Patents
Literature
43results about How to "Simplify the authorization process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
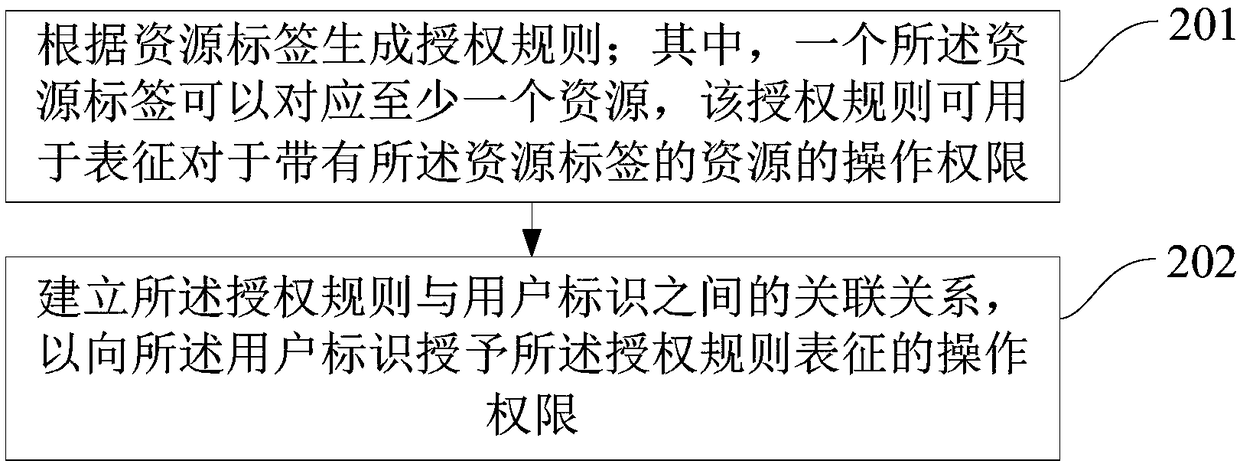
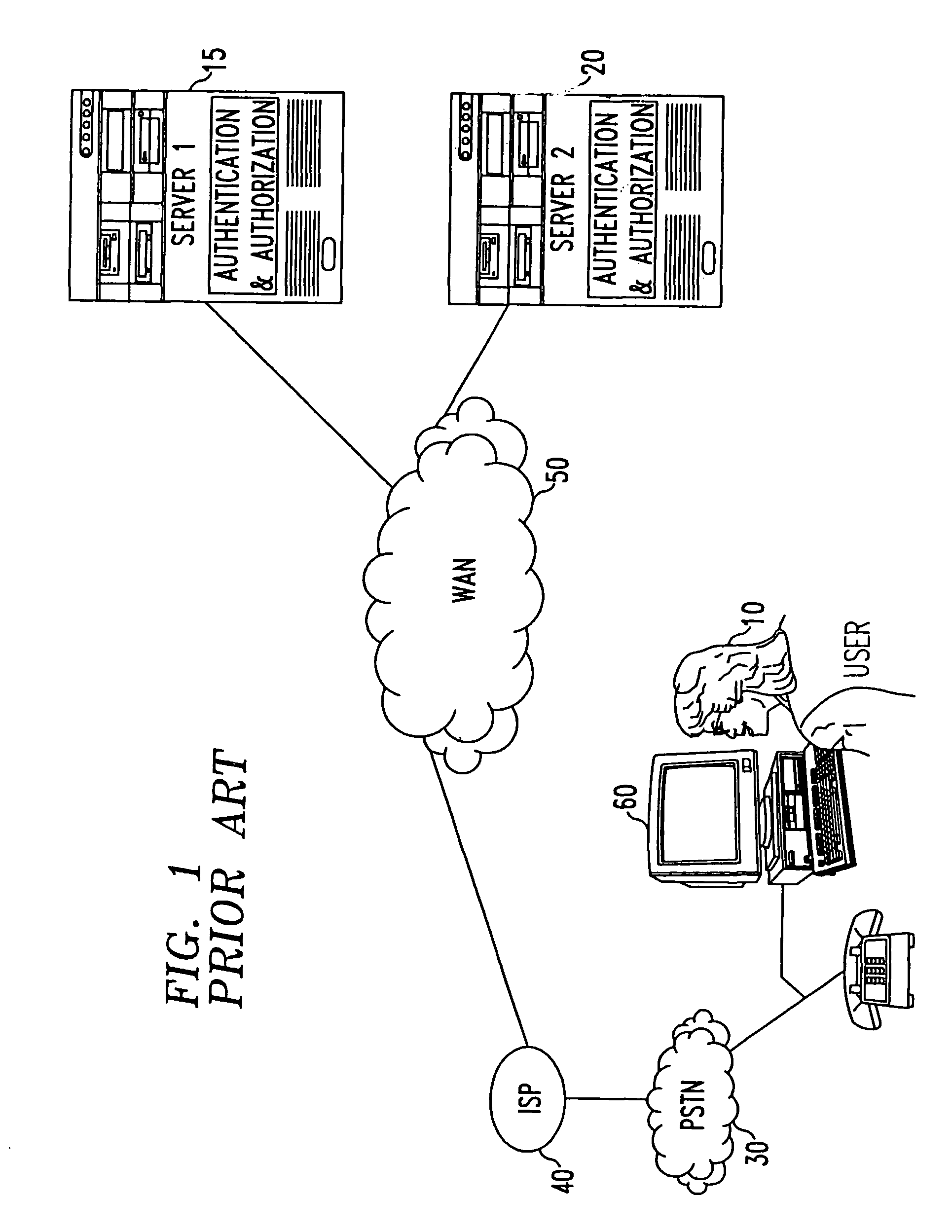
Operation authorization method and device
InactiveCN104283876AProtect propertyPrivacy protectionComputer security arrangementsDetails for portable computersUser privacyText messaging
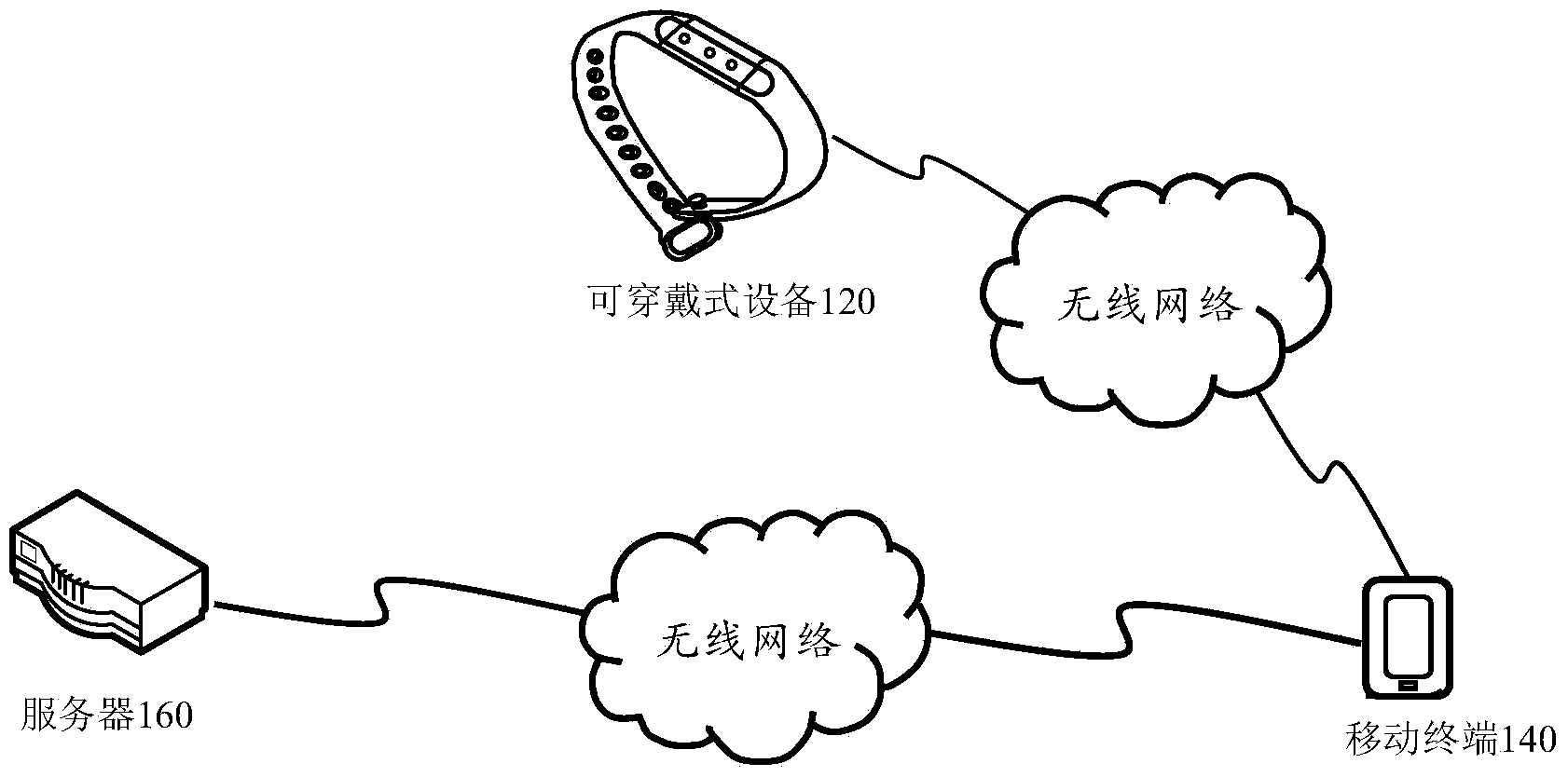
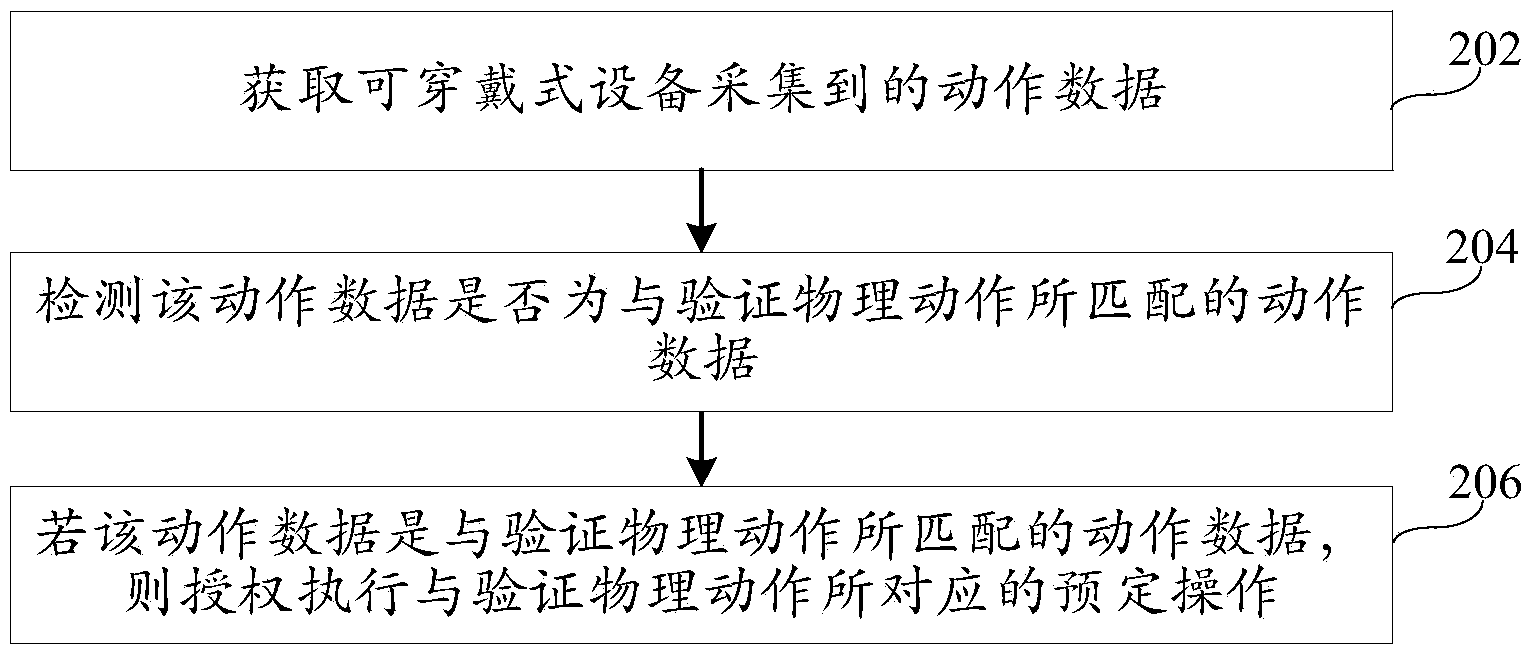
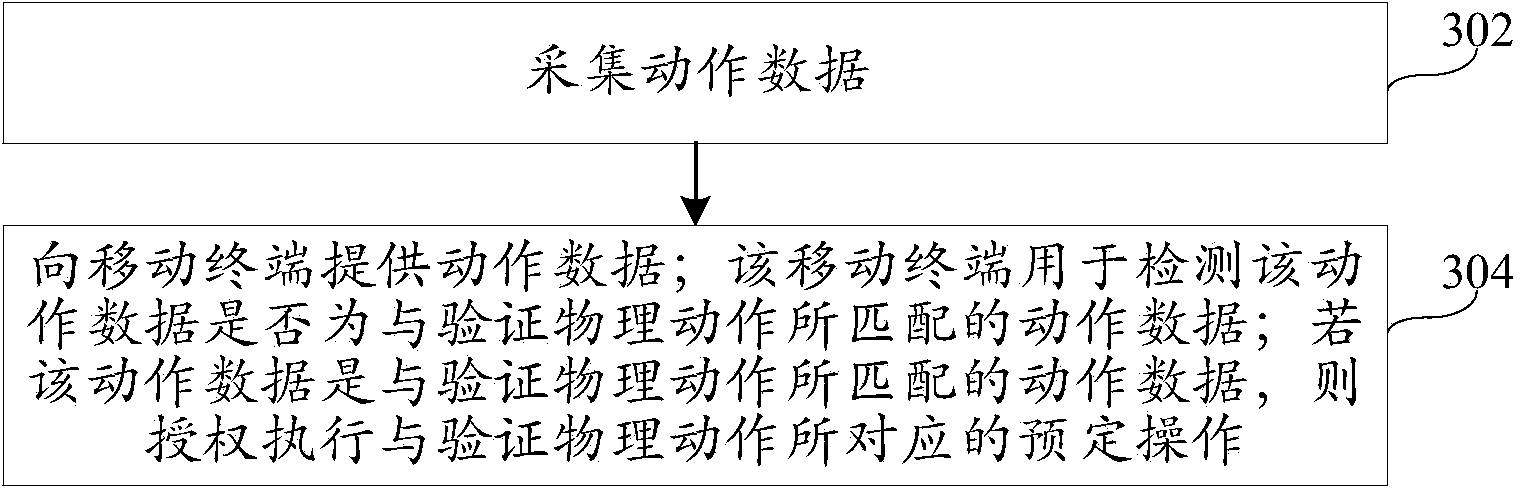
The invention discloses an operation authorization method and device, and belongs to the field of network security. The method includes the steps that motion data collected by a wearable device are obtained; whether the motion data are motion data matched with verification physical motion or not is detected; if yes, the preset operation corresponding to the verification physical motion is authorized to be executed. According to the method, the user identification is verified through the motion data collected by the wearable device, and the problems of complex operation of obtaining a dynamic authorization password in a short message mode and the possibility of leakage are solved; the authorization verification process is simplified, and the authorization execution of the preset operation can be finished only through the wearable device, so that the user property and user privacy are effectively protected, and the safety in using the mobile internet is improved for users.
Owner:XIAOMI INC
Remote authorization method, device and system
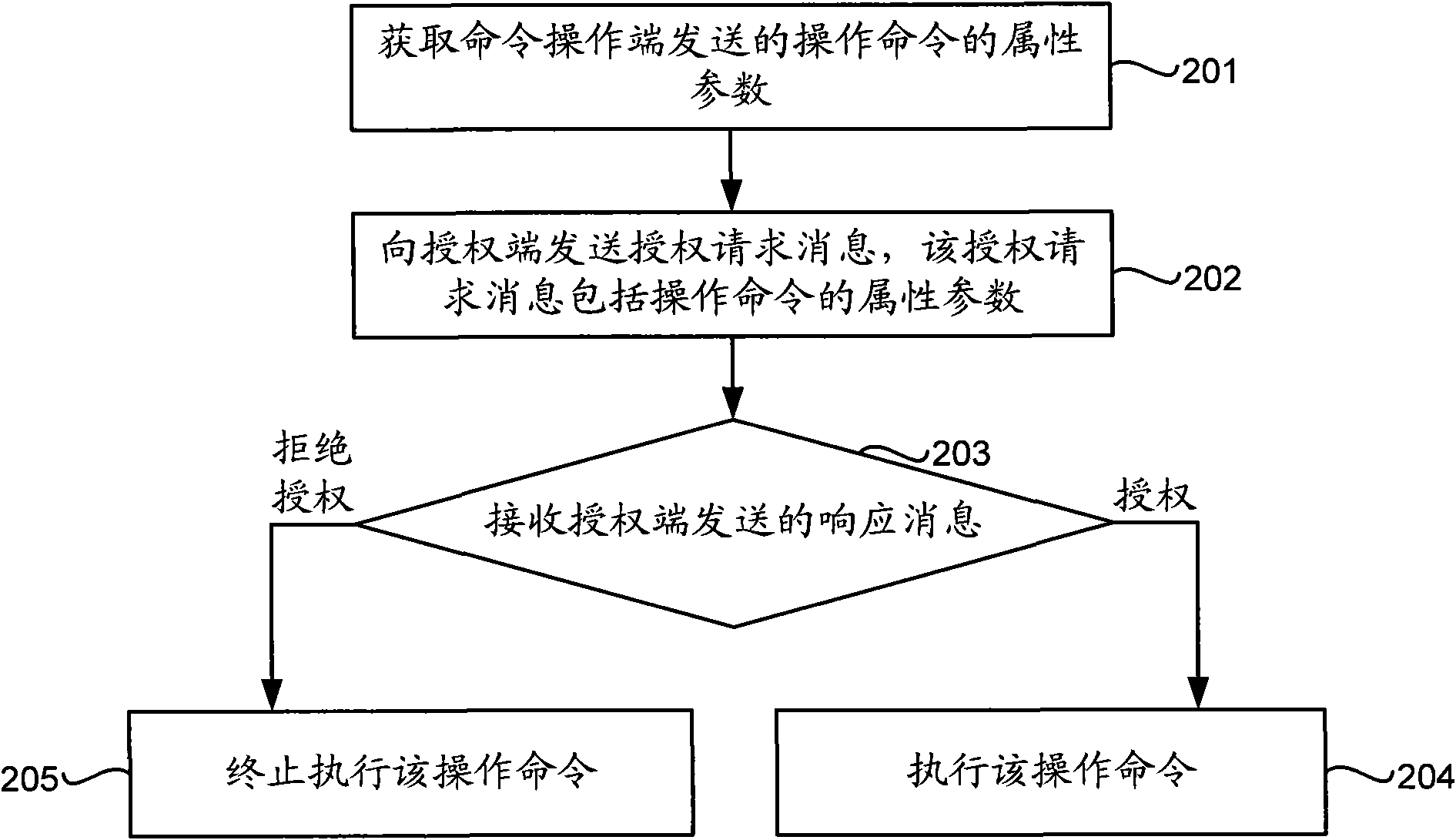
InactiveCN101610155AImprove authorization reliabilityImplement multi-level authorizationUser identity/authority verificationClosed circuit television systemsEmbedded systemAuthorization
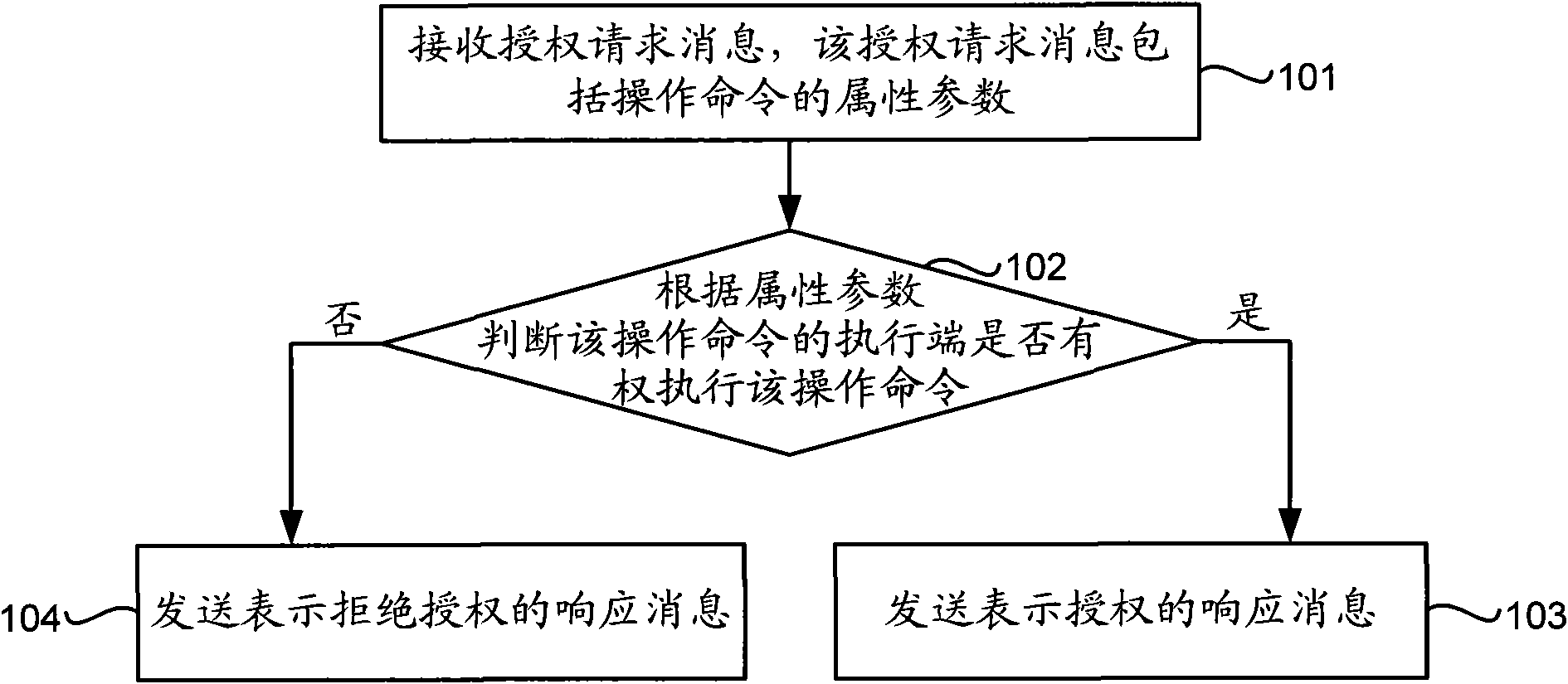
The embodiment of the invention discloses a remote authorization method, a device and a system. The method comprises the steps of receiving an authorization request message which comprises attribute parameters of an operation command and judging whether an enforcement end of the operation command has the right to enforce the operation command or not according to the attribute parameters, if so, sending a response message which represents authorization, otherwise, sending the response message which denies the authorization. The embodiment of the invention further discloses the remote authorization device and the system. The embodiment of the invention improves the reliability of the authorization, realizes multi-level authorization, avoids the problem of difficult operation caused by on-site authorization and simplifies the authorization process.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Supply Medium Exchange System for Mobile Units
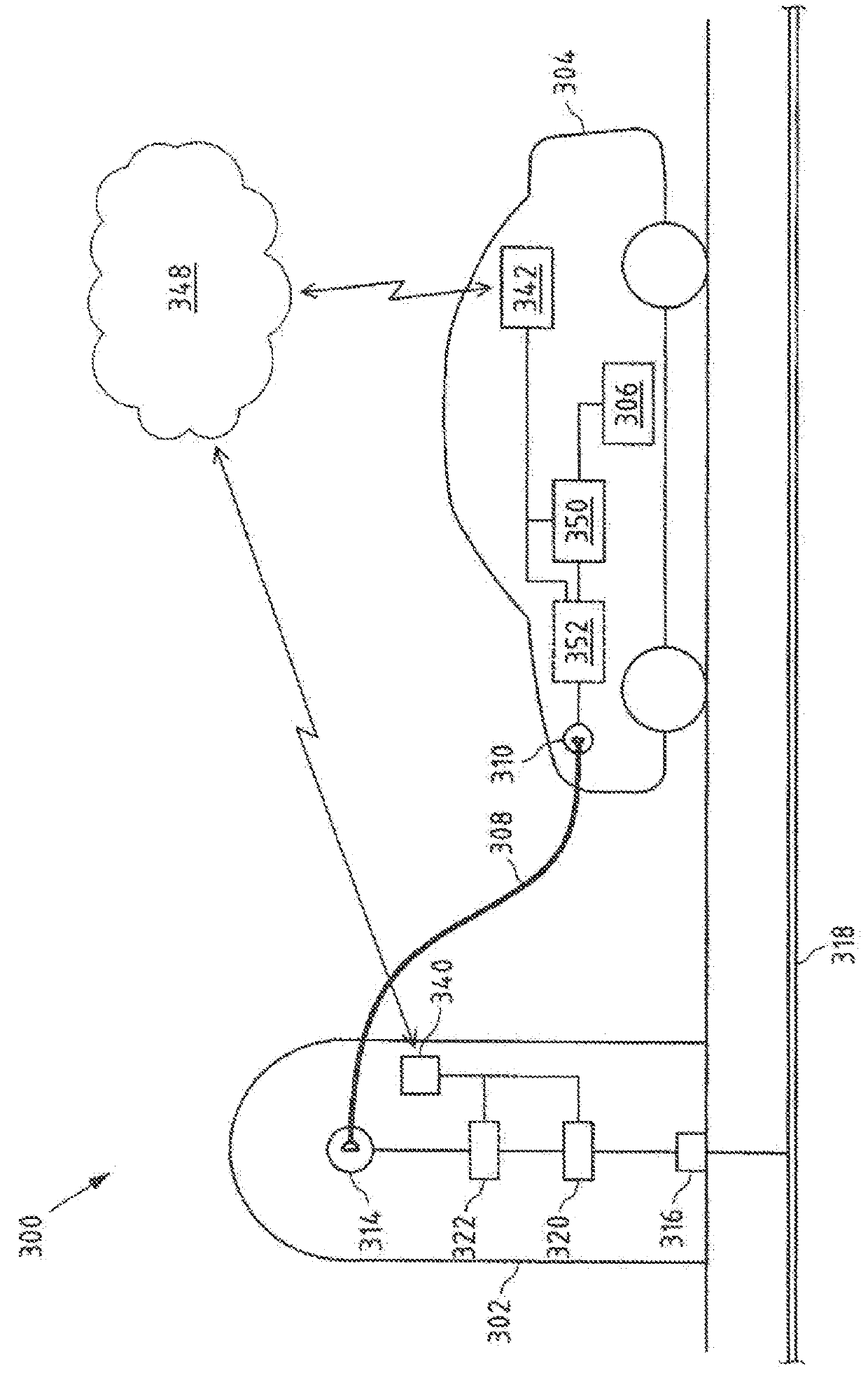
ActiveUS20180272886A1Reduce transaction costsImprove tamper resistanceCharging stationsDigital data protectionComputer moduleEngineering
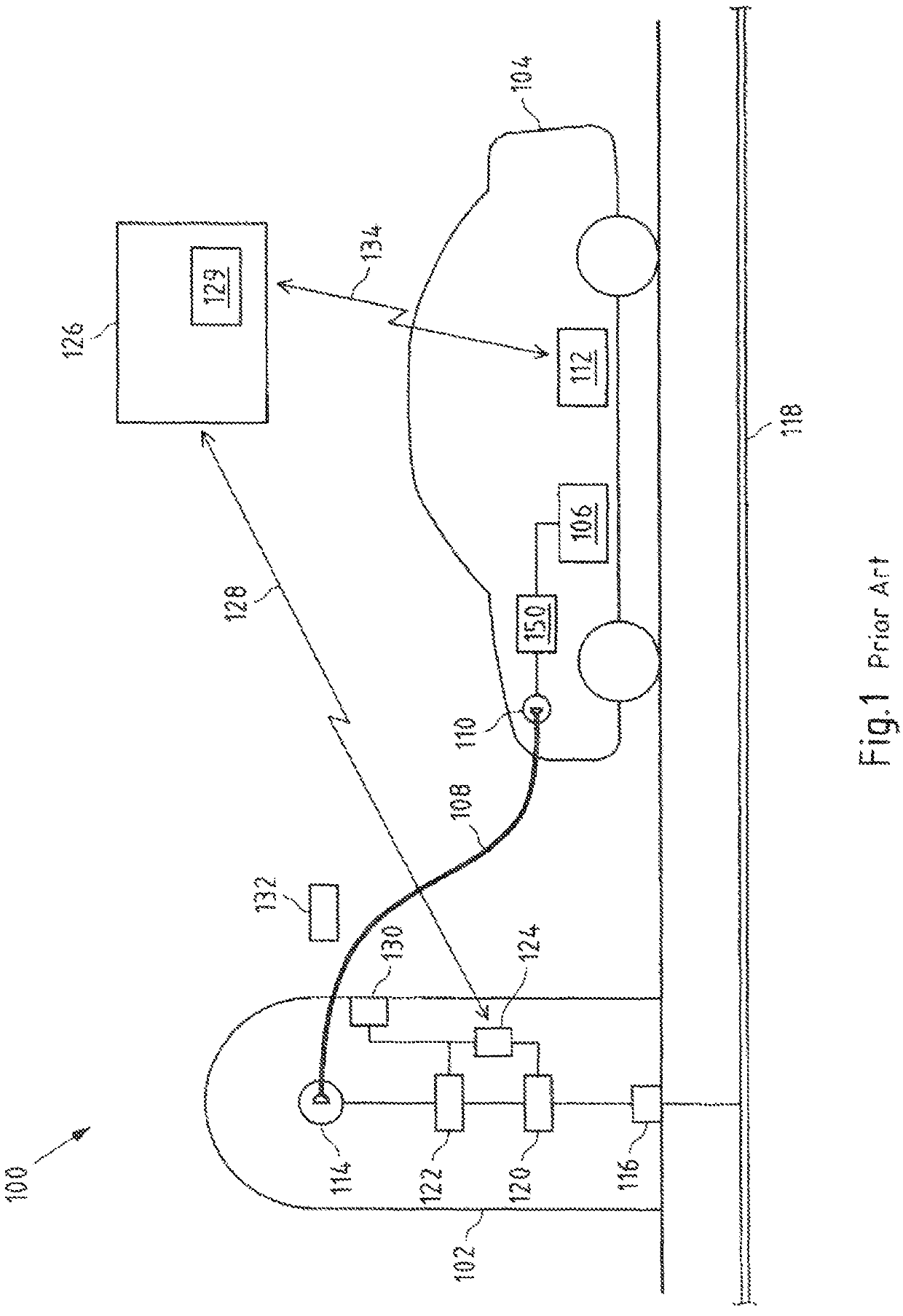
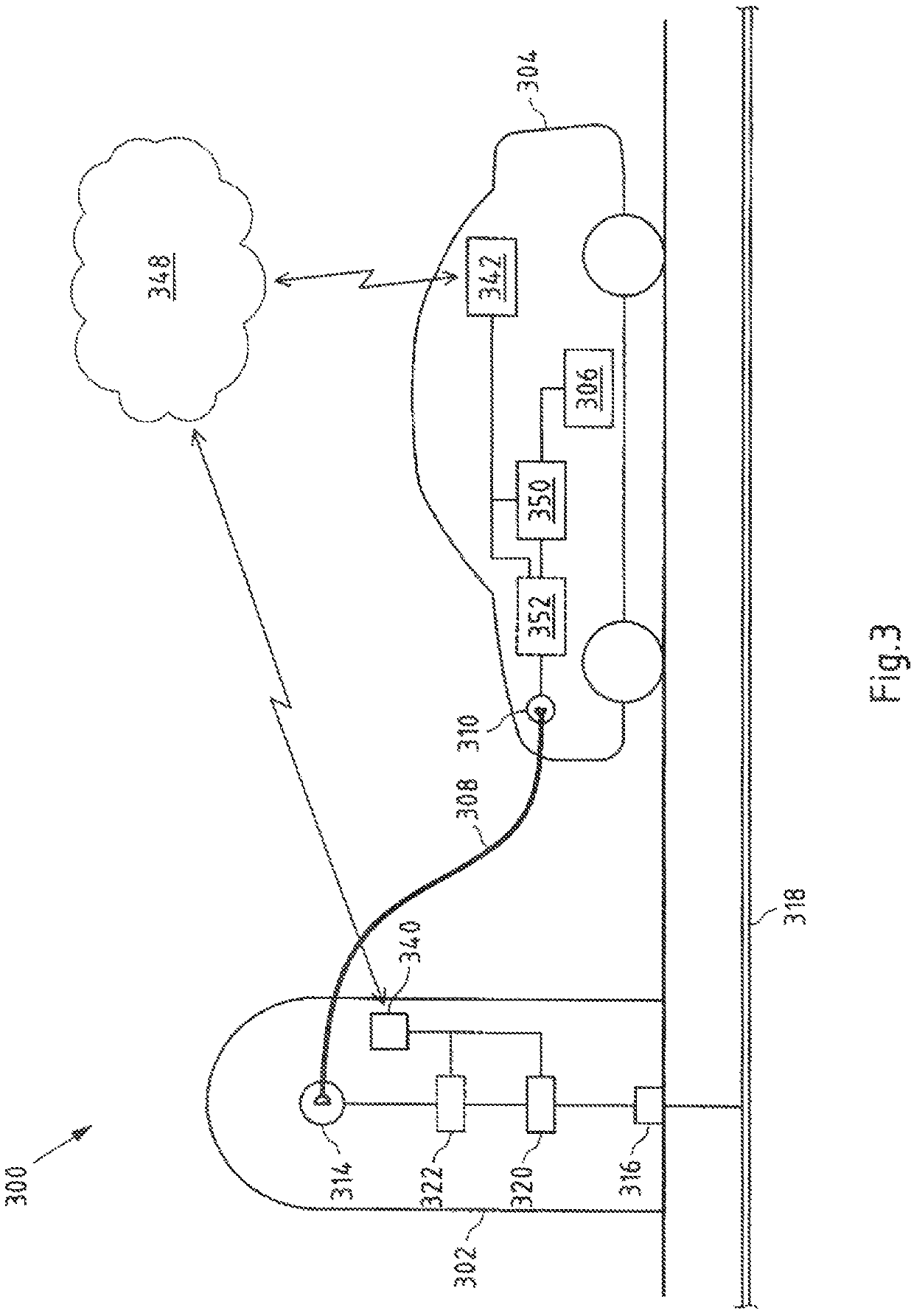
Provided are embodiments of a supply medium exchange system. The system includes at least one supply medium exchange station having at least one supply medium exchange interface. It is configured to exchange a supply medium with at least one mobile unit including at least one supply medium storage and at least one first peer-to-peer module assigned to the mobile unit. It is also configured to communicate with at least one peer-to-peer application of at least one peer-to-peer network. The first peer-to-peer module is configured to cause a generation of a supply medium exchange release message for releasing of the exchange of the supply medium between the mobile unit and the supply medium exchange station by means of the peer-to-peer application.
Owner:INNOGY INNOVATION GMBH
Charging pile parking spot lock management system based on intelligent terminal and charging pile parking spot lock management method based on intelligent terminal
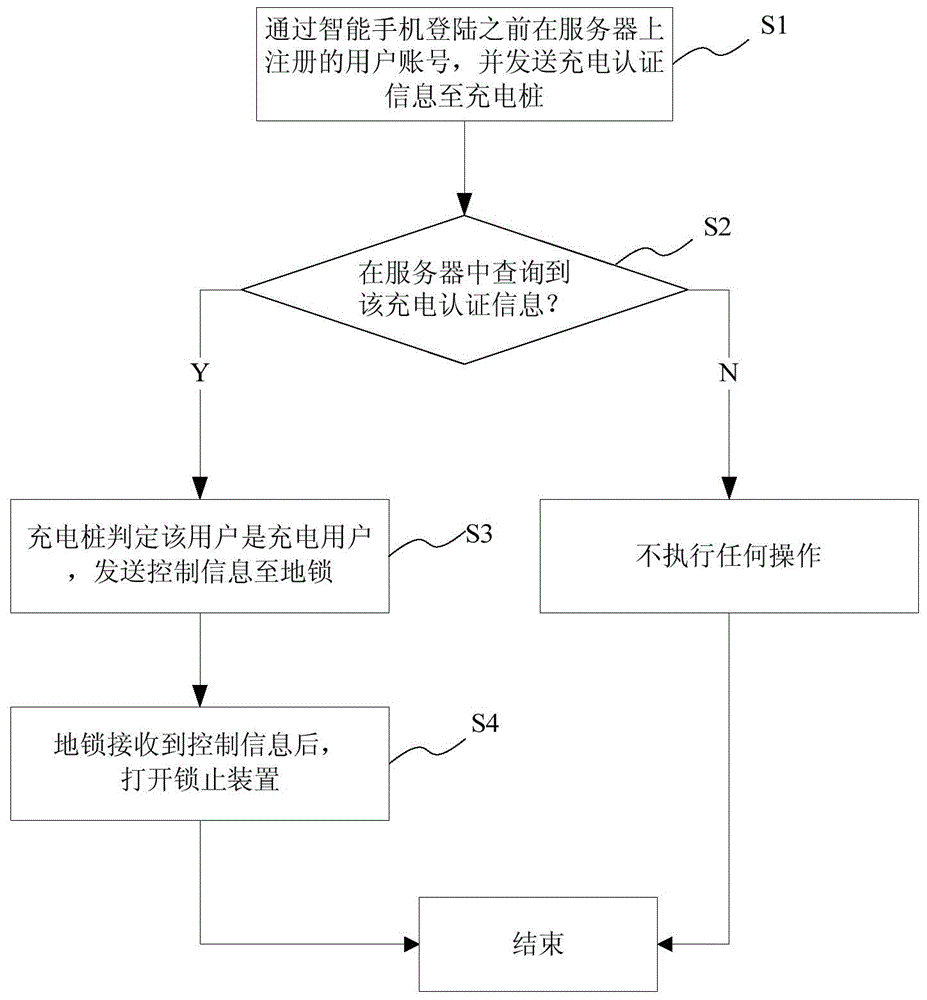
InactiveCN104883355AReduce labor costsSimplify the authorization processIndividual entry/exit registersTransmissionAuthorizationParking space
The present invention provides a charging pile parking spot lock management system based on an intelligent terminal and a charging pile parking spot lock management method based on the intelligent terminal. The charging pile parking spot lock management system comprises the intelligent terminal, a charging pile, a parking spot lock and a server. The intelligent terminal is used to register a user account on the server, set the passwords and send the charging authentication information to the charging pile, the charging pile is used to determine whether a user is an authorization charging user, and controls the parking spot lock to open when the user is determined to be the authorization charging user, the parking spot lock is used to open or lock a parking spot under the control of the charging pile, and the server is used to provide the user account register service to the intelligent terminal and provide the charging authentication information confirmation service to the charging pile. The charging pile parking spot lock management system based on the intelligent terminal and the charging pile parking spot lock management method based on the intelligent terminal of the present invention adopt the intelligent terminal to interact with the charging pile, and control the parking spot lock via the charging pile, thereby obtaining the management authority of the parking spot lock automatically without needing the special management personnel, reducing the manpower cost, and effectively simplifying the authorization process.
Owner:上海ABB联桩新能源技术有限公司
System and method for controlled access to application programming interfaces
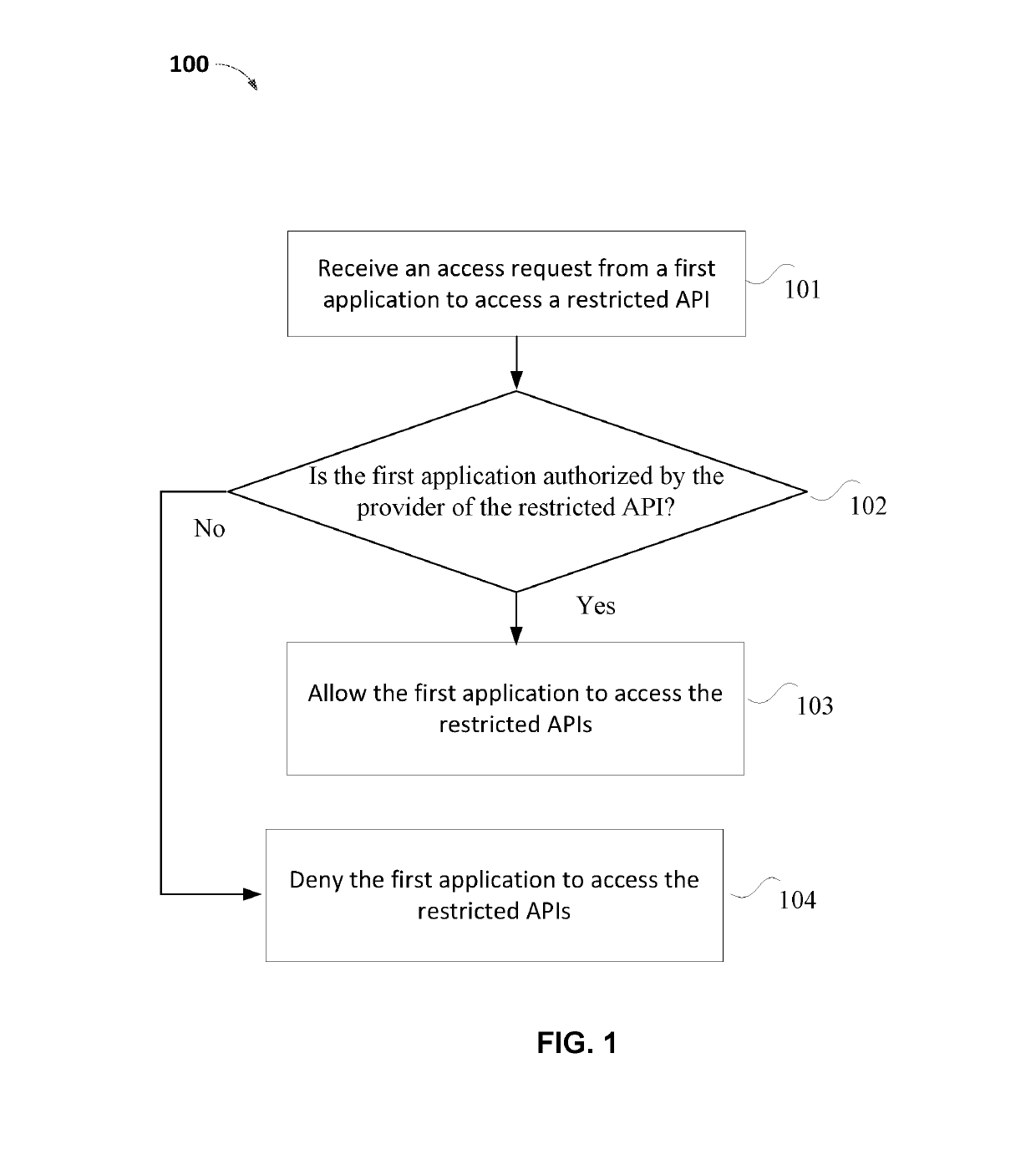
ActiveUS20190138698A1Easy to manageSimplify the authorization processDigital data protectionProgram/content distribution protectionApplication programming interfaceApplication software
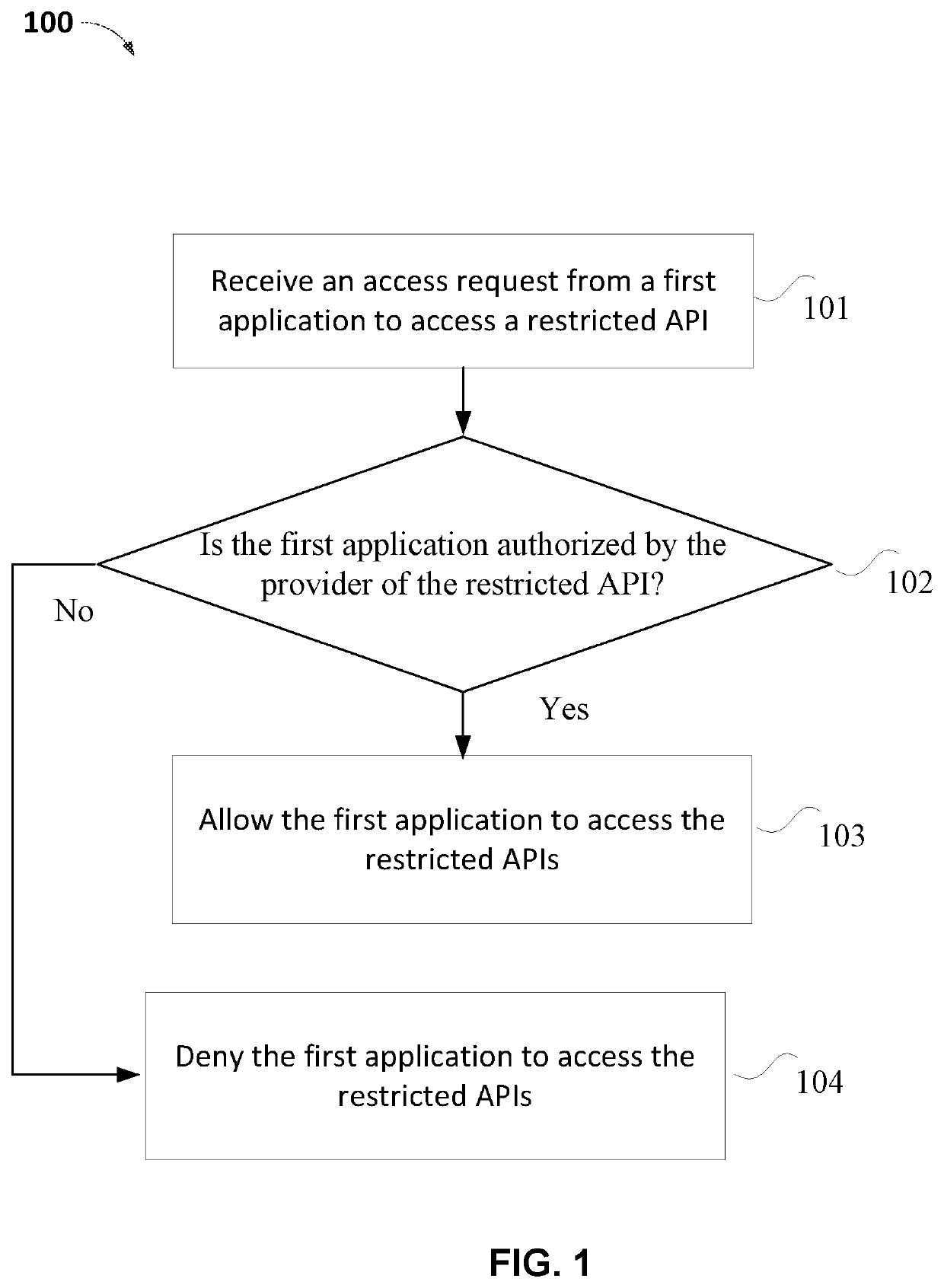
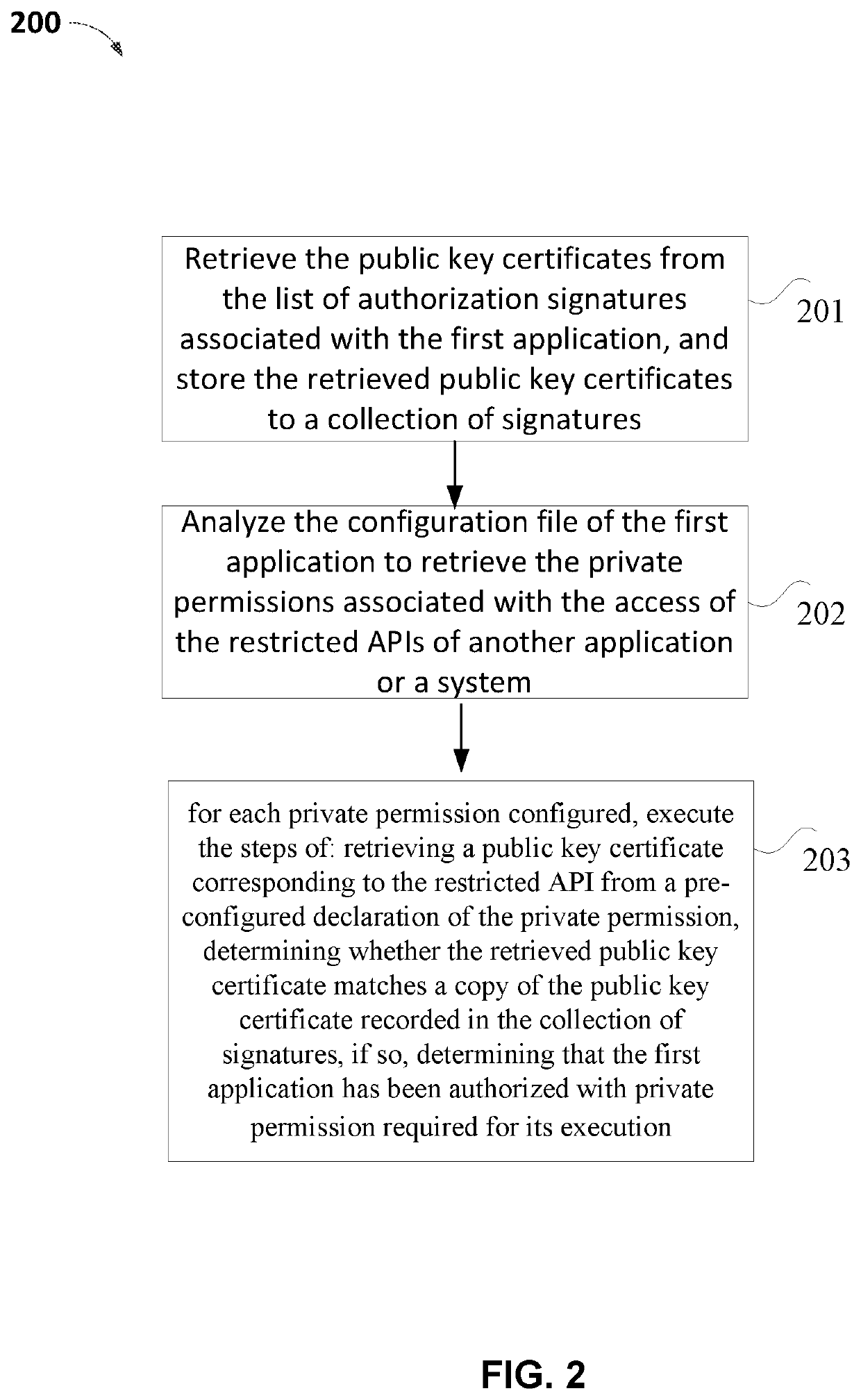
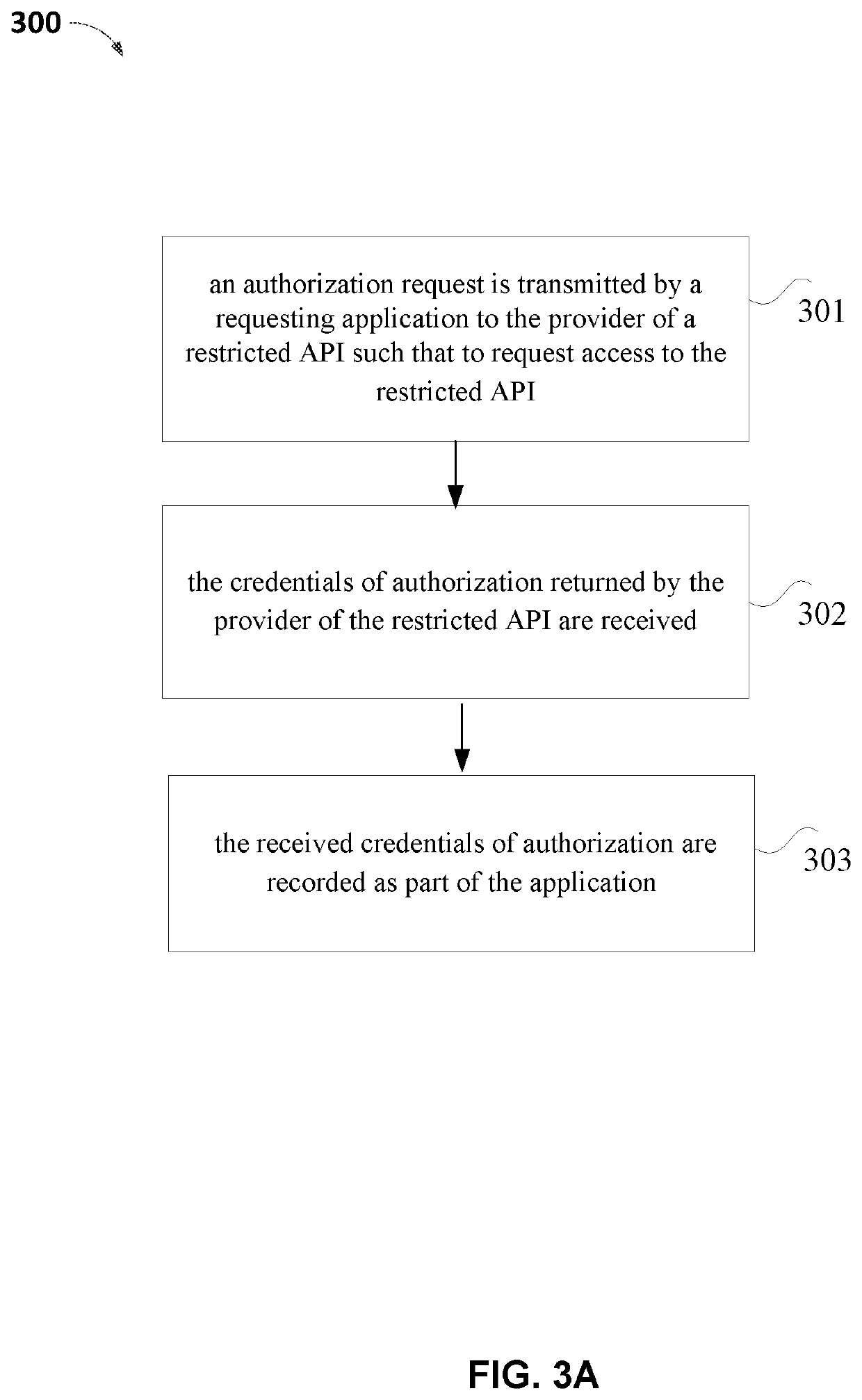
A method for accessing a restricted application programming interface (API) is disclosed, including: receiving, from a first application, a request to access the restricted API, the restricted API not supported by the first application; determining whether the first application is authorized by a provider of the restricted API to access the restricted API; and granting, in response to the determination that the first application is authorized by the provider of the restricted API to access the restricted API, the first application access to the restricted API.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
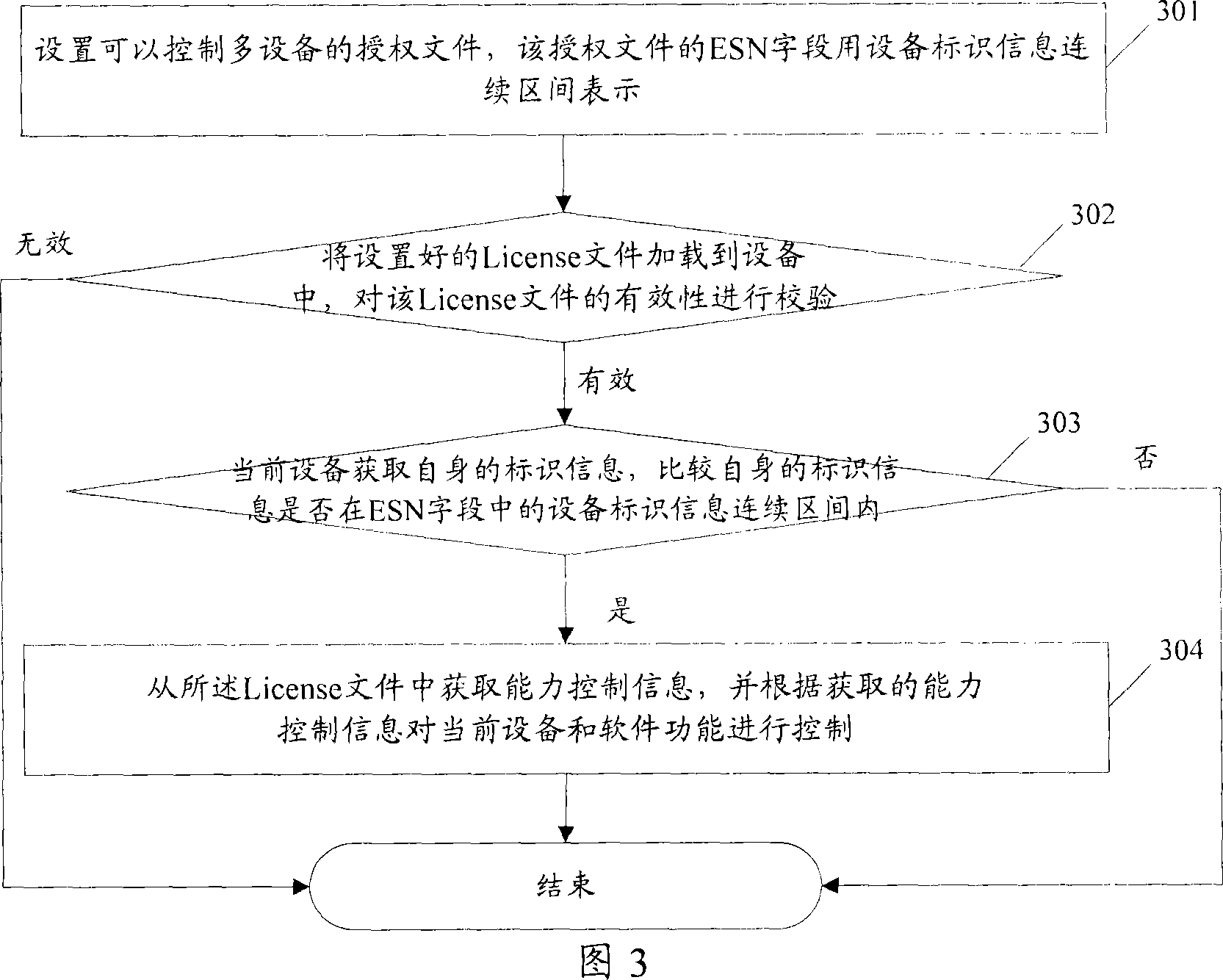
Authorizing method for controling multiple device and commmunication device and server
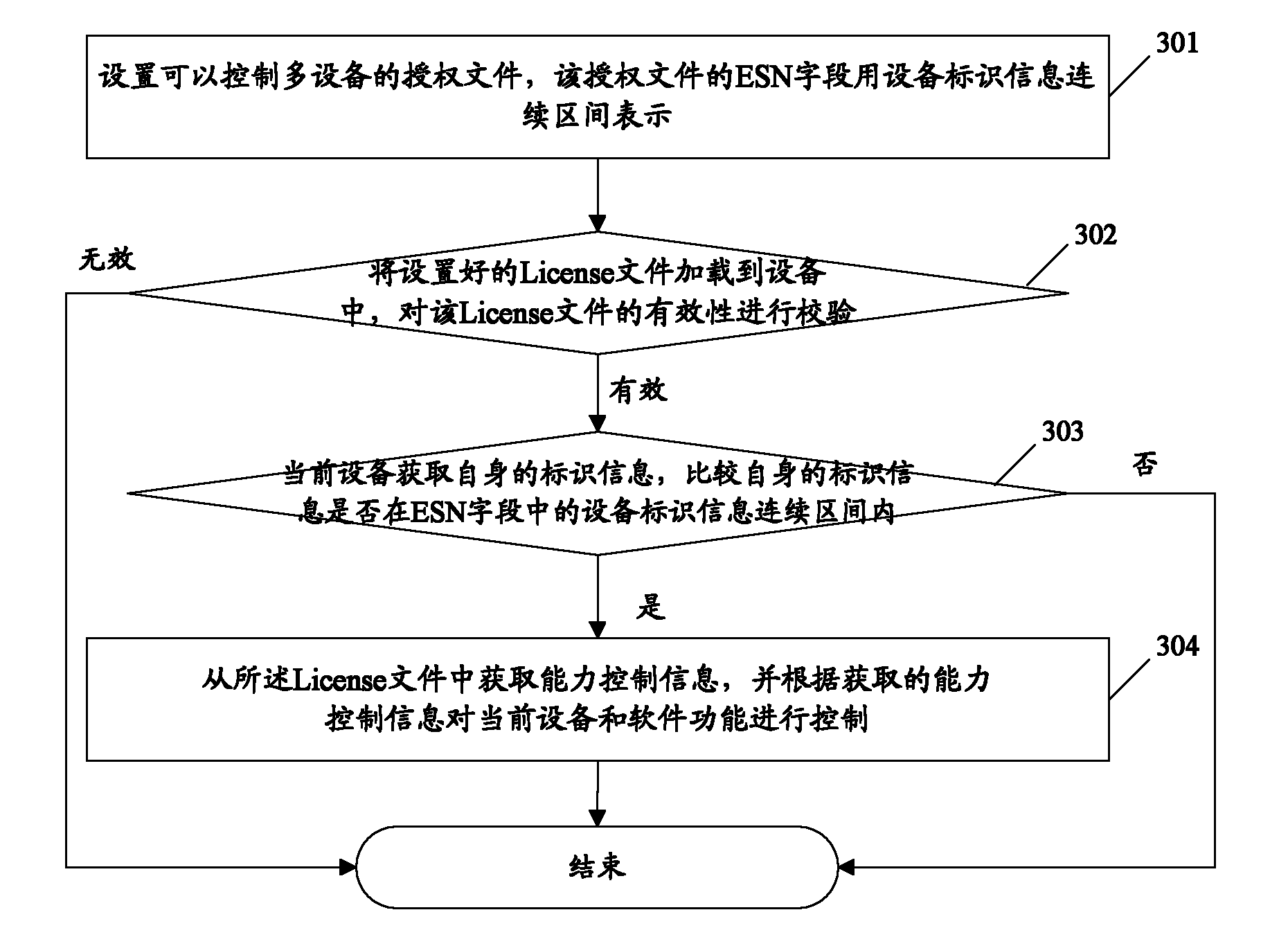
InactiveCN101051909ASimplify the authorization processUser identity/authority verificationProgram/content distribution protectionComputer hardwareAuthorization
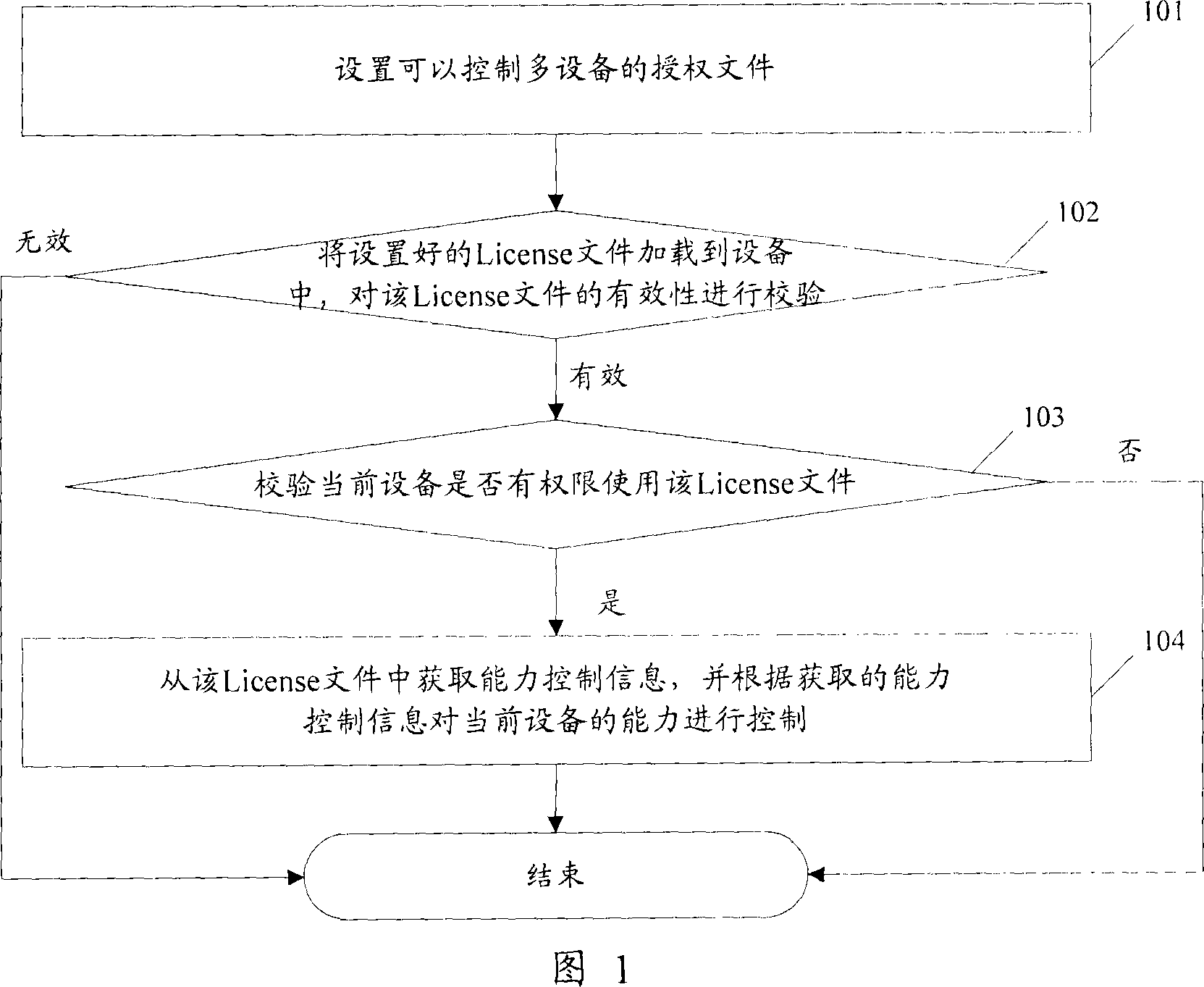
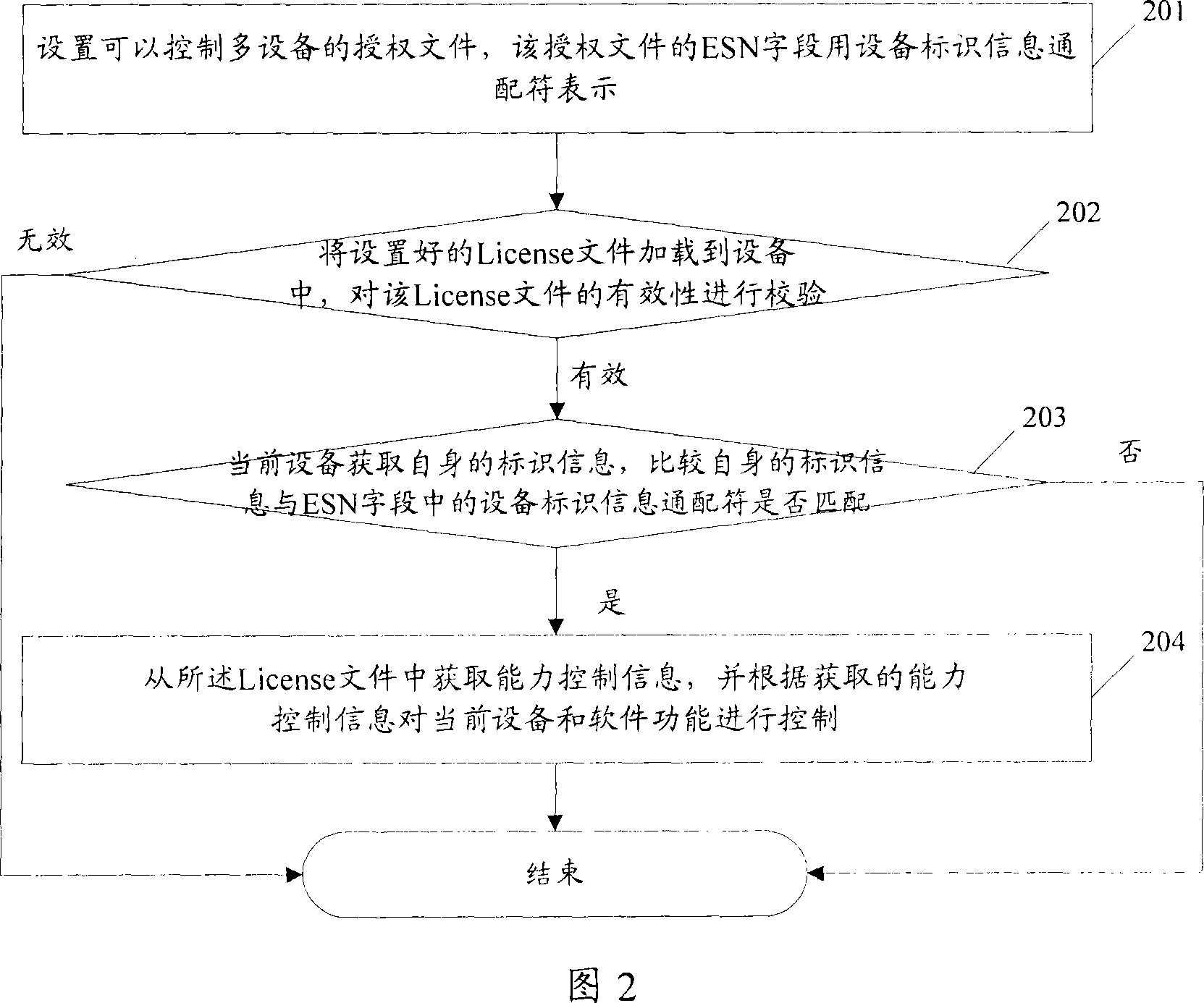
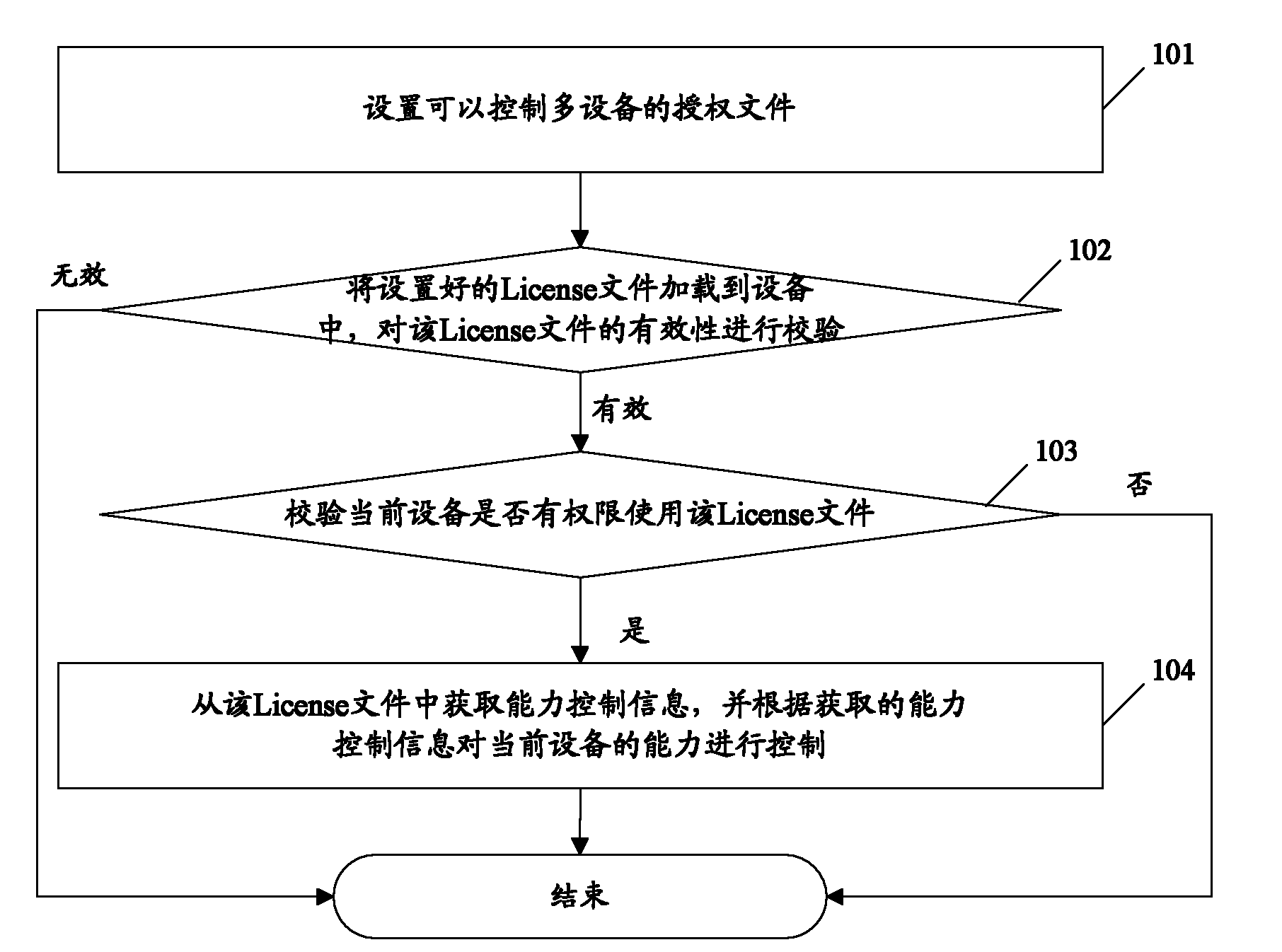
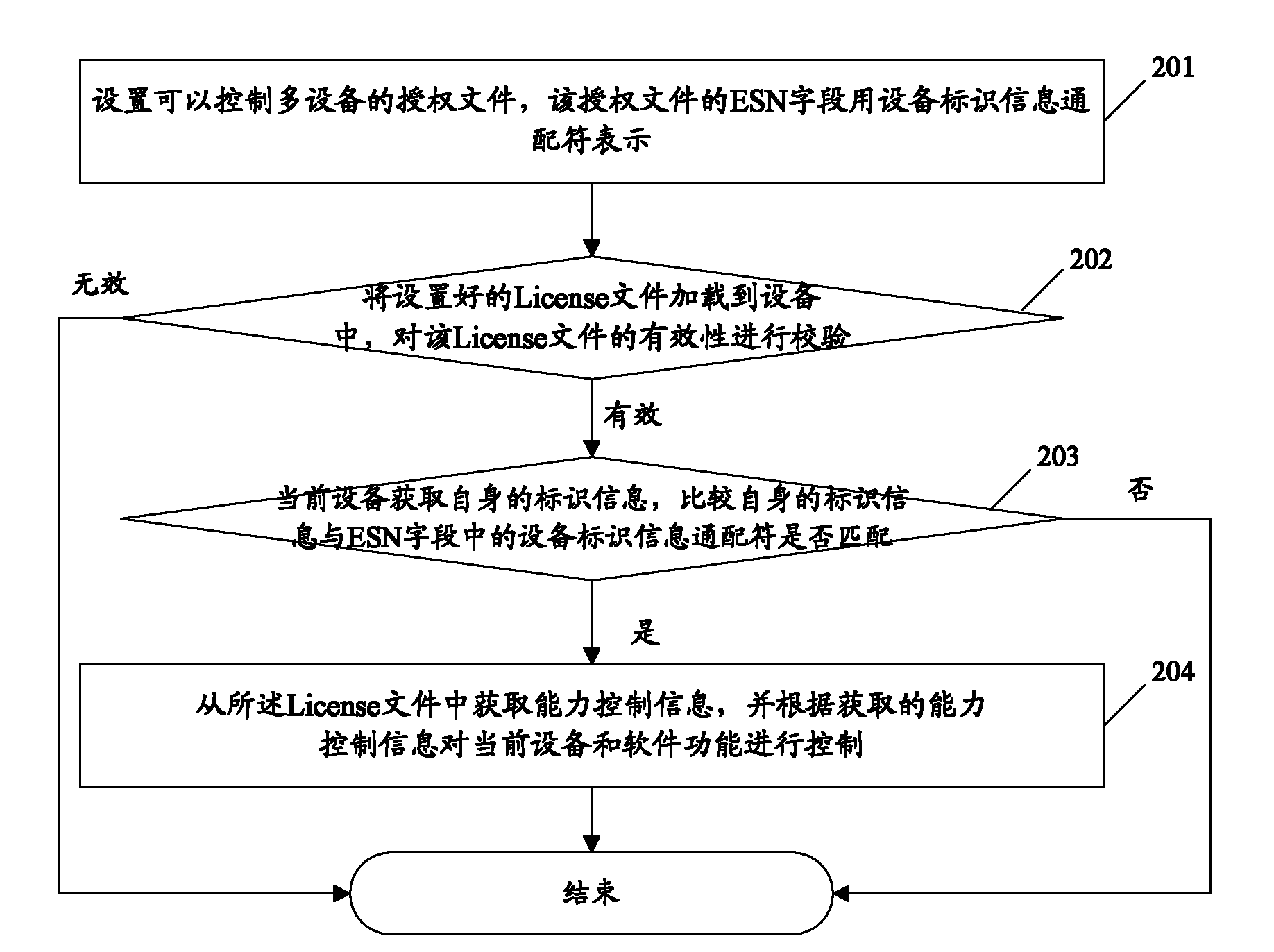
The method includes procedures: receiving authorization file, the authorization file contains information of licensed serviceable range (LSR); LSR is setup by using information wildcard of device ID and / or information continuum of device ID; comparing ID information corresponding to device with information of LSR in the authorization file, the method determines that the device has authorization to use the licensed file if the ID information of the device is existed in range expressed by information of LSR in the authorization file. The implemented example in the invention also discloses communication devices and servers of using the method. Using the method, communication devices and servers can simplify procedure for authorizing devices.
Owner:HUAWEI TECH CO LTD
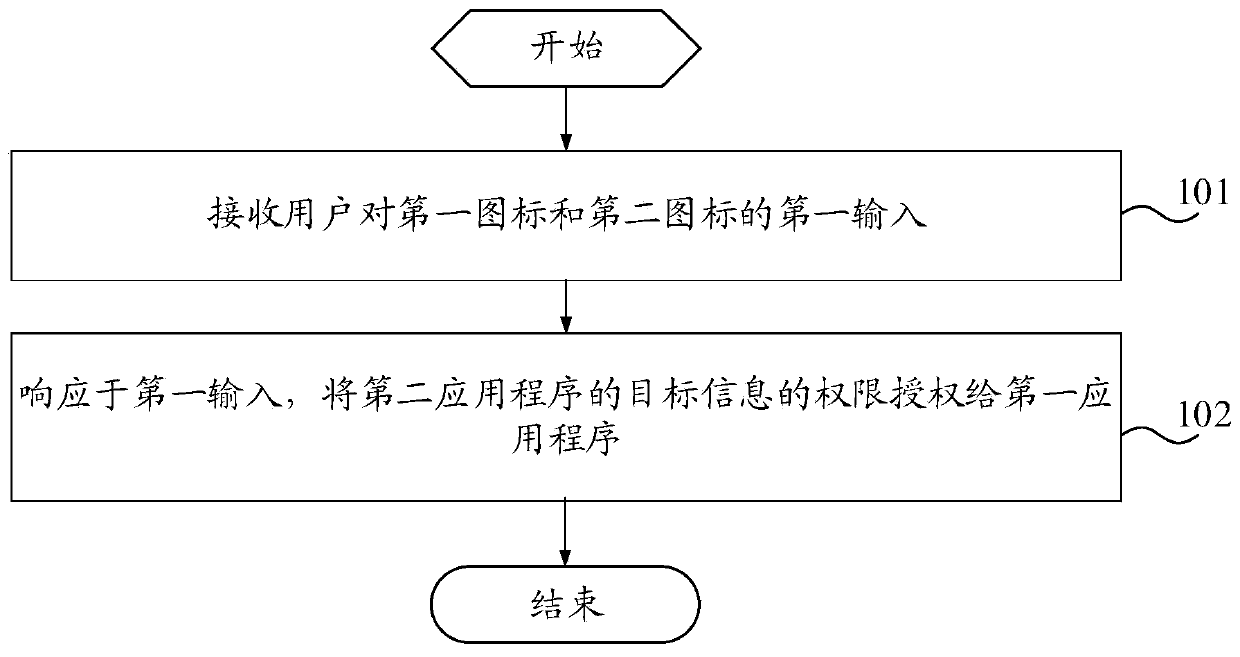
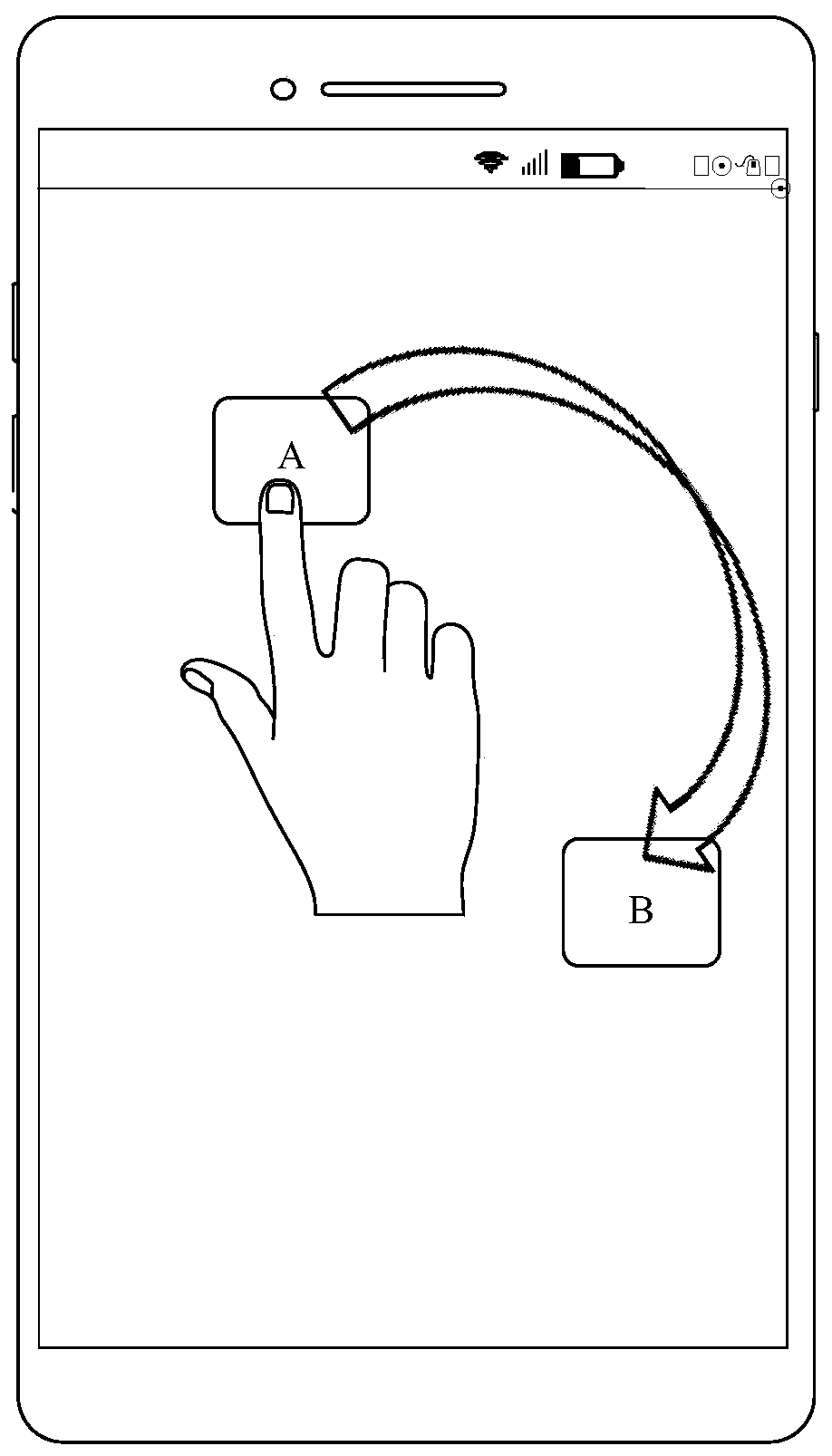
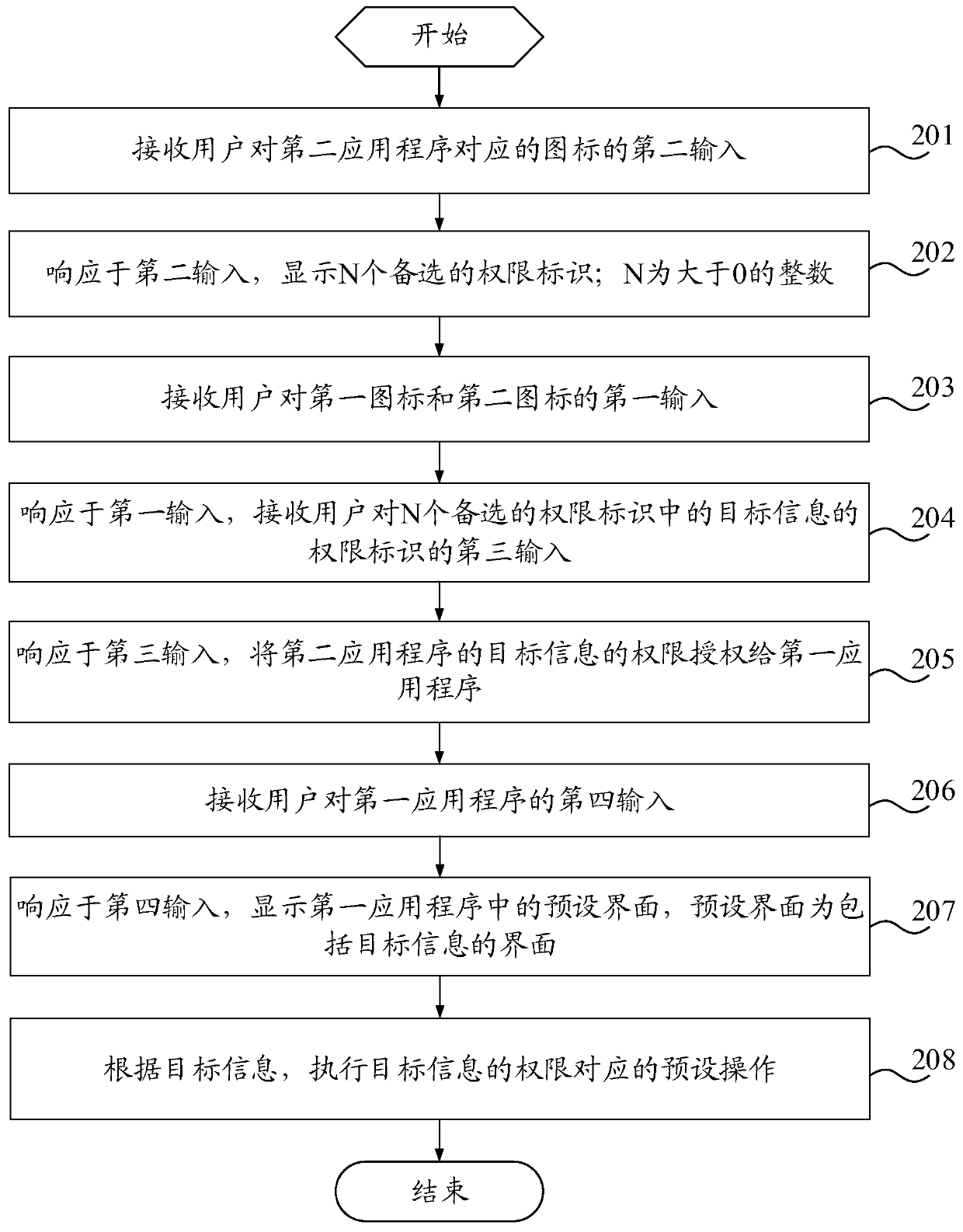
Application authorization method, electronic equipment and storage medium
ActiveCN111177710ASimplify the authorization processEasy to operateDigital data authenticationPlatform integrity maintainanceAuthorizationOperating system
The embodiment of the invention provides an application authorization method, electronic equipment and a storage medium, and relates to the technical field of communication. The method comprises the following steps: receiving a first input of a user to a first icon and a second icon; authorizing the authority of the target information of the second application program to the first application program in response to the first input, wherein the first application program is a program corresponding to one of the first icon and the second icon, and the second application program is a program corresponding to the other one of the first icon and the second icon. In the embodiment of the invention, the user can complete authority authorization between the first application program and the secondapplication program only by executing the first input of the first icon and the second icon without jumping from the first application program to the interface of the second application program for authorization and then returning to the first application program, so that the authorization process of the application is simplified, and the operation is convenient.
Owner:VIVO MOBILE COMM CO LTD
Automatic authorization method and device of equipment
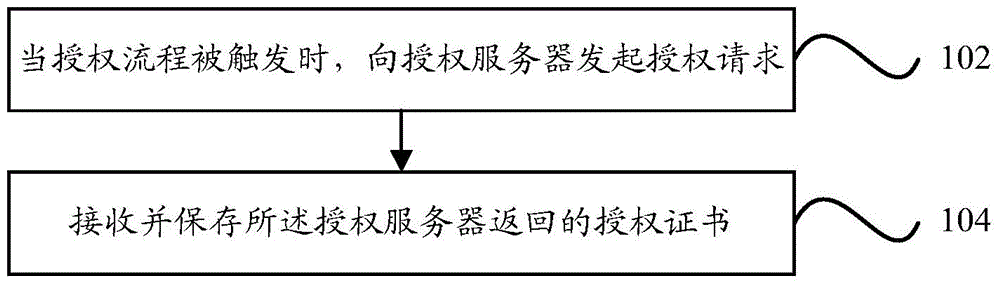
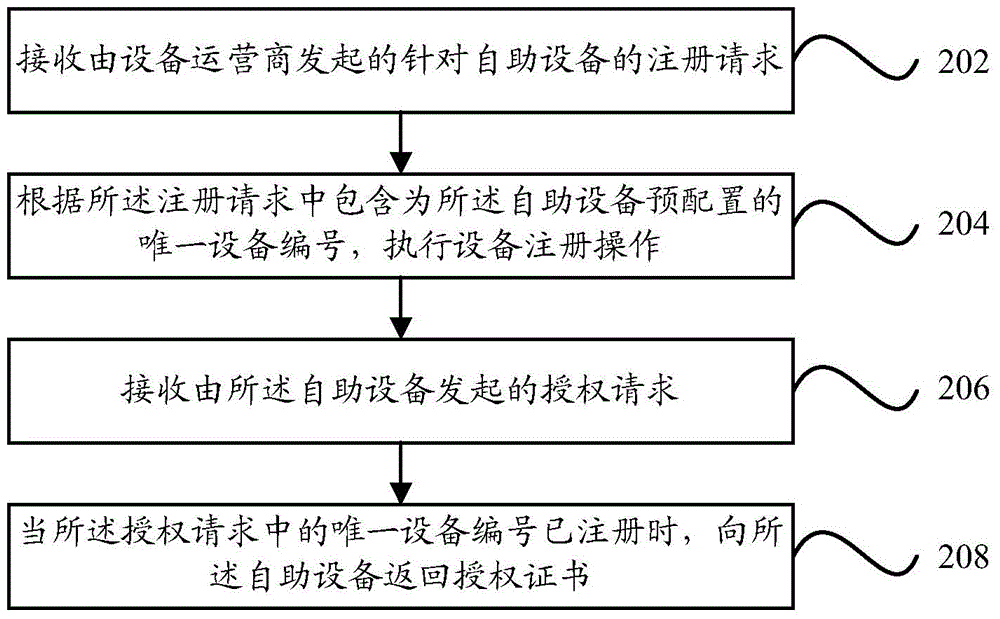
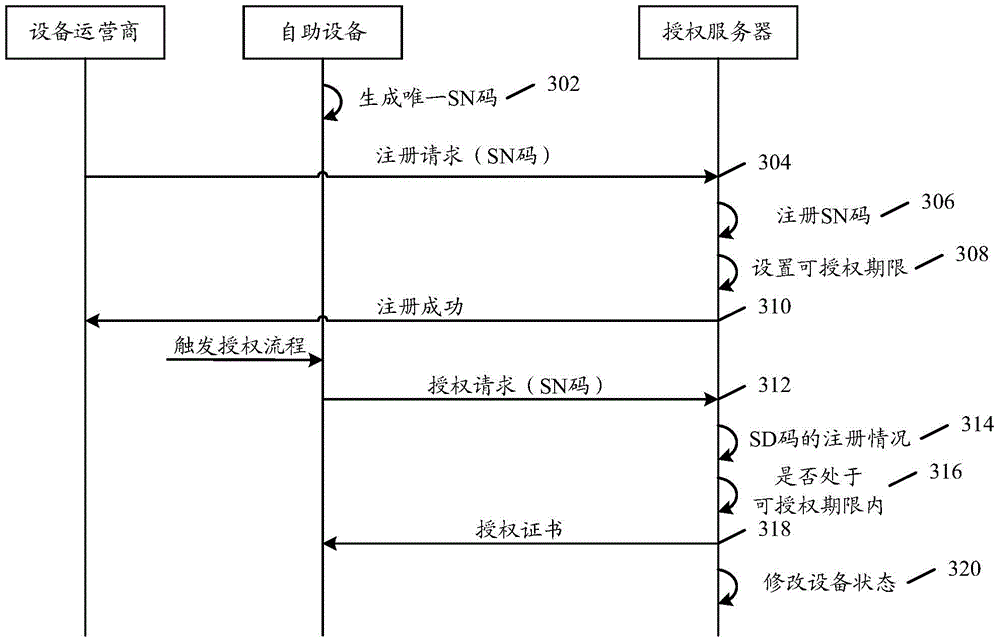
ActiveCN105373723ASimplify the authorization processPrevent leakageDigital data authenticationTransmissionAuthorization certificateEquipment Operator
The invention provides an automatic authorization method and device of equipment. The method is applied to an authorization server and comprises the following steps: receiving a registration request which is initiated from an equipment operator and aims at self-service equipment, and executing an equipment registration operation according to an unique equipment number which is preconfigured for the self-service equipment and is contained in the registration request; and receiving an authorization request initiated from self-service equipment, and returning an authorization certificate to the self-service equipment when the unique equipment number in the authorization request is registered. Through the technical scheme of the invention, the authorization certificate can not be leaked, an authorization process is simplified while authorization safety is improved, and fully-automatic remote authorization can be realized.
Owner:ADVANCED NEW TECH CO LTD
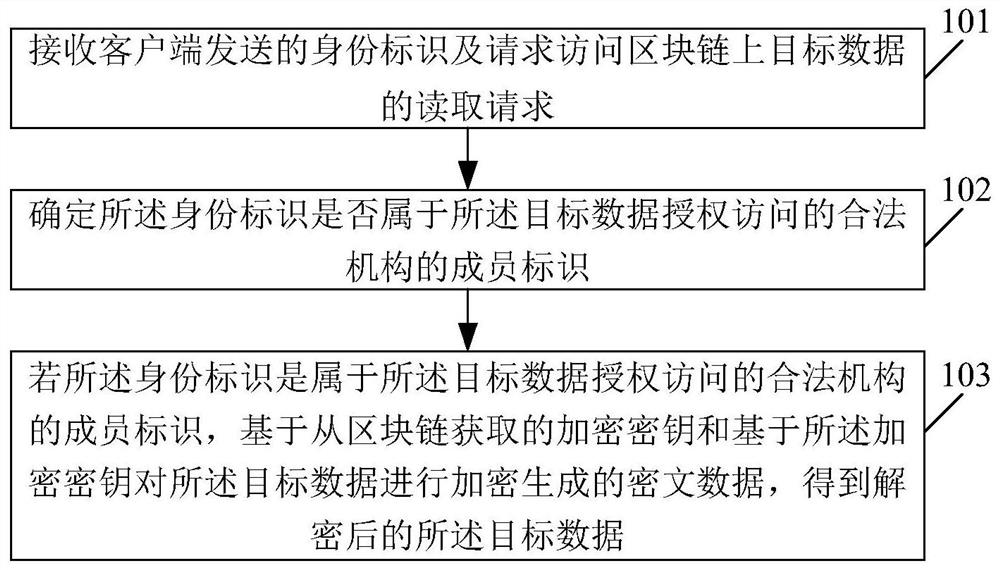
Data reading method and device, data authorization method and device and storage medium
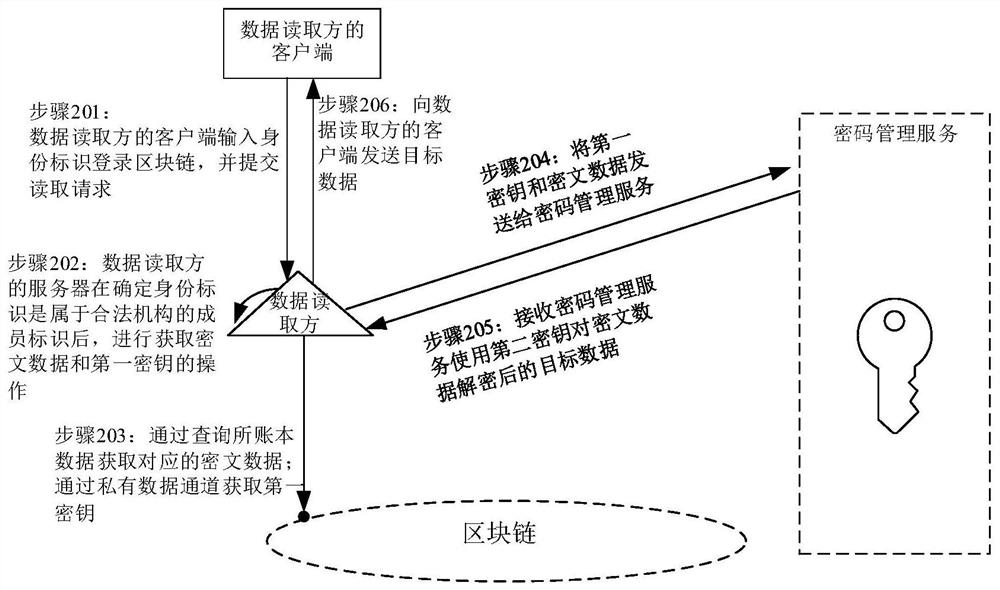
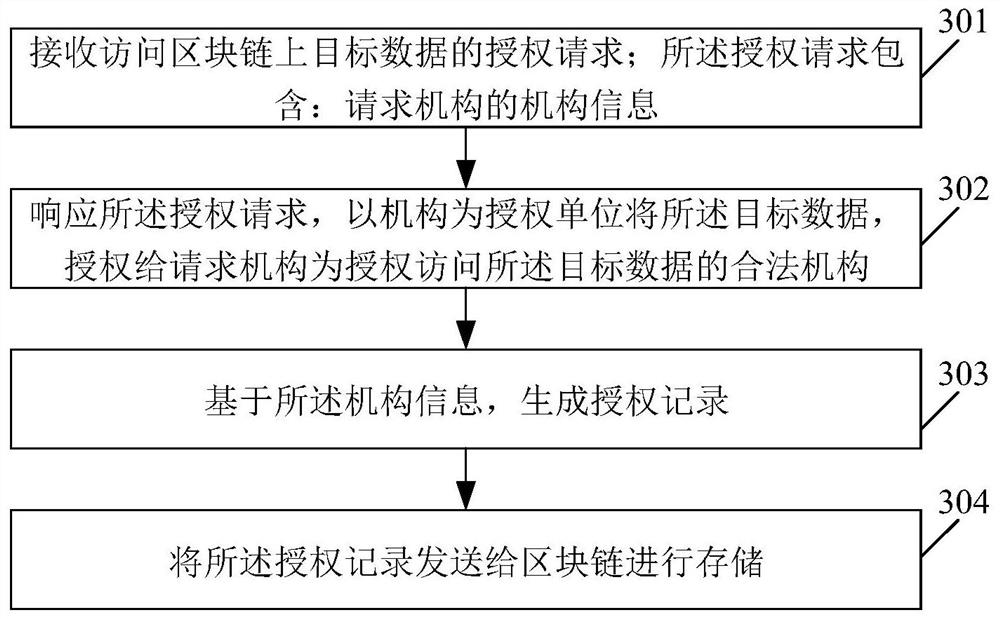
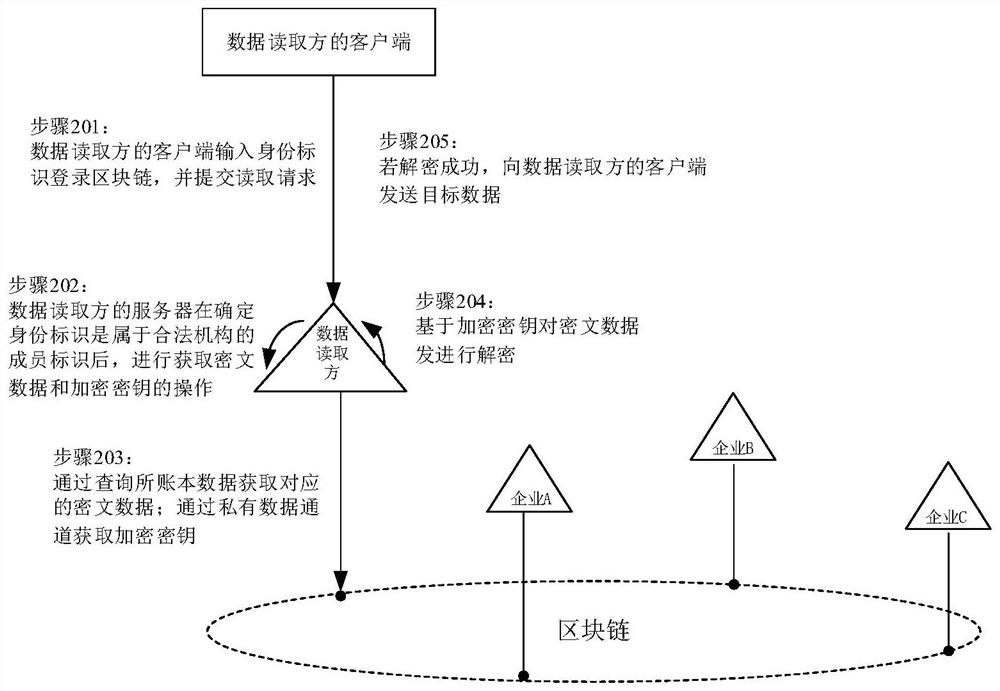
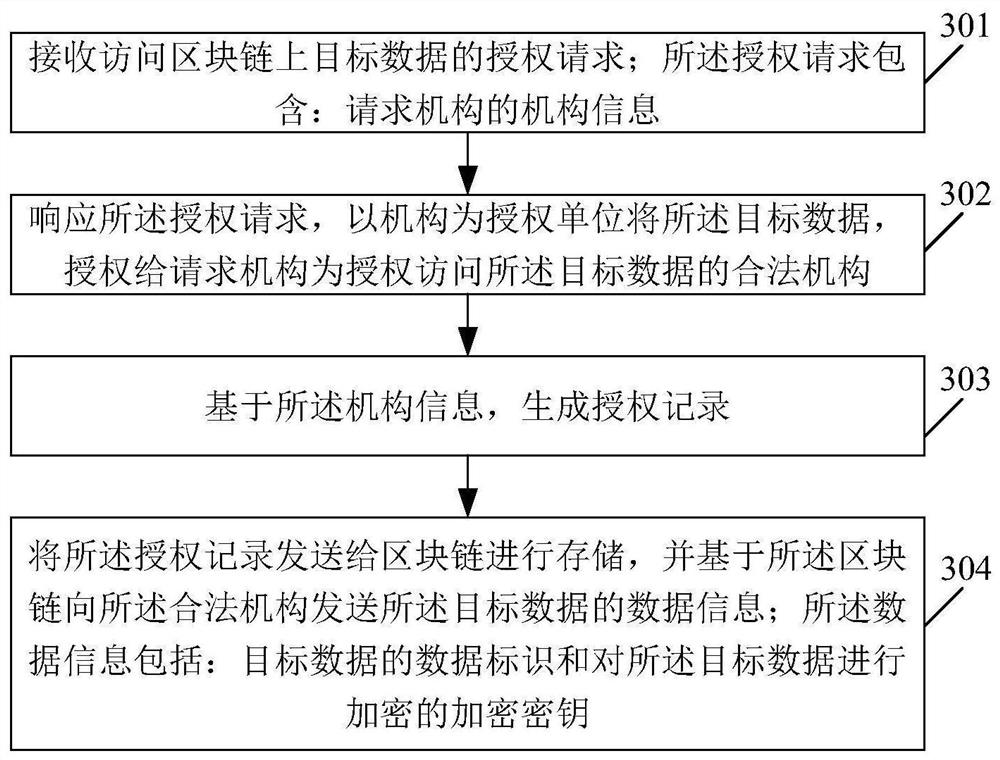
PendingCN112182646ASimplify the authorization processImprove authorization efficiencyDigital data protectionDigital data authenticationInternet privacyCiphertext
The invention relates to a data reading method and device, a data authorization method and device and a storage medium. The data reading method comprises the steps of receiving an identity identifiersent by a client and a reading request for requesting to access target data on a block chain; determining whether the identity identifier belongs to a member identifier of a legal institution authorized to access the target data; and if the identity identifier is a member identifier belonging to a legal institution authorized to access the target data, obtaining decrypted target data according tociphertext data encrypted based on a second key and obtained from a blockchain and a first key obtained by encrypting the second key. Therefore, as long as the reading request of the member identifierof the legal mechanism with authorized access can be responded, the data reading is more convenient and reasonable.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
Lock management system and lock management method
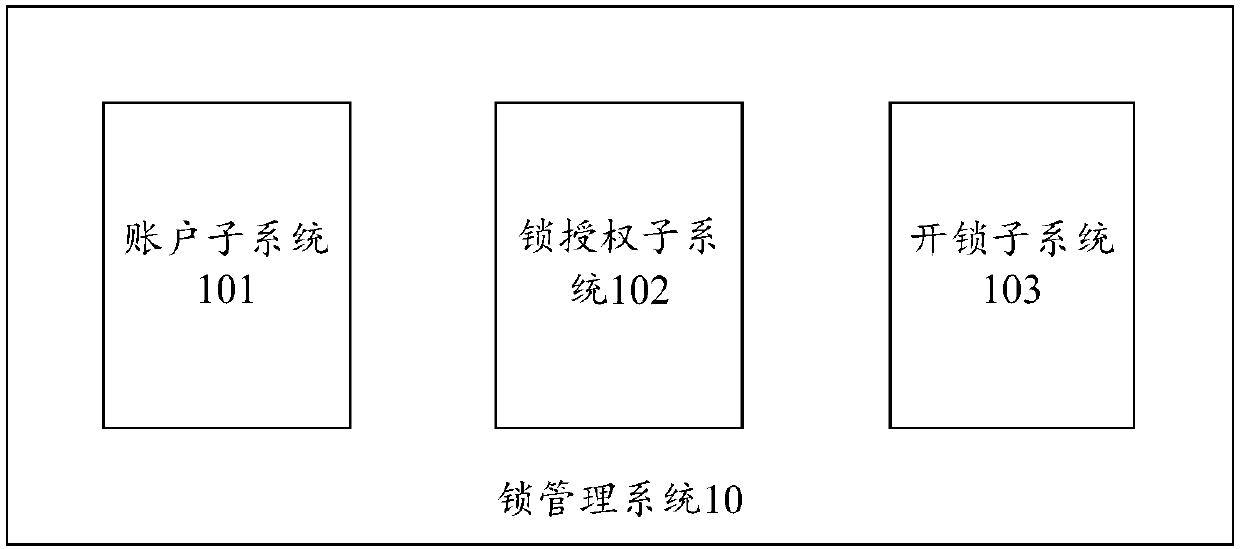
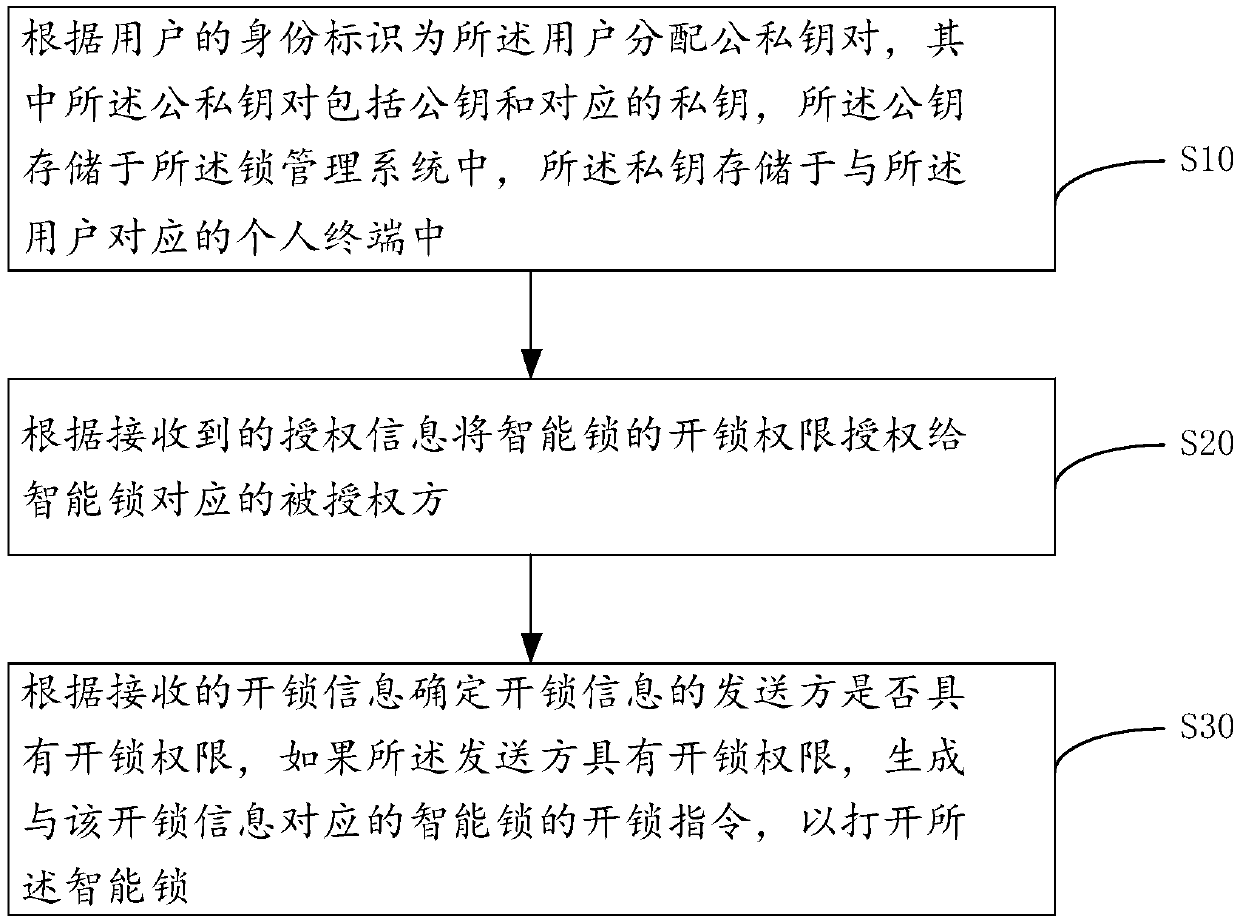
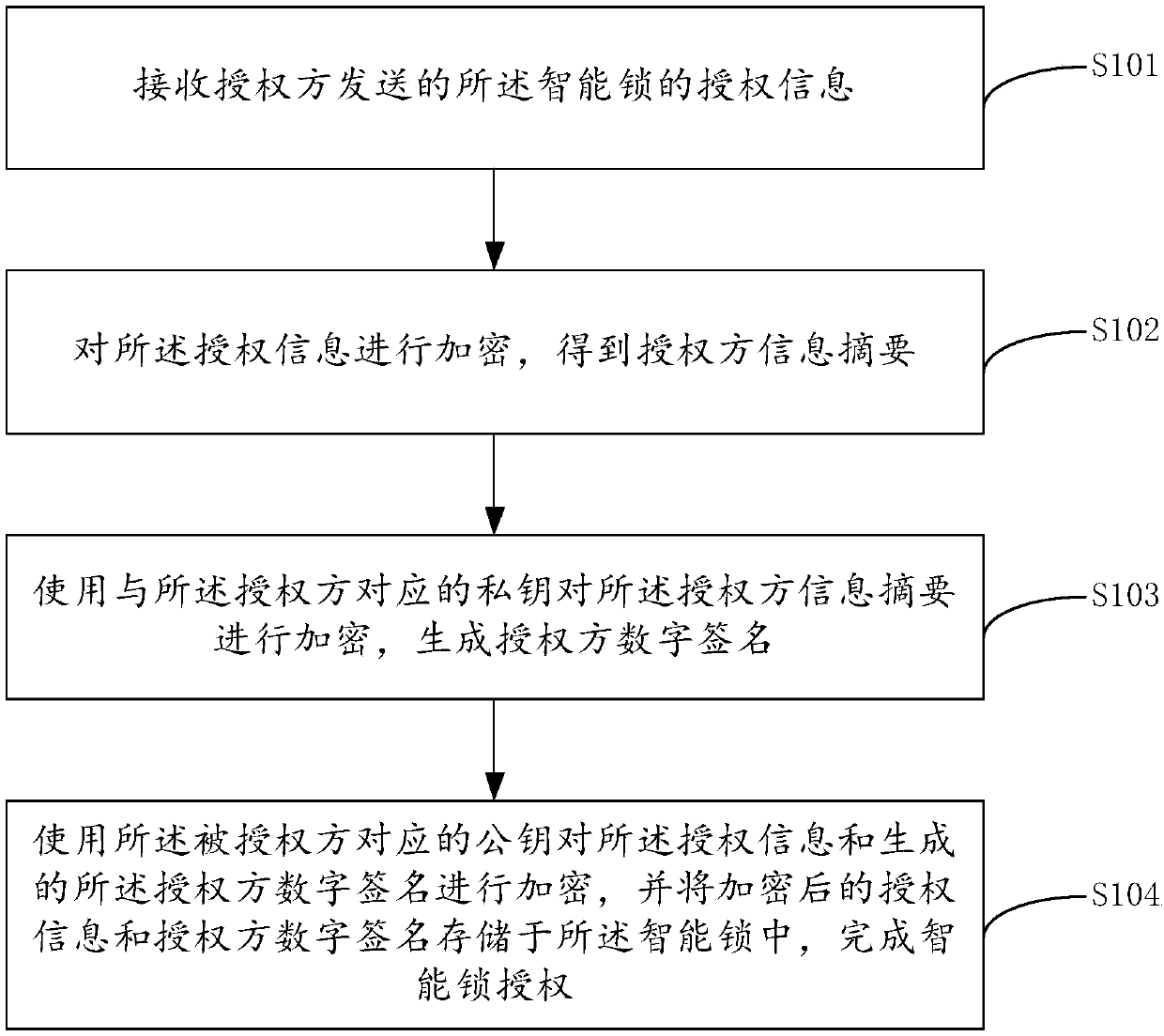
InactiveCN108055124ASimplify the authorization processSafe unlocking processKey distribution for secure communicationUser identity/authority verificationSmart lockAuthorization
The invention provides a lock management system and a lock management method, and relates to the technical field of smart locks. A user can establish a corresponding account through an account subsystem, and can grant the unlocking authority of a smart lock to other authorized parties through an authorization subsystem, in an authorization process, the digital signature of an authorization party needs to be used, and the digital signature of the authorization party has a unique corresponding relationship with the authorization party, so that the authorization information cannot be counterfeited. Meanwhile, only the authorized party obtaining authorization information can decrypt the ciphertext of the smart lock, so that the unauthorized personnel cannot unlock the smart lock. The authorized party can unlock the smart lock only through an electronic device without carrying a physical key, therefore the authorization process is simpler. At the same time, public and private key pairs corresponding to the authorization party are respectively stored in the lock management system and a personal terminal, and authorization and unlocking cannot be achieved through the public key or the private key alone, so that the unlocking process is more secure.
Owner:上海妙联数字科技有限公司
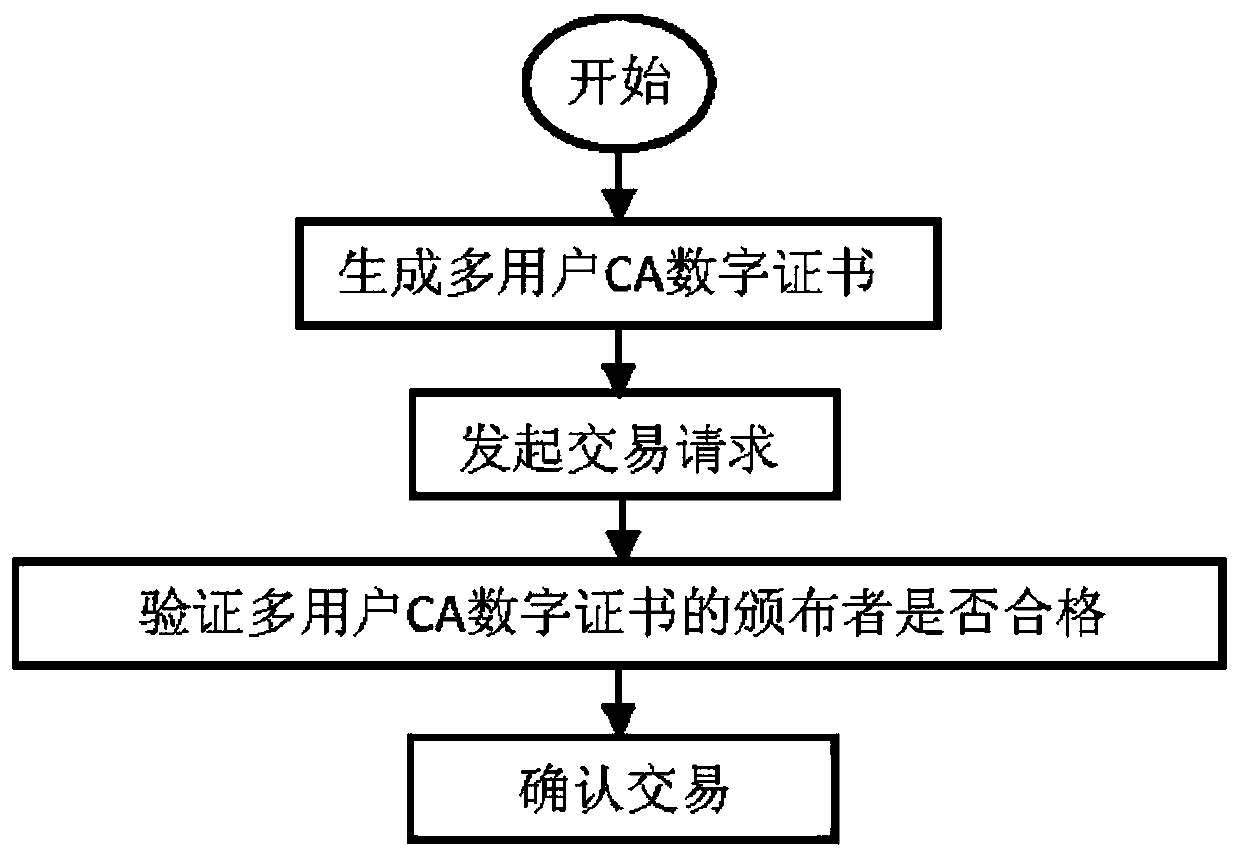
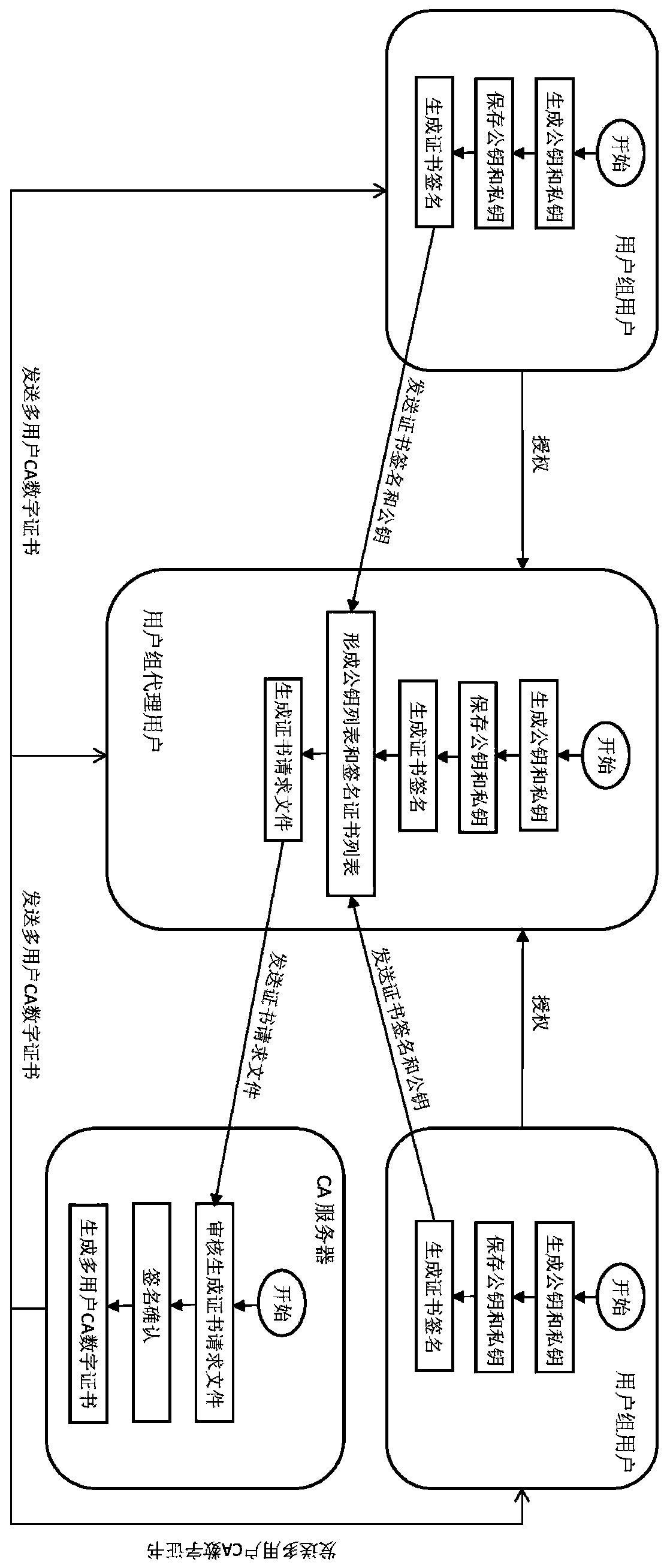
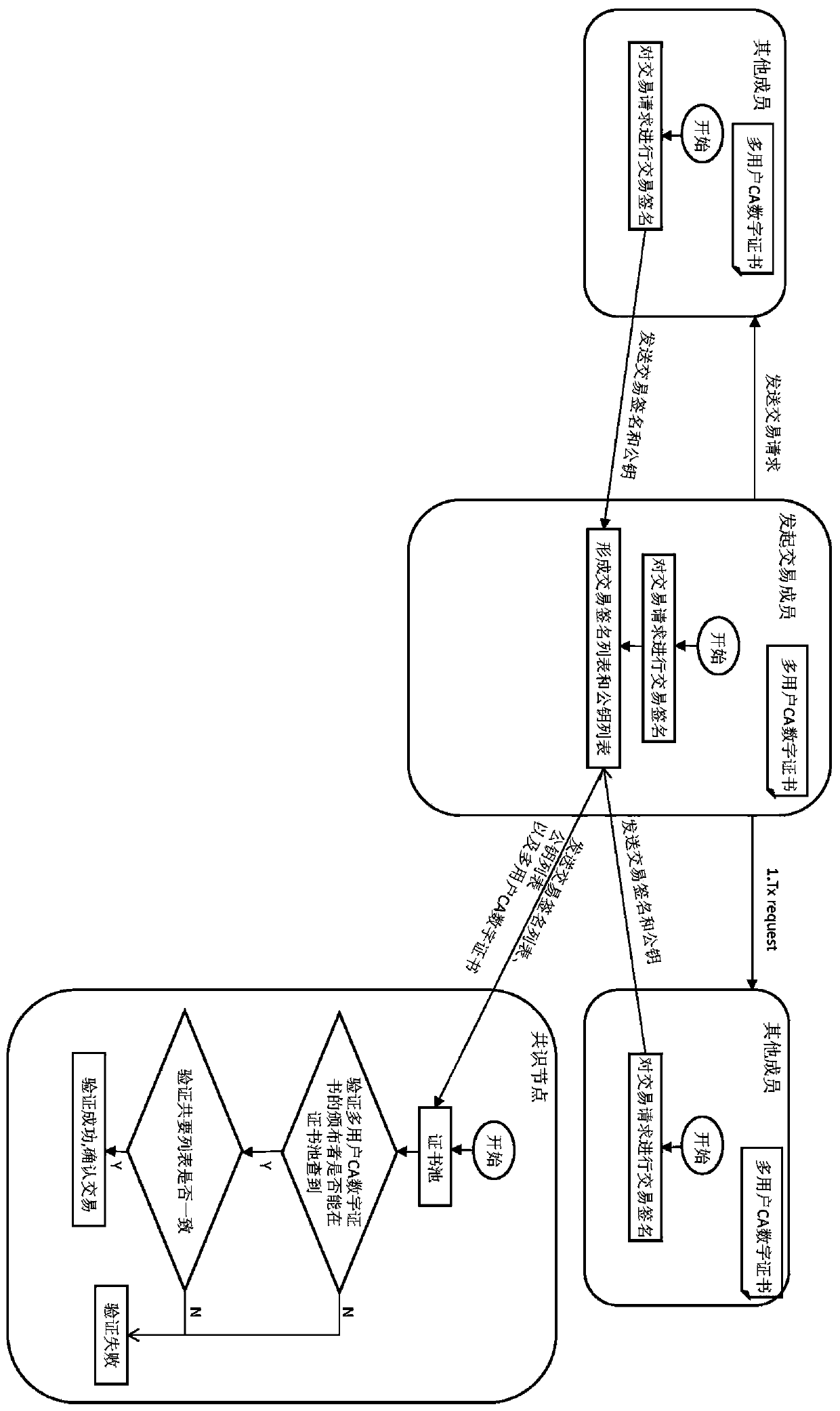
Blockchain transaction method based on multi-user CA digital certificate
ActiveCN110636051AReduce information sizeImprove experienceFinancePublic key for secure communicationFinancial transactionOperating system
The invention discloses a blockchain transaction method based on a multi-user CA digital certificate, which comprises the following steps that: the step 1, applying, by user group members participating in a transaction, for the CA digital certificate to a CA server by using respective public keys and signatures, and generating the multi-user CA digital certificate by the CA server after the auditing is passed; the step 2, initiating a transaction request by a user group member; the step 3, verifying whether an issuer of the multi-user CA digital certificate is qualified or not; and the step 4,confirming a transaction. According to the blockchain transaction method based on the multi-user CA digital certificate, the complexity in the multi-user transaction process can be effectively reduced, and the transmission efficiency and the processing speed are improved.
Owner:中芯昊月(深圳)科技控股有限公司
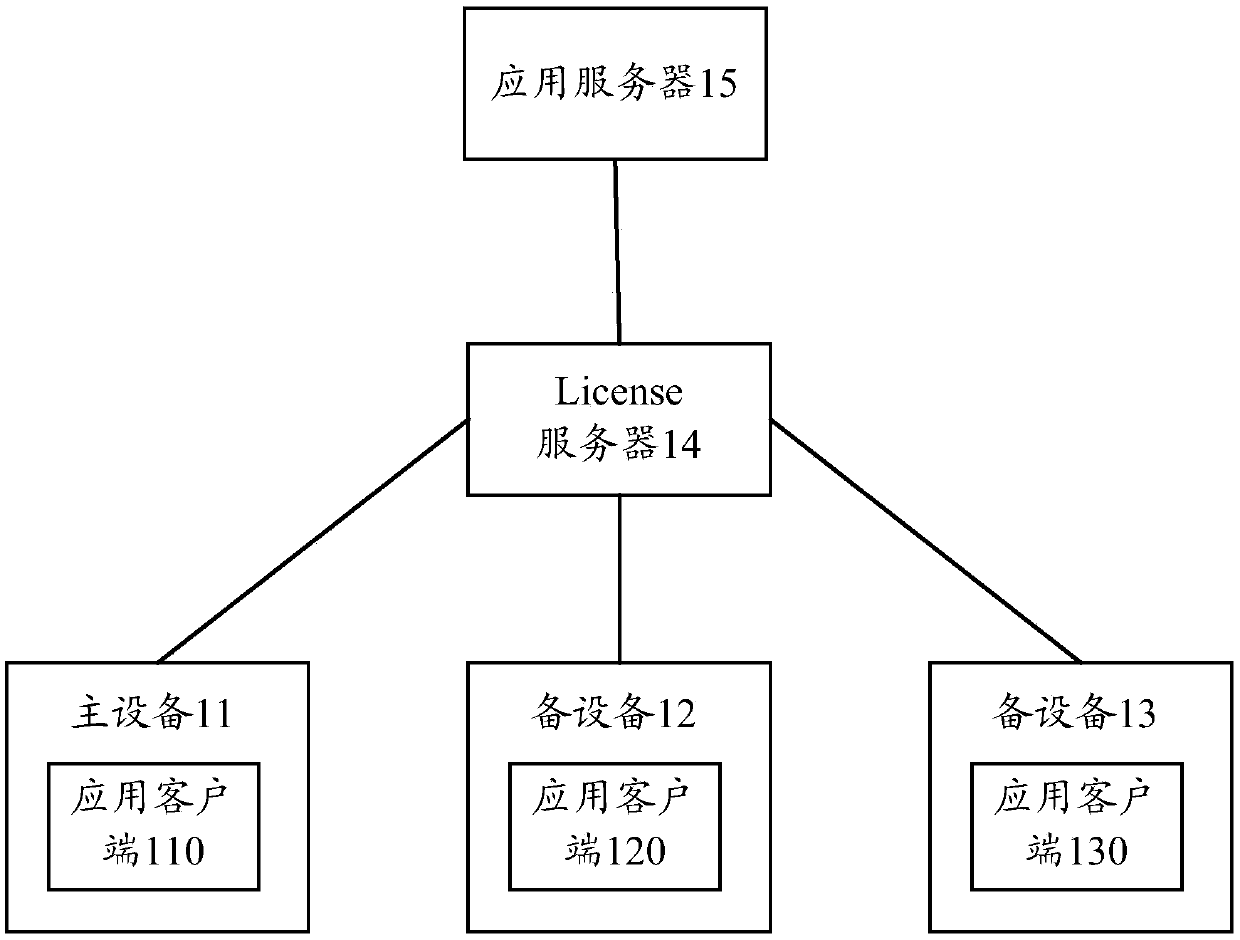
Authorization method and device
ActiveCN109543365AGood experienceSimplify the application process and authorization processProgram/content distribution protectionClient-sideAuthorization
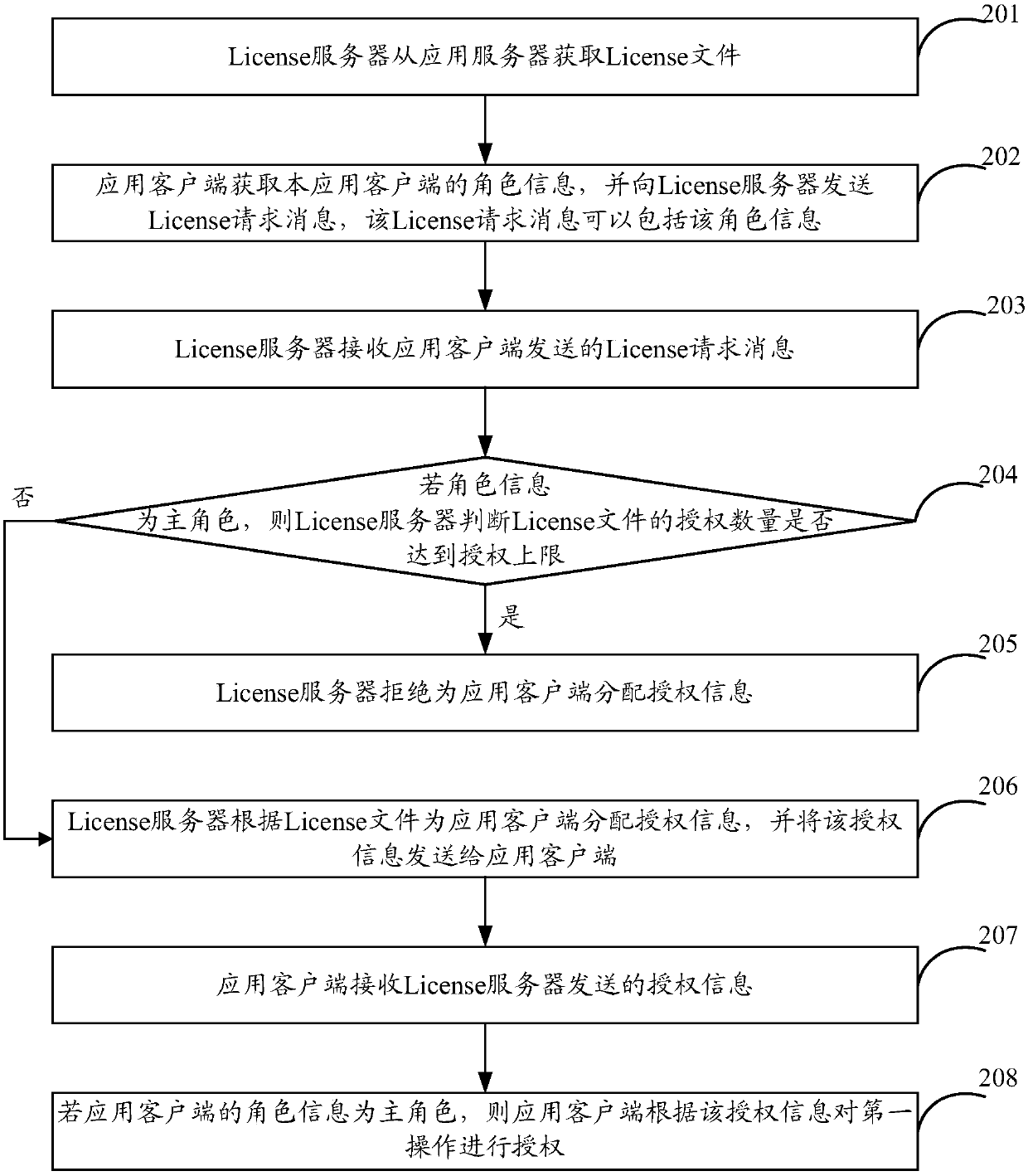
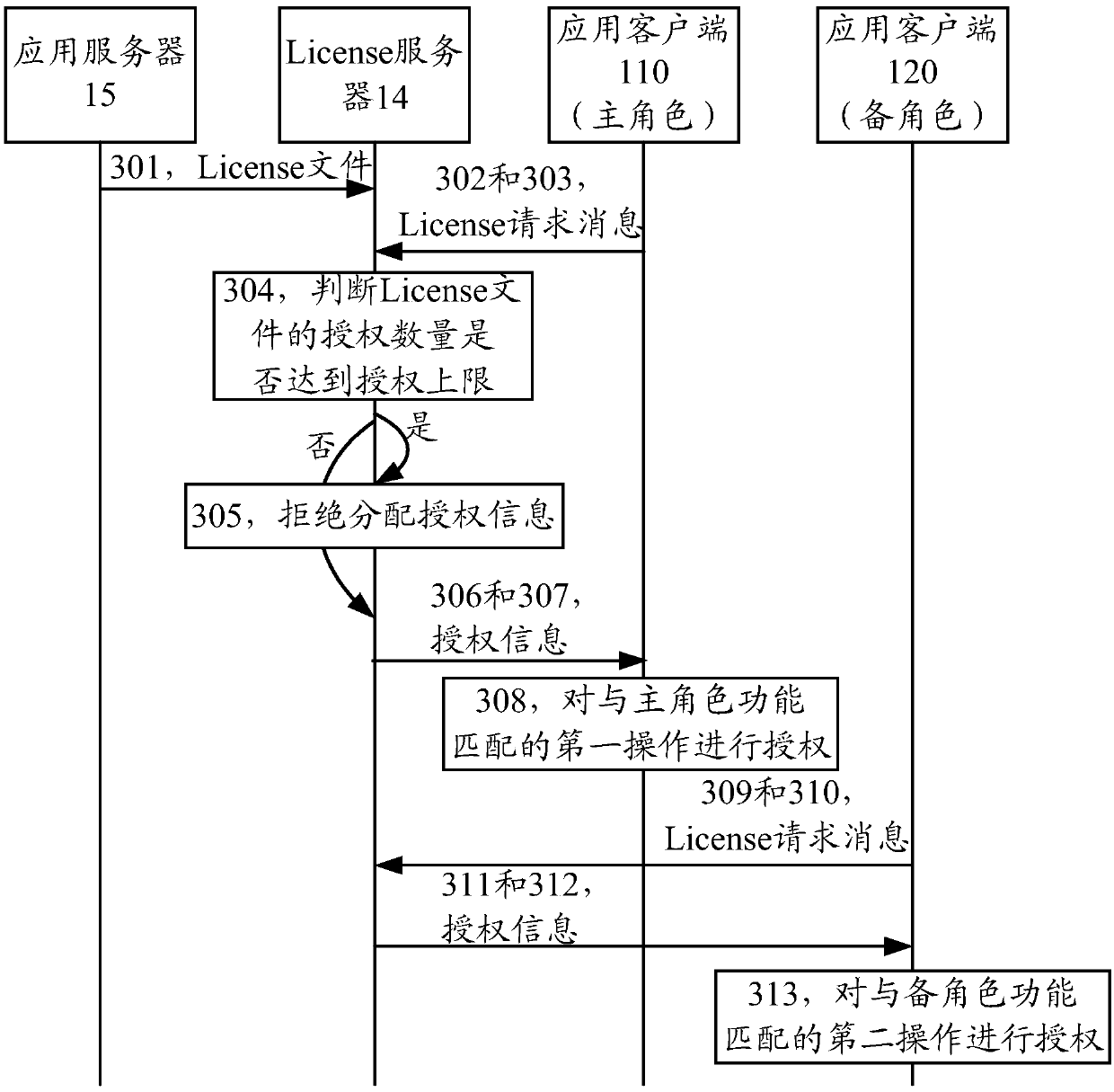
The invention provides an authorization method and device. The method includes obtaining a License file from an application serv; Receiving a License request message sent by an application client, wherein the License request message comprises role information of the application client, and the role information is a main role or a backup role; If the role information is the main role, judging whether the authorization quantity of the License file reaches the authorization upper limit; If so, refusing to assign authorization information to the application client; If not, allocating authorizationinformation to the application client according to the License file, and sending the authorization information to the application client, so that the application client authorizes the first operationaccording to the authorization information. Through the technical proposal of the application, the user does not need to purchase multiple License files, and the user has a better experience.
Owner:NEW H3C TECH CO LTD
Authorization method for controlling plurality of equipment, communication equipment and server
InactiveCN101917300ASimplify the authorization processUser identity/authority verificationData switching networksAuthorizationSoftware engineering
The embodiment of the invention discloses an authorization method for controlling a plurality of equipment. The method comprises the following steps of: receiving an authorization file which contains permission usable range information, wherein the permission usable range information is set by adopting an equipment identification information wildcard and / or an equipment identification information continuous interval; comparing the identification information corresponding to the equipment with the permission usable range information in the authorization file; and confirming that the equipment has the right to use the authorization file if the identification information of the equipment exists in a range shown by the permission usable range information of the authorization file. The embodiment of the invention also provides communication equipment and a server which can use the method. The authorization method for controlling a plurality of equipment, communication equipment and the server, which are provided by the embodiment of the invention, can simplify the authorization process of the equipment.
Owner:HUAWEI TECH CO LTD
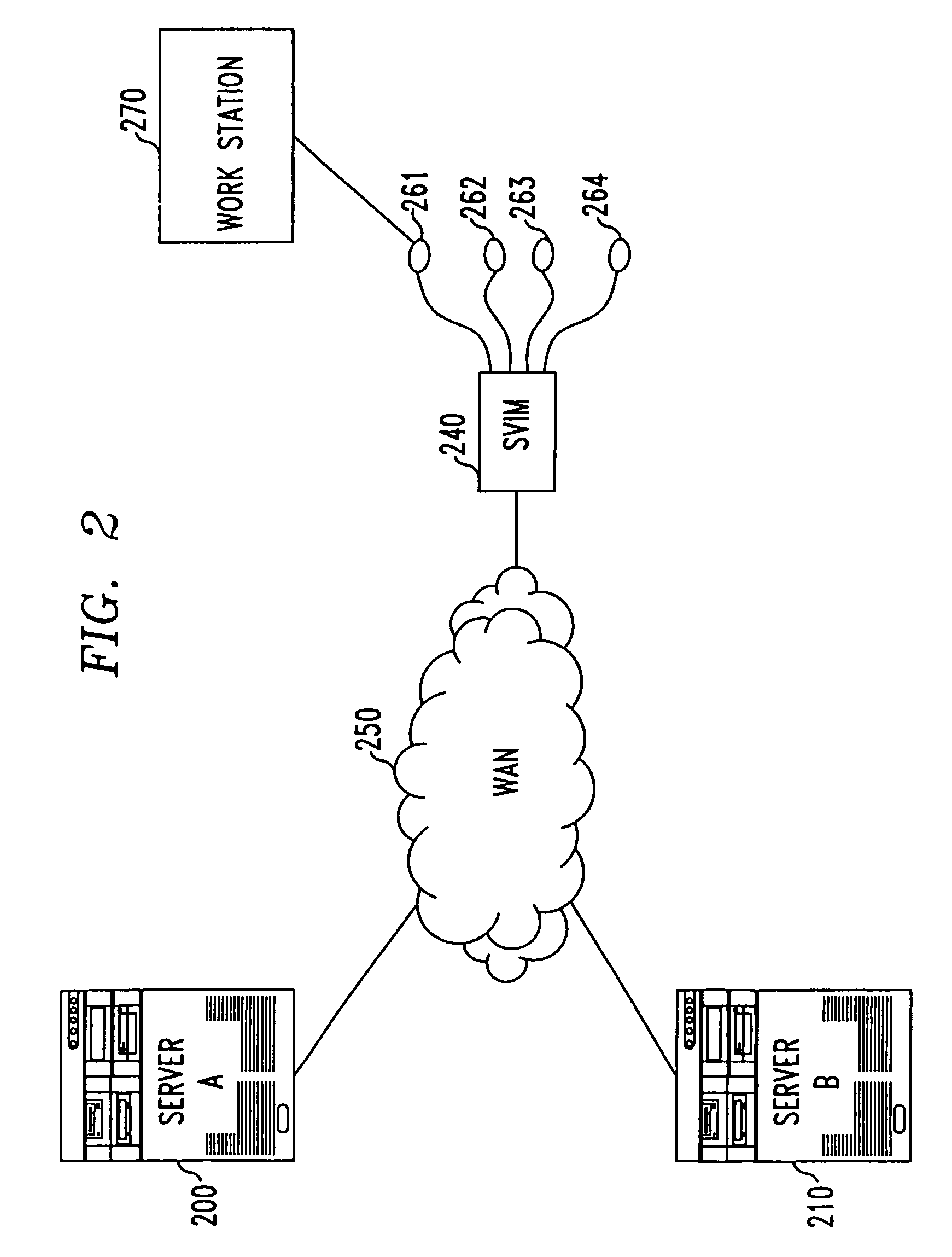
System for securing inbound and outbound data packet flow in a computer network
InactiveUS20080263639A1Simplify the authorization processDigital data processing detailsUser identity/authority verificationNetwork packetEnd user
A method provides for control of access to network resources. A virtual identity machine resides in the network and is pre-authorized to access certain network resources. End users desiring access to those network resources attempt to logically connect to the virtual identity machines. If the logical connection attempt is successful, then the end user assumes the virtual identity of the virtual identity machine and has access to all of the same information that was available to the virtual identity machine.
Owner:AMERICAN PATENTS LLC
Terminal software authorization system and method based on machine fingerprint and USBkey
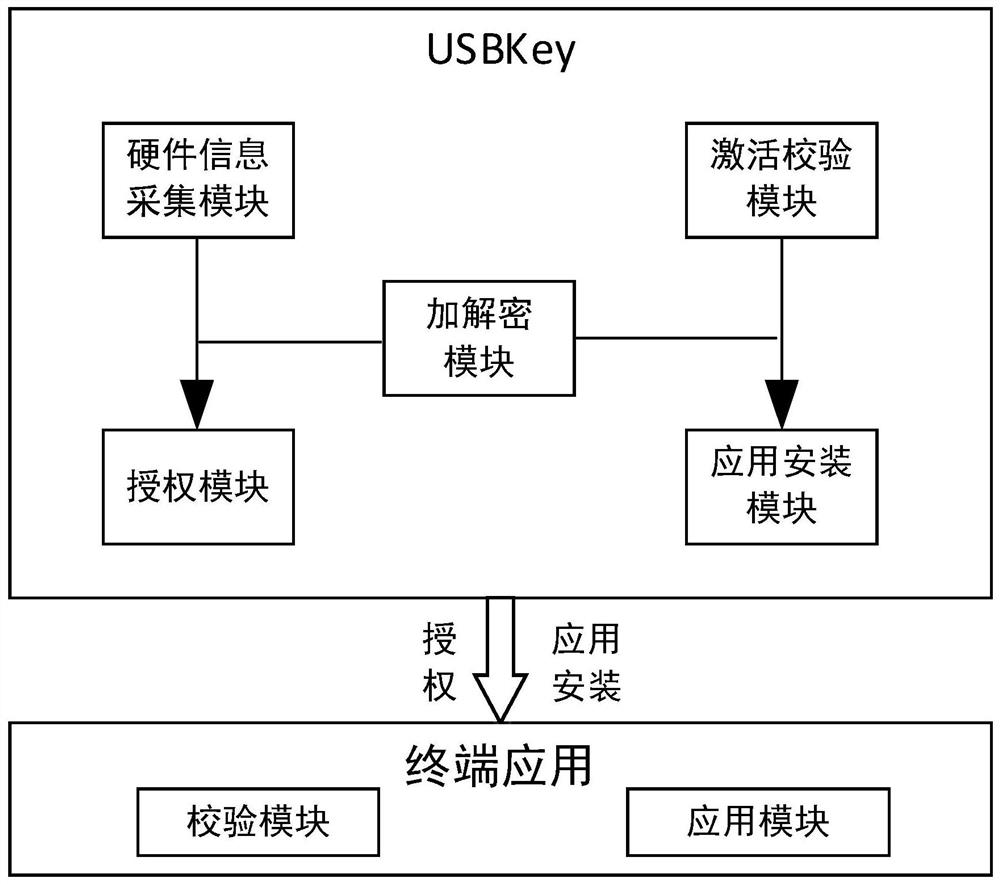
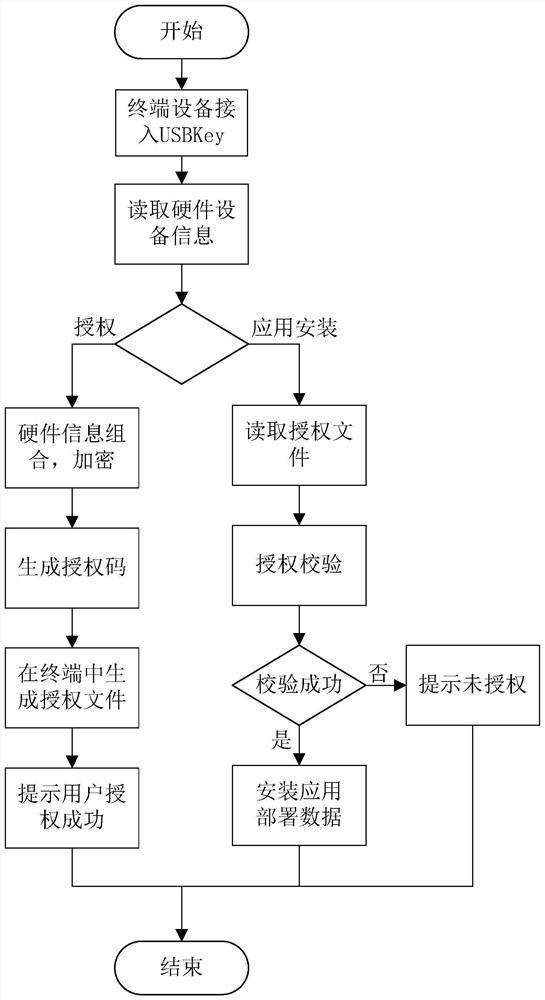
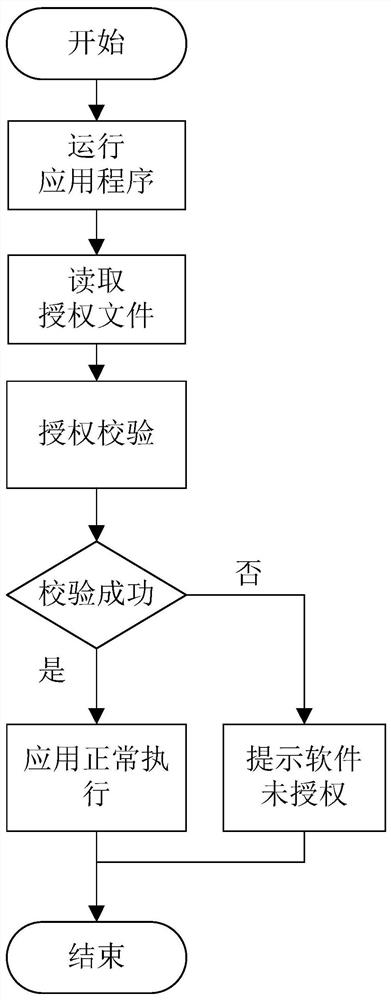
PendingCN113901401ASimplify the authorization processImprove adaptabilityProgram/content distribution protectionSoftware engineeringApplication software
The invention provides a terminal software authorization system and method based on a machine fingerprint and a USBkey, and the system comprises the following modules: a hardware information collection module which collects hardware information and transmits the hardware information; an authorization module which is used for receiving the hardware information, combining the hardware information and generating an authorization file; an activation verification module which is used for verifying the authorization file; and an application installation modulewhich is used for carrying out application software installation and data deployment after the authorization file passes verification. According to the invention, the authorization process is simple and easy to use, and authorization is carried out by adopting an independent USBkey without depending on other hardware; the adaptability and the flexibility are high, and the cost is low.
Owner:EAST CHINA INST OF COMPUTING TECH
Authorization method for accepting communication service and authorization device thereof
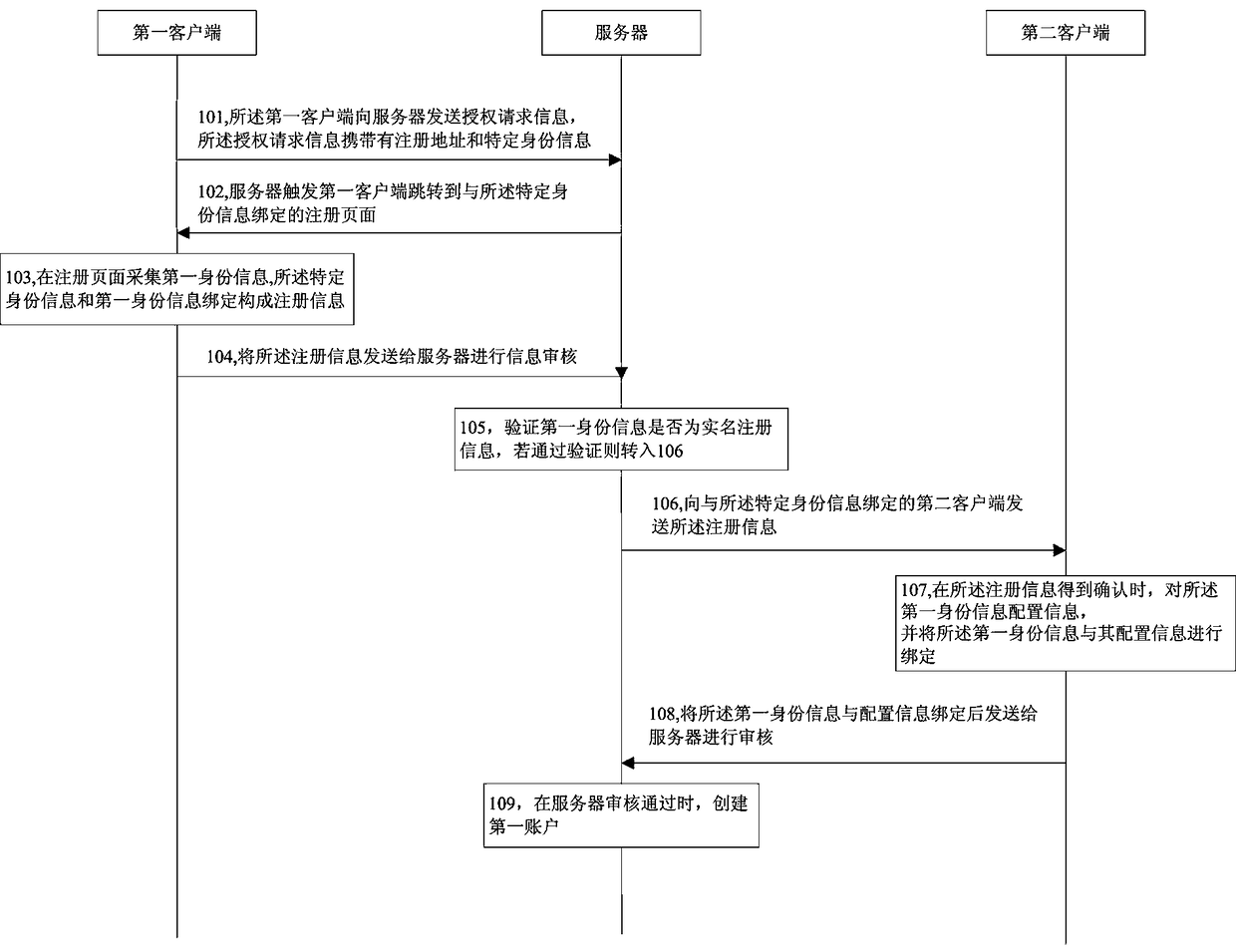
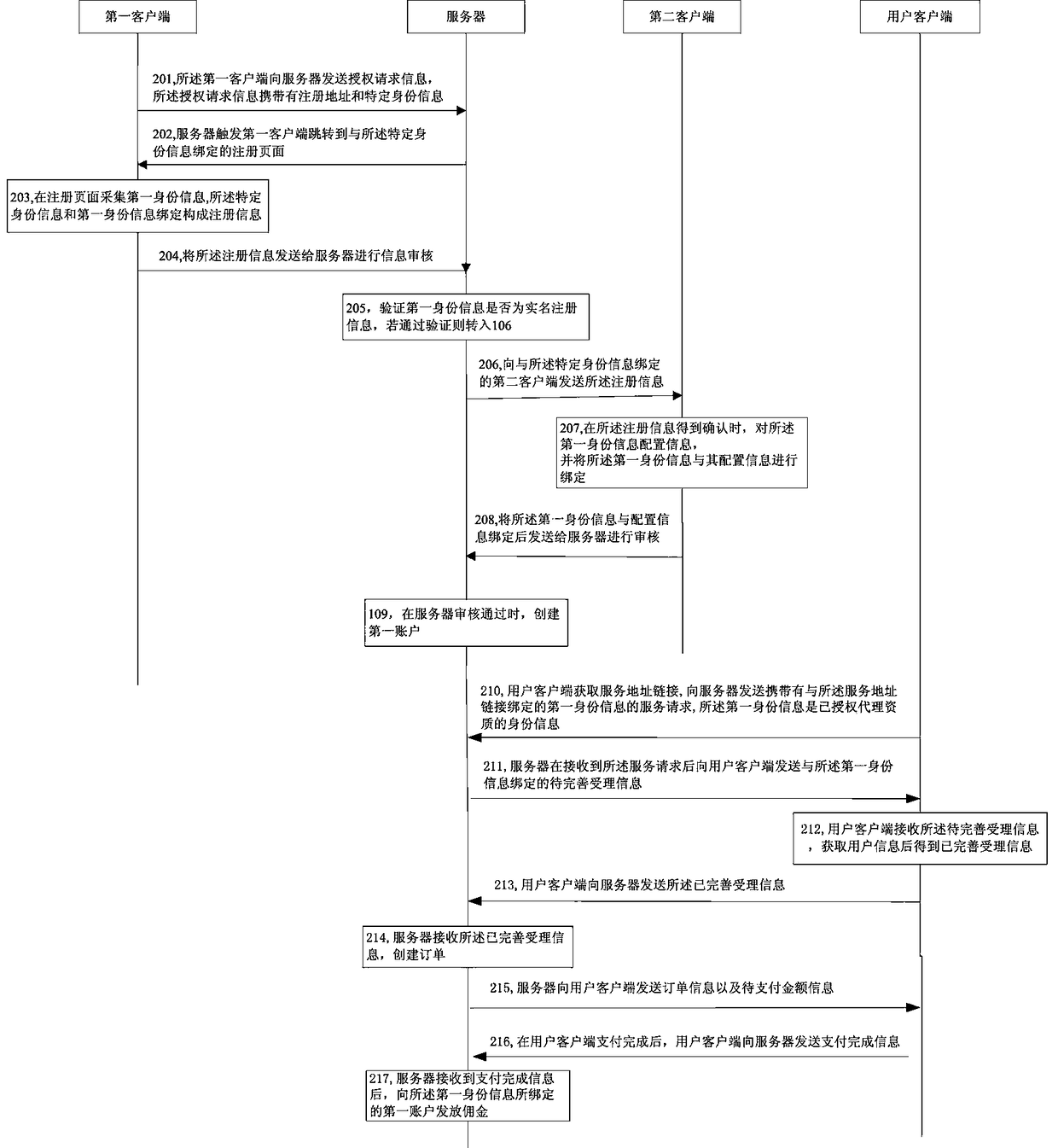
InactiveCN109302481ASimplify the authorization processImprove work efficiencyTransmissionClient-sideAuthorization certificate
The invention relates to the technical field of telecom operations, and specifically relates to an authorization method for accepting a communication service and an authorization device thereof. The method comprises the following steps: sending authorization request information carrying a registration address and specific identity information to a server through a first client; triggering the first client to jump to a registration page bound to the specific identity information by the server; acquiring first identity information by a registration page, and binding the first identity information with the specific identity information to form registration information; sending the registration information to the server for auditing by the first client; sending the registration information toa second client when the server verifies that the first identity information is real-name registration information; when the registration information is confirmed, configuring information for the first identity information by the second client, binding the first identity information with the configuration information, and sending the information to the server for auditing; and creating a first account when the auditing is passed. The authorization method for accepting the communication service provided by the invention solves the technical problem that an authorization process is more complicated when the communication service is authorized to be handled.
Owner:CHINA UNITED NETWORK COMM HENAN BRANCH
Application authorization method and device
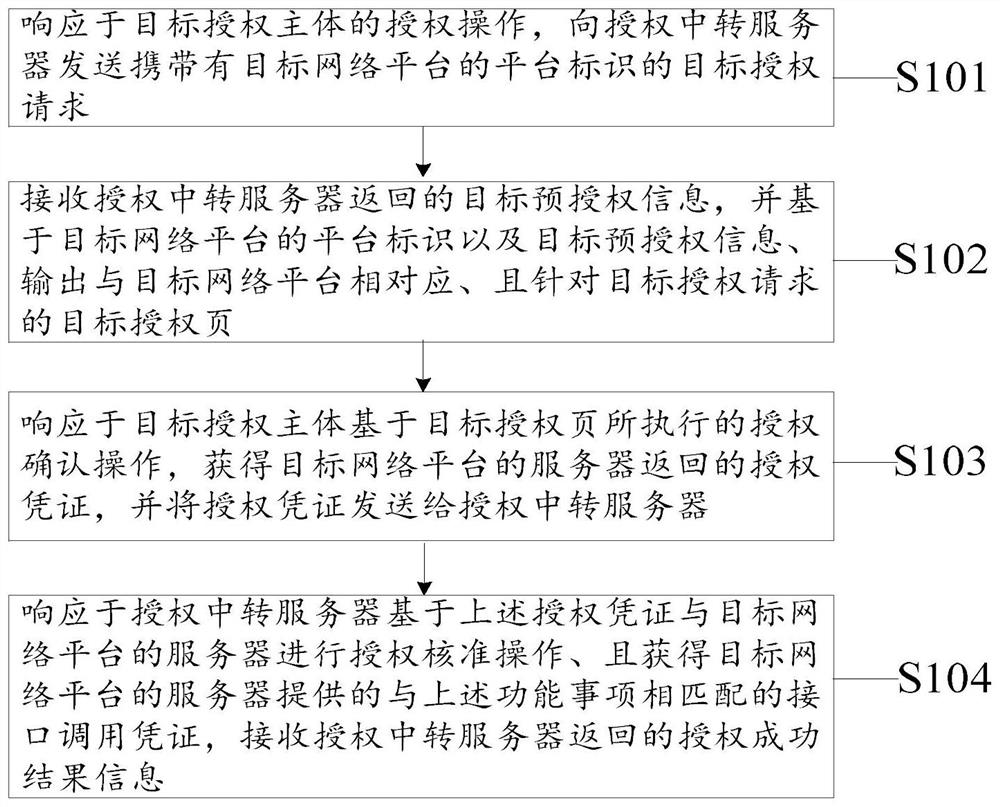
PendingCN112948809AImprove experienceSimplify the authorization processDigital data authenticationThird partyEngineering
The invention discloses an application authorization method and device. The method comprises the following steps: sending a target authorization request to an authorization transit server; receiving target pre-authorization information returned by the authorization transit server, and outputting a target authorization page based on the platform identifier of the target network platform and the target pre-authorization information; in response to an authorization confirmation operation executed based on the target authorization page, obtaining an authorization certificate returned by the server of the target network platform, and sending the authorization certificate to an authorization transit server; and in response to the authorization transit server, obtaining an interface calling voucher provided by the server of the target network platform based on the authorization voucher, and receiving authorization success result information returned by the authorization transit server. By using the method, a standardized and normalized authorization mode for each channel open platform can be provided, a merchant can authorize official accounts or applets corresponding to different channel open platforms to a third-party ISV through the normalized authorization mode, the authorization process is simplified, and the user experience is improved.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
Authorization device of carrier wave prepayment electric energy meter
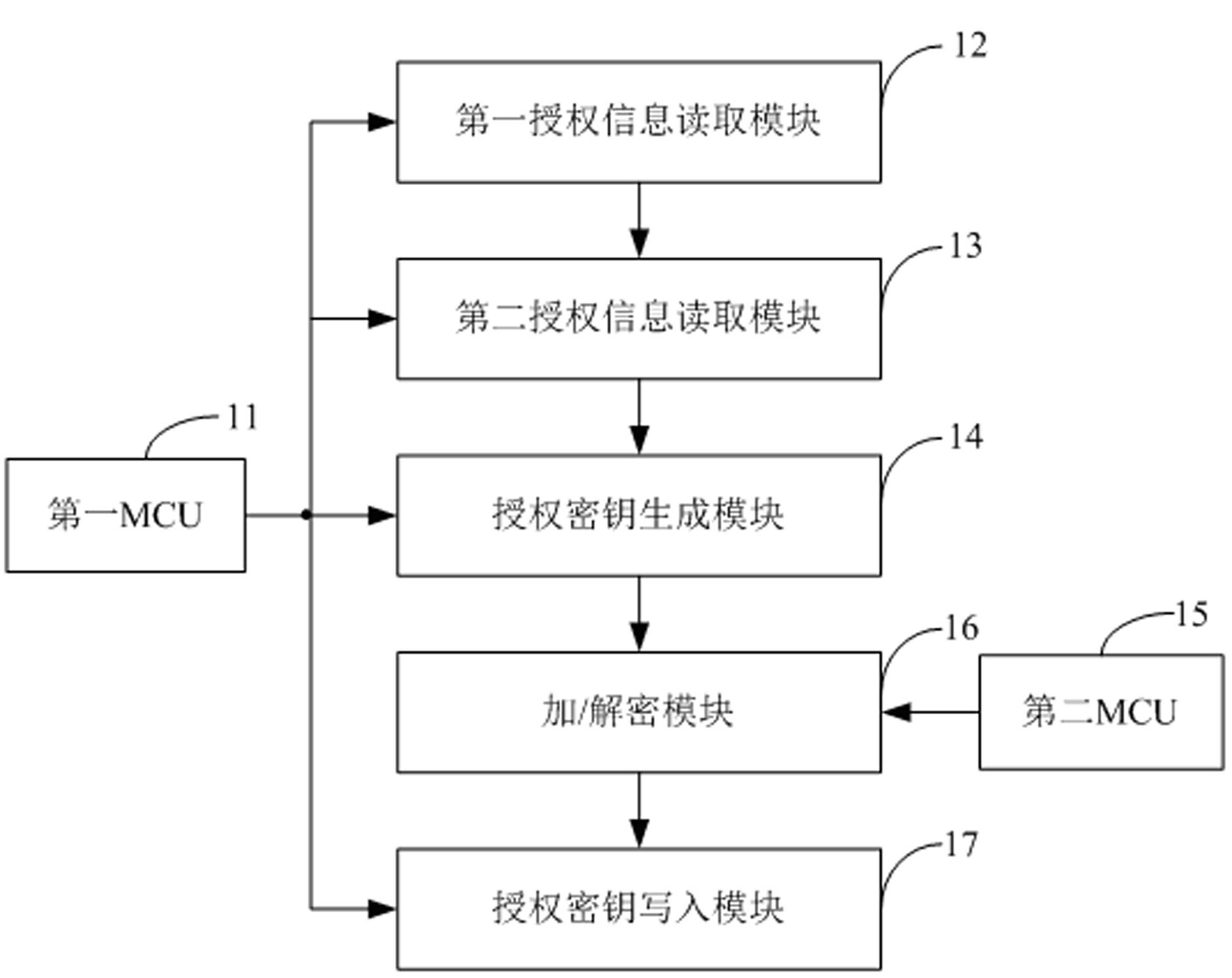
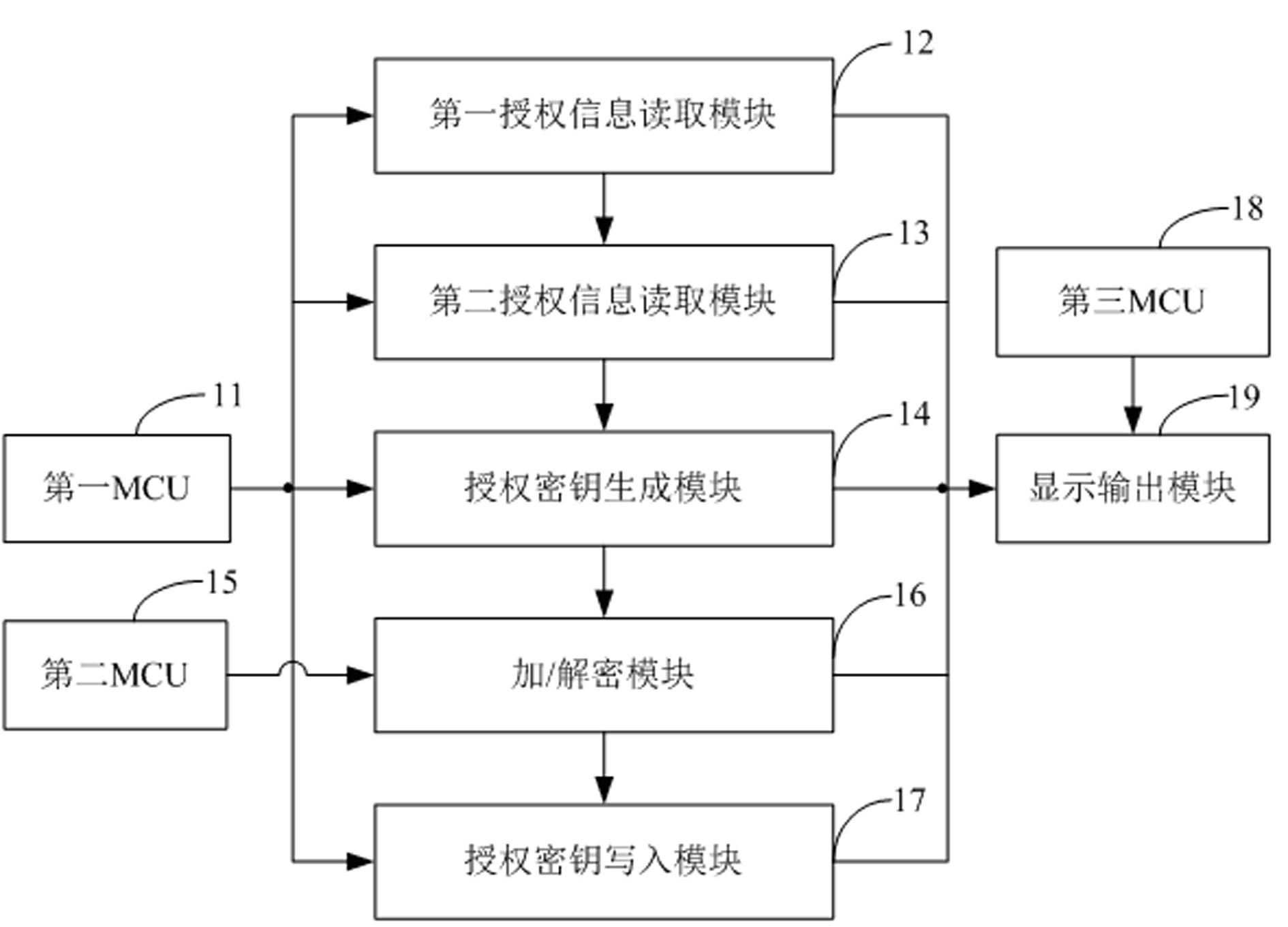
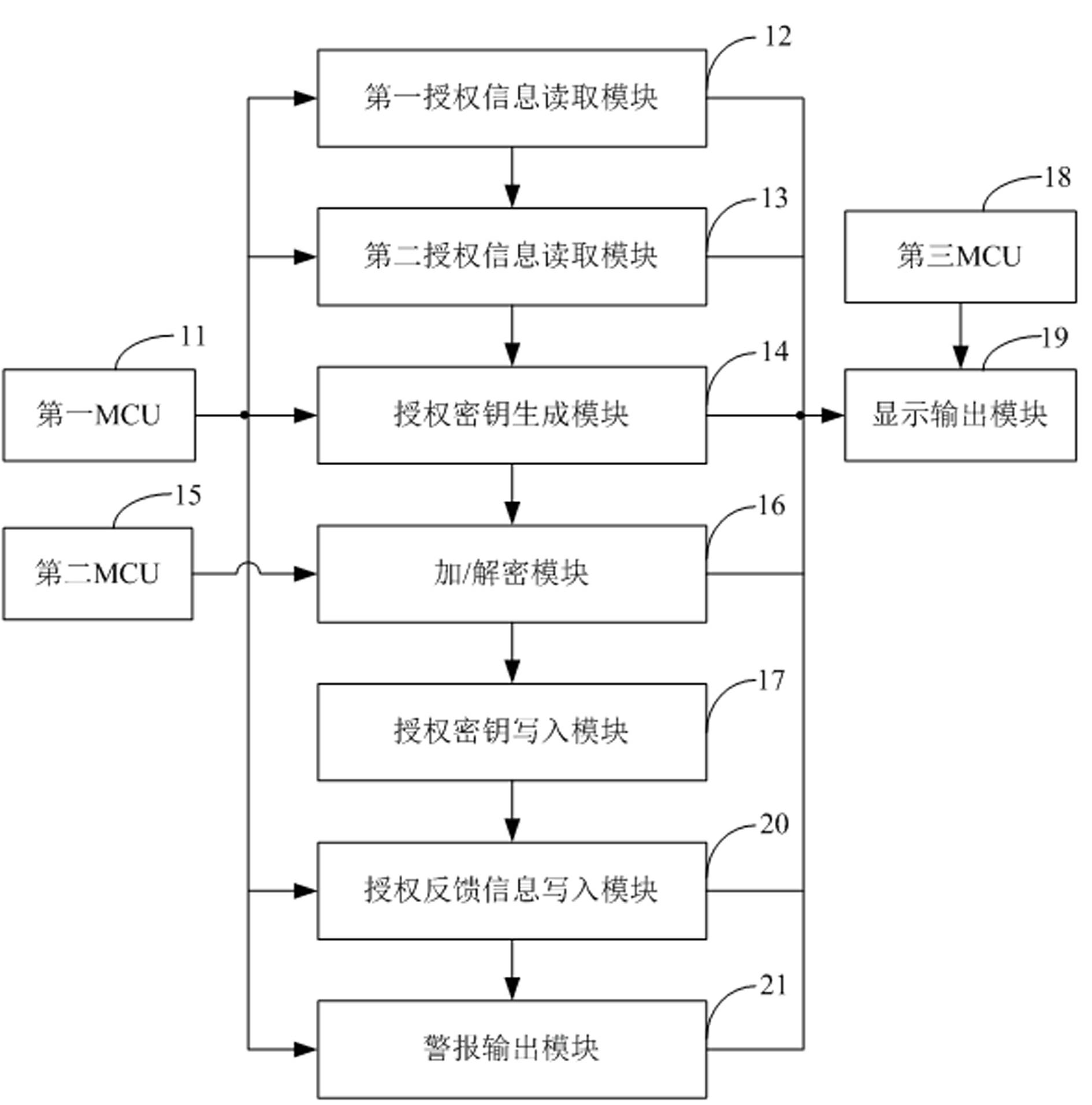
ActiveCN102637324ASimplify the authorization processEnsure safetyApparatus for hiring articlesCarrier signalEngineering
The invention applies to the field of electric energy metering, and provides an authorization device of a carrier wave prepayment electric energy meter. The device comprises a first MCU (Microprogrammed Control Unit), a second MCU, a first authorization information reading module for communicating with an outer computer through an RS232 interface under the control of the first MCU to acquire first authorization information, a second authorization information reading module for reading second authorization information from an authorization information storage device under the control of the first MCU, an authorization key generation module for generating a authorization key according to the first authorization information and the second authorization information under the control of the first MCU, an encrypting / decrypting module for encrypting the authorization key generated by the key generation module under the control of the second MCU, and an authorization key writing-in module for writing the authorization key encrypted by the encrypting / decrypting module into a safety module of the carrier wave prepayment electric energy meter through a carrier wave under the control of the first MCU. The authorization device simplifies the authorization process of the carrier wave prepayment electric energy meter and ensures the authorization safety at the same time.
Owner:SHENZHEN TECHRISE ELECTRONICS
Data reading method and device, data authorization method and device and storage medium
PendingCN112182647ASimplify the authorization processImprove authorization efficiencyDigital data protectionDigital data authenticationInternet privacyCiphertext
The invention relates to a data reading method and device, a data authorization method and device and a storage medium. The data reading method comprises the steps of receiving an identity identifiersent by a client and a reading request for requesting to access target data on a blockchain; determining whether the identity identifier is a member identifier belonging to a legal institution authorized to access the target data; and if the identity identifier is a member identifier belonging to a legal institution authorized to access the target data, obtaining decrypted target data based on anencryption key obtained from a blockchain and ciphertext data generated by encrypting the target data based on the encryption key. Therefore, as long as the reading request of the member identifier ofthe legal mechanism with authorized access can be responded, the data reading is more convenient and reasonable.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
Network resource access control method, device and related equipment
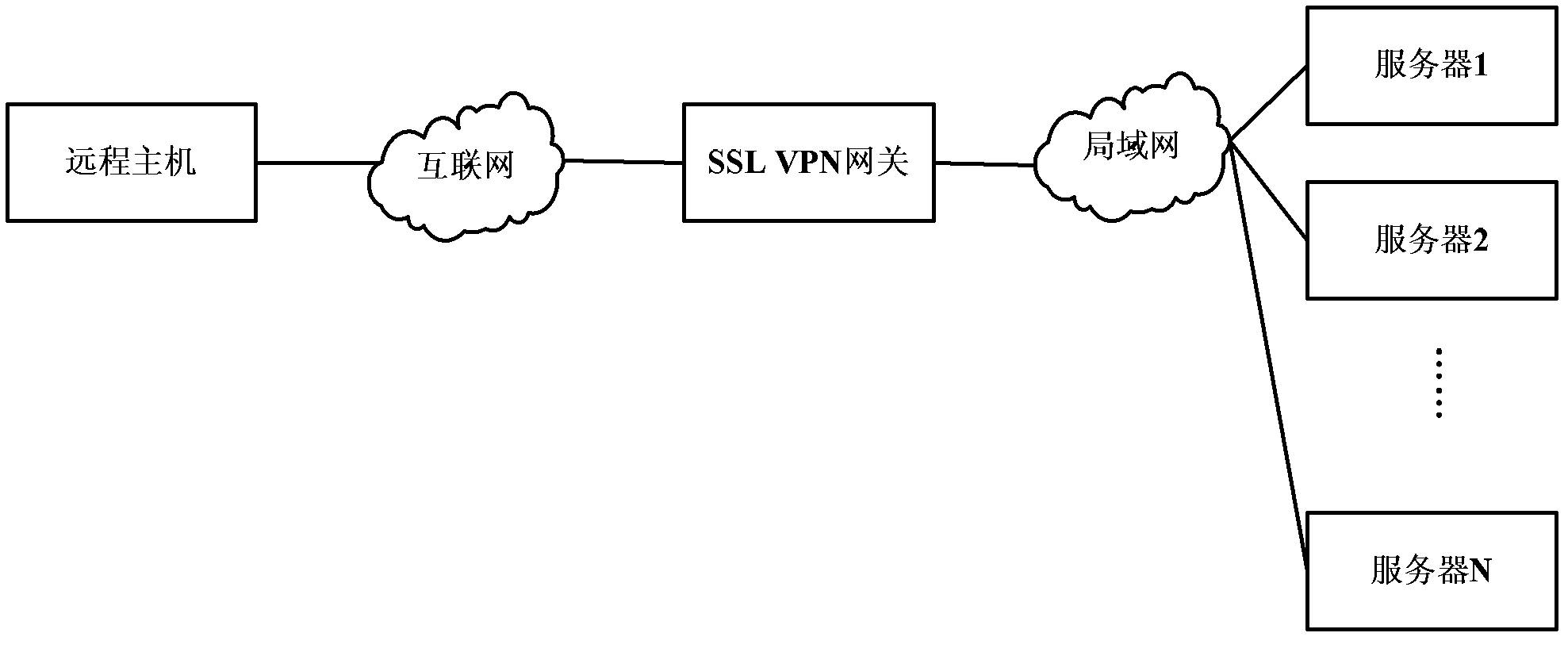
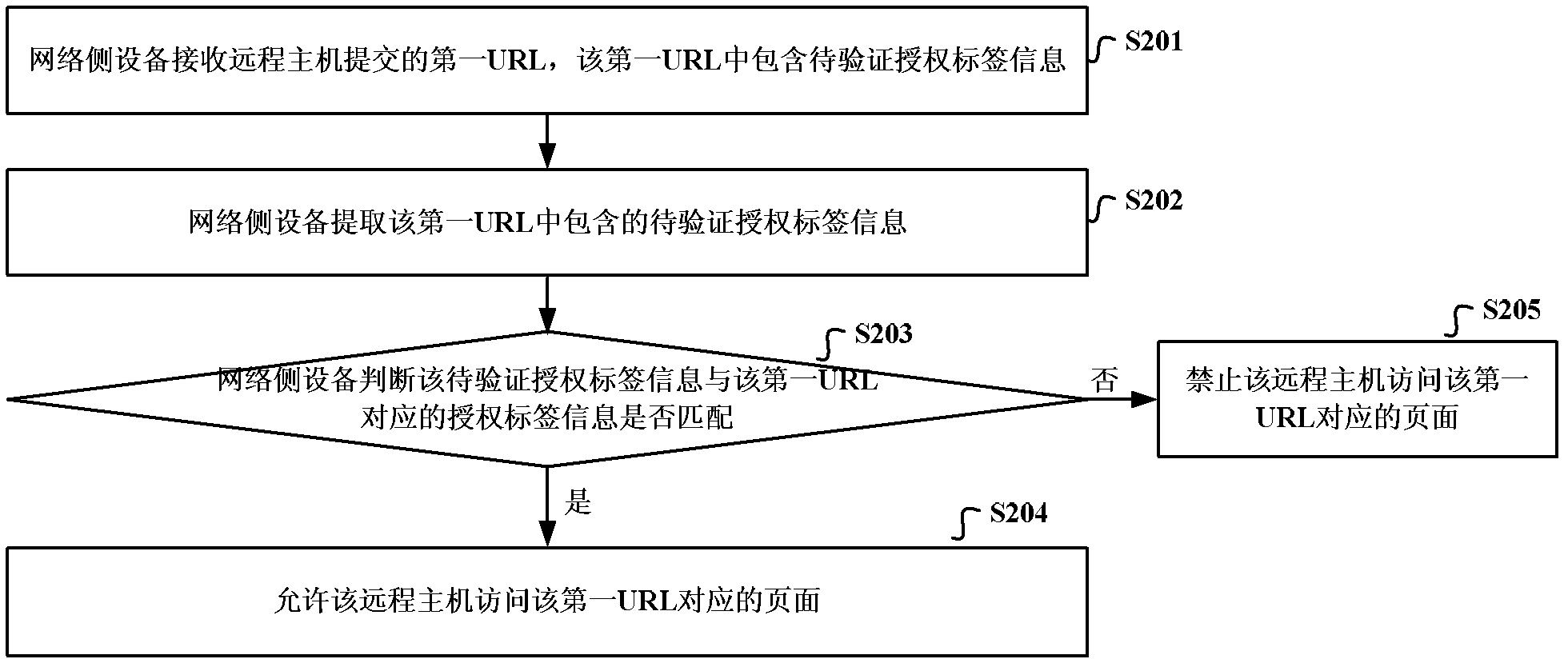
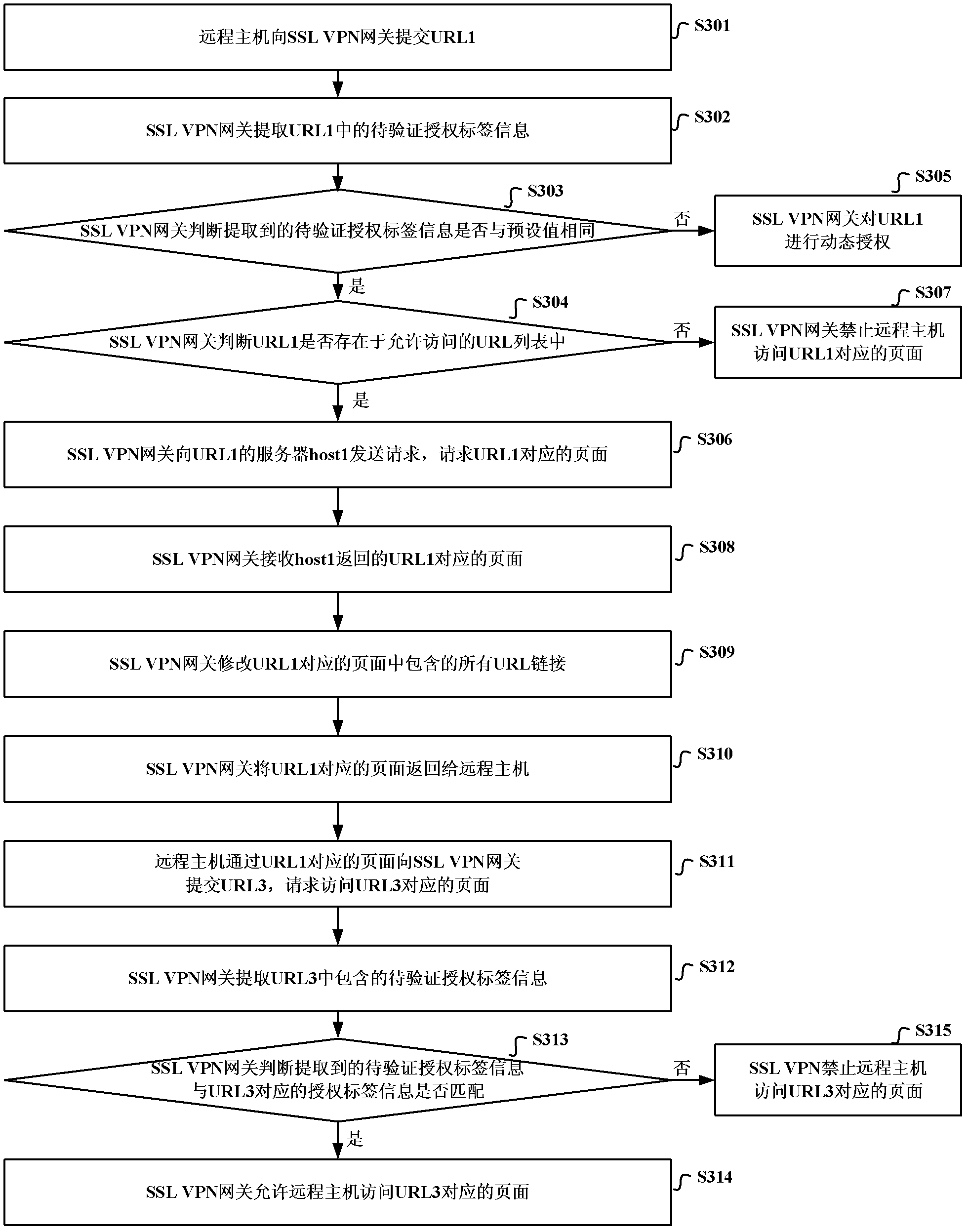
ActiveCN102546594BImplement dynamic authorizationEnsure safetyTransmissionUniform resource locatorAuthorization
The invention discloses a network resource access control method, device and related equipment, which are used for accurately recognizing whether a distance host accesses a URL (Uniform Resource Locator) which does not exist in an access allowed URL list on the basis of a page corresponding to the access allowed URL list for simplifying an authorization process of network side equipment and ensuring safety of network resource access, wherein the network resource access control method comprises the steps: the network side equipment receives a first URL submitted by the distance host, wherein the first URL comprises authorization label information to be verified; the authorization label information to be verified is extracted from the first URL; and the network side equipment judges whether the authorization label information to be verified is matched with authorization label information corresponding to the first URL, if yes, allows the distance to access the page corresponding to the first URL, and if not, prohibits the distance host from accessing the page corresponding to the first URL.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Using distributed state machines for human-to-computer dialogs with automated assistants to protect private data
PendingCN111316276AReduce or even eliminate the need for direct integrationImprove latencyDigital data information retrievalSemantic analysisComputer networkSoftware engineering
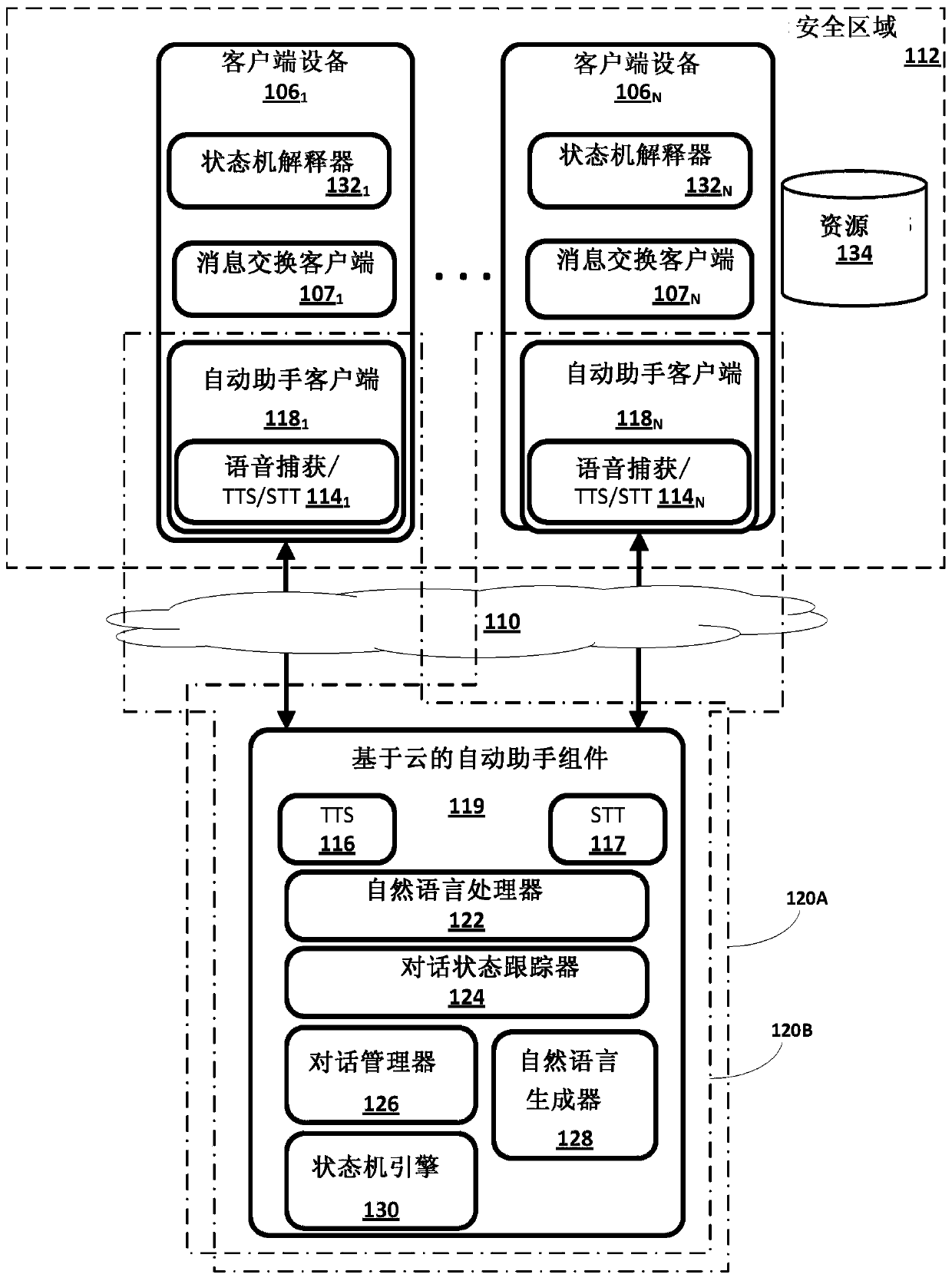
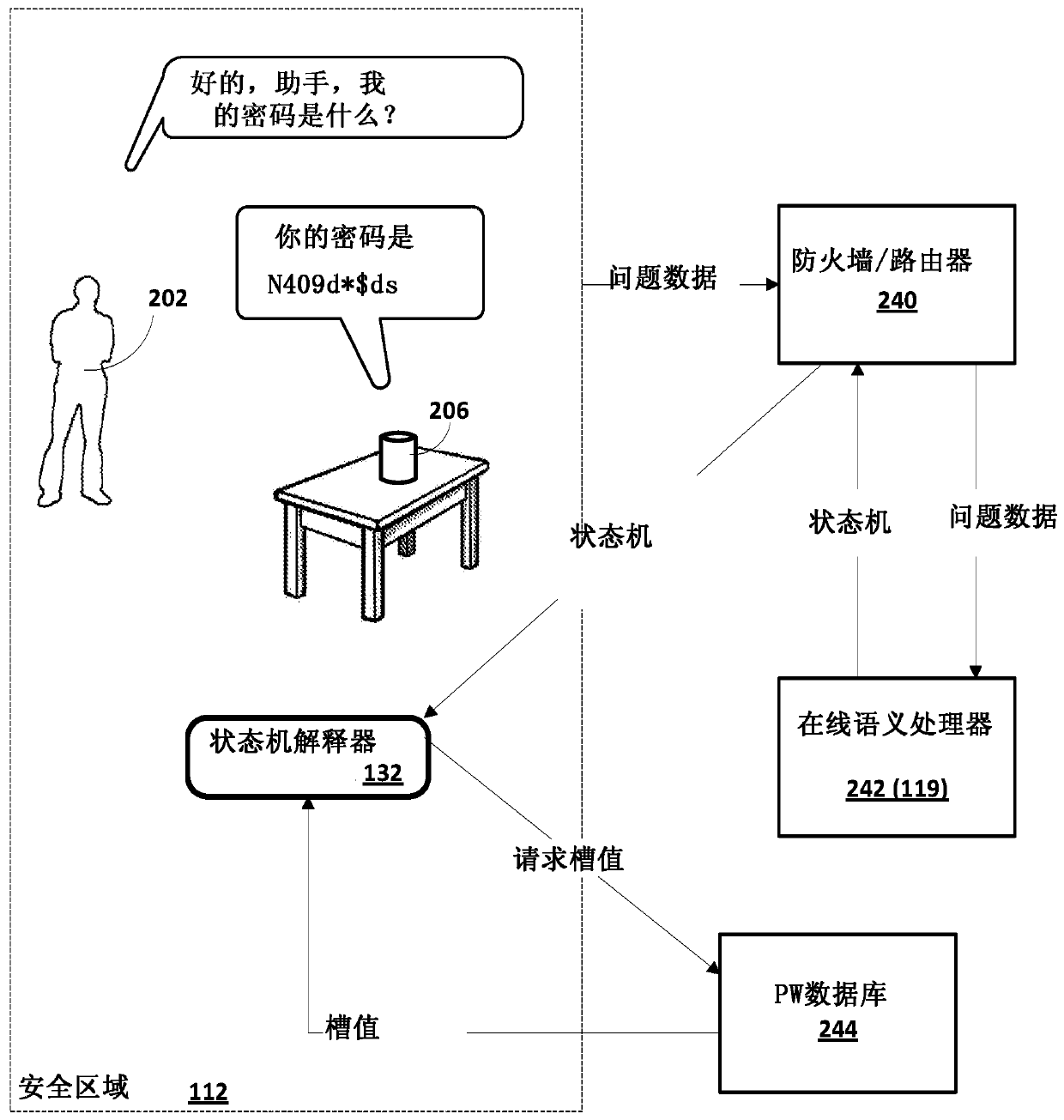
Techniques are described related to for generating / distributing state machines that are implemented within a security zone to obtain private information from one or more resources within the securityzone. In various implementations, an automated assistant client implemented by processor(s) within the security zone may receive a free form natural language query (FFNLQ) that is answerable using private information available from resource(s) within the security zone. Data indicative of the FFNLQ may be provided to a semantic processor outside of the security zone, and the online semantic processor may return a state machine that is implemented by processor(s) within the security zone to obtain the private information from resource(s) within the security zone. Based on the state machine and the obtained private information, natural language output may be generated and presented to convey information responsive to the FFNLQ.
Owner:GOOGLE LLC
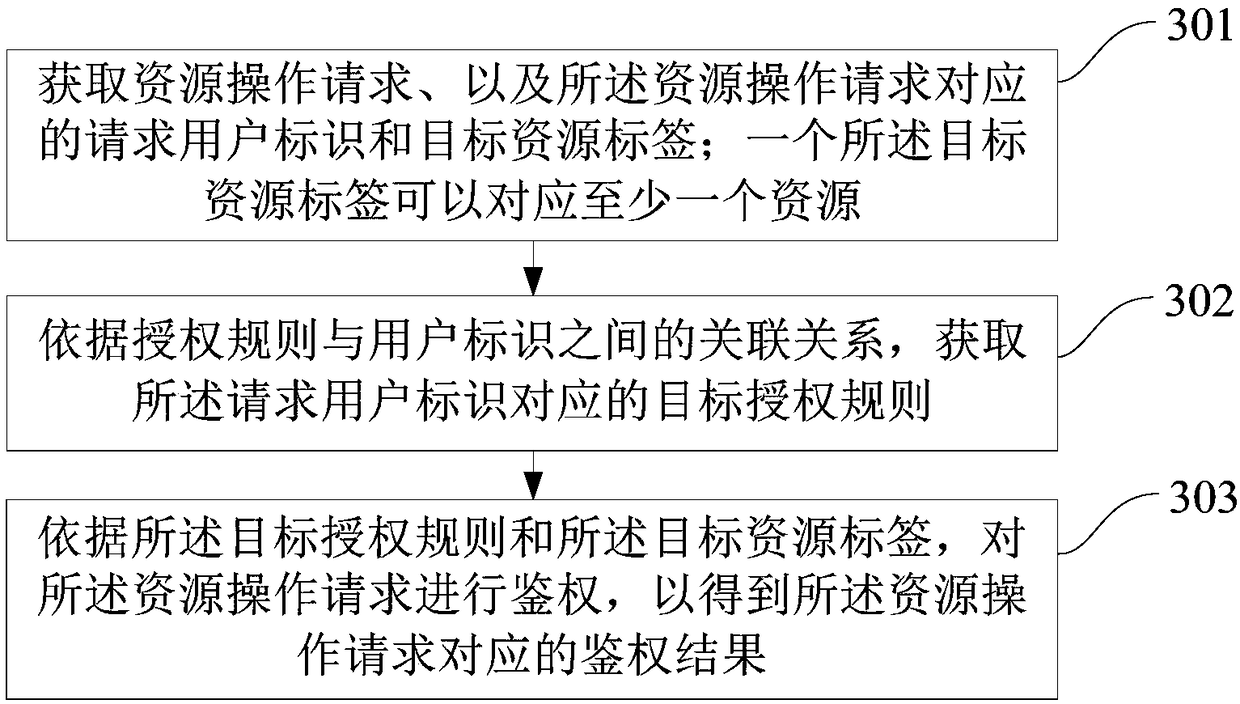
Resource processing method, device and machine readable medium
ActiveCN109150815AImprove securitySimplify the authorization processTransmissionUser identifierComputer science
The embodiments of the present invention provide a resource processing method, a resource processing device, and a machine readable medium. The method includes the following steps that: a resource operation request as well as a requesting user identifier and a target resource label which are corresponding to the resource operation request are acquired; a target authorization rule corresponding tothe requesting user identifier is obtained according to association relationships between authorization rules and user identifiers; and the resource operation request is authenticated according to thetarget authorization rule and the target resource label, so that an authentication result corresponding to the resource operation request can be obtained. With the resource processing method, the resource processing device, and the machine readable medium provided by the embodiments of the present invention adopted, an authorization process can be simplified, and authorization efficiency can be improved.
Owner:ALIBABA GRP HLDG LTD
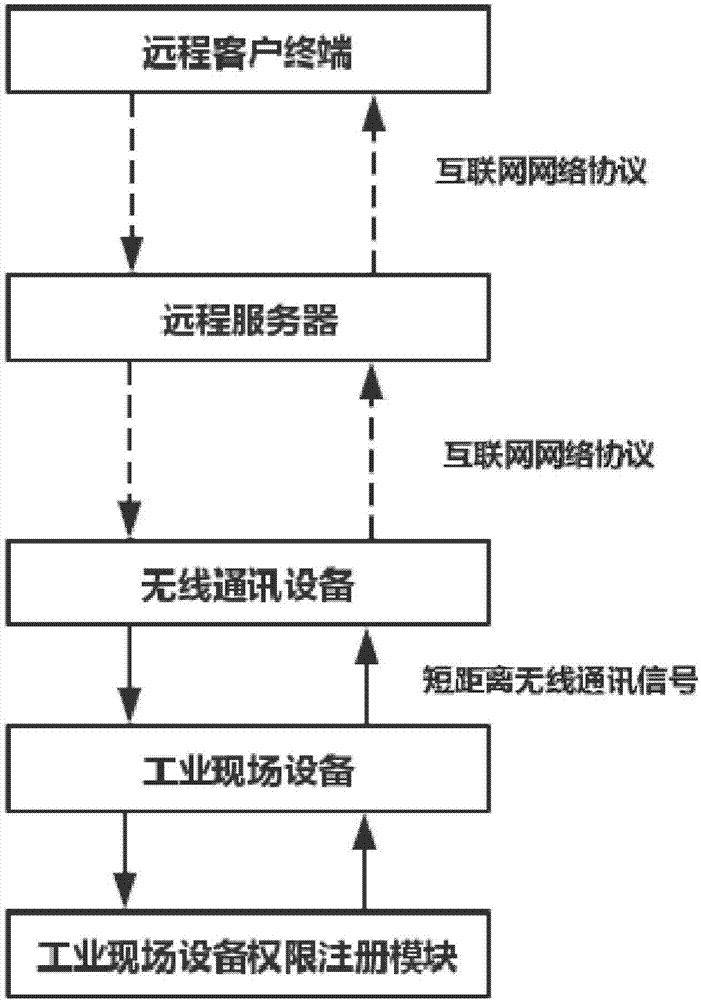
Method for industrial equipment positioning and authorization service through wireless communication equipment
InactiveCN106878924ASimplify the authorization processAvoid regional disorder circulation problemsWireless commuication servicesLocation information based serviceShortest distanceIndustrial equipment
The invention discloses a method for industrial equipment positioning and authorization service through wireless communication equipment, and the method comprises the steps: enabling industrial equipment and the wireless communication equipment which starts a positioning function to build stable bidirectional short-distance wireless communication; enabling the wireless communication equipment to serve as a gateway, and enabling onsite industrial equipment and a remote client terminal to be build the stable bidirectional connection through a network; enabling the wireless communication equipment to transmit an authority registration request from the industrial equipment and the geographic position of the wireless communication equipment to a remote client terminal; and enabling the remote client terminal to judge whether the authority registration operation of the industrial equipment is carried out or not. Through the short-distance wireless communication and an Internet bridge, the method achieves the bidirectional communication between the remote client and the onsite industrial equipment, and achieves a purpose that the remote client terminal carries out positioning and remote authorization service of the onsite industrial equipment. The method simplifies the authorization process of the industrial equipment, and reduces the time cost and manpower cost of the remote authorization service of an equipment producer. Meanwhile, the method effectively avoids a regional disordered circulation problem of sold equipment.
Owner:ZHEJIANG UNIV
Application authorization method, terminal and server
ActiveCN108476226BReduce the burden onAvoid abuseMultiple keys/algorithms usagePublic key for secure communicationThird partyApplication server
Owner:HUAWEI TECH CO LTD
Public security monitoring and identification network for mobile phone number
InactiveCN107991958AReal-time recordingQuick snapProgramme controlComputer controlCommunications systemPublic place
The invention relates to a public security monitoring and identification network for a mobile phone number. Just like a 'camera'of a mobile phone number, the network is a network for monitoring and identifying the number of a mobile phone which is carried by a person in a monitoring region. The network is a new monitoring management tool used for public safety of public places, buses, subway stations, subway cars and other public regions. A plurality of independent small monitoring regions, a communication system and a central computer form the network; each small monitoring region includes but not limit to one or more of a rectangular monitoring area, a sector monitoring area, a circular monitoring area, a three-dimensional multi-layer monitoring area, and a flow monitoring area. Throughthe technology of a direction limiting plate set, the device is like a 'special camera'which can 'see'and detect the mobile phone number, the mobile phone number in the monitoring region can be recorded in real time, and once the person starts the mobile phone, the mobile phone number can be recorded. To crack a gang-crime case, a convenient tool is provided.
Owner:西安立东行智能技术有限公司
System for securing inbound and outbound data packet flow in a computer network
InactiveUS7934090B2Simplify the authorization processDigital data processing detailsUser identity/authority verificationNetwork packetEnd user
A method provides for control of access to network resources. A virtual identity machine resides in the network and is pre-authorized to access certain network resources. End users desiring access to those network resources attempt to logically connect to the virtual identity machines. If the logical connection attempt is successful, then the end user assumes the virtual identity of the virtual identity machine and has access to all of the same information that was available to the virtual identity machine.
Owner:AMERICAN PATENTS LLC
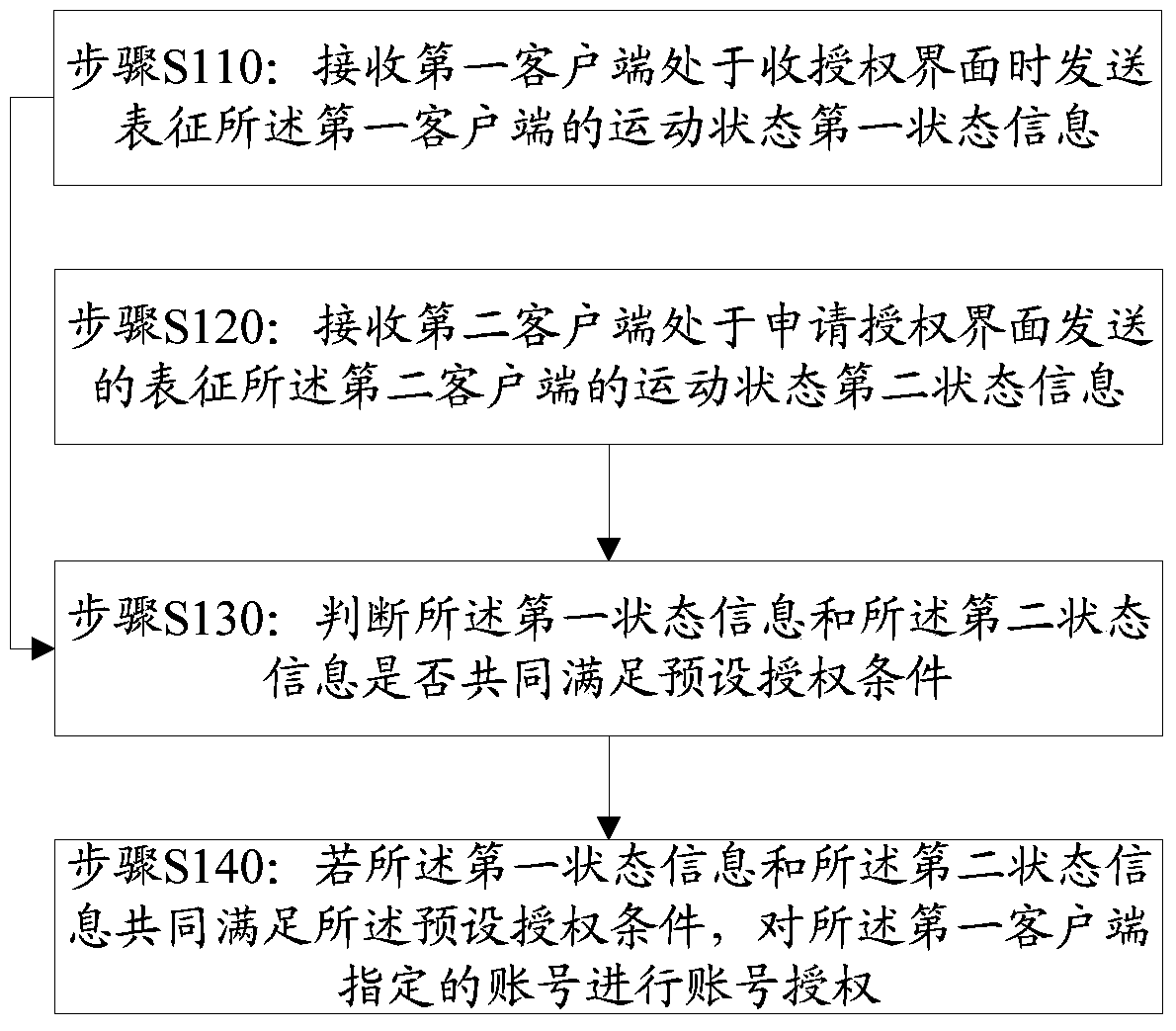
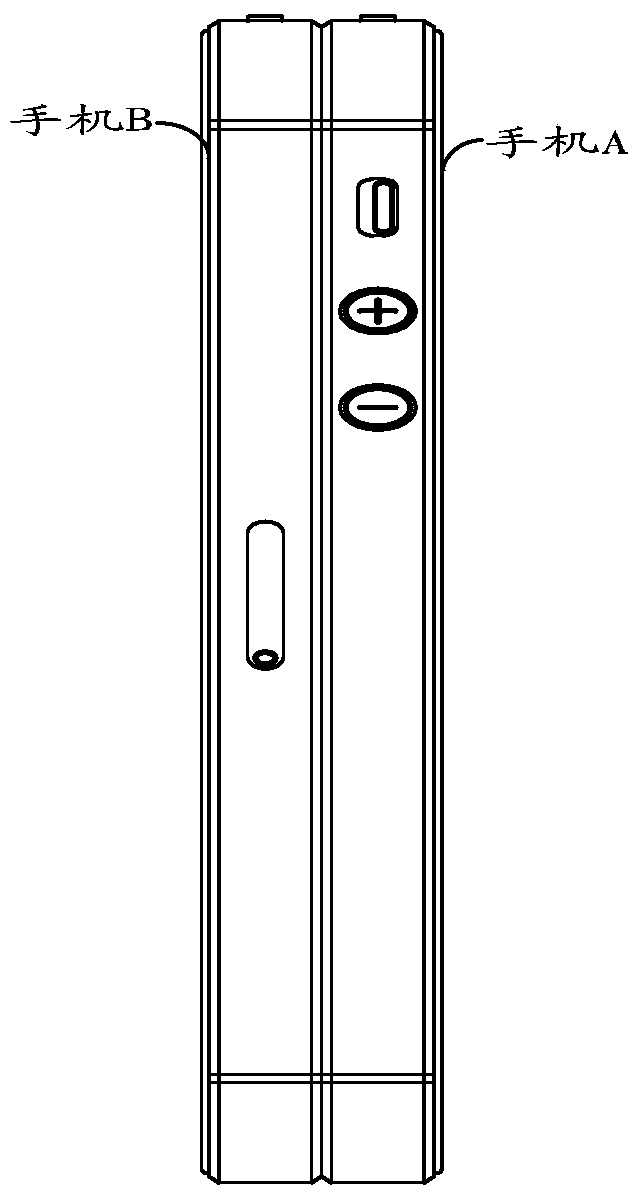
Account authorization method, server and client
ActiveCN105245542BSimplify the authorization processImprove securityTransmissionEngineeringAuthorization
The embodiment of the invention discloses an account authorization method, a server and clients. The method can comprise the following steps: receiving first state information representing a motion state of a first client and transmitted when the first client is in an authorization receiving mode; receiving second state information representing a motion state of a second client and transmitted when the second client is in an authorization application mode; judging whether the first state information and the second state information satisfy a preset authorization condition at the same time or not; and if the first state information and the second state information satisfy the preset authorization condition at the same time, performing account authorization on a specified account corresponding to the first client.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System and method for controlled access to application programming interfaces
ActiveUS10878066B2Easy to manageSimplify the authorization processDigital data protectionProgram/content distribution protectionApplication programming interfaceSoftware engineering
A method for accessing a restricted application programming interface (API) is disclosed, including: receiving, from a first application, a request to access the restricted API, the restricted API not supported by the first application; determining whether the first application is authorized by a provider of the restricted API to access the restricted API; and granting, in response to the determination that the first application is authorized by the provider of the restricted API to access the restricted API, the first application access to the restricted API.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
Supply medium exchange system for mobile units
ActiveUS11305660B2Simplify the authorization processReduce transaction costsCharging stationsDigital data protectionStationEngineering
Provided are embodiments of a supply medium exchange system. The system includes at least one supply medium exchange station having at least one supply medium exchange interface. It is configured to exchange a supply medium with at least one mobile unit including at least one supply medium storage and at least one first peer-to-peer module assigned to the mobile unit. It is also configured to communicate with at least one peer-to-peer application of at least one peer-to-peer network. The first peer-to-peer module is configured to cause a generation of a supply medium exchange release message for releasing of the exchange of the supply medium between the mobile unit and the supply medium exchange station by means of the peer-to-peer application.
Owner:INNOGY INNOVATION GMBH
Method for realizing management authorization in network management system
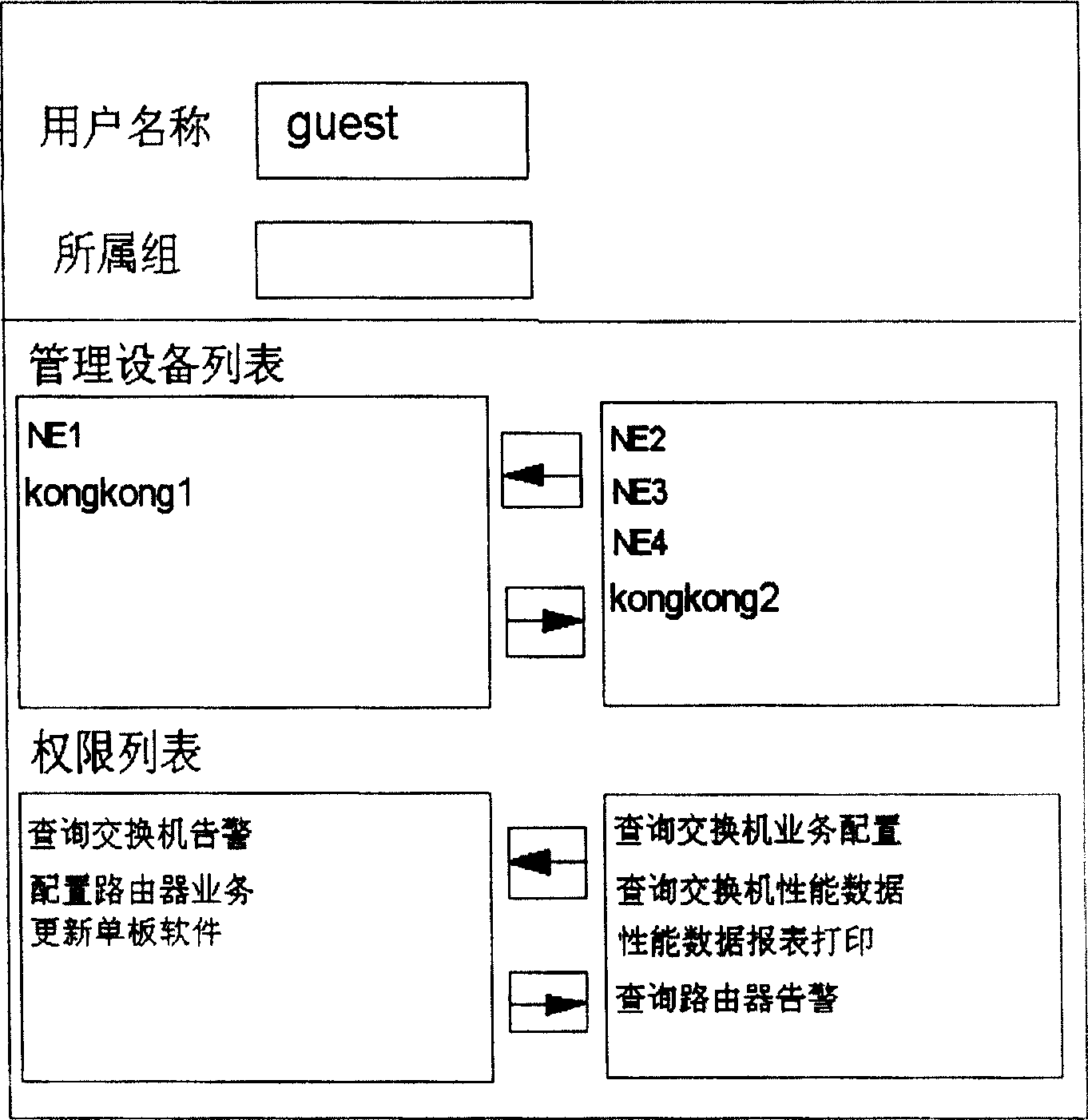
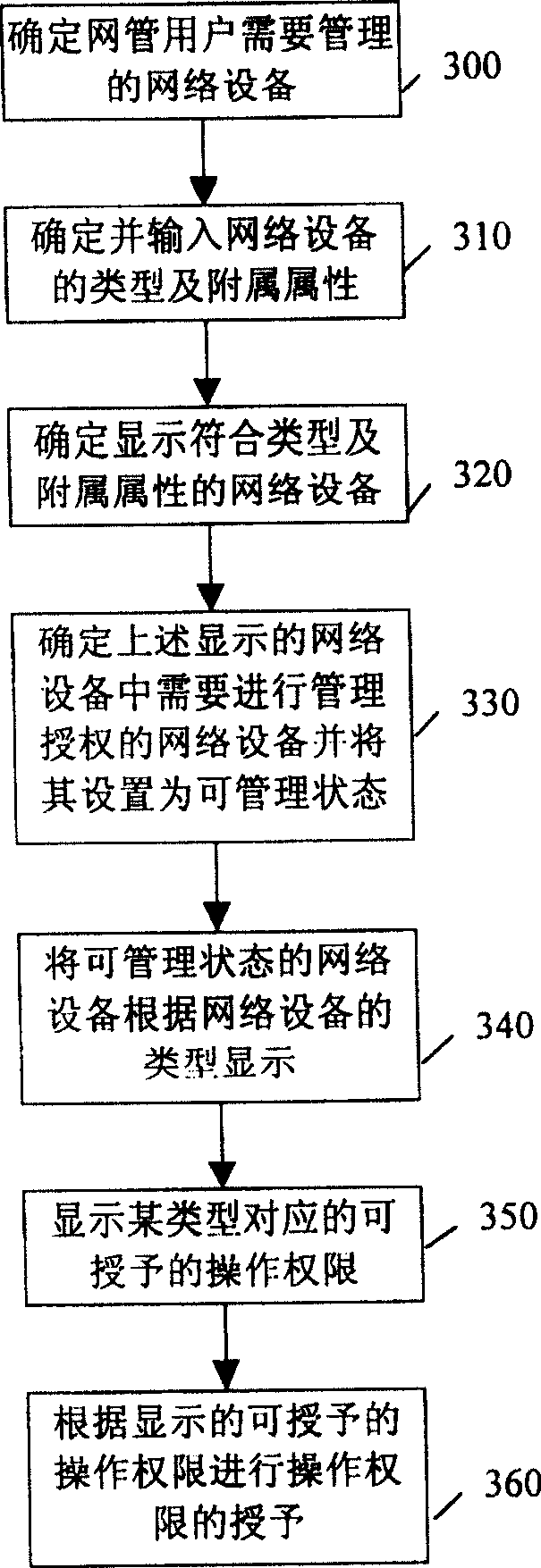
InactiveCN100502298CSure flexibleImprove work efficiencyData switching networksUser deviceNetwork management
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com