Patents
Literature
46 results about "Marketed products" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
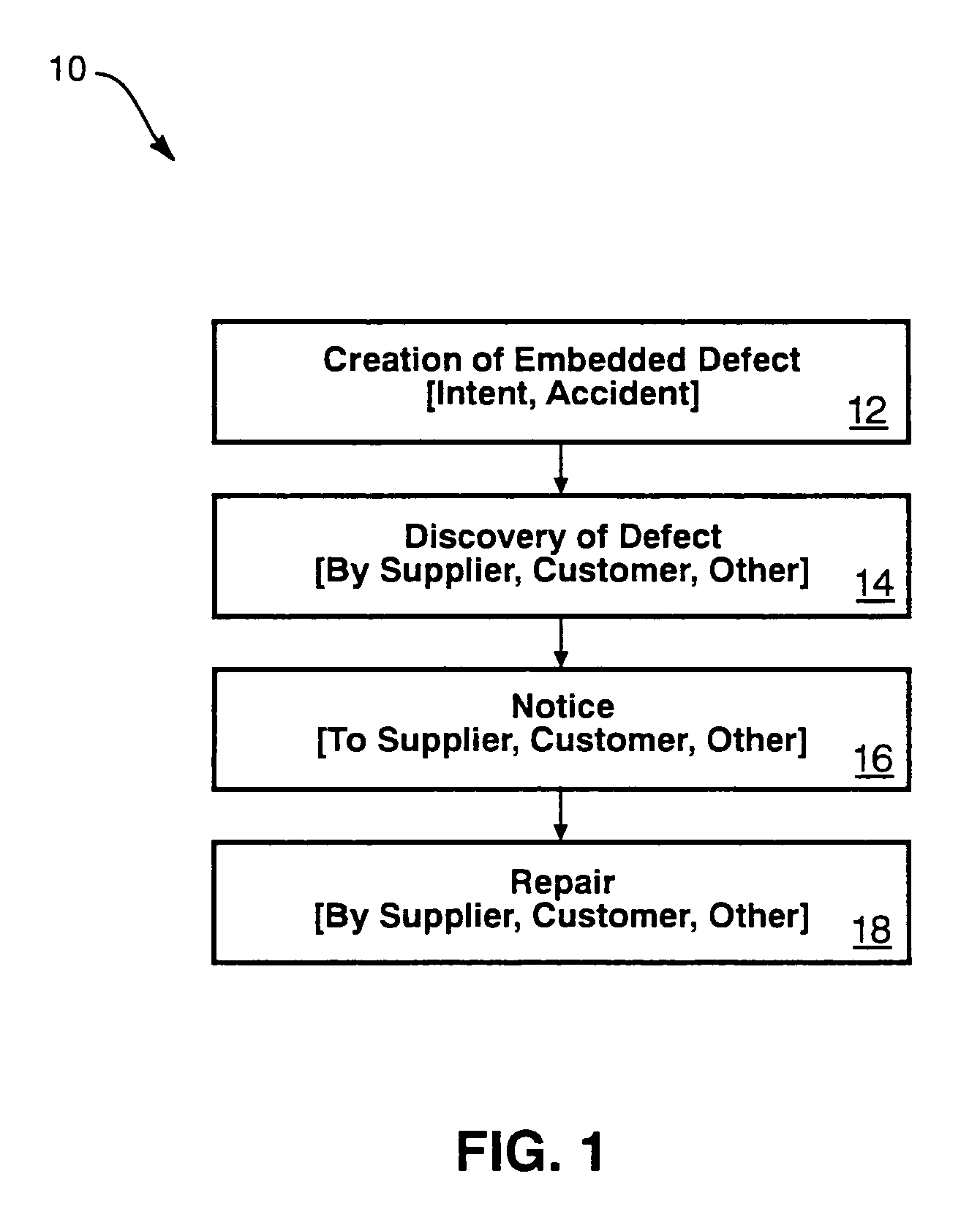
Patent Status
Application Year
Inventor
The marketplace in which a final good or service is bought and sold. A product market does not include trading in raw or other intermediate materials, and instead focuses on finished goods purchased by consumers, businesses, the public sector and foreign buyers.
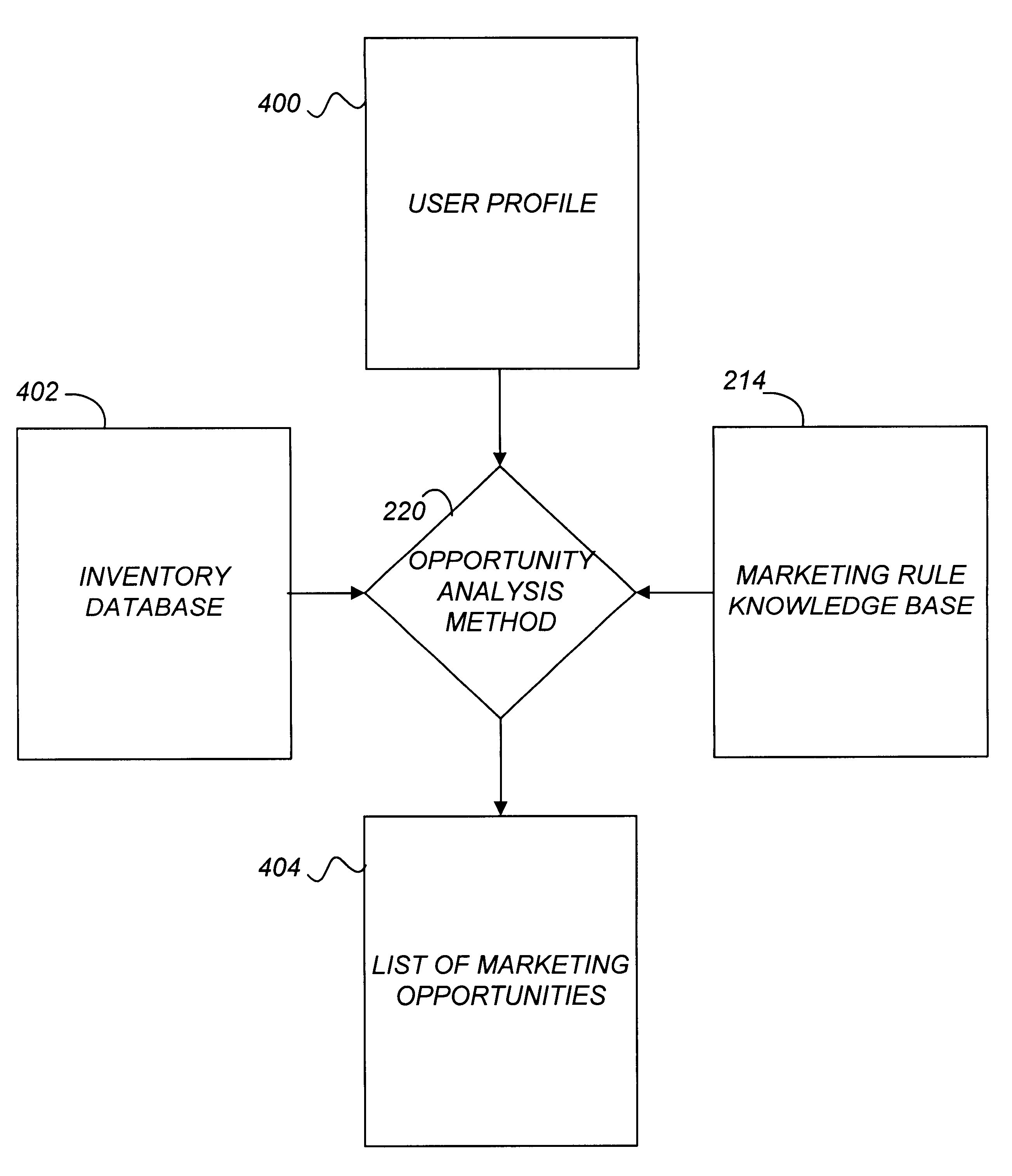
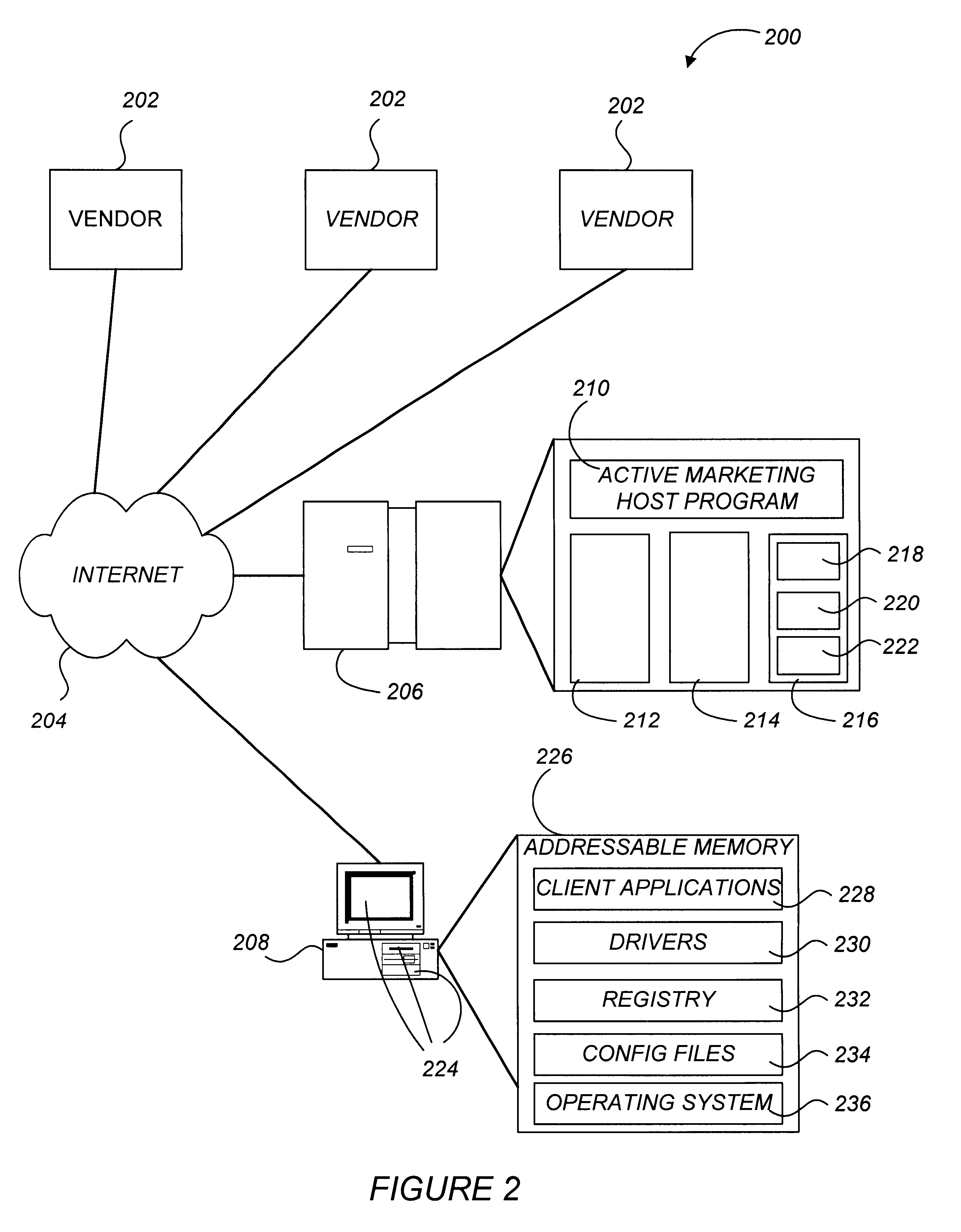
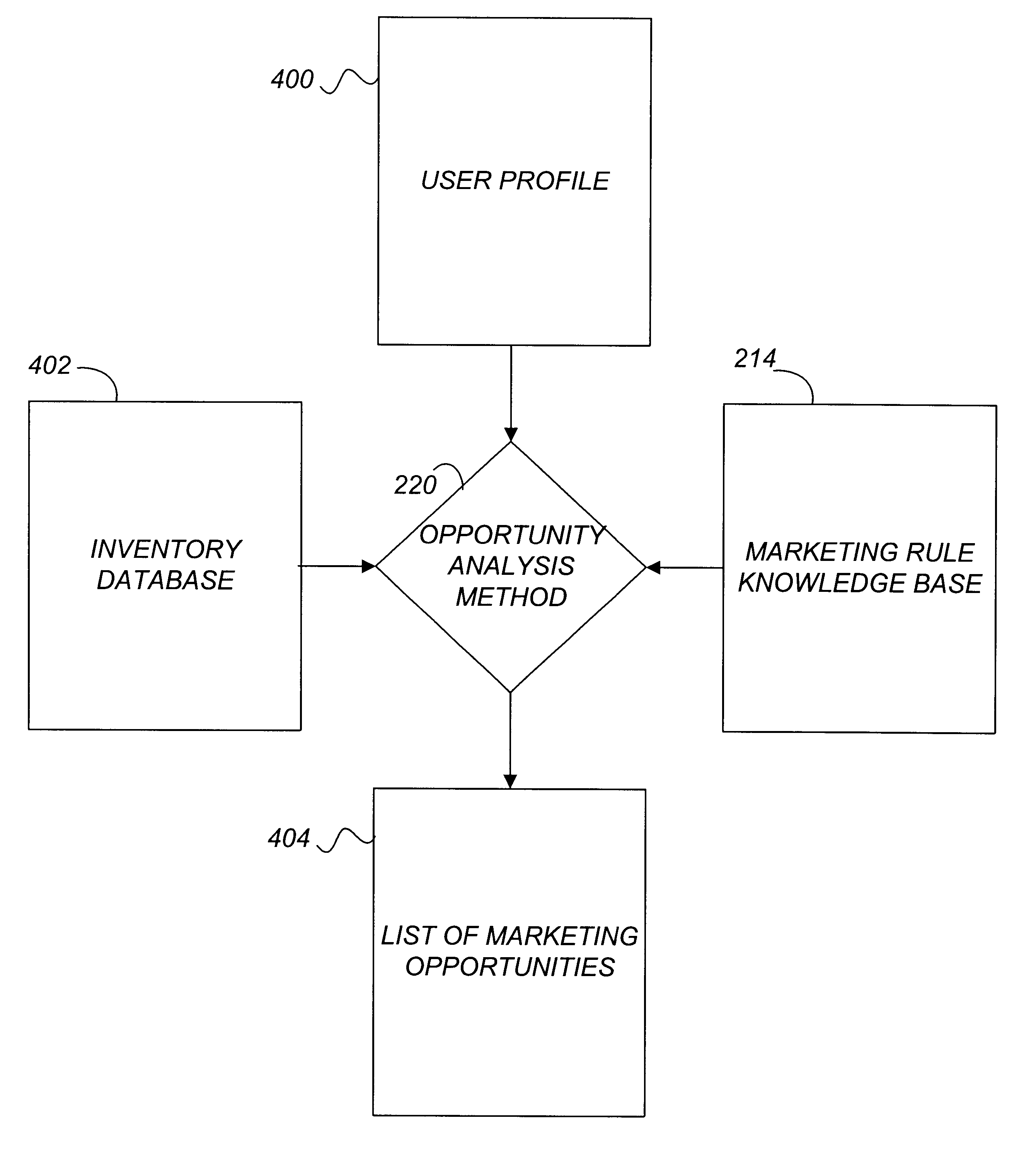
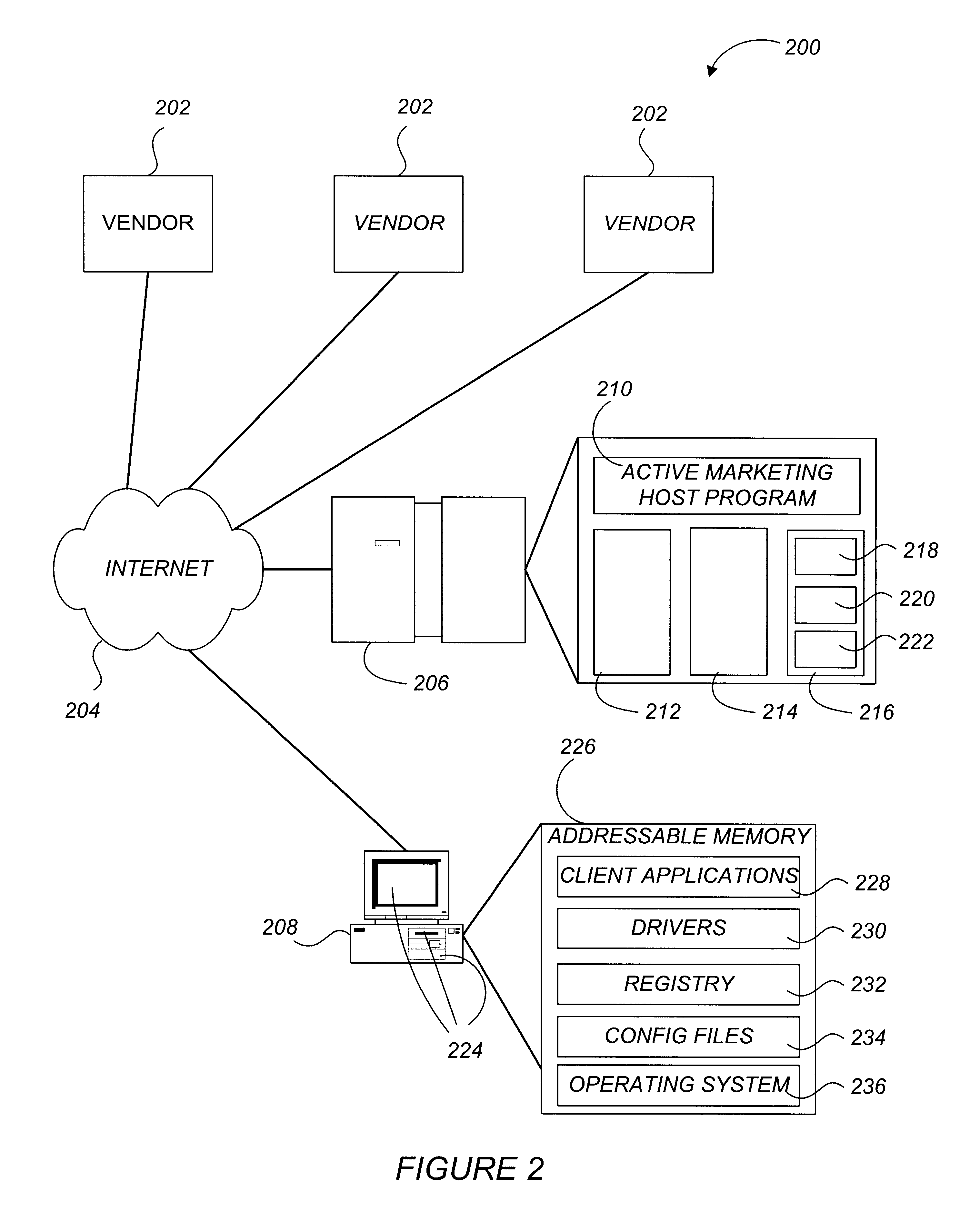
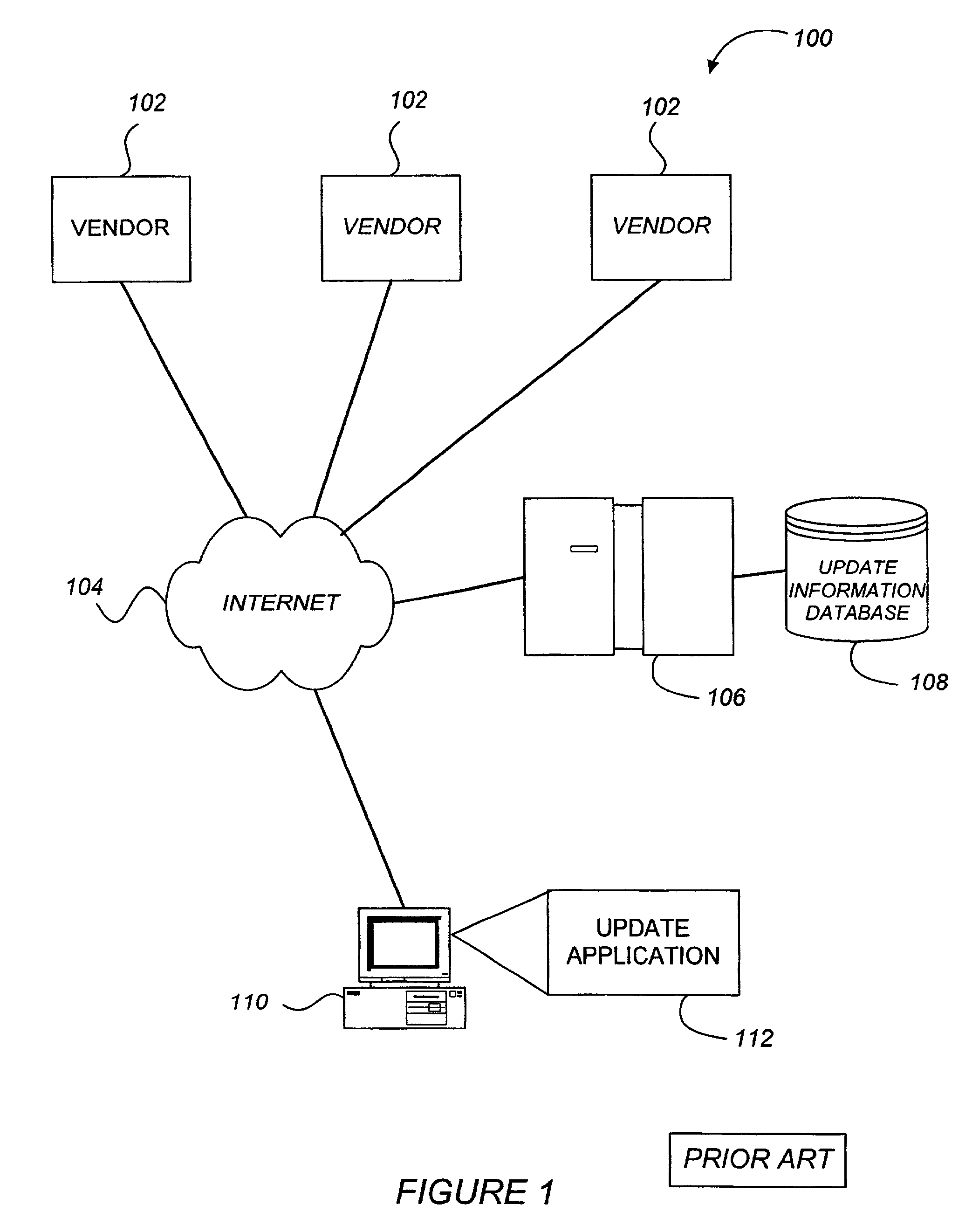
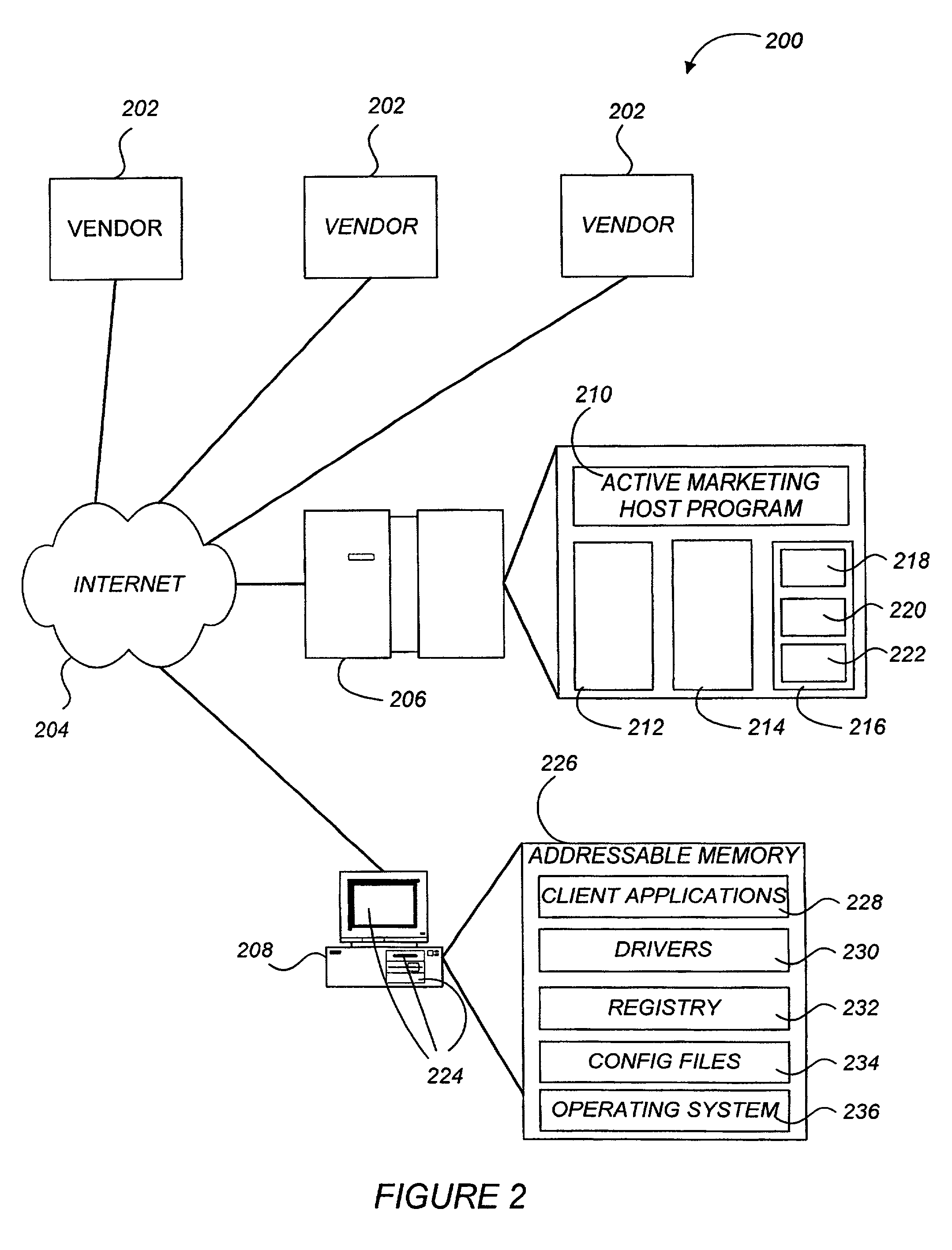
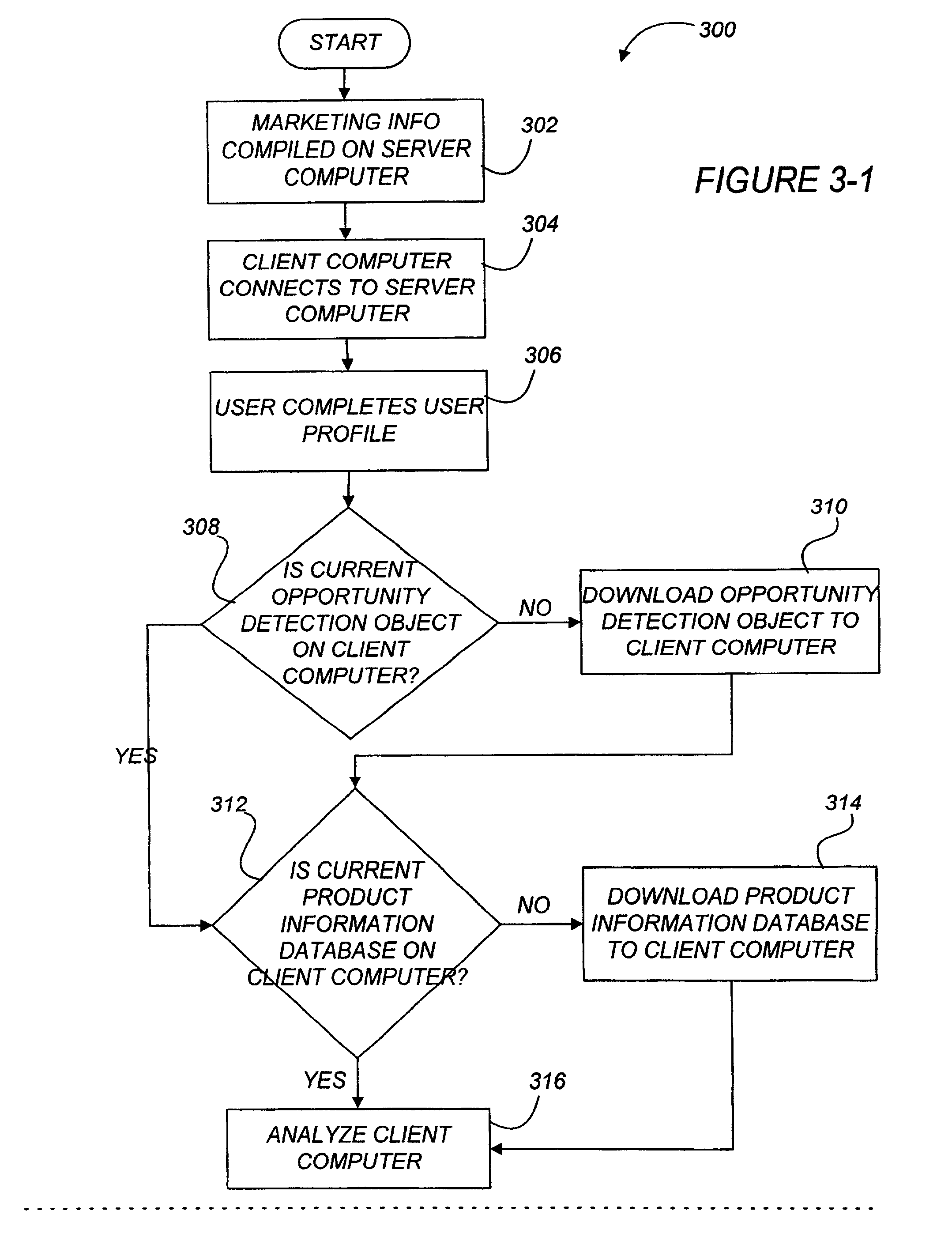
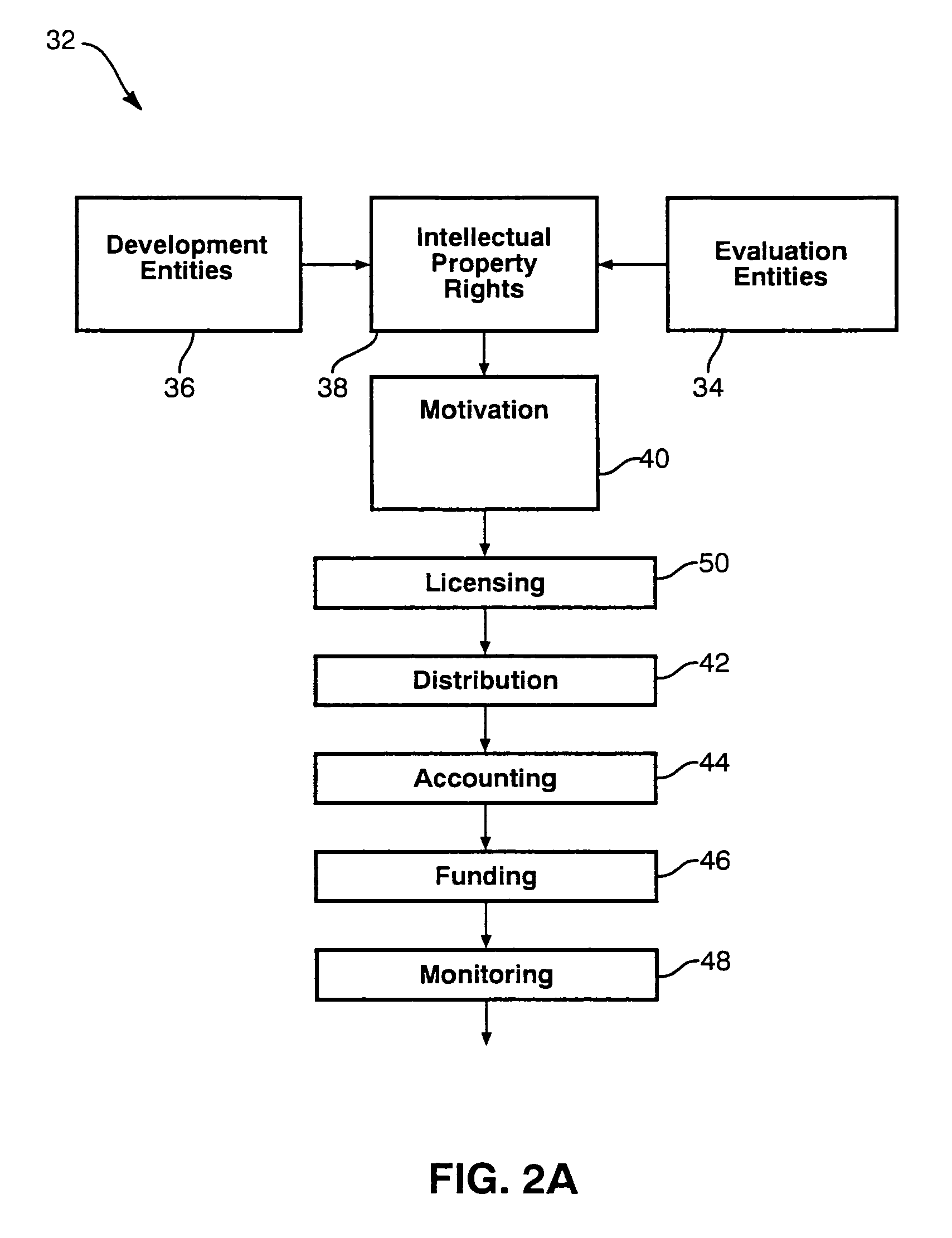
Active marketing based on client computer configurations
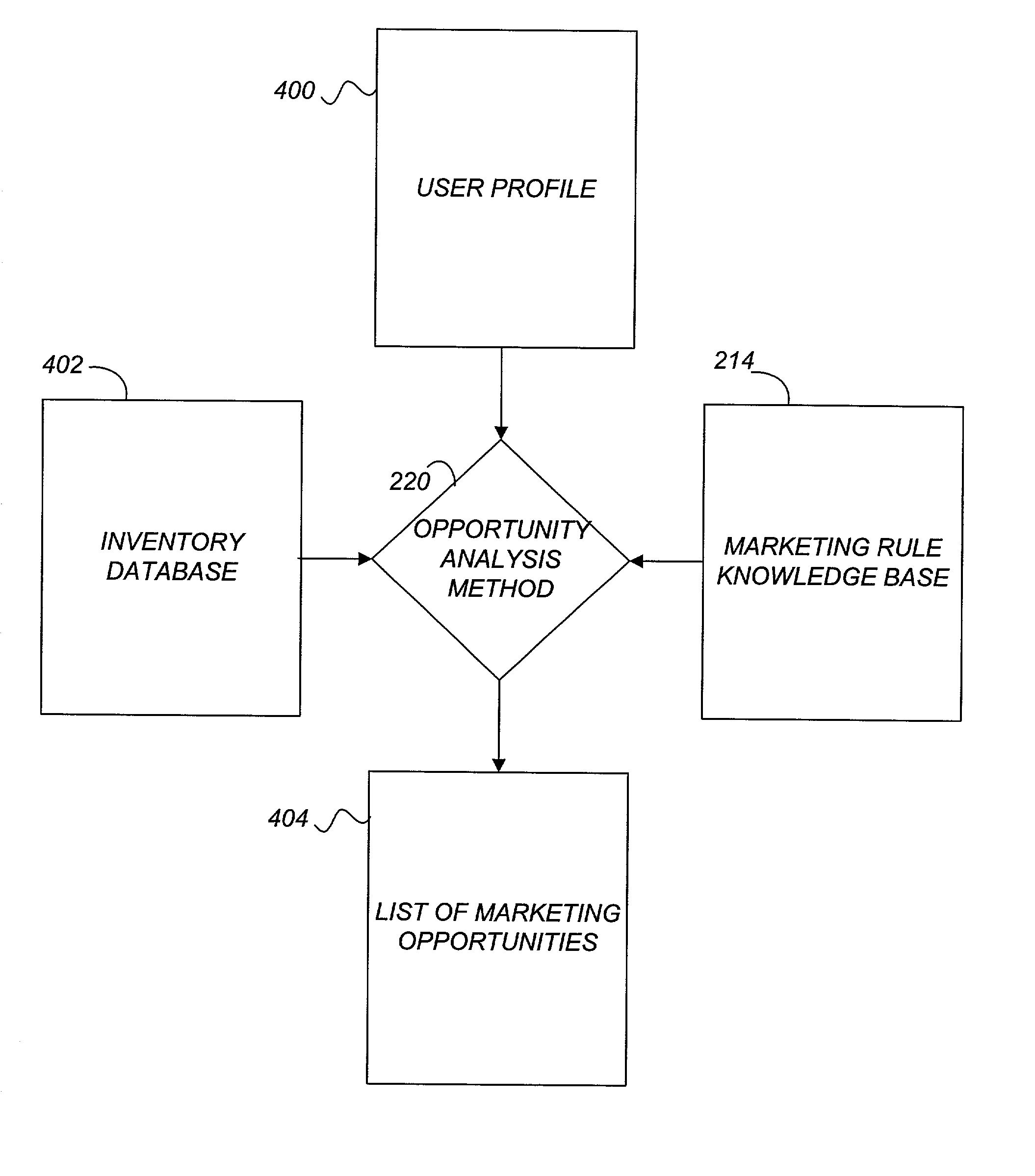
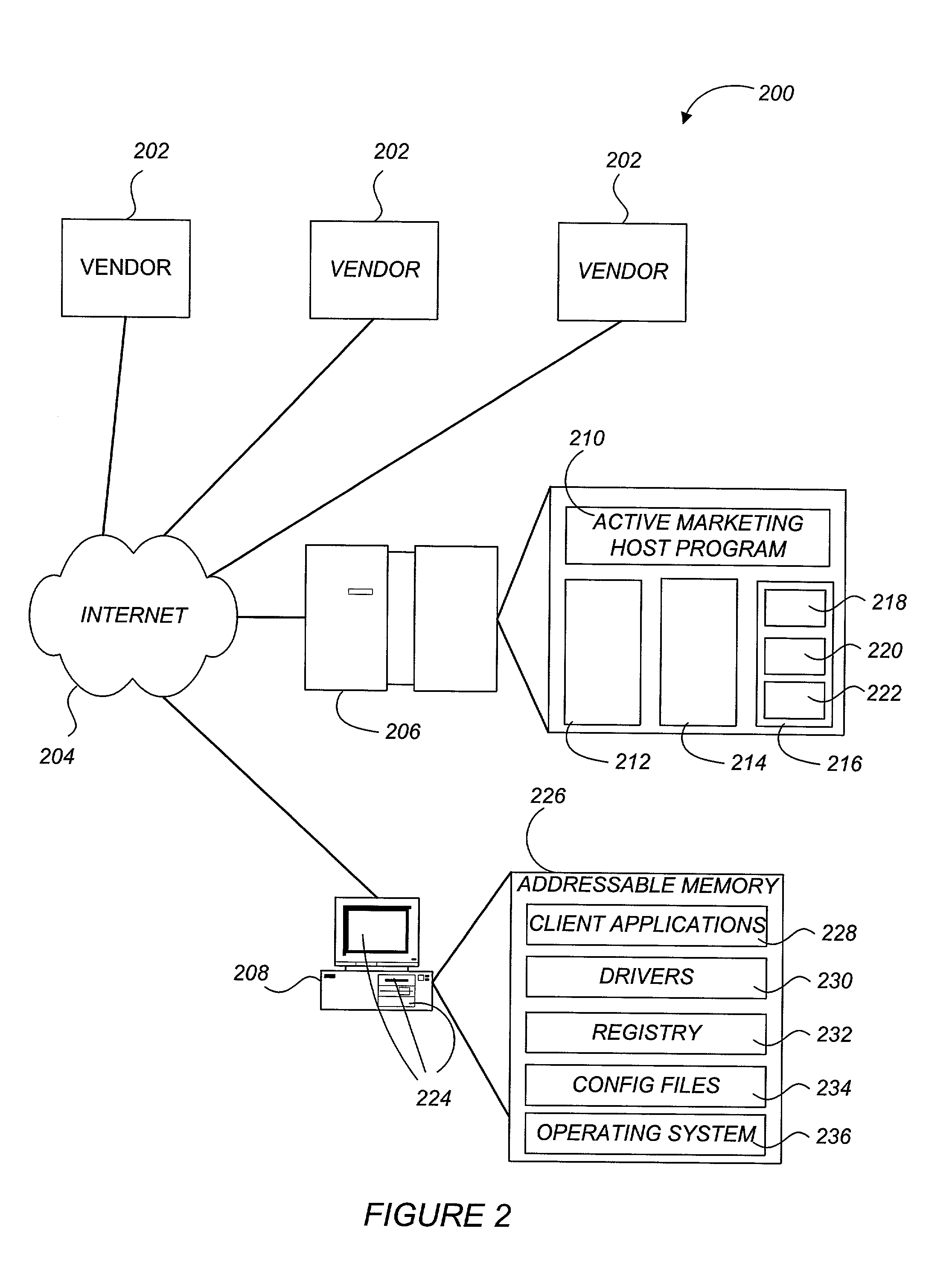
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
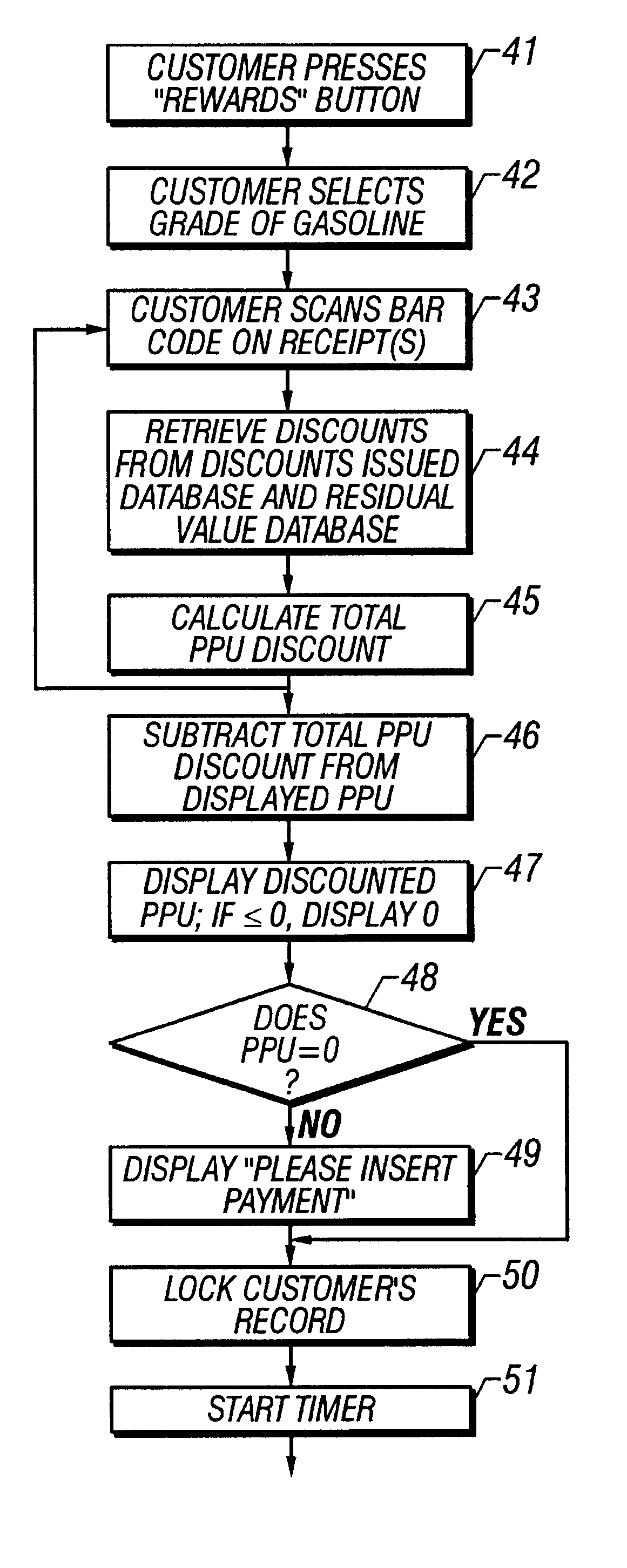
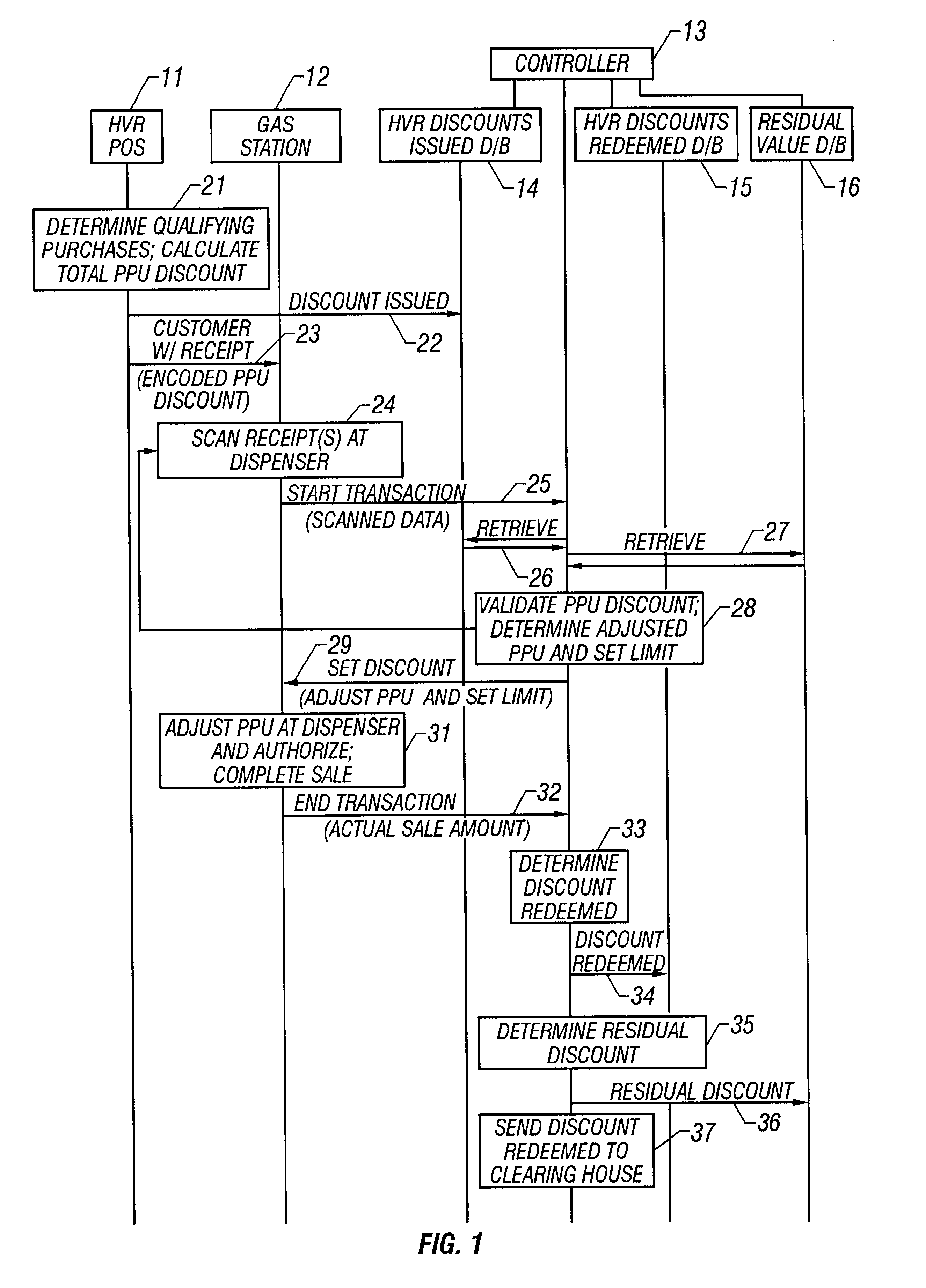
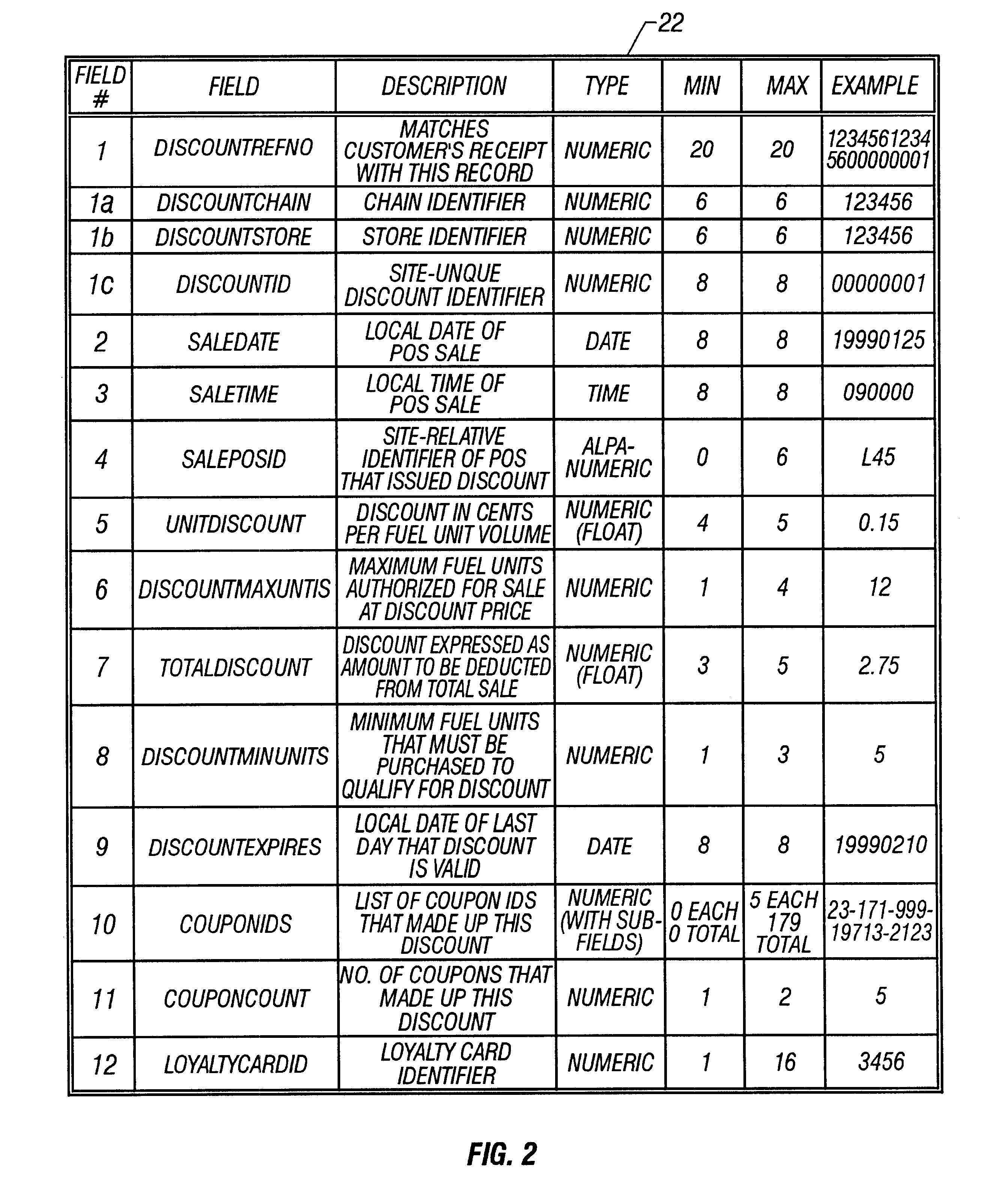
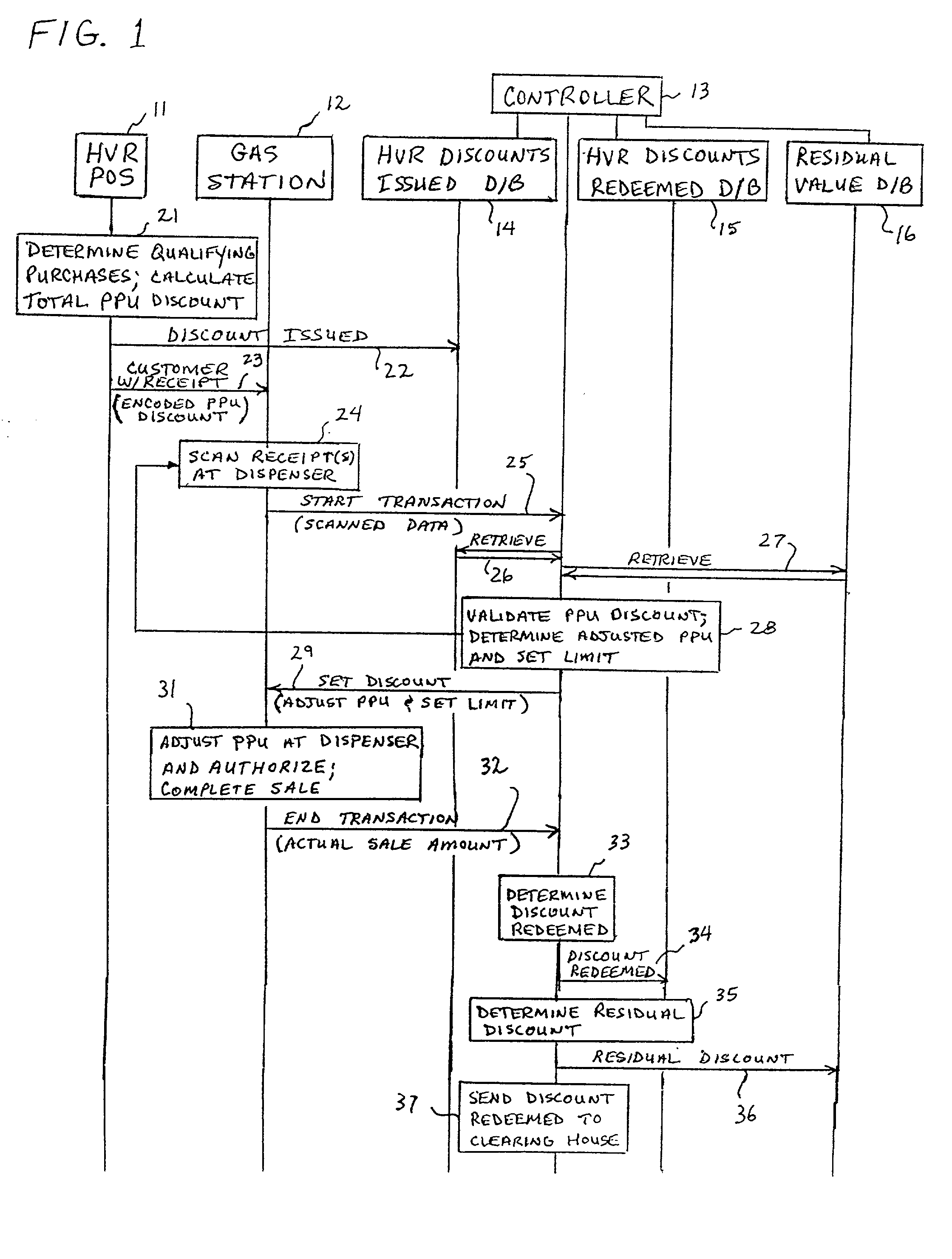
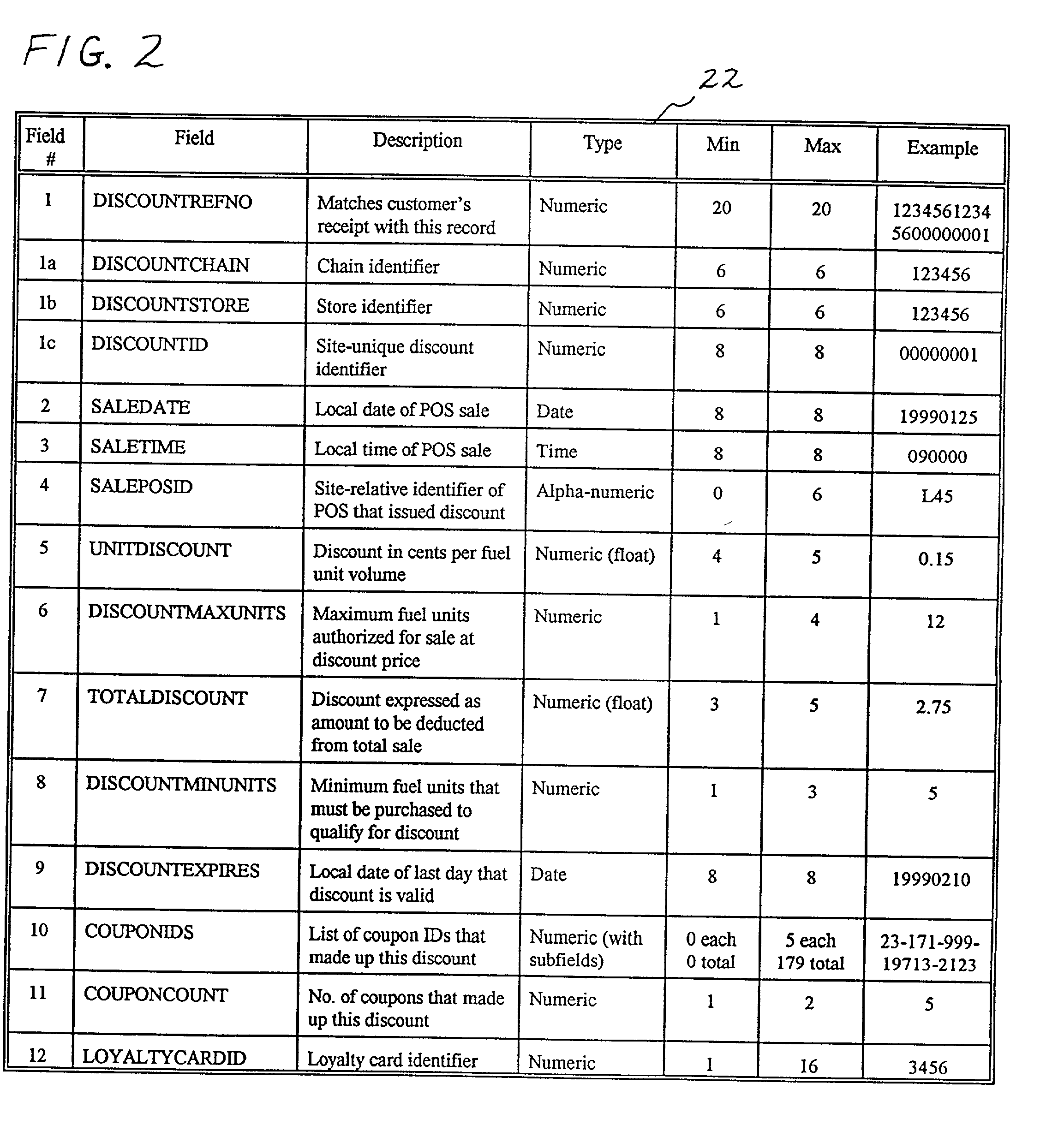
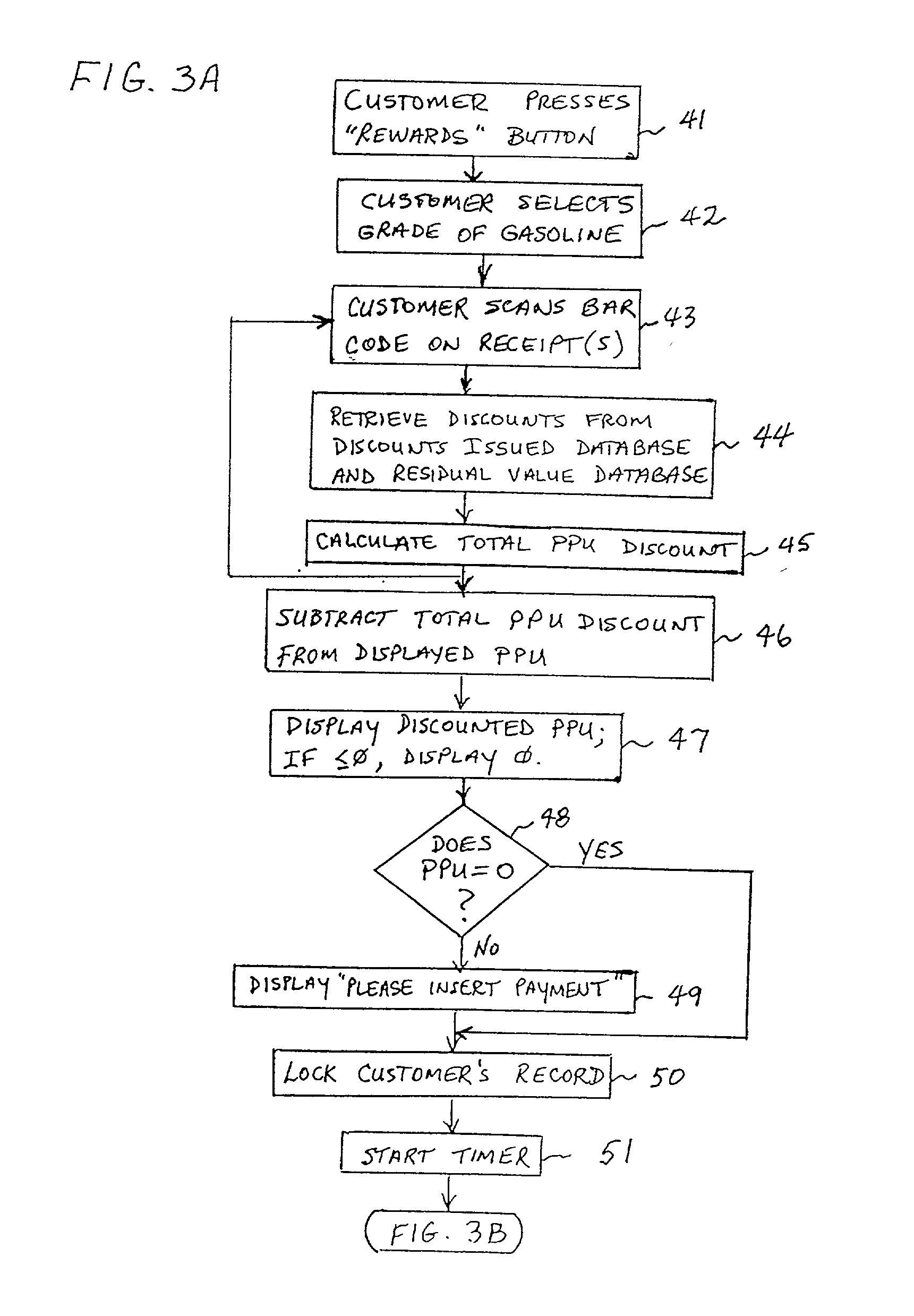
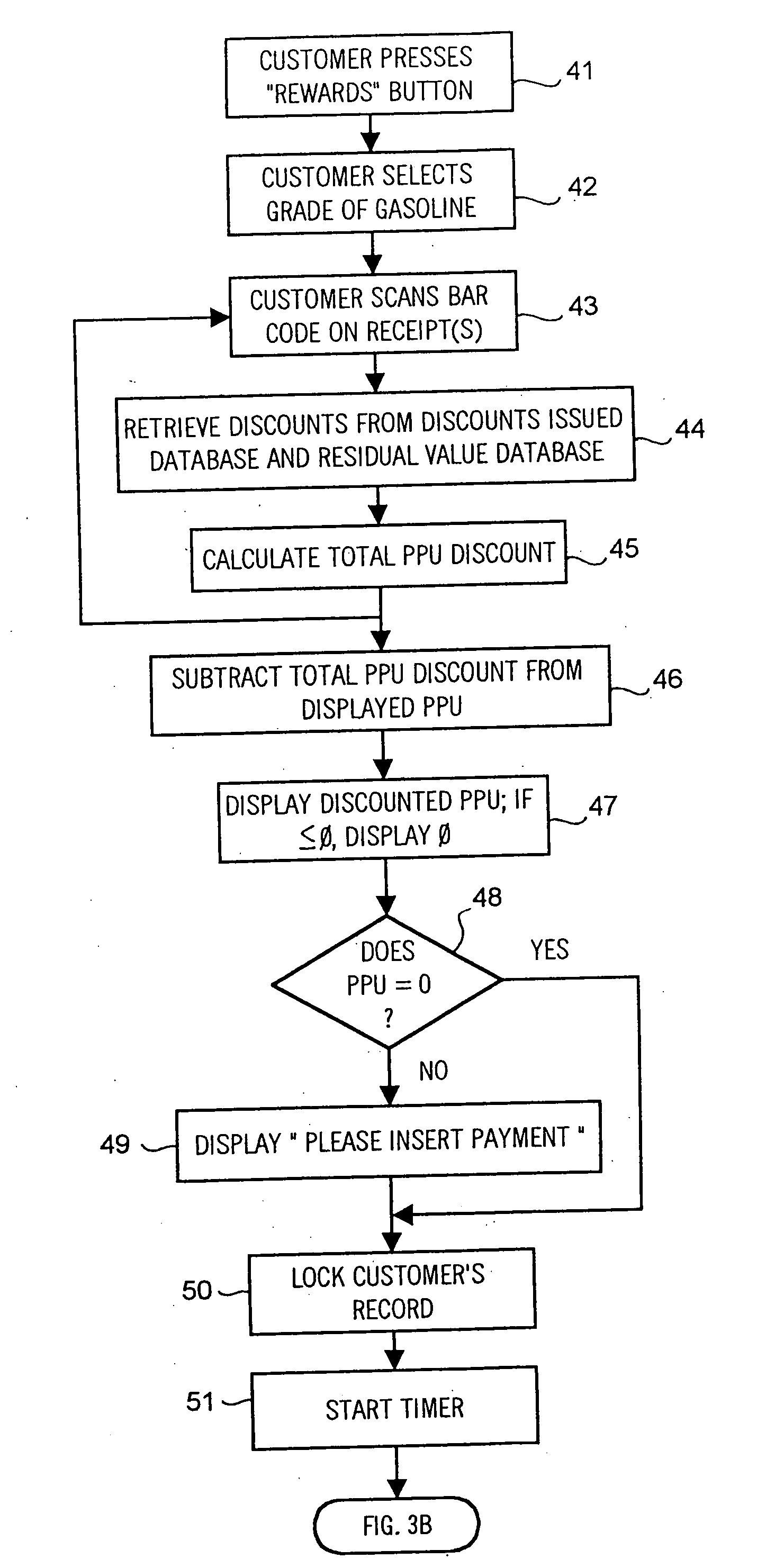
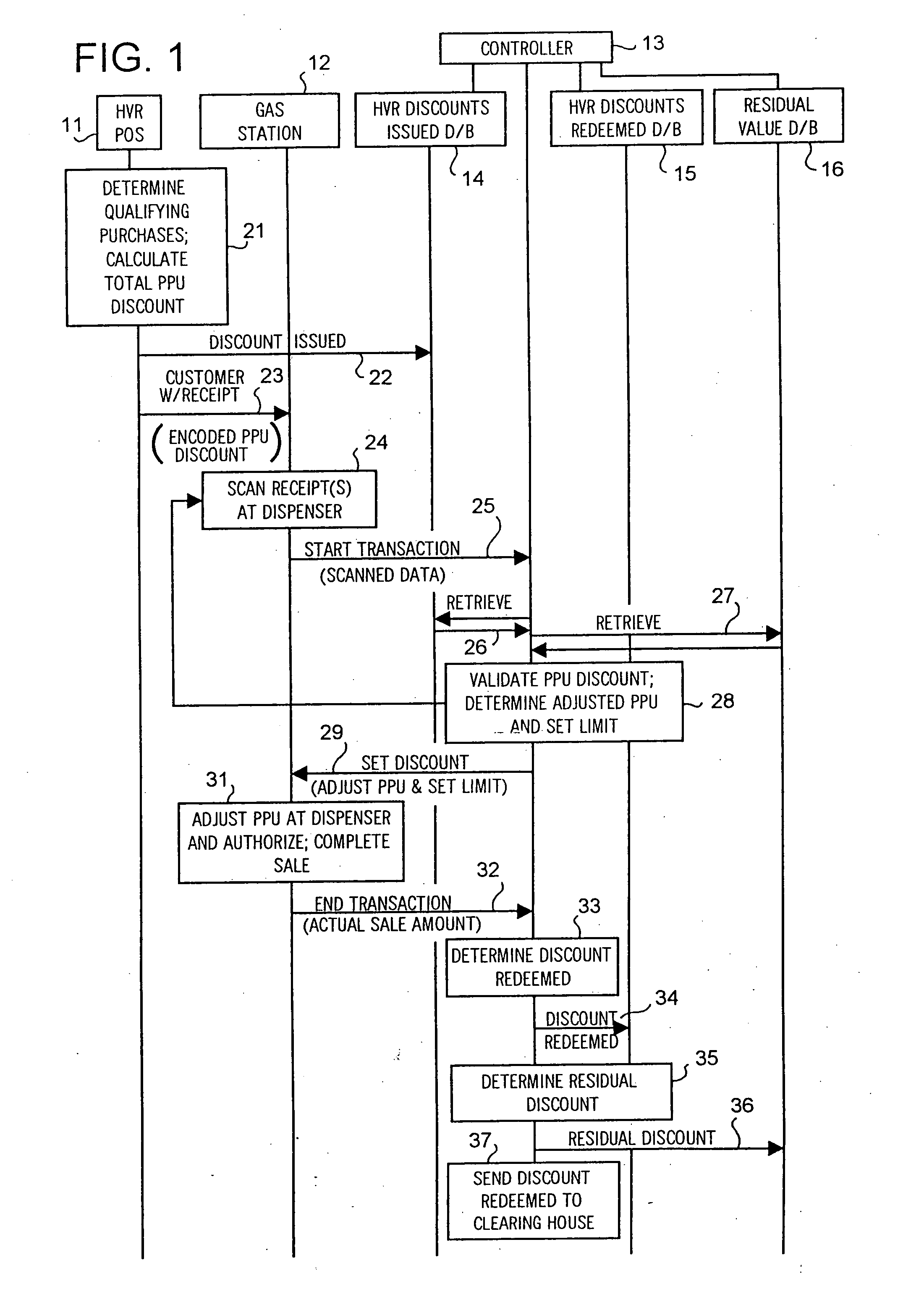
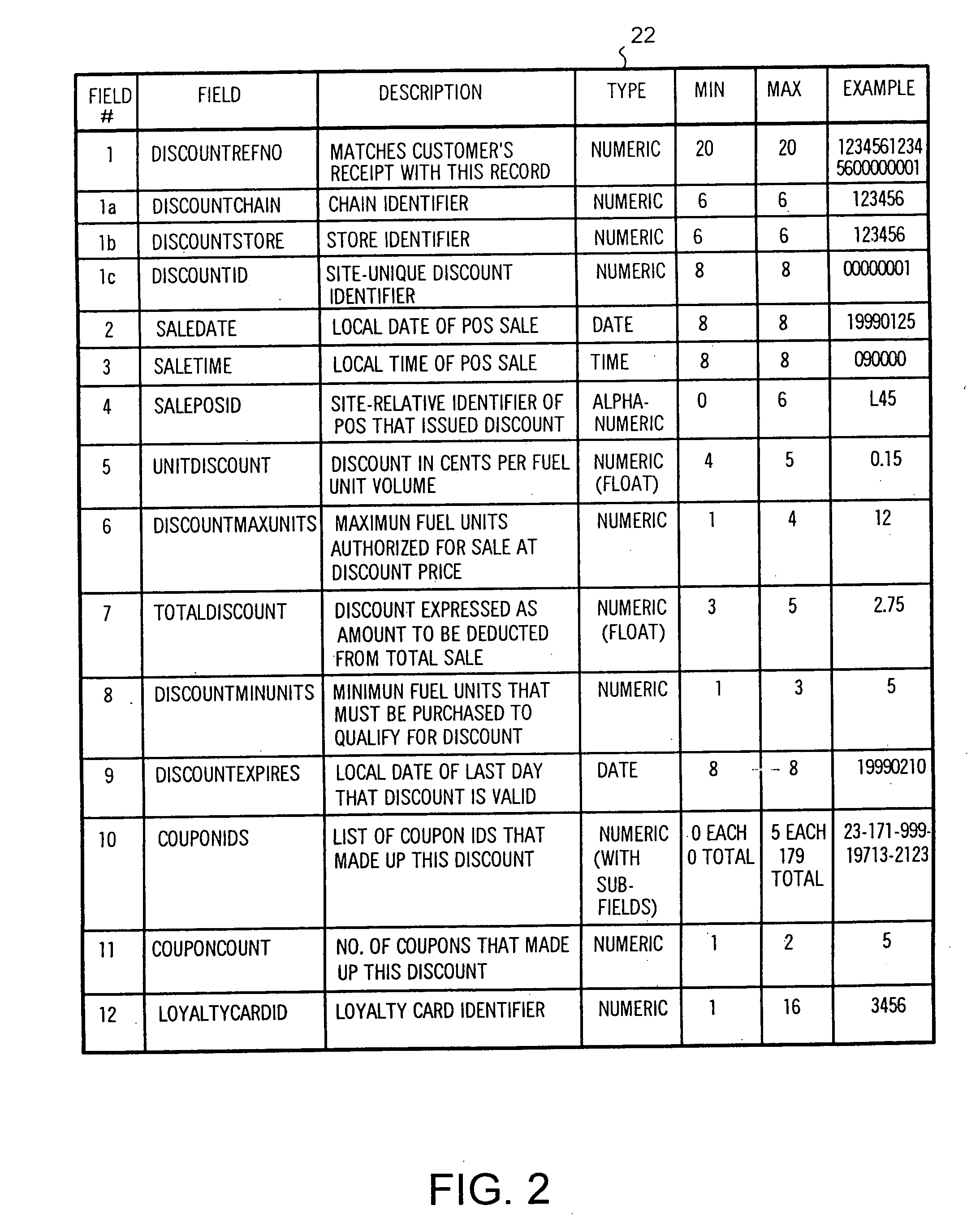
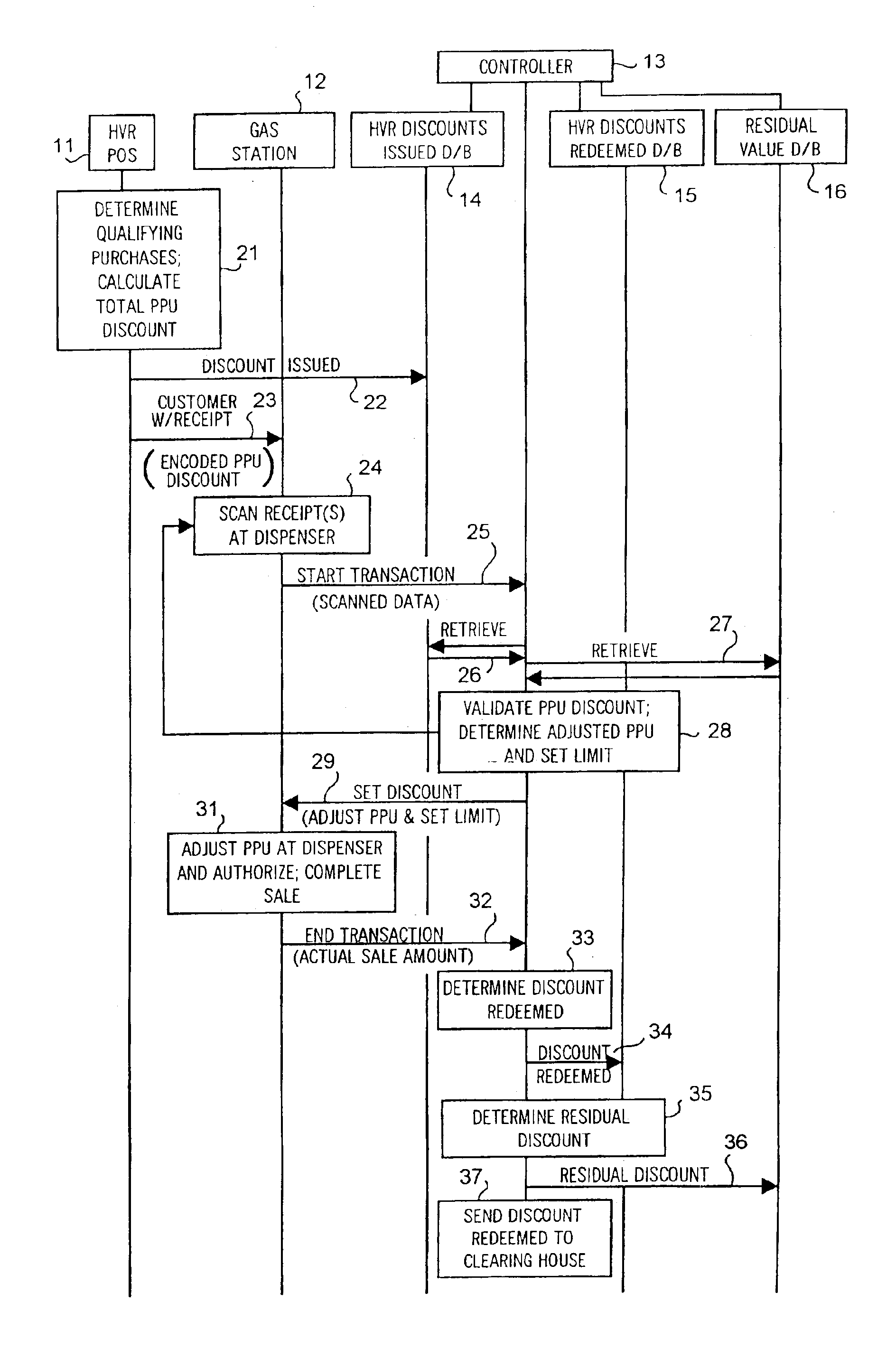
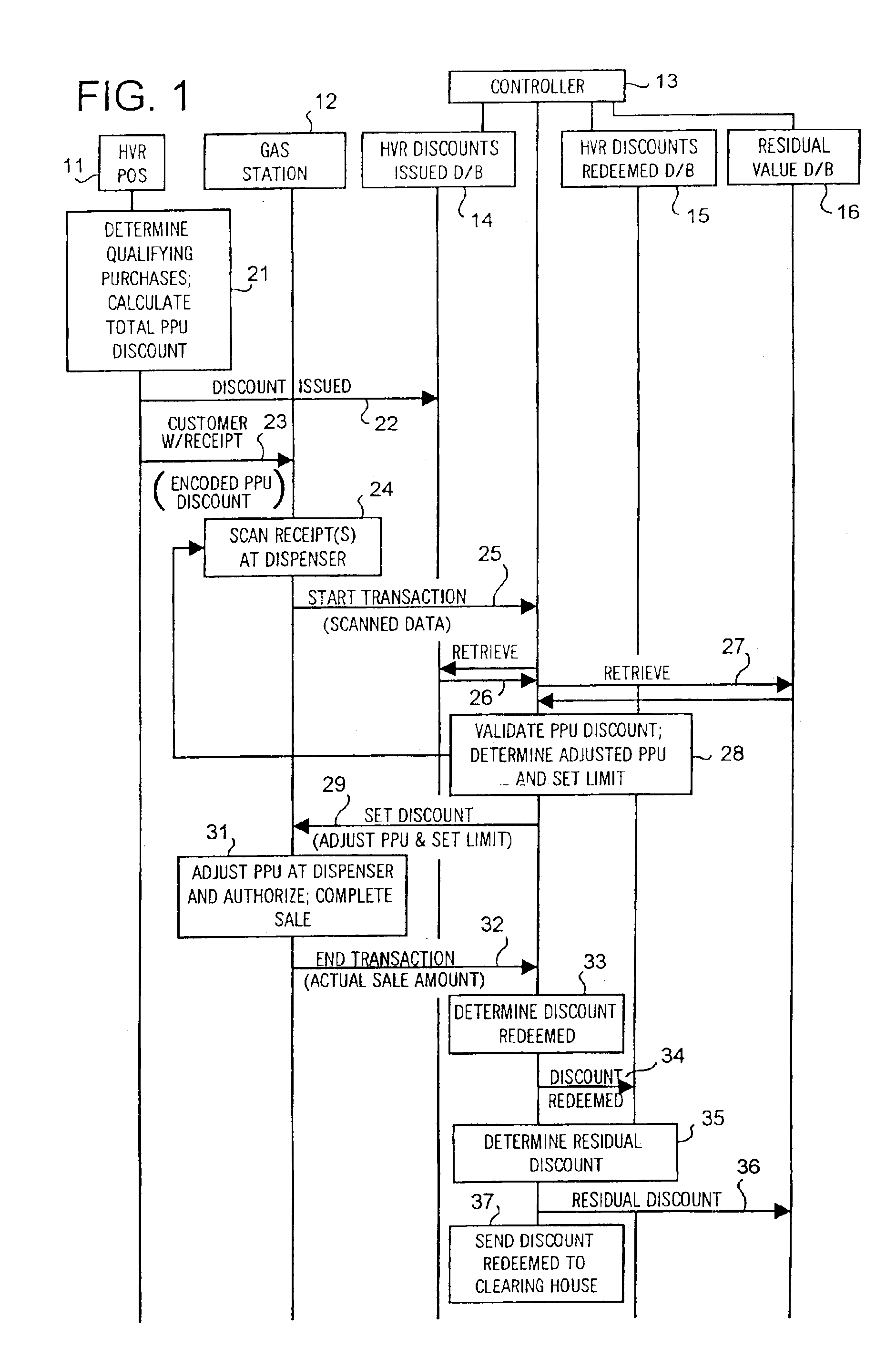
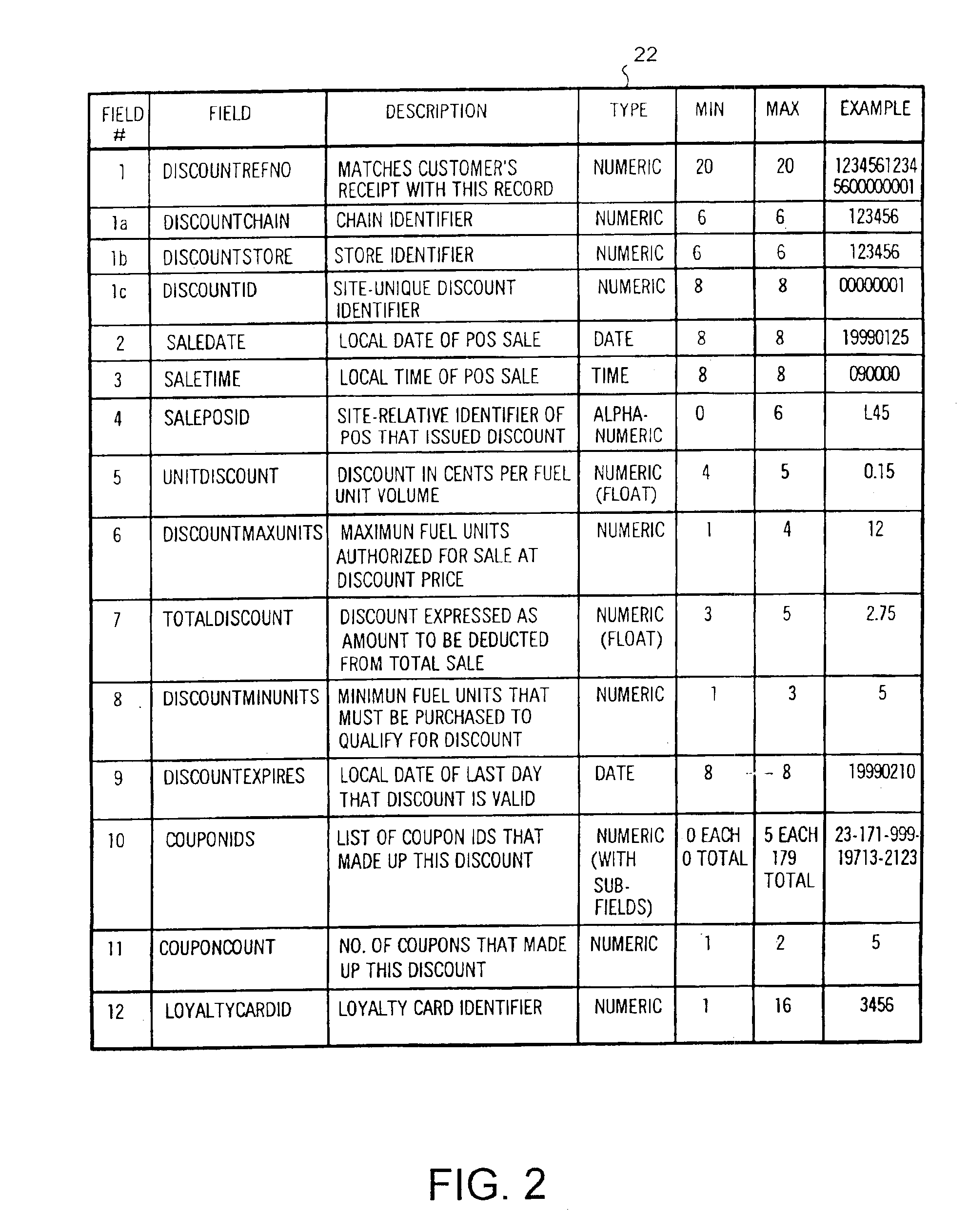
System and method of providing multiple level discounts on cross-marketed products and discounting a price-per-unit-volume of gasoline
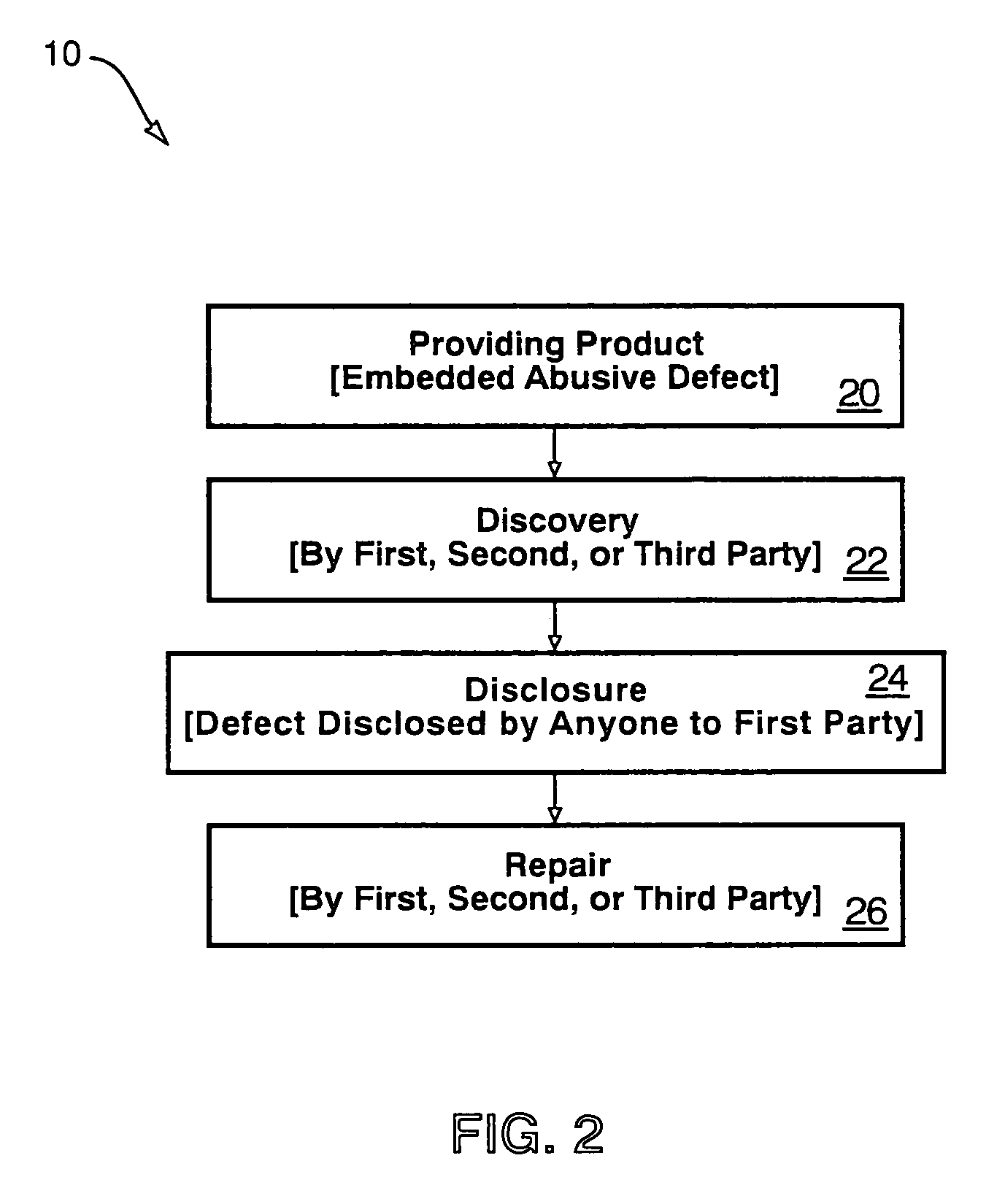
A method of providing multiple level, price-per-unit (PPU) discounts on gasoline to a customer who purchases at least one cross-marketed product. The customer is awarded a first PPU discount on the gasoline based on a purchase by the customer of a first cross-marketed product, and is awarded a second PPU discount based on the purchase of a second cross-marketed product. The first discount is then added to the second discount to determine a total PPU discount, and a paper receipt is printed for the customer with a customer identification and a transaction identification encoded in a bar code thereon. The total discount is stored in a discounts issued database. The customer then scans the encoded bar code with a bar code scanner at a gasoline dispenser to redeem the discount. The total discount is retrieved from the discounts issued database, and the gasoline station then reduces the price-per-unit-volume of the gasoline by an amount equal to the total discount. When the customer completes the gasoline purchase, a value of the total discount redeemed is determined and stored in a discounts redeemed database. Portions of the discount redeemed are then allocated to vendors of the first and second cross-marketed products according to predetermined criteria.
Owner:EXCENTUS CORP +1
Active marketing based on client computer configurations
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
System and method of maintaining a posted street price for fuel while offering different prices to identified customers
InactiveUS20010039512A1Address rising pricesSpecial data processing applicationsMarketingBarcodeMarketed products
A method of providing multiple level, price-per-unit (PPU) discounts on gasoline to a customer who purchases at least one cross-marketed product. The customer is awarded a first PPU discount on the gasoline based on a purchase by the customer of a first cross-marketed product, and is awarded a second PPU discount based on the purchase of a second cross-marketed product. The first discount is then added to the second discount to determine a total PPU discount, and a paper receipt is printed for the customer with a customer identification and a transaction identification encoded in a bar code thereon. The total discount is stored in a discounts issued database. The customer then scans the encoded bar code with a bar code scanner at a gasoline dispenser to redeem the discount. The total discount is retrieved from the discounts issued database, and the gasoline station then reduces the price-per-unit-volume of the gasoline by an amount equal to the total discount. When the customer completes the gasoline purchase, a value of the total discount redeemed is determined and stored in a discounts redeemed database. Portions of the discount redeemed are then allocated to vendors of the first and second cross-marketed products according to predetermined criteria.
Owner:CONOCOPHILLIPS CO +1
Method of cross-marketing utilizing electronic coupons
InactiveUS20040158493A1Address rising pricesOther washing machinesPayment architectureBarcodeMarketed products
A method of providing multiple level, price-per-unit (PPU) discounts on gasoline to a customer who purchases at least one cross-marketed product. The customer is awarded a first PPU discount on the gasoline based on a purchase by the customer of a first cross-marketed product, and is awarded a second PPU discount based on the purchase of a second cross-marketed product. The first discount is then added to the second discount to determine a total PPU discount, and a paper receipt is printed for the customer with a customer identification and a transaction identification encoded in a bar code thereon. The total discount is stored in a discounts issued database. The customer then scans the encoded bar code with a bar code scanner at a gasoline dispenser to redeem the discount. The total discount is retrieved from the discounts issued database, and the gasoline station then reduces the price-per-unit-volume of the gasoline by an amount equal to the total discount. When the customer completes the gasoline purchase, a value of the total discount redeemed is determined and stored in a discounts redeemed database. Portions of the discount redeemed are then allocated to vendors of the first and second cross-marketed products according to predetermined criteria.
Owner:EXCENTUS CORP
Method of providing price-per-unit discounts for fuel to a customer
InactiveUS6885996B2Address rising pricesOther washing machinesPayment architectureMarketed productsEngineering
Owner:EXCENTUS CORP
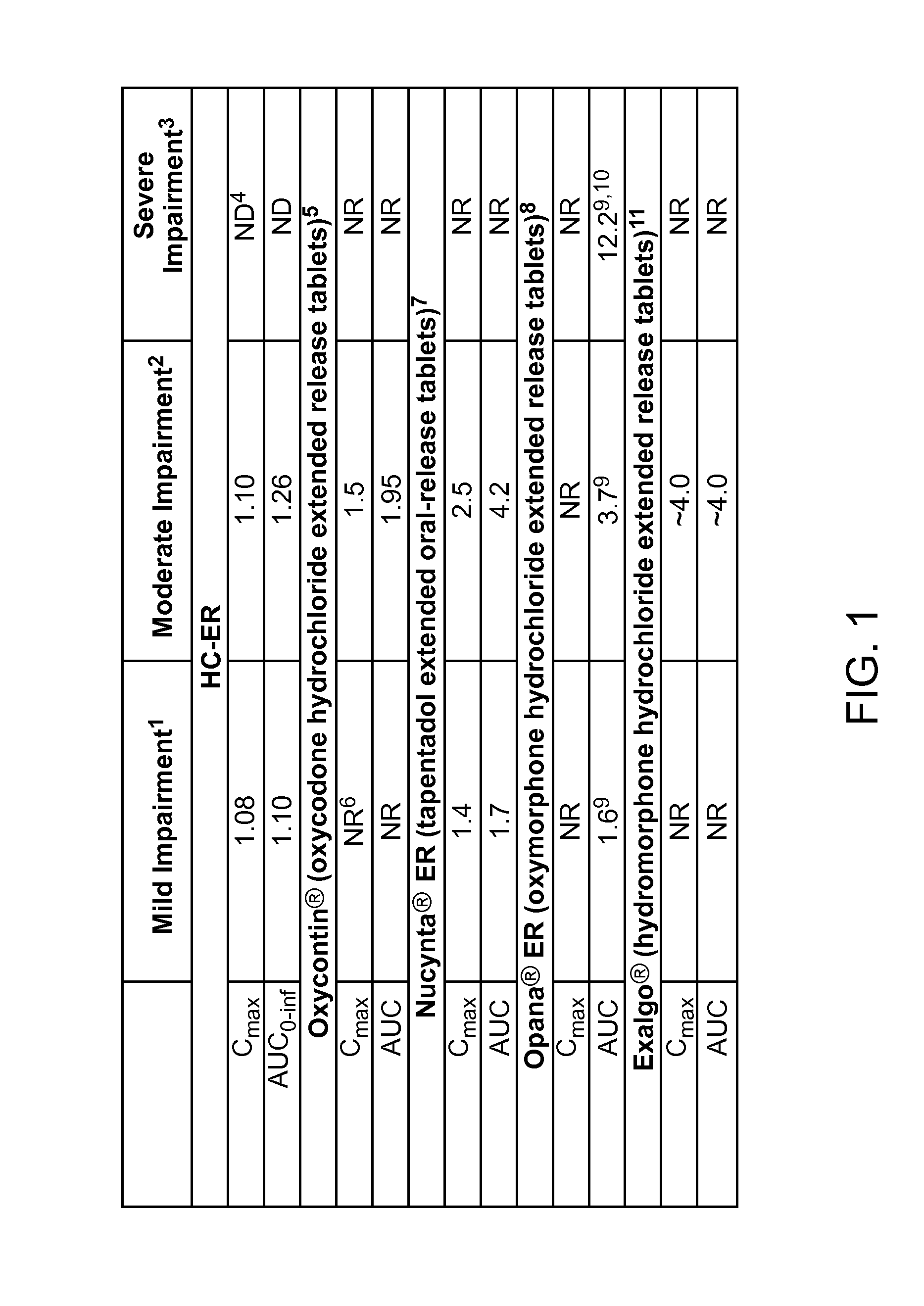
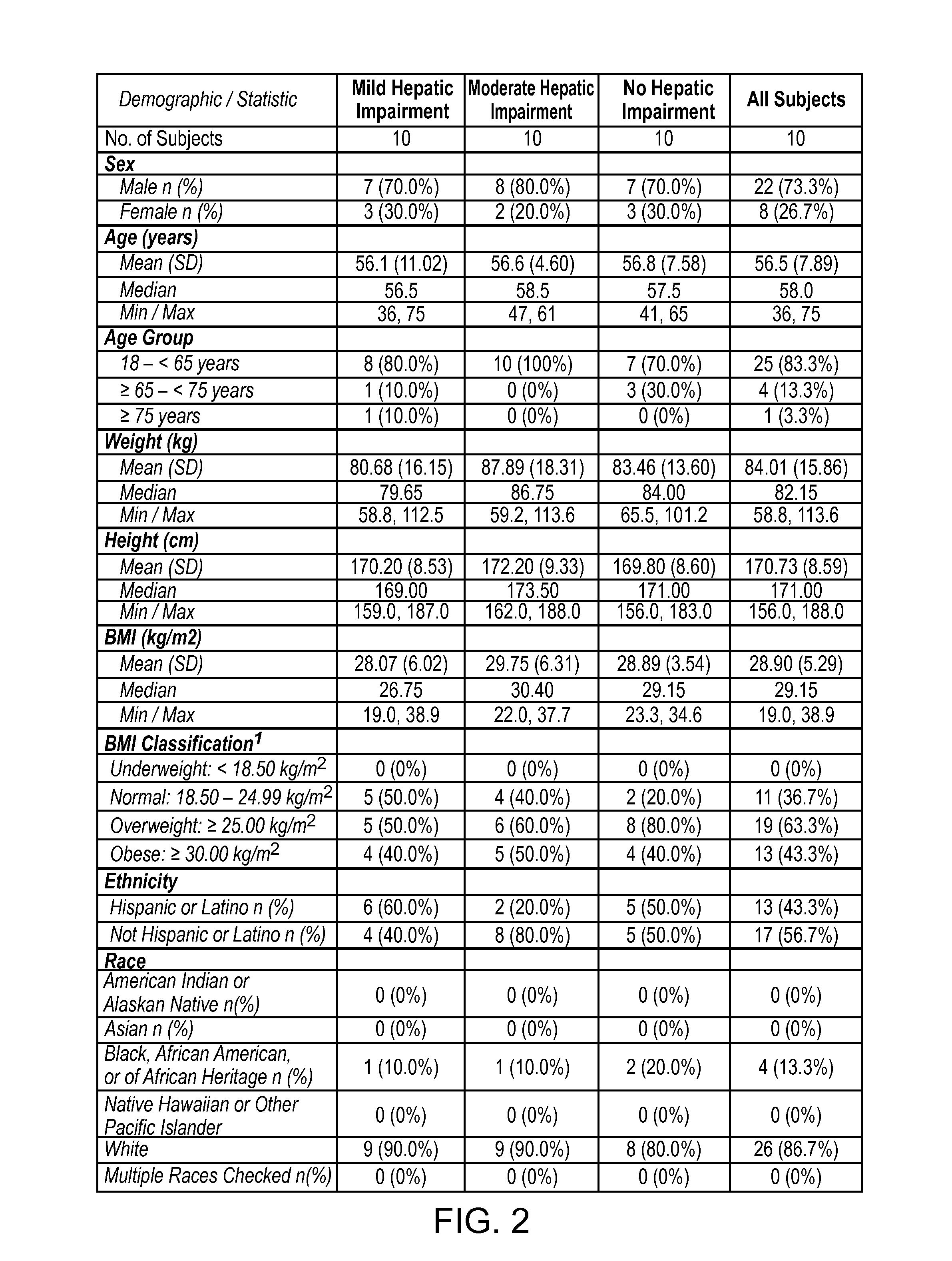
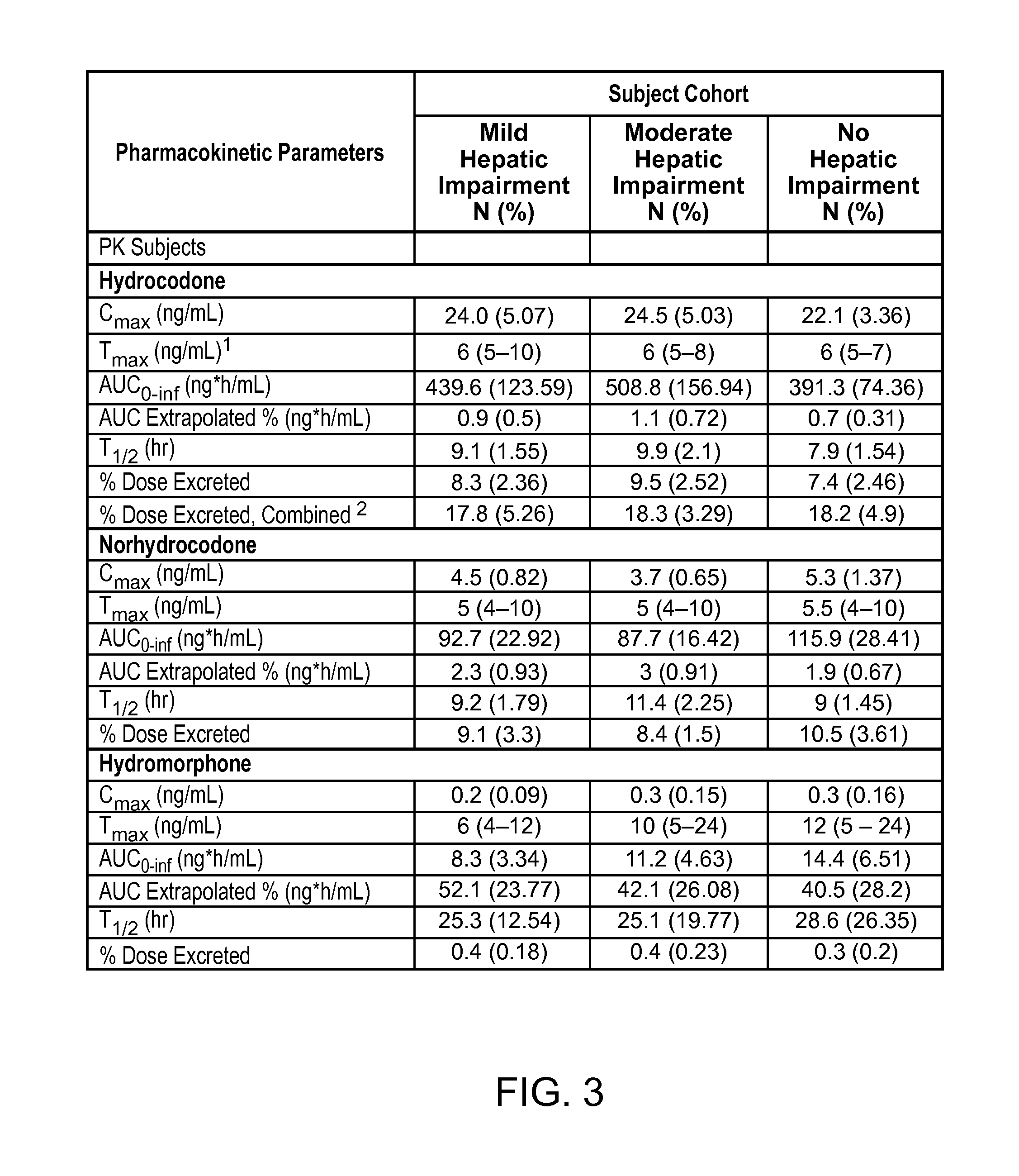
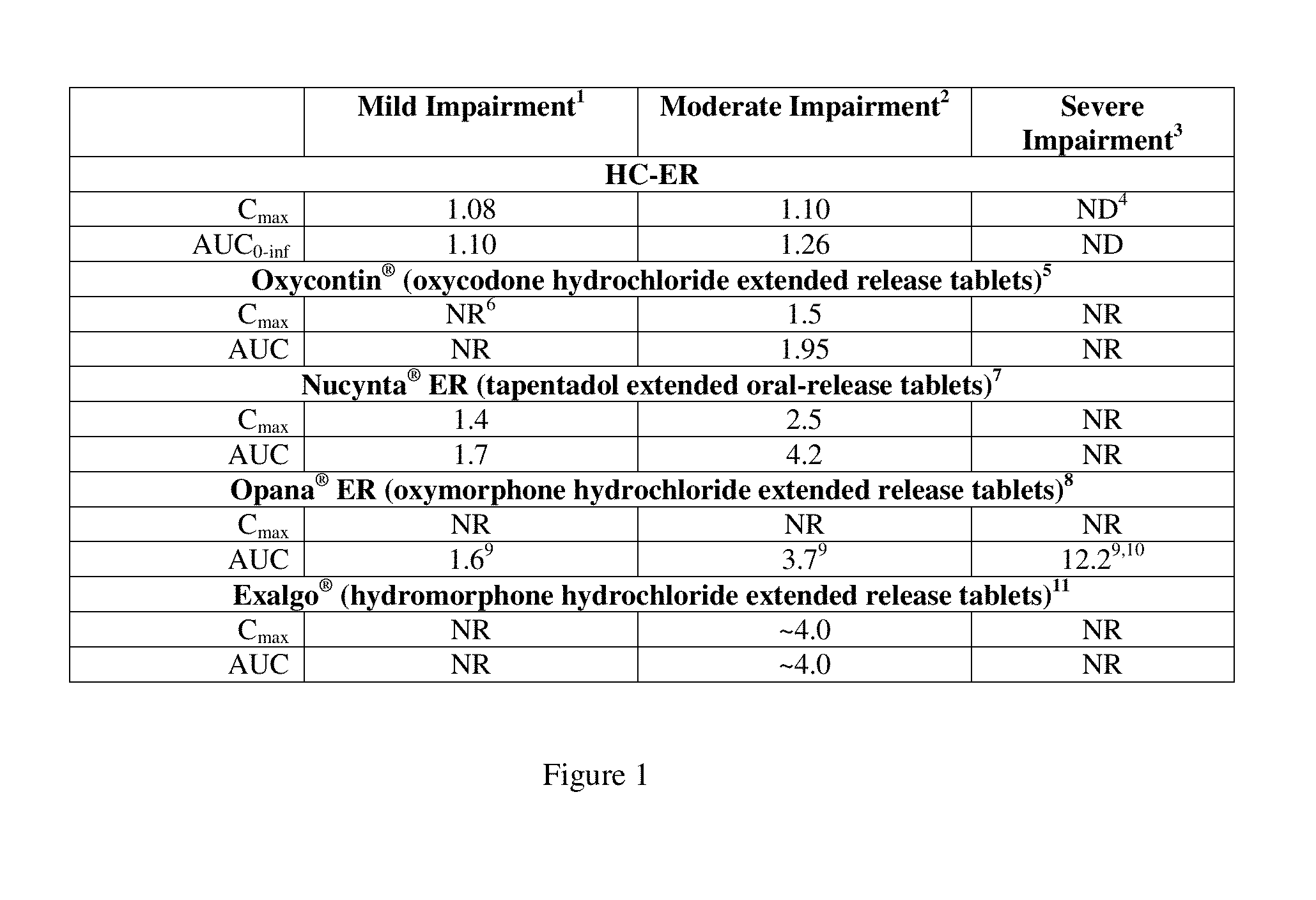
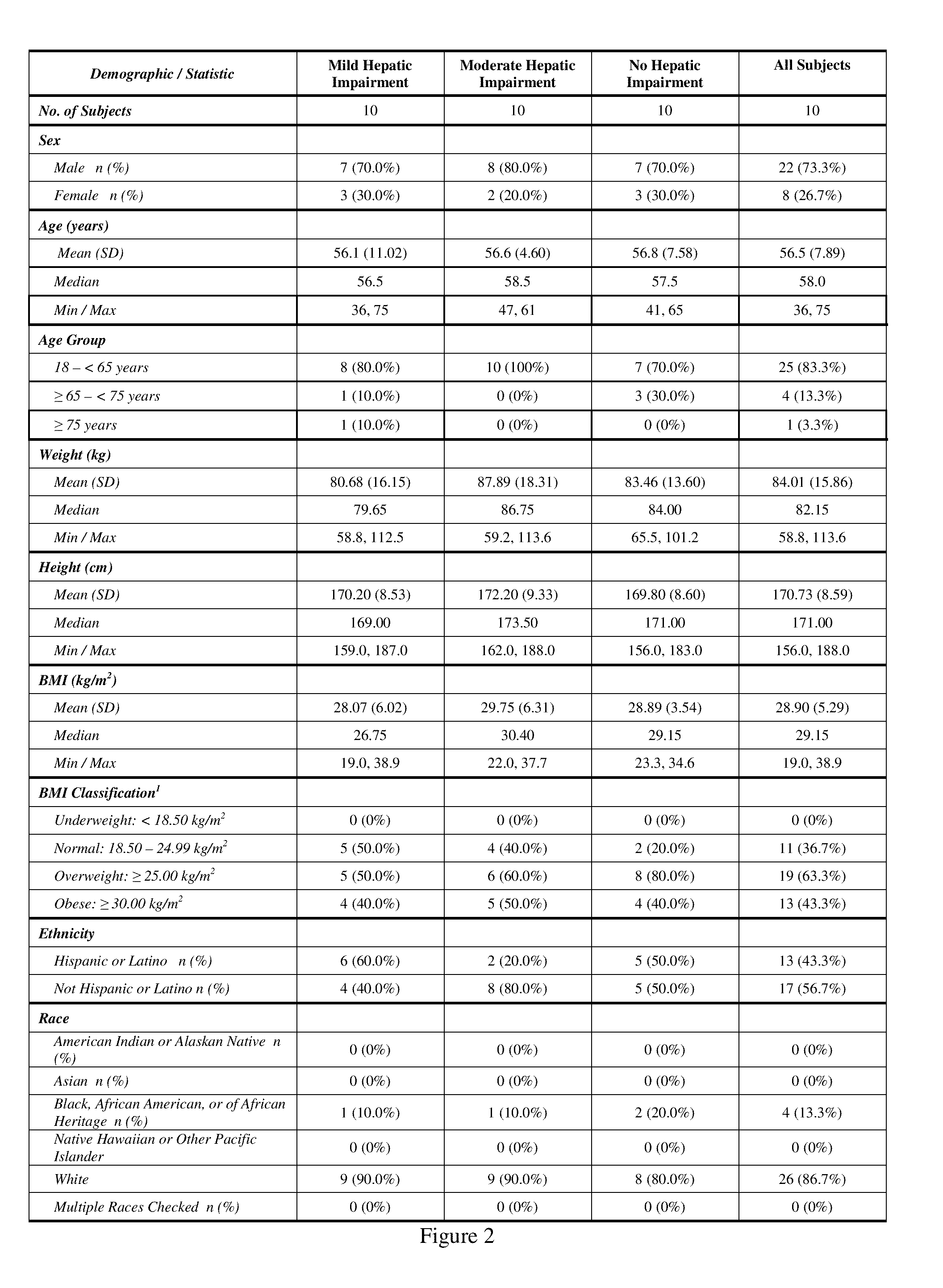
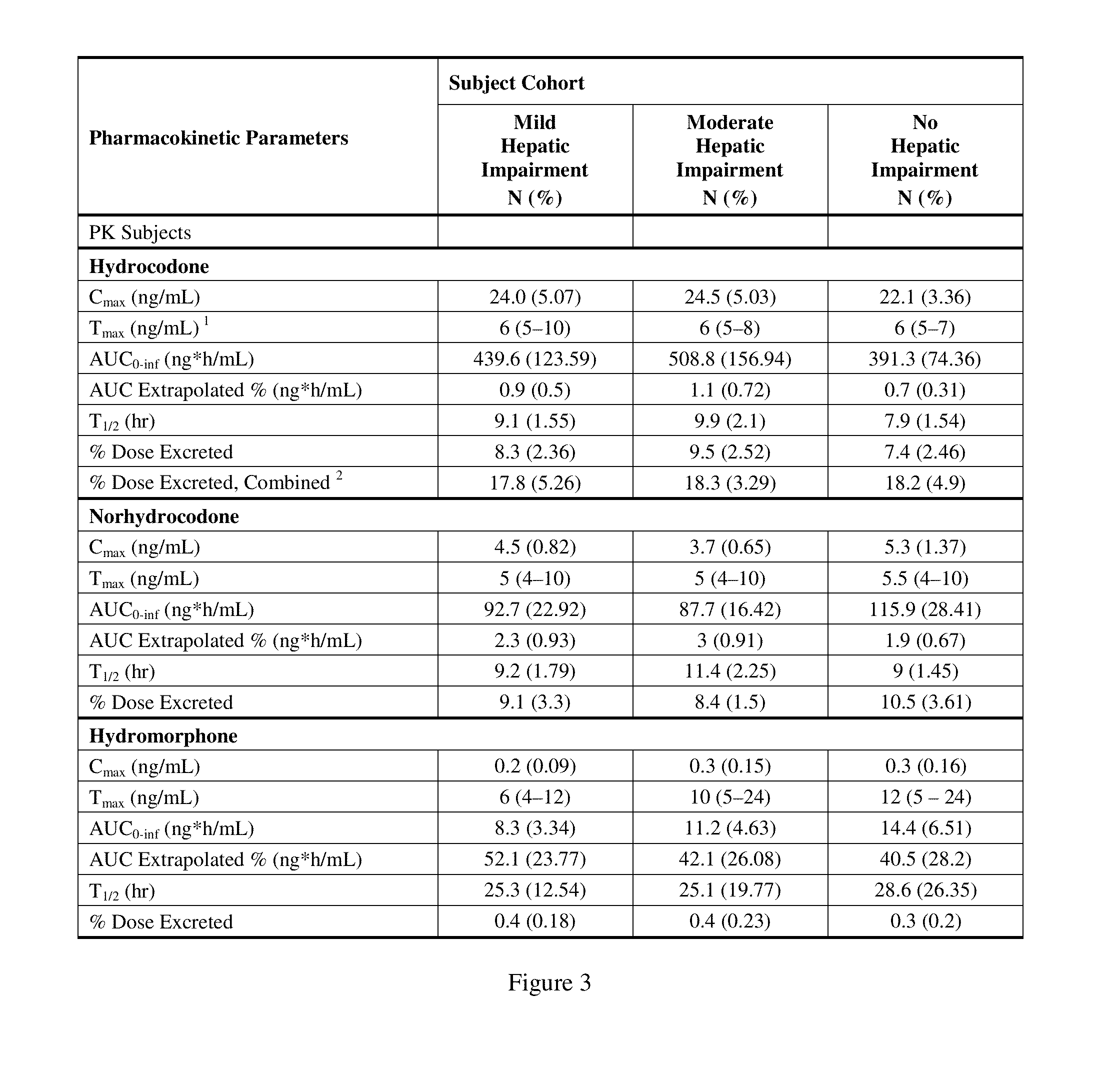
Treating pain in patients with hepatic impairment
An extended release composition for an analgesic active pharmaceutical ingredient which may be an opioid, preferably hydrocodone as the only active ingredient. The extended release composition comprises a multiparticulate modified release composition which may be in the form of beads contained in an oral dosage form such as gelatin capsules as the primary package. The oral dosage units are supplied as part of a kit, which also includes a package insert all sold as a commercially marketed product. The primary package and package insert are contained in an optional secondary package and the package insert does not contain a warning, a dosing instruction, or a dosing table specifically directed to patients suffering from mild, moderate or severe hepatic impairment.
Owner:PERSION PHARMA LLC
Active marketing based on client computer configurations
InactiveUS20010007100A1AdvertisementsMultiple digital computer combinationsComputer usersComputer configuration
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
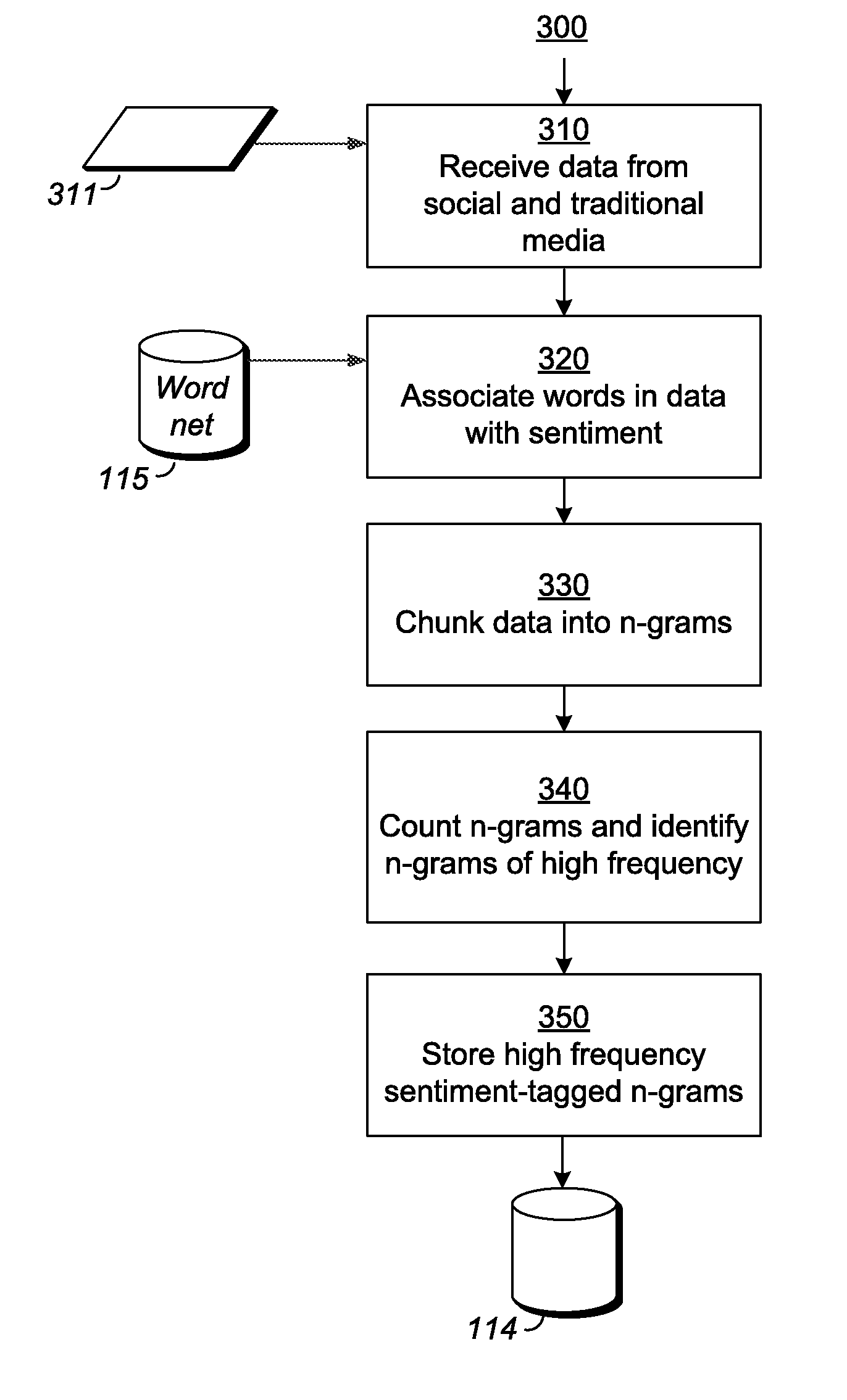
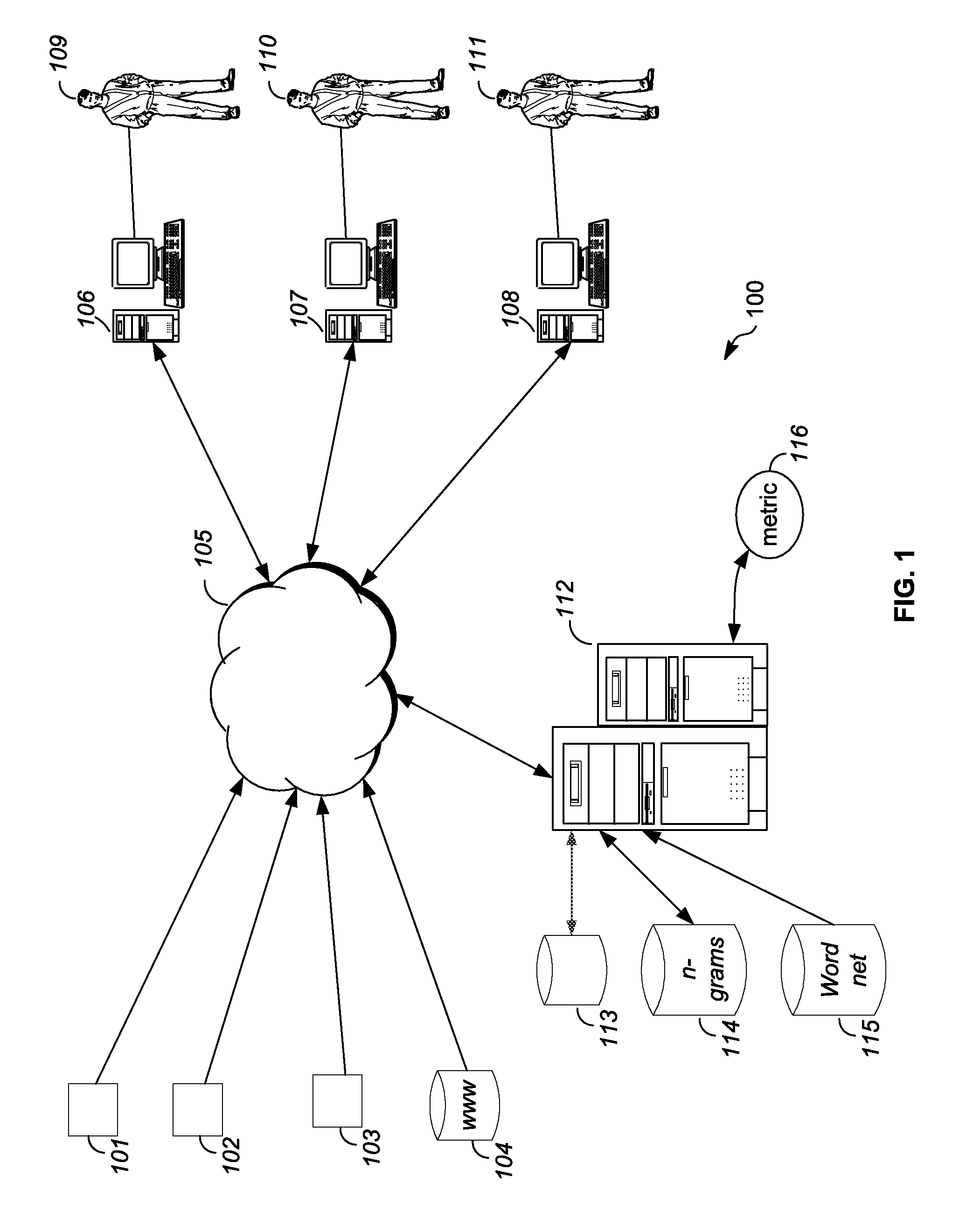
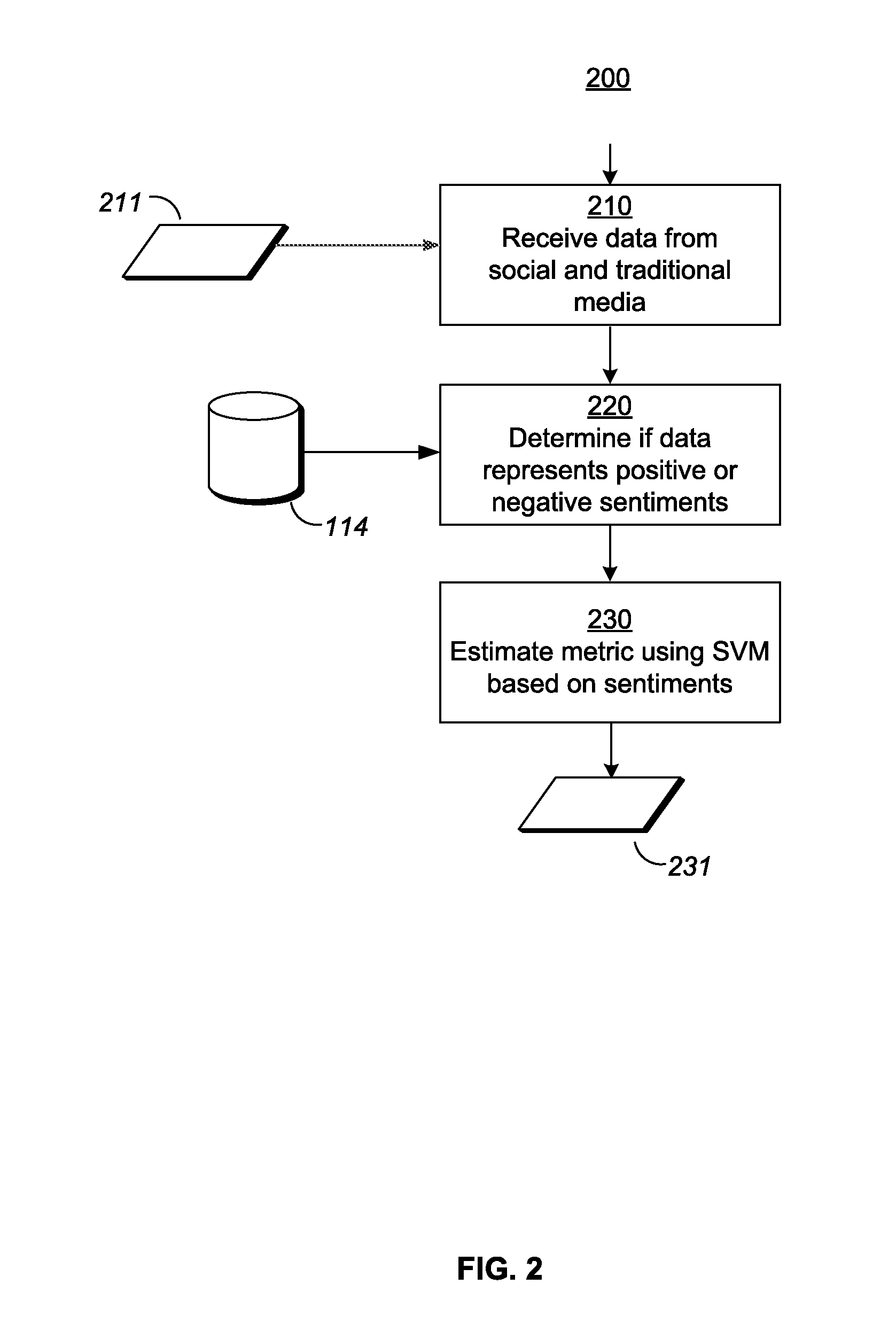
Researching exchange-listed products using sentiment
A metric, such as price, is estimated for an exchange-listed product based on public sentiment regarding the exchange-listed product. A system for estimating a metric for an exchange-listed product receives data from an external server. The data may be received from a social media website, and may represent user-generated data in natural language form. The system identifies a portion of the data and determines whether the portion represents a positive sentiment or a negative sentiment. The system estimates a metric for the exchange-listed product based on the sentiment represented by the data. The system may combine the metric based on sentiment with other metrics to create an averaged metric. The other metrics may be obtained using analyst consensus estimates as well as technical analyses of market information for the exchange-listed product.
Owner:INVESTLAB TECH
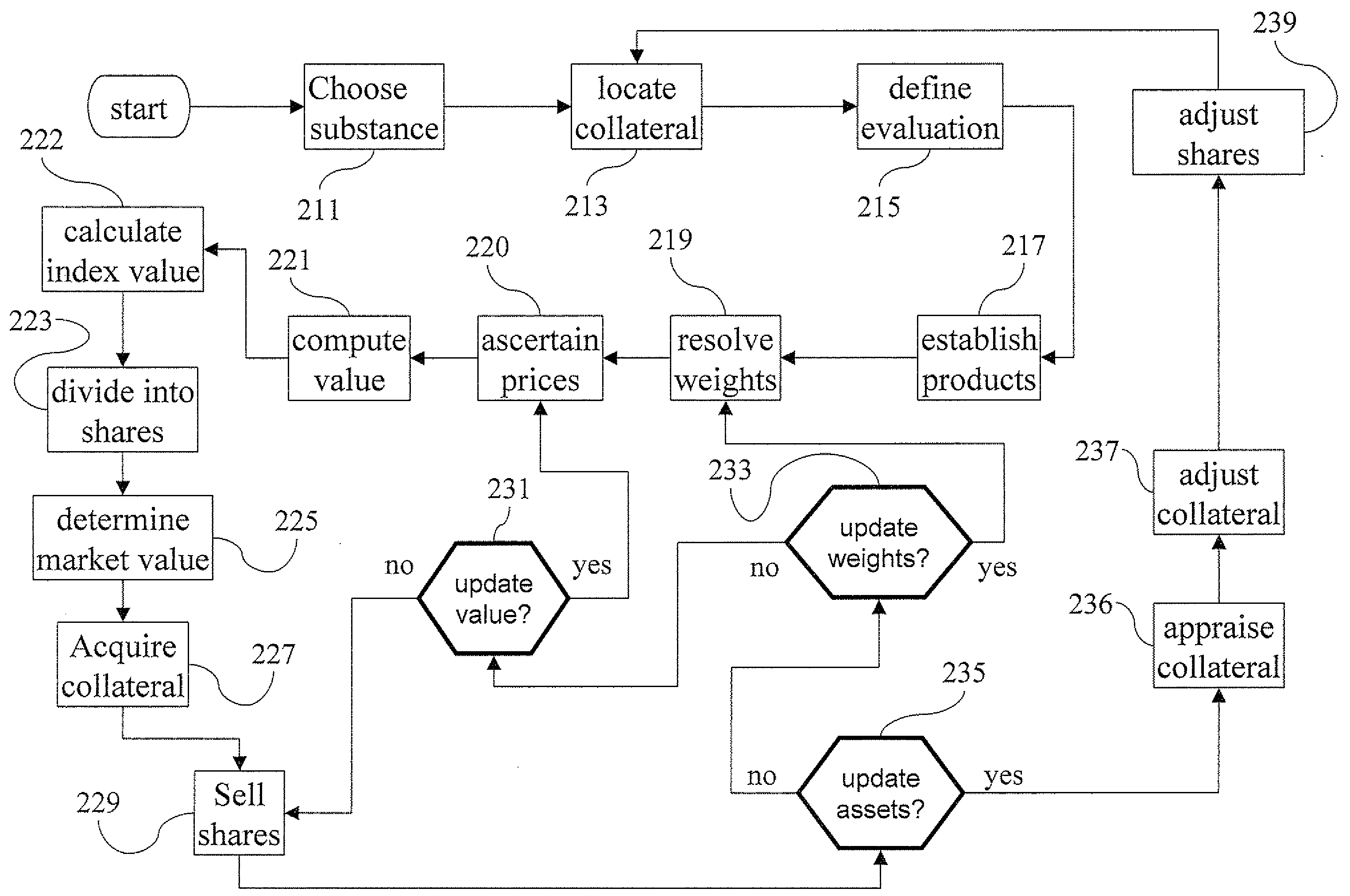
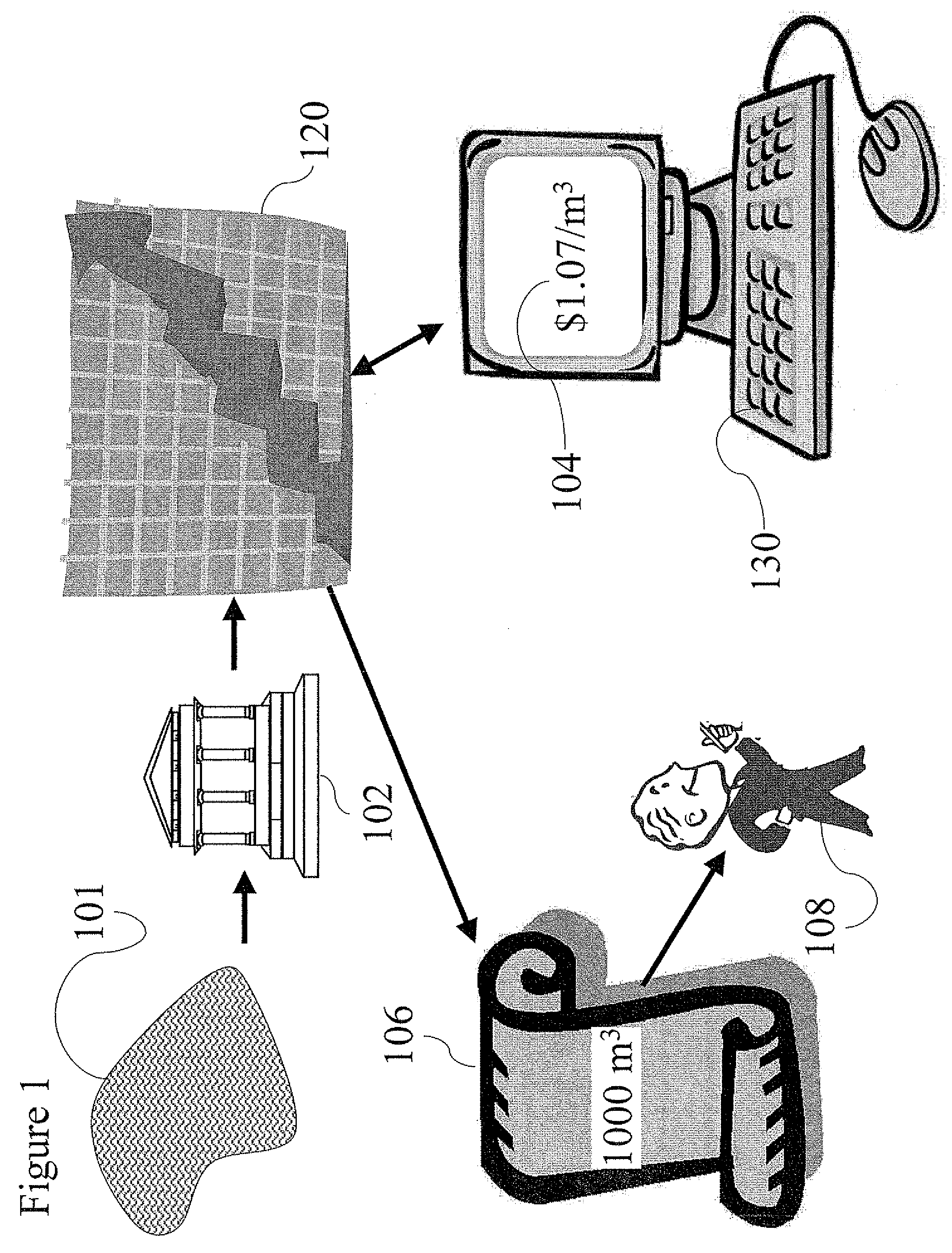
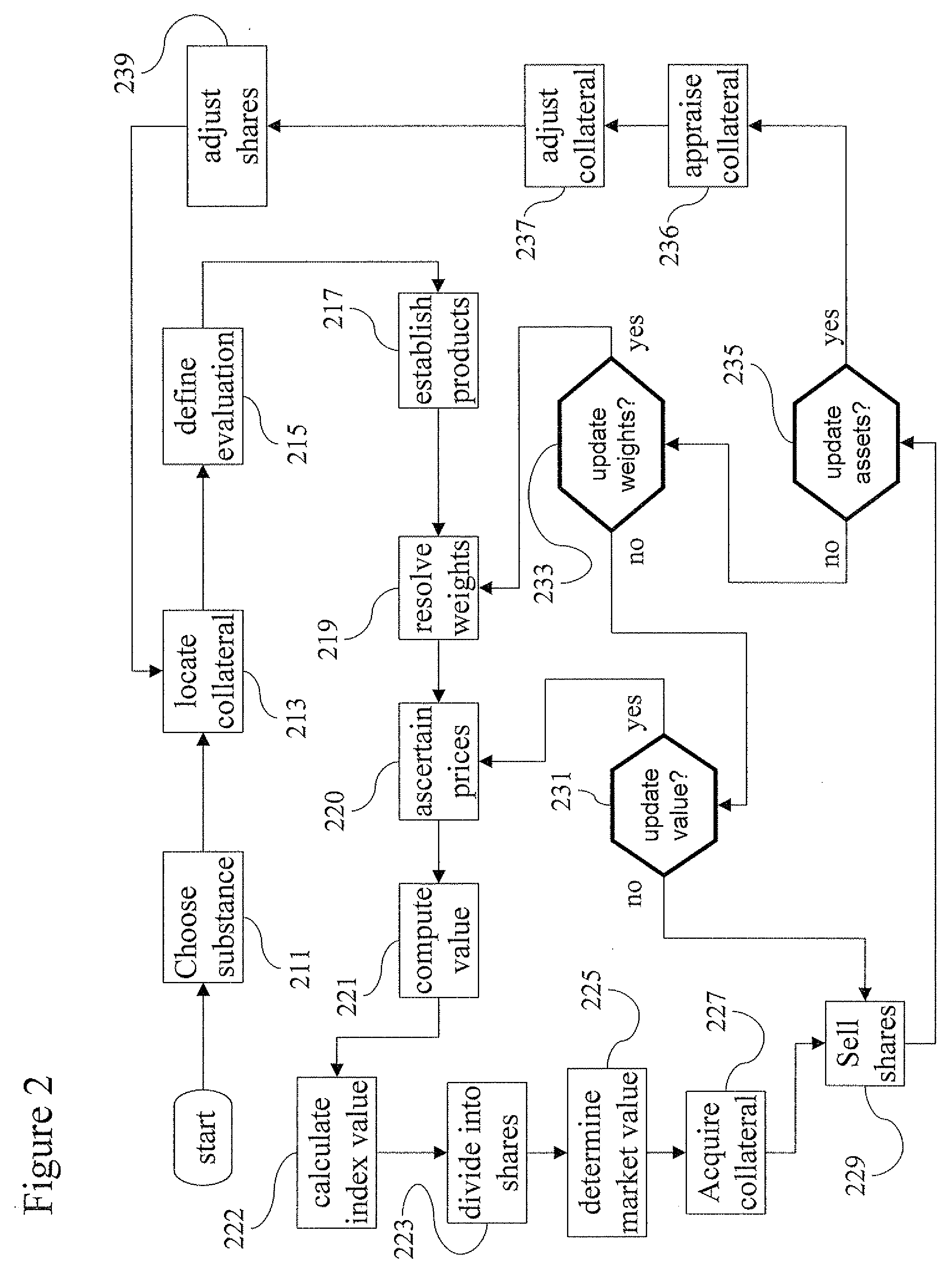
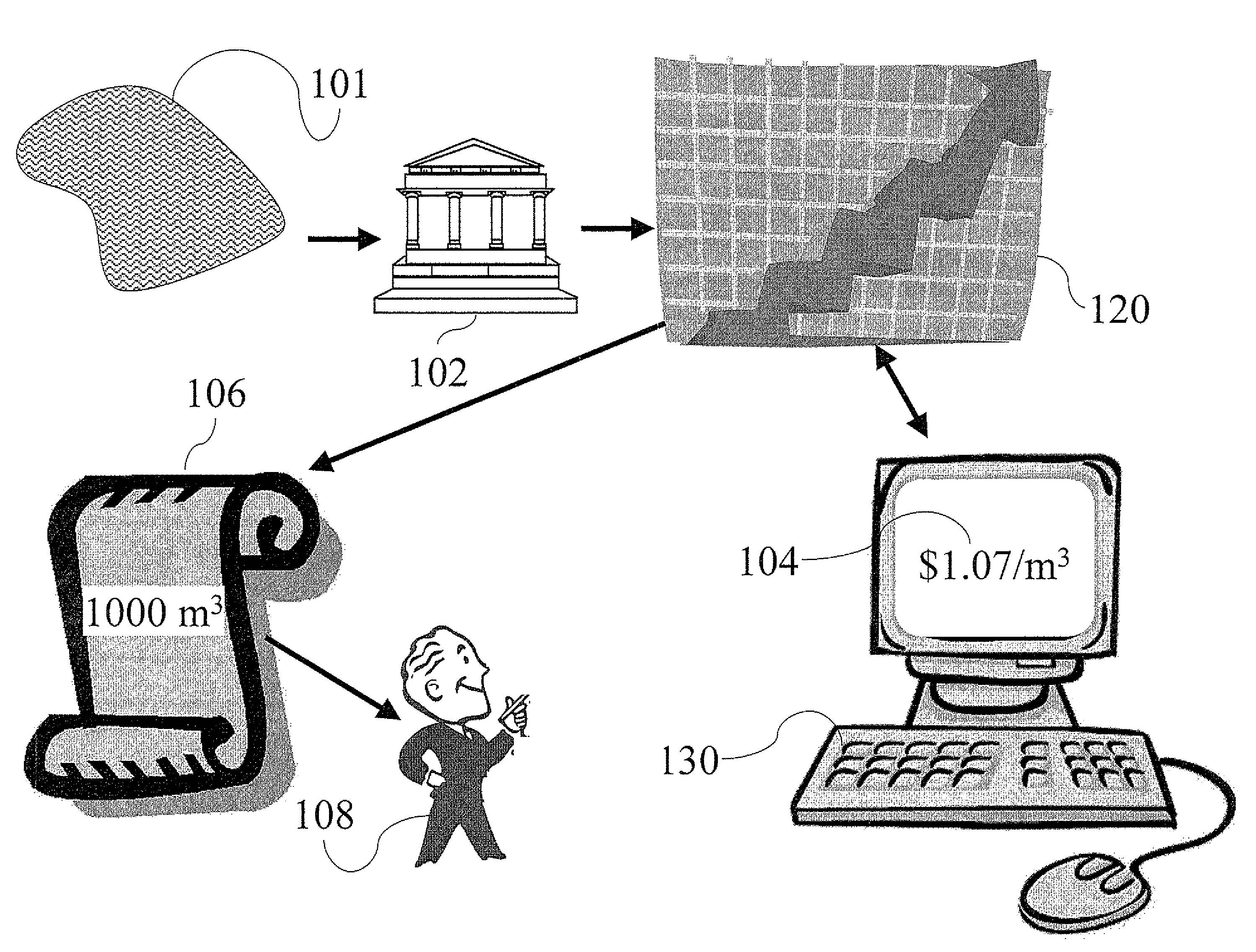
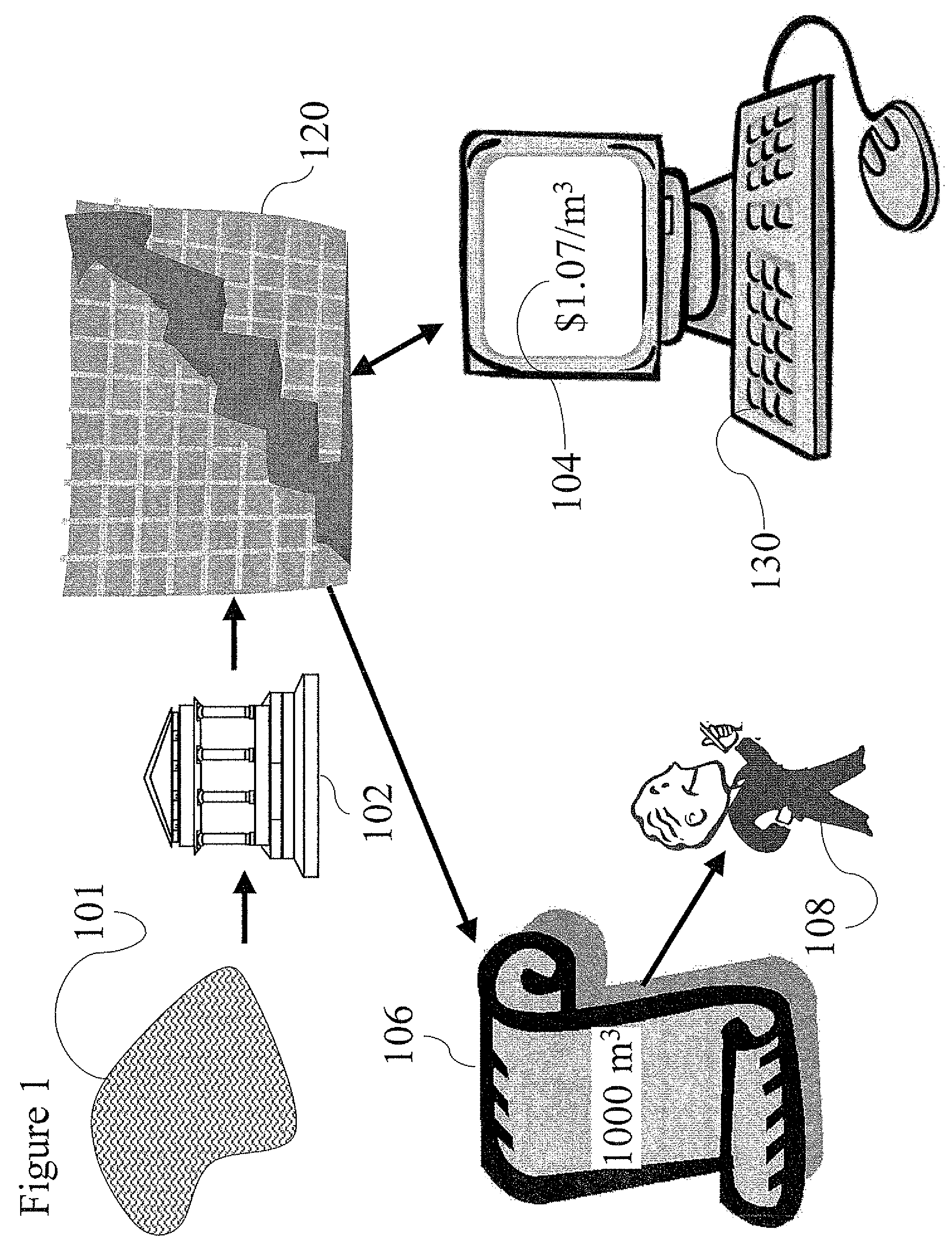
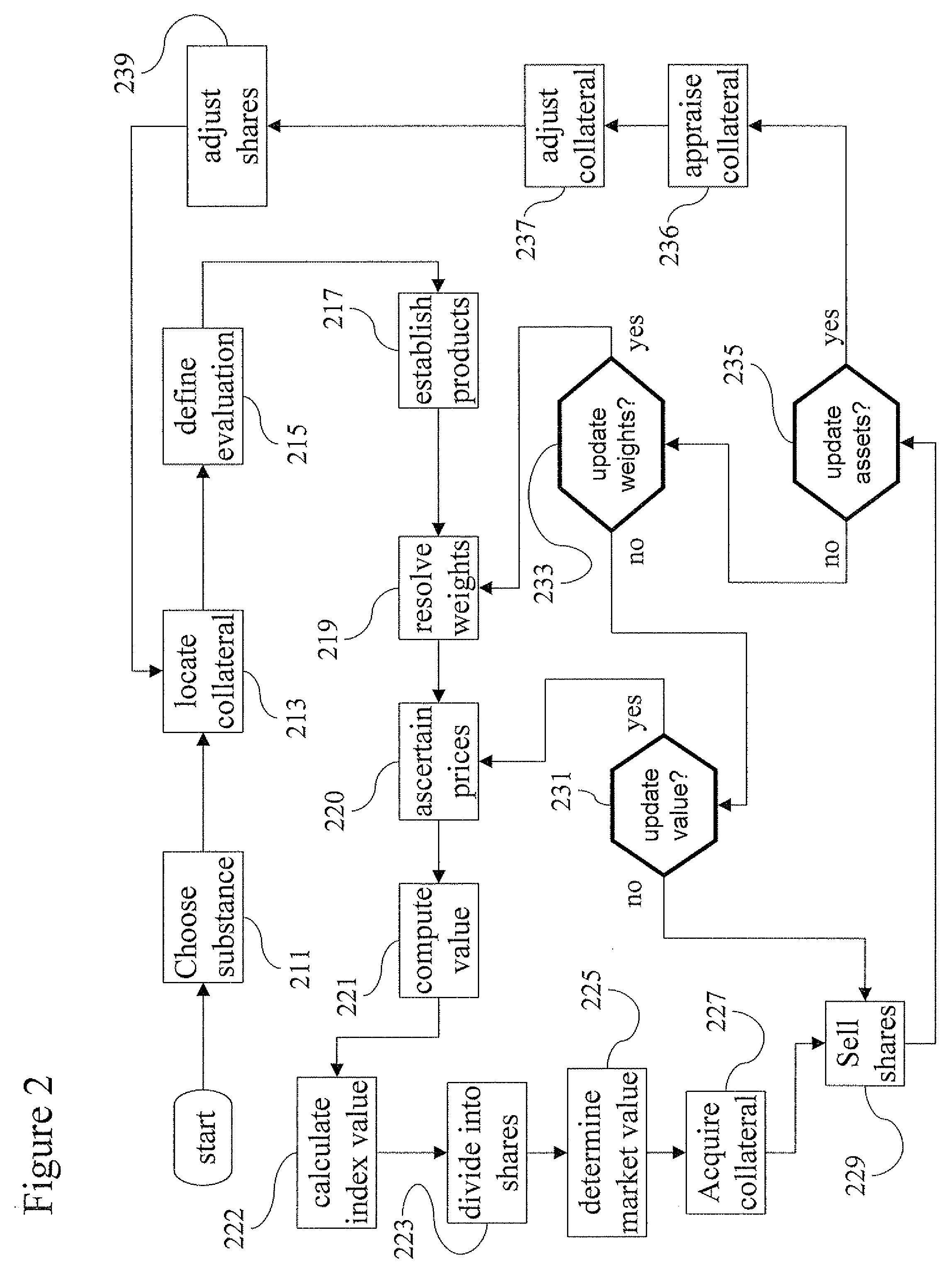
Aqua index
ActiveUS20090055294A1Facilitate in substanceComplete banking machinesGeneral water supply conservationMedicineMarketed products
A method and system for computing a stable index value of a regulated substance by computing a virtual value of the substance based on the value of a freely marketed product of the substance. Particularly the invention may be applied to develop a stable investment instrument for investing in fresh water.
Owner:AQUA INDEX
Aqua index
A method and system for computing a stable index value of a regulated substance by computing a virtual value of the substance based on the value of a freely marketed product of the substance. Particularly the invention may be applied to develop a stable investment instrument for investing in fresh water.
Owner:AQUA INDEX
Security inherent wrap label with patterned adhesive
A patterned adhesive tag applied to separable-lid containers, hinged-lid containers, film-lid containers, and other packaged products. The patterned tag adhesive is designed to add security to the packaging of the goods, such that when an unauthorized person tries to remove the tag, it will tear, indicating an unauthorized entry, and caution against purchase or usage of the product. The tag is designed to wrap around a plurality of sides of the packaged product. The tag may be multi-layered through the usage of additional adhesives and substrates to facilitate couponing and booklet applications for the marketed product.
Owner:WILLIAMS ROBERT E
Methods and systems for monitoring the efficacy of a marketing project
ActiveUS7349865B2Mitigate compliance riskReduce the burden onCash registersMarketingMarketed productsComputer science
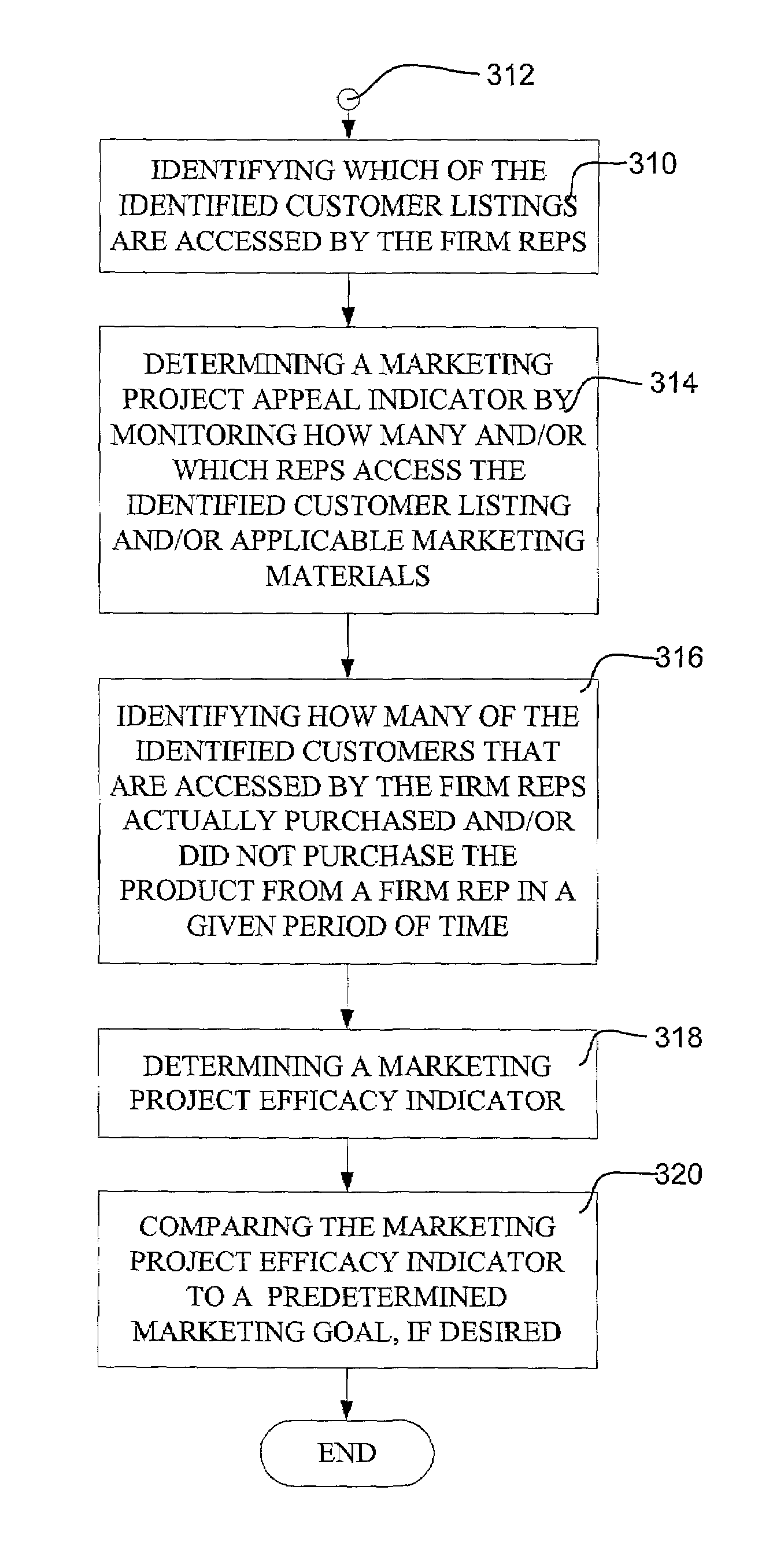
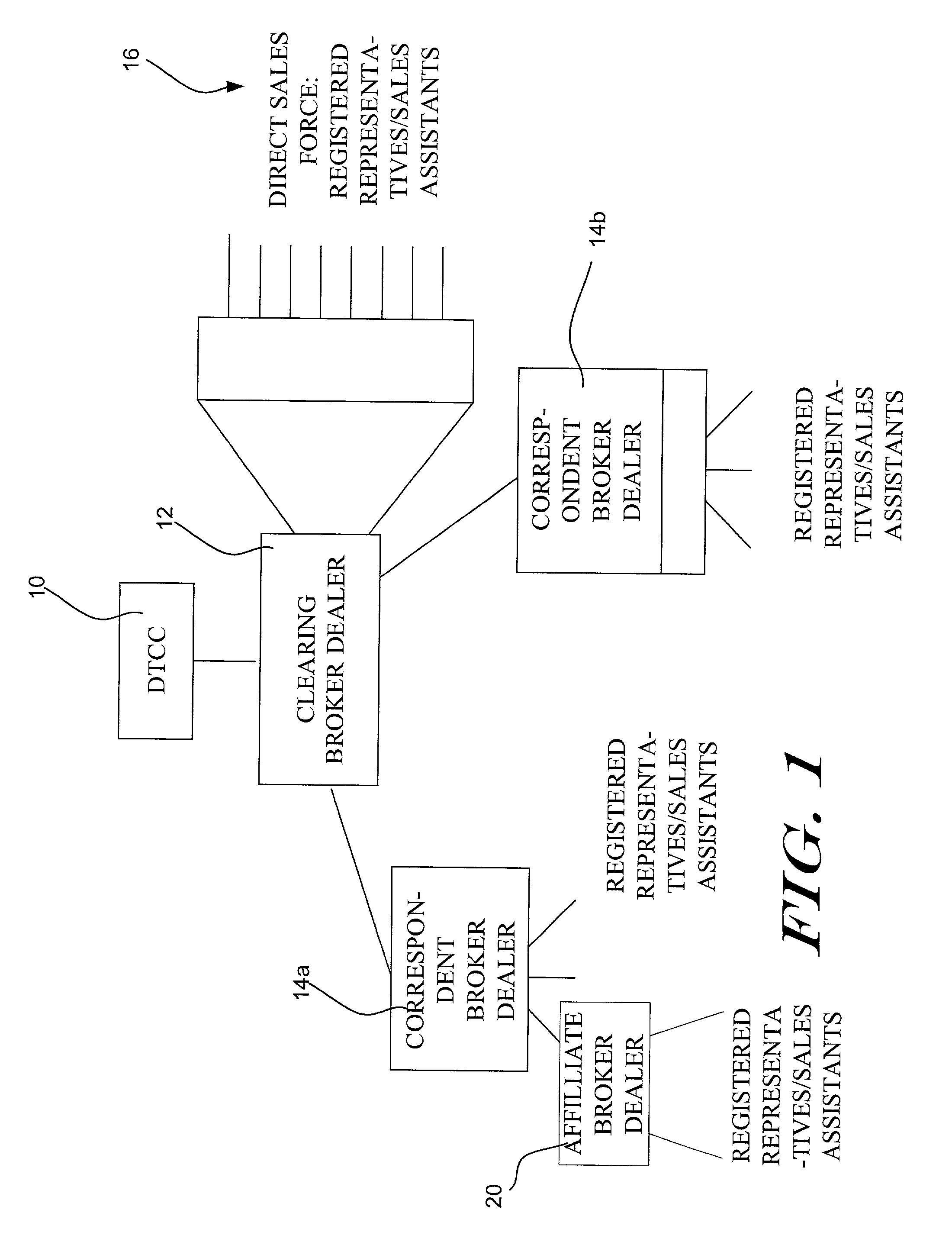
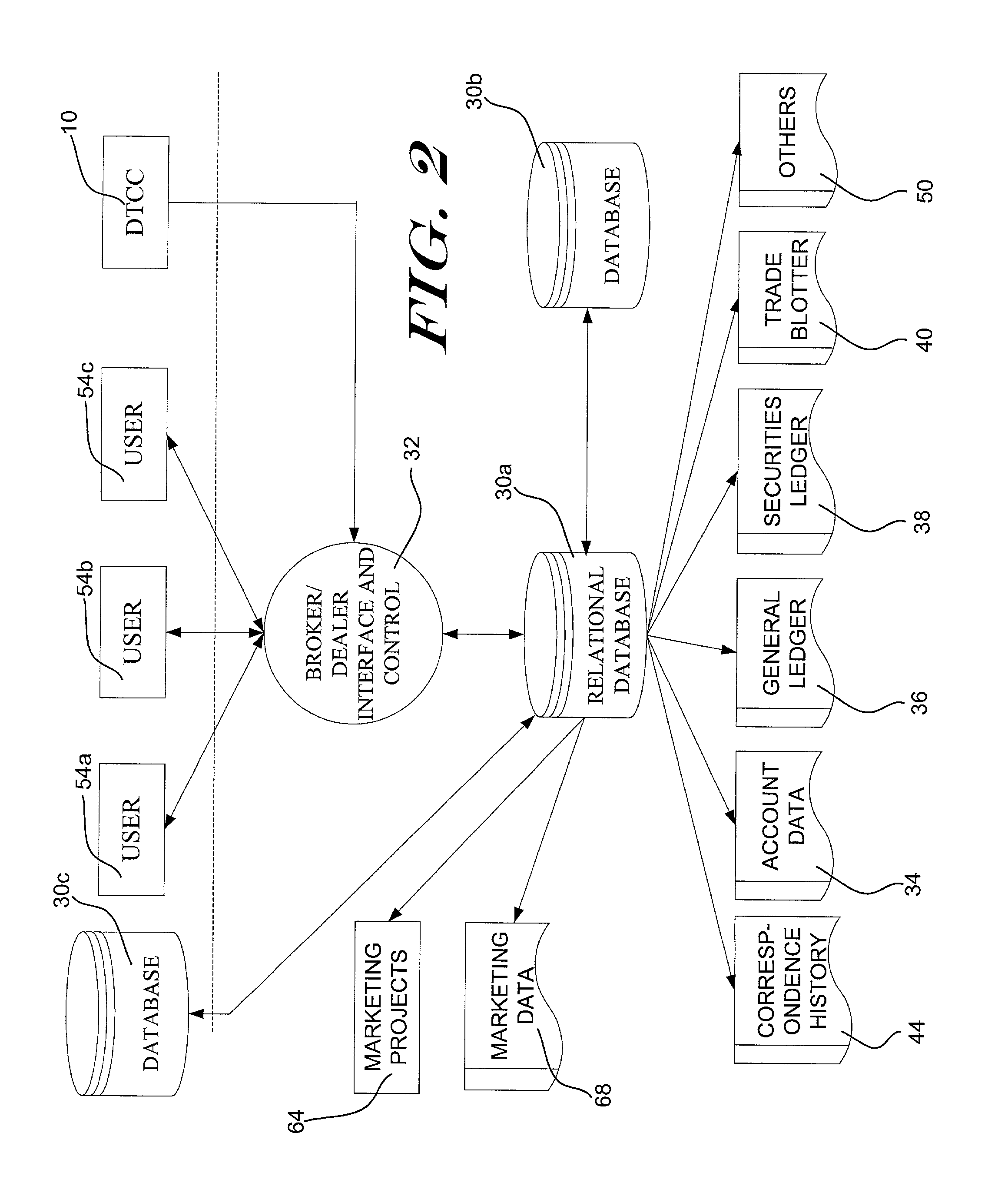
Methods and systems for monitoring the efficacy of a marketing campaign or project. In one embodiment, a customer database stores information about each customer of a firm or business. A number of marketing project parameters are then defined, and run against the information in the customer database to identify those customers that are likely to be interested in a marketed product. The identified customers are notified about the marketed product, preferably through a representative of the firm or business. Then, each sale of the marketed product to the identified customers is recorded. A marketing project efficacy indicator can then be determined by, for example, comparing the number of customers that were notified about the product with the number of customers that actually purchased or did not purchase the product, preferably within a given time period. Preferably, marketing efforts can then be refined based on a timely analysis of the marketing project efficacy.
Owner:BROADRIDGE SECURITIES PROCESSING SOLUTIONS
Precision tourism marketing method based on Internet big data
PendingCN110942337AAdjust in timeMarket predictionsDigital data information retrievalPersonalizationDemographic Accounting
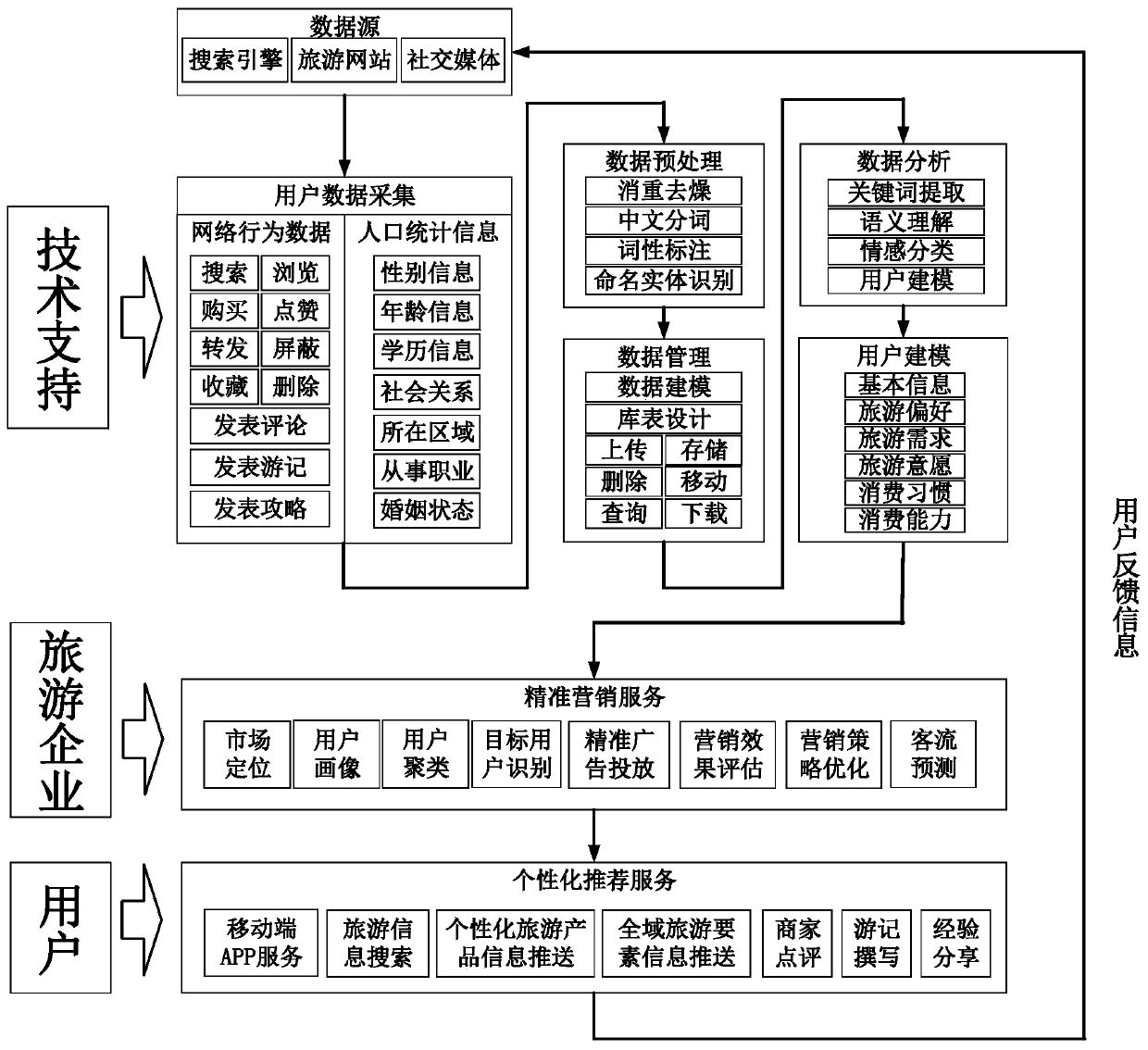
The invention discloses a precision tourism marketing method based on Internet big data. The method comprises the following steps: extracting target features of a user from user behavior data acquiredby the Internet, establishing a dynamic label in combination with demographic information data, performing user portraying by tagging the user, and then identifying a target user by analyzing, locking and identifying on the basis of user clustering; and calculating the matching degree of the target user and the to-be-marketed product, sending corresponding marketing information by means of the Internet according to the matching degree, continuously obtaining user feedback, and reprocessing the marketing information. According to the method, personalized and differentiated marketing strategiescan be implemented, and the marketing strategies can be adjusted in time according to real-time effect feedback.
Owner:天津中科智能识别有限公司
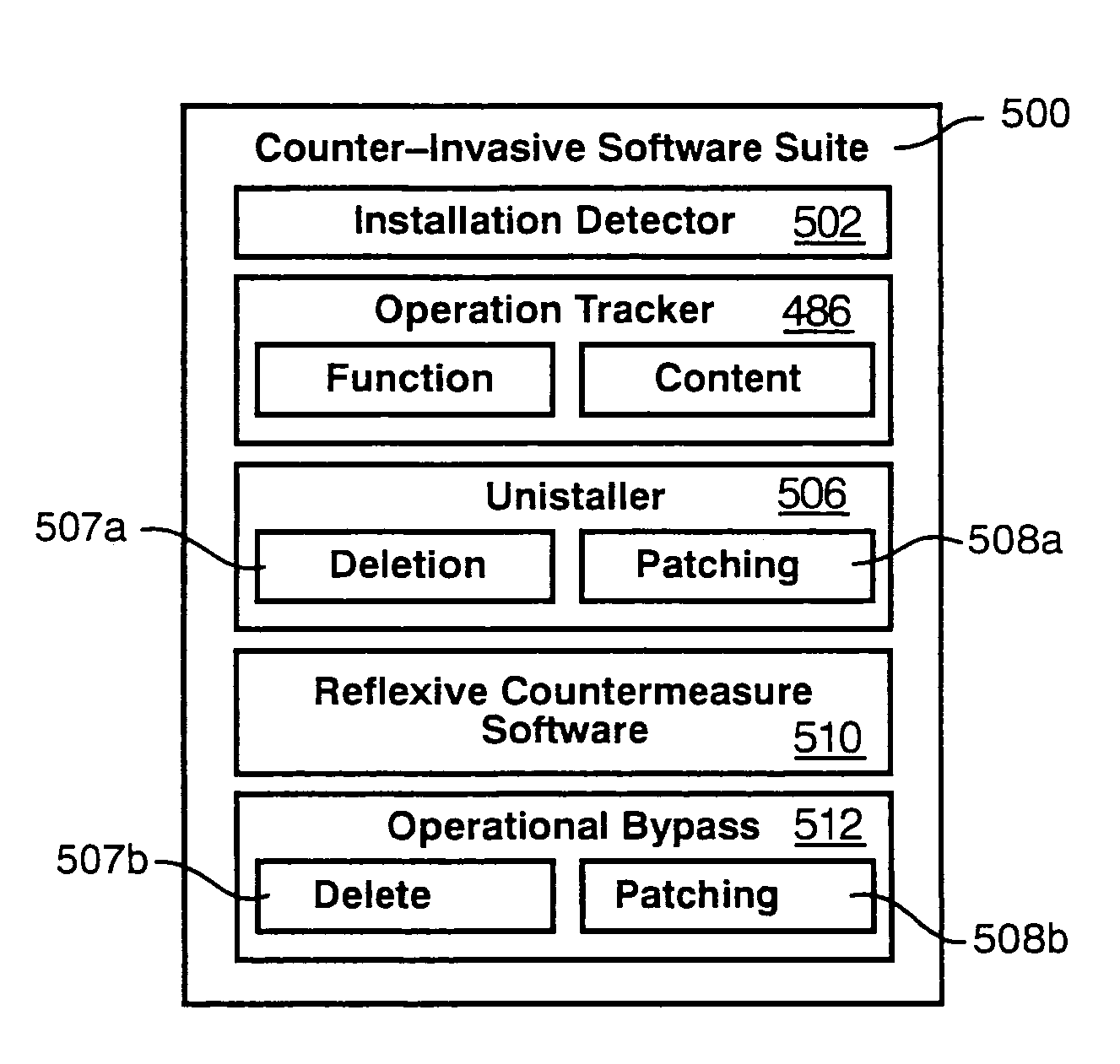
Counter-invasive software system and method
ActiveUS7430689B1Improper installationUnauthorized memory use protectionHardware monitoringRegimenSoftware system
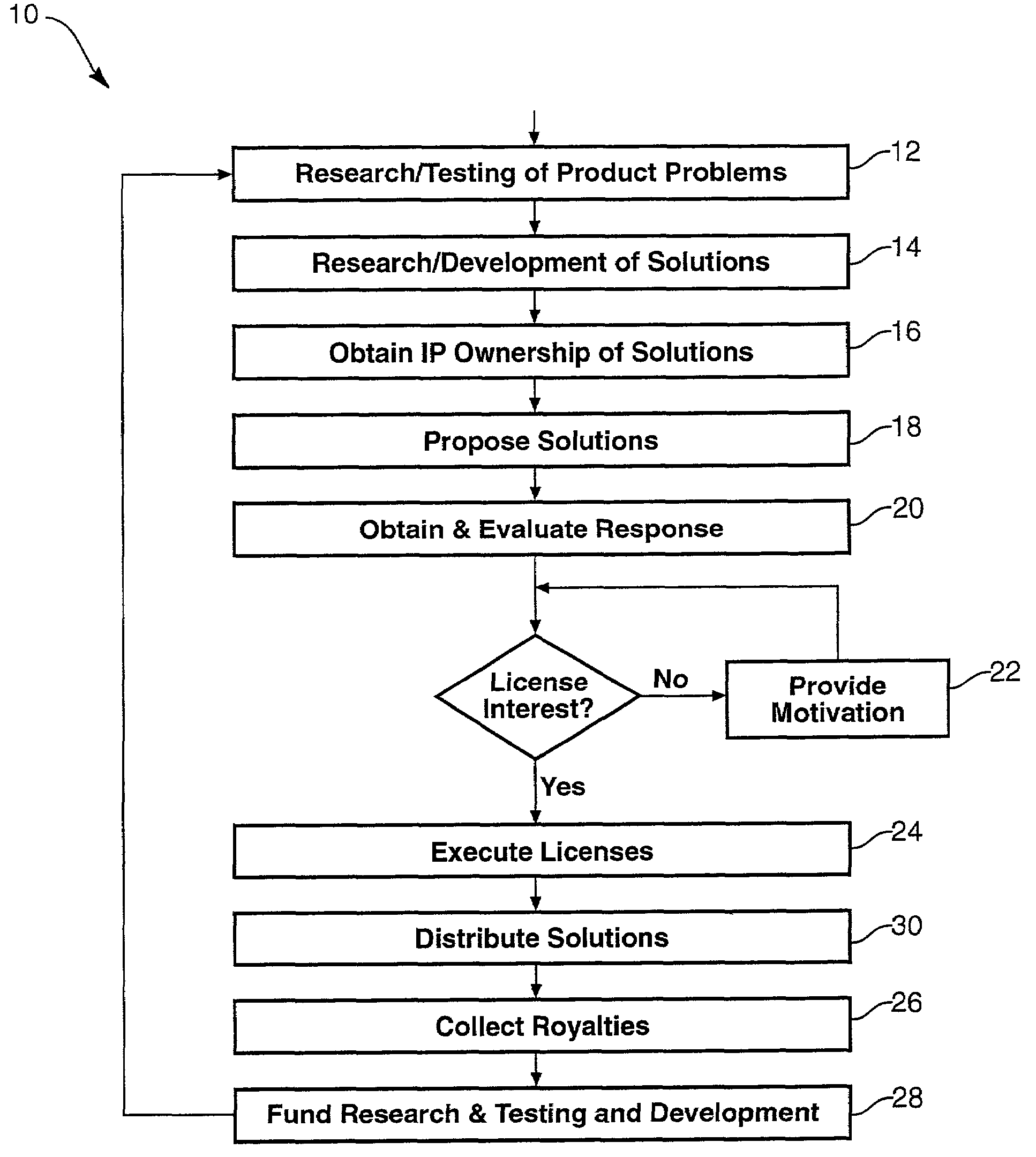
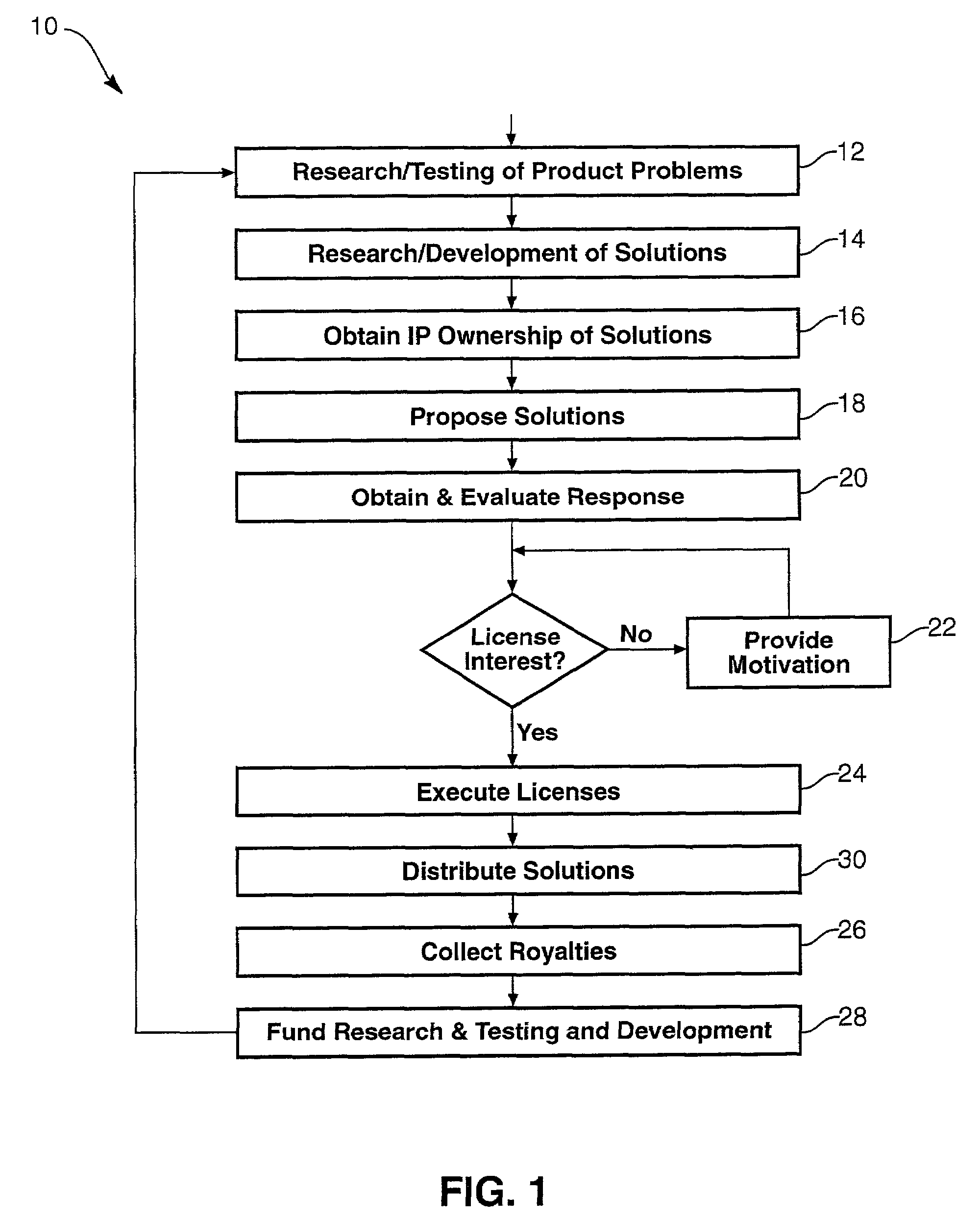
A method and apparatus for detecting, curing and remedying invasive software installation inadvertently, negligently, or intentionally marketed by a vendor. A party may procure a product that sends back invasive data to a source. A testing regimen may identify and defeat sources of any invasive executables found. Accordingly, a party may identify those software packages deemed invasive, and may optionally provide a solution to either defeat or monitor them, where practicable. An independent developer may obtain intellectual property rights in the testing, solution or both of the counter-invasive software system or product. An independent developer may become a supplier of testing or solution systems, motivating a supplier by one of several mechanisms. The developer or damaged party may obtain a legal status with respect to the vendor or of a host of software as a customer, user, clients, shareholder, etc., in order to exercise rights and remedies or provide motivation to a vendor who does not take responsibility for its actions as executed by its marketed products.
Owner:ADAMS PHILLIP M
Active marketing based on client computer configurations
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
Composition for double clutch gearbox oil, use of composition and lubricating oil comprising composition
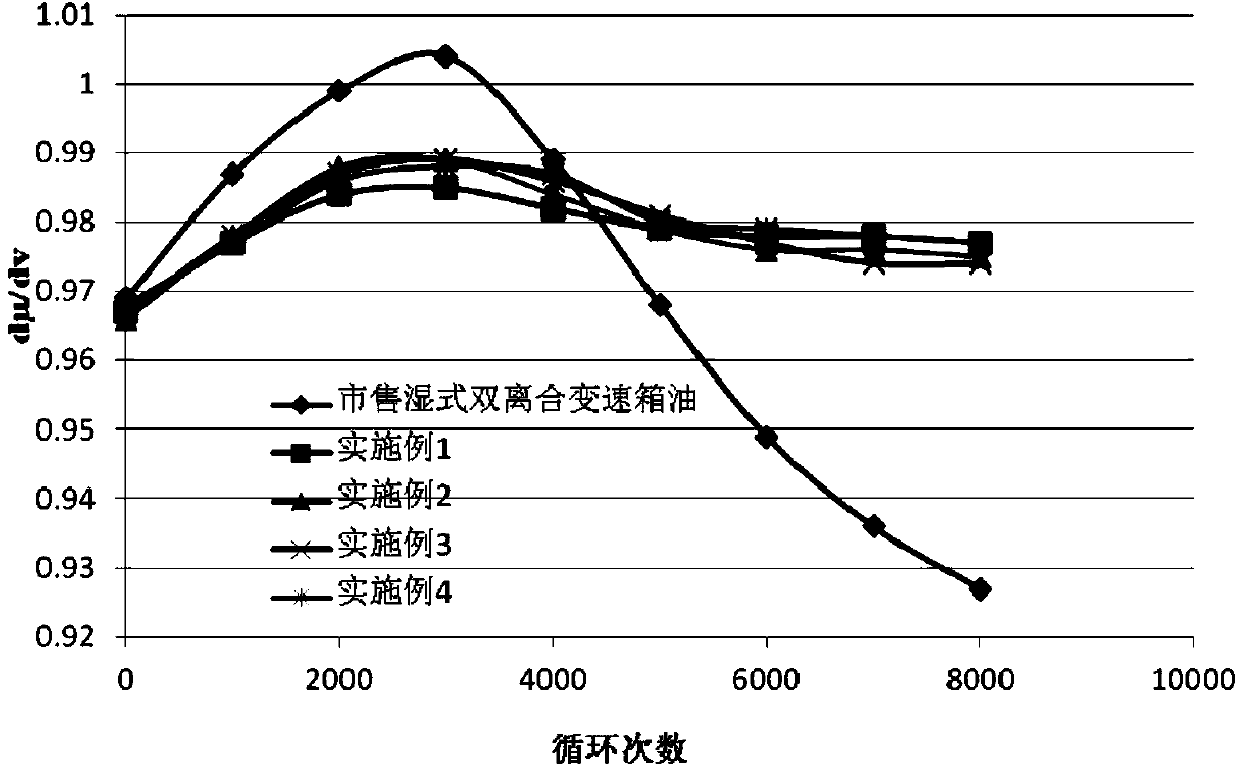
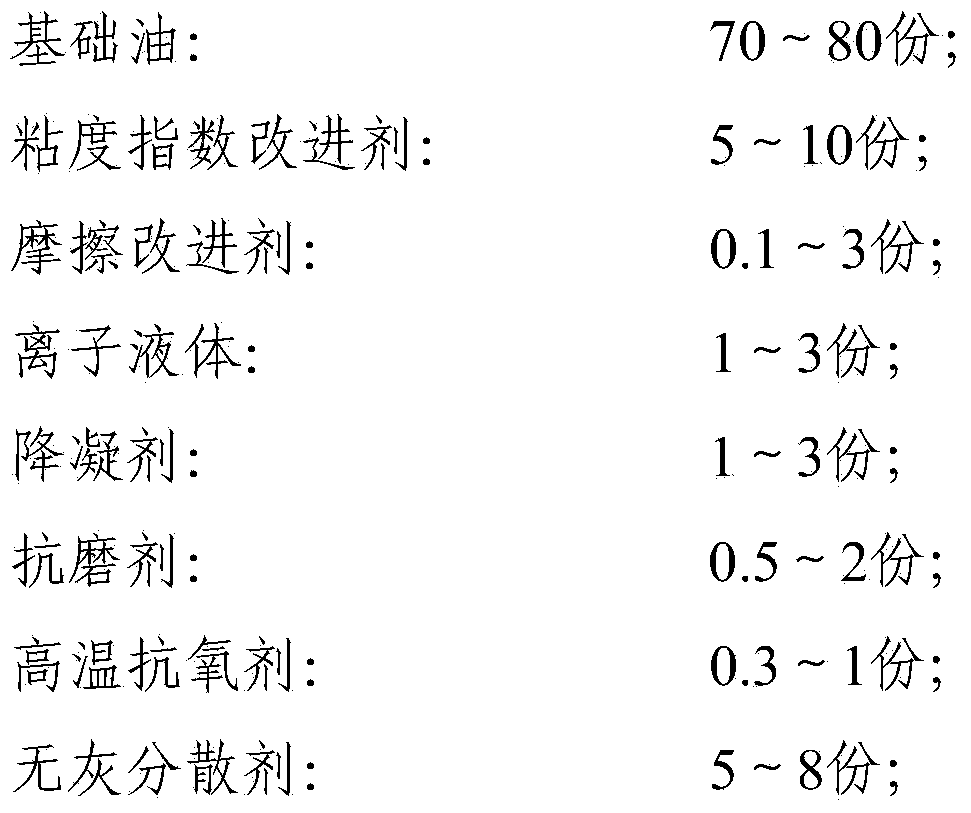
InactiveCN104194881AGood low temperatureImprove friction characteristicsAdditivesMarketed productsViscosity index
The invention relates to a composition for double clutch gearbox oil. The composition comprises the following components in parts by mass: 0.5-15 parts of viscosity index improver, 0.05-10 parts of friction improver and 0.1-10 parts of ionic liquid. The invention further relates to use of the composition and wet type double clutch gearbox lubricating oil comprising the composition. The composition provided by the invention can satisfy the lubricating requirements of clutches, a synchronizer, a gear and a bearing in a wet type double clutch gearbox, and thus can be used for the wet type double clutch gearbox lubricating oil. The lubricating oil has excellent low temperature performance, frictional characteristic, performance of the synchronizer and rust and corrosion resistance. Compared with similar marketed products, the lubricating oil added with the composition has a remarkable advantage in wearing endurance and is simple in ingredients and simple and convenient in manufacturing process.
Owner:CHINA PETROLEUM & CHEM CORP
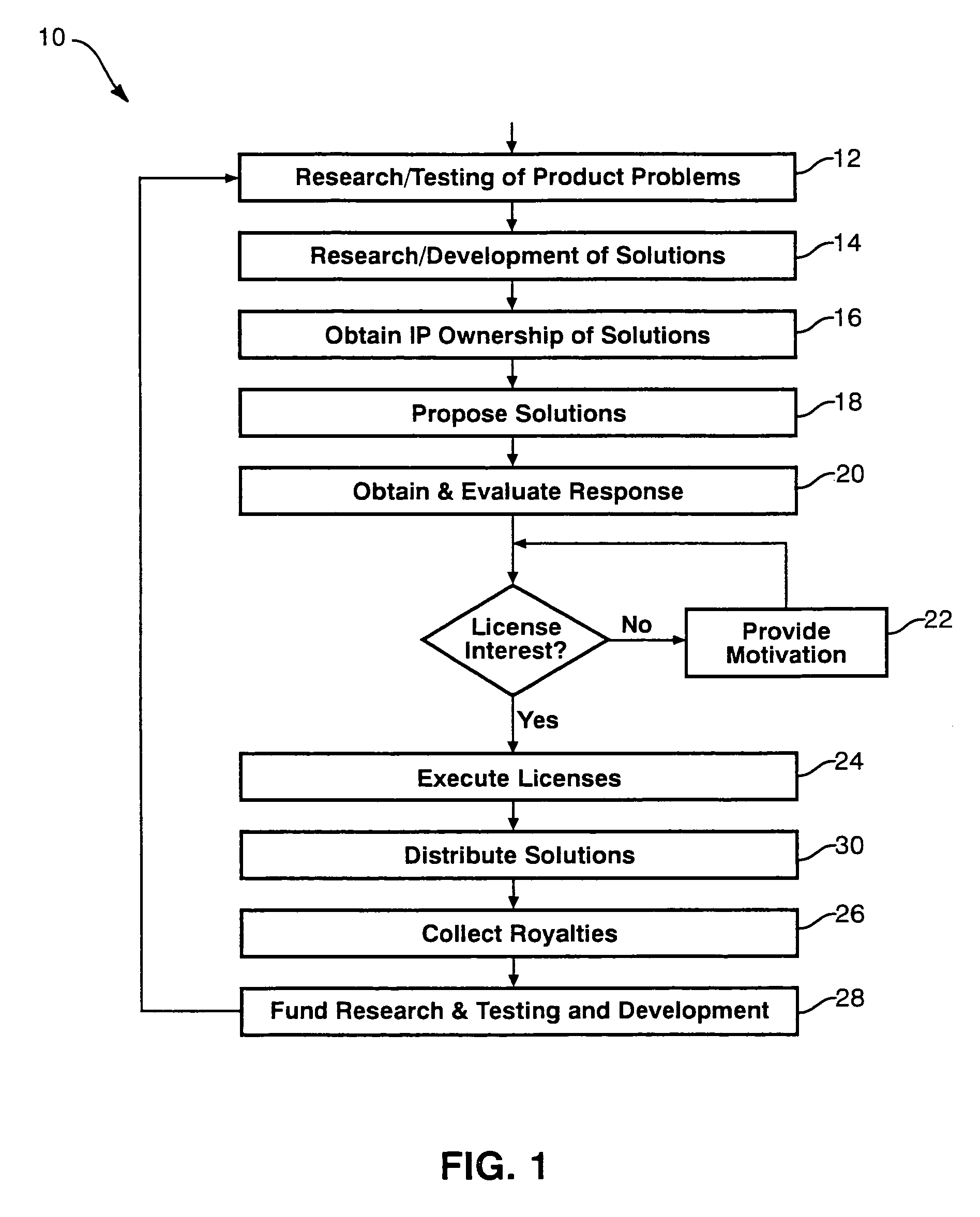
Computerized product improvement apparatus and method
ActiveUS7251752B2Error detection/correctionComputer security arrangementsRegimenIntellectual property
A method and apparatus for improvement of computer-related products by an independent developer may solve problems in hardware or software inadvertently, negligently, or intentionally left in products marketed by a vendor. An independent developer may procure access to a product, develop a testing regimen for functionality of the product, and perform evaluations to identify sources of any operational defects found. Accordingly, the developer may then provide a generalized testing regimen to test instances of product provided by a vendor, identify those containing the flaw, and may optionally provide a solution to the flaw, where practicable. The independent developer may obtain intellectual property rights in the testing, solution or both for the product. Thus, by notifying a vendor, an independent developer may become a supplier of testing or solution systems, motivating a supplier by one of several mechanisms. The developer may obtain a legal status with respect to the vendor by becoming a customer or user, in order to provide motivation to a recalcitrant vendor not designed to take responsibility for defects known and continued in marketed products.
Owner:ADAMS PHILLIP M
Novel crystal form of valnemulin hydrogen tartrate and preparation method thereof
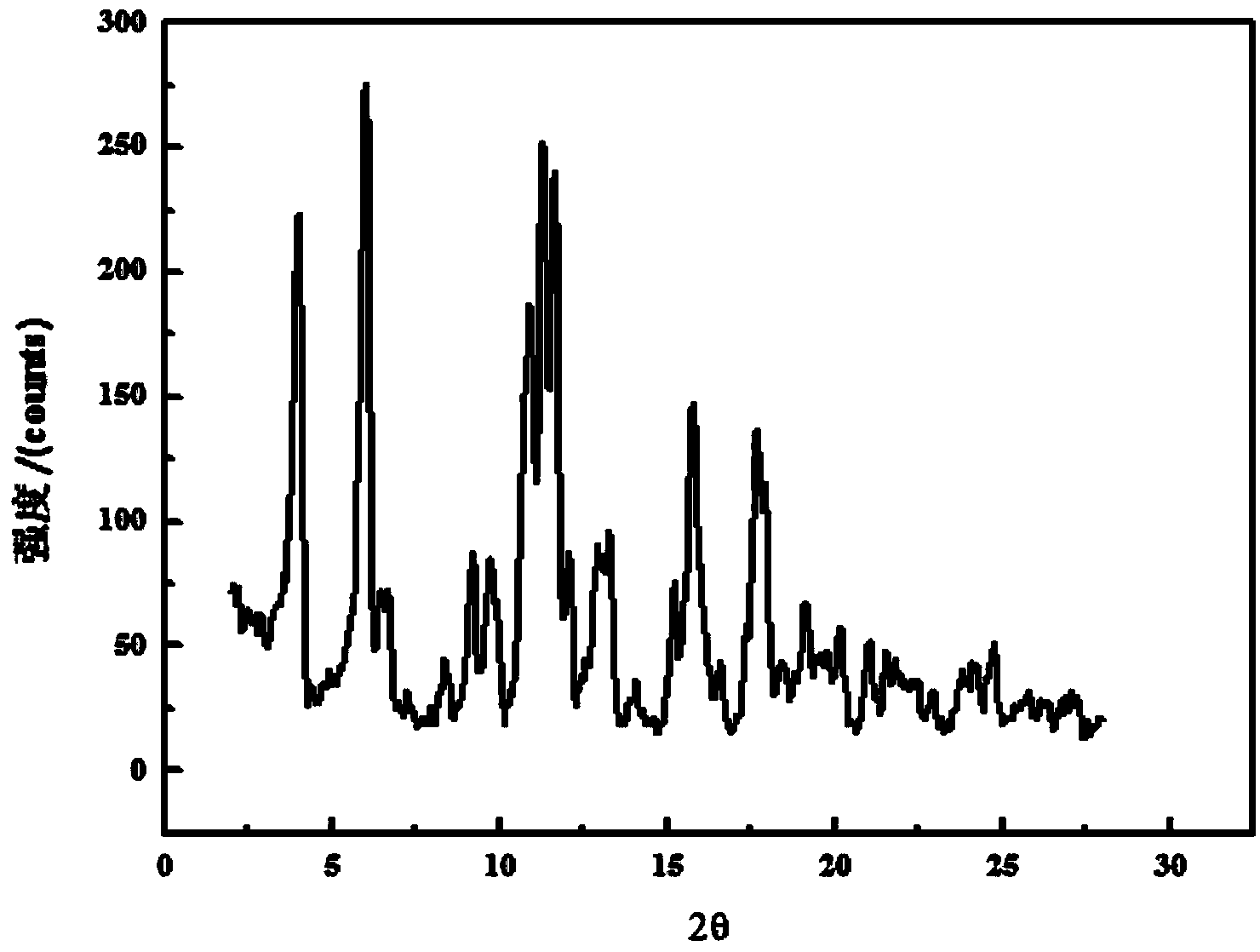
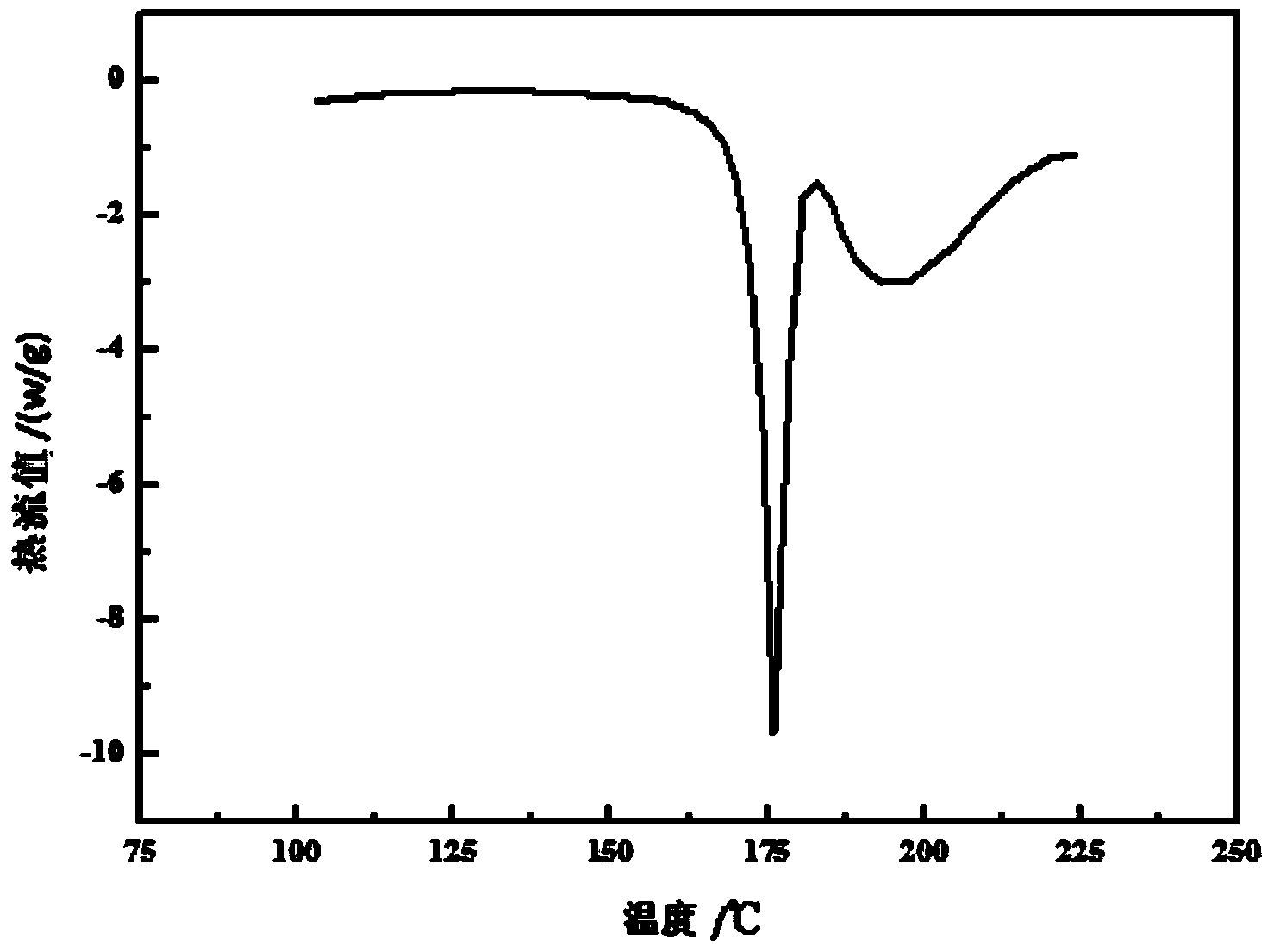
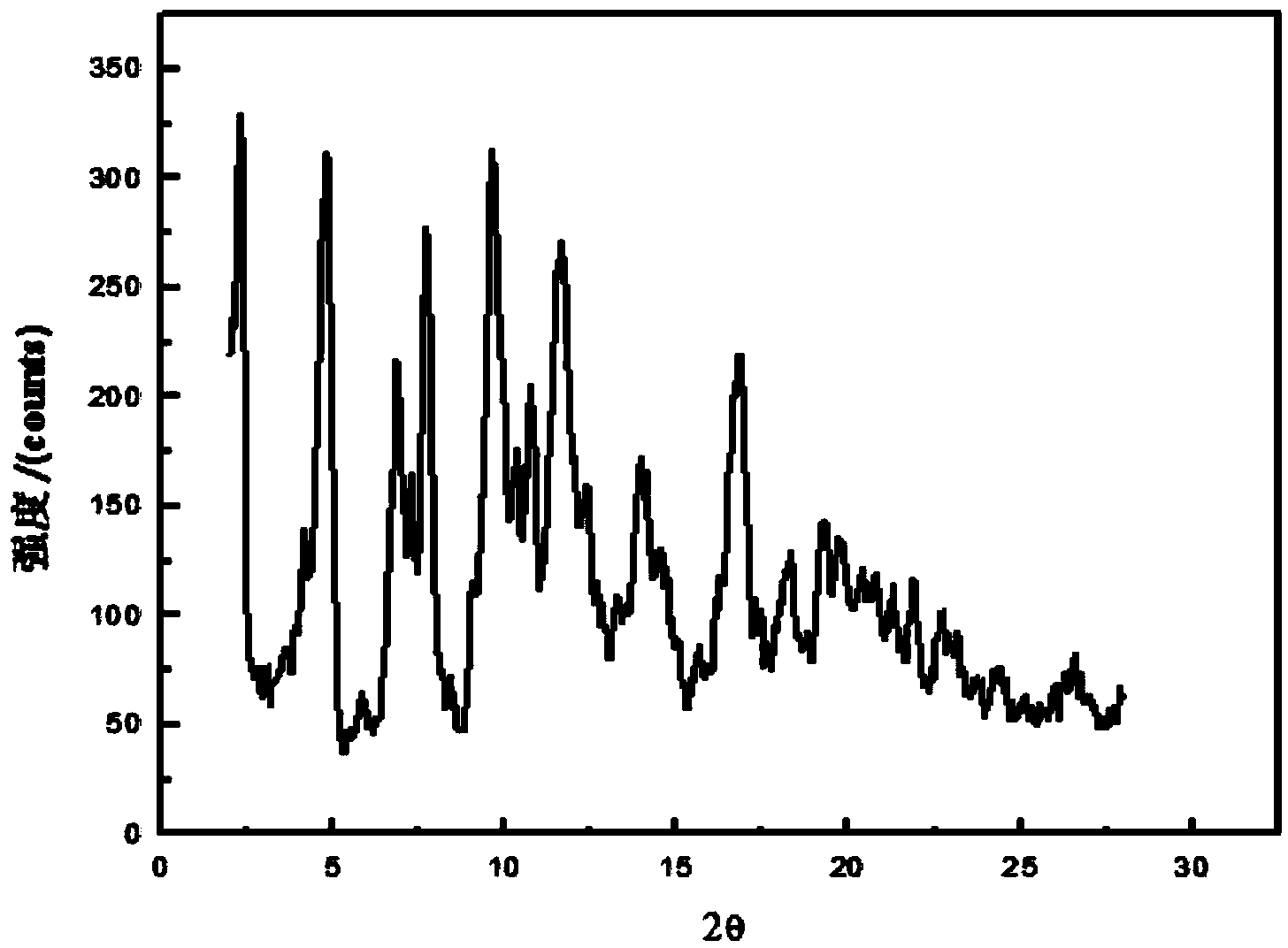
ActiveCN103755609AHigh crystallinityXRD pattern peak intensityOrganic compound preparationCarboxylic acid salt preparationSolubilityN dimethylformamide
The invention relates to a novel crystal form of valnemulin hydrogen tartrate and a preparation method thereof. The method comprises the steps of dissolving valnemulin hydrogen tartrate with the purity being over 95% into a mixed solvent of an ester solvent and N,N-dimethylformamide, adding an elution agent after complete dissolution so as to carry out elution crystallization, then, cooling a solution to the temperature of 5-15 DEG C, and washing, filtrating and drying crystal slurry, thereby obtaining a valnemulin hydrogen tartrate product. An X-ray powder diffraction atlas of the crystal has characteristic peaks when a diffraction angle 2[theta] is equal to 2.5, 4.8, 7.4, 7.5, 10.1, 11.2, 11.7, 13.8 or 17.1 degrees. According to the novel crystal form, during crystallization, the yield reaches over 90%, the product purity reaches over 98%, the product is high in crystallinity, good in stability, difficult in moisture absorption and high in solubility, the water solubility at normal temperature reaches 6.5g / 100mL and is increased by about 30% compared with that of the currently marketed products, and the water stability is good, so that the product can be conveniently prepared into a premix.
Owner:TIANJIN UNIV
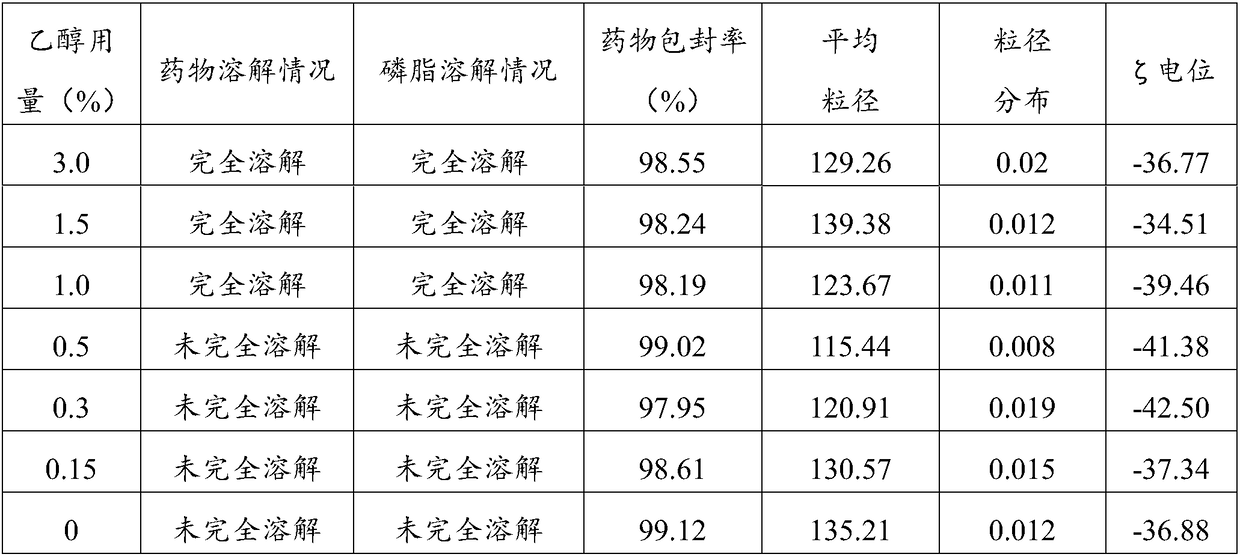
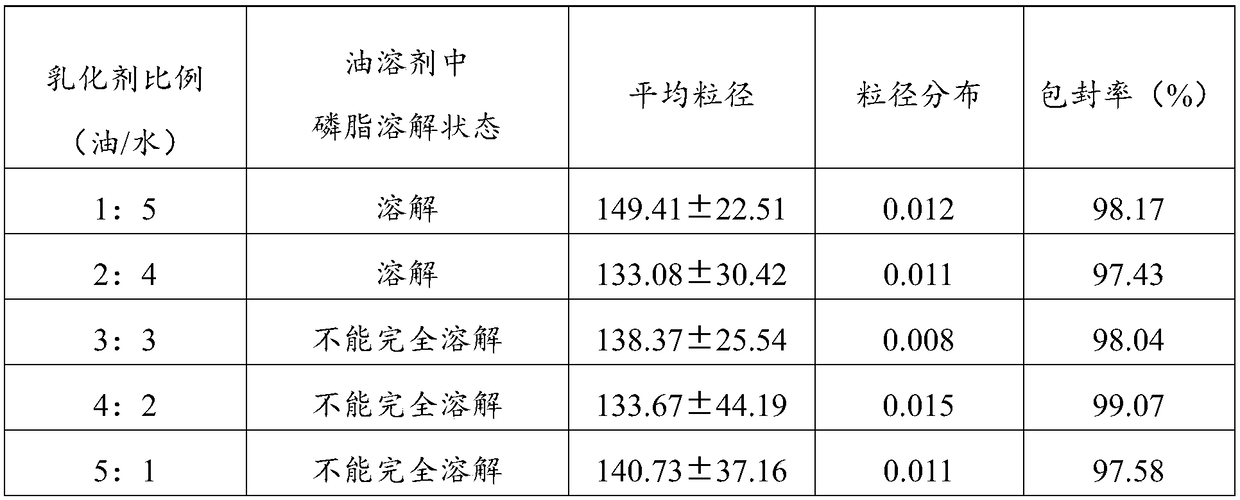
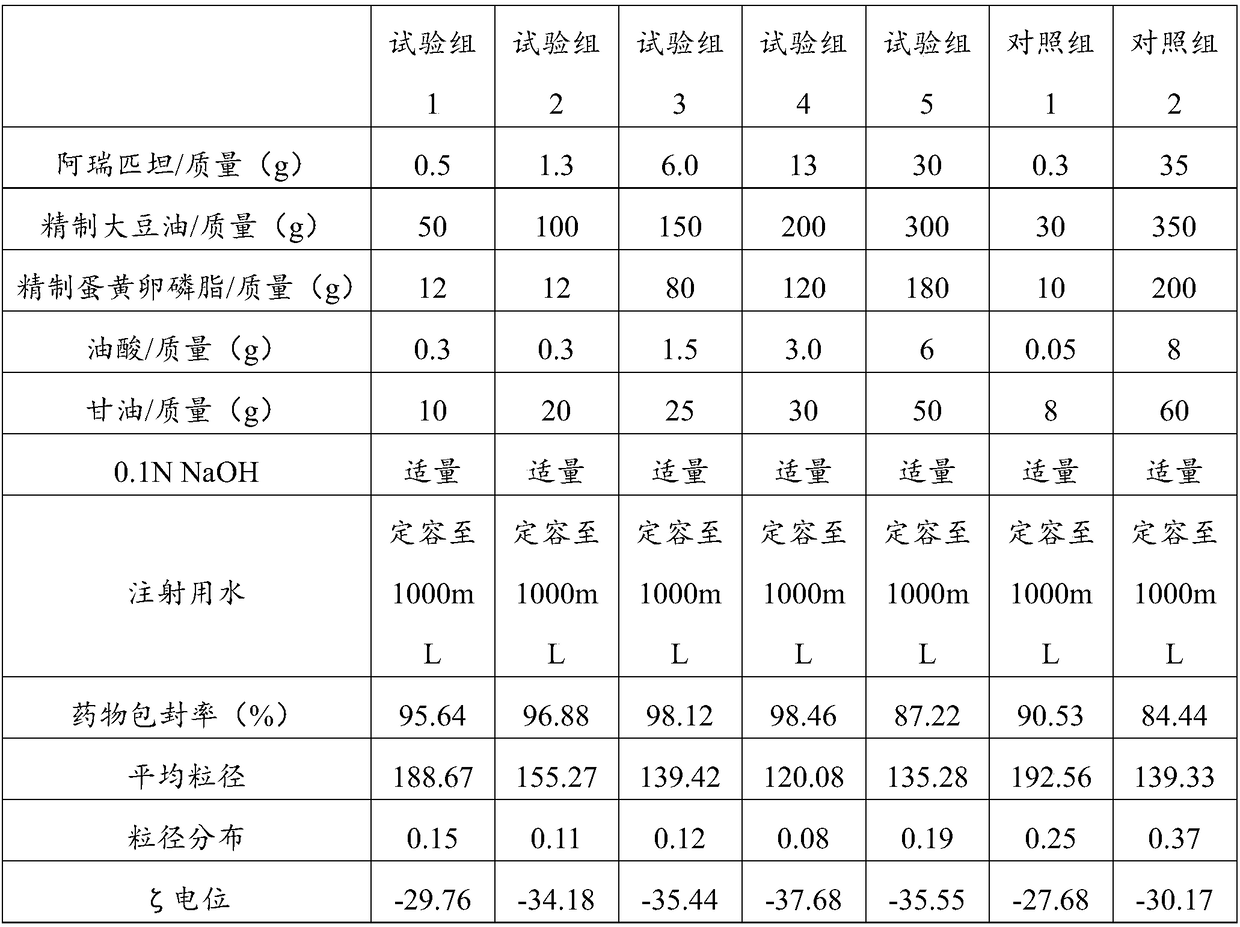
Aprepitant intravenous injection emulsion as well as preparation method and application thereof
PendingCN109364023AImprove liquidityNo hanging phenomenonOrganic active ingredientsDigestive systemHigh dosesMarketed products
The invention relates to aprepitant intravenous injection emulsion as well as a preparation method and an application thereof, and belongs to the technical field of pharmaceutics. The aprepitant intravenous injection emulsion is prepared from components in percentage by mass as follows: 0.05%-3% of aprepitant, 5%-30% of an oil phase solvent, 1.2%-18% of an emulsifier, 0.03%-0.6% of a stabilizer and 1%-5% of an isoosmotic adjusting agent, the injection emulsion further contains a pH regulating agent and the balance of water for injection, and pH value of the injection emulsion is 5.5-8.0. The aprepitant intravenous injection emulsion contains no low-carbon chain alcohol such as ethanol and the like, meanwhile, the quality requirement for a marketed product can be met by technological innovation and adjustment, and clinical use safety of the aprepitant intravenous injection emulsion is greatly improved; direct intravenous injection is utilized during clinical using, and dilution is not needed; the aprepitant intravenous injection emulsion can be used for treating acute and tardive nausea and vomiting caused by high-dose cis-platinum combined high-dose sensitizing cancer chemotherapy,and nausea and vomiting in early stage and middle stage of tumor chemotherapy are reduced.
Owner:GUANGZHOU HANFANG PHARMA
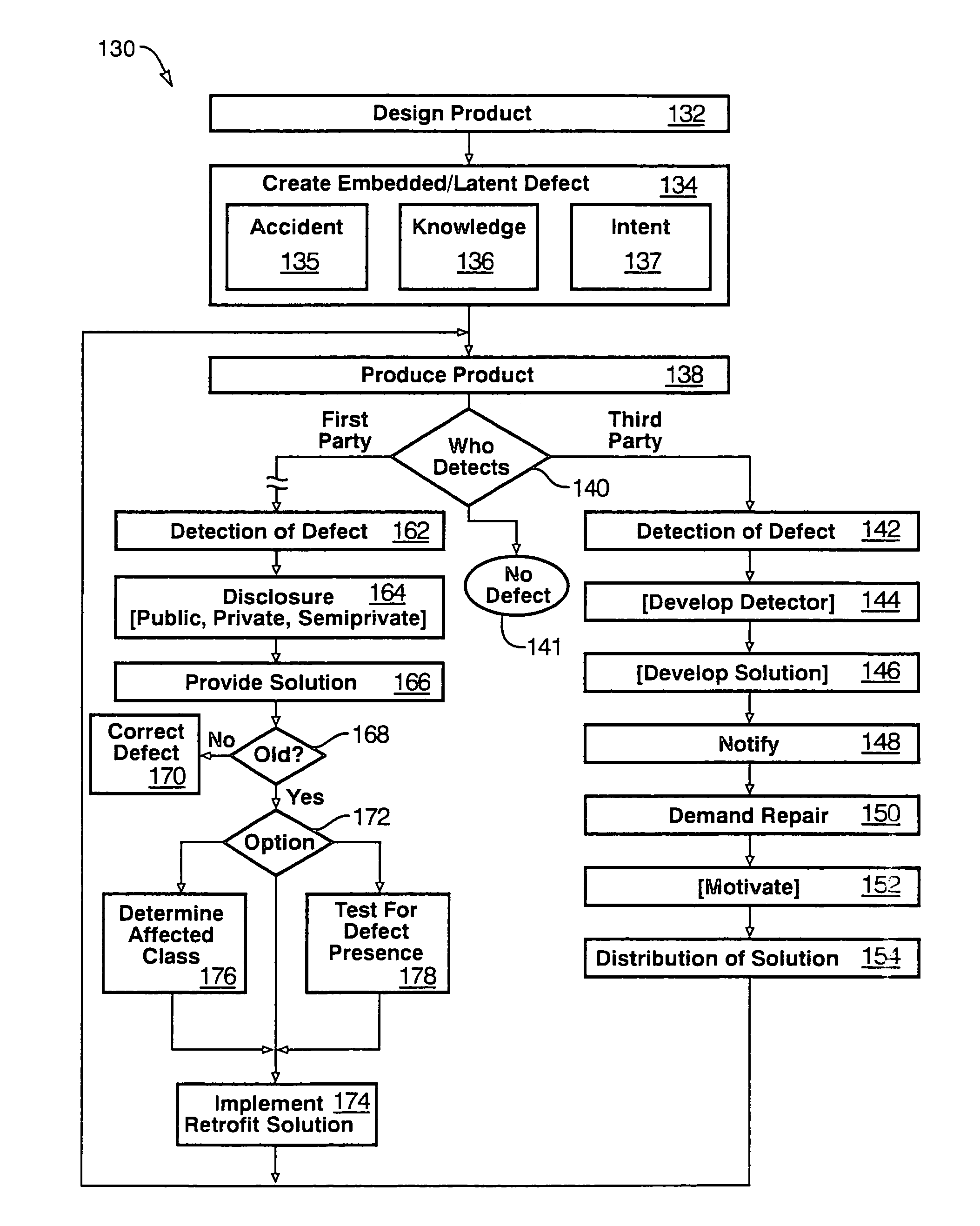
Enforcement process for correction of hardware and software defects
InactiveUS7363237B1Extended service lifeAvoid operation failureData processing applicationsManufacturing computing systemsComputer hardwareRegimen
A method and apparatus for improvement of computer-related products to solve problems caused by artificially embedded locks, barriers, defects, and the like, that force a consumer to needlessly upgrade hardware or software on a computer. An independent developer may procure access to a product, develop a testing regimen for functionality of the product, and perform evaluations to identify sources of any operational defects found. Accordingly, the developer may then provide a generalized testing regimen to test instances of product provided by a supplier, identify those containing the flaw, and may optionally provide a solution to the flaw, where practicable. The independent developer may obtain intellectual property rights in the testing, solution or both for the product. Thus, by notifying a supplier, an independent developer may become a supplier of testing or solution systems, motivating a supplier by one of several mechanisms. The developer may obtain a legal status with respect to the supplier by becoming a customer or user, in order to provide motivation to a recalcitrant supplier not designed to take responsibility for defects known and continued in marketed products.
Owner:ADAMS PHILLIP M
Medicinal composition containing Aerican ginseng and tuber of dwarf lily turf effective part and its preparing method
InactiveCN1616055AEnhance pharmacological effectsPowder deliveryAntiviralsMarketed productsTraditional medicine
The present invention discloses one medicinal composition containing the effective parts of American ginseng and ophiopogon root and its preparation process. The present invention features that extracted and purified effective parts of American ginseng and ophiopogon root and medicinal supplementary material are prepared into the injection preparation, and that the medicine composition has excellent pharmacological effect and limited content of panoxadiol saponin with bad hemolytic reaction, and thus safe clinical application. Pharmacological experiment shows that the medicine composition preparation has even high pharmacological effect and safety compared with similar marketed product.
Owner:张平
Decontamination liquid for protecting human bodies from being burned by chemical substances
InactiveCN105079030AImprove permeabilityProtection securityInorganic boron active ingredientsDermatological disorderAlcoholMarketed products
The invention relates to human body decontamination liquid in the field of industrial safety protection. The human body decontamination liquid can protect human bodies from being burned by chemical substances. The human body decontamination liquid comprises chelating agents, sugar, alcohol, complexing agents, univalent metal salt and water. The human body decontamination liquid which is a composition has the advantages that chemical hazardous articles such as acid, alkali, oxidizing agents, reducing agents, complexing agents and solvents can be converted into products which are harmless to the human bodies and environments, and accordingly secondary injury and pollution can be prevented; the composition has merits and potential in the aspects of chemical hazardous article decontamination potency, safety and the like as compared with products with single corrosion-resistant components on markets; the human body decontamination liquid is suitable for emergency protection and rescue during industrial production, so that burning and erosion on the human bodies due to the chemical substances can be relieved.
Owner:重庆市化工研究院有限公司
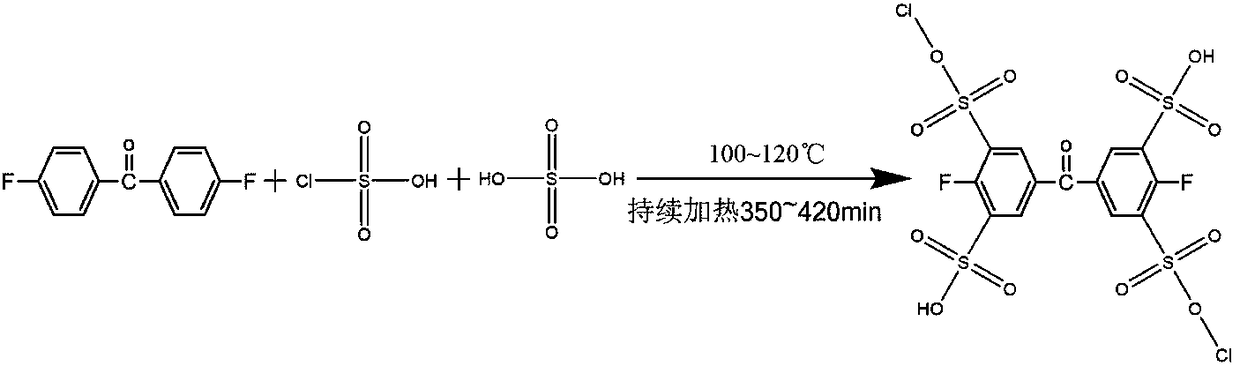
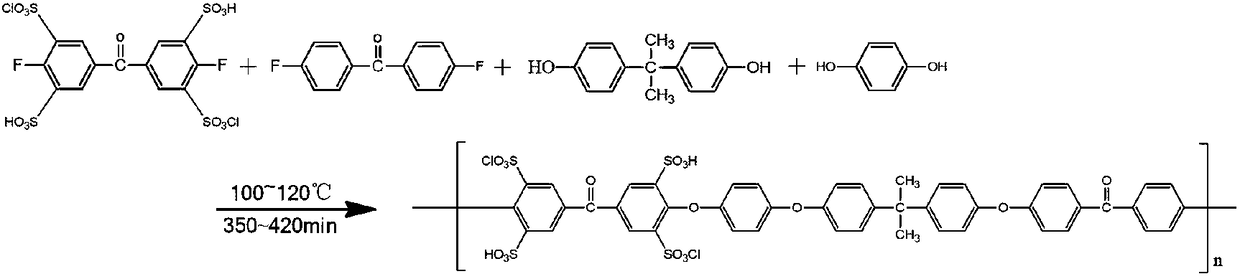
Preparation method of chlorosulfonated polyether-ether-ketone composite material film
The invention belongs to the field of polyether-ether-ketone materials, and in particular discloses a preparation method of a chlorosulfonated polyether-ether-ketone composite material film. The preparation method comprises the following steps: (1) synthesis of chlorosulfonated fluorine; (2) synthesis of chlorosulfonated polyether-ether-ketone; and (3) preparation of the chlorosulfonated polyether-ether-ketone composite material film. Sulfonic acid groups and chlorosulfonic acid groups are introduced to a compound of a polyether-ether-ketone strtucture through reaction principles such as in-situ polymerization, nucleophilic substitution and electrophilic substitution of an aromatic compound. The prepared composite film can be used for a long time at 250 DEG C, is relatively good in high-temperature resistance, has a relatively high alcohol resisting rate, can ensure the safety of an electrode to the maximum extent, and prevents scrap of a battery as a result of poisoning of the electrode. The mechanical property is enhanced greatly compared with that of a marketed product. The film has better strength and toughness.
Owner:YIBIN TIANYUAN GRP CO LTD
Dextromethorphan hydrobromide chewable tablet and preparation method thereof
The invention belongs to the technical field of medicinal preparations, and discloses dextromethorphan chewing gum tablets and an industrially applicable preparation method thereof. The preparation is delivered through a chewing process, so that the defects of the marketed products at present can be overcome, and the tablets have the advantages of no need of water for taking, convenience in taking, good mouthfeel, less adverse effects, quick response, capability of eliminating thirst and the like. The dextromethorphan chewing gum tablets prepared by the invention are mainly used for dry coughand are suitable for cold, acute or chronic bronchitis, bronchial asthma, faucitis, phthisis and cough during other upper respiratory tract infections. The dextromethorphan chewing gum tablets provided by the invention have the advantages of simple preparation process, low cost, easiness in control and easiness for industrial production.
Owner:CHONGQING MEDICAL UNIVERSITY
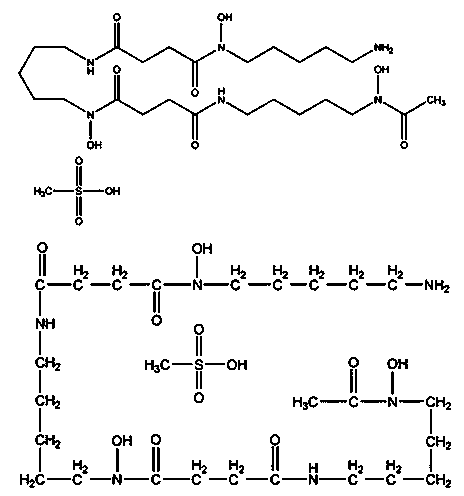
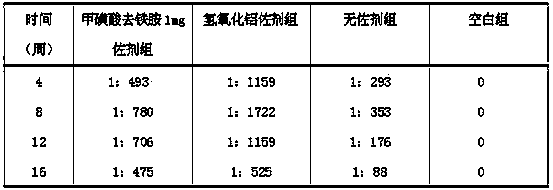
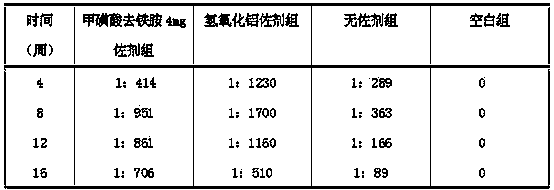
Methanesulfonic acid deferoxamine adjuvant and vaccine comprising methanesulfonic acid deferoxamine adjuvant
ActiveCN103736090ASmall side effectsRaw materials are easy to getImmunological disordersAntibody medical ingredientsResponse effectSide effect
The invention provides a methanesulfonic acid deferoxamine adjuvant and a vaccine comprising the methanesulfonic acid deferoxamine adjuvant. A single part of the vaccine comprising the methanesulfonic acid deferoxamine adjuvant comprises 0.6-8mg methanesulfonic acid deferoxamine adjuvant. The methanesulfonic acid deferoxamine adjuvant is applied to clinical treatment for a long term, has small toxic and side effects, is safe and reliable to use within an immunizing dose scope, and can effectively induce antigen-specific humoral immunity response, the induced humoral immunity response effect is better than that of a group without the adjuvant, a raw material of the methanesulfonic acid deferoxamine adjuvant is easy to obtain and is a marketed product, and the methanesulfonic acid deferoxamine adjuvant is simple in preparation technology, low in cost and stable in performance, and can be added to various traditional vaccines and genetic engineering vaccines as a vaccine adjuvant.
Owner:INST OF MEDICAL BIOLOGY CHINESE ACAD OF MEDICAL SCI
Suede-like coating
InactiveCN104341863AImprove scratch resistanceMildew-resistantMulticolor effect coatingsCarboxymethyl celluloseAcrylic resin
The invention relates to a suede-like coating which is prepared from the following raw materials in parts by mass: 25 parts of polymeric microsphere powder, 30 parts of acrylic resin, 40 parts of a cellulose acetate-butyrate solution, 2 parts of castor oil, 2 parts of dioctyl phthalate, 3 parts of a defoamer, 3 parts of an anti-settling agent, 8 parts of a diluent, 6 parts of a diphenyl guanidine curing agent and 20 parts of carboxymethyl cellulose sodium. Compared with the prior art, the suede-like coating has the characteristics that the process formula of the suede-like coating is obtained by exploration and the scratch resistance of the suede-like coating is better than that of the existing marketed product and the suede-like coating has a certain anti-mould property.
Owner:QINGDAO YIQUN PANT GRP
Treating pain in patients with hepatic impairment
InactiveUS20150045383A1Convenient and cost methodBiocideGranular deliveryMarketed productsBULK ACTIVE INGREDIENT
An extended release composition for an analgesic active pharmaceutical ingredient which may be an opioid, preferably hydrocodone as the only active ingredient. The extended release composition preferably comprises a extended release composition which may be in the form of beads contained in an oral dosage form such as gelatin capsules. The composition is designed to release hydrocodone in a way such that the increase in hydrocodone exposure in hepatically impaired patients is not clinically significant. The oral dosage units are supplied as part of a kit, which also includes a primary package and a package insert all sold as a commercially marketed product. The primary package and package insert are contained in an optional secondary package and the package insert does not contain a warning, a dosing instruction, or a dosing table specifically directed to patients suffering from mild, moderate or severe hepatic impairment, and preferably explicitly states that dosing adjustment is not required for mild or moderate hepatic impairment
Owner:PERSION PHARMA LLC
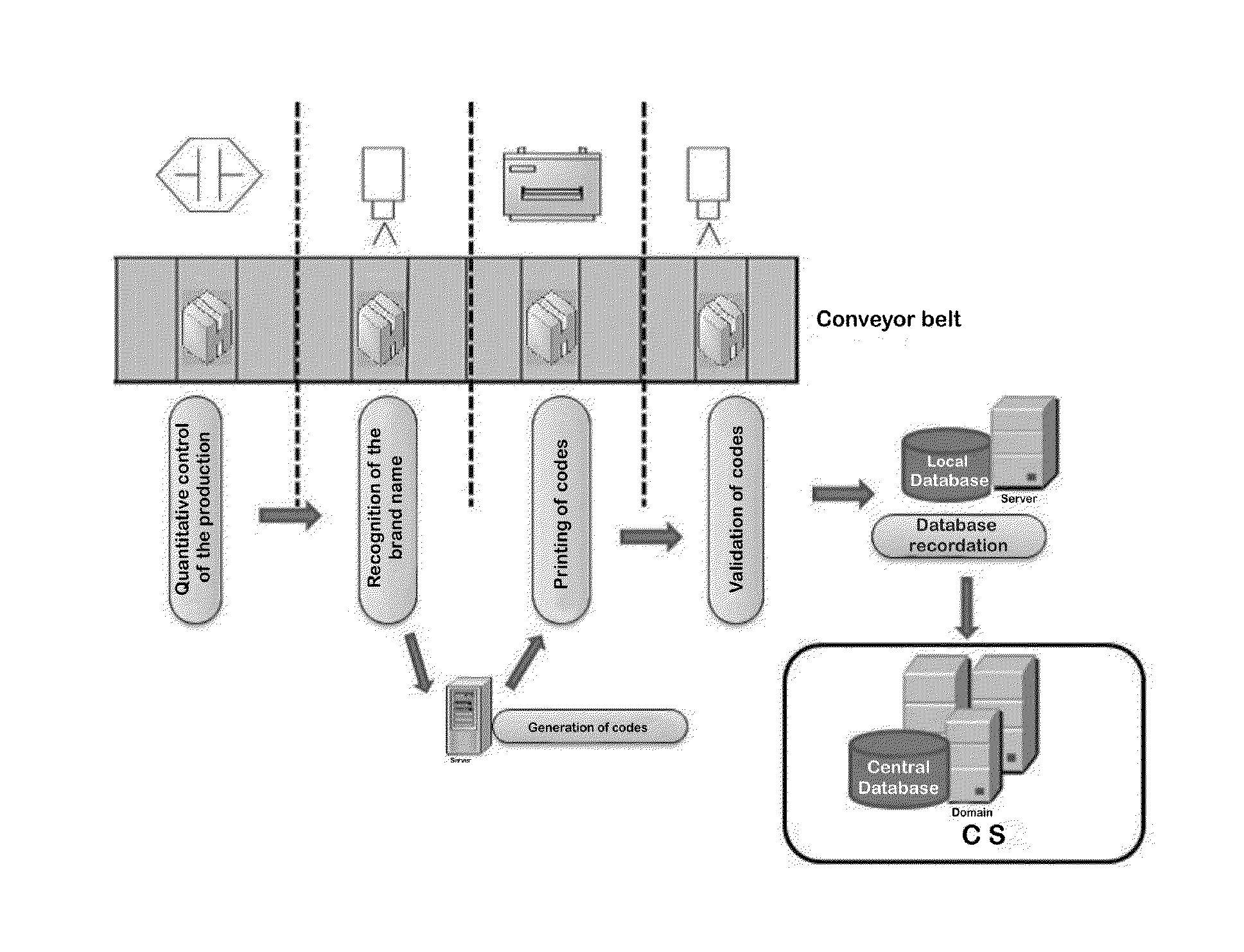
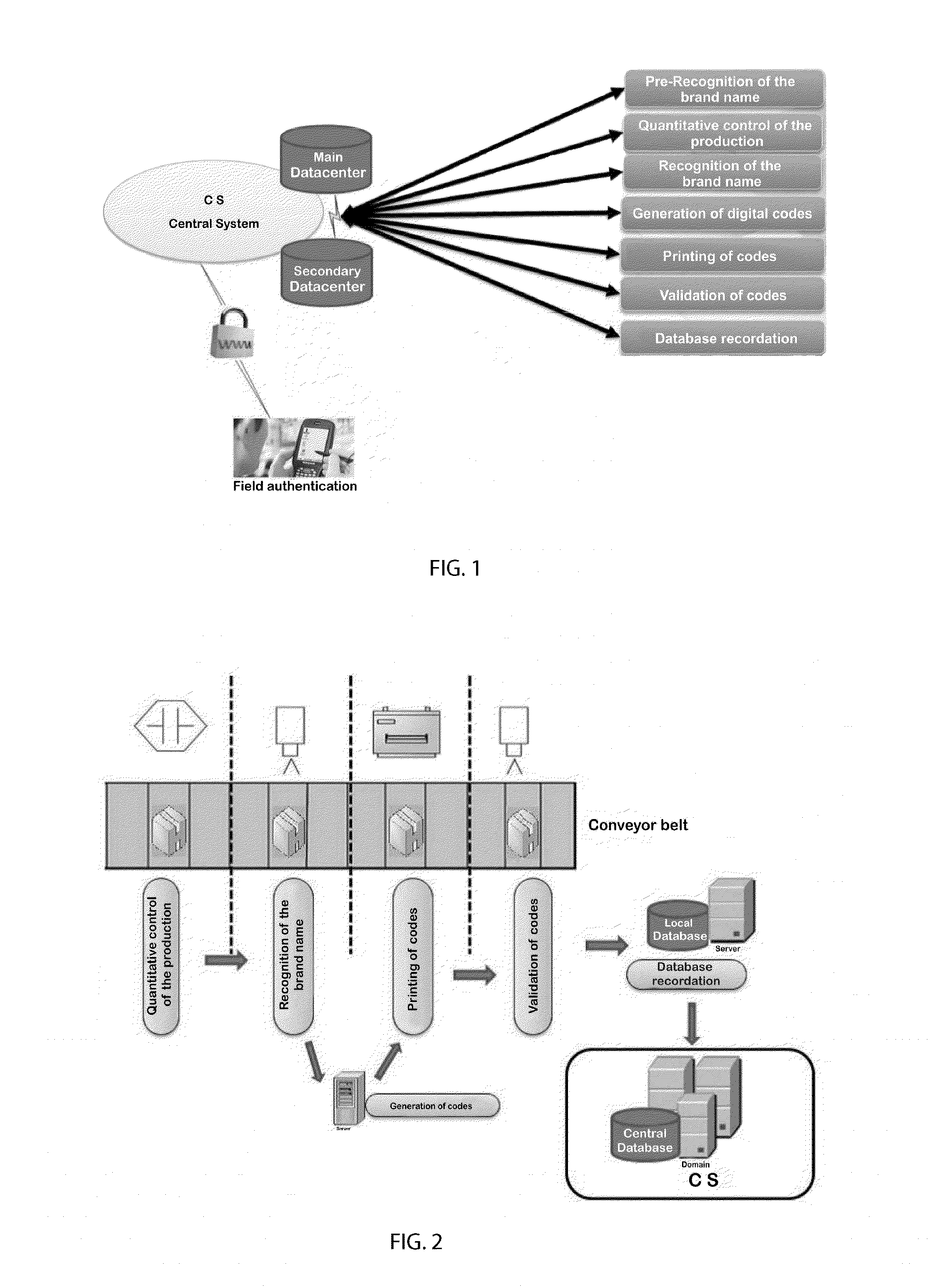
Process and system for the identification and tracking of products in a production line
InactiveUS20150136845A1Efficient mannerEfficient and unambiguousCommerceSpecial data processing applicationsProduction lineMarketed products
The present invention is related to processes used to combat counterfeiting. To that end, there is provided an efficient process and system for the identification and tracking of products in a production line, thereby allowing the marketed products to be further tracked in an efficient and unambiguous manner. More particularly, the present invention provides a process for the identification and tracking of products in a production line, comprising the steps: (a) recognizing each of the products, (b) digitally generating at least one identification code for each of the products, (c) printing, for each of the products, the at least one code directly on the corresponding product, and (d) validating each of the codes printed on the products. The present invention further provides a system capable of carrying out the above process.
Owner:VALID SOLUCOES E SERVICOS DE SEGURANCA EM MEIOS DE PAGAMENTO E IDENTIFICACAO
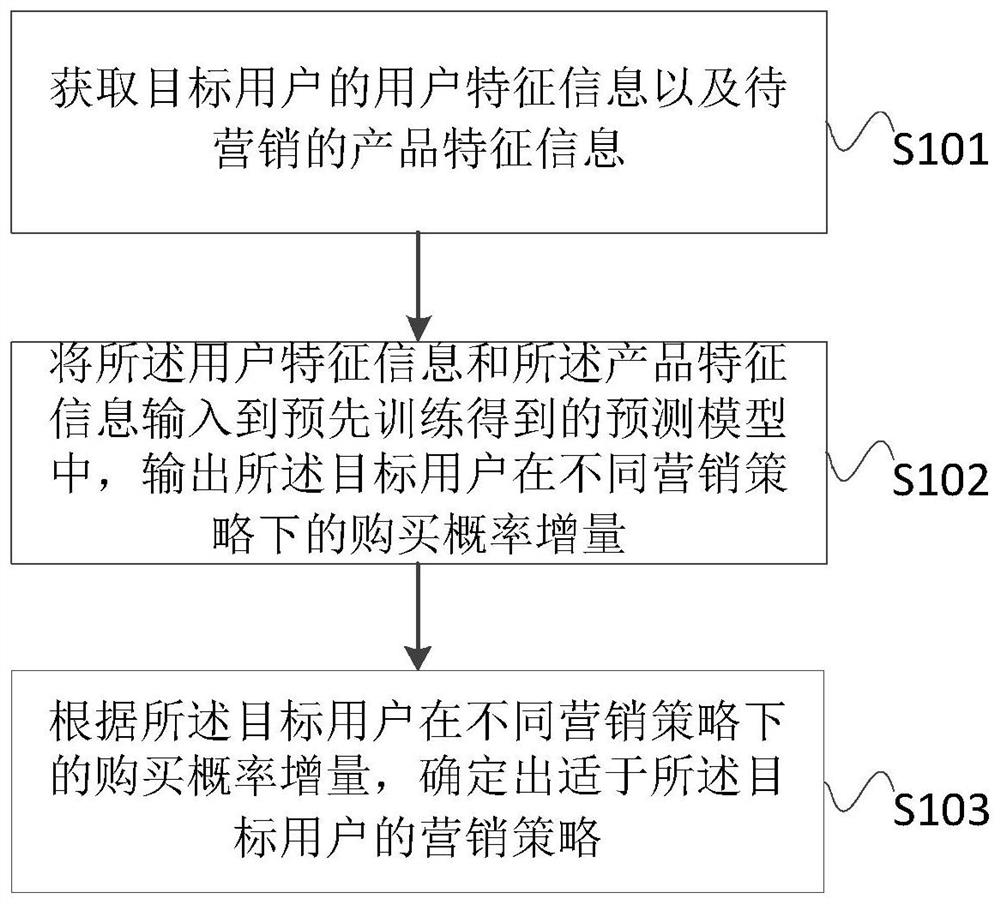
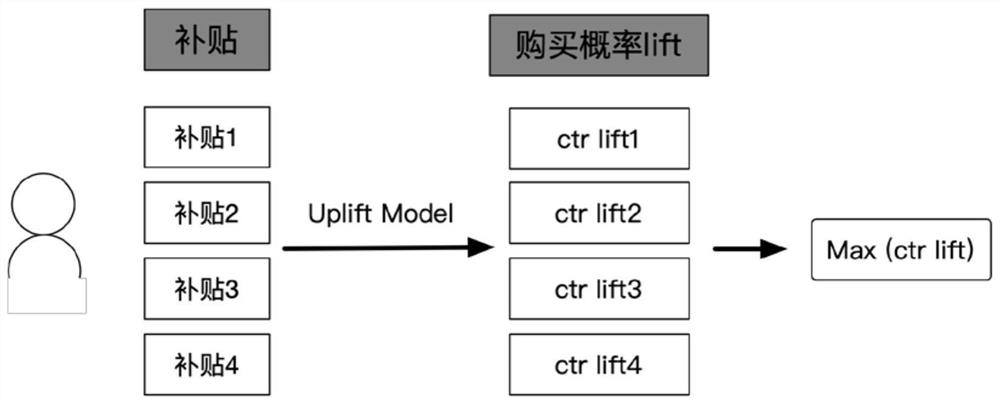
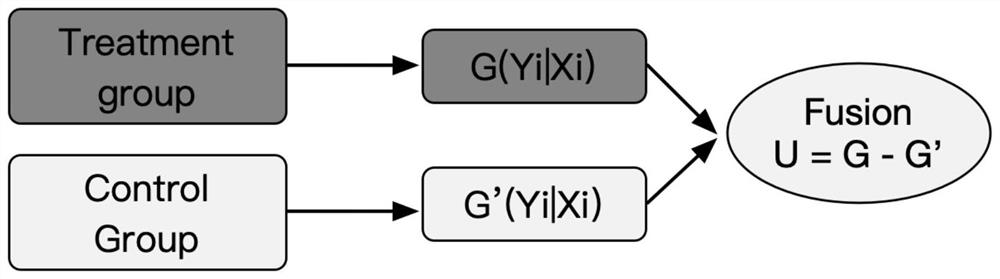
Marketing strategy determination method and device, computer equipment and storage medium
PendingCN114549071APrecise marketing strategyUnderstand the purposeCharacter and pattern recognitionMarket data gatheringMarketed productsOperations research
The invention discloses a marketing strategy determination method and apparatus, a computer device and a storage medium. The method comprises the steps of obtaining user feature information of a target user and feature information of a to-be-marketed product; inputting the user feature information and the product feature information into a pre-trained prediction model, and outputting purchase probability increments of the target user under different marketing strategies; and determining a marketing strategy suitable for the target user according to the purchase probability increment of the target user under different marketing strategies. According to the invention, the pre-trained prediction model is utilized, the user feature information and the product feature information are used as input, the purchase probability increment of the target user under different marketing strategies is predicted, and the specific quantification result brought by the marketing strategies to the purchase probability improvement is determined. And a corresponding marketing strategy is determined according to the quantification result, so that a more accurate marketing strategy is determined.
Owner:SHANGHAI JUNZHENG NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com