Using distributed state machines for human-to-computer dialogs with automated assistants to protect private data
An automatic assistant and state machine technology, applied in digital data protection, electronic digital data processing, digital data information retrieval, etc., can solve problems such as inaccessibility, privacy or sensitive information exposure, and achieve the effect of simplifying audit and improving delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
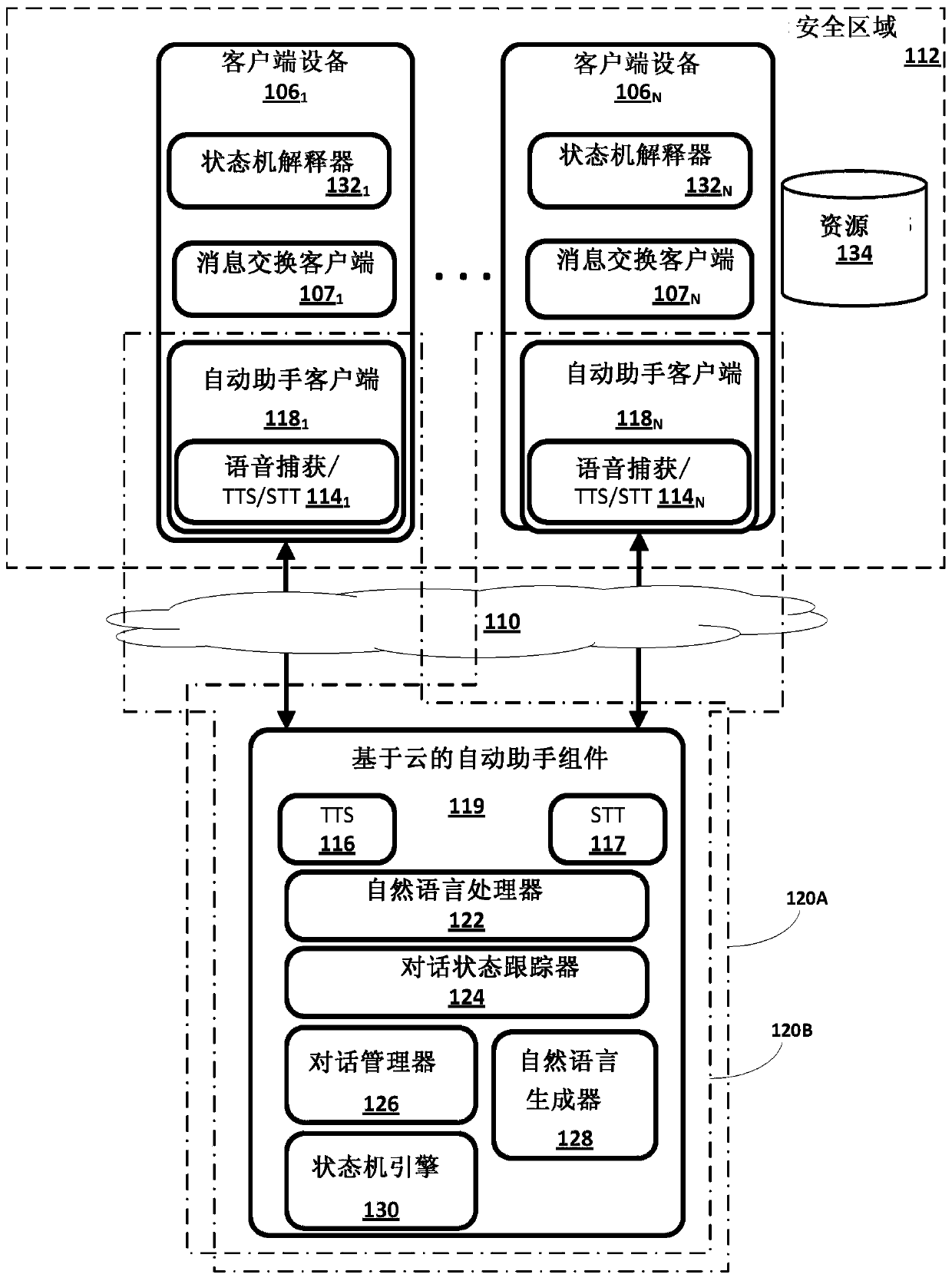
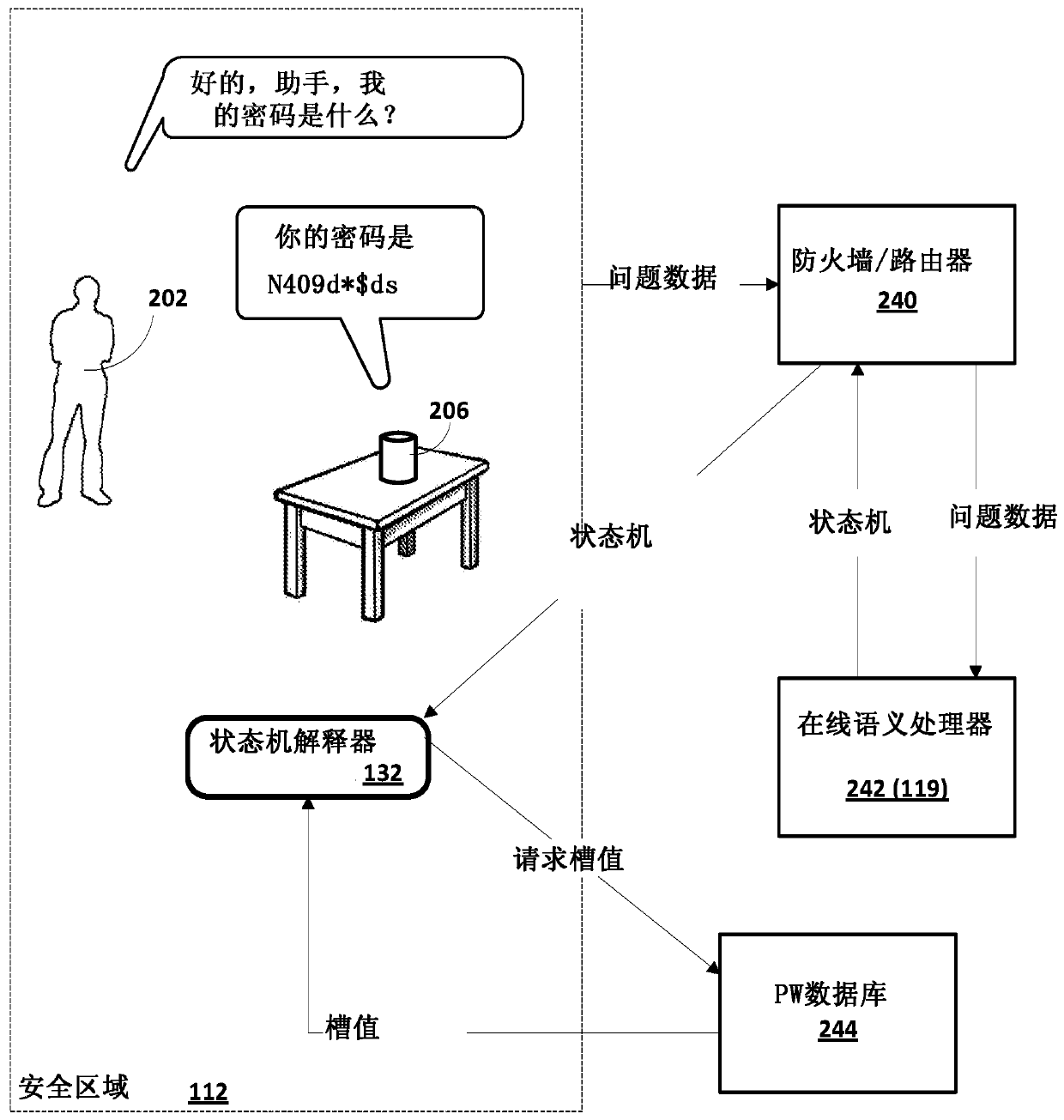
[0024] now go to figure 1 , illustrating an example environment in which the techniques disclosed herein may be implemented. The example environment includes one or more client computing devices 106 1-N . Each client device 106 may execute a respective instance of the automated assistant client 118 . Can be communicatively coupled to client device 106 via one or more local area networks and / or wide area networks (e.g., the Internet), generally indicated at 110 1-N One or more cloud-based automated assistant components 119 (such as natural language processor 122) are implemented on one or more computing systems in the cloud (collectively referred to as "cloud" computing systems).
[0025] In various implementations, an instance of auto-assistant client 118 through its interaction with one or more cloud-based auto-assistant components 119 may form a logical instance of what appears to be auto-assistant 120 from the user's perspective. A user may engage this logical instance ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com