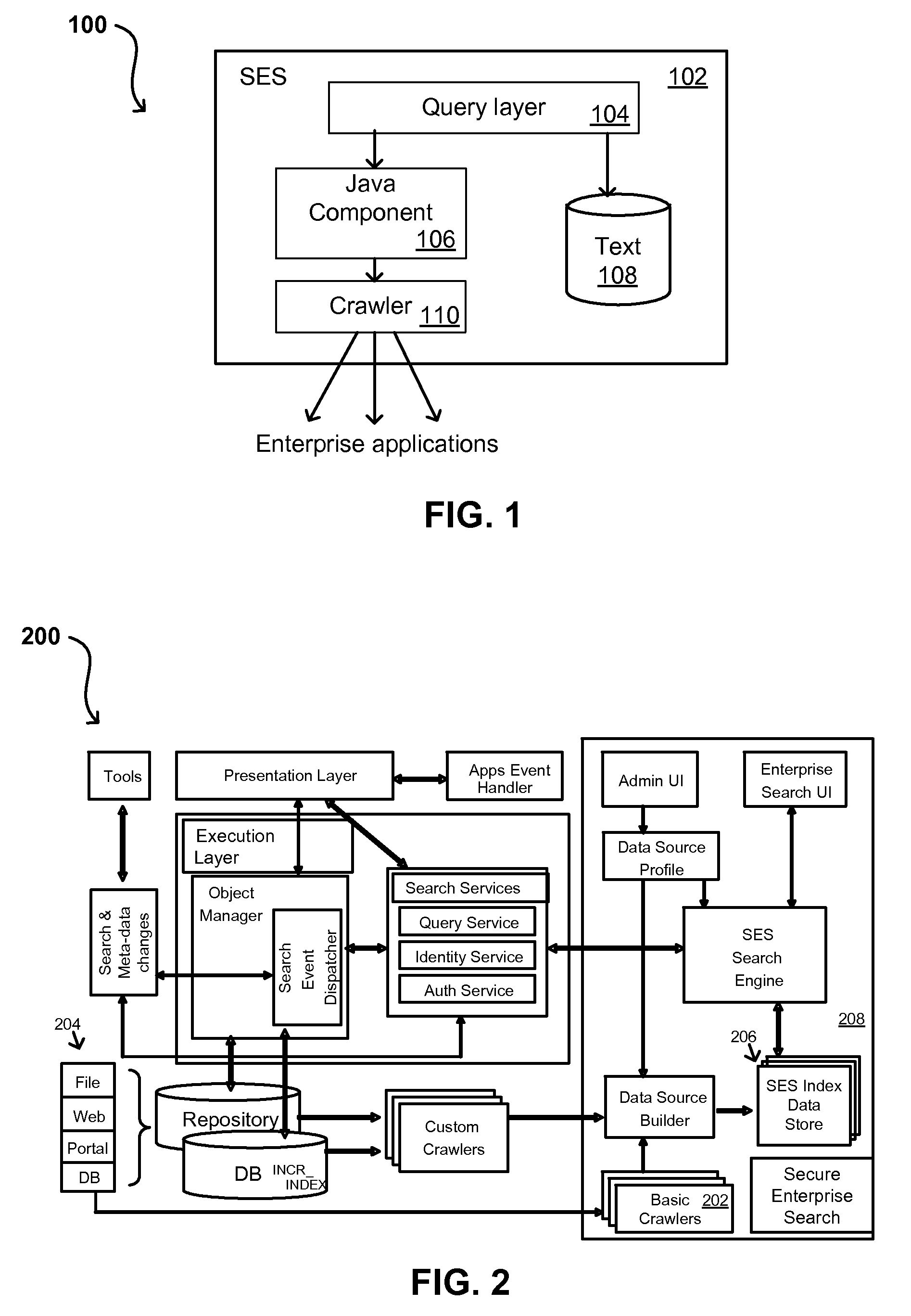
Patents
Literature
43 results about "Extensible architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
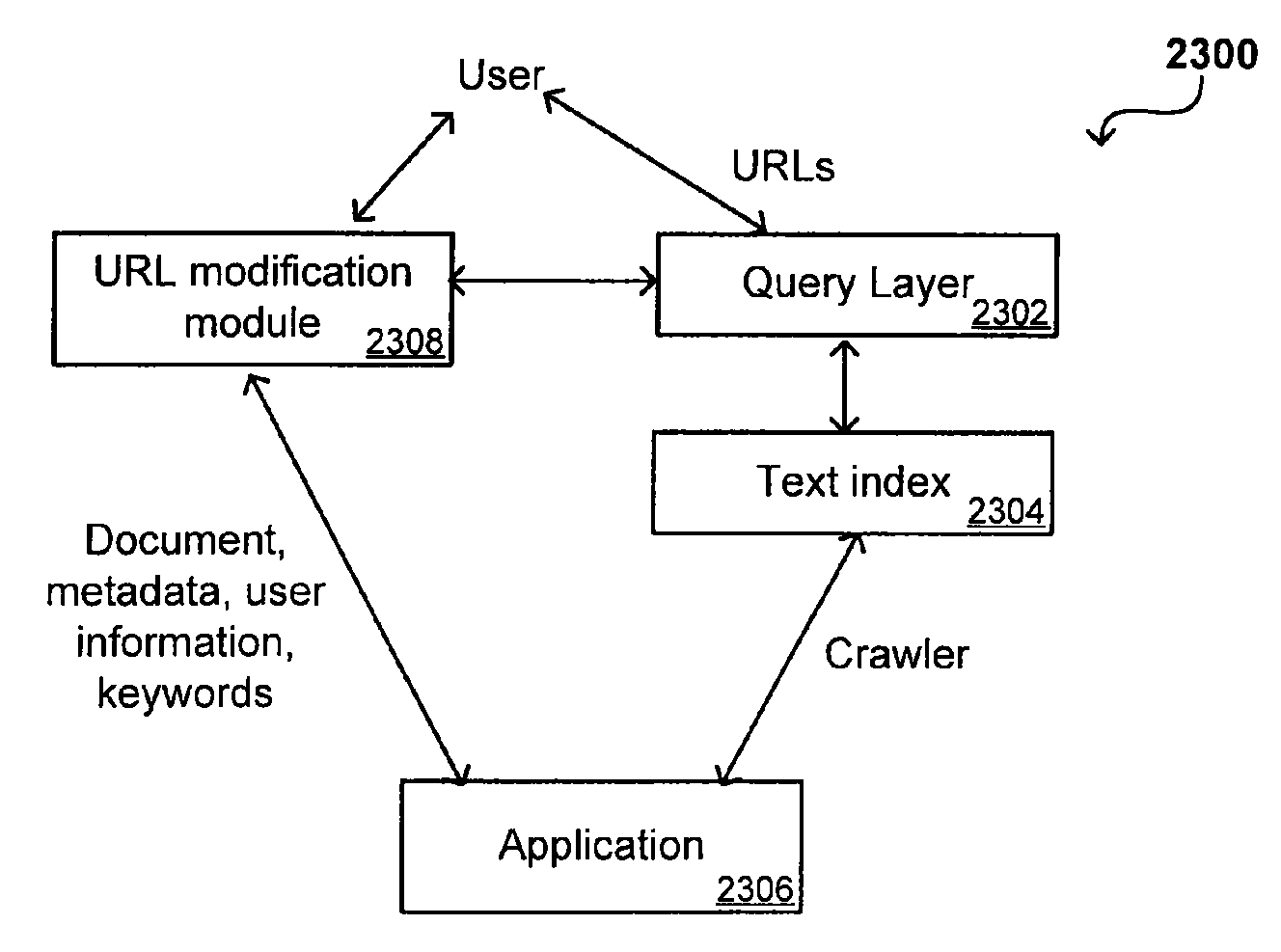
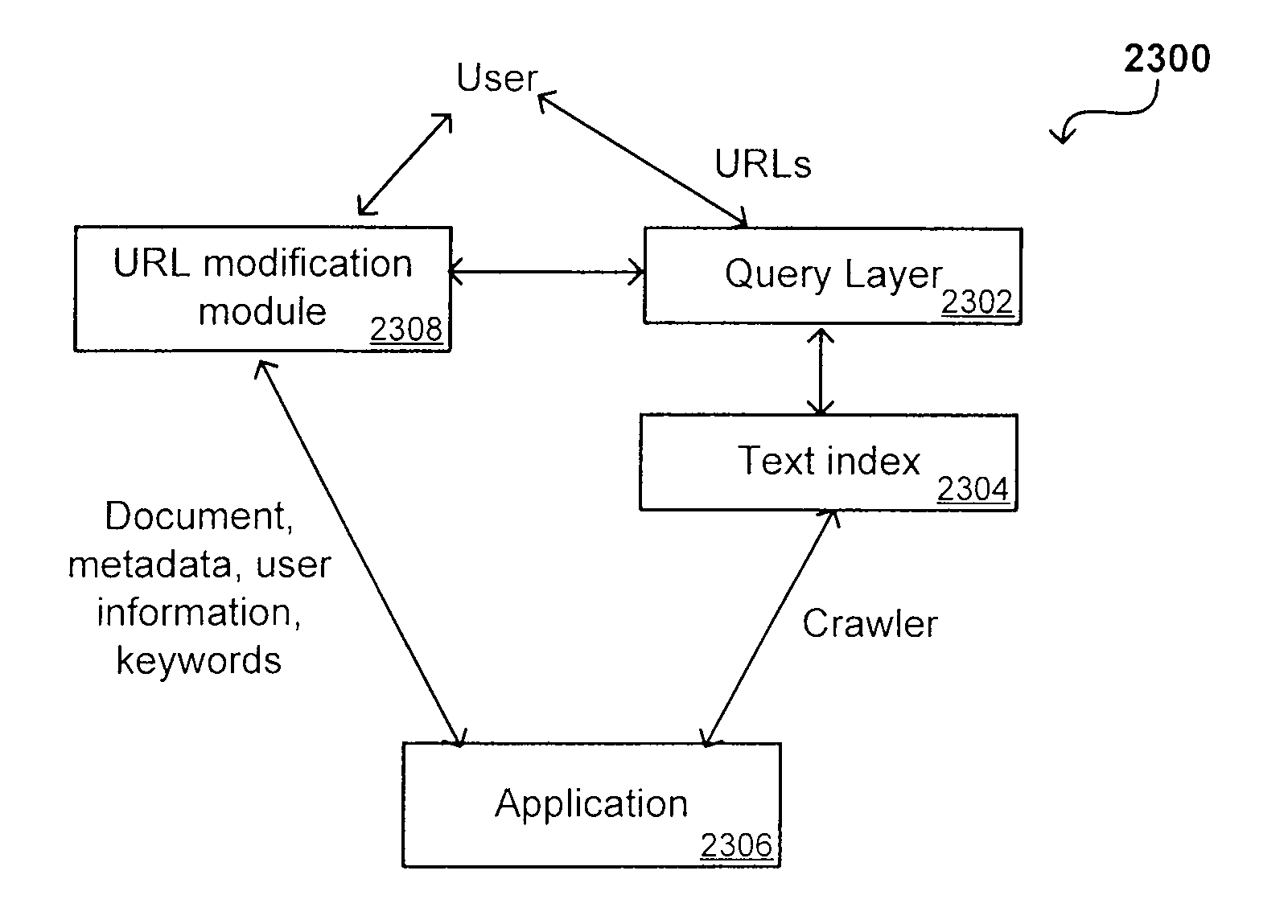
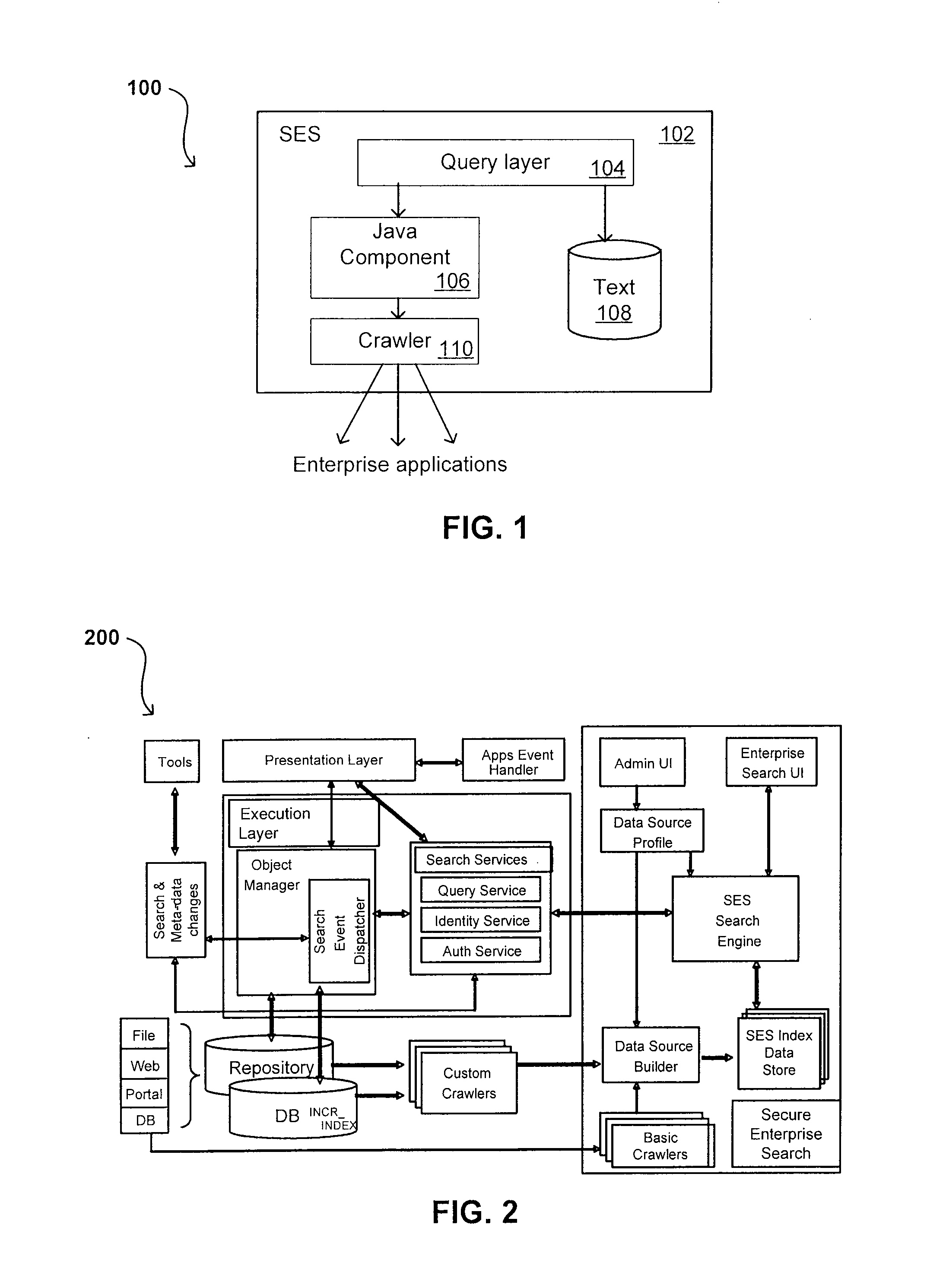
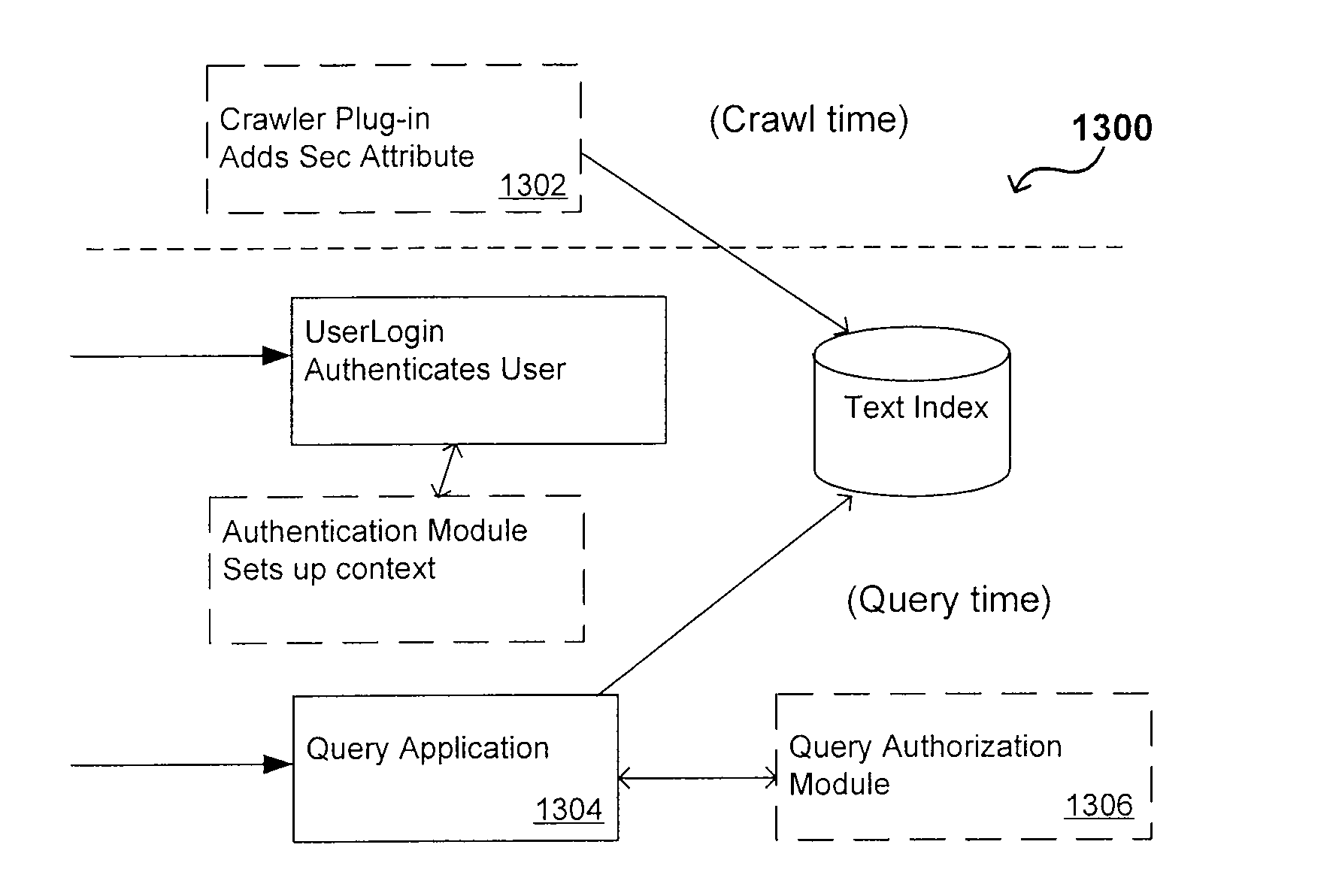
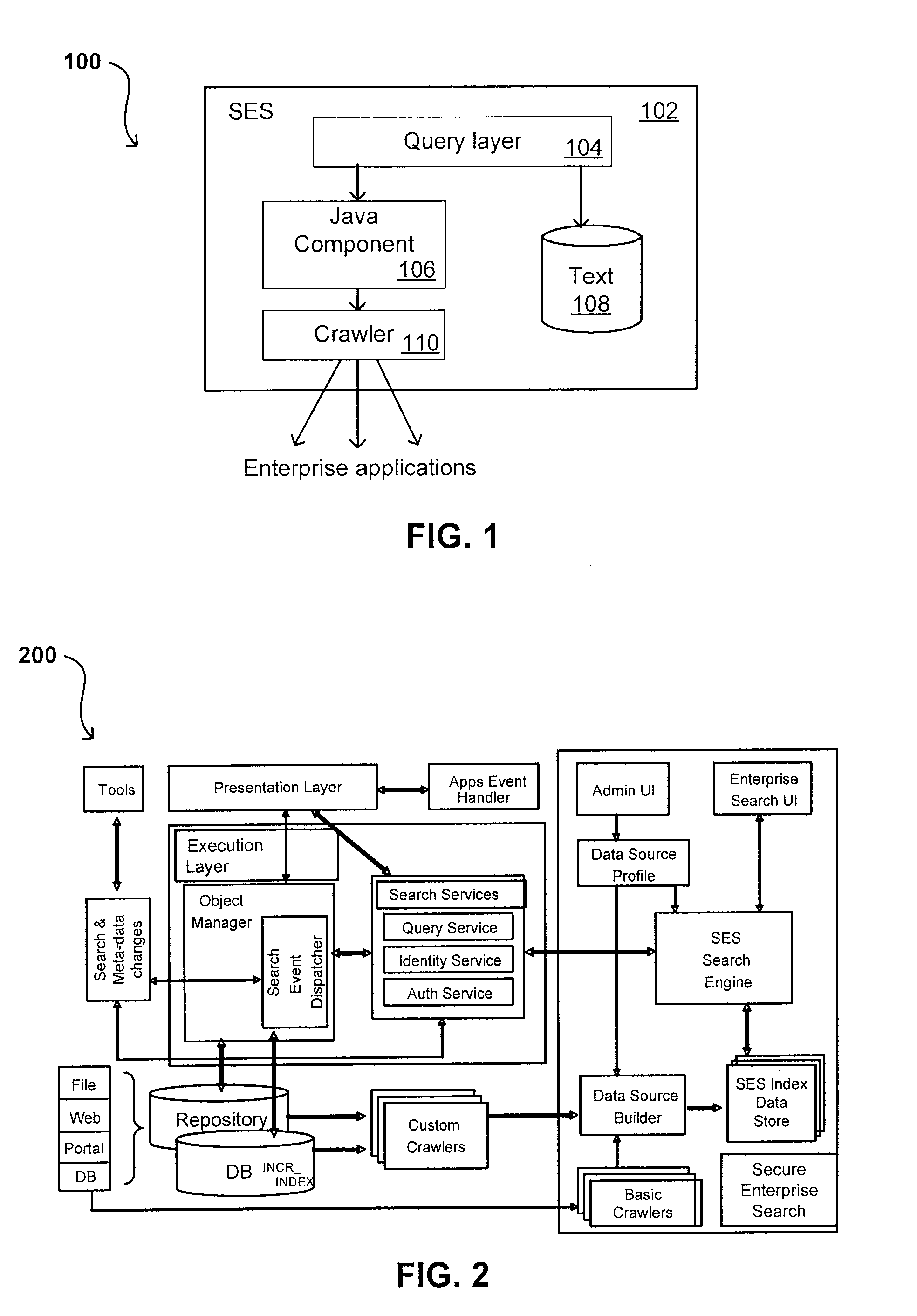
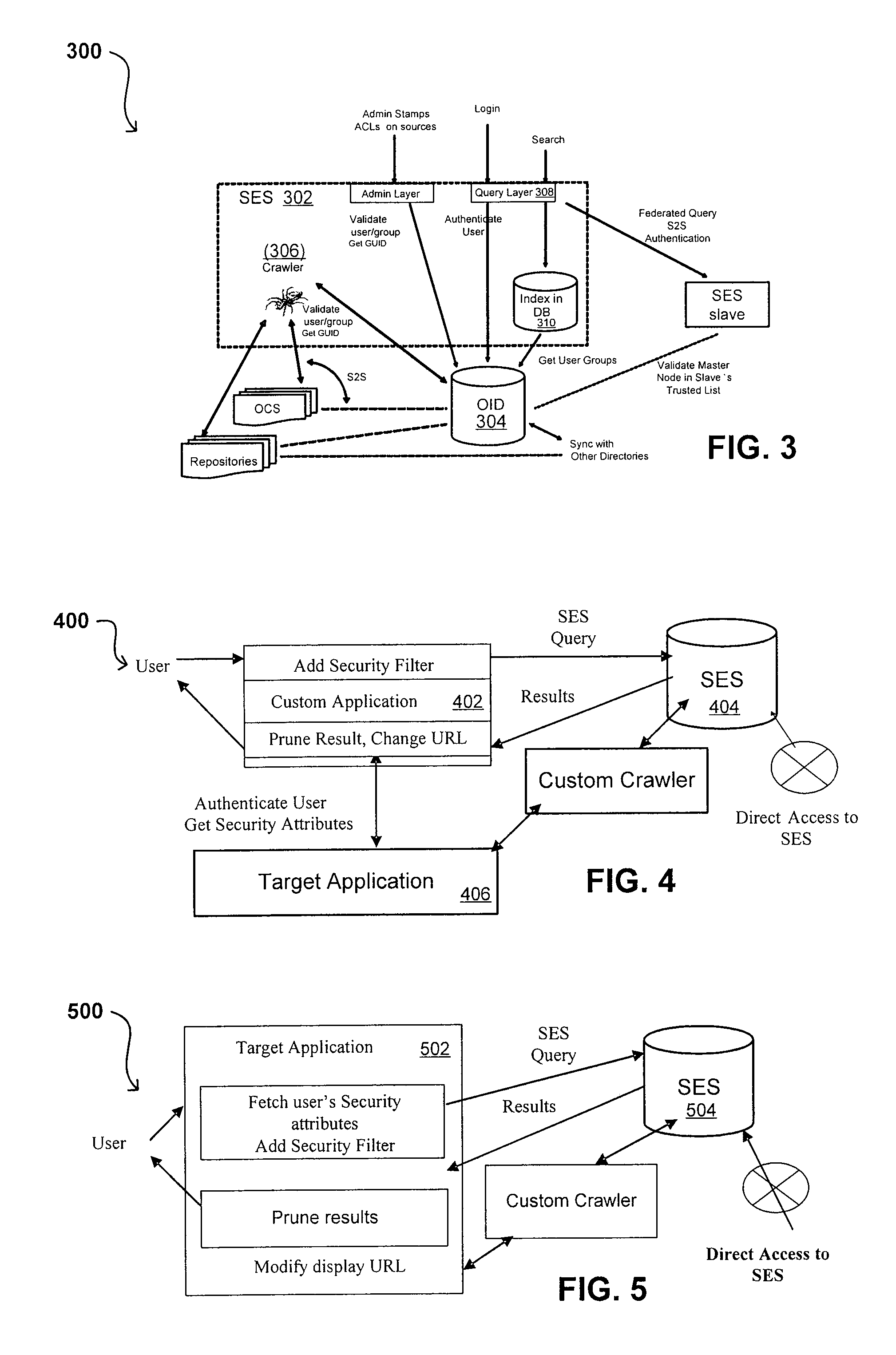
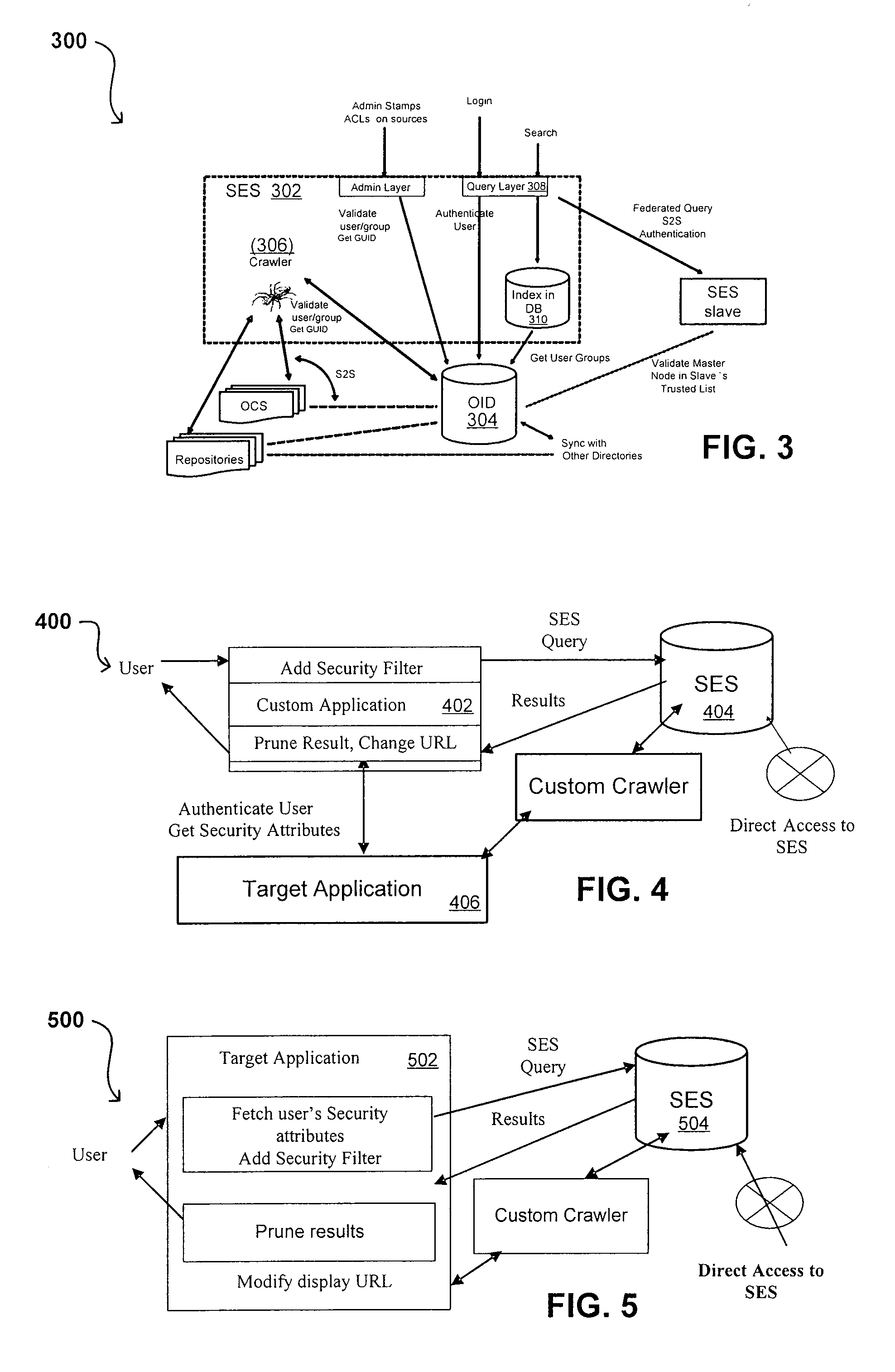
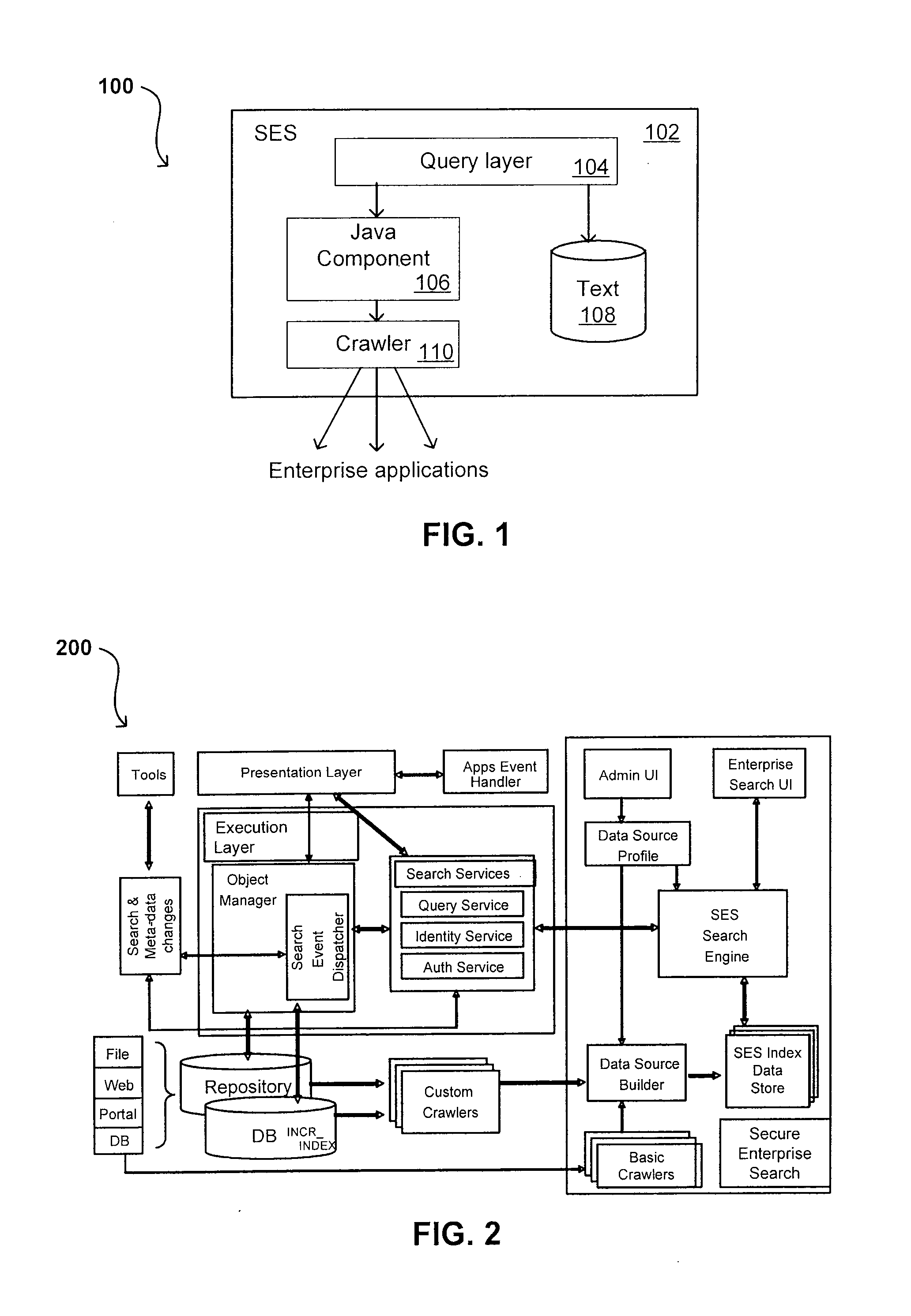
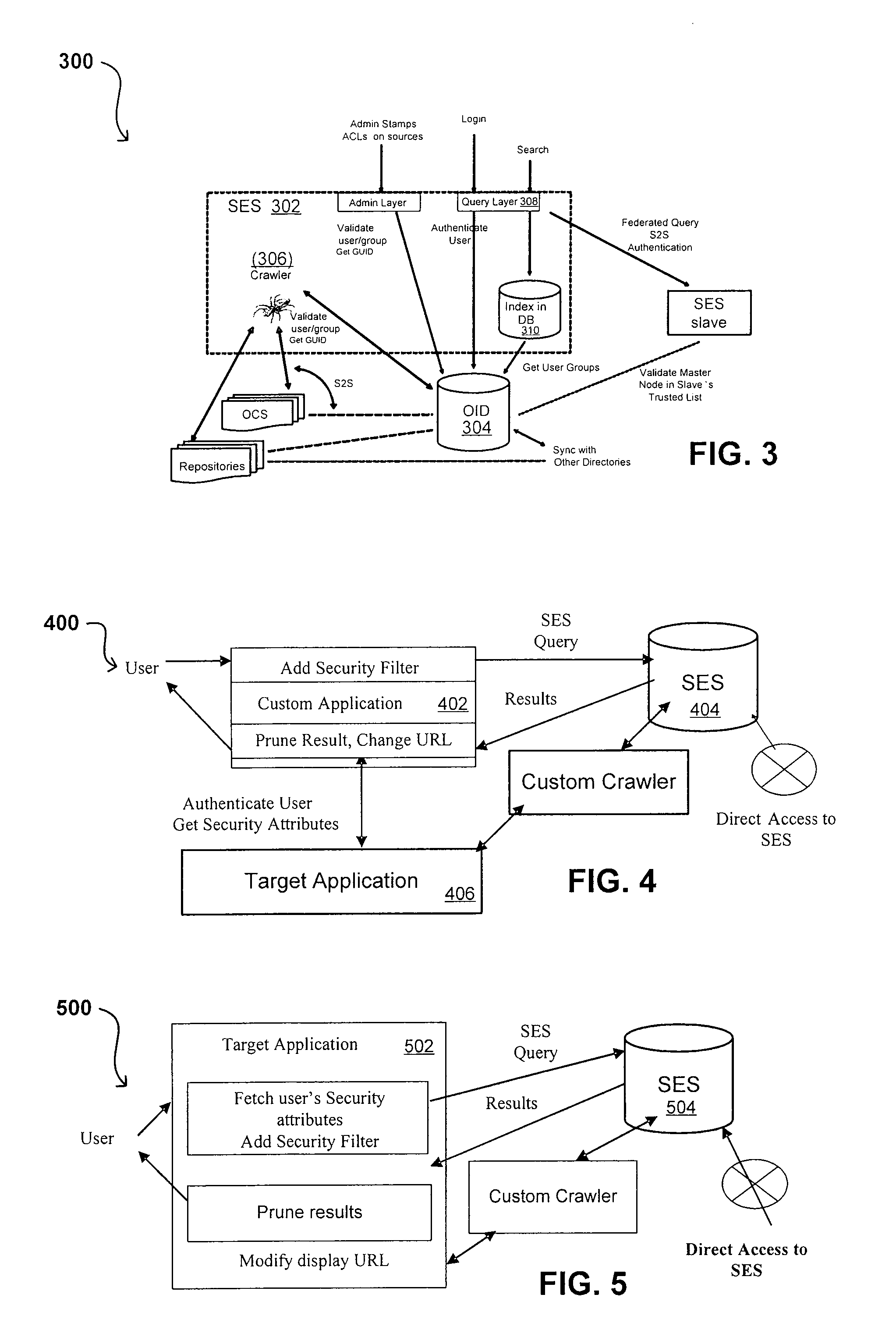
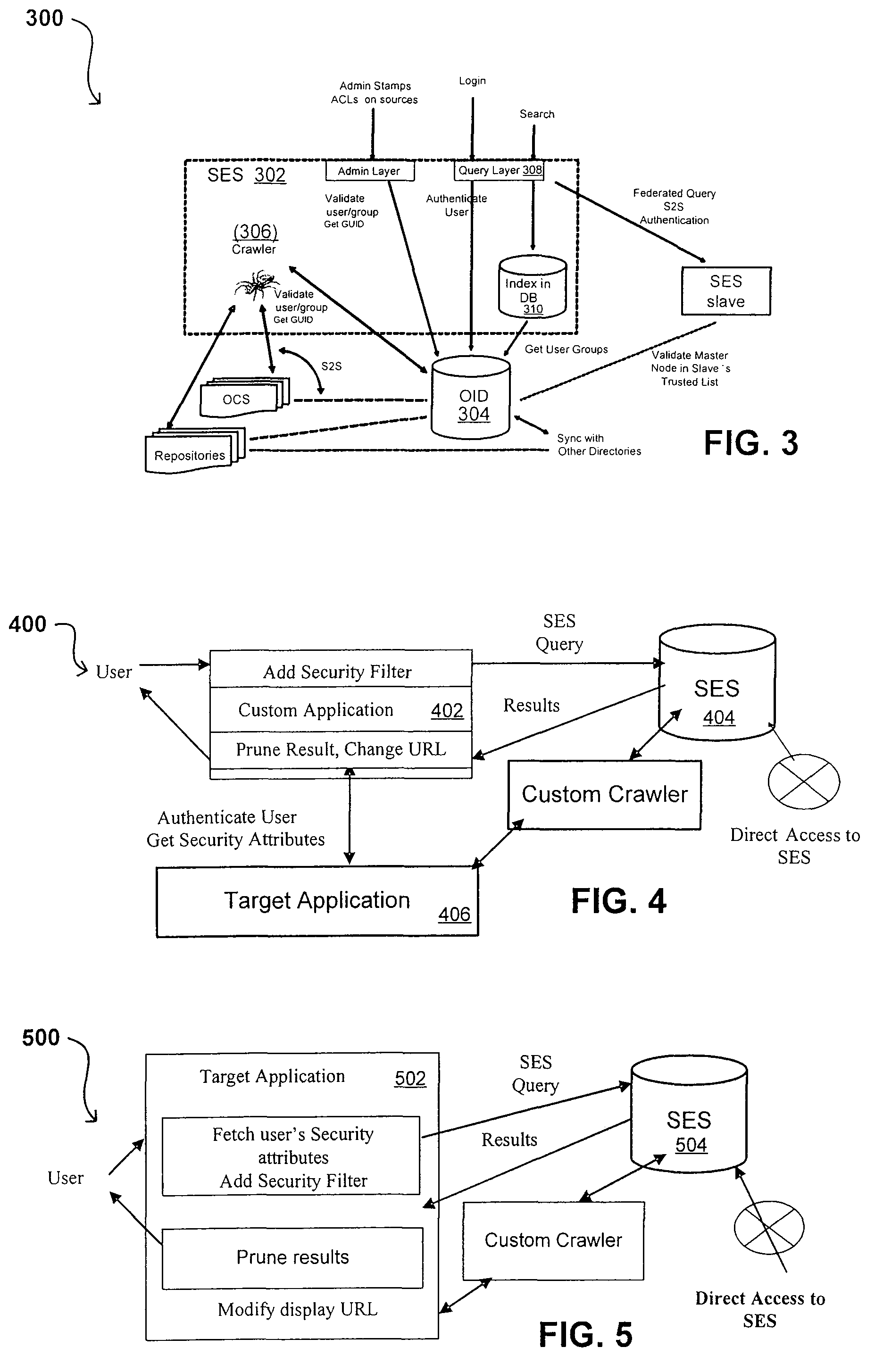
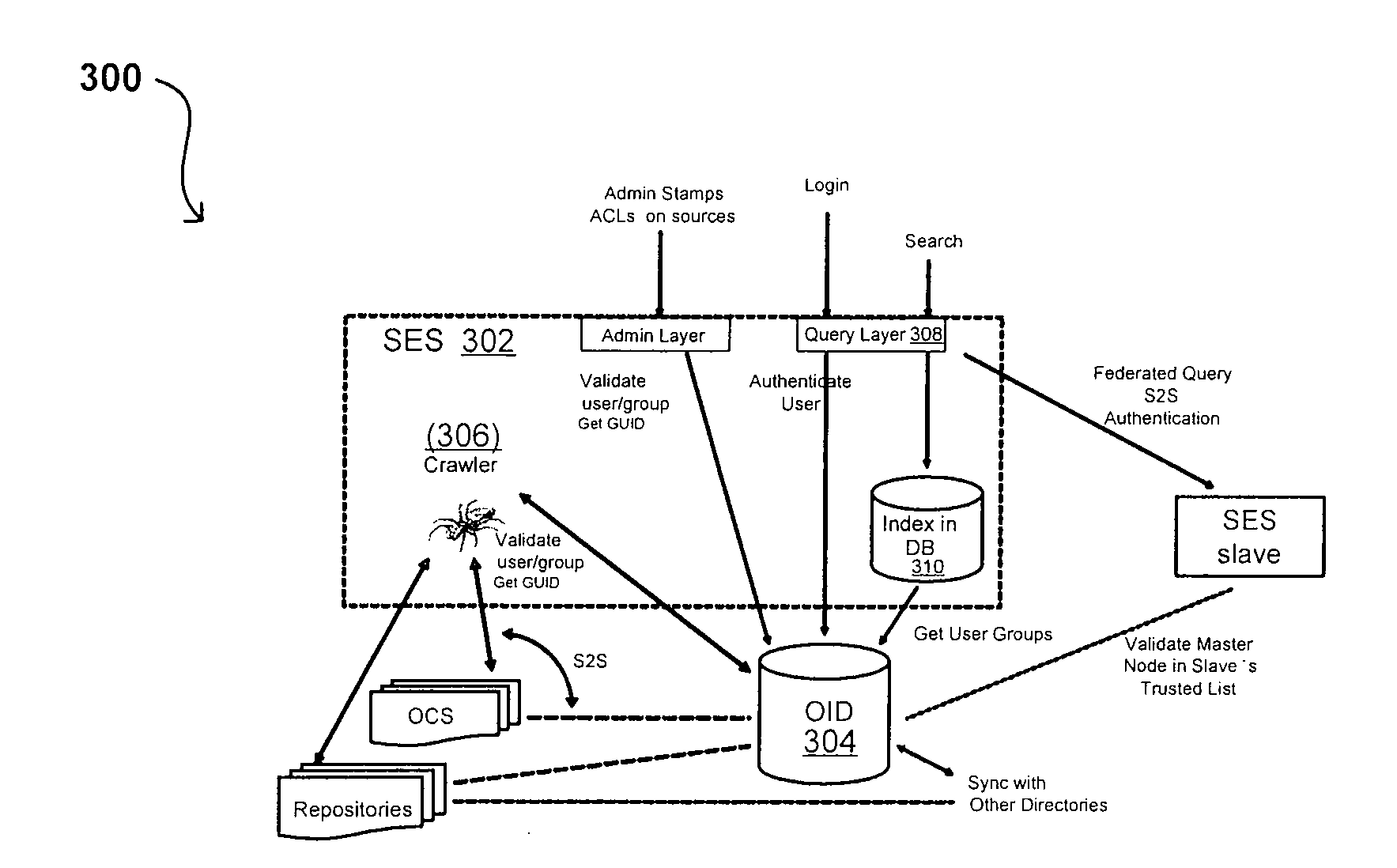
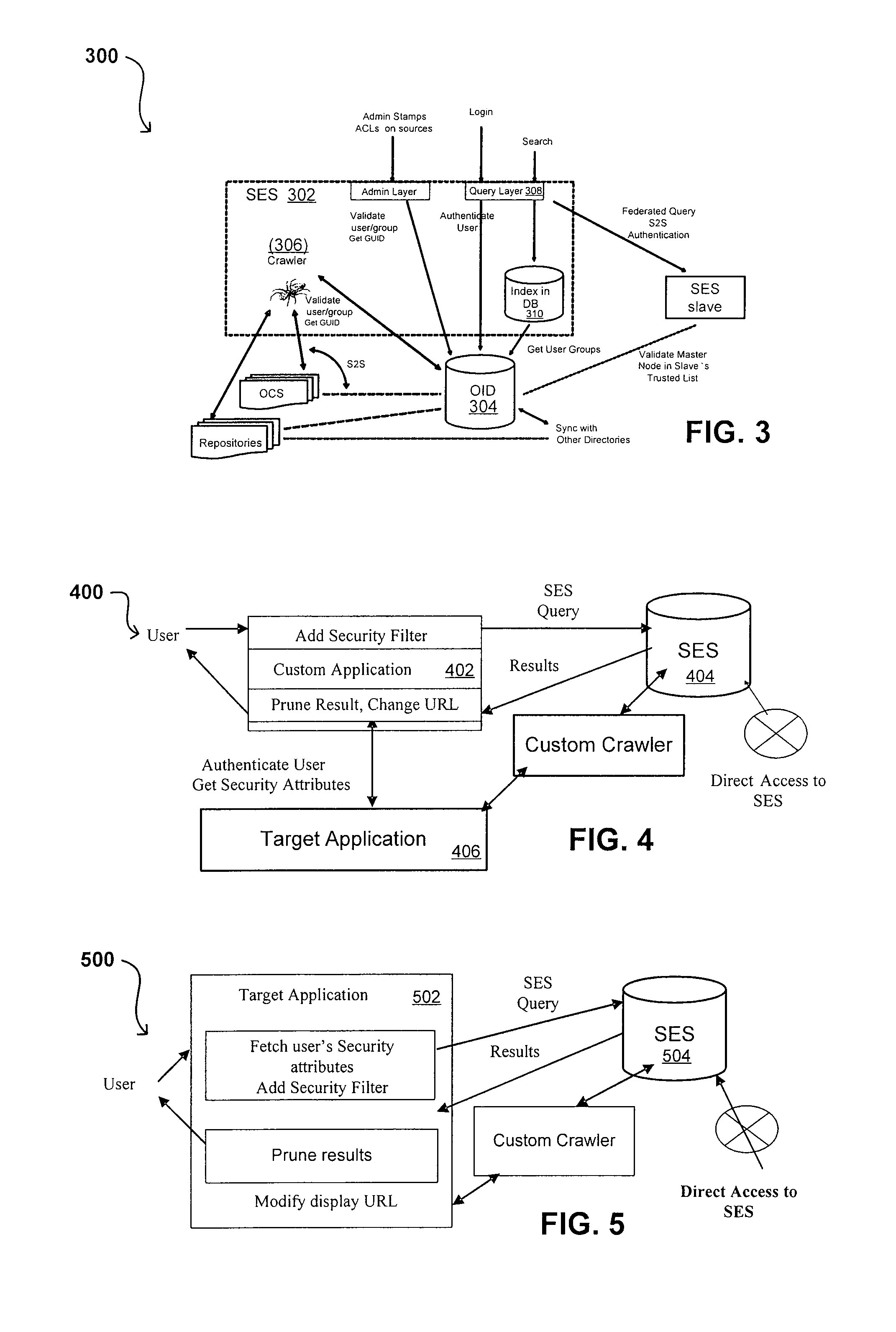
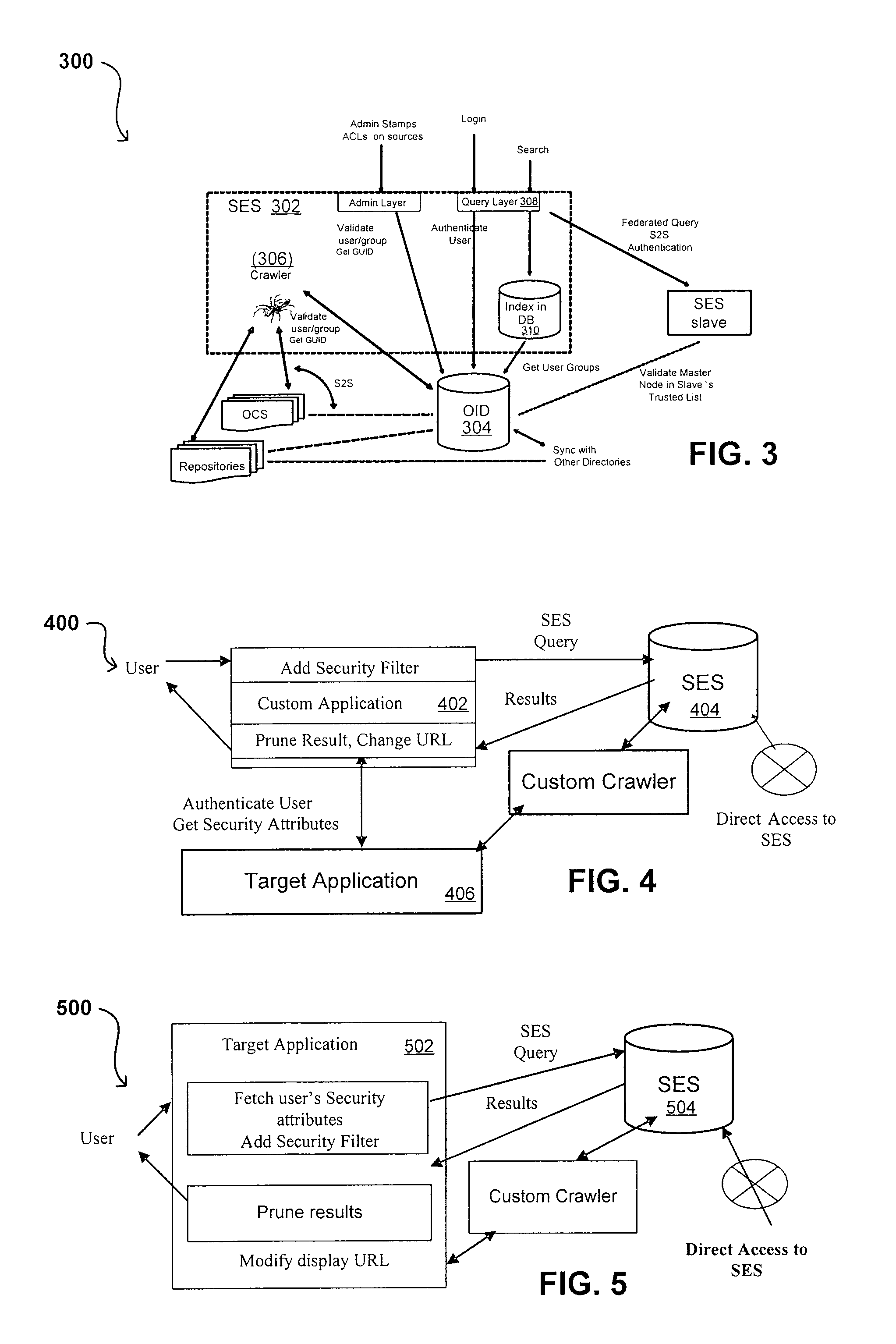
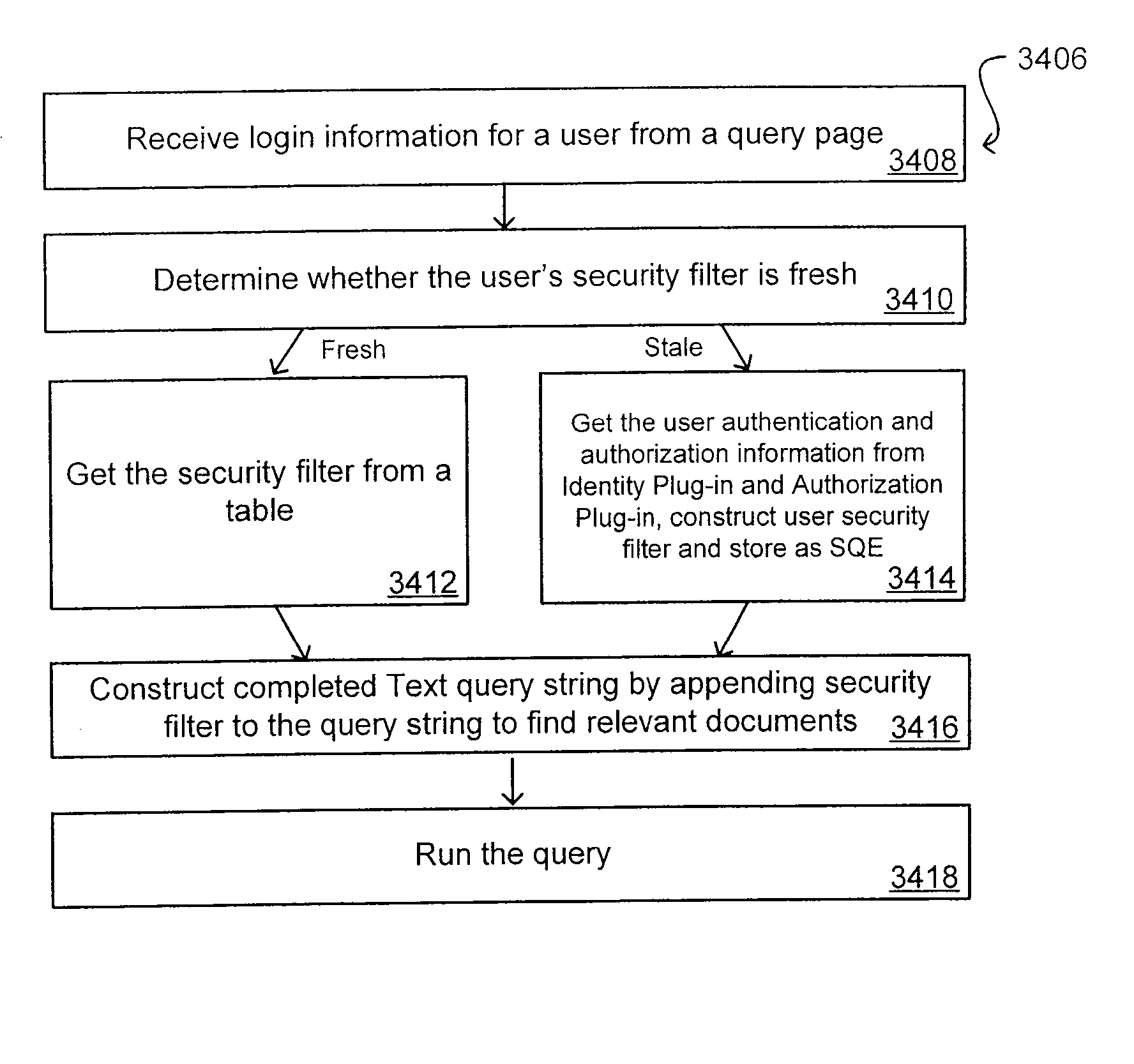
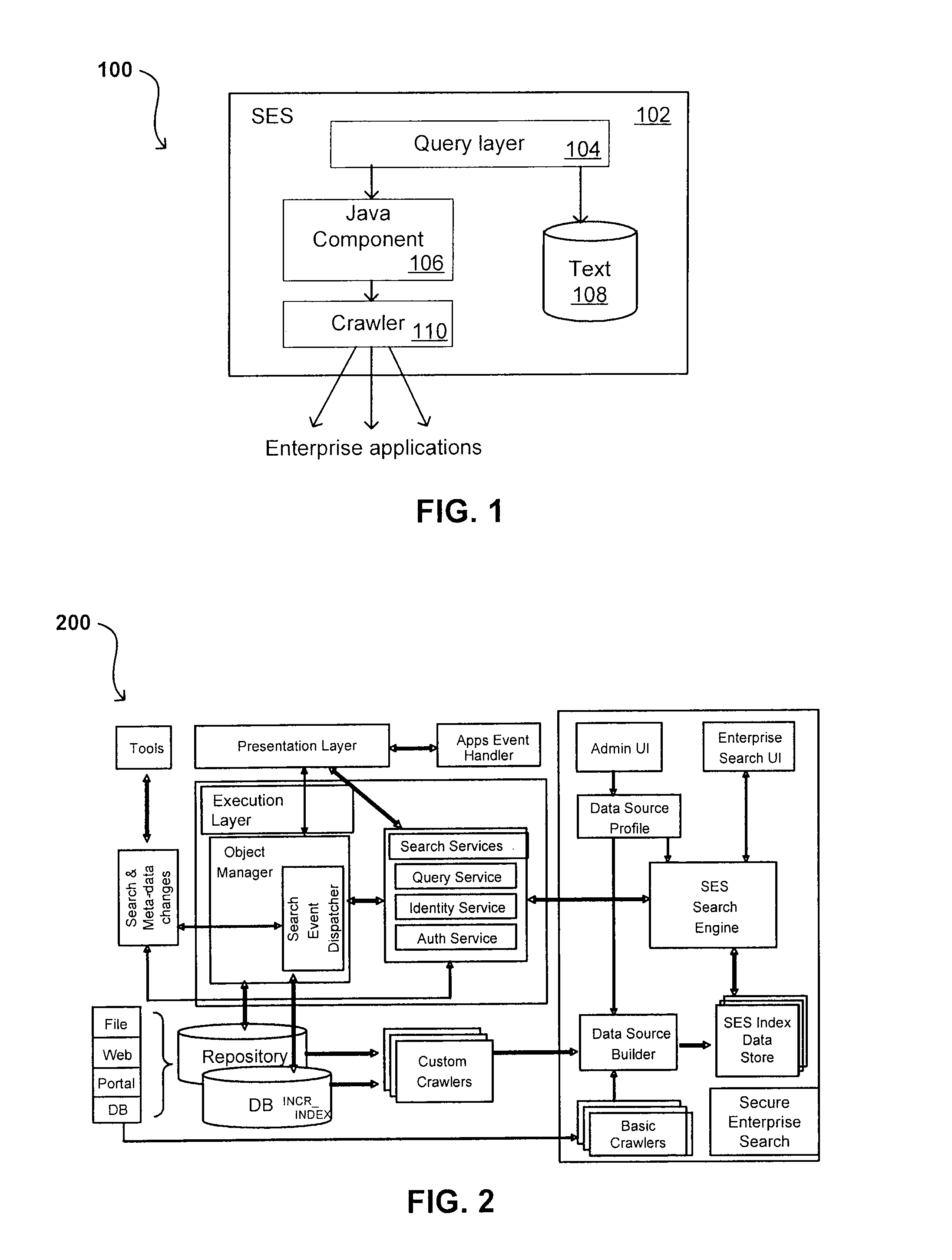
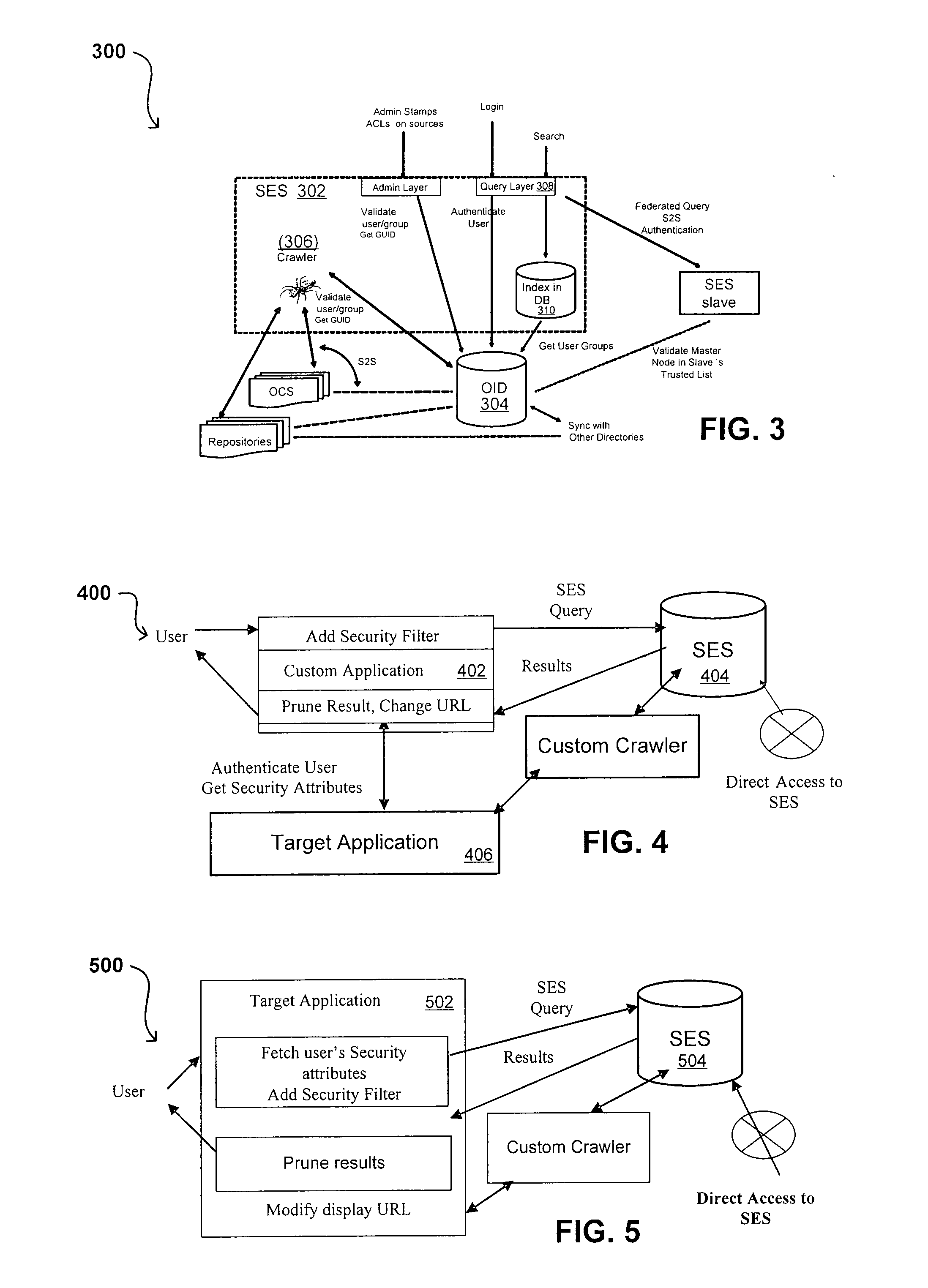
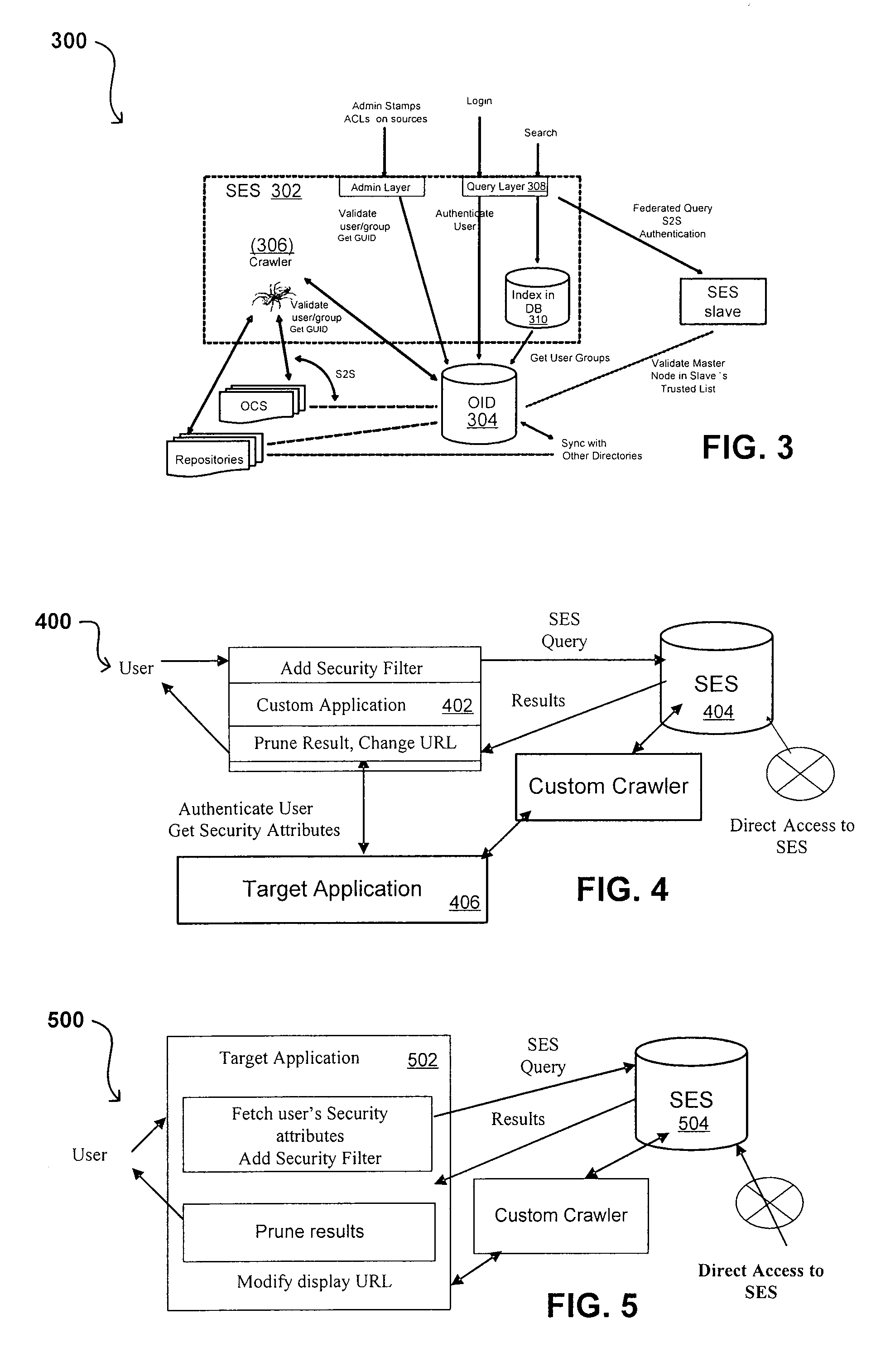
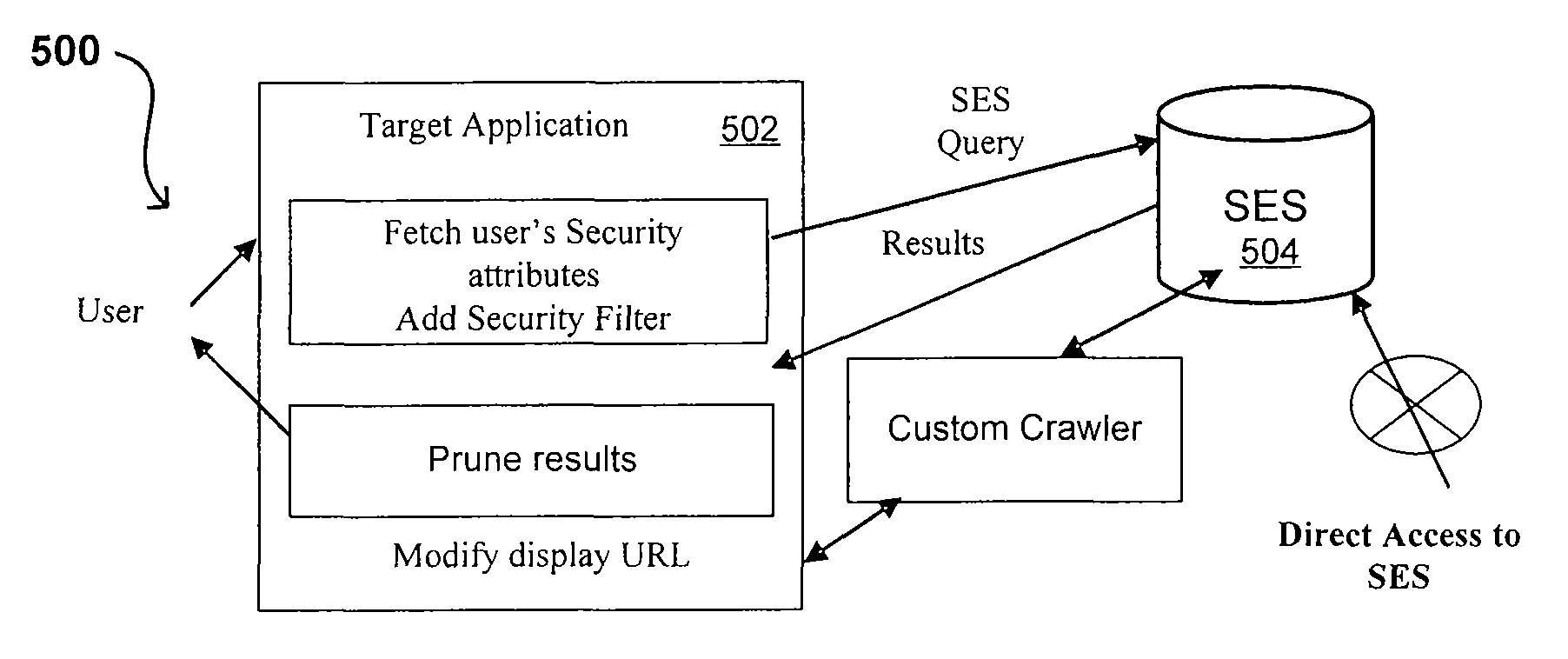
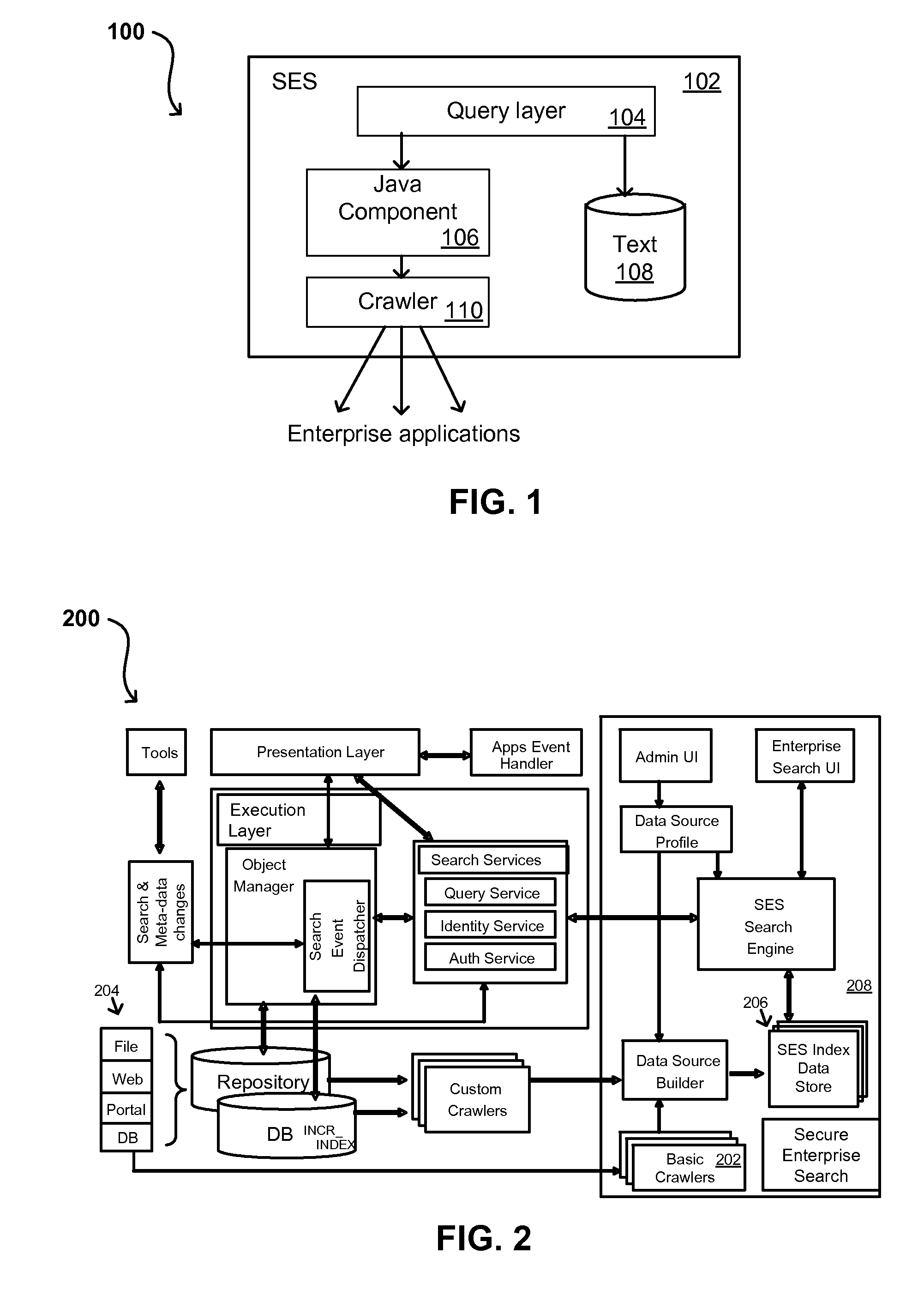
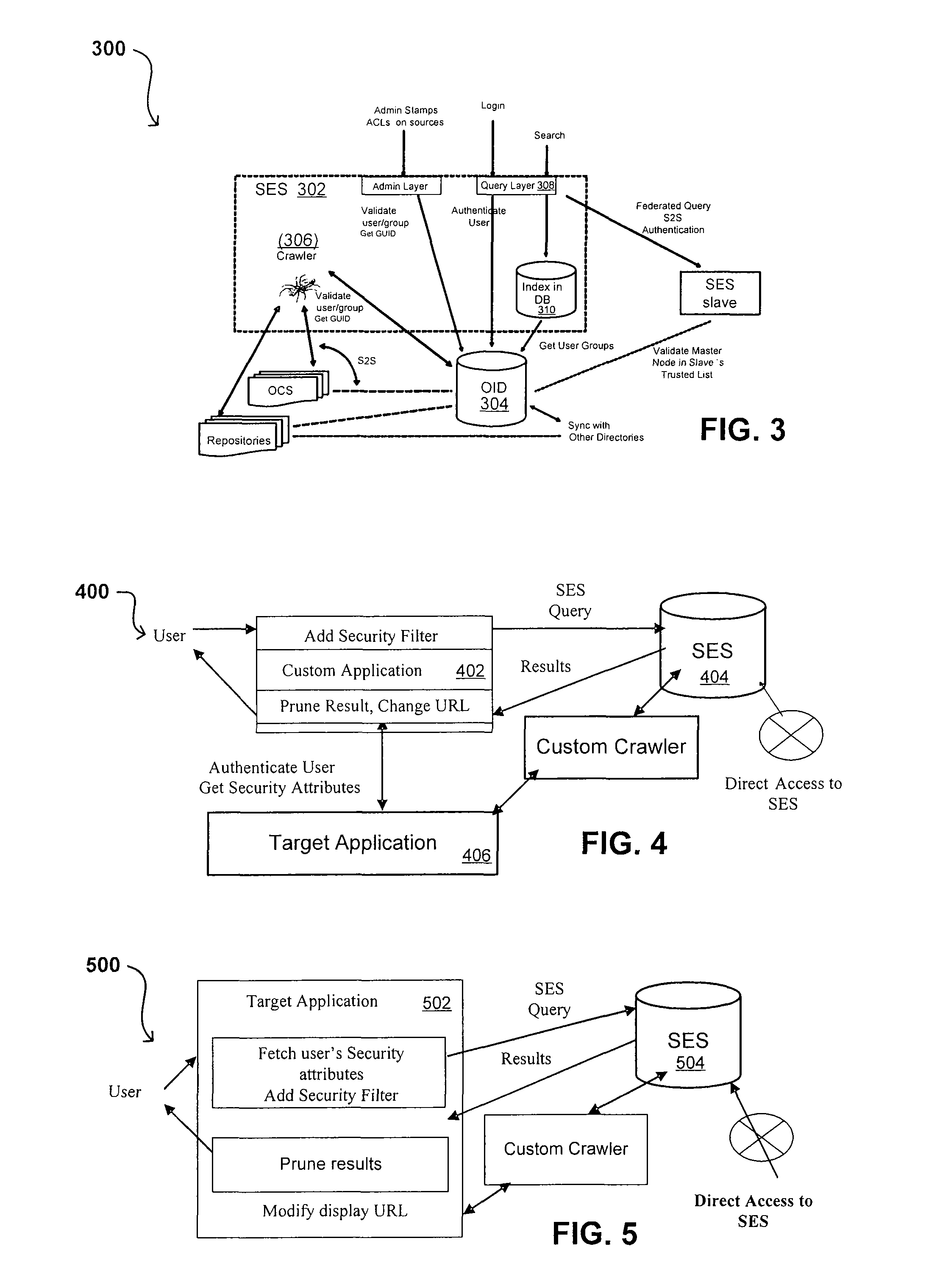
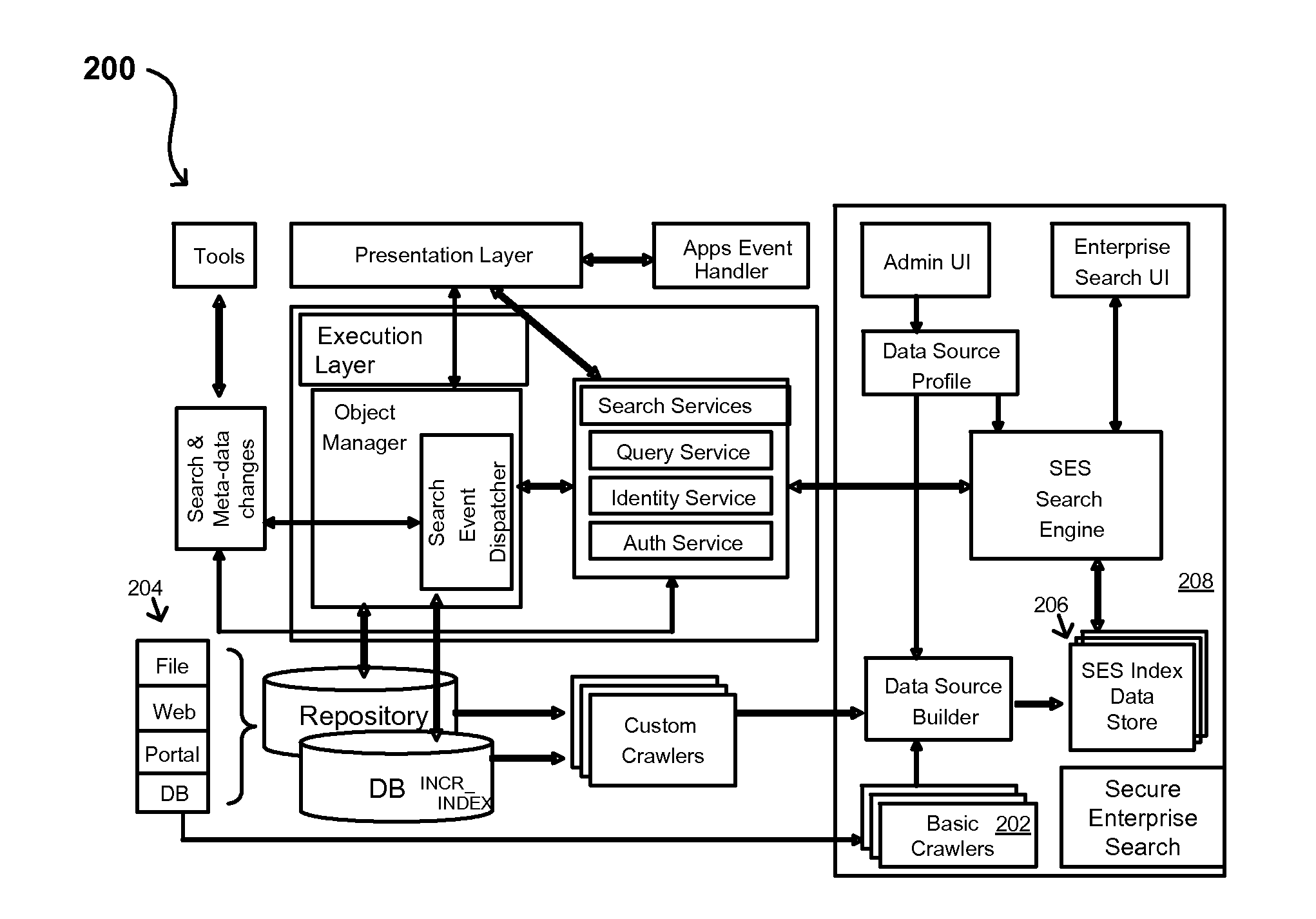
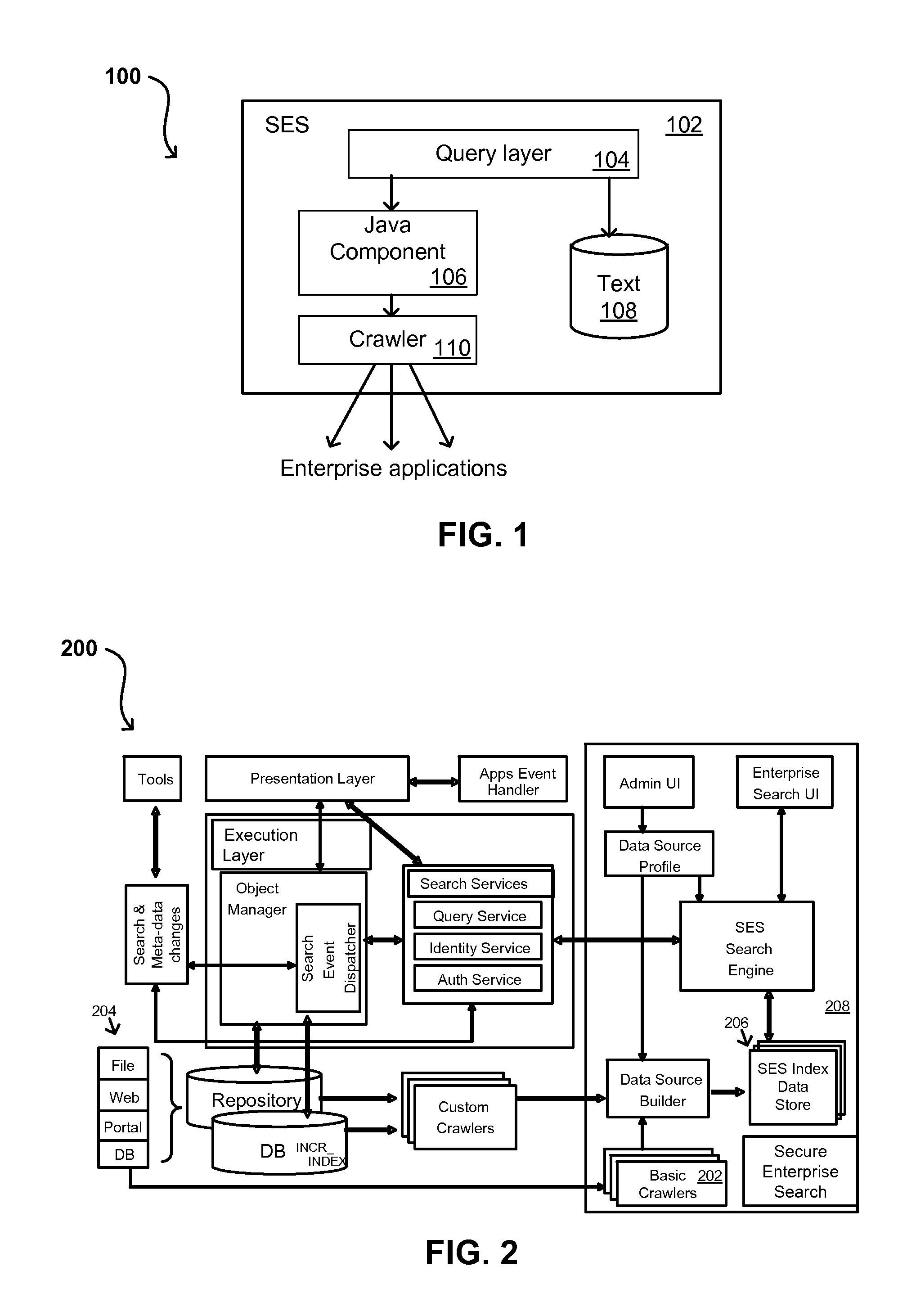
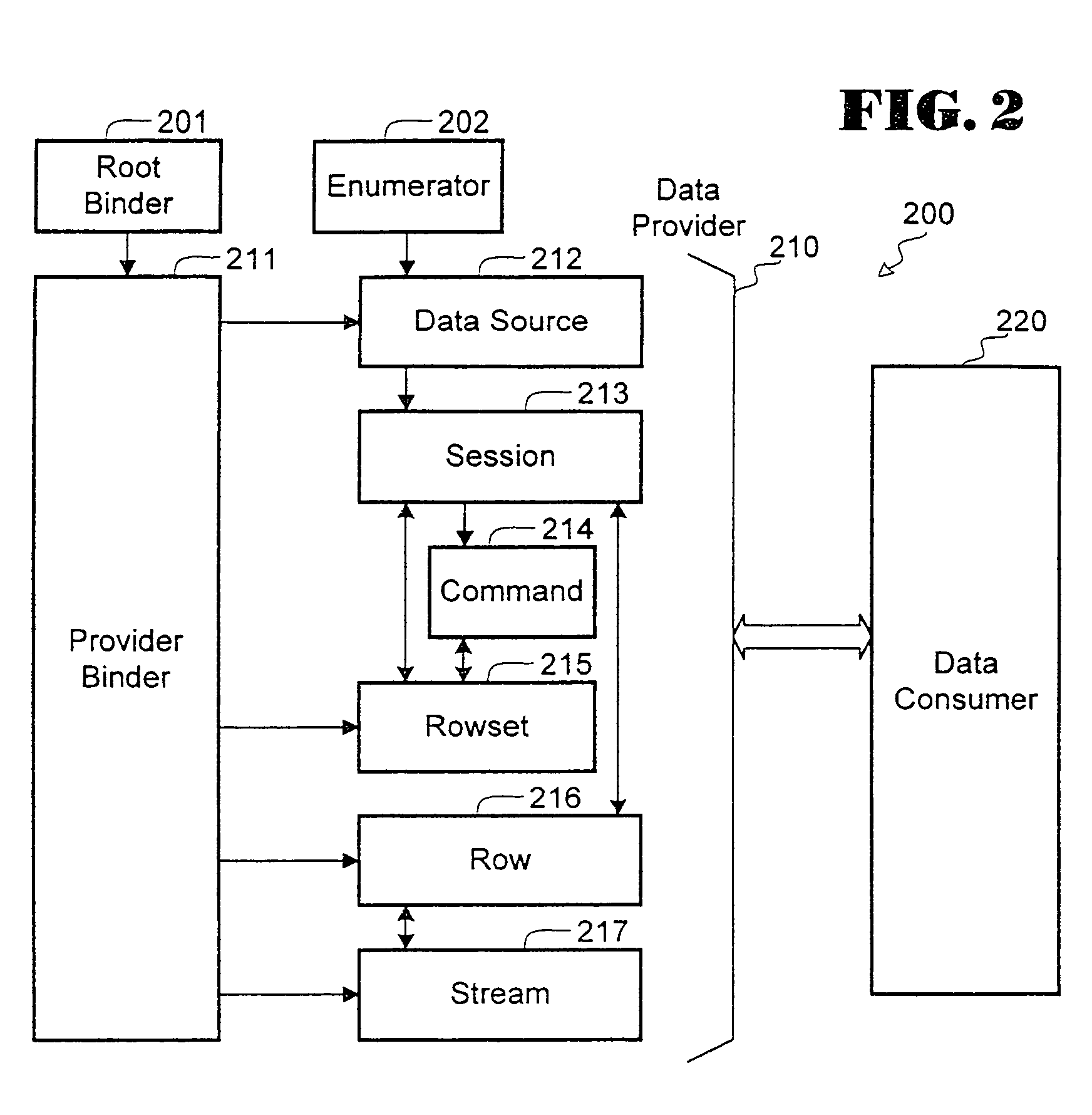
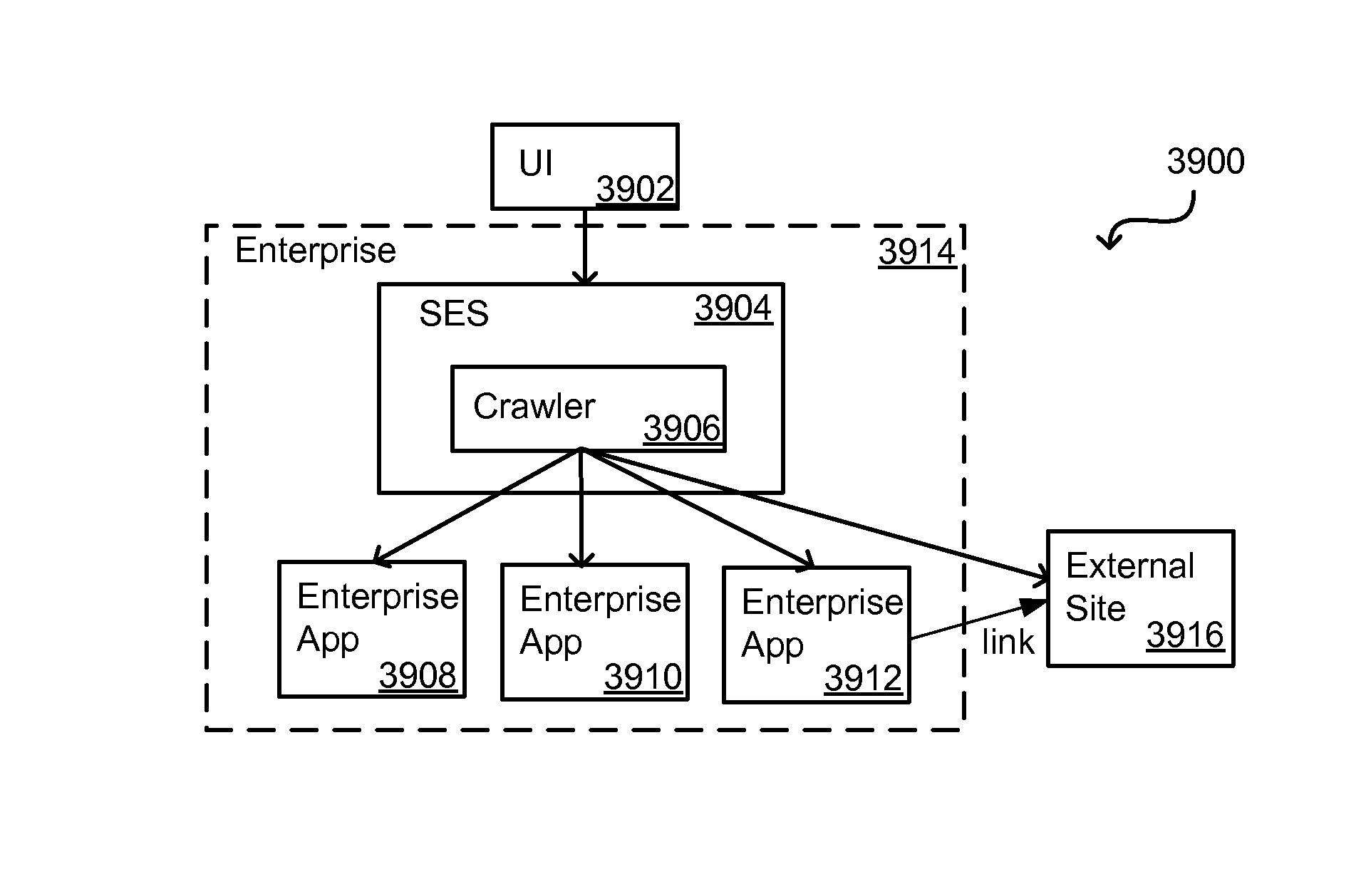
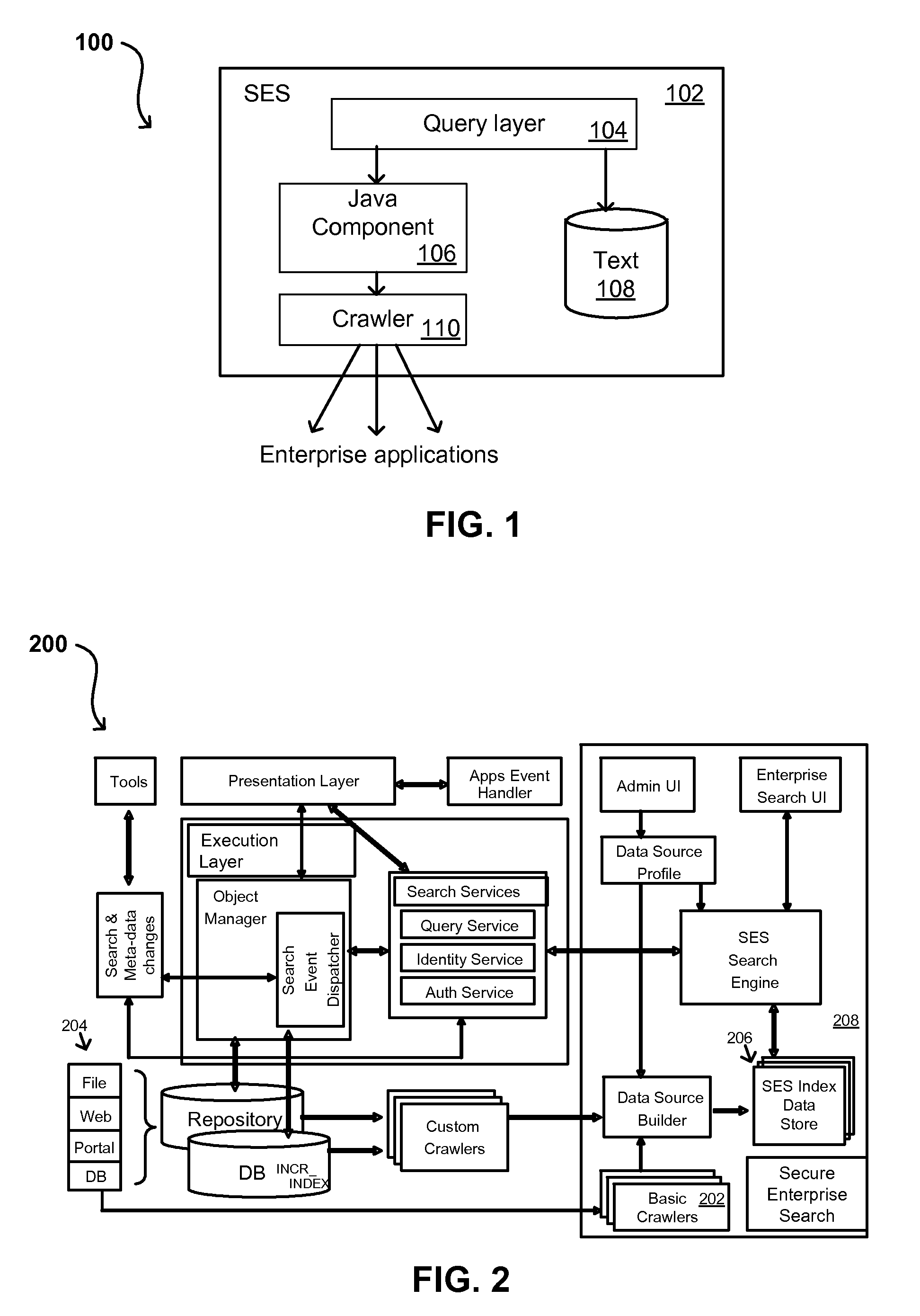
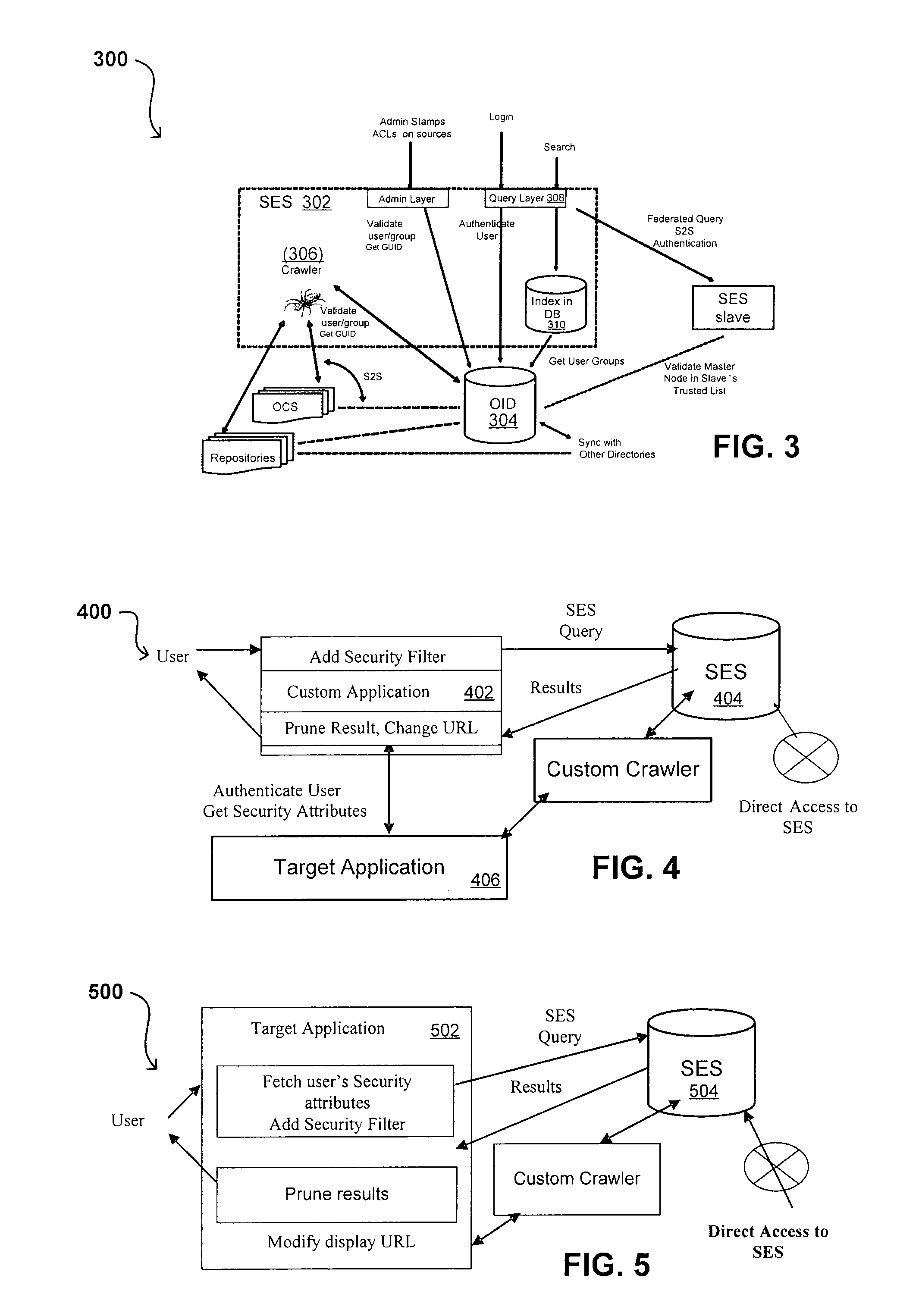
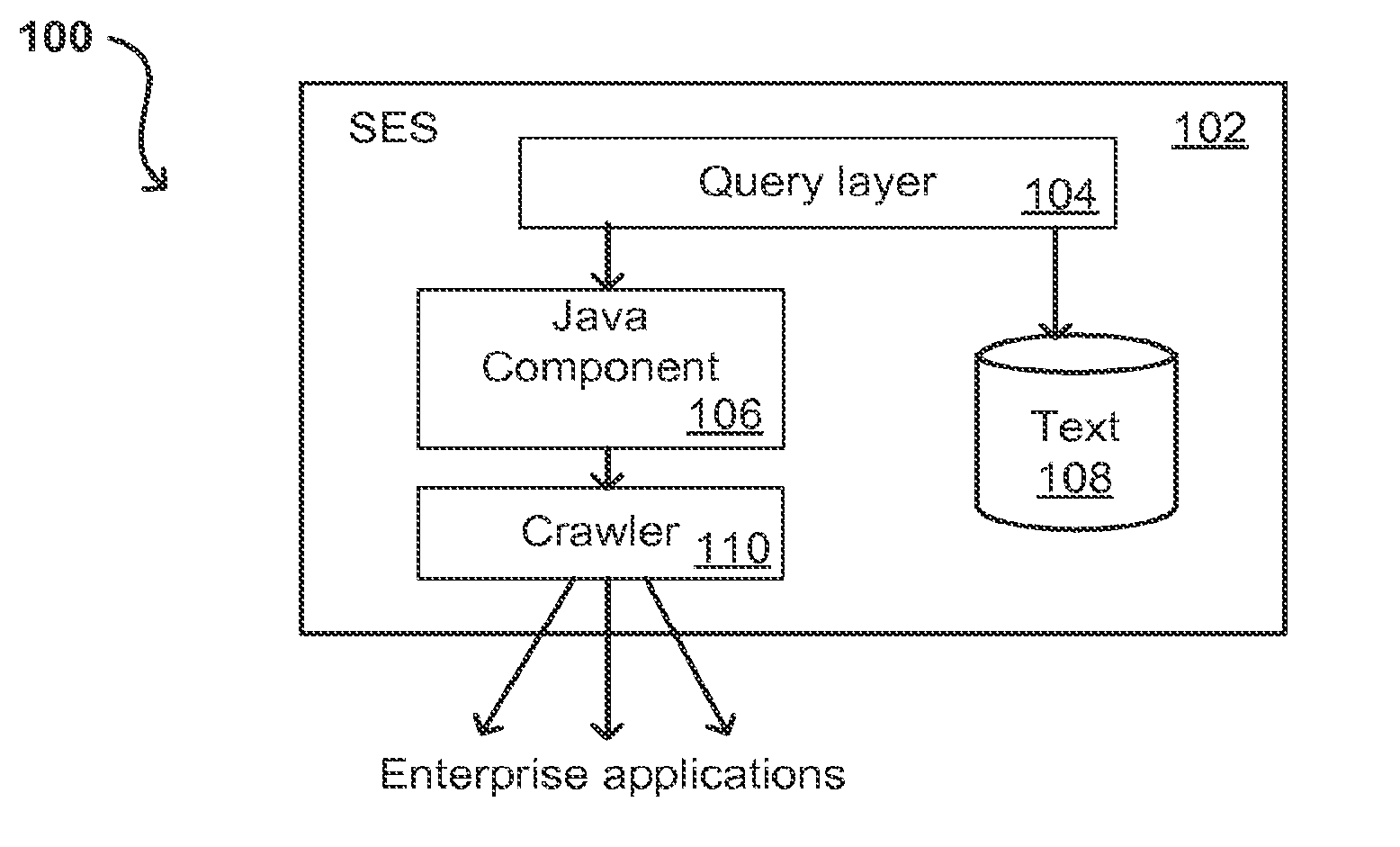
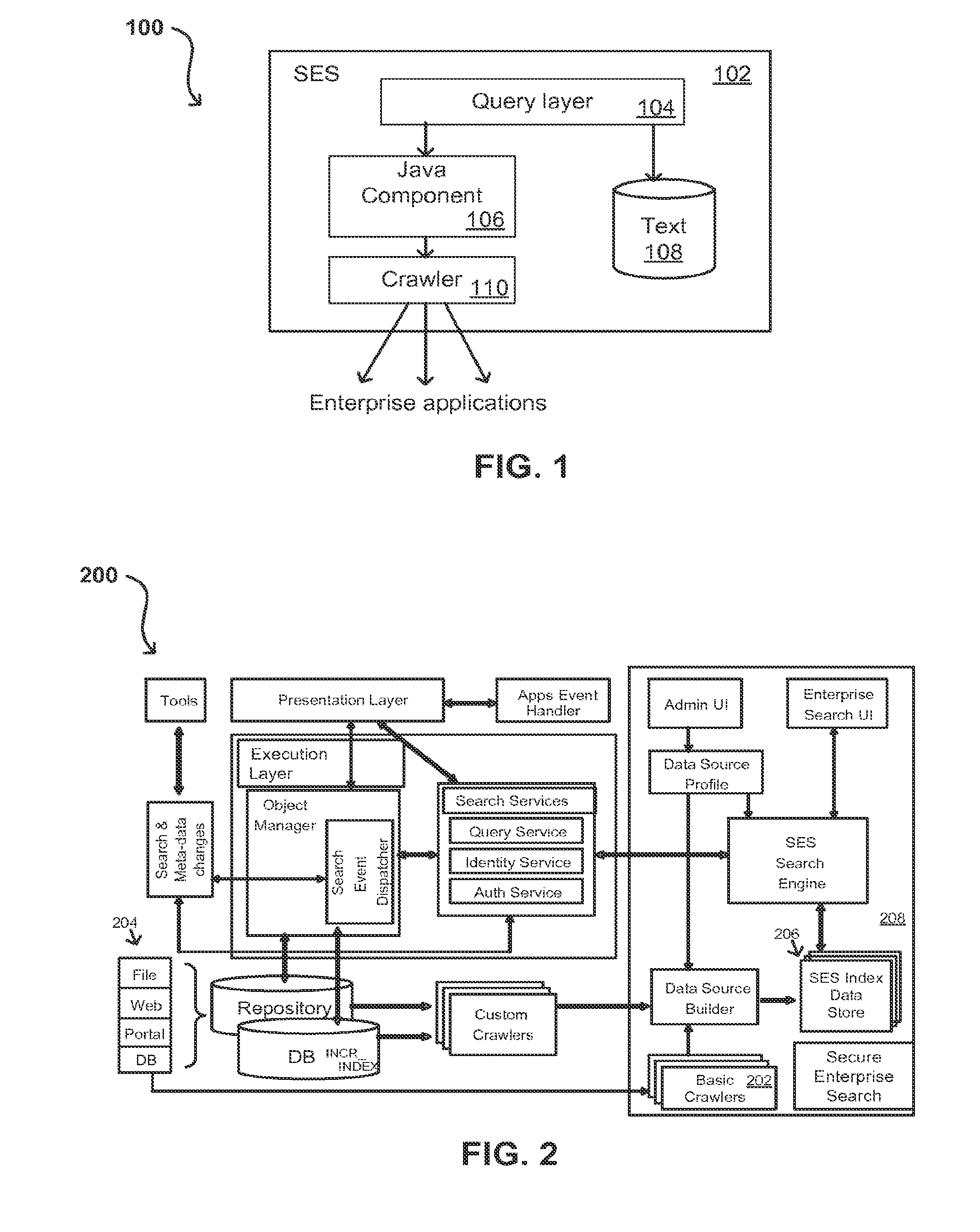
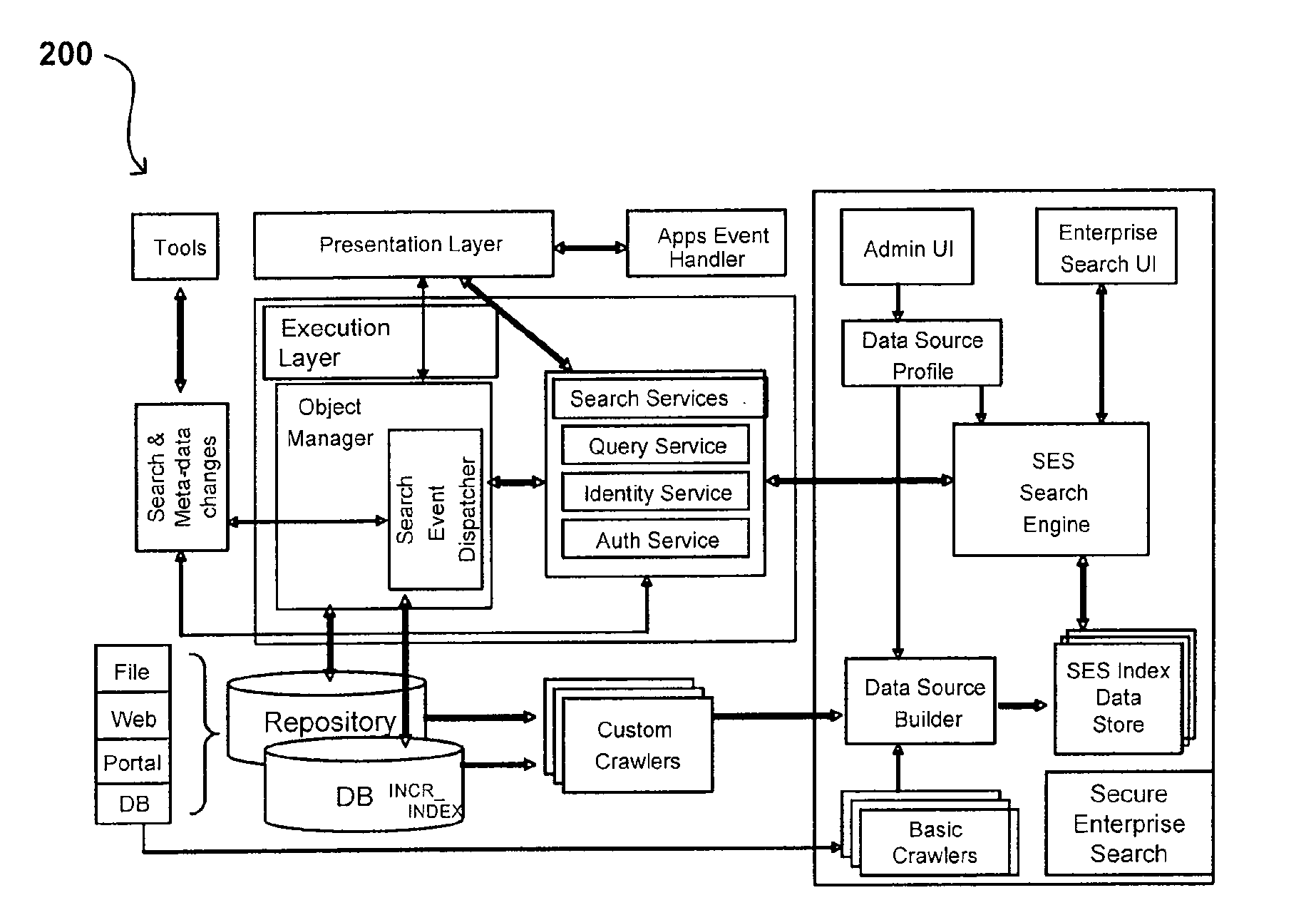
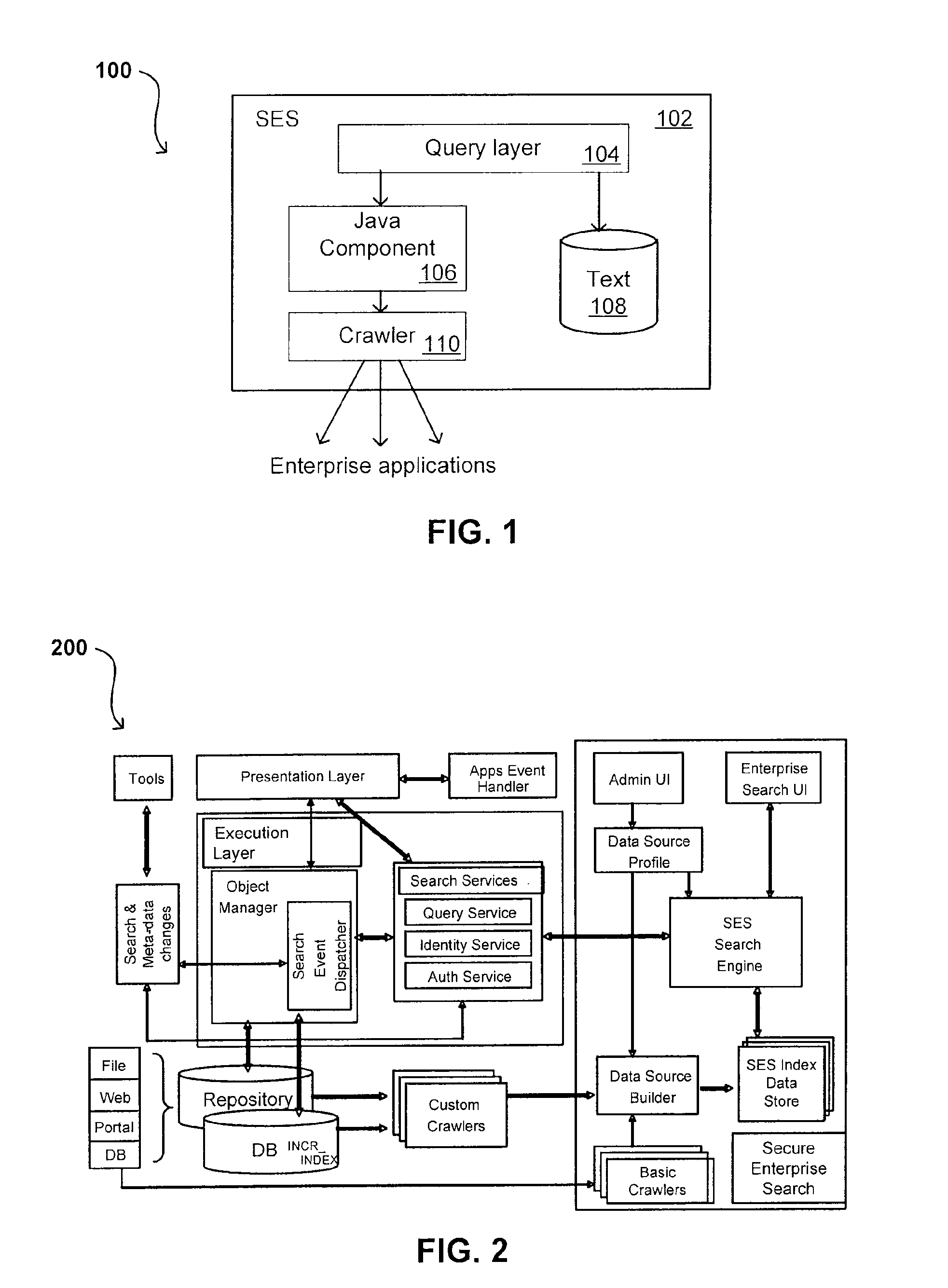
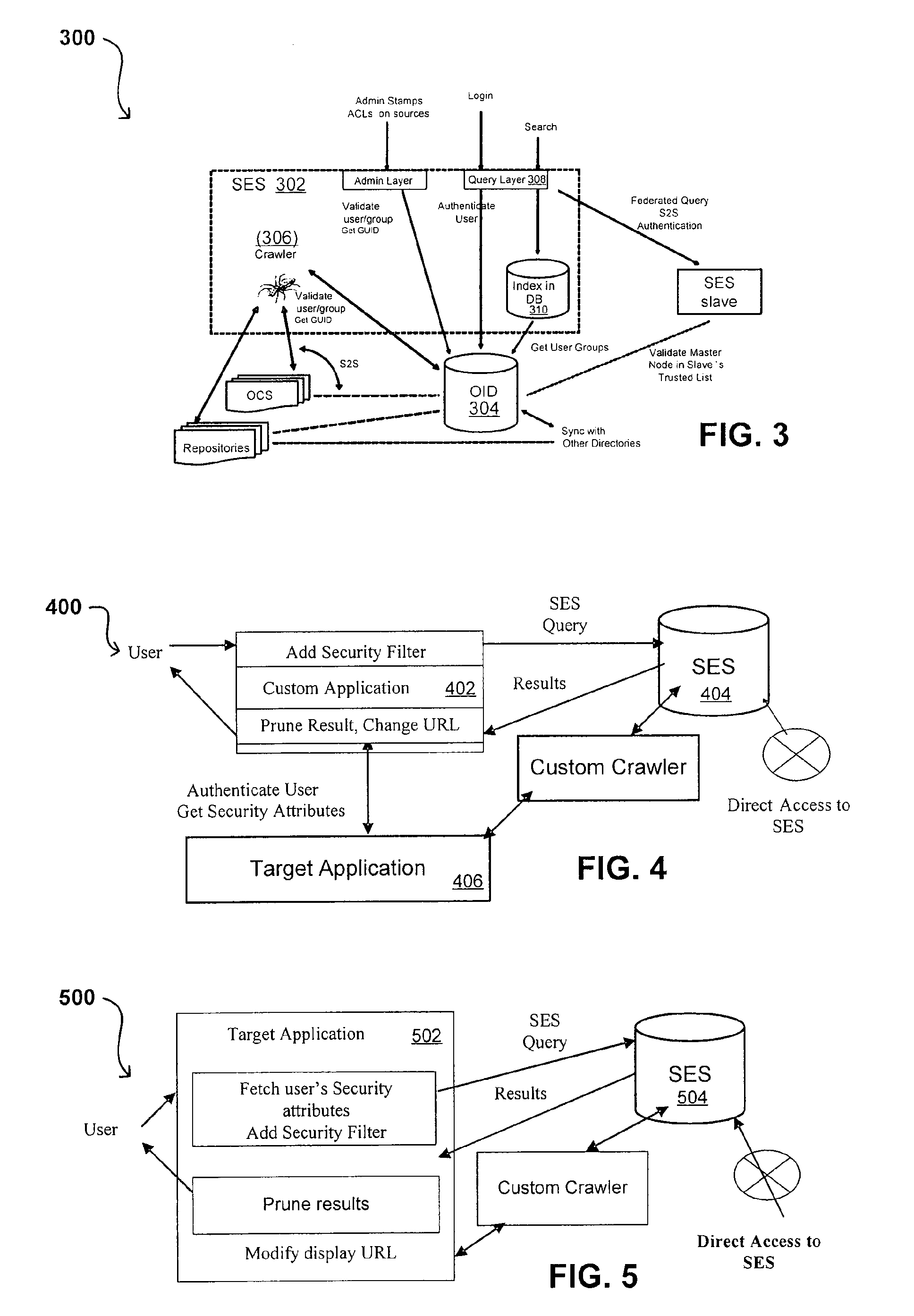
Search hit URL modification for secure application integration
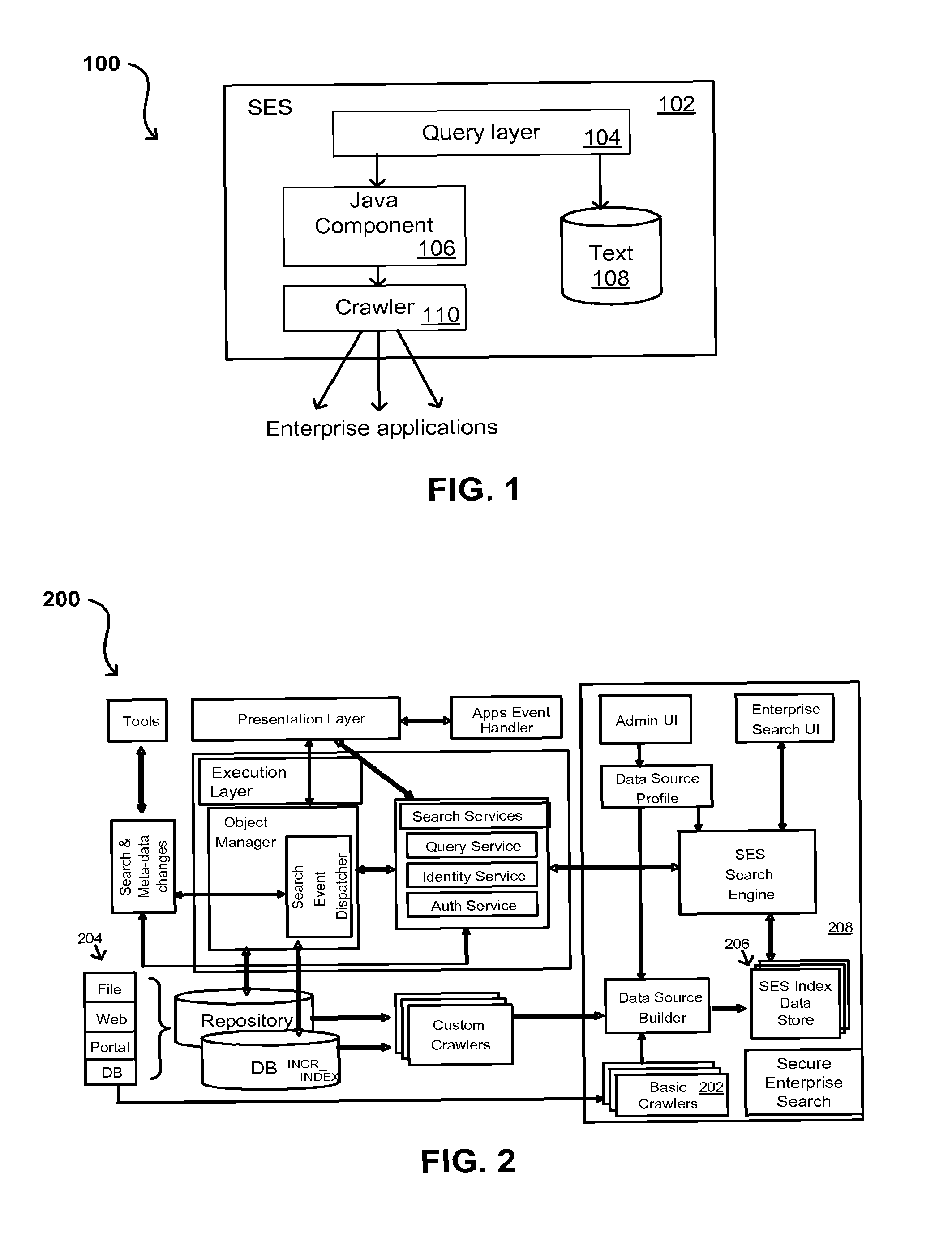
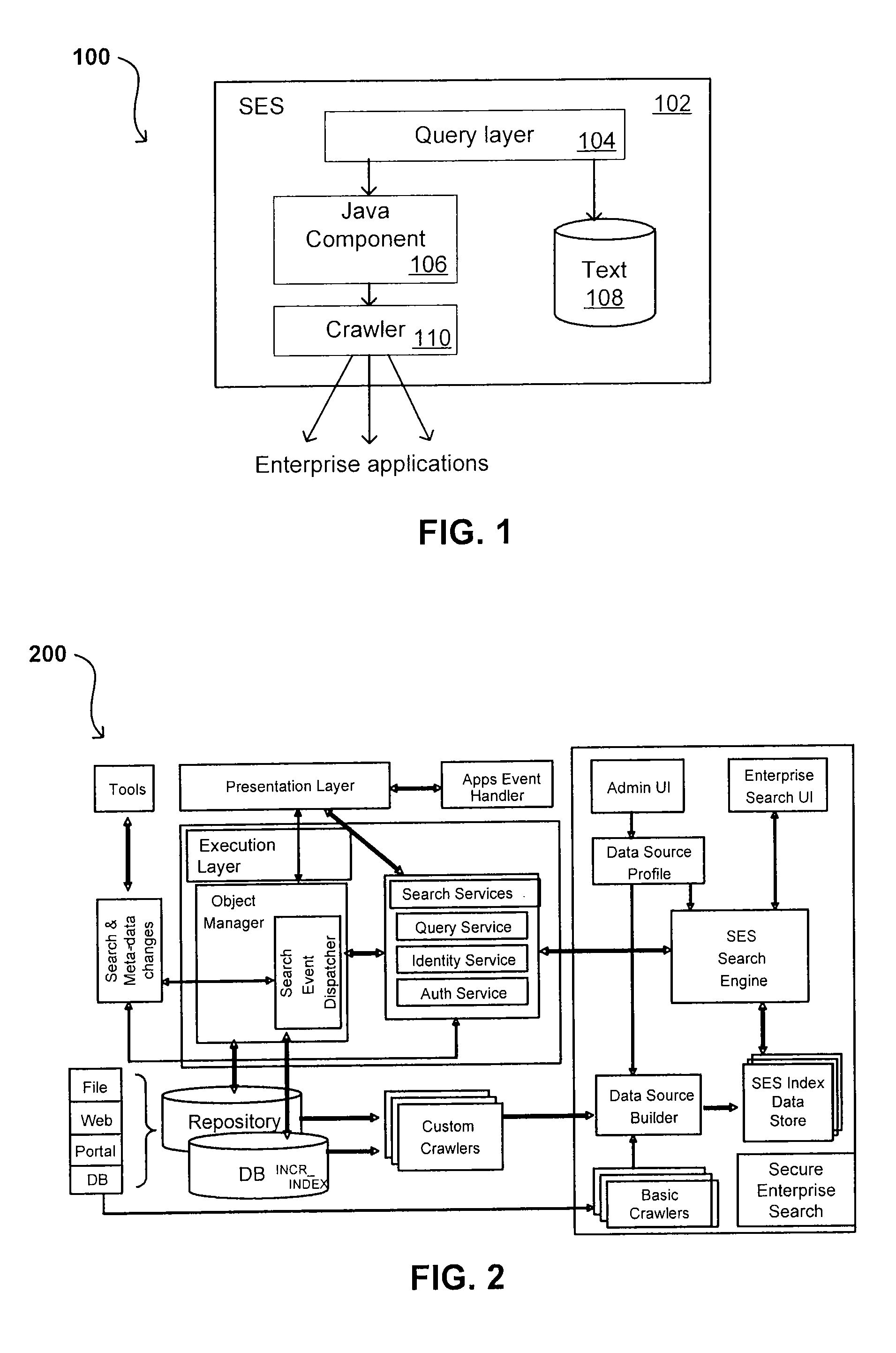
ActiveUS8707451B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsExtensible architectureThe Internet
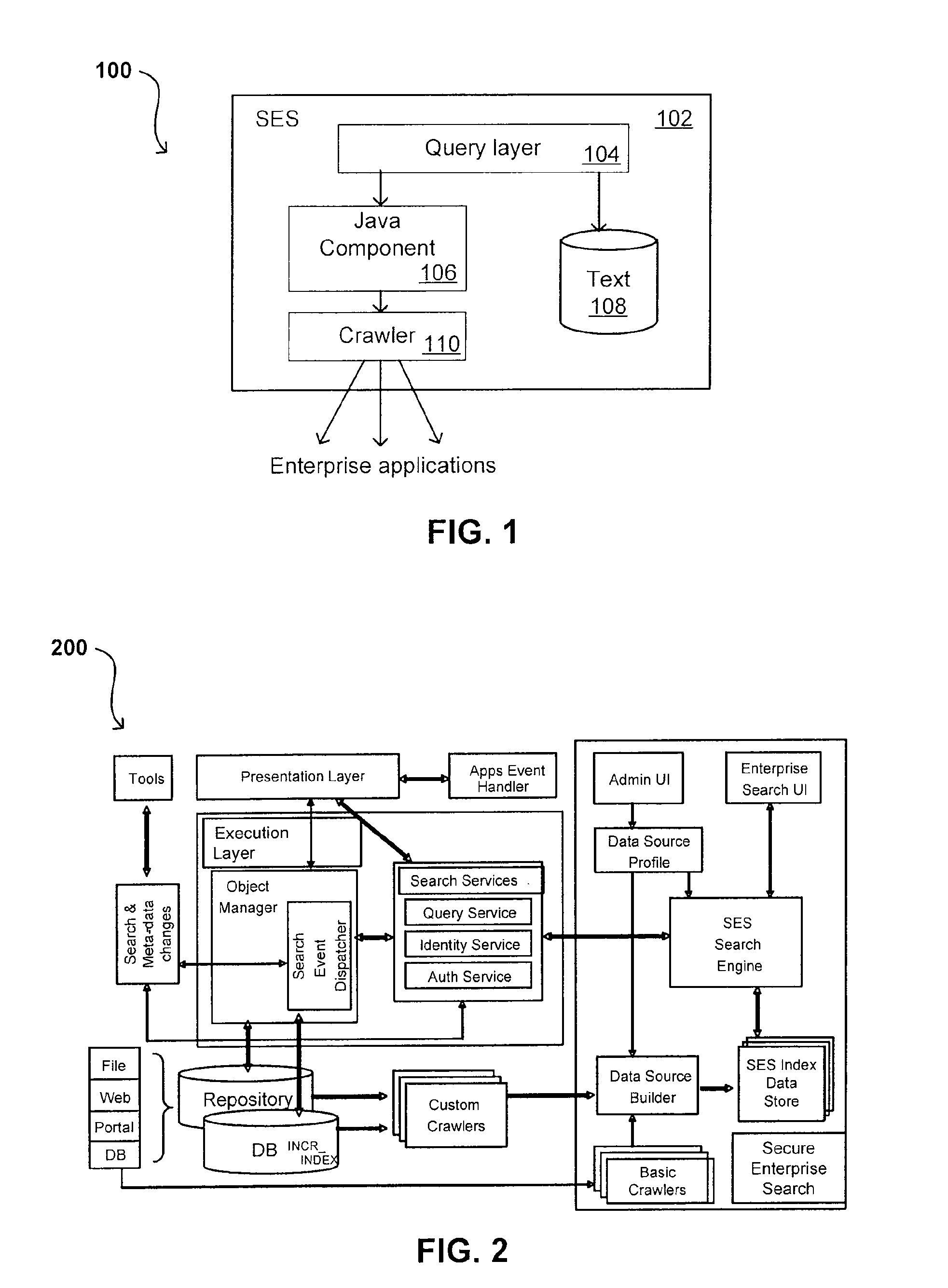
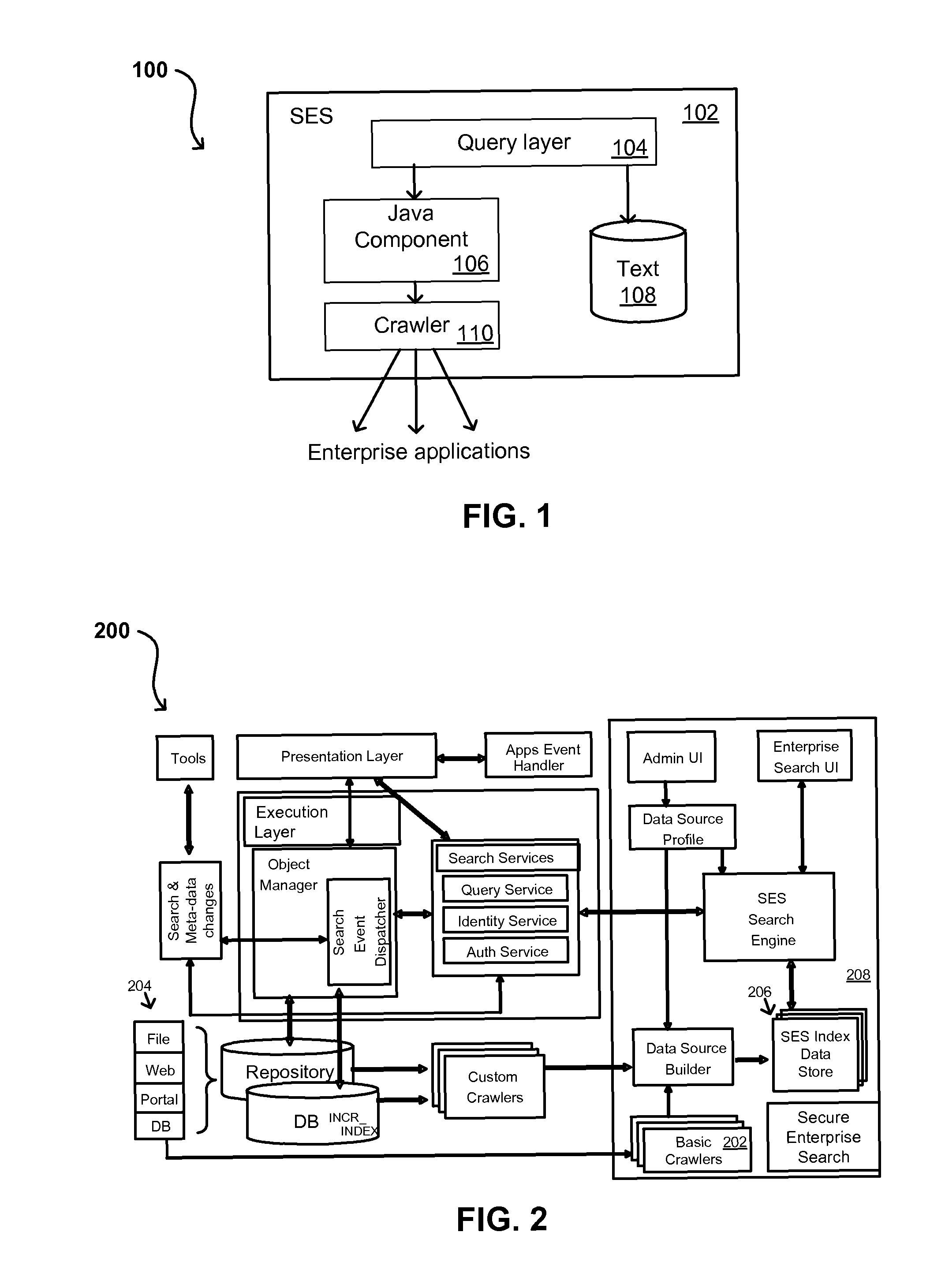
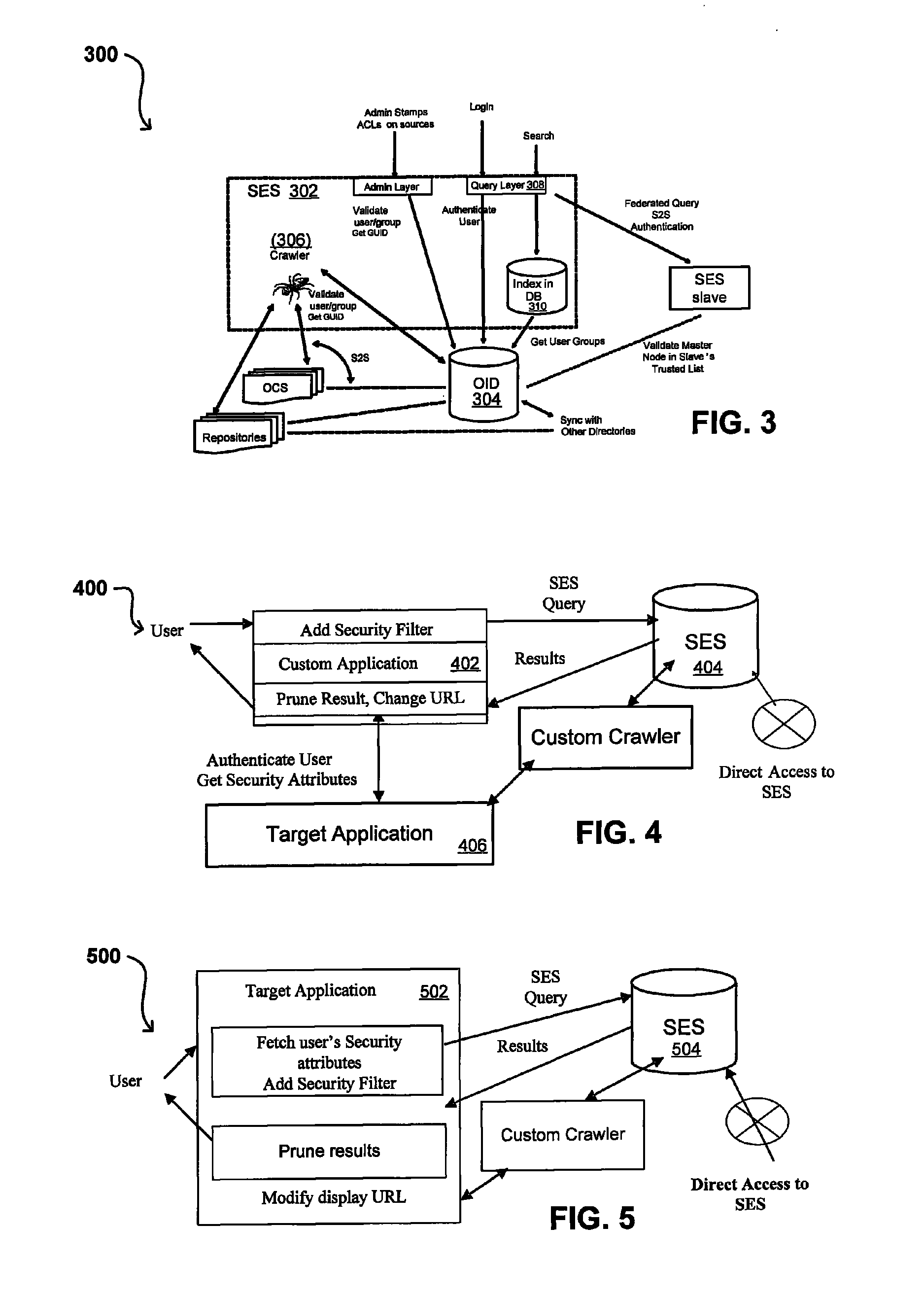
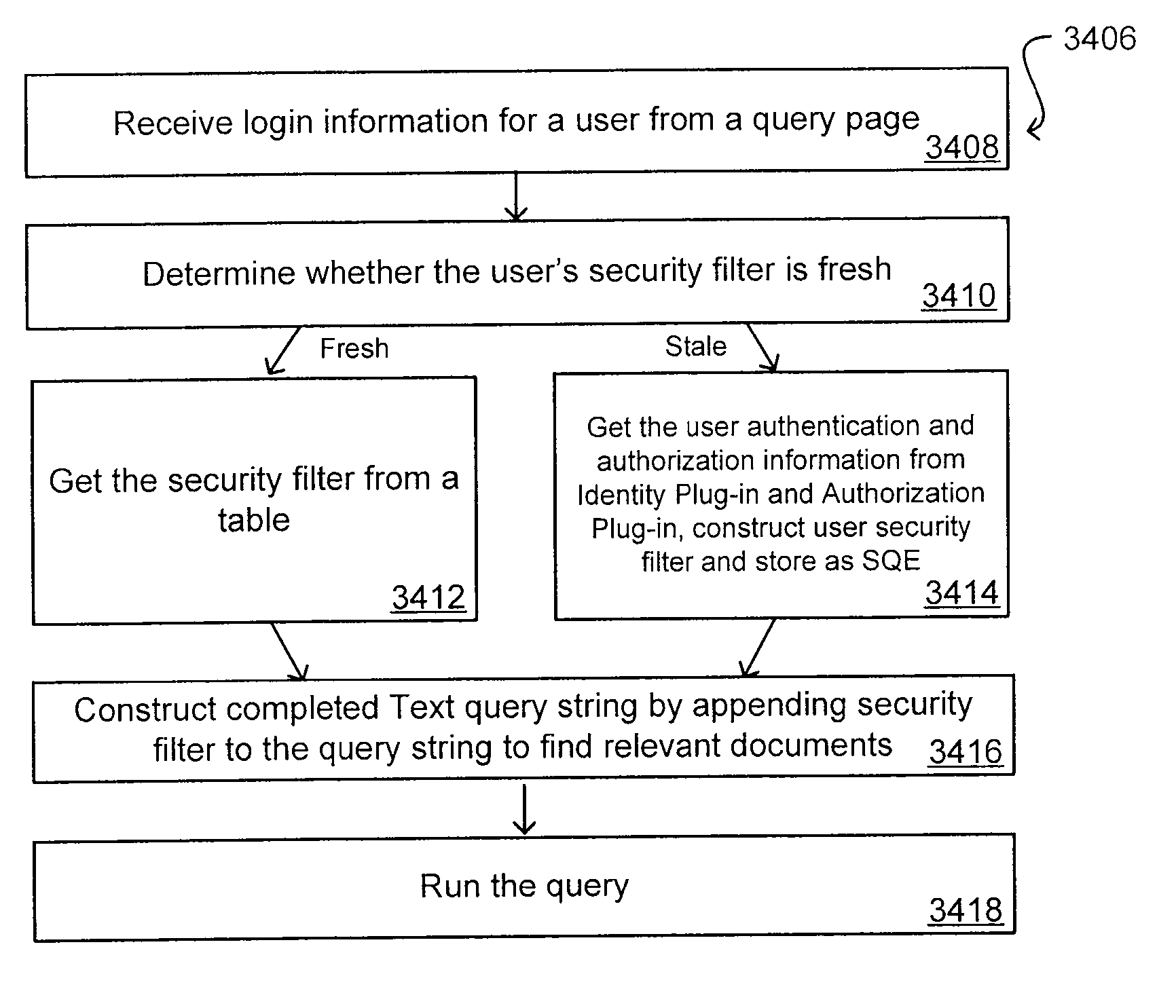
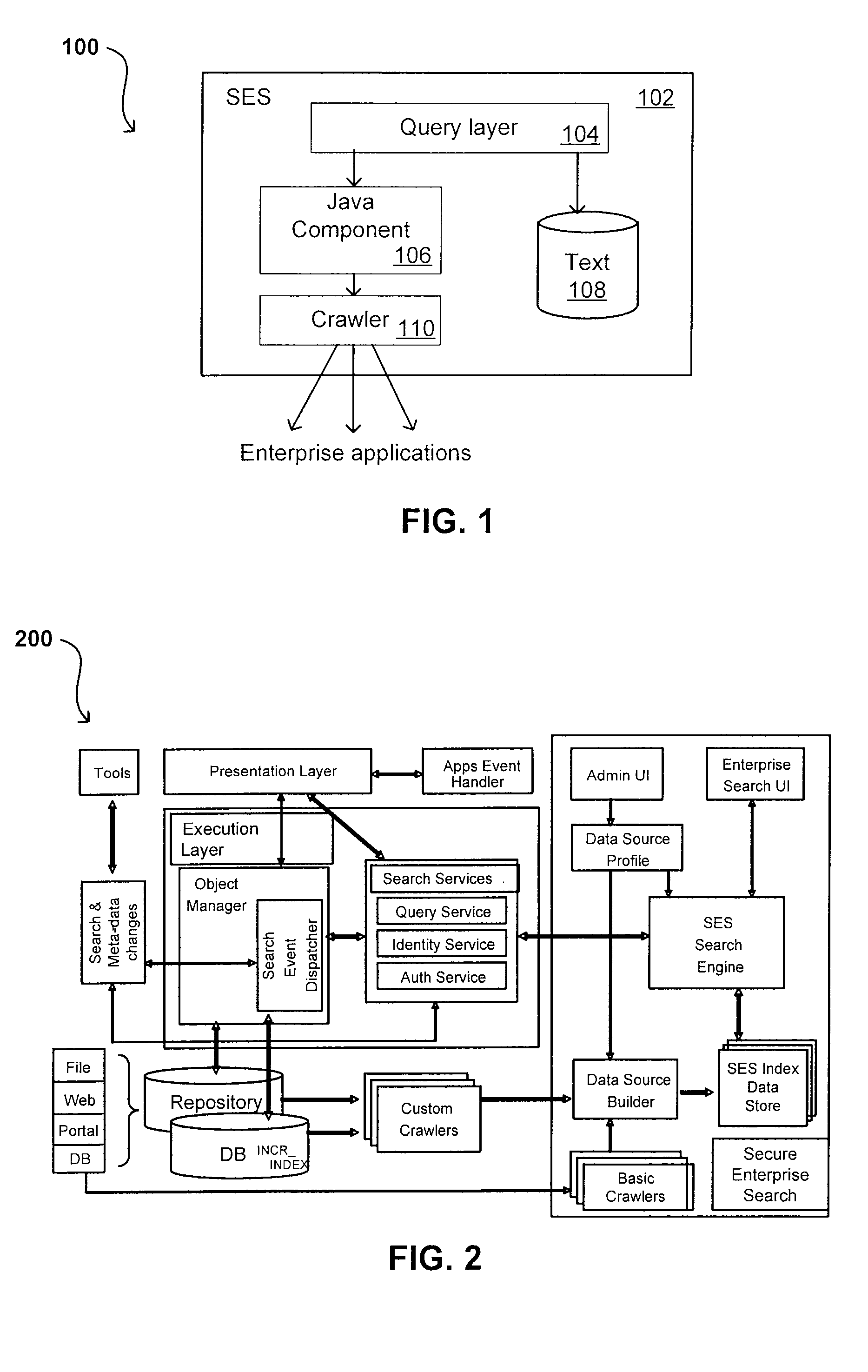
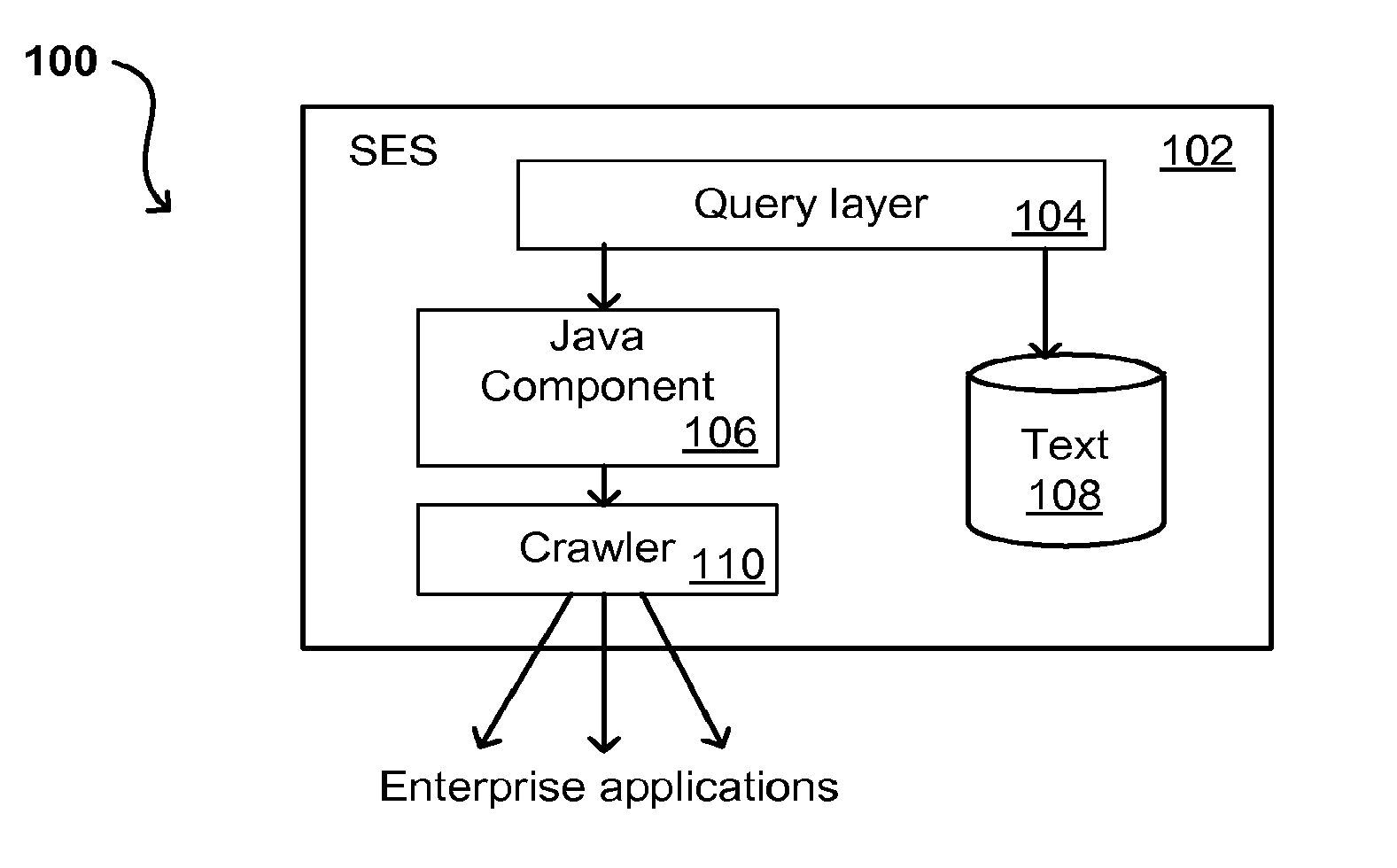
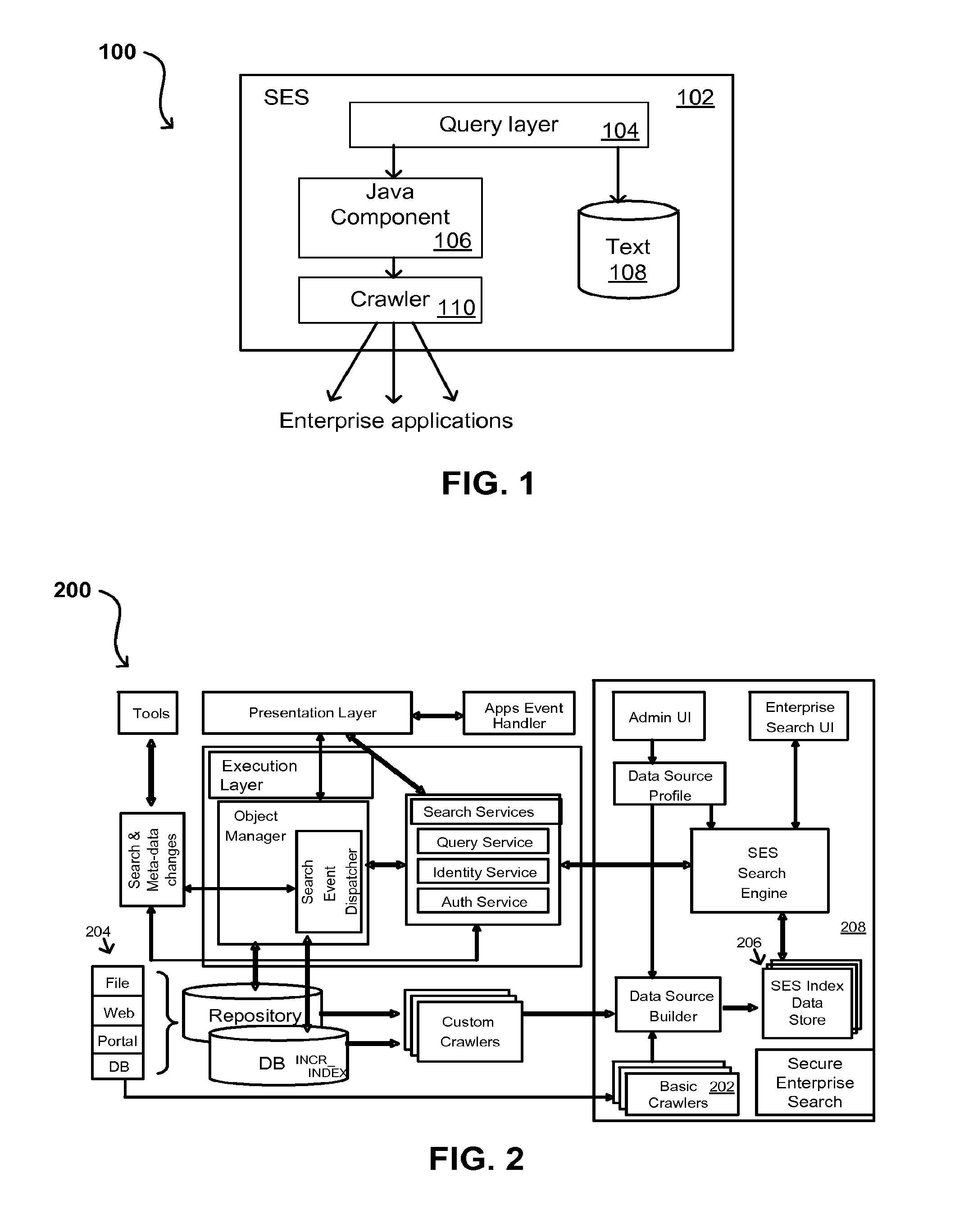
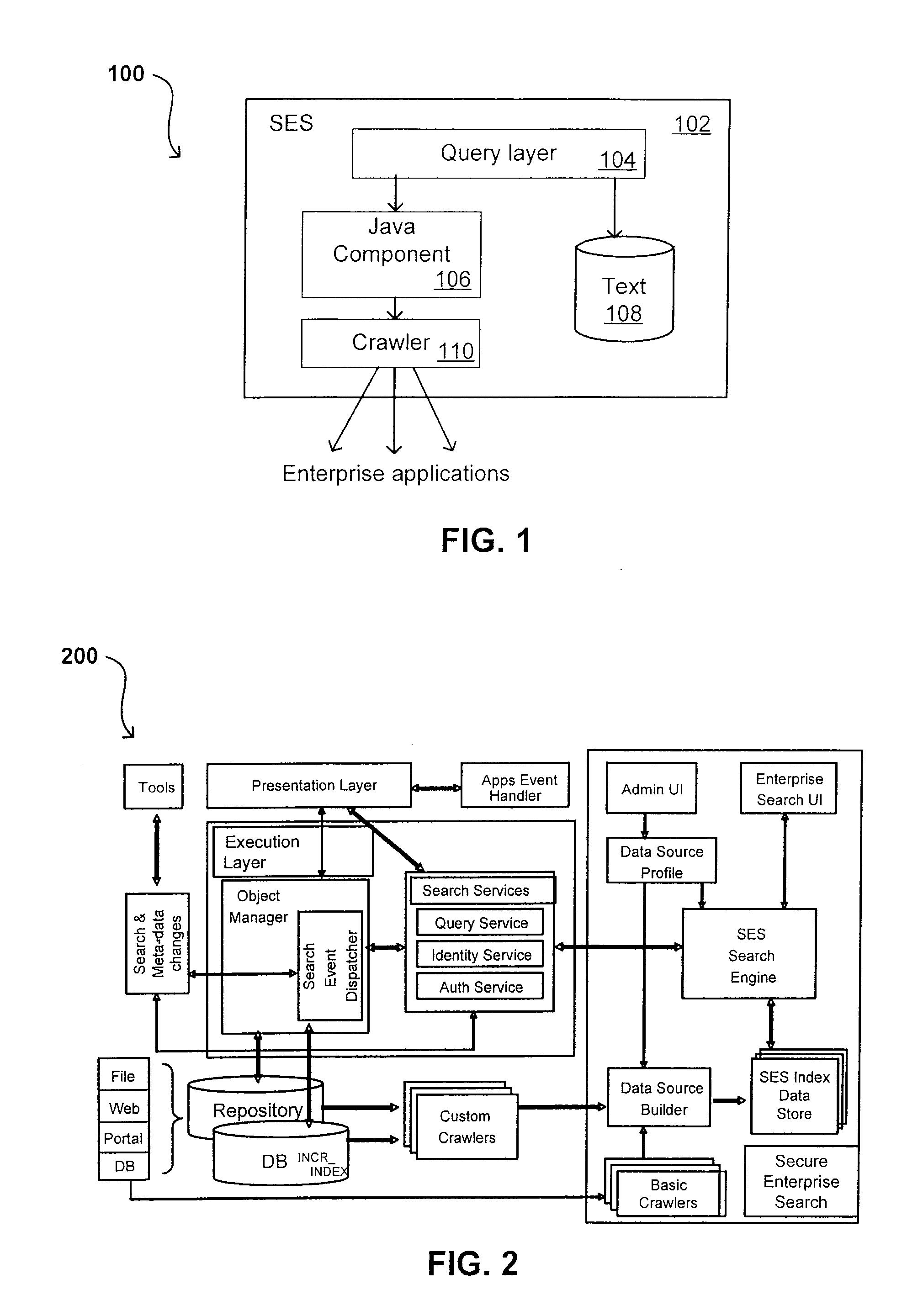
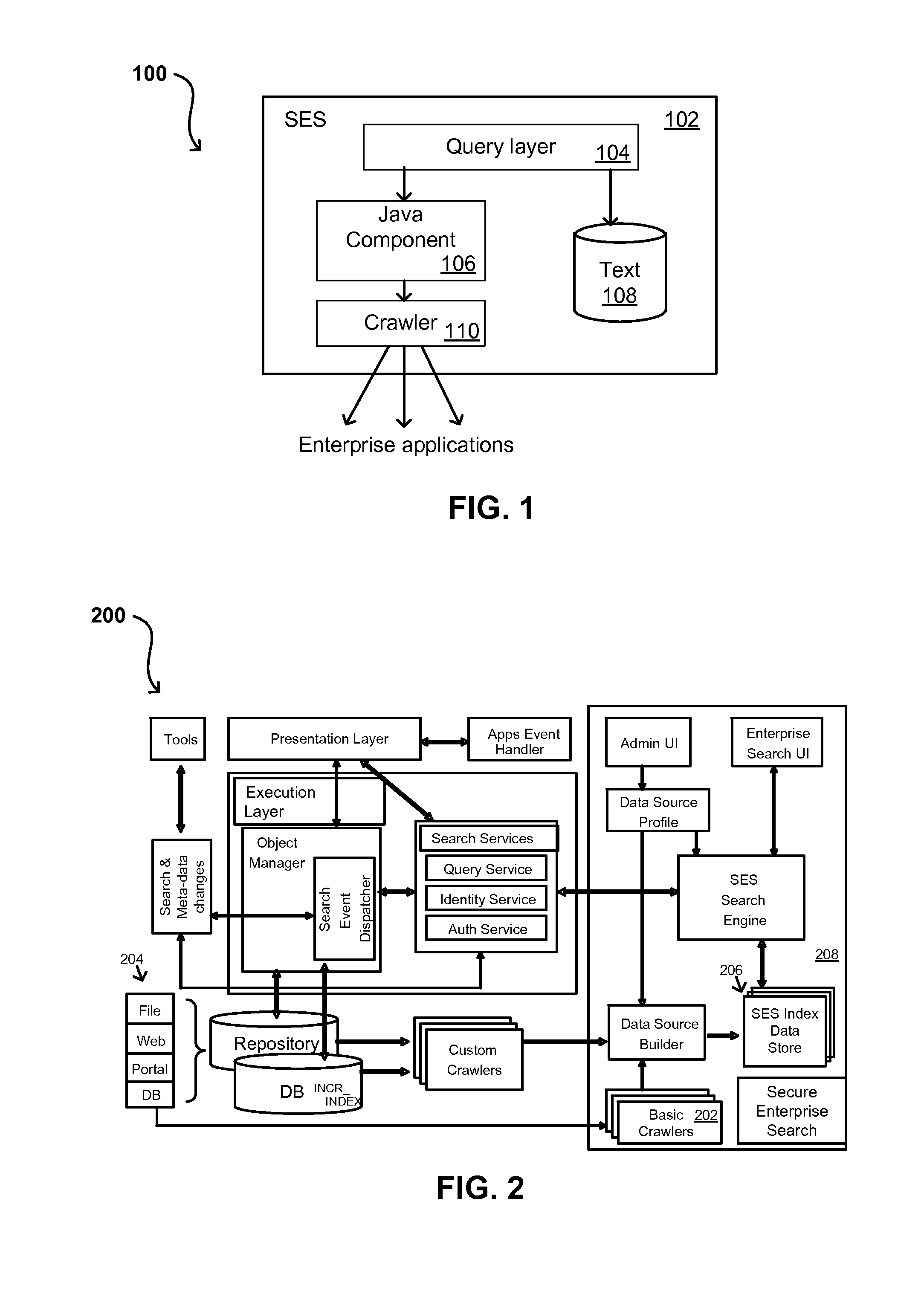
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Search Hit URL Modification for Secure Application Integration
ActiveUS20070209080A1Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Flexible Authentication Framework
ActiveUS20070208744A1Limited lifetimeImprove performanceWeb data indexingDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
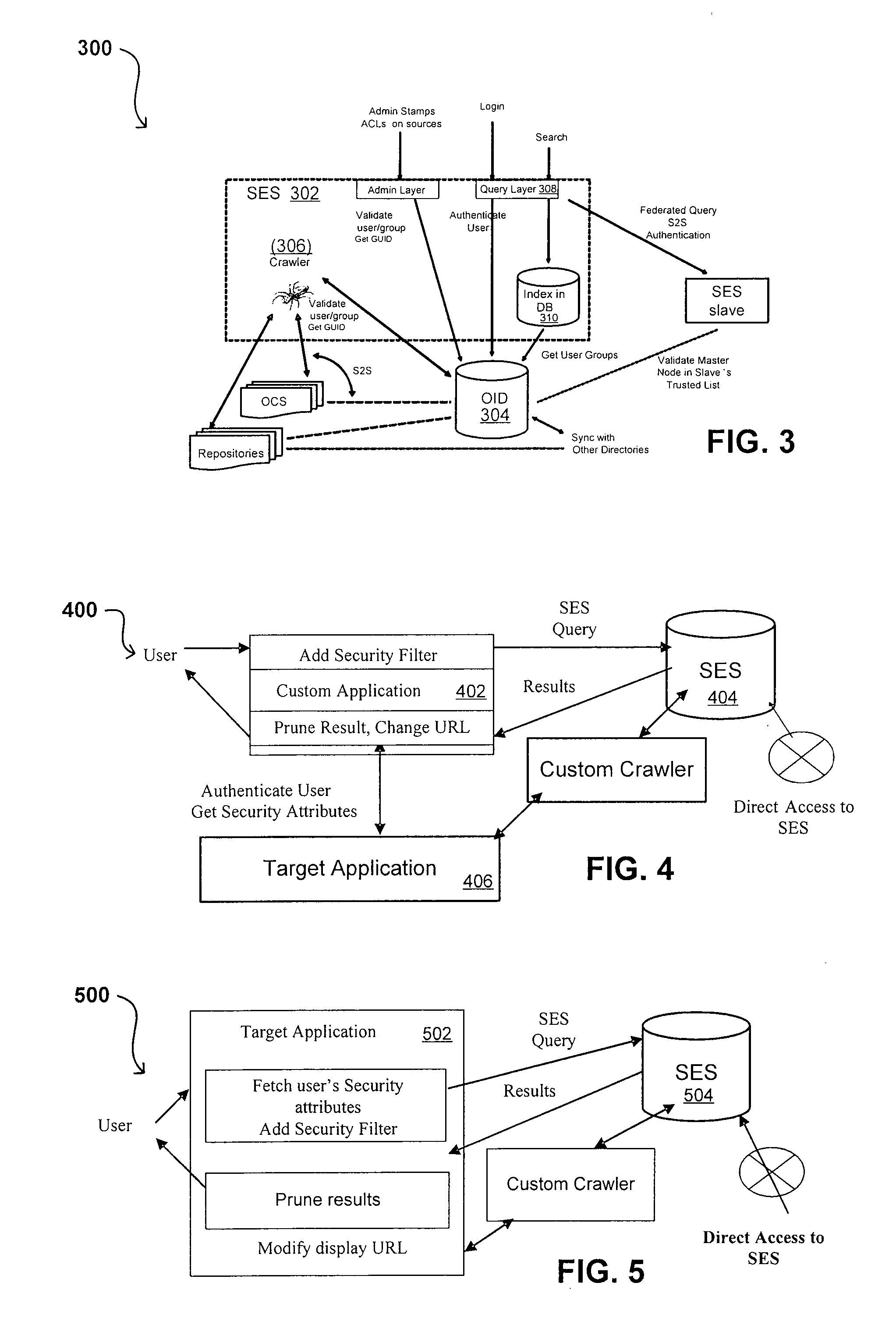
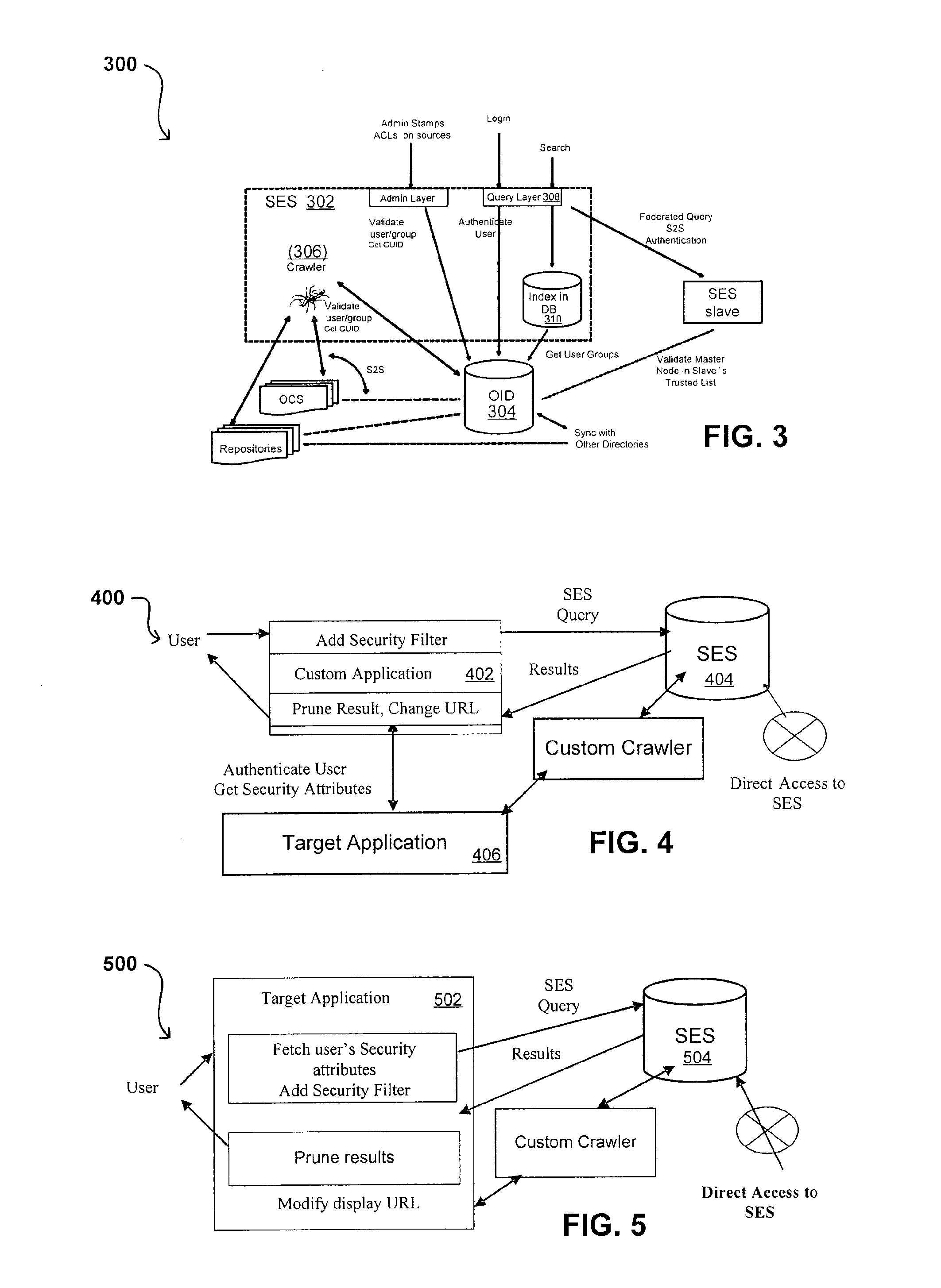
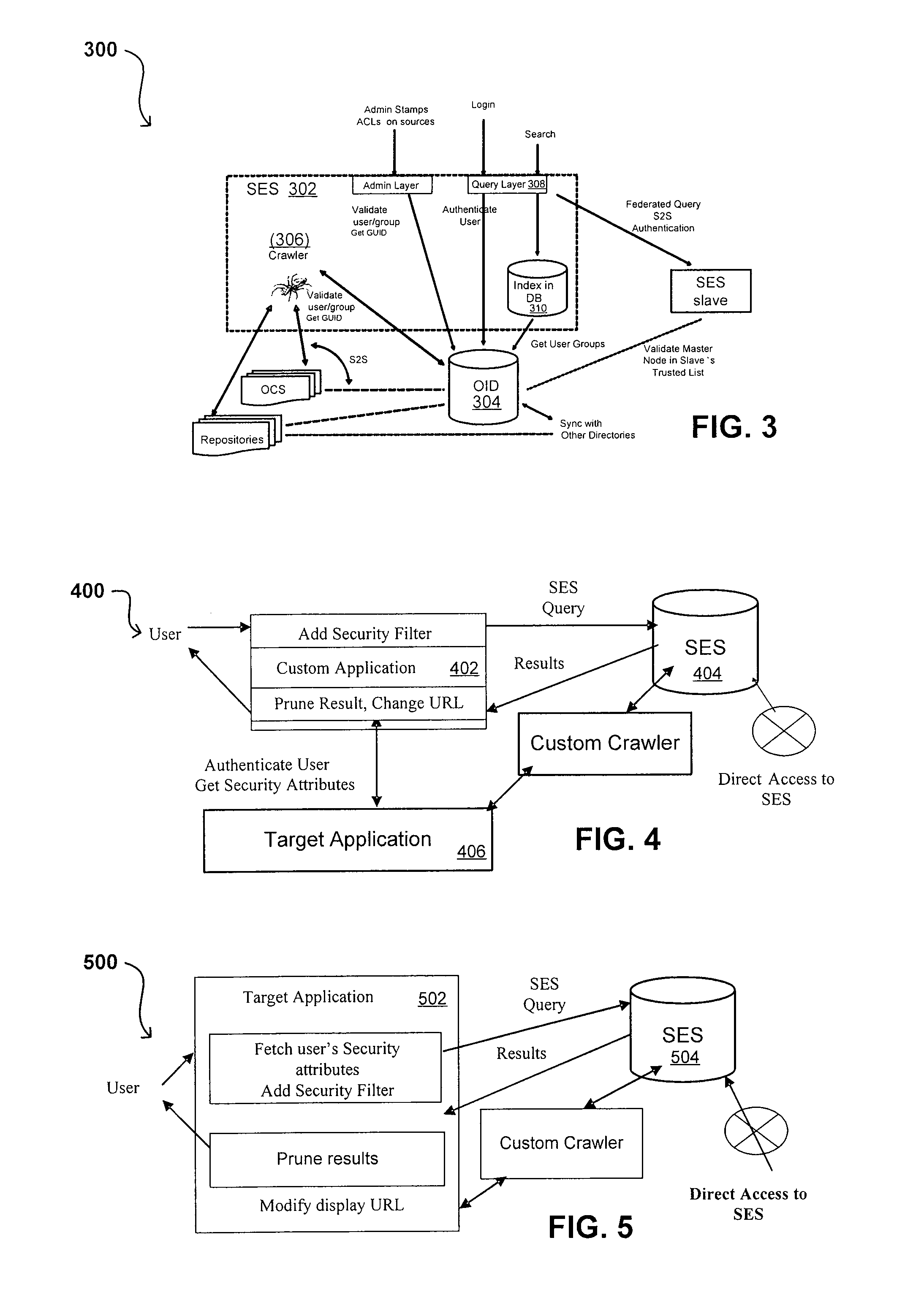
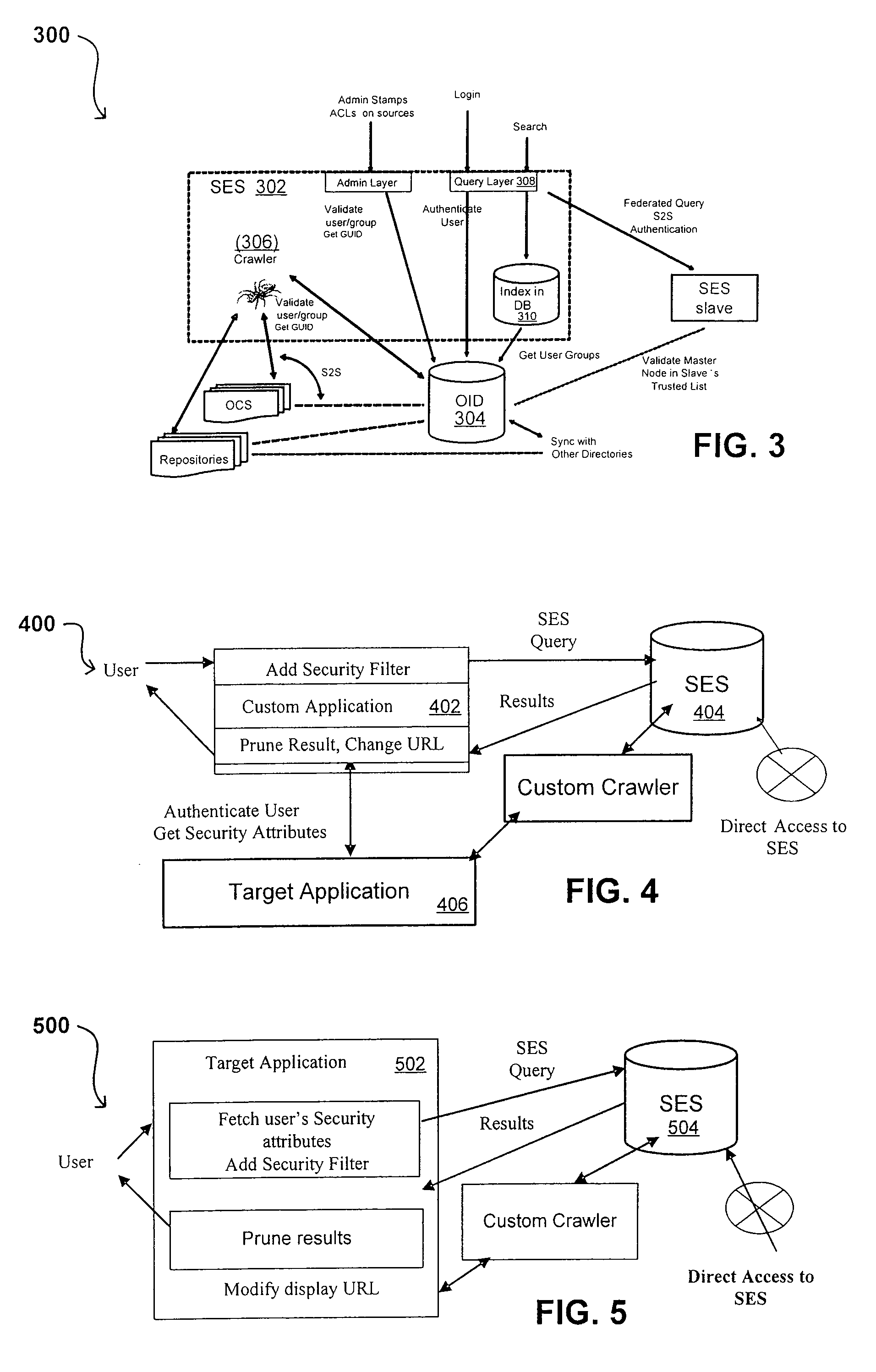
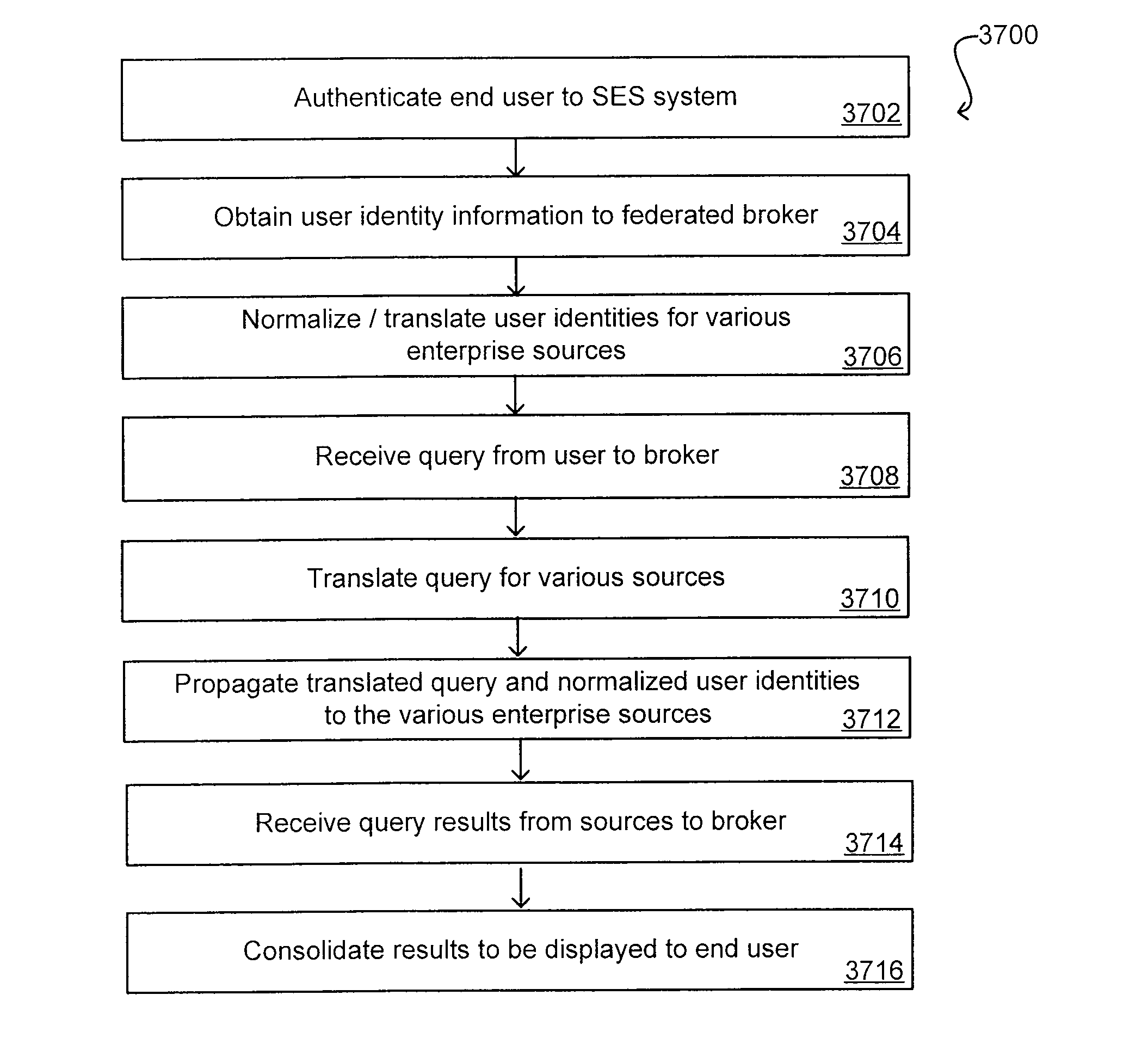
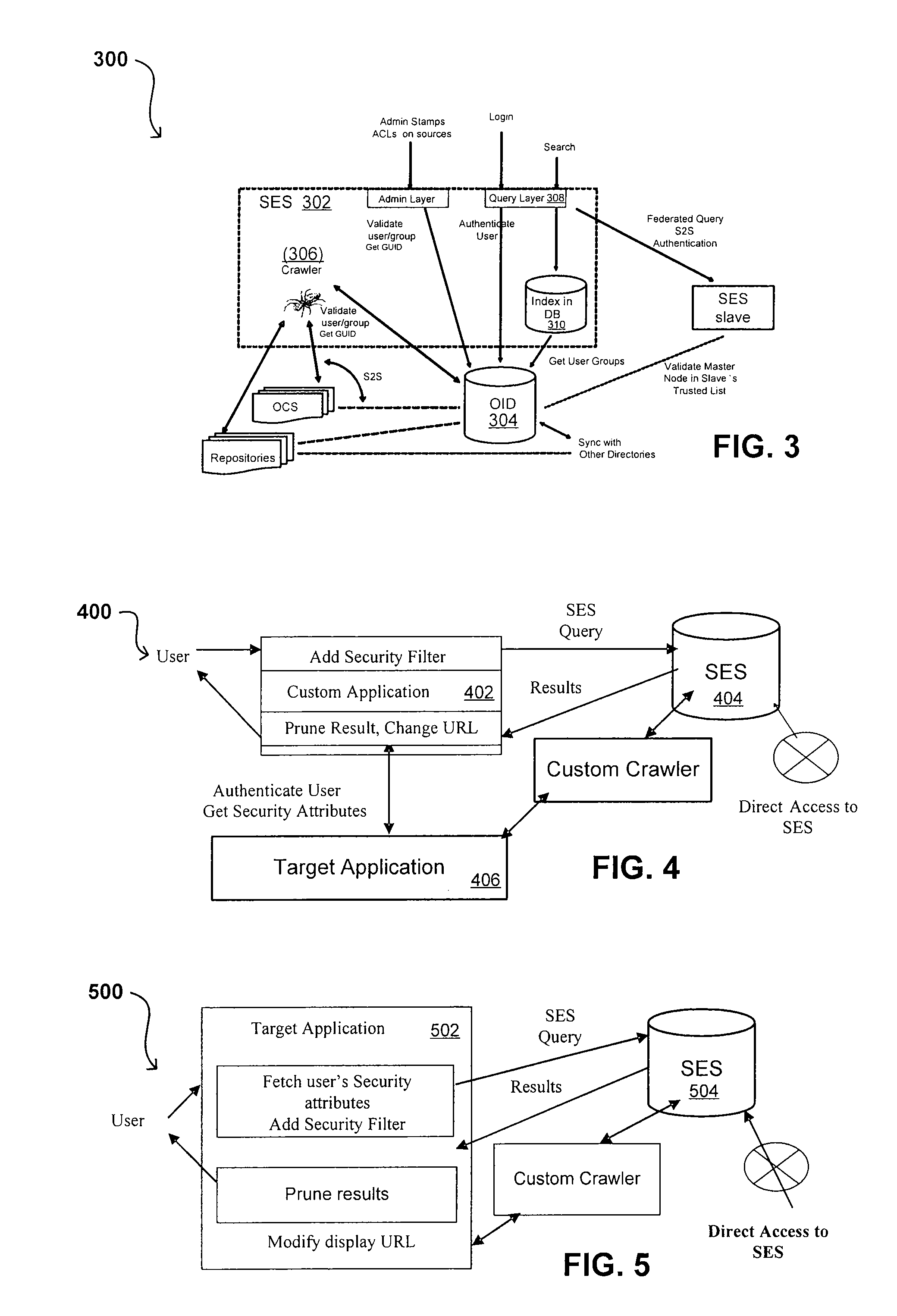
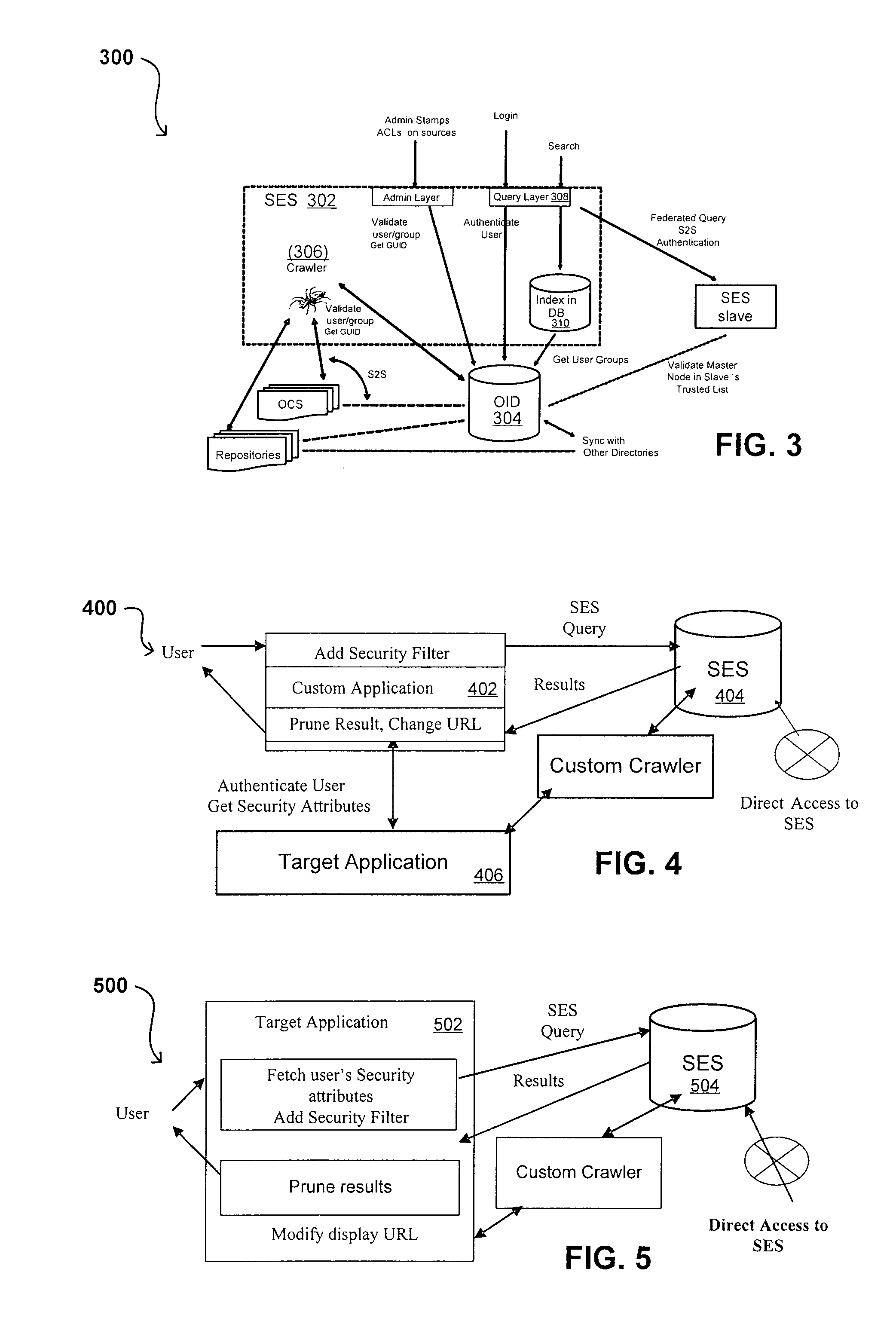
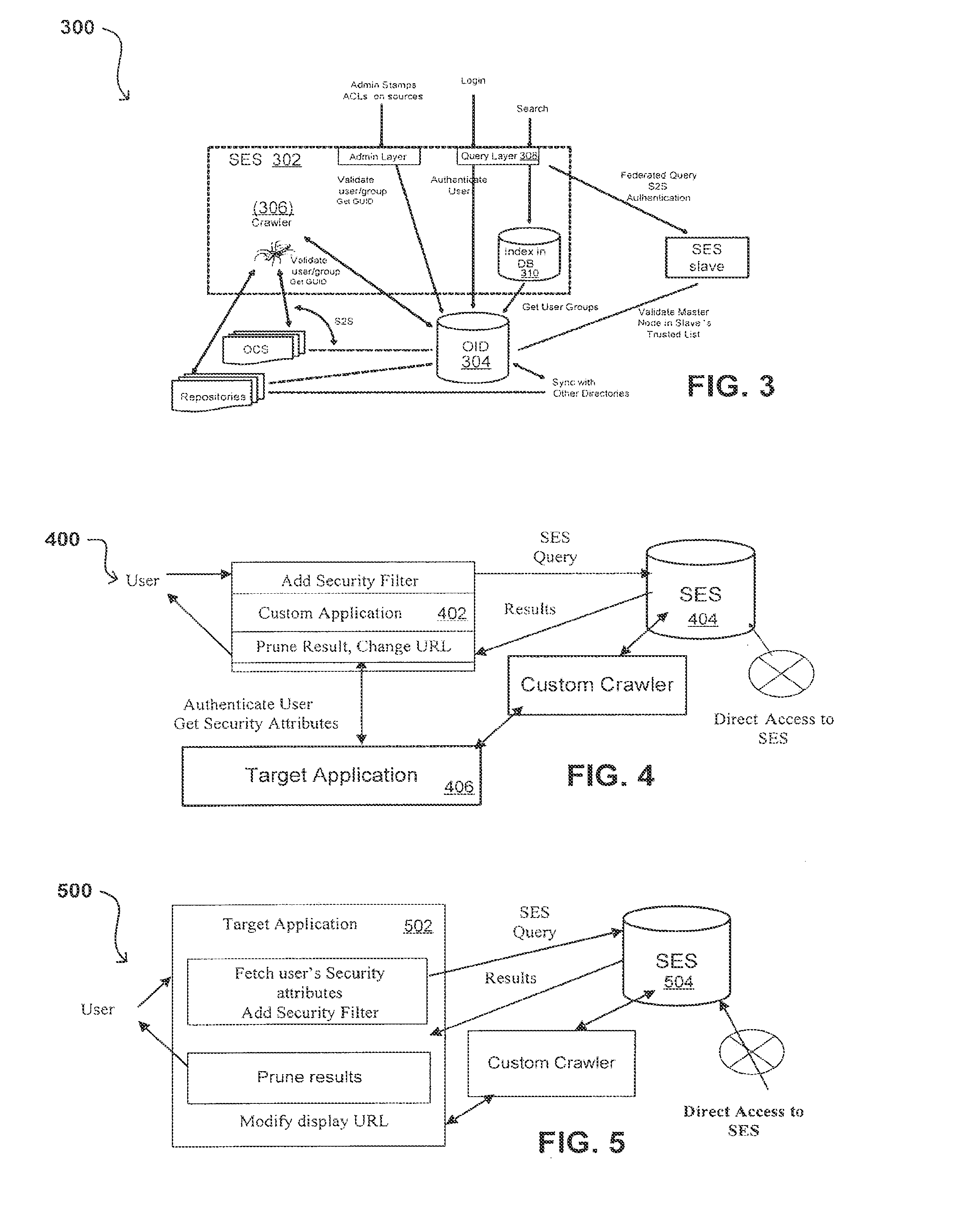
Propagating User Identities In A Secure Federated Search System
ActiveUS20070220268A1Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
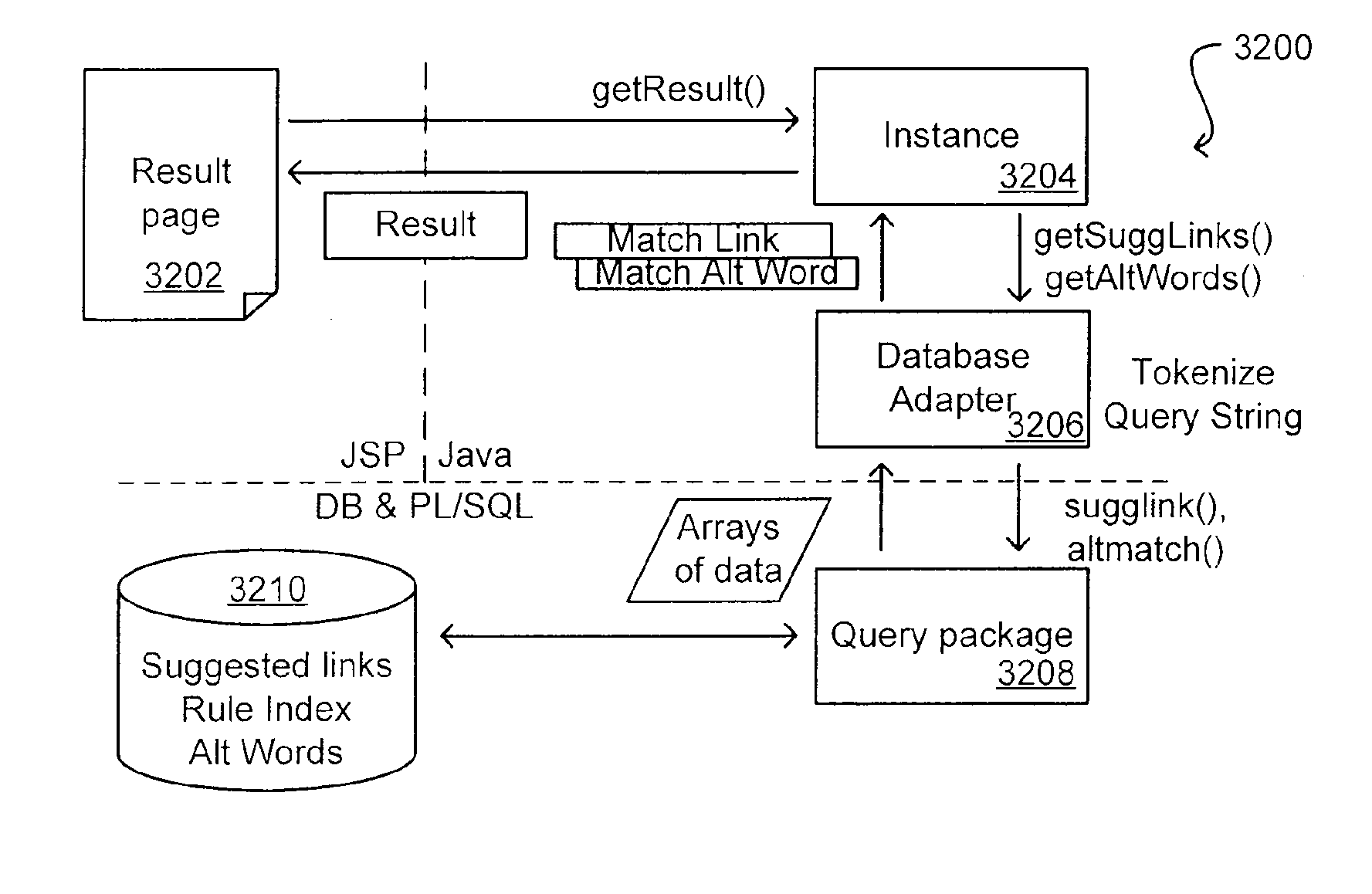
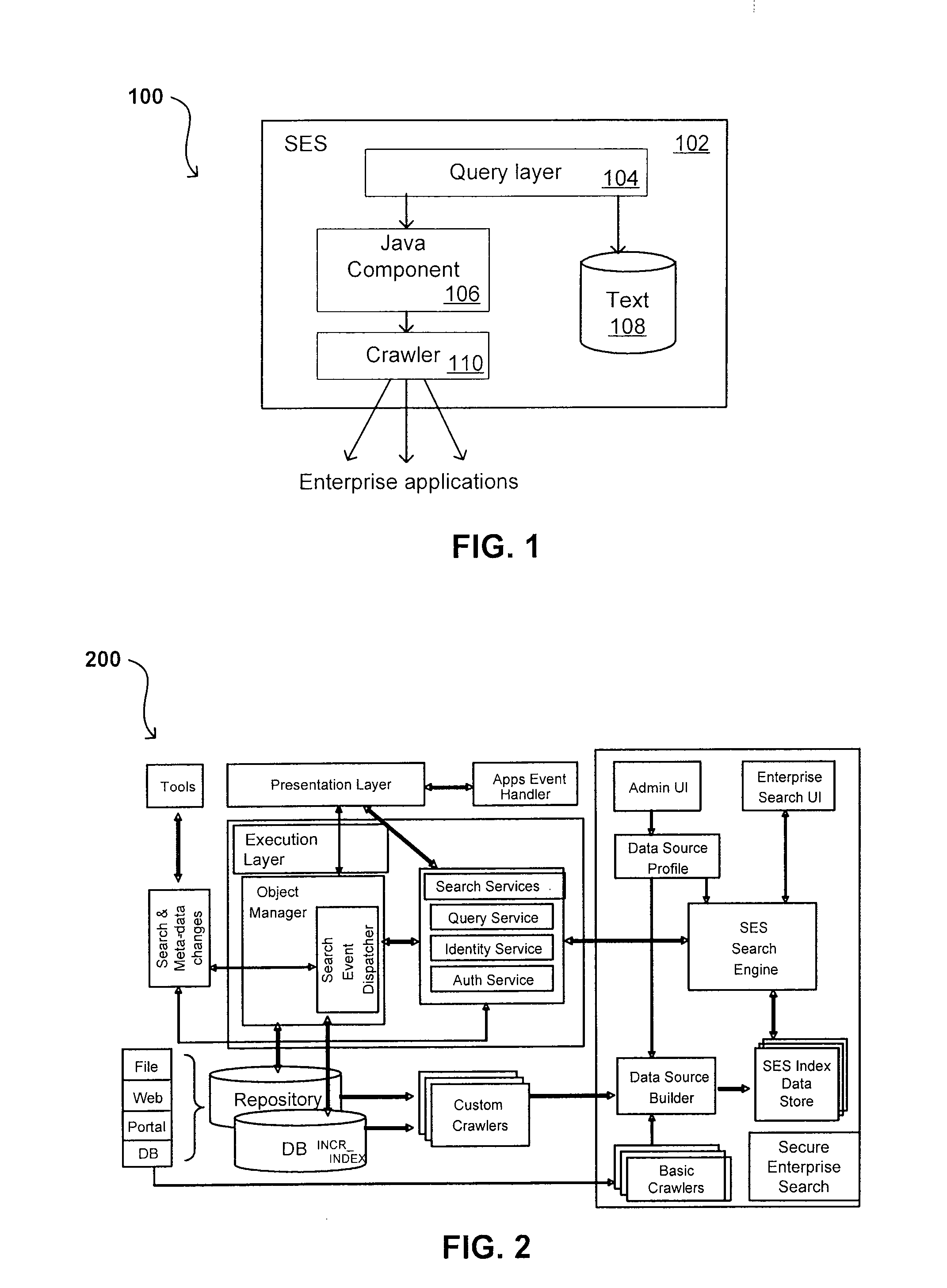
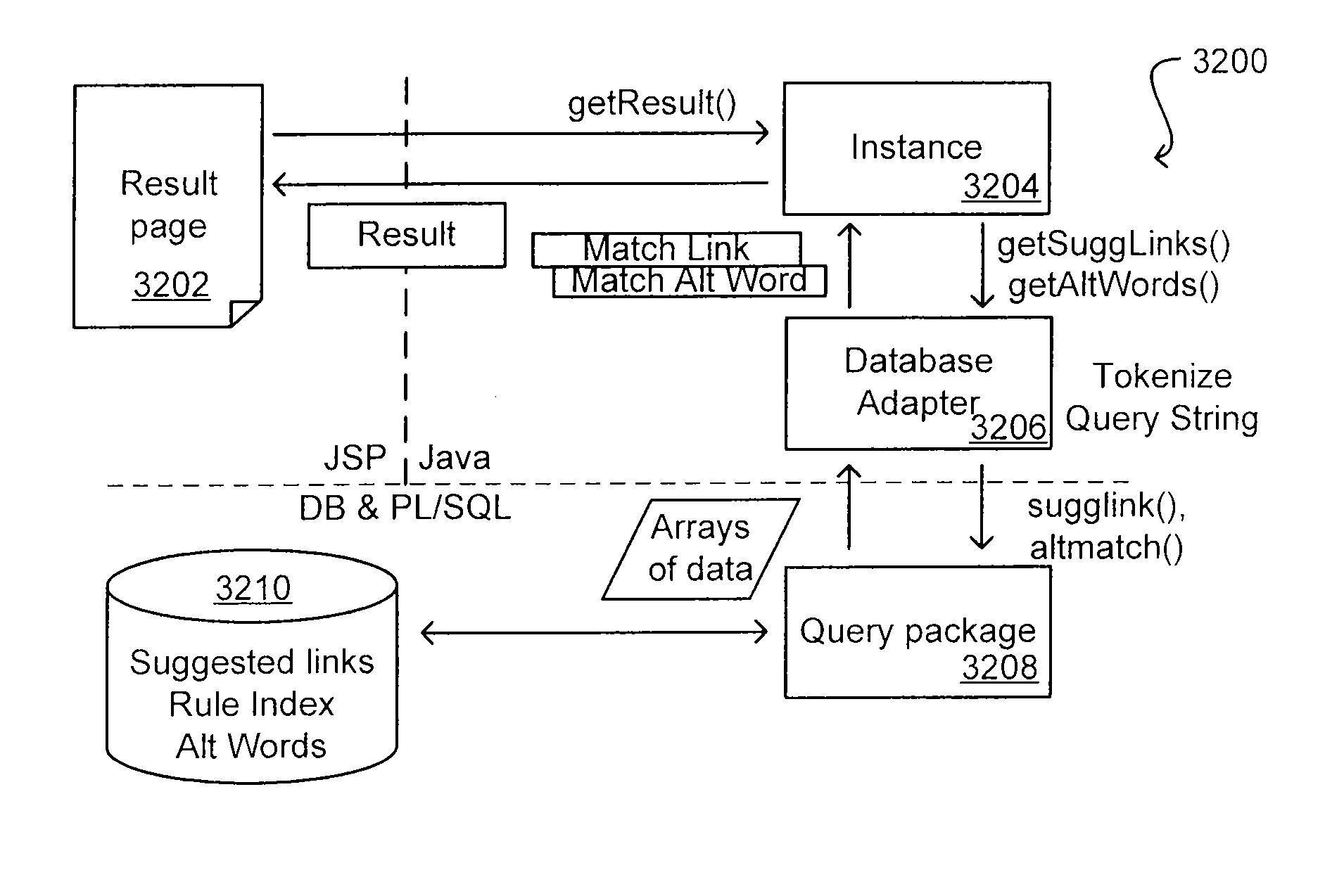
Method for Suggesting Web Links and Alternate Terms for Matching Search Queries
ActiveUS20070208714A1Limited lifetimeImprove performanceWeb data indexingComputer security arrangementsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
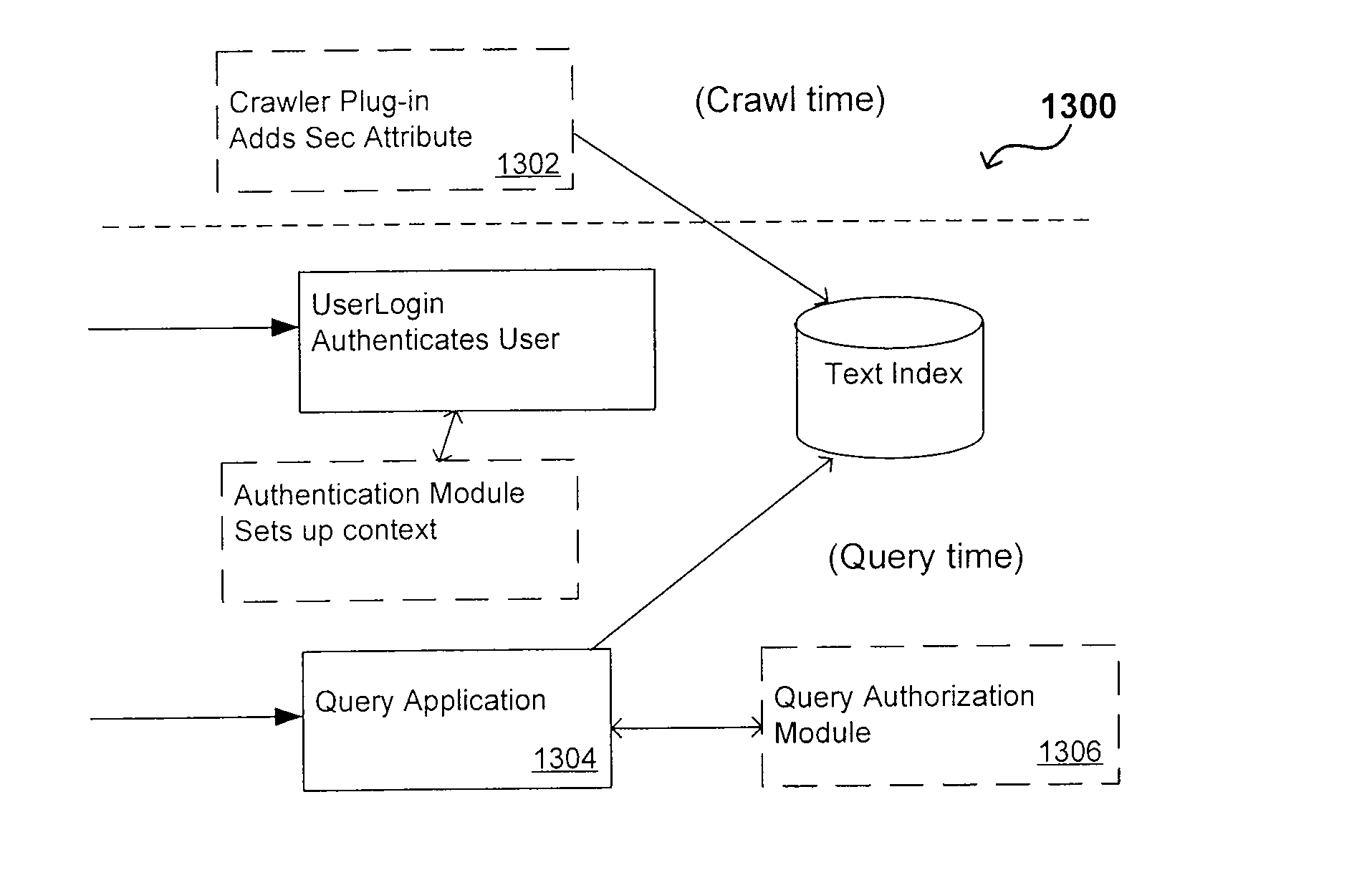
Flexible Authorization Model for Secure Search
InactiveUS20070214129A1Limited lifetimeImprove performanceWeb data indexingSpecial data processing applicationsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
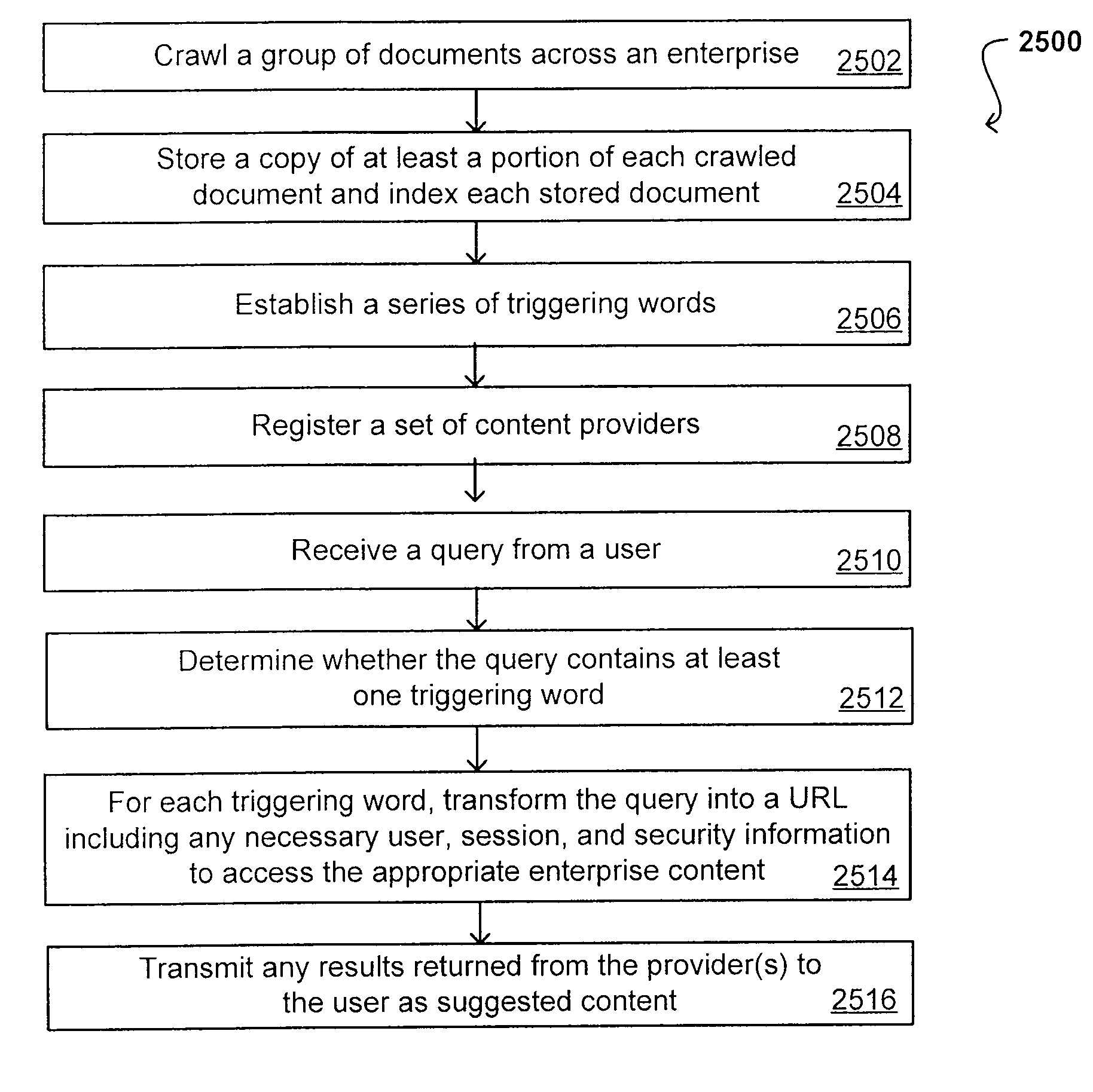
Suggested Content with Attribute Parameterization
ActiveUS20070208755A1Limited lifetimeImprove performanceDigital data processing detailsDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
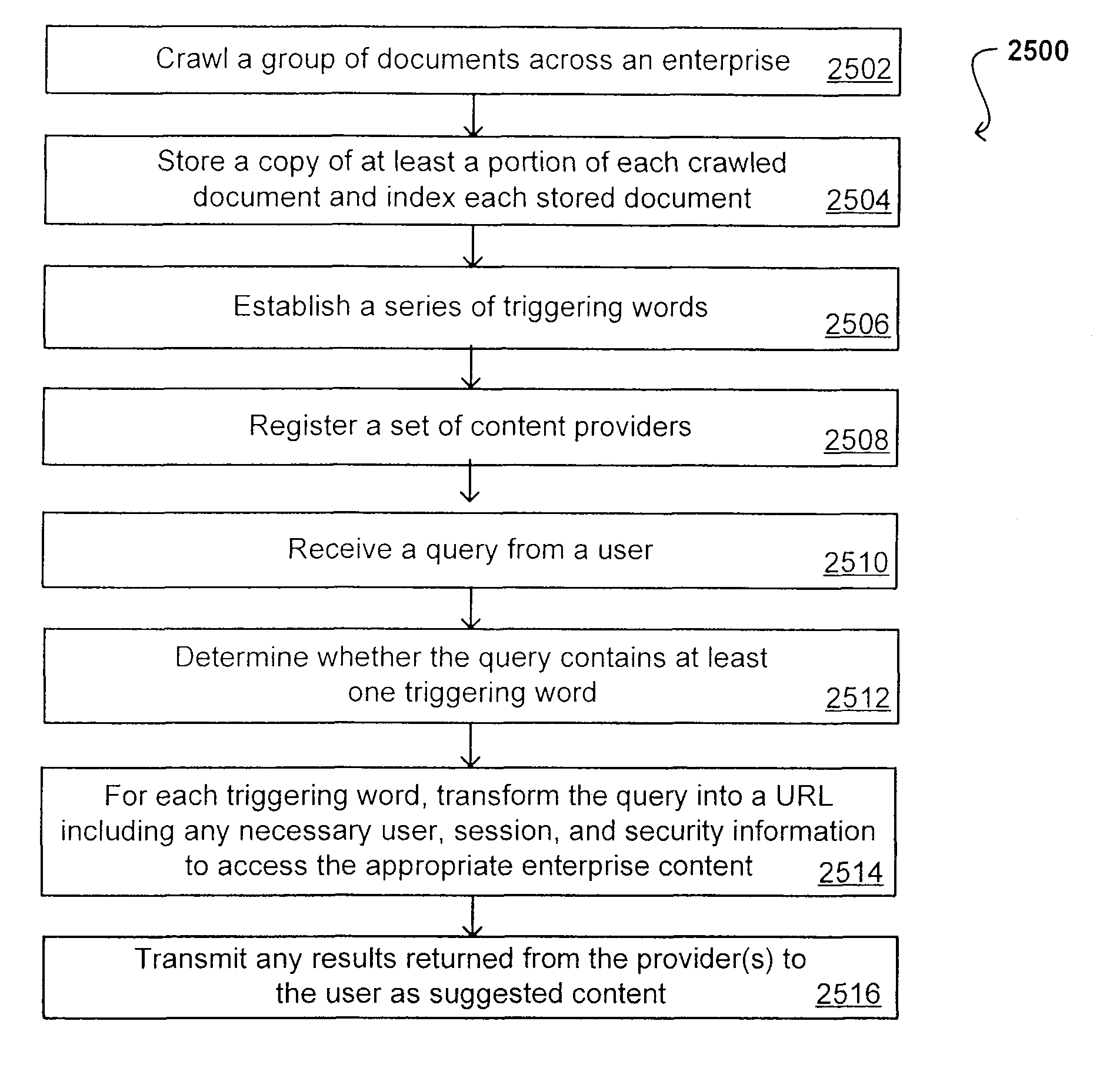
Document date as a ranking factor for crawling
ActiveUS7725465B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security, recency, or other attributes to be submitted at query time, for example, in order to re-rank query results from enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Minimum Lifespan Credentials for Crawling Data Repositories
ActiveUS20070283425A1Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Auto generation of suggested links in a search system
ActiveUS8005816B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Secure Search Performance Improvement
ActiveUS20070208746A1Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Suggested content with attribute parameterization
ActiveUS7941419B2Limited lifetimeImprove performanceDigital data processing detailsDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Document date as a ranking factor for crawling
ActiveUS20070250486A1Limited lifetimeImprove performanceWeb data indexingDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
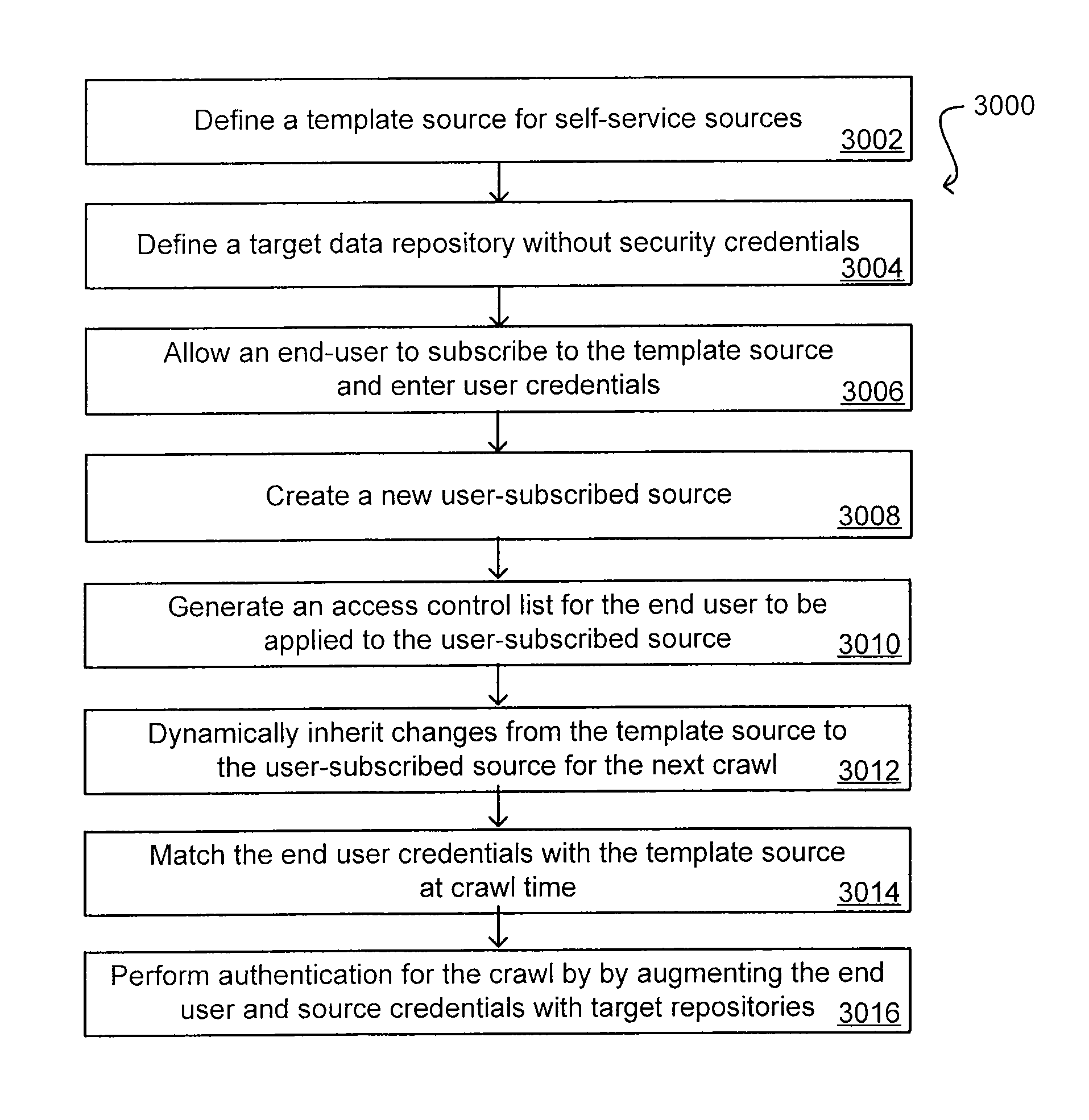
Self-Service Sources for Secure Search
ActiveUS20070208745A1Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
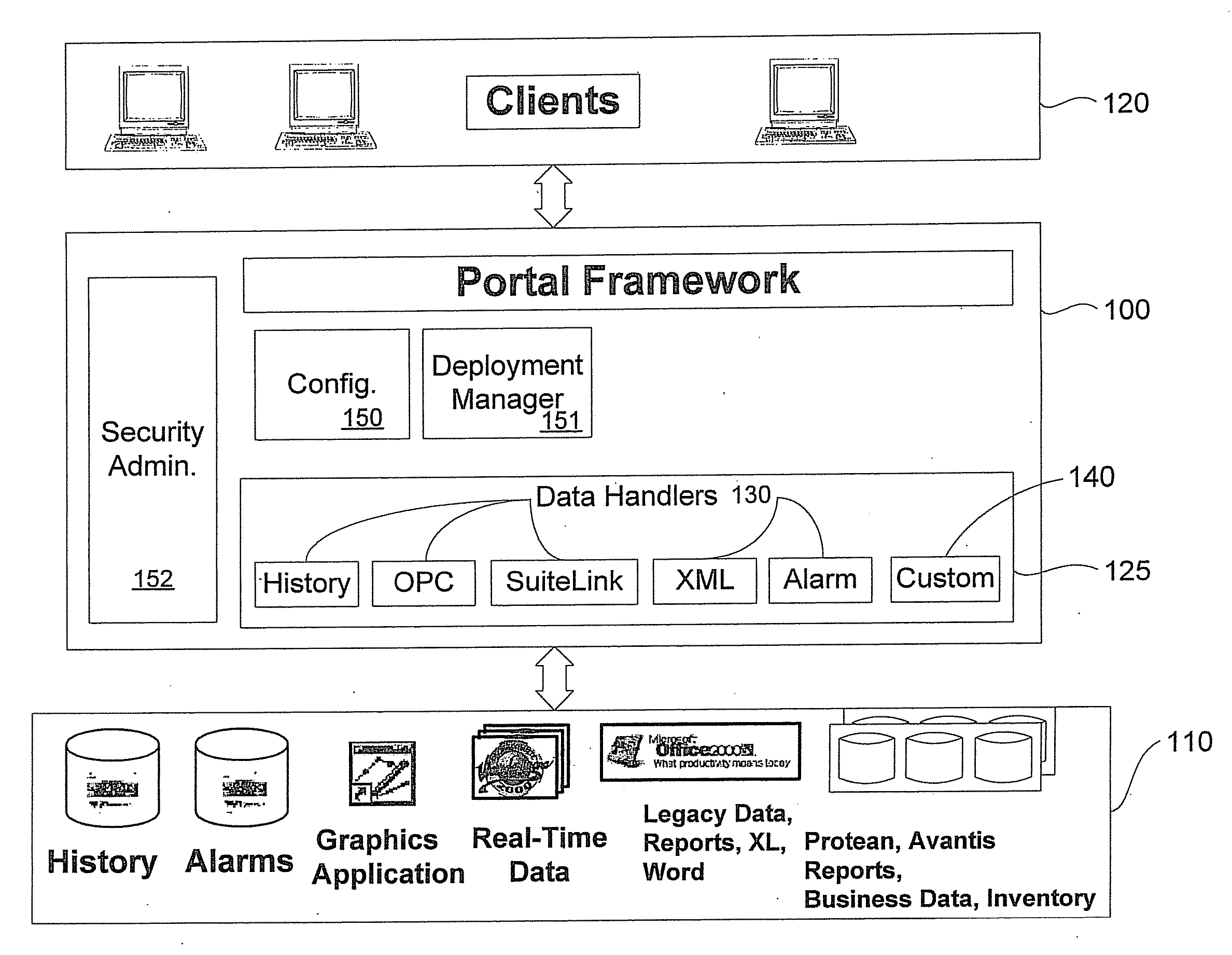
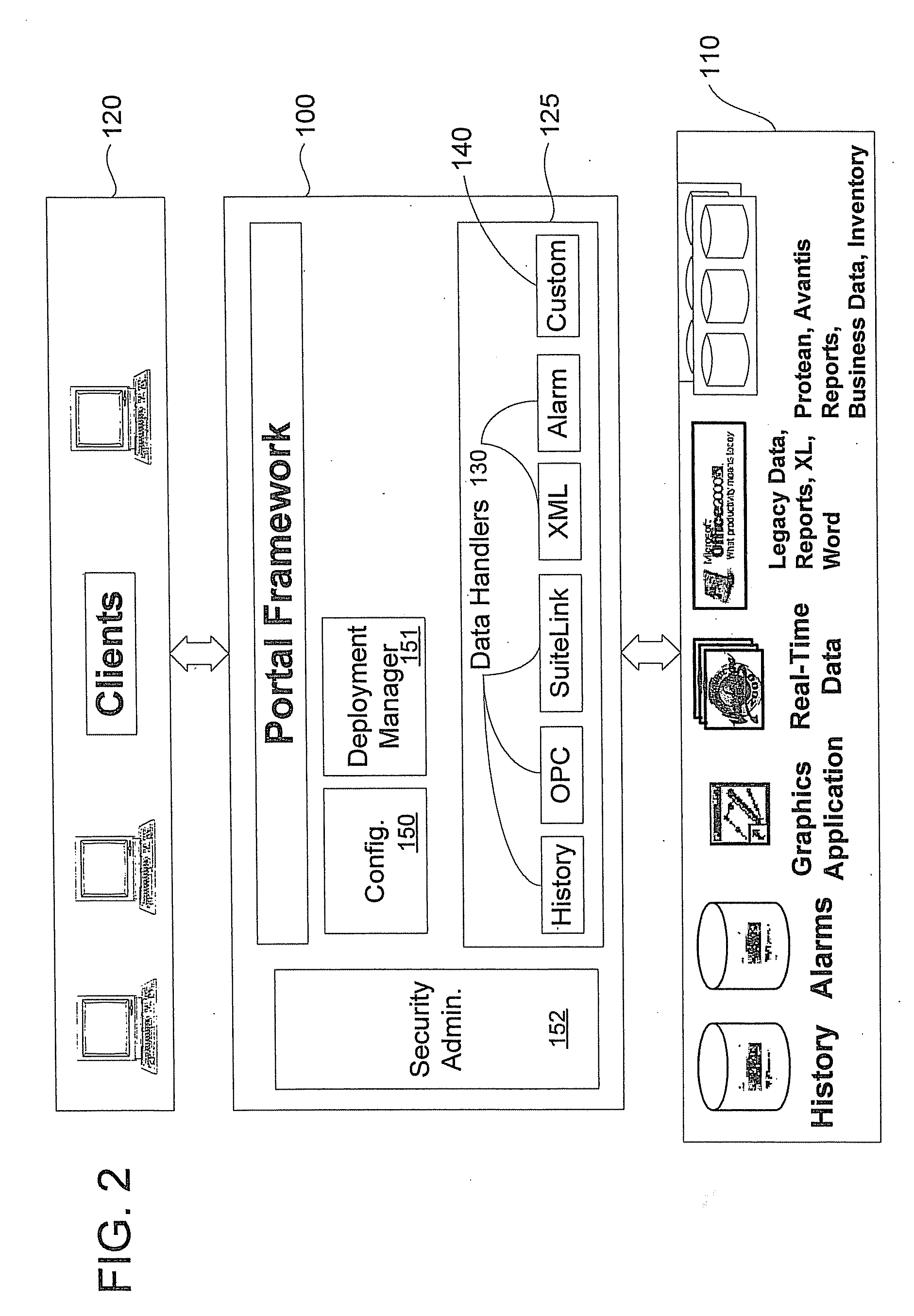
Extensible manufacturing/process control information portal server
InactiveUS20080097622A1Easy to customizeComputer controlCathode-ray tube indicatorsData providerInformation access
A manufacturing / process control system information access provider architecture is disclosed. Manufacturing / process control system data provider flexibility is achieved through a user-configurable manufacturing / process control information portal server that comprises multiple selectable data provides (sources) and / or data types that a particular data provider accommodates. A user configures the portal server to deliver manufacturing / process control information associated with a controlled process environment, such as a food processing plant floor or an oil refinery reactor, to the user via a browser client over the Internet or a corporate intranet. Furthermore, an extensible architecture is provided that enables adding new components to the portal server. Such extensions include new data sources and new data types / handlers. The new architecture enables a user to select particular ones of the available data handlers and then their associated data sources thereby facilitating customizing the configuration of the portal server to the particular needs / interests of the user.
Owner:INVENSYS SYST INC
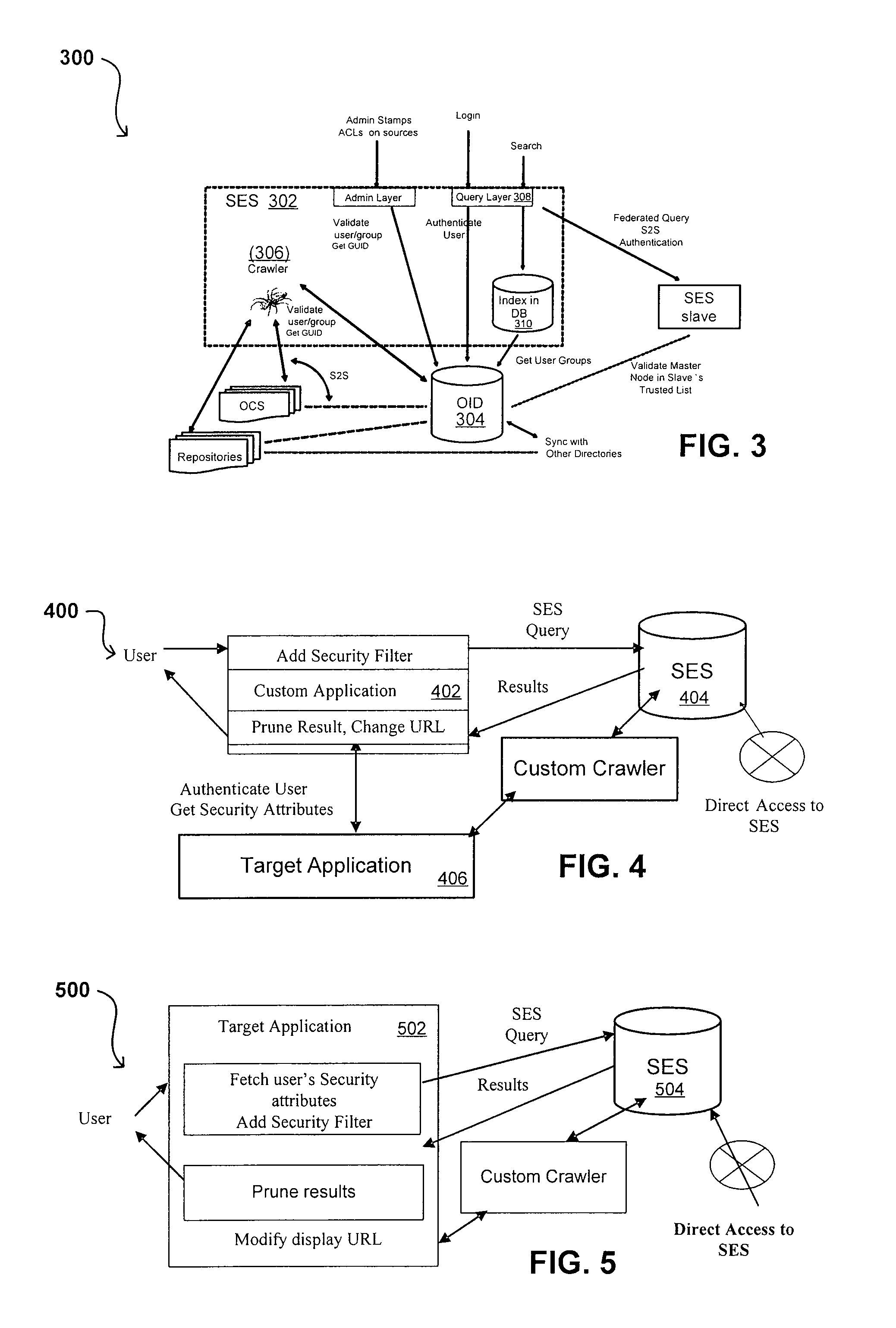
Propagating user identities in a secure federated search system
ActiveUS8214394B2Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
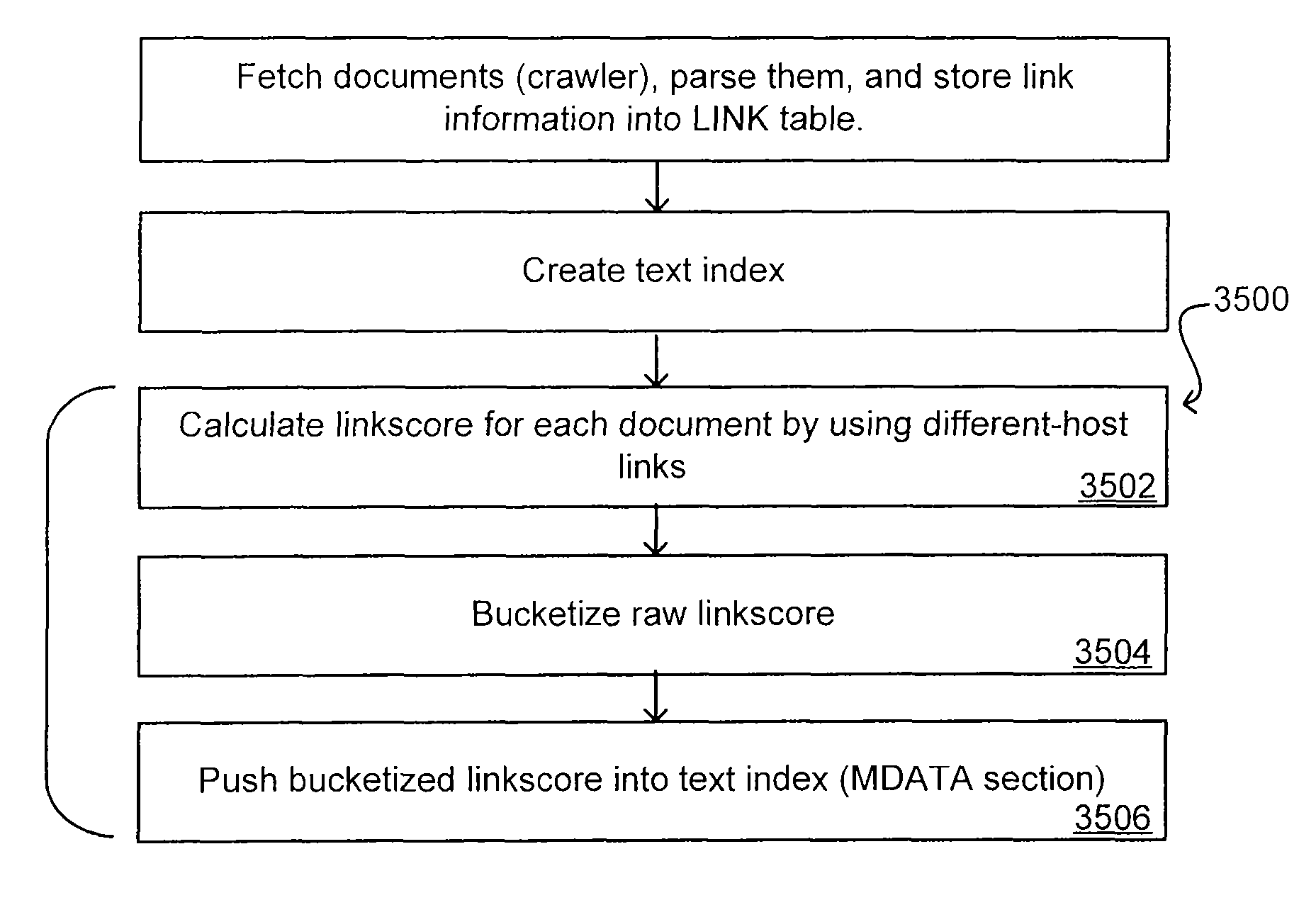
Link Analysis for Enterprise Environment
ActiveUS20070208734A1Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
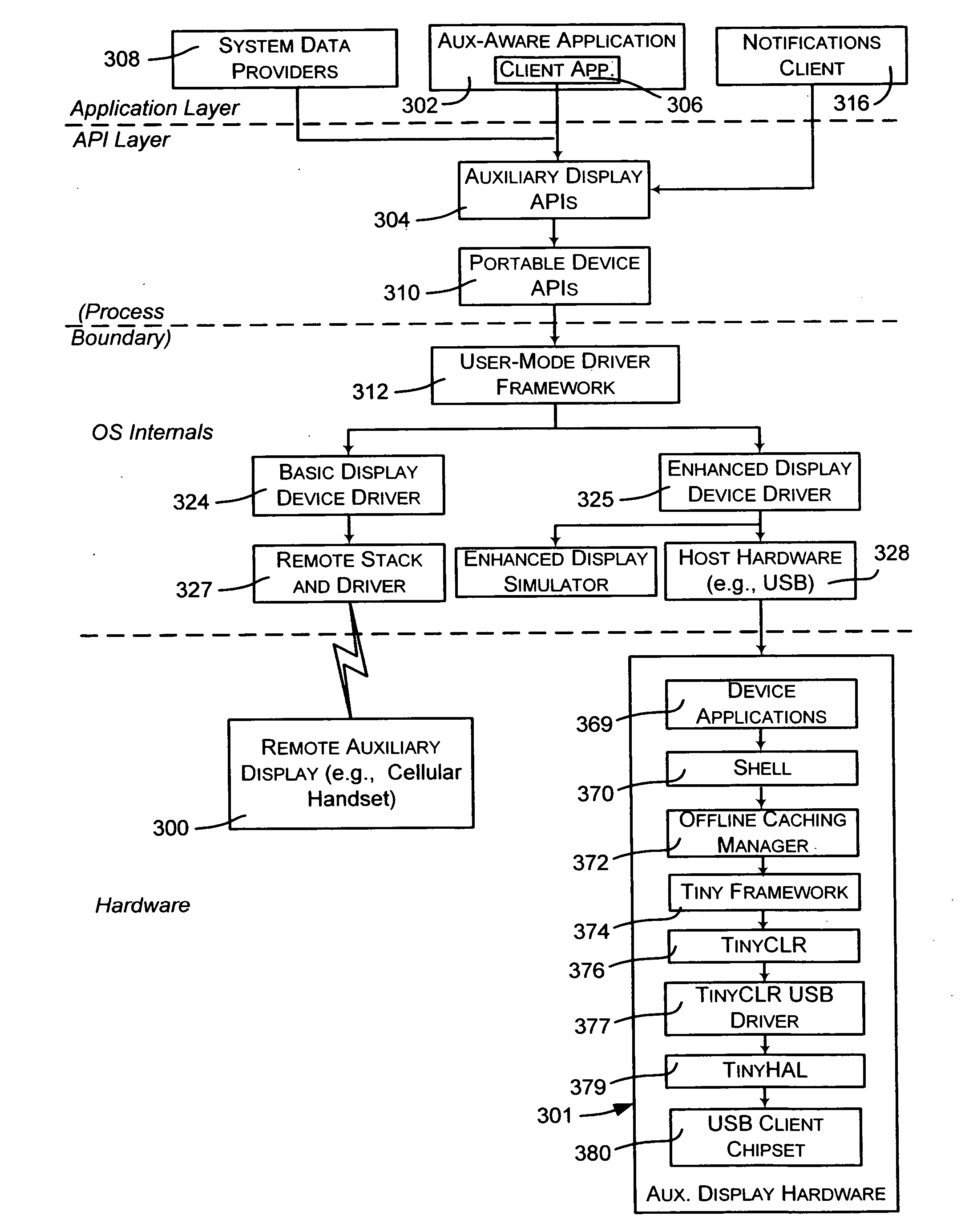
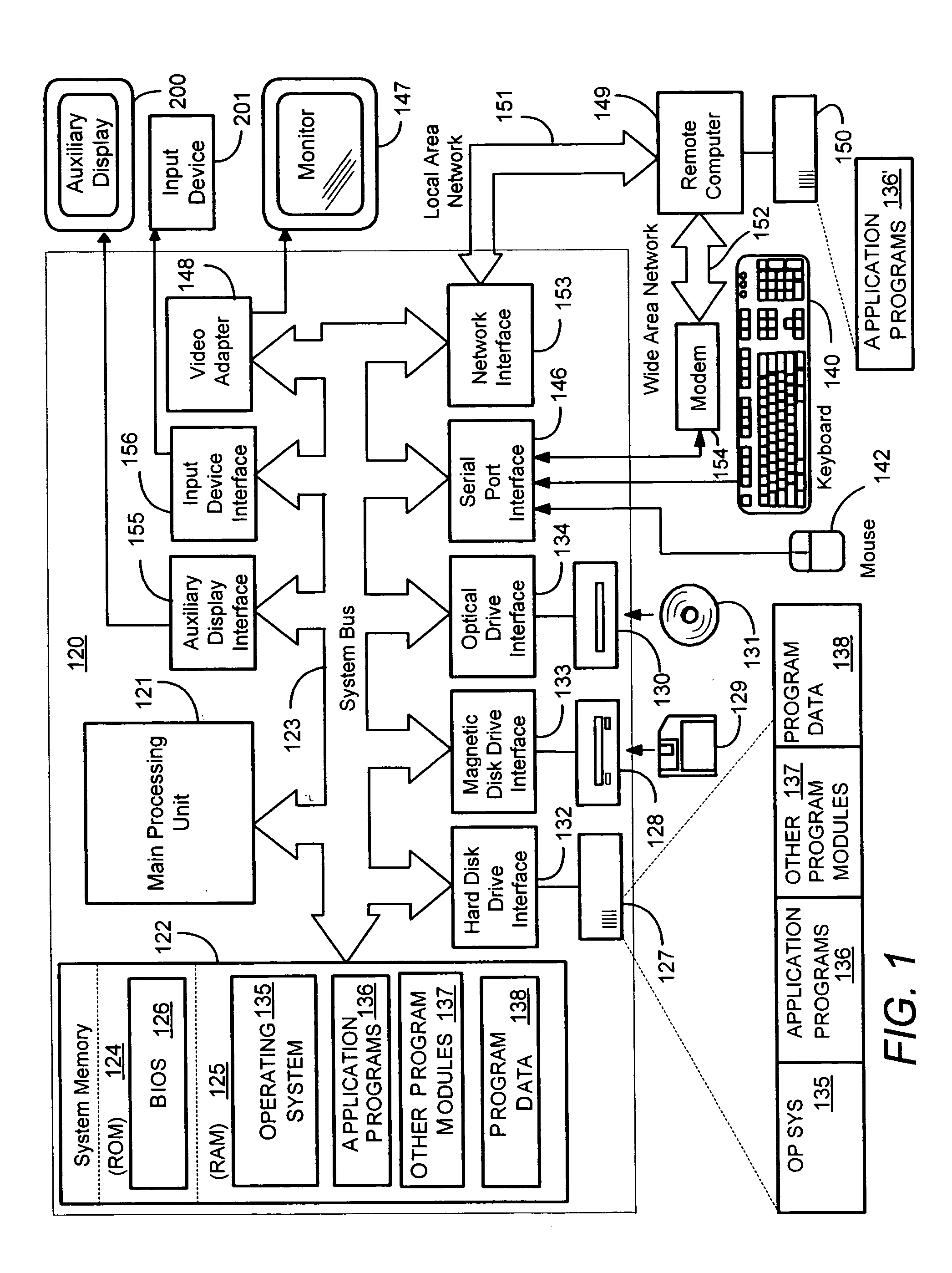
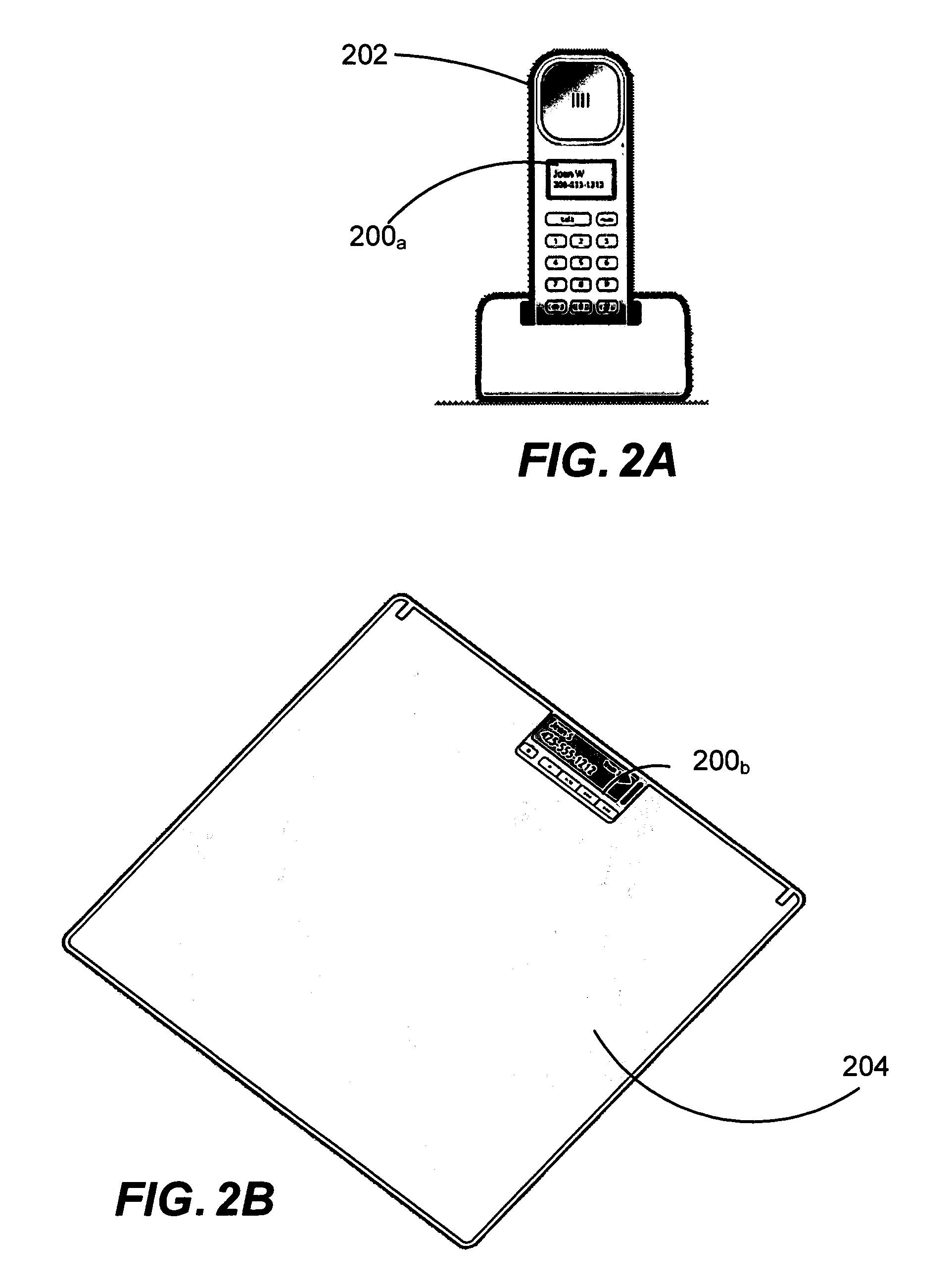
Extensible architecture for auxiliary displays
ActiveUS20060130072A1Reduce the amount requiredQuality improvementComputing modelsMultiprogramming arrangementsComputer hardwareRadio receiver
Described is a system and method by which an auxiliary computing device having an auxiliary display platform that displays information corresponding to data that originated on the main computer system may be extended by a device manufacturer. Extended hardware is added to the device, such as a radio receiver and / or an audio decoder. The auxiliary display platform is layered and extensible at each layer, and includes an extensible hardware abstraction layer that is extensible to support extended hardware if needed, and a driver layer that is extensible by adding driver code for the extended hardware. A runtime layer is also extensible to support the extended hardware as needed, as are libraries, the auxiliary shell program and other managed code. The client API is also extensible to allow applications on the main computer system to communicate with extended hardware via the device runtime layer.
Owner:MICROSOFT TECH LICENSING LLC
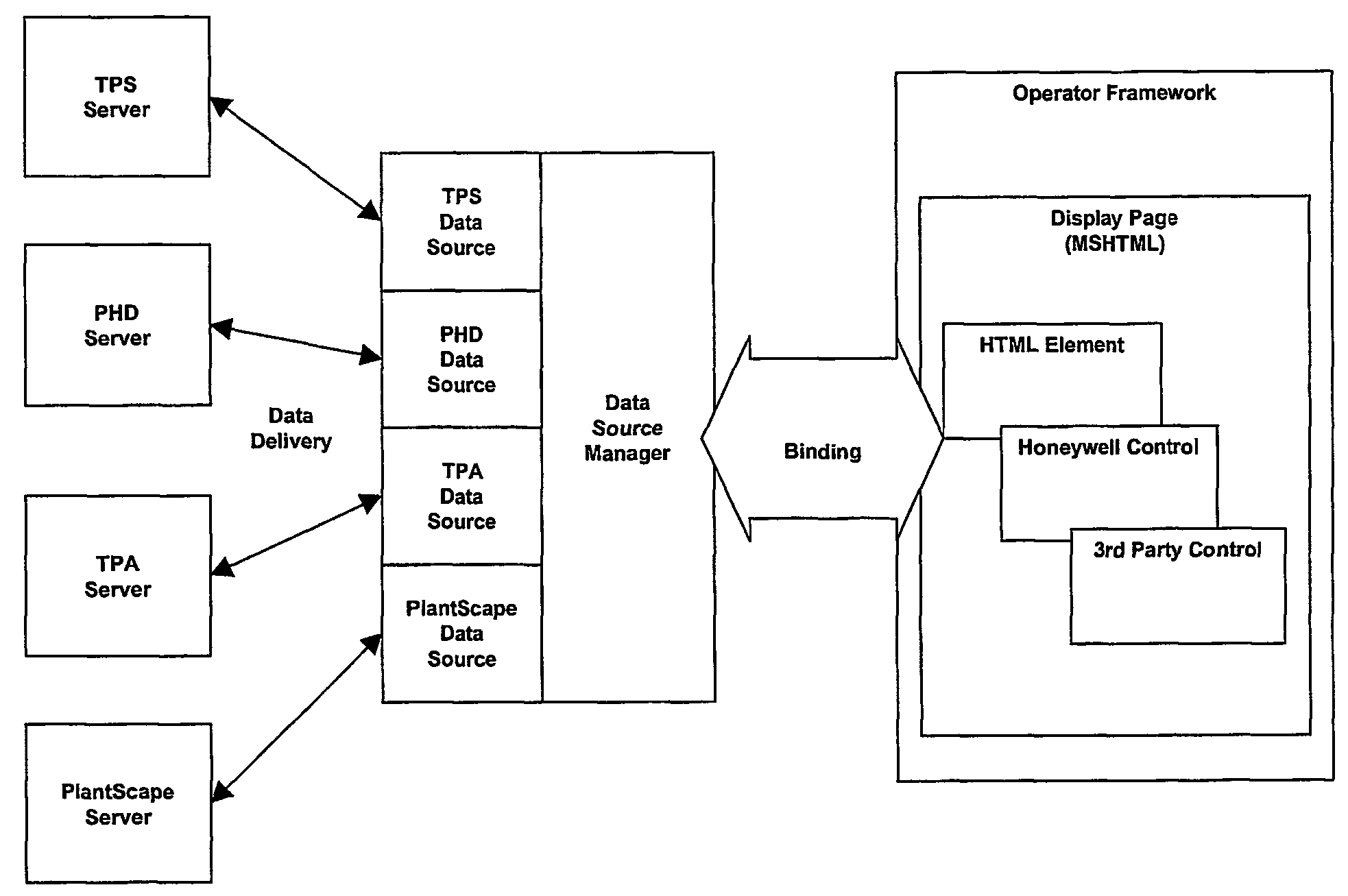
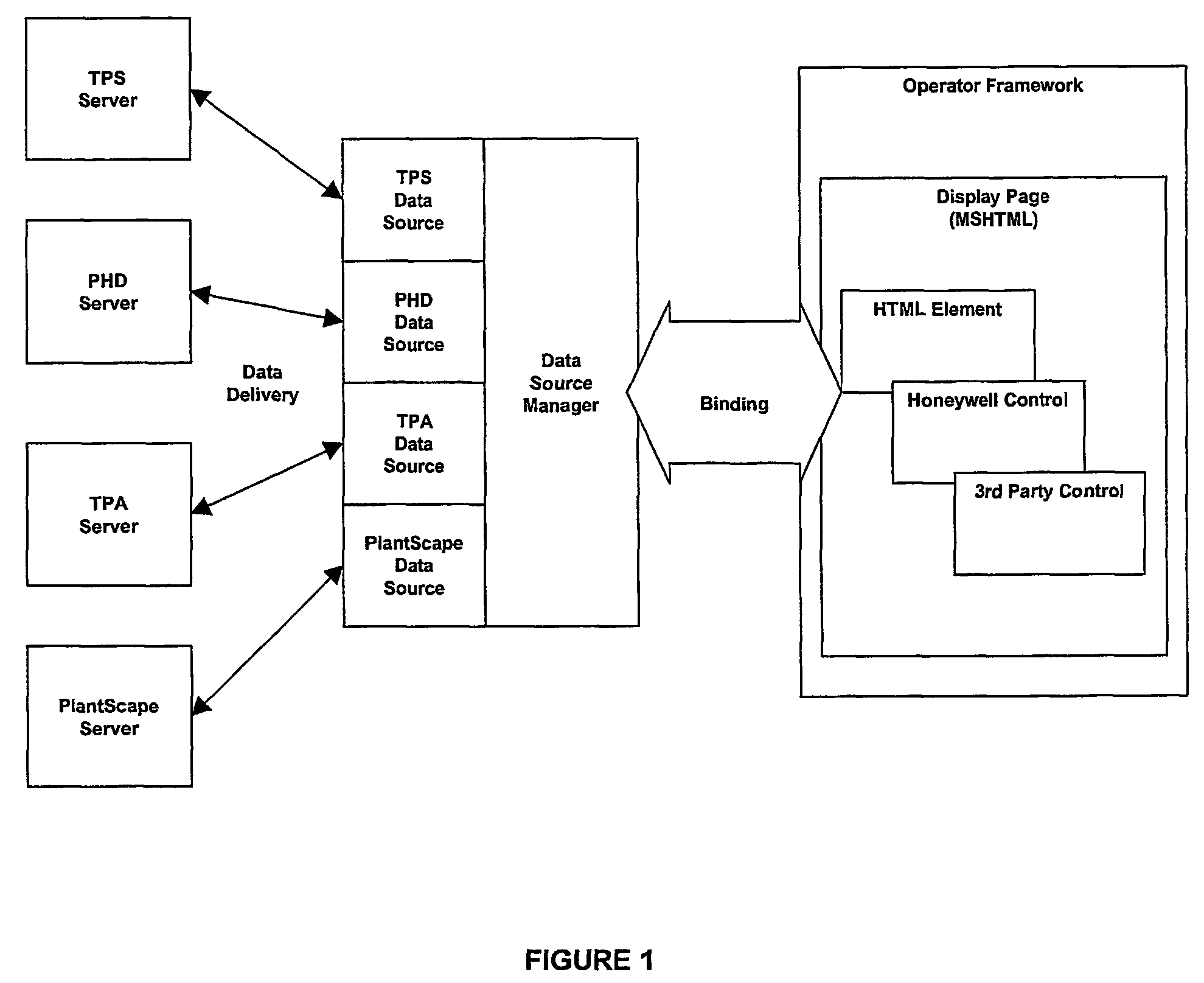
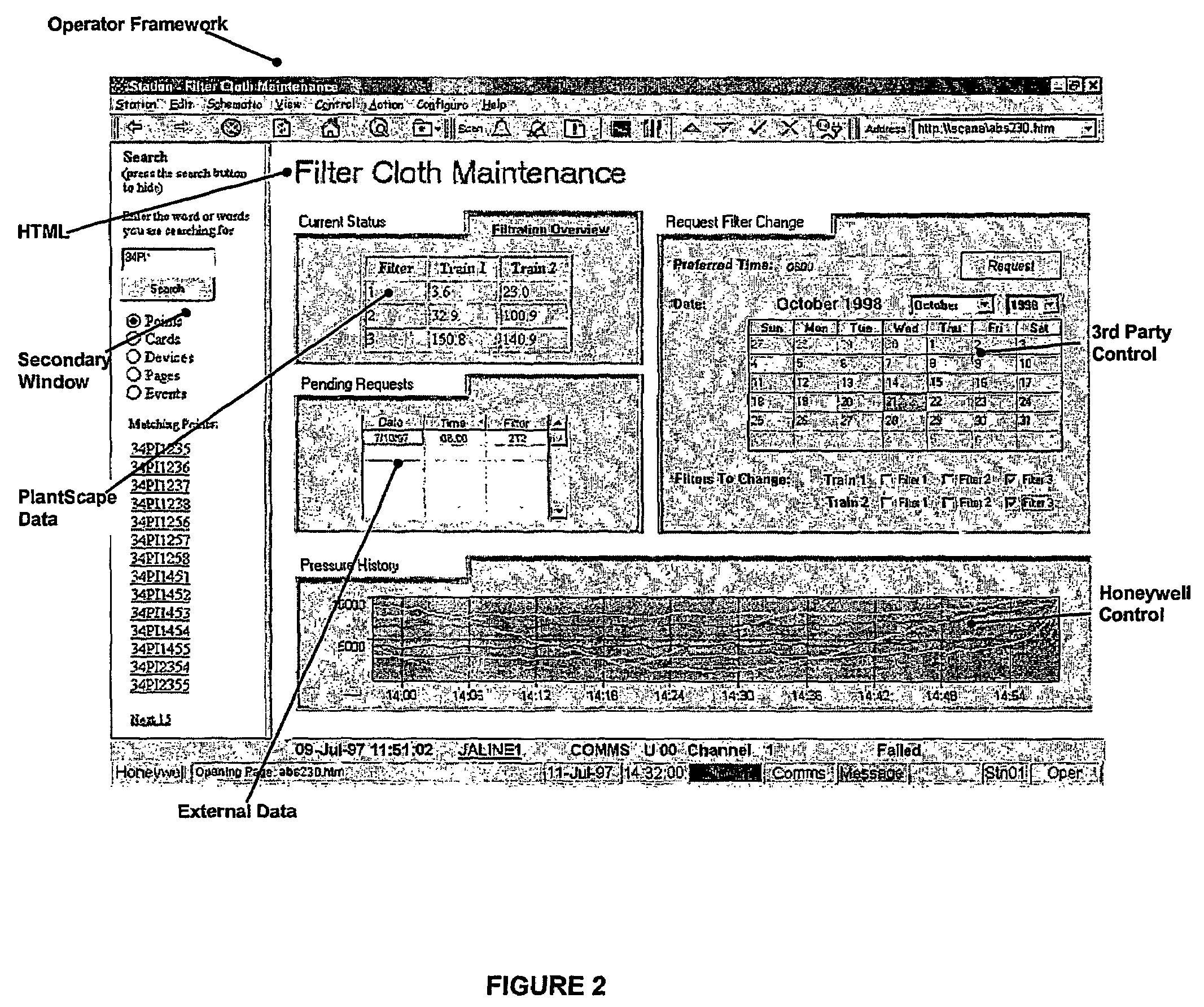
Human machine interface
InactiveUS7555706B2Efficient transferComputer controlSimulator controlHuman–machine interfaceTechnology fusion
An industrial control user interface provides a flexible, extensible architecture for the provision of real-time process data to a state-of-the-art user interface, using MSHTML as the underlying rendering engine. The architecture of the interface provides a user interface that is designed to harness key industry standard technologies in an open, adaptable, architecture that facilitates the technological convergence of disparate HMI products. The preferred embodiments offer open display page architecture via the separation of the provision of data and server specific user interactions from the implementation of individual page elements. The only real assumption made about a page element is that it is part of the HTML display page and accessible via the Document Object Model.
Owner:HONEYWELL INC
Self-service sources for secure search
ActiveUS8027982B2Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Secure search performance improvement
ActiveUS8332430B2Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
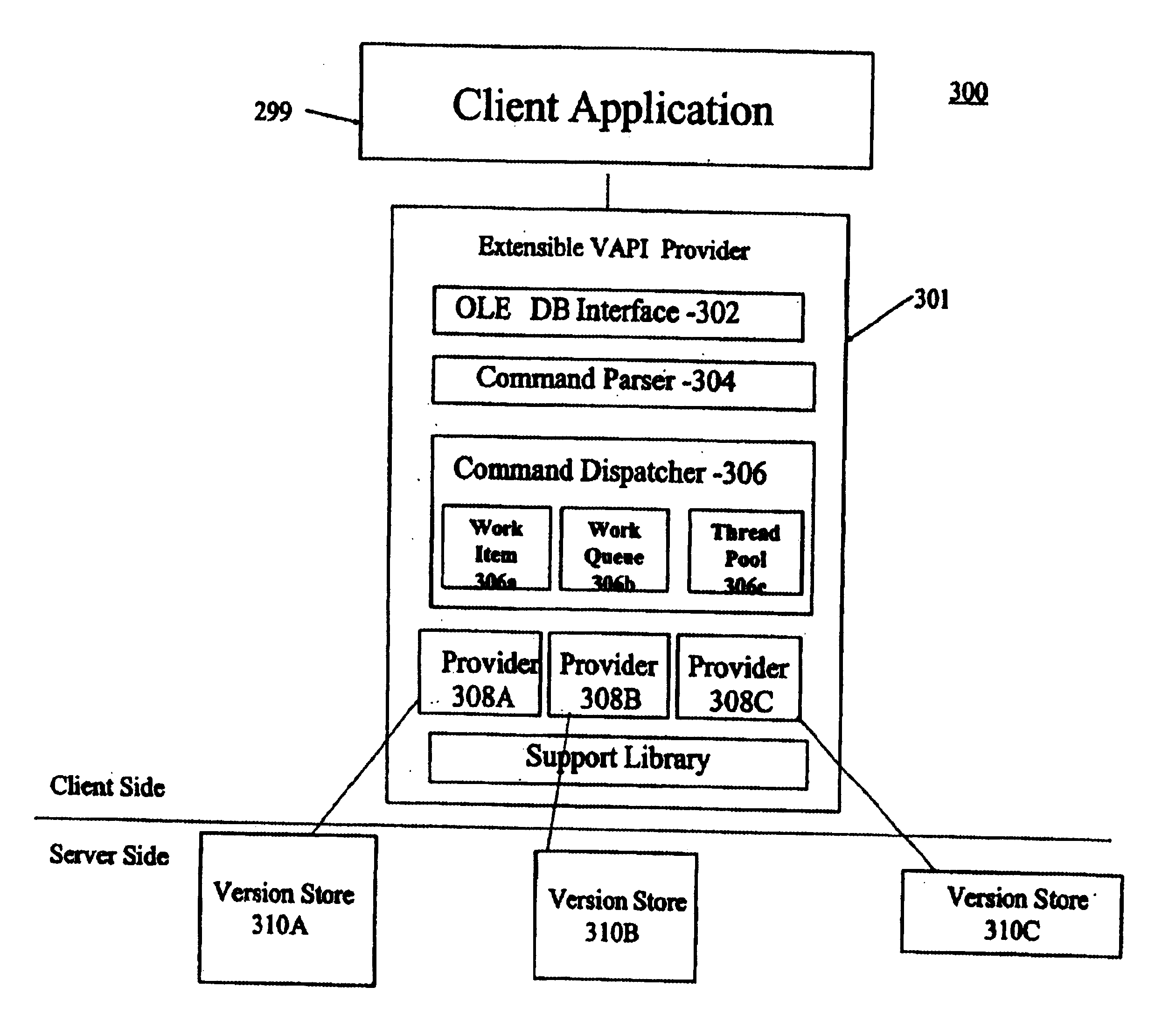
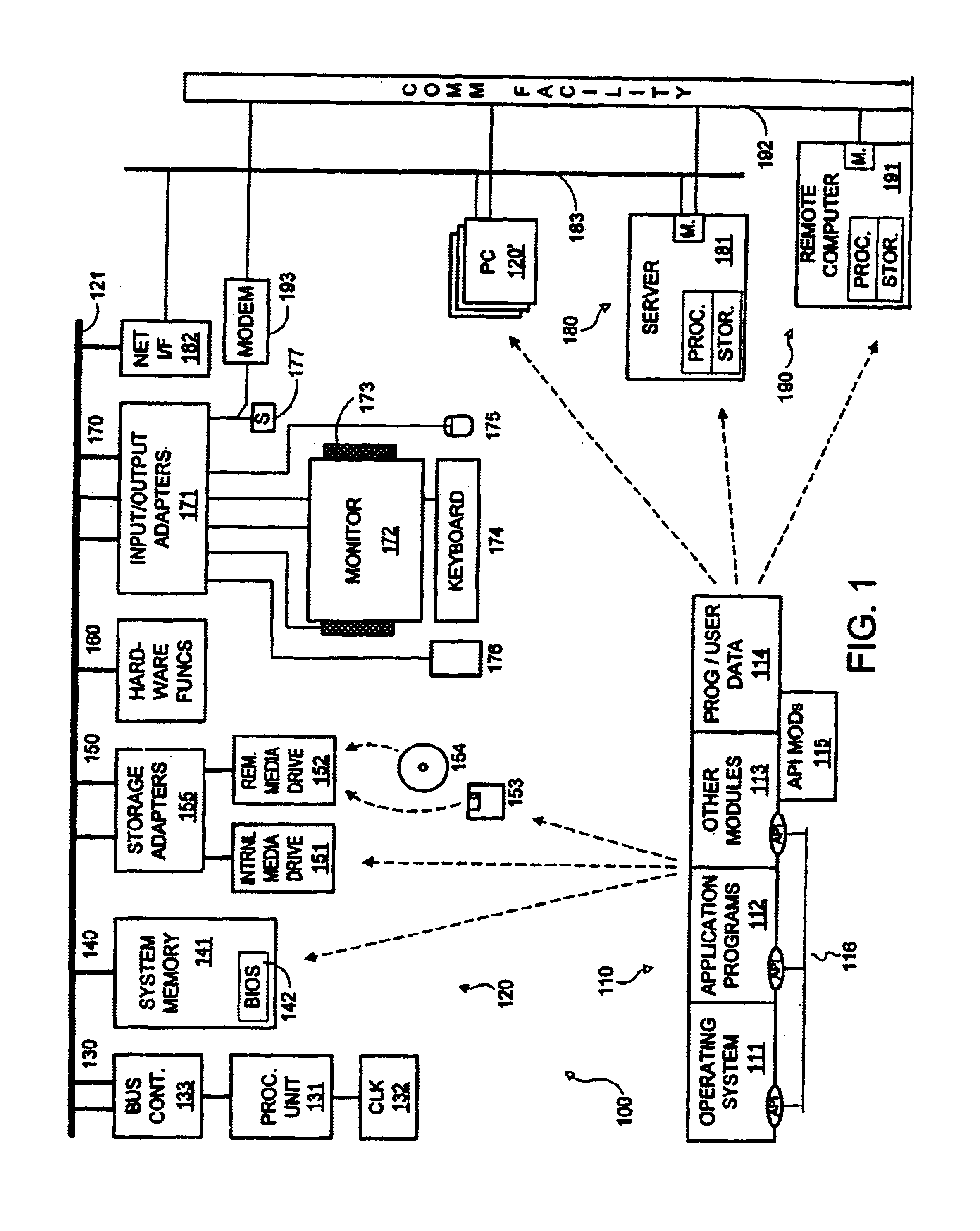
Extensible architecture for versioning APIs
InactiveUS6842904B1Data processing applicationsDigital data processing detailsComputer hardwareDocumentation procedure
Some large software development projects need more than one versioning system to accommodate not only a diversity of document formats and data types, but also the geographic diversity of its programmers. However, having more than one versioning systems is generally very expensive. A major factor in this expense is the requirement for a separate application program interface (API) for each separate versioning system. Accordingly, the inventors devised an exemplary API architecture which can be extended with “plug-in” protocol providers to include virtually any number of separate version stores or versioning systems. The exemplary architecture includes a generic command parser and a command dispatcher. The command dispatcher operatively couples to one or more protocol providers, each coupled to at least one version store. Inclusion of the OLE DB-compliant interface and the command parser in the exemplary embodiment saves the protocol providers the effort and expense of replicating these features, thereby reducing the cost of adding version stores.
Owner:MICROSOFT TECH LICENSING LLC
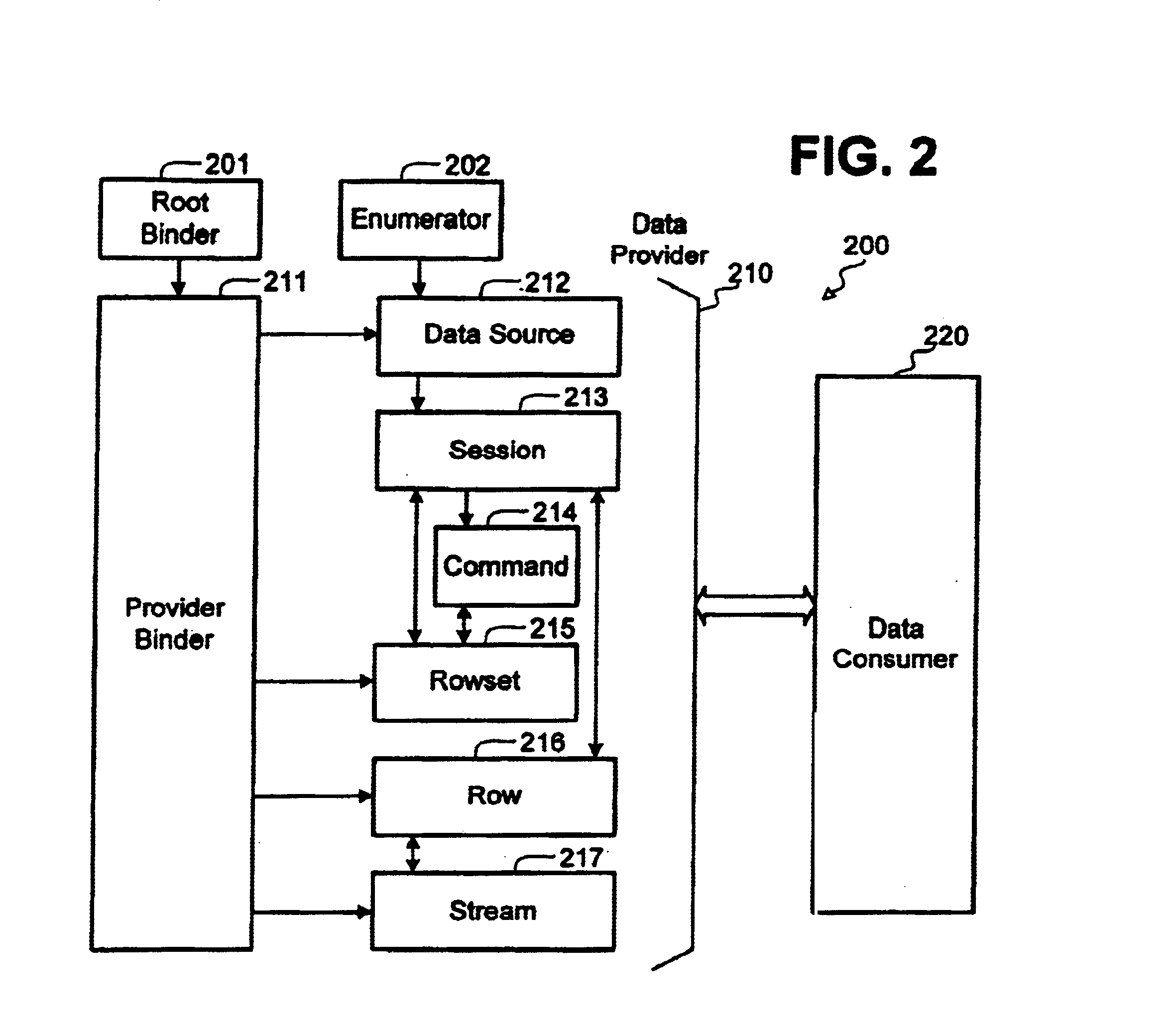
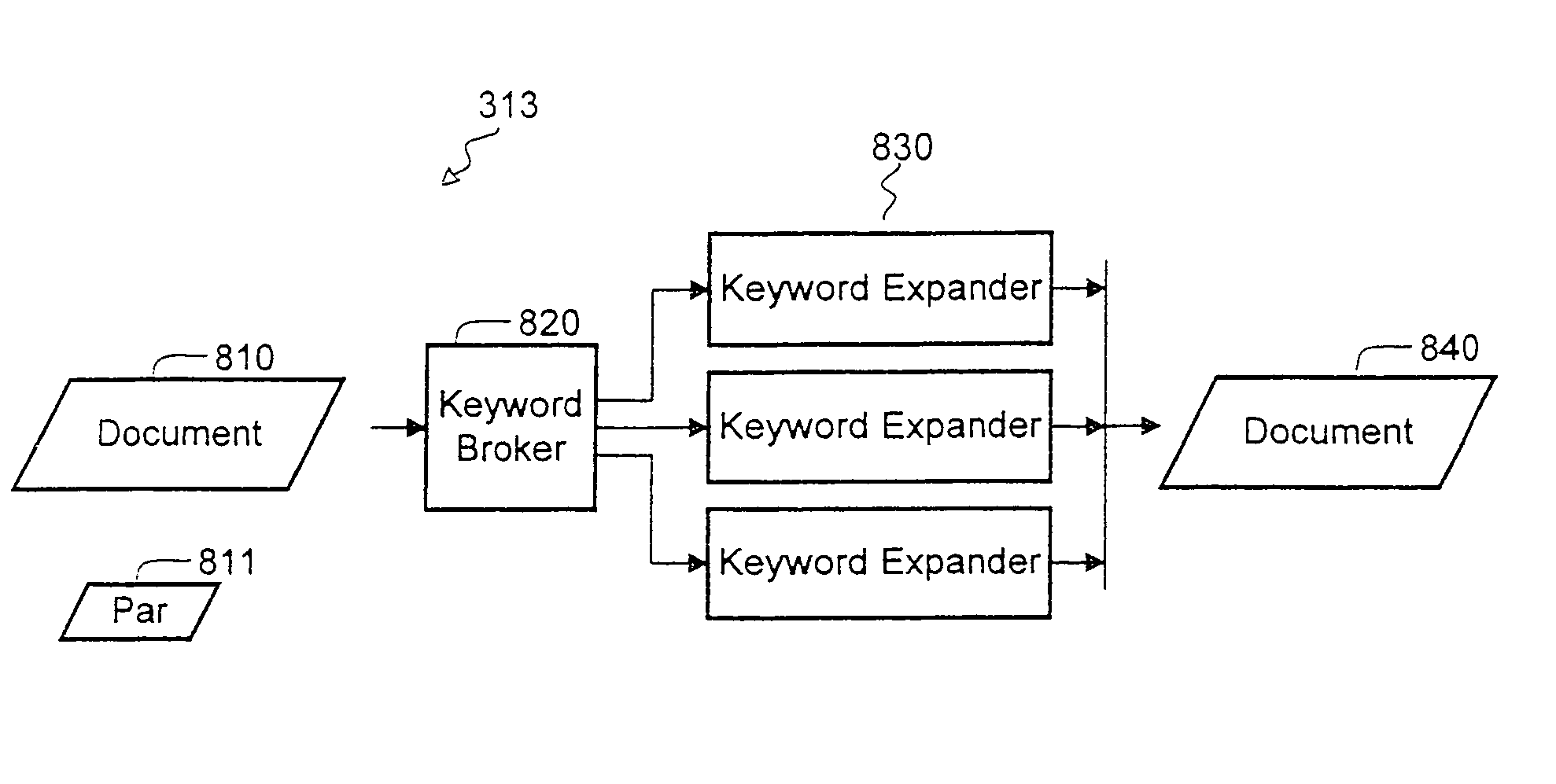
Extensible architecture for project development systems
InactiveUS7631298B2Medical devicesVolume/mass flow by electric/magnetic effectsControl systemComputer module
A software-development system or versioning system has a collection of modules for performing individual development functions such as document editing, keyword processing, and private-copy management. Each module has an interface compatible with that of the others, so that modules can be added to or substituted for the original modules, if the new modules conform to the interface. The architecture of this system supports the performance of development actions such as document merging and keyword expansion at any location within the system. The system operates upon documents and files as objects in an object space, rather than in name spaces.
Owner:MICROSOFT TECH LICENSING LLC
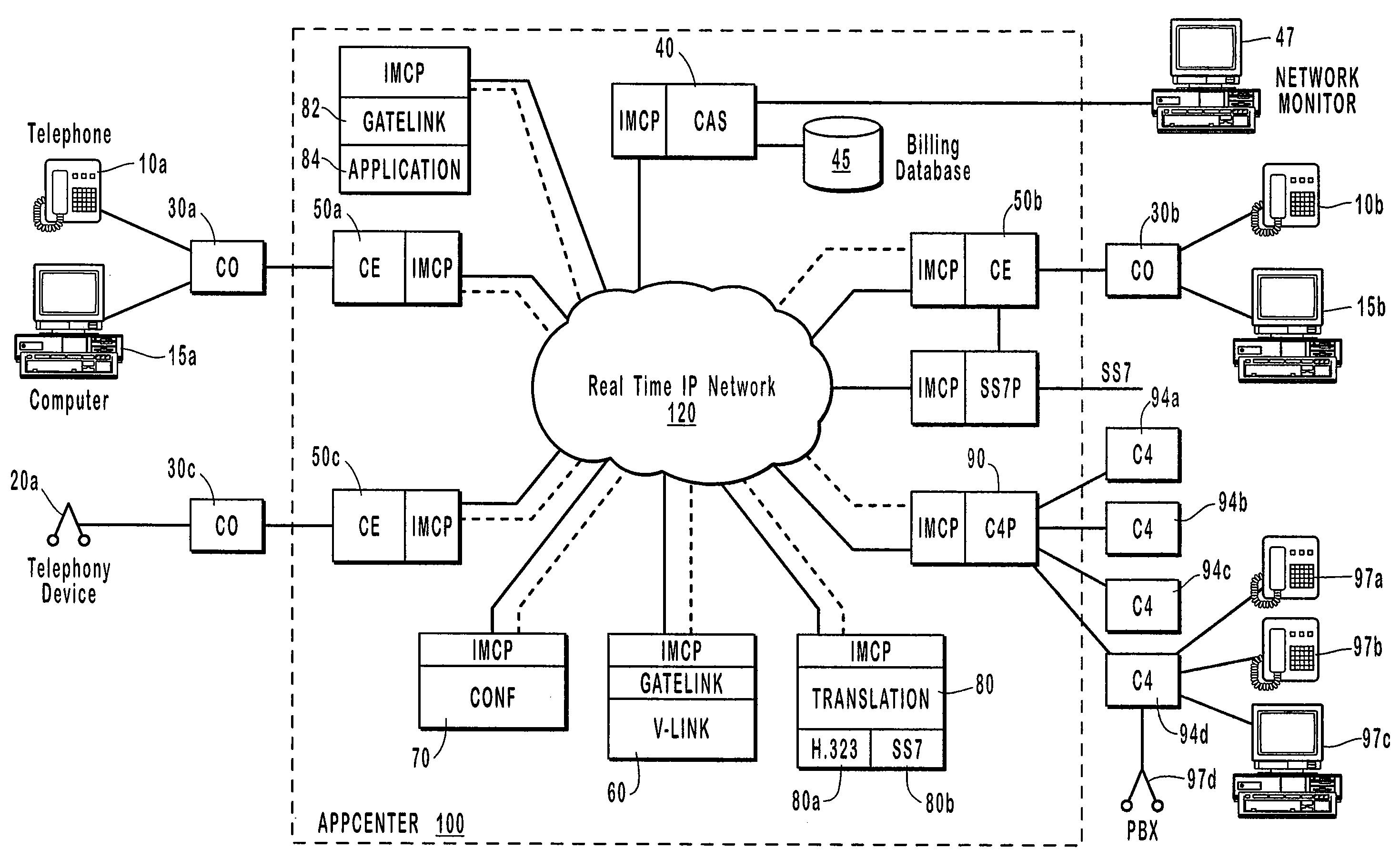
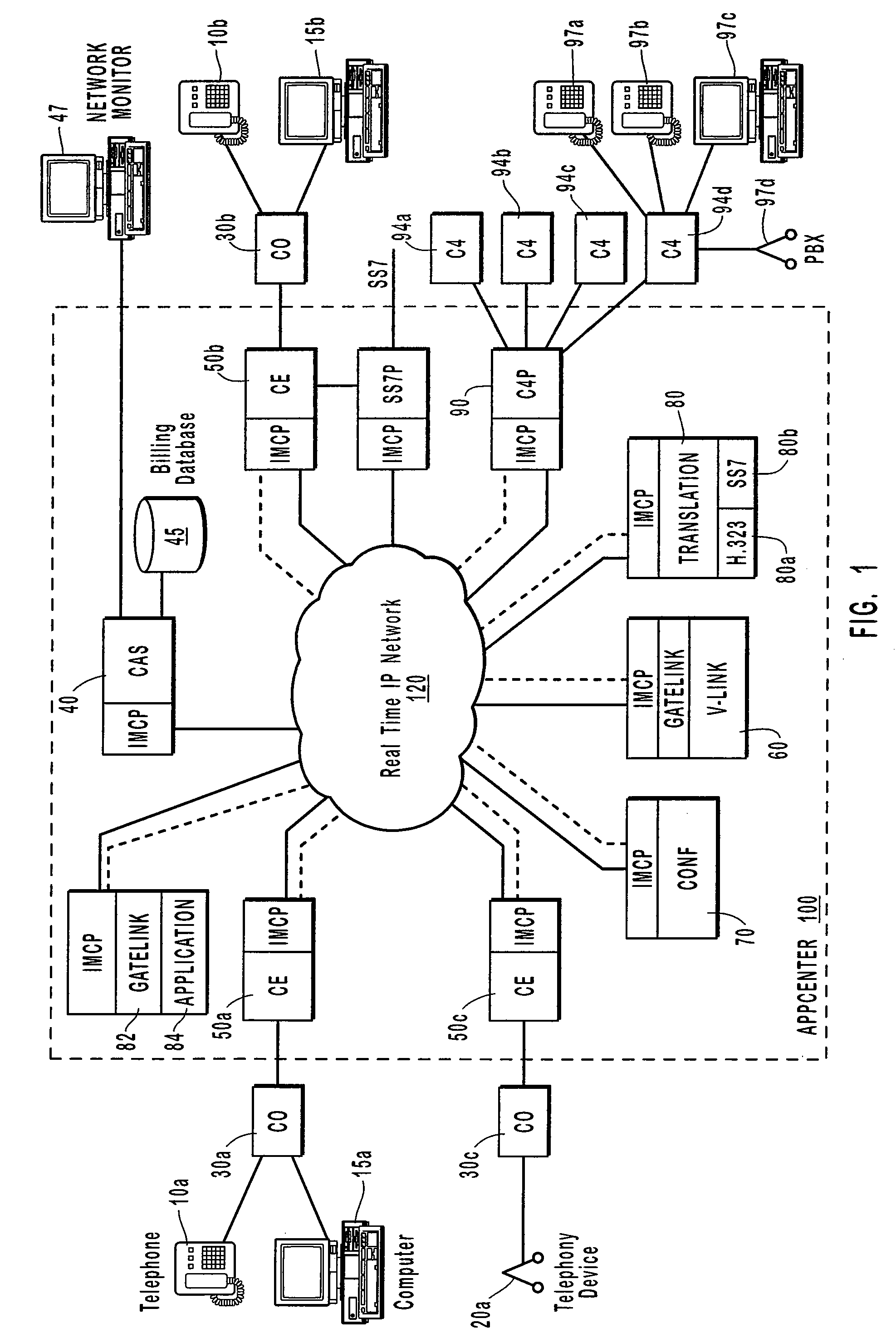
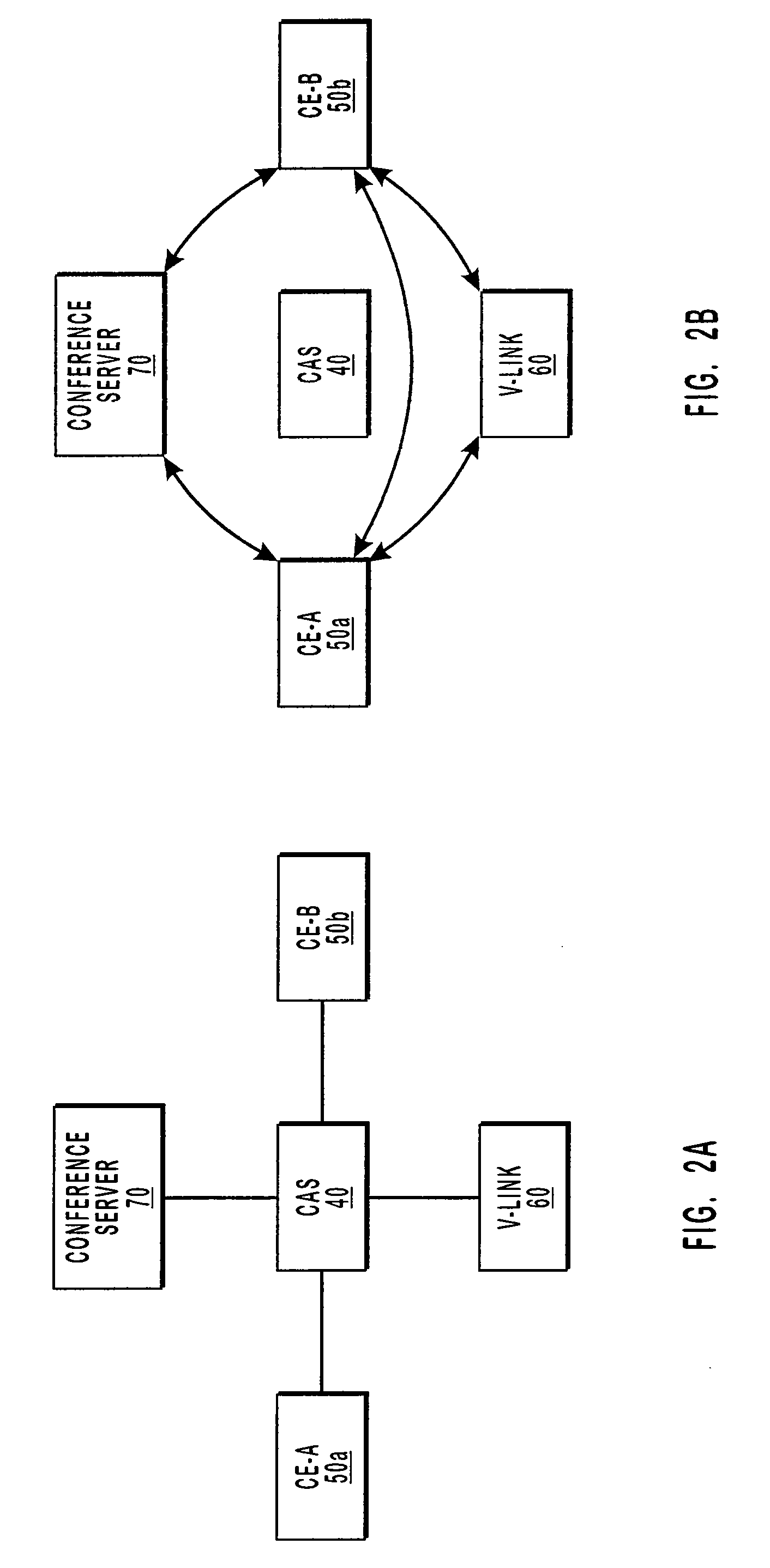
Private IP communication network architecture
InactiveUS20070206576A1Enhanced connectivity and scalabilityCost complexityMetering/charging/biilling arrangementsInterconnection arrangementsDigital dataNetwork connection
A disclosed Internet Linked Network Architecture delivers telecommunication type services across a network utilizing digital technology. The unique breadth and flexibility of telecommunication services offered by the Internet Linked Network Architecture flow directly from the network over which they are delivered and the underlying design principles and architectural decisions employed during its creation. The present invention supports current telecommunication and voice over IP standards and applications. This new network not only replaces the telecommunication network presently in place, but it also offers a more feature rich and cost effective alternative. For example, traditional telecommunication switches are more expensive, less reliable and slower than the faster digital data switches utilized in the present invention. Furthermore, the programmable nature of the digital devices comprising the present invention allows the new network to be built with a scalable and extensible architecture, providing the flexibility necessary to incorporate new or future digital enhancements. The inventive network is designed as a complete replacement for the traditional telecom network. The disclosed architecture allows for this network to connect to traditional networks and allows for an upgrade path. The design is robust and scalable so this network can introduce new features and functionality while preserving the quality of traditional networks.
Owner:RPX CORP
Minimum lifespan credentials for crawling data repositories
ActiveUS8875249B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsExtensible architectureThe Internet
Owner:ORACLE INT CORP
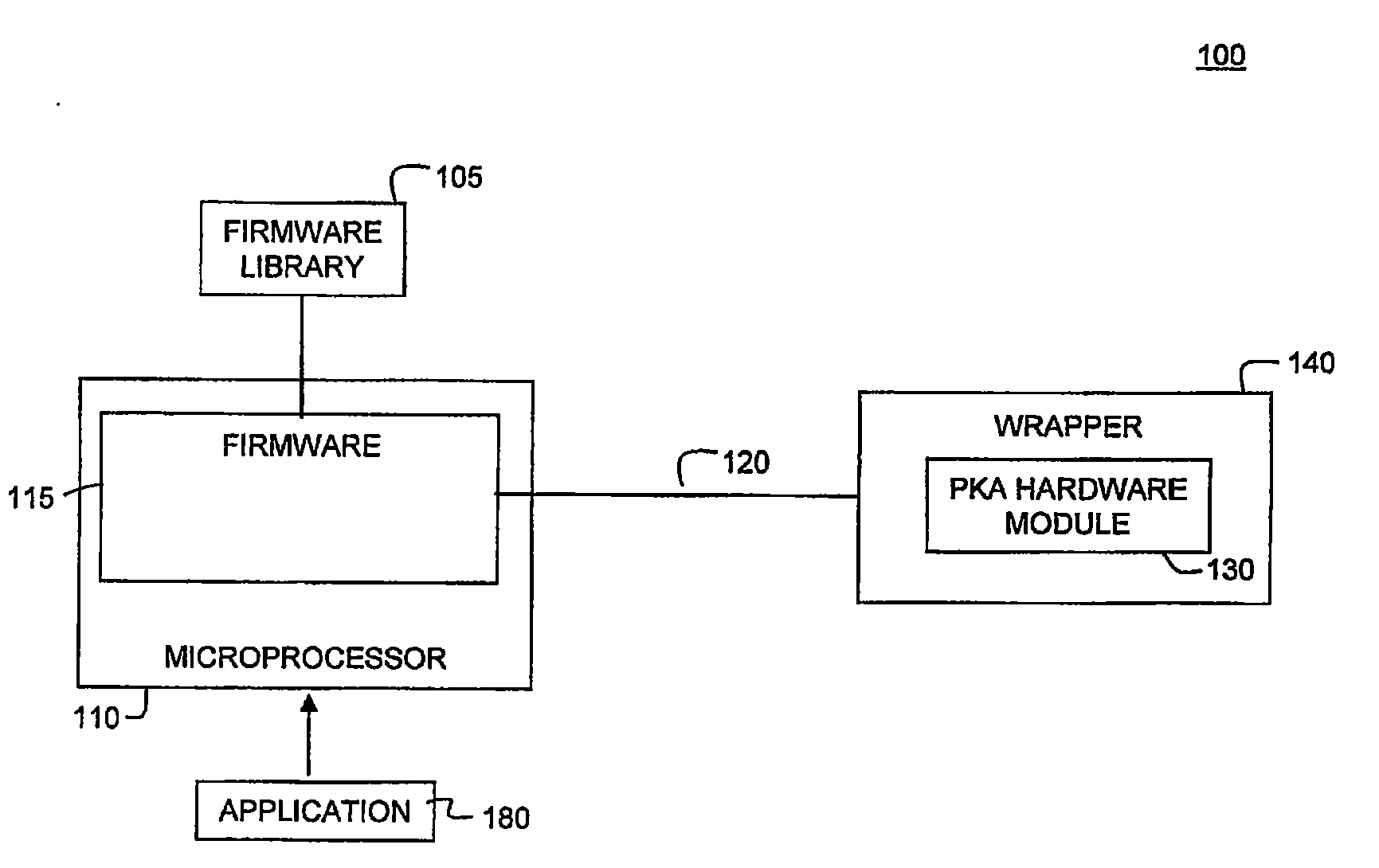
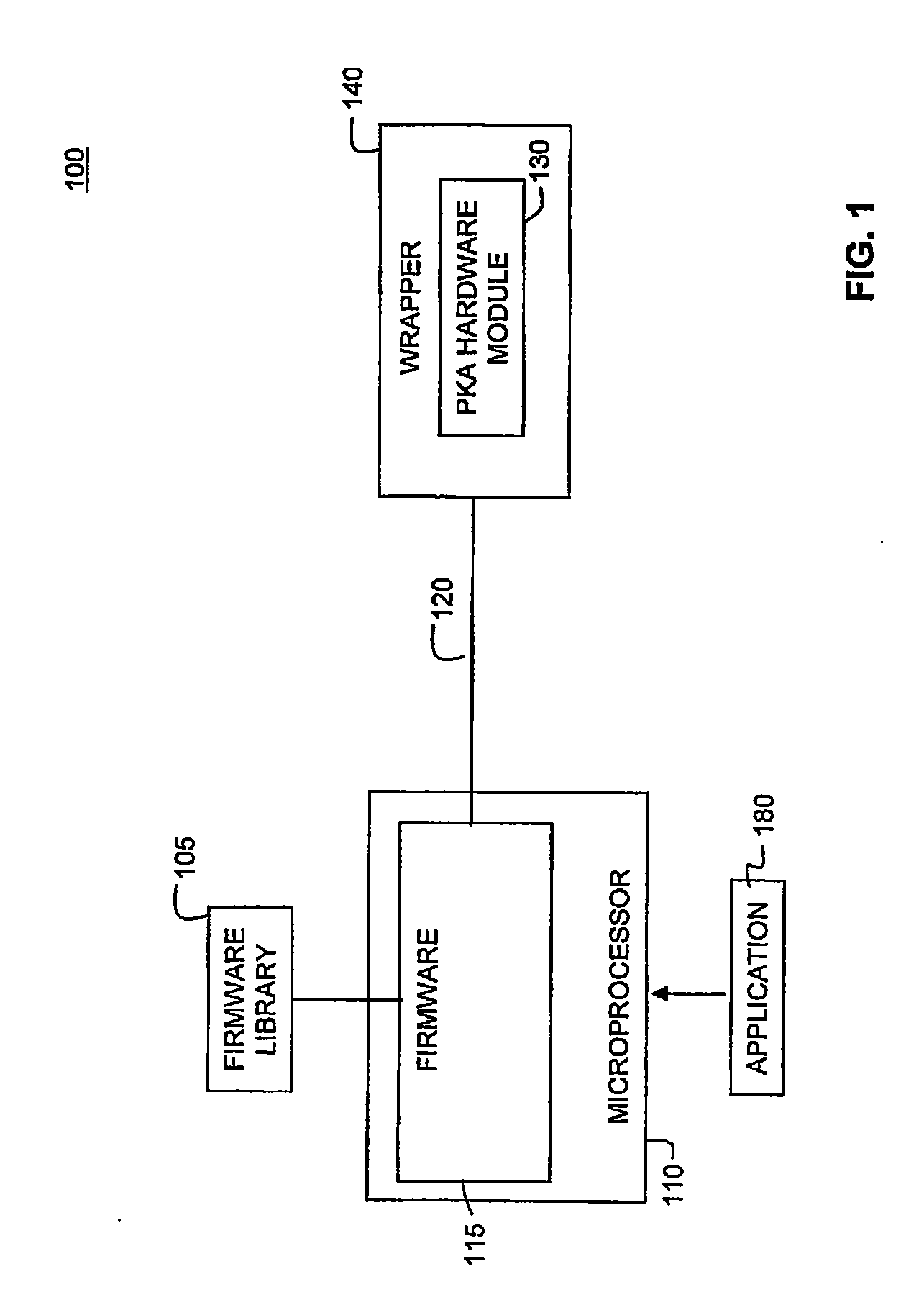
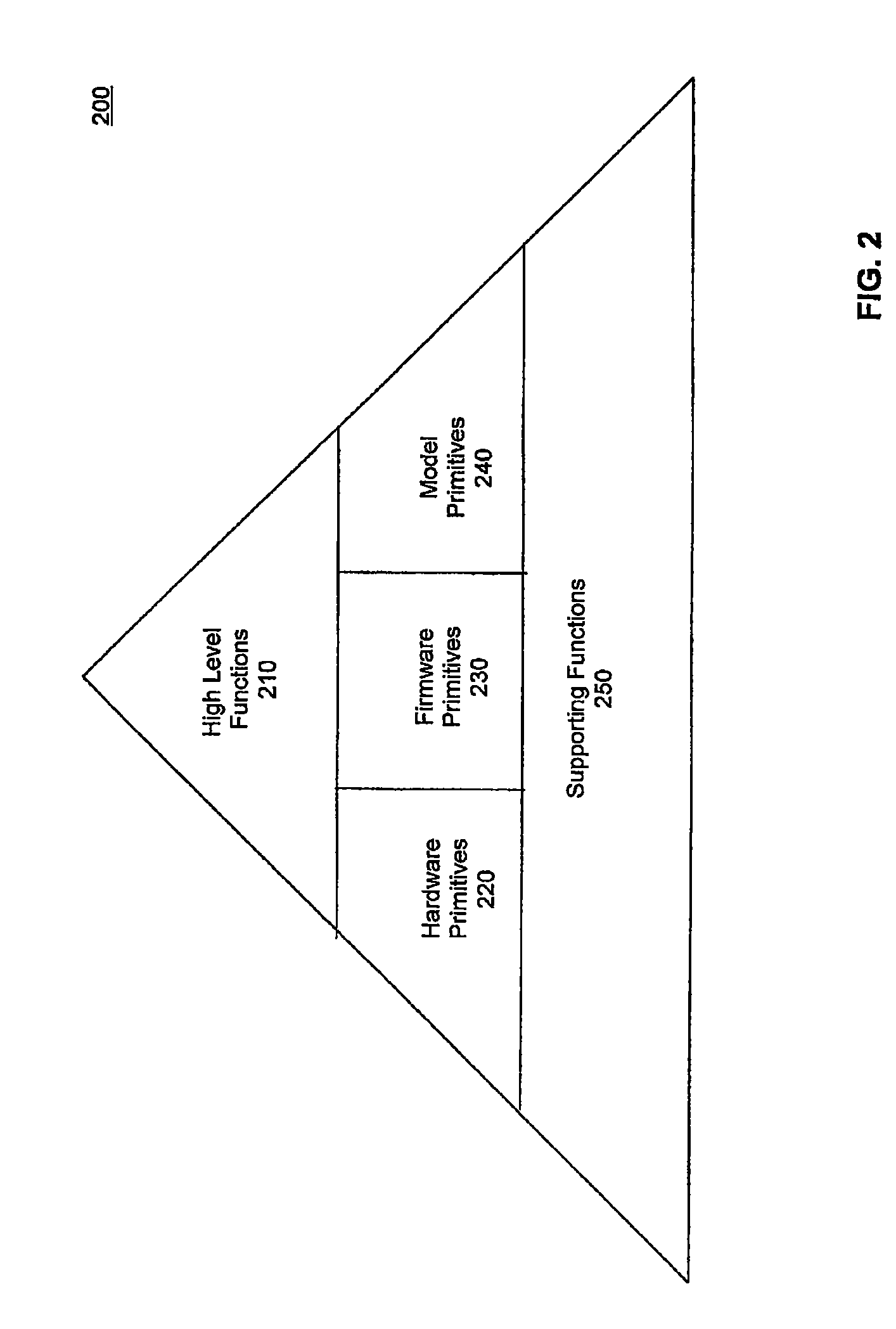
Scalable and Extensible Architecture for Asymmetrical Cryptographic Acceleration
InactiveUS20090319804A1Instruction analysisUnauthorized memory use protectionCryptographic acceleratorExtensible architecture
Systems and methods for providing asymmetrical cryptographic acceleration are provided. The scalable asymmetric cryptographic accelerator engine uses a layered approach based on the collaboration of firmware and hardware to perform a specific cryptographic operation. Upon receipt of a request for a cryptographic function, the system accesses a sequence of operations required to perform the requested function. A micro code sequence is prepared for each hardware operation and sent to the hardware module. The micro code sequence includes a set of load instructions, a set of data processing instructions, and a set of unload instructions. An instruction may include a register operand having a register type and a register index. Upon receipt of a load instruction, the hardware module updates size information in a content addressable memory for a register included in the instruction. The hardware module continuously monitors the content addressable memory to avoid buffer overflow or underflow conditions.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Link analysis for enterprise environment
ActiveUS8433712B2Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
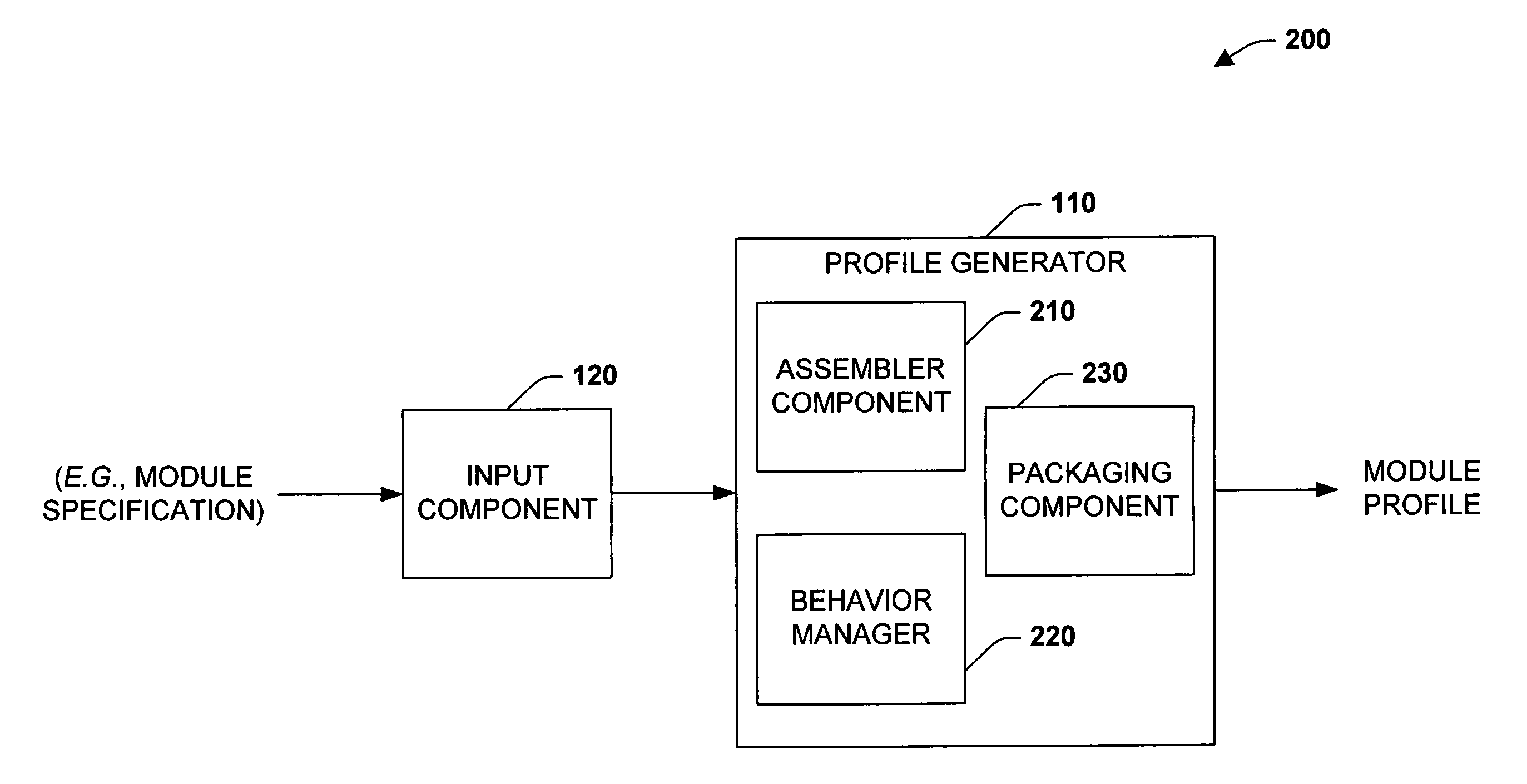
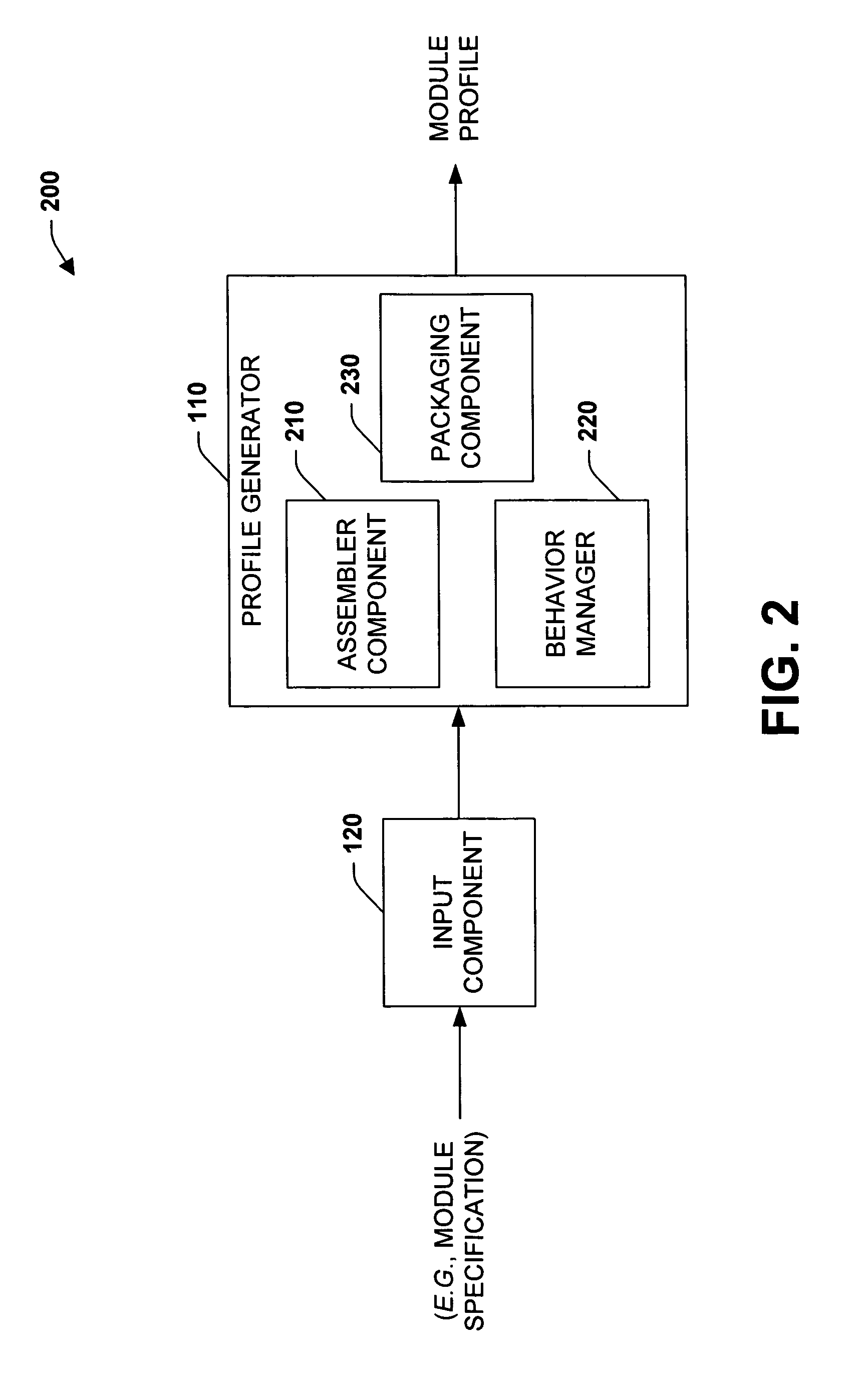
Systems and methods that employ an extensible architecture to define configuration functionality
ActiveUS7861223B1Improve development productivityEasy to determineProgramme controlSpecific program execution arrangementsGraphicsIndustrial software
The subject invention relates to systems and methods that generate modules profiles for industrial control modules (e.g., I / O, scanners, adapters . . . ). A module profile generally includes a set of components, interfaces and / or plug-ins that determine possible configurations for a module. Such entities are packaged in an XML based format to provide a dynamic module profile, wherein a definition type can be dynamically changed. Development and / or configuration of a module can be achieved through an industrial software development environment via a graphical hierarchical representation of configuration options defined in the module profile. In addition, the module profile provides for separately installable / release independent utilization via XML and COM based interfaces, wherein an end-user does not have to wait for a new software release in order to add a new module.
Owner:ROCKWELL AUTOMATION TECH
Search hit URL modification for secure application integration
ActiveUS20140114946A1Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsEnterprise application integrationThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com