Patents
Literature
143 results about "Corporate network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
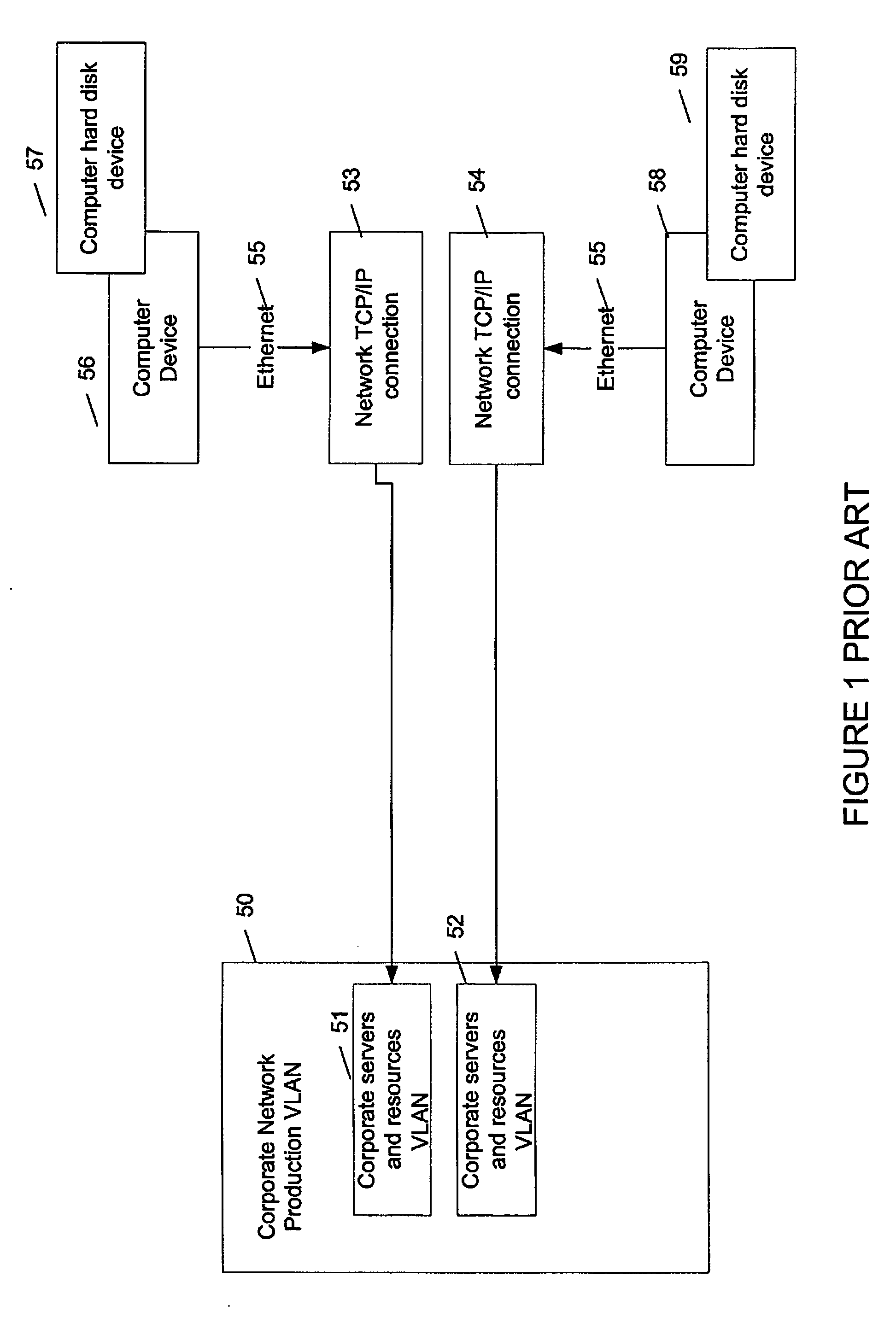
Corporate network. A corporate network is a group of computers, connected together in a building or in a particular area, which are all owned by the same company or institutions.
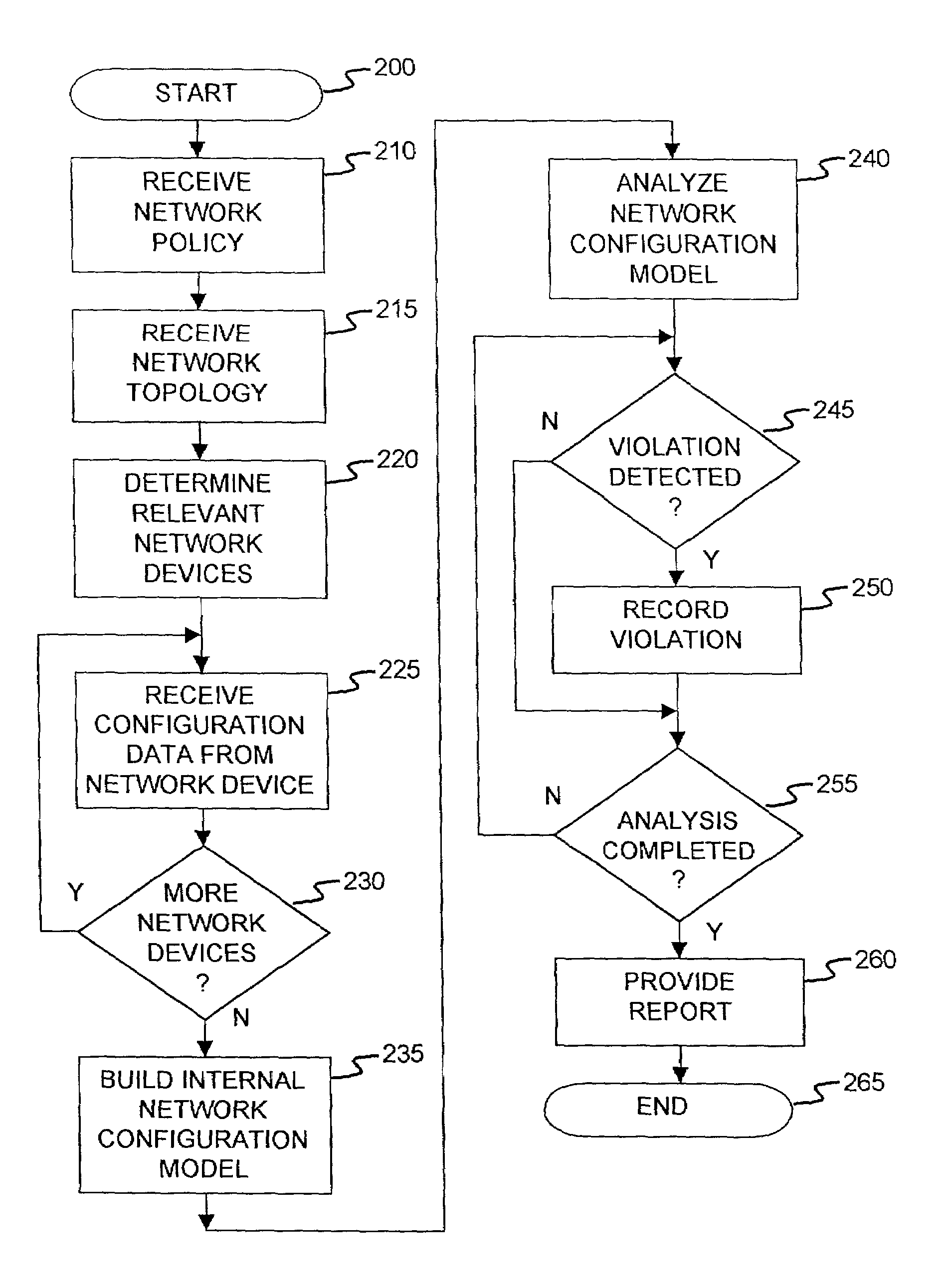
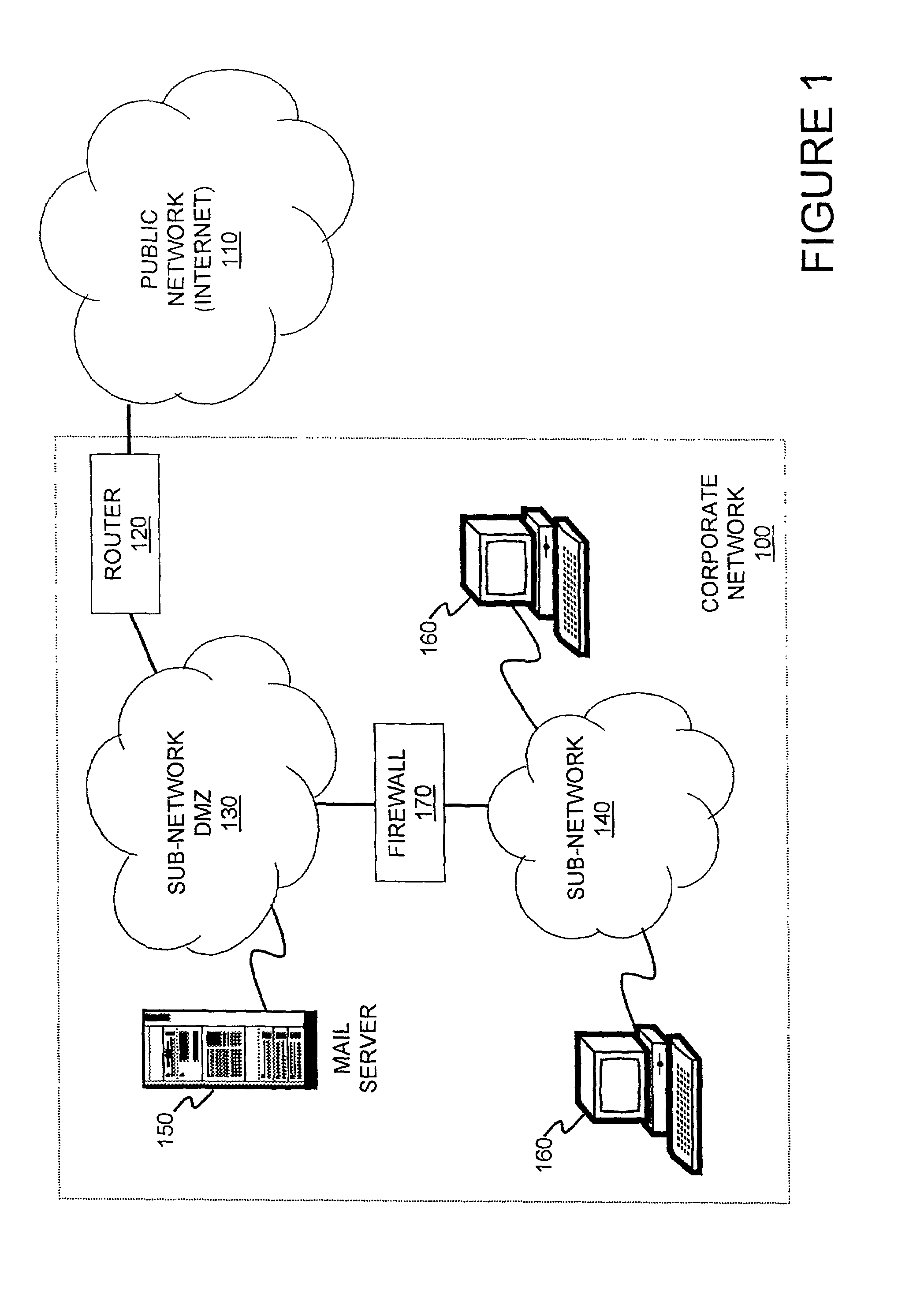
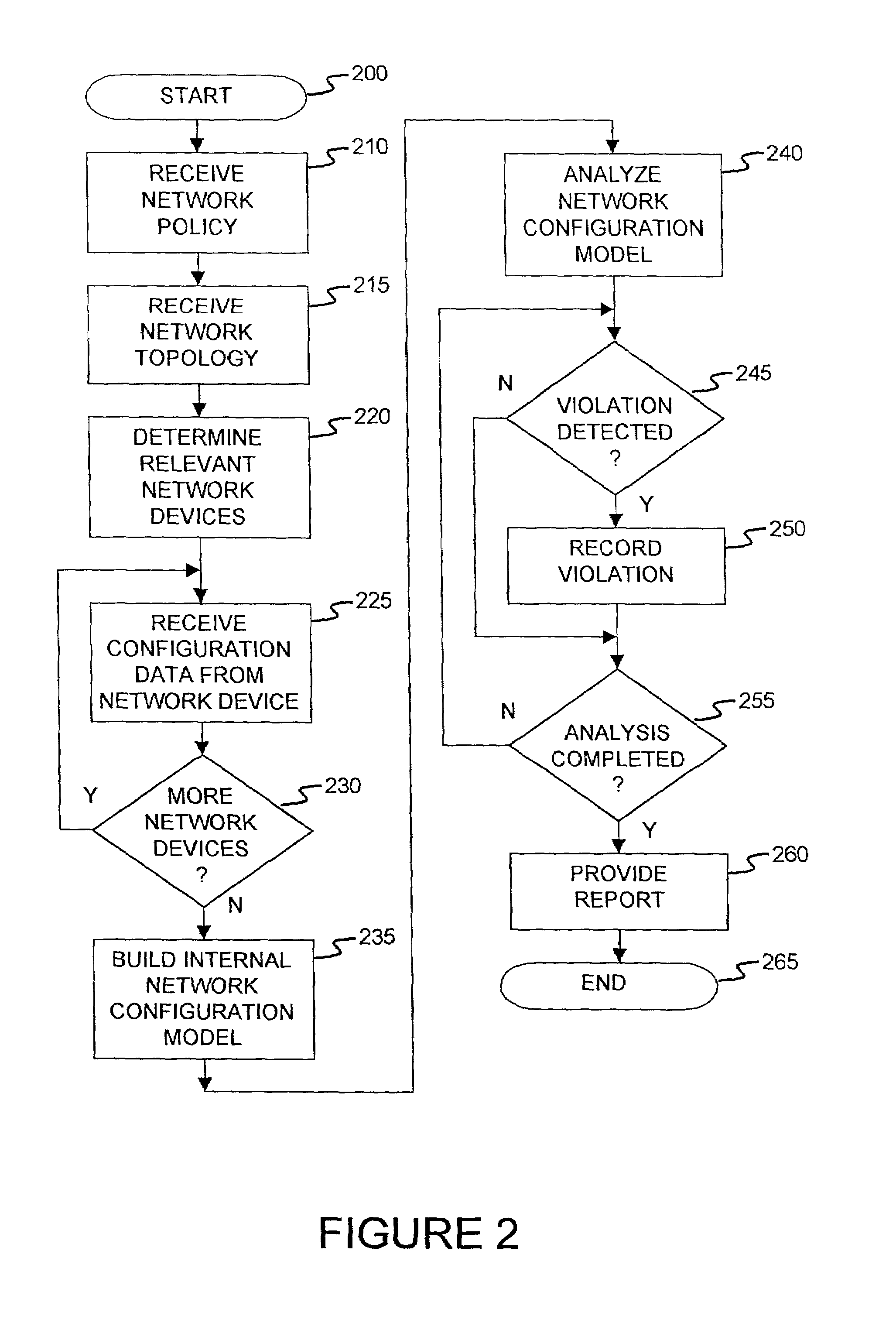
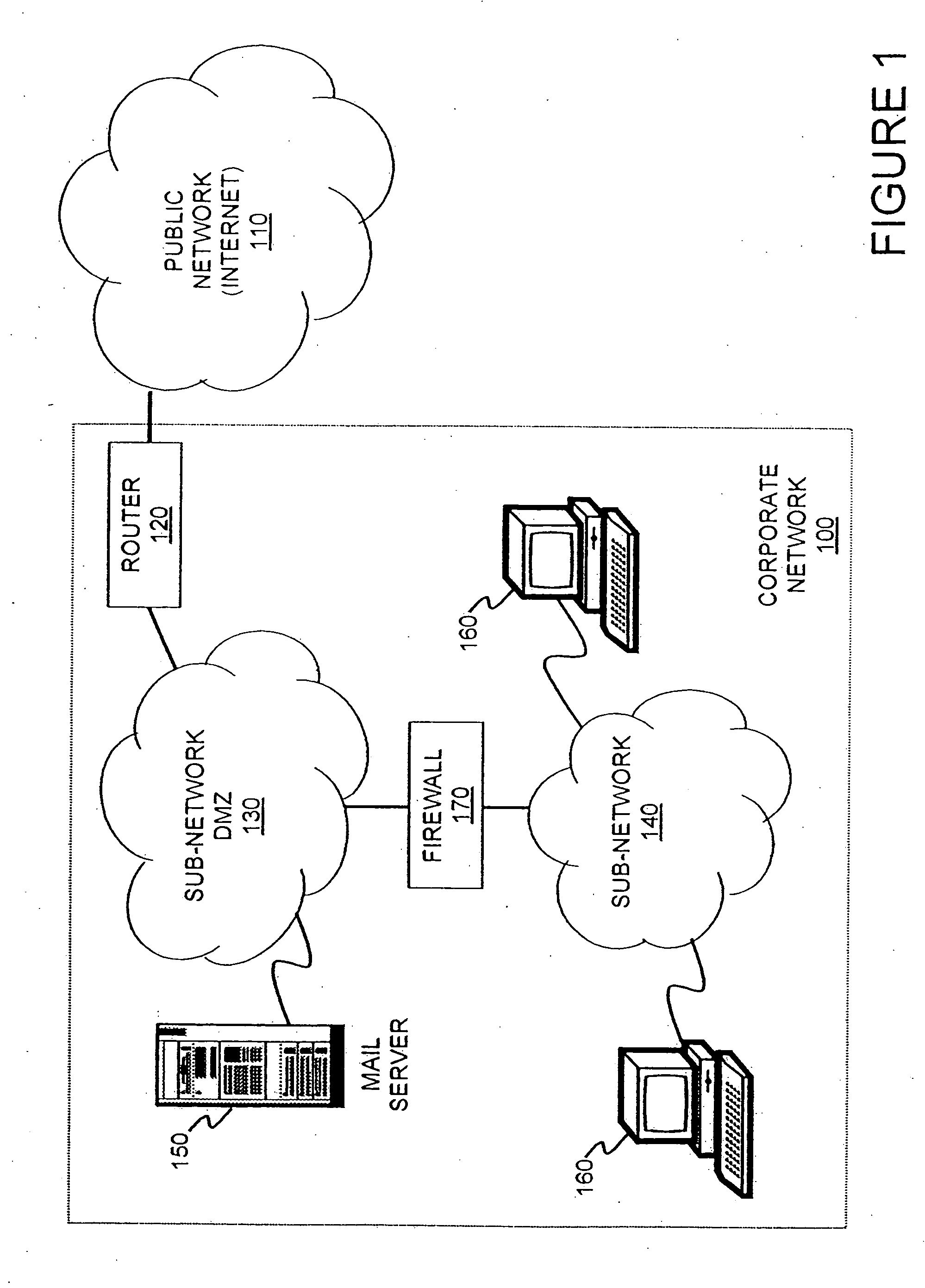
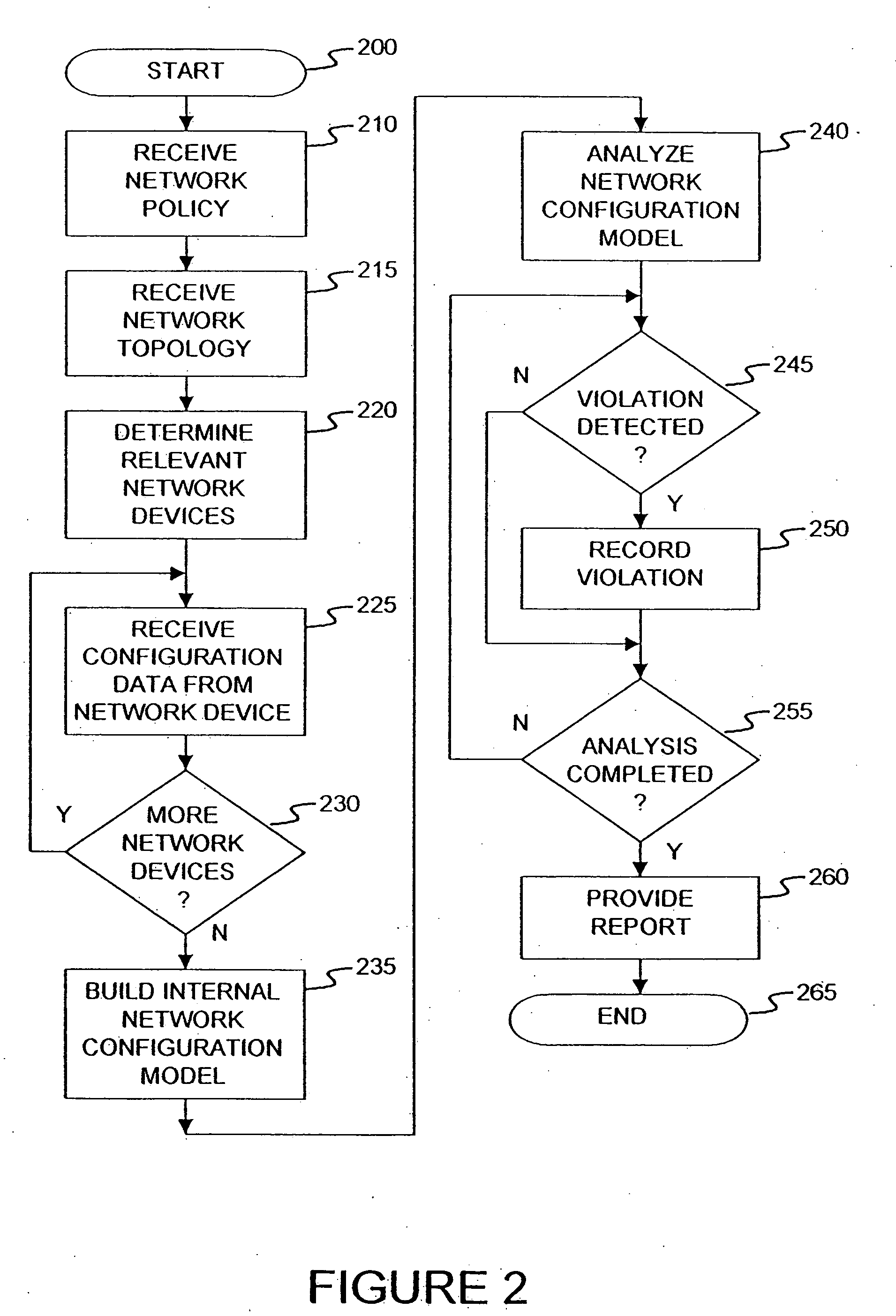
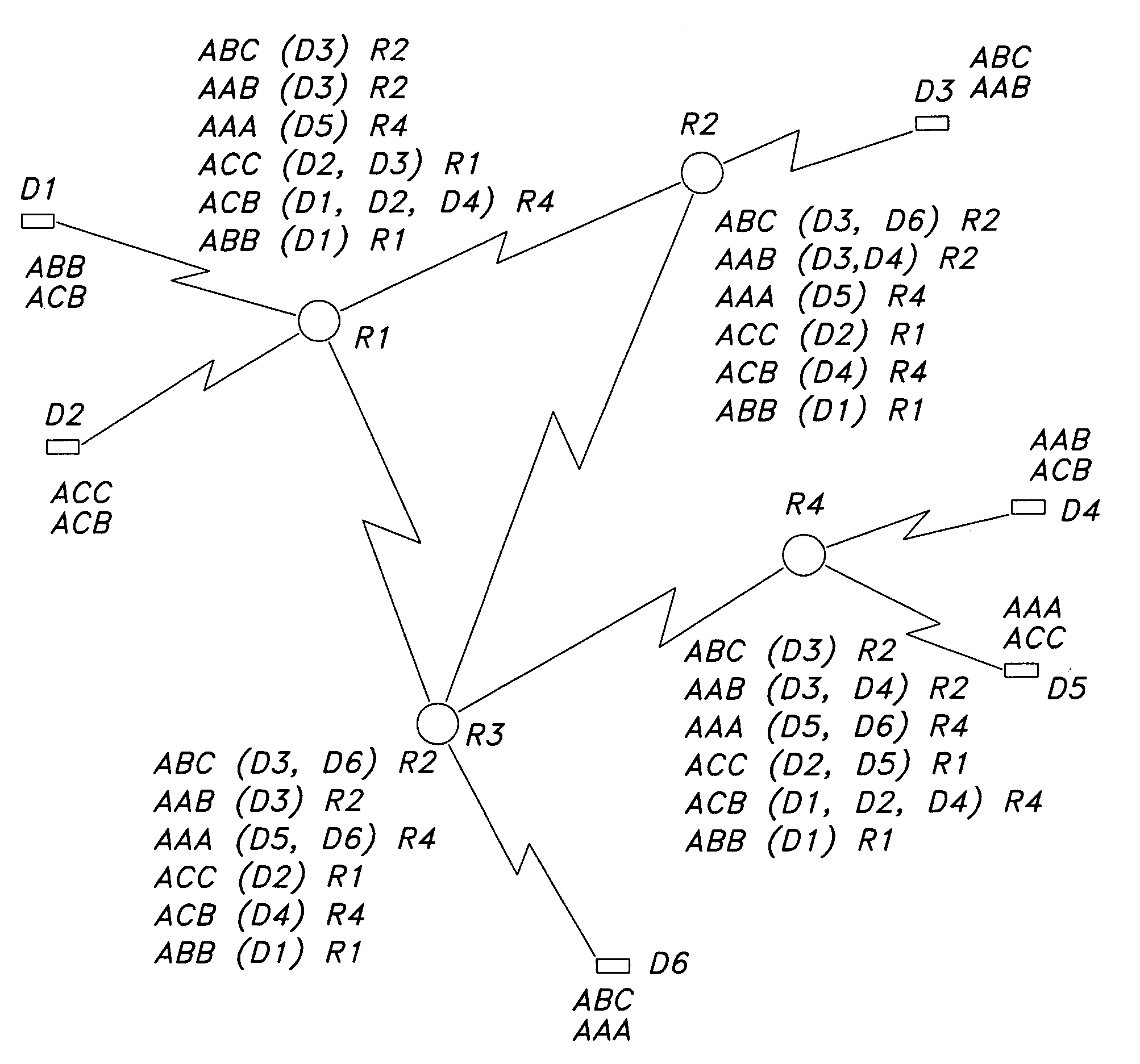
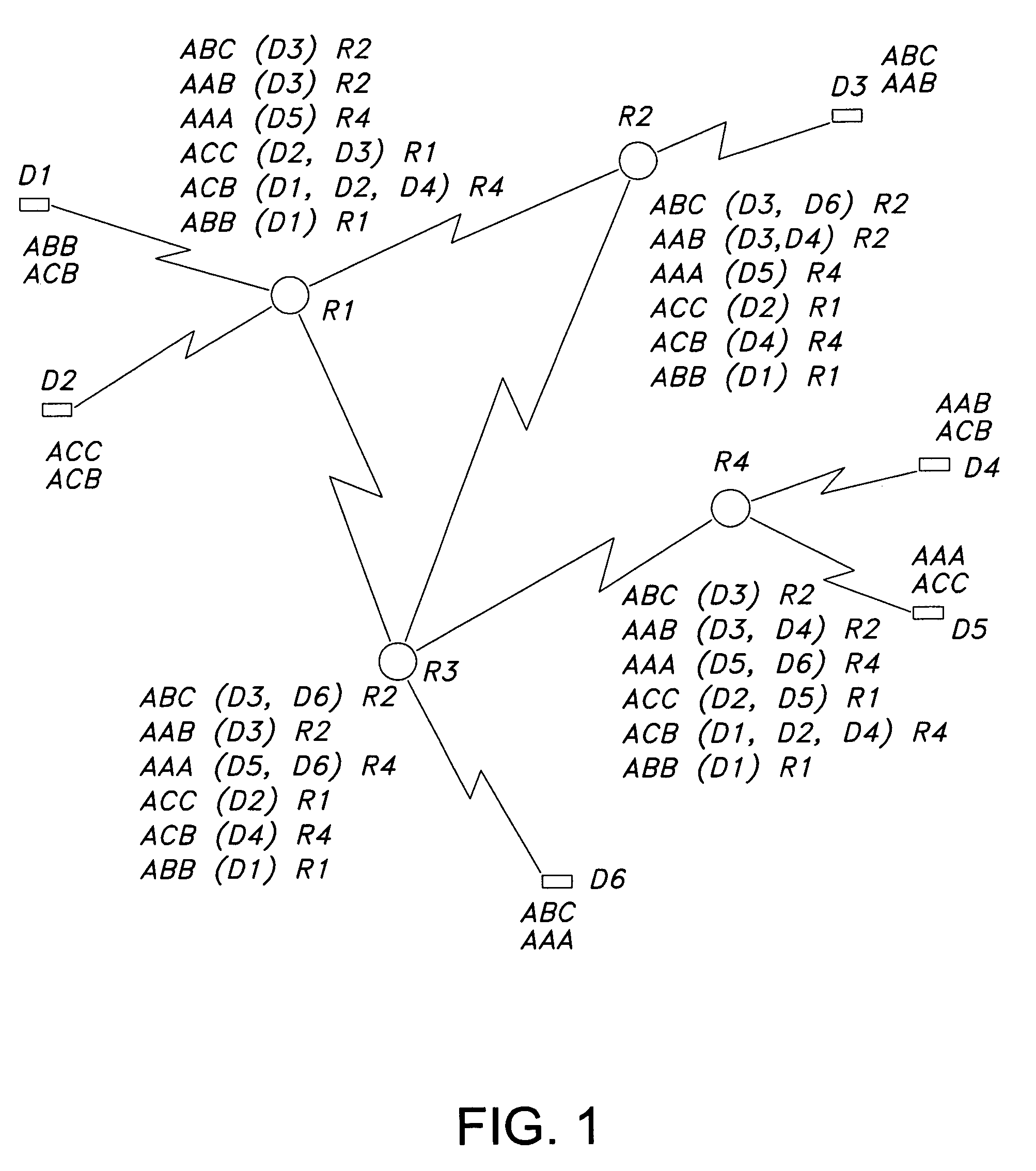
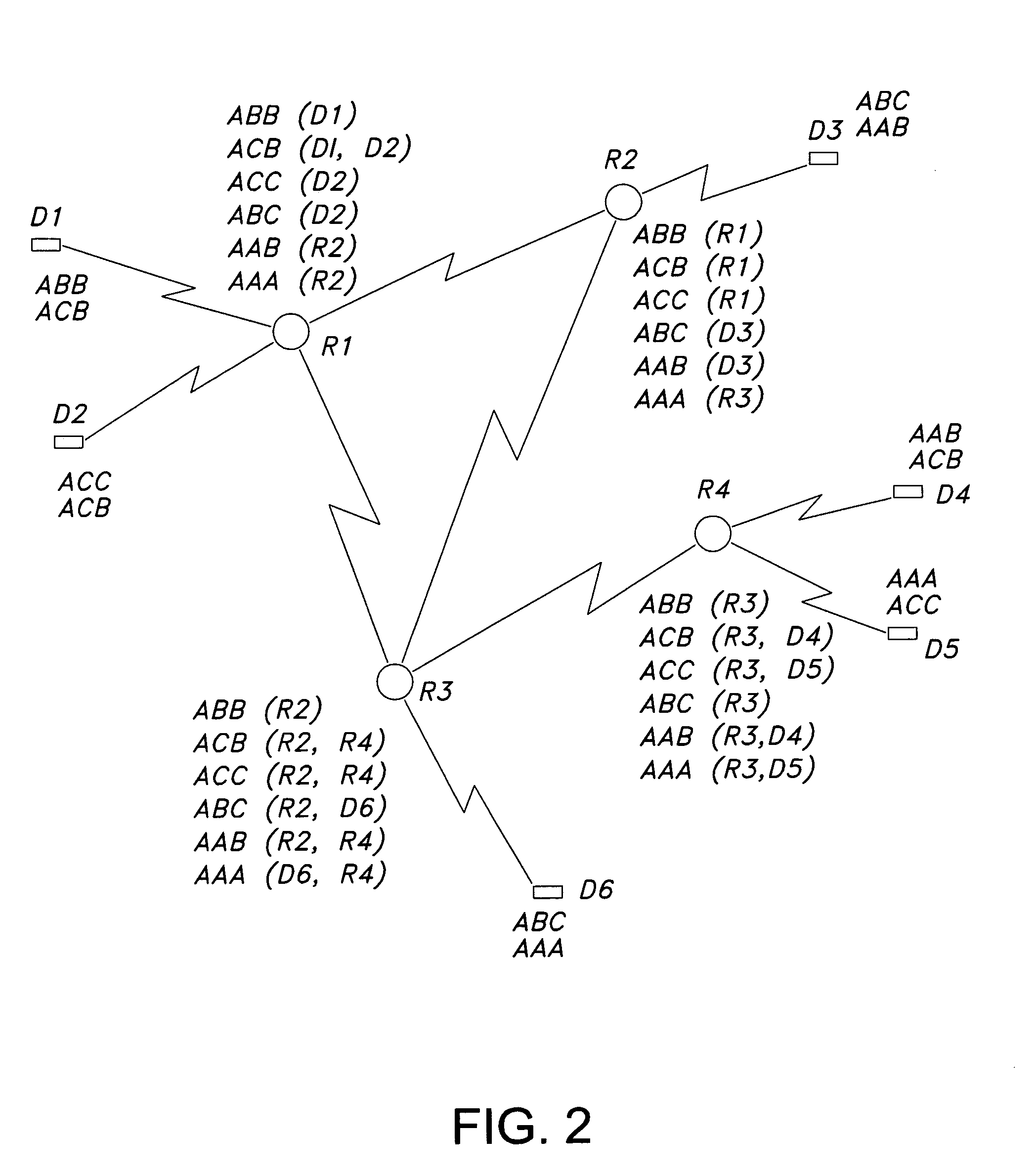
Method and apparatus for network wide policy-based analysis of configurations of devices
ActiveUS7003562B2Traffic controlDigital computer detailsData switching networksNetwork strategyNetwork topology
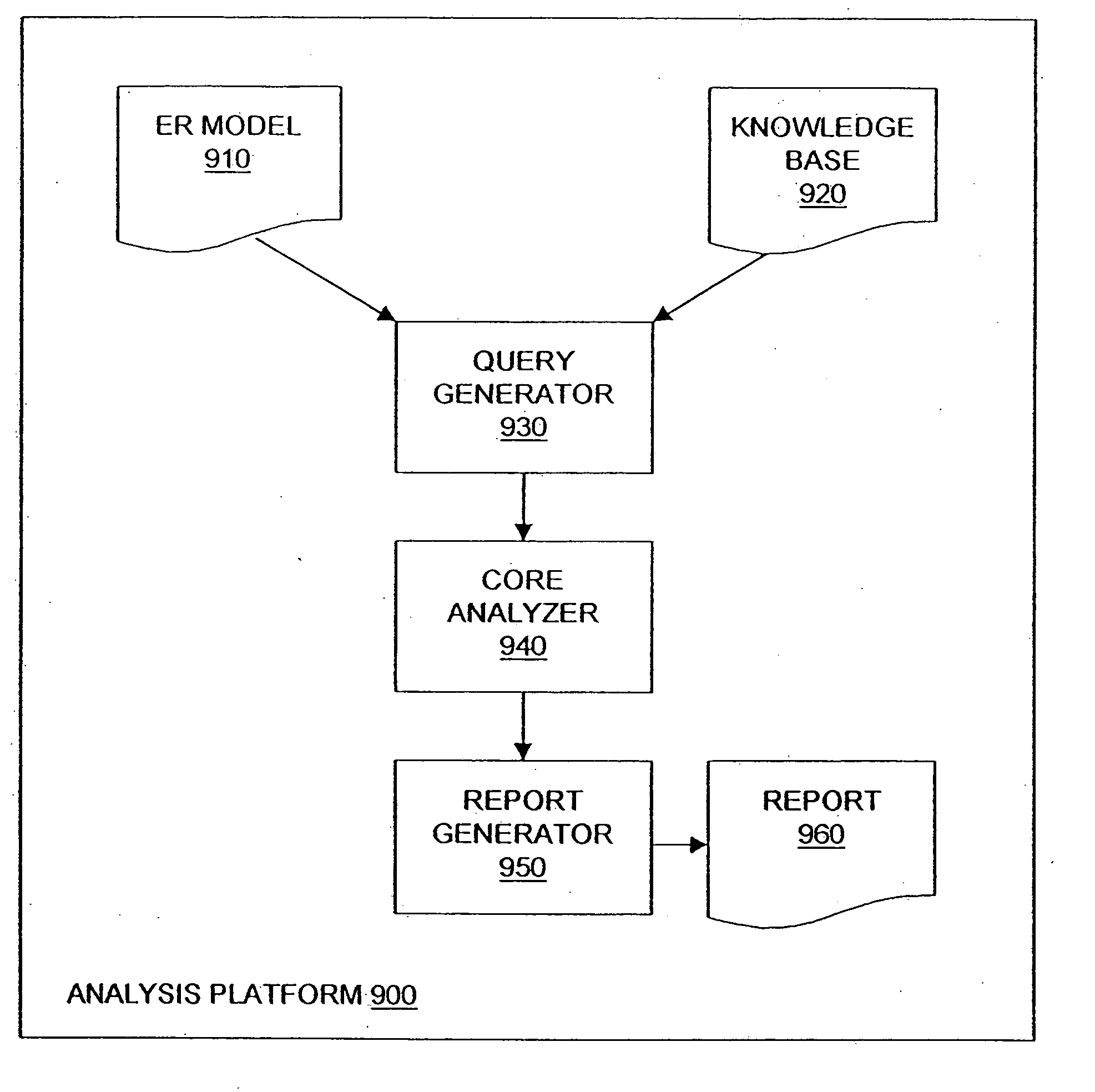
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL
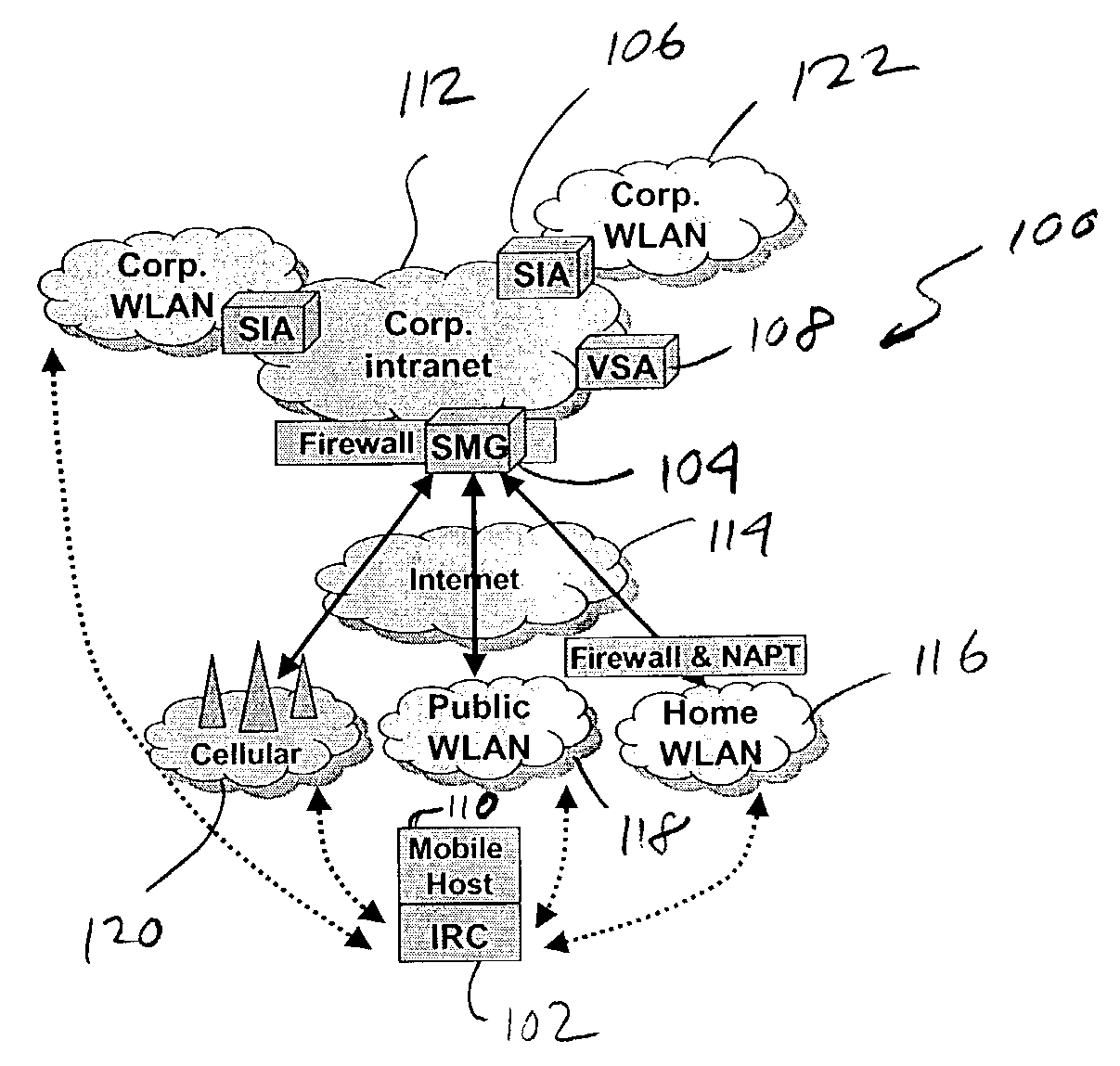
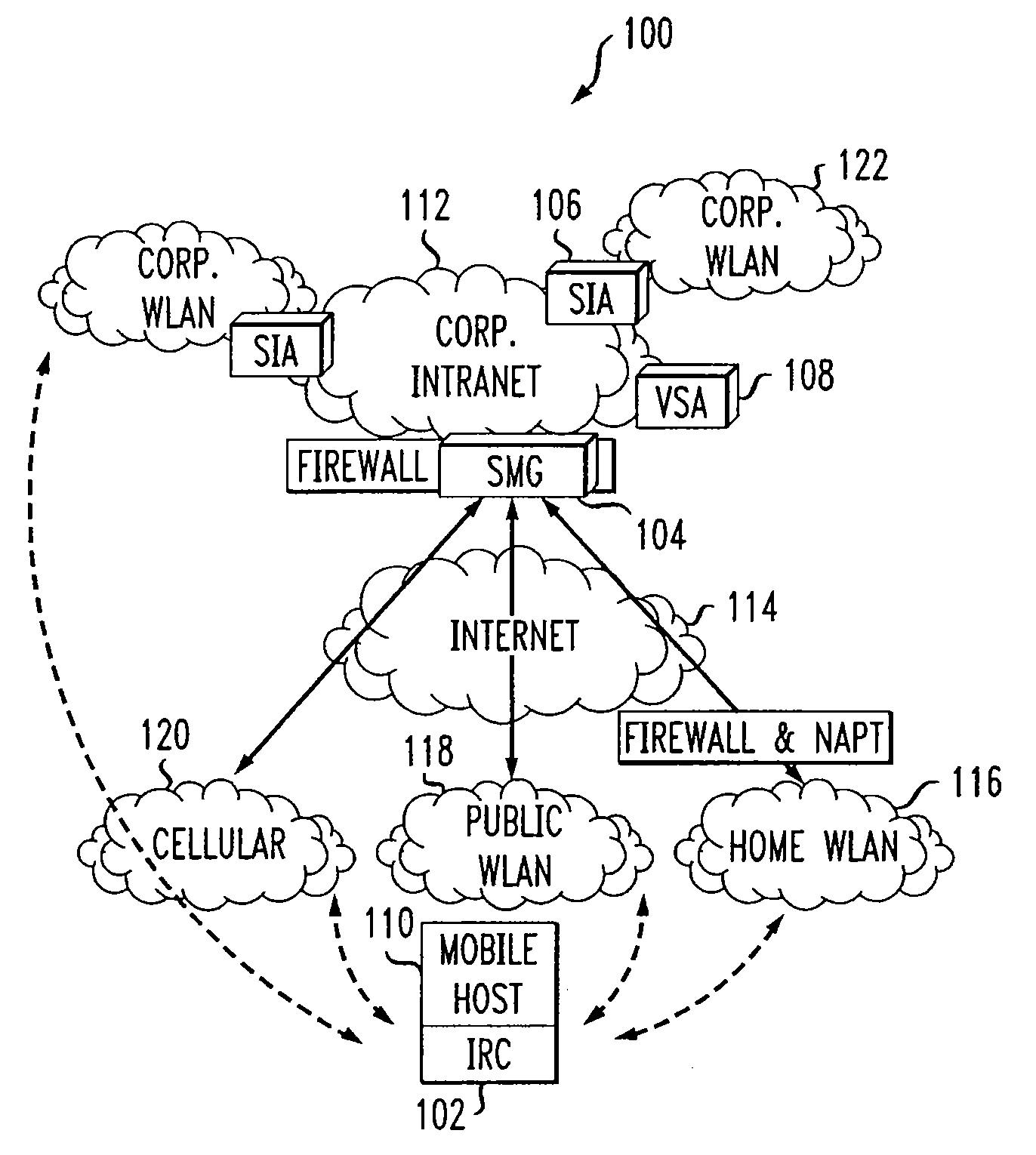
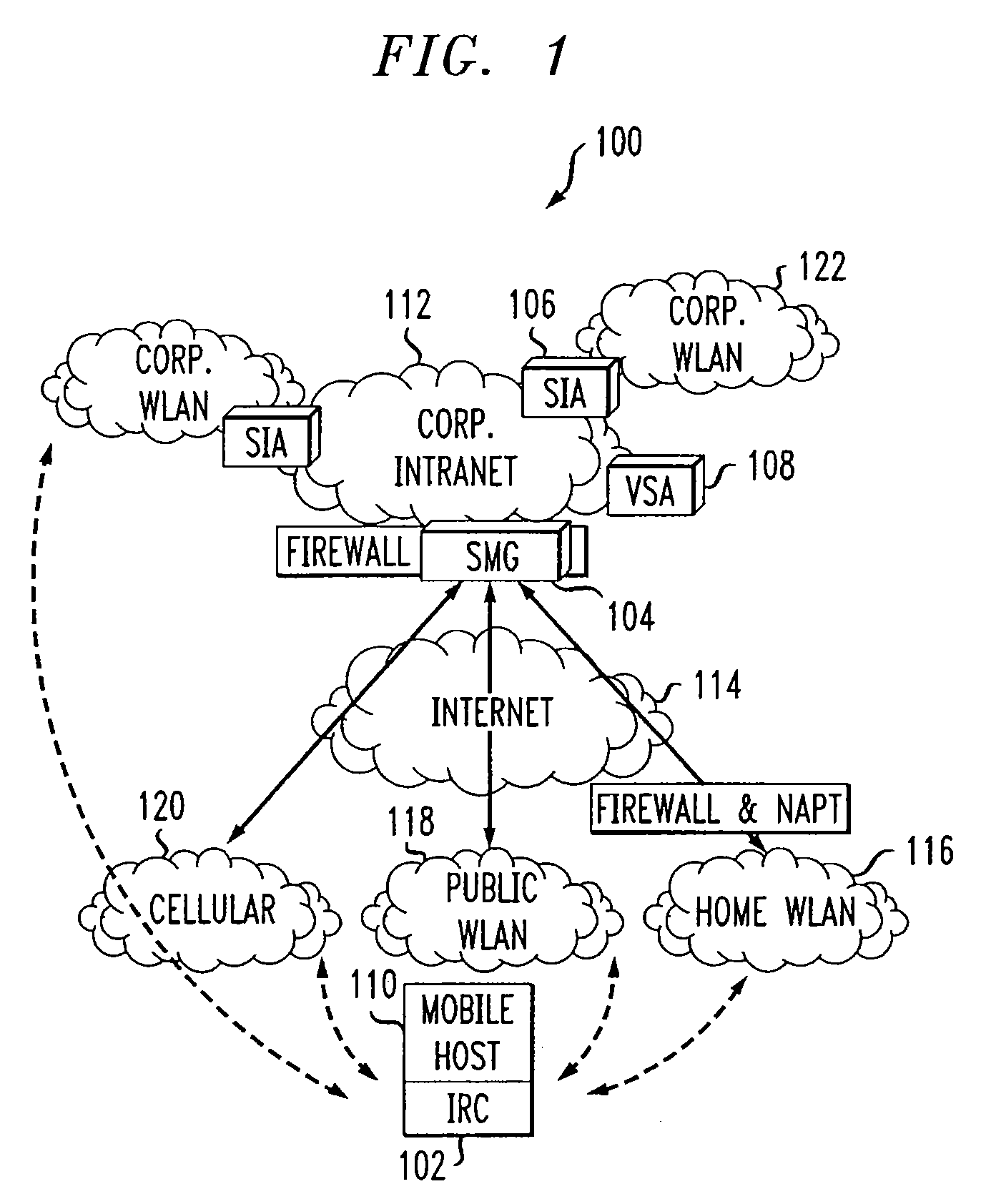
System and method to support networking functions for mobile hosts that access multiple networks
InactiveUS7441043B1Multiple digital computer combinationsWireless network protocolsModem deviceIp address
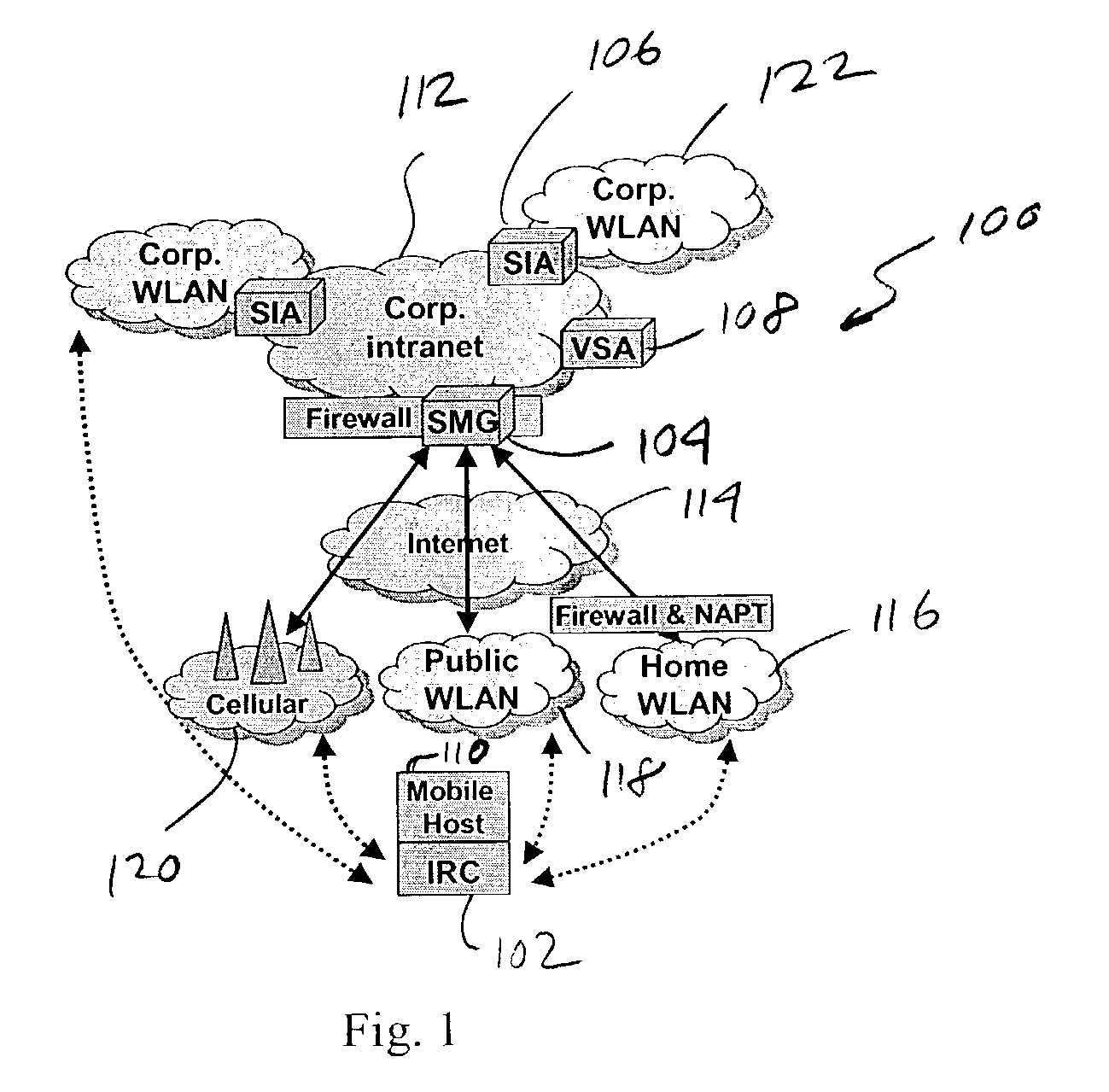
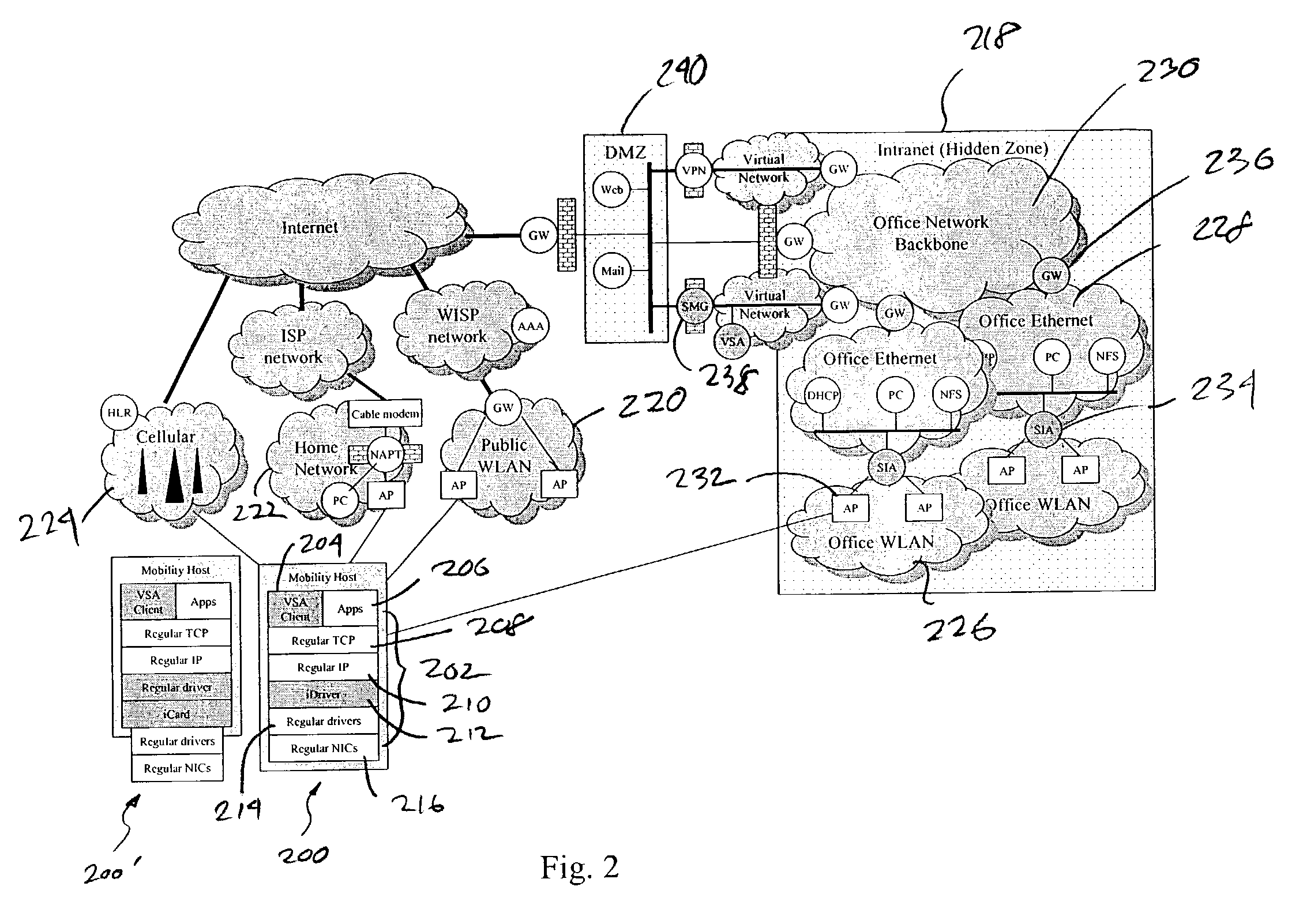
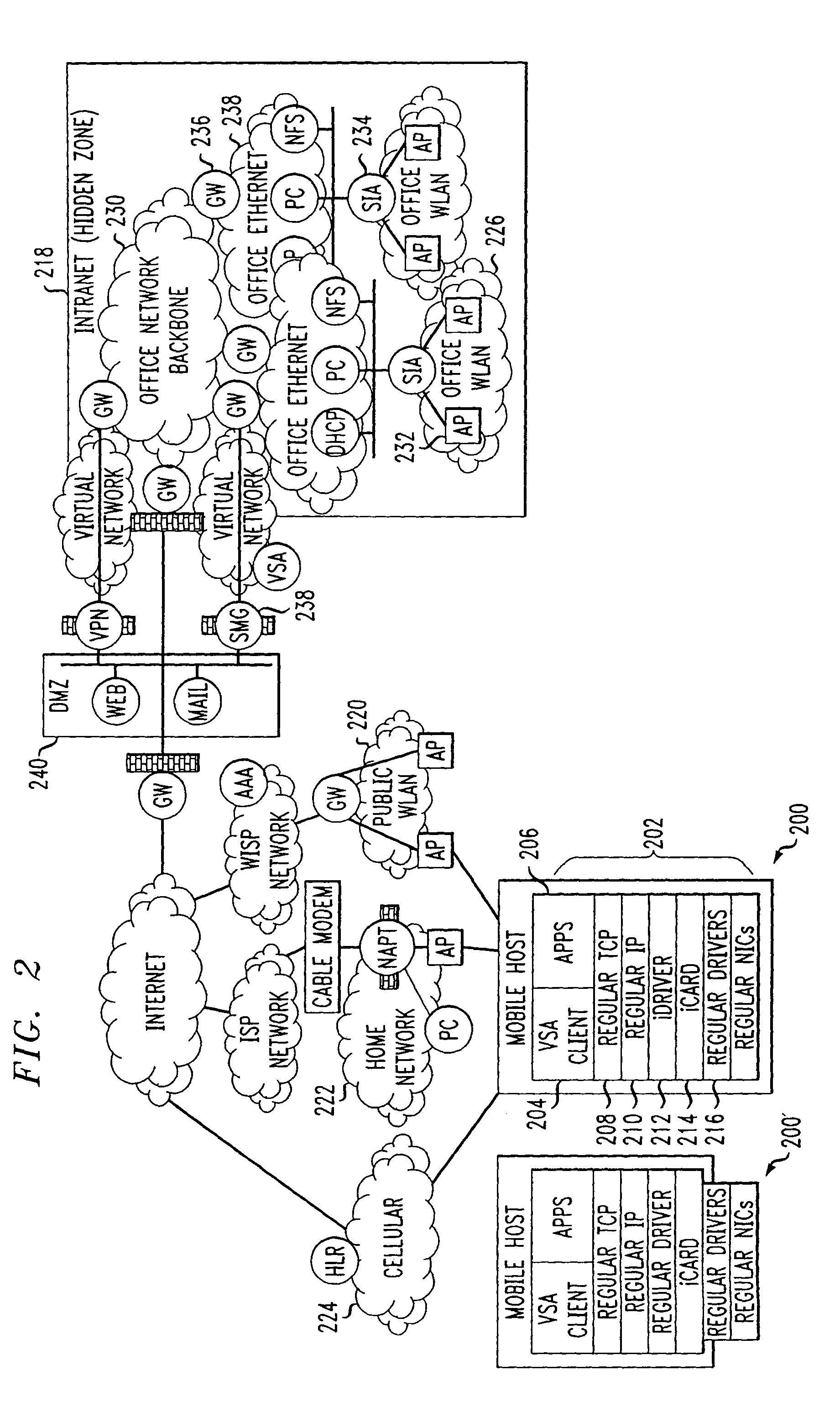
An IP-based corporate network architecture and method for providing seamless secure mobile networking across office WLAN, home WLAN, public WLAN, and 2.5G / 3G cellular networks for corporate wireless data users. The system includes Internet roaming clients (IRCs), a secure mobility gateway (SMG), optional secure IP access (SIA) gateways, and a virtual single account (VSA) server. The IRC is a special client tool installed on a mobile computer (laptop or PDA) equipped with a WLAN adaptor and a cellular modem. It is responsible for establishing and maintaining a mobile IPsec tunnel between the mobile computer and a corporate intranet. The SMG is a mobile IPsec gateway installed between the corporate intranet and the Internet. It works in conjunction with the IRC to maintain the mobile IPsec tunnel when the mobile computer is connected on the Internet via a home WLAN, a public WLAN, or a cellular network. The SIA gateway is a special IPsec gateway installed in the middle of the wired corporate intranet and an office WLAN. It works with the IRC to ensure data security and efficient use of corporate IP addresses when the mobile computer is connected to the office WLAN. The VSA server manages authentication credentials for every corporate user based on a virtual single account concept. The Internet Roaming system can provide secure, always-on office network connectivity for corporate users no matter where they are located using best available wireless networks.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
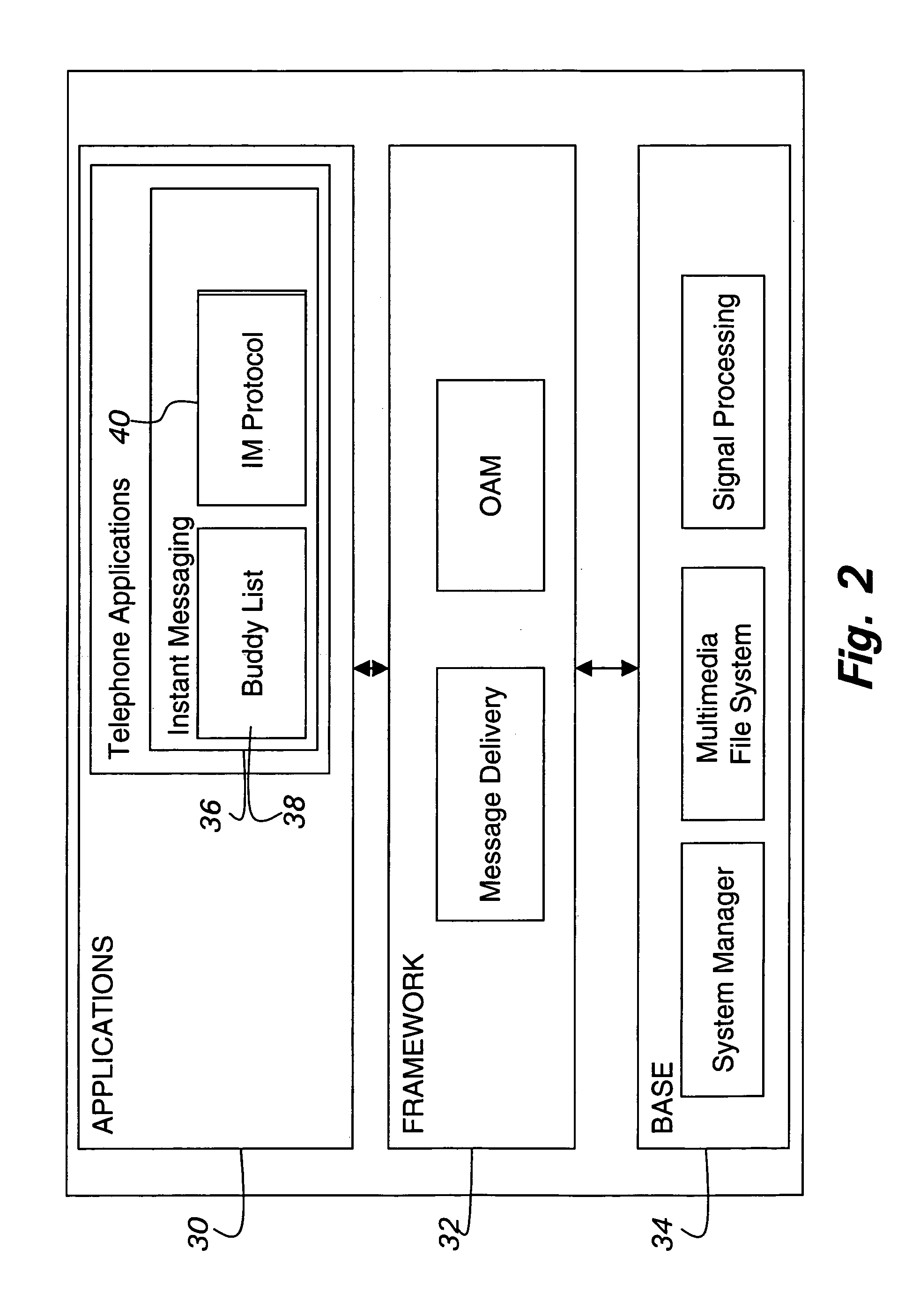
Telephone based access to instant messaging
InactiveUS7065186B1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersThe InternetInstant messaging
The present invention allows Internet instant messaging to be accessed via a telephone. Instant messaging access from any telephone in the world may be provided via a telephone messaging system. Alternatively, access can be embodied independently as a stand-alone telephone service, for example provided by a telephone company, provided by a company network, or provided by a user's personal IVR service implemented on his PC. An advantage of the present invention is providing simple, cost effective and readily available access to data network instant messaging from a telephone.
Owner:RPX CLEARINGHOUSE
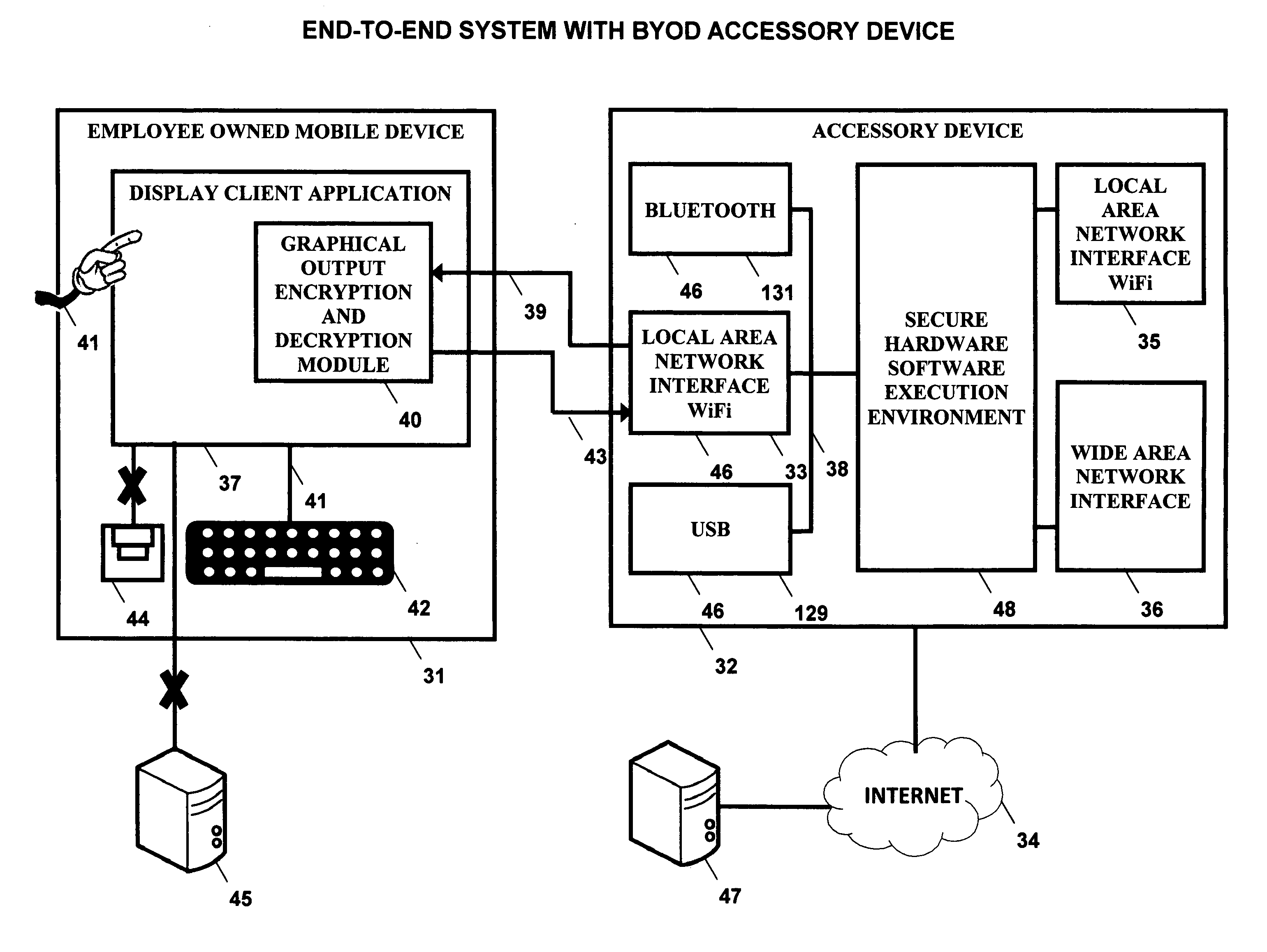
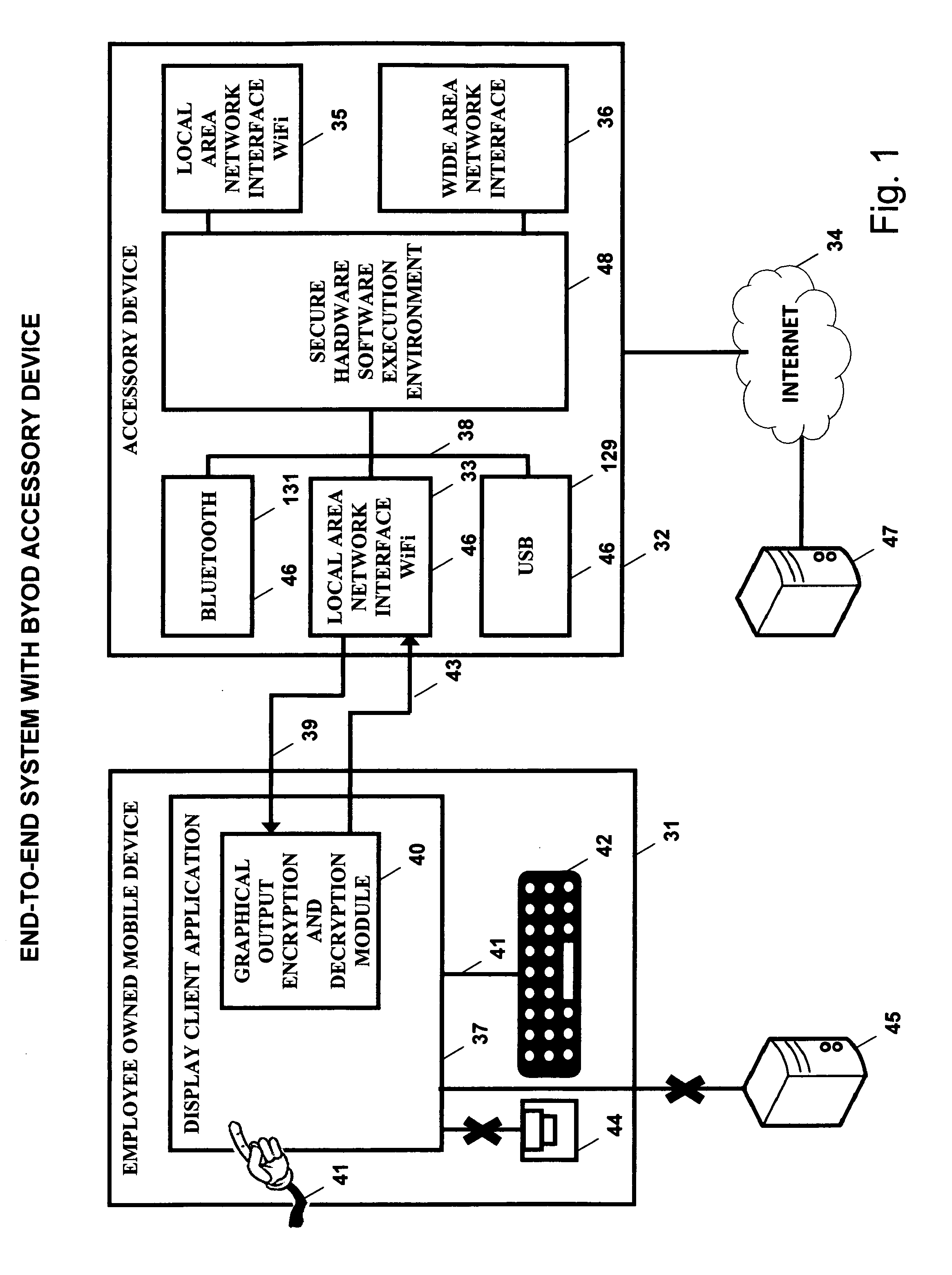
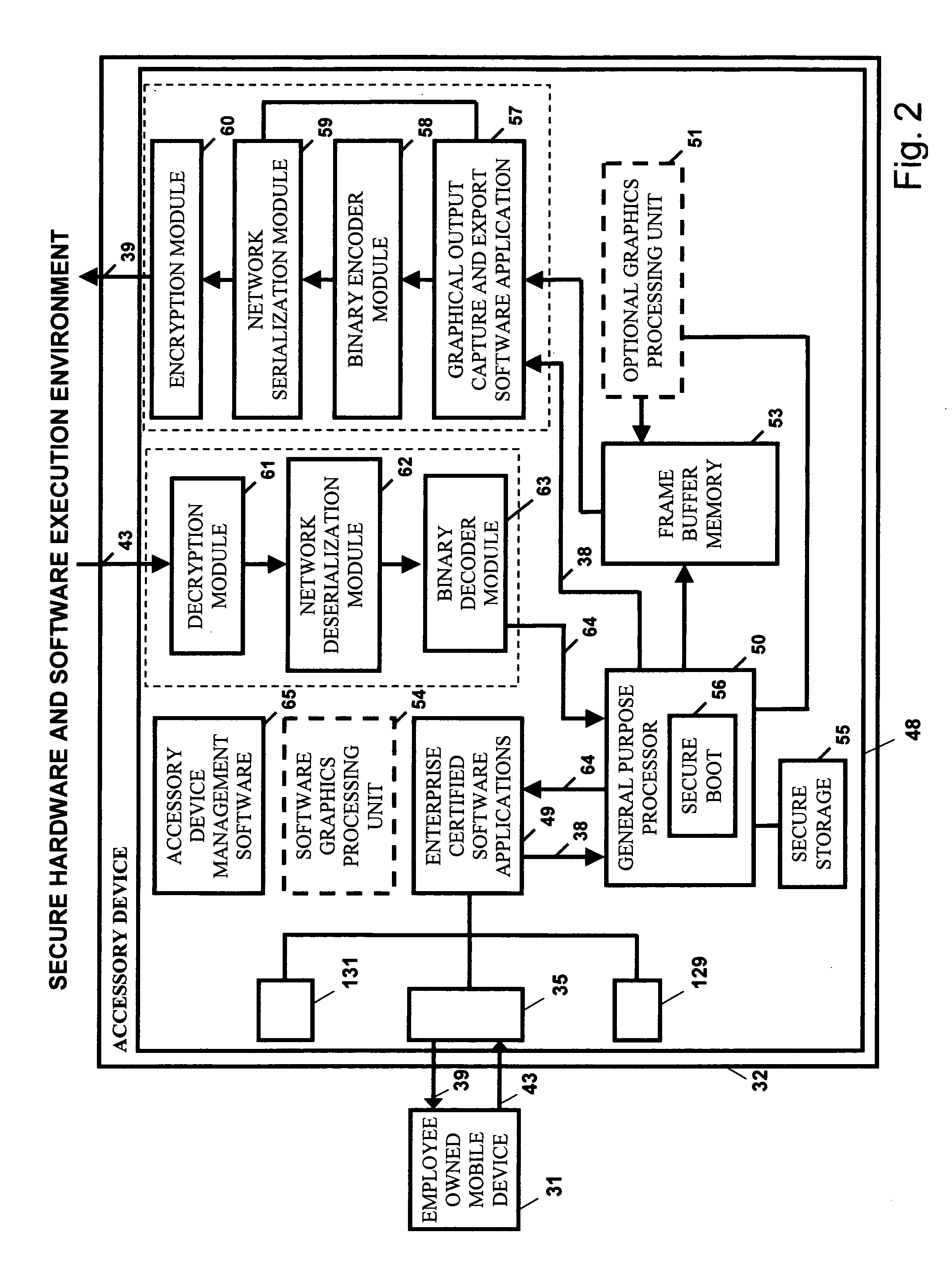
Bring your own device system using a mobile accessory device
InactiveUS20140173692A1Improve application performanceImprove securityDigital data processing detailsMultiple digital computer combinationsCorporate networkInternet network
A BYOD solution using a combination device is described. This combination device is comprised of an employee owned smart mobile device (31) and an accessory device (32) used together using a wireless local area network (46).Mobile device (31) is an employee owned device that is used as a remote display of display output of enterprise certified applications (49) executing at accessory device (32).Accessory device (32) is comprised of a general purpose processor, optional graphics processing unit, one or more local wireless area network interfaces that connect the mobile device (31) to accessory device (32), and one or more Internet network interfaces (52) that connect accessory to enterprise network.The BYOD accessory device acts as a secure hardware gateway to connect the mobile device to corporate network.The BYOD accessory device also acts as a secure execution environment of corporate applications in addition to providing secure storage of corporate data.
Owner:SRINIVASAN SUDHARSHAN +2
Wireless mobility gateway
ActiveUS20070091862A1Efficient forwardingEasy to moveData switching by path configurationRadio/inductive link selection arrangementsTelecommunicationsThe Internet
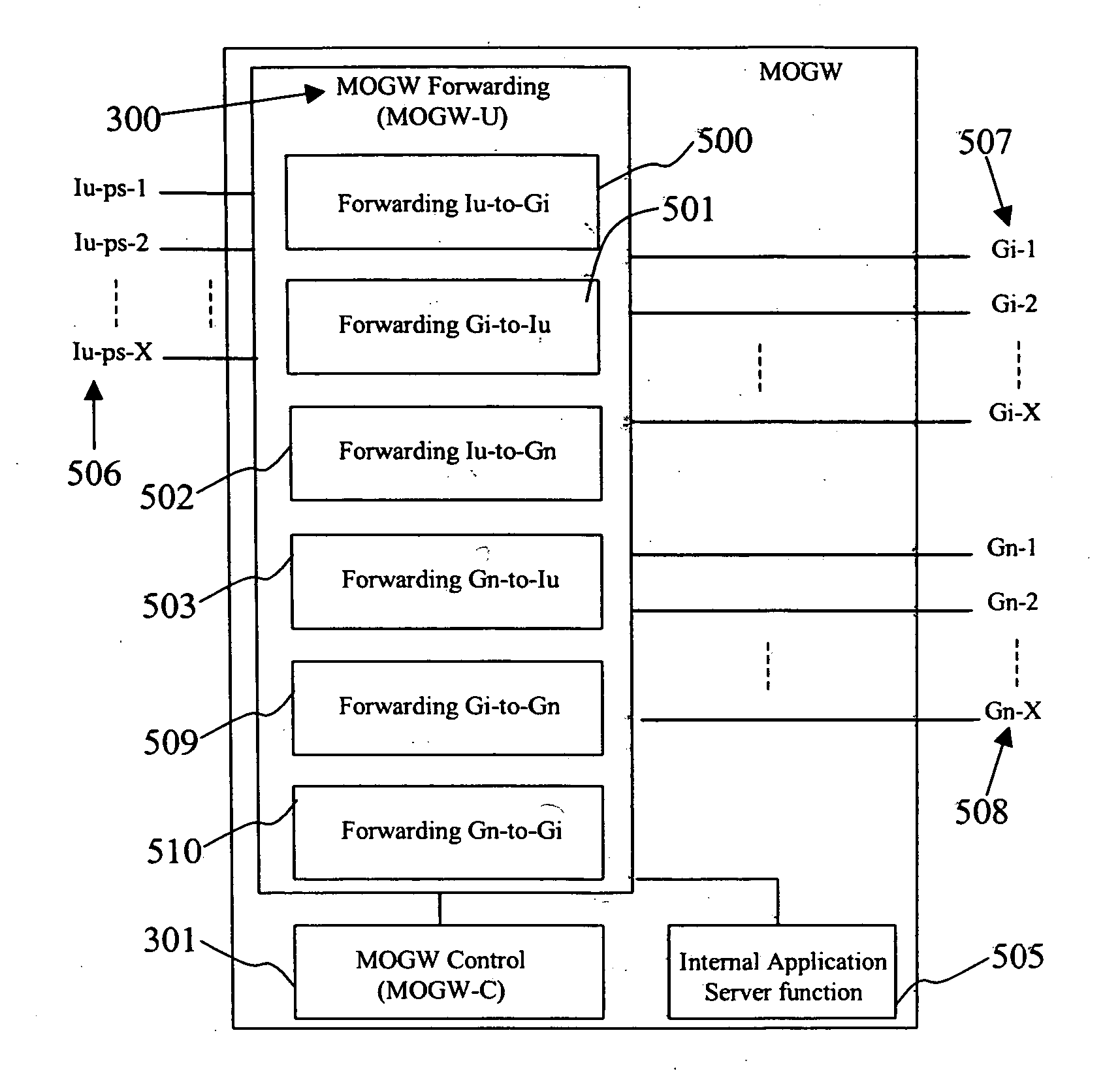
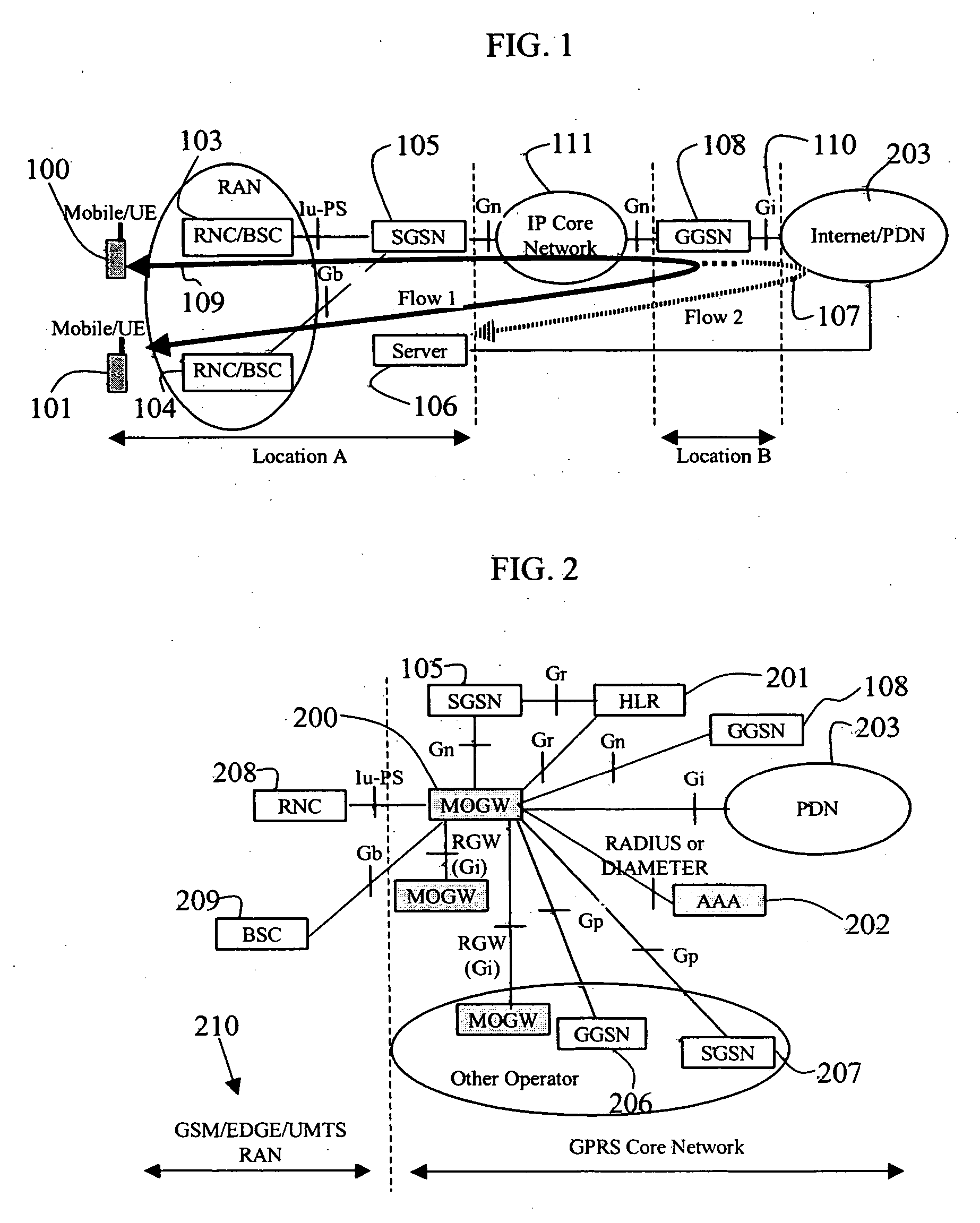
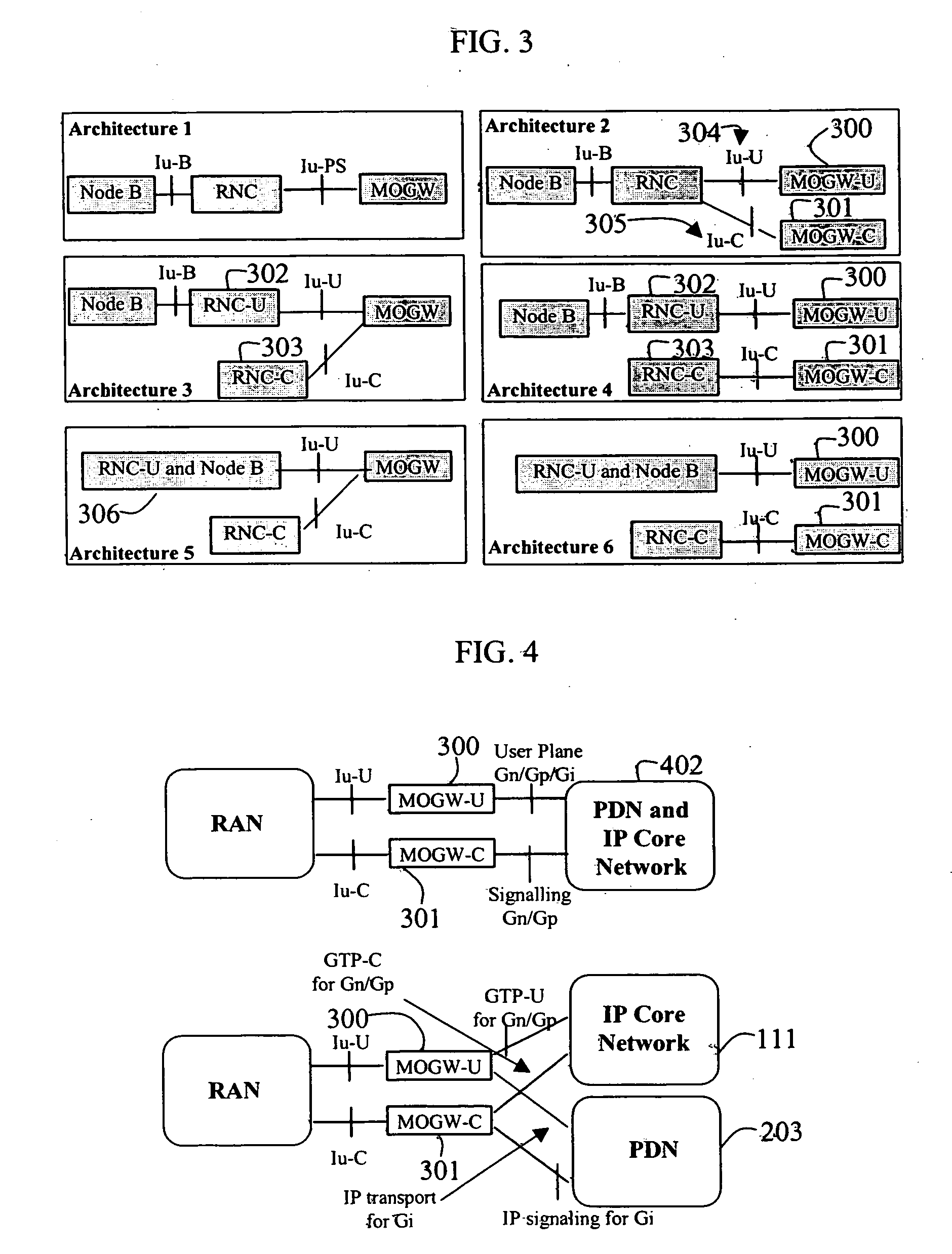
According to certain embodiments of the present invention, Wireless Mobility Gateway (MOGW) method and apparatus determines whether a wireless connection has been requested by a mobile terminal. As a consequence it performs security functions to authenticate the mobile user and grant access. If requested by the mobile user it then also creates a wireless connection to allow it to perform IP packet transmission and reception and therefore make use of mobile data services. The MOGW is able to directly route packets to Internet and Corporate Networks, thus rendering the whole mobile network more efficient and simpler to construct and manage. The MOGW generates a special tunnel identifier to identify the wireless connection that must be contained in all packets received from the RAN. The MOGW generates such a tunnel identifier by concatenating a number of values that characterize the connection. Therefore, simply by reading this tunnel identifier, the MOGW can more efficiently forward packets appropriately. The Mobility protocol and function between MOGWs allows Mobile terminals to easily move between geographical areas served by different MOGWs.
Owner:ATHONET
Method and apparatus for network wide policy-based analysis of configurations of devices
InactiveUS20060129672A1Digital computer detailsData switching networksNetwork strategyNetwork topology
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL NETWORKS
System and method to support networking functions for mobile hosts that access multiple networks
InactiveUS20090022152A1Data switching by path configurationWireless network protocolsModem deviceIp address
An IP-based corporate network architecture and method for providing seamless secure mobile networking across office WLAN, home WLAN, public WLAN, and 2.5 G / 3 G cellular networks for corporate wireless data users. The system includes Internet roaming clients (IRCs), a secure mobility gateway (SMG), optional secure IP access (SIA) gateways, and a virtual single account (VSA) server. The IRC is a special client tool installed on a mobile computer (laptop or PDA) equipped with a WLAN adaptor and a cellular modem. It is responsible for establishing and maintaining a mobile IPsec tunnel between the mobile computer and a corporate intranet. The SMG is a mobile IPsec gateway installed between the corporate intranet and the Internet. It works in conjunction with the IRC to maintain the mobile IPsec tunnel when the mobile computer is connected on the Internet via a home WLAN, a public WLAN, or a cellular network. The SIA gateway is a special IPsec gateway installed in the middle of the wired corporate intranet and an office WLAN. It works with the IRC to ensure data security and efficient use of corporate IP addresses when the mobile computer is connected to the office WLAN. The VSA server manages authentication credentials for every corporate user based on a virtual single account concept. The Internet Roaming system can provide secure, always-on office network connectivity for corporate users no matter where they are located using best available wireless networks.
Owner:AT&T INTPROP II L P
Authentication
InactiveUS20120047563A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwarePassword
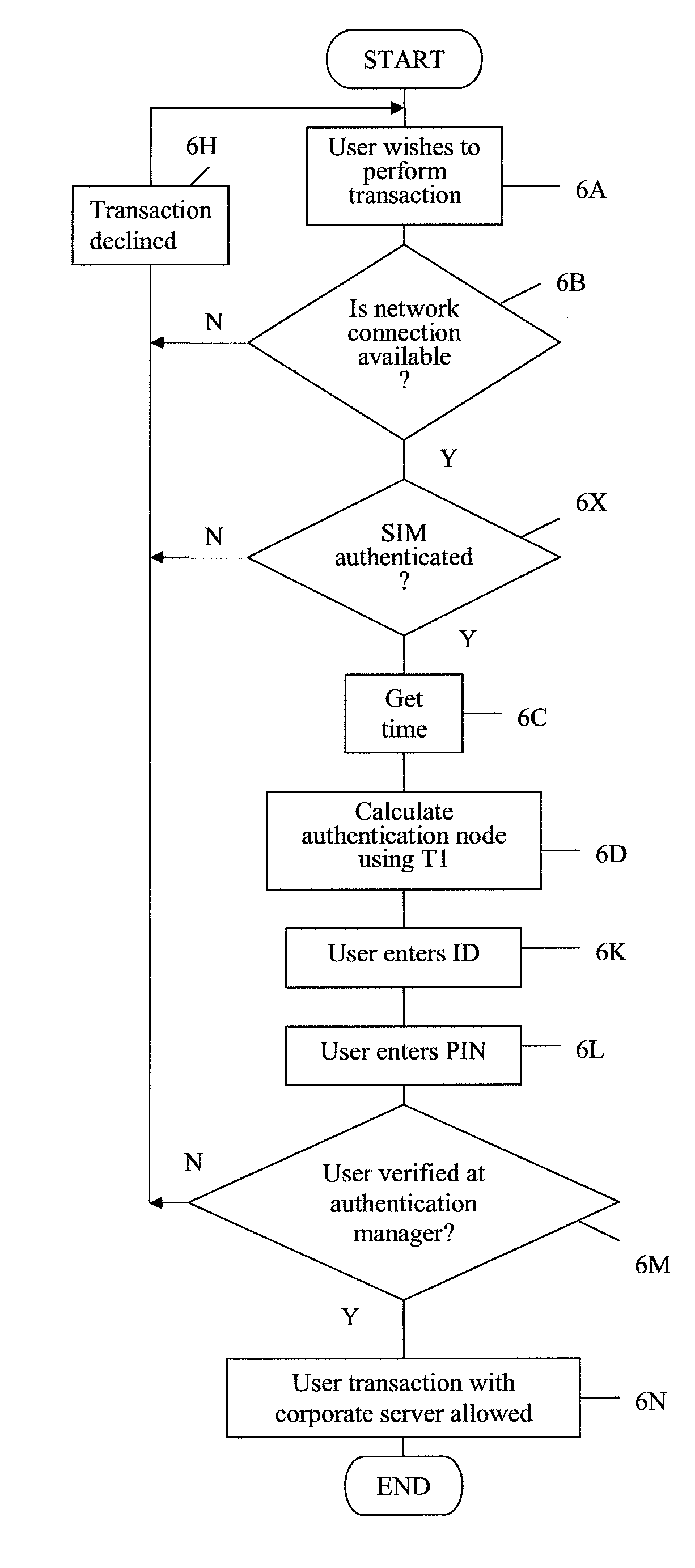
An arrangement for authenticating a transaction between a user's mobile device and an entity such as a corporate server is disclosed. The user's universal integrated circuit card (UICC) is adapted to generate a time-dependent authentication code which is dependent on a time value and which is usable to authenticate the transaction only during a predetermined period. A time verification processor verifies a time value to ensure that the time-dependent authentication code was generated based on the correct time value. The time value is based on the UTC time obtained from UTC clock. The verified time is used to generate a “one-time” password (authentication code) by the authentication code calculator of the UICC. This is used to authenticate a transaction with the corporate network.
Owner:VODAFONE IP LICENSING
Personal remote firewall
InactiveUS20050060328A1Digital data processing detailsMultiple digital computer combinationsPrivate networkCorporate network
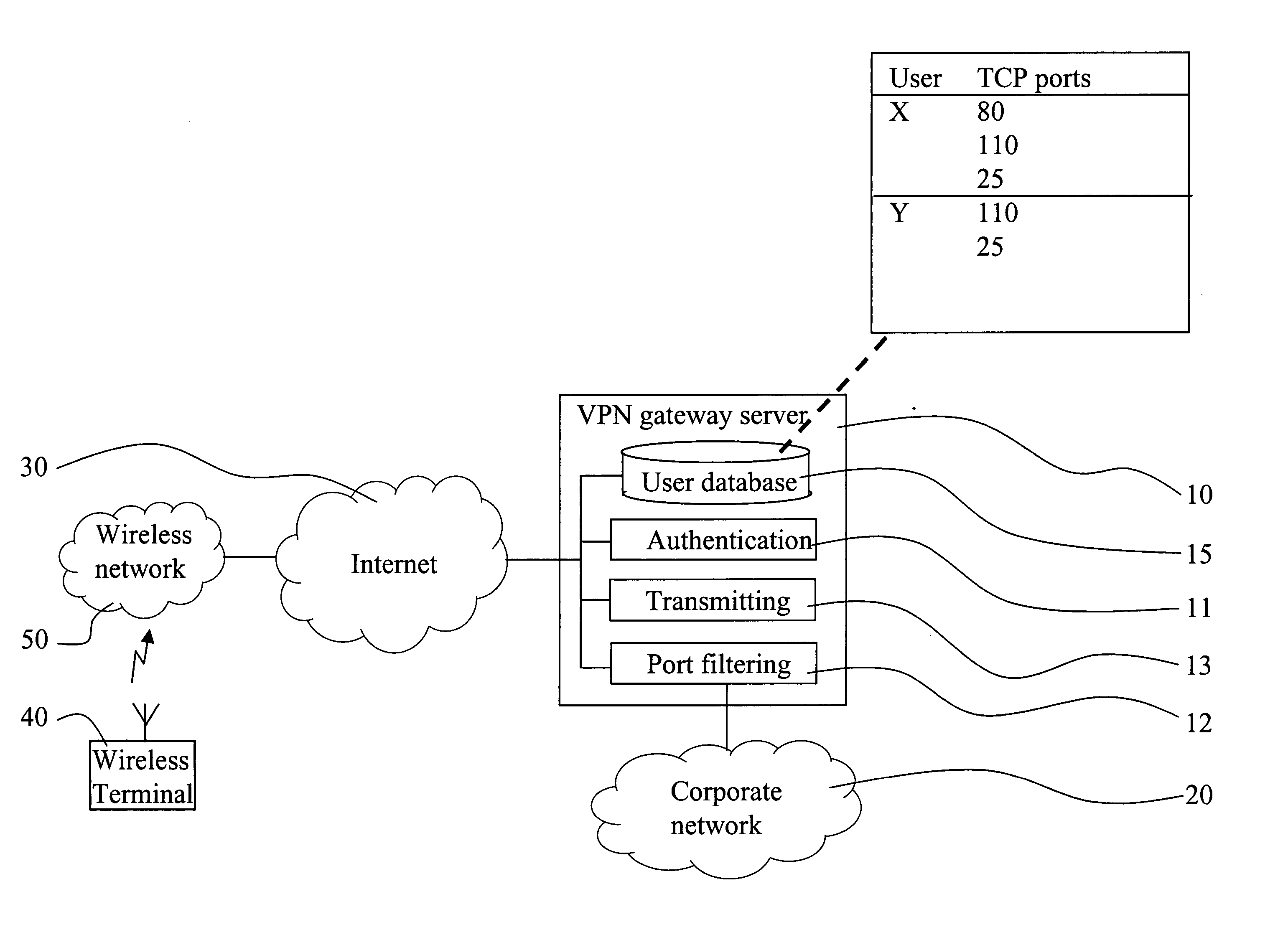
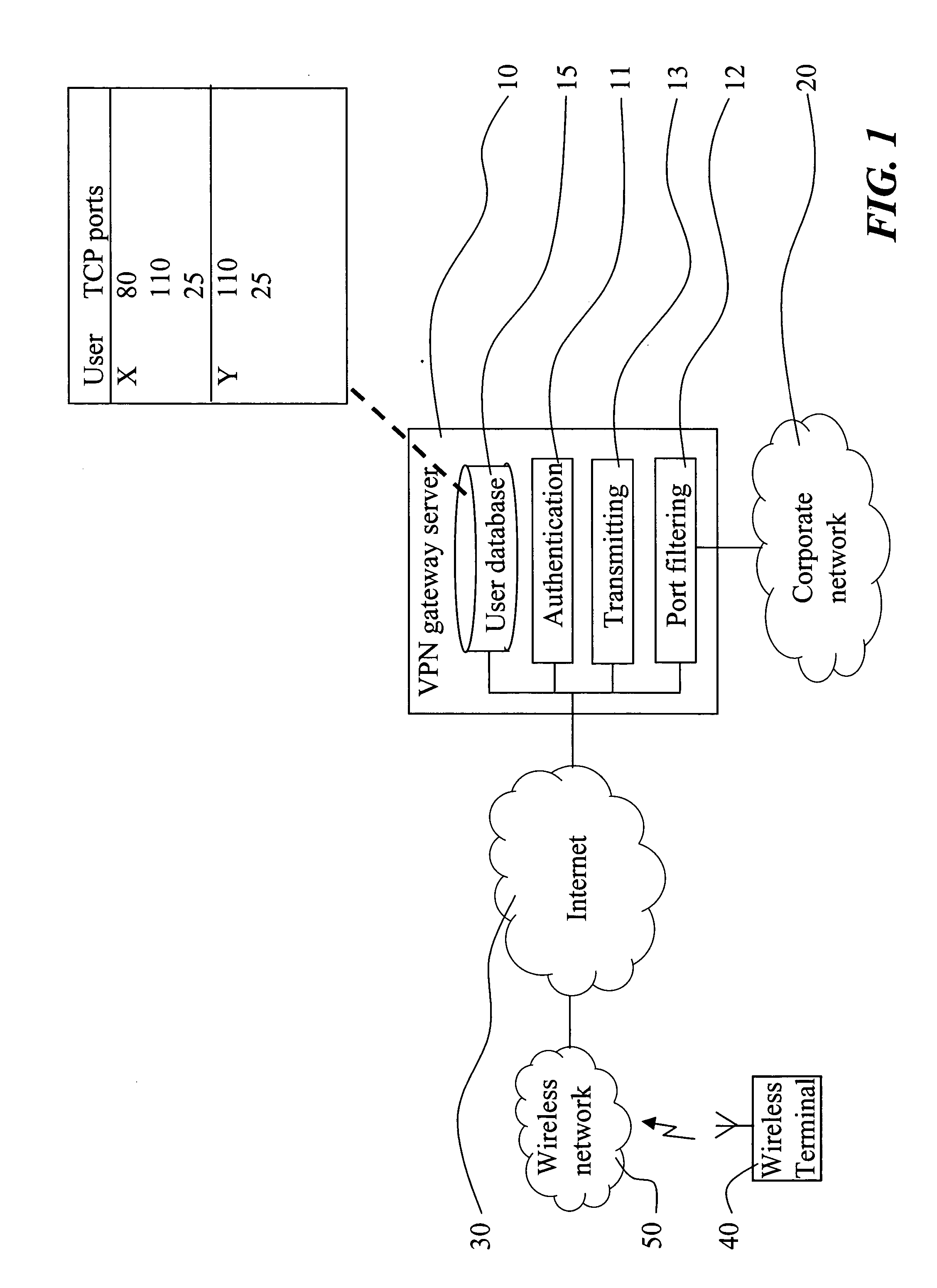
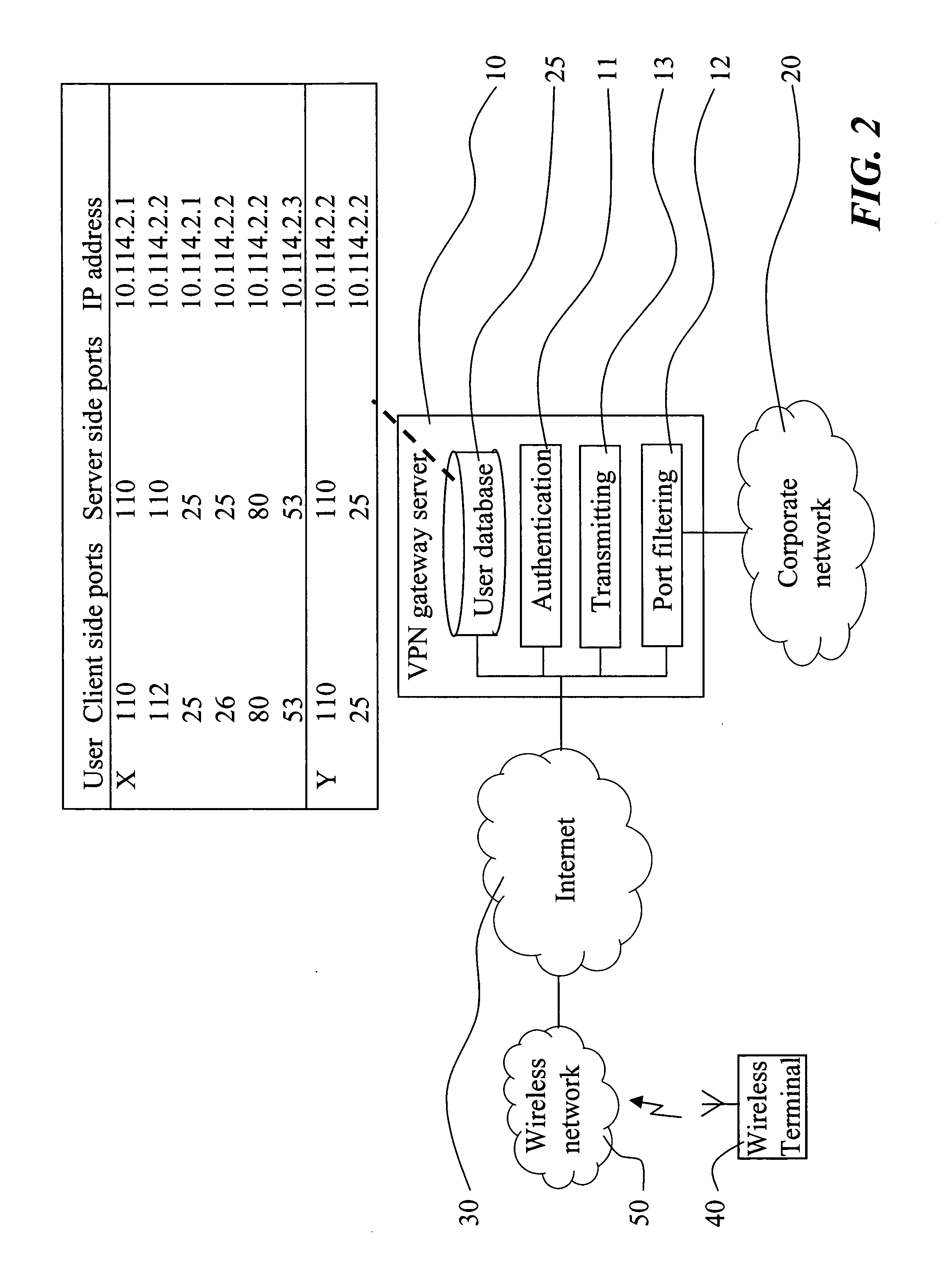
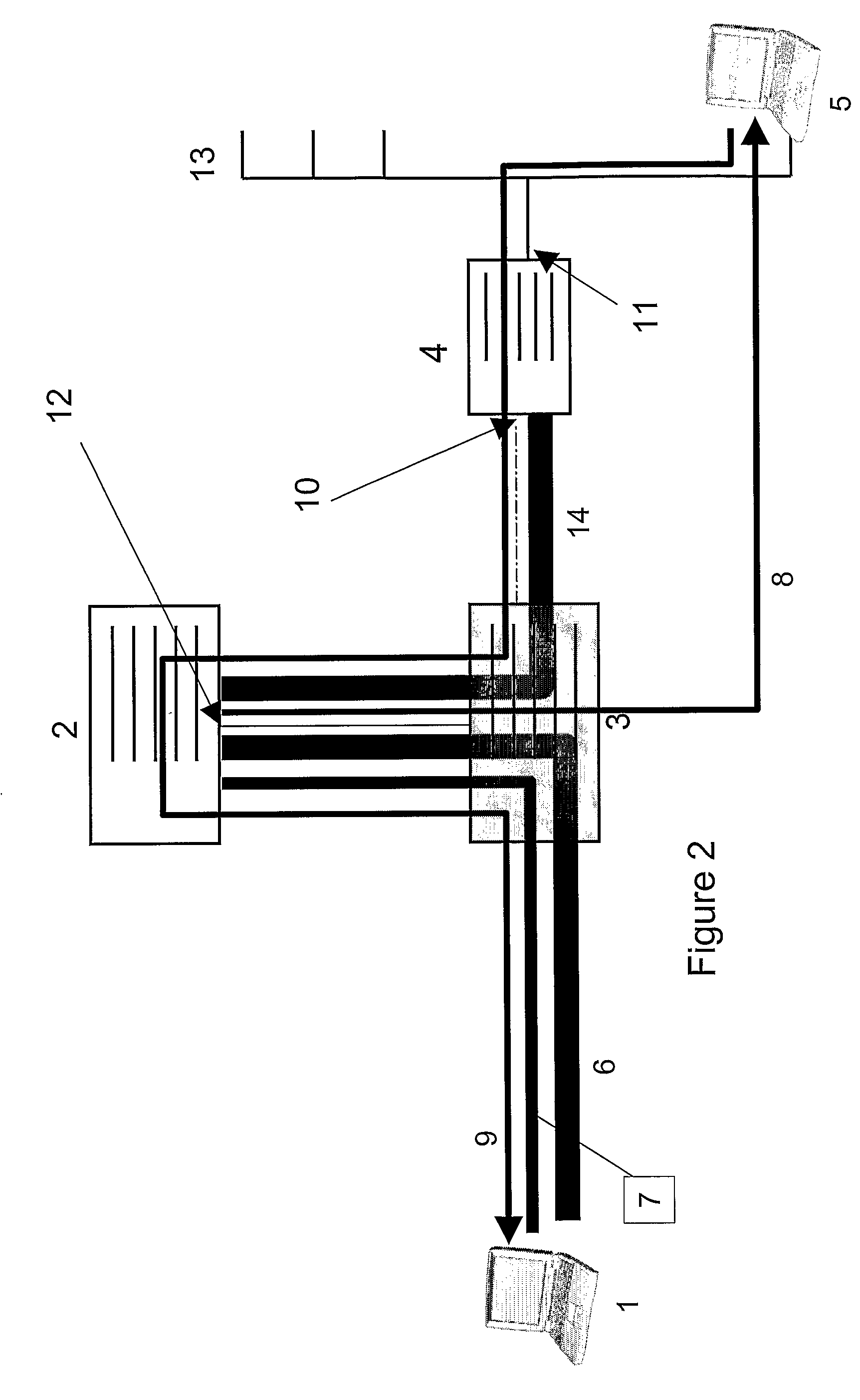
The present invention relates to a method and a virtual private network (VPN) gateway server 10 providing rules for wireless access over a secure tunnel connection to a corporate network 20. The corporate network 20 is protected by firewall functionality, with different access configurations for different remote users. The VPN gateway server 10 includes a user database 15 which provides rules specific for each user for the access to the corporate network 20 using the secure tunnel. The rules include specific sets of TCP ports associated with respective specific users. The gateway server 10 limits an authenticated user's access to the corporate network 20, which access is performed by means of the tunnel connection provided by the gateway server 10, to the associated allowed TCP server ports.
Owner:NOKIA CORP
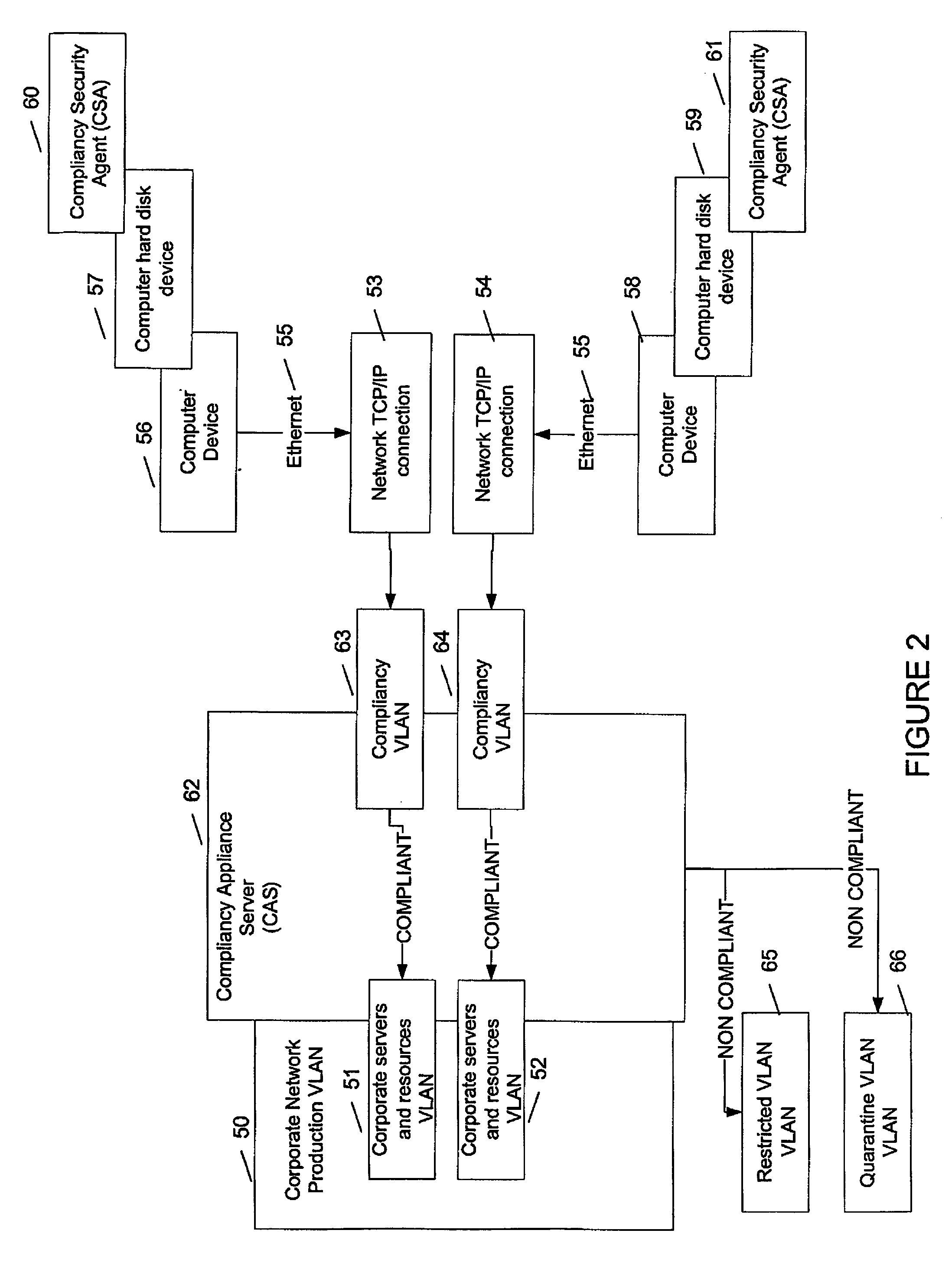
Compliance verification and OSI layer 2 connection of device using said compliance verification
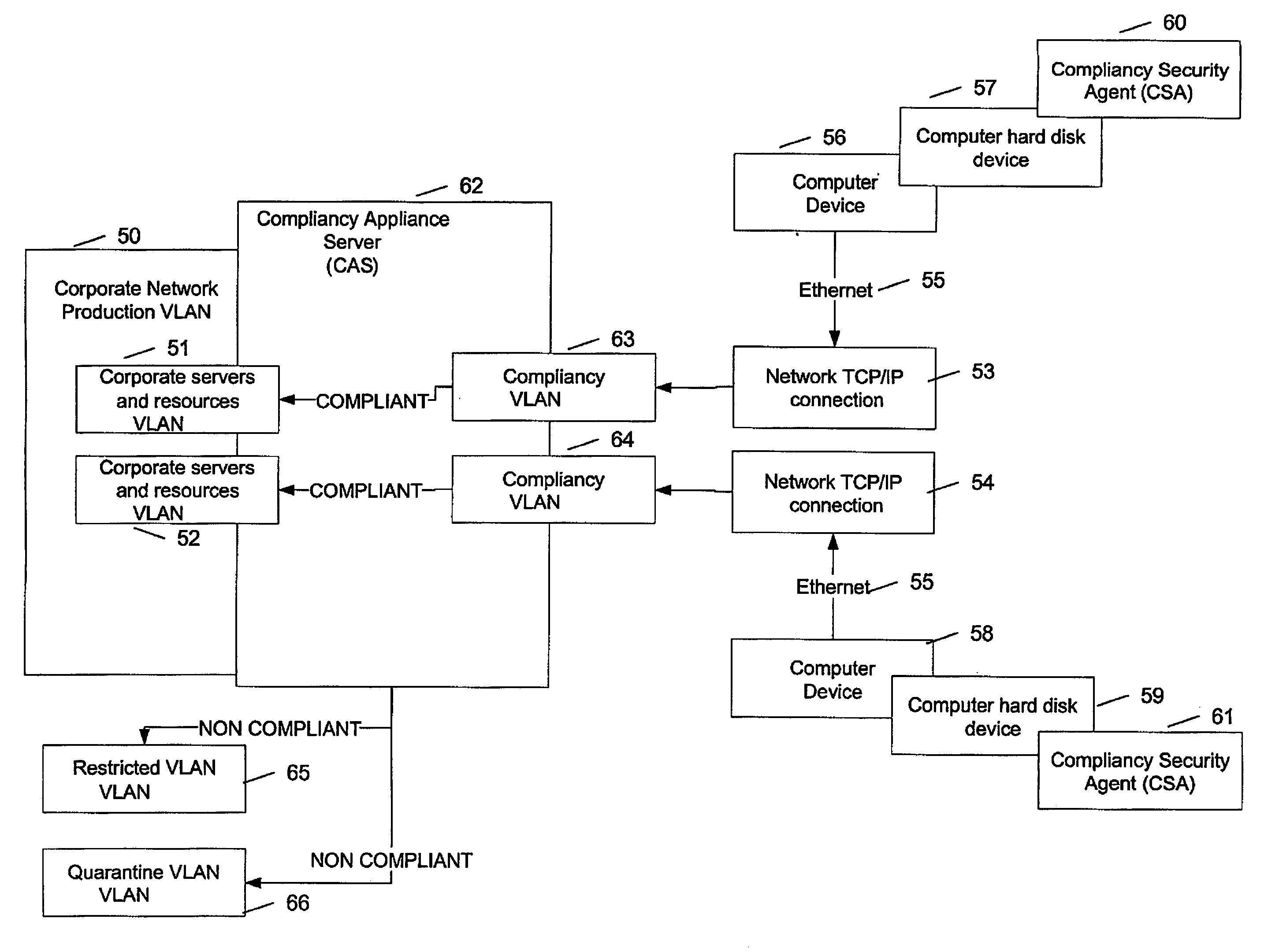
InactiveUS20060203815A1Avoid loopholesPreserving network integrityData switching by path configurationNetwork connectionsCorporate networkIp address
The method comprises installing an agent software on the device; detecting a boot-up of the device; providing the device with a temporary IP address upon boot-up, the temporary IP address being within a compliancy network, logically separate from the corporate network; providing a list of compliance rules to be verified for the device; sending the agent the list of compliance rules; verifying a state of the device for each rule; transmitting a result of the state obtained for each compliance rule; deciding on compliance of the device using the result; instructing a switch port at OSI layer 2 to connect the device to the corporate network if the decision determines compliance; instructing a switch port at OSI layer 2 to connect the device to a network logically separate from the corporate network in case of non-compliance.
Owner:TELUS COMM
Device to facilitate the deployment of mobile virtual private networks for medium/large corporate networks
InactiveUS20070008924A1Substantial tunneling overheadFacilitating optimal traffic flowWireless network protocolsRadio/inductive link selection arrangementsIPsecUser authentication
A mobile agent device in a Mobile Virtual Private Network, said device comprising: termination of Mobile IP tunnel (6) from a remotely connecting Mobile Node (1); termination of an IPSec VPN tunnel (7) from the remotely connecting Mobile Node; dynamic Selection of Internal Mobile IP Home Agent based on user Authentication; tunneling of traffic to and / or from the assigned Internal Mobile Home Agent for this Mobile Node; and, provision of extended authentication, after Mobile IP connection establishment, and during the VPN negotiation phase, based on extra user credentials, one-time-password mechanism or similar.
Owner:RADIO IP SOFTWARE
Thin client end system for virtual private network
InactiveUS20050198532A1Reduce vulnerabilityLess susceptibleMemory loss protectionError detection/correctionPrivate networkEnd system
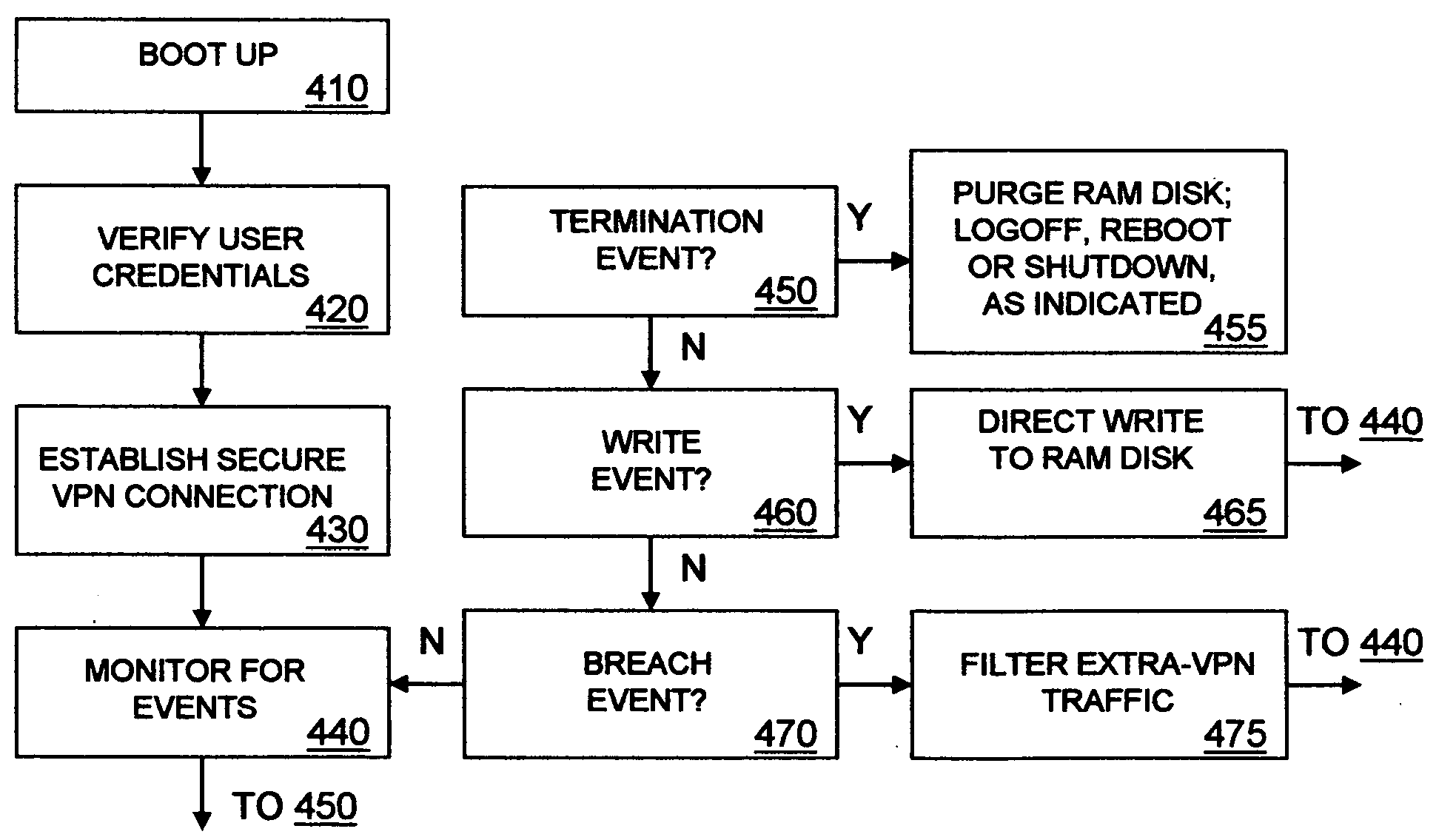
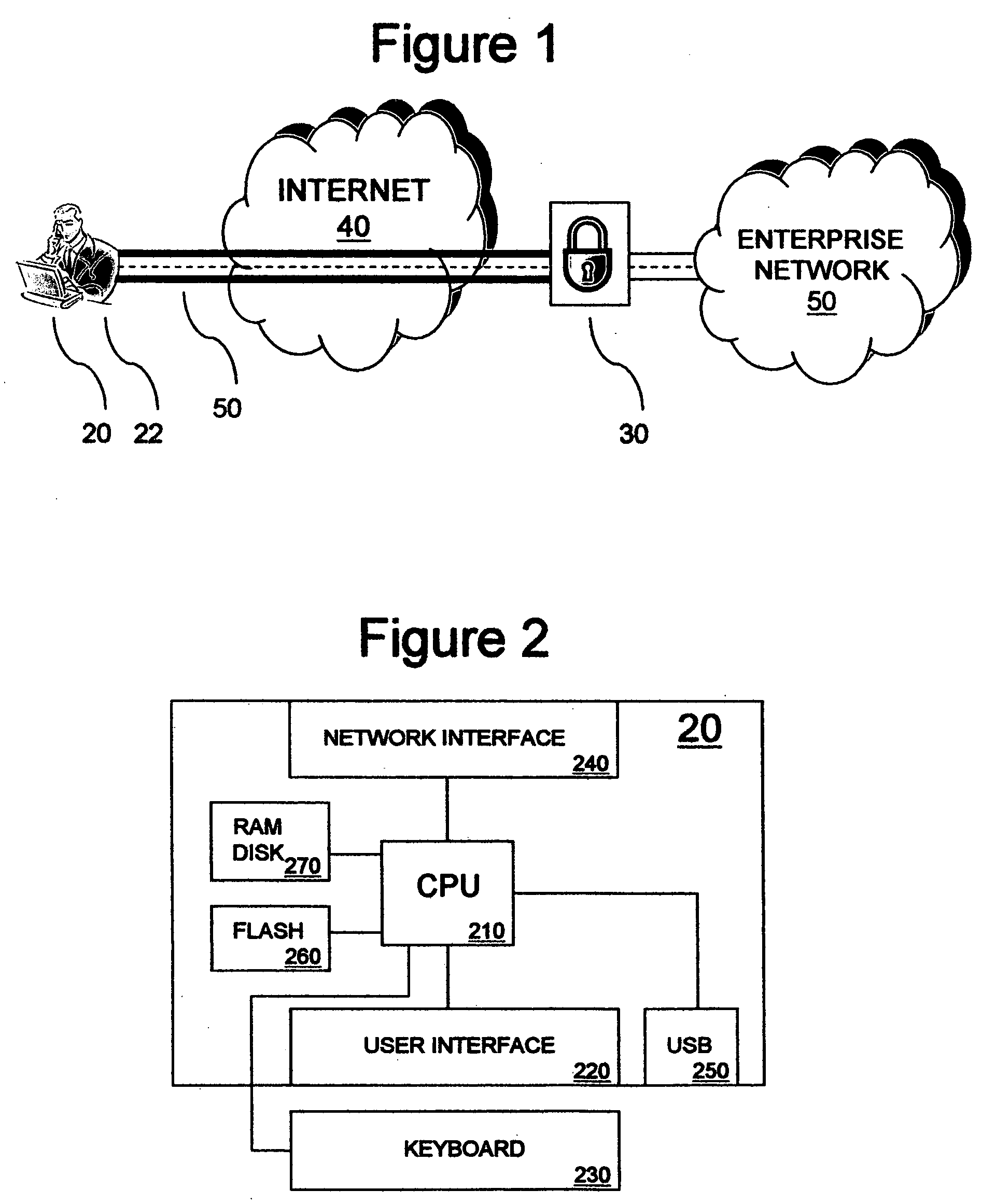
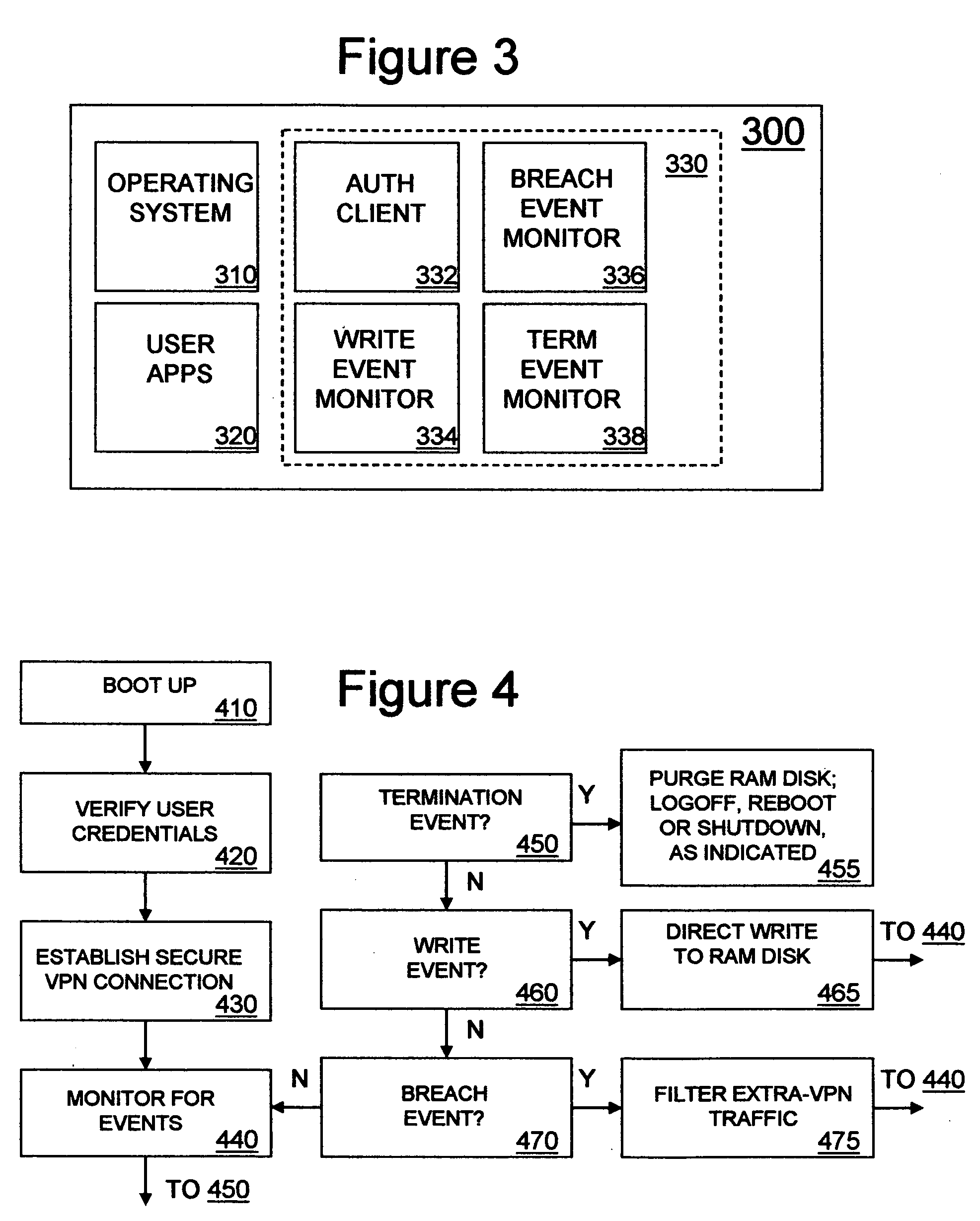
A thin client VPN capable end system reduces the vulnerability of corporate networks to malicious code introduced by remote workers. The end system is denied network connectivity except for conducting VPN sessions. The end system is made virtually impervious to permanent infection by directing all data writes during VPN sessions to a temporary memory that is purged at the end of the session. Thus, the end system cannot acquire malicious code in personal sessions and the corporate network administrator can eradicate any malicious code acquired by the end system in a VPN session by shutting down the VPN and cleaning up the corporate network.
Owner:COMLEKOGLU FATIH +1
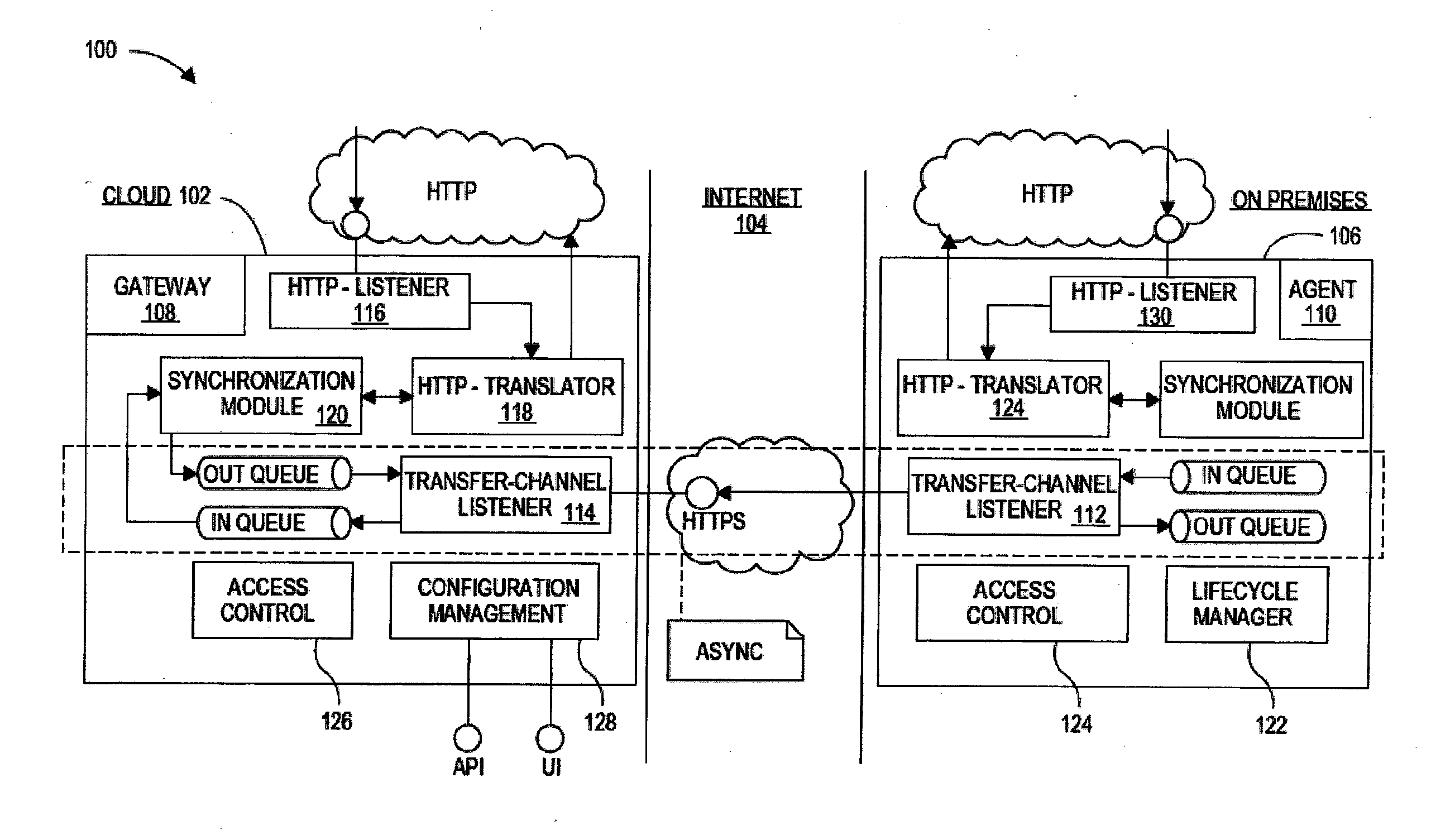
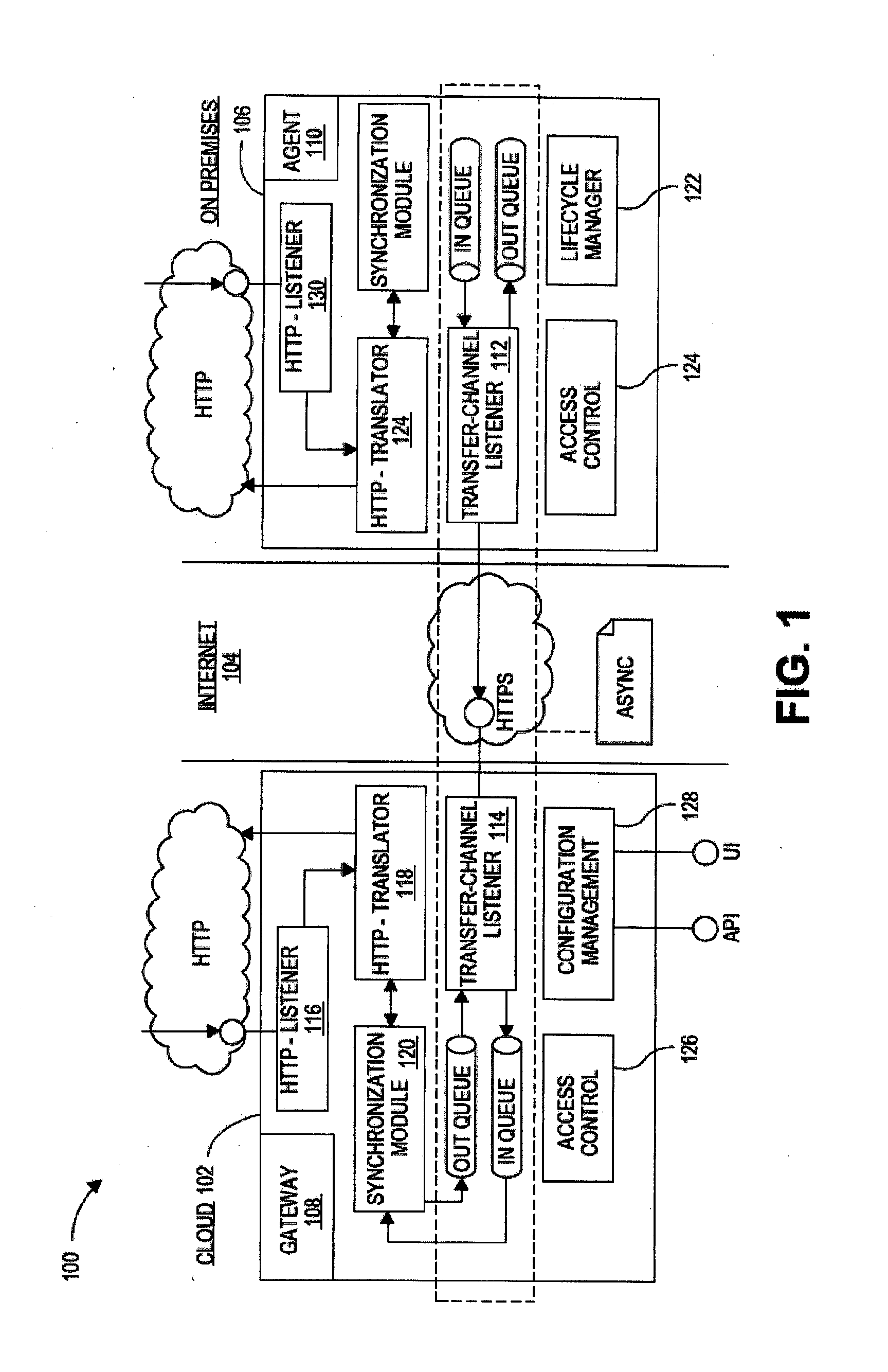
On-premises agent for mobile cloud service
Systems, devices, and methods are disclosed for an agent device within a company's network firewall to initiate an HTTP connection with a cloud-based gateway and then upgrade the connection to a WebSockets protocol in order to have an interactive session. Over this interactive session, a mobile device, which connects to the cloud-based intermediary, can request data from servers inside the company's firewalls. Because the firewall is traversed using HTTP protocols (with WebSockets), it can be as safe as letting employees browse the web from inside the company's network.
Owner:ORACLE INT CORP
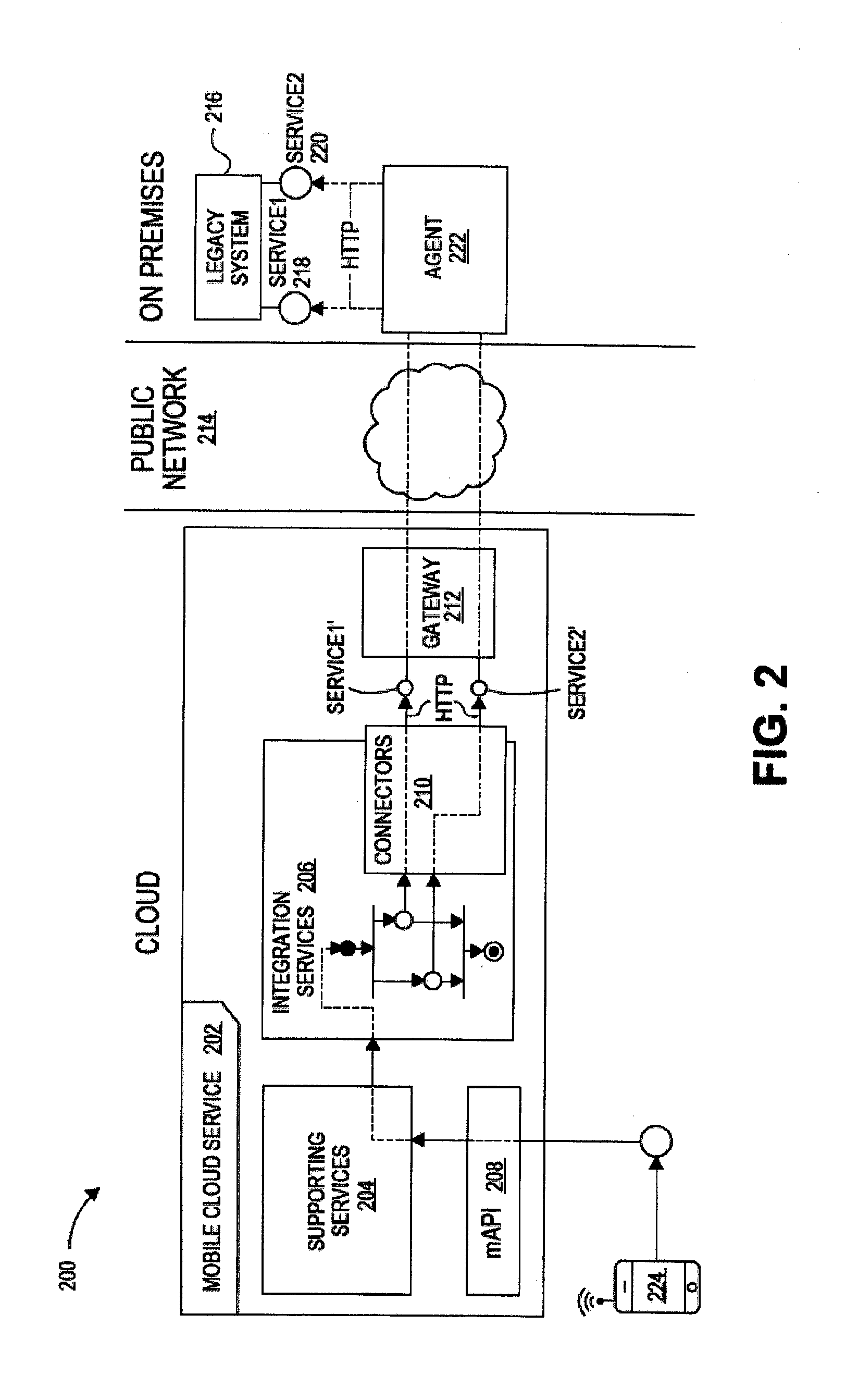
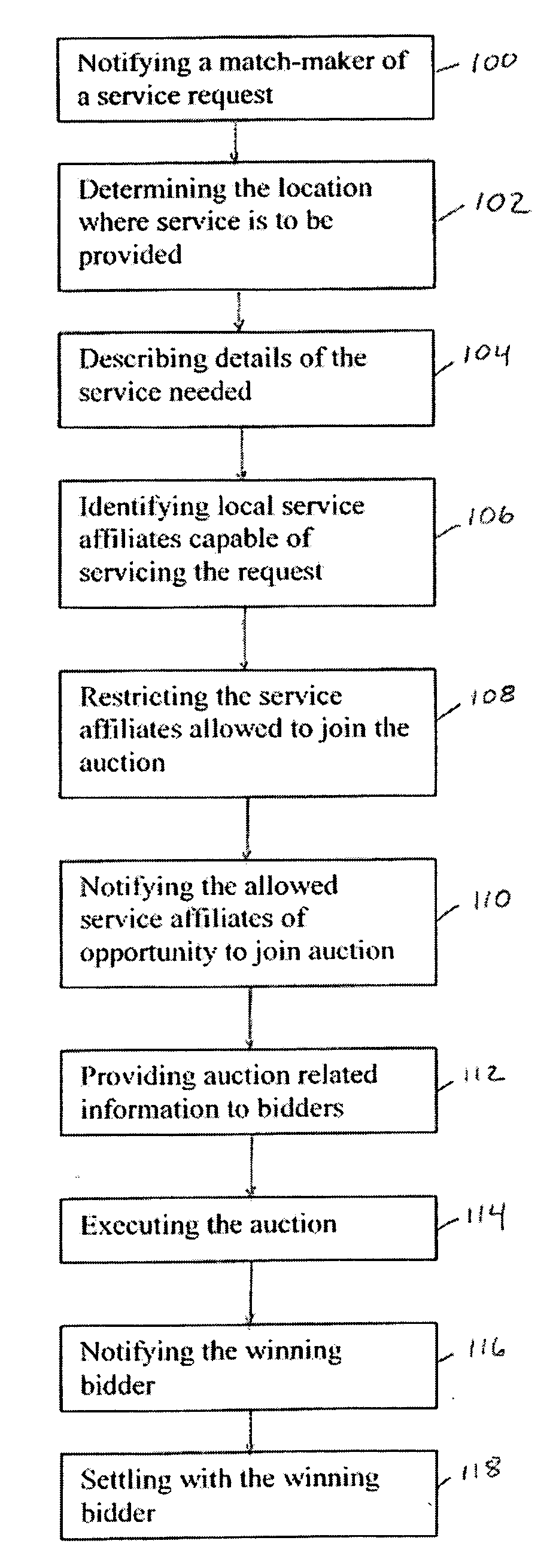
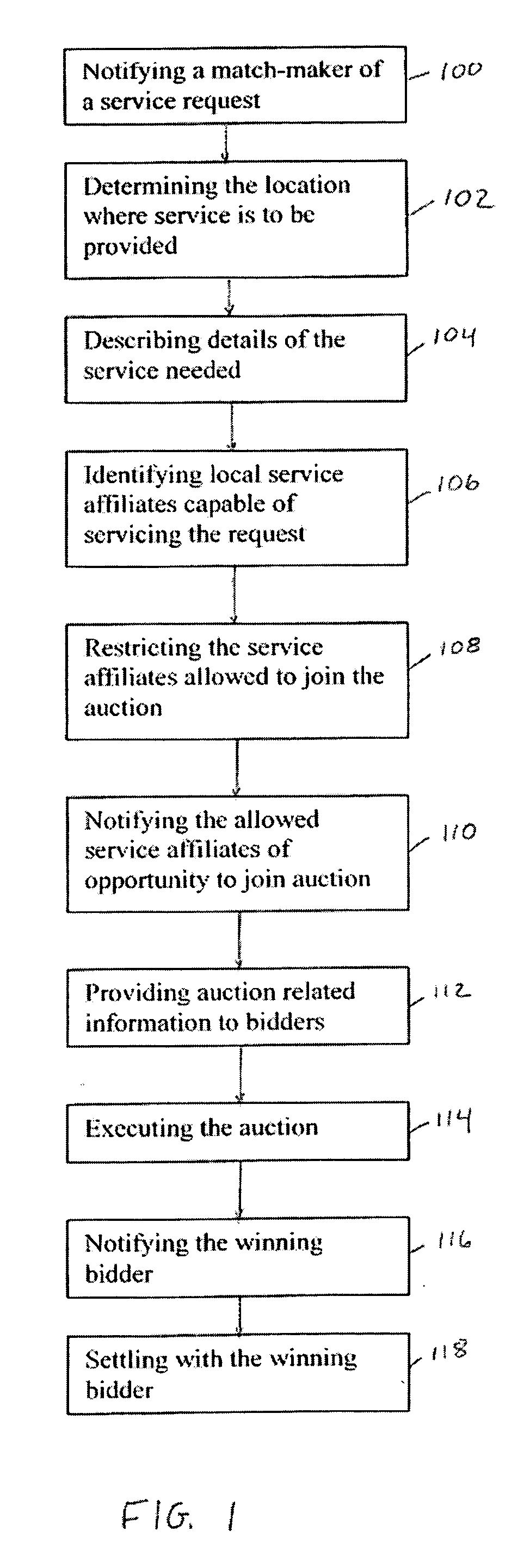
System and method for enabling service providers to create real-time reverse auctions for location based services
InactiveUS20080177653A1Drive down priceIncrease incomeFinanceCommerceClient dataCustomer information
A system and method facilitates the matching of service providers based on certain criteria such as, but not limited to, location of the provider in relation to a customer location, customer requests based on the location of the customer, the type of service requested and other possible attributes such as customer profile, customer past behavior and preferences and service price and quality. Service providers create real-time reverse auctions by using advanced data collection, filtering and disseminating algorithms. In addition, market-makers can provide value-added services, such as real-time traffic conditions and route planning, to their local affiliates. Such a scheme can allow market-makers to economically service customer requests by leveraging the real-time conditions and circumstances of their vast network of local service affiliates. Open competition will drive down prices for these services and increase revenues for the market-makers who will be able to service customer requests at the best prices available. This system will also benefit local service affiliates by notifying them and allowing them to compete for a broader number of service requests. A feedback mechanism will also encourage superior customer service since affiliates will want to ensure that they are considered for more jobs.
Owner:TELCORDIA TECHNOLOGIES INC
Method and apparatus for securely providing billable multicast data
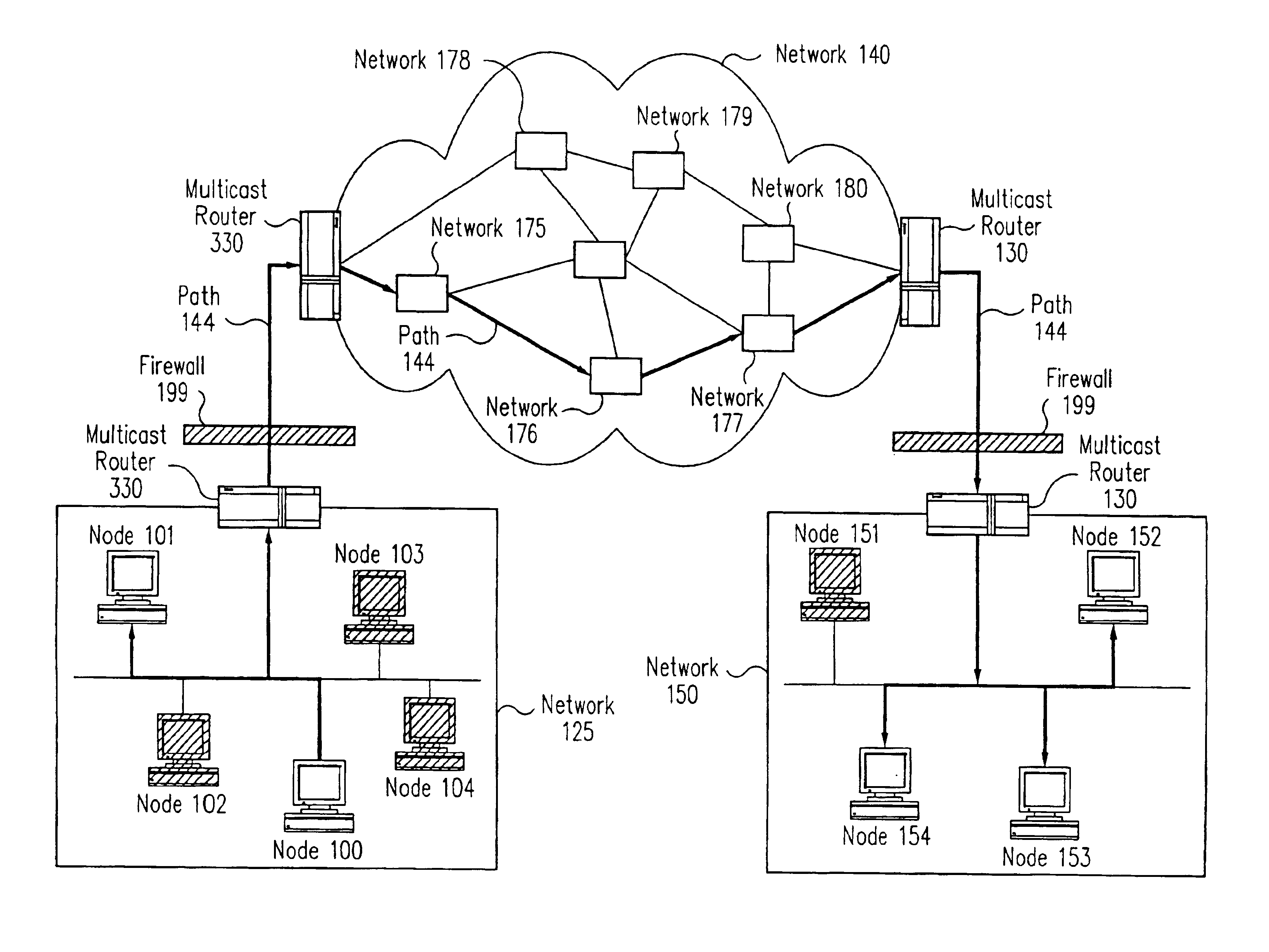
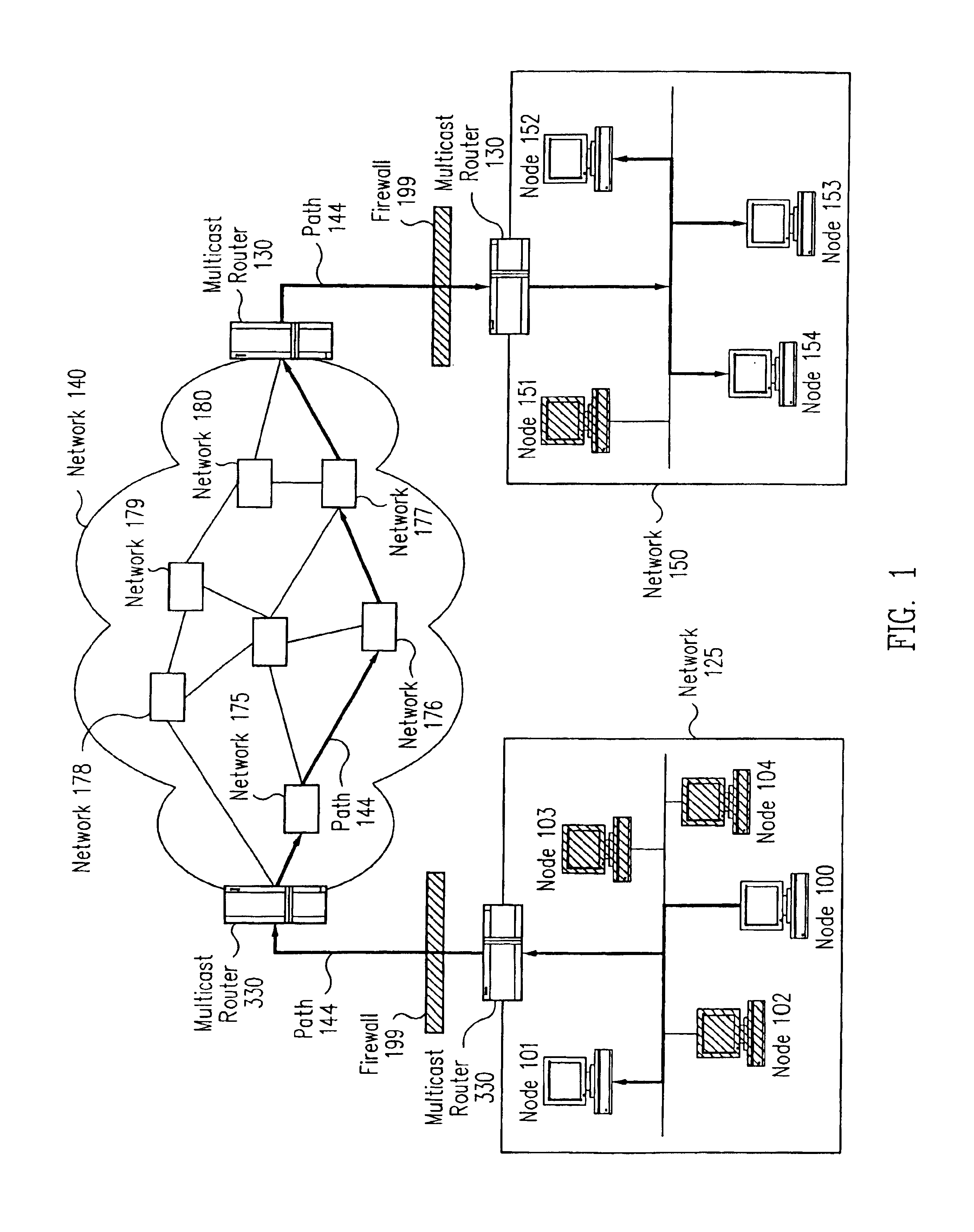
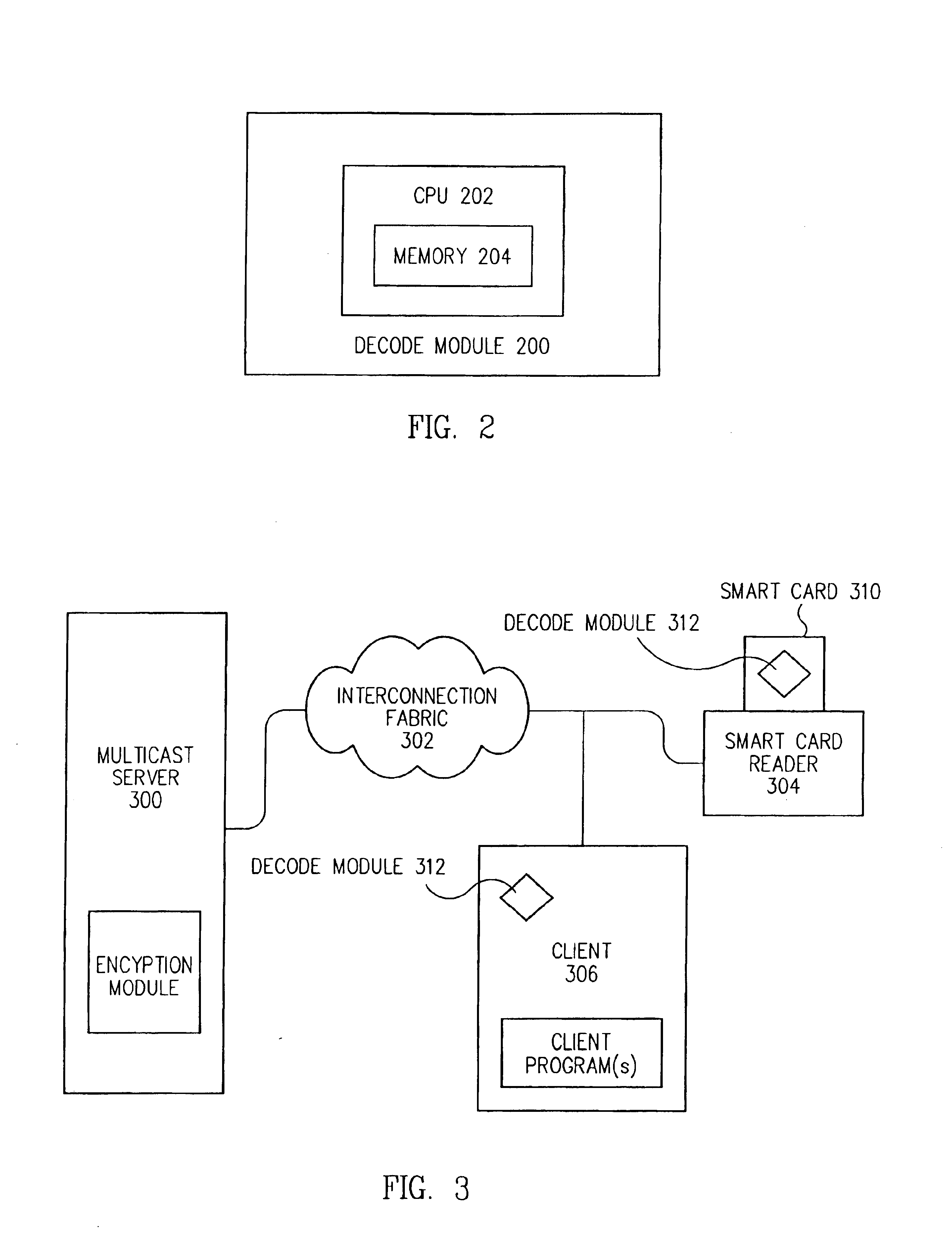
InactiveUS6862684B1Special service provision for substationMetering/charging/biilling arrangementsClient-sideCorporate network
The present invention comprises a method and apparatus for securely providing billable multicast data. The invention describes a solution that provides an architecture for enabling different types of security devices to operate interchangeably in very large consumer networks, corporate networks, for authentication and metered access to services, as well as payment. An embodiment of the invention comprises a mechanism for ensuring that only authorized parties may obtain access to a particular data stream. For example, the present invention provides a way build a restricted-channel system. In a restricted-channel system, a multicast server transmits encrypted information that can be deciphered by authorized multicast client programs or multicast client programs operating under authorized conditions. Access to the multicast data is allowed when the data is appropriately decrypted or otherwise verified and / or the payment is obtained from a portable device such as a smart card.
Owner:ORACLE INT CORP
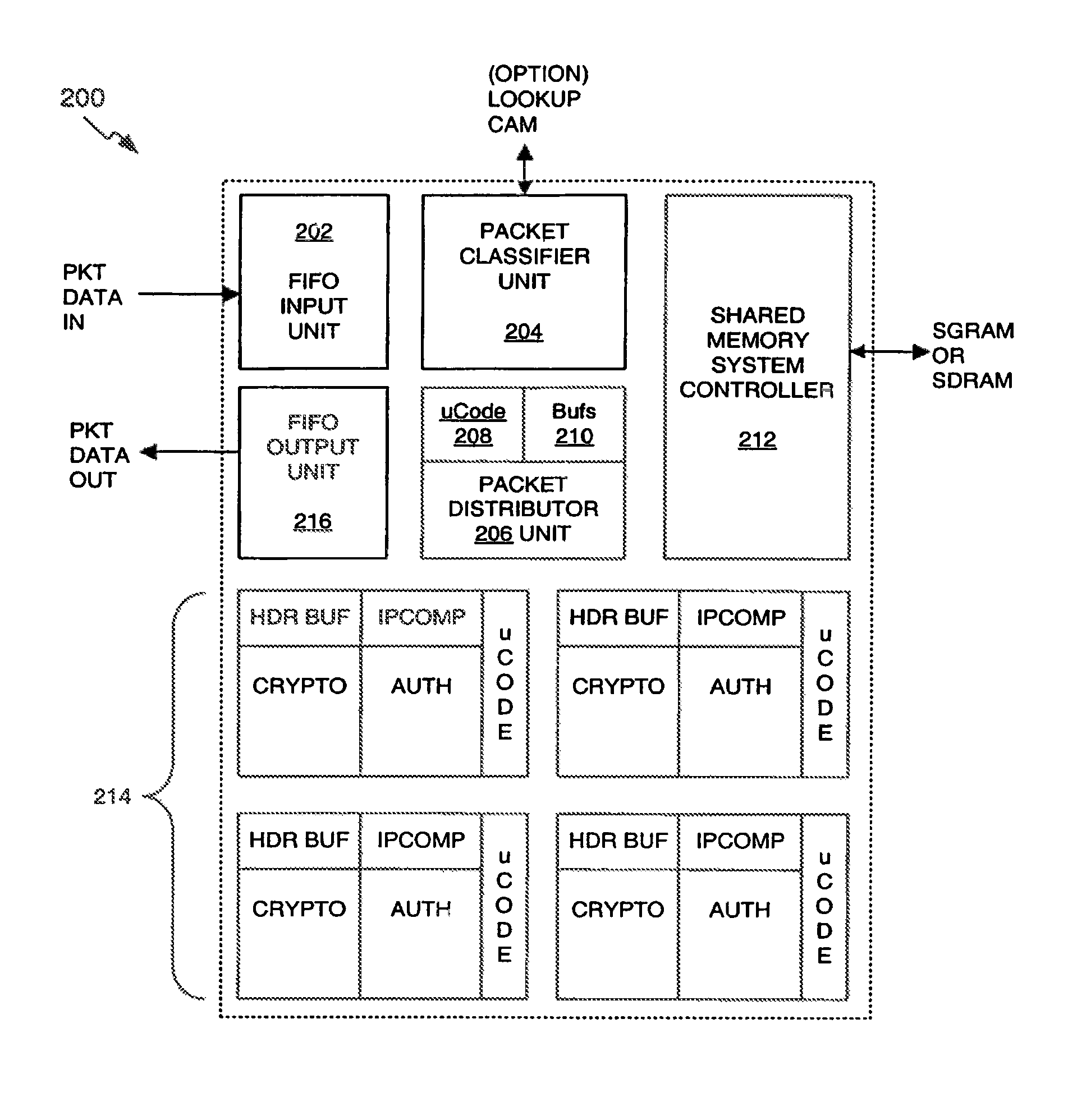
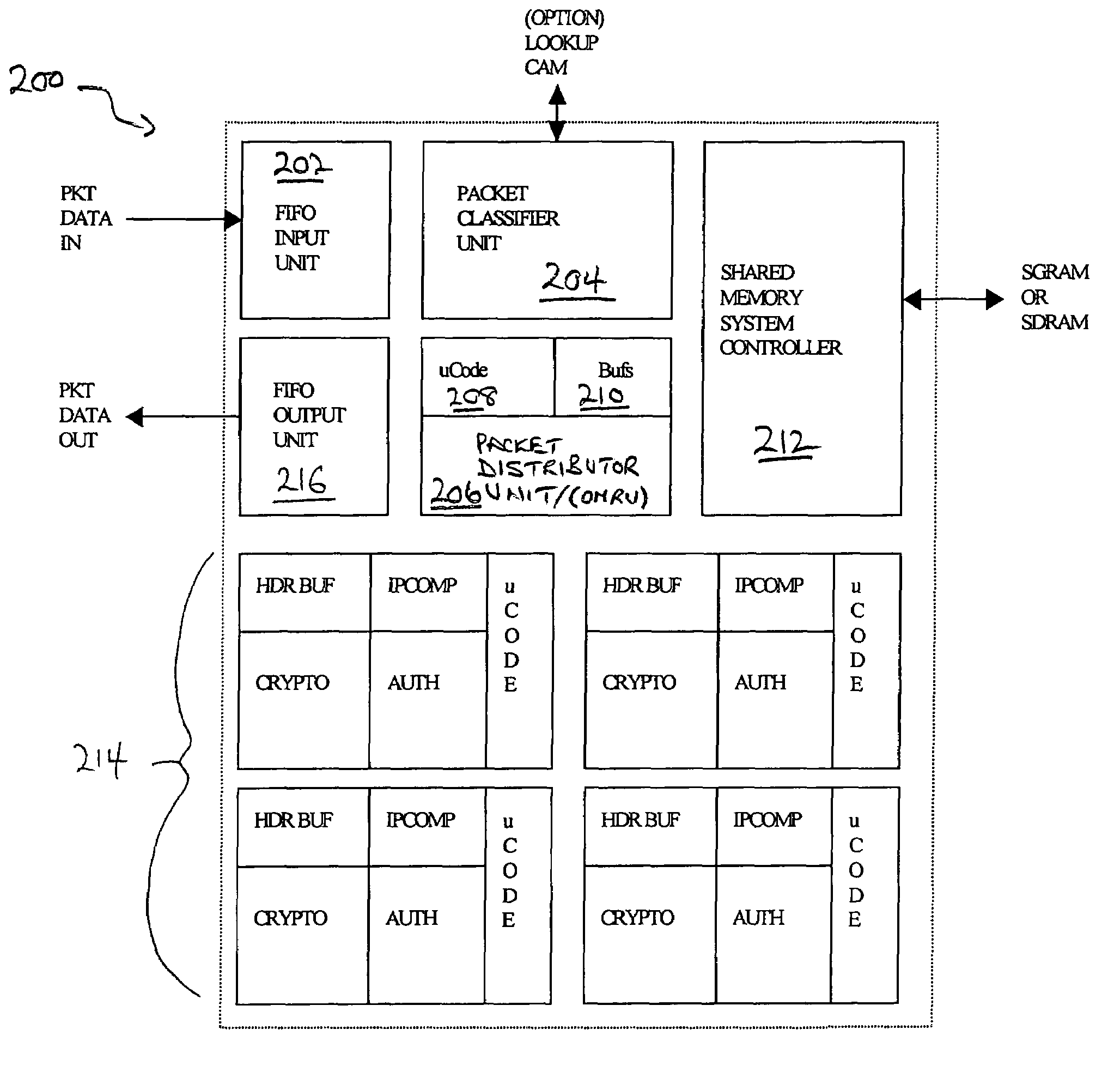
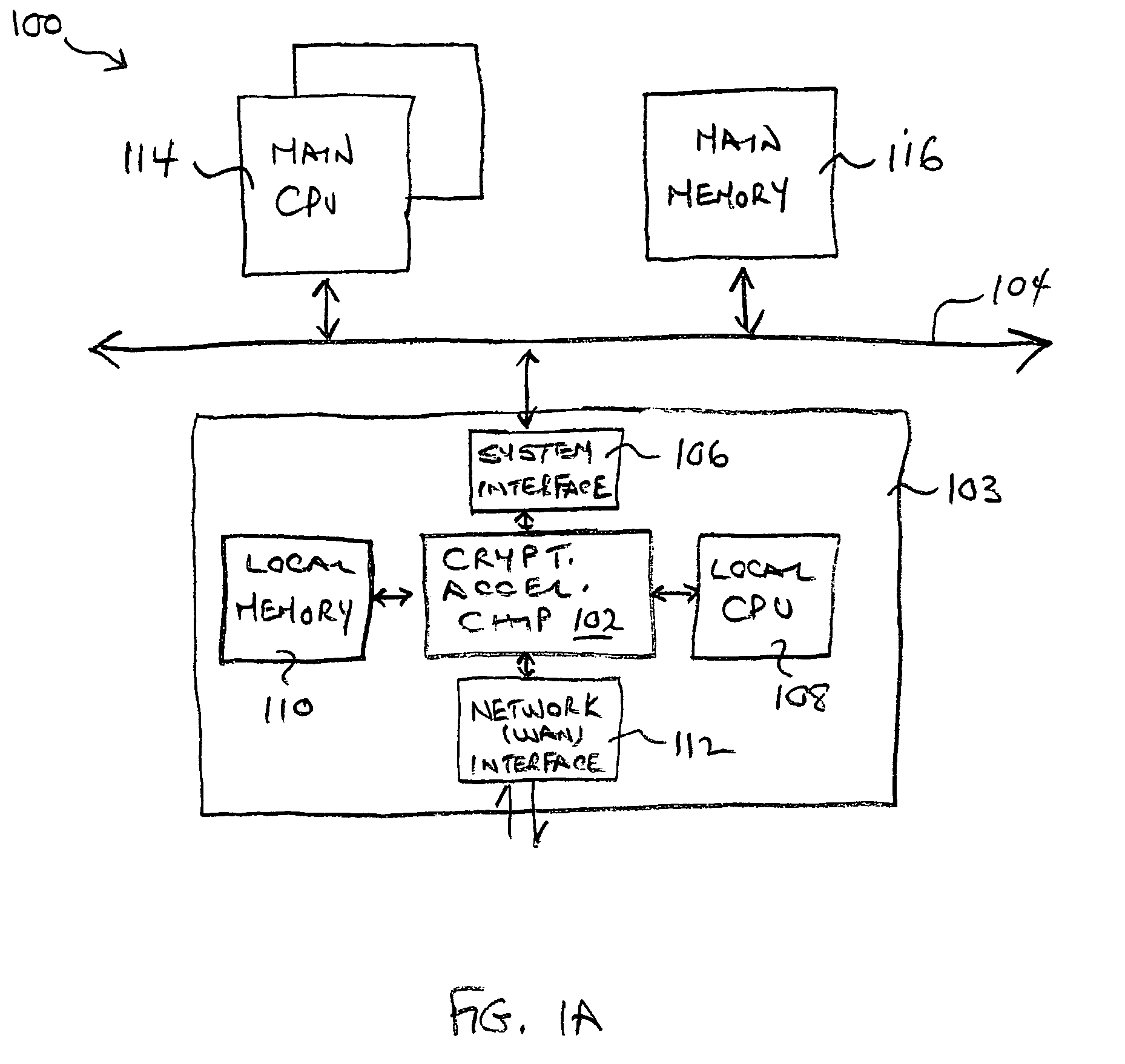
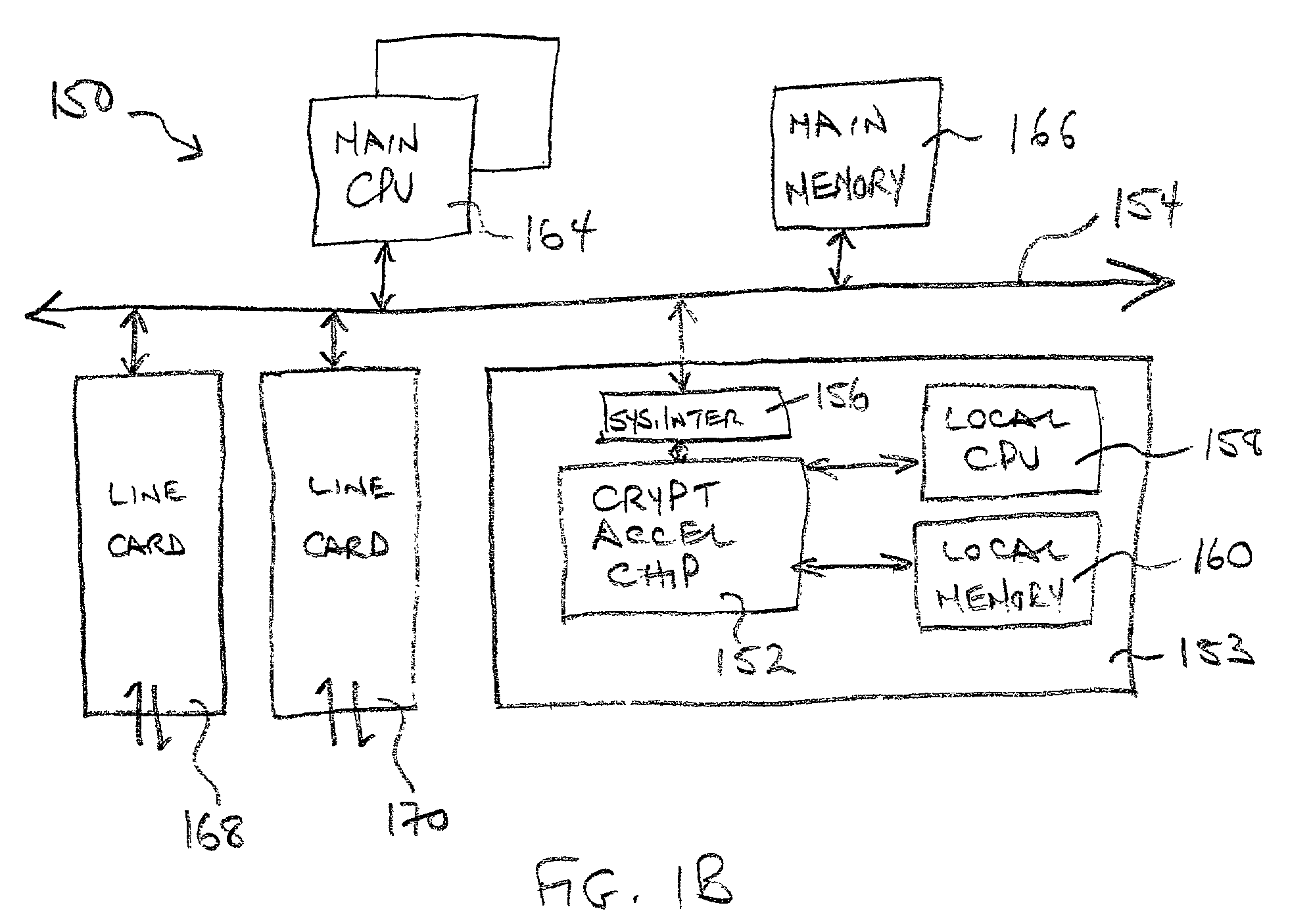
Classification engine in a cryptography acceleration chip
InactiveUS7996670B1Efficient processingMaximum performanceDigital data processing detailsConcurrent instruction executionCryptographic acceleratorNetwork service
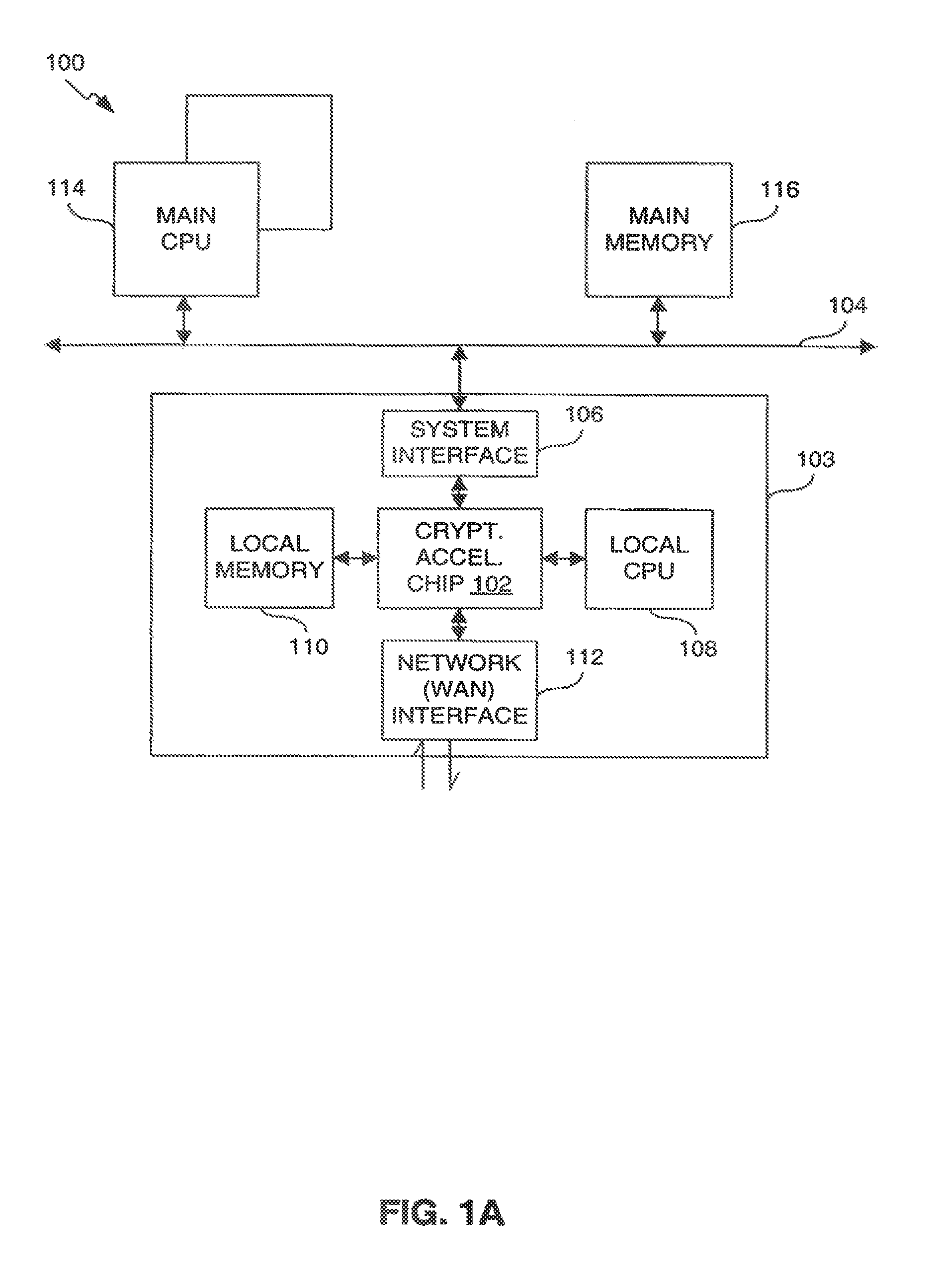
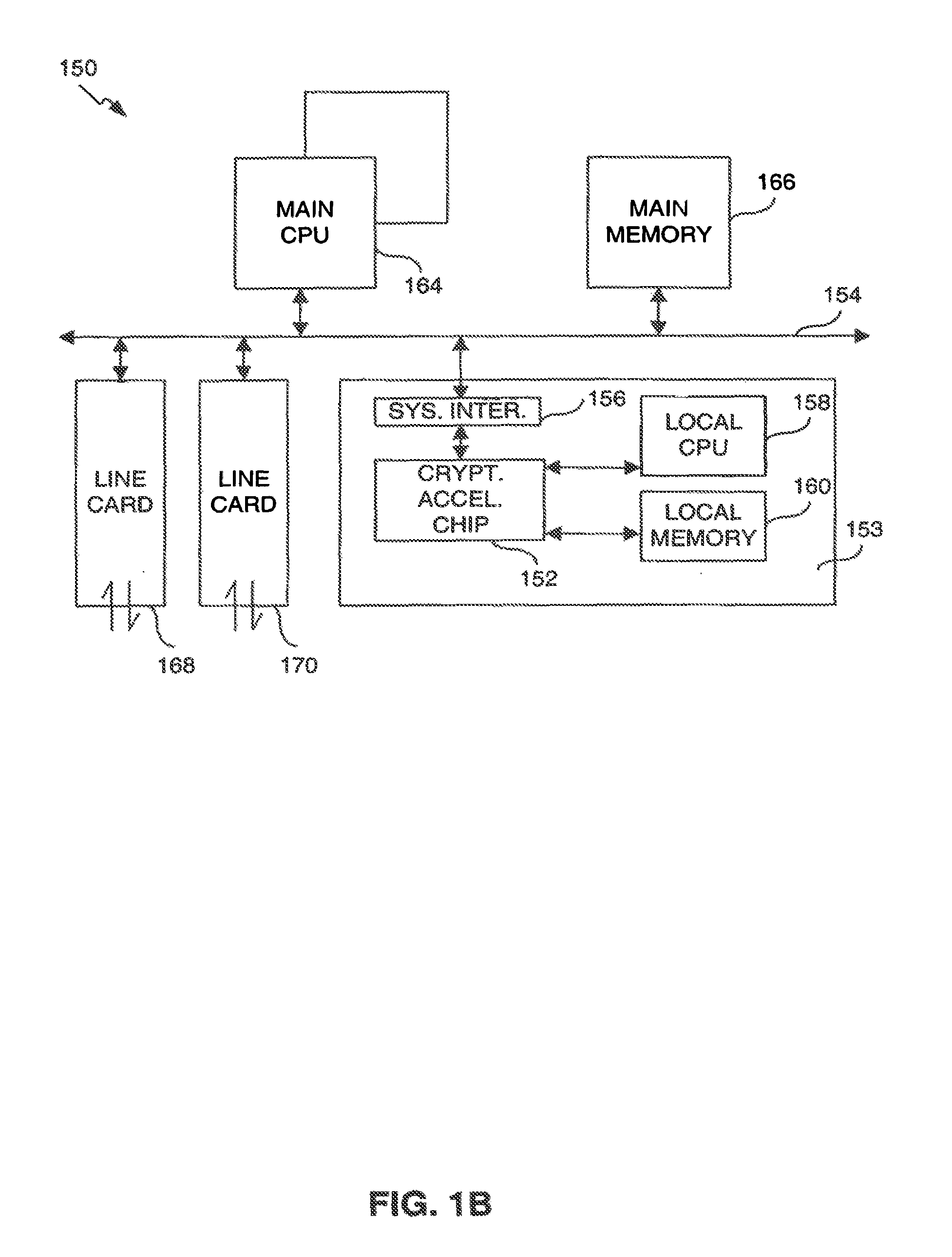
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
Distributed processing in a cryptography acceleration chip
InactiveUS7600131B1Efficient processingImprove performanceDigital data processing detailsUnauthorized memory use protectionCryptographic acceleratorNetwork service
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
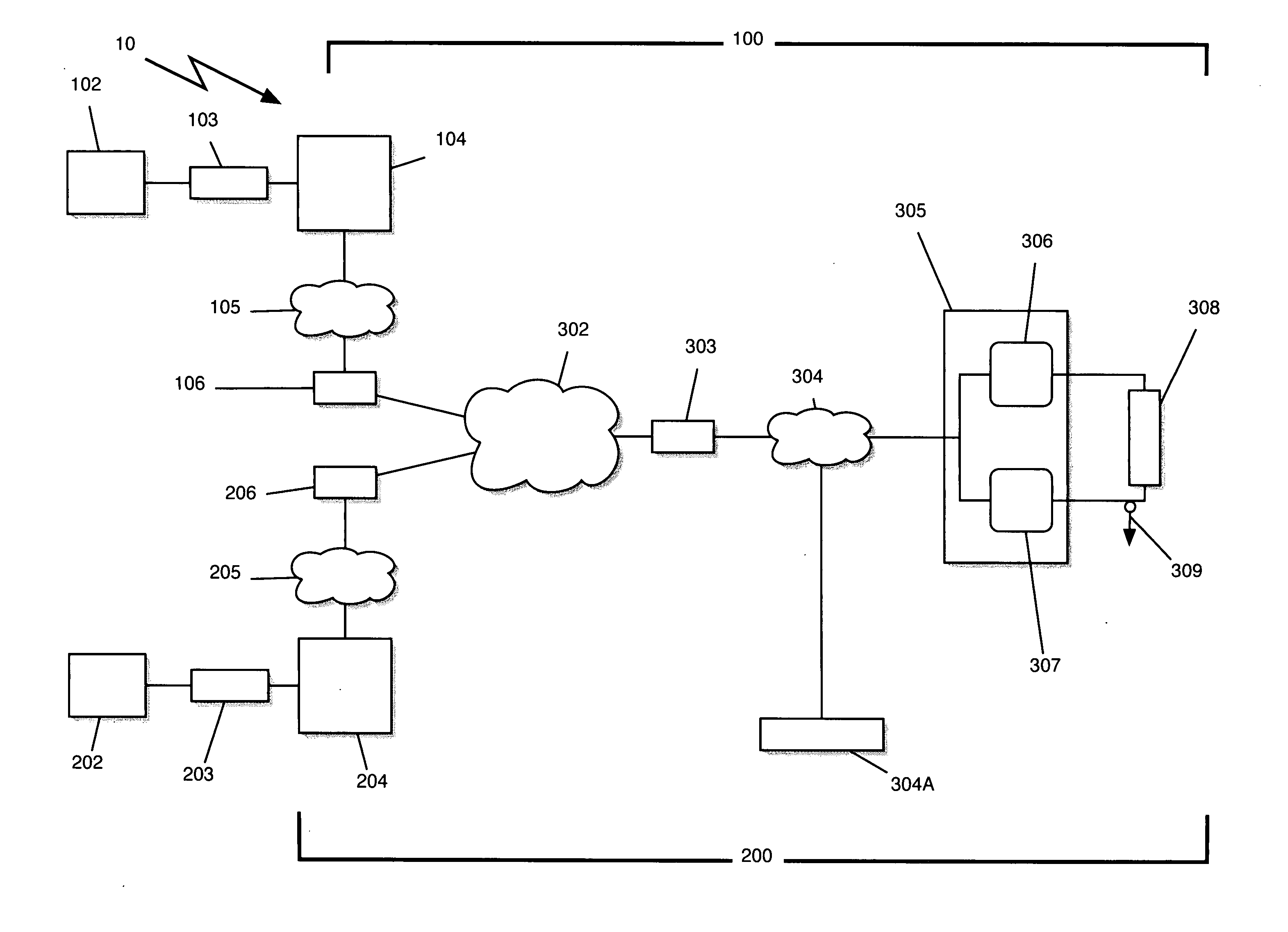
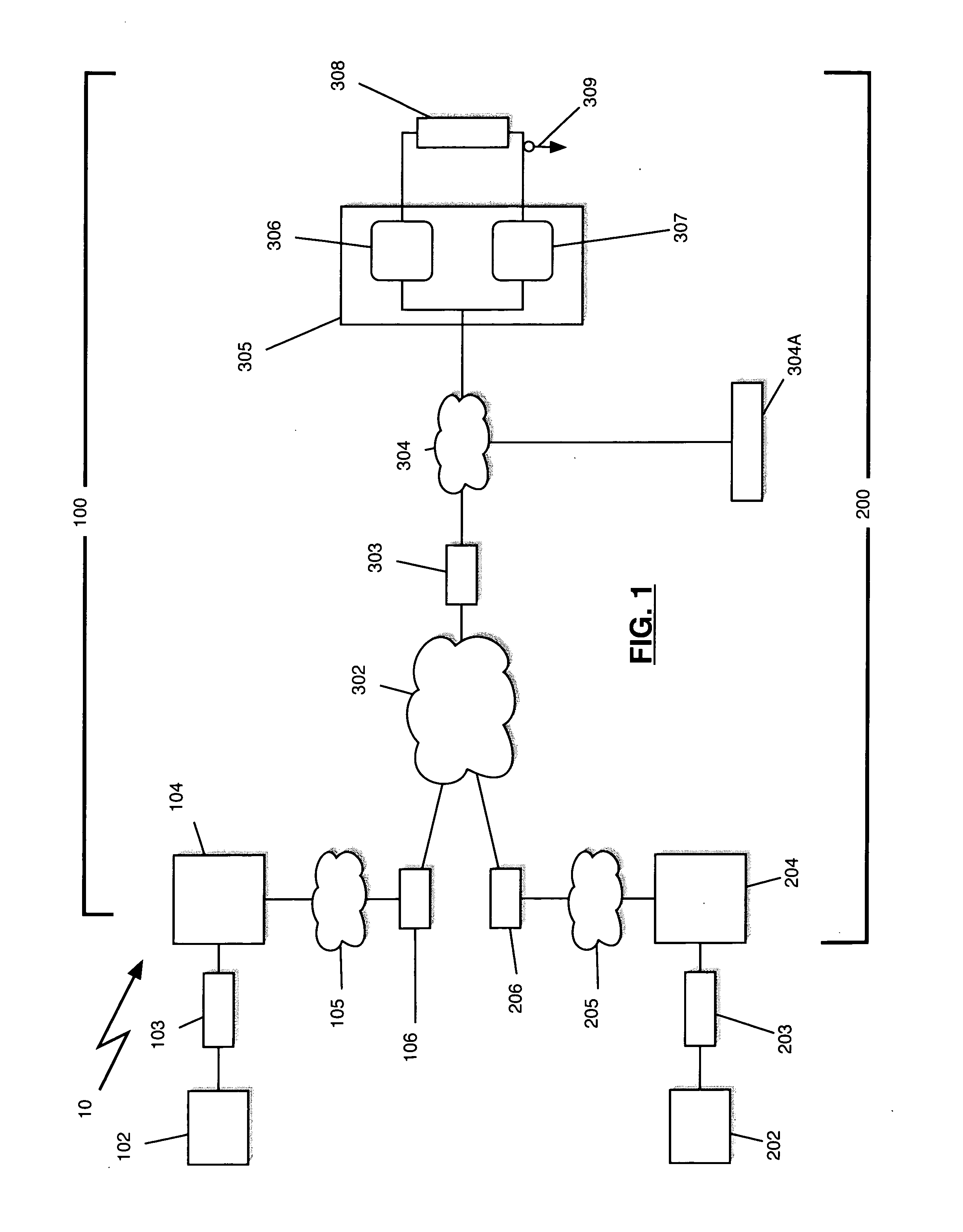
Method and system for layer-2 pseudo-wire rapid-deployment service over unknown internet protocol networks
An International Standards Organization (“OSI”) Layer-2 (“Ethernet”) Pseudo-wire (“OSI Layer-1 type service”) appliance, method, system and hub service is disclosed. The method and system facilitate the rapid deployment of Layer-2 Pseudo-wires over unknown and untrusted Internet Protocol (“IP”) networks. The method and system facilitate the fluid edge of corporate networks and any situation where the Layer-3 network addresses cannot be changed.
Owner:YR20 GROUP
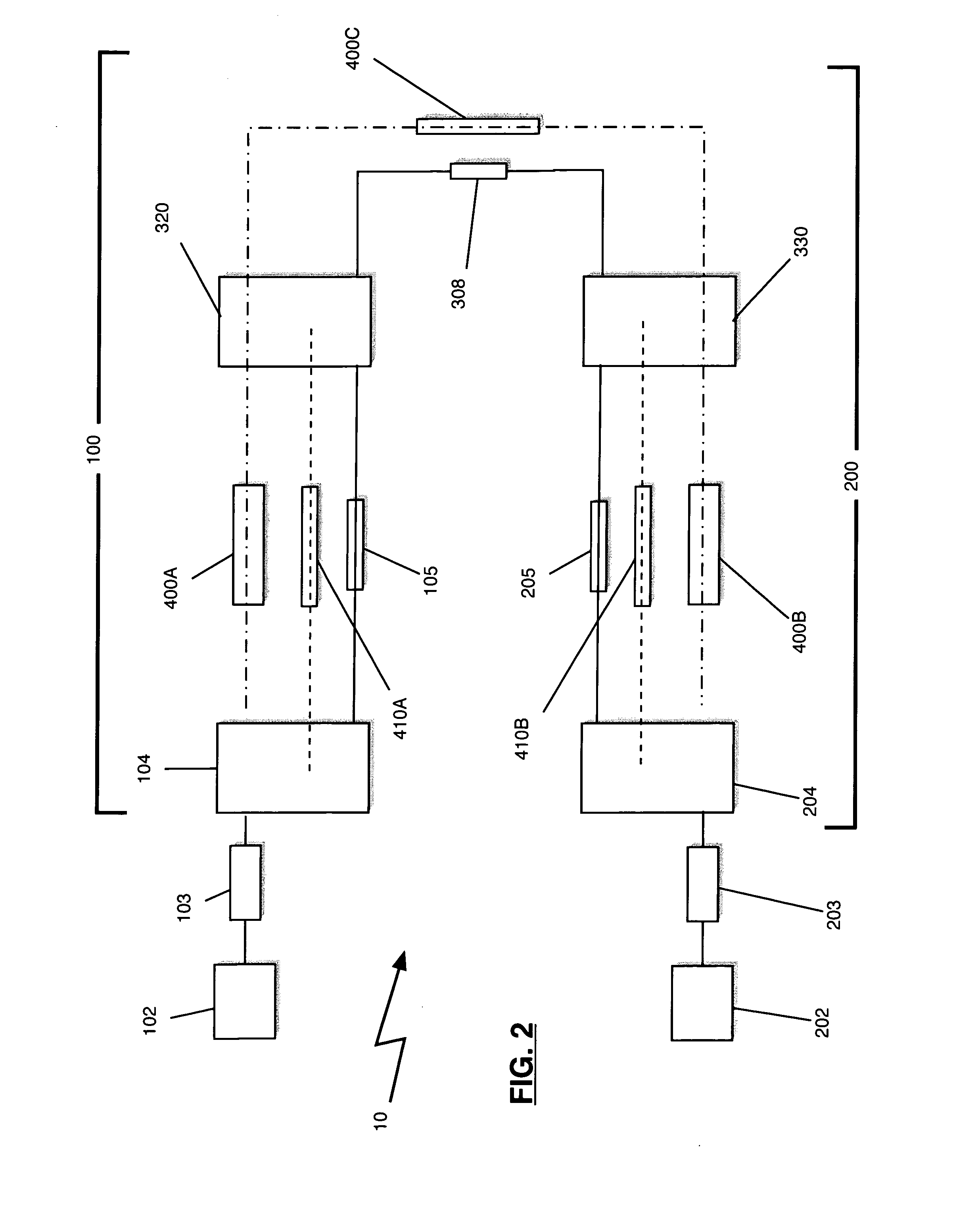
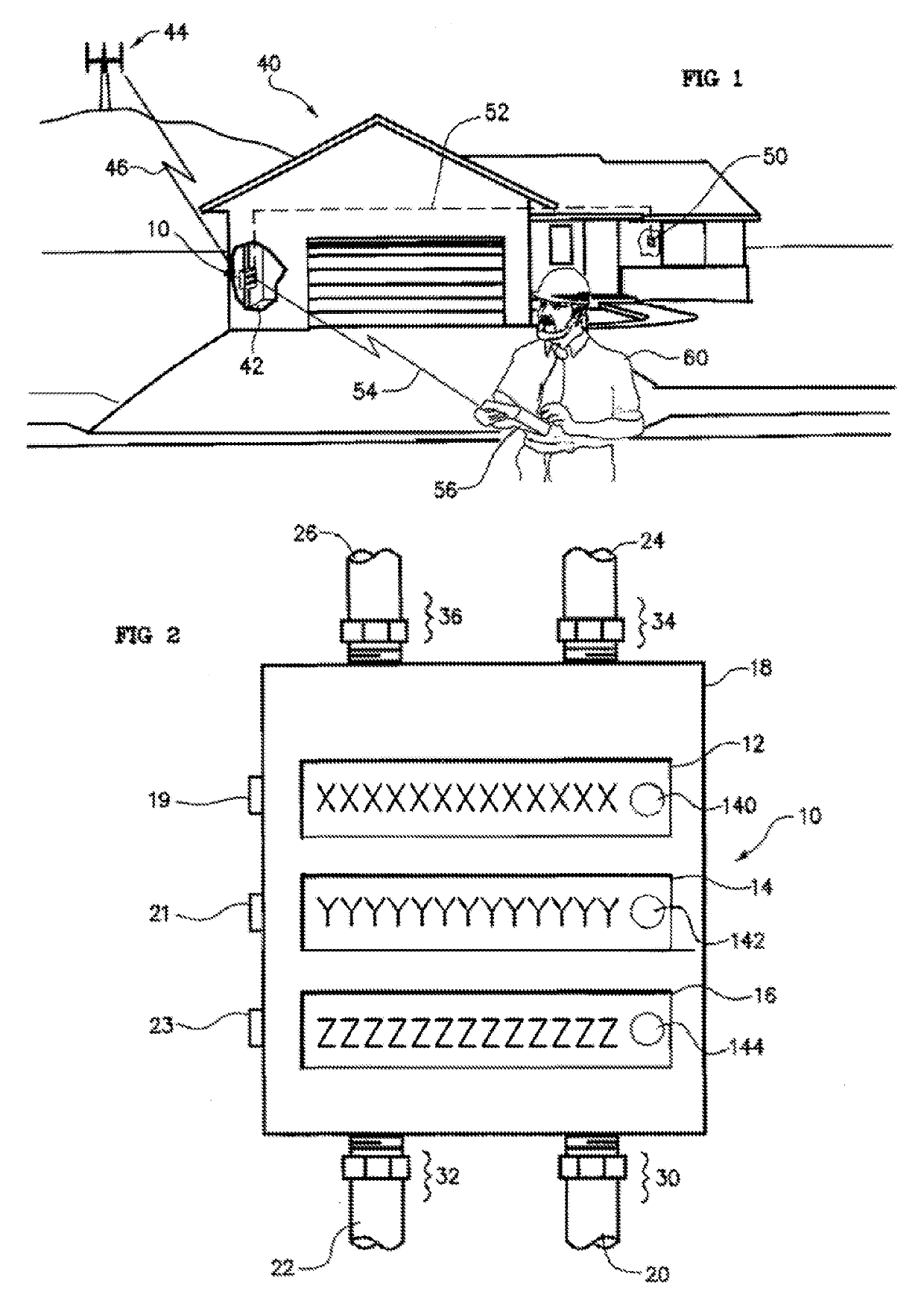
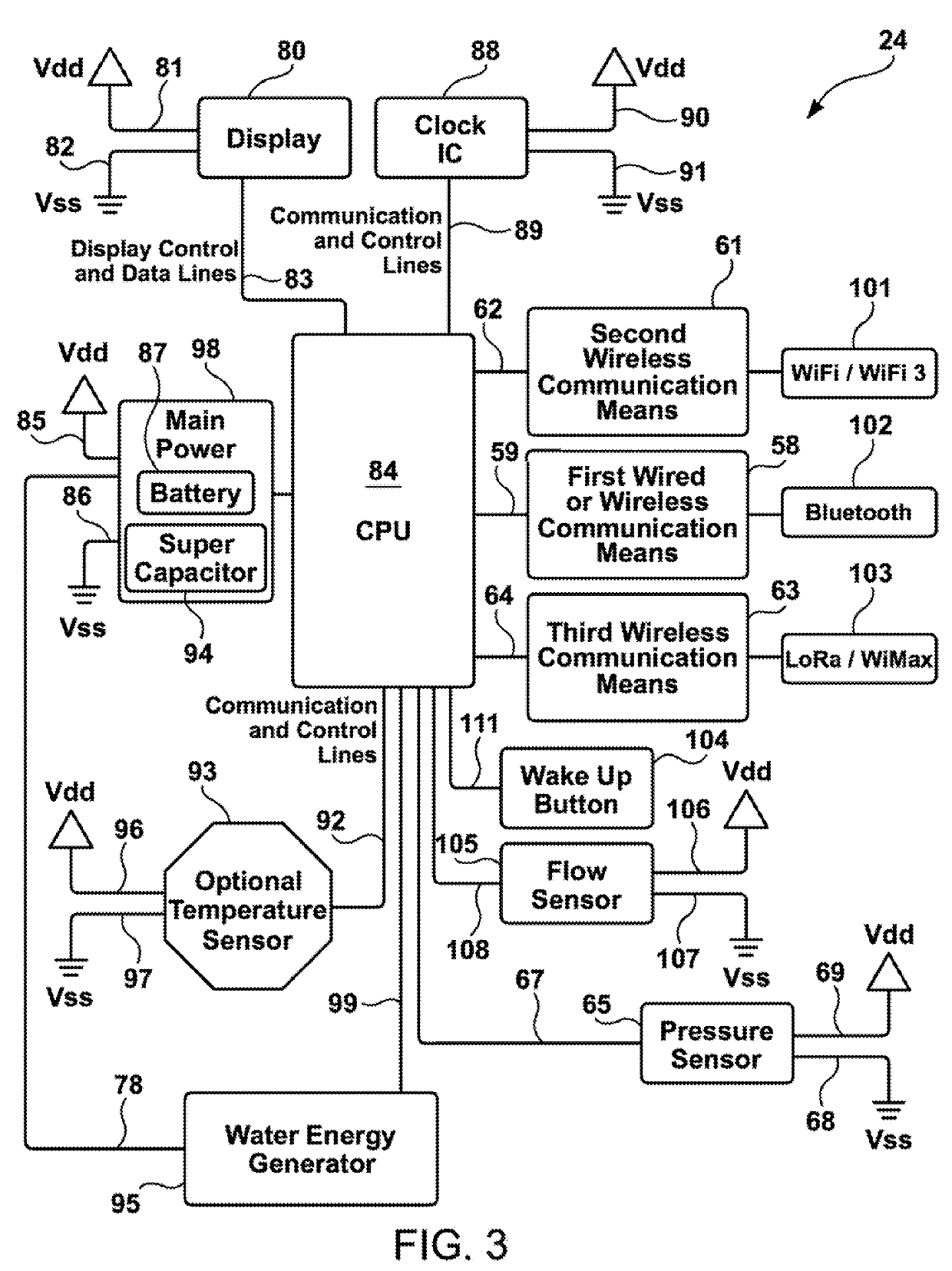
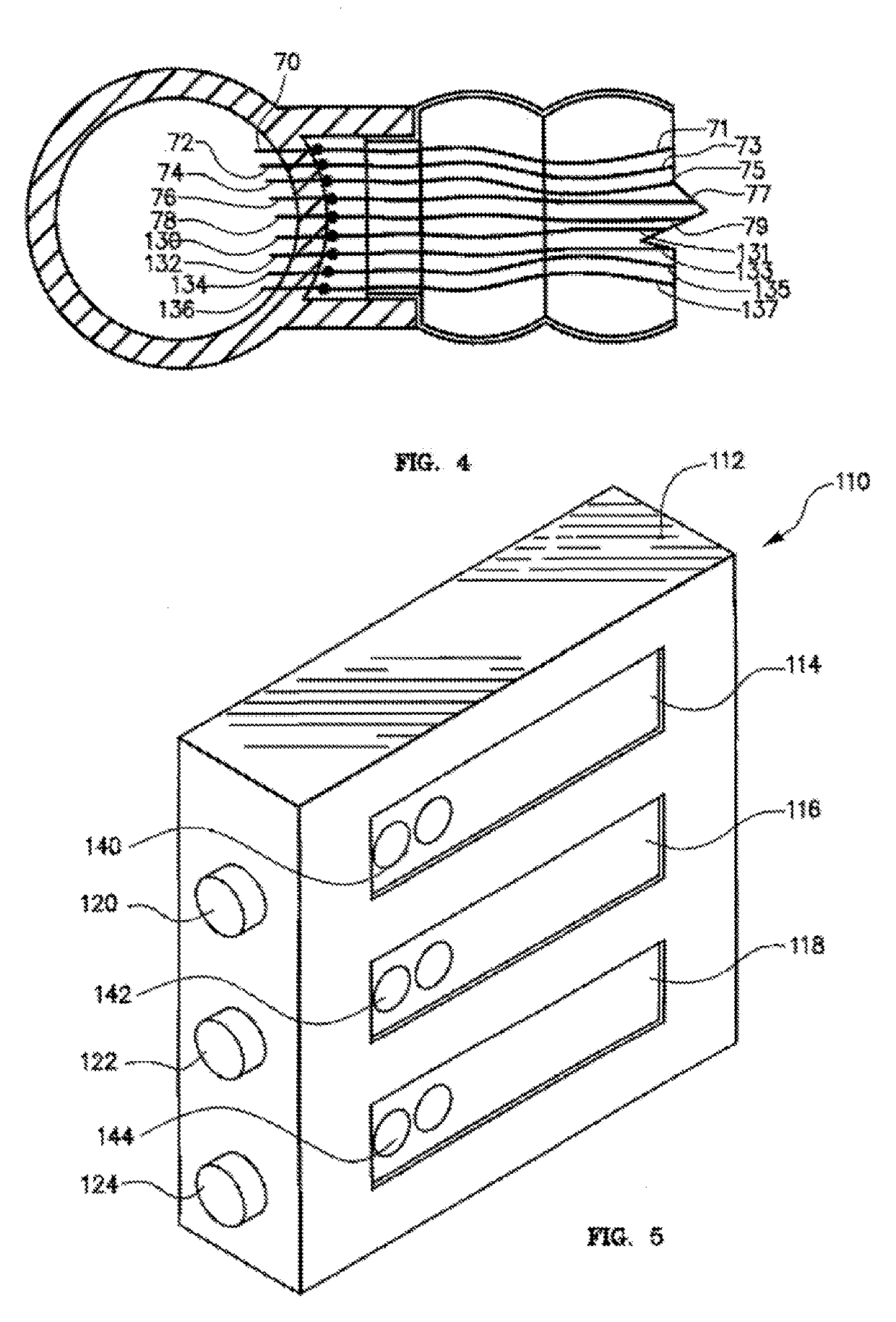
Water Meter and Leak Detection System
ActiveUS20190234786A1Long wireless range capabilityMeasurement of fluid loss/gain rateData processing applicationsWi-FiTTEthernet
The present invention is a water meter and leak detection system that has a private or public property(ies) facility water supply interruption system. The system is comprised of a water meter collection node system with shut-off / on mechanism that has wireless Bluetooth, Bluetooth low energy, Zigbee, Z-wave LoRa, Wi-Fi, radio frequency and cellular technology with a private or corporate network, or internet connection that transfer water parameter data to a remote computer or server. Or the system can consist of a water meter collection node that communicates by Bluetooth, Bluetooth low energy, Zigbee, Z-wave LoRa, Wi-Fi, radio frequency and cellular technology with a data communication hub whereby the communication hub is in wired or wireless communication with an internet router that communicates with an internet connection, or with a private or commercial network system, to a remote computer / server or a cloud-computing commercial service.
Owner:REIN TECH INC
Encryption mechanism in advanced packet switching system
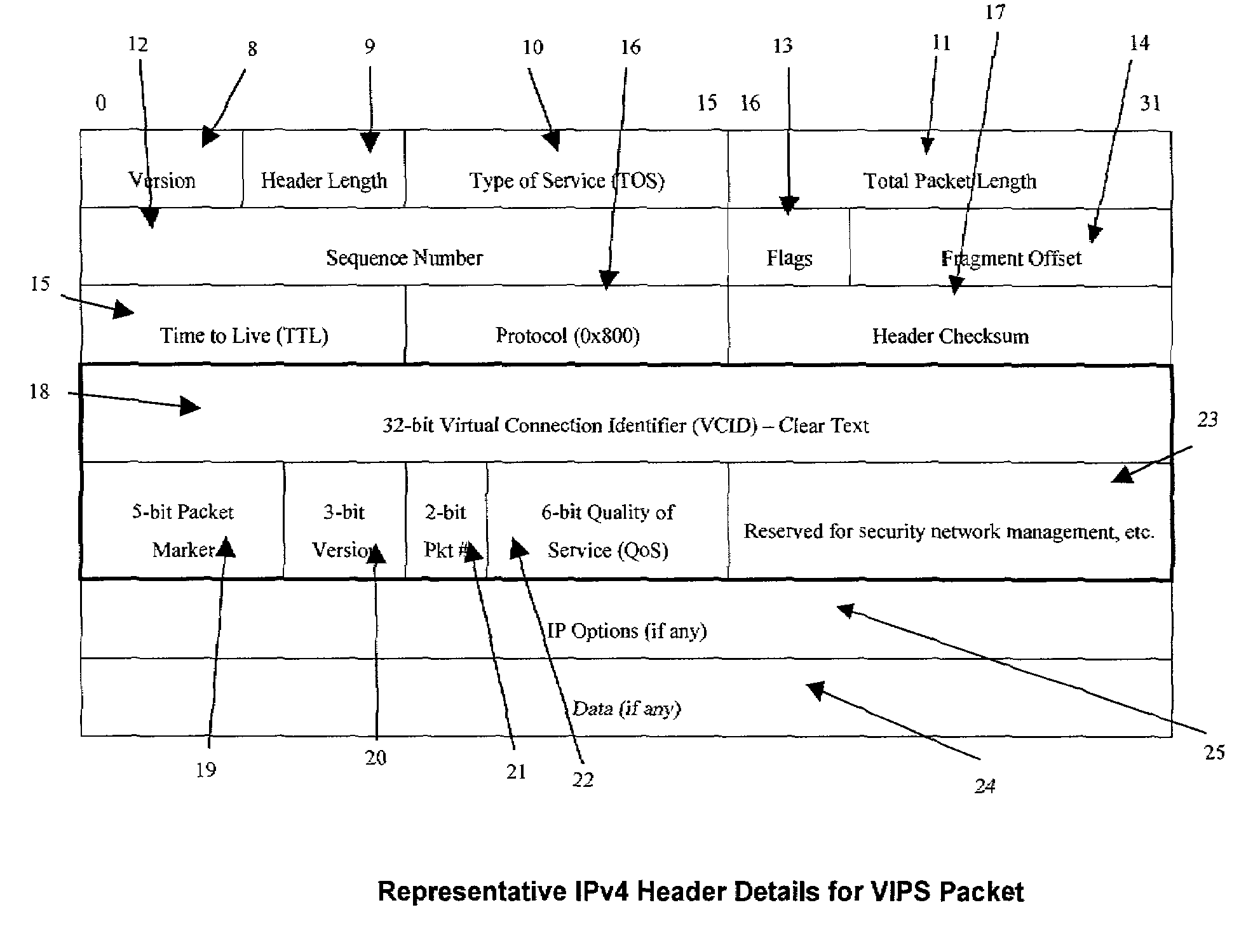
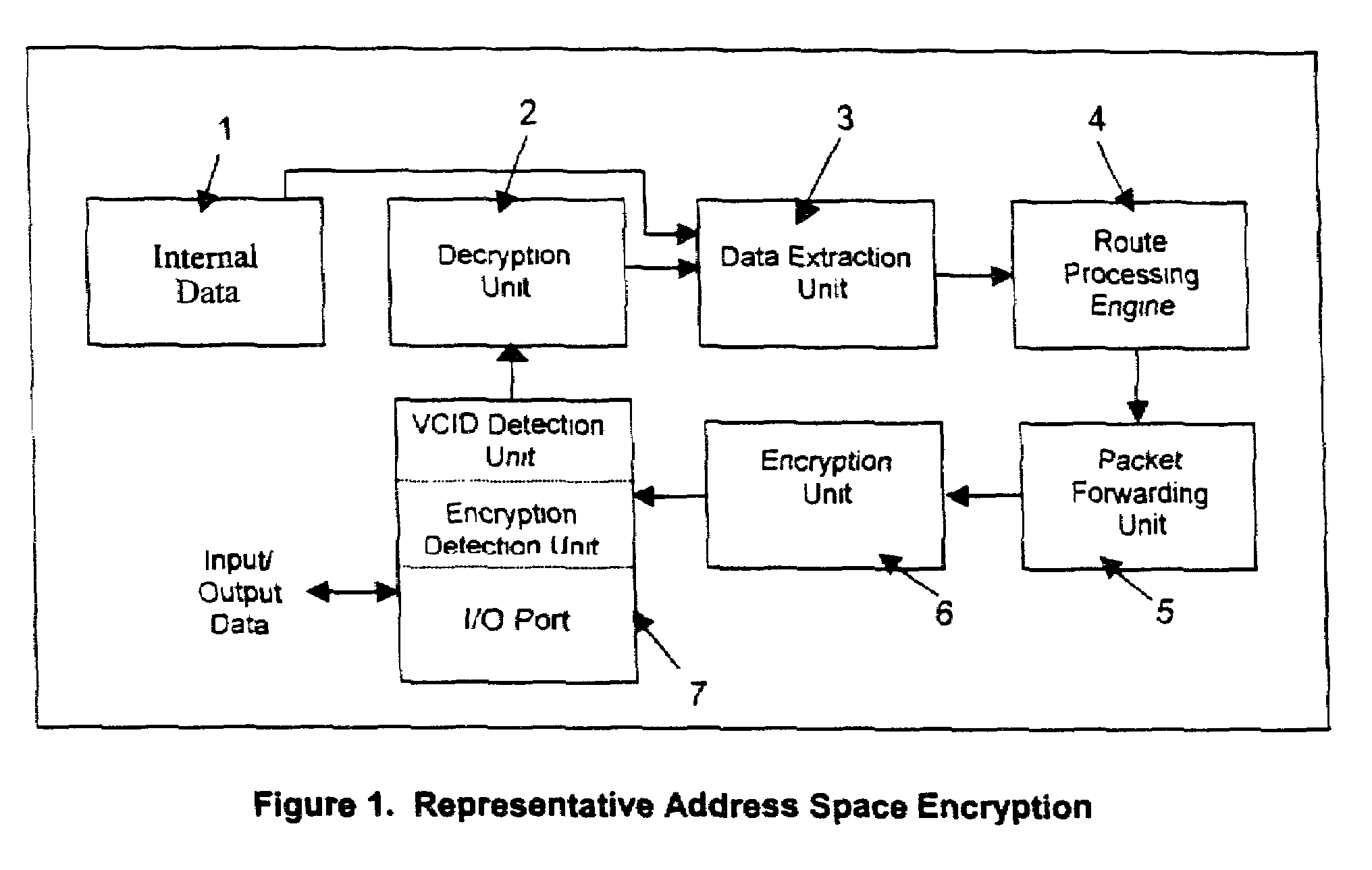
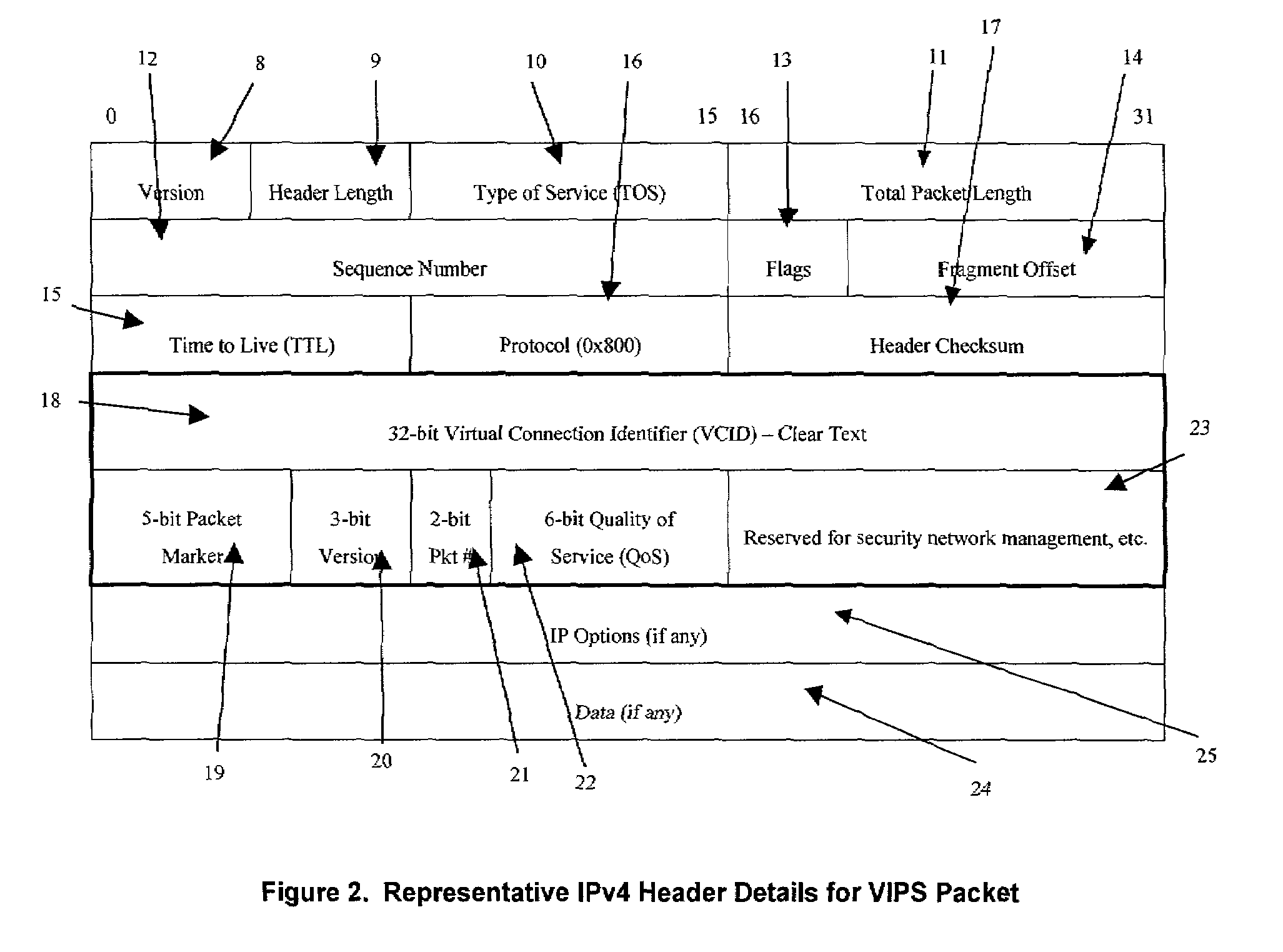
A packet switching system for switching packets over corporate networks and the Internet using Internet Protocol (IP) suite of protocols is provided with an encryption detecting unit that determines whether at least a section of a portion of an incoming packet allocated for Internet Protocol (IP) address fields comprises encrypted data. If the encrypted data is detected, a decrypting unit decrypts the encrypted data. A packet identifying unit detects a virtual connection identifier (VCID) marker indicating that a VCID is provided in the portion of the incoming packet allocated for IP address fields. A data extracting unit extracts the VCID from the decrypted data. For example, the data extracting unit may extracts original source and destination IP addresses, or a Quality of Service (QoS) field for identifying parameters of Quality of Service. A route processing engine determines a route for forwarding the packet, and a packet forwarding unit places the packet into a queue for transmission. An encrypting unit encrypts the VCID of packets transmitted to a network that uses virtual connection identifiers for switching packets.
Owner:SIGNAFOR
Cryptographic communication system and gateway device
InactiveUS20110016309A1Avoid affecting performanceIntensively disposeMultiple digital computer combinationsProgram controlCommunications systemIp address
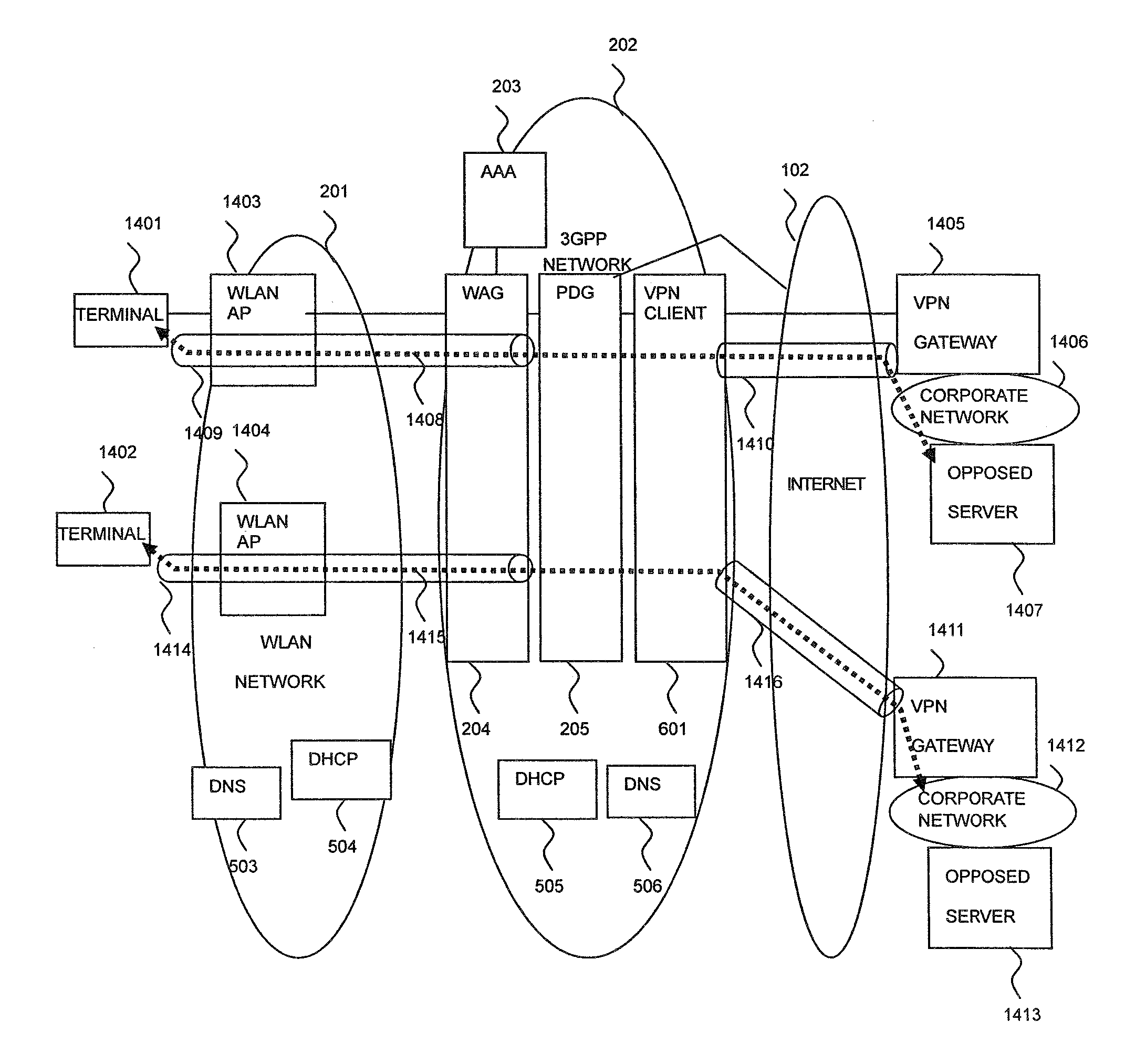
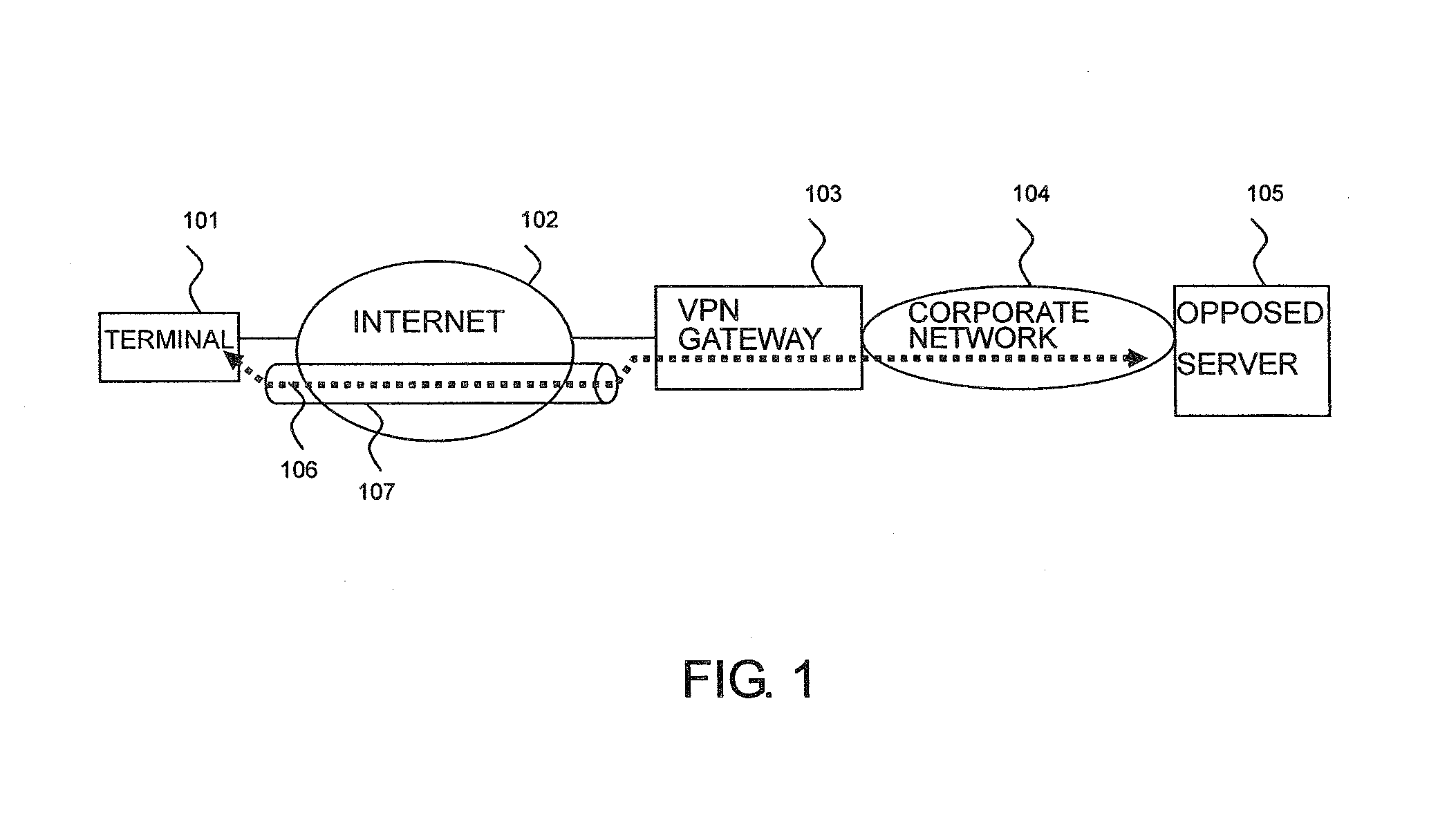
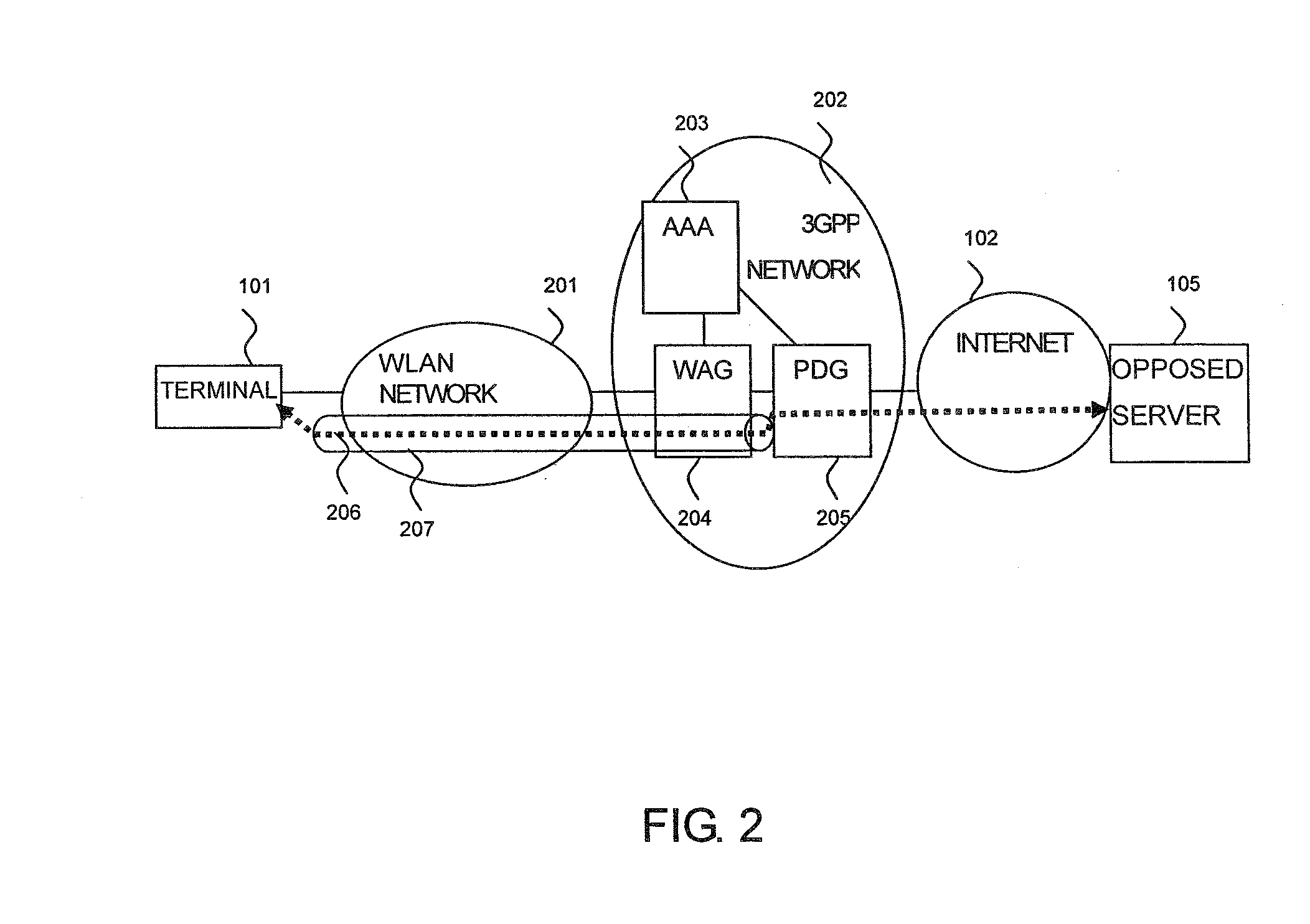
A GW (PDG) at the termination of remote access is installed in the 3GPP system. After an IPSec tunnel between a terminal and the GW is opened, an IPSec tunnel between a VPN client and the corporate network GW is opened, whereby the data from the terminal is transferred via two tunnels between the terminal and the GW and between the VPN client and the corporate network GW to the corporate network. Also, the GW checks if the destination network uses the global address from the destination IP address of a message received from the terminal making the remote VPN access. If the global address is required, the source IP address of the message received from the terminal is translated from the private address for use within the corporate network to which the terminal is allocated to the global address to transfer the message.
Owner:HITACHI LTD
Industrial network security
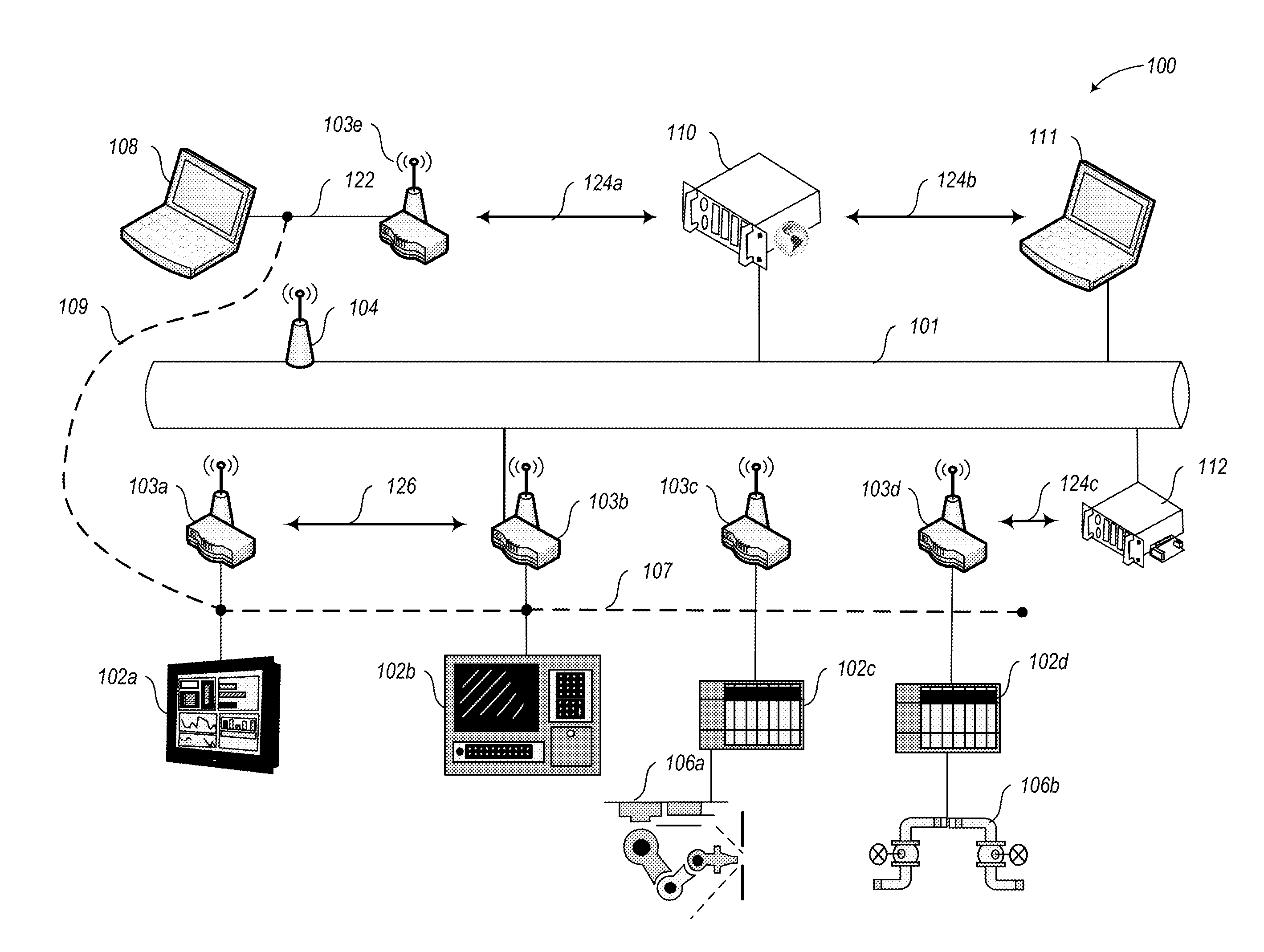
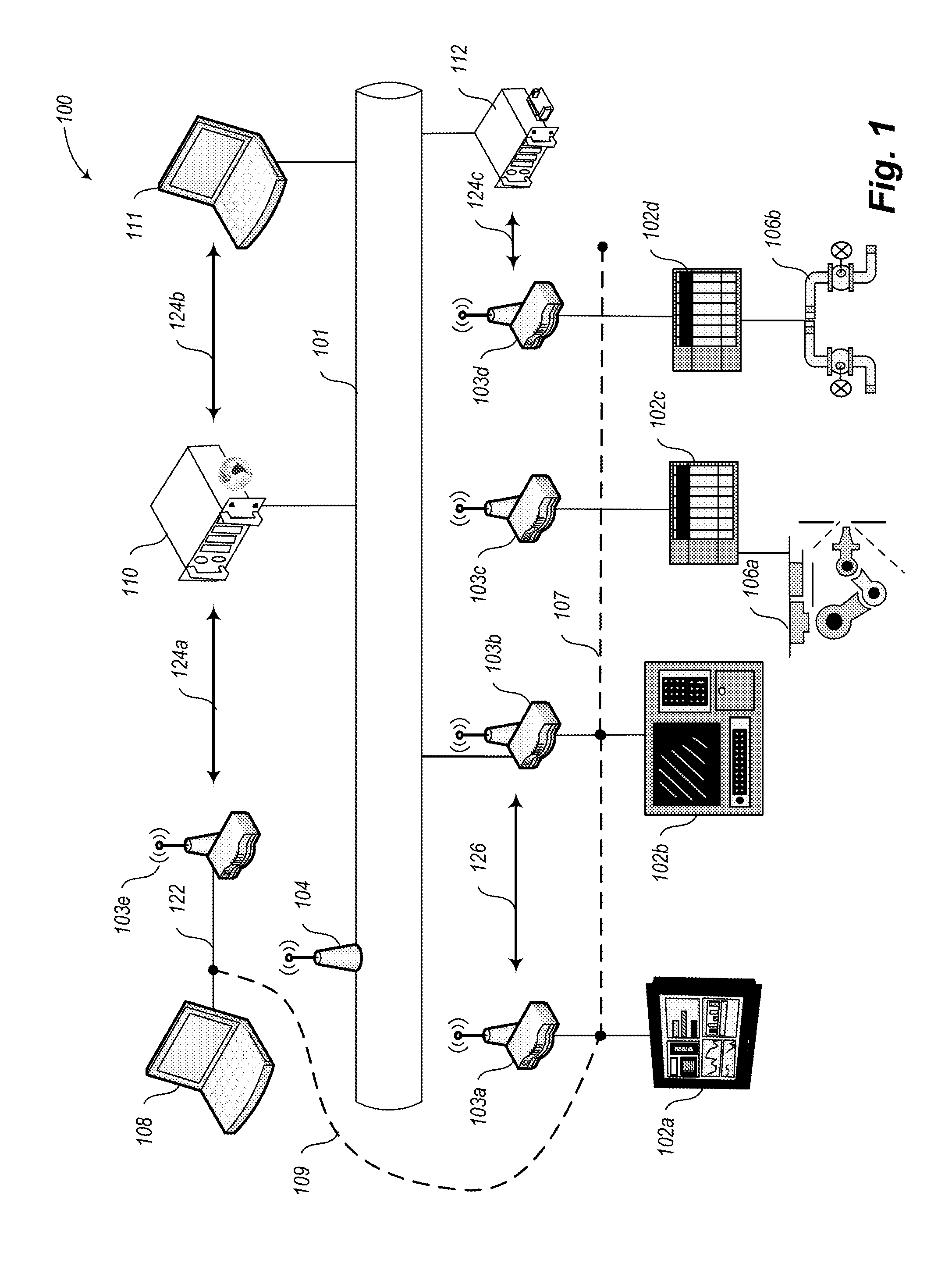
ActiveUS20140282850A1Facilitate communicationImprove network securityTransmissionSpecial data processing applicationsIndustrial safety systemNetwork link
A private overlay network is introduced into an existing core network infrastructure to control information flow between private secure environments. Such a scheme can be used to connect a factory automation network linking operations devices to a corporate network linking various business units, with enhanced network security. Such a connection can be facilitated by introducing into the existing infrastructure a set of industrial security appliances (ISAs) that work together to create an encrypted tunnel between the two networks. The set of ISAs can be scalable to overlay differently sized core networks, to create the private overlay network. Connections to the private overlay network can be managed by the ISAs in a distributed fashion, implementing a peer-to-peer dynamic mesh policy. The industrial security system disclosed may be particularly advantageous in environments such as public utility systems, medical facilities, and energy delivery systems.
Owner:TEMPERED NETWORKS
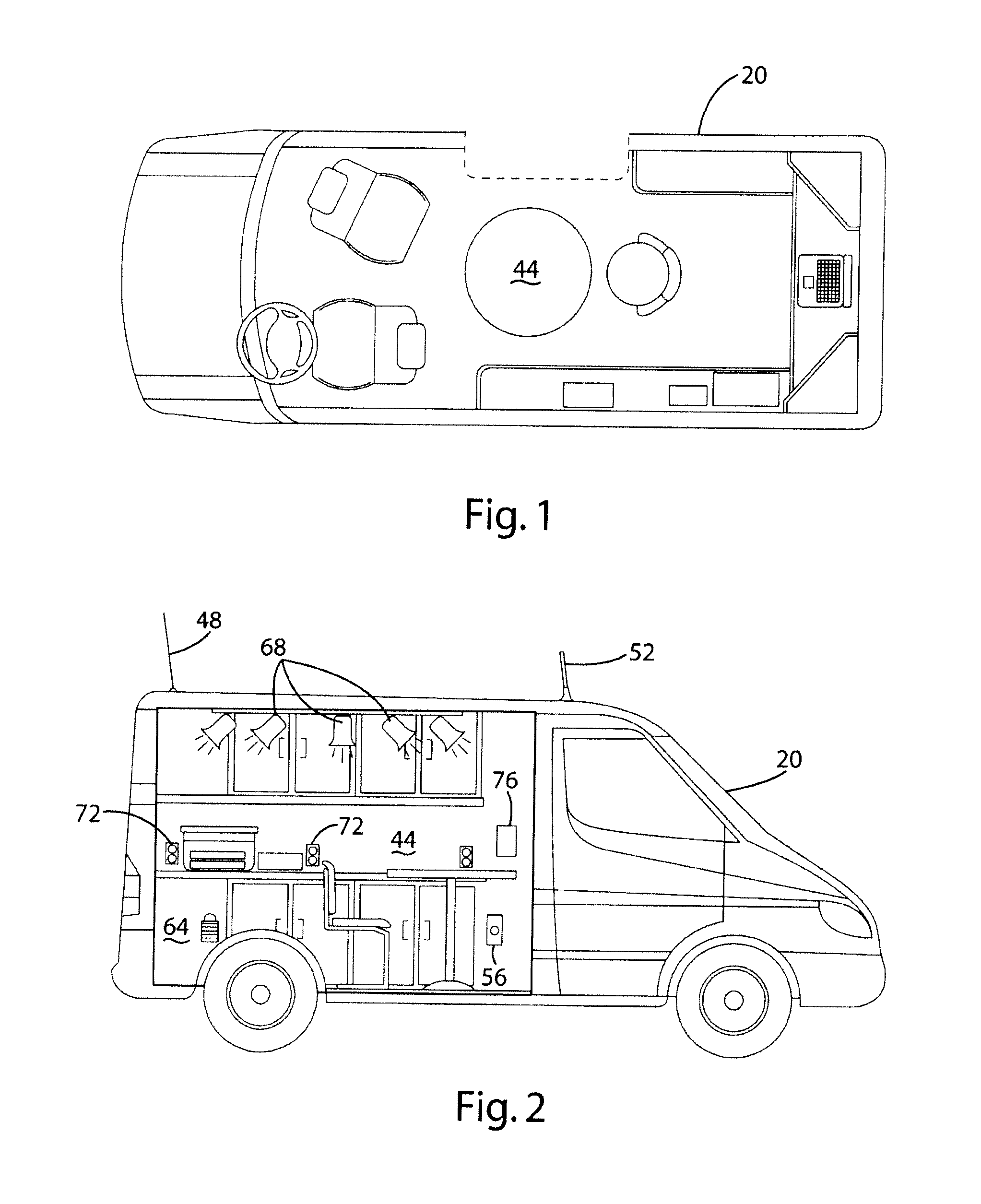
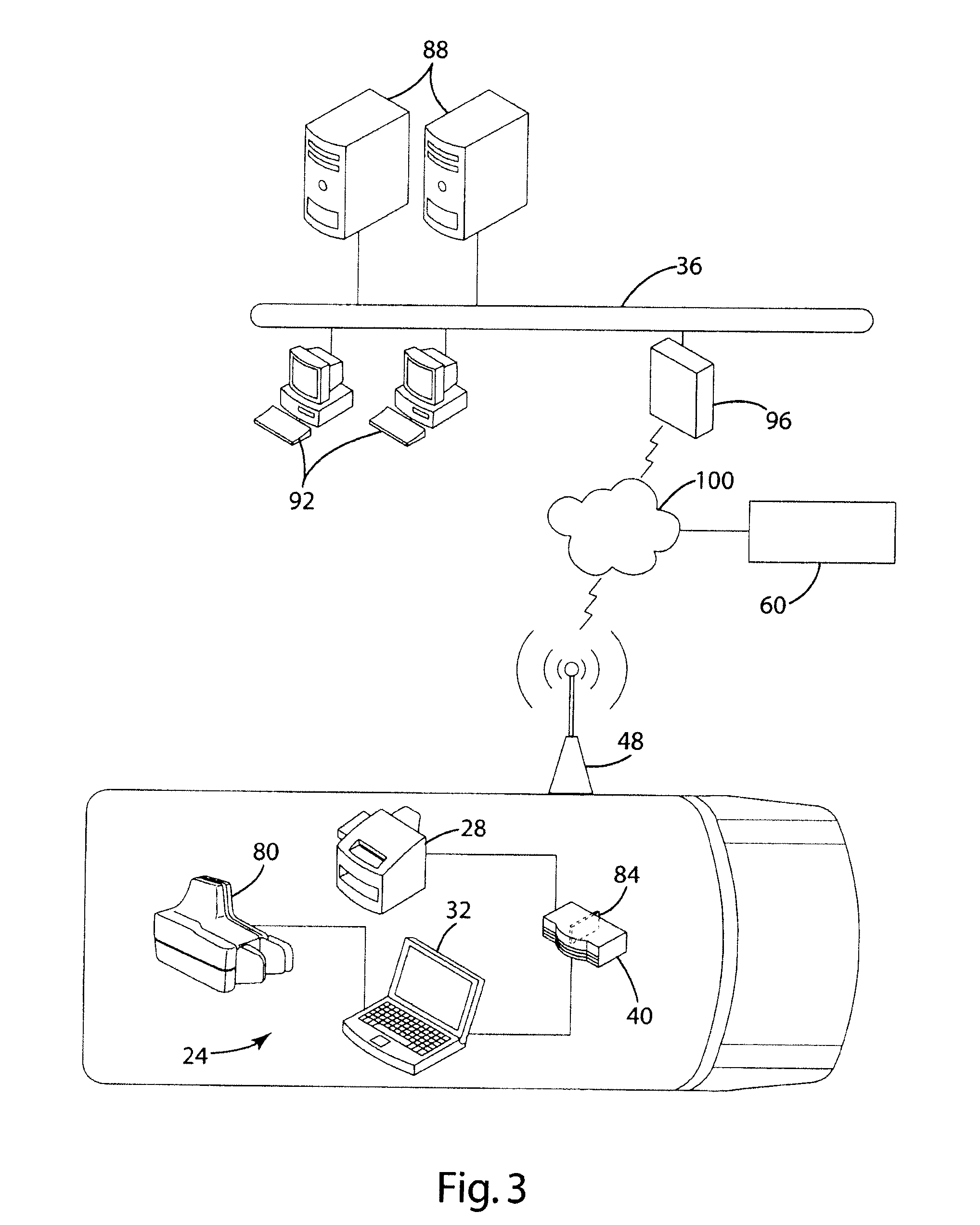
Mobile system and method for processing secure remote in person transactions
ActiveUS20120030124A1Maximize efficiencyMaximize timingFinanceOffice automationTelecommunicationsDocumentation
A mobile system and method are provided for securely sending, receiving and signing documents remote from a home office. A mobile unit capable of connecting to a home corporate network where documents are stored relating to a transaction is used as part of the system. While in route to or at the remote signing location, the mobile unit connects to the corporate network and prints the documents, or the home office sends the documents through a secure wireless connection to the mobile unit. The transaction is conducted at a remote location, and the executed documents are scanned and sent securely to the corporate network. The housing and mobile unit may be moved to a subsequent location and the mobile unit connects, while in route to or at the subsequent location, prints the documents for the subsequent transaction.
Owner:MOBILE TITLE AGENCY OF MICHIGAN
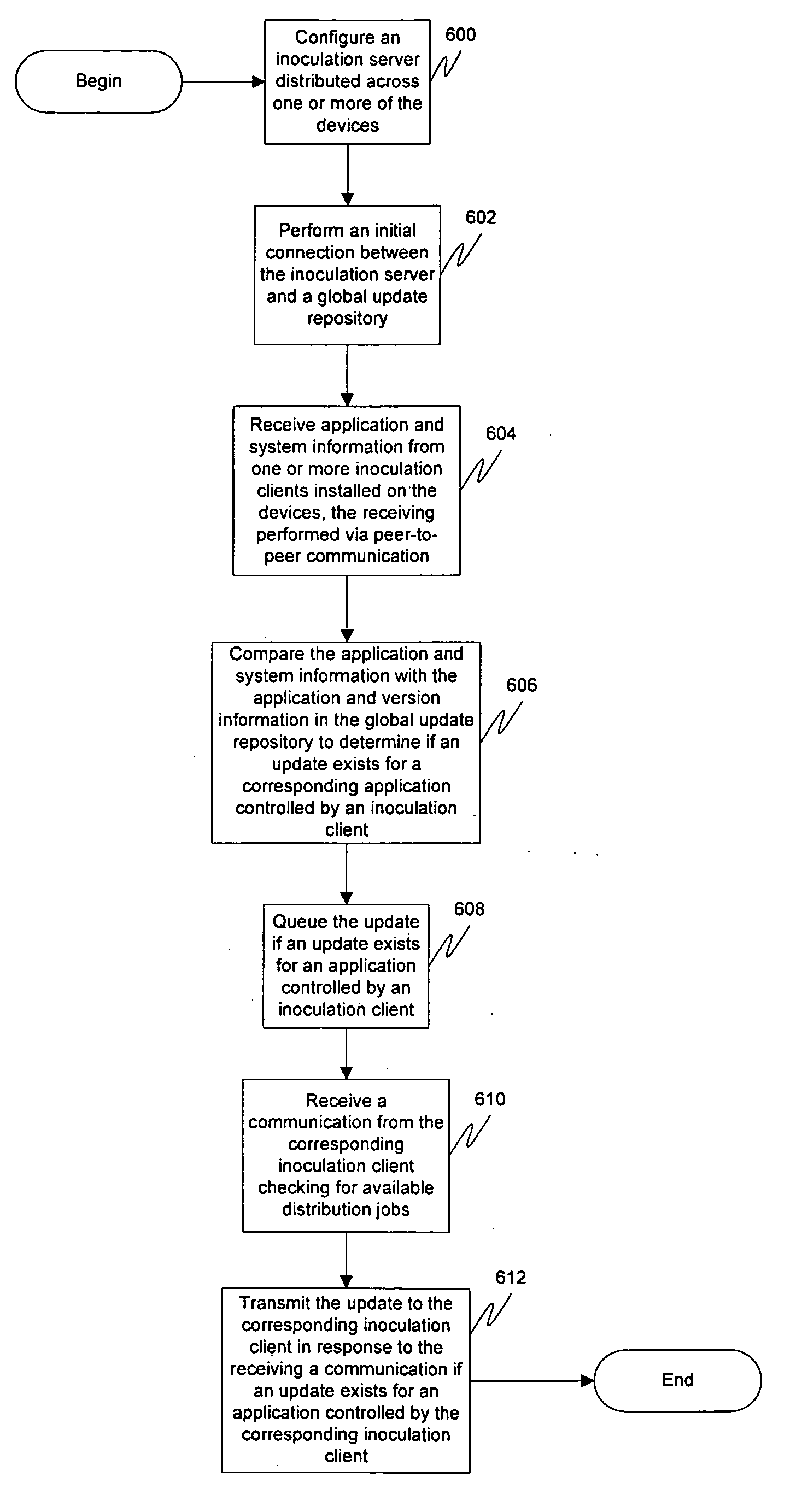
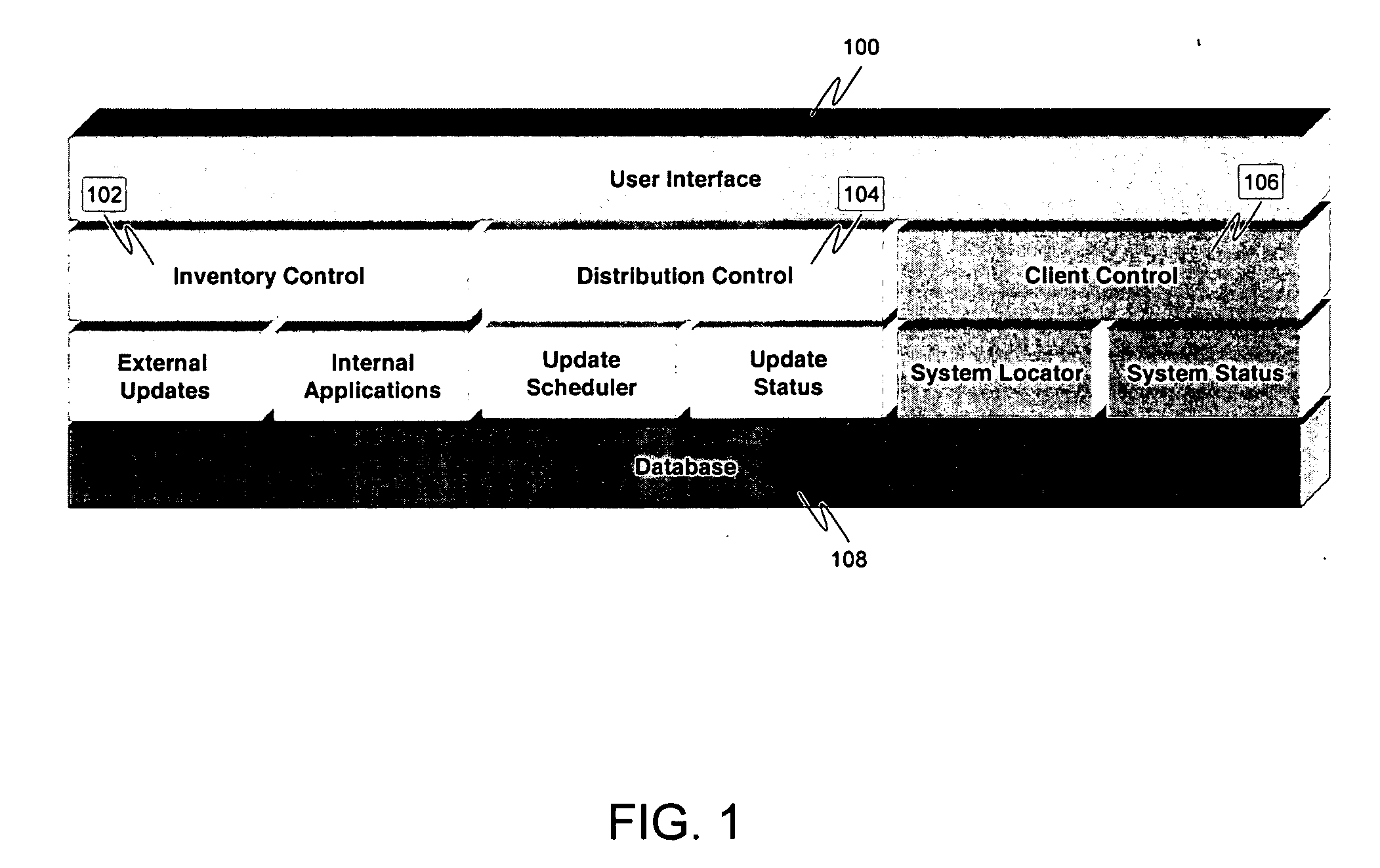
Distributed policy driven software delivery
InactiveUS20050166198A1Reduce business lossesSave resourcesPlatform integrity maintainanceSpecific program execution arrangementsWeb siteDistributed computing
A system may scan various reporting services and application manufacturers' websites for recent security upgrades, hot fixes, and service packs. The system may then retrieve these patches and automatically apply these patches on every computer within the corporate network. By inoculating systems before viruses are able to take advantage of their weaknesses, corporations can prevent many of the modern viruses from entering their network and reduce their corporate losses. Furthermore, as a sufficient amount of network and system administrator time is currently utilized on keeping track of security fixes, downloading these patches, and applying them across the corporate network, the implementation of this solution saves money and resources.
Owner:AUTONOMIC SOFTWARE
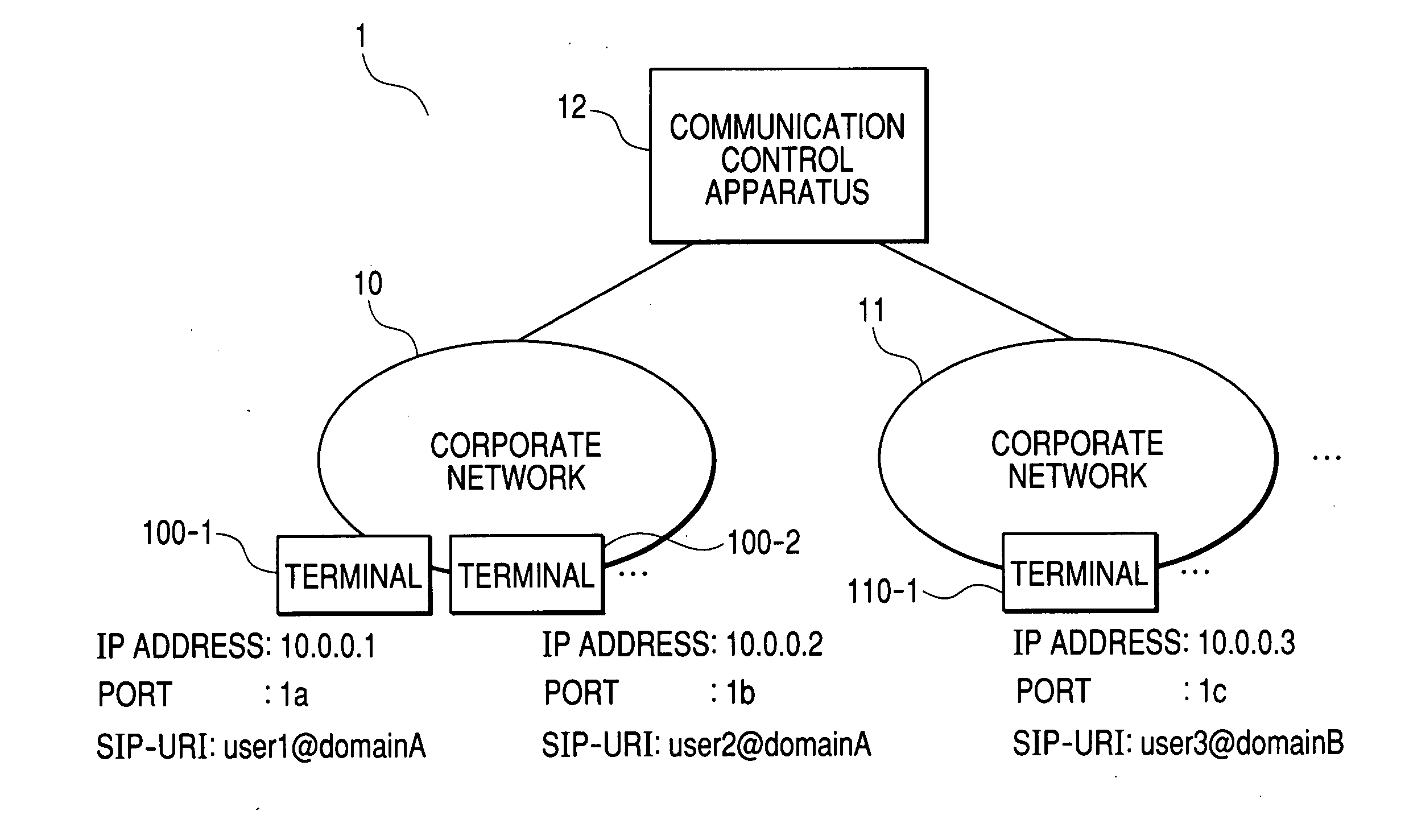
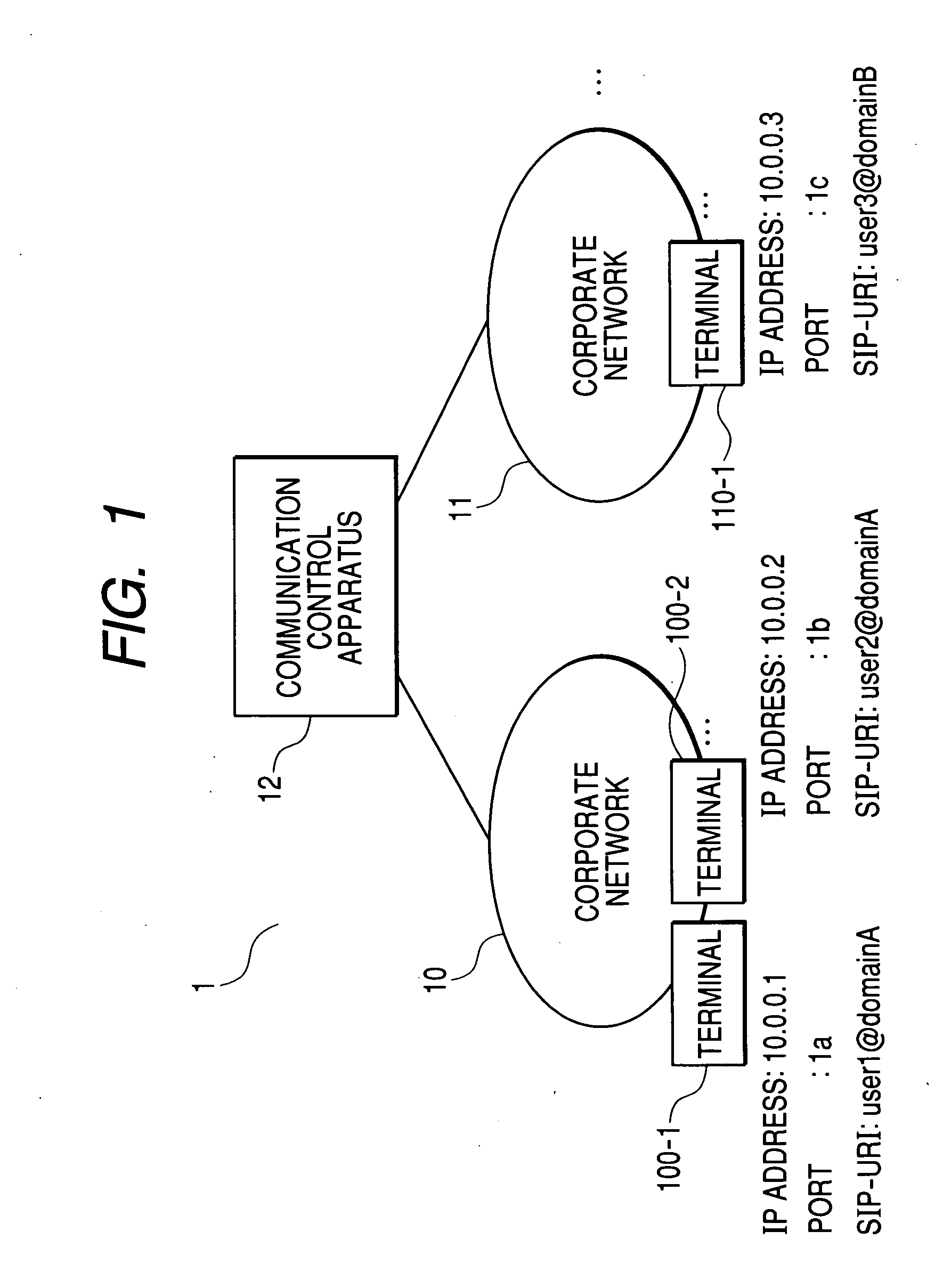
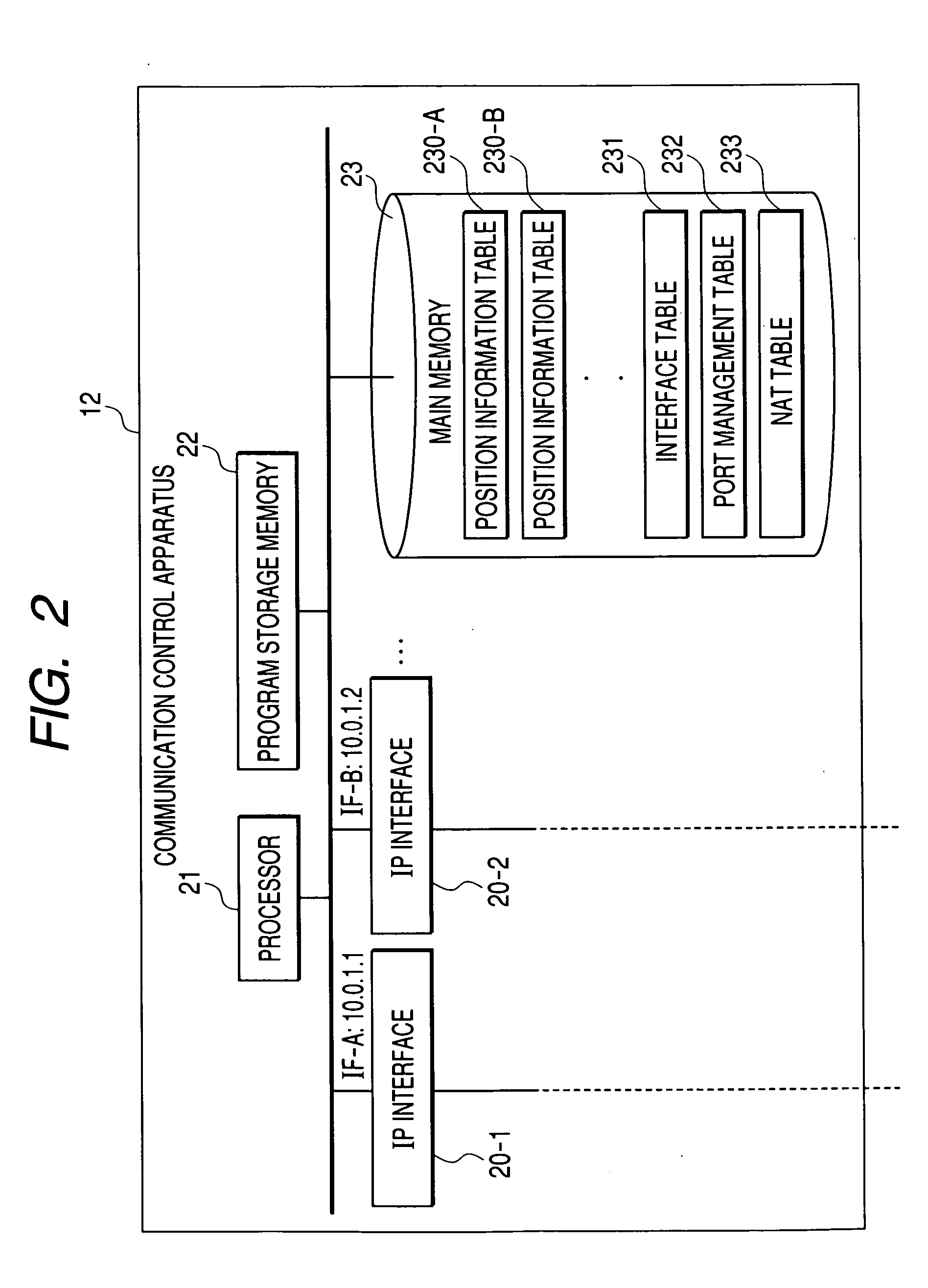
Communication control apparatus
InactiveUS20050111450A1Automatic exchangesNetworks interconnectionTelephone networkCommunication control
The present invention provides a communication control apparatus for controlling incoming and outgoing telephone calls (communication) in a corporate private telephone network and among a plurality of corporate telephone networks by using the IP. The communication control apparatus includes a plurality of interfaces connected to the plurality of corporate networks and processor, wherein when the processor receives an IP packet from a terminal that belongs to a first corporate network through any of the plurality of interfaces, the processor determines which of the corporate networks an incoming terminal for the packet belongs to based on outgoing SIP-URI and incoming SIP-URI contained in the header of the IP packet and performs necessary control so as to connect the outgoing terminal and the incoming terminal depending on each of the network to which the outgoing terminal belongs and other networks.
Owner:HITACHI LTD
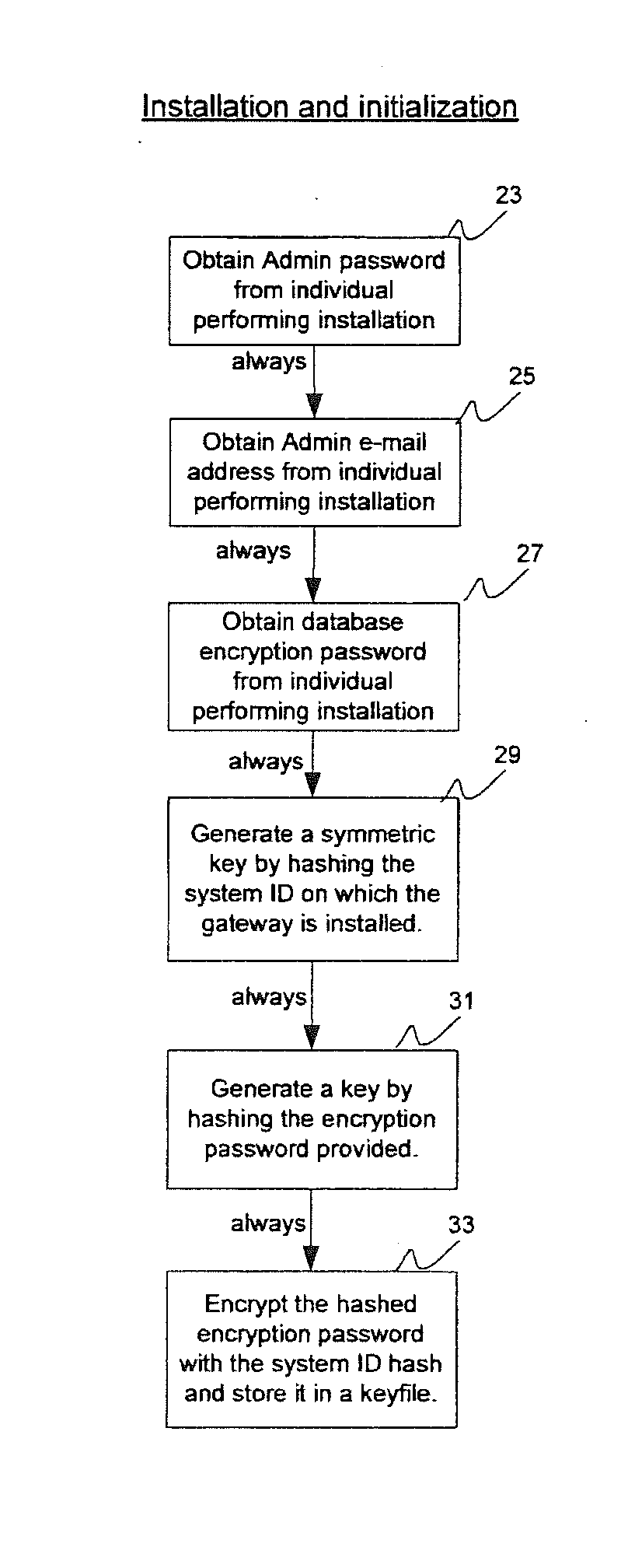
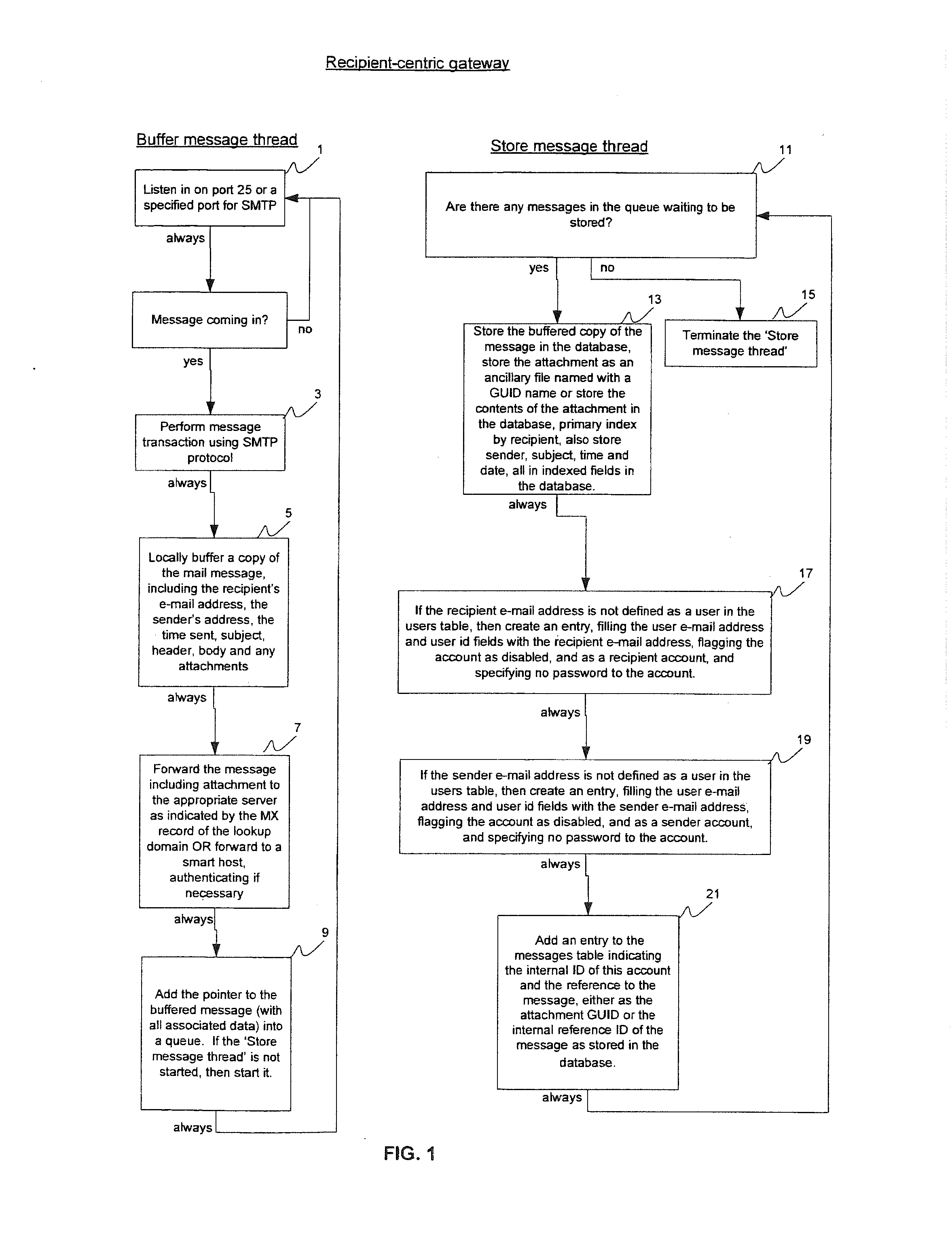
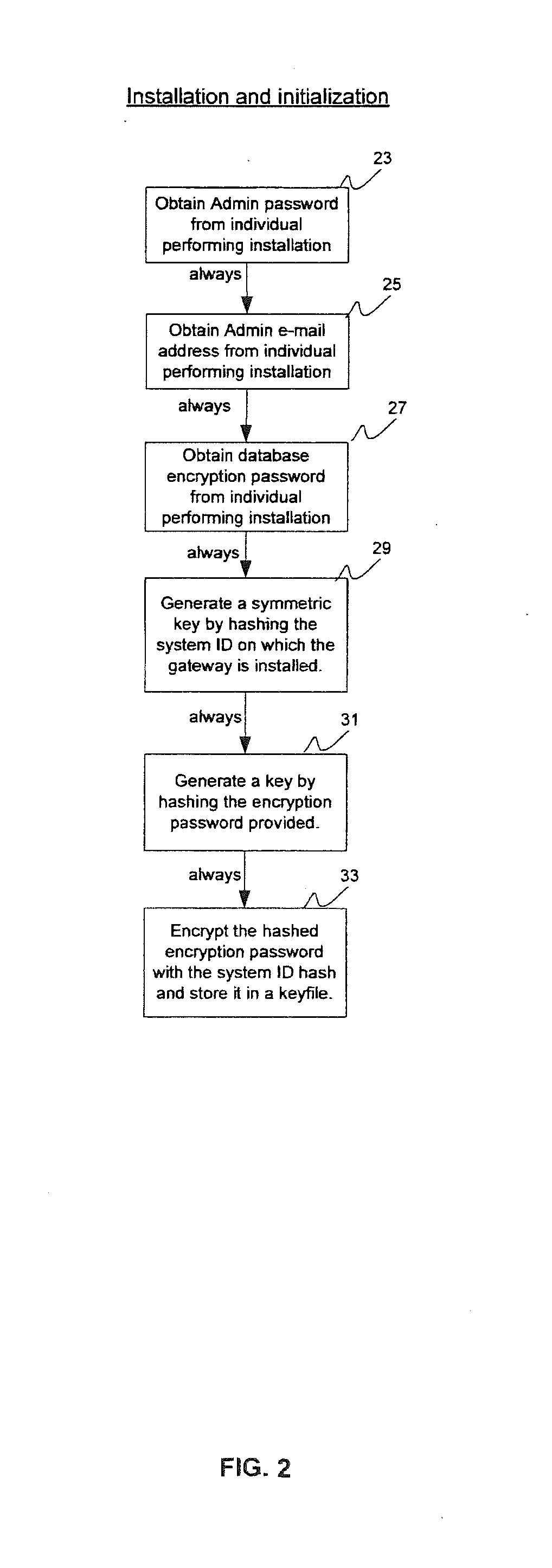
System and method for managing email and email security
InactiveUS20160269440A1Maximizing responsiveness of systemPassword reset costMultiple keys/algorithms usagePublic key for secure communicationThird partyDomain name
A recipient-centric gateway sits at the corporate network perimeter, retaining all outgoing e-mail, organizing the e-mail by recipient so that senders or other designated individuals can view the retained mail from the perspective of the recipient. A login retry limit is based on password strength. A system that guarantees the sender that the recipient is not phished with e-mail fraudulently purported to be from the sender's domain. A system that, without communicating certificates or publishing certificates to third parties and without requiring any workflow changes, enables the transparent two way sending of secure e-mail. A system that, based on feedback and usage, optimizes mailbox responsiveness across the network.
Owner:HARTMAN ROBERT
Routing XML queries
InactiveUS7664806B1Digital data information retrievalDigital data processing detailsSchema for Object-Oriented XMLData node
A vast amount of information currently accessible over the Web, and in corporate networks, is stored in a variety of databases, and is being exported as XML data. However, querying this totality of information in a declarative and timely fashion is problematic because this set of databases is dynamic, and a common schema is difficult to maintain. The present invention provides a solution to the problem of issuing declarative, ad hoc XPath queries against such a dynamic collection of XML databases, and receiving timely answers. There is proposed a decentralized architectures, under the open and the agreement cooperation models between a set of sites, for processing queries and updates to XML data. Each site consists of XML data nodes. (which export their data as XML, and also pose queries) and one XML router node (which manages the query and update interactions between sites). The architectures differ in the degree of knowledge individual router nodes have about data nodes containing specific XML data. There is therefore provided a method for accessing data over a wide area network comprising: providing a decentralized architecture comprising a plurality of data nodes each having a database, a query processor and a path index, and a plurality of router nodes each having a routing state, maintaining a routing state in each of the router nodes, broadcasting routing state updates from each of the databases to the router nodes, routing path queries to each of the databases by accessing the routing state.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
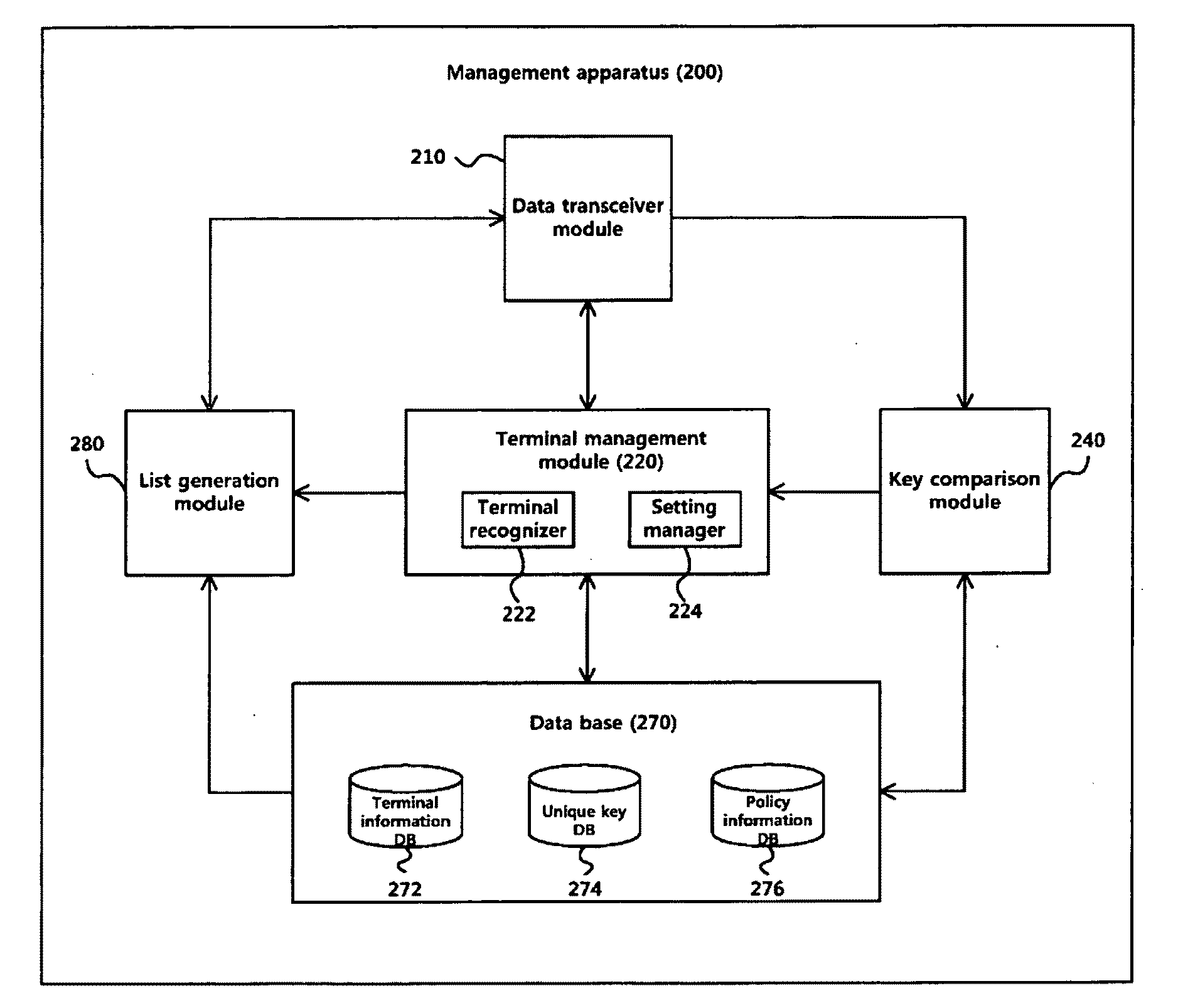
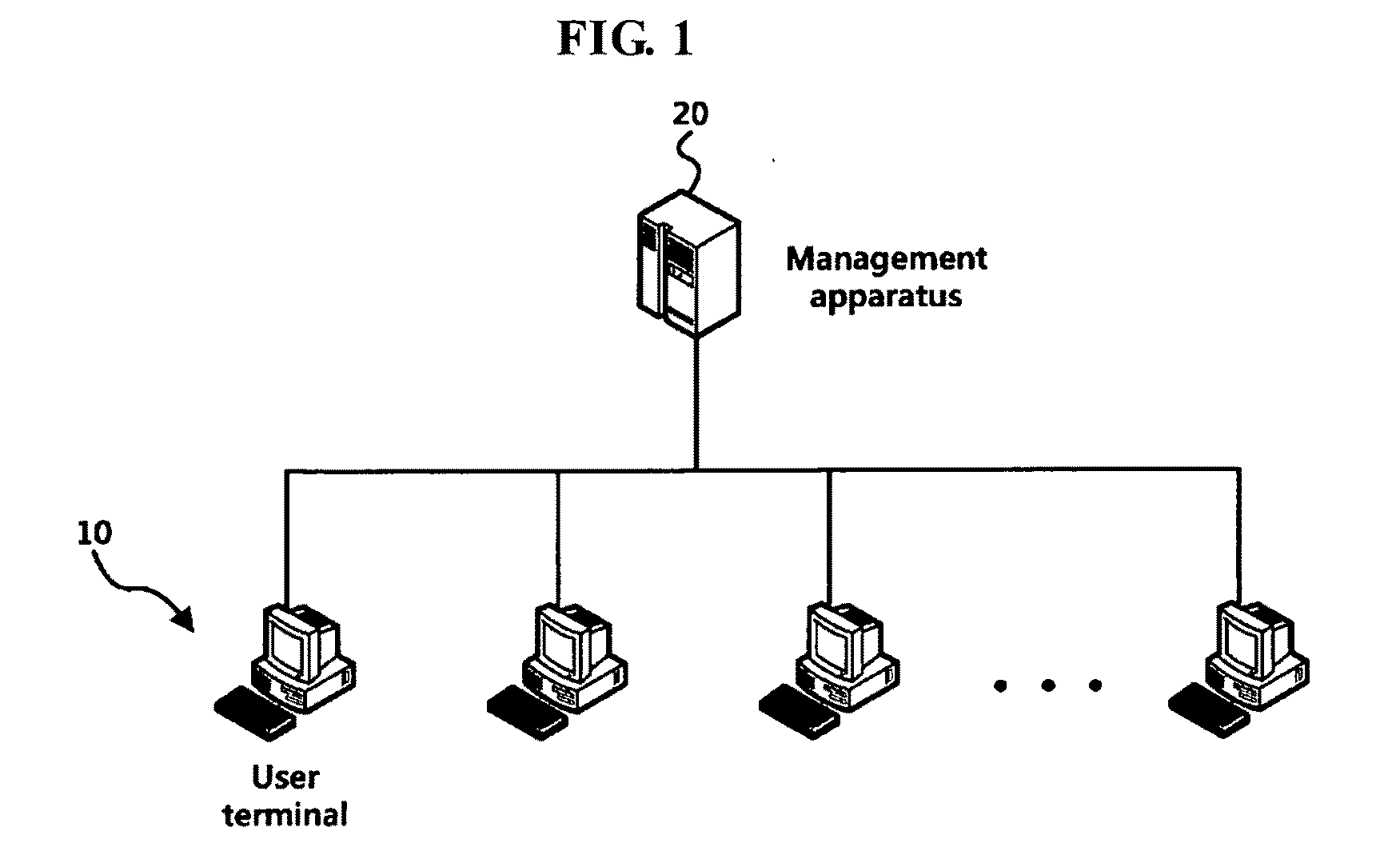
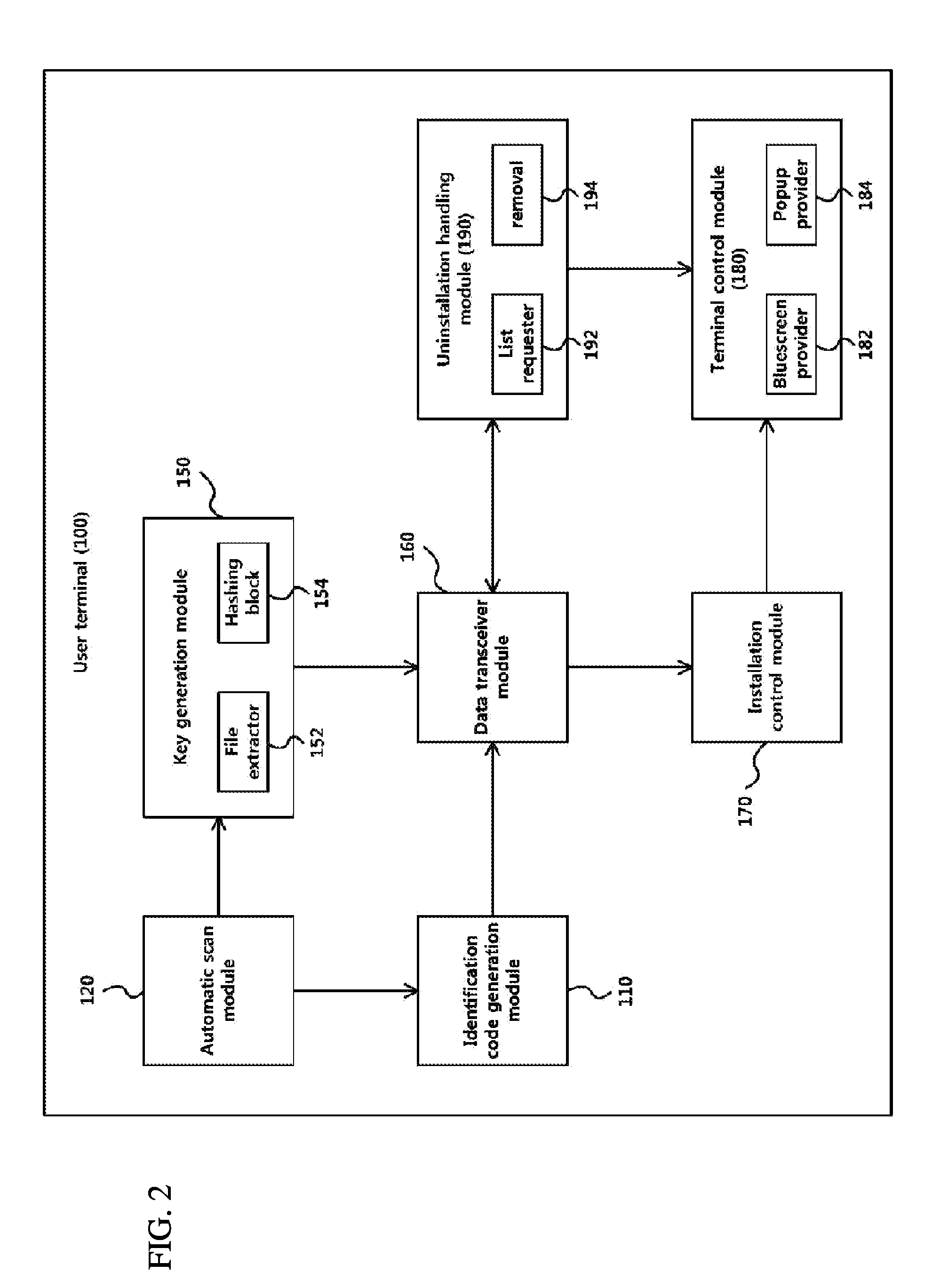
Software management apparatus and method, and user terminal controlled by the apparatus and management method for the same
InactiveUS20100275252A1Avoid installationReduce usageDigital data processing detailsUser identity/authority verificationSystems managementSoftware engineering
A software management apparatus and method are disclosed. A software installation attempt made in one of multiple user terminals connected through a corporate network is detected, and a management operation is performed to permit software installation, to block the use of the user terminal, or to provide a popup notification according to the rights assigned to the user terminal. In addition, unlike existing approaches to prevention of unauthorized software installation that may not handle already installed software, the software management apparatus and method enable the system manager to handle and remove software that is already installed in a user terminal before installation of the apparatus and method. As a result, unauthorized installation of software in corporate computers can be effectively prevented.
Owner:GYEYEONG TECH&INFORMATION
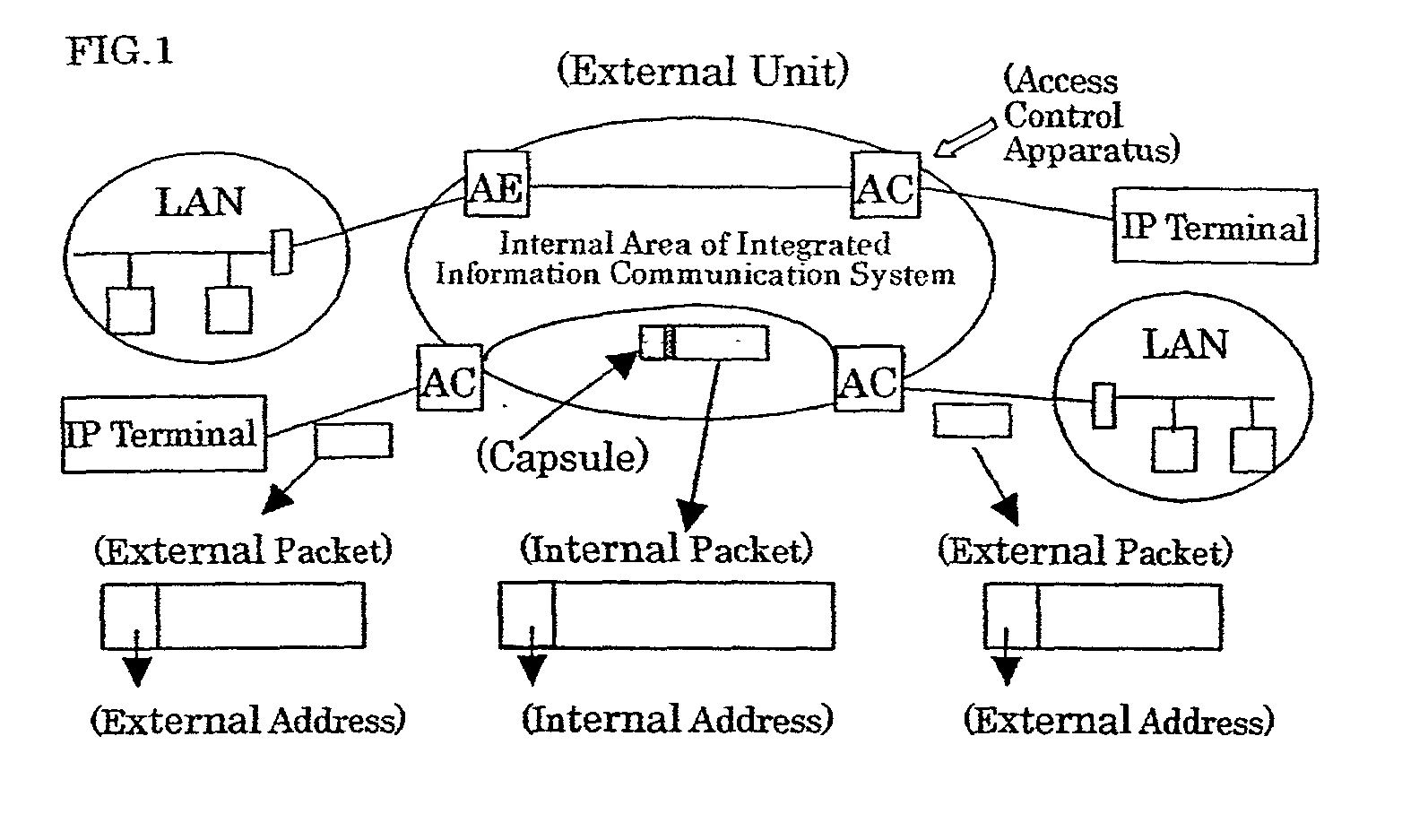
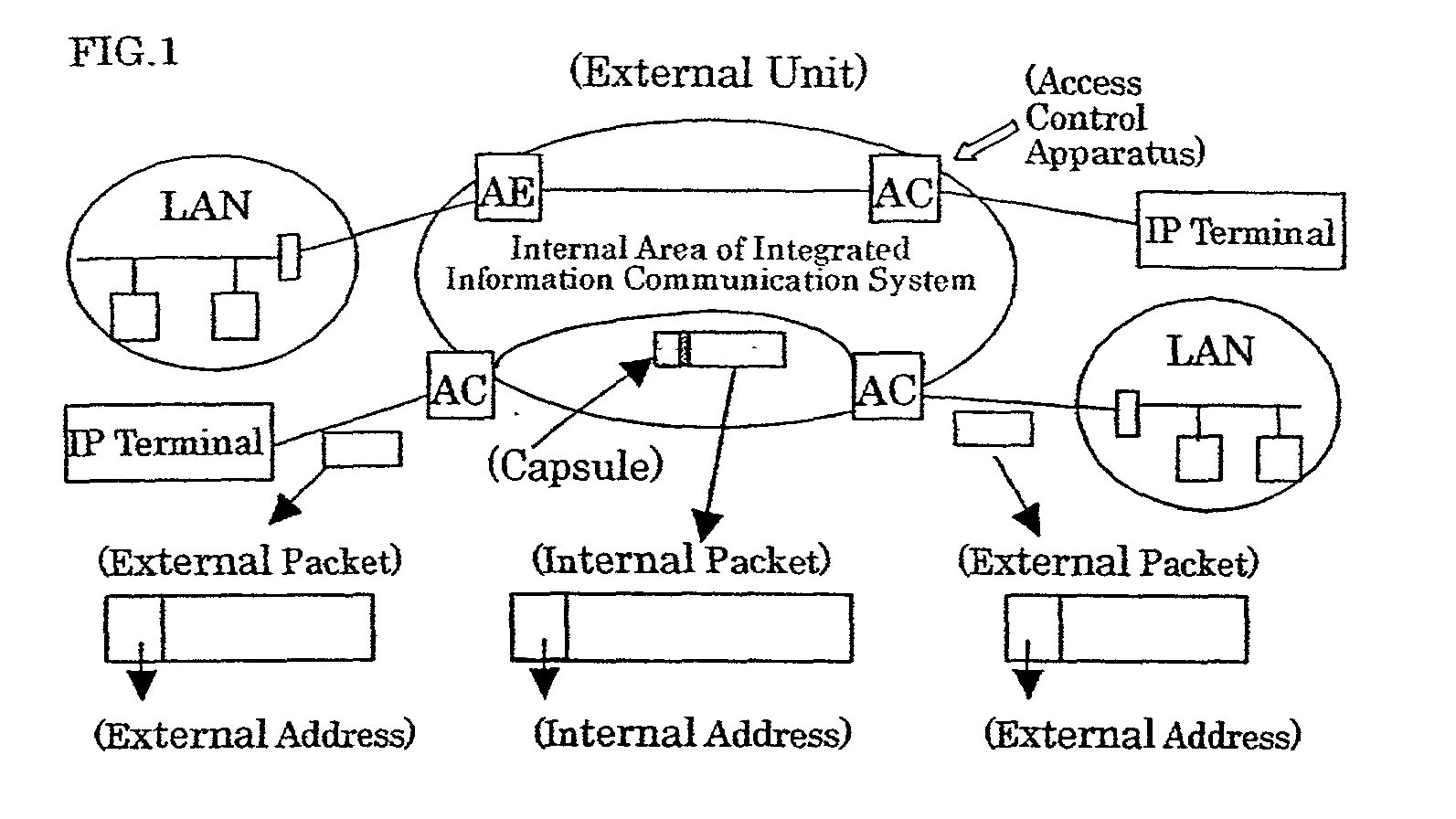
Integrated information communication system
InactiveUS20020124084A1Multiple digital computer combinationsNetworks interconnectionCommunications systemAddress control
An integrated information communication system capable of improving information security is provided, in which an IP packet is detected which is sent from an external area toward either an operation management server or a relay apparatus, the detected IP packet is not entered inside the integrated information communication system in order to reduce such a chance that the operation management server and the relay apparatus are unfairly attacked. Also, such an IP packet is detected and discarded, which violates an address application rule established so as to keep secret of a communication company network. An address which is applied to either an operation management server or a relay apparatus employed in the integrated information communication system is sectioned, or classified as an "address which is not opened outside network" with respect to an external area of the communication system. A packet filter is installed in an address control apparatus.
Owner:THE DISTRIBUTION SYST RES INST
SyncML based OMA connectivity object to provision VPN connections
InactiveUS20060212937A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivate networkMobile device
Mobile devices are provisioned automatically with VPN (Virtual Private Network) information so that users can automatically connect to their corporate networks using their devices. The OMA SyncML standard is extended to define VPN connections and provision them onto the devices automatically either over-the-air or by an IT application provided by the corporation.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com