Big data platform protection device deployed at gateway and protection method thereof
A big data platform and protection device technology, applied in the field of big data security, can solve the problems of poor scalability and single function, and achieve the effects of strong scalability, wide application scenarios, and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
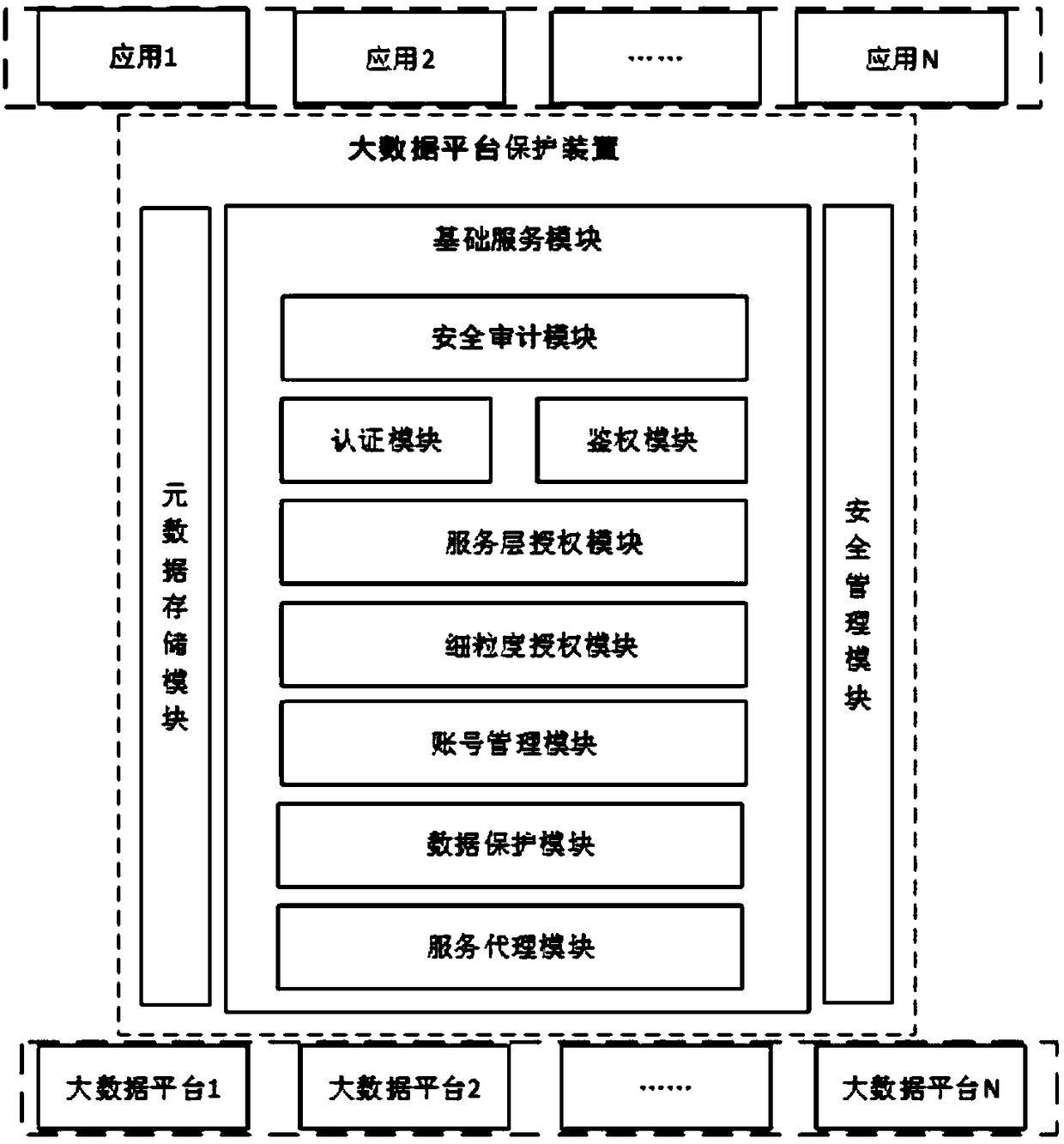
[0049] Such as figure 1 As shown, this embodiment provides a big data platform protection device deployed at the gateway, including an authentication module, an authorization module, a security audit module, a service agent module, a data protection module, an authentication module, an account management module, and a metadata storage module. module, security management module and basic service module,
[0050] Authentication module: through the authority control model, the access request is authenticated at the gateway. The authentication module includes an external authentication module and an internal authentication module. The external authentication module is responsible for the identity authentication between the user and the protection device, and the internal authentication module is responsible for the protection device. Identity authentication with the protected big data platform;
[0051] The external authentication module adopts the ApacheShiro authentication fram...
Embodiment 2
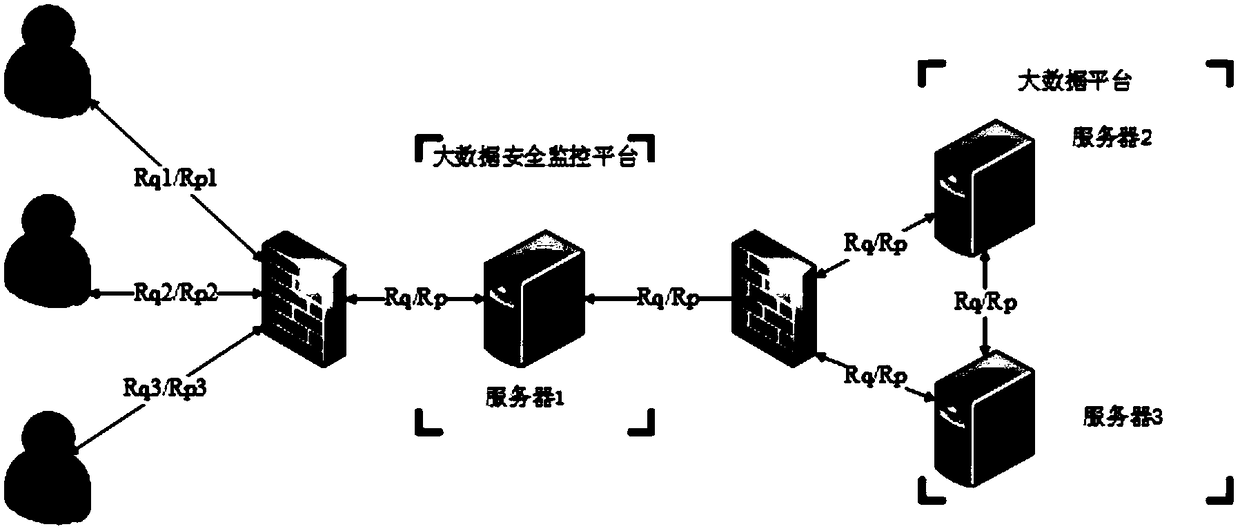
[0077] In this embodiment, on the basis of Embodiment 1, taking the protection of the Hadoop platform as an example, it is described in detail, specifically:
[0078] Such as figure 2As shown, the experimental environment contains a total of 3 servers, where the protection device is deployed on server 1, and the big data platform is deployed on server 2 and server 3, where server 2 is the management node of the Hadoop platform, and server 3 is the working node. The server 1 where the protection device is located includes two IP addresses, an external network IP address and an internal network IP address. The external network IP address is visible to the user, and the user accesses the big data security monitoring platform through the external network IP address. The big data security monitoring platform is a platform on which the protection device in Embodiment 1 is deployed, and the intranet IP address is the communication IP between the big data security monitoring platform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com