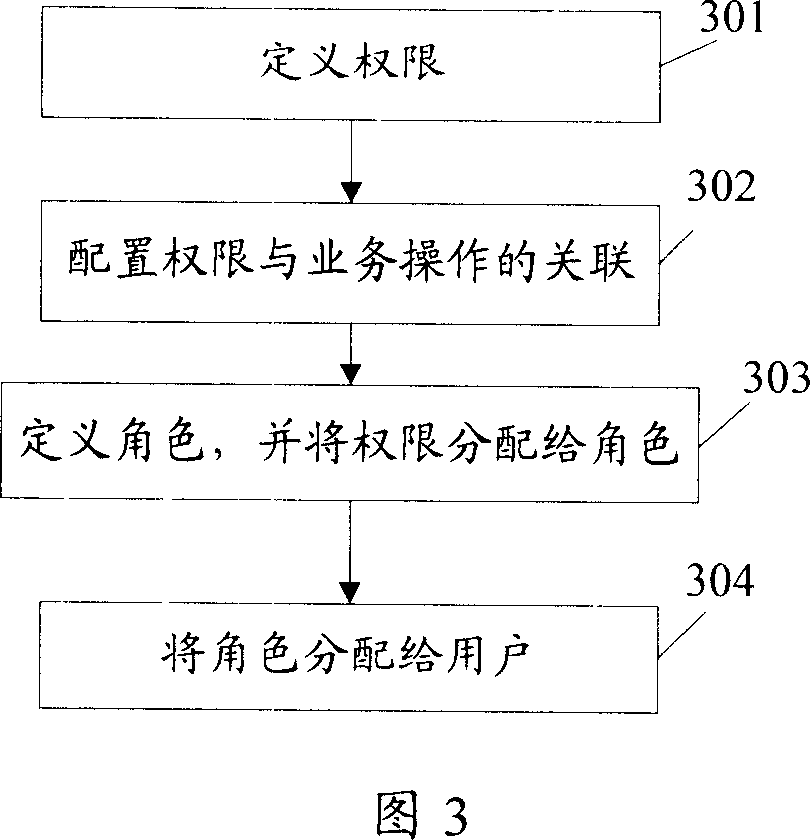
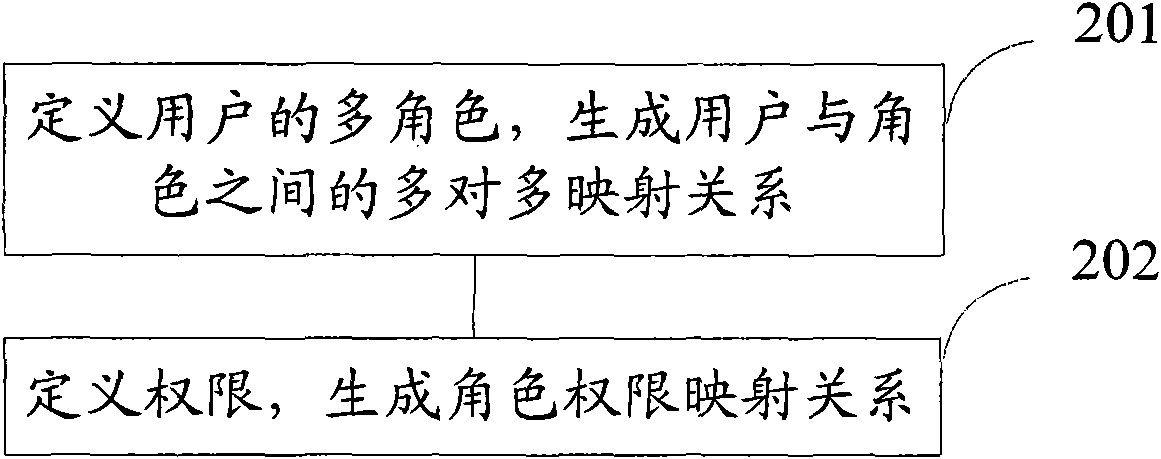
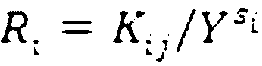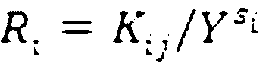Patents
Literature
1071 results about "Authority control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In library science, authority control is a process that organizes bibliographic information, for example in library catalogs by using a single, distinct spelling of a name (heading) or a numeric identifier for each topic. The word authority in authority control derives from the idea that the names of people, places, things, and concepts are authorized, i.e., they are established in one particular form. These one-of-a-kind headings or identifiers are applied consistently throughout catalogs which make use of the respective authority file, and are applied for other methods of organizing data such as linkages and cross references. Each controlled entry is described in an authority record in terms of its scope and usage, and this organization helps the library staff maintain the catalog and make it user-friendly for researchers.
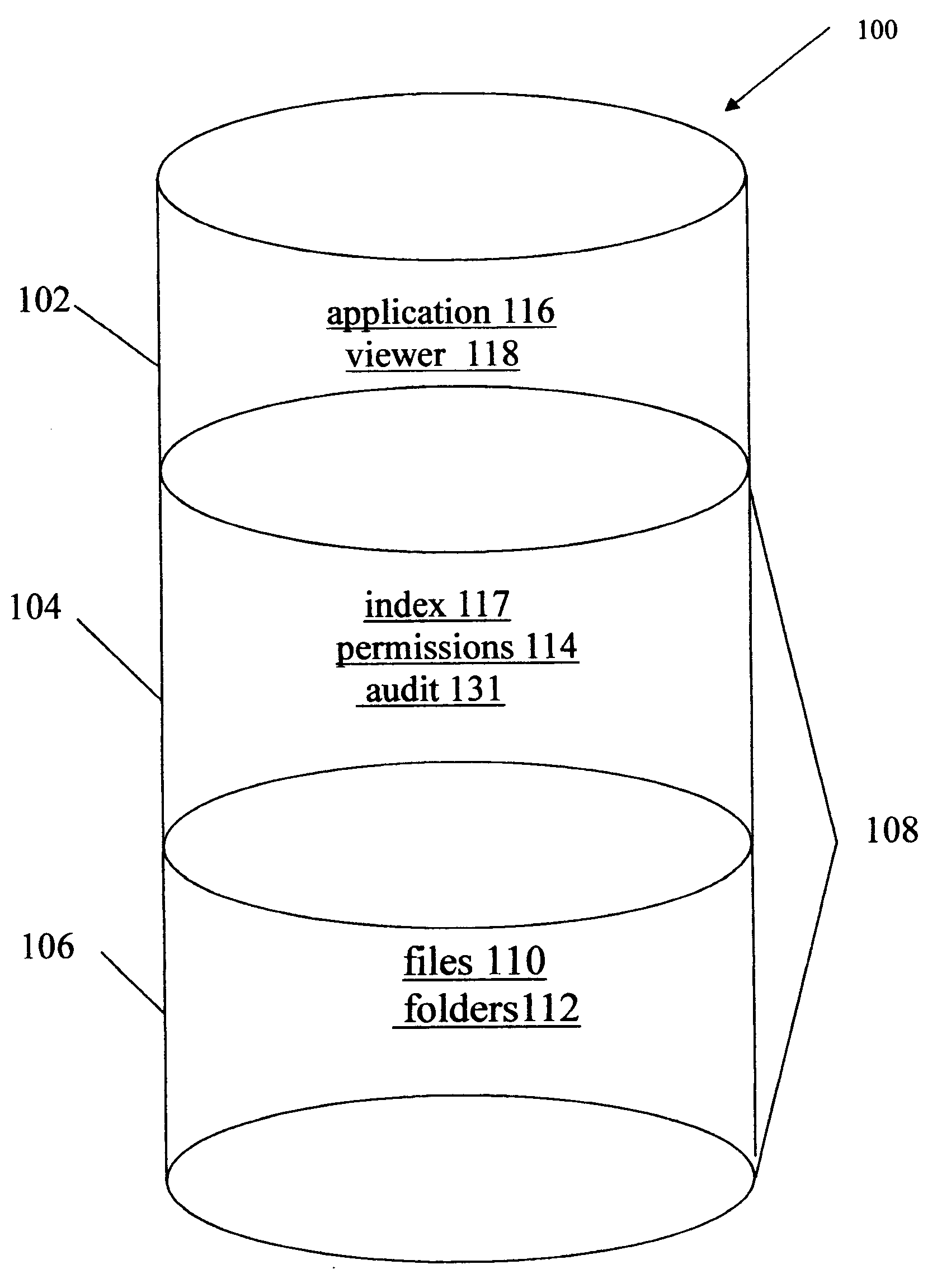
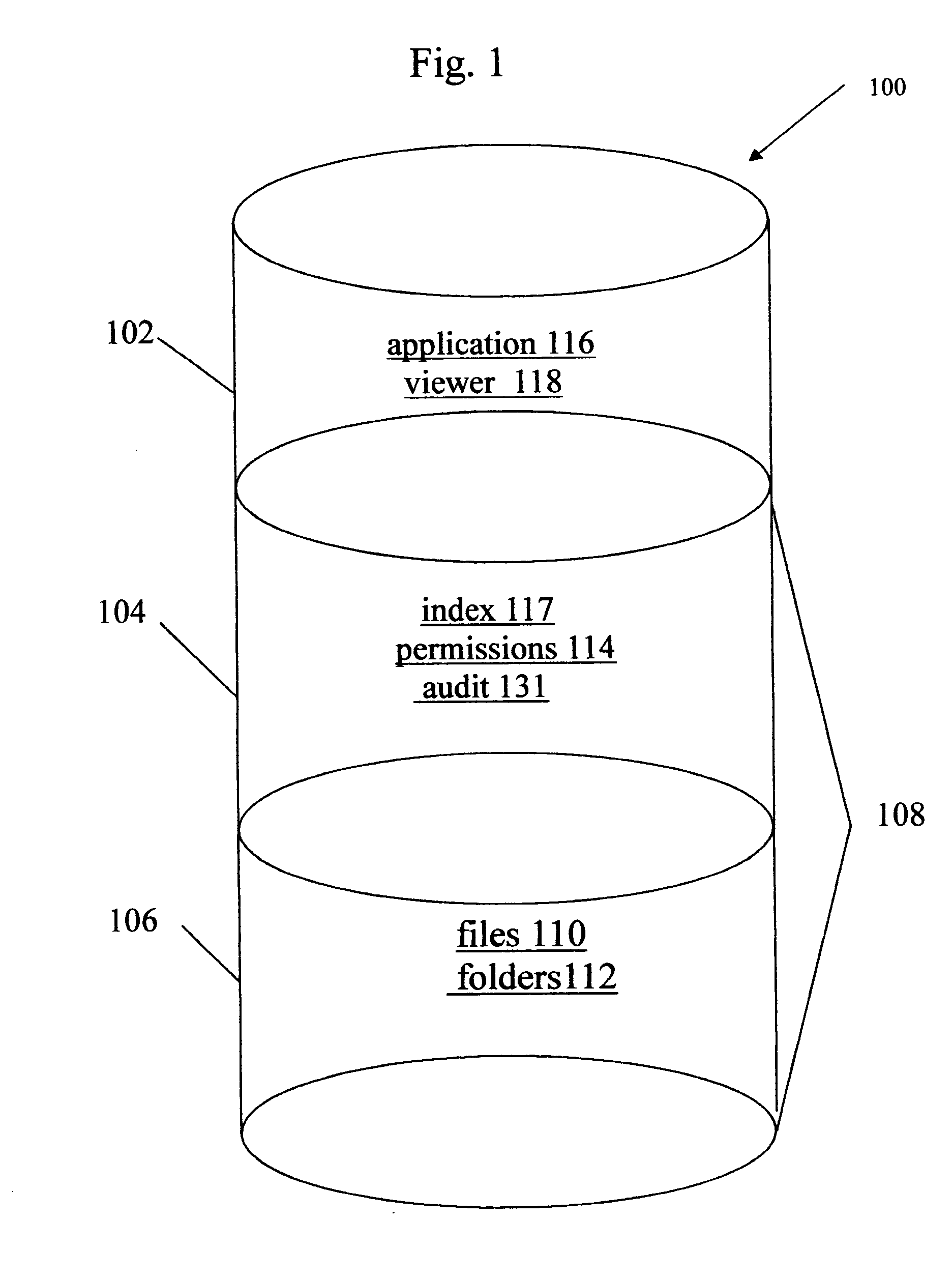
Data rights management of digital information in a portable software permission wrapper
InactiveUS20050114672A1Minimize impactImprove protectionSecret communicationProgram/content distribution protectionEmbedded securityTransaction management
The present invention provides systems and methods for secure transaction management and electronic rights protection. The invention is a software permission control wrapper that is used to encrypt and encapsulate digital information for the purpose of enforcing discretionary access control rights to the data contained in the wrapper. The permission control wrapper enforces rules associated with users, and their rights to access the data. Those rights are based on deterministic security behavior of the permission wrapper based on embedded security policies and rules contained therein and that are based, in part, on the user type, network connectivity state, and the user environment in which the data is accessed.
Owner:ENCRYPTX CORP
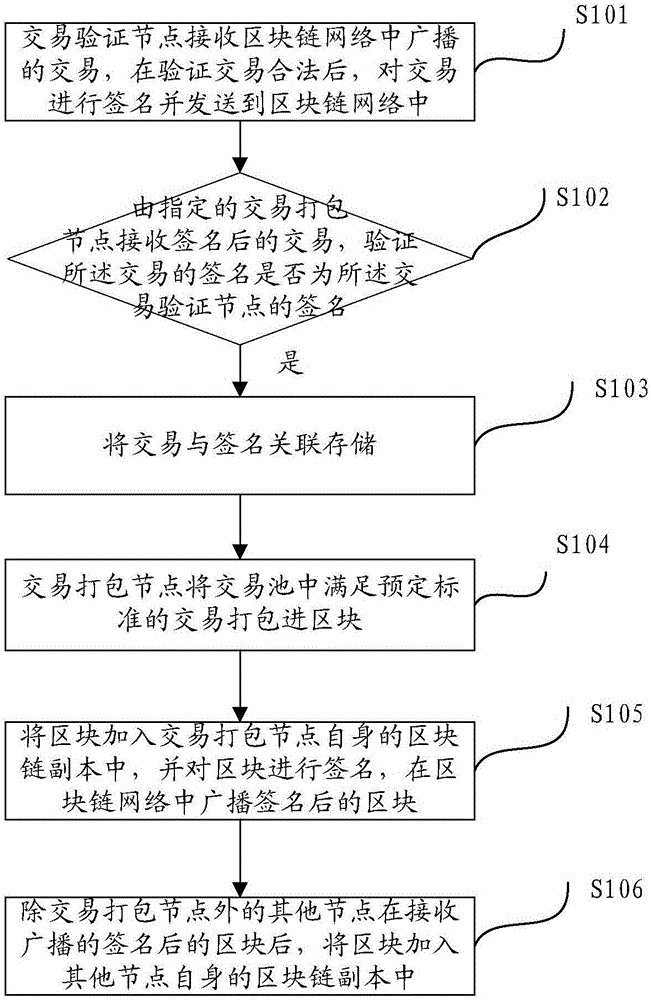
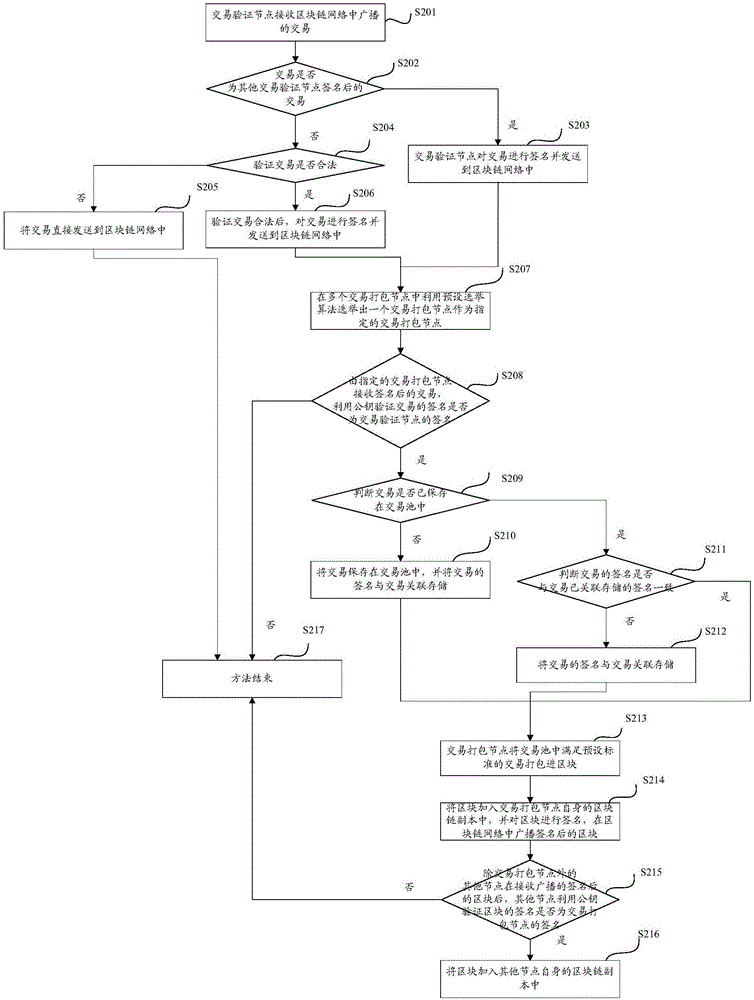
Block chain grouping consensus method and system
ActiveCN106656974AFast formingImplement permission controlTransmissionProtocol authorisationFinancial transactionChain network
The invention discloses a block chain grouping consensus method and system. The method comprises the following steps: transaction verification nodes receive transactions broadcasted in a block chain network, sign the transactions and send the signed transactions to the block chain network when the transactions are checked to be legal; a specific transaction packaging node receives the signed transactions, verifies whether the signatures of the transactions are signatures of the transaction verification nodes, and if so, carries out associated storage on the transactions and the signatures; the transaction packaging node enables transactions meeting preset standard in a transaction pool to be packaged into blocks; the blocks are added to a block chain copy of the transaction packaging node itself, the blocks are signed, and the signed blocks are broadcasted in the block chain network; and after other nodes except the transaction packaging nodes receive the broadcasted signed blocks, and the blocks are added to block chain copies of the other nodes. According to the scheme, the system and method can carry out grouping on the nodes, realize different functions, and realize authority control.
Owner:JIANGSU PAYEGIS TECH CO LTD
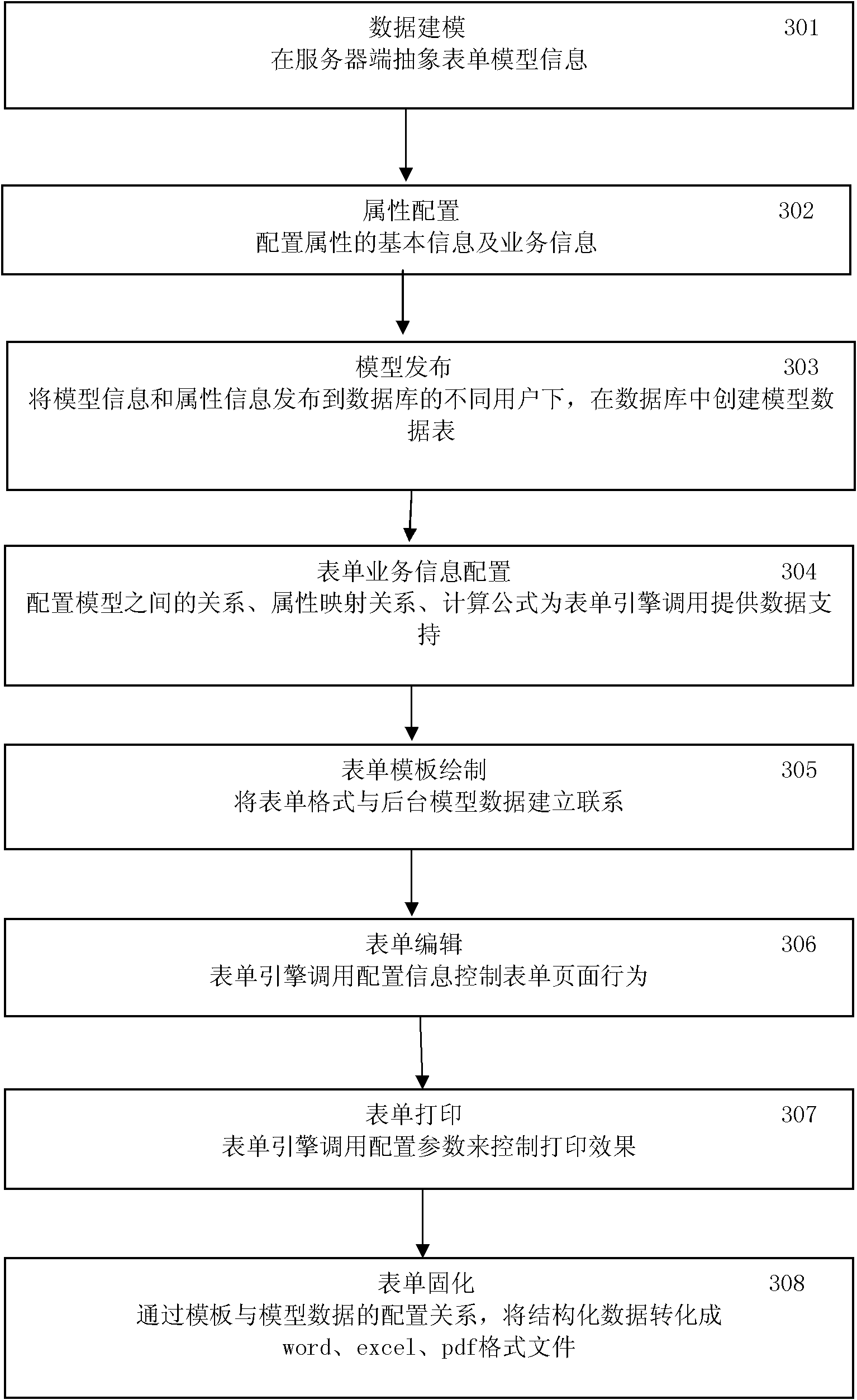
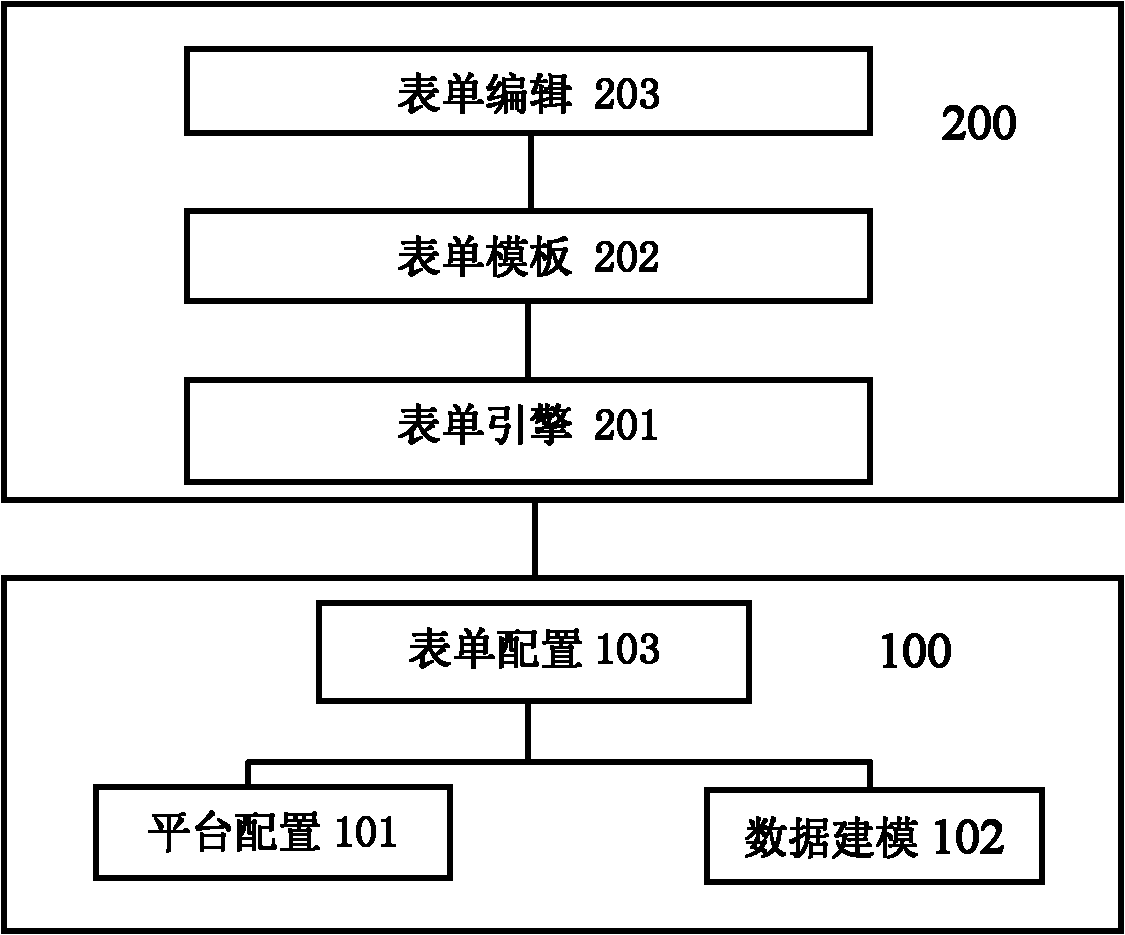
Java server page (JSP) template-based intelligent table system capable of being defined freely and generating method
InactiveCN102135990AQuick buildTight and seamless integrationSpecial data processing applicationsExtensibilityData modeling
The invention relates to a java server page (JSP) template-based intelligent table system capable of being defined freely, which controls a table through system configuration under the driving of a table engine to complete various service functions on the basis of data modeling. The (JSP) template-based intelligent table system provides implementing mechanisms of data modeling, service configuration, table drawing, table editing and the like and can realize user-oriented free customization of the table, and a user can realize most service logics by configuring various parameters through pages, thereby greatly improving the flexibility and extensibility of the intelligent table system. In the system, the JSP file is used as a template of the table, and various configuration information controlling the table and the table template are connected through the table engine, thus that the effect that the table service comes into effect as long as configured can be realized. In the part of table editing, the system can realize automatic calculation of table attribute, addition and delete of sub-table rows, secondary authority control of the table, service implementation and control of the table and the like.
Owner:北京神舟航天软件技术股份有限公司
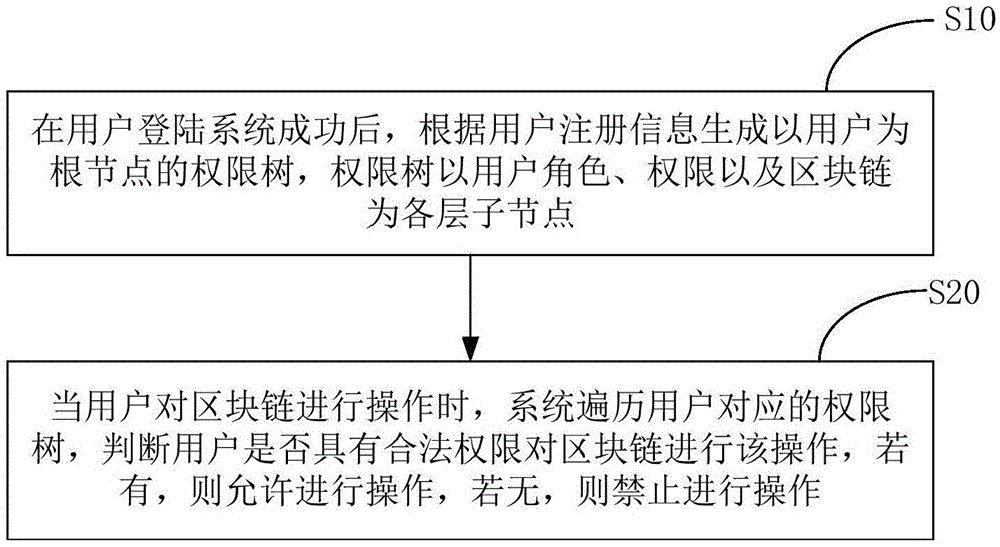
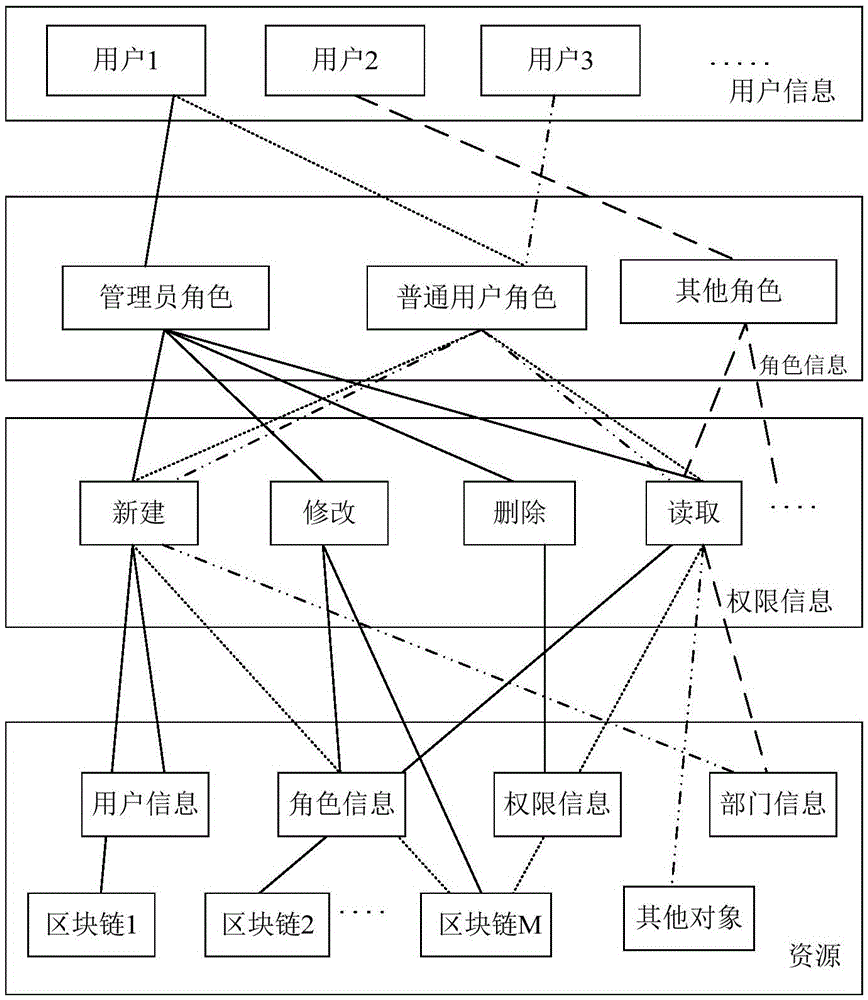
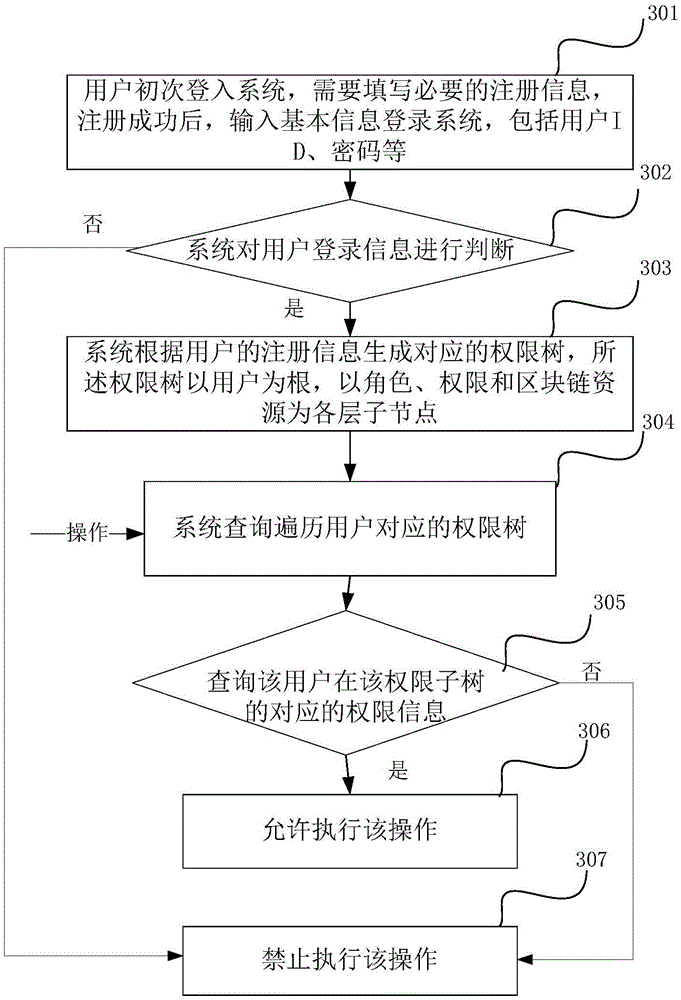
Authority management method and device for block chain system
ActiveCN105488431AReduce the number of layersQuick updateDigital data protectionResource consumptionRights management
The invention discloses an authority management method and device for a block chain system. The method comprises the following steps of generating an authority tree with a user as a root node according to user registration information after the user logs in to the system successfully, wherein the authority tree takes a user role, user permission and a block chain as a sub-node of each layer; and when the user carries out an operation on the block chain, informing a control module to traverse the authority tree corresponding to the user, judging whether the user has legal permission to carry out the operation on the block chain according to a traversing result of the control module, if yes, allowing the operation, and if no, forbidding the operation. According to the method and the device, the flexible authority control is carried out on the authority management by the authority tree, and furthermore, the authority tree has the characteristics of less number of layers and quick updating, so that the authority resource consumption can be reduced, and the efficiency for authority management is also guaranteed.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Method and system for managing authority
ActiveCN101414253AConvenience for follow-up developmentEasy maintenanceSpecific program execution arrangementsRights managementAuthority control
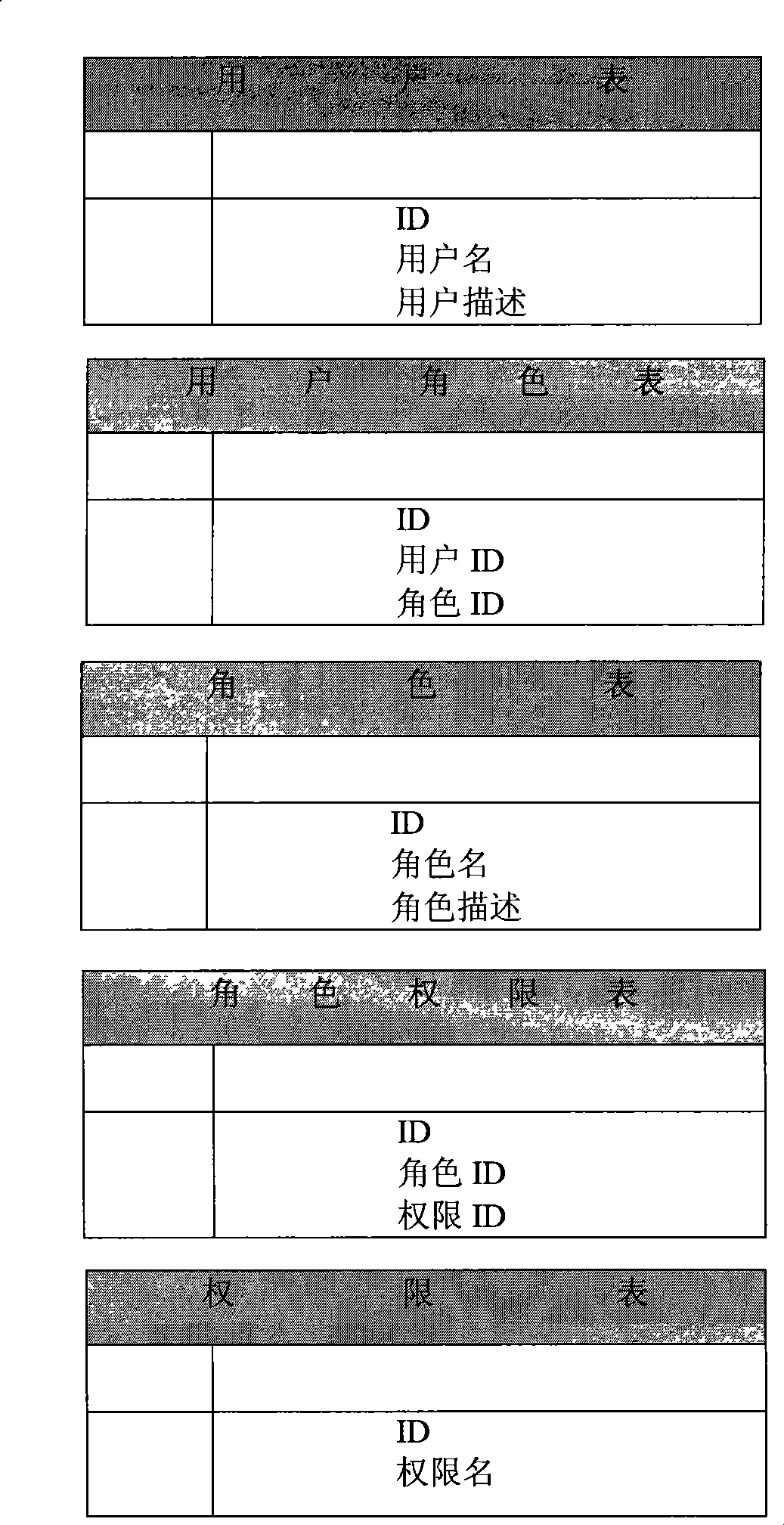
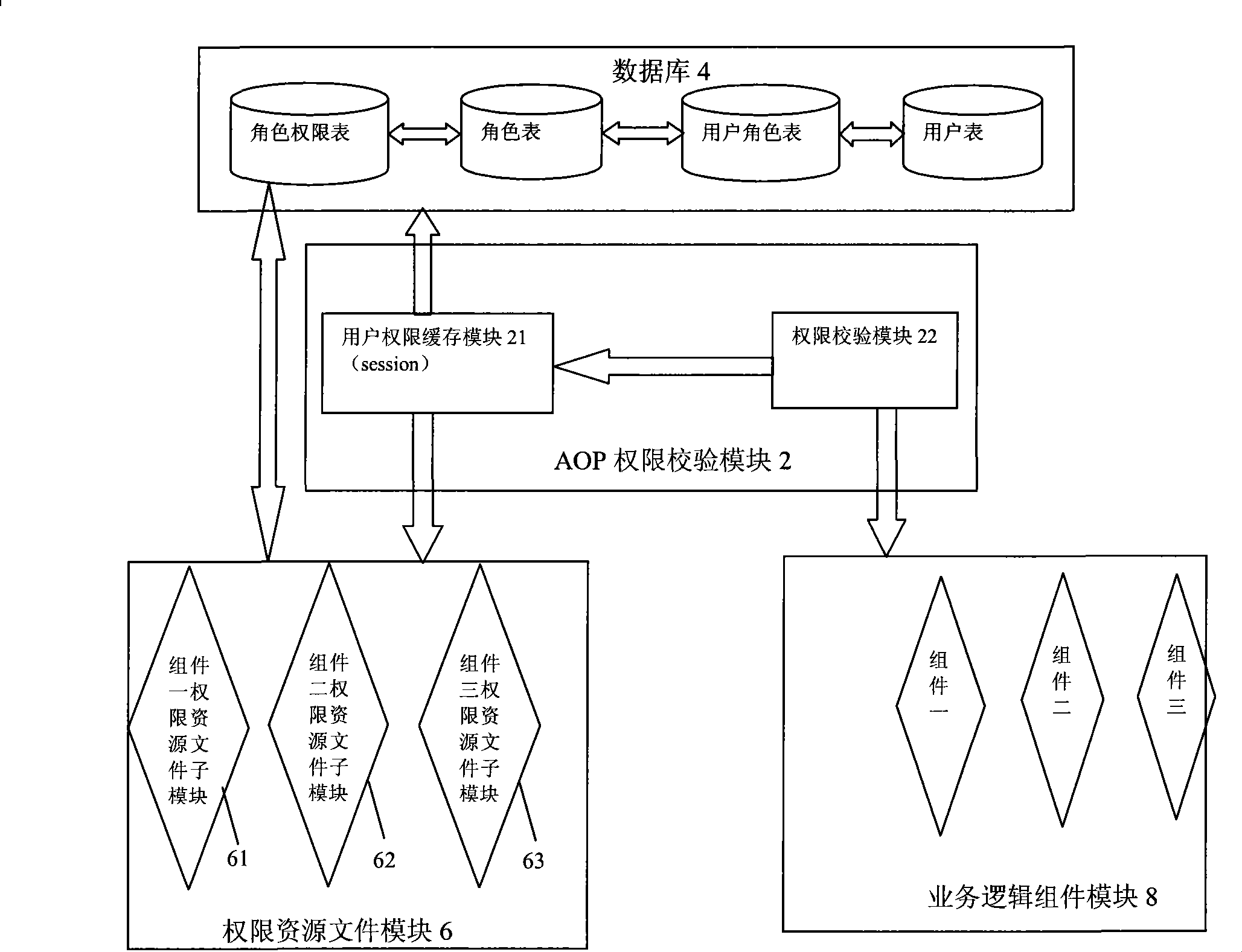
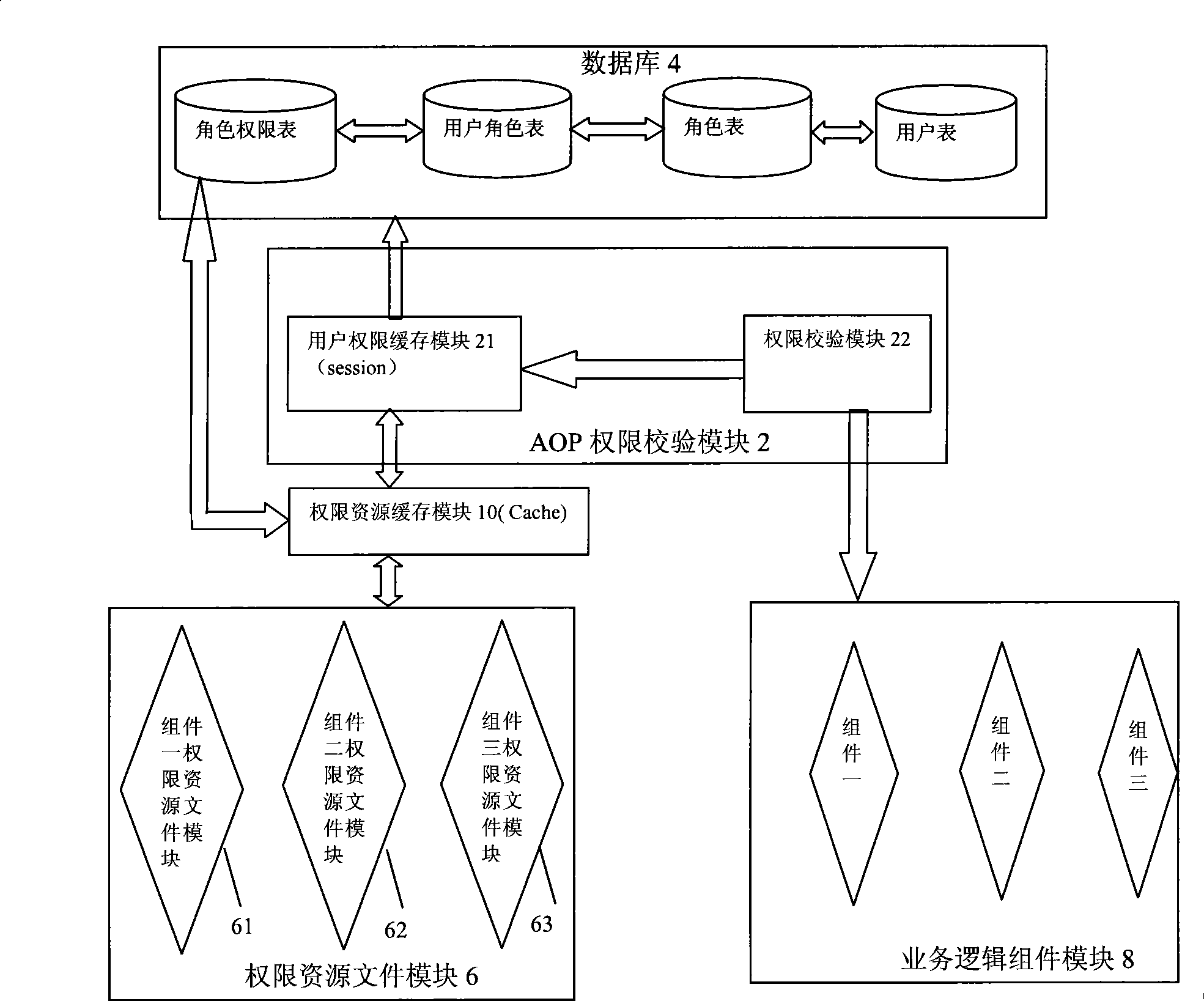
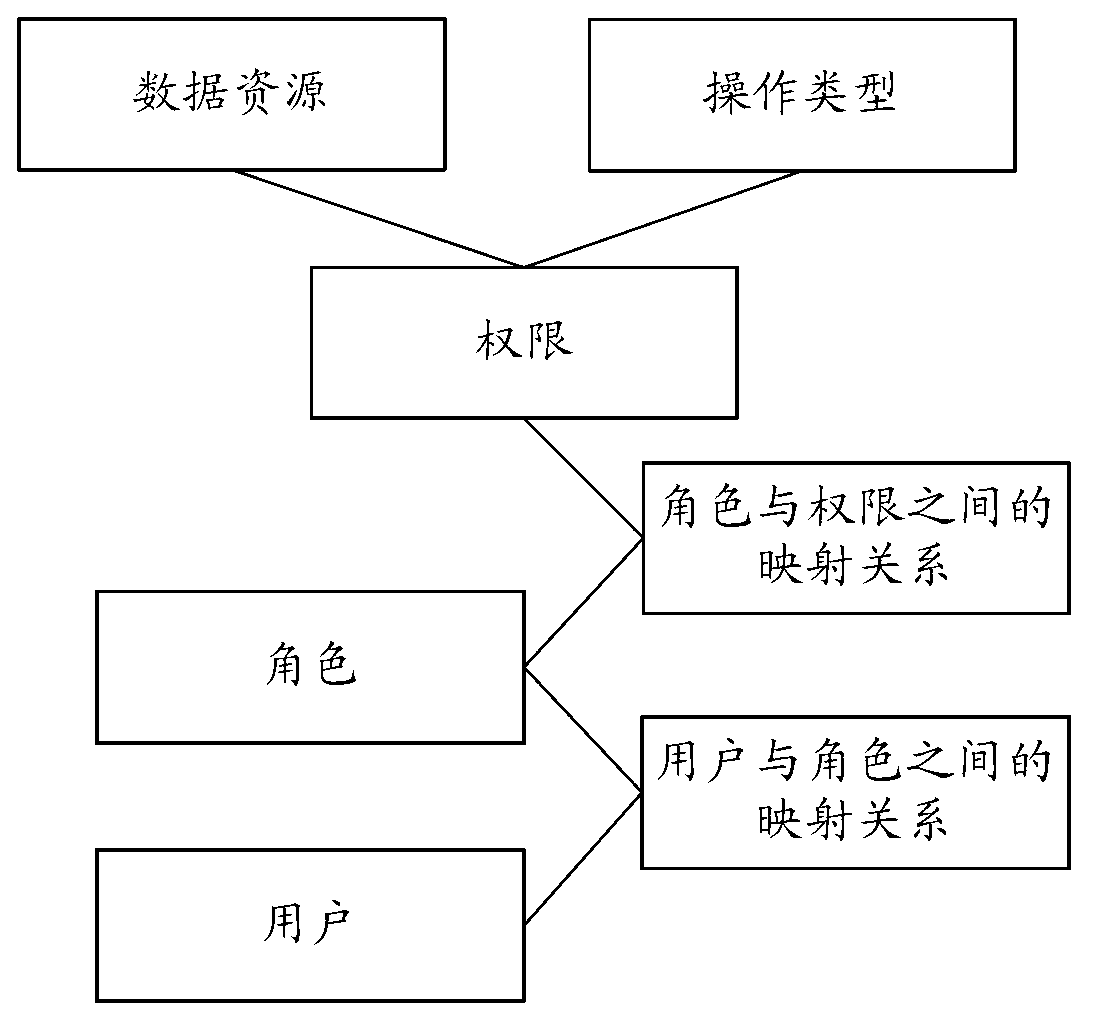
The invention discloses an authority management method, the method is used for carrying out the verification of an operation request of a user in an authority management system, the method comprises: the operation request which is put forward by the user is received; an authority identifier distributed for a character which the user belongs to is obtained from a database, the database stores the corresponding relation among the user, the character and the distributed authority identifier for the character; authority resources which are corresponding to the authority identifier are obtained from various authority resource subfiles in the system and cached, the various authority resource subfiles are corresponding to various business logic component modules in the system, each authority resource subfile stores the authority resources of the corresponding business logic component module; the operation request of the user is intercepted, whether the authority resources distributed to the user contain the operation request or not is judged, if yes, the operation request is accepted, otherwise, the operation request is refused. Meanwhile, the invention also discloses the authority management system. The use of the method and the system can meet the detailed authority control needs of each operation of each operation interface of the system, realize the convenient follow-up development and maintenance of the authority resources of the business modules and also realize the flexible customization of the business modules of the user according to the needs.
Owner:XFUSION DIGITAL TECH CO LTD
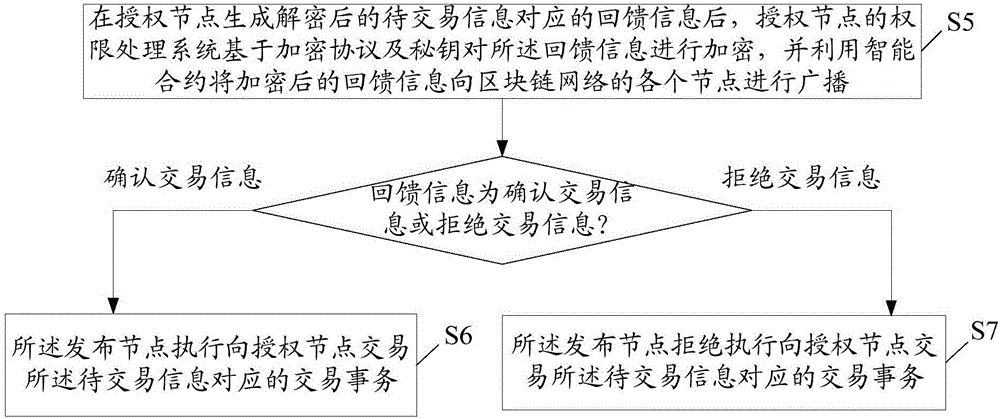
Block chain trading based authority control method and system
ActiveCN106534097AImprove reliabilityTransmissionProtocol authorisationHandling systemSmart contract
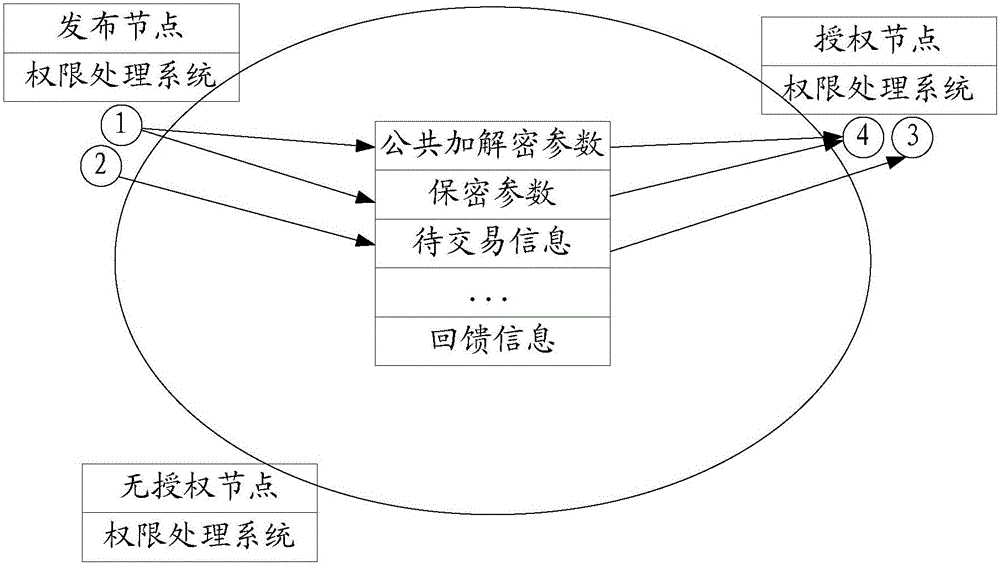
The invention relates to a block chain trading based authority control method and system. The block chain trading based authority control method comprises the steps of establishing an authority processing system for each node of a block chain network and deploying an intelligent agreement; if an issuing party has encrypted to-be-trade information for decrypting and authorizing at least an authorized party, obtaining public encryption and decryption parameters corresponding to each authorized party by the authority processing system on the issuing node, encrypting a key of the encrypted to-be-traded information through confidential parameters corresponding to the authorized party, and issuing the public encryption and decryption parameters and the confidential parameters in the block chain network by utilizing the intelligent agreement; issuing the to-be-traded information to each node of the block chain network through the intelligent agreement by the authority processing system of the issuing node; and after the authorized node receives the to-be-traded information, decrypting the key of the to-be-traded information by utilizing the decryption parameters by the authority processing system, and decrypting the to-be-traded information based on the decrypted key and the public encryption and decryption parameters. The block chain trading based authority control method and system can efficiently control affair processing authority in the block chain network.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
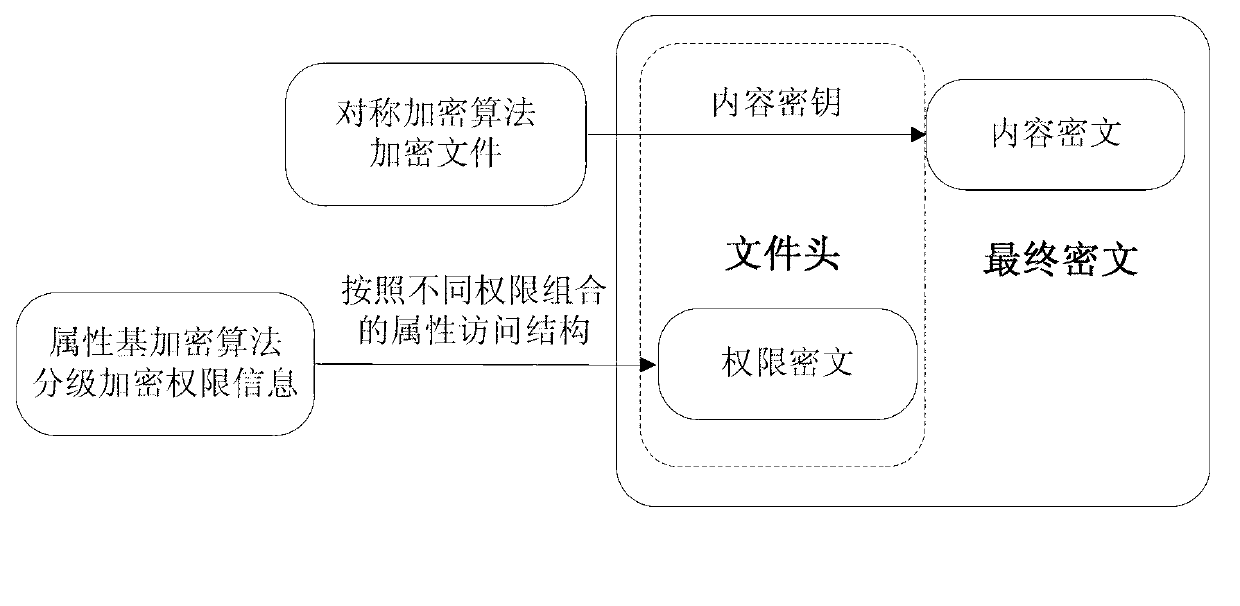
Multistage authority management method for cloud storage enciphered data sharing
ActiveCN103107992AReduce complexityEasy to implementTransmissionAttribute-based encryptionCiphertext
The invention relates to a multistage authority management method for cloud storage enciphered data sharing. The methods such as attribute based encryption, access control and authority management are used for providing a reliable method for access and multistage authority management of a shared cipher text in the cloud storage environment. Through mixing encrypt system, the multistage authority management method for cloud storage enciphered data sharing comprises steps: firstly applying a symmetric encryption algorithm to encrypt data, and generating a content cipher text; then adopting the attribute based encryption to encrypt according to different authority information, and generating an authority cipher text; adopting the attribute based encryption scheme to encrypt a symmetric key and the authority cipher text, regarding the symmetric key and the authority cipher text as a file header of the content cipher text, and generating a final cipher text. The multistage authority management method for cloud storage enciphered data sharing has the advantages of being convenient to achieve, strong in user information protectiveness, fine in authority control grit and the like. Under the premise that a server is not credible, the flexible and extensible authority management to the shared enciphered data is supported, the privacy and the security of the user data and authority information are effectively ensured, and the multistage authority management method for cloud storage enciphered data sharing has good practical value and wide application prospect in the cloud storage field.
Owner:HANGZHOU YUANTIAO TECH CO LTD
Management system and method for user safety authority limit
InactiveCN1485746AEnsure safetyGuaranteed scalabilityUnauthorized memory use protectionExtensibilitySafety management systems
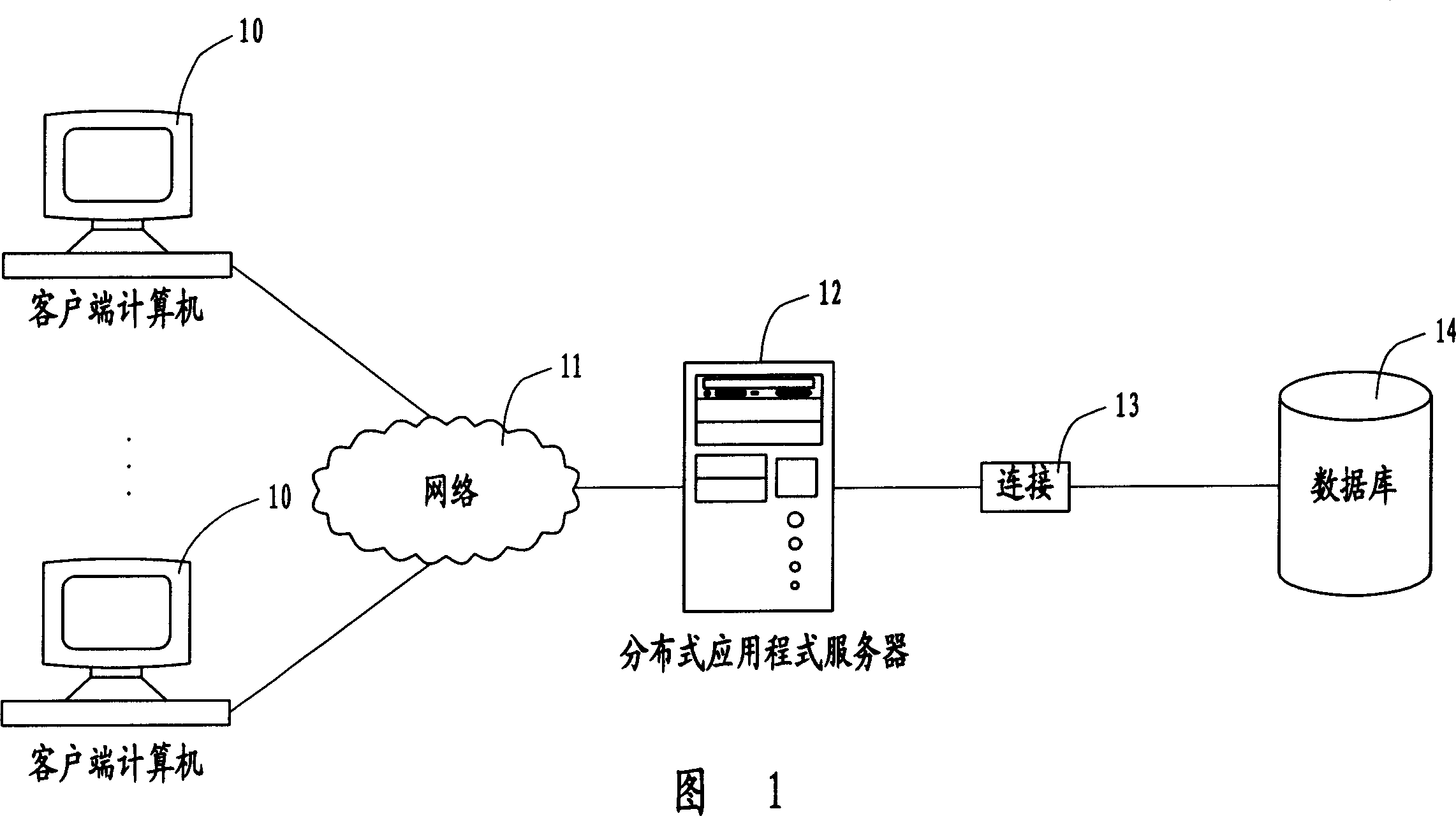
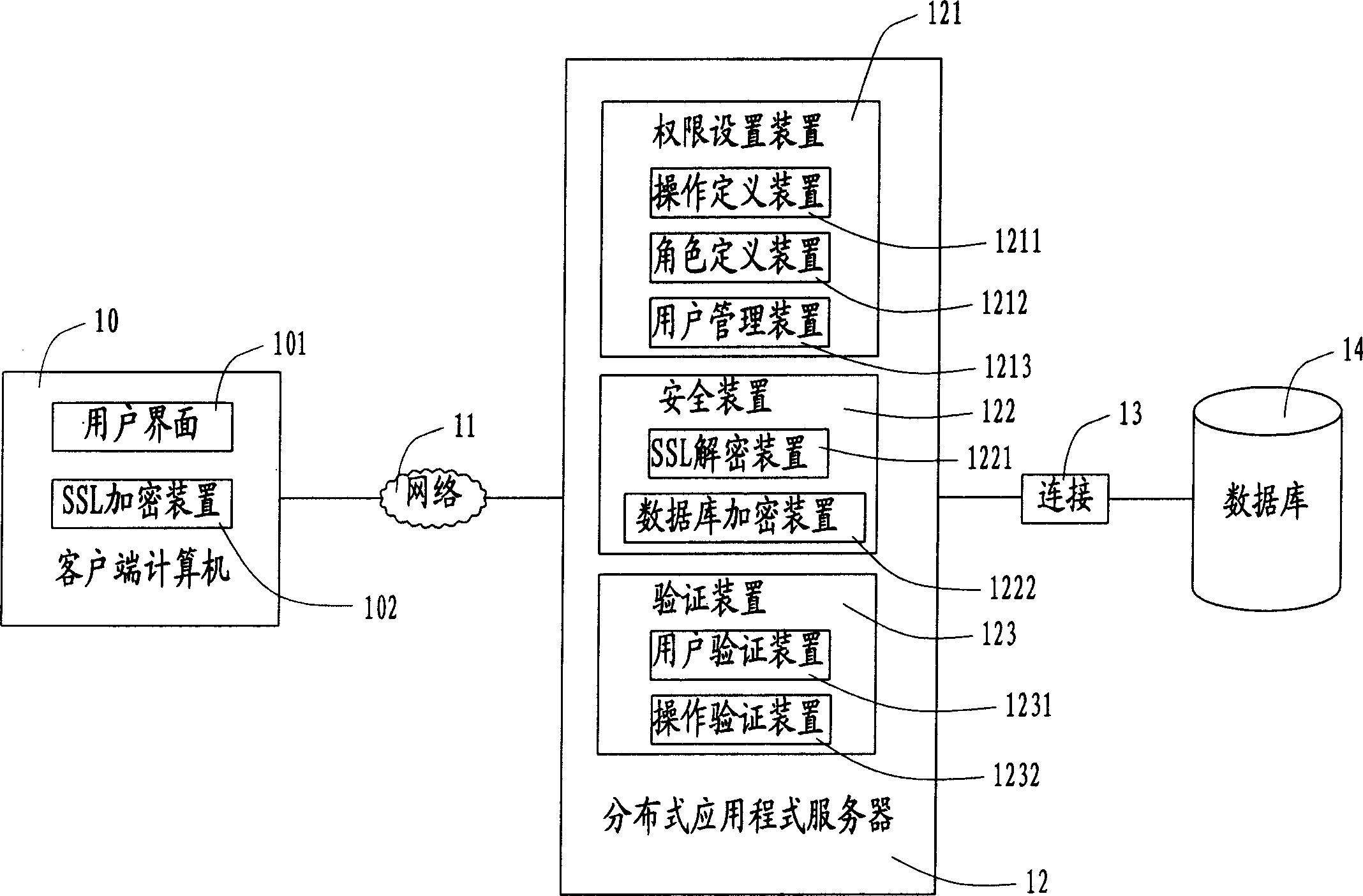
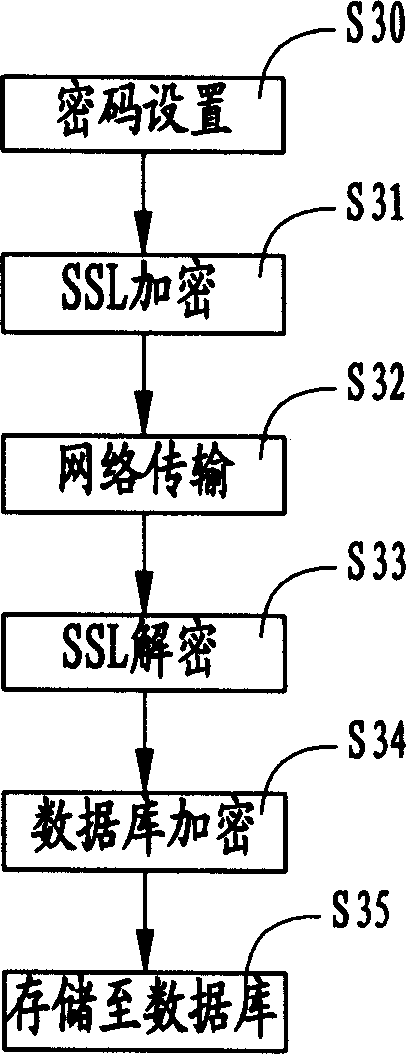
The user authority safety management system and method, wherein the system comprises a plurality of client end computers, a distributed application program server and a data base, the user calls the application program device for proceeding operation definition and role definition through the user interface on the client end computer, and store the information into the database. The invention realizes the user authority control based the system operation, thus guaranteeing the expandability of the system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Mobile equipment privacy authority control method, mobile equipment privacy authority control device and corresponding mobile phone equipment
InactiveCN105072255ARealize managementEasy to manageDigital data protectionSubstation equipmentInternet privacyData access
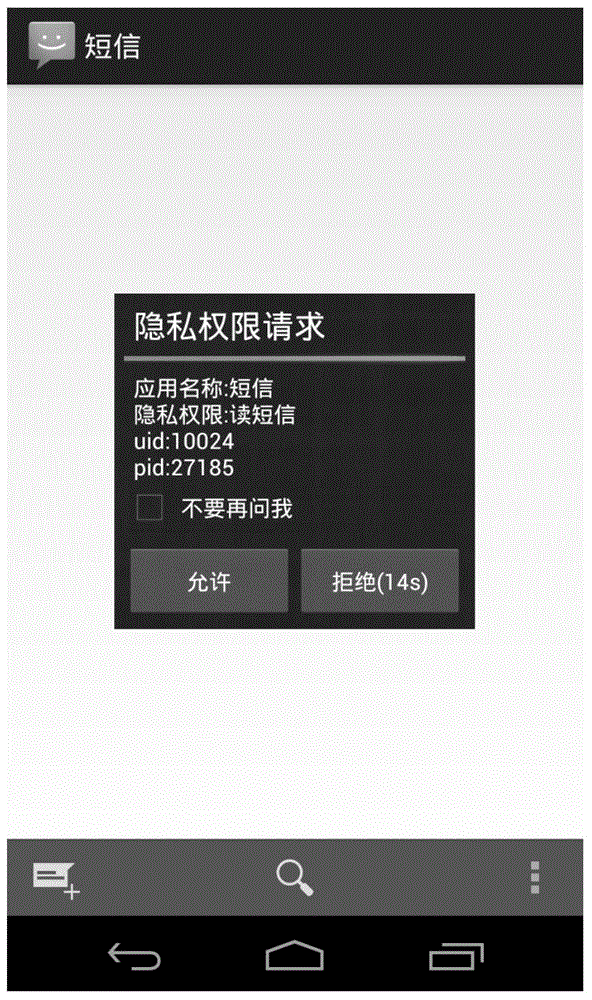
The invention provides a mobile equipment privacy authority control method. The method comprises the steps: receiving a preset event notification, sent by a background service, of privacy data access, wherein the event notification of the privacy data access is generated based on a behavior that the background service intercepts an application program calling a privacy data access interface; in response to the event notification, providing a visual interface to receive a user's authorization instruction for the access privacy data; and, according to the corresponding authorization instruction, notifying the background service to release or prohibit the privacy data access. At the same time, the invention further provides a mobile equipment privacy authority control device and mobile phone equipment. On the condition that an obtaining system root is prevented from causing a system risk, the method and the device can effectively control an access authority of the application program for user privacy data, prevent a leakage of the user privacy data and improve the experience degree.
Owner:BEIJING QIHOO TECH CO LTD +1
Service system authority management method, equipment and system
ActiveCN103078859AImprove the ability of authority managementDigital data authenticationTransmissionGranularityComputer terminal
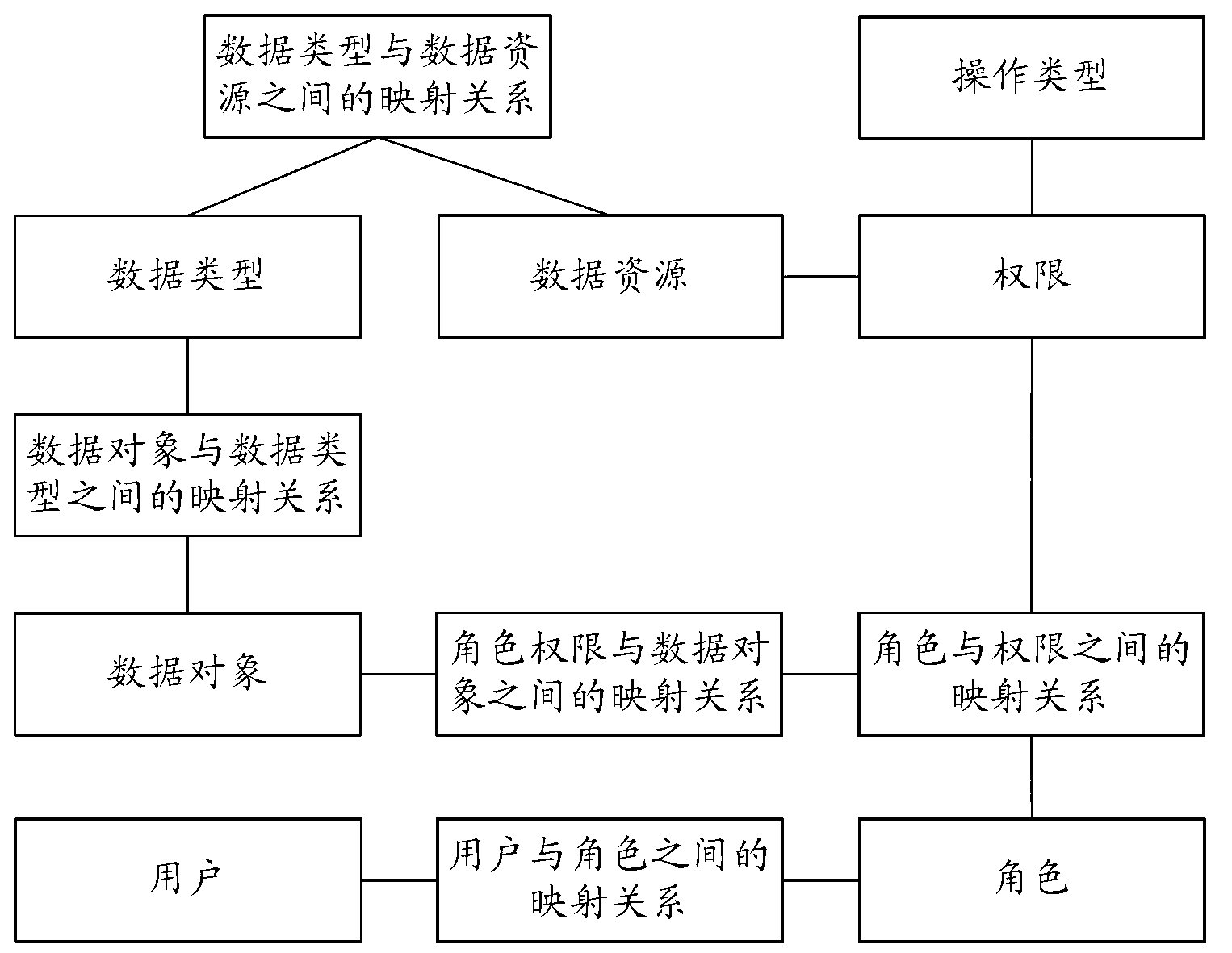
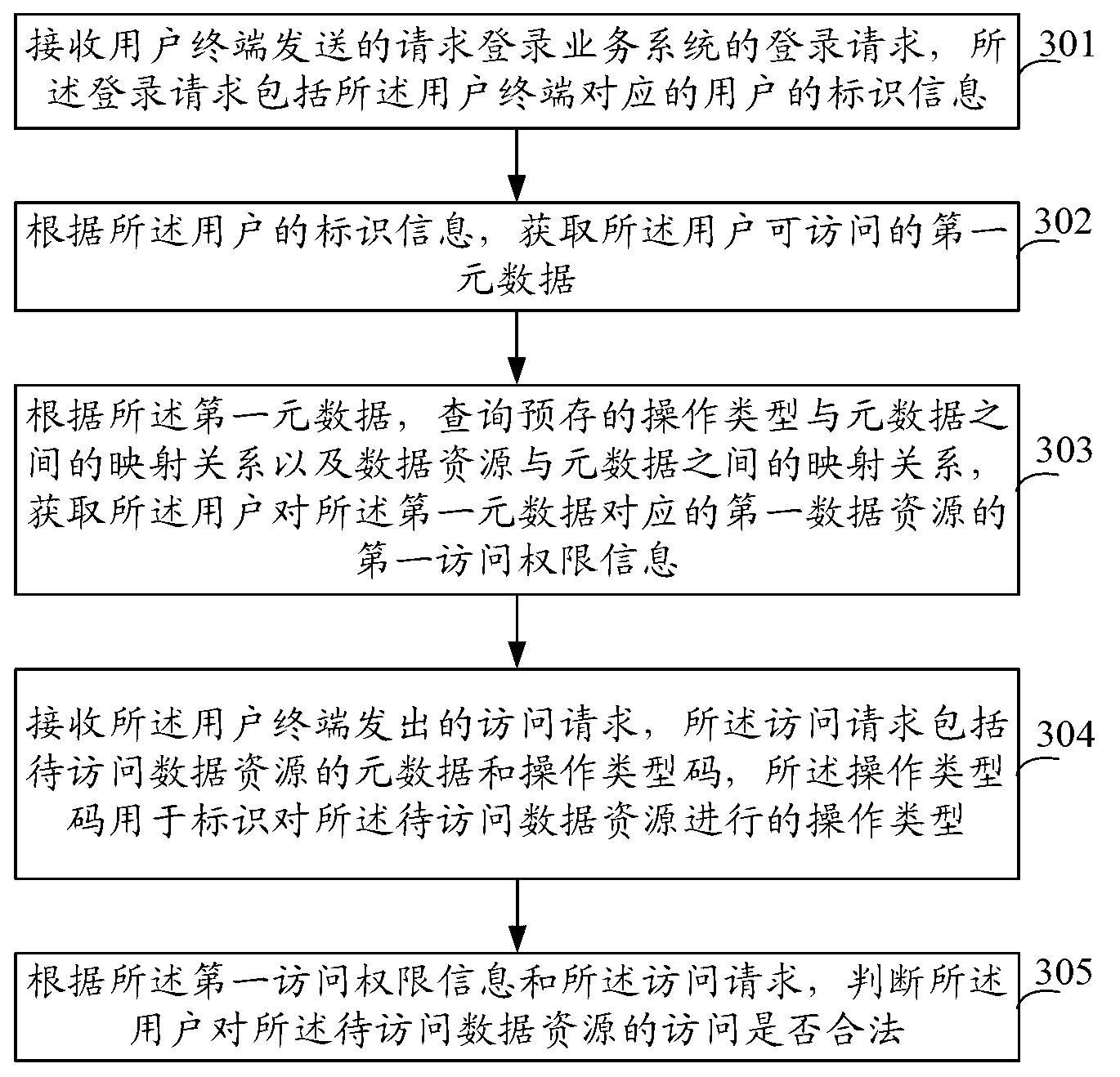
The embodiment of the invention provides a service system authority management method, service system authority management equipment and a service system authority management system. The method comprises the following steps that the login request sent by a user terminal is received, the login request comprises marking information of users, a first metadata capable of being visited by the users is obtained according to the marking information of the users, the mapping relationship between the preset operation type and the metadata and the mapping relationship between the data resource and the metadata are inquired according to the first metadata, the first visit authority information of the users is obtained, the visit request sent by the user terminal is received, the visit request comprises the metadata of data resources to be visited and the operation type codes, and whether the visit to the data resources to be visited by the users is legal or not is judged according to the first visit authority information and the visit request. The mapping relationship is built in advance, the fine granularity grading visit authority control on the data resources of the service system is realized, and the authority management capability on the service system is improved.
Owner:PUTIAN NEW ENERGY
Method and system for detecting and defending multichannel network intrusion
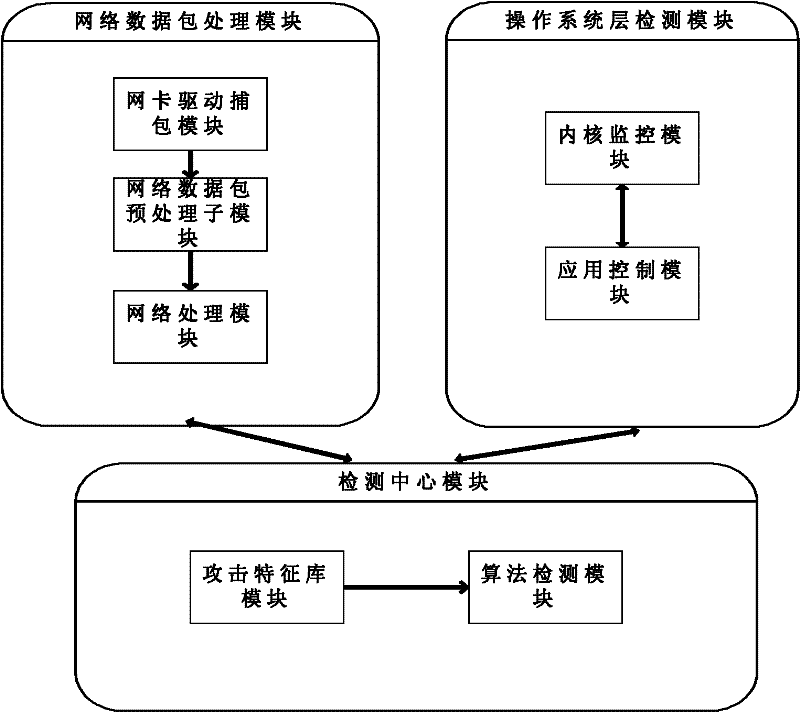
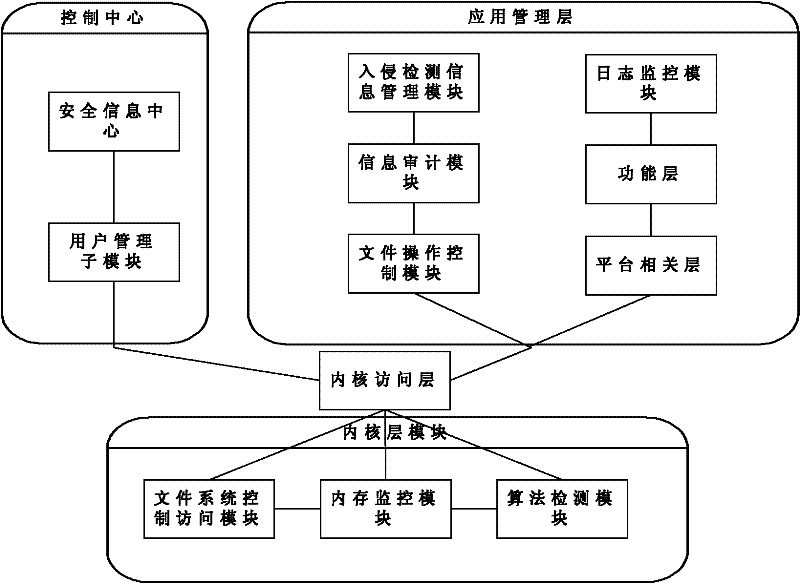
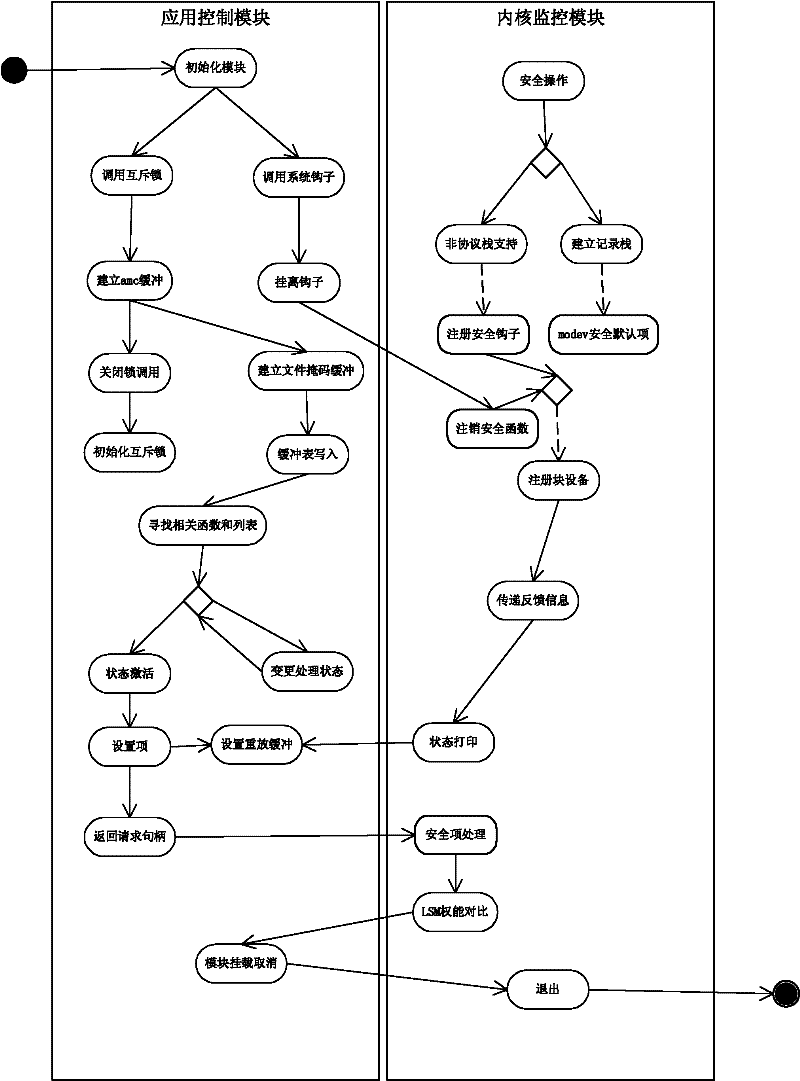
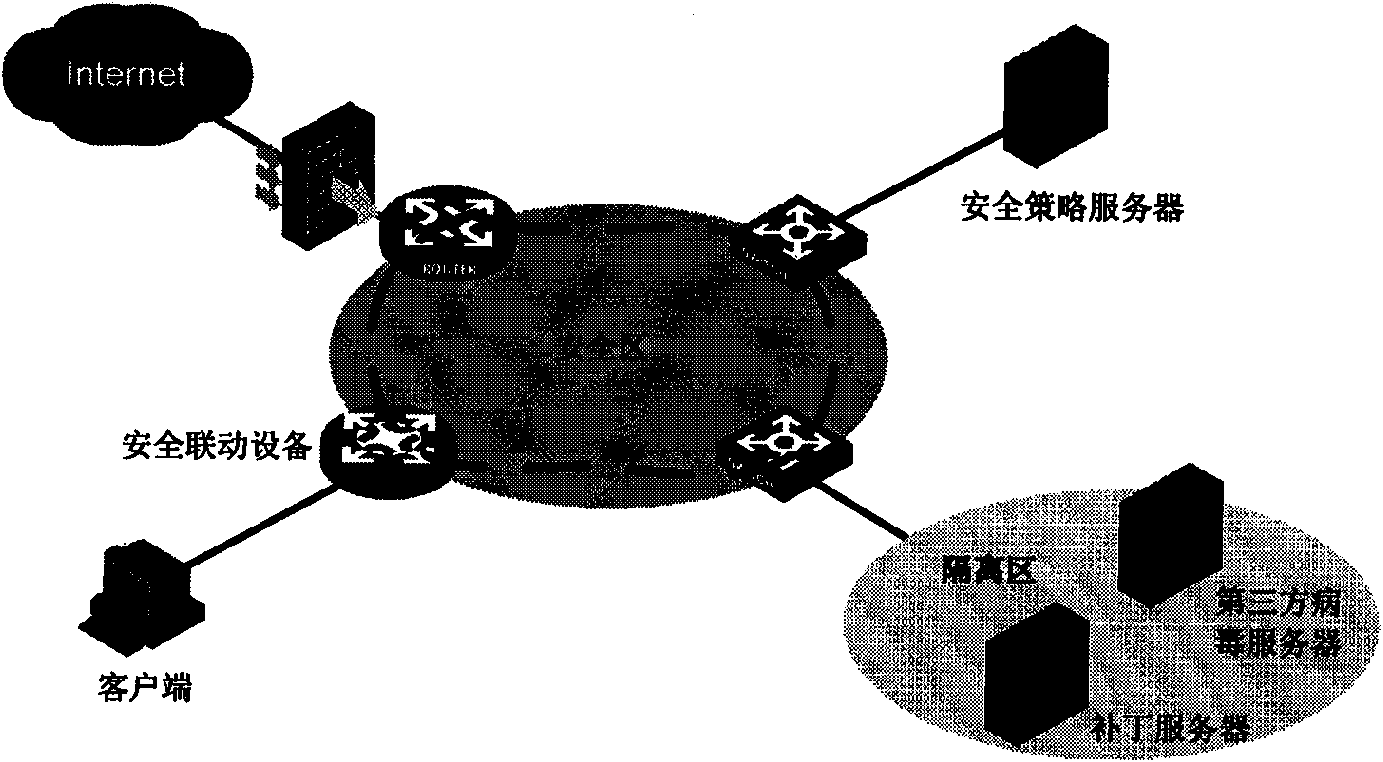
InactiveCN102546624AImprove real-time performanceImprove execution efficiencyData switching networksOperational systemPacket processing
The invention relates to a method and a system for detecting and defending multichannel network intrusion, wherein a half-polling manner is used in a network card driver at a network side to capture a data packet and from a rule for judging abnormal traffic. At an operating system side, secure access control is realized by additionally setting authority control in a Capability module of Linux, meanwhile, monitoring and control treatment is performed on a kernel layer of an operating system, and the monitoring of Trojan and other abnormal operations or virus destruction is realized by carrying out credential privilege arbitration on processes, operating an i-node and carrying out secure control on an application layer. Formed feature data are gathered and sent to a Bayes model for classification, an improved backward propagation neural network (BPNN) is guided in to carry out data training so as to make the produced rule capable of defending corresponding attacks. The system disclosed by the invention comprises three modules and five submodules, wherein the three modules include a network data packet processing module, an operating system layer detecting module ad a detection center module.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
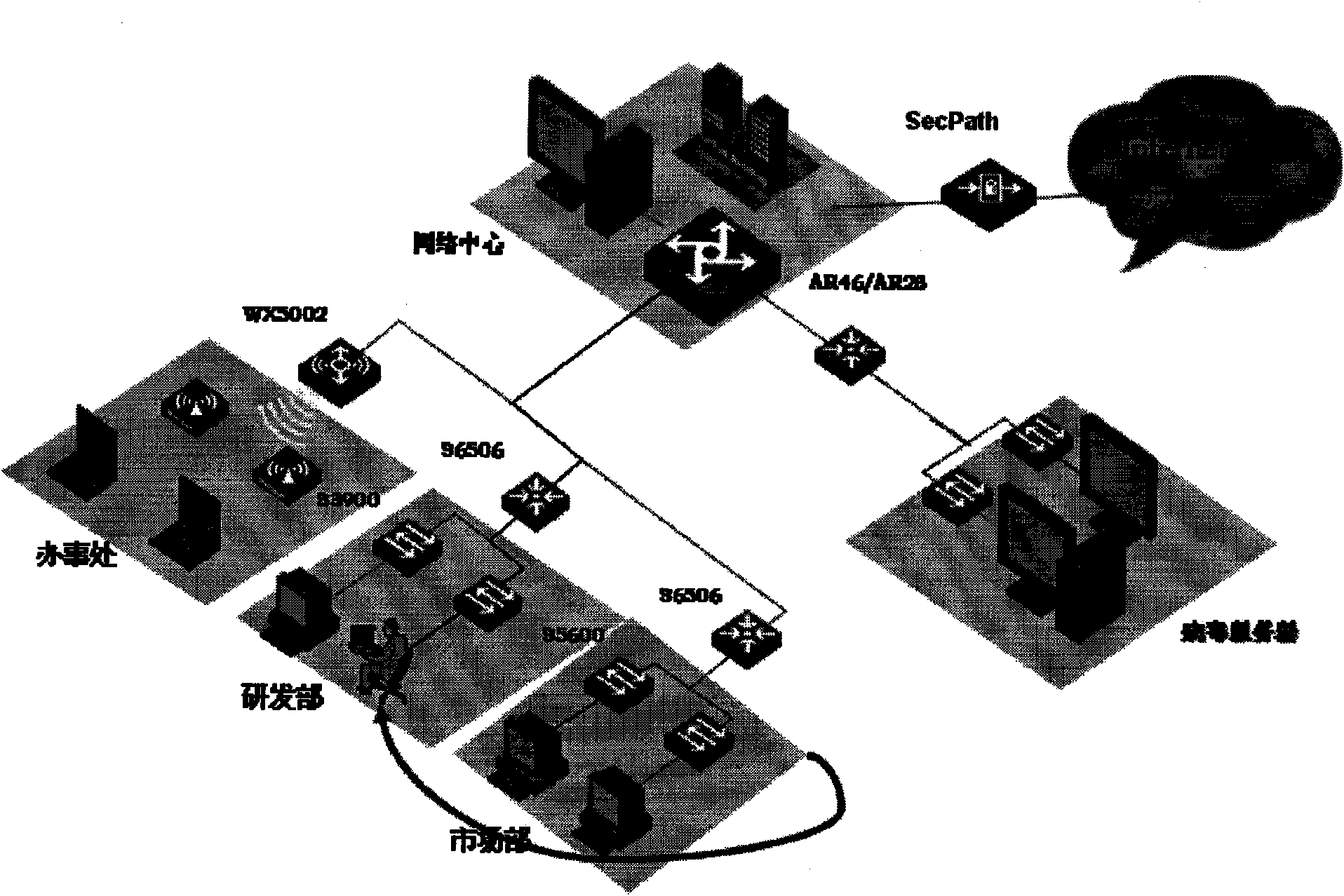
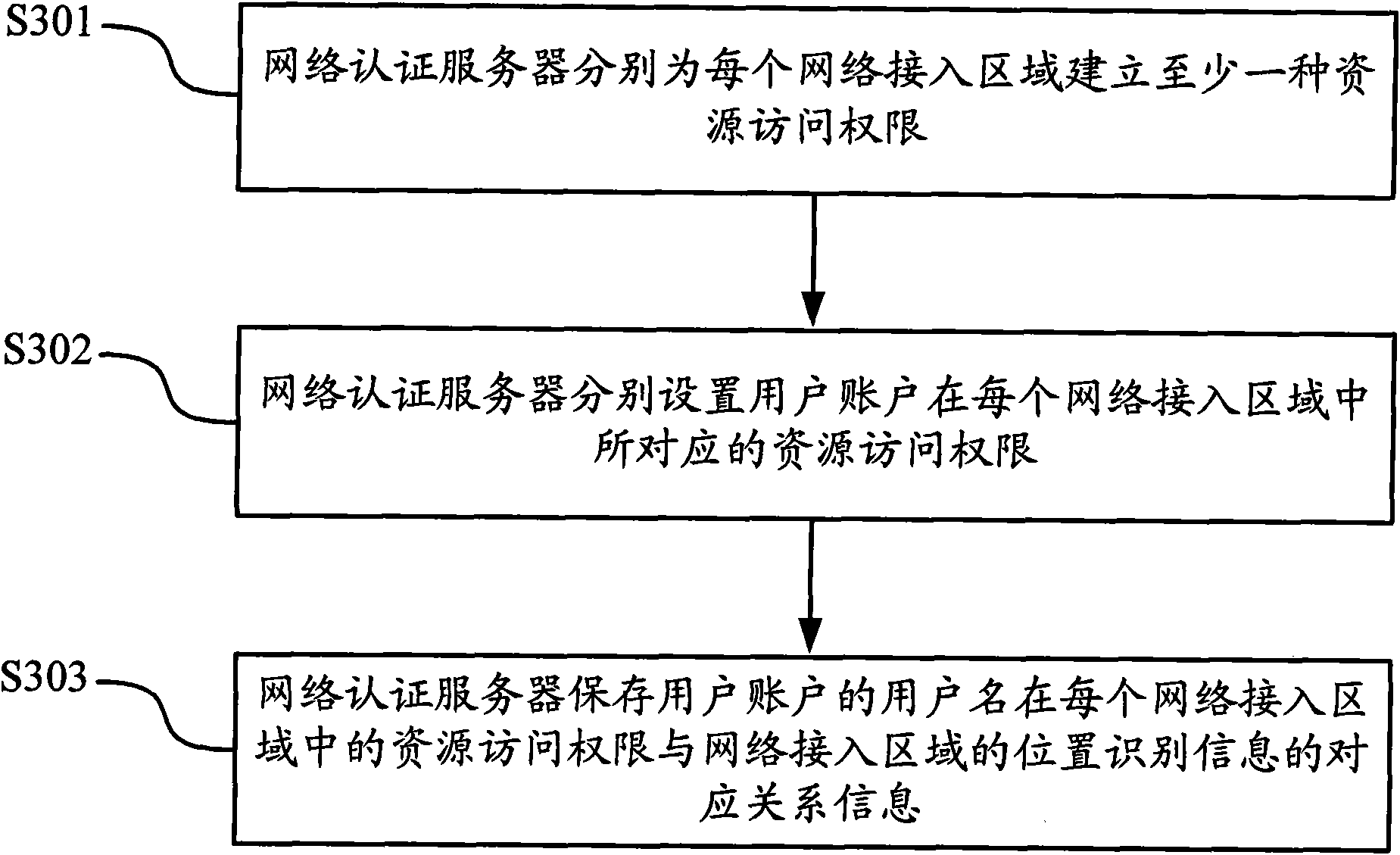
Authority setting method of user access network and equipment
ActiveCN101582769AEasy to useImprove experienceUser identity/authority verificationLocation information based serviceAccess networkWeb authentication
The invention discloses an authority setting method of a user access network and equipment, which are applied to a network system comprising a network authentication server and a plurality of network access areas. The network authentication server stores access authority information of at least one user name in the plurality of network access areas respectively; when a user request is accessed, the user name and the position recognition information of the current network access area are provided, the corresponding resource access authority is obtained and network access is carried out. The invention realizes access authority allocation based on the actual access position of the user, can avoid that the access authority can not be controlled due to change of the access area, can adopt uniform access authority control for unfixed staff in all access areas, and adopts a single account number mode to access, thus providing convenience for use of users, improving network security of the network and simultaneously user experience.
Owner:NEW H3C TECH CO LTD
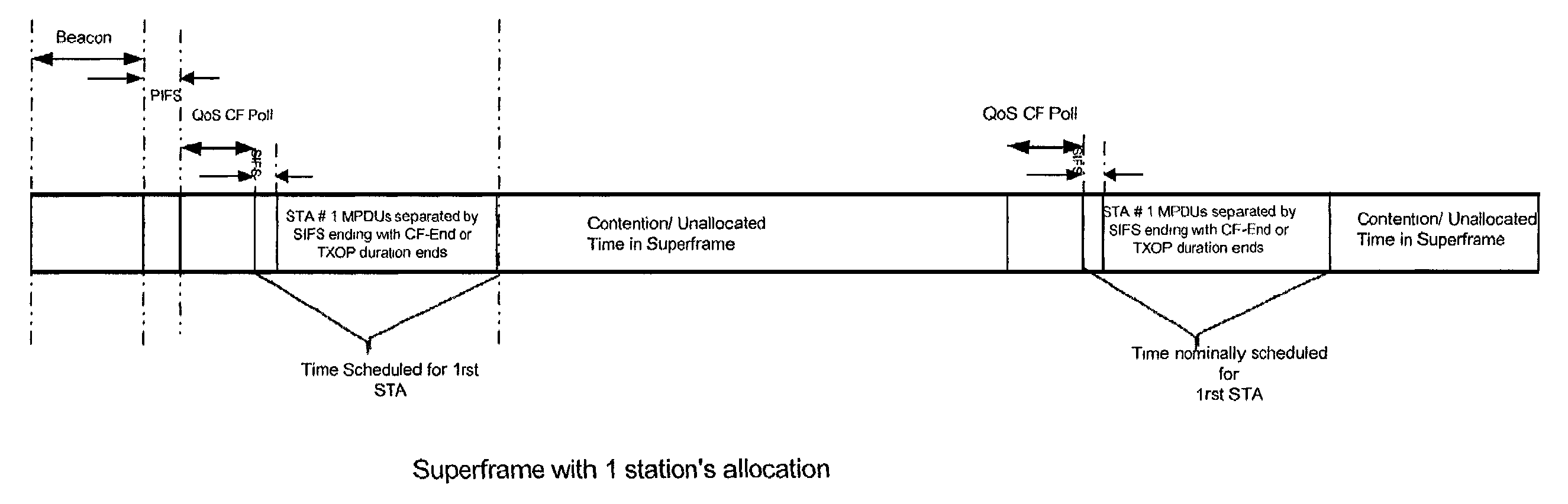
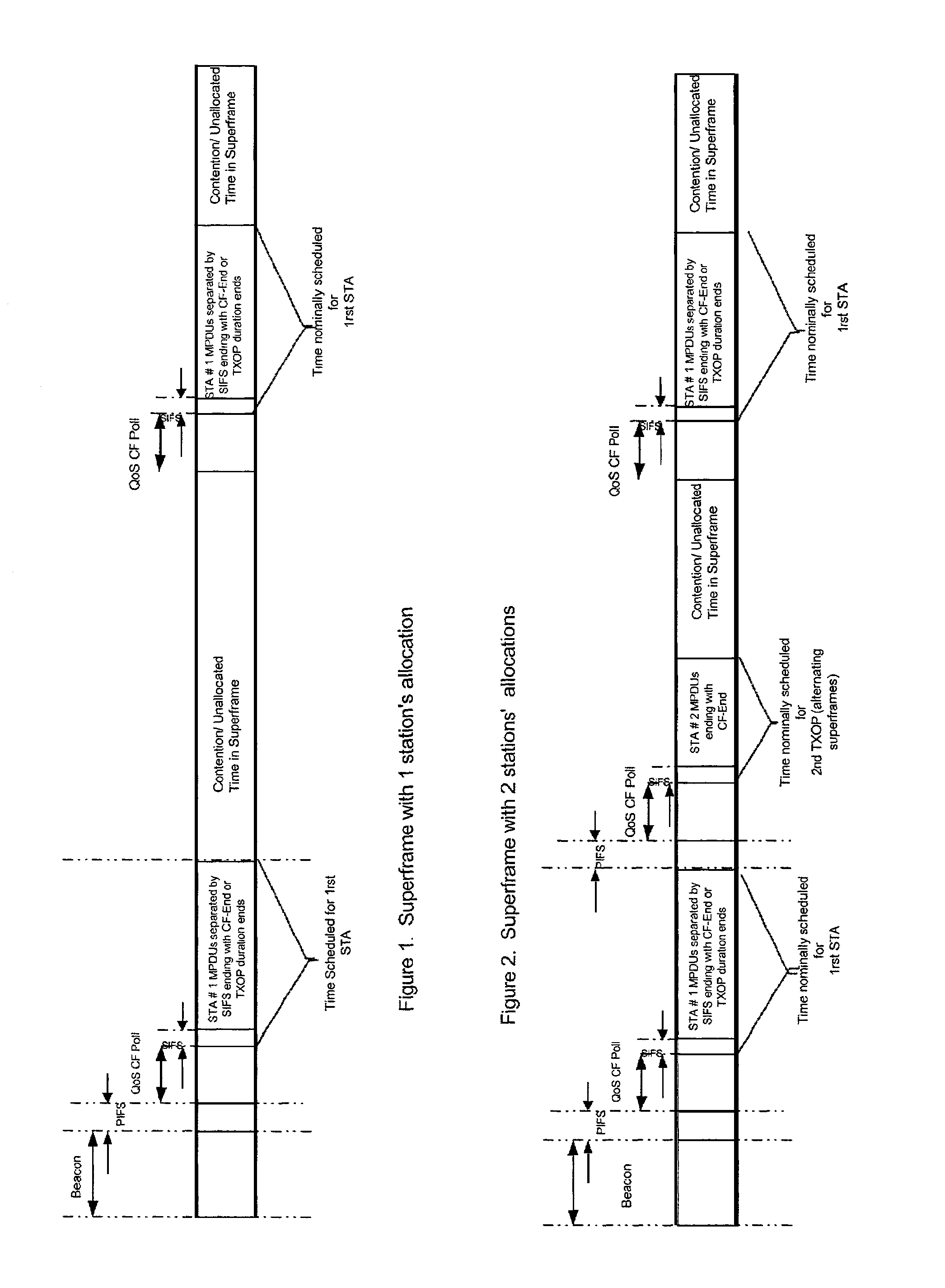
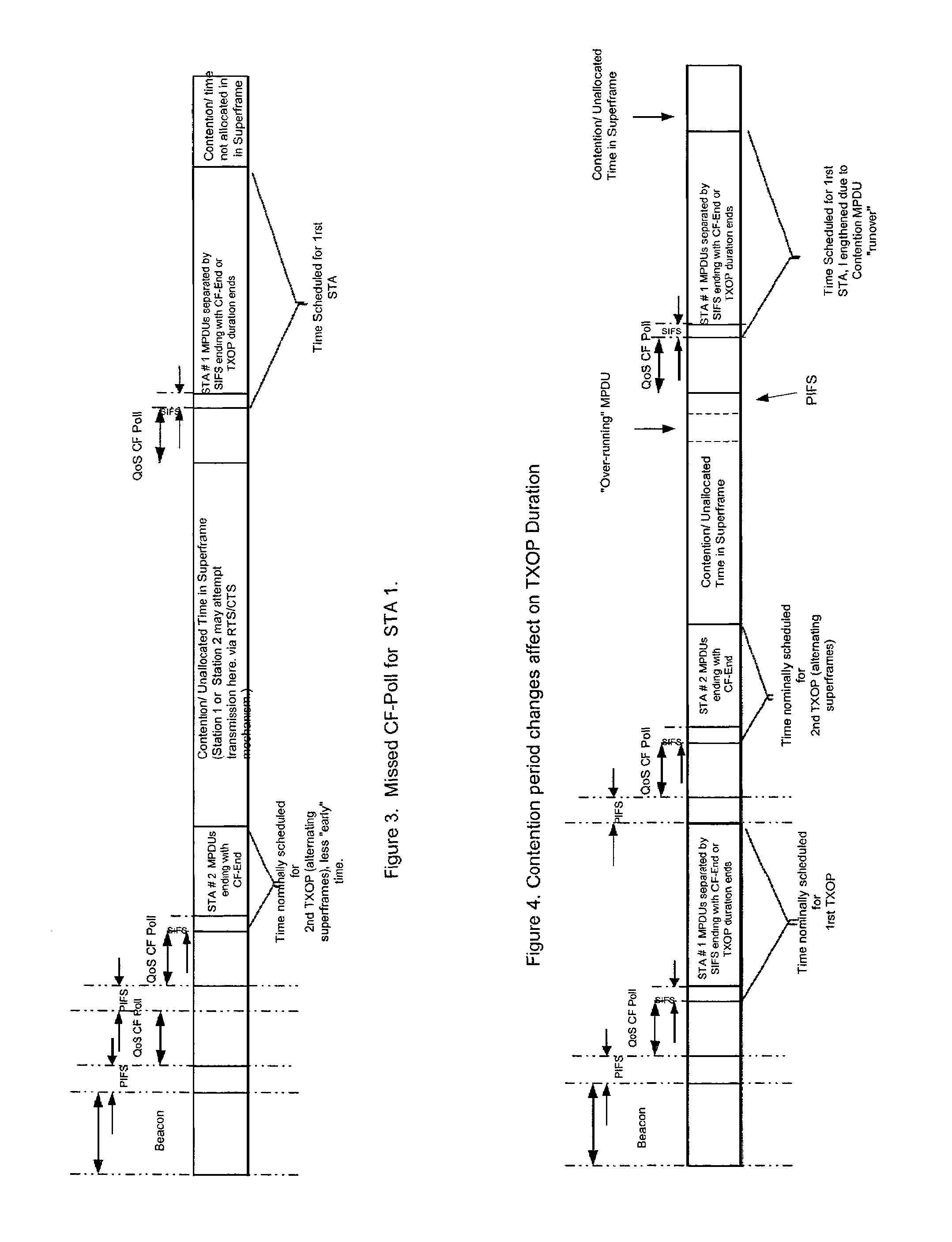
Class of computationally parsimonious schedulers for enforcing quality of service over packet based AV-centric home networks
A scheduler for providing quality of service in a local area network, wherein the local area network includes a plurality of stations, and wherein data flow moves over the network in superframes, includes a mechanism for governing channel resources in the local area network, including a transmit specification controller for granting a transmit specification to a data flow from one station on the network to another station on the network; and a TXOP mechanism for terminating transmits opportunities for stations which have successfully completed data transmission, thereby changing the length of a superframe. A method of providing quality of service in the local area network, includes governing channel resources in the local area network, including controlling transmit specifications for granting a transmit specification to a data flow from one station on the network to another station on the network; and terminating transmits opportunities with a TXOP mechanism for stations which have successfully completed data transmission, thereby changing the length of a superframe.
Owner:SHARP KK
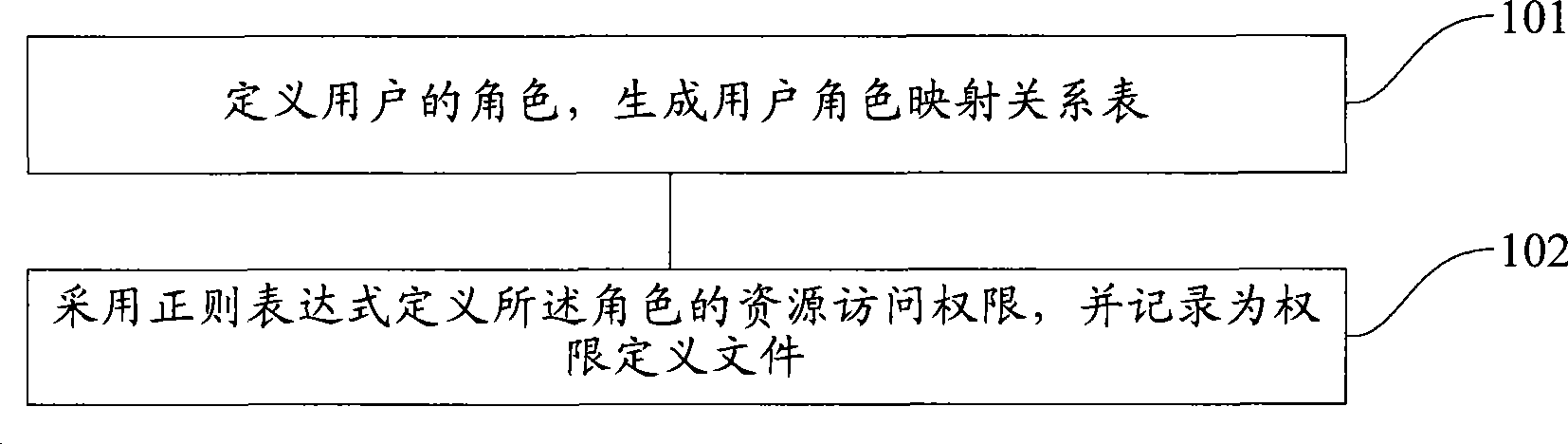
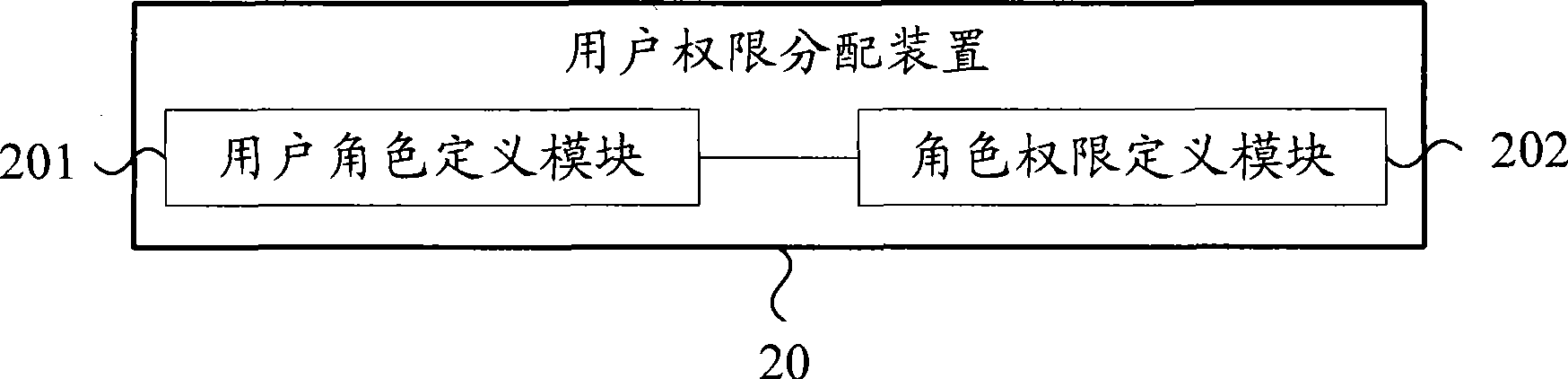
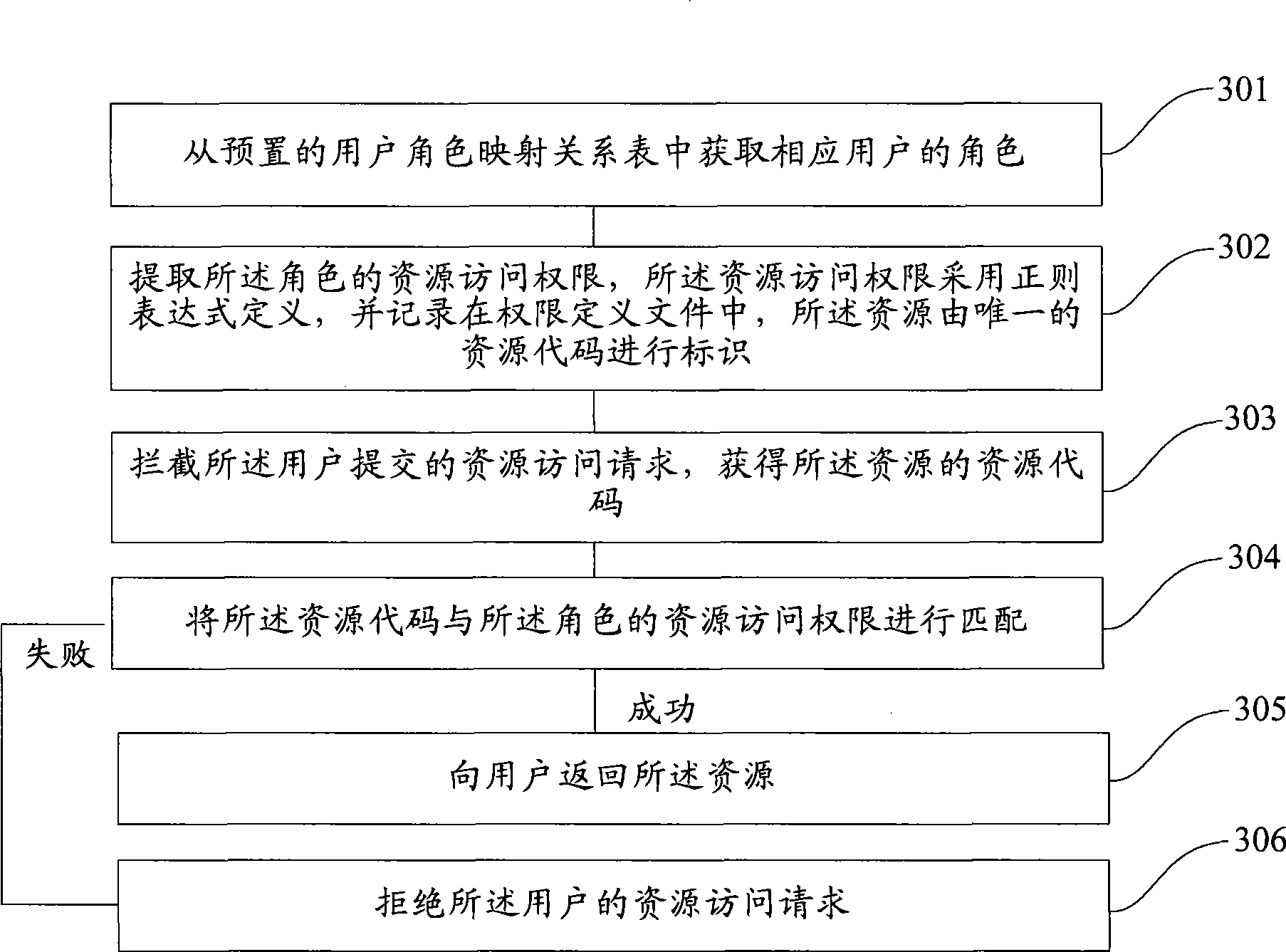
User authority allocation method and user authority control method
ActiveCN101441688APermission definitions are highly descriptiveSupport access controlDigital data authenticationUser PrivilegeSystem development
The invention provides a method for controlling user rights. The method comprises the following steps: a user role is correspondingly acquired from a preset user role mapping relational table; the resource access right of the role is picked up, and the resource access right is defined by a regular expression, recorded in a right definition file, and marked by an exclusive resource code; the resource access request from the user is intercepted, and the resource code of the resource is acquired; by matching the resource code with the resource access right of the role, if matched, the resource is returned to the user; and if not matched, the resource access request from the user is refused. In the inserting mode, the method can be applied to e various system structural frames; moreover, the method also has the advantages of wide application range, flexible definition, and obvious lowering of system development and operation costs.
Owner:ALIBABA GRP HLDG LTD
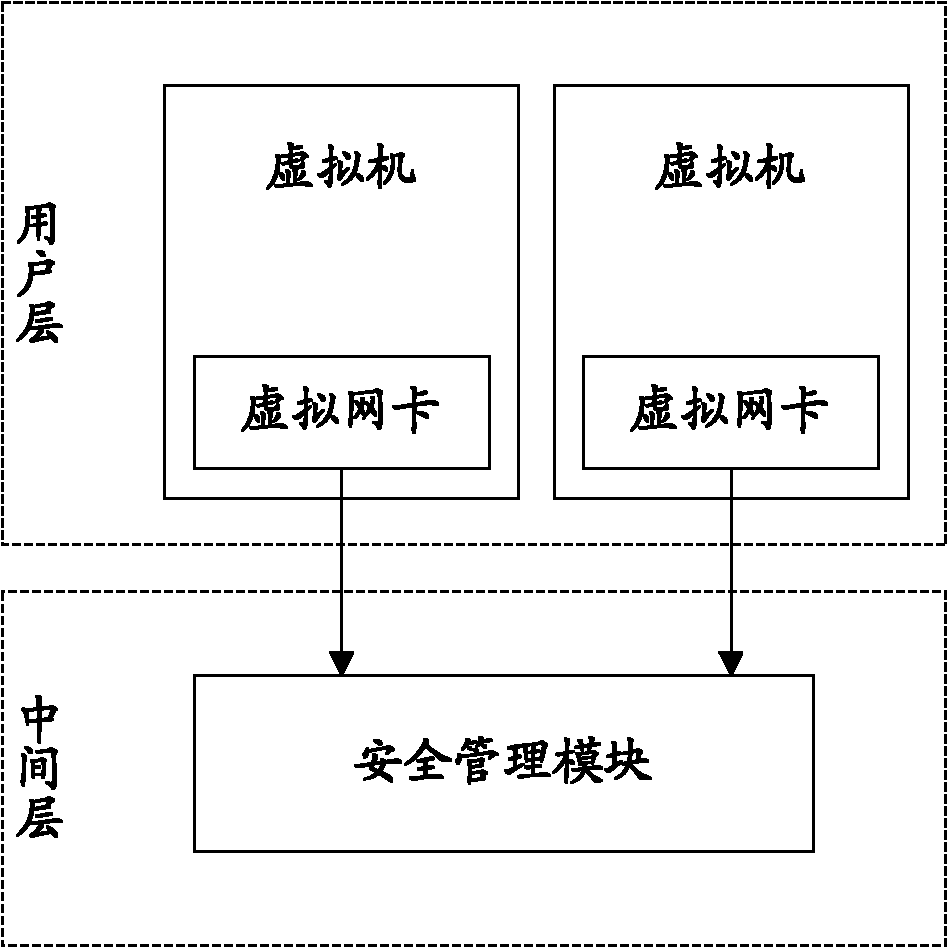
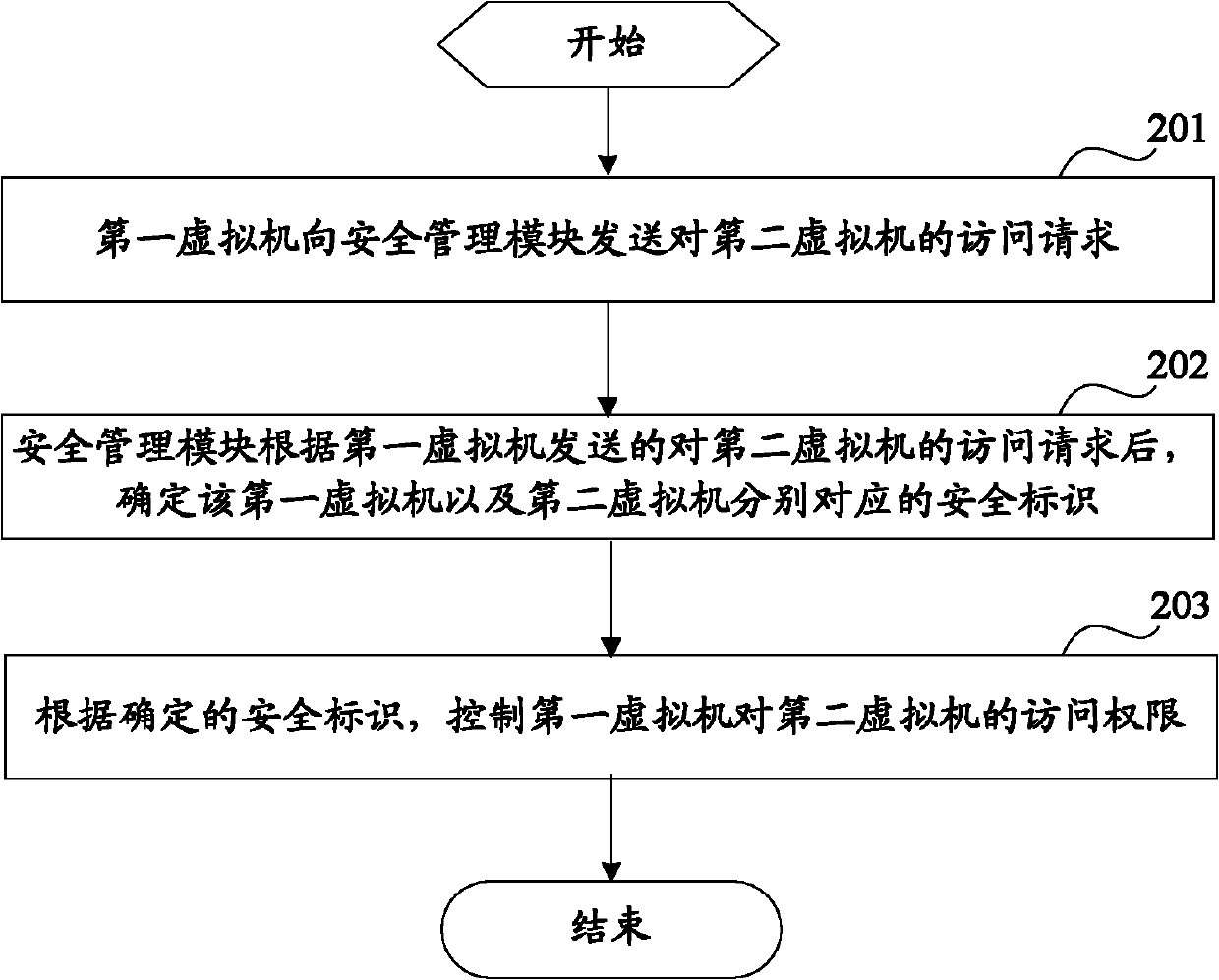
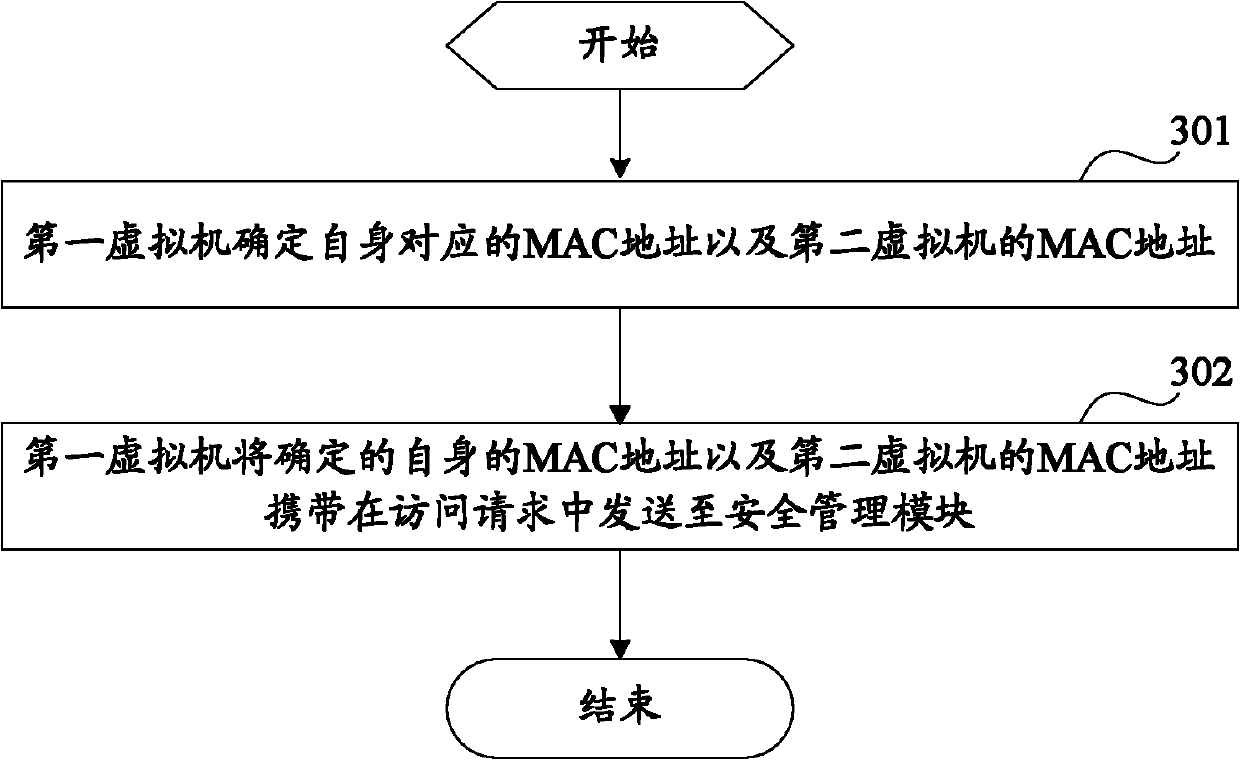
Access authority control method, system and device for virtual machine
The invention discloses an access authority control method, a system and a device for a virtual machine. The main technical scheme is as follows: receiving an access request of a second virtual machine sent by a first virtual machine; determining security identifiers respectively corresponding to the first virtual machine and the second virtual machine; and allowing the first virtual machine to access the second virtual machine after comparing that the determined security identifiers are consistent with each other. According to the technical scheme, whether to allow the first virtual machine to access the second virtual machine can be determined according to the security identifiers of the virtual machines, so that the security control of the virtual machine can be performed according to security requirements of the virtual machine.
Owner:CHINA MOBILE COMM GRP CO LTD
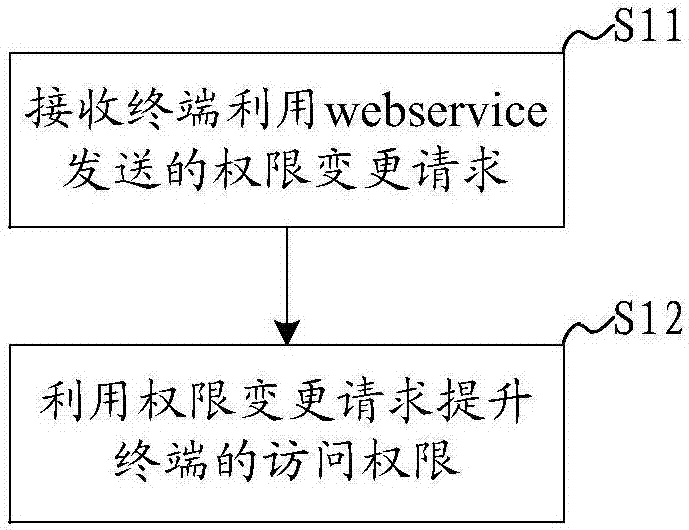
Cloud management authority control method and system
ActiveCN106941504AEasy accessImprove securityTransmissionProgram/content distribution protectionWeb serviceComputer terminal
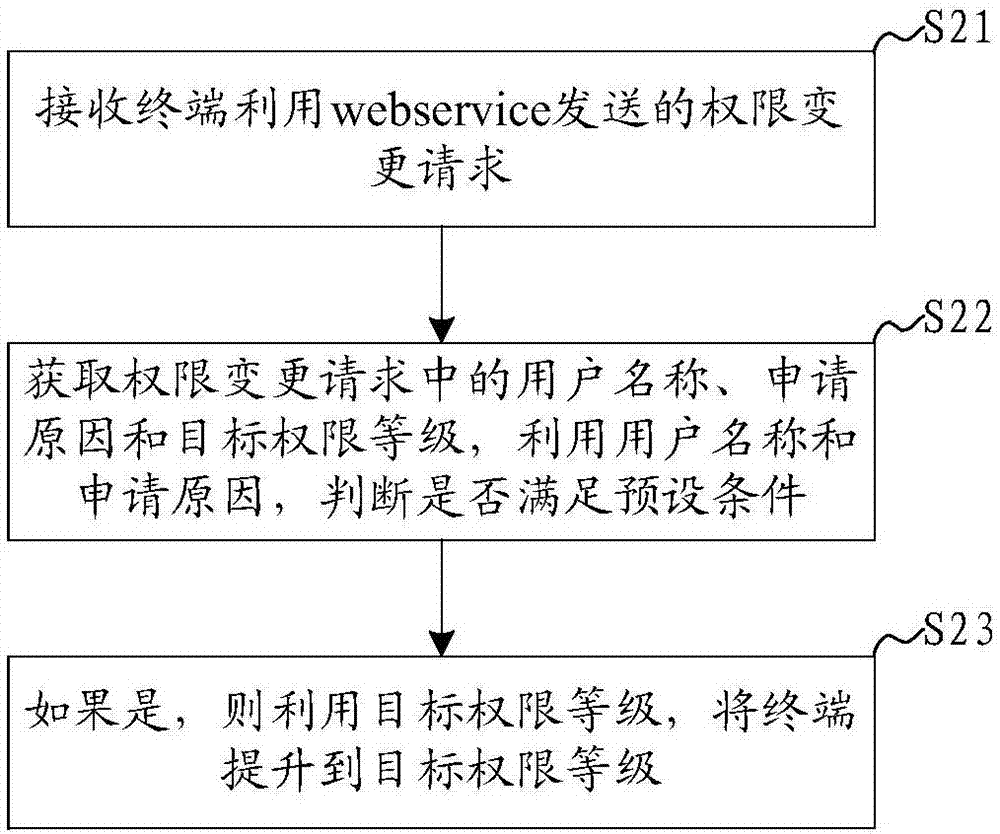
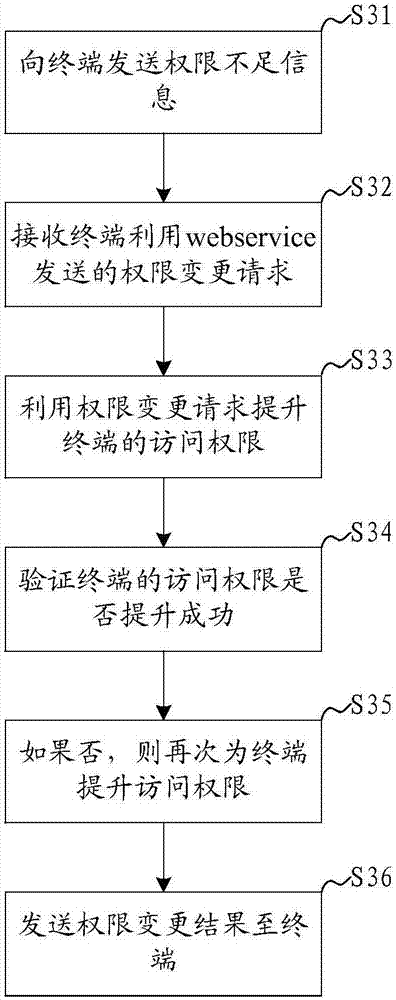
The application discloses a cloud management authority control method and system. The method comprises the following steps: an authority change request sent by a terminal via web service is received, and access authority of the terminal is improved via use of the authority change request. According to the cloud management authority control method and system, the terminal and a server communicate with each other via the web service, whether the authority of the terminal is to be changed is examined and approved by the server, other administrators can be prevented from directly improving the authority of the terminal, and safety of a cloud management system is increased.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Controlling method of business operations competence and generating method of relational database
InactiveCN1967560ARich permission control strategyMeet the needs of dynamic business changesDigital data authenticationSpecial data processing applicationsRelational databaseKnowledge management
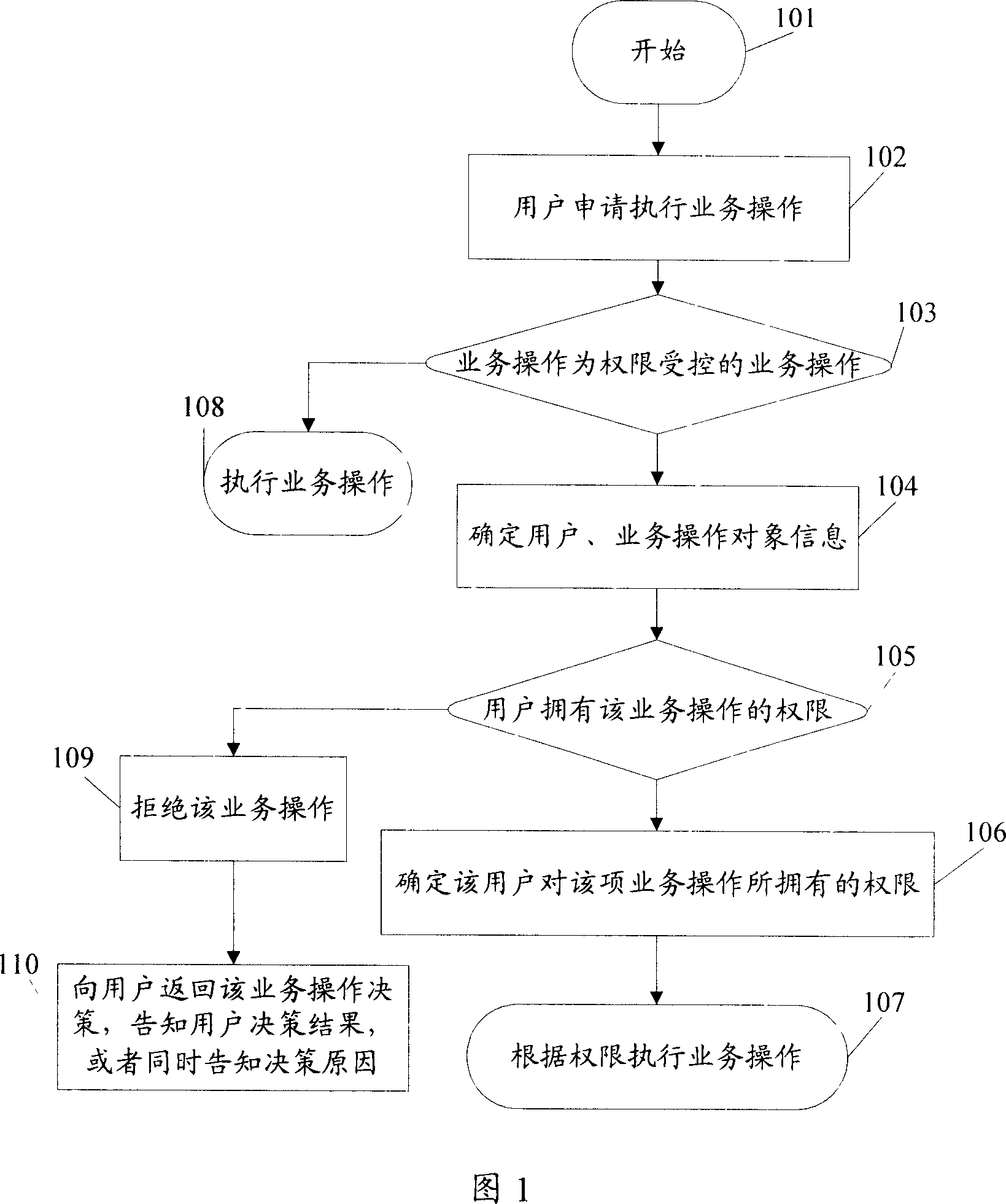
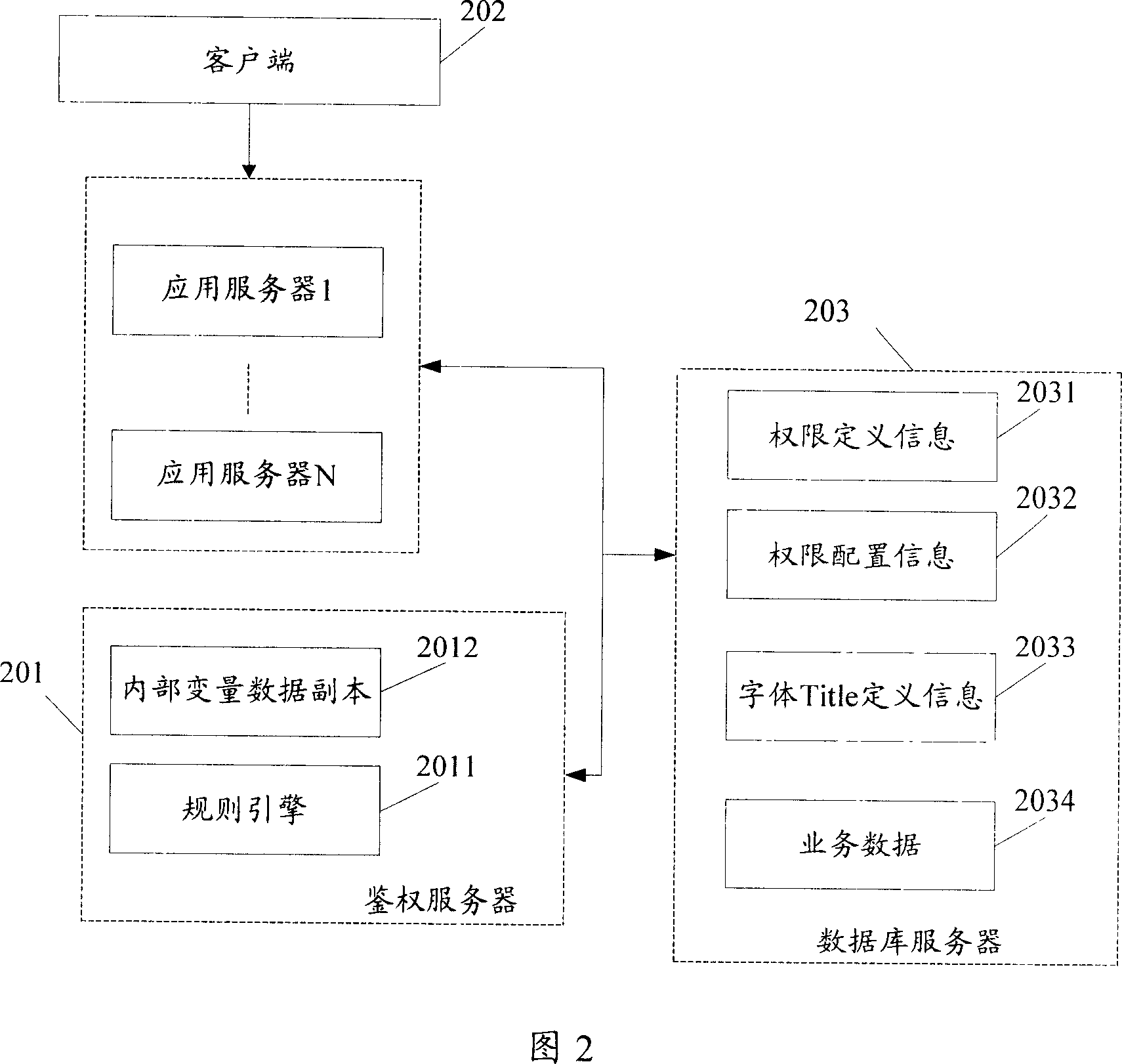
The invention relates to the computer field, and the invention discloses a business operational authority control method, the relational database generation method. The business operational authority control method in the invention includes: identification of user business operations and business operational targets; according to the said users and the business operational target information, to determine whether the said user has operational right to the said business operational targets, and if ownership, executing the said business operations according to the semantic information of the said operational right; otherwise, refused to execute the said business operations. The invention not only implements the fine-grained right control of user's business operation, but also makes right control more flexible.
Owner:HUAWEI TECH CO LTD
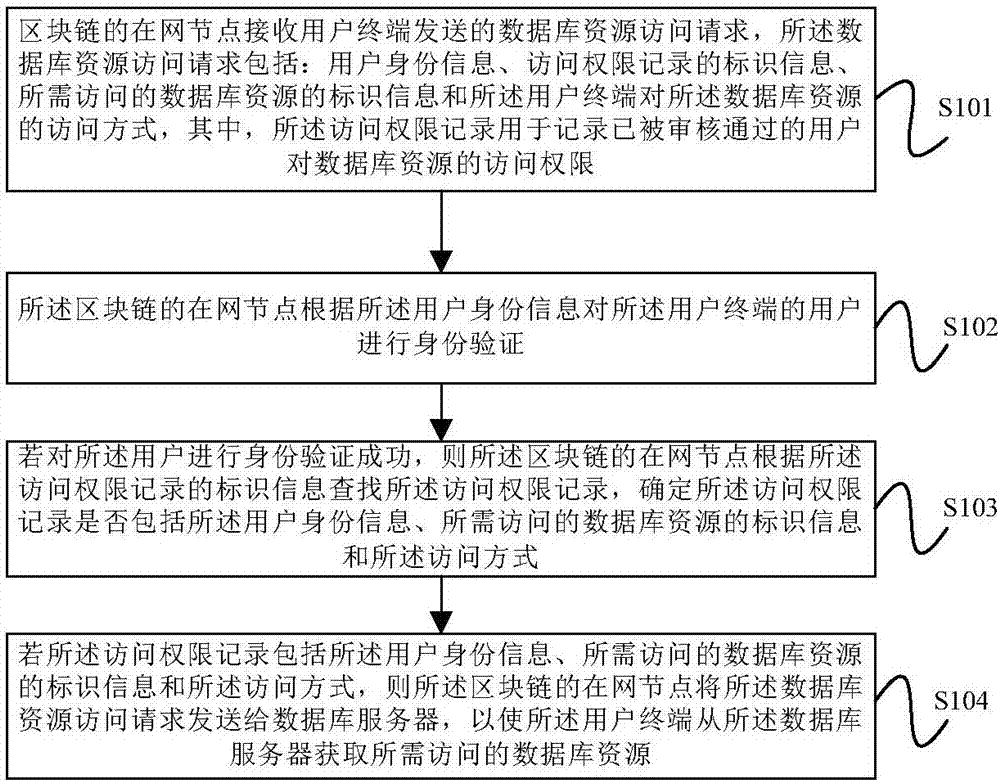
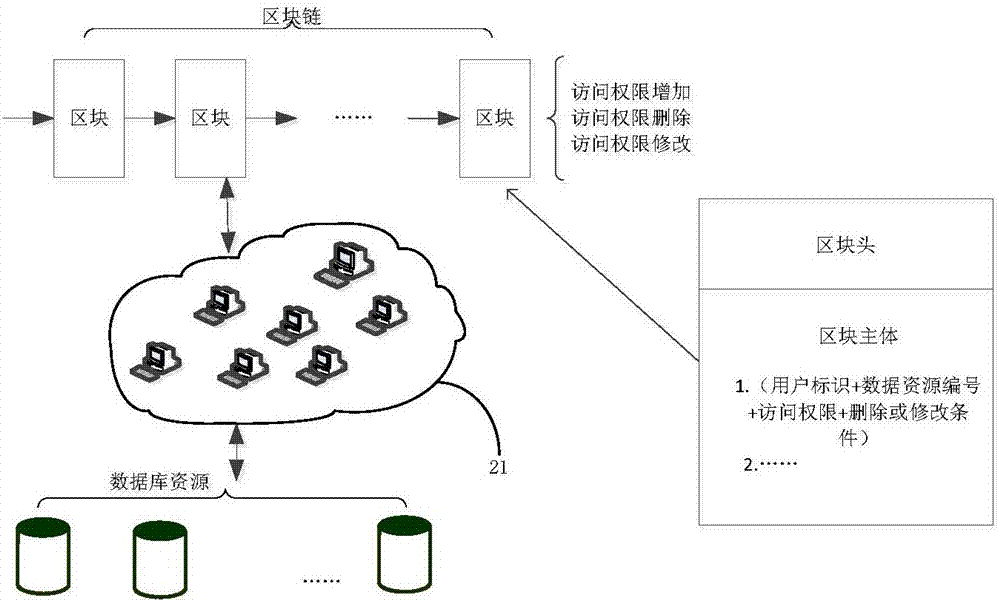
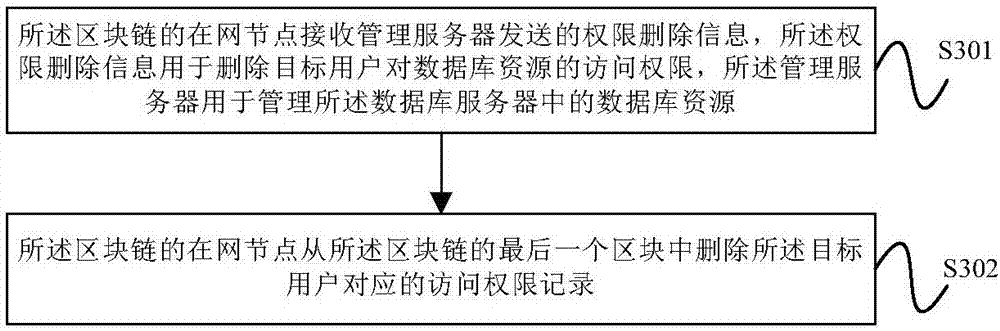
Database accessing authority control method and equipment based on block chain
ActiveCN107480555AImprove securityPrevent leakageDigital data protectionTransmissionDatabase serverComputer terminal
The embodiment of the invention provides a database accessing authority control method and equipment based on a block chain. The method comprises the steps that the block chain receives a database resource accessing request sent by a user terminal in a net node; the block chain looks up an accessing authority record at the net node according to identification information of the accessing authority record; if the accessing authority record comprises user identity information, identification information of a database resource which needs to be accessed and an accessing mode, the block chain sends the database resource accessing request to a database server at the net node, so that the user terminal obtains the database resource which needs to be accessed from the database server. The database server only stores the database resource and does not store the information about the database resource accessing authority of the user, the situation that the data resource accessing authority is possibly completely let out when the centralized storage method is damaged and falsified is avoided, the safety of the data resource in the database is improved, and the safety of the accessing authority of the user terminal is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Authority control method, device and system
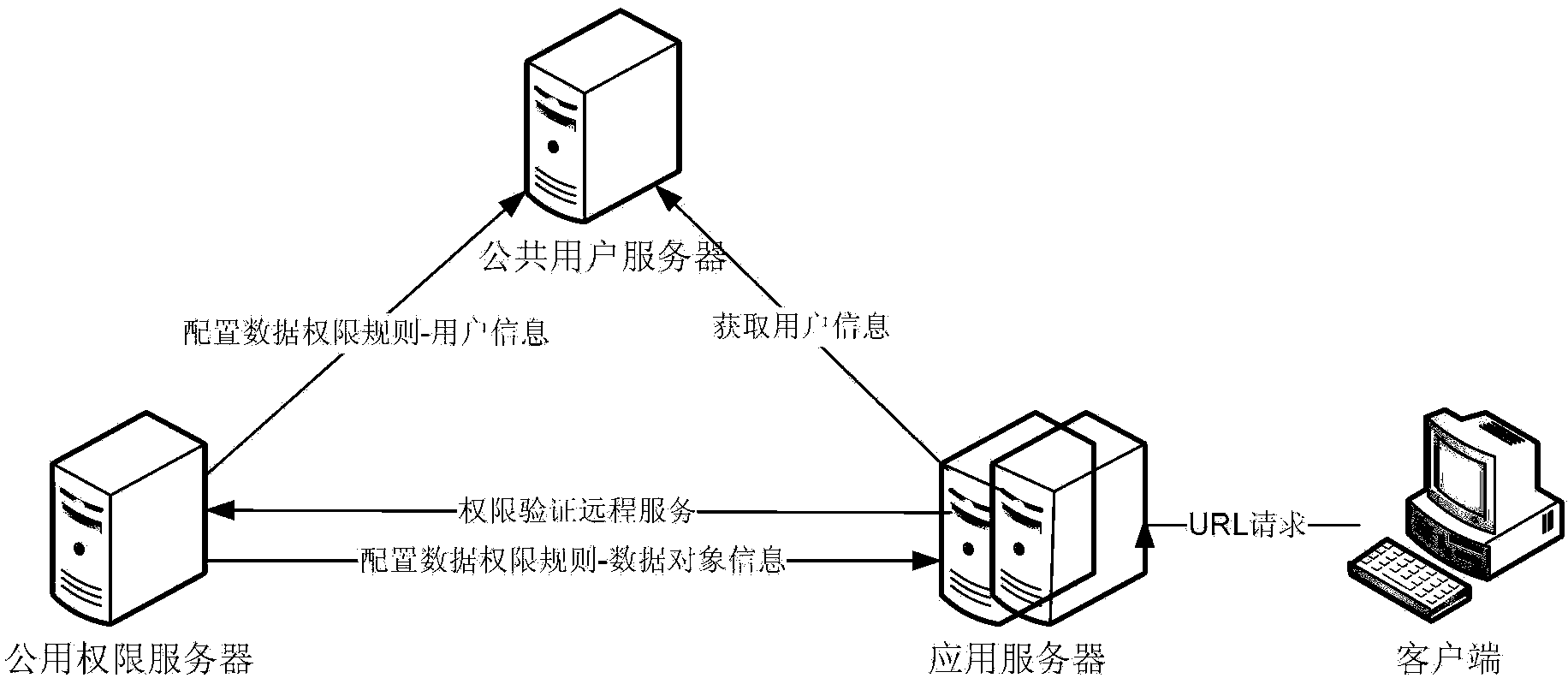
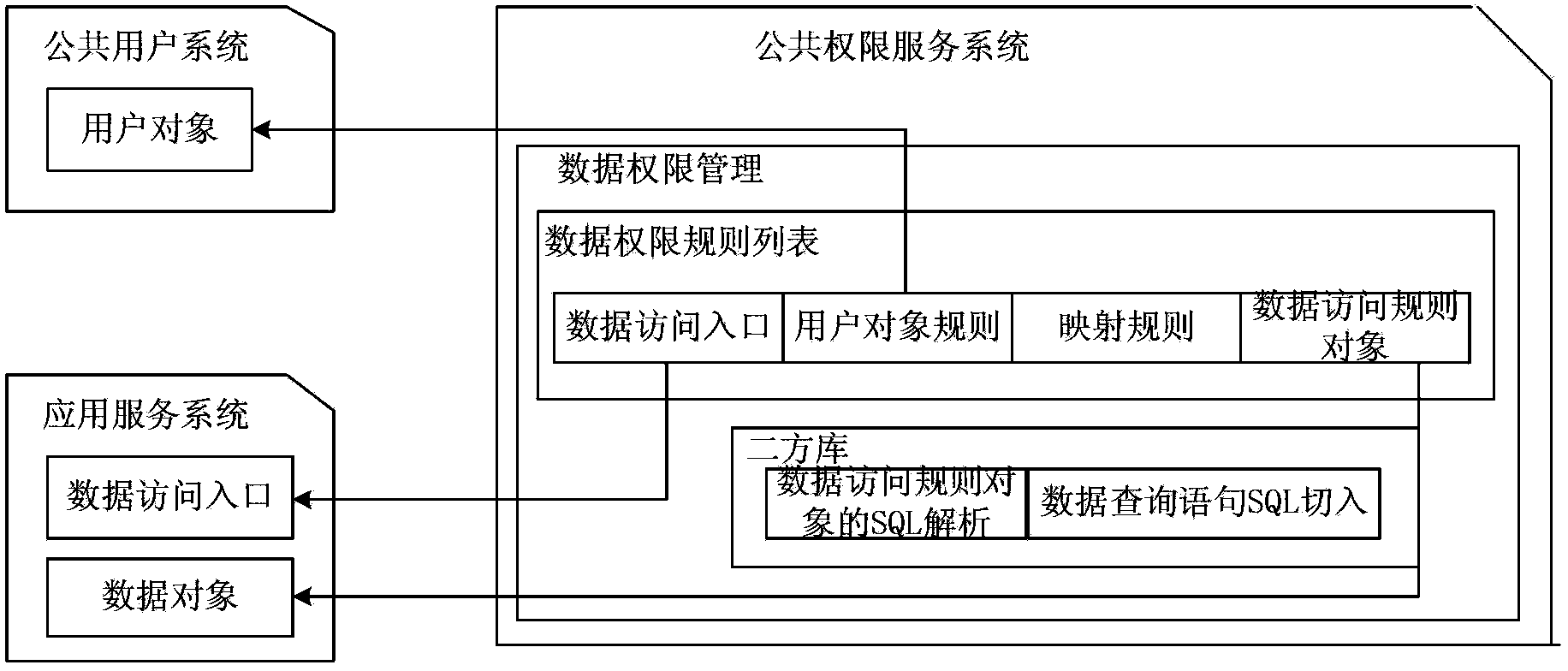
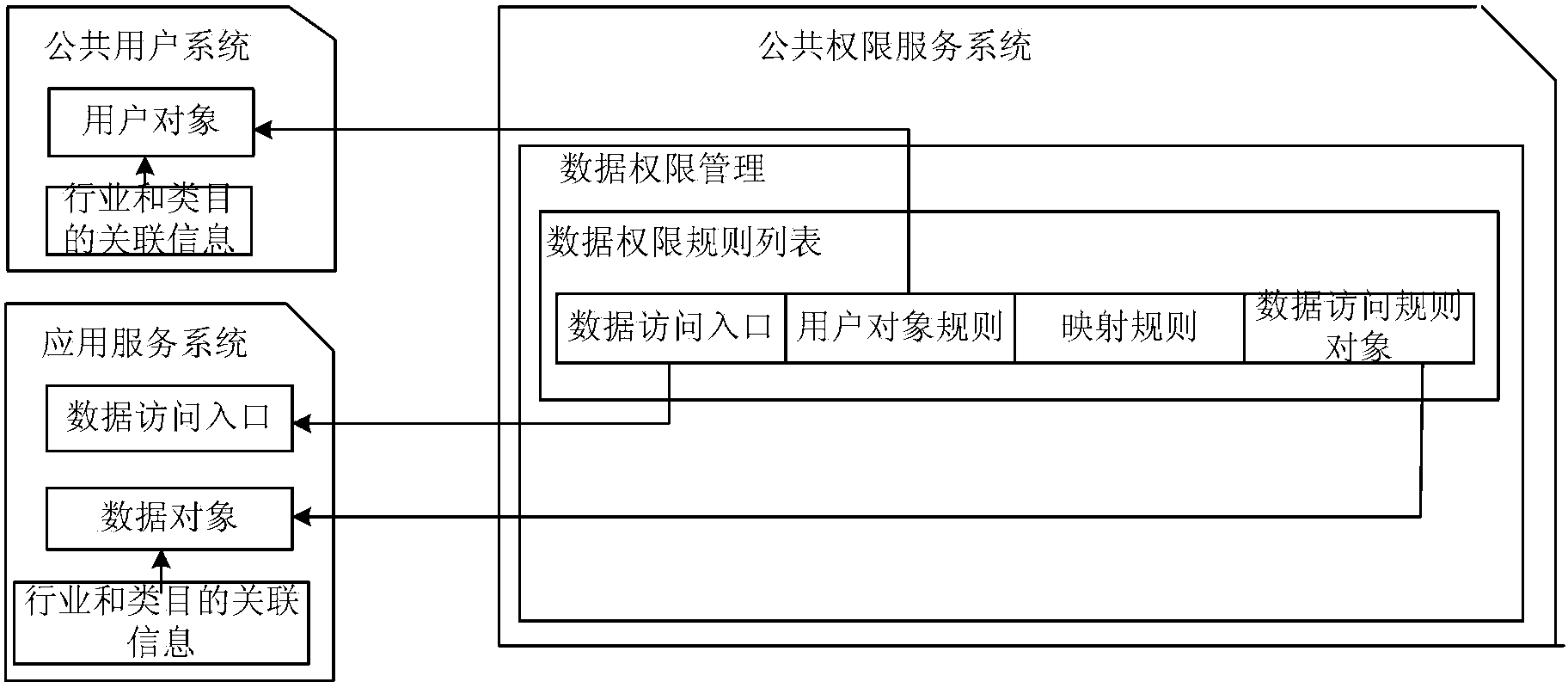
ActiveCN103530568AAchieve unified controlRealize managementDigital data protectionSpecial data processing applicationsData accessAuthority control
The invention discloses an authority control method, device and system. The method includes the steps of obtaining user information of a log-in user, combining the user information with an application data access entry identification needing data authority inquiry so as to obtain a data authority verification parameter, sending a data authority verification request carrying the data authority verification parameter to a public authority server to carry out data authority inquiry so that a data visit rule object corresponding to the application data access entry identification can be obtained, receiving and analyzing the data visit rule object so as to obtain a data authority inquiry condition, and inserting the data authority inquiry condition into an authority inquiry SQL statement corresponding to the application data access entry identification so that a new inquiry statement under the control of data authority can be obtained and a data inquiry result corresponding to the user information can be obtained according to the new inquiry statement. According to the authority control method, management authority service can be independently deployed and uniformly configured, and fine-grained data authority control is achieved.
Owner:ALIBABA GRP HLDG LTD
Authority management method and device, and authority control method and device
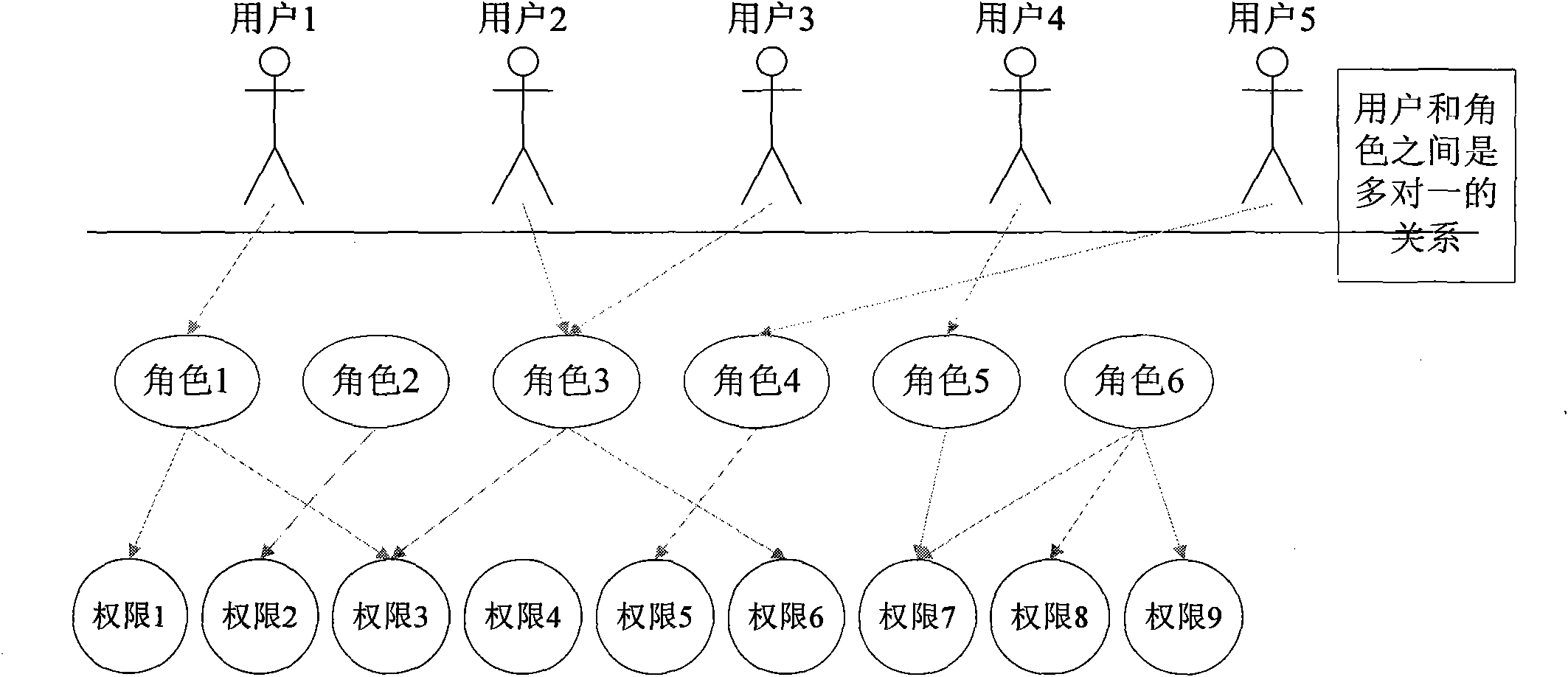
InactiveCN102468971AImprove convenienceImprove work efficiencyData switching networksRights managementAuthority control
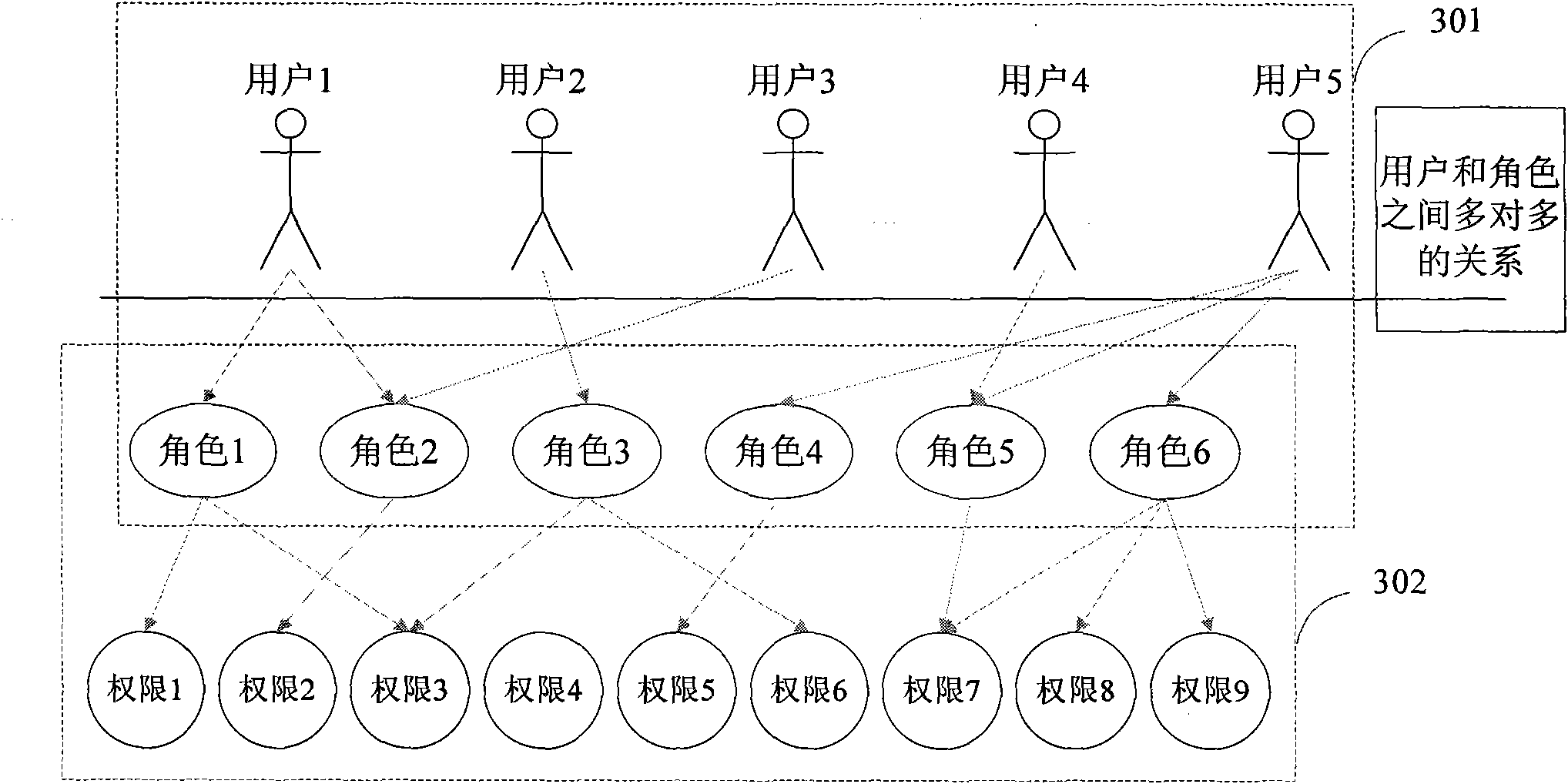
The invention provides an authority management method, an authority management device, an authority control method and an authority control device. The authority control method specifically comprises the following steps of: acquiring a plurality of roles corresponding to the current users according to a preset many-to-many mapping relation between the users and the roles; acquiring authorities corresponding to the plurality of roles according to a preset role authority mapping relation; and opening the authorities to the current users according to the authorities corresponding to the plurality of roles. By the invention, the working efficiency of the users can be improved, and the convenience in authority use is enhanced.
Owner:BEIJING NAURA MICROELECTRONICS EQUIP CO LTD
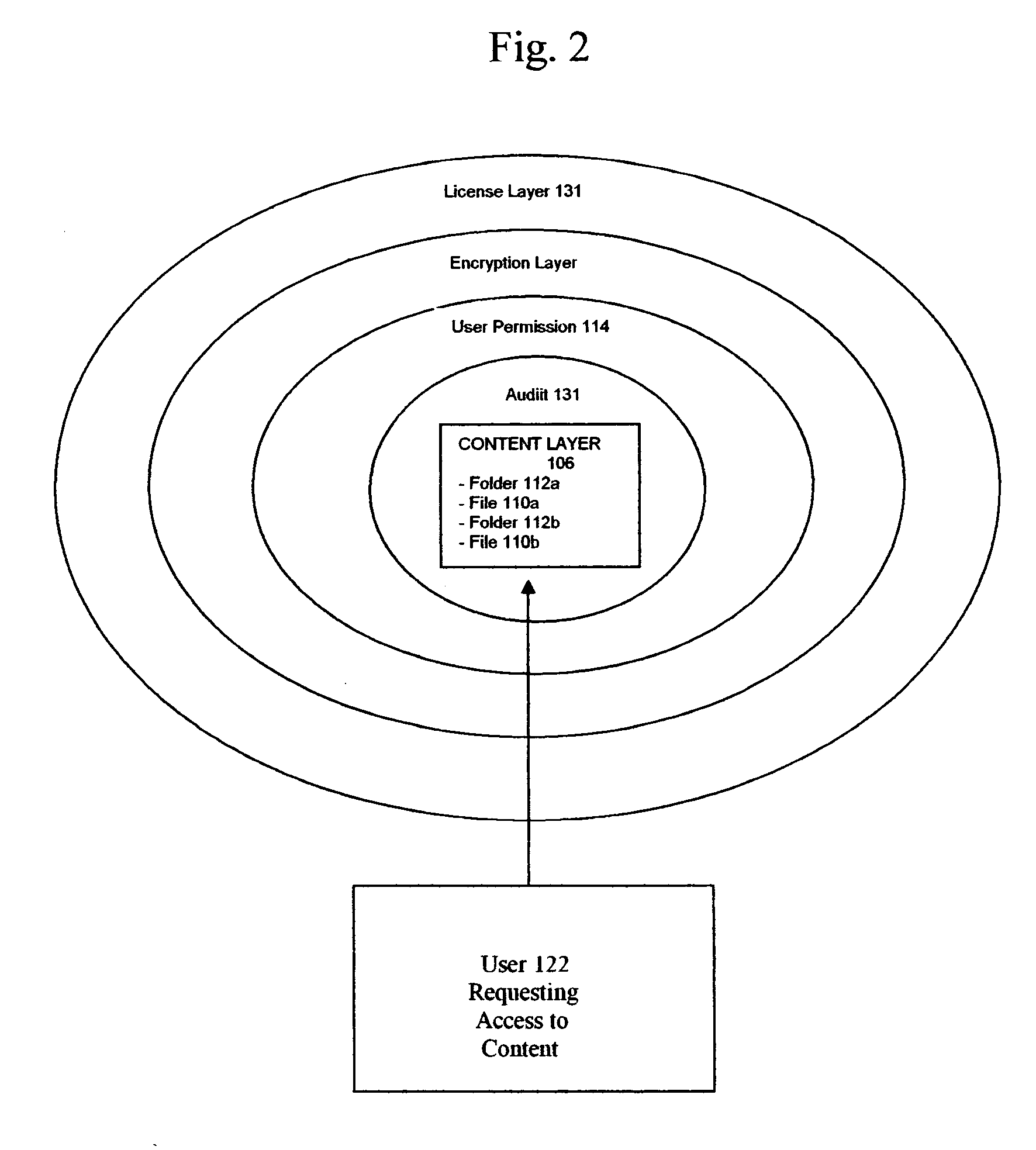
Access control method, access control system, metadata controlling device, and transmitting apparatus
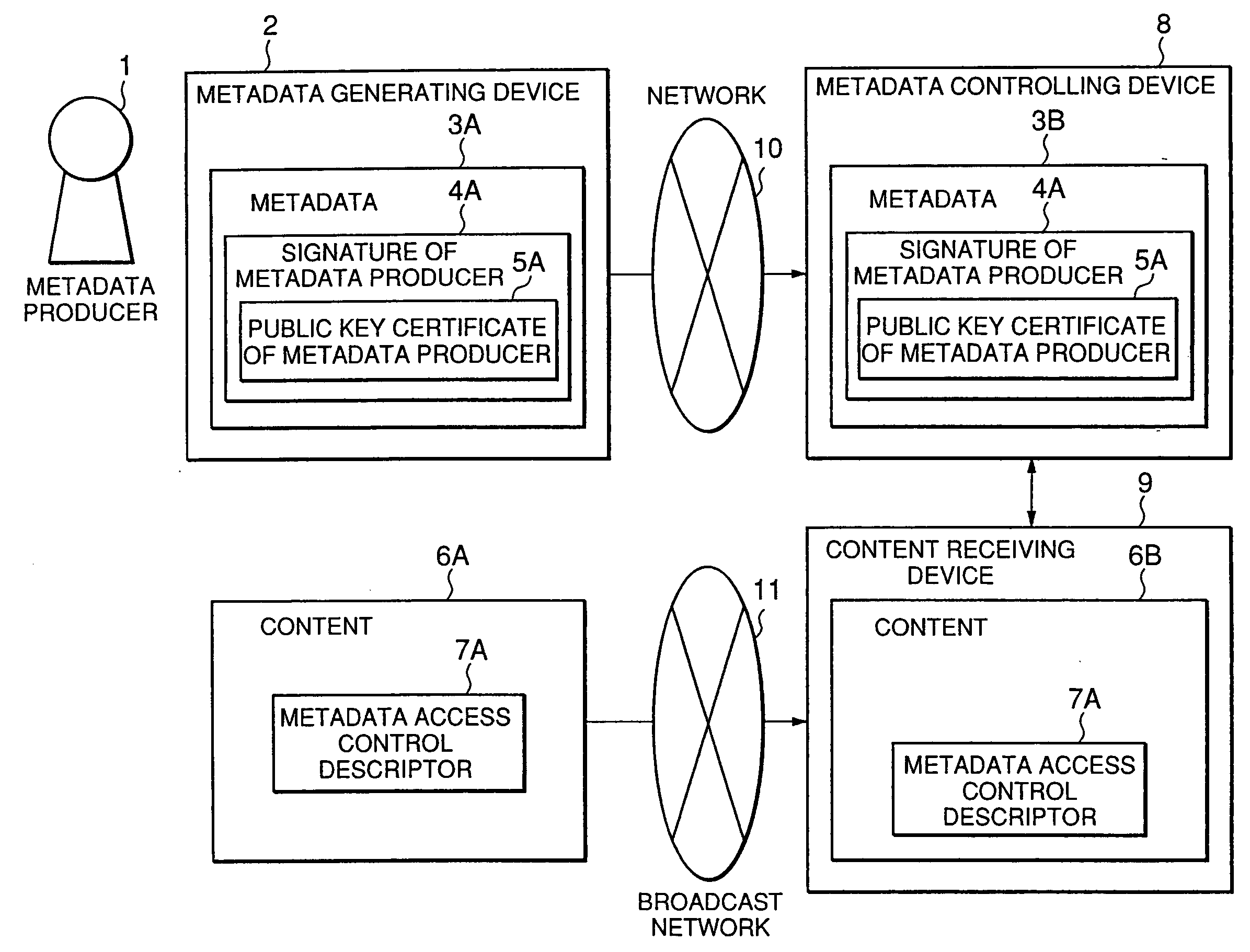
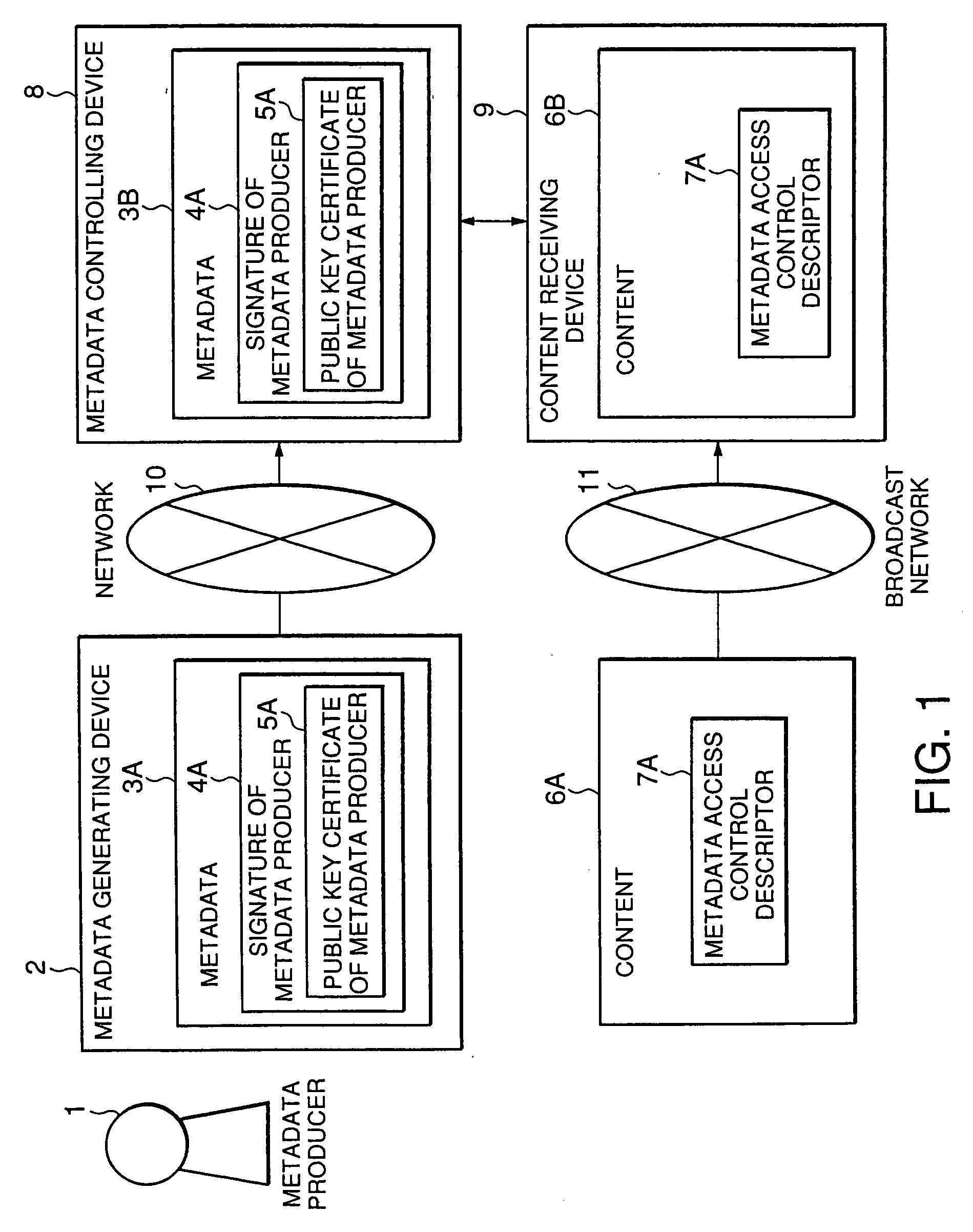
ActiveUS20070277245A1Determine access propriety to contentDigital data processing detailsUser identity/authority verificationDigital signatureAuthority control
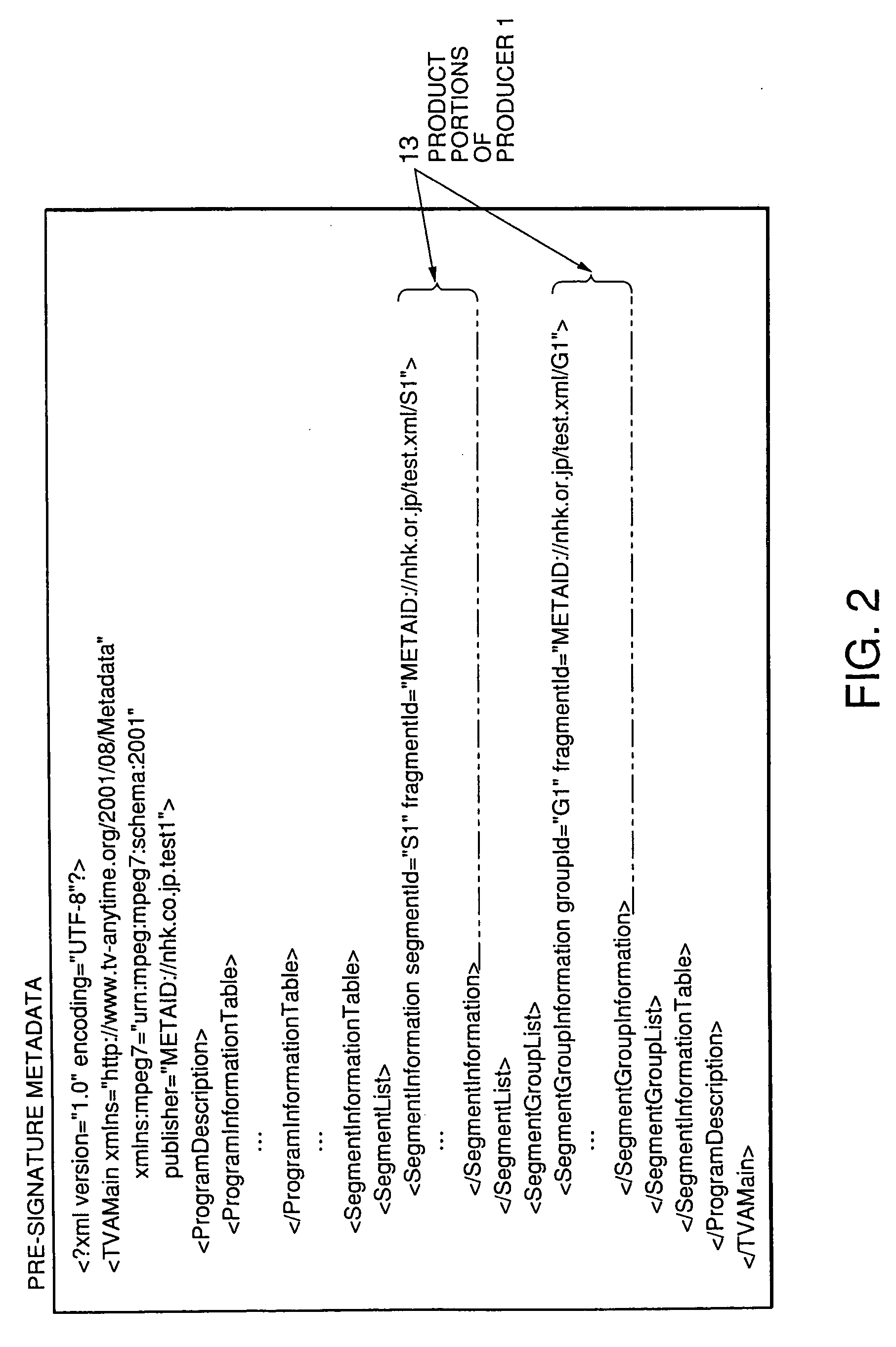
The present invention provides an access control method of controlling acceptance or rejection of access to content from metadata. The access control method according to the present invention includes a step of producing metadata 3A for content 6A and embedding a digital signature 4A of a producer who has produced the metadata as producer information in the produced metadata 3A, a step of embedding an identifier 5A indicating which metadata are accessible to the content in license information required to play back the content 6A, and an access propriety control step of comparing the digital signature 4A with the identifier 5A to control propriety of access to the content 6A from the produced metadata 3A.
Owner:NEC CORP +2
Method for solving access control in authority management
ActiveCN101478536AImplement secure access controlEnrich the connotation of rights managementData switching networksGranularityBusiness data
The invention provides a method for solving access control in an authority management. Based on the RBAC model access control technology, the method divides resource fine granularity into a function resource and a data resource and achieves a centralization management and an authorization to the resource, wherein the function resource is layered designed and realized according to the system, module, function and resource, and visiting sensitive business data is performed a flexible definition and a management by the data resource type management from the business view; finally the operation page authorization is finished by a client-role-function resource authority mode and the data authorization is finished by a client-data resource mode. The method of the invention realizes the security access control of the resource in the system, module, function and resource fine granularity, effectively enriches the authority management connotation, increases the authority control force, prolongs the management size, and improves the management aspect.
Owner:INSPUR SOFTWARE CO LTD
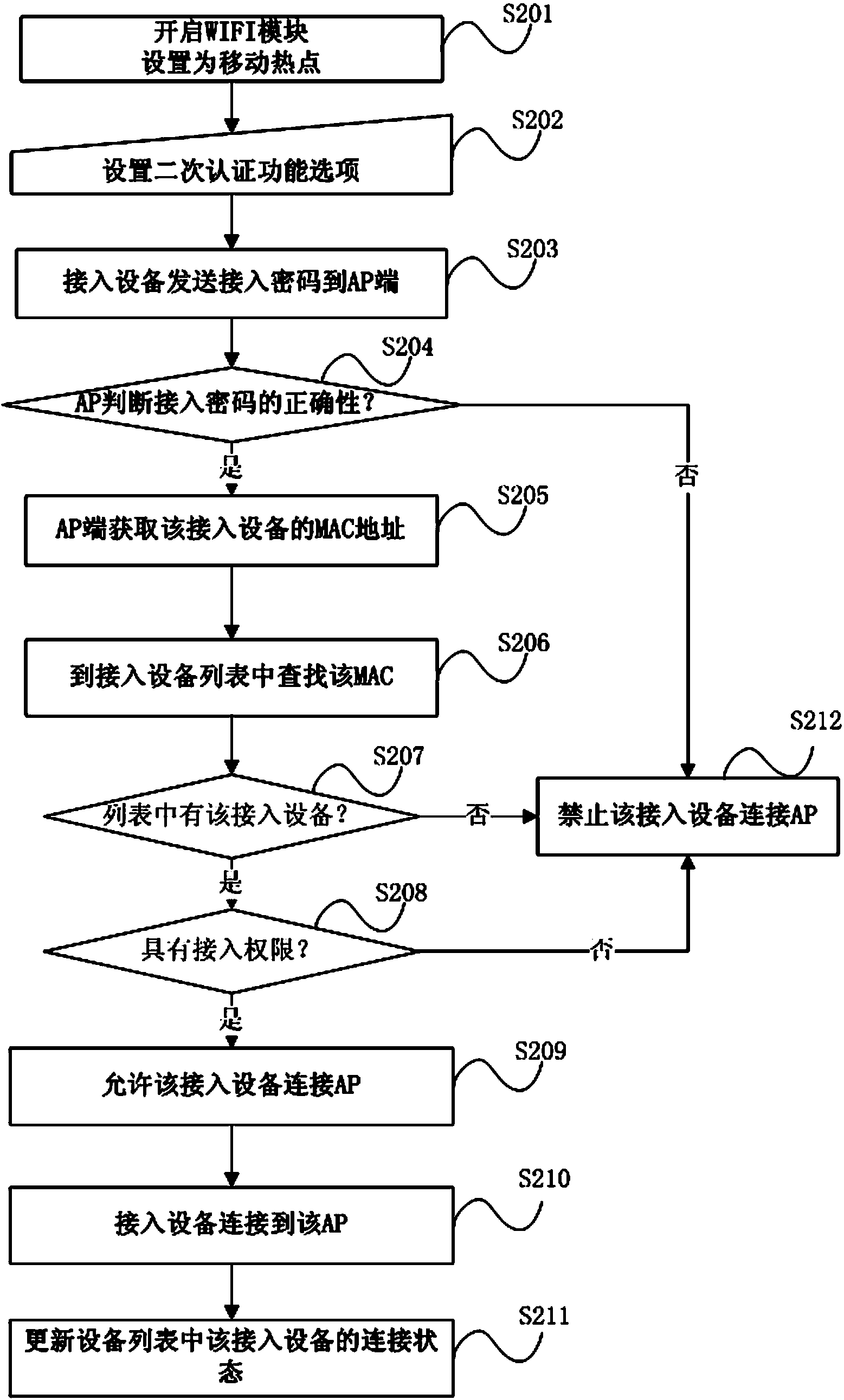
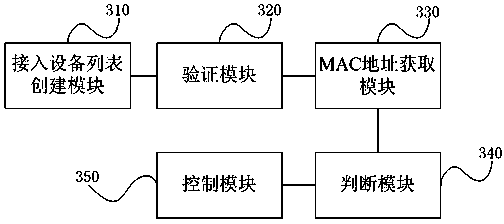
Mobile WIFI hotspot connection processing method and system
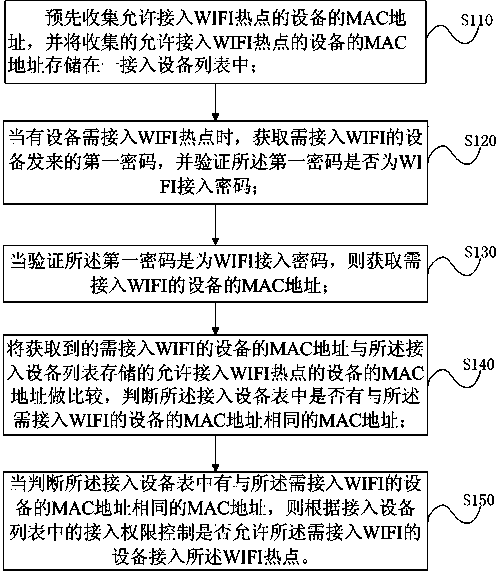
InactiveCN103415016AImprove securityProtect normal useConnection managementSecurity arrangementPasswordSecret code
The invention discloses a mobile WIFI hotspot connection processing method and system. The mobile WIFI hotspot connection processing method includes: a MAC address of a device which is allowed to access a WIFI hotspot is pre-collected and stored in an access device list; when the device requires to access the WIFI hotspot, a first password from the access device is obtained and verified whether the first password is an access password; when the first password is verified as the access password, the MAC address of the access device is obtained; the obtained MAC address of the access device is compared with the MAC address of the device which is allowed to access the WIFI hotspot and stored in the access device list, the obtained MAC address of the access device is judged whether to be the same as the MAC address of the device which is allowed to access the WIFI hotspot; when the obtained MAC address of the access device is judged to be the same as the MAC address of the device which is allowed to access the WIFI hotspot, according to the access authority control in the access device list, the device requiring the access to the WIFI hotspot is judged whether to be capable of accessing the WIFI hotspot or not. With adoption of the method and the system of the invention, the safety of the WIFI hotspot access can be improved, and the convenience for users is provided.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
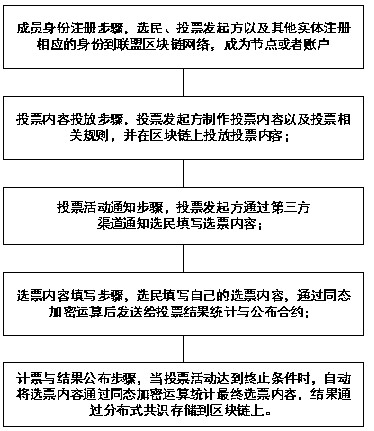
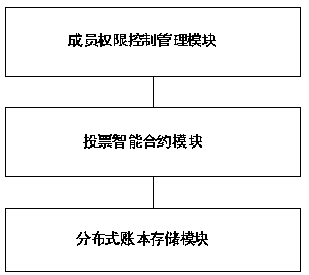
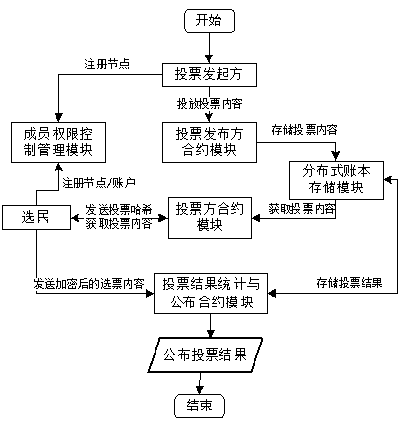
Encrypted electronic voting system and method based on alliance block chain technology
InactiveCN110245183AGuaranteed credibilityGuaranteed reliabilityKey distribution for secure communicationVoting apparatusChain networkSmart contract
The invention relates to the technical field of electronic voting, and discloses an encrypted electronic voting system and method based on an alliance block chain technology, and the system comprises a member authority control management module, a voting intelligent contract module, and a distributed account book storage module. The voters and the voting initiators register the entity identities of the voters and the voting initiators through the member authority control management module to join the alliance chain network. The voting intelligent contract module is used for achieving specific encrypted voting process automation and comprises a voting party contract, a voting publisher contract and a voting result statistics and contract publishing module. The distributed account book storage module is maintained by nodes in a block chain network, adopts a Raft consensus algorithm for accounting, is public and transparent for the voting party and the voting initiator, and can carry out traceability verification on the voting result. The electronic voting system solves the problem that an existing electronic voting system is suspected by the public in voting secrecy, voting anonymity and voting result correctness and fairness, and is used for various elections and voting activities.
Owner:上海链度科技有限公司
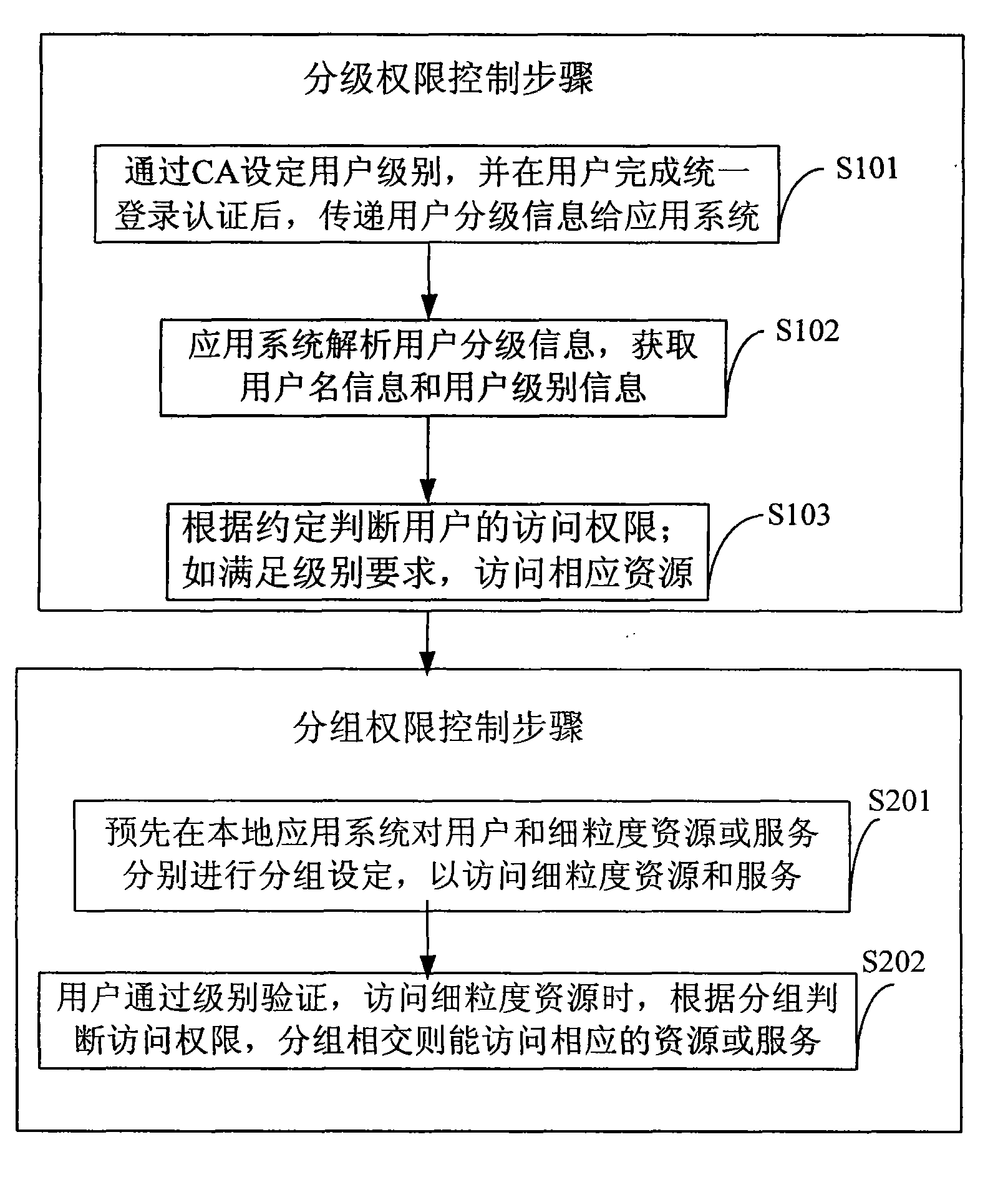
Distributed dual-license and access control method and system
InactiveCN101631116AReduce couplingImprove authorization efficiencyTransmissionControl systemAuthority control
The invention discloses a distributed dual-license and access control method and a system, the method is applied in the control system including a universal certificate licensing sensor and a plurality of different types of application systems, and the method comprises the grade authority control step which is used for setting the grade of a user through the universal certificate licensing sensor, transferring grade information of the user to the application systems and deciding the access authority of the user to resources or services by verifying the matching relationship between the grade of the user and the grade of coarse-grained resources or services of the application systems; and the group authority control step which is used for respectively carrying out grouping setting on the user and the resources / services through the application systems and deciding the access authority of the user to the coarse-grained resources or the services by verifying the intersection relationship between user grouping and data service grouping.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS
Block chain permission control method, device, and node apparatus
ActiveUS20190140822A1Ensure safetyImprove securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationAuthority controlBlockchain
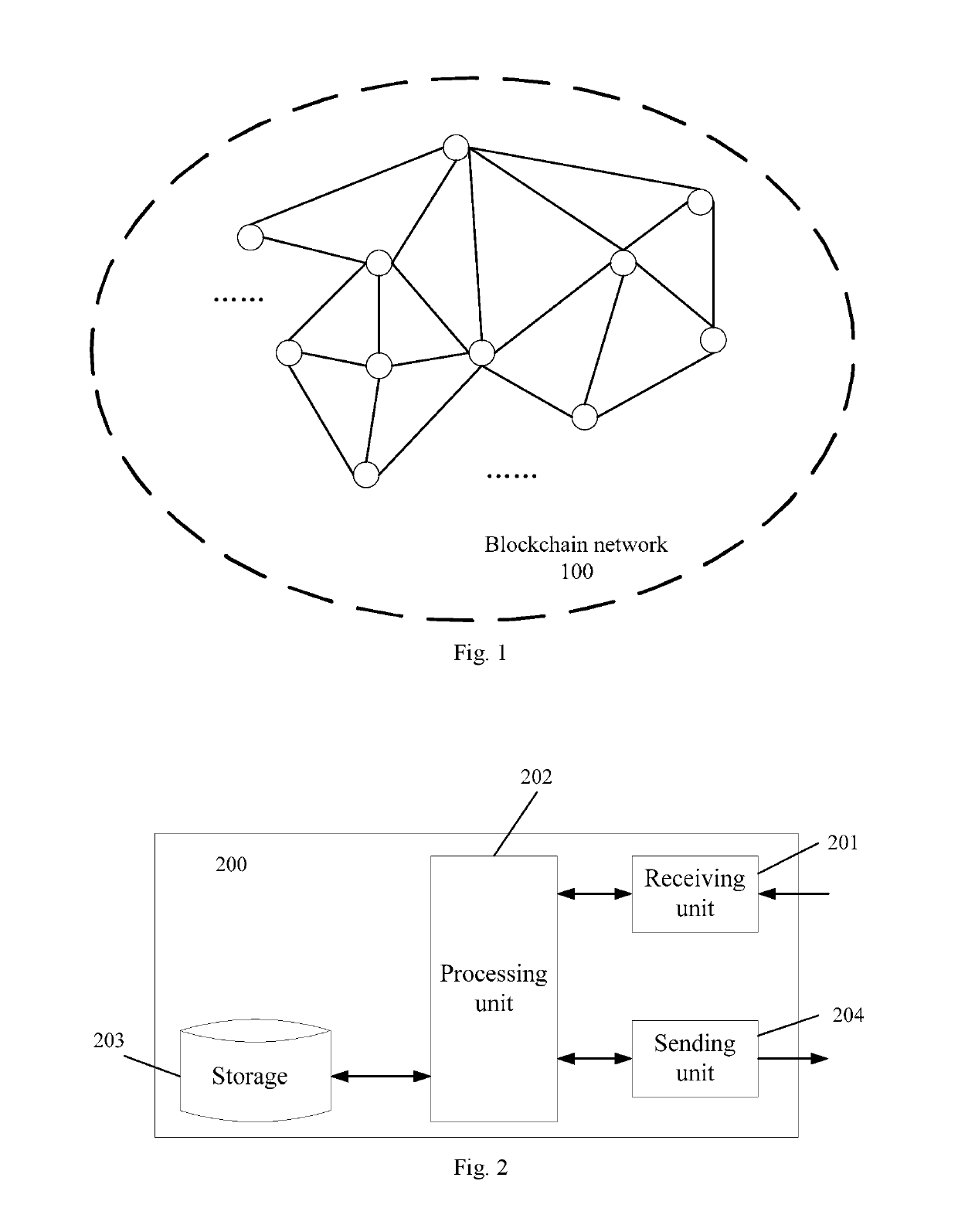
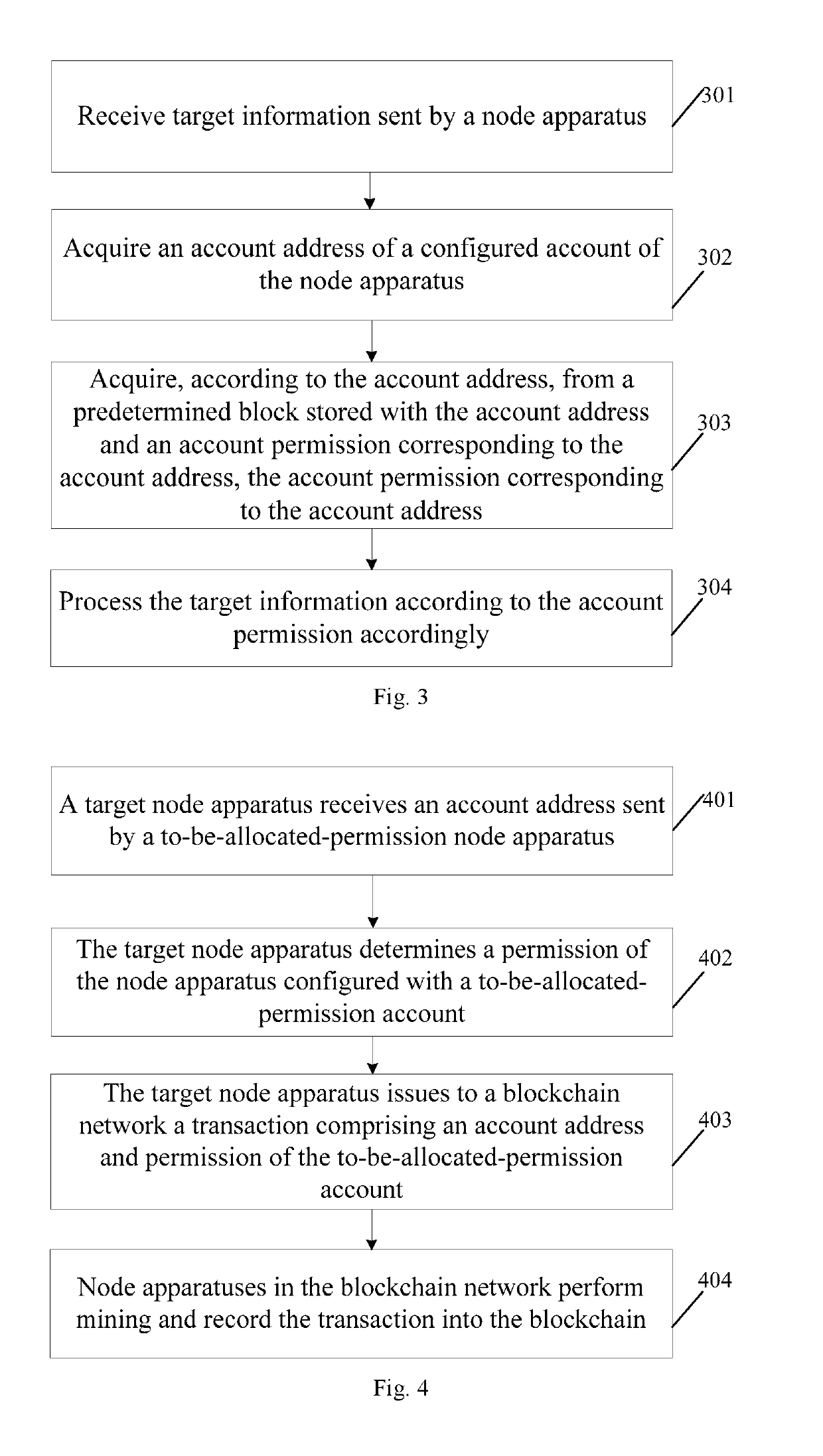
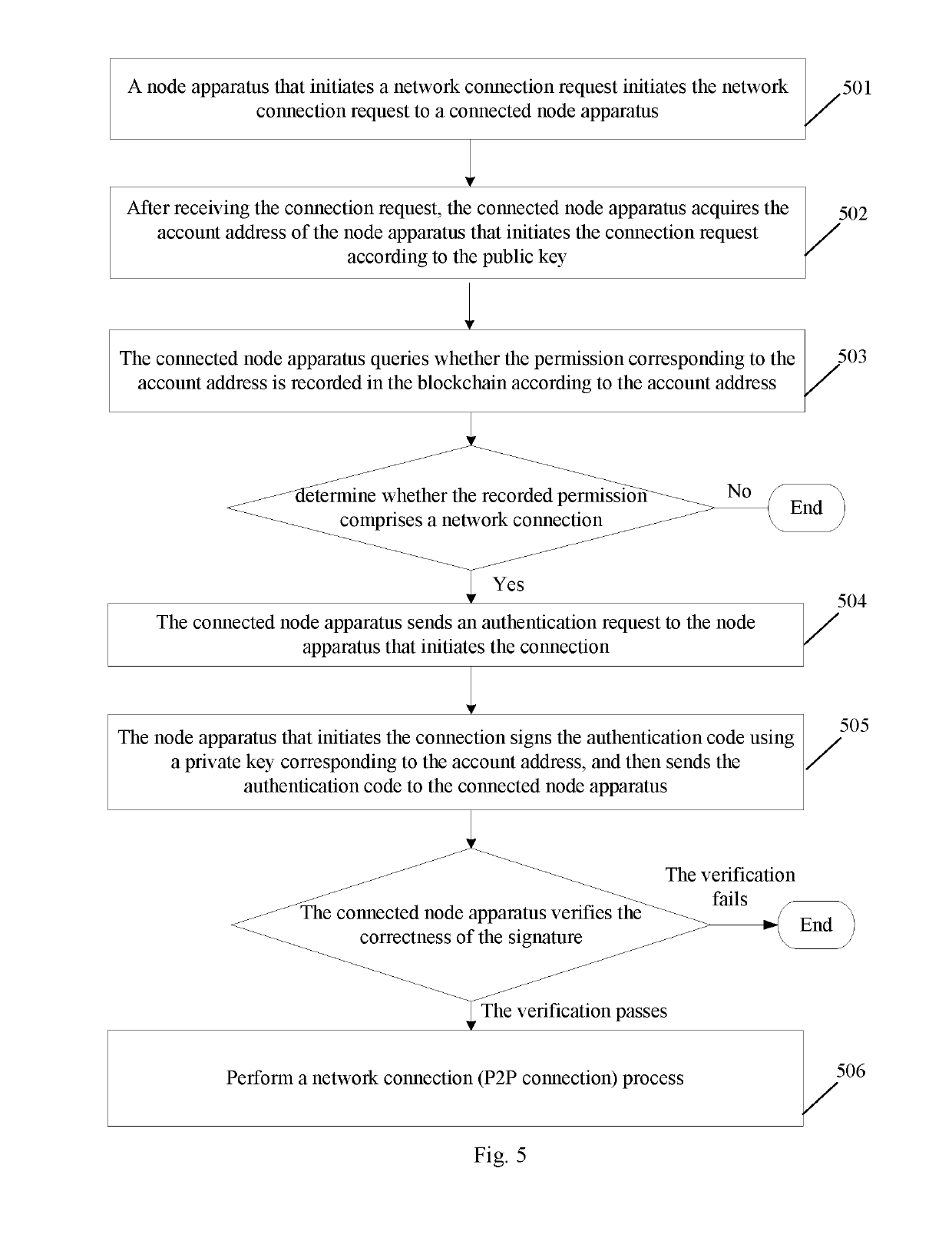
The present disclosure discloses a method, device and node apparatus for blockchain permission control. The method comprises: receiving target information sent by a node apparatus; acquiring an account address of a configured account of the node apparatus; acquiring, according to the account address, from a predetermined block stored with the account address and an account permission corresponding to the account address, the account permission corresponding to the account address; and processing the target information according to the account permission accordingly. In the present disclosure, node apparatuses are configured with corresponding accounts, and performing permission control on the accounts can restrict permissions of different node apparatuses so as to ensure security and privacy of blockchain data.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Man-machine dialogue system, controls dialogue between system and user using dialogue specification employing augmented transition networks propagating tokens
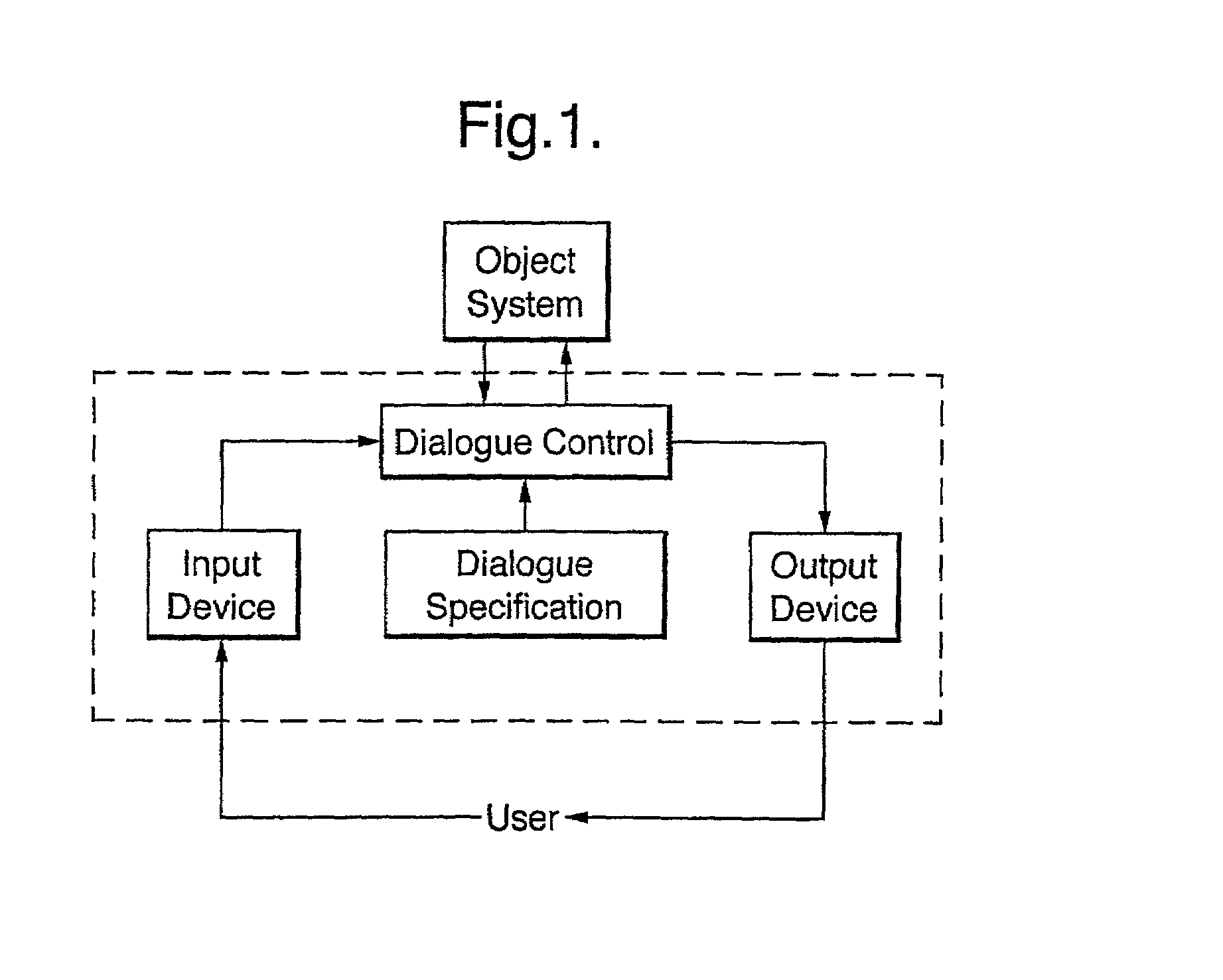
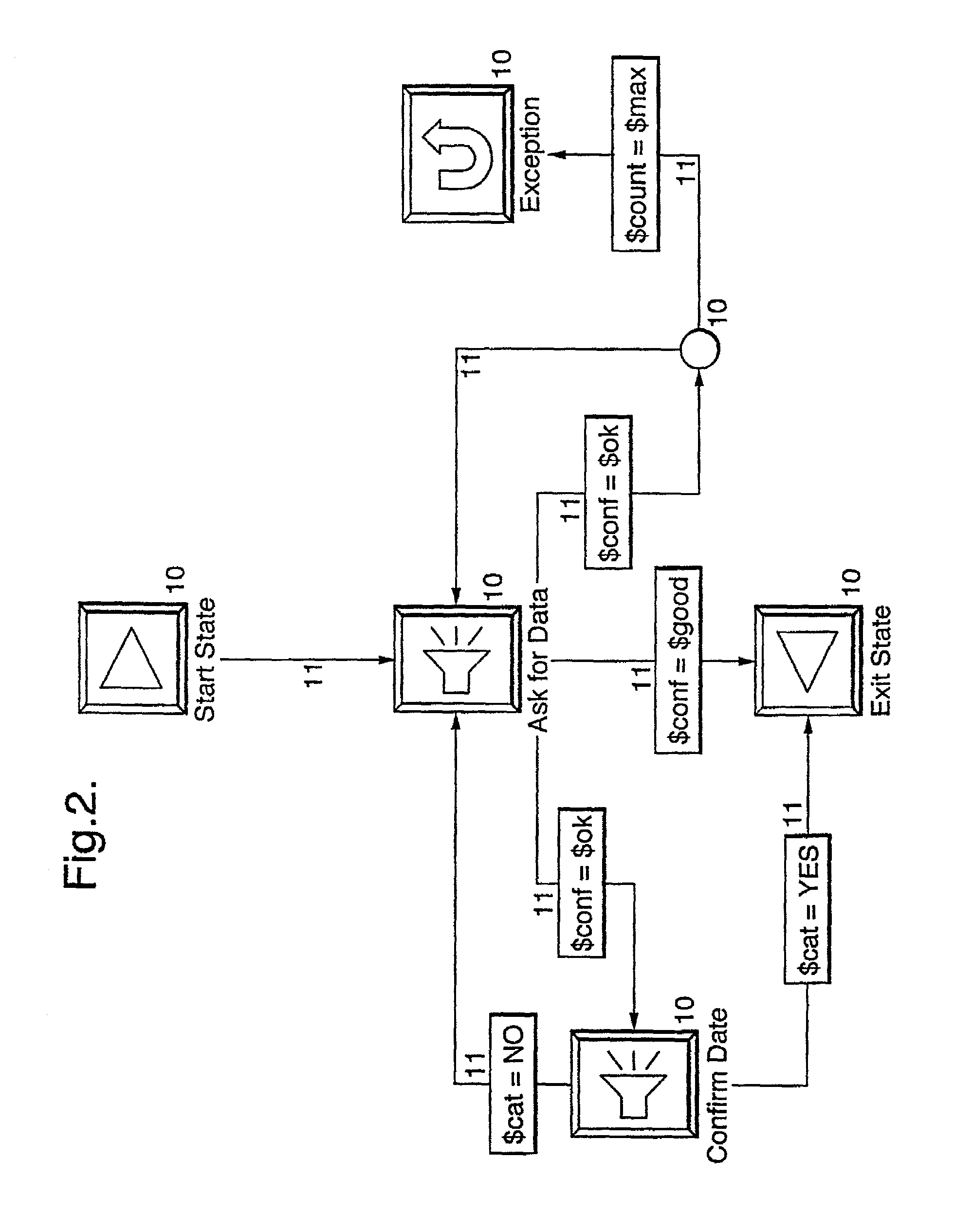
A man-machine dialogue system employing an interactive computer system comprising an input device for receiving input from the user. An output device generating output to the user. There is provided an object system which is an information source or store, or a command and control device. The system has a dialogue manager, which orchestrates the dialogue between the object system and user dependent upon a dialogue specification. The specification employs a set of augmented transition networks (ATNs), through which are propagated one or more tokens, the token comprising a set of fields which together define the current state of belief of the dialogue controller, dependent upon the preceding user-system interchanges and information obtained from the object system.
Owner:MICROSOFT TECH LICENSING LLC
A method and system for controlling the user network access right
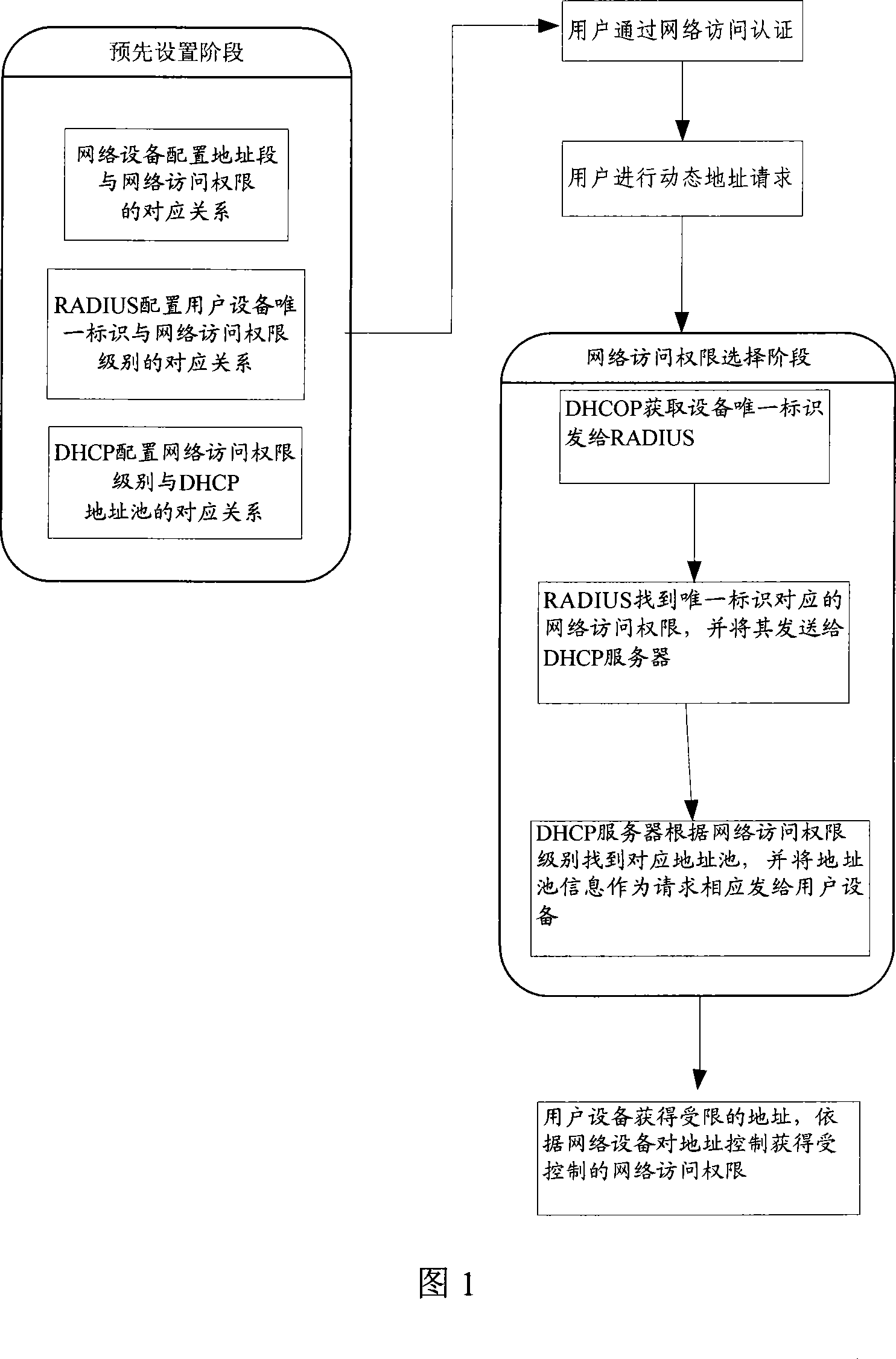
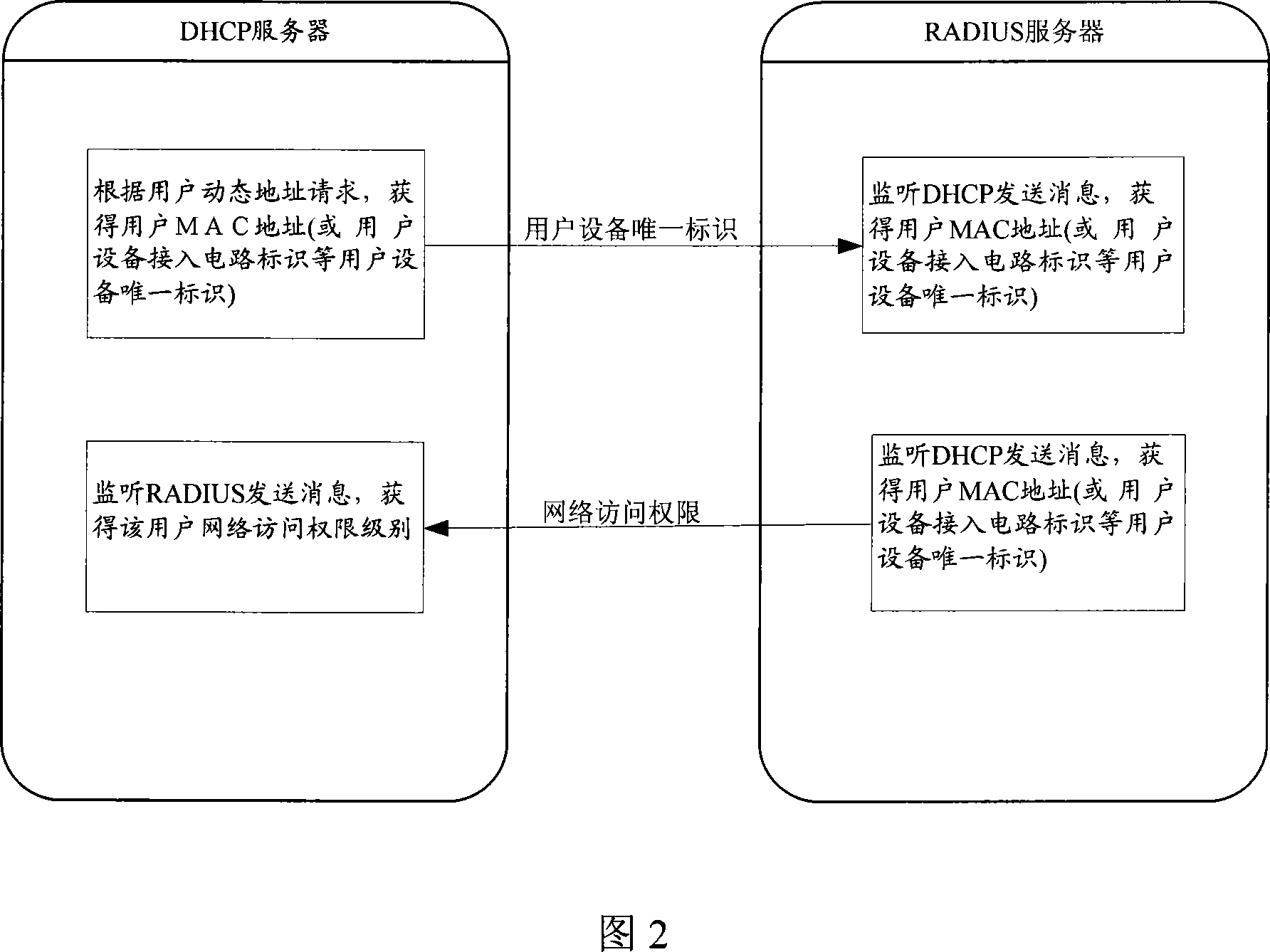
ActiveCN101056178AEasy to controlSimplify dependenciesUser identity/authority verificationUnique identifierUser authentication
The invention provides a method and system for controlling the user network access authority, including the presetting phase: the corresponding relationship between the network equipment configuration address portion and the network access authority; the corresponding relationship between the combination configured unique user equipment identifier for RADIUS server and DHCP server and address pool information. After the user authentication, IP address allocation phase for dynamic address request and network access authority selection, controlling of user network access authority: the DHCP server and RADIUS server may get the address pool information according to the unique identifier of user equipment and return to the user equipment, the user equipment may get the network access authority for corresponding network equipment configuration according to this address pool information. With the invention, directly control during the authentication, and dynamic address acquisition, simply and effectively realize the network access authority control for different user authenticated, simplify the dependency for network equipment.
Owner:ZTE CORP
Information processing method and apparatus thereof
InactiveUS20070146768A1Computer security arrangementsVisual presentationComputer hardwareInformation processing
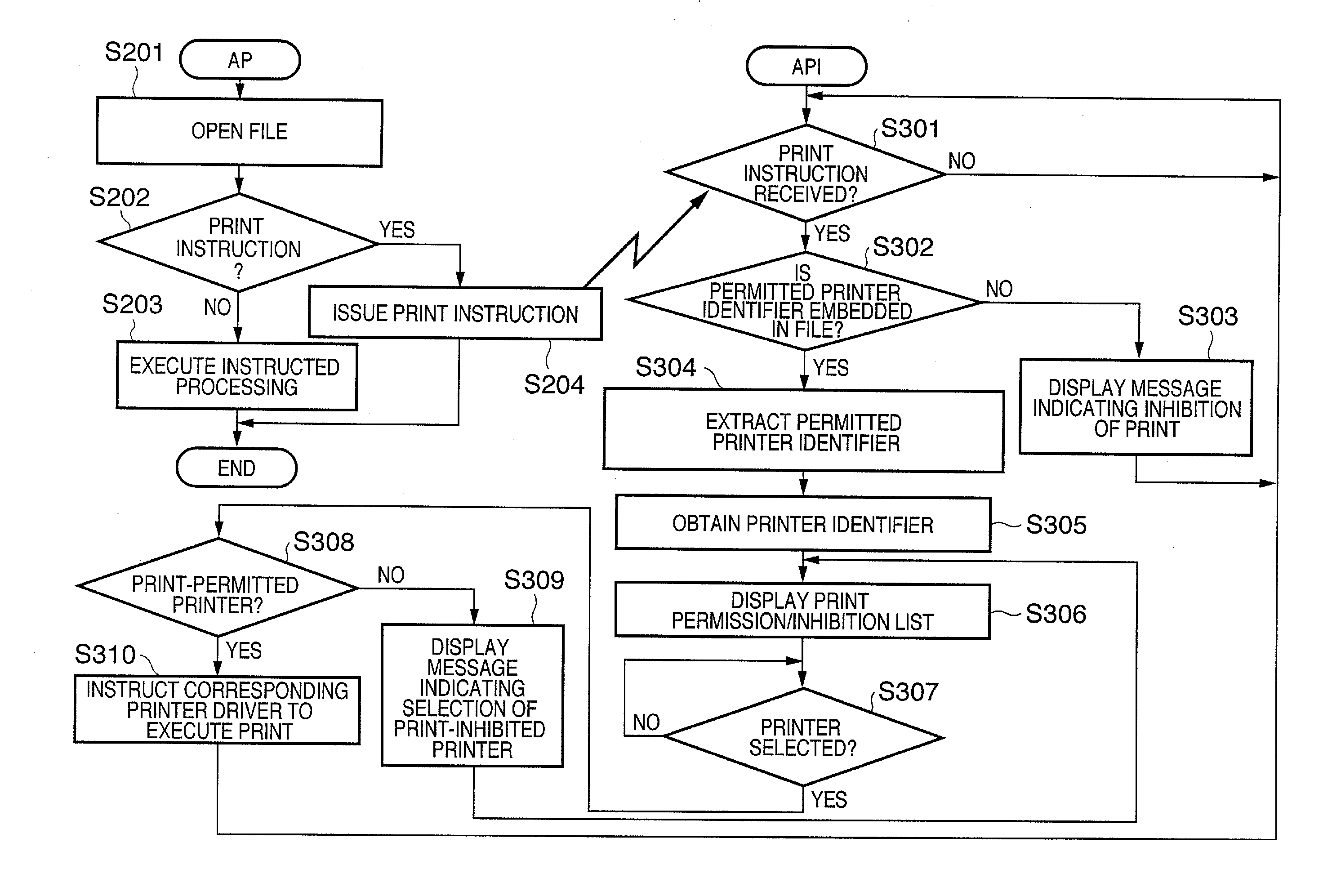
An access rights control system can set permission / inhibition of print processing for respective users and files, but it cannot set permission / inhibition of print processing for respective printer devices. Hence, a first identifier required to identify a printer device is obtained from data, a second identifier required to identify an available printer device is obtained from a memory, and a printer device which is permitted to print the data is determined based on the relationship between the first identifier and the second identifier.
Owner:CANON KK
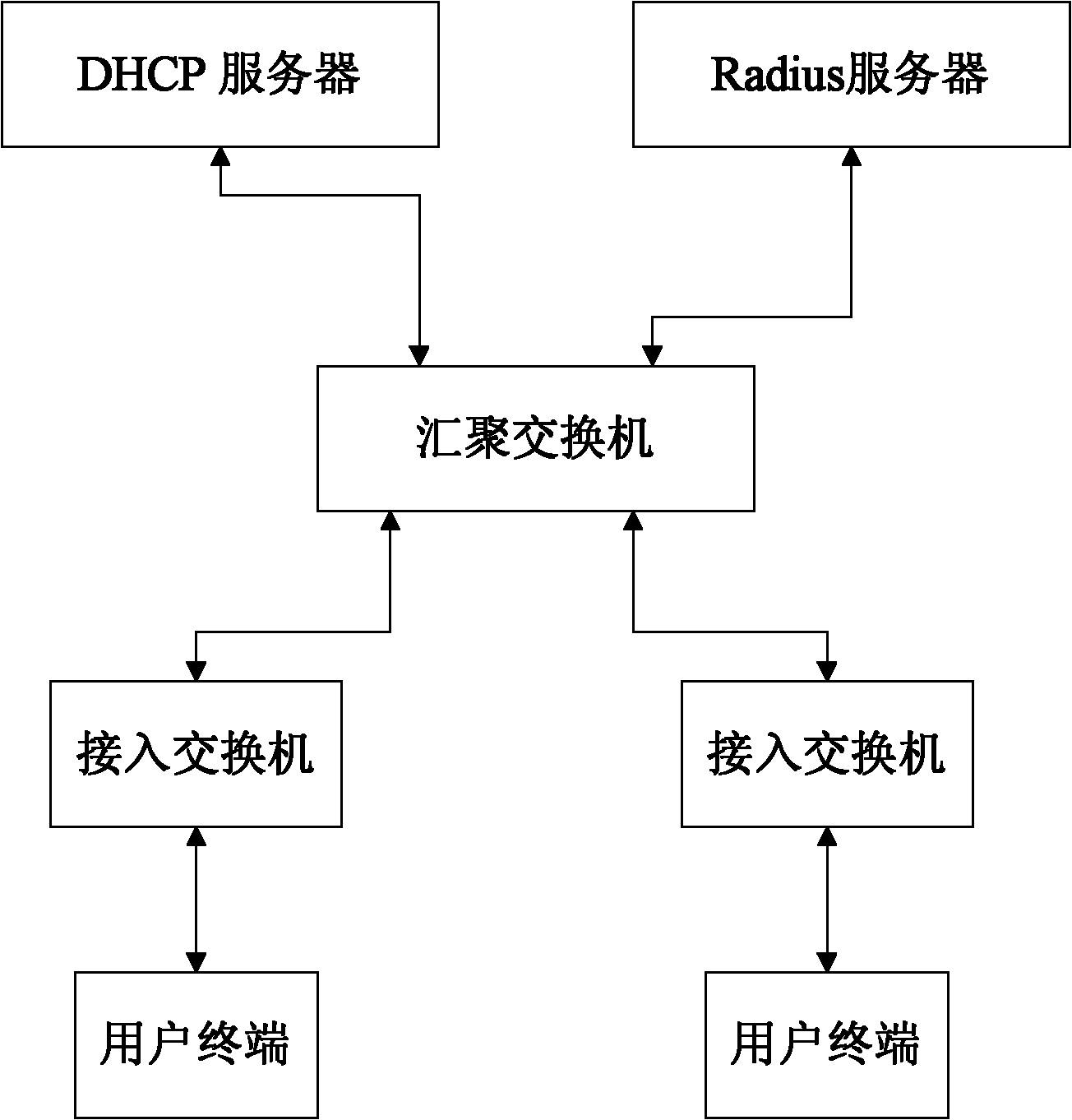
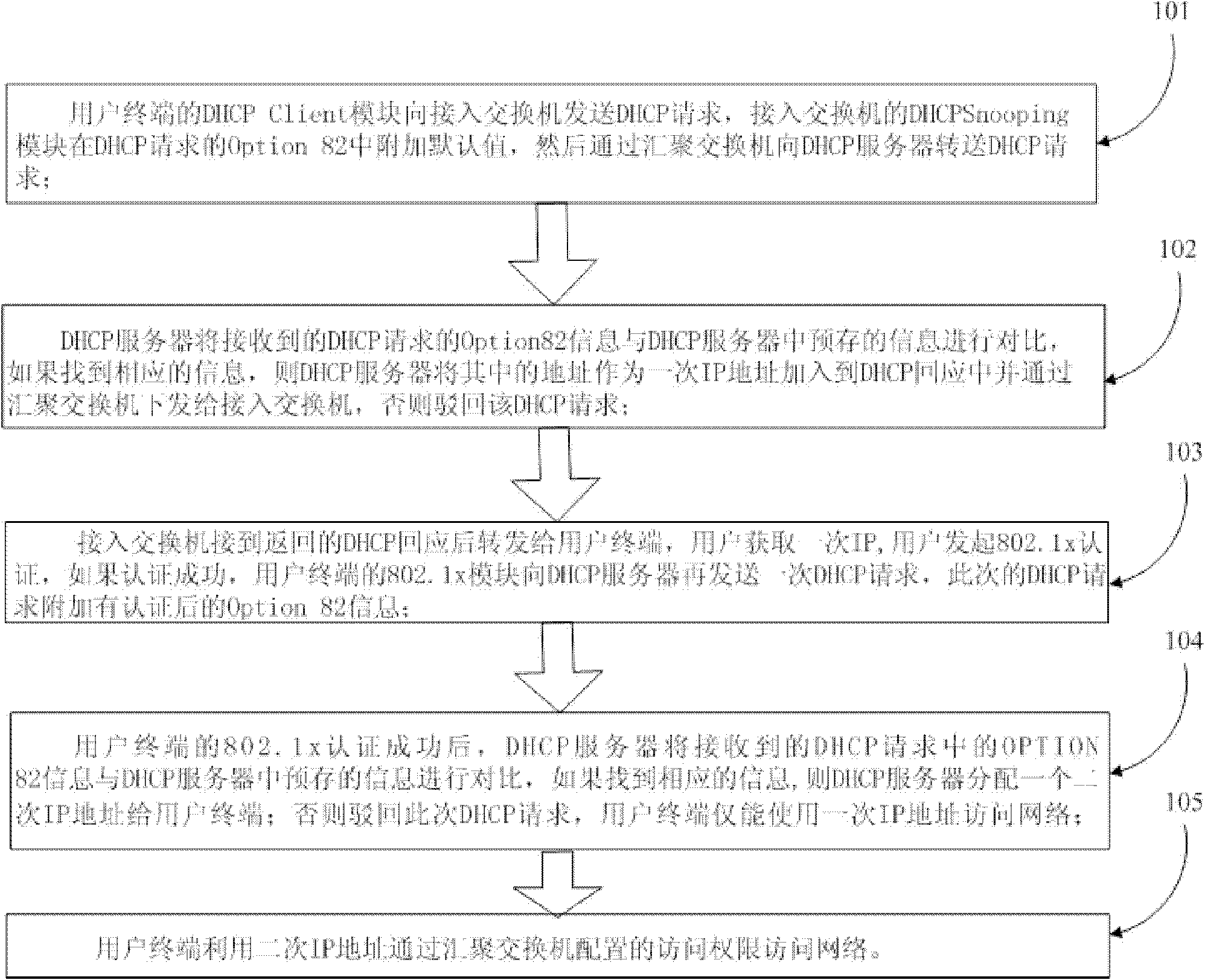
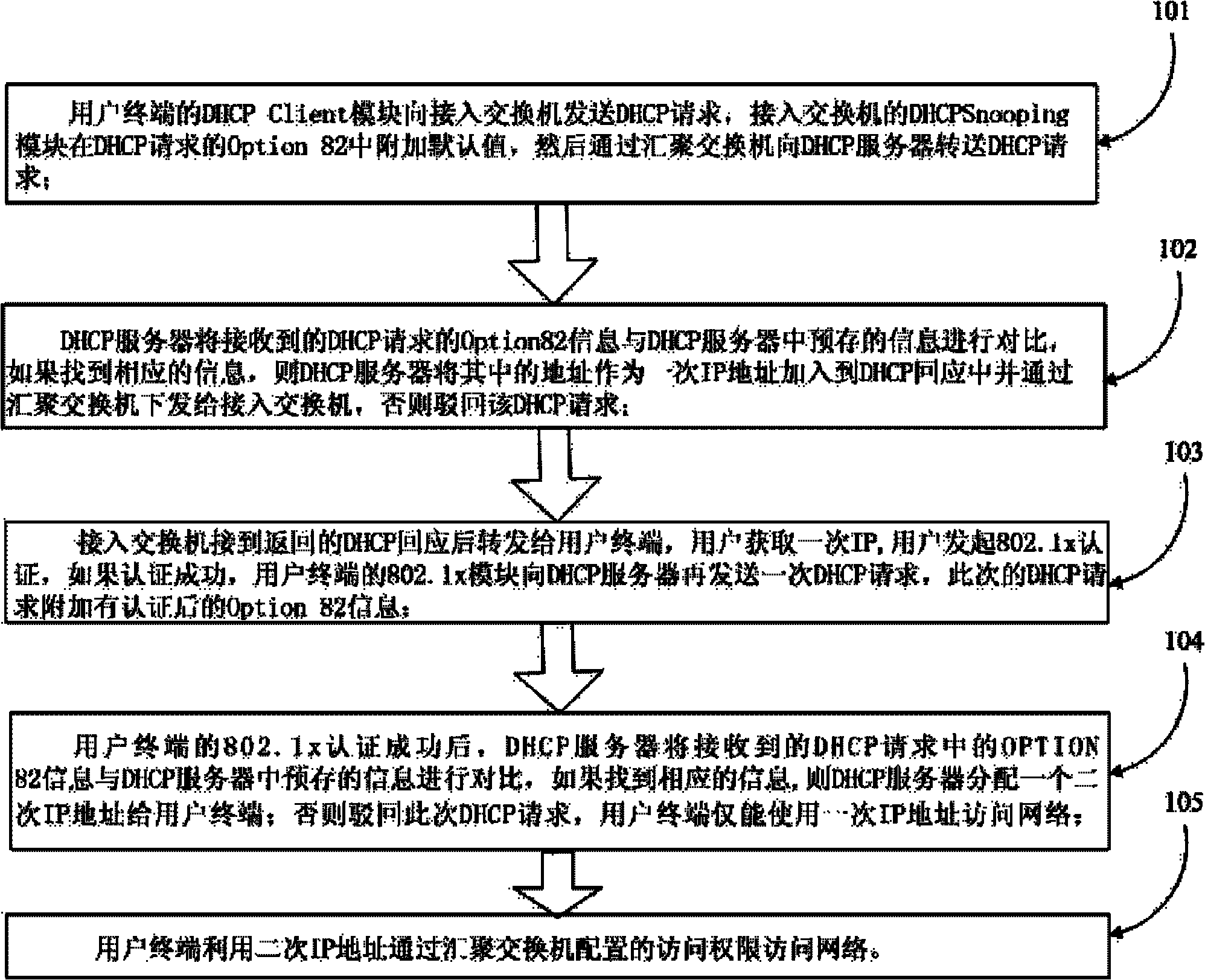
DHCP (Dynamic Host Configuration Protocol) Option 82 based user accessing authority control method
The invention discloses a DHCP (Dynamic Host Configuration Protocol) Option 82 based user accessing authority control method and belongs to the field of computer data communication. The method comprises the following steps: adding Option 82 information when a DHCP Snooping module is used for monitoring a DHCP request of a user terminal; sending Option 82 authenticating information of a user by a Radius server after the user terminal successfully acquires an address and passes the authentication; reapplying an address by 802.1x, after the user terminal successfully passes the authentication; adding the authenticated Option 82 information to the DHCP request by the DHCP Snooping module; and allocating another address to the user by a DHCP server according to the Option 82 information. A hardware ACL (Access Control List) item is configured on a converging switcher, thereby limiting the resources which can be accessed by the users with different source IP addresses and further controlling the access authority of the user terminal before and after authentication.
Owner:北京神州数码云科信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com