Patents
Literature
38 results about "Cryptographic accelerator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
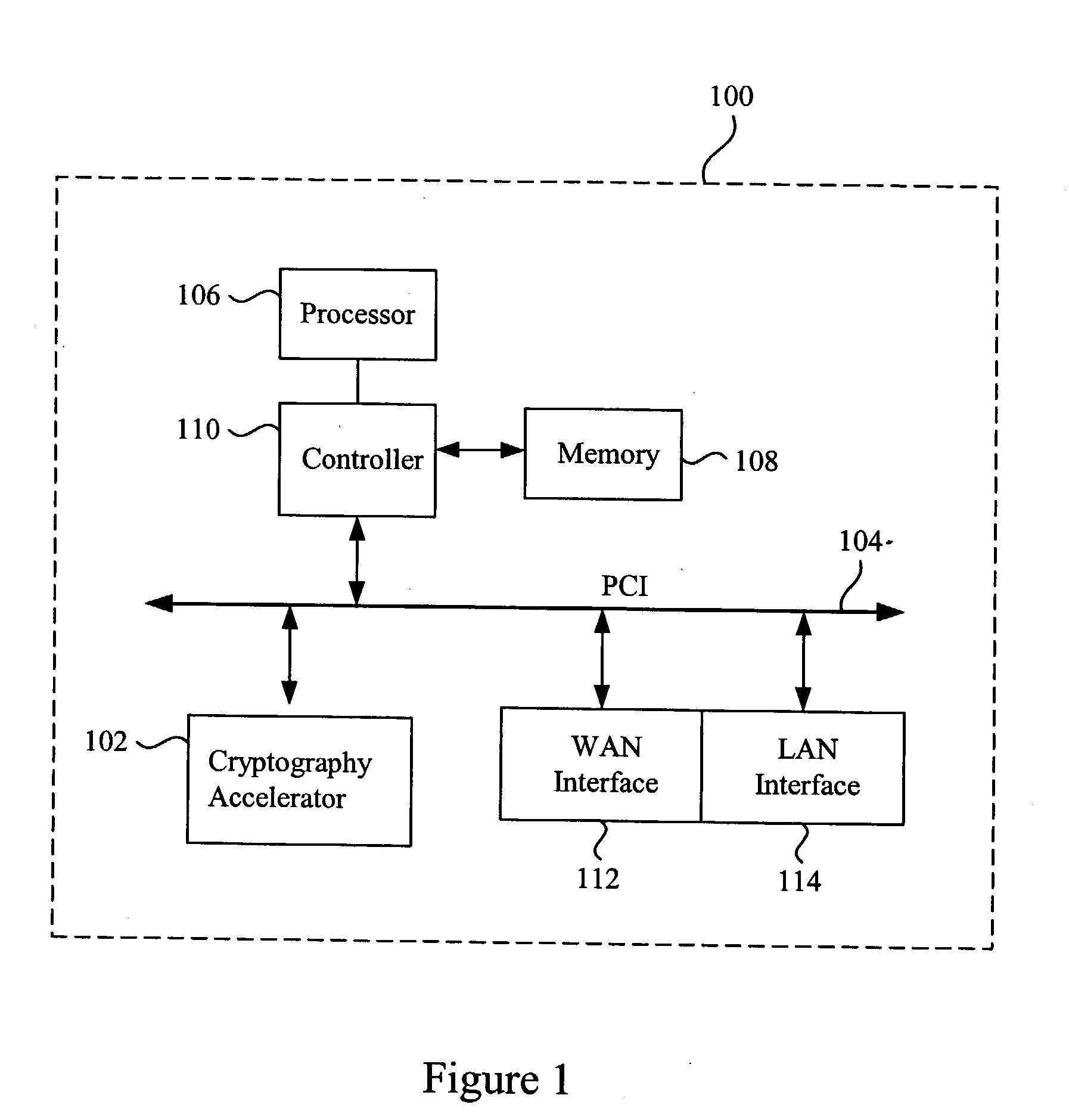
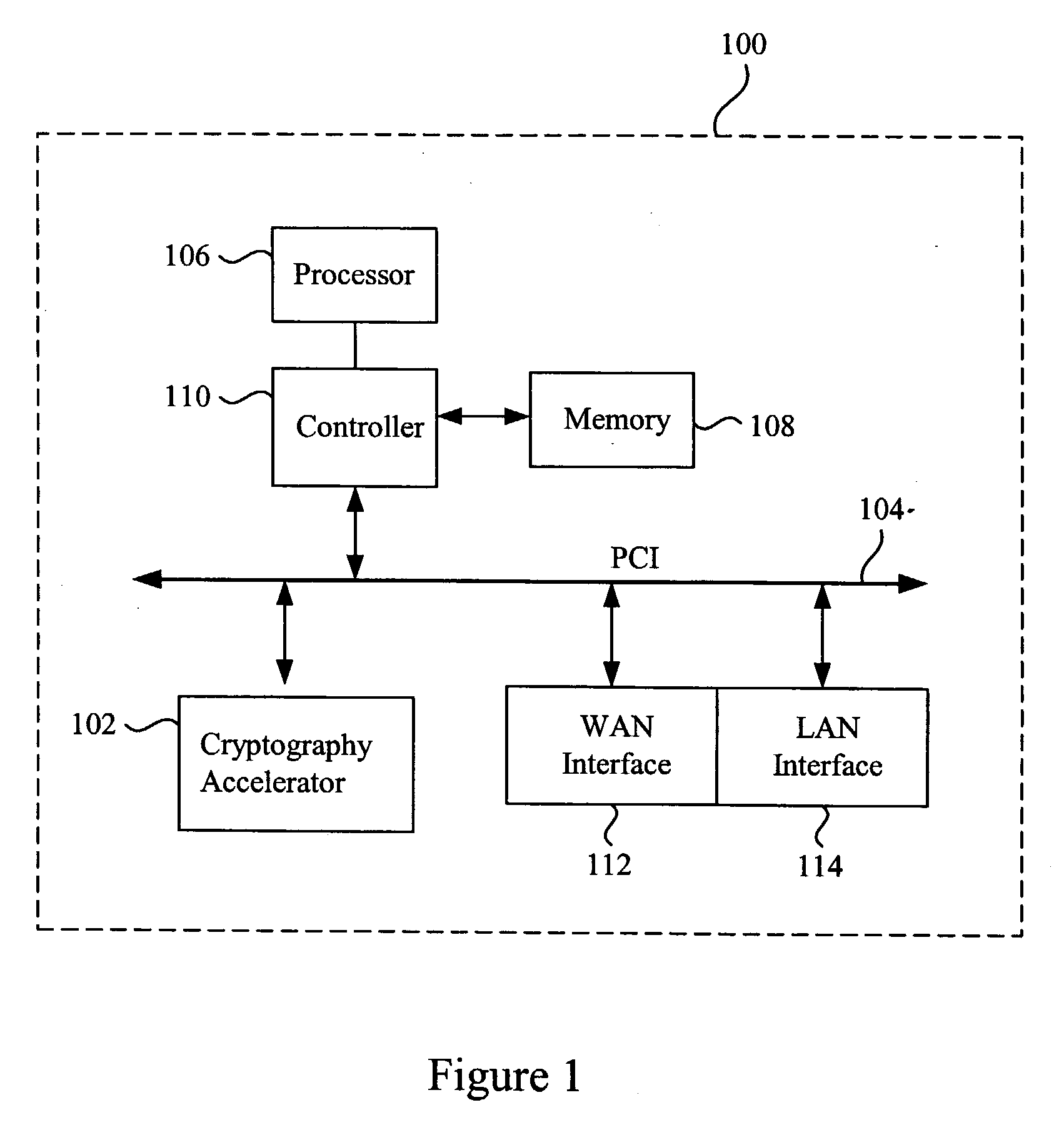
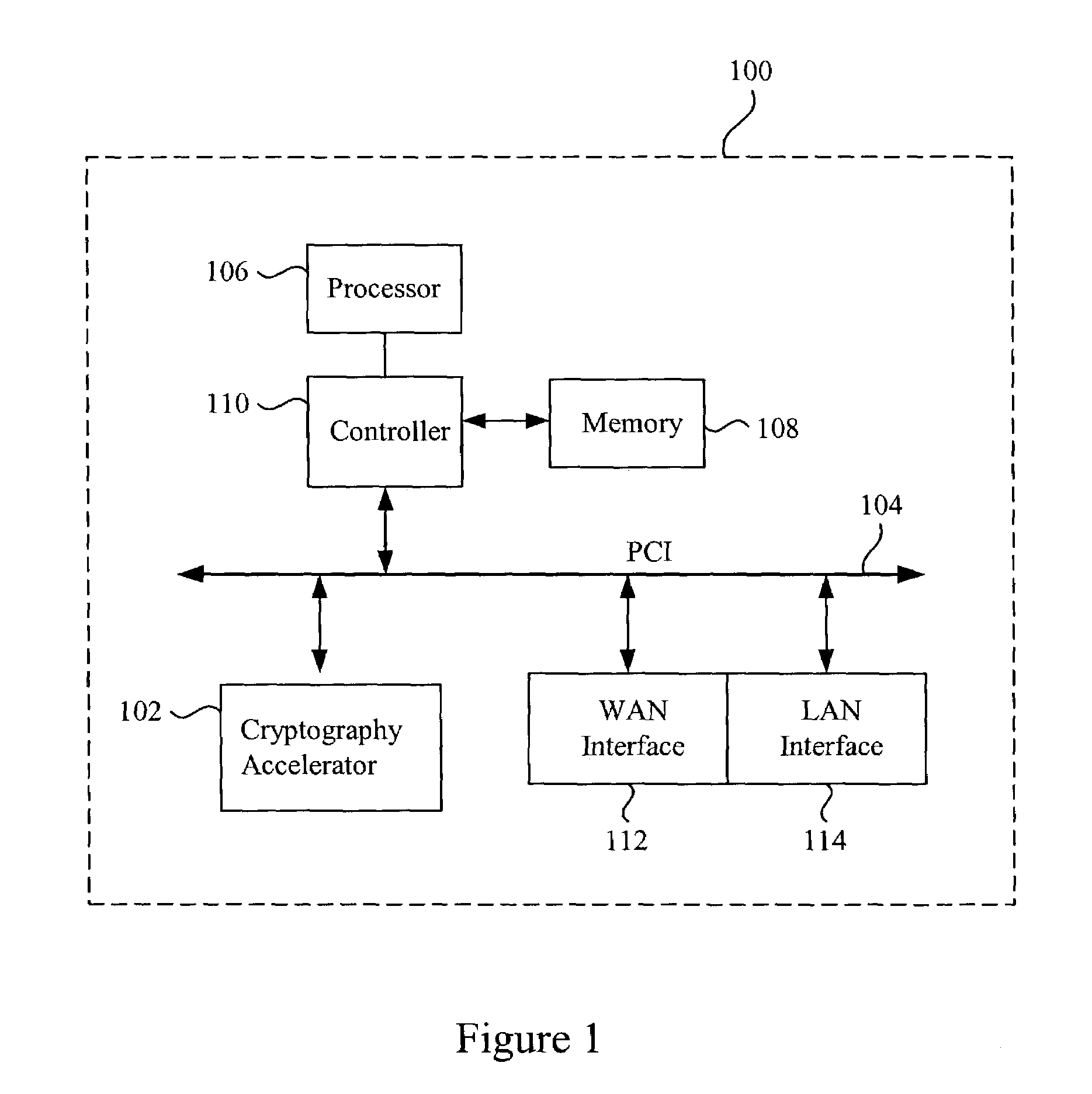
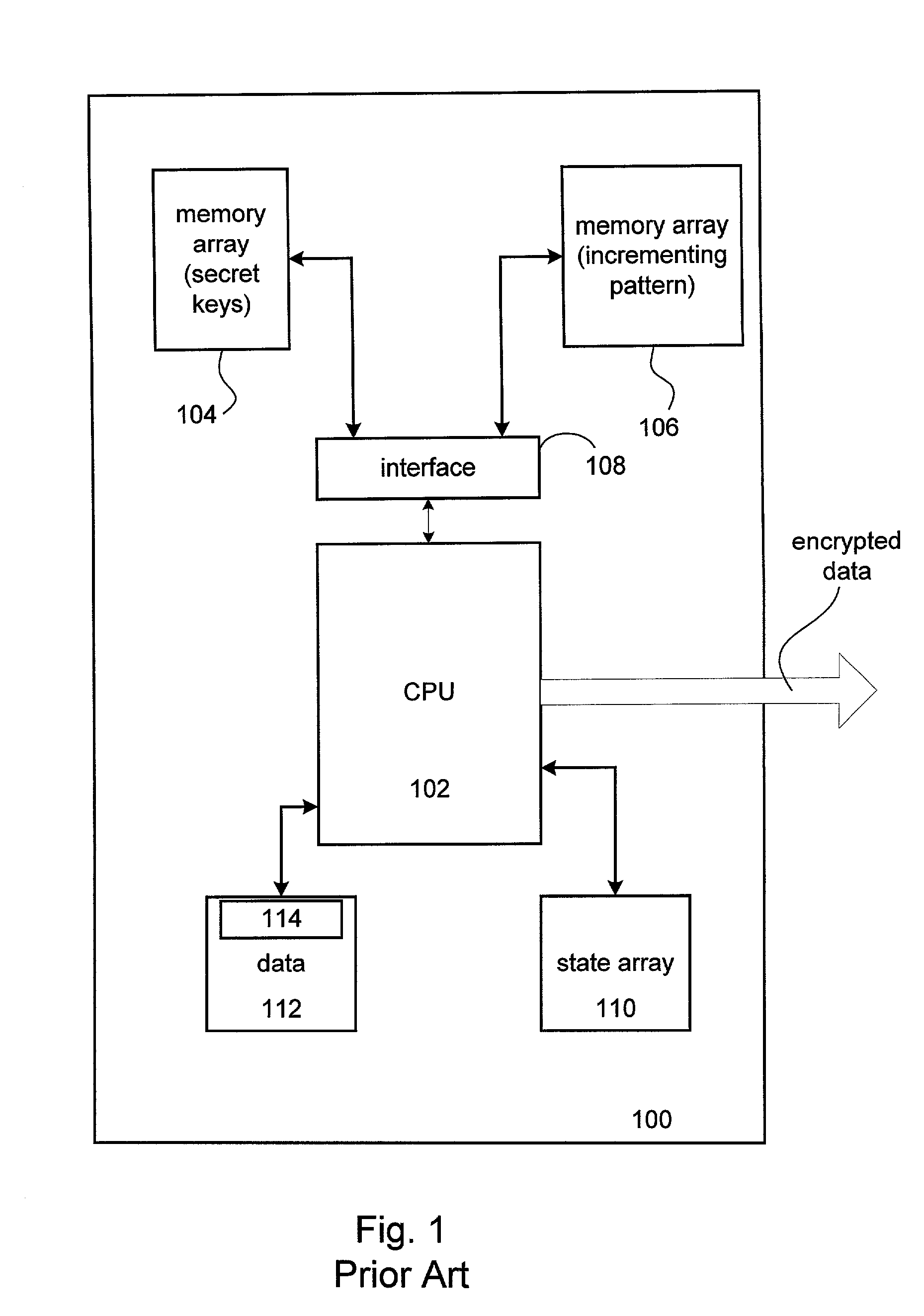
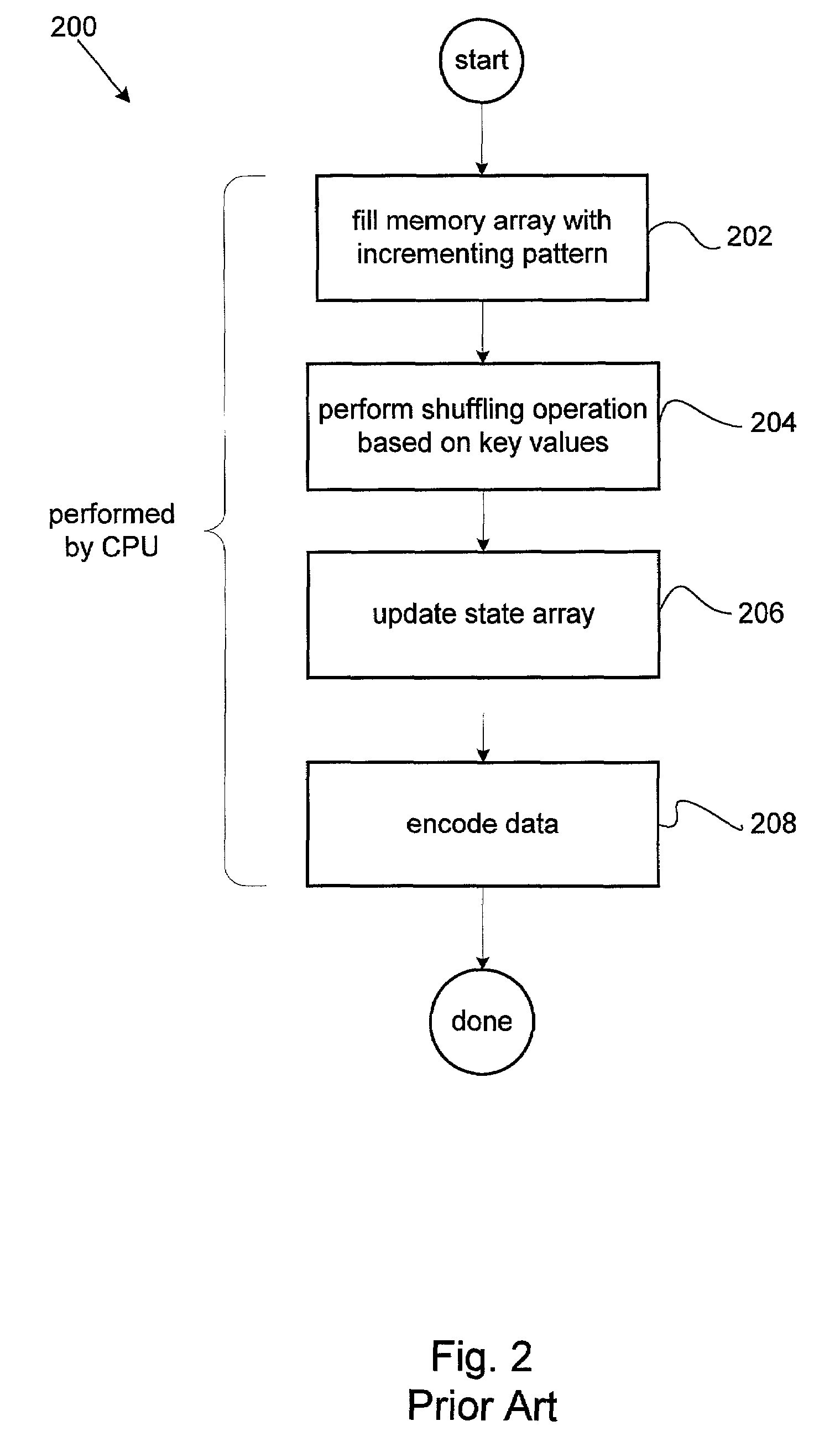
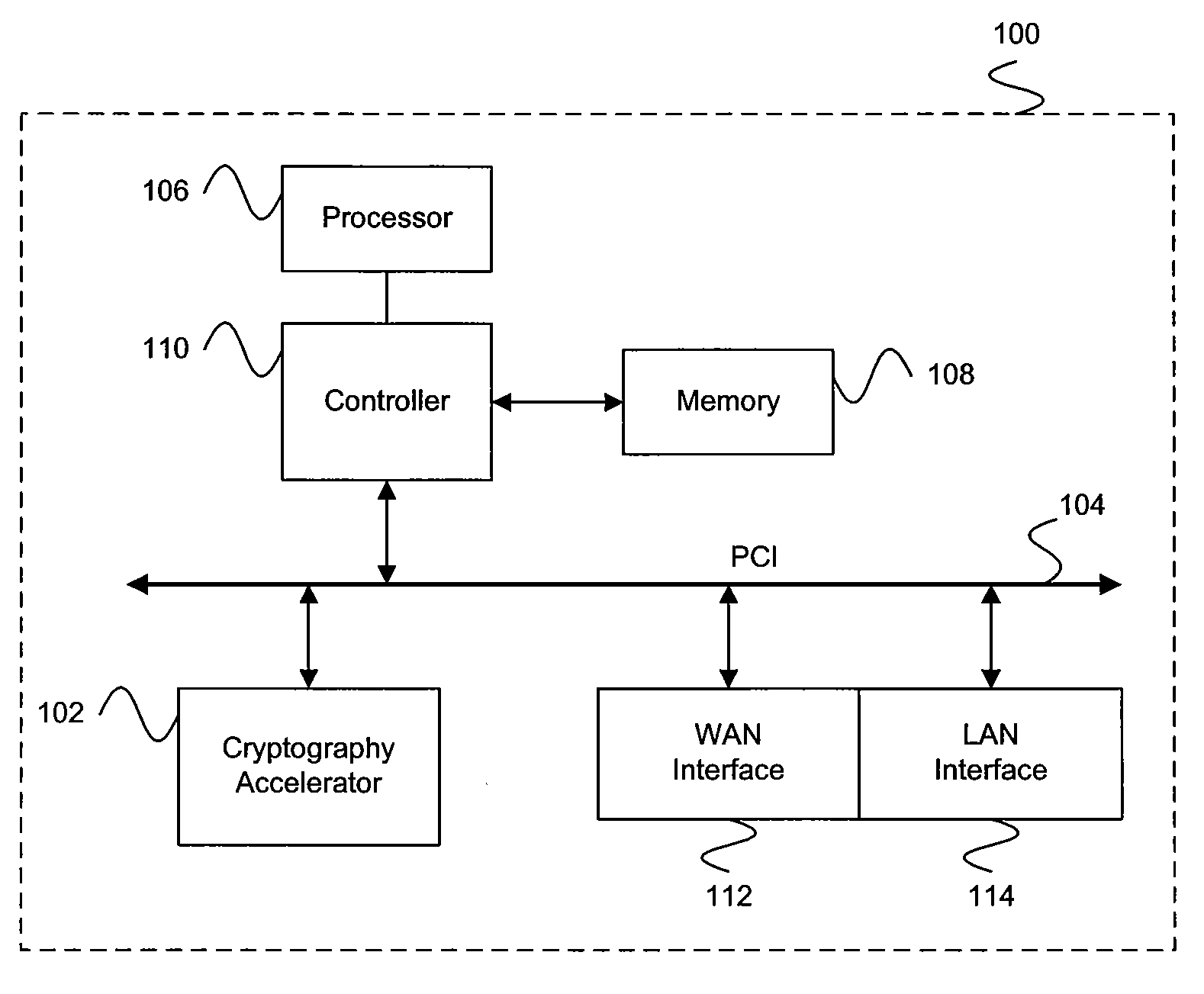
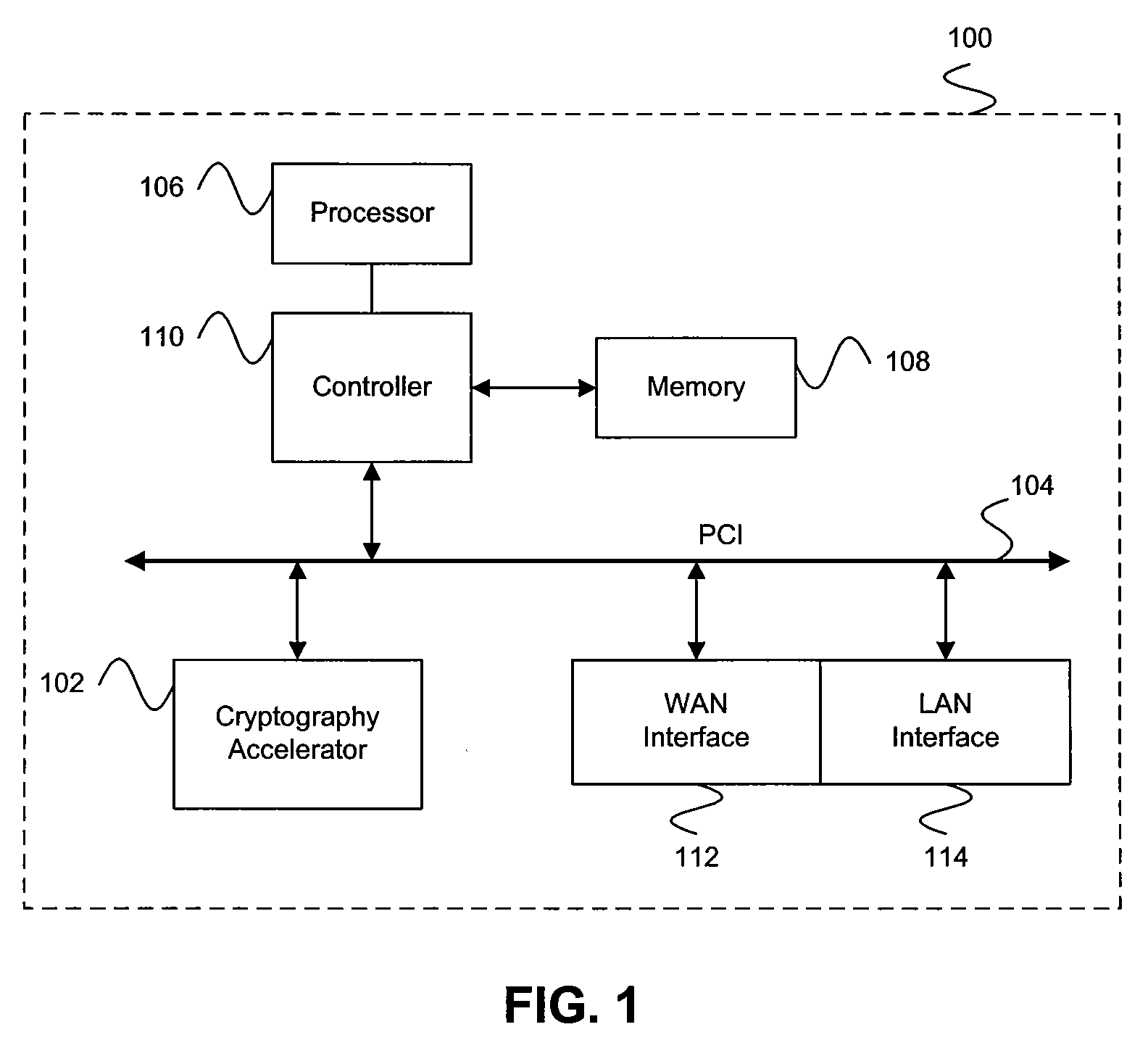
In computing, a cryptographic accelerator is a co-processor designed specifically to perform computationally intensive cryptographic operations, doing so far more efficiently than the general-purpose CPU. Because many servers' system load consists mostly of cryptographic operations, this can greatly increase performance.
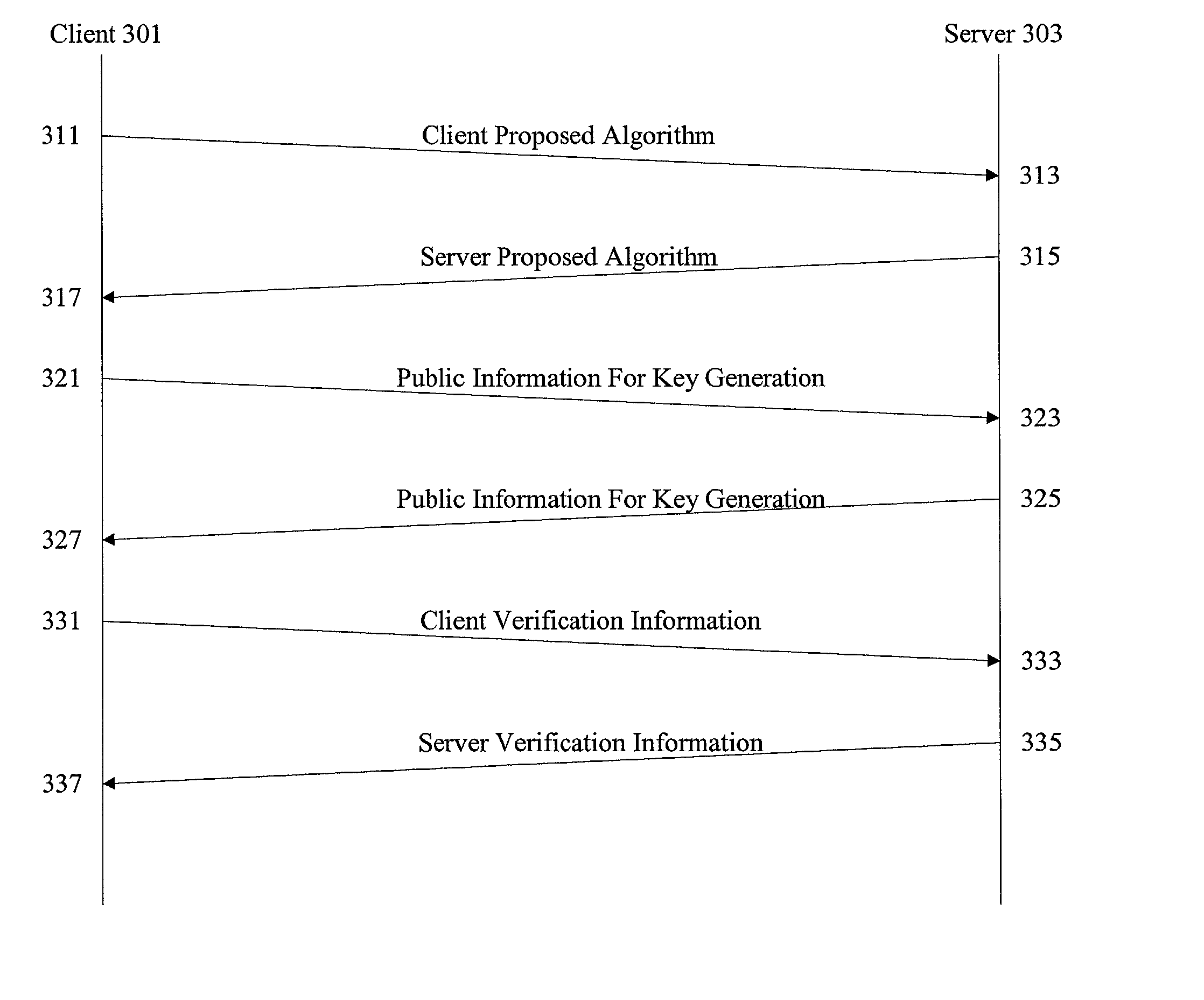
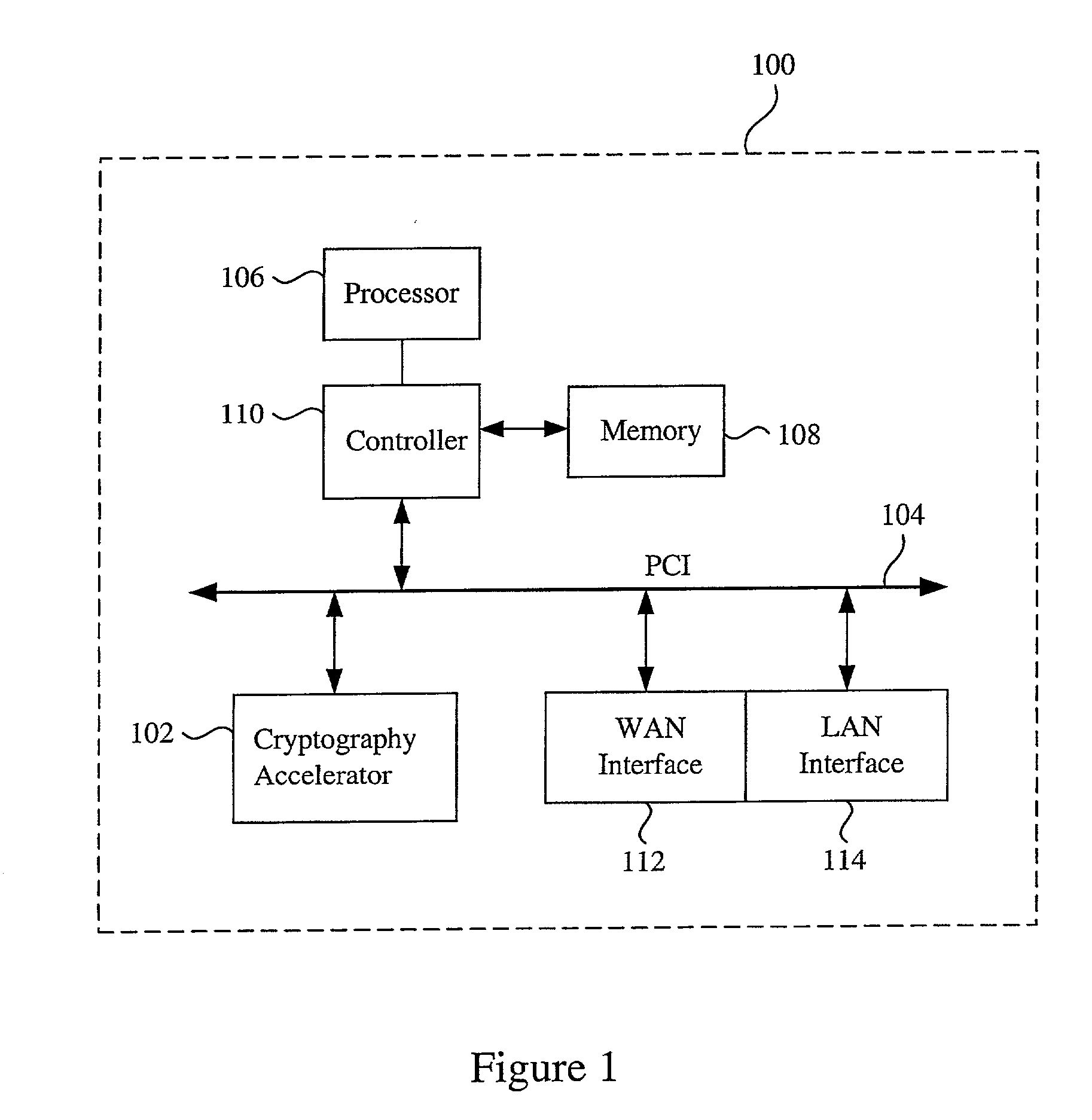
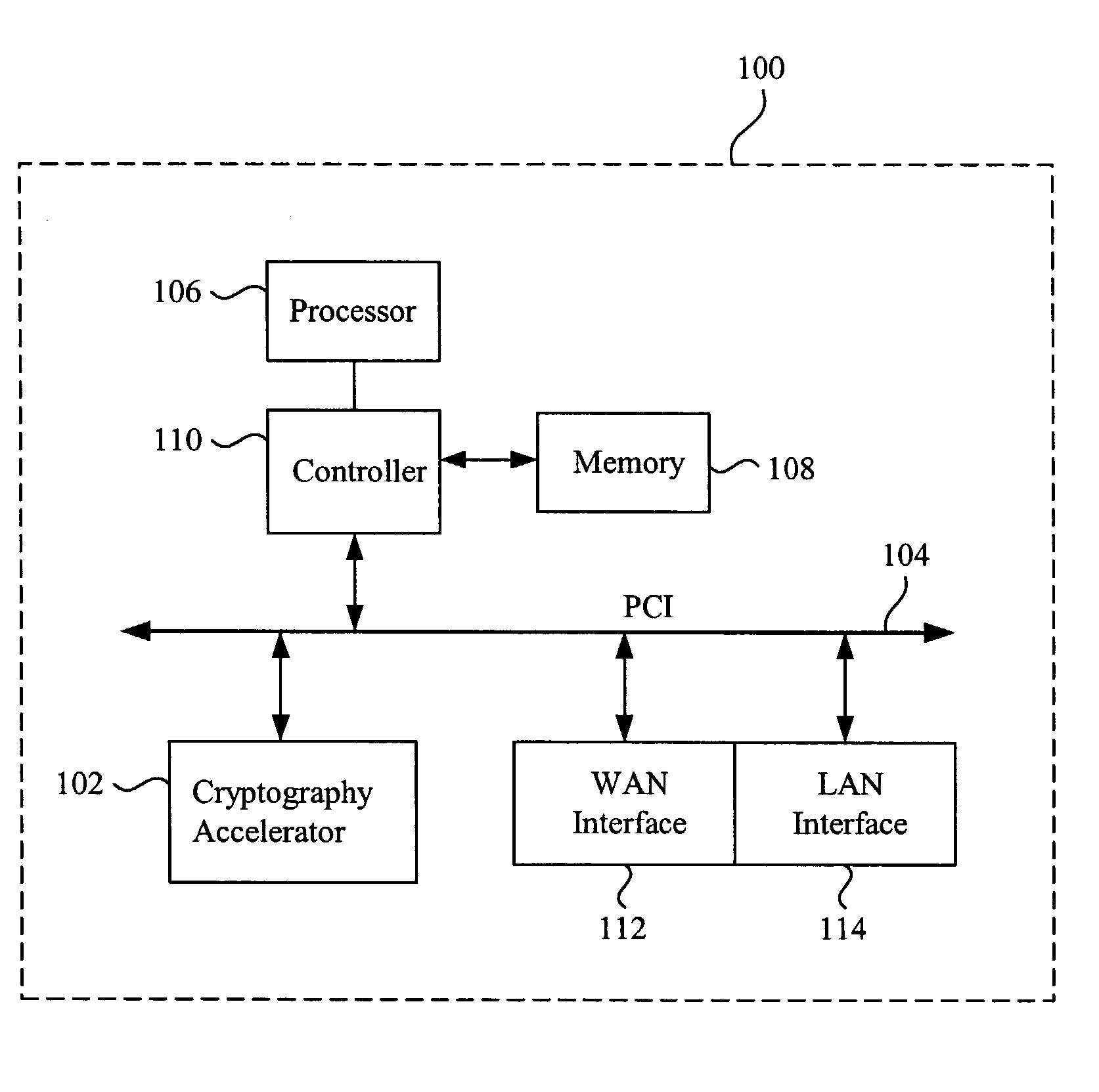
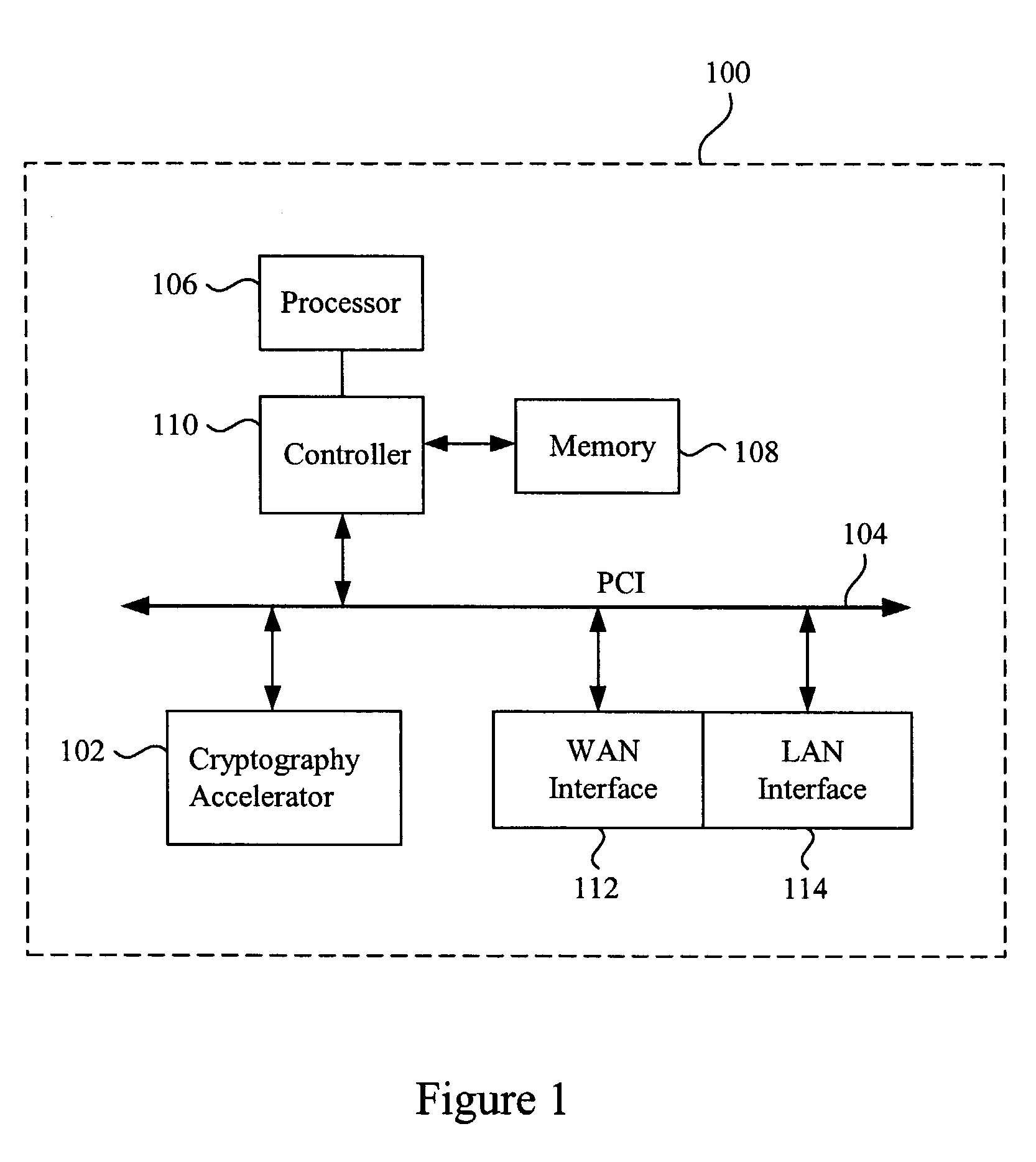
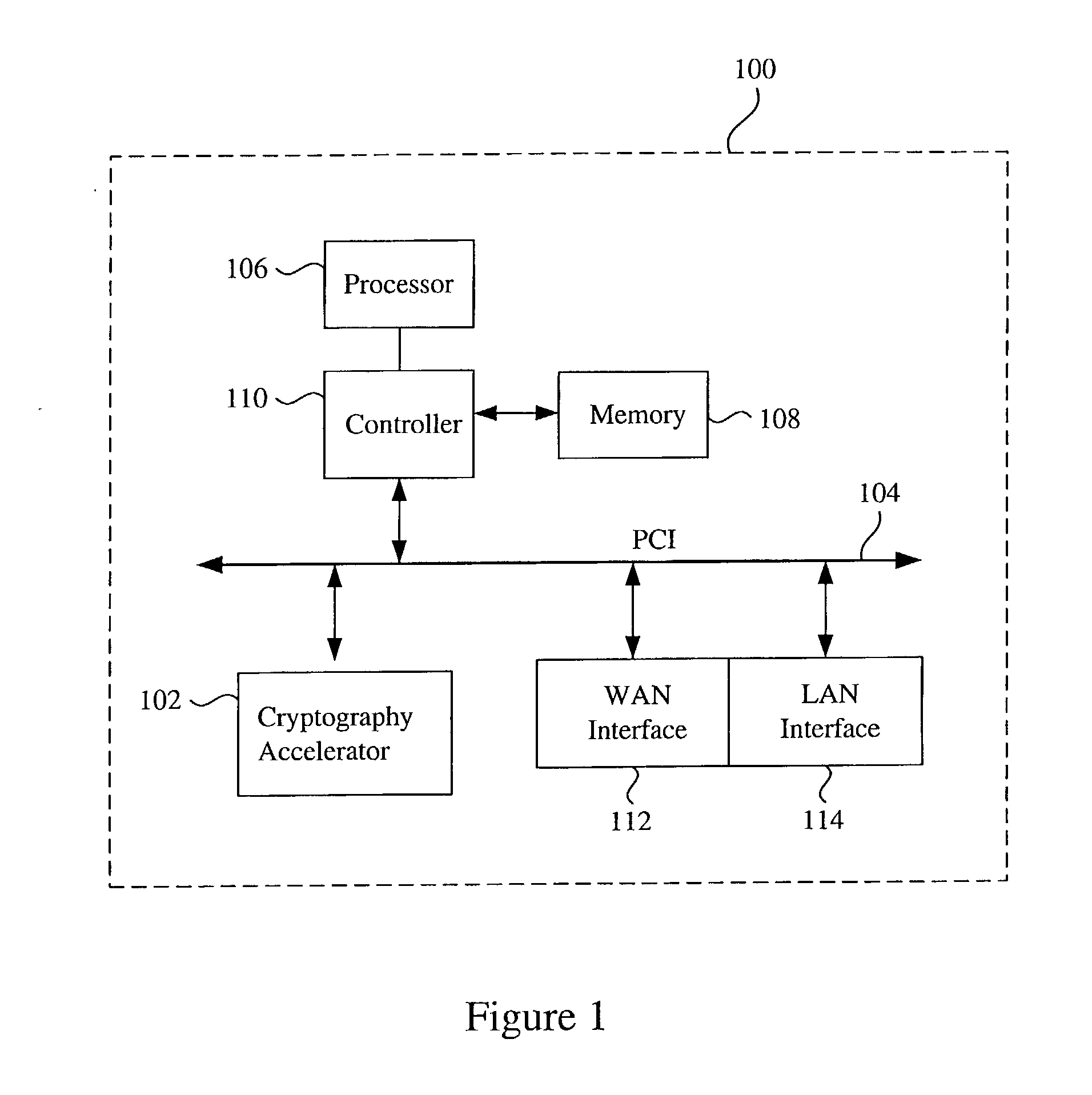
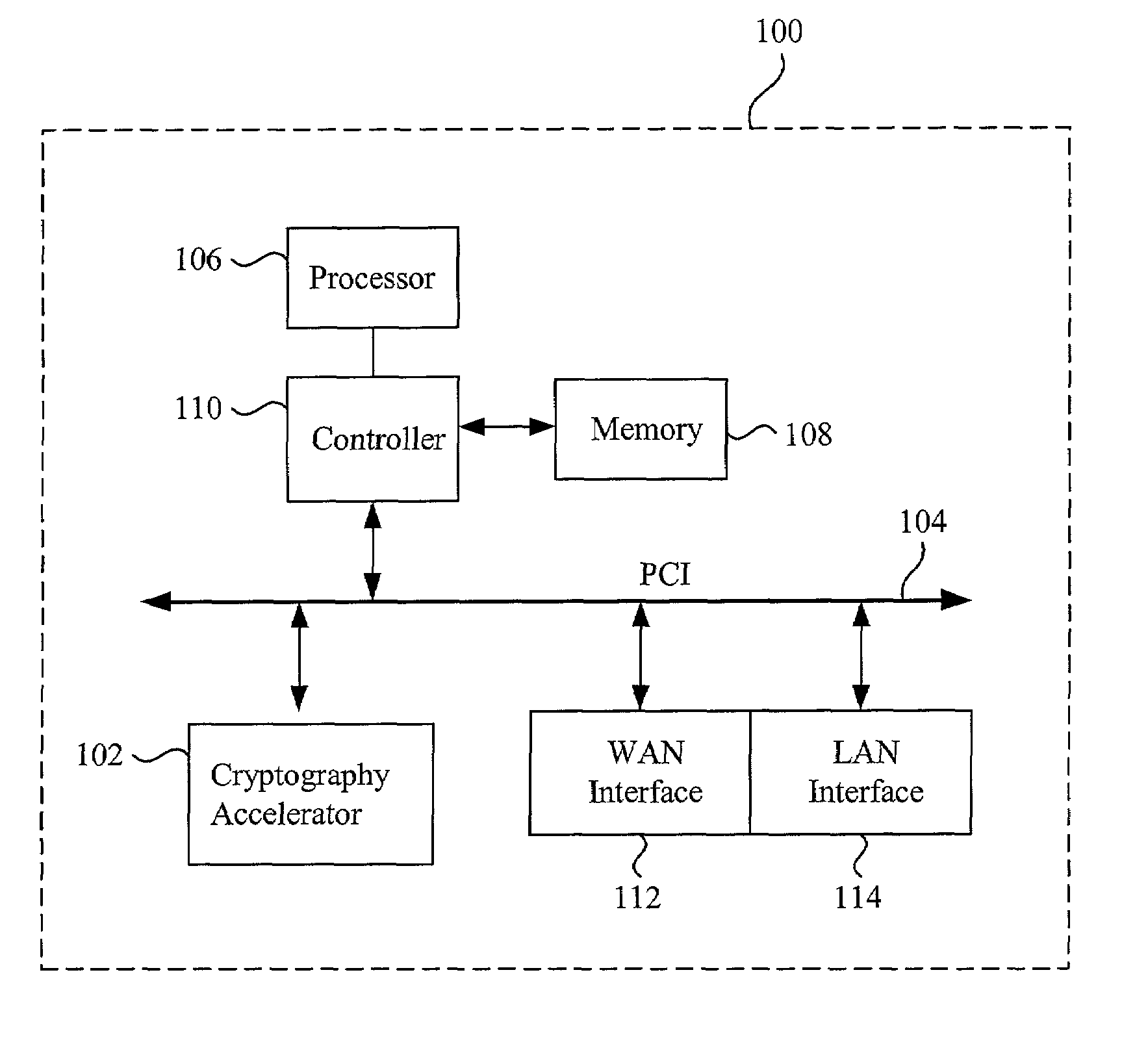
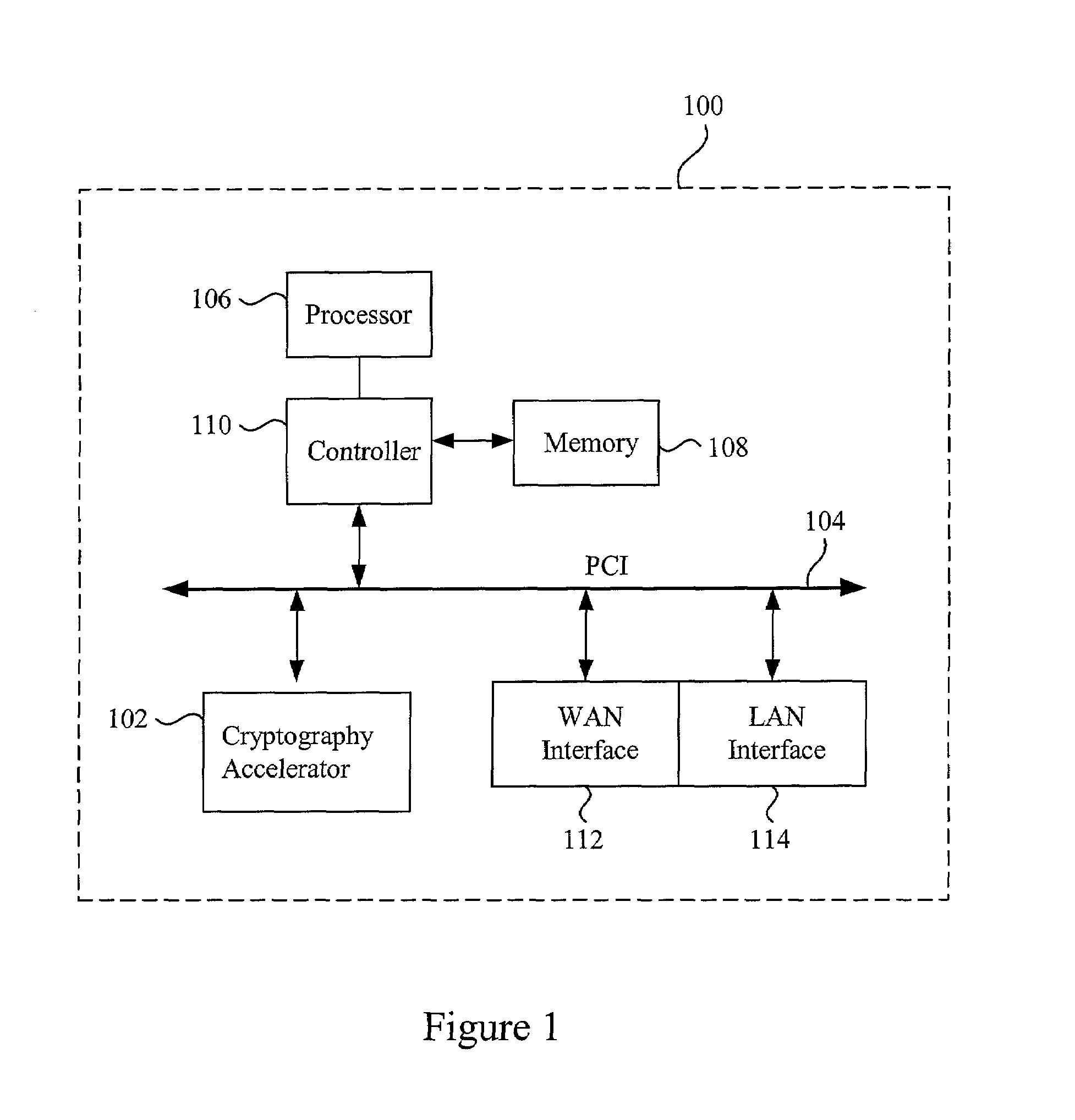
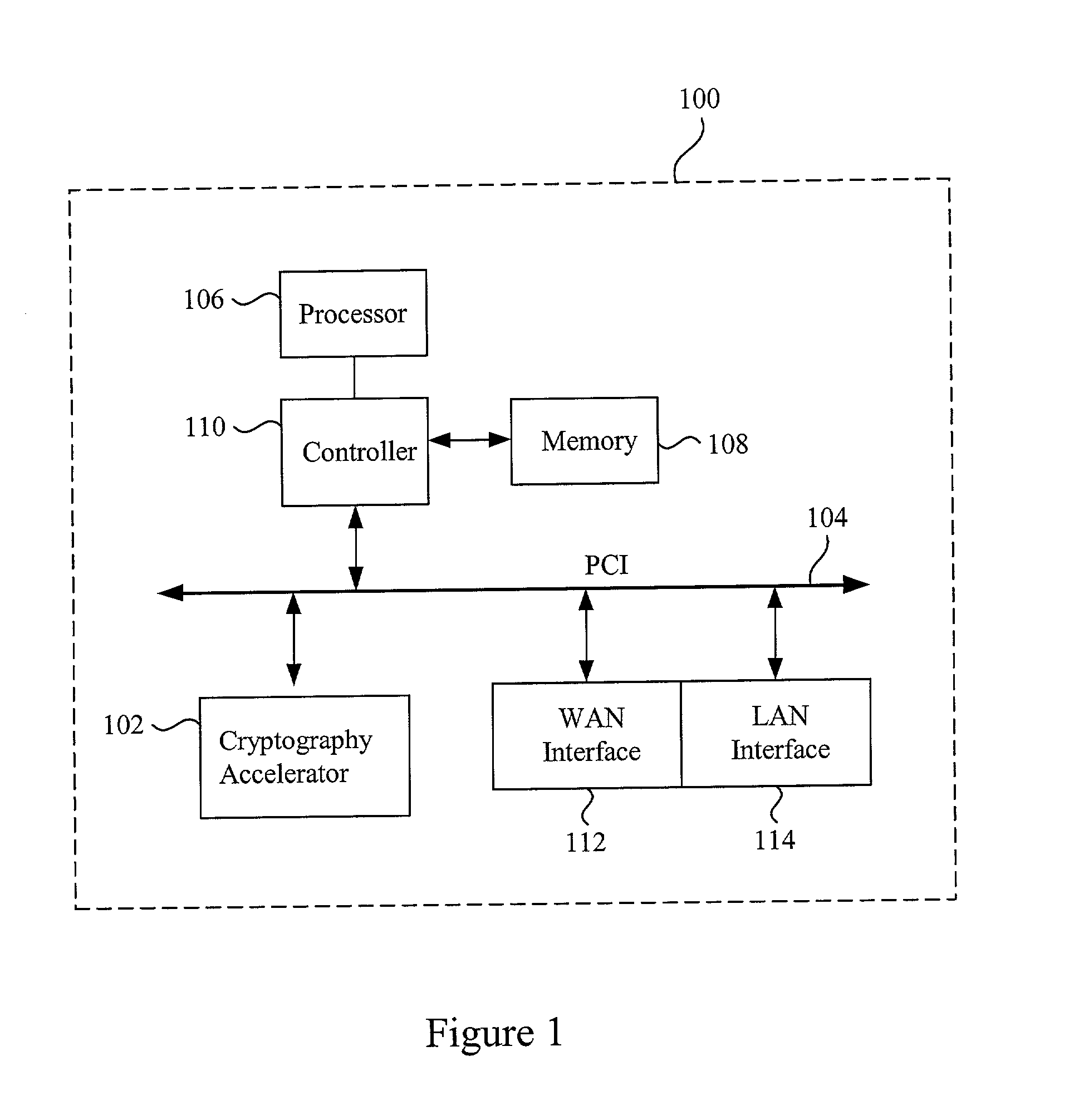
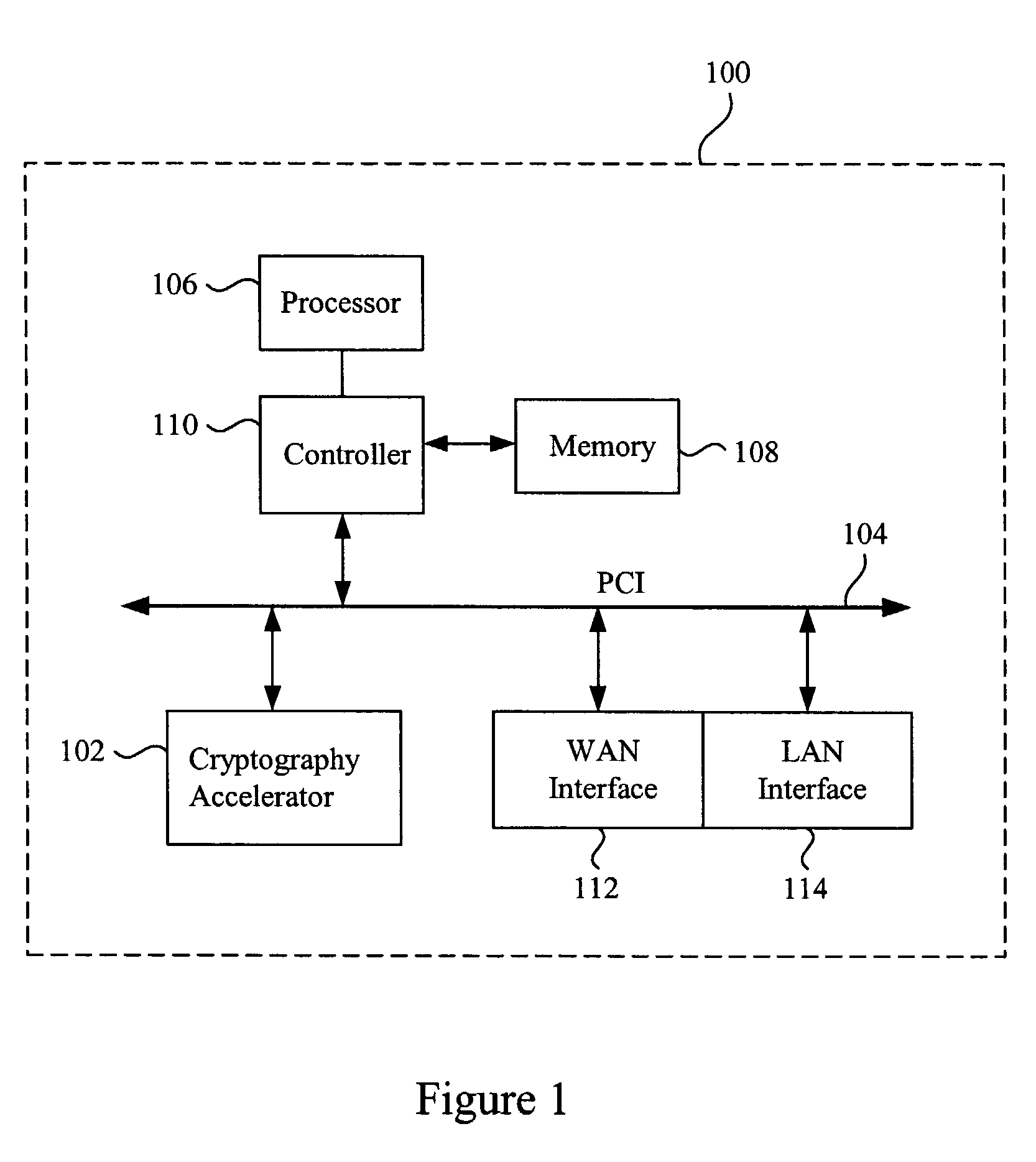
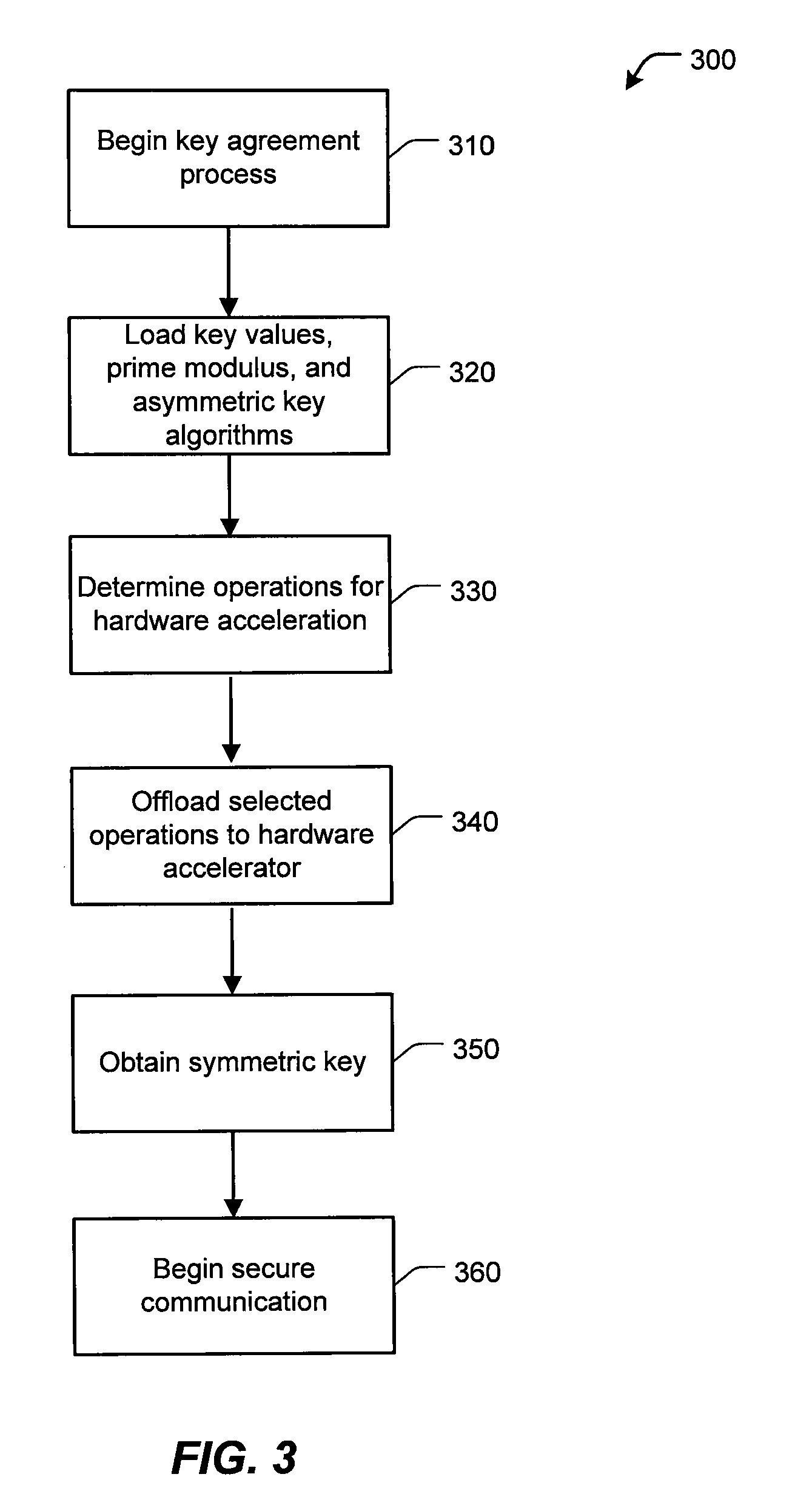
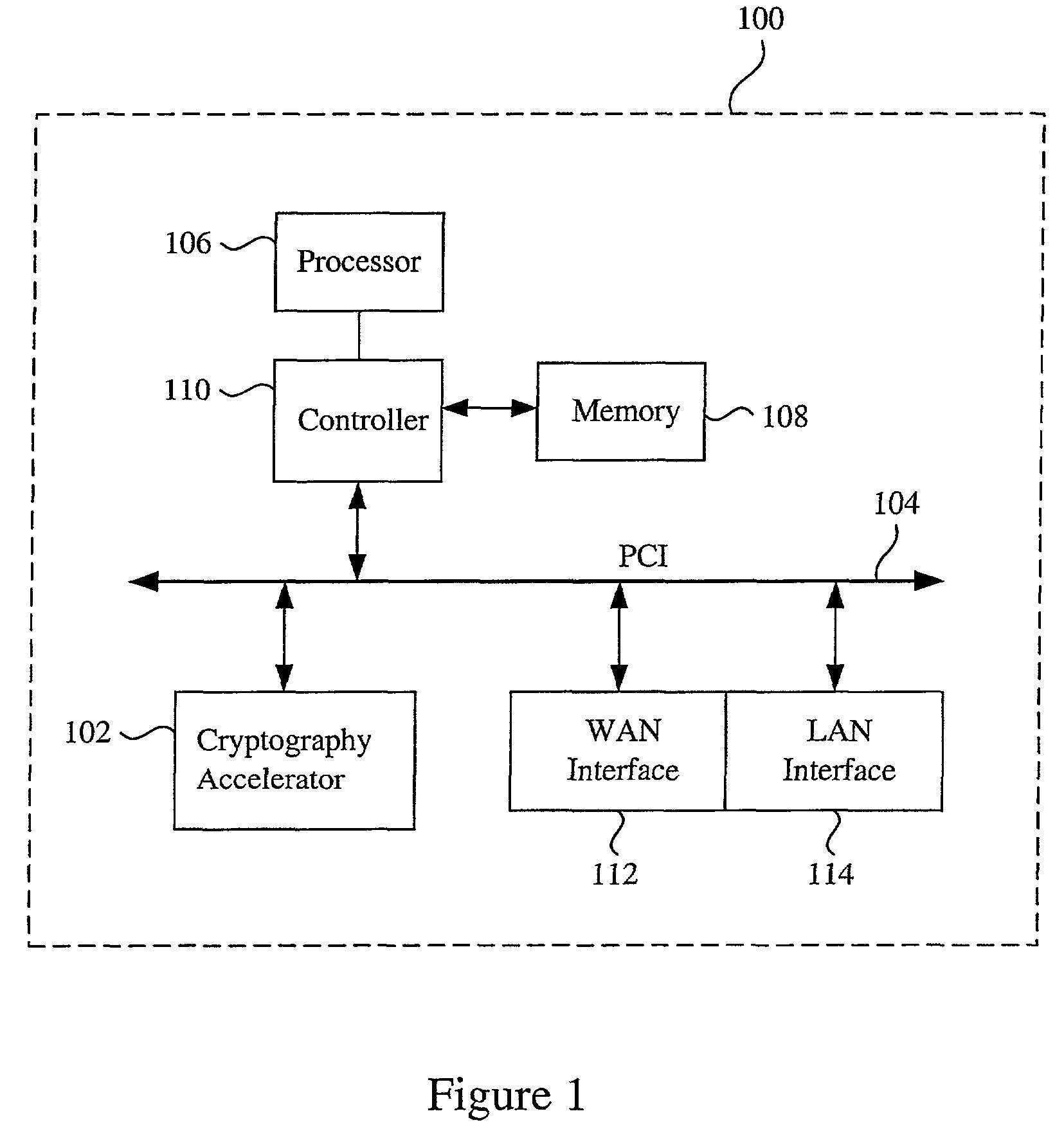
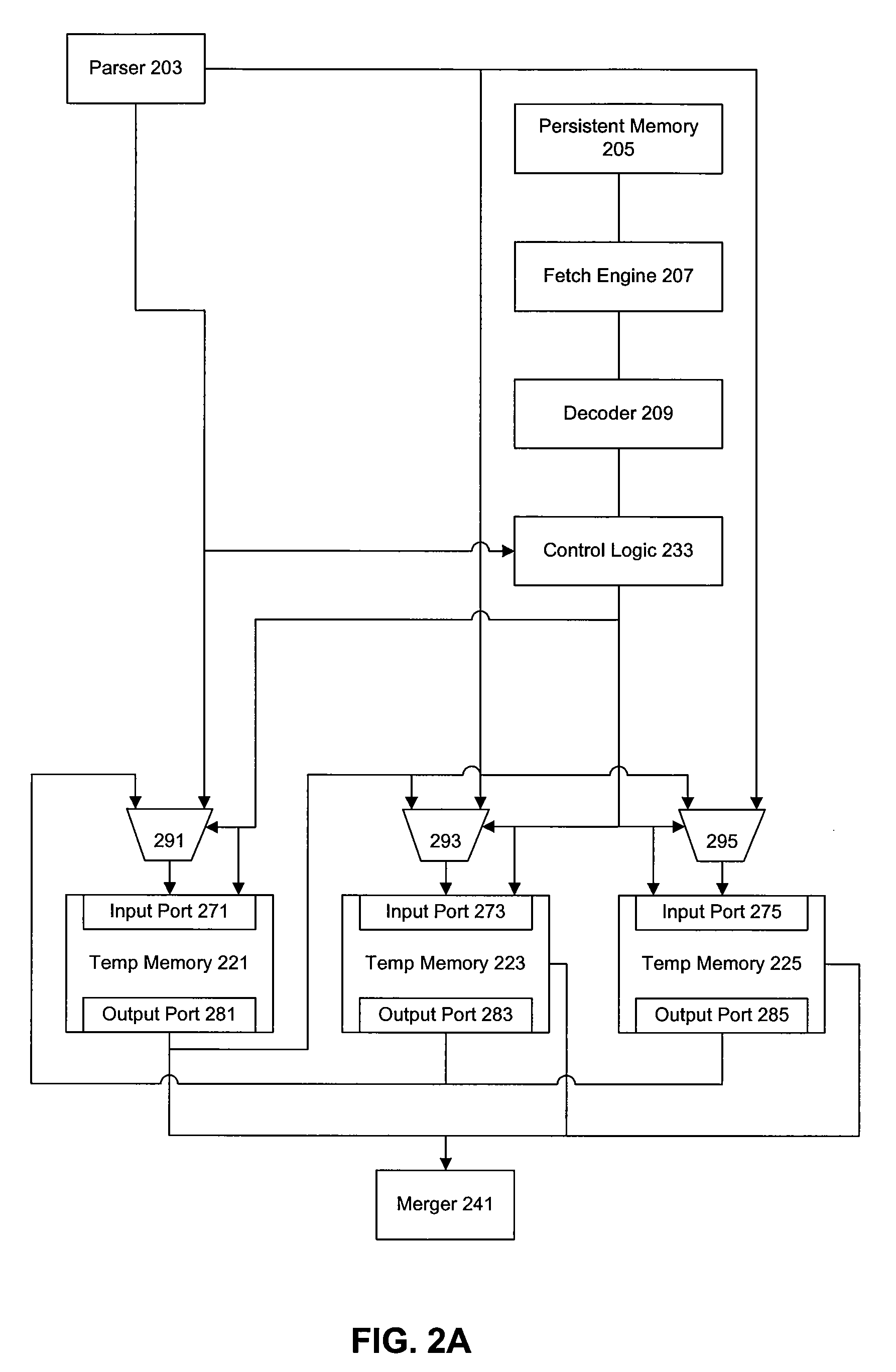
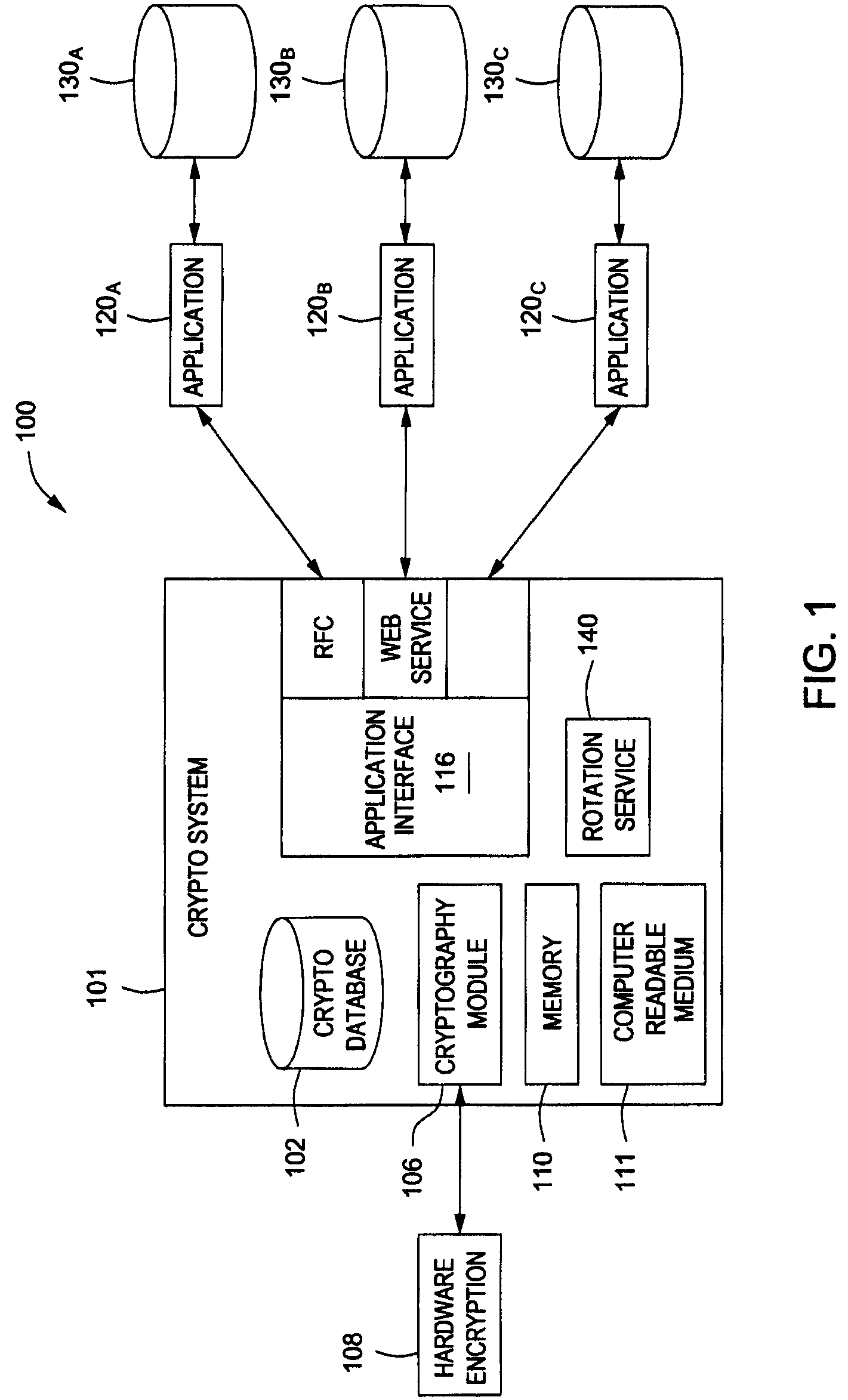
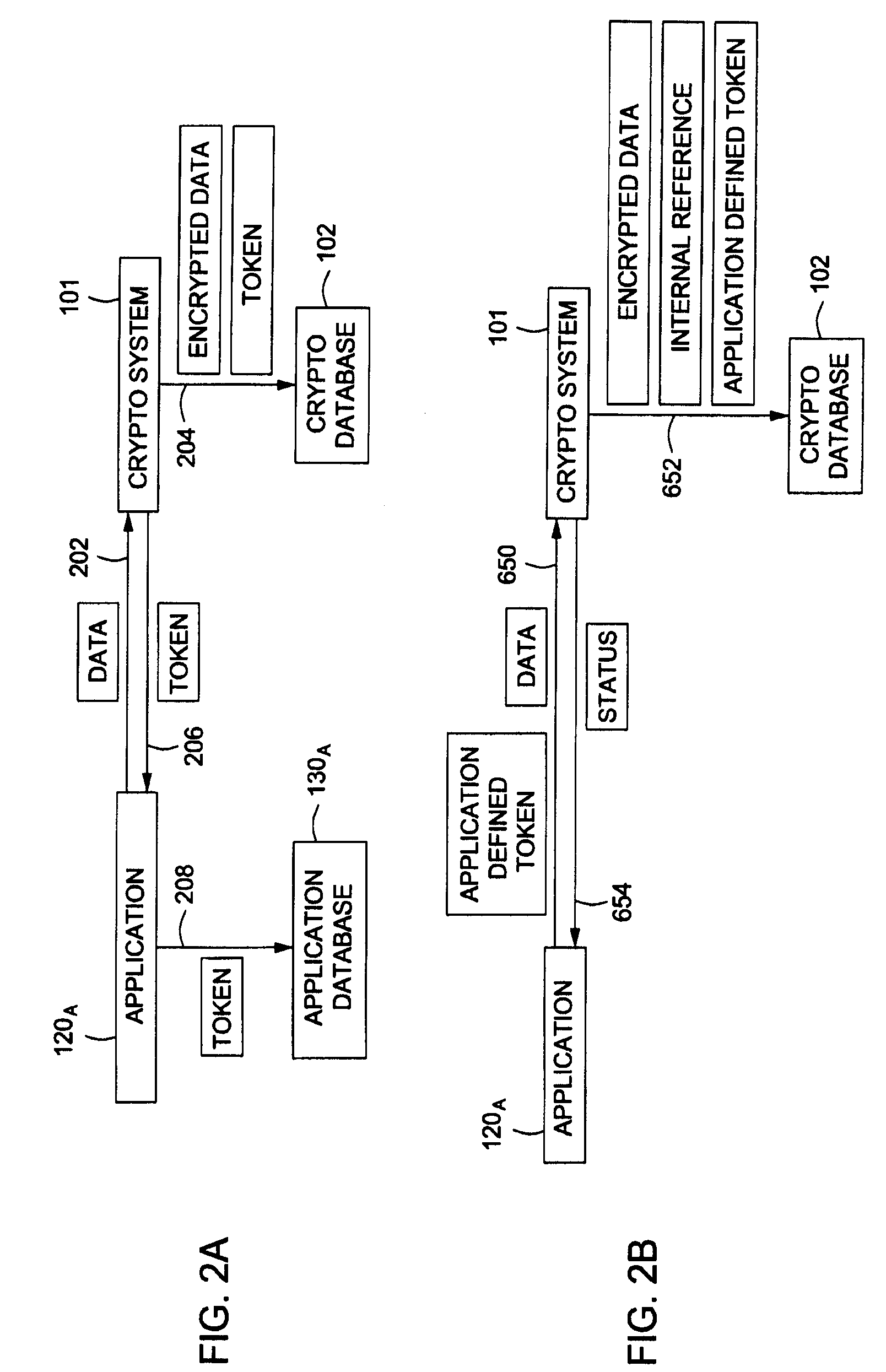
Data transfer efficiency in a cryptography accelerator system
InactiveUS20030226018A1User identity/authority verificationInternal/peripheral component protectionCryptographic acceleratorChecksum
Methods and apparatus are provided for performing authentication and decryption operations in a cryptography accelerator system. Input data passed to a cryptography accelerator from a host such a CPU includes information for a cryptography accelerator to determine where to write the processed data. In one example, processed data is formatted as packet payloads in a network buffer. Checksum information is precalculated and an offset for a header is maintained.
Owner:AVAGO TECH INT SALES PTE LTD
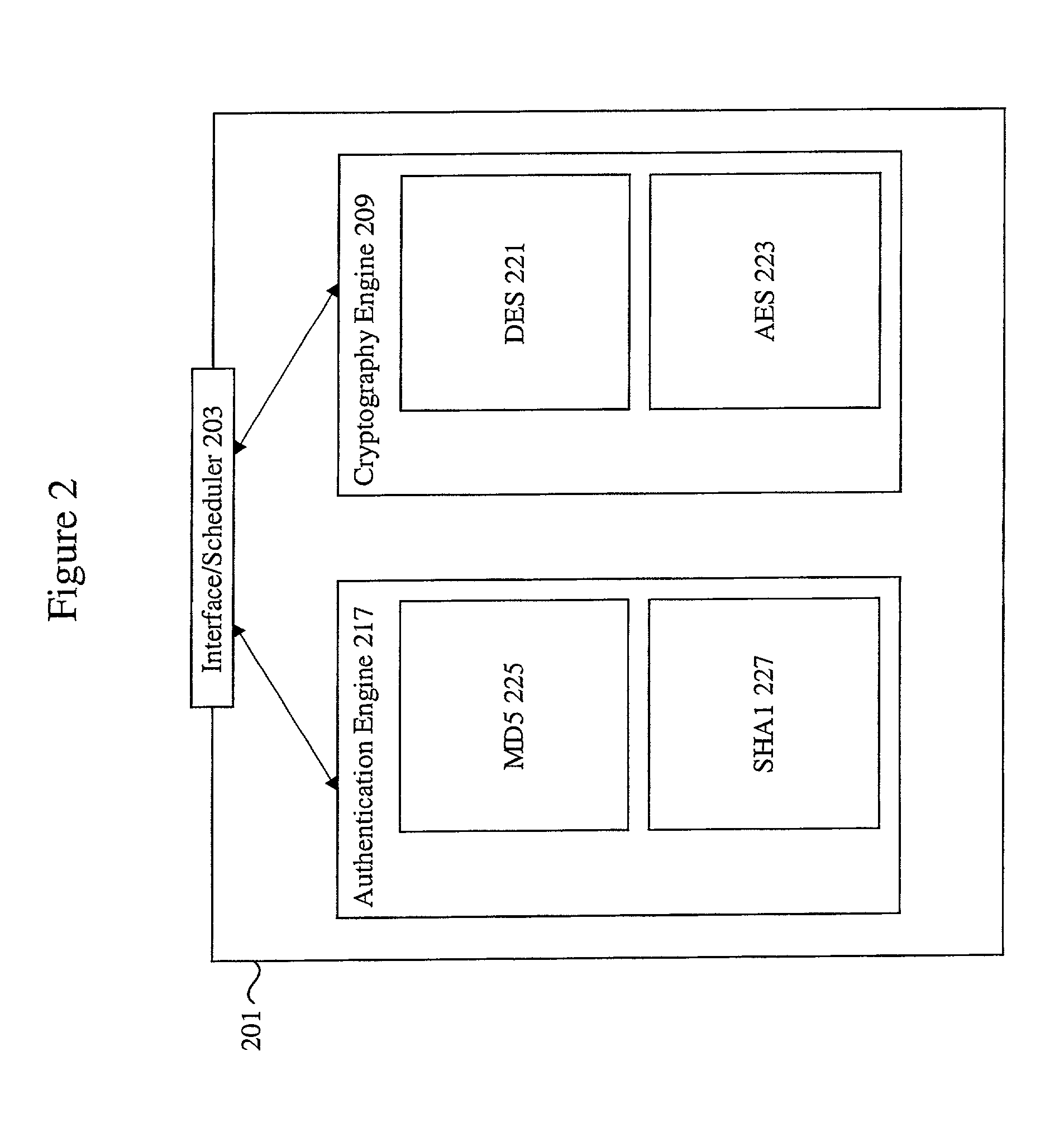
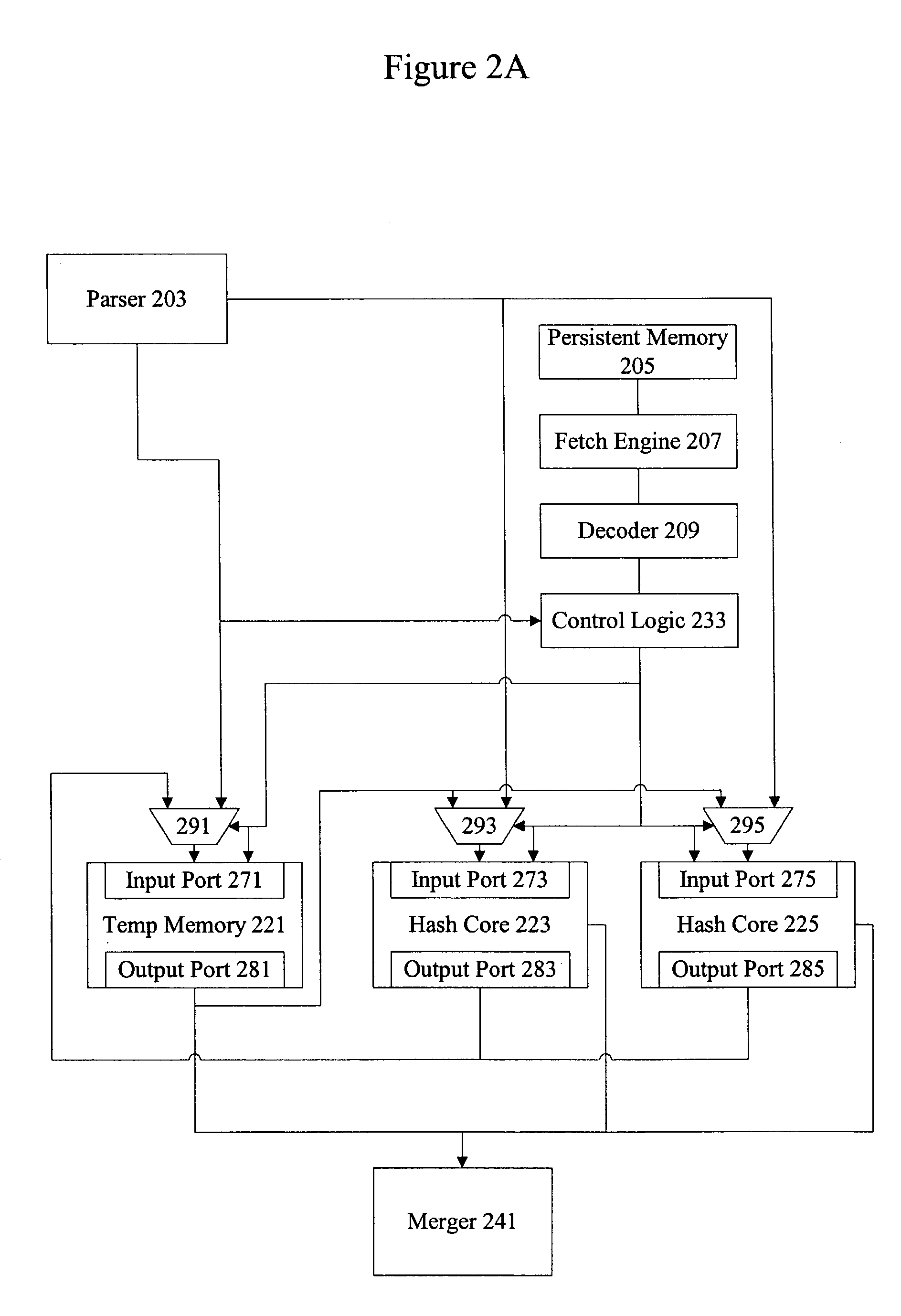
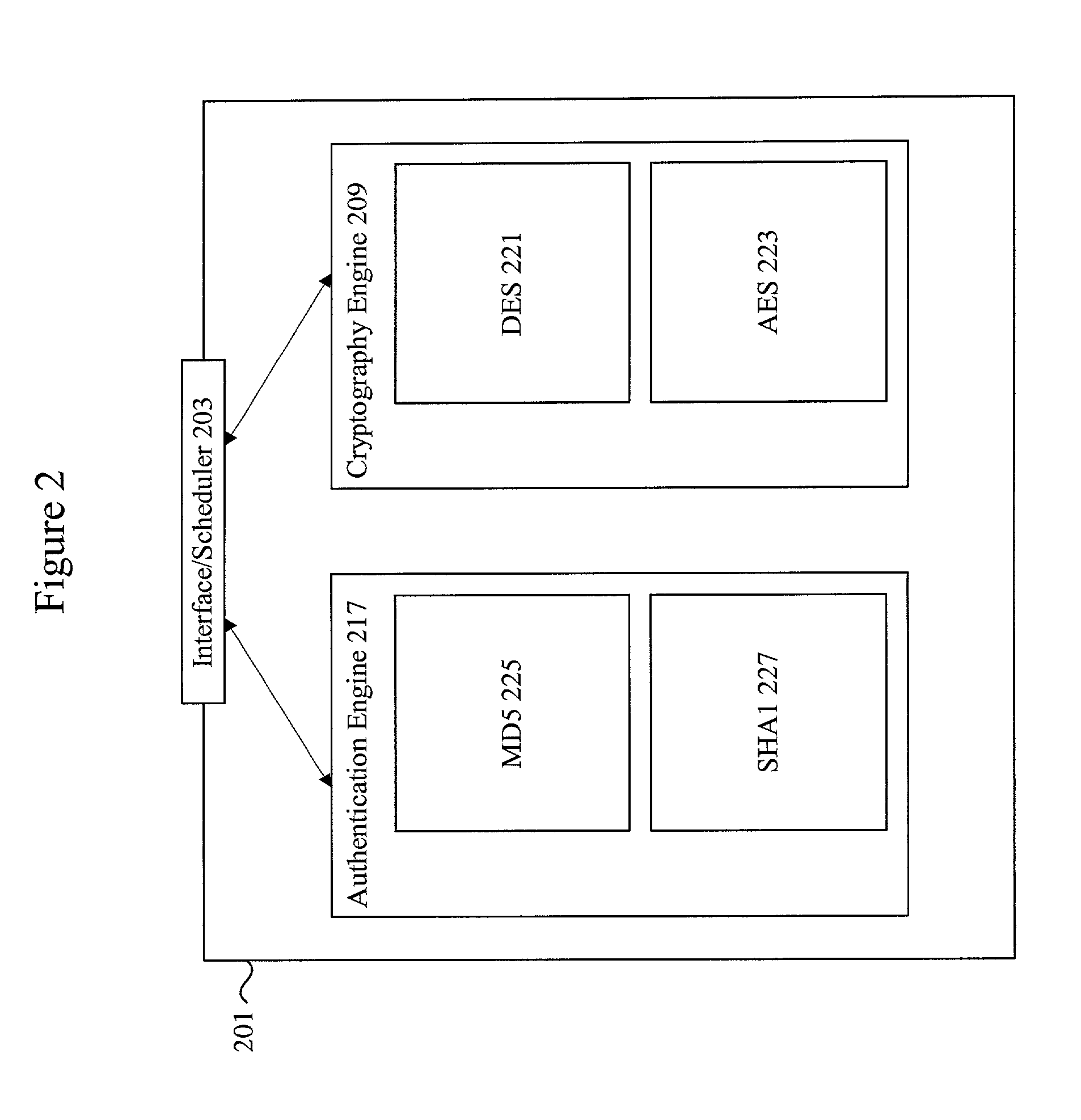
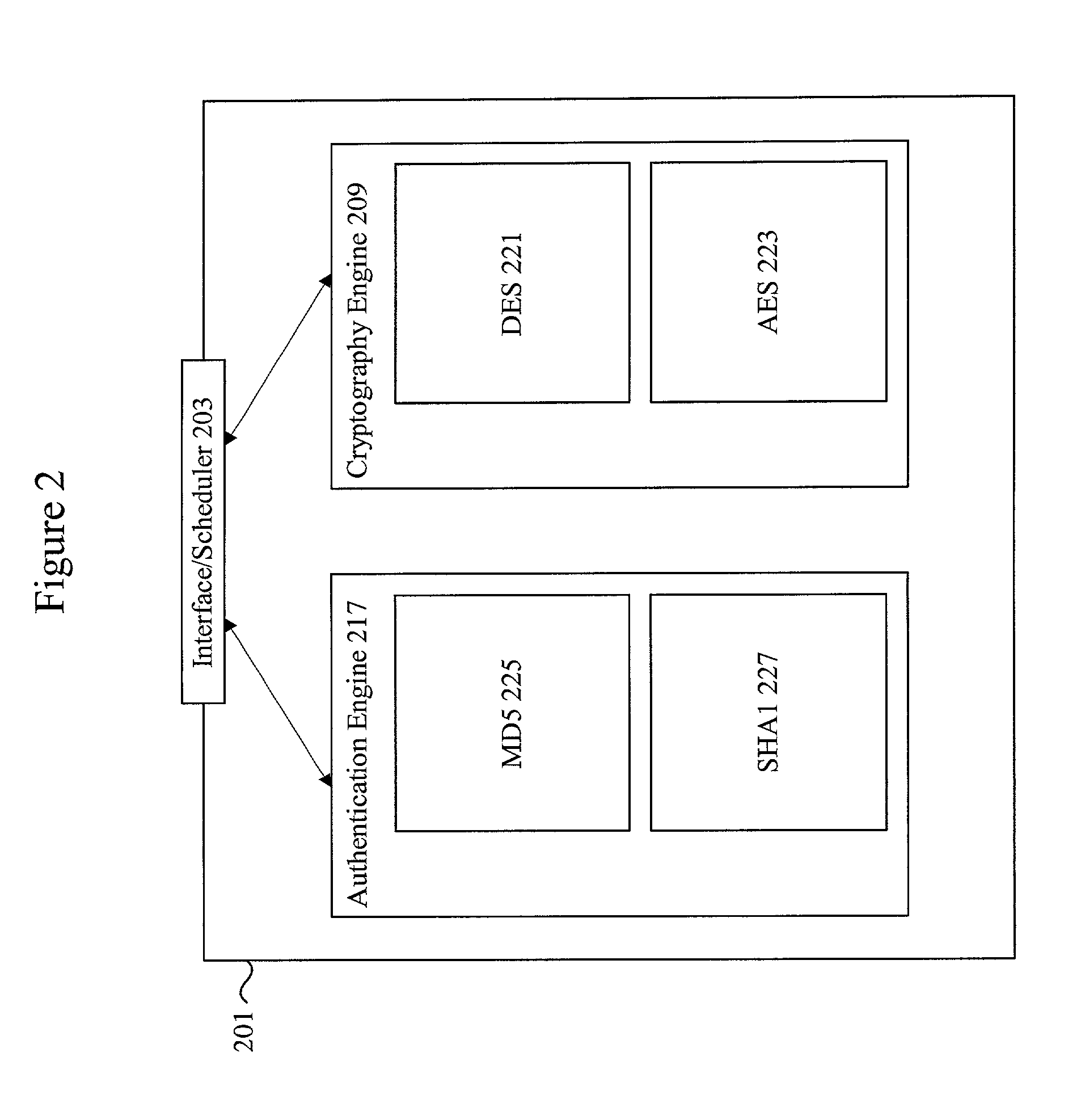
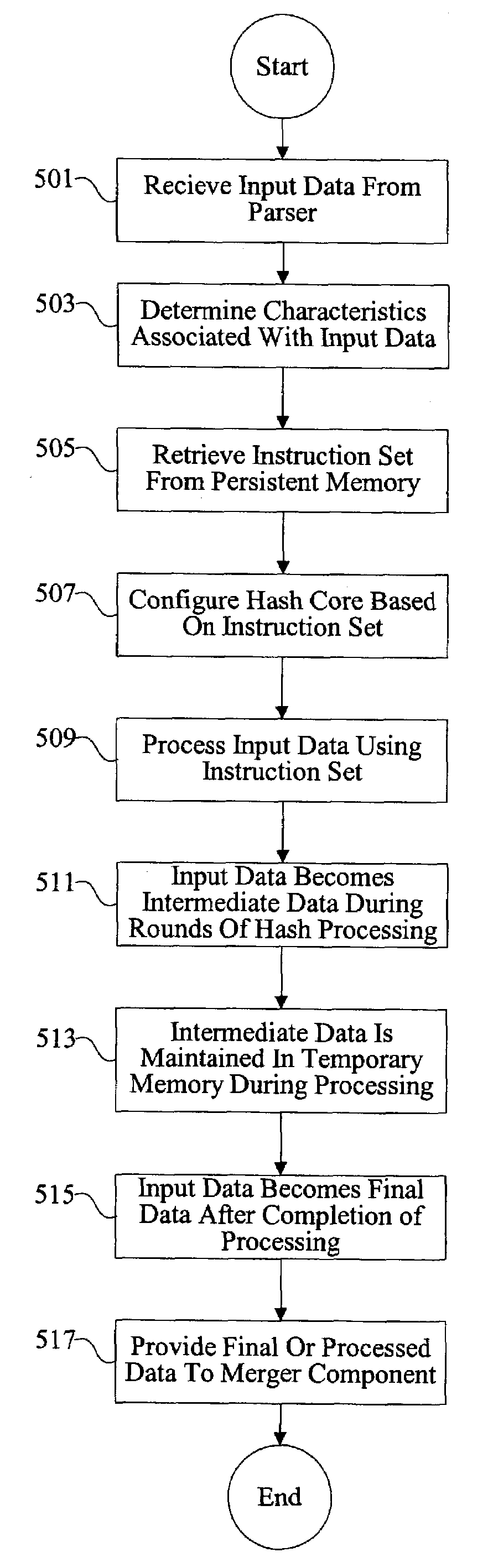
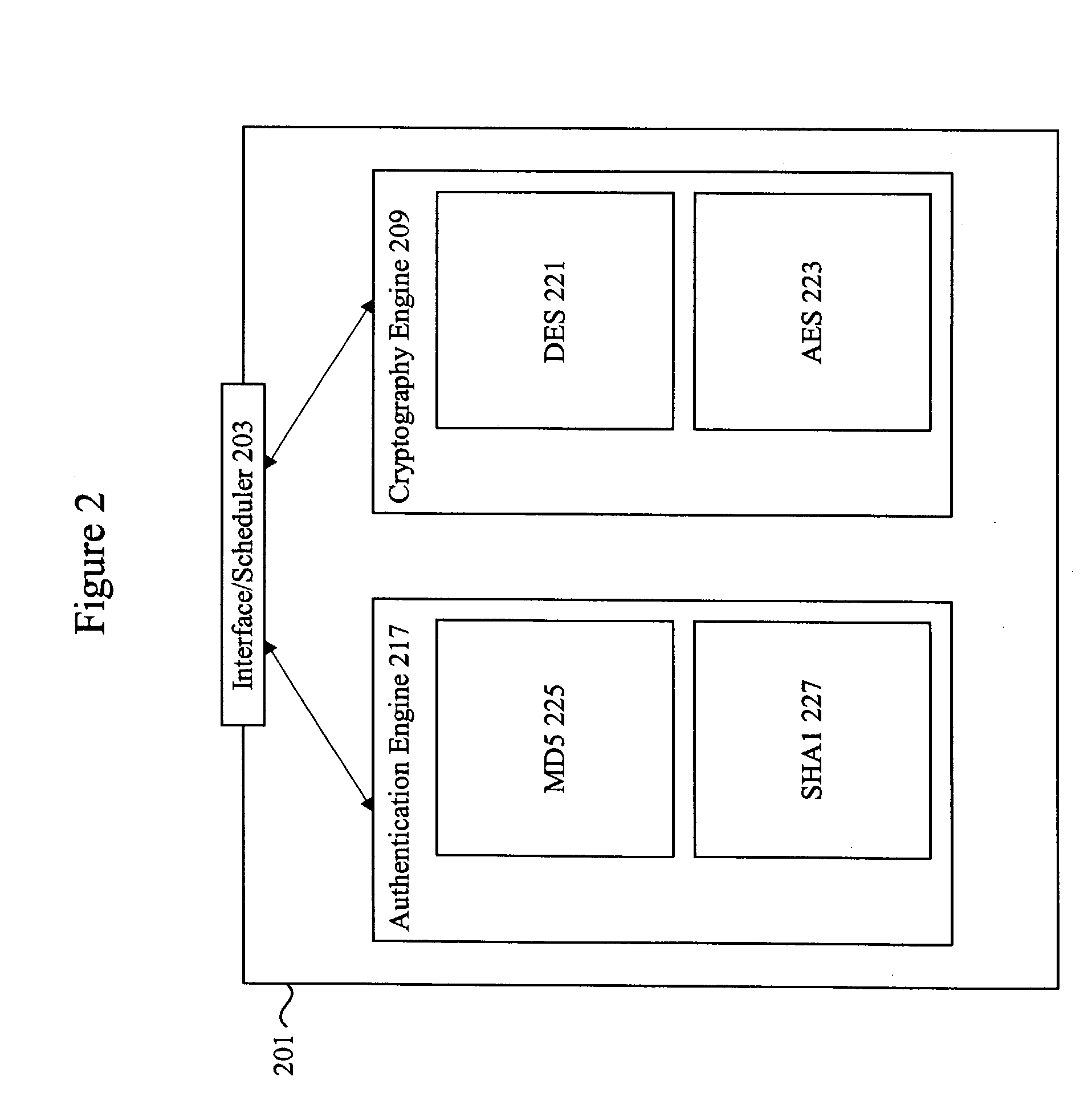
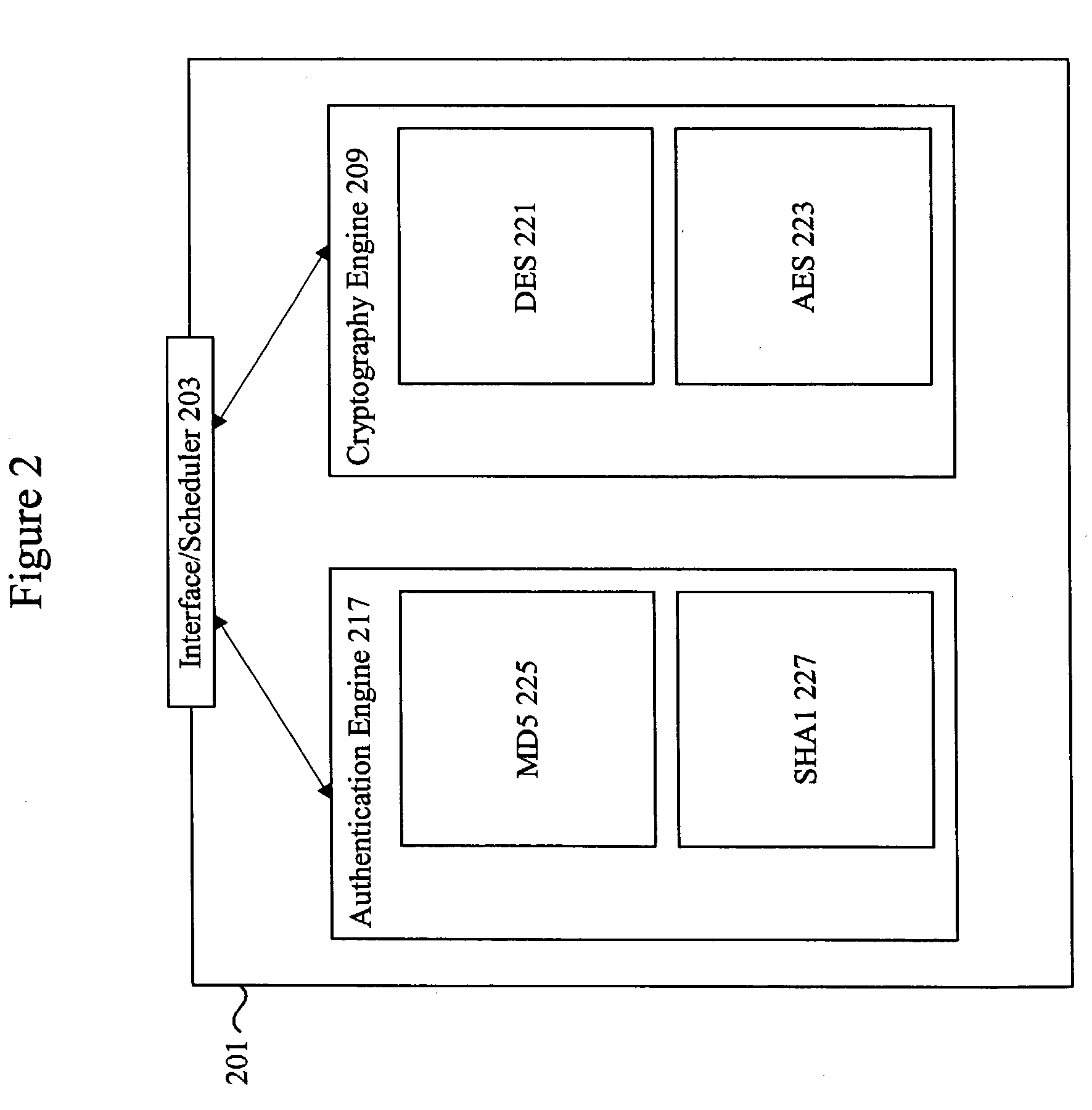
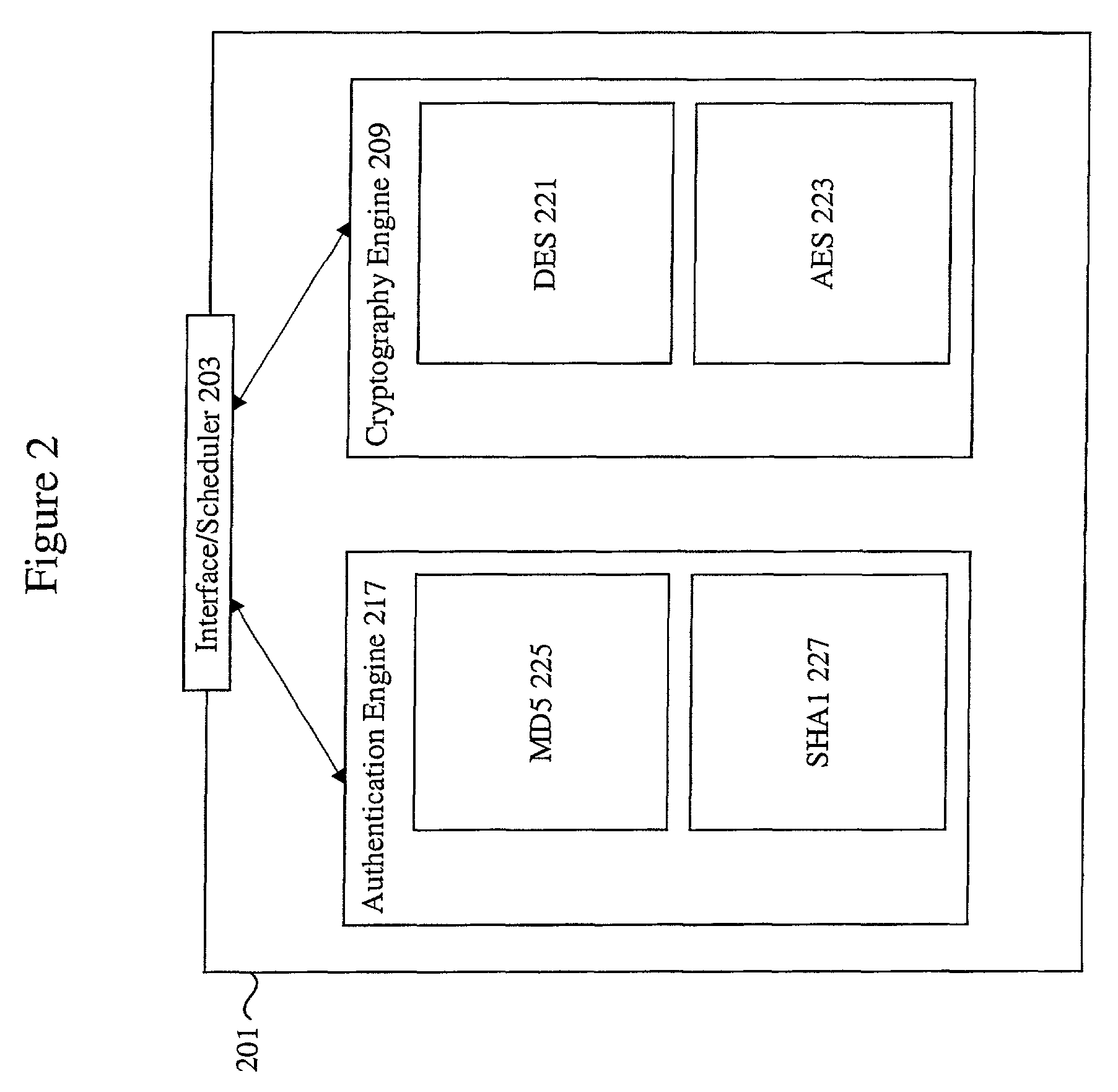
Methods and apparatus for performing hash operations in a cryptography accelerator
ActiveUS20030185391A1User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic accelerator
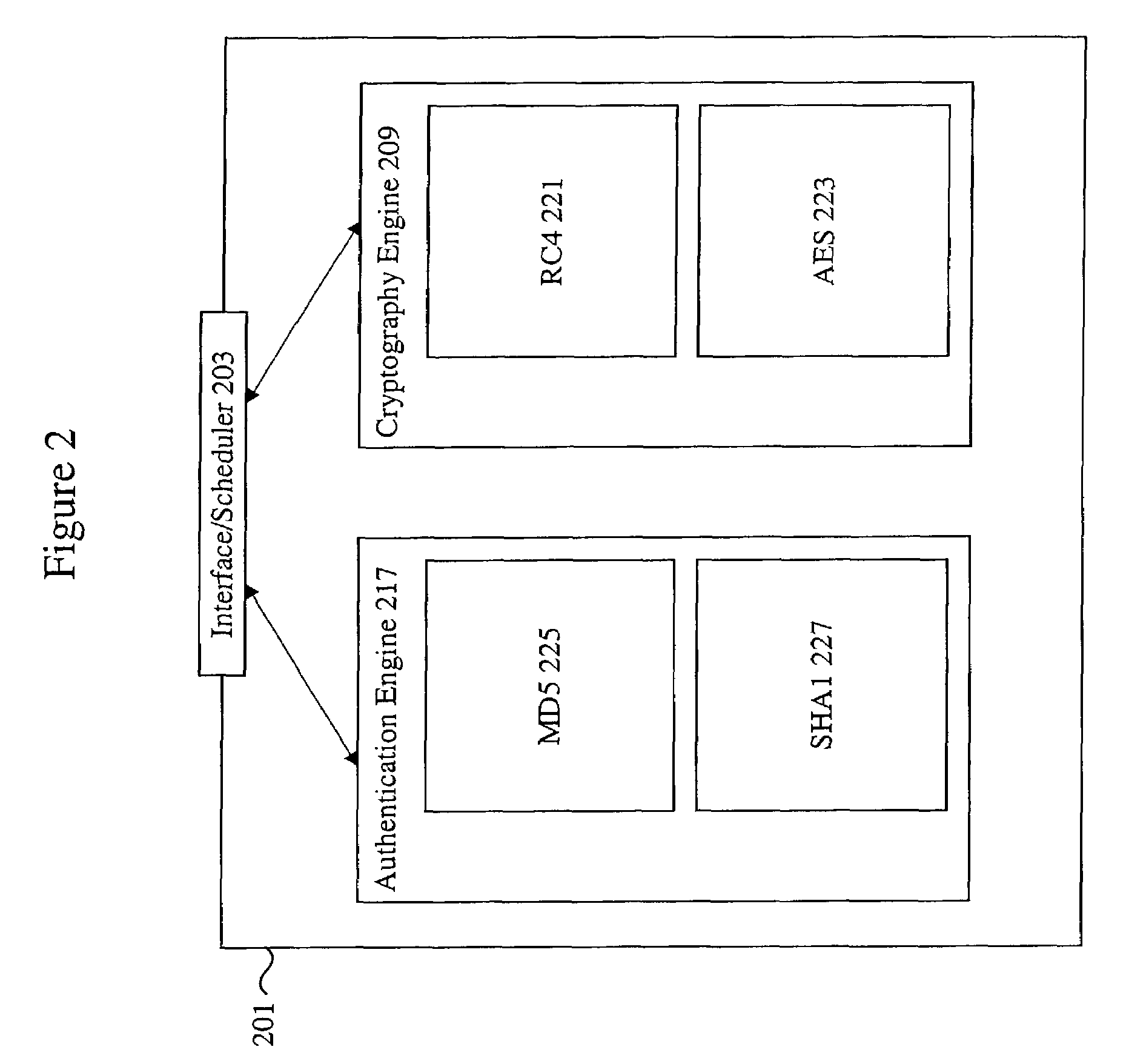
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
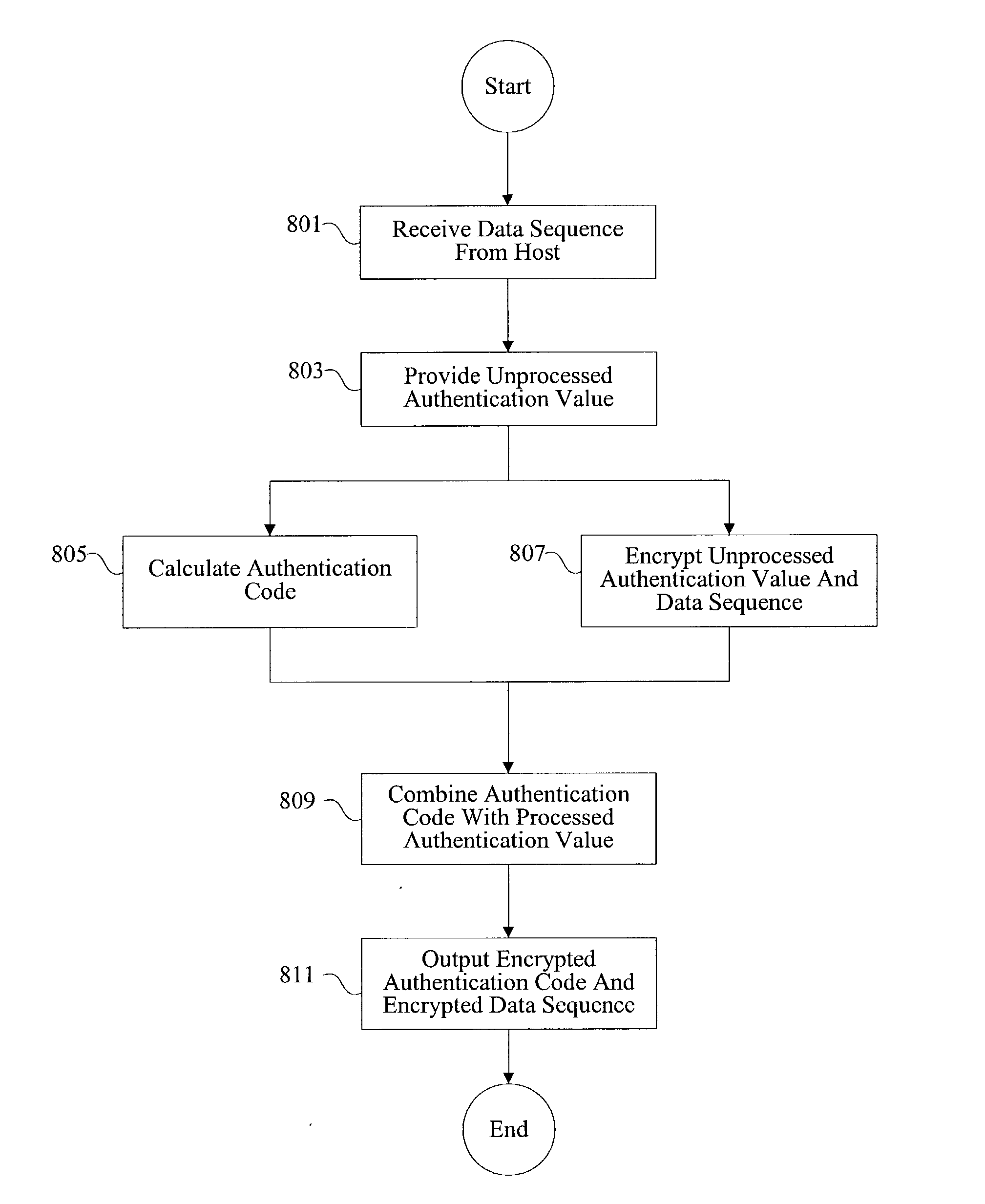
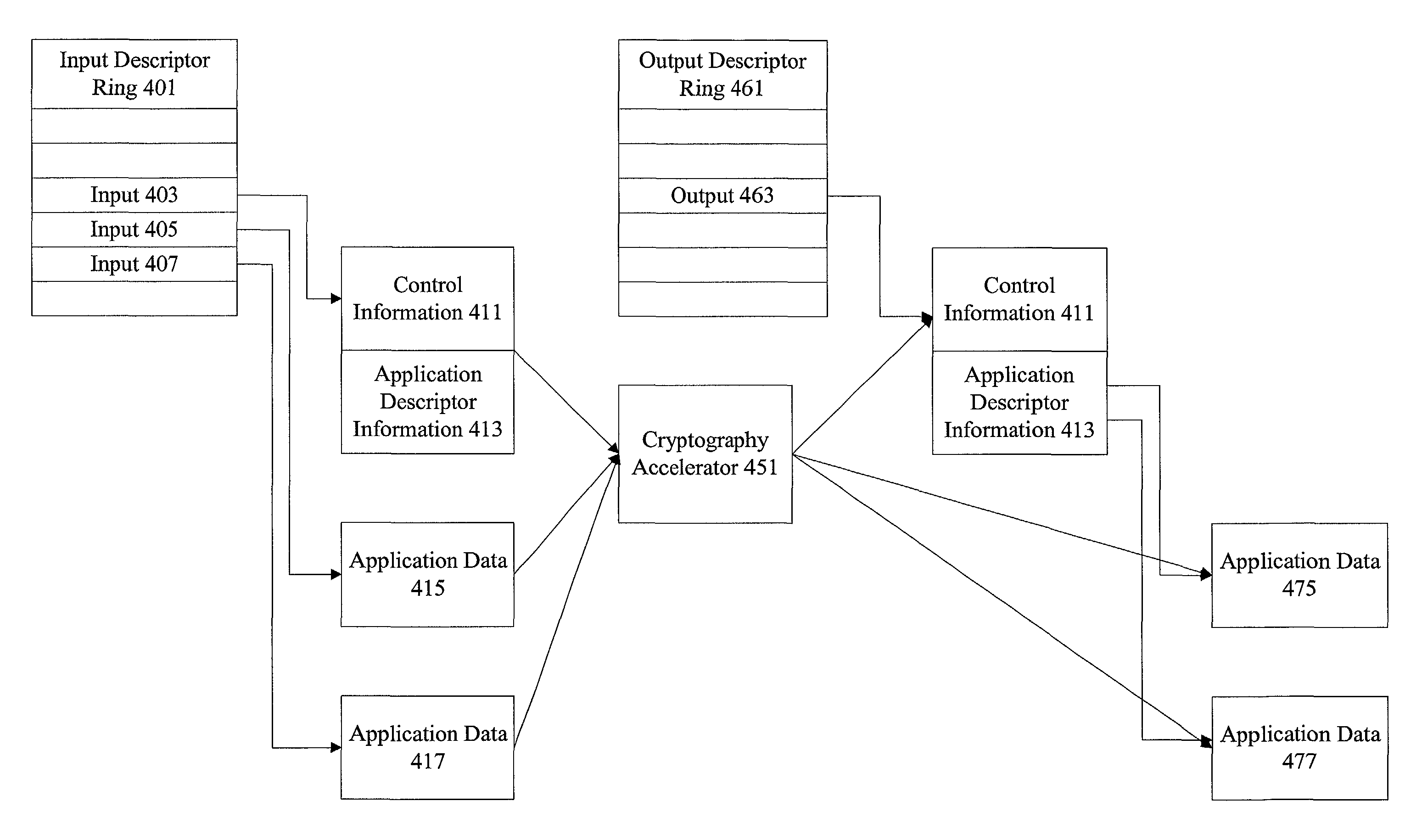
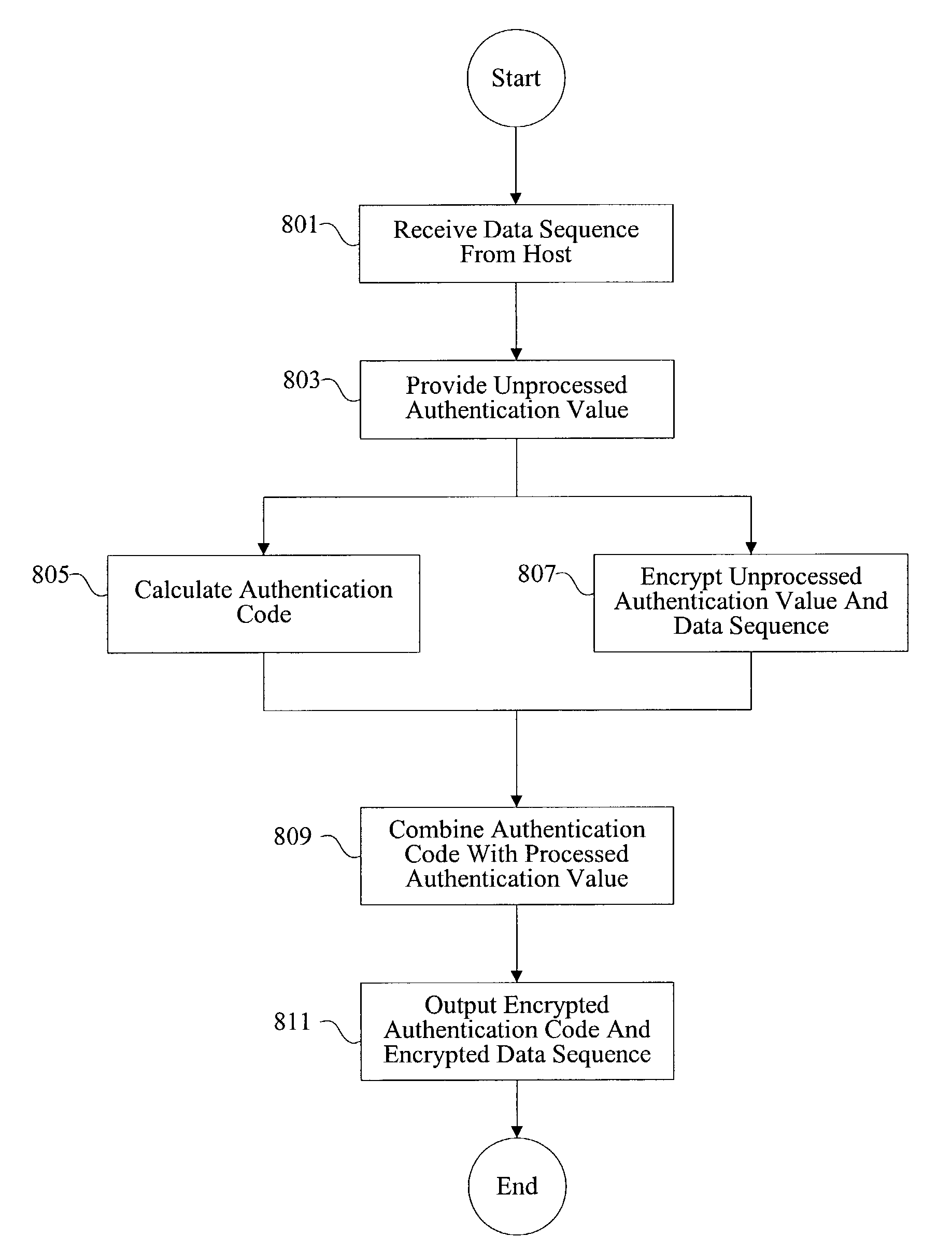
Methods and apparatus for performing encryption and authentication
InactiveUS20030223585A1User identity/authority verificationUnauthorized memory use protectionCryptographic acceleratorData sequences
Methods and apparatus are provided for a cryptography accelerator to efficiently perform authentication and encryption operations. A data sequence is received at a cryptography accelerator. An encrypted authentication code and an encrypted data sequence is provided efficiently upon performing single pass authentication and encryption operations on the data sequence.
Owner:AVAGO TECH INT SALES PTE LTD
Virtualized shared security engine and creation of a protected zone
ActiveUS7634650B1Error detection/correctionUser identity/authority verificationInternal managementCryptographic accelerator
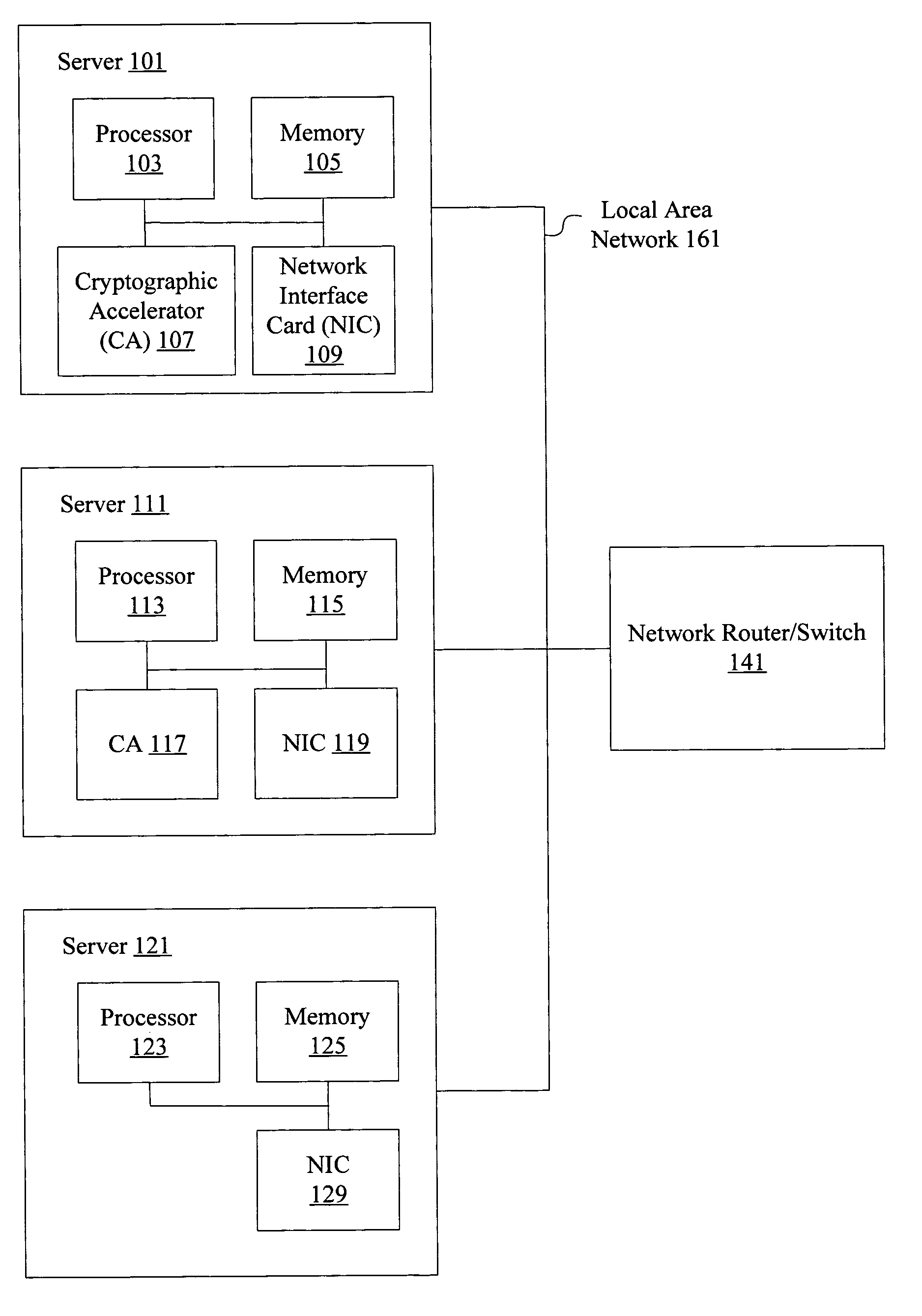
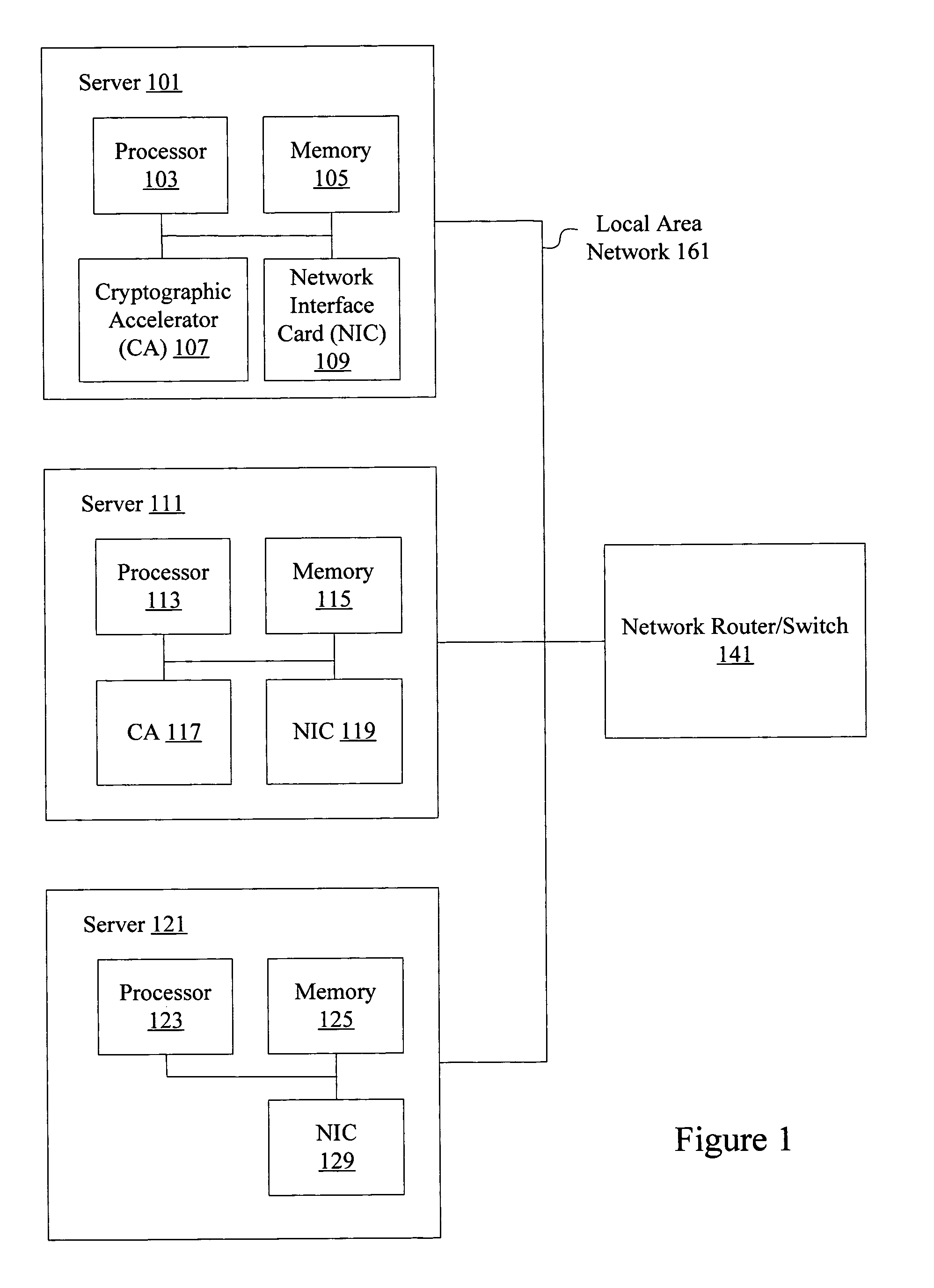
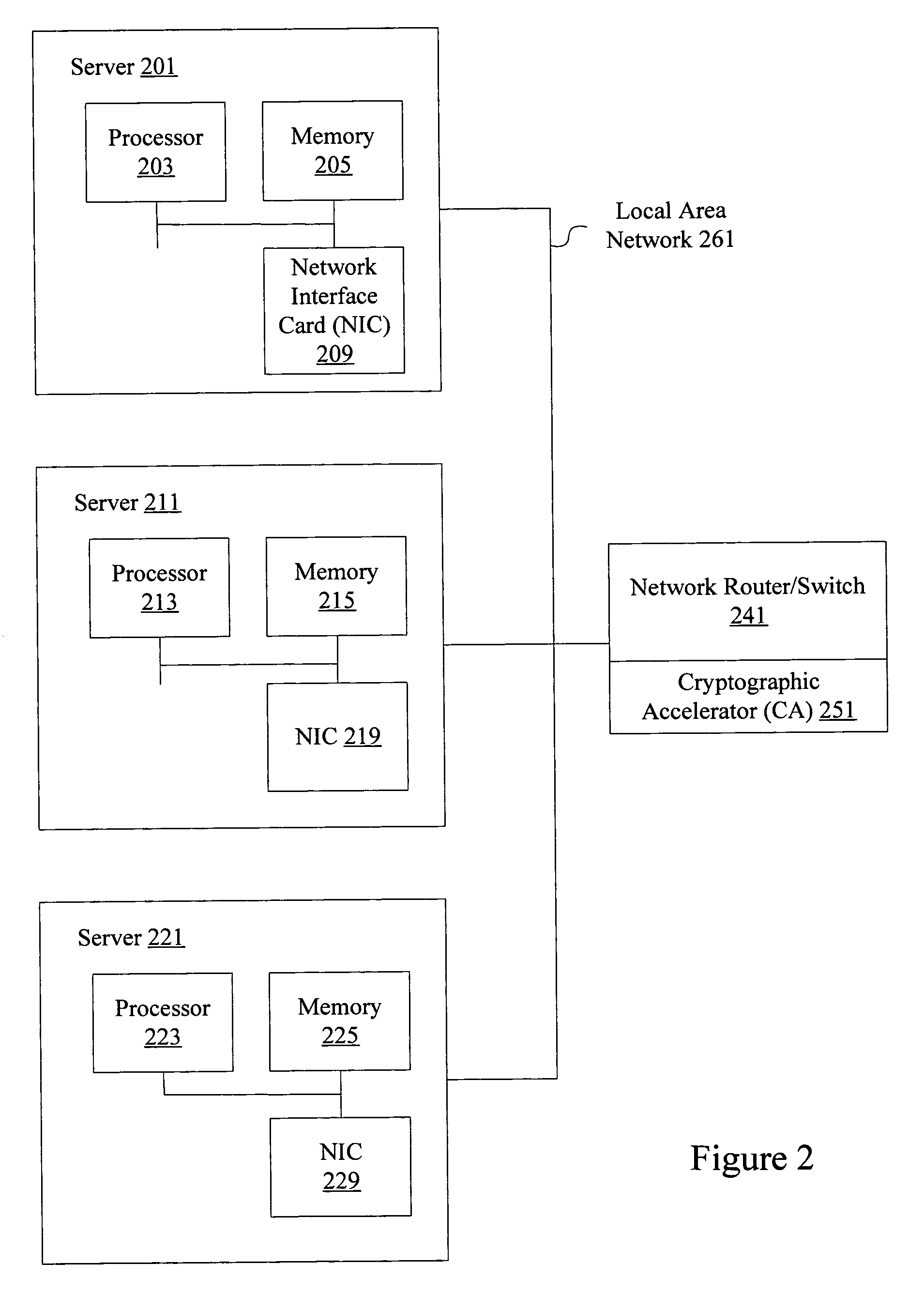
Methods and apparatus are provided for creating a secure zone having multiple servers connected to a resource virtualization switch through I / O bus interfaces, such as PCI Express or PCI-AS. Servers connected to the resource virtualization switch using I / O bus interfaces share access to one or more virtualized cryptographic accelerators associated with the resource virtualization switch. Applications on a server or system images running on hypervisor inside server can use cryptographic accelerators associated with the resource virtualization switch as though the resources were included in the server itself. Connections between multiple servers and the resource virtualization switch are secure non-broadcast connections. Data provided to a resource virtualization switch can be cryptographically processed using one or more shared and virtualized cryptographic accelerators.
Owner:ORACLE INT CORP
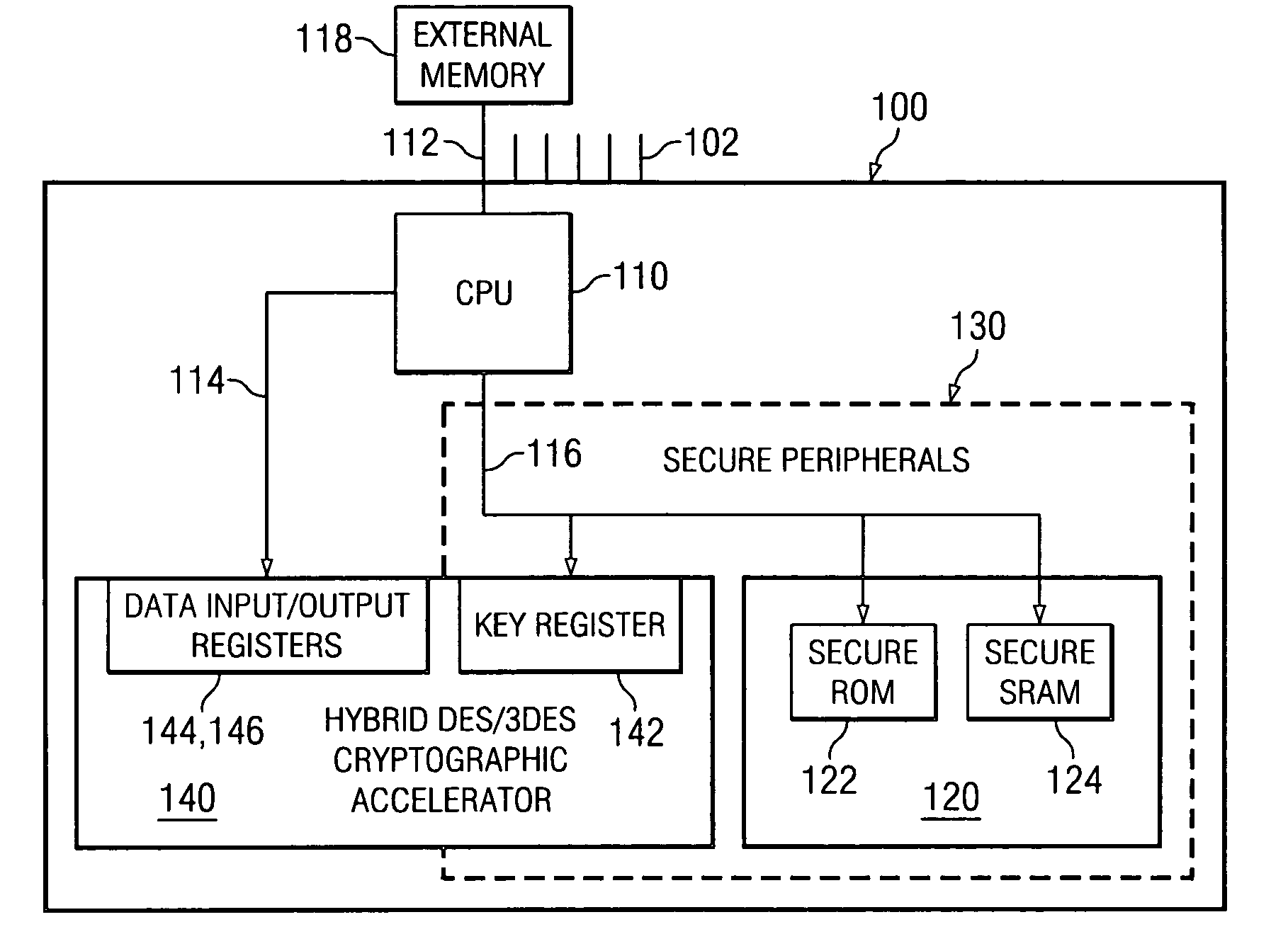
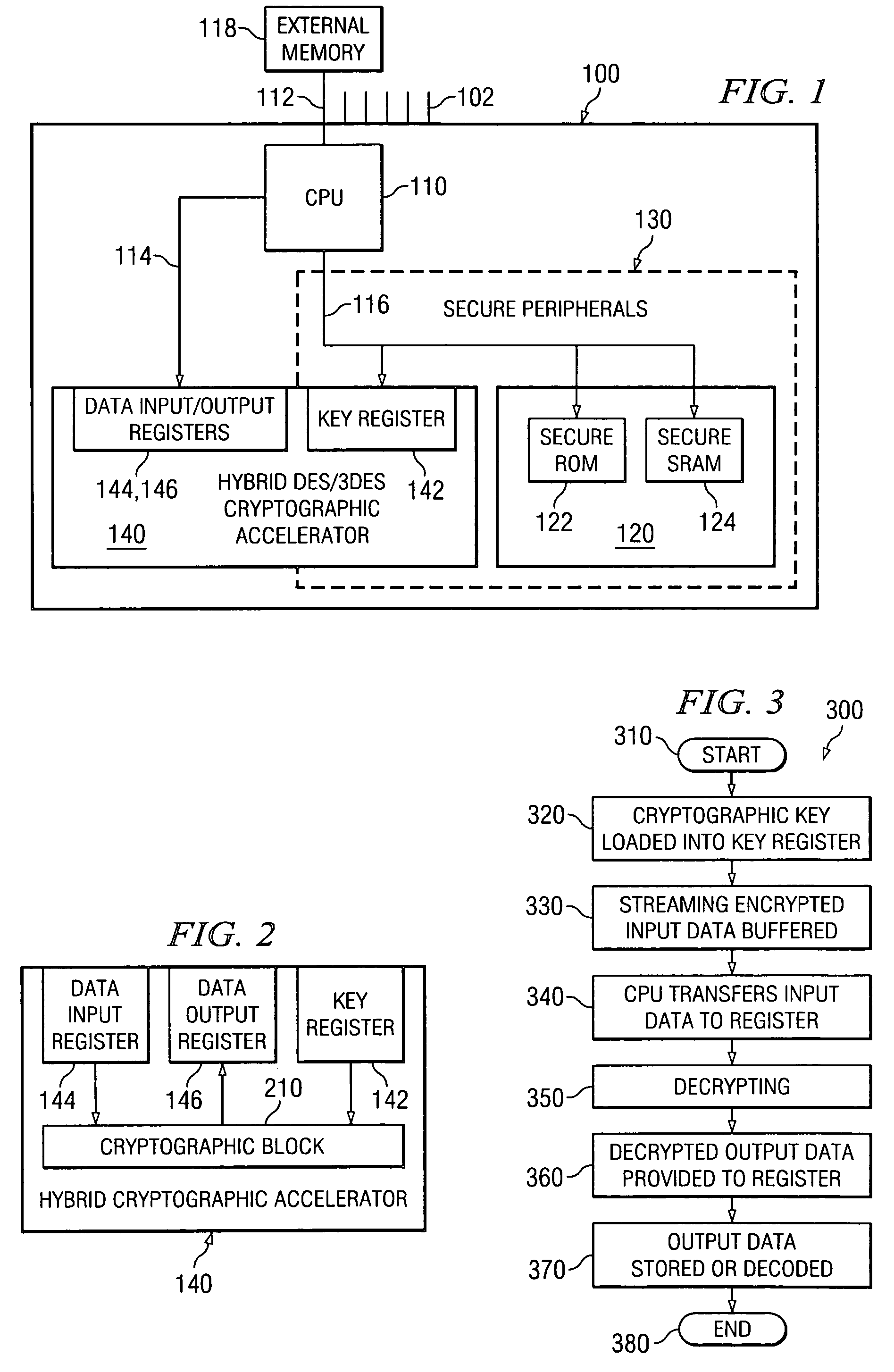
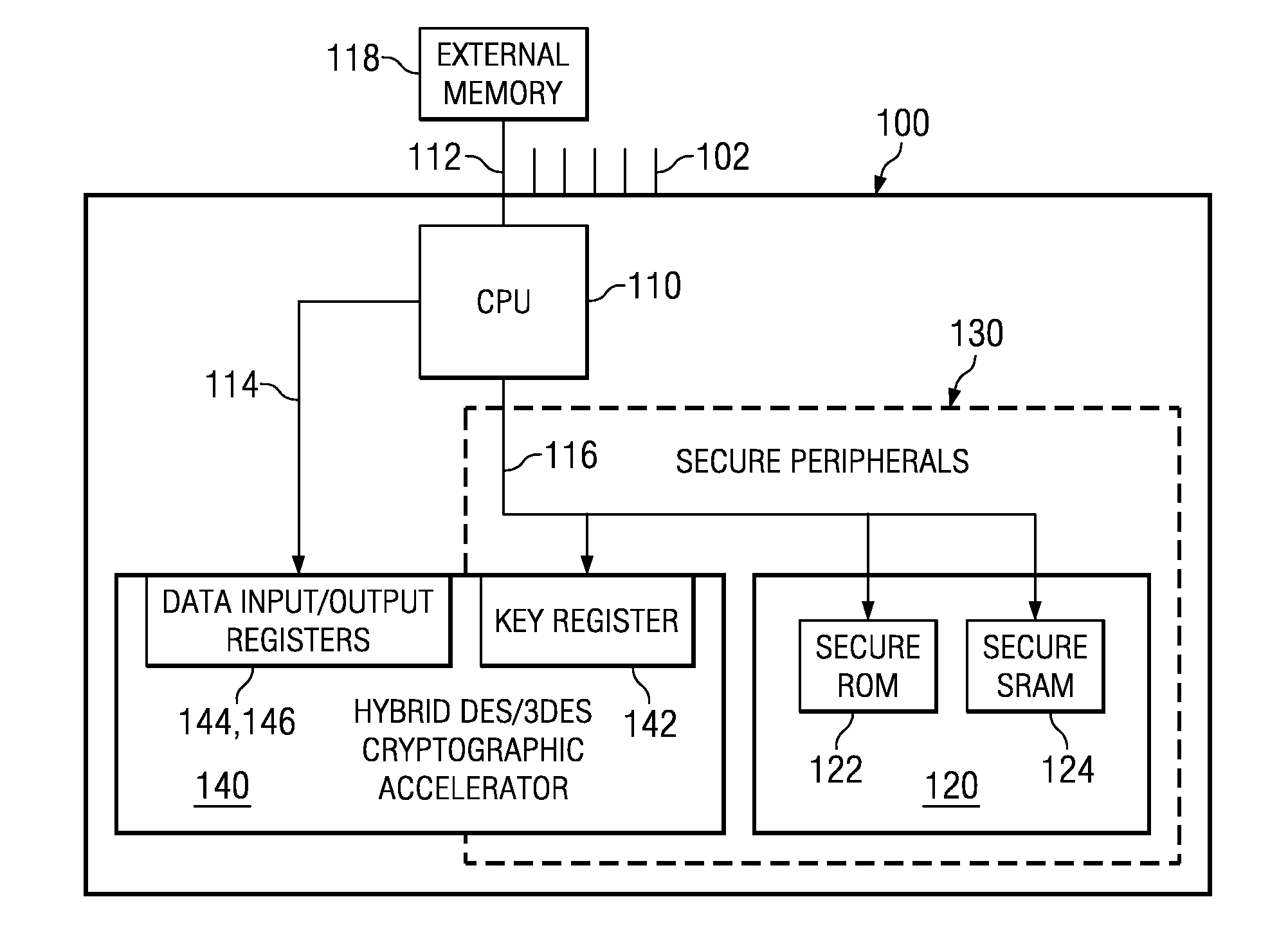
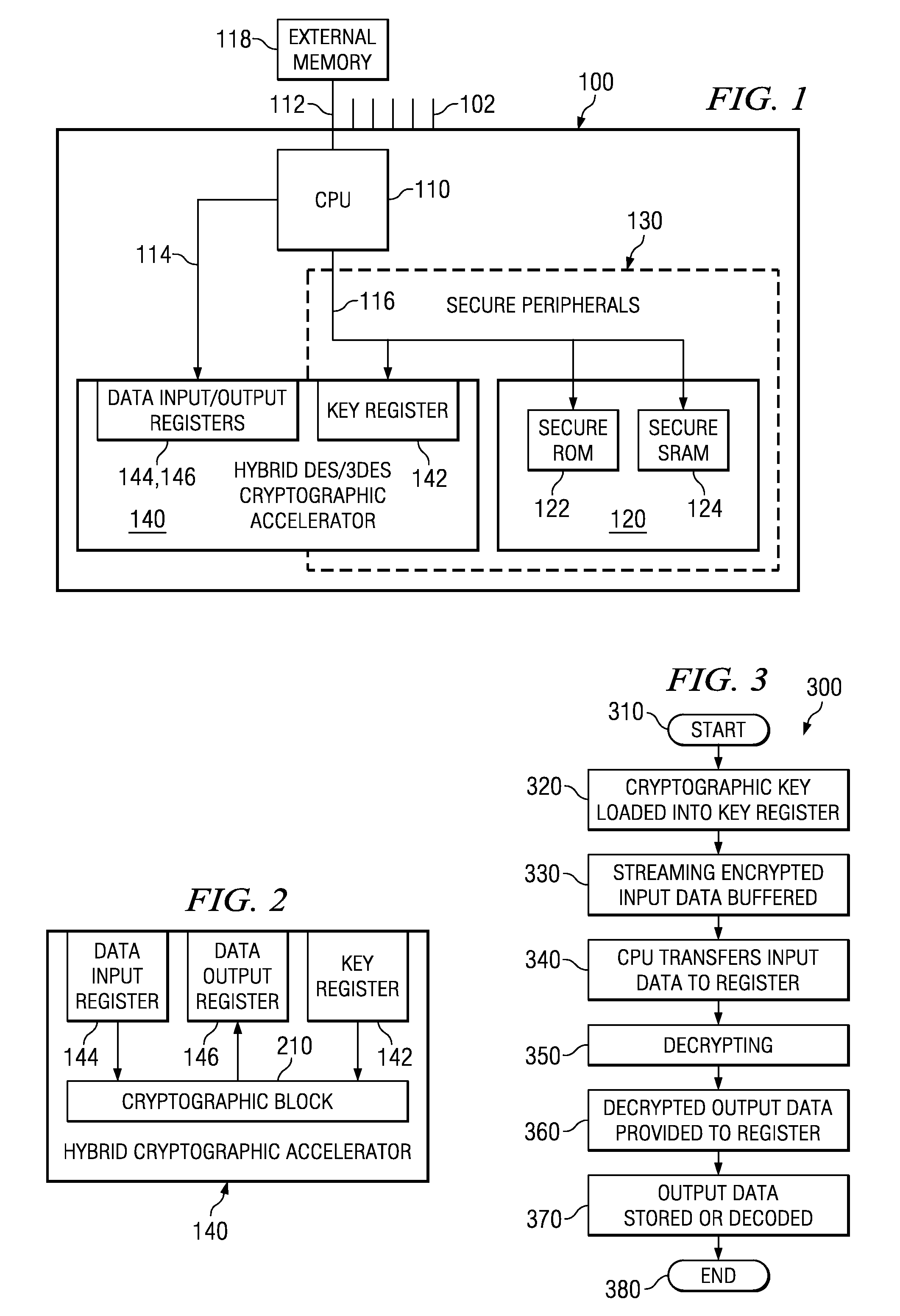
Hybrid cryptographic accelerator and method of operation thereof
ActiveUS20050213766A1Public key for secure communicationUnauthorized memory use protectionCryptographic acceleratorProcessor register
For use in a system-on-a-chip (SoC) having a secure execution environment (SEE) containing secure memory, a cryptographic accelerator, a method of performing cryptography therewith and an SoC incorporating the cryptographic accelerator or the method. In one embodiment, the cryptographic accelerator includes: (1) a key register located within the SEE and coupled to the secure memory to receive a cryptographic key therefrom and (2) data input and output registers located outside of the SEE and coupled to the key register to allow the cryptographic key to be applied to input data arriving via the data input register to yield output data via the data output register.
Owner:TEXAS INSTR INC
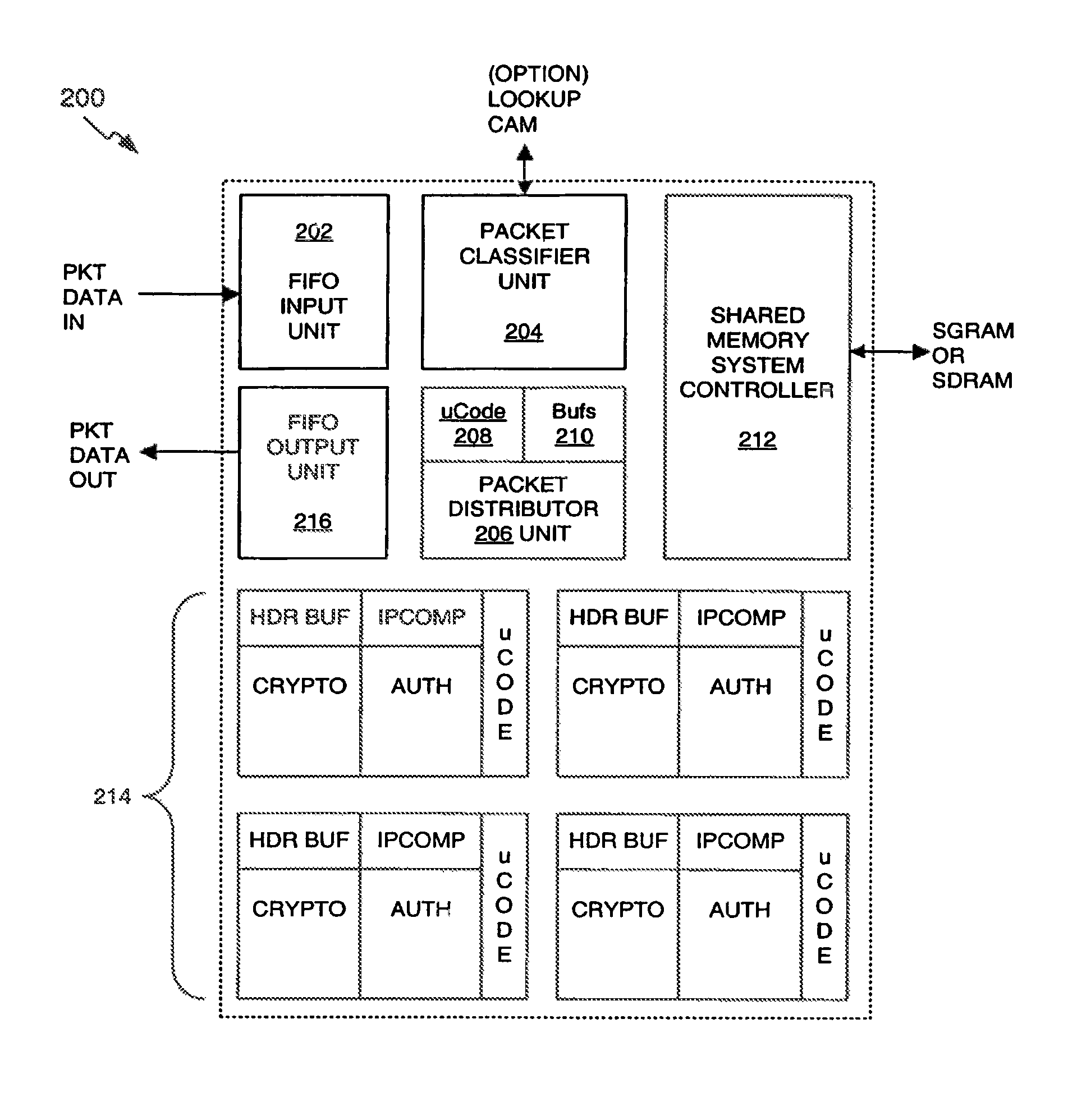
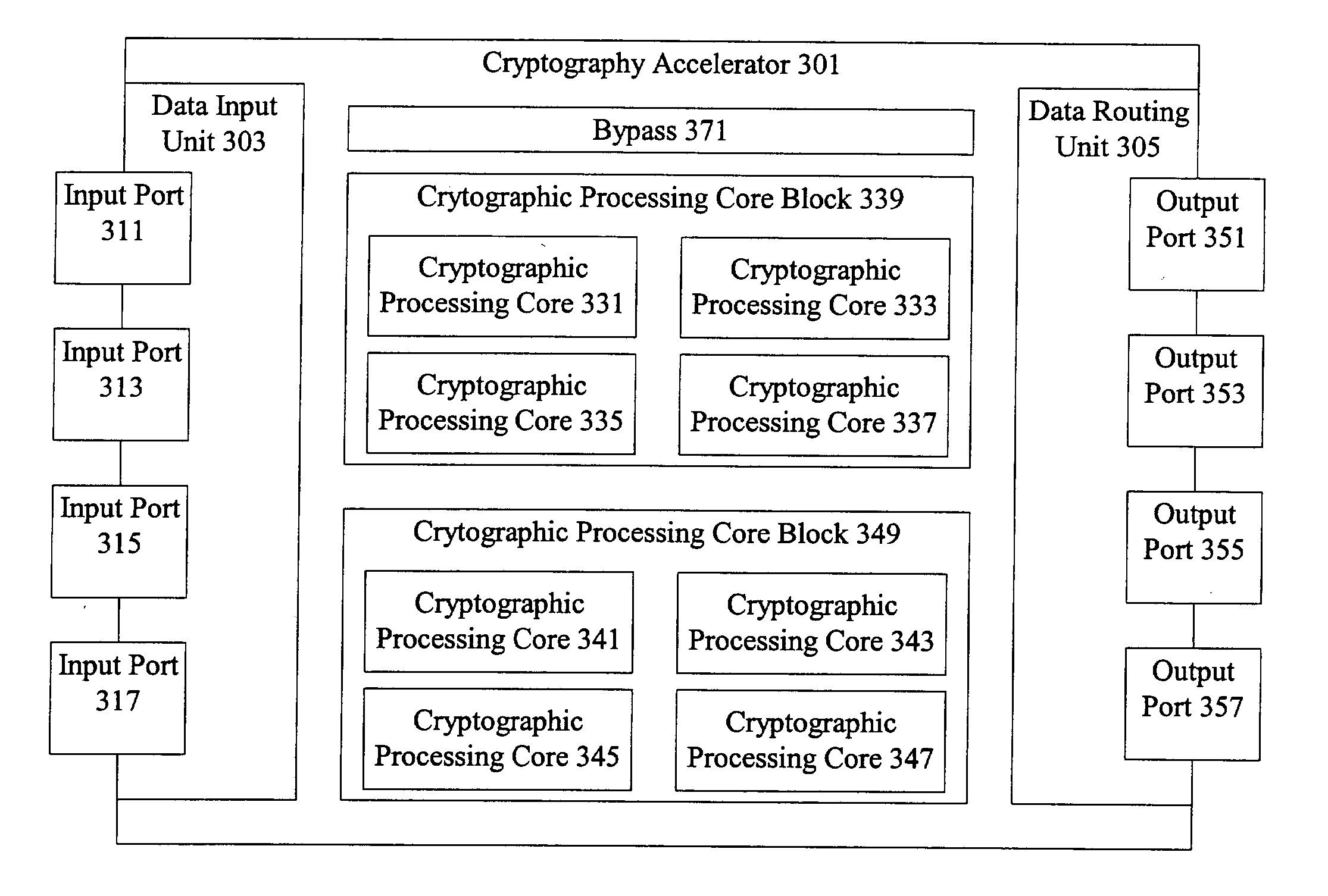
Classification engine in a cryptography acceleration chip
InactiveUS7996670B1Efficient processingMaximum performanceDigital data processing detailsConcurrent instruction executionCryptographic acceleratorNetwork service
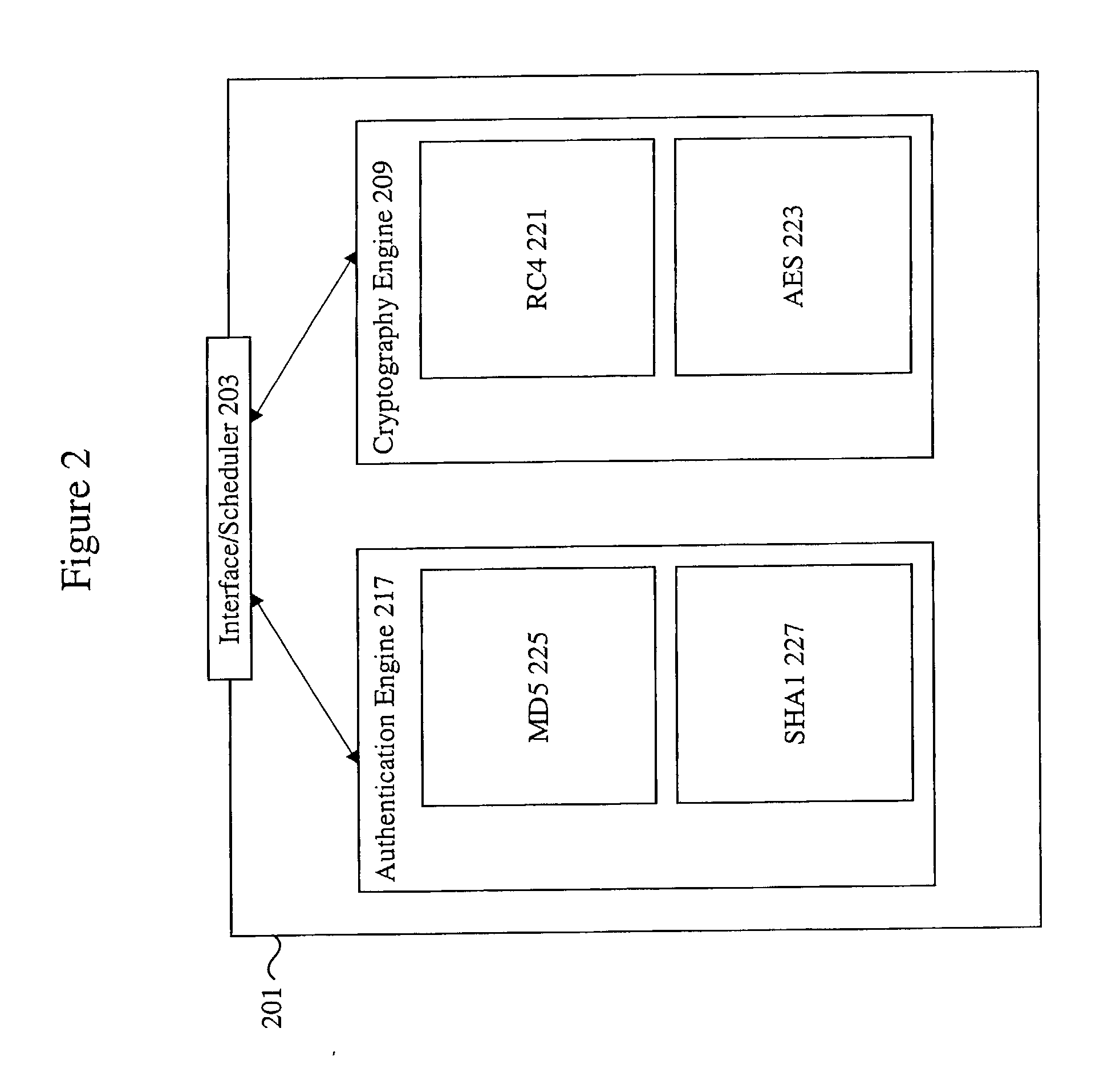
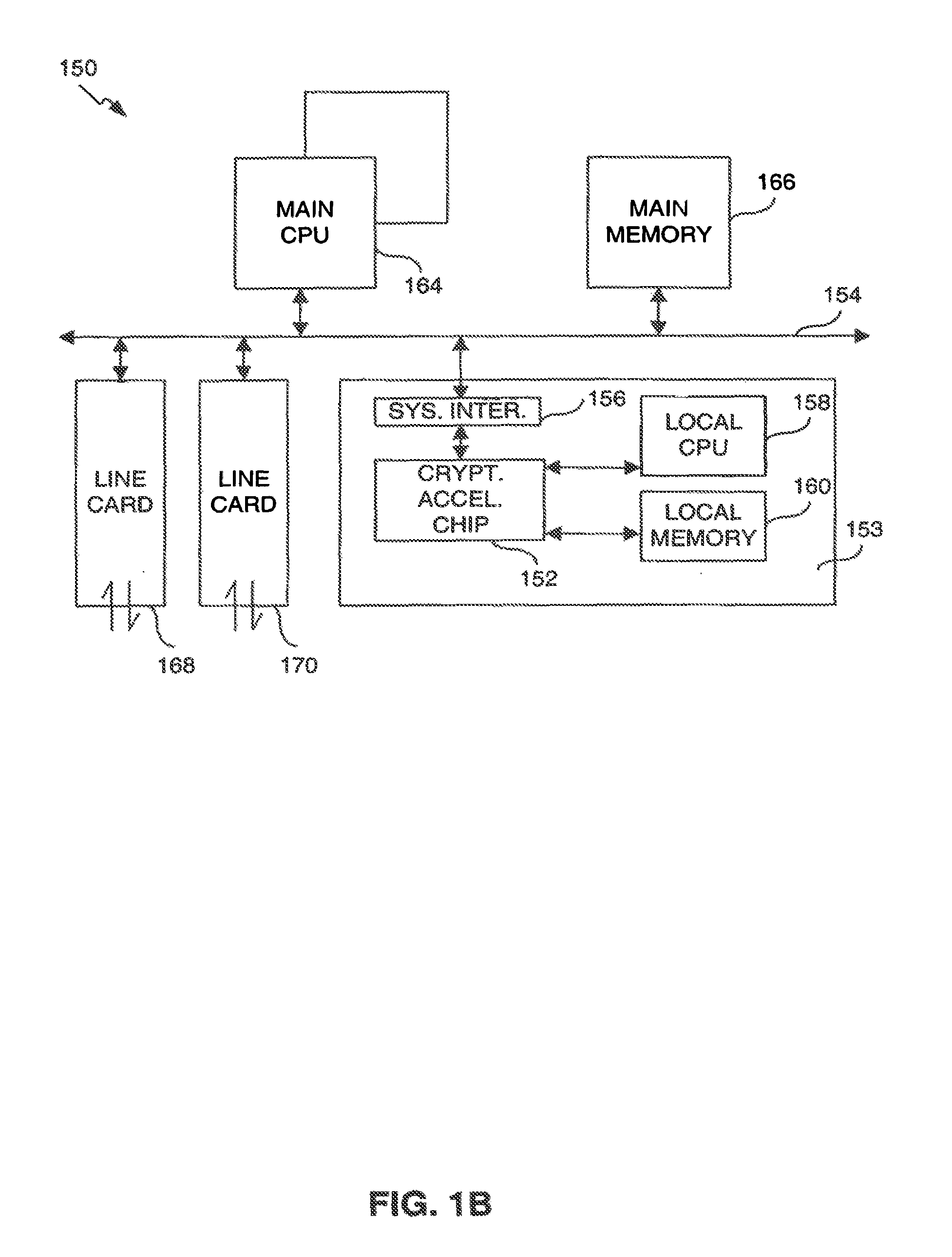
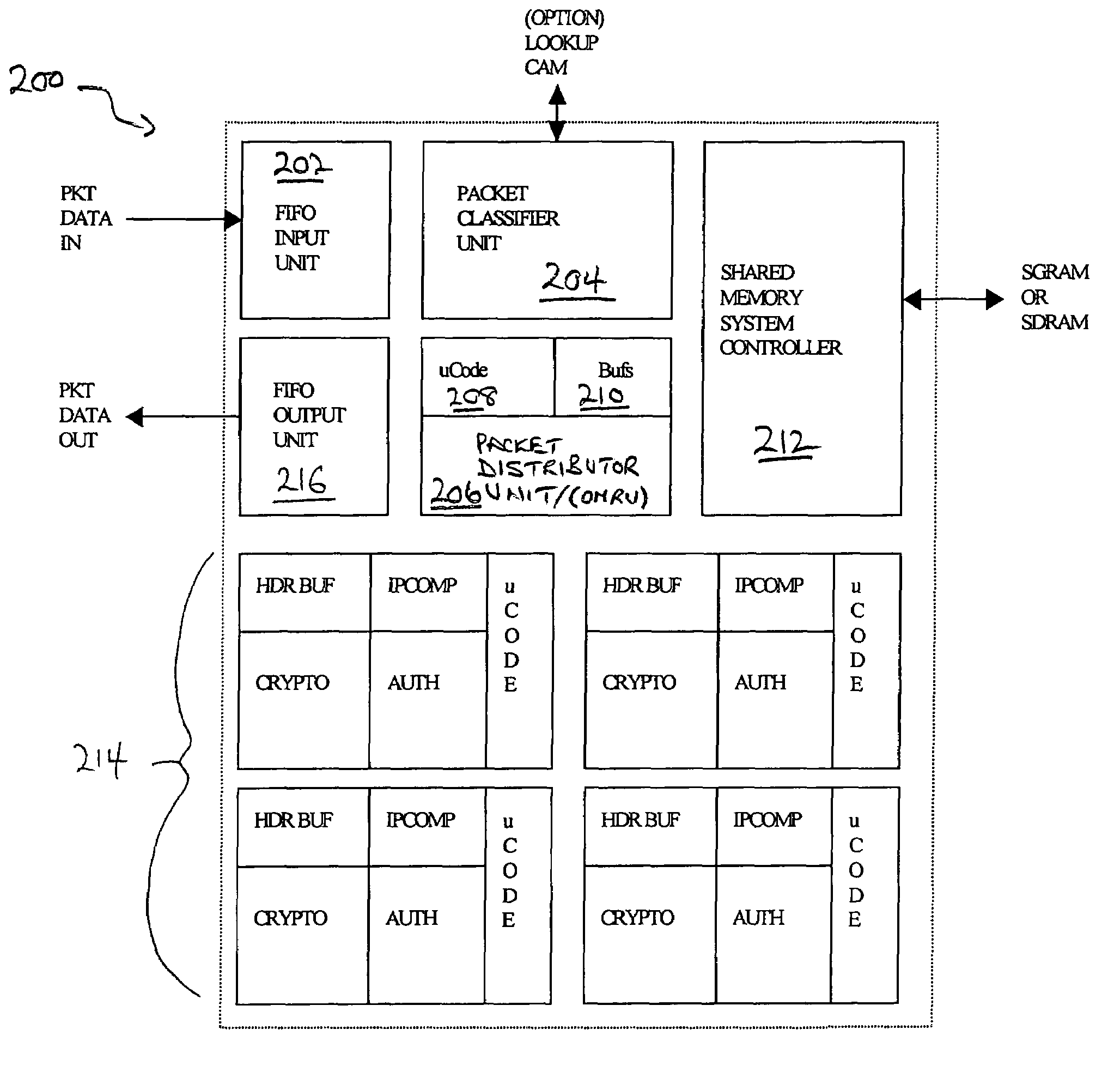
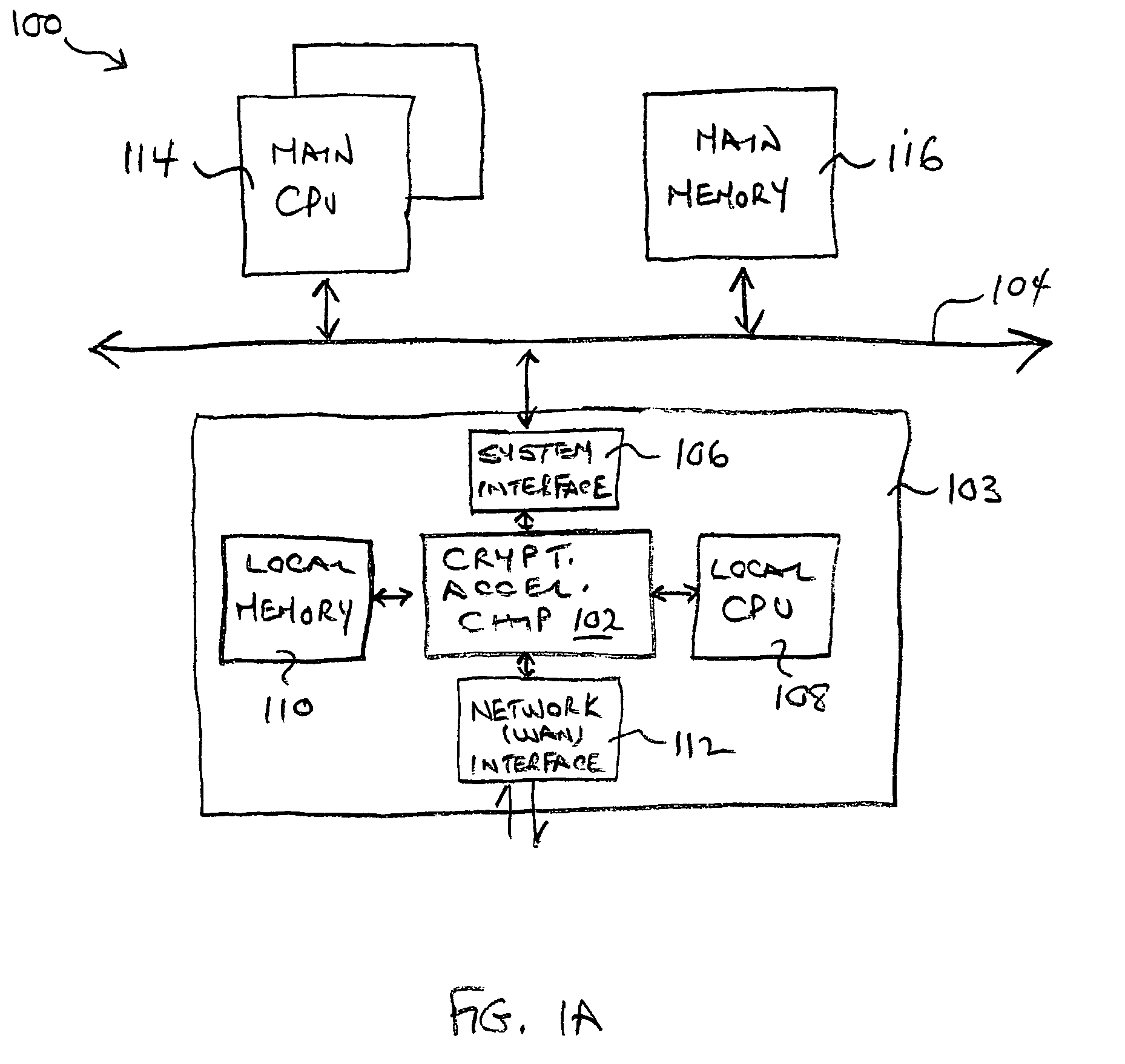
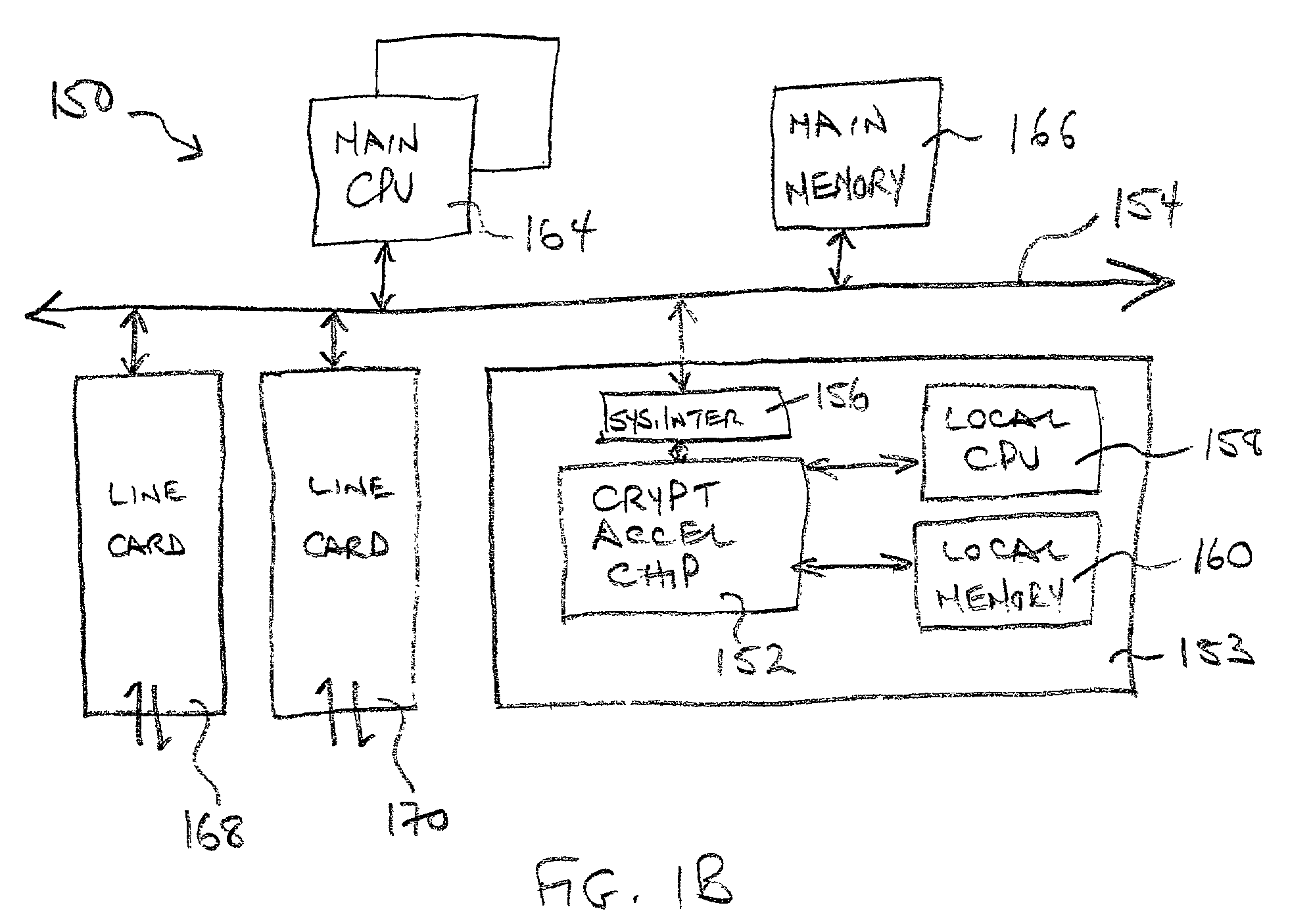
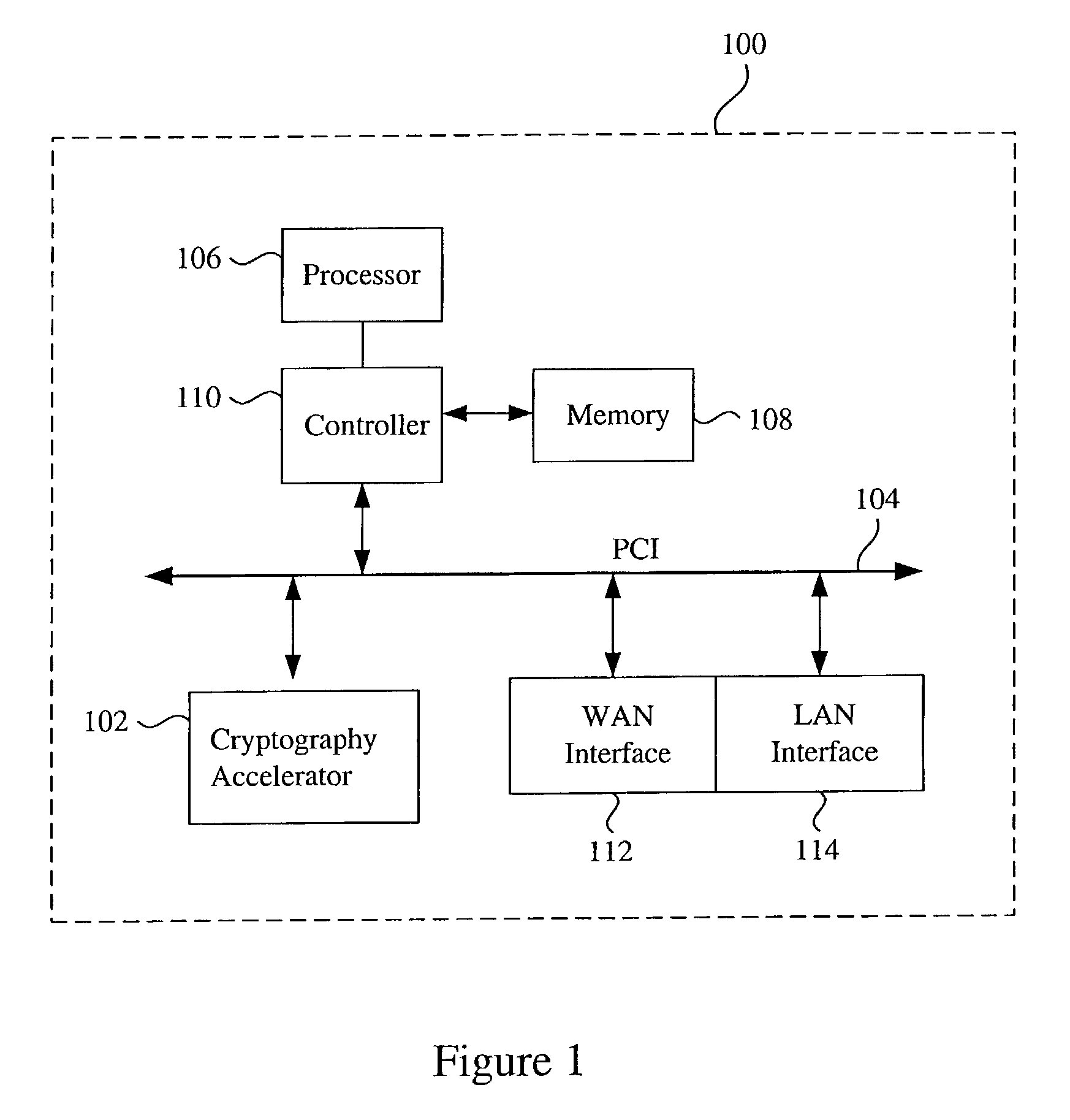
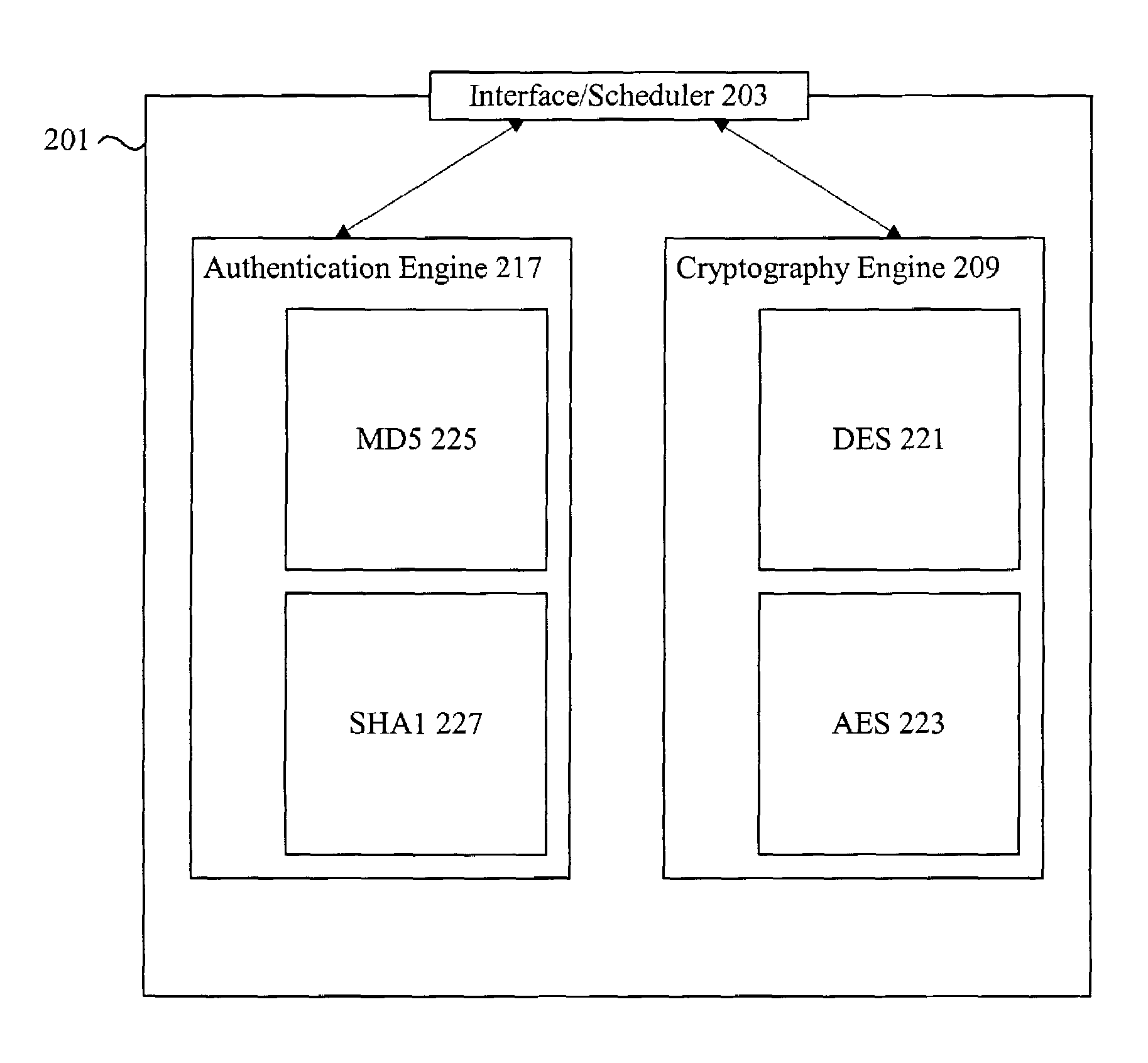
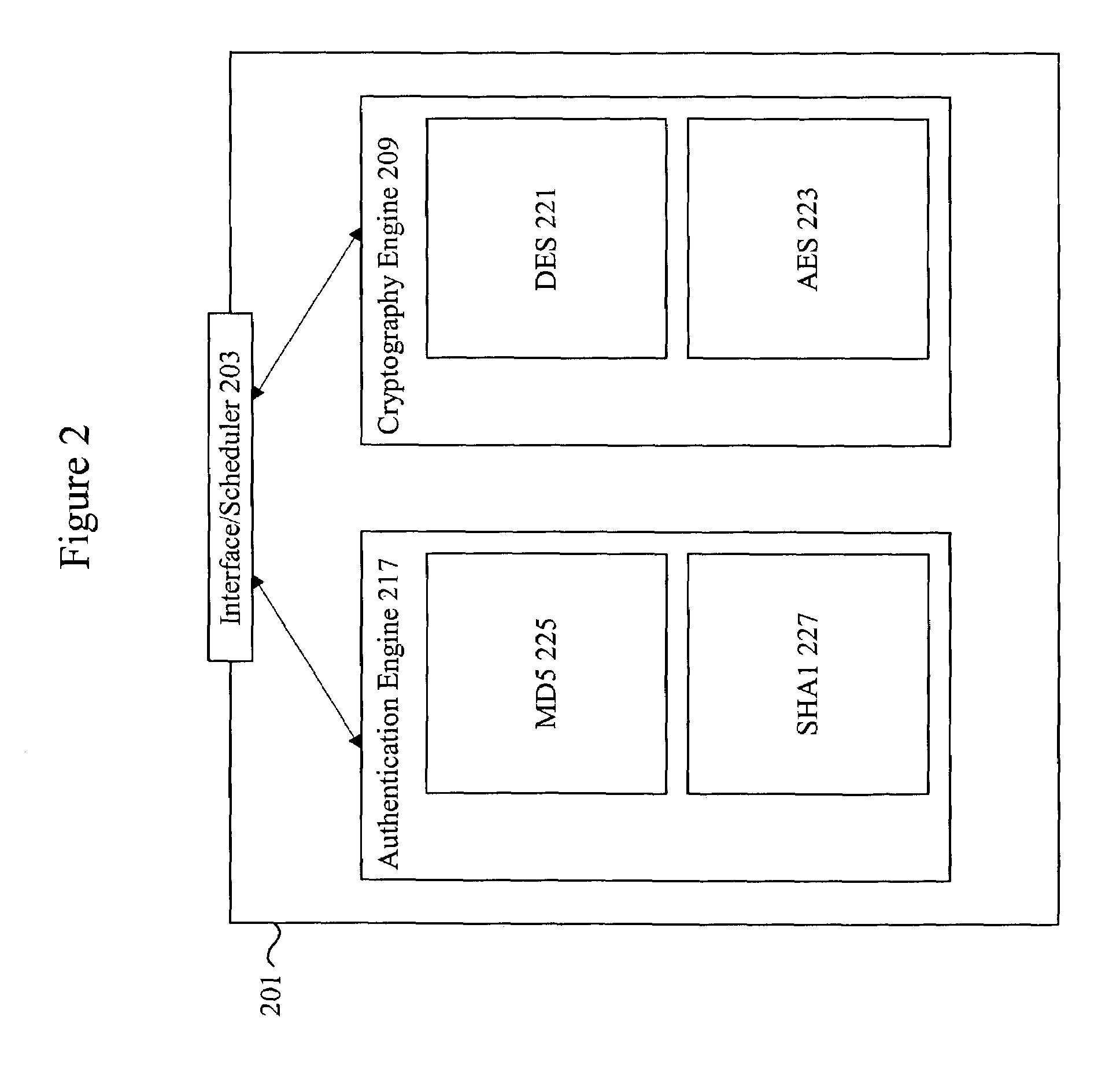
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
Distributed processing in a cryptography acceleration chip
InactiveUS7600131B1Efficient processingImprove performanceDigital data processing detailsUnauthorized memory use protectionCryptographic acceleratorNetwork service
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
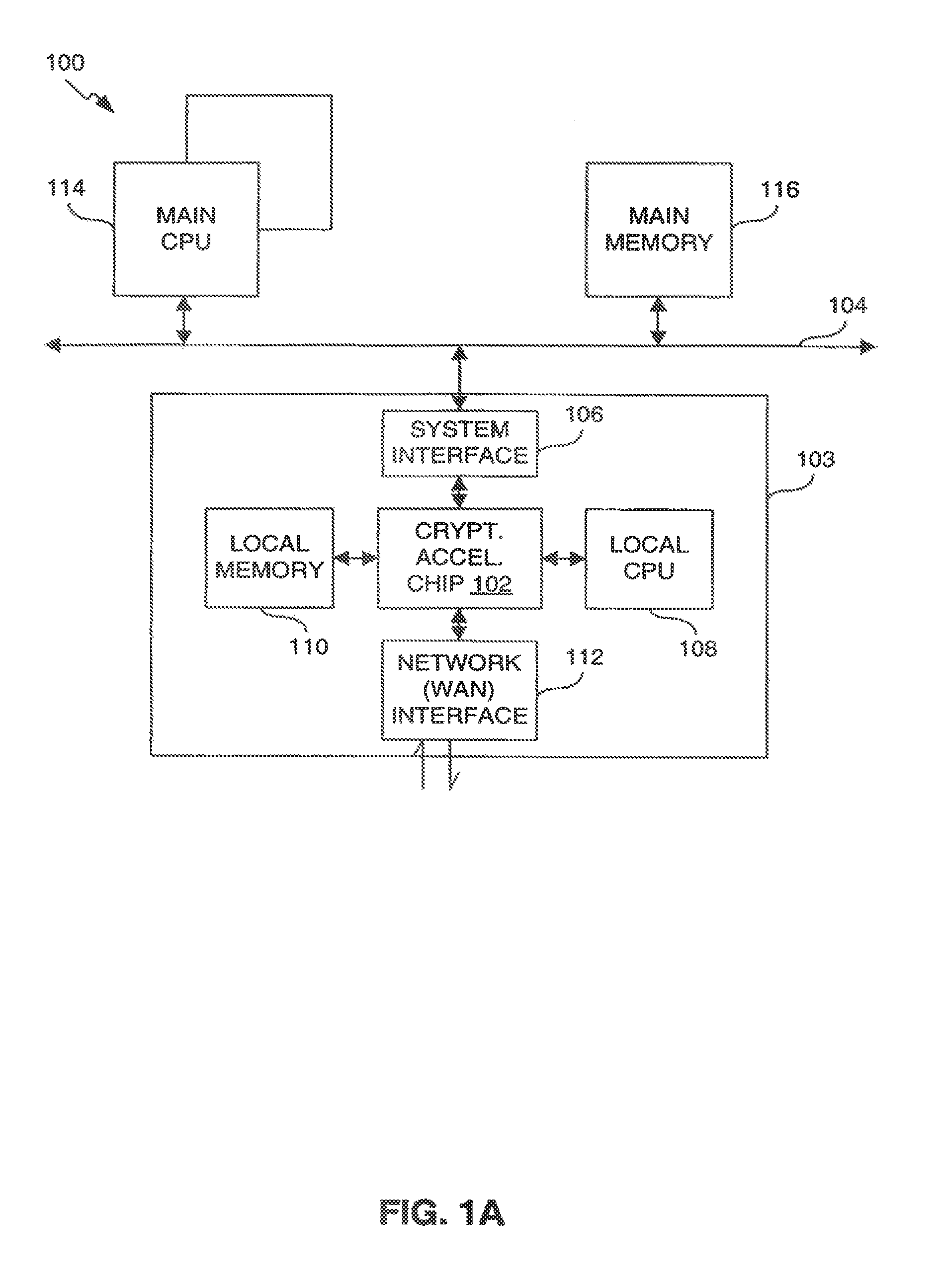
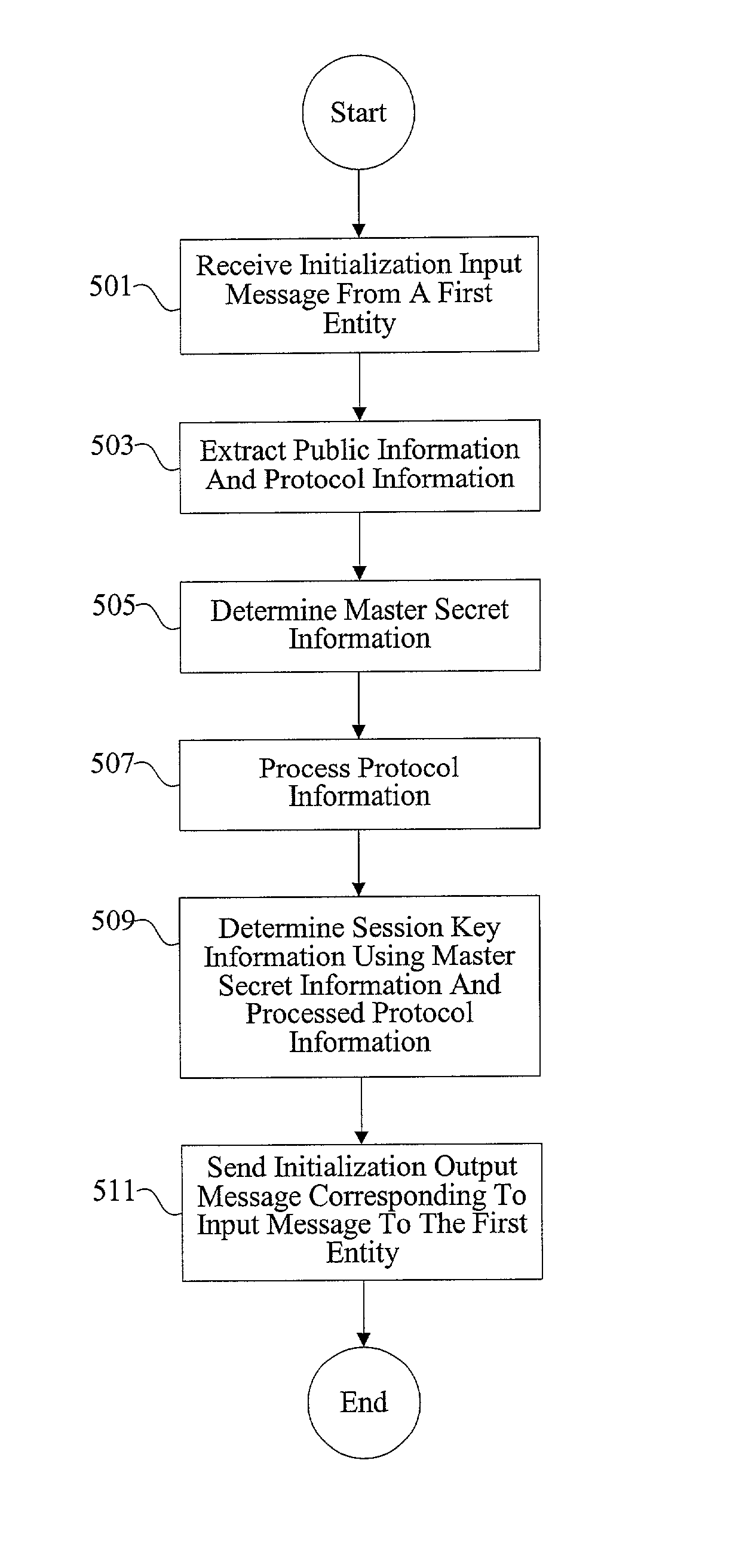
Methods and apparatus for accelerating secure session processing
ActiveUS7007163B2Efficient callEasy to useKey distribution for secure communicationDigital data processing detailsCryptographic acceleratorMemory interface
Owner:AVAGO TECH INT SALES PTE LTD
Methods and apparatus for accelerating secure session processing
ActiveUS20030233539A1Key distribution for secure communicationDigital data processing detailsCryptographic acceleratorMemory interface
Methods and apparatus are provided for an entity such as a CPU to efficiently call a cryptography accelerator to perform cryptographic operations. A function call causes the cryptography accelerator to execute multiple cryptographic operations in a manner tailored for specific processing steps, such as steps during a handshake phase of a secured session. The techniques provide efficient use of hardware processing resources, data interfaces, and memory interfaces.
Owner:AVAGO TECH INT SALES PTE LTD
Methods and apparatus for performing hash operations in a cryptography accelerator
ActiveUS7400722B2User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic accelerator
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
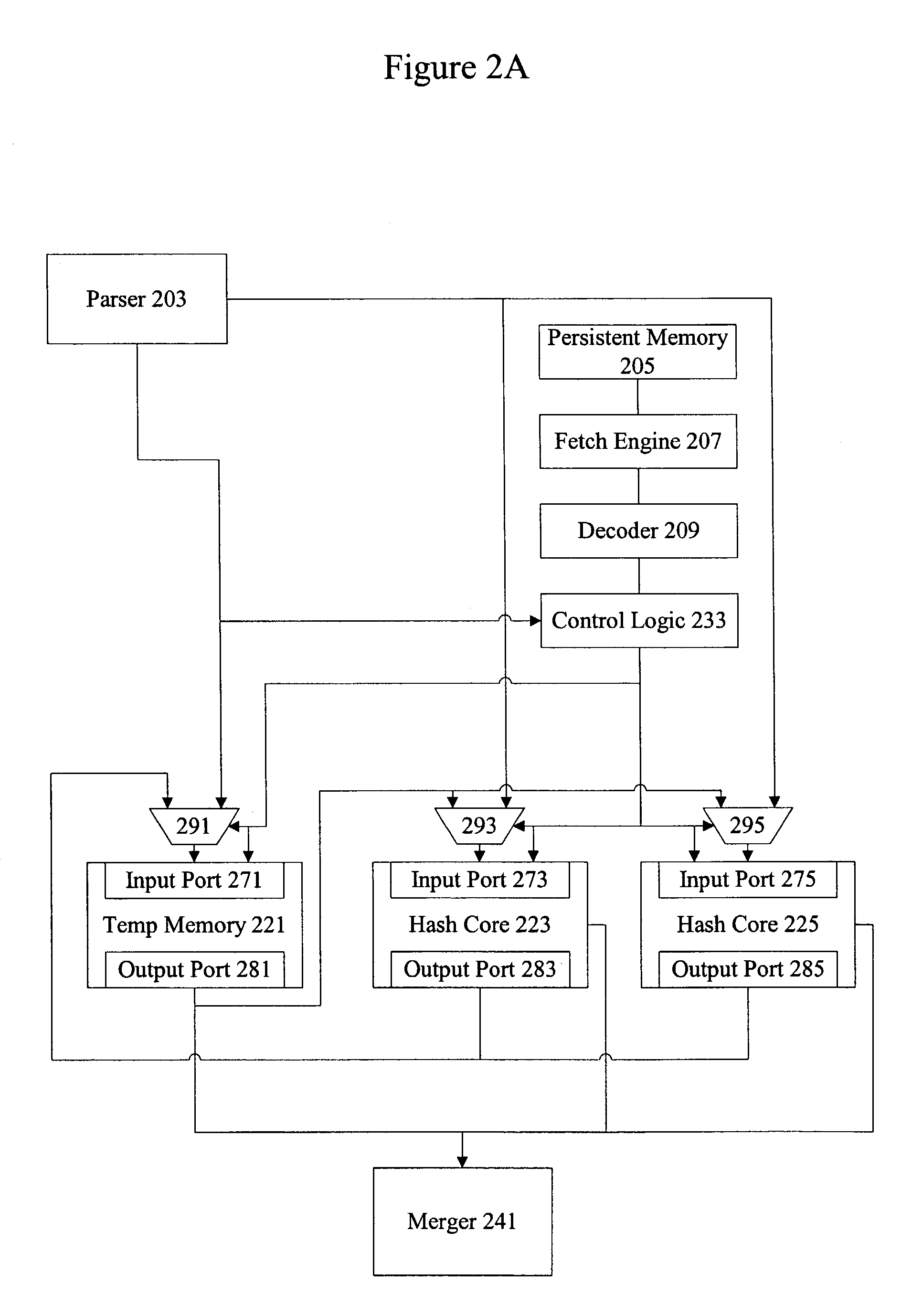
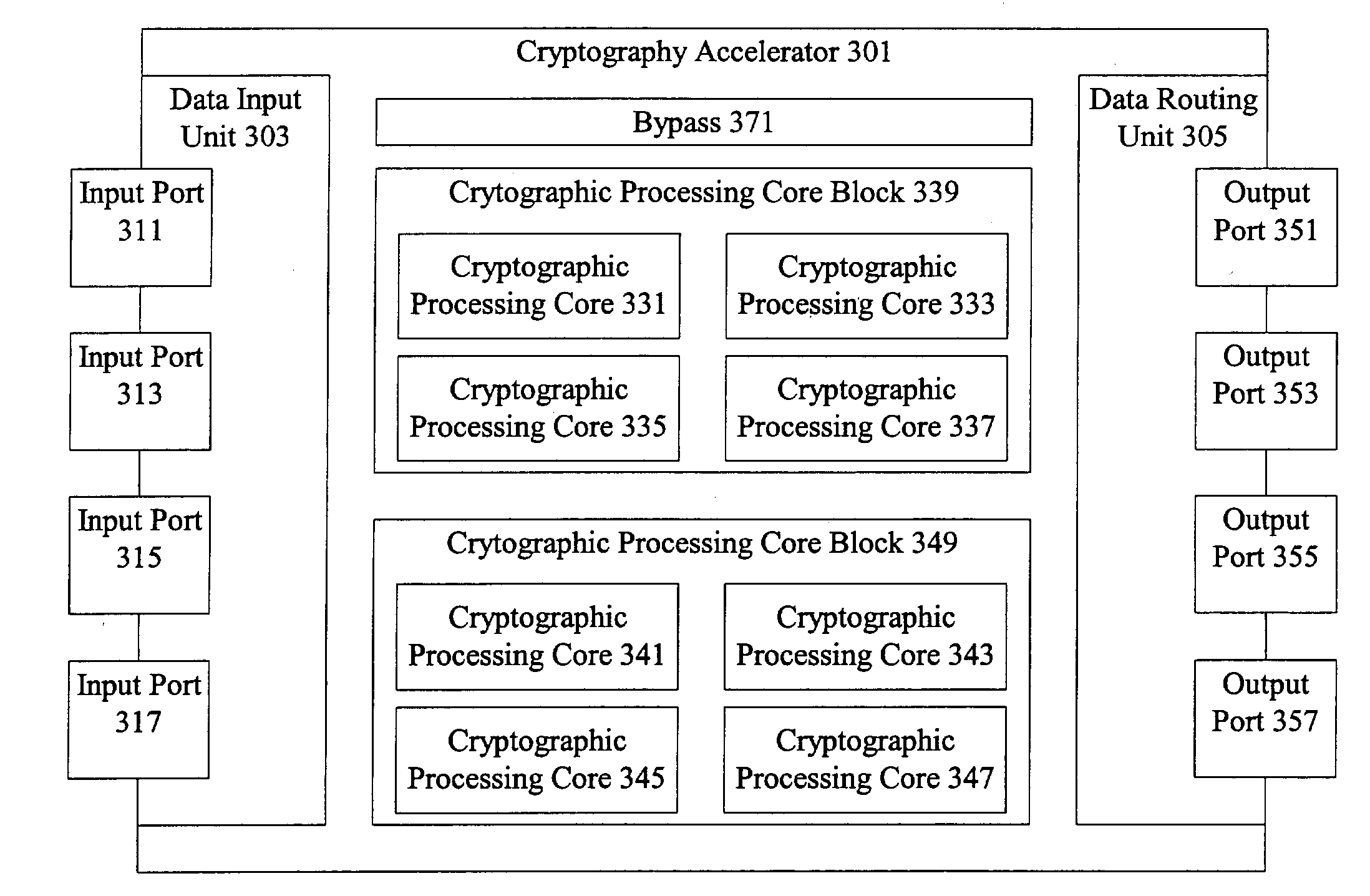
Cryptography accelerator interface decoupling from cryptography processing cores
InactiveUS20040123119A1Unauthorized memory use protectionHardware monitoringProcessing coreCryptographic accelerator
Methods and apparatus are provided for decoupling a cryptography accelerator interface from cryptographic processing cores. A shared resource is provided at the cryptography accelerator interface having multiple input ports. References to data in the shared resource are provided to allow processing and ordering of data in preparation for processing by cryptographic processing cores without substantial numbers of separate buffers in the cryptographic processing data paths.
Owner:AVAGO TECH INT SALES PTE LTD
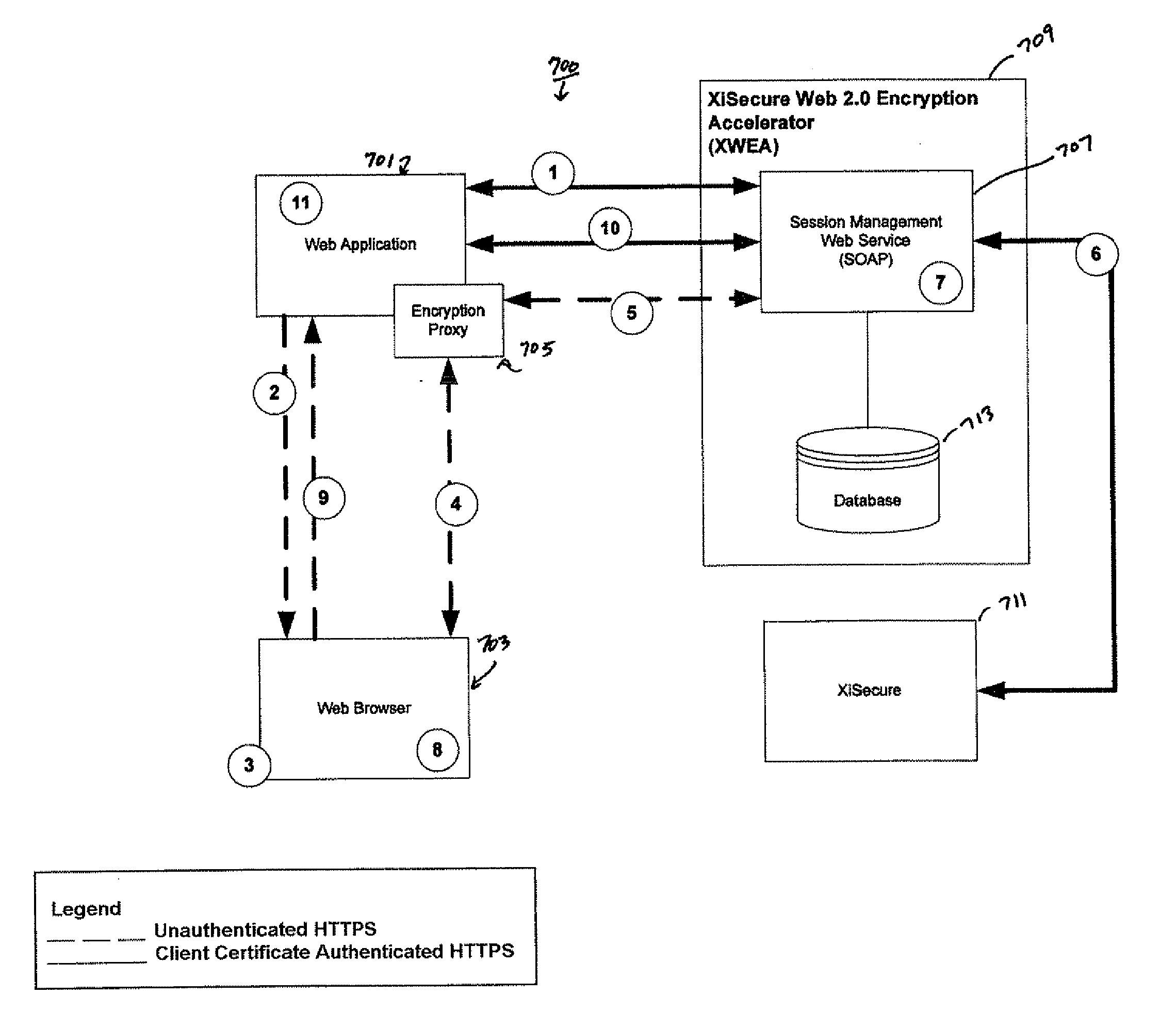
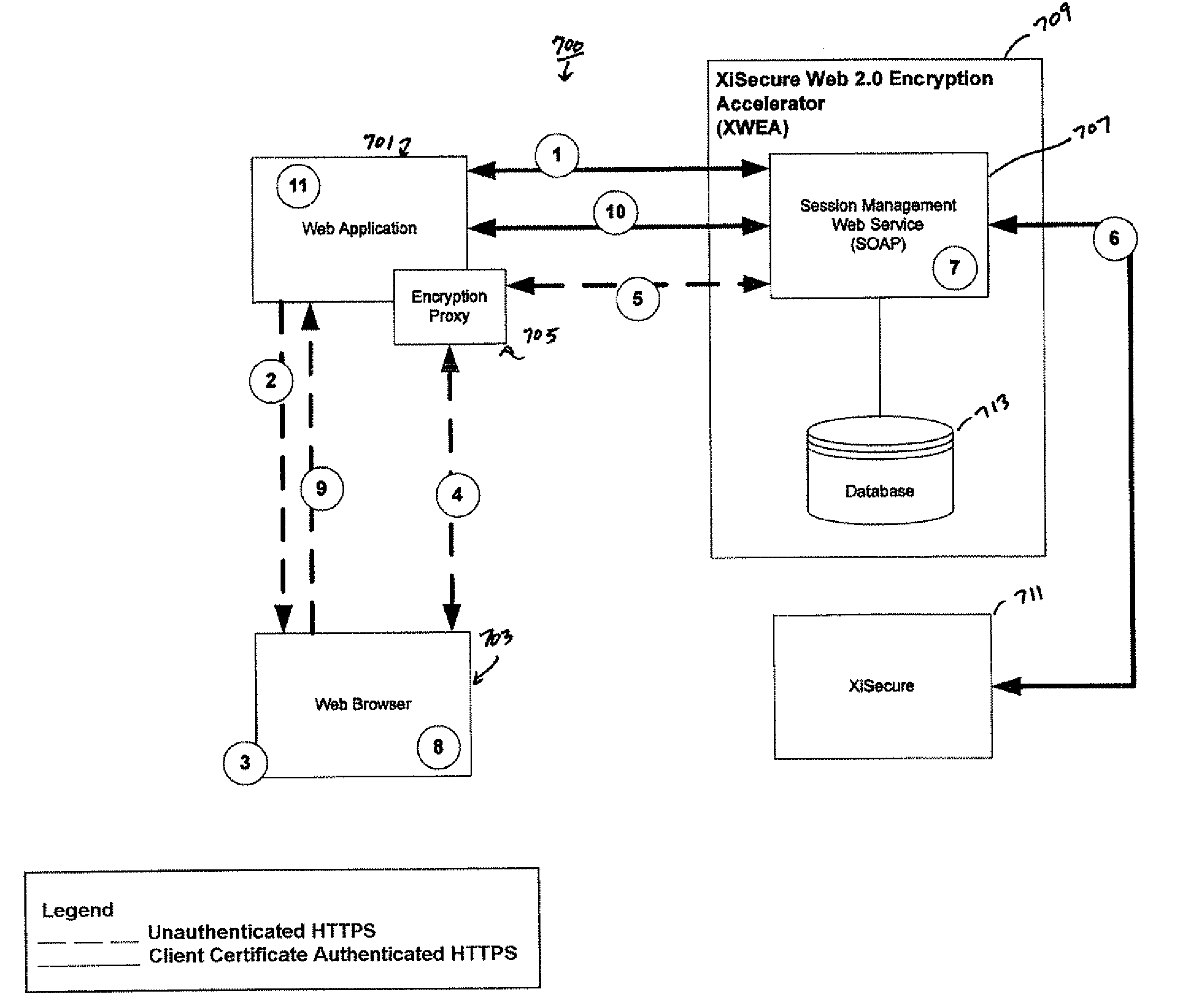
Payment encryption accelerator
Embodiments of the invention provide a system for encrypting web session data which may include a session management module adapted to receive data from a web application module and provide a token that represents the data in encrypted form to the web application, wherein the web application is adapted to use the token to represent the data. The system may also include a tokenizer module communicably coupled to the session management module, wherein the tokenizer module is adapted to receive the data and generate the token. Further, the system may include a database communicably coupled to the session management module, wherein the database is adapted to receive the token and the data, associate the token with the data, and store the token and the data.
Owner:PAYMETRIC
Hybrid cryptographic accelerator and method of operation thereof
ActiveUS7543158B2Public key for secure communicationUnauthorized memory use protectionComputer hardwareCryptographic accelerator
For use in a system-on-a-chip (SoC) having a secure execution environment (SEE) containing secure memory, a cryptographic accelerator, a method of performing cryptography therewith and an SoC incorporating the cryptographic accelerator or the method. In one embodiment, the cryptographic accelerator includes: (1) a key register located within the SEE and coupled to the secure memory to receive a cryptographic key therefrom and (2) data input and output registers located outside of the SEE and coupled to the key register to allow the cryptographic key to be applied to input data arriving via the data input register to yield output data via the data output register.
Owner:TEXAS INSTR INC
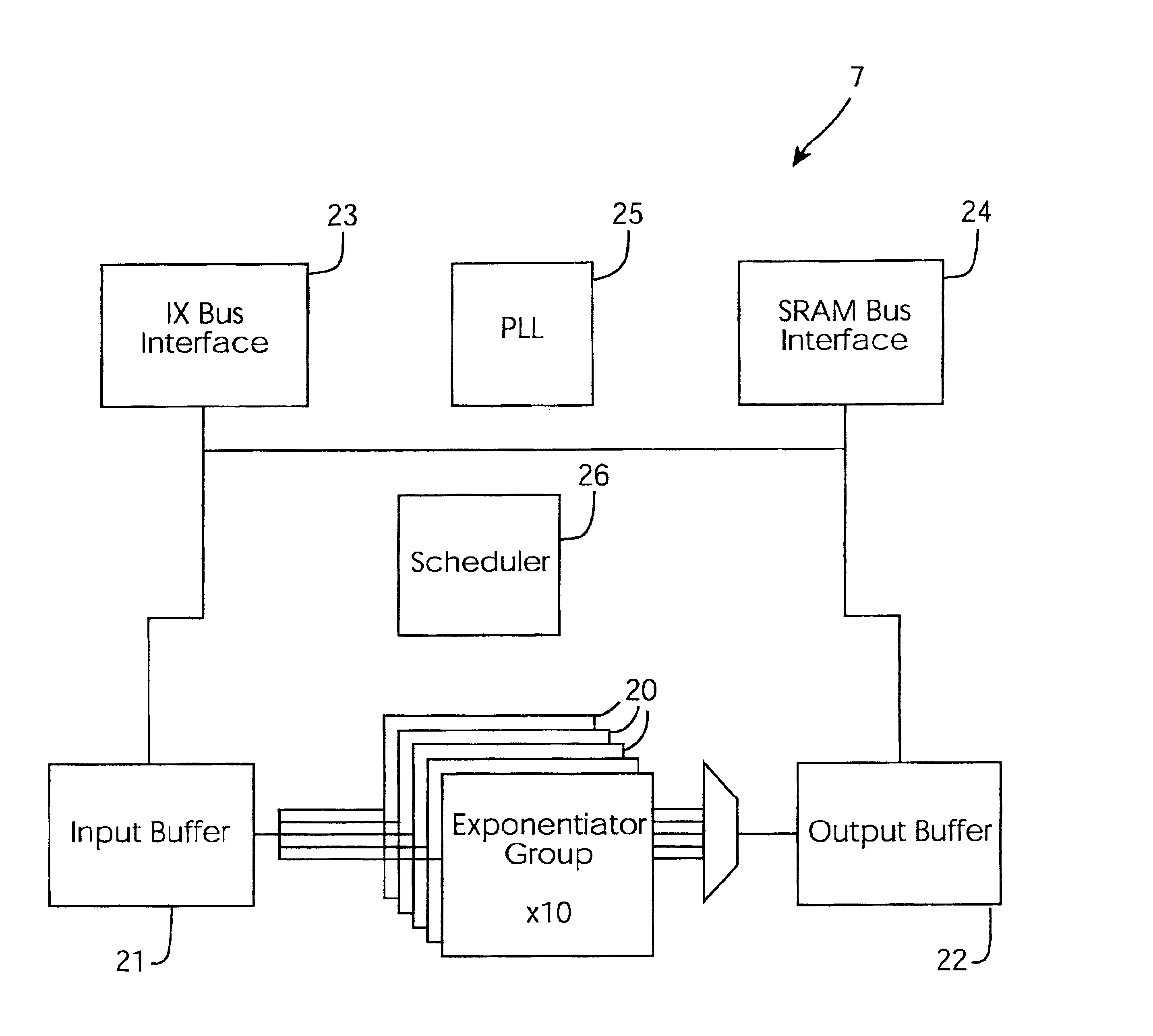
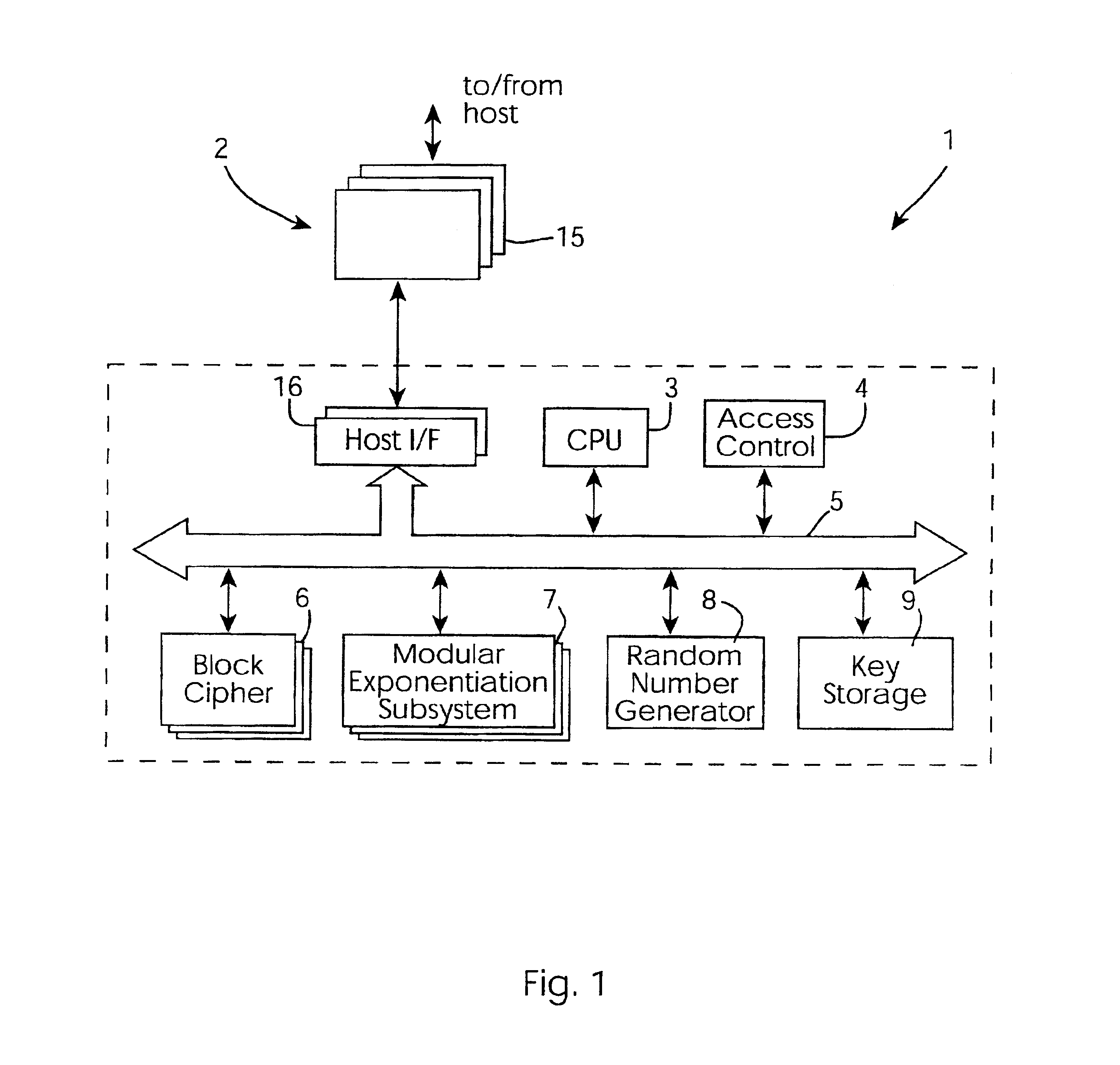
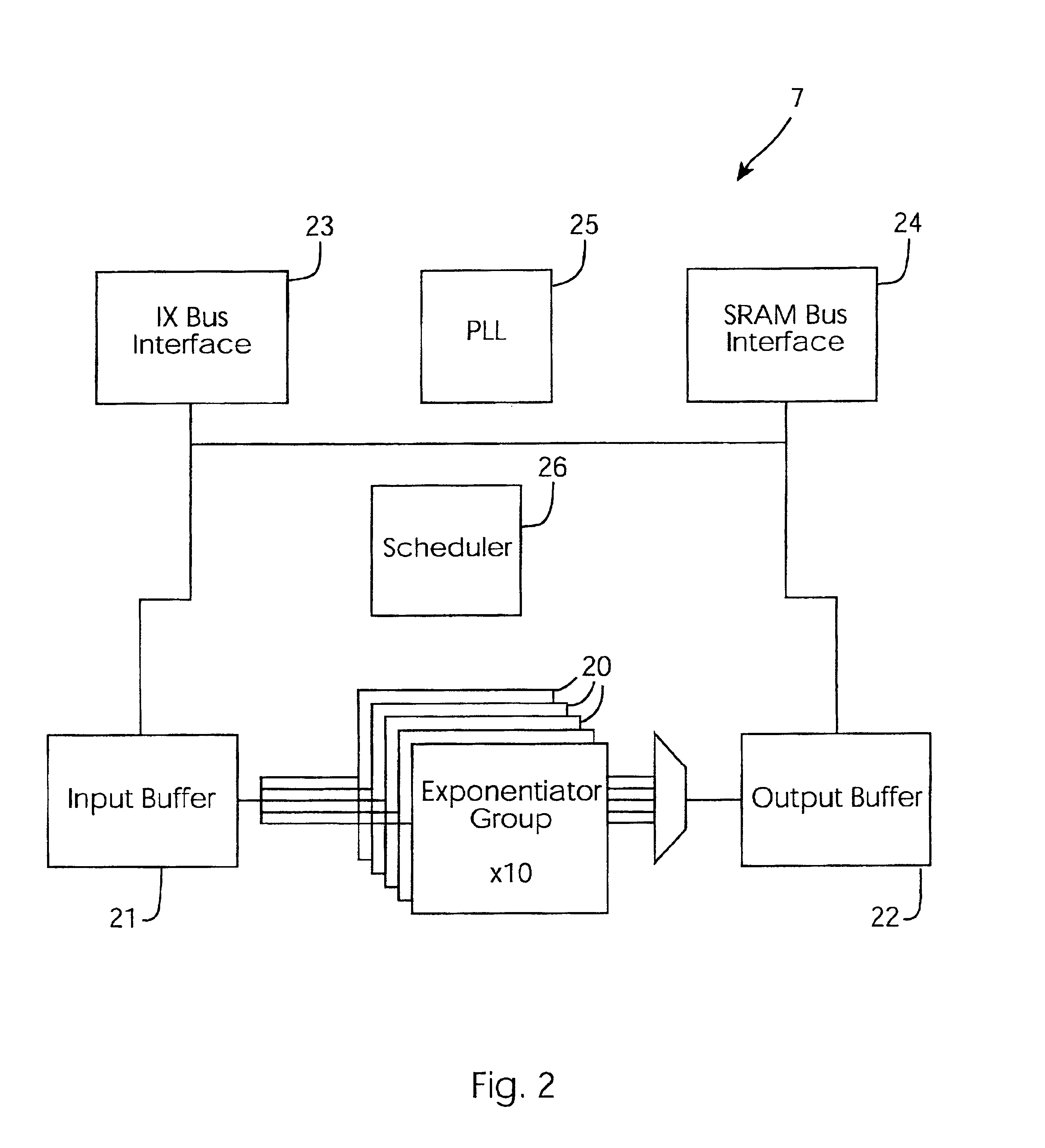
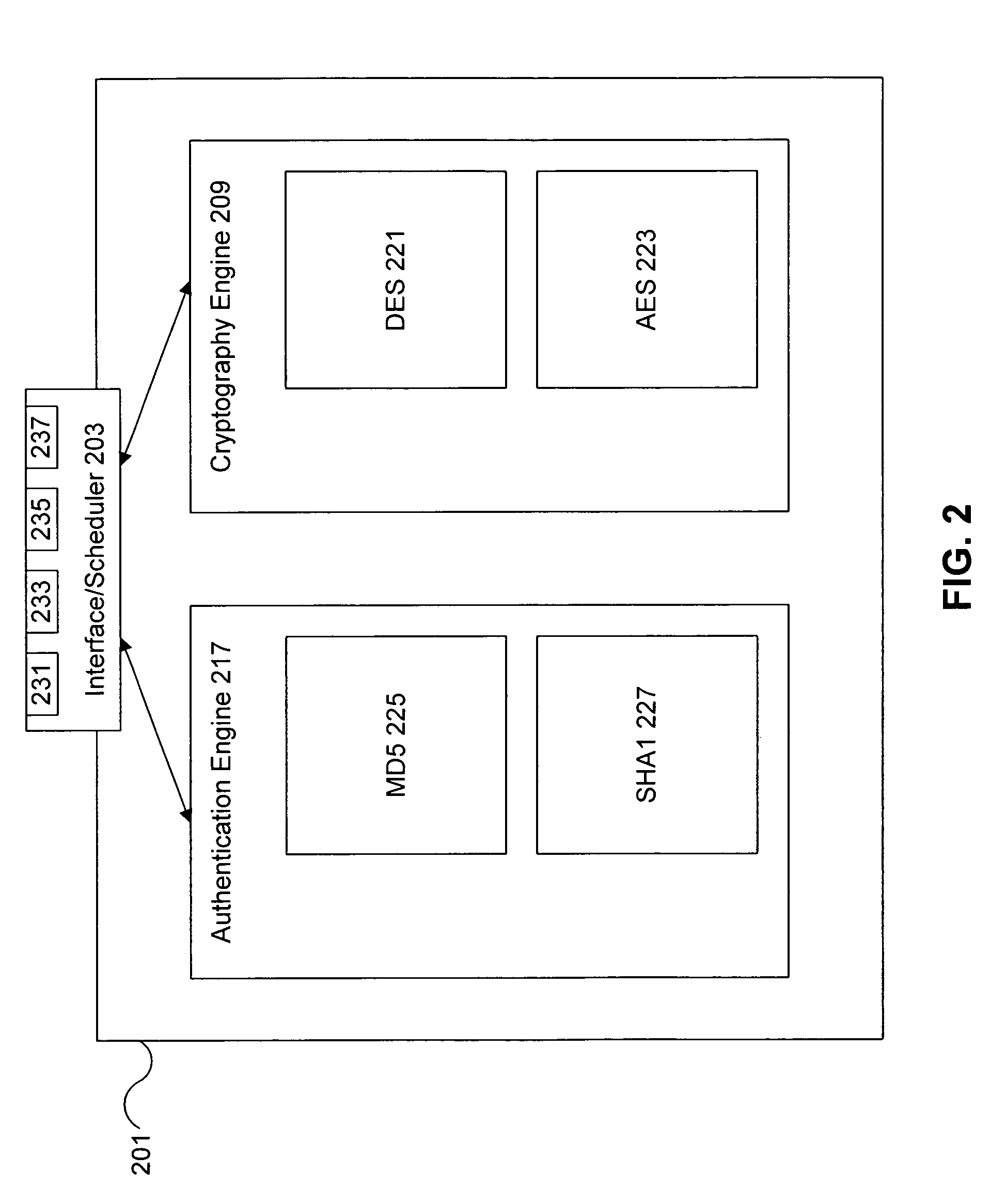
Cryptographic accelerator
InactiveUS6963979B2Public key for secure communicationUser identity/authority verificationCryptographic acceleratorControl register
A cryptographic accelerator (1) has a host interface (2) for interfacing with a host sending cryptographic requests and receiving results. A CPU (3) manages the internal logical unit in an exponentiation sub-system (7) having modulator exponentiators (30). The exponentiators (30) are chained together up to a maximum of four, in a block (20). There are ten blocks (20). A scheduler uses control registers and an input buffer to perform the scheduling control.
Owner:AEP SYSTEMS LIMITED
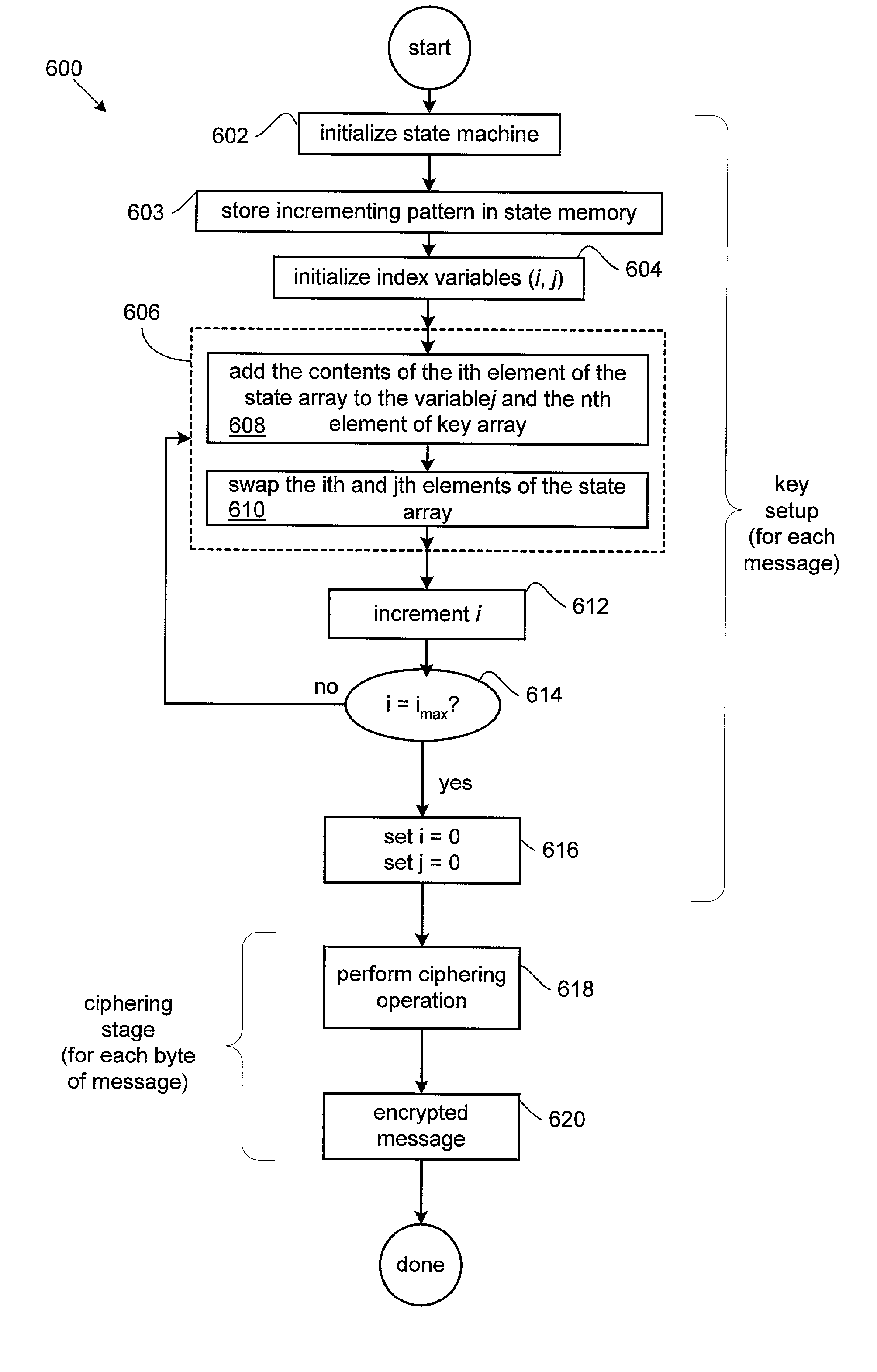
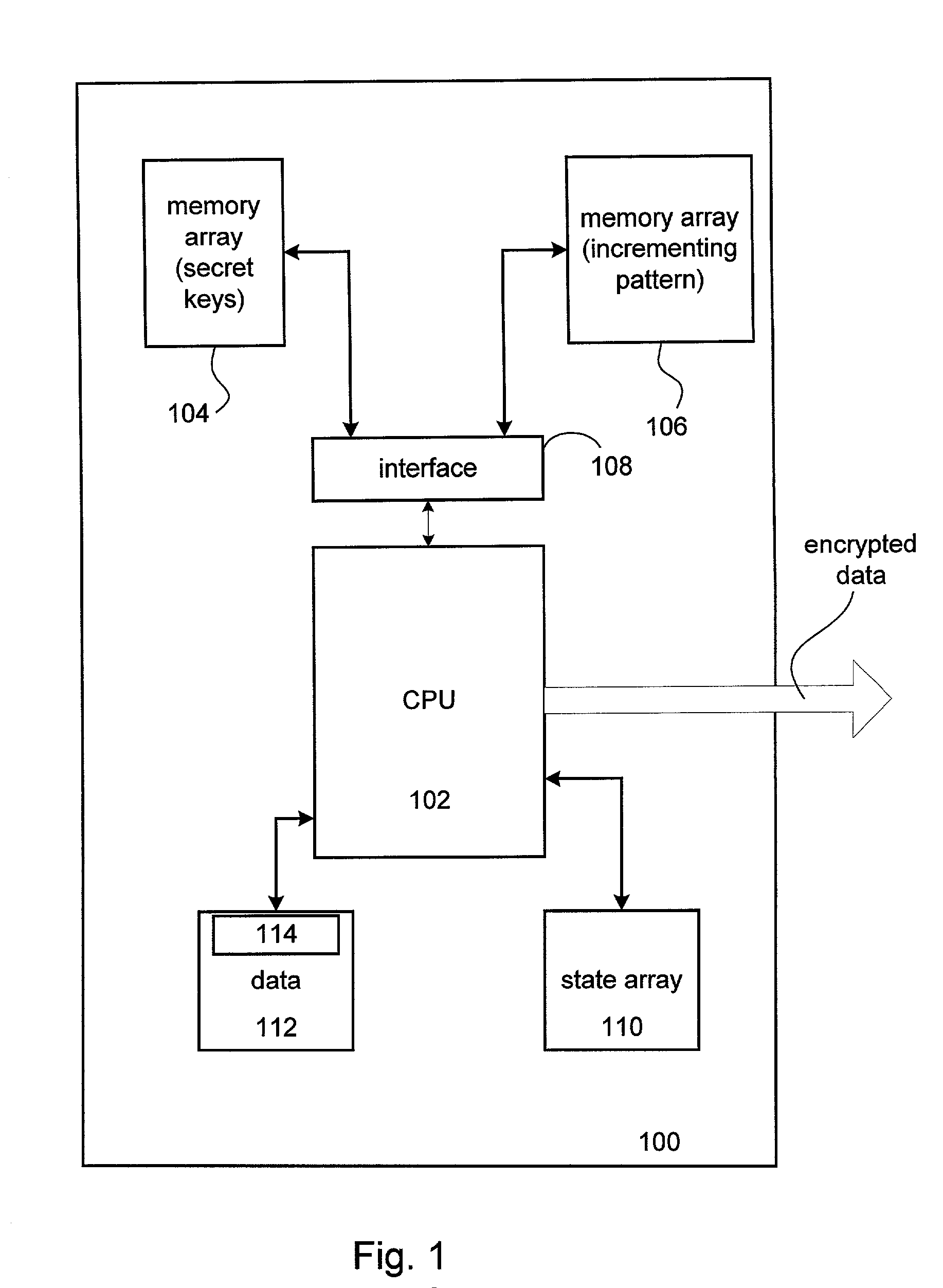
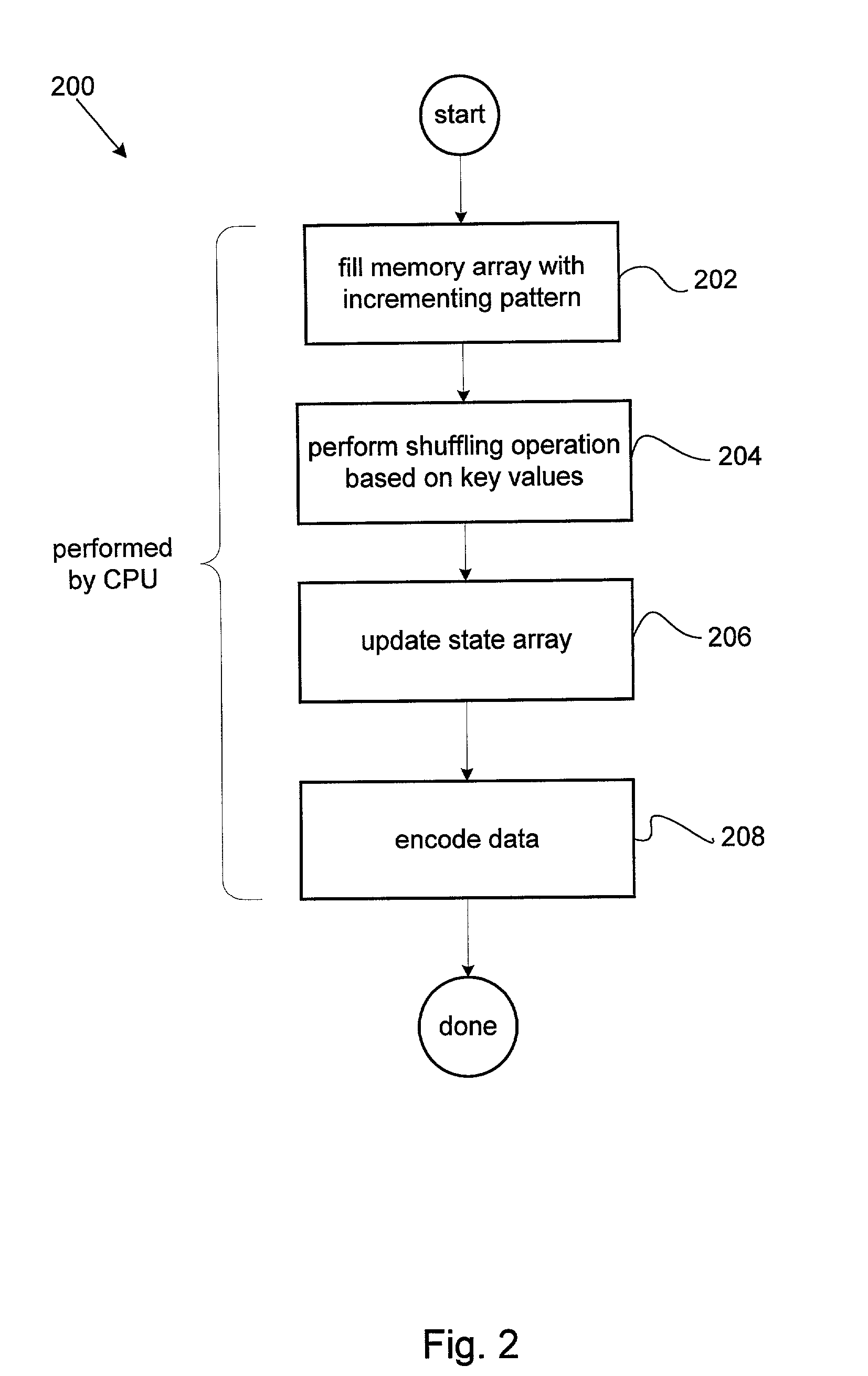
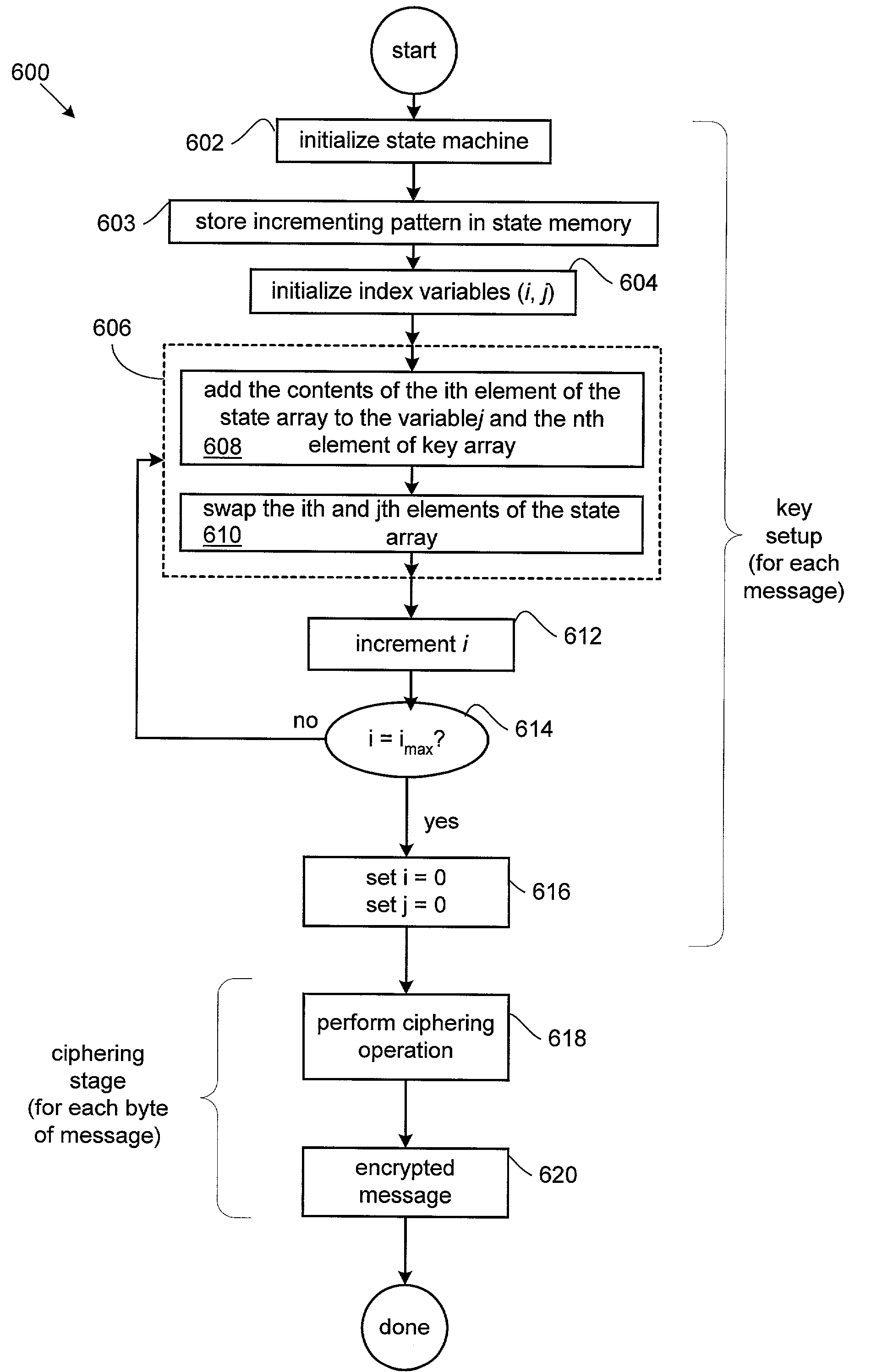
Stream cipher encryption application accelerator and methods thereof
InactiveUS20020037079A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCryptographic acceleratorByte
A system for encrypting and decrypting data formed of a number of bytes using the ARCFOUR encryption algorithm is disclosed. The system includes a system bus and an encryption accelerator arranged to execute the encryption algorithm coupled to the system bus. A system memory coupled to the system bus arranged to store a secret key array associated with the data and a central processing unit coupled to the system bus wherein encryption accelerator uses substantially no central processing unit resources to execute the encryption algorithm.
Owner:AVAGO TECH INT SALES PTE LTD
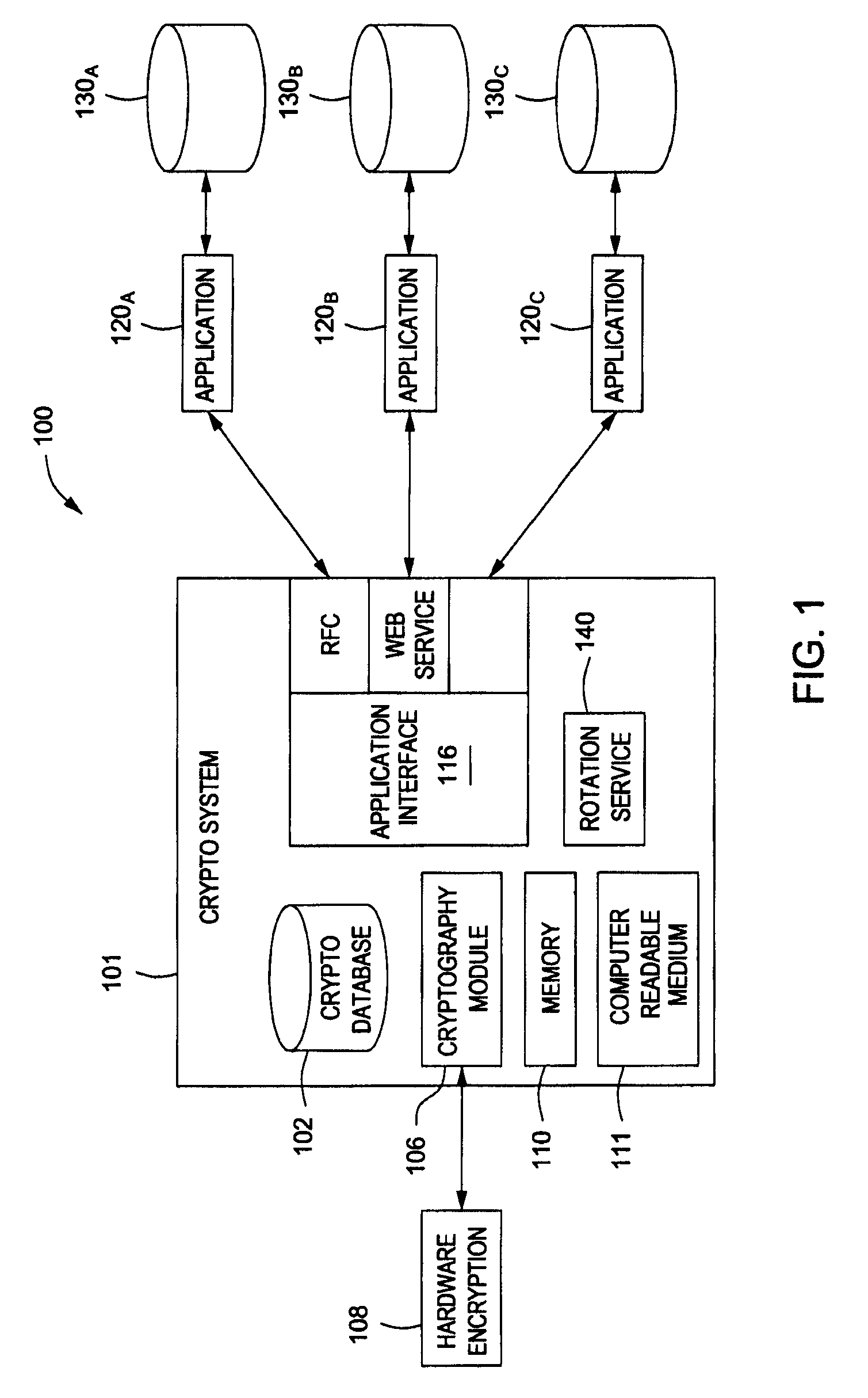
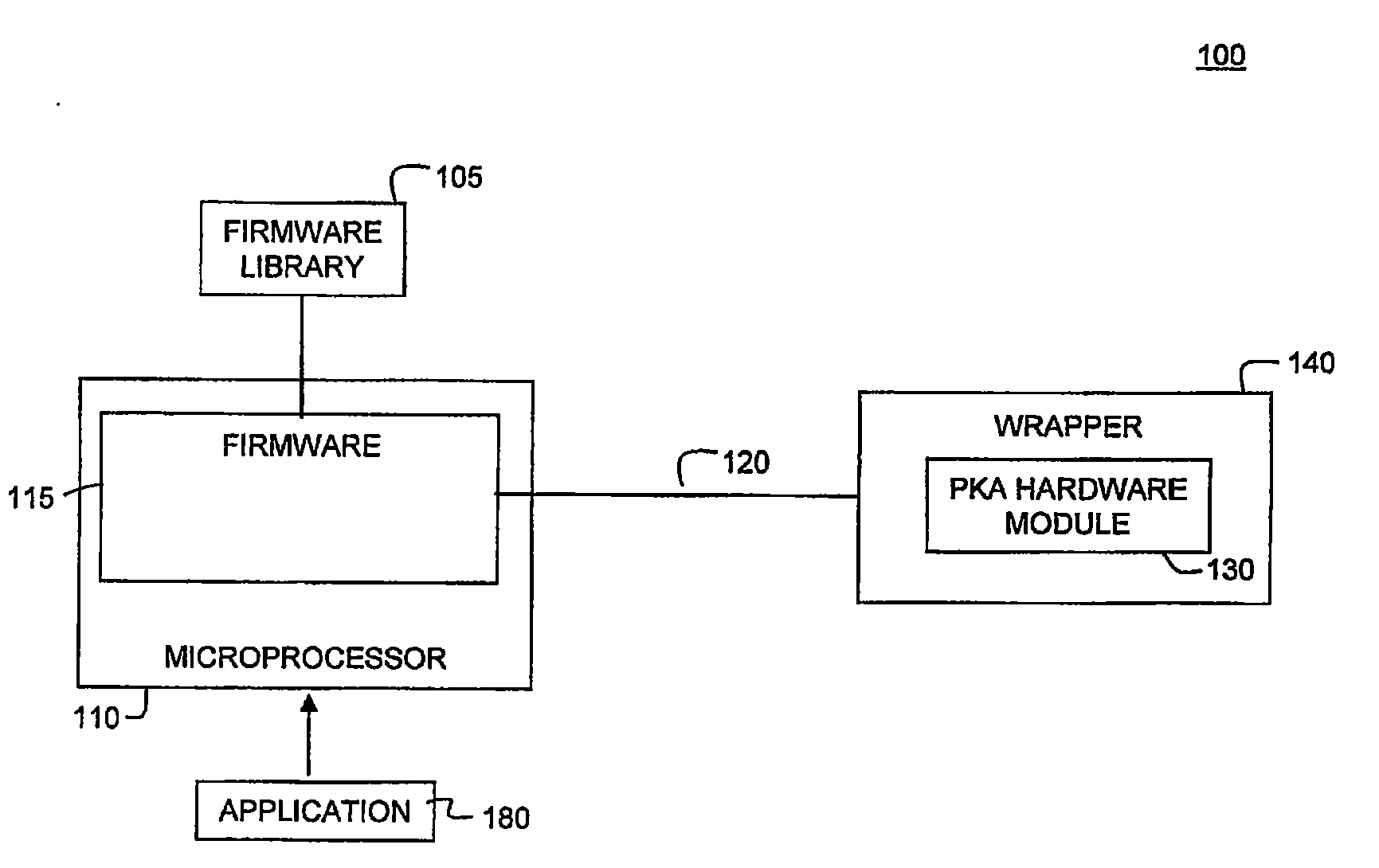
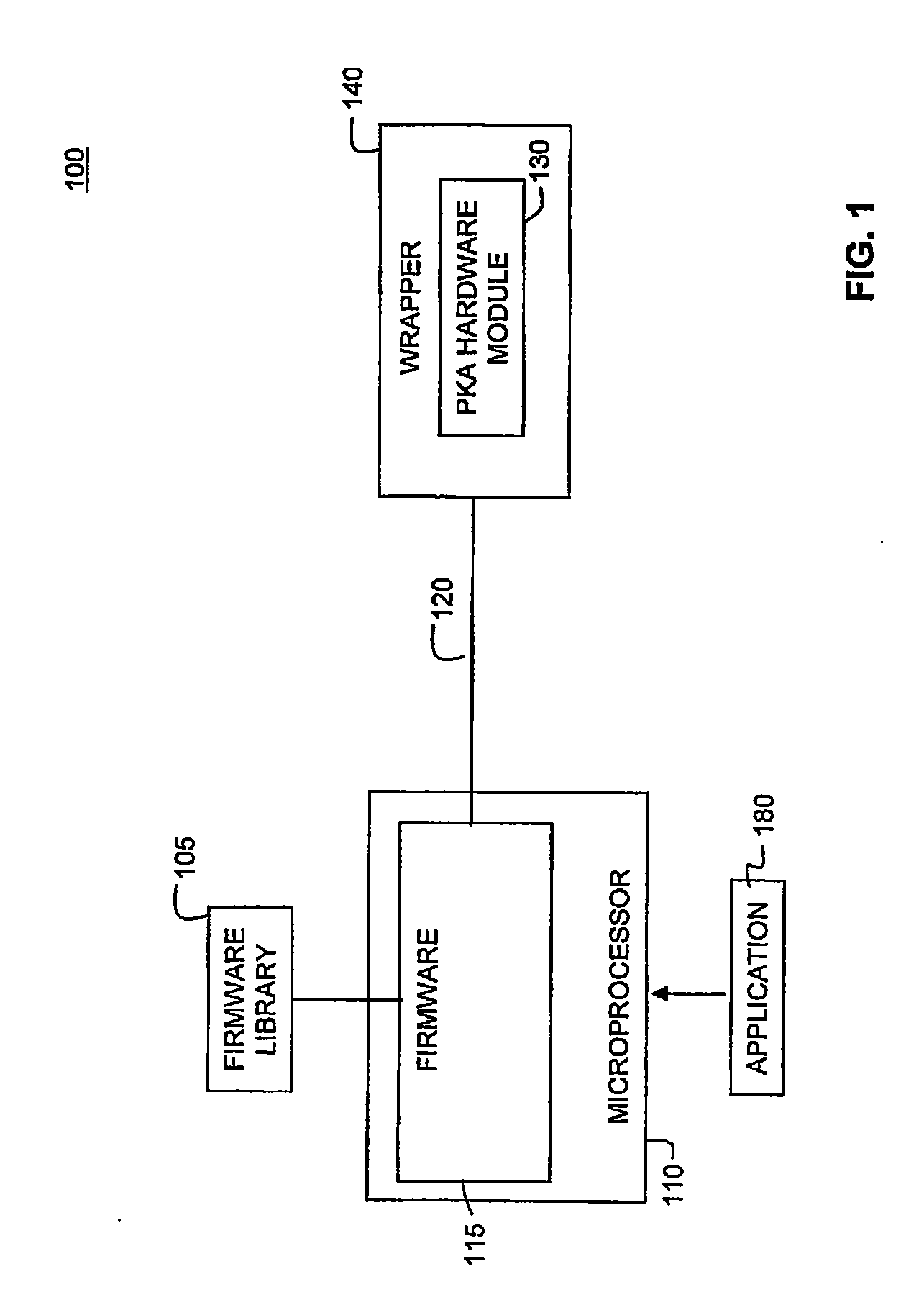
Scalable and Extensible Architecture for Asymmetrical Cryptographic Acceleration
InactiveUS20090319804A1Instruction analysisUnauthorized memory use protectionCryptographic acceleratorExtensible architecture
Systems and methods for providing asymmetrical cryptographic acceleration are provided. The scalable asymmetric cryptographic accelerator engine uses a layered approach based on the collaboration of firmware and hardware to perform a specific cryptographic operation. Upon receipt of a request for a cryptographic function, the system accesses a sequence of operations required to perform the requested function. A micro code sequence is prepared for each hardware operation and sent to the hardware module. The micro code sequence includes a set of load instructions, a set of data processing instructions, and a set of unload instructions. An instruction may include a register operand having a register type and a register index. Upon receipt of a load instruction, the hardware module updates size information in a content addressable memory for a register included in the instruction. The hardware module continuously monitors the content addressable memory to avoid buffer overflow or underflow conditions.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
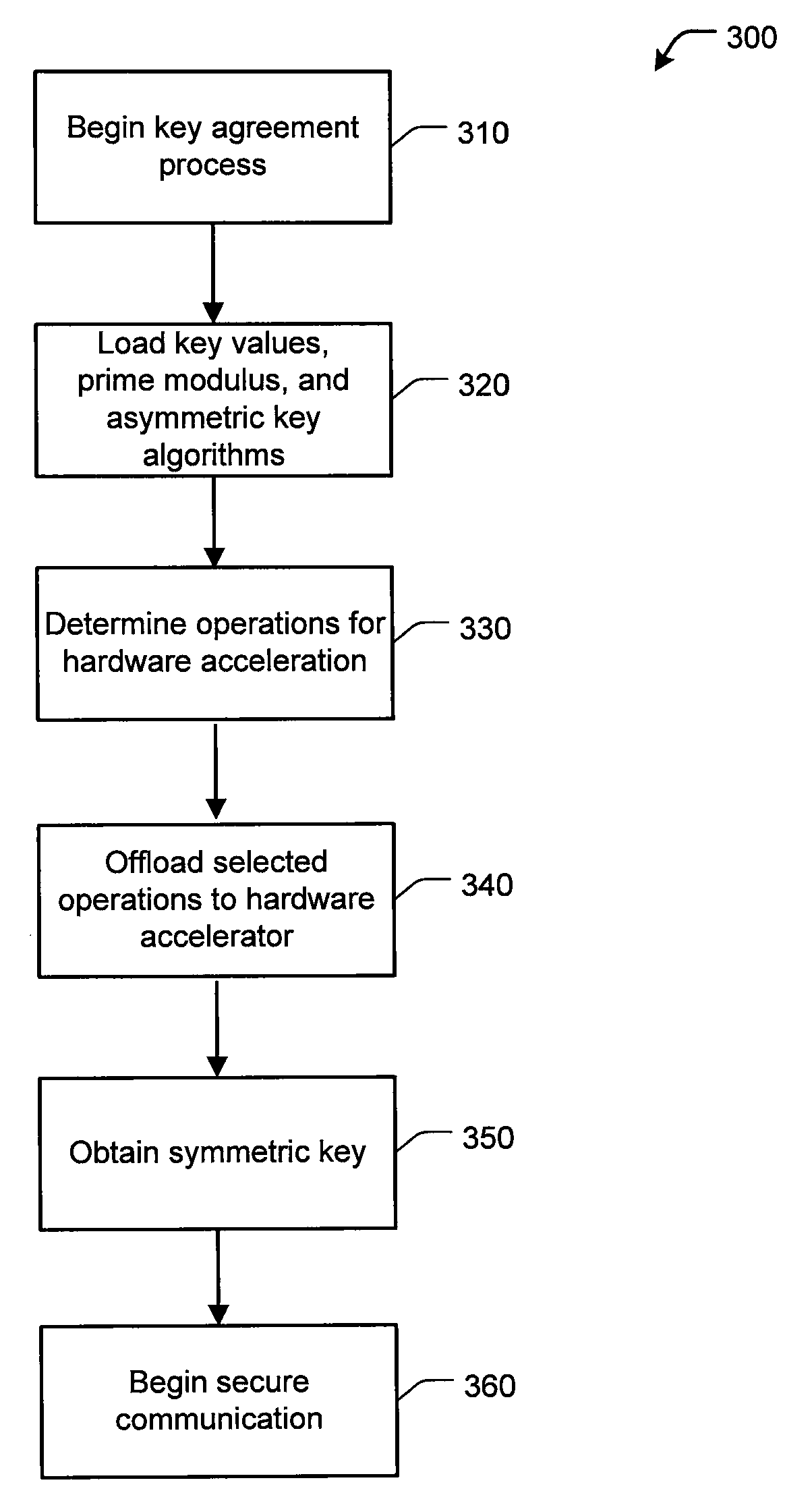
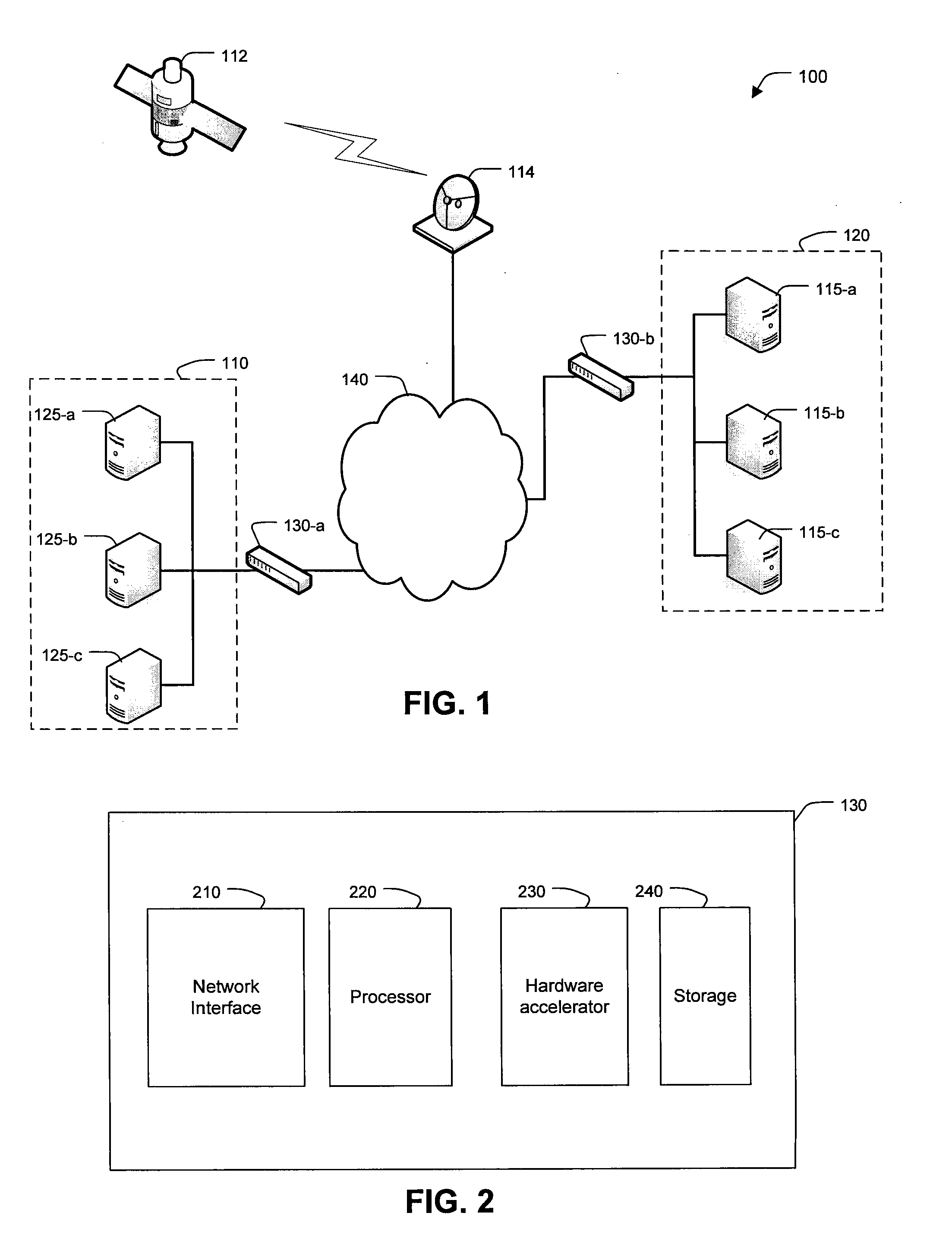
Hardware-Based Cryptographic Accelerator
InactiveUS20100011047A1Encryption apparatus with shift registers/memoriesComputation using non-contact making devicesCryptographic acceleratorProgrammable logic device
A system, method, and apparatus for performing hardware-based cryptographic operations are disclosed. The apparatus can include an encryption device with a hardware accelerator having an accumulator, a multiplier circuit, an adder circuit, and a state machine. The state machine can control successive operation of the hardware accelerator to carry out a rapid, multiplier-based reduction of a large integer by a prime modulus value. Optionally, the hardware accelerator can include a programmable logic device such as a field-programmable gate array with one or more dedicated multiple-accumulate blocks.
Owner:VIASAT INC
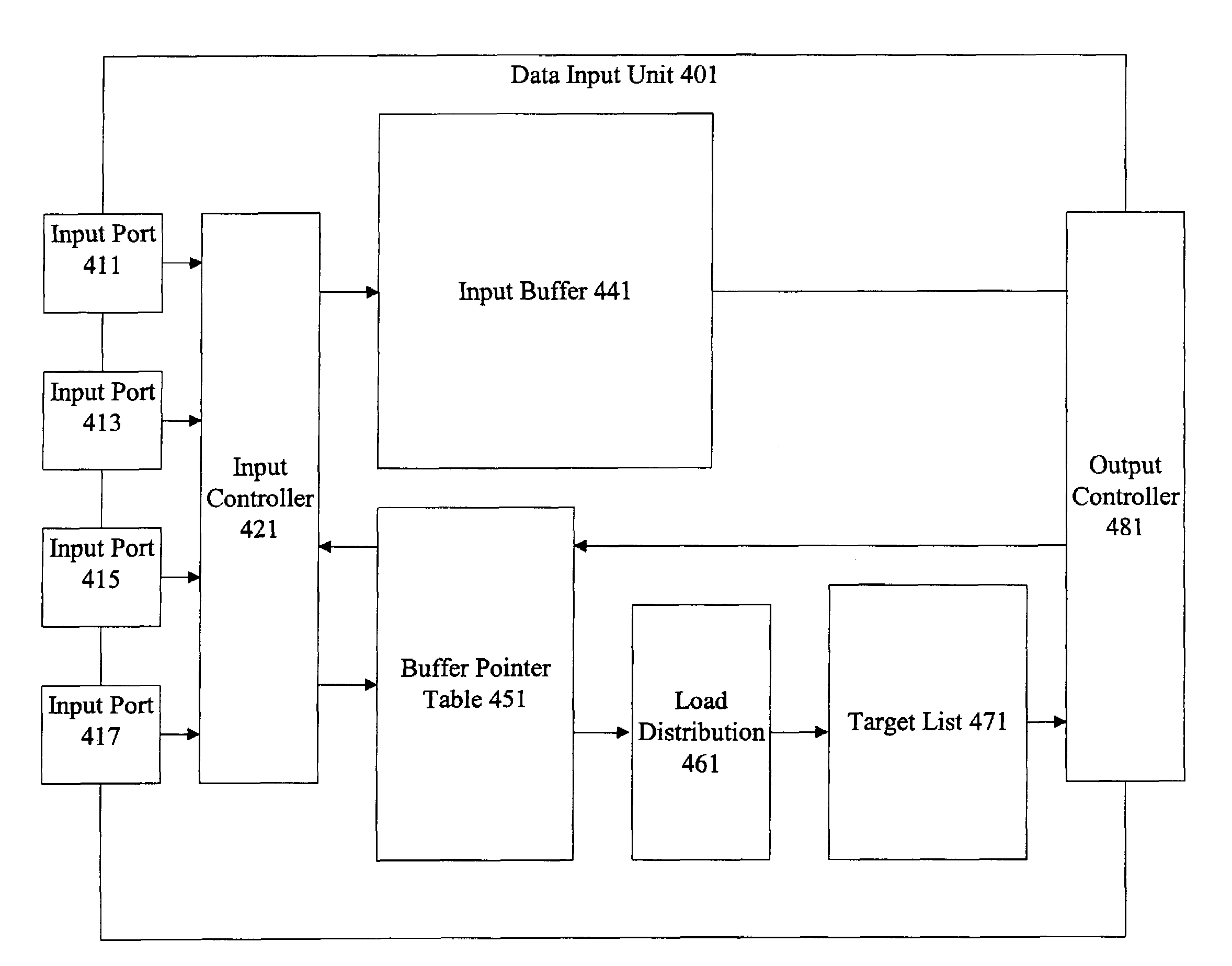
Cryptography accelerator data routing unit
InactiveUS20040123096A1Unauthorized memory use protectionHardware monitoringProcessing coreCryptographic accelerator
Methods and apparatus are provided for handling data at a cryptography accelerator output interface. A shared resource such as a shared output buffer is provided at the cryptography accelerator output interface having multiple output ports. The output interface shared resource can be allocated amongst the various output ports based on characteristics and requirements of the various input ports. References to data in the shared resource allow processing and ordering of data following processing by cryptographic processing cores.
Owner:AVAGO TECH INT SALES PTE LTD
Data transfer efficiency in a cryptography accelerator system
InactiveUS7941662B2User identity/authority verificationInternal/peripheral component protectionCryptographic acceleratorChecksum
Methods and apparatus are provided for performing authentication and decryption operations in a cryptography accelerator system. Input data passed to a cryptography accelerator from a host such a CPU includes information for a cryptography accelerator to determine where to write the processed data. In one example, processed data is formatted as packet payloads in a network buffer. Checksum information is precalculated and an offset for a header is maintained.
Owner:AVAGO TECH INT SALES PTE LTD
Methods and apparatus for performing encryption and authentication
InactiveUS7376826B2Efficient executionEfficiently provideUser identity/authority verificationUnauthorized memory use protectionCryptographic acceleratorComputer science
Methods and apparatus are provided for a cryptography accelerator to efficiently perform authentication and encryption operations. A data sequence is received at a cryptography accelerator. An encrypted authentication code and an encrypted data sequence is provided efficiently upon performing single pass authentication and encryption operations on the data sequence.
Owner:AVAGO TECH INT SALES PTE LTD
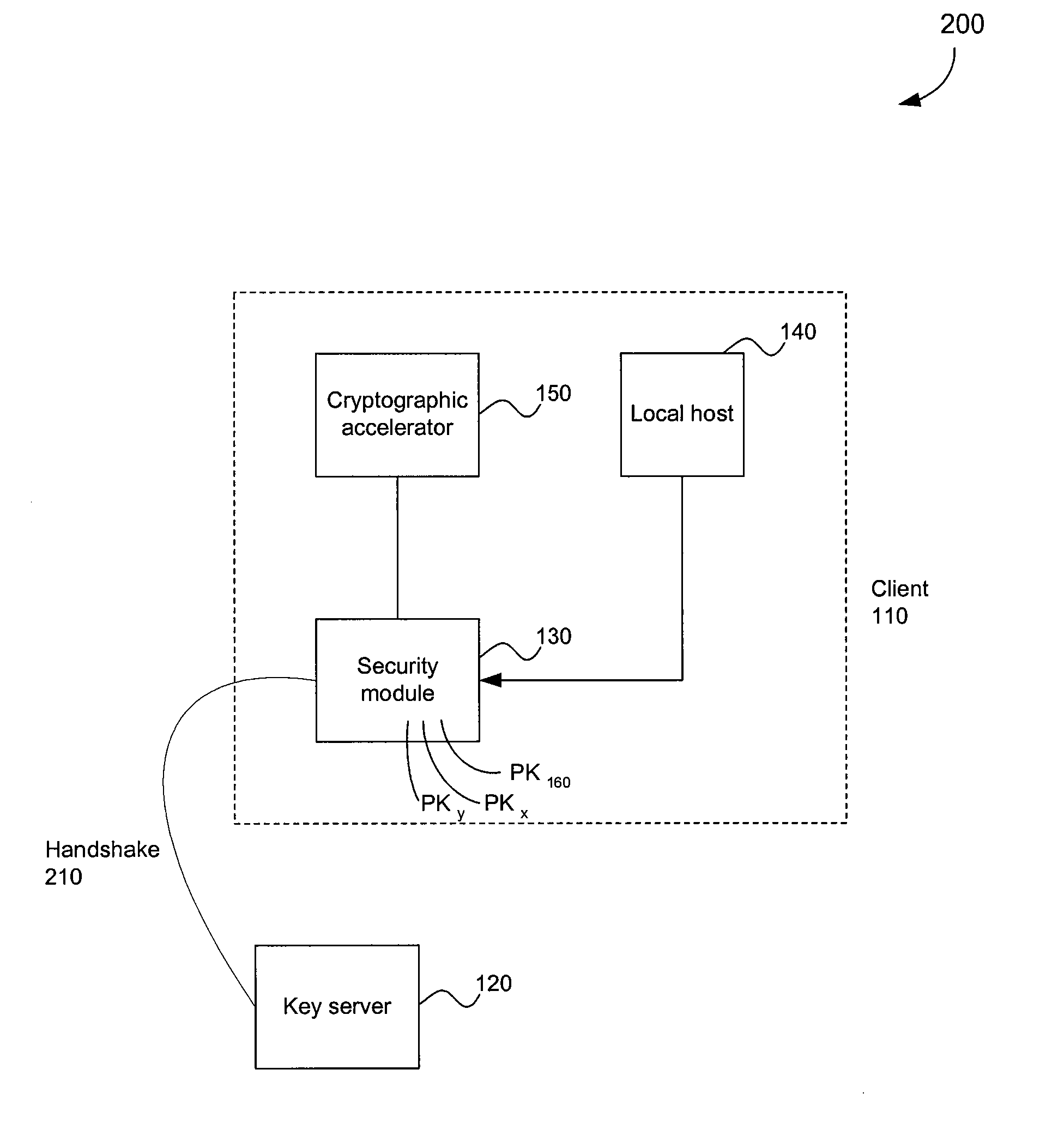
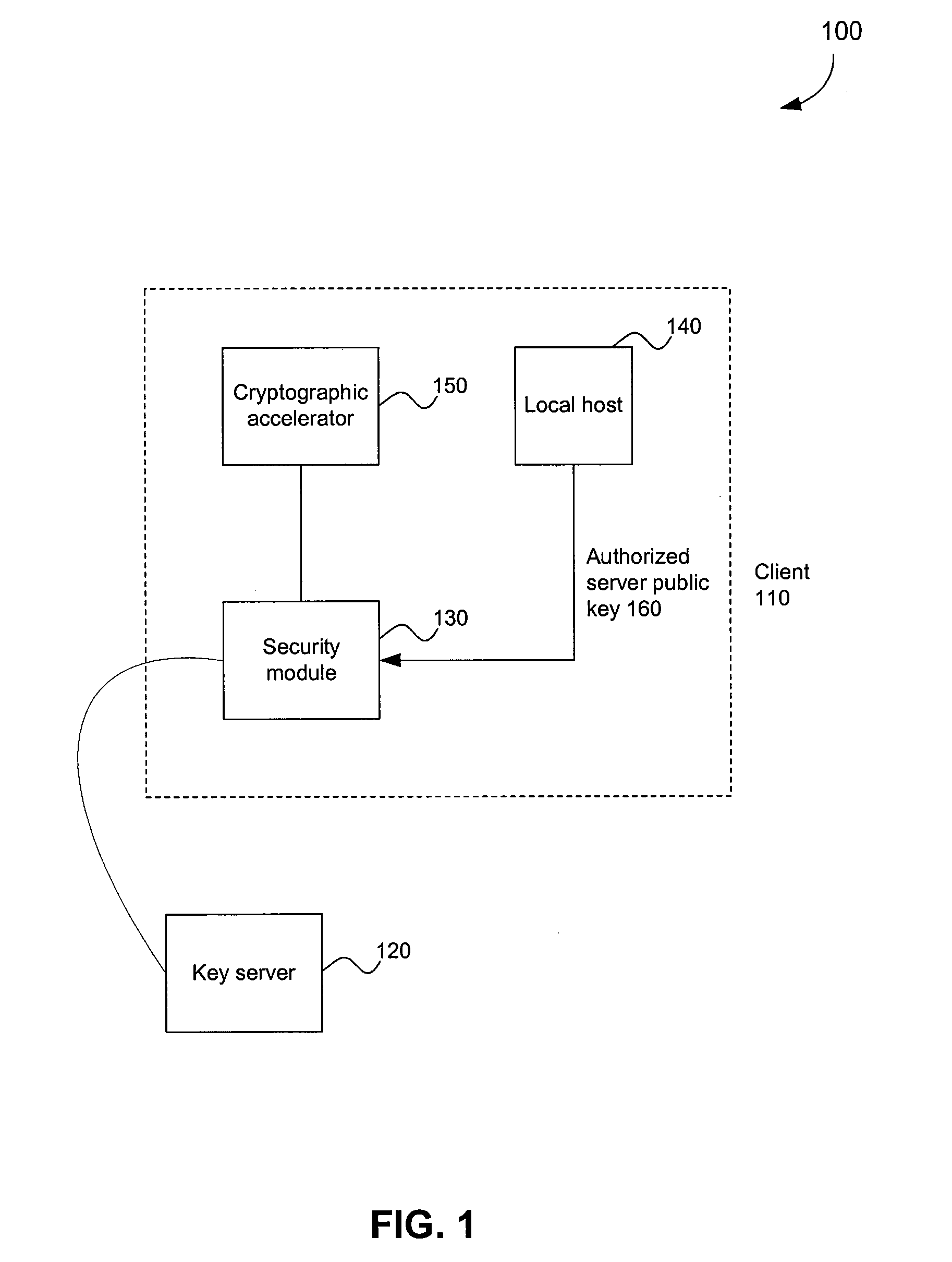
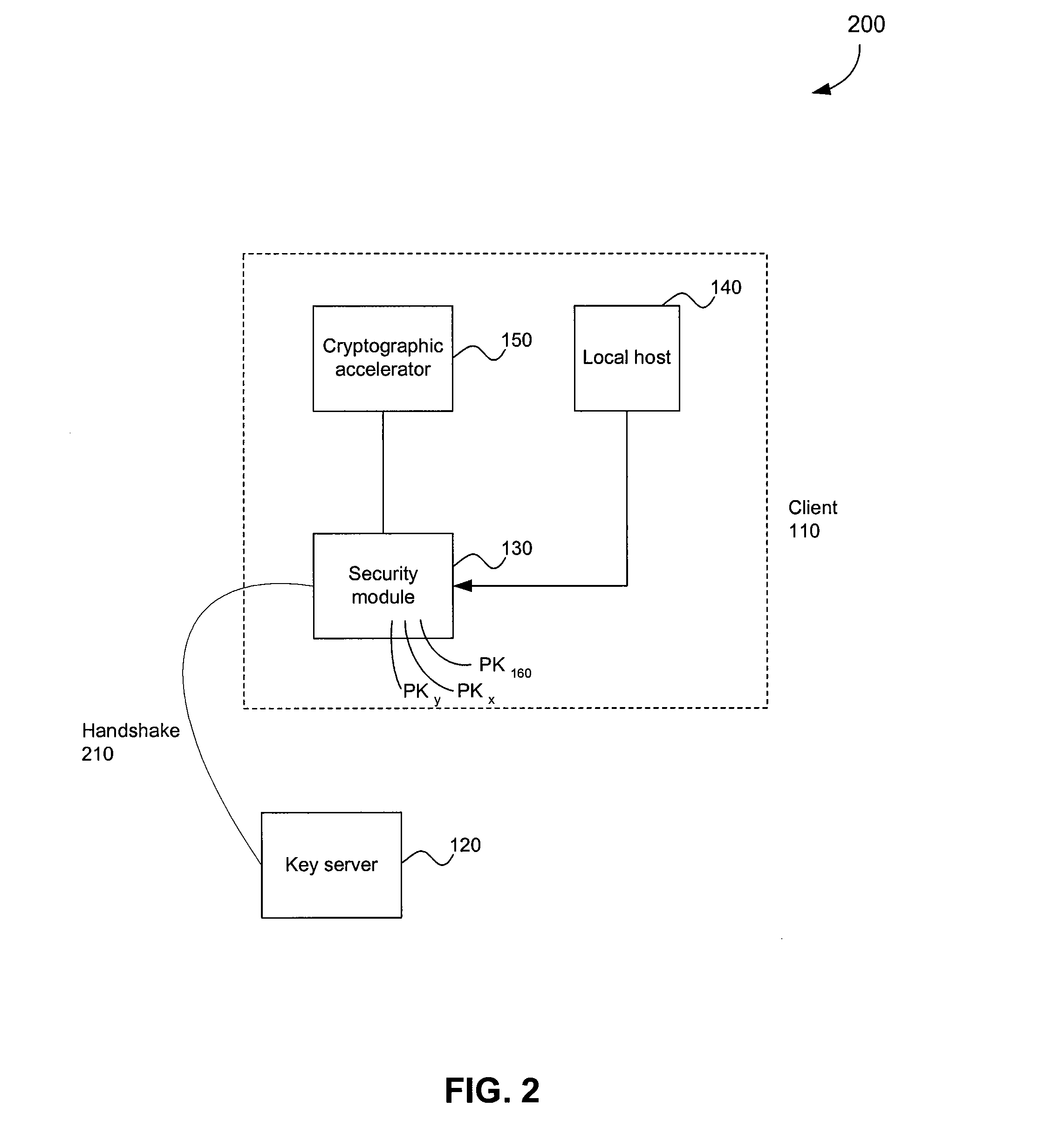
System and method for distributed security
InactiveUS7289632B2Security functionality is enhancedImprove functionalityKey distribution for secure communicationUser identity/authority verificationCryptographic acceleratorClient-side
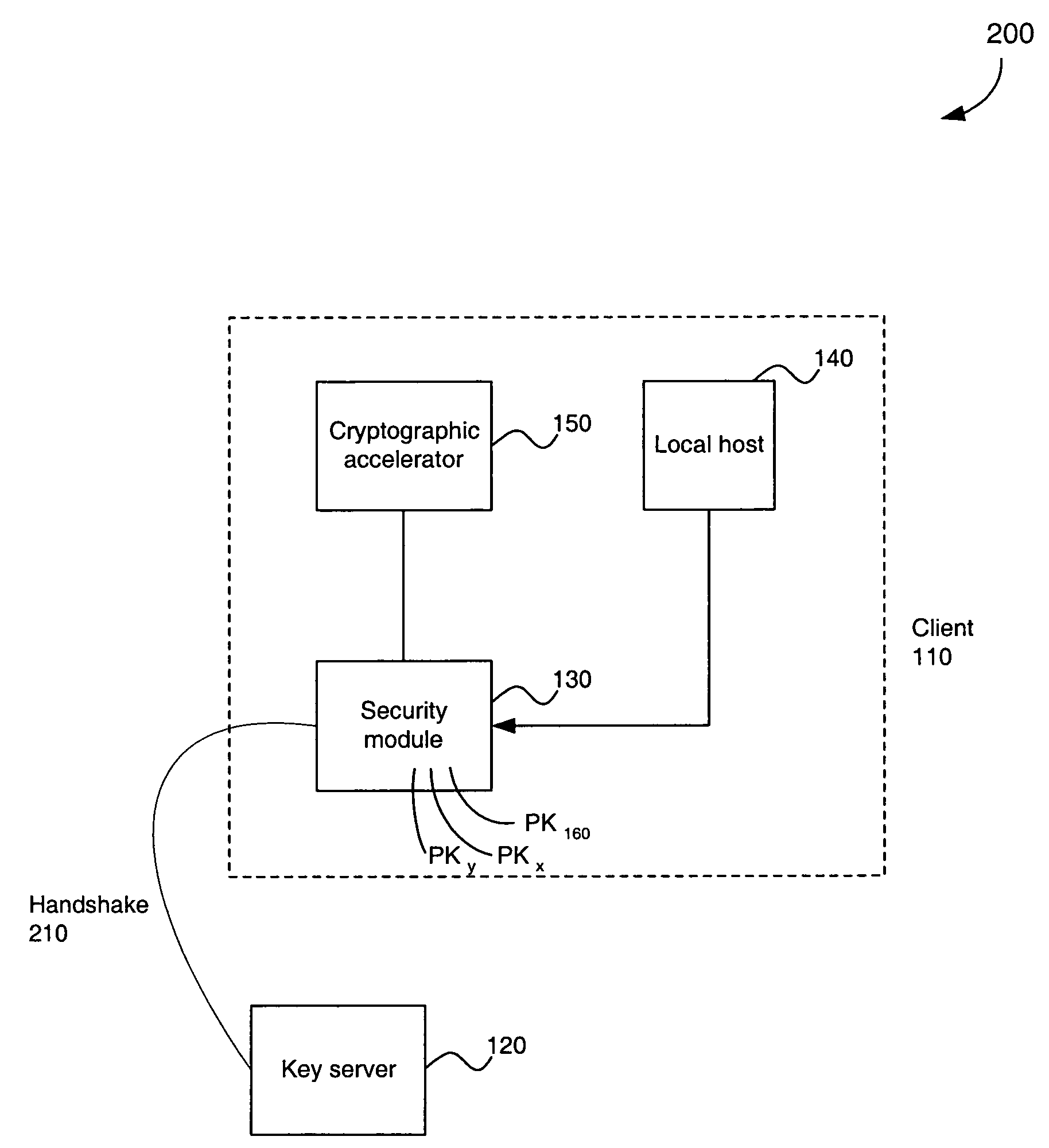
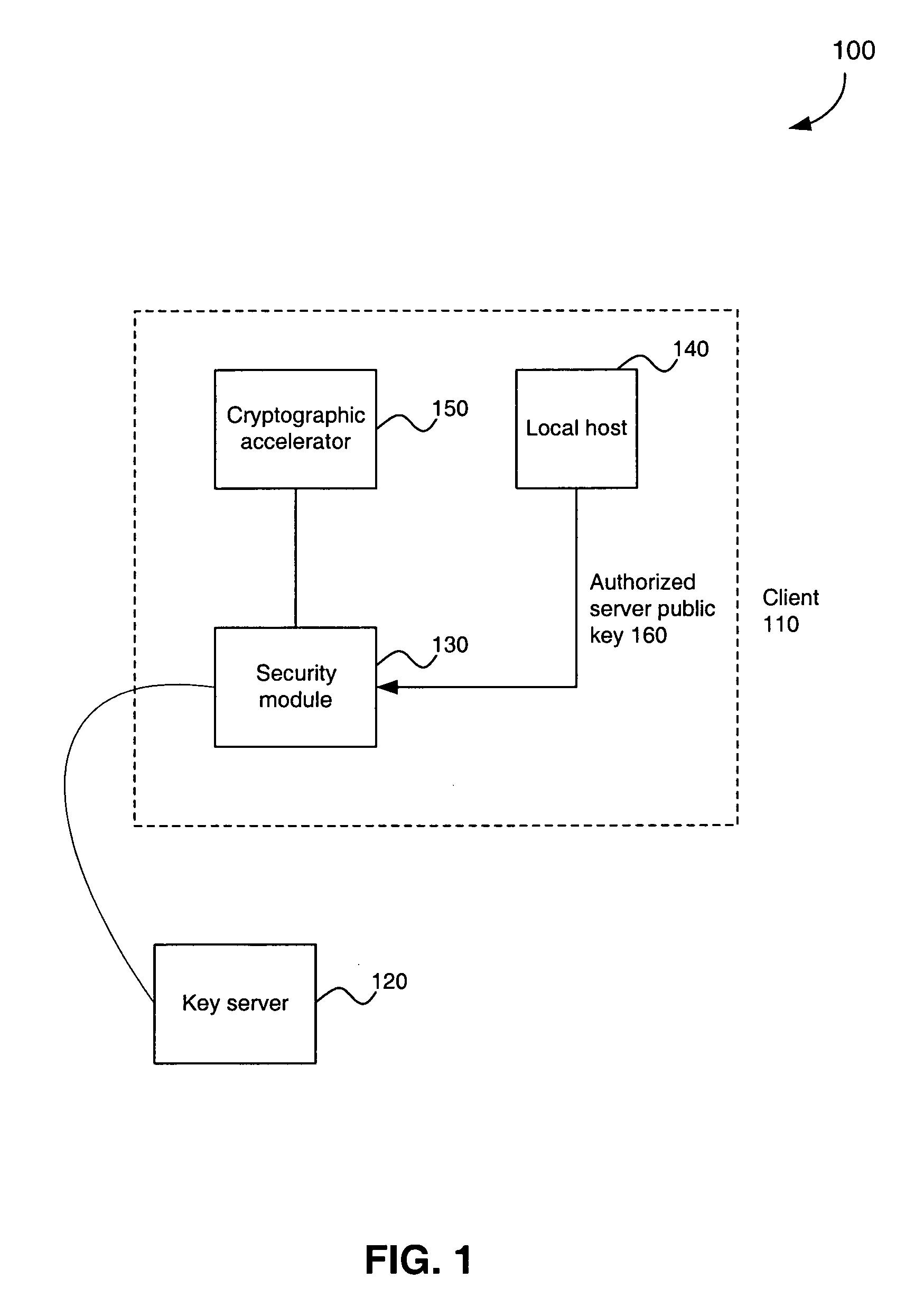
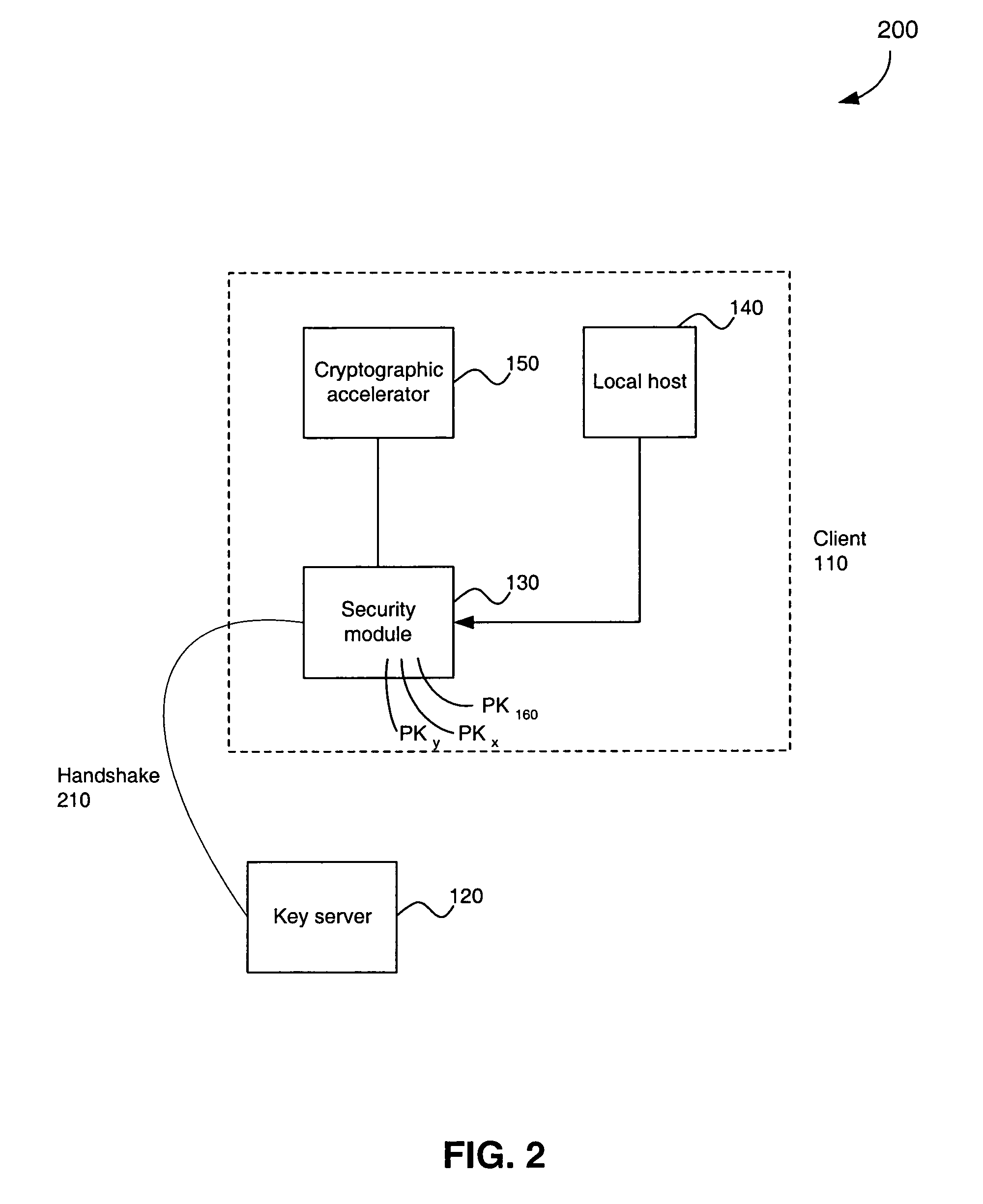
A security architecture in which a security module is integrated in a client machine, wherein the client machine includes a local host that is untrusted. The security module performs encryption and decryption algorithms, authentication, and public key processing. The security module also includes separate key caches for key encryption keys and application keys. A security module can also interface a cryptographic accelerator through an application key cache. The security module can authorize a public key and an associated key server. That public key can subsequently be used to authorize additional key servers. Any of the authorized key servers can use their public keys to authorize the public keys of additional key servers. Secure authenticated communications can then transpire between the client and any of these key servers. Such a connection is created by a secure handshake process that takes place between the client and the key server. A time value can be sent from the key server to the client, allowing for secure revocation of keys. In addition, secure configuration messages can be sent to the security module.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Cryptography accelerator application program interface
InactiveUS7369657B2Internal/peripheral component protectionSecret communicationAbstraction layerCryptographic accelerator
Owner:AVAGO TECH INT SALES PTE LTD
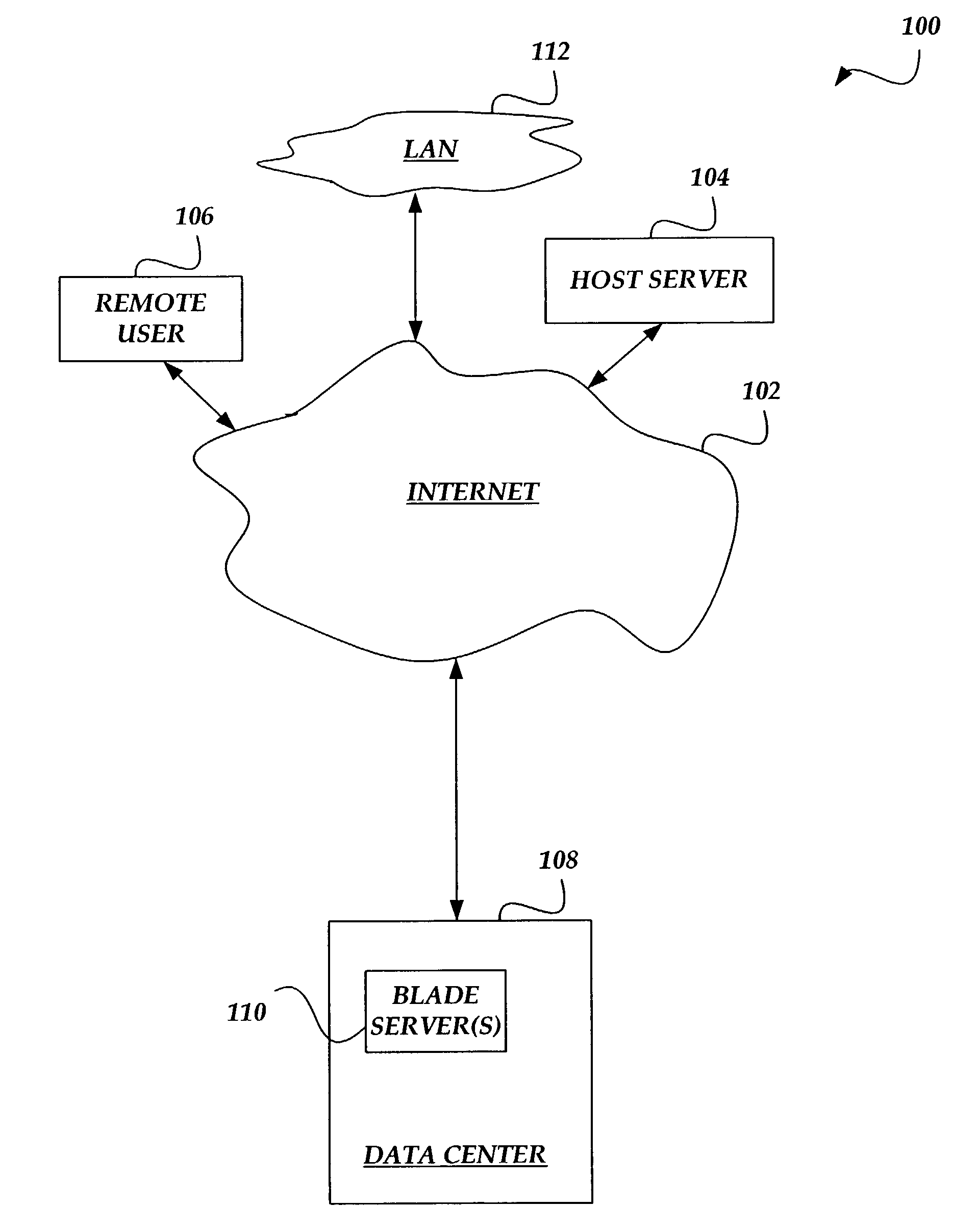
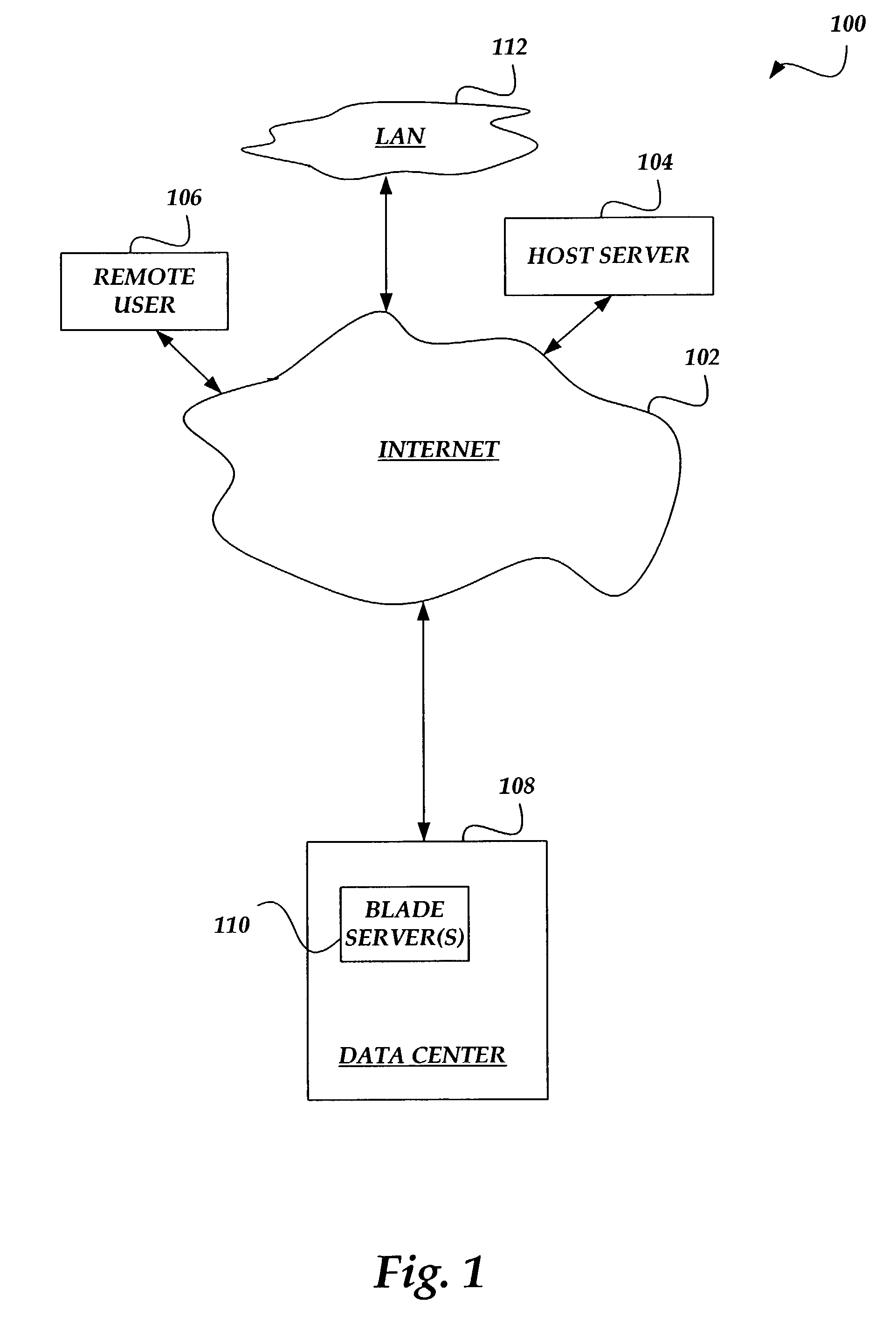
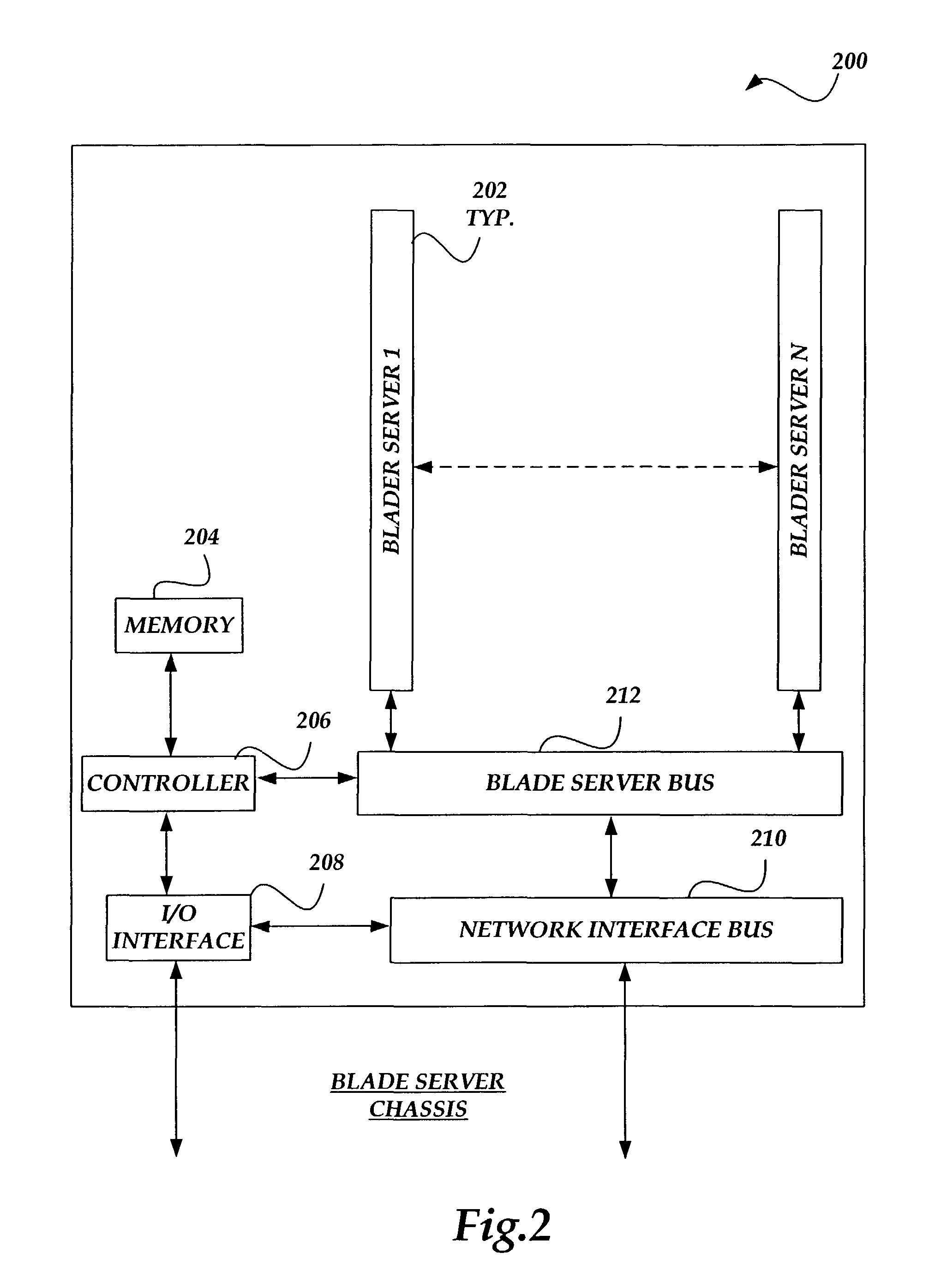
Method and system for hard disk emulation and cryptographic acceleration on a blade server
ActiveUS8850223B1Unauthorized memory use protectionHardware monitoringCryptographic acceleratorModular exponentiation
An inventive apparatus that integrates the operation of a hard disk emulator and a cryptographic accelerator on a single blade server card. An application with cryptographic operations can off load computationally intensive calculations to the cryptographic accelerator so that the speed at which the application performs actions can be increased significantly. Typically, the hard disk emulator is a flash memory component and the accelerator can perform at least modular exponentiation calculations. One bus is employed for communication between the hard disk emulator and the accelerator. Another bus is employed to communicate with other resources off the card. Often, the card is configured to operate as one of a several blade servers in a chassis.
Owner:F5 NETWORKS INC
Stream cipher encryption application accelerator and methods thereof
InactiveUS7277542B2Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCryptographic acceleratorByte
A system for encrypting and decrypting data formed of a number of bytes using the ARCFOUR encryption algorithm is disclosed. The system includes a system bus and an encryption accelerator arranged to execute the encryption algorithm coupled to the system bus. A system memory coupled to the system bus arranged to store a secret key array associated with the data and a central processing unit coupled to the system bus wherein encryption accelerator uses substantially no central processing unit resources to execute the encryption algorithm.
Owner:AVAGO TECH INT SALES PTE LTD
Methods and apparatus performing hash operations in a cryptography accelerator
InactiveUS20090028326A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareCryptographic accelerator
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
System and Method for Distributed Security
ActiveUS20080037793A1Improve functionalityKey distribution for secure communicationRandom number generatorsCryptographic acceleratorComputer module
A security architecture in which a security module is integrated in a client machine, wherein the client machine includes a local host that is untrusted. The security module performs encryption and decryption algorithms, authentication, and public key processing. The security module also includes separate key caches for key encryption keys and application keys. A security module can also interface a cryptographic accelerator through an application key cache. The security module can authorize a public key and an associated key server. That public key can subsequently be used to authorize additional key servers. Any of the authorized key servers can use their public keys to authorize the public keys of additional key servers. Secure authenticated communications can then transpire between the client and any of these key servers. Such a connection is created by a secure handshake process that takes place between the client and the key server. A time value can be sent from the key server to the client, allowing for secure revocation of keys. In addition, secure configuration messages can be sent to the security module.
Owner:AVAGO TECH INT SALES PTE LTD
Payment encryption accelerator
ActiveUS8751788B2Digital data processing detailsUnauthorized memory use protectionPaymentSession management
Embodiments of the invention provide a system for encrypting web session data which may include a session management module adapted to receive data from a web application module and provide a token that represents the data in encrypted form to the web application, wherein the web application is adapted to use the token to represent the data. The system may also include a tokenizer module communicably coupled to the session management module, wherein the tokenizer module is adapted to receive the data and generate the token. Further, the system may include a database communicably coupled to the session management module, wherein the database is adapted to receive the token and the data, associate the token with the data, and store the token and the data.
Owner:PAYMETRIC
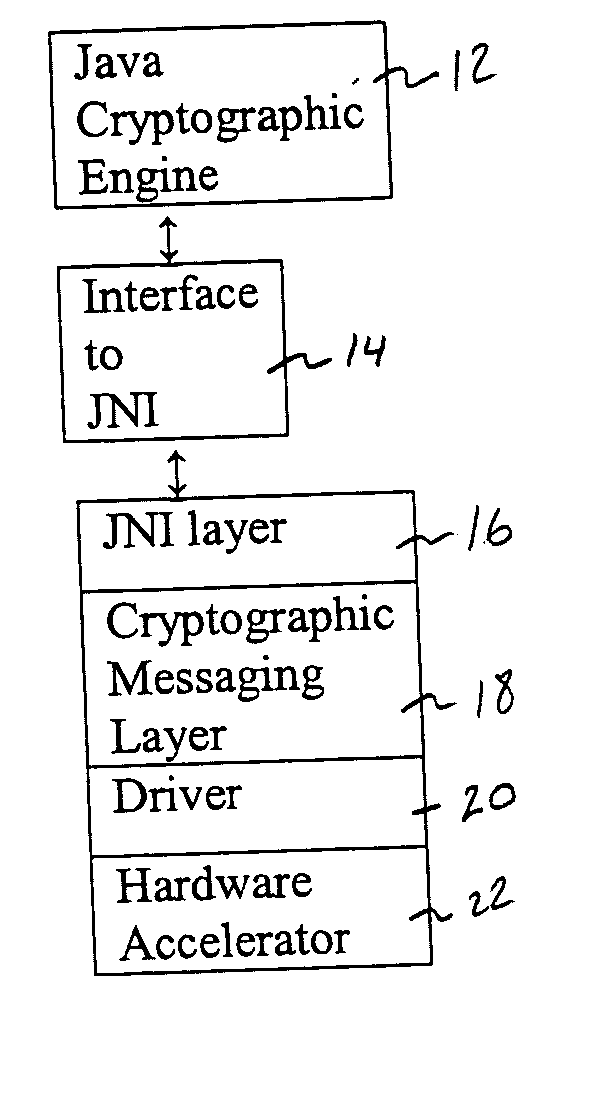
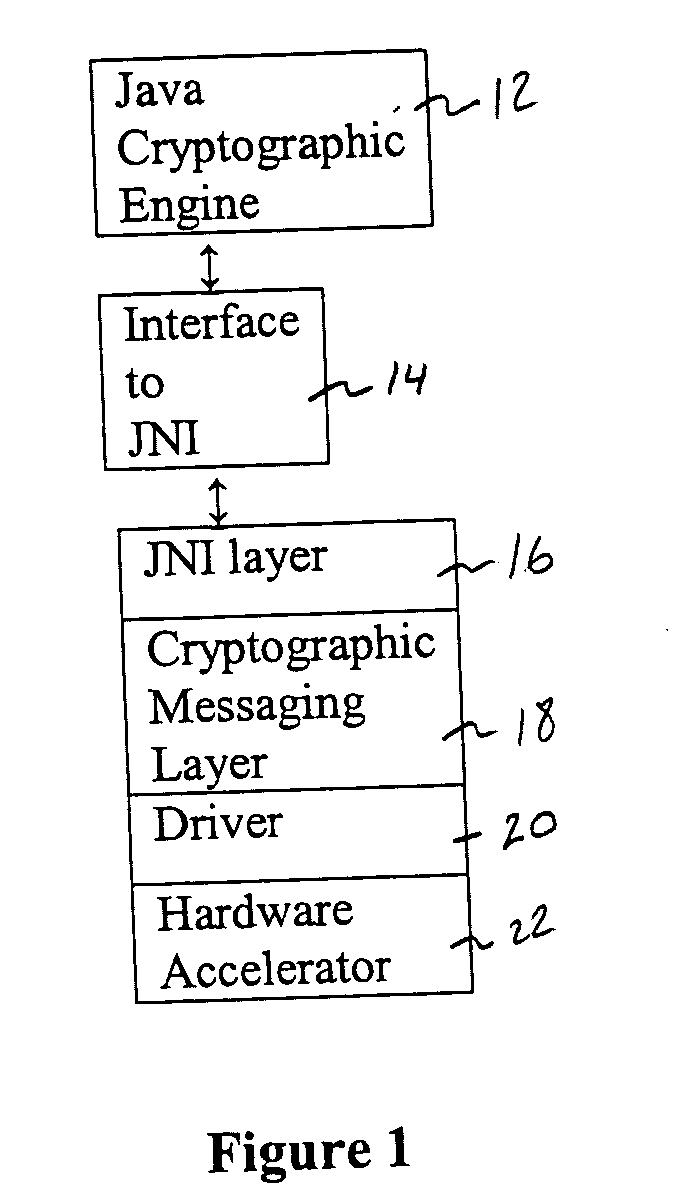
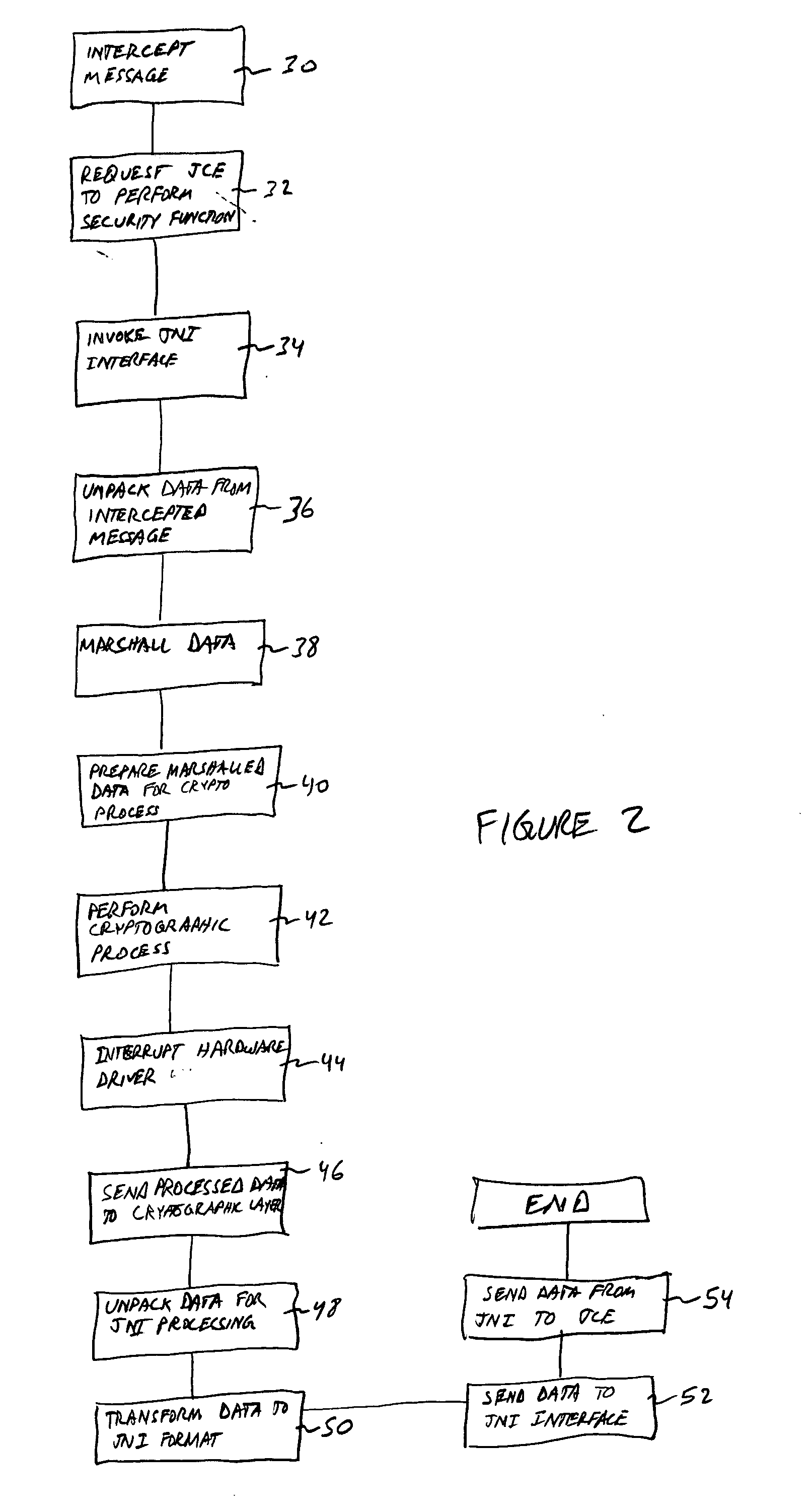
Java cryptographic engine to crypto acceleration integration
InactiveUS20050132211A1Fast formingIncrease speedUnauthorized memory use protectionHardware monitoringCryptographic acceleratorRapid prototyping
A networking appliance having a Java proxy engine that transparently offloads security functions into a cryptographic accelerator, thereby enabling rapid prototyping and platform independence, while increasing the speed of cryptographic and other security functions.
Owner:YUNUS MAMOON +2
Cryptography accelerator data routing unit
InactiveUS7434043B2Unauthorized memory use protectionHardware monitoringProcessing coreCryptographic accelerator
Methods and apparatus are provided for handling data at a cryptography accelerator output interface. A shared resource such as a shared output buffer is provided at the cryptography accelerator output interface having multiple output ports. The output interface shared resource can be allocated amongst the various output ports based on characteristics and requirements of the various input ports. References to data in the shared resource allow processing and ordering of data following processing by cryptographic processing cores.
Owner:AVAGO TECH INT SALES PTE LTD
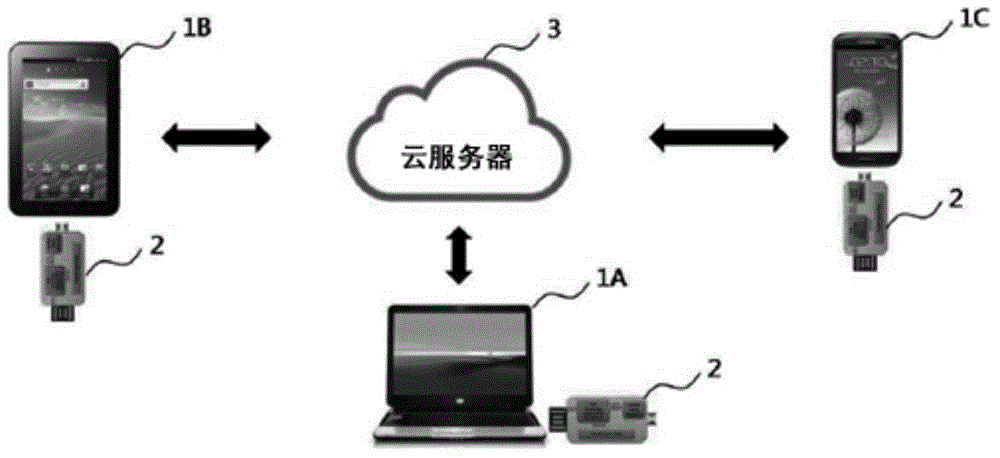
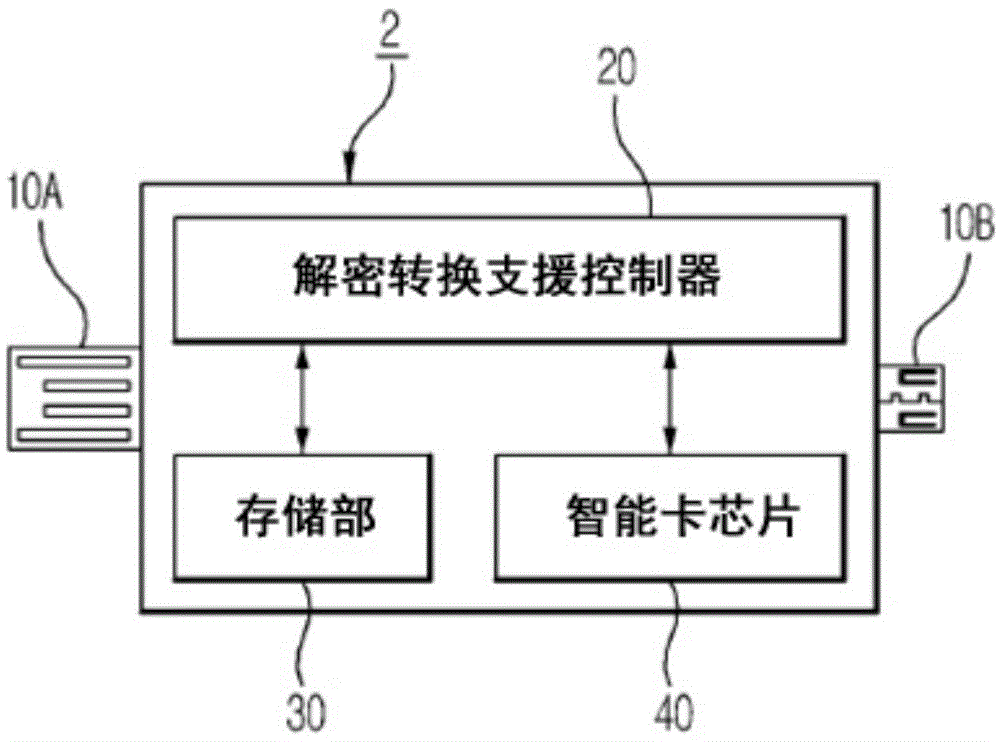
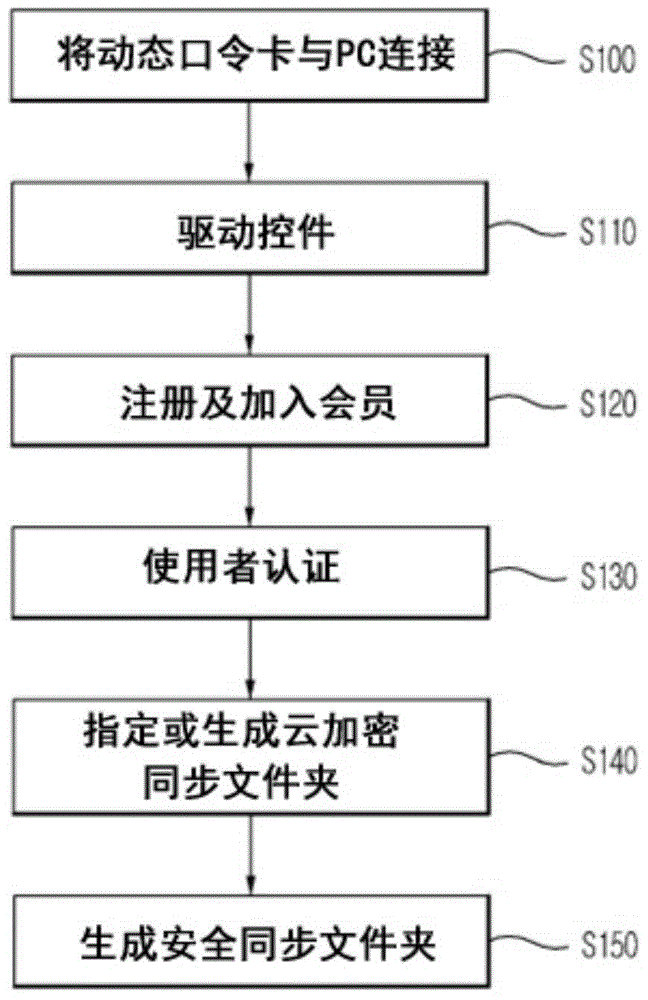
Security key device for secure cloud services, and system and method of providing security cloud services
InactiveCN104615929APrevent leakageImprove securityMultiple digital computer combinationsDigital data authenticationCryptographic acceleratorCloud server
Disclosed is a security key device for cloud services. The security key device includes an interface unit that provides an interface with the user terminal, a storage unit that stores an encrypted user file, and an encryption / decryption conversion support controller that encrypts, when a file to be uploaded to a cloud server is received from the user terminal, the received file and stores the encrypted file in the storage unit to transmit the encrypted file to the user terminal, and stores, when an encrypted file downloaded from the cloud server is received from the user terminal, the received encrypted file in the storage unit and decrypts the encrypted file to transmit the decrypted file to the user terminal. Even when a cloud server is hacked, individual and company's important data cannot be opened, encryption / decryption is processed in a hardware encryption accelerator, and therefore it is possible to prevent leakage of an encryption key even when a personal PC is hacked, thereby significantly improving security compared to the related art.
Owner:SAFERZONE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com