Patents
Literature
36results about How to "Consume bandwidth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
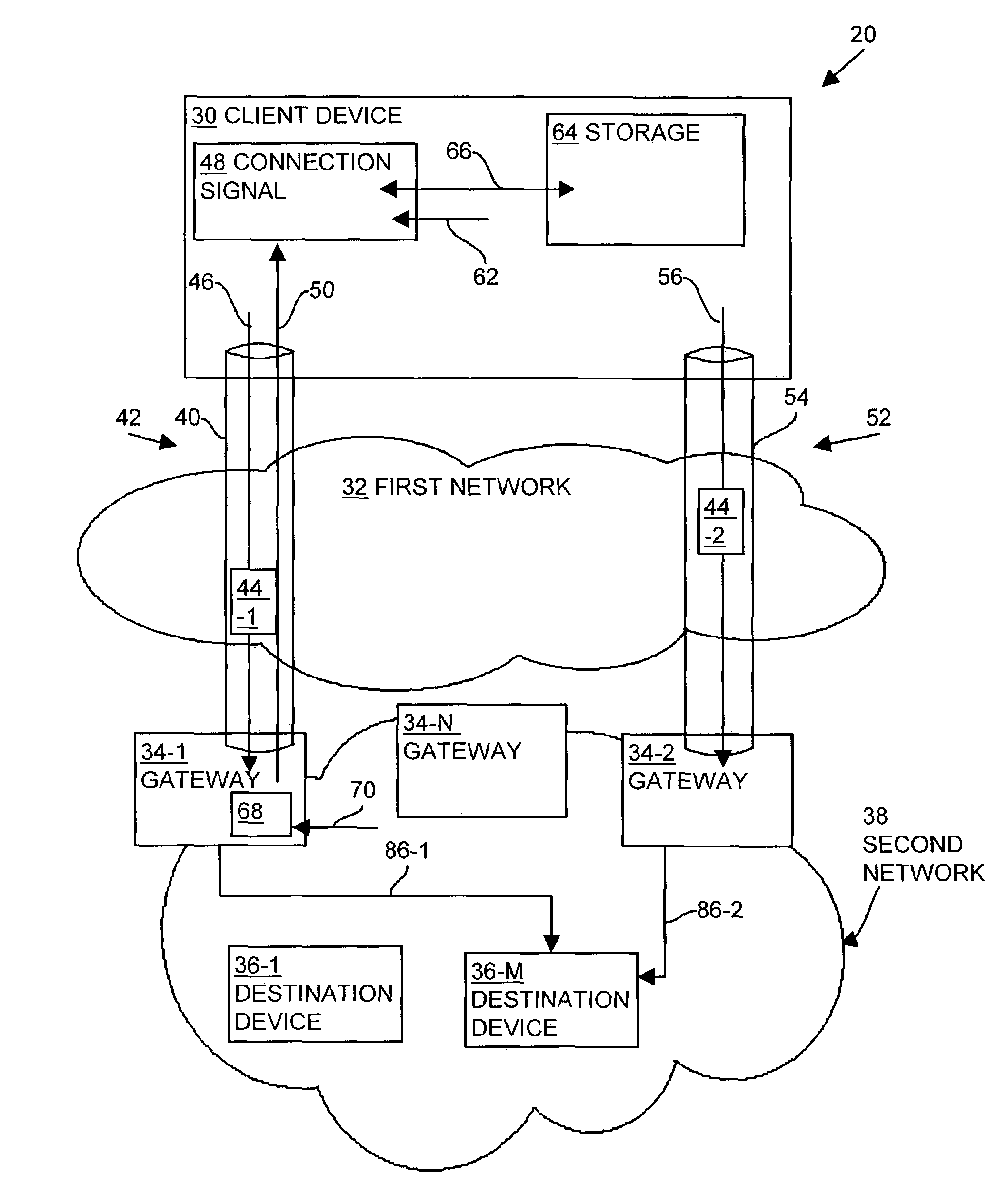
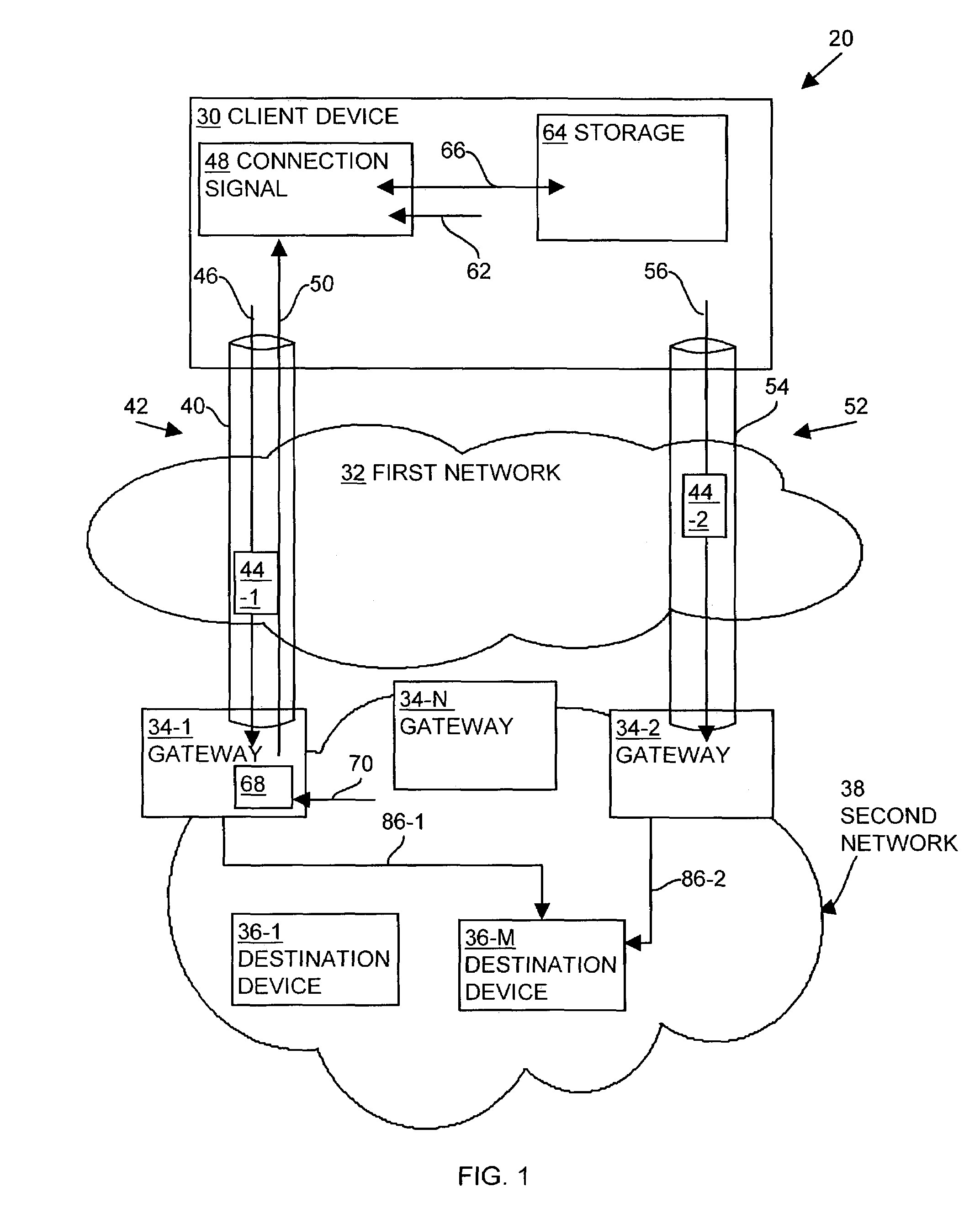
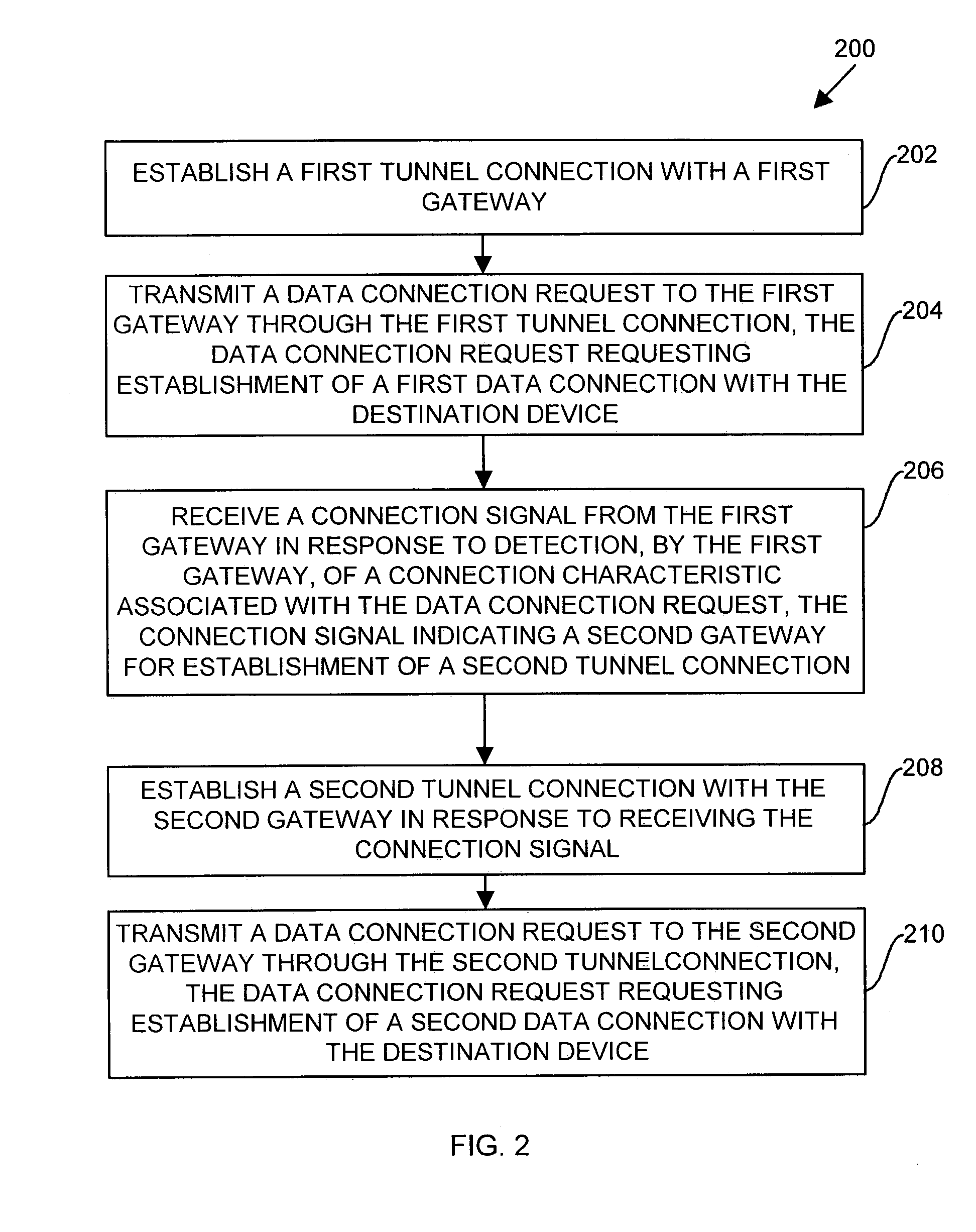
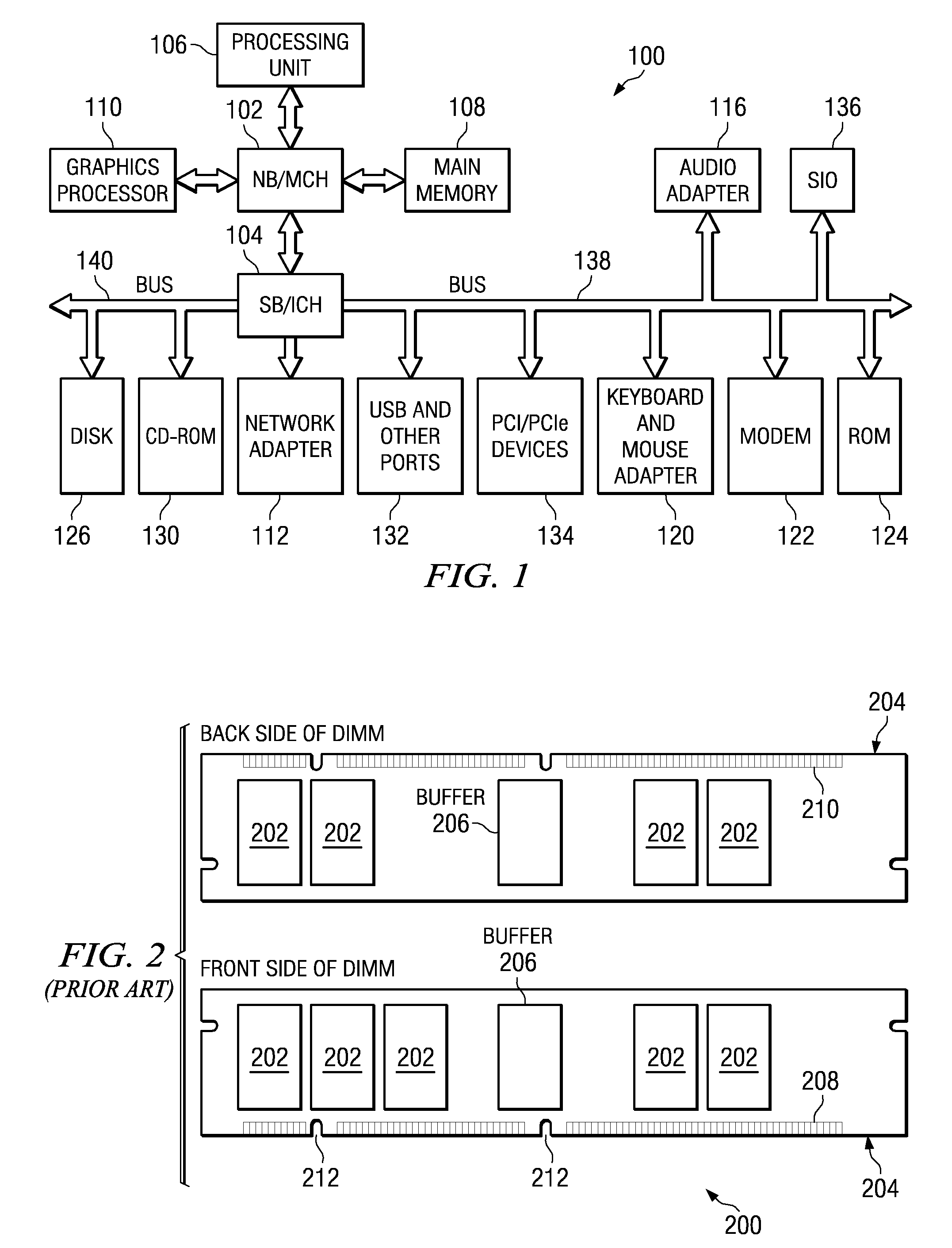
Methods and apparatus for establishing a computerized device tunnel connection
InactiveUS7673048B1Minimize bandwidth utilizationIncrease costError preventionTransmission systemsData connectionTelecommunications
A client device establishes a first tunnel connection or tunnel, through a public network, with a first gateway of a private network and establishes, through the tunnel connection, a data connection with a destination device within the private network. The first gateway monitors or analyzes the geographic locations of the gateways associated with the private network relative to geographic location of the destination device associated with the data connection. Based upon such the monitoring, the first gateway transmits information to the client device relating to establishment of a second tunnel connection or tunnel with a second gateway of the private network. The client device establishes the second tunnel connection with the second gateway and establishes a data connection with the destination device through the second gateway. By establishing the second tunnel connection with the second gateway, the client device utilizes the bandwidth of the public network to exchange data with the destination device, thereby decreasing data transmission costs to the private network and decreasing private network latency.
Owner:CISCO TECH INC
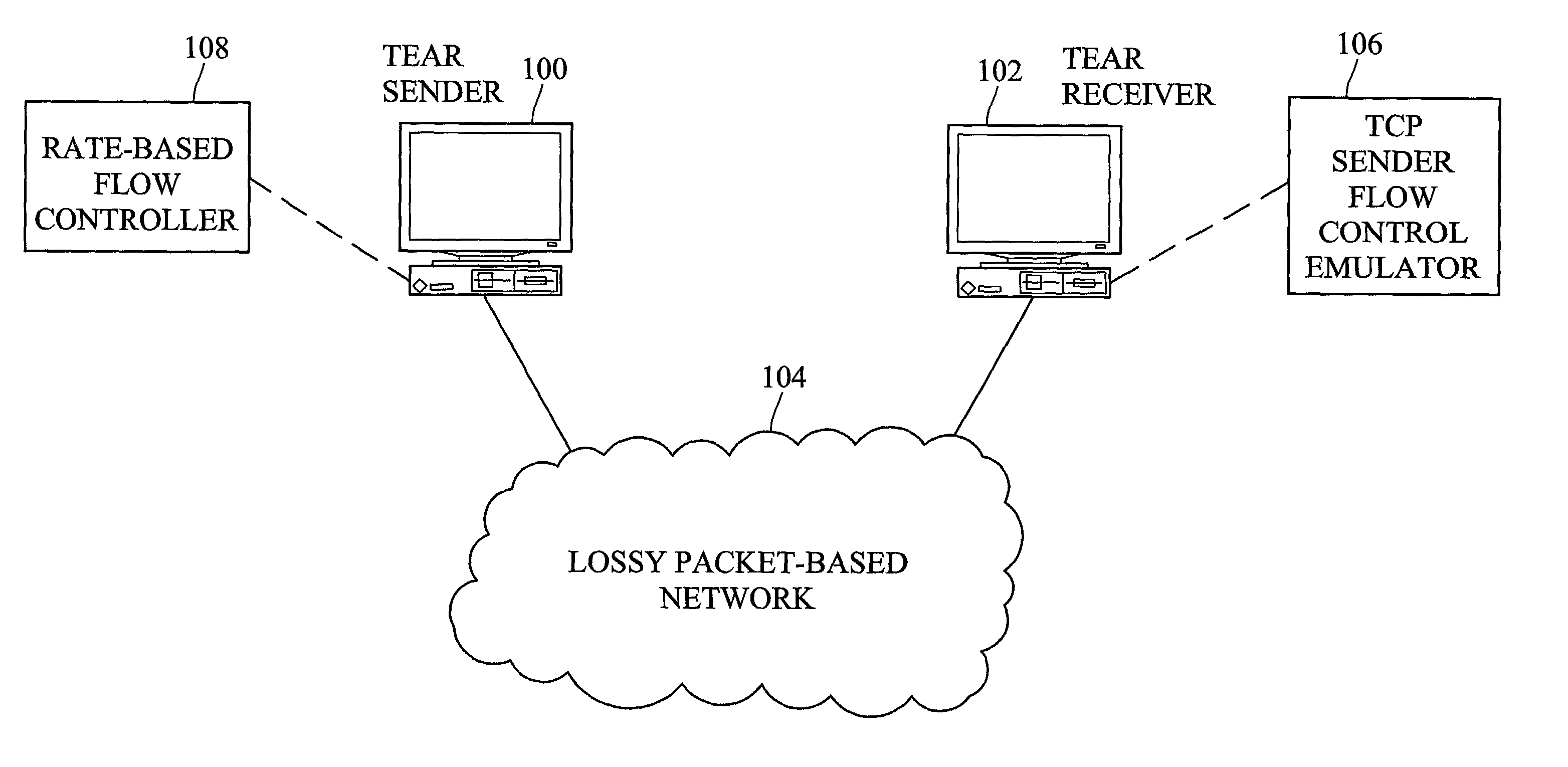
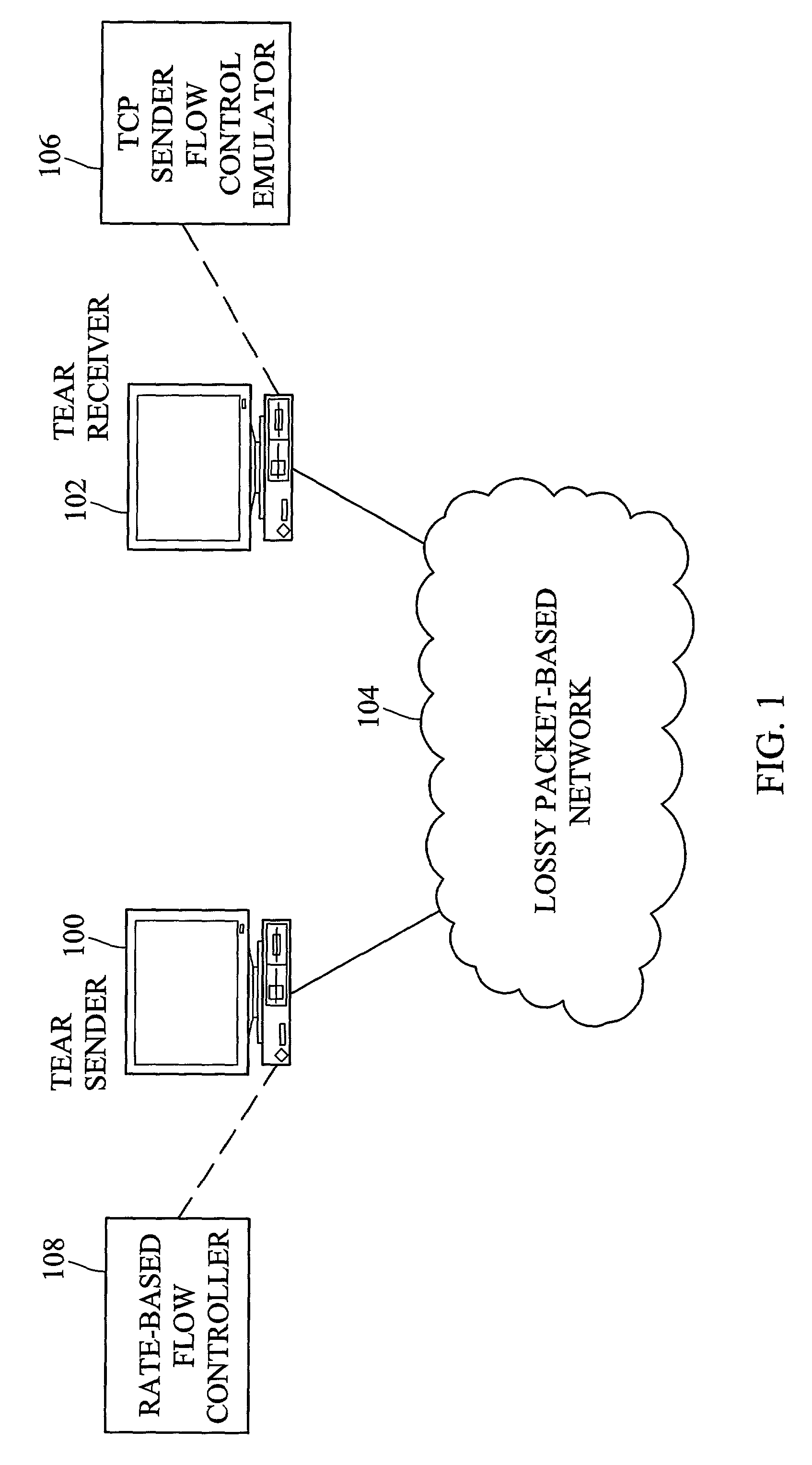
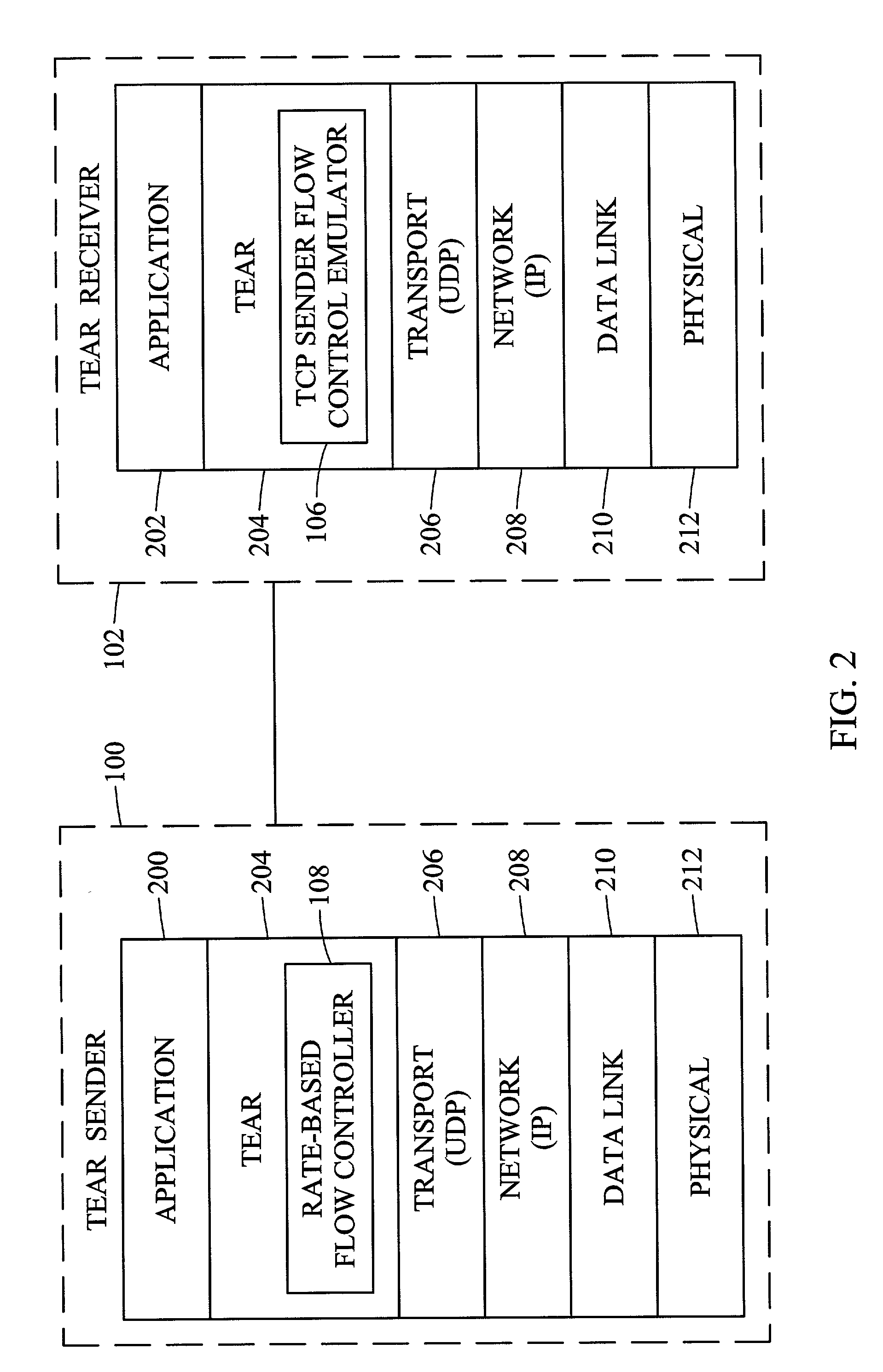
Methods and systems for rate-based flow control between a sender and a receiver
InactiveUS7304951B2Excessive rateFluctuation in rateError preventionTransmission systemsTransmitterReal-time computing
Methods and systems for rate-based flow control between a sender and a receiver are disclosed. A receiver performs TCP-like flow control calculations based on packets received from a sender. The receiver calculates a transmission rate and forwards the transmission rate to the sender. The sender sends packets to the receiver at the rate calculated by the receiver. Thus, rather than having sender-based flow control as in TCP, the receiver controls the rate at which packets are delivered.
Owner:NORTH CAROLINA STATE UNIV
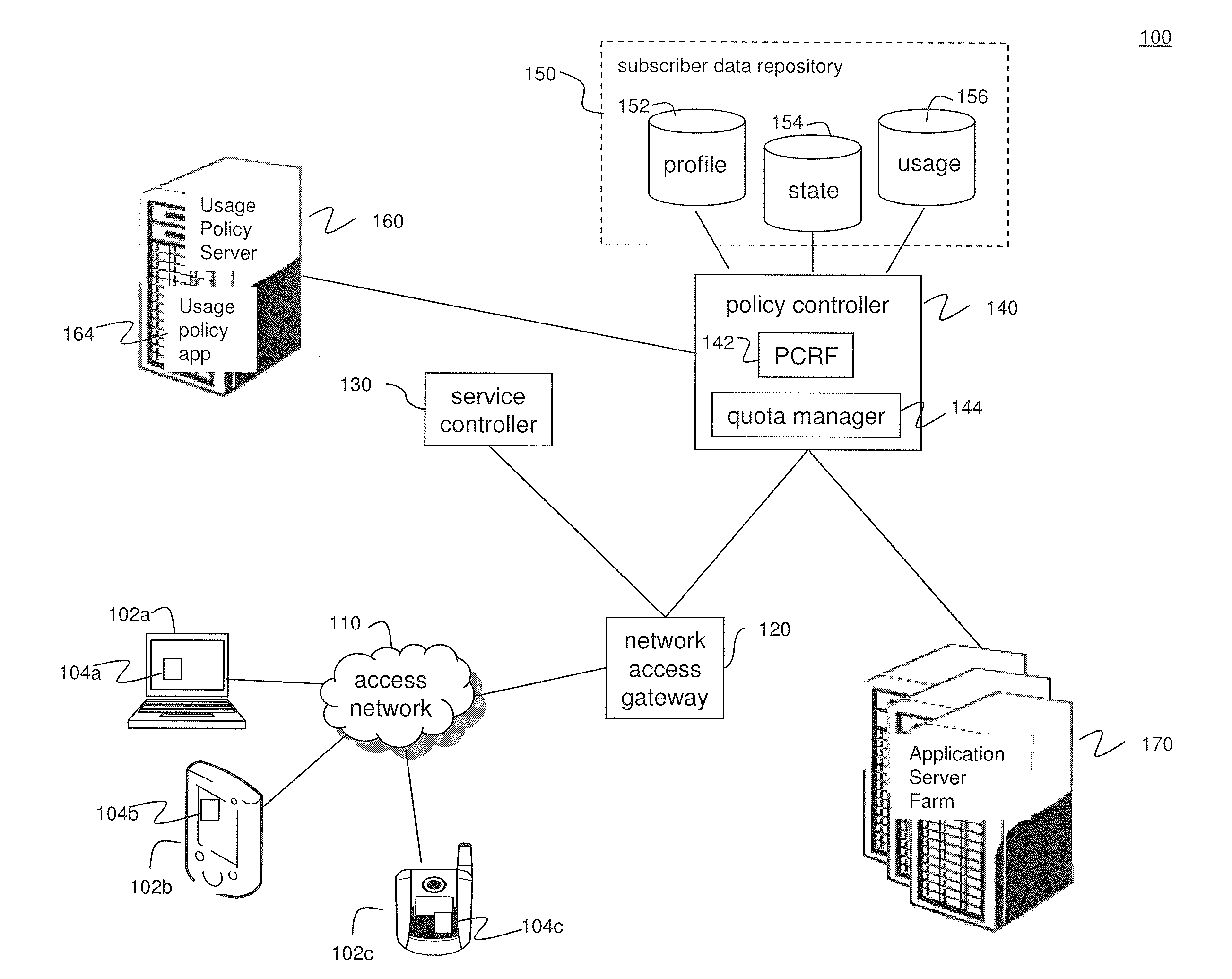
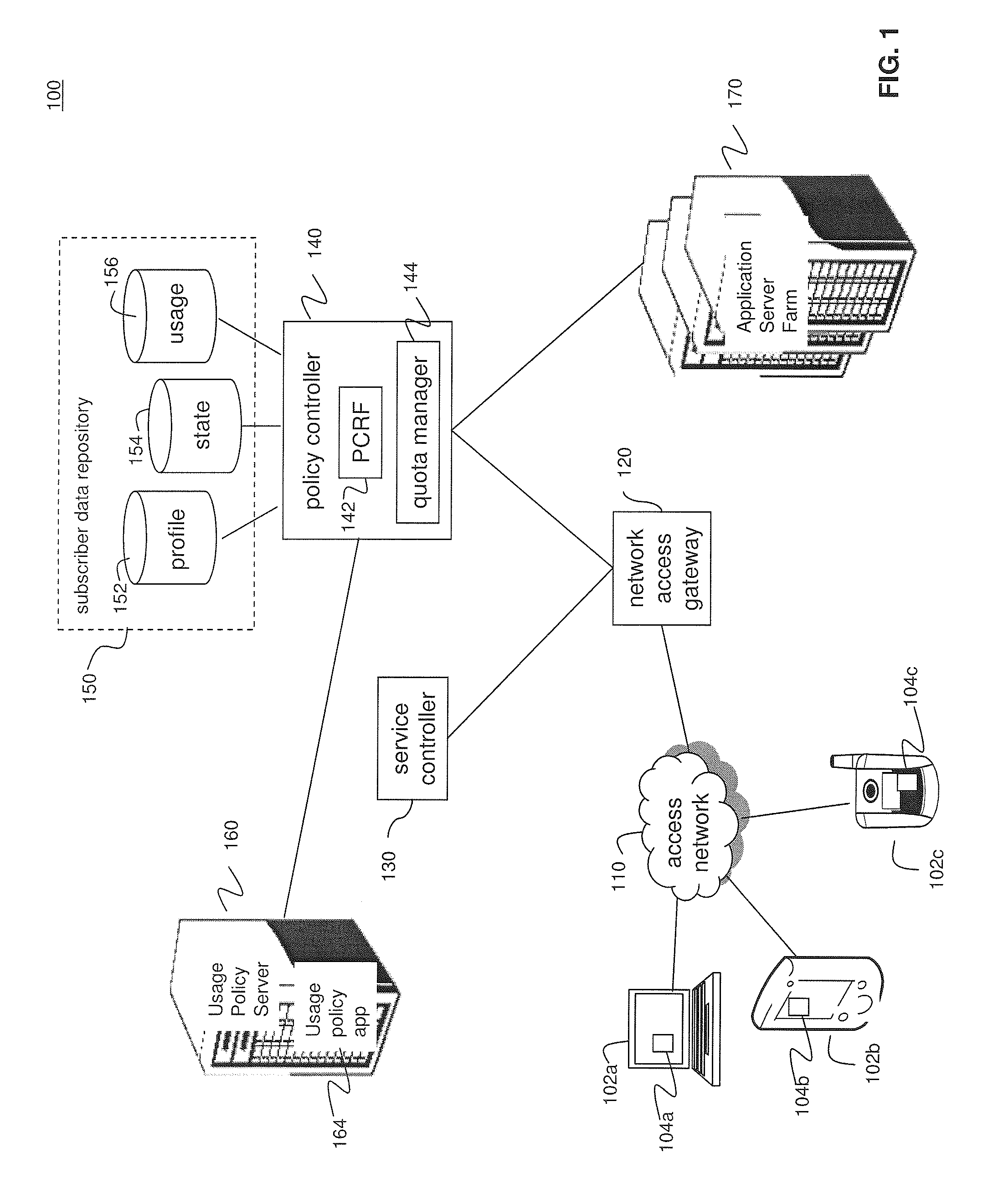
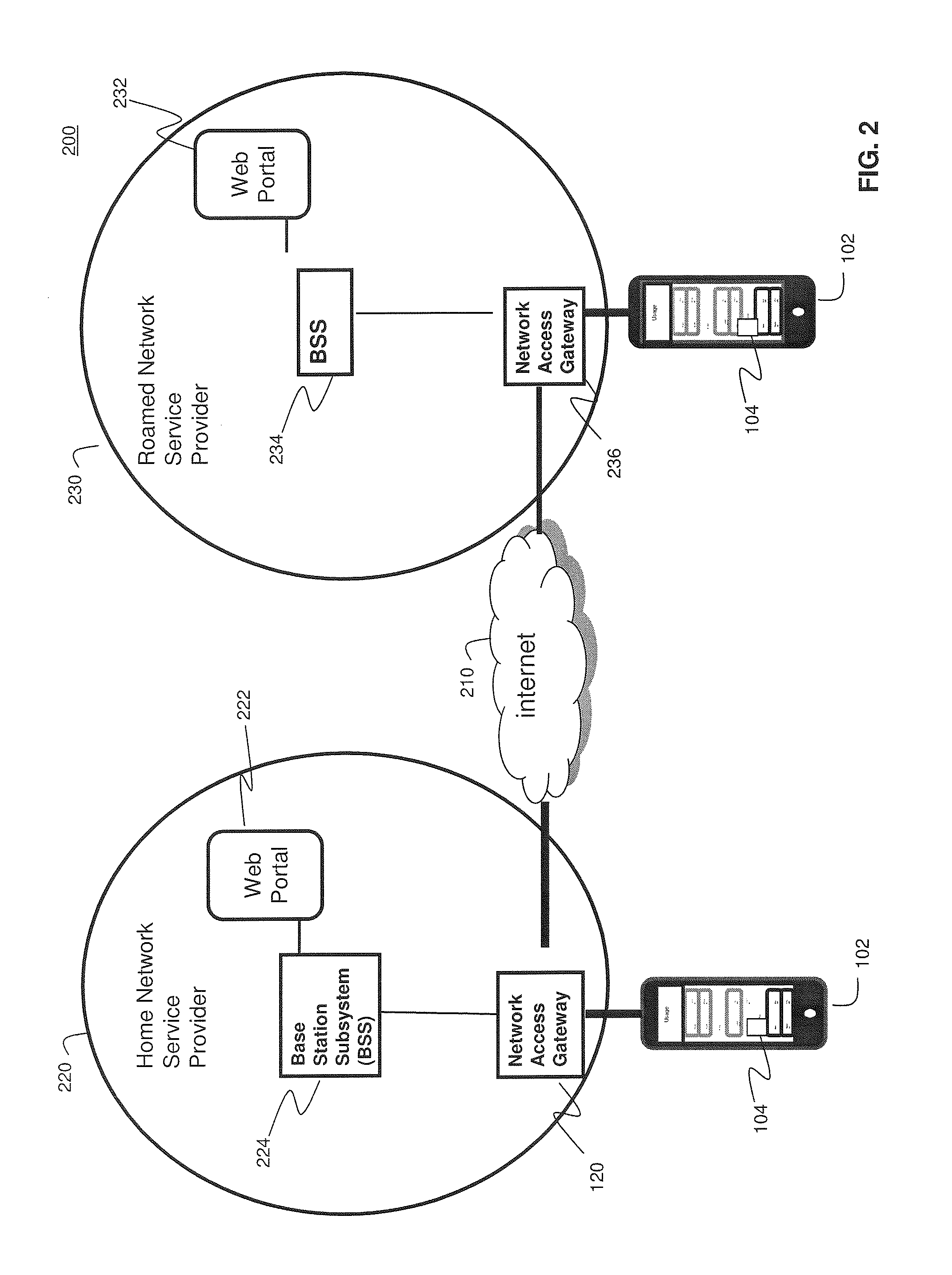
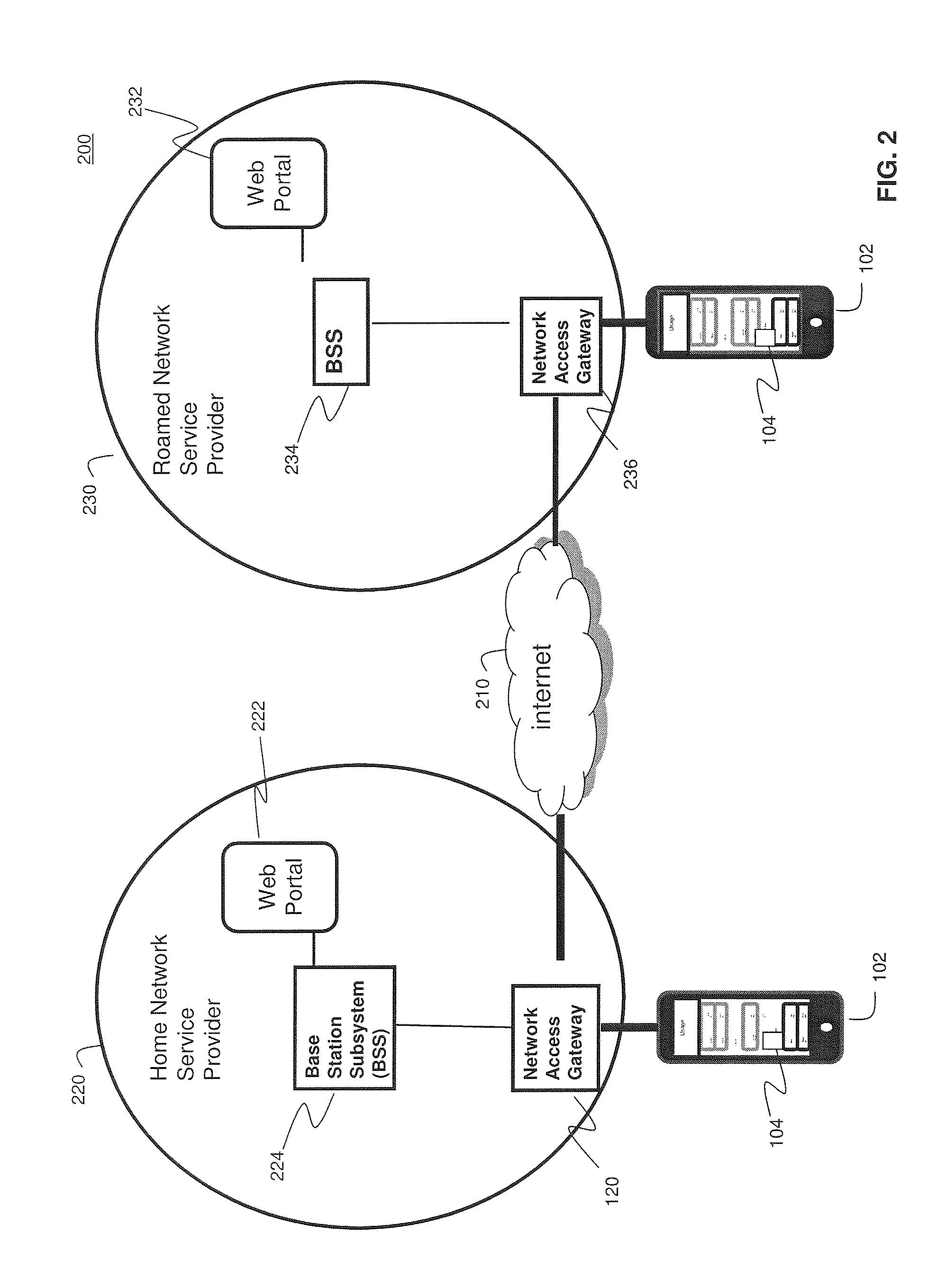
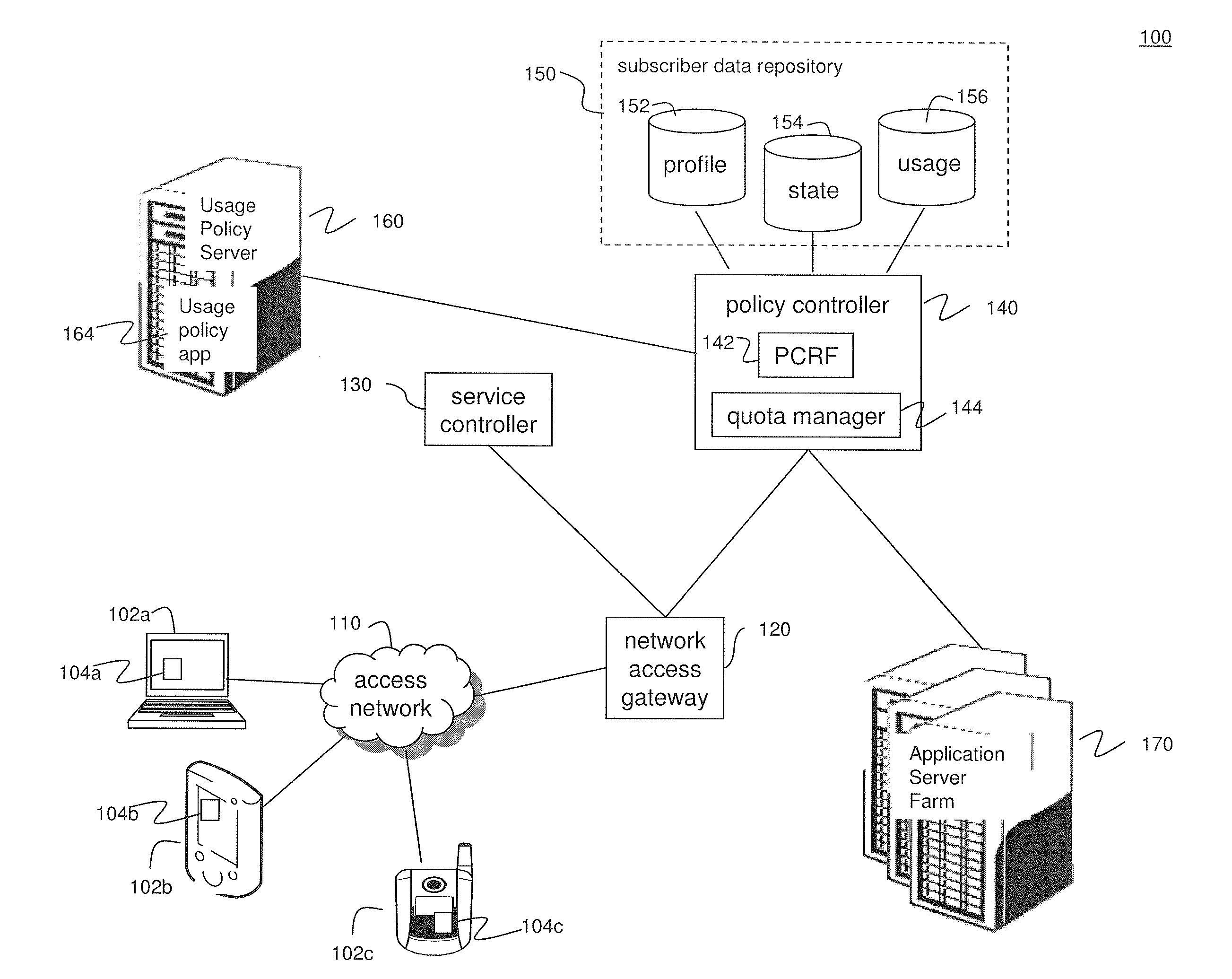
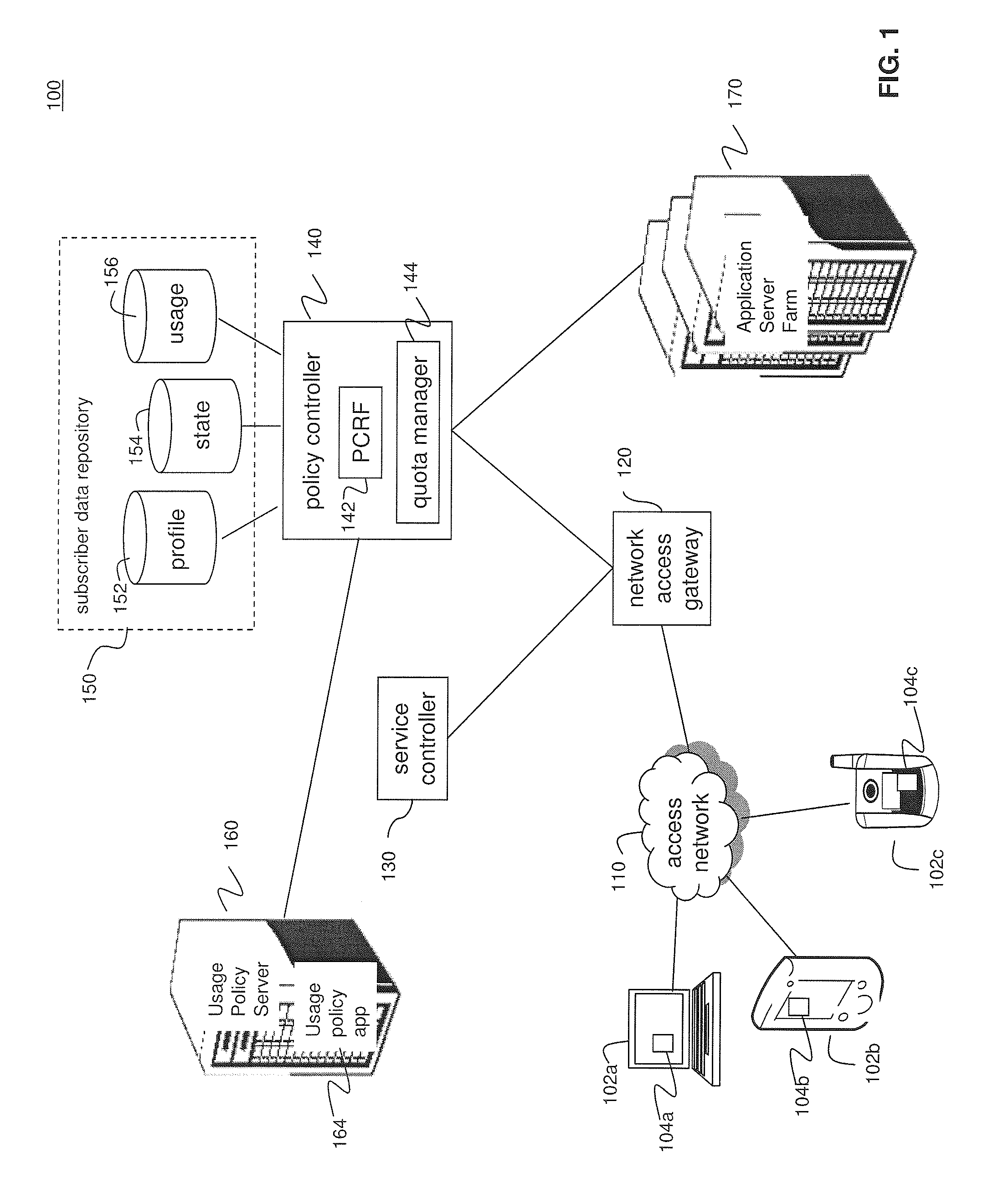
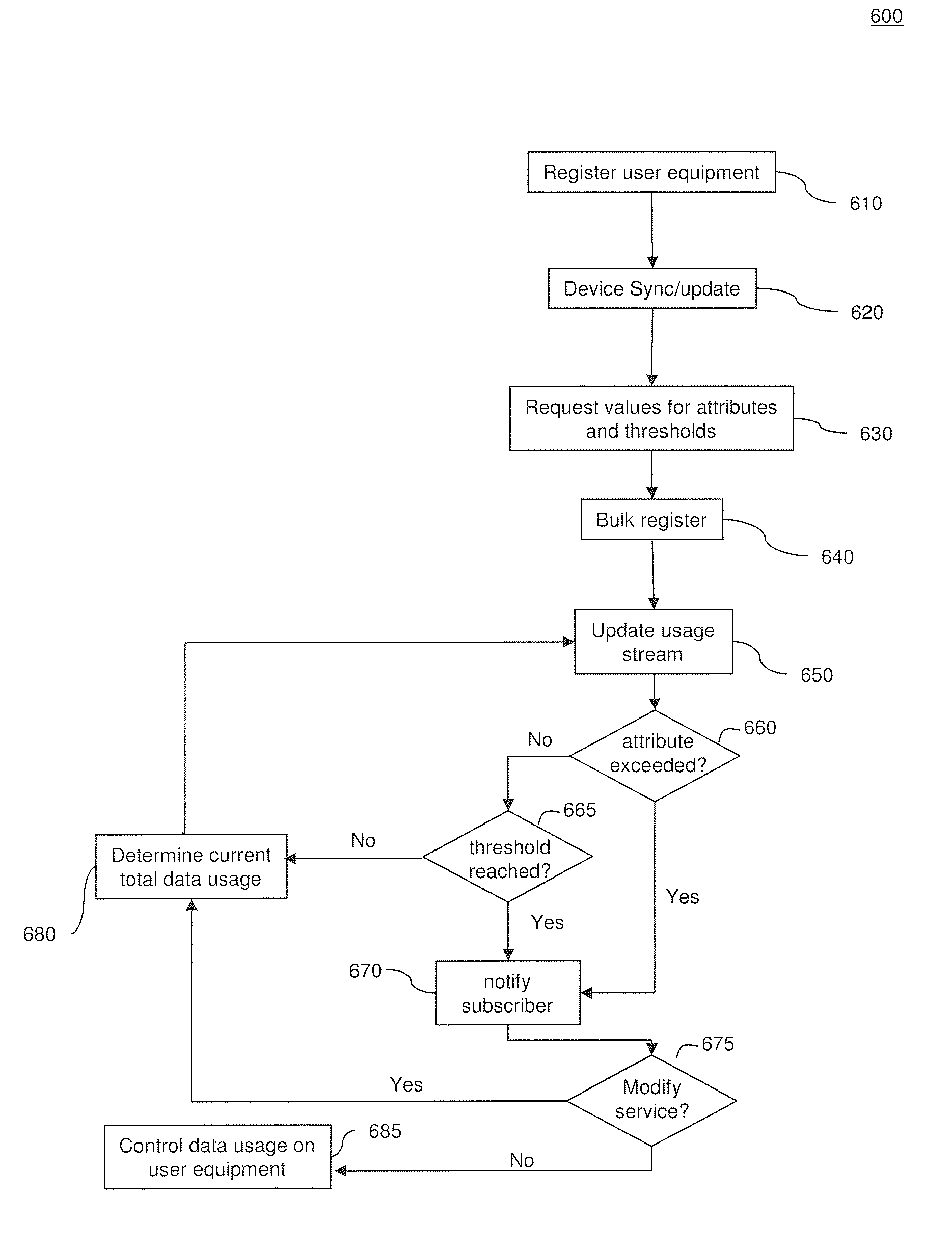
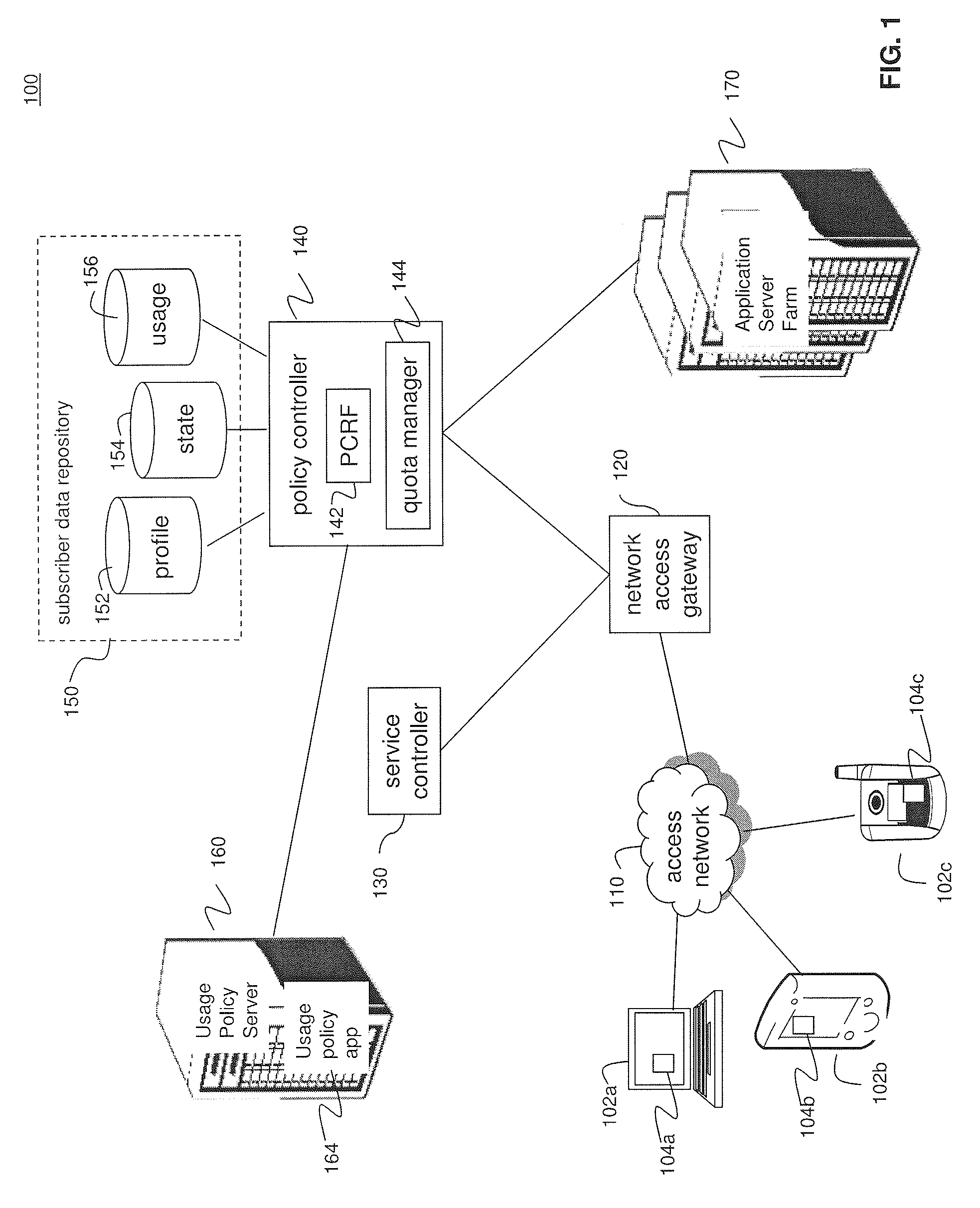
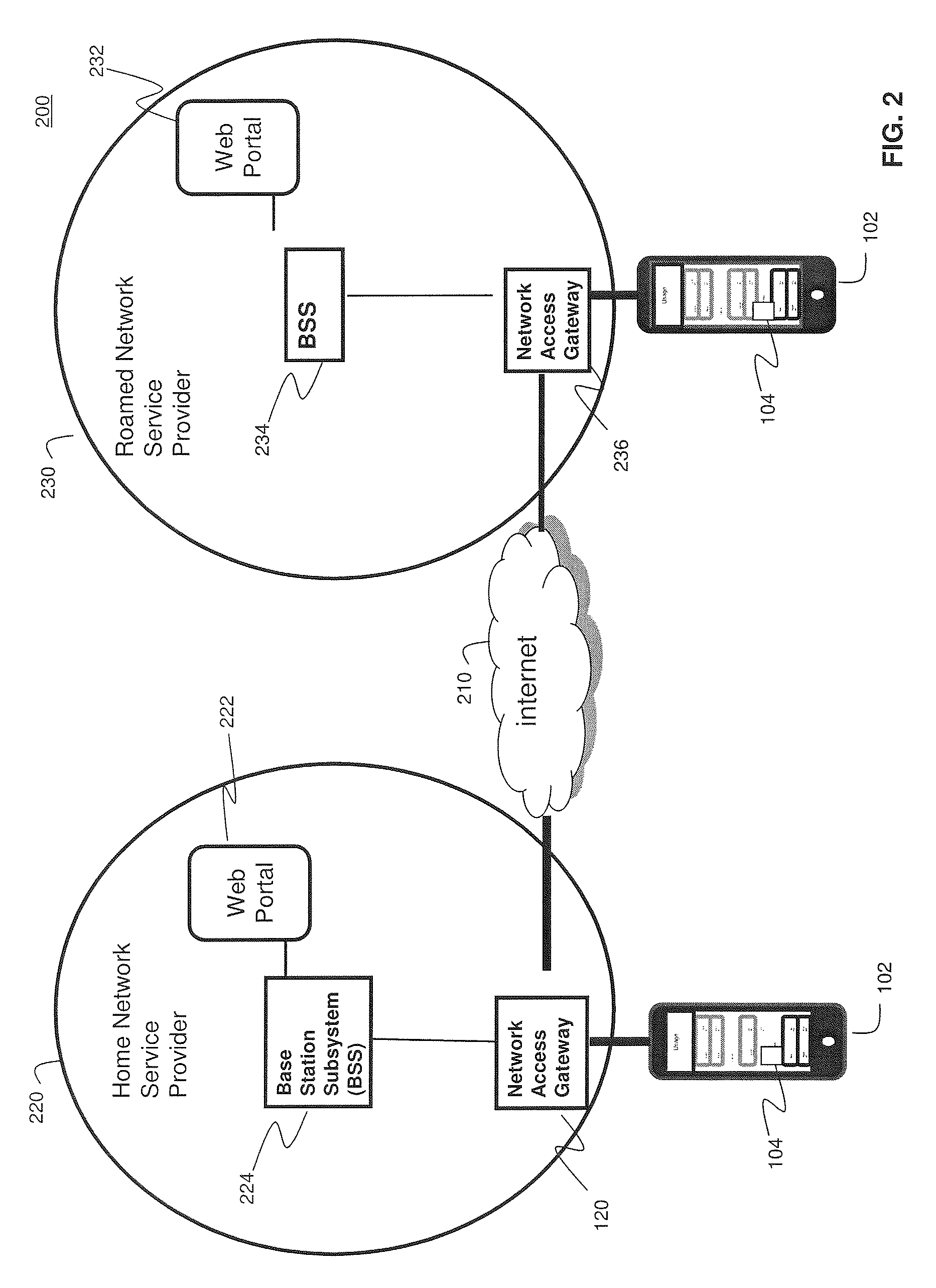
System and Methods for Carrier-Centric Mobile Device Data Communications Cost Monitoring and Control
ActiveUS20110275344A1Improve data communication usageImprove cost monitoring operationMetering/charging/biilling arrangementsAccounting/billing servicesControl systemControl data
Systems and methods for providing carrier-centric data communications cost monitoring and controls are provided. In an embodiment, the method operates by receiving a registration request associated with a subscriber session, determining current data usage associated with the subscriber, and receiving data usage thresholds. The method further comprises receiving quotas associated with the subscriber session and collecting data usage information associated with the subscriber session. The method sends a notification to the subscriber when a pre-determined quota is exceeded during the subscriber session and controls data usage. The cost monitoring and control system comprises a usage policy server and a usage policy application. The usage policy application allows a carrier to offer alterations to terms of a subscription. The usage policy application displays current data usage information on a per-network and per-application basis using subscriber profile information, subscriber session information, and prior subscriber usage history provided by the usage policy server.
Owner:AMDOCS DEV LTD +1
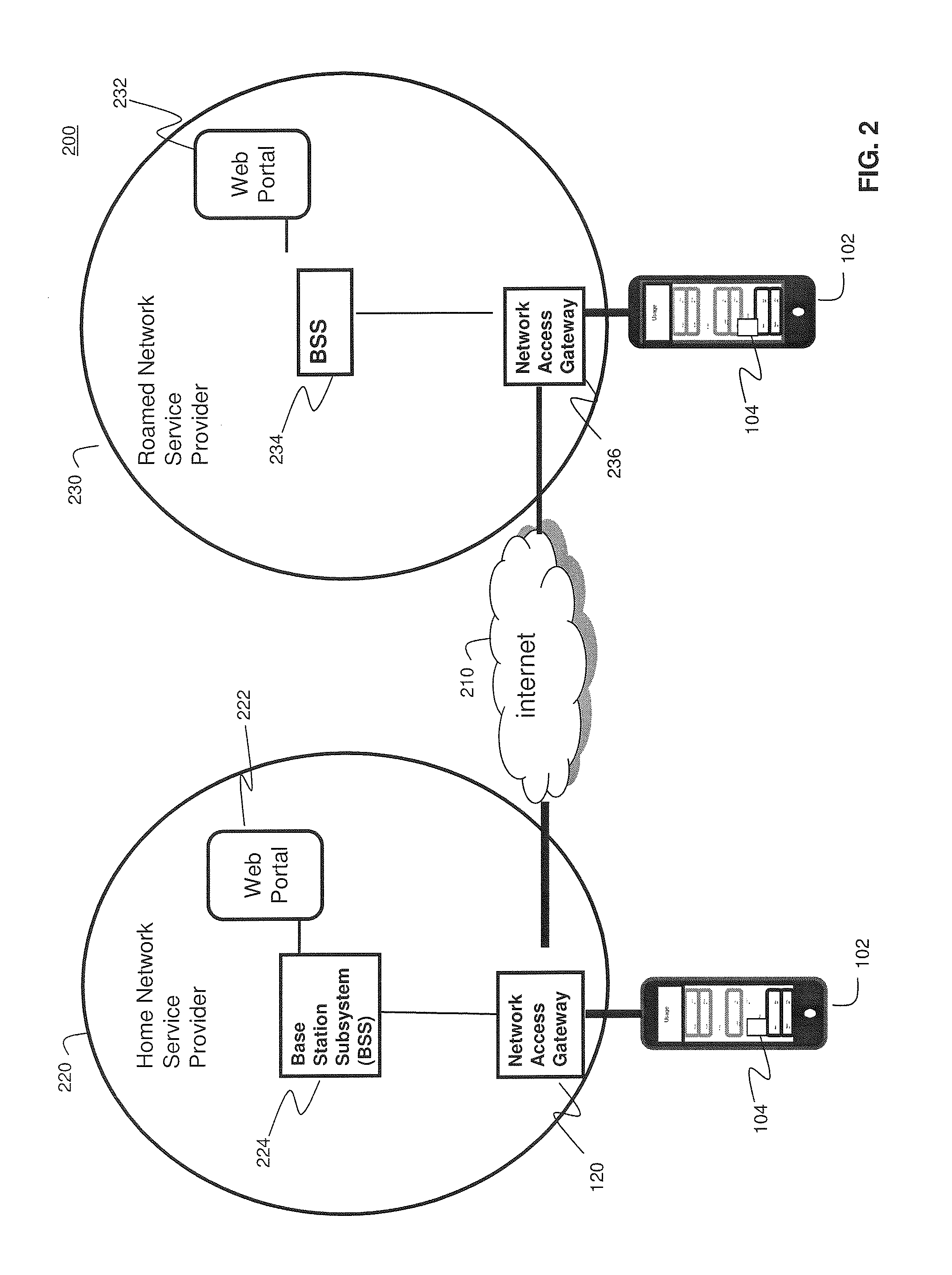
System and Methods for User-Centric Mobile Device-Based Data Communications Cost Monitoring and Control
ActiveUS20110276442A1Improve data communication usageImprove cost monitoring operationComplete banking machinesAccounting/billing servicesComputer networkControl data
Systems and methods for providing user-centric device-based data communications cost monitoring and controls. In an embodiment, the method operates by sending a registration request associated with a subscriber session, determining current data usage associated with the subscriber, and sending data usage thresholds. The method further comprises sending quotas associated with the subscriber session after collecting data usage information associated with the subscriber session. The method receives a notification at the subscriber's mobile device when a pre-determined quota is exceeded during the subscriber session to control data usage. The system communicates with a usage policy server and a usage policy application. The usage policy application allows a subscriber to alter terms and service tiers of a subscription. The usage policy application displays current data usage information on a per-network and per-application basis using subscriber profile information, subscriber session information, and prior subscriber usage history received from the usage policy server.
Owner:AMDOCS DEV LTD +1
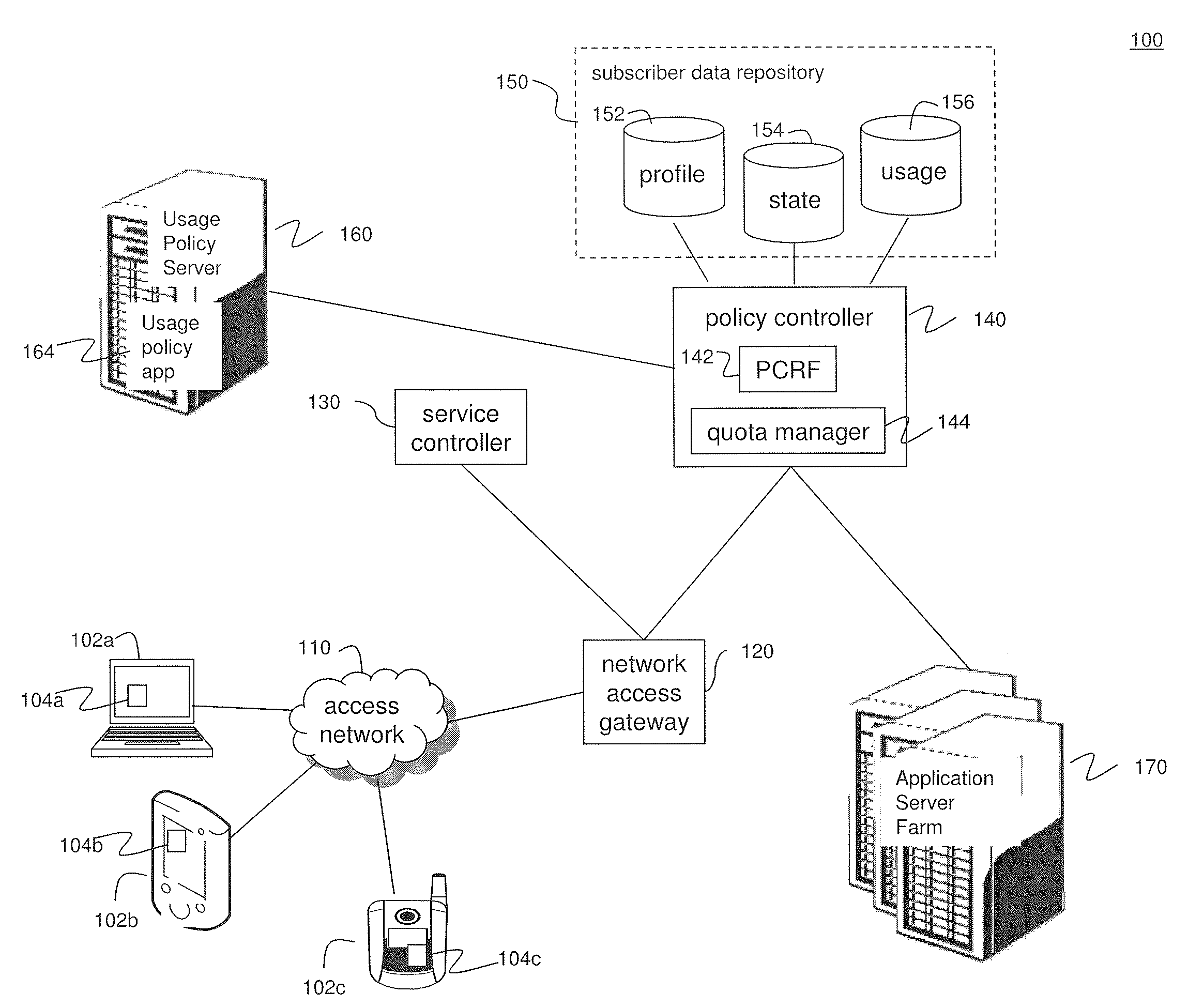
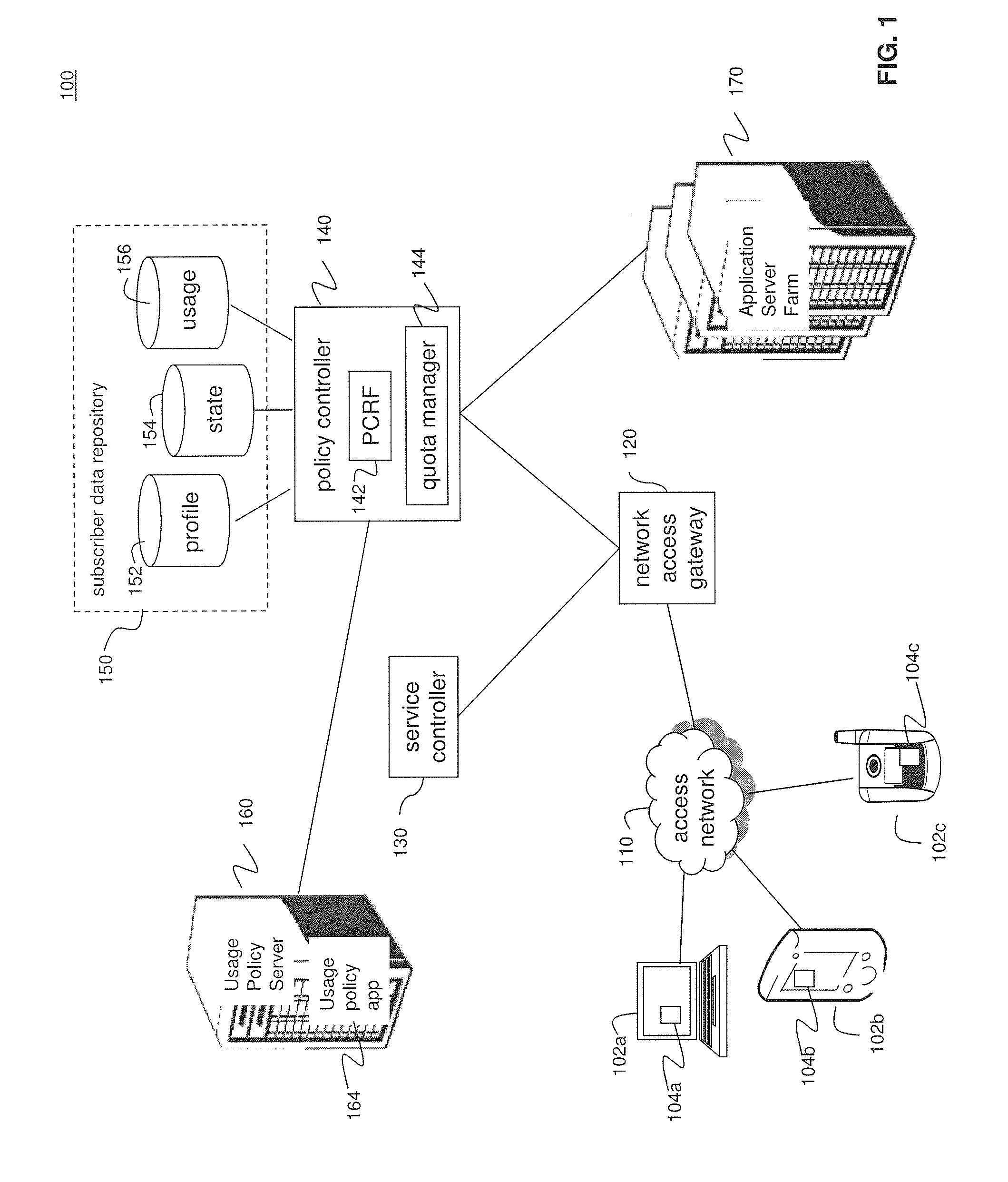
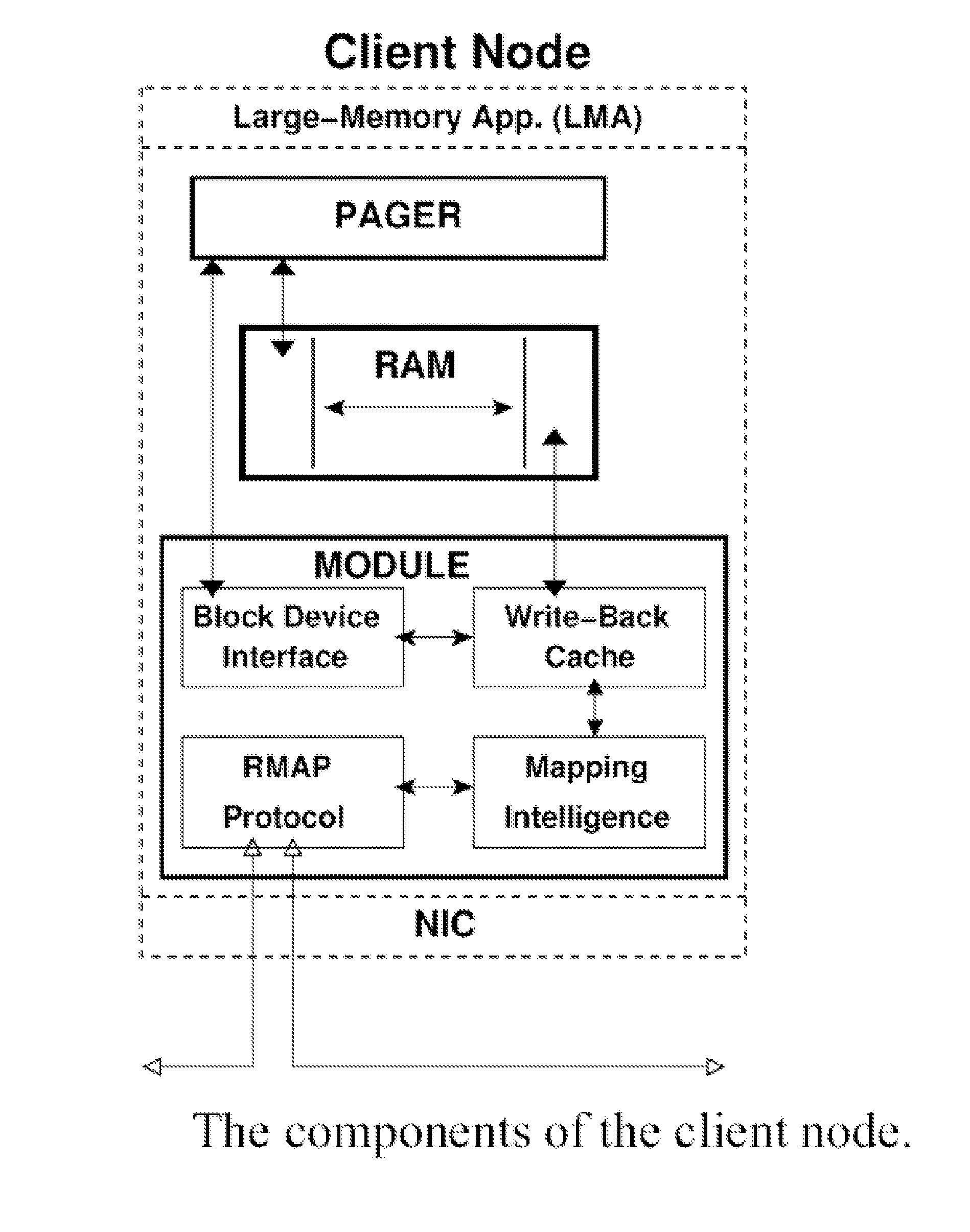
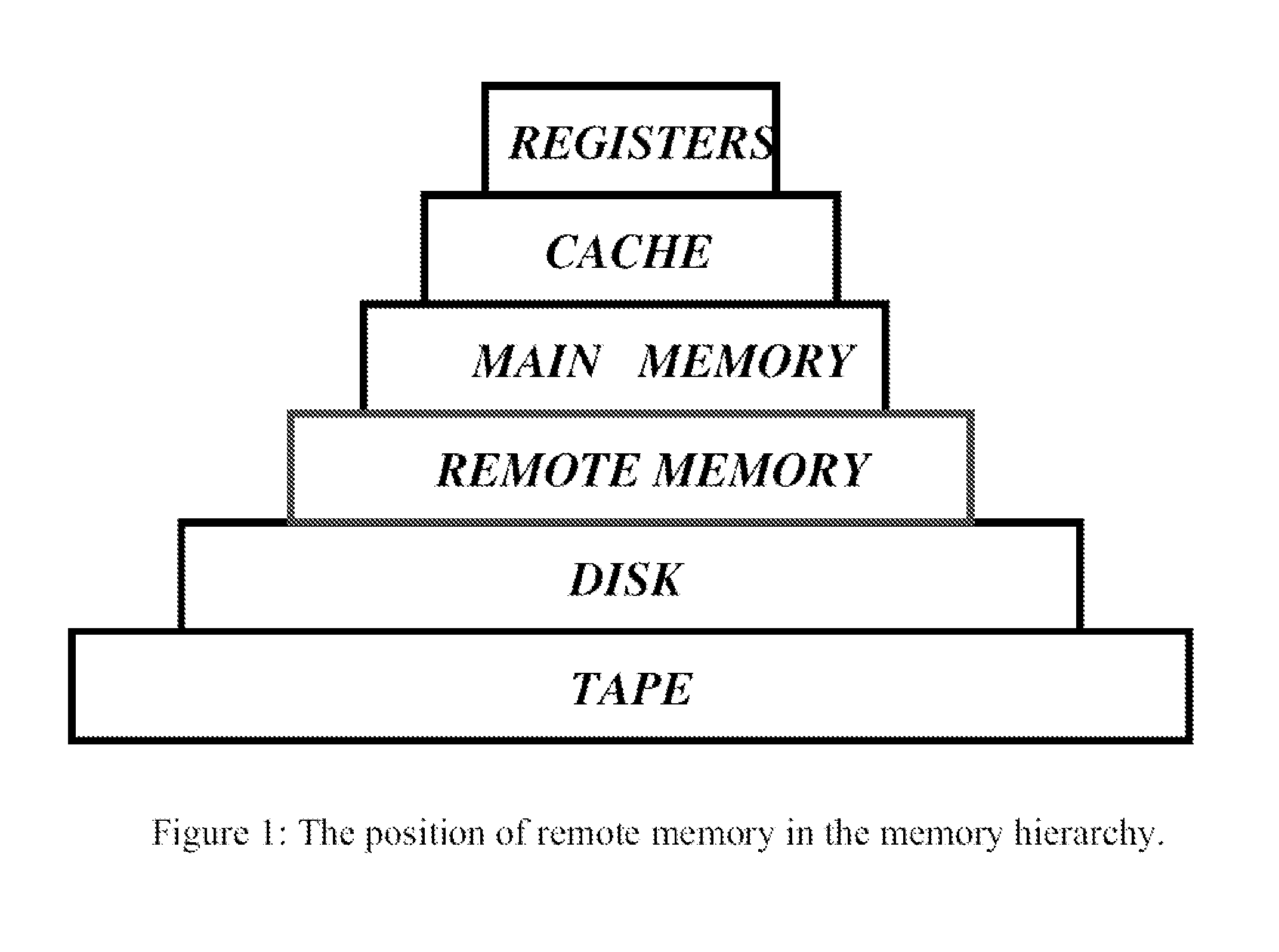
Distributed adaptive network memory engine
ActiveUS7917599B1Processing speedLower latencyMultiple digital computer combinationsTransmissionMass storageOperational system
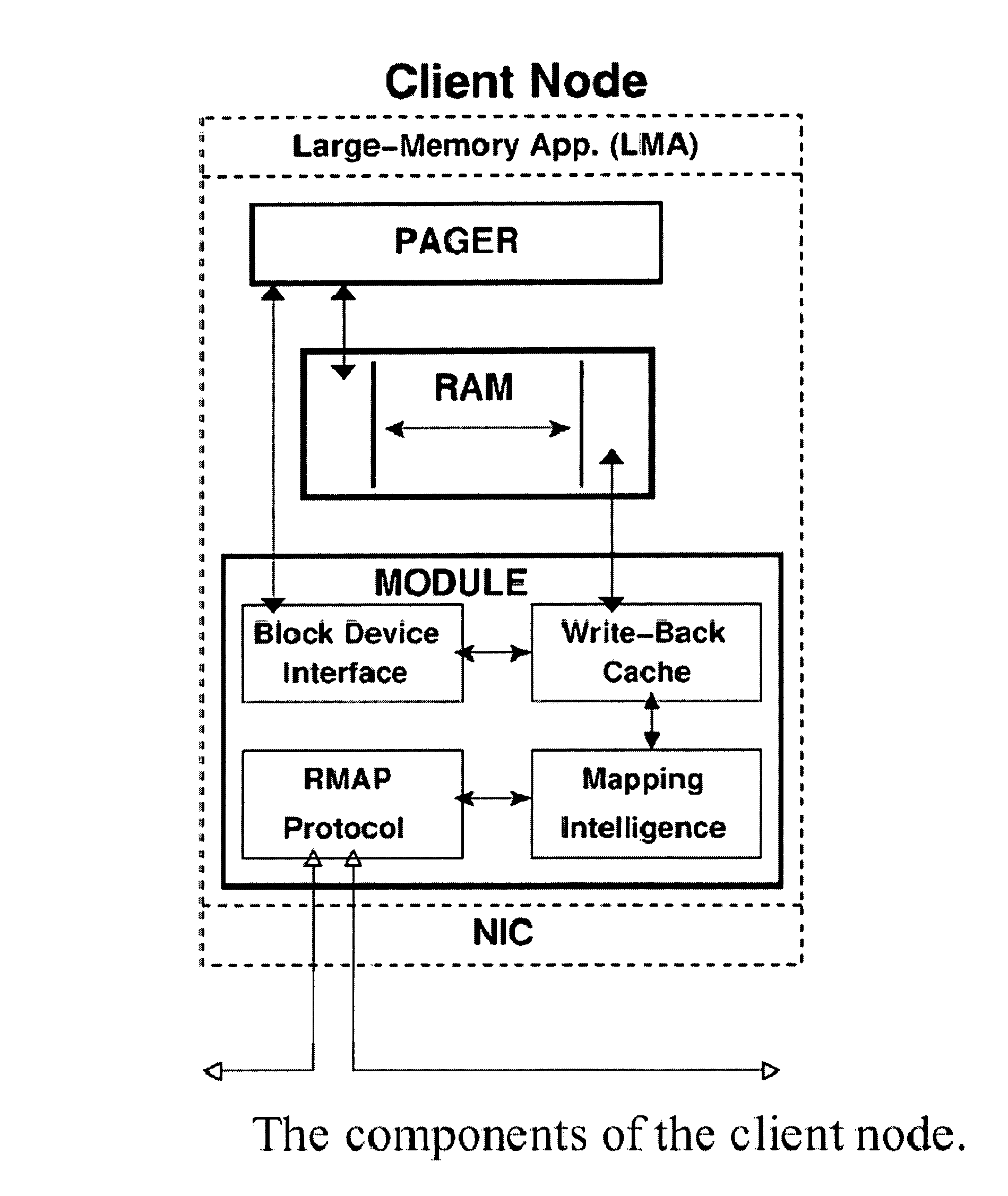
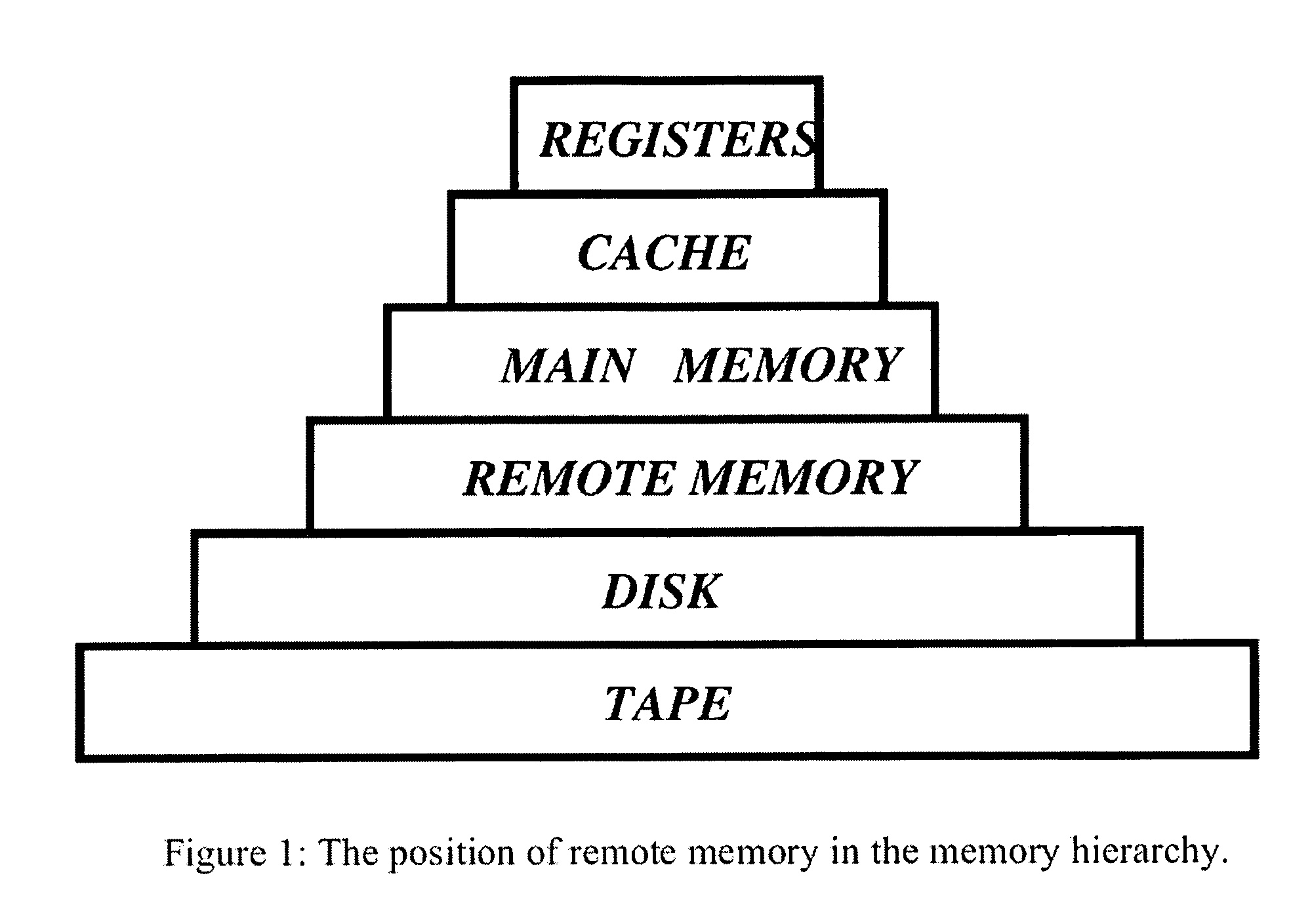
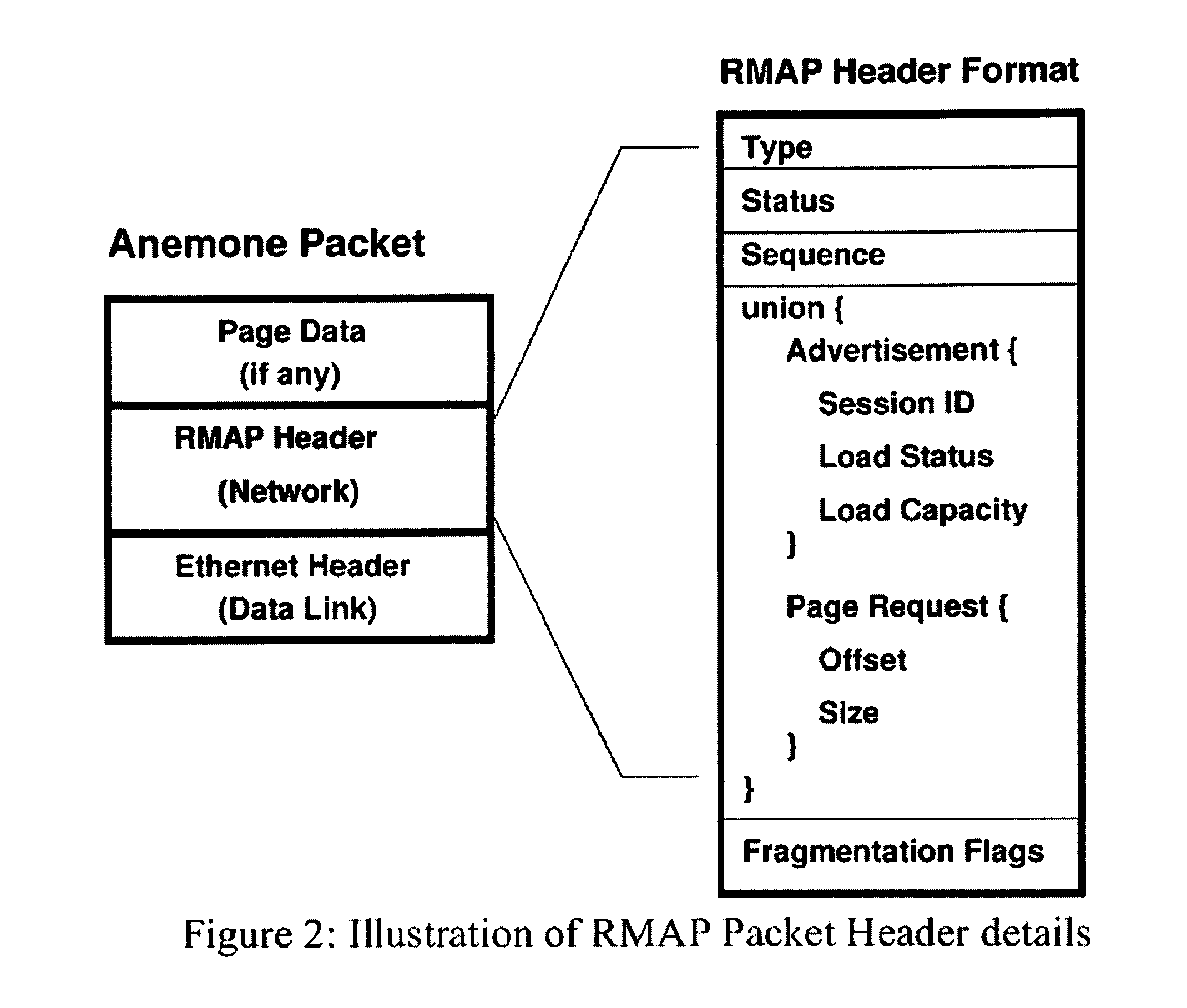
Memory demands of large-memory applications continue to remain one step ahead of the improvements in DRAM capacities of commodity systems. Performance of such applications degrades rapidly once the system hits the physical memory limit and starts paging to the local disk. A distributed network-based virtual memory scheme is provided which treats remote memory as another level in the memory hierarchy between very fast local memory and very slow local disks. Performance over gigabit Ethernet shows significant performance gains over local disk. Large memory applications may access potentially unlimited network memory resources without requiring any application or operating system code modifications, relinkling or recompilation. A preferred embodiment employs kernel-level driver software.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
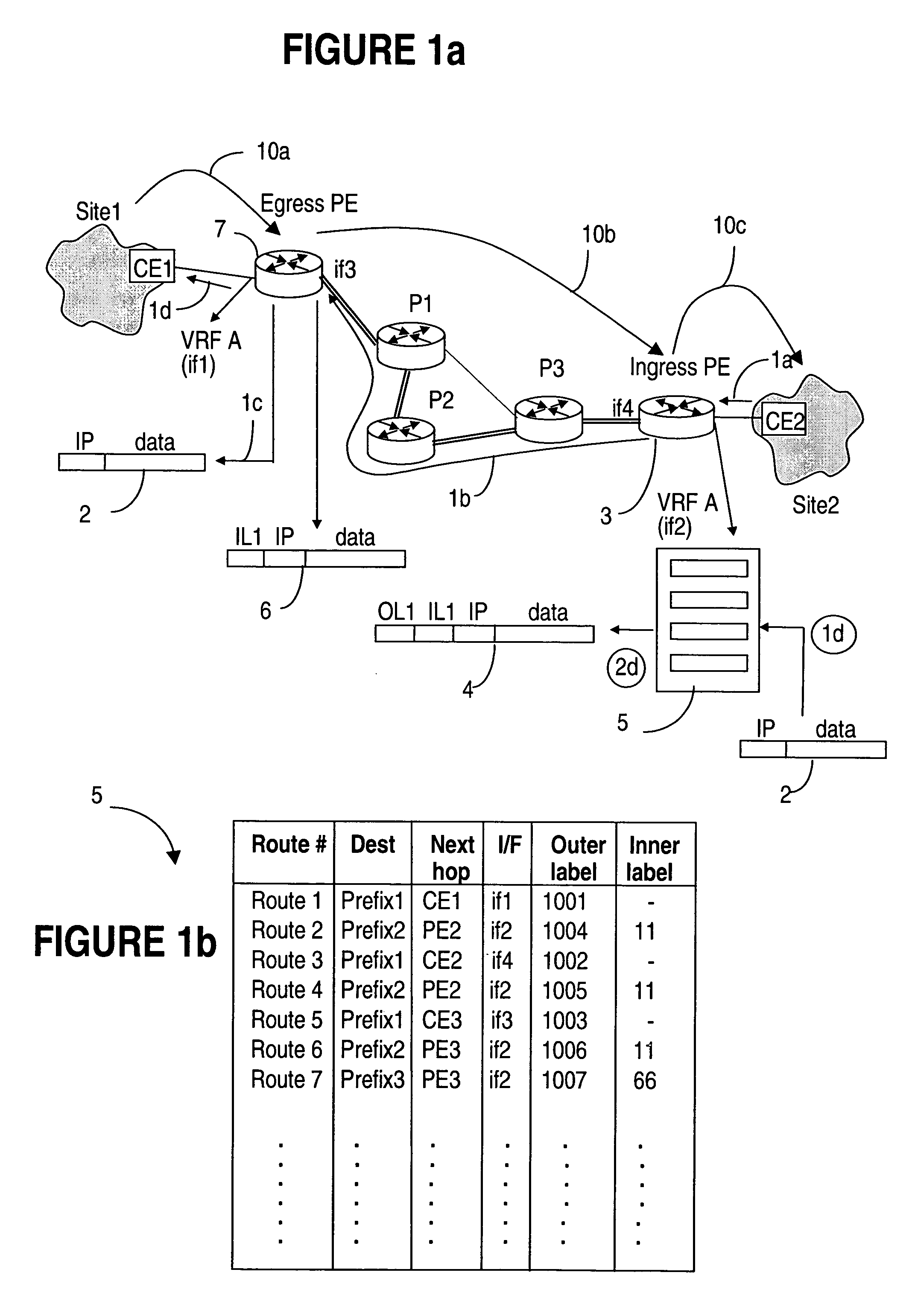
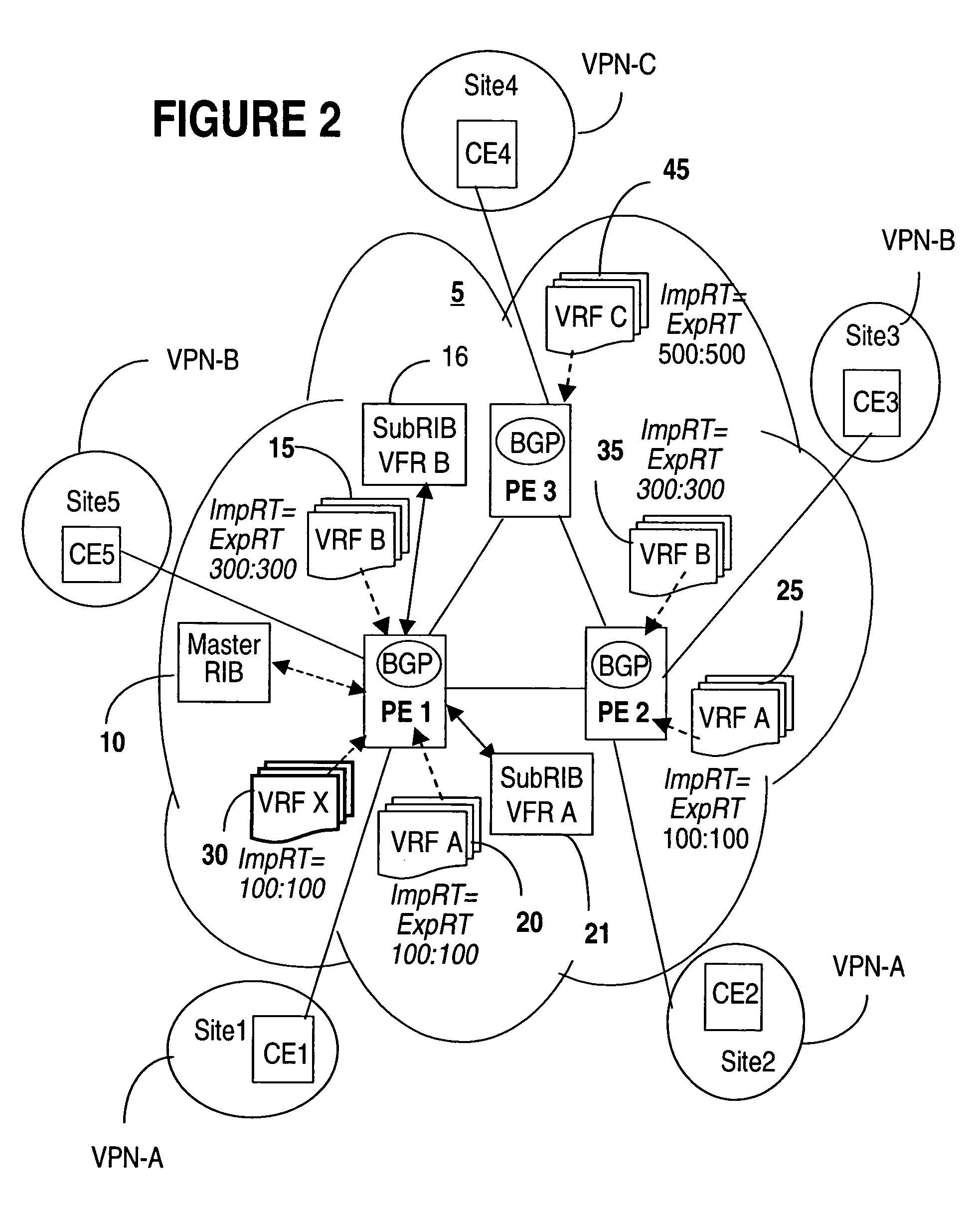
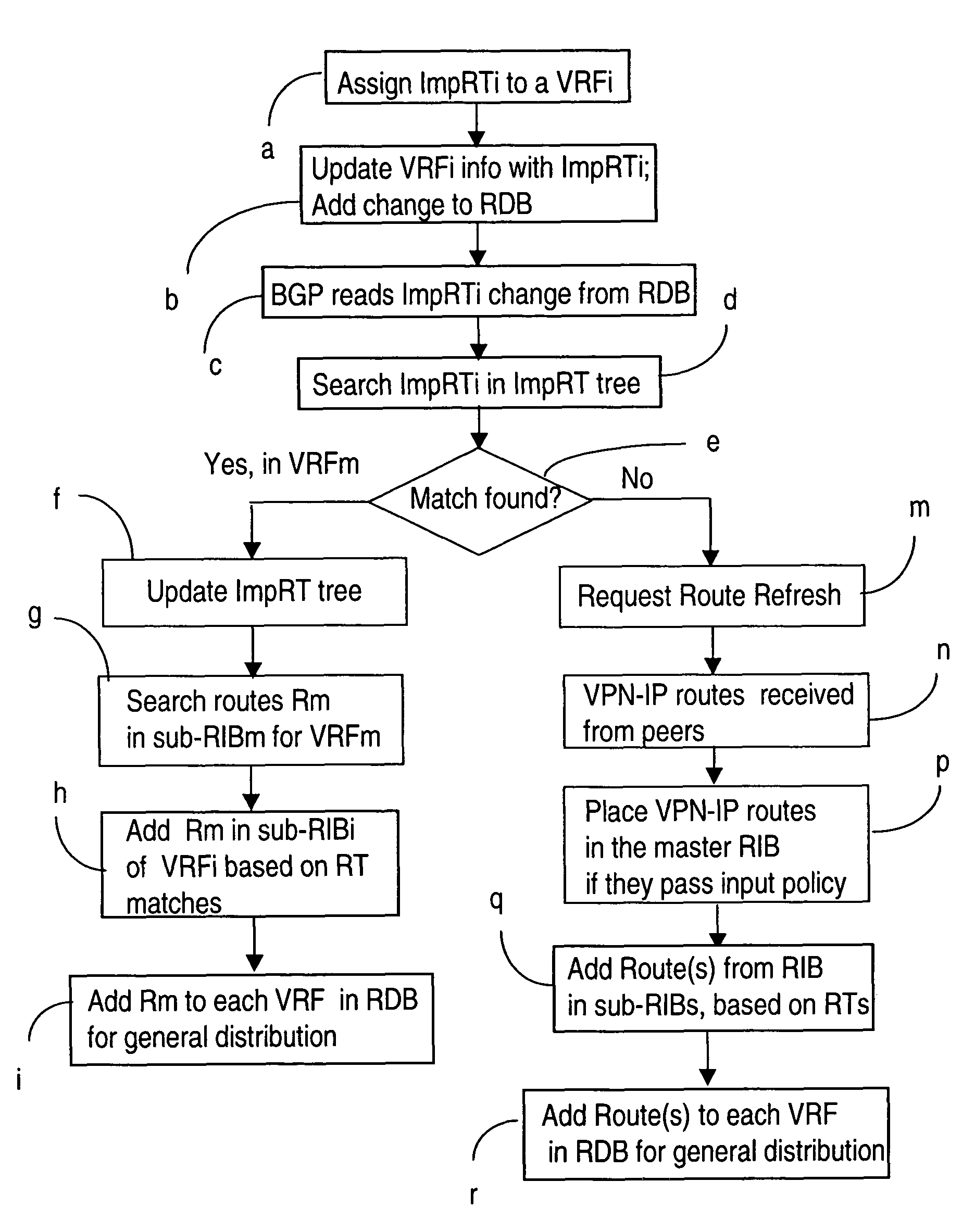
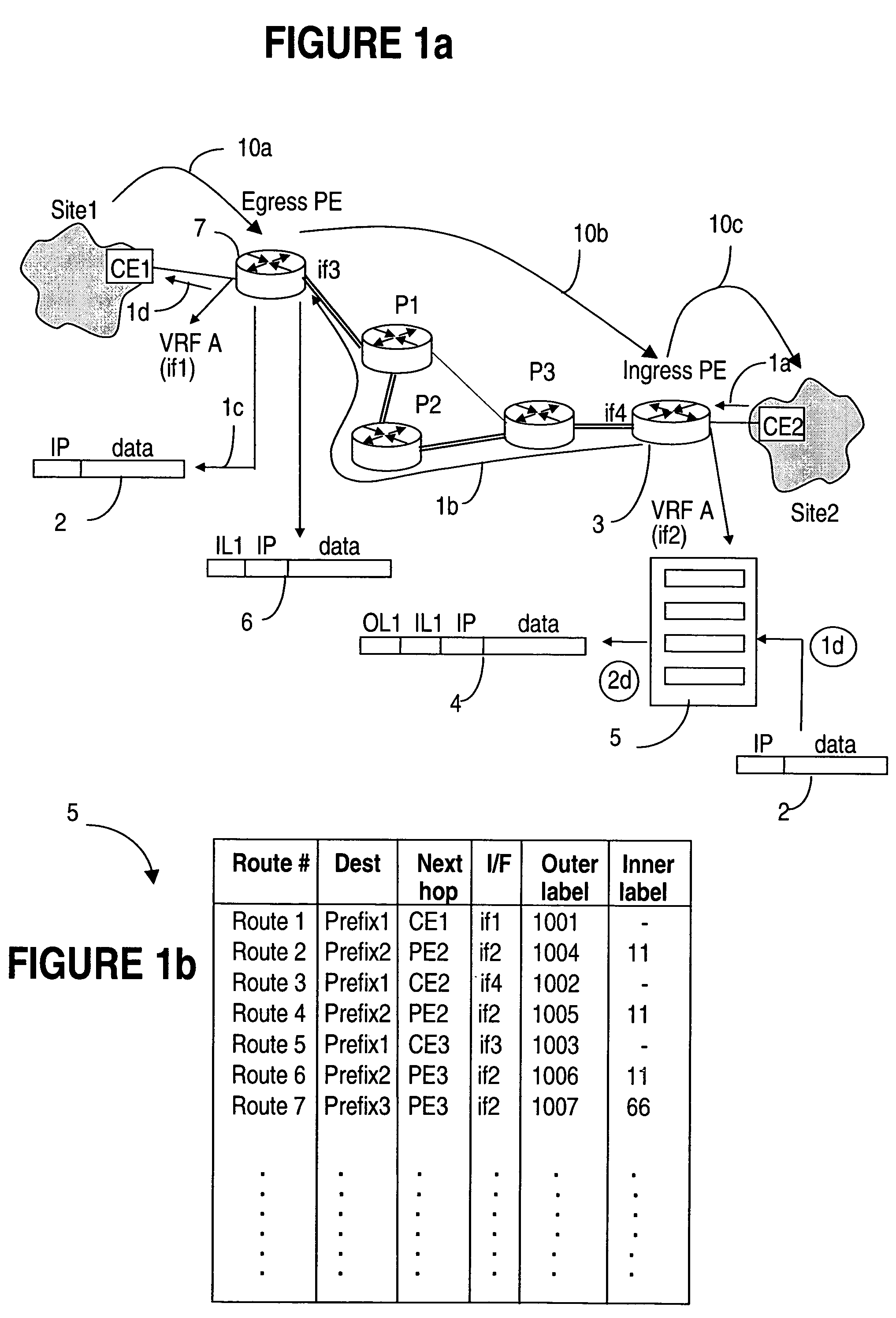
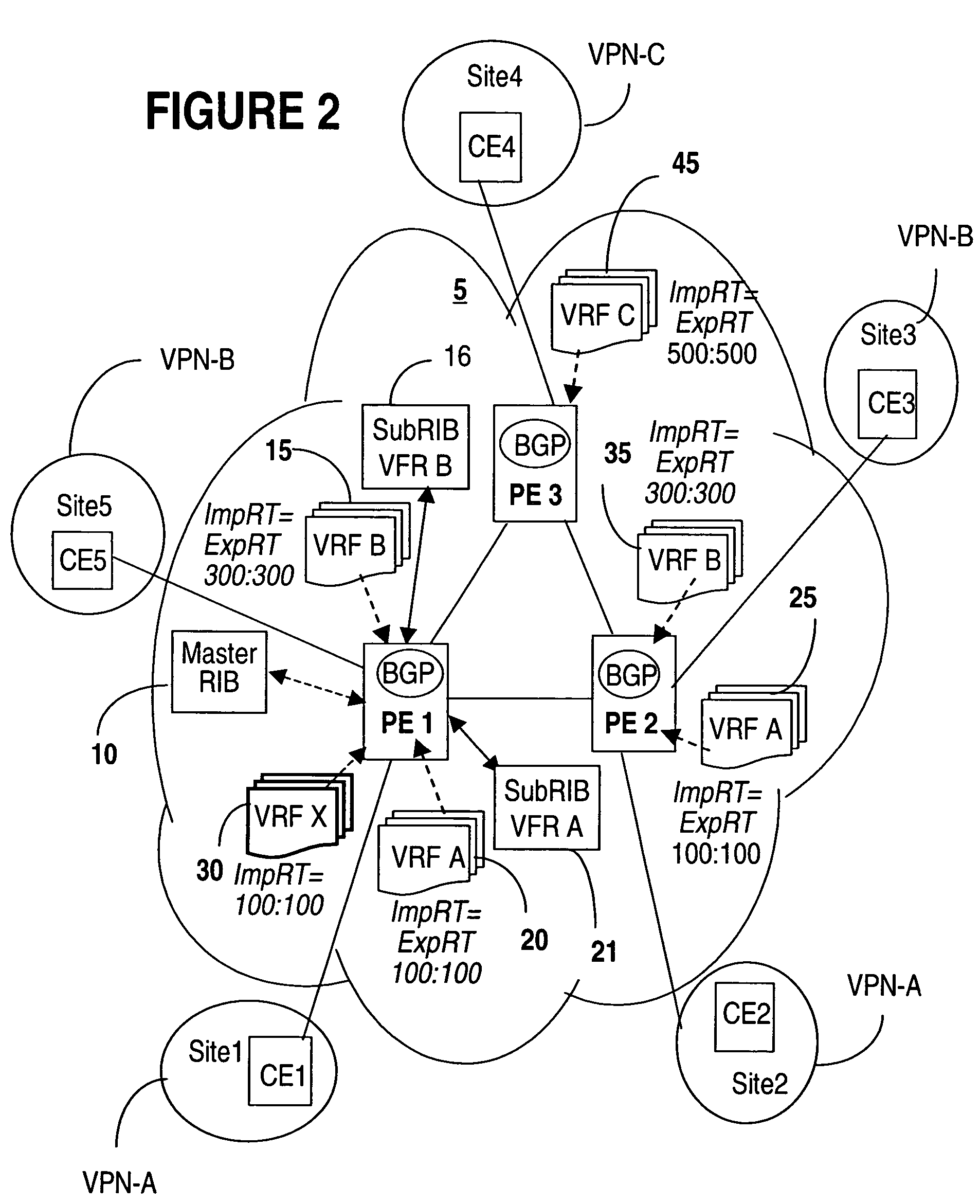
Managing L3 VPN virtual routing tables
InactiveUS20050188106A1Efficiently setupEffective maintenanceDigital computer detailsNetworks interconnectionRouting tablePrivate network
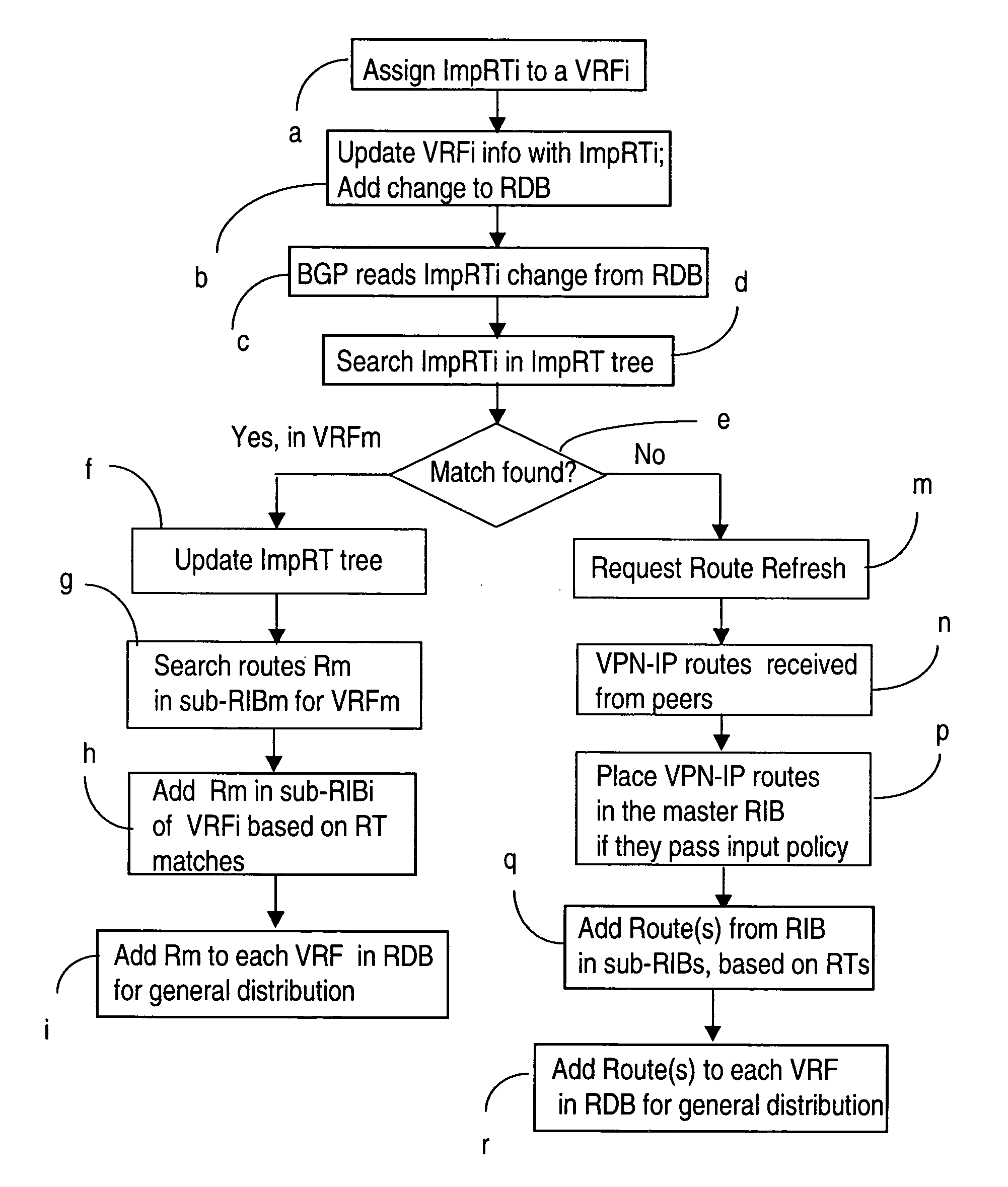
A method of managing virtual routing forwarding (VRF) tables at a provider edge PE router of a L3 virtual private network (VPN) is provided. An import route target (ImpRT) tree is maintained at the PE router, which keeps the association between all ImpRT attributes currently configured on said PE router and the virtual routing table VRF at that router. When an ImpRT attribute is configured on a VRF table, the PE router first searches the tree to identify a local VRF table that contains a route(s) with that ImpRT attribute. If this information is available locally, the VRF is updated by copying the route information, and there is no need to do a route refresh. When an ImpRT is deleted from a VRF, a route refresh is avoided by parsing all the routes in the VRF and removing the routes that no longer have a matching route target. In an alternative implementation, the local source is the master RIB (routing information base) which includes all routes in all VRFs at the router, and optionally even rejected routes that were filtered out using ImpRTs. In this variant, even routes associated with ImpRTs that are new to the router would be available to update the VRF without requiring a route refresh.
Owner:WSOU INVESTMENTS LLC
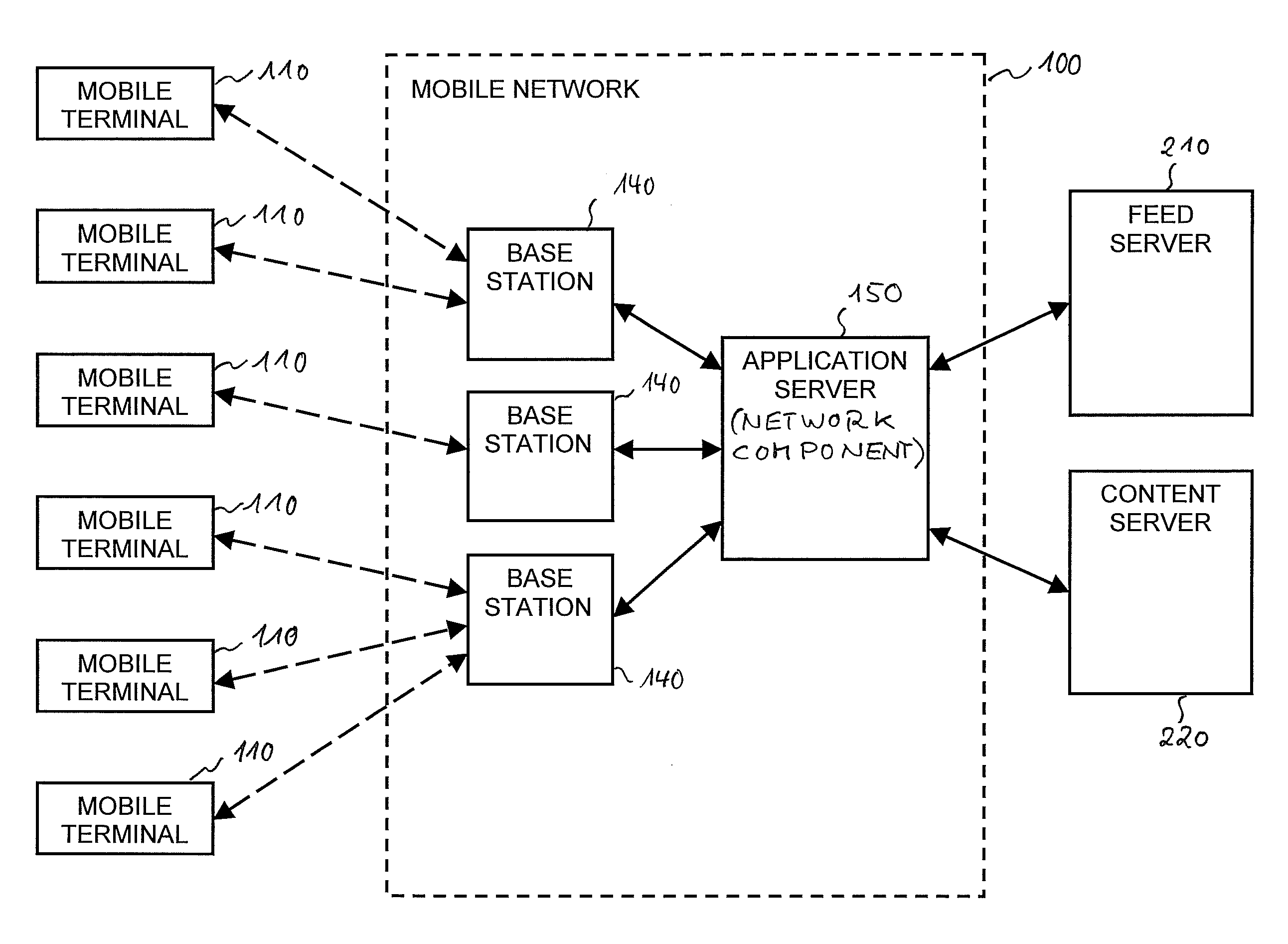
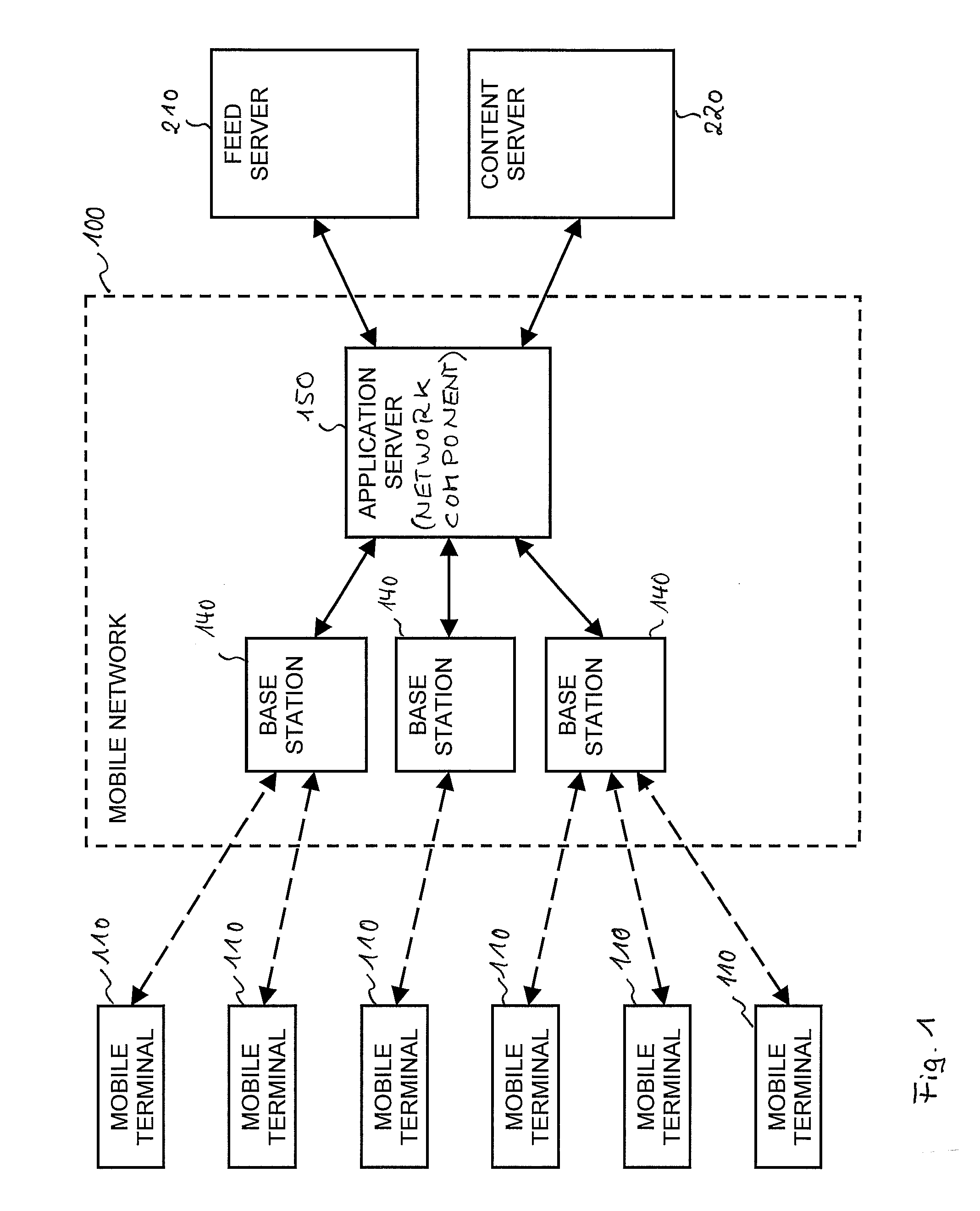
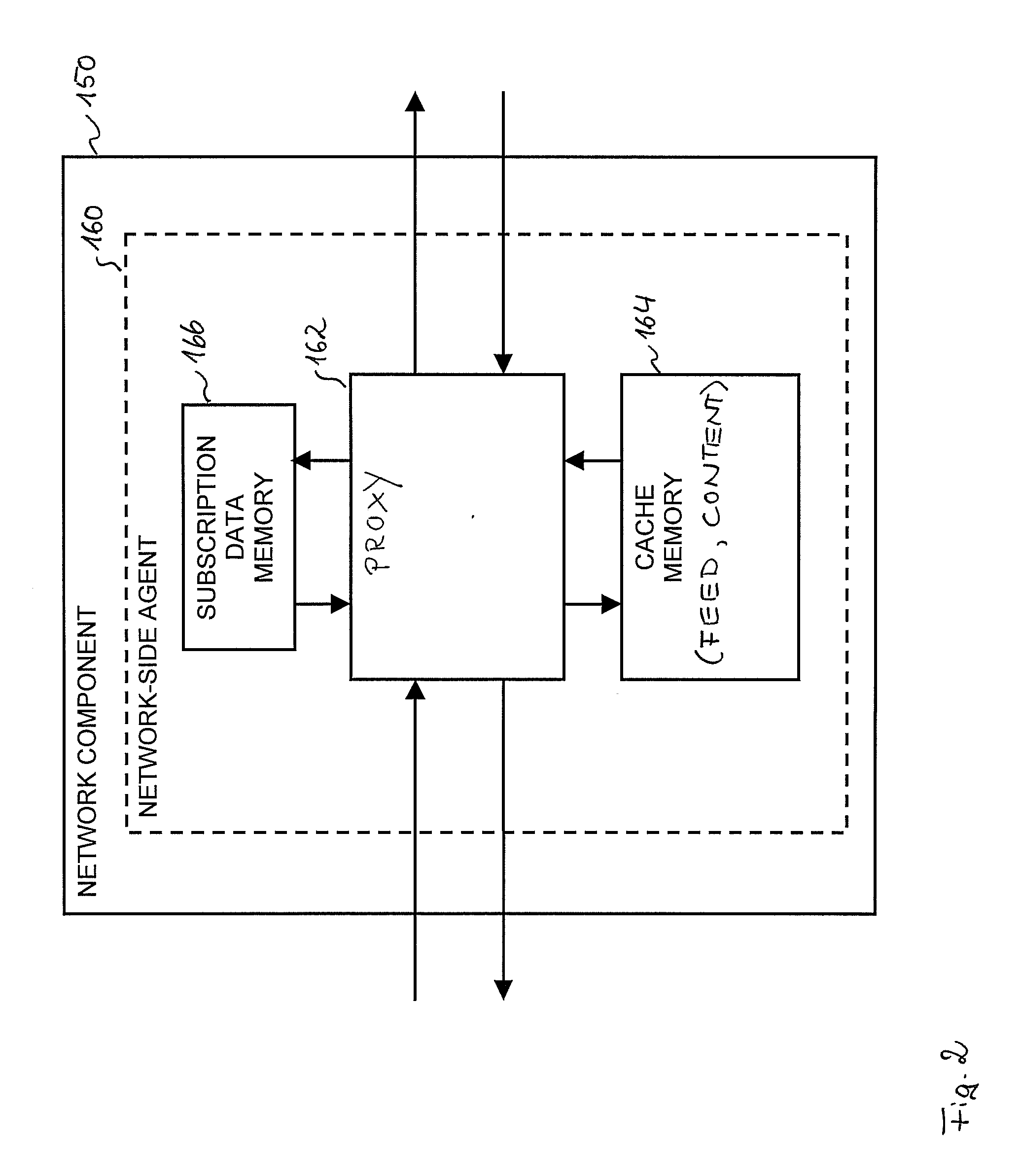
Techniques for Feed-Based Automatic Transmission of Content to a Mobile Terminal
ActiveUS20110066715A1Reduce bandwidth consumptionImprove bandwidth usageDigital computer detailsTransmissionAutomatic transmissionMobile Web
For improving feed-based automatic distribution of content to a mobile terminal via a mobile network, a network component (150) comprises a network-side agent (160). The network-side agent (160) manages the feed-based automatic transmission of content to the mobile terminal and is configured to periodically generate a feed request to a feed server, to receive a requested feed from the feed server in response to the feed request, and to transmit the received feed to the mobile terminal. The network component (150) may also comprise a cache memory (164) for storing copies of feeds and contents and a proxy for processing feed requests and content requests received from the mobile terminal (110).
Owner:TELEFON AB LM ERICSSON (PUBL)
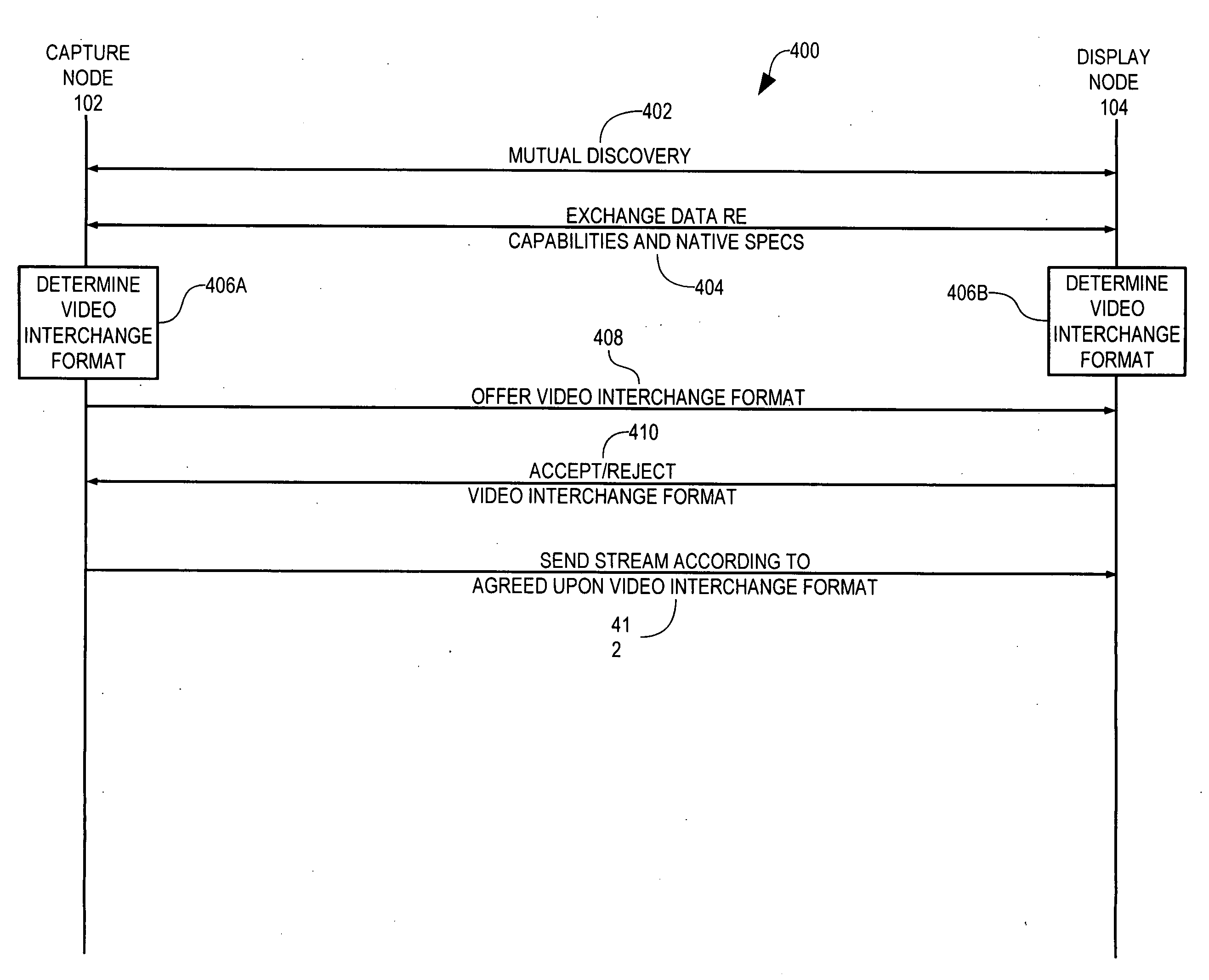
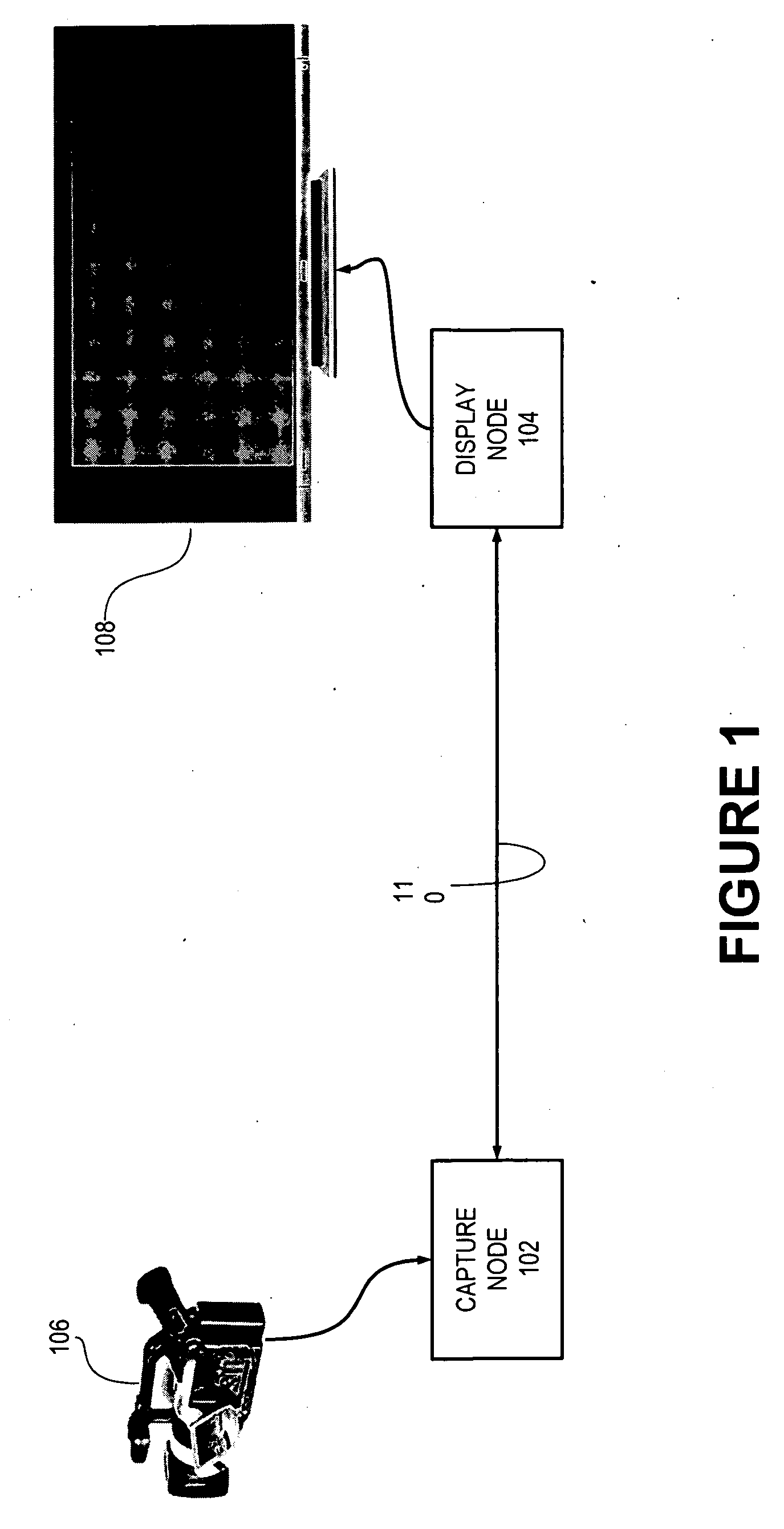
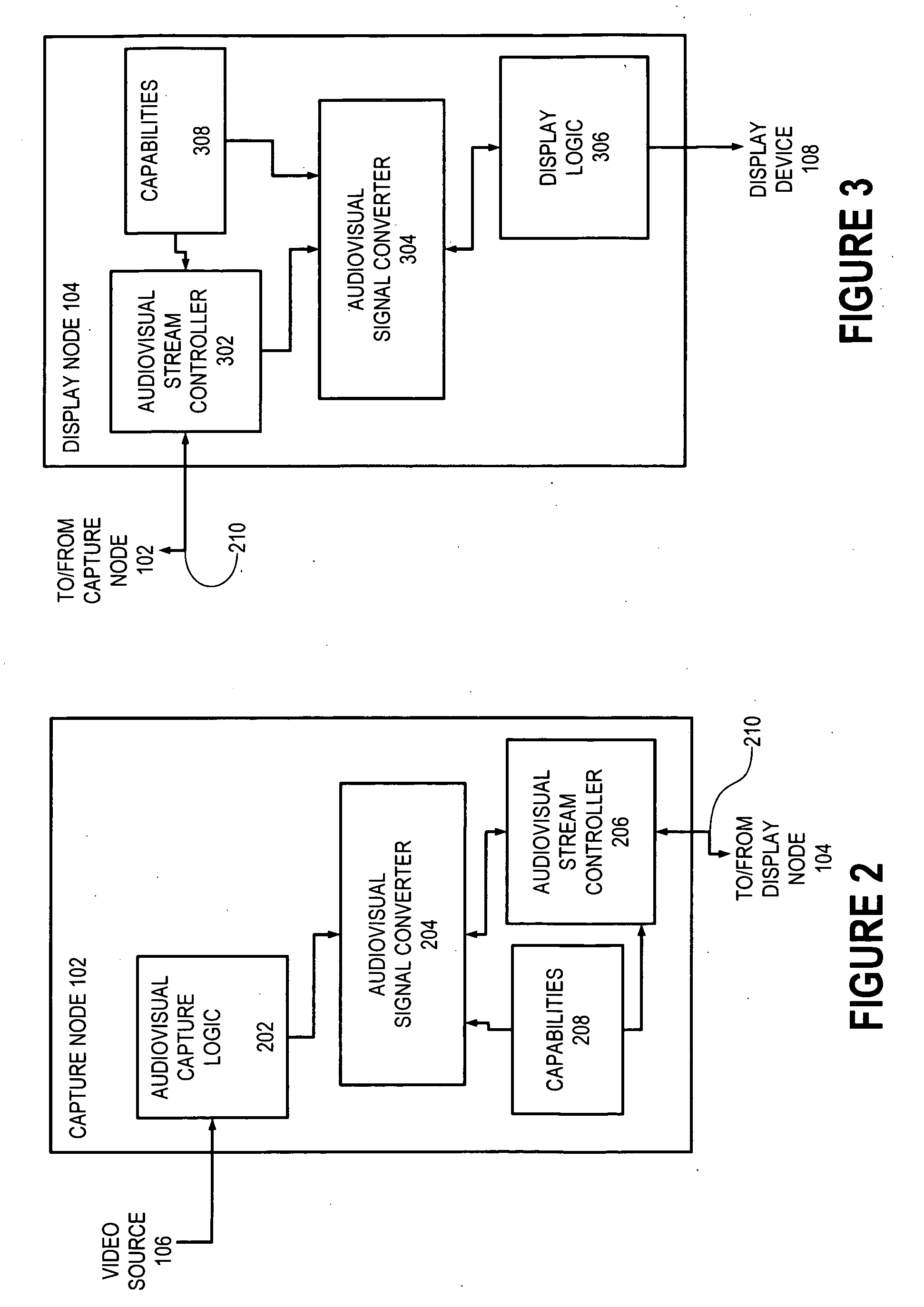
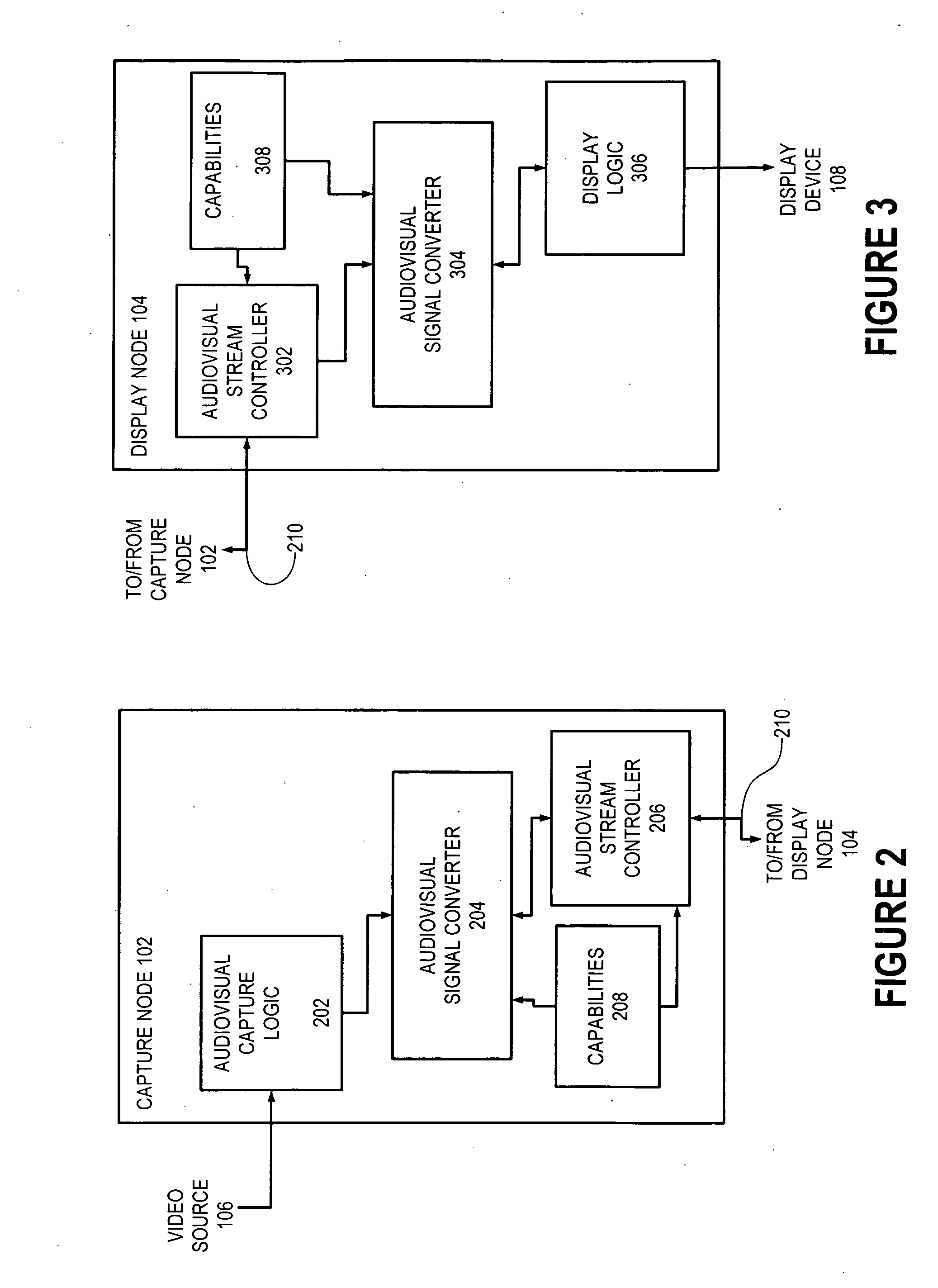
Display node for use in an audiovisual signal routing and distribution system
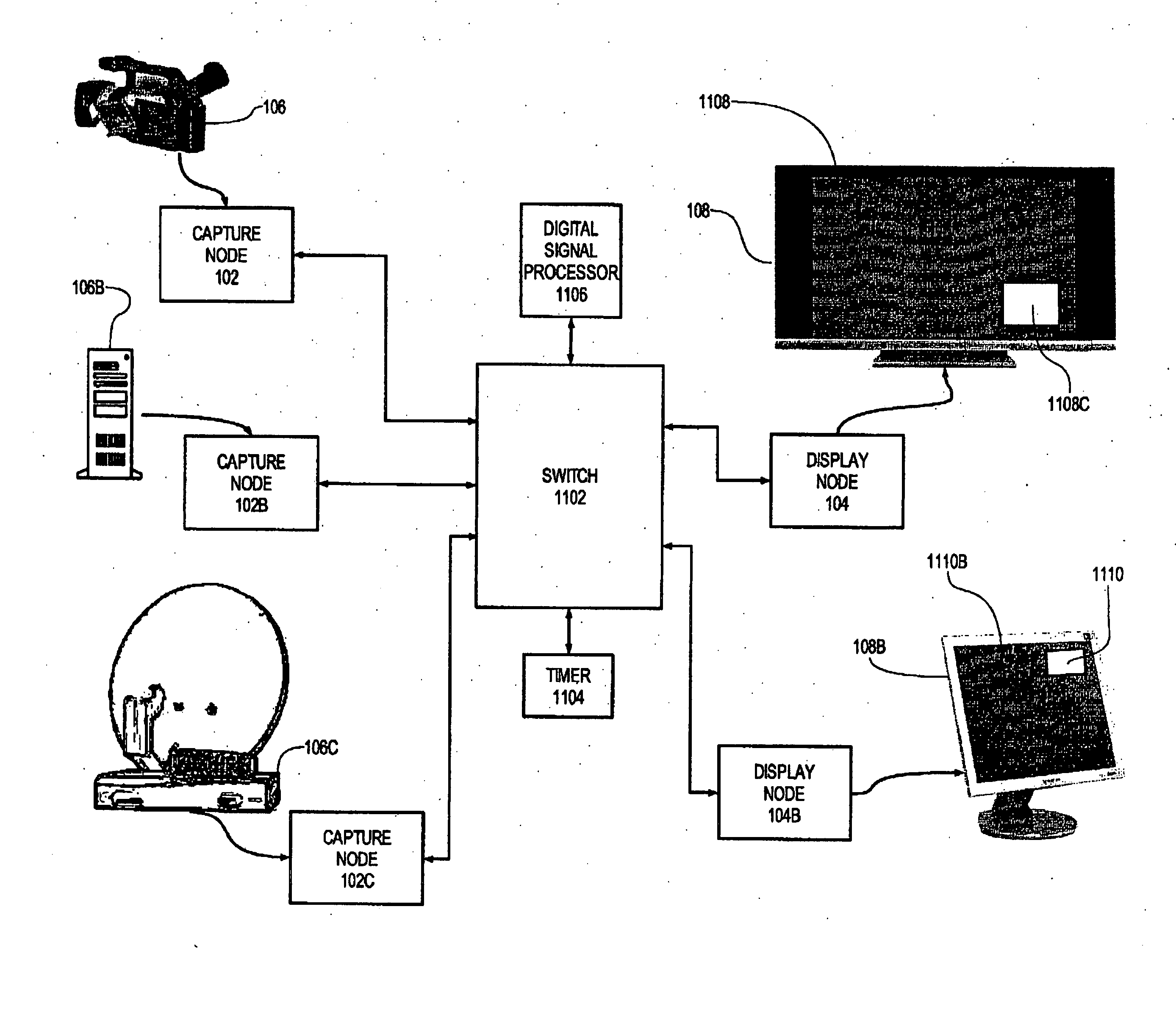
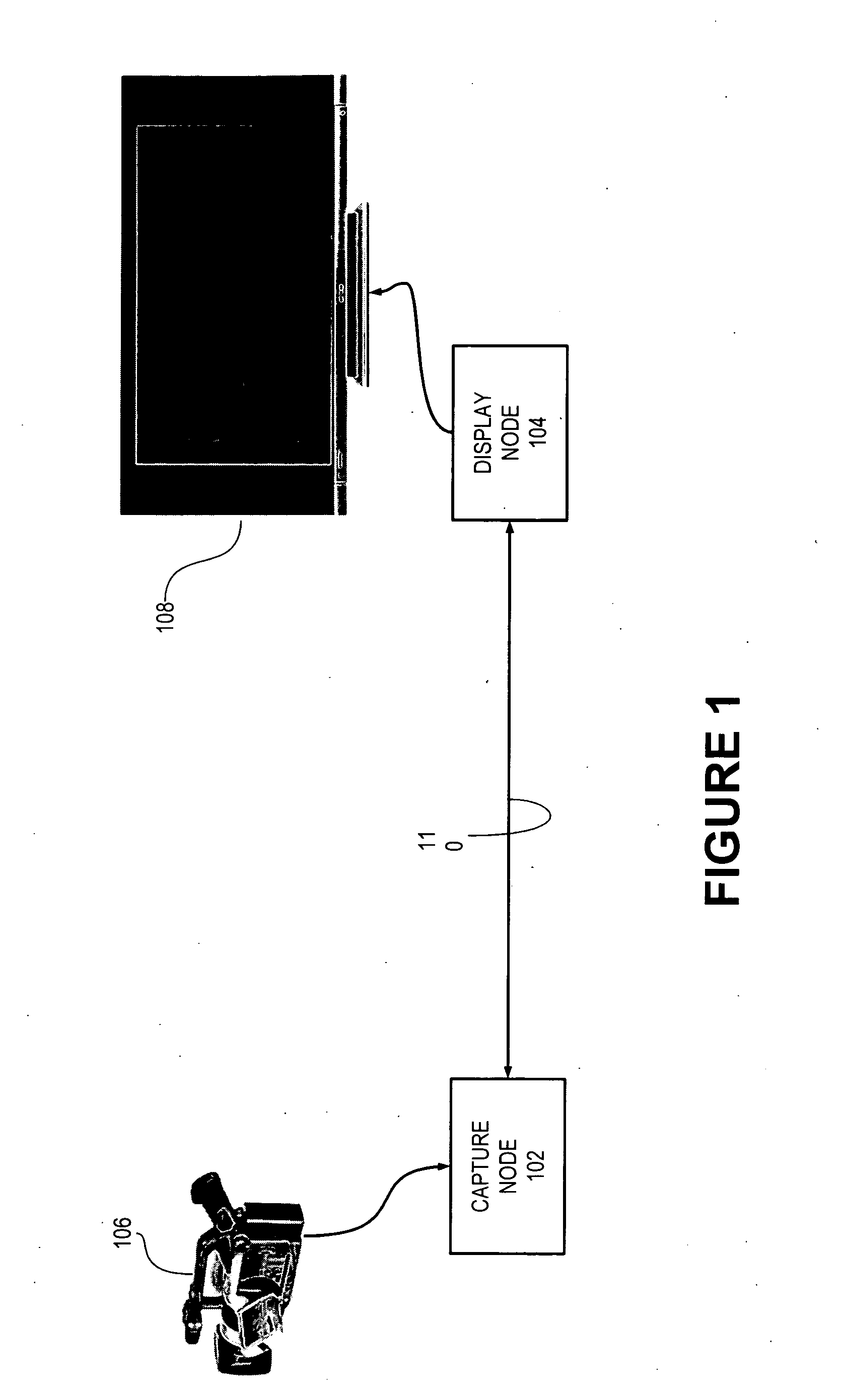
InactiveUS20060242669A1Exceeding bandwidthMinimize excessive use of bandwidthTelevision system detailsAnalogue secracy/subscription systemsSignal routingComputer network
An audiovisual signal is converted from a native format to a digital, packetized interchange format and transported between a capture node and a display node through a switch. The display node converts the audiovisual signal from the interchange format to a displayable format and causes display of the audiovisual signal. The use of a switch for video routing and distribution allows one-to-one, one-to-many, many-to-one, and many-to-many distribution. The use of a device-independent interchange format allows concurrent distribution of multiple heterogeneous audiovisual signals.
Owner:WOGSBERG ERIC
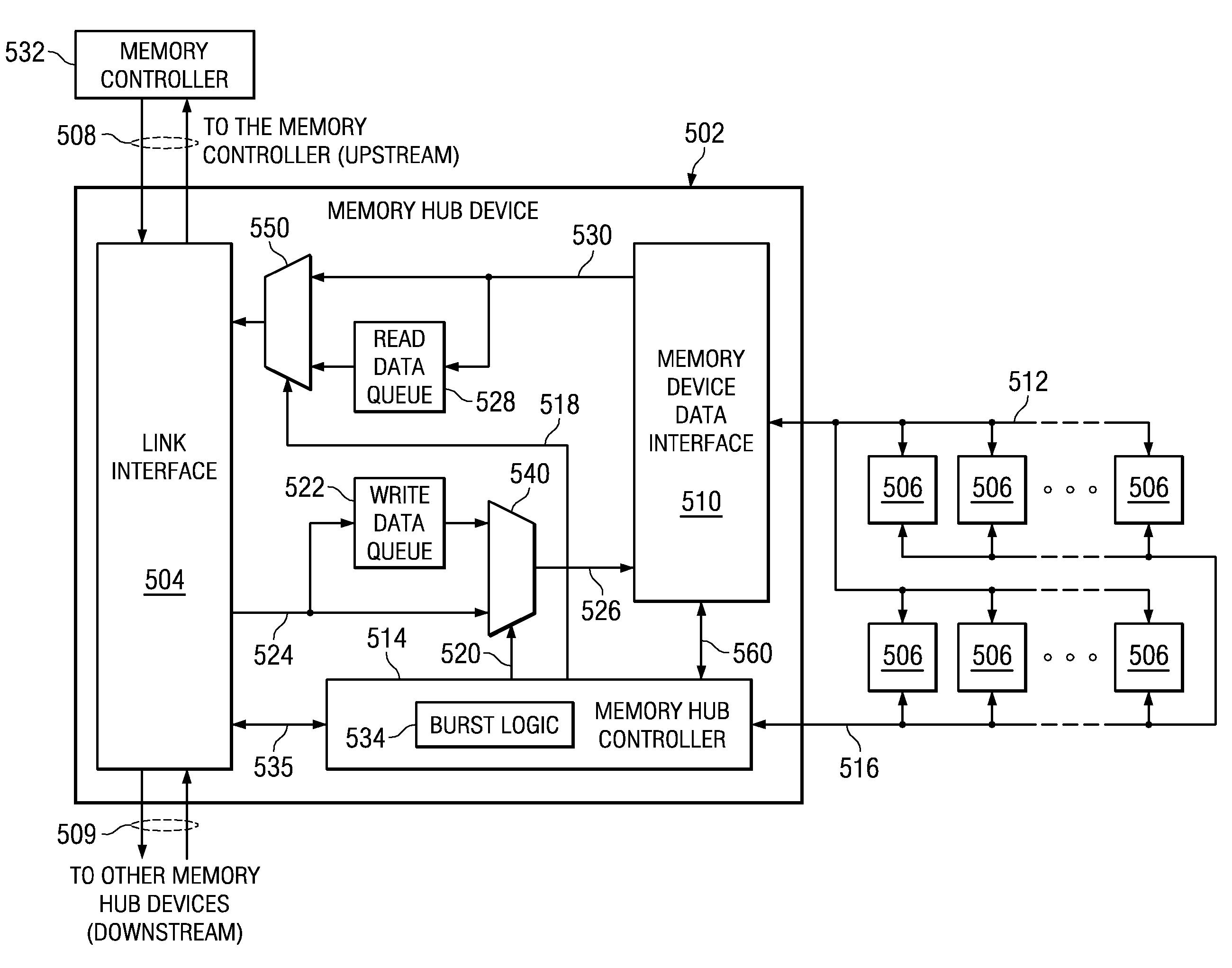
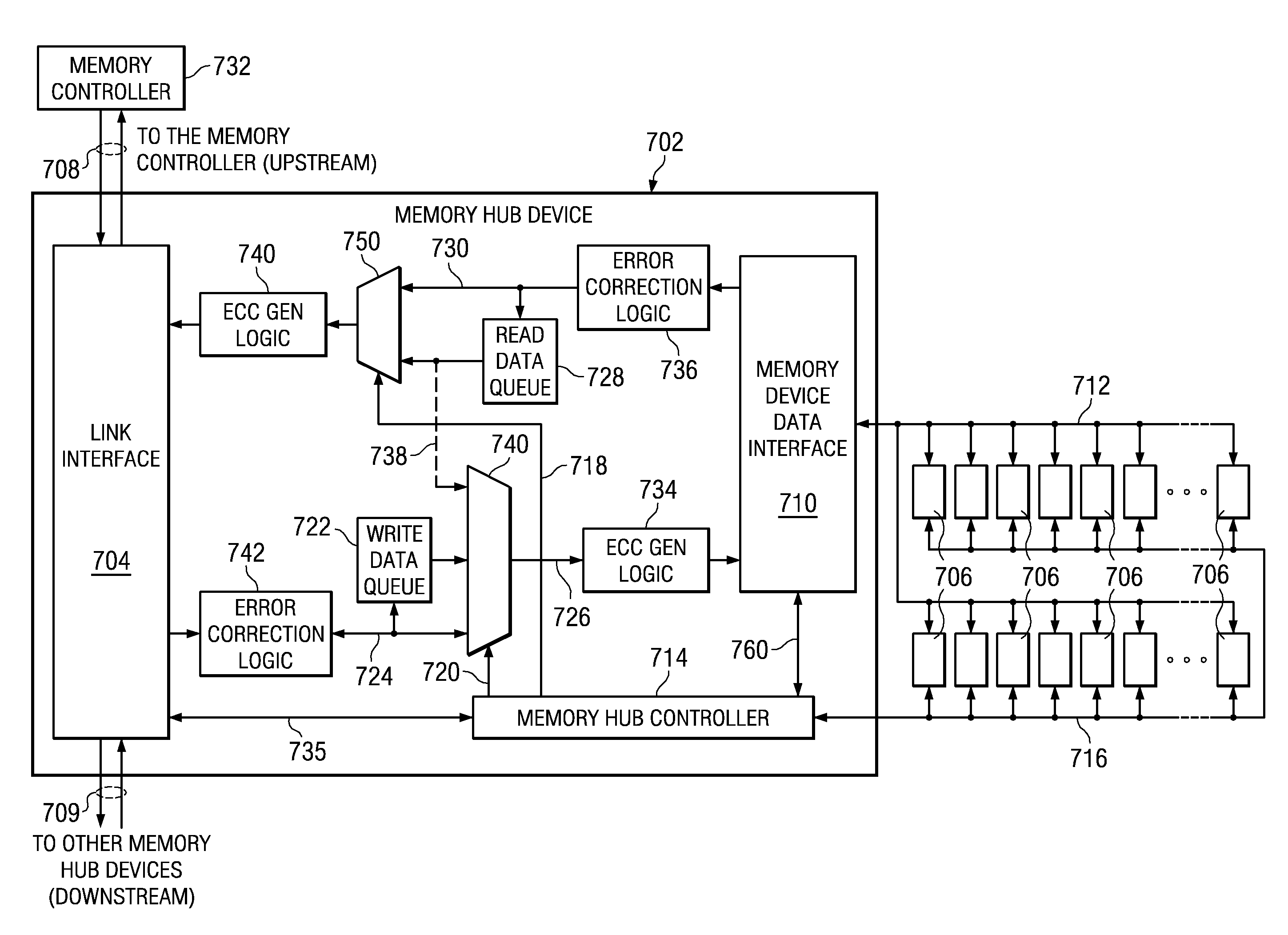
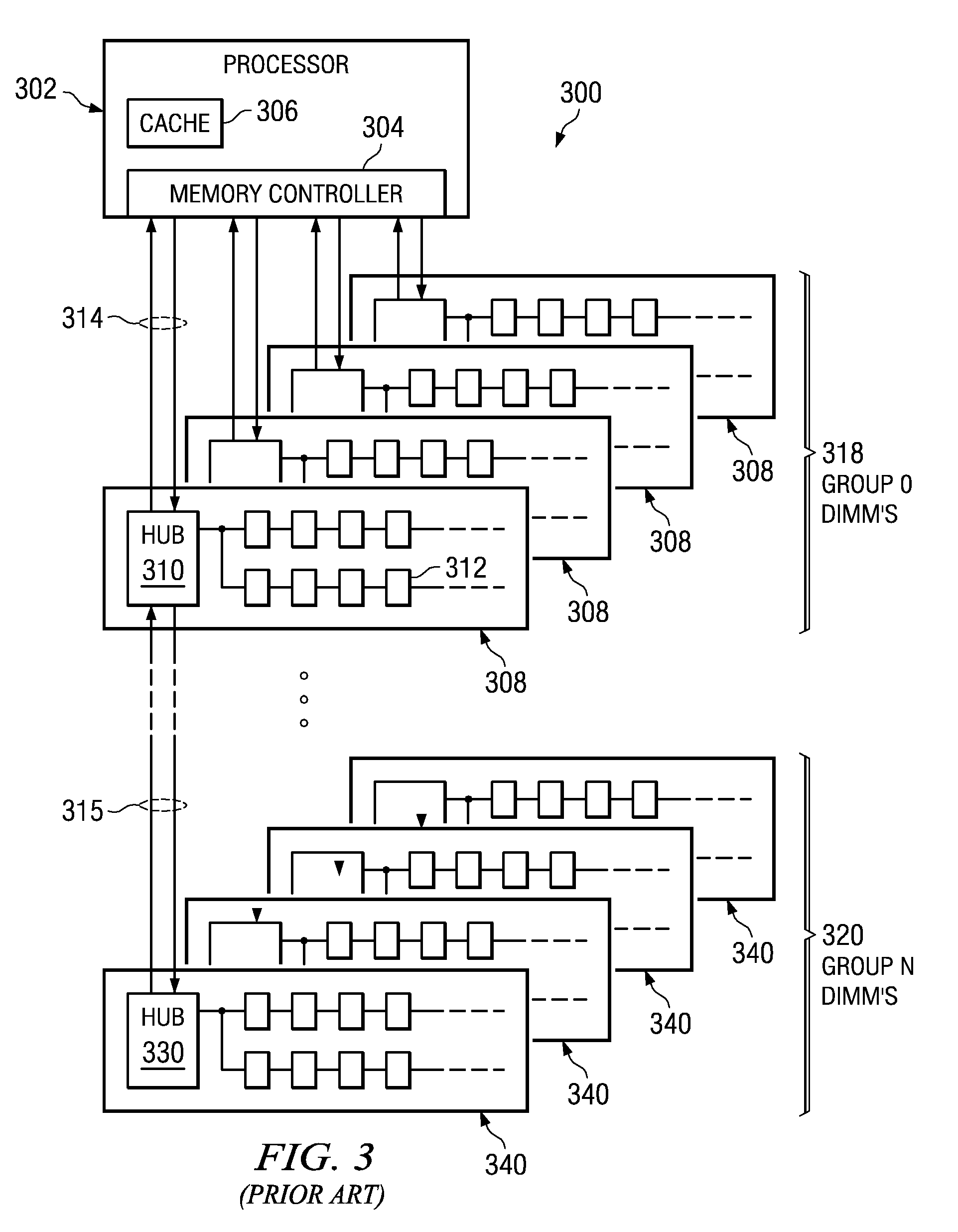
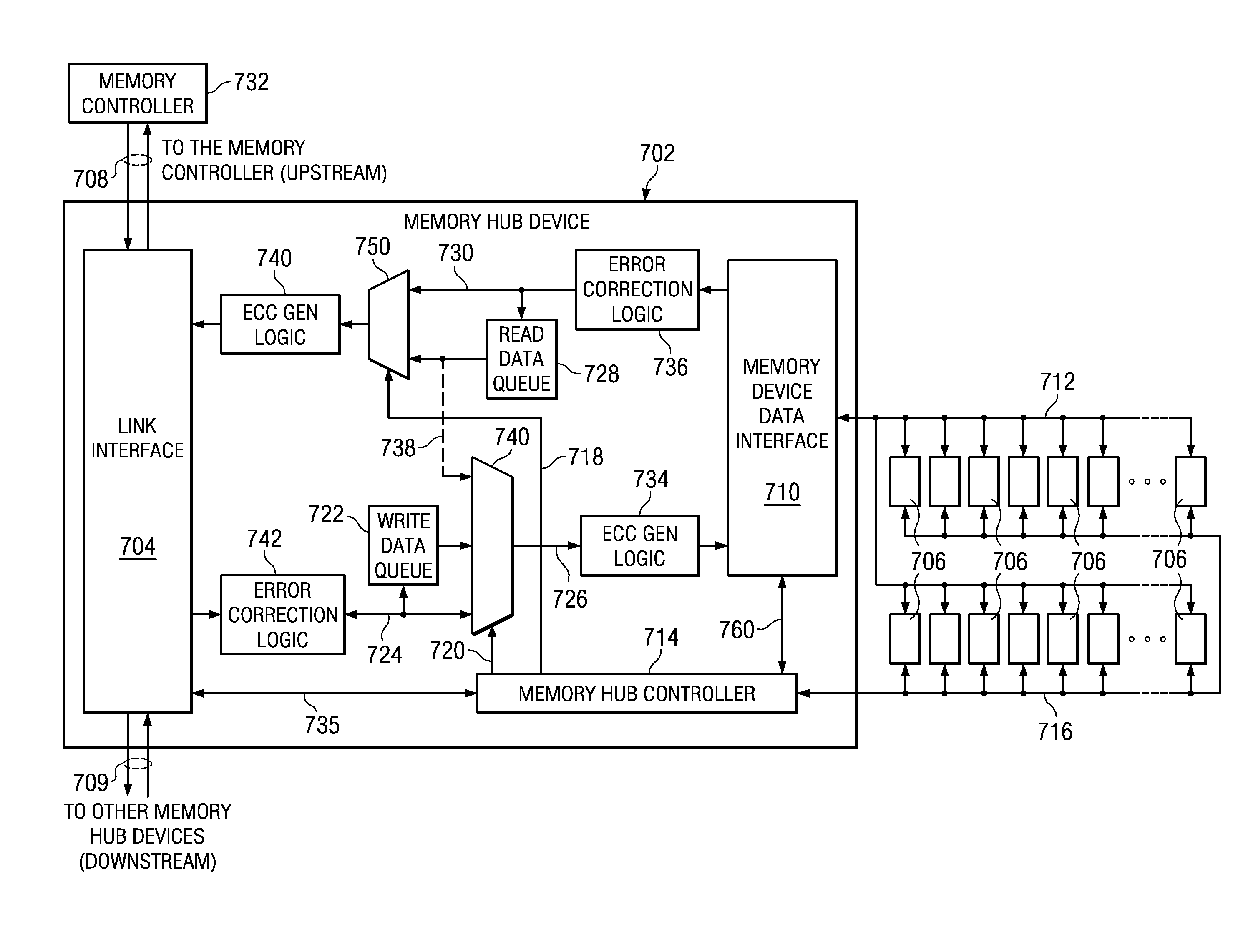
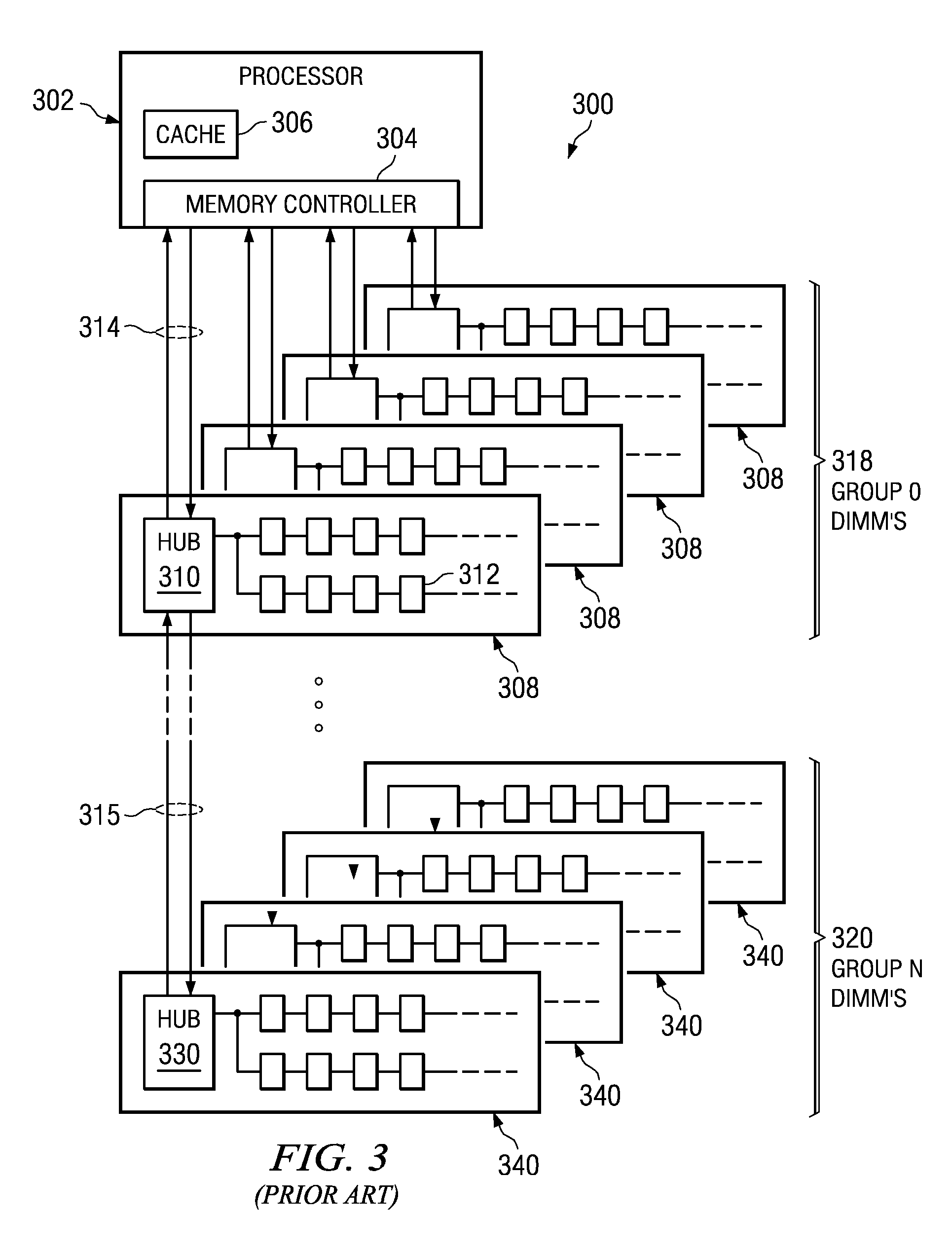
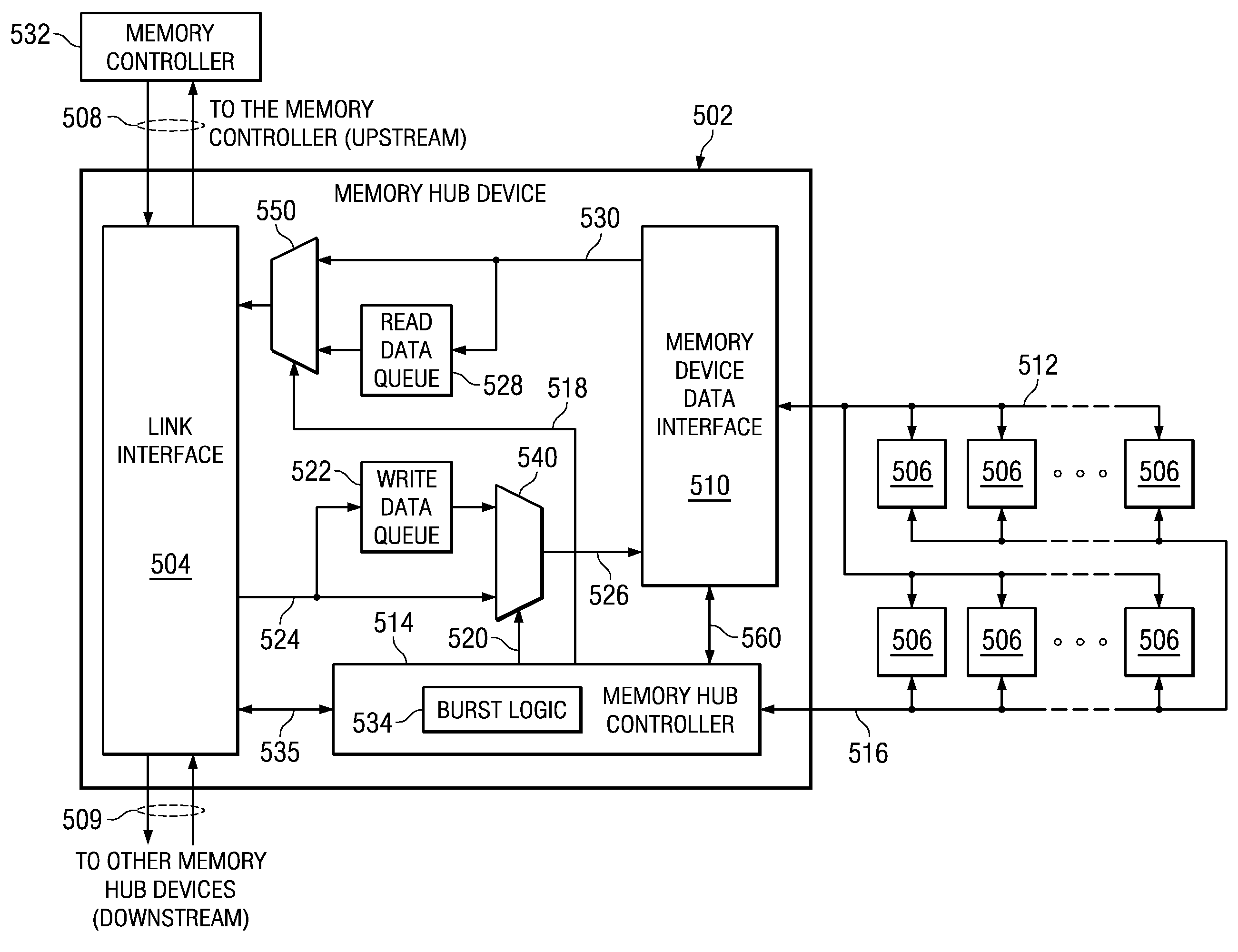
System and Method for Performing Error Correction at a Memory Device Level that is Transparent to a Memory Channel
InactiveUS20090063923A1Increased memory bandwidthReduce the amount requiredError preventionTransmission systemsExternal storageMemory controller
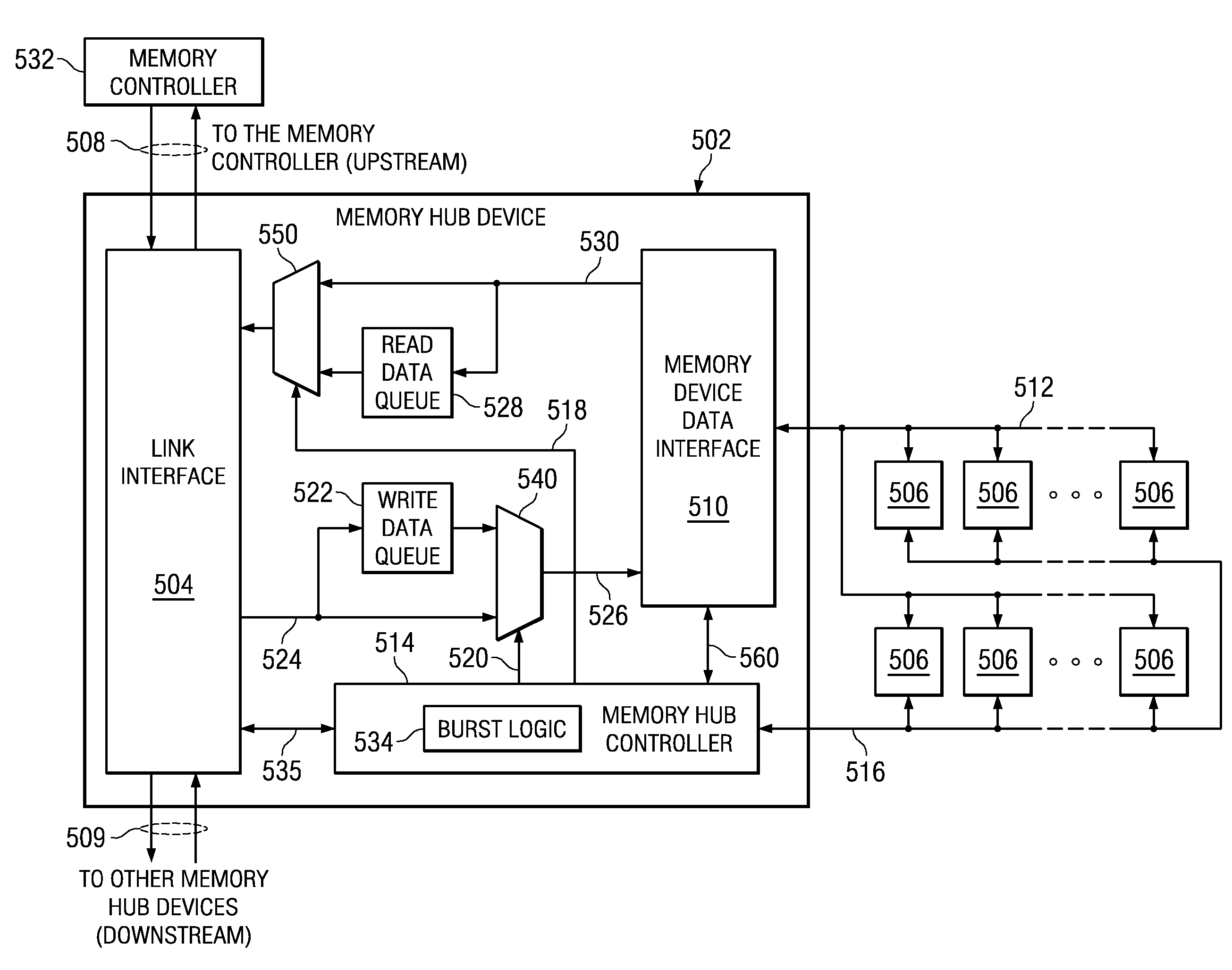
A memory system is provided that performs error correction at a memory device level that is transparent to a memory channel. The memory system comprises a memory hub device integrated in the memory module and a set of memory devices coupled to the memory hub device. The memory hub device comprises first error correction logic provided in write logic integrated in the memory hub device. The memory hub device comprises second error correction logic provided in read logic integrated in the memory hub device. The first error correction logic and the second error correction logic performs error correction operations on data transferred between a link interface and the set of memory devices. The memory hub device transmits and receives data via a memory channel between the external memory controller and the link interface without any error correction code.
Owner:IBM CORP
Method and apparatus for executing a communication session between two terminals
InactiveUS20060013148A1Reduce delaysMinimal bandwidth consumptionError preventionFrequency-division multiplex detailsComputer network
Owner:TELEFON AB LM ERICSSON (PUBL)
Audiovisual signal routing and distribution system
ActiveUS20060238648A1Format conversionHeterogeneous distributionPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningSignal routingComputer network
An audiovisual signal is converted from a native format to a digital, packetized interchange format and transported between a capture node and a display node through a switch. The display node converts the audiovisual signal from the interchange format to a displayable format and causes display of the audiovisual signal. The use of a switch for video routing and distribution allows one-to-one, one-to-many, many-to-one, and many-to-many distribution. The use of a device-independent interchange format allows concurrent distribution of multiple heterogeneous audiovisual signals.
Owner:JUPITER SYST LLC +1
System and Methods for Carrier-Centric Mobile Device Data Communications Cost Monitoring and Control
ActiveUS20130023230A9Facilitate communicationImprove operationMetering/charging/biilling arrangementsAccounting/billing servicesControl systemControl data
Systems and methods for providing carrier-centric data communications cost monitoring and controls are provided. In an embodiment, the method operates by receiving a registration request associated with a subscriber session, determining current data usage associated with the subscriber, and receiving data usage thresholds. The method further comprises receiving quotas associated with the subscriber session and collecting data usage information associated with the subscriber session. The method sends a notification to the subscriber when a pre-determined quota is exceeded during the subscriber session and controls data usage. The cost monitoring and control system comprises a usage policy server and a usage policy application. The usage policy application allows a carrier to offer alterations to terms of a subscription. The usage policy application displays current data usage information on a per-network and per-application basis using subscriber profile information, subscriber session information, and prior subscriber usage history provided by the usage policy server.
Owner:AMDOCS DEV LTD +1
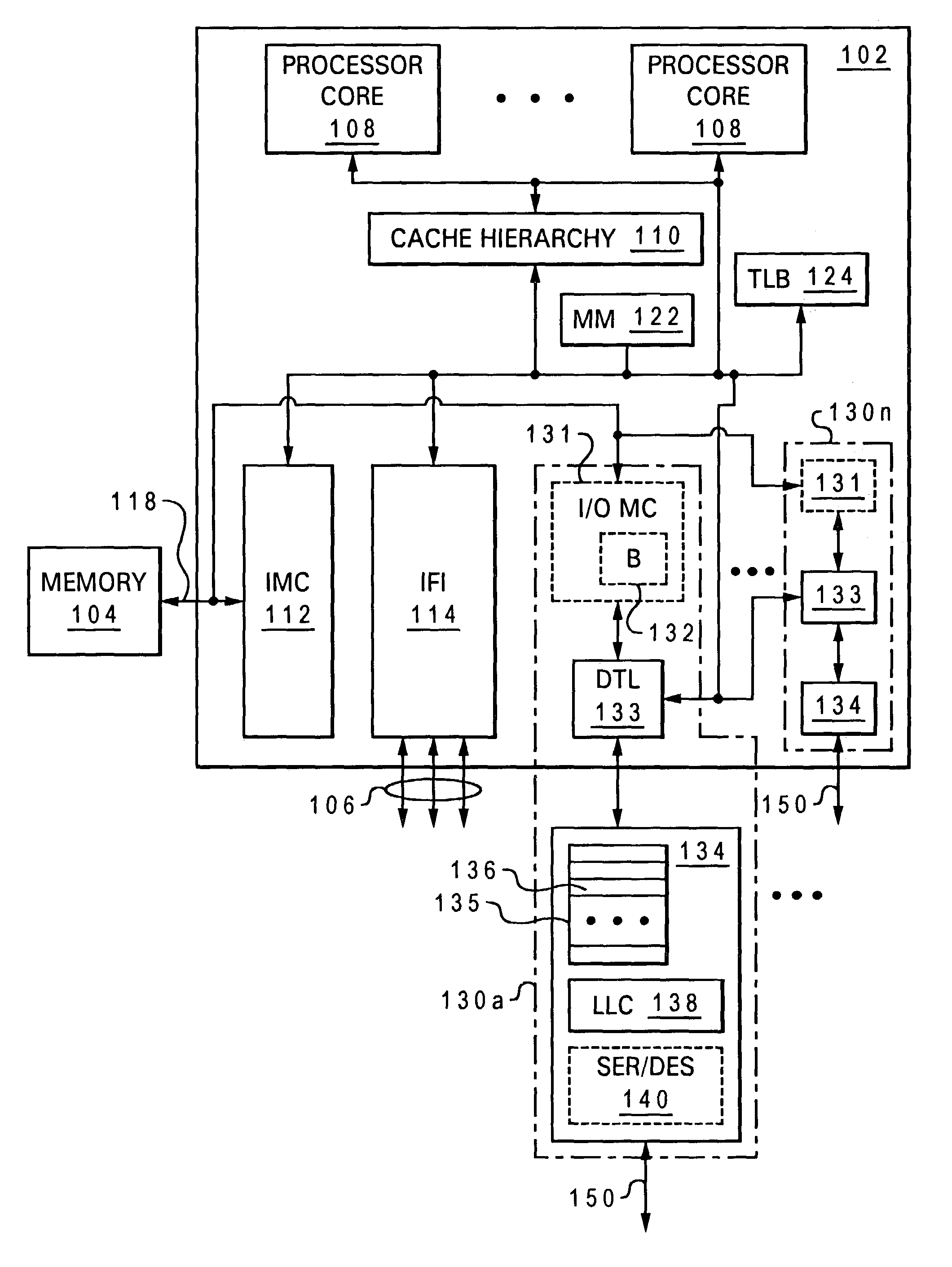
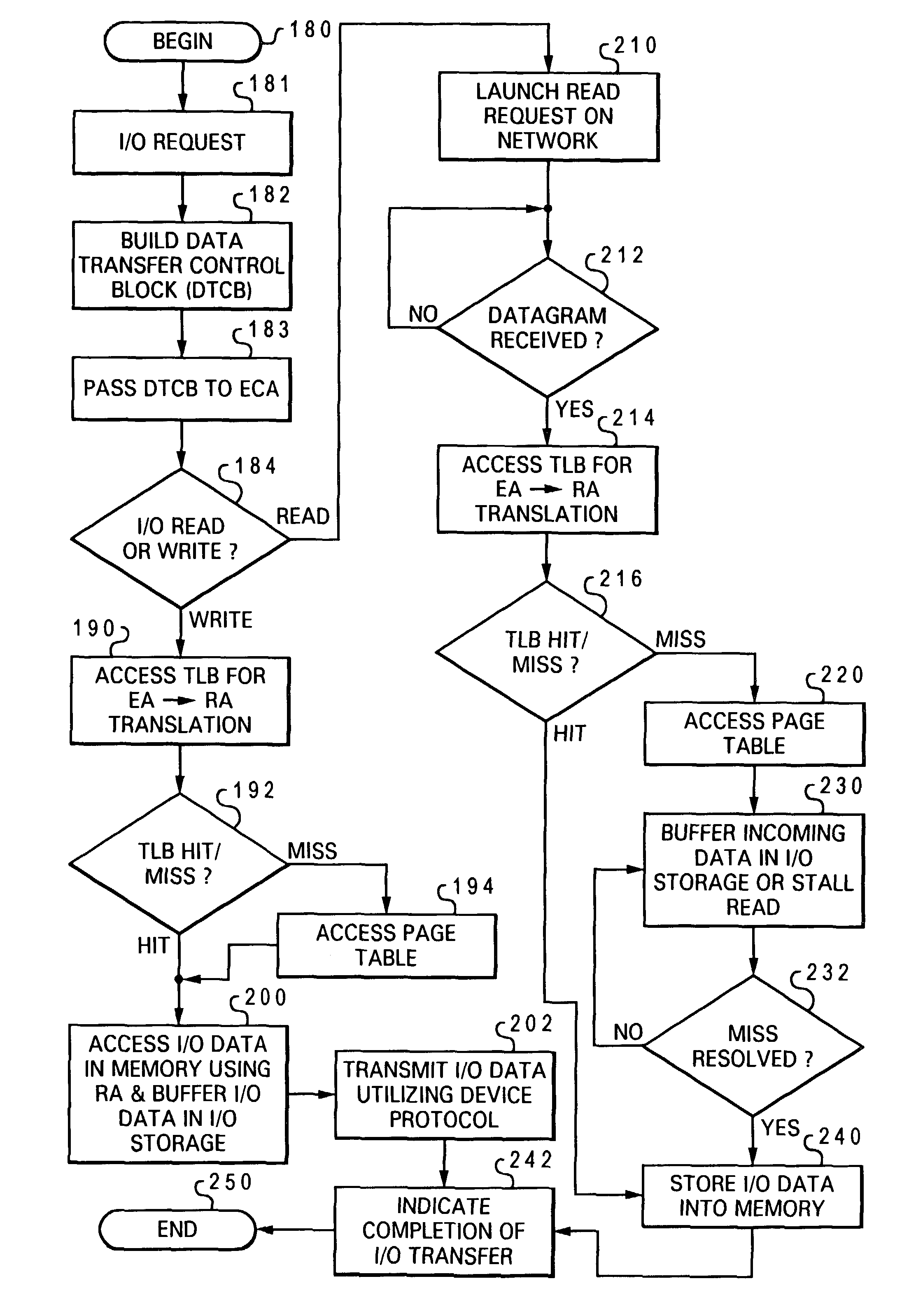
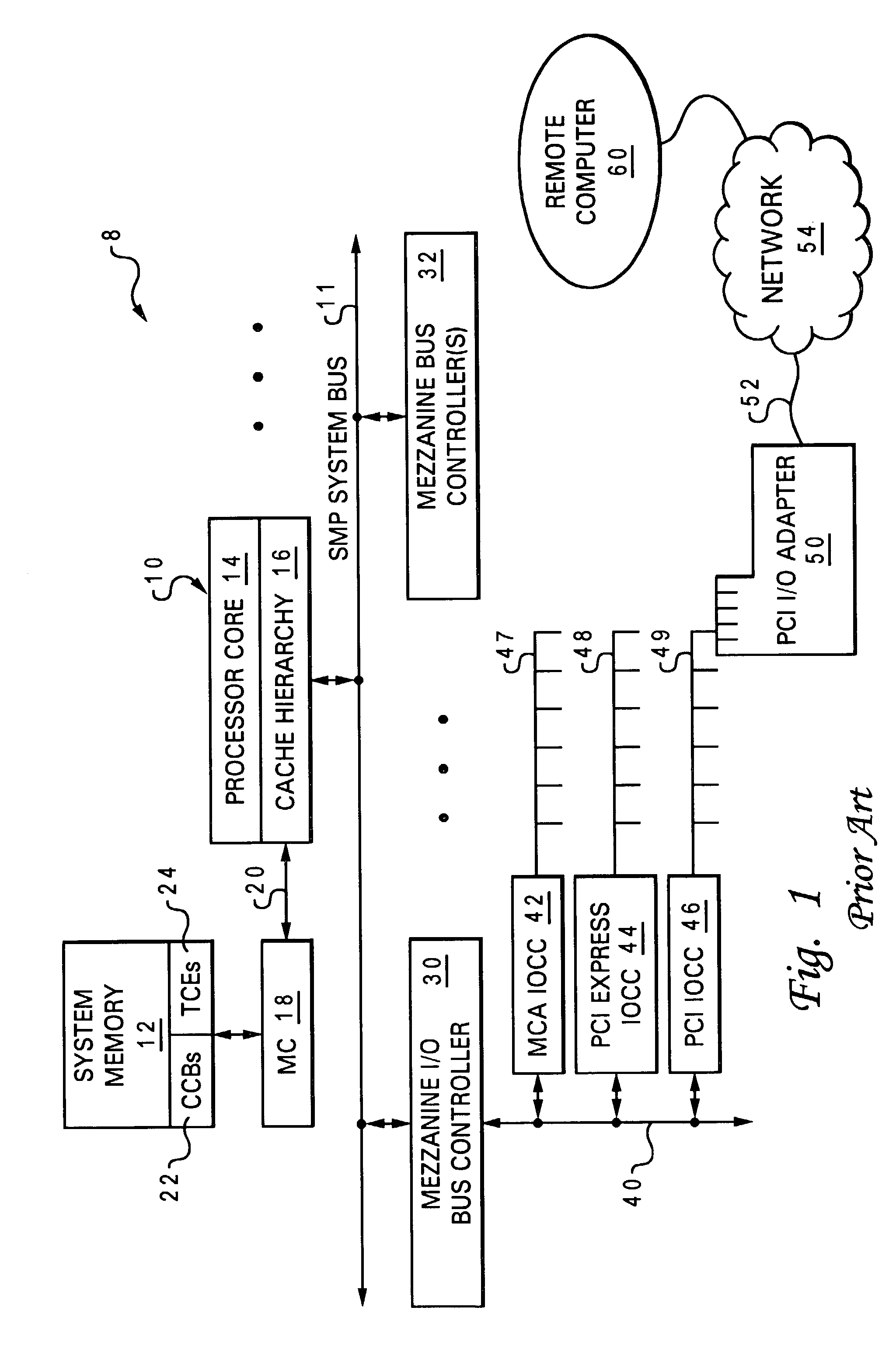
Data processing system providing hardware acceleration of input/output (I/O) communication
ActiveUS7047320B2Improve latencyReduce system performanceMemory adressing/allocation/relocationDigital computer detailsData processing systemTelecommunications link
An integrated circuit, such as a processing unit, includes a substrate and integrated circuitry formed in the substrate. The integrated circuitry includes a processor core that executes instructions, an interconnect interface, coupled to the processor core, that supports communication between the processor core and a system interconnect external to the integrated circuit, and at least a portion of an external communication adapter, coupled to the processor core, that supports input / output communication via an input / output communication link.
Owner:IBM CORP
Method for supporting partial cache line read and write operations to a memory module to reduce read and write data traffic on a memory channel
InactiveUS7558887B2High bandwidthReduce the amount requiredProgram controlMemory systemsTraffic capacityMemory controller
A method is provided that supports partial cache line read and write operations to a memory module to reduce read and write data traffic on a memory channel. In a memory hub controller integrated in the memory module determines an amount of data to be transmitted to or from a set of memory devices of the memory module, in responsive to an access request. The memory hub controller generates a burst length field corresponding to the amount of data. The memory controller controls the amount of data that is transmitted to or from the memory devices using the burst length field. The amount of data is equal to or less than a standard data burst amount of data for the set of memory devices.
Owner:IBM CORP
Performing error correction at a memory device level that is transparent to a memory channel
InactiveUS8086936B2High bandwidthReduce the amount requiredError preventionTransmission systemsExternal storageMemory controller
Owner:INT BUSINESS MASCH CORP
Method for Performing Error Correction Operations in a Memory Hub Device of a Memory Module
InactiveUS20100269021A1Increased memory bandwidthReduce the amount requiredError correction/detection using block codesStatic storageExternal storageComputer module
A method is provided for performing error correction operations in a memory module. A memory hub device, which is integrated in the memory module, receives an access request for accessing a set of memory devices of the memory module coupled to the memory hub device. Data is transferred between a link interface of the memory hub device and the set of memory devices. Error correction logic, which is integrated in the memory hub device, performs one or more error correction operations on the data transferred between the link interface and the set of memory devices. The memory hub device transmits and receives data, via a memory channel between an external memory controller and the link interface, without any error correction code, thereby reducing an amount of bandwidth used on the memory channel.
Owner:IBM CORP
System for supporting partial cache line write operations to a memory module to reduce write data traffic on a memory channel
InactiveUS7584308B2High bandwidthReduce the amount requiredElectric digital data processingData trafficMemory systems
A memory system is provided that supports partial cache line write operations to a memory module to reduce write data traffic on a memory channel. The memory system comprises a memory hub device integrated in the memory module and a set of memory devices coupled to the memory hub device. The memory hub device comprises burst logic integrated in the memory hub device. The burst logic determines an amount of write data to be transmitted to the set of memory devices and generates a burst length field corresponding to the amount of write data. The memory hub also comprises a memory hub controller integrated in the memory hub device. The memory hub controller controls the amount of write data that is transmitted using the burst length field. The memory hub device transmits the amount of write data that is equal to or less than a conventional data burst amount.
Owner:INT BUSINESS MASCH CORP
Prefix caching assisted quality of service aware peer-to-peer video on-demand
InactiveUS20100281509A1Improved admission performanceImprove performanceTwo-way working systemsSelective content distributionSystem capacityClient-side
A multimedia-on-demand peer-to-peer device acting as a receiving peer includes a local cache memory device adapted to store a multimedia prefix. Local storage of the multimedia prefix allows rapid commencement of playback of the requested multimedia program without substantially loading the streaming capacity of an associated server device. The storage of multimedia prefixes in local cache memory of the receiving peer device can take place during periods of relatively low network loading so as to optimize network and server scheduling. Included is a method and apparatus for performing admission control in a peer-to-peer multimedia-on-demand system. The admission control system determines if there is sufficient system capacity to support a new request from a peer-to-peer device acting as a client in light of the presence of stored multimedia prefixes at the peer-to-peer device acting as a receiving peer device, among other factors.
Owner:THOMSON LICENSING SA
Acceleration of input/output (I/O) communication through improved address translation
InactiveUS6976148B2Improve latencyReduce system performanceMemory adressing/allocation/relocationMicro-instruction address formationComputer scienceAddress space
An I / O communication adapter receives from a processor core an I / O command referencing an effective address within an effective address space of the processor core that identifies a storage location. In response to receipt of the I / O command, the I / O communication adapter translates the effective address into a real address by reference to a translation data structure. The I / O communication adapter then accesses the storage location utilizing the real address to perform an I / O data transfer specified by the I / O command.
Owner:INT BUSINESS MASCH CORP
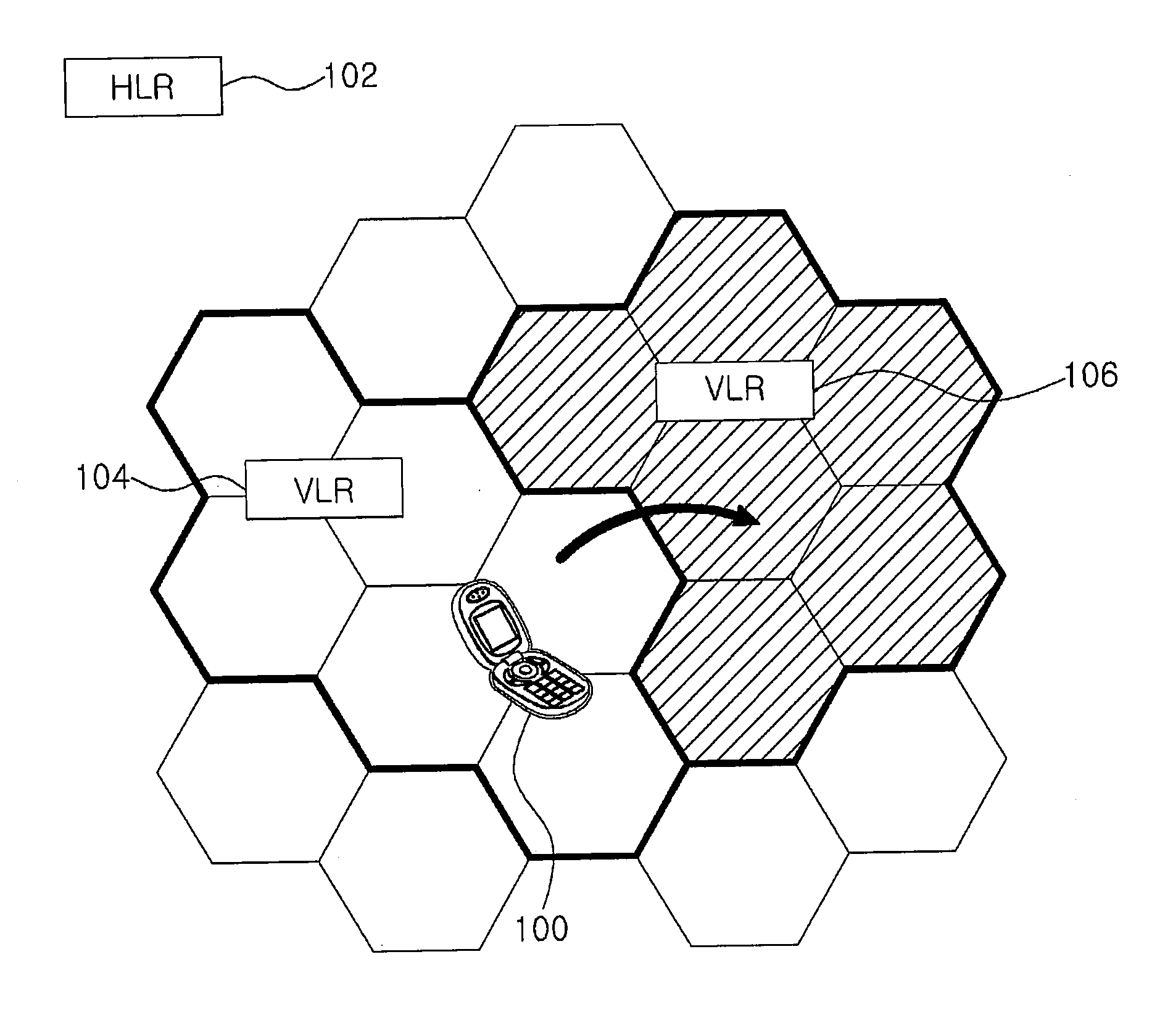
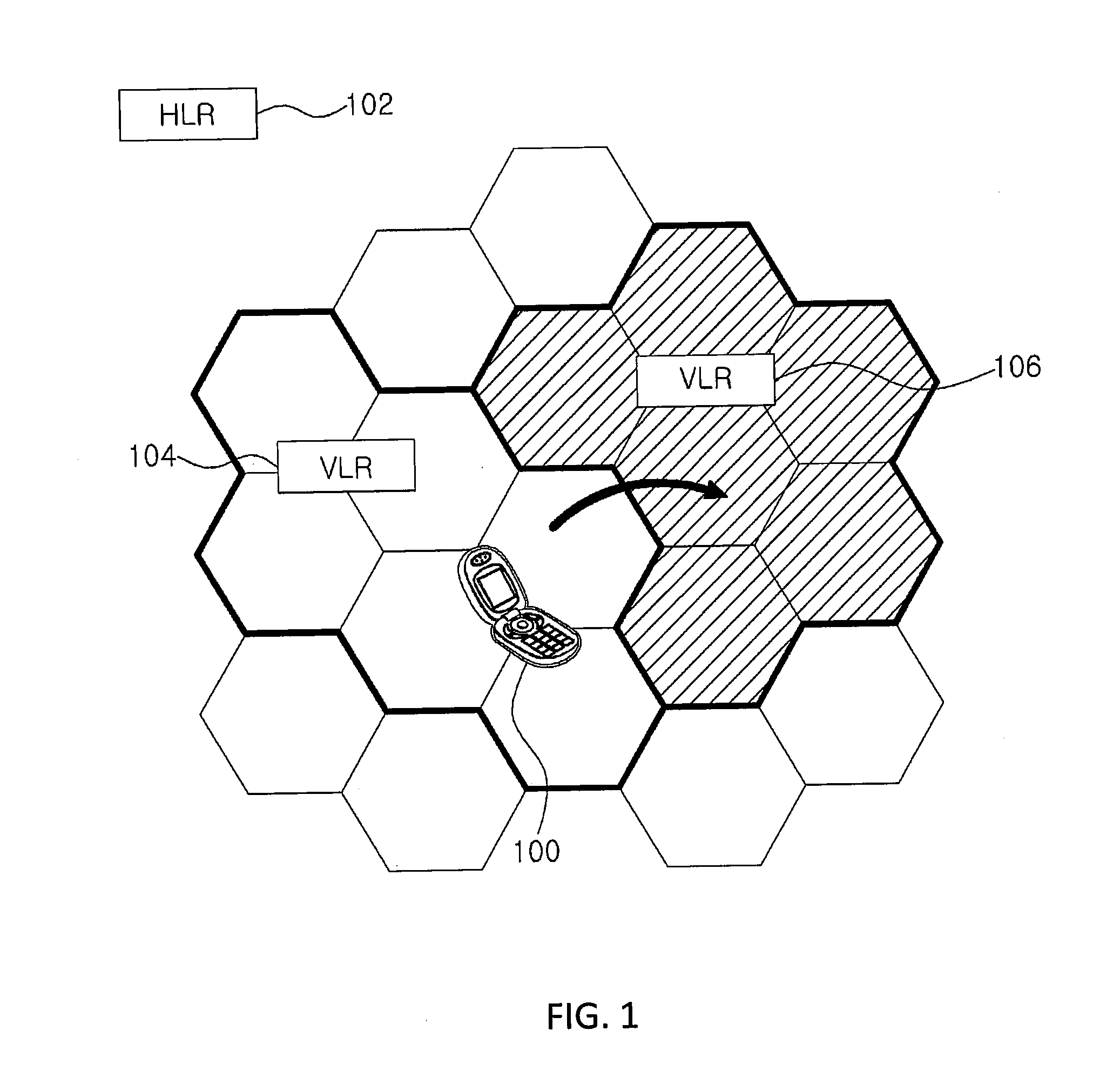
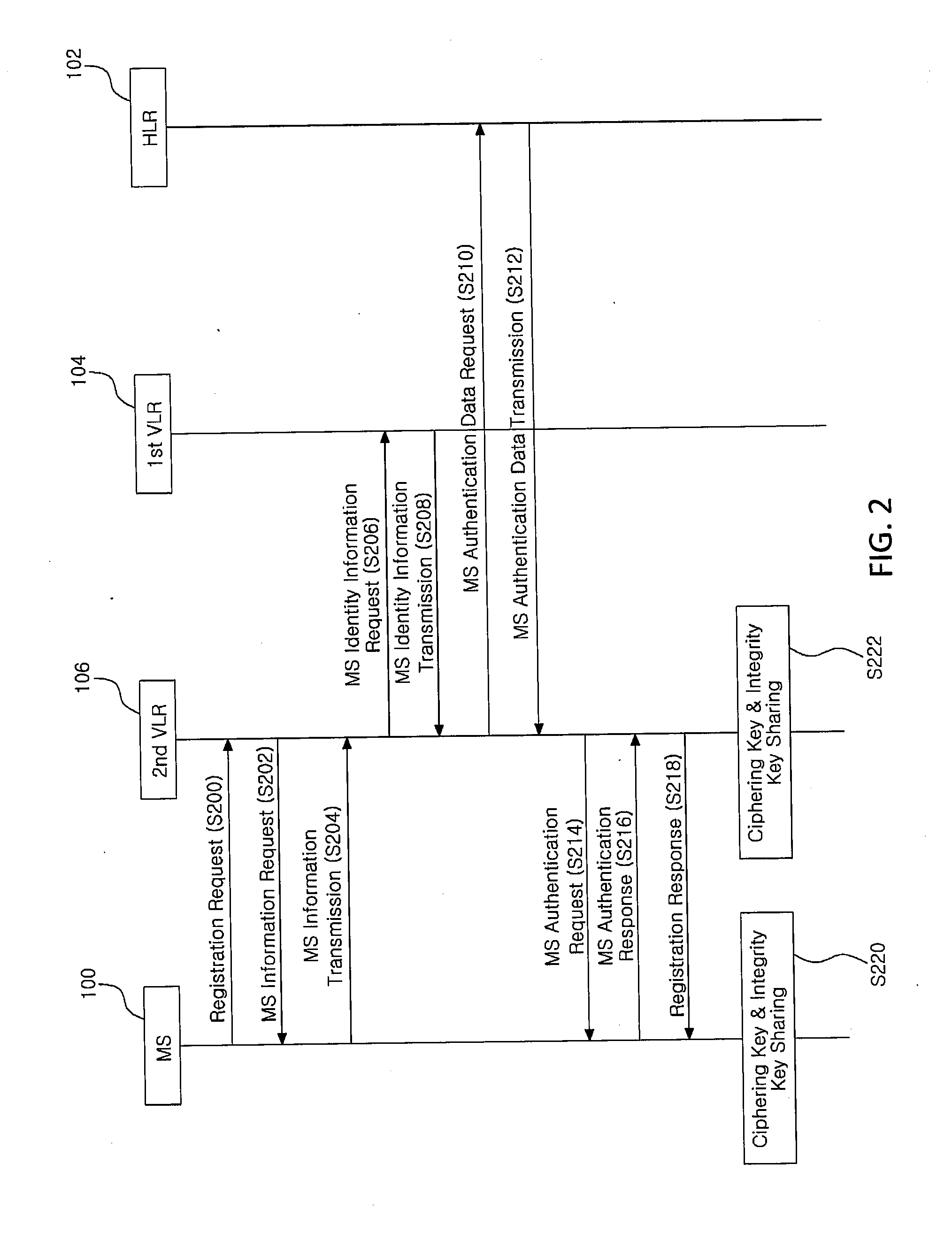
Method for authentication and key establishment in a mobile communication system and method of operating a mobile station and a visitor location register
InactiveUS20120142315A1Simplify the authentication processConsume bandwidthUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsProcessor register
The present invention relates to a method whereby the mobile station and a visitor location register create and share a ciphering key and an integrity key in order to directly authenticate each other. The communication method in a mobile communication system such as this includes registering the mobile station with the home location register; and having the mobile station and the visitor location register directly authenticate each other and mutually share a ciphering key and an integrity when the mobile station moves to the visitor location register.
Owner:IND ACADEMIC CORP FOUND YONSEI UNIV
System and methods for user-centric mobile device-based data communications cost monitoring and control
ActiveUS9203629B2Facilitate communicationImprove operationComplete banking machinesMetering/charging/biilling arrangementsComputer networkControl data
Systems and methods for providing user-centric device-based data communications cost monitoring and controls. In an embodiment, the method operates by sending a registration request associated with a subscriber session, determining current data usage associated with the subscriber, and sending data usage thresholds. The method further comprises sending quotas associated with the subscriber session after collecting data usage information associated with the subscriber session. The method receives a notification at the subscriber's mobile device when a pre-determined quota is exceeded during the subscriber session to control data usage. The system communicates with a usage policy server and a usage policy application. The usage policy application allows a subscriber to alter terms and service tiers of a subscription. The usage policy application displays current data usage information on a per-network and per-application basis using subscriber profile information, subscriber session information, and prior subscriber usage history received from the usage policy server.
Owner:AMDOCS DEV LTD +1
Managing L3 VPN virtual routing tables
InactiveUS7756998B2Reduce needConsume bandwidthMultiple digital computer combinationsNetworks interconnectionRouting tablePrivate network
A method of managing virtual routing forwarding (VRF) tables at a provider edge PE router of a L3 virtual private network (VPN) is provided. An import route target (ImpRT) tree is maintained at the PE router, which keeps the association between all ImpRT attributes currently configured on said PE router and the virtual routing table VRF at that router. When an ImpRT attribute is configured on a VRF table, the PE router first searches the tree to identify a local VRF table that contains a route(s) with that ImpRT attribute. If this information is available locally, the VRF is updated by copying the route information, and there is no need to do a route refresh. When an ImpRT is deleted from a VRF, a route refresh is avoided by parsing all the routes in the VRF and removing the routes that no longer have a matching route target. In an alternative implementation, the local source is the master RIB (routing information base) which includes all routes in all VRFs at the router, and optionally even rejected routes that were filtered out using ImpRTs. In this variant, even routes associated with ImpRTs that are new to the router would be available to update the VRF without requiring a route refresh.
Owner:WSOU INVESTMENTS LLC
Distributed adaptive network memory engine
ActiveUS8046425B1Processing speedLower latencyMultiple digital computer combinationsTransmissionMass storageOperational system
Memory demands of large-memory applications continue to remain one step ahead of the improvements in DRAM capacities of commodity systems. Performance of such applications degrades rapidly once the system hits the physical memory limit and starts paging to the local disk. A distributed network-based virtual memory scheme is provided which treats remote memory as another level in the memory hierarchy between very fast local memory and very slow local disks. Performance over gigabit Ethernet shows significant performance gains over local disk. Large memory applications may access potentially unlimited network memory resources without requiring any application or operating system code modifications, relinkling or recompilation. A preferred embodiment employs kernel-level driver software.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
System for supporting partial cache line read operations to a memory module to reduce read data traffic on a memory channel
InactiveUS7861014B2High bandwidthReduce the amount requiredError detection/correctionMemory adressing/allocation/relocationTraffic capacityData traffic
A memory system is provided that supports partial cache line read operations to a memory module to reduce read data traffic on a memory channel. The memory system comprises a memory hub device integrated in the memory module and a set of memory devices coupled to the memory hub device. The memory hub comprises burst logic integrated in the memory hub device. The burst logic determines an amount of read data to be transmitted from the set of memory devices and generates a burst length field corresponding to the amount of read data. The memory hub also comprises a memory hub controller integrated in the memory hub device. The memory hub controller controls the amount of read data that is transmitted using the burst length field. The memory hub device transmits the amount of read data that is equal to or less than a conventional data burst amount of data.
Owner:INT BUSINESS MASCH CORP
System and method for encrypting data using a cipher text in a communications environment
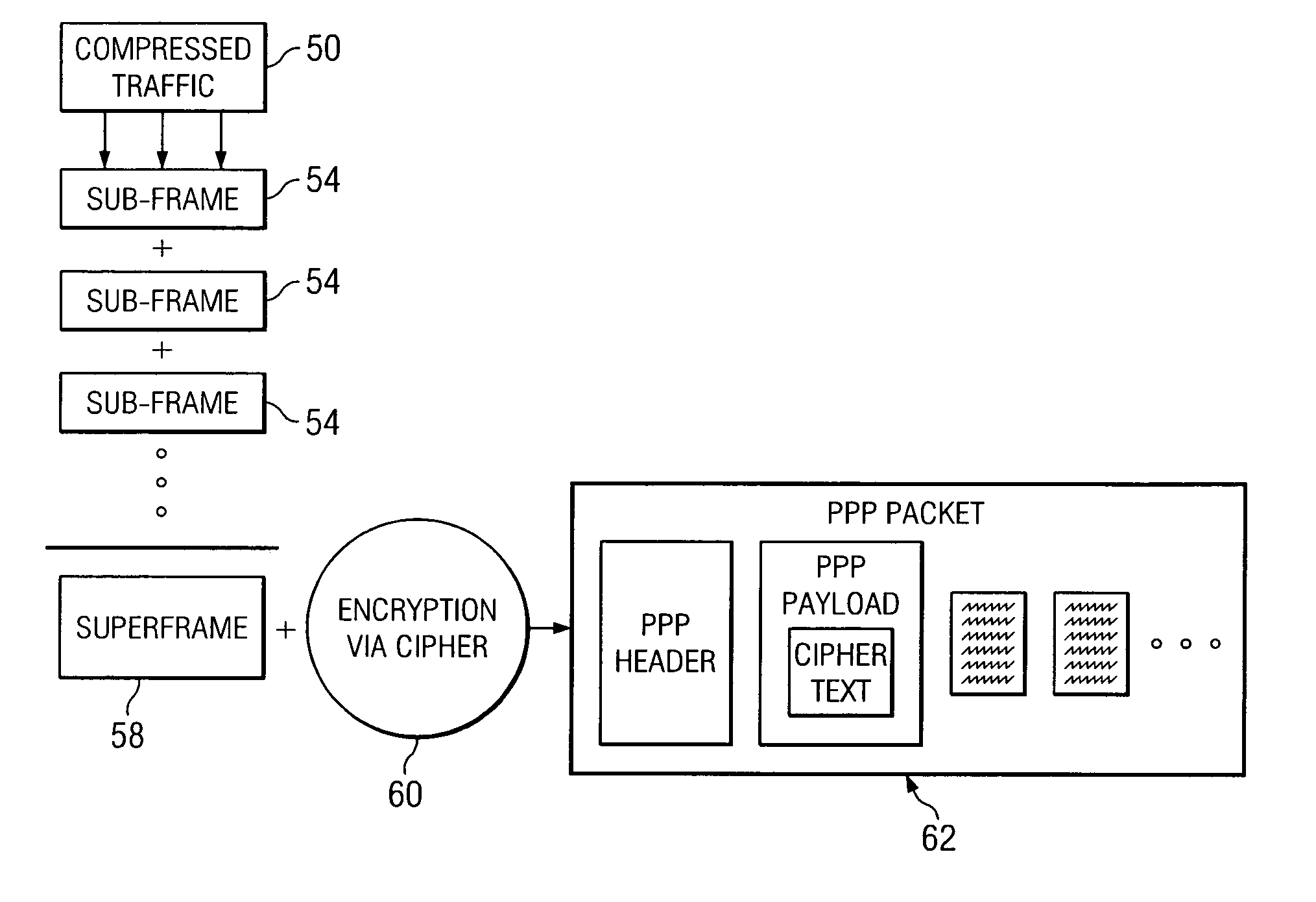
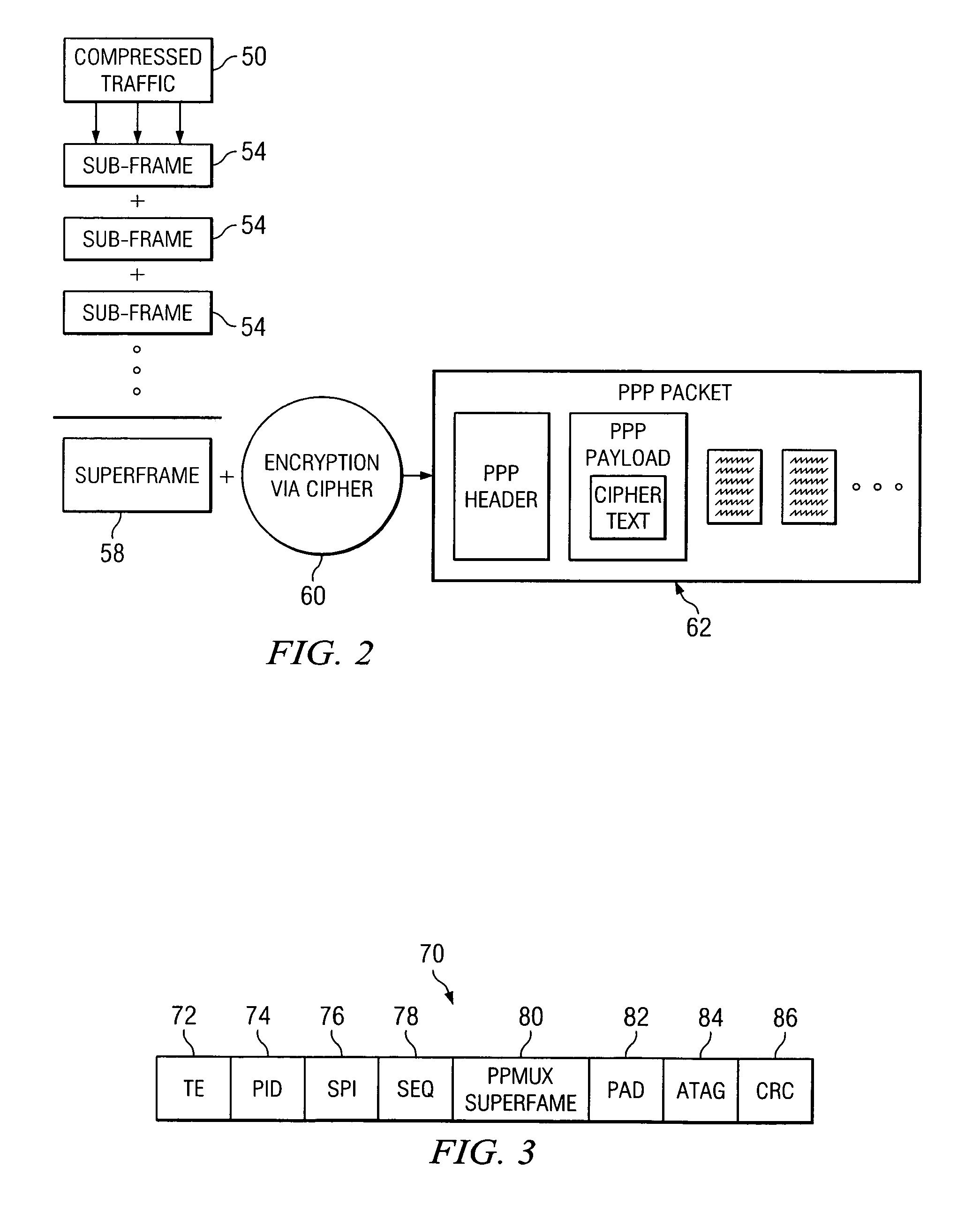
ActiveUS8300824B1Minimum bandwidthFew cost expenditureData stream serial/continuous modificationMultiple keys/algorithms usageComputer networkCiphertext
Data is encrypted by receiving a plurality of bits associated with a communications flow and compressing at least a portion of the bits in order to produce a plurality of sub-frames. The sub-frames may be assembled into a superframe and a stream cipher may be applied to the superframe in order to generate an encrypted packet.
Owner:CISCO TECH INC
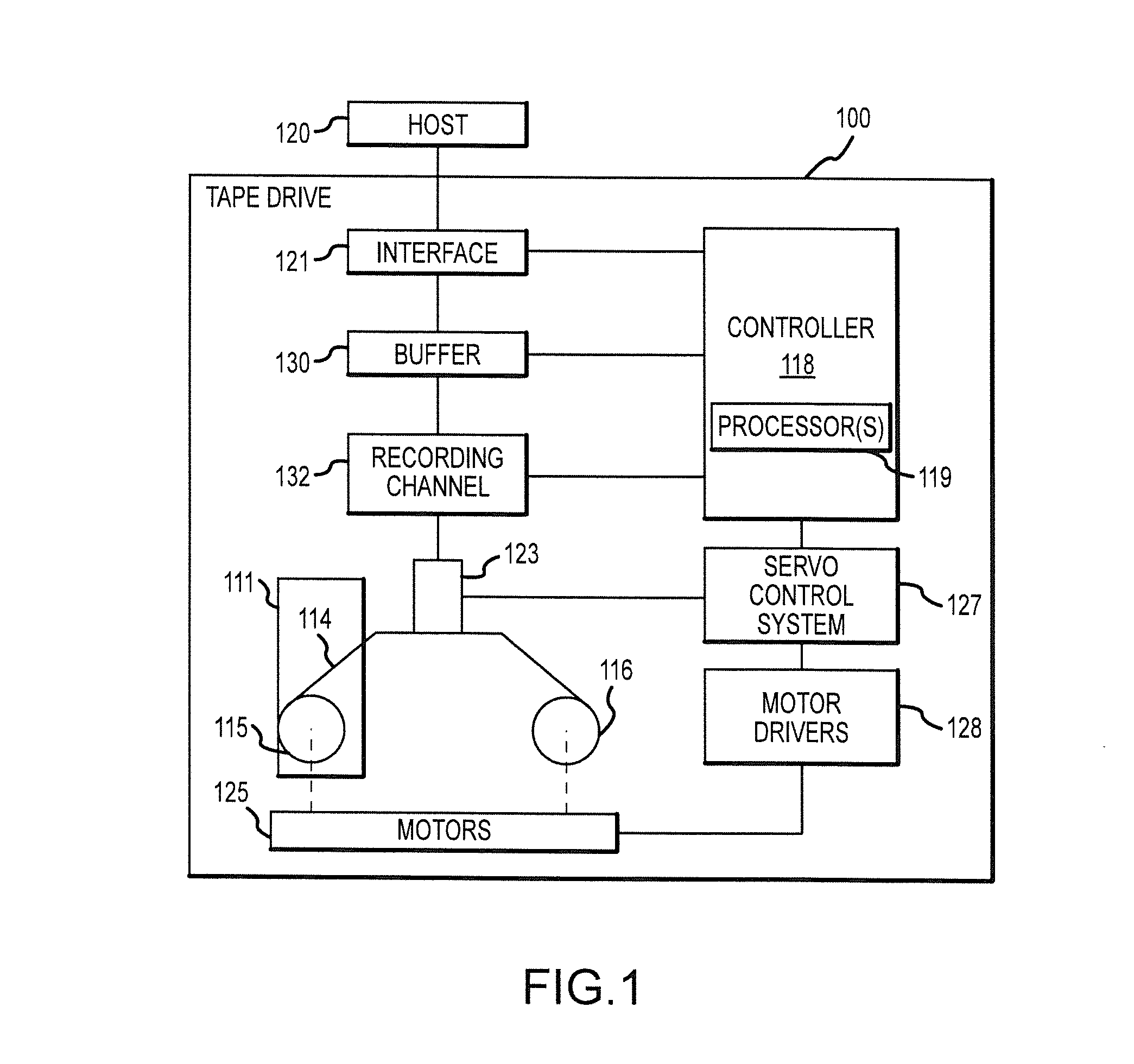
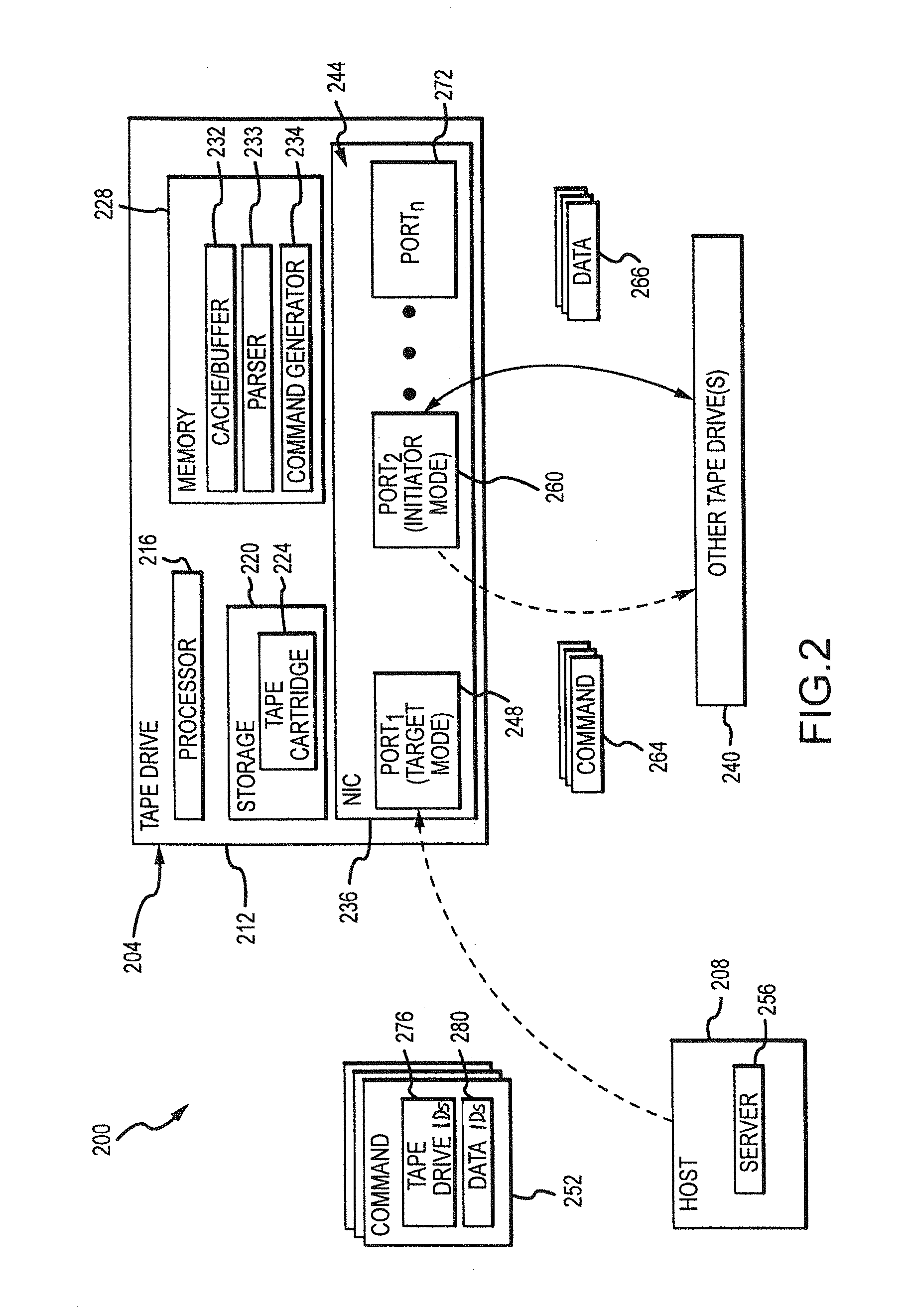
Target and initiator mode configuration of tape drives for data transfer between source and destination tape drives
ActiveUS20160041915A1Increase ratingsImprove system performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationDatapathData transmission
Systems and methods that substantially or fully remove a commanding server from a data path (e.g., as part of a data migration, disaster recovery, and / or the like) to improve data movement performance and make additional bandwidth available for other system processes and the like. Broadly, a network interface card (e.g., host bus adapter (HBA)) of a tape drive may be configured in both a target mode to allow the tape drive to be a recipient of control commands from a server to request and / or otherwise obtain data from one or more source tape drives, and in an initiator mode to allow the tape drive to send commands to the one or more tape drives specified in the commands received from the server to request / read data from and / or write data to such one or more tape drives.
Owner:ORACLE INT CORP
Cache coherent I/O communication
InactiveUS7783842B2Improve latencyReduce system performanceMemory adressing/allocation/relocationParallel computingData storing
A processing unit includes a processor core, an input / output (I / O) communication adapter coupled to the processor core, and a cache system coupled to the processor core and to the I / O communication adapter. The cache system including a cache array, a cache directory and a cache controller. The cache controller snoops I / O communication by the I / O communication adapter and, in response to snooping the I / O communication adapter performing an I / O data write of outgoing data in an exclusive state, invalidates corresponding data stored within the cache array.
Owner:BEIJING PIANRUOJINGHONG TECH CO LTD
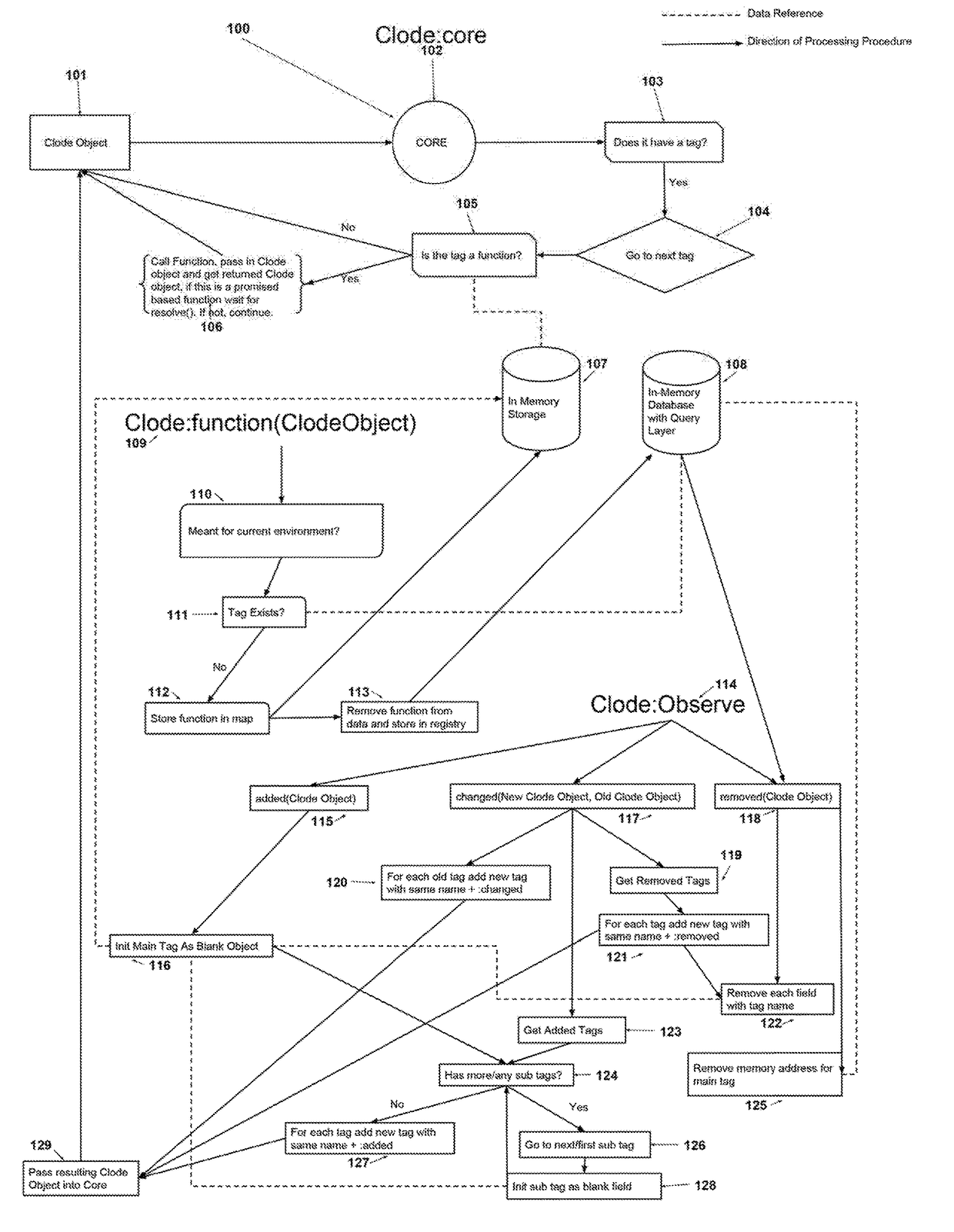
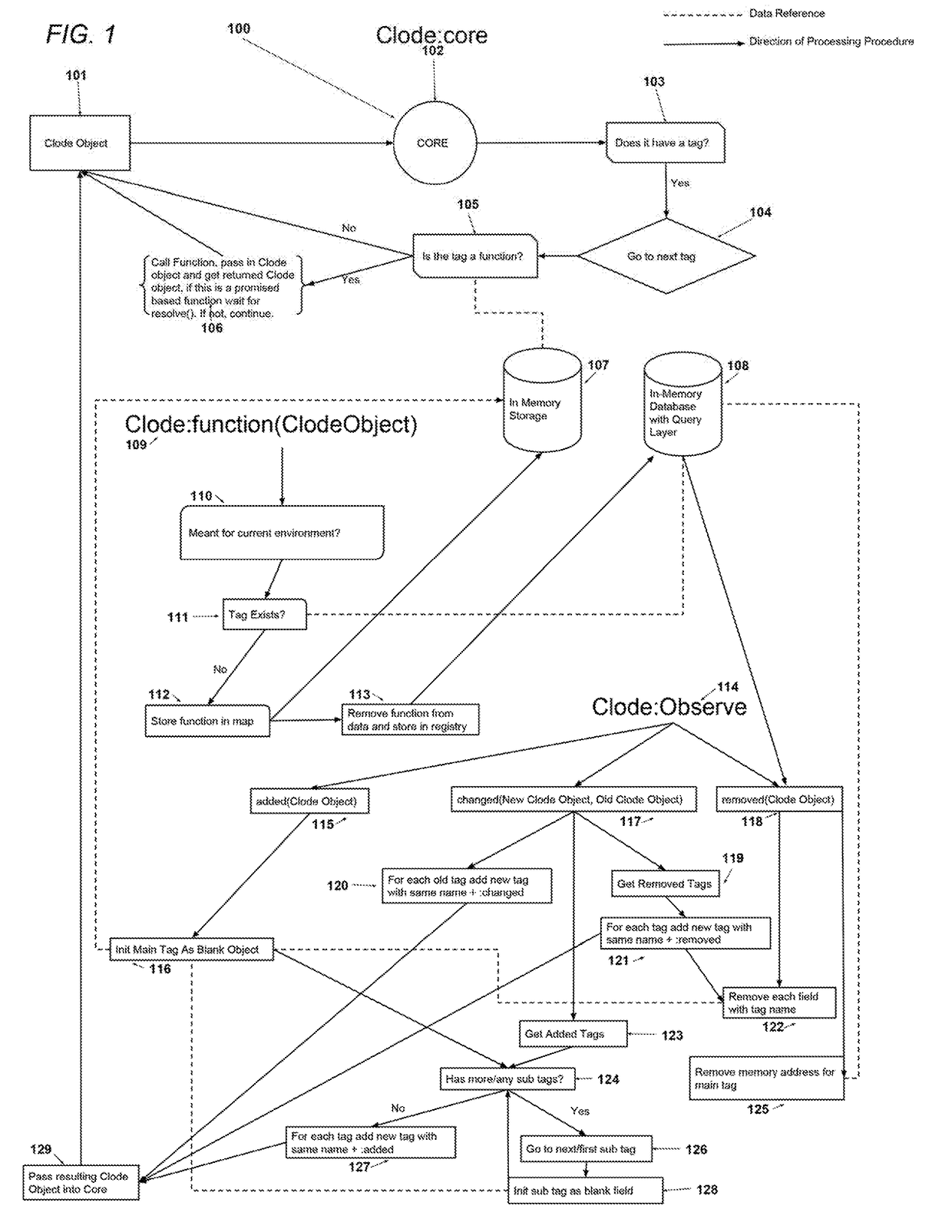
Function and memory mapping registry with reactive management events
ActiveUS20170337291A1Enhanced couplingSimpler and efficient programmingCryptography processingDigital computer detailsThird partyDisplay device
A system for managing data content and data content relationships through resource efficient process structures for cloud and network environments includes a Clode core. The Clode core provides a means to create a resulting object / display / process based on a defined order of processes determined by the object's tags and / or relationships to a function map and / or other objects in the system. This is used in Clode tag modules such as ‘clode:autopublish’ to create a data publication on the server, by ‘clode:autosubscribe’ to make client's automatically subscribe to data related to the tagged object, and by ‘clode:surface’ to manage an object on a display; just to name a few use cases. Tags can then be used to manage third party environments such as a docker container that would be classified as having the tag ‘on’, but when removed could cause the container to shut off. Tag management functions could also change the classifications as to say in the previous example to cause a tag to be added called ‘off’.
Owner:OMEGA SUNRISE GRP SPENDTHRIFT TRUST
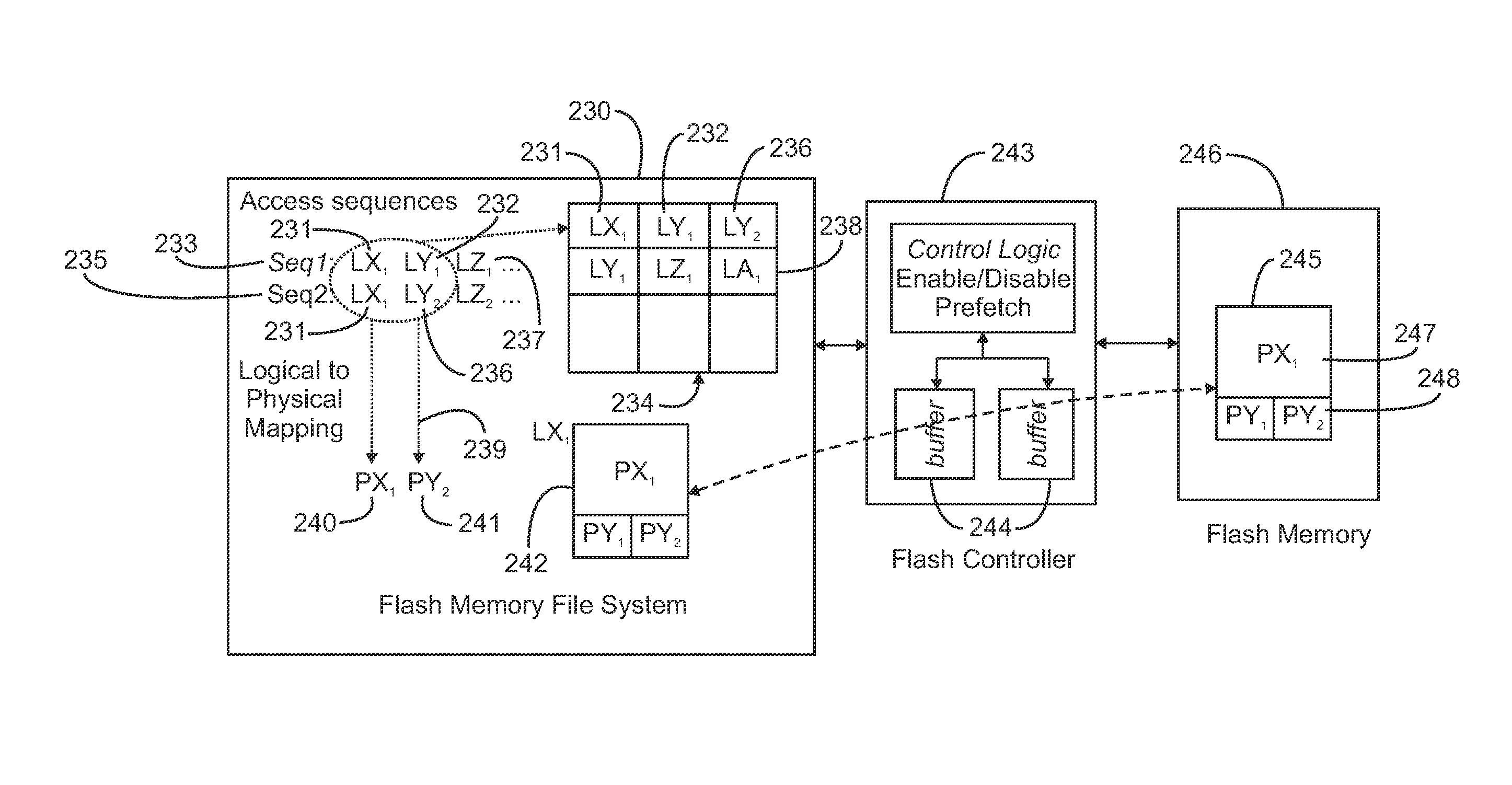
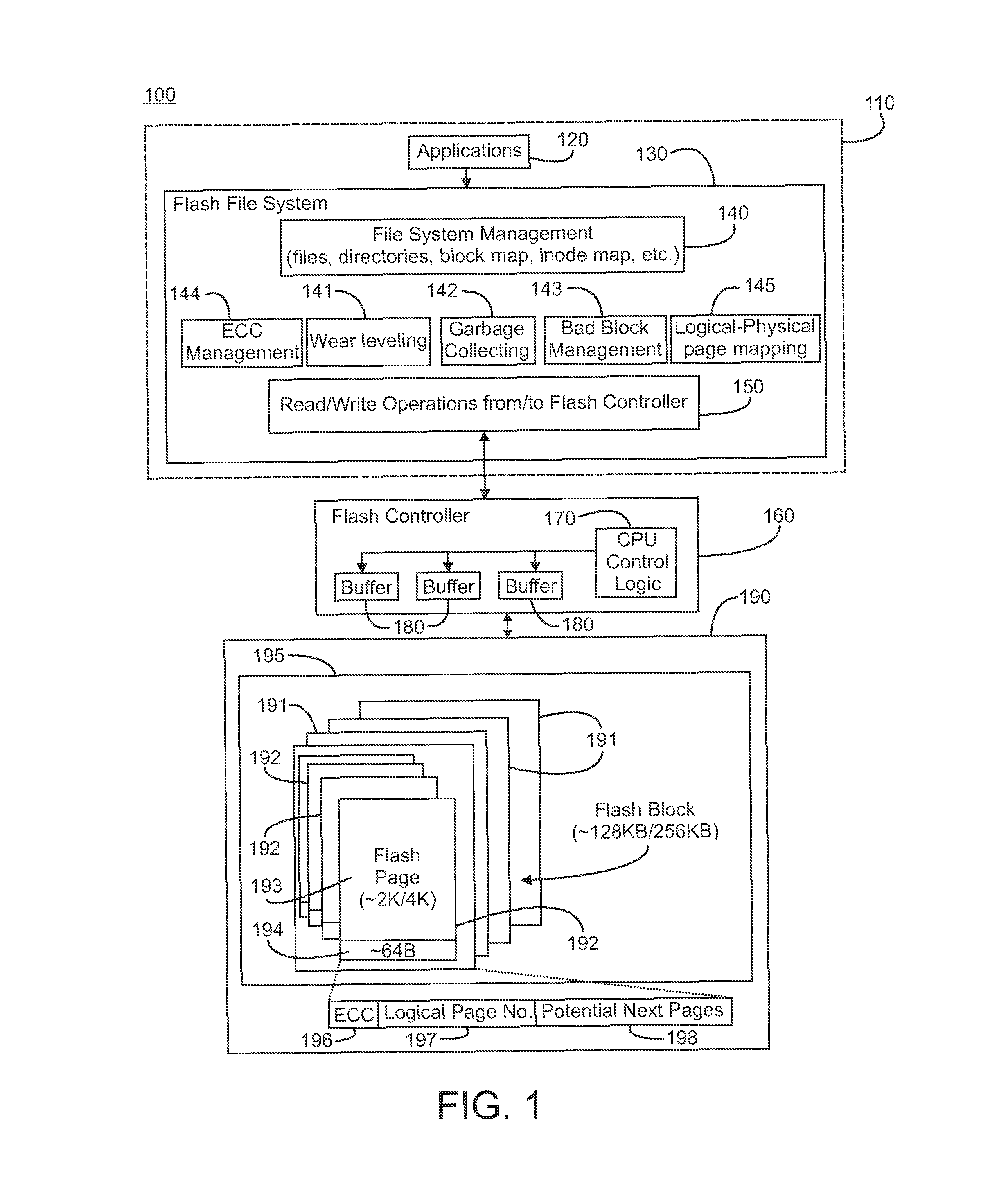
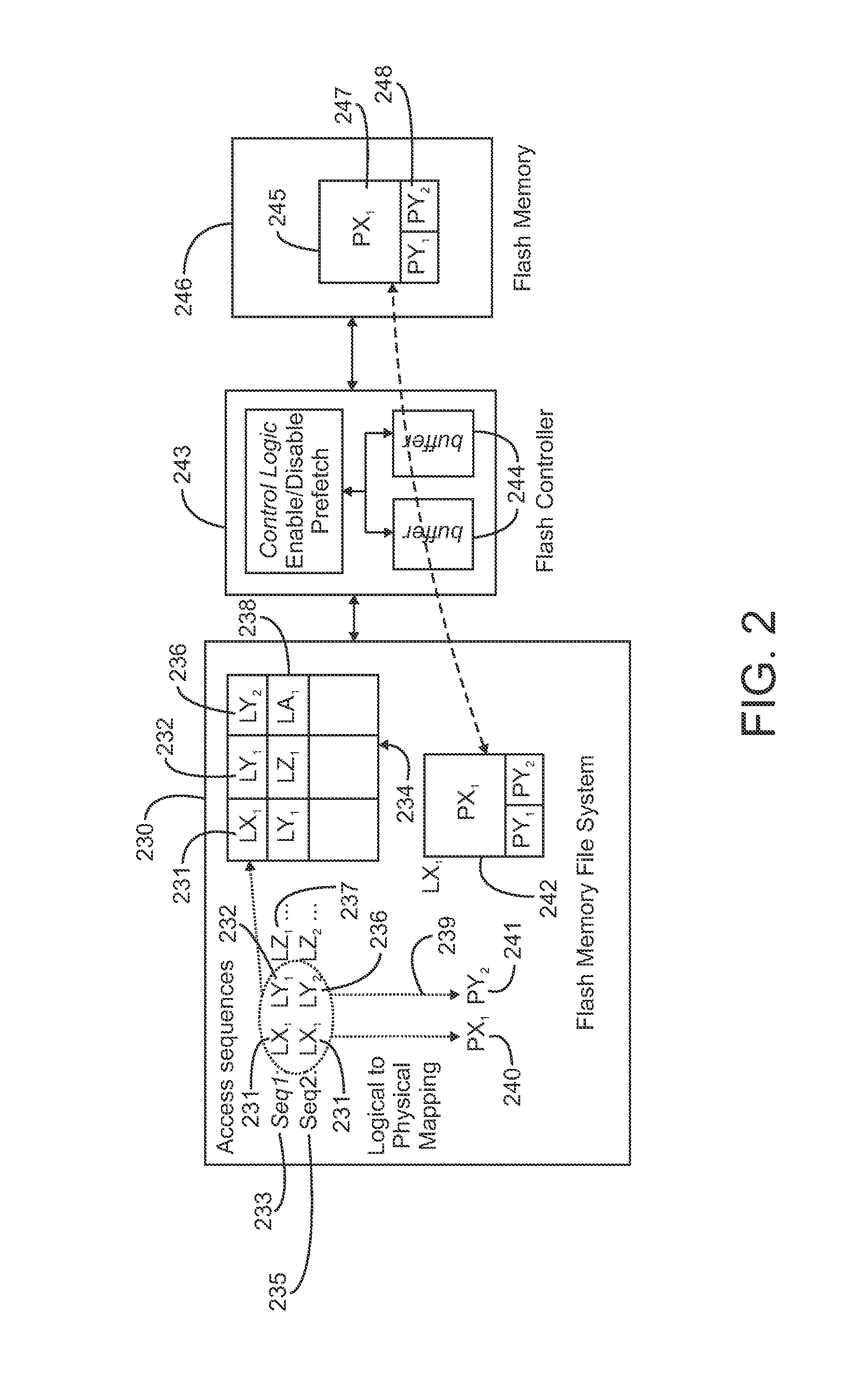
Storing multi-stream non-linear access patterns in a flash based file-system
InactiveUS9164676B2Improve performanceWithout consuming extra storage space and bandwidth overheadMemory architecture accessing/allocationInput/output to record carriersMemory addressFile system
Accesses to logical pages of memory are monitored. Each logical page corresponds to a logical memory address and the accesses defining an access pattern. The logical memory addresses are logged in ordered pairs of consecutive logical pages in the access pattern. Upon receipt of a request to write data to a given logical page, a given ordered pair of consecutive logical pages containing the logical memory address of the given logical page as a first logical memory address in the ordered pair of logical memory addresses associated with that consecutive pair is obtained. A first physical memory address mapping to the first logical memory address is identified, and a second logical memory address from that identified consecutive pair. A second physical memory address mapping to the second logical memory address is identified, and the data and the second physical memory address are written to the first physical memory address.
Owner:IBM CORP
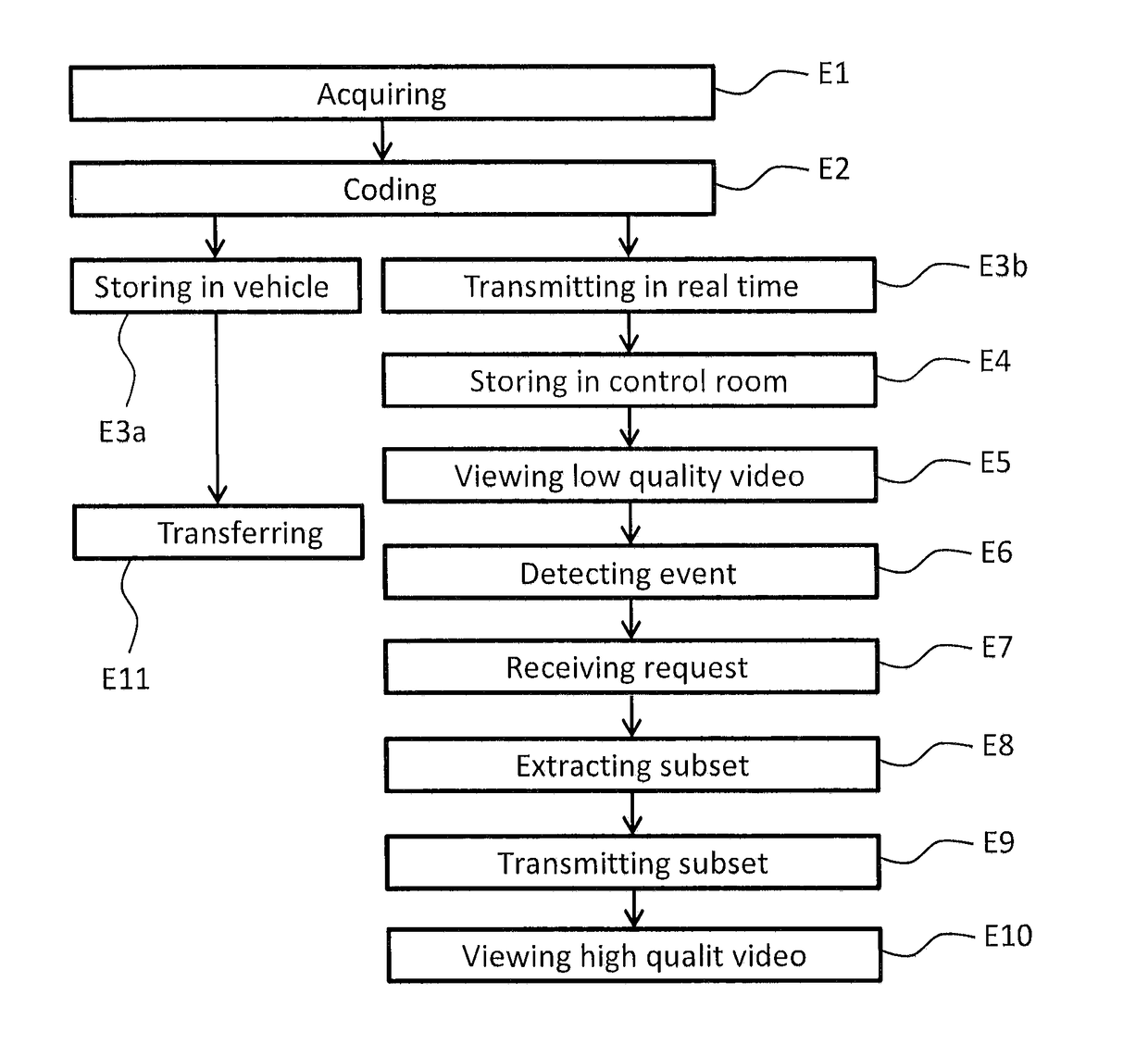
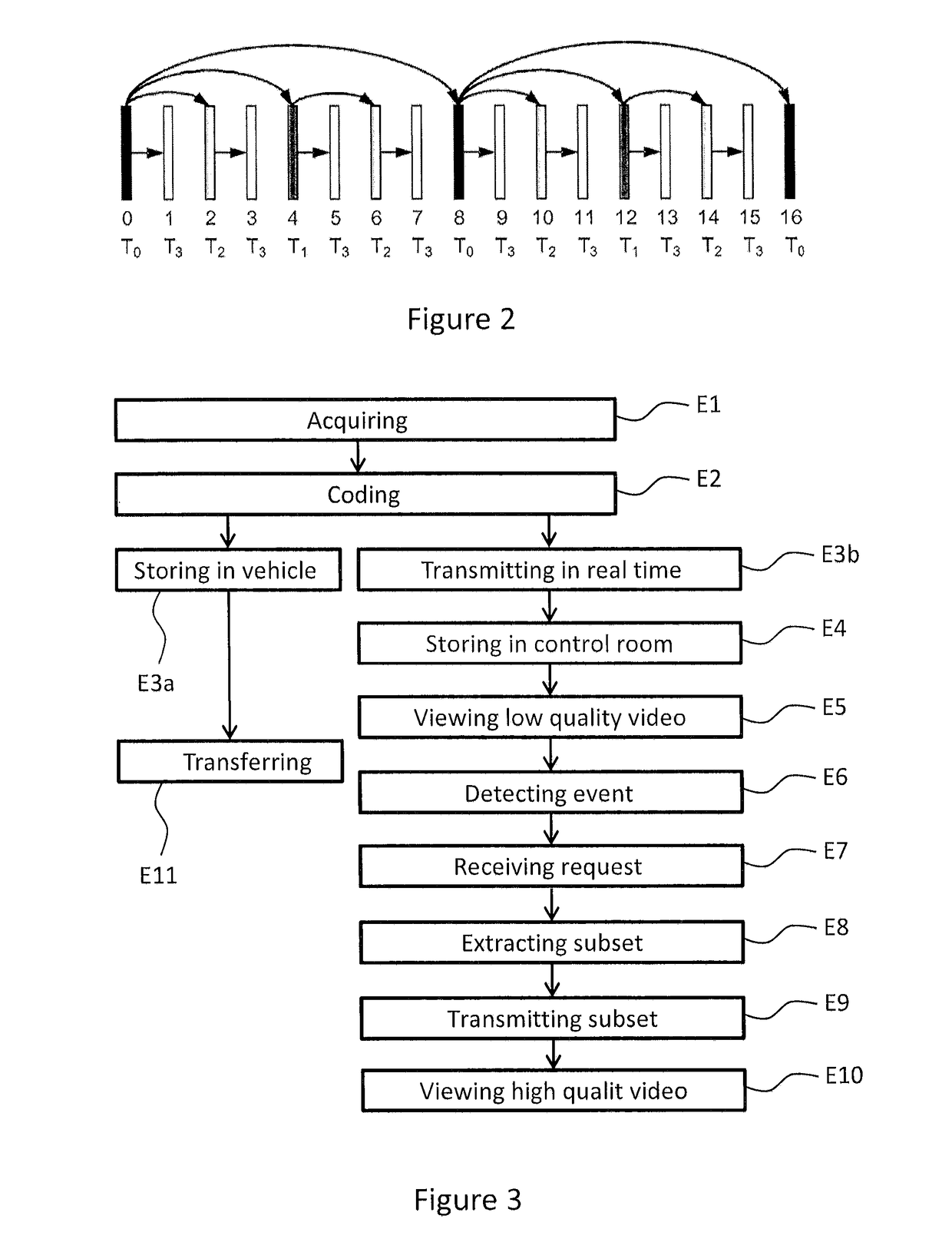
Method for transmitting video surveillance images
ActiveUS20170302977A1Improve image qualityQuality improvementClosed circuit television systemsDigital video signal modificationTelecommunications networkControl room
A method of transmission by a surveillance device to a control room, via a telecommunications network, of a series of images, includes steps, implemented by the surveillance device, of acquisition of a series of images, of coding of the series of images acquired into a series of base video frames including a first quantity of information and into at least one series of enhancement video frames of the series of base video frames, the series of enhancement video frames including a second quantity of information making it possible to enhance the quality of the series of images coded into the series of base video frames, of transmission in real time via the telecommunications network of at least the series of base video frames to the control room, and of storage of at least the series of enhancement video frames.
Owner:AIRBUS DS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com