Method and a device for detecting security deployment of big data
A detection method and big data technology, applied in the detection field of big data security deployment, can solve problems such as omissions or errors, inability to know the status of security deployment, abnormality of big data platform, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
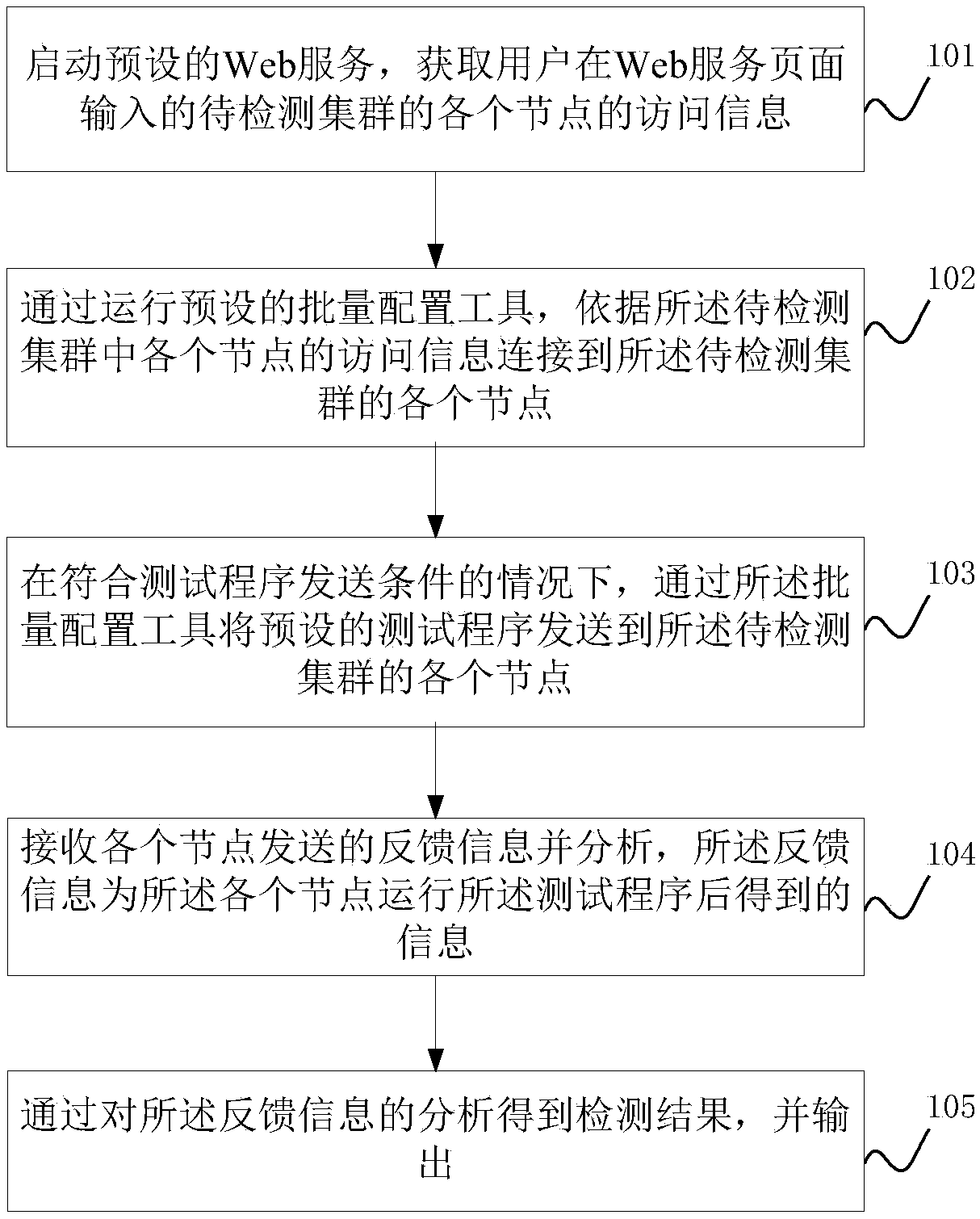
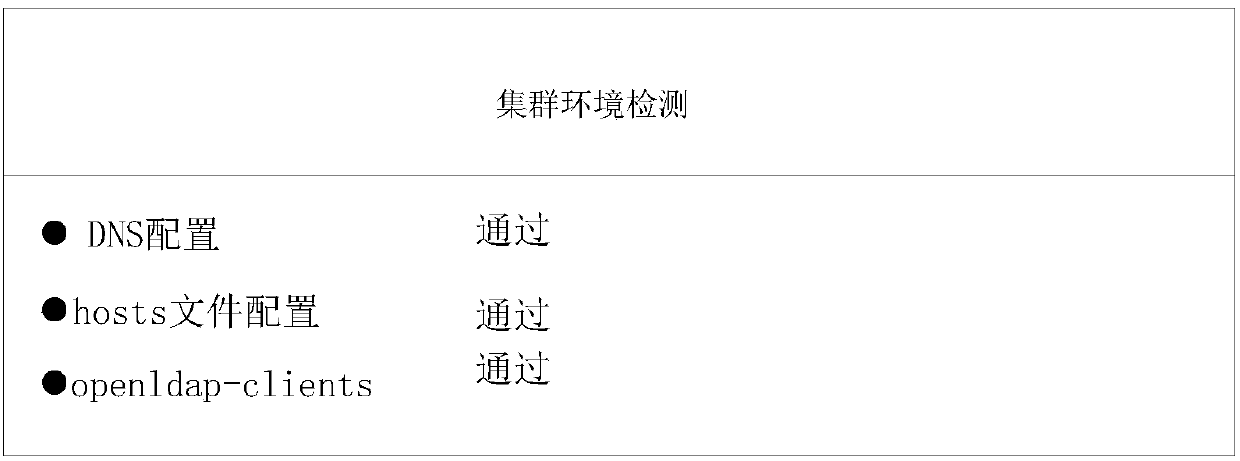
[0095] Implementation mode 1: if all nodes meet the requirements of the cluster environment, output the detection result of the cluster environment security on the web page of the cluster environment detection;
[0096] If all nodes meet the requirements of the service component, output the detection result of the service component security on the web page of the service component detection;
[0097] If all nodes meet the service status requirements, output the detection result of service status security on the Web page of service status detection.
[0098] Among them, for the first embodiment, such as Figure 3-a , Figure 3-b , Figure 3-c As shown: the detection results of each aspect will be displayed on the display page, and each aspect includes different test items, and the detection results of different test items will also be displayed on the web page.
Embodiment approach 2
[0099] Embodiment 2: If all nodes meet the preset cluster environment requirements, whether all nodes meet the preset service component requirements, and all nodes meet the preset service status requirements, output the detection result of the cluster environment security.
[0100] Regarding the second embodiment, it means that when the three aspects of security deployment testing meet the conditions, the information about the security of the testing result is displayed on the output display page.
[0101] In addition, if the test results in any aspect do not meet the conditions, specific abnormal information is output. Specifically, S105 includes:
[0102] If any node does not meet the preset cluster environment requirements, or any node does not meet the preset service component requirements, or any node does not meet the preset service status requirements, output corresponding abnormal information.
[0103]A detection method for big data security deployment provided by an e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com