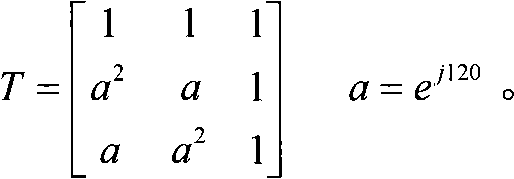Patents
Literature
766 results about "System recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
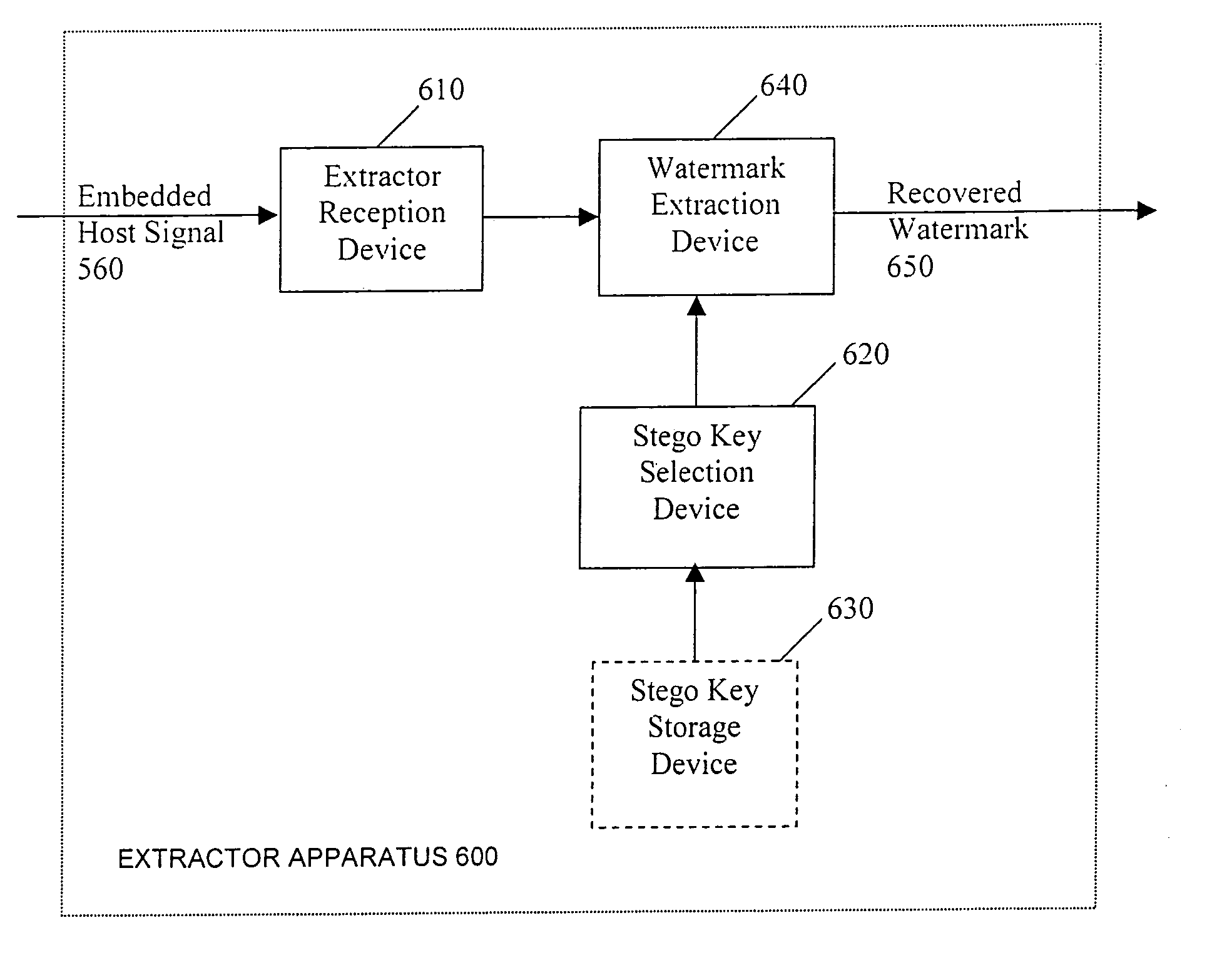
System reactions to the detection of embedded watermarks in a digital host content
InactiveUS7369677B2Increase payload capacitySacrificing complexityUser identity/authority verificationSpeech analysisSystem requirementsSystem recovery
Methods for adapting the operation of a system in response to the detection of embedded watermarks from a digital host content are provided. A digital host content is received and examined for the presence of watermarks. In response to the detection of embedded watermarks and in accordance with the value, type, density or spacing of the detected watermarks, one or more system reactions may take place. These reactions include conditionally allowing the system to resume its normal operation, prohibiting the system from resuming its normal operation, degrading the quality of the digital host content or changing the security status of the digital host content. In response to the extraction of weak watermarks that do not meet the desired system requirements, the extraction operation may be modified or extended to enable the detection of strong watermarks.
Owner:IP ACQUISITIONS LLC
Performing operating system recovery from external back-up media in a headless computer entity
InactiveUS6845464B2Redundant operation error correctionMemory systemsHard disc driveOperational system
A computer entity, particularly but not exclusively a headless computer entity, has operating systems stored on a non-volatile data storage device e.g. a hard disk drive, and has a back-up data storage device. Operating system backup's are taken from an uncorrupted copy of an operating system stored in a separate partition on the data storage device to the primary operating system which is actually used to run the device, thereby ensuring that if the primary operating system of the computer entity becomes corrupted either gradually or catastrophically, the back-up copy which is stored on a back-up media is not effected. Under failure conditions of the computer entity, a pristine copy of the operating system can be reloaded from the back-up tape data storage media and the computer entity rebooted from the pristine operating system back-up copy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
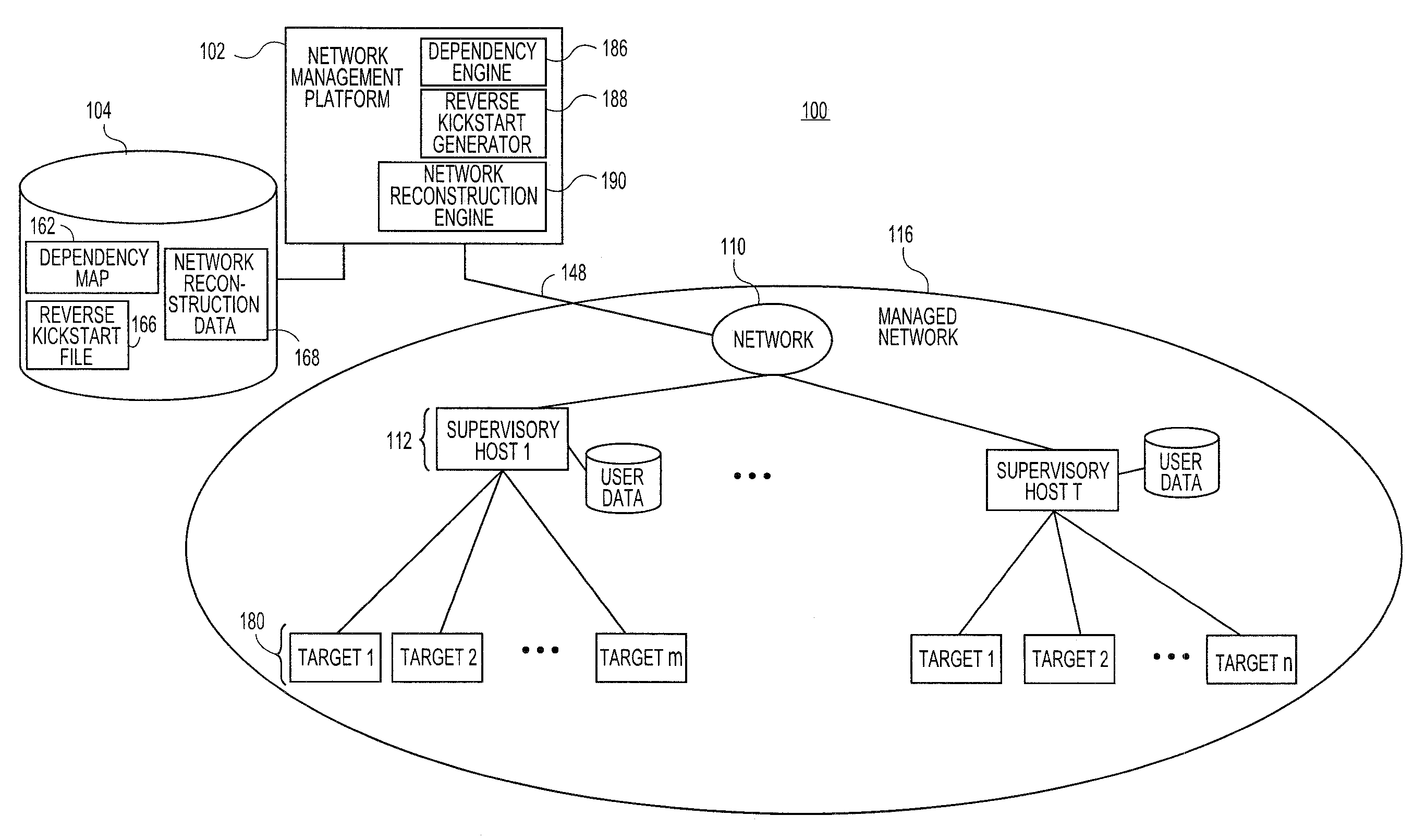
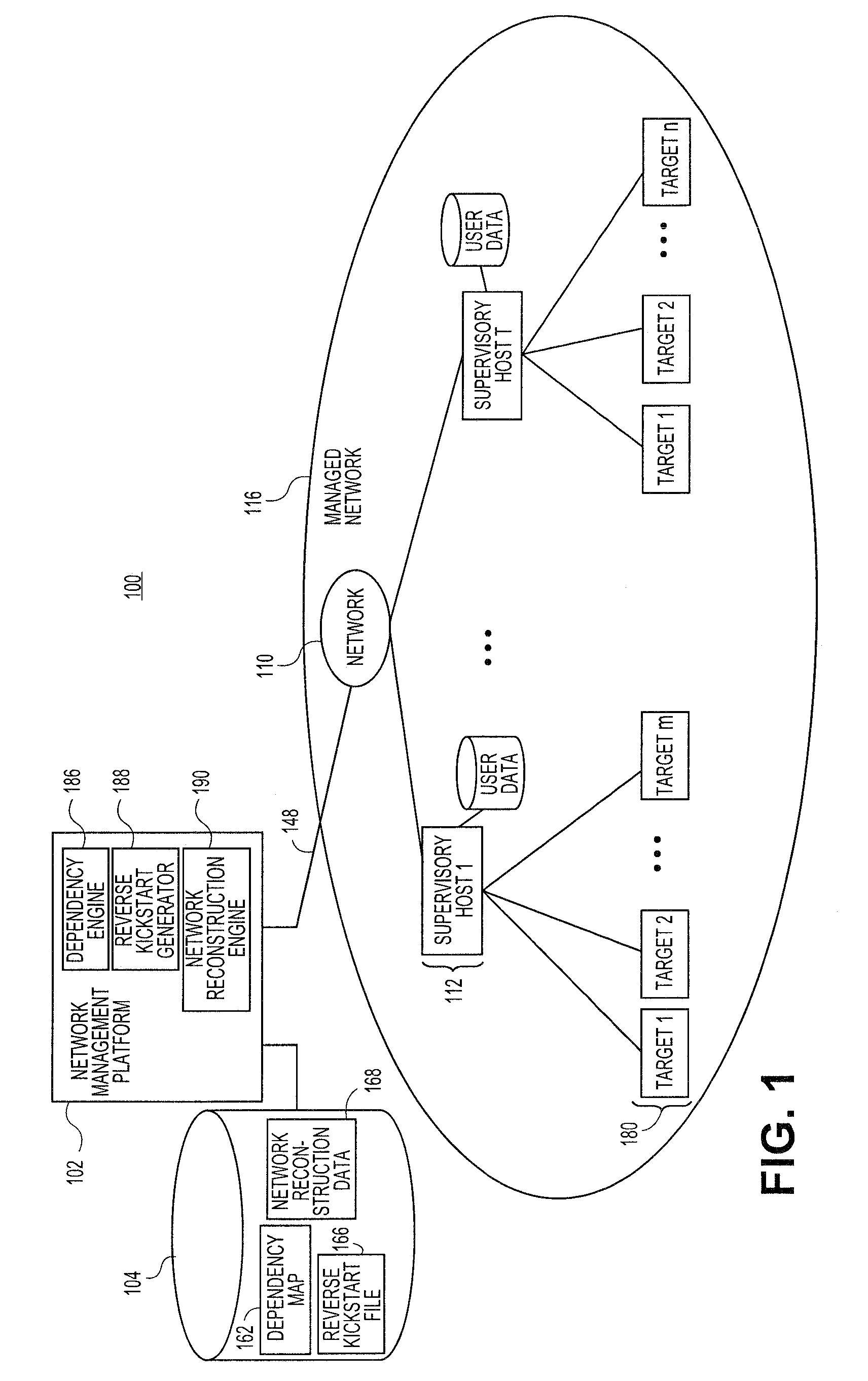
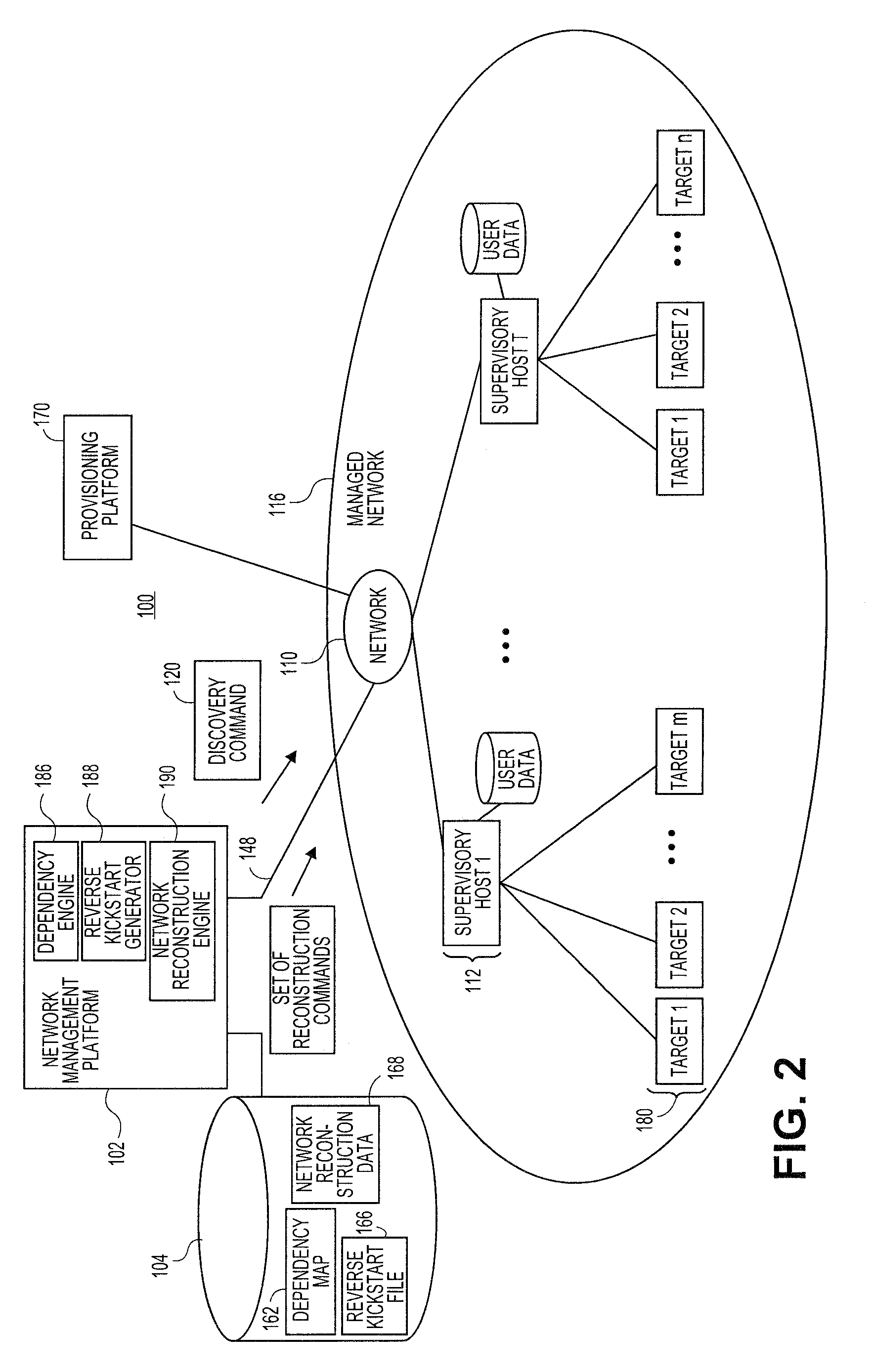
Systems and methods for automatically generating system restoration order for network recovery
Embodiments relate to systems and methods for automatically generating a system restoration order for network recovery. A set of managed machines, such as personal computers or servers, can be managed by a network management platform communicating with the machines via a secure channel. The network management platform can access a dependency map indicating a required order for restoration of machines or nodes on a network. The network management platform likewise access a reverse kickstart file for each machine to be automatically restored in order to ensure proper functioning of the network, and extract a current configuration of that machine for purposes of restoring the overall network.
Owner:RED HAT
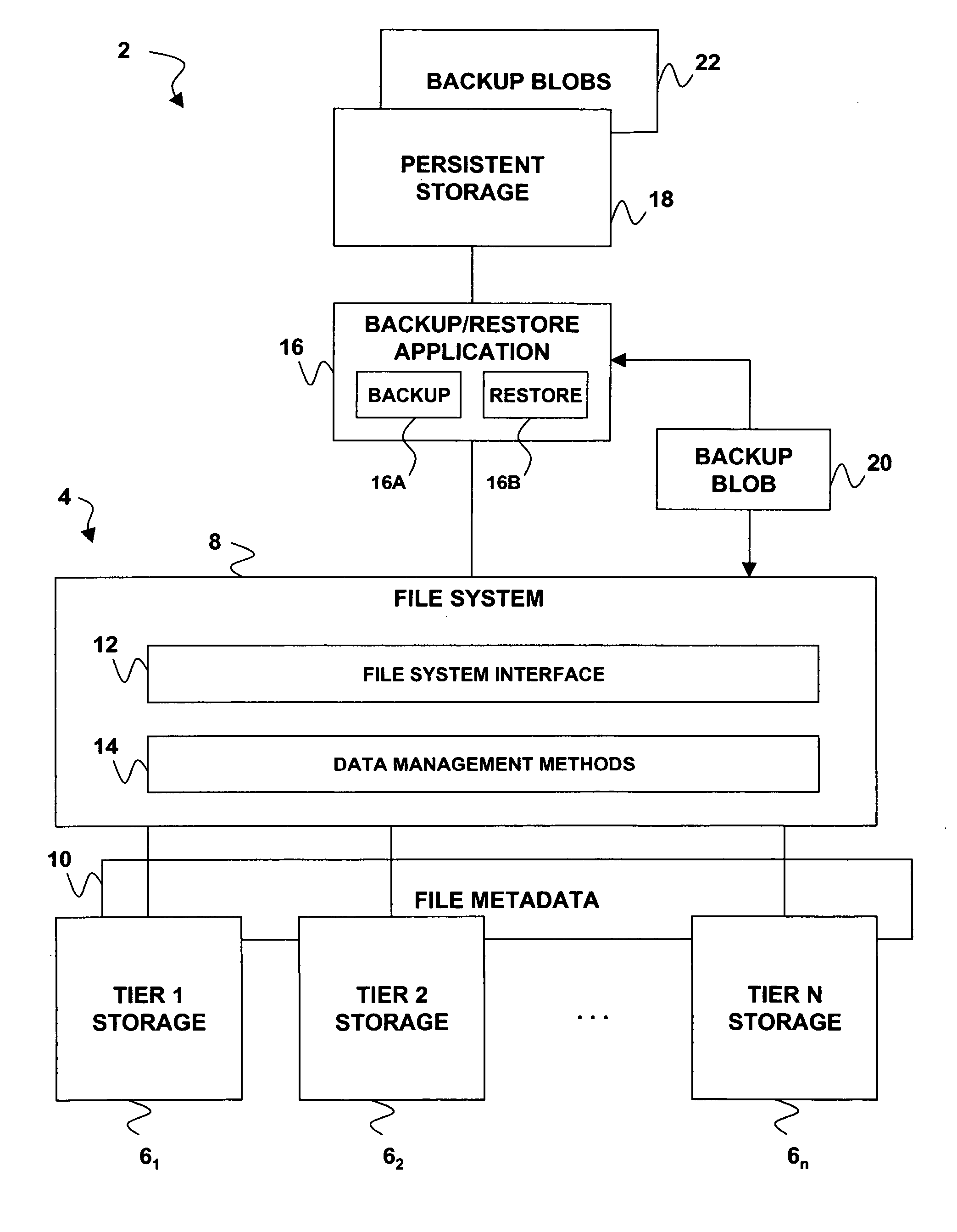
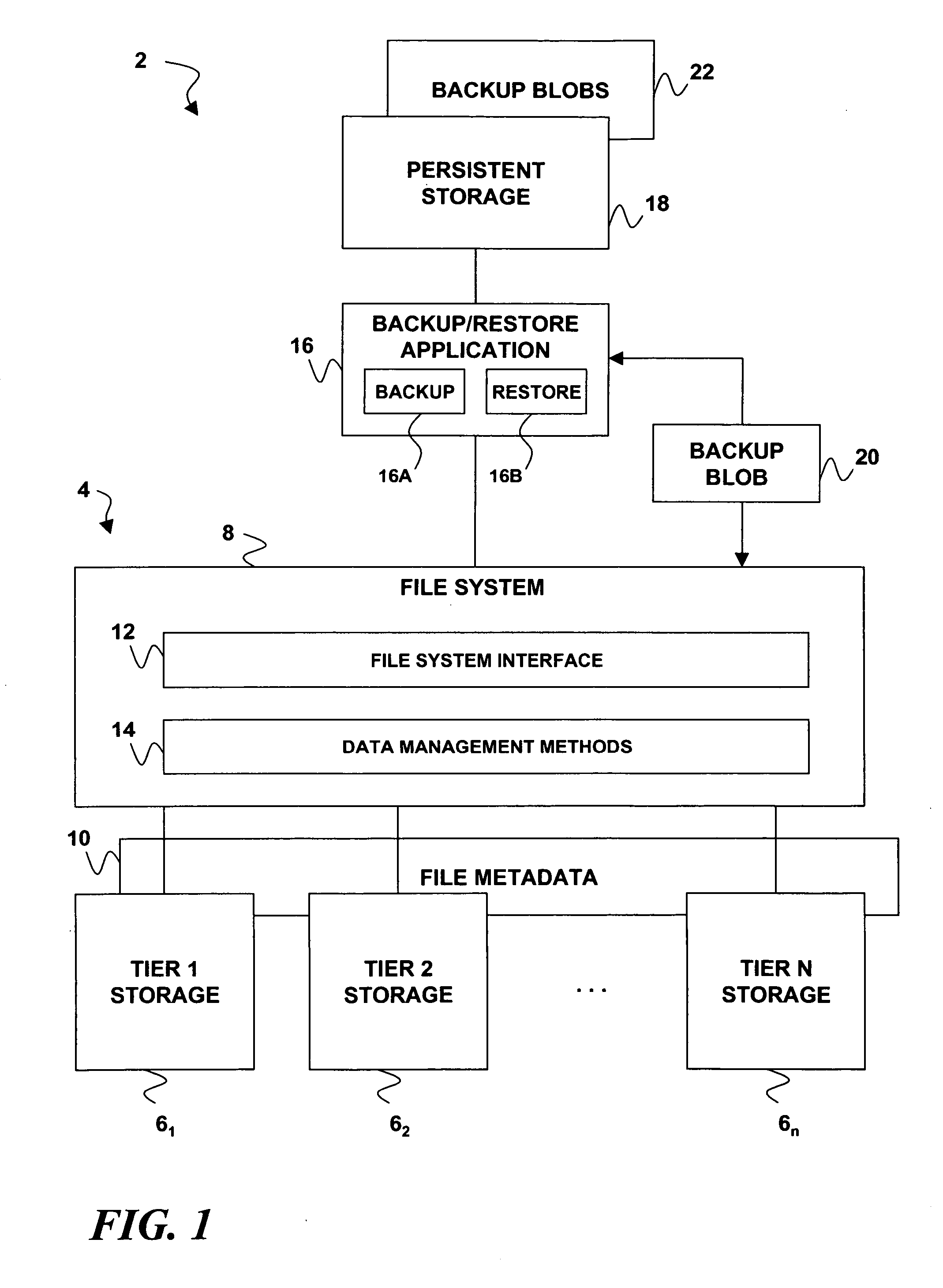
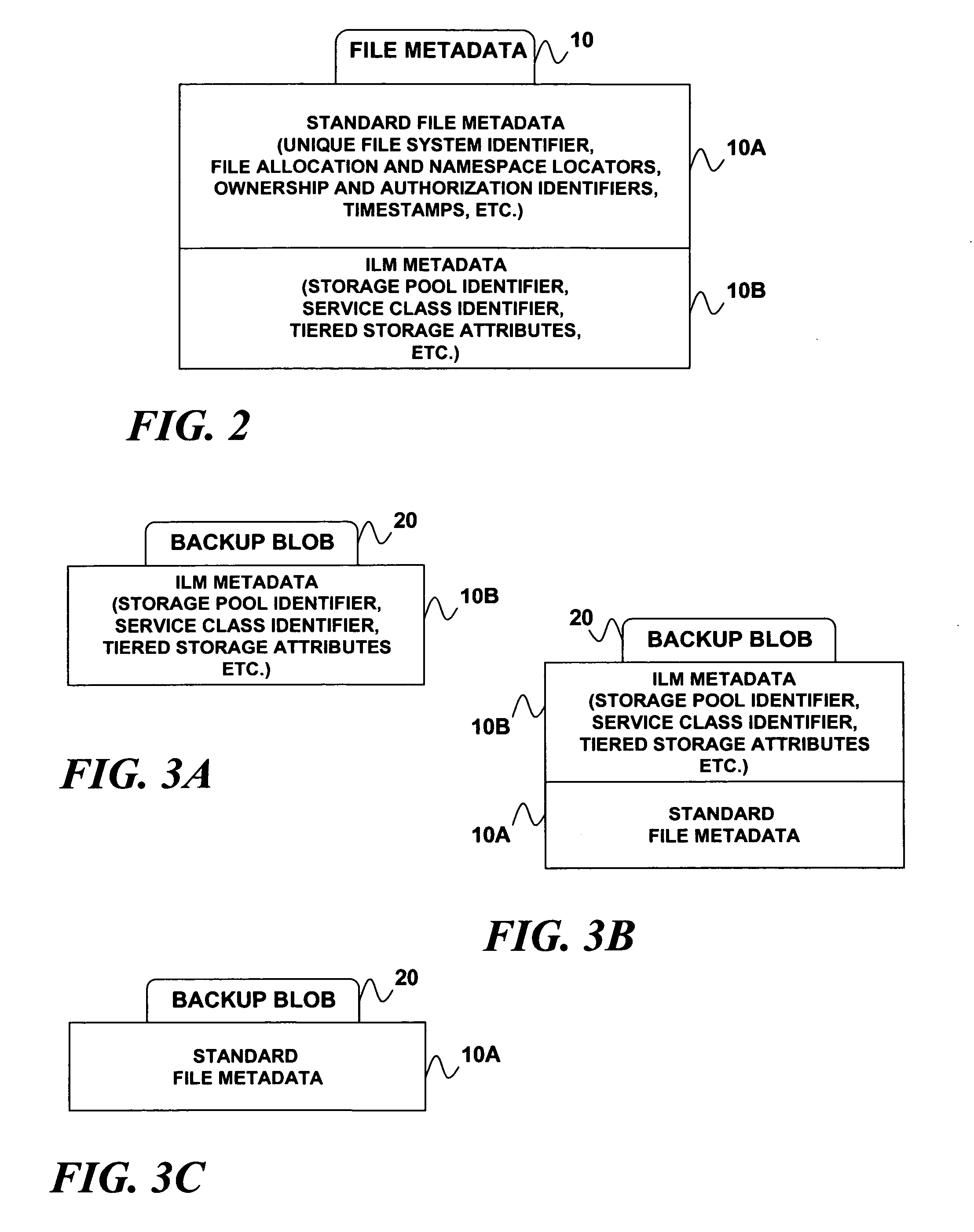
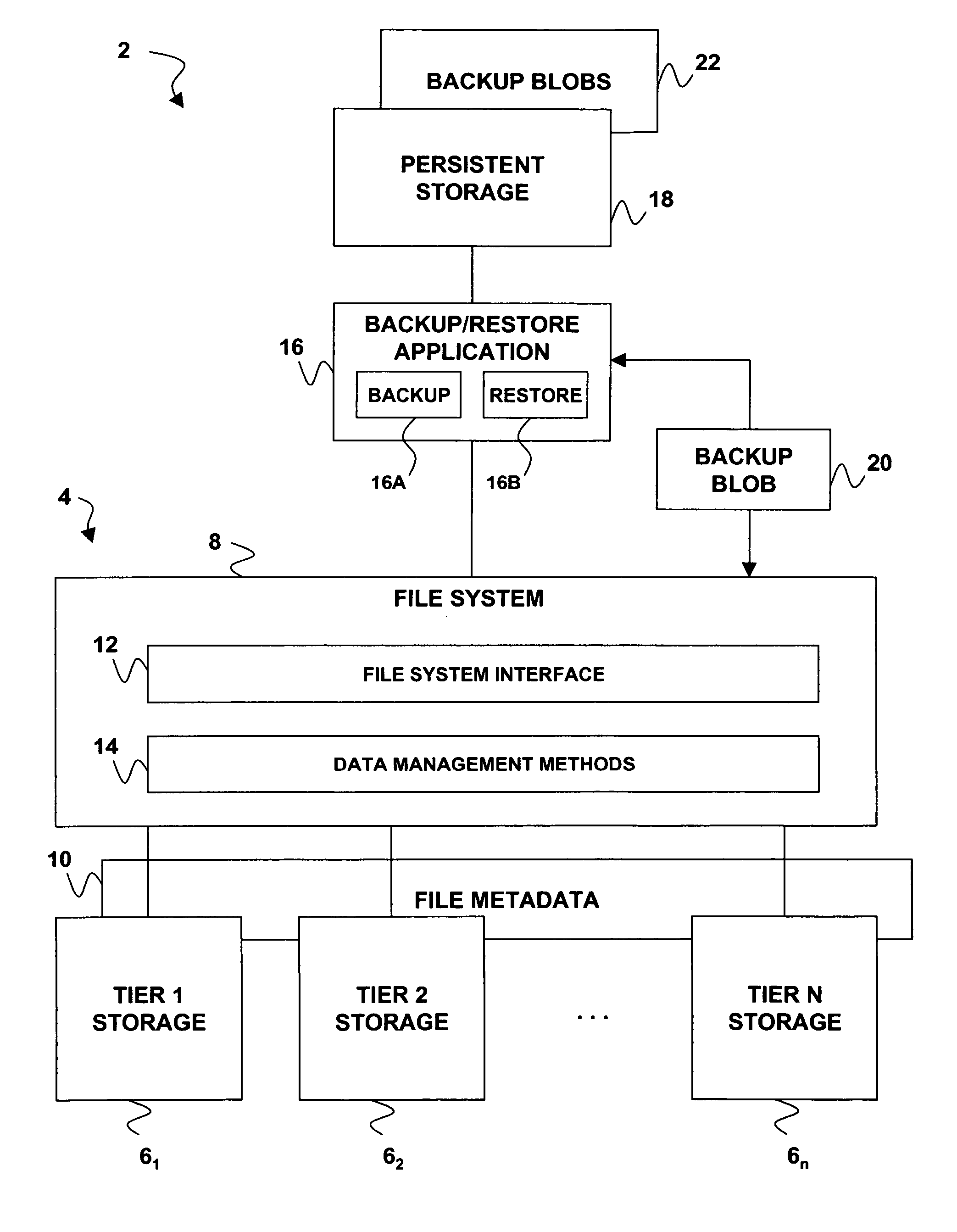
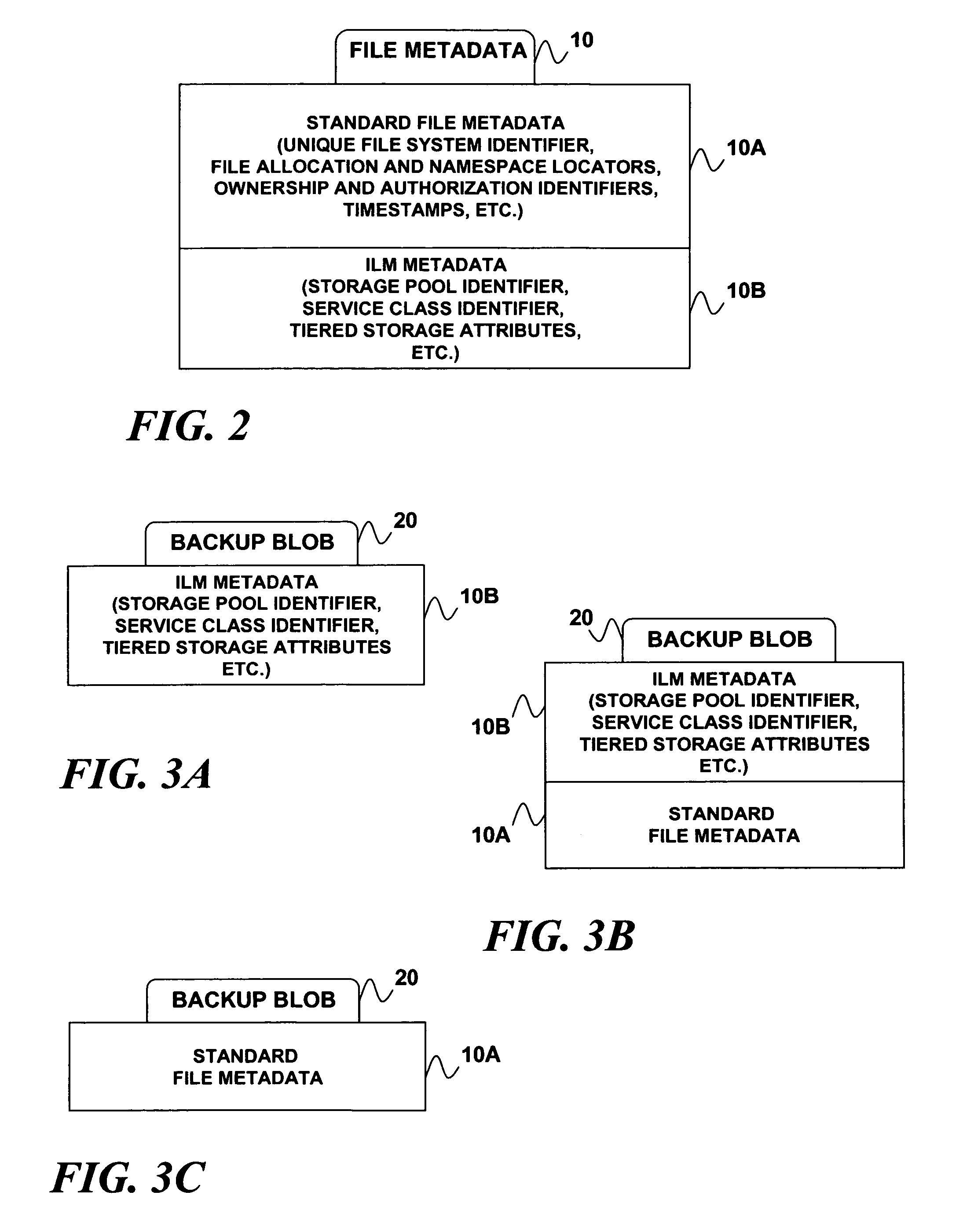
Restoring a file to its proper storage tier in an information lifecycle management environment
ActiveUS20070185934A1Digital data processing detailsError detection/correctionData setSystem recovery
A technique for implementing policy-aware backup and restore capability in a tiered storage system. If a data set's contents are backed up from the tiered storage system to a backup storage system, metadata for the data set may also be backed up. Prior to the data set being restored from the backup storage system to the tiered storage system, the backed up metadata is restored and processed to determine a tier among the tiered storage pools to which the data set will be restored.
Owner:HUAWEI TECH CO LTD
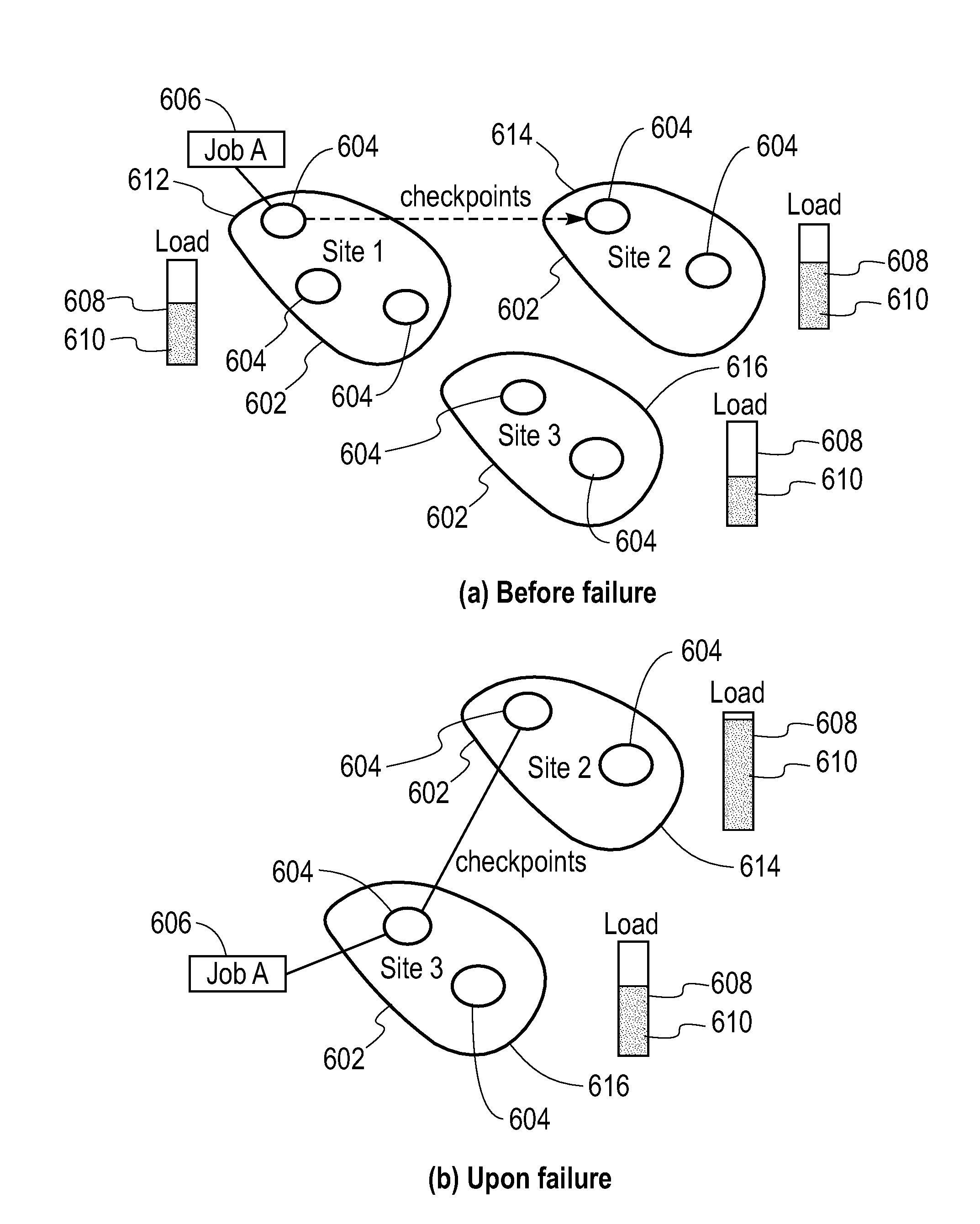
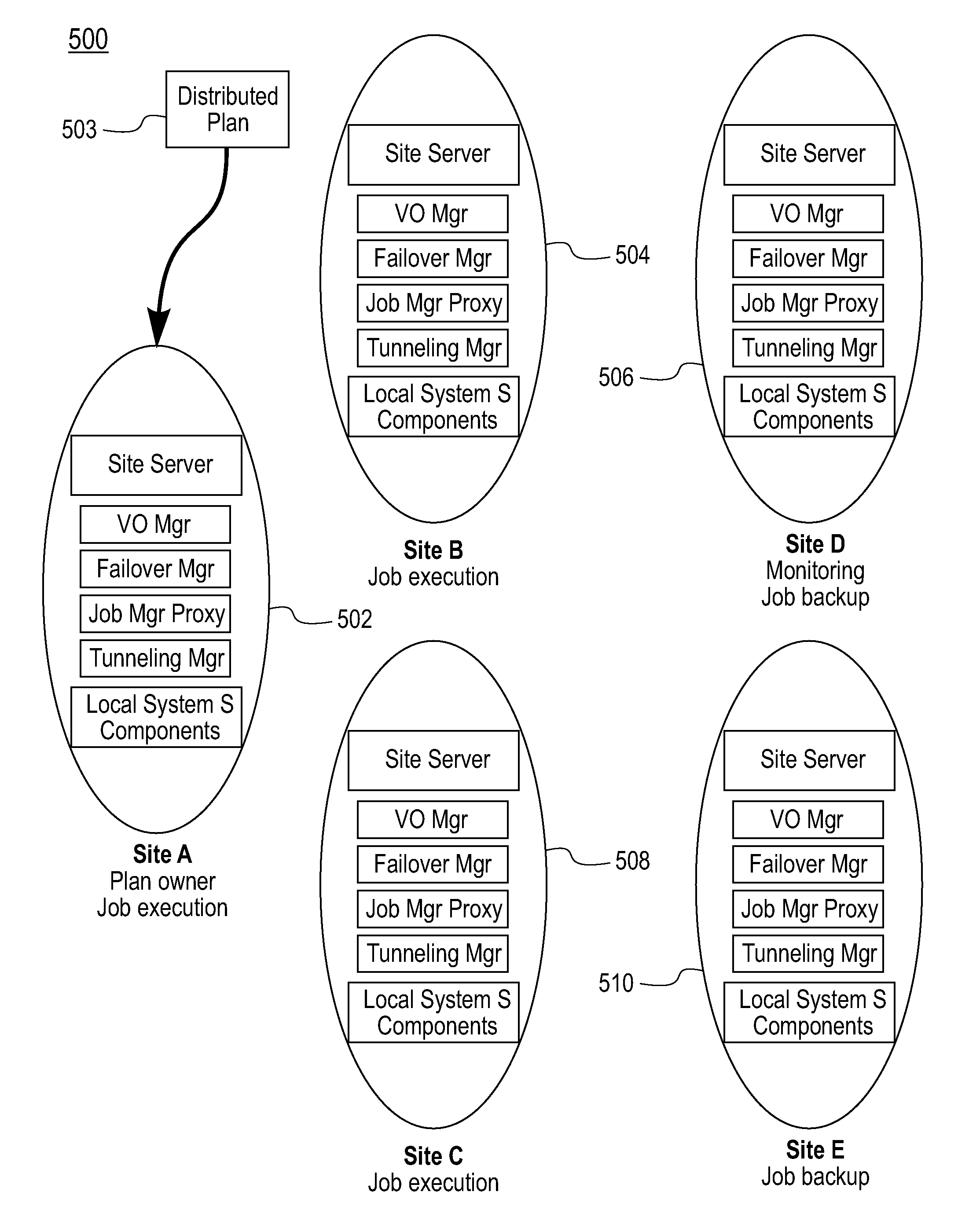
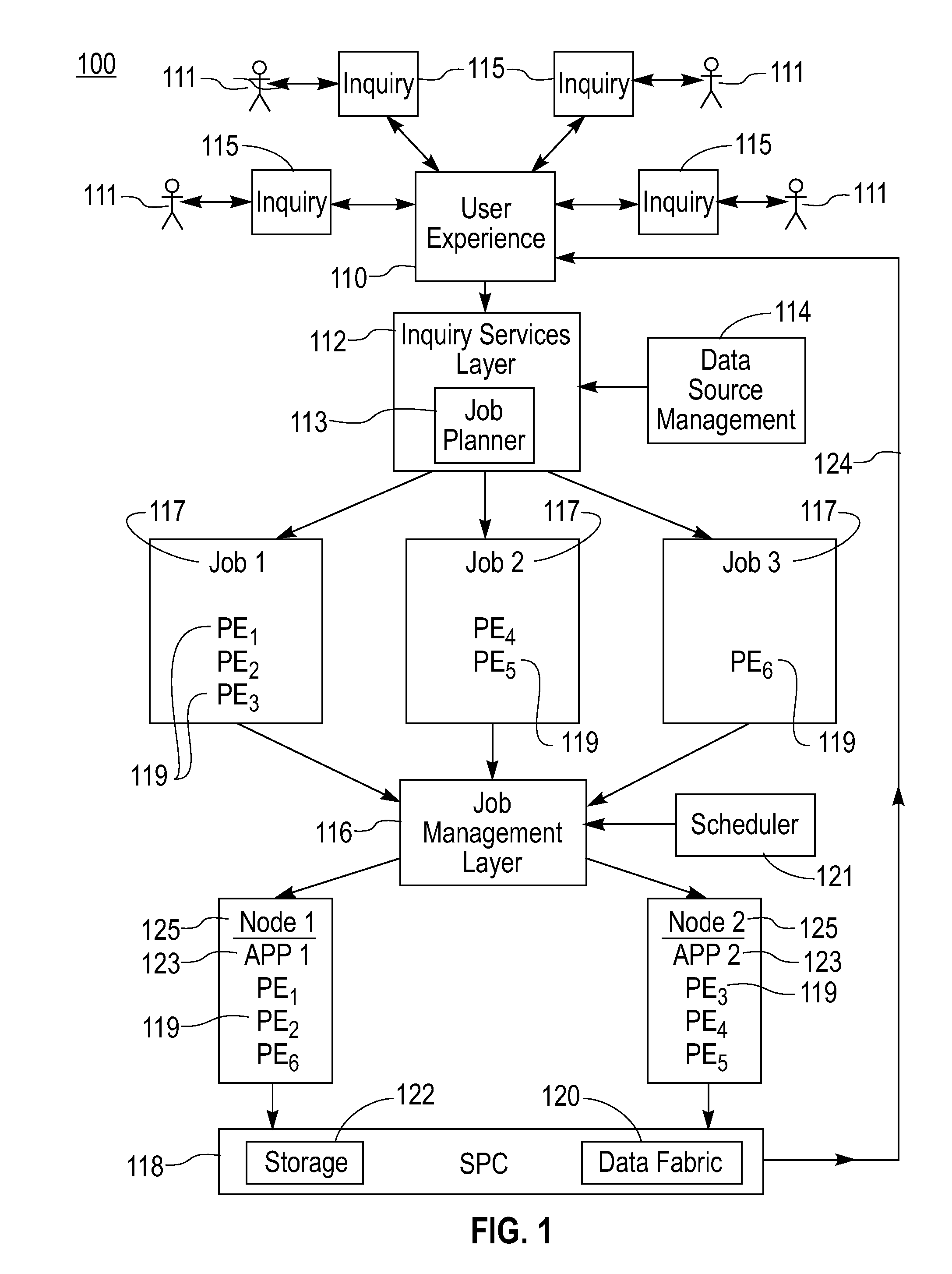
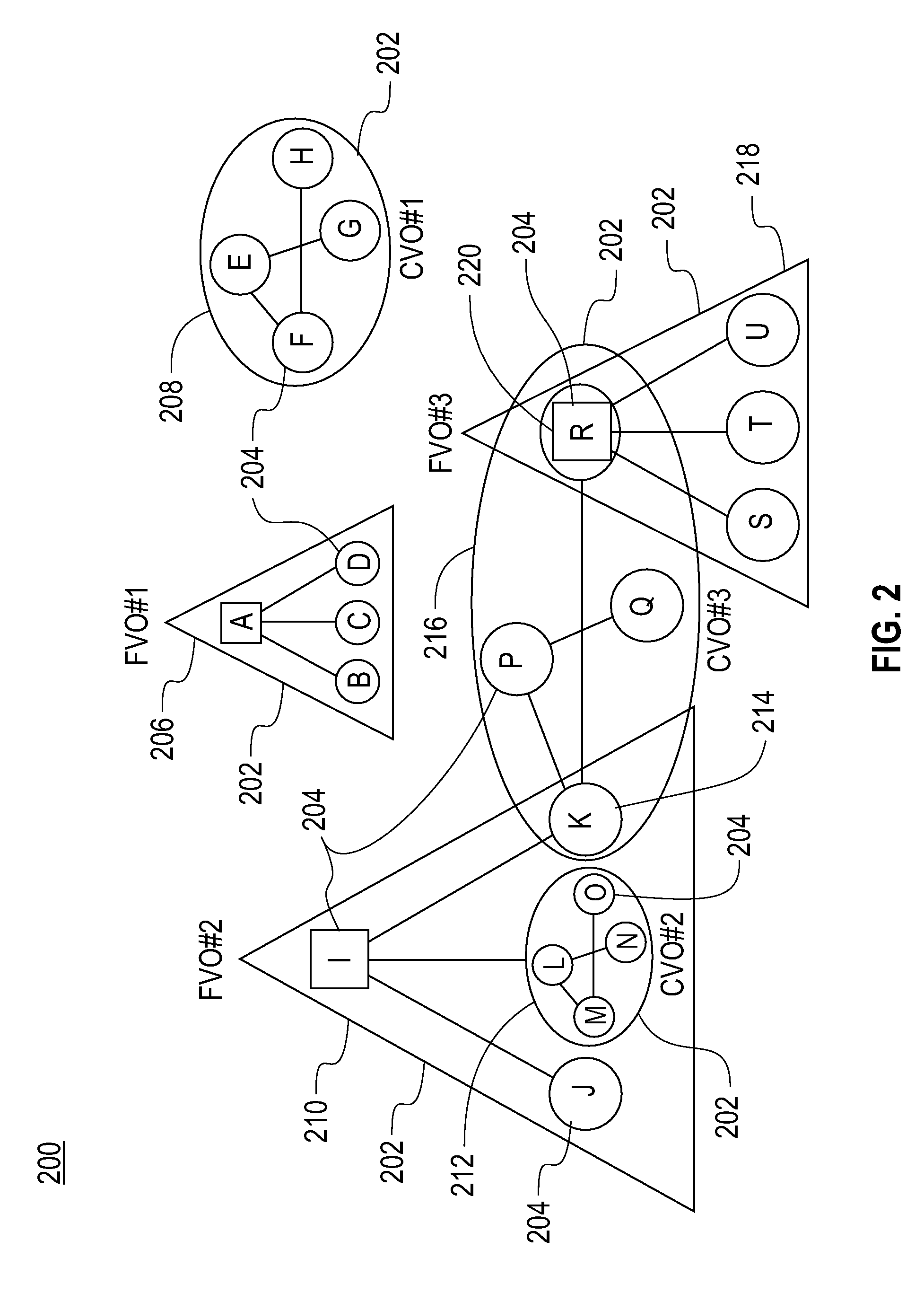
Mechanism for Recovery from Site Failure in a Stream Processing System
InactiveUS20080256384A1Describe wellCompensation differenceFault responseData processing systemPrimary sites
A failure recovery framework to be used in cooperative data stream processing is provided that can be used in a large-scale stream data analysis environment. Failure recovery supports a plurality of independent distributed sites, each having its own local administration and goals. The distributed sites cooperate in an inter-site back-up mechanism to provide for system recovery from a variety of failures within the system. Failure recovery is both automatic and timely through cooperation among sites. Back-up sites associated with a given primary site are identified. These sites are used to identify failures within the primary site including failures of applications running on the nodes of the primary site. The failed applications are reinstated on one or more nodes within the back-up sites using job management instances local to the back-up sites in combination with previously stored state information and data values for the failed applications. In additions to inter-site mechanisms, each one of the plurality of sites employs an intra-site back-up mechanism to handle failure recoveries within the site.
Owner:IBM CORP
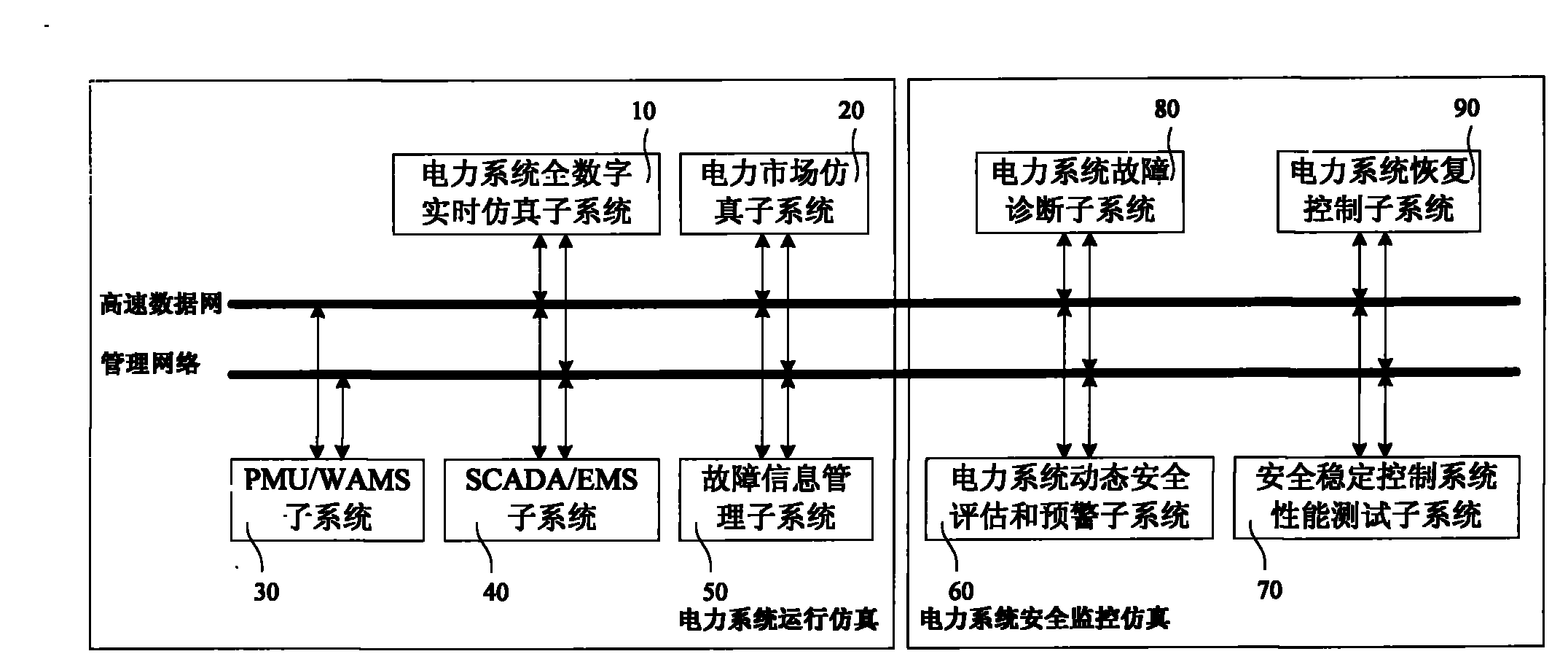
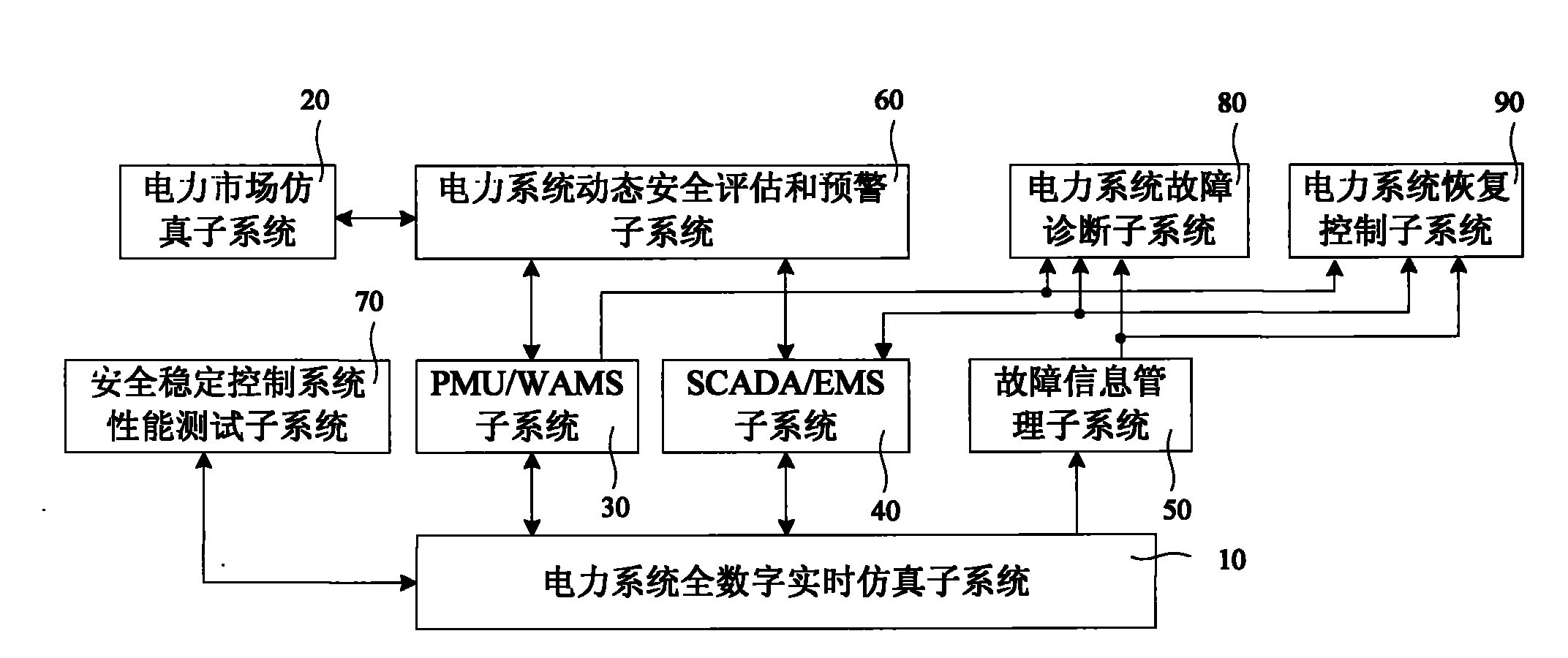
Operation and safety monitoring simulation system for power system
ActiveCN101944766AComprehensive effectComprehensive performance testingCircuit arrangementsSpecial data processing applicationsElectricity marketPower system scheduling
The invention relates to an operation and safety monitoring simulation system for a power system, which comprises a power system full digital real-time simulation subsystem used for simulating the operation of a large-scale power system in real time and providing simulation data to other subsystems, a power market simulation subsystem used for simulating and training power market transaction, a PMU / WAMS subsystem used for carrying out real-time dynamic monitoring and analysis on a simulated power system, an SCADA / EMS subsystem used for monitoring and analyzing the simulated power system, a fault information management subsystem used for managing and comprehensively utilizing fault information, a power system dynamic safety assessment and early warning subsystem used for carrying out safety assessment and early warning on the current power system and carrying out safety verification on the operation mode of a future plan, a safety and stability control system performance test subsystem used for testing the performance of a protective relay device, a power system stabilizer (PSS) and other automated equipment as well as a safety and stability control system and equipment, a power system fault diagnosis subsystem used for carrying out on-line diagnosis and intelligent safety alarming on the fault of the simulated power system and providing a dispatching control decision under the fault condition, and a power system recovery control subsystem used for recognizing the state of the fault of the simulated power system, searching and inferring the power supply path of an outage region and providing a power grid recovery control strategy. The system can simulate the operation of a large-scale power grid in real time, and can be used for searching and comprehensively testing the technology and software of various power systems in dispatching, operation, control and other aspects.
Owner:CHINA ELECTRIC POWER RES INST +1
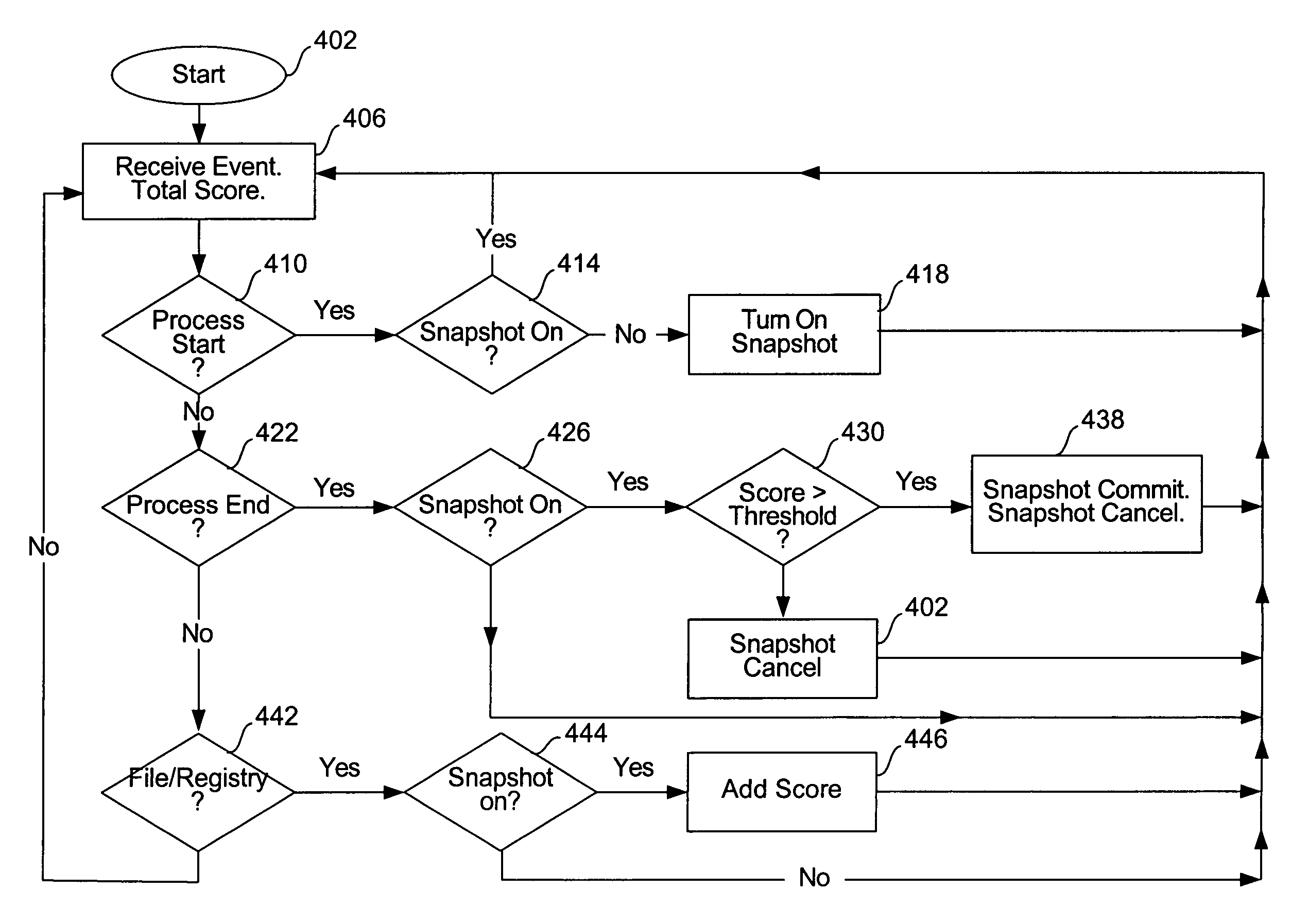
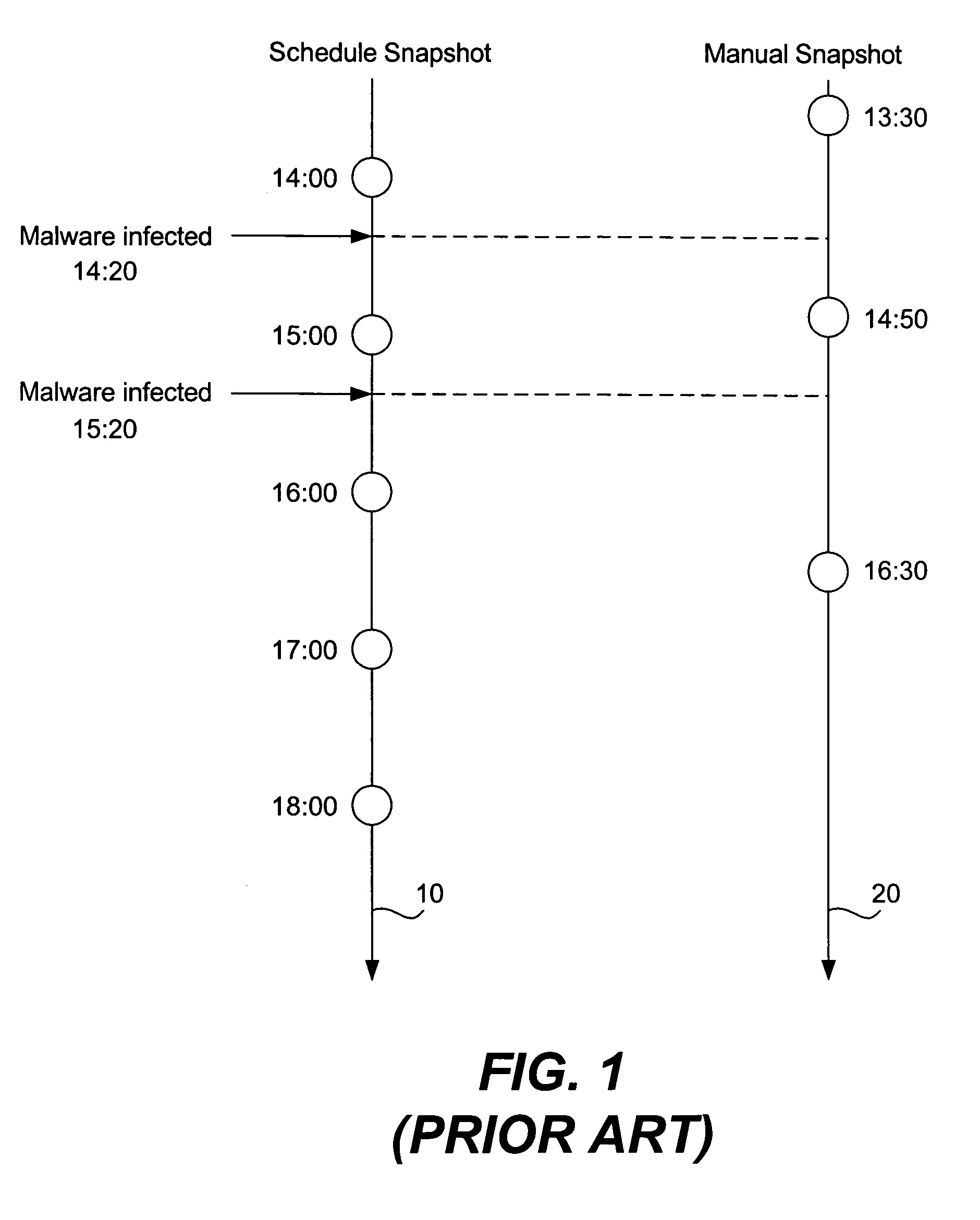
Snapshot and restore technique for computer system recovery
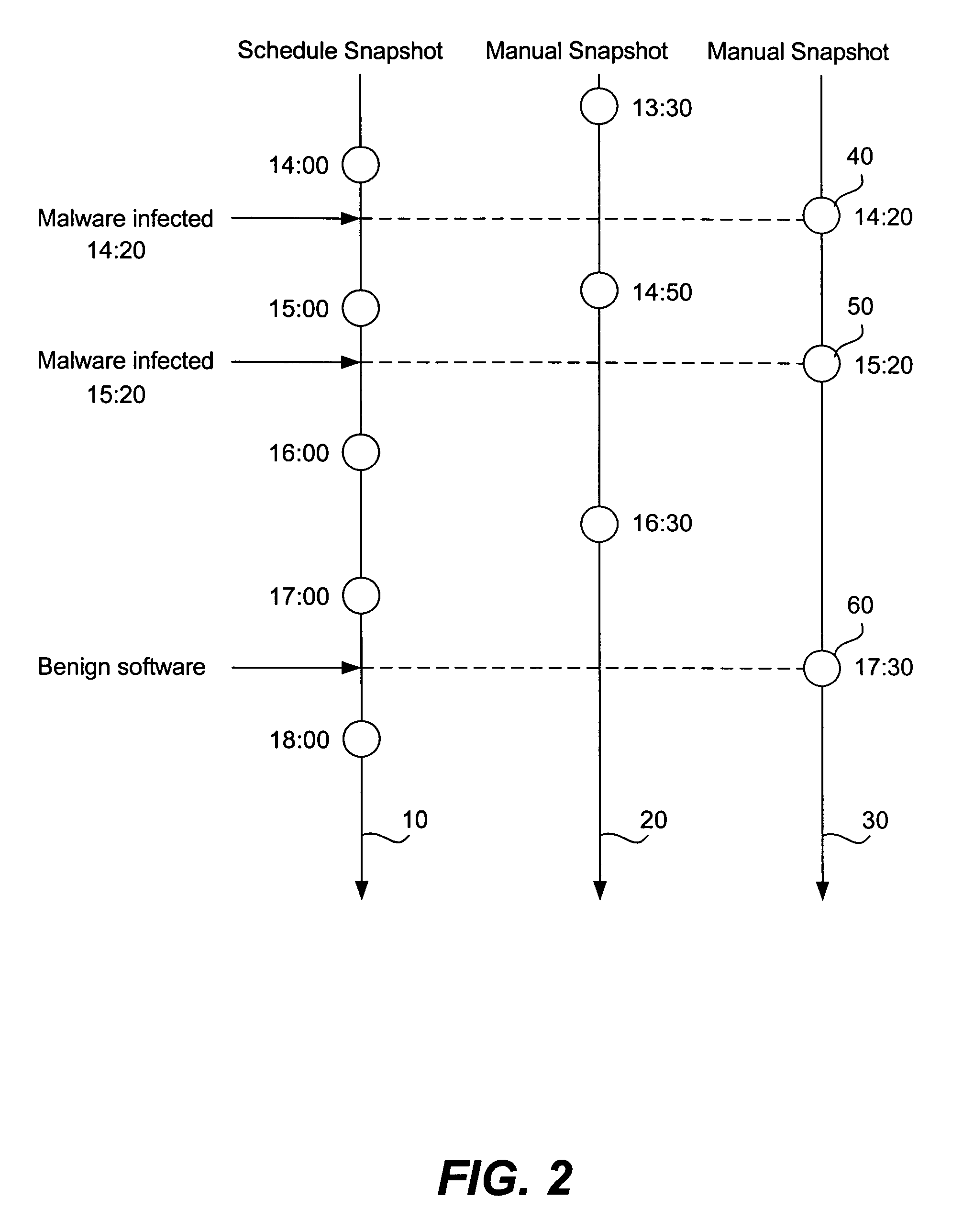
A computer system operation registers as an event when an operation potentially characteristic of malware occurs. Events are scored and when a threshold is reached indicative of a possible malware infection a restore point is created. Many restore points are created. When a user decides to restore the system because of the presence of malware a malware report is retrieved. The malware report describes characteristics of a particular piece of malware. The malware report is compared to the restore point logs that had been created earlier. Any number of malware reports are compared to the restore point logs. A restore point log that shares many of the same system changes or other effects also present in a malware report is likely to be an indication of the beginning of a malware infection. The matched restore point log is recommended to the user as the best restore point.
Owner:TREND MICRO INC
Persistent snapshot management system
InactiveUS20060107006A1Memory loss protectionDigital data processing detailsHard disc drivePrimitive state
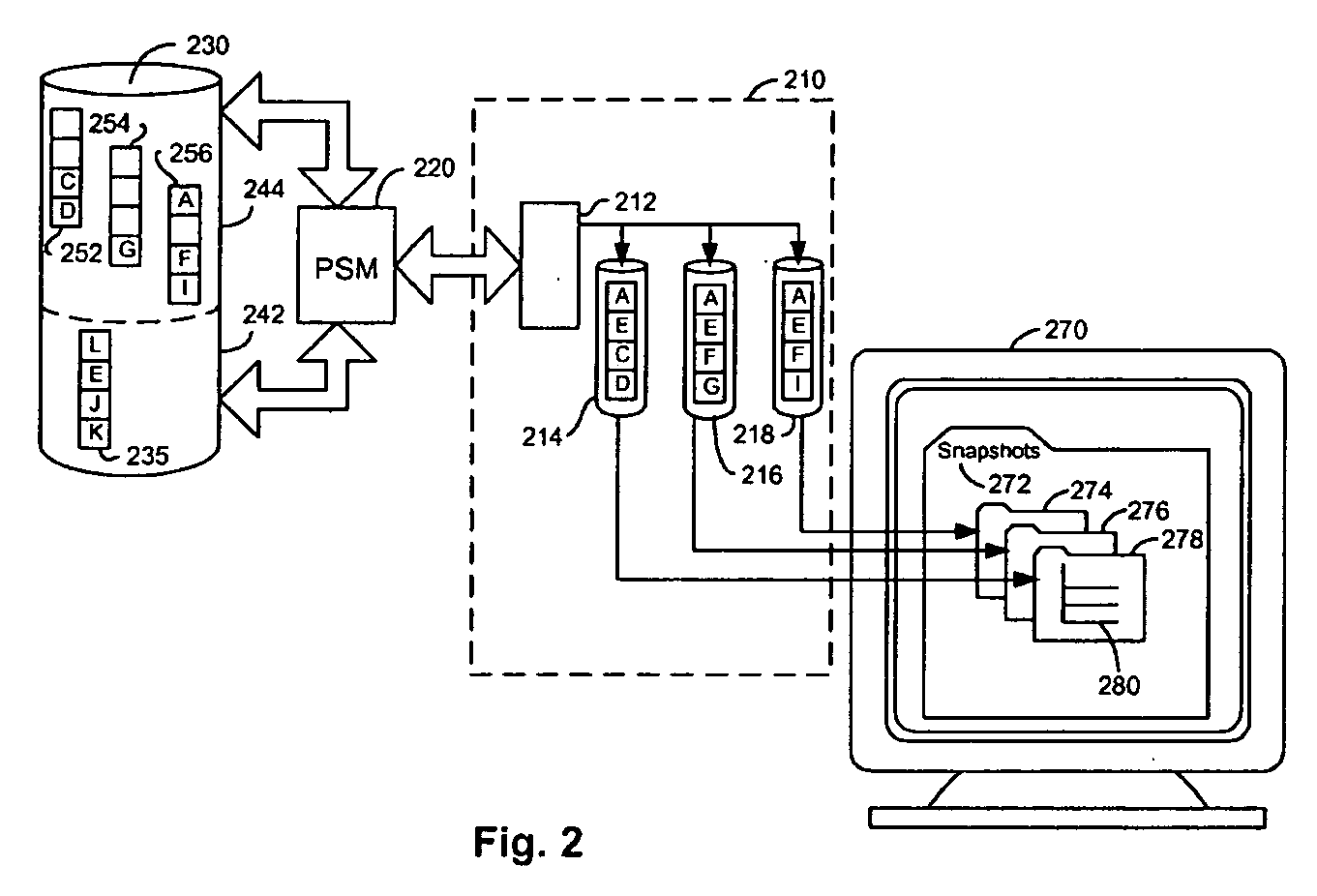
A persistent snapshot is taken and maintained in accordance with a novel method and system for extended periods of time using only a portion of a computer readable medium of which the snapshot is taken. Multiple snapshots can be taken in succession at periodic intervals and maintained practically indefinitely. The snapshots are maintained even after powering down and rebooting of the computer system. The state of the object of the snapshot for each snapshot preferably is accessible via a folder on volume of the snapshot. A restore of a file or folder may be accomplished by merely copy that file or folder from the snapshot folder to a current directory of the volume. Alternatively, the entire computer system may be restored to a previous snapshot state thereof. Snapshots that occurred after the state to which the computer is restored are not lost in the restore operation. Different rule sets and scenarios can be applied to each snapshot. Furthermore, each snapshot can be written to within the context of the snapshot and later restored to its pristine condition. Software for implementing the systems and methods of snapshots in accordance with the present invention may comprise firmware of a hard disk drive controller or a disk controller board or within the HDD casing itself. The present invention further comprises novel systems and methods in which the systems and methods of taking and maintaining snapshots are utilized in creating and managing temporal data stores, including temporal database management systems. The implications for data mining and exploration, data analysis, intelligence gathering, and artificial intelligence (just to name a few areas) are profound.
Owner:COLUMBIA DATA PRODUCTS
Performing operating system recovery from external back-up media in a headless computer entity
InactiveUS20020042892A1Redundant data error correctionRedundant operation error correctionHard disc driveOperational system
A computer entity, particularly but not exclusively a headless computer entity, has operating systems stored on a non-volatile data storage device e.g. a hard disk drive, and has a back-up data storage device. Operating system backup's are taken from an uncorrupted copy of an operating system stored in a separate partition on the data storage device to the primary operating system which is actually used to run the device, thereby ensuring that if the primary operating system of the computer entity becomes corrupted either gradually or catastrophically, the back-up copy which is stored on a back-up media is not effected. Under failure conditions of the computer entity, a pristine copy of the operating system can be reloaded from the back-up tape data storage media and the computer entity rebooted from the pristine operating system back-up copy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
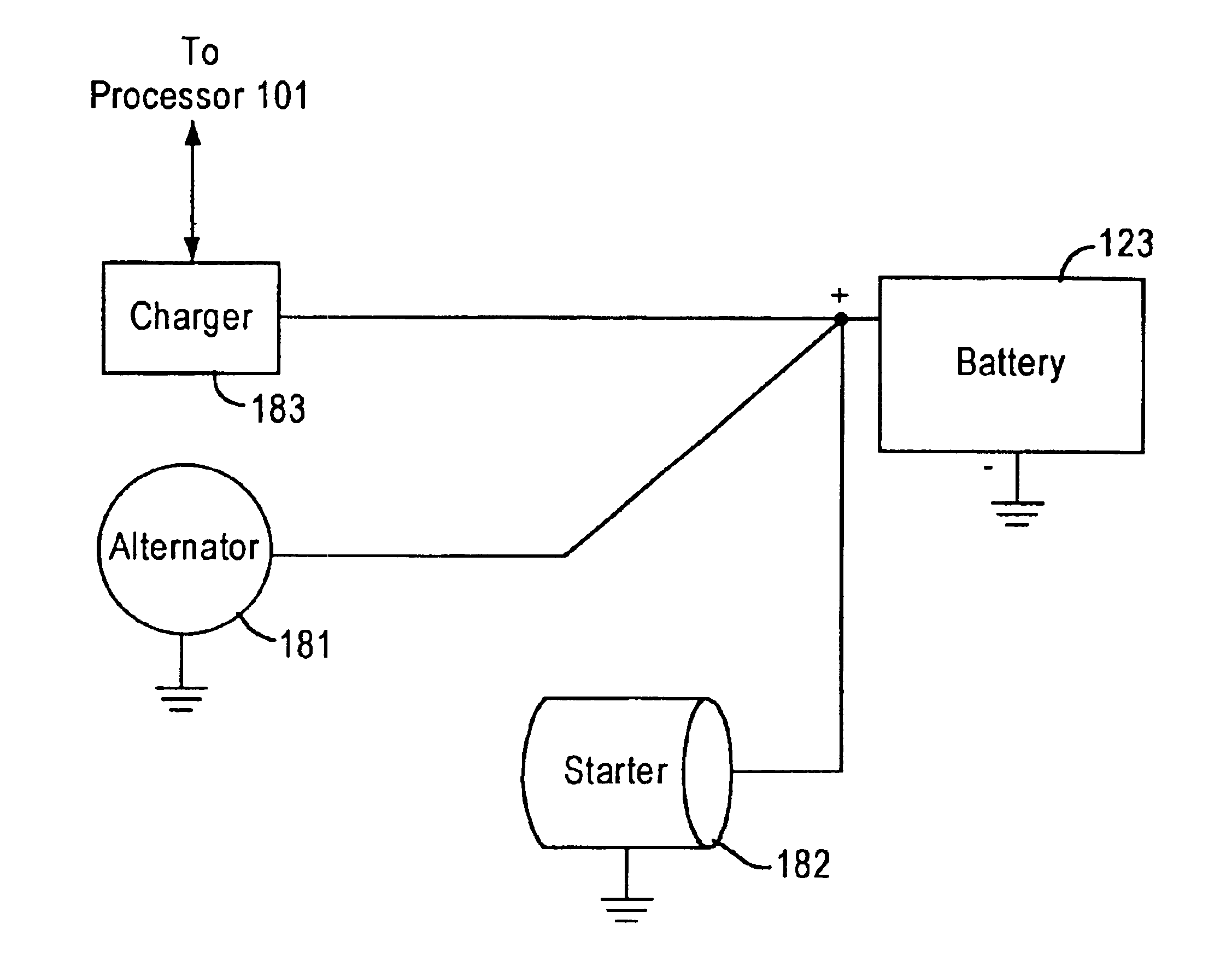
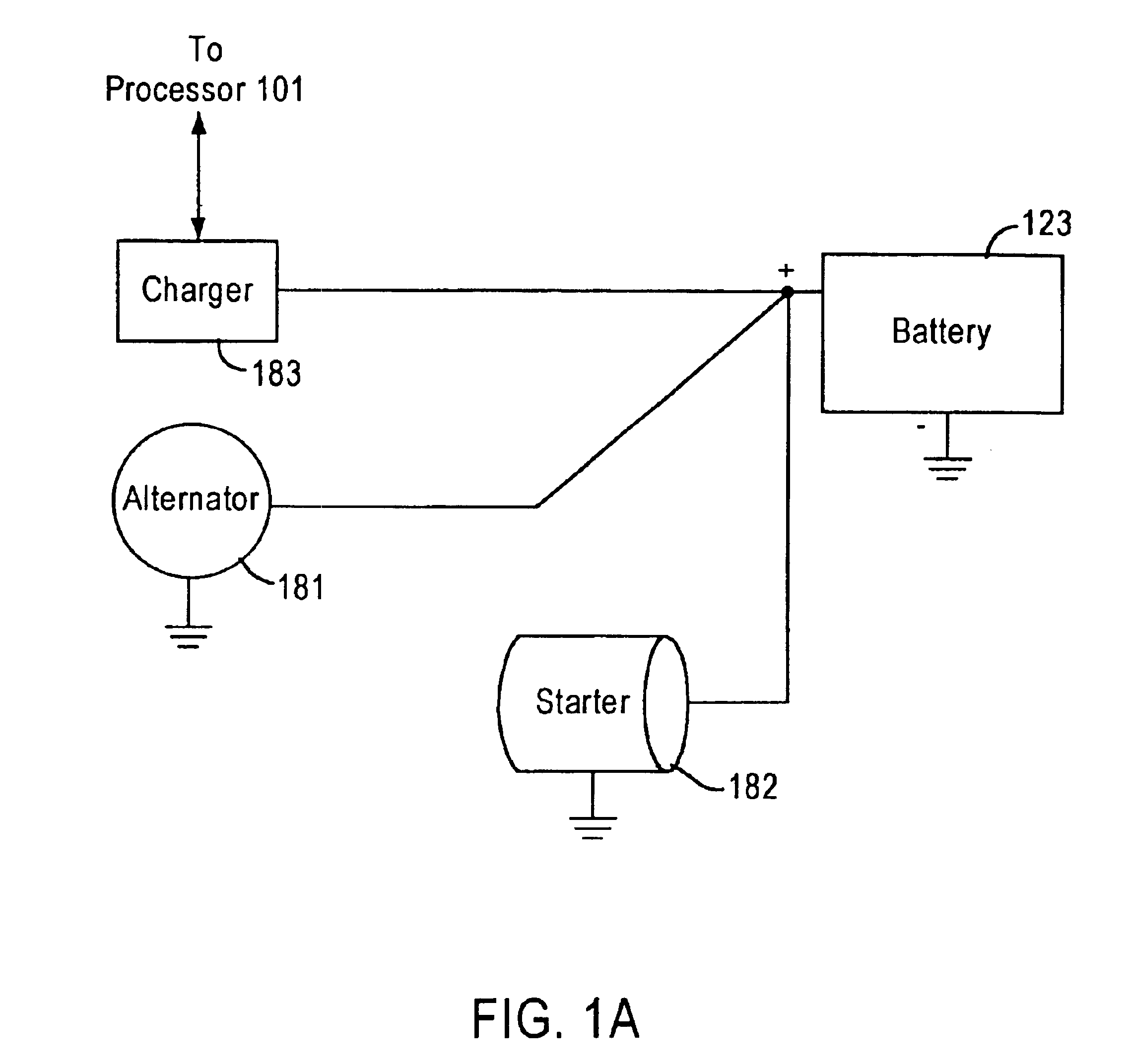
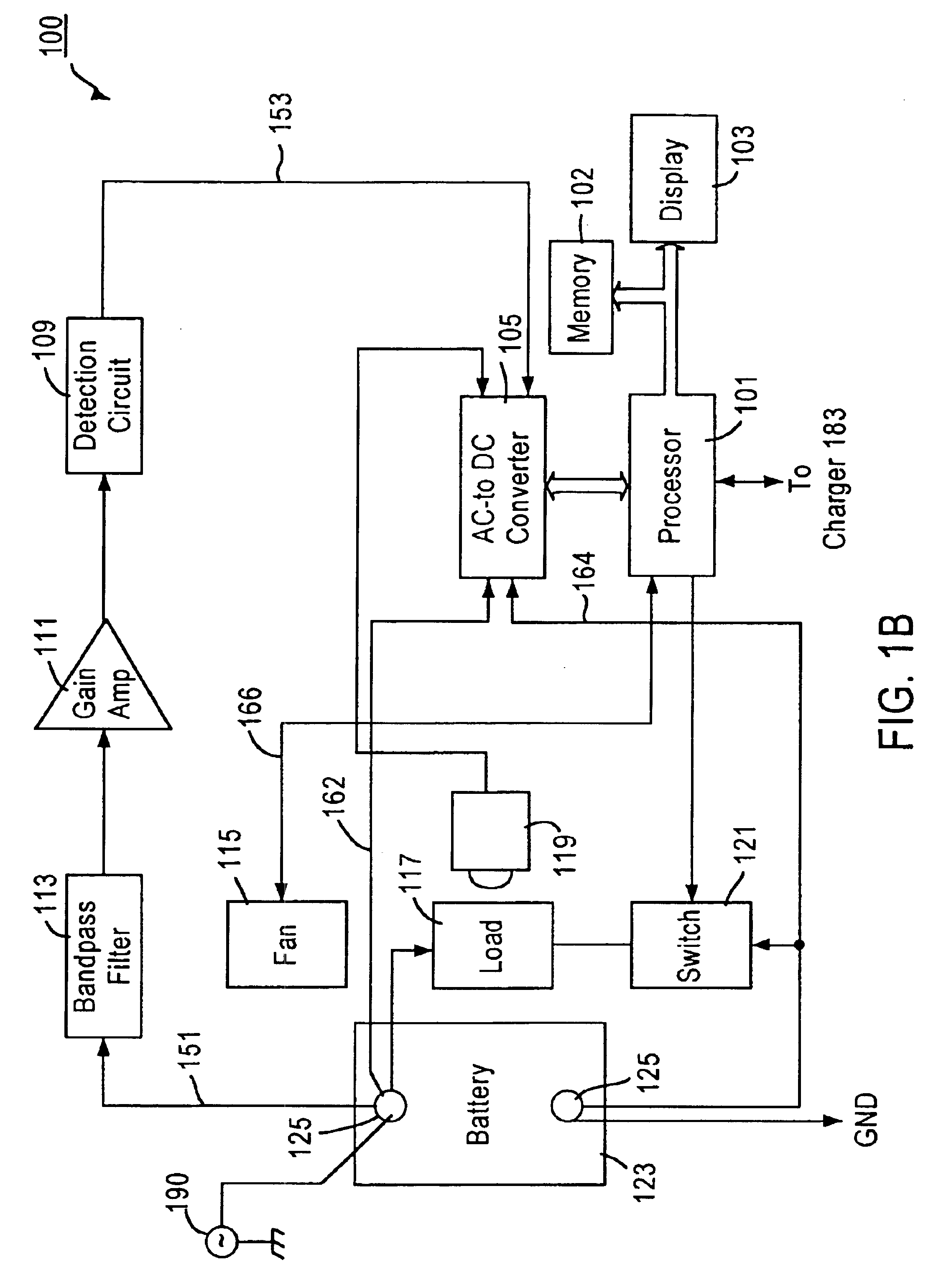
Integrated battery service system
An integrated battery service system performs a plurality of services related to a battery, such as battery testing, battery charging, and the like. In addition, the integrated service system provides services to devices / components that are coupled to the battery, such as starters, alternators, etc. The integrated battery service system allows a user to abort a service and then resume the process from where the process was aborted. When conducting a service, the integrated battery service system determines a noise level caused by devices / components coupled to the battery. The integrated battery service system includes connectors configured to couple to a battery for receiving input signals, a processor coupled to the connectors, and a memory device coupled to the processor for storing control codes and operation history. The control codes, when executed by the processor, control the system to selectively abort a service in response to a user input. Since the memory stores operation histories, the processor may access the memory to retrieve data related to the aborted service and parameters obtained during the service before the process was aborted. The system reinstates the aborted service in response to another user input.
Owner:SOMALTUS
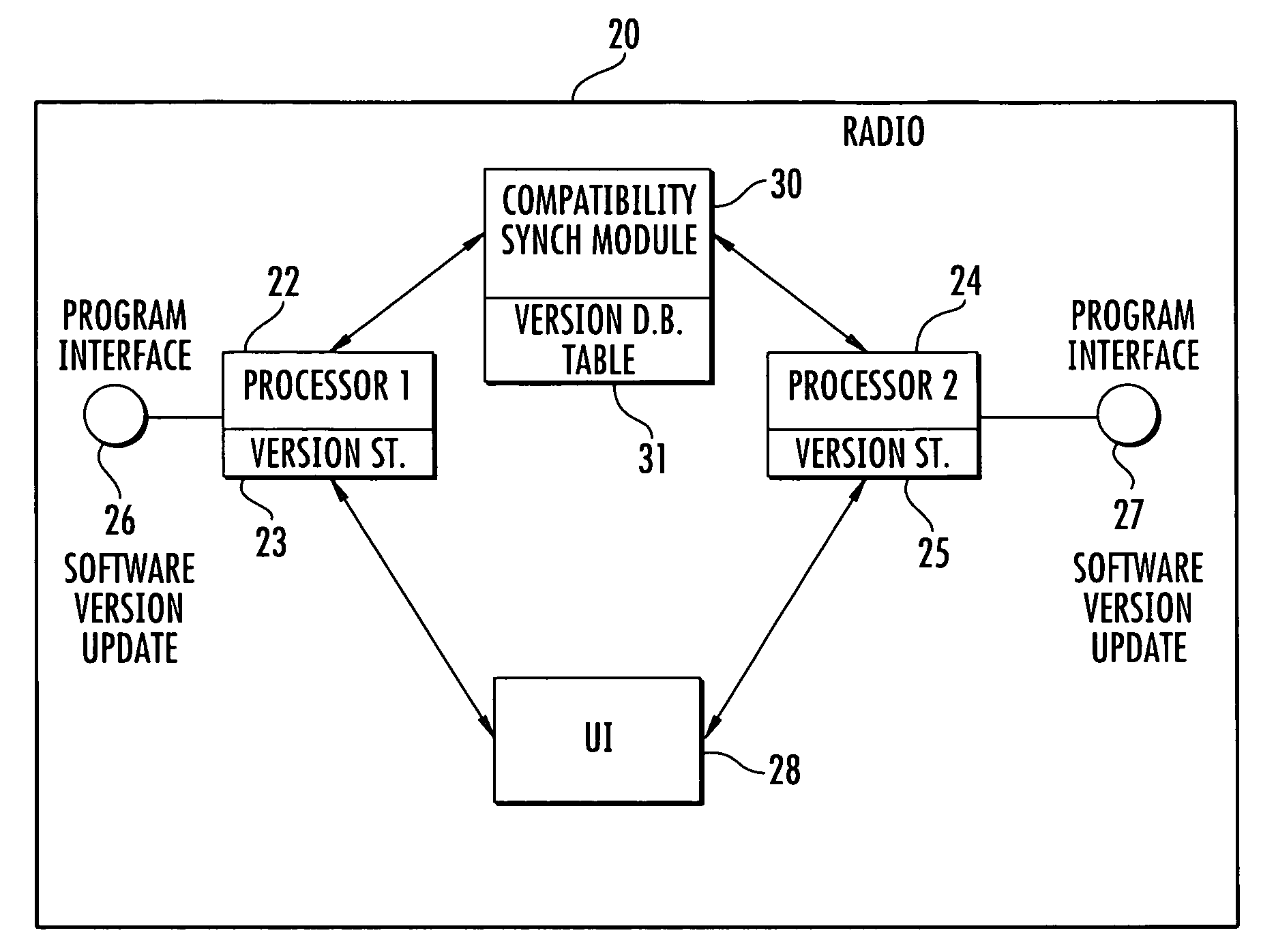
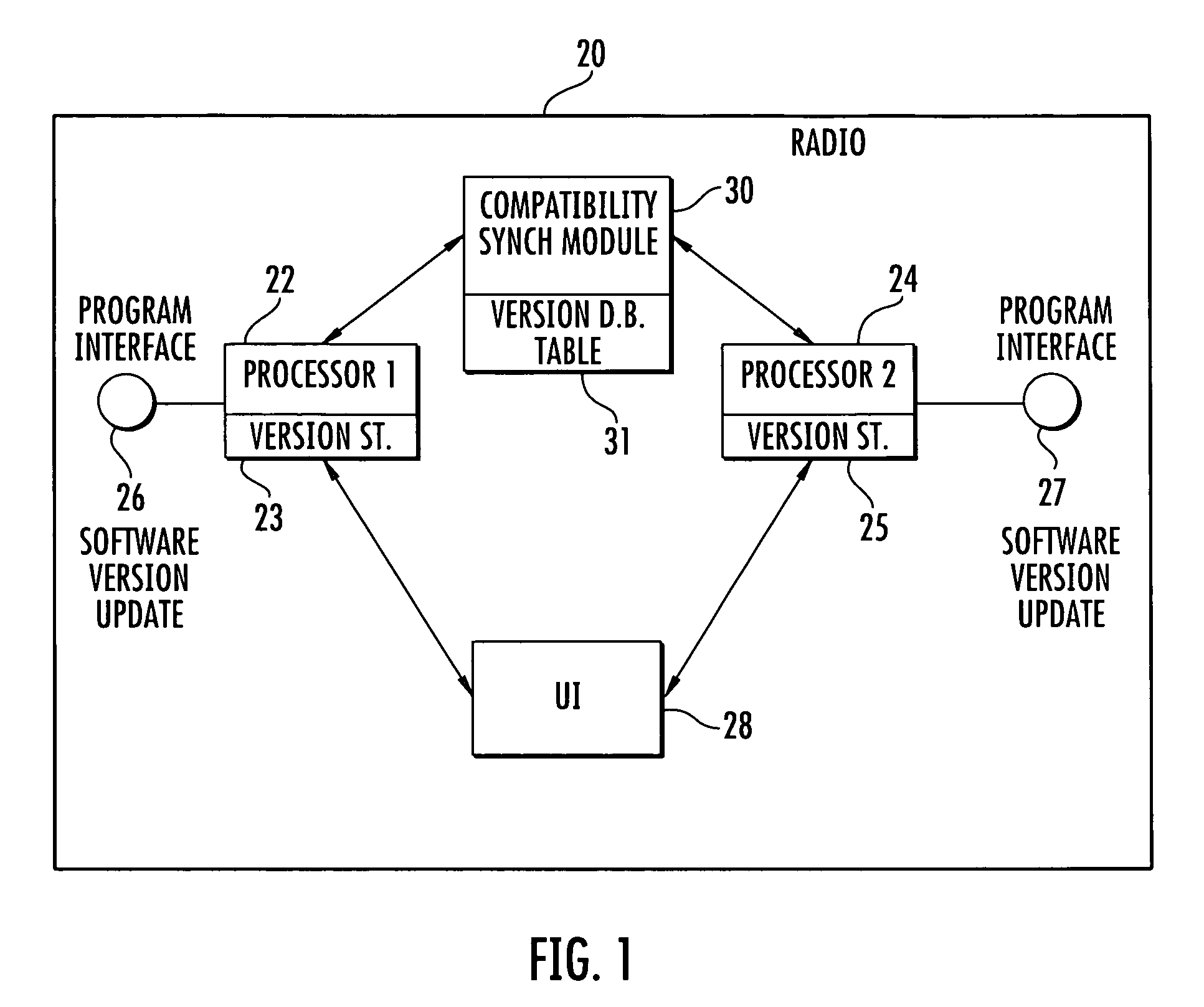
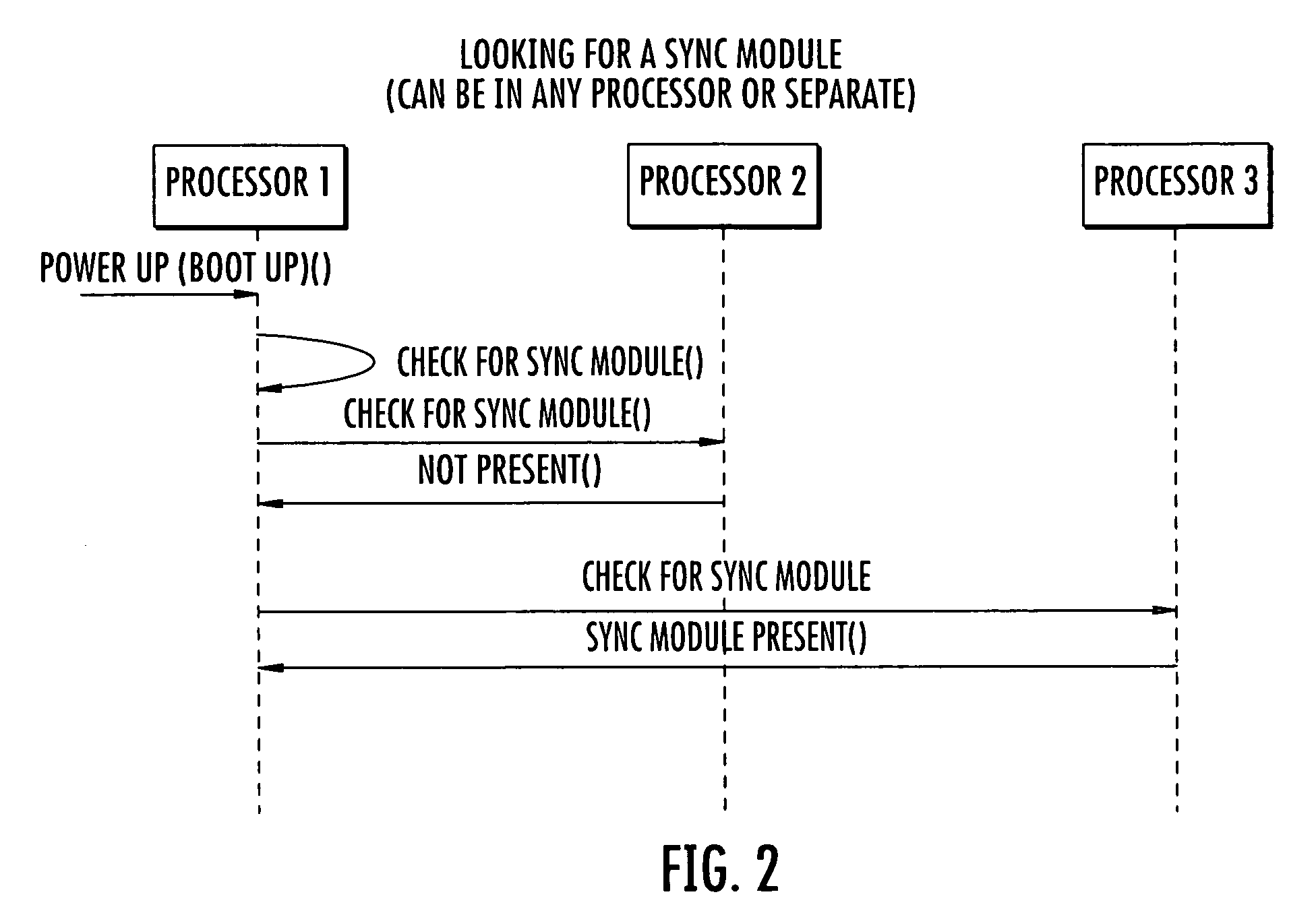
Communications device with a plurality of processors and compatibility synchronization module for processor upgrades and related method
InactiveUS20100146497A1Specific program execution arrangementsSpecial data processing applicationsSystem recoverySoftware update
A multiprocessor device includes a plurality of device subsystems each having a processor dependent on a respective other processor in another device subsystem for device operation. Each processor has at least one independent channel for updating a respective software version within the respective processor. A compatibility synchronization module has a database storing a table of compatible software versions for each processor. It is updated when a new software version for a processor is created. This table is independent of software images for the software versions. The compatibility synchronization module is operative for verifying if the software version for a processor is compatible with other software versions at other processors and instructs a respective device subsystem to revert back to a compatible software version within a respective processor or prevent any incompatible software updates within the processor.
Owner:HARRIS CORP
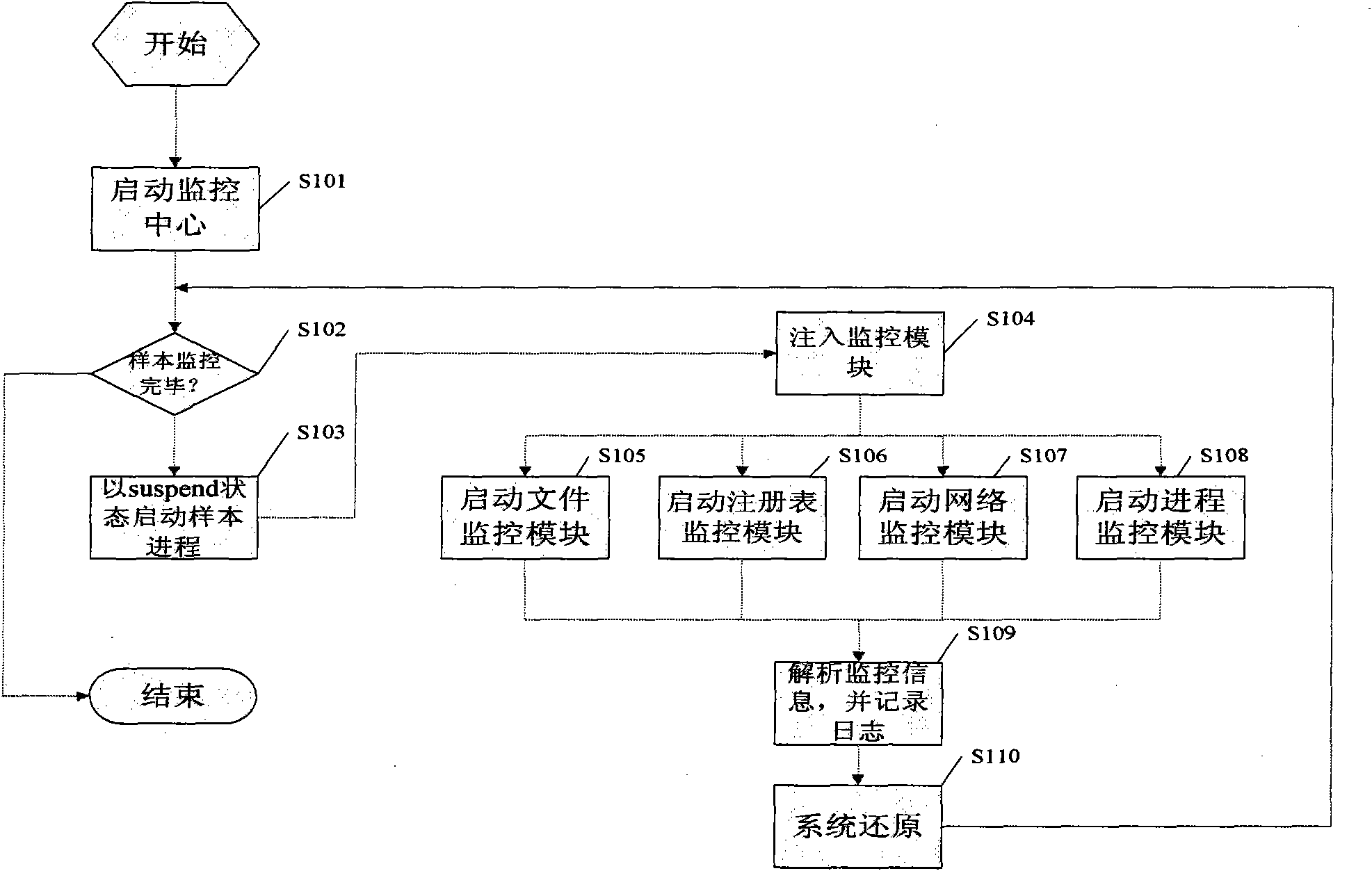
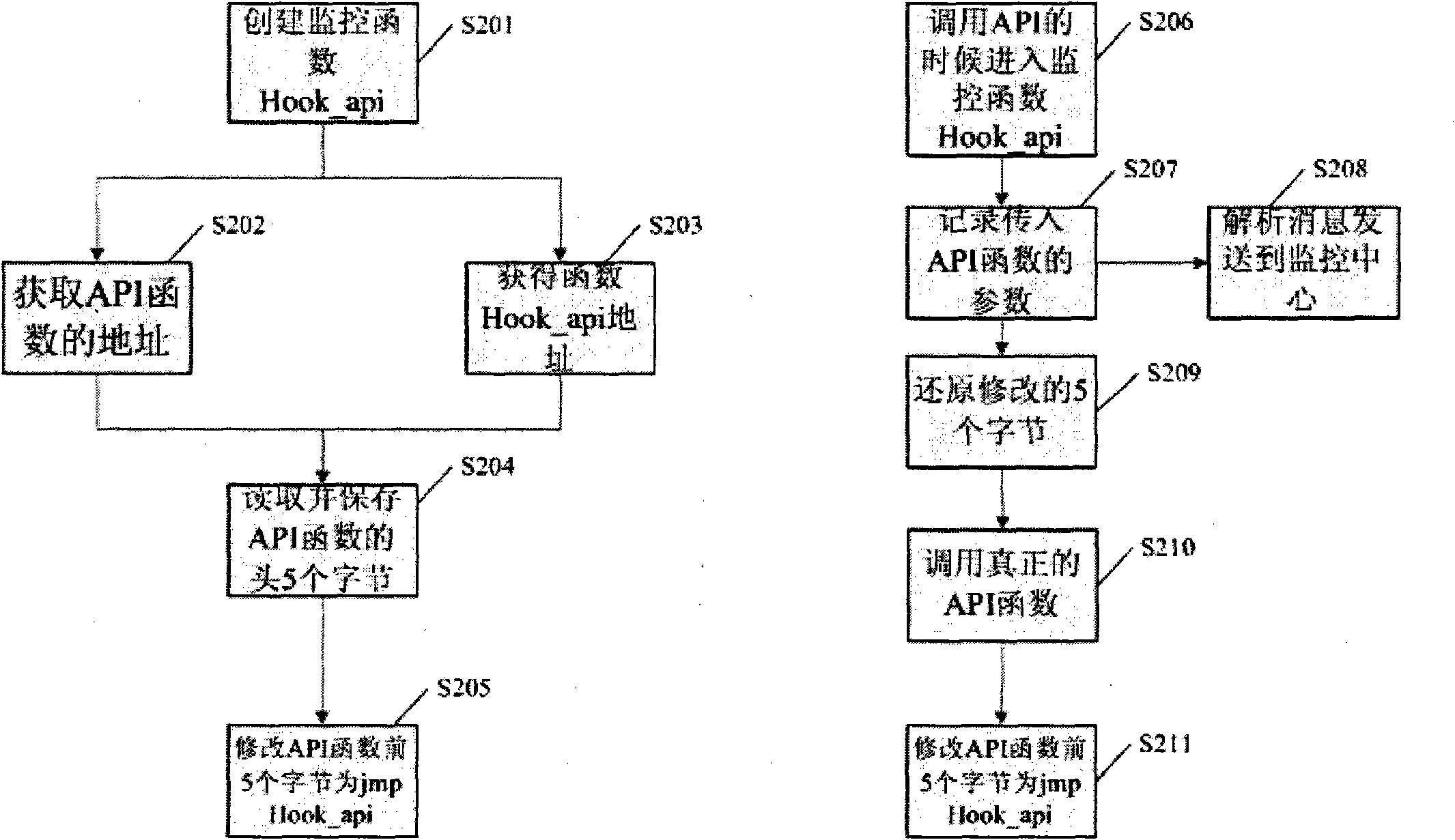
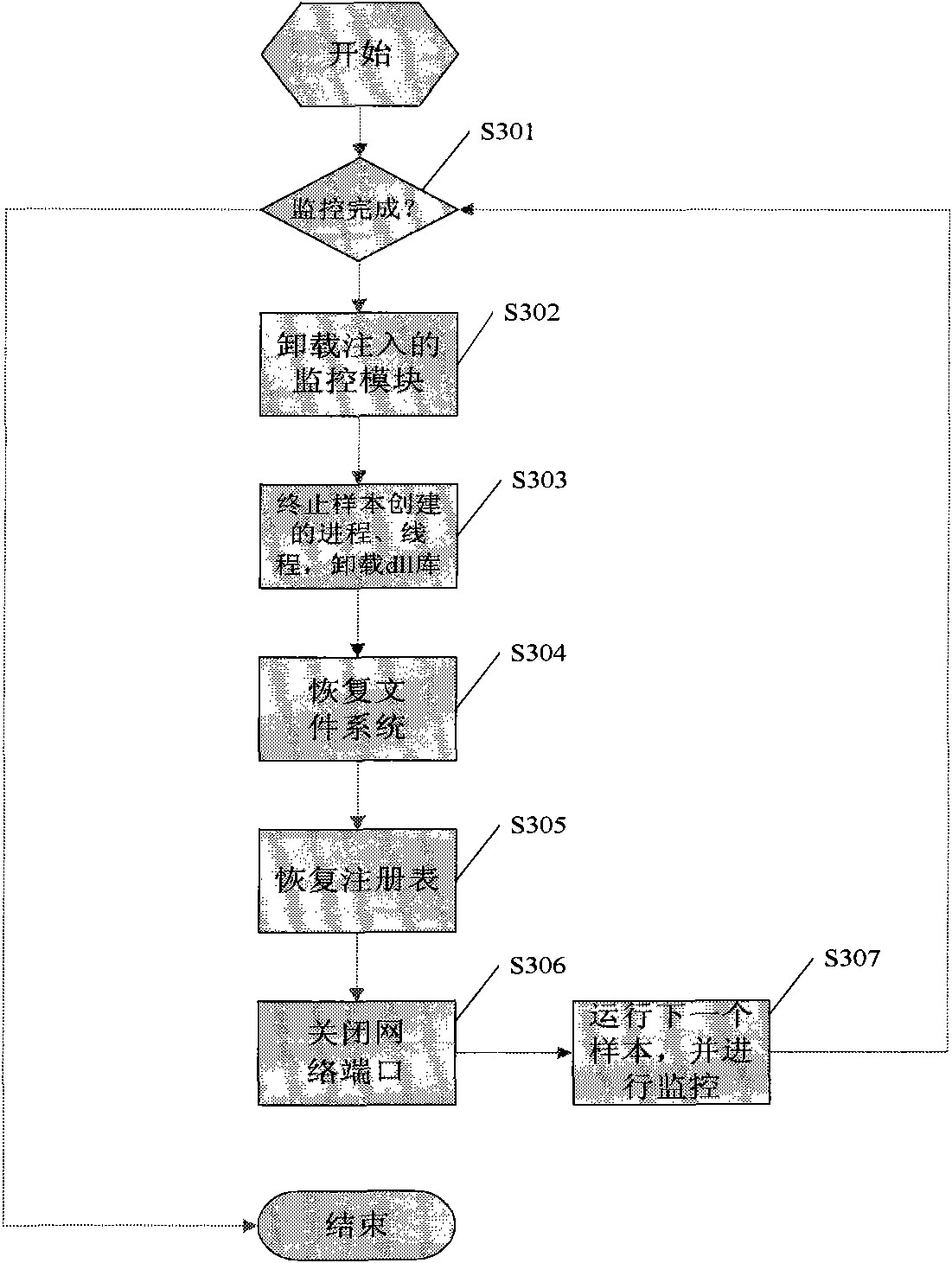
Automatic analysis method and system of malicious codes based on API (application program interface) HOOK
InactiveCN102314561APlatform integrity maintainanceData switching networksOperational systemApplication programming interface
The invention provides an automatic analysis method and system of malicious codes based on an API (application program interface) HOOK. An API HOOK technology and a remote thread implantation technology are utilized to monitor samples; influences of the malicious codes on the whole system in an operation process are recorded, and a dynamic analysis report is automatically generated; influences of malicious code samples on a file, a network, and a registry and a key process are recorded, and when the operation of the samples ends, the system recovers the state before the samples are executed; the whole monitoring, recording and reduction process ends automatically without manual intervention; monitoring software can only run a sample each time, the monitoring software is used for monitoring the host process of the samples and process threads created by the host process of the samples, and when the monitoring software finishes the monitoring, the system recovers the state before the samples are operated; behaviors such as creation, deletion, modification and the like of the malicious code samples on the file are detected, operation behaviors of the malicious code samples on the network are detected, behaviors such as addition, deletion, modification and the like of the malicious code samples on the registry are detected, and operation behaviors of the malicious code samples on the create process are detected; and finally the dynamic monitoring report on the malicious code samples is submitted, and when the monitoring is finished, the monitoring software carries out inversion operation to restore the system to the state before the samples are operated according to the operations and influences of the samples on an operating system. The intelligent analysis technology of the malicious codes is suitable for analyzing a great deal of samples without the manual intervention, and is quicker in analysis speed and less in garbage in the analysis report.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Restoring a file to its proper storage tier in an information lifecycle management environment
A technique for implementing policy-aware backup and restore capability in a tiered storage system. If a data set's contents are backed up from the tiered storage system to a backup storage system, metadata for the data set may also be backed up. Prior to the data set being restored from the backup storage system to the tiered storage system, the backed up metadata is restored and processed to determine a tier among the tiered storage pools to which the data set will be restored.
Owner:HUAWEI TECH CO LTD
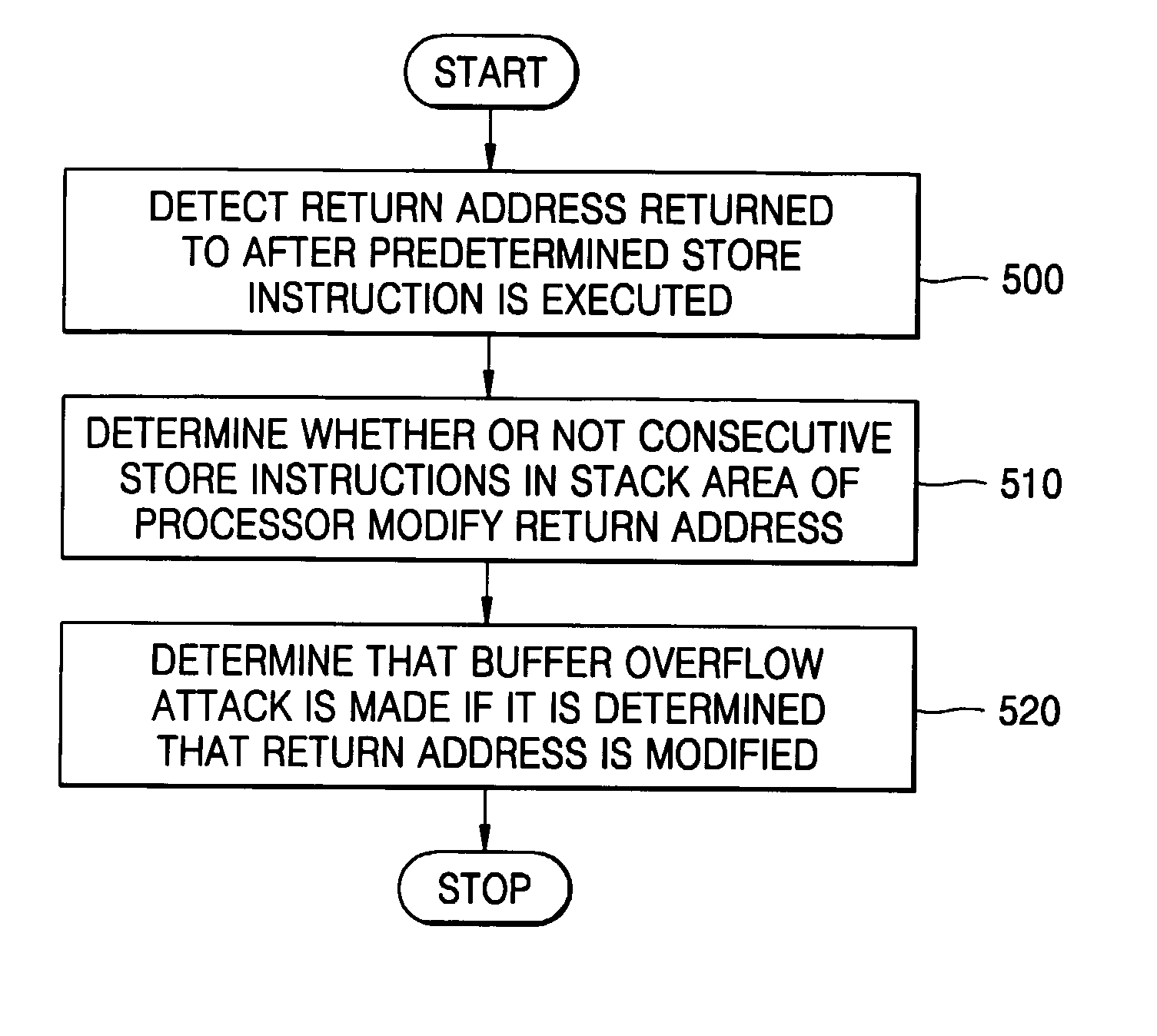
Method for sensing and recovery against buffer overflow attacks and apparatus thereof
ActiveUS20070180524A1Efficient detectionLow computing performanceOperating means/releasing devices for valvesMemory loss protectionSystem recoveryAttack
Methods and apparatuses for detecting and recovering from a buffer overflow attack are provided. A method of recovering an operation state of a processor from a buffer overflow attach includes: detecting whether a buffer overflow attack is made on any write operation while storing write operations that are potential targets of buffer overflow attacks in a predetermined location instead of an original destination to store write operations; storing the contents stored in the predetermined location at a predetermined interval in the original destination for storing write operations if no buffer overflow attack is detected and discarding unsafe write operations subsequent to a buffer overflow attack if a buffer overflow attack is detected; and ignoring the unsafe write operations subsequent to the buffer overflow attack if a buffer overflow attack is detected. Therefore, a buffer overflow attack occurring in a computer can be effectively detected, and damage of a system which is attacked can be minimized and the system can be recovered or return to the original state before the attack. A system can be effectively protected while minimizing reduction in performance of the computer system according to a method used to implement the present invention, thereby greatly improving the environments under which the computer and the Internet are used.
Owner:HANBAT NAT UNIV IND ACADEMIC COOPERATION FOUND
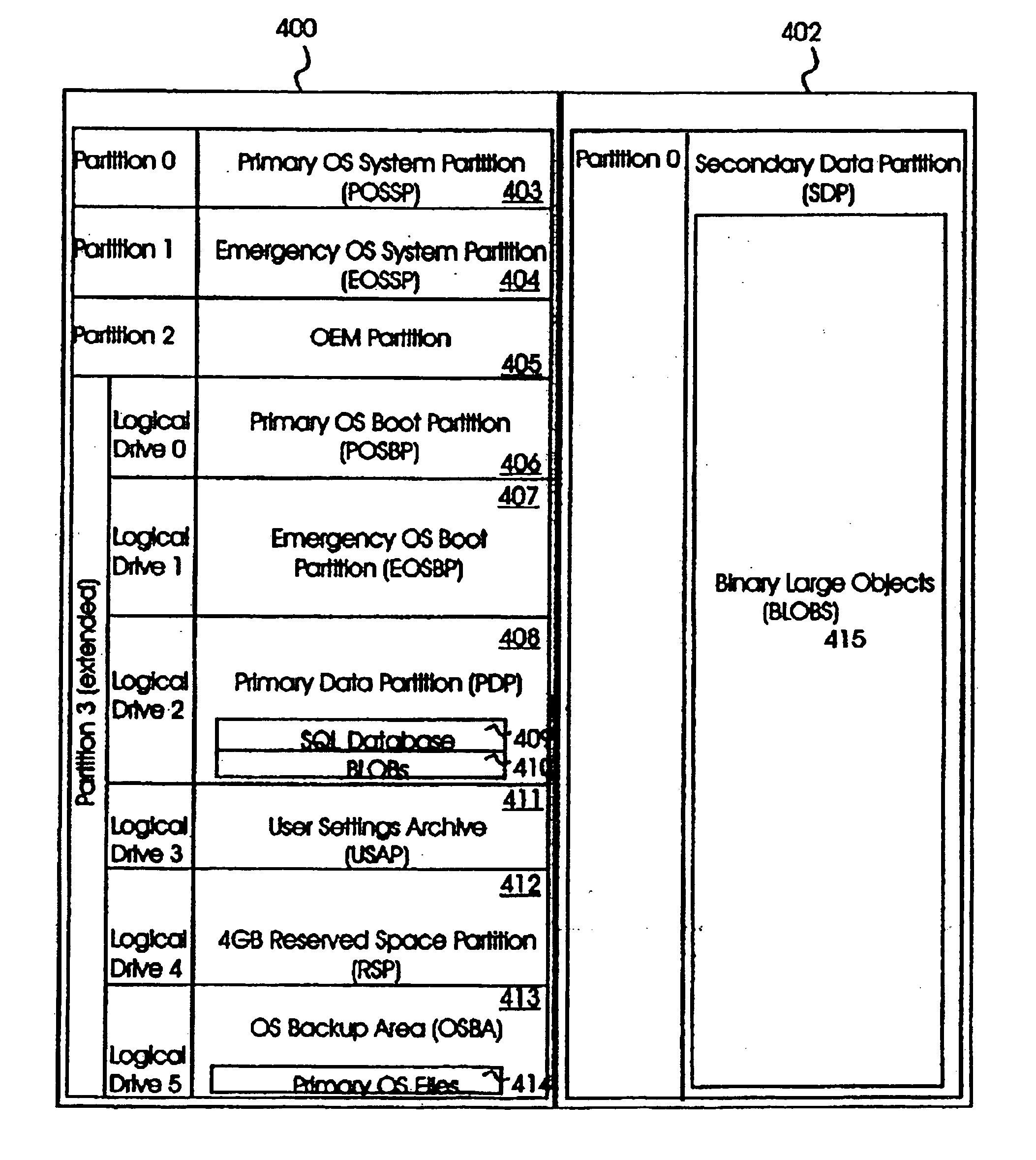
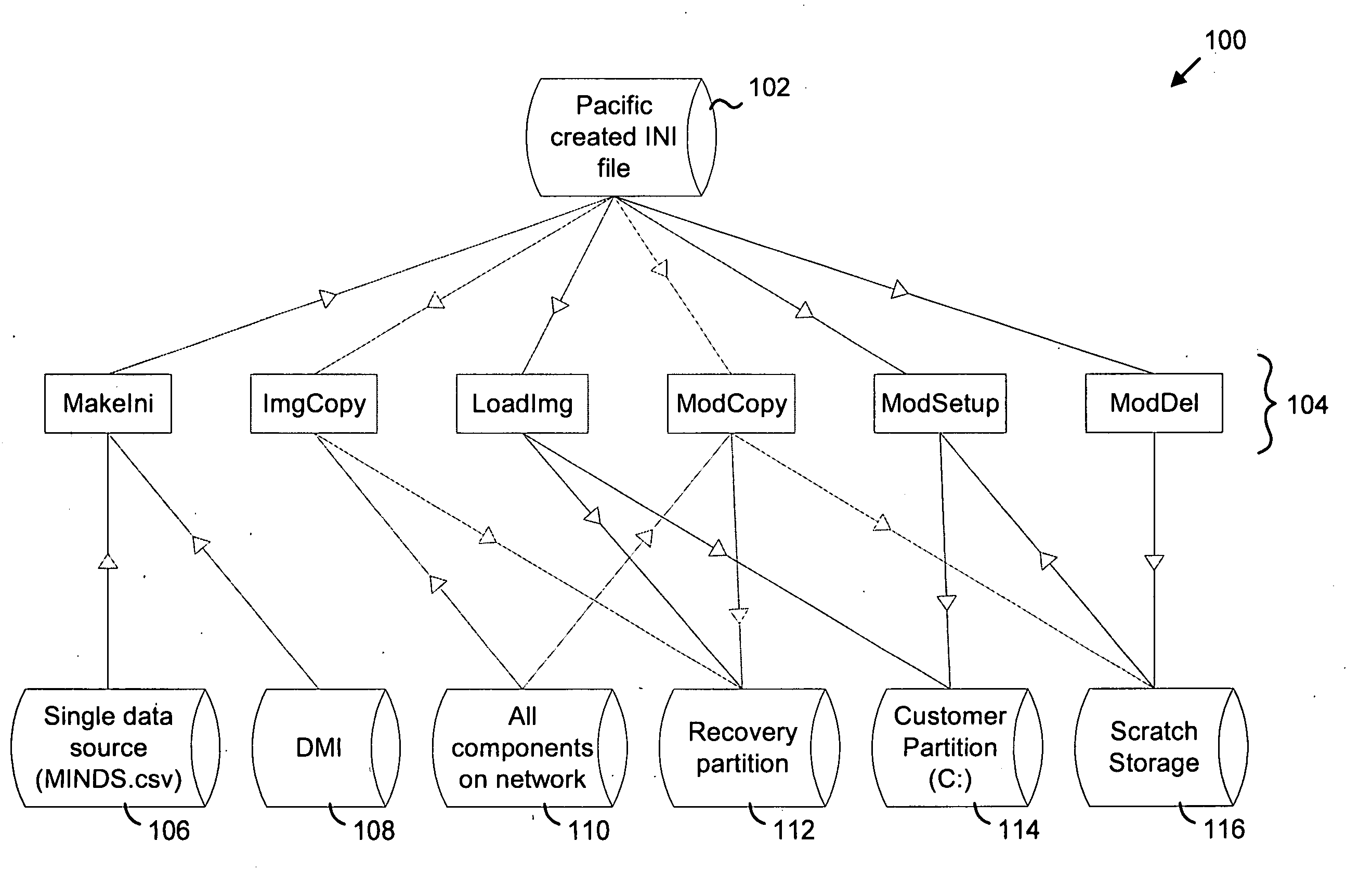
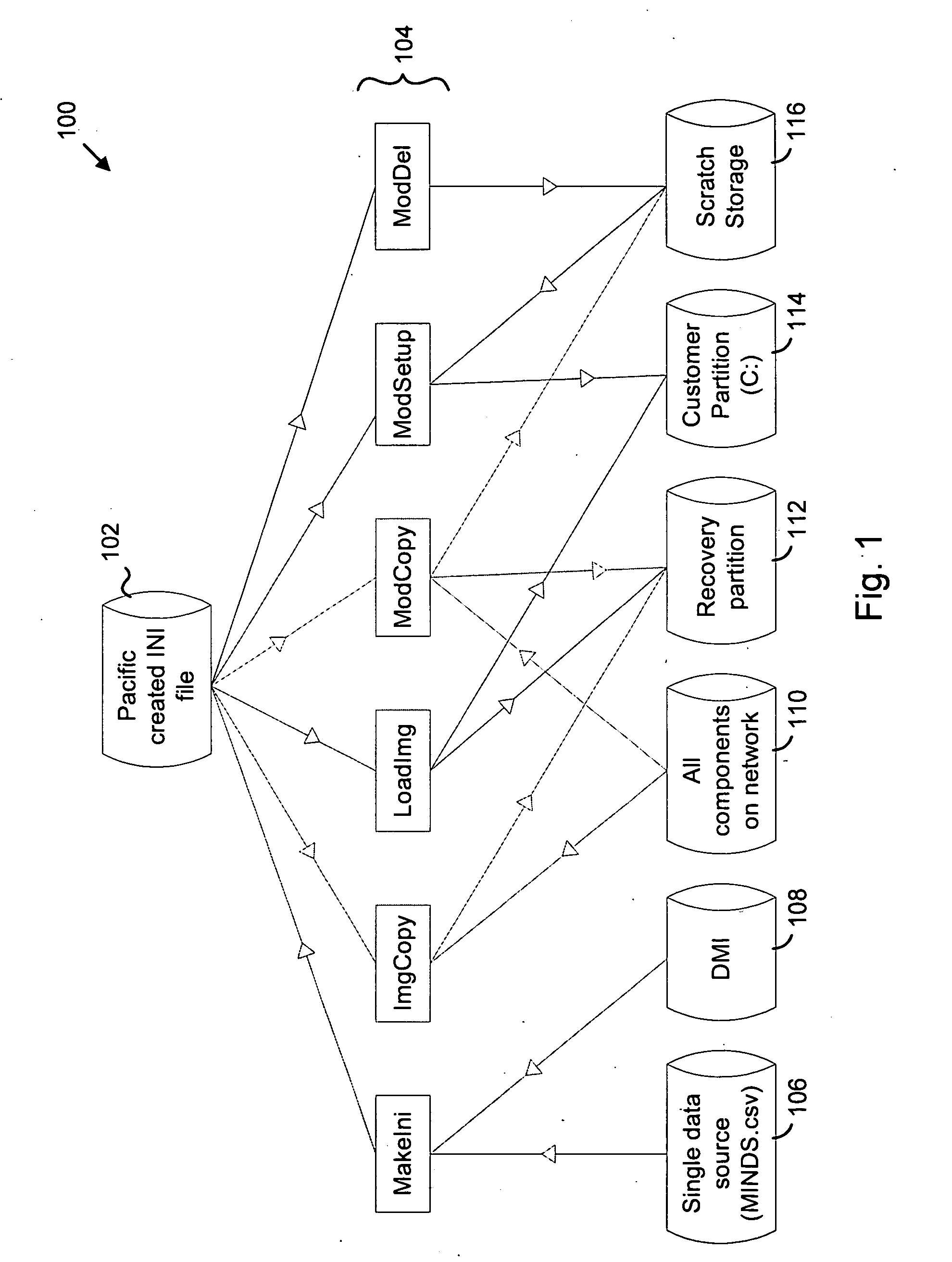
Modular imaging of computer software for system install and restore
InactiveUS20050240815A1Error detection/correctionProgram loading/initiatingDigital videoOperational system
A modular approach to creating a software configuration and to allowing recovery of a configuration. Initial configuration tools can be applied or executed selectively and in different orders at a time of manufacture or shipping of a computer system. Foundation images and modules are stored in a flat directory structure, in one directory, with unique names to make management of, and access to, the images and modules more efficient. Records are used to identify image and module compatibility on specific hardware platforms, or sets (i.e., computer system hardware). In one embodiment a text format is used for the records and other database information to describe and define the images and modules. A hardware set is identified by an identification (ID) code. A recovery set of tools allows a user to selectively restore a system to an original configuration, or to restore selected modules or components. A graphical user interface is described along with facilities for starting and managing a recovery process, application recovery, and Compact Disk (CD) / Digital Video Disk (DVD) media creation from within the computer system's operating system and to recover system and application files and modules; create recovery media and to remind a user to create recovery media.
Owner:SONY CORP +1
Methods and Apparatus for Effective On-Line Backup Selection for Failure Recovery in Distributed Stream Processing Systems
InactiveUS20080253283A1Error preventionFrequency-division multiplex detailsPrimary sitesSystem recovery
A failure recovery framework to be used in cooperative data stream processing is provided that can be used in a large-scale stream data analysis environment. Failure recovery supports a plurality of independent distributed sites, each having its own local administration and goals. The distributed sites cooperate in an inter-site back-up mechanism to provide for system recovery from a variety of failures within the system. Failure recovery is both automatic and timely through cooperation among sites. Back-up sites associated with a given primary site are identified. These sites are used to identify failures within the primary site including failures of applications running on the nodes of the primary site. The failed applications are reinstated on one or more nodes within the back-up sites using job management instances local to the back-up sites in combination with previously stored state information and data values for the failed applications. In additions to inter-site mechanisms, each one of the plurality of sites employs an intra-site back-up mechanism to handle failure recoveries within the site.
Owner:IBM CORP
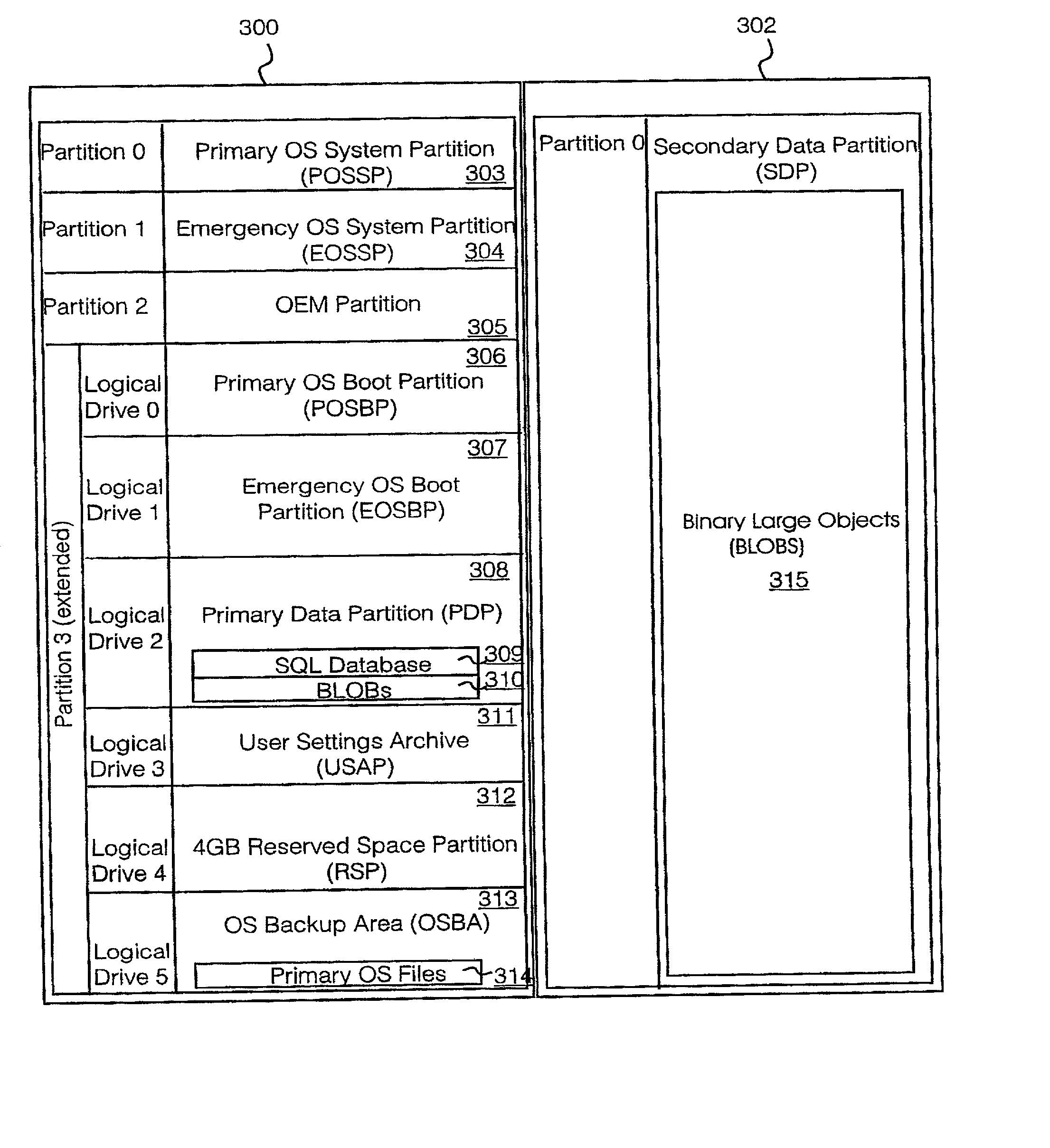
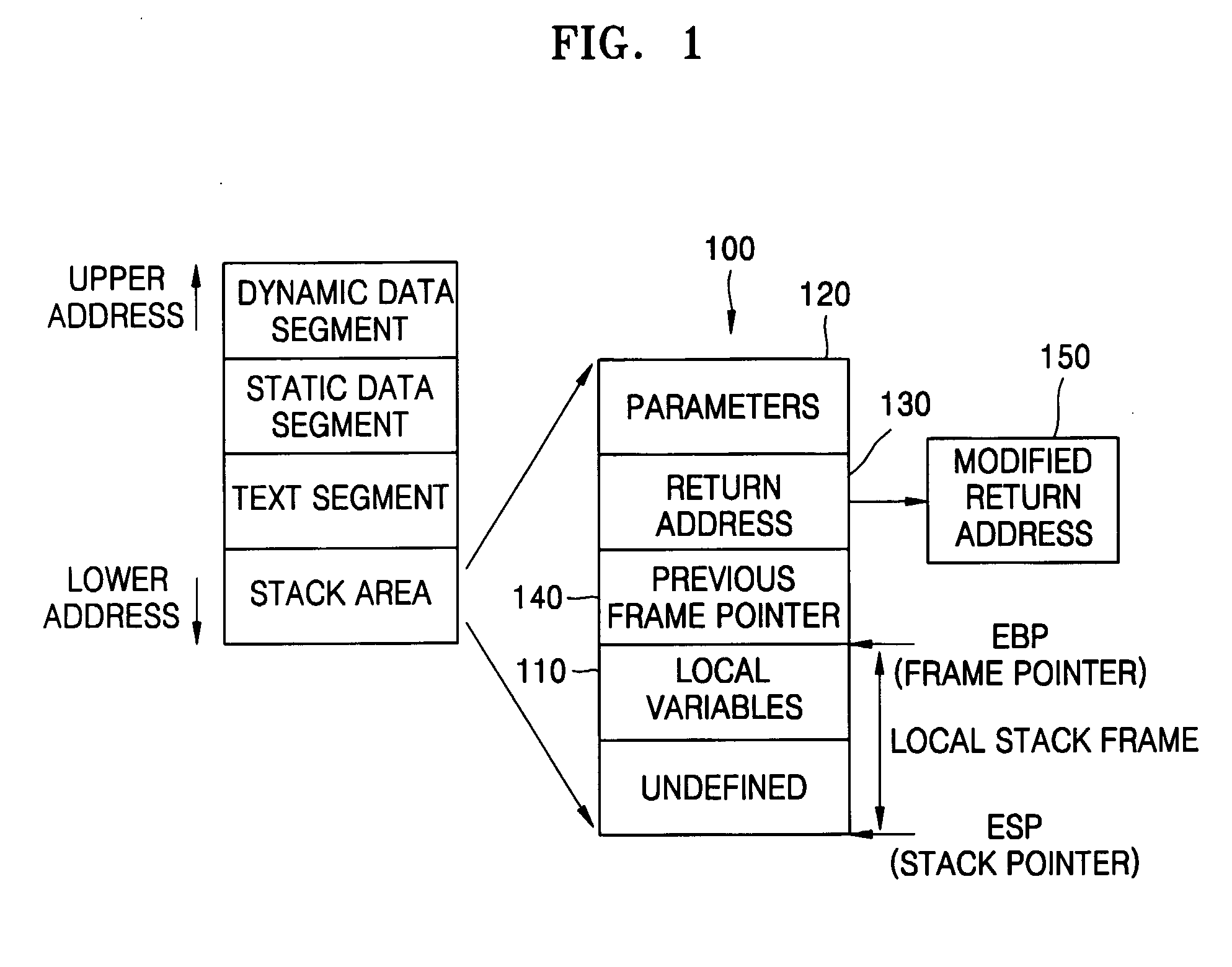
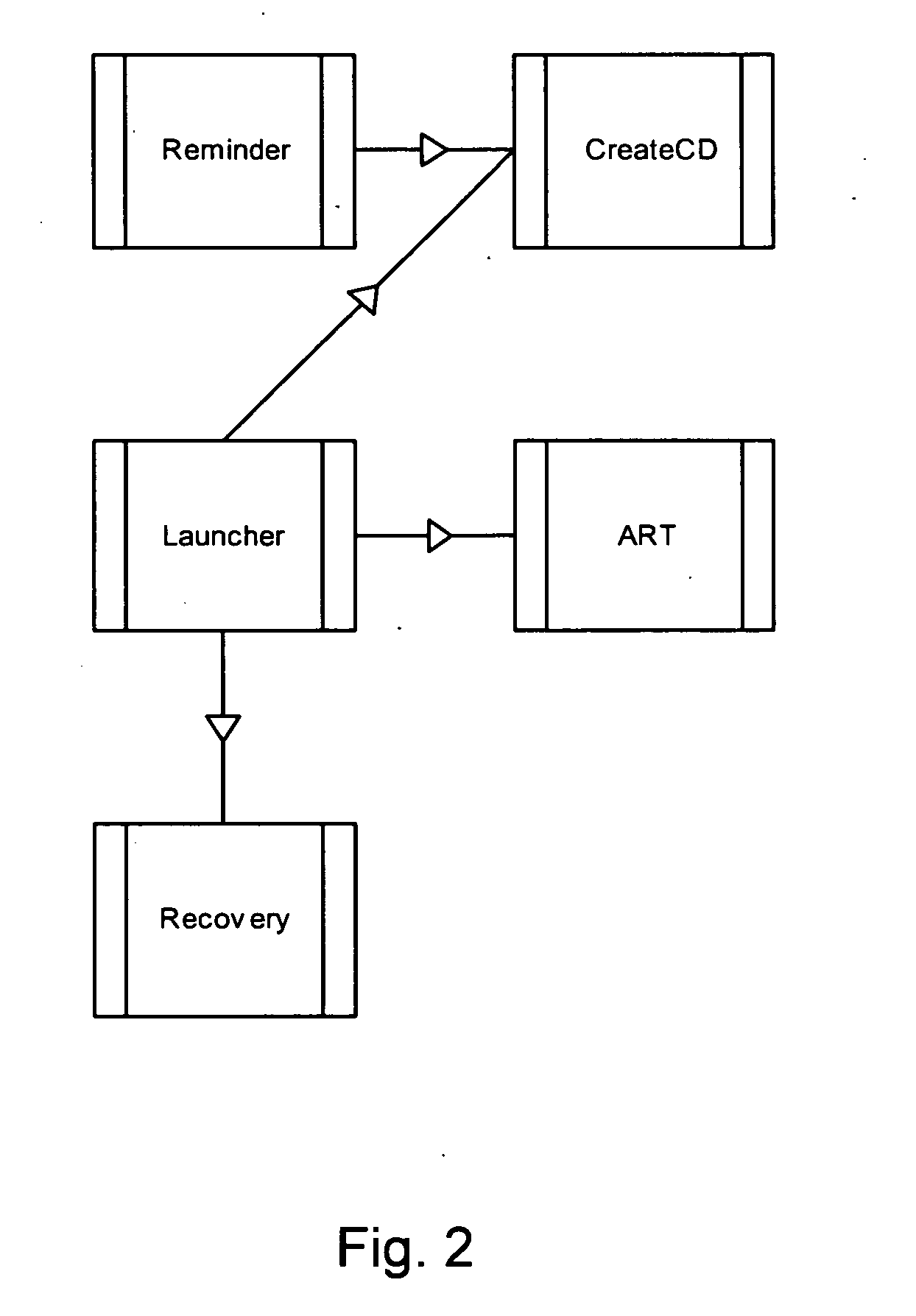
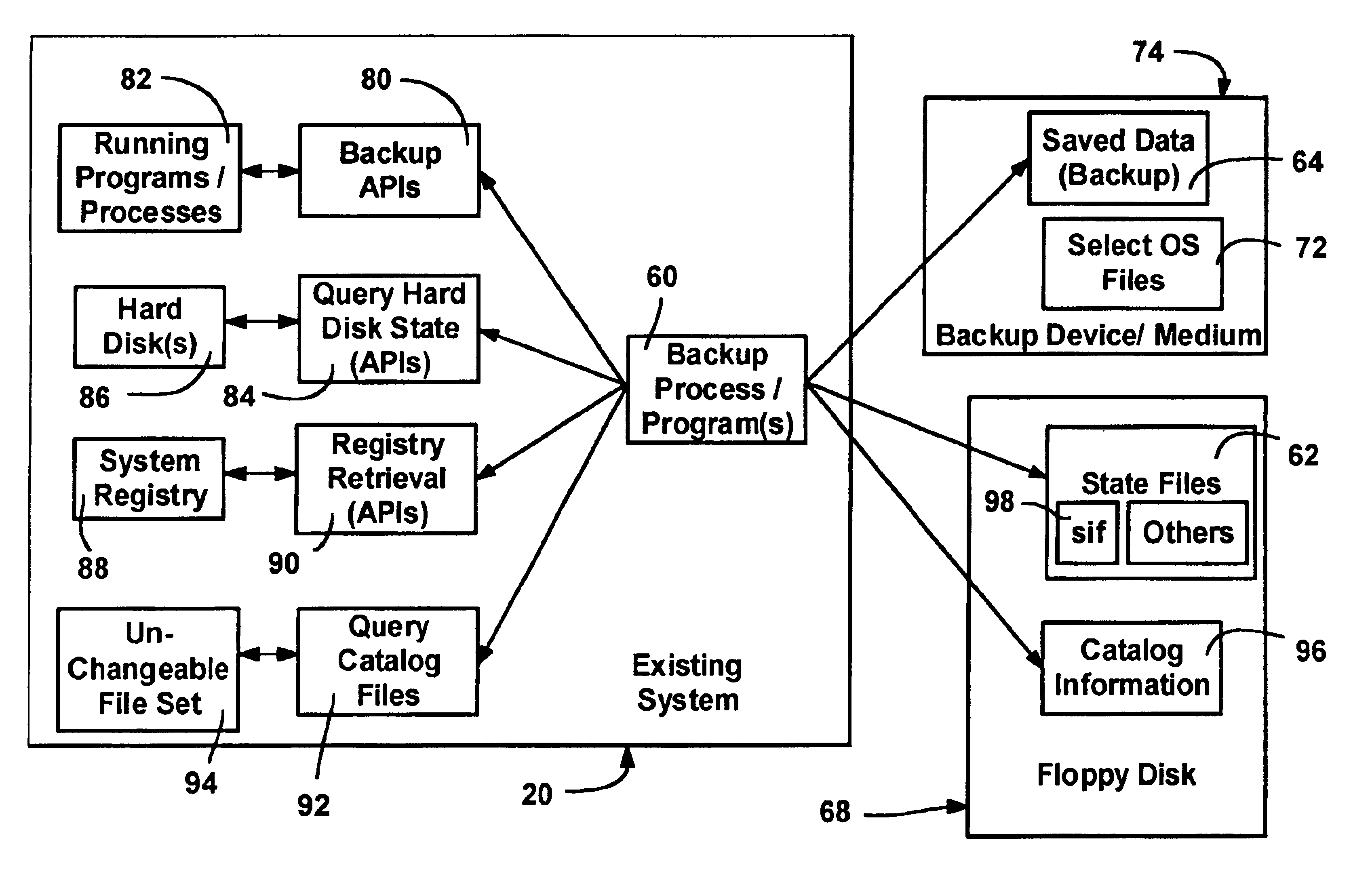
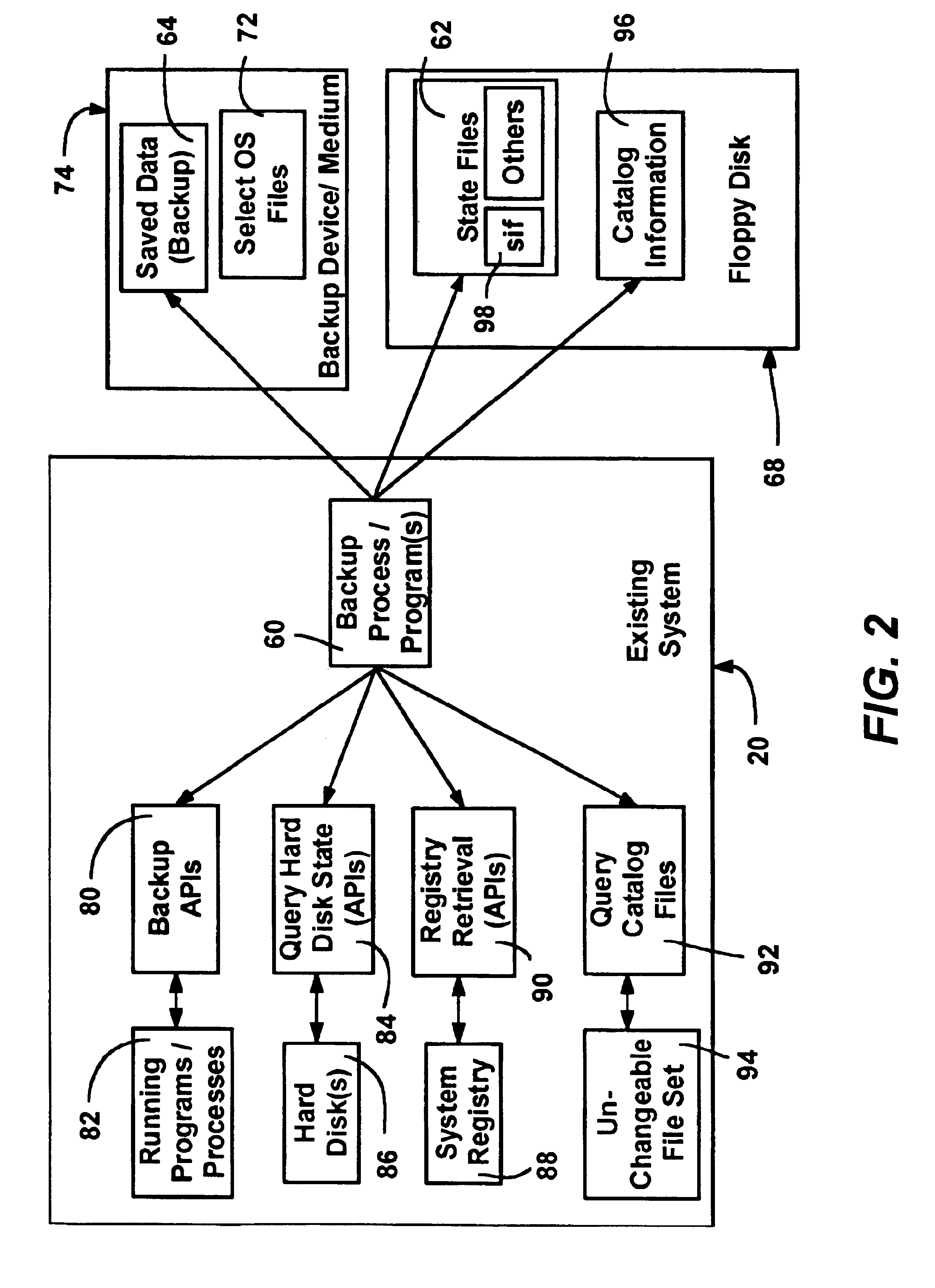
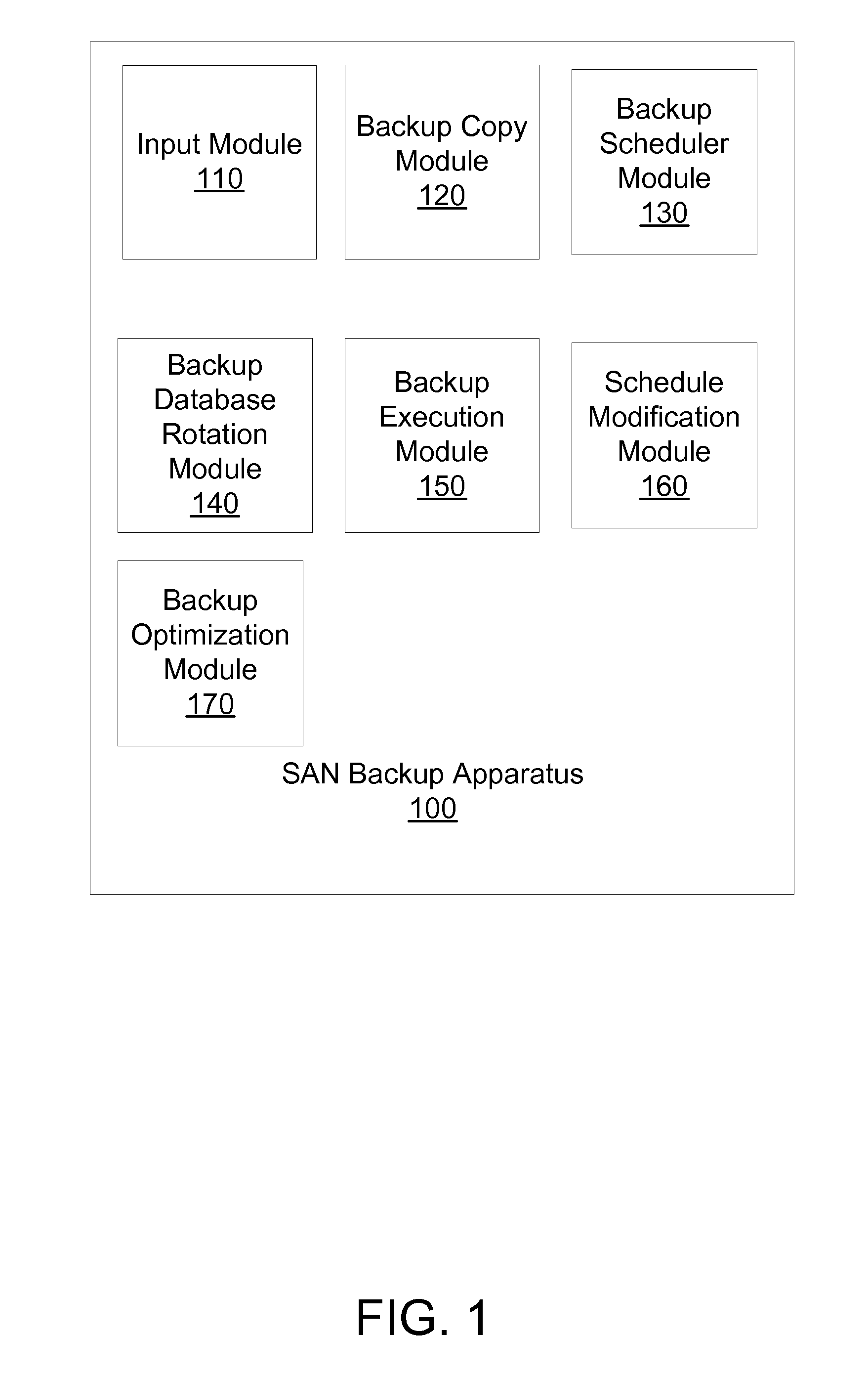
Extensible system recovery architecture
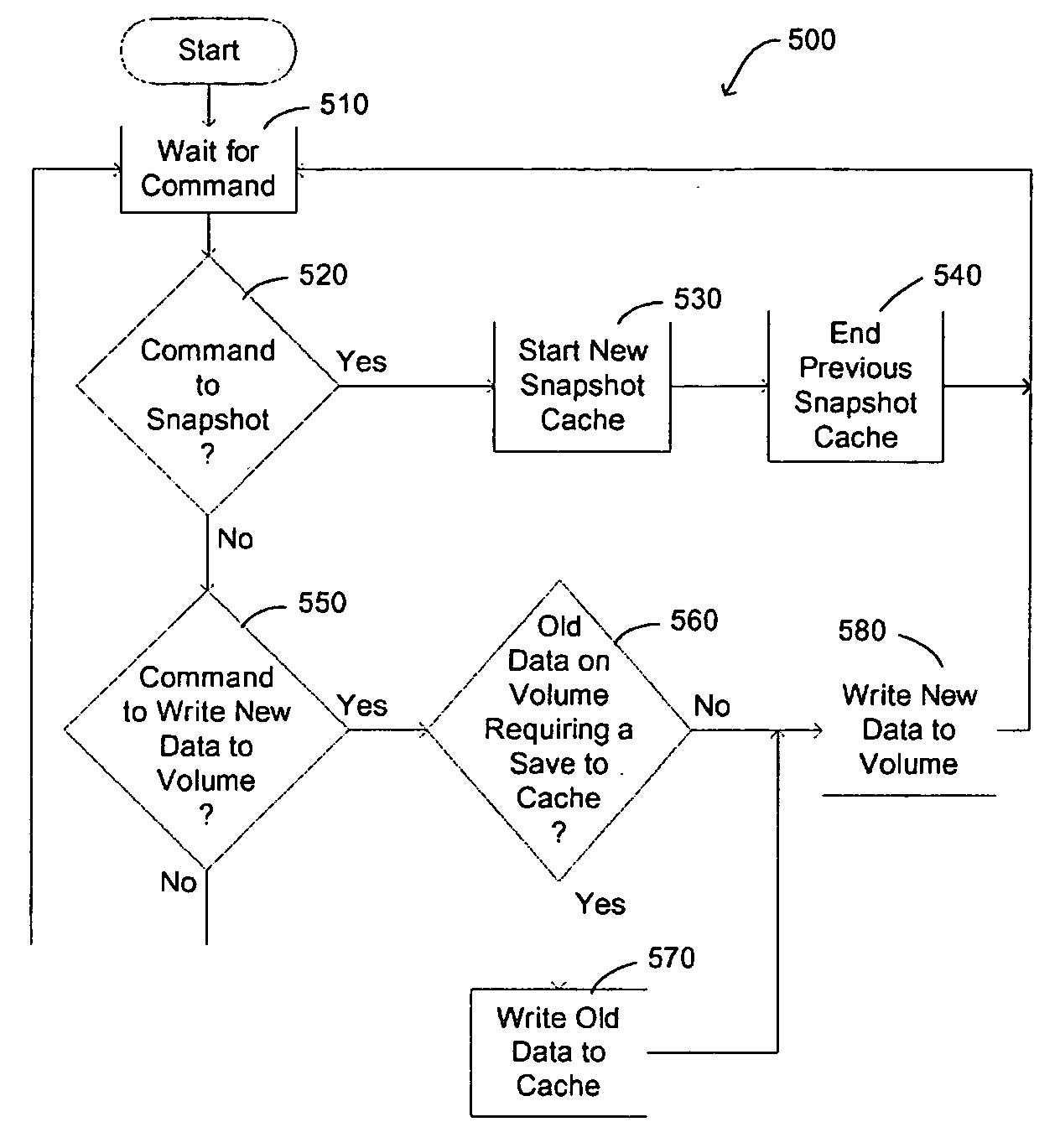
A system recovery method and framework for backing up and restoring a system that cannot reboot. The framework defines a common process, environment, and syntax, whereby backup programs integrate with this framework by collecting and writing appropriate information to be used during system recovery in the proper format. The format is a System Information File, a text file that specifies the hard disk state of the system and the location of key partitions where key components of the operating system are located. The file also includes instructions for specifying programs to launch during the restore phase, and any commands that need to be run in error handling cases. The file also includes or references any additional drivers or files to copy to assist in the restore process. A framework for restoring is also provided, and includes reading the file to restore the disk partition state, creating a common environment, and configuring (initializing) the common environment. When the environment is configured, the programs specified in the file are run to restore the remainder of the system.
Owner:MICROSOFT TECH LICENSING LLC
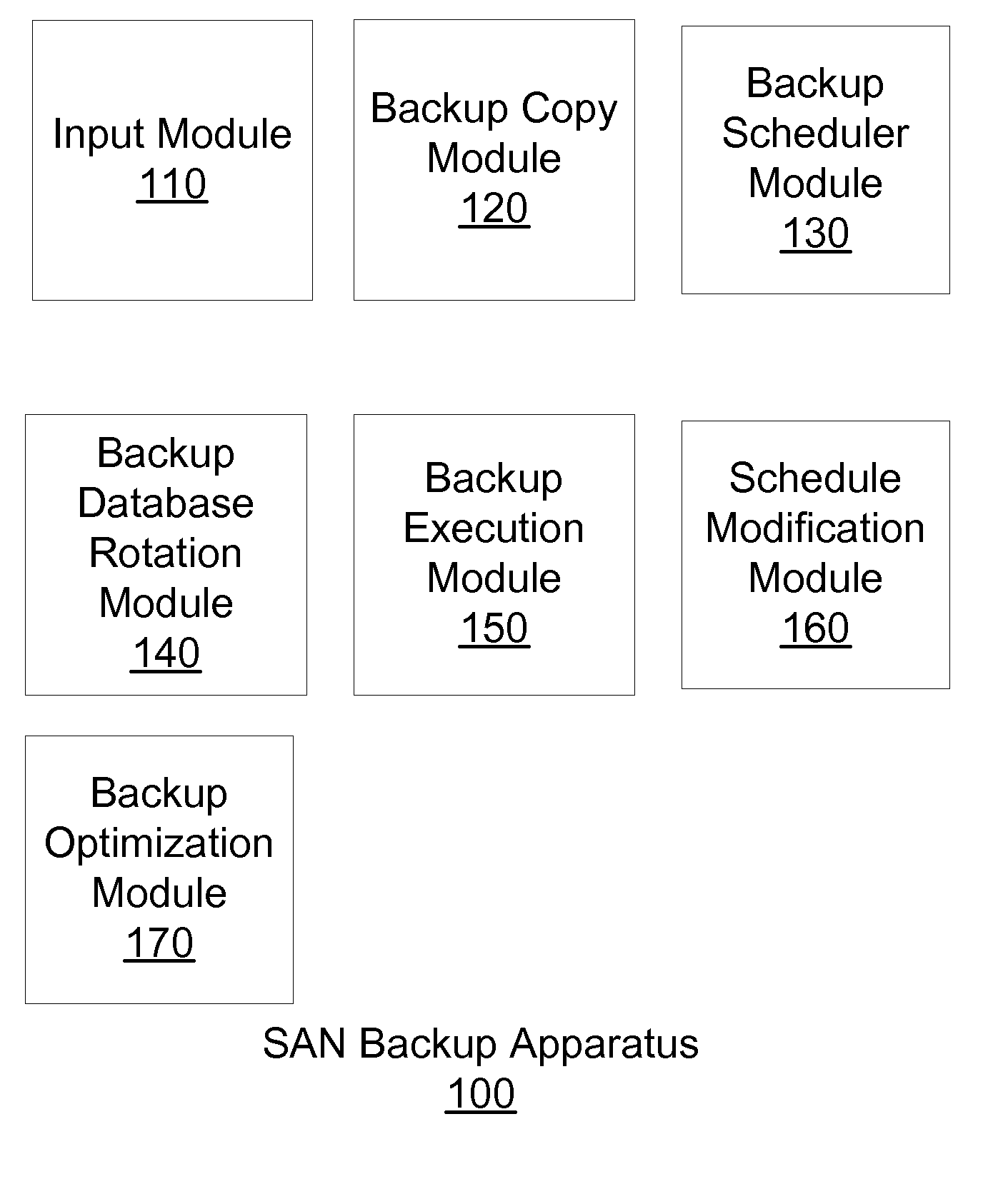
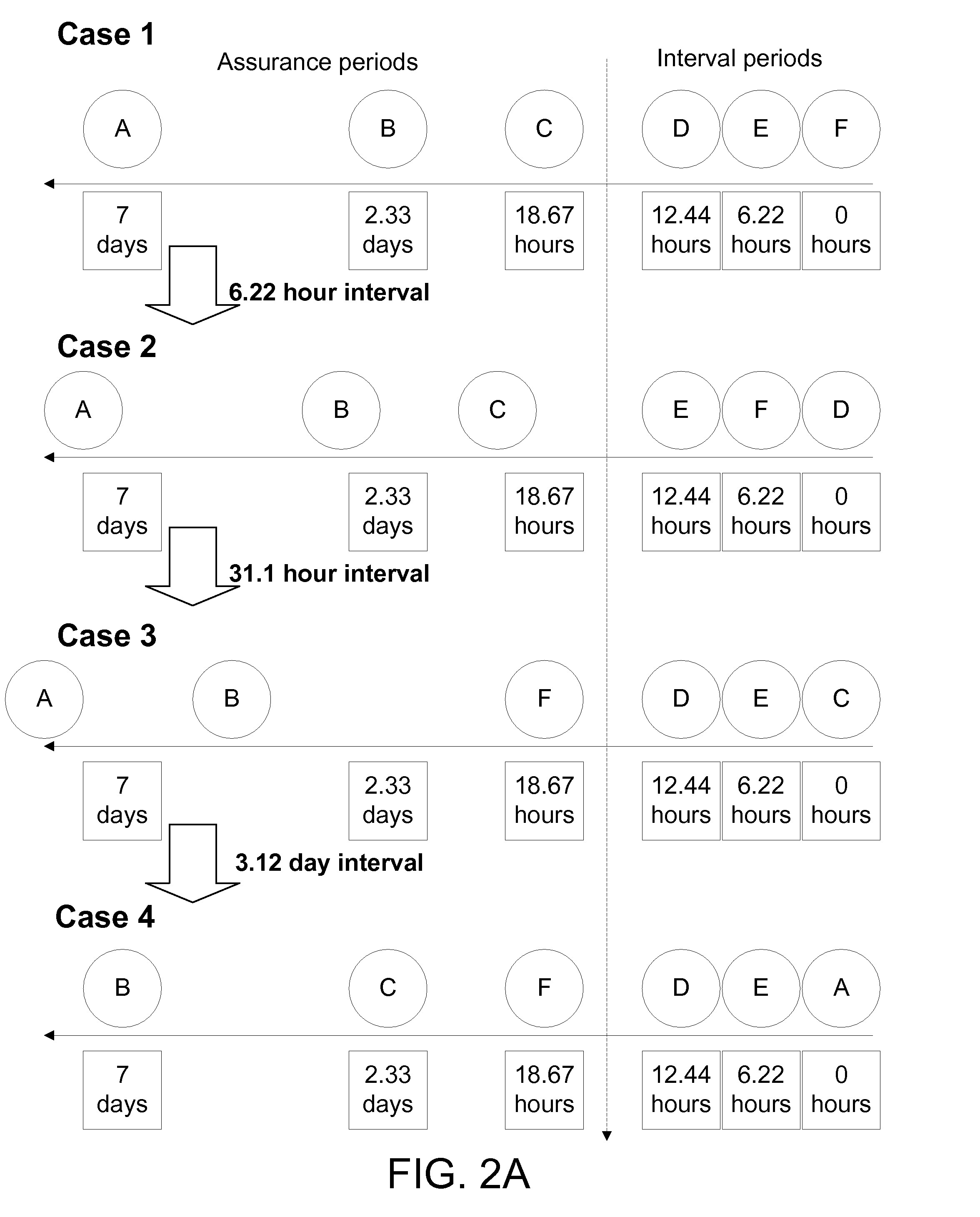
Apparatus, system, and method for creating a backup schedule in a san environment based on a recovery plan
InactiveUS20080154979A1Minimal disruptionError detection/correctionSpecial data processing applicationsDatabase backupSystem recovery
An apparatus, system, and method for creating a database backup schedule in a SAN environment based on a recovery plan. A user provides a desired recovery point objective (RPO) from a system recovery plan and an identifier of a database for back up. The present invention determines a priority (w) for a recent recovery point and determines a number (N) of volumes for storing backup images and a number (n) of database volumes used by the database. The present invention generates a scheduling formula where RPO is divided by the priority (w) of the most recent recovery point raised to the power of the truncated integer value of the ratio of volumes for storing backup images (N) and the number of volumes in use by the database (n) minus a scheduling interval determinant (i). The scheduling formula is used to determine a backup interval and backup assurance points.
Owner:IBM CORP
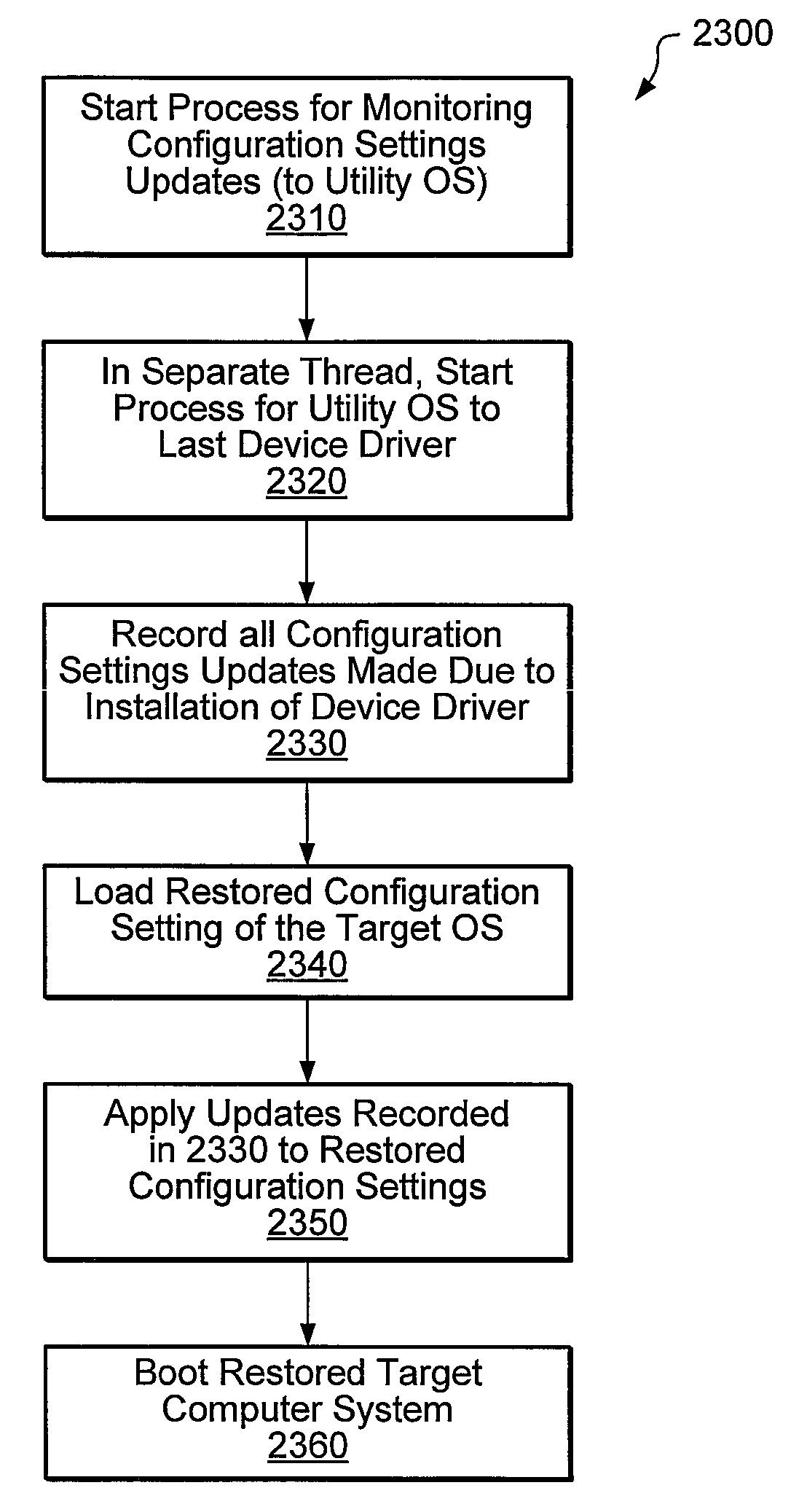
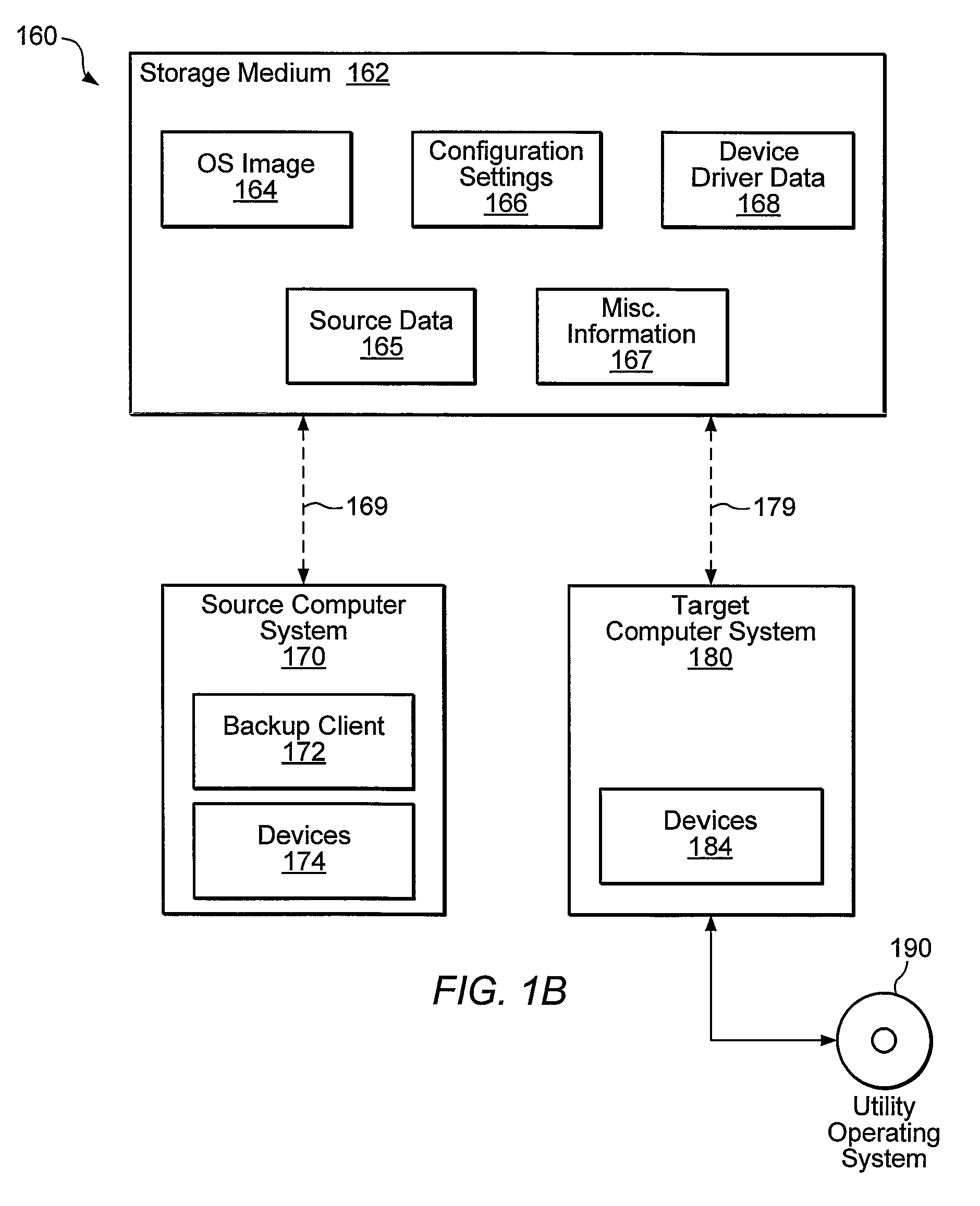
Using a monitoring process to update system configuration settings during restore operations
InactiveUS7769990B1Error detection/correctionDigital computer detailsOperational systemSystem recovery
Systems, methods, and computer-readable memory media for performing various computer configuration tasks are disclosed. One such configuration task is dissimilar system restore (DSR). Another such task is software deployment. In various embodiments, these configuration tasks operate on a target computer system using a utility operating system to perform detection of certain target system devices, determination of critical device classes on the source computer system, and updating of target computer configuration settings. Other tasks may be performed upon a computer system such as a backup server. These tasks include locating device drivers for the target operating systems and the installing utility operating system, as well as creating device driver packages that are usable to install device drivers for a plurality of devices.
Owner:VERITAS TECH
Data redundancy for writes using remote storage system cache memory
A technique for using a remote array cache memory for data redundancy. A computer system includes a first storage system having cache memory and mass storage. Data to be written to the mass storage is written to the cache memory. Redundant data is stored elsewhere in case the cache experiences a fault before the data can be written to mass storage. Otherwise, data not yet written to the mass storage may be lost. The first storage system is in communication with a second storage system which is typically located remotely from the first storage system. When the first storage system receives a write request, the first storage system forwards the data to the second storage system for redundant storage. Where the data is forwarded to the second storage system, this is referred to herein as "remote mode."The first storage system may include redundant cache memories and enters remote mode only in the event a fault affects one of the cache memories. The data can then be recovered from the second storage system if needed.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
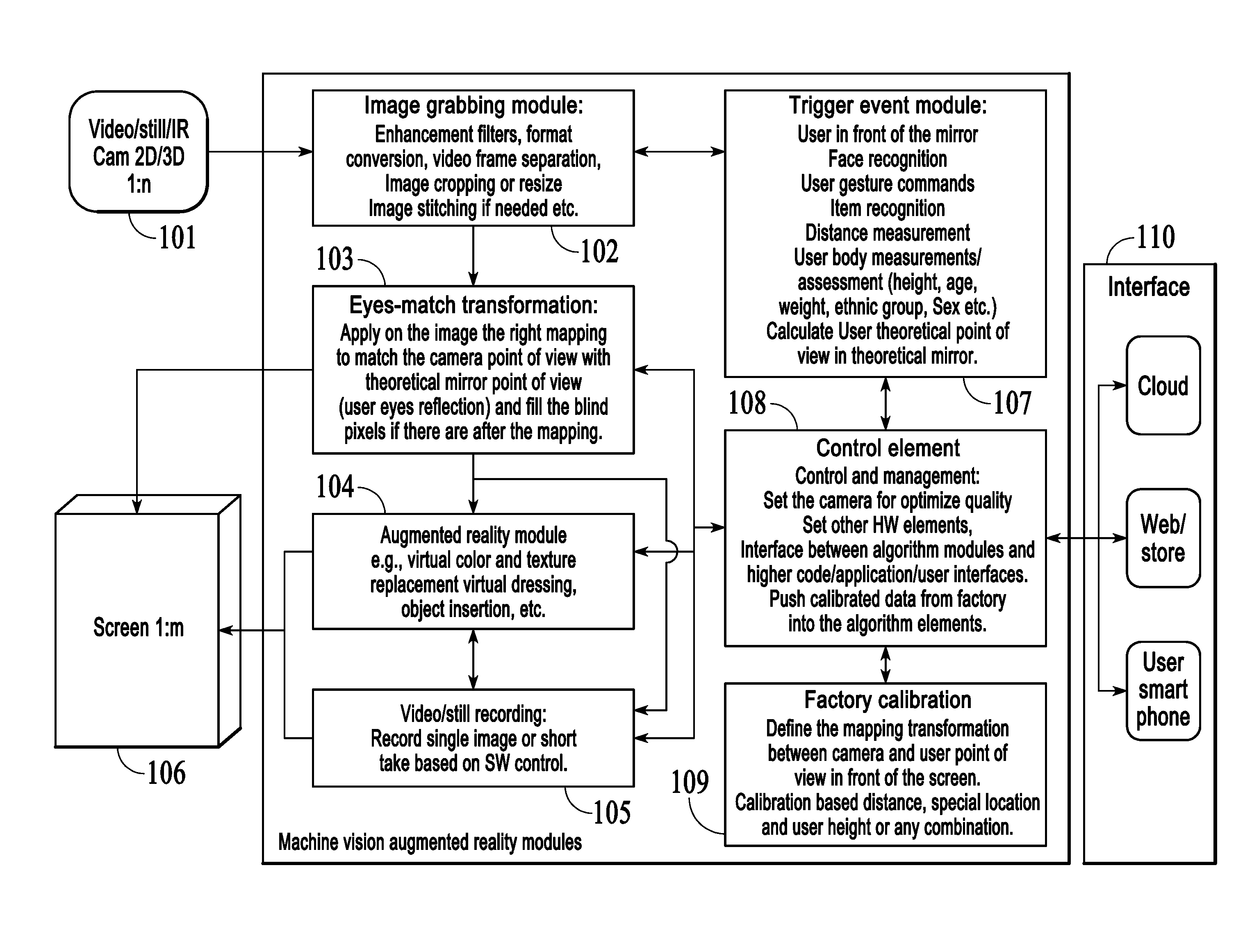
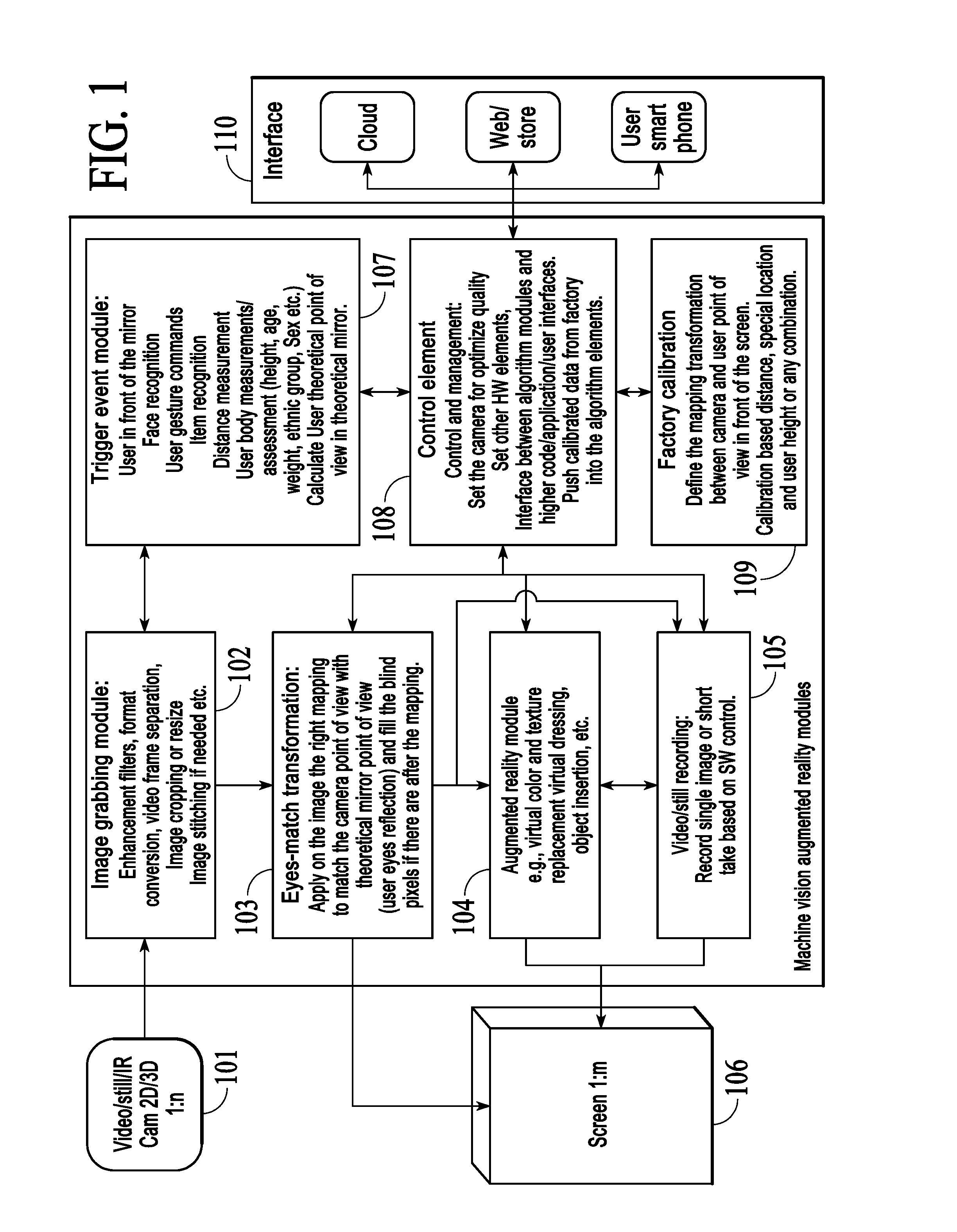
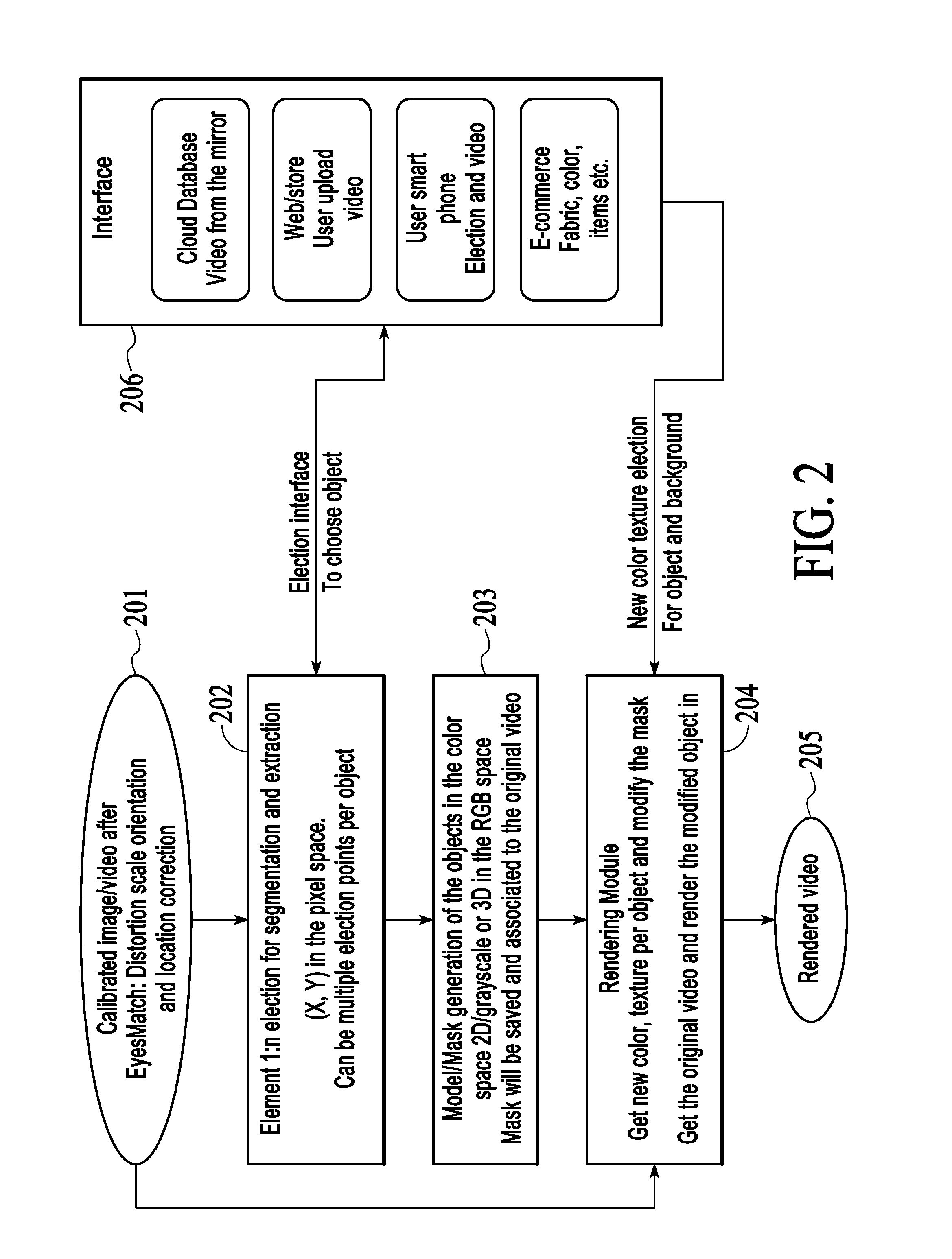
Devices, systems and methods for auto-delay video presentation
ActiveUS20160127710A1Interfere with flowImprove viewing experienceTelevision system detailsMirrorsDelayed periodsSystem recovery
A computer implemented method for automatic presentation of delayed video. During normal operation real-time video feed is sent to a digital screen for presentation and is also sent to memory for storage. When a delay trigger is issued, the system either freezes the frame presented in that instance or stores a time indicator. The system then monitors delay time and, when the delay time is reached, the system starts fetching frames from the memory, starting either from the frame immediately following the frozen frame or from the frame that was stored at the time indicator, and sends these frames to the digital screen for presentation. The system then monitors delay period and, when the delay period arrive, the system reverts to normal mode wherein real-time video feed is sent to a digital screen for presentation and is also sent to memory for storage.
Owner:EYESMATCH
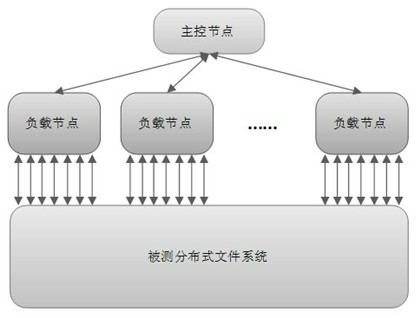
Concurrent connections performance testing system and method for file system
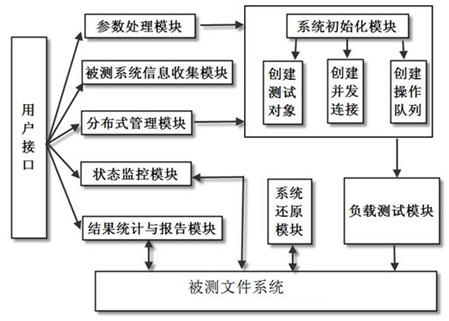
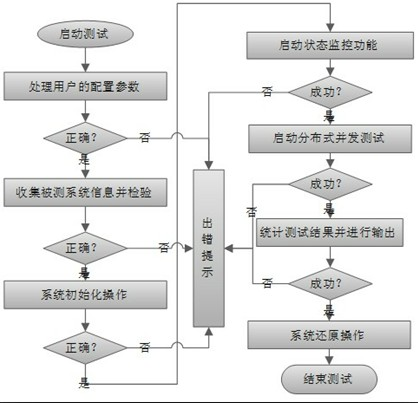
ActiveCN102035697AUnderstand the actual situationIncrease profitData switching networksSystem under testTask management
The invention discloses a concurrent connections performance testing system and a concurrent connections performance testing method for a file system. A master control node and at least one testing node are arranged, wherein the testing node is arranged on an application server of a storage system, is mainly used for simulating an application load to test a tested system, is connected with the tested file system through a storage network, and is used for testing the tested system; and the master control node performs centralized management which comprises process scheduling and task management on the testing node through a local area network, and is used for performing centralized management on all testing nodes and counting a test result. The system comprises a parameter processing module, a tested system information collecting module, a system initialization module, a condition monitoring module, a distributed management module, a load testing module, a result counting and reporting module and a system recovery module, solves the problems that the concurrent connections of the file system are not definitely defined and a detailed and useable testing method is lacked in the prior art, and is particularly suitable for the concurrent connections performance test of a distributed file system.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP
Highly available TCP systems with fail over connections
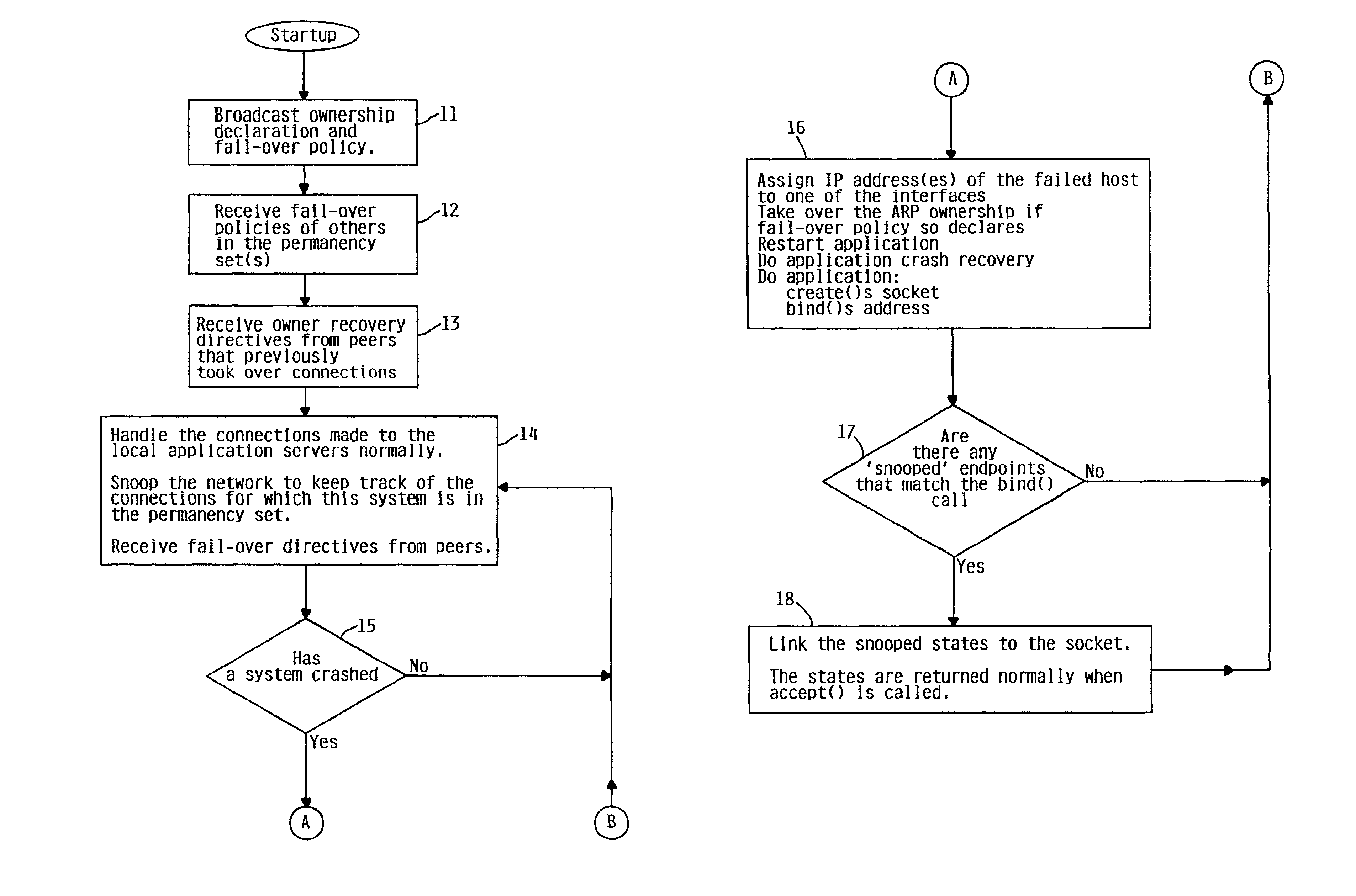
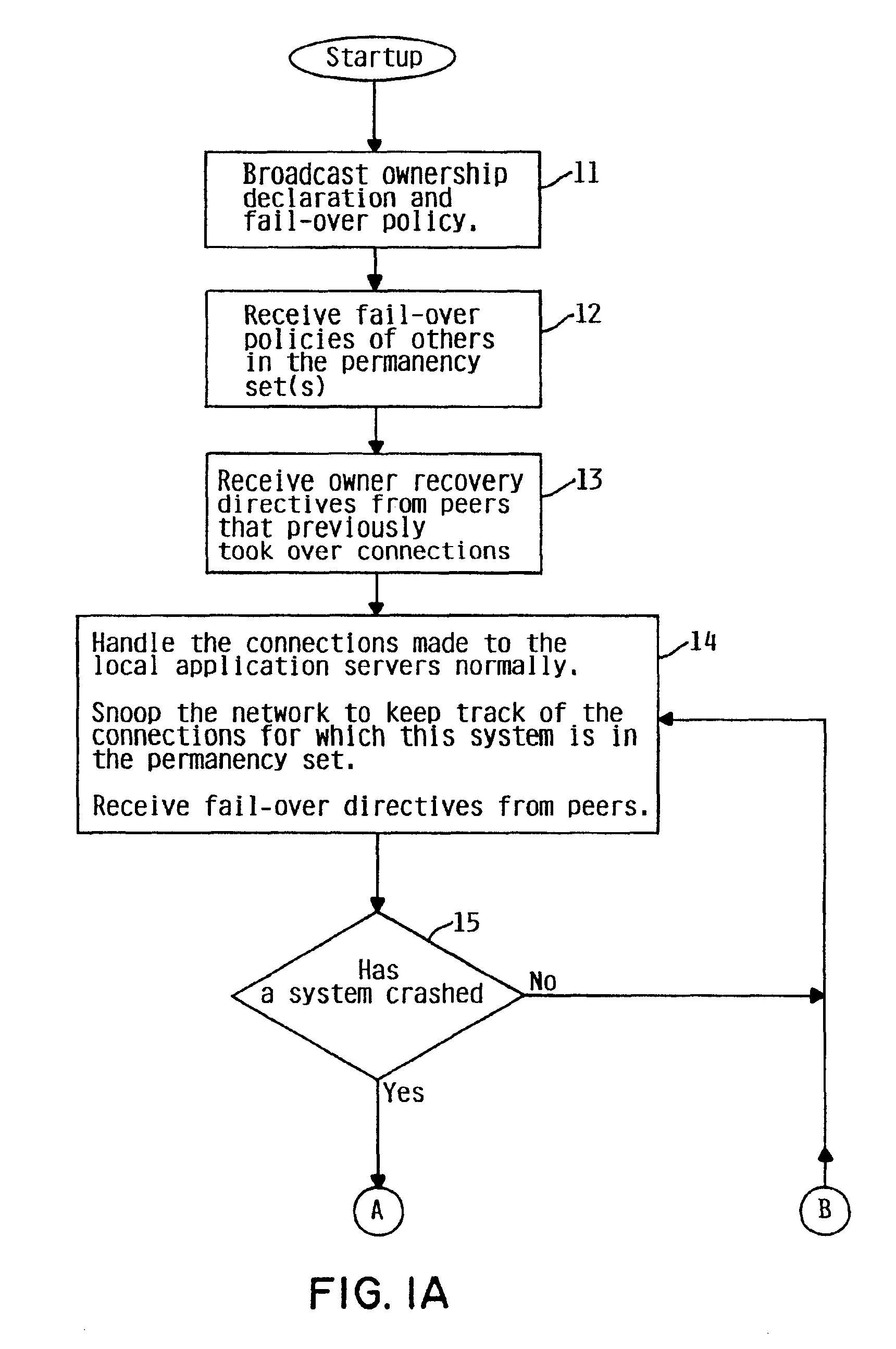
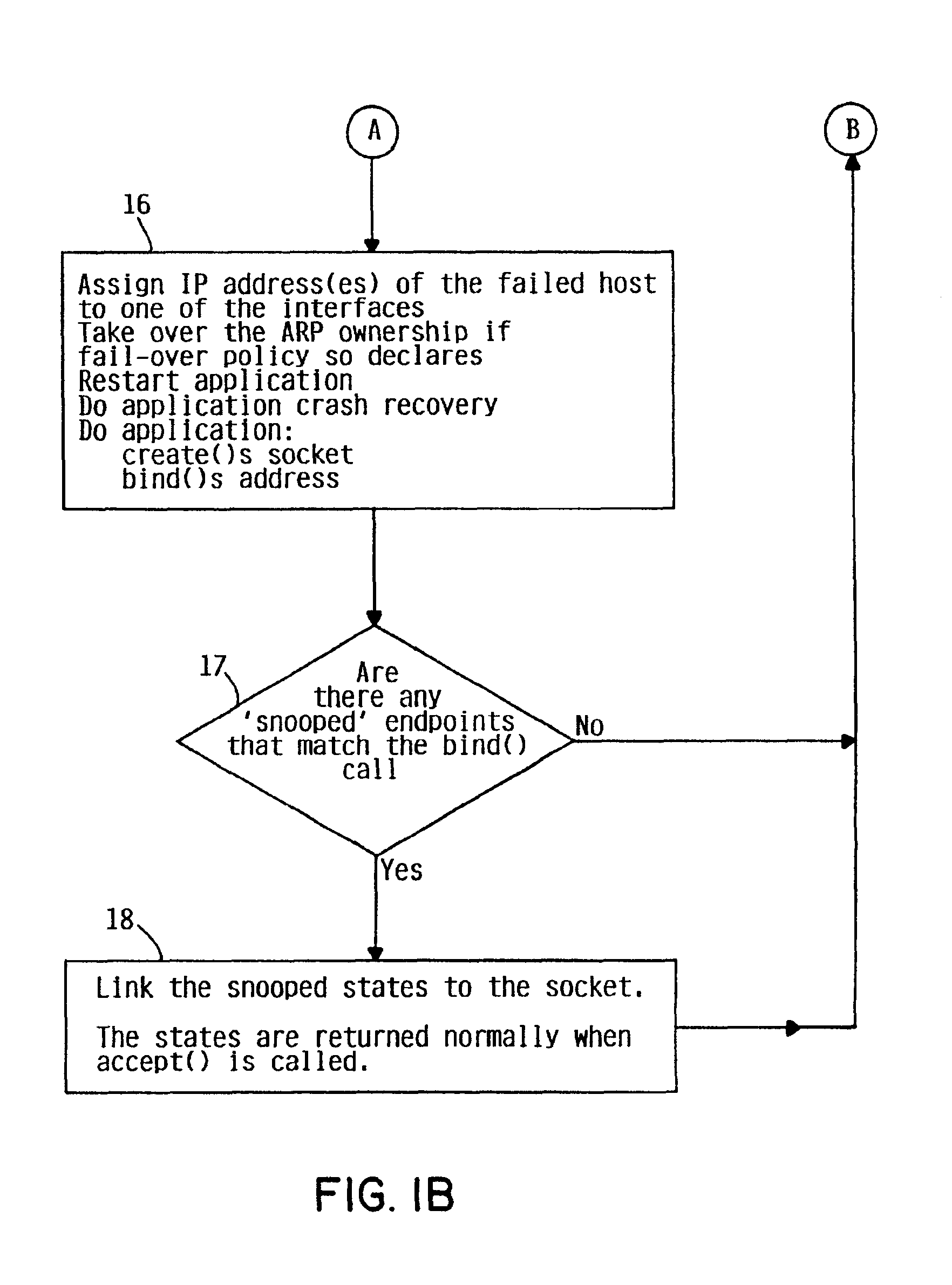
InactiveUS6871296B2Special service provision for substationMultiple digital computer combinationsFailoverSystem recovery
The present invention provides a method, system and apparatus by which TCP connections may be failed-over from one system to another within a highly available network service, and appear transparent to the remote client. The connection state and ownership information of a system is broadcast within the network, so that if a first system crashes while running an application, a predetermined take-over policy causes a peer system to assume connection without loss of data such that a permanent connection has been established from the client's point of view. After the failed system has been restored to a normal state, new connections are established by the first system.
Owner:IBM CORP
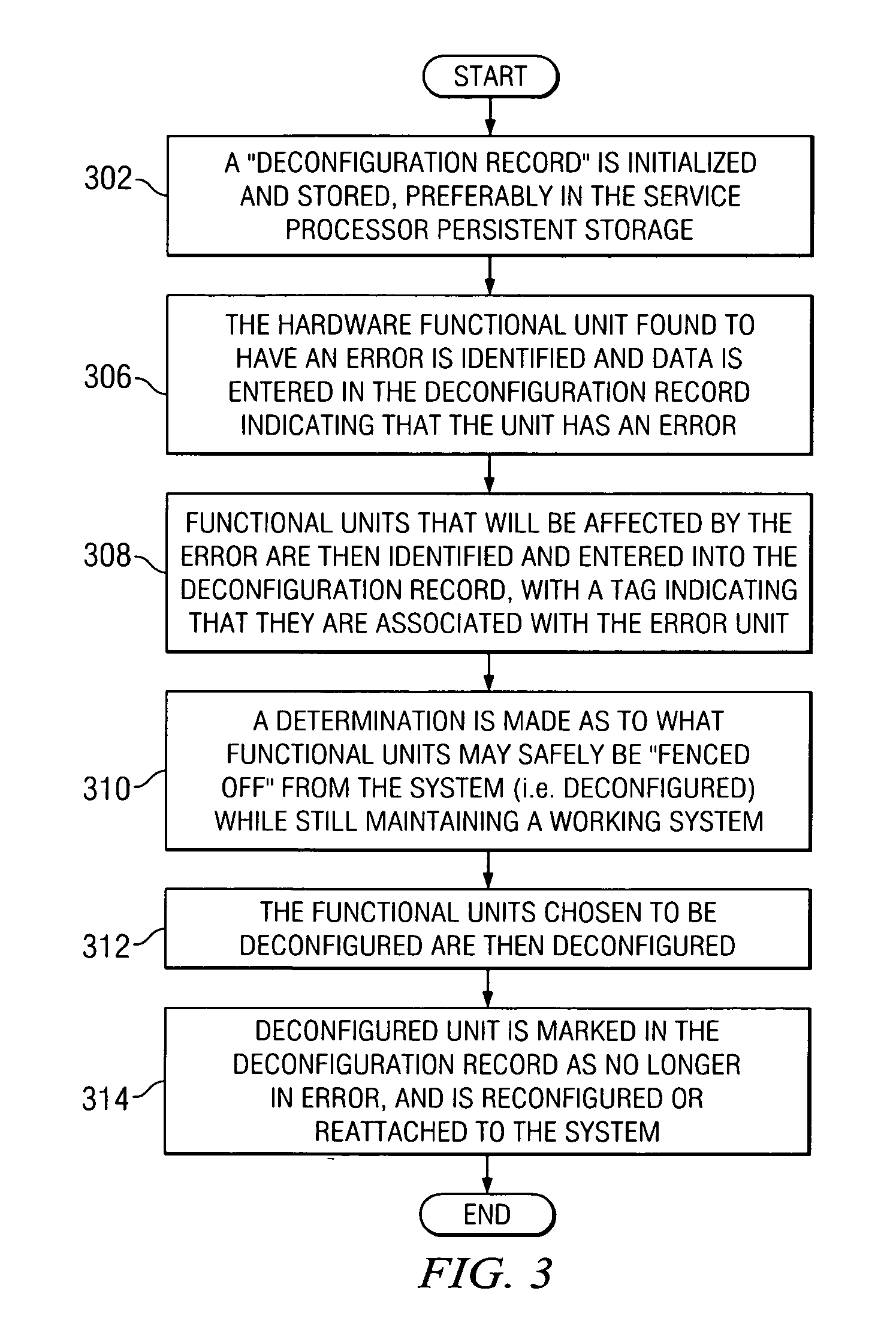
Method for fast system recovery via degraded reboot
InactiveUS20050229039A1Reduce downtimeDigital computer detailsBootstrappingSystem recoverySystem failure
A system and method for fast system recovery that bypasses diagnostic routines by disconnecting failed hardware from the system before rebooting. Failed hardware and hardware that will be affected by removal of the failed hardware of the system are disconnected from the system. The system is restarted, and because the failed hardware is disconnected, diagnostic routines may safely be eliminated from the reboot process.
Owner:IBM CORP
Method for closing processes
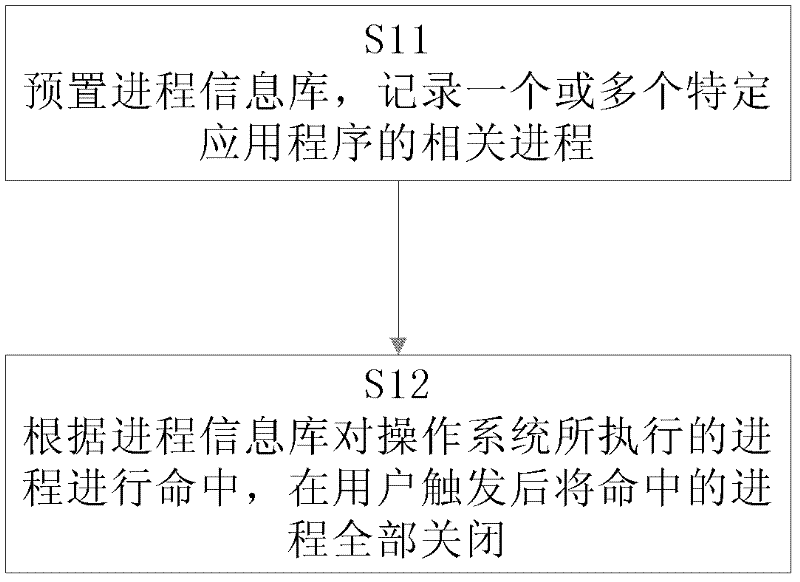
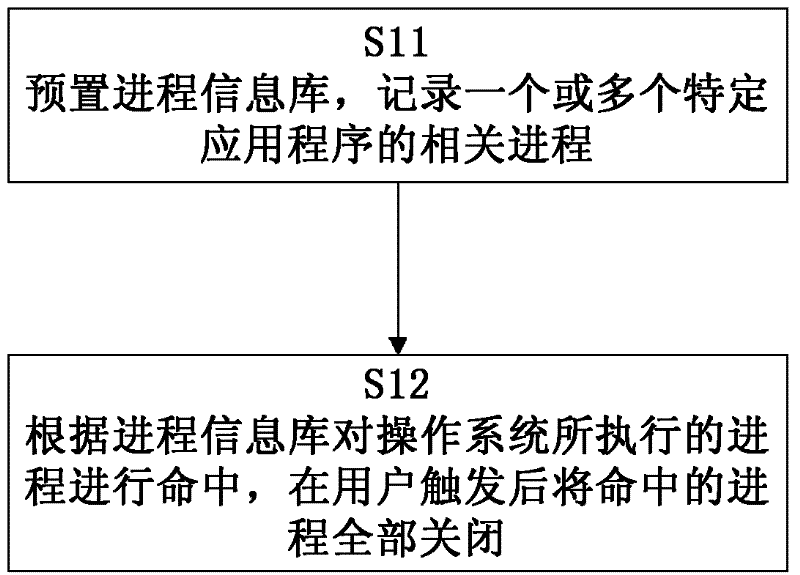
ActiveCN102253863AAvoid lostSave time and costError detection/correctionInformation repositoryOperational system
The invention discloses a method for closing processes, comprising the following steps of: presetting a process information bank for recording processes associated with one or more special application programs; and according to the process information bank, selecting the processes executed by an operating system, and closing all the selected processes after being trigged by a user. The method disclosed by the invention has the following advantages of: enabling the operating system to recover to the normal state, saving time cost and use cost for the user, and simultaneously ensuring that the user can open and use other application programs without being influenced after closing a multitude of processes.
Owner:三六零数字安全科技集团有限公司
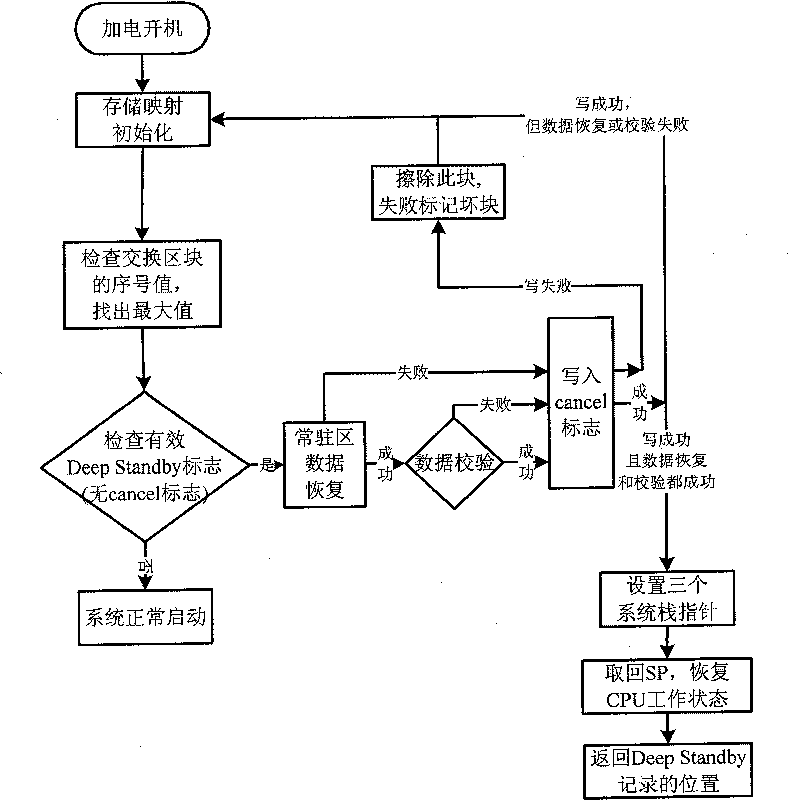
Deep-sleep method of embedded system
ActiveCN101710253AReduce standby power consumptionImprove boot speedEnergy efficient ICTPower supply for data processingElectricitySystem recovery
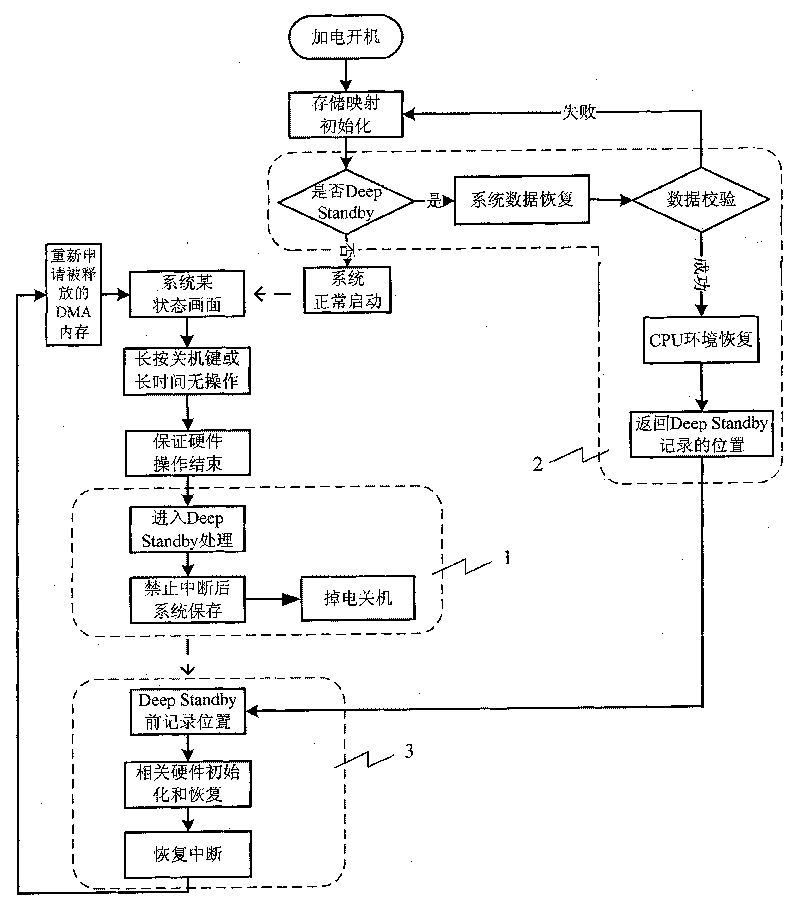
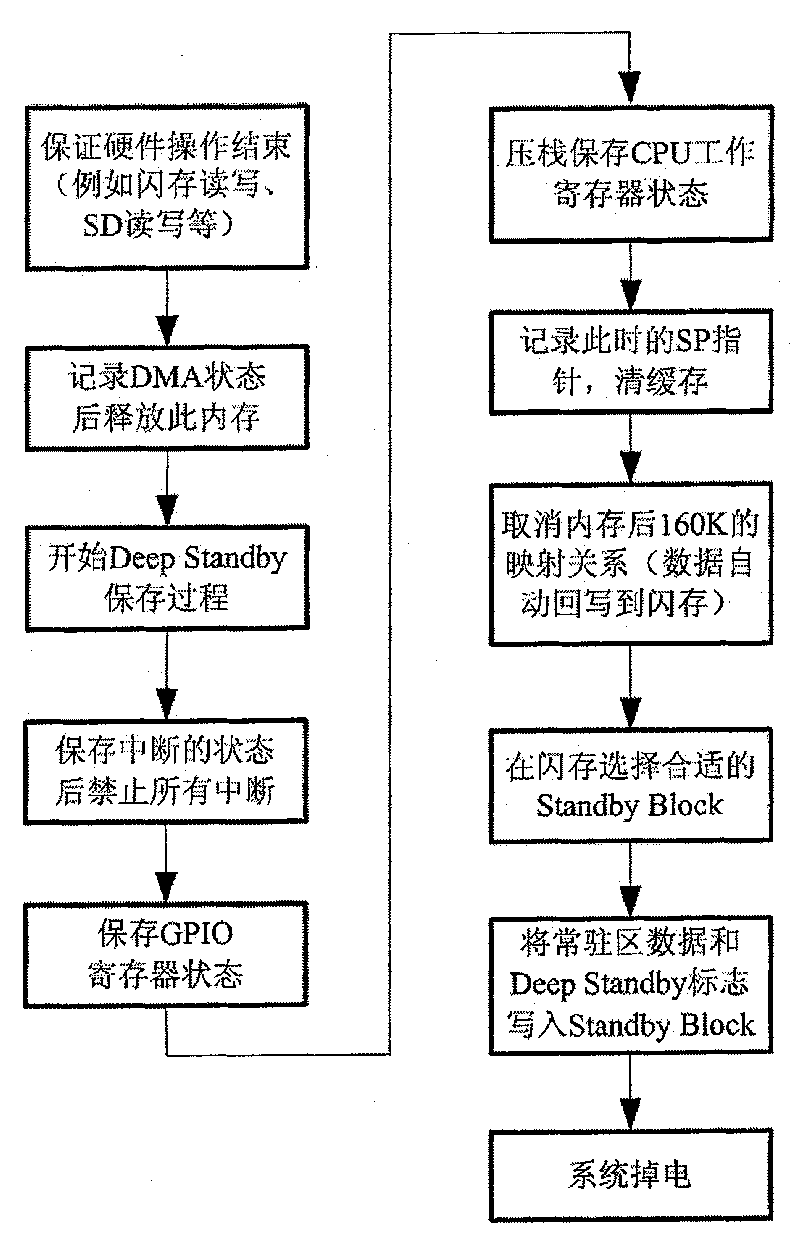
The invention provides a deep-sleep method of embedded system. The method mainly comprises the following processing steps: 1, in the system operating status, judging whether no operation is performed for long time to ensure that if so, the system preservation process is carried out after the hardware operation is ensured to be completed and then the system is closed to enter the deep-sleep mode, or receiving a system-closing signal; 2, starting the system, searching a deep-sleep block after the mapping and initializing of memory; after finding the effective deep-sleep sign, performing system data recovery process; and 3. after successfully recovering the system, performing the initializing of the related hardware, and returning to the state before the deep-sleep mode. By using the method of the invention, after the device is powered down or powered off and powered on again, the device can automatically return to the original interface to greatly reduce the power consumption of the stand-by system and save energy and electrical energy, thus prolonging the service time of the battery and ensuring the service life of the related hardware while largely increasing the startup speed of the system.
Owner:浙江金华凯宇电子科技有限公司
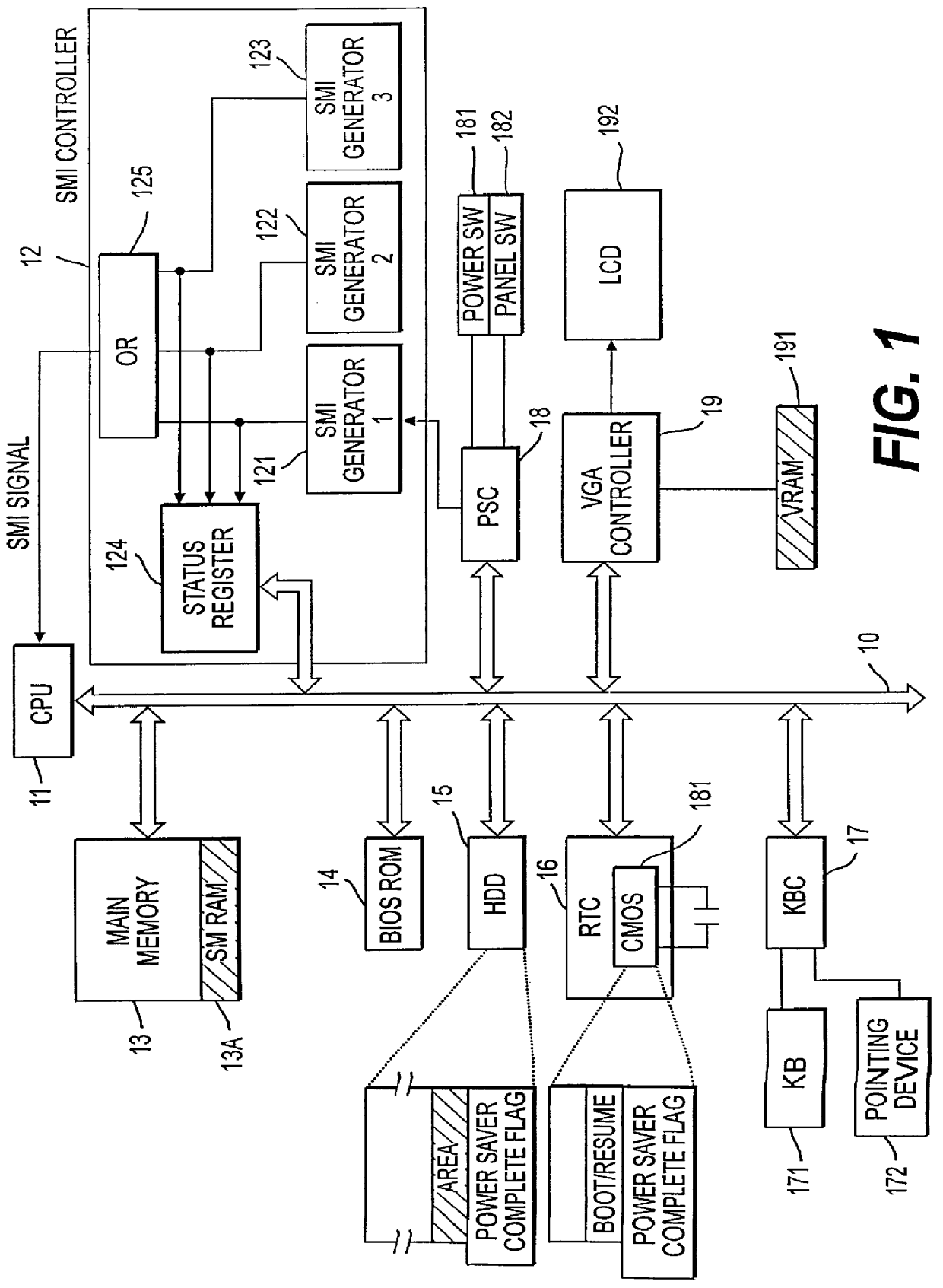
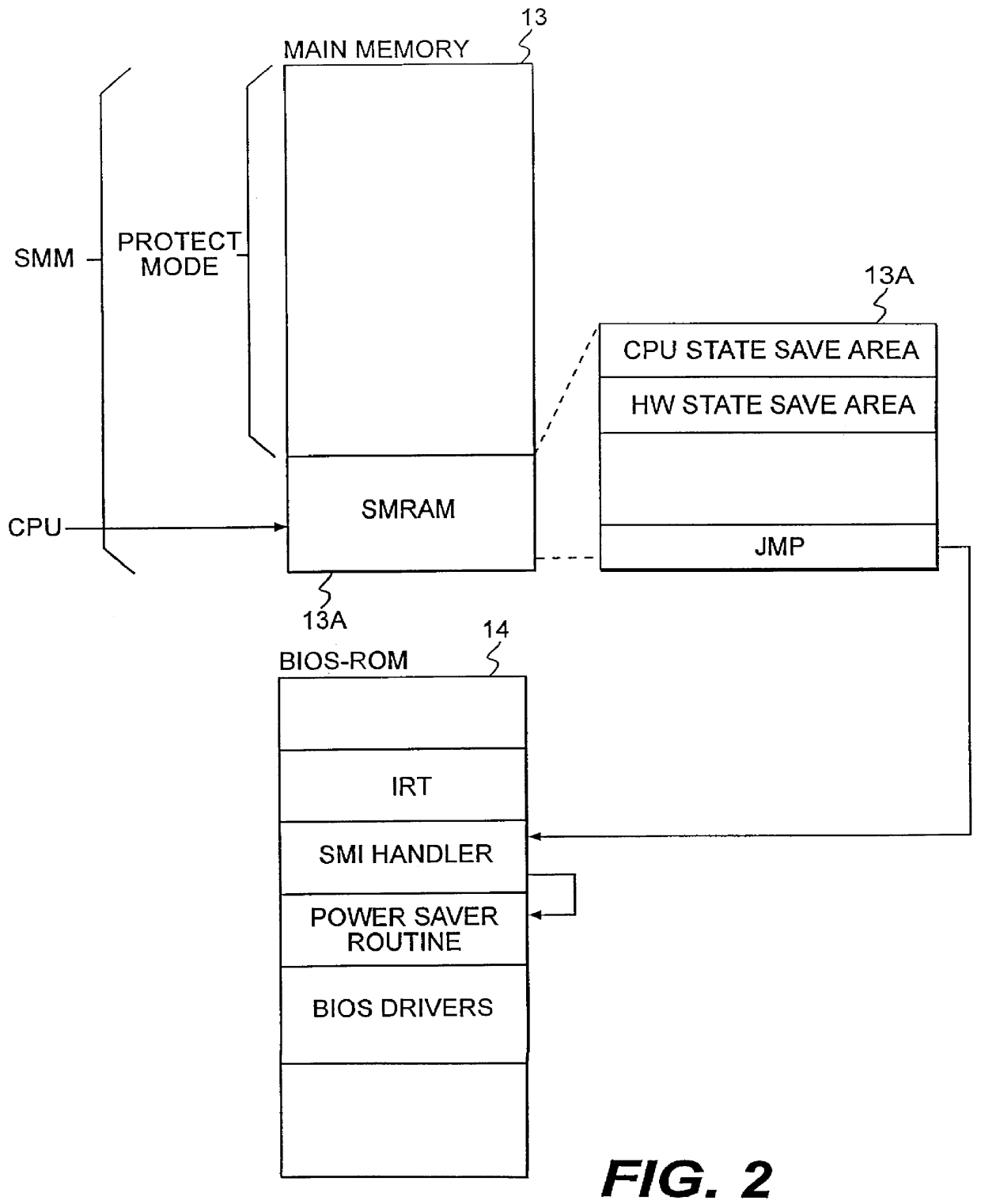
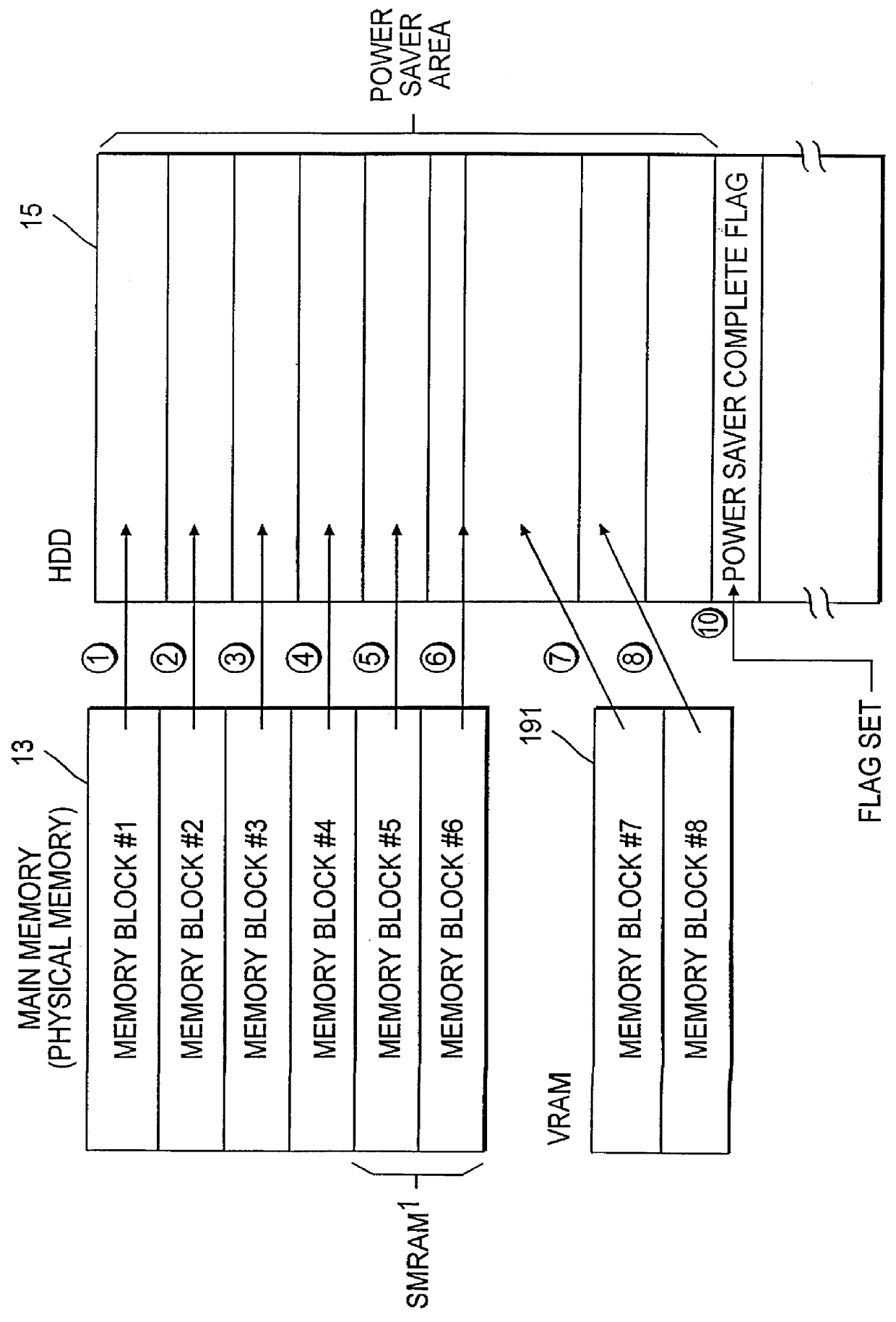
System for controlling a power saving mode in a computer system
InactiveUS6154846AVolume/mass flow measurementPower supply for data processingHard disc driveSystem recovery
A power saving process in a computer system that can be suspended, allowing for immediate restoration of an operating state just before the power saving process without waiting for completion of the process. During the power saving process, the contents of the main memory are saved to a hard disk drive in memory block units. Every time the saving of a memory block is completed, the key buffer of a keyboard controller is checked to confirm the existence of any key input. When a key input is detected, the power saving process is suspended, and the system is restored to the previous operating state.
Owner:KK TOSHIBA
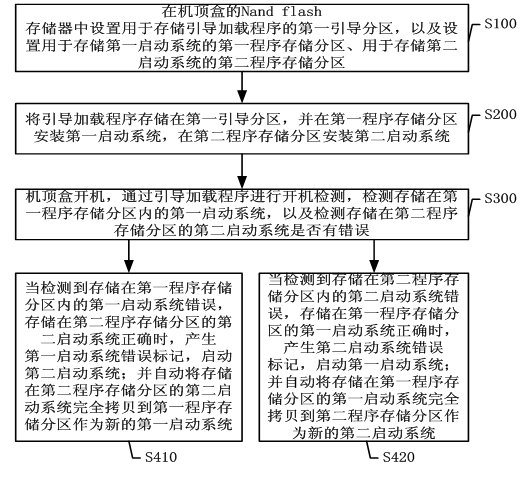
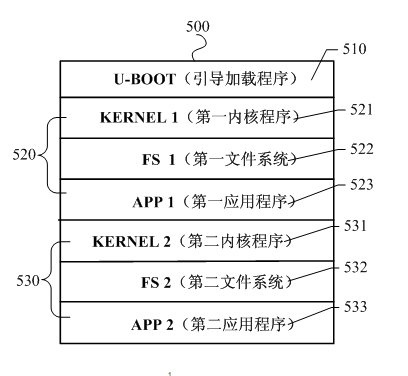
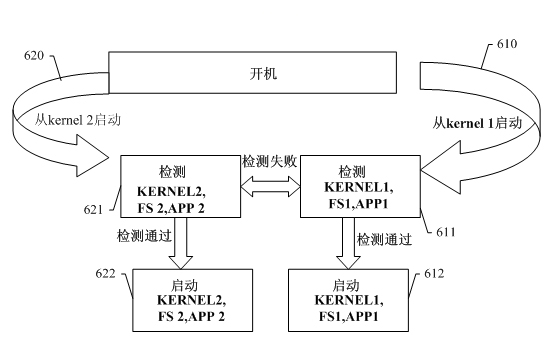
Embedded system automatic recovery method and device of a set-top box
ActiveCN102289397ASolve the problem of not startingNo impact on uptimeSelective content distributionRedundant operation error correctionRecovery methodSystem recovery
The invention discloses a method and a device for automatically restoring an embedded system of a set top box. The method comprises the steps of: carrying out power-on detection through a bootstrap loader so as to detect whether a first start system which is stored in a first program storage subarea and a second start system which is stored in a second program storage subarea are wrong or not; generating a first start system error flag and starting the second start system when detecting that the first start system which is stored in the first program storage subarea is wrong and the second start system which is stored in the second program storage subarea is correct; and automatically and completely copying the second start system which is stored in the second program storage subarea to the first program storage subarea to serve as a new first start system. In the invention, rapid restoration of system start of the set top box can be realized by using double systems, and automatic andrapid restoration can be realized without influencing the normal running time of the system, so that convenience is provided for users and the maintenance cost is reduced.
Owner:ZHUHAI GOTECH INTELLIGENT TECH
Device, Method And Program Product To Automatically Detect And Break Gas Locks In An ESP
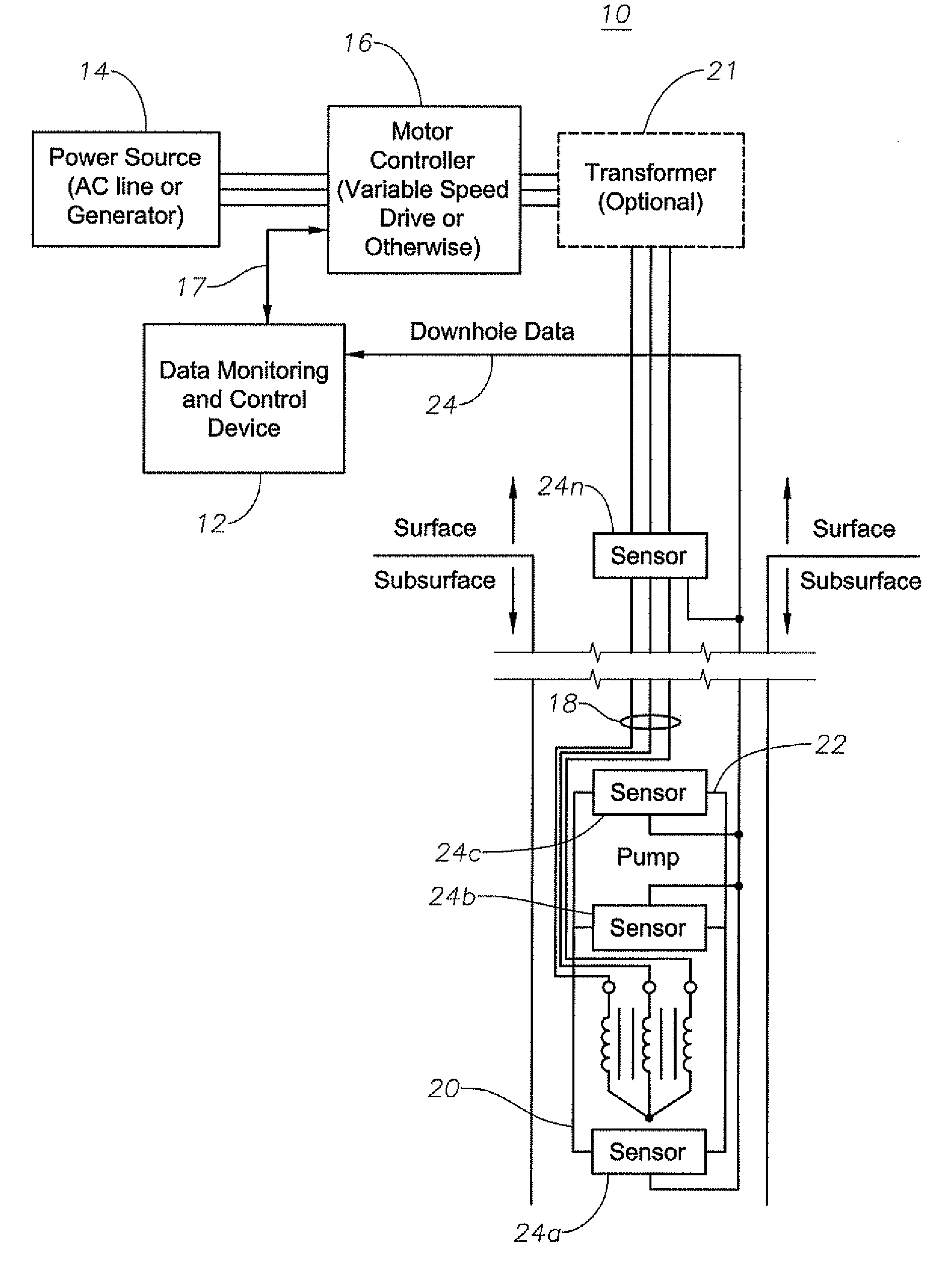
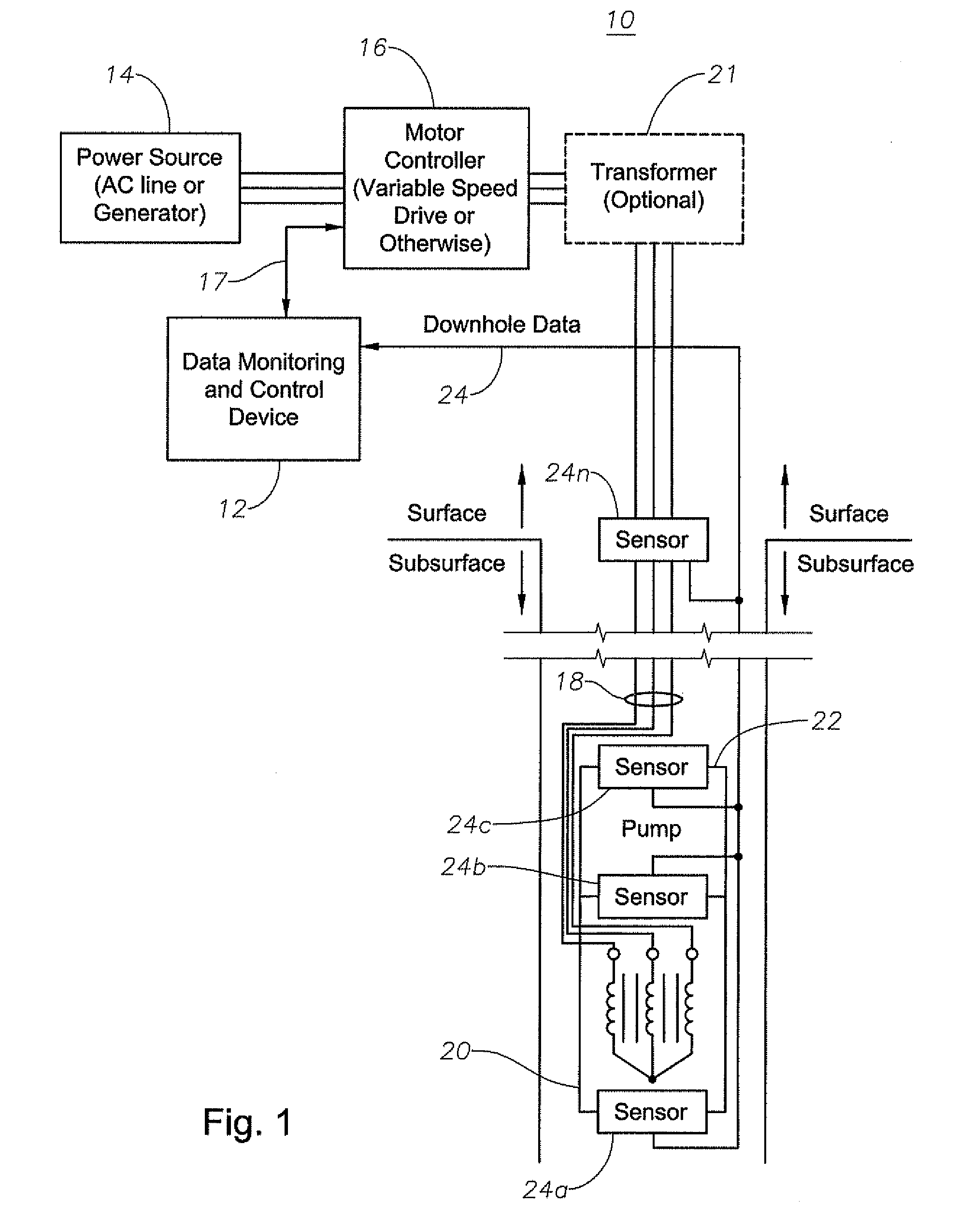
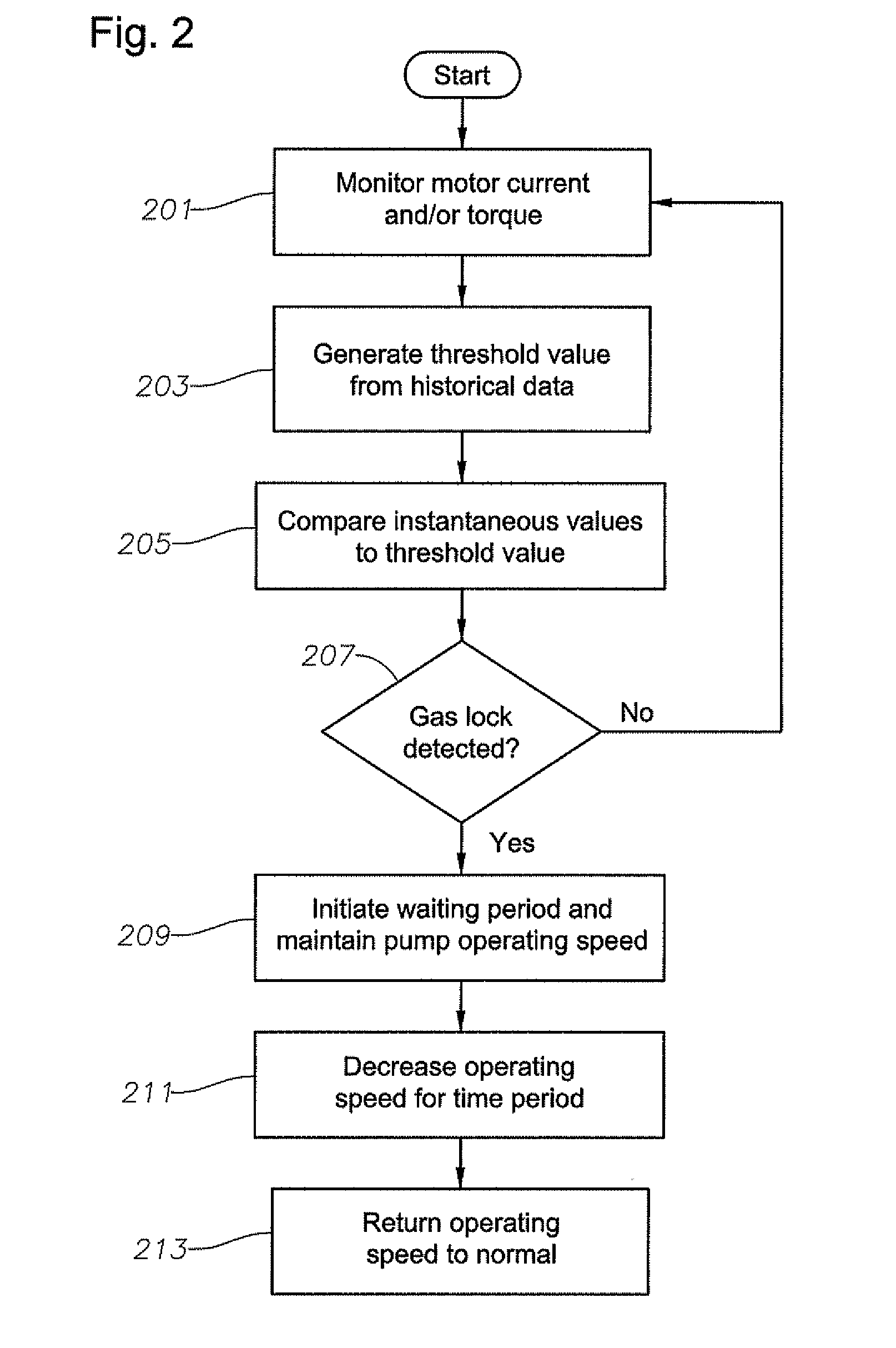
A device, method, and program product detect and break an occurrence of gas lock in an electrical submersible pump assembly in a well bore based upon surface or downhole data without the need for operator intervention. The system provides the ability to flush the pump and return the system back to production without requiring system shutdown. In addition, the system provides an algorithm for controlling a pump operating speed of the electrical submersible pump assembly to maximize production from the well bore.
Owner:BAKER HUGHES INC
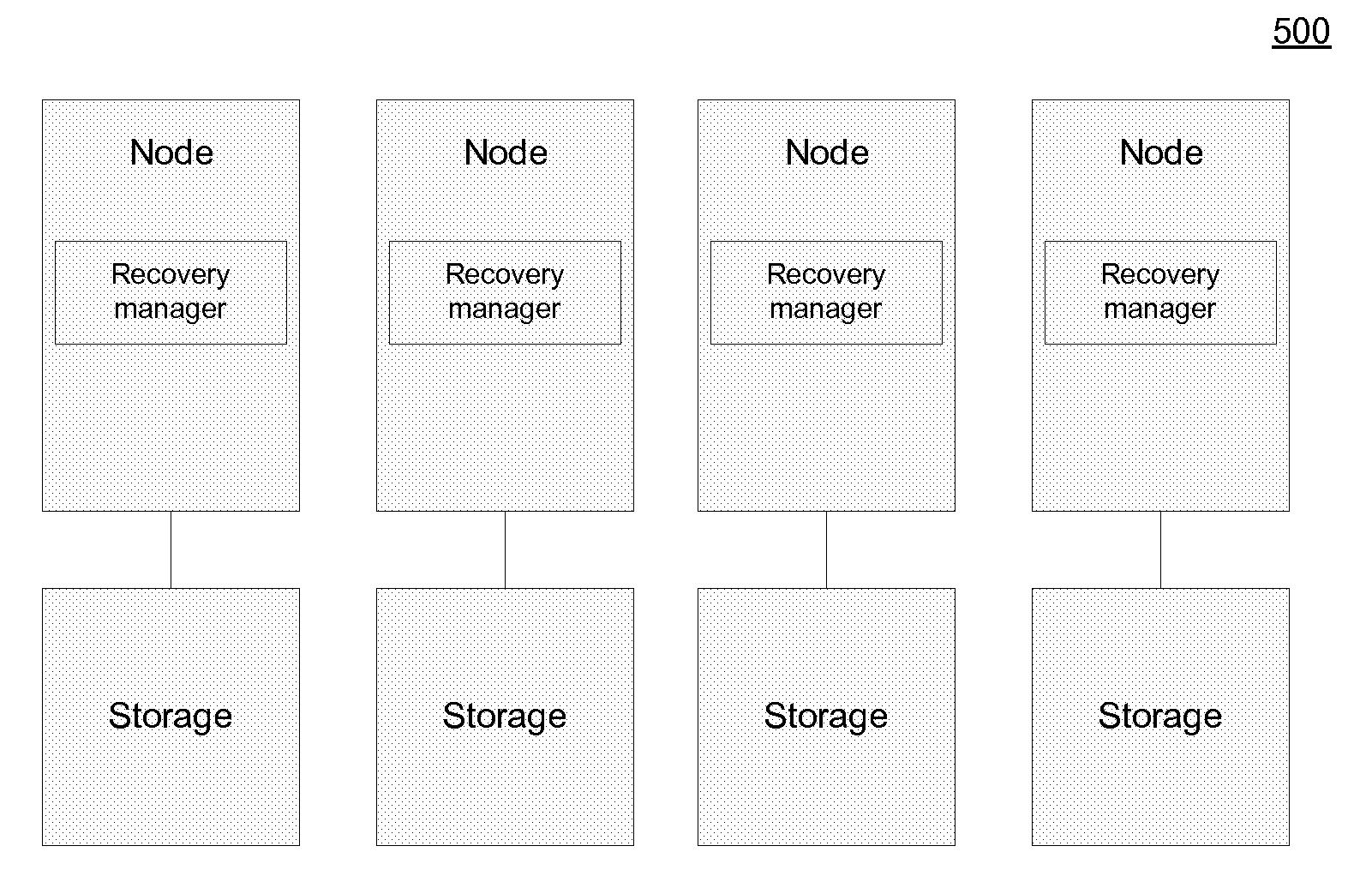
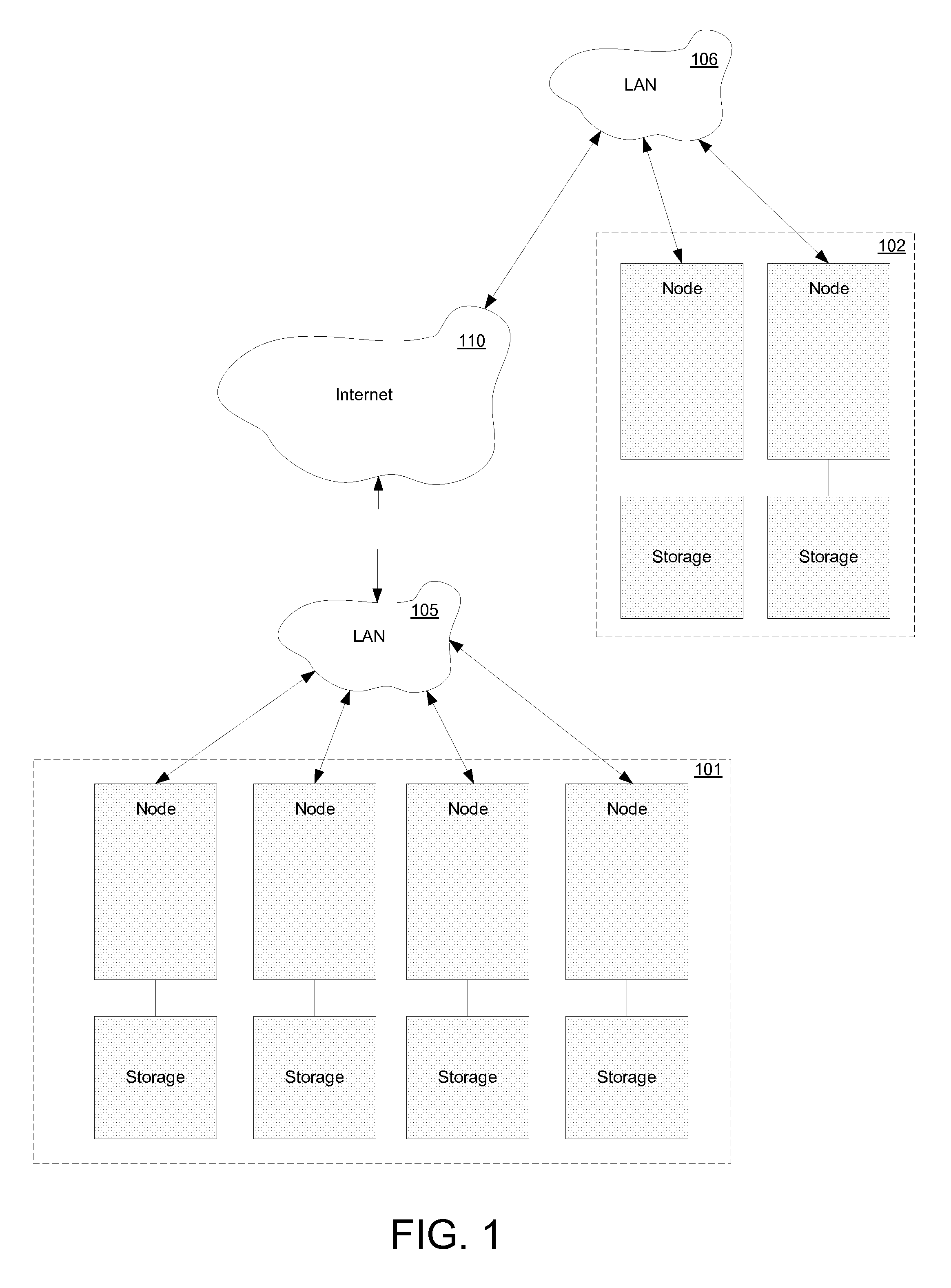
Multistage system recovery framework
A method and system for multi-staged recovery of a distributed computer system. The method includes receiving a failure event notification from at least one node of the distributed computer system and executing a plurality of recovery stages upon receiving the failure event notification by using a recovery manager, wherein each of the plurality of recovery stages performs a defined recovery task. The progress of recovery is tracked by using at least one state machine executed by the recovery manager, wherein the state machine reflects progress of each of the recovery stages. The progress of recovery is monitored to a completion by using the state machine and the recovery manager.
Owner:VERITAS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com