Patents
Literature
1394 results about "Error message" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
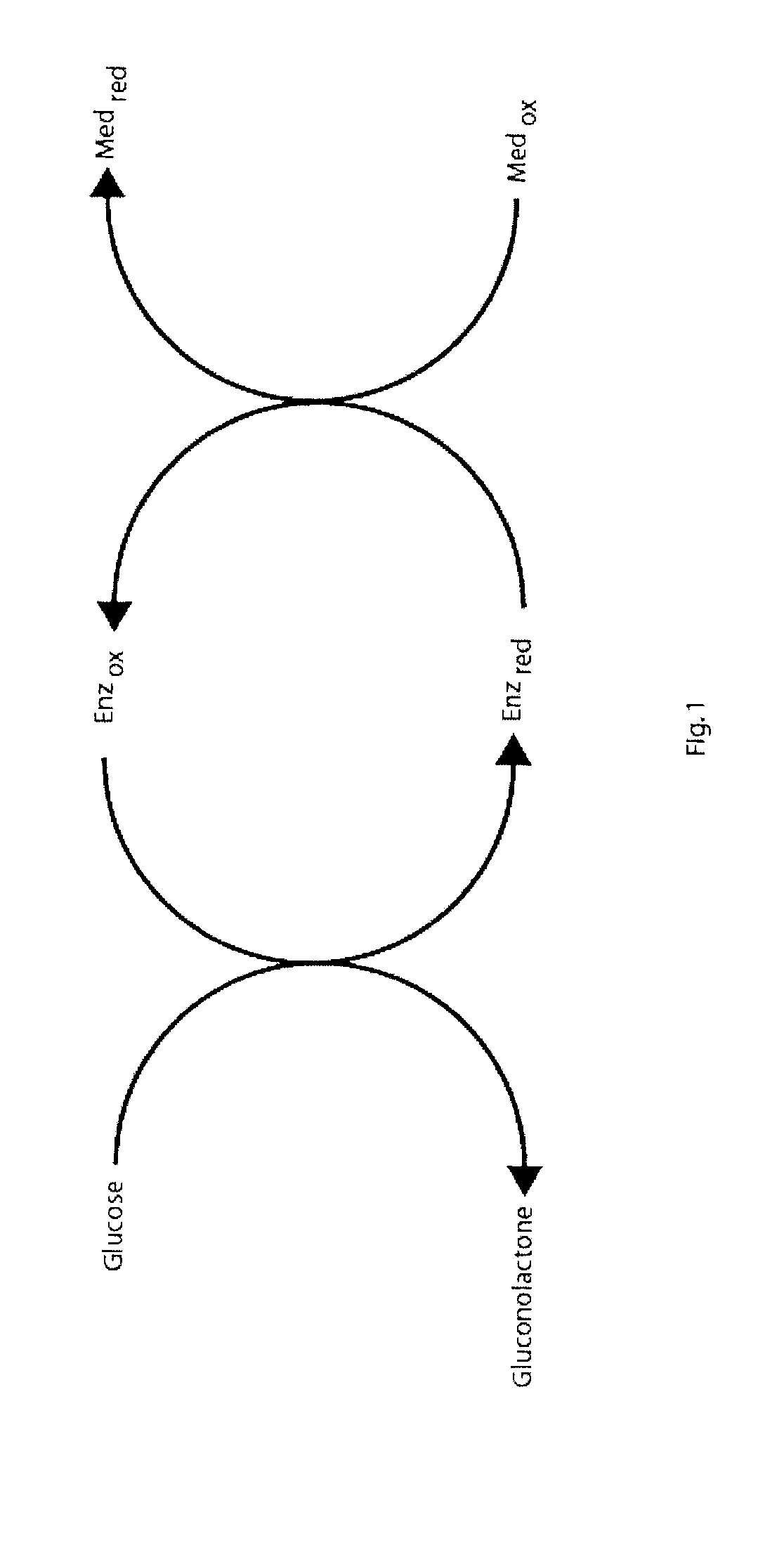
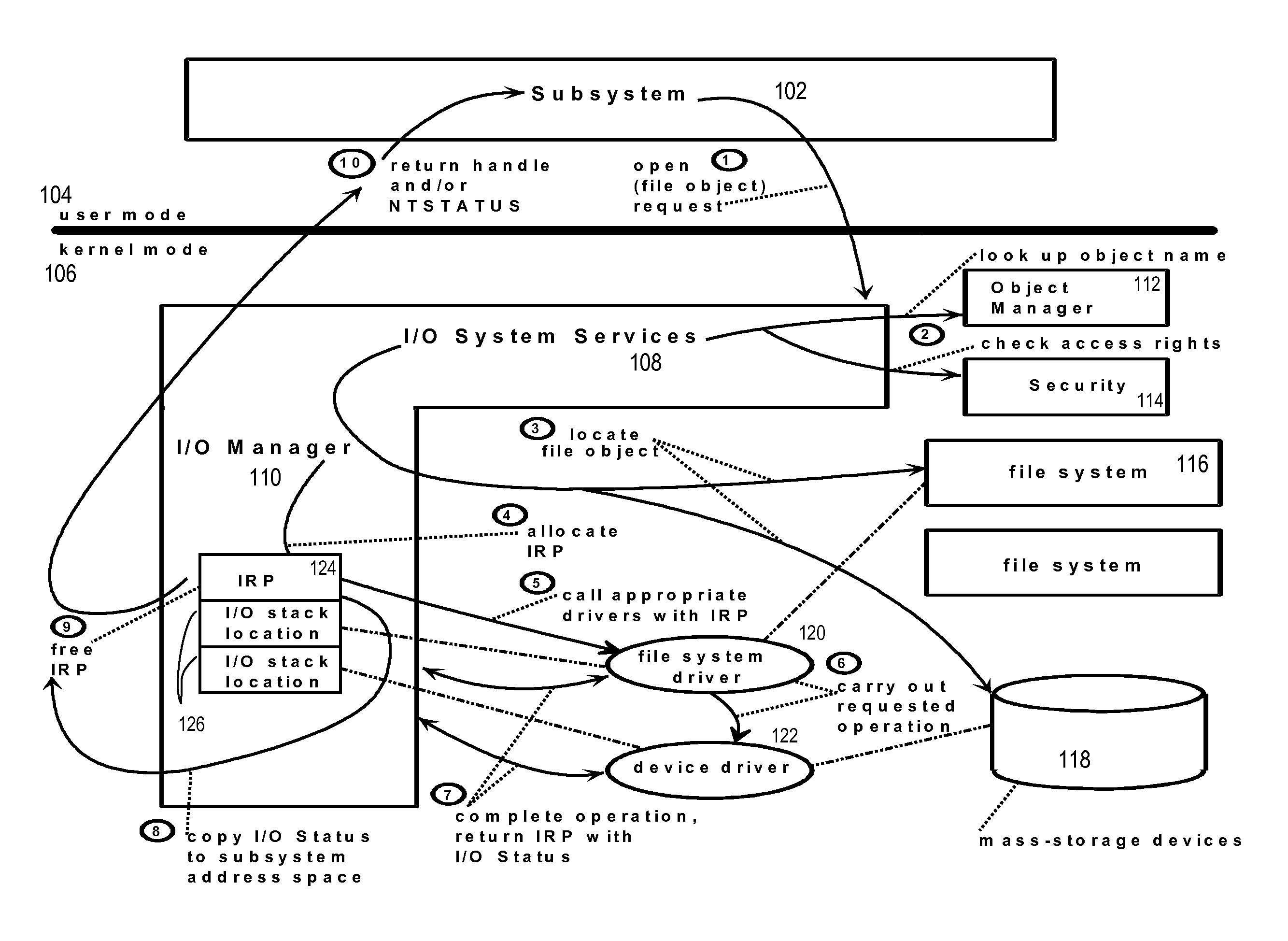
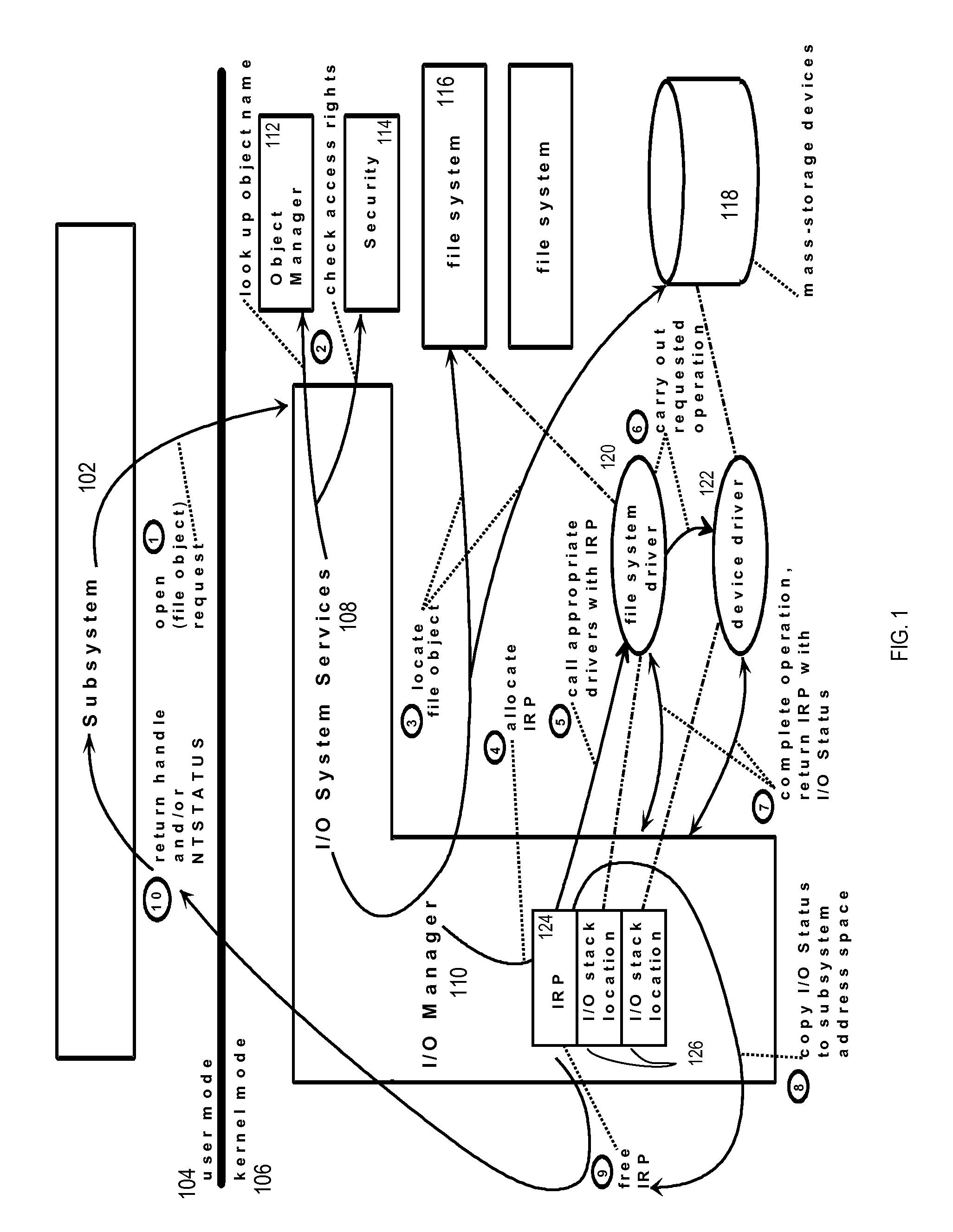
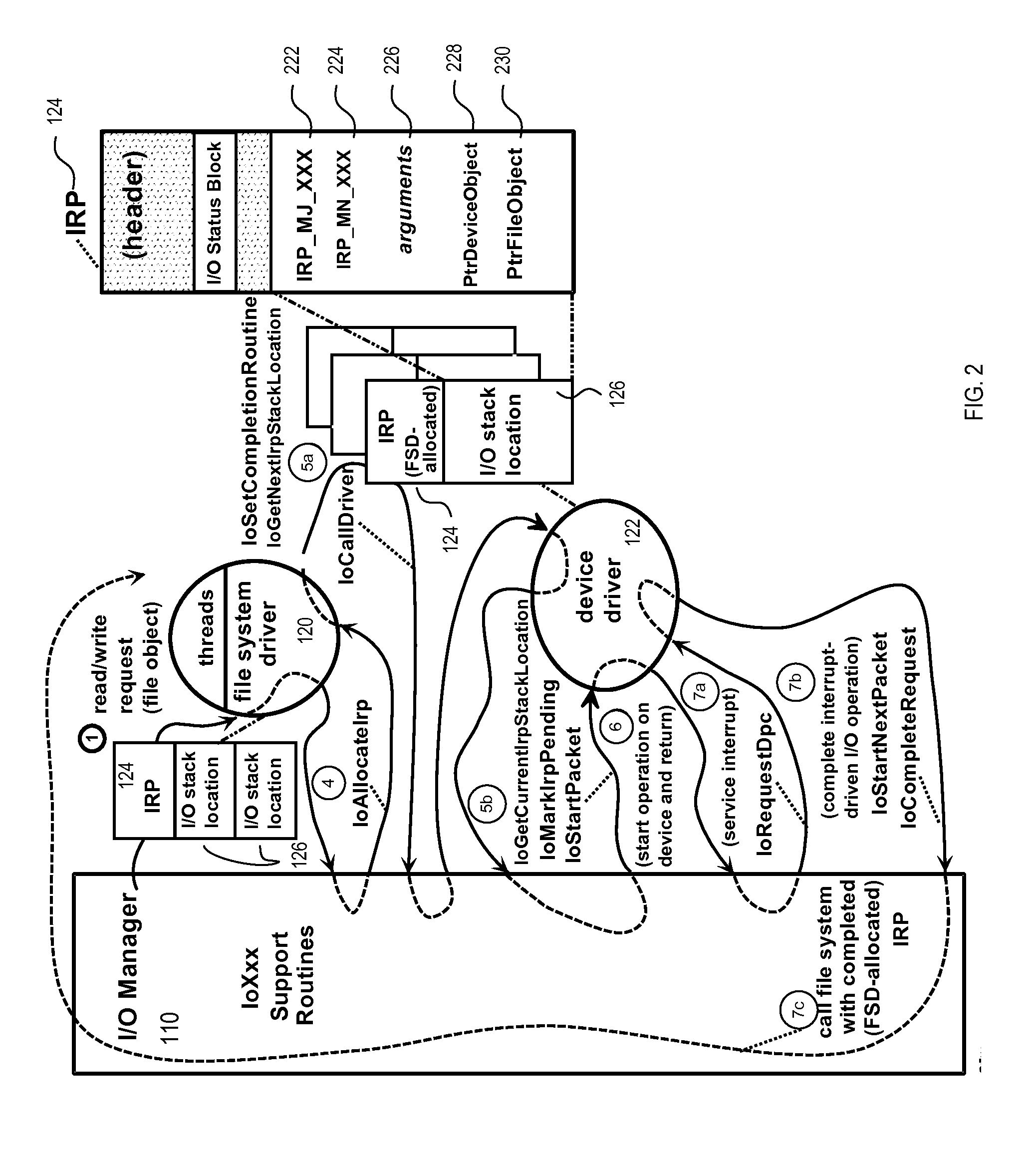
An error message is information displayed when an unexpected condition occurs, usually on a computer or other device. On modern operating systems with graphical, error messages are often displayed using dialog boxes. Error messages are used when user intervention is required, to indicate that a desired operation has failed, or to relay important warnings (such as warning a computer user that they are almost out of hard disk space). Error messages are seen widely throughout computing, and are part of every operating system or computer hardware device. Proper design of error messages is an important topic in usability and other fields of human–computer interaction.
Debugging site errors by an admin as a guest user in a multi-tenant database environment
An approach for debugging site errors in a multi-tenant database system is disclosed. An example method can include receiving a request from a site administrator to access an enhanced error message and determining if the site administrator is approved for viewing the enhanced error message by evaluating exceptions associated with the enhanced error message, the request, and the site administrator. The example method further includes modifying a detailed error message related to the request for generating the enhanced error message, and providing the enhanced error message to the site administrator based on the approval determination.
Owner:SALESFORCE COM INC
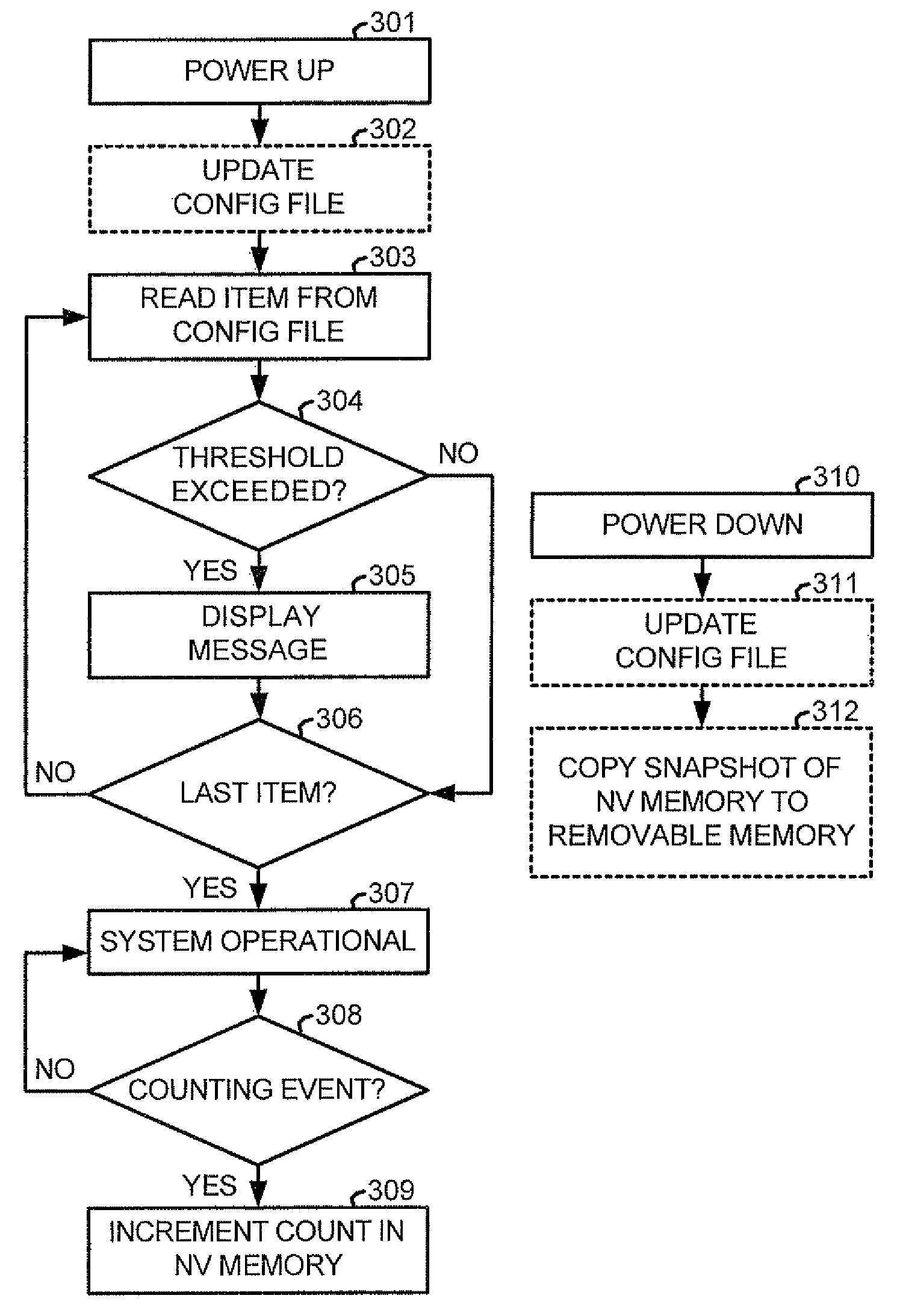
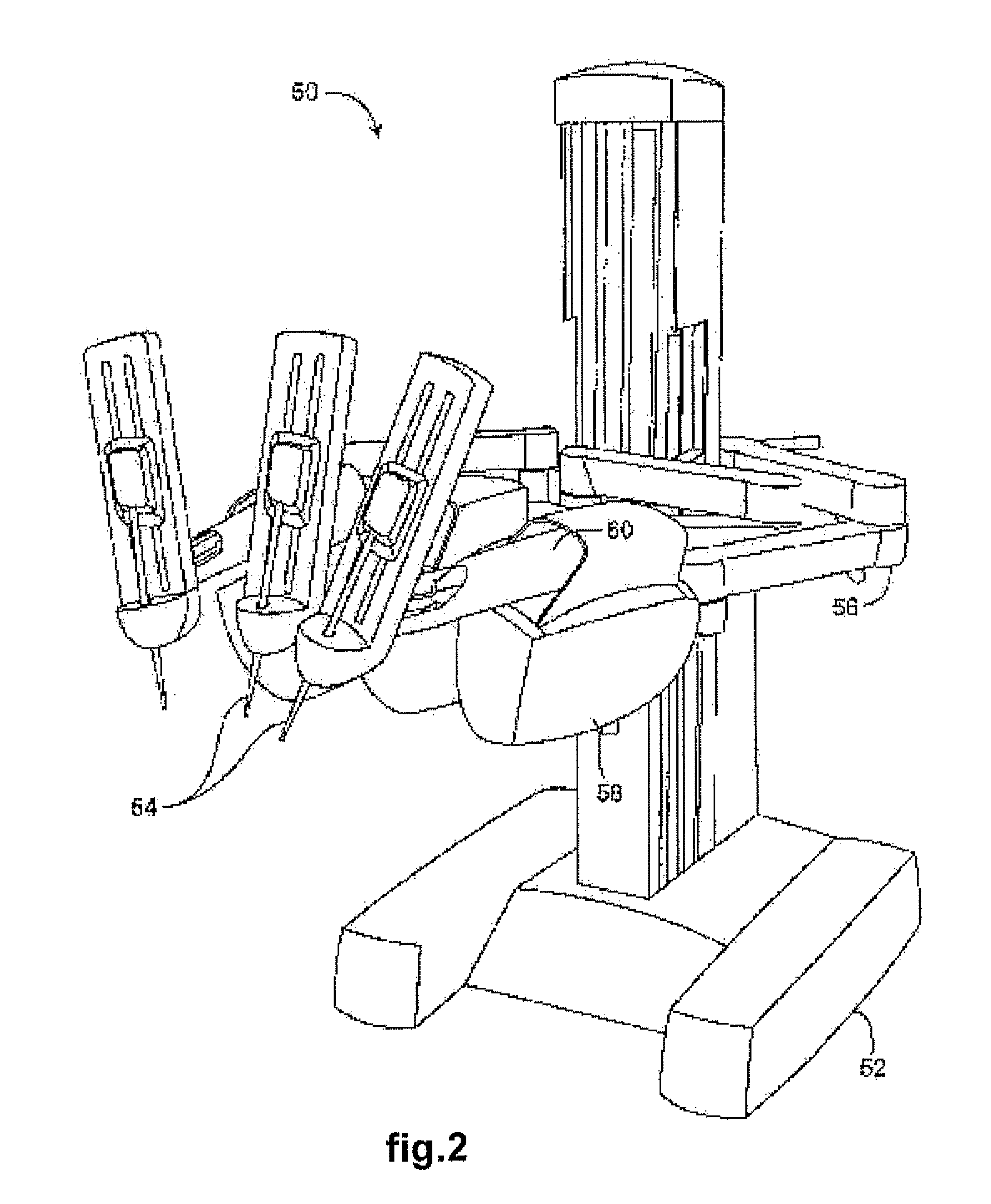
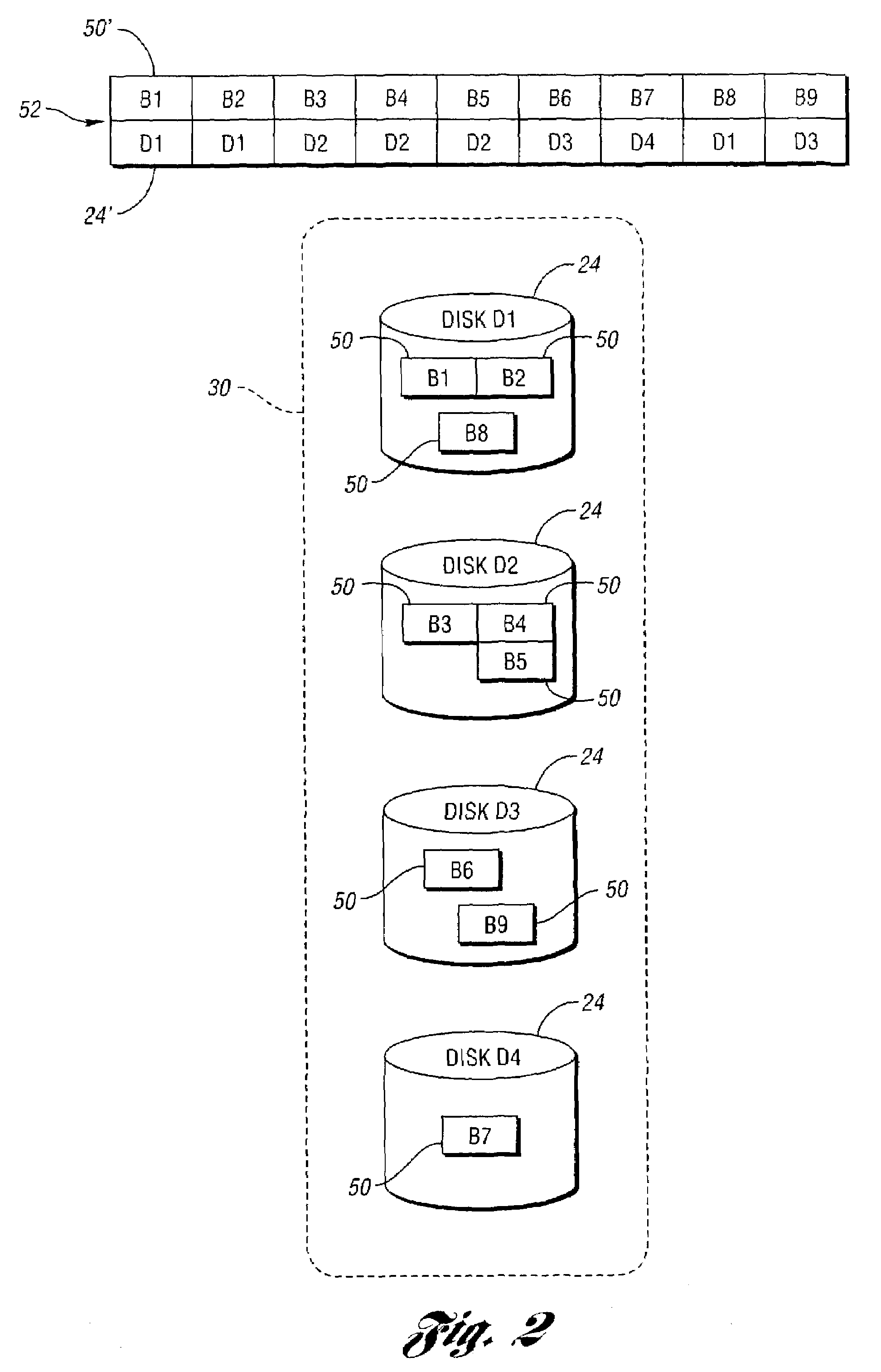
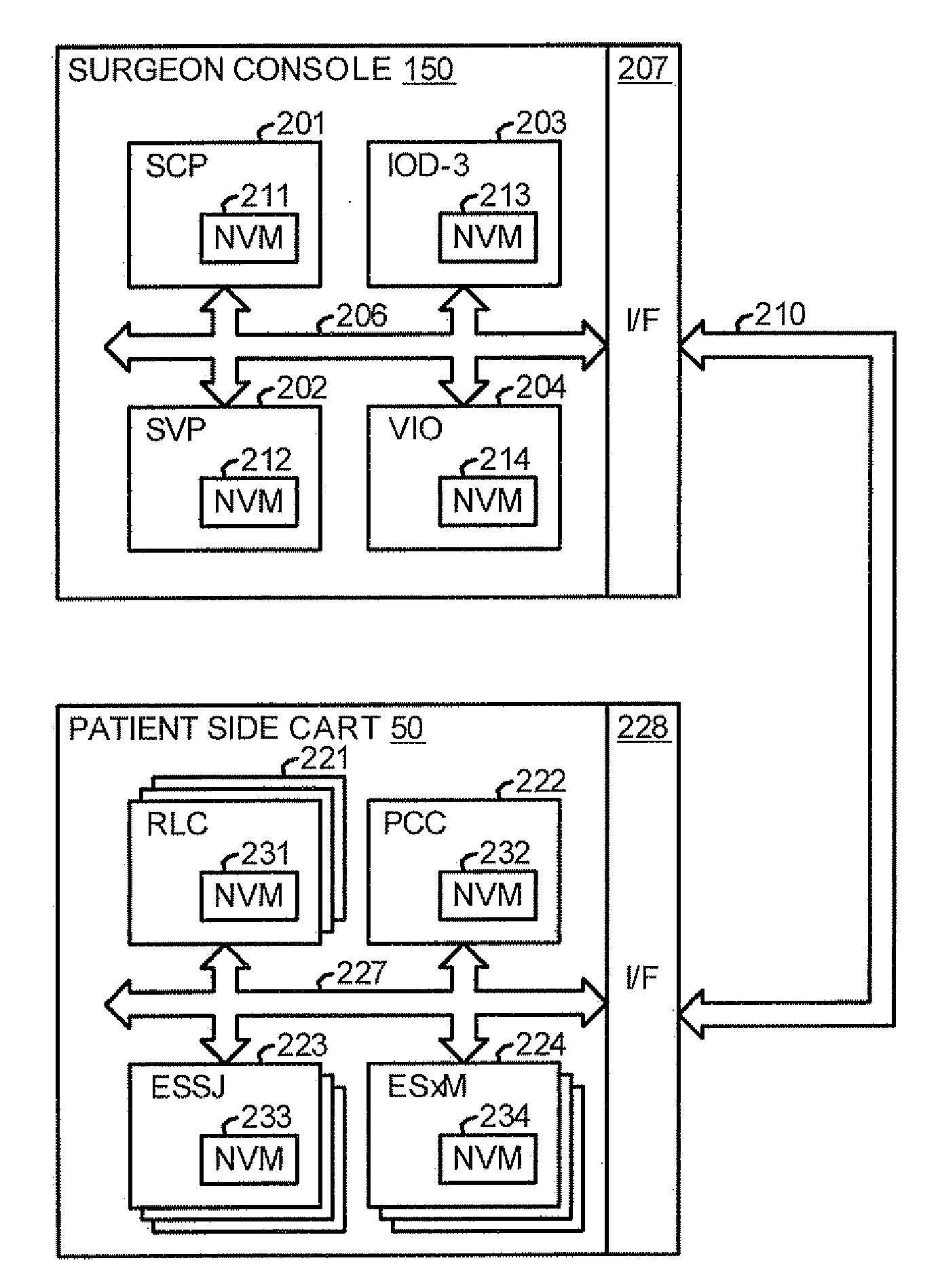
Method for tracking and reporting usage events to determine when preventive maintenance is due for a medical robotic system
A medical robotic system comprises a number of components that may be monitored to determine their preventive maintenance needs by recording usage-related information for the monitored components into associated non-volatile memories. When usage of the component exceeds a specified usage threshold, the system displays a warning message on its display screen to have preventive maintenance performed for the component. If the usage continues without such maintenance and exceeds a higher usage threshold, the system displays an error message on its display screen and the system transitions into an error state during which medical procedures are not allowed to be performed. The usage-related information may also be communicated to a remote computer which gathers and processes usage-related information from a number of medical robotic systems to estimate resource requirements for timely performing preventive maintenance on the medical robotic systems, and anticipated service revenues from such maintenance.
Owner:INTUITIVE SURGICAL OPERATIONS INC
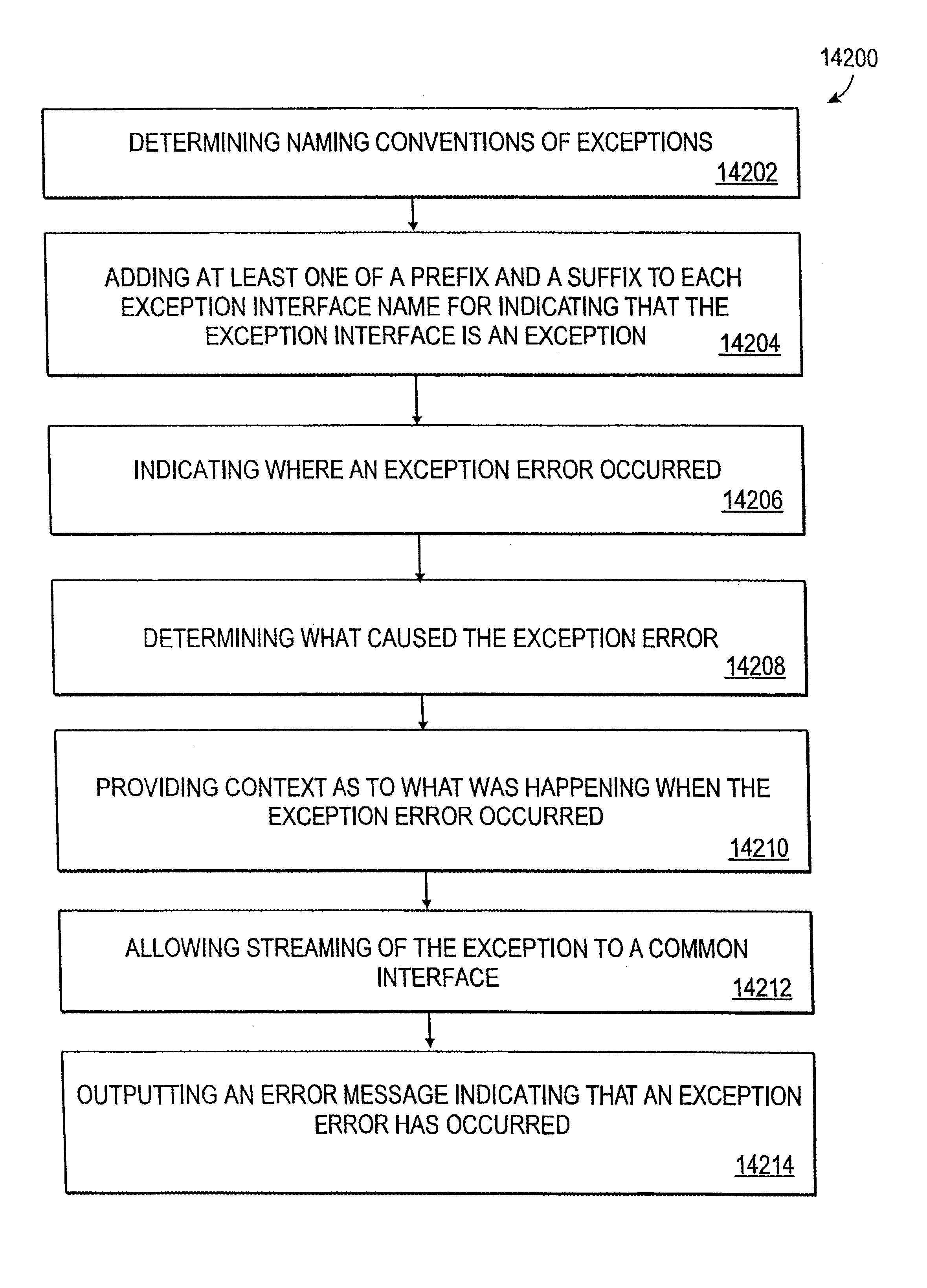
Common interface for handling exception interface name with additional prefix and suffix for handling exceptions in environment services patterns
A system, method and article of manufacture are provided for creating a common interface for exception handling. Naming conventions of exceptions are determined. A prefix and / or a suffix is added to each exception interface name for indicating that the exception interface is an exception. Where an exception error occurred is indicated and a determination is made as to what caused the exception error. Context is provided as to what was happening when the exception error occurred. Streaming of the exception is allowed to a common interface. An error message is outputted indicating that an exception error has occurred.
Owner:ACCENTURE GLOBAL SERVICES LTD
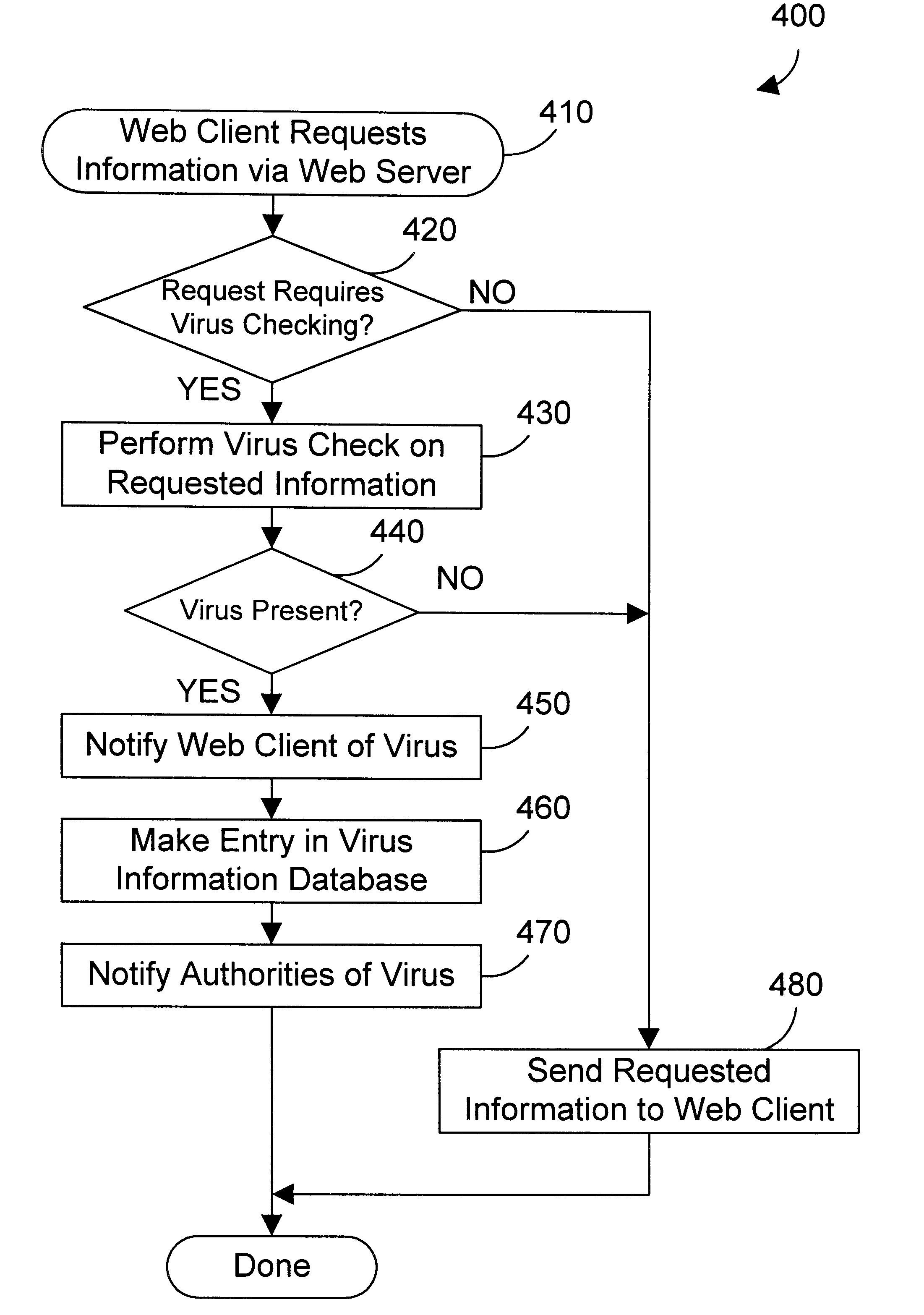
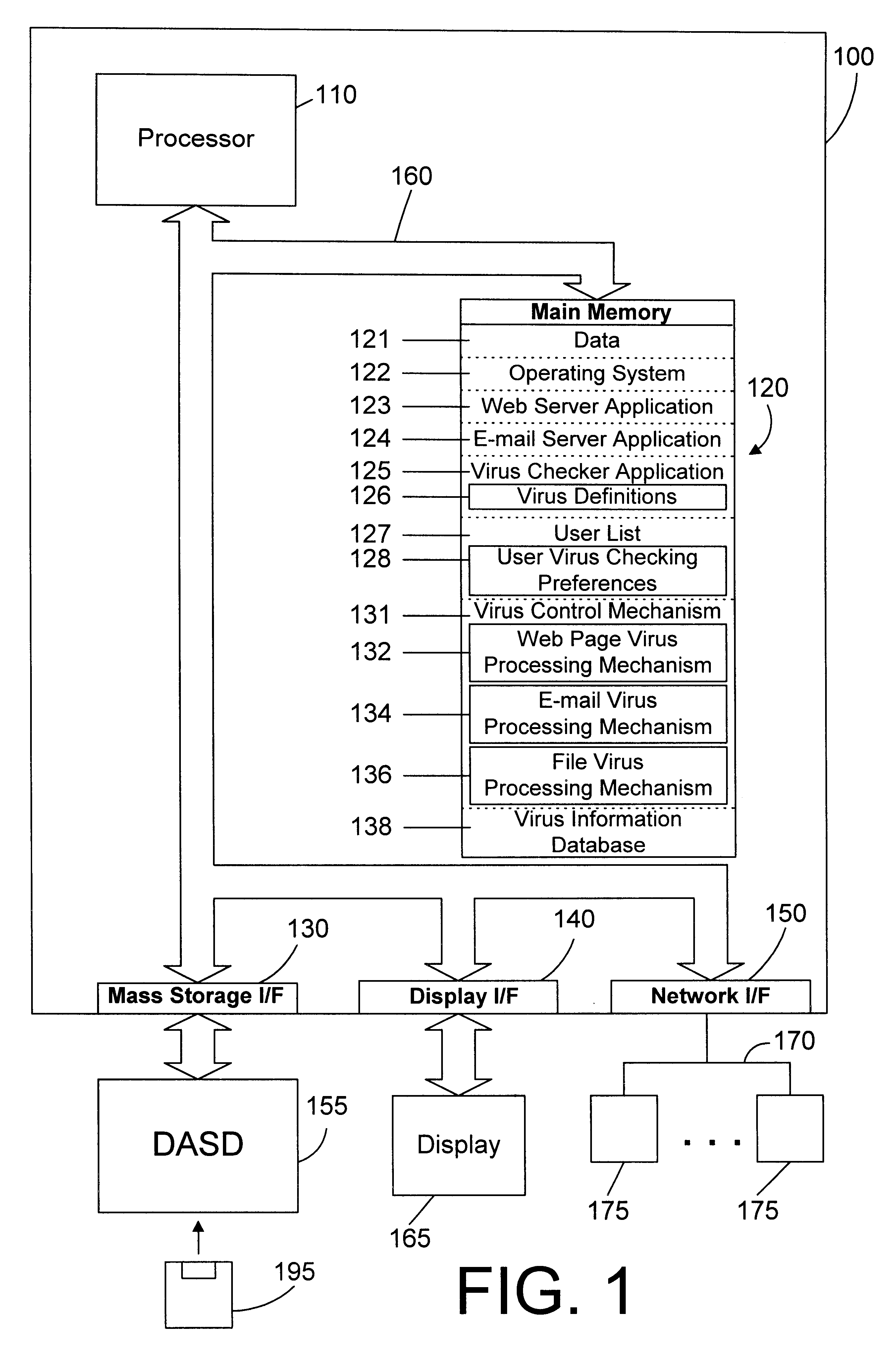
Web server apparatus and method for virus checking
InactiveUS6785732B1Eliminate needPrevent proliferationMemory loss protectionDigital data processing detailsWeb serviceUniform resource locator
A web server computer system includes a virus checker and mechanisms for checking e-mails and their attachments, downloaded files, and web sites for possible viruses. When an e-mail message contains a detected virus, the message is discarded, and both the sender and recipient are informed via e-mail that the message contained a virus. When an e-mail attachment contains a detected virus, the attachment is deleted, and the e-mail message without the attachment is sent to the web client, along with a message explaining that the e-mail message had an attachment that was automatically deleted because it had a virus. When a downloaded file contains a virus, the downloaded file is deleted, and an error message is sent to the web client to inform the web client that the requested file had a virus. When a requested web site (i.e., Uniform Resource Locator (or URL)) has been labeled as a source for a known virus, a message is sent to the web client stating that a virus may have been downloaded from that URL. In addition, if the requested URL has not been labeled as a source for a known virus, but it contains links that have been so labeled, the web page is processed before being sent to the user to identify those potentially dangerous links. In this manner a web server can perform virus checking of different types of information real-time as the information is requested by a web client. In addition, a web client may also request that the server perform virus checking on a particular drive on the web client. If this case, the web server may receive information from the web client drive, scan the information for viruses, and inform the web client whether any viruses were found. In the alternative, the web server may download a client virus checker to the web client and cause the client virus checker to be run on the web client. The preferred embodiments thus allow a virus checker on a web server to dynamically scan incoming data, and to scan web clients coupled to the web server, thereby eliminating the need for virus checking software to be installed on each web client.
Owner:FINJAN BLUE INC
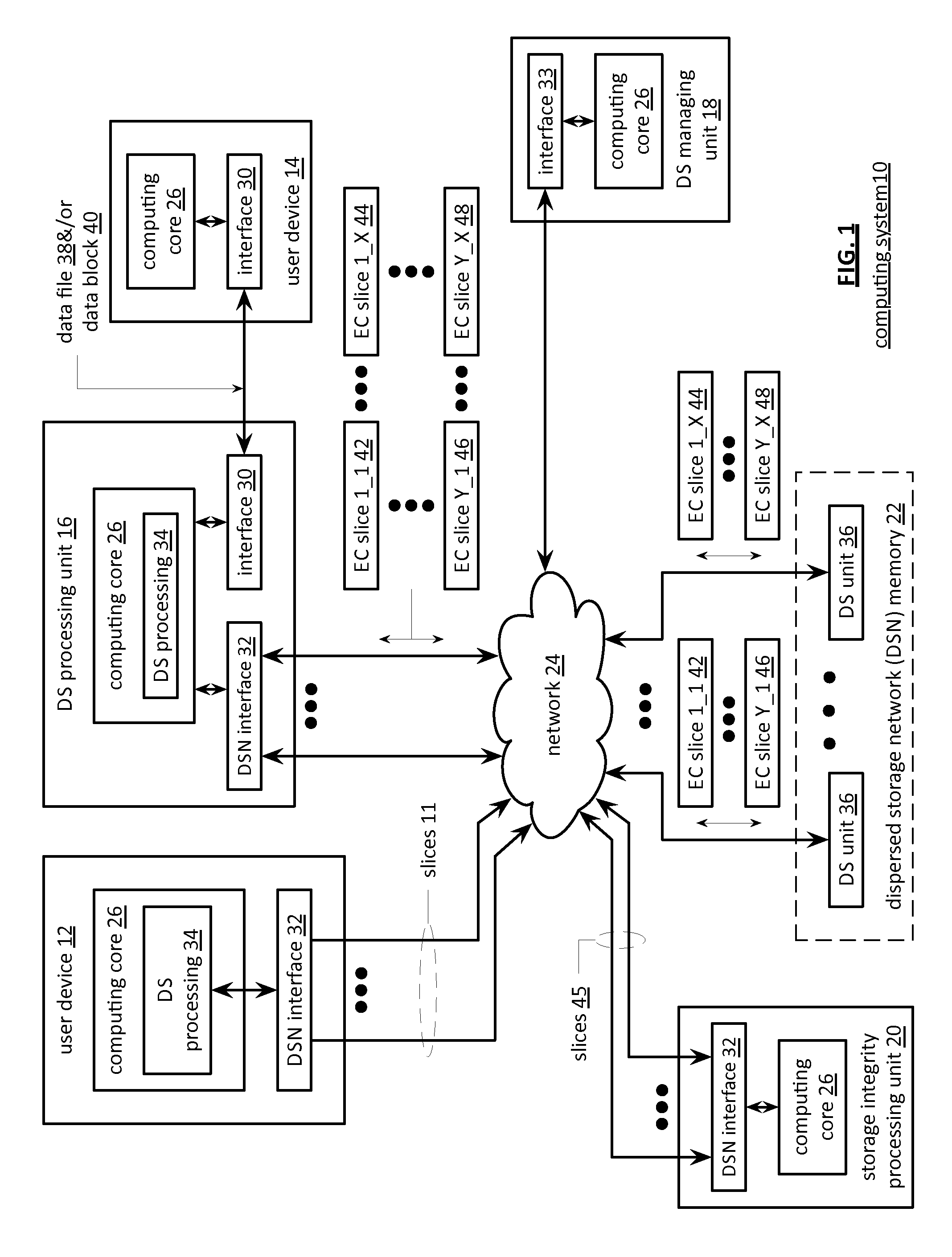
Identifying an error cause within a dispersed storage network
A method begins by a dispersed storage (DS) processing module selecting two or more correlated error messages of a plurality of error messages. The method continues with the DS processing module identifying two or more collection of records corresponding to the selected two or more correlated error messages such that a collection of records includes an event record including information regarding an event, a first record including information regarding a dispersed storage (DS) processing module processing an event request to produce a plurality of sub-event requests, and a plurality of records including information regarding a plurality of DS units processing the plurality of sub-event requests. The method continues with the DS processing module identifying a correlation cause of one or more errors corresponding to the two or more correlated error messages based on the two or more collections of records.
Owner:PURE STORAGE
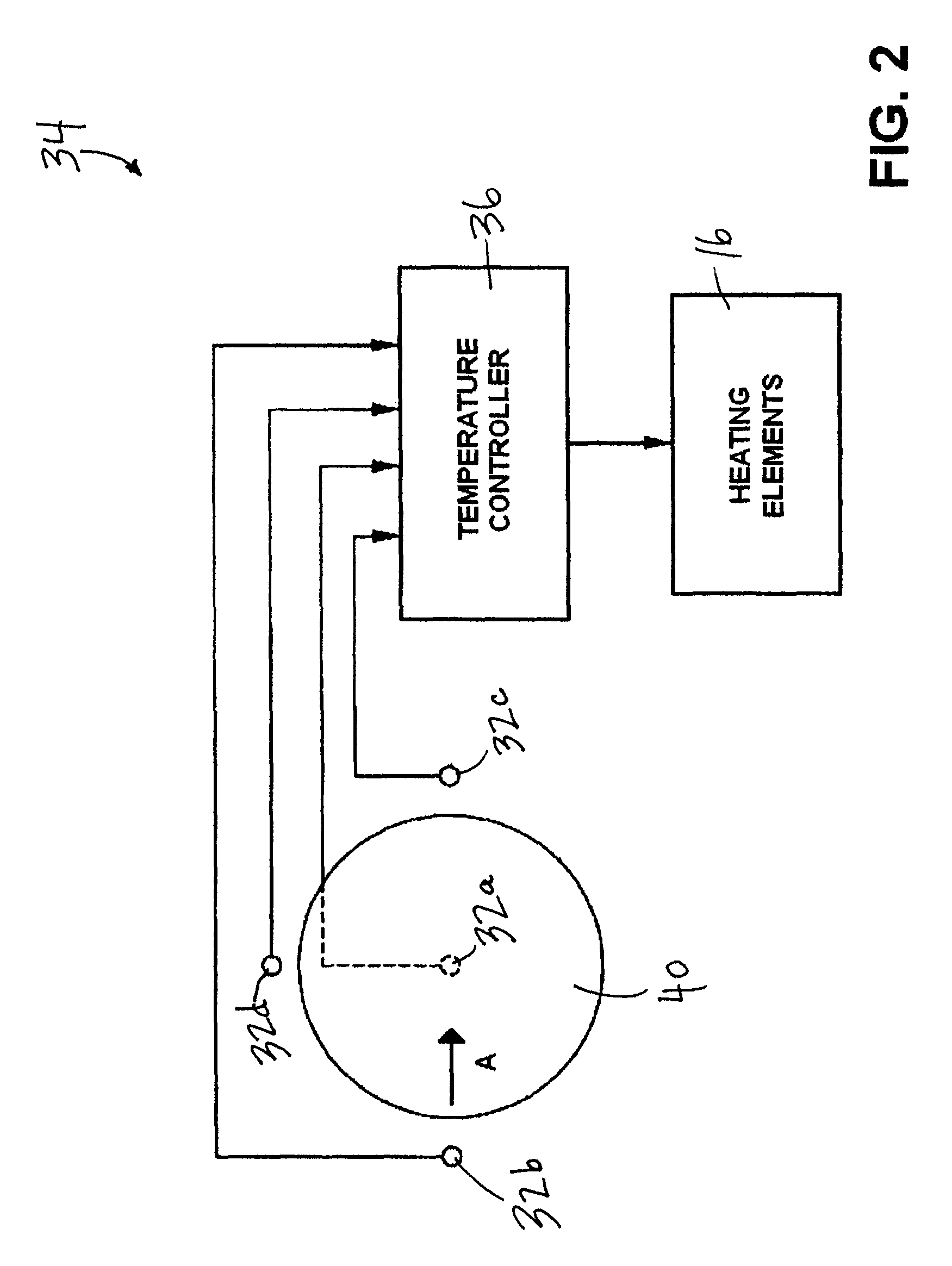
Smart temperature measuring device
ActiveUS9297705B2Avoid data transferThermometer detailsThermometers using electric/magnetic elementsTemperature controlGraphics
A temperature measuring device having a smart chip, or electronic circuit, integrated therein is provided. The smart chip, or electronic circuit, includes at least a unique identification number or data specific to the particular temperature measuring device stored thereon. The electronic circuit further includes calibration data of the temperature measuring device stored thereon. A module controller of a temperature control system is configured to verify the unique identification number of the thermocouple assembly prior to allowing data to be transferred between the temperature measuring device and a temperature controller. A graphical user interface allows an operator to enter the unique identification number or data to verify the temperature measuring device and display an error message if the number or data entered is not equivalent, or does not match, the unique identification number or data stored on the electronic circuit.
Owner:ASM IP HLDG BV
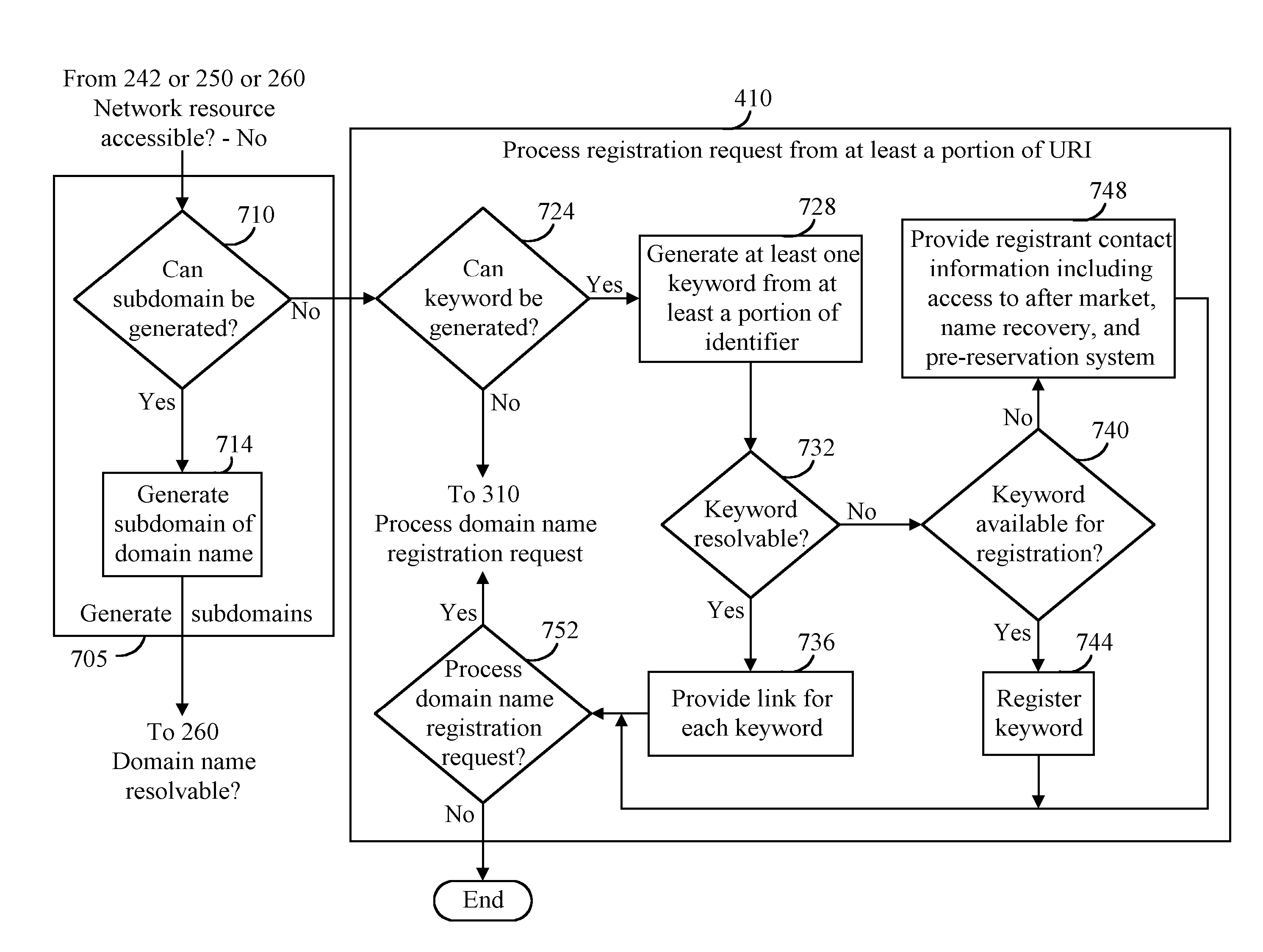
Method, product, and apparatus for resource identifier registration and aftermarket services
InactiveUS7188138B1Easy to understandReduce extra bandwidth requiredMultiple digital computer combinationsMarketingDomain nameWeb browser
When a network resource request having a domain name is received, it is determined whether the network resource can be accessed from the domain name. Rather than, or in addition to, displaying an error message or processing a search request in response to determining that a network resource can not be accessed, the domain name can instead be redirected to a registration service where the domain name can be automatically used to perform a registration request and determine domain name availability. When the domain name is not available for registration, domain name registrant information is provided. However, when the domain name is determined available, a registration form is provided. For example, such a domain name may be redirected from the autosearch feature of a web browser to a service, which determines that the domain name is available for registration enabling a potential registrant to register the available domain name by selecting a domain name registration provider from a list of domain name registration providers.
Owner:MEC MANAGEMENT LLC
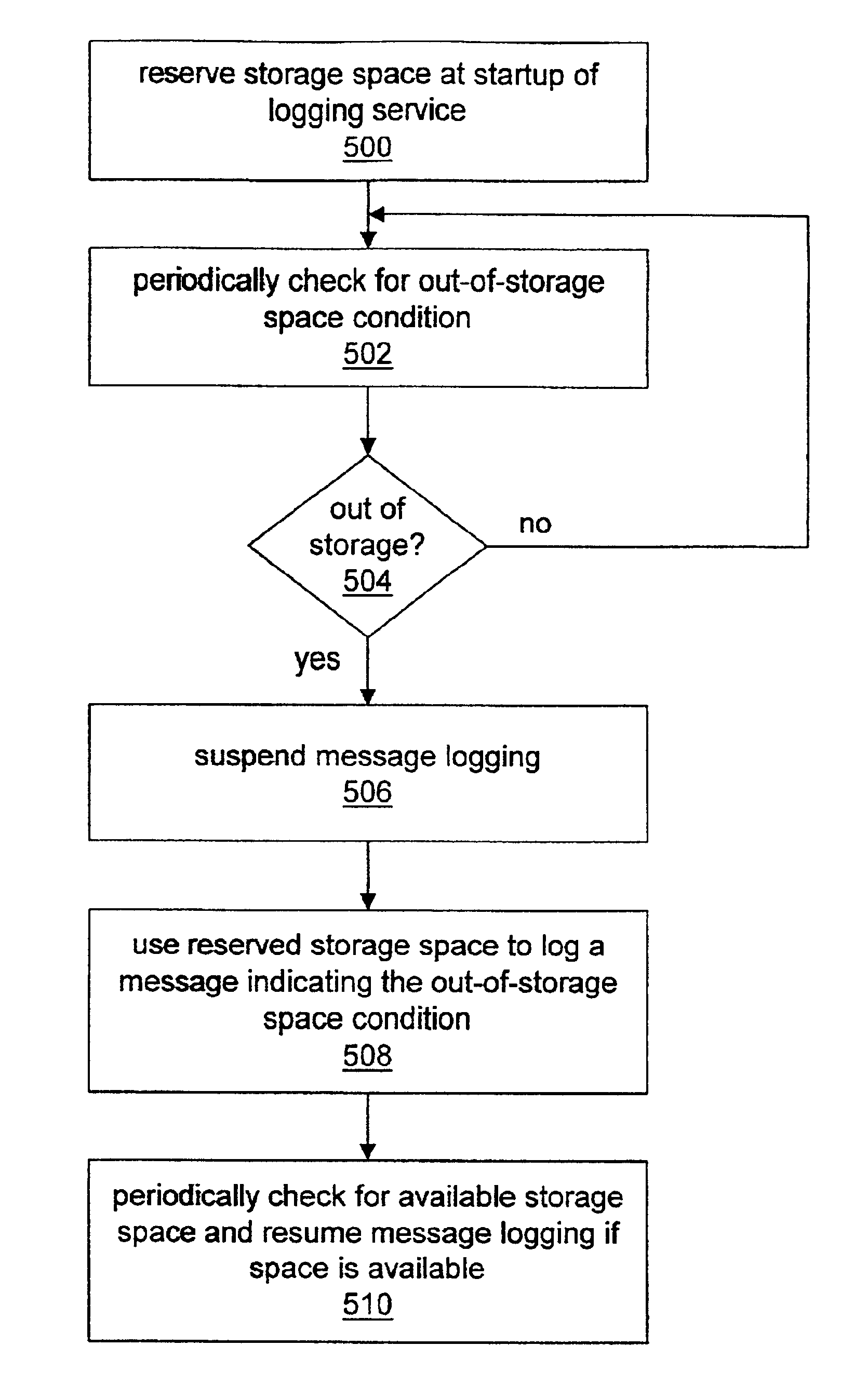
Application server message logging
InactiveUS6879995B1Multiple digital computer combinationsTransmissionApplication serverComputer module
System and method for performing message logging for networked applications running on application servers. The application server may run a process referred to as a “logging service” that accepts requests from client processes to log messages regarding various types of runtime events or conditions. These client processes may include any of various types of processes, such as modules or components running on the application server. Any of various types of information may be recorded when a message is logged. For example, the information may include the date and time the message was created, the type of message, such as a warning message, an error message, etc., the message text to be recorded, the ID of a service or component requesting the message to be logged, or any of various other types of information. The logging service may also be operable to handle low-storage-space or out-of-storage space conditions.
Owner:ORACLE INT CORP
Hierarchical system and method for centralized management of thin clients
InactiveUS20030061323A1Digital computer detailsData switching networksInformation dispersalInformation transmission
A system and method for managing a network of thin clients is disclosed. The thin clients may be organized into a hierarchy with multiple administrative servers in a hierarchy, each managing one or more thin clients. Updates to thin client configurations may be performed by propagating update information to a top-level master administrative server, which in turn conveys the update information to one or more lower-level remote administrative servers, which in turn convey the update information to their managed thin clients. To simplify network management, the thin clients may be organized into arbitrary clusters, regardless of their position within the hierarchy structure. The hierarchy may also be used to control the propagation of error messages from thin clients. The hierarchy may be implemented using a thin client management program that configures thin clients according to their position within the hierarchy.
Owner:EAST KENNETH H +4
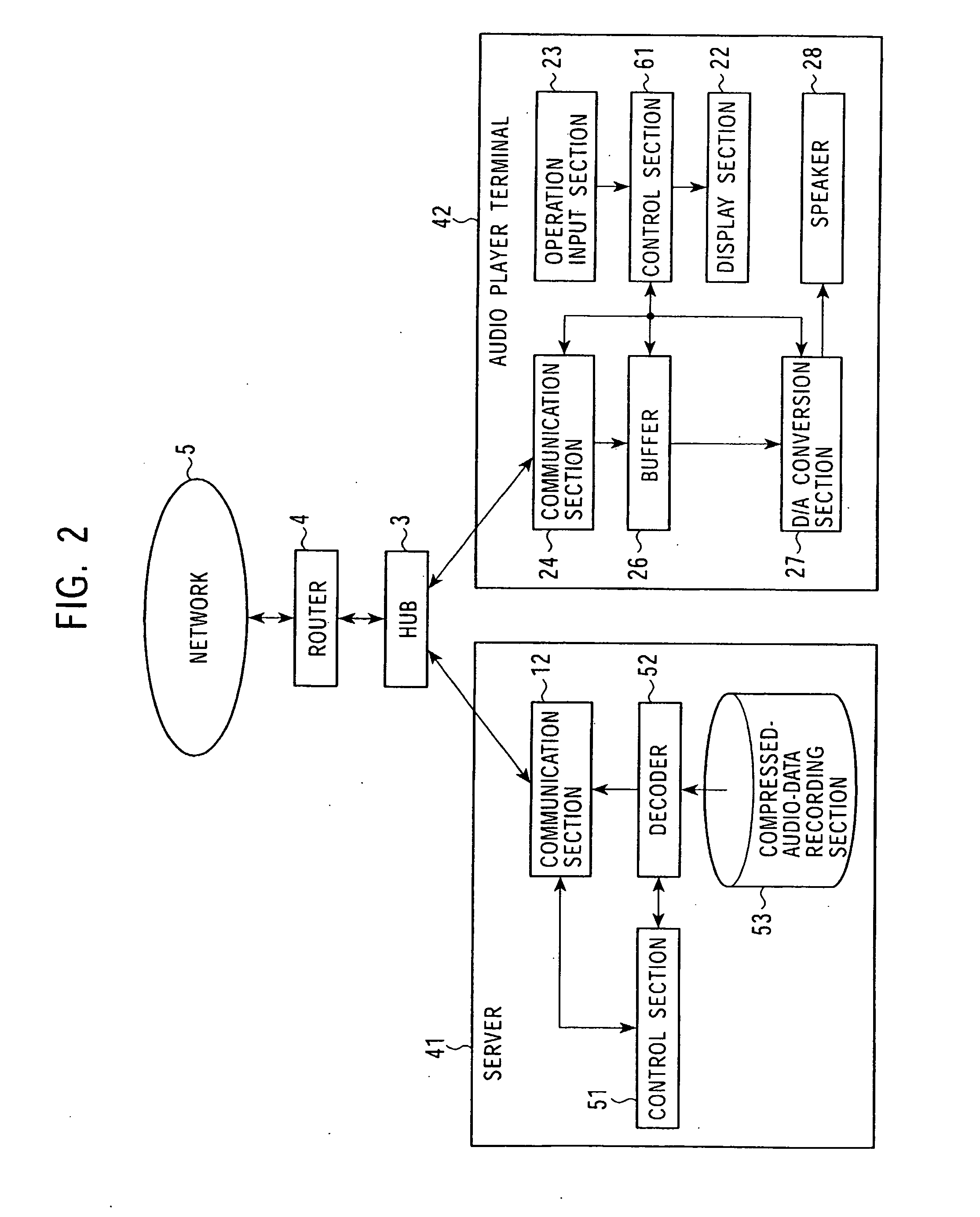
Data stream-distribution system and method therefor
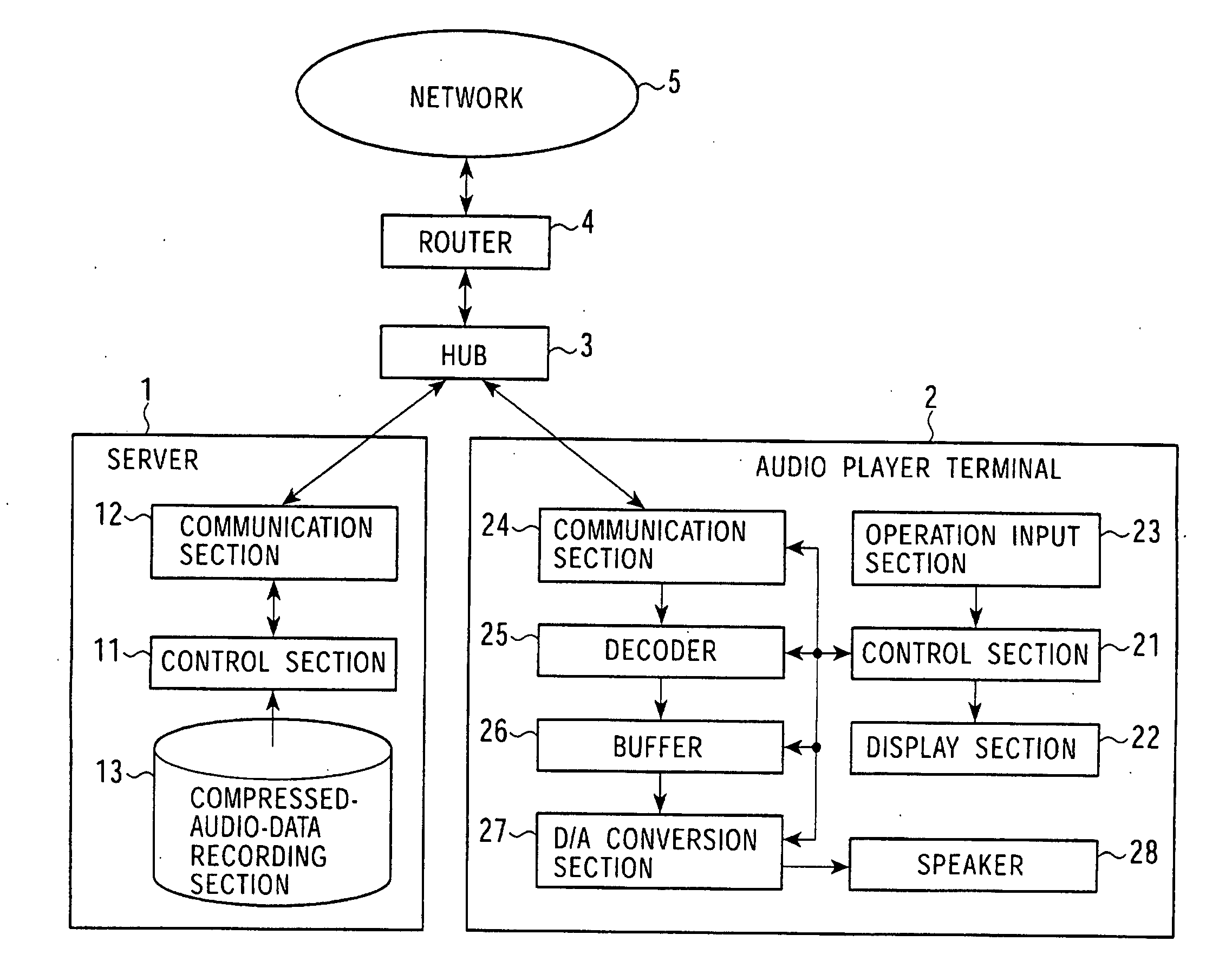
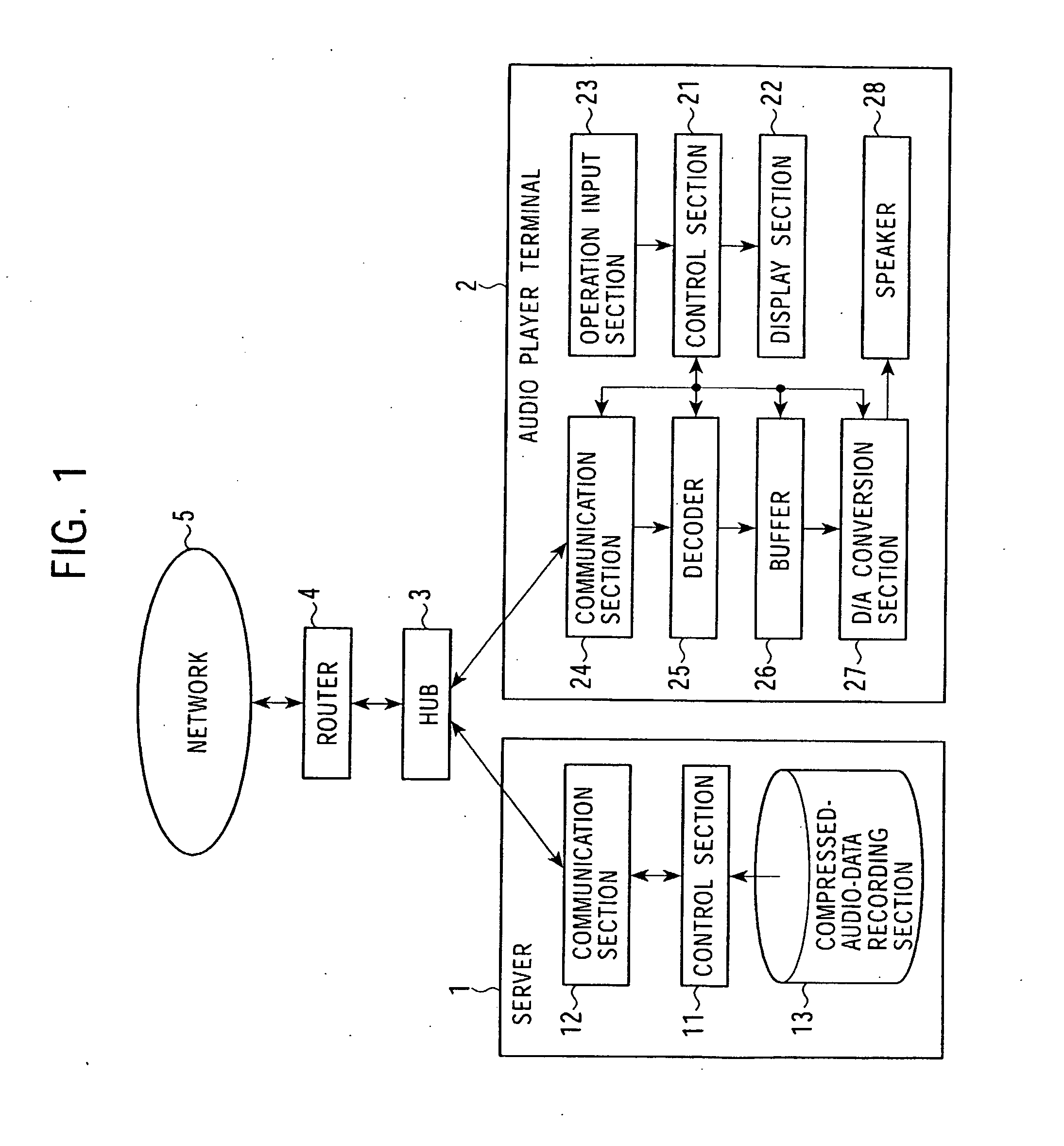
InactiveUS20080147874A1Low data rateReproducing dataSpeech analysisData switching by path configurationData streamDistribution system
A mutual recognition process is performed in step S1. When it is determined in step S2 that a request for sending a list of musical pieces has been received, the list of musical pieces is sent in step S3. When a request for sending audio data has been received in step S4, a transfer-rate measurement process is executed in step S5. When it is determined according to the transfer rate in step S6 that the audio can be transmitted, the corresponding compressed audio data is extracted in step S7, the compressed audio data is decoded to generate linear PCM data suited to the transfer rate in step S8, and transmitted in step S9. When the audio data cannot be transmitted, an error message is transmitted in step S10. The present invention can be applied, for example, to a server for distributing audio data and an audio player terminal for reproducing the distributed audio data.
Owner:SONY CORP
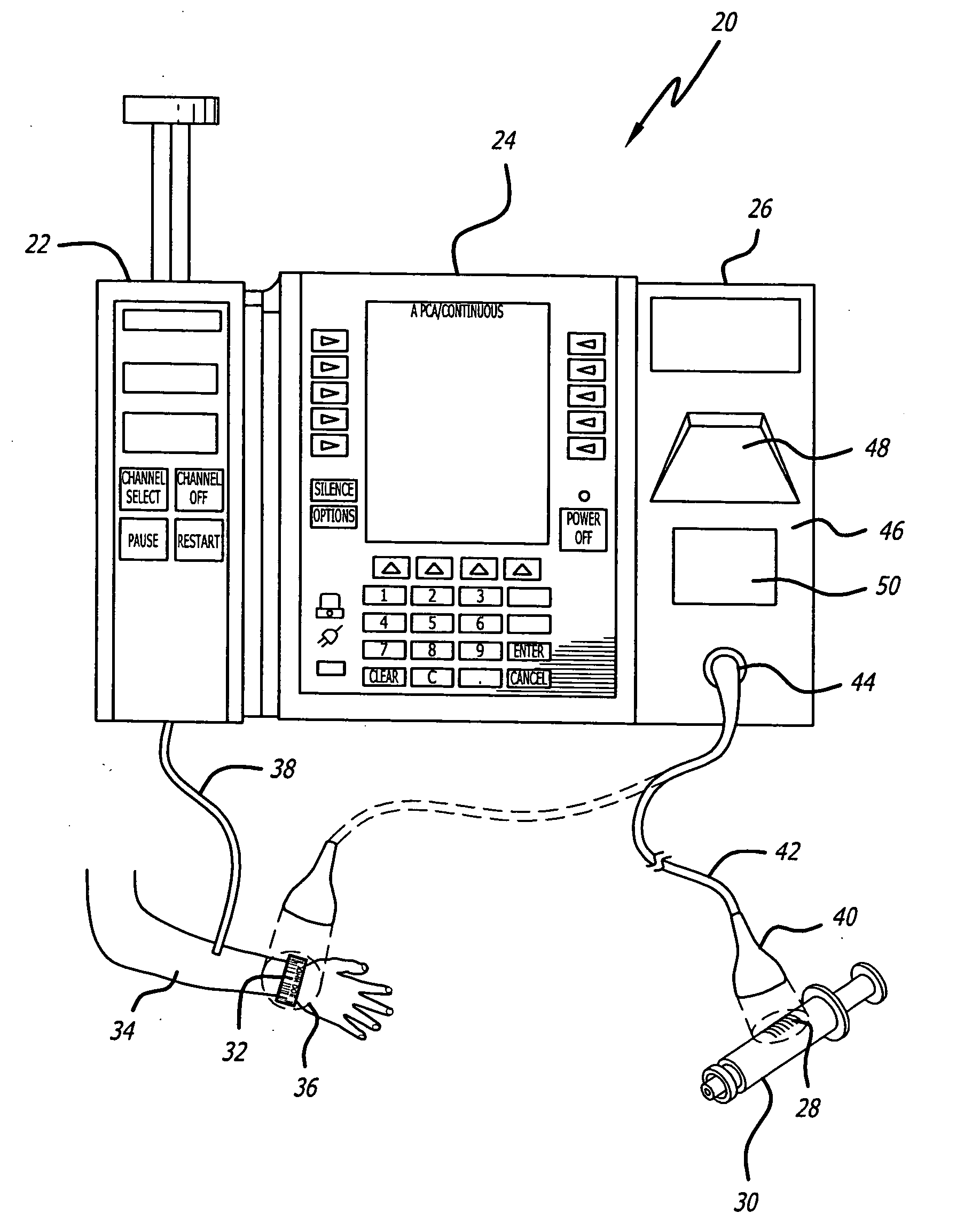
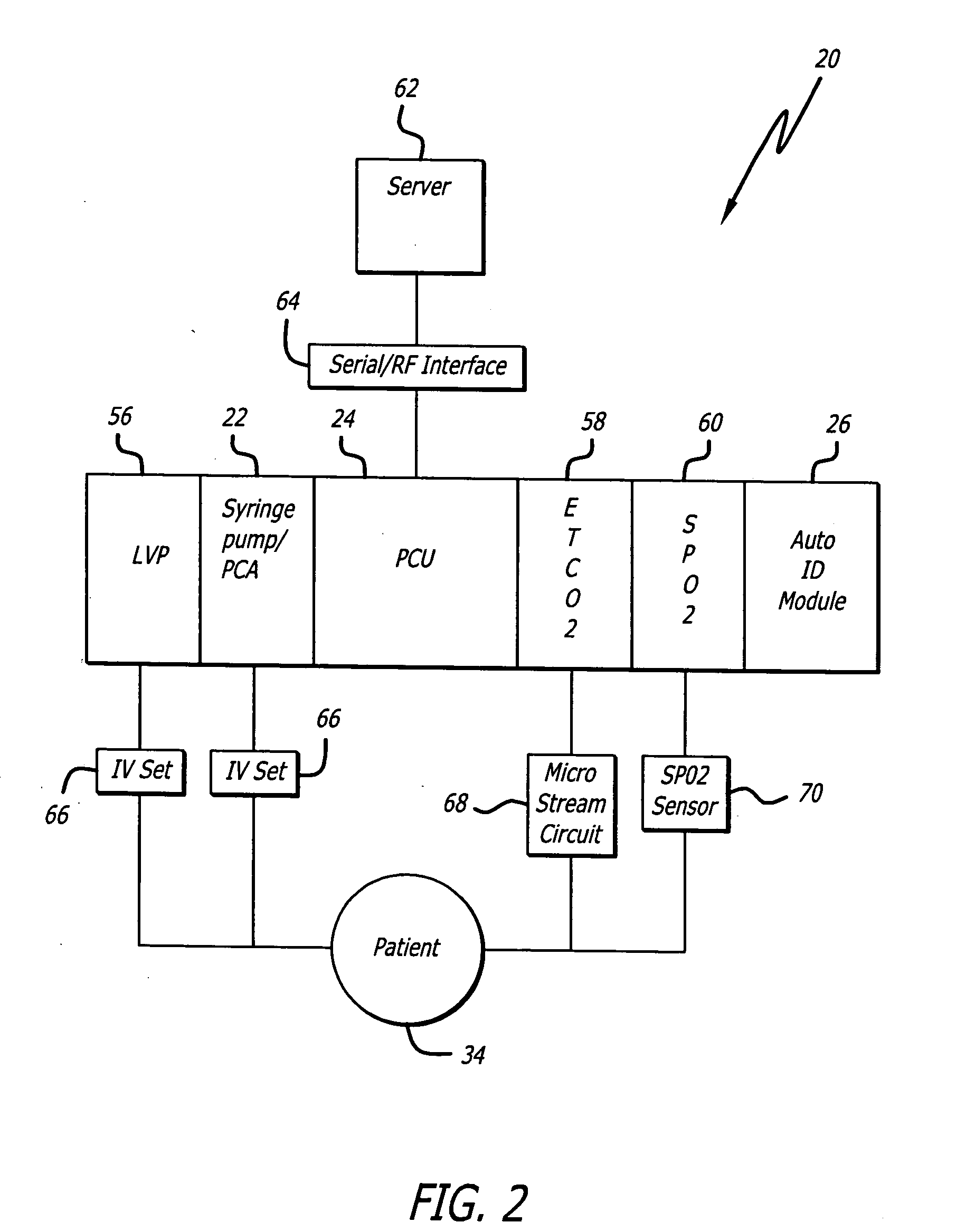
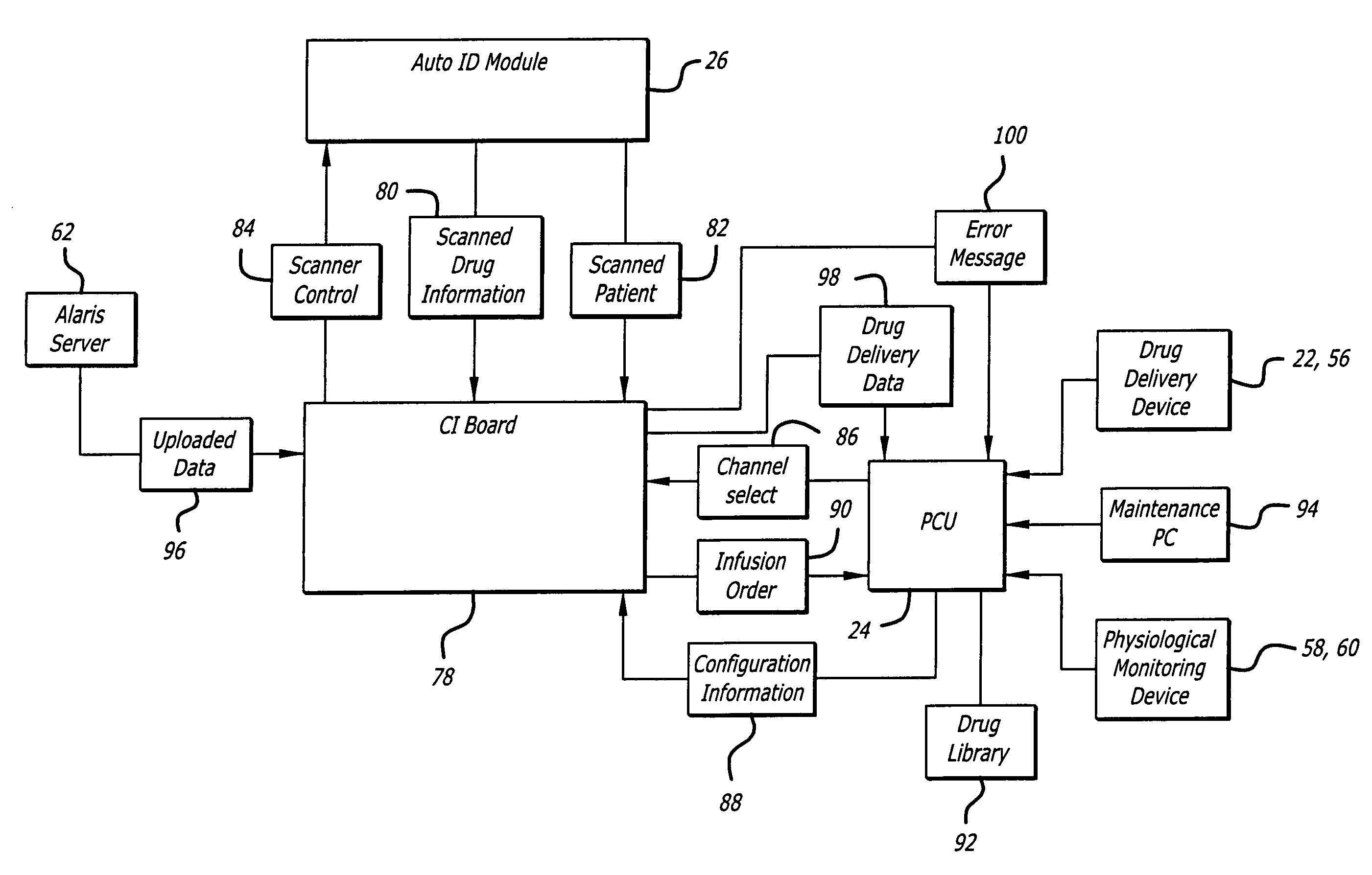
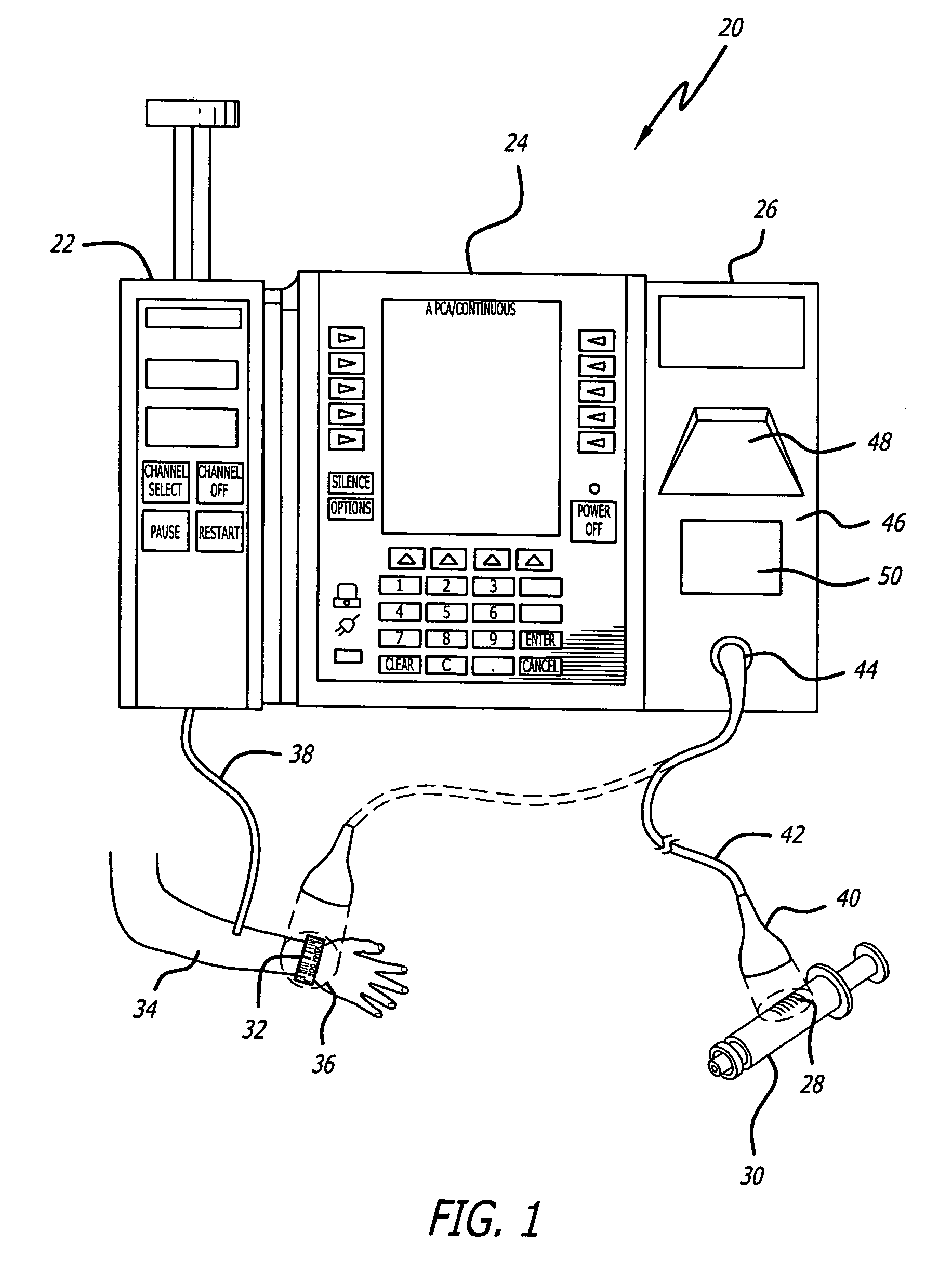
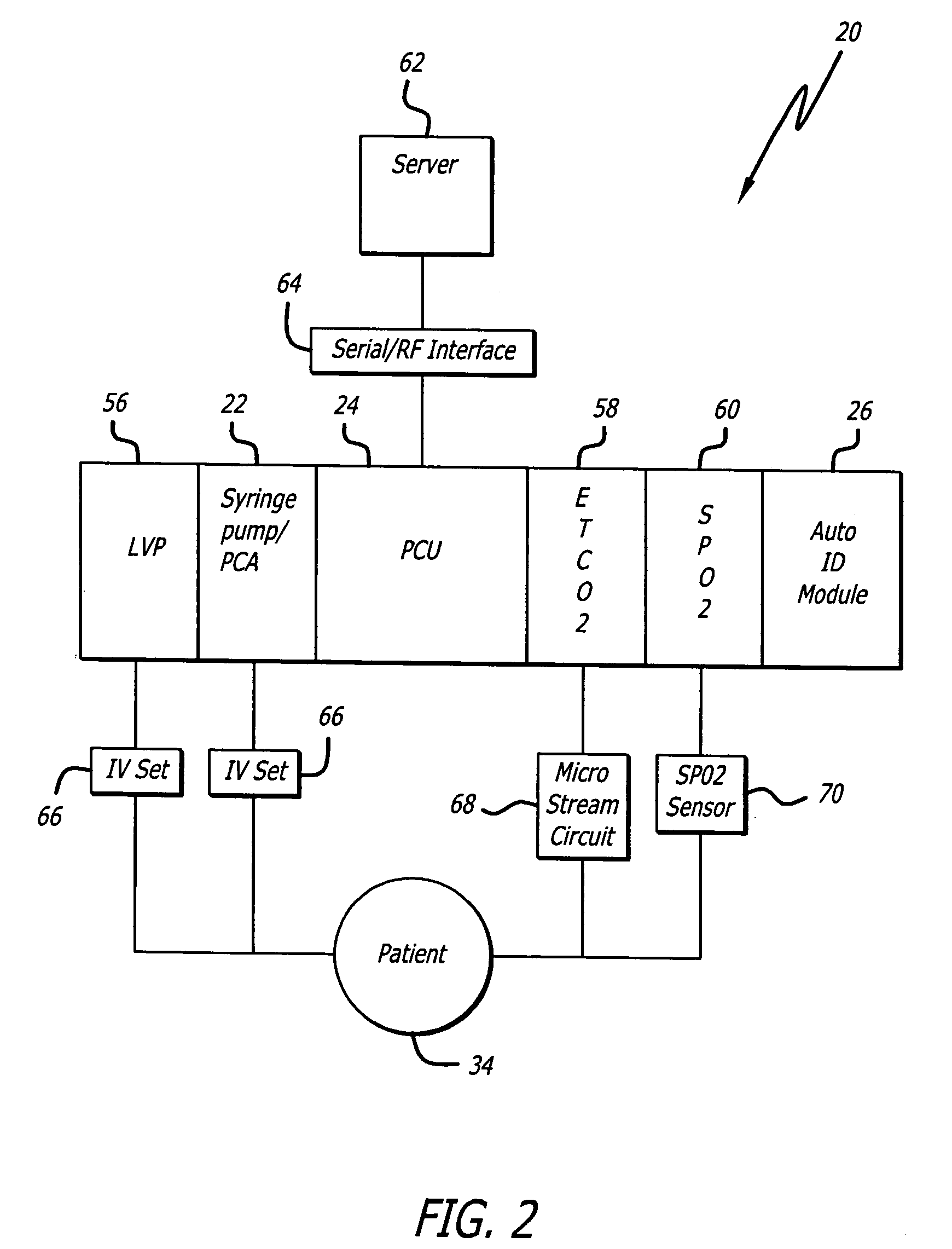
Identification system and method for medication management
An identification system and method for medication management comprises a controller, a drug library accessible by the controller, the drug library containing drug library profiles including a data set of drug information, and an identification module configured to read patient identification information from machine-readable identification devices worn by patients and to read drug information from machine-readable identification devices affixed to drugs or containers of drugs. The controller compares the read information to each other and to the drug library profile and provides alerts or error signals in the event of an inconsistency. In one case, identification devices are read by an optical reader fixedly mounted to the identification module. In another case, identification devices are read by an optical reader that is hand-held and mobile and can be moved to the location of the identification device. The hand-held reader communicates with the identification module by wired or wireless means. In another case, a third reader that is non-optical and wireless is fixedly mounted to the identification module. The controller is also configured to provide alerts or error messages in the event that there is an inconsistency between the drug information on the drug or drug container when compared to the drug library profile associated with the controller.
Owner:CAREFUSION 303 INC
Method, product, and apparatus for requesting a network resource
InactiveUS8635340B1Easy to understandSaving distribution costMultiple digital computer combinationsTransmissionDomain nameIndex term
When a network resource request having a domain name is received, it is determined whether the network resource can be accessed from the domain name. Rather than displaying an error message or processing a search request in response to determining that a network resource can not be accessed, the domain name can instead be redirected to a registration service for domain names or keyword advertiser registration.
Owner:MEC MANAGEMENT LLC
Identification system and method for medication management
An identification system and method for medication management comprises a controller, a drug library accessible by the controller, the drug library containing drug library profiles including a data set of drug information, and an identification module configured to read patient identification information from machine-readable identification devices worn by patients and to read drug information from machine-readable identification devices affixed to drugs or containers of drugs. The controller compares the read information to each other and to the drug library profile and provides alerts or error signals in the event of an inconsistency. In one case, identification devices are read by an optical reader fixedly mounted to the identification module. In another case, identification devices are read by an optical reader that is hand-held and mobile and can be moved to the location of the identification device. The hand-held reader communicates with the identification module by wired or wireless means. In another case, a third reader that is non-optical and wireless is fixedly mounted to the identification module. The controller is also configured to provide alerts or error messages in the event that there is an inconsistency between the drug information on the drug or drug container when compared to the drug library profile associated with the controller.
Owner:CAREFUSION 303 INC
Method and apparatus for automatic downloading of URLs and internet addresses
InactiveUS6393462B1Data processing applicationsDigital data information retrievalWeb browserUser input
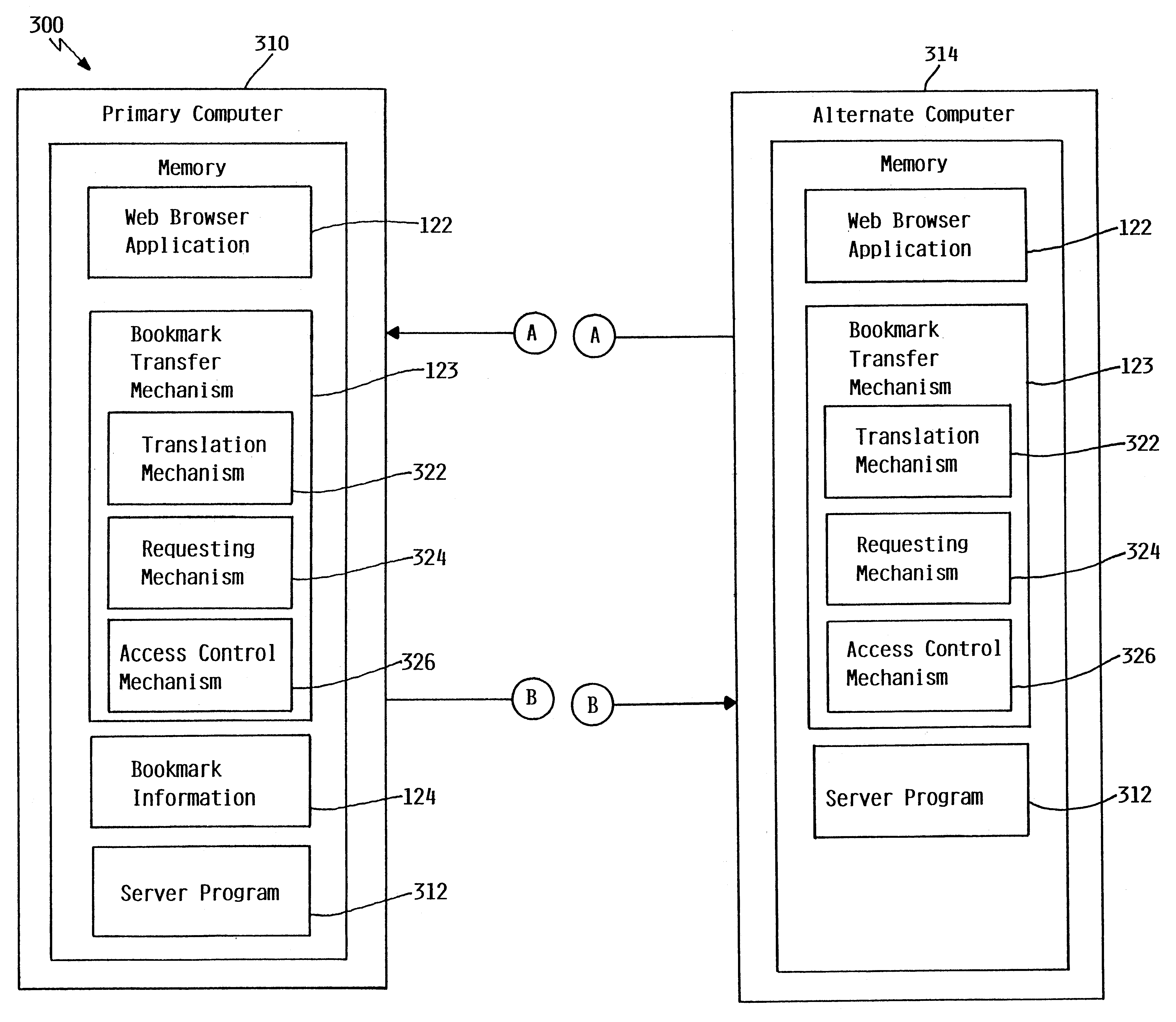
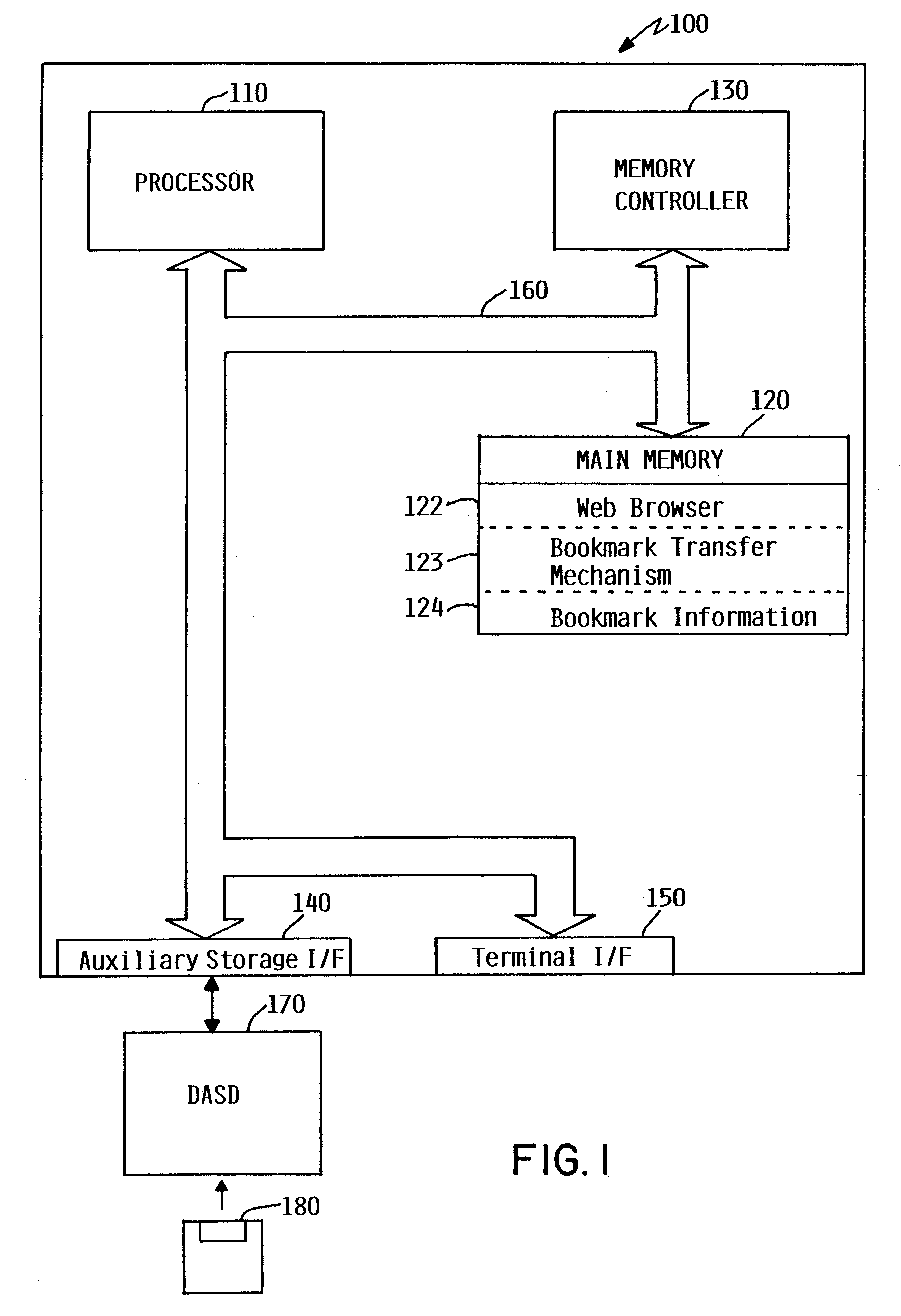
A bookmark transfer mechanism allows a user to transfer bookmark information from a primary computer to an alternate computer to customize a bookmarks menu on a web browser displayed on the alternate computer. The alternate computer prompts the user for a base address which is used by the web browser on the alternate computer to locate the primary computer where bookmark information is stored. The base address should correspond to a primary computer that has been configured for automatic download of bookmark information. Once the primary computer is located, the alternate computer transfers the base address and prompts the user for security information. The alternate computer then delivers the security information to the primary computer. The primary computer then authenticates the security information. If the security information is not valid, the primary computer delivers an error message to the alternate computer indicating that access to the primary computer has been denied. If the security information is valid, the primary computer transfers the bookmark information to the alternate computer. If necessary, the alternate computer translates the received bookmark information to the proper web browser format and updates the bookmarks menu on the web browser to include the transferred bookmark information. The bookmark information may be either temporarily or permanently incorporated into the web browser.
Owner:IBM CORP
Location system and method for client terminals which provide location-based service to mobile terminals
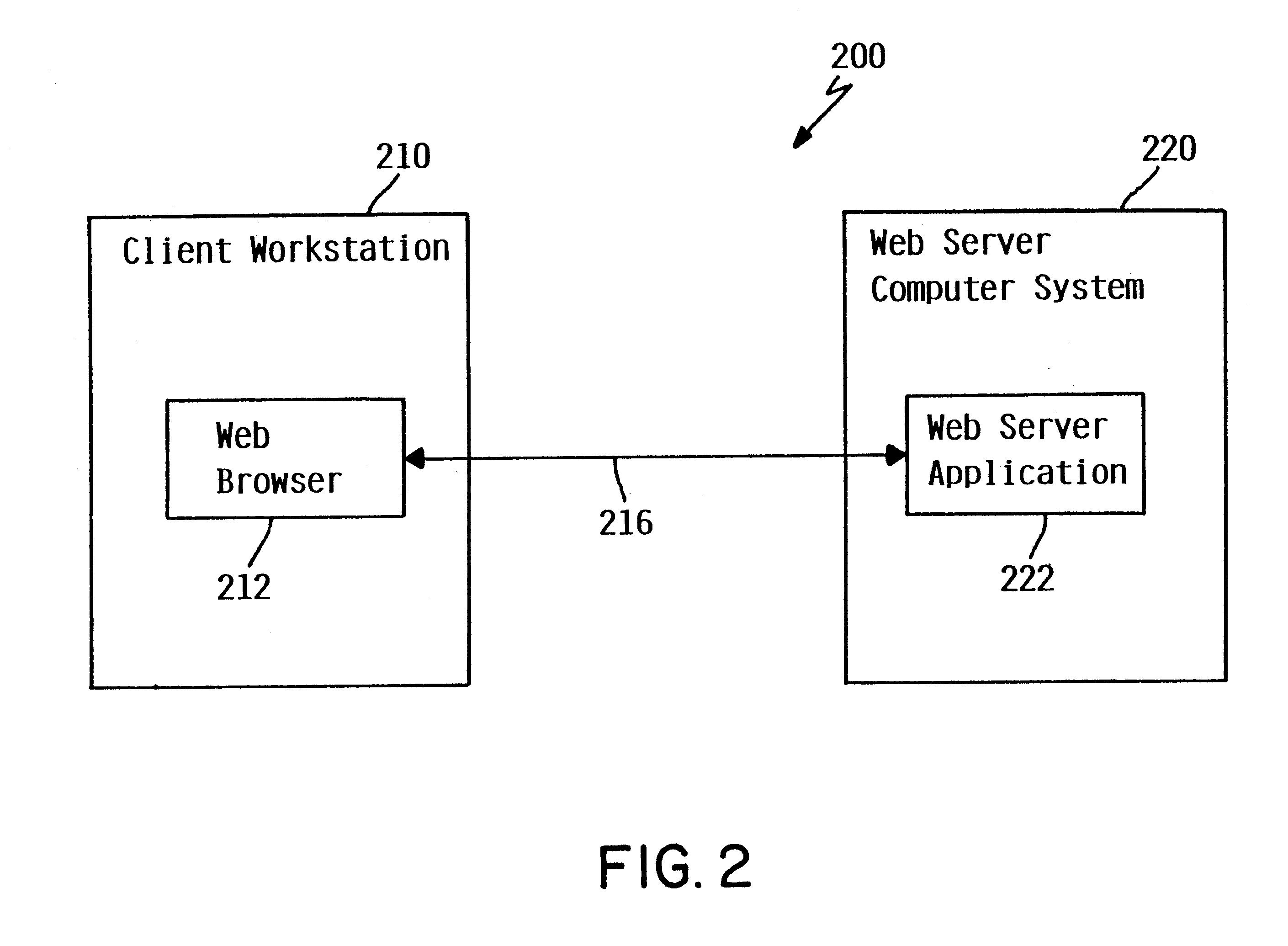
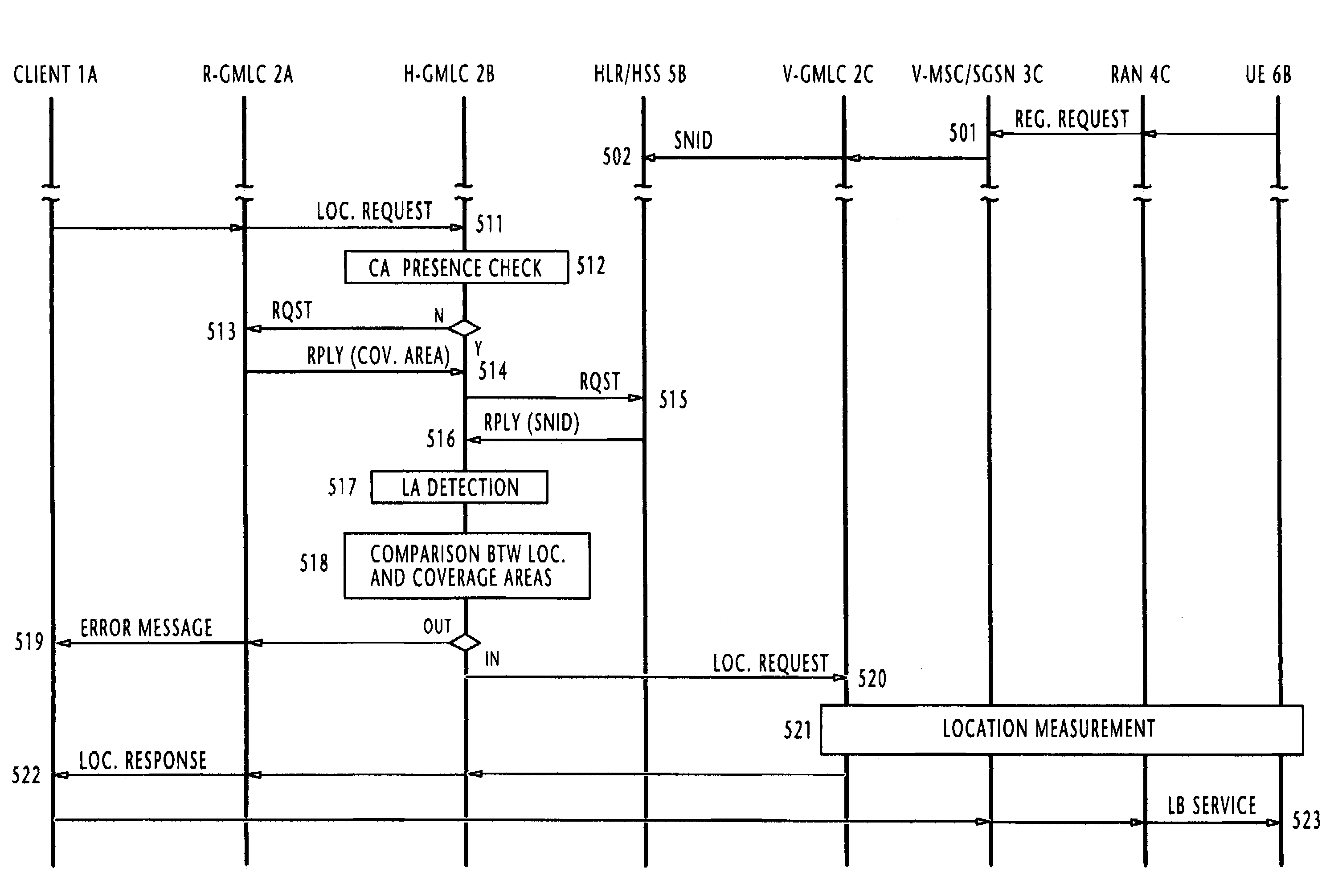
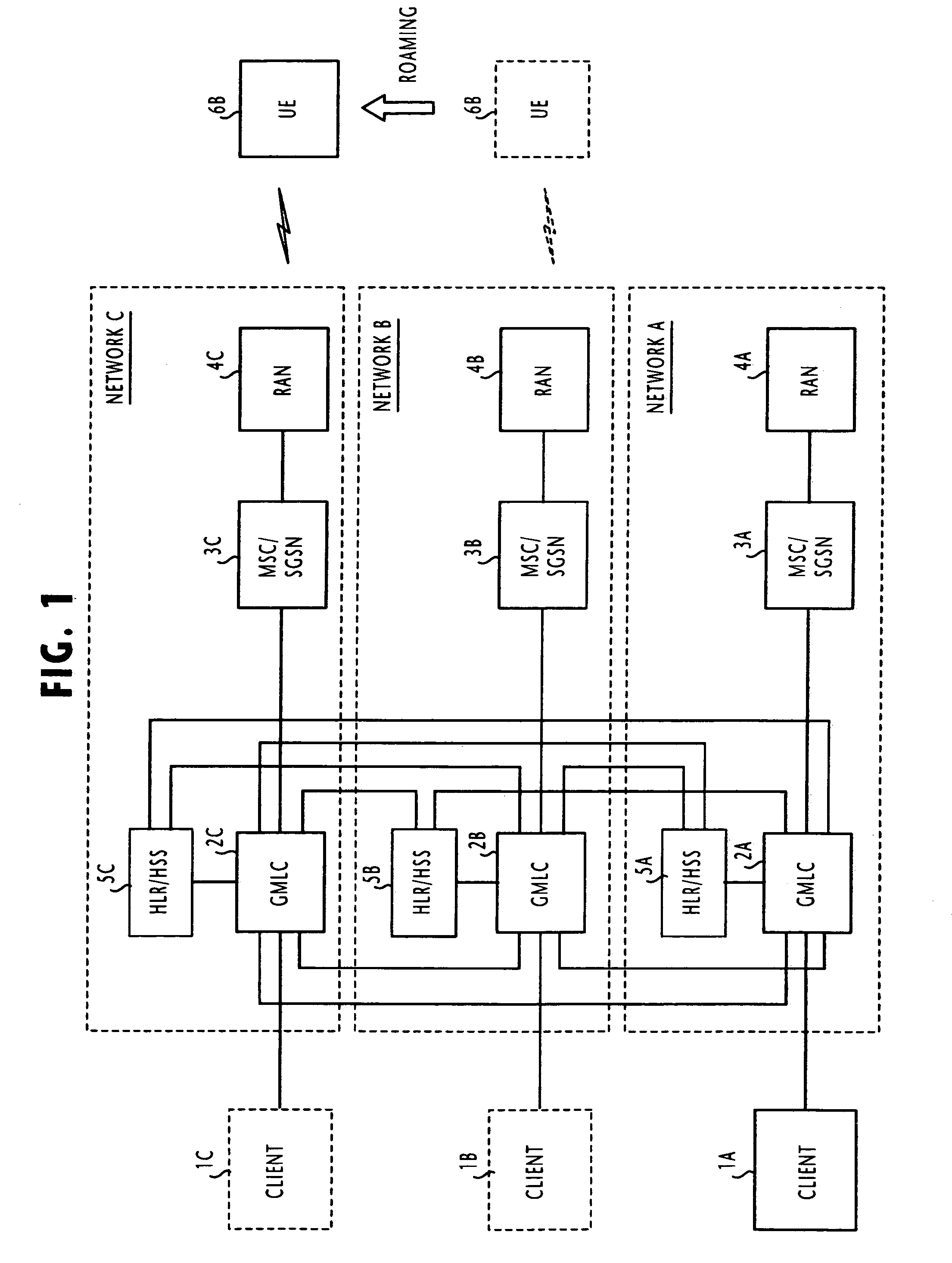
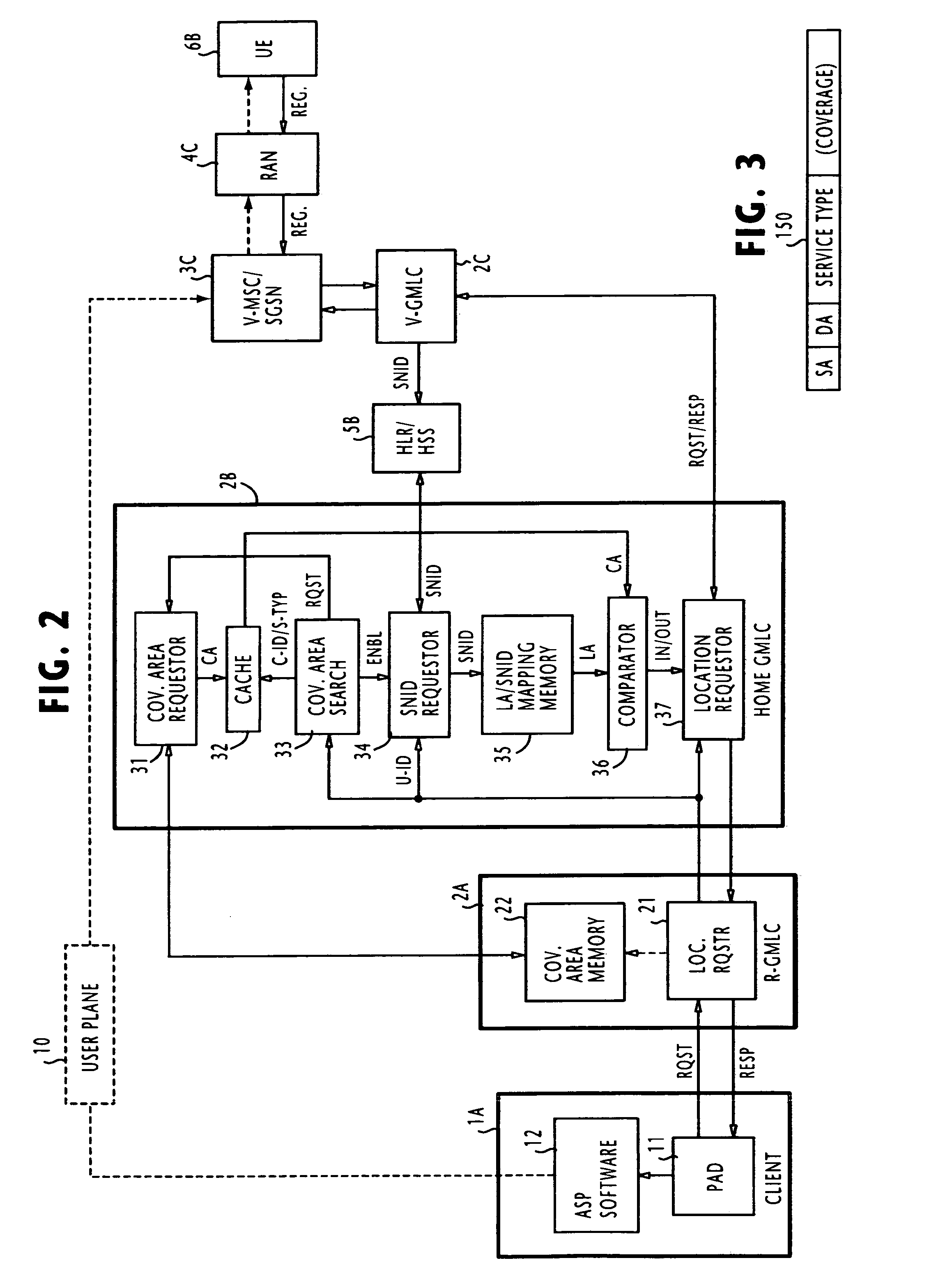
ActiveUS7277711B2Consume resourcesUseless trafficSpecial service for subscribersServices signallingClient-sideLocation area
In one of multiple mobile communication networks, a serving node responsible for locating mobile terminals is responsive to a registration request from a mobile terminal for storing the serving node identity in a home location database to which the mobile terminal is subscribed. In response to a location request message from a client terminal requesting the location of a target mobile terminal, a serving node identity is retrieved from the home location database of the target mobile terminal. The serving node identity represents the current location of the target mobile terminal. If the current location area is within the coverage area of location-based service provided by the client terminal, the location request message is forwarded to a serving node identified by the retrieved serving node identity. Otherwise, an error message is transmitted to the client terminal to indicate that the target mobile terminal is roaming outside of the coverage area.
Owner:NEC CORP
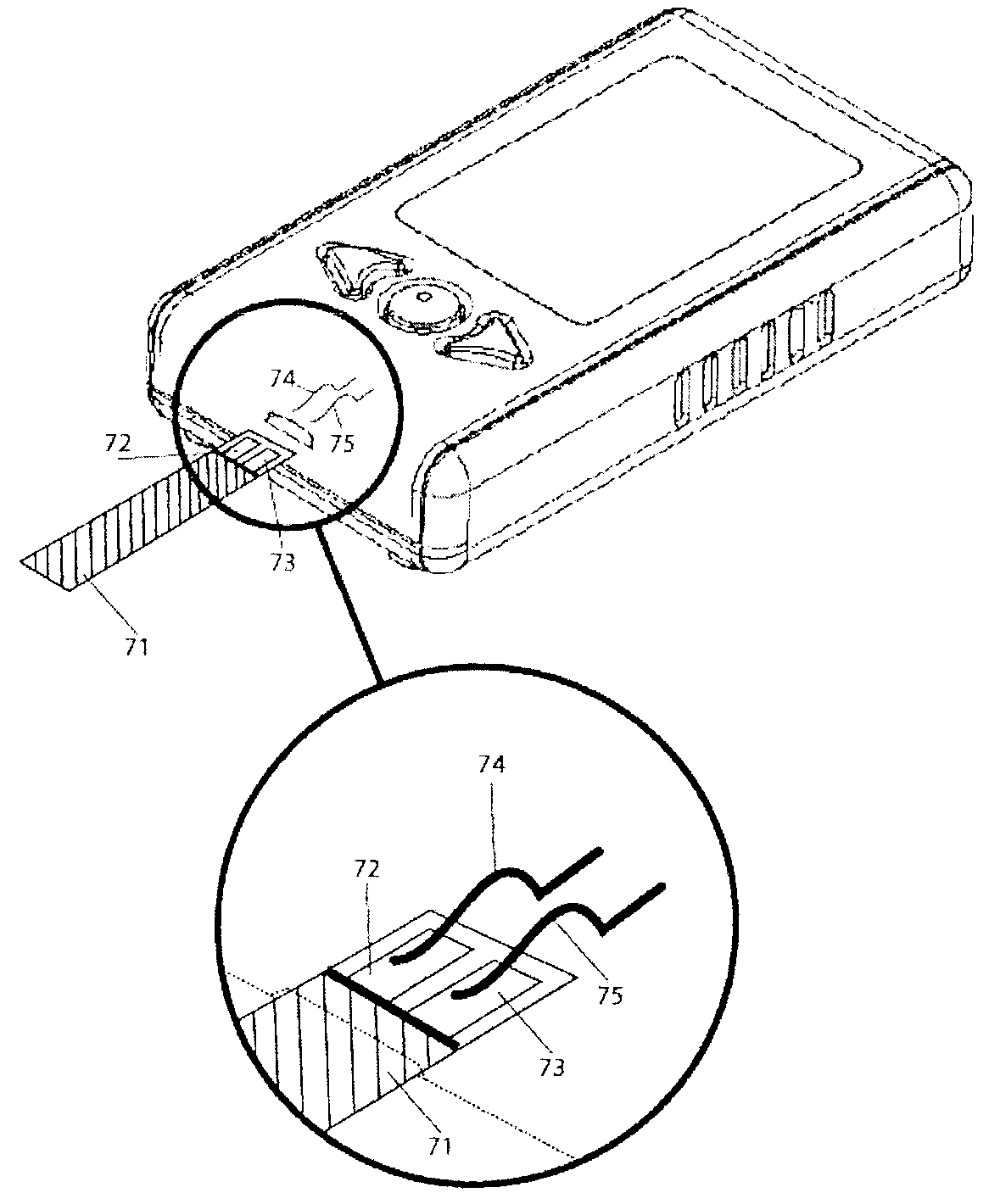
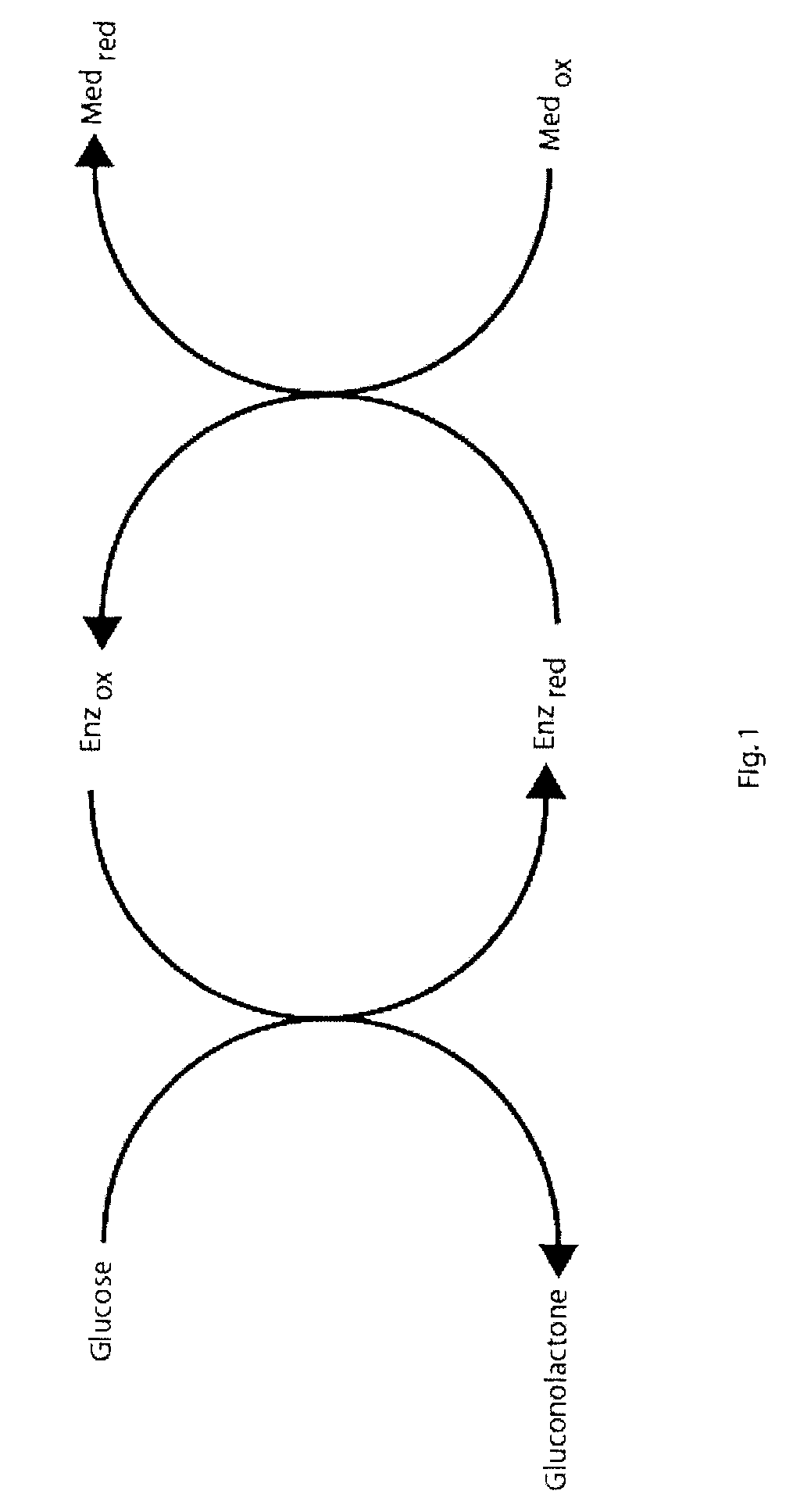
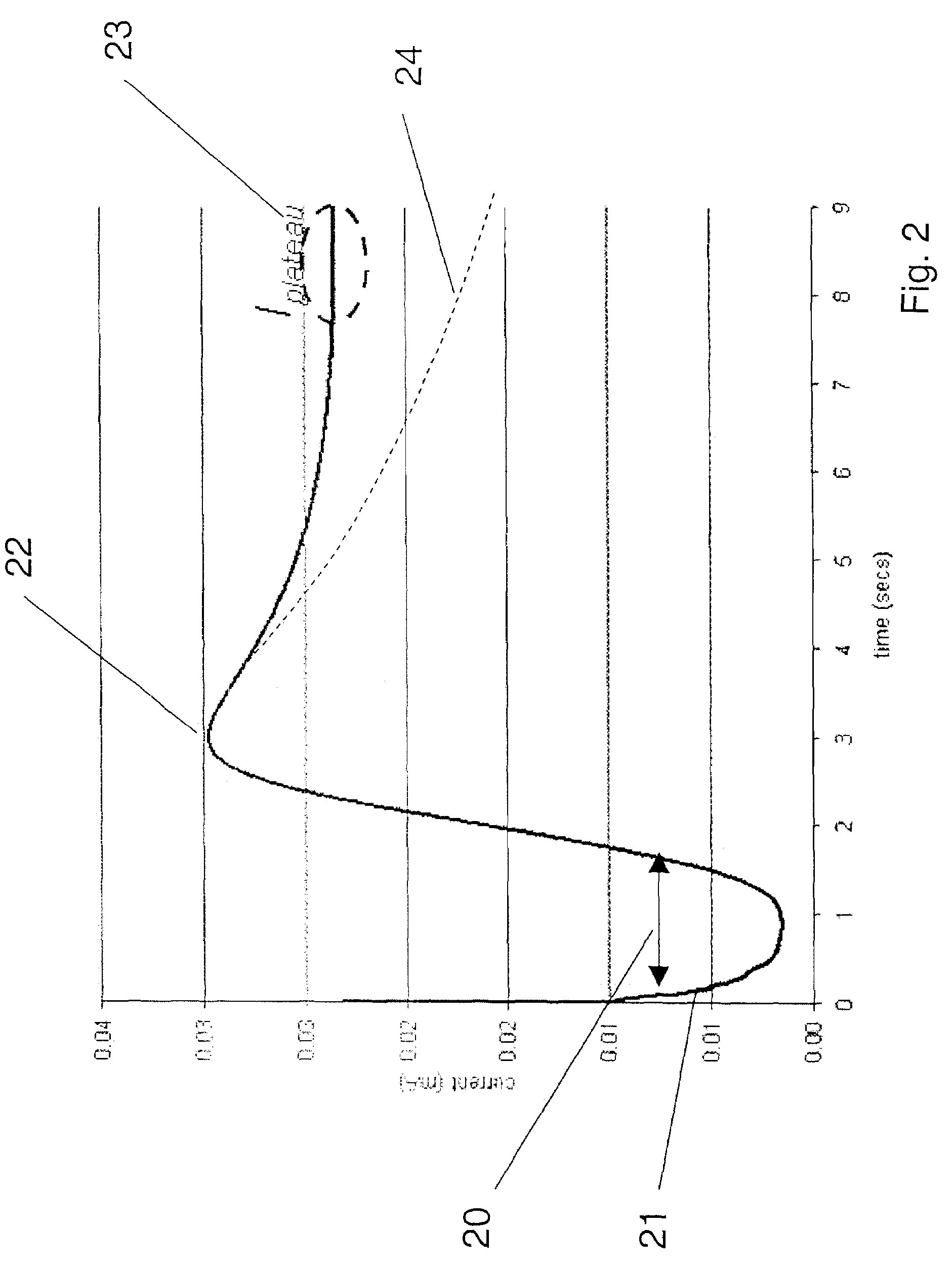
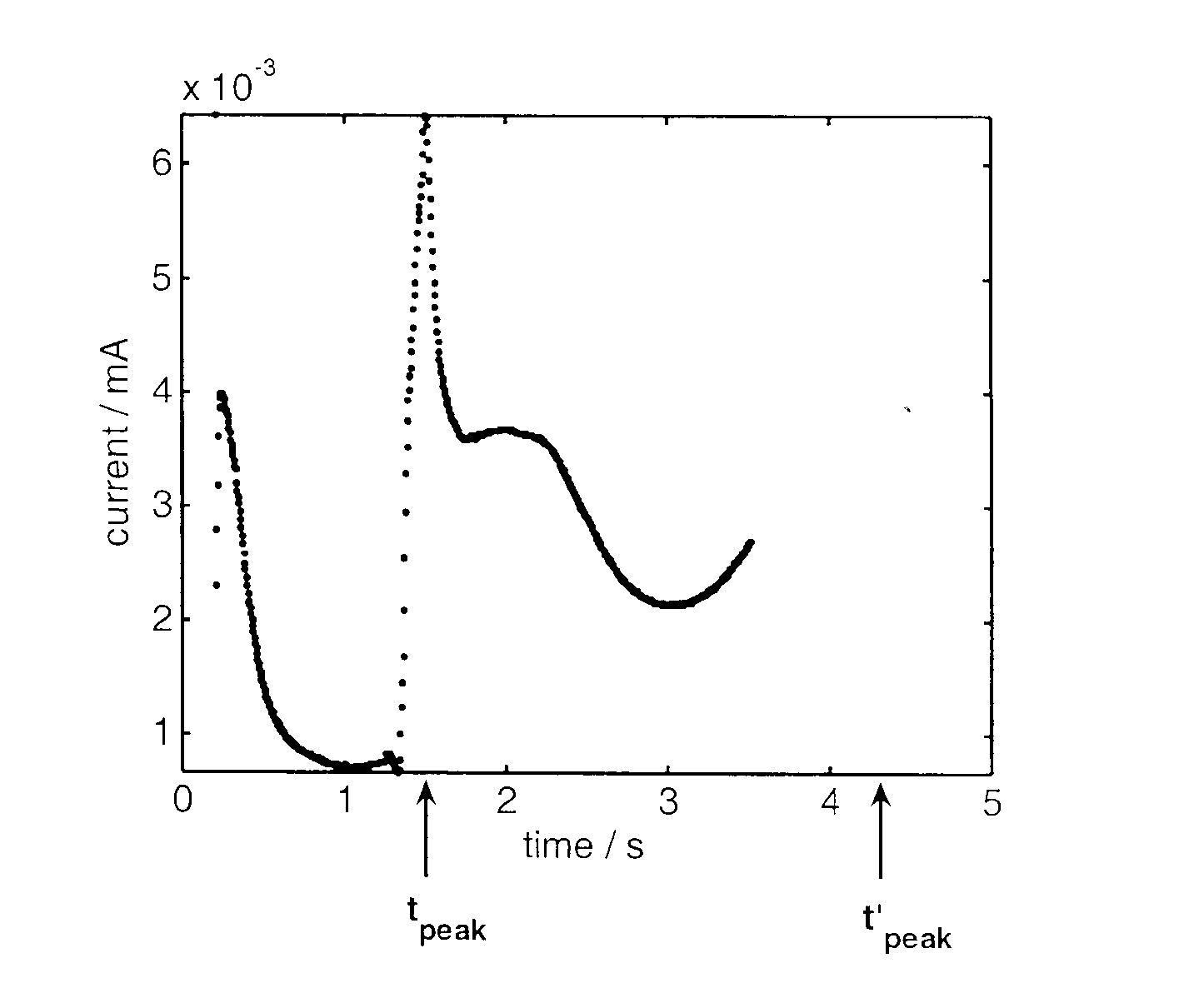
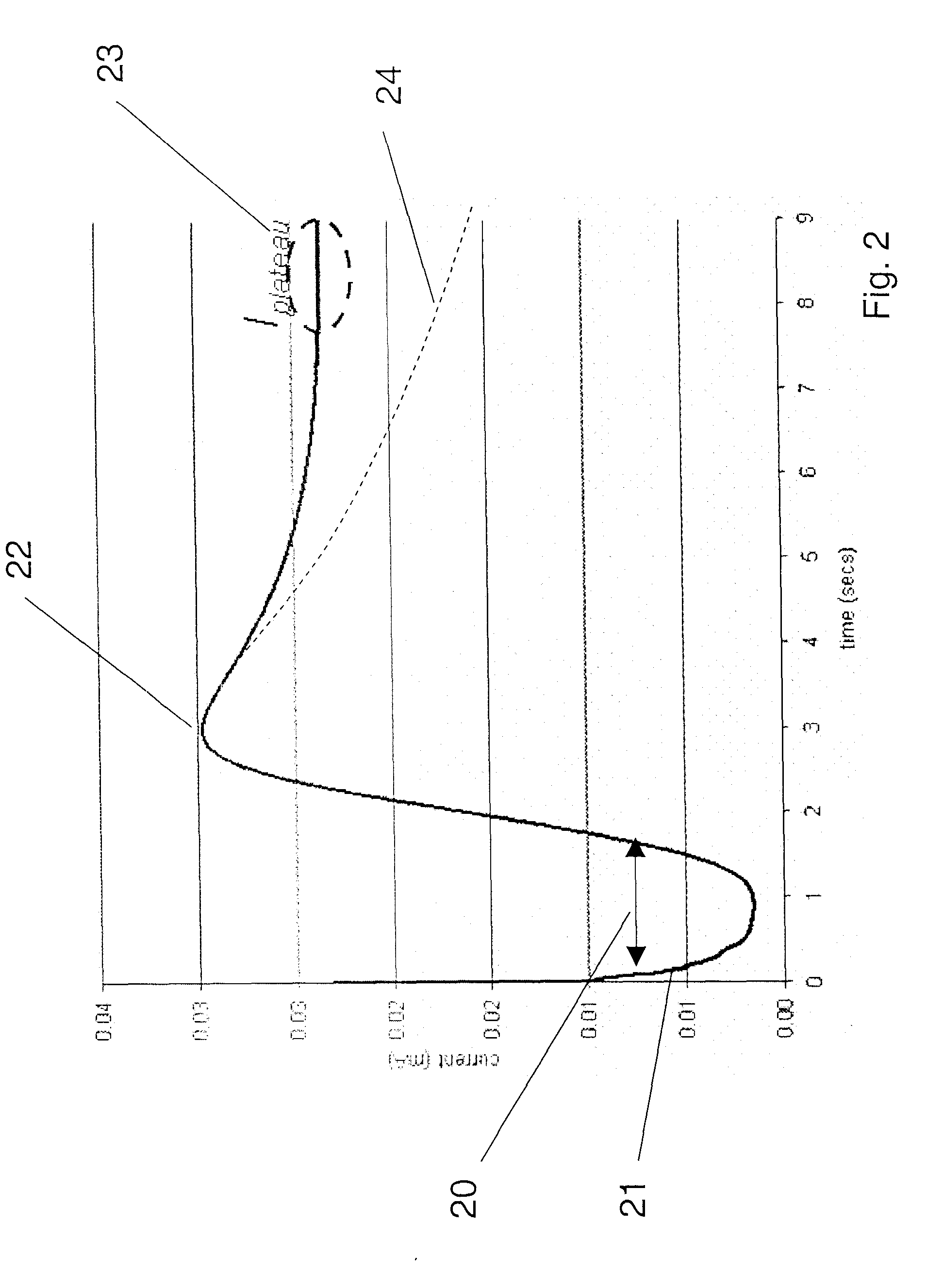
Method and apparatus for detection of abnormal traces during electrochemical analyte detection
Detection of abnormal signal traces in electrochemical measurements generated using an electrochemical test strip to which a potential is applied allows for an indication of an erroneous analyte determination. The current trace has an expected shape in which a peak current is observed a time tpeak after which there is a decrease in current. To detect abnormal signal traces, the time tpeak is determined experimentally and compared with an expected value, t′peak, and if the difference between the two values to over a predetermined threshold, an error message is provided to the user instead of a test result. The value of t′peak is determined as a function of a mobility term that is determined during a potentiometry phase following the amperometric measurements.
Owner:AGAMATRIX INC
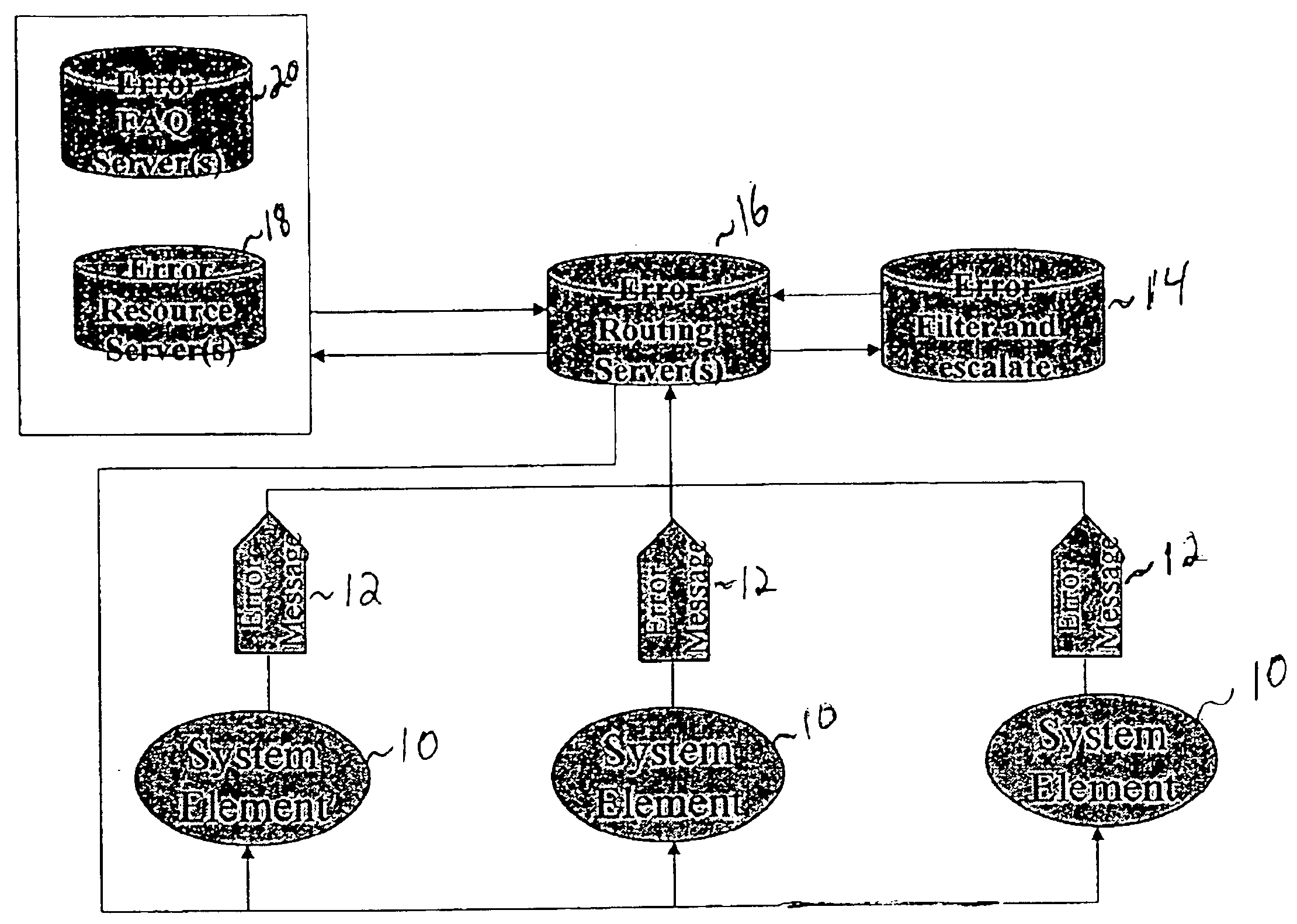
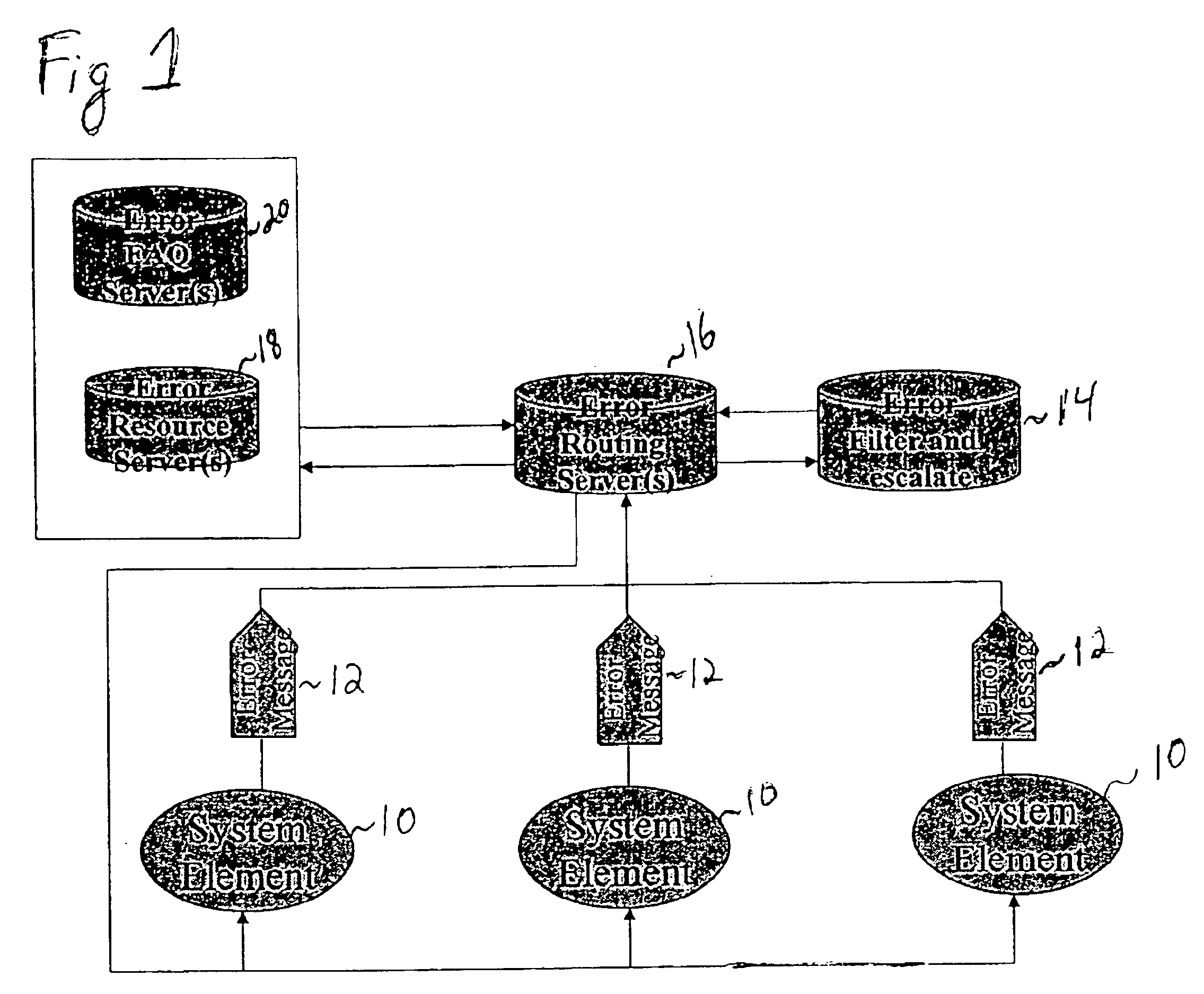
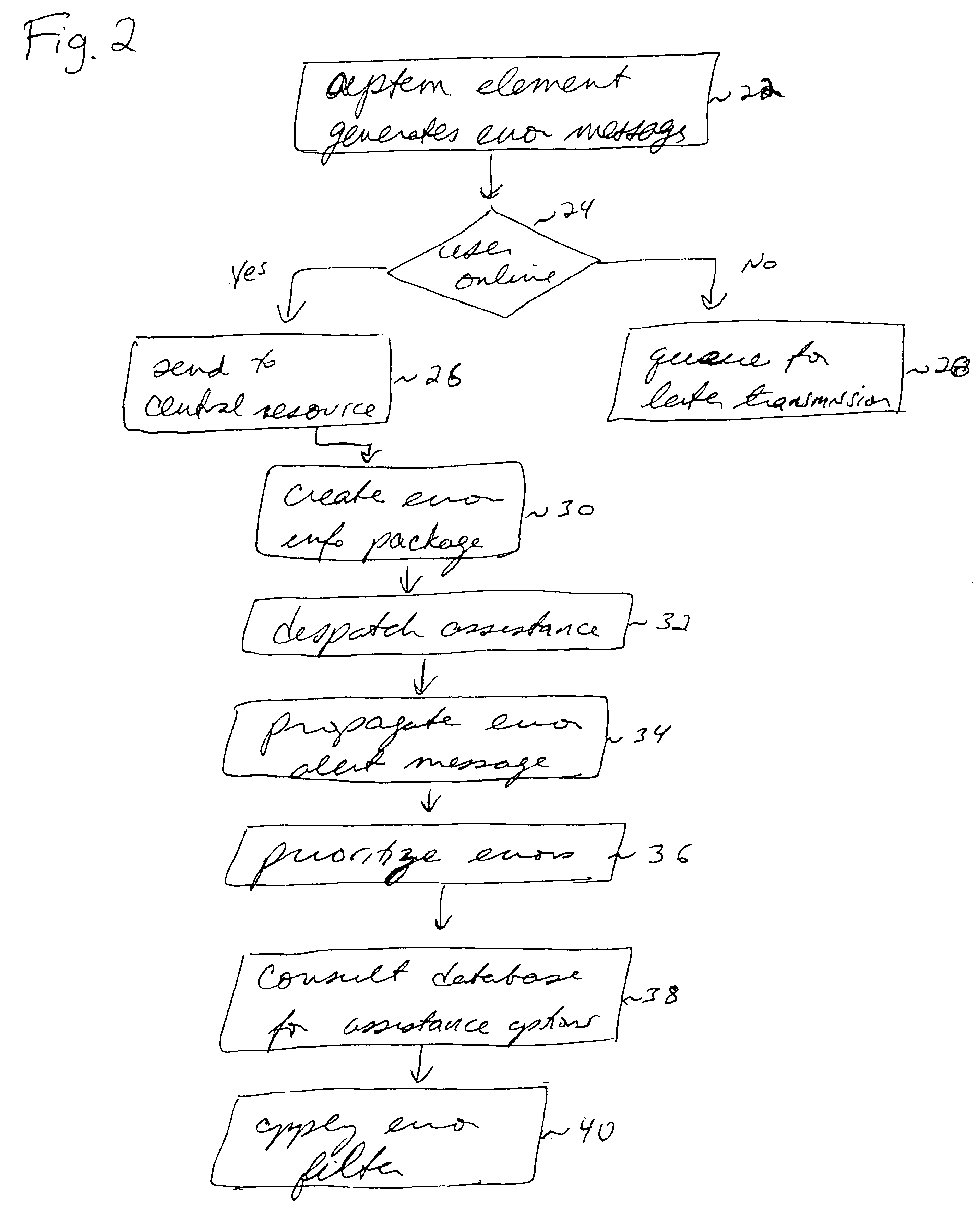
Method and system for handling errors in a distributed computer system
InactiveUS6918059B1Avoid the correction processNon-redundant fault processingData switching networksError processingComputerized system
A method and system for tracking and processing errors in a distributed computer system. As an application encounters an error, a centralized system intercepts and assumes the processing of that error event. The central error processing may be used with a distributed network connecting the applications running on various user computers. Upon receipt of an error message from an application, the system creates an informative error package, propagates appropriate error alert to relevant subsystems, and attempts to resolve the error. The error may be resolved in various ways. For example, the system may select and dispatch appropriate help information to the user; or the system may locate an alternative resource to substitute for the failed resource. The system may prioritize errors when there is more than one error still unresolved at any given time. In addition, the system may filter errors that require different levels of response and the system may direct errors to resources capable of assisting in resolving the error.
Owner:SALESFORCE COM INC
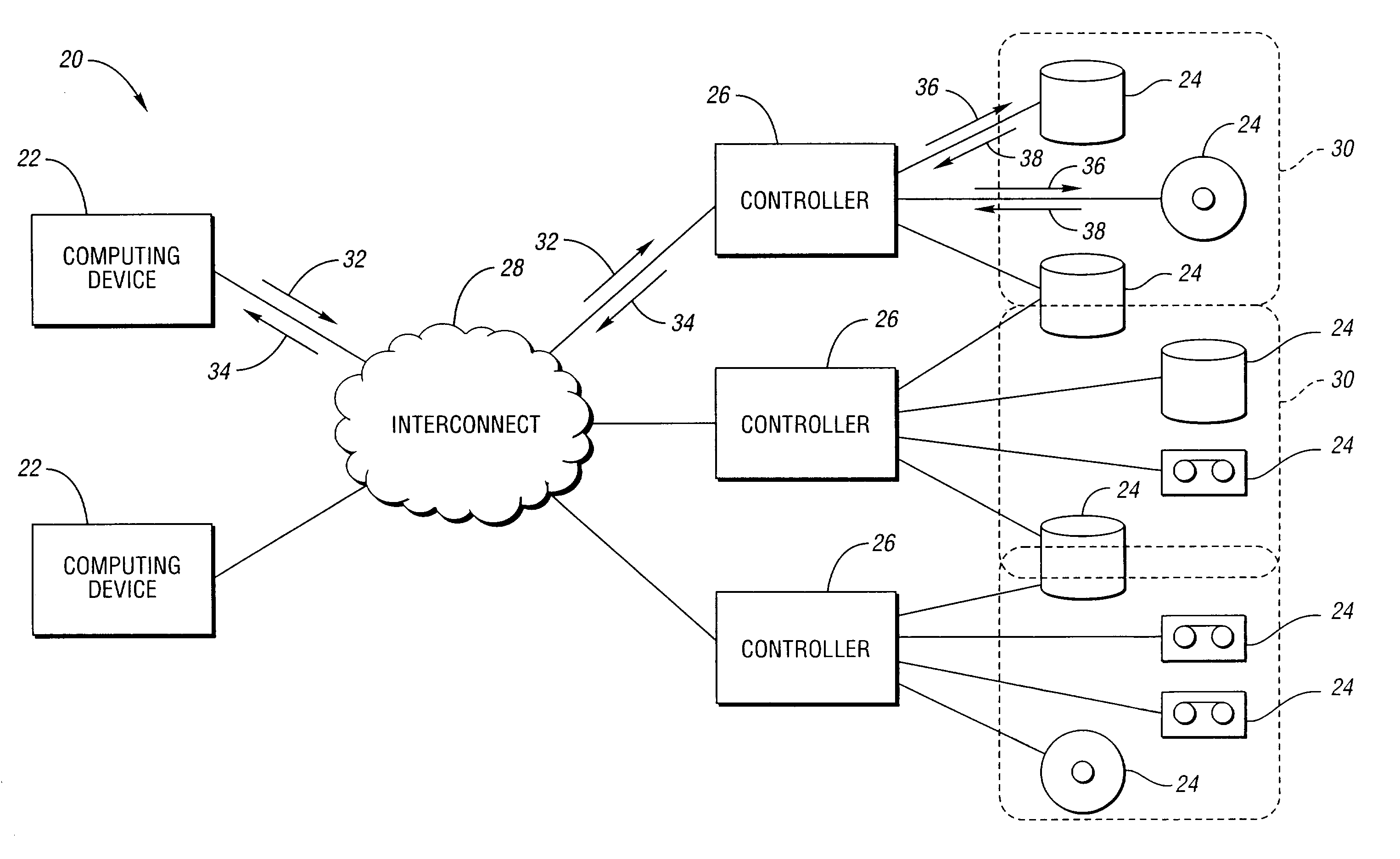
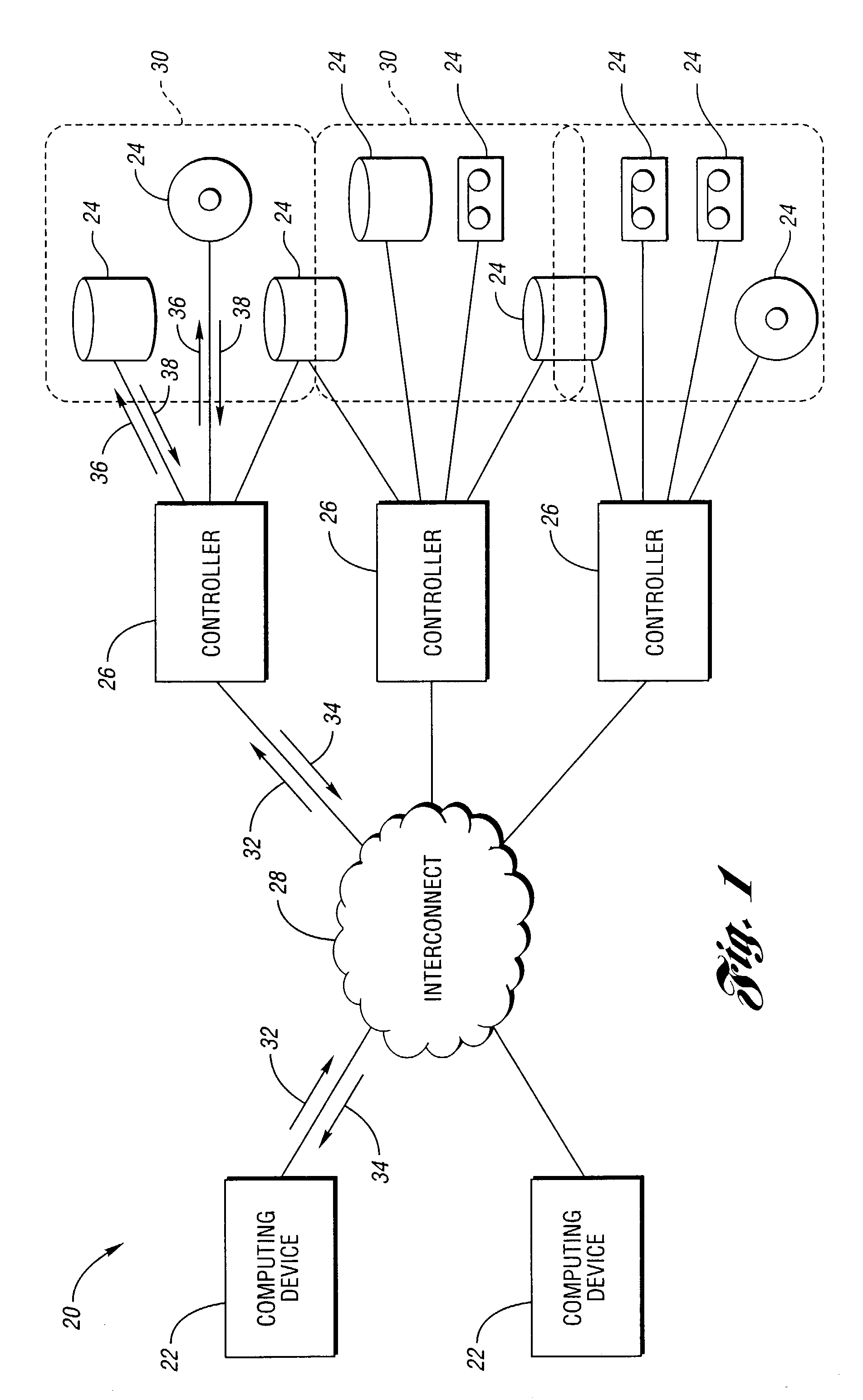
Virtual storage status coalescing with a plurality of physical storage devices
ActiveUS6990604B2Reduce difficultyNon-redundant fault processingInput/output processes for data processingData accessPhysical access
Error messages generated when accessing more then one physical storage device are handled by coalescing the status from each accessed physical storage device. A controller receives a virtual storage request from a computing device specifying a virtual data access. The virtual data access includes a plurality of blocks, each block associated with one of at least two target physical storage devices. An access sequence associating one target storage device with each block in the received virtual storage access request is determined. At least one physical access request is sent to each target storage device. At least one error message is received from a target storage device, each error message having an error type. An error response is determined based on the error message type and on the access sequence.
Owner:ORACLE INT CORP
Method for tracking and reporting usage events to determine when preventive maintenance is due for a medical robotic system
A medical robotic system comprises a number of components that may be monitored to determine their preventive maintenance needs by recording usage-related information for the monitored components into associated non-volatile memories. When usage of the component exceeds a specified usage threshold, the system displays a warning message on its display screen to have preventive maintenance performed for the component. If the usage continues without such maintenance and exceeds a higher usage threshold, the system displays an error message on its display screen and the system transitions into an error state during which medical procedures are not allowed to be performed. The usage-related information may also be communicated to a remote computer which gathers and processes usage-related information from a number of medical robotic systems to estimate resource requirements for timely performing preventive maintenance on the medical robotic systems, and anticipated service revenues from such maintenance.
Owner:INTUITIVE SURGICAL OPERATIONS INC
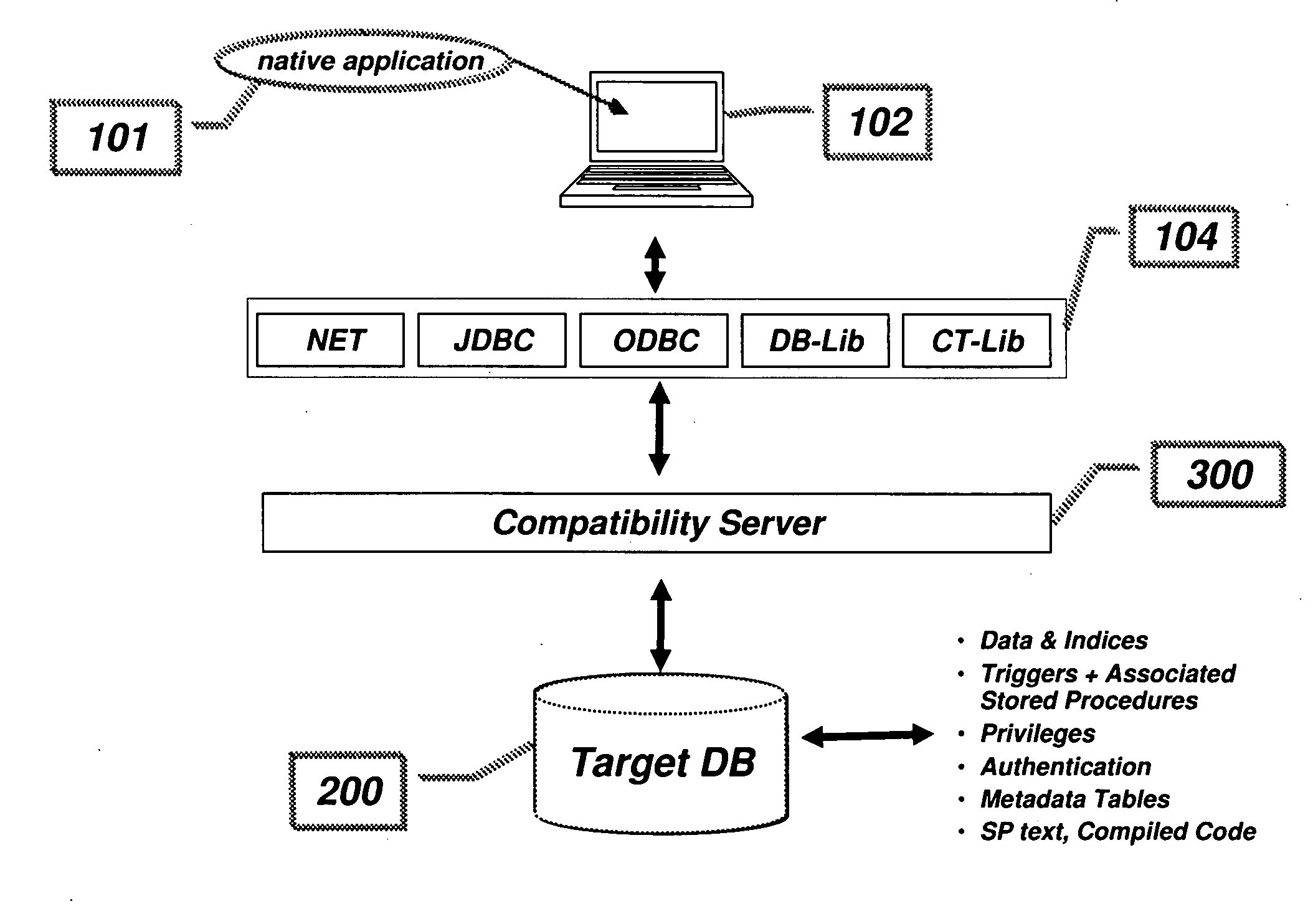
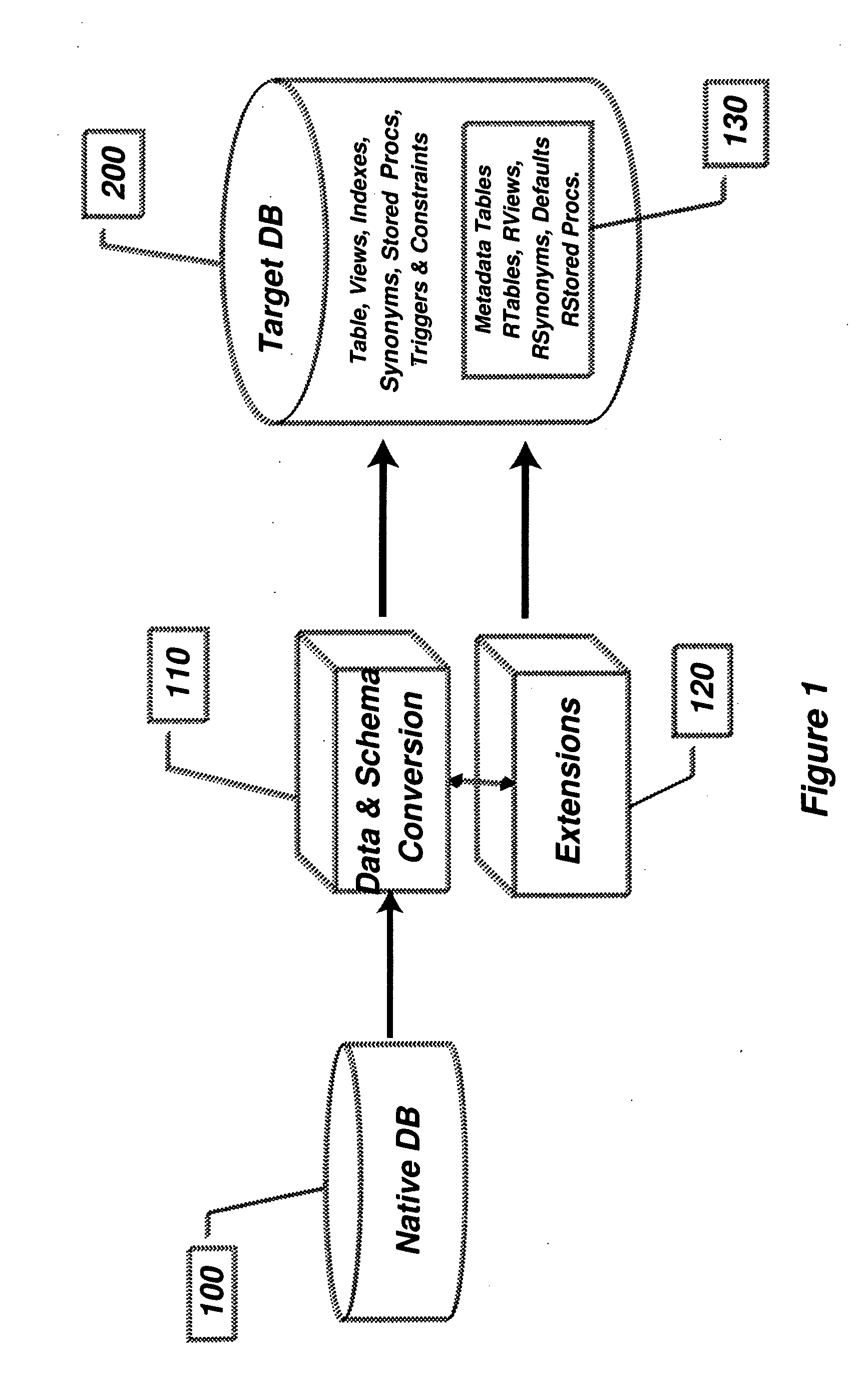
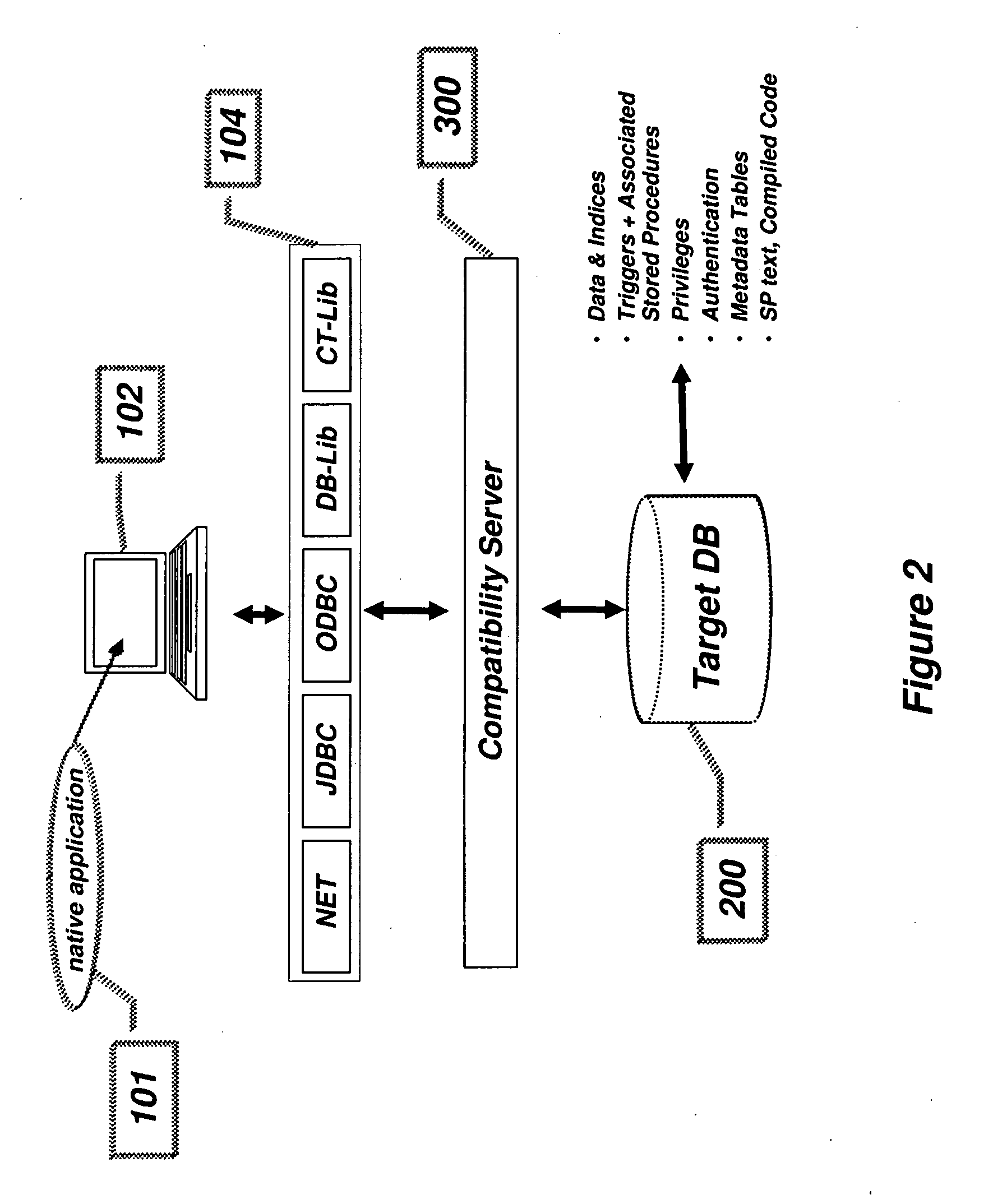
Compatibility Server for Database Rehosting
InactiveUS20100094838A1Digital data information retrievalDigital data processing detailsApplication programming interfaceDatabase application
A system and method describing a compatibility server for rehosting database applications written for a specific vendor's database on the database of a second vendor, without the need of rewriting the application to take into account differences in the application programming interfaces between the first vendor's database and the second vendor's database. Requests for access to the database are translated from one format to another at execution time. The server is also capable of translating error messages, data types and data formatting from the format used by the second database to that expected when making requests to the first database. Stored procedures defined in the first database are migrated to the second database as text blocks, and are translated at execution time into a high level programming language, compiled and executed against the second database. All information necessary for the mapping of schema, data, data types, error and status messages and data formatting, as well as information necessary to execute stored procedures, is stored in a plurality of metadata tables in the second database, which are created during a migration phase prior to executing the application.
Owner:ANTS SOFTWARE
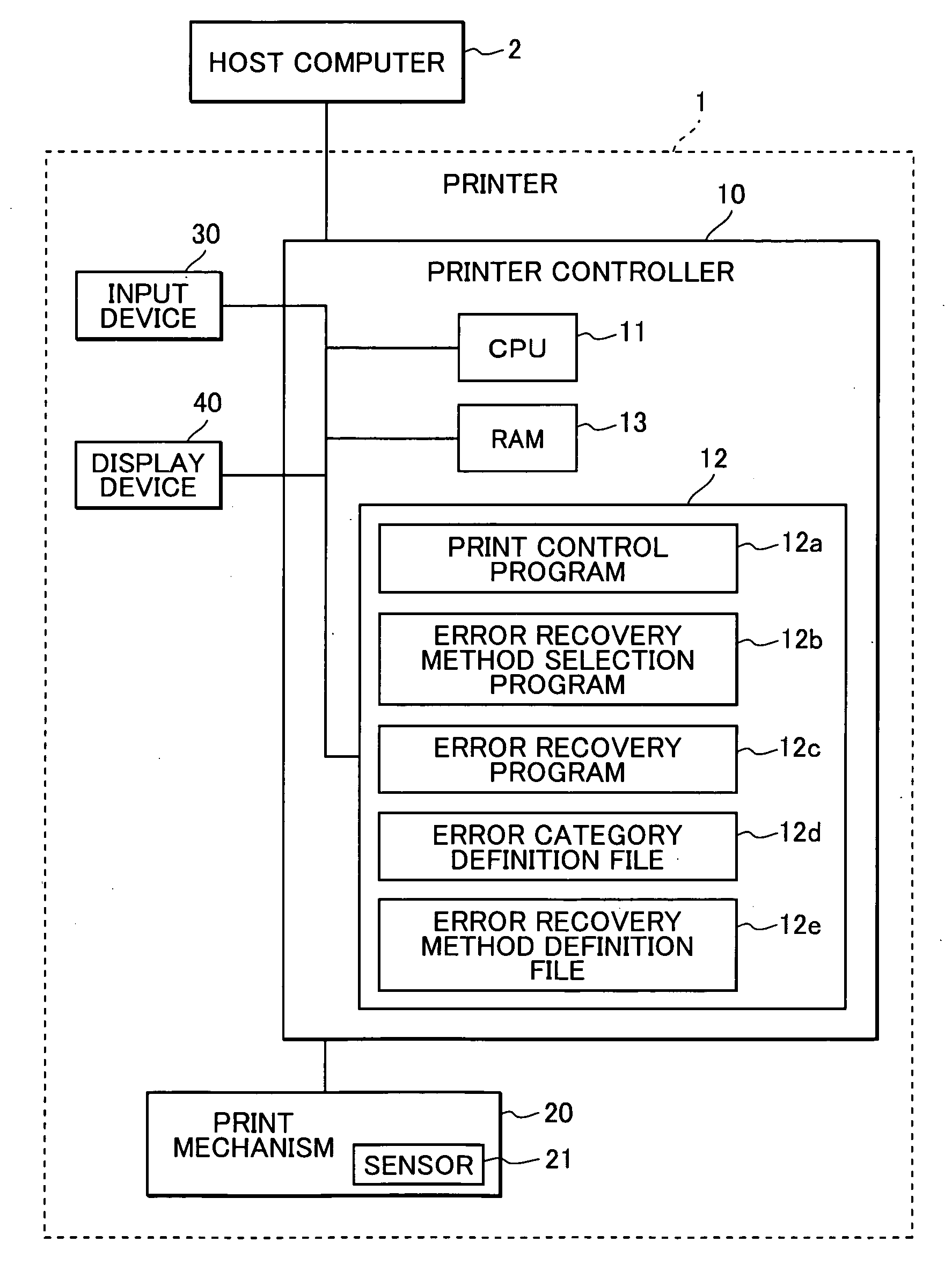
Printer enabling user to set error recovery method for each error category
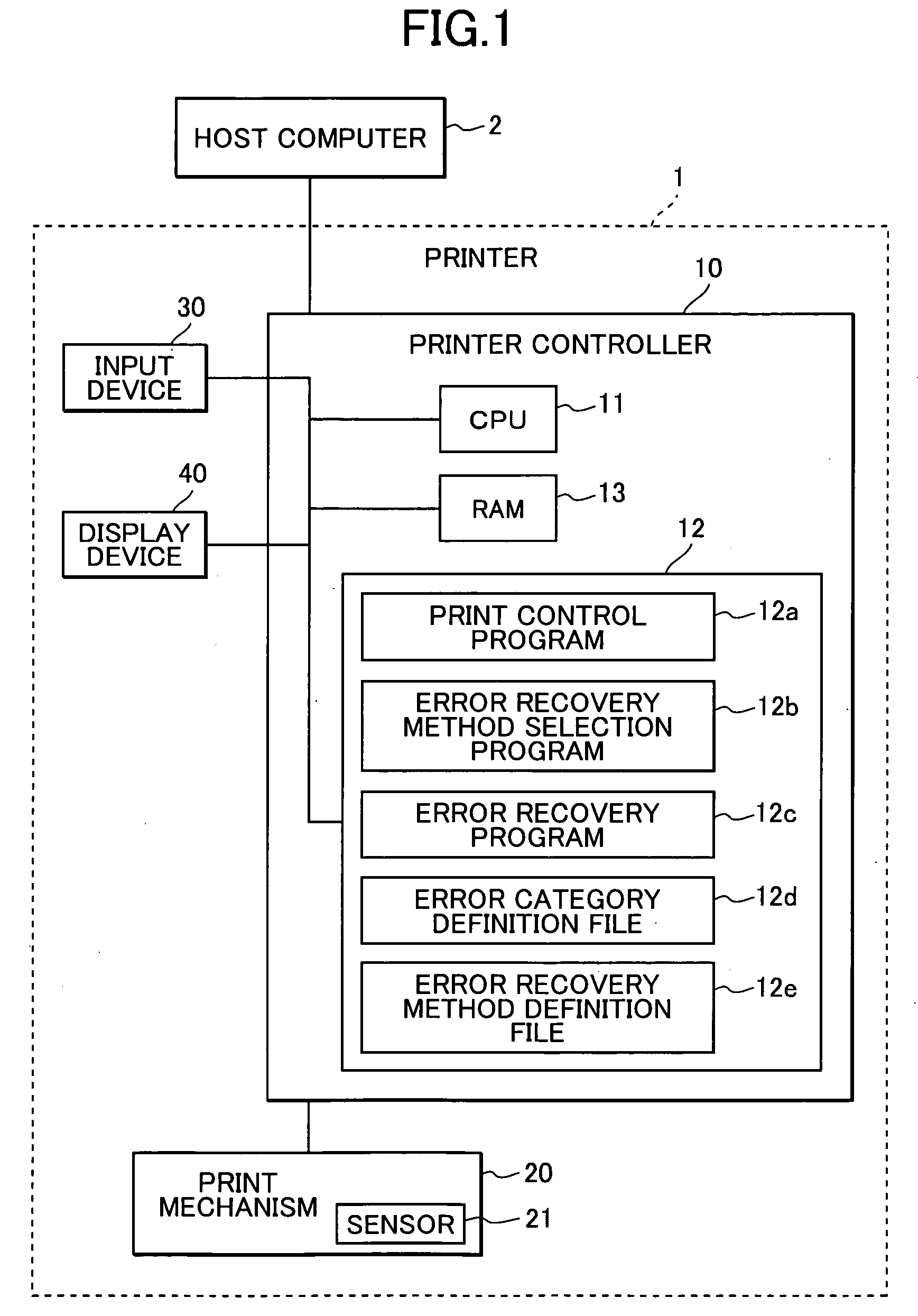
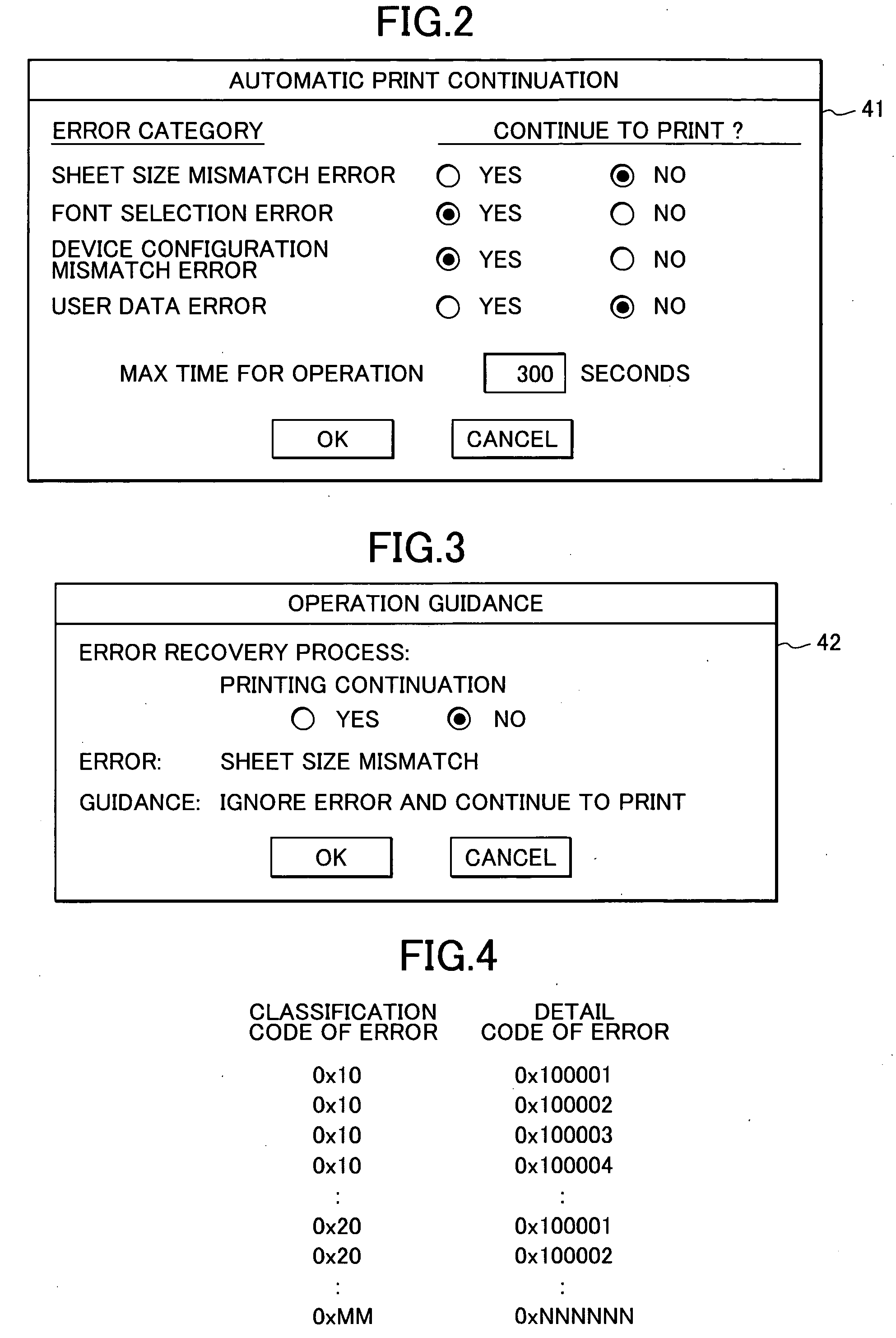
InactiveUS20040165209A1Digitally marking record carriersDigital computer detailsRecovery methodComputer science
As a user selects one of error recovery methods for each error category, and the selected method is stored in a memory. When an error occurs, an error recovery method corresponding to an error category of the error is detected. If the detected method is automatic print continuation, then the error is ignored and print operation is automatically continued. If the detected method is a recovery by user's operation, then an error message is displayed, and a procedure is performed in accordance with an instruction from the user.
Owner:RICOH KK
Dual band unidirectional scheme in a cellular mobile radio telecommunications system
InactiveUS20030104816A1Time-division multiplexFrequency-division multiplexCellular radioTelecommunications network
A cellular radio telecommunications system and method of operating the same is described which includes a first cellular radio telecommunications network for providing frequency division duplex radio transmissions over an air interface to one or more fixed or mobile terminals and a second cellular unidirectional radio telecommunications network which at least partly overlaps the first cellular radio telecommunications network for providing unidirectional simplex radio transmissions over an air interface to the one or more fixed or mobile terminals. At least one of access to the unidirectional second cellular network and handover of a communication supported by the unidirectional second cellular network is managed by the first cellular network. A special dedicated uplink channel may be provided in the first network for trasmitting uplink control and / or error messages of the second network.
Owner:RPX CLEARINGHOUSE
Method and Apparatus for Detection of Abnormal Traces during Electrochemical Analyte Detection
ActiveUS20060231425A1Sufficient materialImmobilised enzymesBioreactor/fermenter combinationsAnalytePeak current
Detection of abnormal signal traces in electrochemical measurements generated using an electrochemical test strip to which a potential is applied allows for an indication of an erroneous analyte determination. The current trace has an expected shape in which a peak current is observed a time tpeak after which there is a decrease in current. To detect abnormal signal traces, the time tpeak is determined experimentally and compared with an expected value, t′peak, and if the difference between the two values to over a predetermined threshold, an error message is provided to the user instead of a test result. The value of t′peak is determined as a function of a mobility term that is determined during a potentiometry phase following the amperometric measurements.
Owner:AGAMATRIX INC
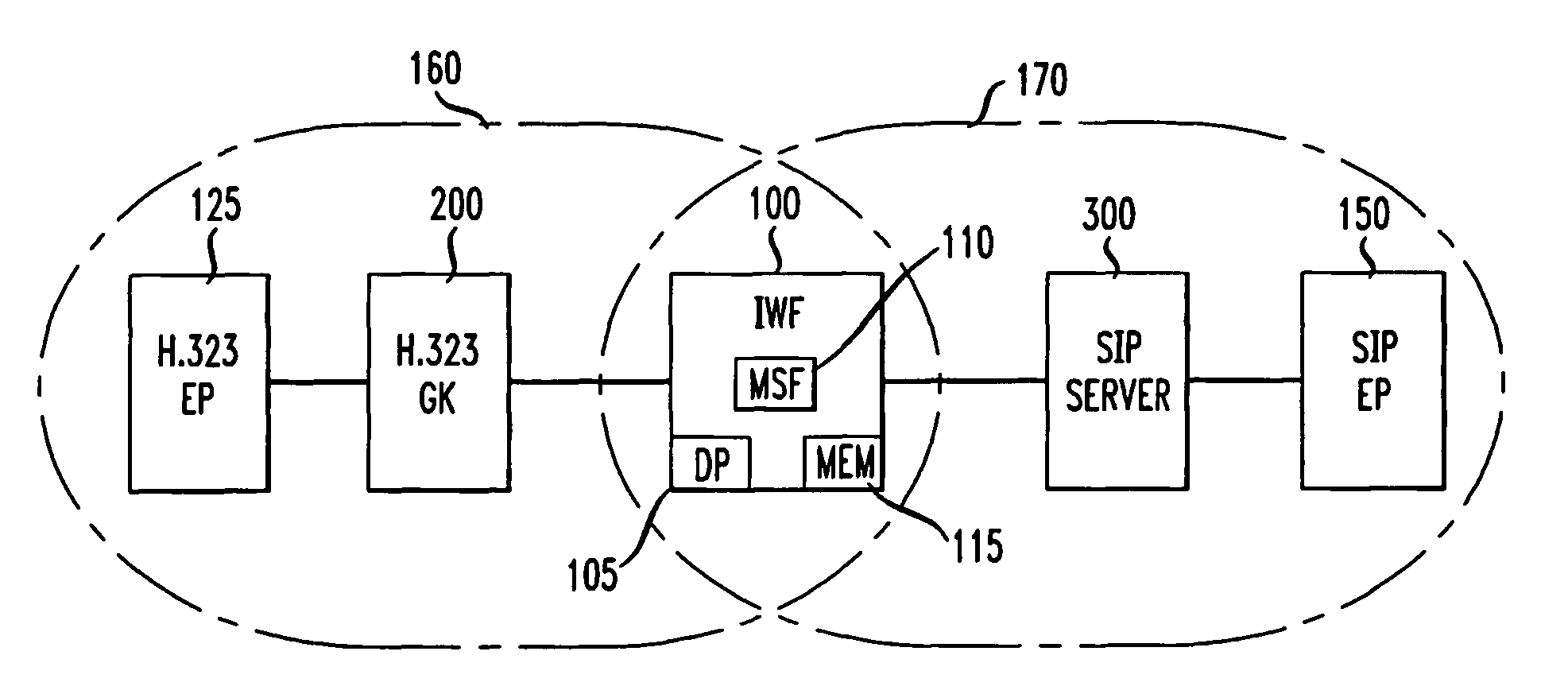
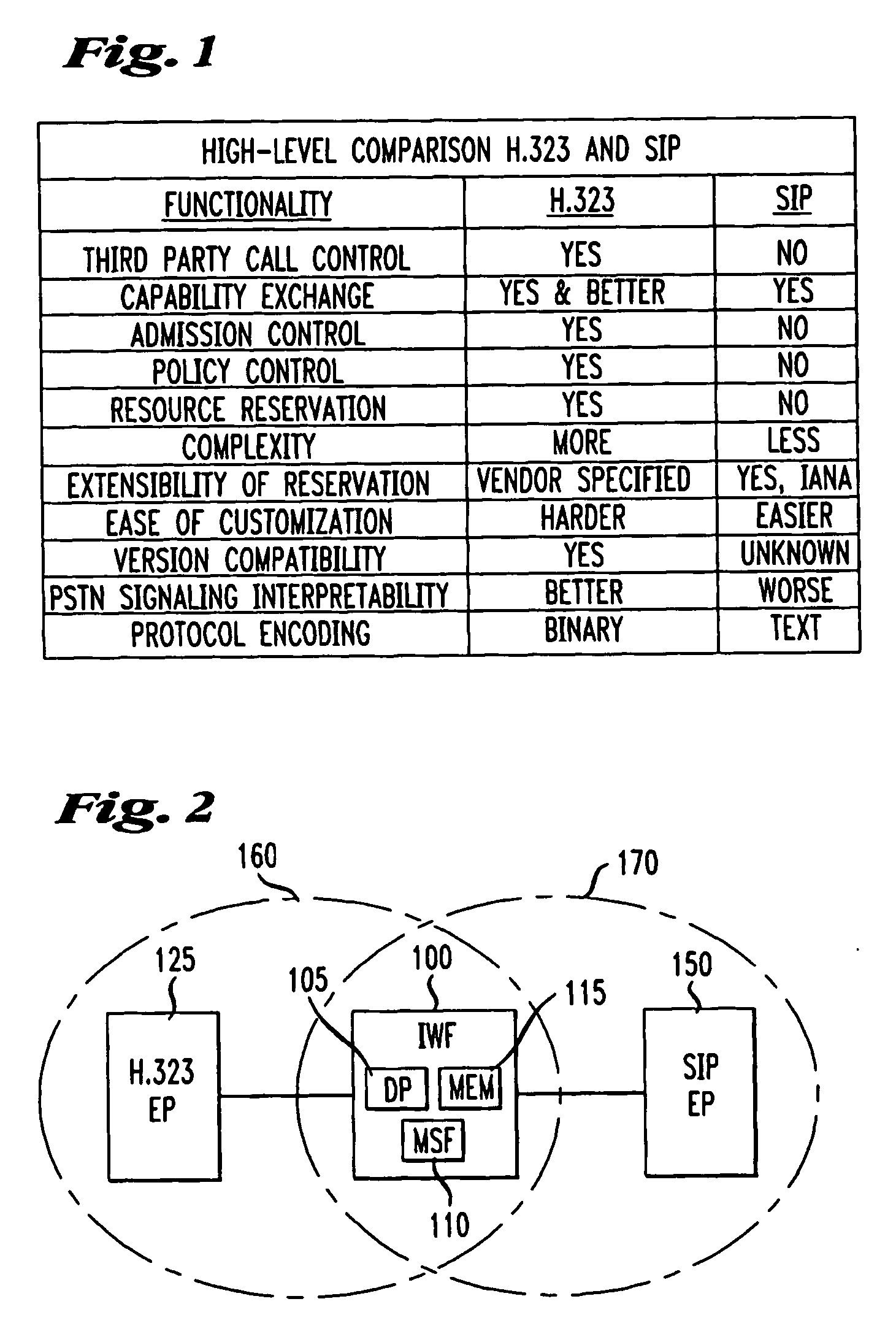
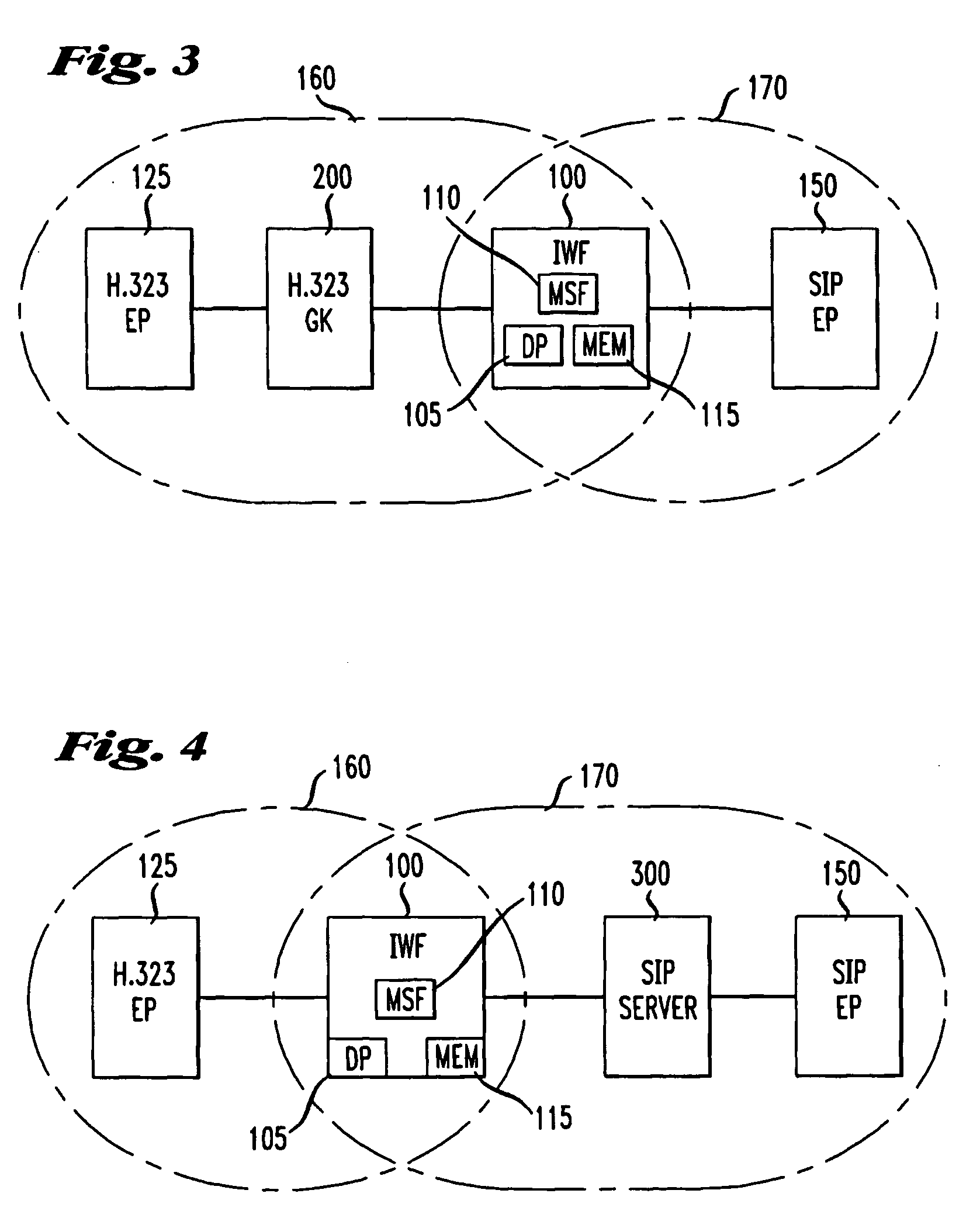
Method and apparatus for S.I.P./H.323 interworking
InactiveUS20060007954A1Time-division multiplexData switching by path configurationState dependentStructure of Management Information
An interworking function (IWF) for a first and second protocol based network, for example, an H.323 protocol based network and an SIP protocol based network comprises an interworking gateway server including a state machine for defining each call processing state and a translation table for use in translating addresses formatted in each protocol. A method of interworking for use in interworking between said first protocol based network and said second protocol based network comprises the steps of receiving at said interworking gateway server serving said first and second protocol based networks a request from an endpoint in the first or second protocol based networks, establishing a state machine in memory whereby, for each state of said state machine, a message associated with that state is categorized as one of a triggering message, a non-triggering message and an error message, establishing a translation table in said memory whereby an address formatted in said first protocol has a one-for-one correspondence with an address formatted in said second protocol, processing said request in accordance with said translation table and said state machine and permitting communication between said first and second endpoints utilizing a realtime transport protocol. In the event media is terminated at said interworking gateway server, the interworking gateway server, in one embodiment, comprises a media switching fabric for switching media terminated at the gateway to an addressed endpoint capable of receiving it.
Owner:AT&T INTPROP II L P
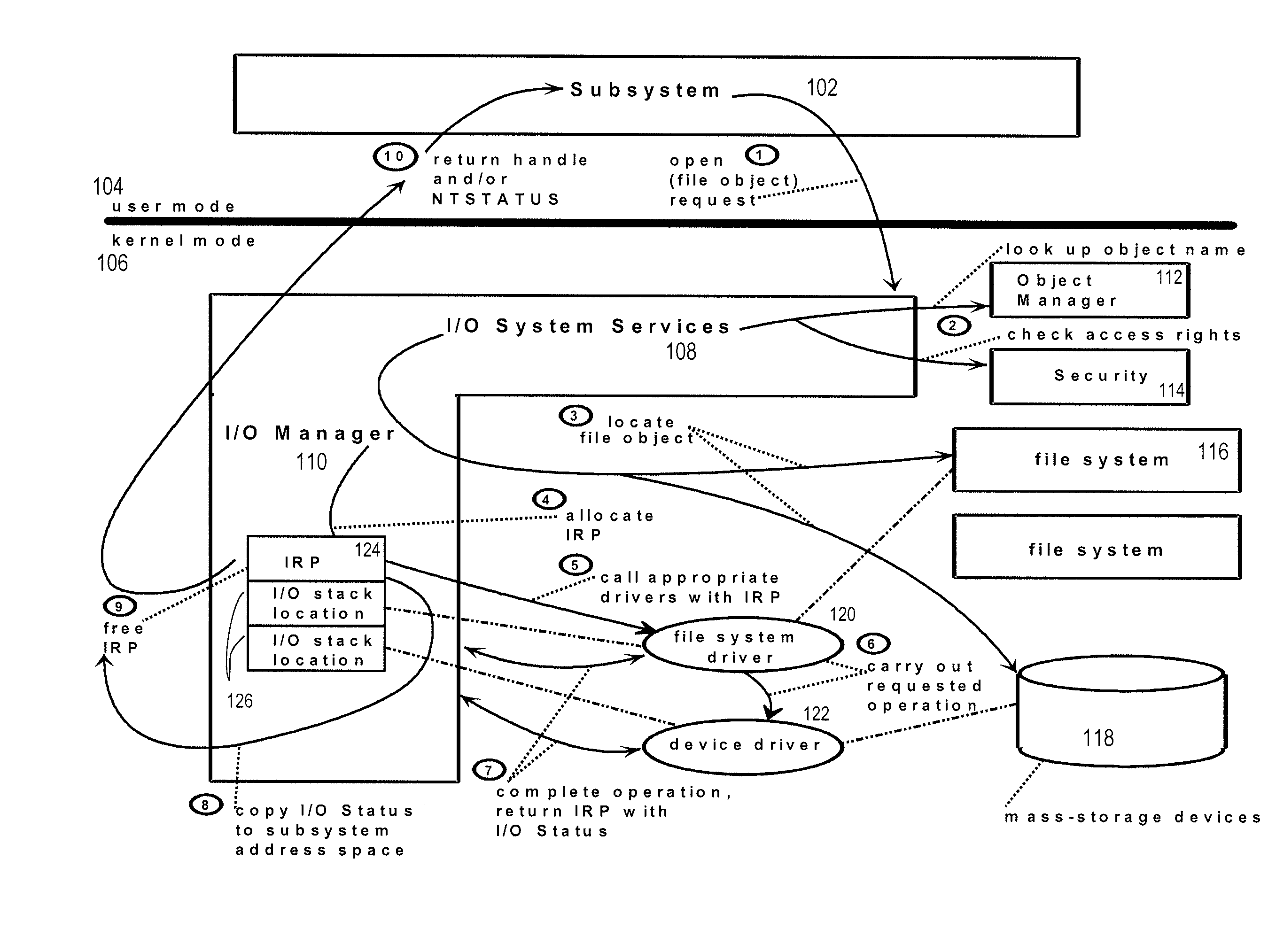
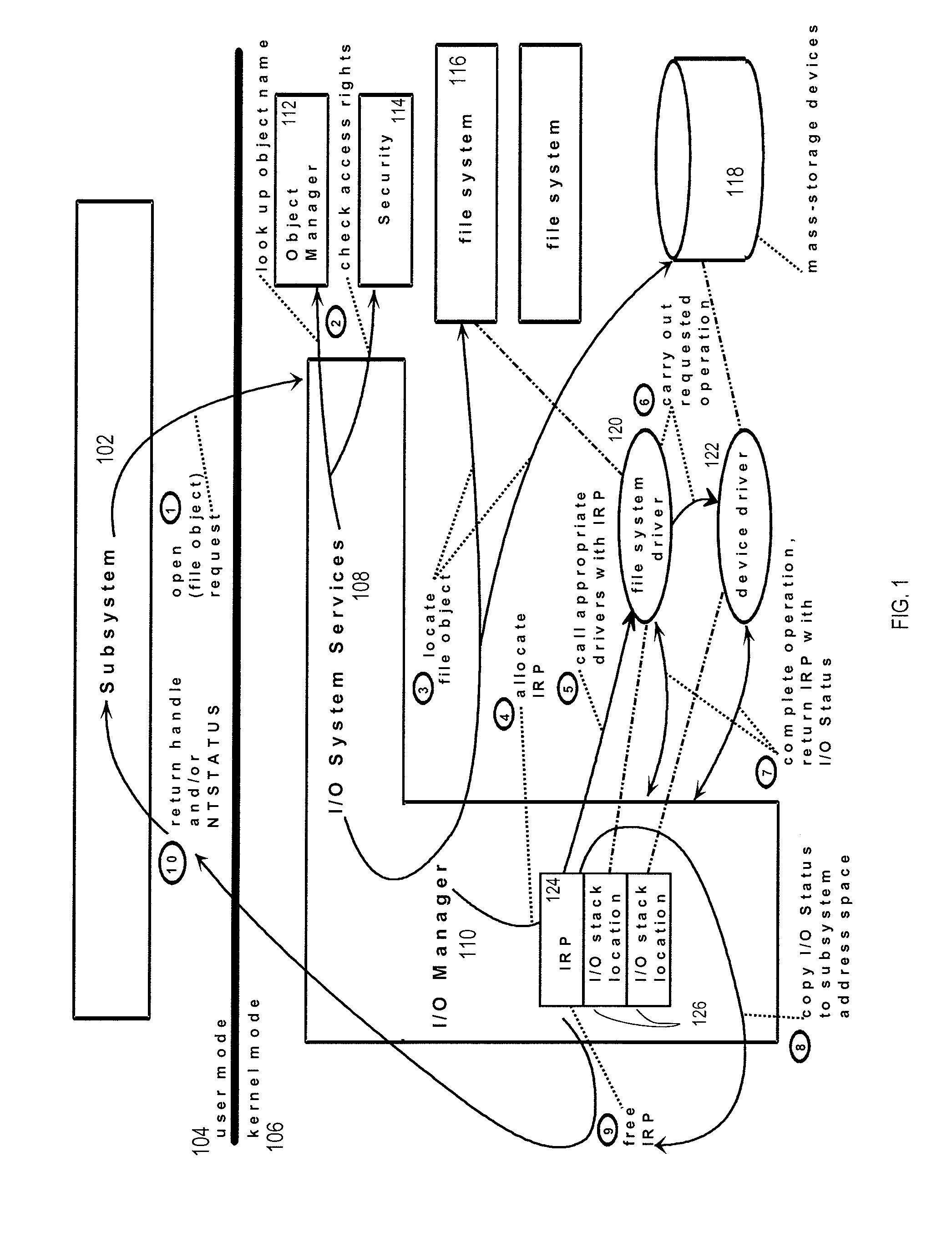
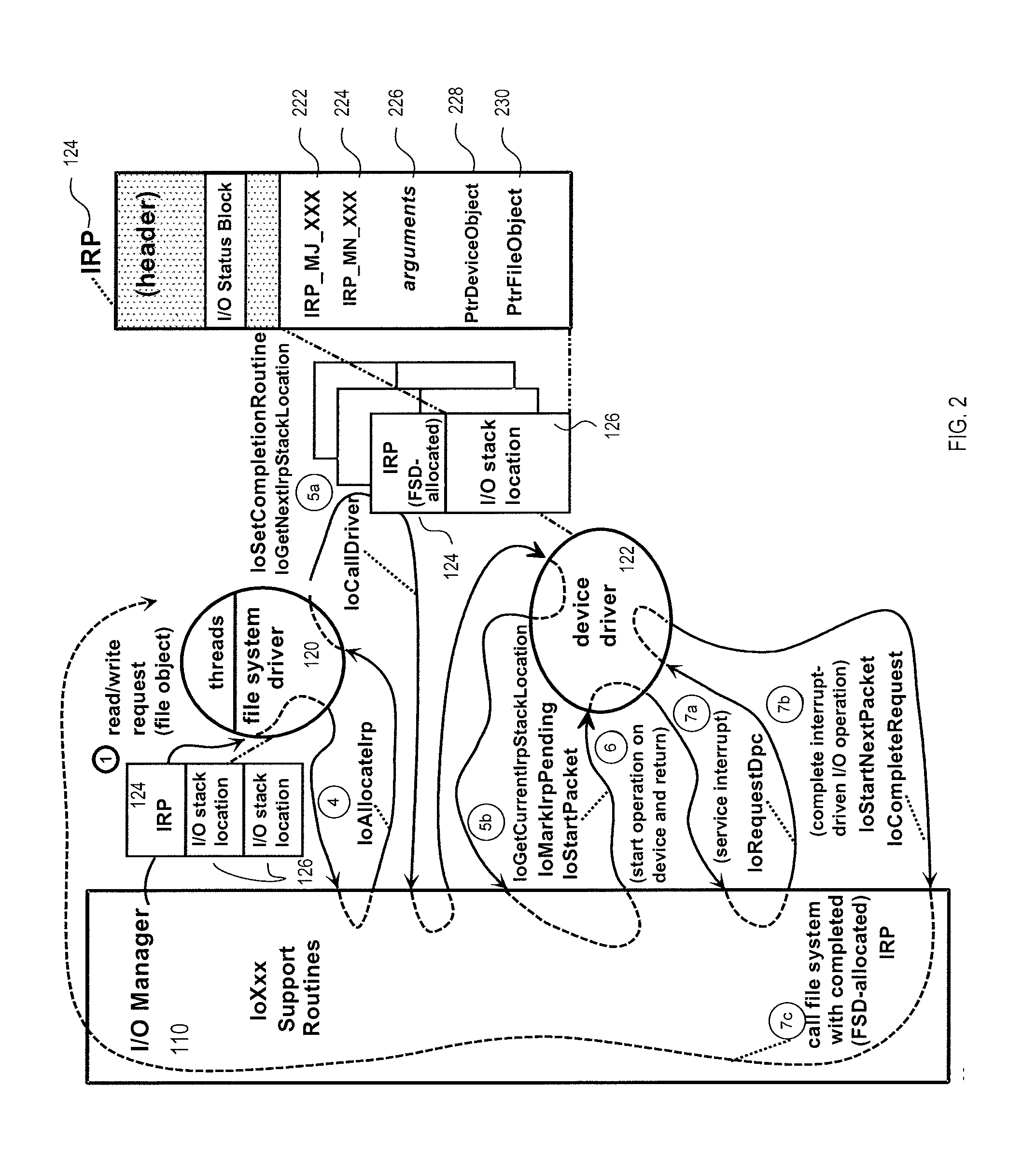
Method and system for providing restricted access to a storage medium
InactiveUS20090271586A1Digital data processing detailsUnauthorized memory use protectionFile systemData storing
A method of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
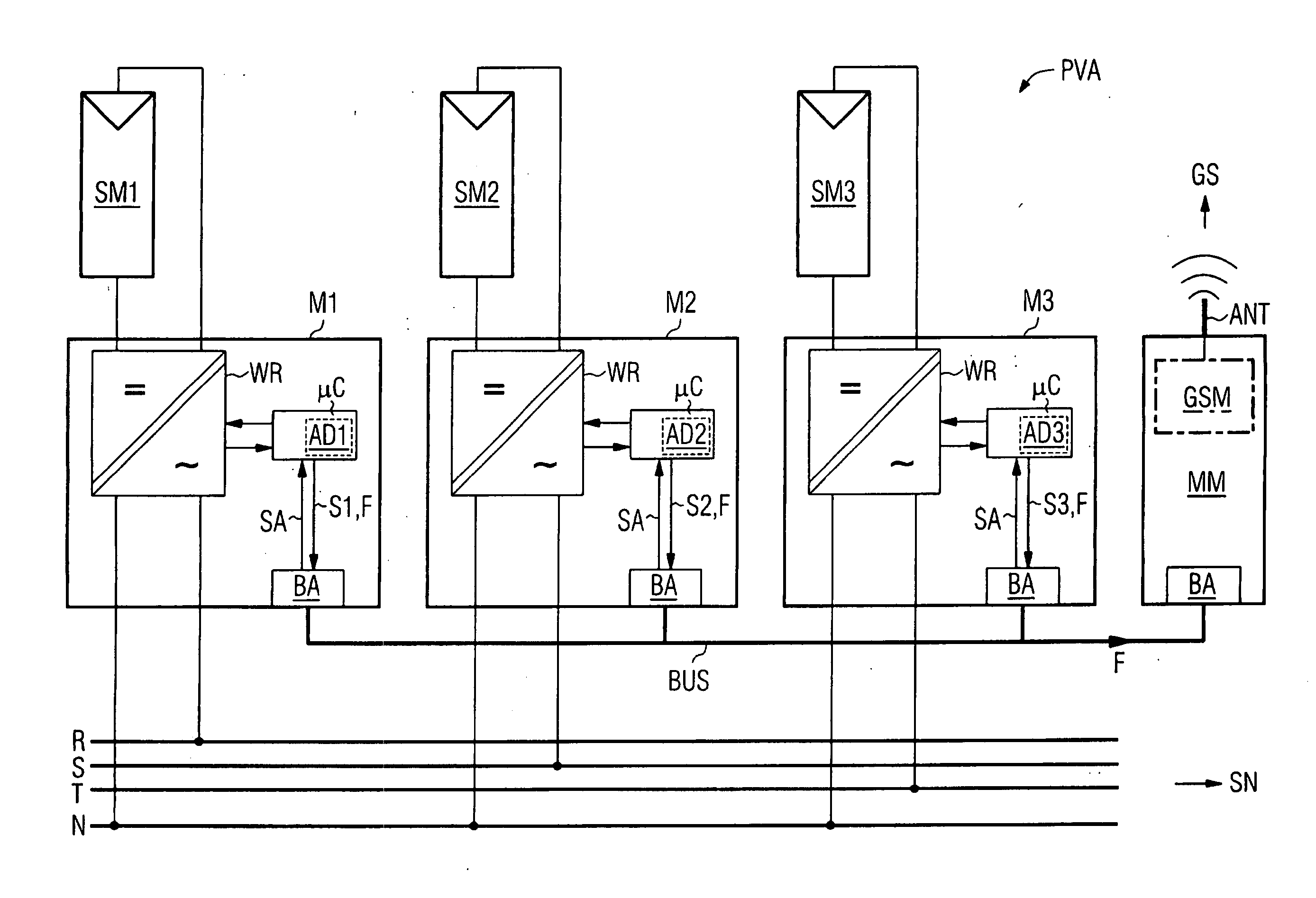
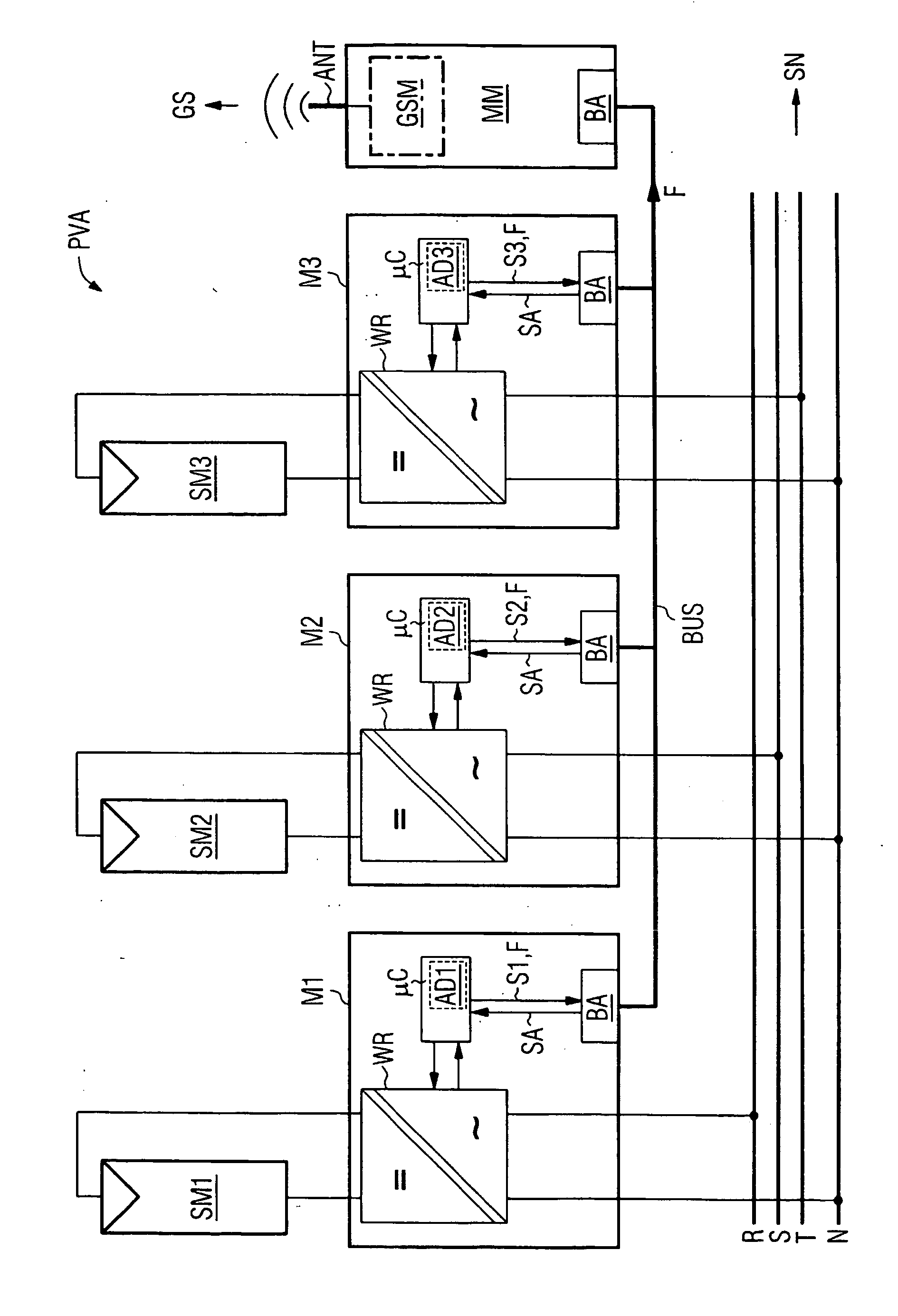
Solar Inverter and Photovoltaic Installation Comprising Several Solar Inverters
InactiveUS20070252716A1Compact implementationBatteries circuit arrangementsSingle network parallel feeding arrangementsElectric power systemComputer module
In one aspect, a solar inverter which can be connected to at least one photovoltaic generator at the input end and to a power system at the output end is provided. The solar inverter includes an inverter module, an electronic control unit at least for diagnosing an inverter module, and a bus interface for technically connecting the electronic control unit to a communication bus. The electronic control unit cyclically outputs a piece of status information of the solar inverter on the communication bus, and outputs an error message on the communication bus, cyclically reads status information of other solar inverters that are connected to the communication bus, and outputs an error message on the communication bus in case at least one expected additional piece of status information fails to be output. Whereby, the need for a separate monitoring unit is eliminated.
Owner:SIEMENS AG
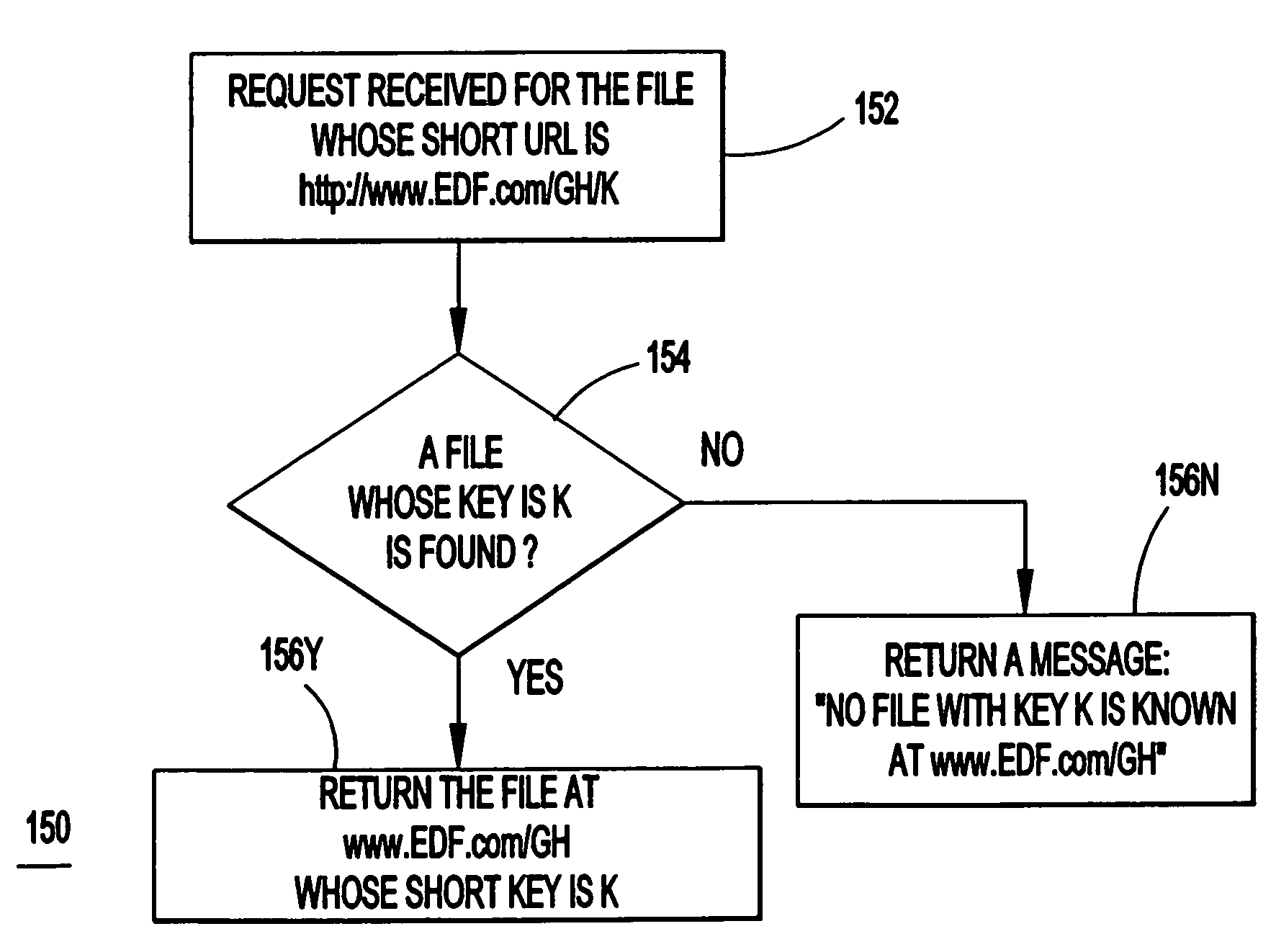
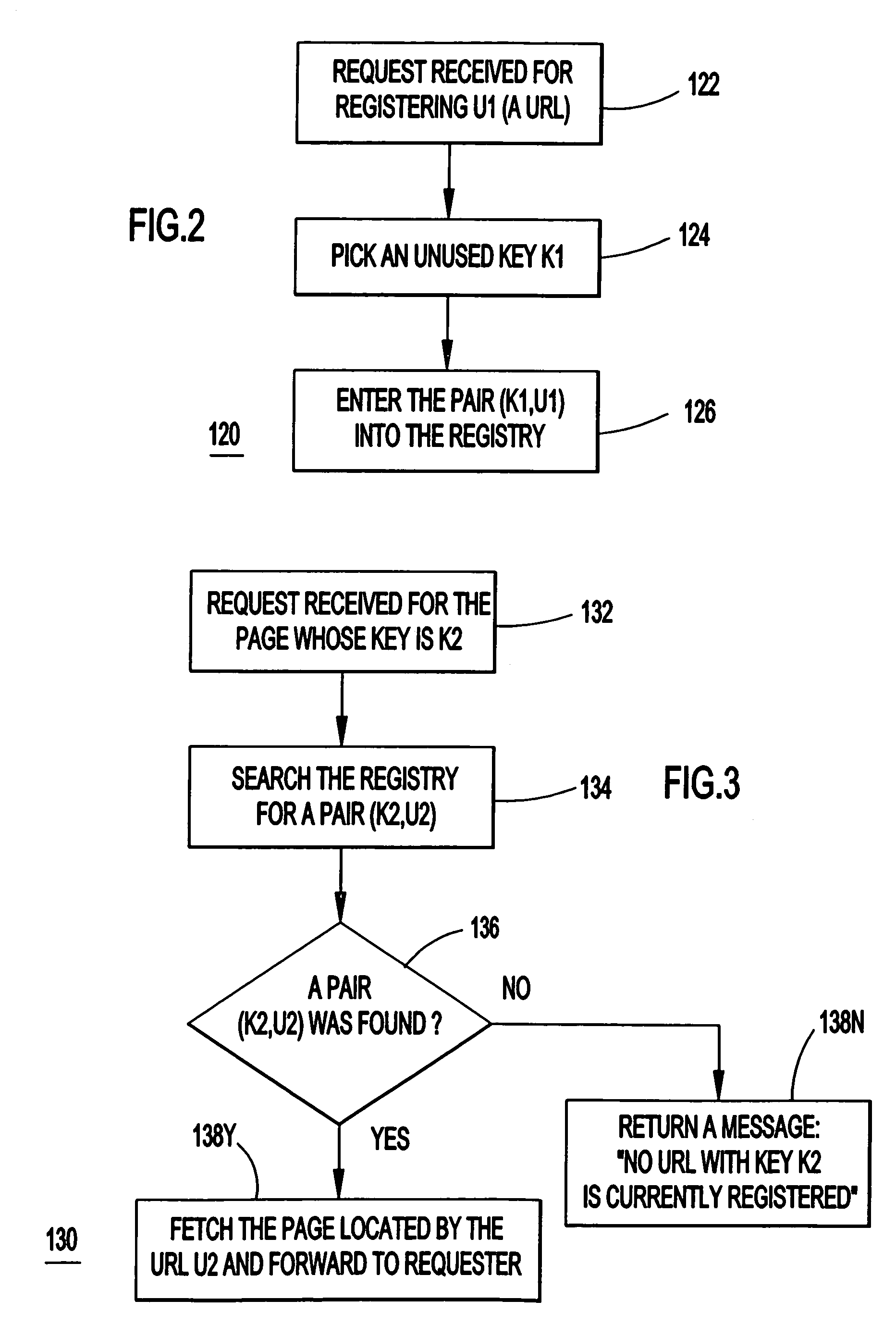
Efficient retrieval of uniform resource locators
InactiveUS6957224B1Small sizeReduce loadData processing applicationsTransmissionRegistry dataUniform resource locator
A system, method and computer program product for providing links to remotely located information in a network of remotely connected computers. The system may or may not include a server providing an interface between shorthand codes and corresponding original files. If the server is included, a uniform resource locator (URL) is registered with a server. A shorthand link is associate with the registered URL. The associated shorthand link and URL are logged in a registry database. When a request is received for a shorthand link, the registry database is searched for an associated URL. If the shorthand link is found to be associated with an URL, the URL is fetched, otherwise an error message is returned. If the server is not included, all URLs located at a root page may be listed and associated with shorthand keys or links. Associated files and keys are indexed in an index file. The shorthand codes or keys are combined with the root page to form shorthand URLs. Requests are made for the shorthand URLs and the index file is searched for the requested shorthand URL. If the requested shorthand URL is encountered, the corresponding file is returned; otherwise, an error message is returned.
Owner:TWITTER INC
Method and apparatus for verifying the contents of a global configuration file
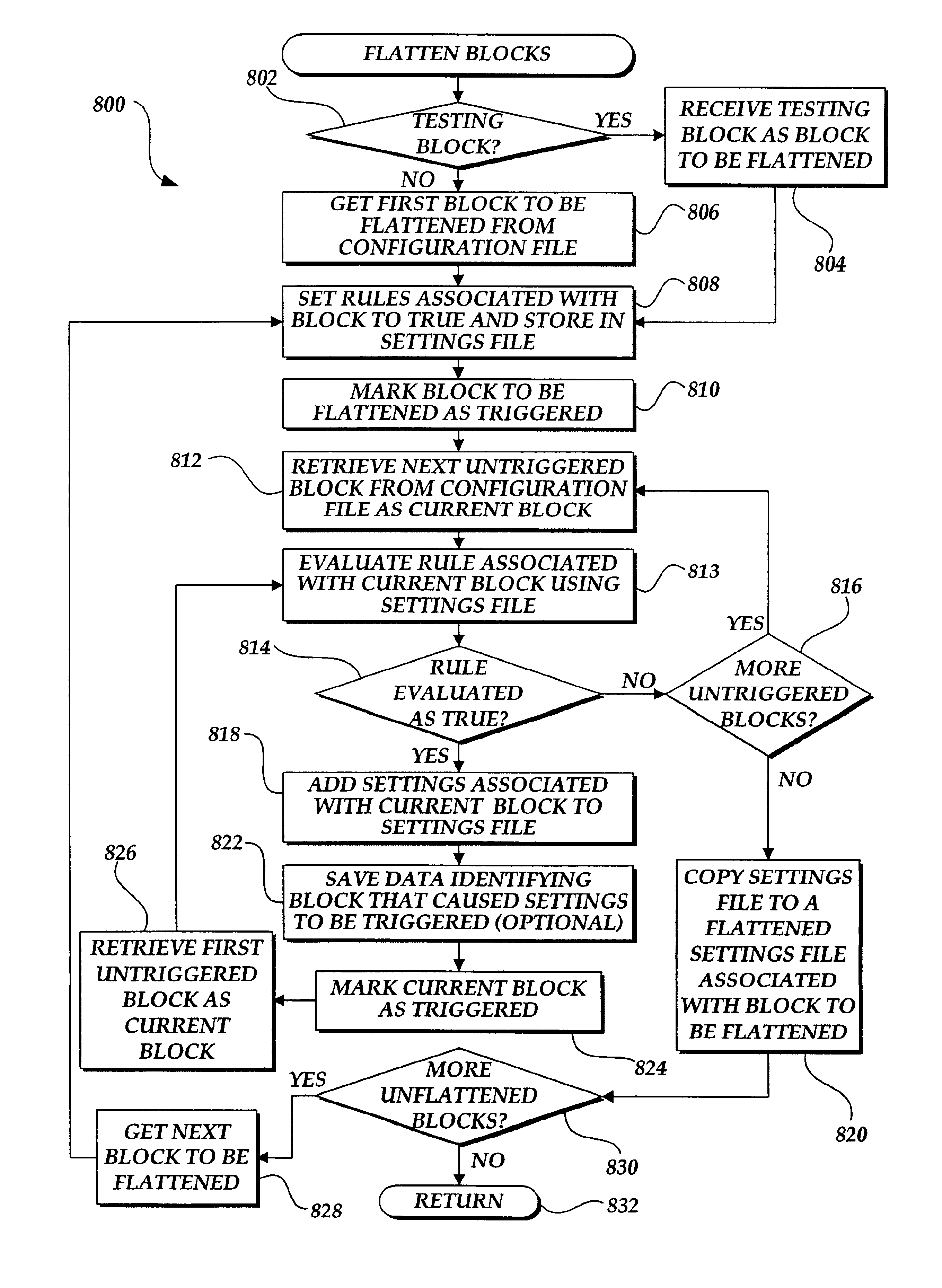
InactiveUS6892231B2Simplify the configuration processFast processingDigital computer detailsData switching by path configurationIdentifying problemsSyntax error
A method and apparatus are provided for determining the validity of a global configuration file. In order to verify the global configuration file, the configuration file is first “flattened.” To flatten the configuration file, the rules in the first block of the configuration file are identified. A settings file is then created with the rules set as true. The normal configuration process is then performed on the configuration file. The resulting settings file constitute the flattened settings for the block and are associated with the block. A determination is then made as to whether any conflicting settings, inconsistently set related settings, or syntax errors exist within the flattened settings. If any such settings do exist, an error message is generated. This process is then repeated for each block in the configuration file so that flattened settings are created for each block. A testing block may also be utilized to identify problems with the settings file generate by the testing block. Reverse queries may also be performed on the settings file. Changes in the flattened configuration files caused by changes in the global configuration file can also be identified. The flattened files may also be used to simplify the server computer configuration process.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for providing restricted access to a storage medium
InactiveUS20130198474A1Unauthorized memory use protectionComputer security arrangementsFile systemData storing
A system, apparatus, method, or computer program product of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
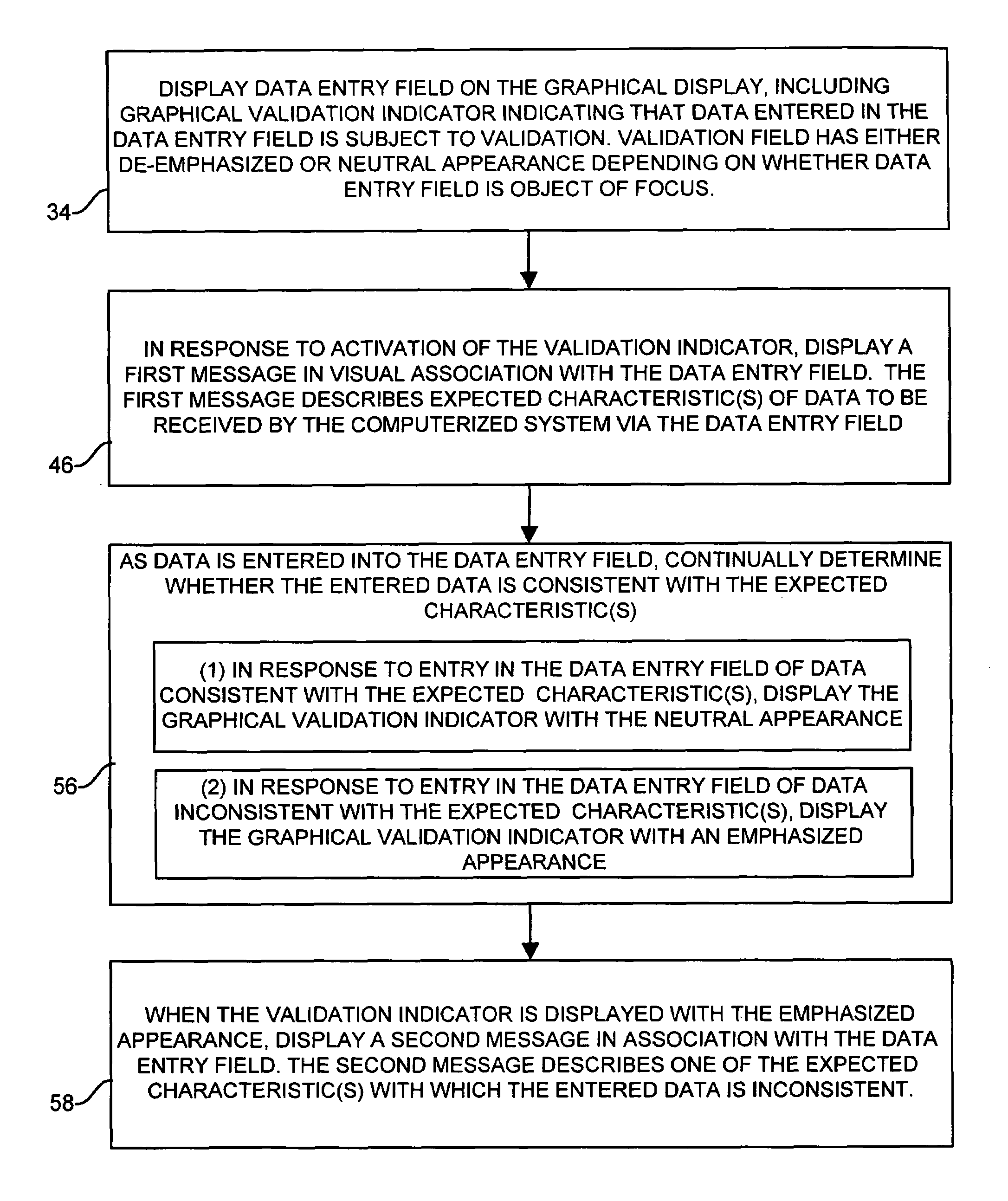
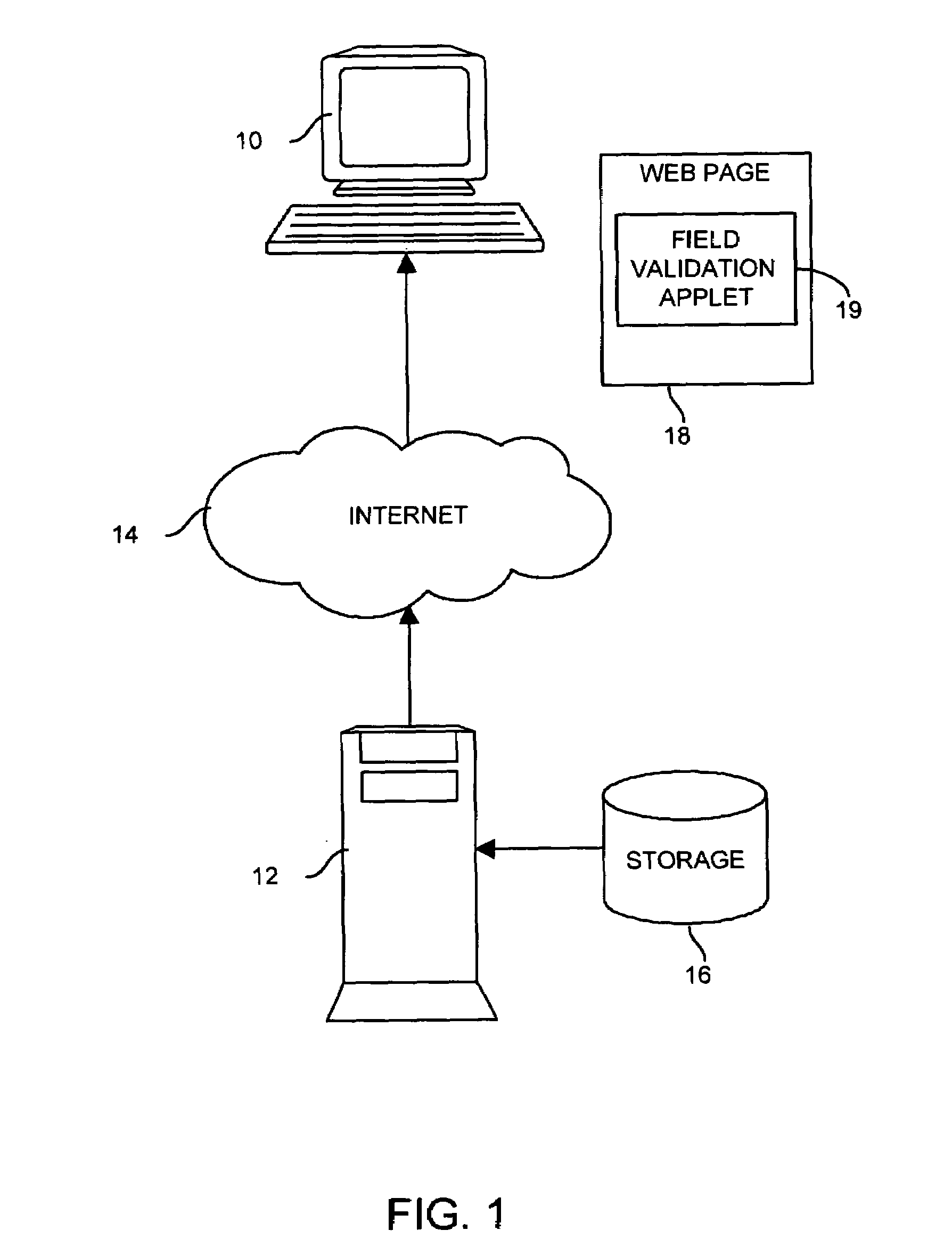
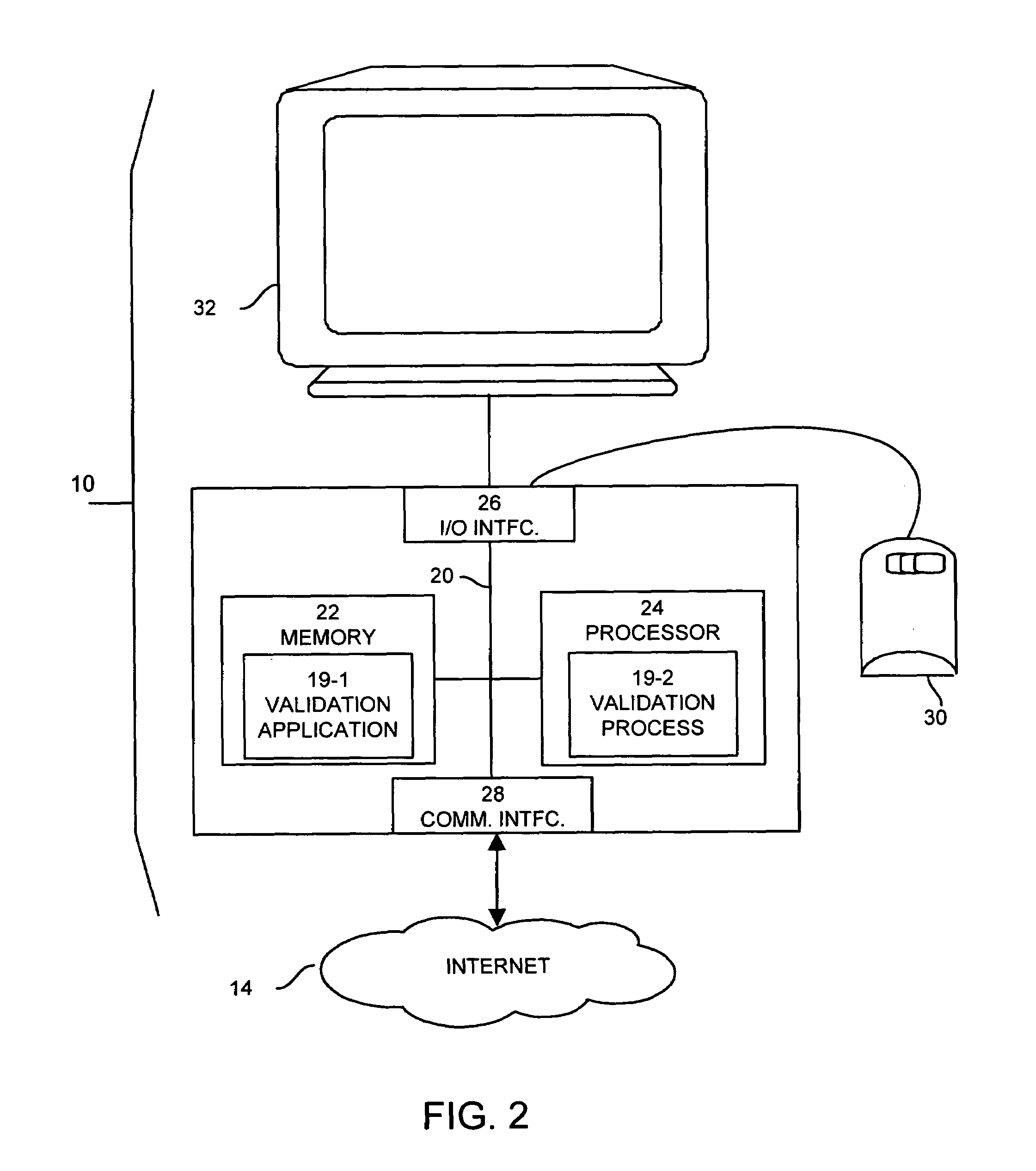
Method and apparatus for validating user input fields in a graphical display
ActiveUS7251782B1High strengthEmphasized appearanceInput/output for user-computer interactionGraph readingGraphicsComputer hardware
For validating user input fields in a graphical user interface, a data entry field includes a graphical validation indicator. In response to user activation of the validation indicator, such as by hovering with an on-screen pointer, a message is displayed in visual association with the data entry field. The message describes one or more expected characteristics of the data to be entered, for example that the data is numerical. As the user enters data consistent with the expected characteristics, the validation indicator is displayed with a neutral appearance, indicating that no errors have been detected. If incorrect data is detected, the validation indicator takes on an emphasized appearance, such as a higher intensity and / or an error-indicating color such as red, providing an immediate error indication to the user. An error message may also be displayed in visual association with the data entry field. The error message is preferably displayed with an emphasized appearance, and may specifically identify the error in the entered data.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com