Patents
Literature
225 results about "Computer configuration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
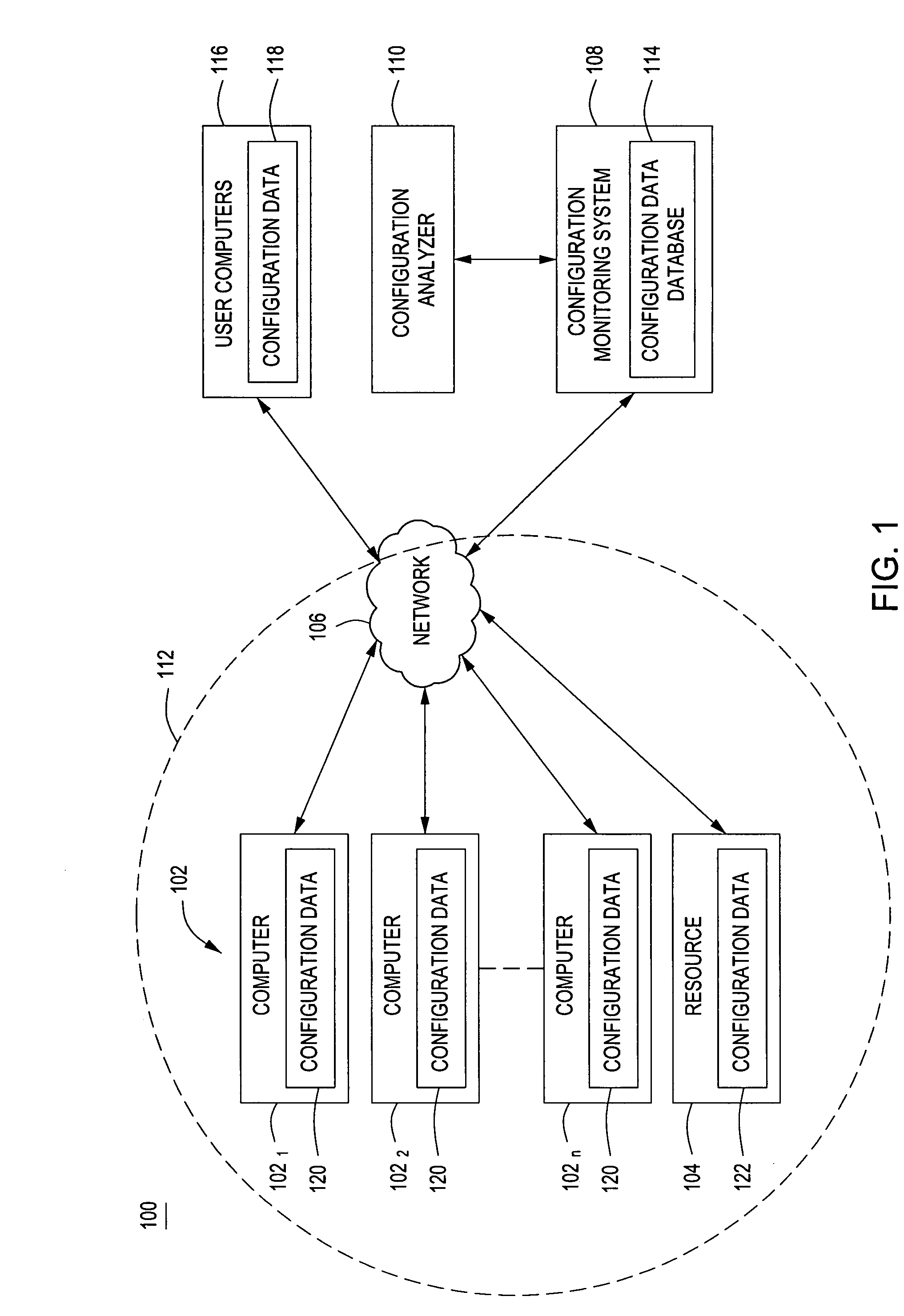
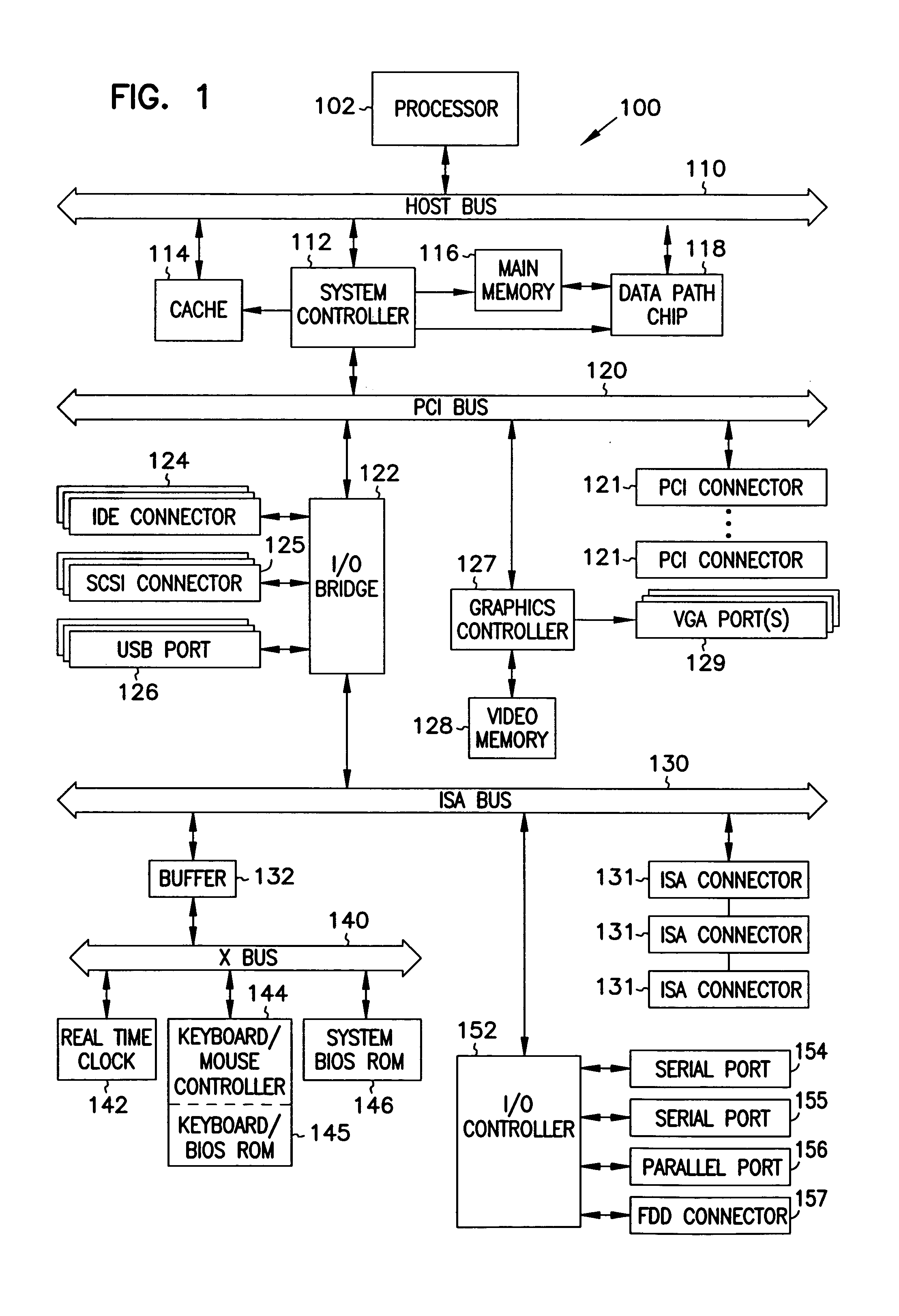
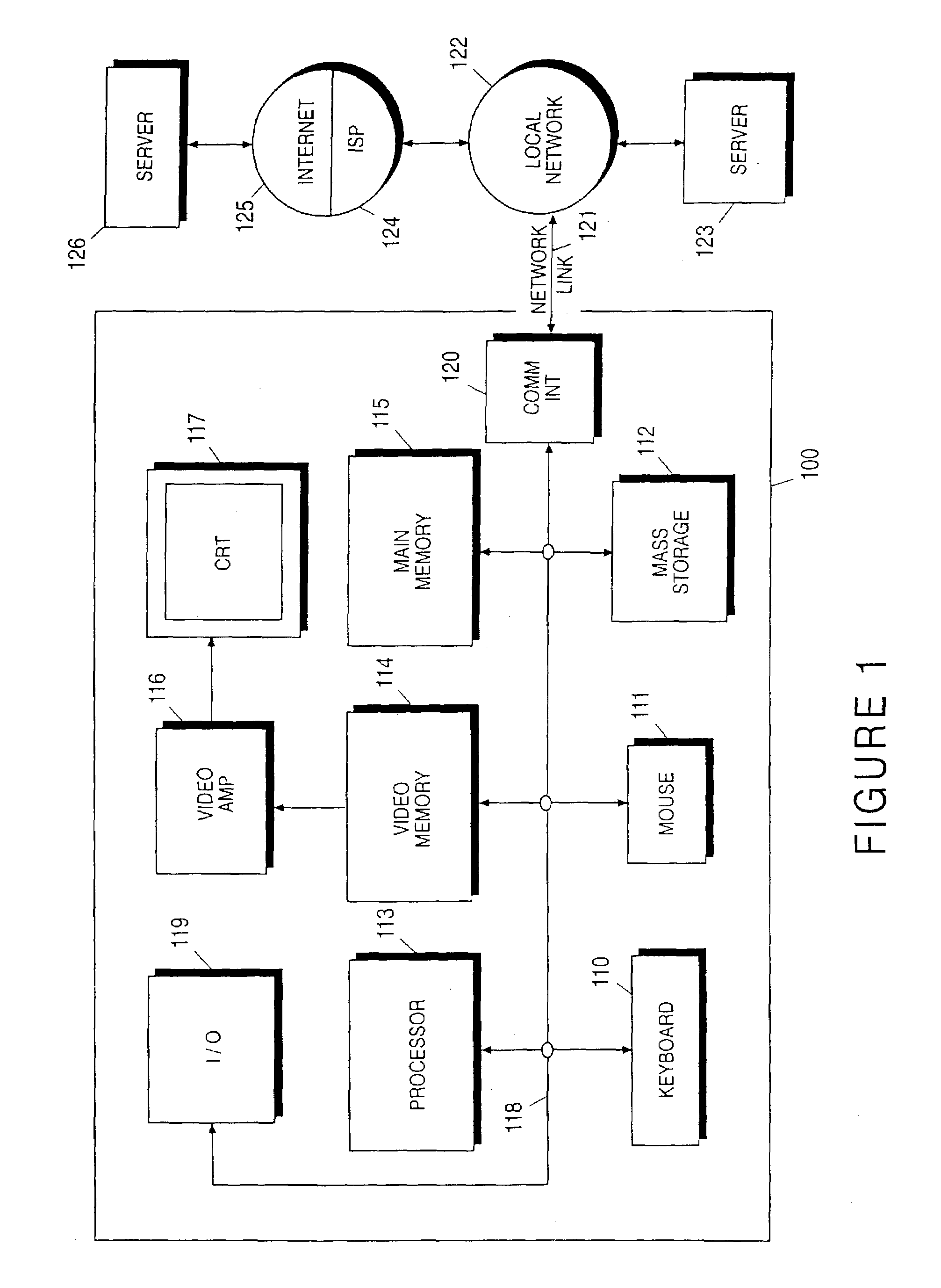
In communications or computer systems, a configuration of a system refers to the arrangement of each of its functional units, according to their nature, number and chief characteristics. Often, configuration pertains to the choice of hardware, software, firmware, and documentation. Along with its architecture, the configuration of a computer system affects both its function and performance.
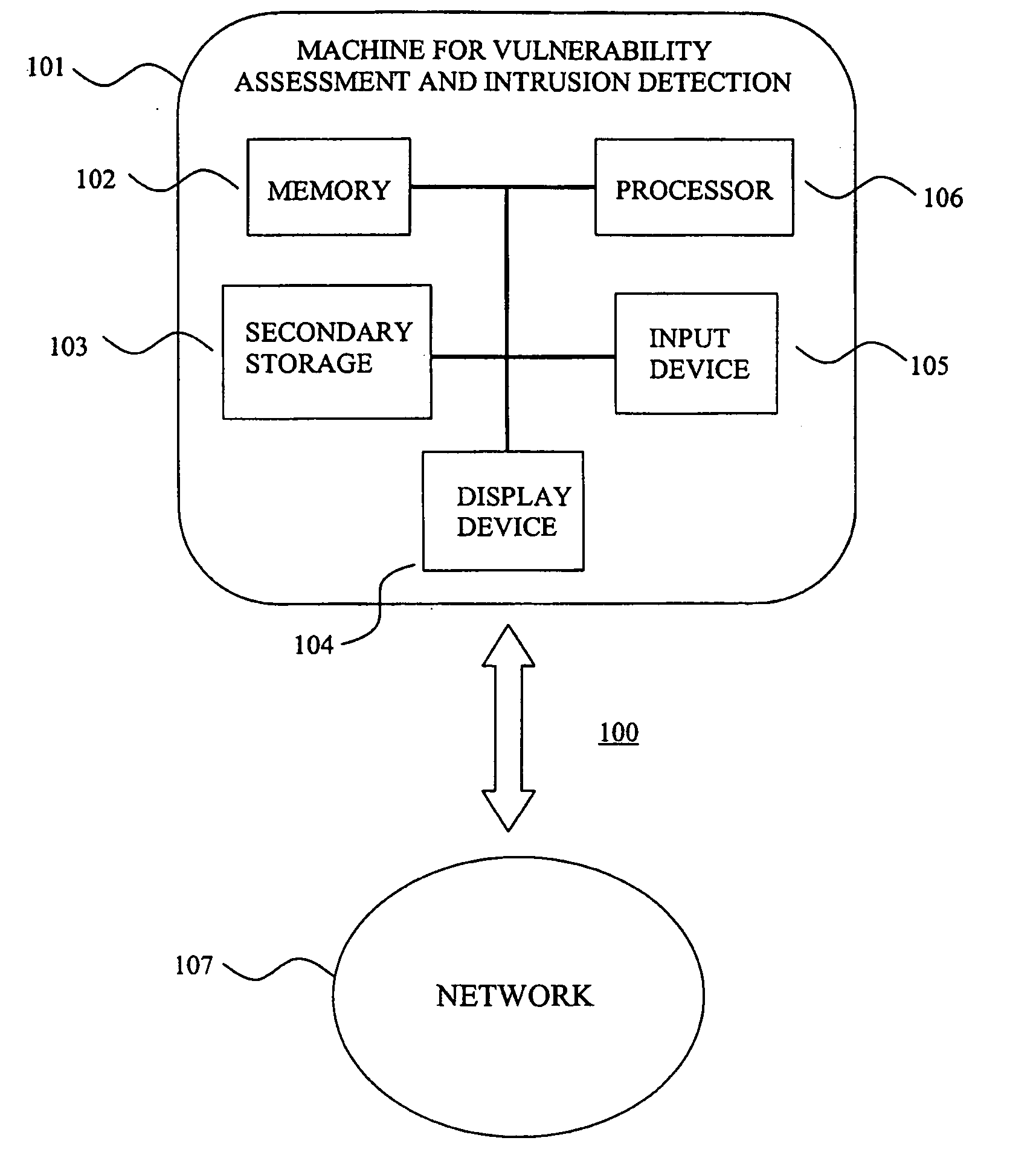
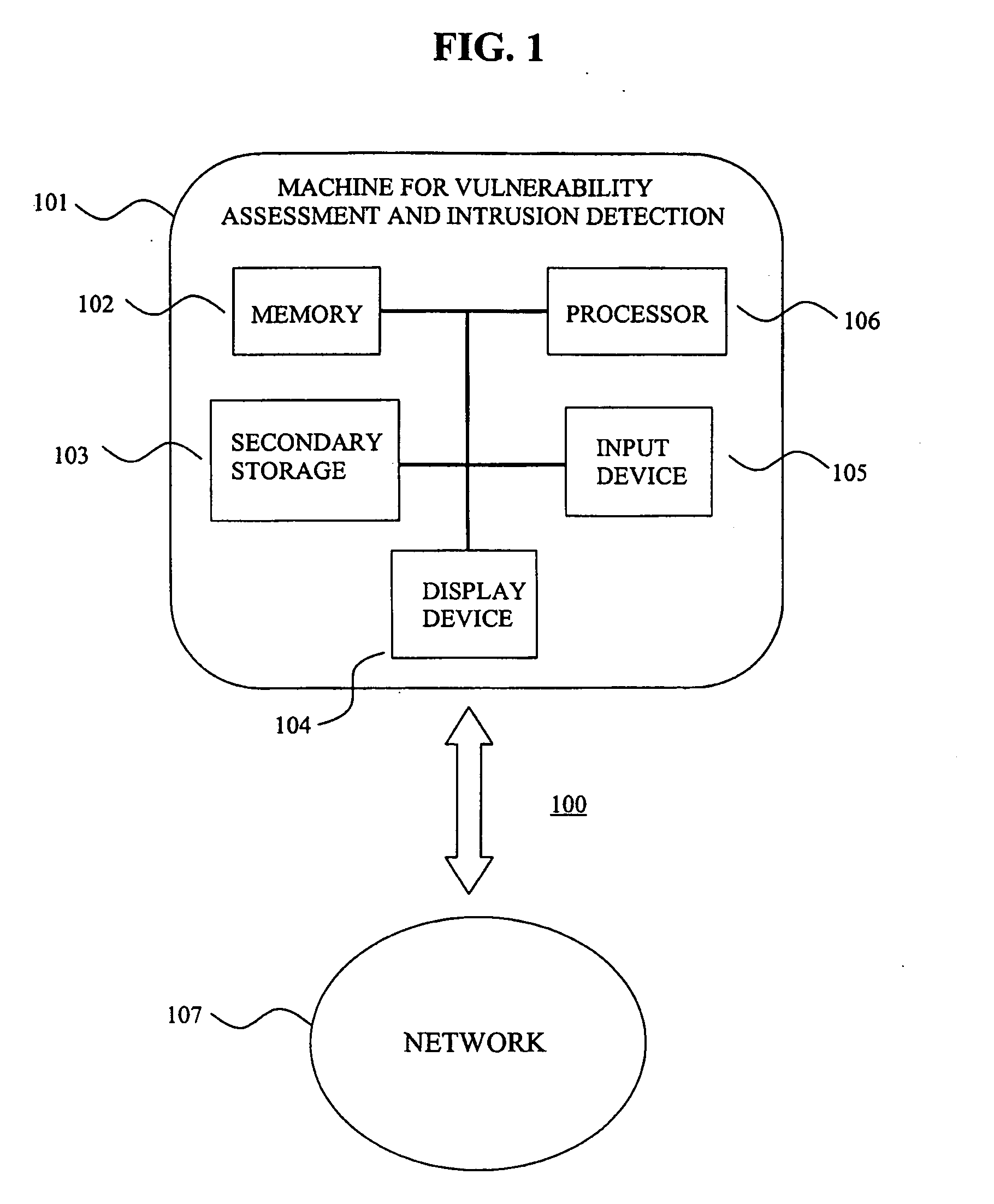
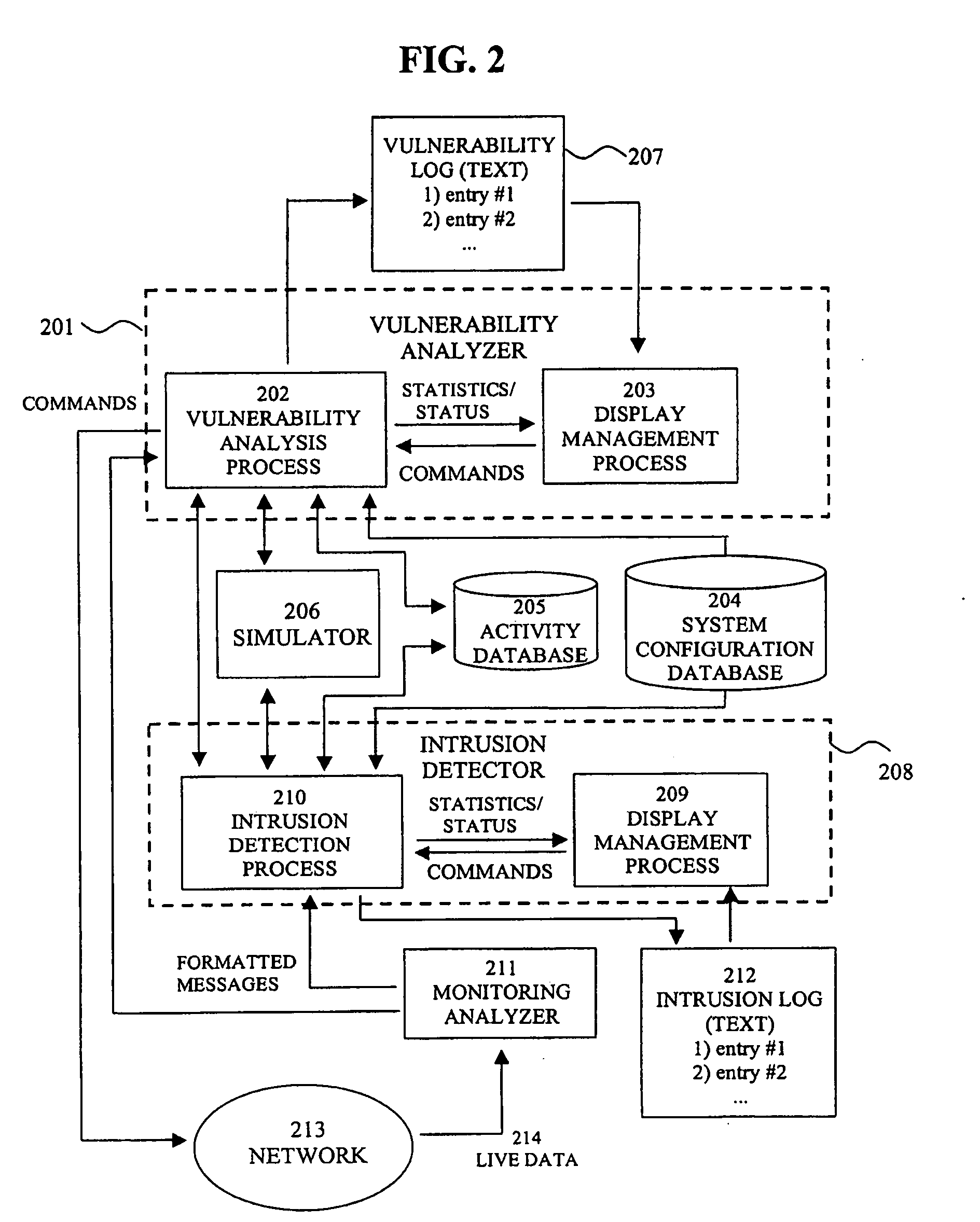
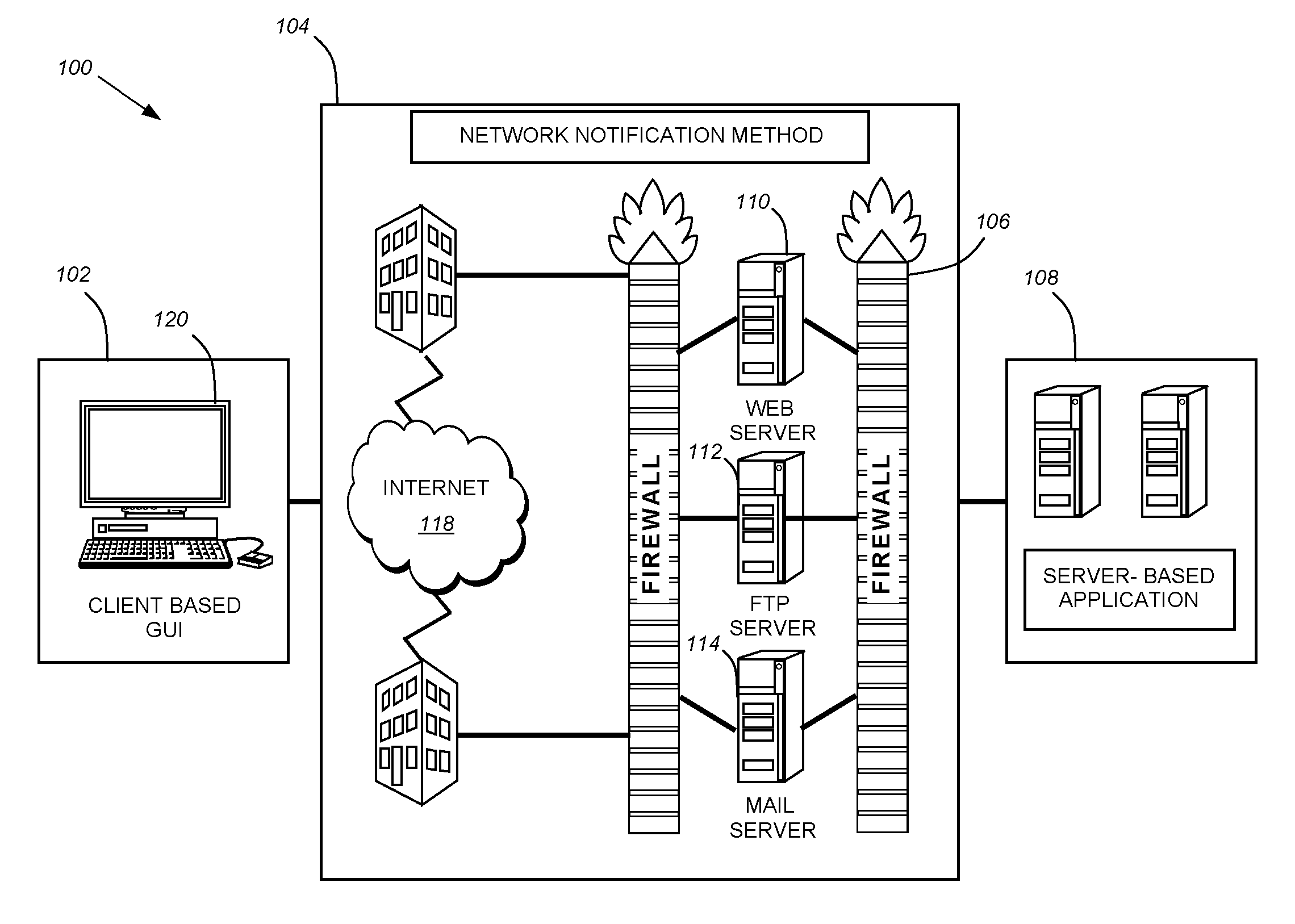
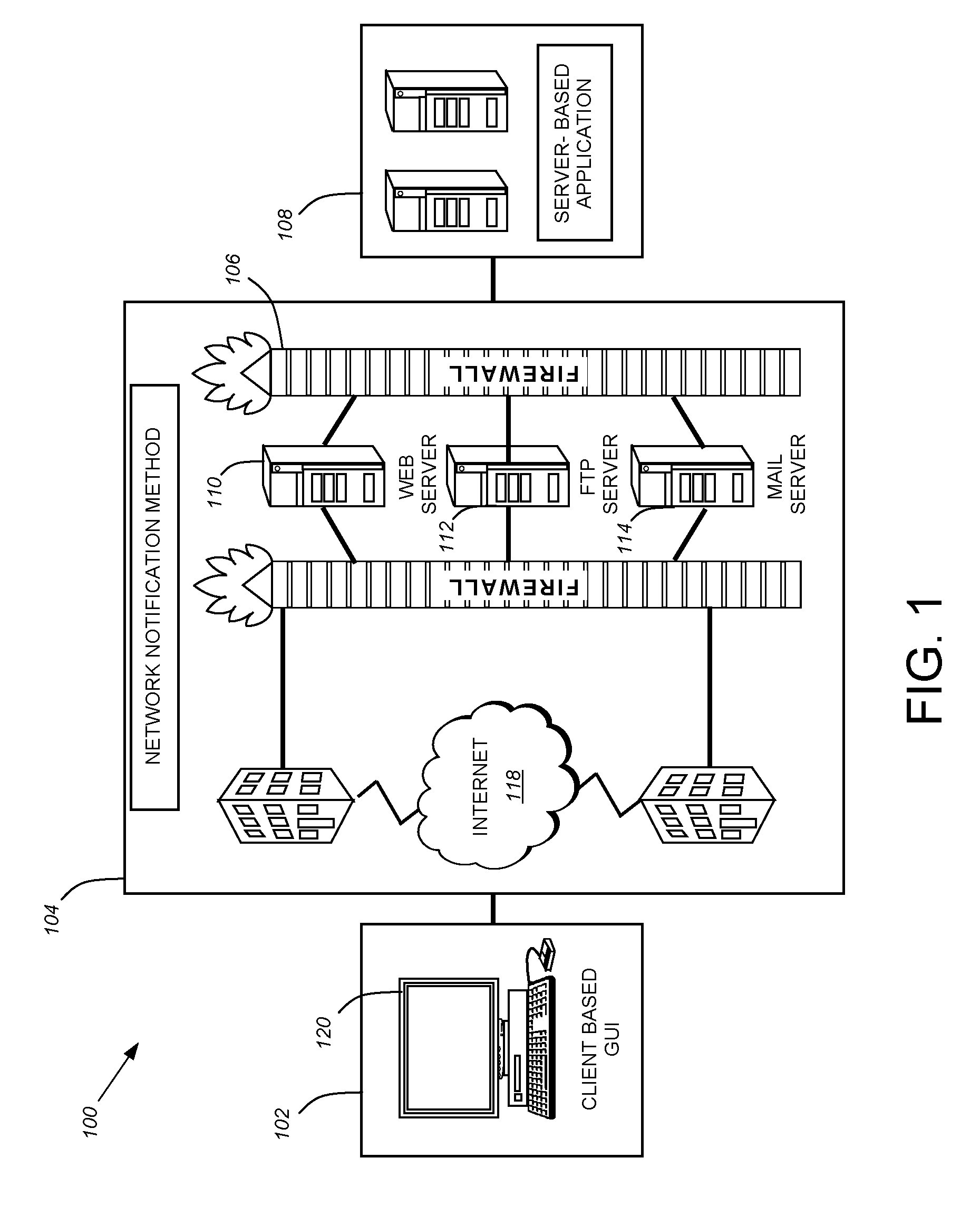
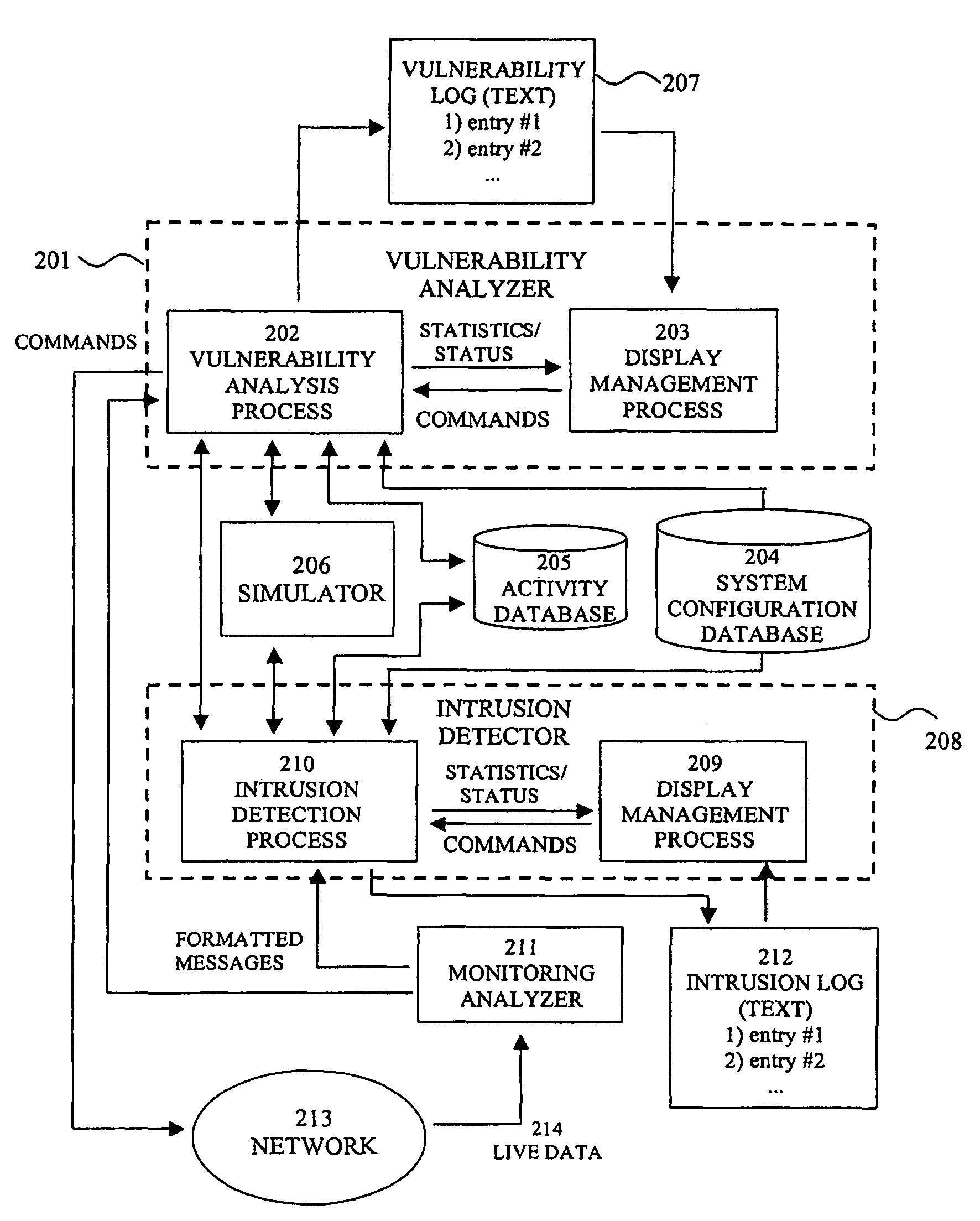
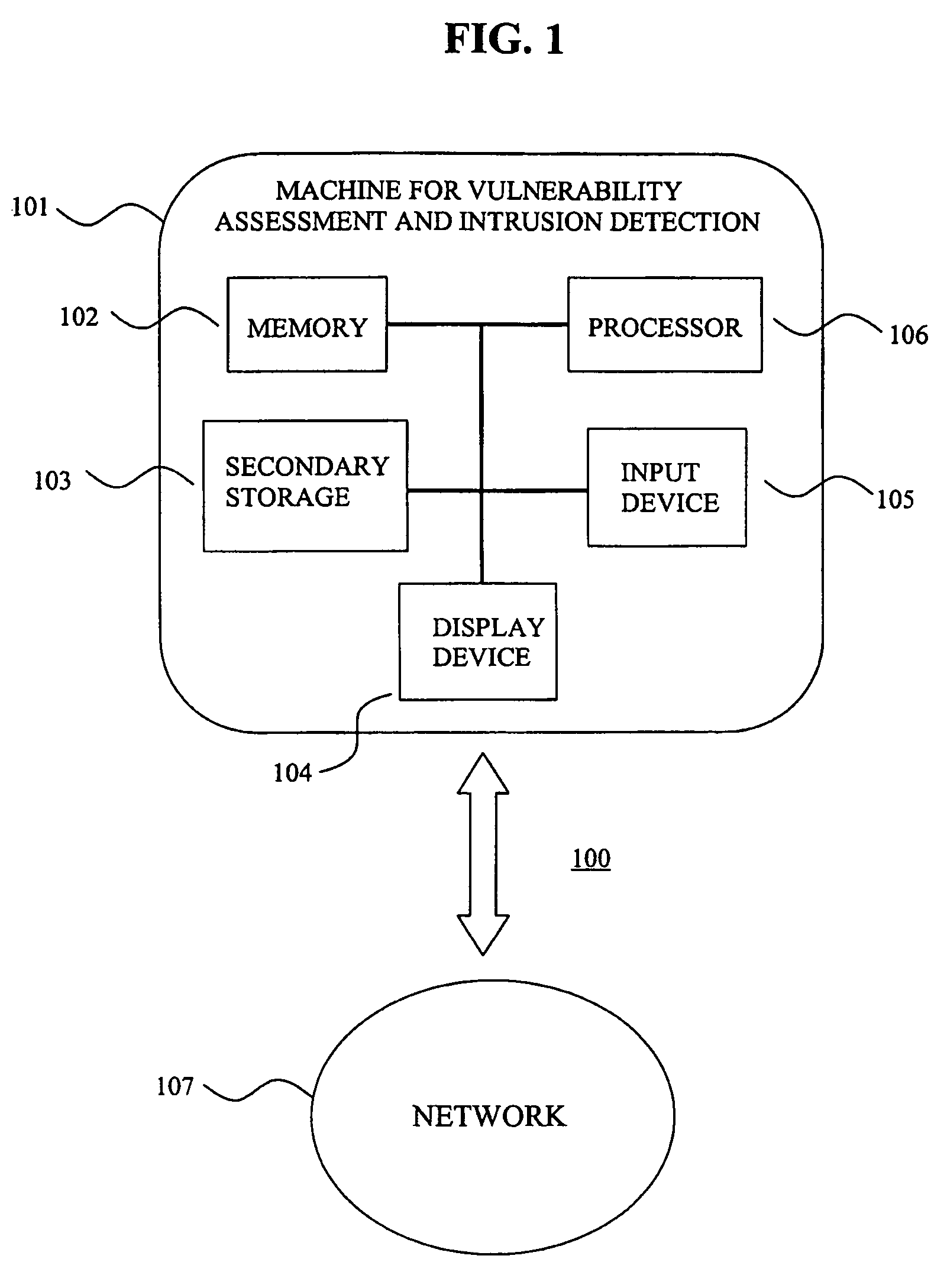
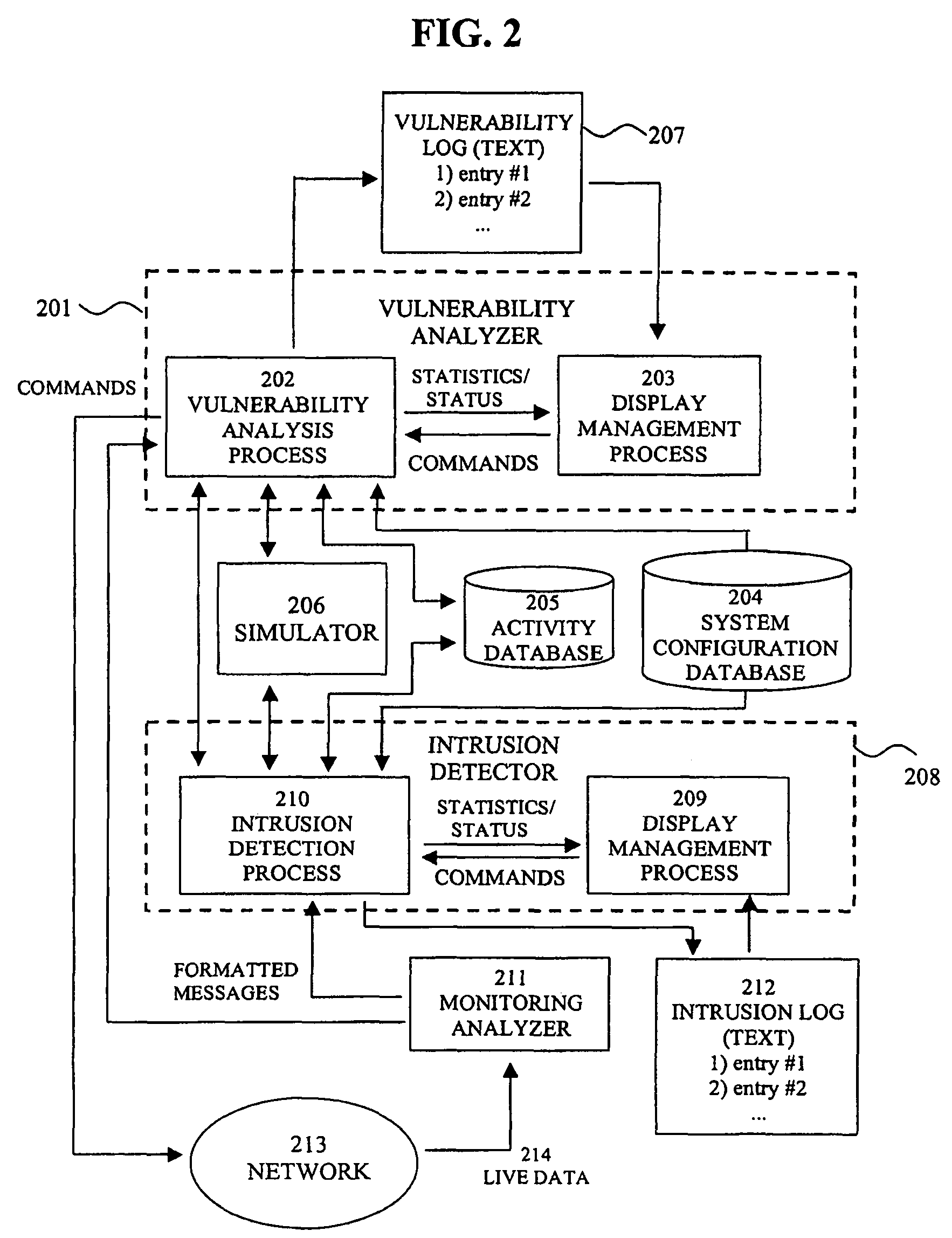
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
Computer configuration for resource management in systems including a virtual machine
InactiveUS6961941B1Avoiding multiple recurrenceBootstrappingSoftware simulation/interpretation/emulationOperational systemComputer configuration
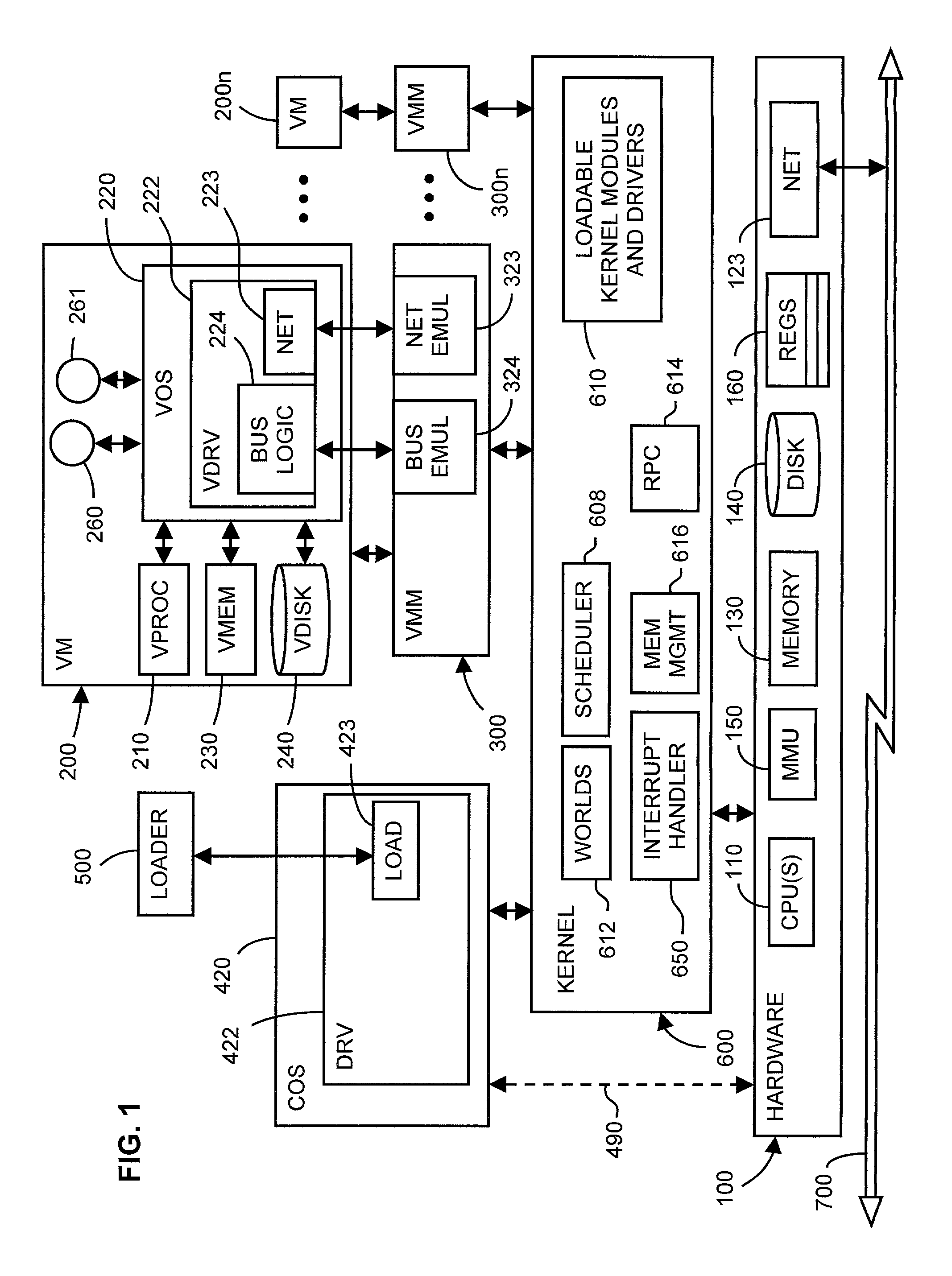
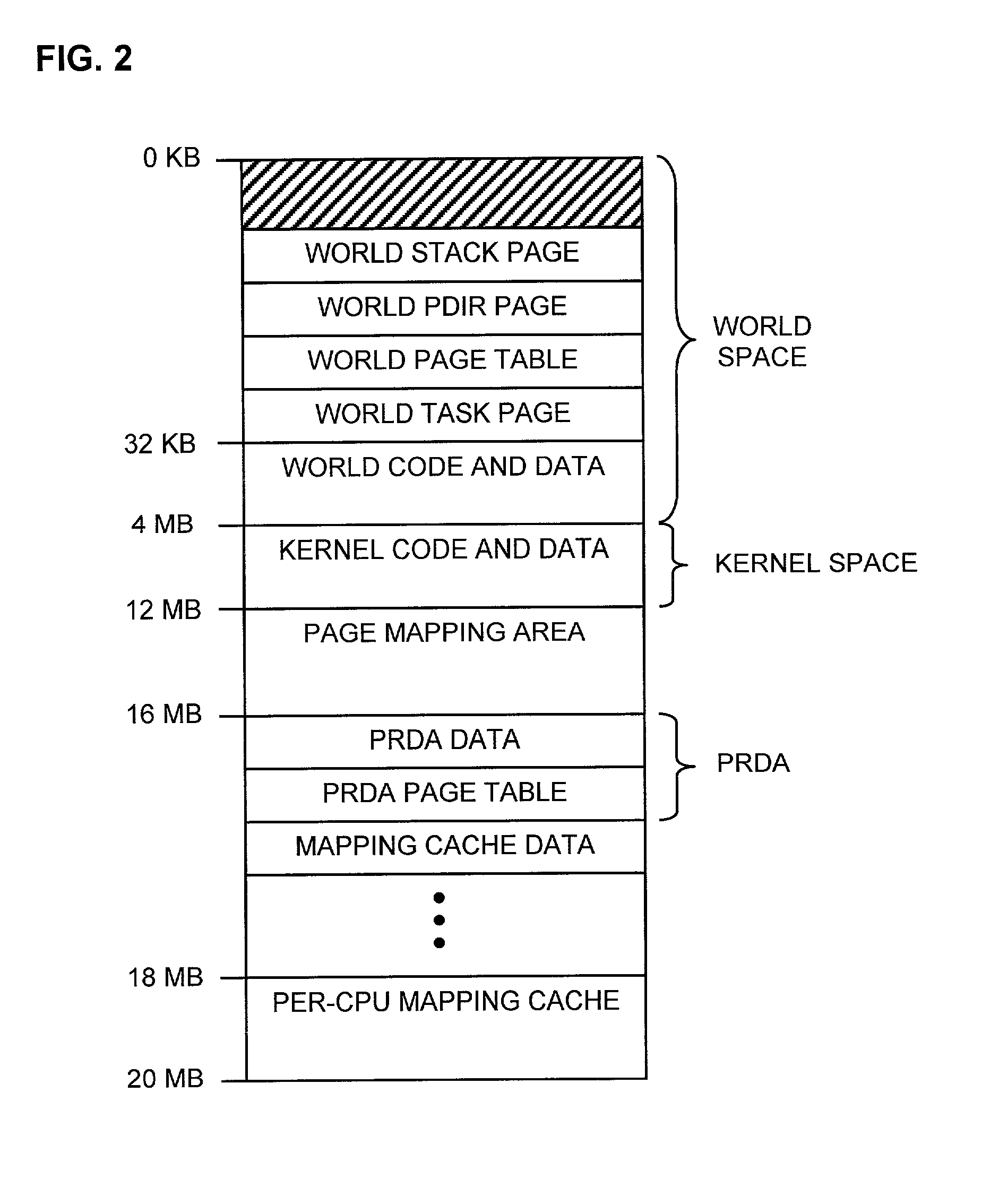
A computer architecture includes a first operating system (COS), which may be a commodity operating system, and a kernel, which acts as a second operating system. The COS is used to boot the system as a whole. After booting, the kernel is loaded and displaces the COS from the system level, meaning that the kernel itself directly accesses predetermined physical resources of the computer. All requests for use of system resources then pass via the kernel. System resources are divided into those that, in order to maximize speed, are controlled exclusively by the kernel, those that the kernel allows the COS to handle exclusively, and those for which control is shared by the kernel and COS. In the preferred embodiment of the invention, at least one virtual machine (VM) runs via a virtual machine monitor, which is installed to run on the kernel. Each VM, the COS, and even each processor in a multiprocessor embodiment, are treated as separately schedulable entities that are scheduled by the kernel. Mechanisms for high-speed I / O between VM's and I / O devices are also included.
Owner:VMWARE INC
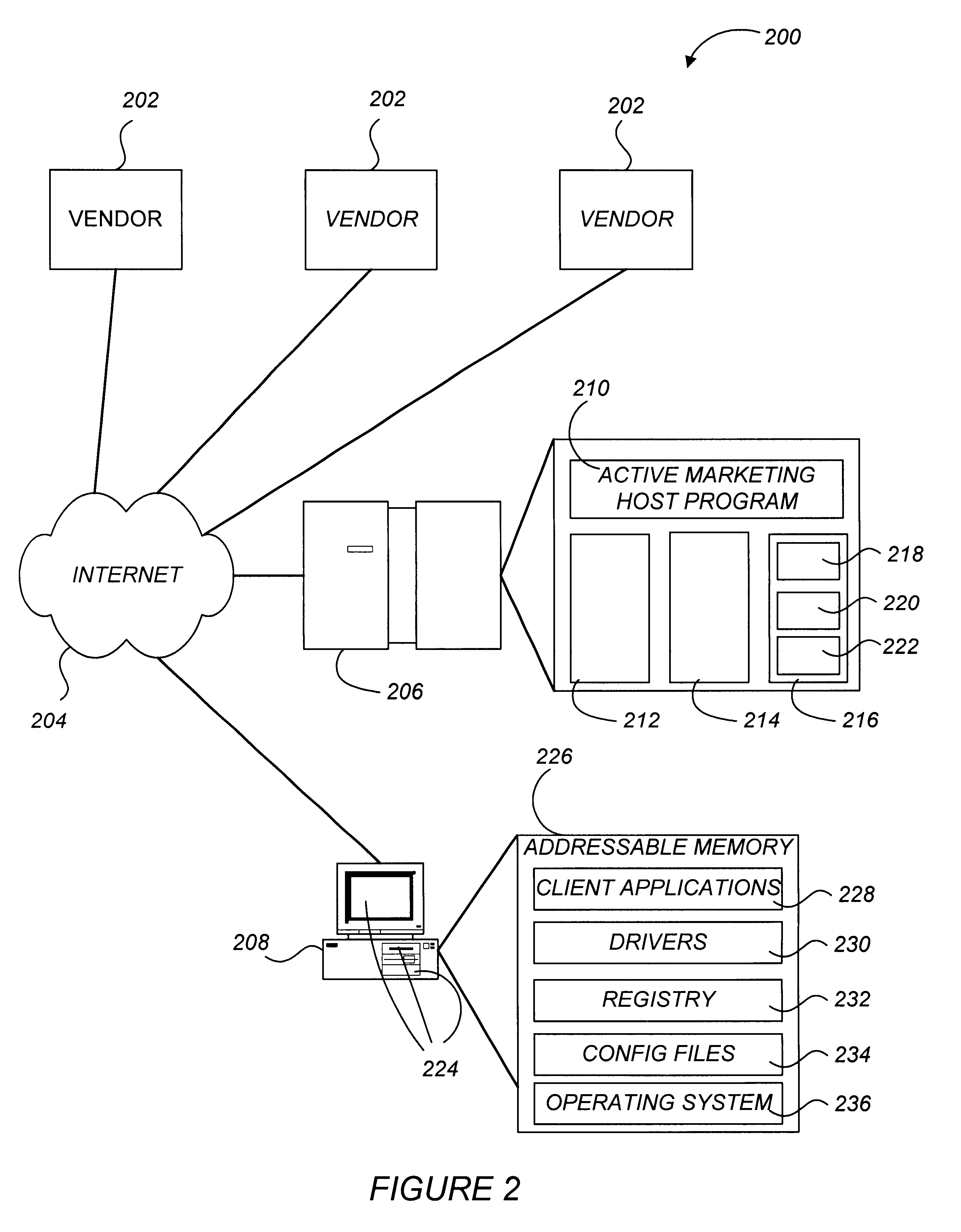
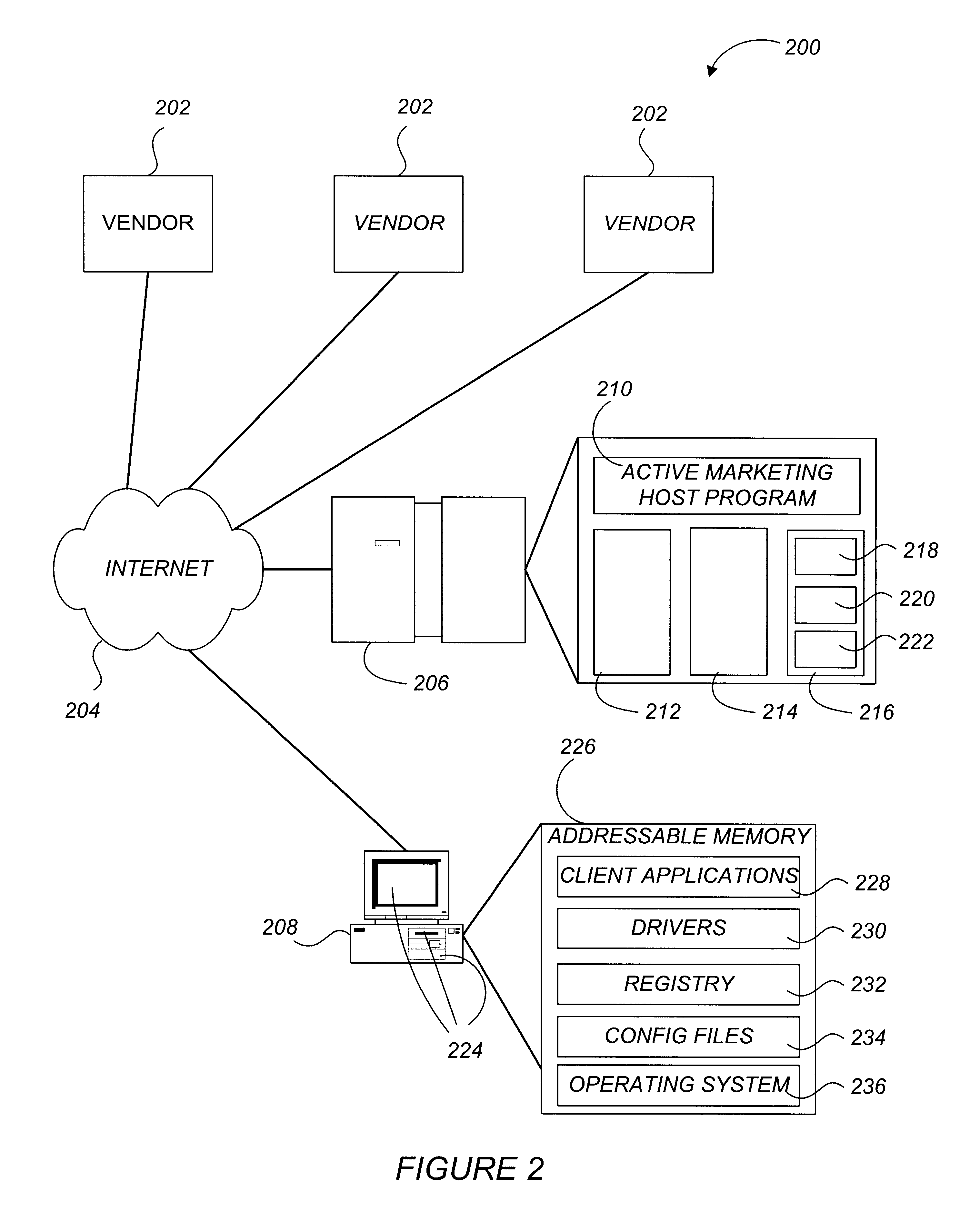
Active marketing based on client computer configurations
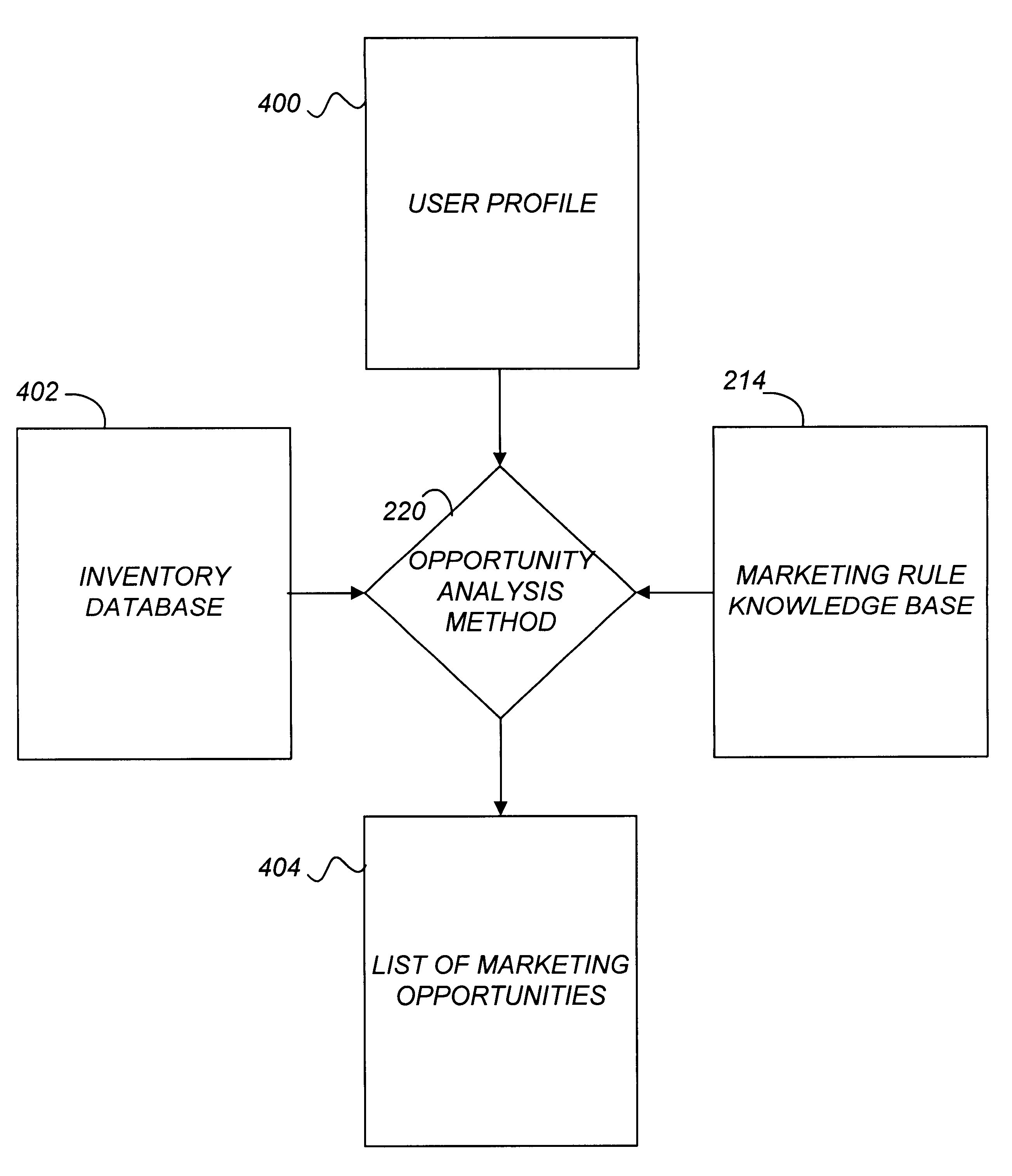
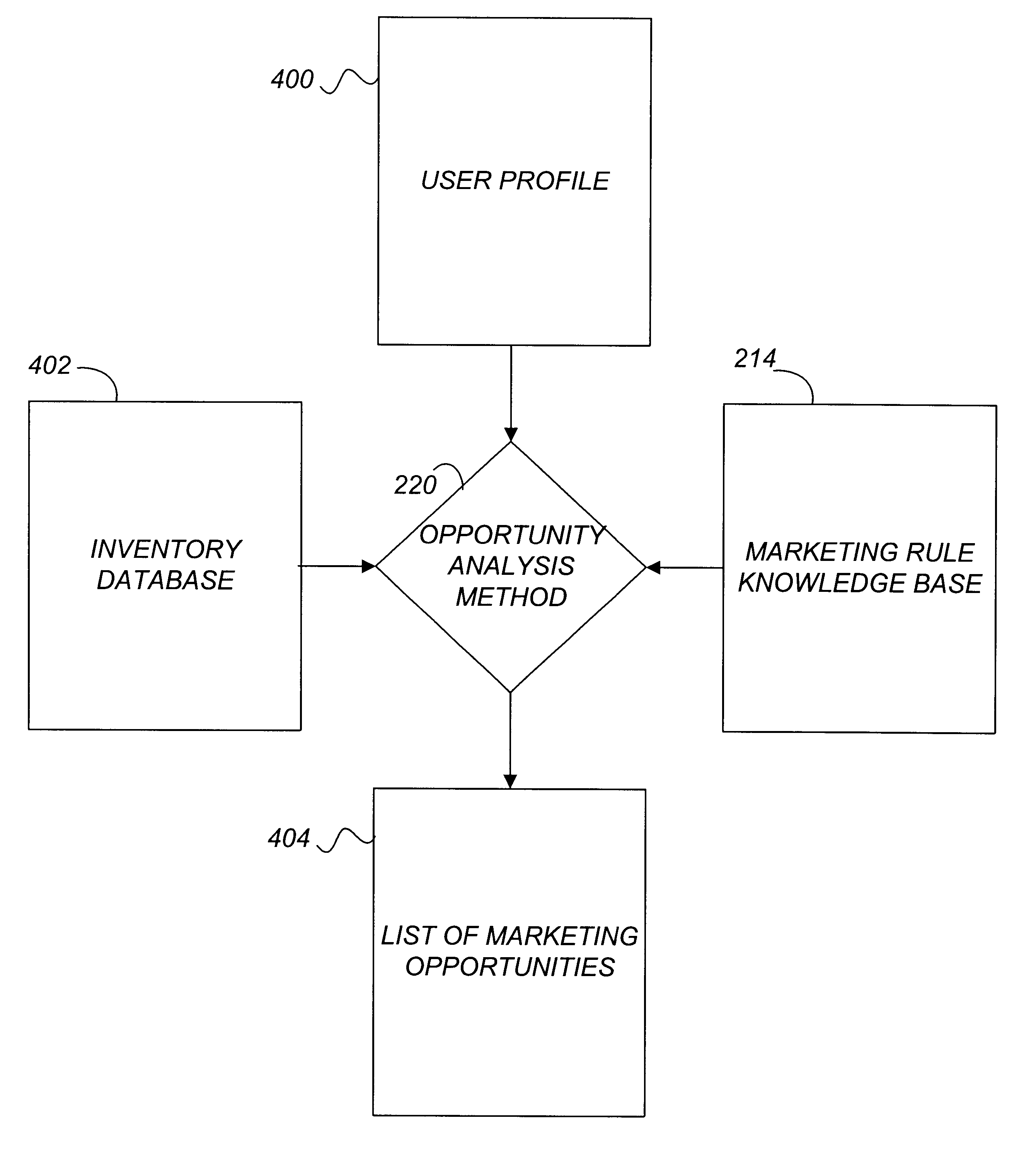
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
Active marketing based on client computer configurations
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
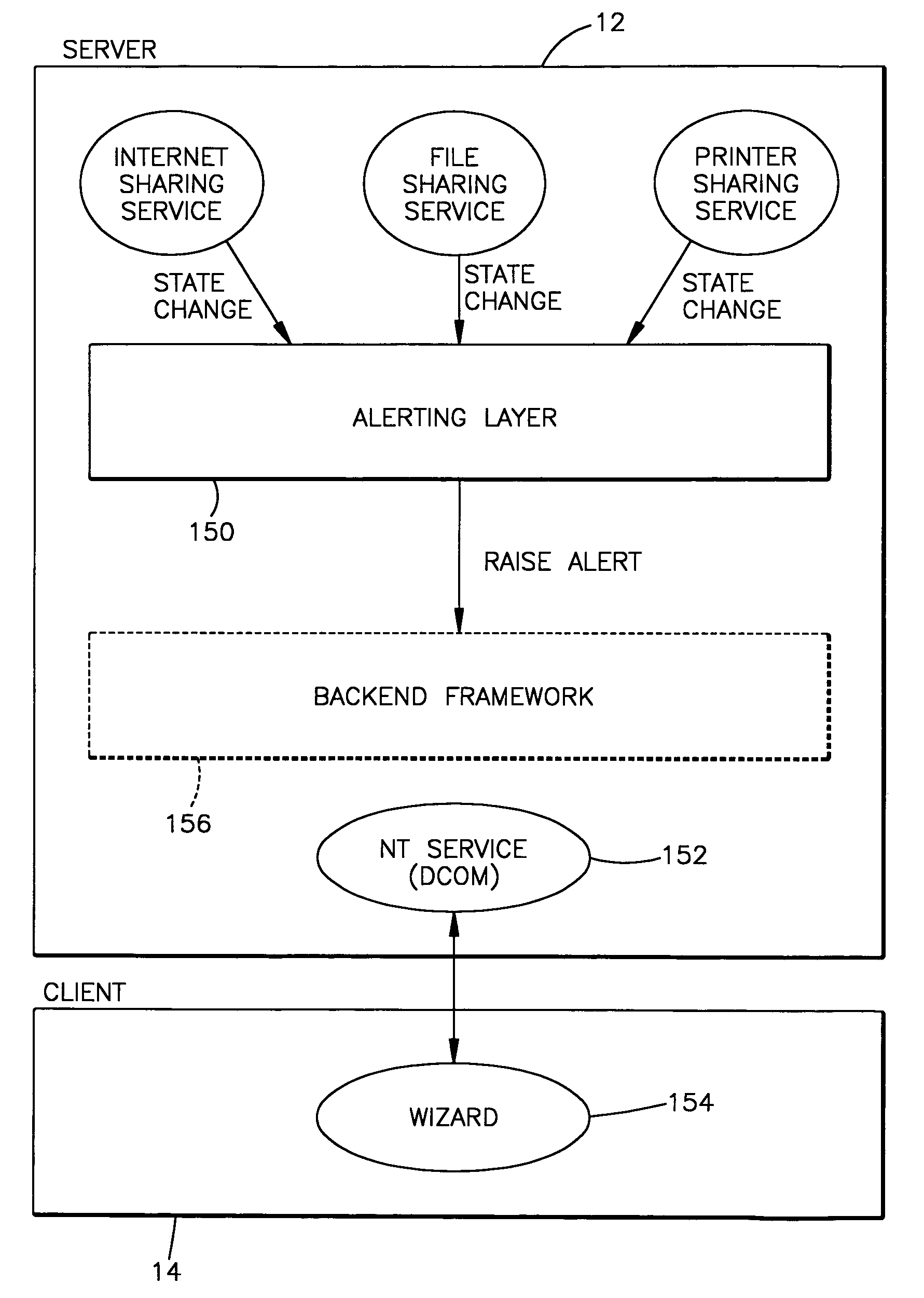
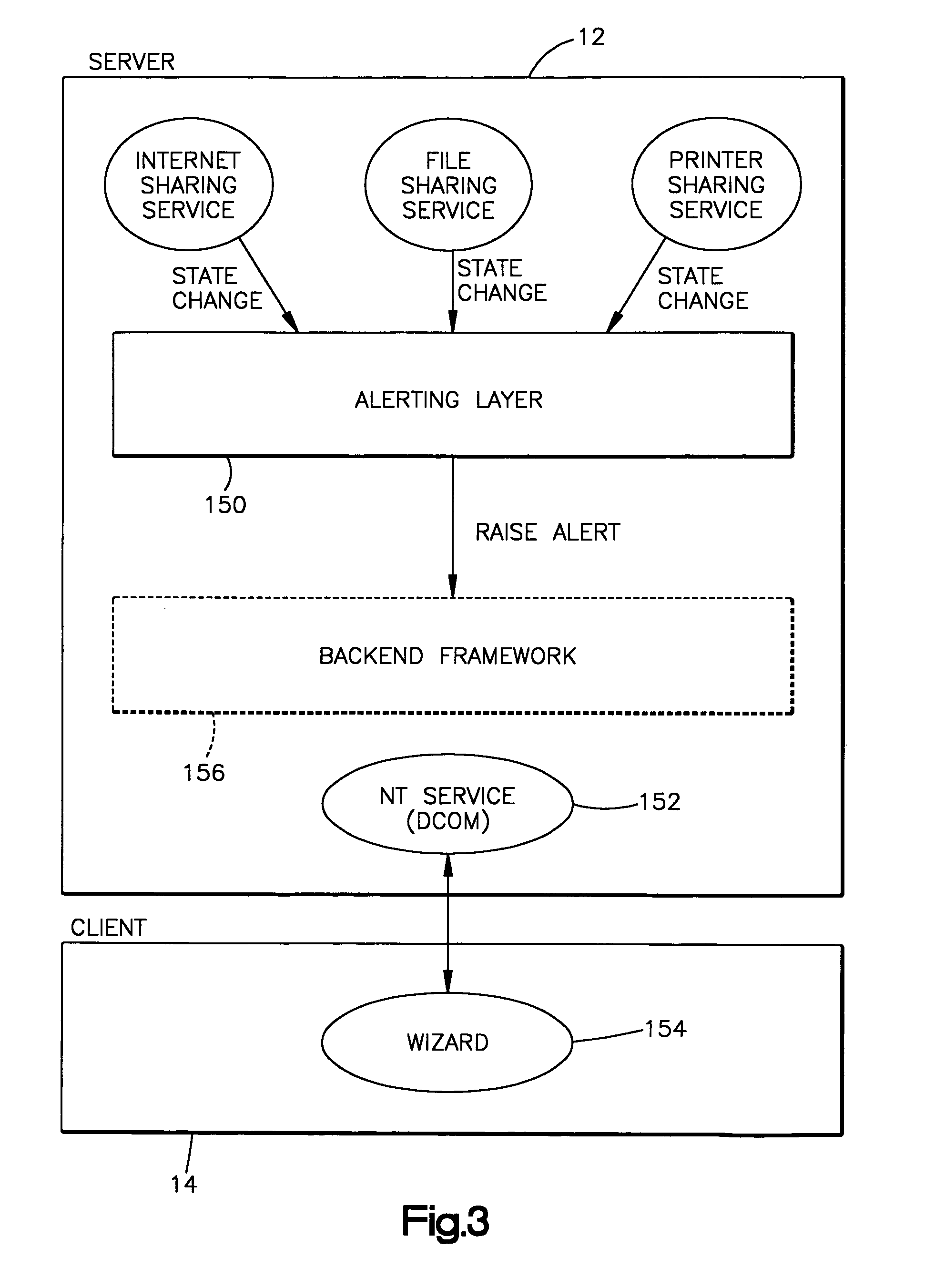
Client computer configuration based on server computer update
InactiveUS7103650B1Multiple digital computer combinationsTransmissionHard disc driveComputer configuration
The invention includes method and apparatus for updating a configuration of a client computer coupled by means of a network to a server computer. The updating process begins with a change in the status of a server computer. This change can be necessitated by addition of hardware such as an additional hard drive or the addition of an additional service such as shared Internet access. A status message is transmitted by means of the network between the server computer and the client computer regarding the changed status of the server computer. This message can be either an alert message from the server to all connected client computer nodes or can be accomplished by client polling for an updated status of the server. A message is displayed at the client computer to apprise a user that a status of the server computer has changed. Additionally, a communications between the client computer and the server computer takes place over the network to inform the client computer regarding details of the change of status in the server computer. This updated status allows a computer setup wizard running on the client computer to upgrade the status of the client.
Owner:MICROSOFT TECH LICENSING LLC
Computer configuration tracking system able to restore a previous configuration
Owner:SERVICENOW INC
Method and apparatus for verifying the contents of a global configuration file
InactiveUS6892231B2Simplify the configuration processFast processingDigital computer detailsData switching by path configurationIdentifying problemsSyntax error
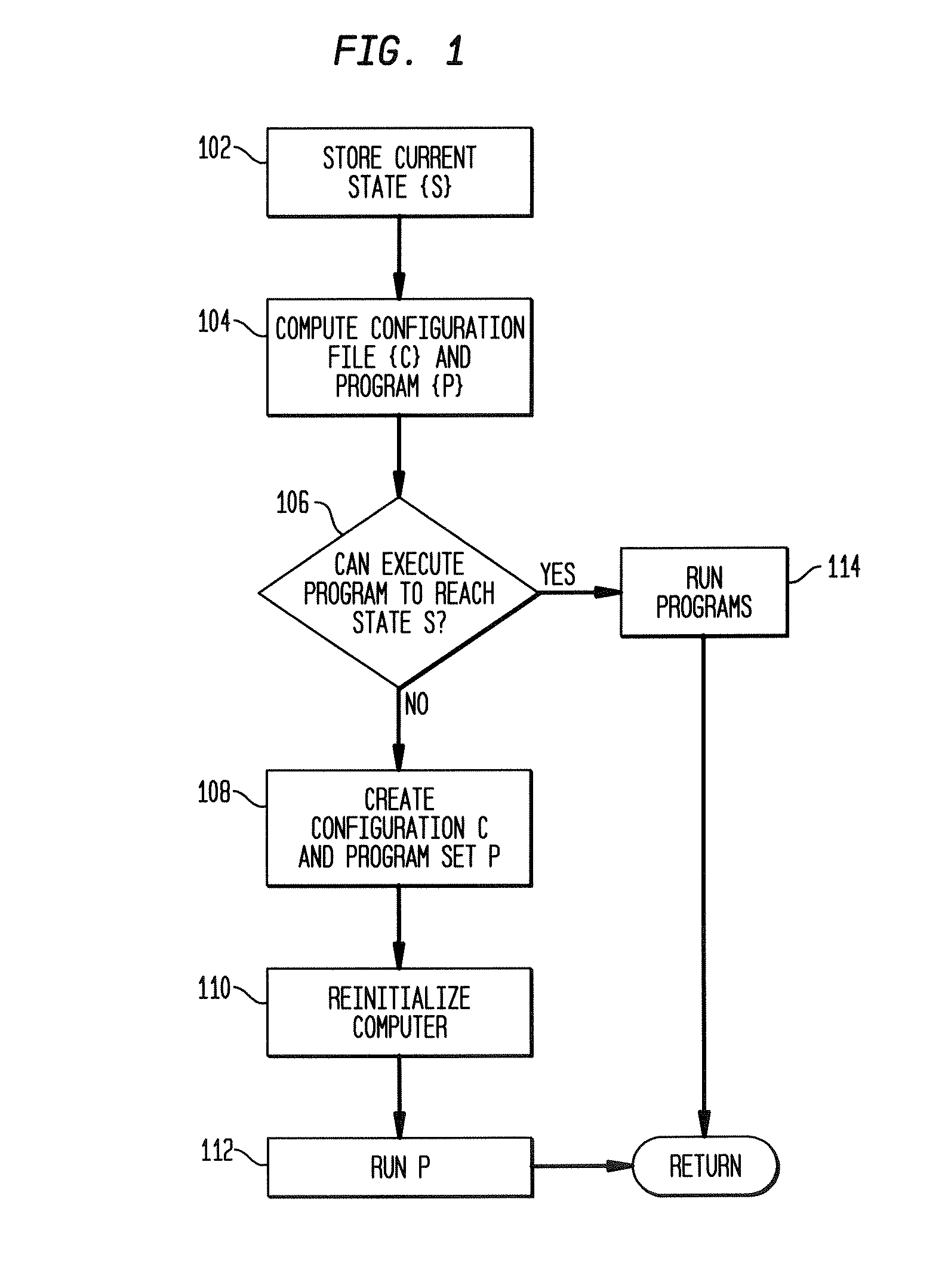
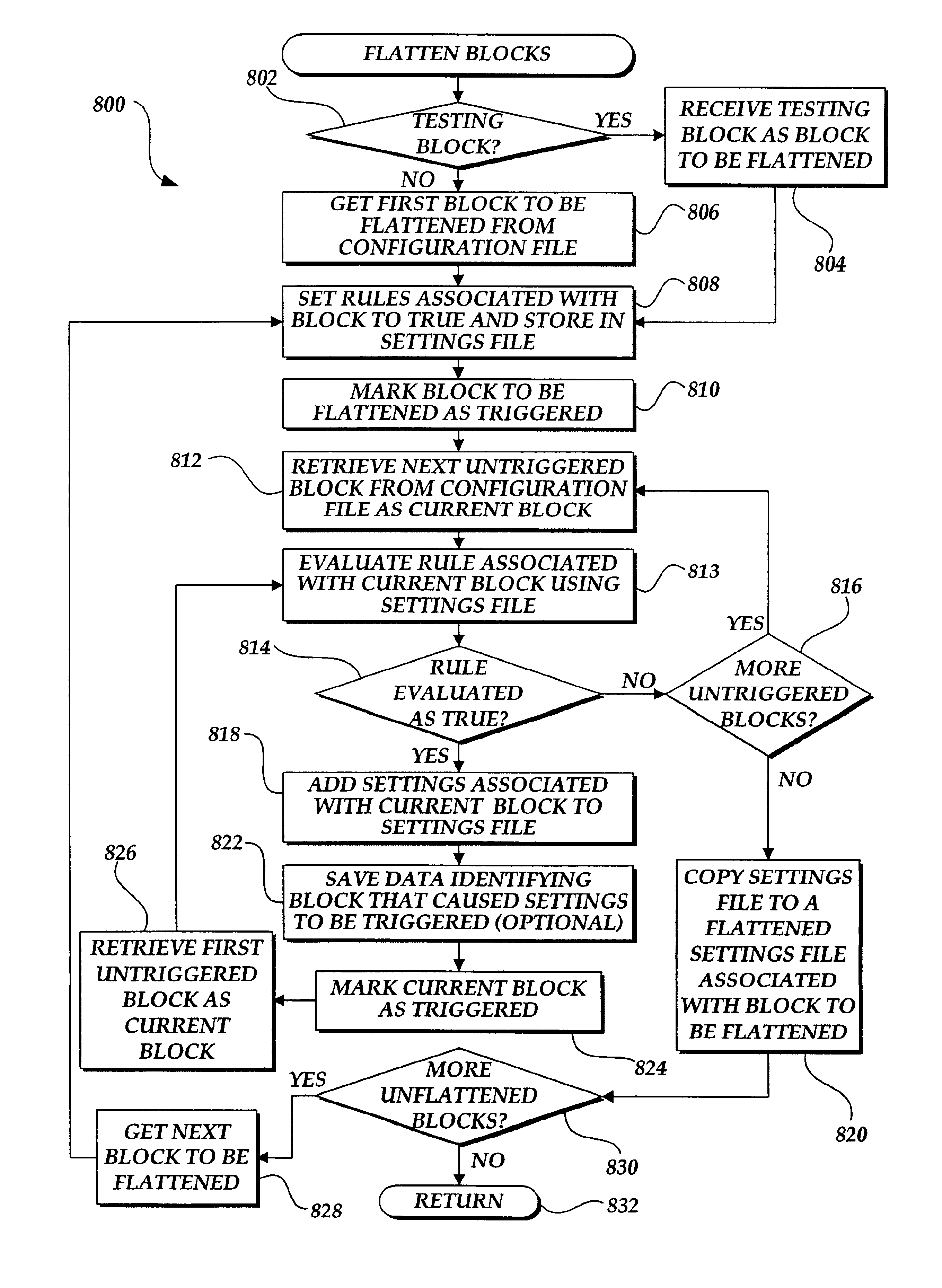
A method and apparatus are provided for determining the validity of a global configuration file. In order to verify the global configuration file, the configuration file is first “flattened.” To flatten the configuration file, the rules in the first block of the configuration file are identified. A settings file is then created with the rules set as true. The normal configuration process is then performed on the configuration file. The resulting settings file constitute the flattened settings for the block and are associated with the block. A determination is then made as to whether any conflicting settings, inconsistently set related settings, or syntax errors exist within the flattened settings. If any such settings do exist, an error message is generated. This process is then repeated for each block in the configuration file so that flattened settings are created for each block. A testing block may also be utilized to identify problems with the settings file generate by the testing block. Reverse queries may also be performed on the settings file. Changes in the flattened configuration files caused by changes in the global configuration file can also be identified. The flattened files may also be used to simplify the server computer configuration process.
Owner:MICROSOFT TECH LICENSING LLC
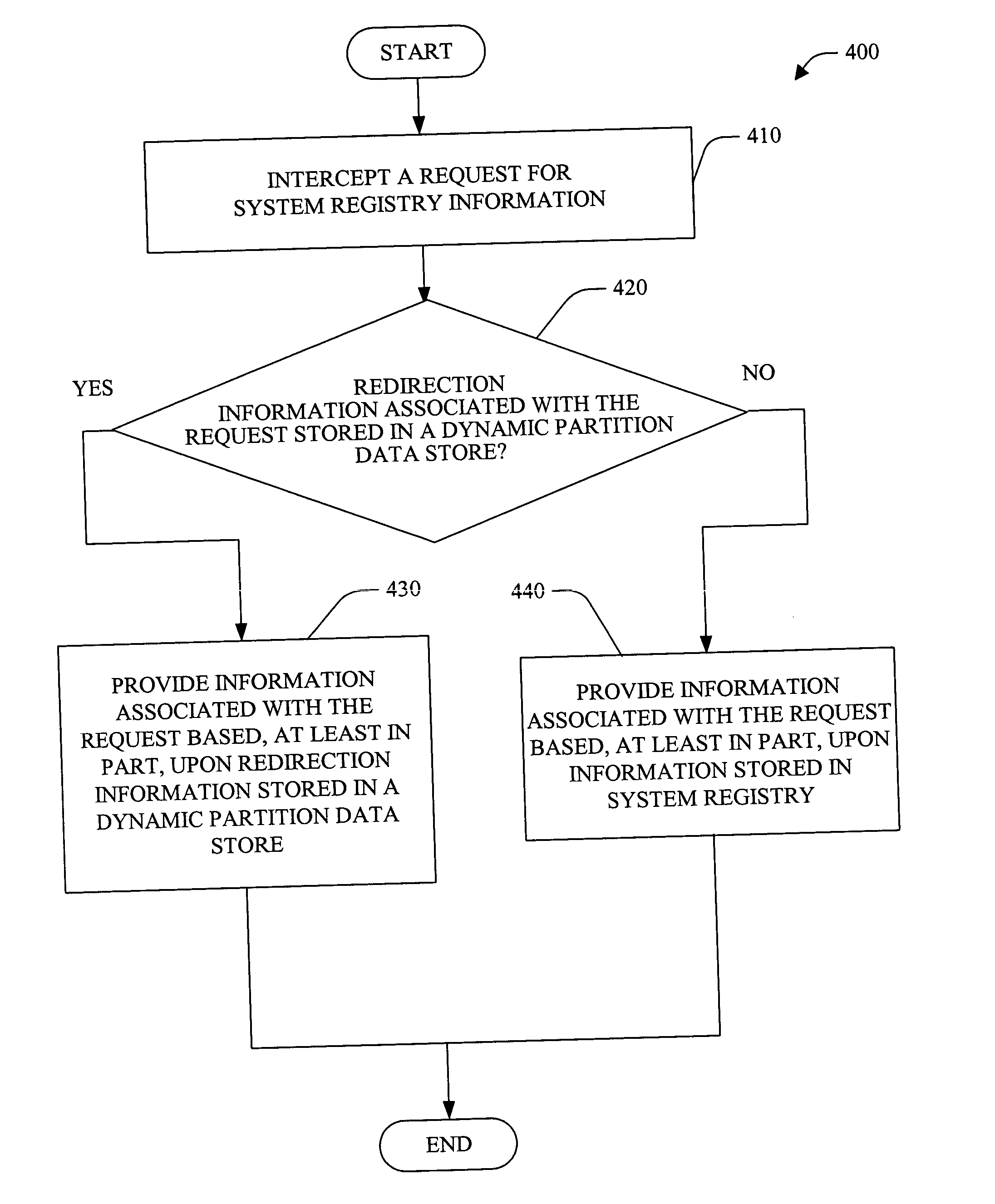
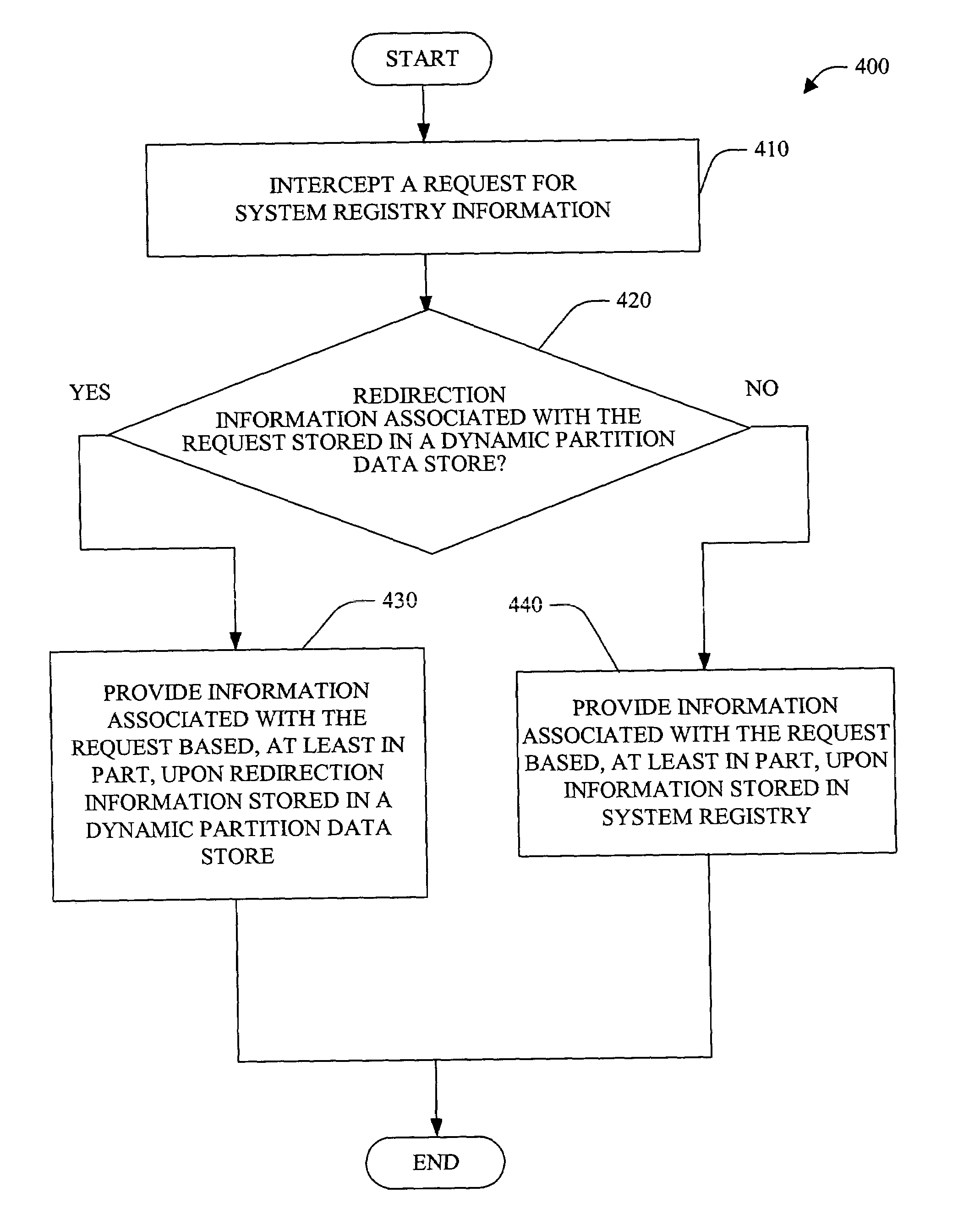
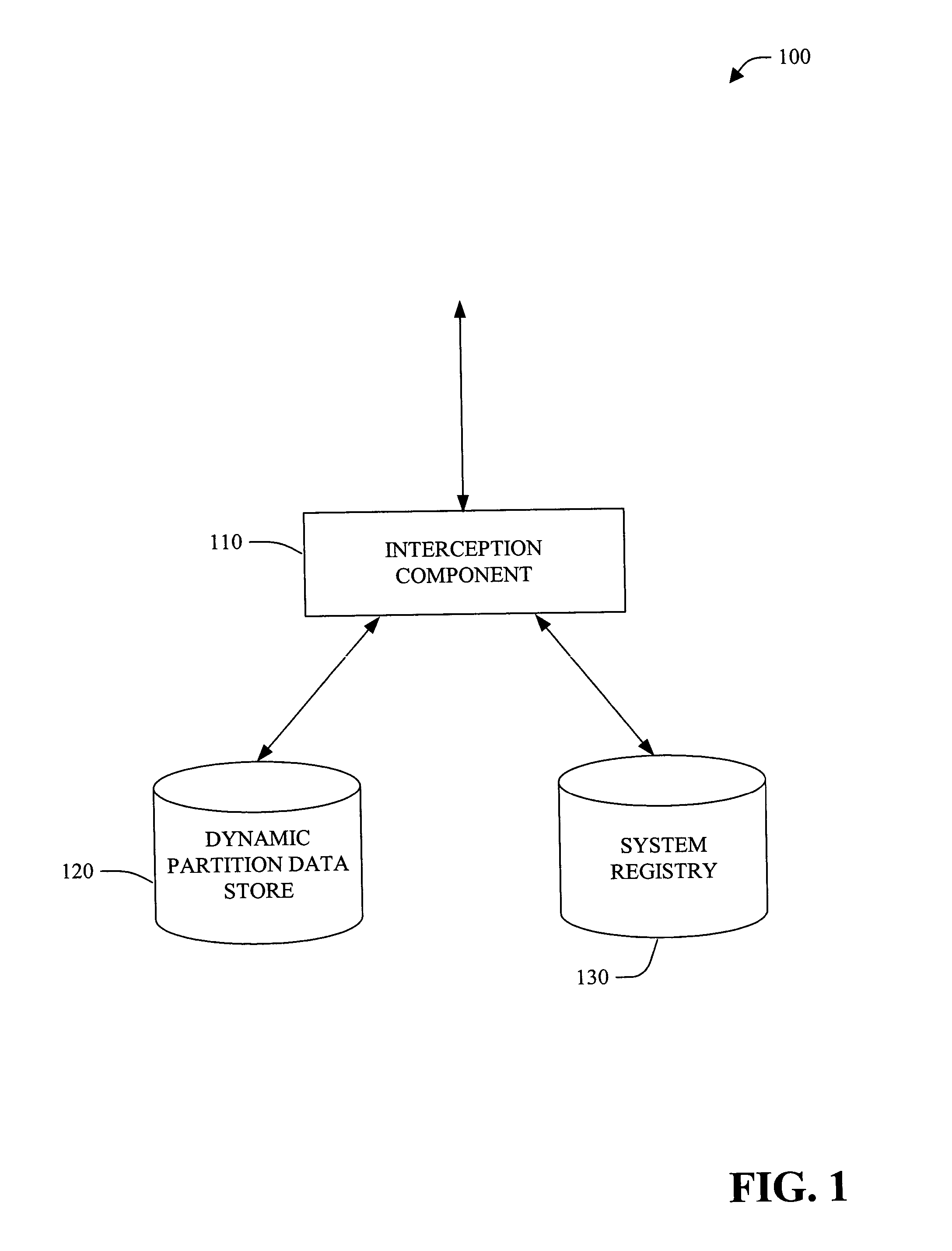
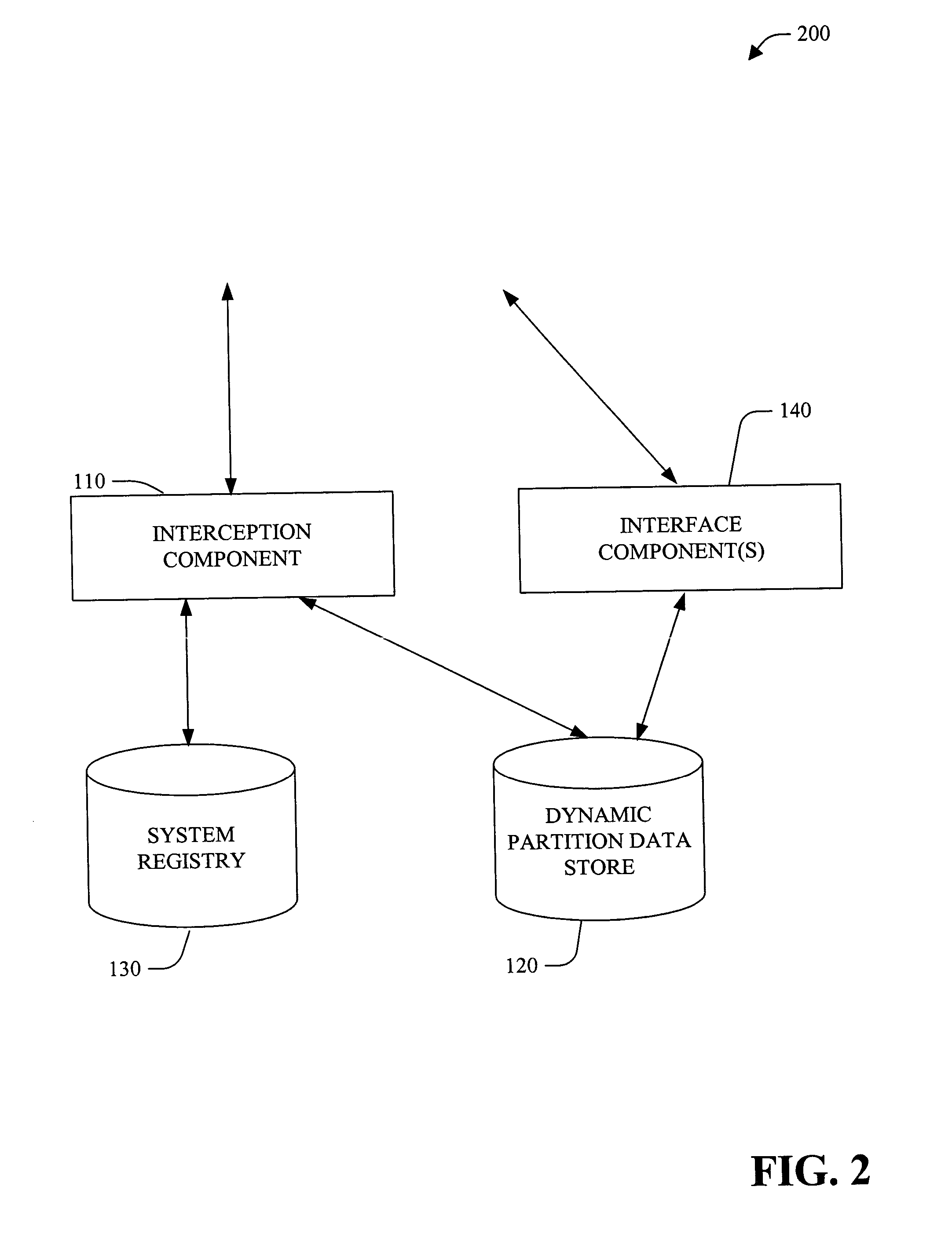
Dynamic registry partitioning
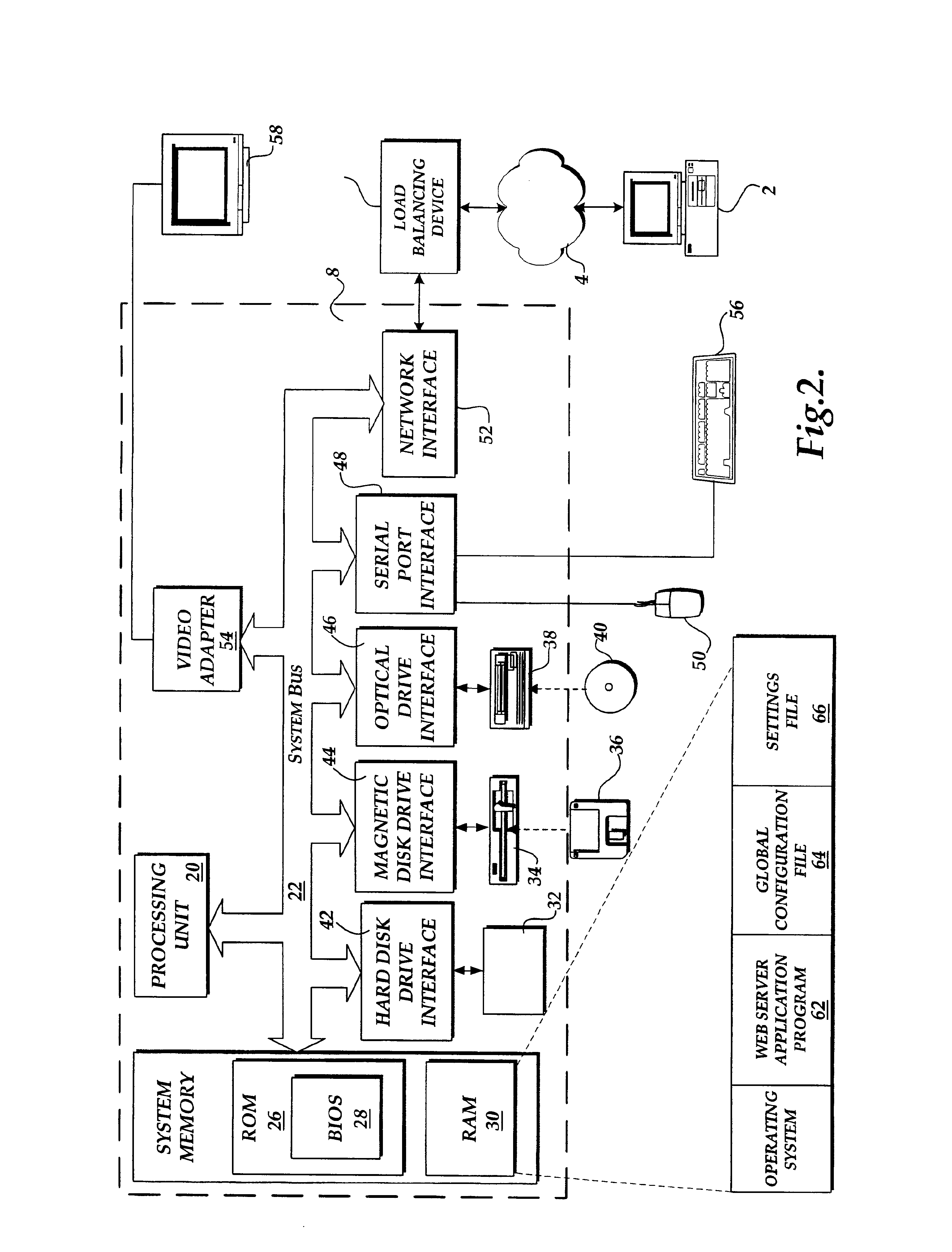
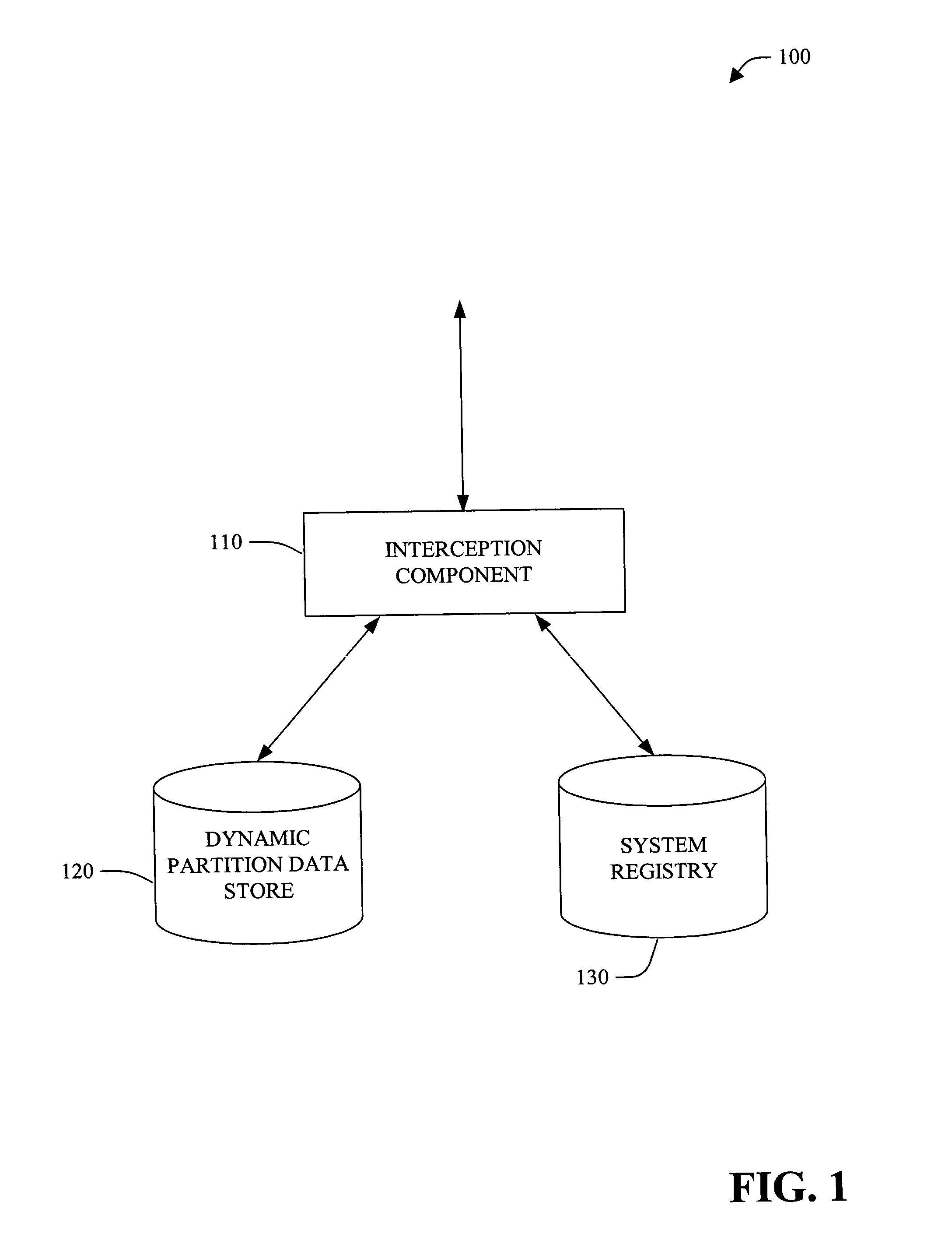
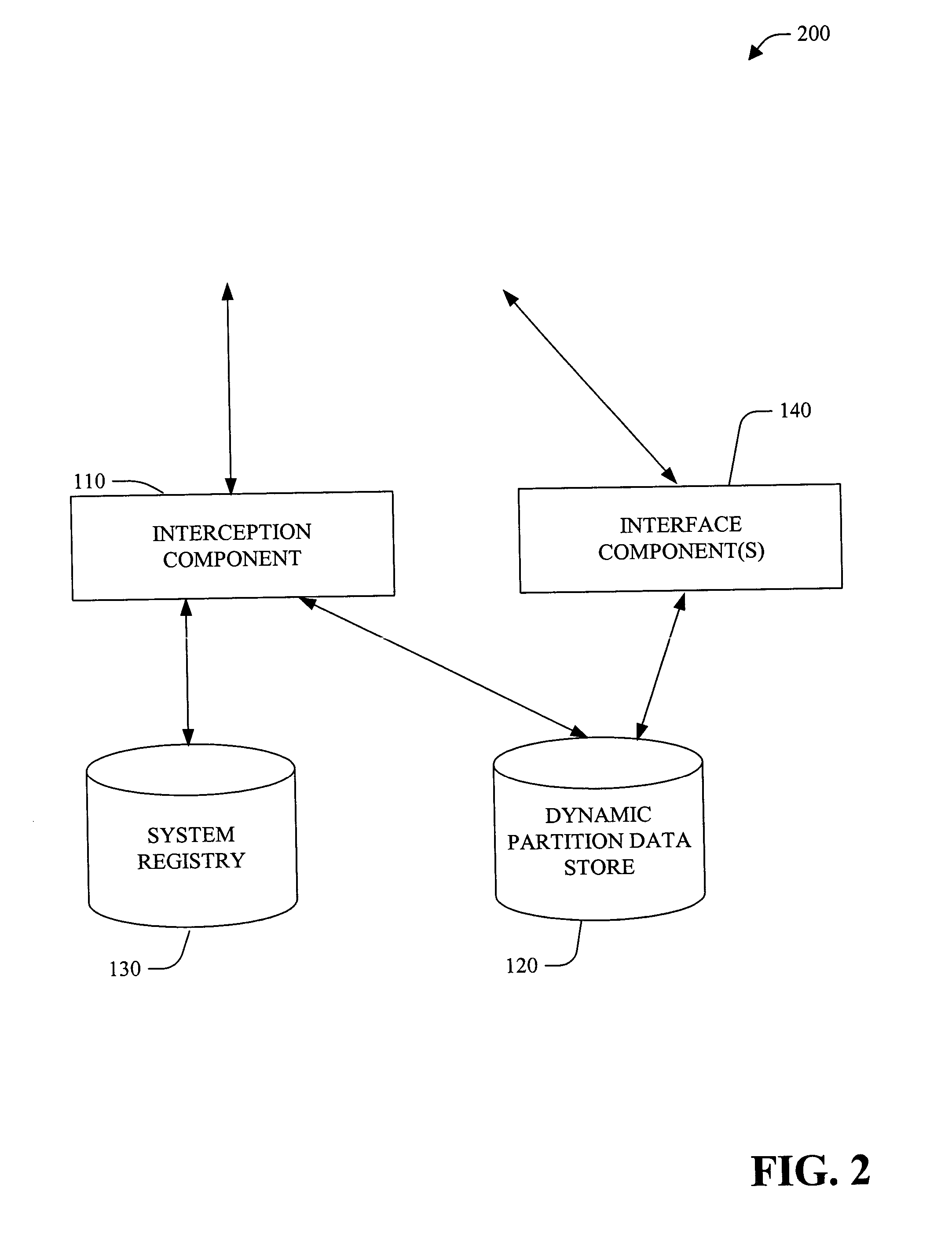
InactiveUS20050050084A1Data processing applicationsProgram control using stored programsOperational systemComputer configuration
A system and method of providing access to information stored in a system registry is provided. The system and method can further facilitate a generic (e.g., application and / or operating system independent) manner for dynamic partitioning of the system registry. The present invention facilitates providing of customized view(s) of the system registry to client(s), component(s) and / or application(s). Customization can be based on version, computer configuration, user and / or other suitable information. Further, the customized view of the system registry can be manipulated at runtime. Additionally and / or alternatively, low level component(s) (e.g., client(s) and / or application(s)) can also be given access to a dynamic partition data store to manipulate (e.g., add, delete and / or modify) redirection information (e.g., via interface component(s)).
Owner:MICROSOFT TECH LICENSING LLC
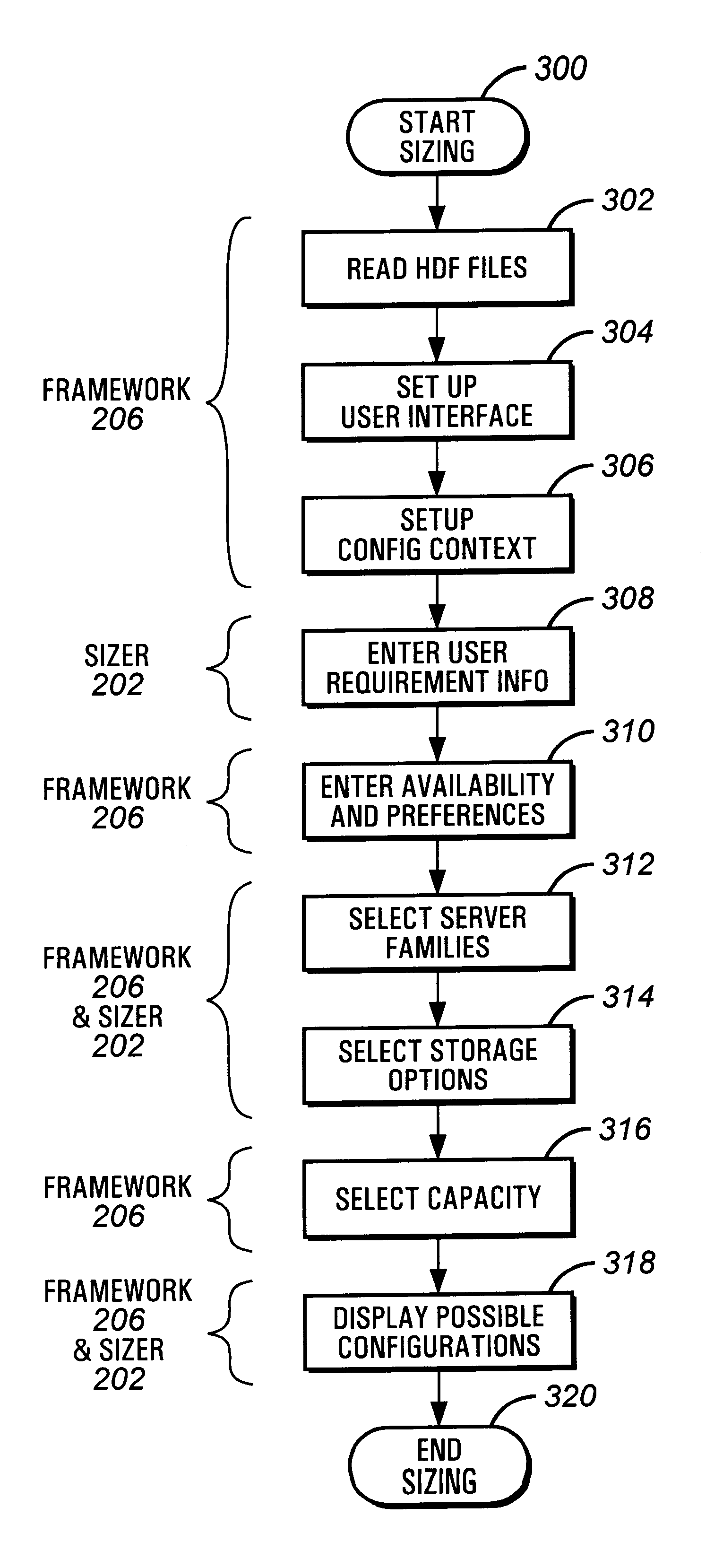
Configuration sizer for selecting system of computer components based on price/performance normalization
InactiveUS6192470B1Minimal effortAnalogue computers for electric apparatusGeneral purpose stored program computerComputer configurationComputerized system
A computer system is implemented according to the invention when an computer process allows a user to determine a desired computer configuration by in part determining performance relative to price candidate configurations.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Video editing method and apparatus
InactiveUS20060206526A1Improve user interactionElectronic editing digitised analogue information signalsUsing non-detectable carrier informationComputer configurationData store
A computer video editing system and method in a network of computers is disclosed. The system and method include a datastore or other source of subject video data, a transcription module and an assembly member. The transcription module generates a working transcript of the corresponding audio data of subject source video data. The working transcript includes original source video time coding for the passages (statements) forming the transcript. The assembly member enables user selection and ordering of transcript portions. For each user selected transcript portion, the assembly member, in real-time, (i) obtains the respective corresponding source video data portion and (ii) combines the obtained video data portions to form a resulting video work. The resulting video work is displayed to users and may be displayed simultaneously with display of the whole original working transcript to enable further editing and / or user comment. A text script of the resulting video work is also displayed. The video editing system and method may be implemented in a local area network of computers, as a browser based application on a host in a global computer network, as well as on stand alone computer configurations with a remote or integrated transcription service. The subject video data may be from a video blog, email, a user discussion thread or other user forum based on a computer network.
Owner:PORTALVIDEO
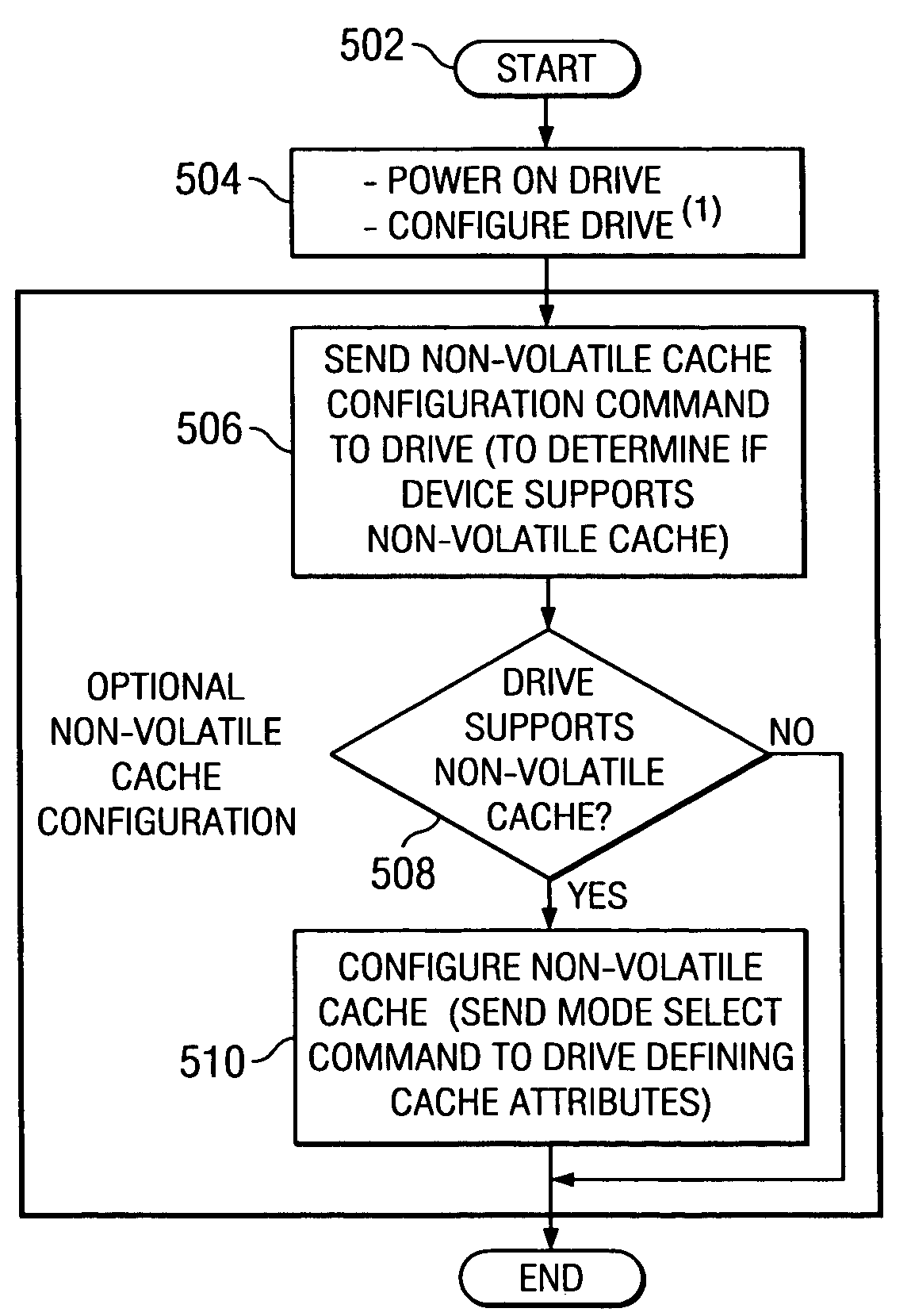
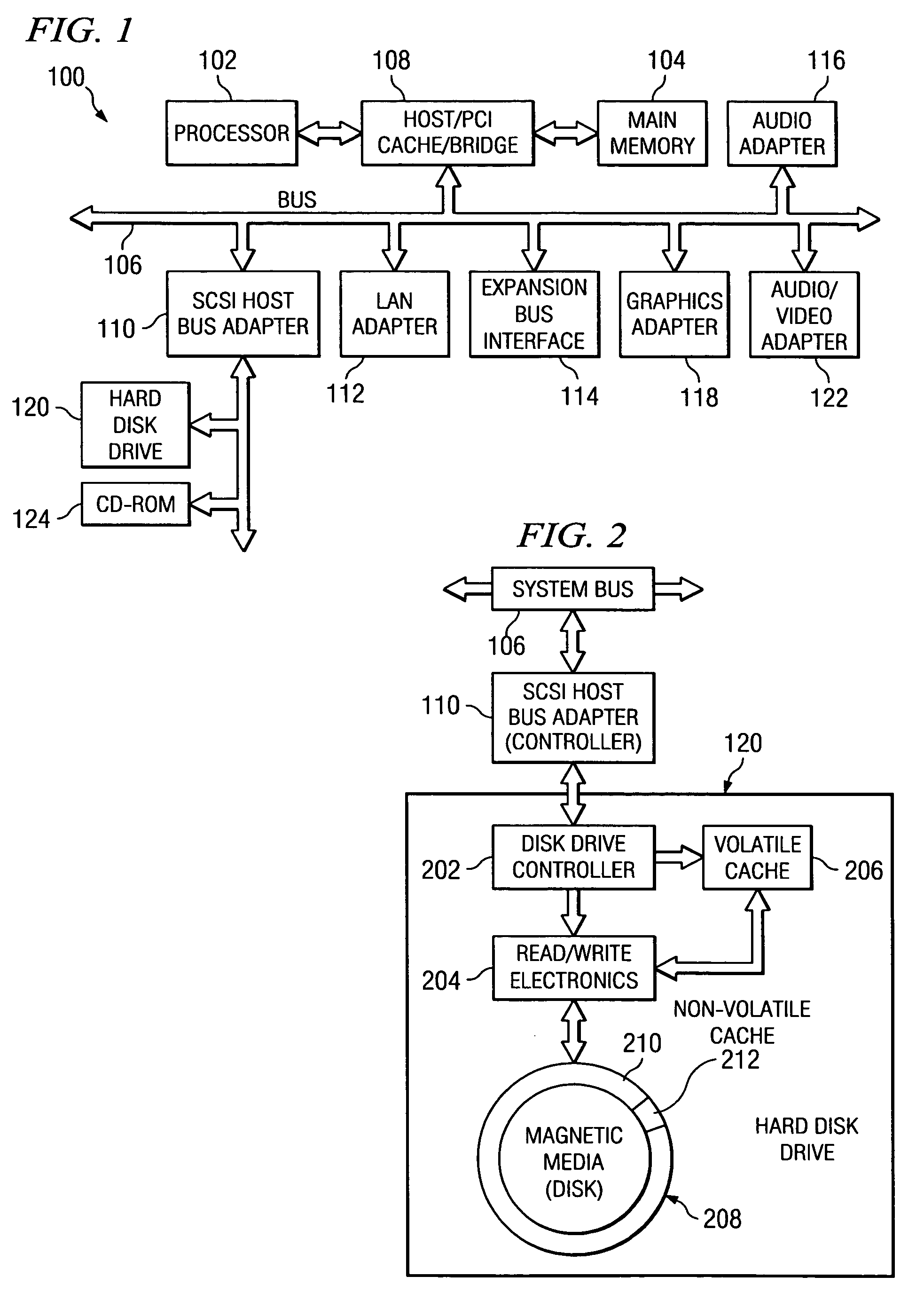
Method and apparatus using hard disk drive for enhanced non-volatile caching
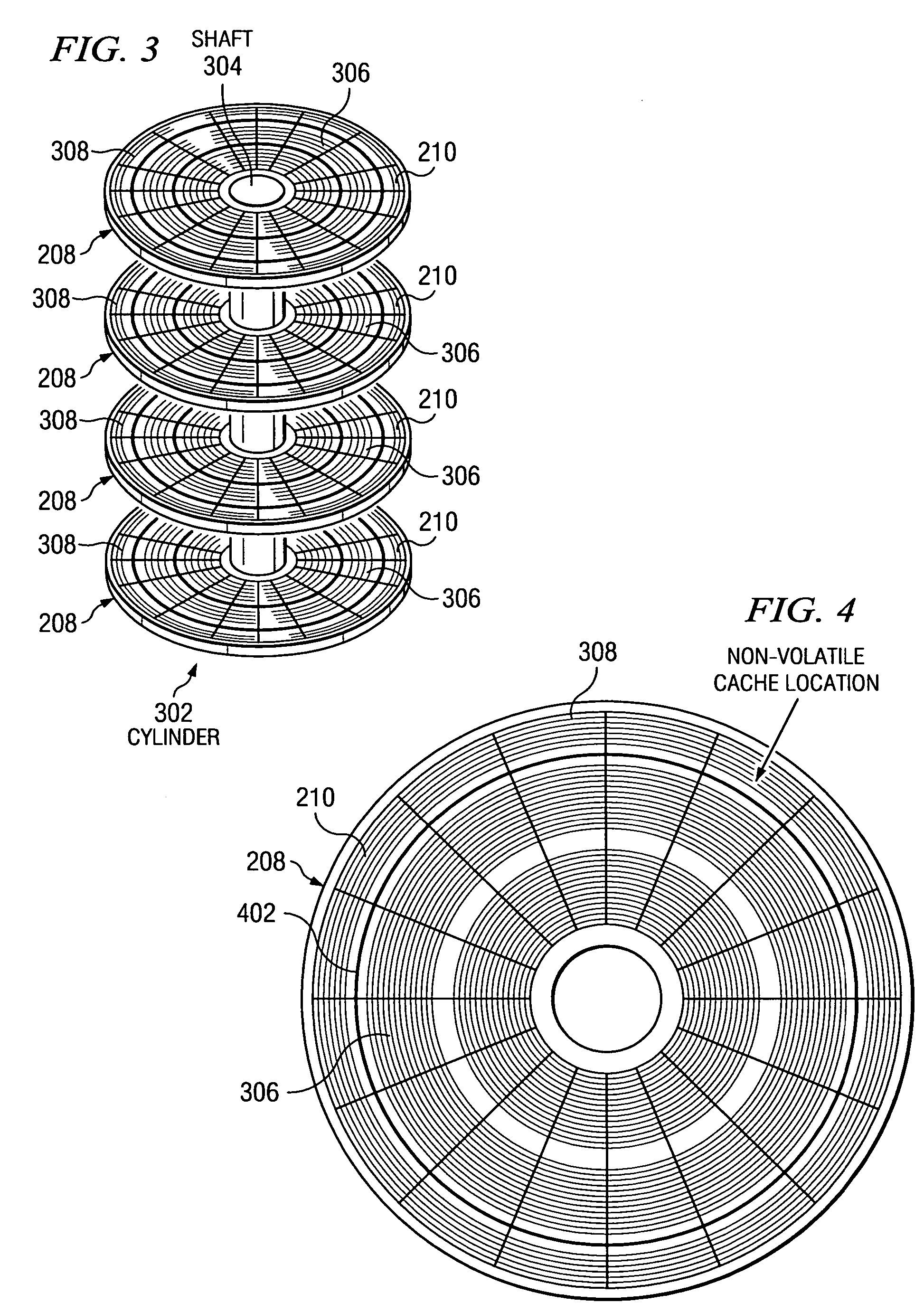
InactiveUS7461202B2Increase speedAddressing slow performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationHard disc driveComputer configuration
A method and apparatus is provided for allocating a portion of the OD zone of a hard drive disk to be a non-volatile (NV) caching space, where all writes to the disk are carried out. These write operations can be performed much faster than with conventional techniques, and storage costs may be significantly reduced. The disk drive controller manages the cache, and the host system sees improved throughput, especially for write intensive operations. In one embodiment a method is provided for writing specified data to a disk drive in a computer configuration, the disk drive having a magnetic disk and a volatile cache memory. A specified portion of the OD zone of the disk is reserved for an NV cache space, and the specified data is initially stored in the volatile memory, in response to a write command. The method further includes writing the specified data from the volatile memory to the NV cache space at the disk OD, and subsequently writing the specified data from the NV cache space to a selected longer-term storage location on the disk.
Owner:INT BUSINESS MASCH CORP
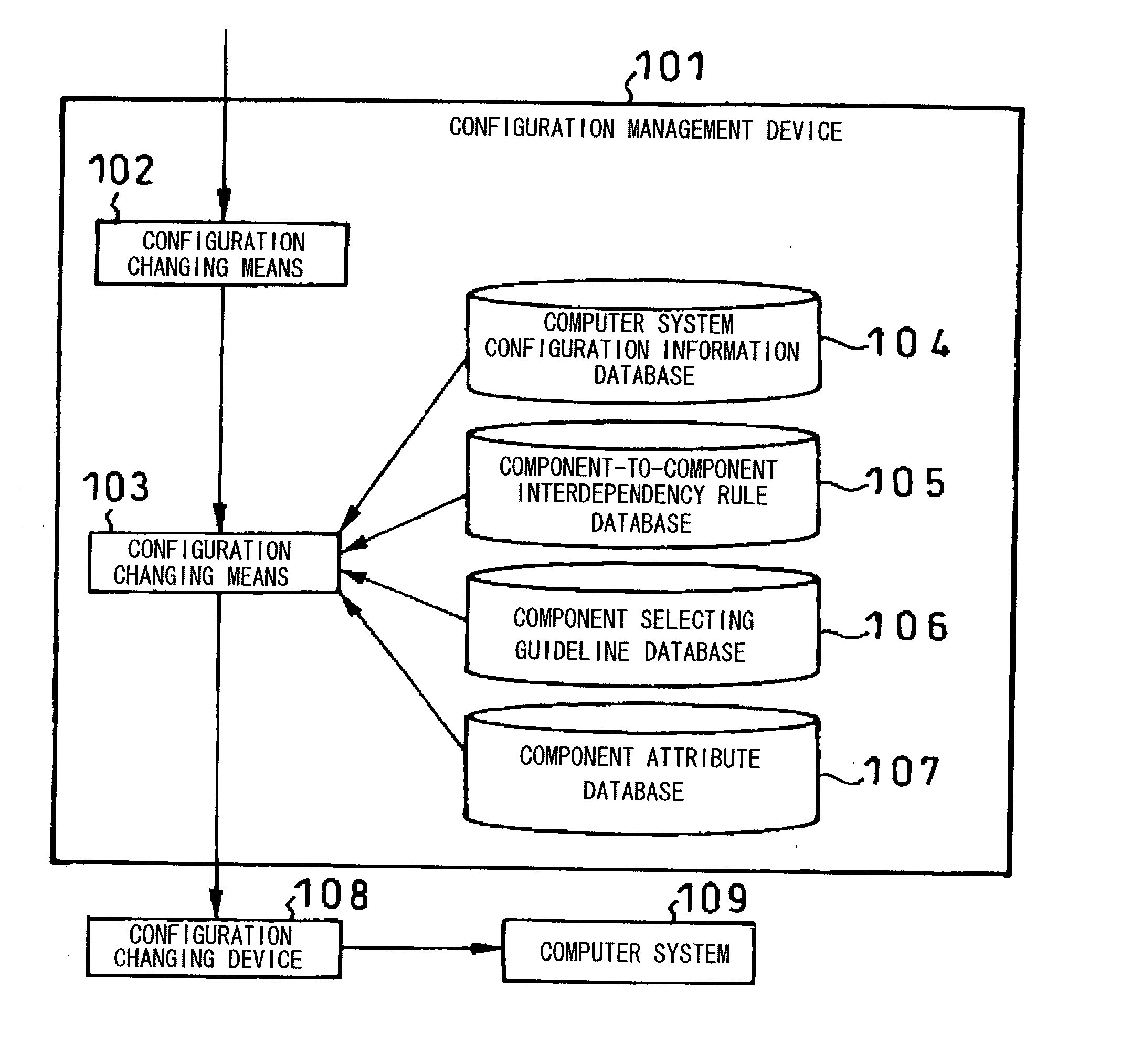
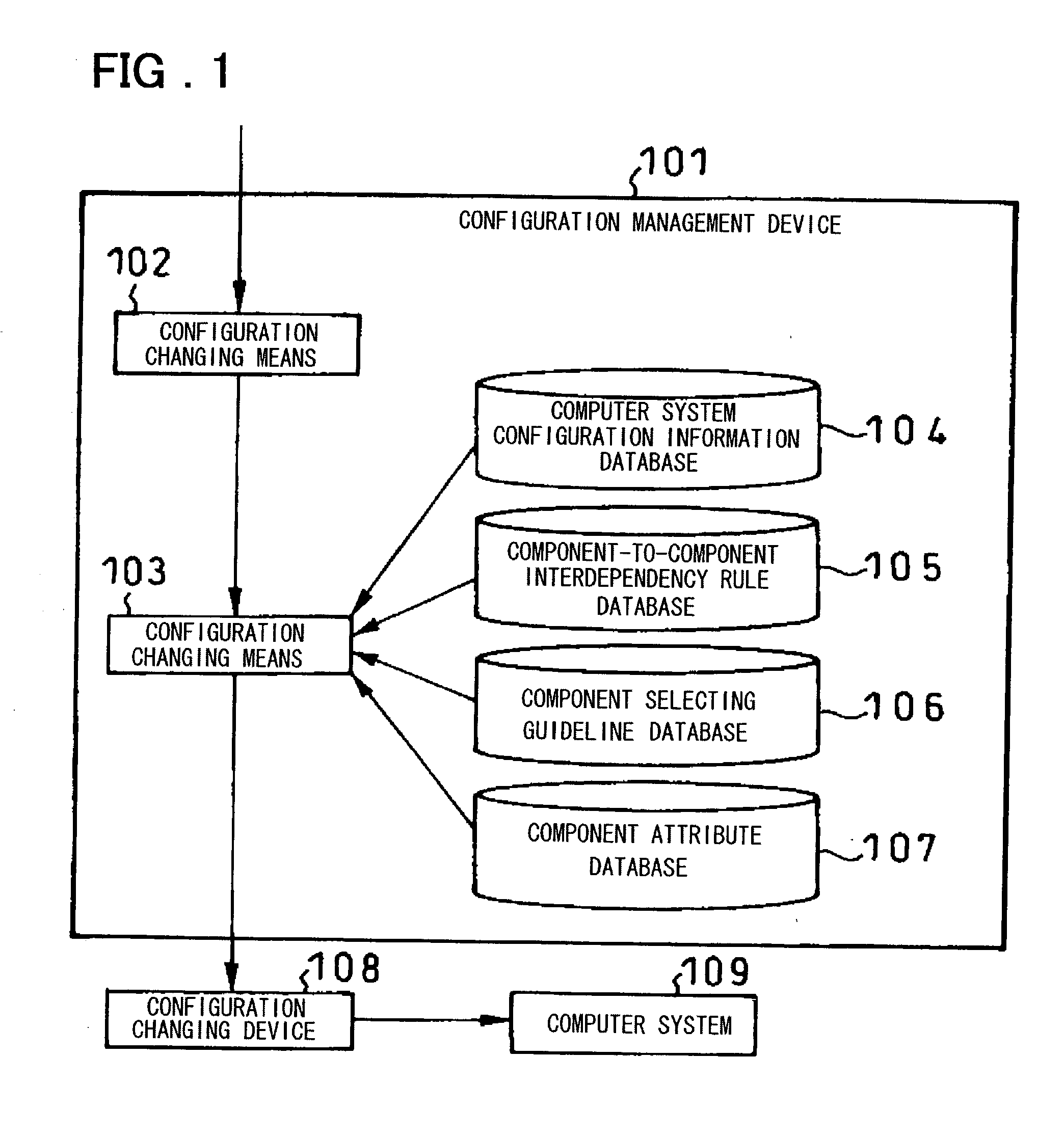
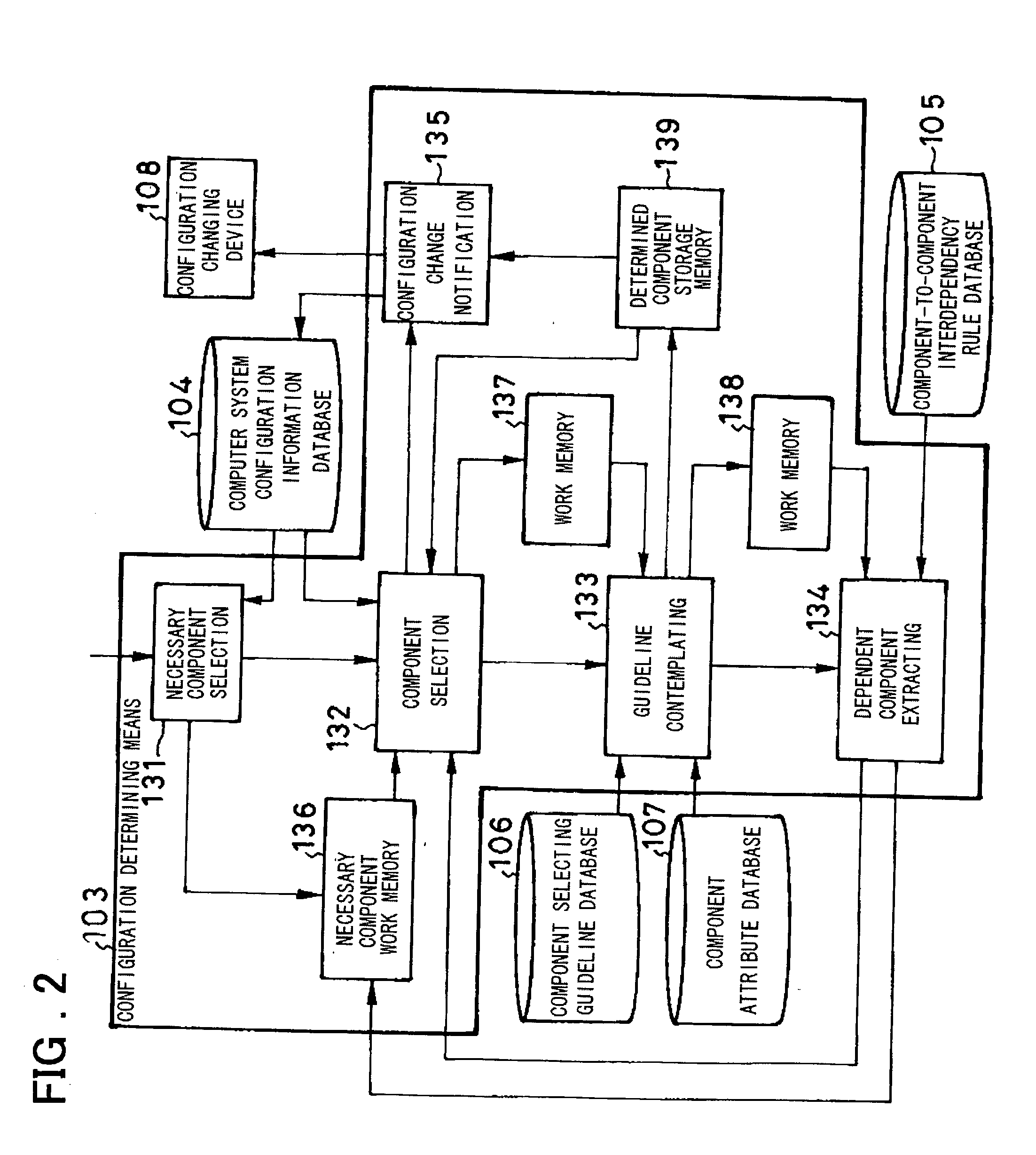
System for automatically changing computer system configuration
InactiveUS20030055529A1Increase workforceDigital data processing detailsDigital computer detailsGuidelineComputer configuration
Owner:NEC CORP
Method for modifying computer configuration and configuration of program which operates on computer, and computing device and system for implementing the method
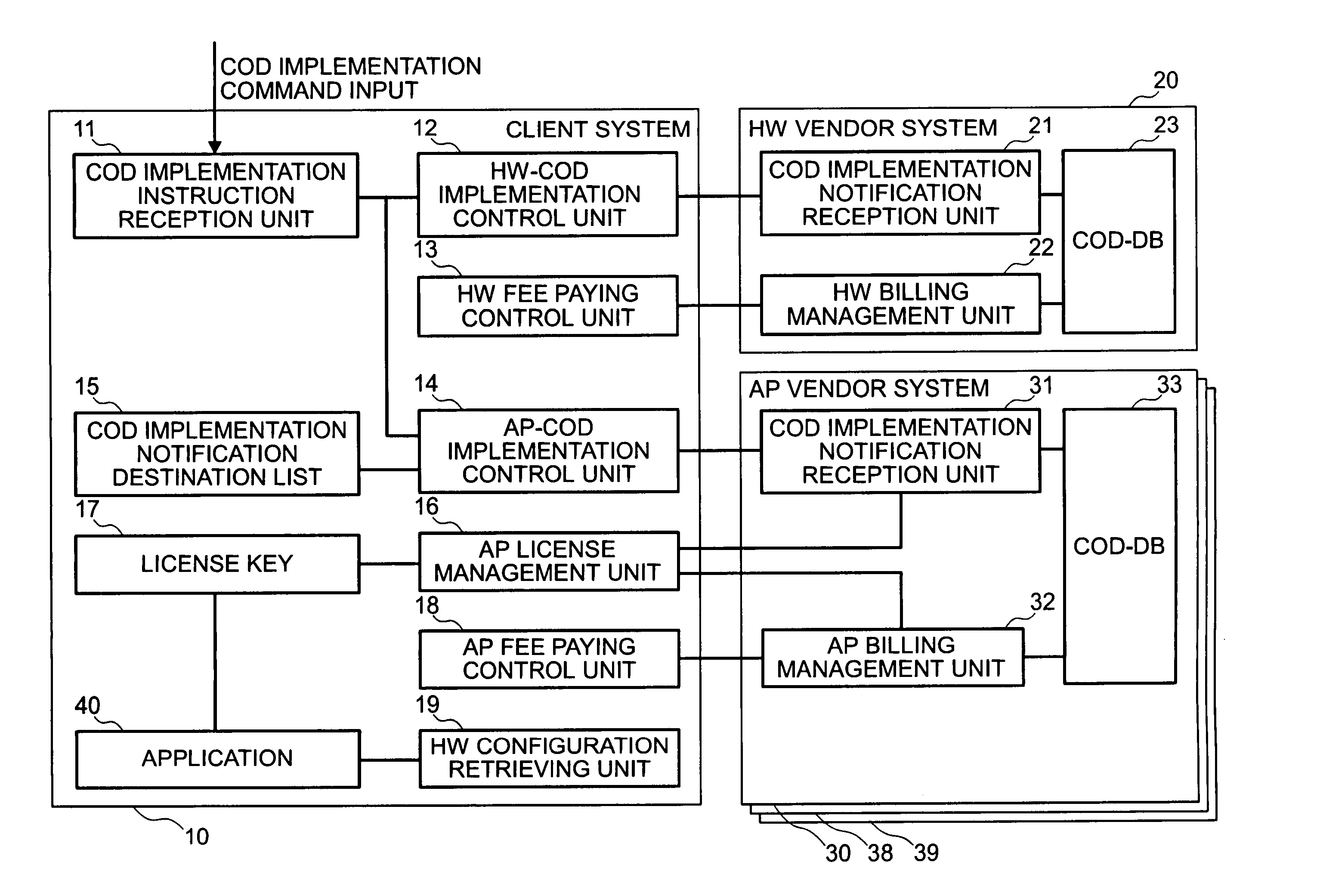
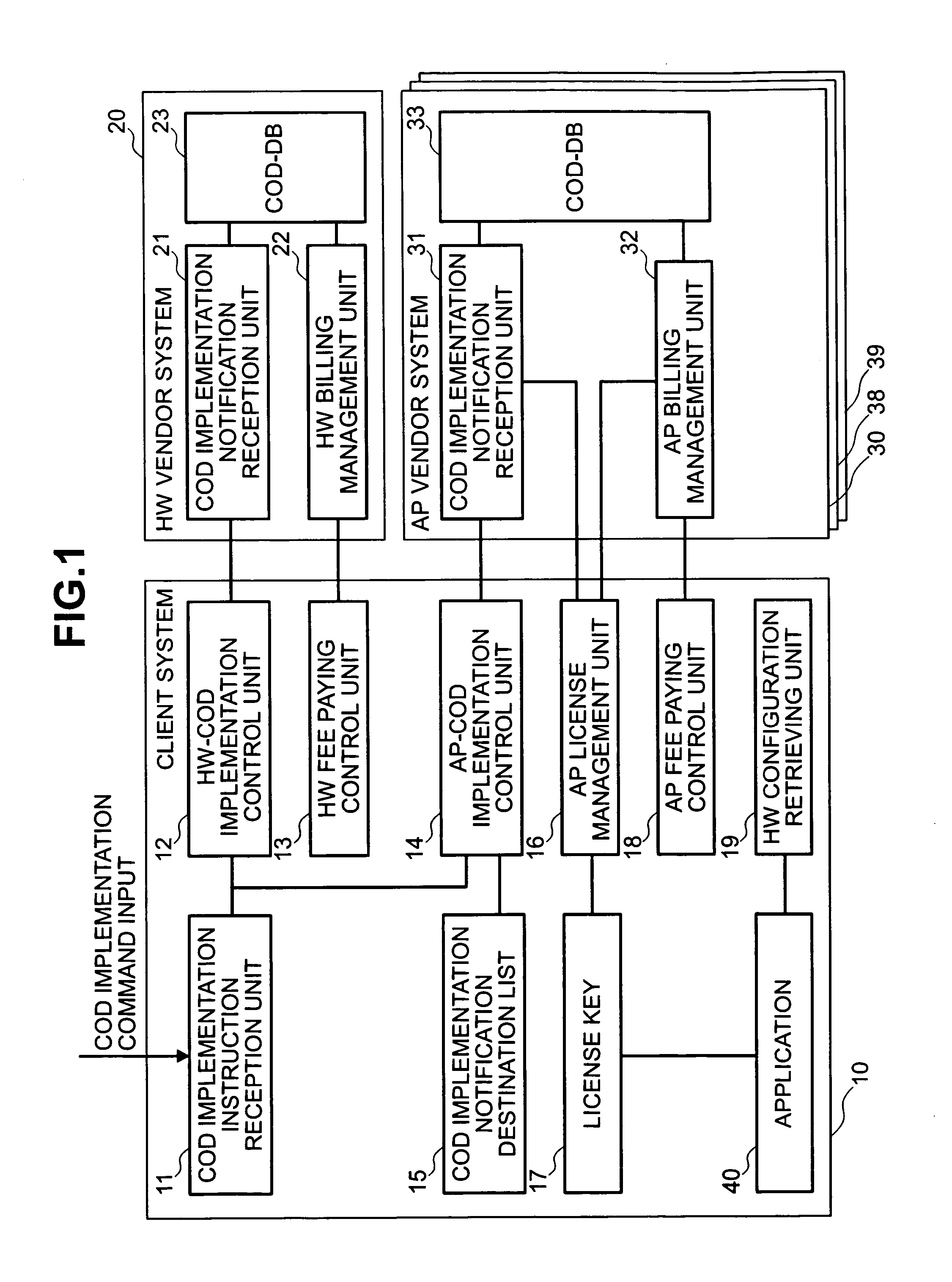
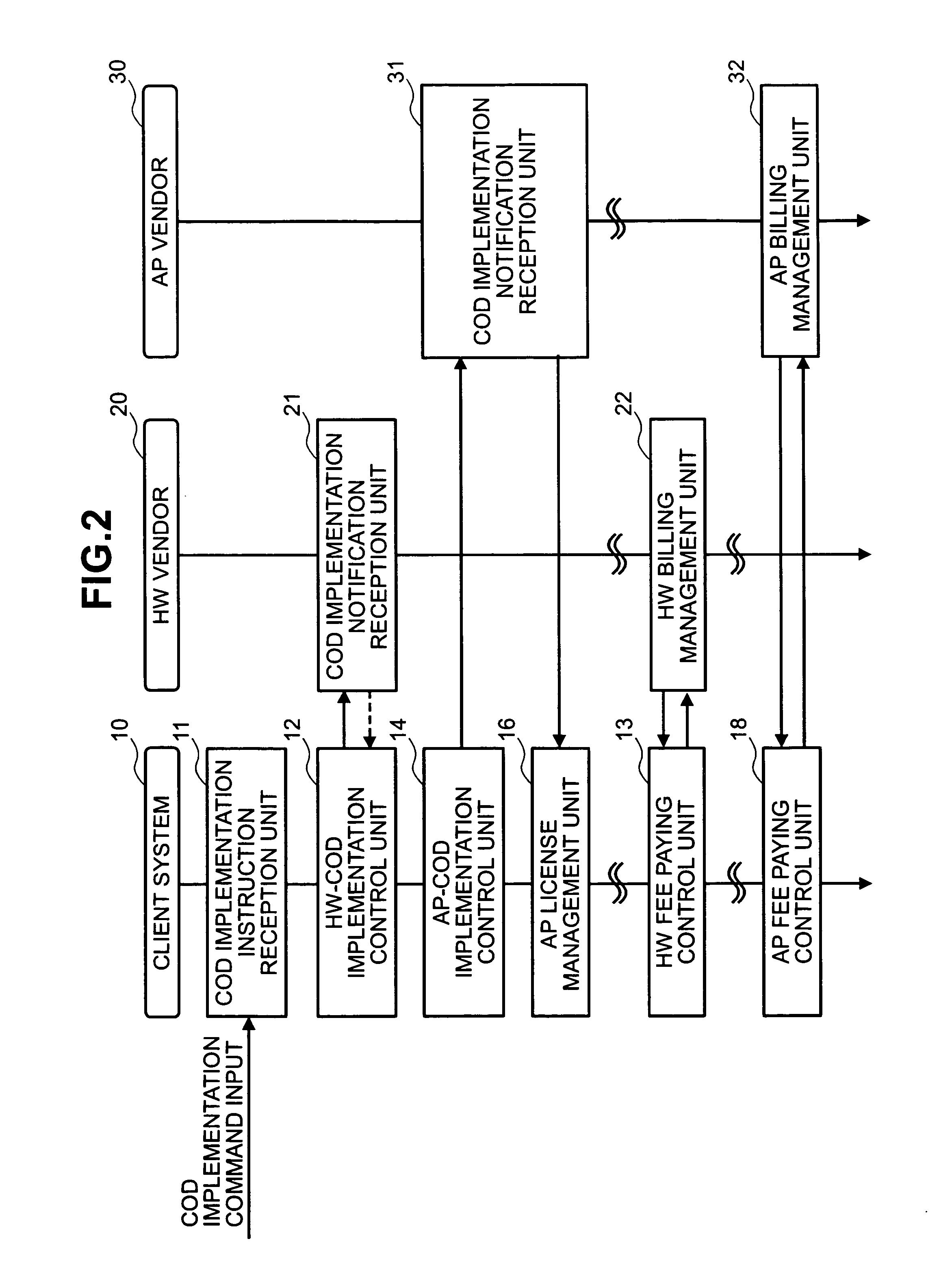
InactiveUS20050060388A1Increasing hardware capacityDigital data processing detailsDigital computer detailsComputer configurationModified method
This invention relates to modifying hardware and program configuration of a computer. In one embodiment, a computer configuration modification method comprises, upon reception of a configuration modification request for the hardware configuration and program configuration of the computer to be modified, transmitting the information regarding the hardware configuration to be modified to a hardware contract renewal notification destination in order to modify the fee to be paid for the modified hardware, and transmitting the information regarding the hardware configuration to be modified and the information regarding the program configuration to be modified to a program contract renewal notification destination in order to modify the fee to be paid for the modified program. When license information transmitted from the program contract renewal notification destination is inputted, the hardware configuration is modified based on the information regarding the hardware configuration to be modified and the program configuration is modified based on the information regarding the hardware configuration to be modified and the information regarding the program configuration to be modified.
Owner:HITACHI LTD
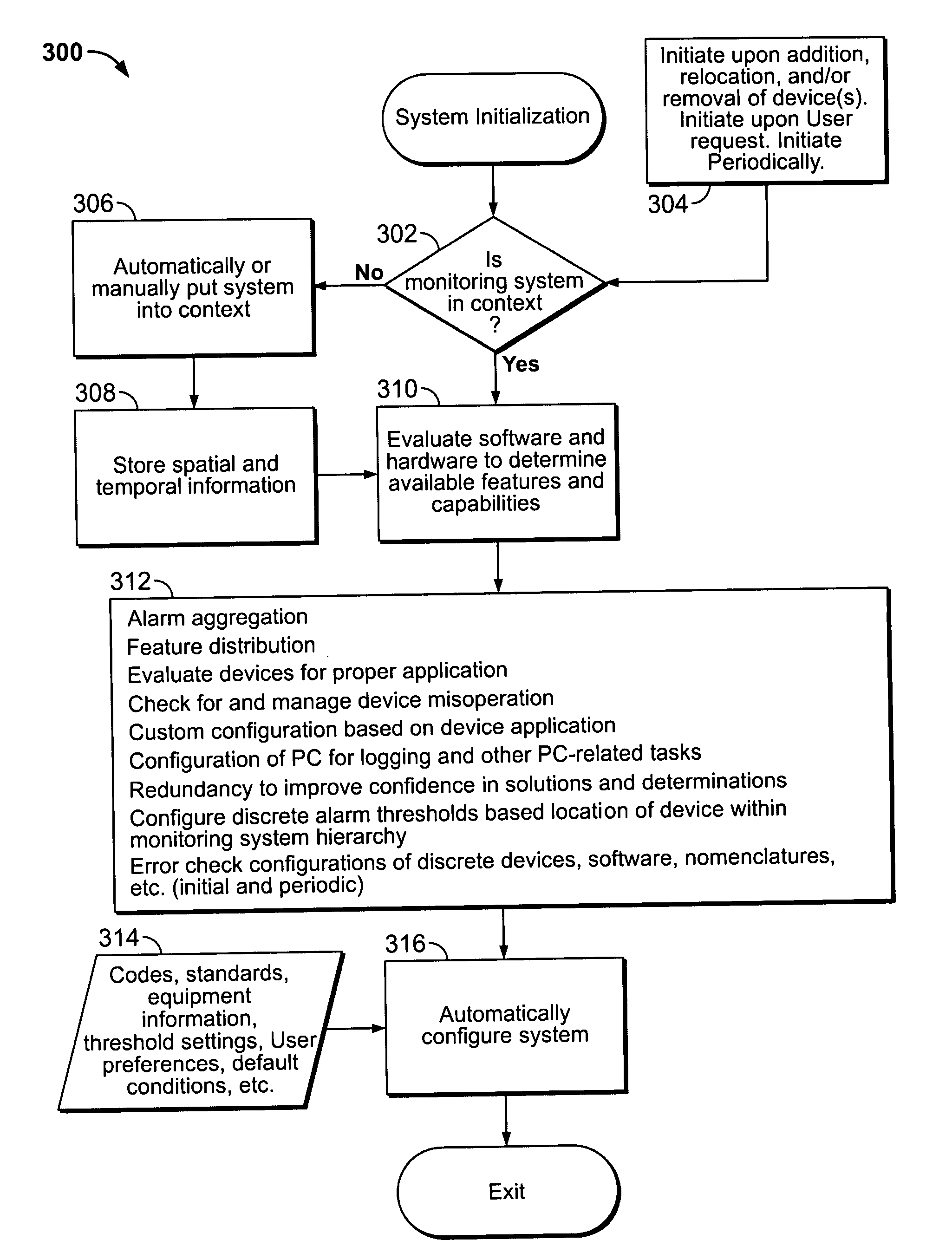
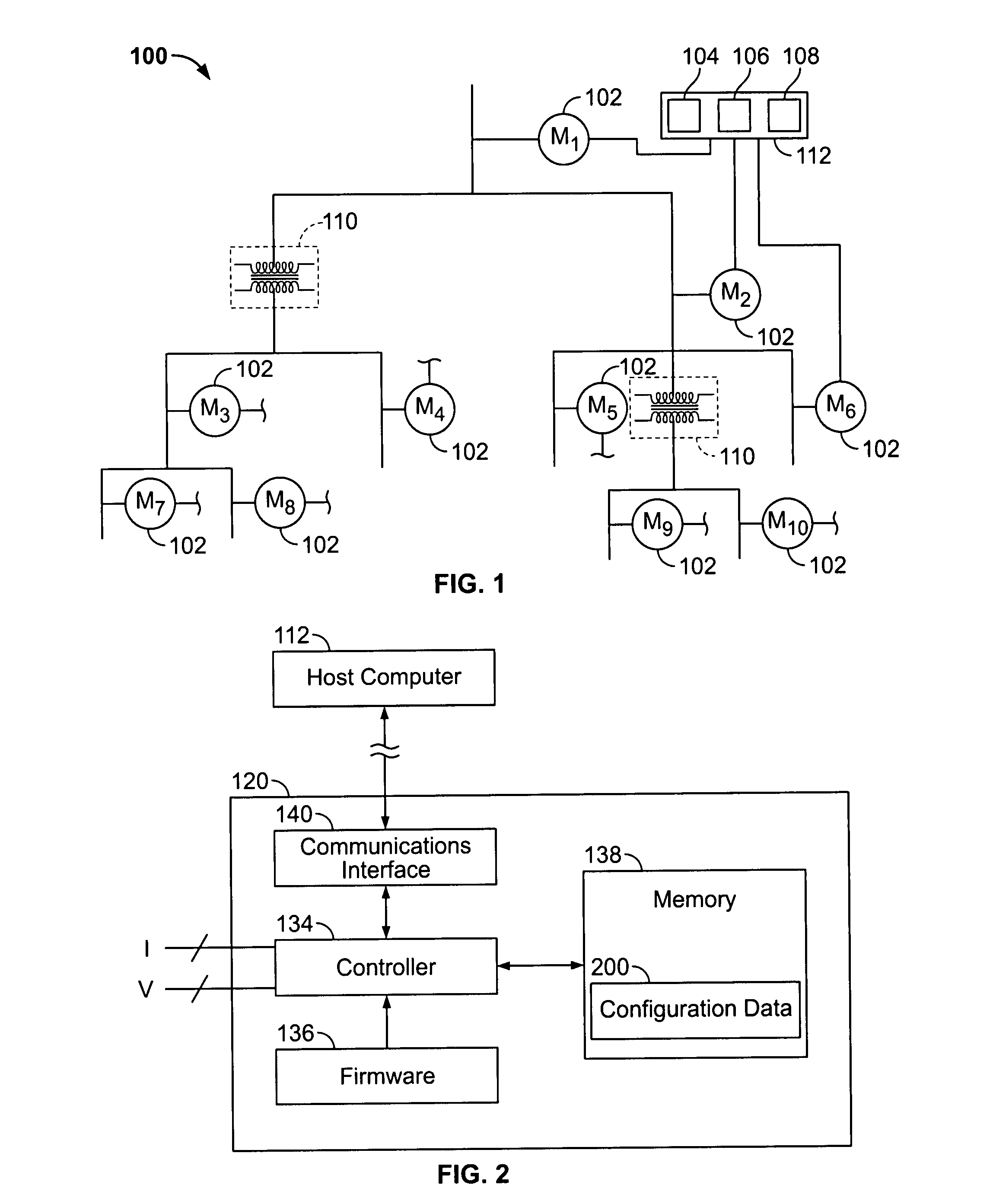
Automated configuration of a power monitoring system using hierarchical context
ActiveUS20090066528A1Increase short-termMinimizing orLevel controlFrequency-division multiplex detailsError checkAuto-configuration
Methods of automatically configuring a power monitoring system based upon the locations of the monitoring devices in a hierarchy representing the spatial interrelationships of the monitoring devices. The power monitoring system includes a host computer communicatively coupled to a plurality of monitoring devices arranged in a hierarchy in an electrical system. Software on the host computer may execute any or all of an alarm aggregation algorithm for aggregating multiple alarms based on device location; a feature distribution algorithm for enabling / disabling selected device features; an evaluation algorithm for evaluating device applications; a device check algorithm for detecting flawed data; a custom configuration algorithm for customized configuration of thresholds on device-by-device basis; a host computer configuration algorithm for configuring the host computer; a redundancy algorithm for verifying an electrical event; an alarm configuration algorithm for configuring device thresholds; and a configuration error checking algorithm for detecting nomenclature issues.
Owner:SQUARE D CO
Pipeline path analysis
This disclosure relates to path analysis, determination, and optimization for pipelines. The methods, systems, and computer executable code disclosed herein contemplate the evaluation of numerous aspects and constraints of an area around a potential pipeline path in a project. Further the methods, systems, and computer executable code may be deployed in a variety of platforms including various stand-alone and client-server computer configurations.
Owner:TRIMBLE PLANNING SOLUTIONS
Device case and mounting apparatus
A multi-function case and support for an electronic device, such as a tablet computer. The case may be adapted to support the tablet in a variety of configurations, such as similar to a laptop computer configuration, and as a raised support. The case may also protect the electronic device from rough contact and other wear. In the raised support configuration, the case and support may be adapted to allow for rotation of the tablet from a landscape to a portrait attitude.
Owner:VITEC HLDG ITAL SRL
Method and apparatus for generating configuration rules for computing entities within a computing environment using association rule mining
ActiveUS20080301081A1Digital computer detailsKnowledge representationComputer configurationRule mining
A method and apparatus for generating computer configuration rules comprising receiving configuration data regarding a plurality of computers, analyzing the configuration data to determine associations within the configuration data, and generating configuration rules from a result of the analysis.
Owner:CA TECH INC
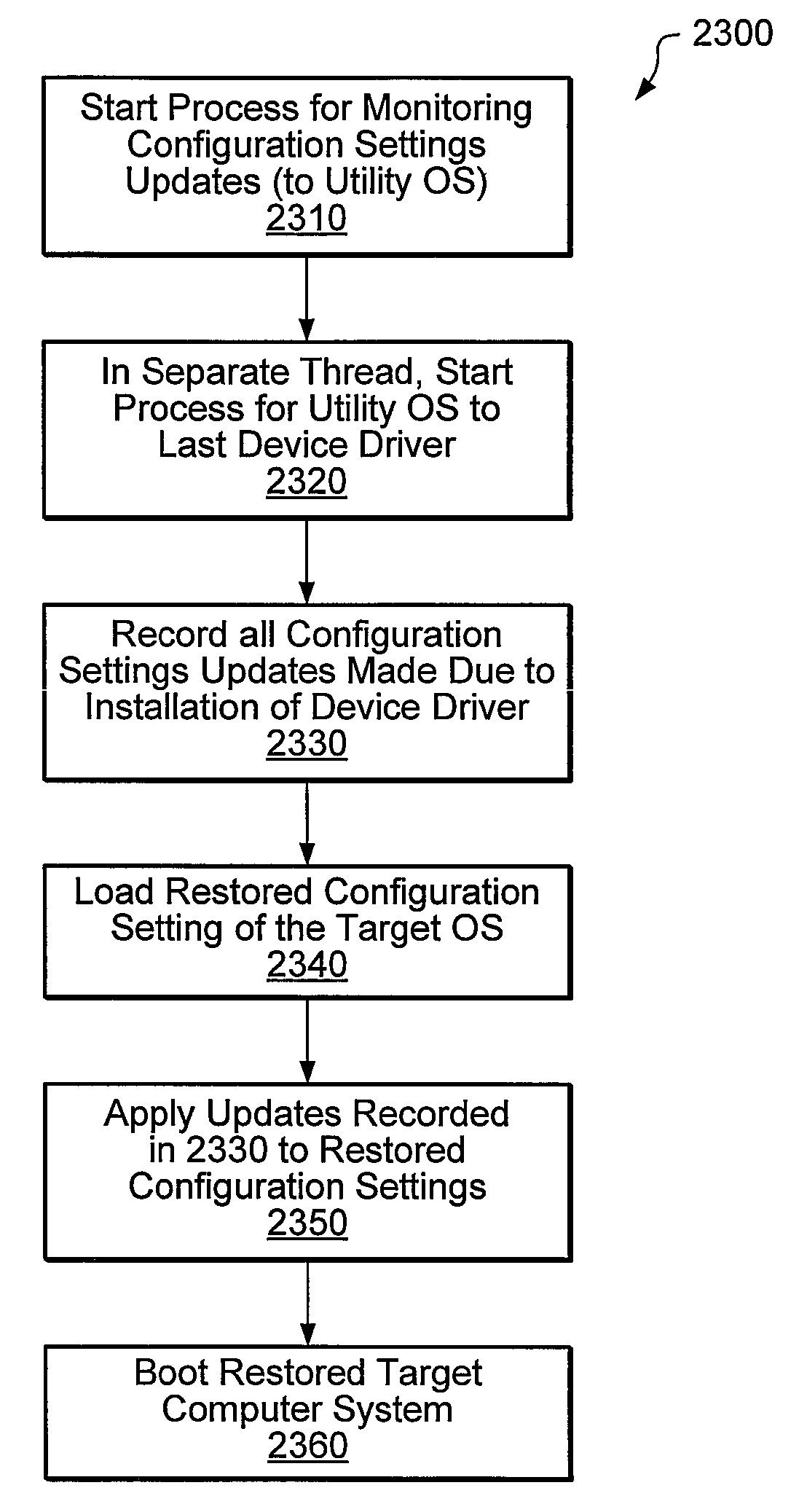
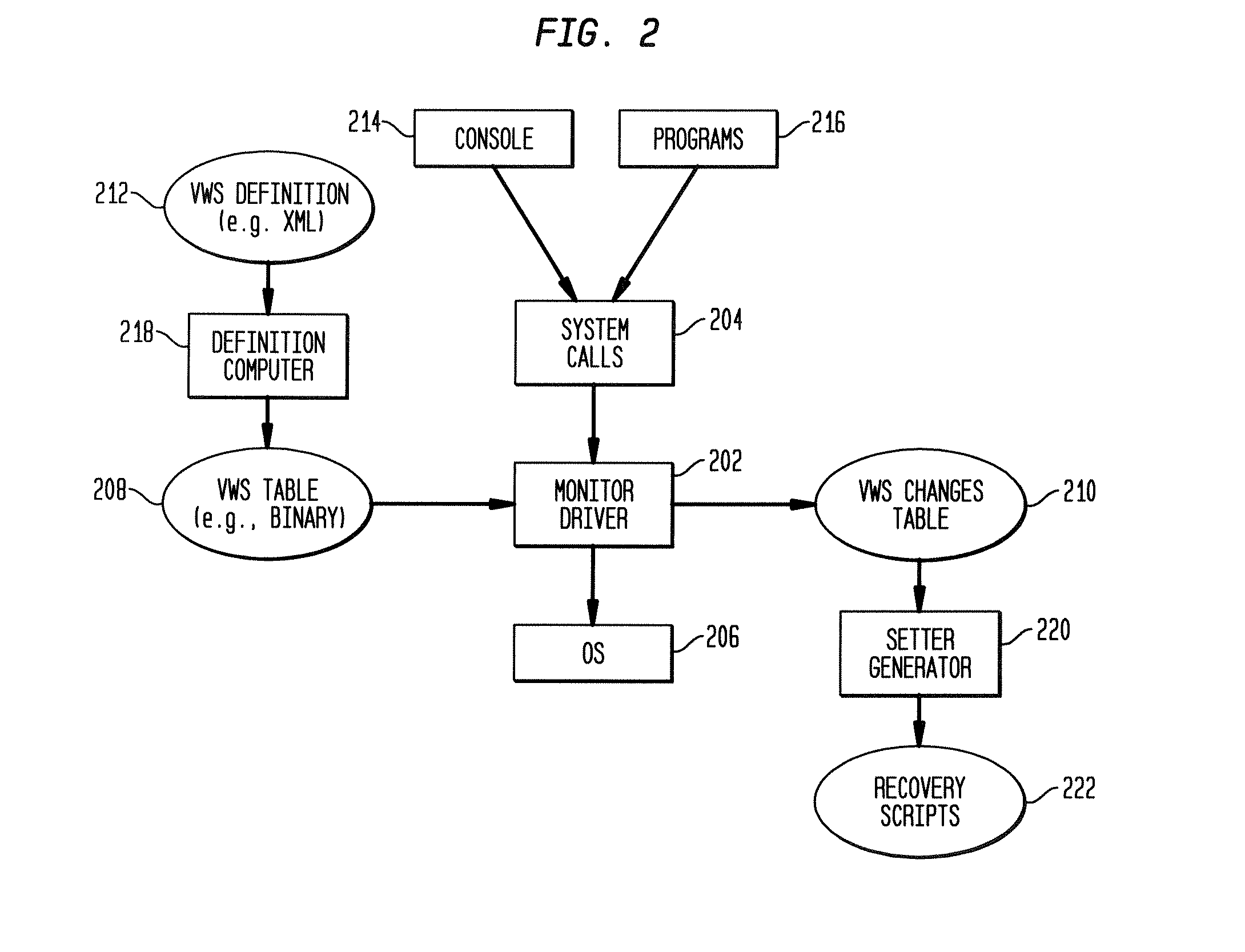
Using a monitoring process to update system configuration settings during restore operations
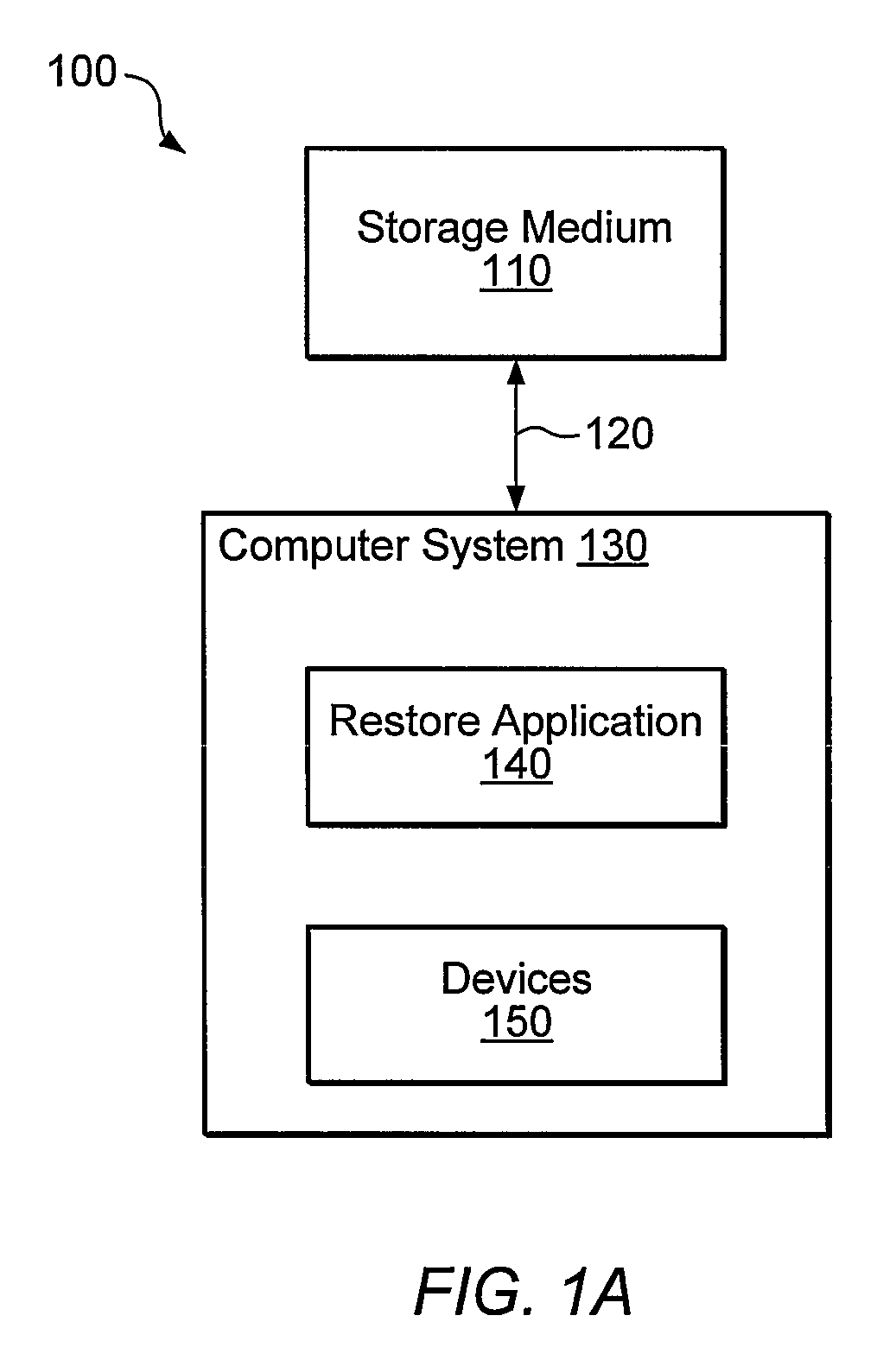
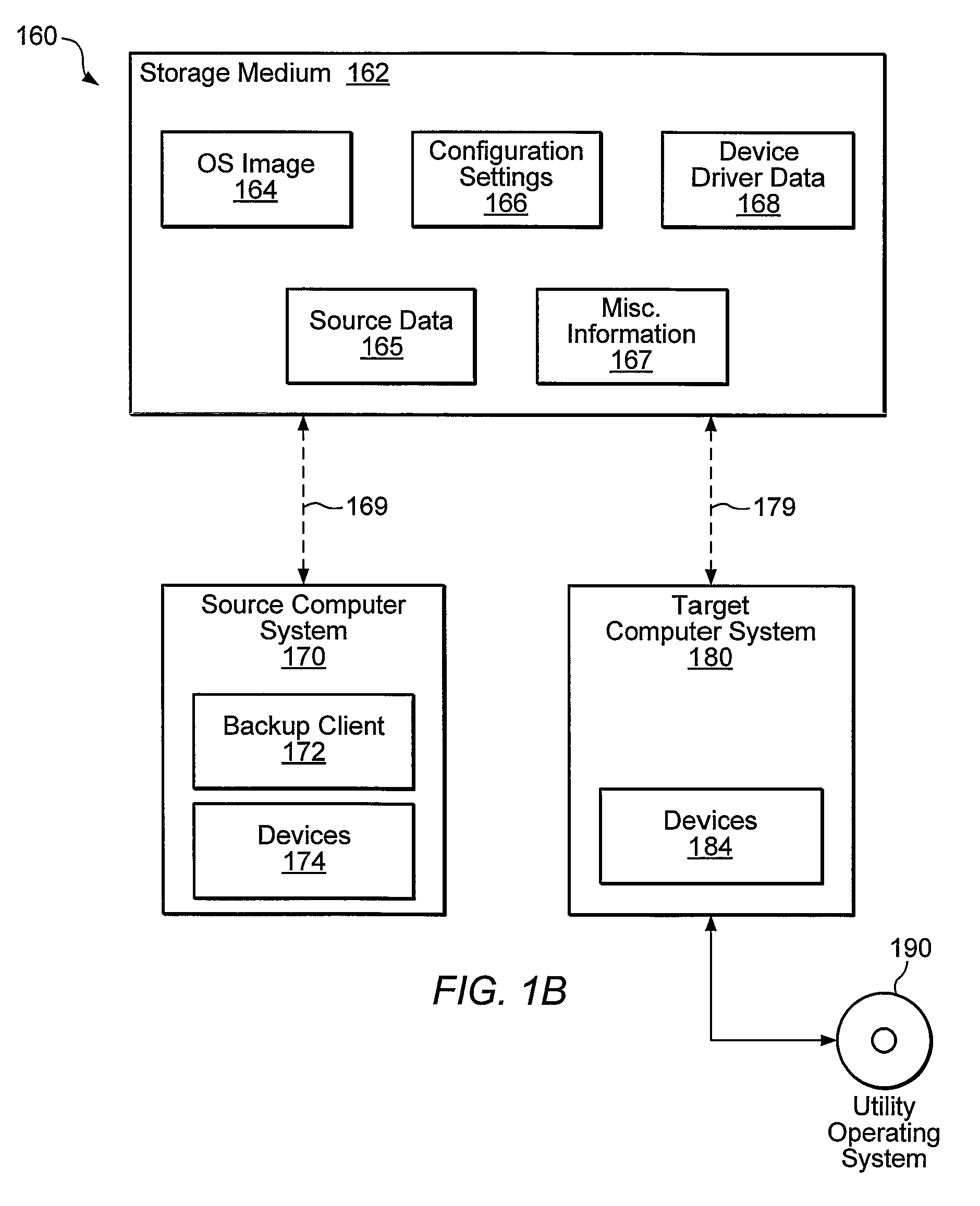
InactiveUS7769990B1Error detection/correctionDigital computer detailsOperational systemSystem recovery
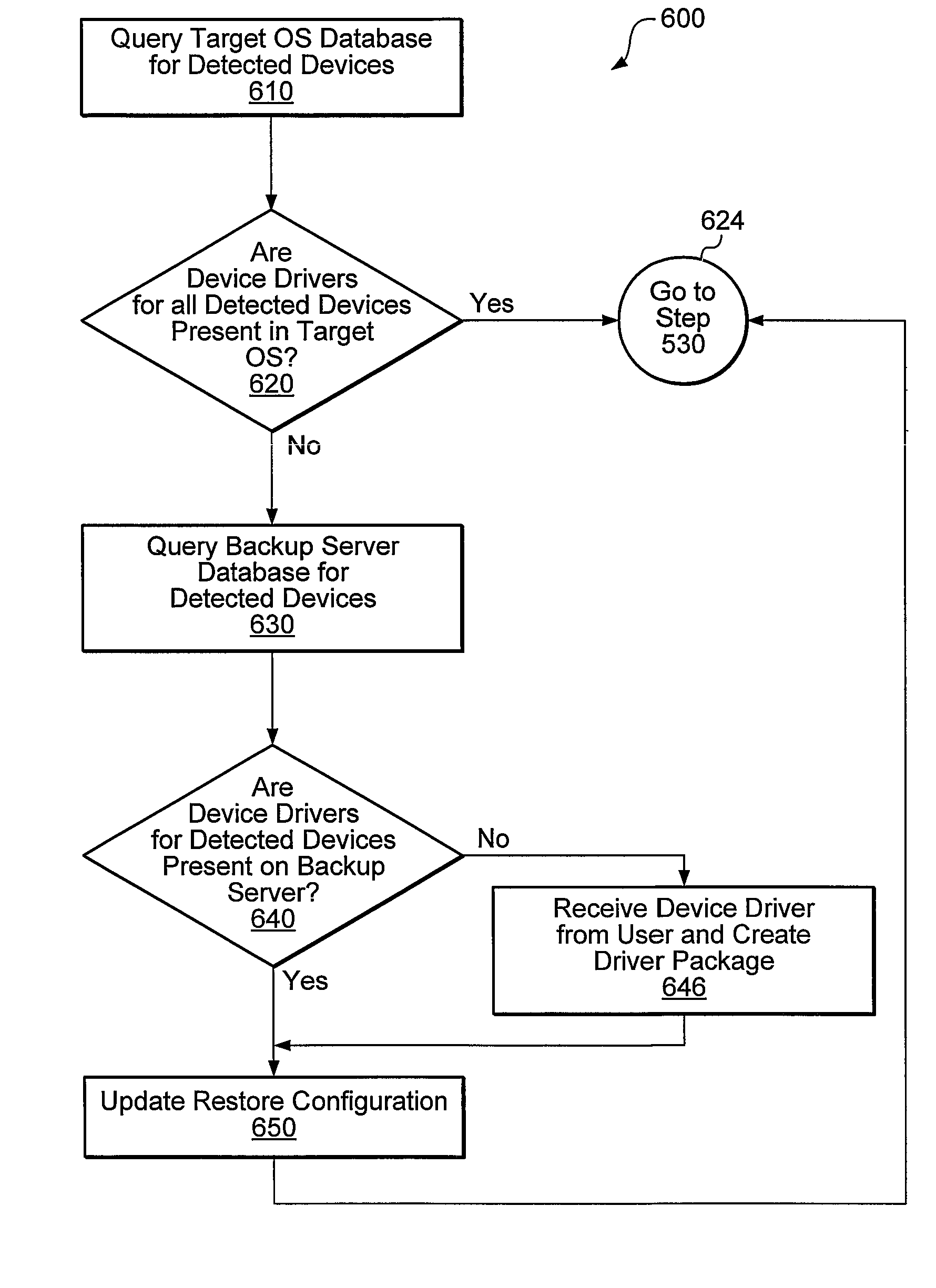
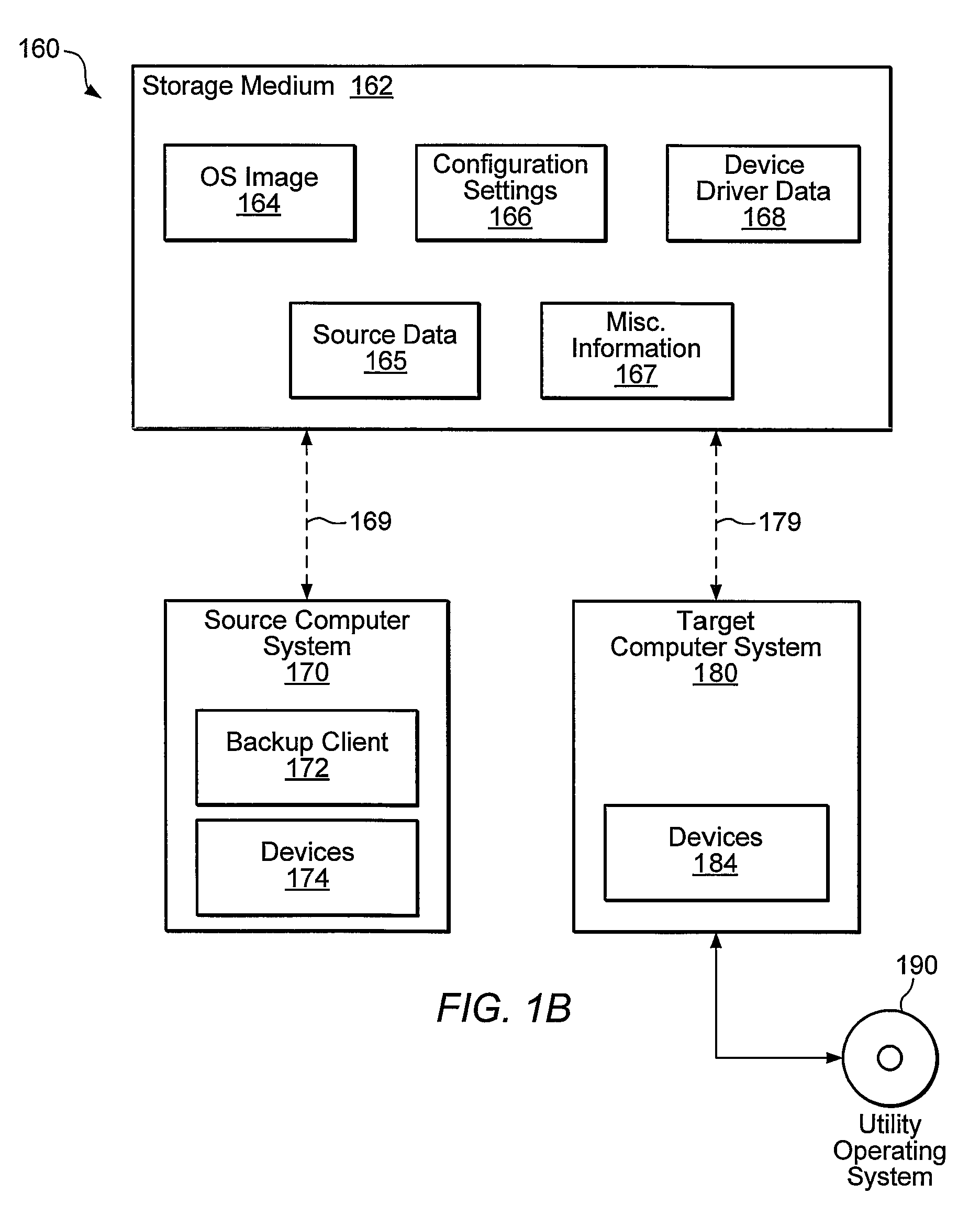
Systems, methods, and computer-readable memory media for performing various computer configuration tasks are disclosed. One such configuration task is dissimilar system restore (DSR). Another such task is software deployment. In various embodiments, these configuration tasks operate on a target computer system using a utility operating system to perform detection of certain target system devices, determination of critical device classes on the source computer system, and updating of target computer configuration settings. Other tasks may be performed upon a computer system such as a backup server. These tasks include locating device drivers for the target operating systems and the installing utility operating system, as well as creating device driver packages that are usable to install device drivers for a plurality of devices.
Owner:VERITAS TECH
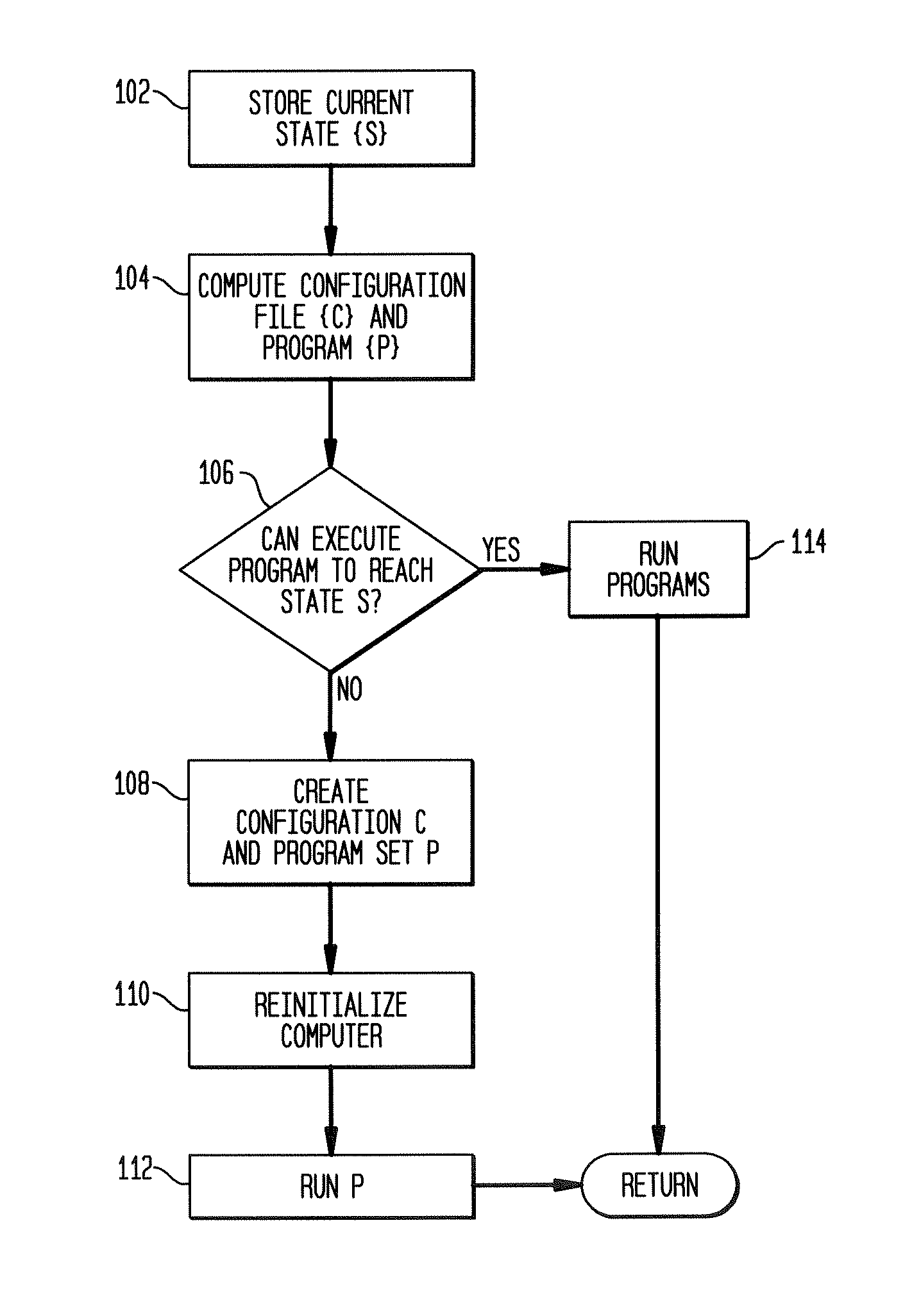
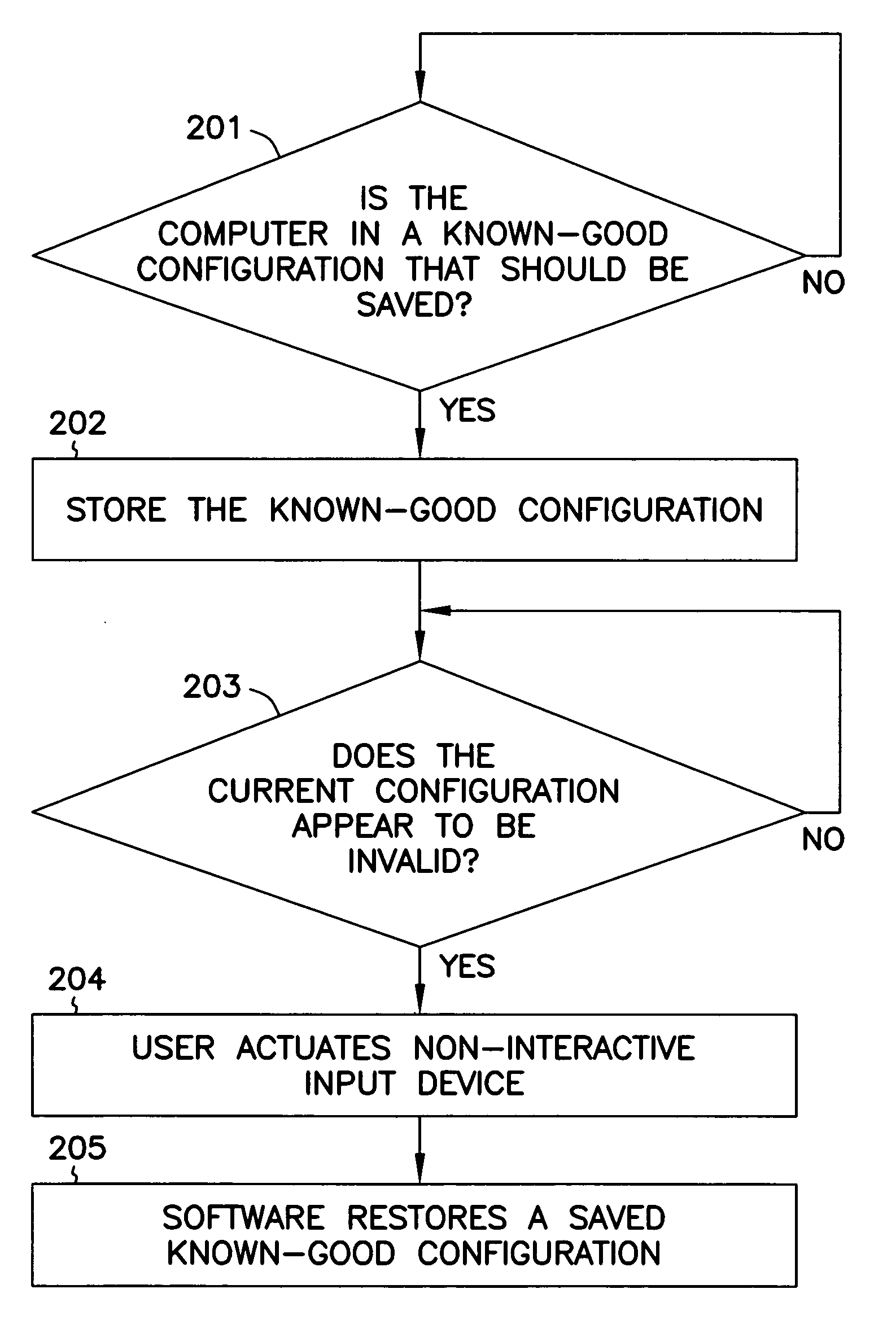
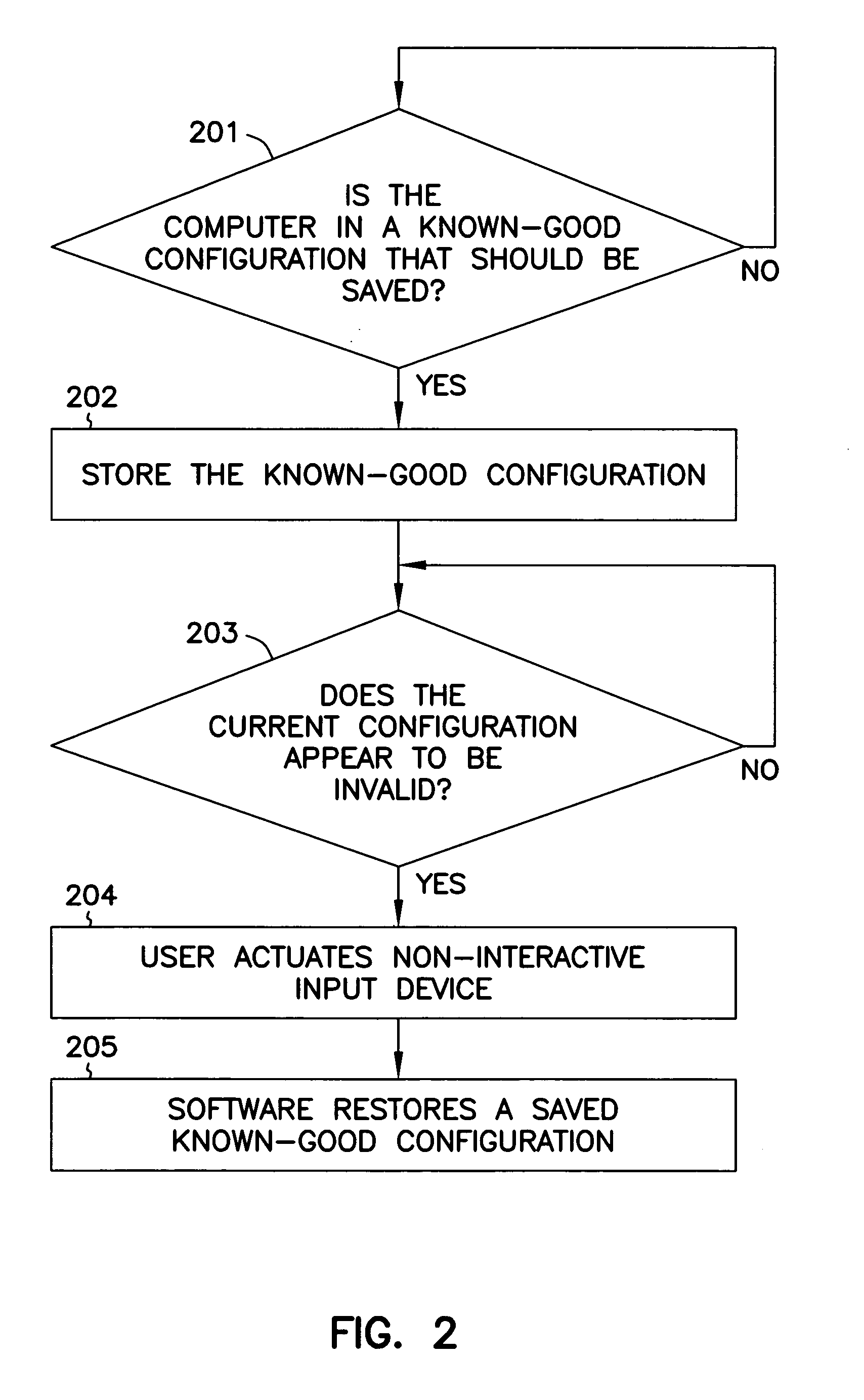
System and method for re-storing stored known-good computer configuration via a non-interactive user input device without re-booting the system
The invention includes a method of providing a known-good configuration for a computer, comprising storing a known-good computer configuration and restoring the known-good configuration via non-interactive user input. The configuration includes in various embodiments hardware and software configuration parameters. The known-good configuration is stored in some embodiments in computer storage such as a hard disc drive, and is loaded from storage upon restoration of the configuration. The non-interactive user input of some embodiments is a protected switch, hot key combination of keyboard keys, or is a special-purpose key or switch. The configuration is determined to be a known-good configuration to be stored in various embodiments by user determination that a configuration is good, by computer determination that the configuration is good based on a predetermined period of successful computer operation, or via other similar methods that suggest a proper configuration.
Owner:GATEWAY
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS7784099B2Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
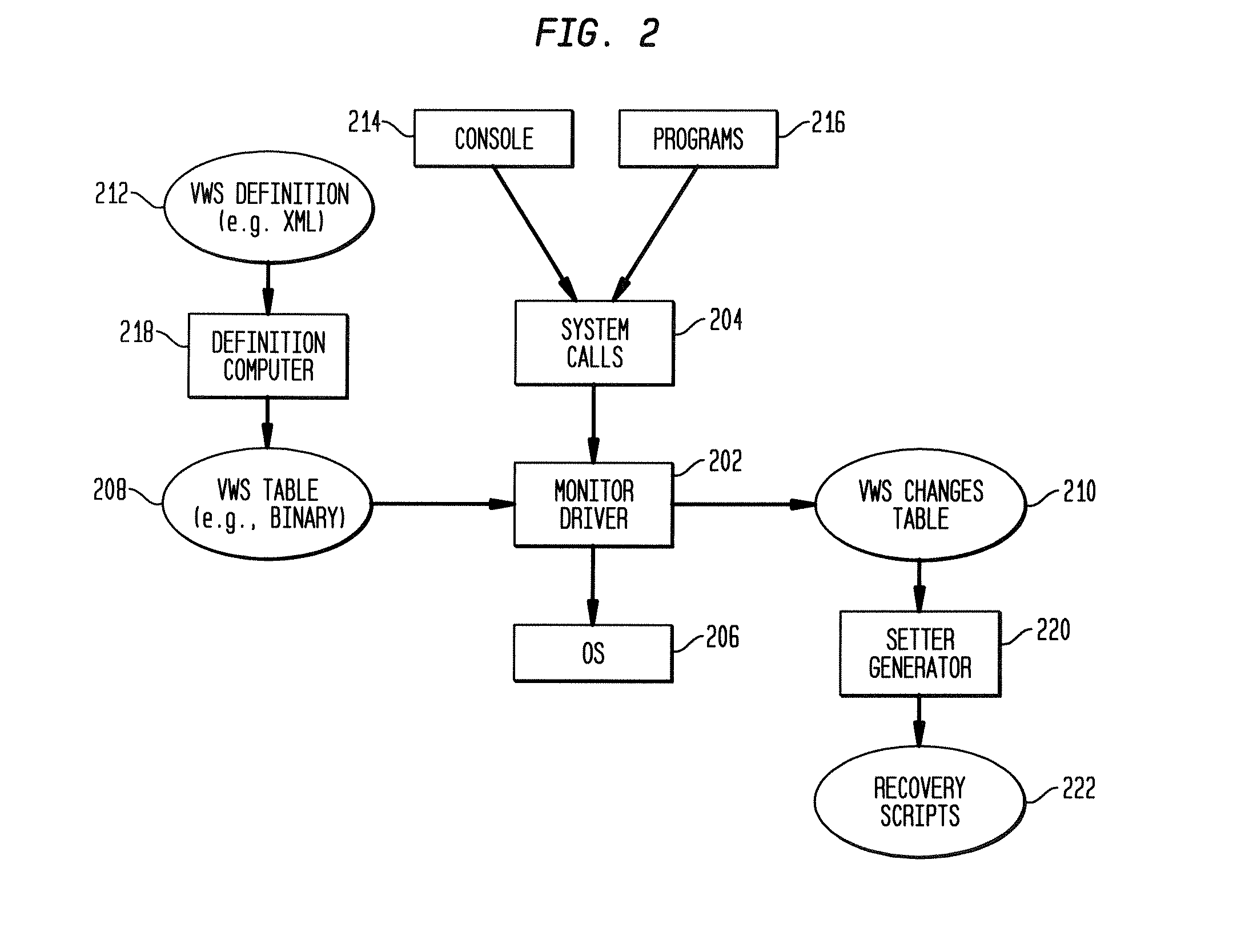
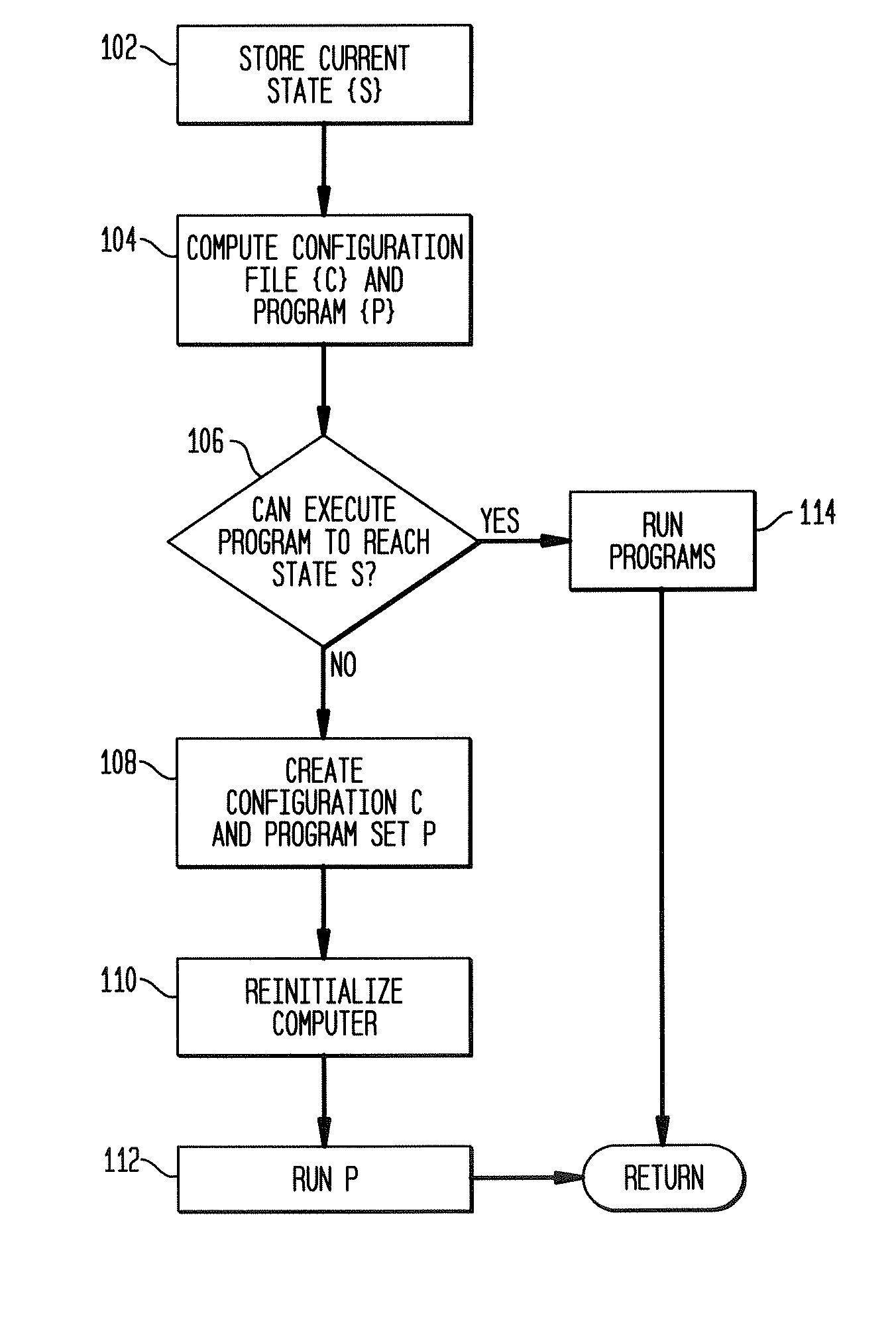
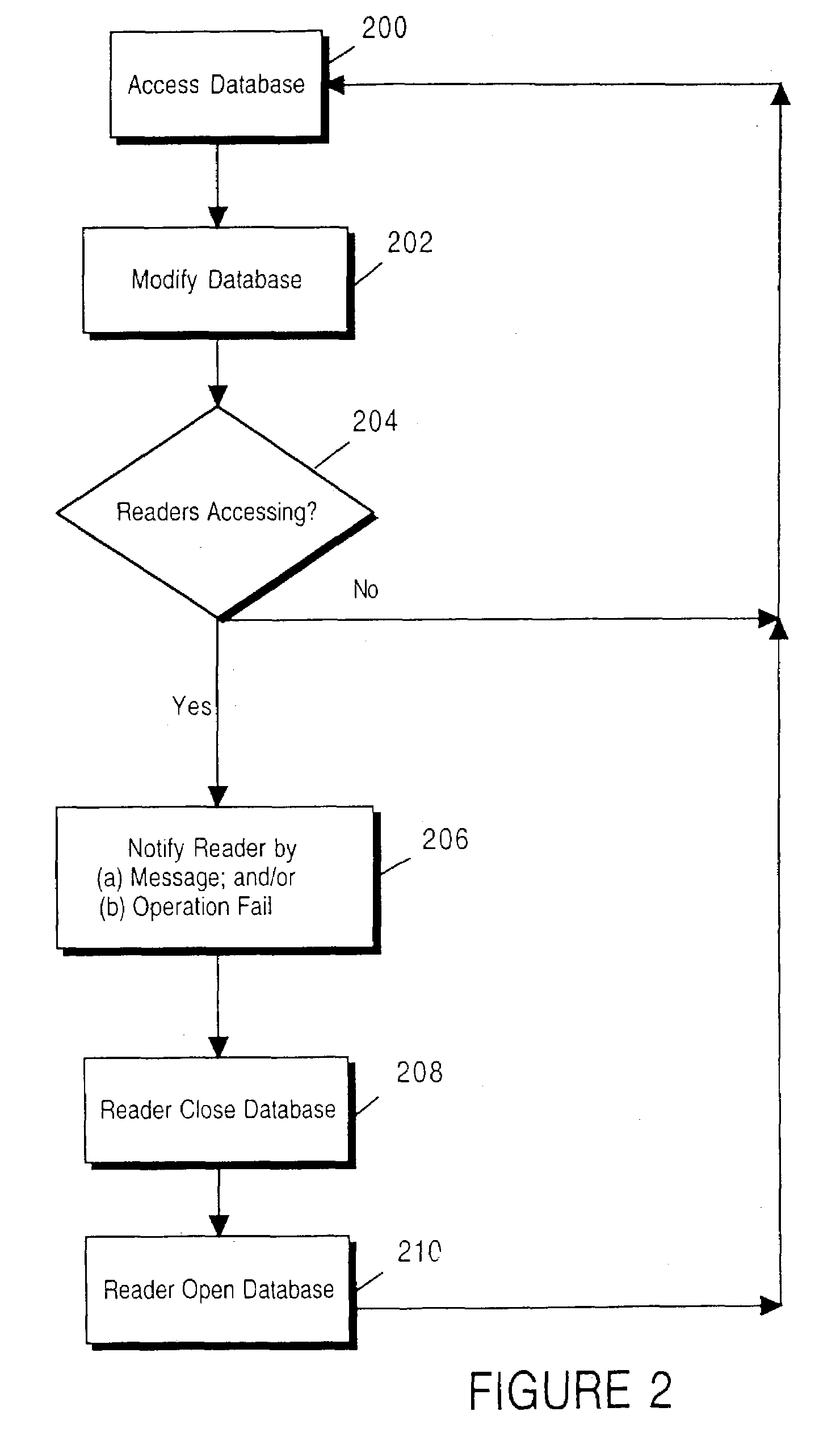
Computer configuration tracking system able to restore a previous configuration
ActiveUS20080126302A1Redundant data error correctionSpecial data processing applicationsComputer configurationSystem call
A system and method for tracking and restoring computer configuration are disclosed. In one aspect, the system and method monitors for a series of changes in watched one or more computer configuration variables. The changes are registered into a series of saved states. The one or more computer configuration variables may be restored to a desired saved state using the registry of saved states. In one aspect, the system and method monitors the changes by intercepting system calls, determining which system calls affect the one or more computer configuration variables, and logging the system calls and the results of the system calls that affect the one or more computer configuration variables. A recovery script may be dynamically generated to restore to a saved state.
Owner:SERVICENOW INC
System for integrated utilization of data to identify, characterize, and support successful farm and land use operations
InactiveUS7991754B2Digital data processing detailsFuzzy logic based systemsFarm levelComputer configuration
Computer configurations, search processors (2), software, and methods of viewing and analyzing information regarding agriculture or land use automatically located relationally-linked agronomic entities with both real (18) and virtual (8) displays. Relational linking exist through broad assessment of commonality information with fuzzy logic heuristics. Dynamic link presentation (6) can exist with congregated and hierarchical information displays (29) such as at the farm level, at a location level, at a physically aggregated parcel level with hierarchical display of farms or agronomic entity ownership, management, organization, and crop usages that afford users an unprecedented series of views into the businesses of land use, food production, and resource conservation. A meta-syntactic agronomic information generator (31) can facilitate imputed information through the integration of multiple databases (32). Predictive and application-specific configurations can allow at-a-glance understanding of agronomic organizations and agronomic decision-making to see where to most optimally devote resources for higher success or efficiency.
Owner:VISUAL FARMS LLC
Autonomic computer configuration based on location
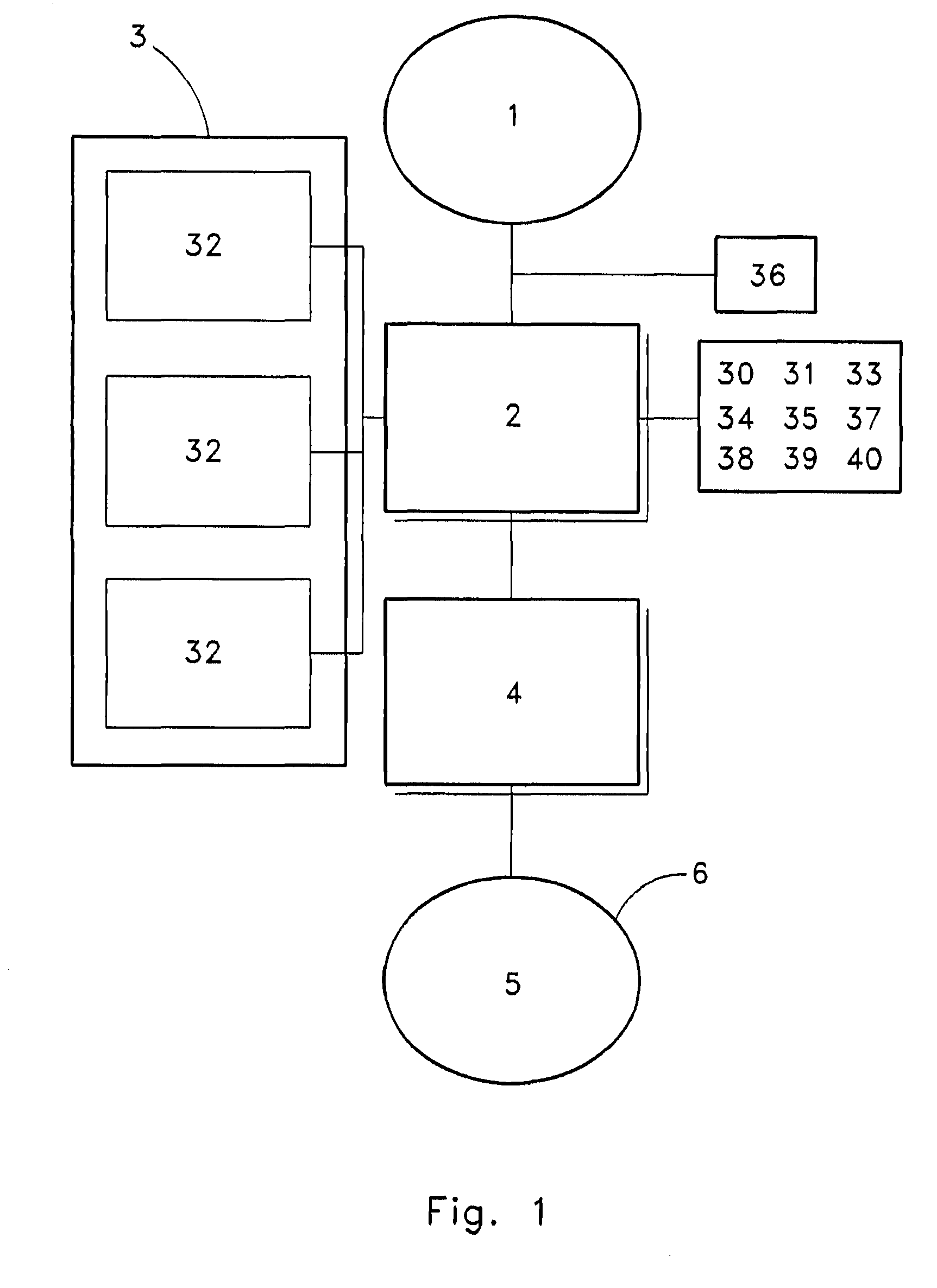
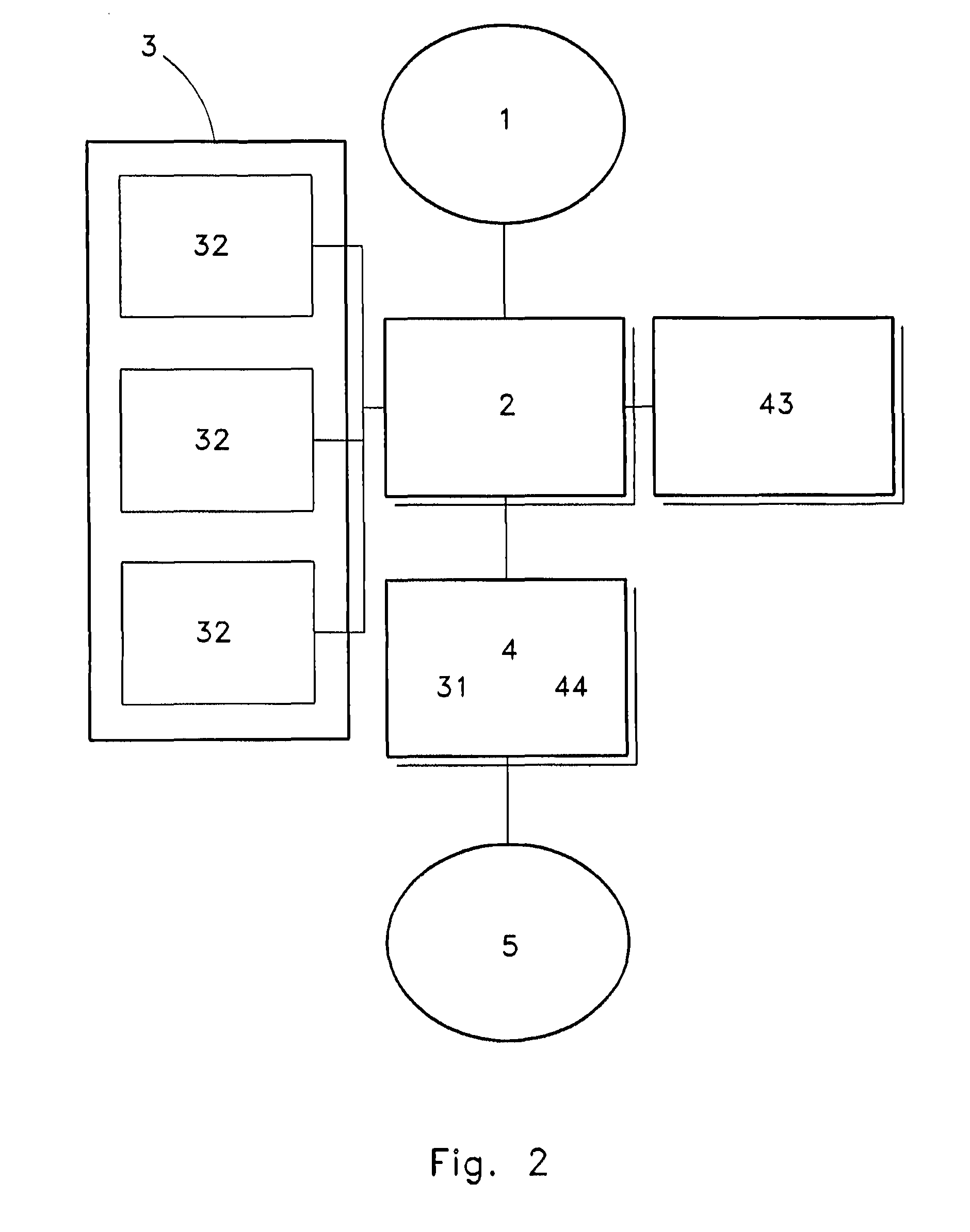
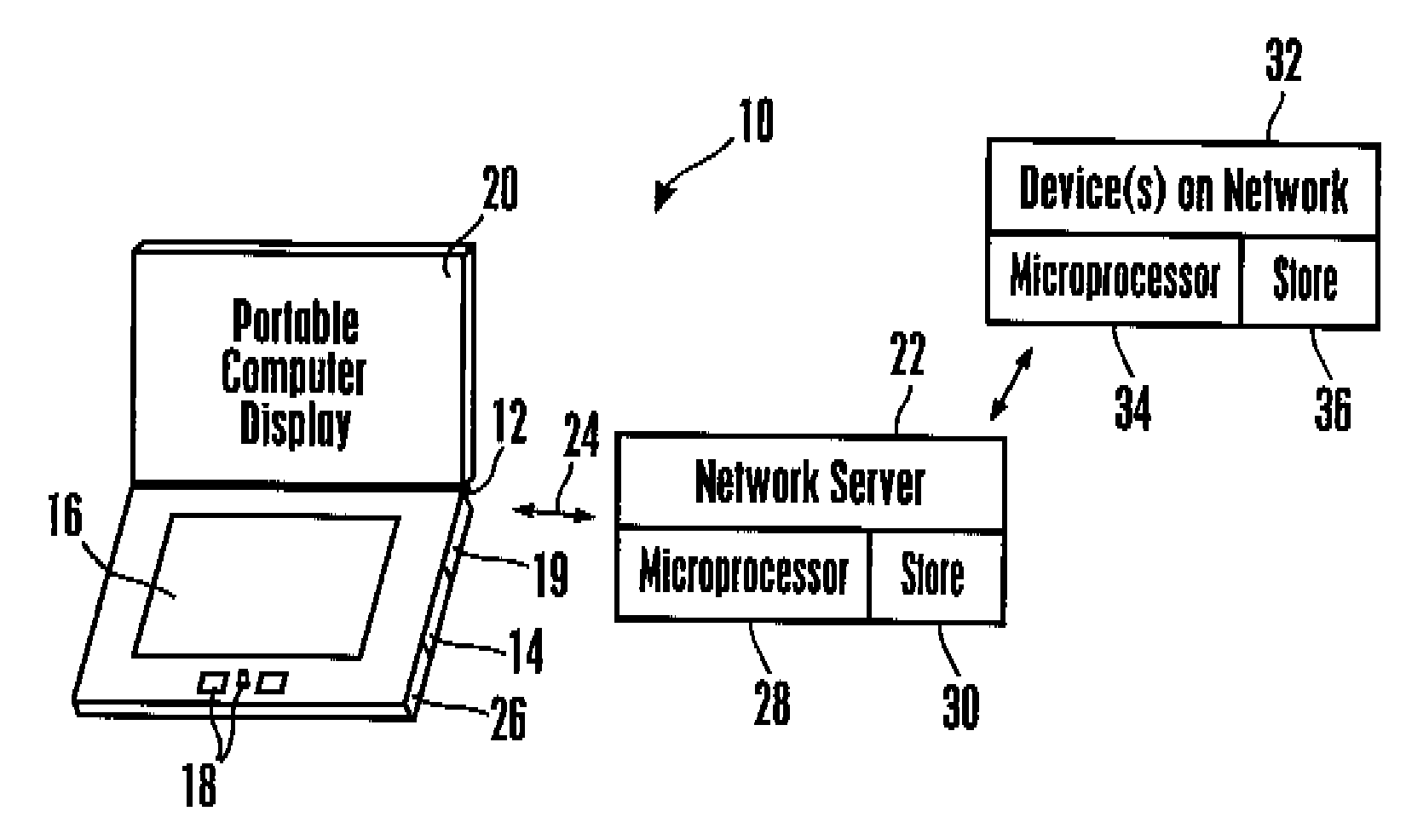
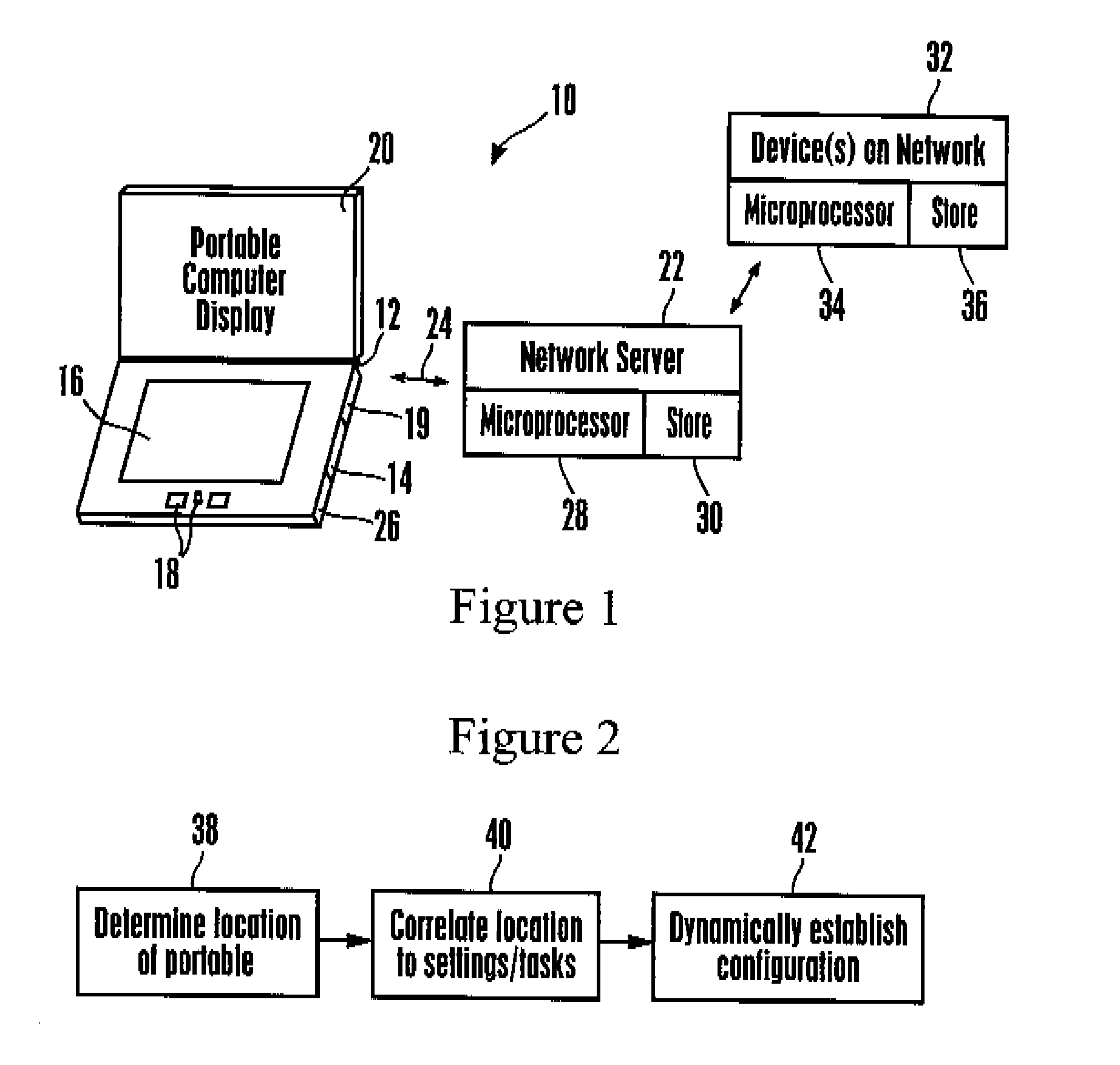
ActiveUS20090106542A1Beacon systems using radio wavesDigital computer detailsComputer configurationAutonomic computing
A system and apparatus for noticing and creating relational settings, actions, profiles, and tasks by tying resources to a location based on user behavior.
Owner:LENOVO PC INT
Computer resource management method in distributed processing system
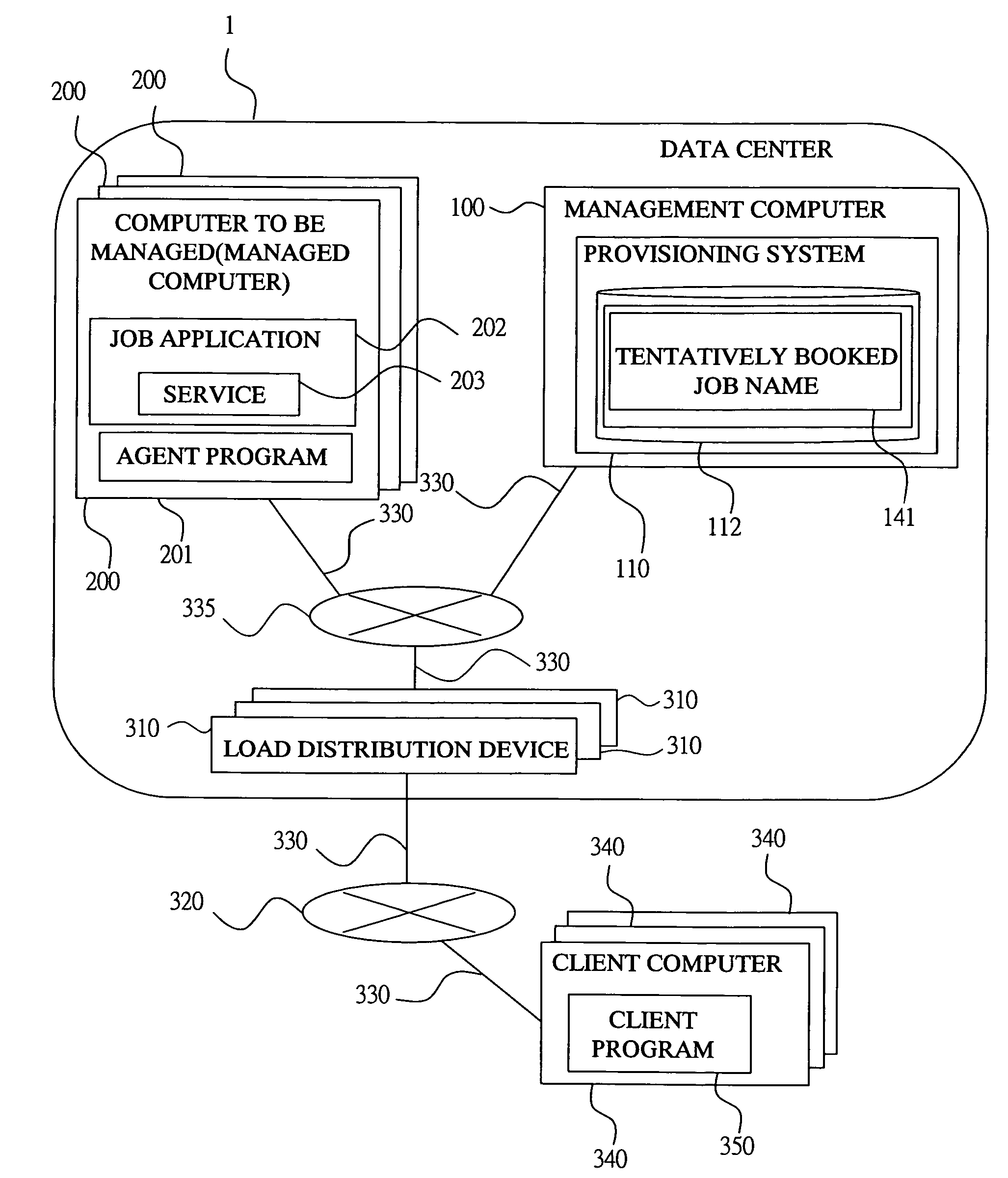
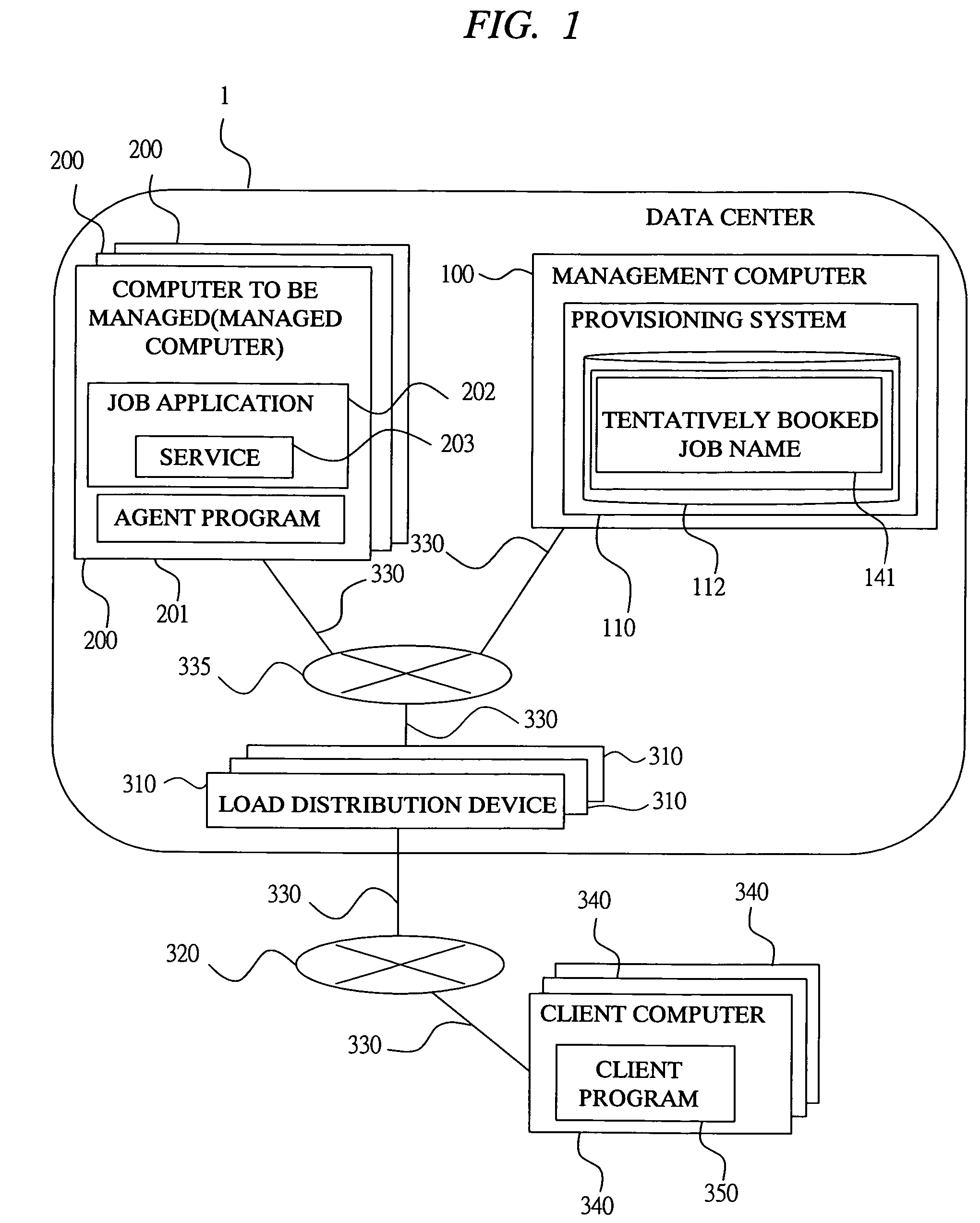
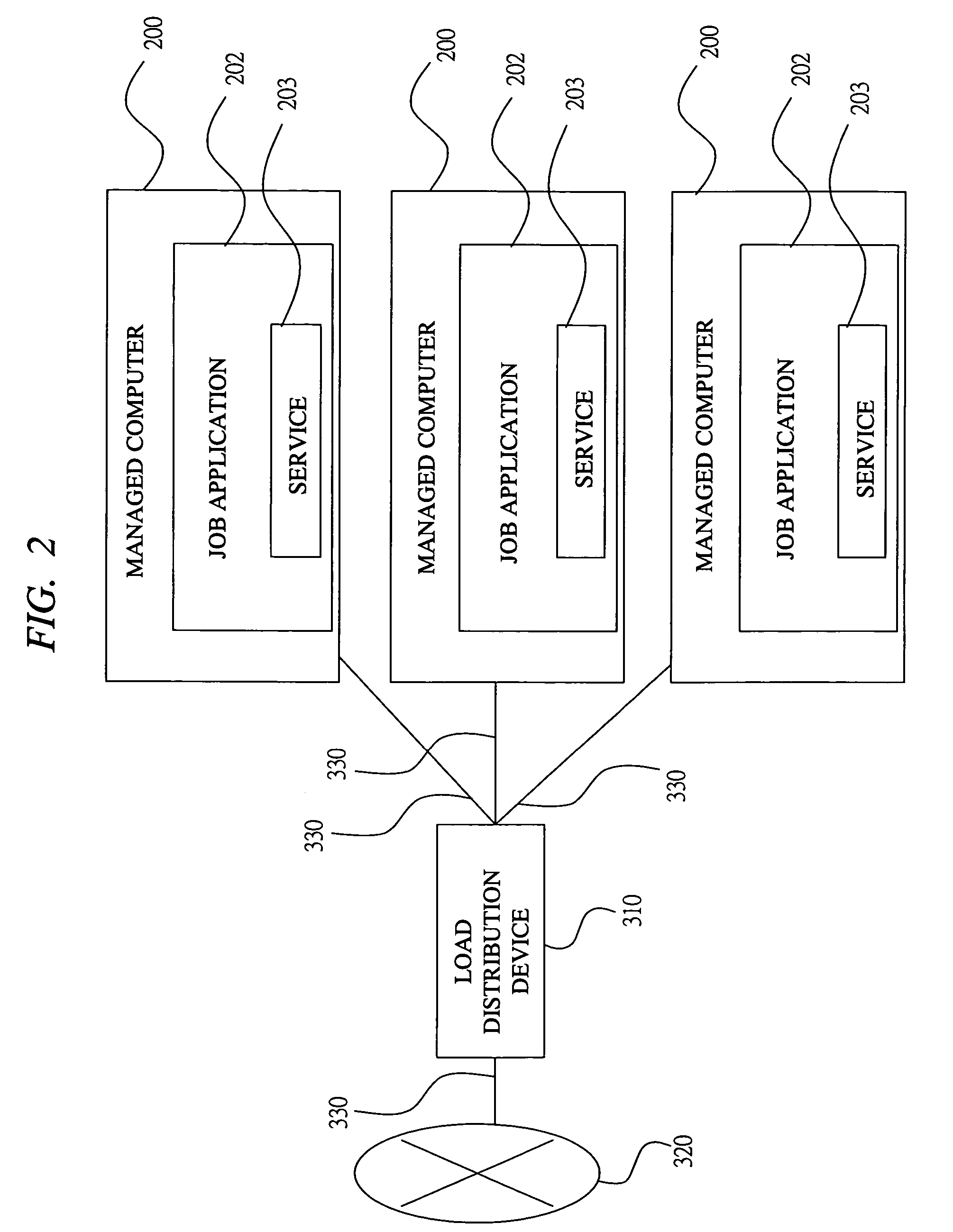
InactiveUS7730488B2Unified performanceSure easyResource allocationElectrical testingComputer resourcesComputer configuration
The hardware information showing a type of hardware constituting the computer resource and the software information showing a type of software mounted in the computer resource are stored in the entry corresponding to each computer resource in the computer configuration table managed by a management computer. Further, when a computer resource allocated to a certain job is determined, a computer resource which may be used for the job in the aftertime is selected with reference to the hardware information and the software information, and the job name is registered as a tentatively booked job name in the entry corresponding to the selected computer resource in the computer configuration table. When additionally allocating the computer resource, the computer resource which is tentatively booked is selected with priority, and the computer resource tentatively booked to another job is excluded from the additional allocation.
Owner:HITACHI LTD
Dynamic registry partitioning
InactiveUS7203696B2Data processing applicationsProgram control using stored programsOperational systemComputer configuration
Owner:MICROSOFT TECH LICENSING LLC
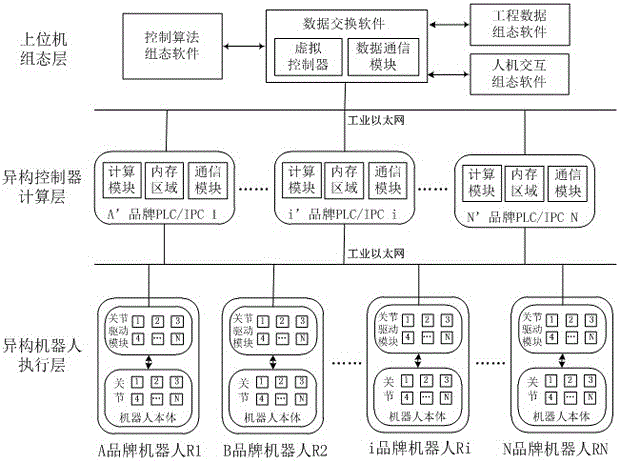
Multiple-heterogeneous industrial robot control system
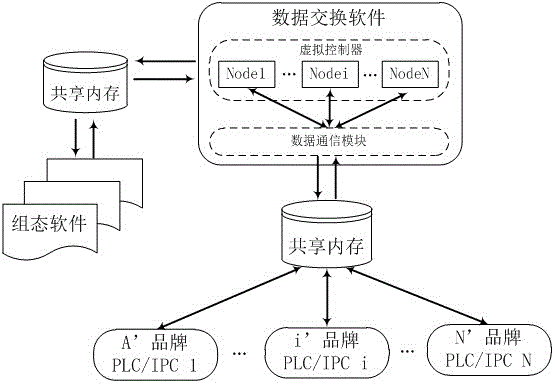
ActiveCN106272484AImprove scalabilityIncrease flexibilityProgramme-controlled manipulatorComputer configurationProgrammable logic controller
The invention relates to a multi-heterogeneous industrial robot control system. The system provides a distributive multi-heterogeneous industrial robot control system structure. The system consists of three parts, namely, a heterogeneous robot execution layer, a heterogeneous controller calculation layer and a principal computer configuration layer. Specifically, a same set of control algorithm configuration programs can run between the heterogeneous controllers of an industrial robot, different types of programmable logic controllers (PLC) or industrial process controllers (IPC) can share and synchronize control data of different robots in real time by virtue of data exchanging software, so that the real-time performance and effectiveness of the synergistic control of a plurality of heterogeneous robots can be improved.
Owner:FUZHOU UNIV
Method and system for the distribution of configurations to client computers
InactiveUS20090172136A1Significant positive effectSave storage spaceDigital data processing detailsUser identity/authority verificationOperational systemComputer configuration
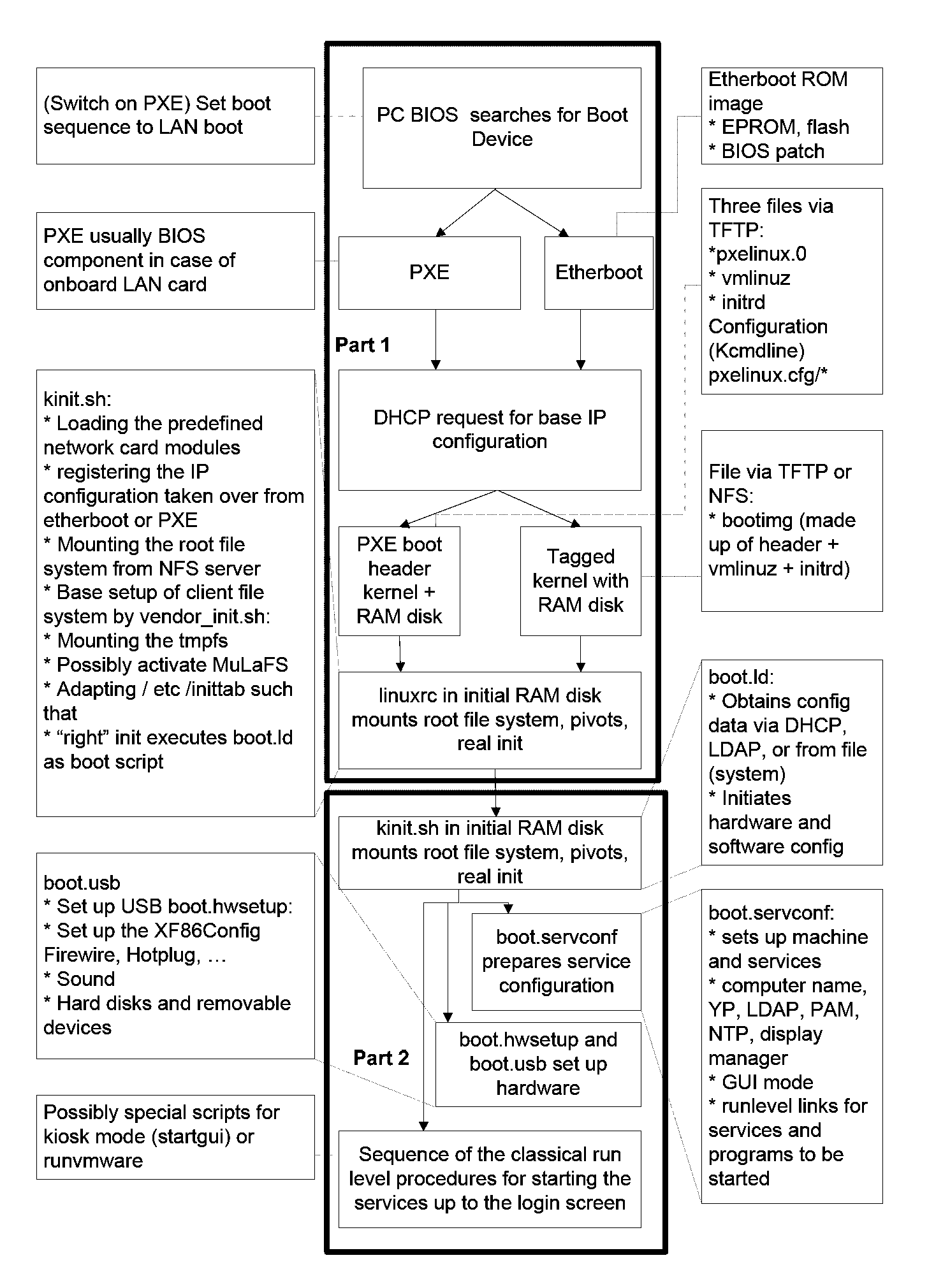
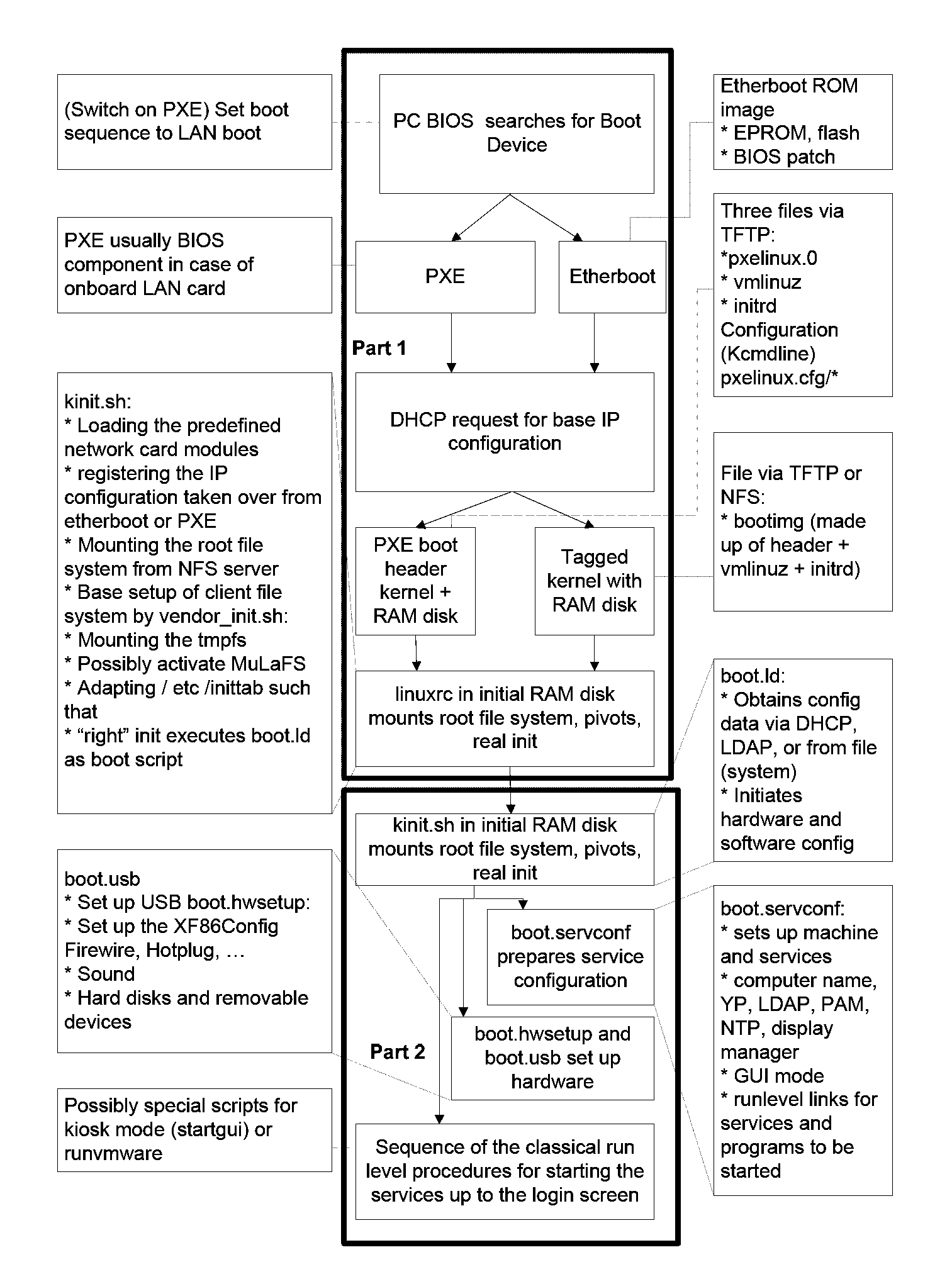
A method for distributing computer configurations to at least one client from a server, comprising the following steps: Network-booting a first operating system for the clients from a server, automatically loading a virtual machine having an elective second operating system on the basis of the booted (first) operating system while taking into consideration one or more of the following parameters: user login, network address. Consequently, providing a full fat client (standard PC) functionality under an elective operating system on a (diskless) client hardware by using exclusively volatile storage media (on the new thin client system).
Owner:SCHULZ ULRICH +1
Method and apparatus for configuring a computer
InactiveUS7065533B2Data processing applicationsDigital computer detailsAs DirectedComputer configuration
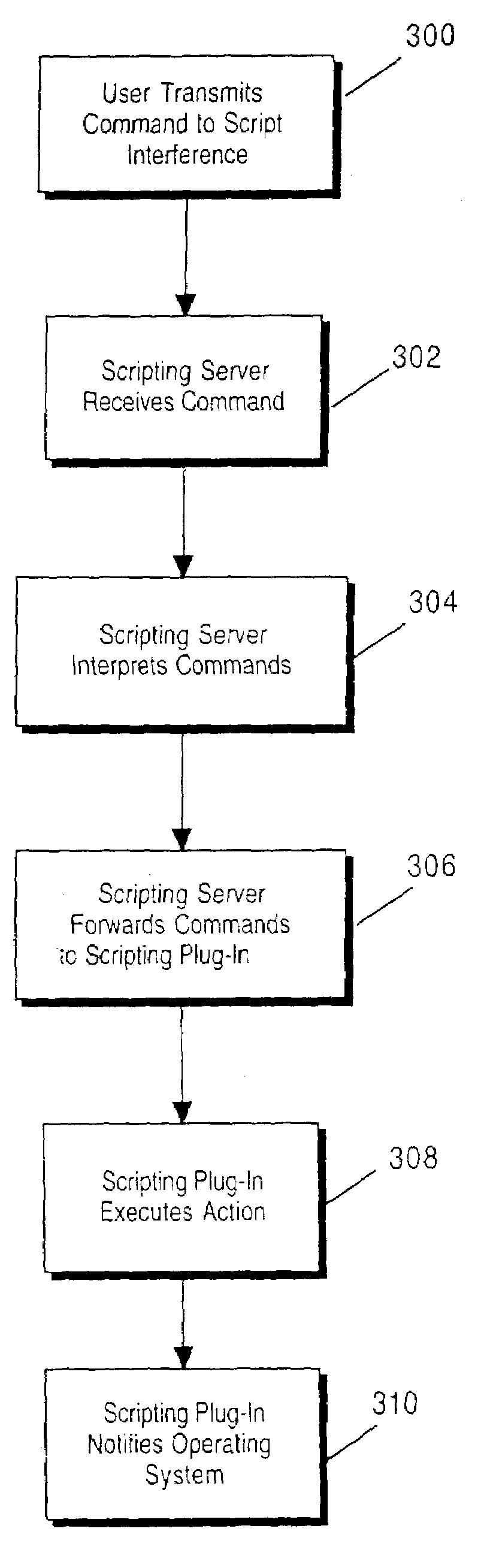
A method and apparatus for configuring a computer. One embodiment of the invention combines all of the prior art control panels related to networking into a consolidated Network Setup Control Panel. In addition, the invention provides for computer configuration by scripting. The configuration may be for a type of system setting or for network configurations and protocols. Through scripting, a computer may be configured locally or remotely on a network. One embodiment of the invention provides for a centralized database or Configuration Library consisting of collected data relating to available configuration settings. This database is not limited to configuration information and can be used as a general database containing information the user desires to store. To modify a configuration by scripting, the invention provides for a Scripting Interface consisting of a Scripting Server and Scripting Plug-In. The Scripting Server receives the script forwarded from a user or network administrator, parses the script and determines the appropriate Scripting Plug-In to forward the desired action to. The Scripting Plug-In receives the commands and executes the appropriate actions to modify the configuration as directed.
Owner:APPLE INC
Mobile device, wireless router, route configuration method and system
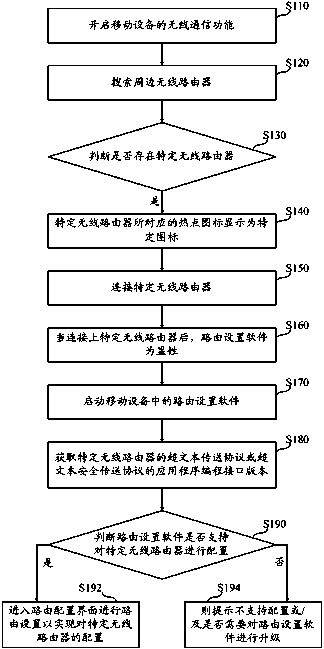
InactiveCN103873359AEasy to operateImprove experienceData switching networksWireless communicationWireless routerComputer configuration
The invention provides a mobile device, a wireless router, and a route configuration method and system. The route configuration method comprises the steps of: a) starting the radio communication function of the mobile device; b) searching for peripheral wireless routers; c) determining whether specific wireless routers exist; d) connecting the specific wireless routers when the specific wireless routers exist; e) starting the route setting software in the mobile device; and f) entering a route configuration interface to perform route configuration in order to realize the configuration of the specific wireless routers. According to the invention, the specific wireless routers are configured through the route setting software in the mobile device; compared with a computer configuration mode, the configuration mode of the invention is more convenient; and compared with a handset configuration mode through a browser web, the configuration mode of the invention has a more friendly configuration interface (such as larger characters and buttons), which is easier for a user to operate and can raise user experience.
Owner:PHICOMM (SHANGHAI) CO LTD
Automatic detection of hardware and device drivers during restore operations
ActiveUS8132186B1Error identificationProgram loading/initiatingOperational systemComputer configuration
Systems, methods, and computer-readable memory media for performing various computer configuration tasks are disclosed. One such configuration task is dissimilar system restore (DSR). Another such task is software deployment. In various embodiments, these configuration tasks operate on a target computer system using a utility operating system to perform detection of certain target system devices, determination of critical device classes on the source computer system, and updating of target computer configuration settings. Other tasks may be performed upon a computer system such as a backup server. These tasks include locating device drivers for the target operating systems and the installing utility operating system, as well as creating device driver packages that are usable to install device drivers for a plurality of devices.
Owner:VERITAS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com