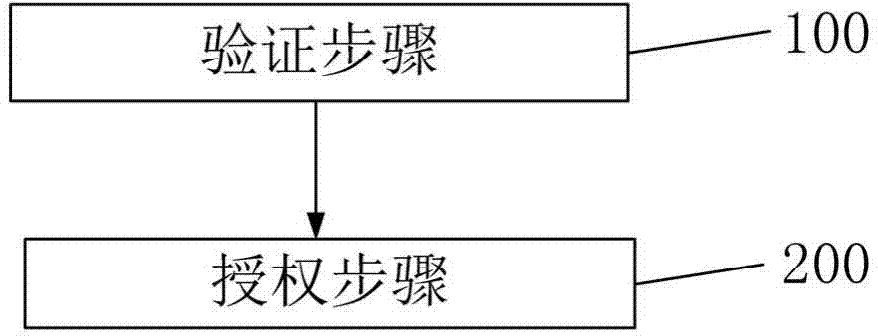
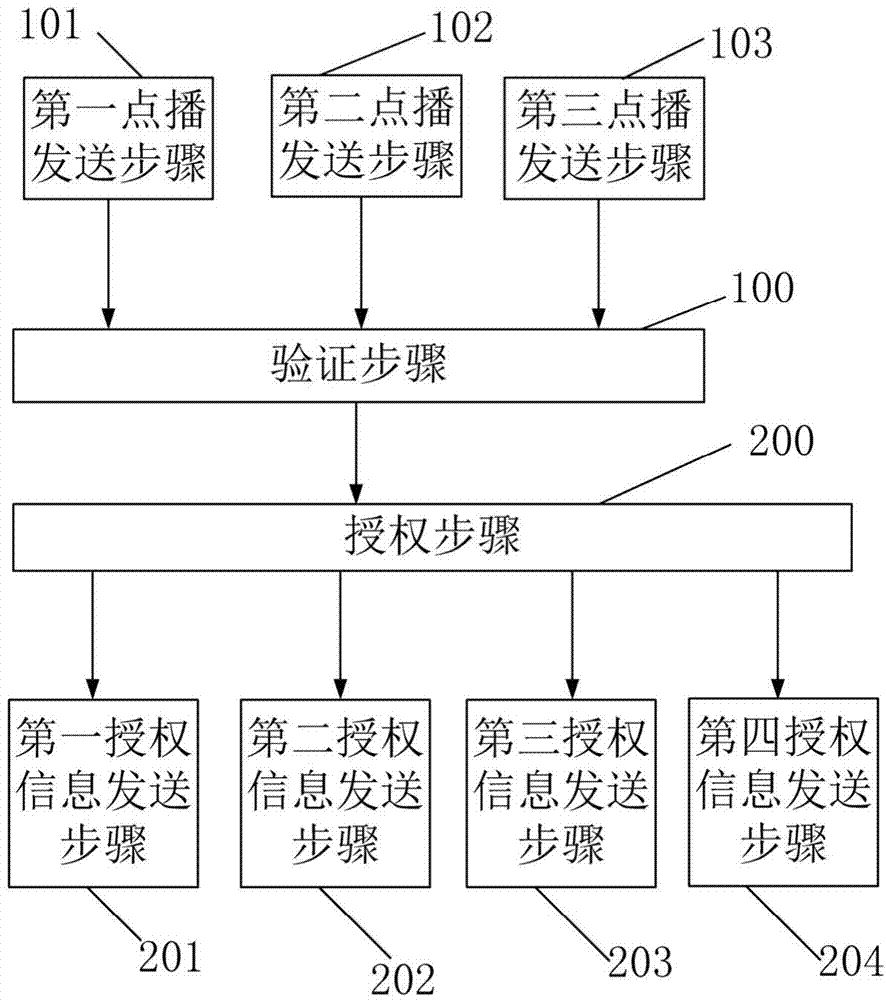
Patents
Literature
82results about How to "Improve authorization efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
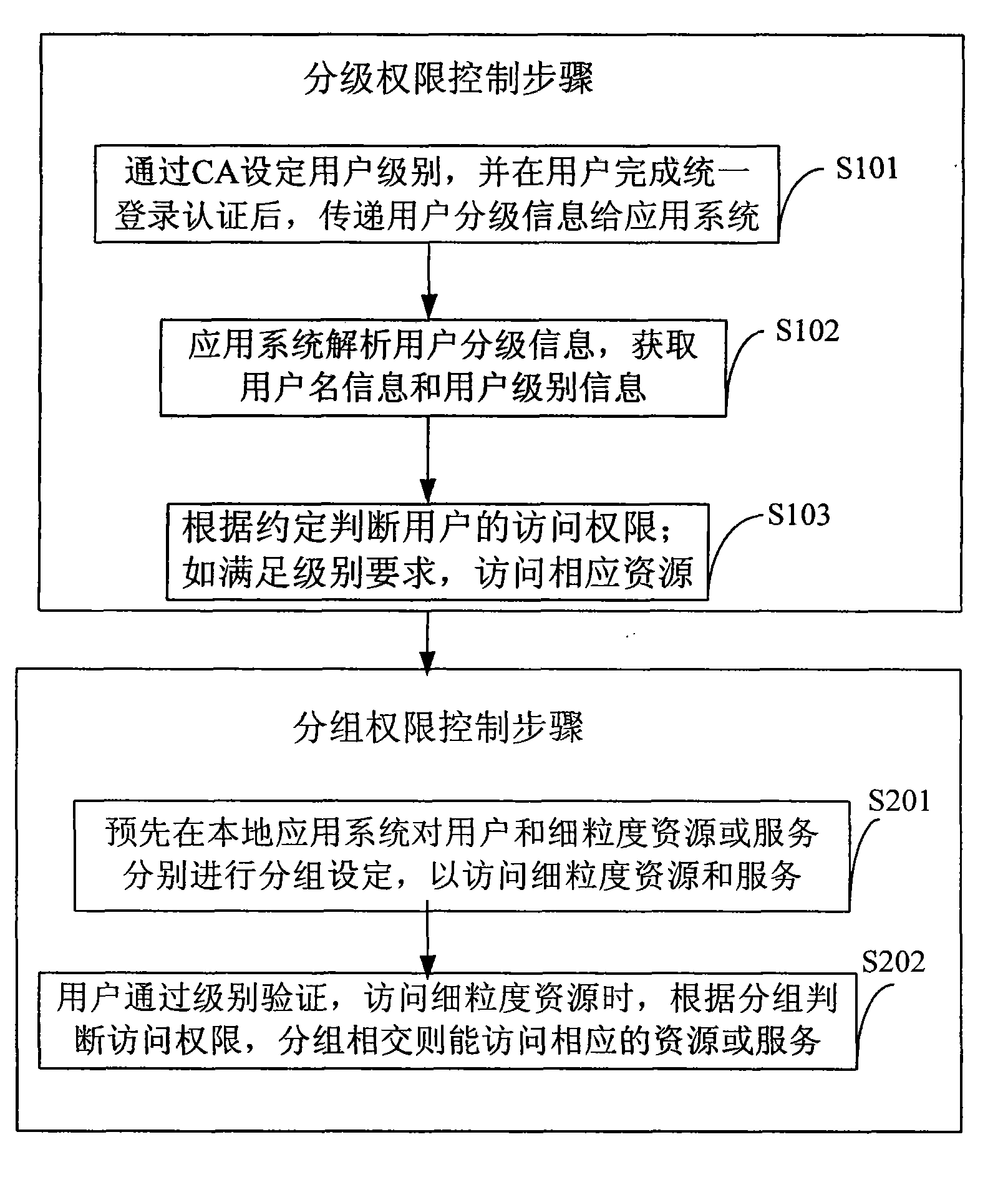
Distributed dual-license and access control method and system
InactiveCN101631116AReduce couplingImprove authorization efficiencyTransmissionControl systemAuthority control
The invention discloses a distributed dual-license and access control method and a system, the method is applied in the control system including a universal certificate licensing sensor and a plurality of different types of application systems, and the method comprises the grade authority control step which is used for setting the grade of a user through the universal certificate licensing sensor, transferring grade information of the user to the application systems and deciding the access authority of the user to resources or services by verifying the matching relationship between the grade of the user and the grade of coarse-grained resources or services of the application systems; and the group authority control step which is used for respectively carrying out grouping setting on the user and the resources / services through the application systems and deciding the access authority of the user to the coarse-grained resources or the services by verifying the intersection relationship between user grouping and data service grouping.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS
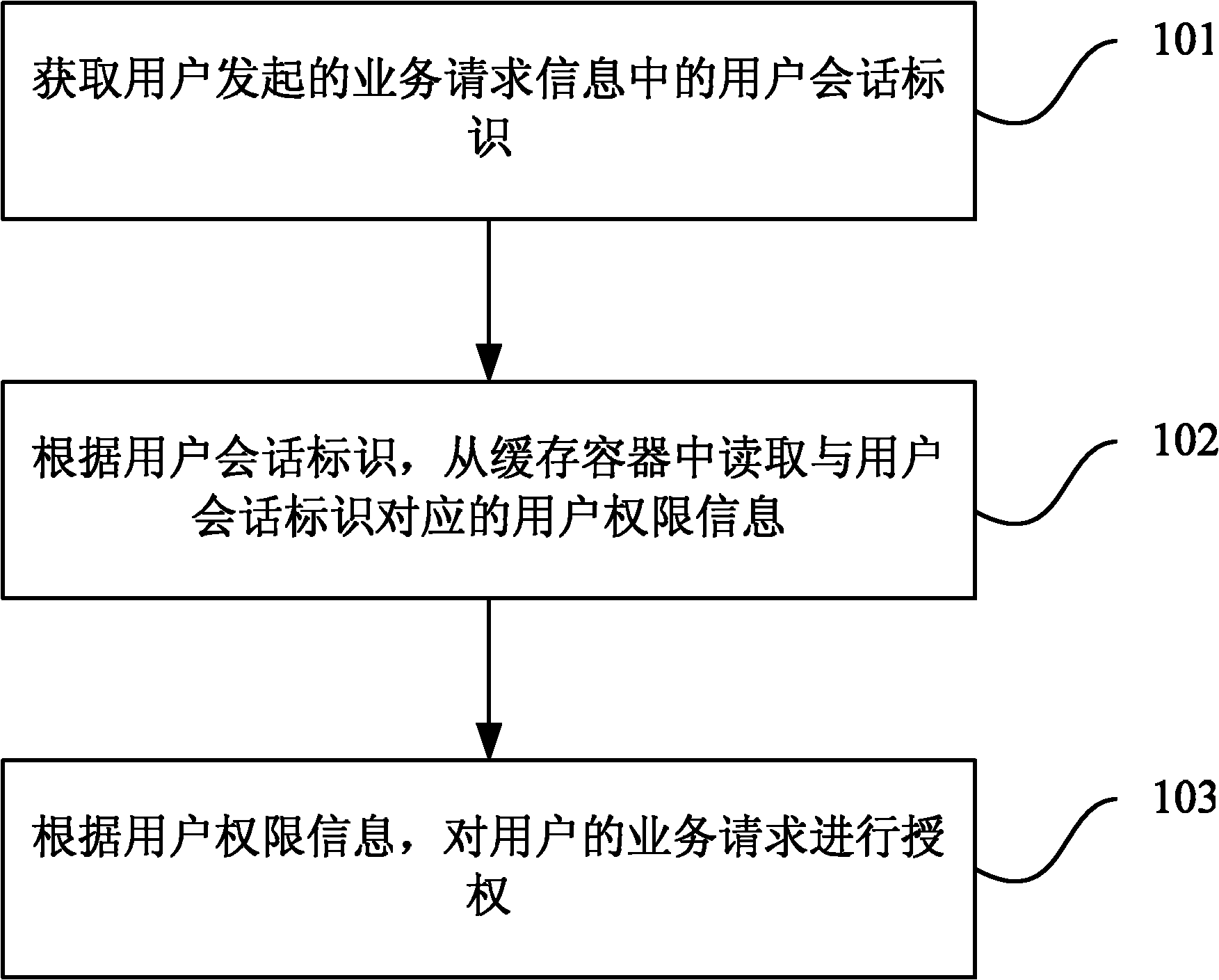
Method, device and system for controlling safety of service access
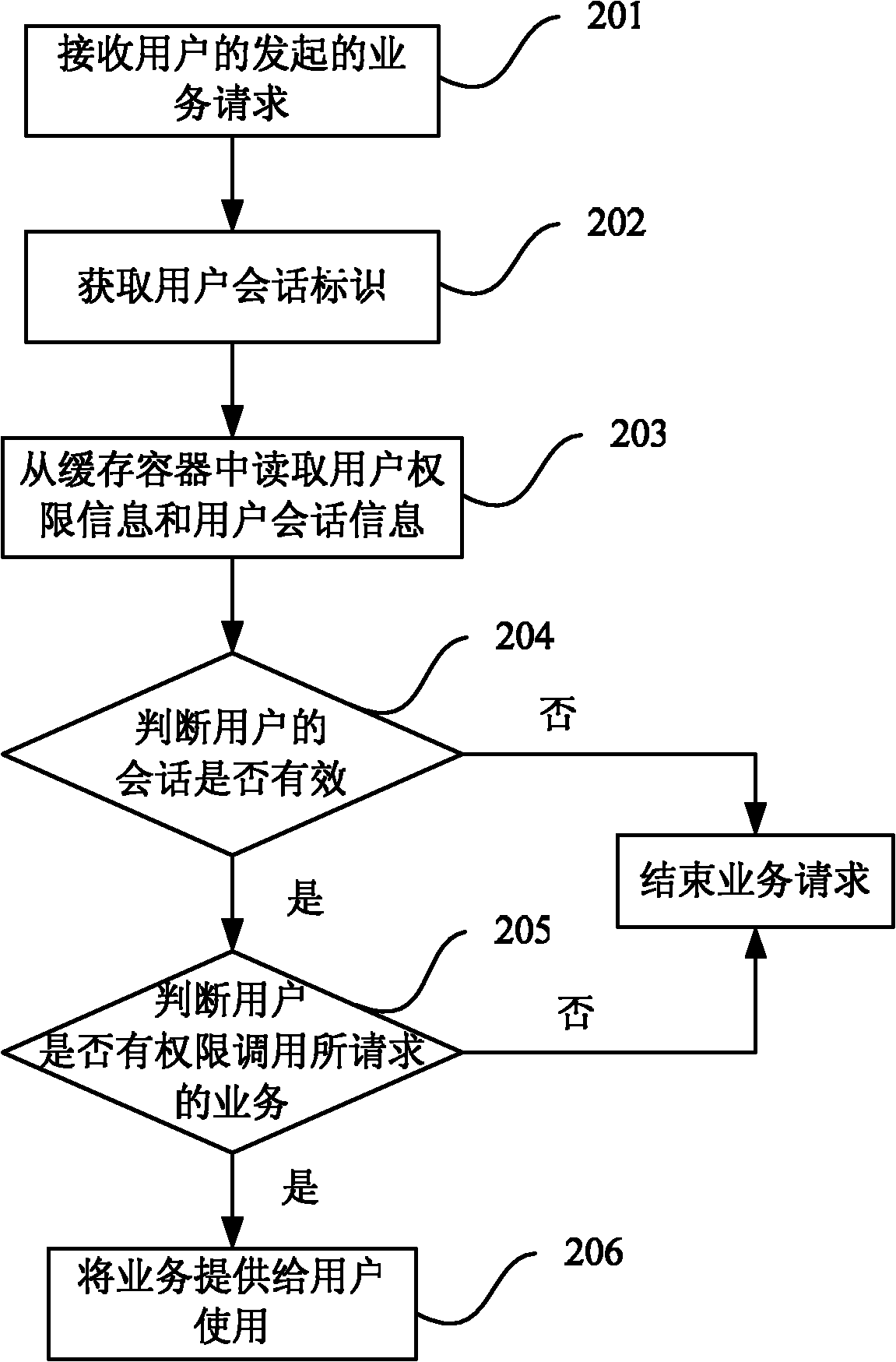
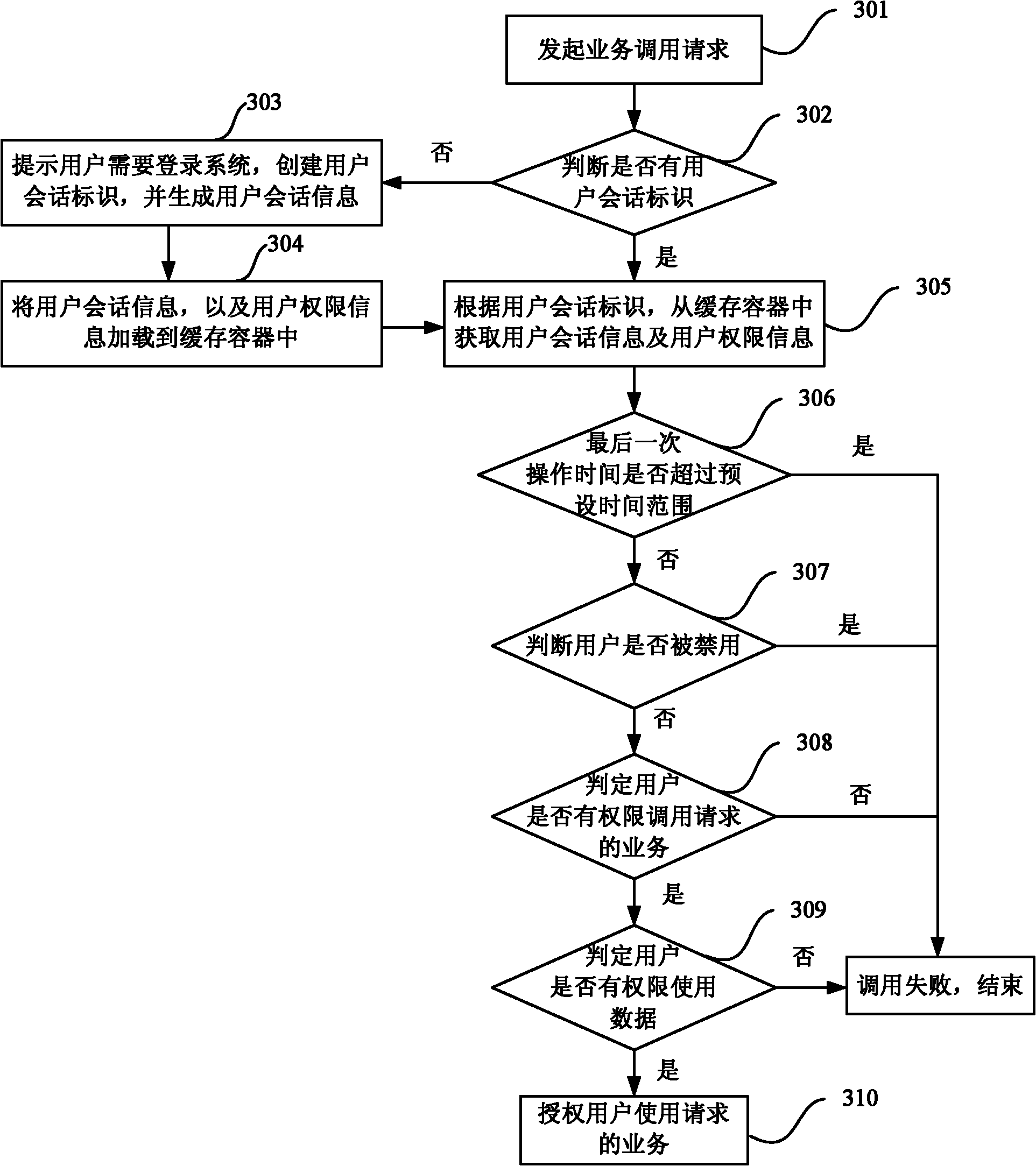
The invention discloses a method, device and system for controlling safety of service access. The method comprises the following steps: acquiring a user session identification from a service request message initiated by a user; based on the user session identification, reading user permission information corresponding to the user session identification from a cache container, wherein the cache container caches the user permission information; and authorizing the service request of the user based on the user permission information. In the technical scheme adopted by the invention, a caching technology is used, thus the safety of user service access is effectively improved, and the service access efficiency is enhanced.
Owner:易程(苏州)软件股份有限公司
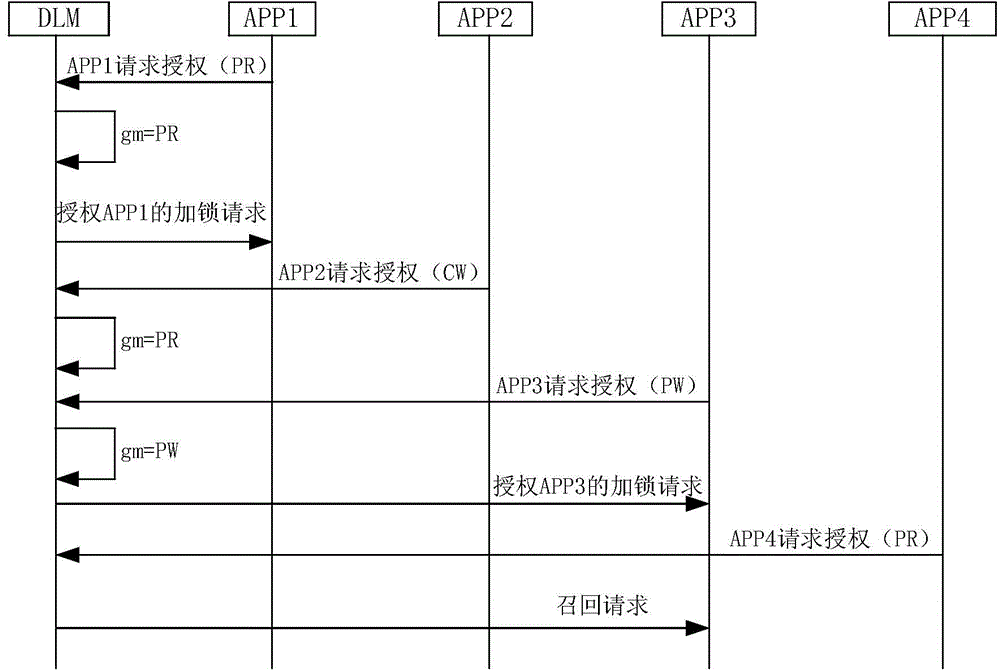
Method for authorizing lock permission and distributed lock manager
InactiveCN104536834AImprove the efficiency of authorizationShorten Authorization Wait TimeProgram synchronisationTransmissionFull PermissionResource management
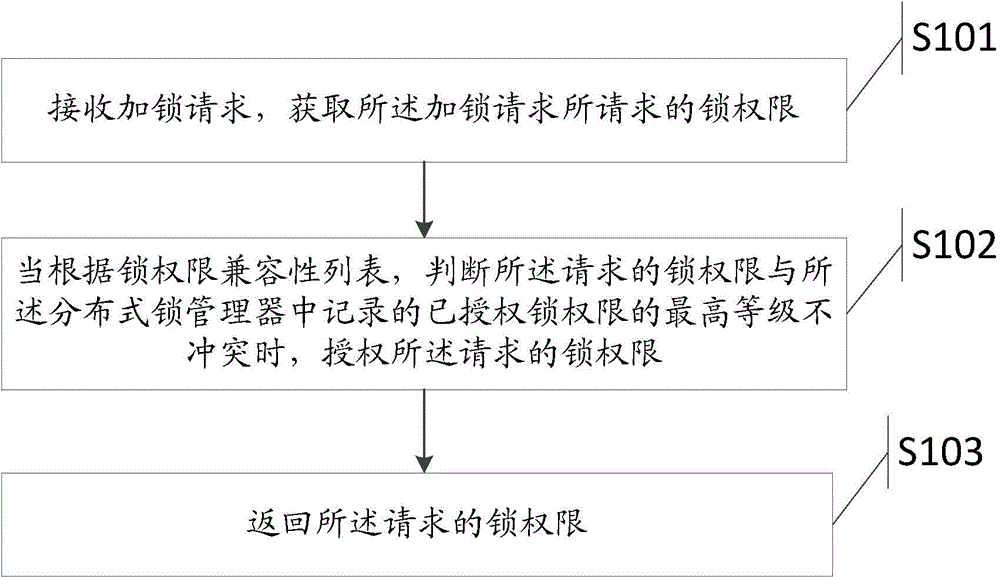
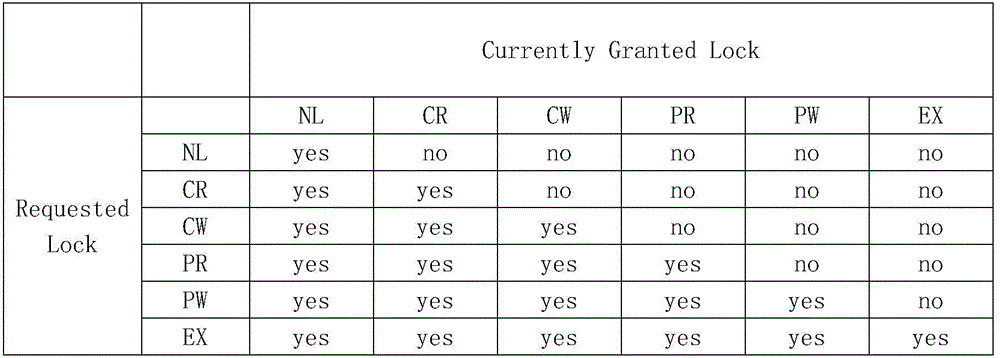
The embodiment of the invention provides a method for authorizing lock permission and a distributed lock manager, and aims to increase the authorizing efficiency of a lock resource manager in a distributed system for requested lock permission. The method comprises the following steps: receiving a lock request, and acquiring the lock permission requested by the lock request; when a judgment indicating that the requested lock permission does not conflict with the highest level of authorized lock permission recorded in the distributed lock manager is made according to a lock permission compatibility list, authorizing the requested lock permission; and returning the requested lock permission.
Owner:HUAWEI TECH CO LTD
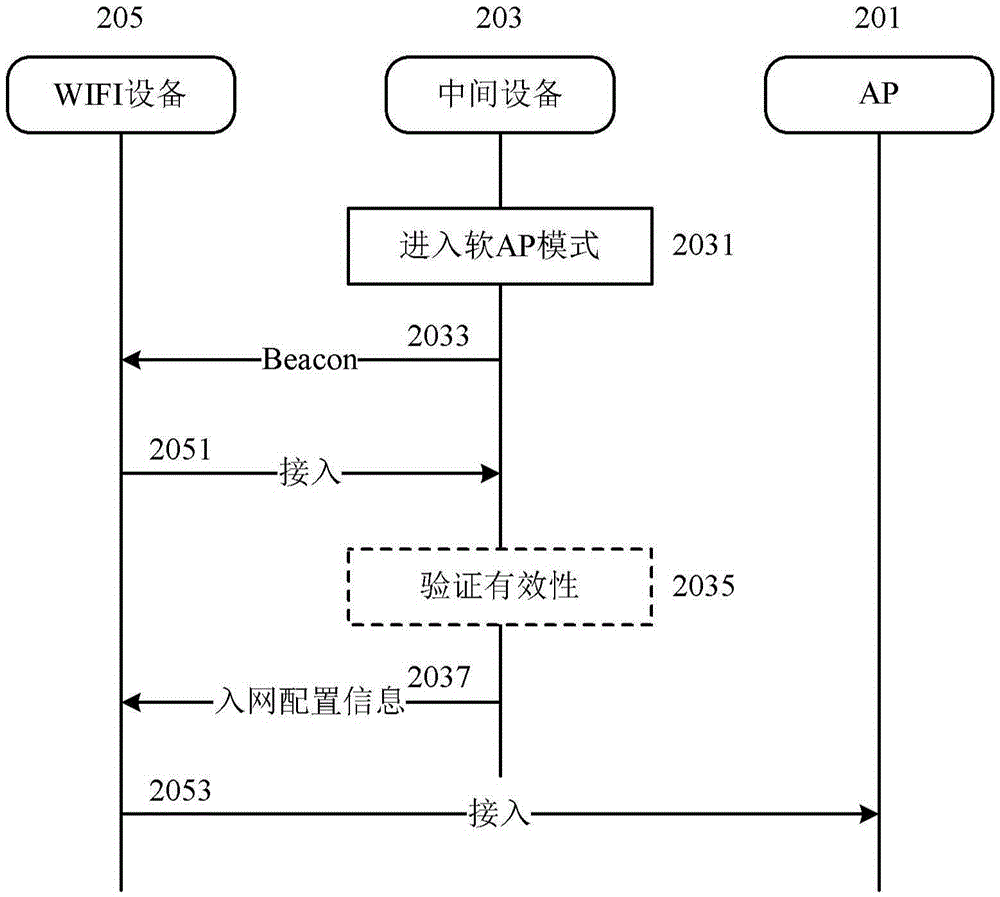
WIFI equipment, electronic device and method for assisting WIFI equipment access to network
The invention discloses WIFI equipment, an electronic device and a method for assisting the WIFI equipment access to a network. According to the embodiment, the electronic device may comprise a WIFI unit which is configured to establish WIFI connection with other devices, wherein the WIFI unit has a soft AP (Access Point) mode, sends a beacon when the WIFI unit is in the soft AP mode, and sends configuration information used for the AP to the accessed WIFI equipment when the WIFI device accessing the WIFI unit exists.
Owner:BEIJING JINGDONG CENTURY TRADING CO LTD
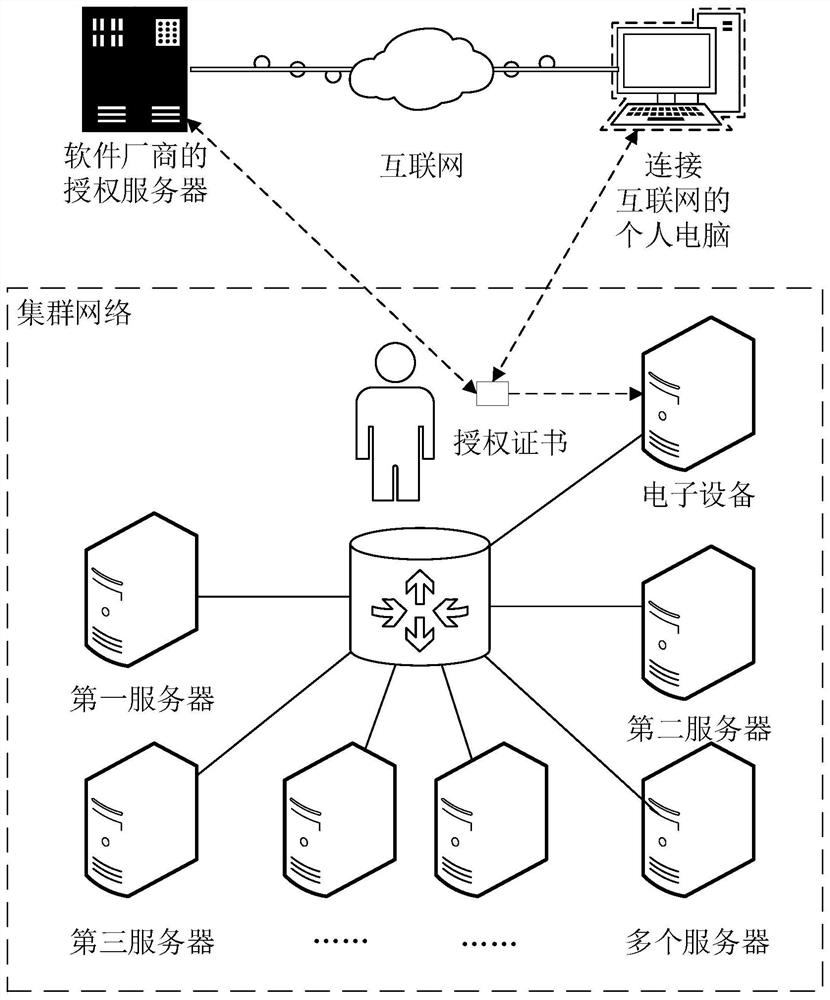
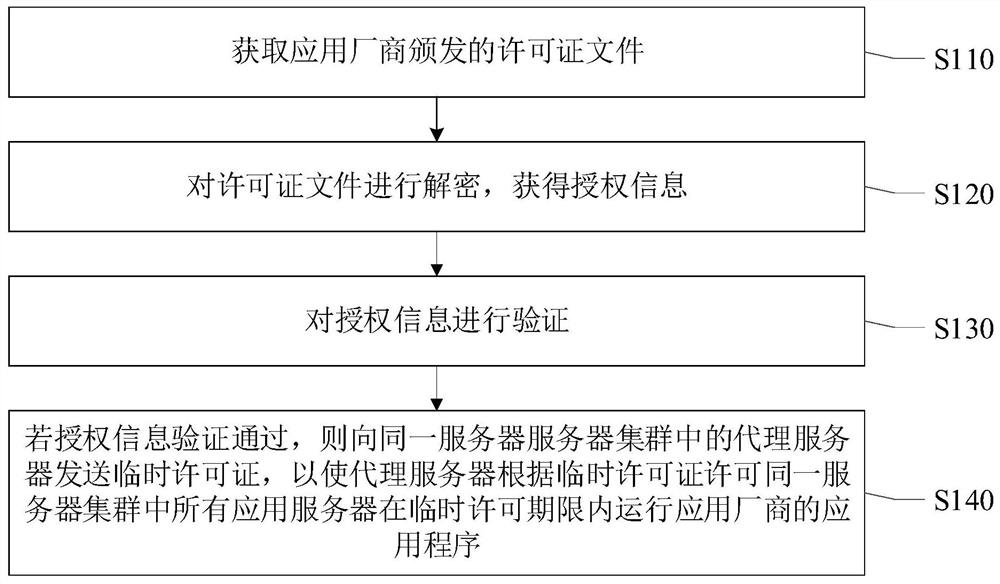
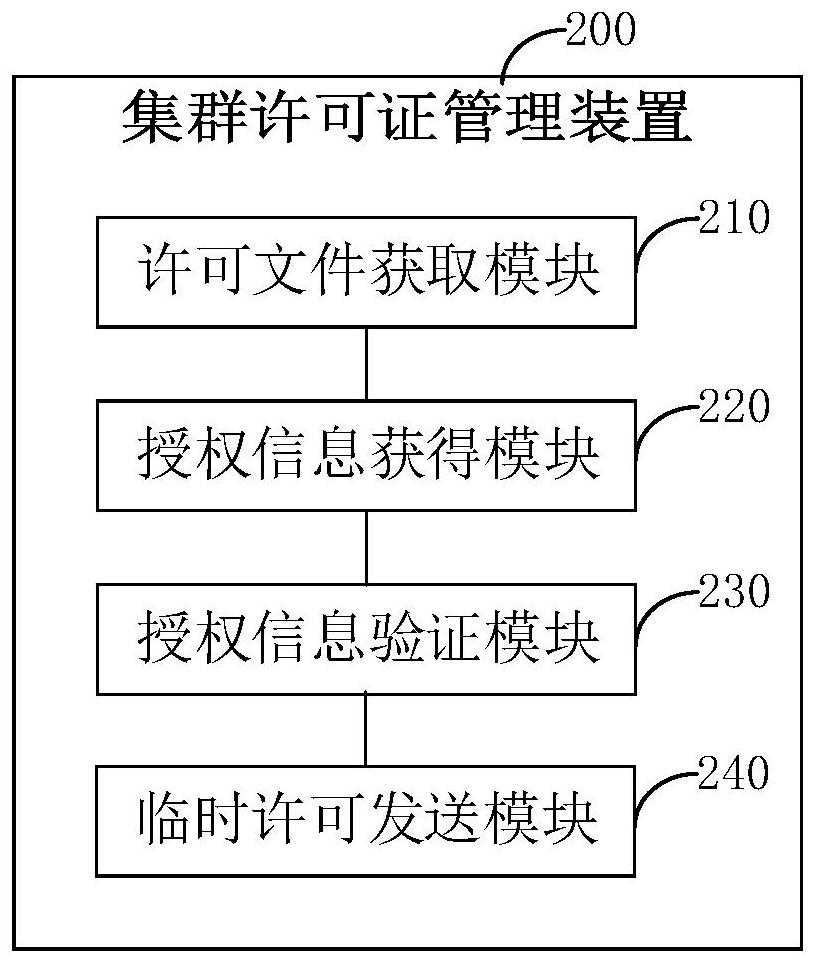
Cluster license management method and device, authorization server and storage medium
ActiveCN112417379AImprove re-authenticationImprove authorization efficiencyDigital data protectionProgram/content distribution protectionApplication serverEngineering
The invention provides a cluster license management method, a cluster license management device, an authorization server and a storage medium, which are used for solving the problem that the maintenance of a cluster server activated by hardware or software is very tedious. The method comprises the steps of obtaining a license file issued by an application manufacturer; decrypting the license fileto obtain authorization information, wherein the authorization information is the basis whether the behavior that the authorization server sends the license in the same server cluster is authorized ornot; verifying the authorization information; and if the authorization information passes the verification, sending a temporary license to the proxy server in the same server cluster, so that the proxy server permits all application servers in the same server cluster to run the application programs of the application manufacturer within a temporary permission period according to the temporary license.
Owner:MAIPU COMM TECH CO LTD
Block chain community face recognition access control security system and method thereof
InactiveCN109064591AReduce workloadImprove certificationIndividual entry/exit registersComputer terminalWorkload
The invention provides a block chain community face recognition access control security system and a method thereof. The system comprises a community access control device and a user, wherein the useris a person about to enter or leave a community, a block chain face recognition system is arranged beside the community access control device, a resident in the community uses a user terminal to receive and send information, the block chain face recognition system and the user terminal perform information interaction with a remotely erected cloud platform, and other users make contact with the user terminal through other personnel terminals. Through the block chain face recognition system, personnel hoping to enter the community are recognized; through different authentication methods, authentication efficiency is improved, community entering time is shortened, and the workload of community property and security staff is lowered; and by adopting different recognition modes on different personnel, the authentication strength of unfamiliar personnel is improved, and the security in the community is guaranteed.
Owner:安徽灵图壹智能科技有限公司
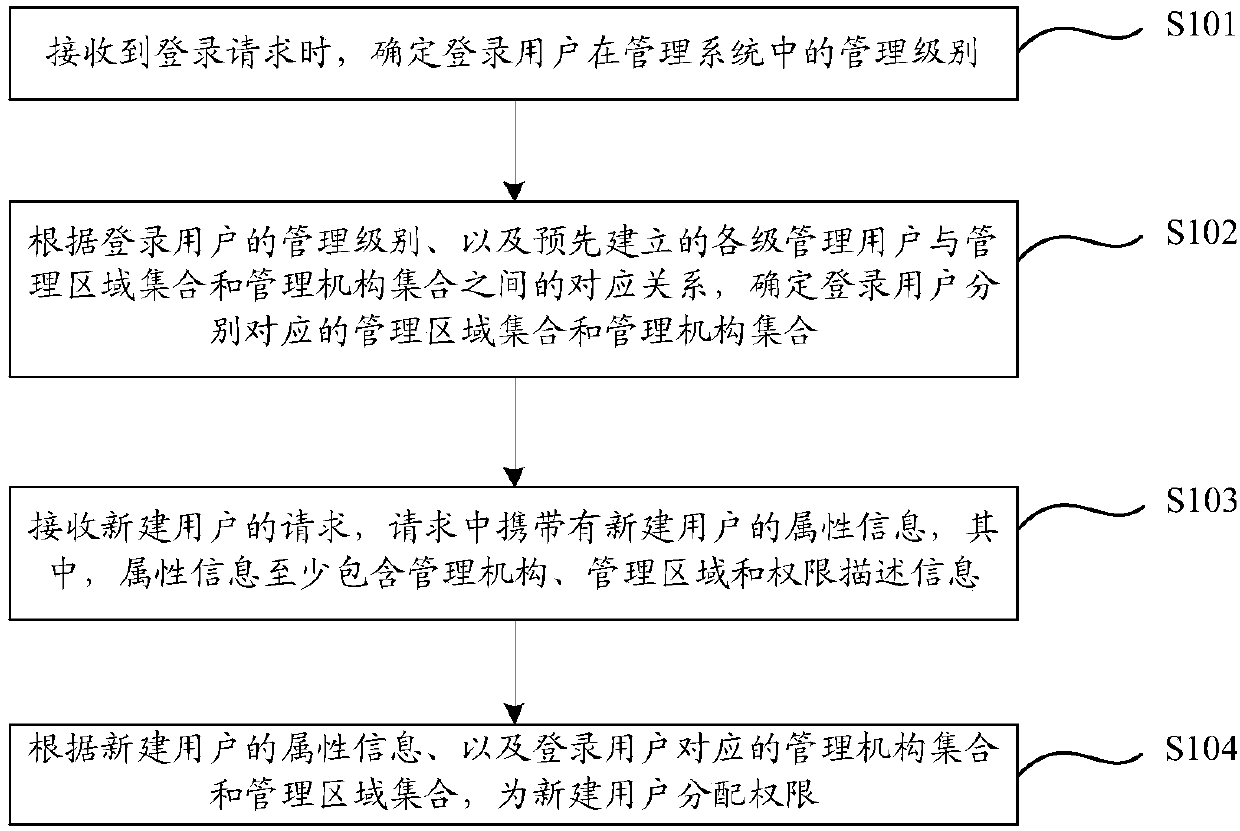
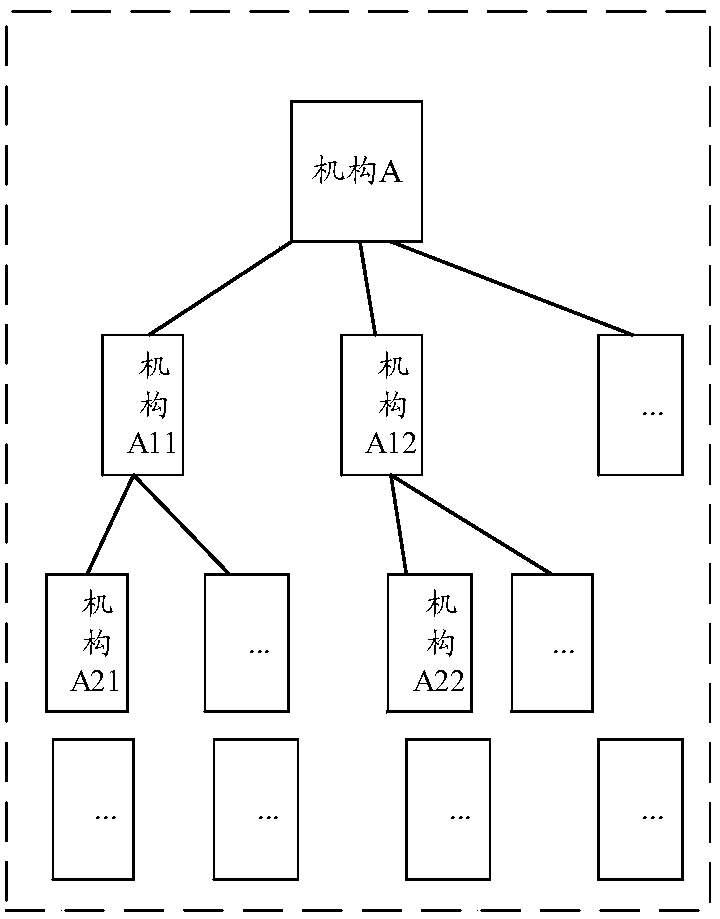
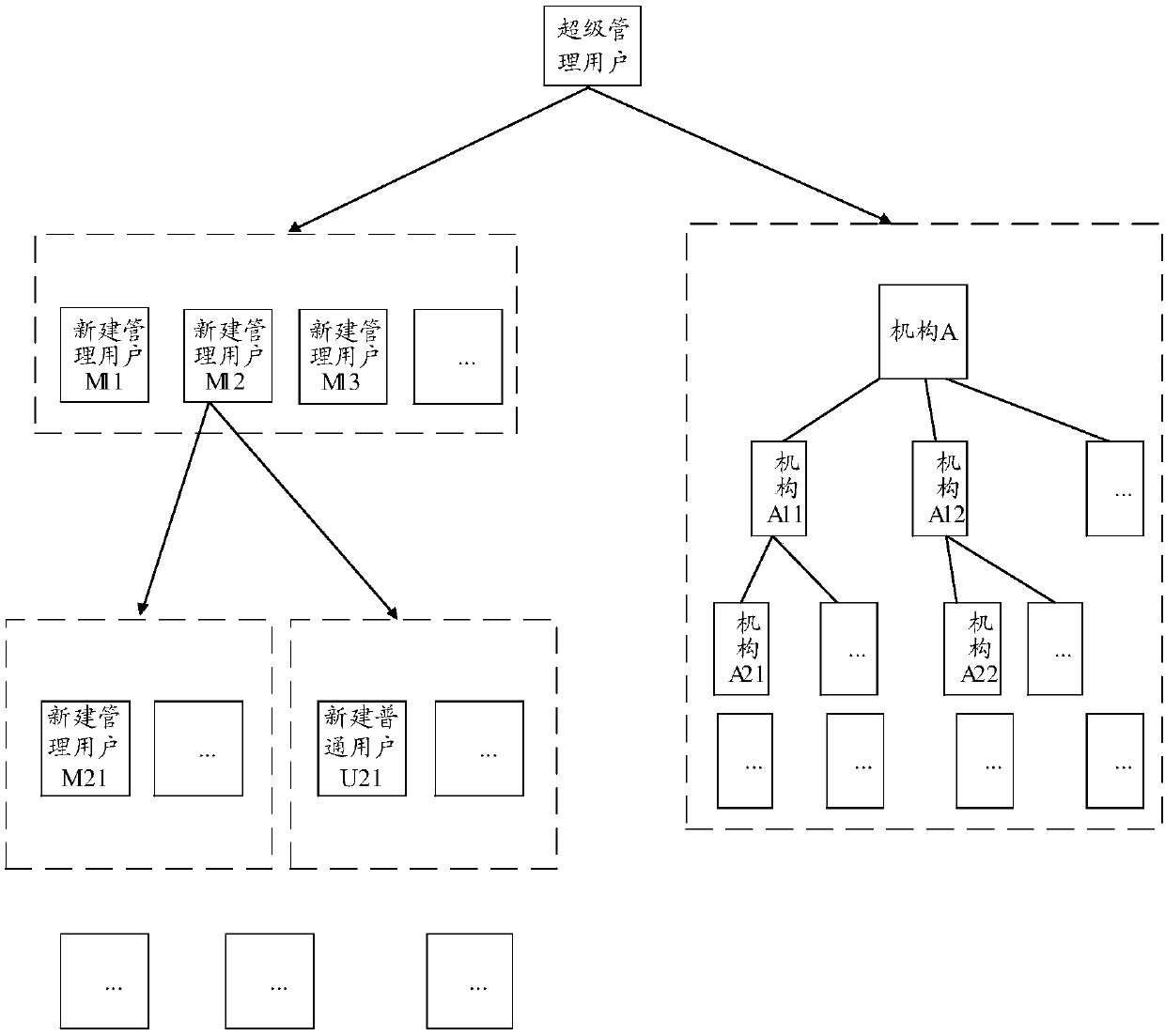
Permission allocation method and device
ActiveCN109981552AAllocation fineAppropriate distribution of authorityTransmissionDistribution methodThe Internet
The invention relates to the technical field of Internet, in particular to an authority distribution method and device, and aims to solve the problem that an authority distribution method for a systemwith a relatively complex hierarchical structure is unreasonable in the prior art. The authority distribution method provided by the embodiment of the invention is applied to a management system comprising multiple levels of management users, and comprises the following steps: when receiving a login request, determining the management level of the login user in the management system; determininga management area set and a management mechanism set corresponding to the login user according to the management level of the login user and the established corresponding relationship between each level of management user and the management area set and the management mechanism set; receiving a request of a new user, the request carrying attribute information of the new user, the attribute information at least comprising a management mechanism, a management area and authority description information; and distributing permission to the new user according to the attribute information of the newuser and the management mechanism set and the management area set corresponding to the login user.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
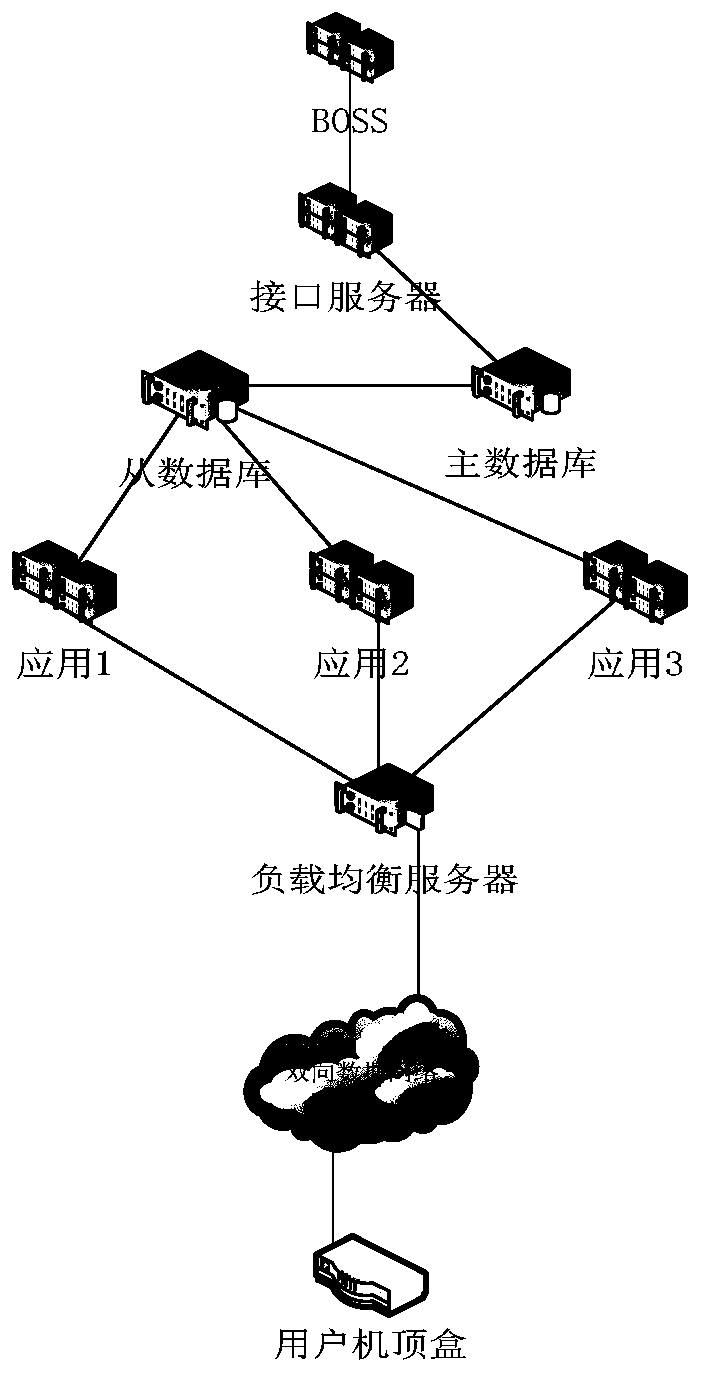
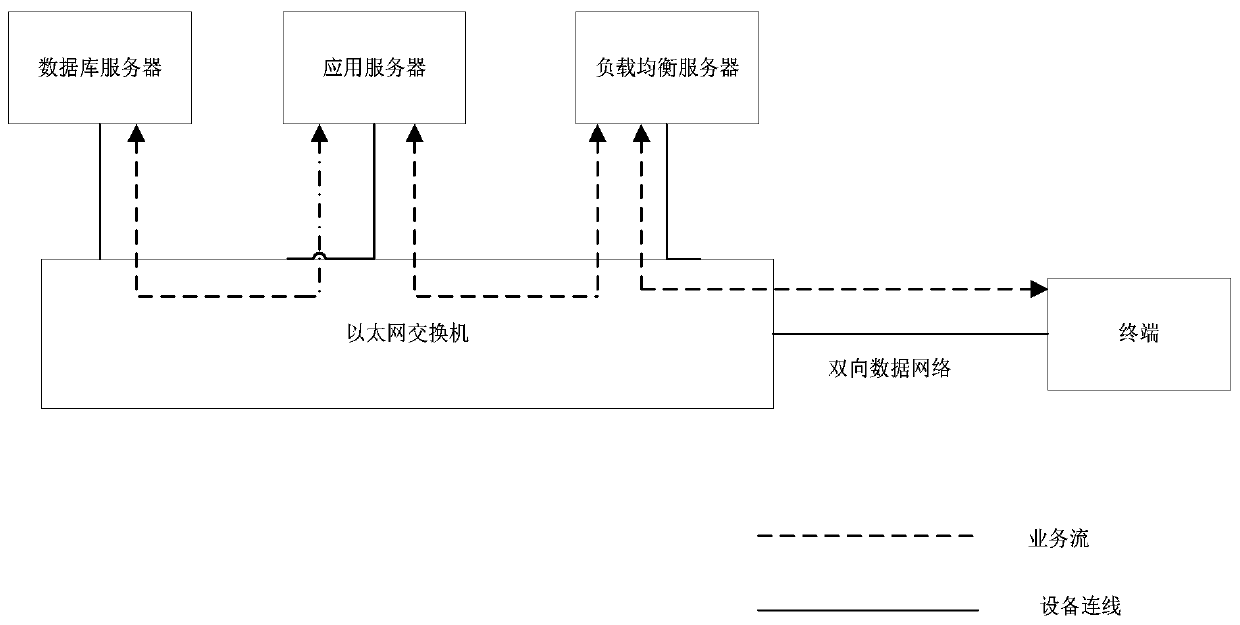
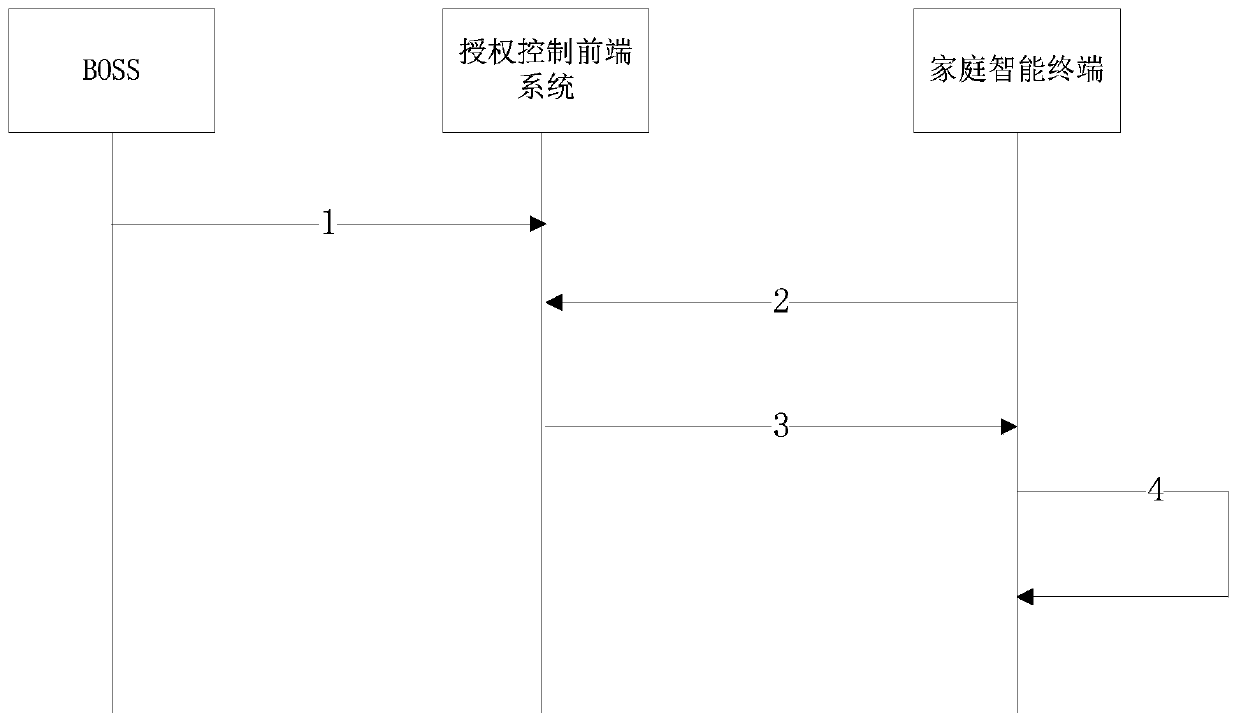
Program authorization control method of household intelligent terminal
InactiveCN110891187ATroubleshoot authorization issuesImprove authorization efficiencySelective content distributionService flowEngineering
The invention relates to a program authorization control method of a home intelligent terminal, a front-end system is composed of a database server, an application server and a load balancing server,servers of the front-end system are interconnected through an Ethernet switch, and the home intelligent terminal and the load balancing server of the front-end system are interconnected through a datatransmission network. The data interface server is used for synchronizing user ordering information in the BOSS system; the application server calls the data information of the database server. Verification and encrypted service flow processing are finished in a whole system at the same time. Encrypted related information of user authorization is sent to a load balancing server. A home intelligent terminal is received and returned by a load balancing server, and authorization control of a program is completed on the home intelligent terminal based on the received encrypted authorization information. The method can be widely applied to operator-level program authorization control based on the intelligent home terminal in the all-IP two-way network, and the rights and interests of operatorsare guaranteed.
Owner:GUANGXI RADIO & TV NETWORK
Method and system for authenticating satellite digital on-demand services
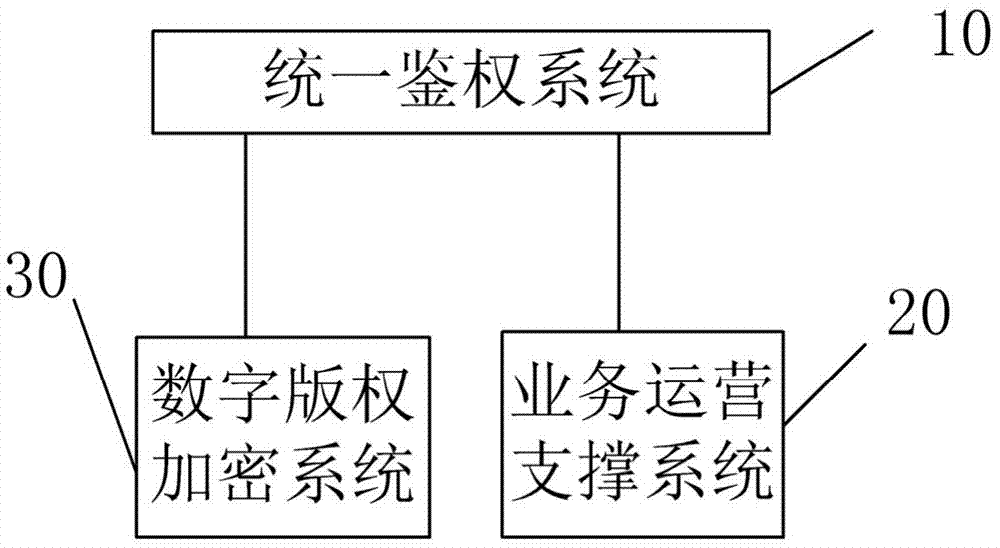
InactiveCN103763583AImprove efficiencyReduce utilizationSelective content distributionAuthentication systemSatellite
The invention provides a method and system for authenticating satellite digital on-demand services. The method includes the steps of calling a service running supporting system after a unified authentication system receives on-demand information, verifying the user identity, the product information and the user subscription relation through the service running supporting system, generating on-demand request success information under the condition that the user identity, the product information and the user subscription relation are all correct, and generating authentication information according to the on-demand information through a digital copyright encryption system. A user inputs the on-demand information, the on-demand information is received by the unified authentication system, verified by the service running supporting system and then authenticated by the digital copyright encryption system so that authentication information can be formed, a product receiving terminal with configuration codes receives the authentication information and on-demand products according to the authentication information, the user can timely watch the on-demand products, and therefore the problems that the user can not conveniently watch the on-demand products and the utilization rate of satellite digital services is low due to the fact that no product on-demand services exist in existing satellite digital services are solved.
Owner:CHINA DBSTAR
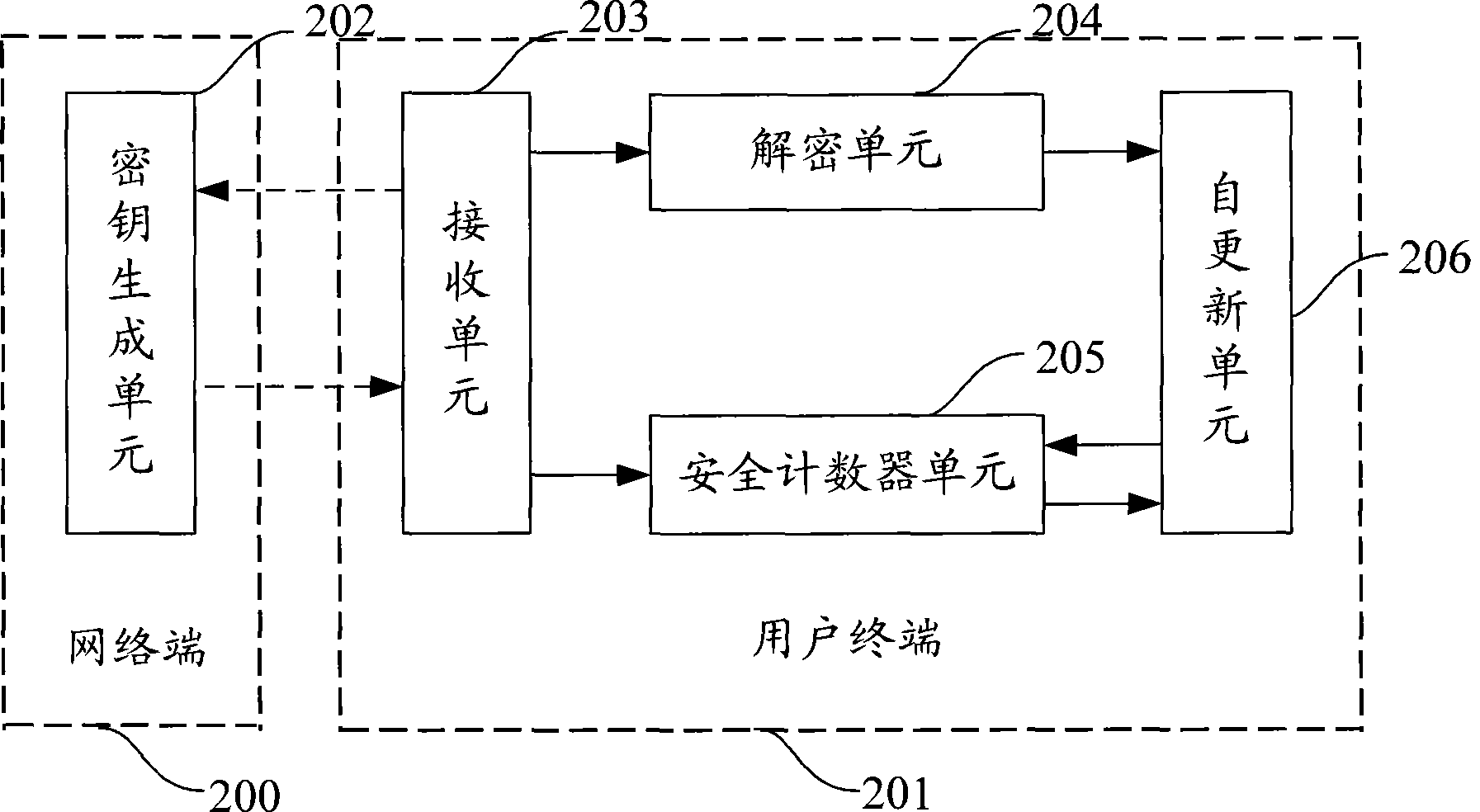
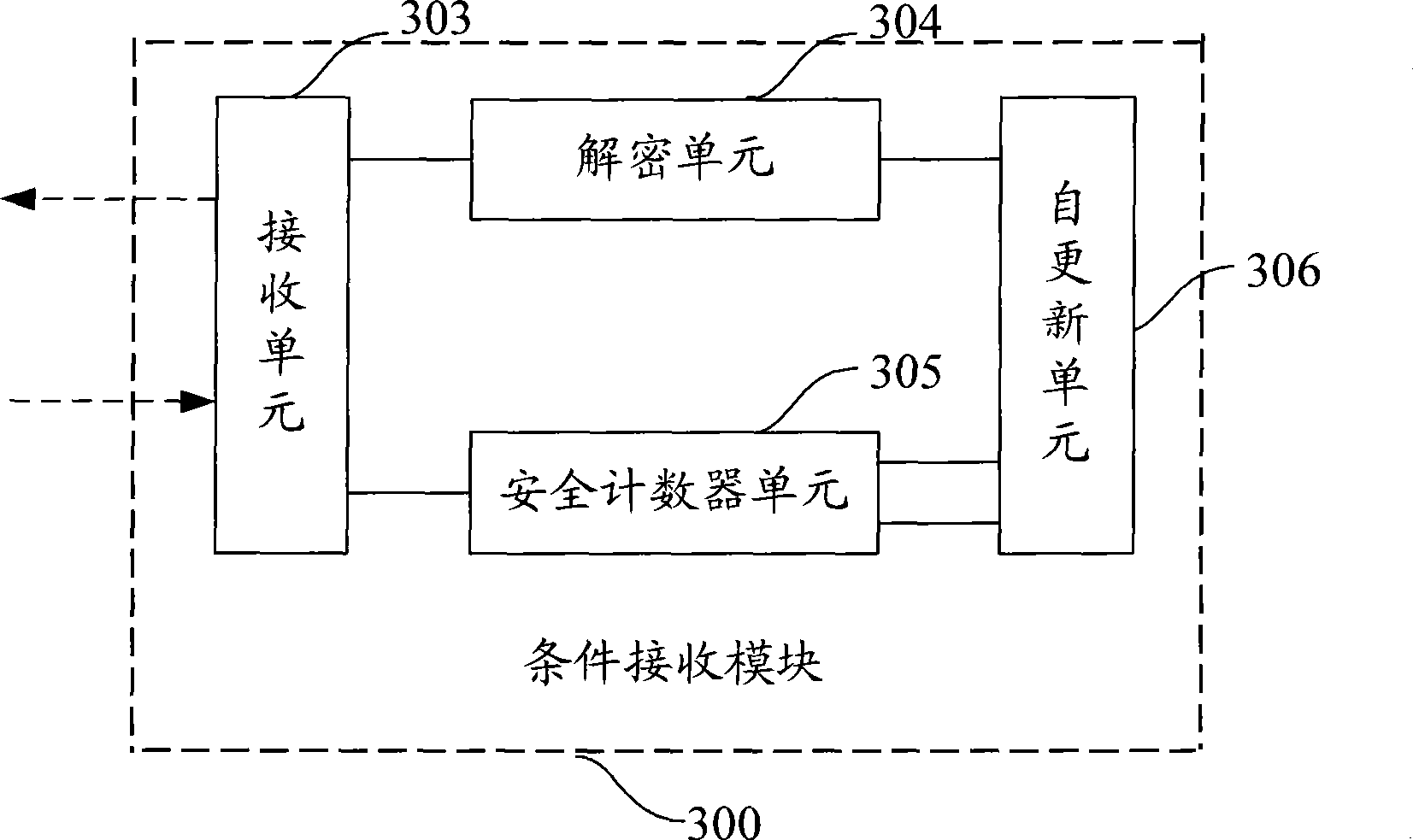
Method, system, conditional receiving module and customer terminal for obtaining service key
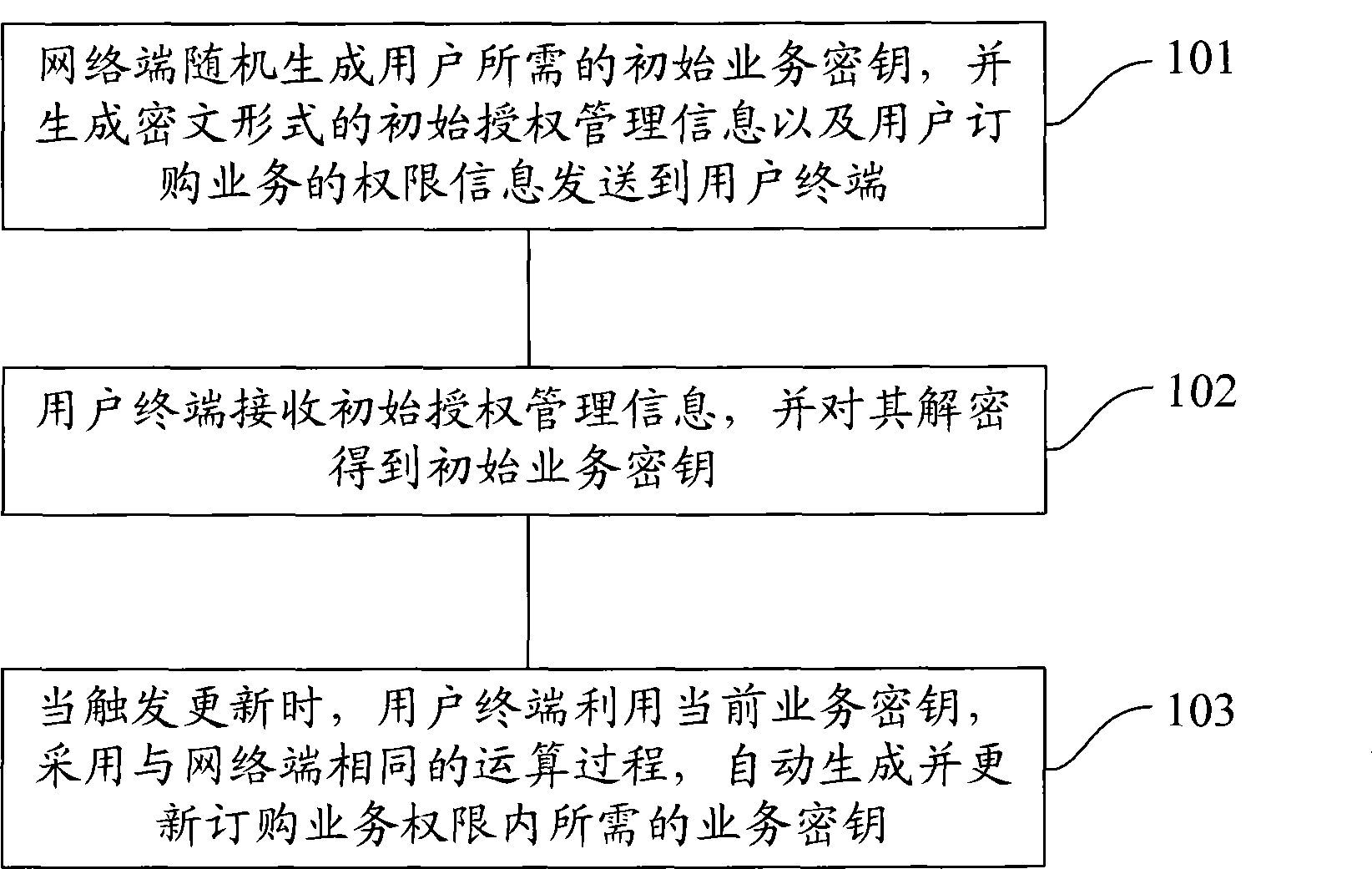
InactiveCN101399662AImprove authorization efficiencyImprove experienceKey distribution for secure communicationAnalogue secracy/subscription systemsCiphertextConditional access
The invention provides a method for acquiring a service key and a system thereof. The method comprises the following steps: a network terminal generates an initial service key required by a user randomly, and generates initial authorization management information with a cryptograph mode and authority information of user subscription service to be transmitted to a user terminal; the user terminal receives the initial authorization management information, and decrypts the information to obtain an initial service key; when updating is triggered, the user terminal automatically generates and updates the service key required in the authority of subscription service by current service key by adopting the operation process being same as the network terminal. The invention also provides a condition receiving module and a user terminal. The invention can improve the authorization efficiency of the user terminal and save resource of the network terminal by a simple and easy service authorization method, thereby saving transmission bandwidth.
Owner:新奇点智能科技集团有限公司
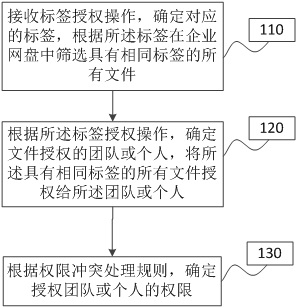
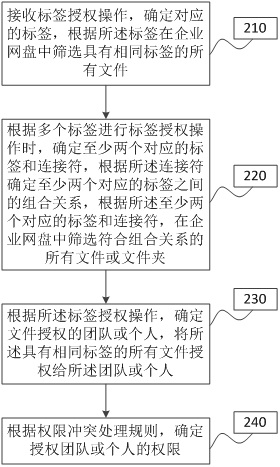
File authorization method and system under enterprise network disk, network disk and storage medium
ActiveCN114003963ARealize quick authorizationImprove authorization efficiencyDigital data protectionBusiness enterpriseEngineering
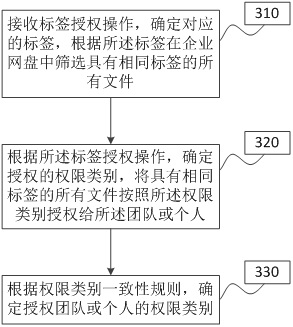
The invention provides a file authorization method and system under an enterprise network disk, the network disk and a storage medium, and the method comprises the steps: receiving a label authorization operation, determining a corresponding label, and screening all files with the same label in the enterprise network disk according to the label; according to the label authorization operation, determining a team or an individual authorized by the file, and authorizing all the files with the same label to the team or the individual; and determining the authority of the authorized team or individual according to the authority conflict processing rule. According to the file authorization method and system under the enterprise network disk, the network disk and the storage medium, the files can be screened and authorized according to the labels of the files, so that quick authorization of the files under the enterprise network disk is realized, and the authorization efficiency of the files is improved.
Owner:天津联想协同科技有限公司
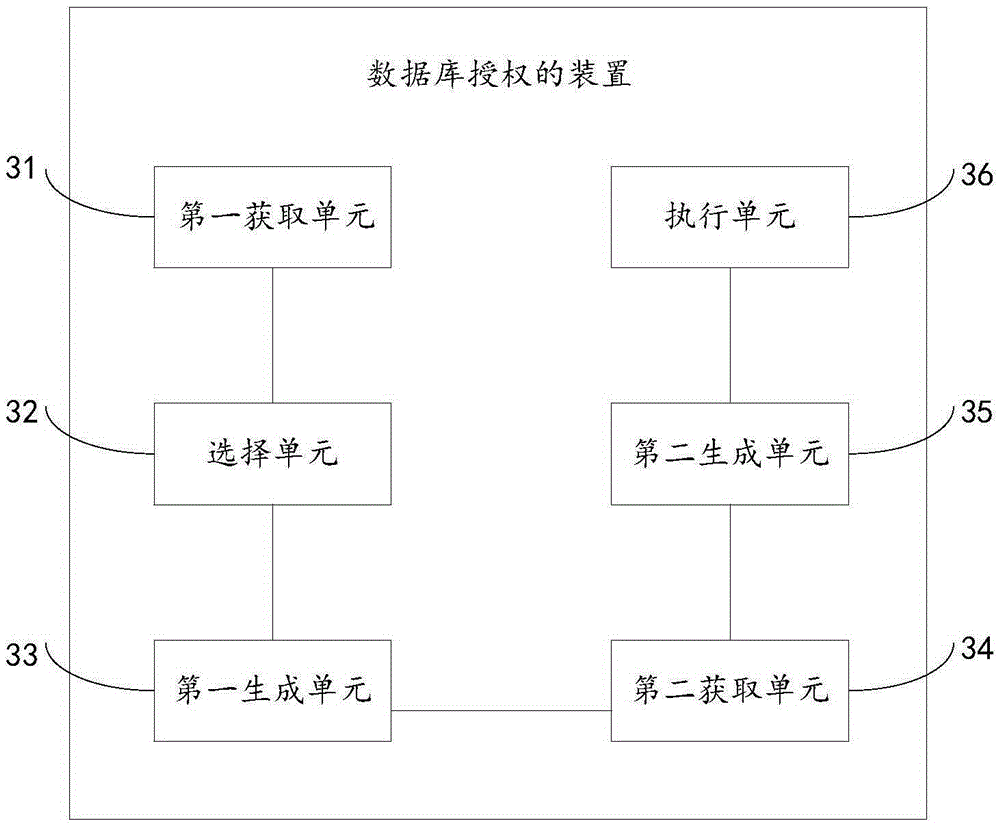
Automatic authorization access method for database
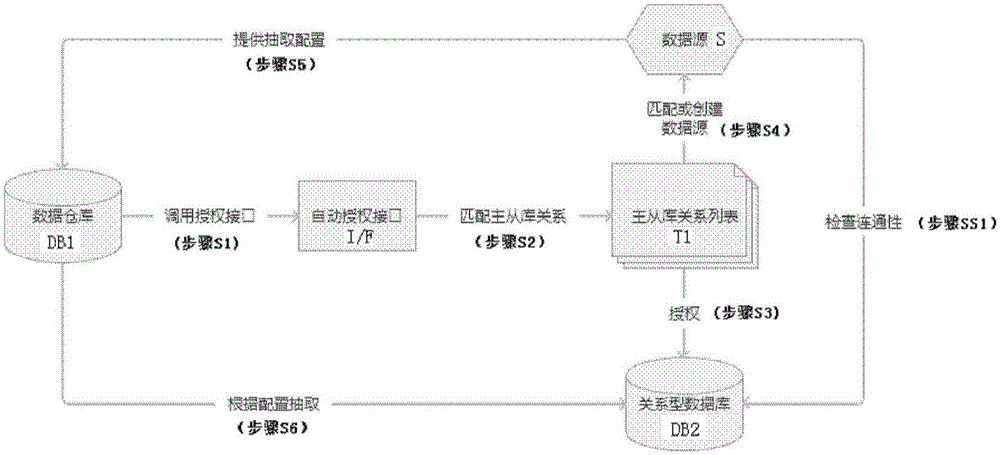
ActiveCN105069370AImprove authorization efficiencyRelieve stressDigital data protectionAccess methodData source
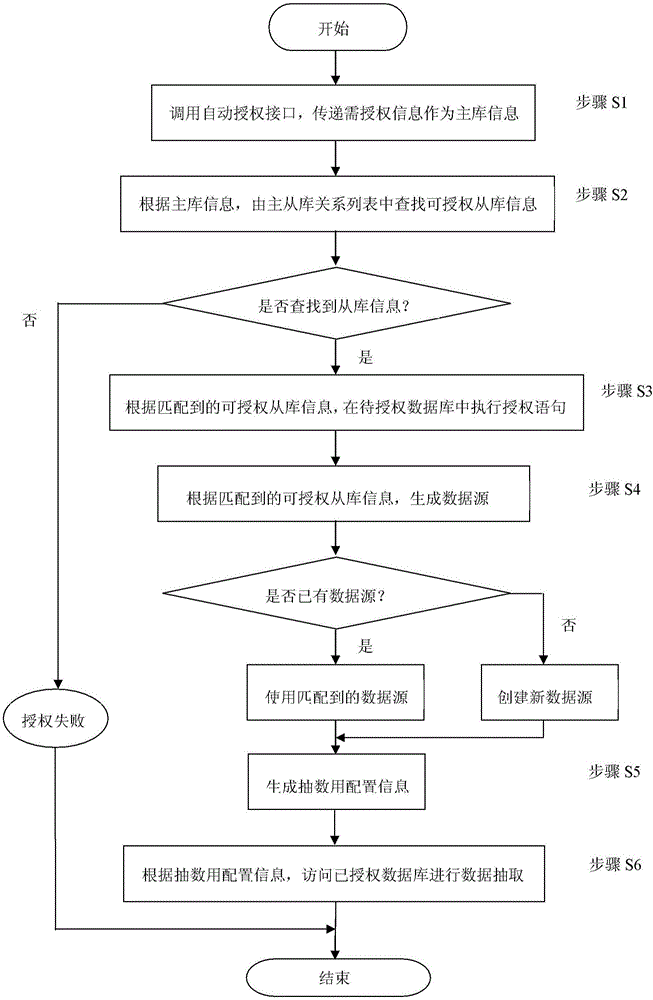
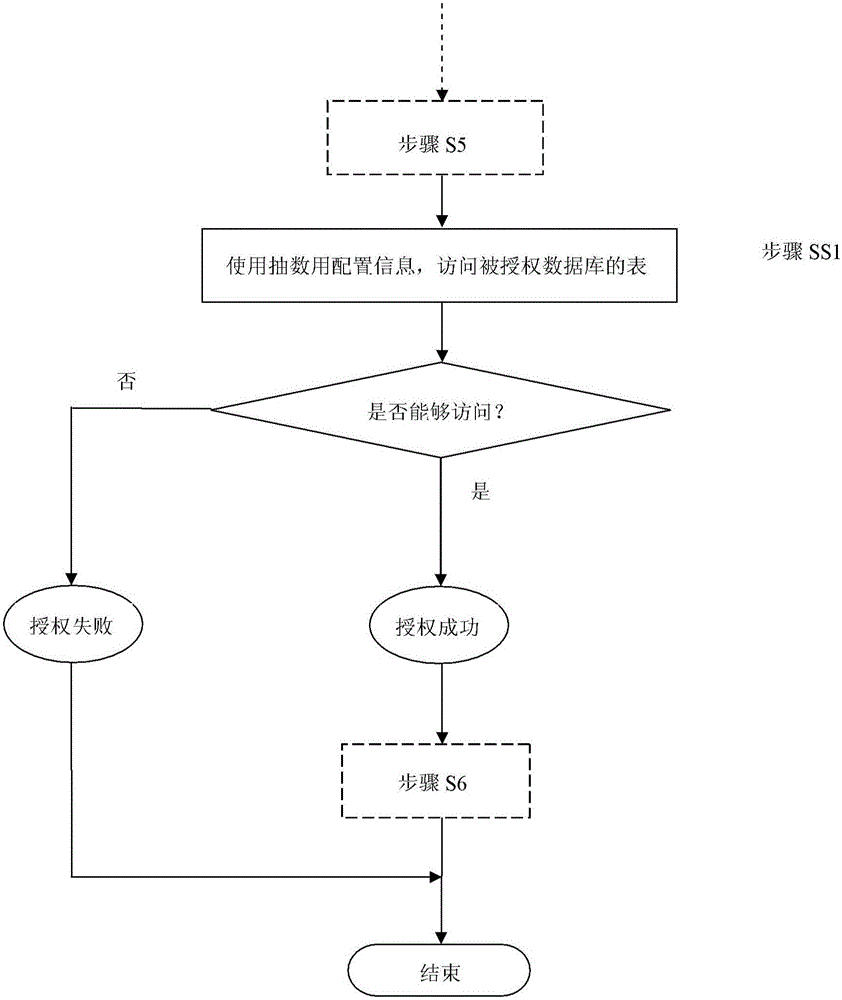
The invention discloses an automatic authorization access method for a database. The automatic authorization access method is a method for automatically authorizing and accessing to the accessed database by an object required to be subjected to authorization access. The method comprises: step (S1), transmitting information of the accessed database as main library information; step (S2), according to the main library information, matching authorizable slave database information of a slave database corresponding to the accessed database in a preset main and slave database relation list; step (S3), according to the authorizable slave database information, executing an authorization statement in the accessed database to enable the slave database to be provided with an access right; step (S4), according to the authorizable slave database information, generating a data source accessed by the object required to be subjected to authorization access; step (S5), according to the data source, generating access configuration information accessed by the object required to be subjected to authorization access; and step (S6), according to the access configuration information, accessing to the accessed database by the object required to be subjected to authorization access.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Intelligent terminal authorization method and device
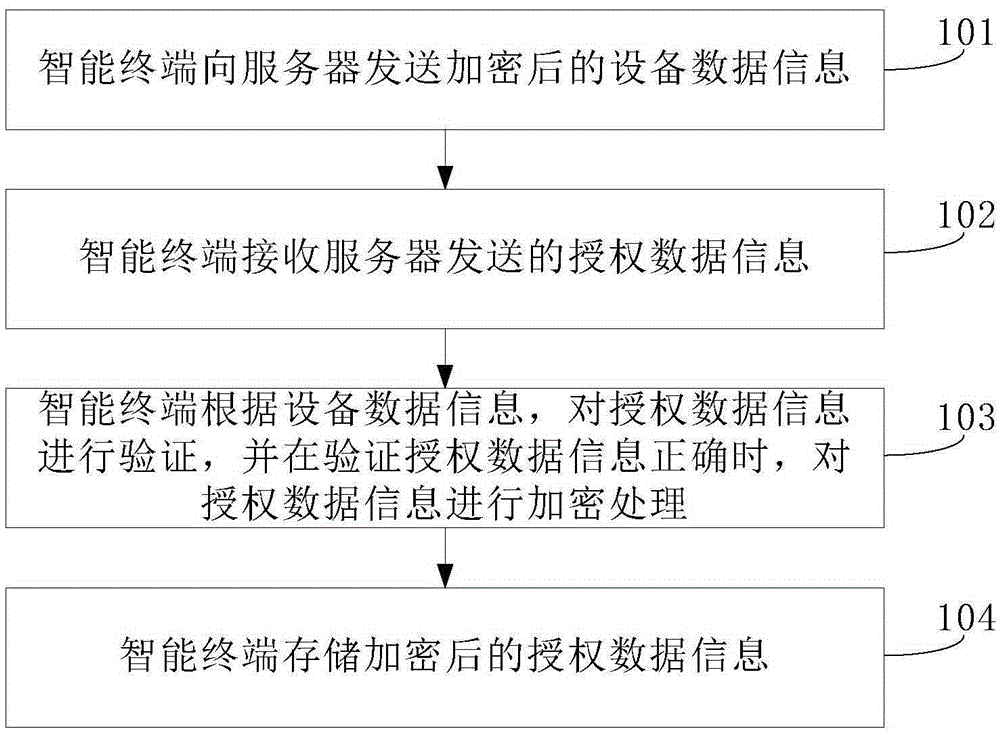
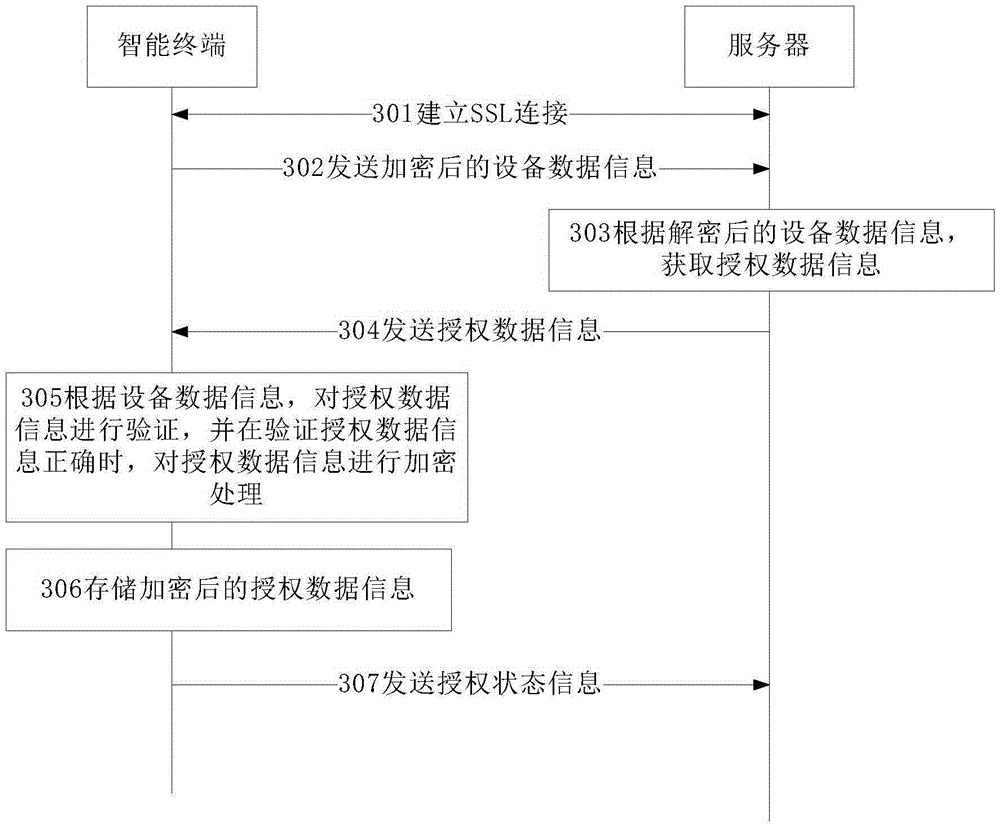
InactiveCN105391693AImprove authorization efficiencyReduce the chance of errorTransmissionComputer hardwareData information
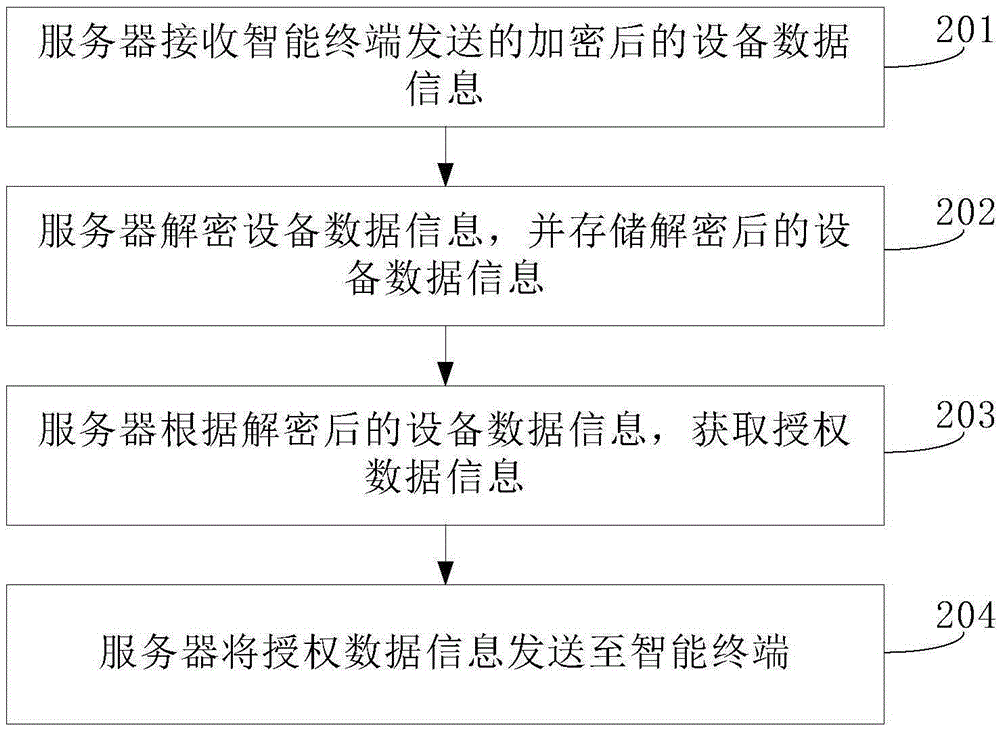
The embodiment of the invention provides an intelligent terminal authorization method and an intelligent terminal authorization device, which relate to the field of Internet of Things, and used for achieving the purposes of reducing manual participation and increasing intelligent terminal authorization efficiency. The intelligent terminal authorization method comprises the steps that: an intelligent terminal sends encrypted equipment data information to a server; the intelligent terminal receives authorization data information sent by the server; the intelligent terminal verifies the authorization data information according to the equipment data information, and encrypts the authorization data information when the authorization data information is verified to be correct; and the intelligent terminal stores the encrypted authorization data information. The intelligent terminal authorization method and the intelligent terminal authorization device are applicable to the automatic authorization scene.
Owner:INSPUR QILU SOFTWARE IND
A method and equipment for generating an income report
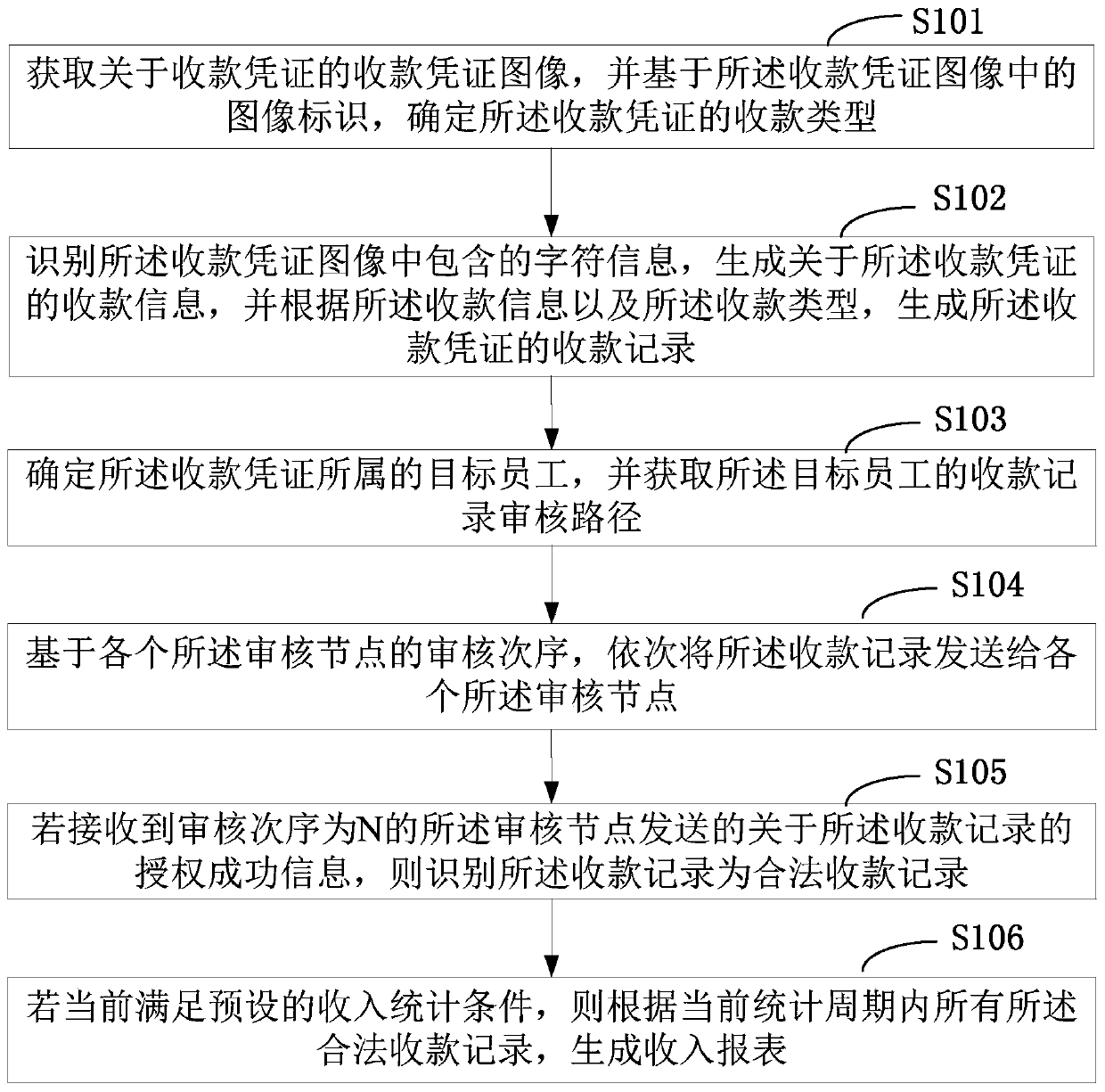
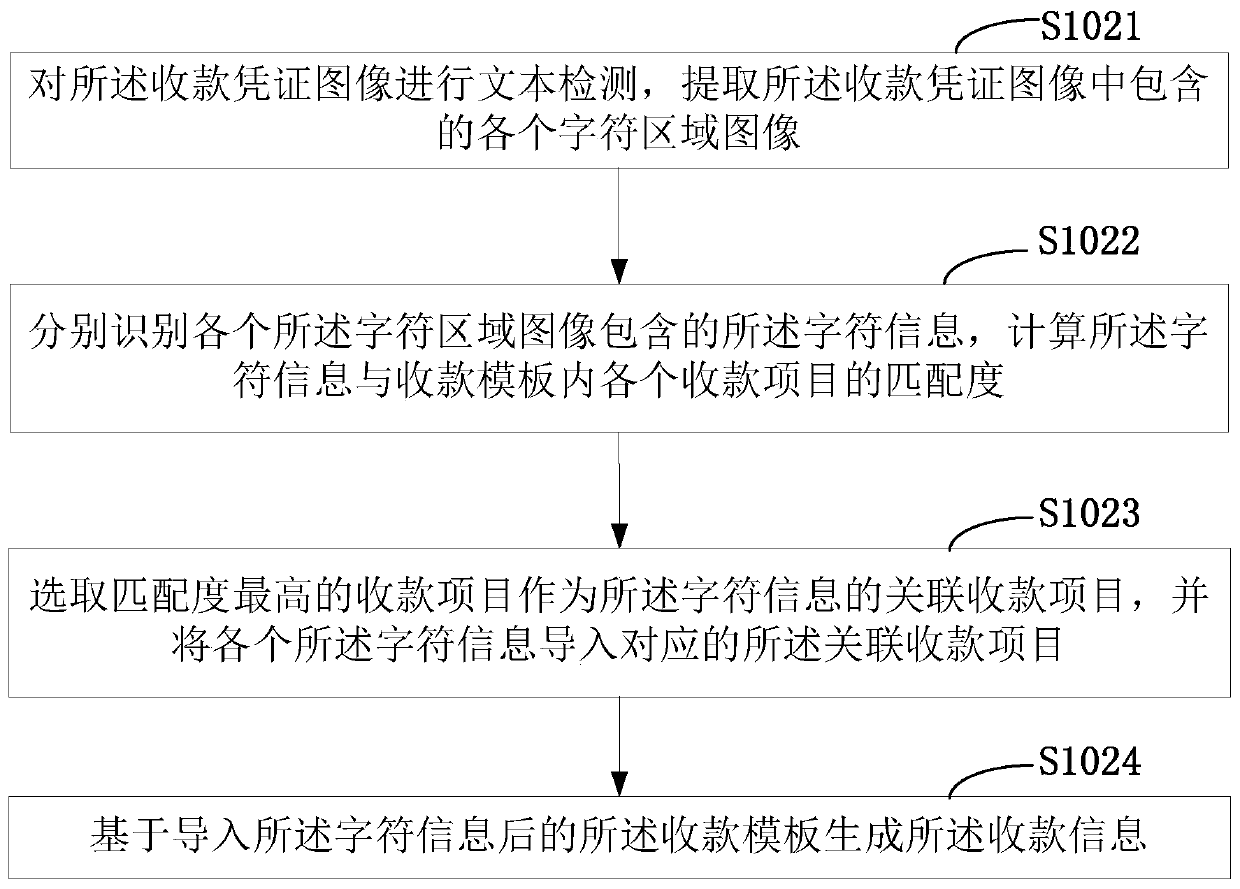
PendingCN109784833AImprove production efficiencyImprove accuracyFinanceCharacter and pattern recognitionVoucherAuthorization
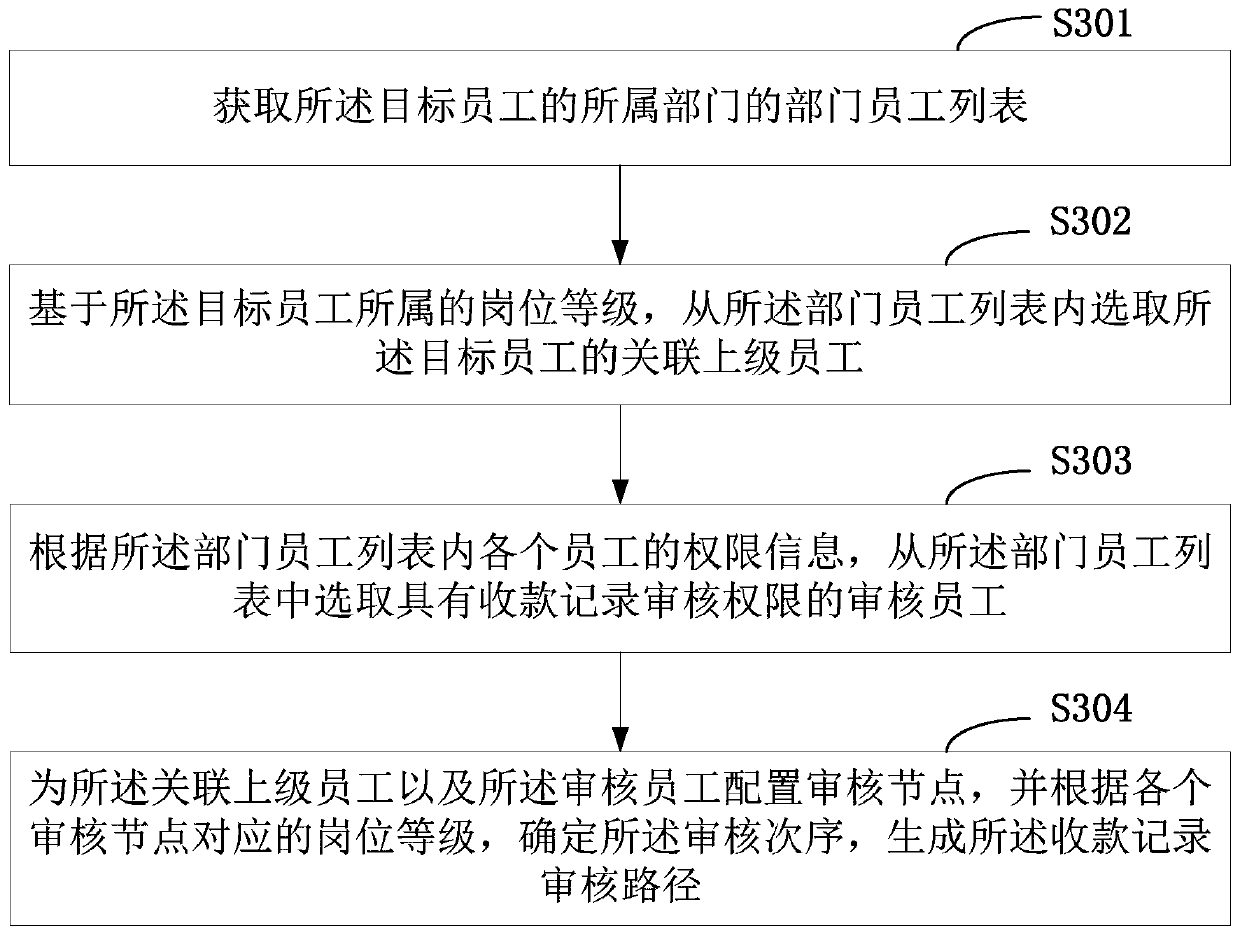
The invention is applicable to the technical field of data processing, and provides an income report generation method and device, and the method comprises the steps: obtaining a collection voucher image about a collection voucher, and determining the collection type of the collection voucher; Identifying character information contained in the collection voucher image, generating collection information about the collection voucher, and generating a collection record of the collection voucher according to the collection information and the collection type; Acquiring a collection record auditingpath; Based on the audit order of each audit node, sequentially sending the collection record to each audit node; If authorization success information of which the auditing order is N is received, identifying the collection record as a legal collection record; And if the income statistics condition is met, generating an income report according to all legal collection records in the current statistics period. According to the invention, the collection voucher image can be converted into the collection information, and finally the income amount is counted, and the income report is generated, sothat the generation efficiency and accuracy of the income report are improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
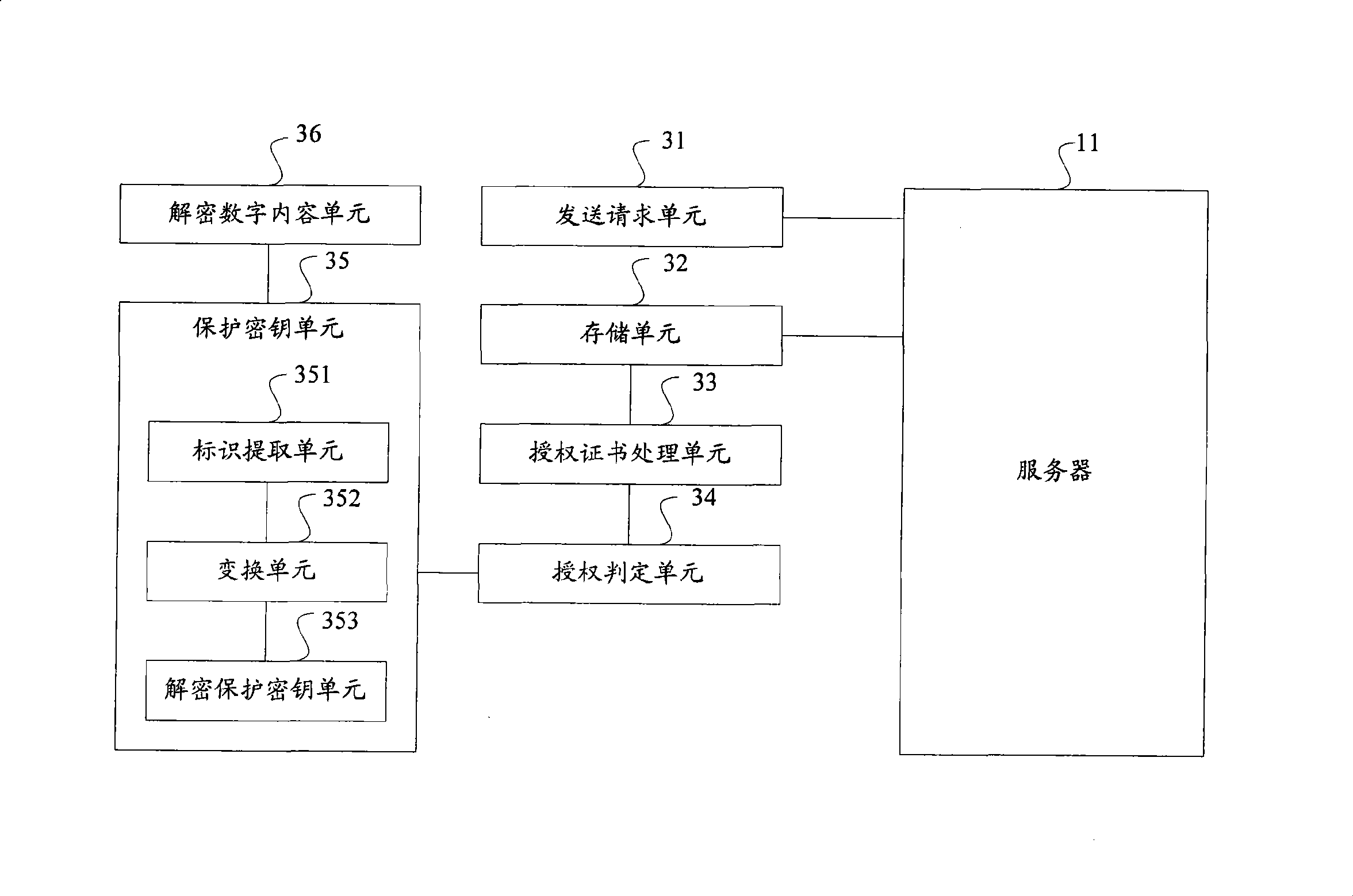
Method, system and device for digital content authentication
InactiveCN101399663AImprove authorization efficiencyKey distribution for secure communicationProgram/content distribution protectionDigital contentNumber content
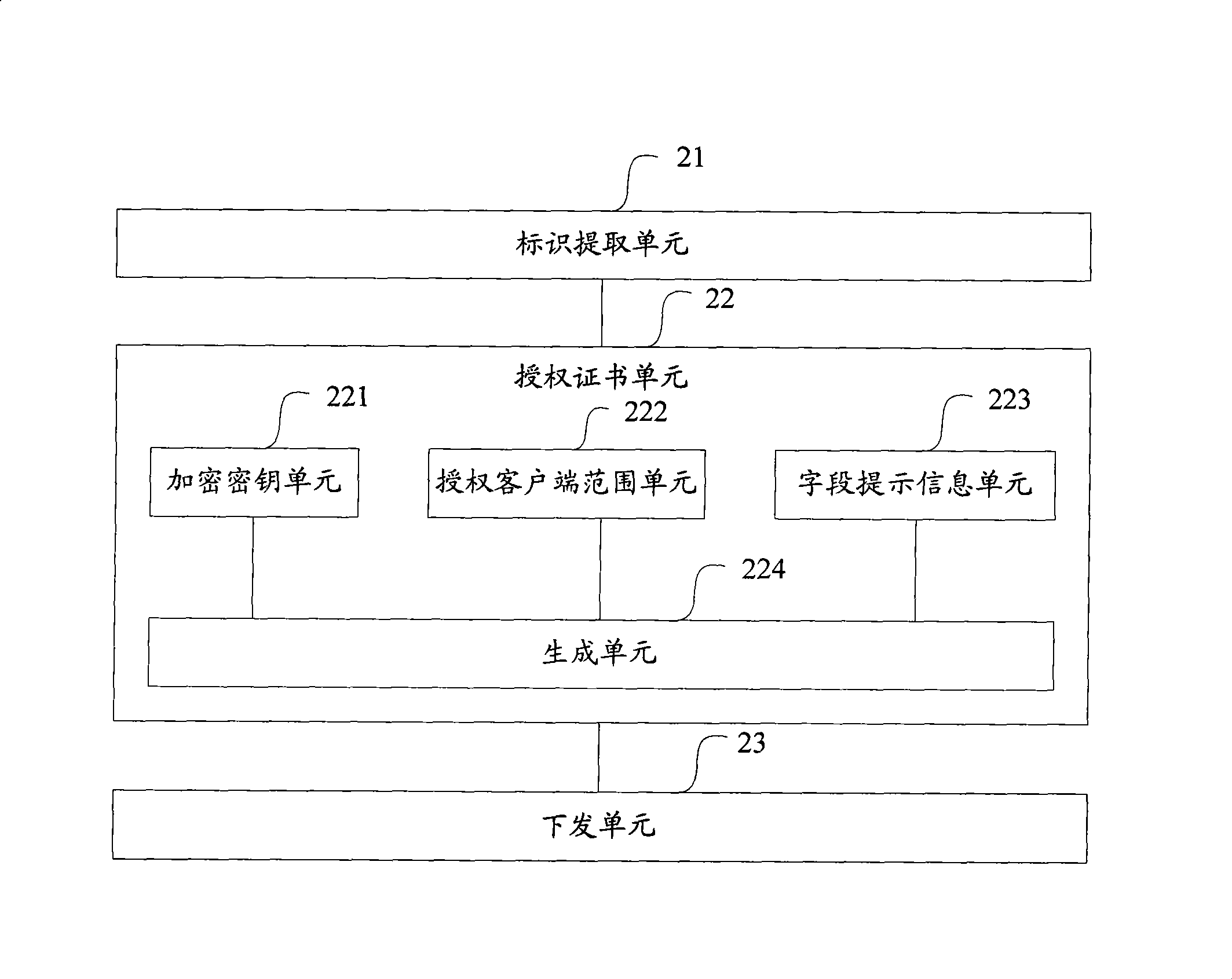
The invention discloses a method for authorizing digital content, a system and a device thereof, which is used for improving the authorizing efficiency of the digital content. The method for authorizing the digital content comprises the following steps: a server acquires the same part and different parts of a plurality of client identifications by analyzing on a plurality of client identifications; the server generates an encryption key by the same part, and encrypts a protective key for decrypting the digital content by the encryption key; moreover, the server generates an authorized client range of the digital content by the different parts; the server generates a certificate of authorization to the client by the protective key encrypted by the encryption key and the certificate of authorization generated by the authorized client range according to the request of the client to the digital content. The invention also provides a method for acquiring the digital content and a device thereof. The invention can be used for uniformly awarding the right that a plurality of clients can access the same digital content, thereby improving the authorizing efficiency of the digital content.
Owner:PEKING UNIV +2
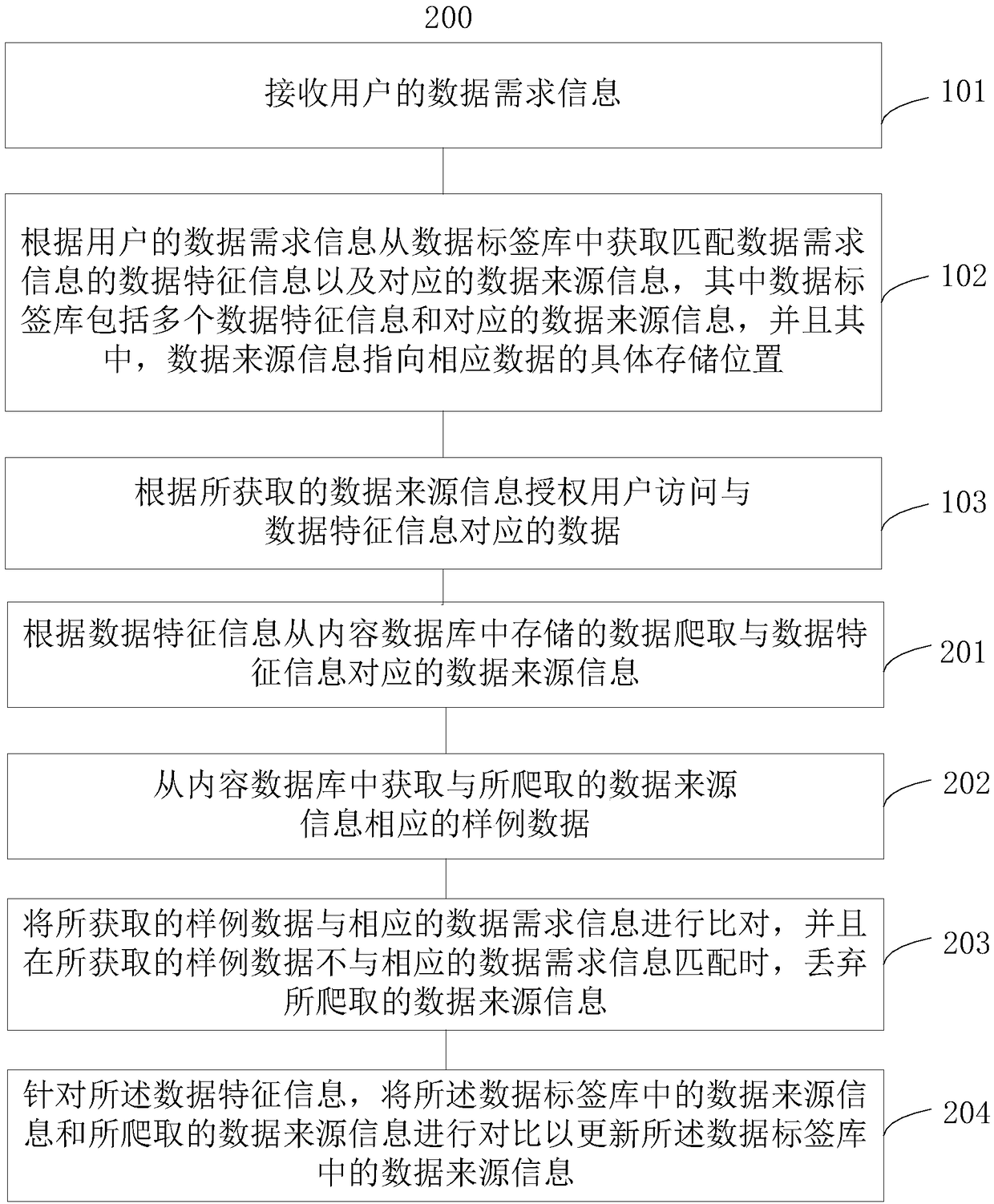
Method and system for executing data access authorization on user
InactiveCN108268769AImprove authorization efficiencyEnsure Authorization AccuracyDigital data protectionDigital data authenticationData sourceData access
The invention discloses a method and a system for executing data access authorization on a user. The method for executing the data access authorization on the user comprises the steps of receiving data demand information of the user; according to the data demand information of the user, obtaining data feature information matched with the data demand information and corresponding data source information from a data tag library, wherein the data tag library comprises multiple pieces of data feature information and corresponding data source information, and the data source information points to specific storage positions of corresponding data; and according to the obtained data source information, authorizing the user to access the data corresponding to the data feature information.
Owner:CHINA MOBILE GROUP SICHUAN +1
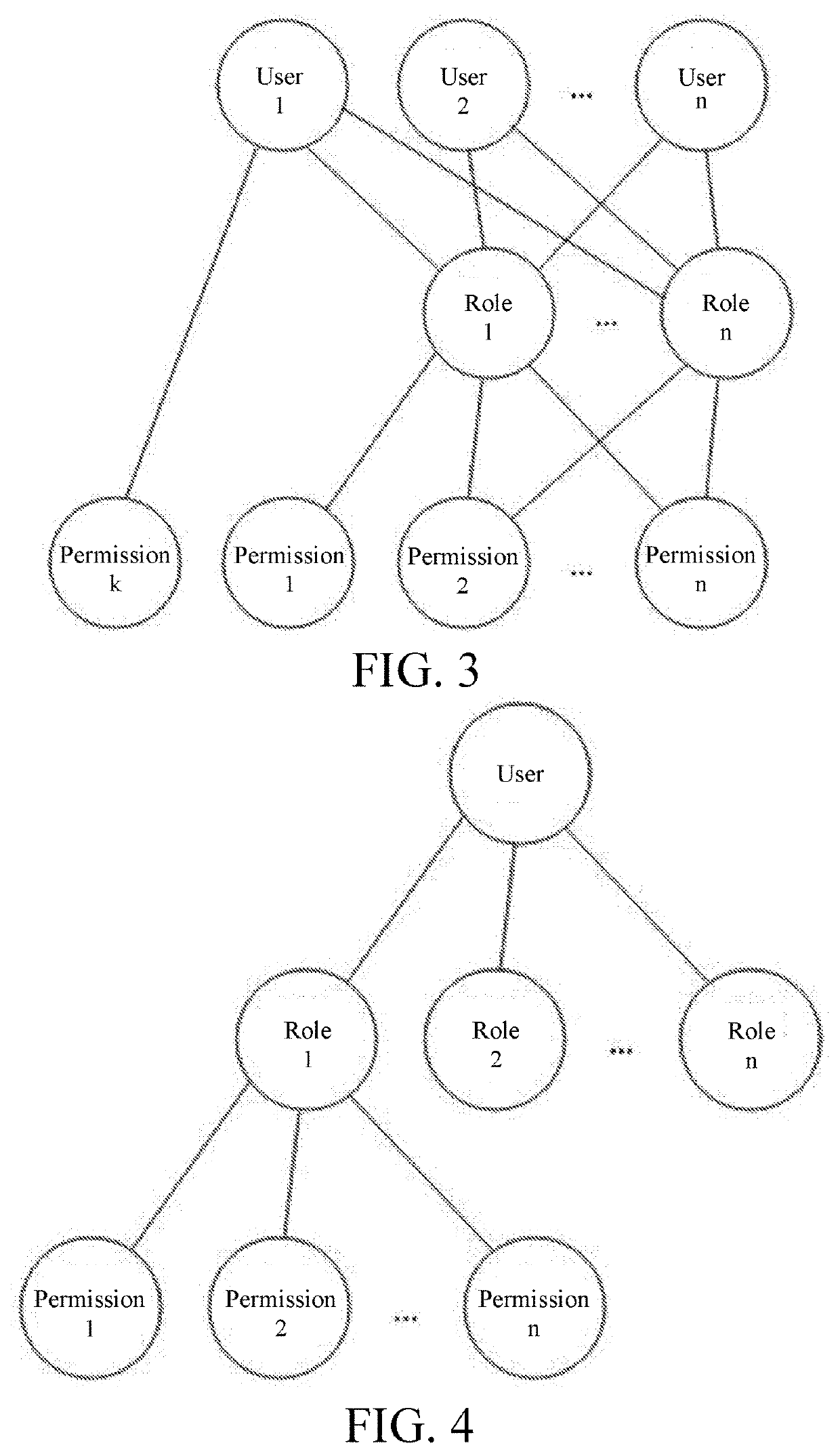
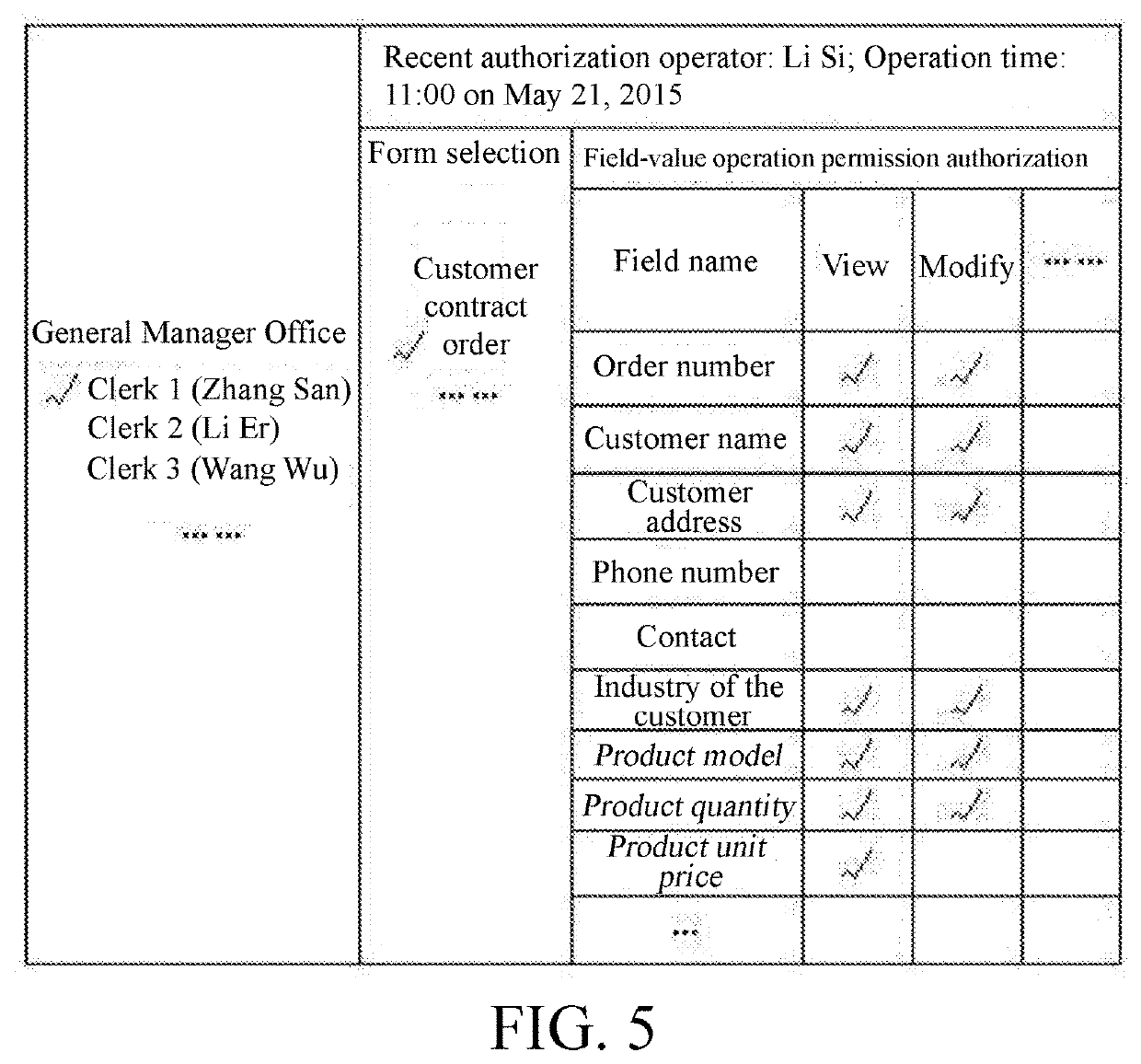
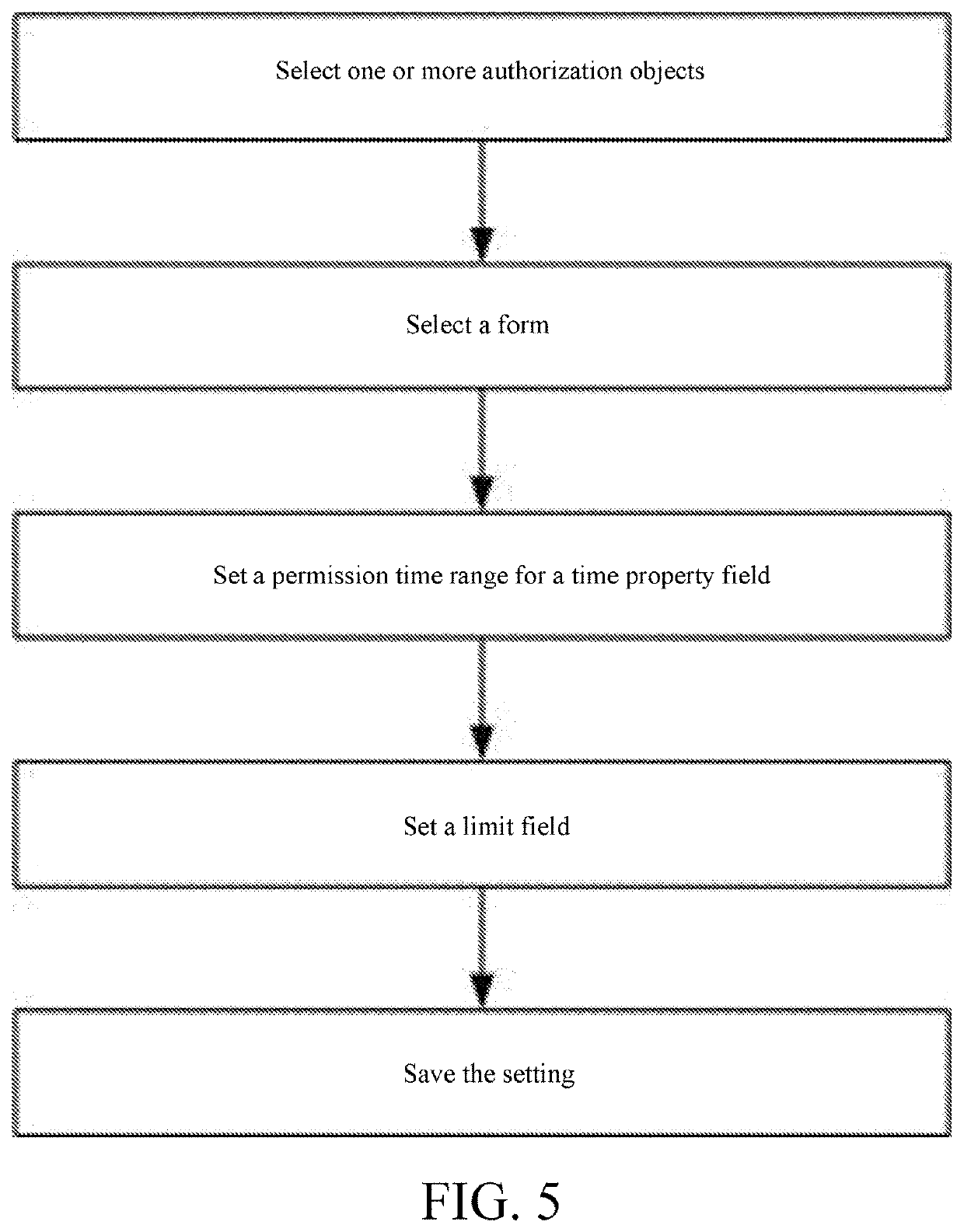
Method for authorizing operation permissions of form-field values
ActiveUS20200218796A1Improve finenessPermission setting rapidlyNatural language data processingDigital data authenticationSystems managementEngineering
A method for authorizing operation permissions of form-field values is disclosed in the present invention, including a step of authorizing operation permissions of form-field values and a step of selecting a grantee; the step of authorizing operation permissions of form-field values includes: S1: selecting a form to be authorized, and displaying fields in the form that need operation permission control; and S2: authorizing the operation permissions to each value of the fields respectively, where the grantee is one or more roles, the role is an independent individual rather than a group or class, one role can only be related to a unique user during the same period, and one user is related to one or more roles. The present invention can achieve respective authorization for the operation permissions of form-field values, and improves the fineness of system management. In this method, multiple authorized roles can be selected at the same time to batch authorization, thus improving the authorization efficiency. In addition, this method supports template authorization. Two methods are combined, so that the authorization efficiency of operation permissions of form-field values in a system is greatly improved.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
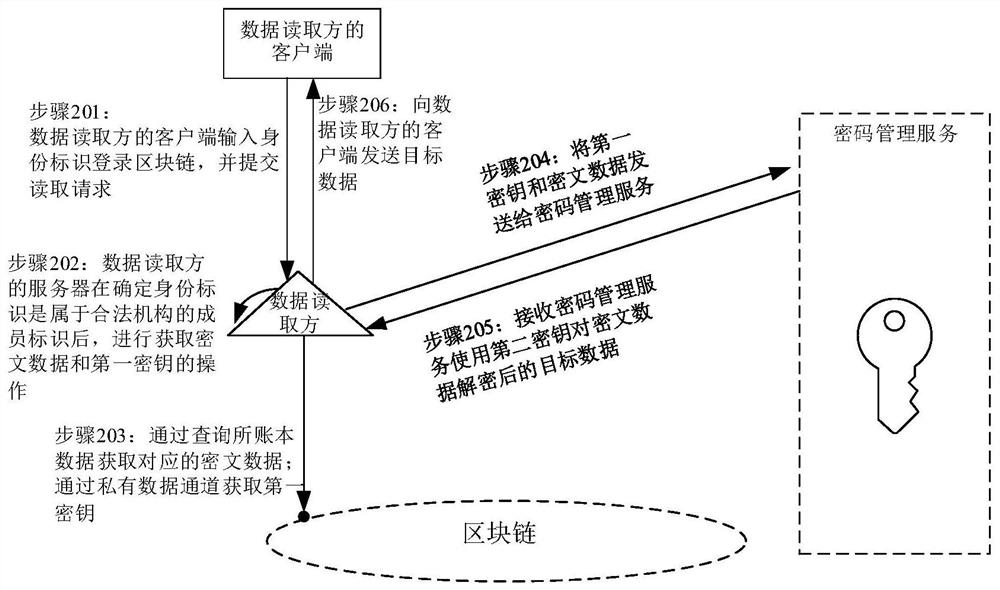
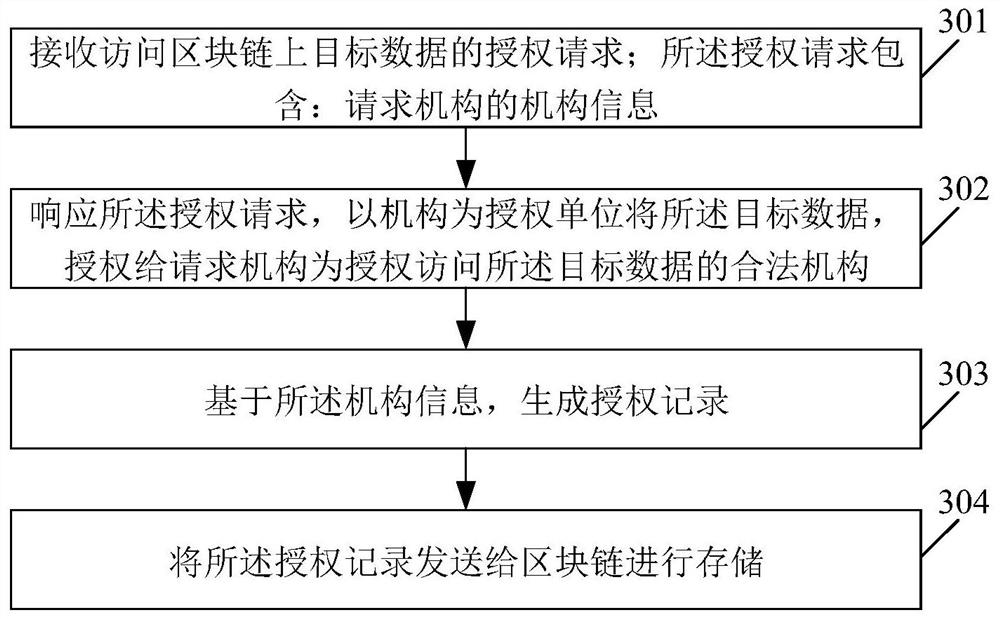
Data reading method and device, data authorization method and device and storage medium
PendingCN112182646ASimplify the authorization processImprove authorization efficiencyDigital data protectionDigital data authenticationInternet privacyCiphertext
The invention relates to a data reading method and device, a data authorization method and device and a storage medium. The data reading method comprises the steps of receiving an identity identifiersent by a client and a reading request for requesting to access target data on a block chain; determining whether the identity identifier belongs to a member identifier of a legal institution authorized to access the target data; and if the identity identifier is a member identifier belonging to a legal institution authorized to access the target data, obtaining decrypted target data according tociphertext data encrypted based on a second key and obtained from a blockchain and a first key obtained by encrypting the second key. Therefore, as long as the reading request of the member identifierof the legal mechanism with authorized access can be responded, the data reading is more convenient and reasonable.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
Agent-based business span-domain operation supporting system and method
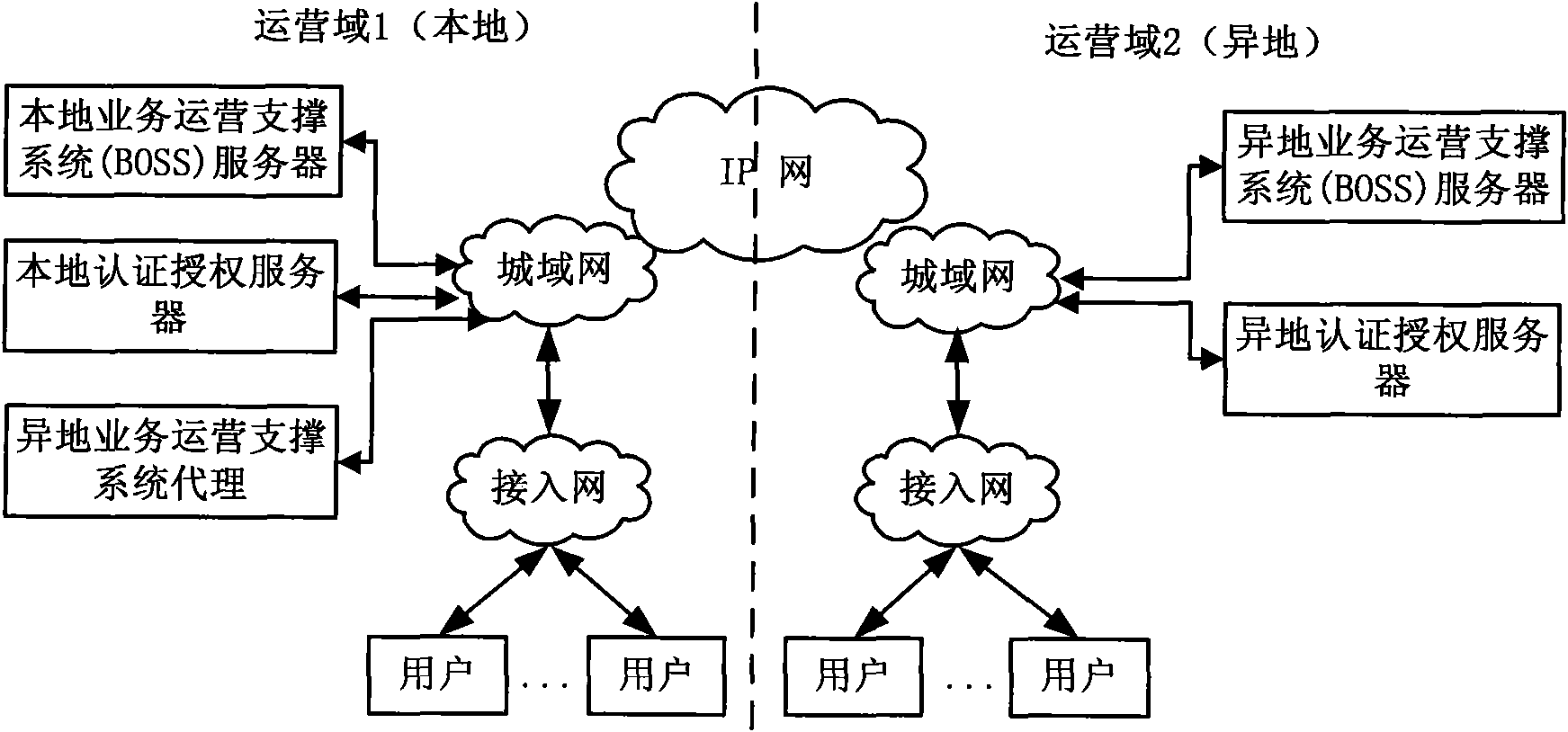
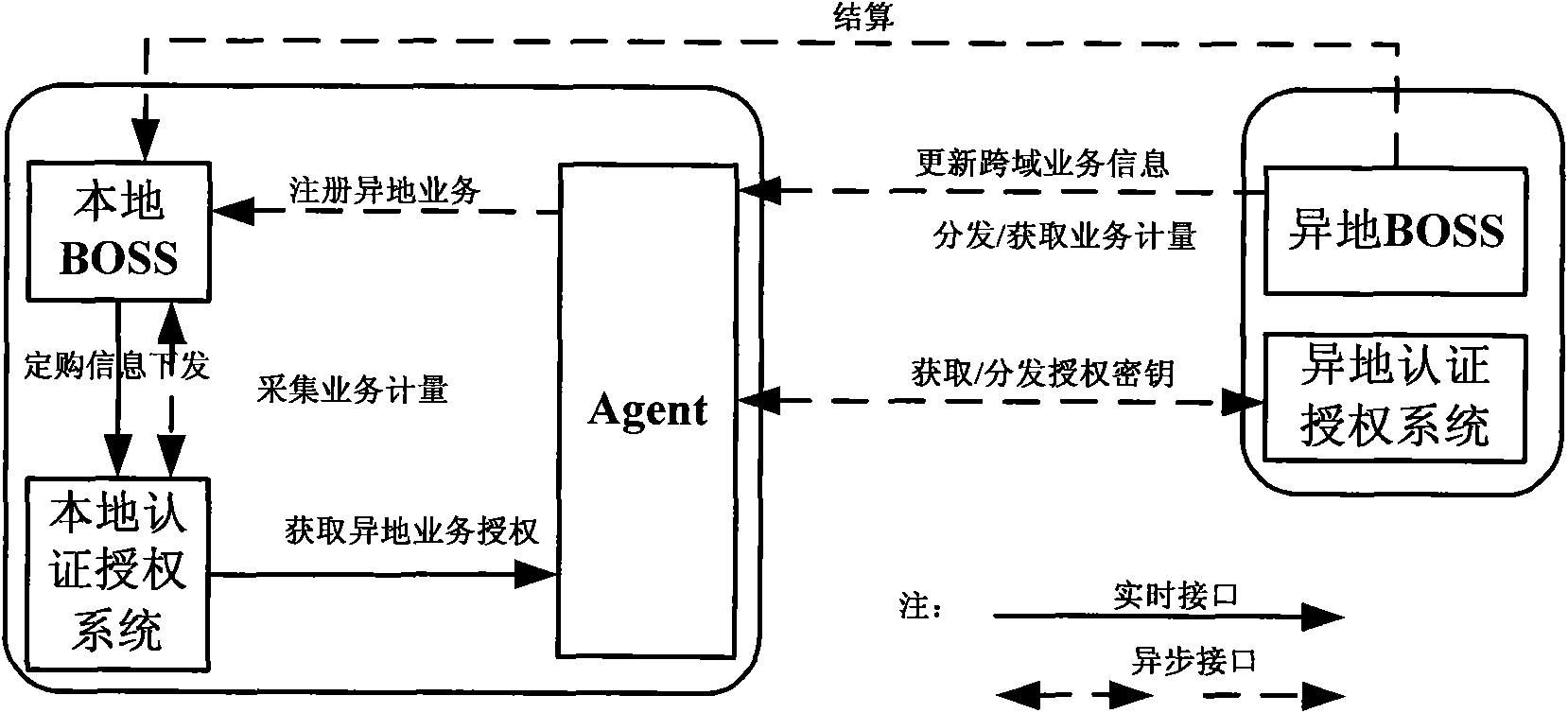
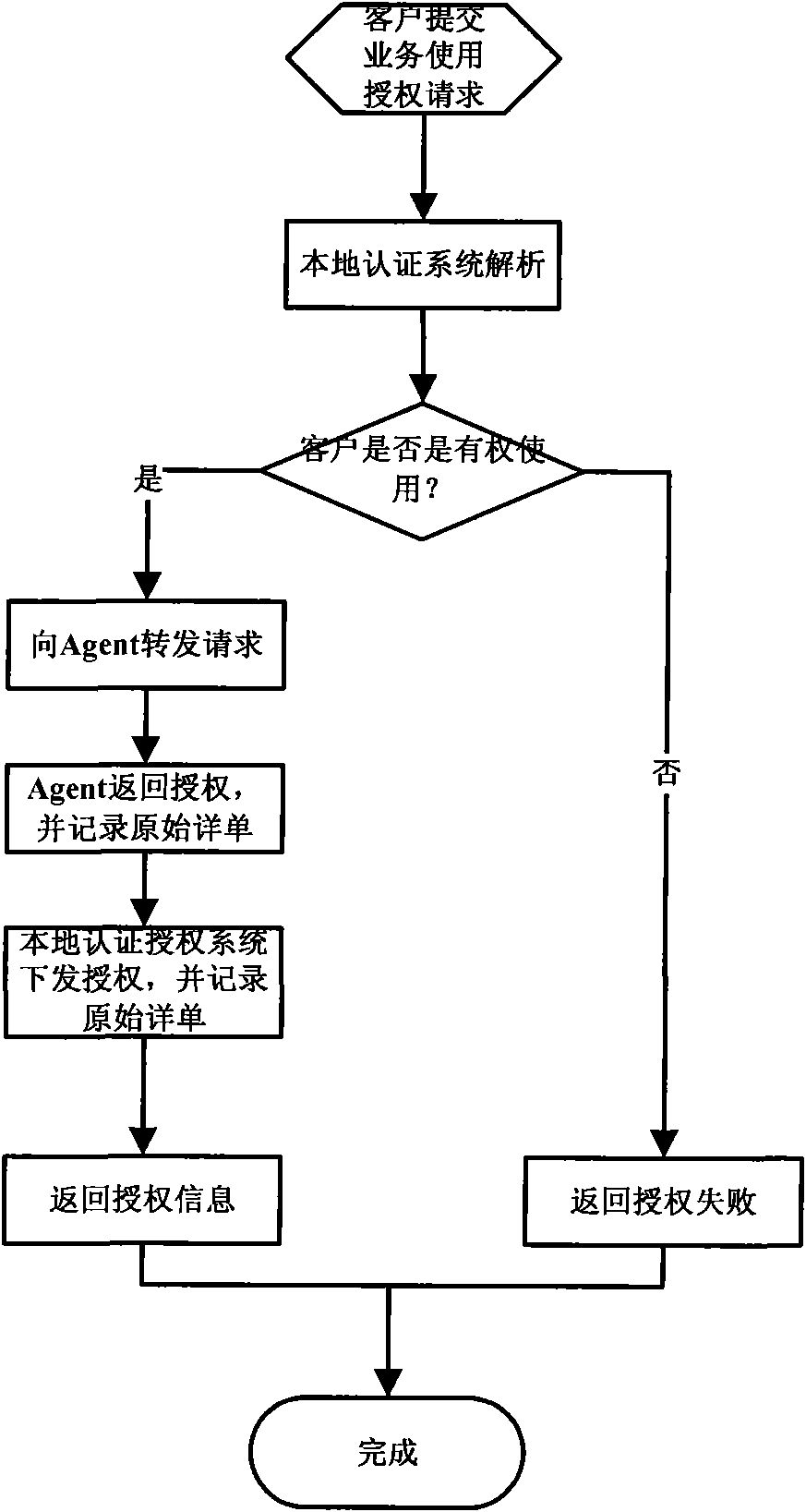
InactiveCN101645984AResolving heterogeneityMeet the needs of sharingSpecial service for subscribersSelection arrangementsSupporting systemClient data
The invention discloses an agent-based business span-domain operation supporting system and a method. A locally-running operation supporting system agent of an allochthonous operator is utilized to authorization and measurement of business. When a client uses the allochthonous business, a local authorization system requests the locally-running agent for authorization information and issues the authorization information to the client; and two operator bosses can accurately record the usage amount of the allochthonous business according to the issuing number of the authorization information. Themethod not only can separate concrete certificate authority methods of two parties, but also can ensure the usage amount consistency of the business, and meanwhile, synchronization of client data andorder information between the two bosses are avoided, thereby being beneficial to protecting the local client data. The amount of the allochthonous business is processed by the agent and sent to allochthonous bosses in fixed time, and remote communication adopts an asynchronous mode to reduce the transinformation amount of remote information and lessen the dependence on the reliability of a remote network.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
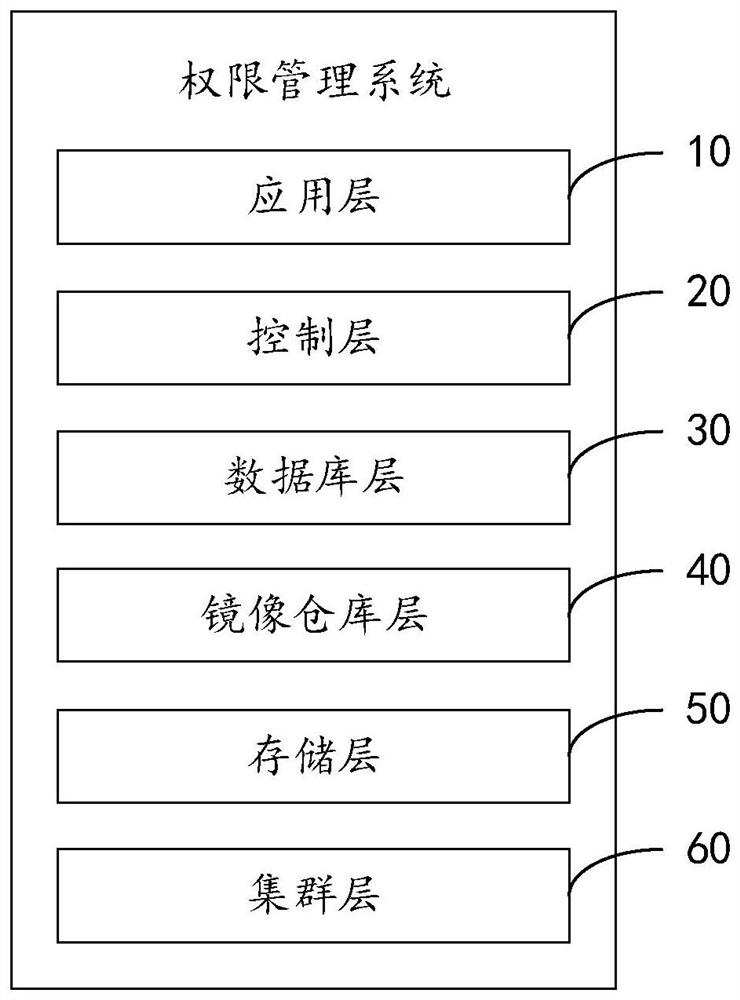
Authority management system
PendingCN113239373AEasy to operateImprove authorization efficiencyDatabase management systemsDigital data protectionUser PrivilegeControl layer
The invention provides an authority management system which comprises an application layer which comprises a unified authority management module used for unified user management, unified resource management and unified authentication management; a control layer for gathering and compiling front-end interface operation, and calling APIs of different modules according to instructions of the front-end interface operation; a database layer used for storing data; a mirror image warehouse layer used for localized storage of system service mirror images and user operation service mirror images; a storage layer which is an integrated management layer of system storage and is integrated with multiple storage types; and a cluster layer realizing arrangement and scheduling management of service applications. According to the invention, each business module is split into independent sub-services by adopting a micro-service architecture to independently provide interfaces to the outside, and the sub-services communicate with each other to complete data sharing and authority control among the cross-business modules; and a visual operation interface is adopted to configure and associate roles, users and permissions, so that the operation is convenient, and the authorization efficiency is improved.
Owner:CHINA NUCLEAR POWER OPERATION TECH +1
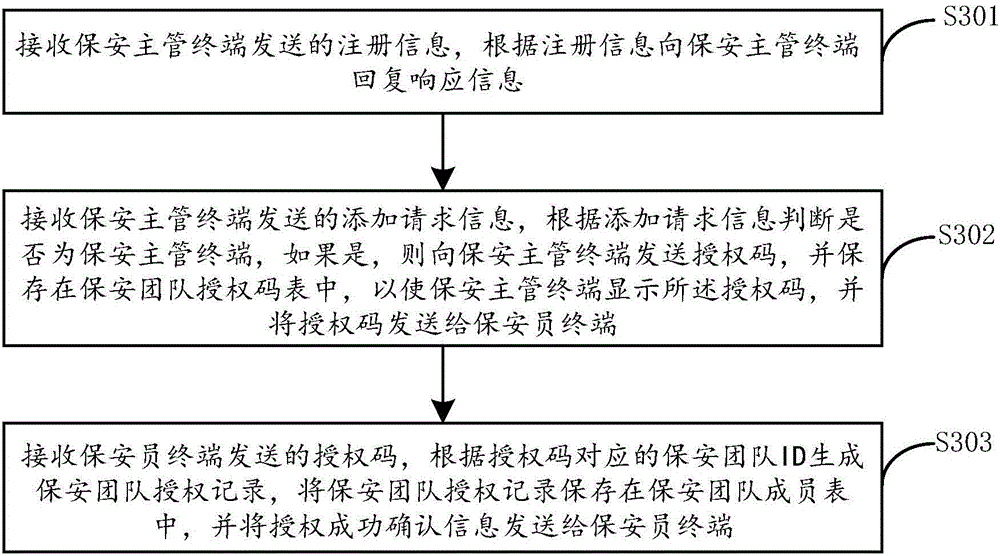
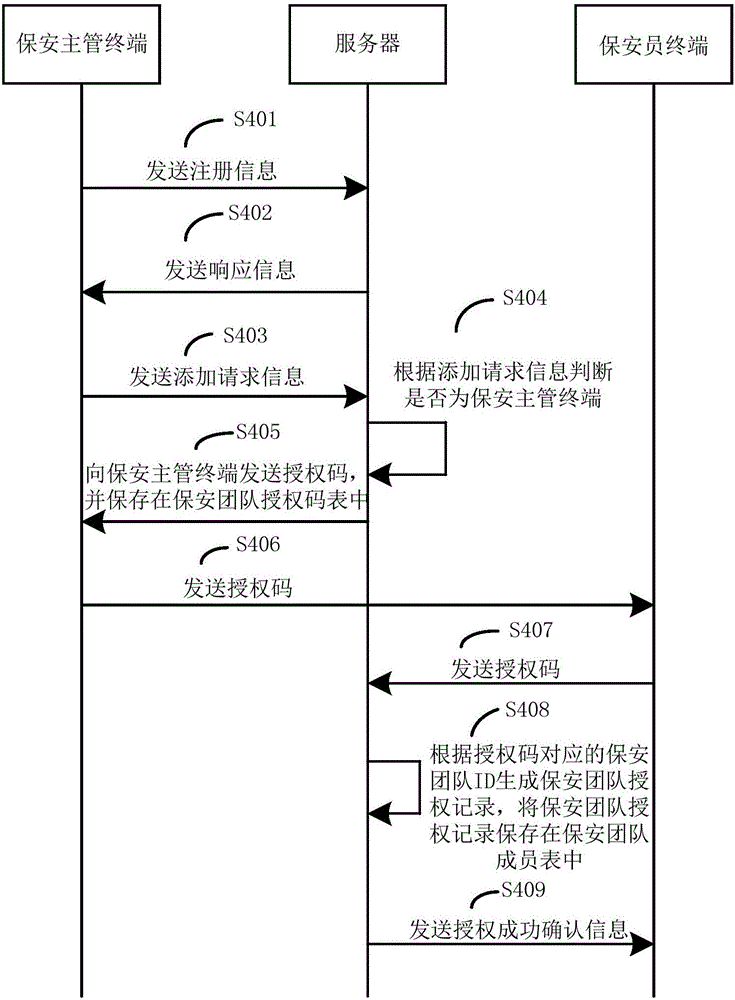
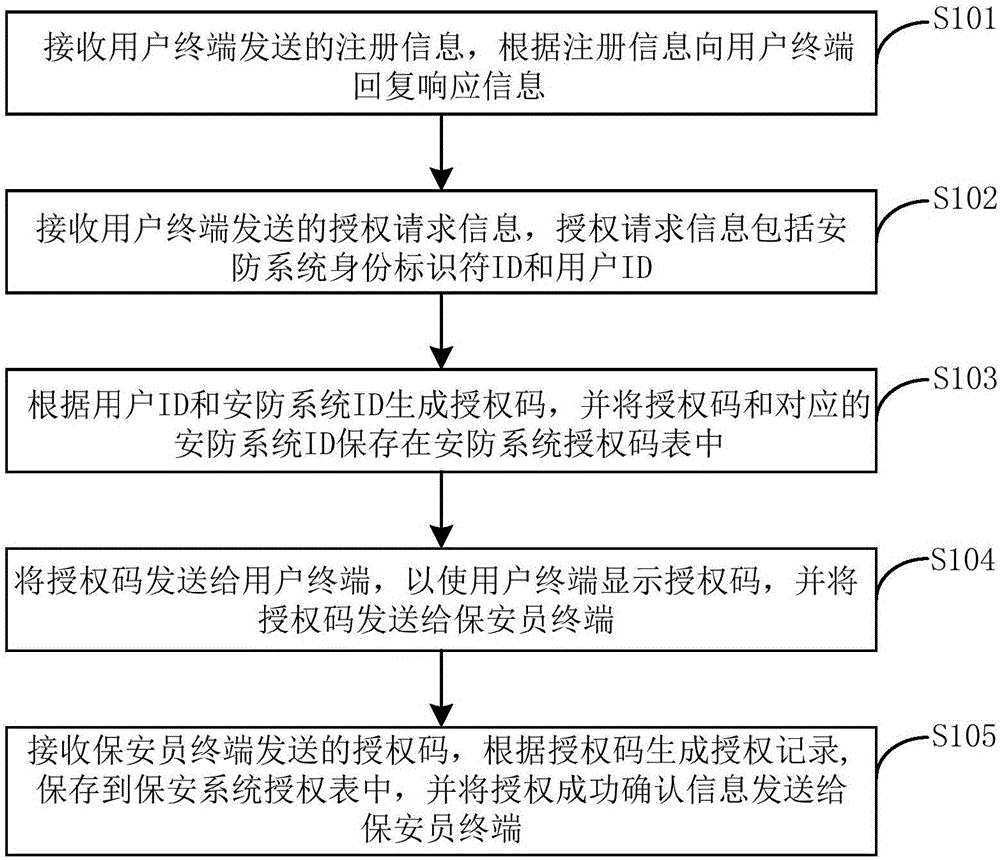
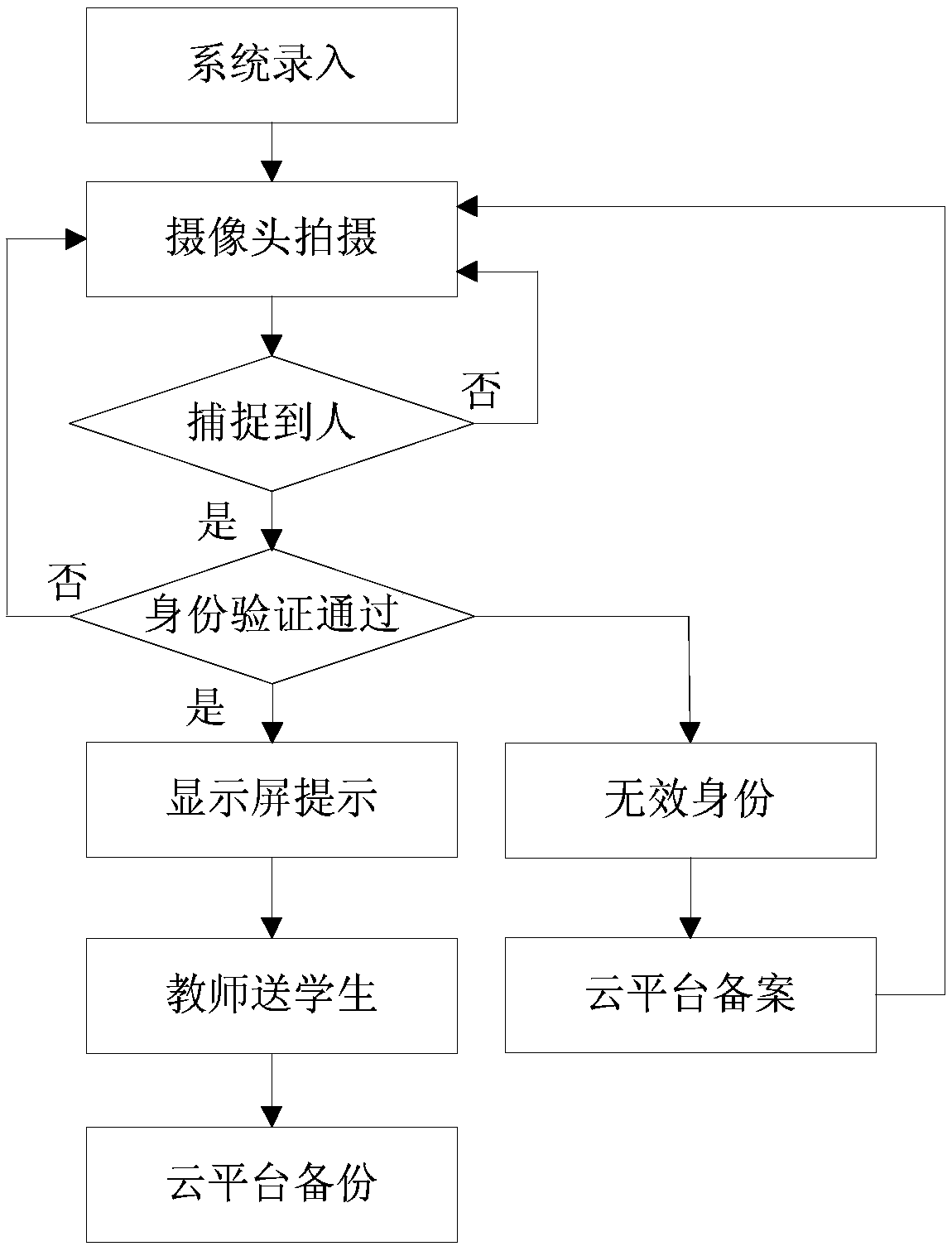
Method for authorizing security team of security and protection system and authorizing security team by user
InactiveCN106780191AMonitor for Unforeseen ConditionsImprove authorization efficiencyData processing applicationsComputer terminalUser identifier
The invention provides a method for authorizing a security team of a security and protection system and authorizing the security team by a user; the method includes steps of receiving a request adding information sent by a security charging terminal; according to the request adding information, judging if it is the security charging terminal; if yet, sending an authorization code to the security charging terminal so that the security charging terminal sends the authorization code to a security guard terminal; receiving the authorization code sent by the security guard terminal; according to the security team ID corresponding to the authorization code, generating a security team authorization record, and sending the confirmation information of successful authorization to the security guard terminal, and receiving the authorization request information sent by the user terminal; according to the user ID and the security system ID, generating the authorization code; sending the authorization code to the user terminal so that the user terminal sends the authorization code to the security guard terminal; receiving the authorization code sent by the security guard terminal; according to the authorization code, generating the authorization record, storing the record to the security system authorization table, and sending the confirmation information of successful authorization to the security guard terminal.
Owner:温州风暴智能科技有限公司
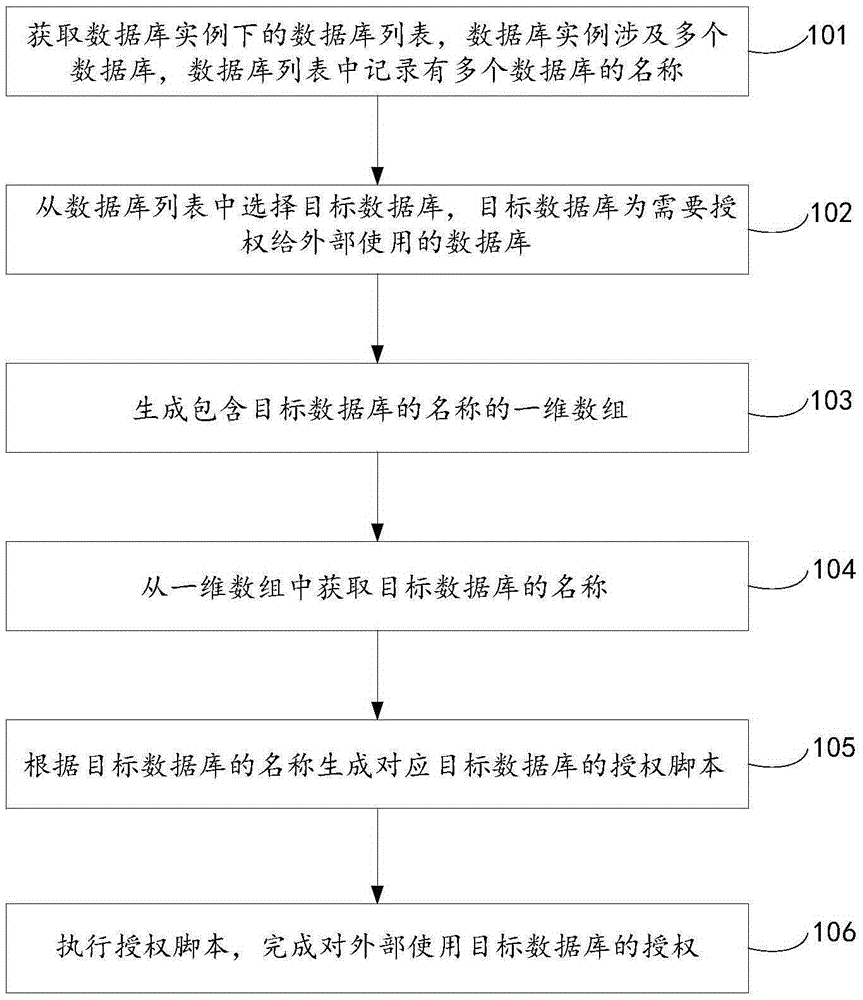
Database authorization method and device
ActiveCN106570035AImprove authorization efficiencyDigital data protectionSpecial data processing applicationsArray data structureThe Internet
The invention discloses a database authorization method and a database authorization device, relates to the technical field of the Internet, and is invented for solving the problem that in the prior art, manual database authorization is low in efficiency. The method provided by the invention comprises the steps of acquiring a database list under database instances, wherein the database instances relate to a plurality of databases, and names of a plurality of databases are recorded in the database list; selecting a target database from the database list, wherein the target database is the database needing to be authorized for external use; generating a one-dimensional array including the name of the target database; acquiring the name of the target database from the one-dimensional array; generating an authorization script corresponding to the target database according to the name of the target database; and executing the authorization script to complete the authorization for external use of the target database. The method and the device are applicable to a batch authorization process of database users.
Owner:BEIJING GRIDSUM TECH CO LTD
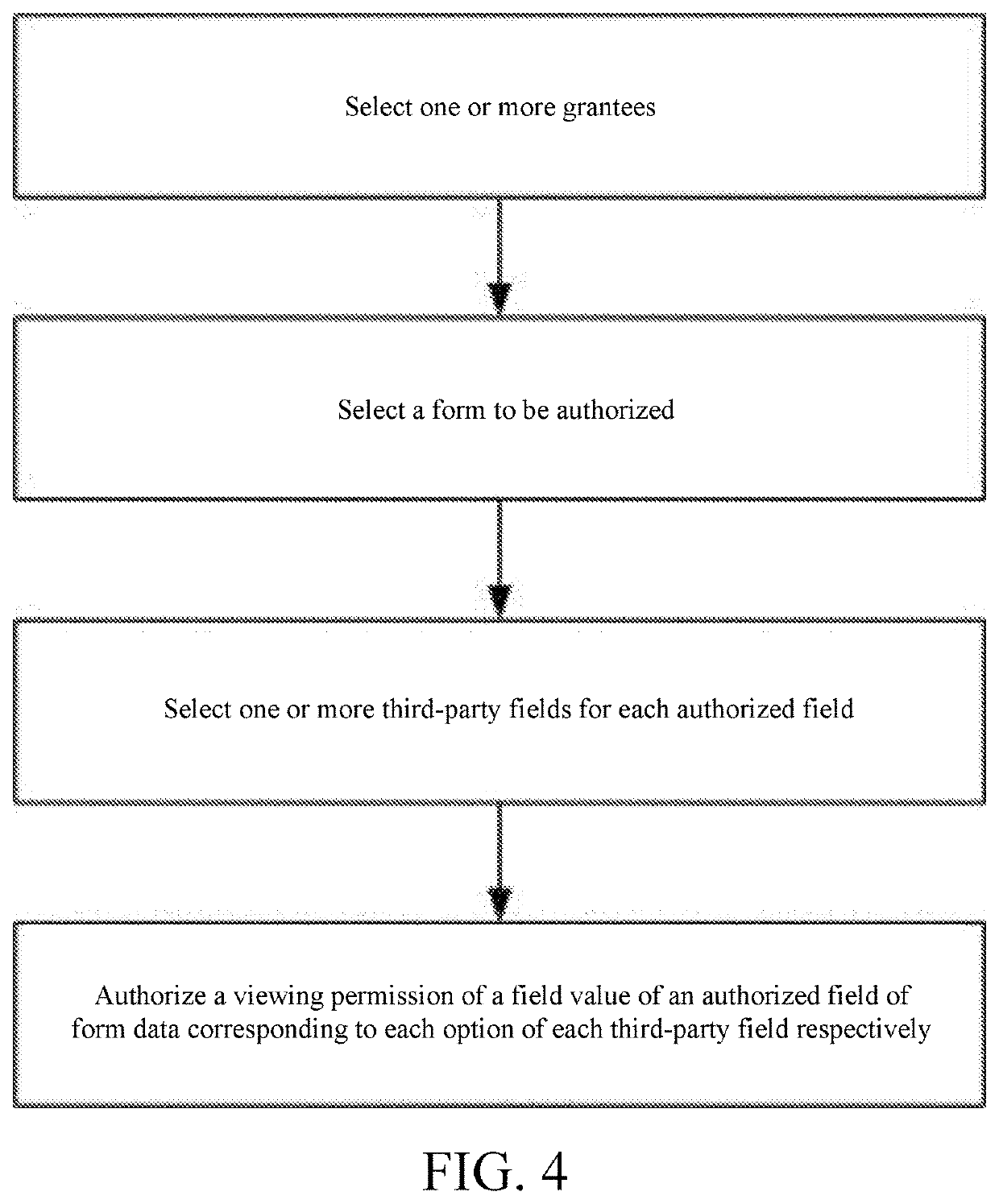
Method for authorizing field values of form fields through third-party fields
InactiveCN107358093APrevent viewing/modificationReduce the possibility of leaksDigital data authenticationOffice automationThird partyComputer science
The invention discloses a method for authorizing field values of form fields through third-party fields. The method comprises the steps of selecting one or more authorized objects; selecting a form to be authorized, and displaying authorized fields, meeting a condition that authorization of viewing permissions of the field values of the authorized fields needs to be controlled through the third-party fields, in the form; selecting one or more third-party fields for each authorized field, wherein each third-party field comprises one or more options; and authorizing the viewing permission of the field value of the authorized field of form data corresponding to each option of each third-party field. By setting the third-party fields to limit the authorized fields needed to be subjected to the authorization of the viewing / modification permissions of the field values in the form, the viewing / modification permissions of the authorized objects can be set to be consistent with job responsibilities of the authorized objects, so that the authorized objects can be prevented from viewing / modifying form information unrelated to work of the authorized objects, and the possibility of company information leakage is reduced.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
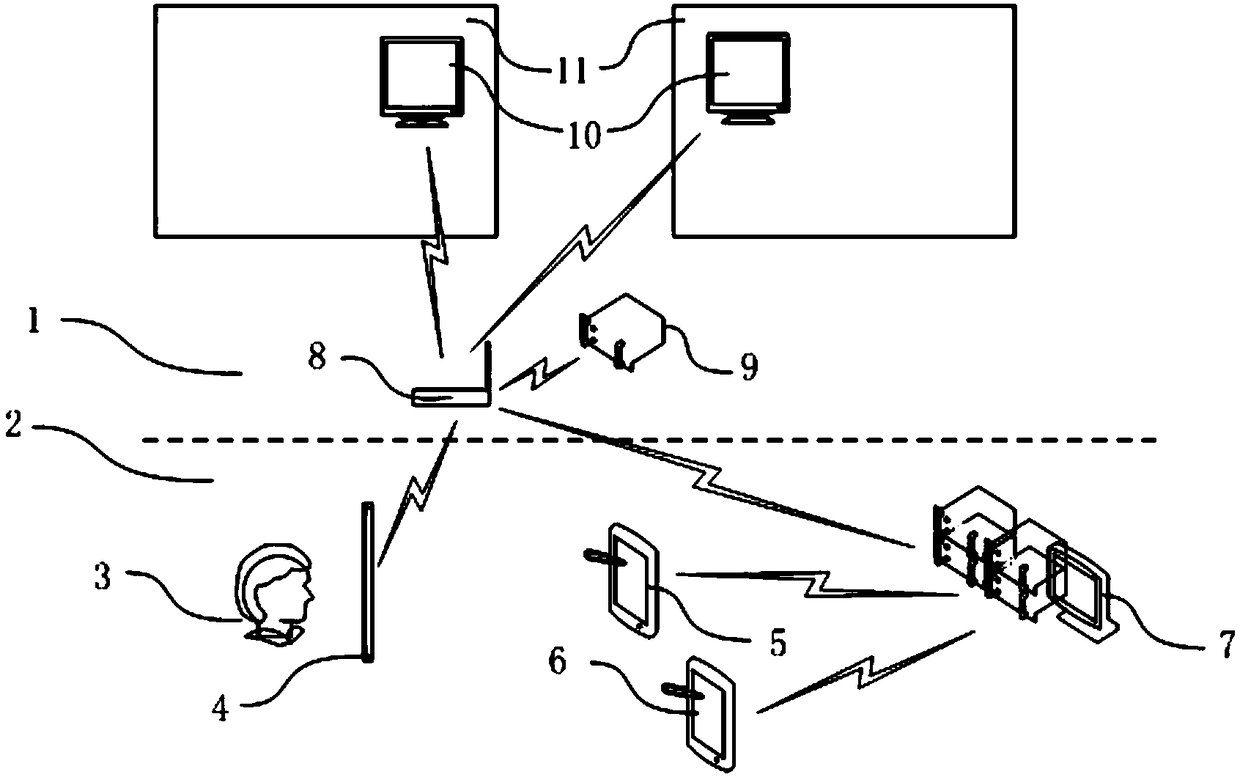
Blockchain face recognition campus student pickup system and blockchain face recognition campus student pickup method
InactiveCN108932778AEnsure safetyGo home safe and timelyData processing applicationsIndividual entry/exit registersUser inputLAN switching
The invention provides a blockchain face recognition campus student pickup system and a blockchain face recognition campus student pickup method. The blockchain face recognition campus student pickupsystem comprises a campus area, an off-campus area and a user who picks up a student, a railing and a school gate are arranged between the campus area and the off-campus area, the user is located outside the campus area, a blockchain face recognition system is arranged in the off-campus area, the user inputs and obtains information by using a student's parent user terminal or other user terminal,a cloud platform is arranged in the off-campus area, a campus internal server is arranged in the campus area, information exchange is carried out by the cloud platform and the campus internal server,a local area network switch is arranged in the campus area to distribute the information in the campus, display screens are arranged in the campus area, and the display screens are arranged in classrooms. A face recognition technology and a blockchain technology are used to ensure the safety of students in the student pickup process, and the personnel who picks up the student is recognized throughthe face recognition technology in order to improve safety.
Owner:安徽灵图壹智能科技有限公司
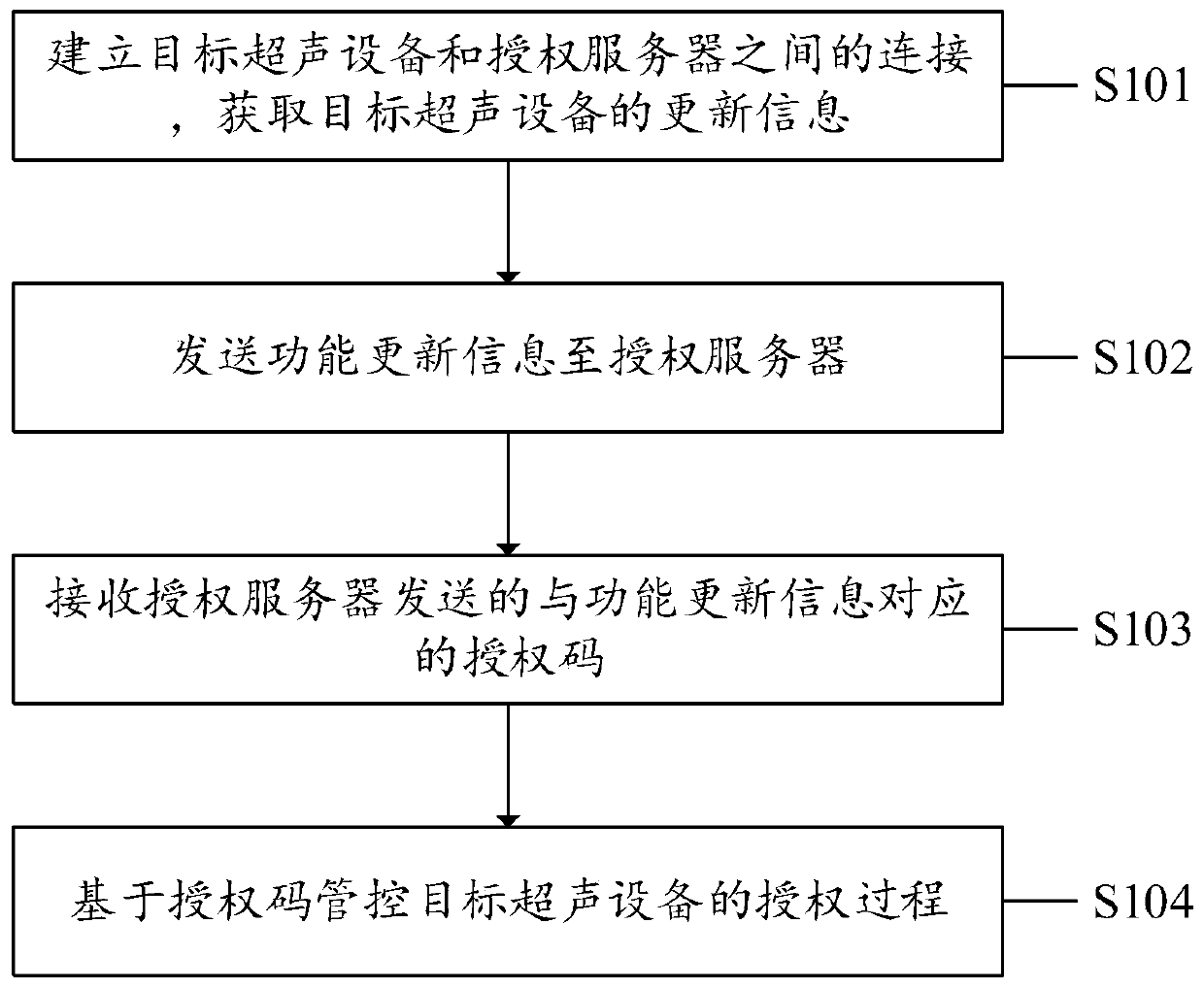
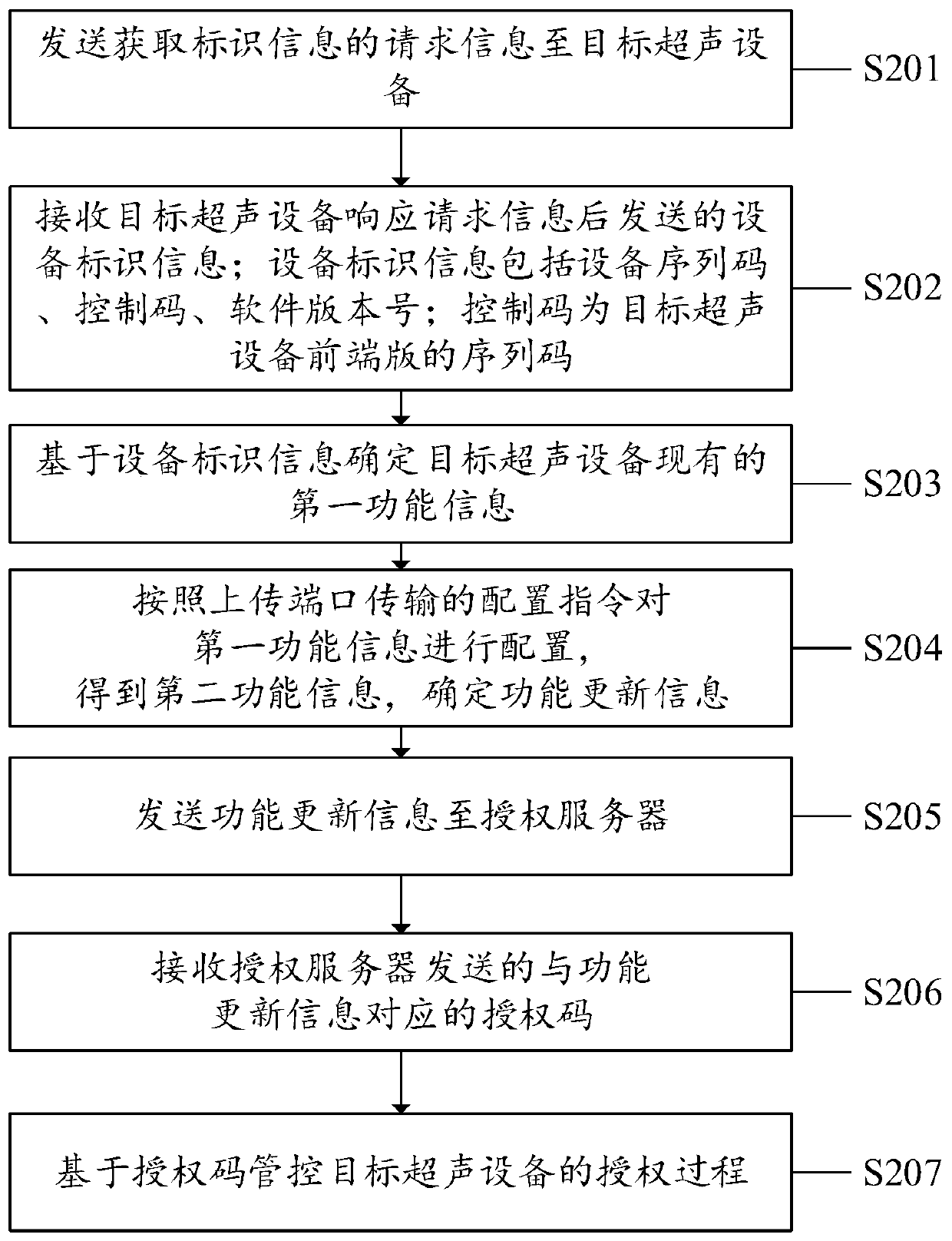
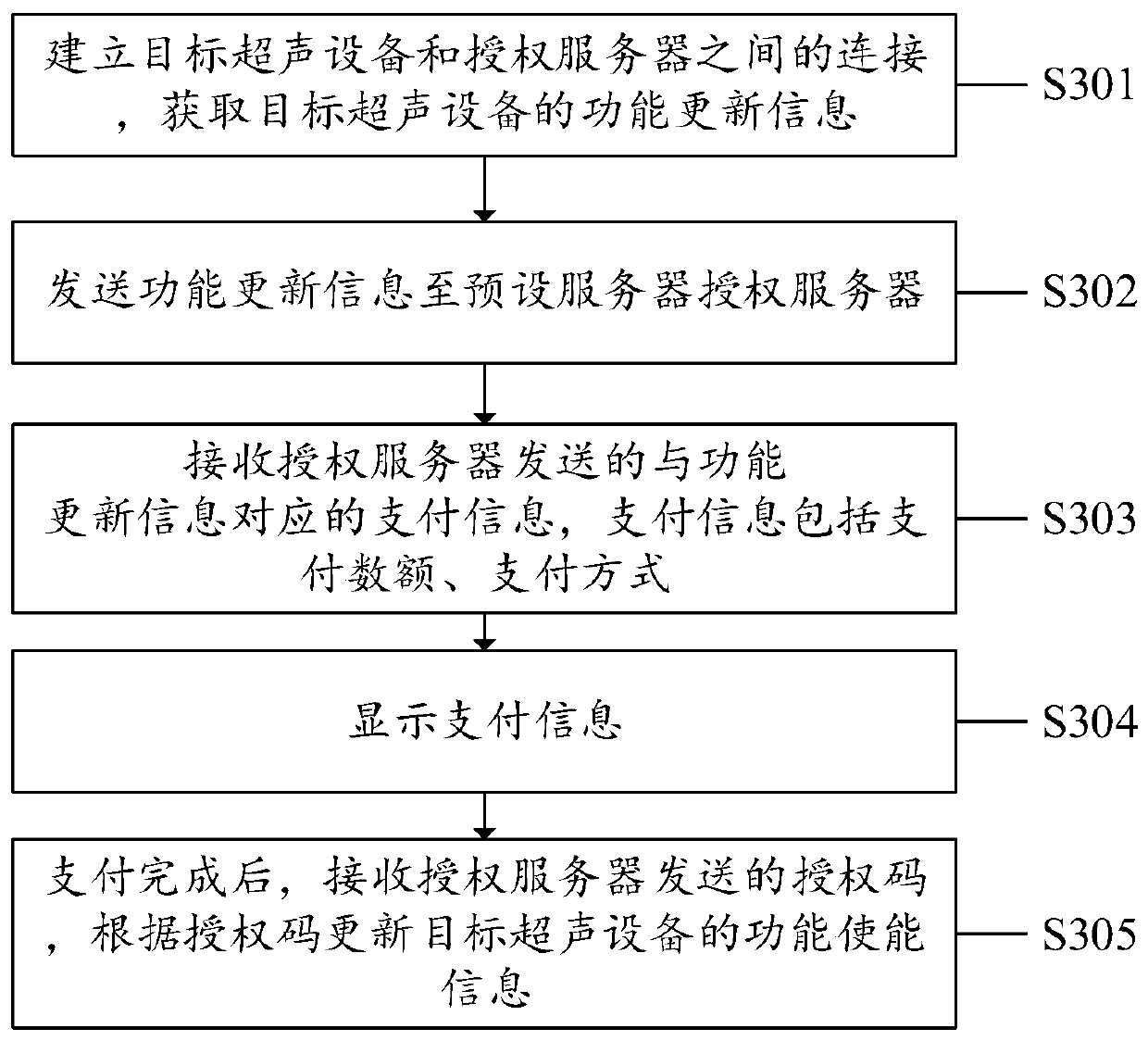
Ultrasonic equipment authorization method, system and device and computer storage medium
ActiveCN110233857AImprove authorization efficiencyImprove information transmission efficiencyData switching networksSoftware engineeringAuthorization
The invention discloses an ultrasonic device authorization method, system and device and a computer storage medium, and the method comprises the steps: building the connection between a target ultrasonic device and an authorization server, and obtaining the function updating information of the target ultrasonic device; sending the function updating information to an authorization server; receivingan authorization code which is sent by the authorization server and corresponds to the function updating information; and controlling the authorization process of the target ultrasonic equipment based on the authorization code. The invention provides the ultrasonic equipment authorization method. The acquired function updating information of the target ultrasonic equipment can be automatically sent to the authorization server, the authorization code which is sent by the authorization server and corresponds to the function updating information is received, the authorization process of the target ultrasonic equipment is controlled based on the authorization code, and the authorization efficiency of the ultrasonic authorization equipment can be improved. The ultrasonic equipment authorization system and equipment and the computer readable storage medium provided by the invention also solve the corresponding technical problems.
Owner:SONOSCAPE MEDICAL CORP
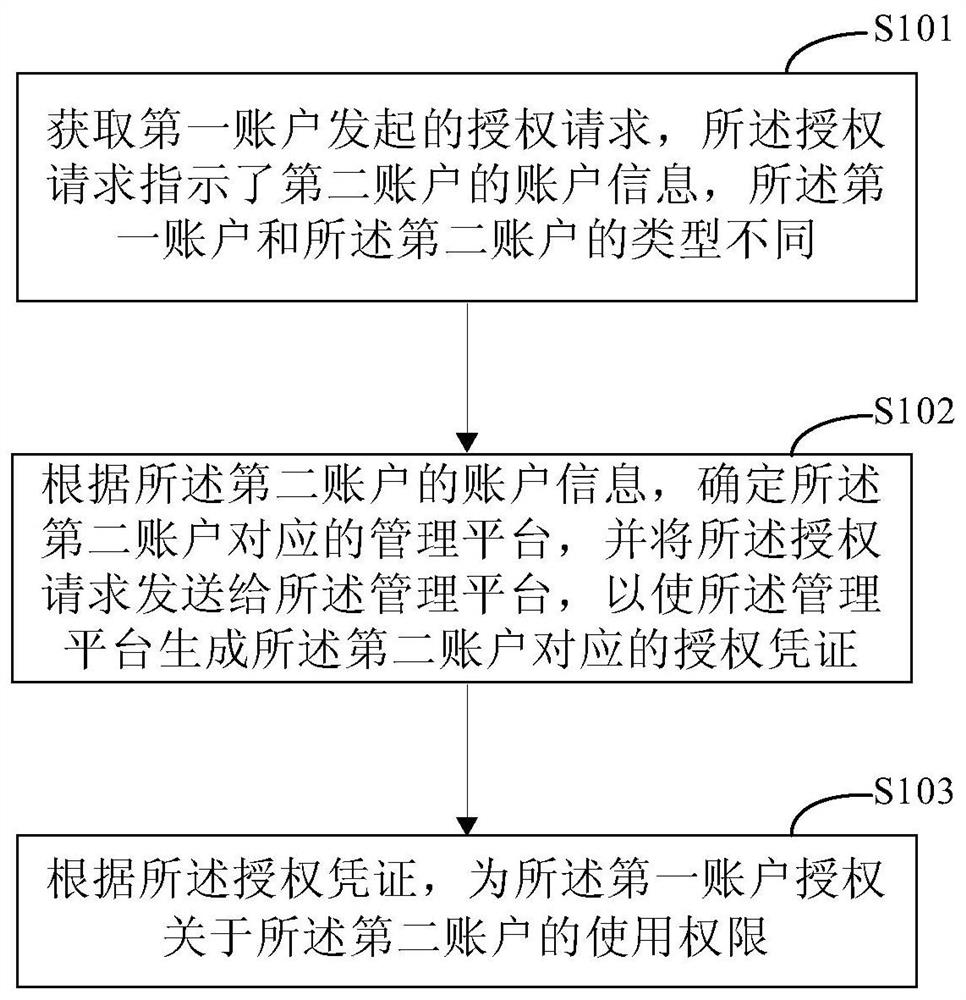
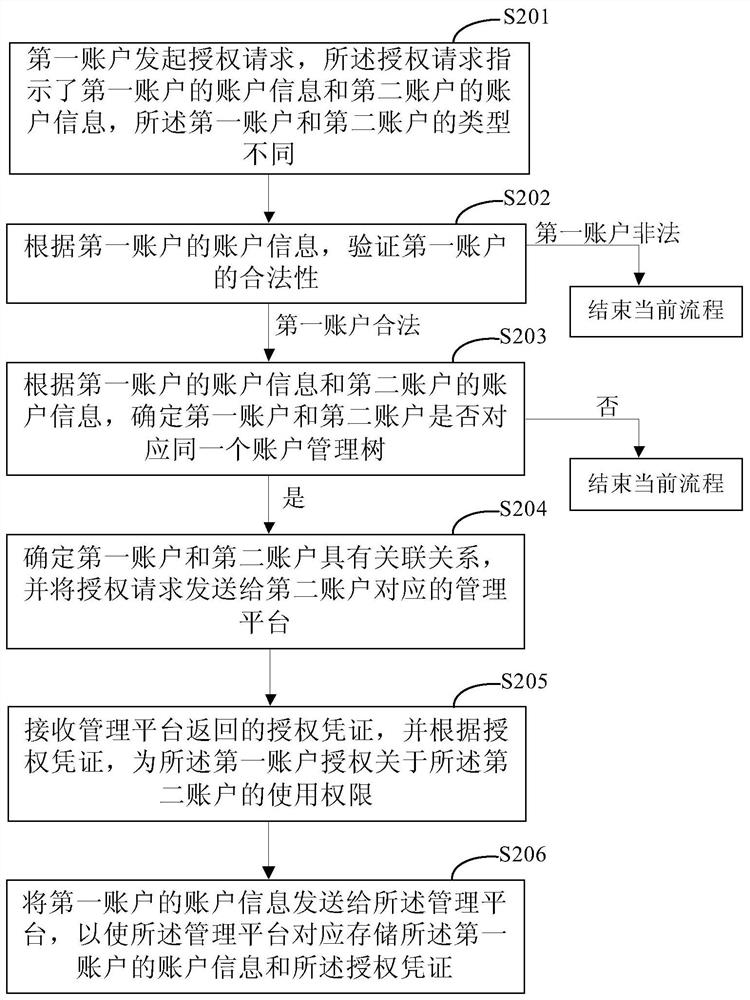
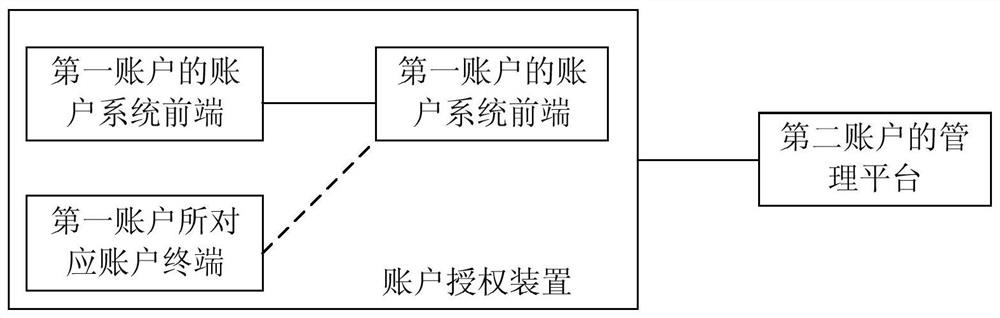
Account authorization method, device and system
PendingCN111833066AImprove authorization efficiencyImprove experienceProtocol authorisationAuthorization certificateEngineering
The invention discloses an account authorization method, device and system, and relates to the technical field of computers. One specific embodiment of the method comprises the steps of obtaining an authorization request initiated by a first account, the authorization request indicating account information of a second account, and the first account and the second account being different in type; determining a management platform corresponding to the second account according to the account information of the second account, and sending the authorization request to the management platform, so that the management platform generates an authorization certificate corresponding to the second account; and authorizing the use permission about the second account for the first account according to the authorization certificate. According to the embodiment, online authorization between different accounts is realized, the account authorization efficiency is improved, and the user experience is improved.
Owner:CHINA CONSTRUCTION BANK
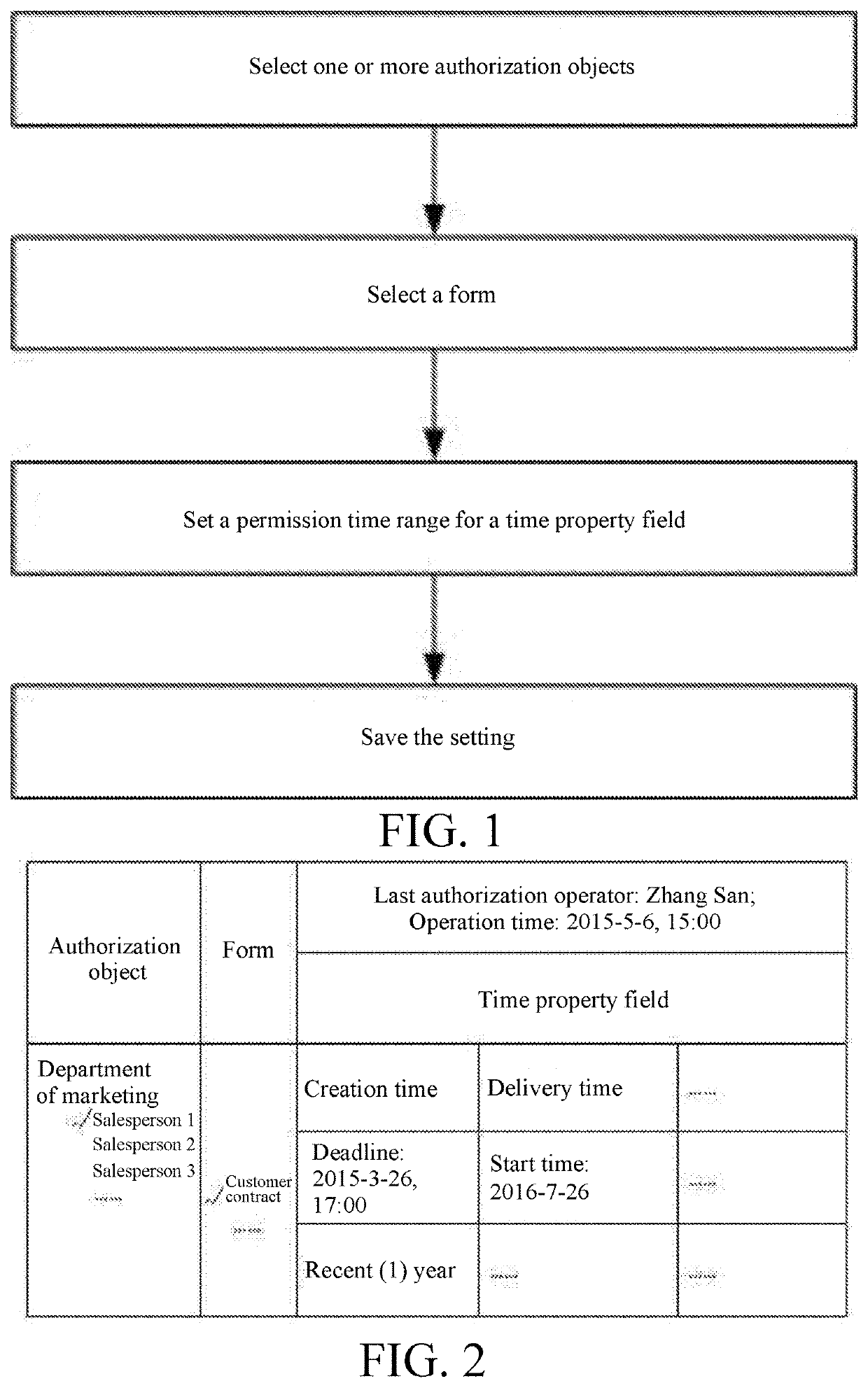
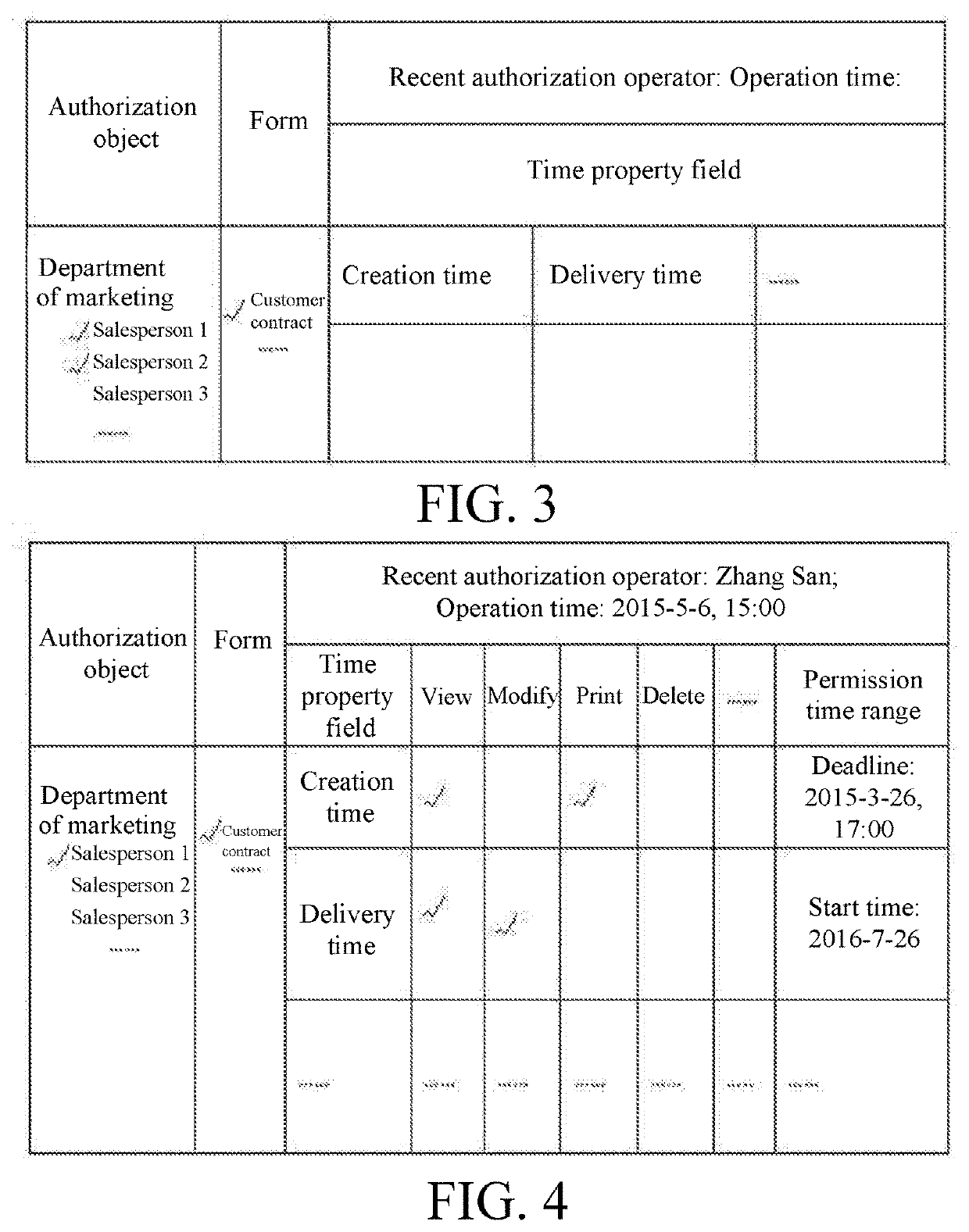
Form authority granting method based on time property fields of form
PendingUS20200219063A1Satisfies requirementReduce leakageNatural language data processingDigital data authenticationTime rangeStart time
A form-authorizing method based on time property fields of a form is disclosed in the present invention, including: selecting one or more grantees; selecting a form, and displaying time property fields of which permission time ranges need to be set in the selected form; respectively setting a permission time range for each time property field, wherein the permission time range comprises one or more of the following six types: a time range from a time point, which is determined by going backwards from a current time for a fixed time length, to the current time, a time range from a start time to a current time, a time range from a deadline to a system initial time, a time range from a start time to a deadline, a time range where a time field value is null, and a time range from a system initial time to a current time; and after completing setting the permission time ranges, saving the settings. In the present invention, the operation permissions within a period of time in the form can be authorized to a grantee according to actual needs, thus satisfying requirements for form authorization in various time-limited cases.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
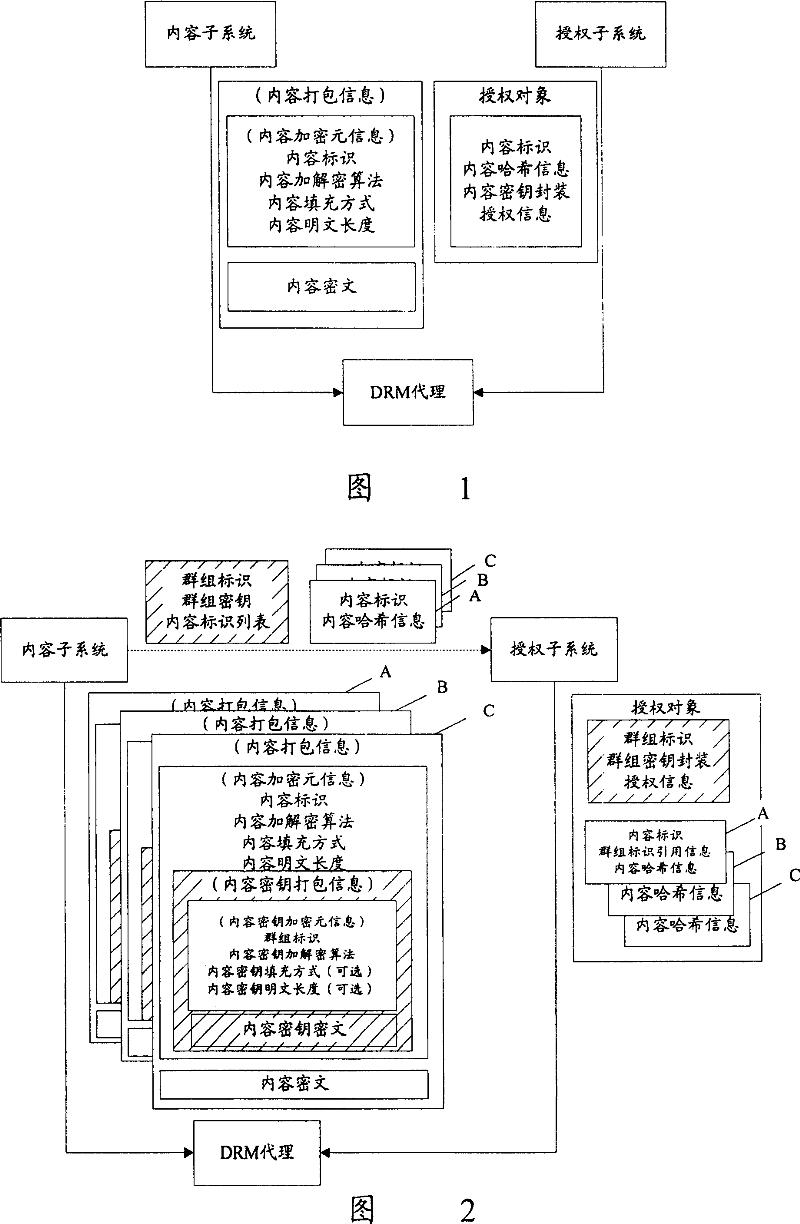
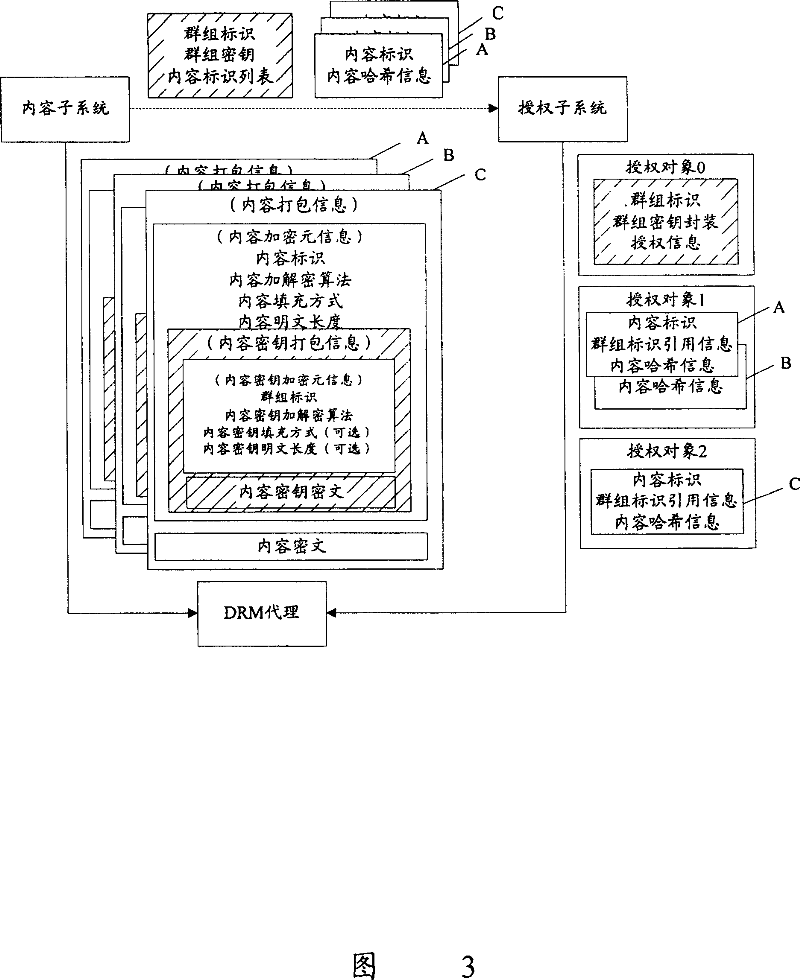
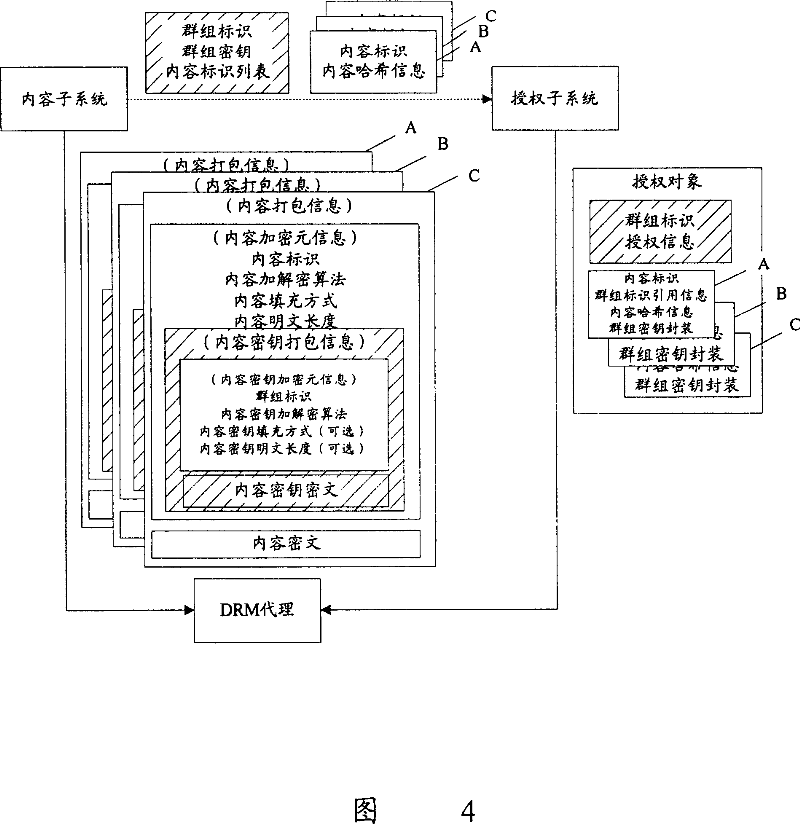
Content group digital copyright protection method and system
ActiveCN100354789CFlexible divisionFlexible Group AuthorizationDigital data processing detailsPlaintextCiphertext
Owner:HUAWEI TECH CO LTD
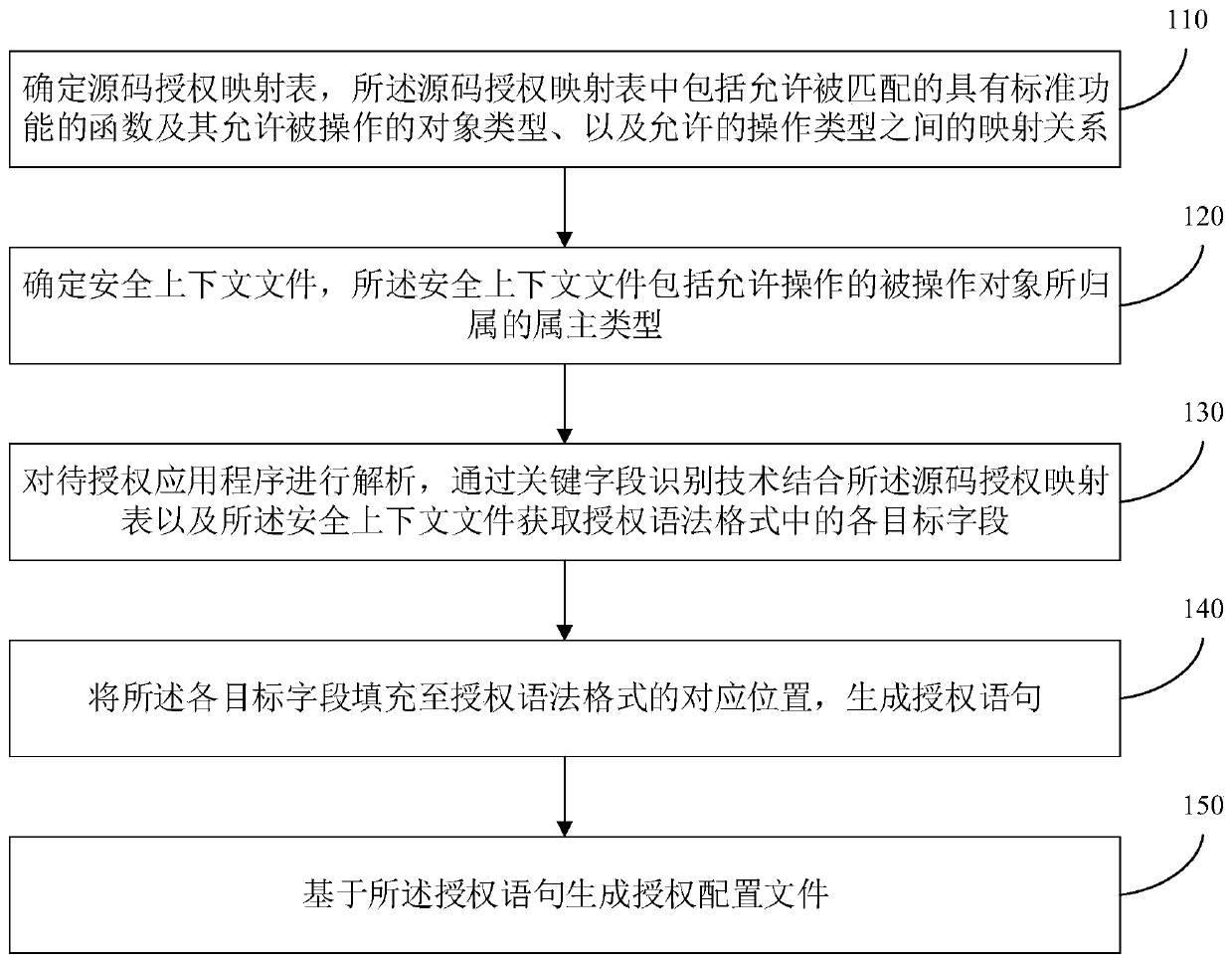
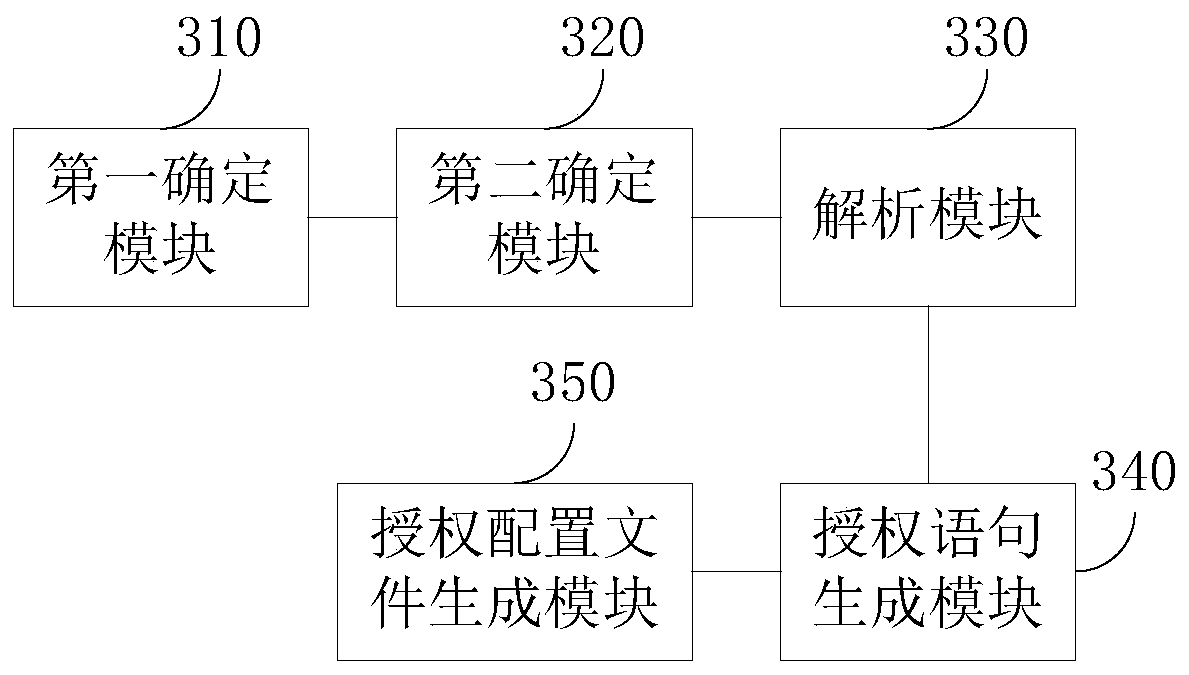
Authorization configuration file generation method and device, equipment and storage medium
ActiveCN110727476ARealize automatic generationImprove authorization efficiencyProgram loading/initiatingProgram/content distribution protectionObject typeApplication procedure
The embodiment of the invention discloses an authorization configuration file generation method and device, equipment and a storage medium, and the method comprises the steps: determining a source code authorization mapping table which comprises a function which is allowed to be matched and has a standard function, an object type which is allowed to be operated by the function, and a mapping relation between allowed operation types; determining a security context file, wherein the security context file comprises an owner type to which the operated object allowed to be operated belongs; analyzing a to-be-authorized application program, and combining the source code authorization mapping table and the security context file through a key field identification technology to obtain each target field in an authorization syntax format; filling each target field into a corresponding position of the authorization grammar format to generate an authorization statement; and generating an authorization configuration file based on the authorization statement. By adopting the technical scheme, the purposes of automatically generating the SELinux authorization configuration file, improving the authorization efficiency and saving human resources are achieved.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Method for authorizing field value of form field by means of third party field
PendingUS20200143068A1Reduce the possibility of leaksImproving form authorization efficiencyDigital data protectionDigital data authenticationThird partyInternet privacy
A method for authorizing a field value of a form field by means of a third-party field is disclosed in the present invention, including: selecting one or more grantees; selecting a form to be authorized, and displaying authorized fields which need to control authorization of the permission to view field values thereof by means of third-party fields in the form; selecting one or more third-party fields for each authorized field respectively, where said third-party field includes one or more options; and authorizing a viewing permission of a field value of an authorized field of form data corresponding to each option of each third-party field respectively. In the present invention, the authorized fields in a form that need to authorize the viewing permission / modification permission of the field values are restricted by setting third-party fields, so that the viewing permission / modification permission of the grantee is set to be consistent with its job responsibility, thus preventing the grantee from viewing / modifying form the information irrelevant to its work and reducing possibility of leakage of company information.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com