Patents
Literature
379 results about "Buffer overflow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
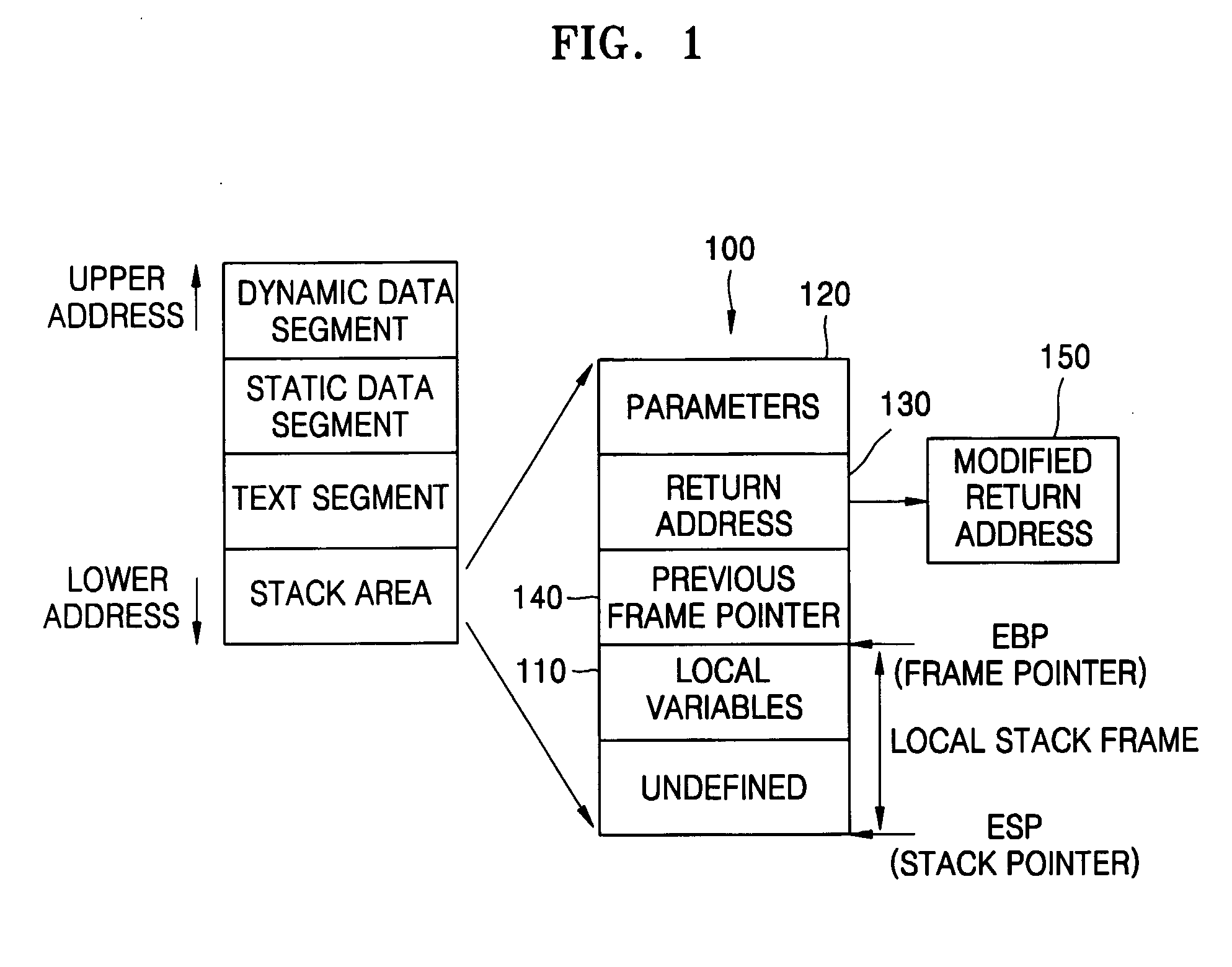
In information security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory locations.
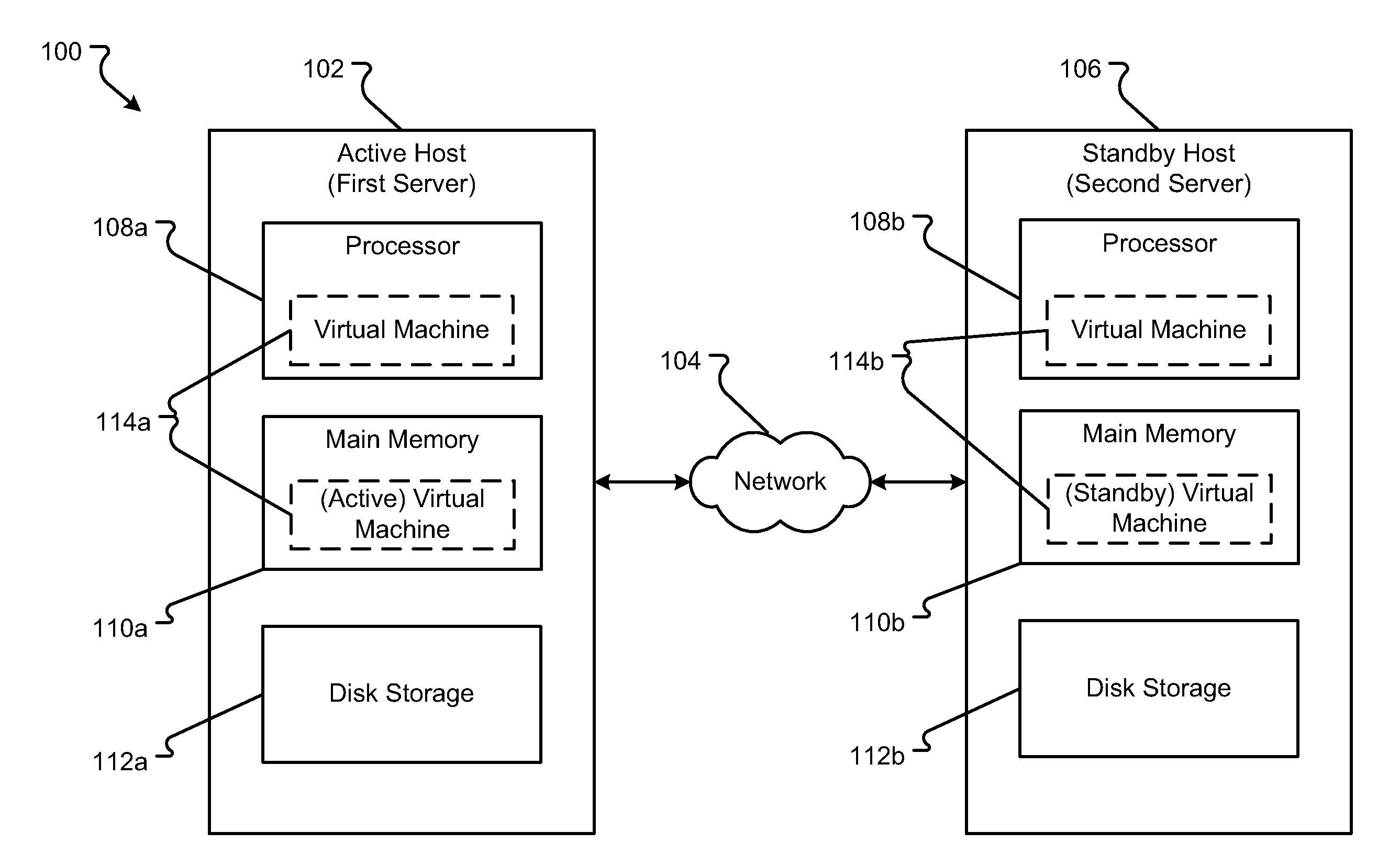
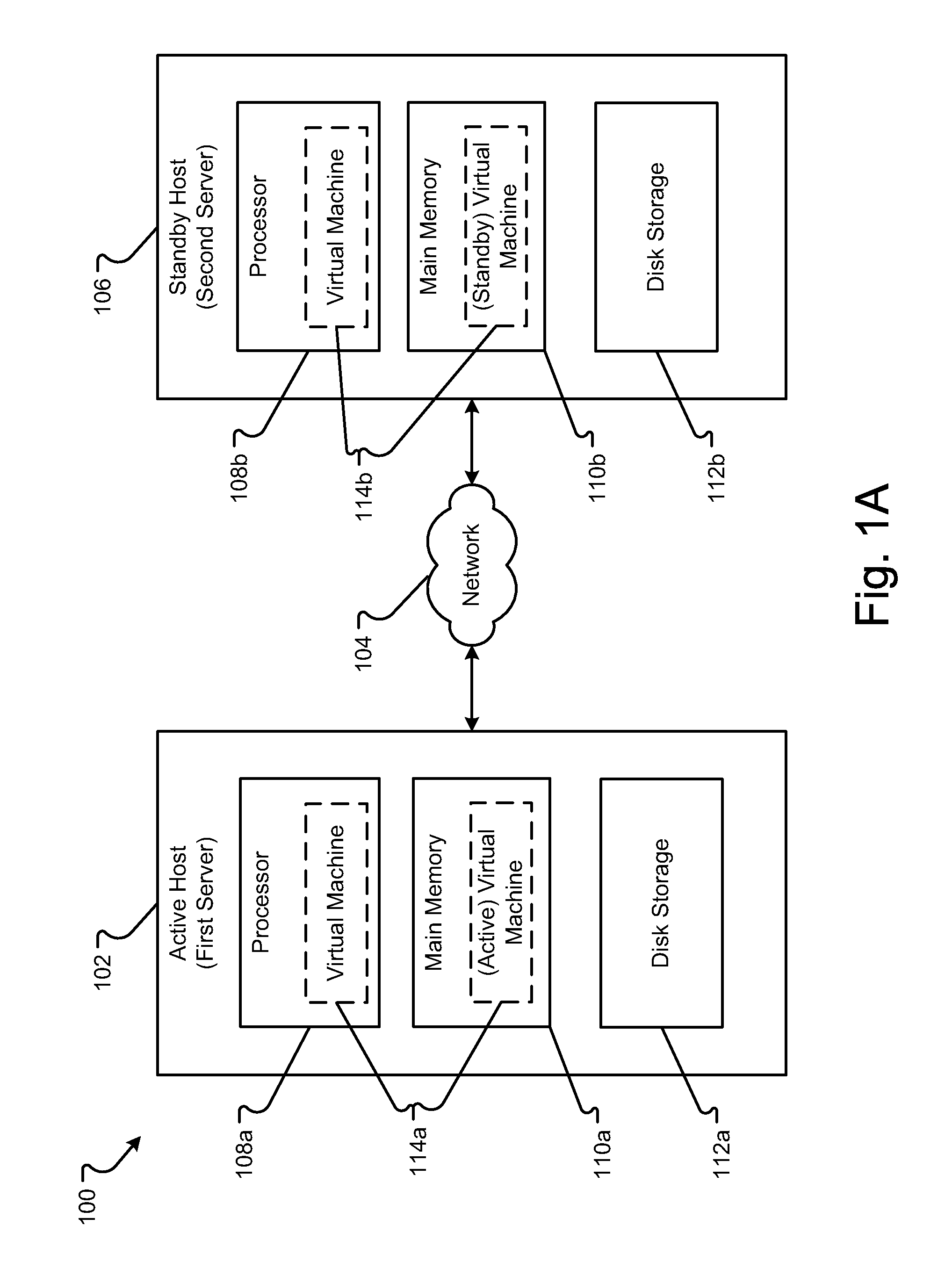
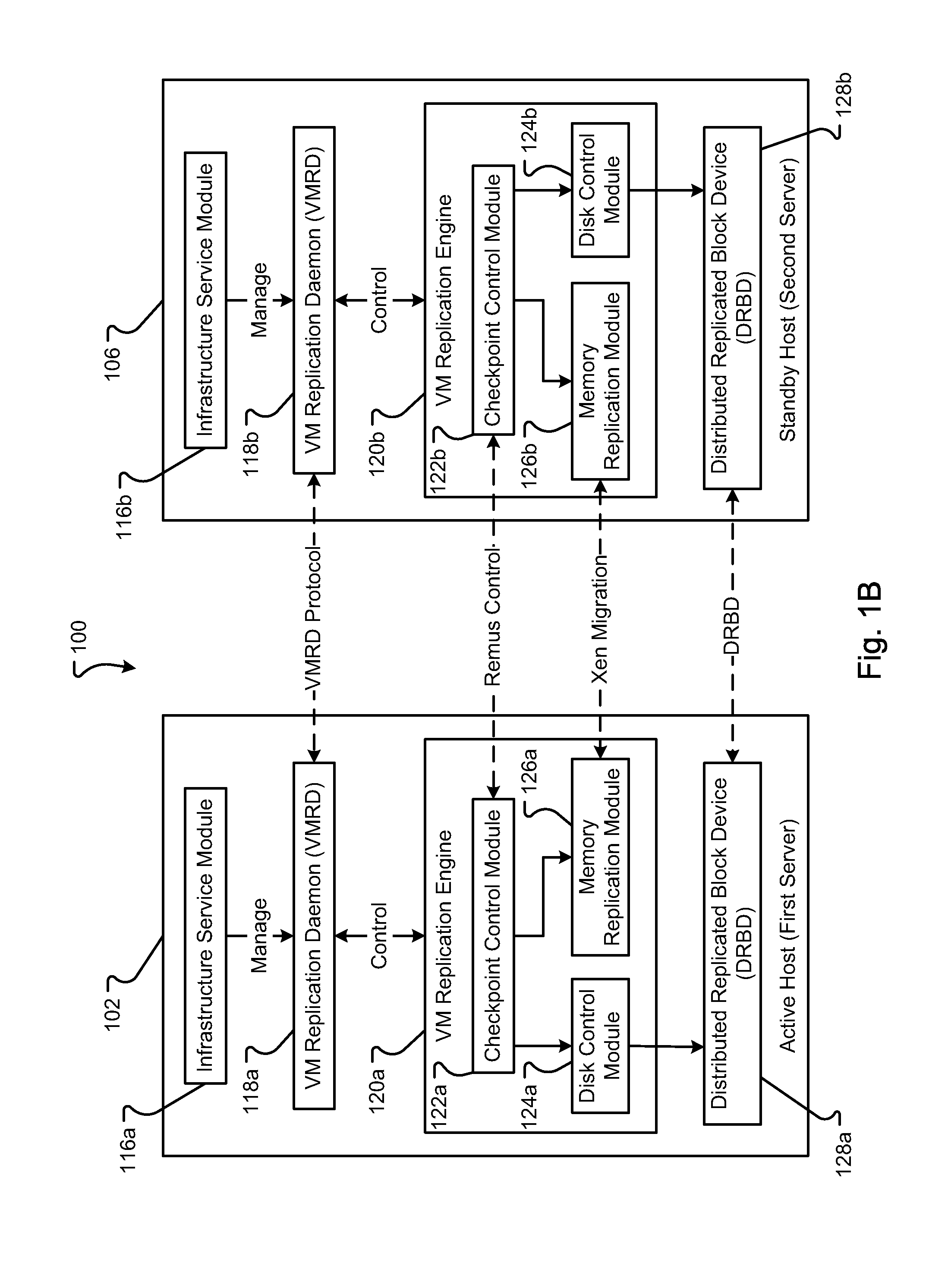
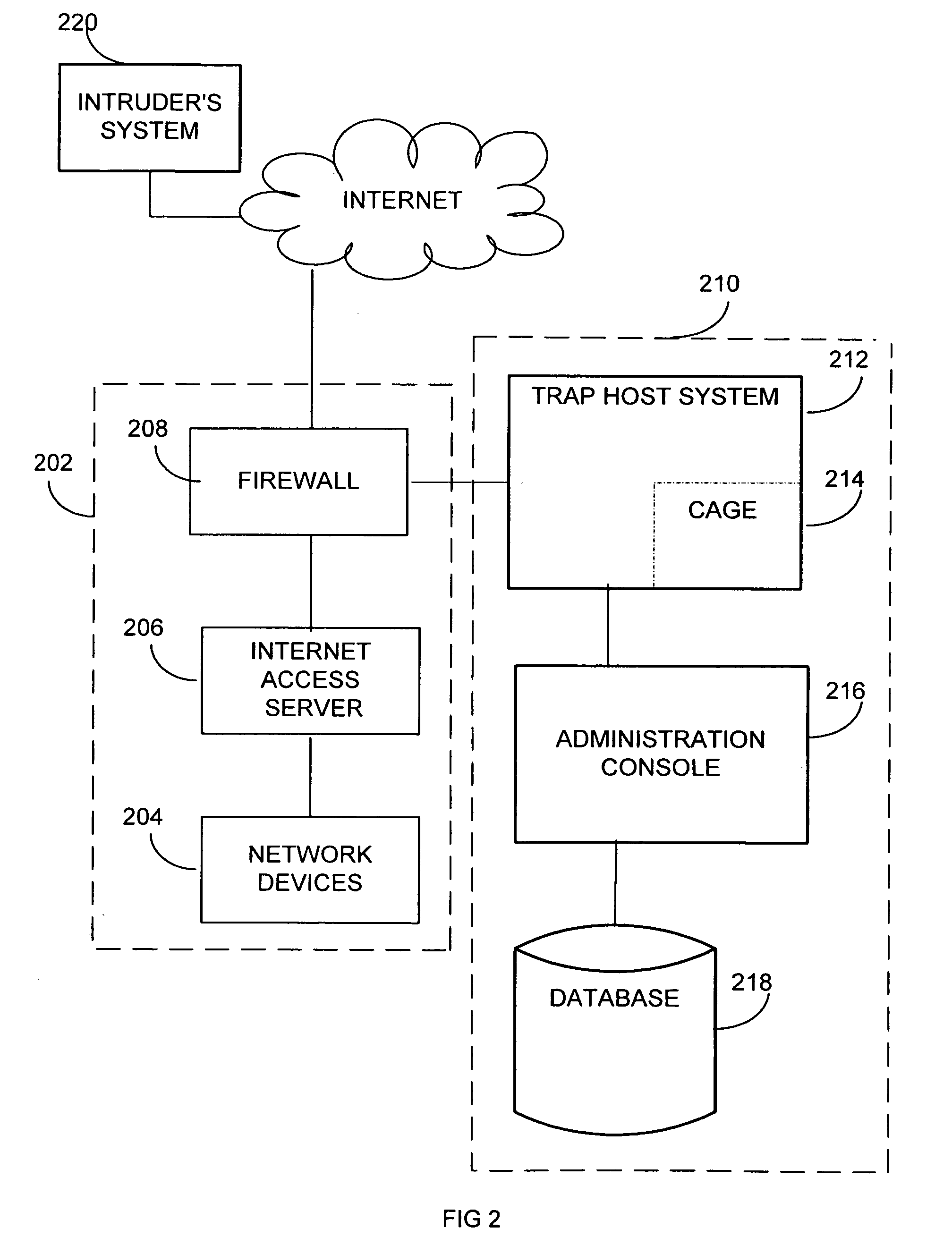
Method and Apparatus for Efficient Memory Replication for High Availability (HA) Protection of a Virtual Machine (VM)
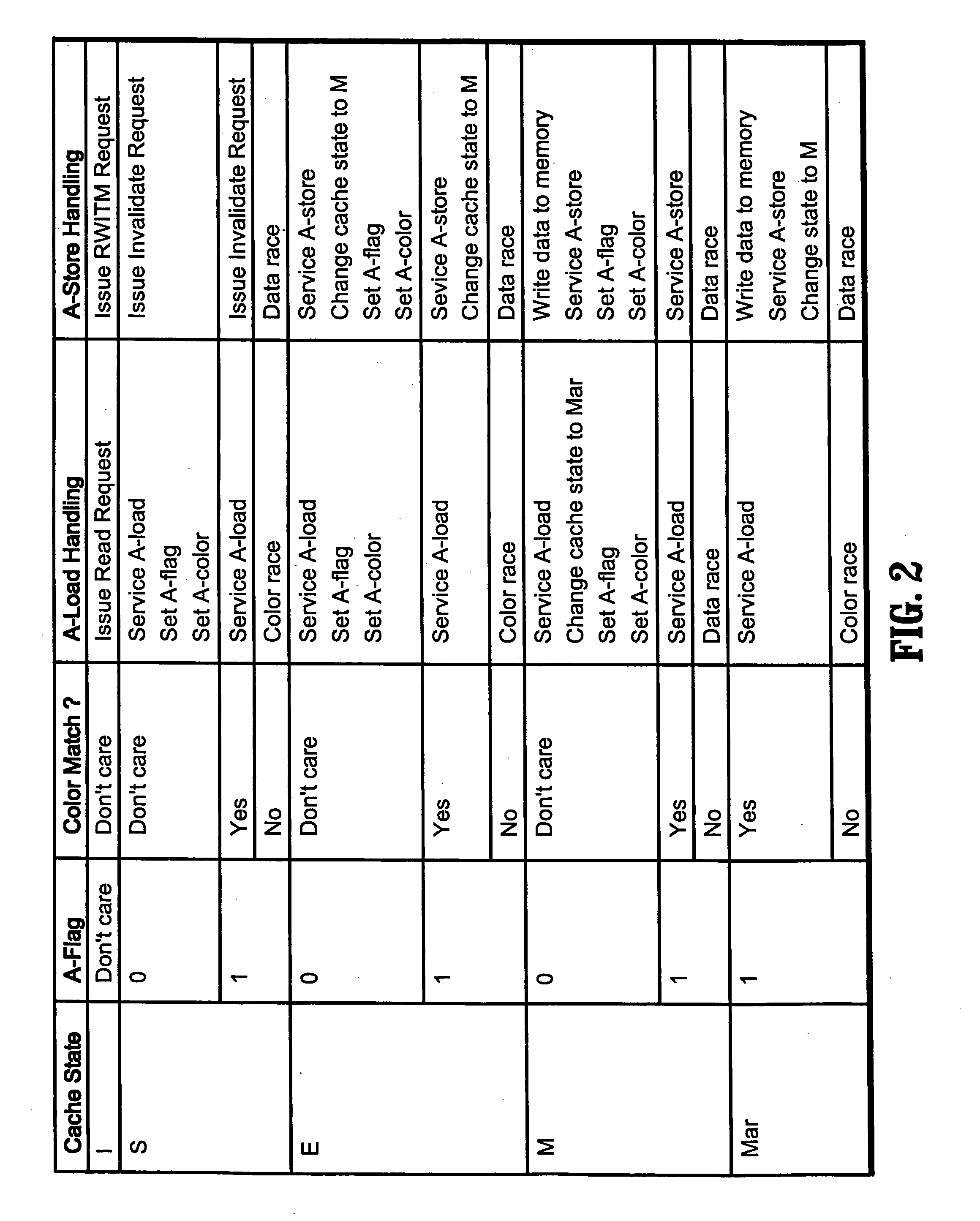
ActiveUS20120084782A1Prevents buffer overflowSmall bufferMemory architecture accessing/allocationError detection/correctionDirty pageBuffer overflow
High availability (HA) protection is provided for an executing virtual machine. At a checkpoint in the HA process, the active server suspends the virtual machine; and the active server copies dirty memory pages to a buffer. During the suspension of the virtual machine on the active host server, dirty memory pages are copied to a ring buffer. A copy process copies the dirty pages to a first location in the buffer. At a predetermined benchmark or threshold, a transmission process can begin. The transmission process can read data out of the buffer at a second location to send to the standby host. Both the copy and transmission processes can operate substantially simultaneously on the ring buffer. As such, the ring buffer cannot overflow because the transmission process continues to empty the ring buffer as the copy process continues. This arrangement allows for smaller buffers and prevents buffer overflows.
Owner:AVAYA INC
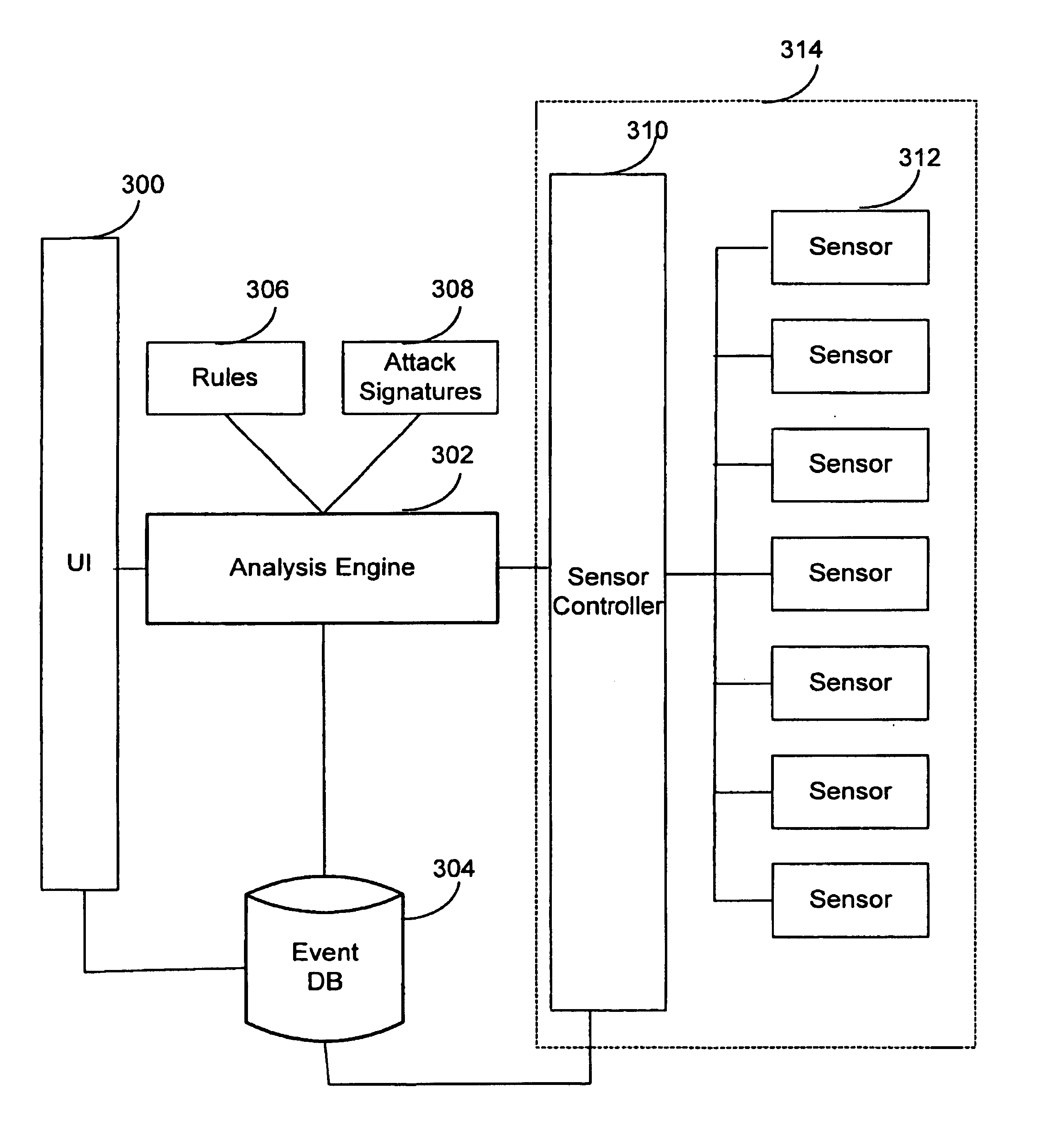
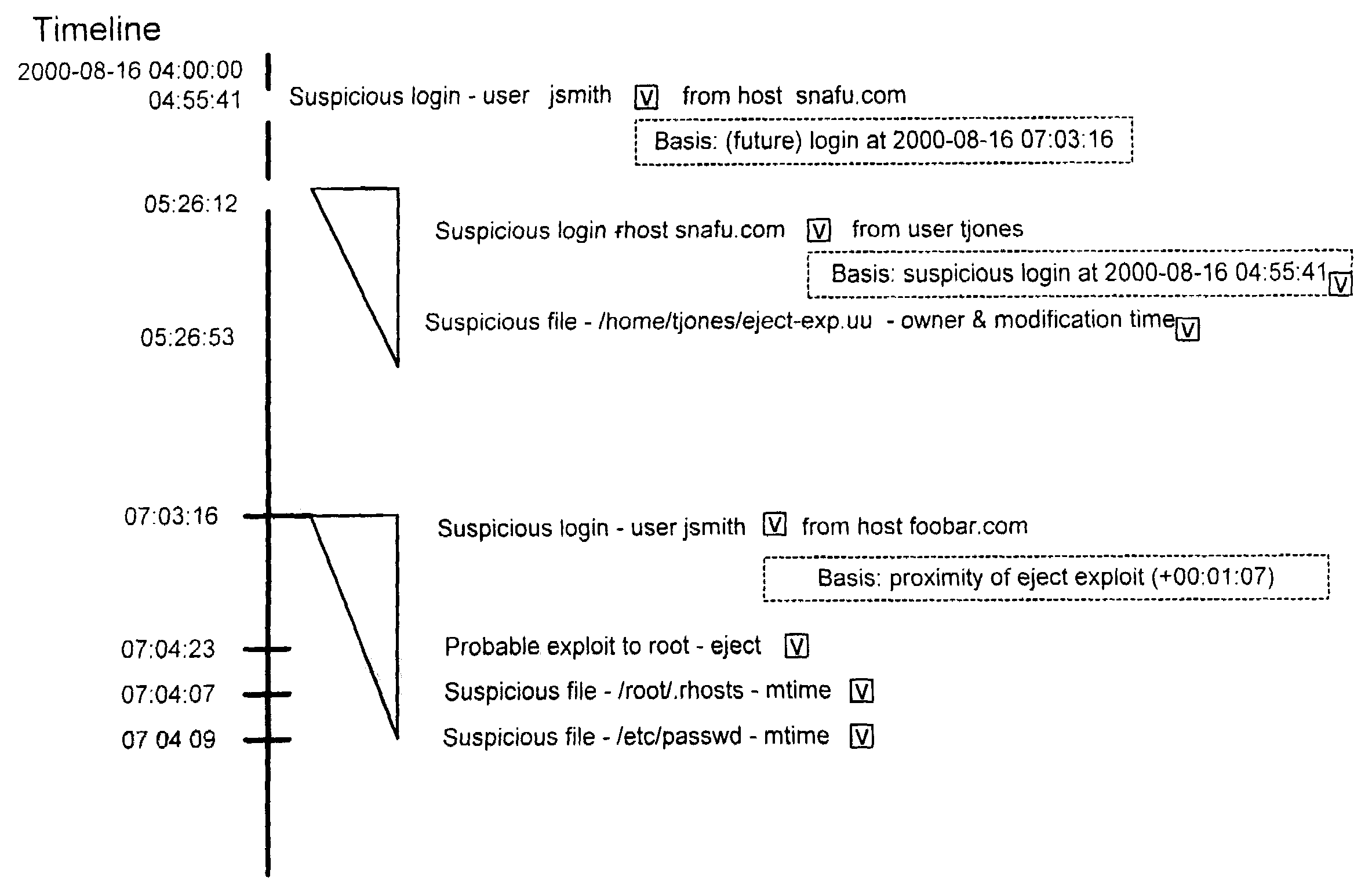
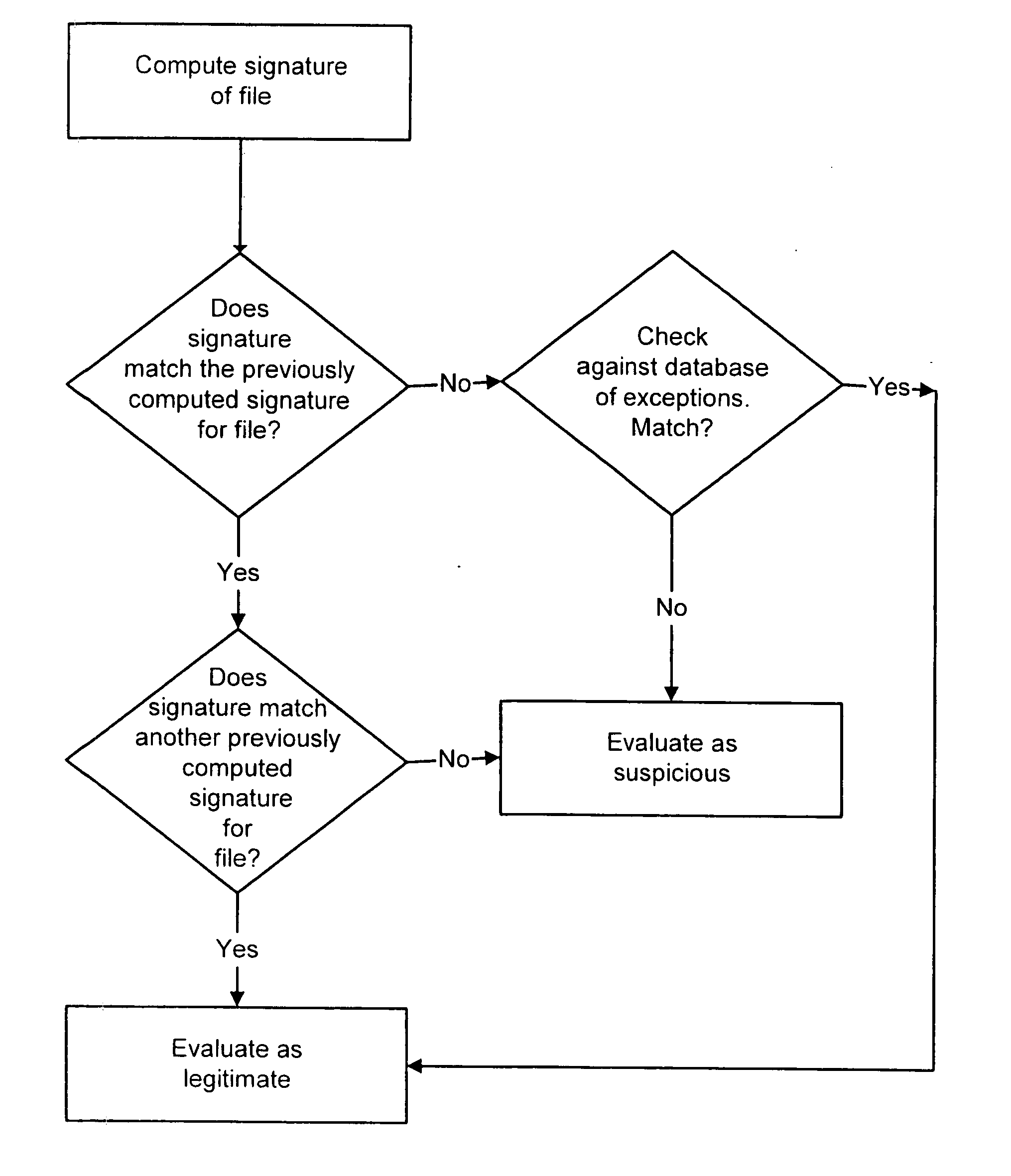
Extensible intrusion detection system
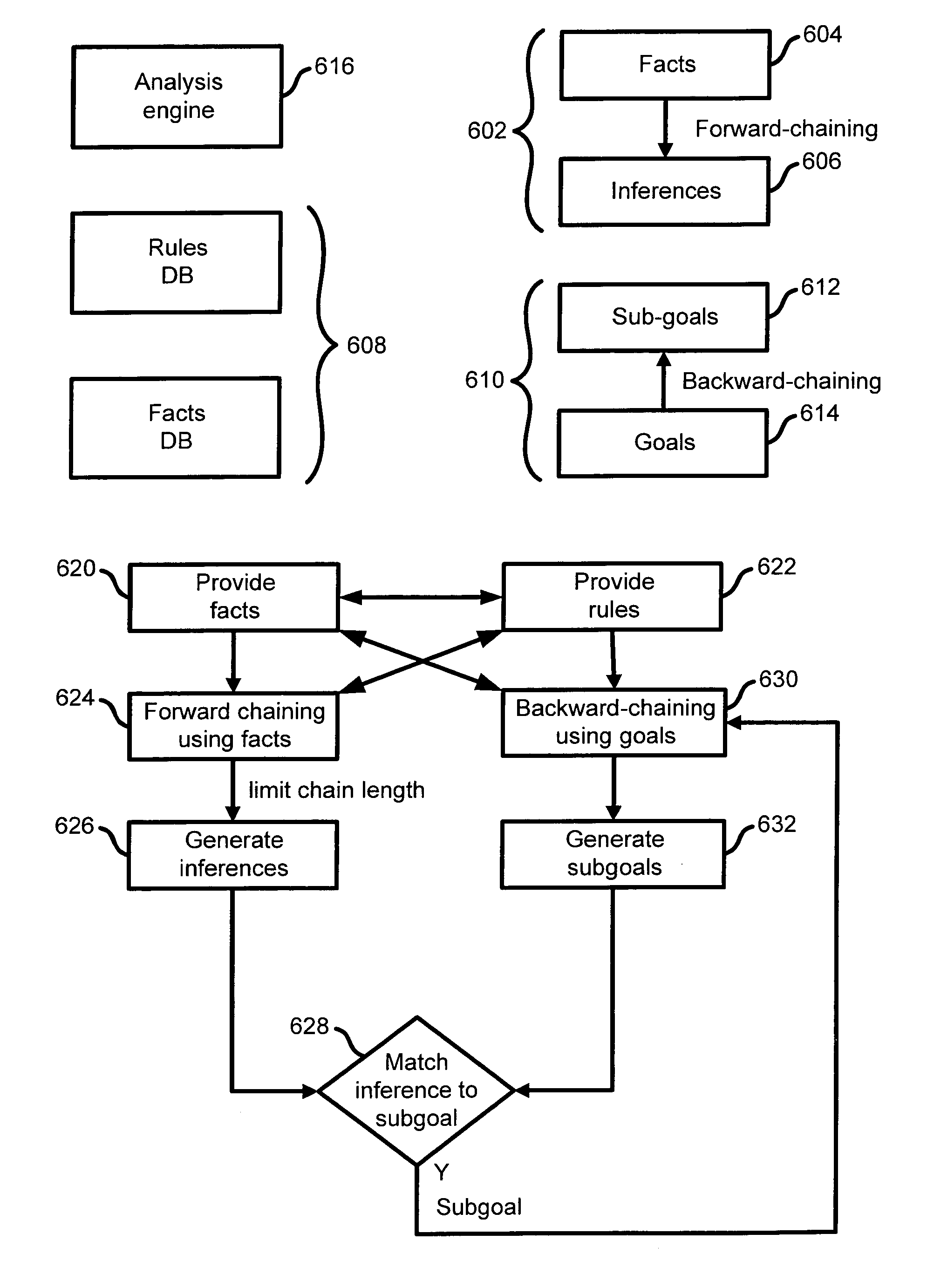
InactiveUS7065657B1Overcome problemsEnabling detectionDigital data processing detailsHardware monitoringTimestampAccess time
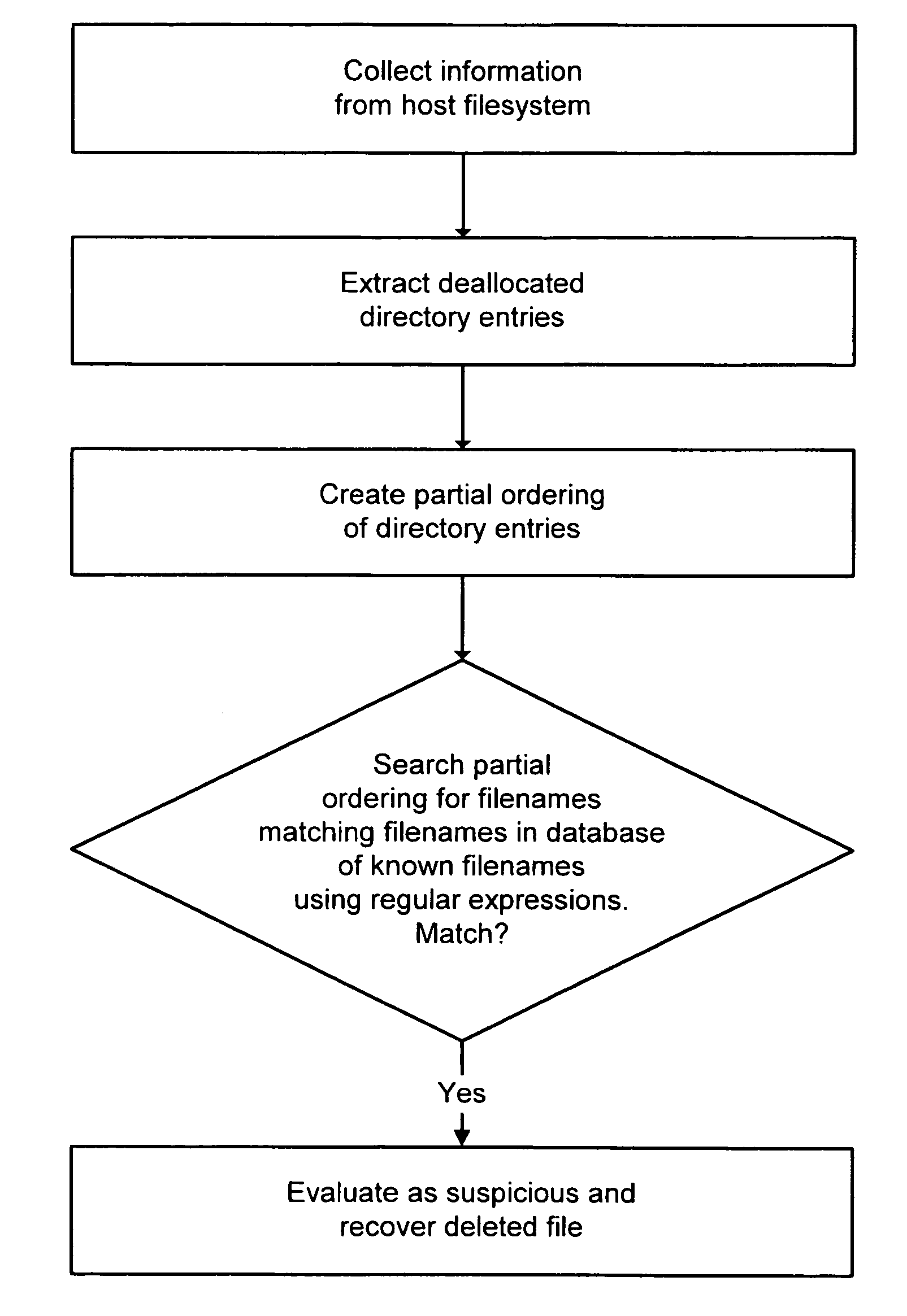
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
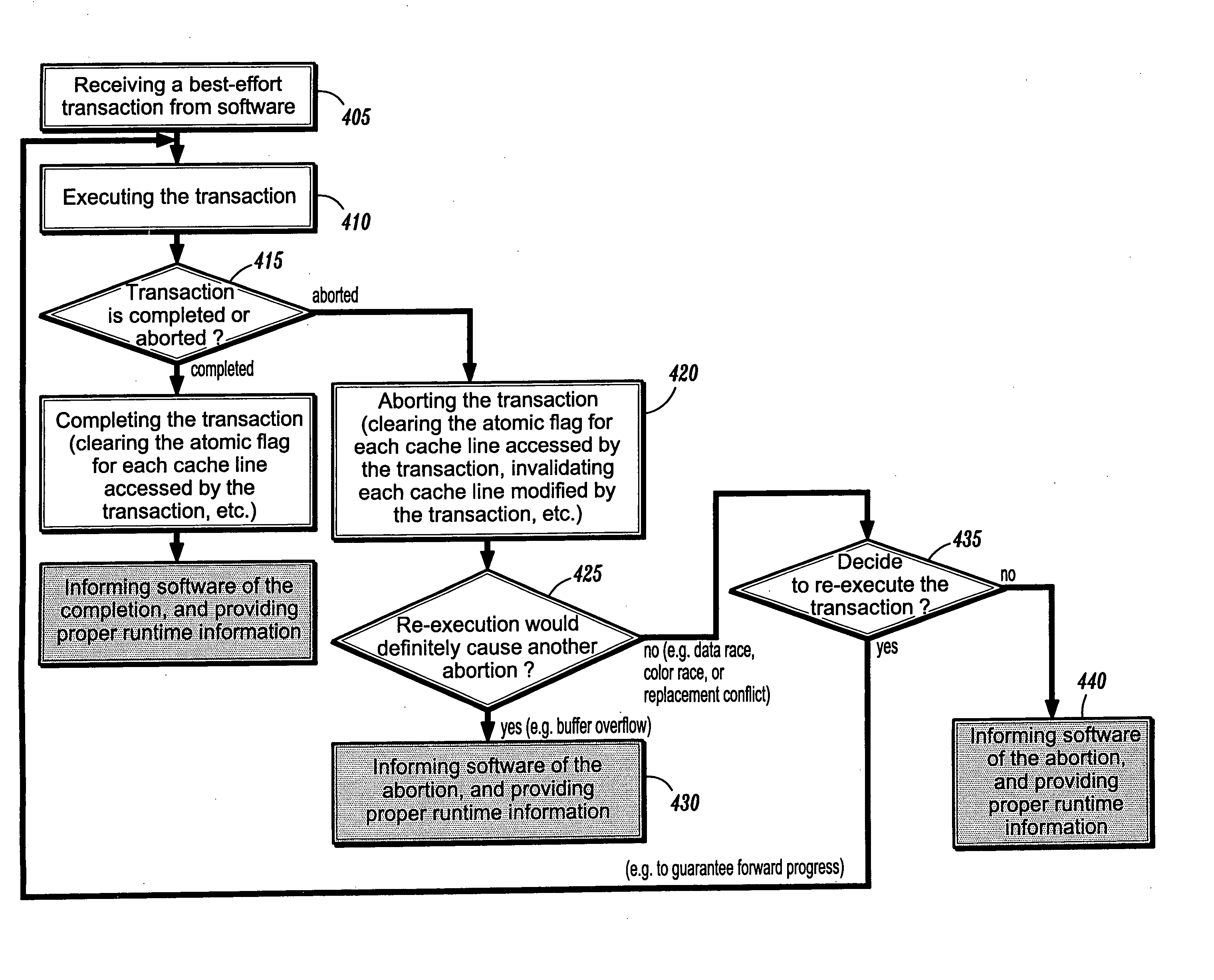
Architecture support of best-effort atomic transactions for multiprocessor systems
An atomic transaction includes one or more memory access operations that are completed atomically. A Best-Effort Transaction (BET) system makes its best effort to complete each atomic transaction without guaranteeing completion of all atomic transactions. When an atomic transaction is aborted, BET may provide software with appropriate runtime information such as cause of the abortion. With proper coherence layer enhancements, BET can be implemented efficiently for multiprocessor systems, using caches as buffers for data accessed by atomic transactions. Furthermore, with appropriate fairness support, forward progress can be guaranteed for atomic transactions that incur no buffer overflow.
Owner:IBM CORP
System and method for detecting computer intrusions
InactiveUS6996843B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS7203962B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS20070157315A1Overcome problemsEnabling detectionMemory loss protectionError detection/correctionData packProcess mechanism
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
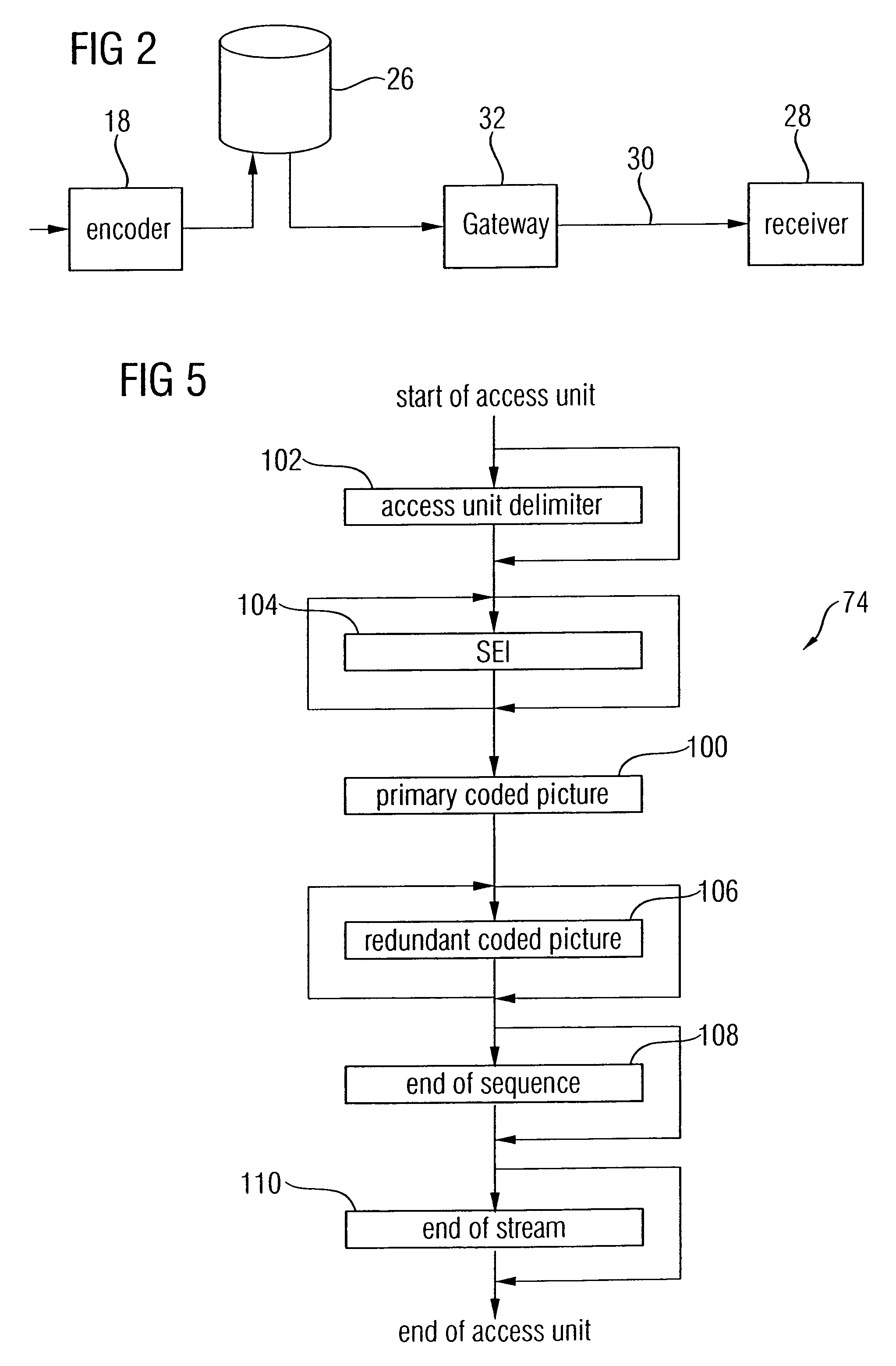
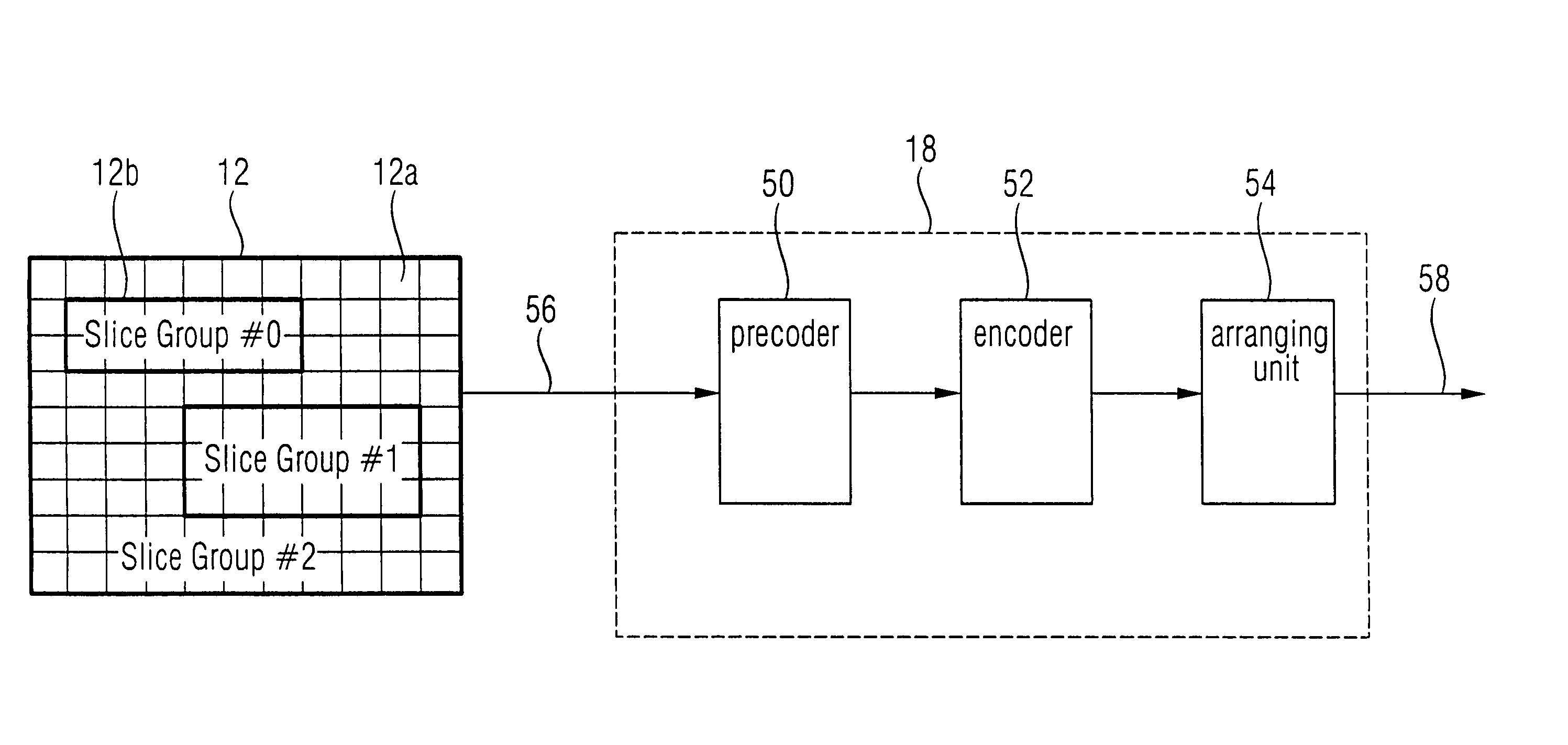
Apparatus and method for coding an information signal into a data stream, converting the data stream and decoding the data stream
ActiveUS7586924B2Increase flexibilityPulse modulation television signal transmissionData switching by path configurationPrecodingData stream
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
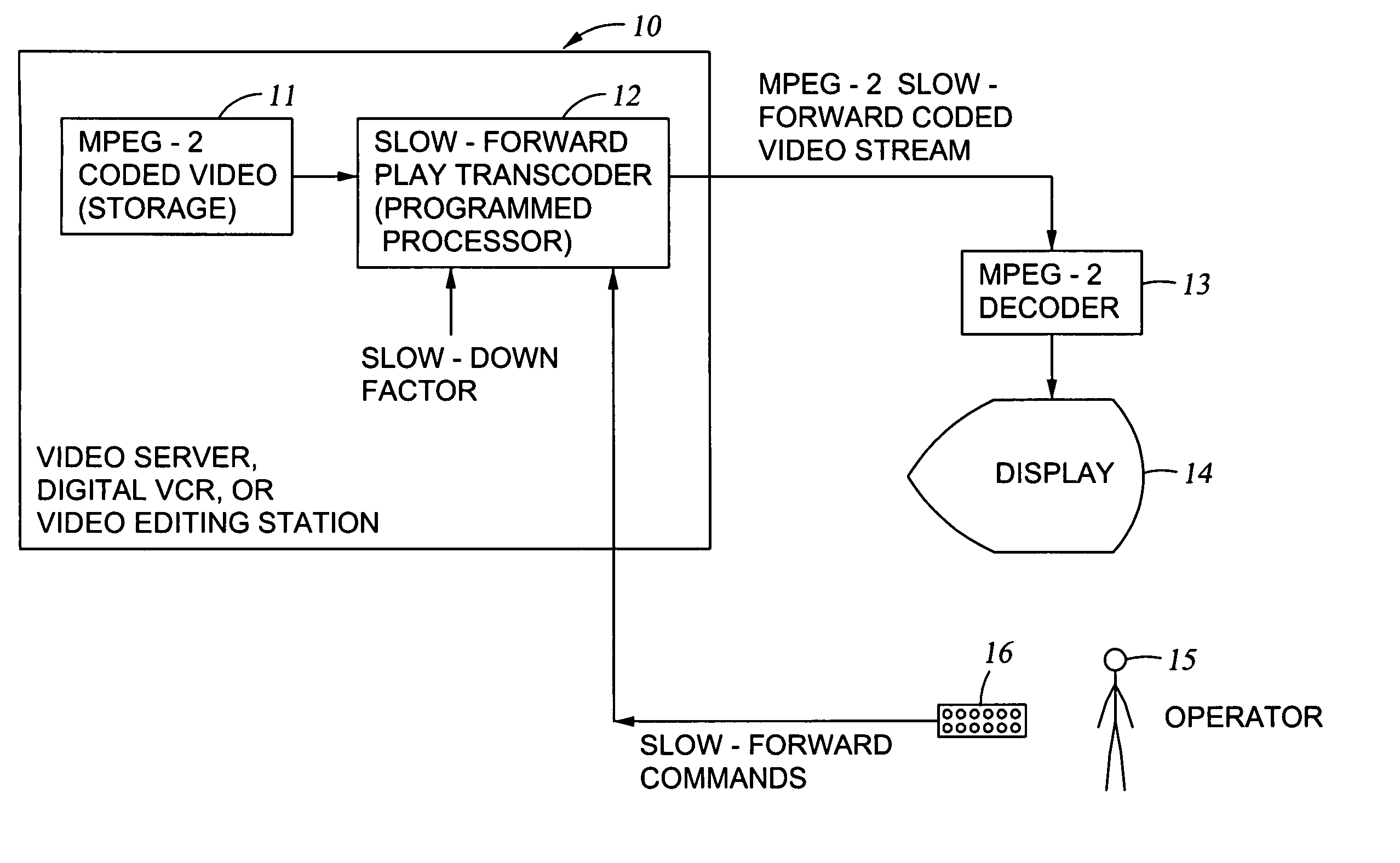
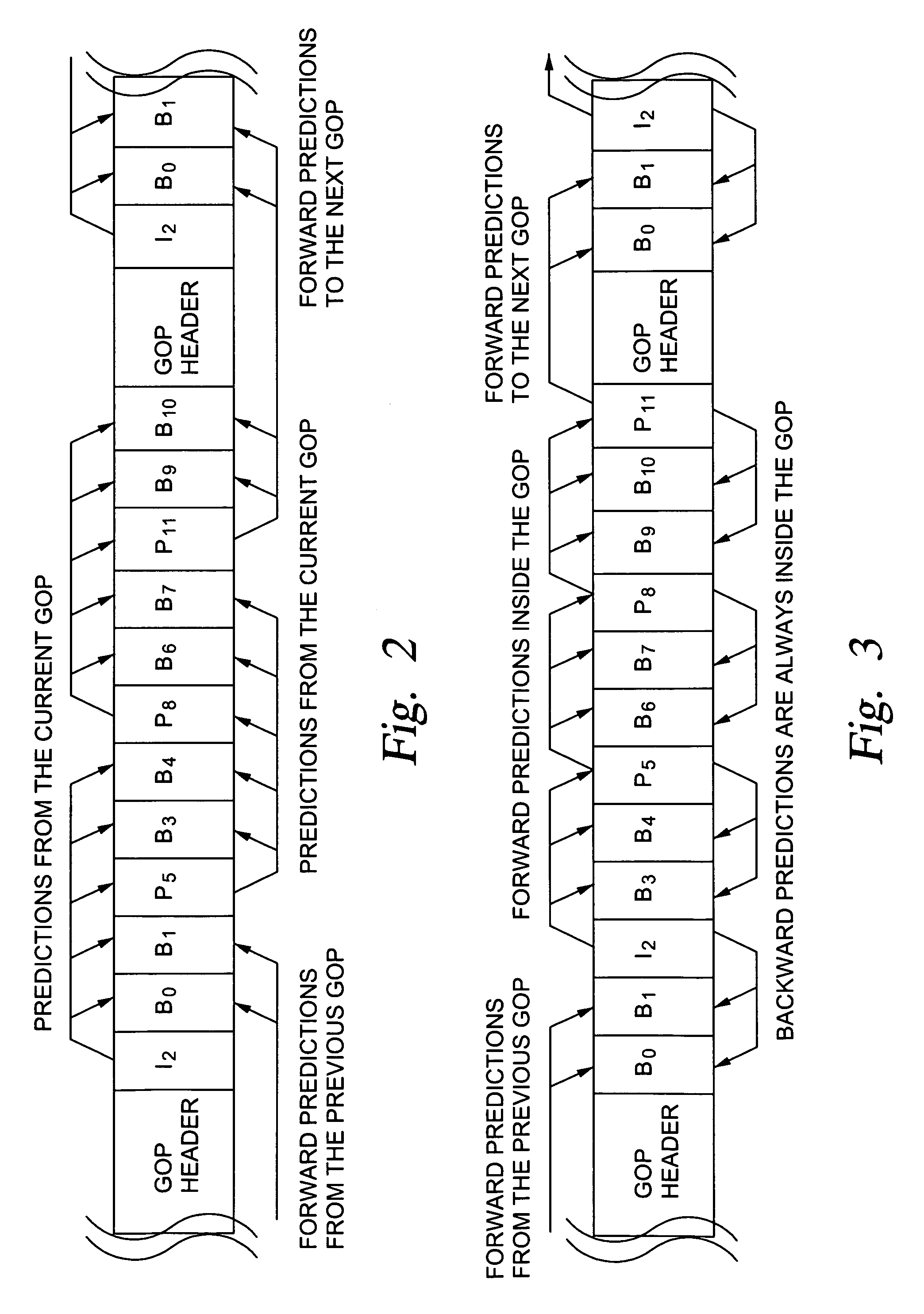
Generation of MPEG slow motion playout
InactiveUS6980594B2Minimal costGuaranteed preservation qualityTelevision system detailsDisc-shaped record carriersGroup of picturesComputer graphics (images)
MPEG coded video data includes groups of pictures (GOPs). Each group of pictures includes one or more I-frames and a plurality of B- or P-frames. To produce an MPEG slow-forward coded video stream, the coding type of each frame in the MPEG coded video data is identified, and freeze frames are inserted as a predefined function of the identified coding type and as a predefined function of a desired slow down factor. In a preferred implementation, for a slow-down factor of n, for each original I- or P-frame, (n−1) backward-predicted freeze frames are inserted, and for each original B-frame, (n−1) copies of the original B-frames are added, and a selected amount of padding is added to each copy of each original B-frame in order to obtain a normal play bit rate and avoid video buffer overflow or underflow.
Owner:EMC IP HLDG CO LLC
Apparatus and method for coding an information signal into a data stream, converting the data stream and decoding the data stream
ActiveUS20050190774A1Increase flexibilityPulse modulation television signal transmissionData switching by path configurationPrecodingData stream
More customization and adaptation of coded data streams may be achieved by processing the information signal such that the various syntax structures obtained by pre-coding the information signal are placed into logical data packets, each of which being associated with a specific data packet type of a predetermined set of data packet types, and by defining a predetermined order of data packet types within one access unit of data packets. The consecutive access units in the data stream may, for example, correspond to different time portions of the information signal. By defining the predetermined order among the data packet types it is possible, at decoder's side, to detect the borders between successive access units even when removable data packets are removed from the data stream on the way from the data stream source to the decoder without incorporation of any hints into the reminder of the data stream. Due to this, decoders surely detect the beginnings and endings of access units and therefore are not liable to a buffer overflow despite a removal of data packets from the data stream before arrival at the decoder.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
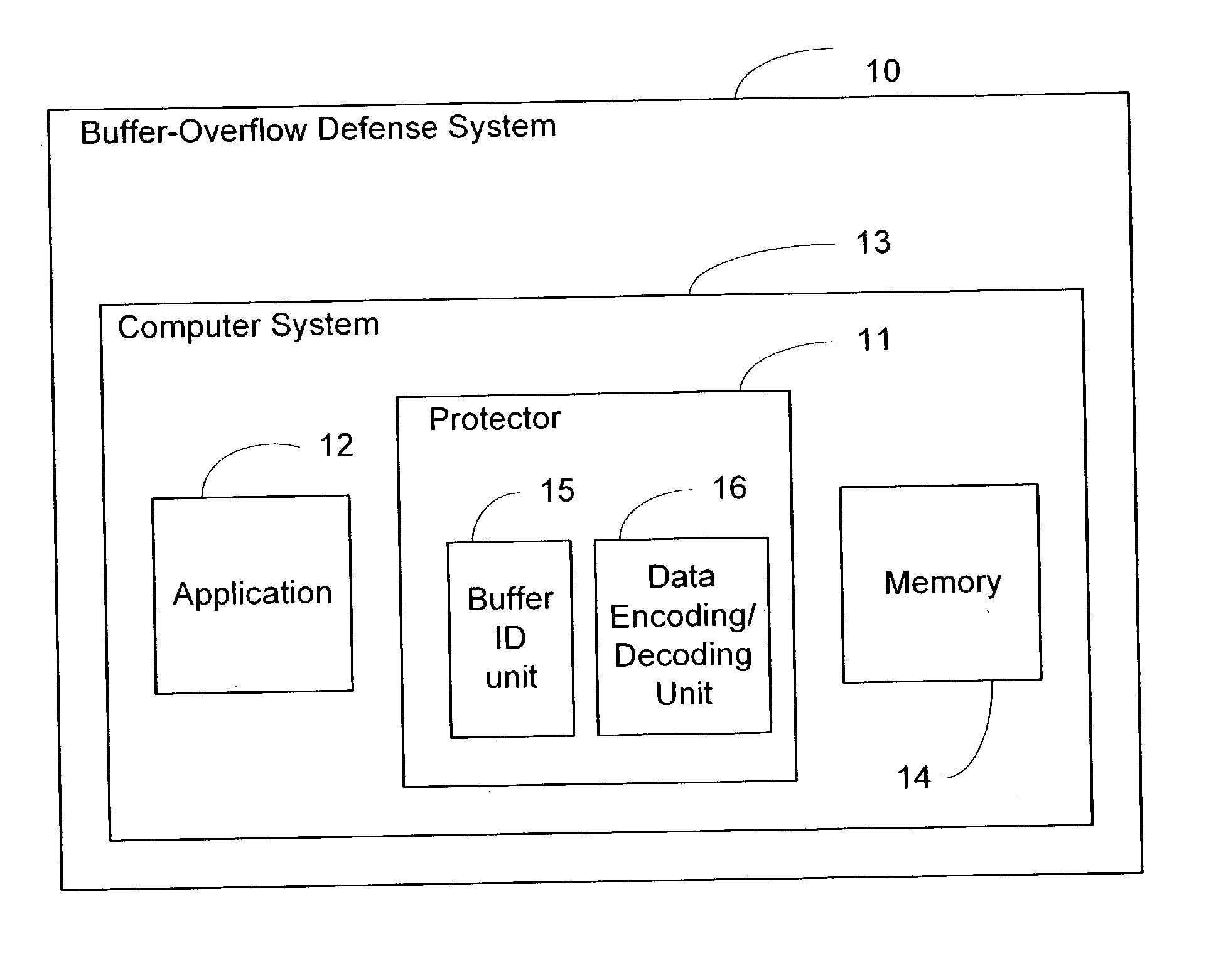
System and method of foiling buffer-overflow and alien-code attacks
InactiveUS20030172293A1Protected growthShuts down buffer overflow attacksMemory loss protectionUnauthorized memory use protectionBuffer overflowApplication software
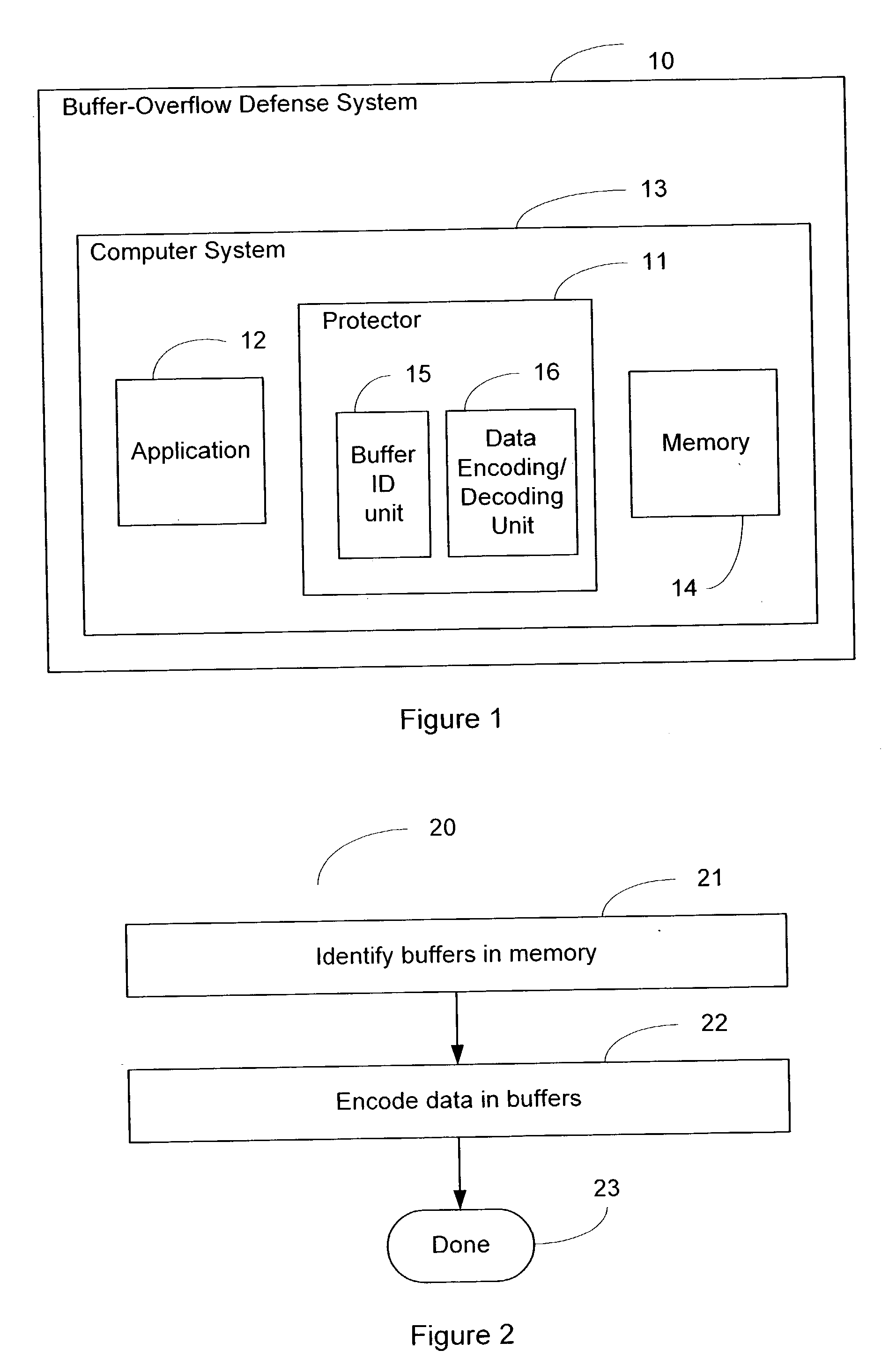
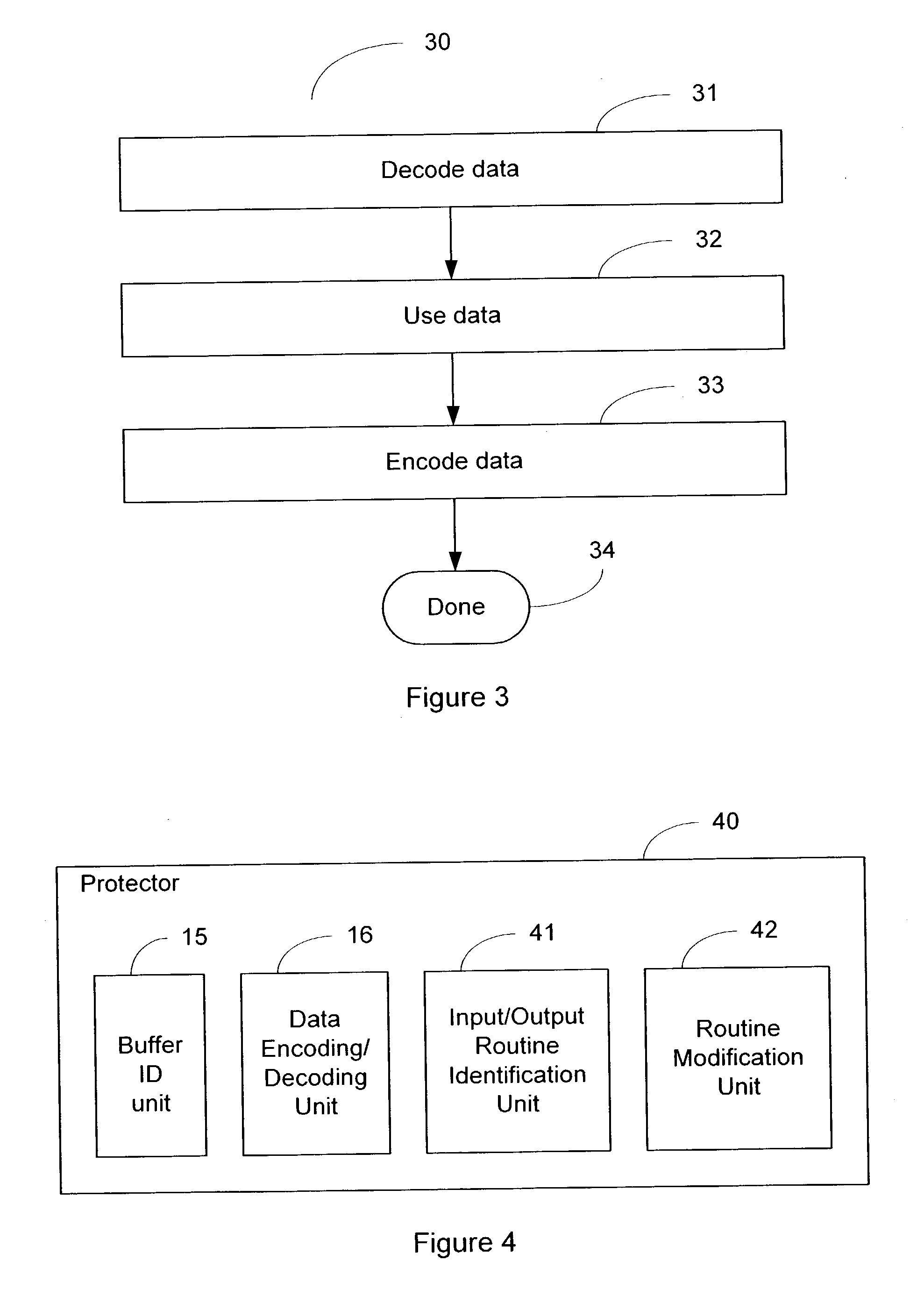
The present invention relates generally to computer software, and more specifically, to a system and method of foiling buffer-overflow and alien-code attacks. The invention protects computers from such attacks by encoding data placed in storage, and varying the encodings used in different storage areas. When the data is needed by a software application, the data is simply decoded in a complementary manner. This prevents storage areas written according to one usage from being used effectively for some other purpose. The method of the invention can be done in a number of ways. For example, a "protector" engine can be placed between a software application and memory, or the function calls in the software application itself, could be amended to include encoding and decoding. Other embodiments and alternatives are also described.
Owner:IRDETO CANADA CORP
System and method for using login correlations to detect intrusions
InactiveUS7085936B1Overcome problemsEnabling detectionDigital data processing detailsUnauthorized memory use protectionContinuationTimestamp
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
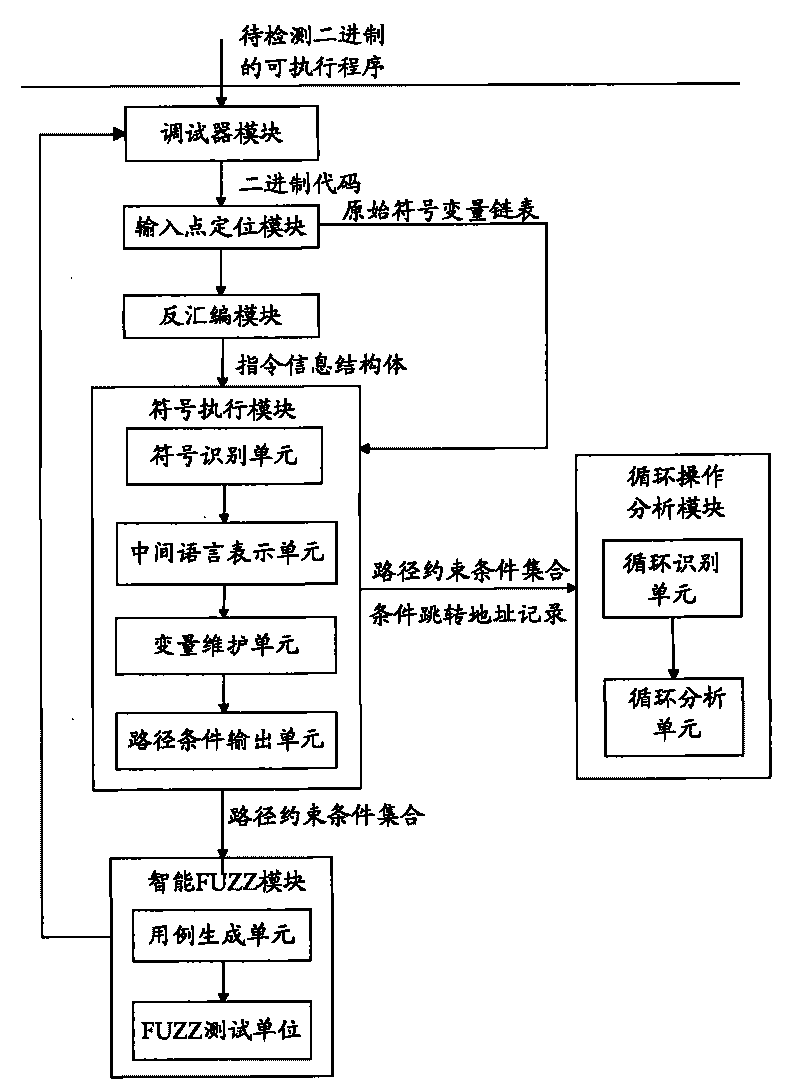
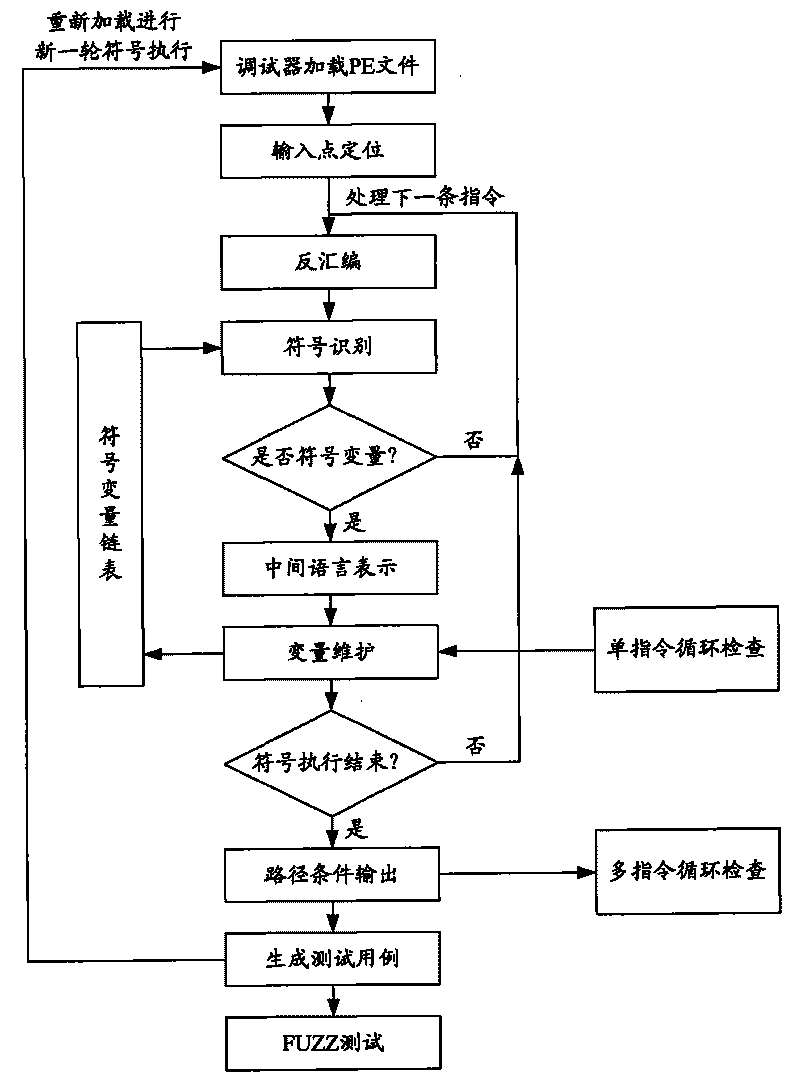
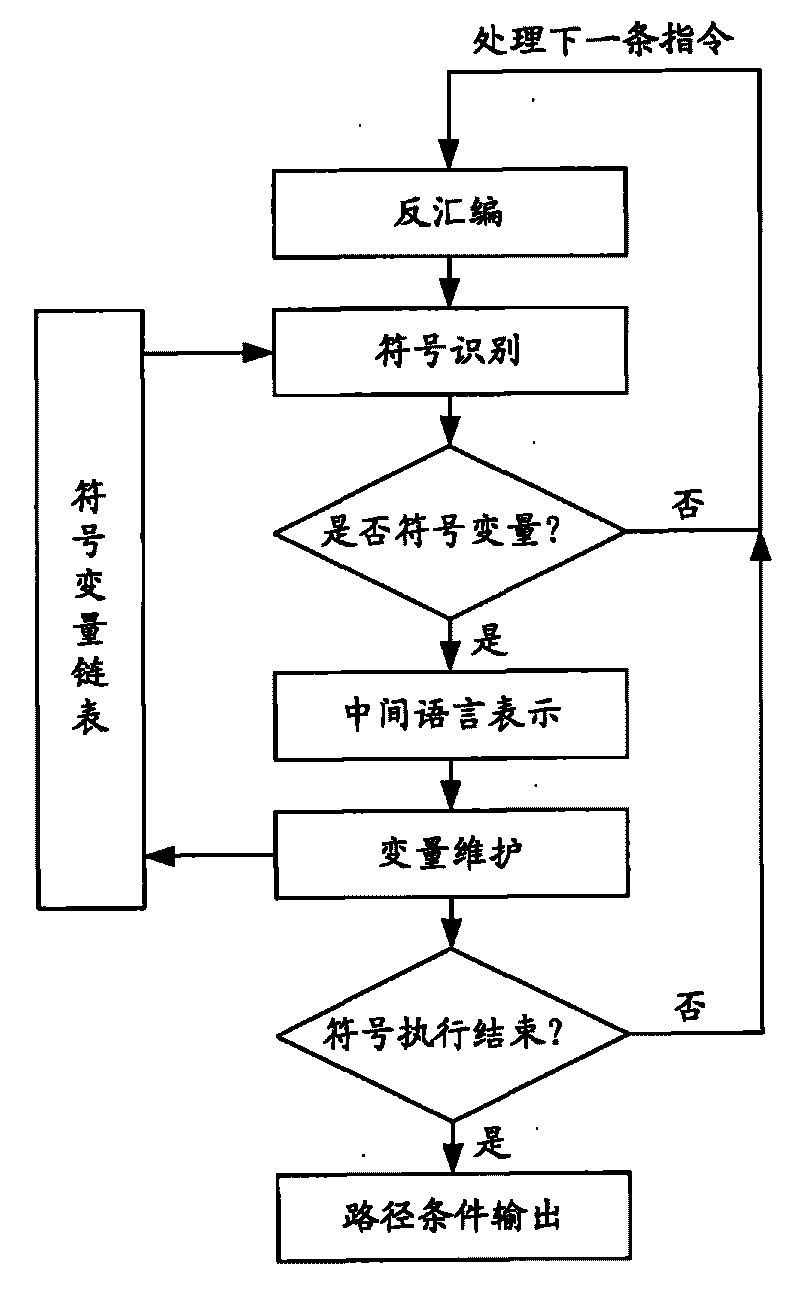
Detector for binary-code buffer-zone overflow bugs, and detection method thereof
InactiveCN101714118AGuaranteed feasibilityGuaranteed accuracyMultiprogramming arrangementsSoftware testing/debuggingBuffer overflowSource code
The invention provides a detector for binary-code buffer-zone overflow bugs, and a detection method thereof. The detector comprises six functional modules, namely a debugger module, an input point positioning module, a disassembling module, a symbolic execution module, a loop operation analysis module and an intelligent FUZZ test module. Differing from static symbolic execution, the detection method dynamically loads programs through the self-developed debugger module to synchronously performing symbolic execution and single-step practical execution, and then applies a model to solve each difficulty in binary code analysis so as to test path coverage and detect overflow bugs in accordance with all executable programs of PE format under a Windows platform. The detection can also provide propagation paths of input data and other important information related to bug formation cause while positioning the bugs, only analyzes the selves of the executable programs, needs no source codes, is unrelated to the species of source codes and development tools, and is extensive in applicable occasions, so the detection method has good prospects for popularization and application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
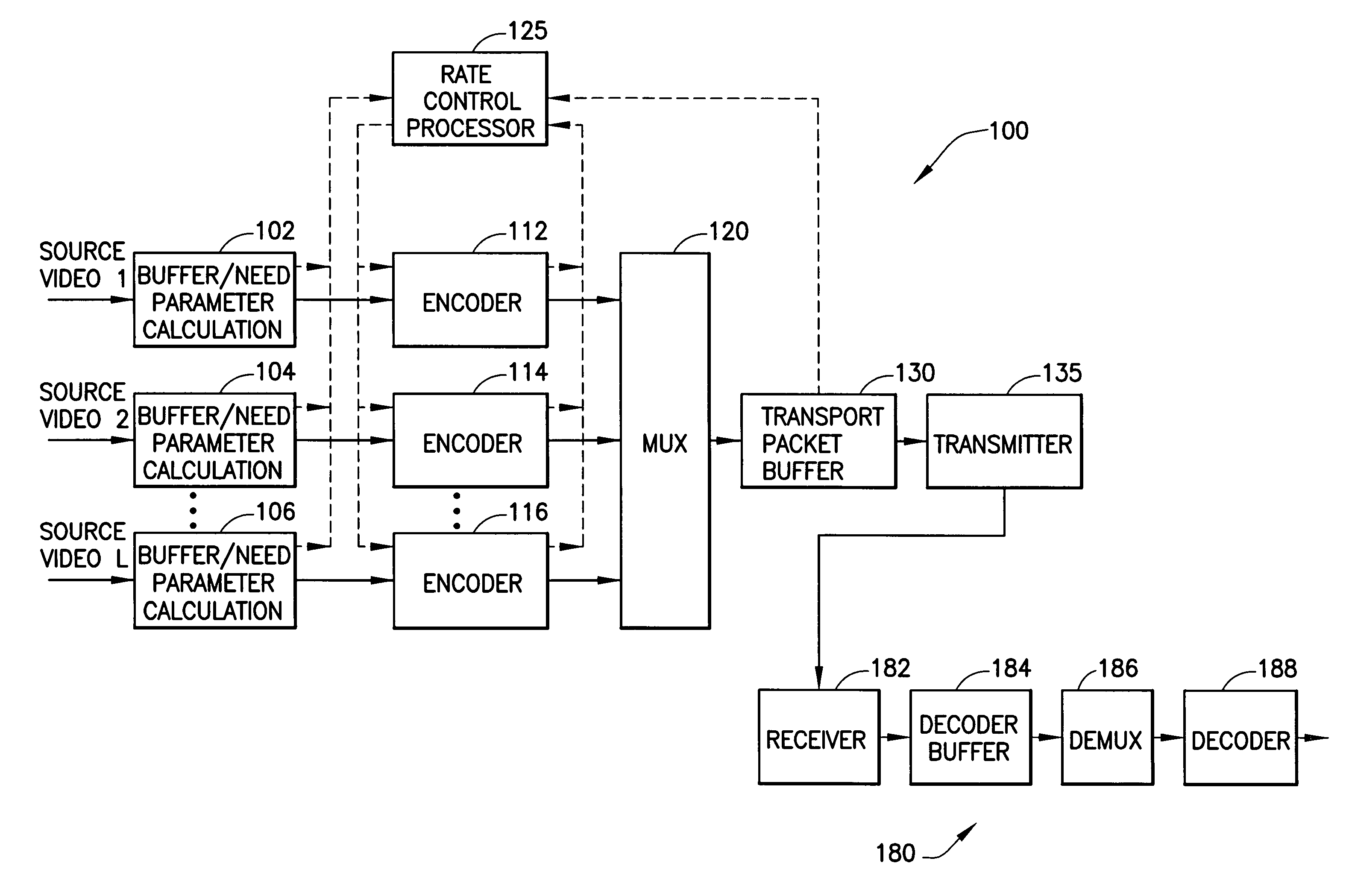
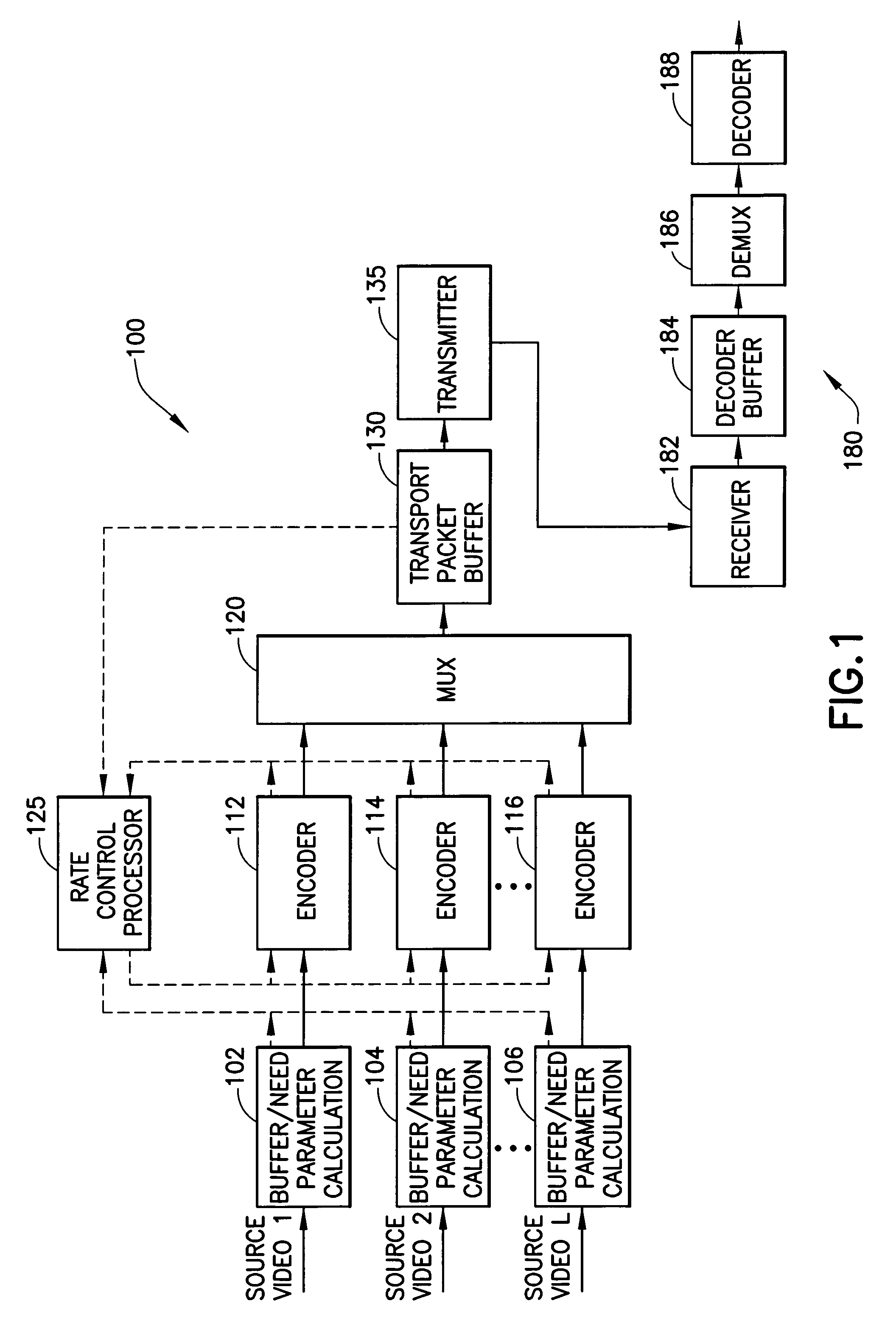
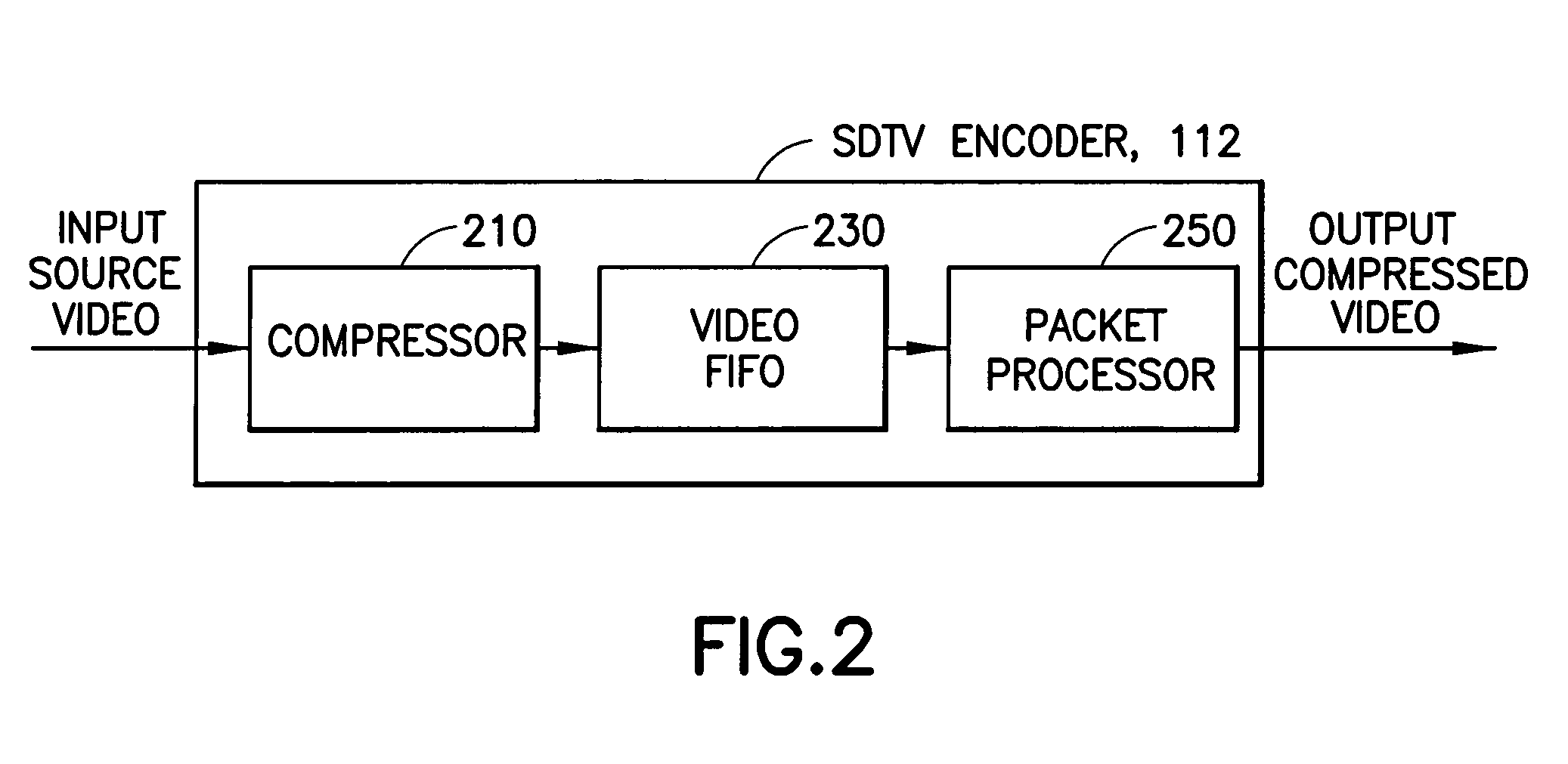
Method and apparatus for determining a transmission bit rate in a statistical multiplexer
ActiveUS7418007B1Minimizing ratePicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningMultiplexingMultiplexer
A statistical multiplexer for coding and multiplexing multiple channels of digital television data, or multiple panels of HDTV digital television data. A bit rate need parameter is determined for each encoder in a stat mux group, and an encoding bit rate is allocated to each channel based on its need parameter. A transmission bit rate is allocated to each channel as a time-lagged version of its need parameter to minimize a rate mismatch between the output and the input of a decoder buffer. A packet processor checks for impending decoder buffer overflow or underflow events to set minimum and maximum limits on the transmission bit rate. Moreover, these limits are set based on whether a new transmission bit rate can be implemented before the decoding time stamp (DTS) of the current or next frame.
Owner:GOOGLE TECH HLDG LLC
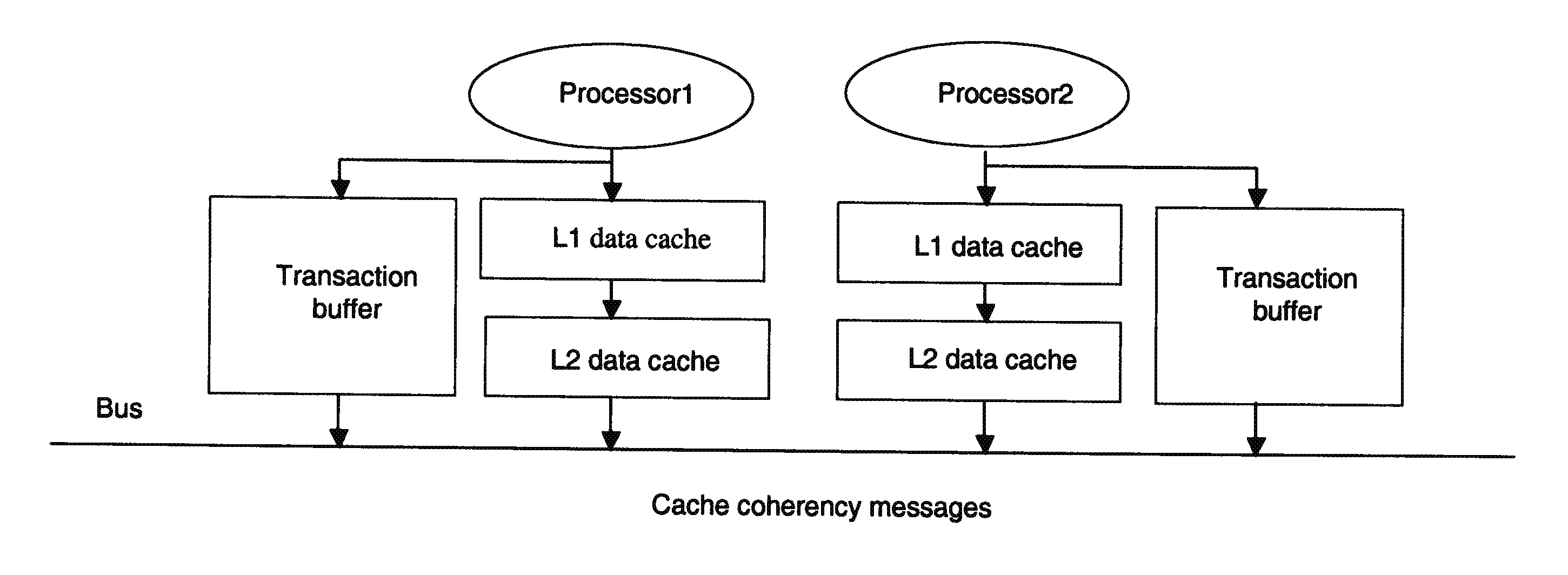
Method and System for Handling Transaction Buffer Overflow In A Multiprocessor System
ActiveUS20090144524A1Simple and efficient solutionMinimal modificationProgram control using stored programsGeneral purpose stored program computerMulti processorBuffer overflow
There is disclosed a method and apparatus for handling transaction buffer overflow in a multi-processor system as well as a transaction memory system in a multi-processor system. The method comprises the steps of: when overflow occurs in a transaction buffer of one processor, disabling peer processors from entering transactions, and waiting for any processor having a current transaction to complete its current transaction; re-executing the transaction resulting in the transaction buffer overflow without using the transaction buffer; and when the transaction execution is completed, enabling the peer processors for entering transactions.
Owner:IBM CORP
Method and apparatus for improved vision detector image capture and analysis
InactiveUS20050226490A1Reduce in quantityIncrease frame rateImage analysisCharacter and pattern recognitionHigh frame rateImaging analysis
Disclosed are methods and apparatus for improvements to image capture and analysis for vision detectors. The improvements provide for asynchronous capture and analysis and allow high frame rates to be maintained when image analysis may under certain conditions comprise a significantly longer time interval than image capture. The improvements prevent memory buffer overflow and provide for short and predictable decision delays even though an arbitrary and potentially unlimited number of images are captured and analyzed for each object.
Owner:COGNEX TECH & INVESTMENT
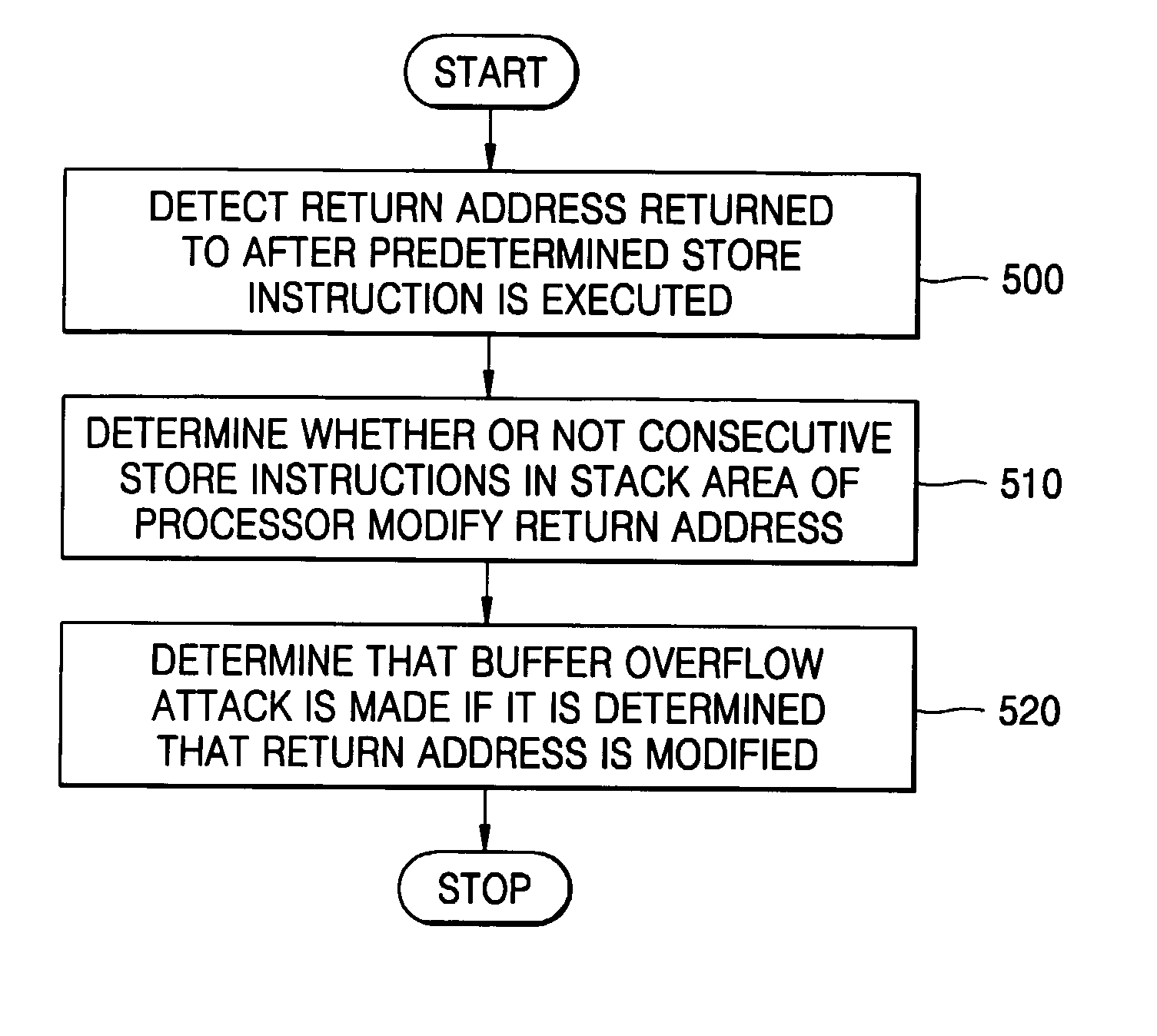
Method for sensing and recovery against buffer overflow attacks and apparatus thereof
ActiveUS20070180524A1Efficient detectionLow computing performanceOperating means/releasing devices for valvesMemory loss protectionSystem recoveryAttack
Methods and apparatuses for detecting and recovering from a buffer overflow attack are provided. A method of recovering an operation state of a processor from a buffer overflow attach includes: detecting whether a buffer overflow attack is made on any write operation while storing write operations that are potential targets of buffer overflow attacks in a predetermined location instead of an original destination to store write operations; storing the contents stored in the predetermined location at a predetermined interval in the original destination for storing write operations if no buffer overflow attack is detected and discarding unsafe write operations subsequent to a buffer overflow attack if a buffer overflow attack is detected; and ignoring the unsafe write operations subsequent to the buffer overflow attack if a buffer overflow attack is detected. Therefore, a buffer overflow attack occurring in a computer can be effectively detected, and damage of a system which is attacked can be minimized and the system can be recovered or return to the original state before the attack. A system can be effectively protected while minimizing reduction in performance of the computer system according to a method used to implement the present invention, thereby greatly improving the environments under which the computer and the Internet are used.
Owner:HANBAT NAT UNIV IND ACADEMIC COOPERATION FOUND
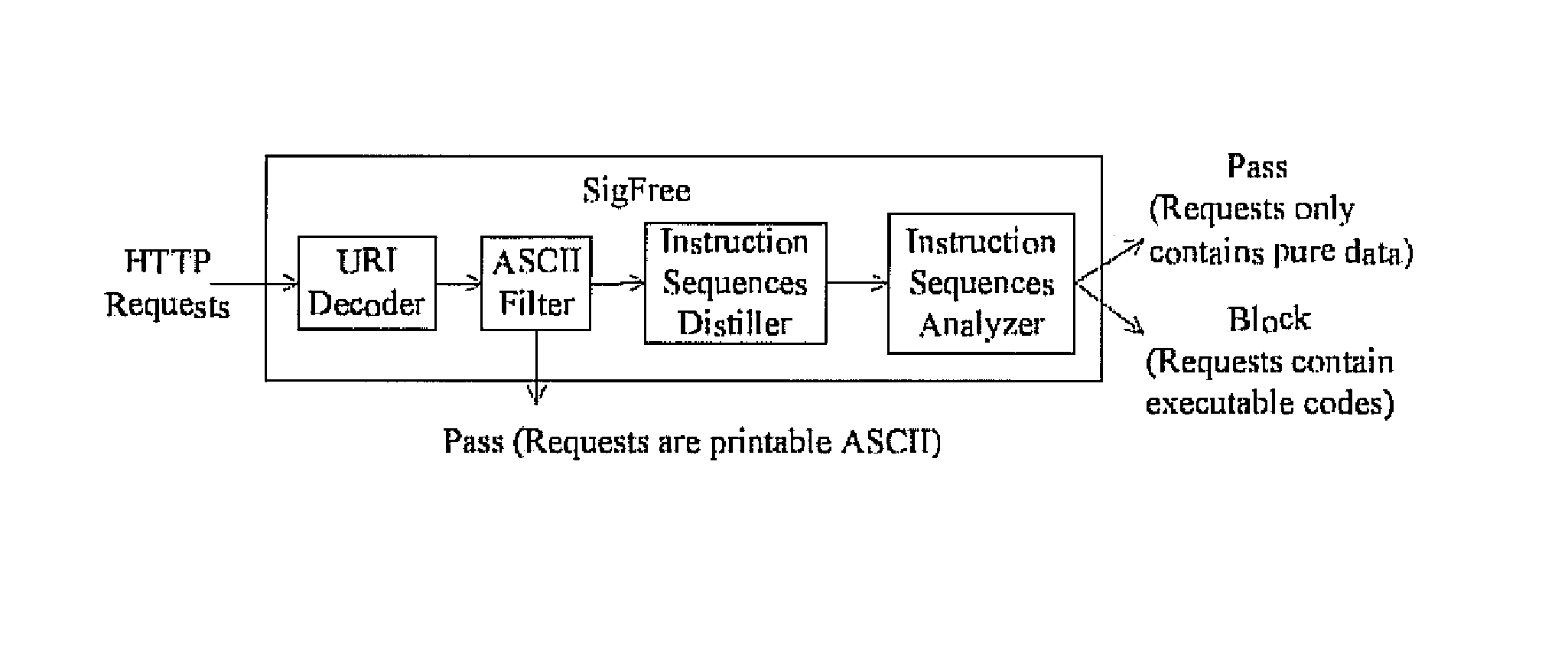
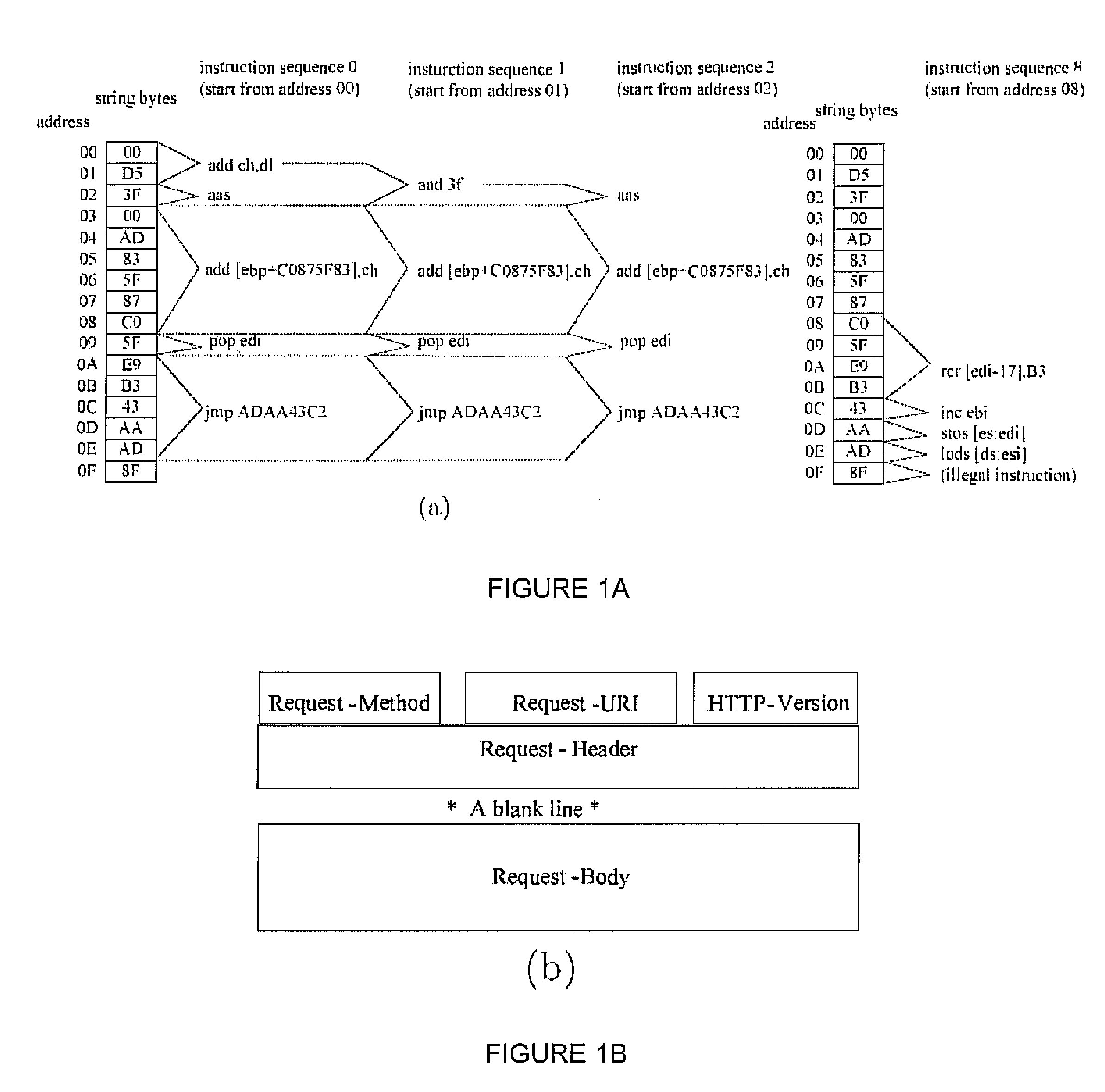
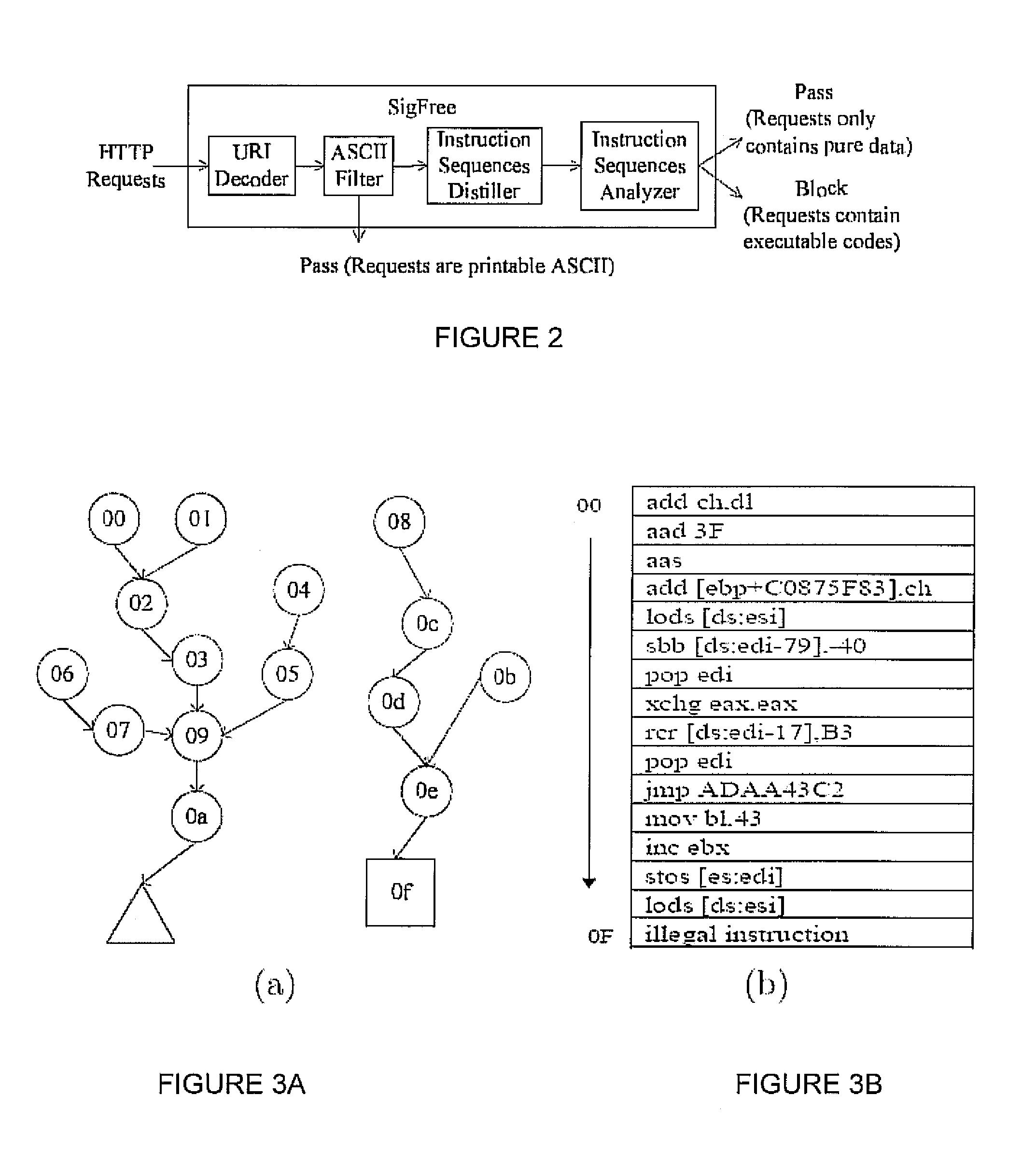
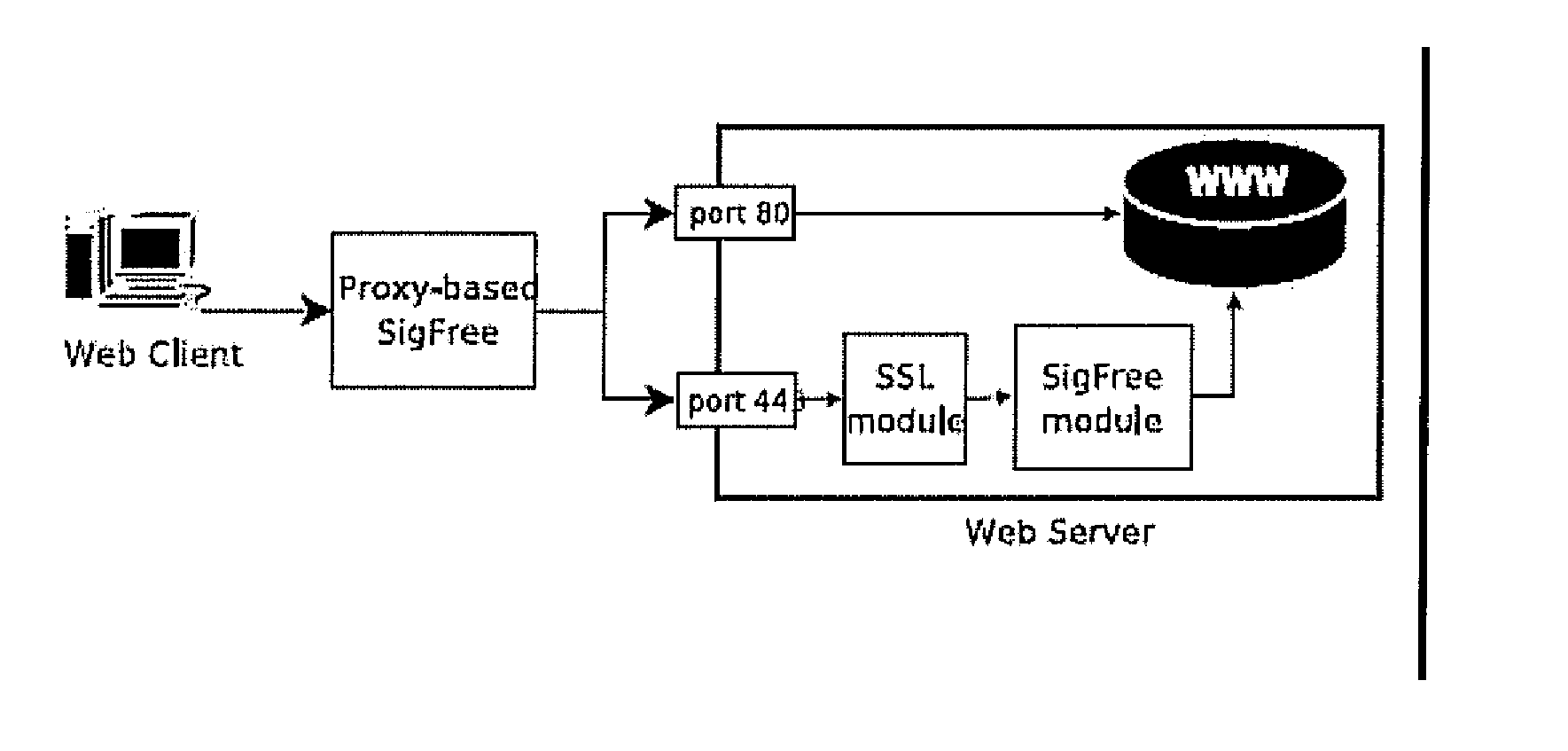
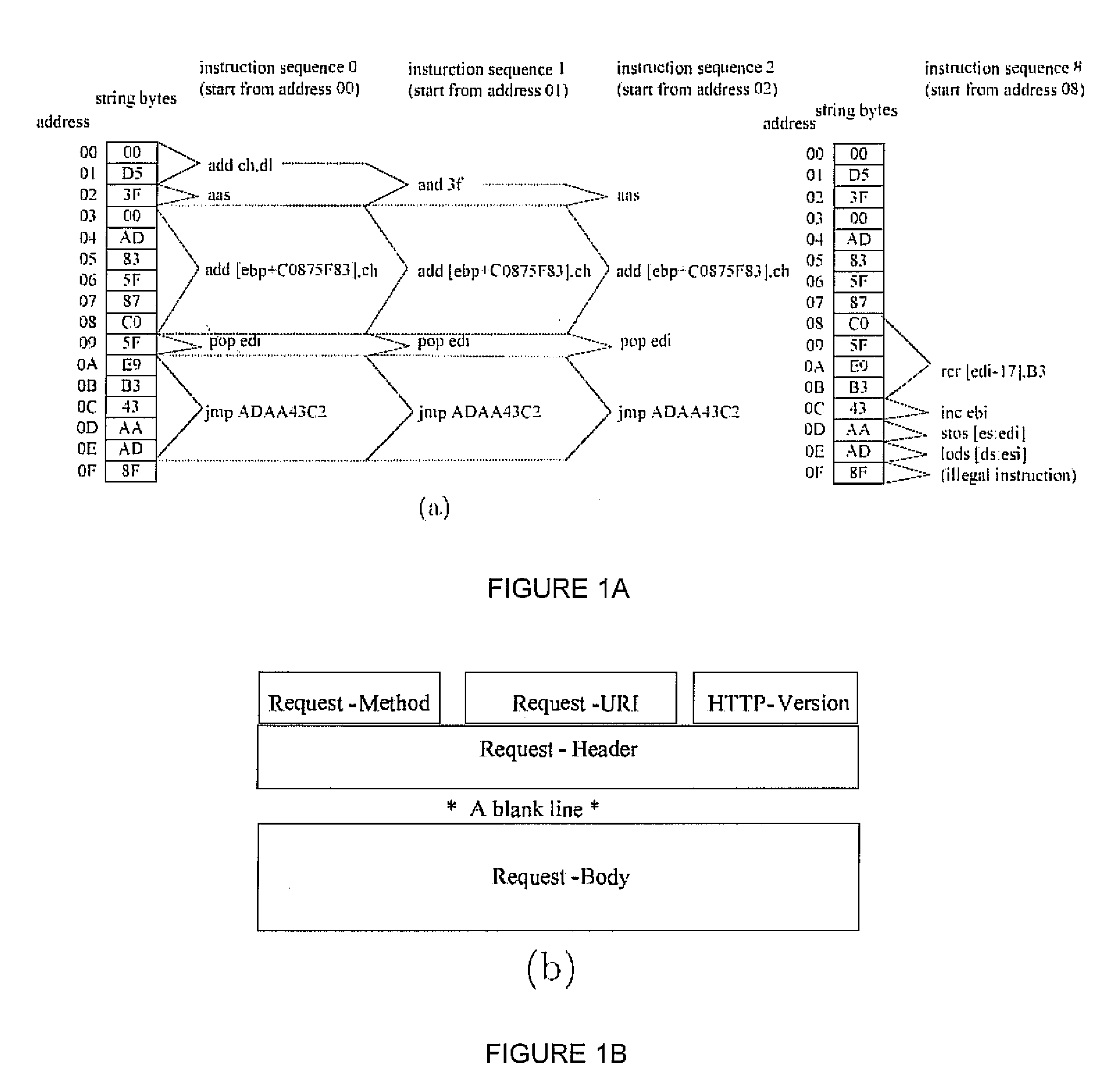
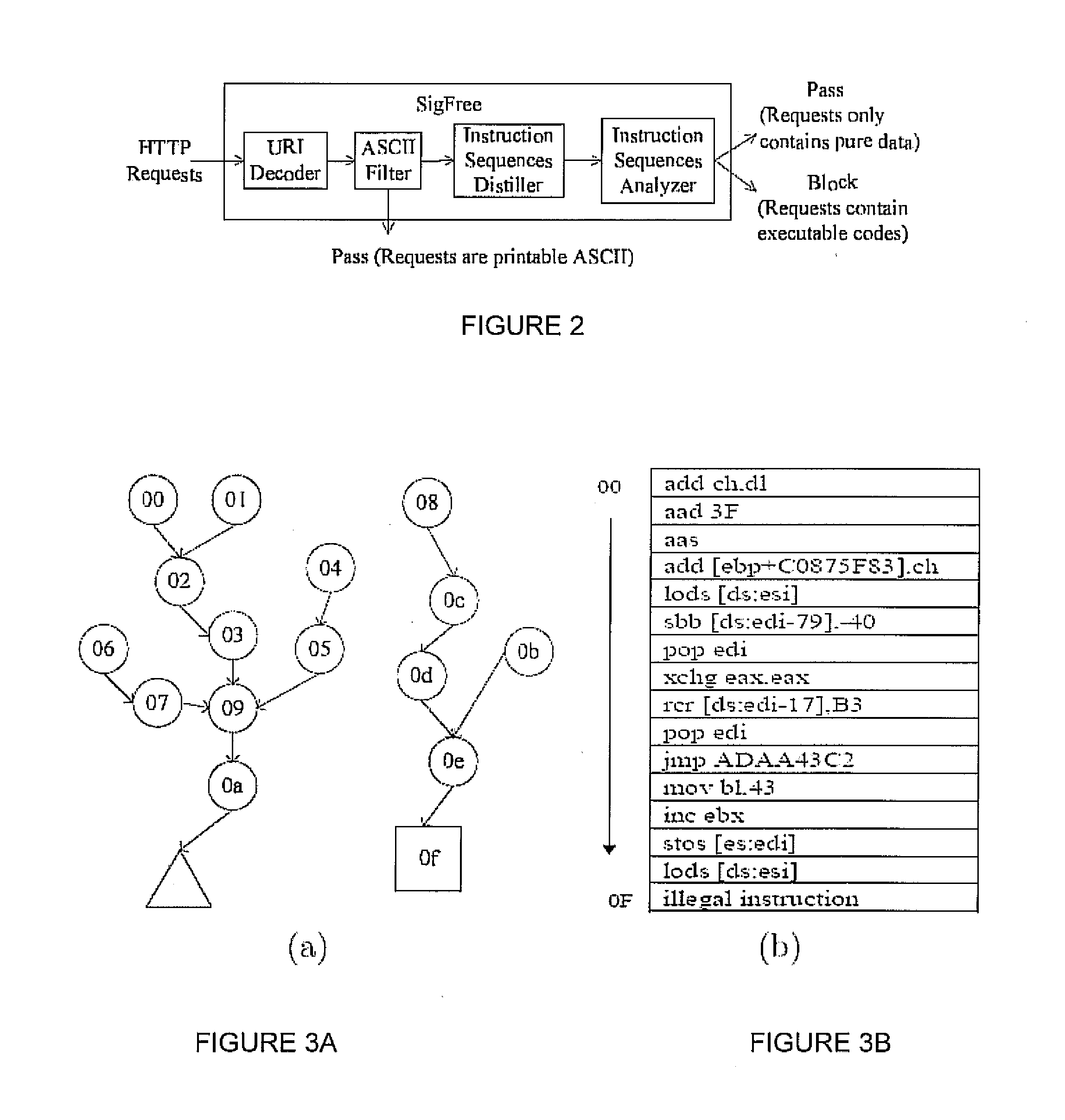
Signature-free buffer overflow attack blocker
ActiveUS8443442B2Transparent to serverLow deploymentMemory loss protectionError detection/correctionObfuscationWeb service
A real-time, signature-free, blocker prevents buffer overflow attacks. The system and method, called SigFree, can filter out code injection buffer overflow attack packets targeting at various Internet services such as web services. Motivated by the observation that buffer overflow attacks typically contain executables whereas legitimate client requests never contain executables in most Internet services, SigFree blocks attacks by checking, without any preknowledge of the real attacks, if “executable” instruction sequences can be blindly disassembled and extracted from a packet. Being signature-free, the invention can block new and unknown buffer overflow attacks. It is immunized from almost every attack-side code obfuscation method, and transparent to the servers being protected. The approach is therefore suited to economical Internet-wide deployment with very low deployment and maintenance costs. SigFree can also handle encrypted SSL packets. An experimental study shows that SigFree can block all types of code-injection attack packets without yielding any false positives or false negatives. Moreover, SigFree causes negligible throughput degradation to normal client requests.
Owner:PENN STATE RES FOUND
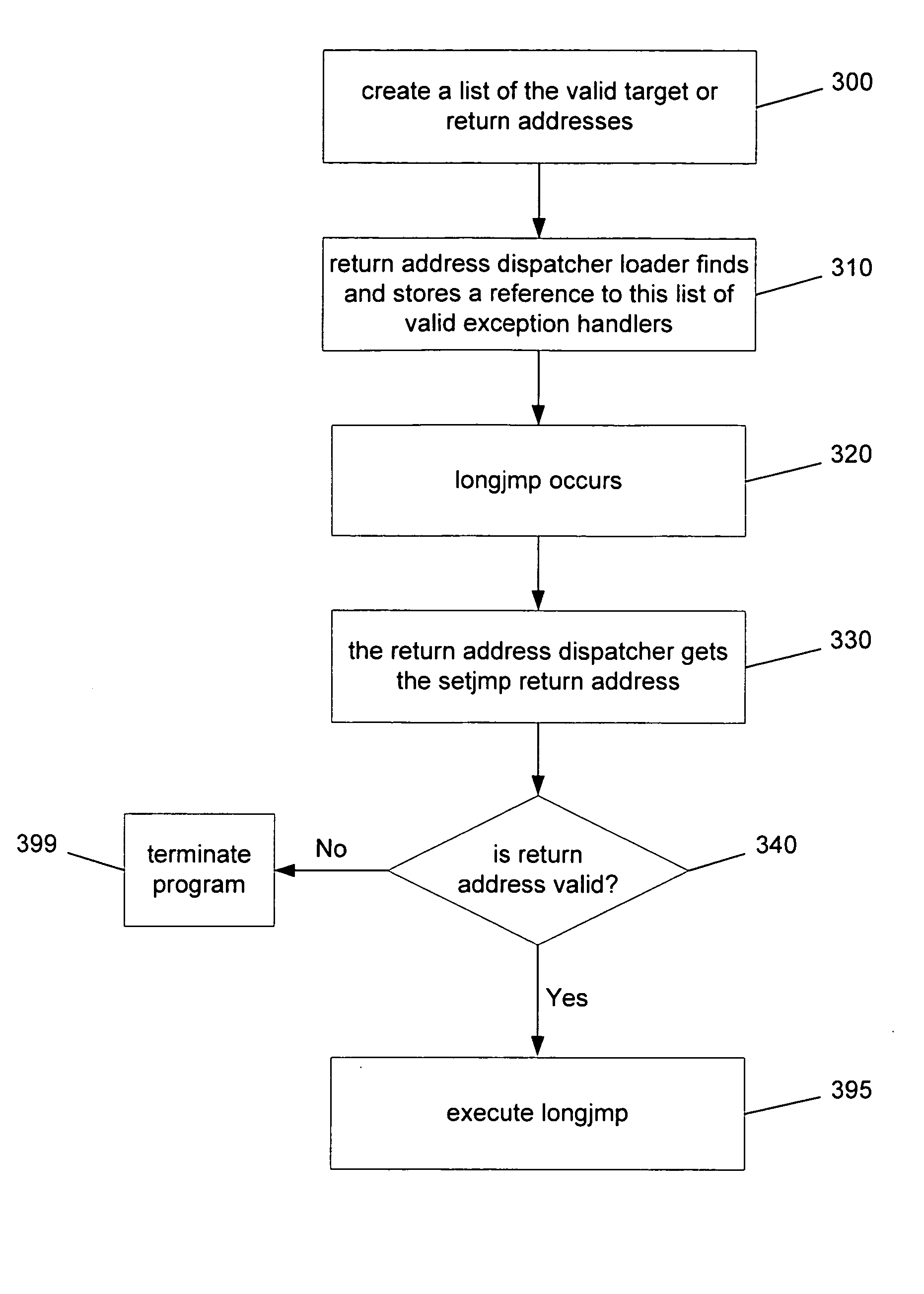
Protection against runtime function attacks
InactiveUS20050144471A1Conservation valueMemory loss protectionUser identity/authority verificationBuffer overflowComputer science
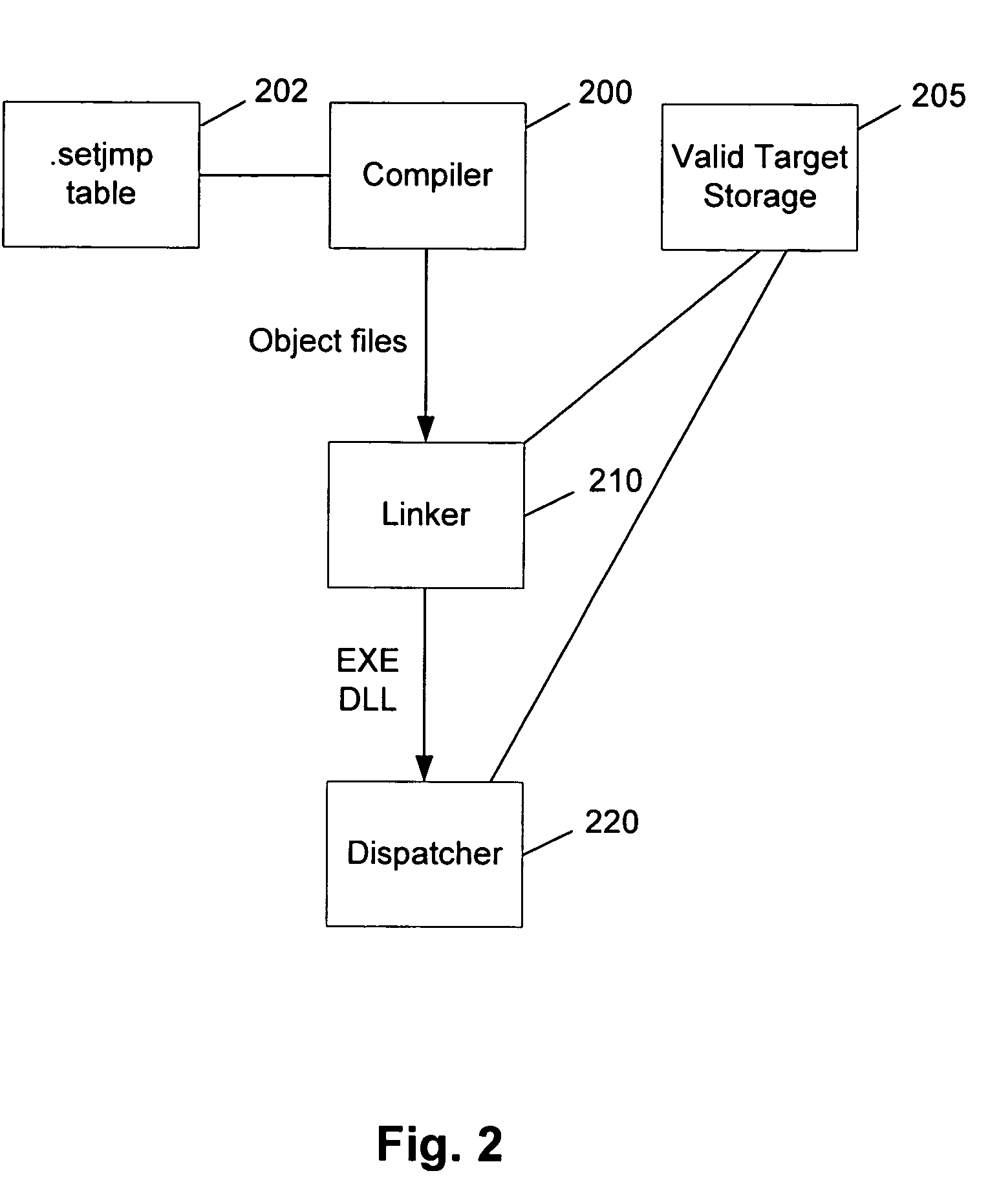
Security mechanisms detect and intervene in a malicious attack against a runtime function, even in the presence of a coding flaw such as a buffer overrun or overflow. One such exemplary mechanism uses a predetermined security list of the valid targets for a first runtime function (such as longjmp). For every call to a second runtime function (e.g., setjmp) that prepares for a later invocation of the first runtime function, the dispatcher finds and stores a reference to this list. When a subsequent attack targets the runtime functions by creating an attacker-provided setjmp target address (e.g., the attack overwrites the longjmp target address so that the pointer points somewhere else, such as code provided by the attacker or code that already exists that will eventually pass control to code provided by the attacker), the new (attacker provided) target address is compared to a reference list of the real (valid) target addresses. The list of real target addresses is stored in memory. If the target address that has been provided is found on the reference list, then the runtime function (e.g., longjmp) is allowed to continue to execute by the dispatcher (which may be the actual runtime function). Otherwise, the dispatcher assumes the application is under attack and terminates the process' execution.
Owner:MICROSOFT TECH LICENSING LLC
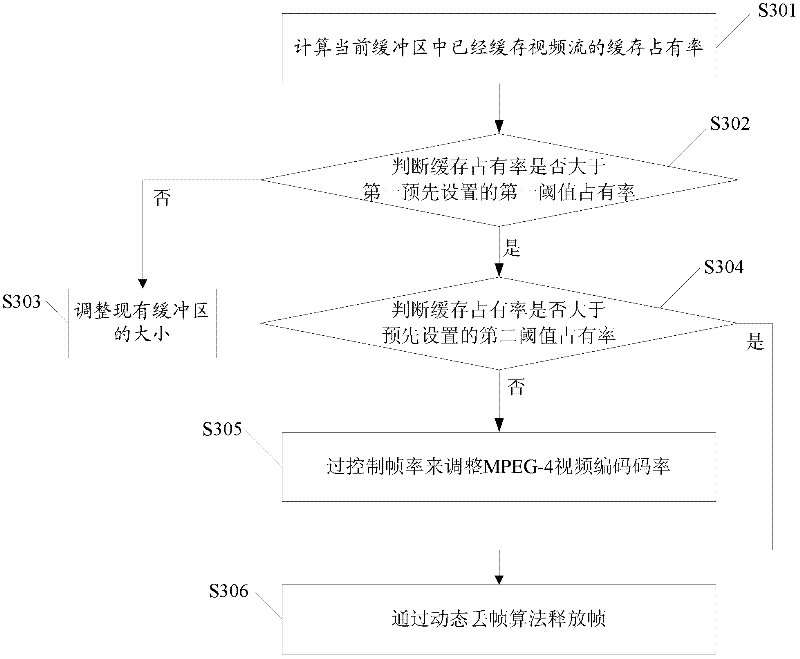
Method and system for configuring buffer area at streaming media server side based on MPEG (Moving Picture Experts Group)-4
InactiveCN102378065APrevent overflowQuality assuranceSelective content distributionOccupancy rateBuffer overflow
The embodiment of the invention discloses a method and system for configuring a buffer area at a streaming media server side based on an MPEG (Moving Picture Experts Group)-4. The method comprises the following steps of: calculating the cache occupancy rate of cached video streaming in the current buffer area; judging whether the cache occupancy rate is greater than a preset first occupancy rate threshold and is smaller than a second occupancy rate threshold, wherein, the second occupancy rate threshold is greater than the first occupancy rate threshold; if the cache occupancy rate is smaller than the first threshold, adjusting the size of the current buffer area; if the cache occupancy rate exceeds the first threshold and is less than the second occupancy rate threshold, adjusting the video coding rate of the MPEG-4 by controlling the frame rate; and if the cache occupancy rate exceeds the second occupancy rate threshold, releasing frames according to a dynamic frame dropping algorithm. The method and the system have the beneficial effects that on the premise of ensuring no drop frame as far as possible, buffer overflow can be well prevented and effective decoding rate can be improved by dynamically configuring the capacity of the buffer area and adjusting the decoding rate of the frames, thus further improving the video quality.
Owner:江西省南城县网信电子有限公司
Methods for combating malicious software
A method for combating malware monitors all attempts by any software executing on a computer to write data to the computer's digital storage medium and records details of the attempts in a system database having a causal tree structure. The method also intercepts unauthorized attempts by executing objects to modify the memory allocated to other executing objects or to modify a selected set of protected objects stored on the digital storage medium, and may also intercept write attempts by executing objects that have a buffer overflow or that are executing in a data segment of memory. The method may include a procedure for switching the computer into a quasi-safe mode that disables all non-essential processes. Preferably, the database is automatically organized into software packages classified by malware threat level. Entire or packages or portions thereof may be easily selected and neutralized by a local or remote user.
Owner:ROBOT GENIUS
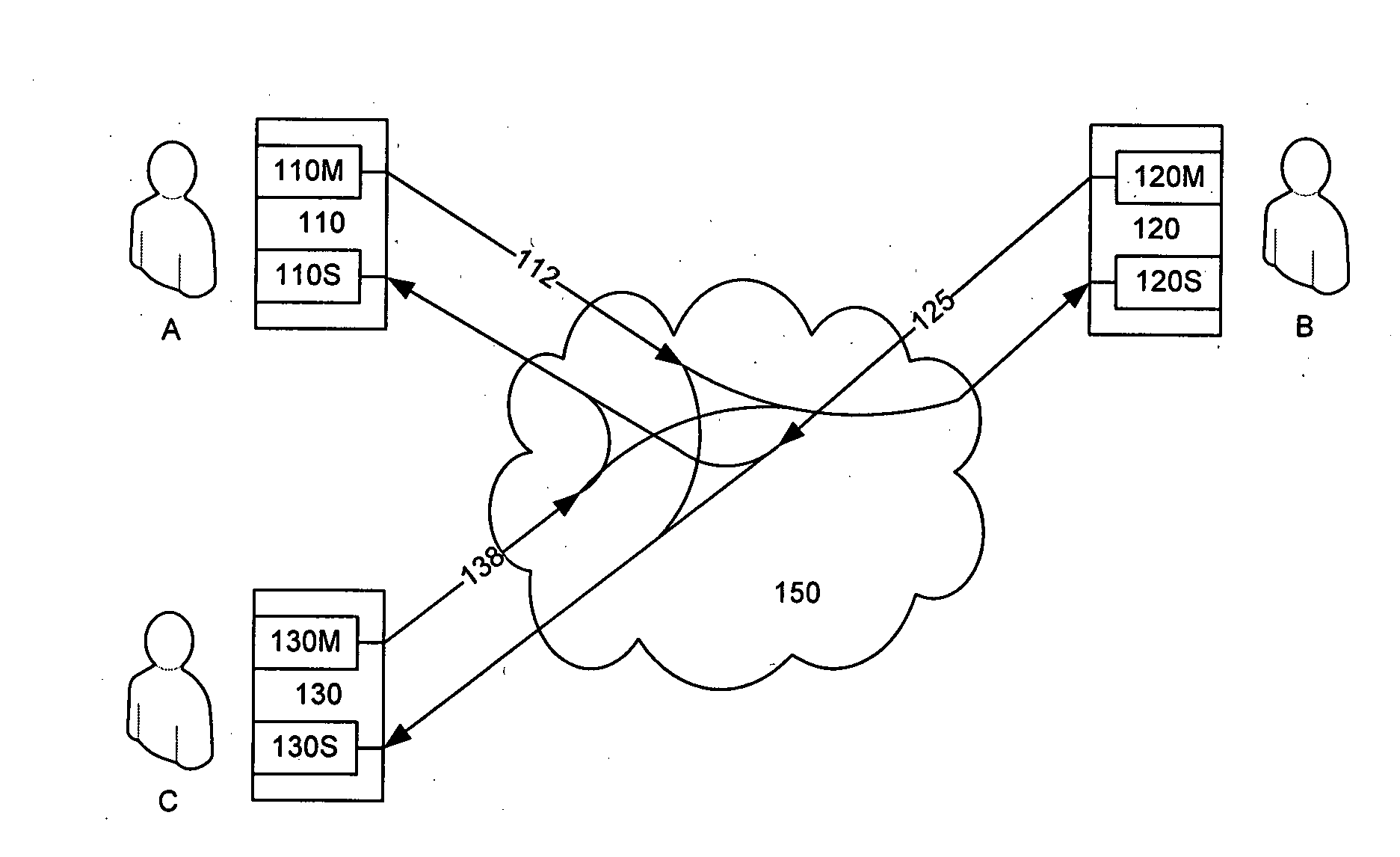
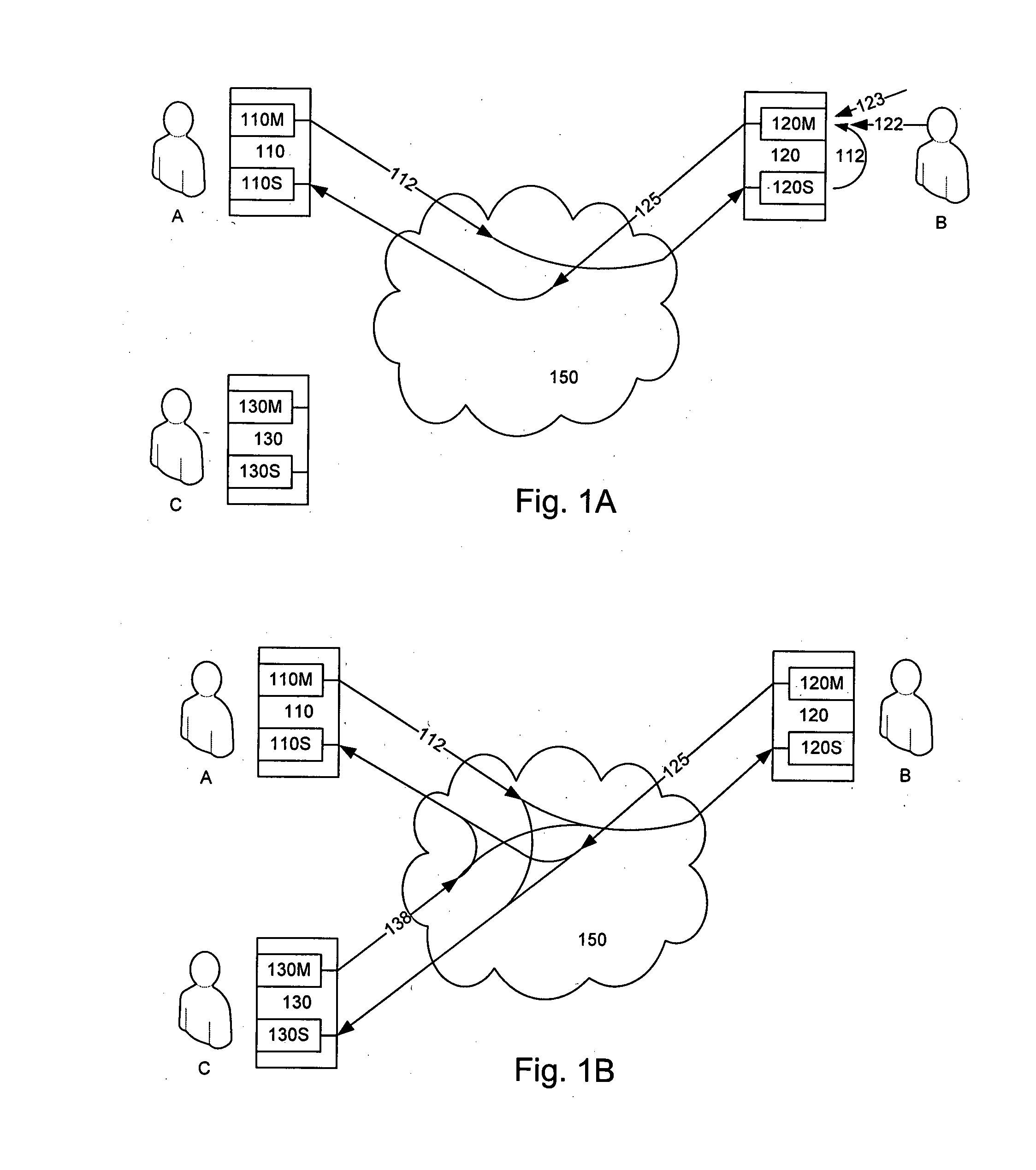
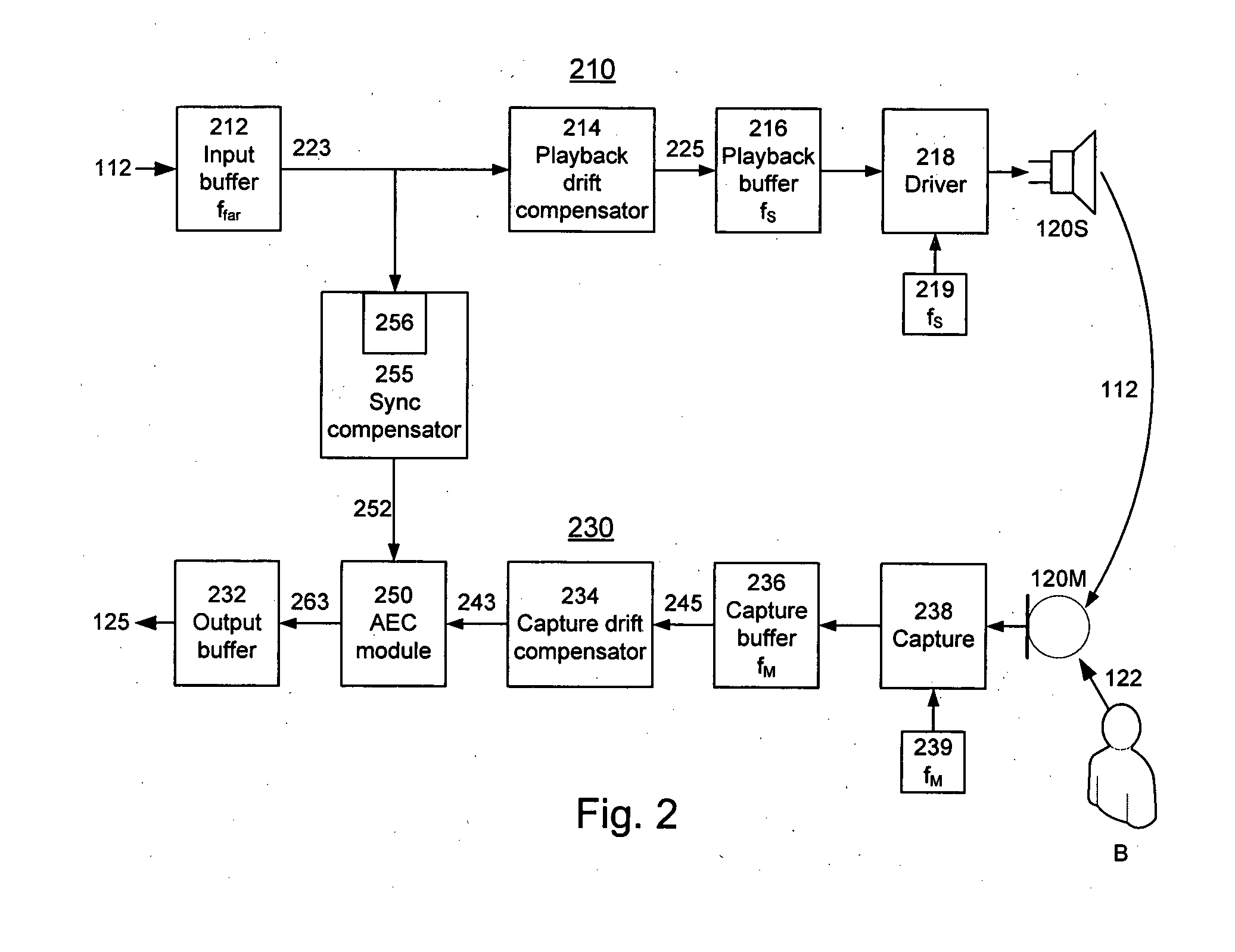
Audio Acoustic Echo Cancellation for Video Conferencing
ActiveUS20130002797A1Two-way loud-speaking telephone systemsTelevision conference systemsProximal pointBuffer overflow
A new audio echo cancellation (AEC) approach is disclosed. To facilitate echo cancellation, the method adjusts for errors (called drift) in sampling rates for both capturing audio and playing audio. This ensures that the AEC module receives both the signals at precisely the same sampling frequency. Furthermore, the far-end signal and near-end mixed signal are time aligned to ensure that the alignment is suitable for application of AEC techniques. An additional enhancement to reduce errors utilizes a concept of native frequency. A by-product of drift compensation allows for excellent buffer control for capture / playback and buffer overflow / underflow errors from drift errors are eliminated.
Owner:RED HAT
Method for detecting web page Trojan horse based on program execution characteristics
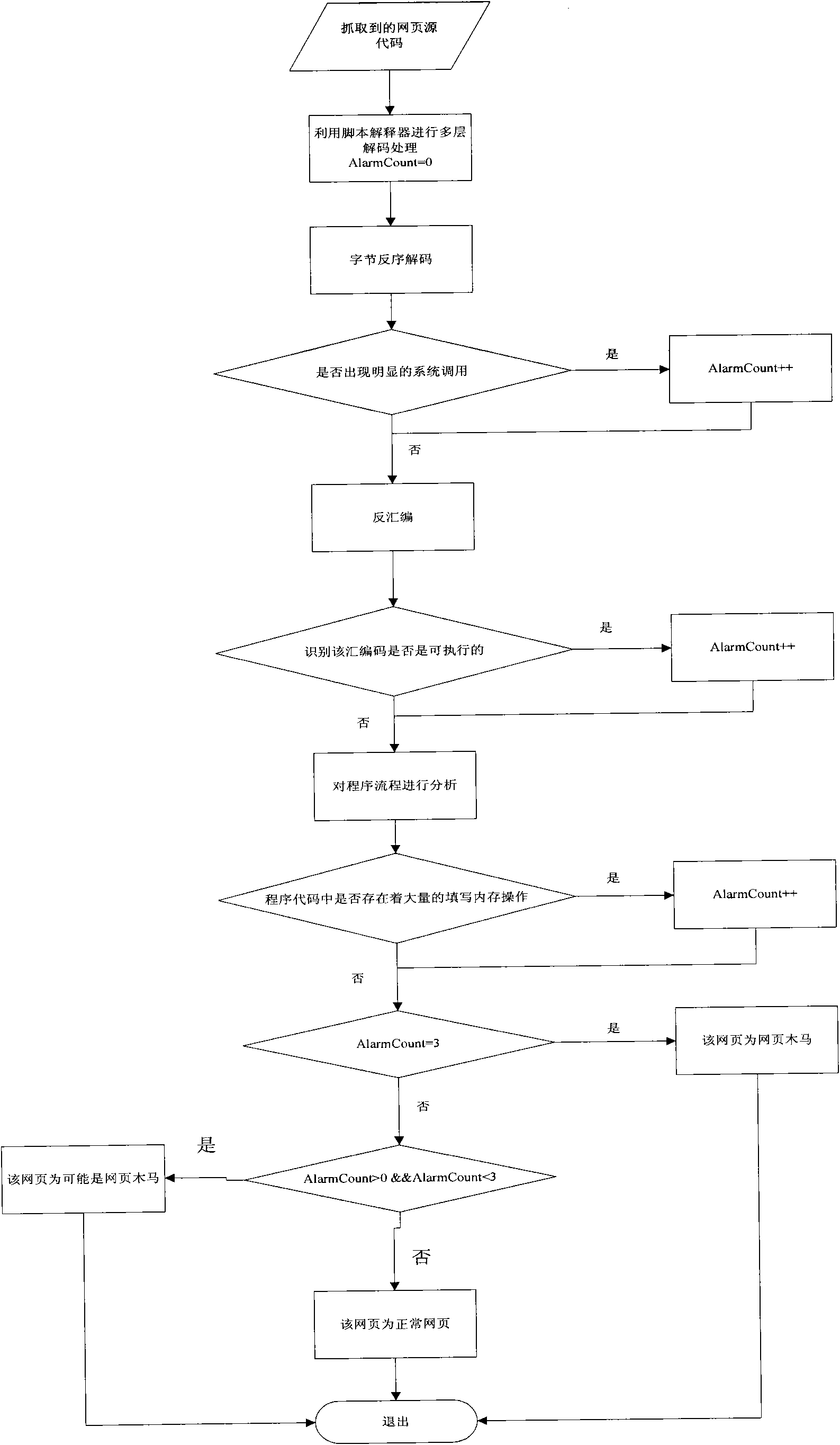
InactiveCN101673326AReduce missed detection rateReduce false detection ratePlatform integrity maintainanceSpecial data processing applicationsWeb siteBuffer overflow
The invention belongs to the field of computer security, and relates to a method for detecting web page Trojan horse based on program execution characteristics, which comprises the following steps: using web crawlers to capture source codes of a web page; then obtaining a recognizable script program through multilevel decoding; carrying out disassembling processing on the script program to obtainassembled source codes while reserving the script program; then, judging whether a large number of filled invalid instructions, calling system level functions and obvious URL links exist in the sourcecodes; and finally detecting whether the Trojan horse exists in the web page through the assembled source codes in a deep level. Because most of the prior web pages with the Trojan horse are embeddedwith ShellCode, to execute the ShellCode in the web pages in a local computer, system vulnerability is needed to realize buffer overflow and enable the program to skip onto the ShellCode code segment. Thus, only by analyzing the condition of executing the ShellCode, and analyzing the source codes according to the execution characteristics, whether the web page to be detected is the web page Trojan horse can be quickly detected.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
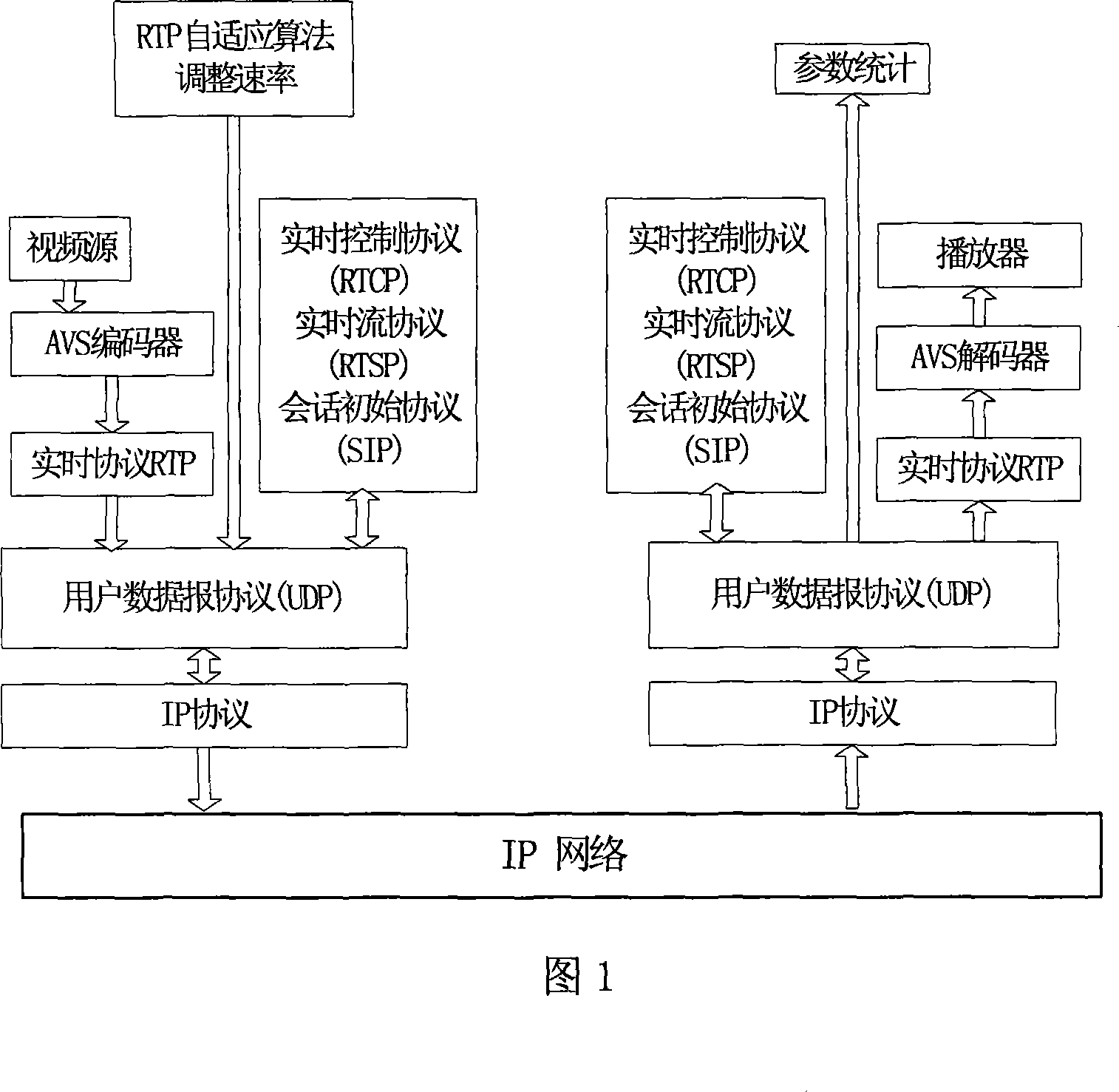
Method for controlling AVS fluid-medium transmission
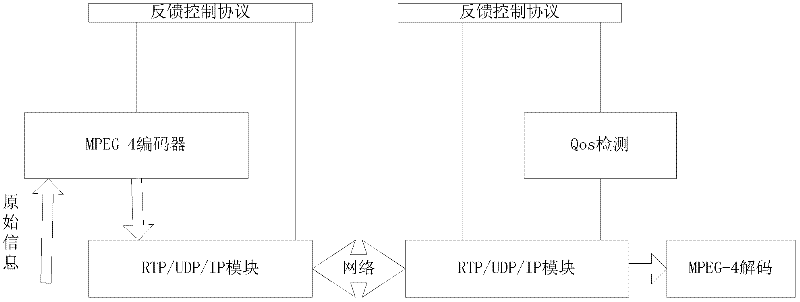
InactiveCN101075957ASuppress overflowGuaranteed service qualityData switching networksQuality of serviceVideo transmission
The method comprises: counting the output rate of the buffer at receiving end; estimating the sending rate of the sending end; feeding back it to the send end via RTCP; at send end, the estimated transmission rate and the transmission rate returned from the receiving end are compared in order to adjust the transmission rate. The invention controls the buffer overflow and keeps the Quos of video transmission.
Owner:SHANGHAI UNIV
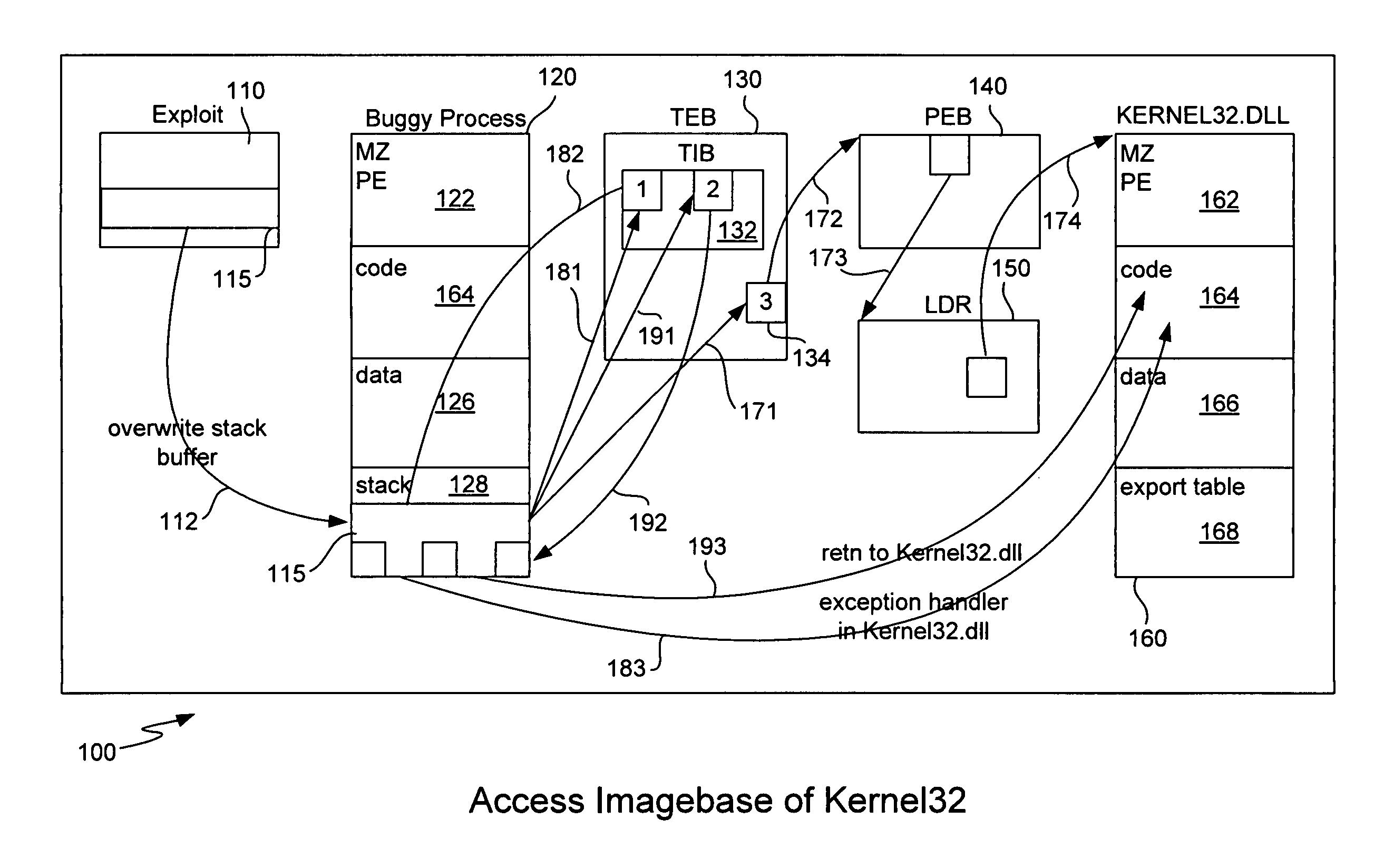
Generic shellcode detection
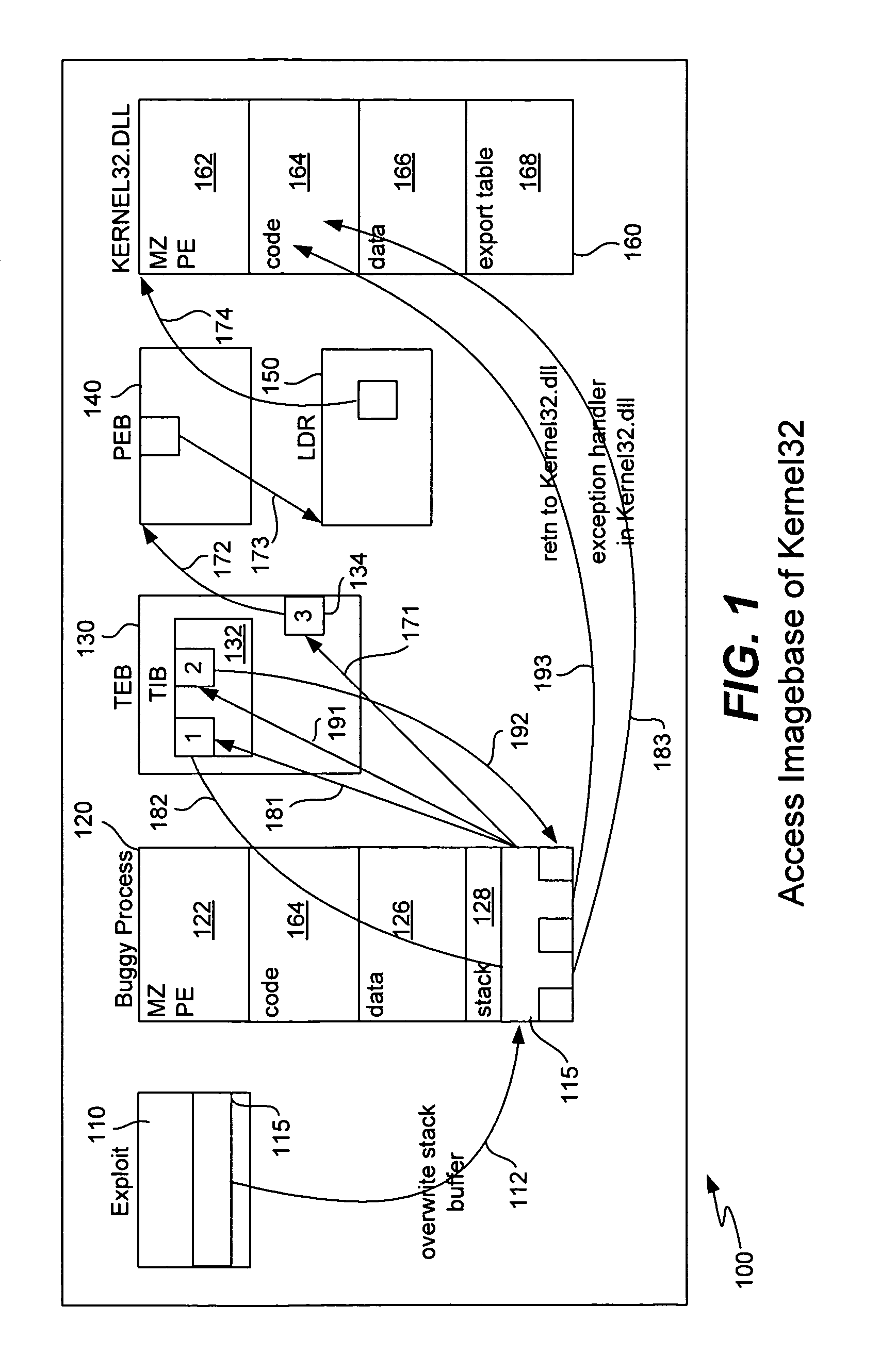
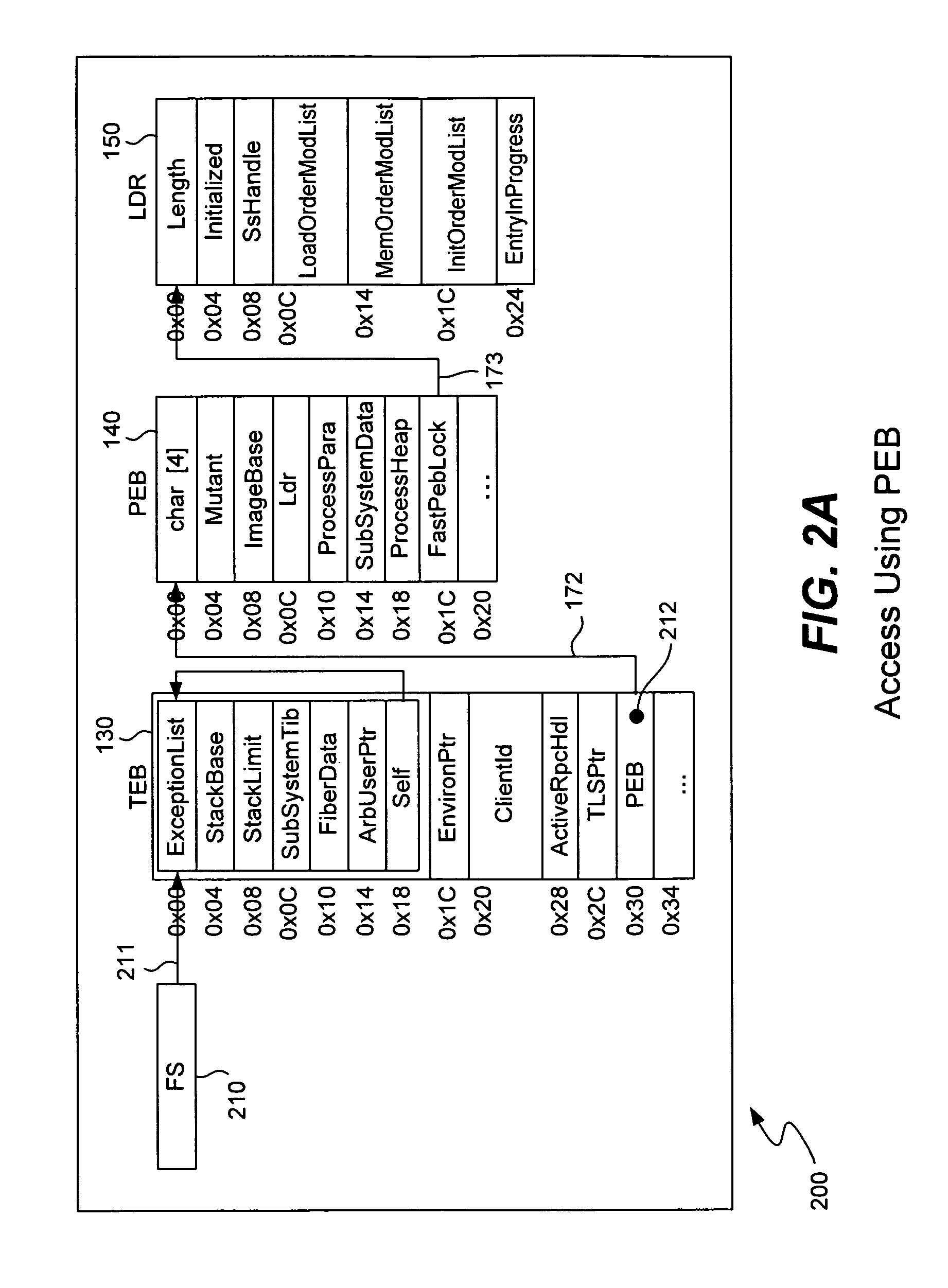
ActiveUS8307432B1Quick analysisImprove the detection rateMemory loss protectionError detection/correctionBuffer overflowShellcode
Detecting buffer-overflow exploits scans generically for shellcode without using virus signatures and maintains close to a zero false-positive rate. Shellcode is detected generically without determining specifically which buffer-overflow exploit is being used. Protection is offered against unknown buffer-overflow exploits. A file is scanned to determine if a vulnerable buffer in that file includes suspect code that has characteristics of shellcode. Next, it is determined if the suspect code contains a routine to find the imagebase of Kernel32.dll using any of the techniques of PEB, TOS or SEH (process environment block, top of stack or structured exception handling). It is next determined if the suspect code contains a routine to search for APIs in the export table of kernel32.dll. Techniques for analyzing the suspect code include static analysis and executing the code in an emulator. A high sensitivity setting determines that shellcode is present when any of the techniques of PEB, TOS or SEH are found.
Owner:TREND MICRO INC
Signature-free buffer overflow attack blocker
ActiveUS20080022405A1Negligible throughput degradationTransparent to serverMemory loss protectionError detection/correctionData packExperimental research
A real-time, signature-free, blocker prevents buffer overflow attacks. The system and method, called SigFree, can filter out code injection buffer overflow attack packets targeting at various Internet services such as web services. Motivated by the observation that buffer overflow attacks typically contain executables whereas legitimate client requests never contain executables in most Internet services, SigFree blocks attacks by checking, without any preknowledge of the real attacks, if “executable” instruction sequences can be blindly disassembled and extracted from a packet. Being signature-free, the invention can block new and unknown buffer overflow attacks. It is immunized from almost every attack-side code obfuscation method, and transparent to the servers being protected. The approach is therefore suited to economical Internet-wide deployment with very low deployment and maintenance costs. SigFree can also handle encrypted SSL packets. An experimental study shows that SigFree can block all types of code-injection attack packets without yielding any false positives or false negatives. Moreover, SigFree causes negligible throughput degradation to normal client requests.
Owner:PENN STATE RES FOUND
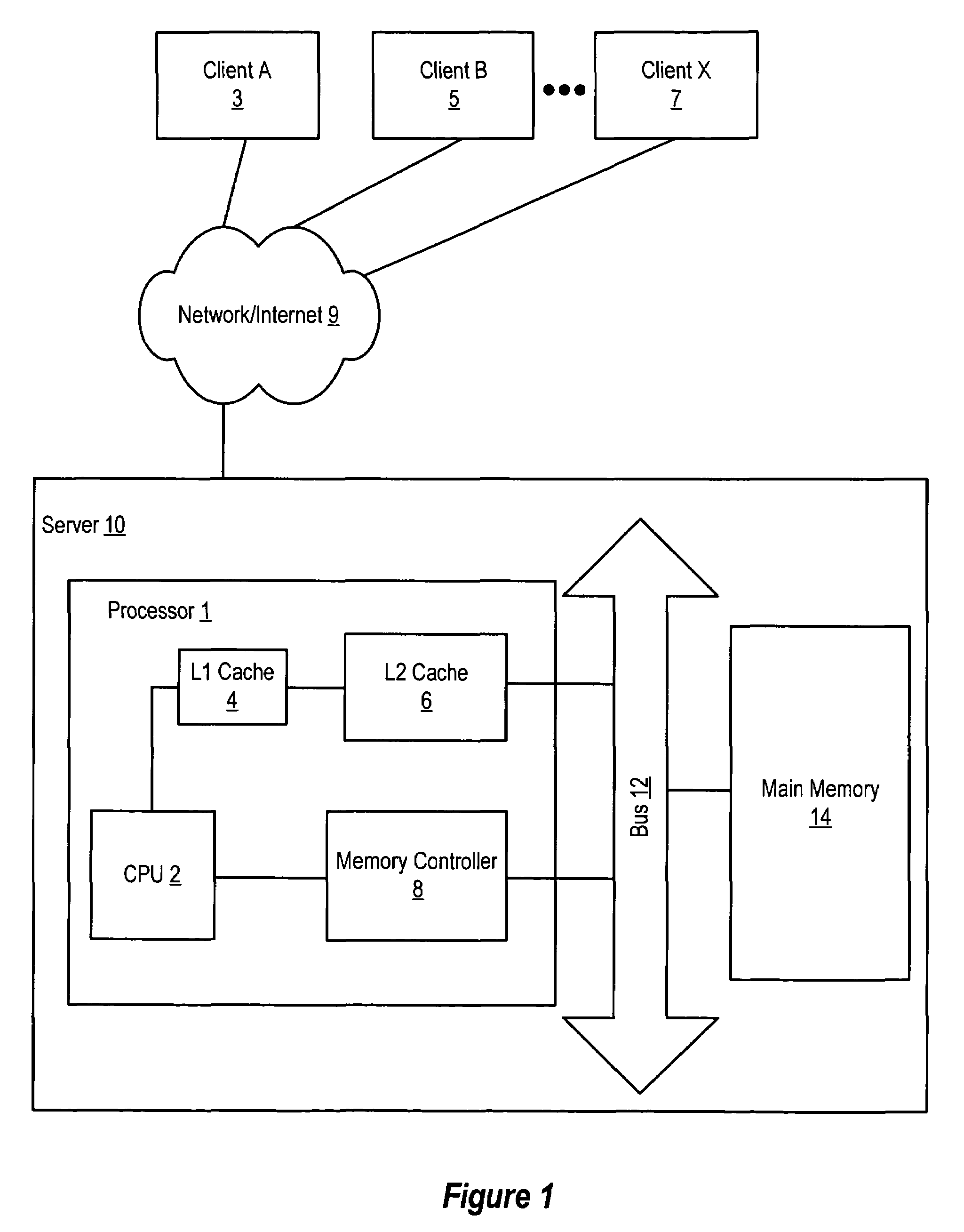
Efficient utilization of a store buffer using counters
ActiveUS7519796B1Efficient processingMinimizes store buffer sizeDigital computer detailsSpecific program execution arrangementsBuffer overflowPower usage
An apparatus and method for efficiently managing store buffer operations is described in connection with a multithreaded multiprocessor chip. A CMT processor keeps track of stores by maintaining two store counters in the instruction fetch unit (IFU). A speculative store counter in the IFU tracks stores in flight to the store buffer as well as stores already in the store buffer. A committed store counter in the IFU tracks the number of stores actually in the store buffer. The store buffer provides allocate and deallocate signals to accurately maintain the committed store counter. The IFU stops issuing stores to the store buffer once the speculative counter has reached a threshold value. Upon a flush, the IFU sets the speculative counter equal to the committed store counter. In this way, an efficient feedback mechanism is provided for preventing store buffer overflow that minimizes the store buffer size, operations time and power usage.
Owner:ORACLE INT CORP
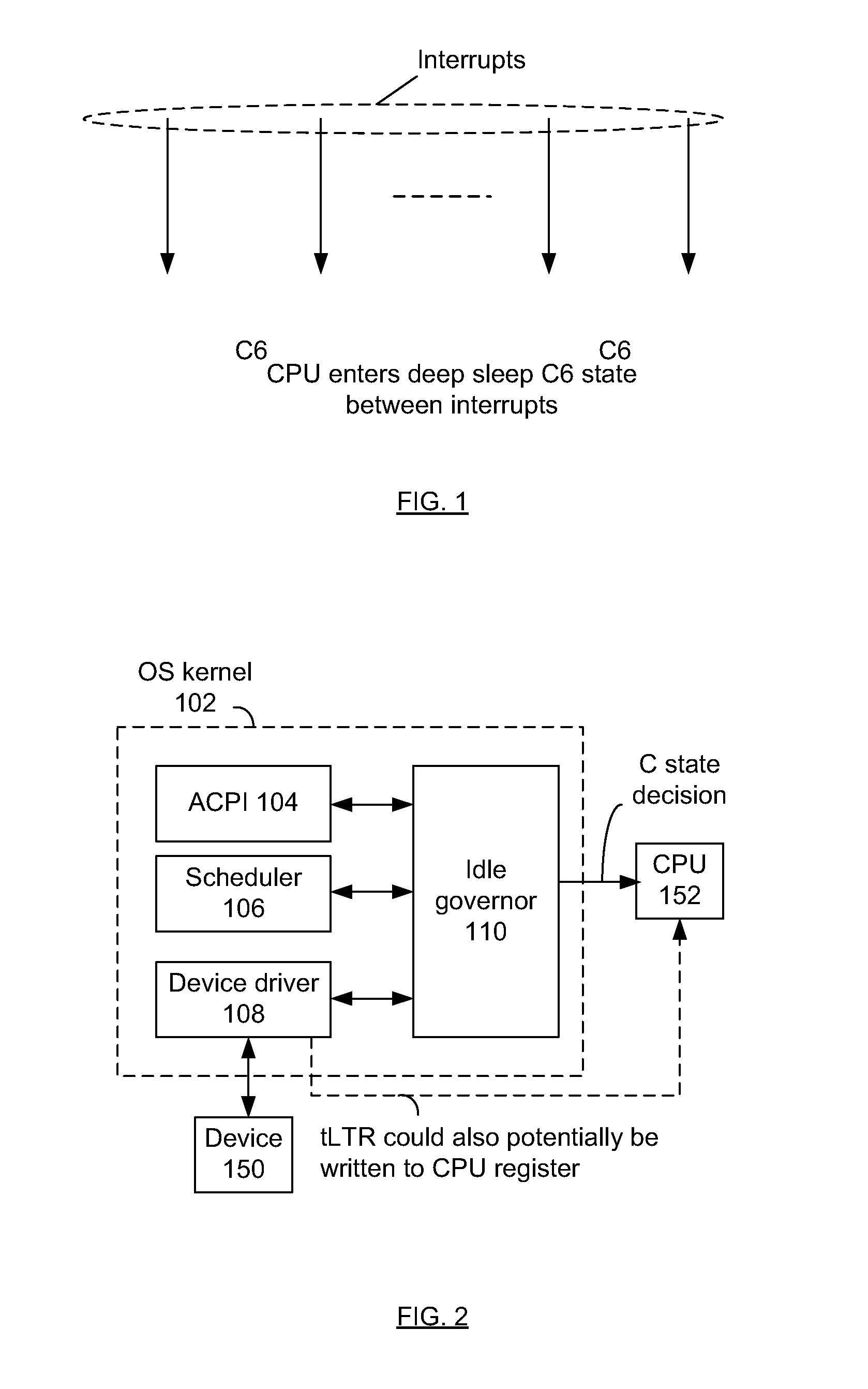
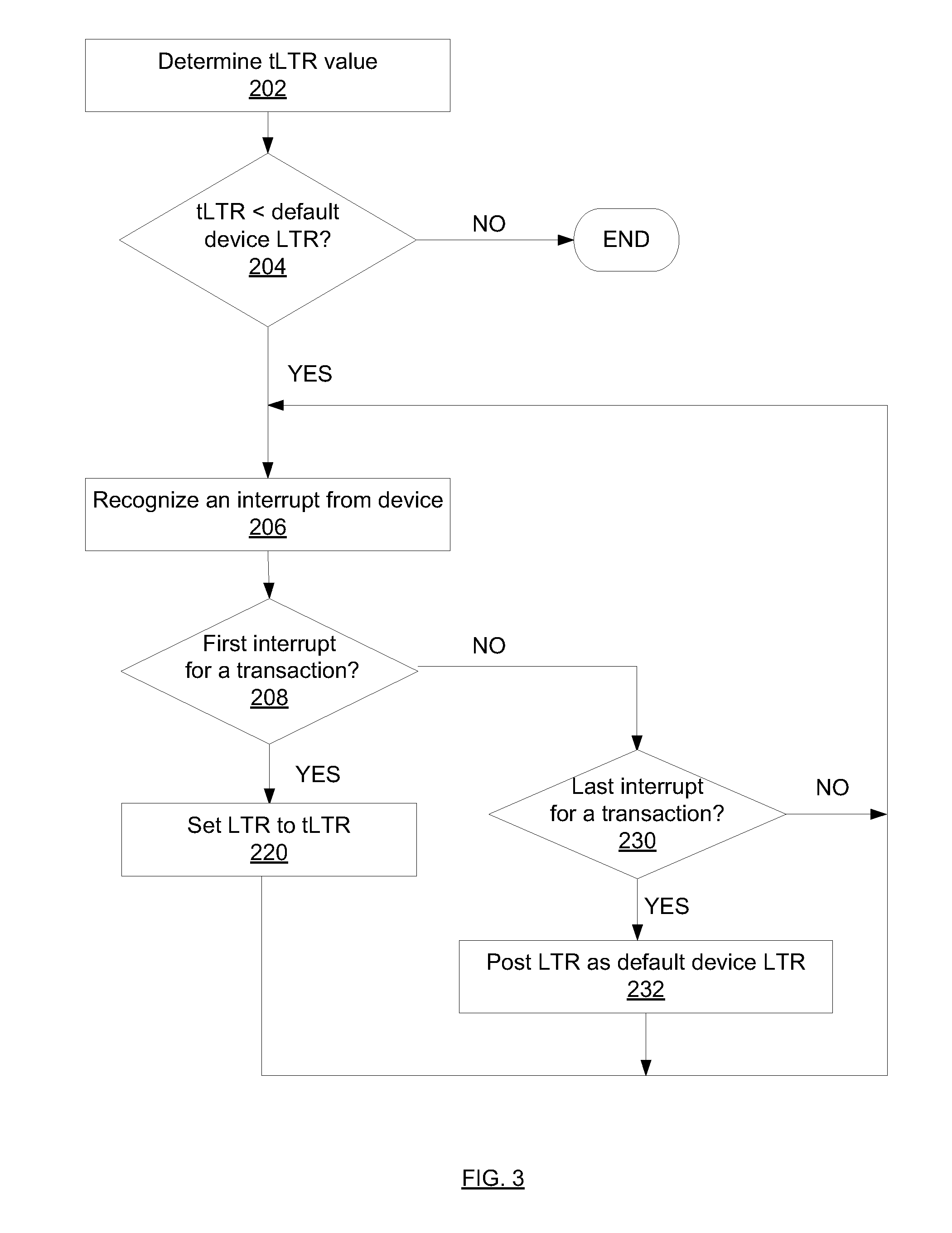
Techniques for managing power consumption state of a processor
InactiveUS20120210032A1Energy efficient ICTDigital data processing detailsSleep stateBuffer overflow
Techniques are described for determining a temporary latency tolerance report (tLTR) value. A processing unit has to respond to a device interrupt within a duration specified by tLTR to ensure no incoming data is lost due to device buffer overflow. The tLTR value can be used to prevent the processing unit from entering too deep a sleep state when a device driver anticipates multiple sequential interrupts for a transaction.
Owner:INTEL CORP
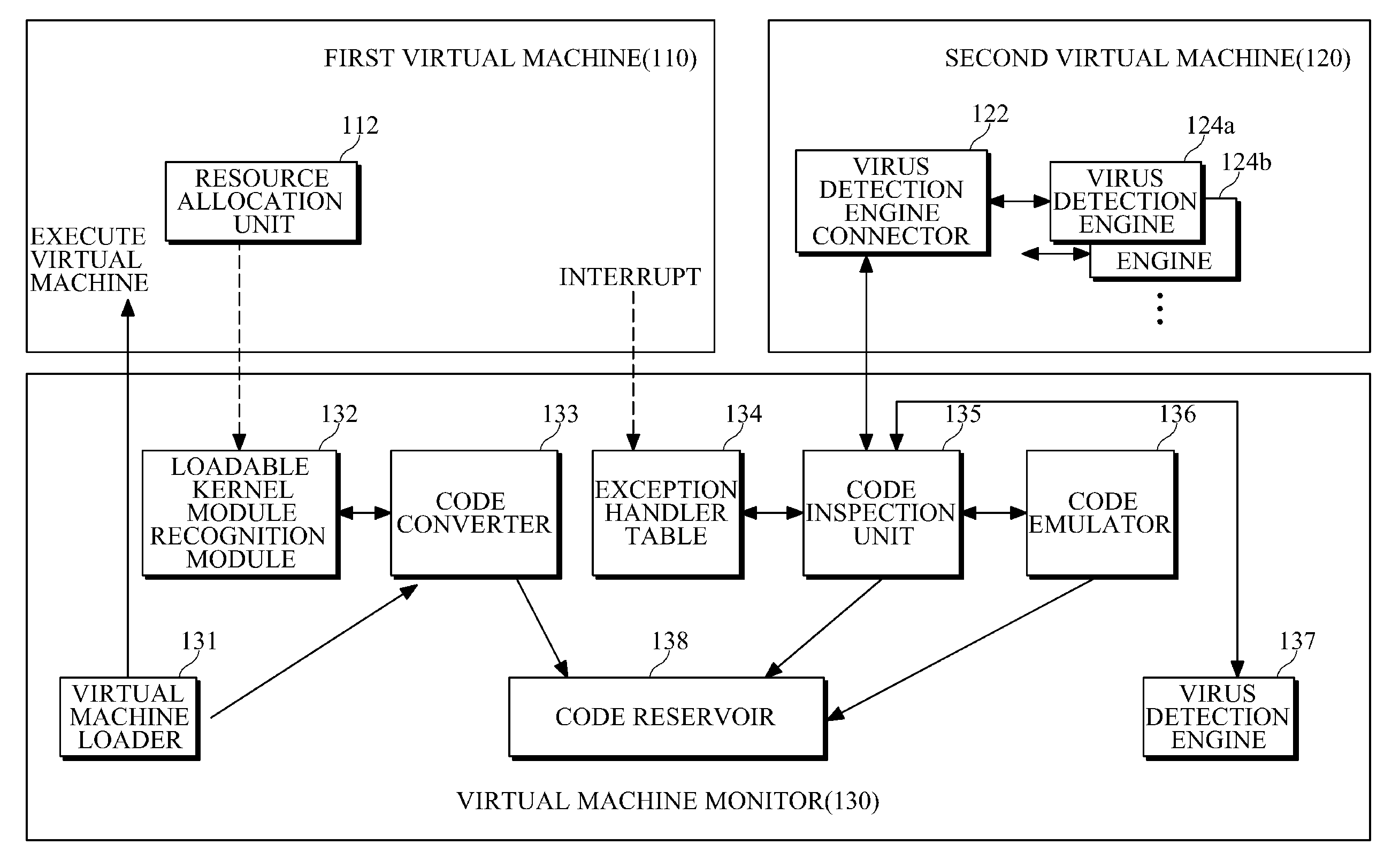
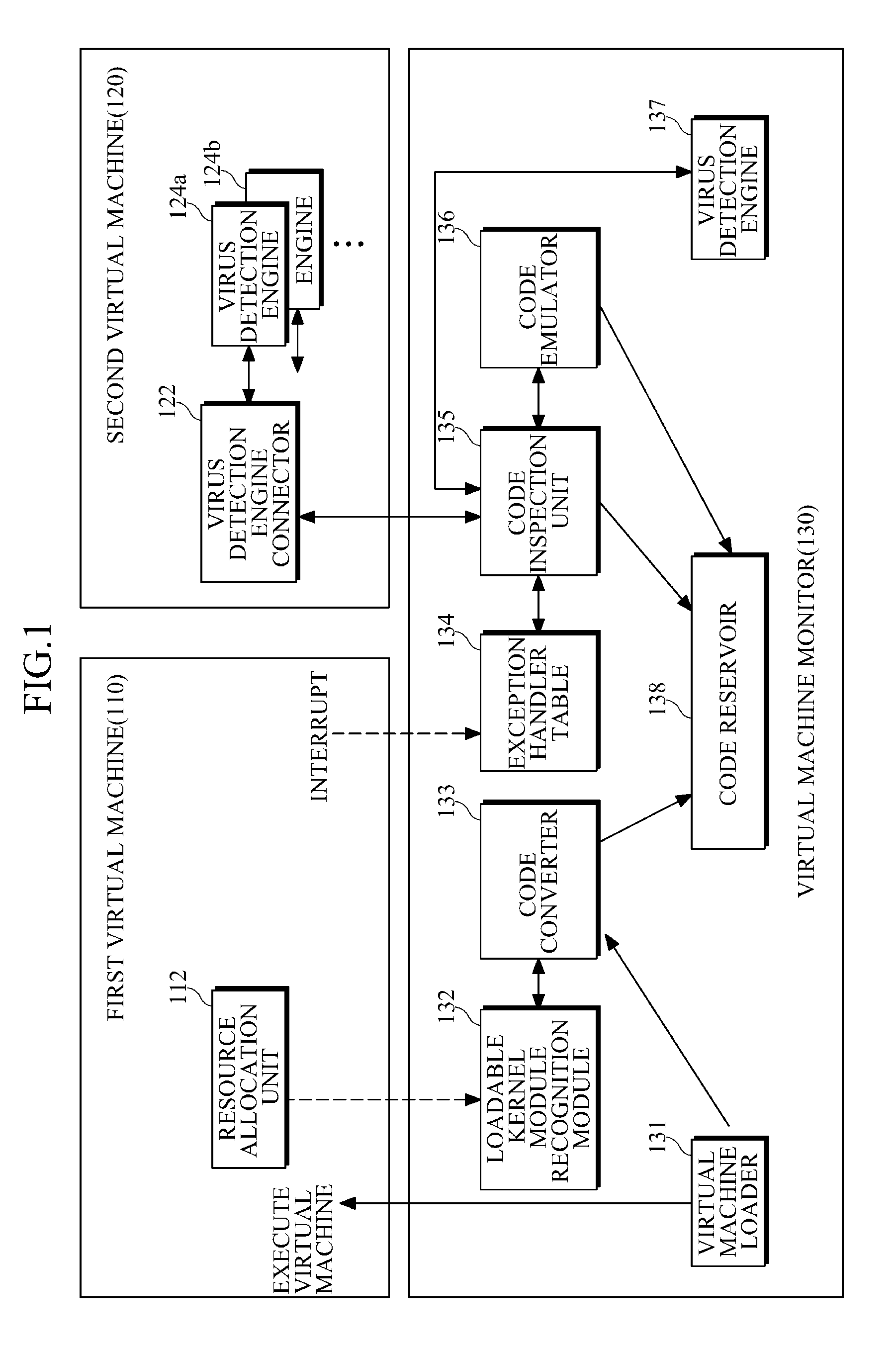
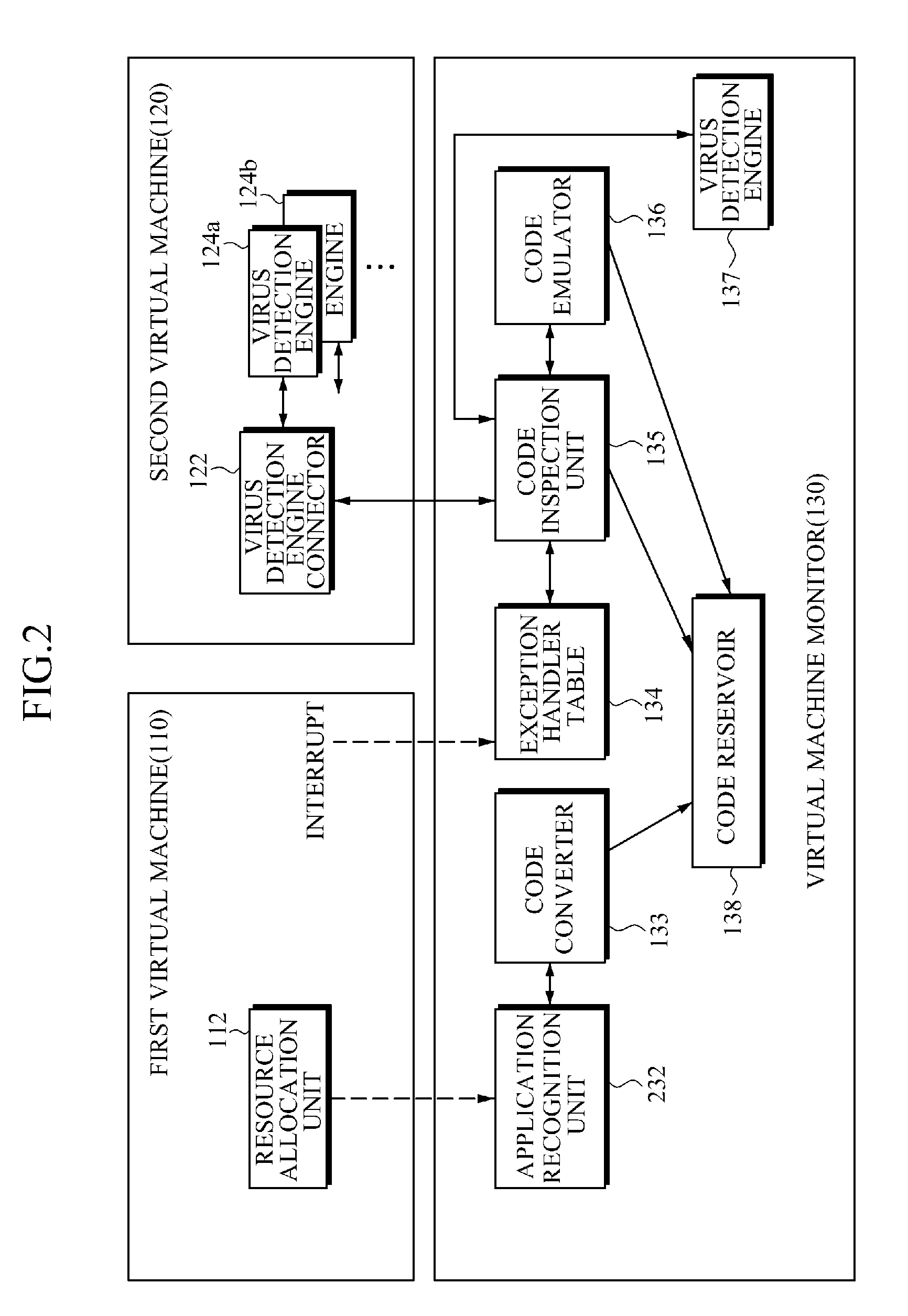
Apparatus and method for preventing virus code execution
An apparatus and method for preventing virus code execution through buffer overflow management are provided. When buffer overflow occurs during execution of a kernel module or application program, the apparatus and method may perform virus inspection on a program execution region moved by the buffer overflow.
Owner:SAMSUNG ELECTRONICS CO LTD
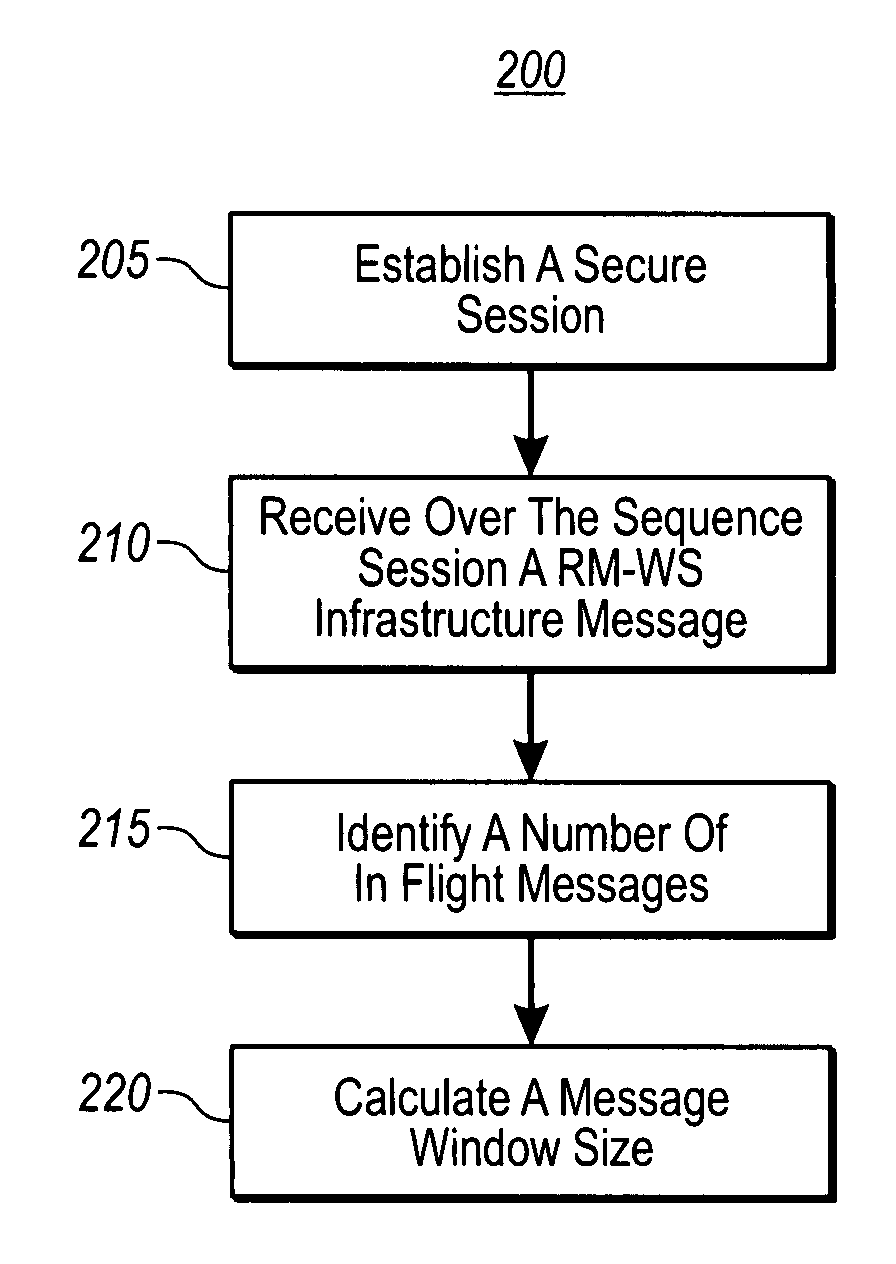
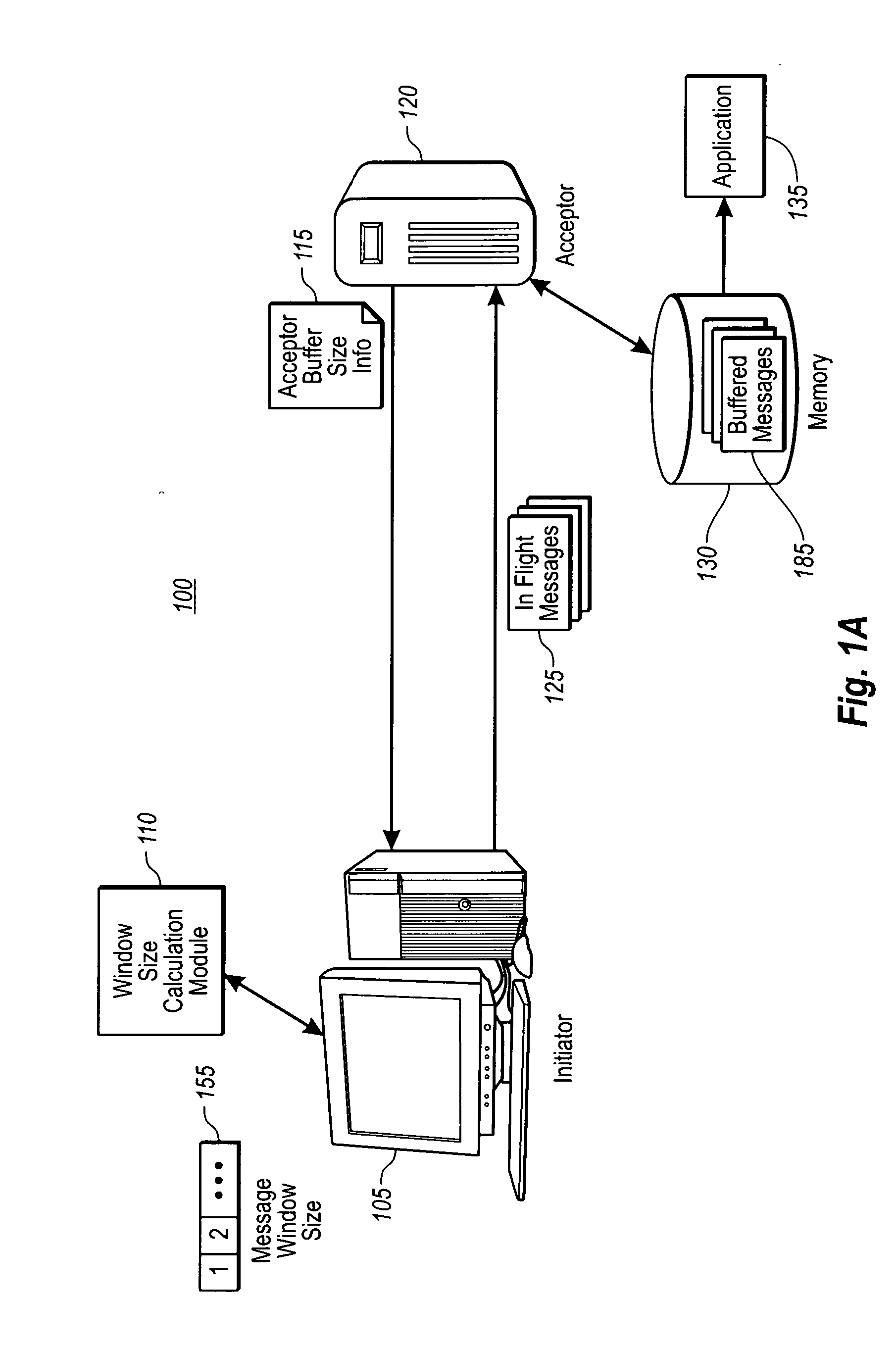
Efficient transfer of messages using reliable messaging protocols for web services
InactiveUS20060133278A1Efficiently transferring messageControlling network congestionData processing applicationsError preventionReliable messagingBuffer overflow
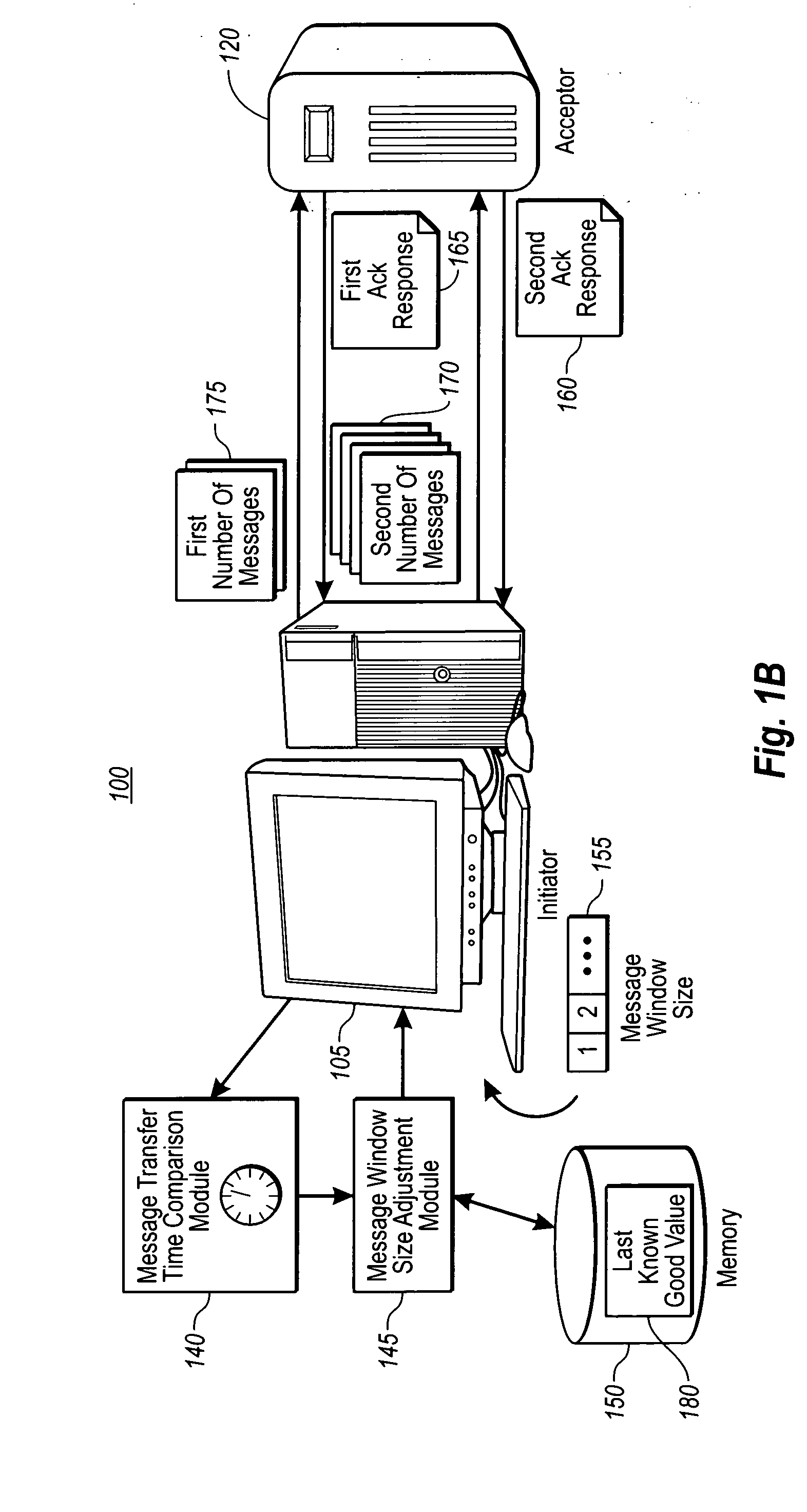
The present invention provides for flow and congestion control mechanisms in accordance with a Reliable Message protocol for Web Services (RM-WS). For flow control, one endpoint informs another endpoint of its available buffer size by including buffer size information in response messages. The response messages, typically RM-WS infrastructure messages, are then used to determine an upper limit on the number of messages that can be sent to the acceptor in order to prevent resending messages due to buffer overrun. In the case of congestion control, embodiments provide for increasing the number of in-flight messages until a failure point is found. The last successful rate below the failure point is the closest known point to the optimum point. Example embodiments then reset and try again raising the rate back to the last known good point and fine tuning from there using an algorithm that asymptotes the optimum rate.
Owner:MICROSOFT TECH LICENSING LLC
Method of performing rate control for a compression system
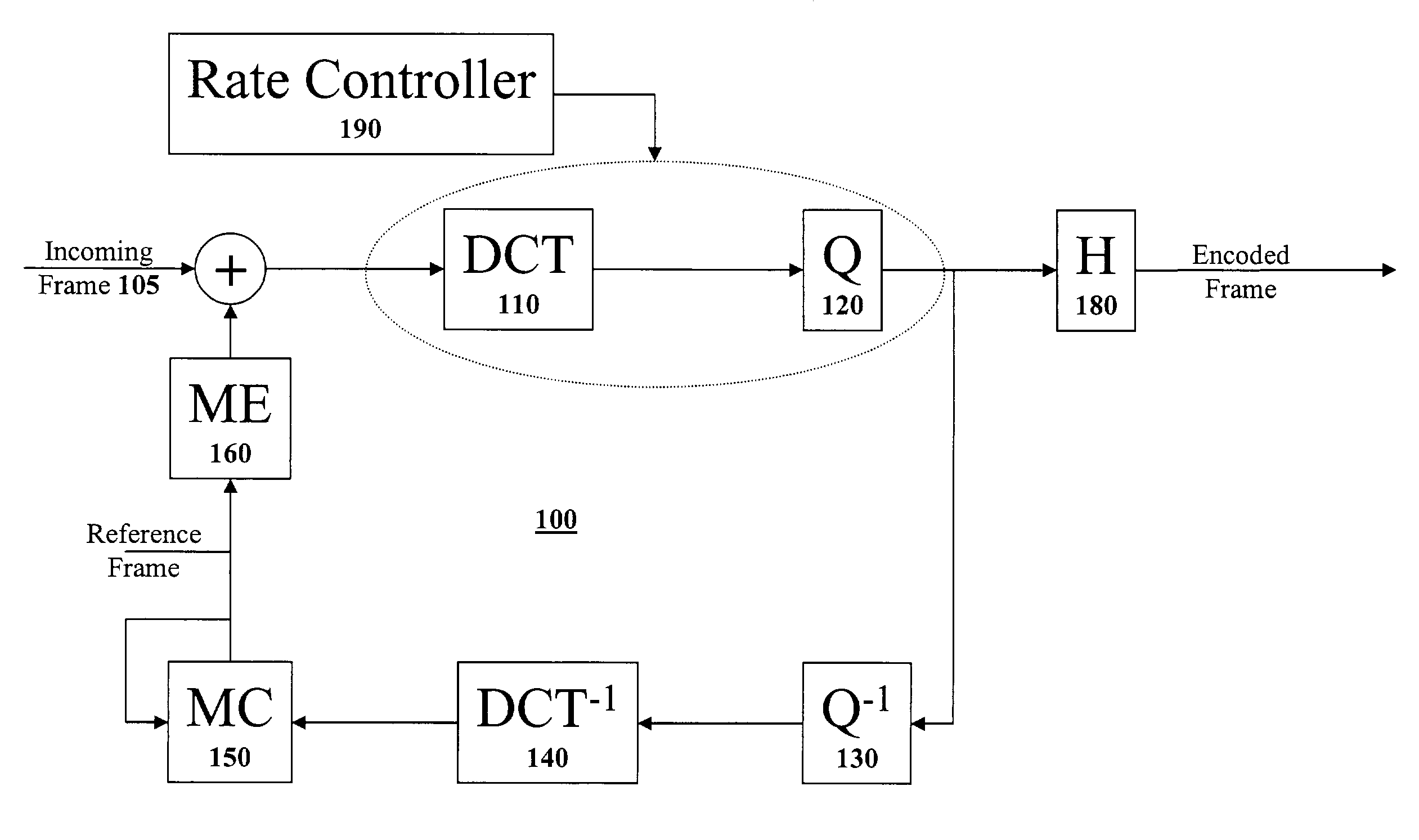
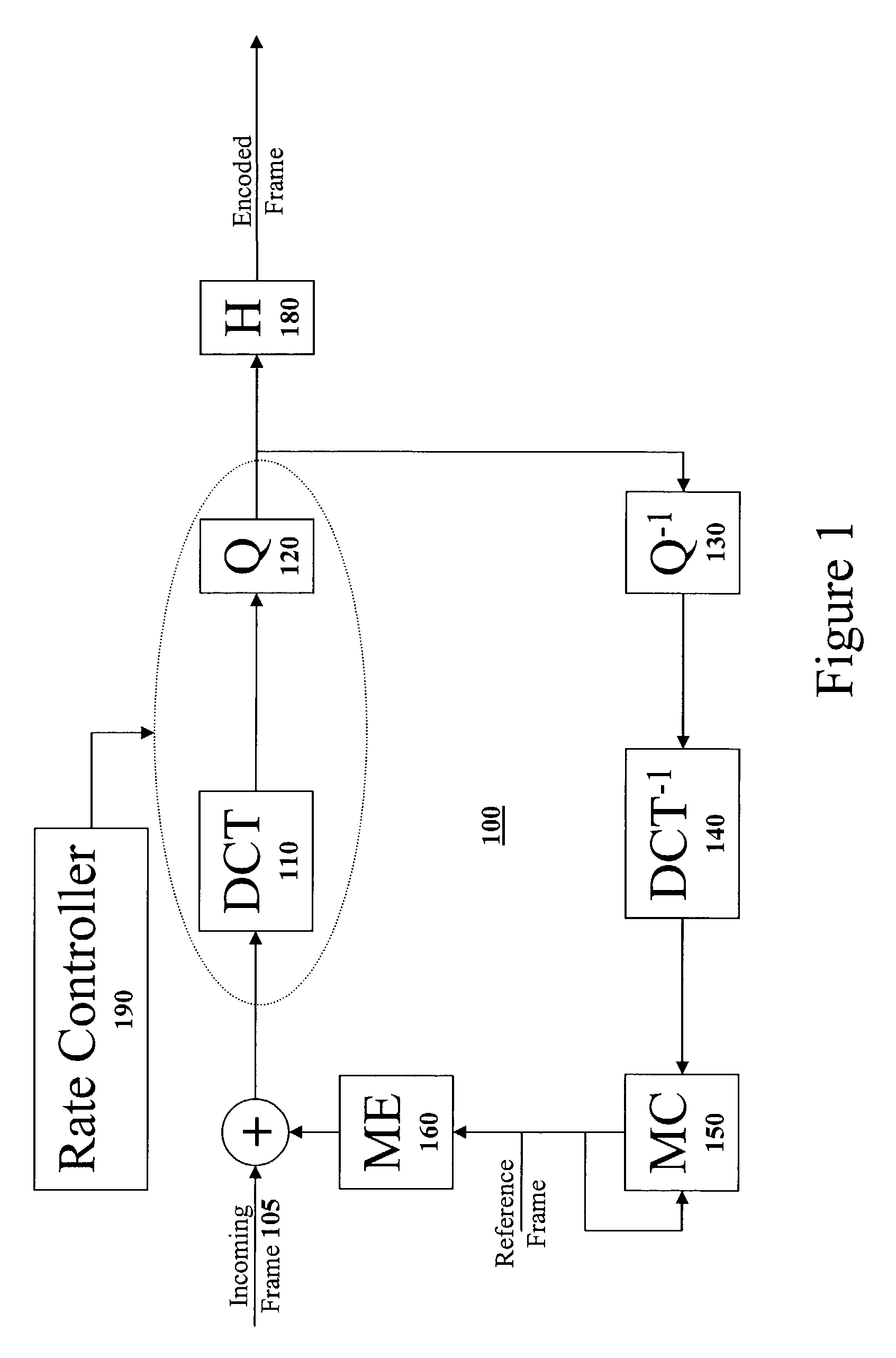
ActiveUS7418037B1Color television with pulse code modulationColor television with bandwidth reductionBuffer overflowVideo quality
A rate controller for allocating a bit budget for video frames to be encoded is disclosed. The rate controller of the present invention considers many different factors when determining the frame bit budget including: desired video quality, target bit rate, frame type (intra-frame or inter-frame), frame duration, intra-frame frequency, frame complexity, intra-block frequency within an intra-frame, buffer overflow, buffer underflow, and the encoded video frame quality for a possible second pass.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com