Patents
Literature
112results about How to "Consume resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Techniques for pruning a data object during operations that join multiple data objects
InactiveUS7020661B1Reduce consumptionReduced computing resourceData processing applicationsDigital data information retrievalData miningDigital object
Techniques for eliminating one or more portions of a data object from any join step of an operation that joins multiple data objects include determining that an operation joins a first data object and a second data object. The second data object includes multiple portions. Each of multiple data units of the first data object is scanned. Based on data in the data units of the first data object, information is generated. The information indicates a portion of the second data object for exclusion. The indicated portion is excluded from an output of the operation. Only one or more portions of the second data object that are not indicated for exclusion in the information are included in a particular join step involving the second data object. By pruning a large second table, such as a fact table, the computational resources consumed by the joins are substantially reduced.
Owner:ORACLE INT CORP
Systems and methods that facilitate software installation customization
ActiveUS7802246B1Consume resourcesEasy to customizeExecution for user interfacesMemory systemsThird partyGraphics
The present invention facilitates customizing software installation such as software updates for a user interface (UI) of a mobile communication device. The systems and methods of the present invention utilize a component that receives software updates (e.g., releases, releases, patches, upgrades, etc.) and presents various installation options to an installer through an interface. The installer can interact with the interface to select one or more components (e.g., controls, menus, menu items, etc) to install and define how such components are installed. For example, the installer can determine a control's location with respect to other controls within a user interface. This can be achieved by moving graphical components within the user interface and / or by providing parameters, setting flags, and / or including suitable arguments. In addition, the installer can add components to an installation. For example, the installer can add proprietary and / or third party applications, features, brands, logos and aesthetics to the installation.
Owner:MICROSOFT TECH LICENSING LLC
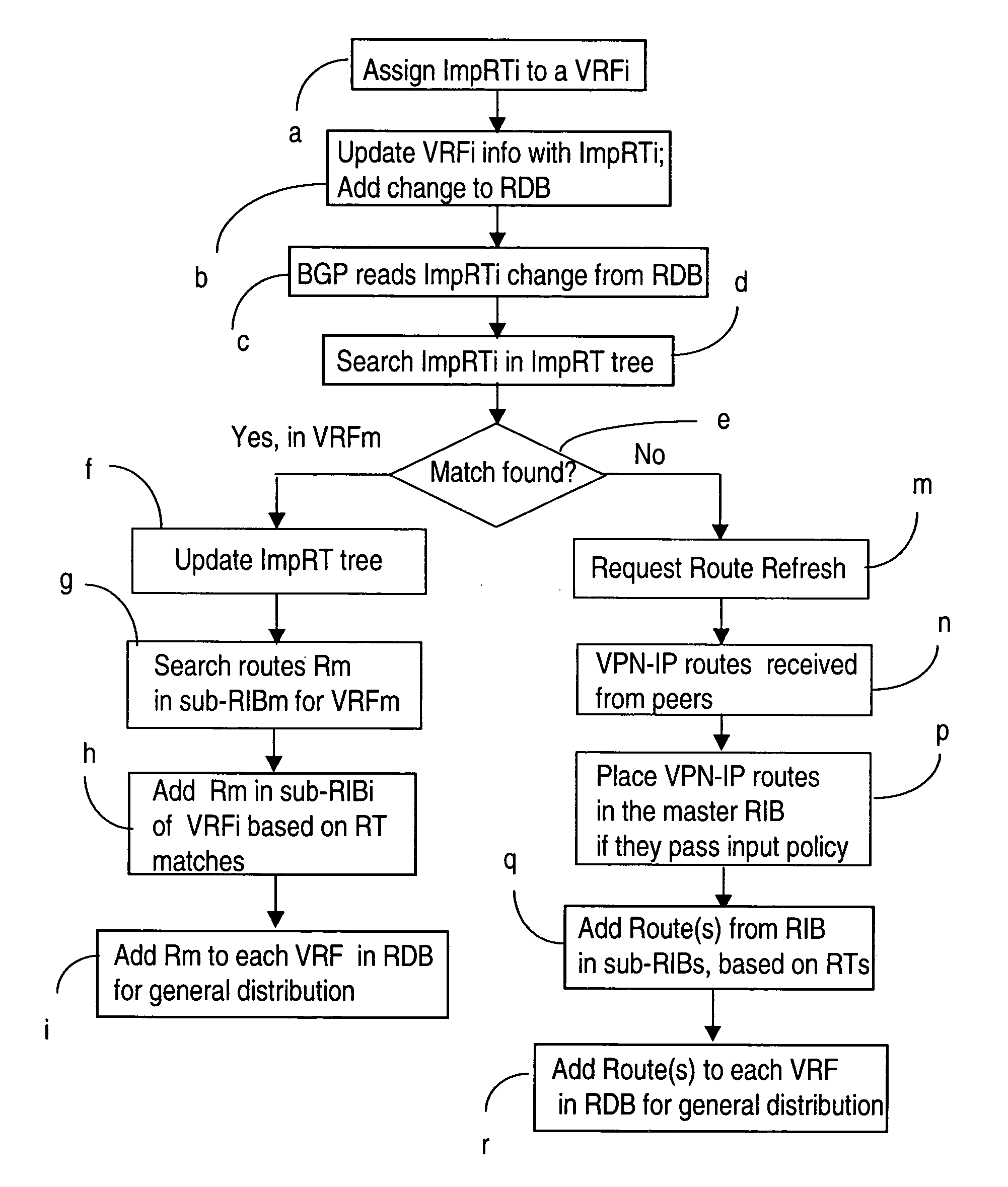
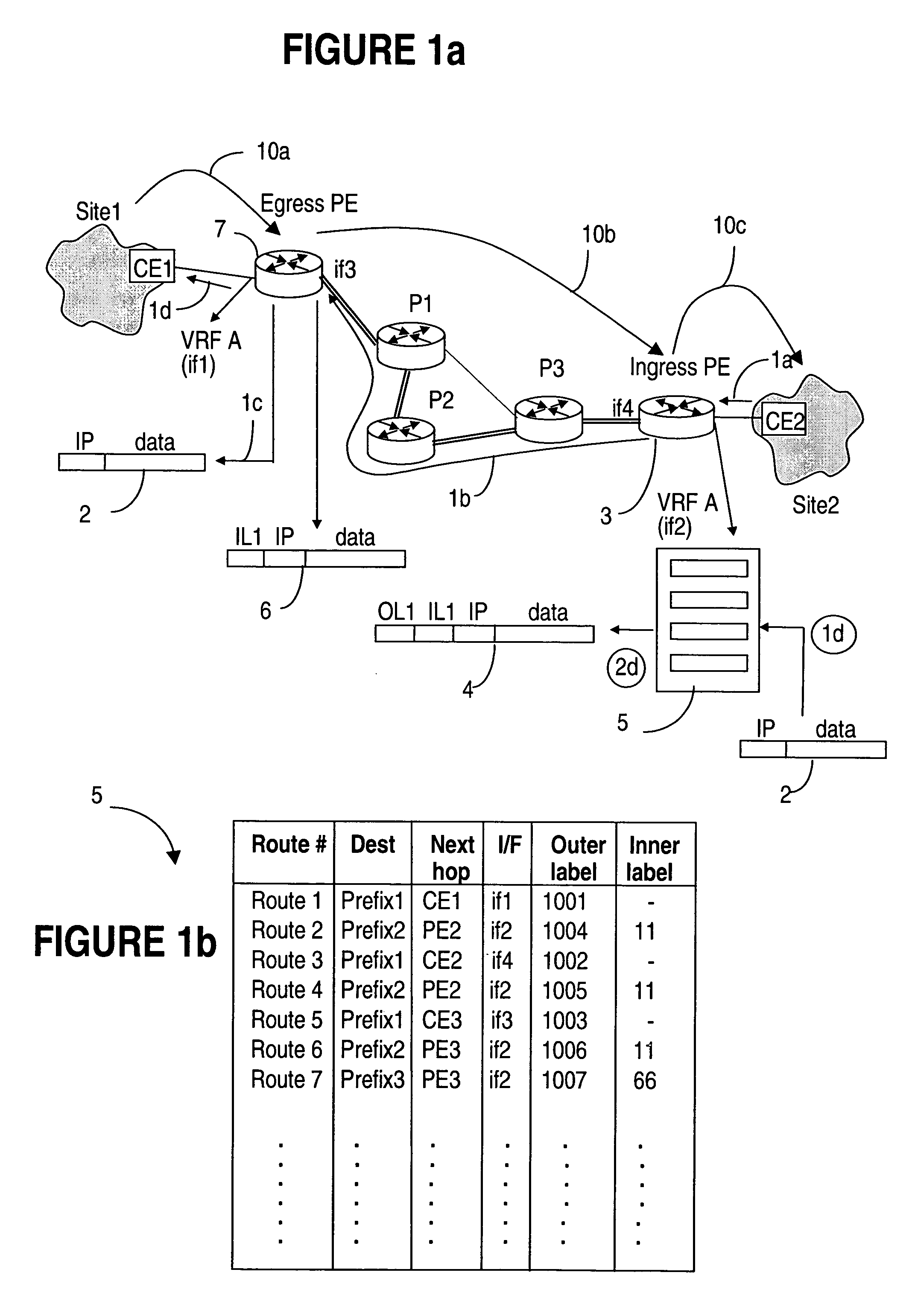
Managing L3 VPN virtual routing tables
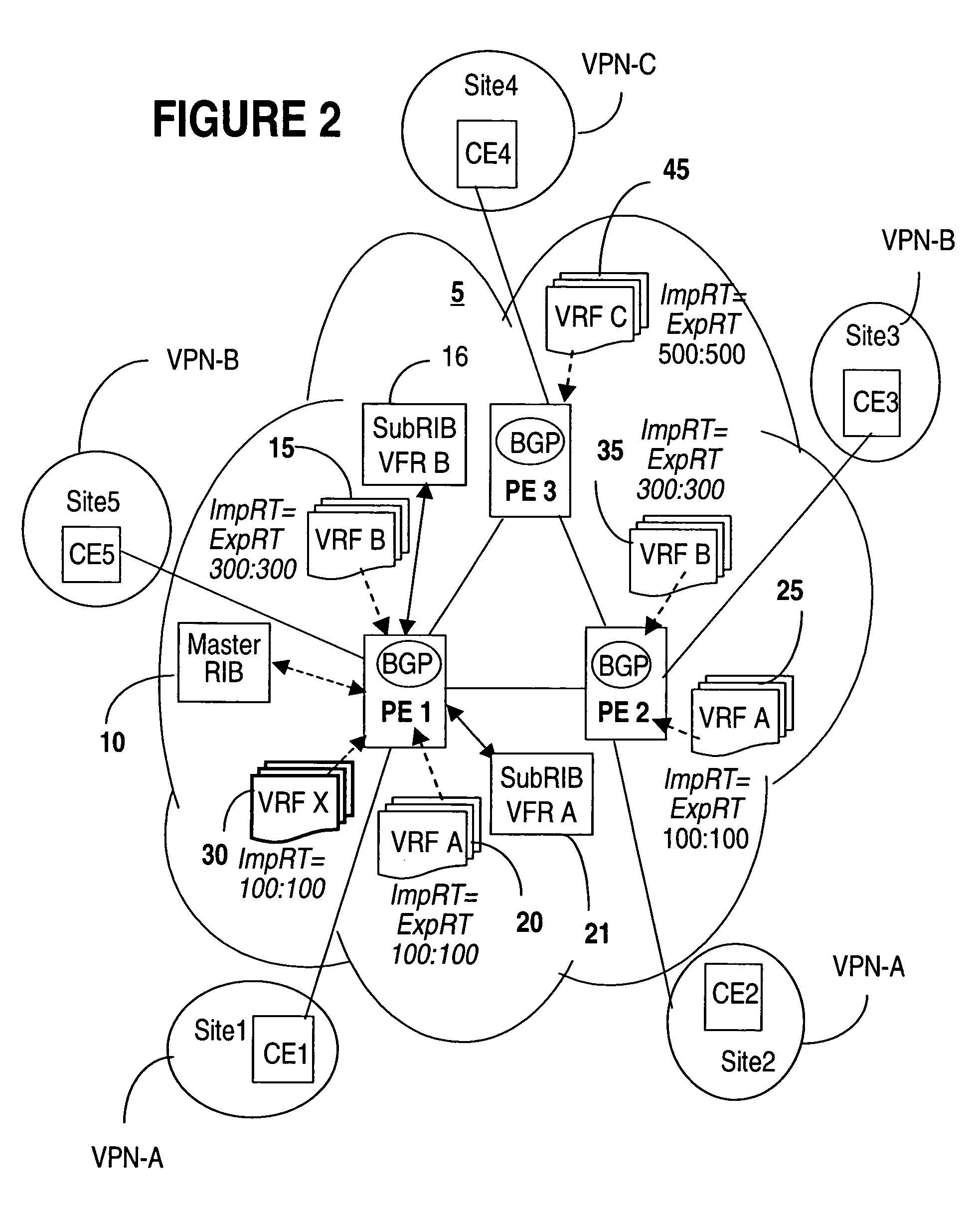
InactiveUS20050188106A1Efficiently setupEffective maintenanceDigital computer detailsNetworks interconnectionRouting tablePrivate network
A method of managing virtual routing forwarding (VRF) tables at a provider edge PE router of a L3 virtual private network (VPN) is provided. An import route target (ImpRT) tree is maintained at the PE router, which keeps the association between all ImpRT attributes currently configured on said PE router and the virtual routing table VRF at that router. When an ImpRT attribute is configured on a VRF table, the PE router first searches the tree to identify a local VRF table that contains a route(s) with that ImpRT attribute. If this information is available locally, the VRF is updated by copying the route information, and there is no need to do a route refresh. When an ImpRT is deleted from a VRF, a route refresh is avoided by parsing all the routes in the VRF and removing the routes that no longer have a matching route target. In an alternative implementation, the local source is the master RIB (routing information base) which includes all routes in all VRFs at the router, and optionally even rejected routes that were filtered out using ImpRTs. In this variant, even routes associated with ImpRTs that are new to the router would be available to update the VRF without requiring a route refresh.
Owner:WSOU INVESTMENTS LLC
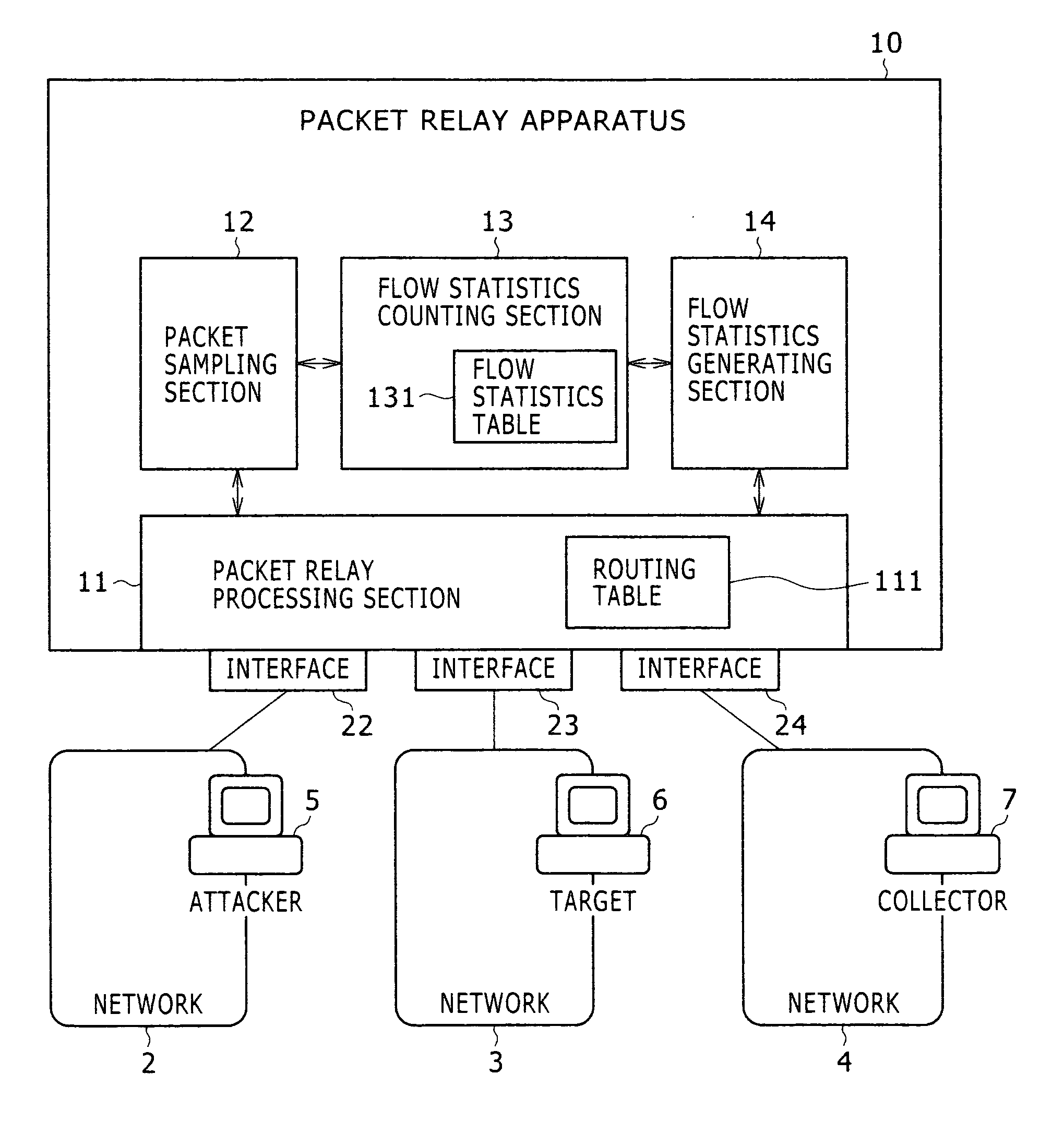
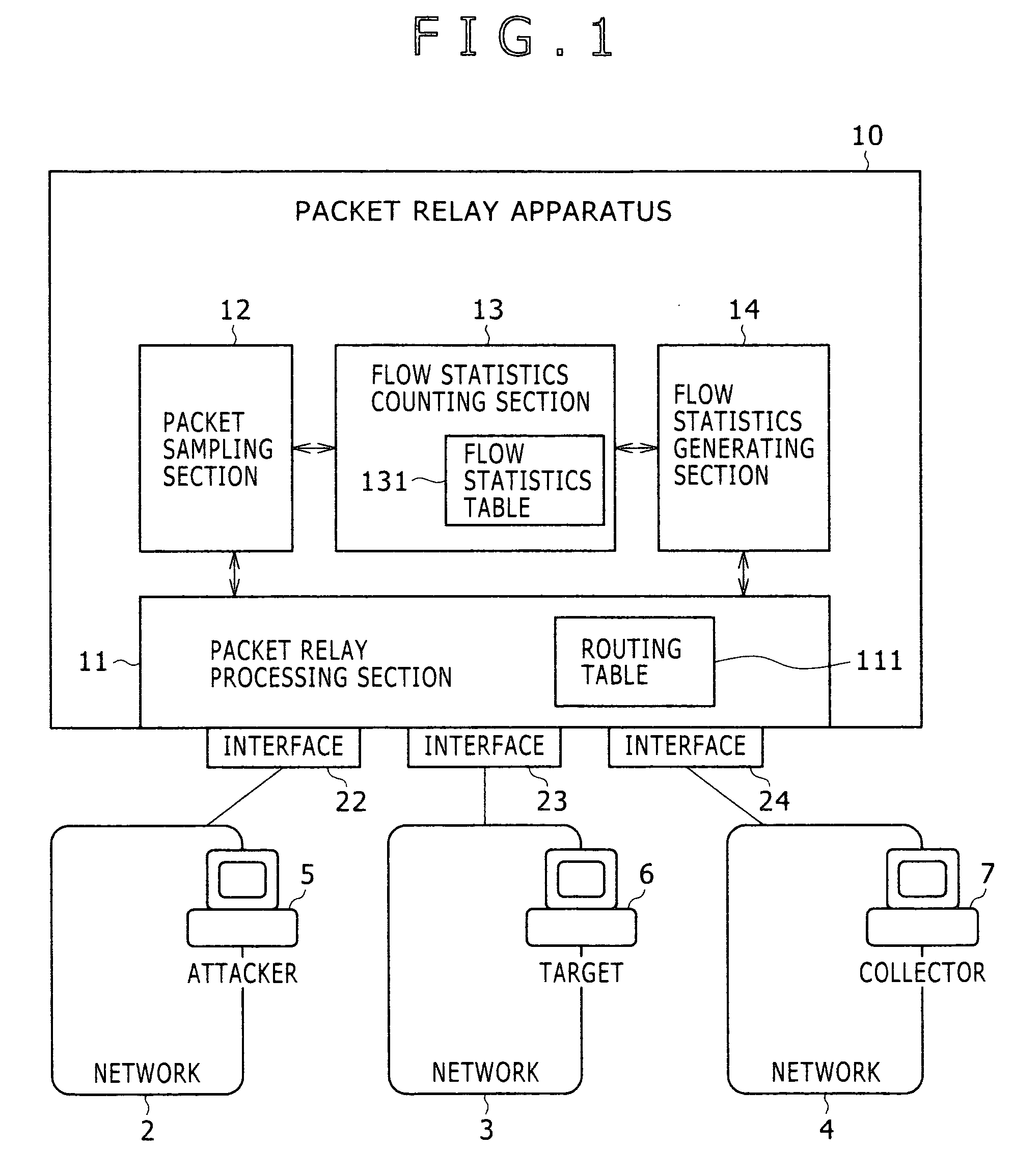
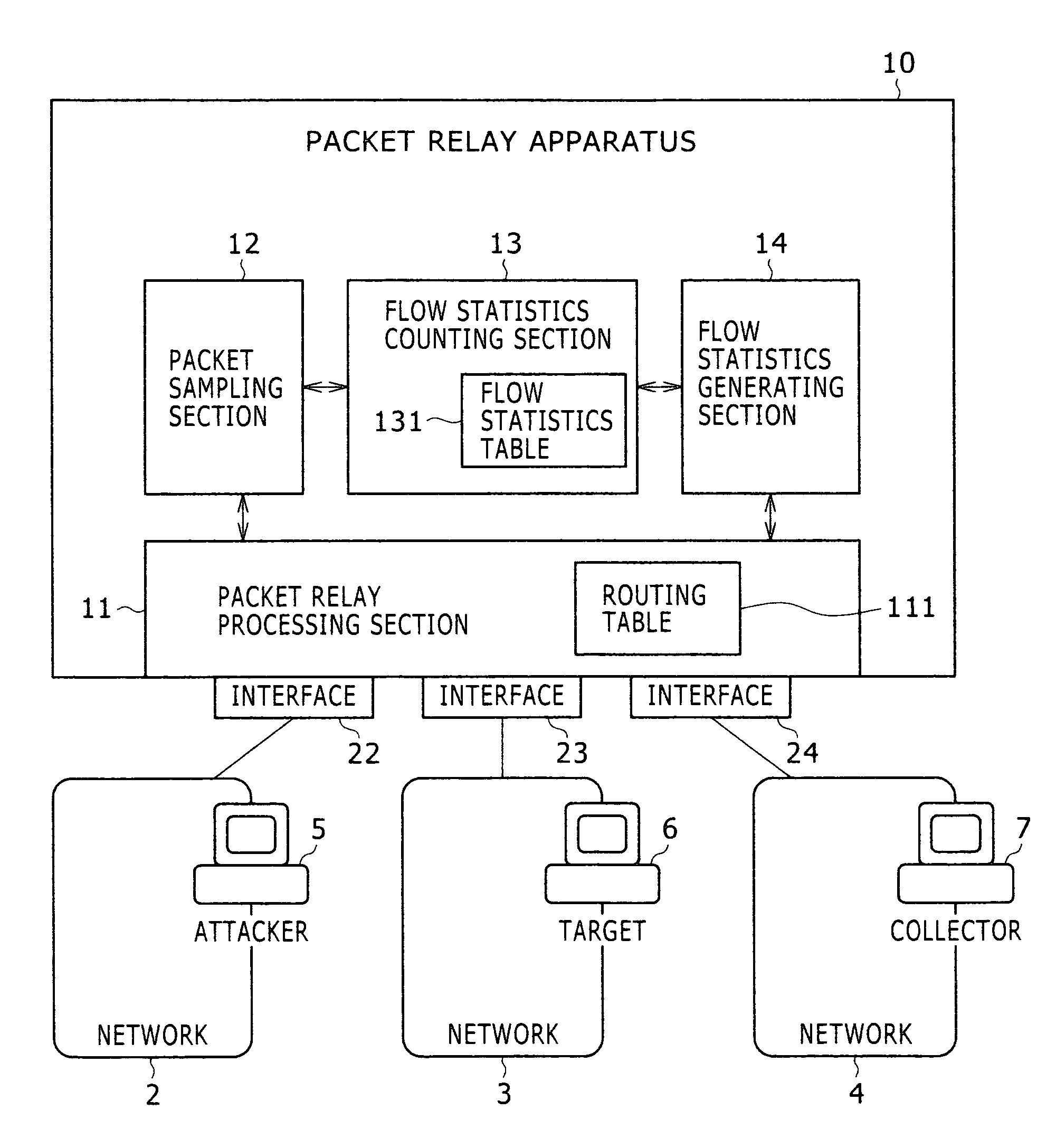
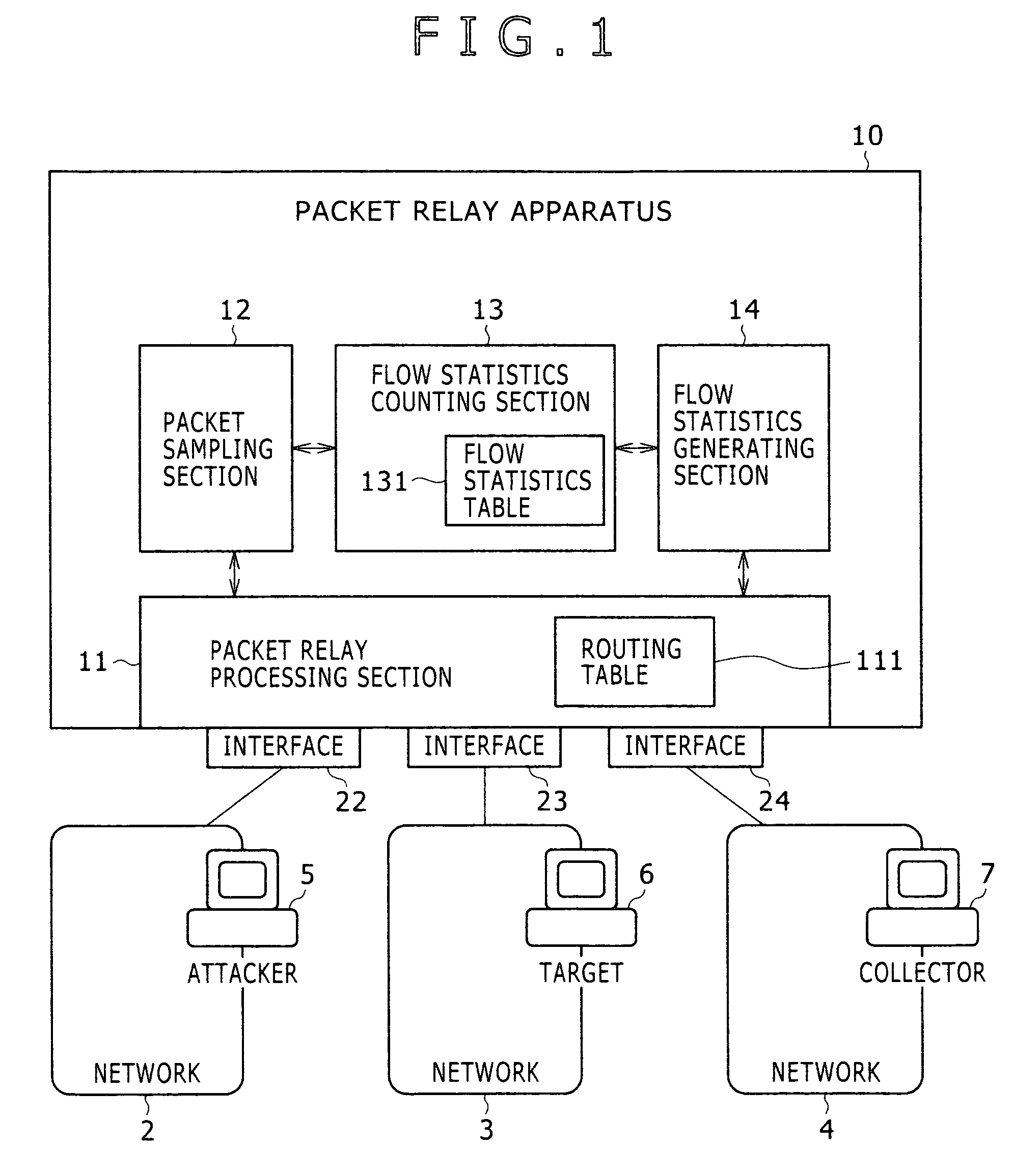
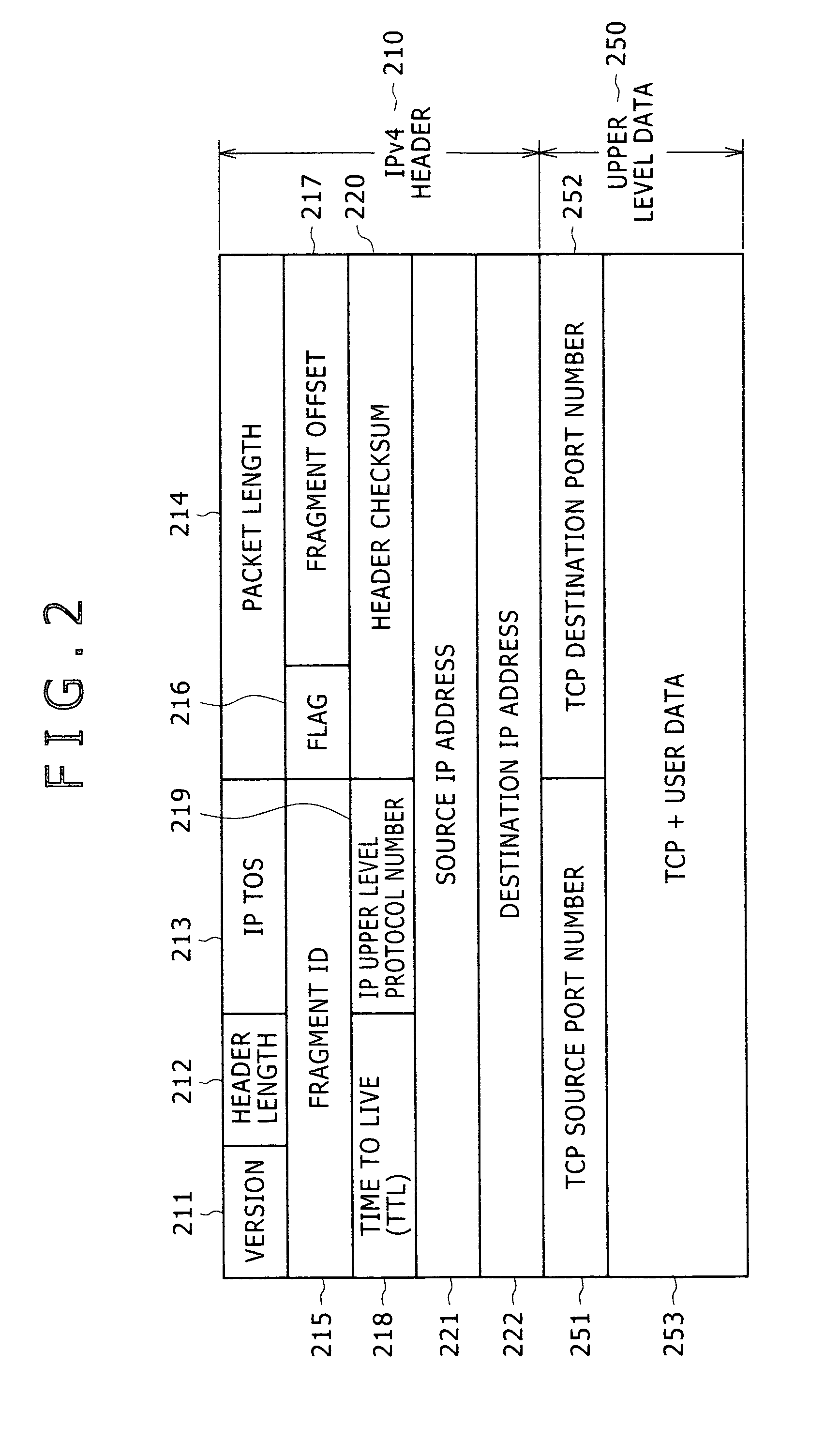
Detection method for abnormal traffic and packet relay apparatus
InactiveUS20070115850A1Efficient detectionMakes the resources of the target consumedError preventionTransmission systemsTraffic capacityByte
The present invention provides a technology including, for example, a packet relay processing section to carry out packet relay, a packet sampling section to carry out packet sampling, a flow statistics counting section to take statistics of each flow, and a flow statistics generating section to generate a NetFlow export datagram, wherein the flow statistics counting section collectively counts the number of the packets or bytes received per unit time when the number does not exceed a threshold value and individually counts the number for each flow when the number exceeds the threshold value, and thereby a flow of abnormal traffic which is suspected to be DoS attack is efficiently detected with small amounts of resources (mainly memories).
Owner:ALAXALA NETWORKS
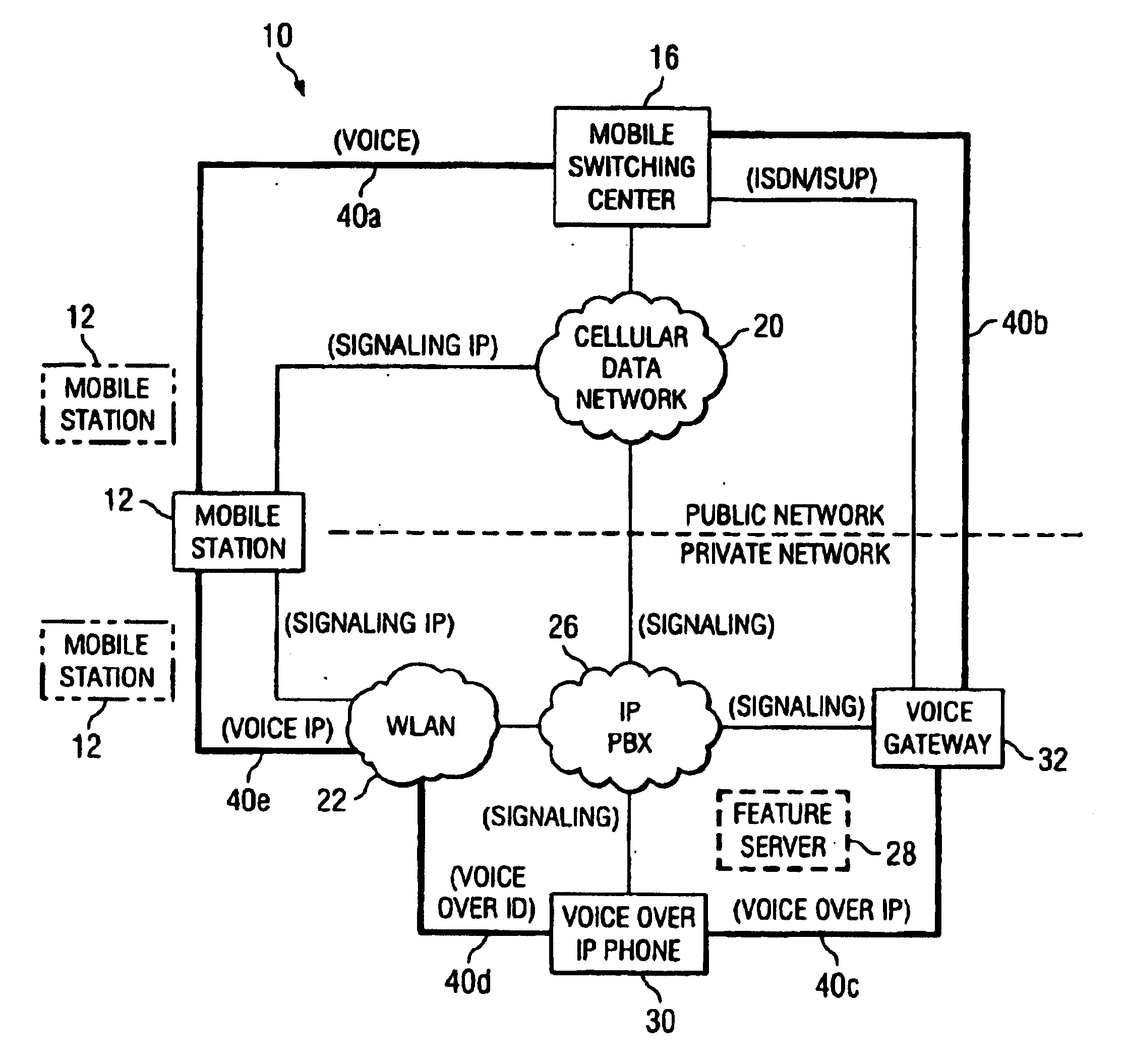
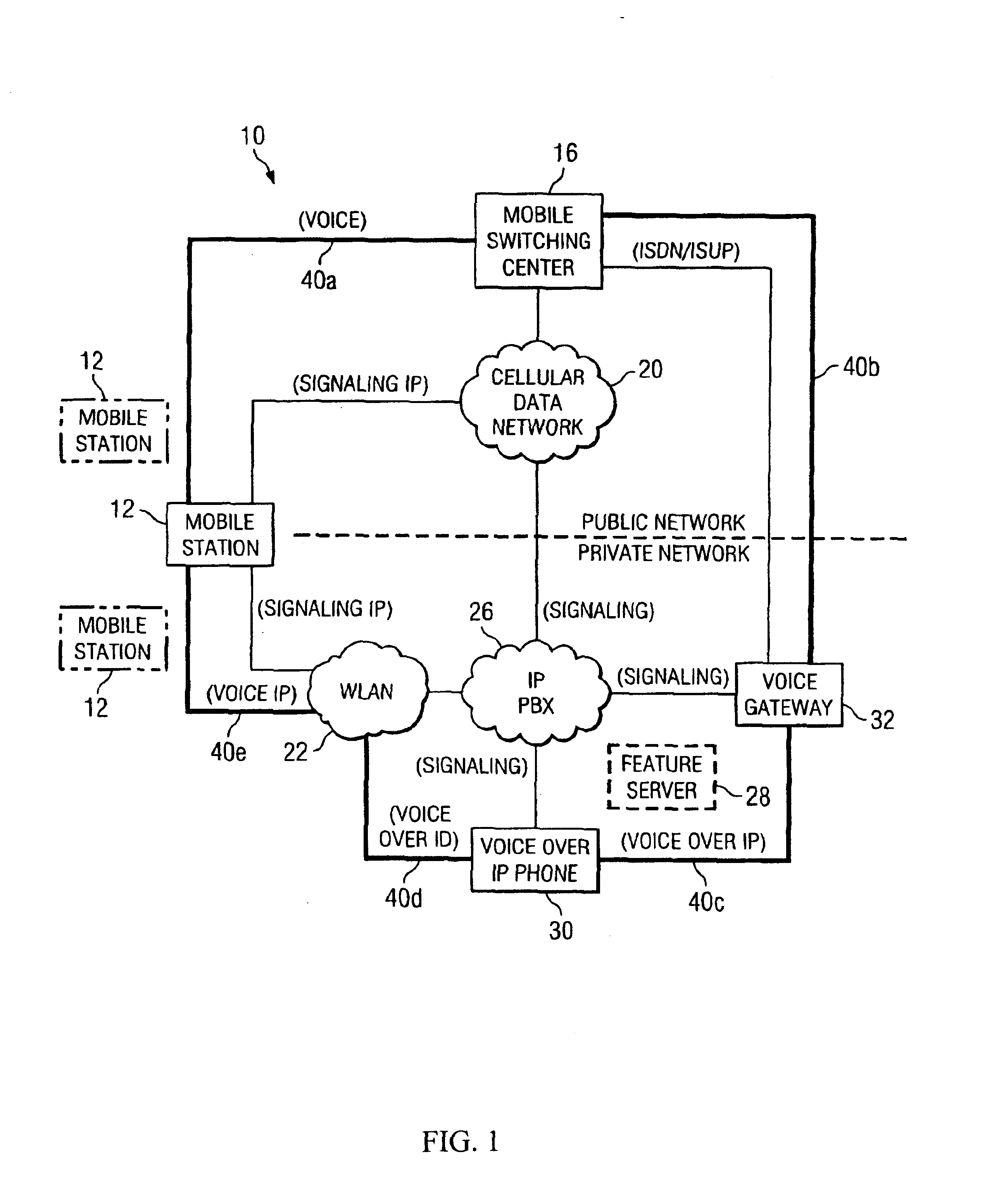
System and method for providing transparency in delivering private network features
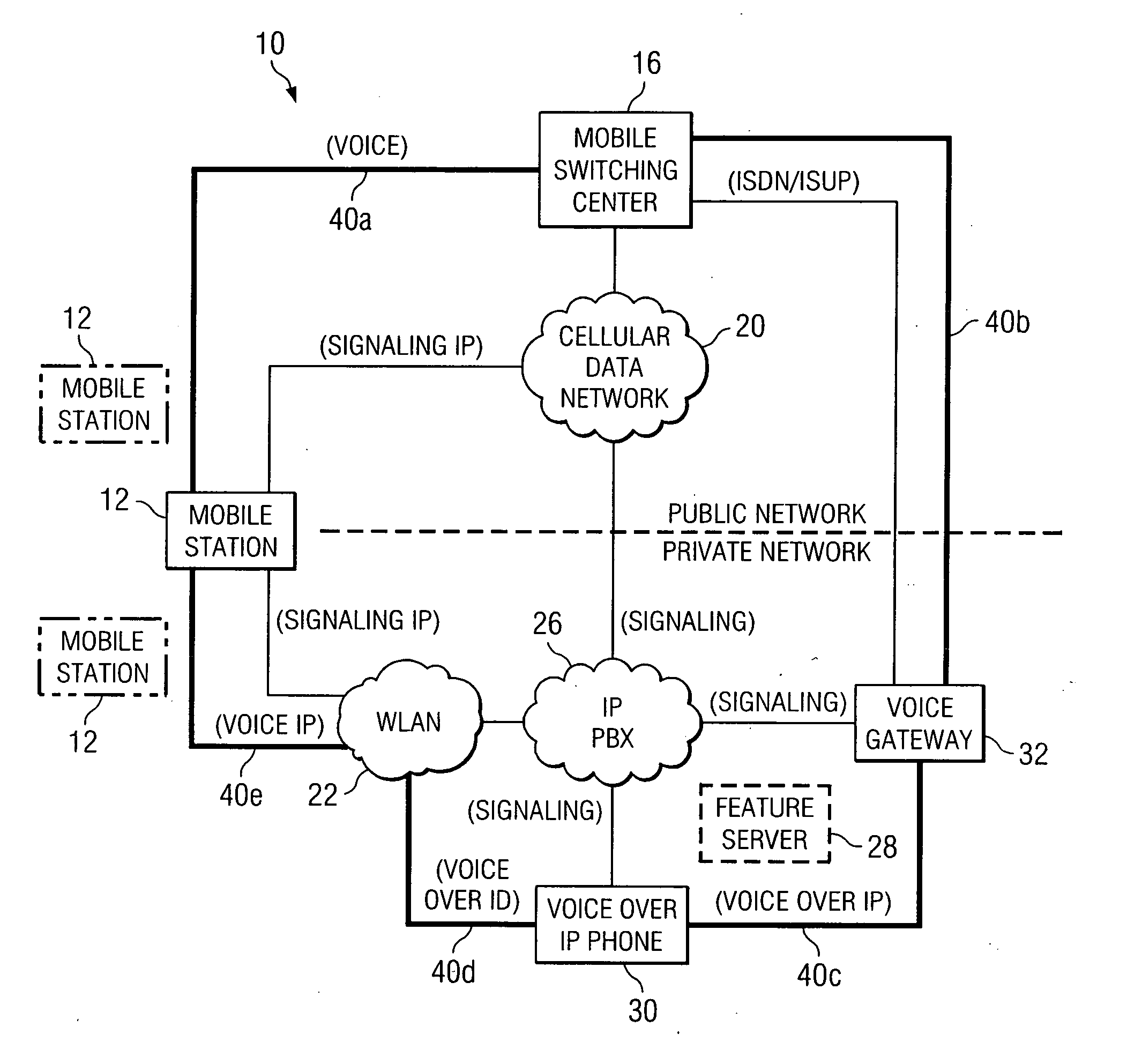
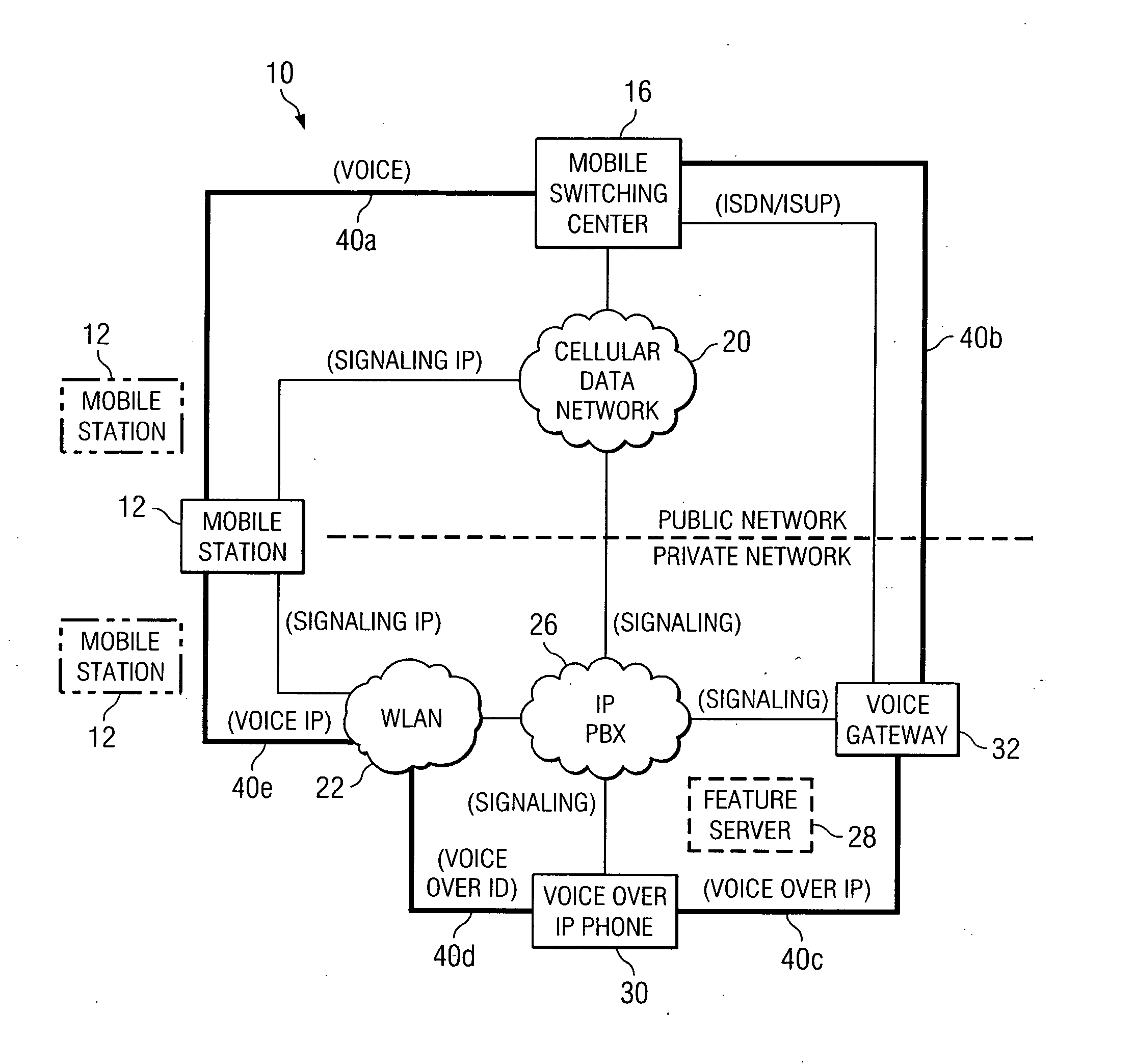
InactiveUS20050063359A1Reduce disadvantagesReduce problemsTelephone data network interconnectionsAccounting/billing servicesTelecommunicationsPrivate network
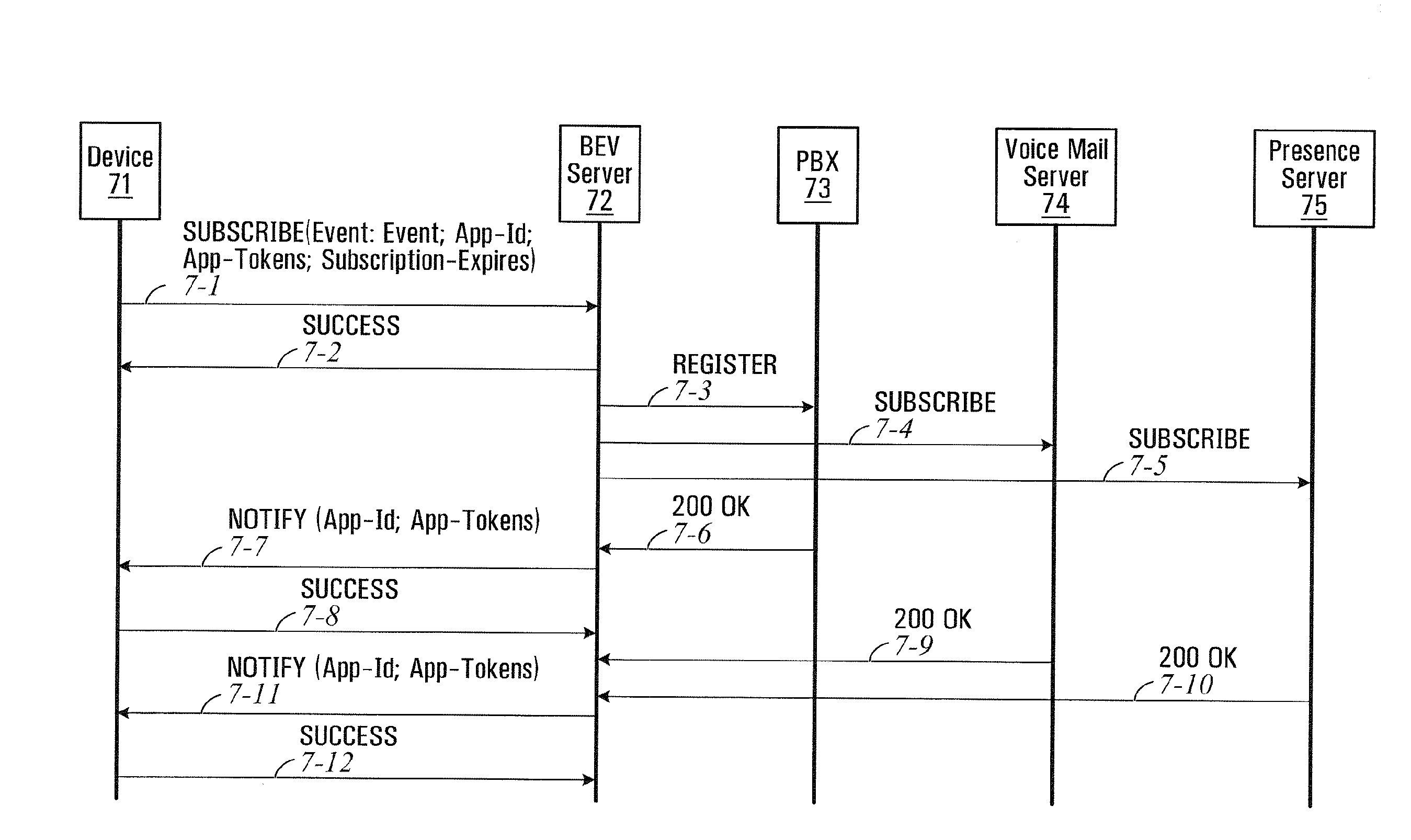
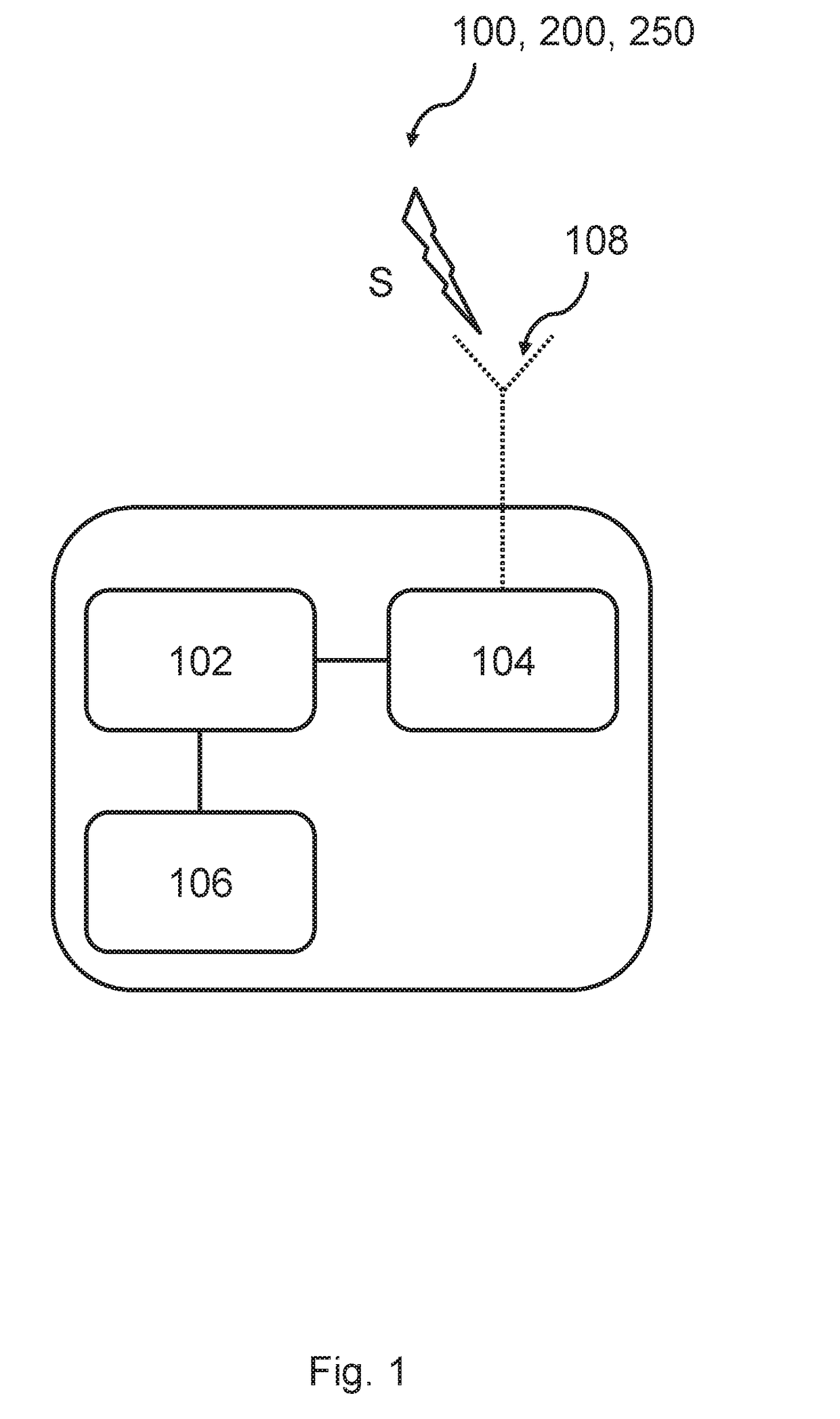
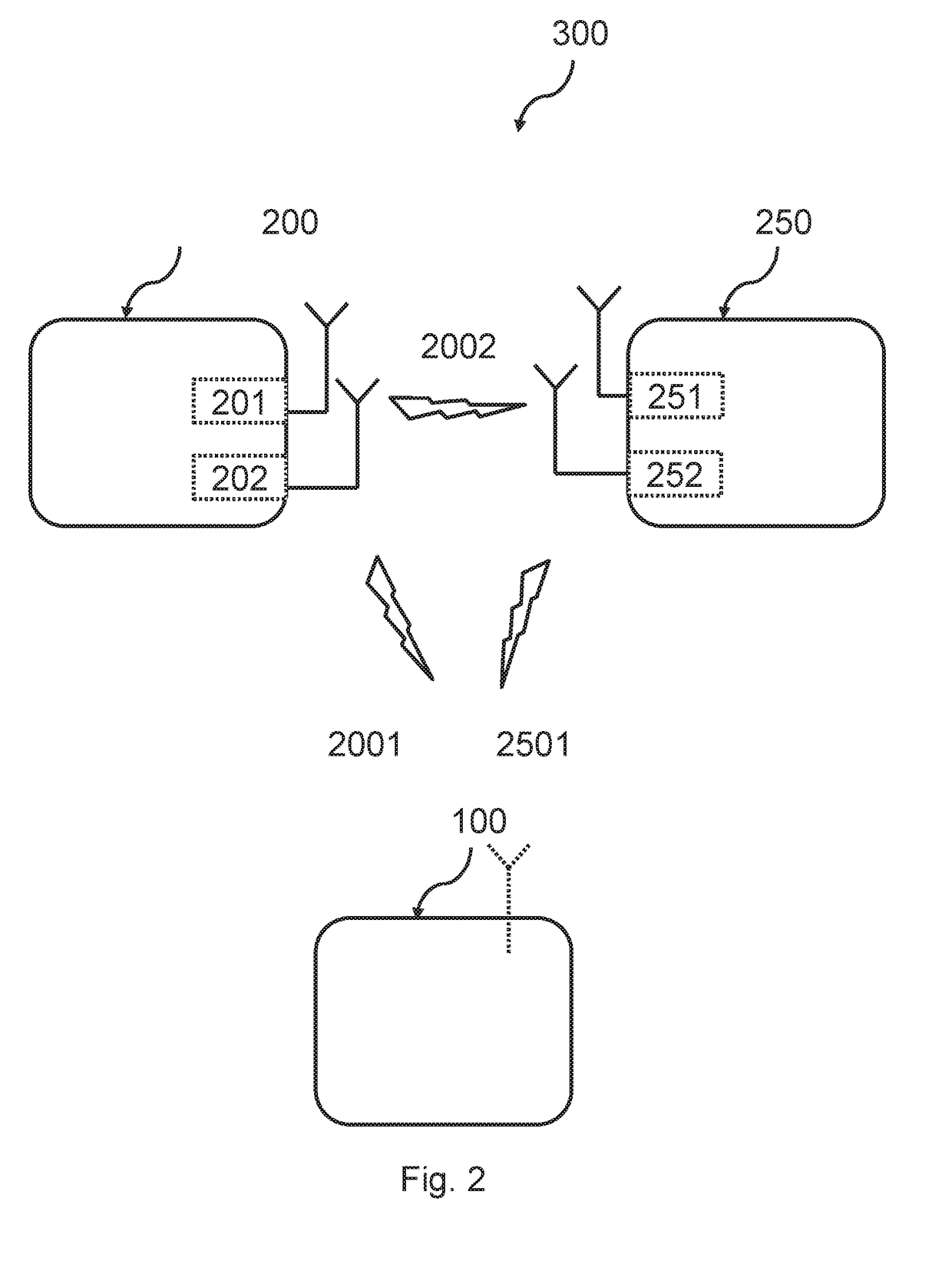
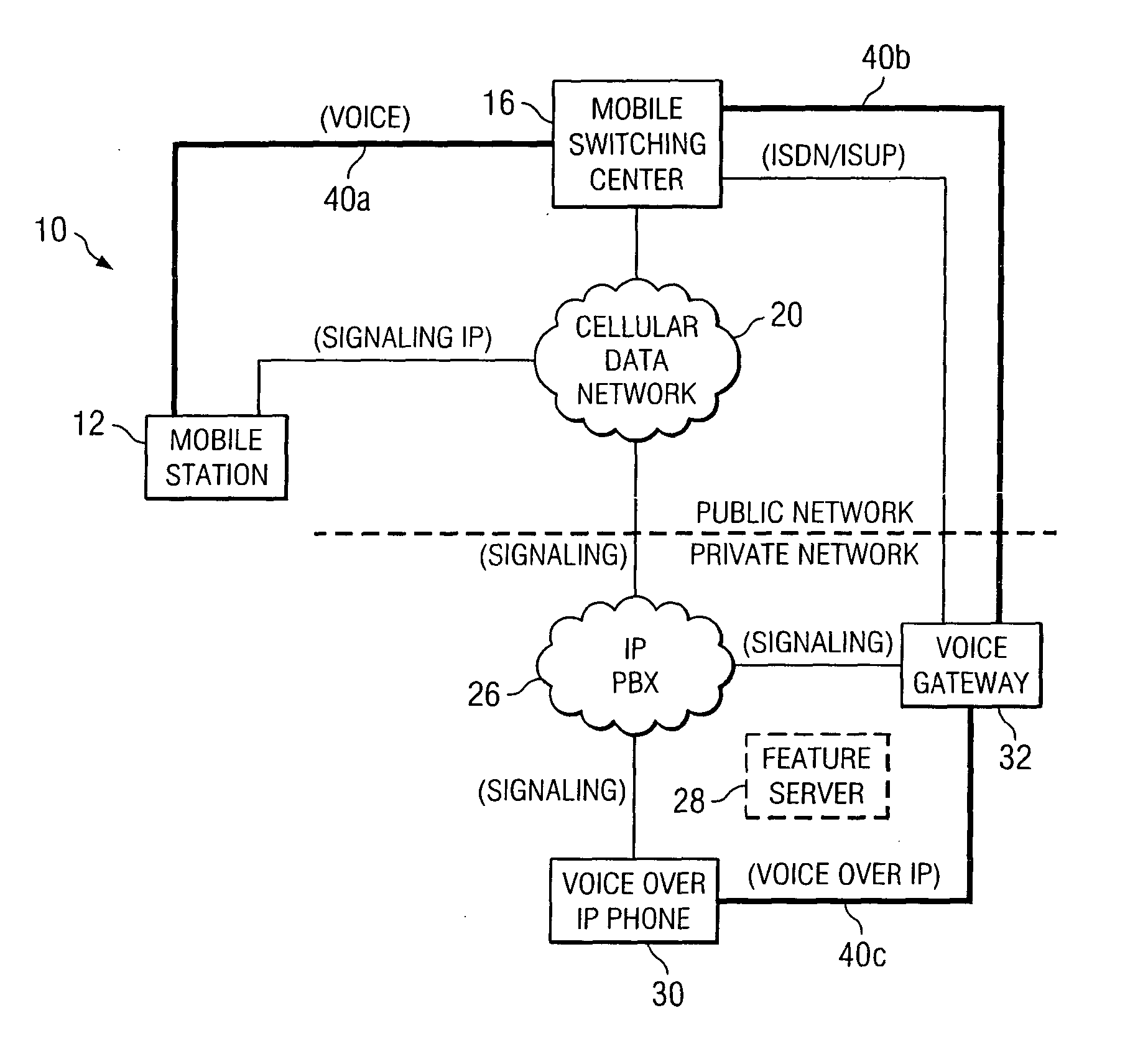
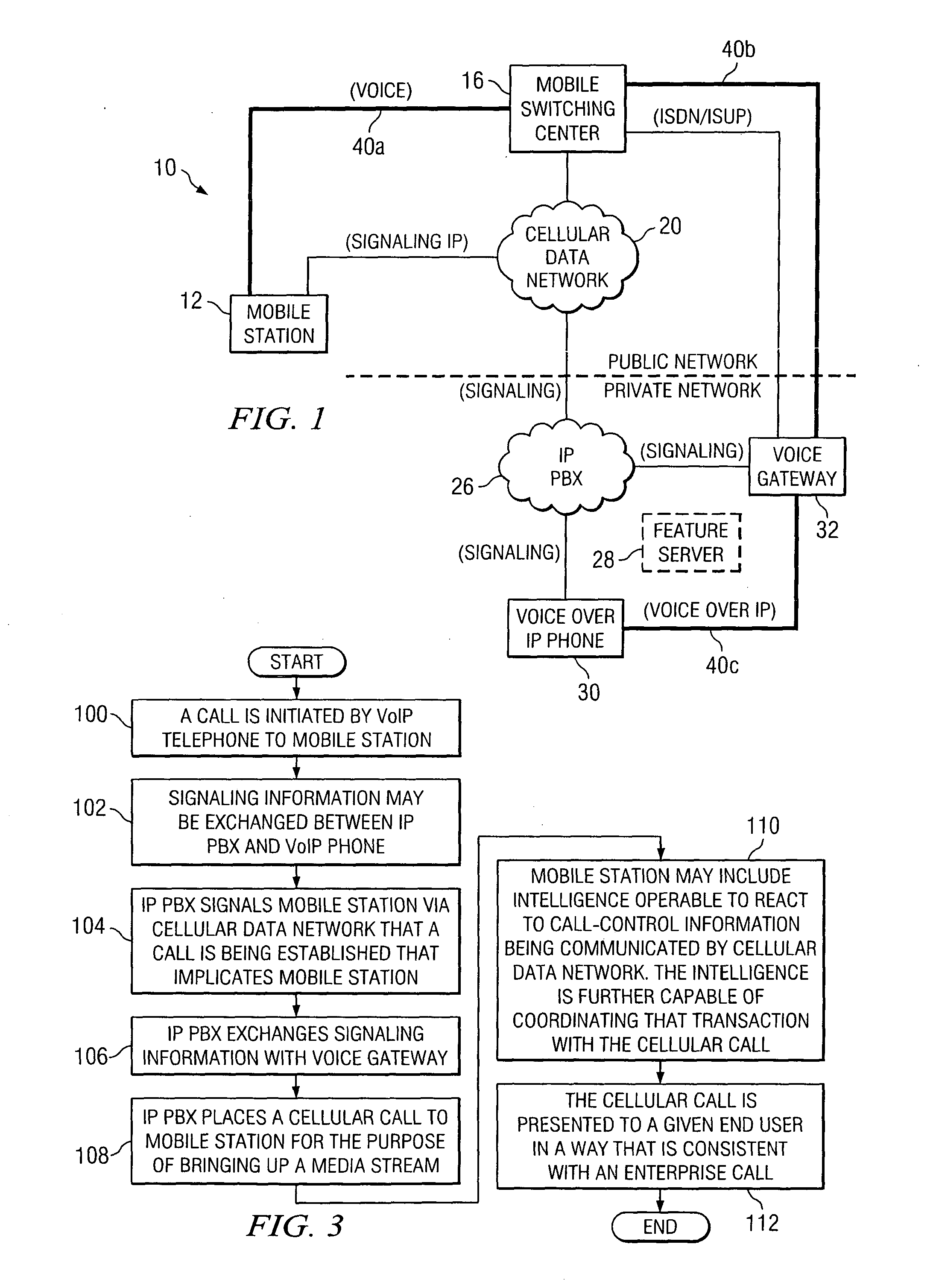
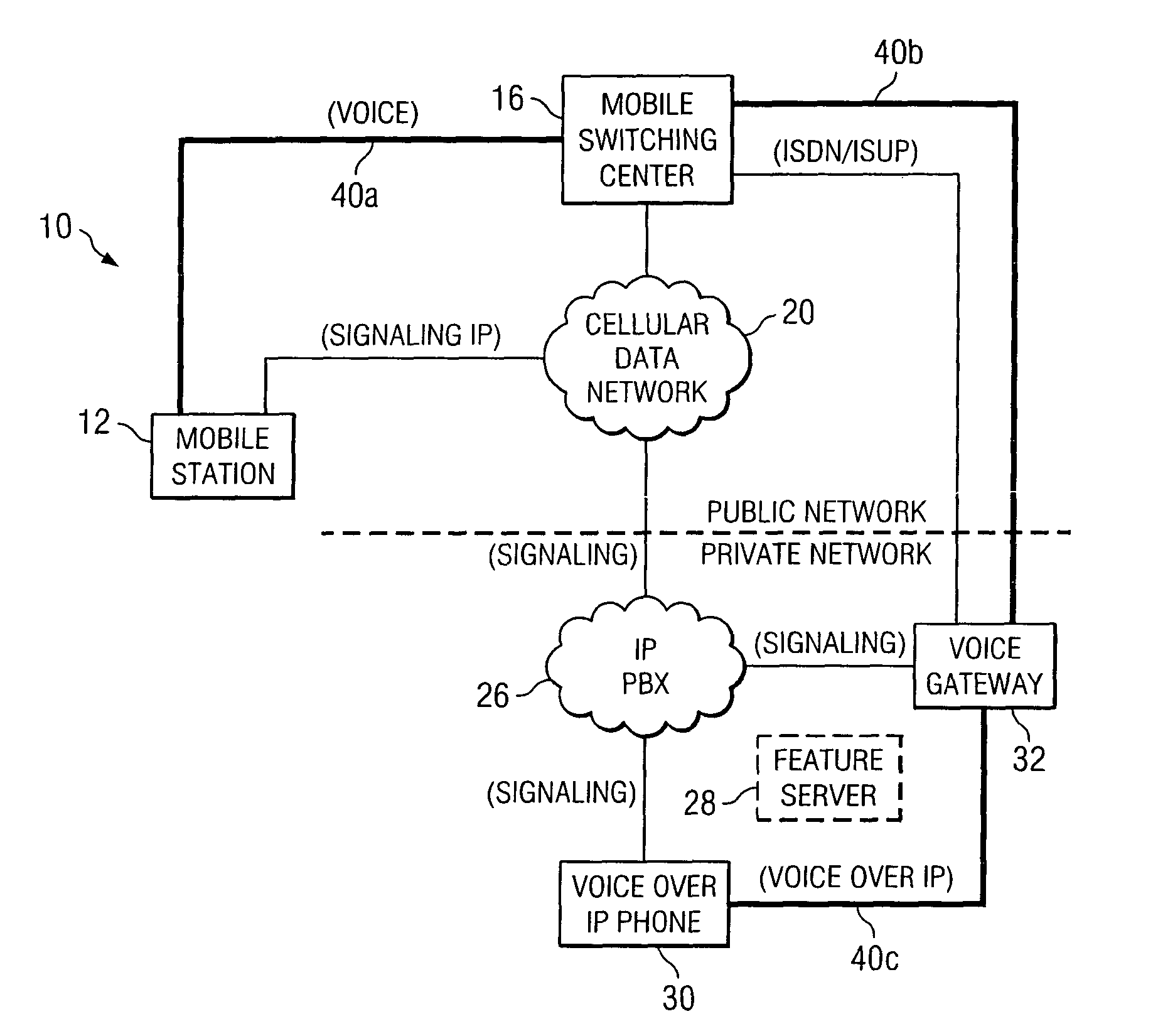
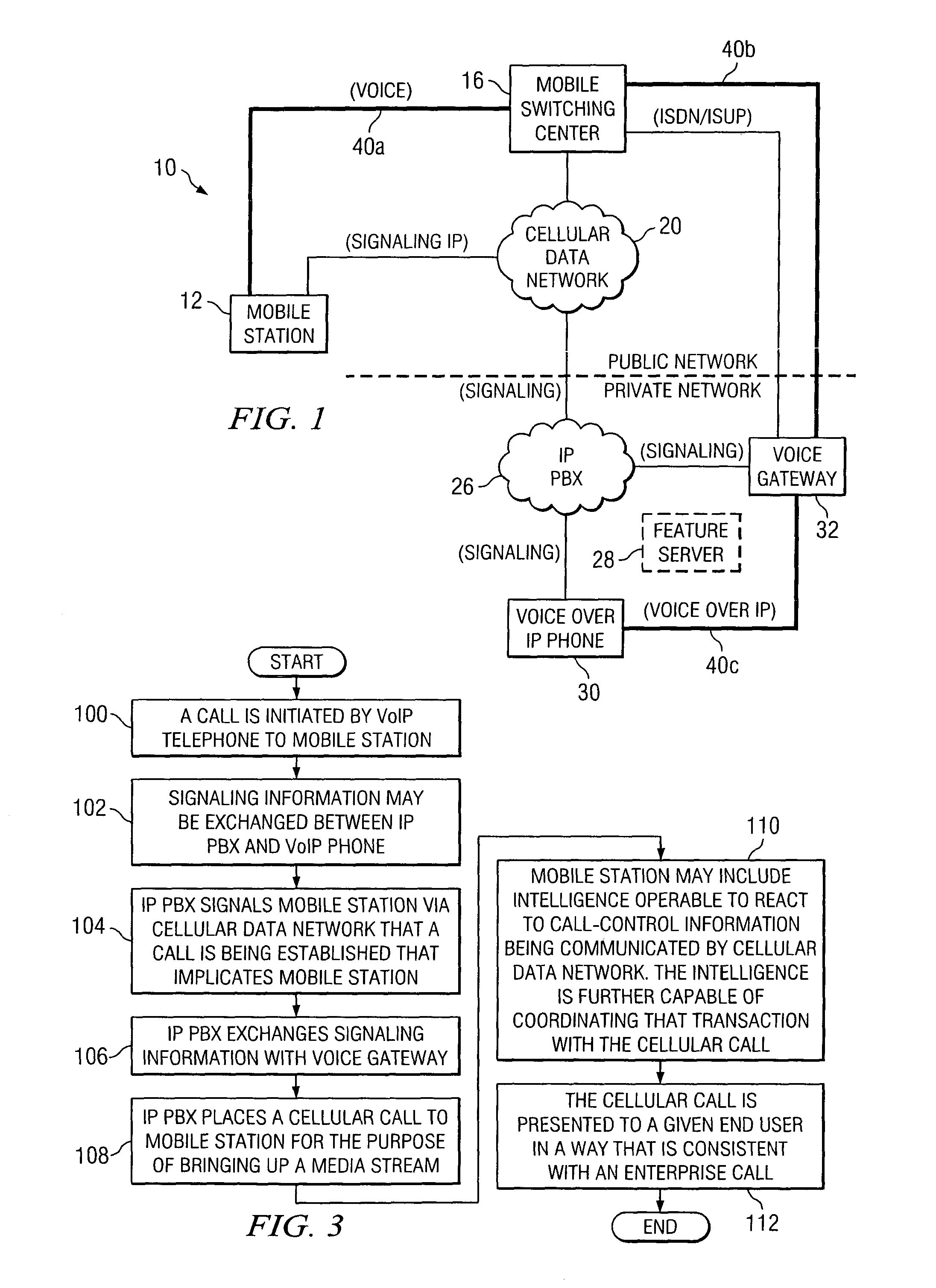
A method is provided that includes receiving a request from a communication device to establish a communication session with a mobile station, the mobile station being operable to roam between a private and a public network. The mobile station is signaled via a cellular data network that a call is being initiated for the mobile station. Signaling information may be exchanged with a voice gateway such that one or more voice circuits are established. A signaling pathway may be established between an Internet protocol private branch exchange (IP PBX) and the mobile station via the cellular data network. The establishment of the signaling pathway is substantially concurrent with the establishment of one or more of the voice circuits. One or more features associated with a private network are delivered to the mobile station during the communication session as an end user moves between the public and private networks.
Owner:CISCO TECH INC
System and method for providing transparency in delivering private network features
InactiveUS6888808B2Reduce disadvantagesReduce problemsData switching by path configurationRadio/inductive link selection arrangementsTelecommunicationsPrivate network
Owner:CISCO TECH INC
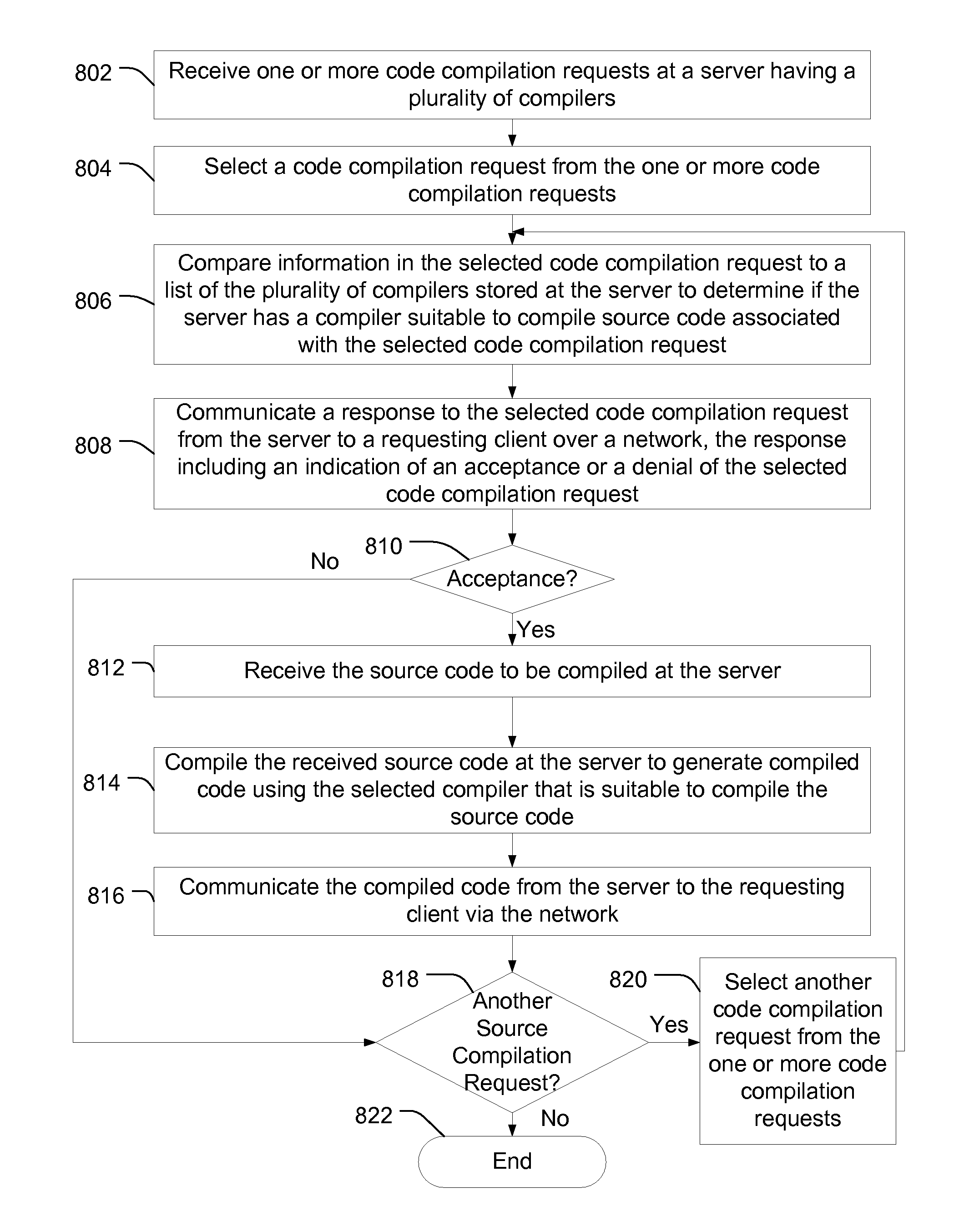
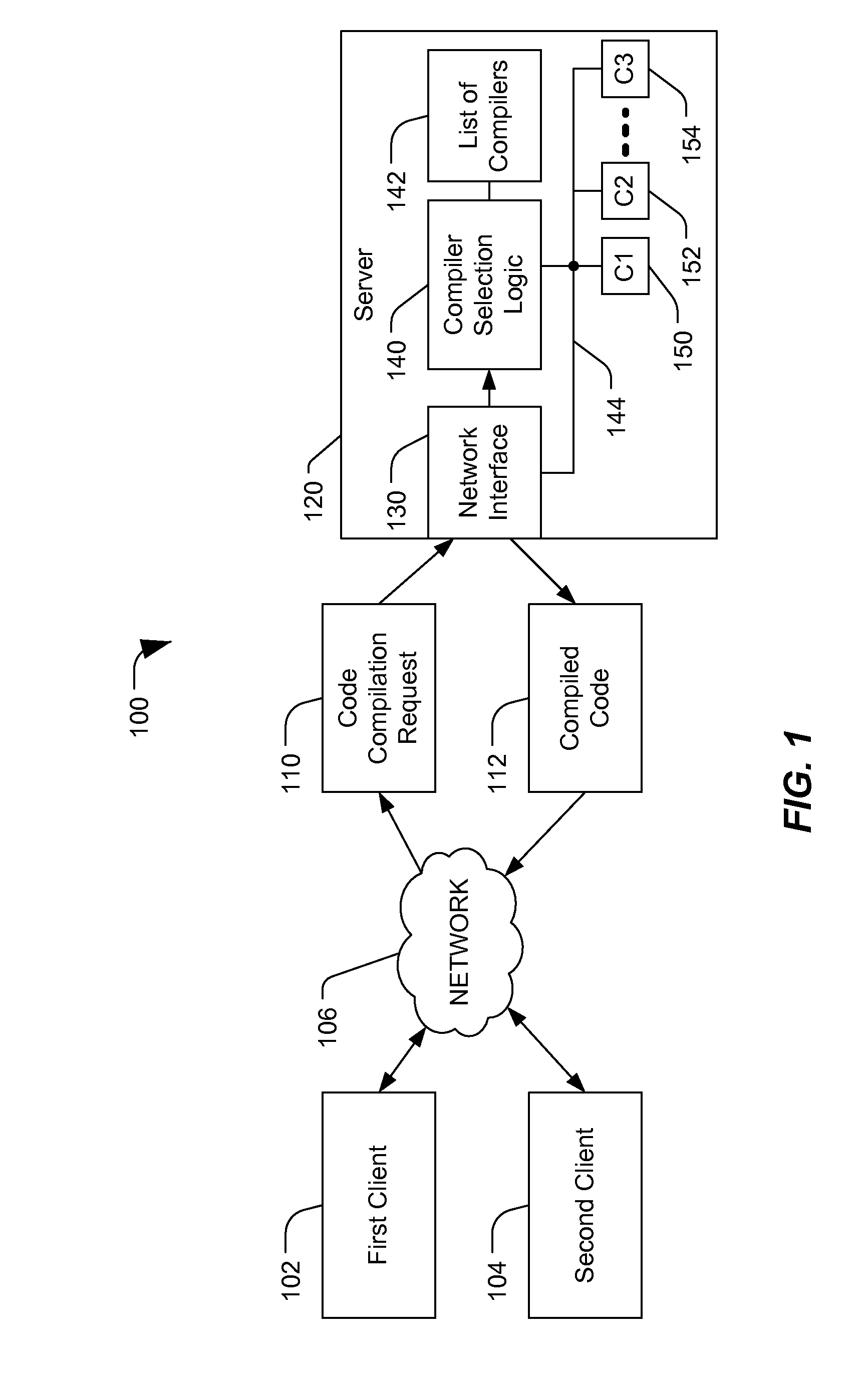
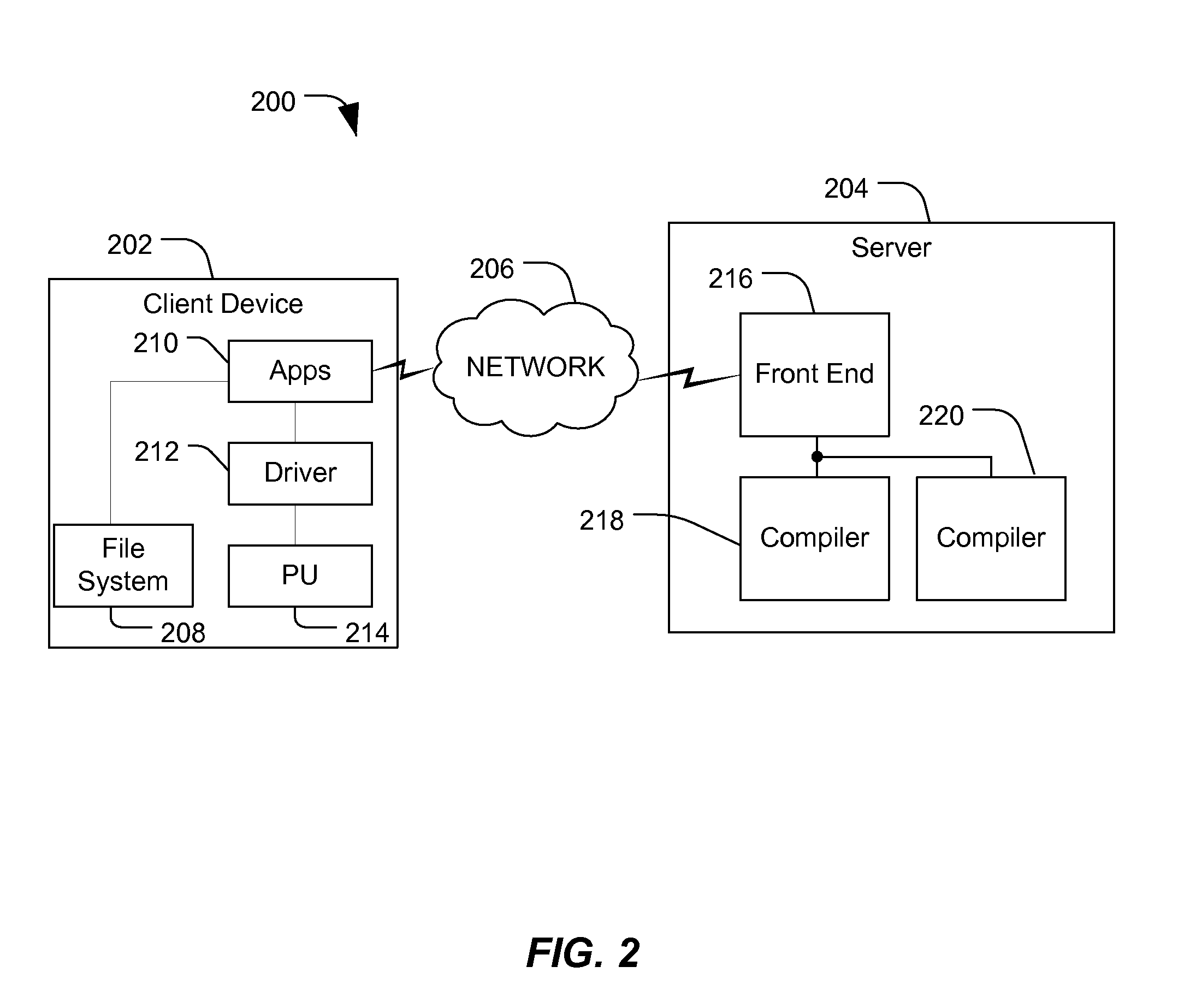
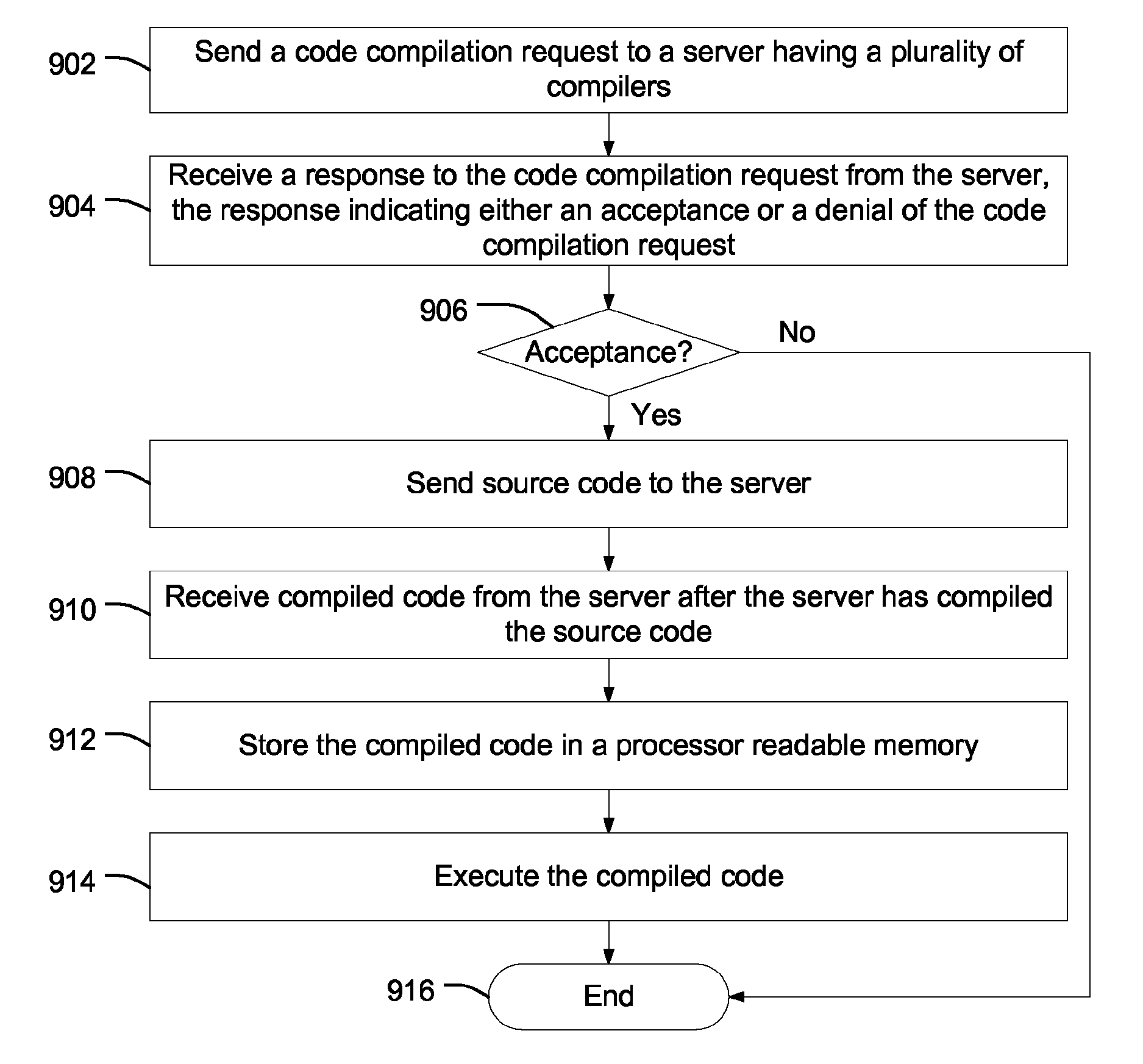
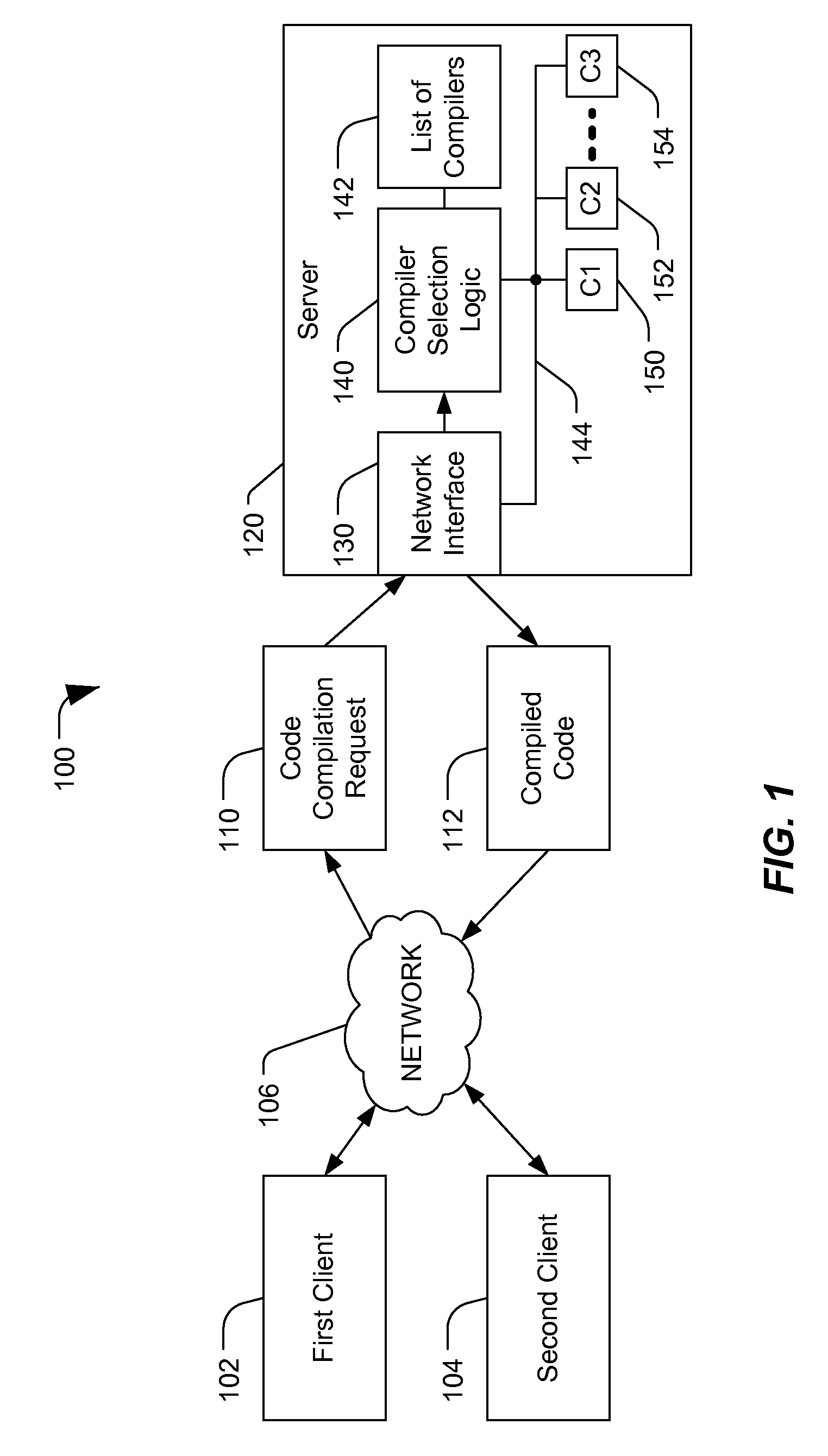
Server-based code compilation
ActiveUS20090113402A1Protection is in progressGreat processing resourceProgram controlMemory systemsClient-sideCompiler
A server is disclosed that includes an interface to a data communication network, a compiler library that stores a plurality of different compilers, and compiler selection logic responsive to data received at the interface and including logic. The compiler selection logic is configured to select one of the plurality of different compilers based on an evaluation of the received data. The selected compiler generates compiled output data and the compiled output data is communicated over the data communication network to a client.
Owner:QUALCOMM INC
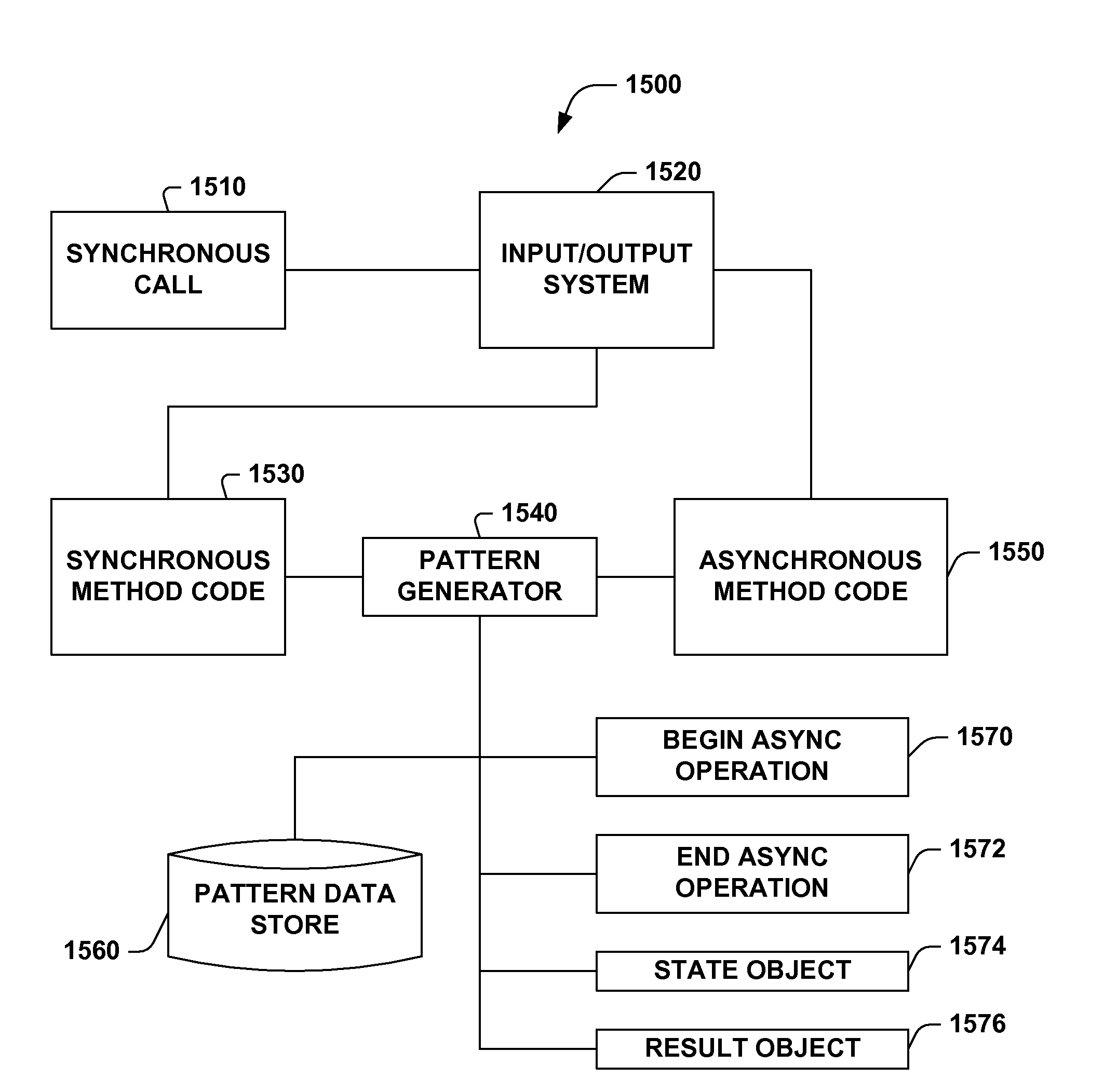
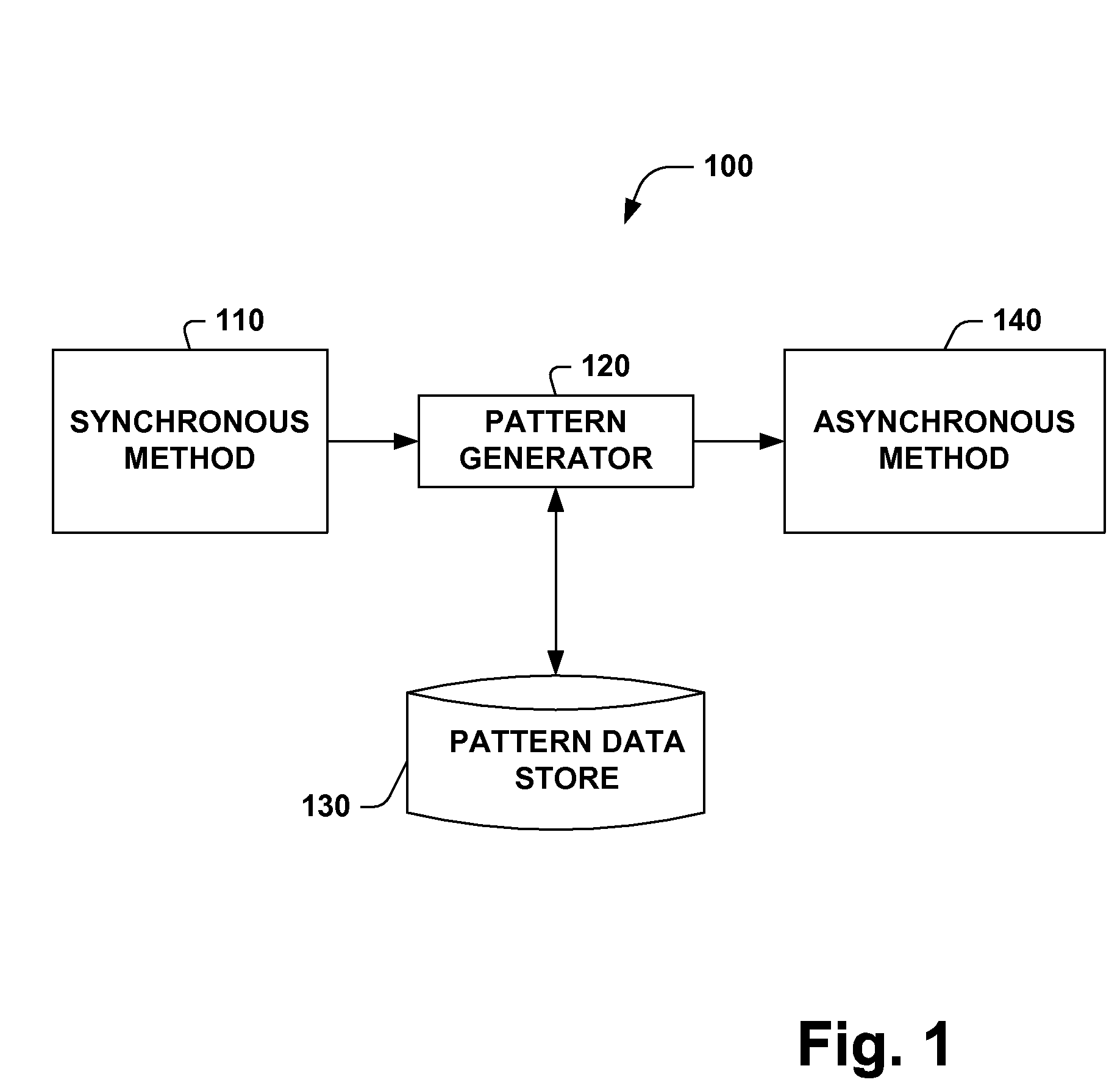
Asynchronous pattern
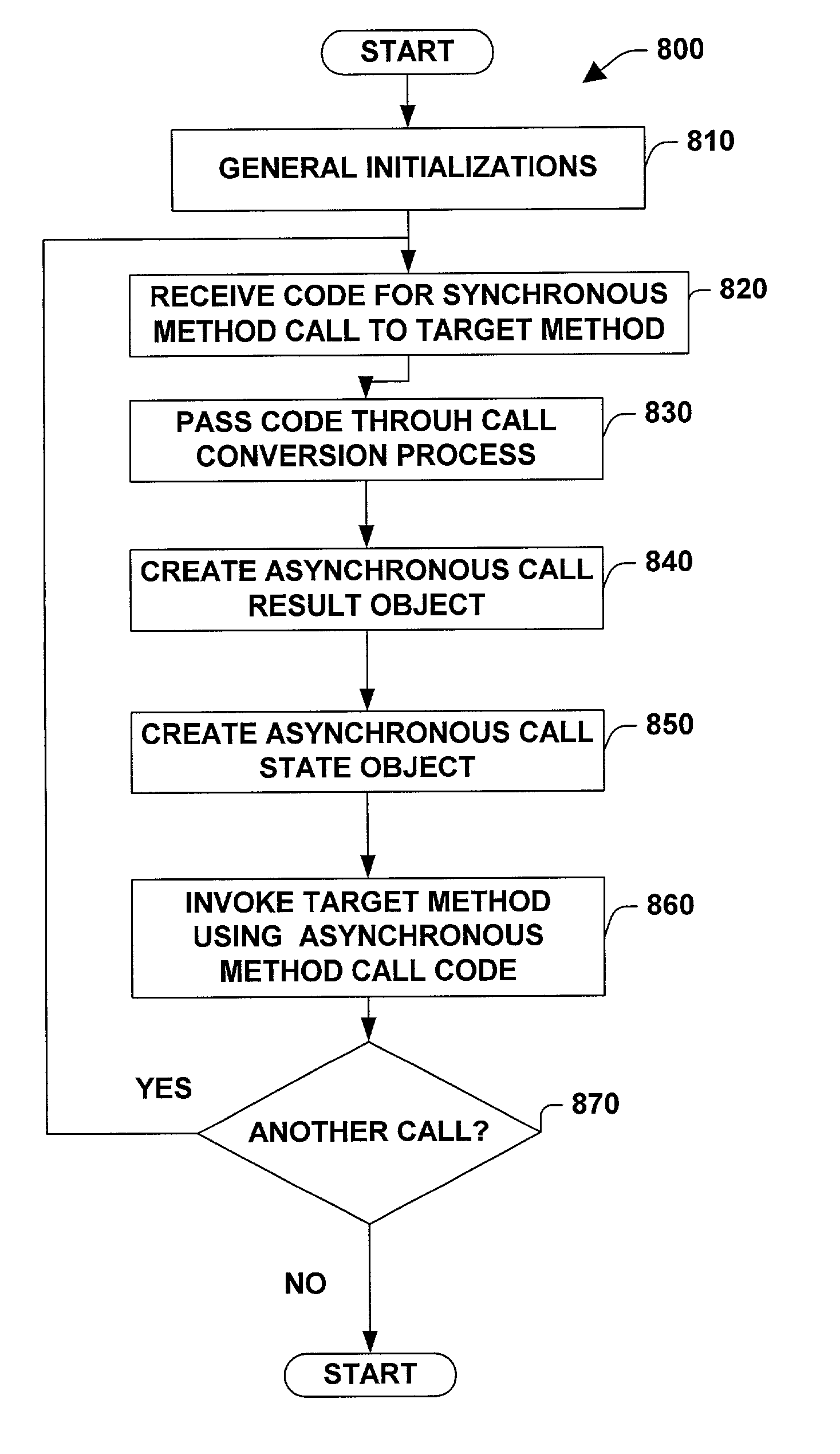
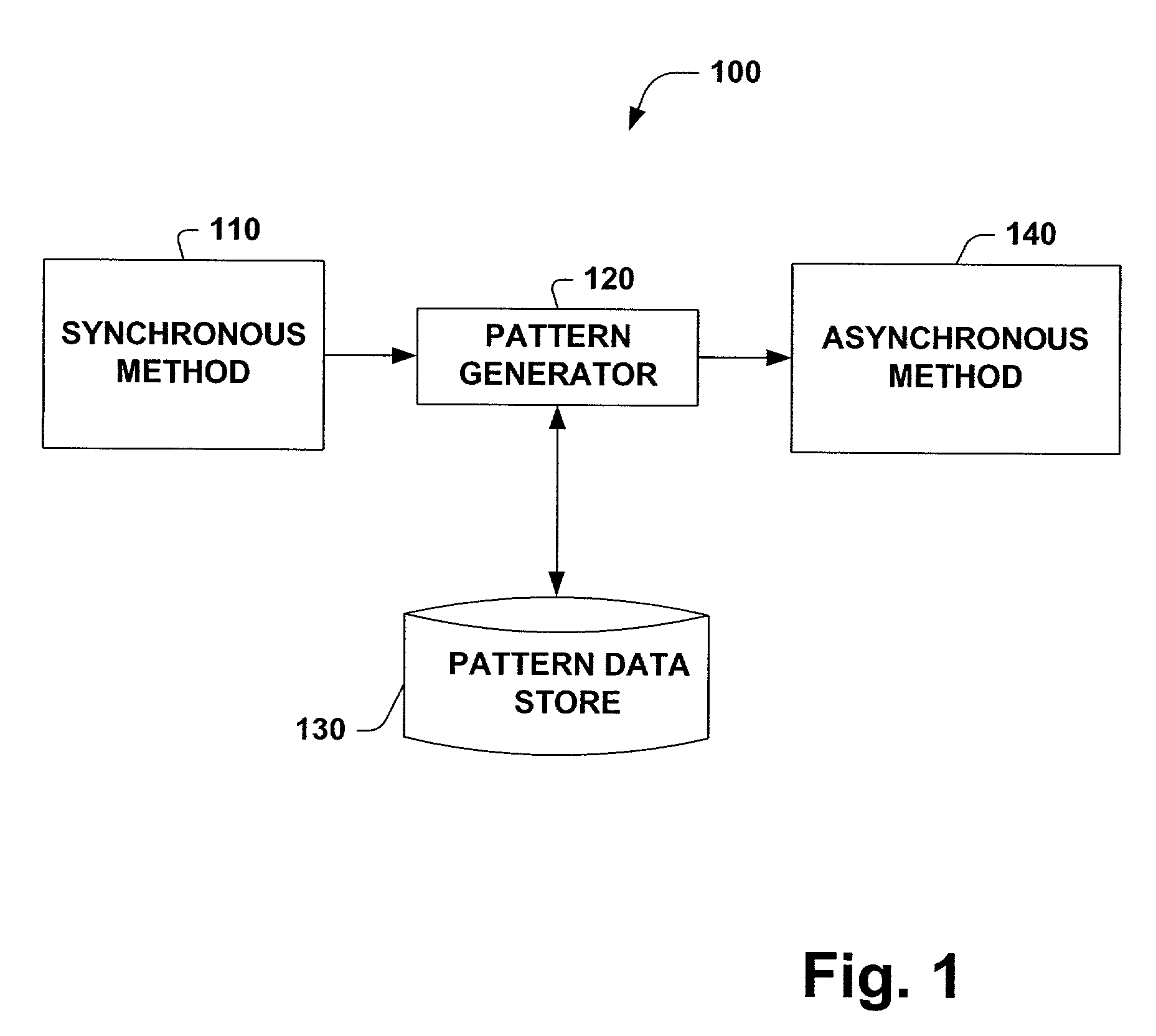
InactiveUS7248603B1Reduce the possibilityImprove processing efficiencyData processing applicationsTime-division multiplexAsynchronous method invocationMessage queue
A system and method for converting code associated with synchronous method calls to code that can be employed to perform asynchronous method calls and for supporting such asynchronous method calls is provided. The system includes a pattern generator that can break code for a synchronous method call into one or more constituent parts including a begin asynchronous operation method, an end asynchronous operation method, an asynchronous call state object and an asynchronous call result object. The system includes a pattern data store that holds data associated with converting a synchronous method call to an asynchronous method call, which facilitates employing the system consistently across environments like file input / output, stream input / output, socket input / output, networking, remoting channels, proxies, web forms, web services and messaging message queues.
Owner:MICROSOFT TECH LICENSING LLC
System and method for providing transparency in delivering private network features
InactiveUS20050148362A1Reduce disadvantagesReduce problemsTelephone data network interconnectionsAccounting/billing servicesTelecommunicationsPrivate network
A method is provided that includes receiving a request from a communication device to establish a communication session with a mobile station, the mobile station being operable to roam between a private and a public network. The mobile station is signaled via a cellular data network that a call is being initiated for the mobile station. Signaling information may be exchanged with a voice gateway such that one or more voice circuits are established. A signaling pathway may be established between an Internet protocol private branch exchange (IP PBX) and the mobile station via the cellular data network. The establishment of the signaling pathway is substantially concurrent with the establishment of one or more of the voice circuits. One or more features associated with a private network are delivered to the mobile station during the communication session as an end user moves between the public and private networks.
Owner:CISCO TECH INC
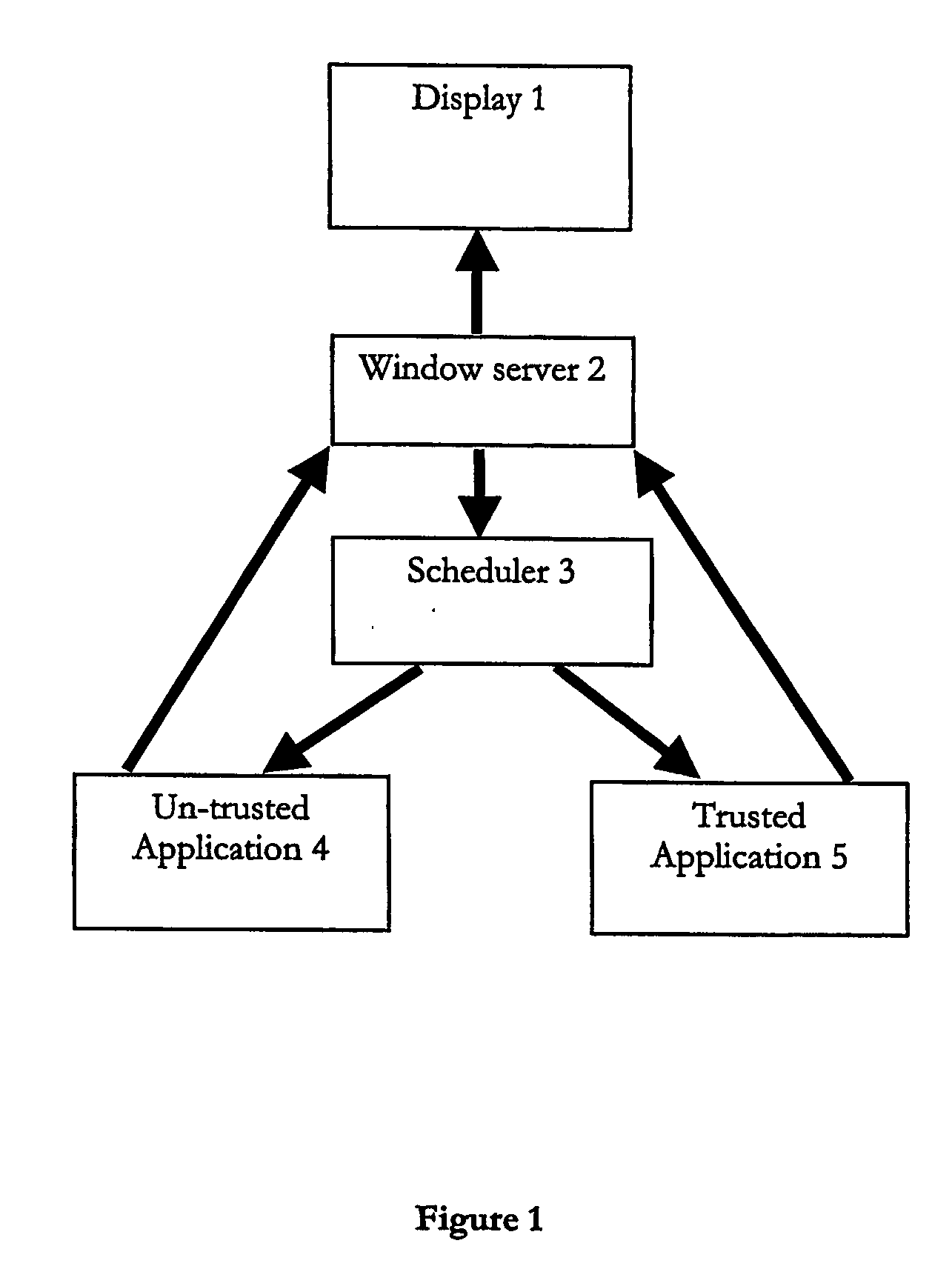
Method of enabling a multitasking computing device to conserve resources
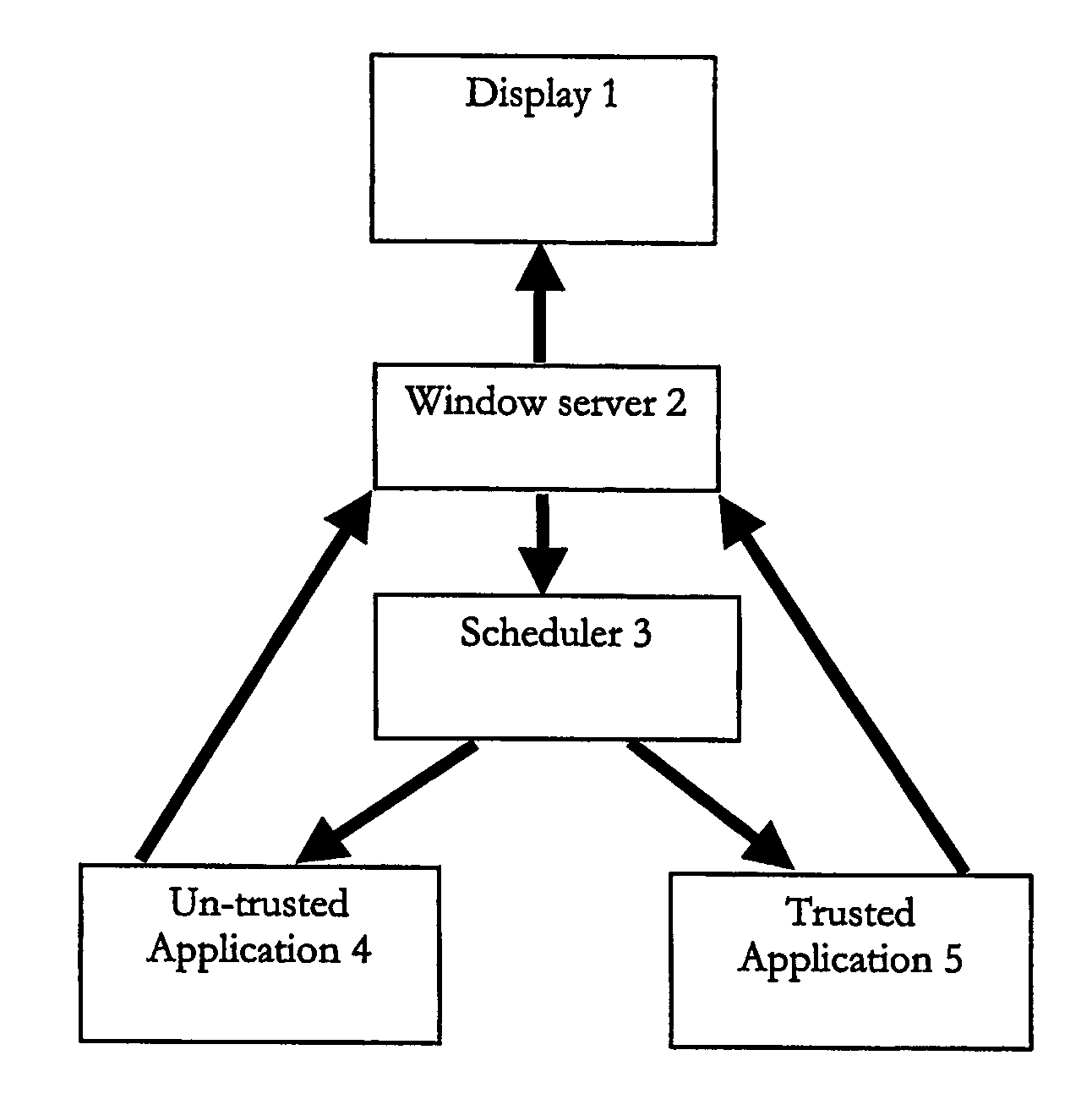
InactiveUS20070038763A1Save system resourcesPreserve system resources (CPU, power)Energy efficient ICTResource allocationTrusted applicationMany-task computing
A multitasking battery operated computing device preserves battery power by determining if an untrusted application is in the background or foreground and preventing an untrusted application that is in the background from running. A window server component may be used to determine if an untrusted application is in the background or foreground; for applications in the background, it can send a control signal to the scheduler or interrupt handler that in effect prevents the untrusted application from running, e.g. being given any services or consuming any resources.
Owner:UIQ TECH
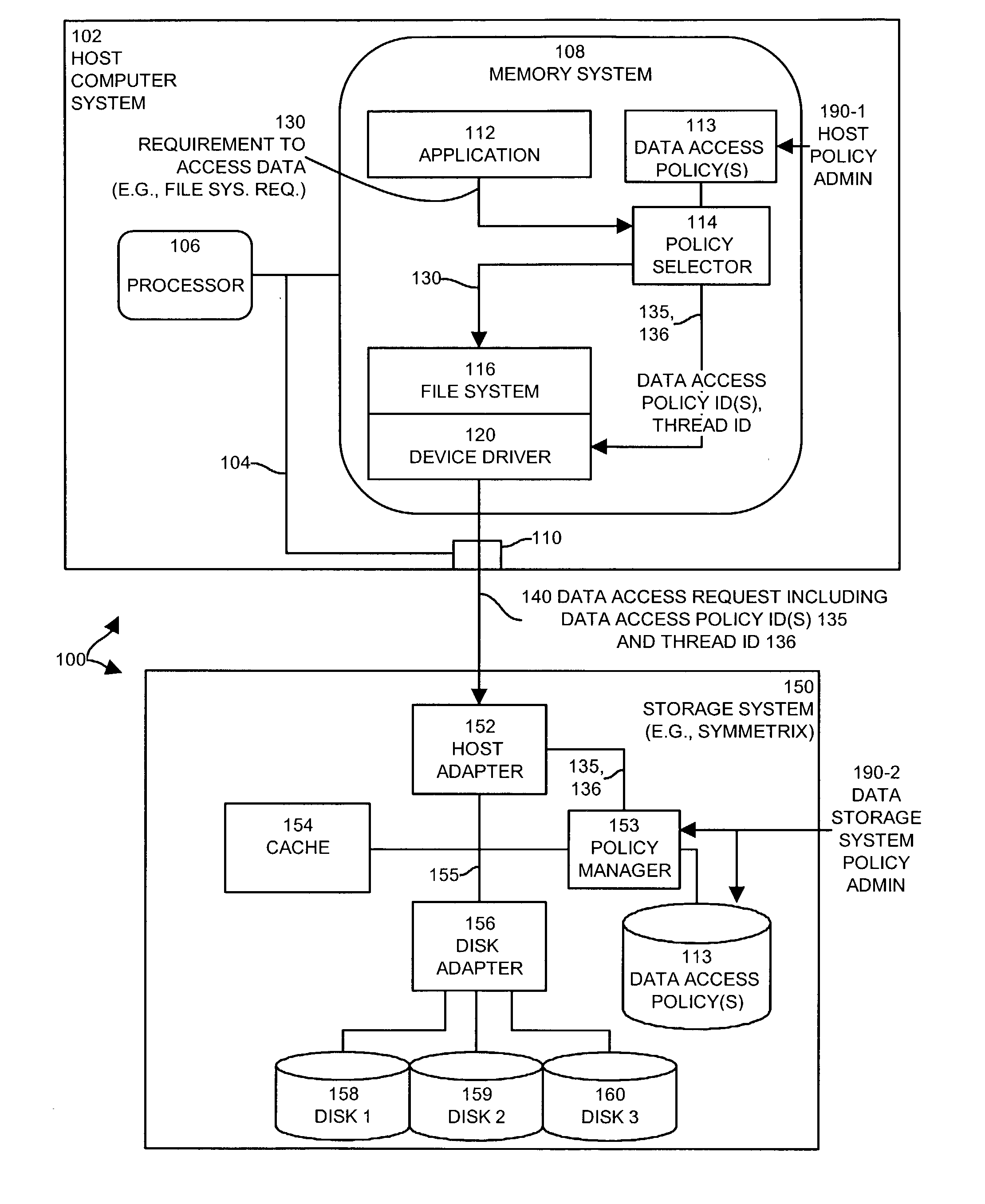
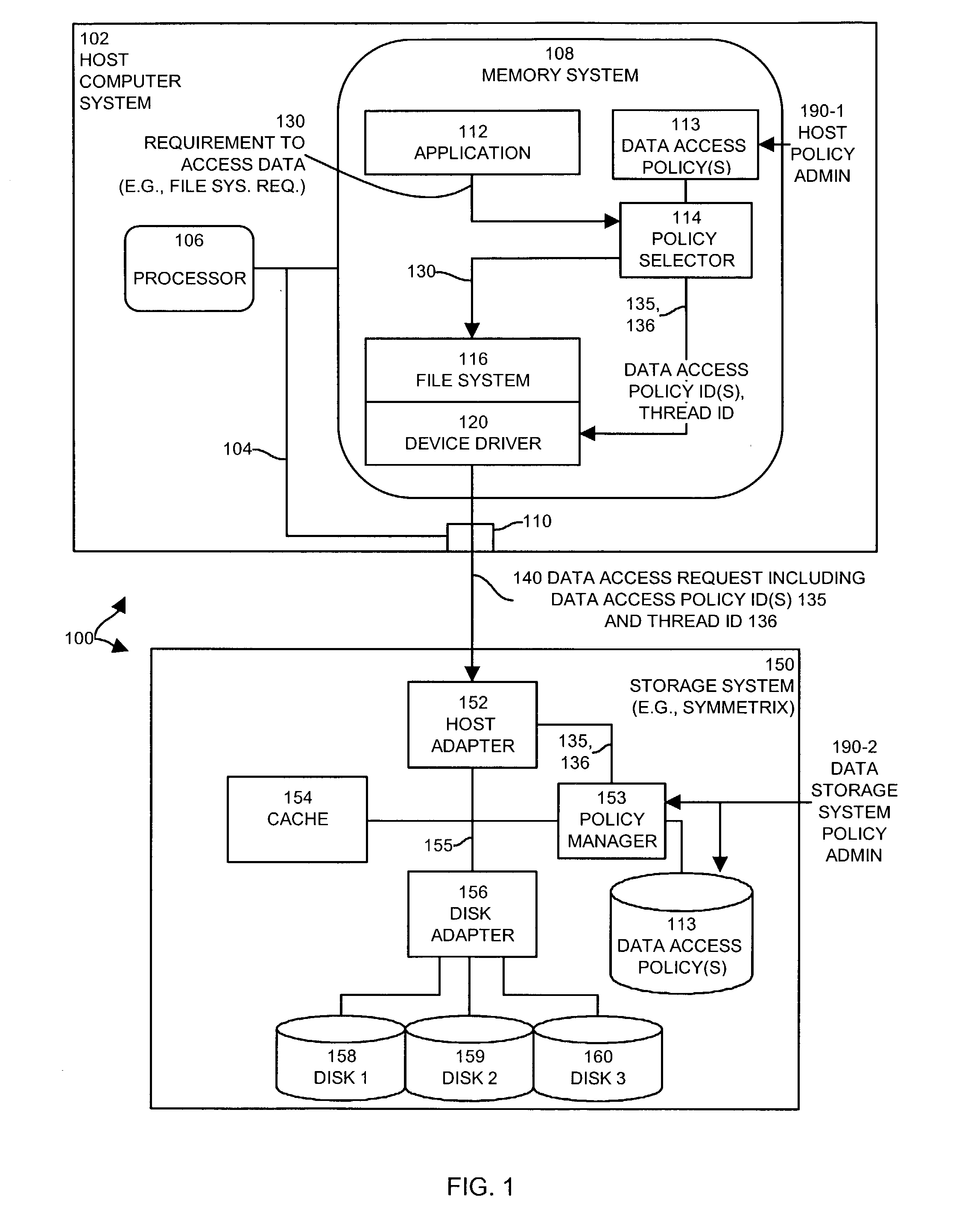
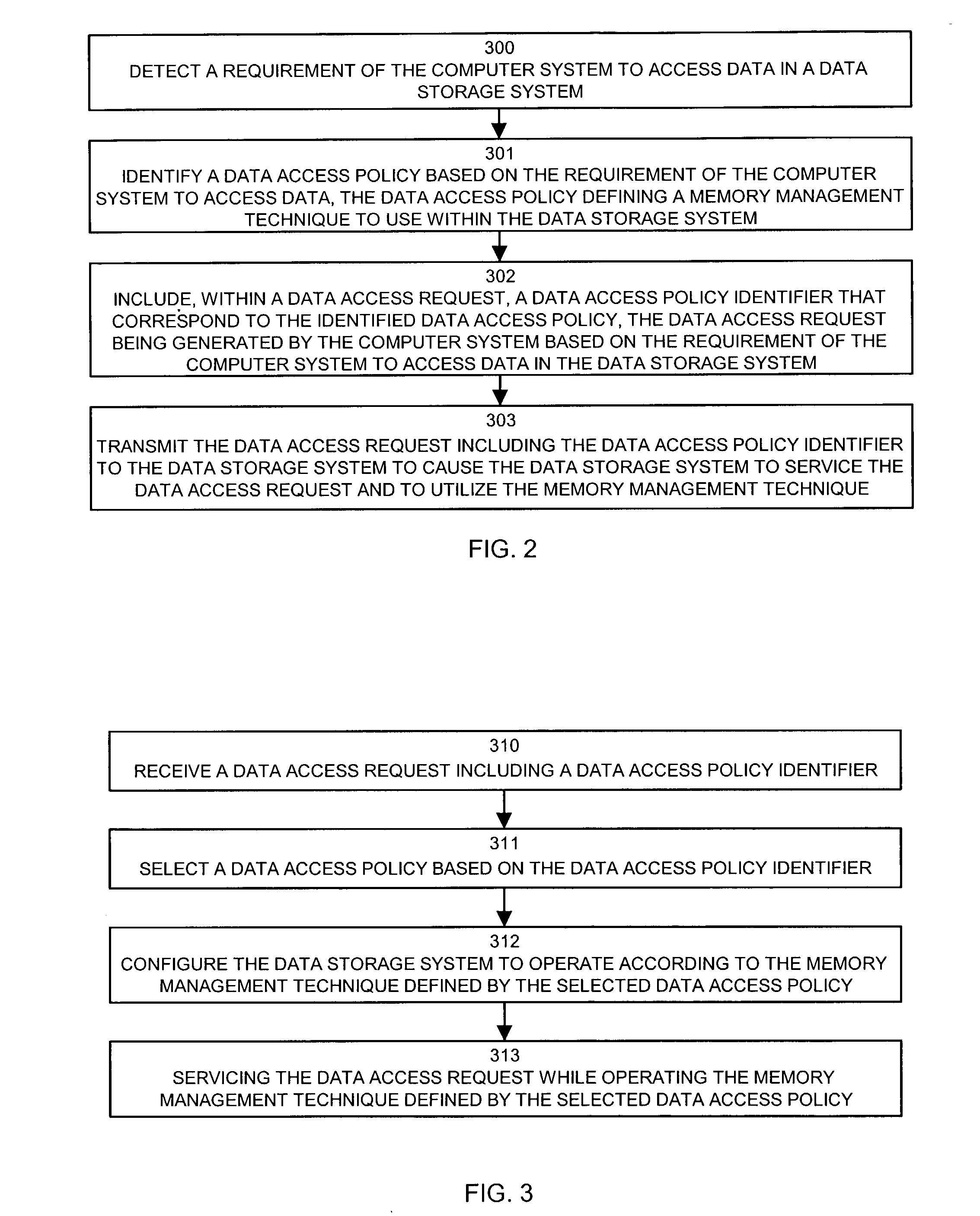
Methods and apparatus for controlling access to data in a data storage system
InactiveUS7266538B1Manipulation is accurateReduce throughputData processing applicationsSpecial data processing applicationsData accessComputerized system
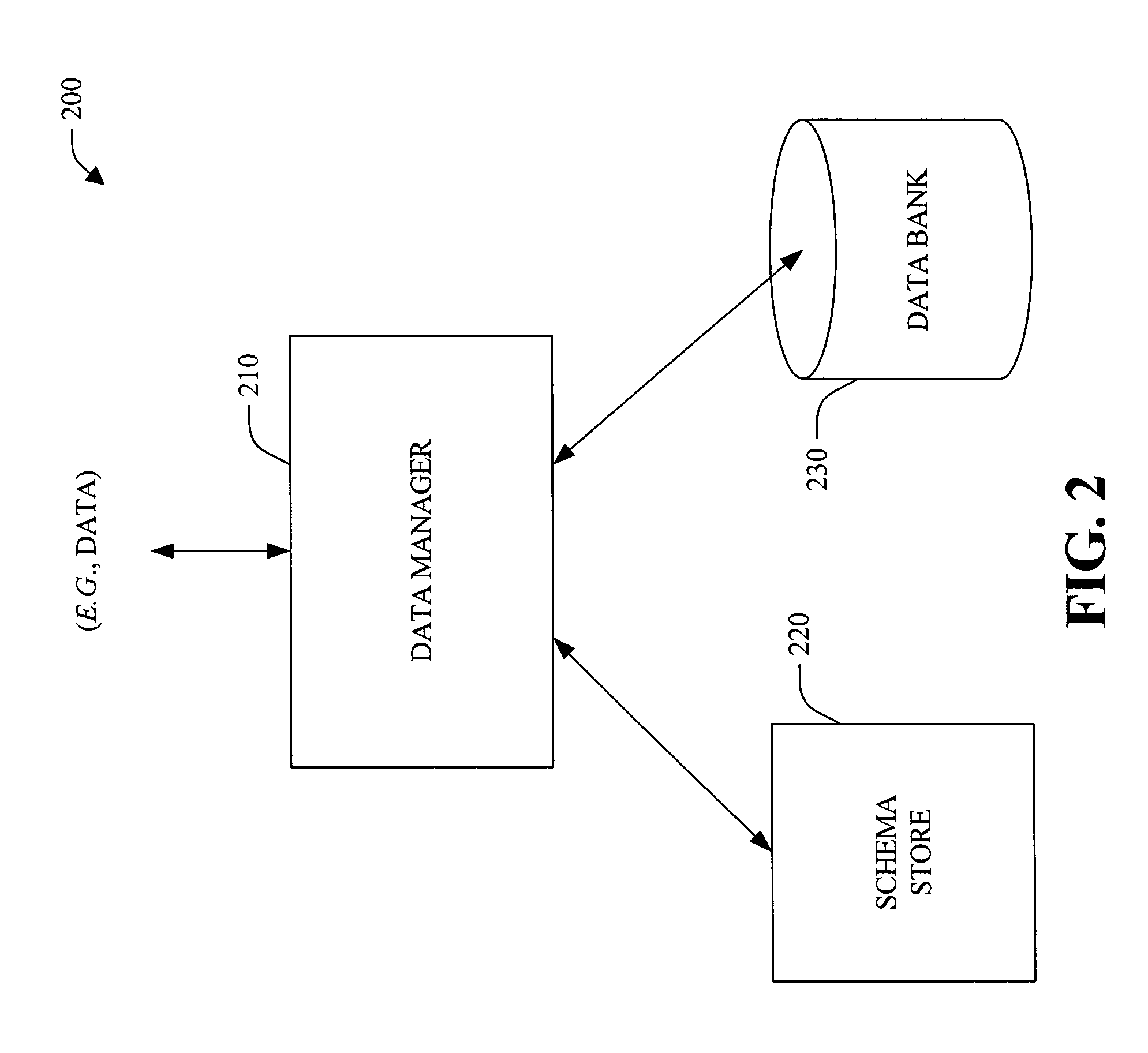
Mechanisms and techniques allow a host computer system to control memory management techniques within a data storage system. The host computer system can detect a requirement of the computer system to access data in the data storage system and can identify a data access policy based on the requirement of the computer system to access data. The host can then include, within a data access request, a data access policy identifier that corresponds to the identified data access policy. The host then transmits the data access request including the data access policy identifier to the data storage system. The data storage system receives the data access request and selects a data access policy based on the data access policy identifier. The selected data access policy defining a memory management technique to use within the data storage system. The data storage system configures itself to operate according to the memory management technique and services the data access request according to the data access policy.
Owner:EMC IP HLDG CO LLC
Micro installation process for software packaging and distribution
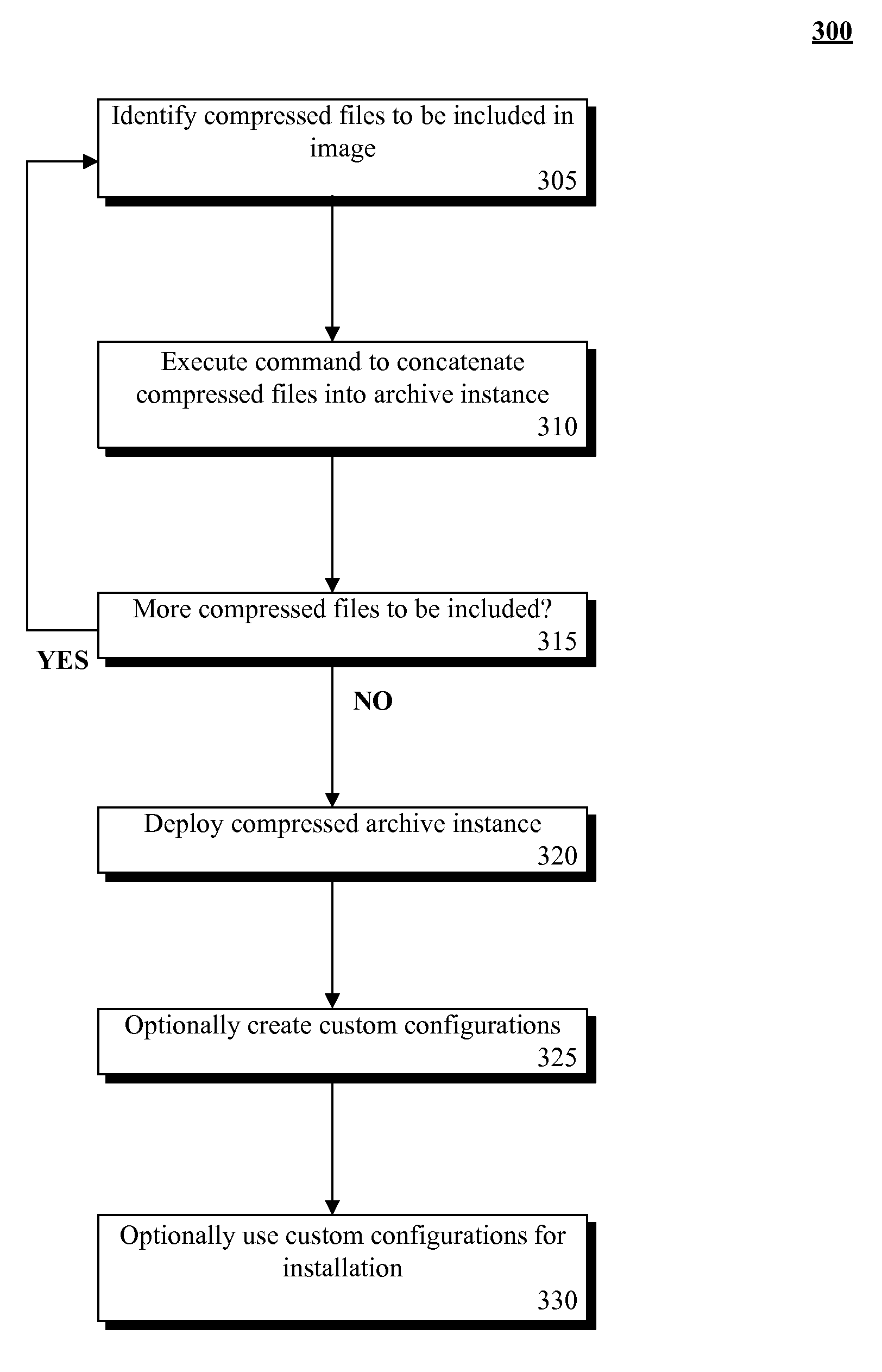
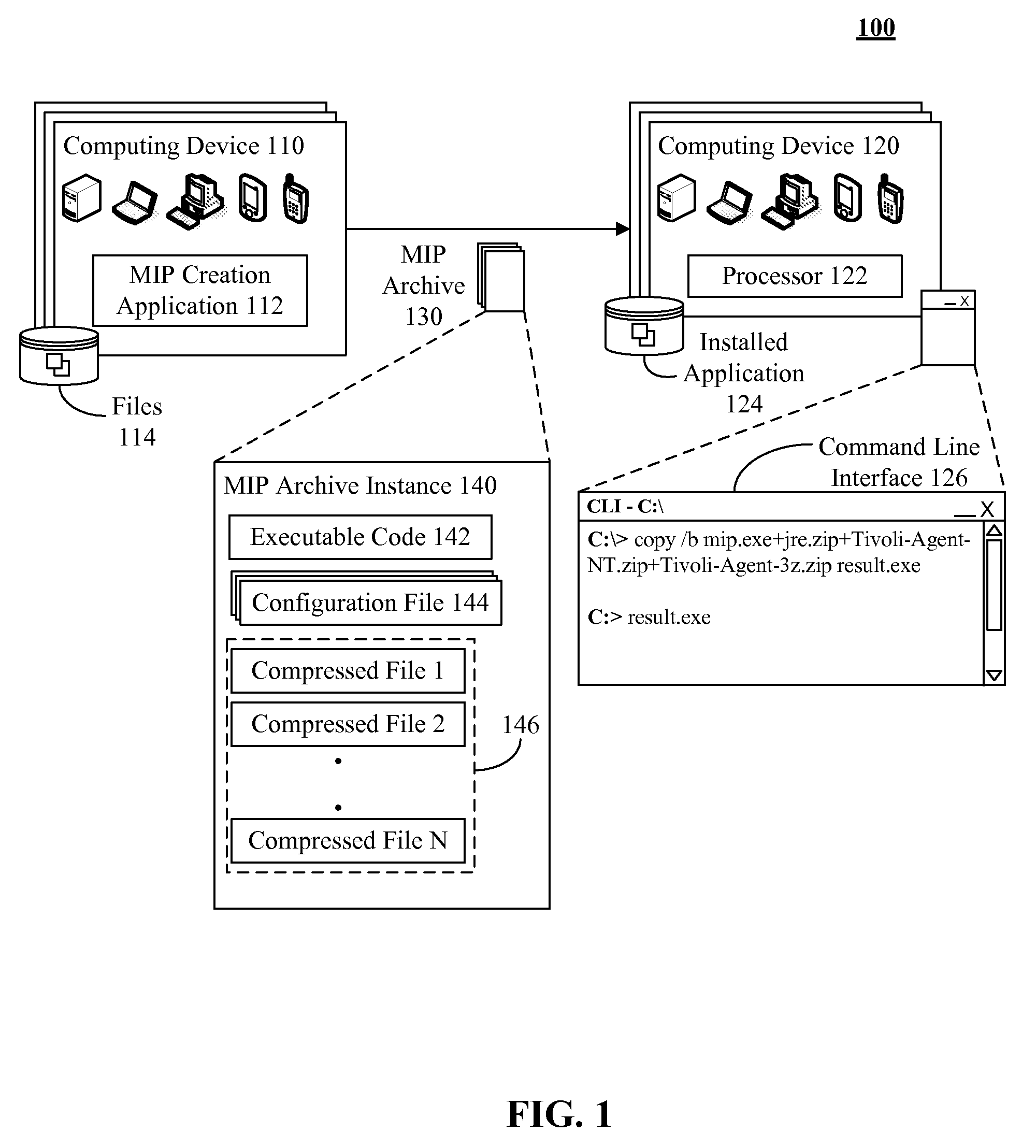
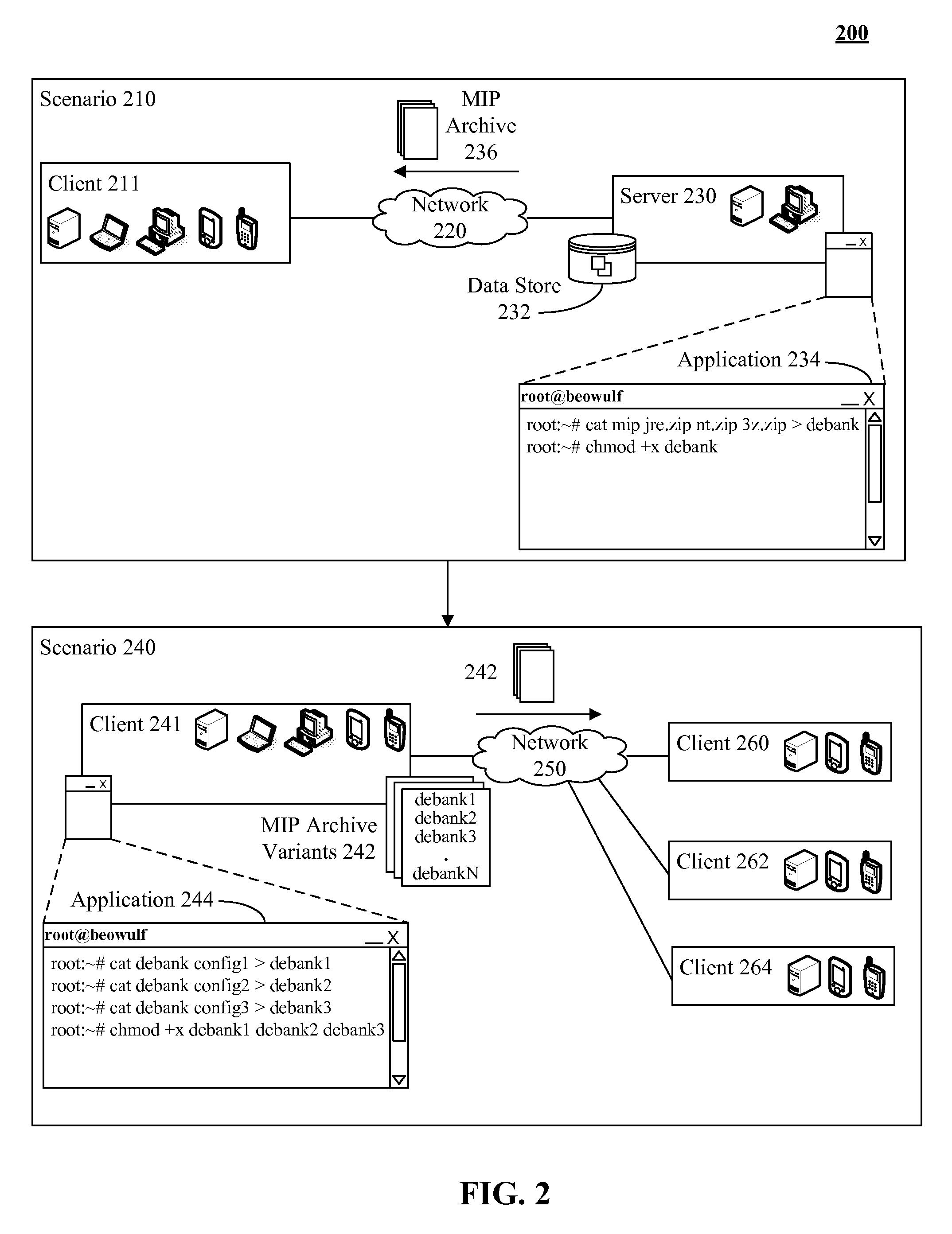
InactiveUS20090119660A1Consume resourcesEasy to deployProgram loading/initiatingMemory systemsSoftware engineeringWeb transport
The present invention discloses a software program that includes a first set of one or more compressed files and an executable file. The executable file can include a second set of one or more compressed files. The software program can be a self-executing program stored in a machine readable medium. Executing the software program can result in an automatic extraction of files contained within the first set and the second set of compressed files. In one embodiment, the software program can be an installation program, which includes a configuration file specifying settings to be applied during an installation process. The installation program can be dynamically constructed at a time an installation file is requested. The installation program can be a network lean file containing only those necessary components for a customized installation, which minimizes an amount of time and bandwidth expended when transferring the installation program over a network.
Owner:IBM CORP +1
Systems and methods that schematize audio/video data
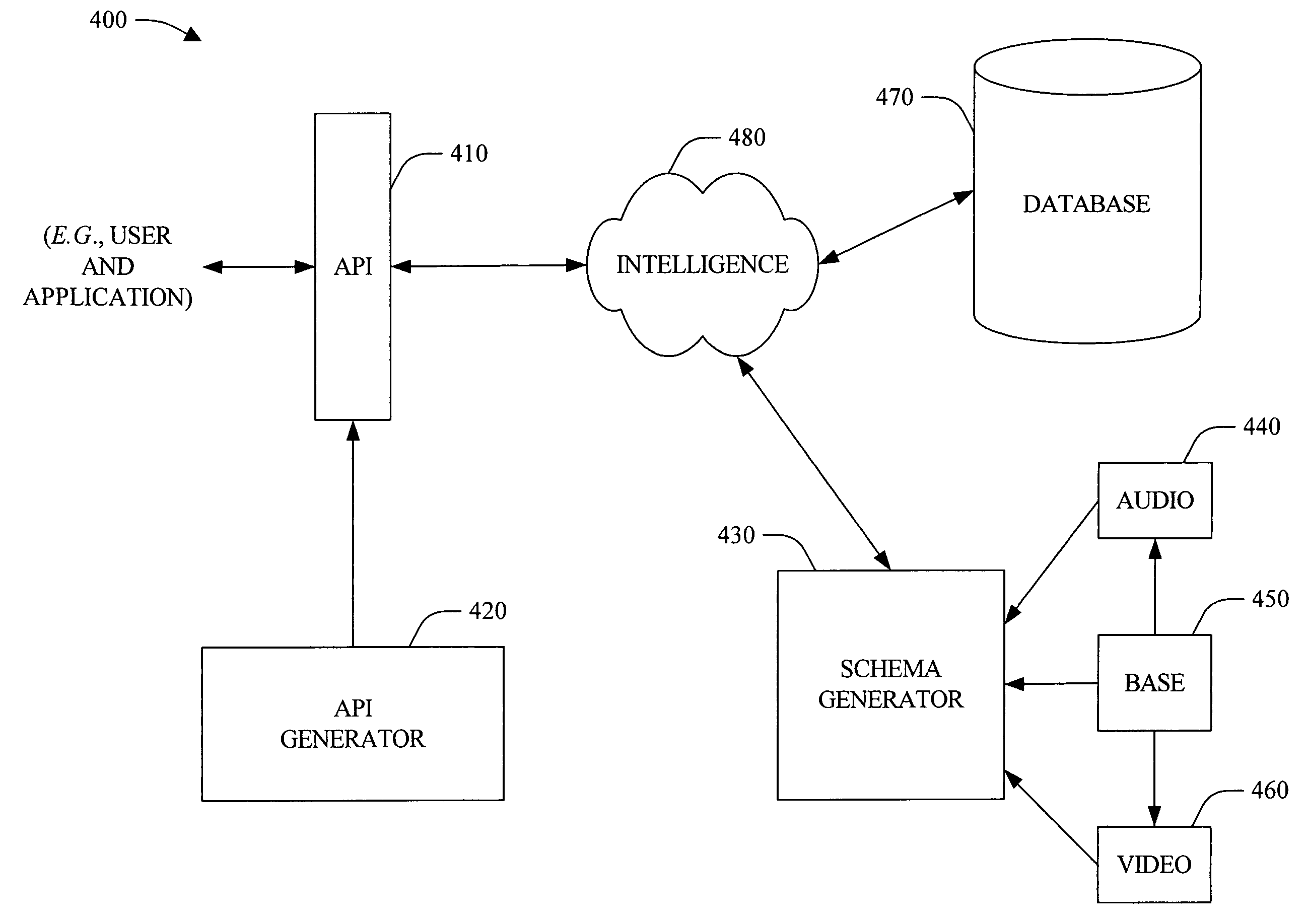
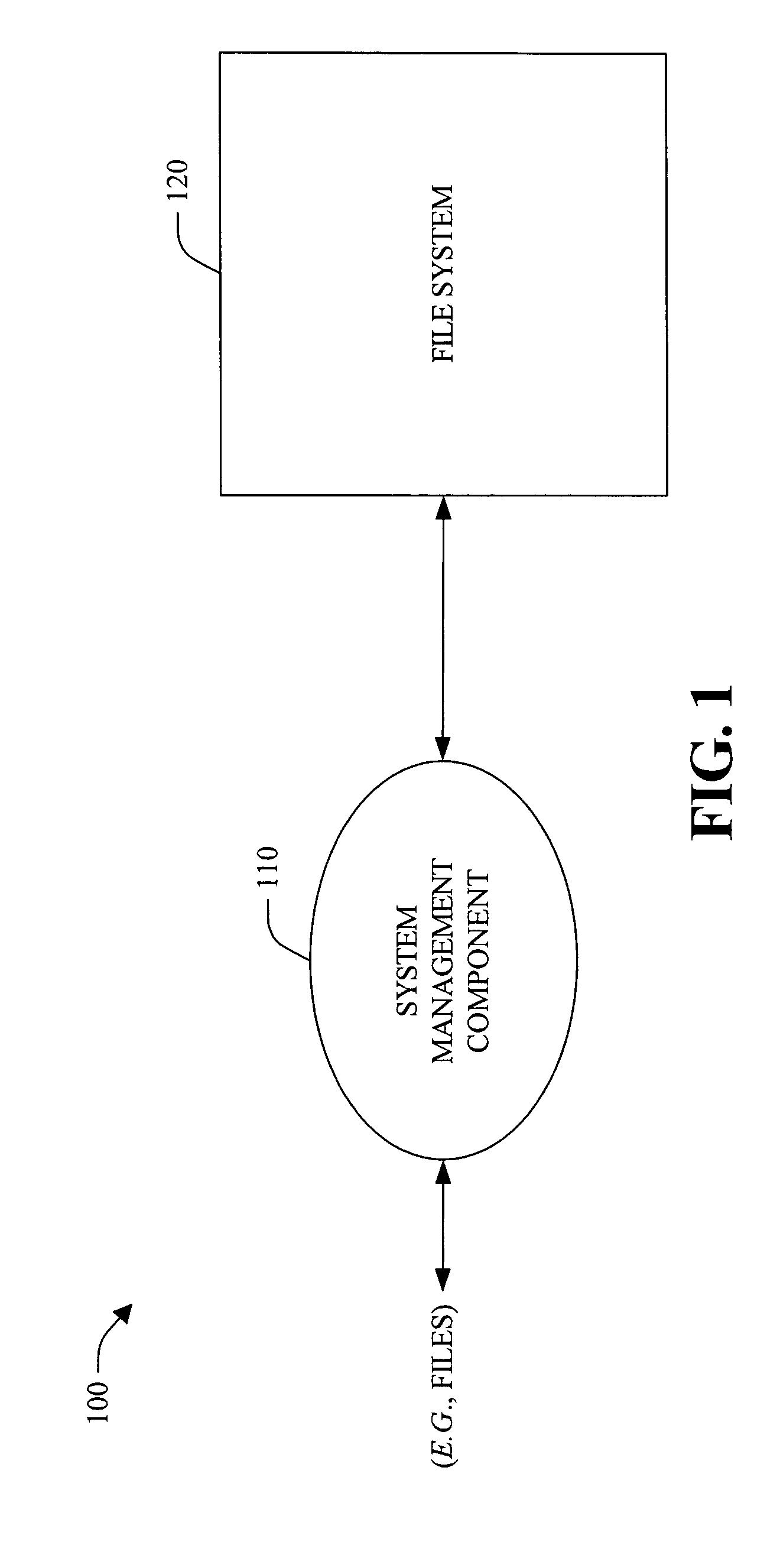
InactiveUS20050091271A1Efficient developmentConsume resourcesData processing applicationsMetadata multimedia retrievalModelicaOperational system
The present invention provides a novel file management approach. The systems and methods comprise a schema-based file management technique that can be integrated within an operating system to provide application developers an efficient and powerful develop utility to build applications. In addition, the system and methods provide for applications that can be employed uniformly across disparate data (e.g., audio and video data) within the operating environment. The schema can include a base schema that is related to known types of data and derived schema that extend the base schema with respect to one or more characteristics of the data. The schema can be employed to generate APIs that can be employed by users and / or applications to exchange information with a file system. In addition, the systems and methods can include configurable intelligence that can be utilized perform actions and / or make decisions, which can automate processes and / or facilitate data storage and / or management.
Owner:MICROSOFT TECH LICENSING LLC
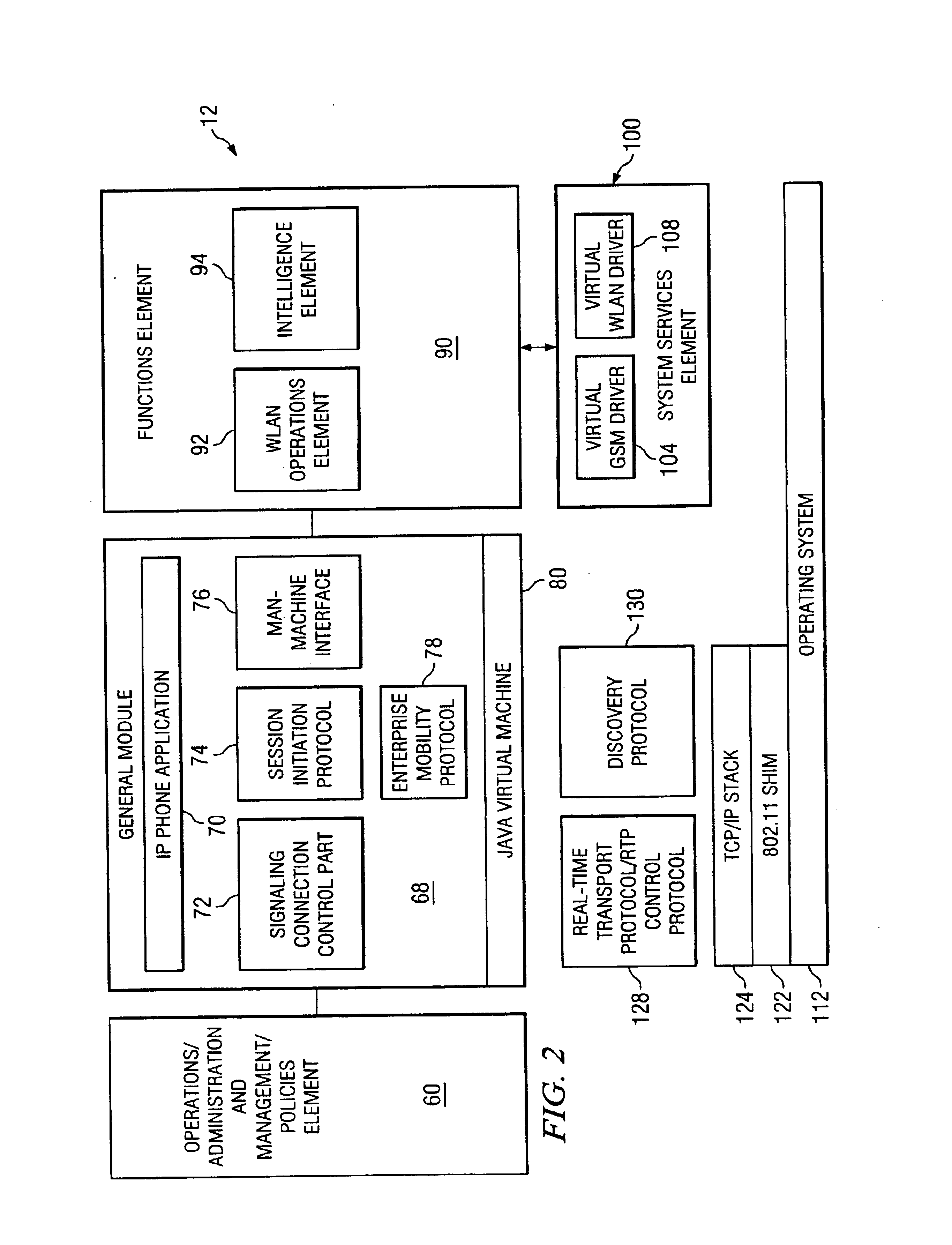
Apparatus and method for reducing responses when executing a session initiation protocol operation
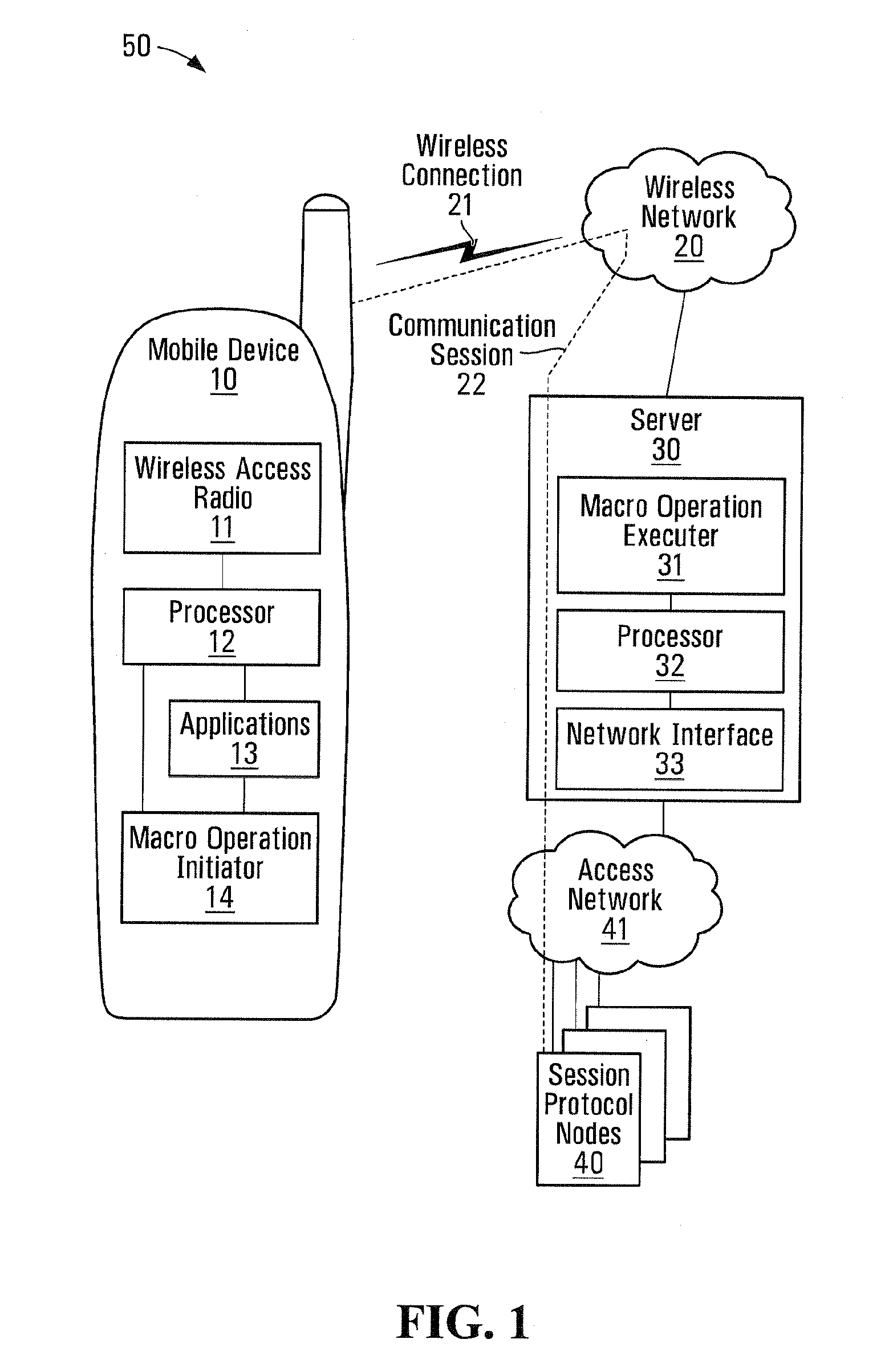
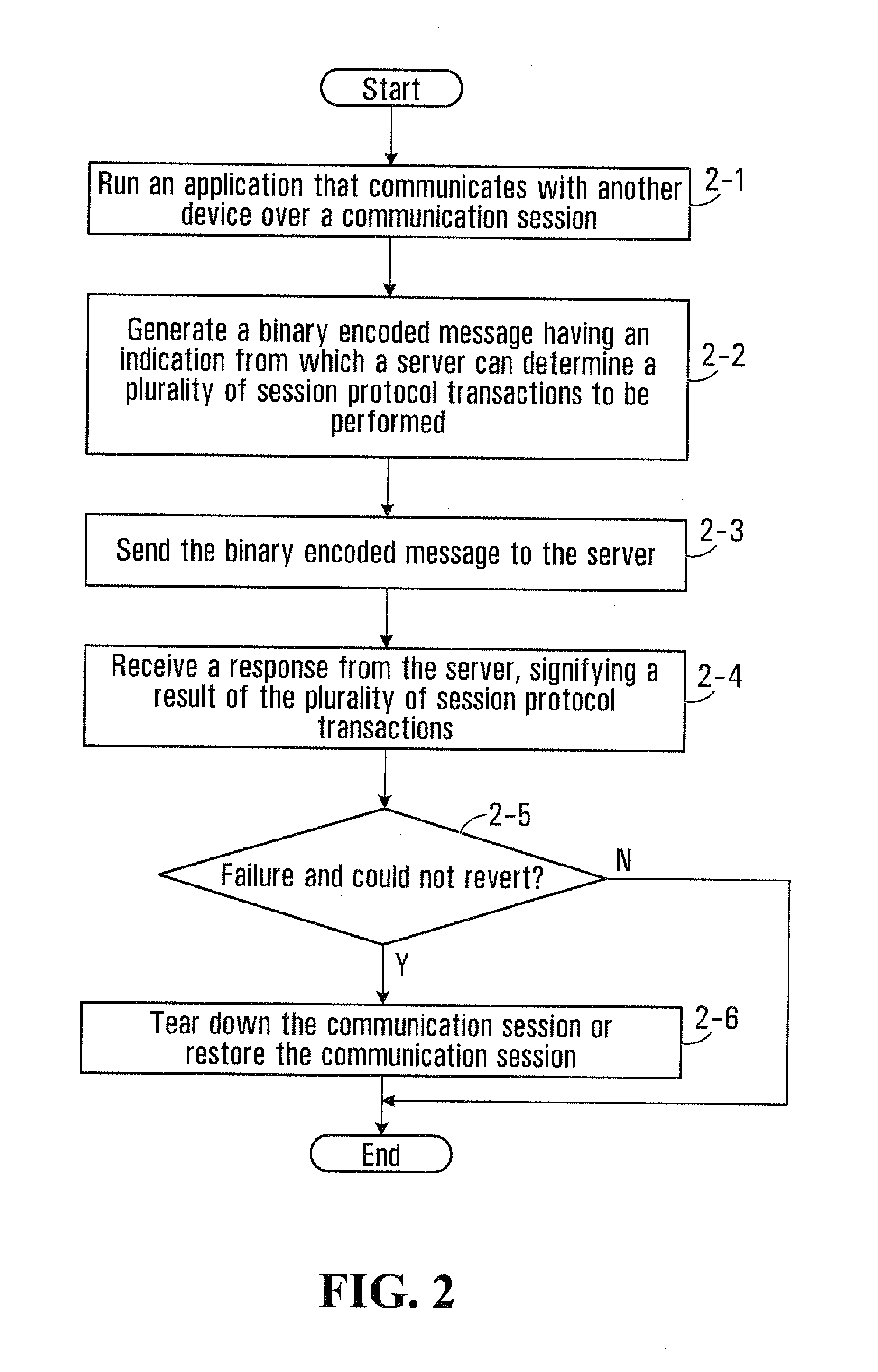
InactiveUS20110225307A1Reduce message sizeSimple processMultiple digital computer combinationsTransmissionComputer hardwareComputer science
An apparatus and method for reducing responses when executing a session protocol operation is disclosed. In accordance with an embodiment of the disclosure, a mobile device generates a binary encoded message having an indication from which a server can determine a session protocol operation to be performed without communicating all responses for the SIP transaction. The binary encoded message is sent from the mobile device and received by the server. In accordance with an embodiment of the disclosure, the server determines, based on the indication in the binary encoded message, the SIP transaction to be performed without communicating all SIP responses relating to the SIP transaction. The server then attempts the SIP transaction. By reducing the number of SIP responses, communication resources for the mobile device can be conserved. Also battery power for the mobile device can be conserved apparatus and method for reducing responses when executing a session initiation protocol operation
Owner:BLACKBERRY LTD
Communication connection bypass method capable of minimizing traffic loss when failure occurs
ActiveUS7058845B2Consume resourcesReduce the amount requiredError preventionTransmission systemsDistributed computingBackup
Backup LSPs (label switched path) are established from LSRs (label switching router) except the egress LSR of a main LSP. Each backup LSP is established between an LSR that functions as a starting node and the egress LSR so as not to include any link or node on the main LSP to be protected. When the backup LSP is established such that it merges into another pre-established backup LSP protecting the same main LSP, merging is performed at the LSR located at the merge point.
Owner:NEC CORP
Detection method for abnormal traffic and packet relay apparatus
InactiveUS7729271B2Efficient detectionMakes the resources of the target consumedError preventionTransmission systemsTraffic capacityByte
The present invention provides a technology including, for example, a packet relay processing section to carry out packet relay, a packet sampling section to carry out packet sampling, a flow statistics counting section to take statistics of each flow, and a flow statistics generating section to generate a NetFlow export datagram, wherein the flow statistics counting section collectively counts the number of the packets or bytes received per unit time when the number does not exceed a threshold value and individually counts the number for each flow when the number exceeds the threshold value, and thereby a flow of abnormal traffic which is suspected to be DoS attack is efficiently detected with small amounts of resources (mainly memories).
Owner:ALAXALA NETWORKS
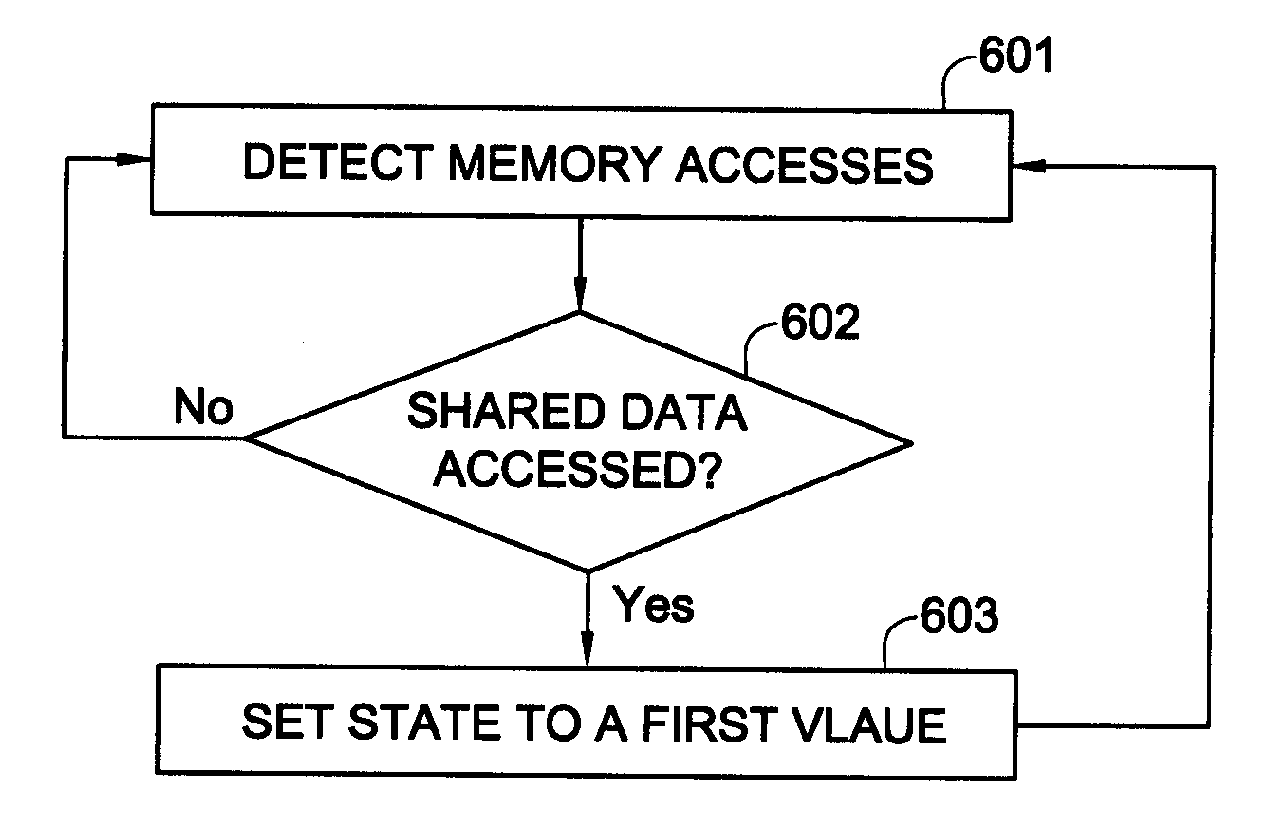
Method and apparatus for synchronizing shared data between components in a group
InactiveUS20060236039A1Reduced delay intervalConsume processing resourceMemory systemsTerm memoryData storing
A method and system for use by a cache-less component contained in a group of two or more components each having access to shared data stored in a shared segment of memory connected to the components, at least one of which is cache-less. Synchronization of the components in the group is assured by detecting memory accesses performed by components in the group. Upon detecting that any one of the components accesses data in the shared segment of memory, a state associated with the data is set to a first value.
Owner:IBM CORP
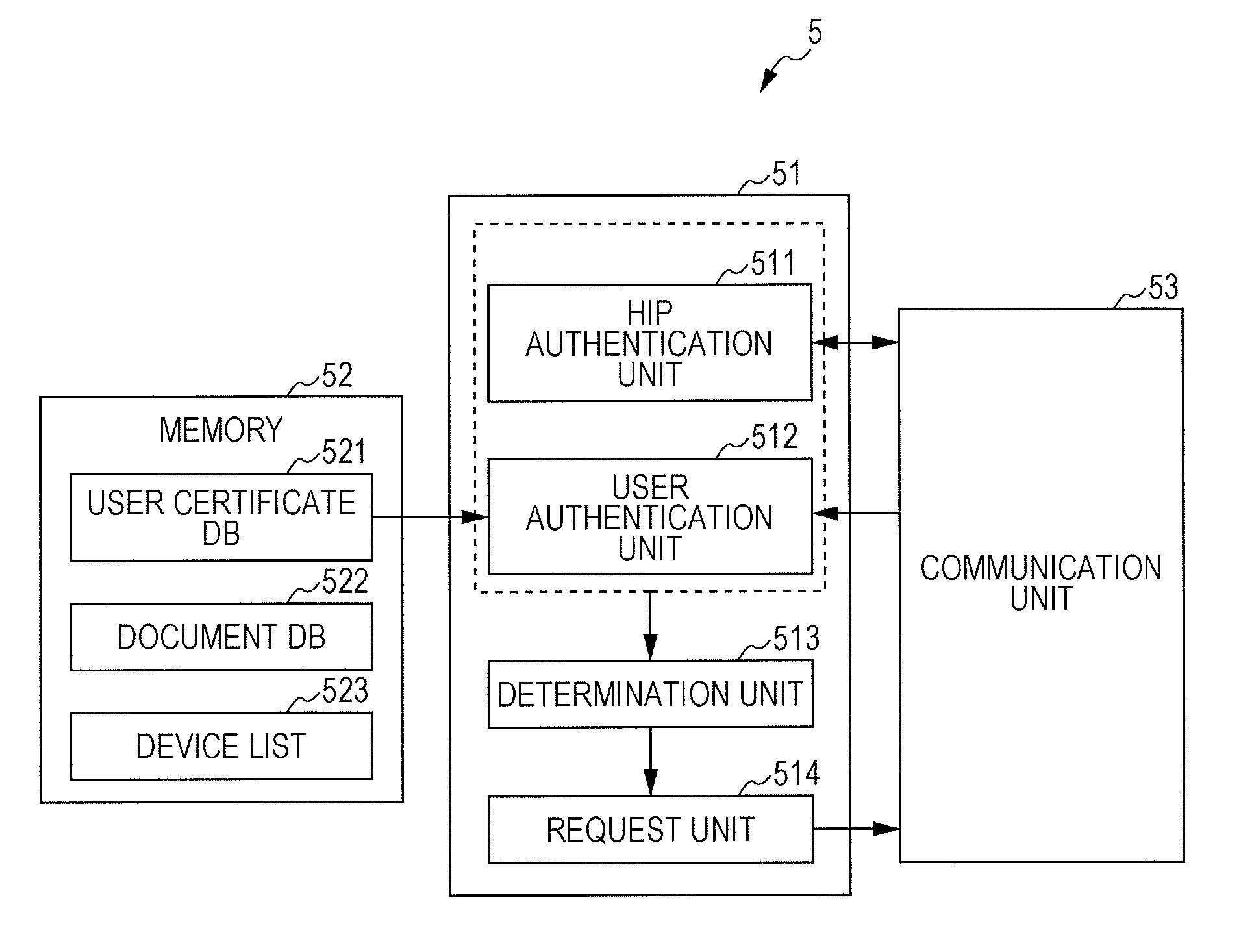
Information processing system, information processing device, server device, and method
InactiveUS20120222101A1Consume resourcesEnergy efficient ICTDigital data processing detailsInformation processingInstruction unit
An information processing system including an information processing device connected to a first communication network, a terminal device connected to the first communication network, and a server device connected to a second communication network. The server device includes a receiving unit, a first request unit, and a providing unit. The receiving unit receives an instruction from the terminal device to provide the information processing device with a predetermined service. The first request unit presents a test to the information processing device to authenticate whether or not the information processing device is being operated by a human. The providing unit provides the information processing device with the service in accordance with the instruction. The terminal device includes an instruction unit and a response unit. The instruction unit sends the instruction to the server device. The response unit makes a response to the test on behalf of the information processing device.
Owner:FUJIFILM BUSINESS INNOVATION CORP
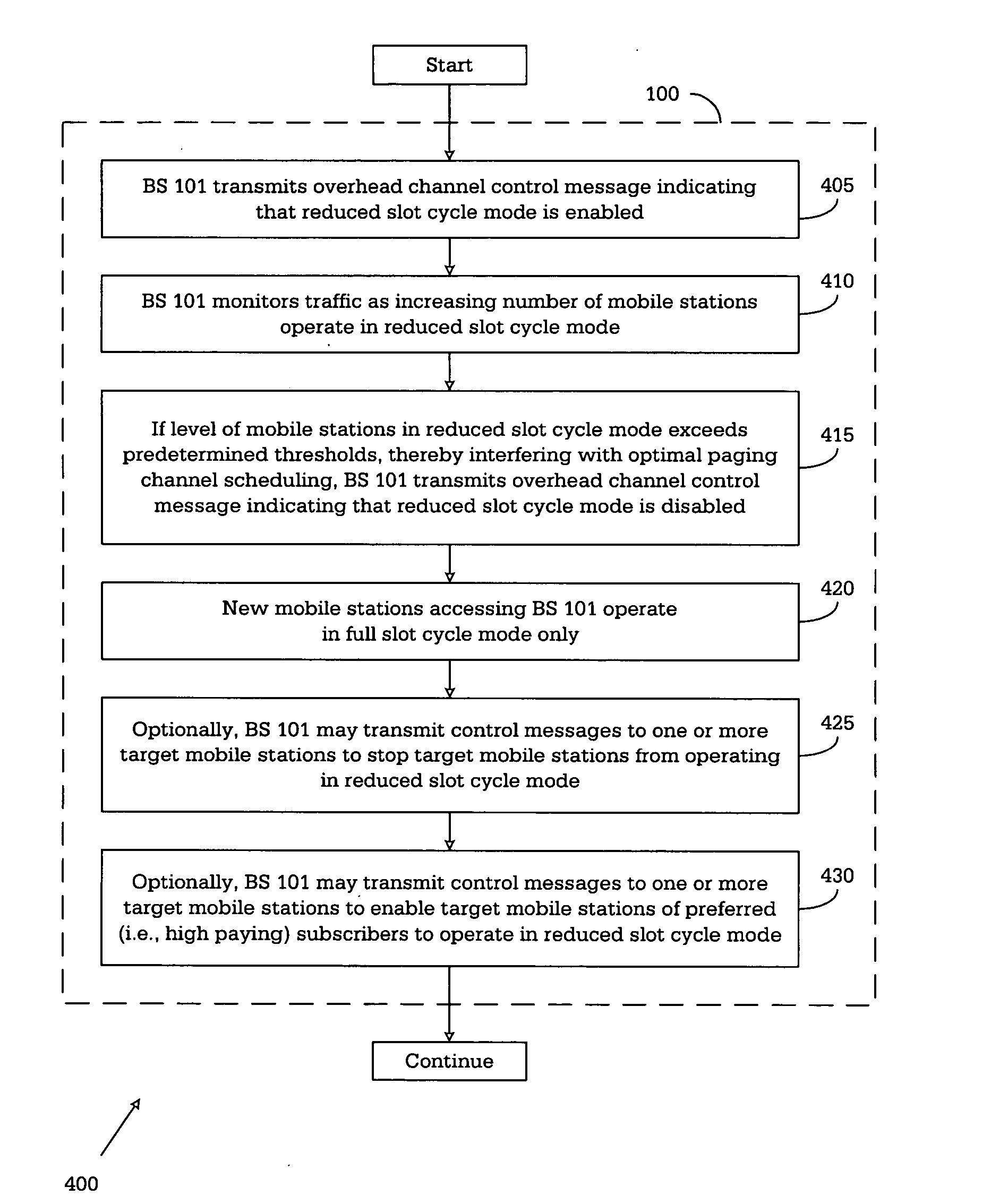
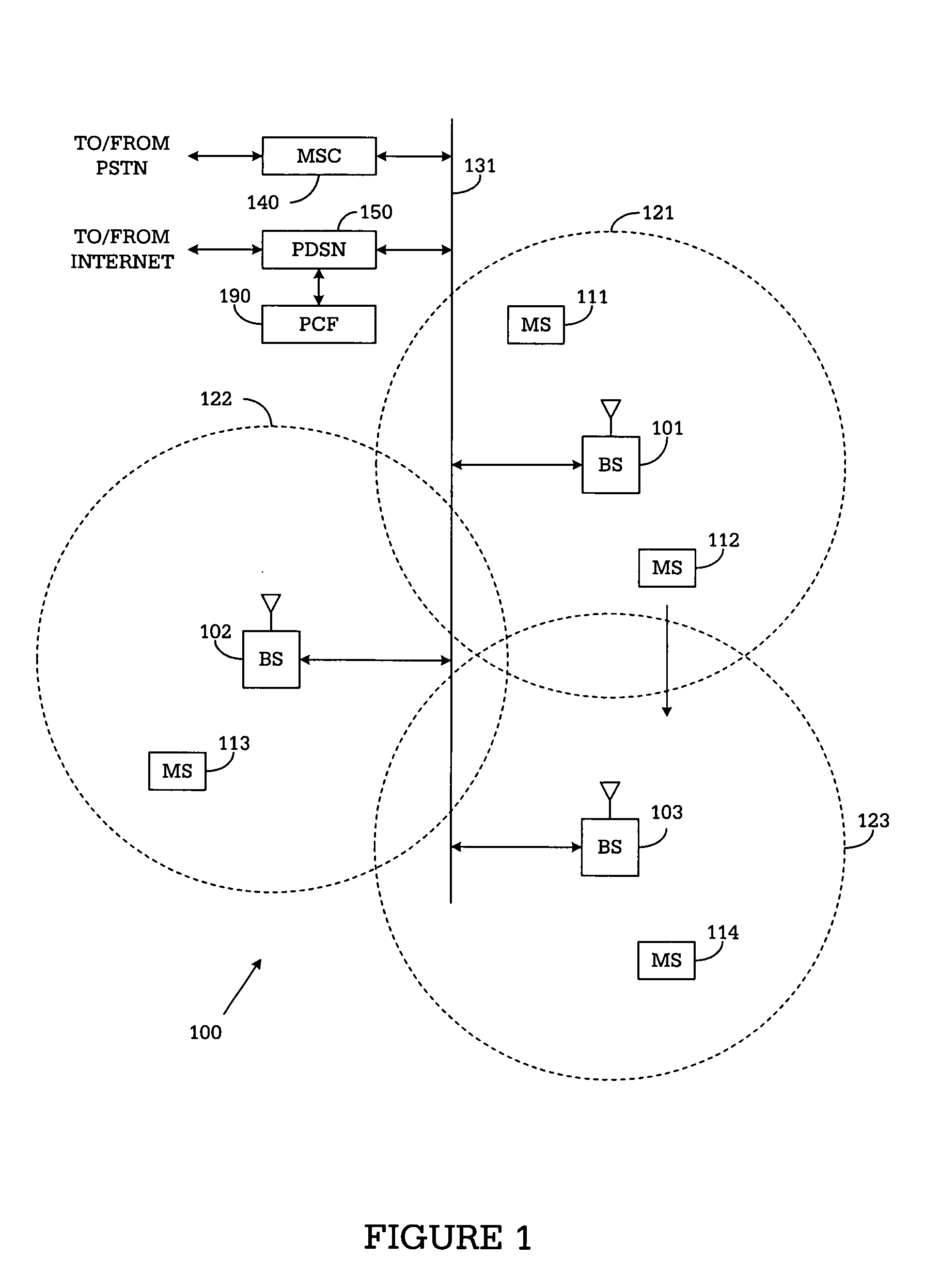
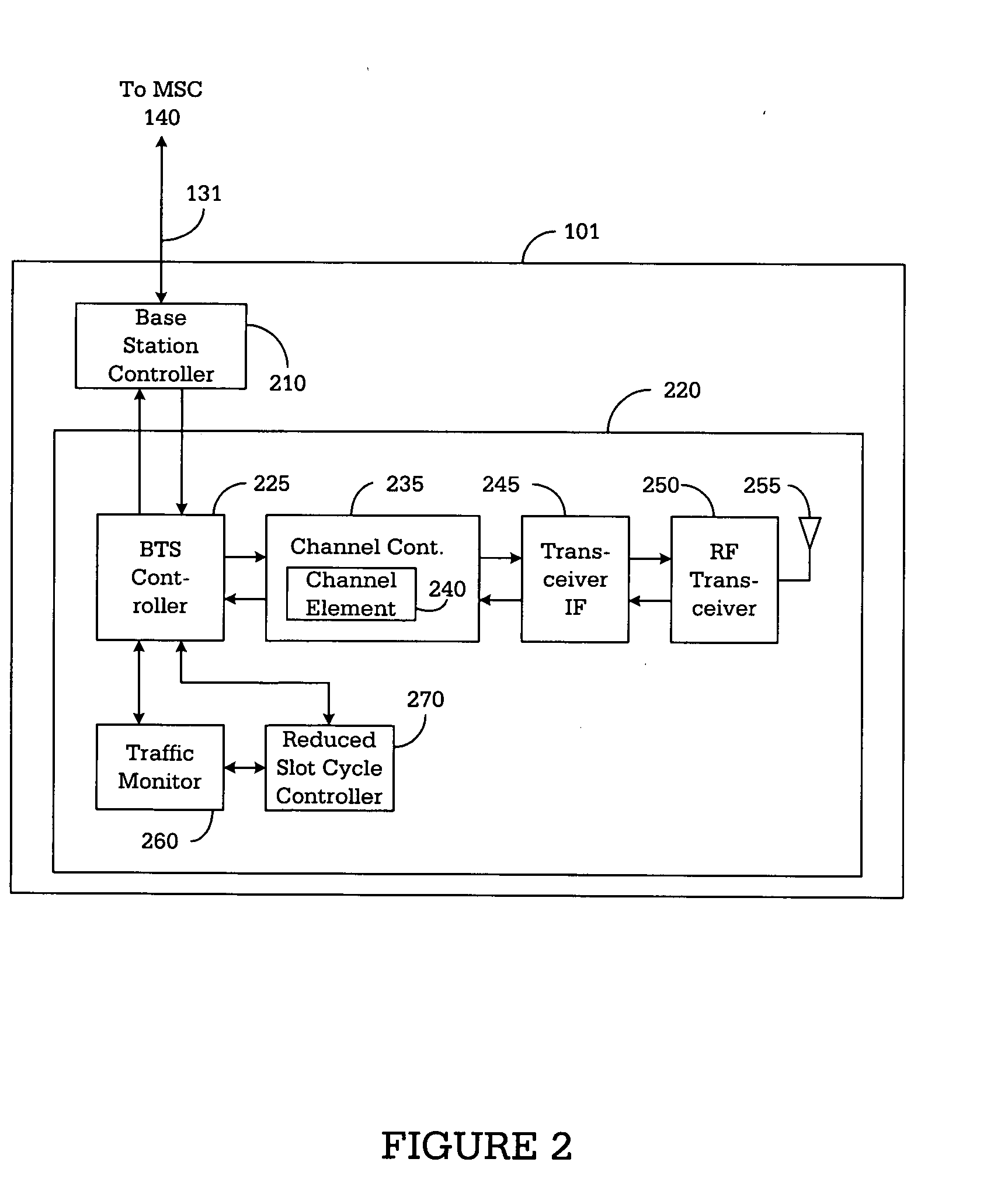
Base station for controlling use of reduced slot cycle mode of operation in a wireless network
InactiveUS20050096060A1Reduce circulationImpact network performanceRadio/inductive link selection arrangementsWireless communicationCycle controlOperation mode
For use in a wireless network, a base station that controls use of the reduced slot cycle mode by mobile stations communicating with the base station. The base station comprises: i) a traffic monitor for monitoring message traffic levels handled by the base station; and ii) a reduced slot cycle controller for receiving traffic statistics information from the traffic monitor and determining whether use of the reduced slot cycle mode by the mobile stations communicating with the base station interferes with scheduling of paging message transmissions by the base station. The reduced slot cycle controller, in response to a determination that use of the reduced slot cycle mode by the mobile stations does interfere with the scheduling of paging message transmissions by the base station, causes the base station to transmit a first control message indicating that the reduced slot cycle mode is disabled in the base station.
Owner:SAMSUNG ELECTRONICS CO LTD
Extensible application platform
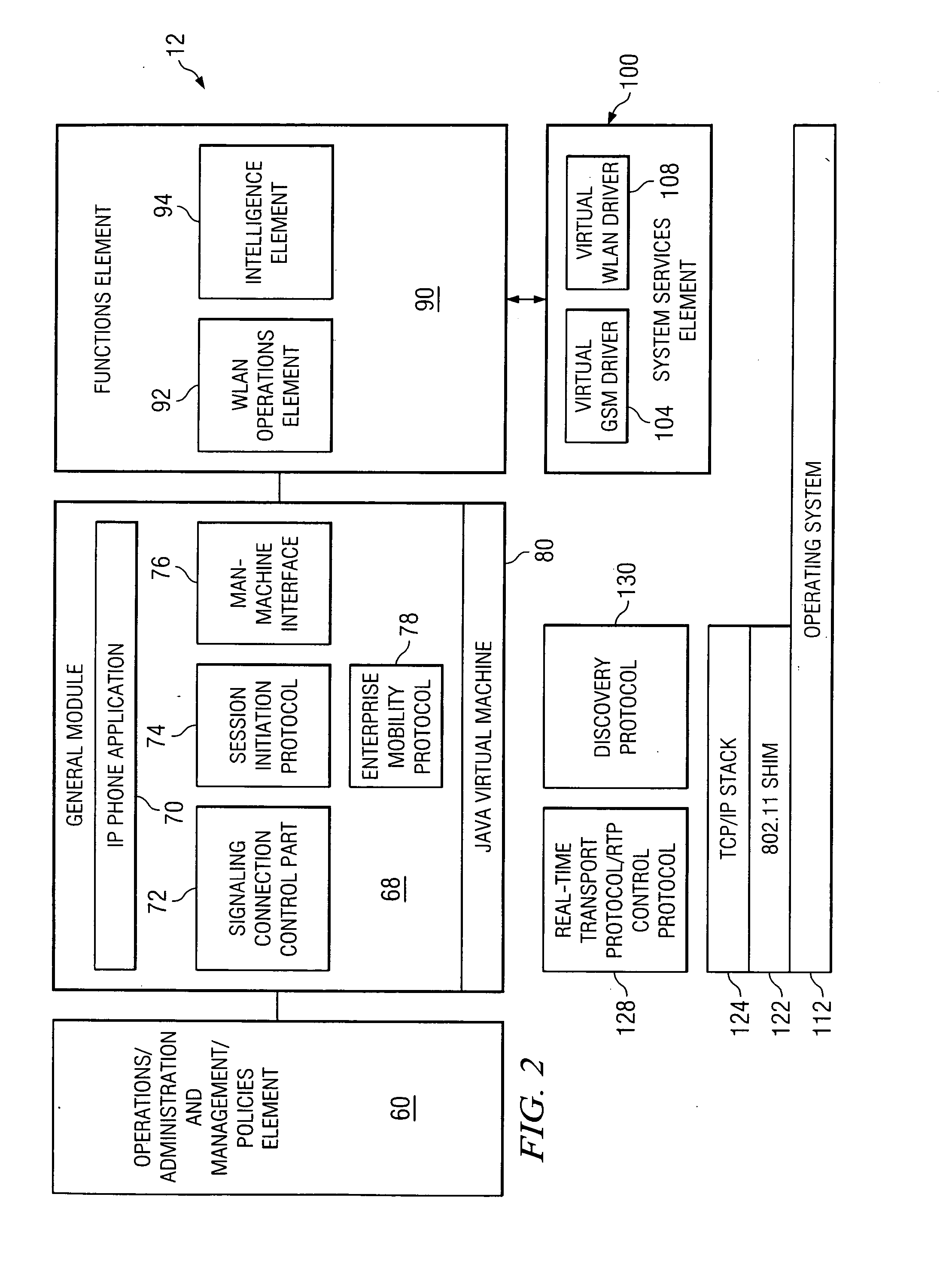
ActiveUS7984115B2Readily developed and deployed and maintainedImprove scalabilityMultiple digital computer combinationsSoftware designThird partyBusiness intelligence
An extensible client-server application platform. Execution of functions may require interactions between client-side and server-side components. Extensions may be provided as pairs of modules, one for the client and one for the server, that interact when performing an extension function. To ensure that the client-side and server-side interact appropriately, extensions modules may be initially supplied to the server and downloaded as appropriate, to the client. An enterprise business intelligence application is used as an example of the extensible client-server application platform. To enable use of third party extension modules, the server-side components may execute on a virtualized server.
Owner:MICROSOFT TECH LICENSING LLC
Wireless Device and Network Node for a Wireless Communication System and Methods Thereof
ActiveUS20180317212A1Reduce overheadImprove network capacity/throughputSynchronisation arrangementTransmission path divisionCommunications systemControl signal
The disclosure relates to a method and a wireless device for communication in a wireless communication network, the method comprising the steps of obtaining information of a level of duplication of one or more common control signals or channels; and receiving the common control signals or channels using the obtained information. The method further relates to a network node and a method thereof.
Owner:TELEFON AB LM ERICSSON (PUBL)
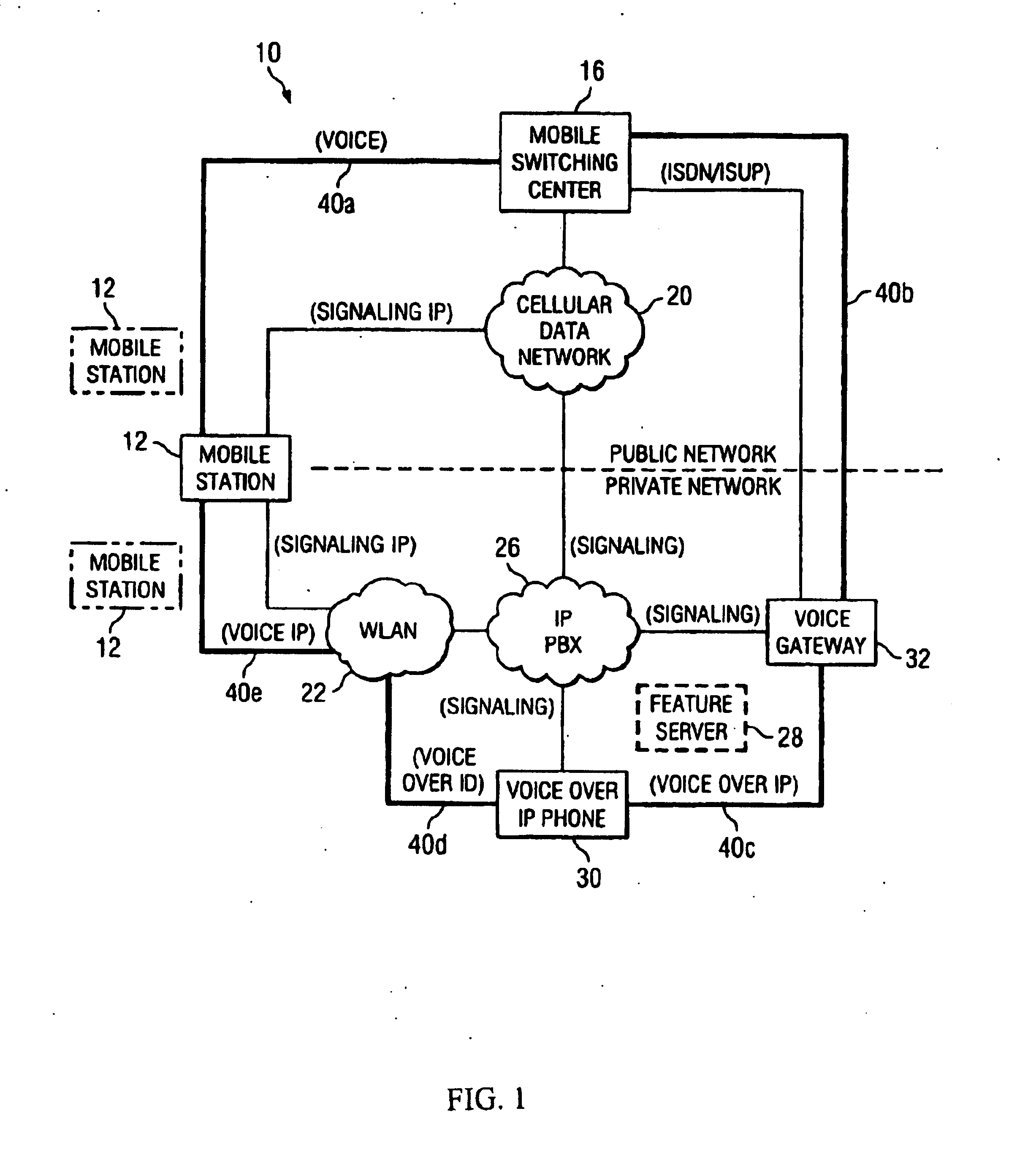
System and method for delivering private network features to a public network
ActiveUS20050059402A1Sacrifice processing timeImpeding versatilityNetwork topologiesSpecial service for subscribersTelecommunicationsPrivate network
A method is provided that includes receiving a request from a communication device to establish a communication session with a mobile station. The request is responded to by signaling the mobile station via a cellular data network that a call is being initiated for the mobile station. Signaling information may be exchanged with a voice gateway such that one or more voice circuits are established to accommodate voice data that may propagate between the communication device and the mobile station. A signaling pathway may be established between an Internet protocol private branch exchange (IP PBX) and the mobile station via the cellular data network. The establishment of the signaling pathway is substantially concurrent with the establishment of one or more of the voice circuits such that one or more features associated with a private network are delivered to the mobile station during the communication session.
Owner:CISCO TECH INC
Asynchronous pattern
InactiveUS7280558B1Reduce the possibilityImprove processing efficiencyData processing applicationsDigital computer detailsAsynchronous method invocationMessage queue
A system and method for converting code associated with synchronous method calls to code that can be employed to perform asynchronous method calls and for supporting such asynchronous method calls is provided. The system includes a pattern generator that can break code for a synchronous method call into one or more constituent parts including a begin asynchronous operation method, an end asynchronous operation method, an asynchronous call state object and an asynchronous call result object. The system includes a pattern data store that holds data associated with converting a synchronous method call to an asynchronous method call, which facilitates employing the system consistently across environments like file input / output, stream input / output, socket input / output, networking, remoting channels, proxies, web forms, web services and messaging message queues.
Owner:MICROSOFT TECH LICENSING LLC
Method, Apparatus, and Computer Program Product for Authenticating Subscriber Communications at a Network Server
ActiveUS20080209522A1Reduce vulnerabilityConsume resourcesDigital data processing detailsUser identity/authority verificationDevice IdentifiersComputer program
An apparatus for authenticating subscriber communications at a network server includes a determining element and an identification element in communication with the determining element. The determining element may be configured to receive an incoming message. The identification extractor may be configured to extract a device identifier and an address identifier from the incoming message. The determining element may be further configured to determine whether the device identifier and the address identifier of the incoming message match both a registered device identifier and a registered address identifier associated with the registered device identifier, respectively.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS
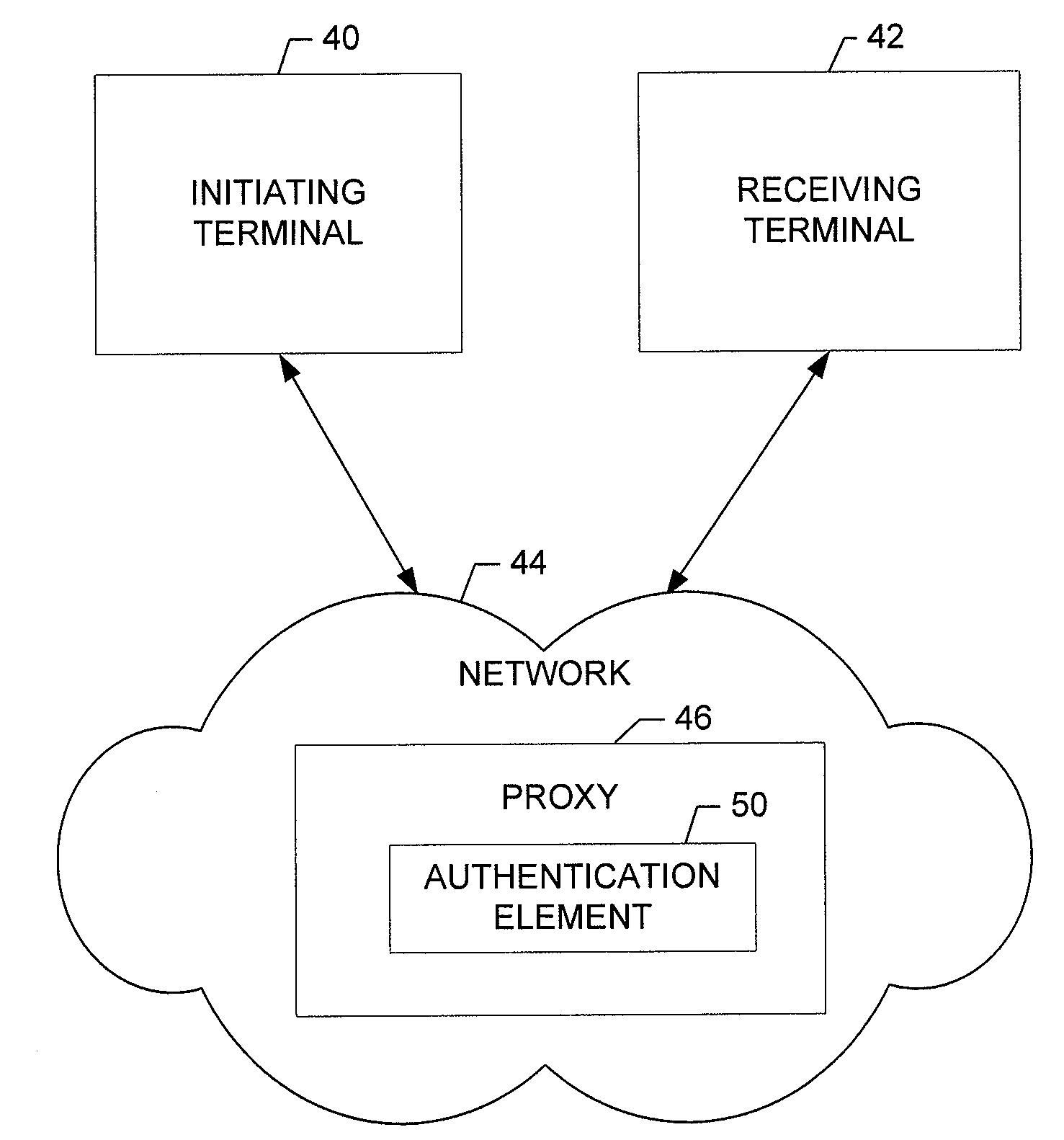
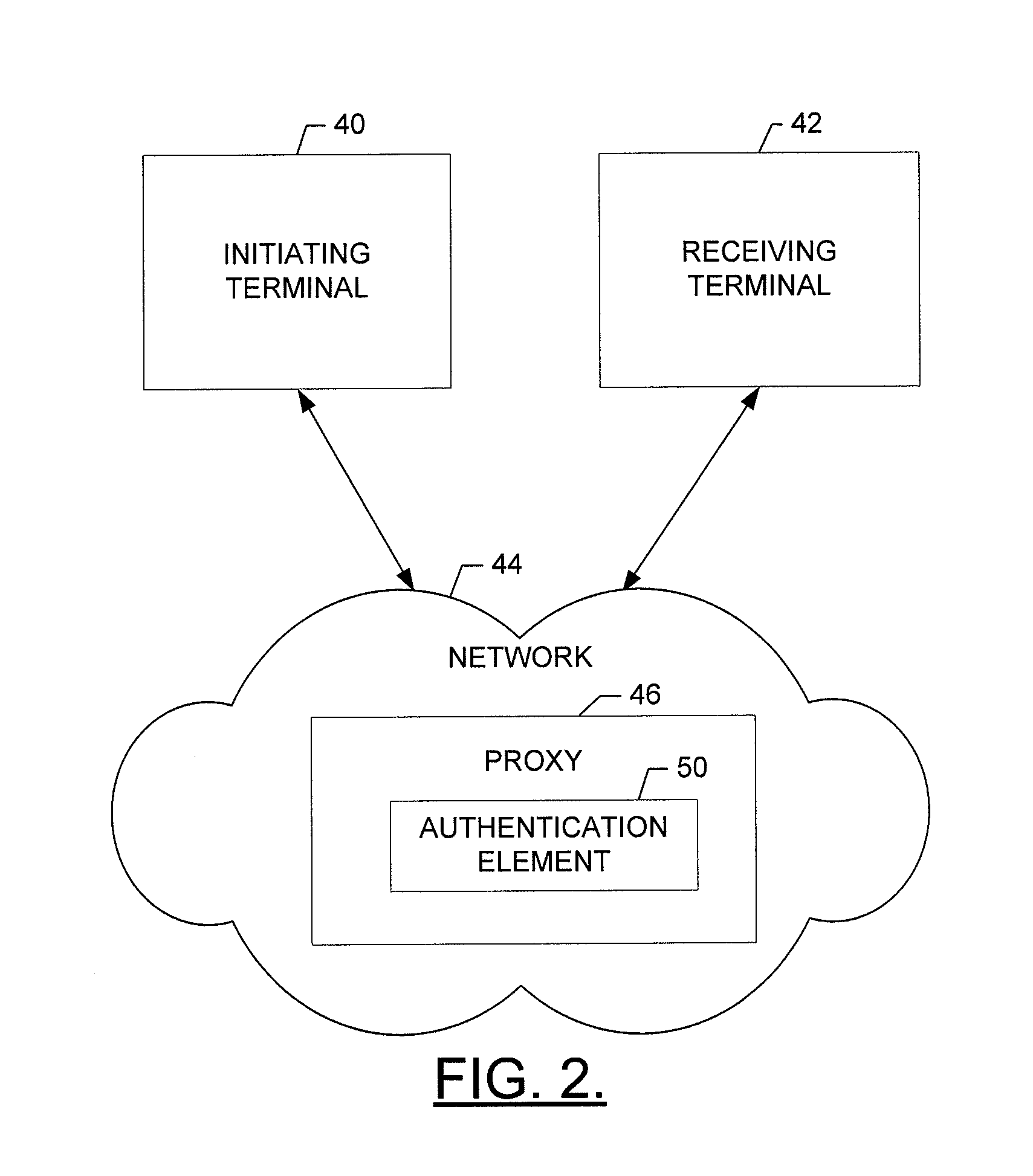
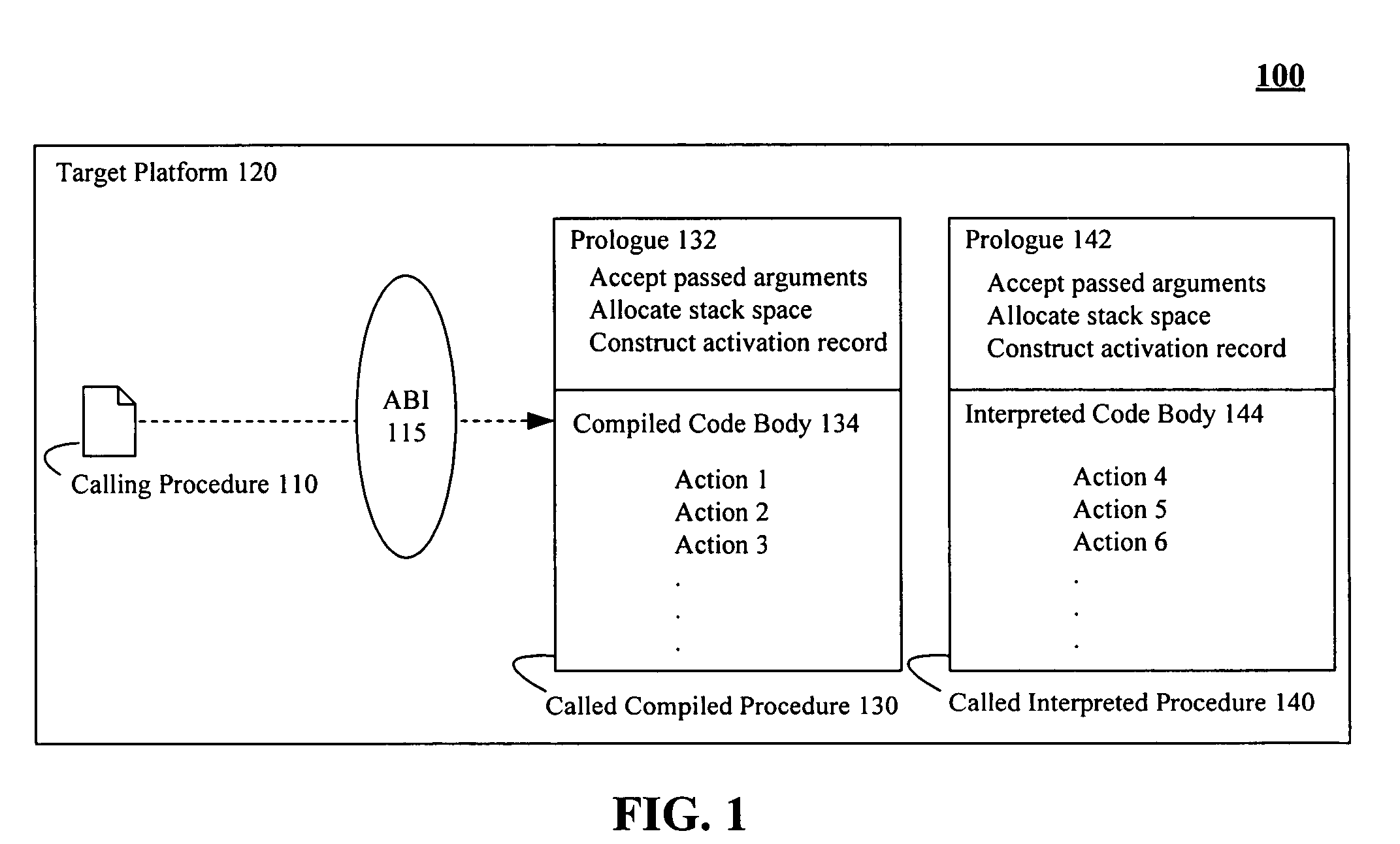
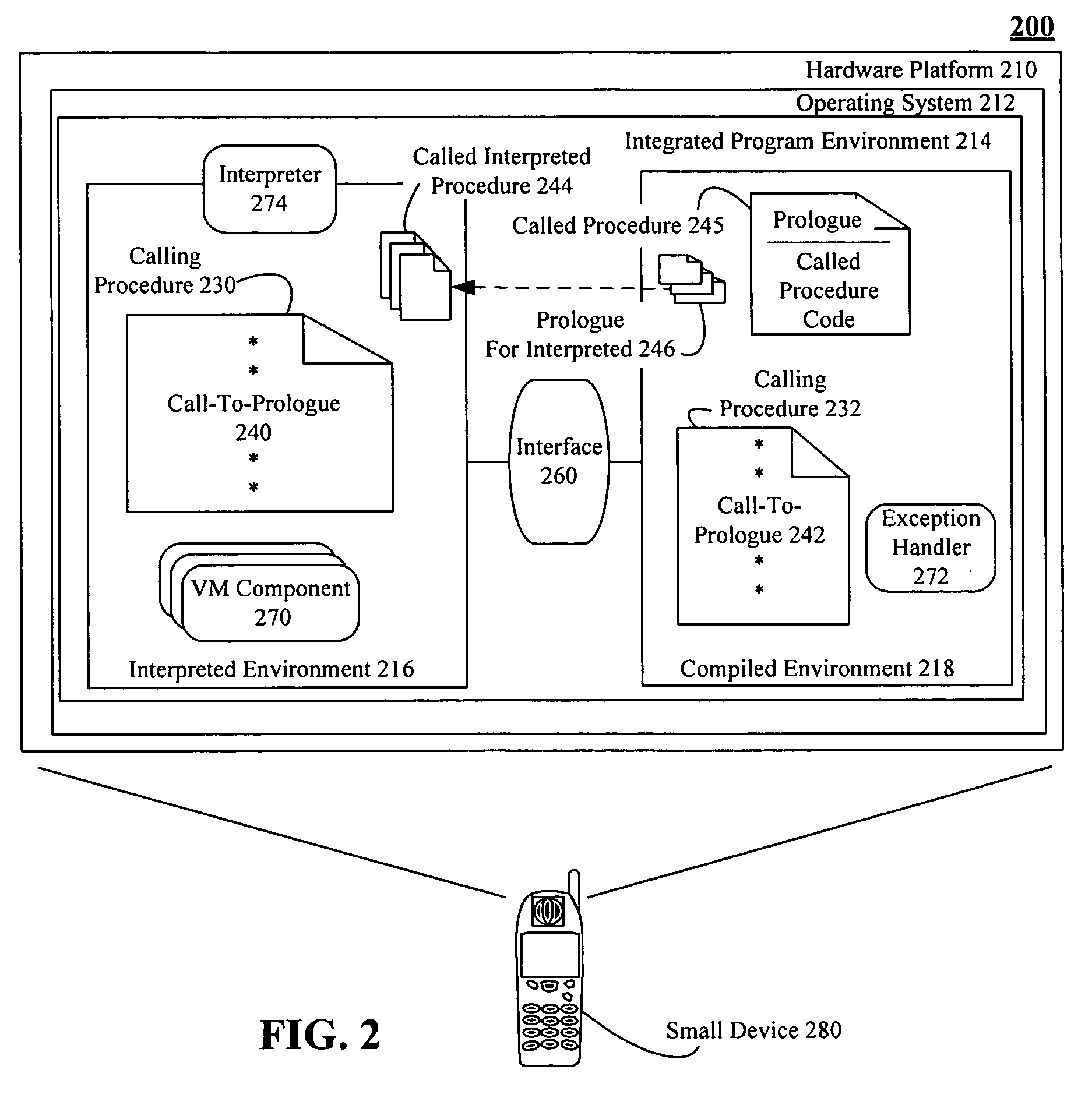
Procedure invocation in an integrated computing environment having both compiled and interpreted code segments
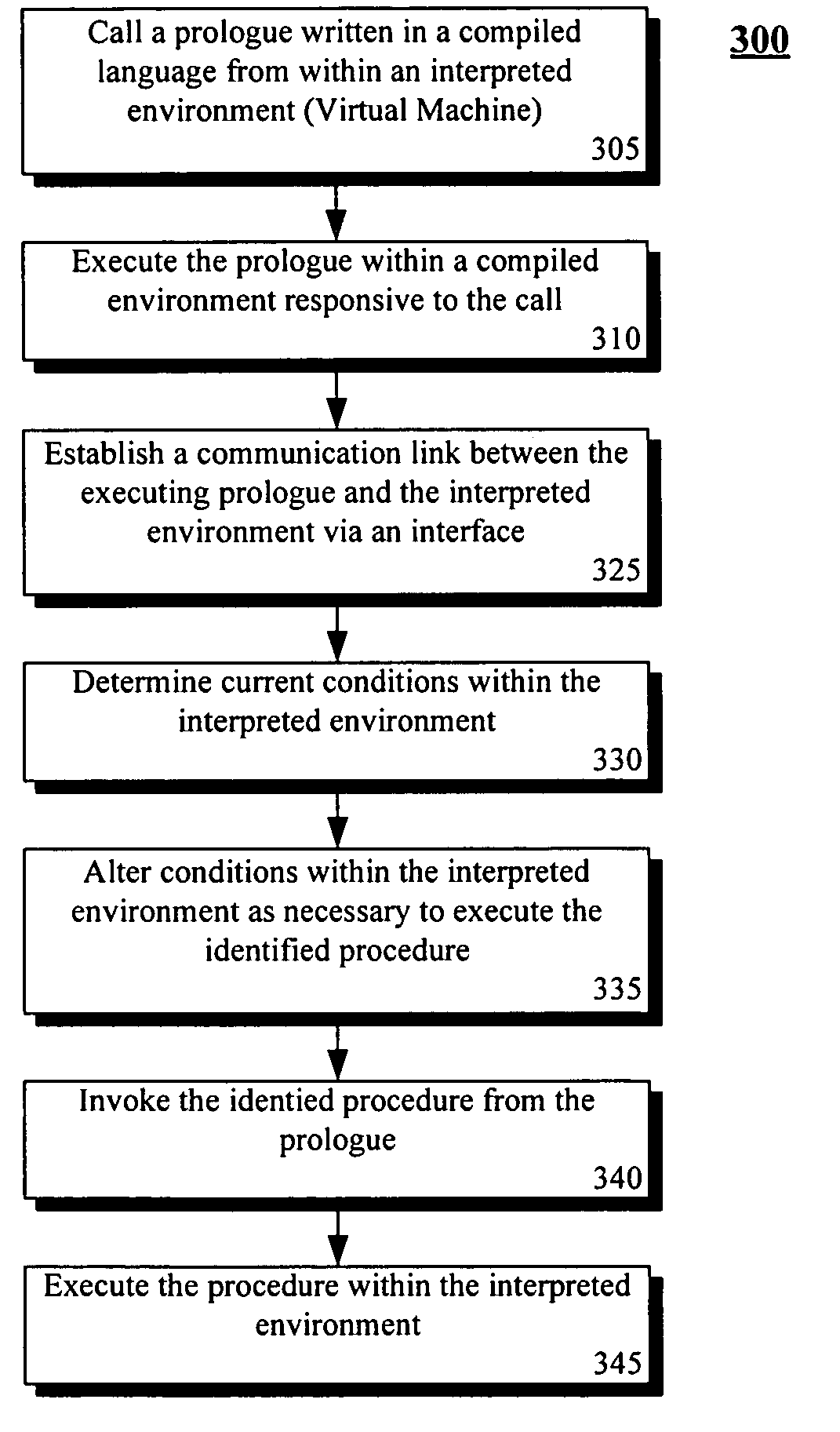
InactiveUS20060070028A1Unwanted overhead checks can be eliminatedEfficient executionSpecific program execution arrangementsMemory systemsProcedure callsCode segment
Software code sections can include at least one calling procedure (110) and a called procedure (140). The called procedure can include an interpreted code body (144). Execution of the interpreted code body can require the use of an associated interpreter. The software code sections can also include prologue (142) associated with the called procedure. The prologue can be invoked by the at least one calling procedure and can responsively actuate the interpreted code body causing programmatic actions defined within the interpreted code body to execute. Execution of the prologue does not require use of an interpreter. In one embodiment, the interpreted code body of the called procedure can execute upon a platform having an application binary interface (115). The prologue can actuate the interpreted code body according to specifications of the application binary interface.
Owner:GOOGLE TECH HLDG LLC
Server-based code compilation
ActiveUS8365153B2Save resourcesResource optimizationMultiple digital computer combinationsMemory systemsBase codeCompiler
A server is disclosed that includes an interface to a data communication network, a compiler library that stores a plurality of different compilers, and compiler selection logic responsive to data received at the interface and including logic. The compiler selection logic is configured to select one of the plurality of different compilers based on an evaluation of the received data. The selected compiler generates compiled output data and the compiled output data is communicated over the data communication network to a client.
Owner:QUALCOMM INC
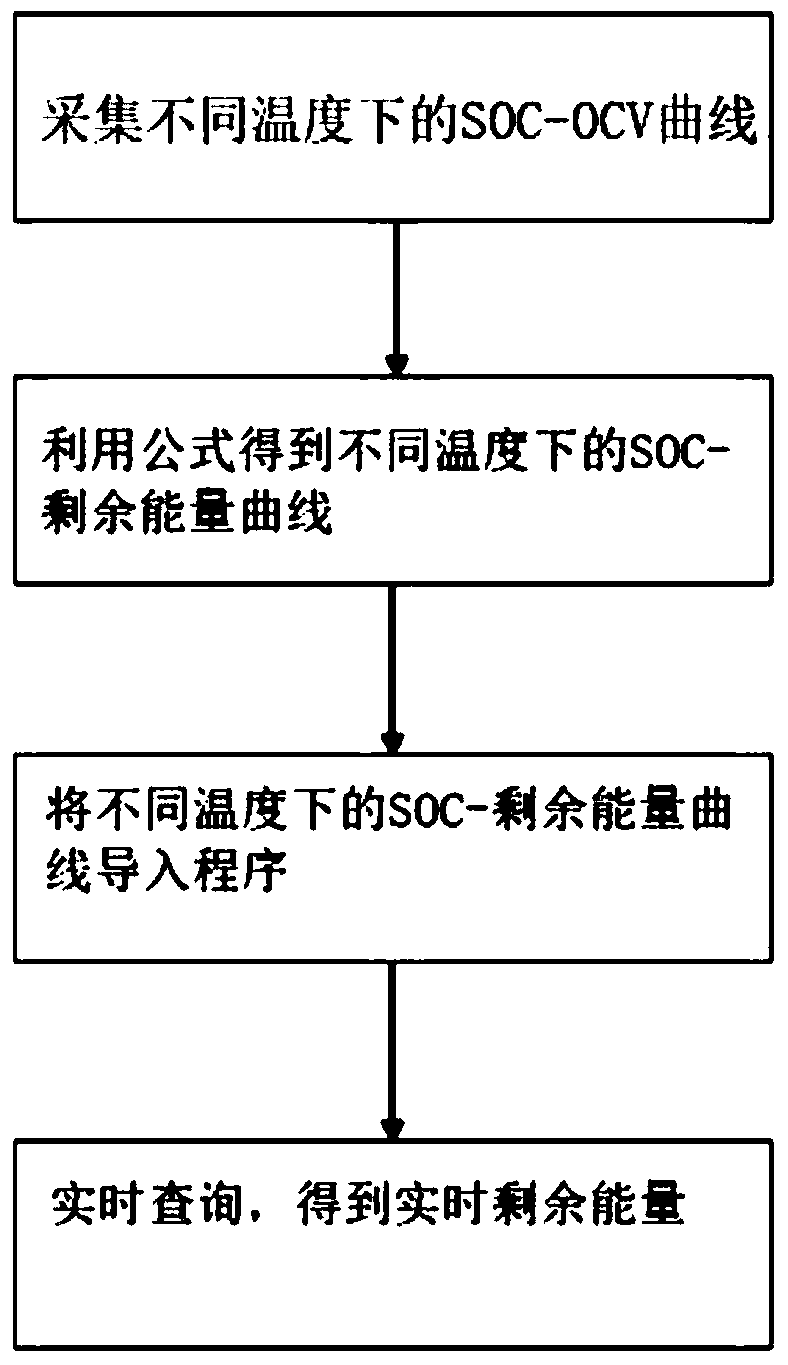
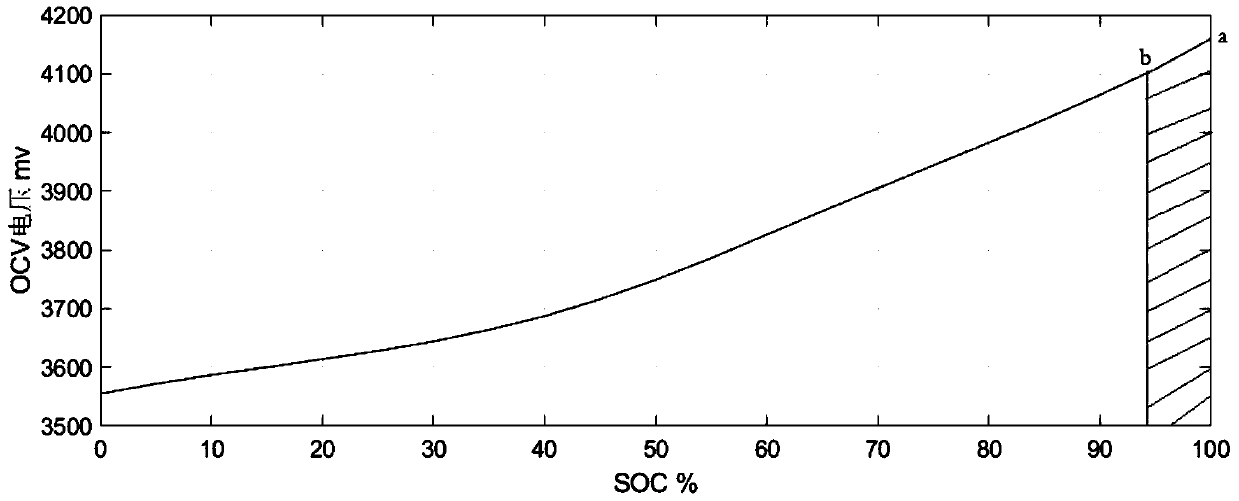
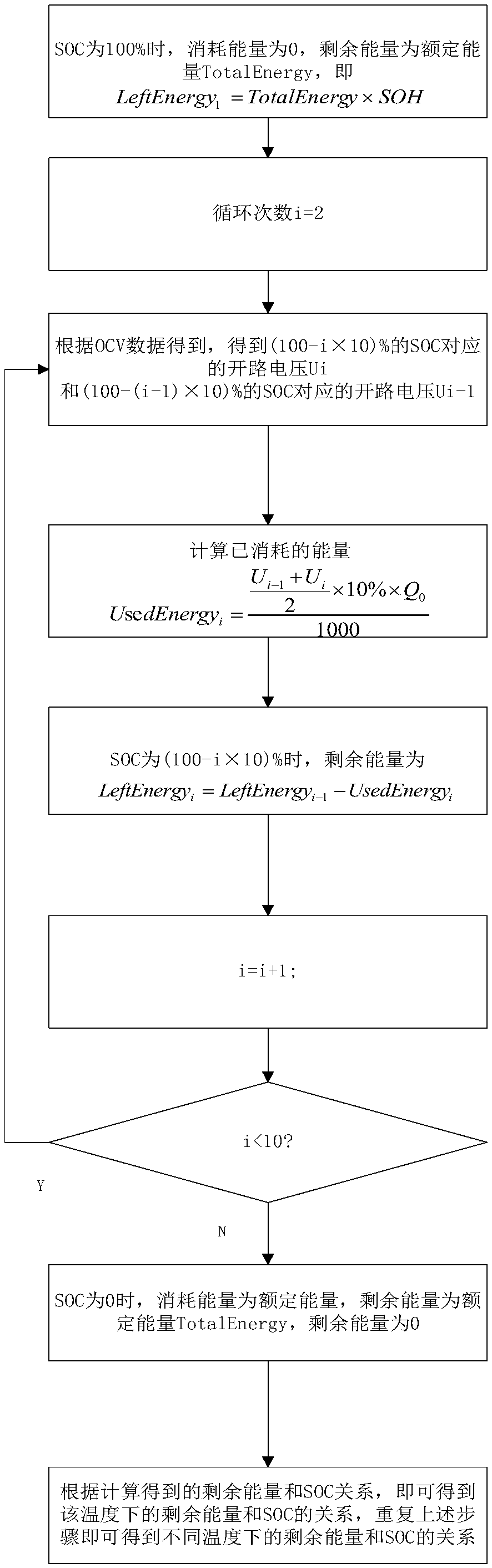
Method for obtaining surplus energy of battery based on SOC-OCV curve
ActiveCN109683101AGuaranteed accuracyReduce computational complexityElectrical testingAutomotive batteryEngineering
The invention discloses a method for obtaining surplus energy of a battery based on an SOC-OCV curve and belongs to the field of vehicle batteries. The method comprises the following steps that S1, atemperature-rated capacity curve, a temperature-total energy curve and SOC-OCV curves at different temperatures are collected; S2, SOC-surplus energy curves at different temperatures are obtained; S3,the SOC-surplus energy curves at different temperatures are input to a BNS program; S4, query is conducted according to a two-dimensional table to obtain the real-time surplus energy. According to the method, the SOC-OCV curves are used for calculating an integral of released energy to obtain the surplus energy of the battery for the first time, and the surplus energy of the battery at differenttemperatures and SOCs is obtained. According to the method, the accurate surplus energy can be obtained just by testing the most basic battery characteristic, the workload of battery testing is lowered, and the real-time surplus energy of the battery can be obtained in the vehicle operation process.
Owner:安徽优旦科技有限公司
Signal processing system for tonal noise robustness
ActiveUS20060265215A1Mitigates and eliminates detectionReliable analysisEar treatmentSpeech analysisComputer scienceSignal processing
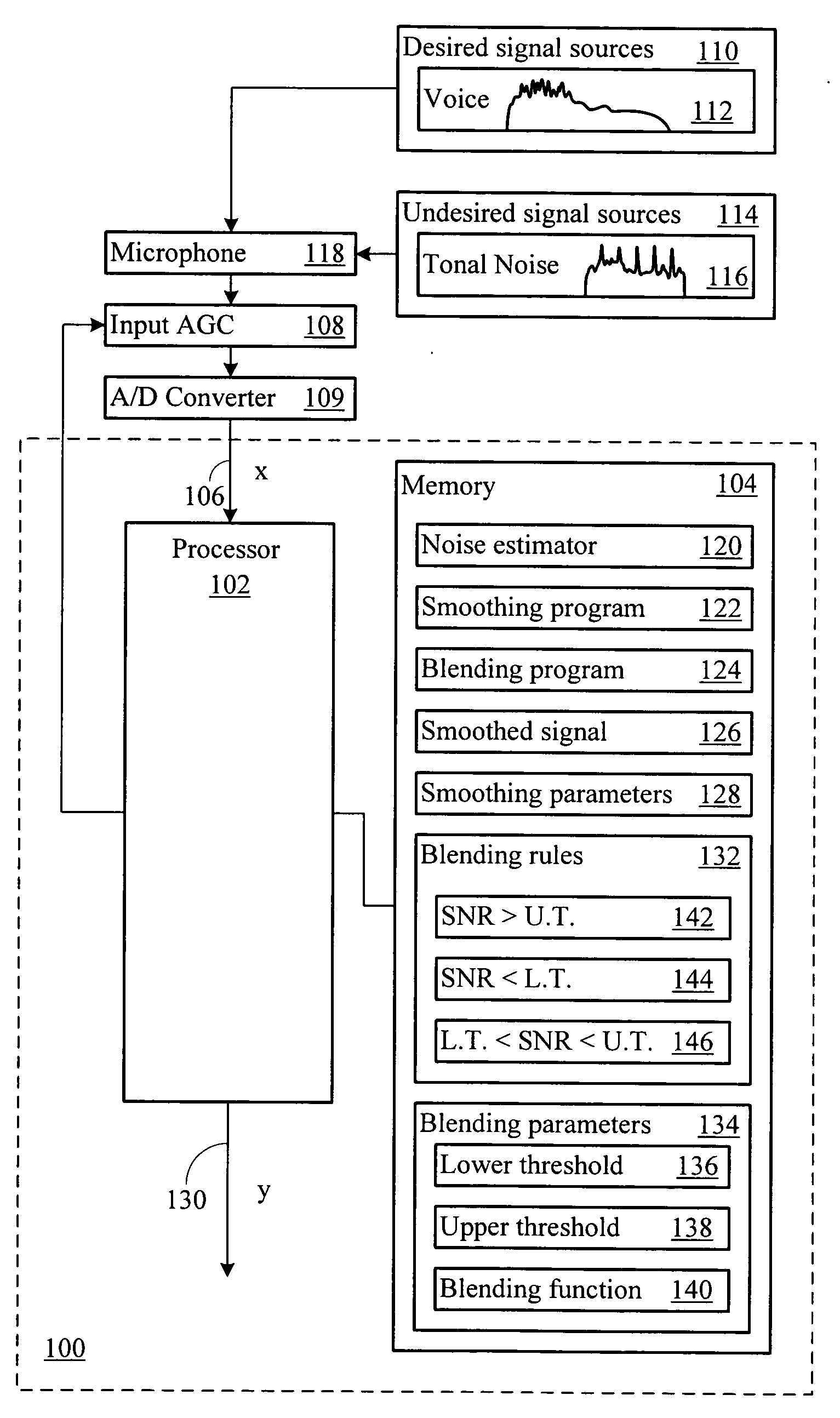
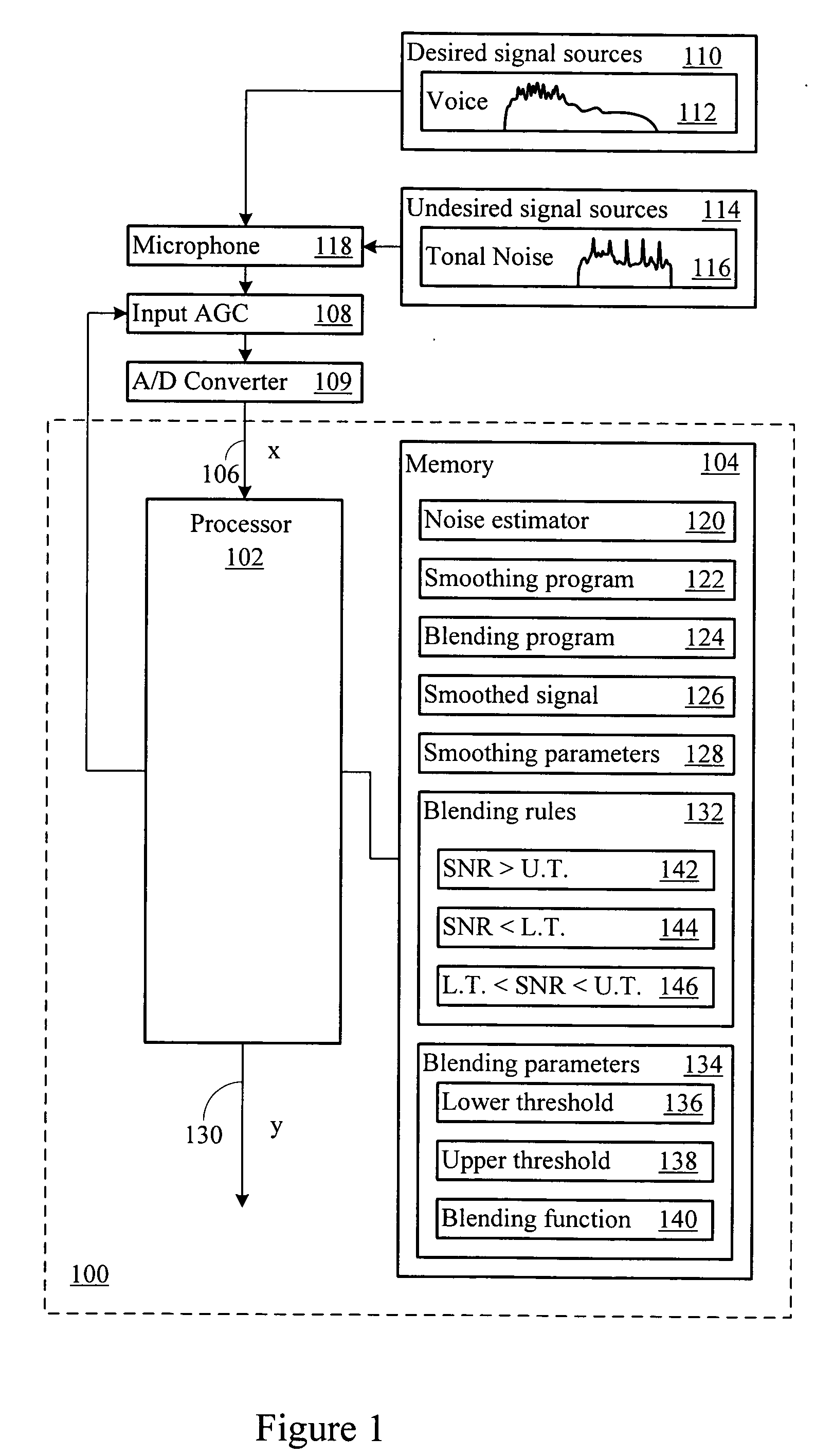
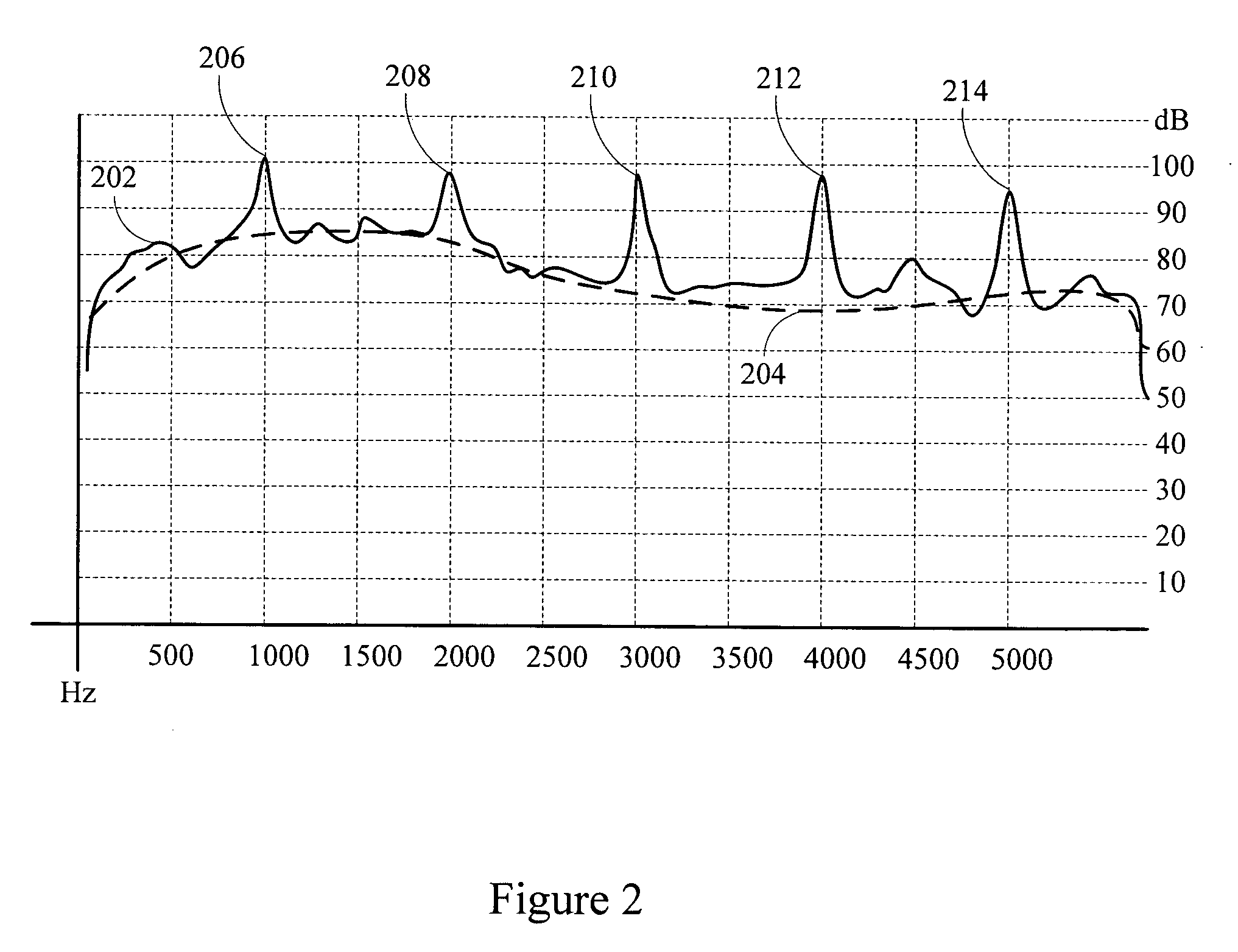
A processing system generates an output signal which includes desired signal components, and reduces or eliminates tonal noise. The output signal may be provided to any subsequent signal processing system, including voice recognition systems, pitch detectors, and other processing systems. The subsequent processing systems are less likely to mistake tonal input signal noise for desired signal content, to needlessly consume computational resources to analyze noise, and to take spurious actions induced by the tonal noise.
Owner:BLACKBERRY LTD
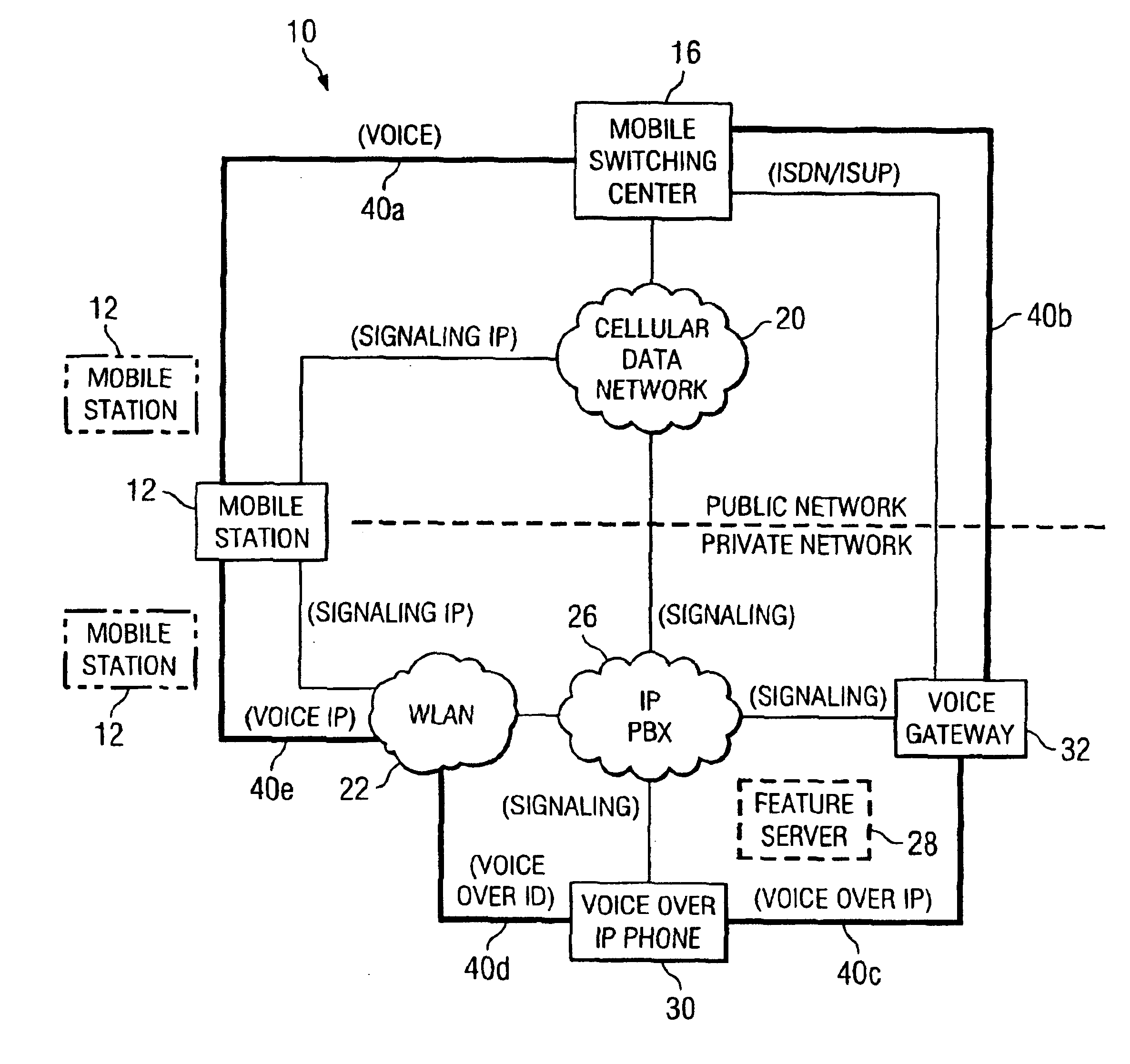
System and method for delivering private network features to a public network
ActiveUS7076251B2Reduce disadvantagesReduce problemsNetwork topologiesSpecial service for subscribersPrivate networkMobile station
Owner:CISCO TECH INC
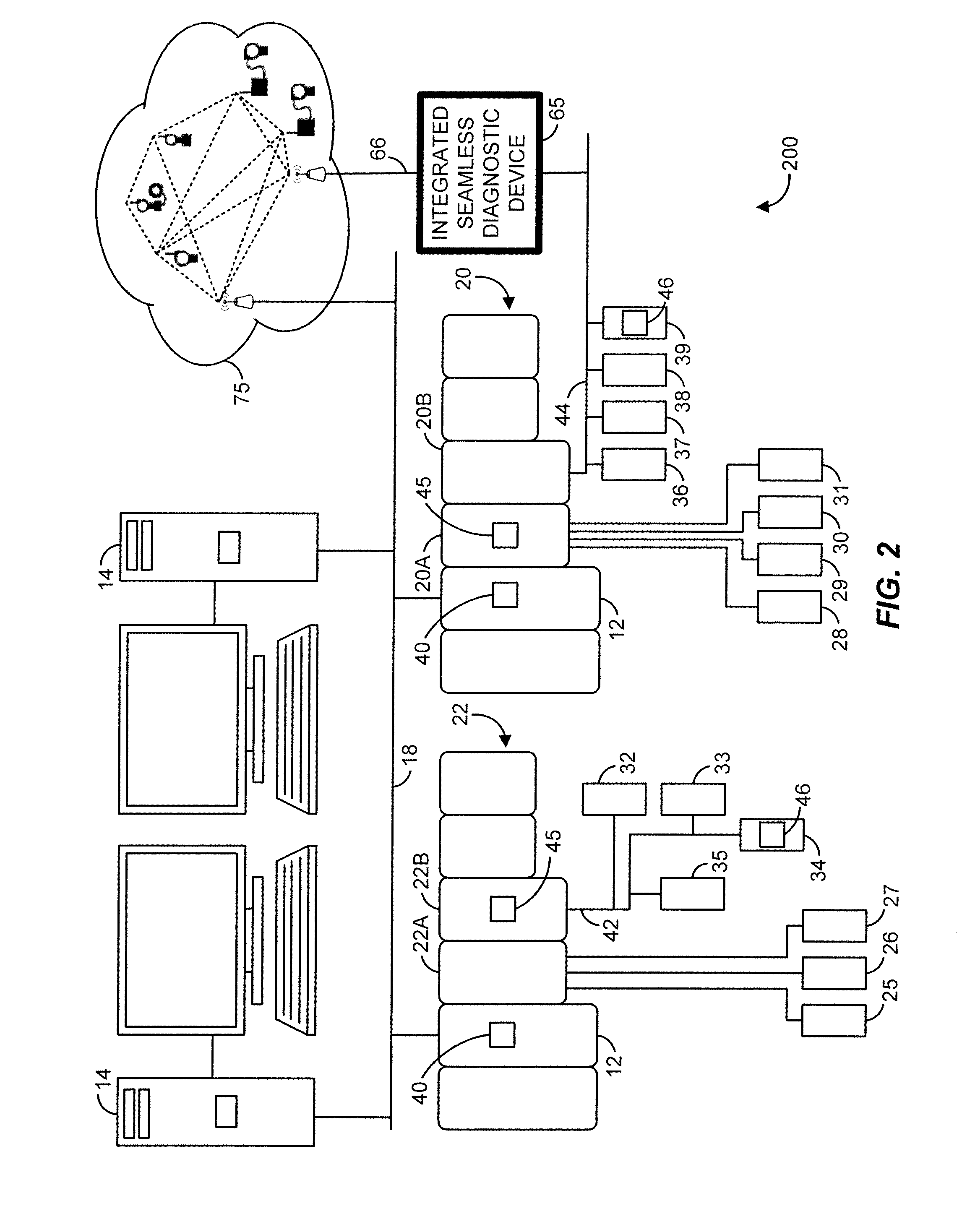
Seamless integration of process control devices in a process control environment
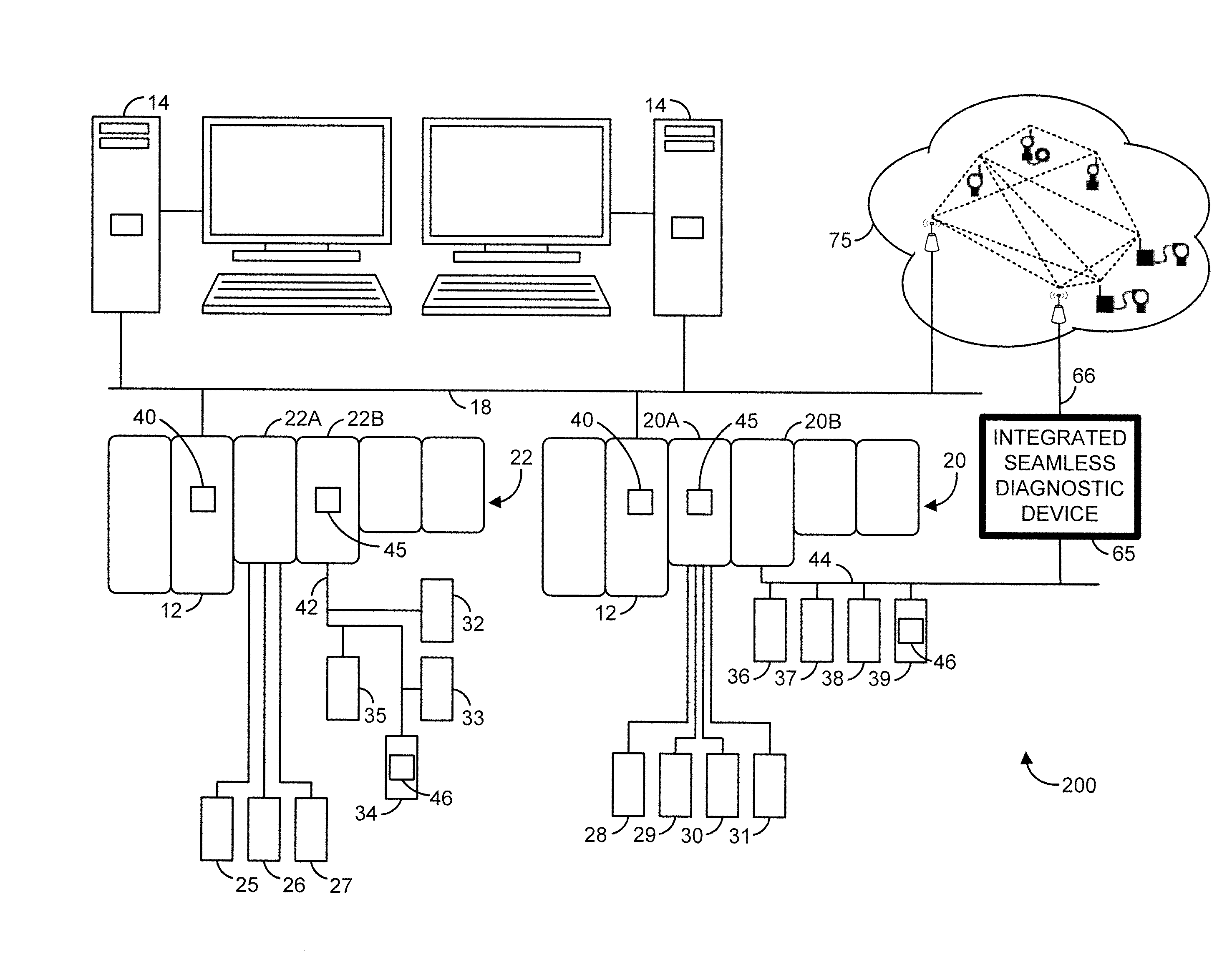
InactiveUS20120035749A1Easy and seamless integrationIncrease variabilityProgramme controlSafety arrangmentsDiagnostic dataTelecommunications link
In order to facilitate seamless integration of process control devices in a process control system, an integrated seamless diagnostic device collects diagnostic data related to the operation of (or problems associated with) one communication link that supports one process control protocol but communicates the collected diagnostic data to other entities in the process control system via another communication link that supports a different process control protocol. As a result, problems with the communication link monitored by the integrated seamless diagnostic device can be reported to the appropriate entities in the process control system as they occur and without unwanted delay. Moreover, problems with the monitored communication link can be communicated to the appropriate entities via process control protocols that are understood by those entities (and other entities in the process control system) and without consuming the potentially valuable resources of the monitored communication link.
Owner:FISHER-ROSEMOUNT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com