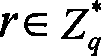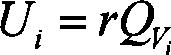Patents
Literature
66results about How to "Simplify the authentication process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
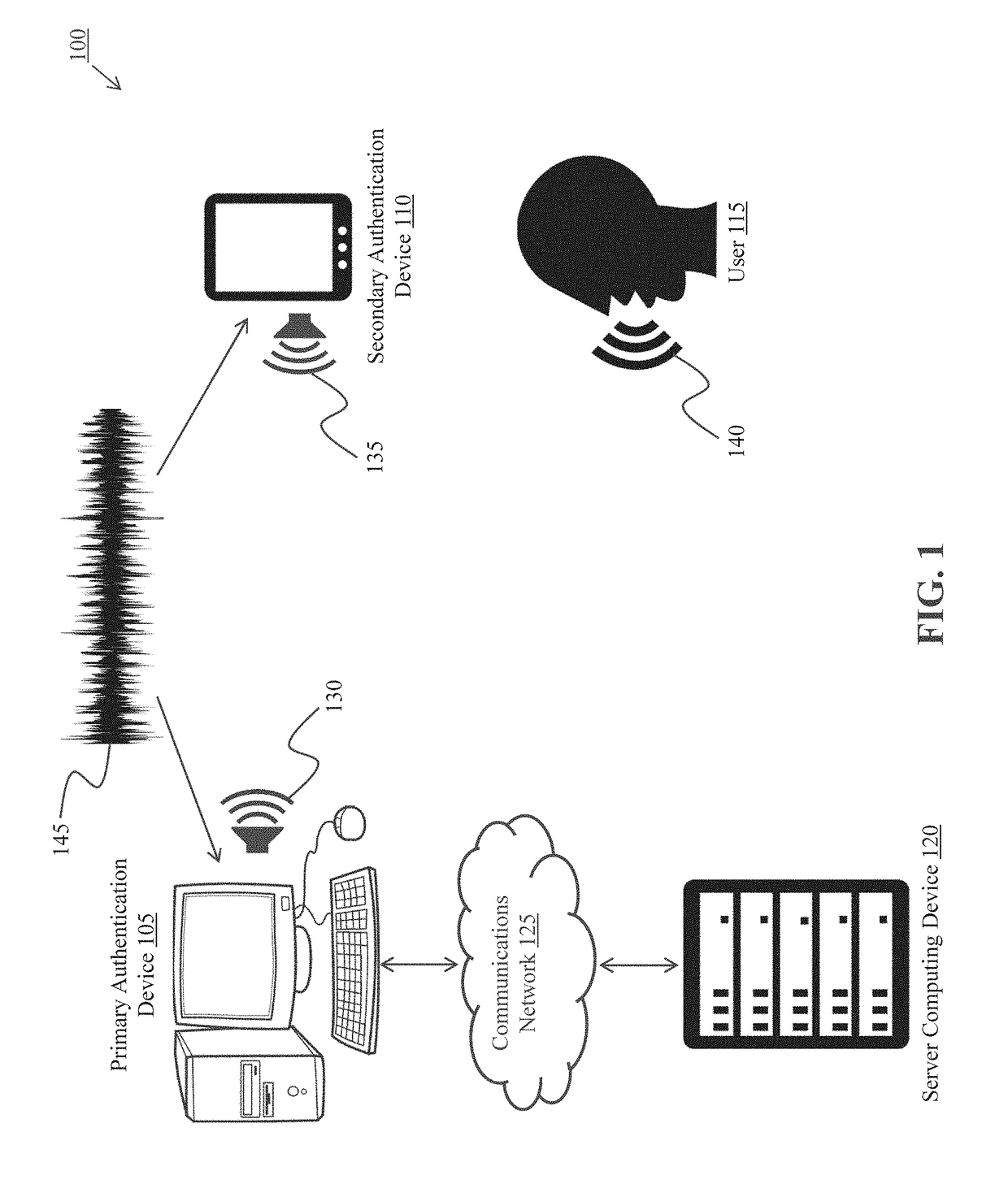
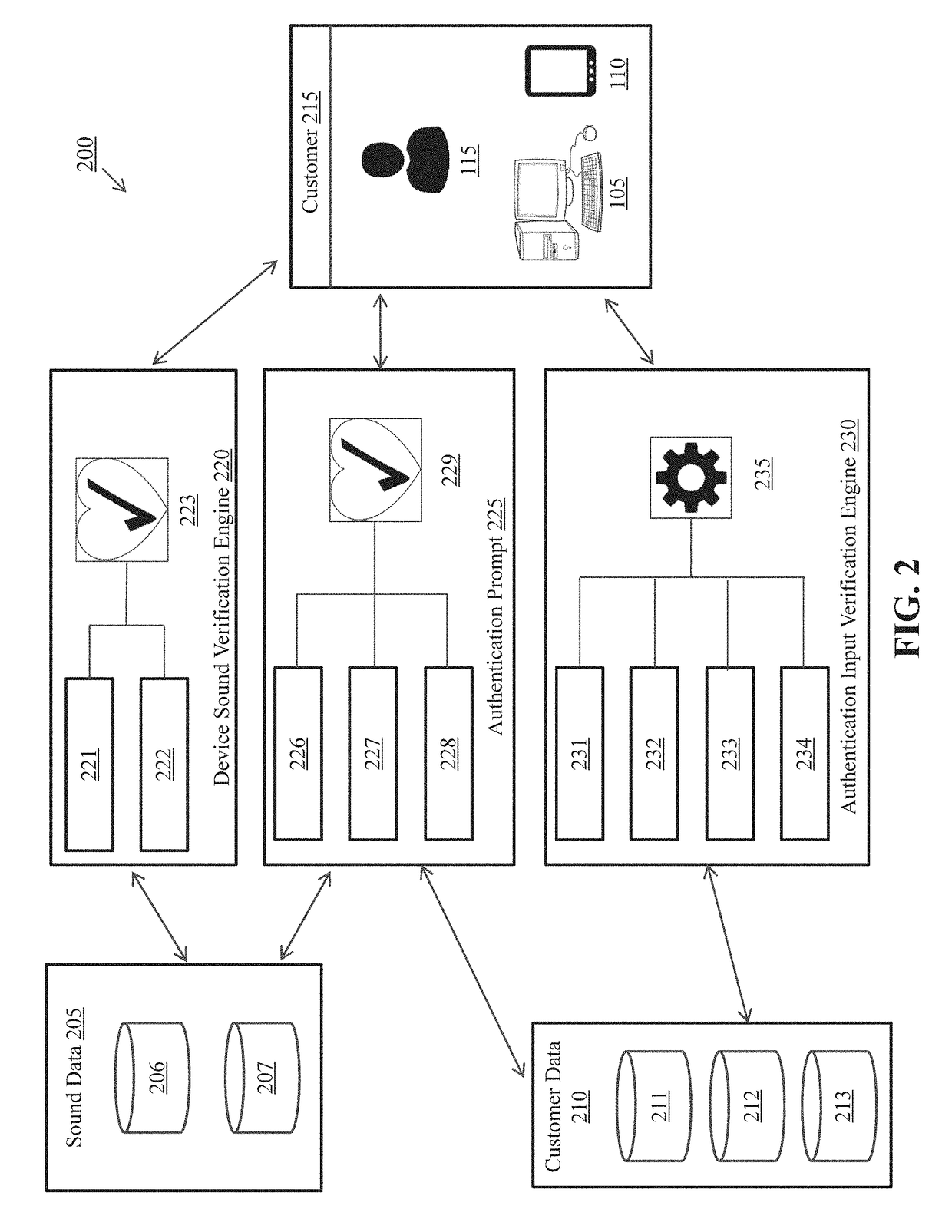
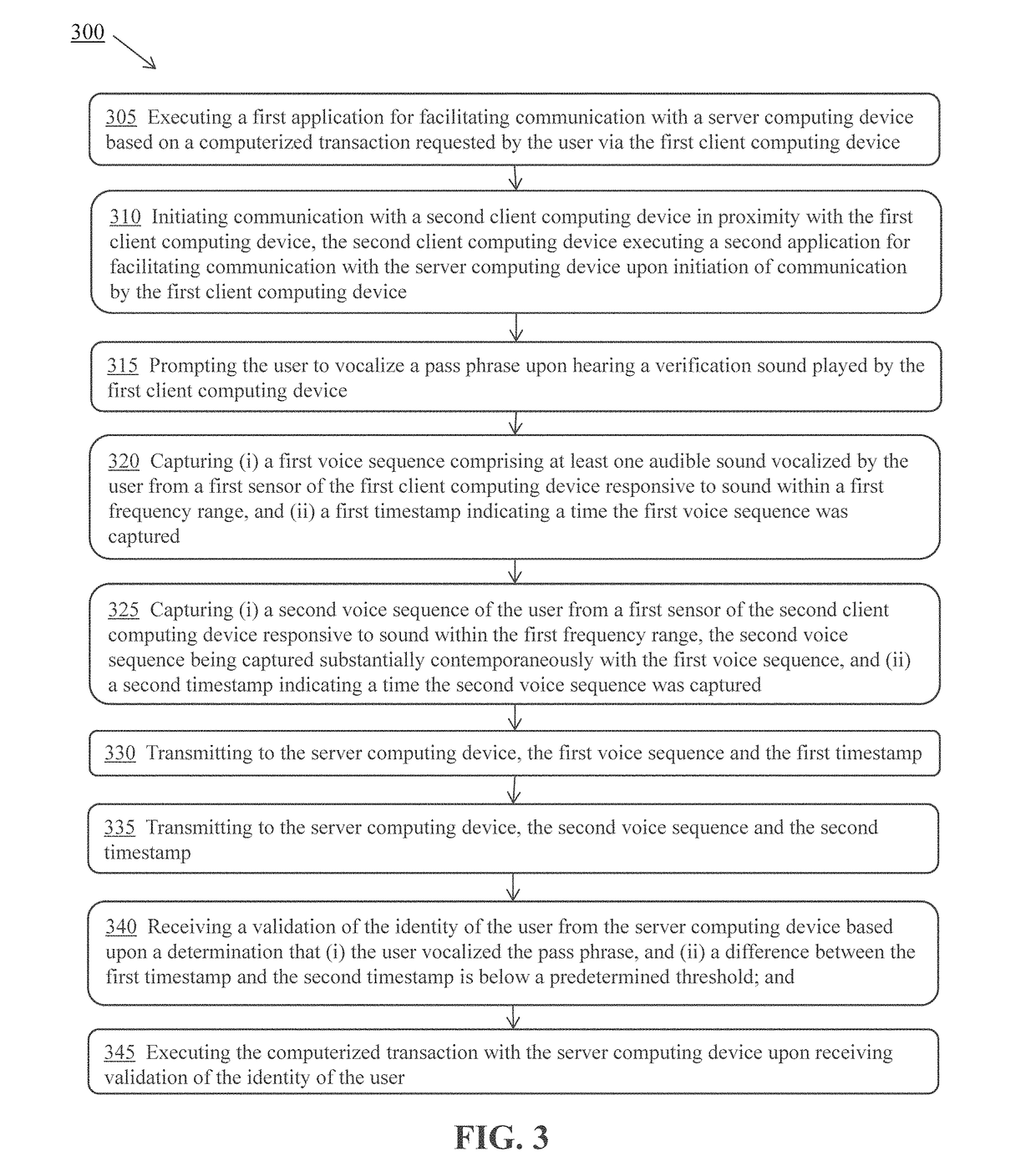
Systems and methods for simultaneous voice and sound multifactor authentication
ActiveUS10063542B1Simplify authentication processImprove robustnessDigital data authenticationSpeech recognitionClient-sideTimestamp
A computer-implemented method is described for authenticating an identity of a user requesting execution of a computerized transaction via a first client computing device. The first device and a second client computing device in proximity each execute applications for communicating with a server. The first and second devices contemporaneously capture voice sequences including at least one audible sound vocalized by the user, and a timestamp indicating when the sound is captured. The identity of the user is validated based upon a determination that the user vocalized the pass phrase, and a difference between the first timestamp and the second timestamp is below a predetermined threshold. The first device executes a computerized transaction with the server computing device upon receiving validation of the identity of the user.
Owner:FMR CORP
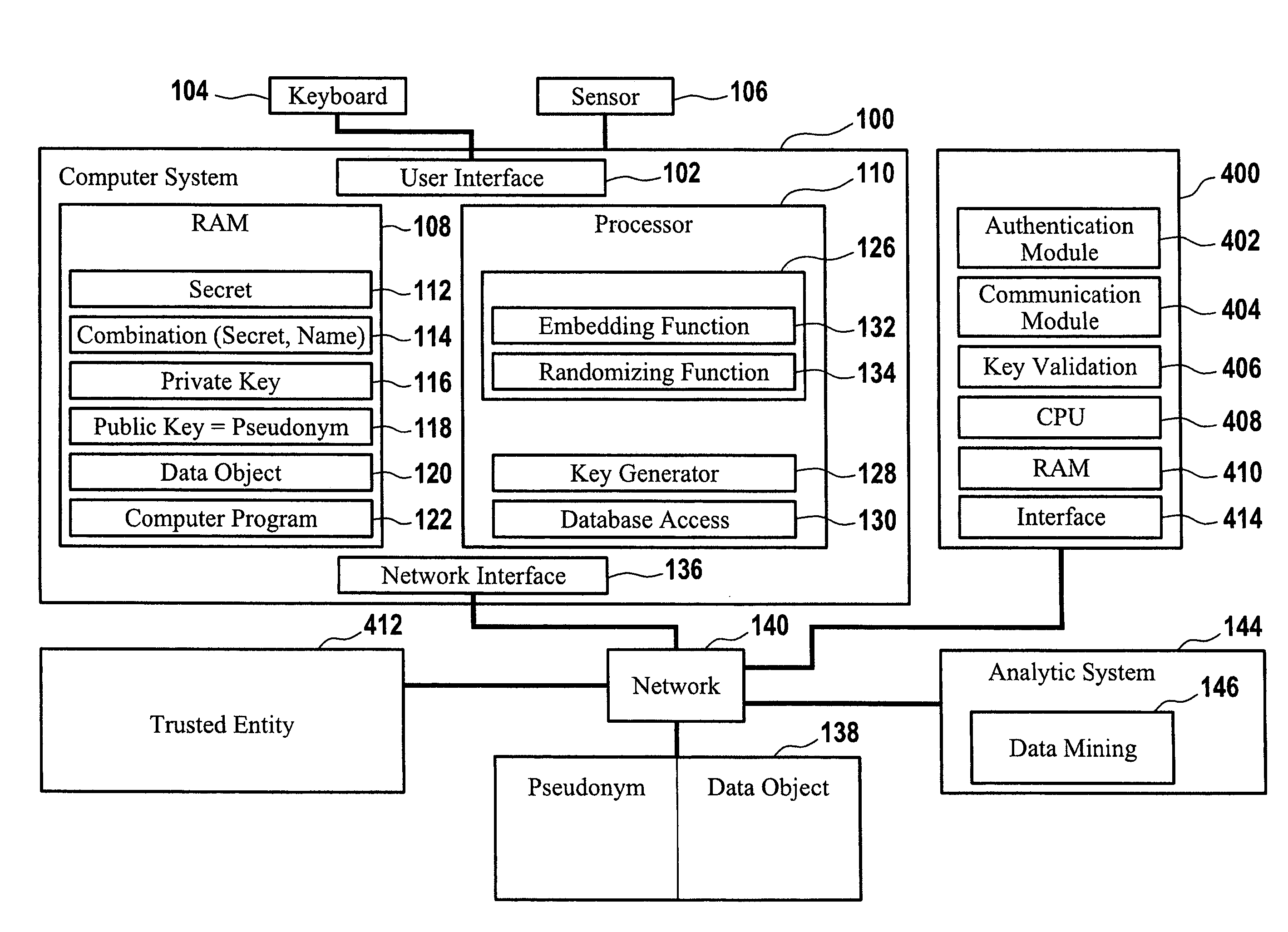
Computer implemented method for authenticating a user
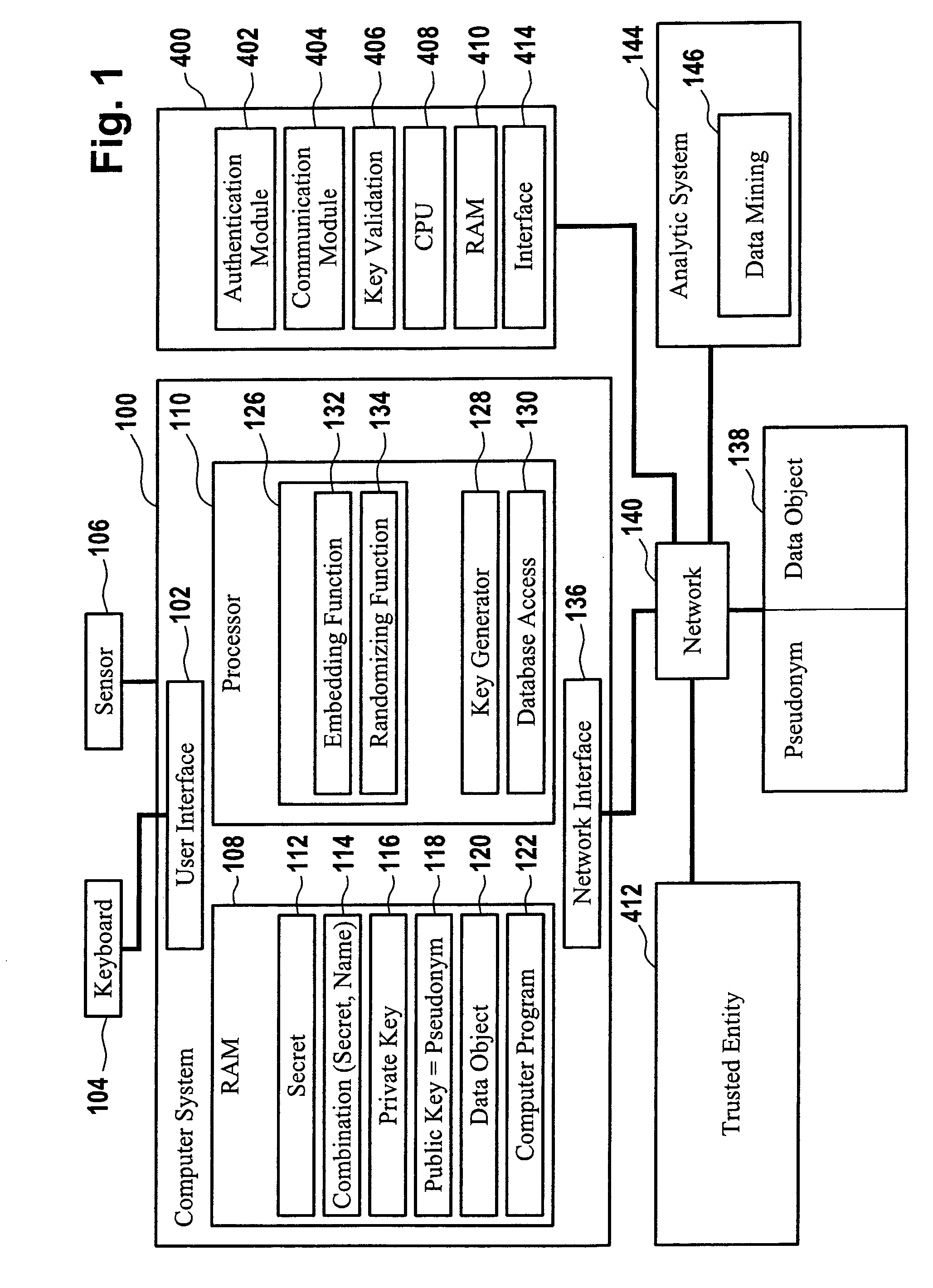
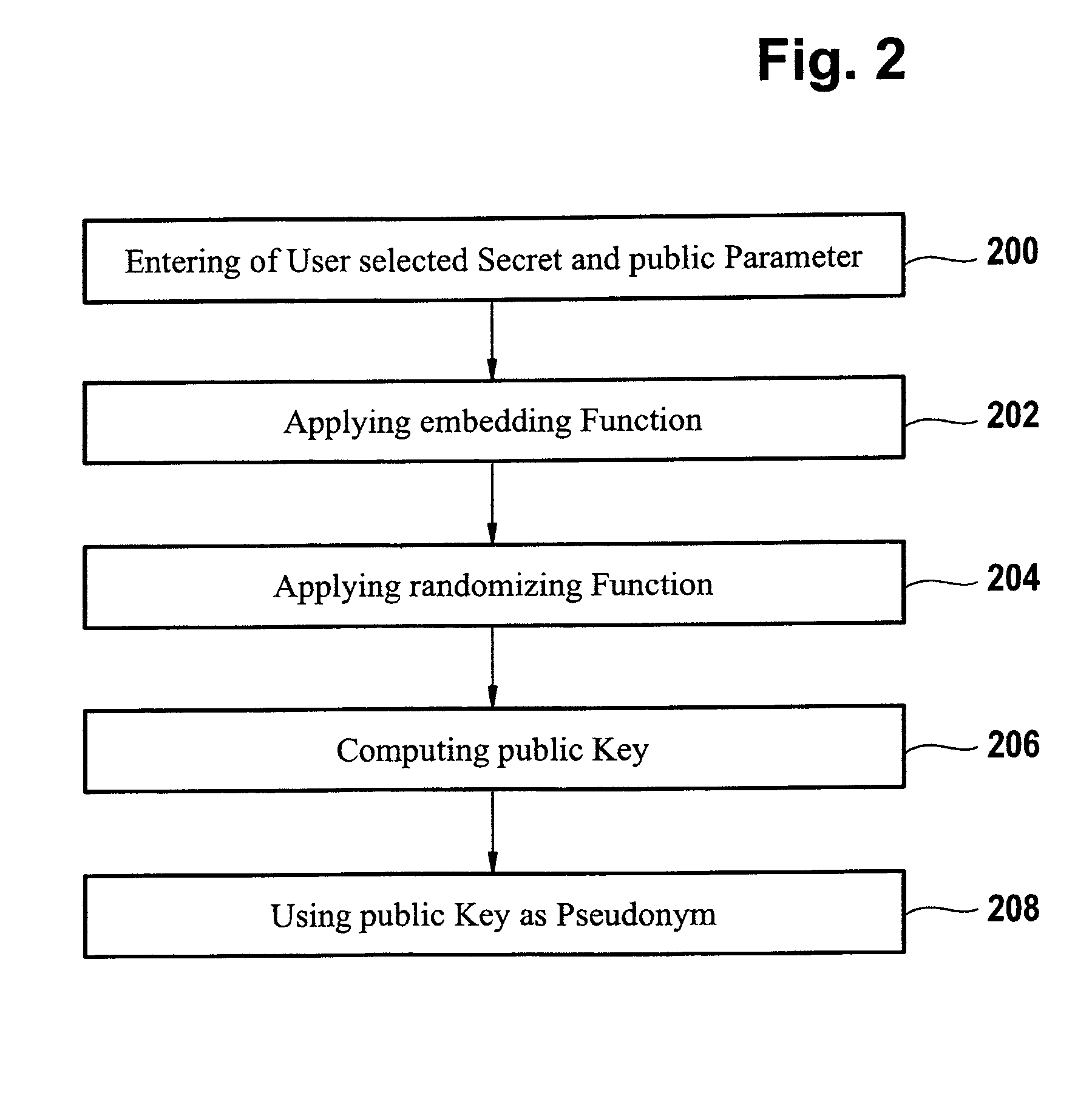
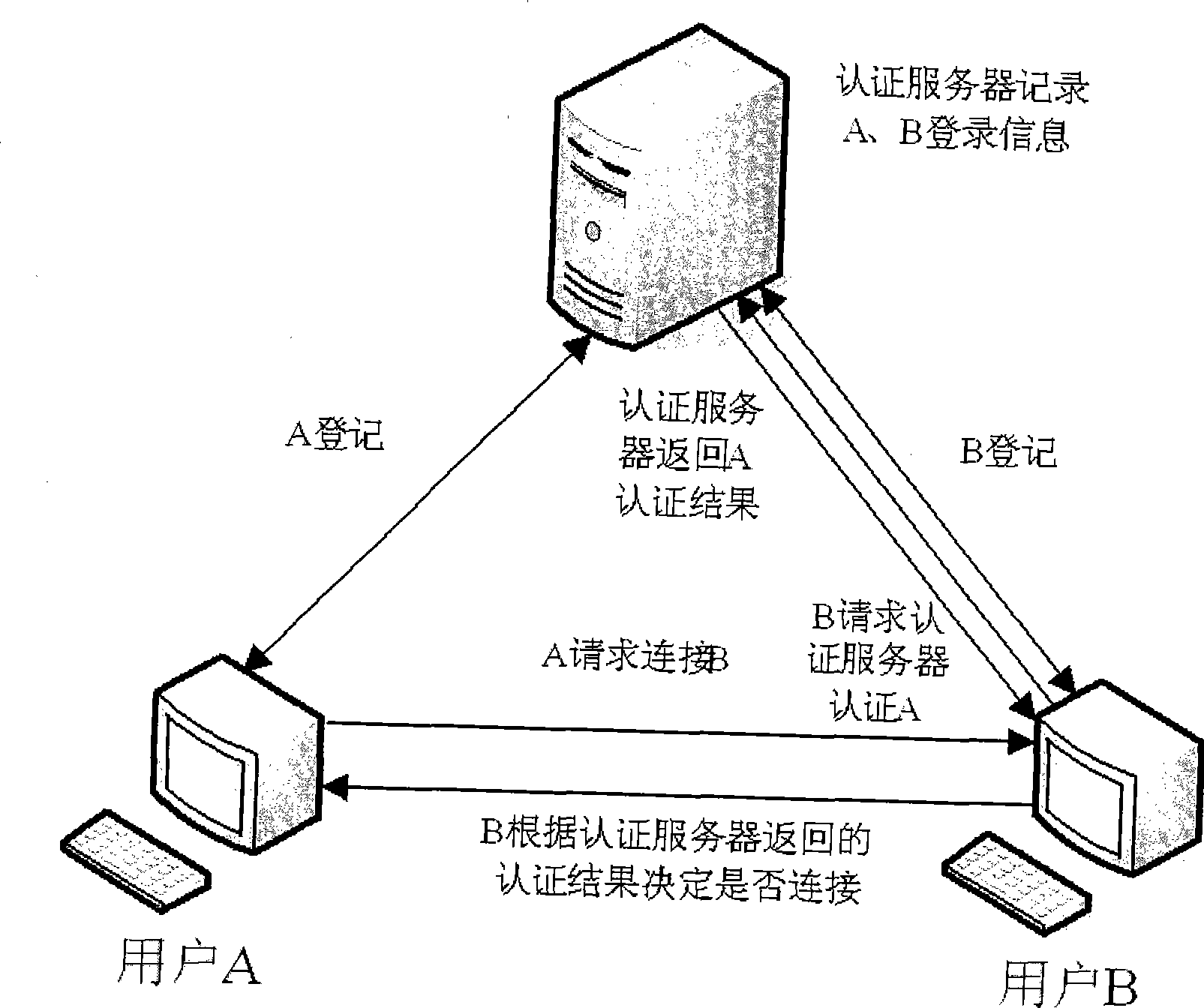
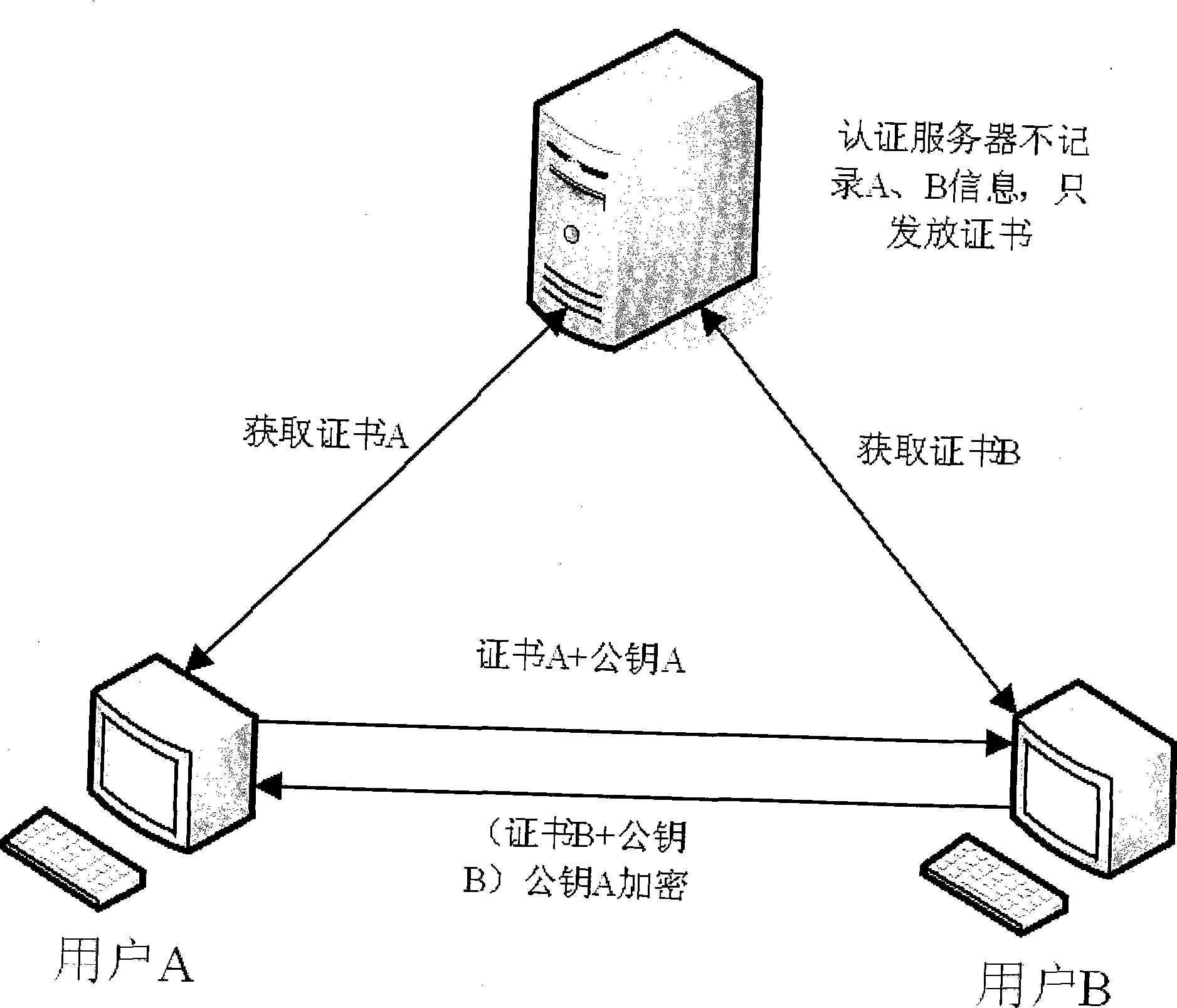
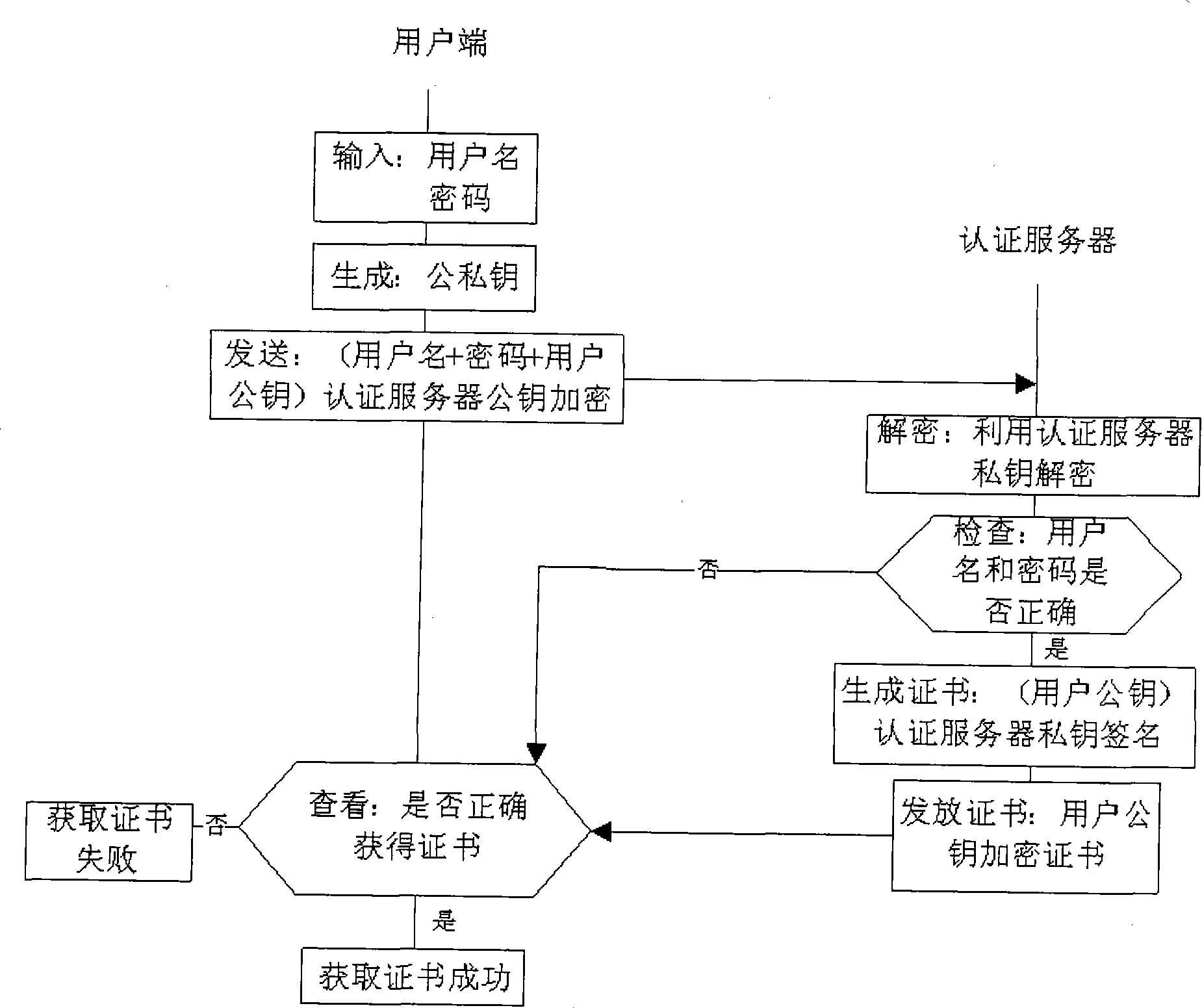
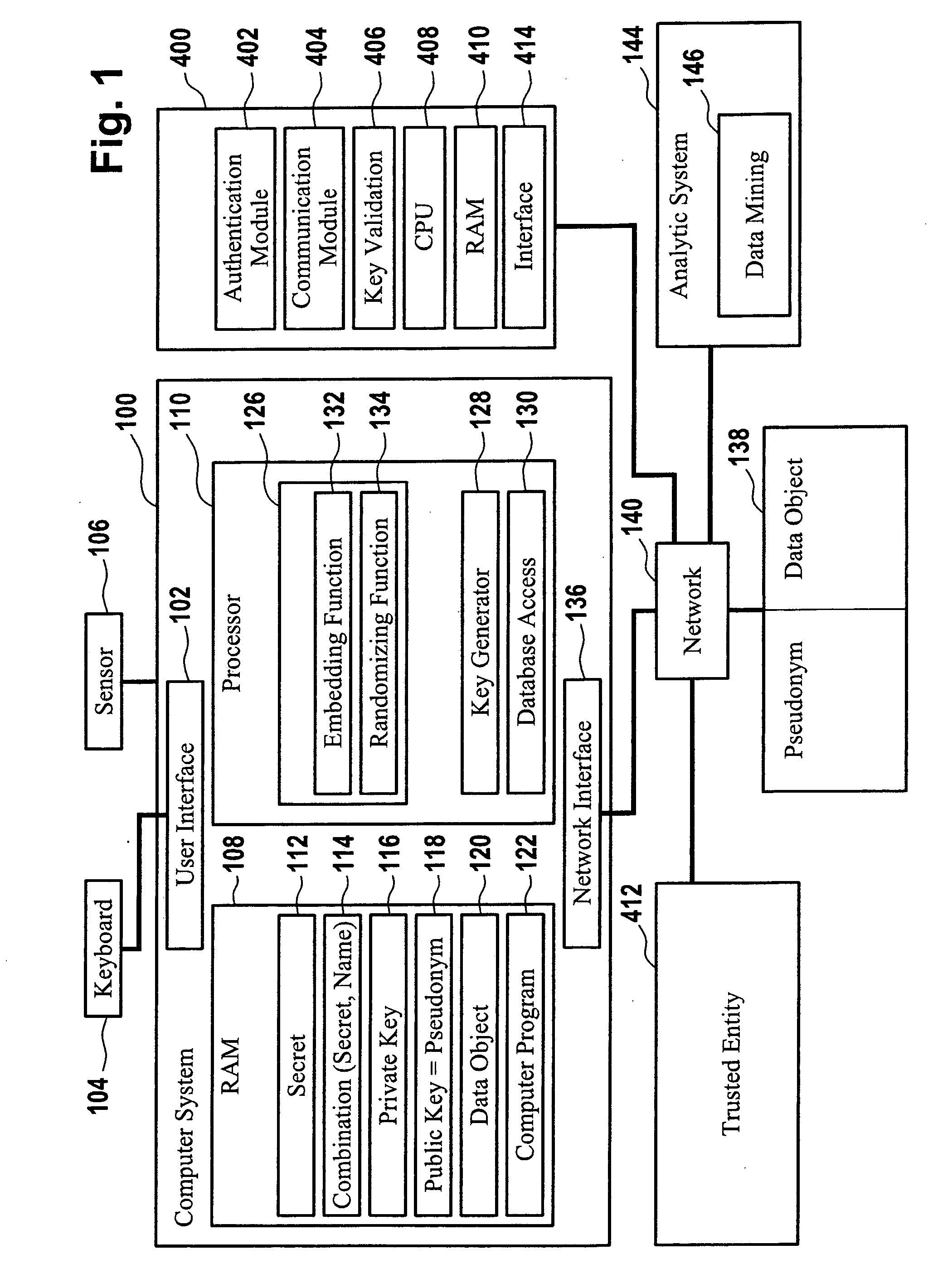
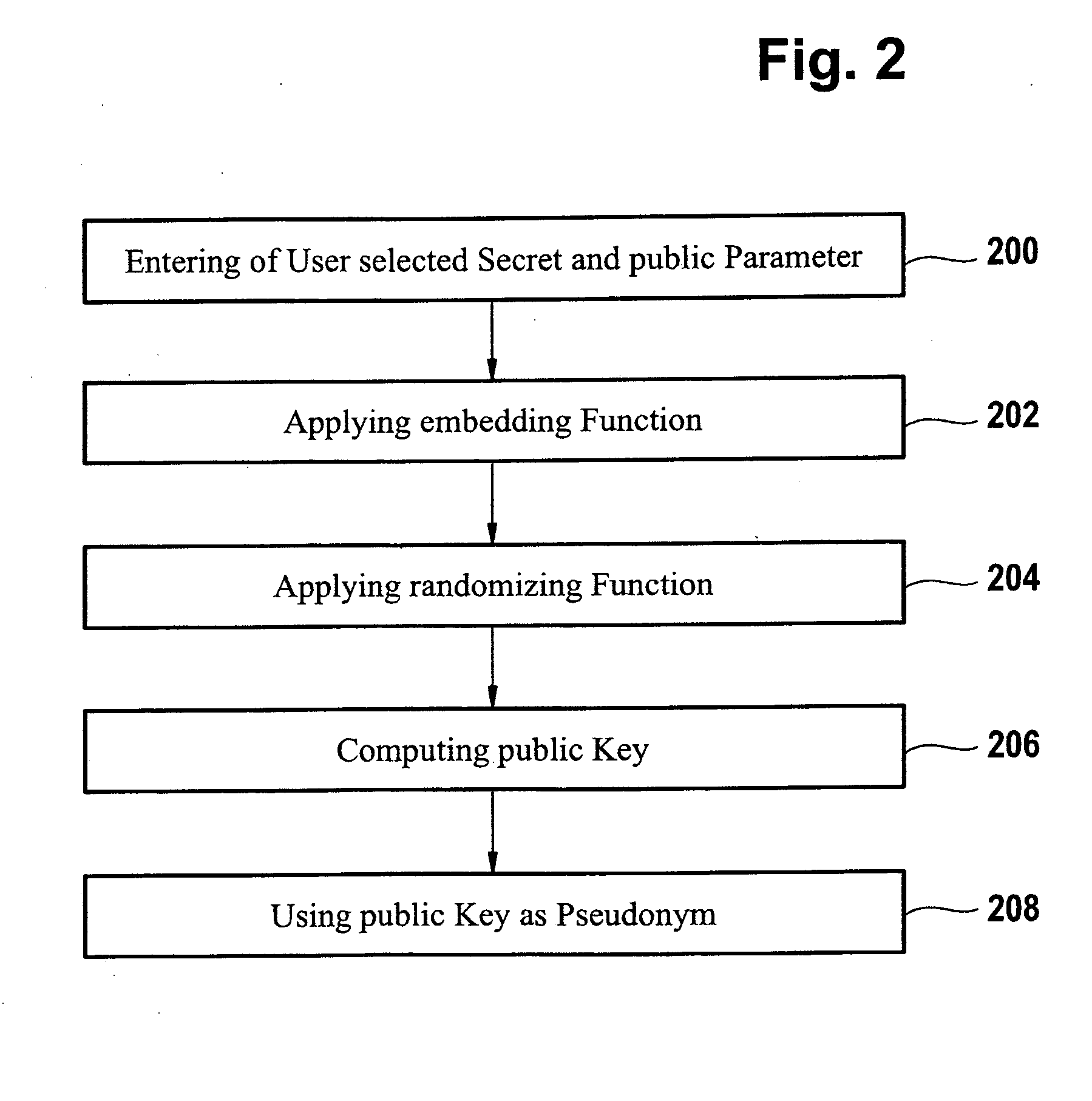
ActiveUS8522011B2Simplify the authentication processEfficient implementationKey distribution for secure communicationPublic key for secure communicationUser authenticationComputer science
The invention relates to a computer implemented method for performing a user authentication, wherein an asymmetric cryptographic key pair is associated with the user, said key pair comprising a public key and a private key, wherein the method comprises selecting the user to be authenticated using a pseudonym of said user, wherein said pseudonym comprises the public key of the user, the method further comprising performing a cryptographic authentication of the user using the asymmetric cryptographic key pair.
Owner:SPALKA ADRIAN +1
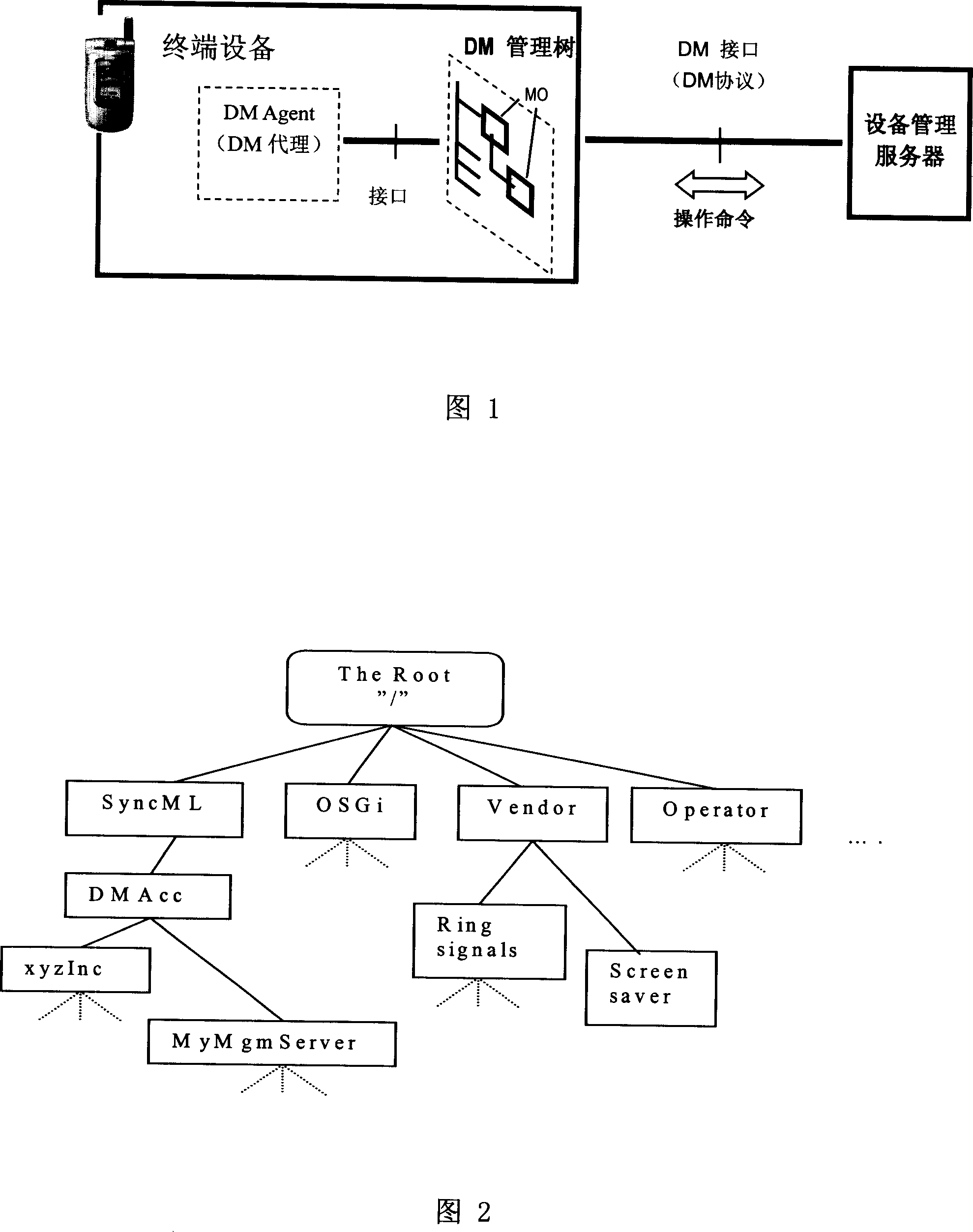
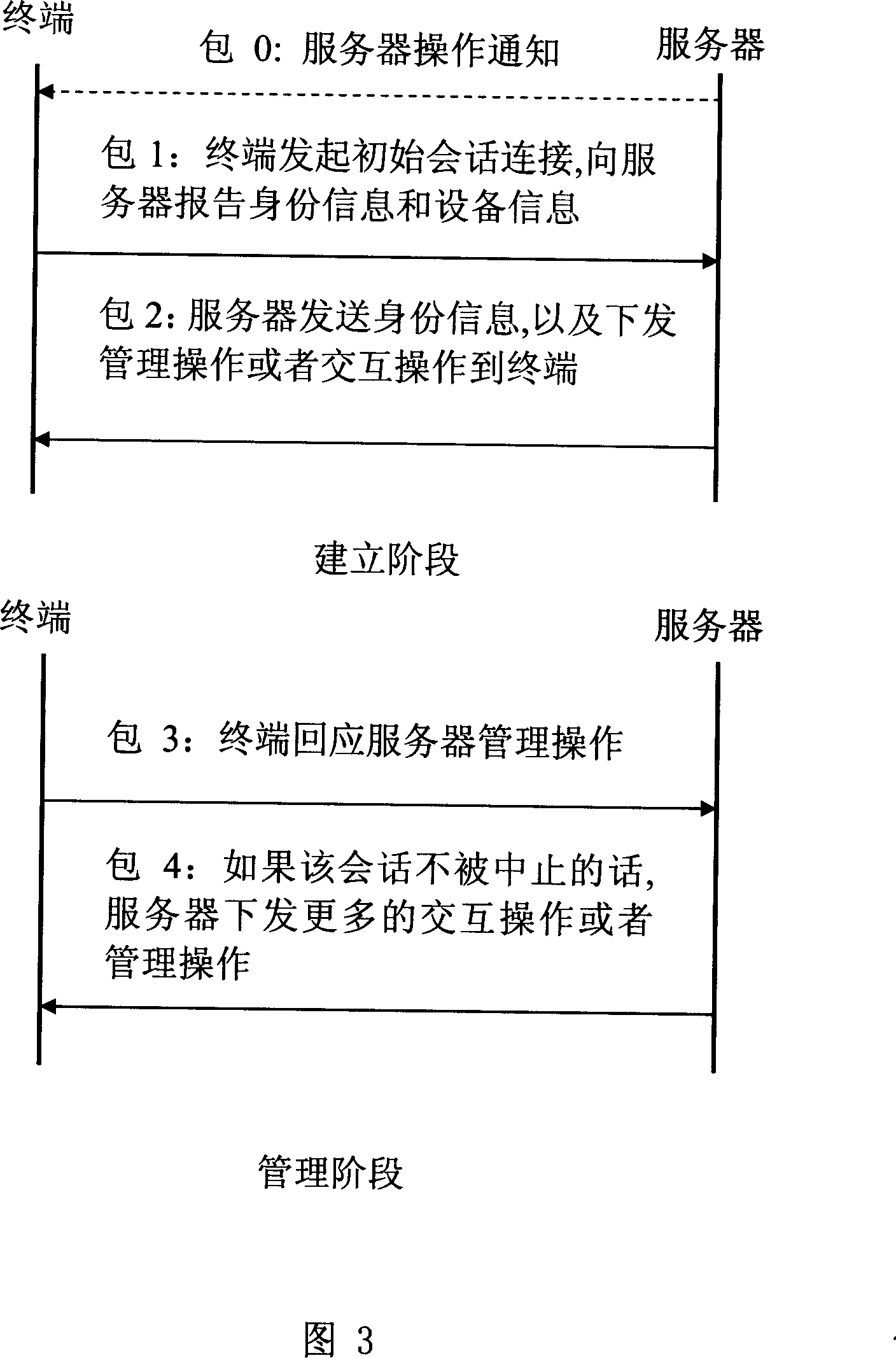
Method, apparatus and system for realizing device management
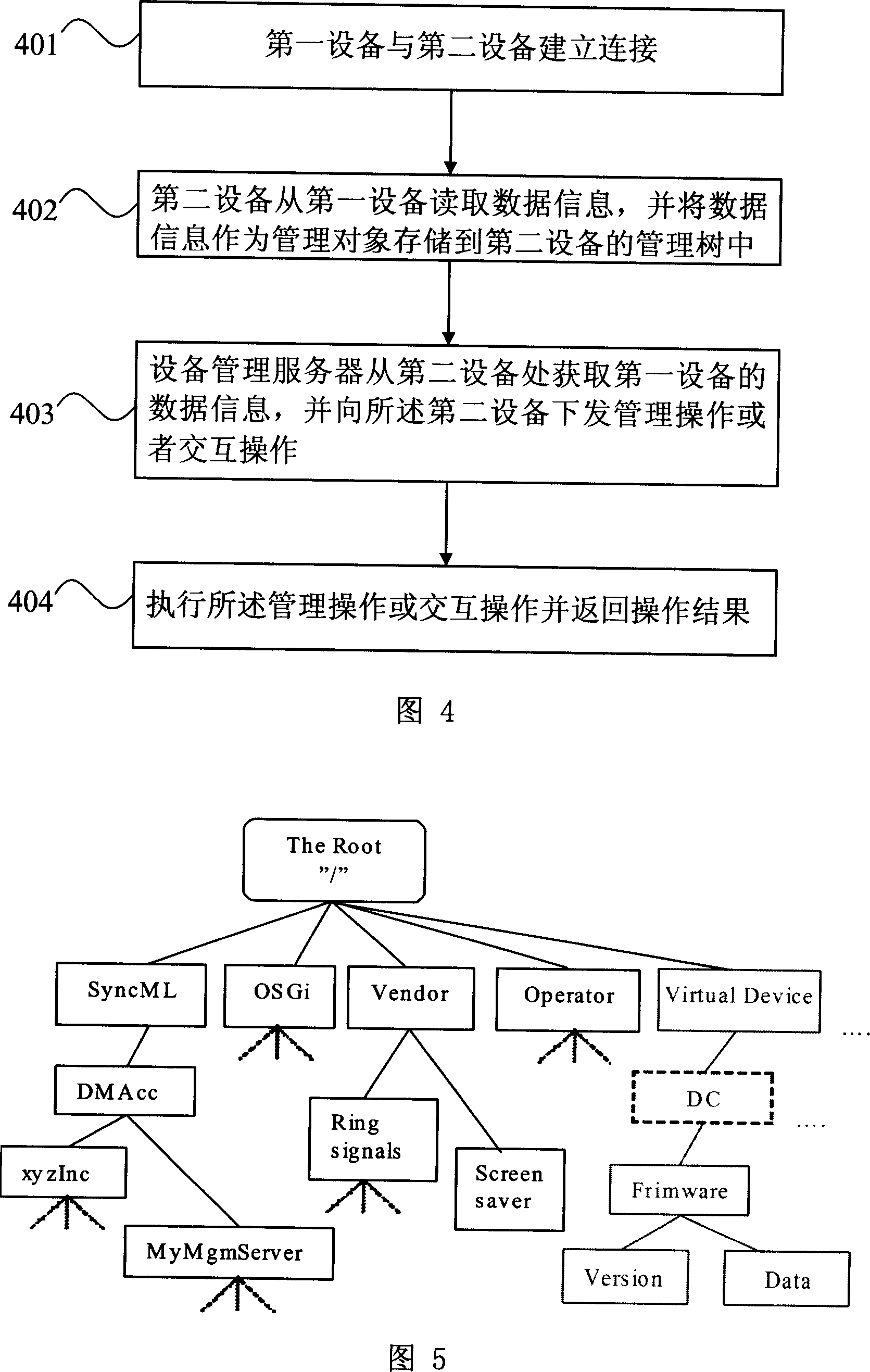
ActiveCN101083537ALess investmentSimplify the authentication processSubstation remote connection/disconnectionManagement objectManaged object
The invention discloses a device management method, device and system, and the method comprises: when first device is connected to second device, the second device reads data from the first device, and uses the data as managed object and stores into its management tree; the device management server obtains data of the first device from the second device and issues management operation or interactive operation to the second device; the second device executes the management operation or interactive operation and returns operation results. And the invention provides a method, device and system of implementing device management by data mapping.
Owner:HUAWEI TECH CO LTD
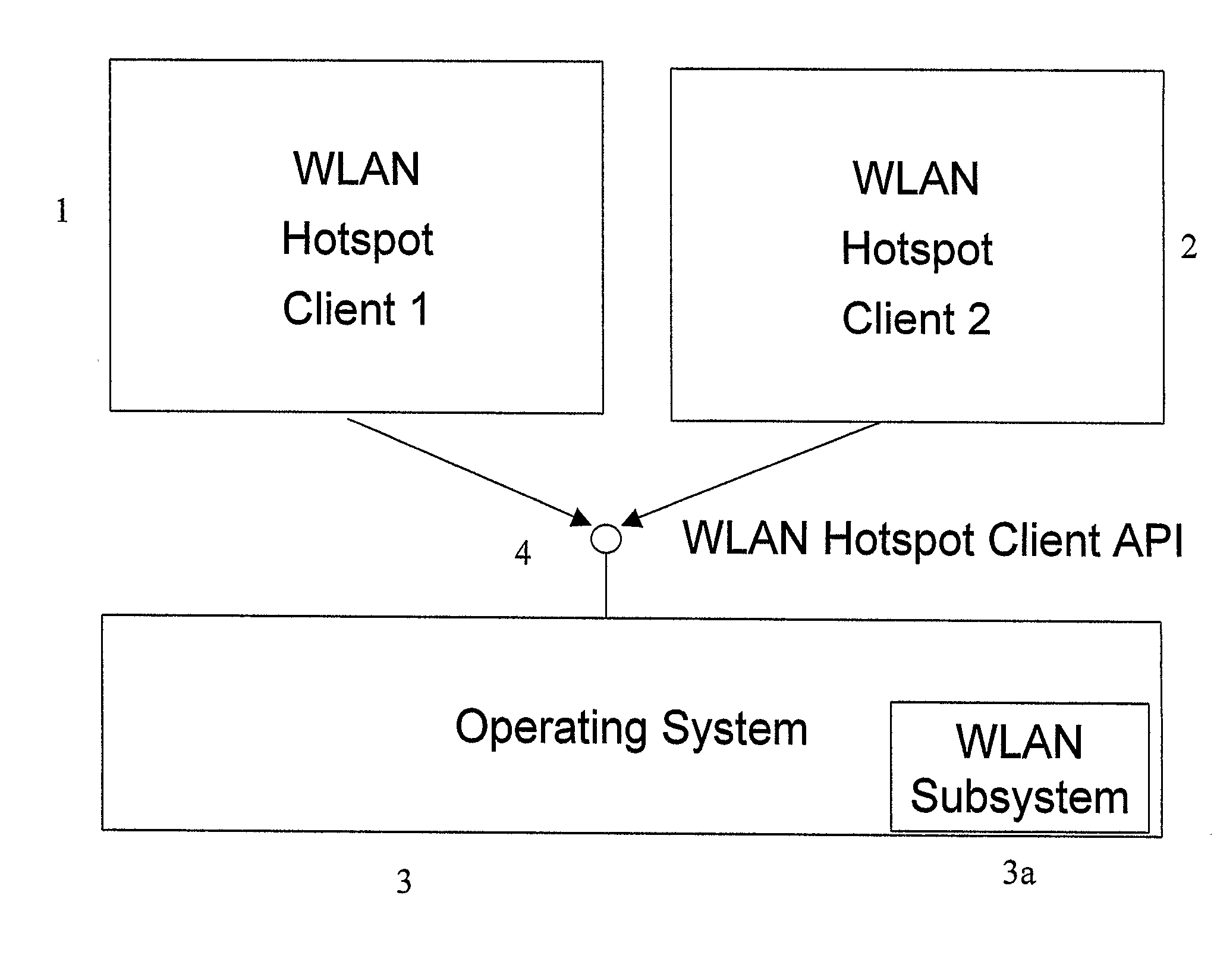
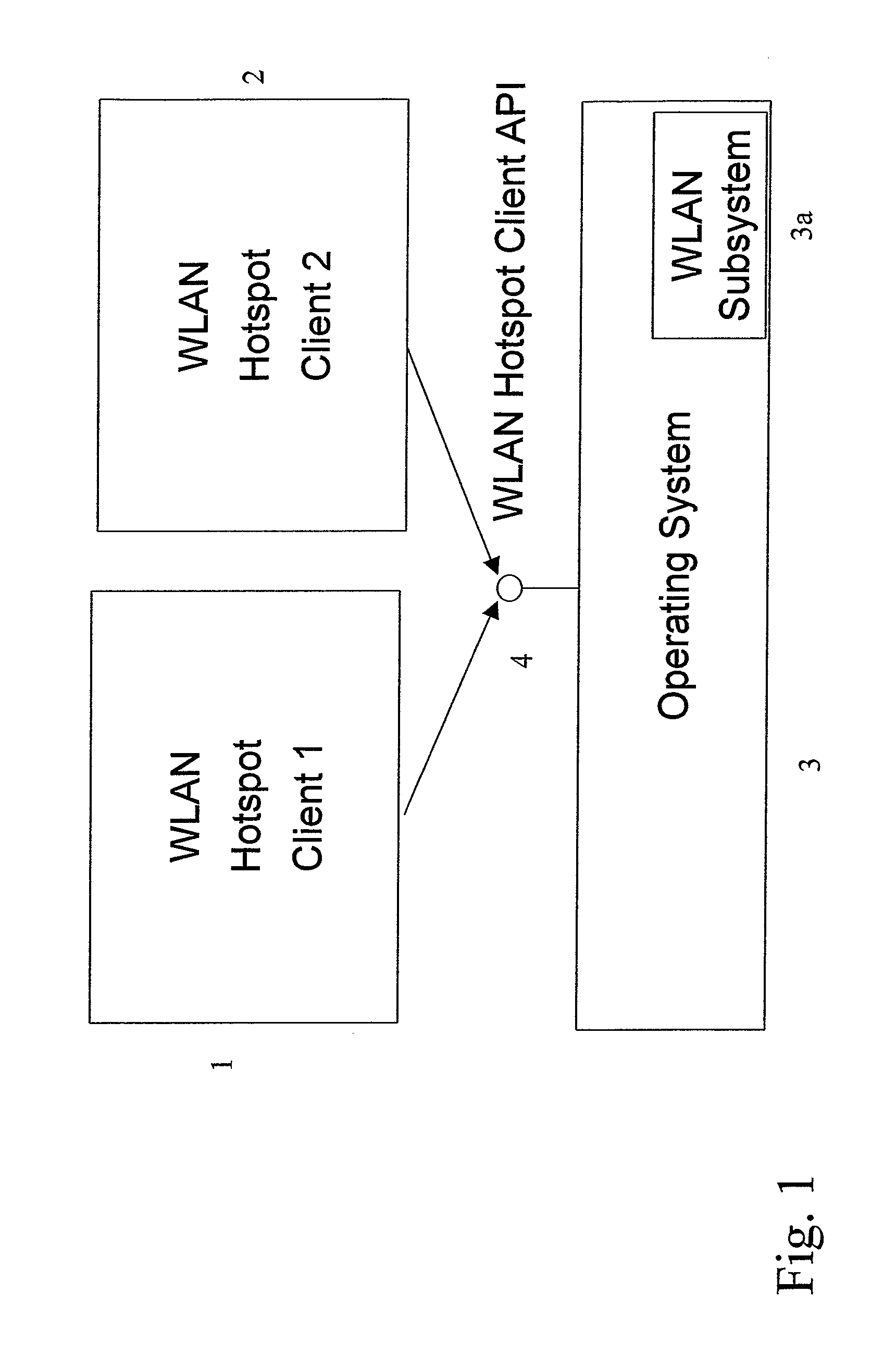
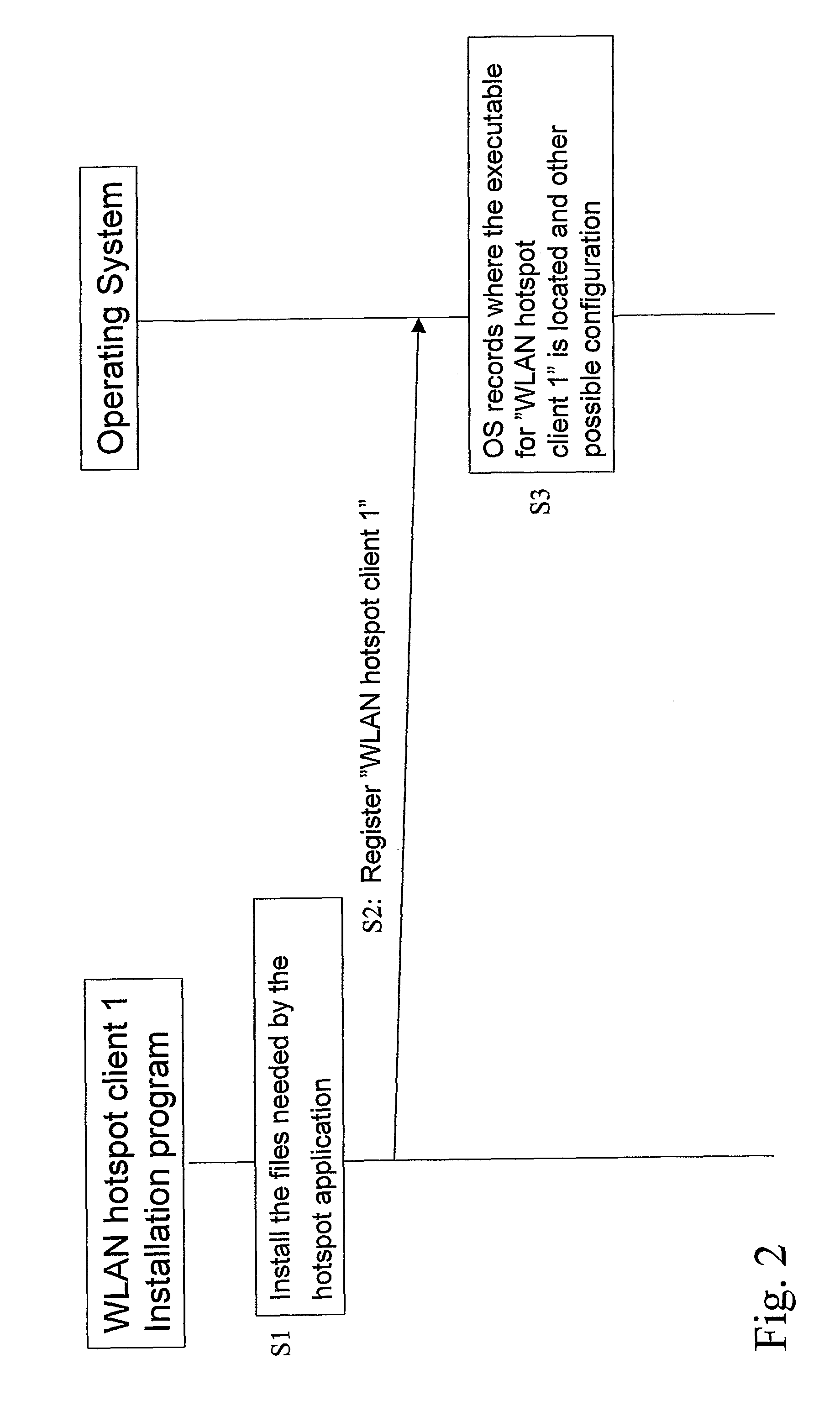
Support for integrated WLAN hotspot clients
InactiveUS20090300722A1Simplify the authentication processDigital data processing detailsData switching by path configurationClient-sideNetwork Access Device
The invention proposes a method and a network device comprising an operation entity (3) for handling network connection and at least one access client entity (1, 2) providing connection handling to a specific network access device, wherein the operation entity is adapted to identify a need for a network connection and to inform the access client entity, and the at least one access client entity is adapted to perform an authentication. Hence, an authentication procedure is delegated to a separate entity so that depending on the specification of a specific network connection, a suitable access entity for performing the authentication can be selected.
Owner:NOKIA TECHNOLOGLES OY
Identification authentication method between peer-to-peer user nodes in P2P network
InactiveCN101442411ARelieve pressureGuaranteed freshnessPublic key for secure communicationUser identity/authority verificationEncryptionPeer-to-peer
The invention provides a method for authenticating identification among peer-to-peer nodes in a P2P network. Each peer-to-peer node in the P2P network has a certificate which is acquired when a user node logs on the network through a certificate server, and the certificate comprises an encryption result of a private key of the certificate server to a public key of the user node. The method comprises the following steps: a first user node transmits an identification authentication message to a second user node in the network, wherein the identification authentication message comprises a certificate of the first user node and the public key of the first user node; a second user node authenticates identification of the first user node by the identification authentication message, after authentication succeeds, the identification authentication message is returned to the first user node, wherein the identification authentication message comprises a certificate of the second user node and the public key of the second user node; and the first user node authenticates the identification of the second user node by the identification authentication message returned by the second user node, and if the authentication succeeds, identification authentication between two user nodes succeeds.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Computer implemented method for authenticating a user
ActiveUS20110154025A1Simplify the authentication processEfficient implementationKey distribution for secure communicationPublic key for secure communicationMethod selectionUser authentication
The invention relates to a computer implemented method for performing a user authentication, wherein an asymmetric cryptographic key pair is associated with the user, said key pair comprising a public key and a private key, wherein the method comprises selecting the user to be authenticated using a pseudonym of said user, wherein said pseudonym comprises the public key of the user, the method further comprising performing a cryptographic authentication of the user using the asymmetric cryptographic key pair.
Owner:SPALKA ADRIAN +1
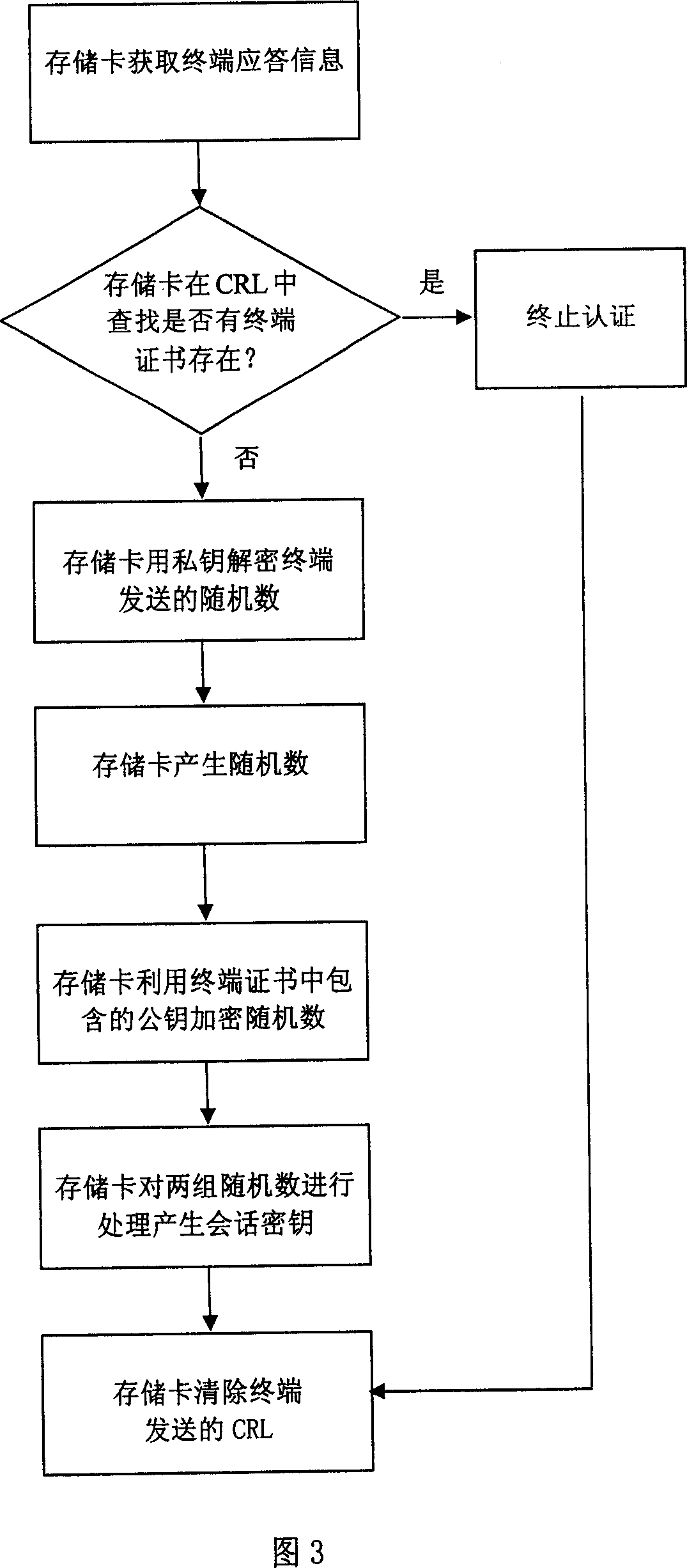
Identify authorization method between storage card and terminal equipment at off-line state
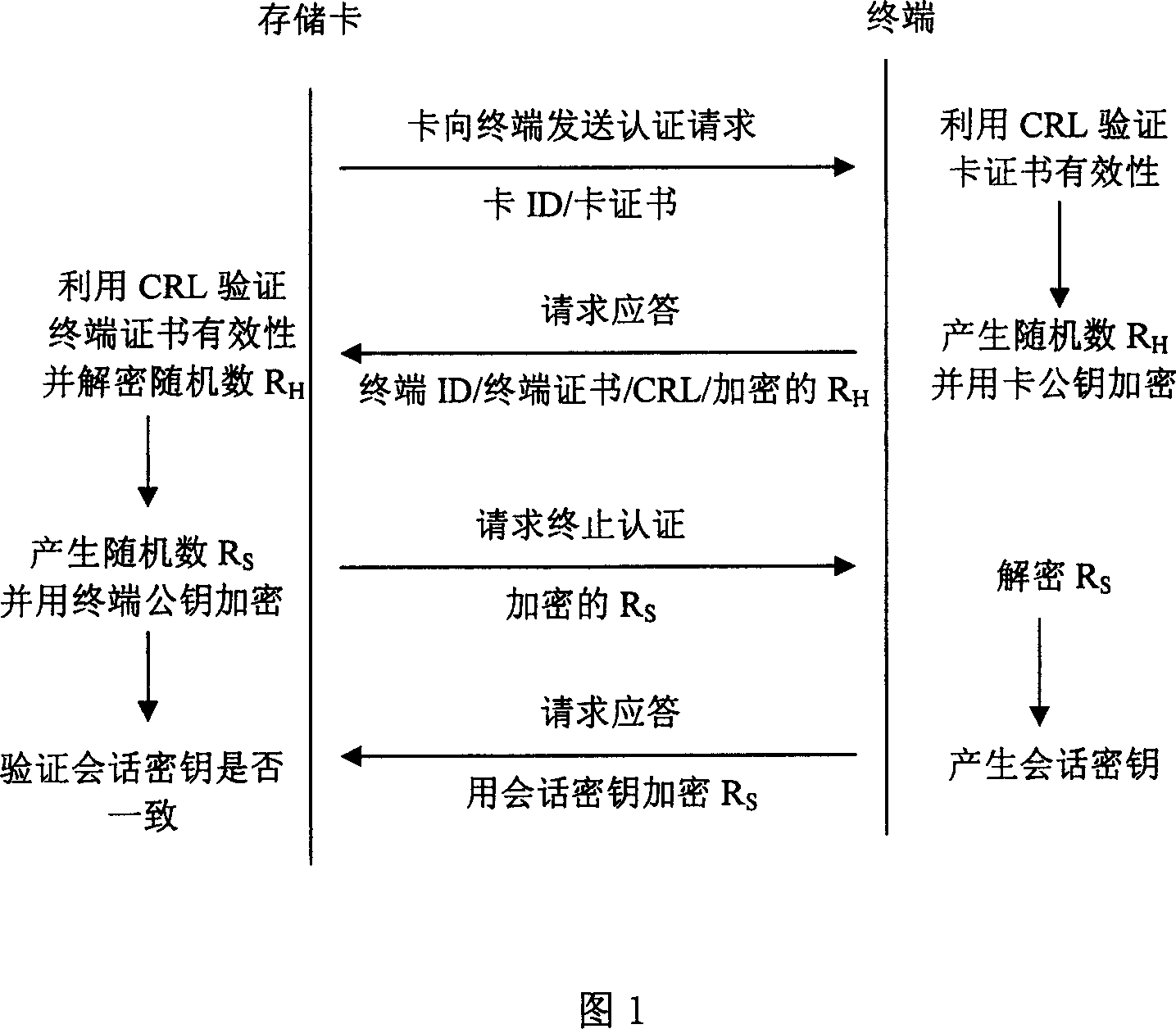
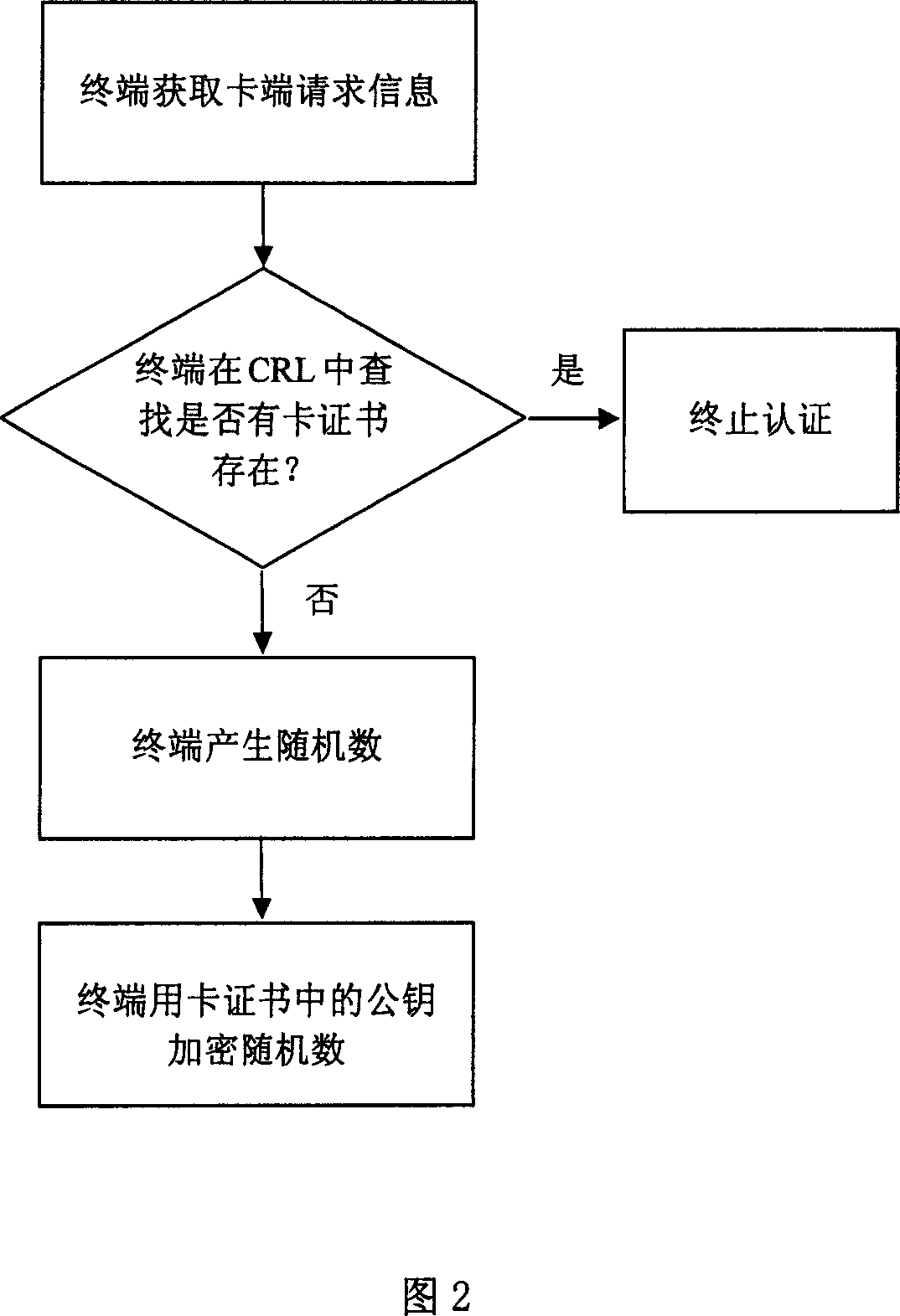
InactiveCN101090316ASimple and effective authentication methodQuick responsePublic key for secure communicationUser identity/authority verificationComputer hardwareTerminal equipment
This invention discloses an identity authentication method between storage cards and a terminal device at the off-line state including: a storage card sends an authentication request to a terminal device including the identity number of the card and the card certificate, the terminal processes the request and sends a response to the card including the identity number of the terminal, a certificate, a list for certificate revoking and a random number of the card ciphered public key, the storage card sends a request for stopping the authentication to the terminal with the random number of the ciphered terminal public key, the terminal sends a stopping request response to the card with the session secret key encryption random number generated by the card, which processes the response request to verify the exclusiveness of the session key.
Owner:POTEVIO INFORMATION TECH
Identity authentication method and equipment
InactiveCN106156702AImprove accuracyImprove experienceCharacter and pattern recognitionTemplate matchComputer science
The invention provides an identity authentication method and equipment. The method comprises the steps that an identity authentication request of a user under authentication is received; the identity authentication request is responded and the face image of the user under authentication is automatically acquired; the face features are extracted from the acquired face image of the user under authentication; and existence of face feature templates matched with the face features extracted from the acquired face image of the user under authentication is determined in a preregistered face feature template library, representative feature screening is performed according to the face features extracted from the acquired face image of the user under authentication and the face feature templates if the judgment result is yes, and the face feature template library is updated by using the selected features through screening.
Owner:BEIJING SENSETIME TECH DEV CO LTD
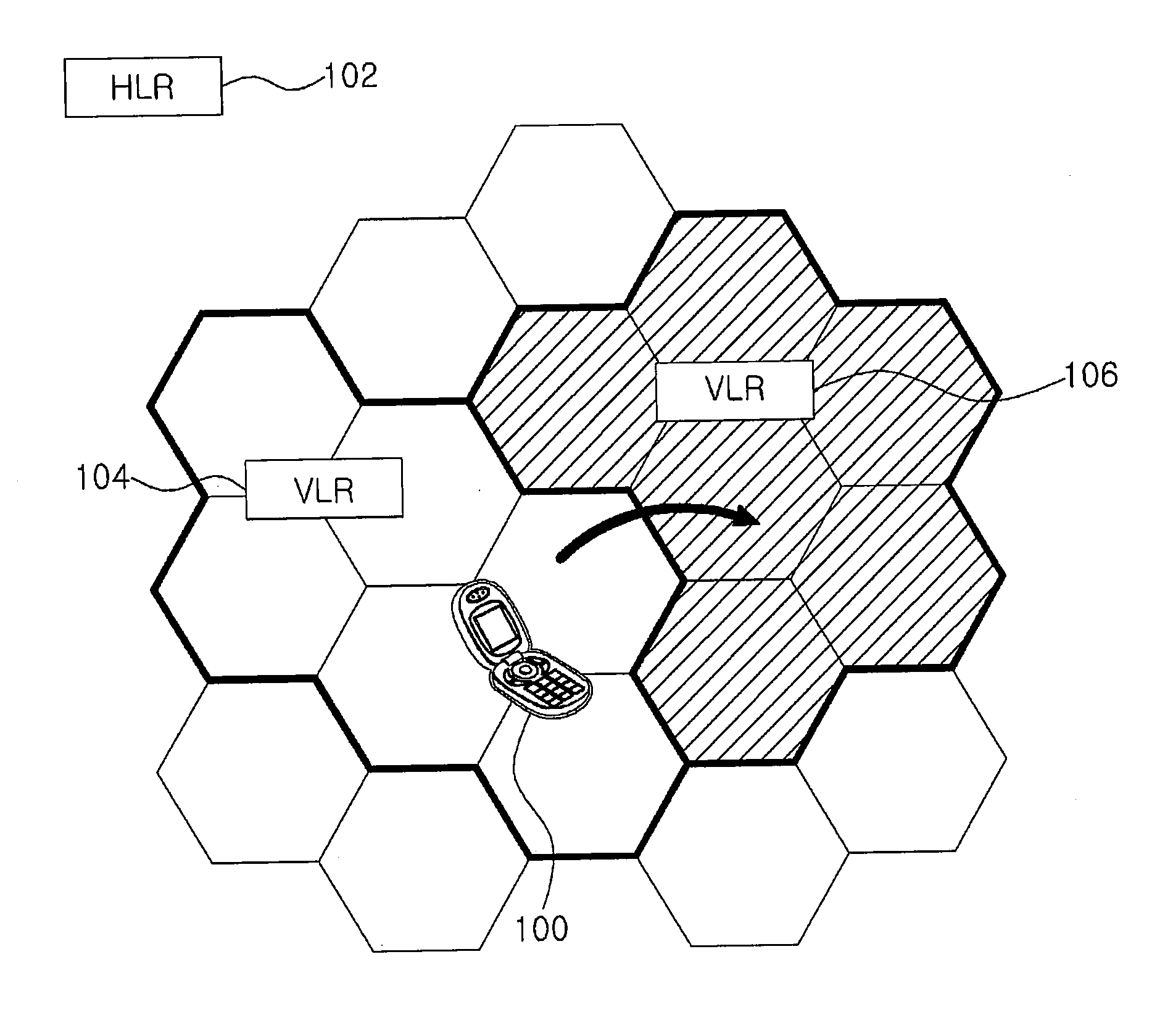
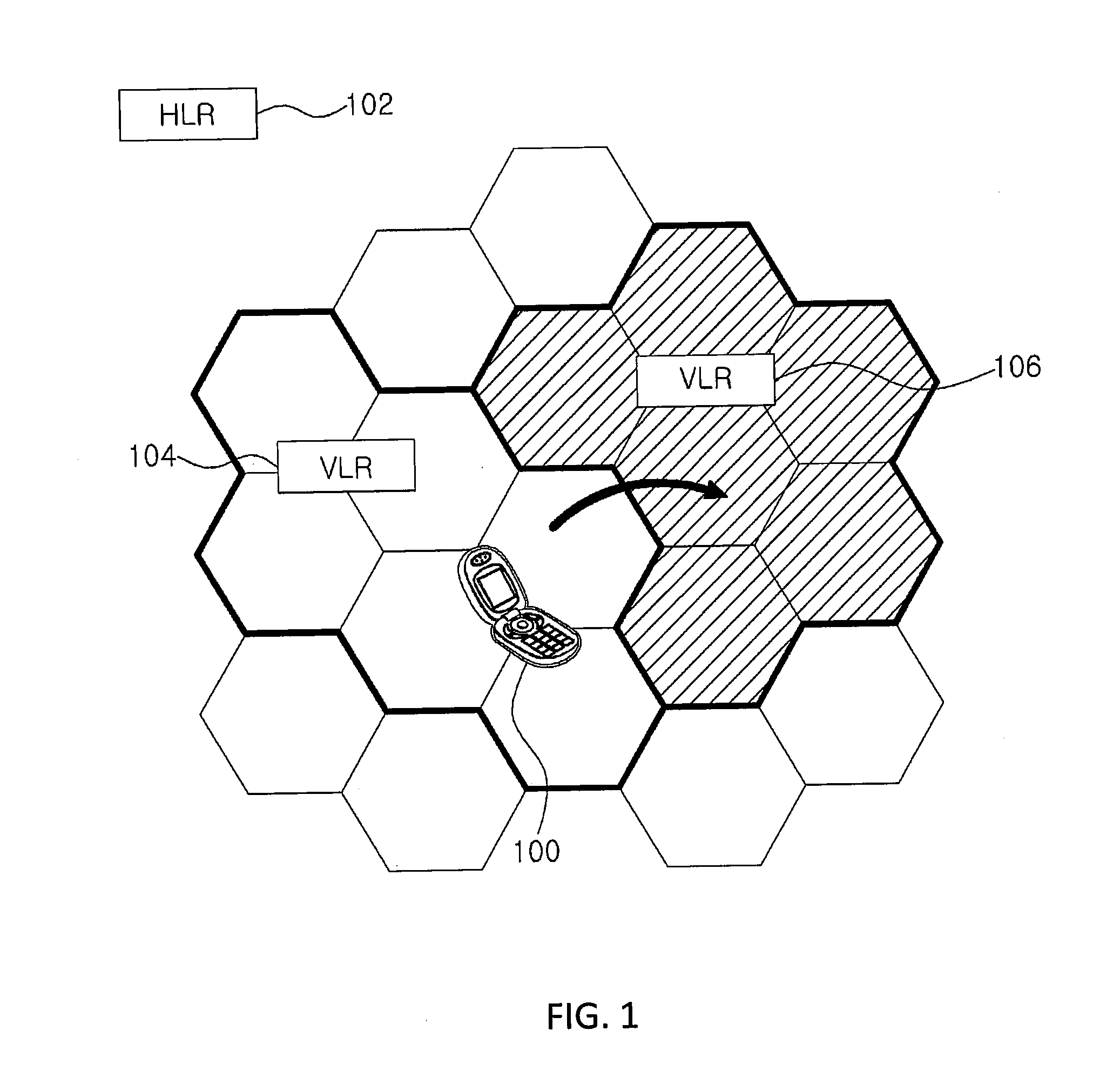
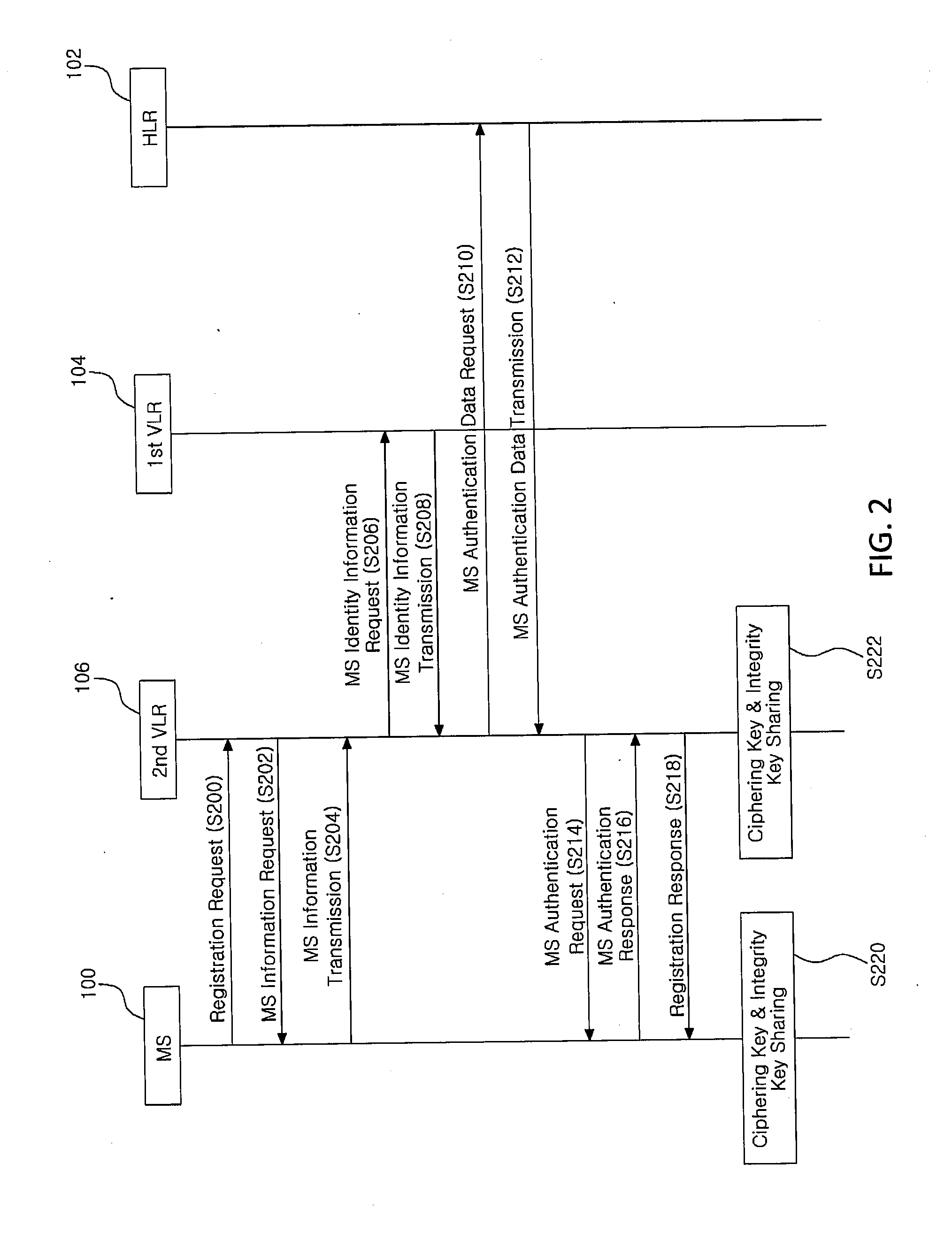
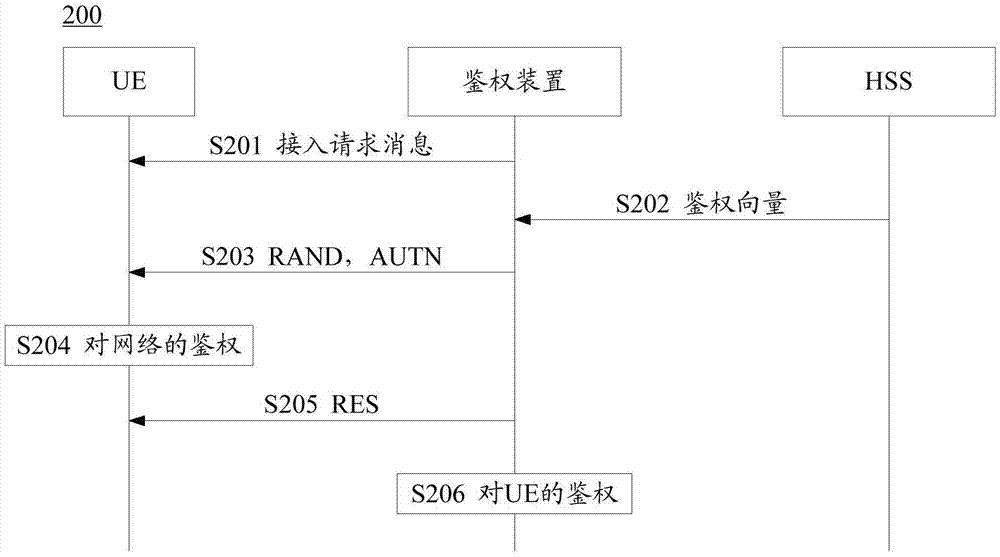
Method for authentication and key establishment in a mobile communication system and method of operating a mobile station and a visitor location register
InactiveUS20120142315A1Simplify the authentication processConsume bandwidthUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsProcessor register
The present invention relates to a method whereby the mobile station and a visitor location register create and share a ciphering key and an integrity key in order to directly authenticate each other. The communication method in a mobile communication system such as this includes registering the mobile station with the home location register; and having the mobile station and the visitor location register directly authenticate each other and mutually share a ciphering key and an integrity when the mobile station moves to the visitor location register.
Owner:IND ACADEMIC CORP FOUND YONSEI UNIV
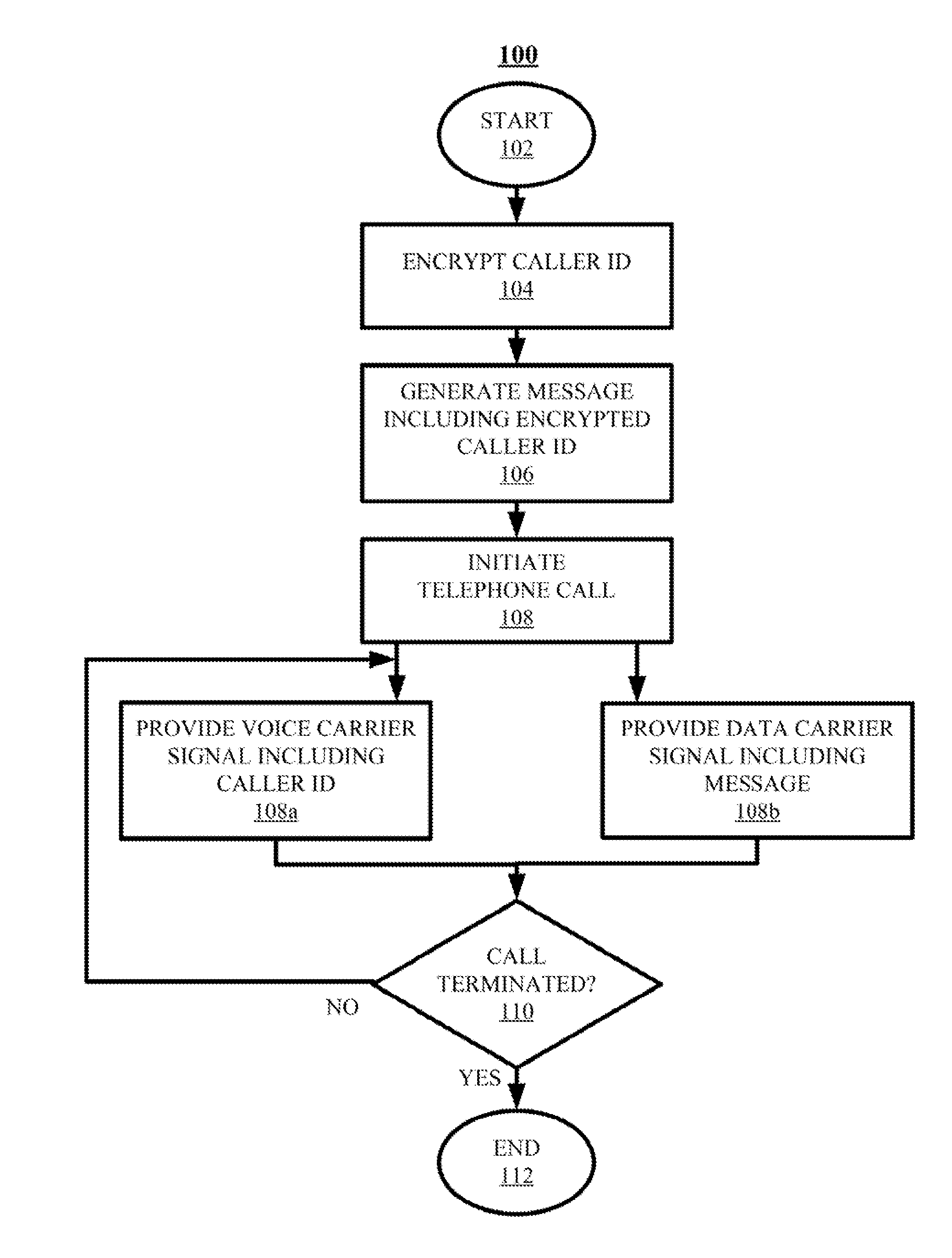
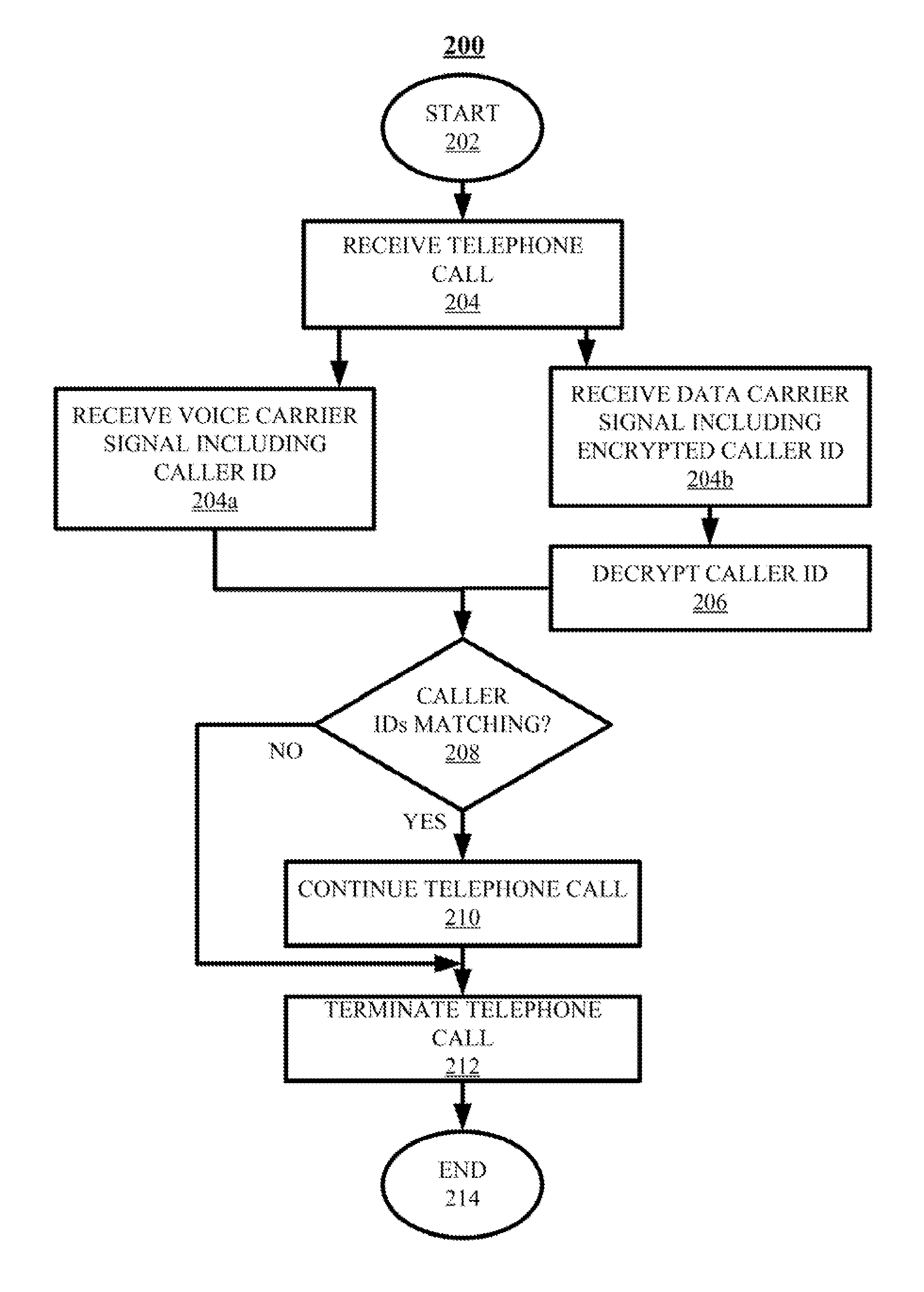
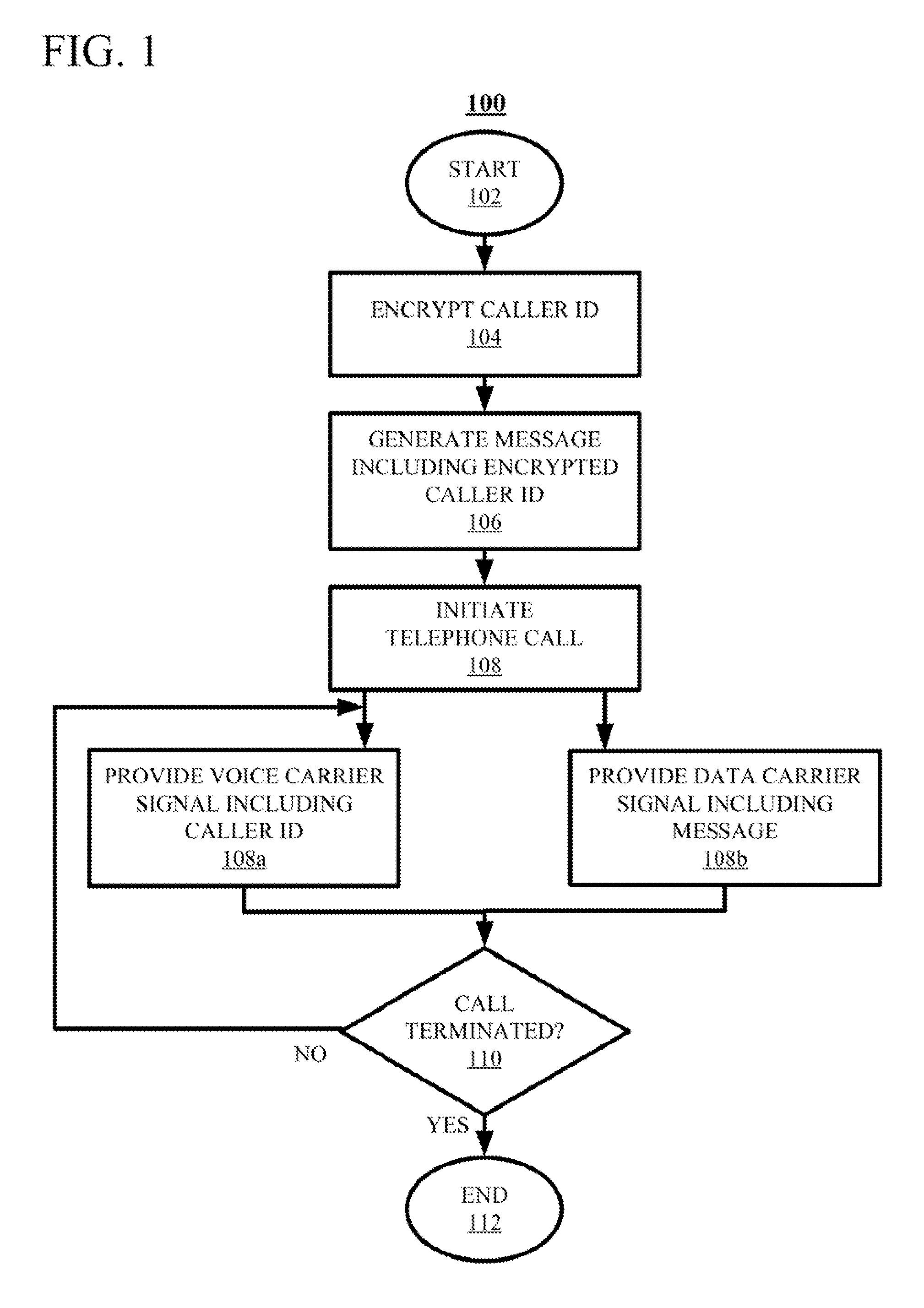
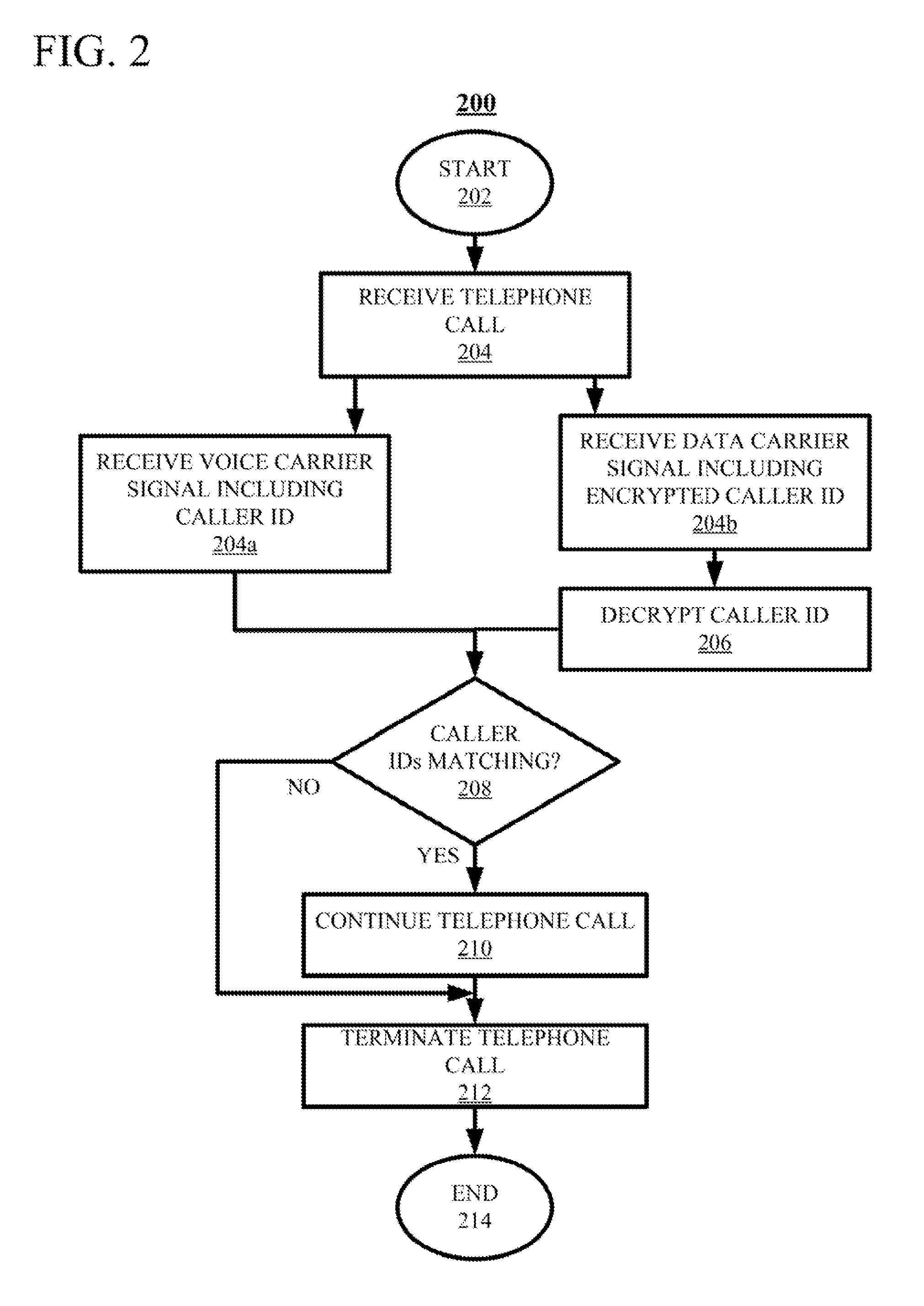
Telephone Caller Authentication
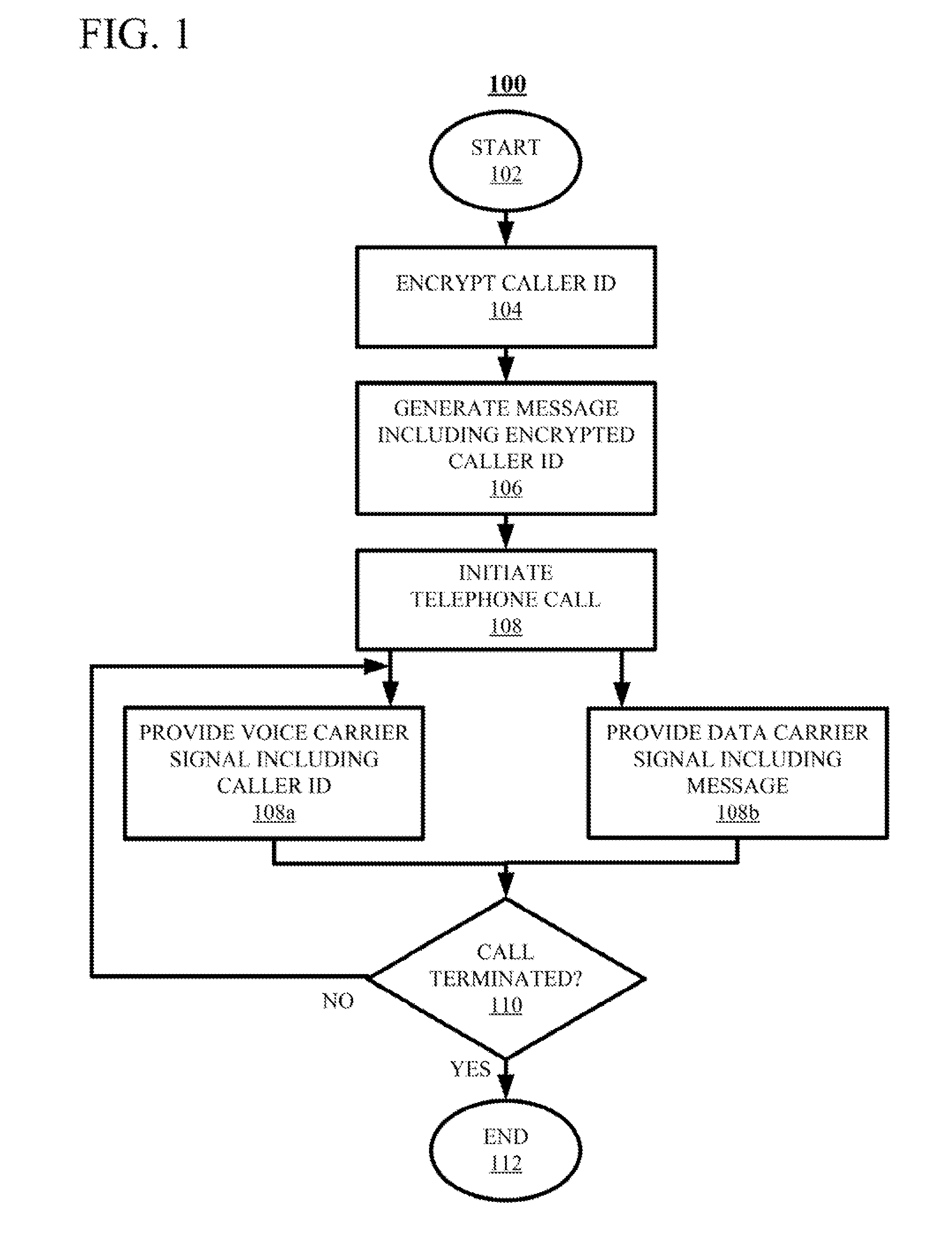
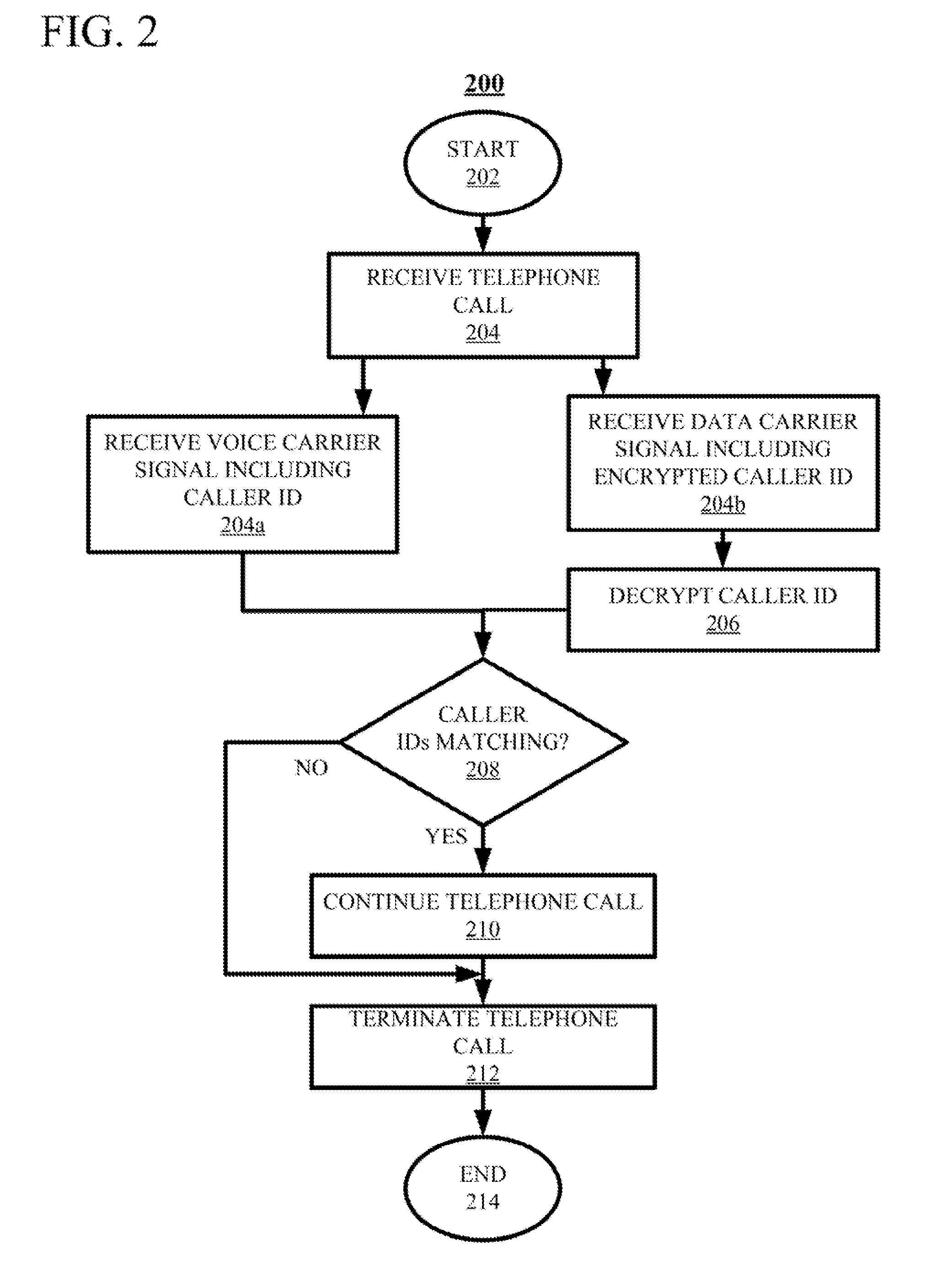
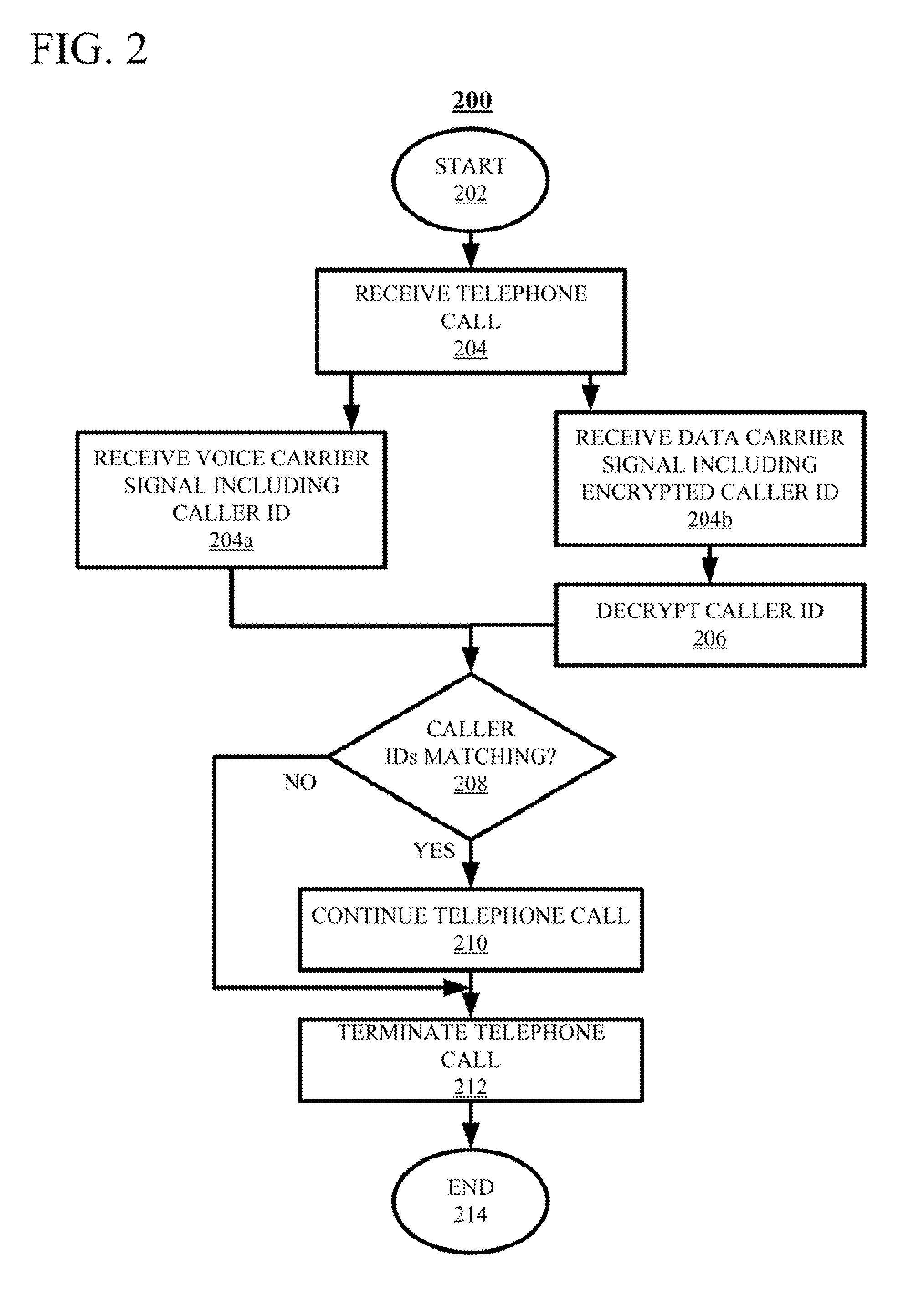
ActiveUS20150236857A1Sacrificing robustnessSimplify the authentication processUser identity/authority verificationCommmunication supplementary servicesCarrier signalSpeech sound
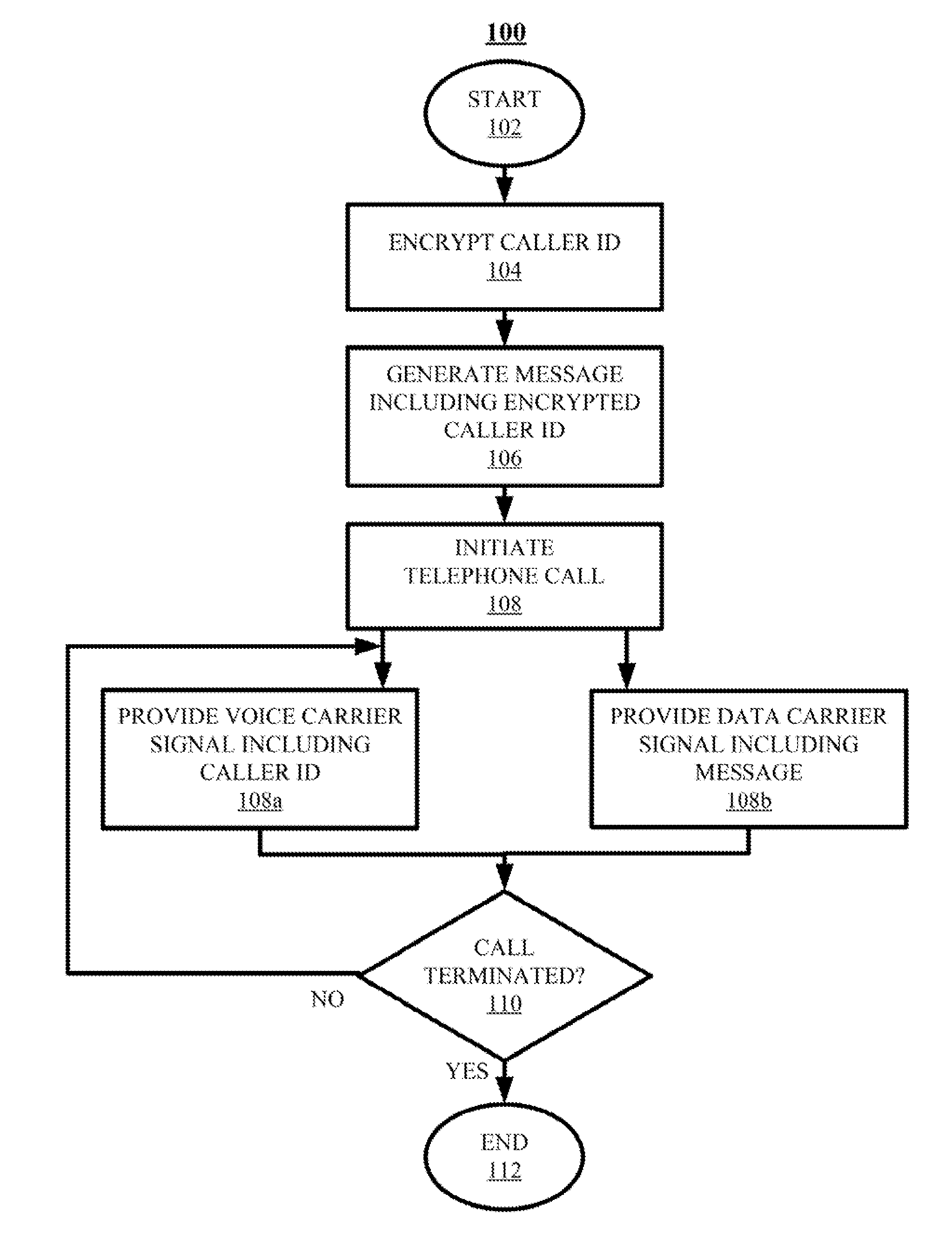
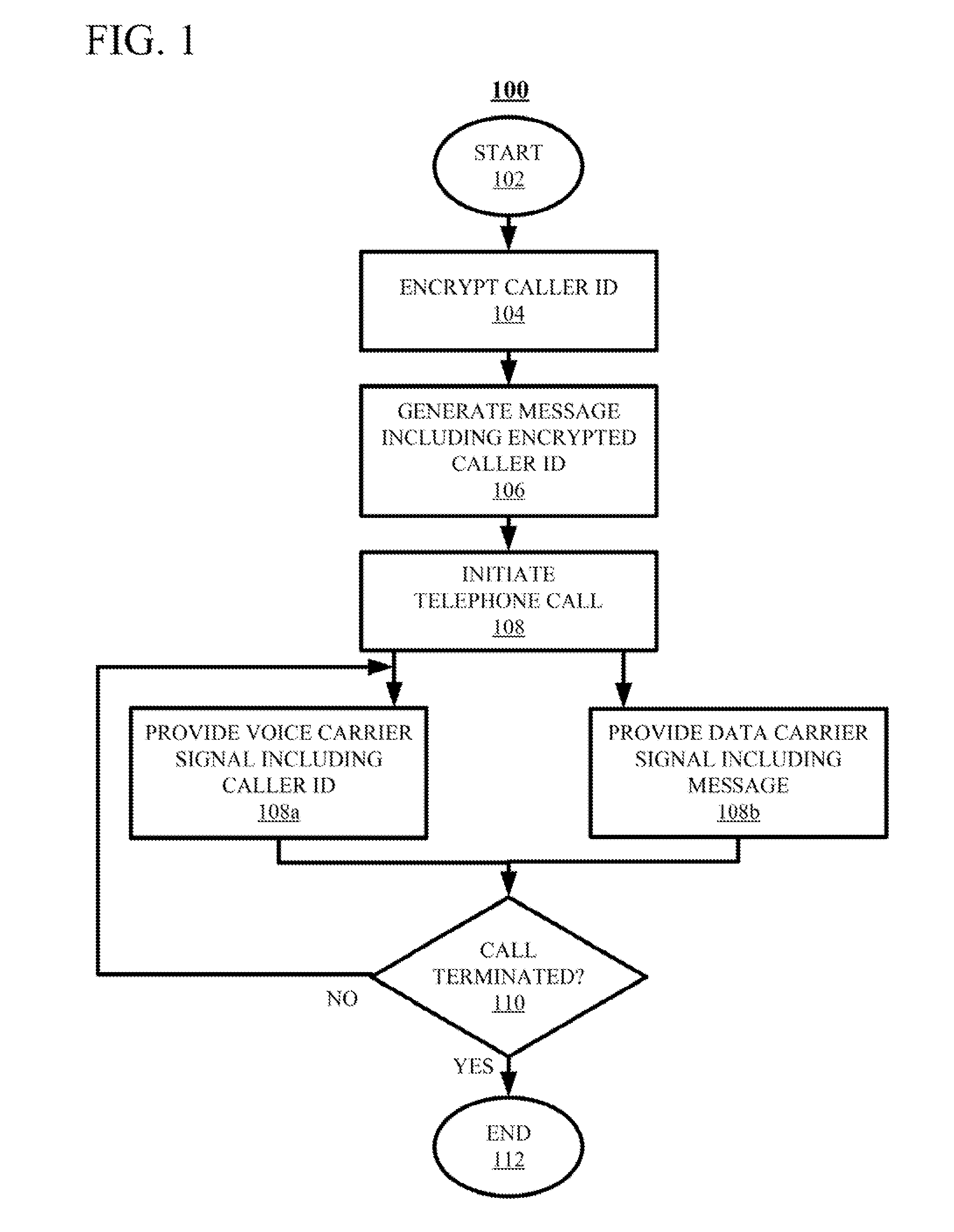
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including the caller identification information; and simultaneously providing a data carrier signal including the encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
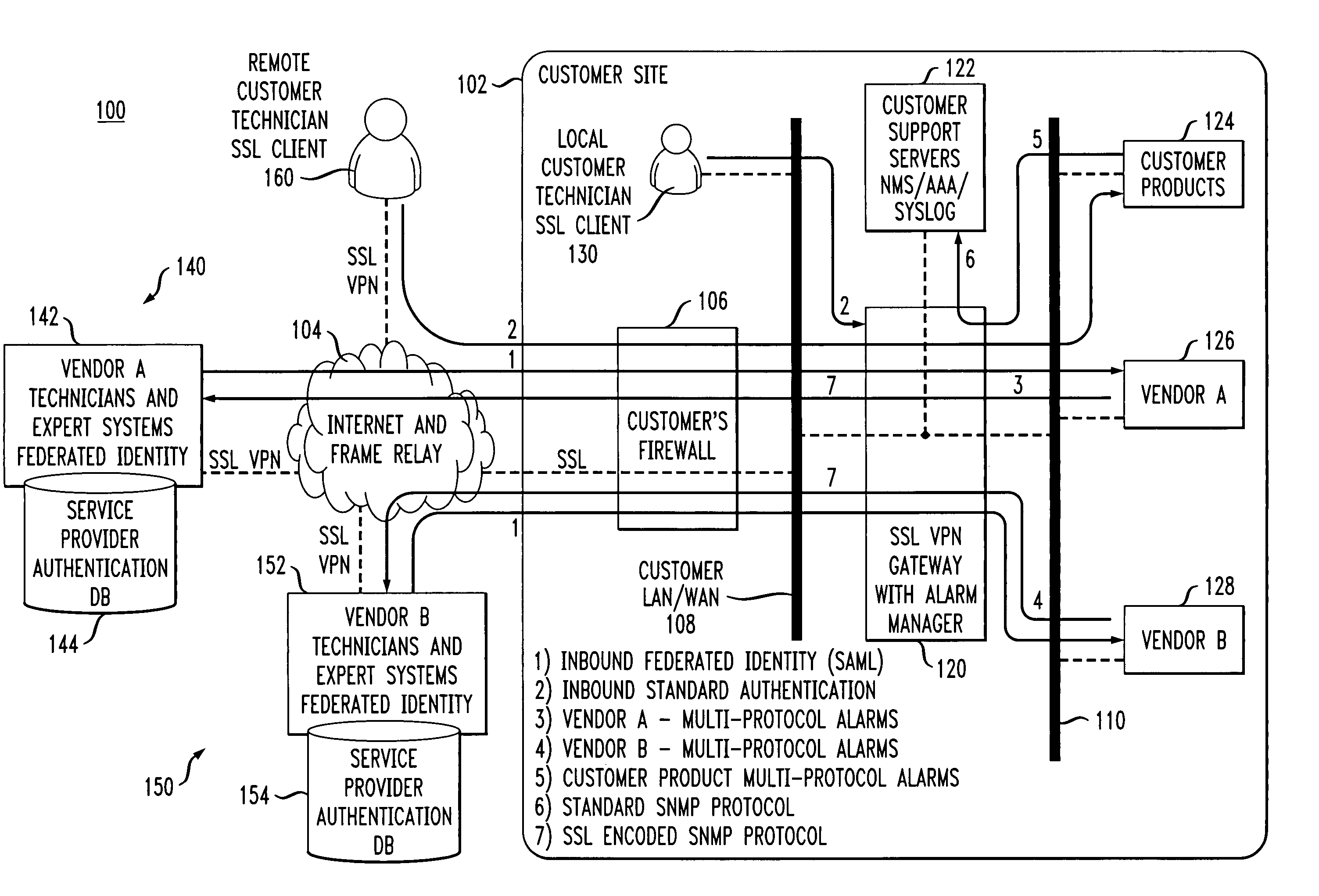
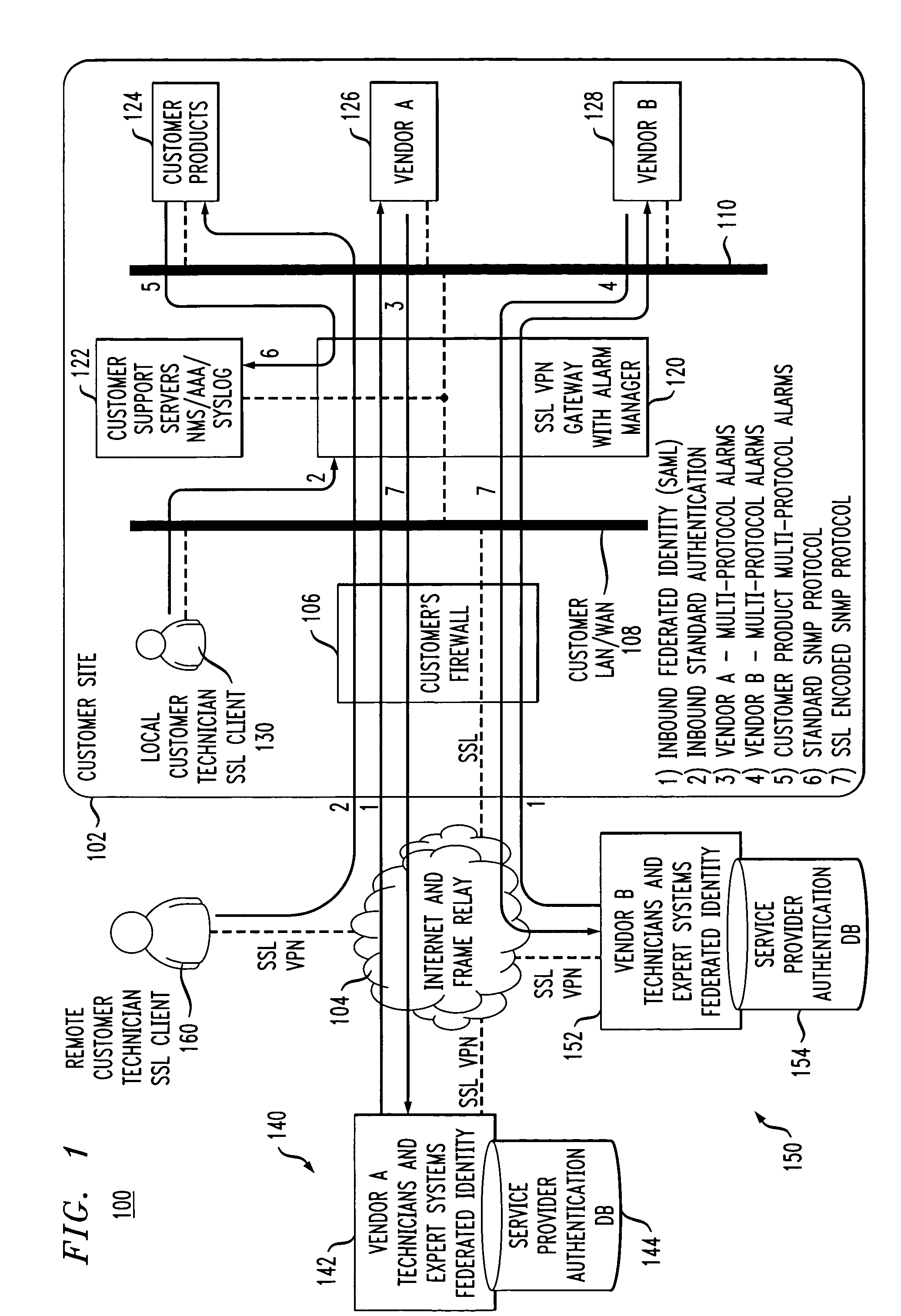
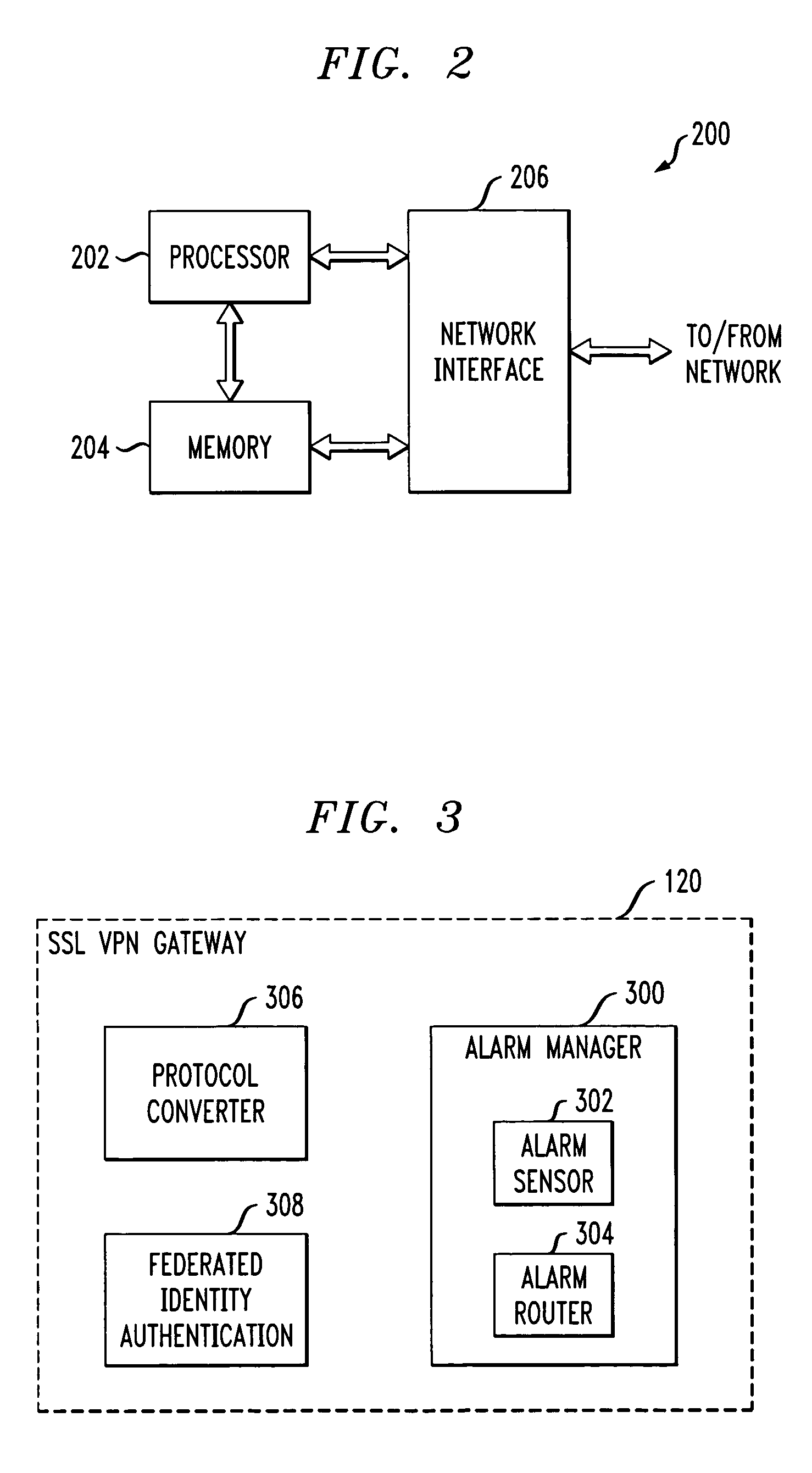
Secure gateway with alarm manager and support for inbound federated identity
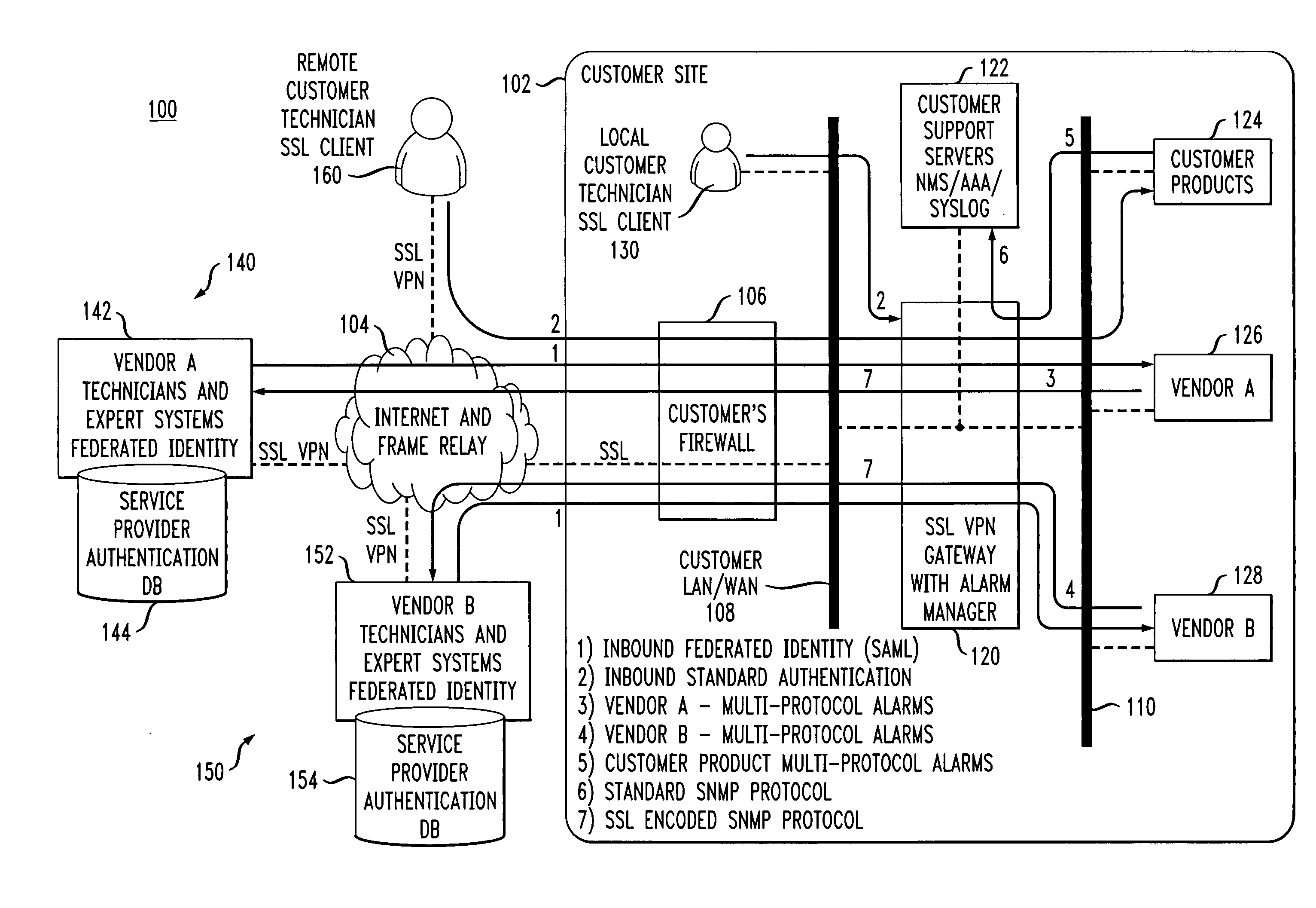
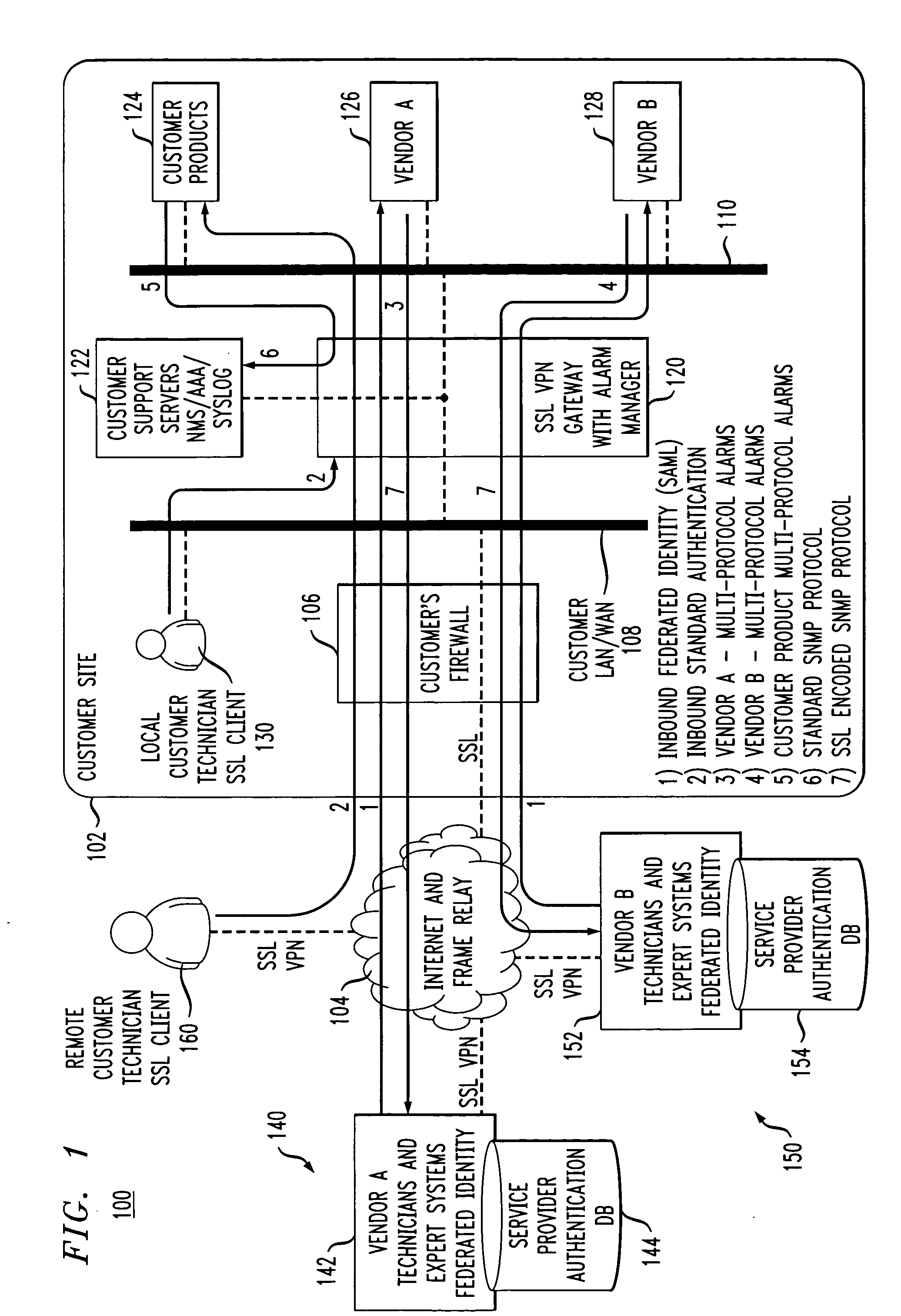
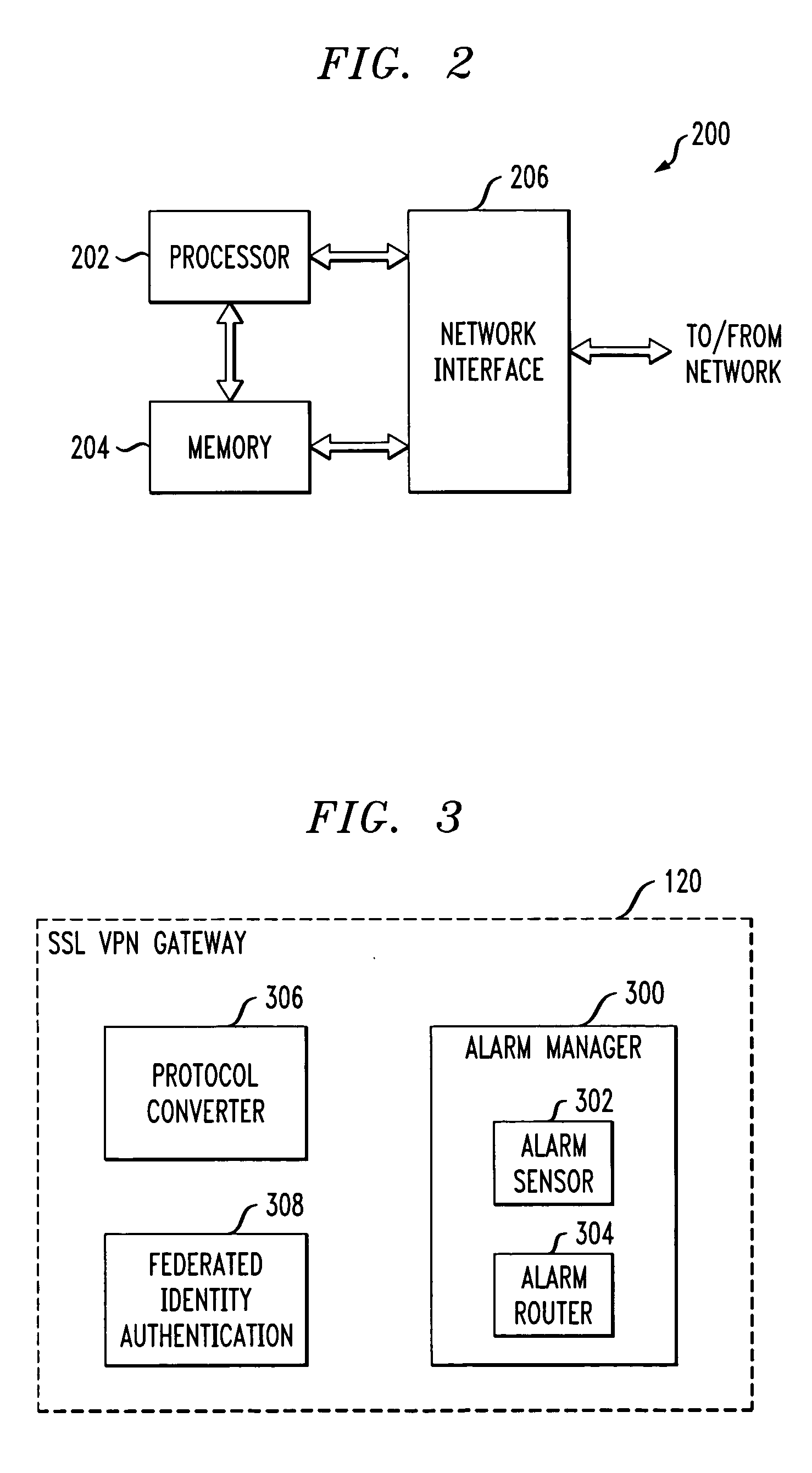
ActiveUS20070130326A1Simplify authentication processFacilitate handlingMultiple digital computer combinationsTransmissionService providerService provision
An SSL VPN gateway or other type of secure gateway is operative to control access to an enterprise network of a communication system. The gateway in accordance with an aspect of the invention comprises an alarm manager. The alarm manager receives an alarm from a vendor product that is part of a set of internal resources of the enterprise network, and routes the alarm to an external service provider for processing. The gateway receives from the service provider, responsive to the alarm, a federated identity which encompasses a plurality of technicians, expert systems or other servicing elements of the service provider. The gateway may grant one or more particular servicing elements of the service provider access to the alarm-generating vendor product based on the federated identity.
Owner:AVAYA INC
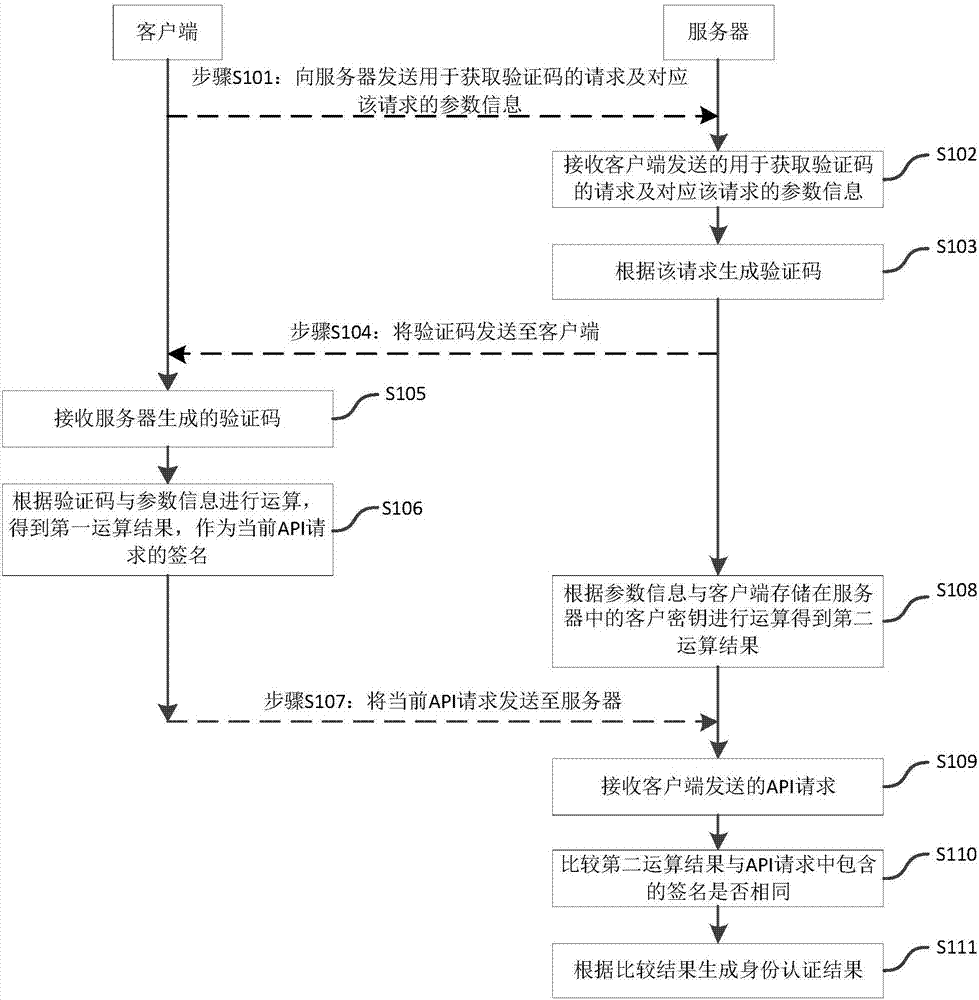
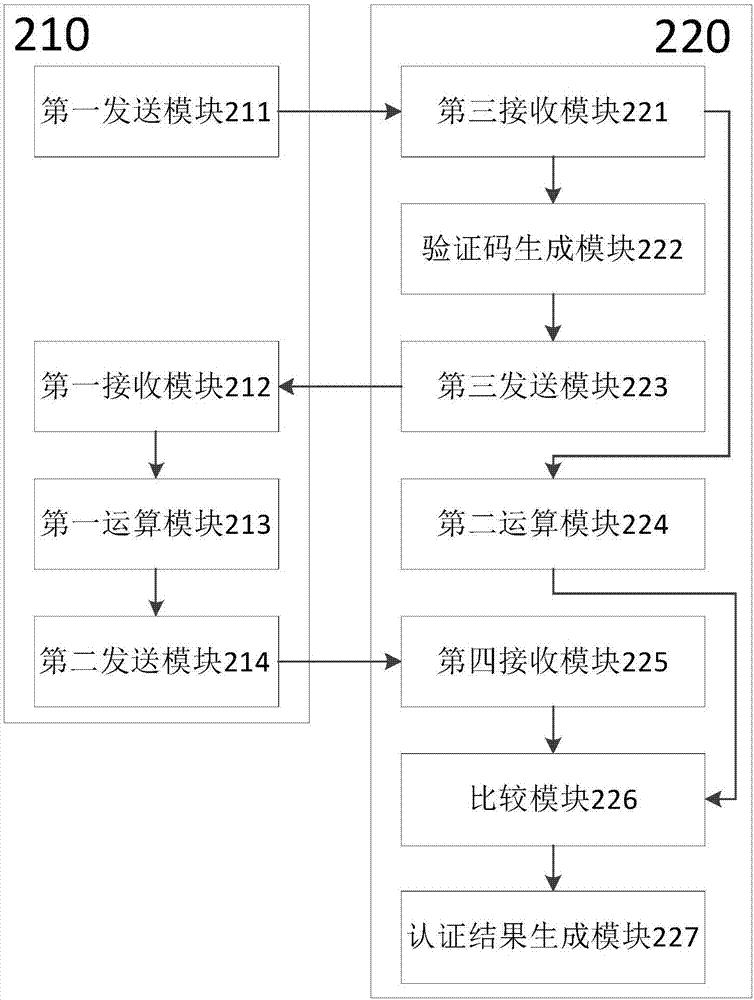
Identity authentication method, device and client
ActiveCN107249004AImprove securitySimplify the authentication processUser identity/authority verificationClient-sideAuthentication
The present invention discloses an identity authentication method, an identity authentication device and a client. The identity authentication method comprises the following steps that: the client sends a request for obtaining a verification code and parameter information corresponding to the request to a server; the server generates the verification code according to the request; the client performs calculation according to the verification code and the parameter information to obtain a first calculation result and adopts the first calculation result as the signature of a current API request; the server performs calculation to obtain a second calculation result according to the parameter information and a client key stored in the server by the client; whether the second calculation result is identical with the signature in the API request is judged through comparison; and an identity authentication result is generated according to a comparison result. With the identity authentication method, the identity authentication device and the client adopted, an identity authentication process is simplified, and the security of identity authentication is improved.
Owner:GUANGZHOU XUANWU WIRELESS TECH CO LTD
System and Method for Quick Authentication between Bluetooth Devices
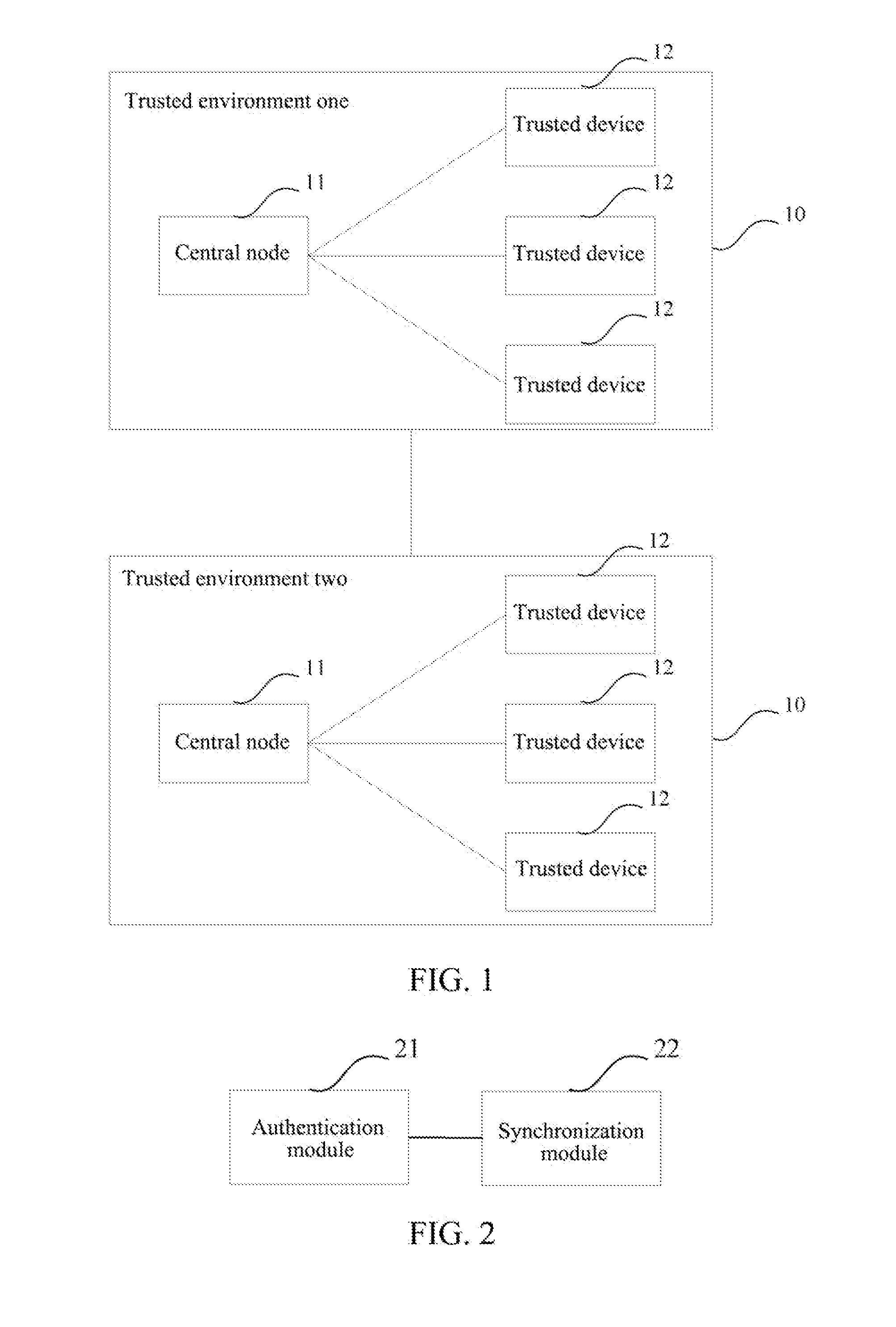
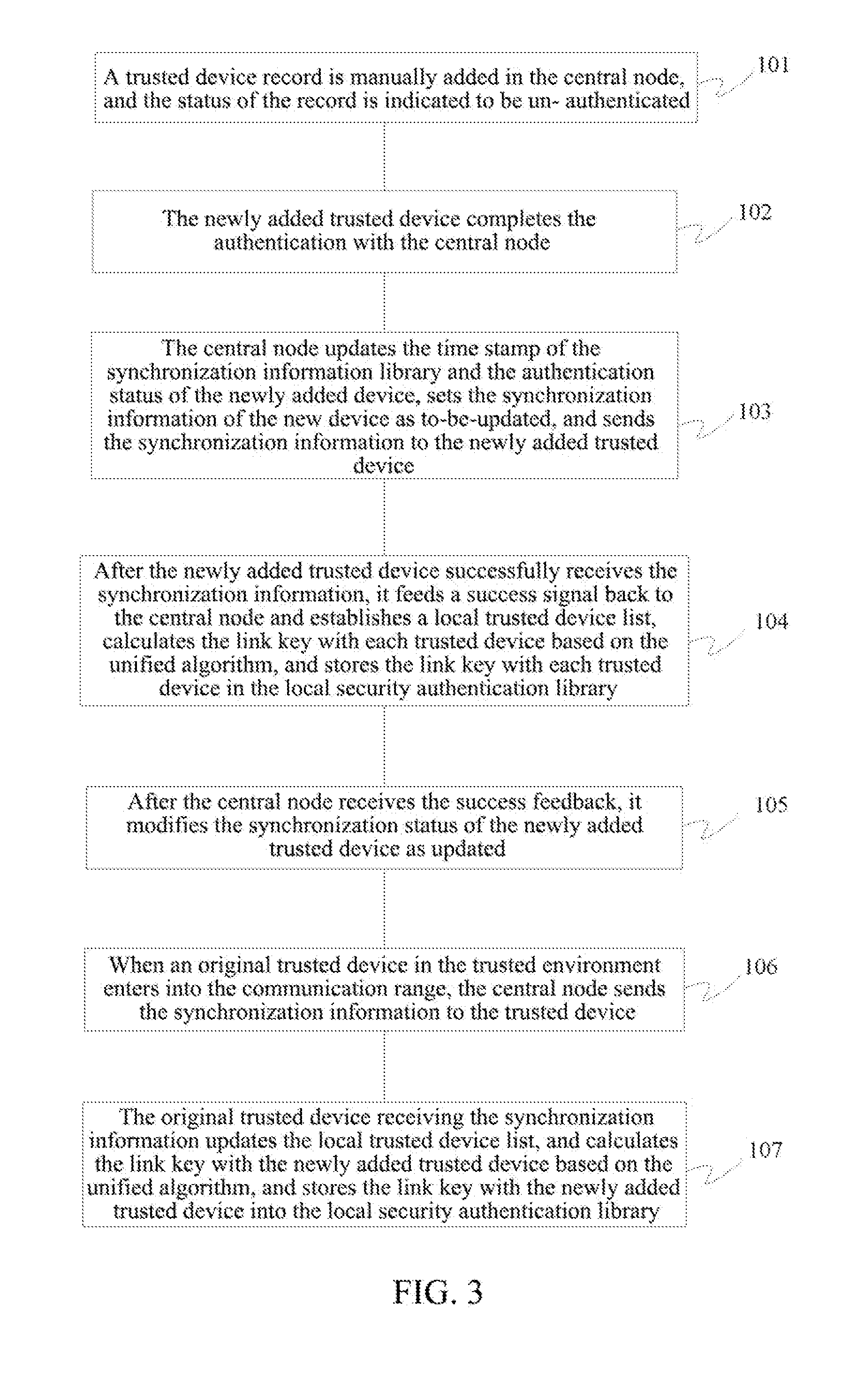
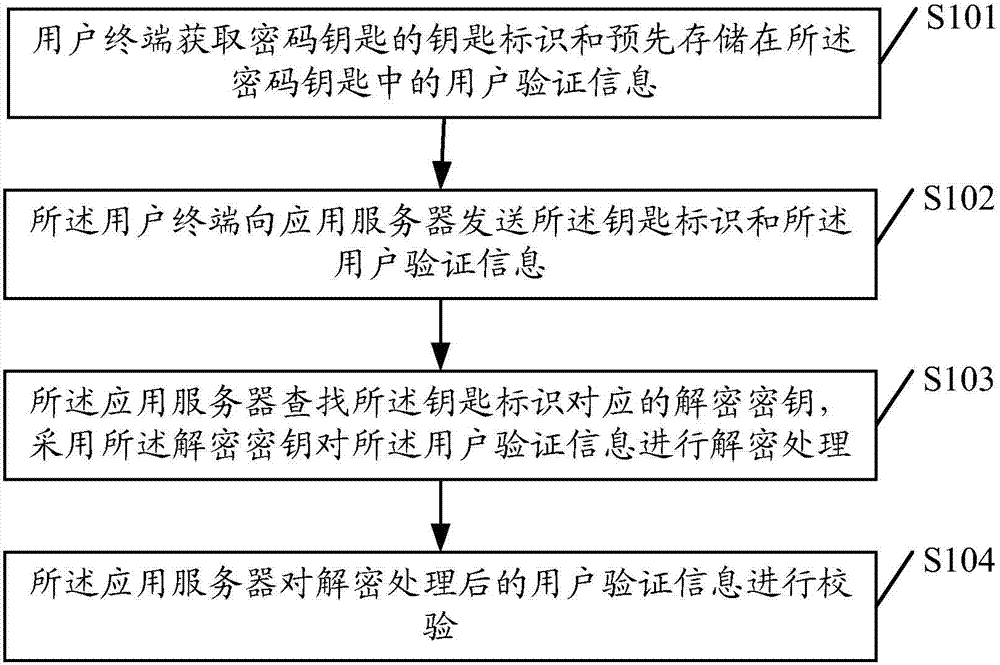
ActiveUS20120171961A1Fast authenticationSimplify the authentication processSynchronisation arrangementNetwork topologiesBluetoothAuthentication
A system and method for quick authentication between Bluetooth devices are disclosed. The method includes: adding a central node (11) in a trusted environment (10, 13) of a Bluetooth device, wherein, said control node makes authentication with each trusted device (12) in the trusted environment and stores an information list containing information of each trusted device; after the information of a trusted device in the trusted environment is updated, the central node sends synchronization information to the trusted device that needs to update the synchronization information, and the trusted device receiving the synchronization information implements the update of the synchronization information.
Owner:DRNC HLDG INC
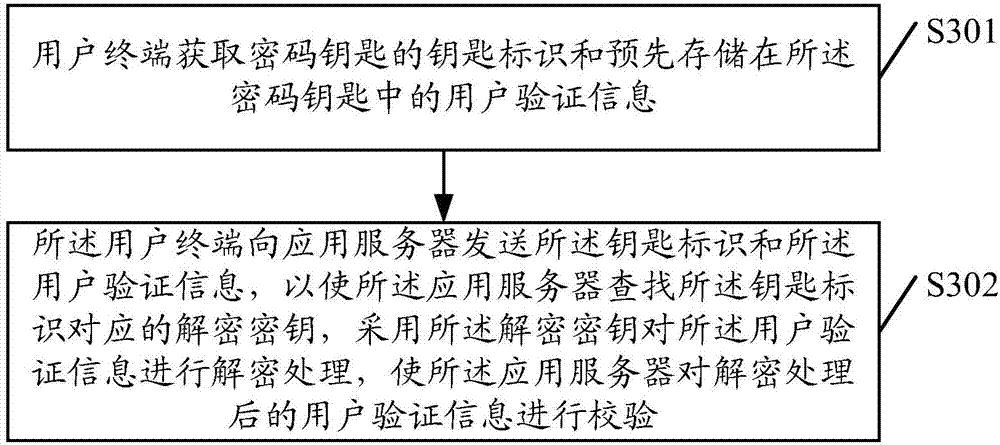
Information verification method, and electronic payment method, terminal, server and system
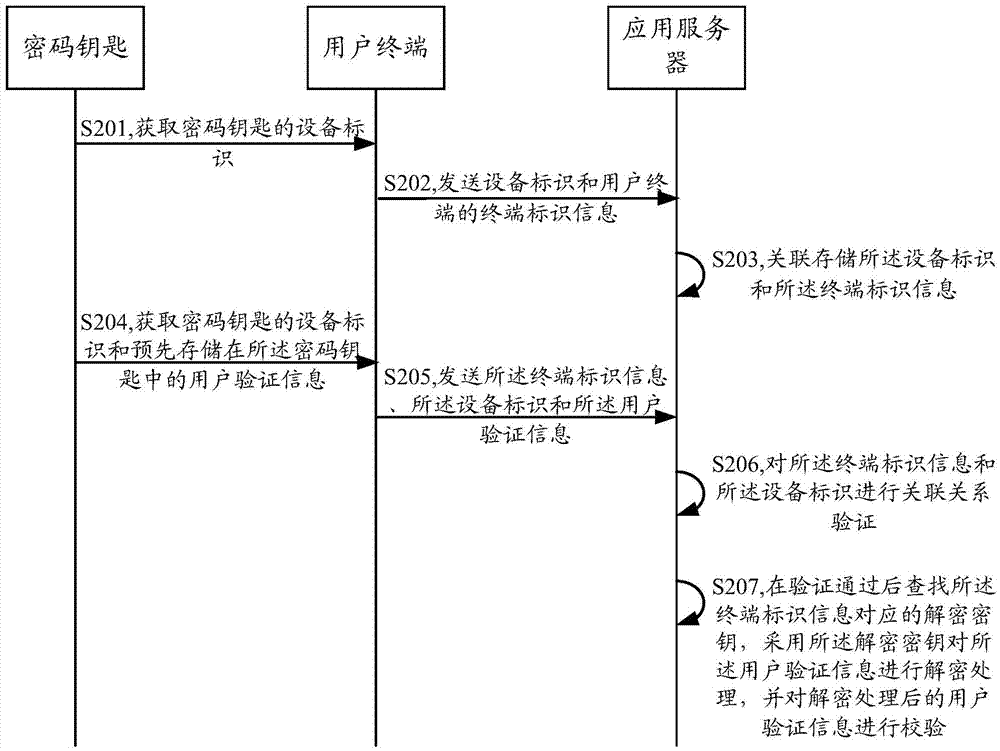
ActiveCN104753675AAvoid exposureImprove convenienceUser identity/authority verificationProtocol authorisationPaymentUser verification
The embodiment of the invention discloses an information verification and electronic payment method, terminal, server and system. The method comprises the steps of acquiring key identification of a password key and user verification information which is pre-stored in the password key through a user terminal; sending the key identification and the user verification information to an application server through the user terminal; finding out an encrypting key corresponding to the key identification through the application server; encrypting the user verification information through the encrypting key; checking the encrypted user verification information through the application server. With the adoption of the device, the service handling safety can be improved, and the service handling efficiency can be increased.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Telephone caller authentication
ActiveUS9288062B2Sacrificing robustnessSimplify the authentication processUser identity/authority verificationCommmunication supplementary servicesCarrier signalSpeech sound
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including the caller identification information; and simultaneously providing a data carrier signal including the encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
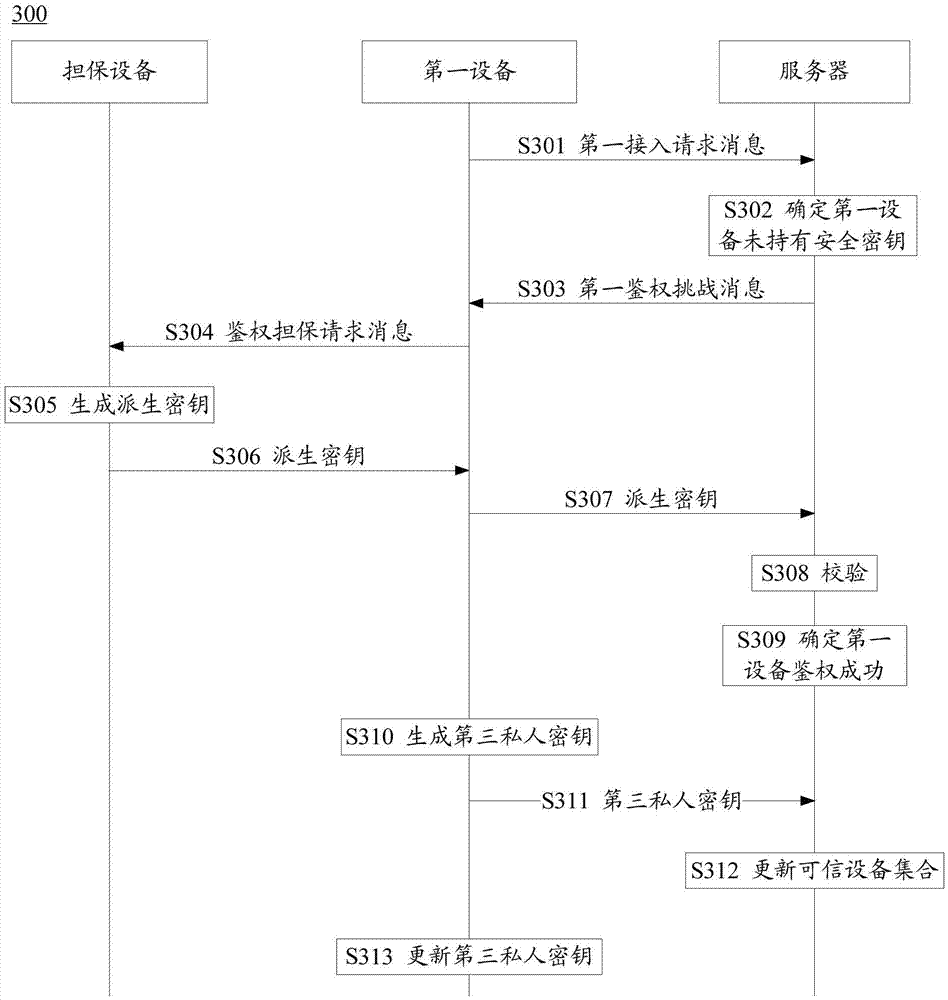
Authentication method, terminal and server
ActiveCN107205208AReduce manual involvementIncrease opennessWireless commuication servicesSecurity arrangementAccess networkTerminal equipment
The invention discloses an authentication method, terminal and server, and the method, terminal and server can reduce the manual participation degree of terminal equipment in an authentication process of an access network. The method is used in a system for the authentication through a safety secret key and a server. The method comprises the steps that first equipment transmits a first access request message to the server in a first time period, wherein the first equipment is equipment which does not hold a shared secret key; the first equipment receives a first authentication challenge message transmitted by the server based on the first access request message, wherein the first authentication challenge message carries authentication parameters, and the authentication parameters are used for generating a derived secret key; the first equipment transmits an authentication assurance request message to assurance equipment, wherein the authentication assurance request message comprises authentication parameters; the first equipment receives a first derived secret key transmitted by the assurance equipment based on the authentication assurance request message, wherein the first derived secret key is generated by the assurance equipment based on the first safety secret key and the authentication parameters; the first equipment transmits the first derived secret key to the server, so as to carry out the authentication with the server.
Owner:HUAWEI TECH CO LTD
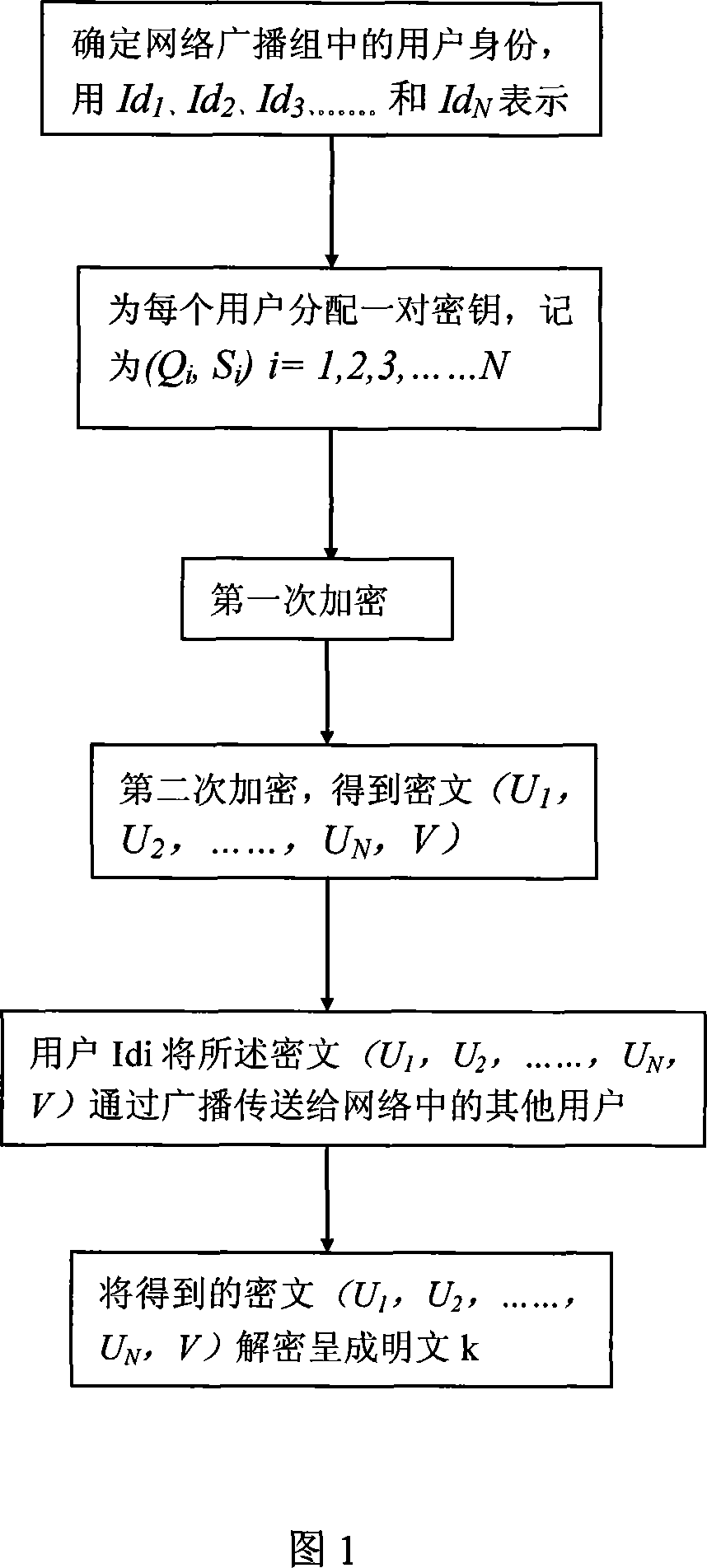
Method for encrypting and decrypting broadcast of network information
InactiveCN101094059AThe encryption algorithm is simpleSimplify the encryption processSecuring communicationHash functionEncryption decryption
The method for encrypting and decrypting a network broadcast comprises: after first encryption, getting n intermediate results QV1,QV2......QVN. Said first encryption comprises: 11) figuring out the value Qi of the hash function H1 of the user Idi in network, namely Qi= H1(Idi); 12) after encryption, figuring out n intermediate results, namely QV1,QV2......QVN; The decryption process is a process of solving a linear equation system.
Owner:JIANGSU WENTRY TECH
Telephone Caller Authentication
ActiveUS20150237201A1Sacrificing robustnessSimplify the authentication processCommmunication supplementary servicesGraded-service arrangementsCarrier signalSpeech sound
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including tire caller identification information; and simultaneously providing a data carrier signal including tire encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
Method for authenticating user terminal
ActiveCN101030853AGuaranteed reliabilityProcess controlUser identity/authority verificationInternet privacy
Owner:HUAWEI TECH CO LTD
Secure gateway with alarm manager and support for inbound federated identity
ActiveUS7590761B2Easy to carrySimplify the authentication processMultiple digital computer combinationsTransmissionCommunications systemService provision
An SSL VPN gateway or other type of secure gateway is operative to control access to an enterprise network of a communication system. The gateway in accordance with an aspect of the invention comprises an alarm manager. The alarm manager receives an alarm from a vendor product that is part of a set of internal resources of the enterprise network, and routes the alarm to an external service provider for processing. The gateway receives from the service provider, responsive to the alarm, a federated identity which encompasses a plurality of technicians, expert systems or other servicing elements of the service provider. The gateway may grant one or more particular servicing elements of the service provider access to the alarm-generating vendor product based on the federated identity.
Owner:AVAYA INC
Online charging engine, real-time charge off engine, and online charging method and system
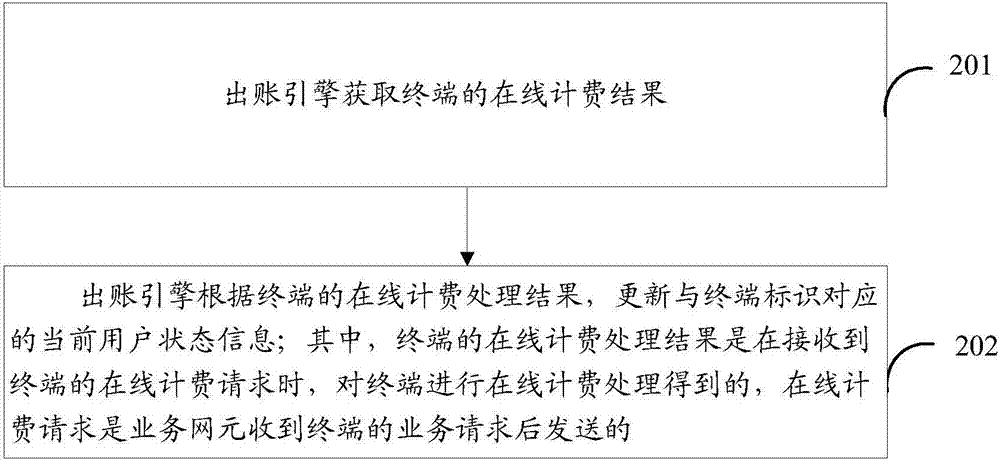
ActiveCN107040387AShorten the response cycleGuaranteed immediacyMetering/charging/biilling arrangementsAccounting/billing servicesReal-time chargingOnline charging system
The invention discloses an online charging engine, a real-time charge off engine, and an online charging method and system. The online charging method comprises the following steps: receiving an online charging request, obtaining current user state information corresponding to a terminal identifier of a terminal, and performing authentication on a service request according to the current user state information, wherein the current user state information is user state information after the online charging processing of the previous online charging request of the terminal is terminated, and an authentication result of the service request is sent to a service network element. By adoption of the online charging method, service authentication and real-time charge off are asynchronous processing procedures, the response period of the service authentication is shortened, the retention rate of the online charging flow of the user is improved, the working load of the online charging system on service peaks is reduced, and thus the technical problem of large working load of the online charging system on service peaks, relatively low retention rate of the online charging flow of the user and influence to the service perception of the user on the flow service in the prior art are solved.
Owner:CHINA MOBILE GROUP JILIN BRANCH
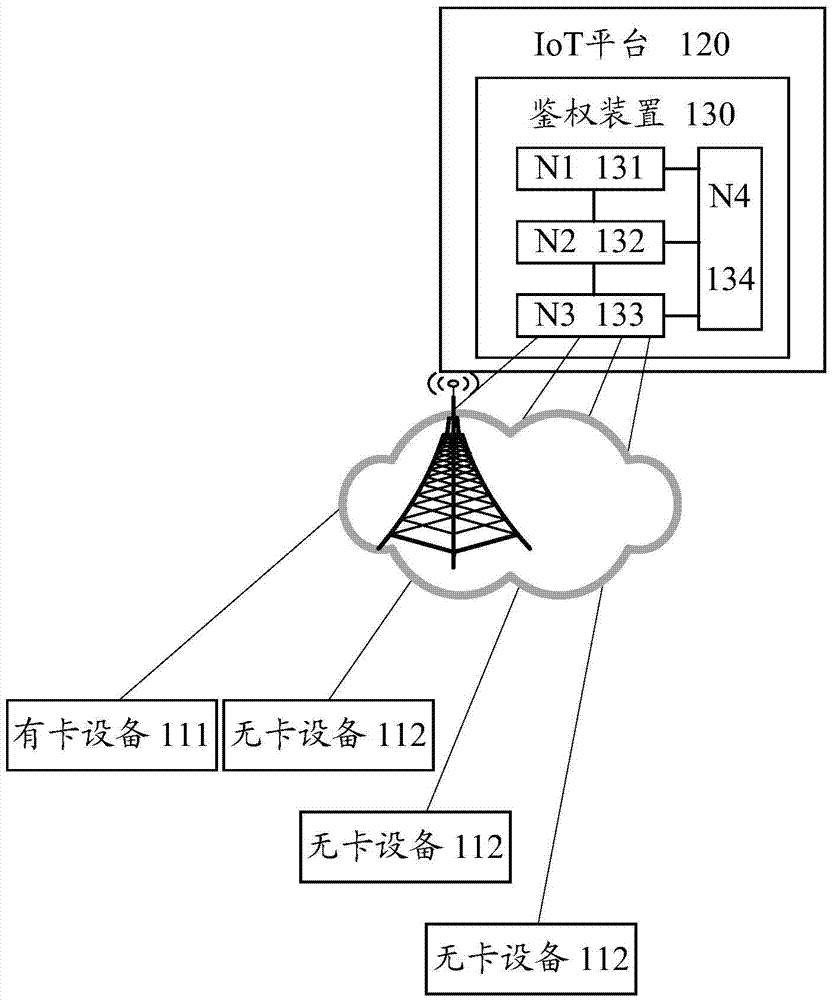
Internet of Things equipment safety communication system and method, networking equipment and server
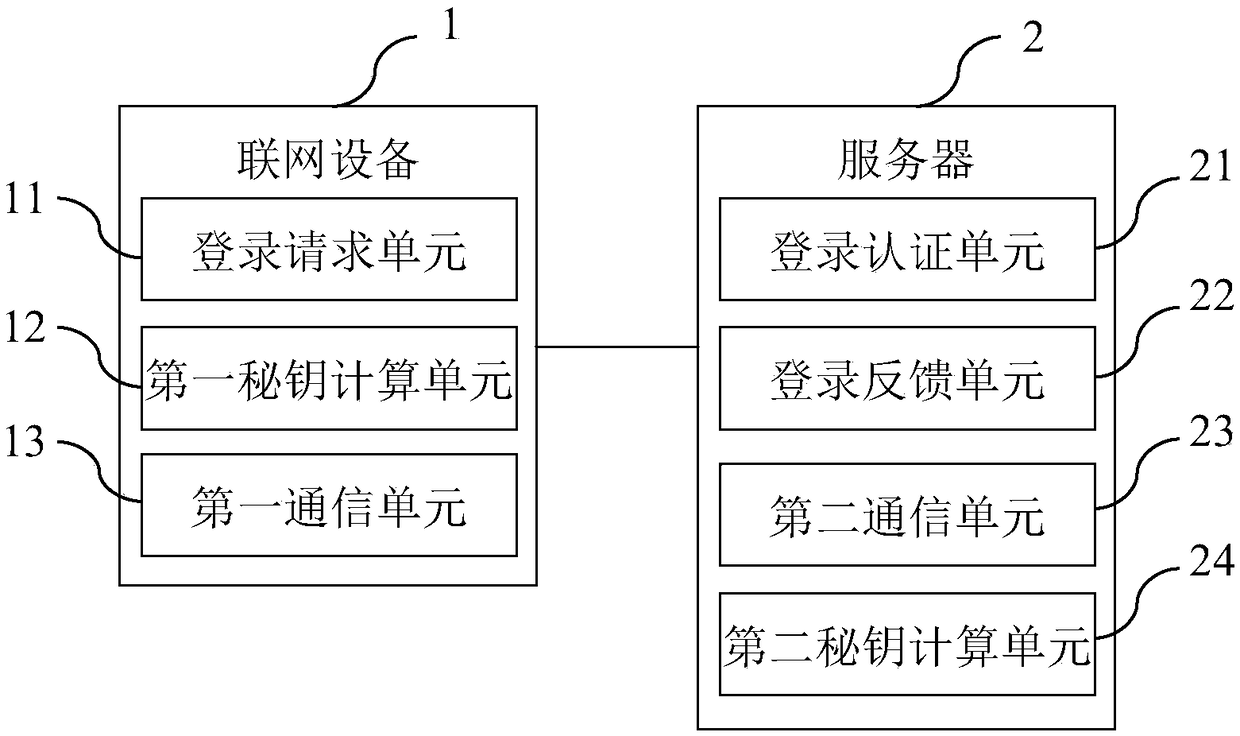
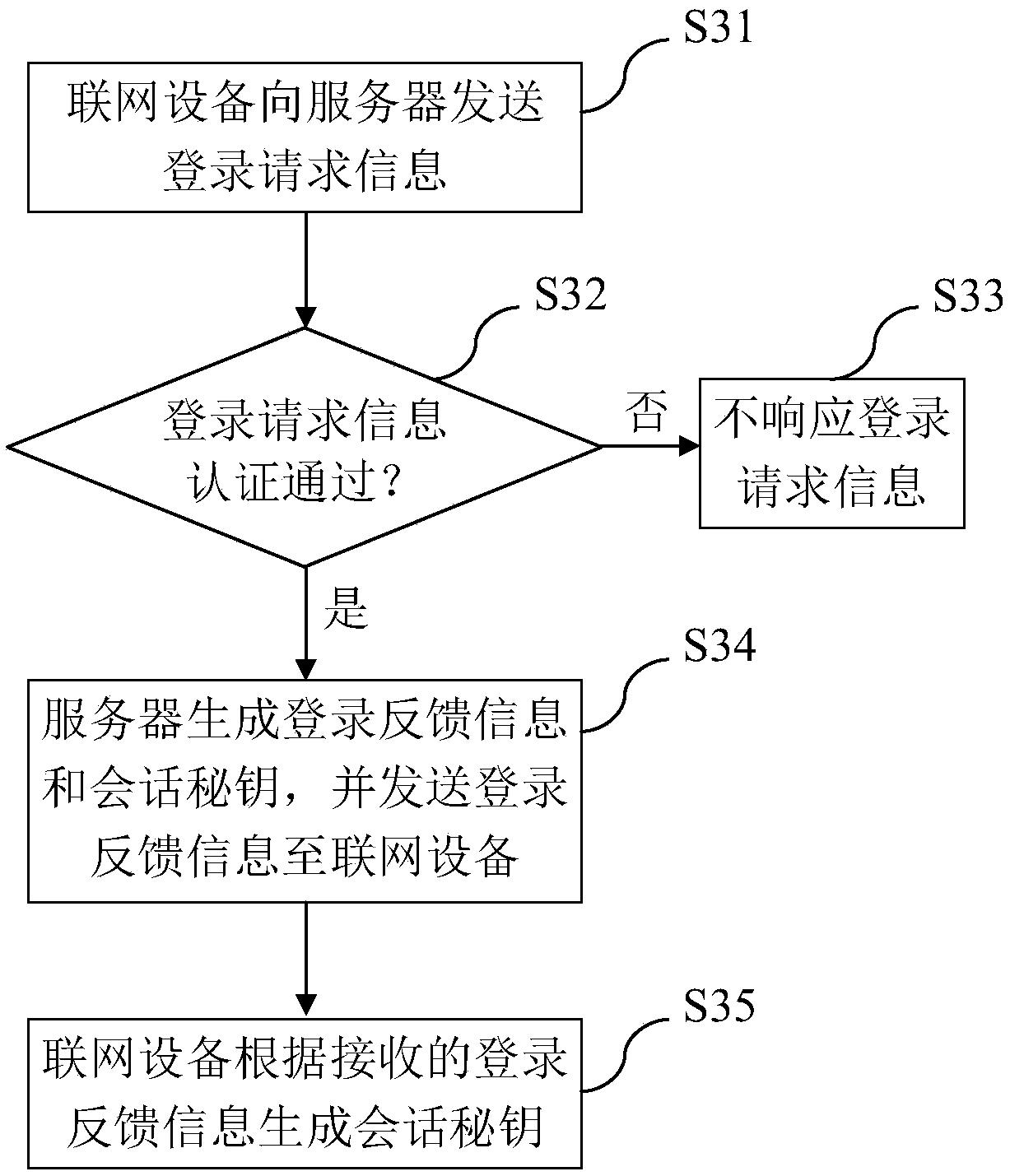
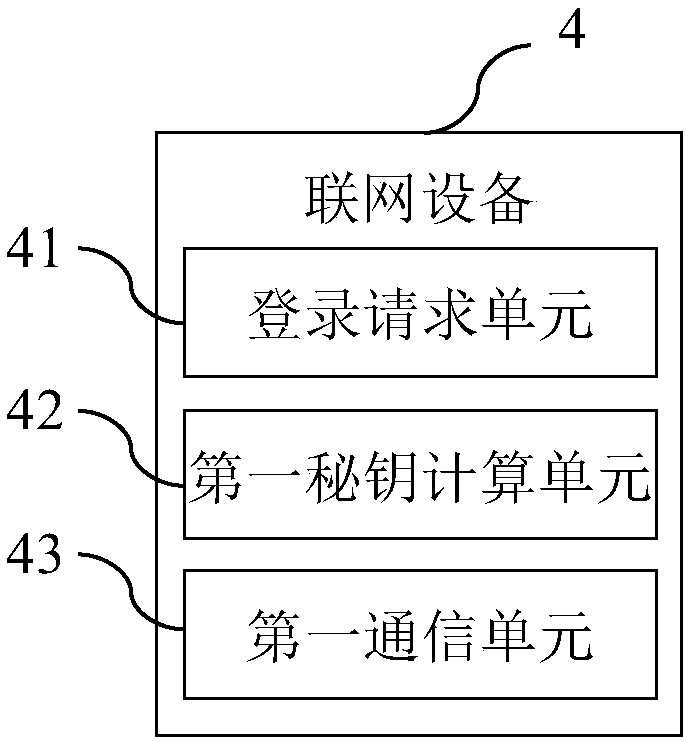
InactiveCN108076062AEnable secure communicationSimplify the authentication processKey distribution for secure communicationCommunications systemCommunication unit
The invention provides an Internet of Things equipment safety communication system and method, networking equipment and a server, which are used for achieving safe communication between the networkingequipment and the server in Internet of Things; the networking equipment comprises a login request unit, a first secret key calculation unit and a first communication unit, wherein the server comprises a login authentication unit, a login feedback unit and a second communication unit, wherein the login request unit is used for sending login request information; the login authentication unit is used for carrying out authentication on the login request information; the login feedback unit is used for generating login feedback information and a session key and sending the login feedback information to the networking equipment; the first secret key calculation unit is used for generating the session key; and the first communication unit and the second communication unit communicate through the session key. According to the Internet of Things equipment safety communication system and method, the networking equipment and the server, the session key is generated in a login authentication process, and safe communication of the Internet of Things equipment can be realized only by occupying a small amount of resources.
Owner:SHENZHEN INOVANCE TECH
Multi-application identity authentication system and method
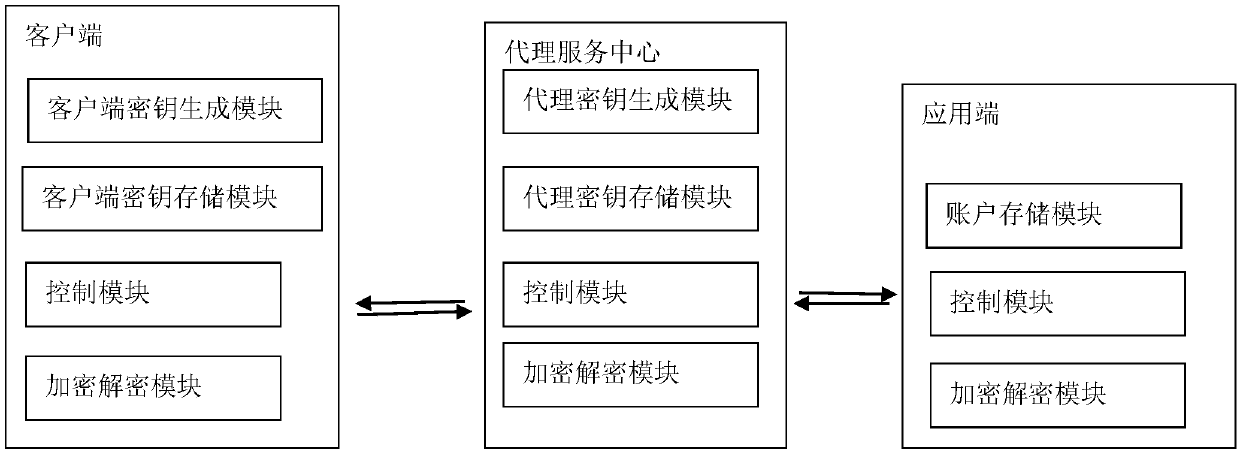
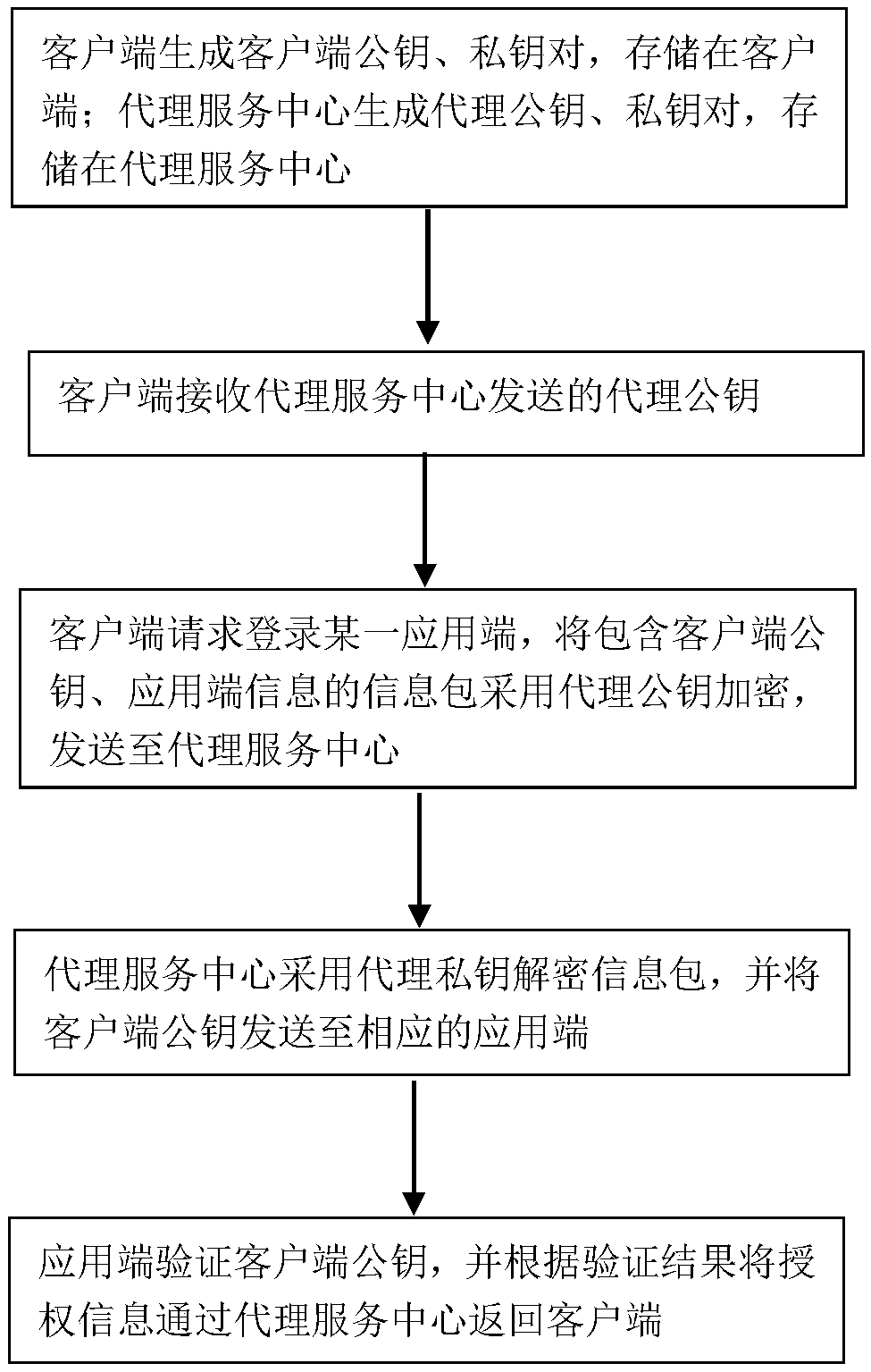
ActiveCN110740116ASimplify the authentication processEnsure safetyUser identity/authority verificationClient agentInternet privacy
The invention provides a multi-application identity authentication system and method. The multi-application identity authentication system comprises a client, an application terminal and a proxy service center, wherein the client establishes connection with the application terminal through the proxy service center; the client and the proxy service center respectively generate a public key pair anda private key pair; the client receives the proxy public key sent by the proxy service center; the client requests to log in a certain application terminal, encrypts the information packet by adopting the proxy public key, and sends the information packet to the proxy service center; the proxy service center decrypts the information packet by adopting the proxy private key, and sends the client public key to the corresponding application terminal; and the application terminal verifies the client public key and returns the authorization information to the client through the proxy service center according to a verification result. According to the multi-application identity authentication system, the standard specifications of the client, the proxy service center and the application terminal are formulated through the preset protocol, and the security mechanism is designed, so that the identity authentication of the client is simplified, and the security in the data transmission processis ensured.
Owner:北京思源理想控股集团有限公司
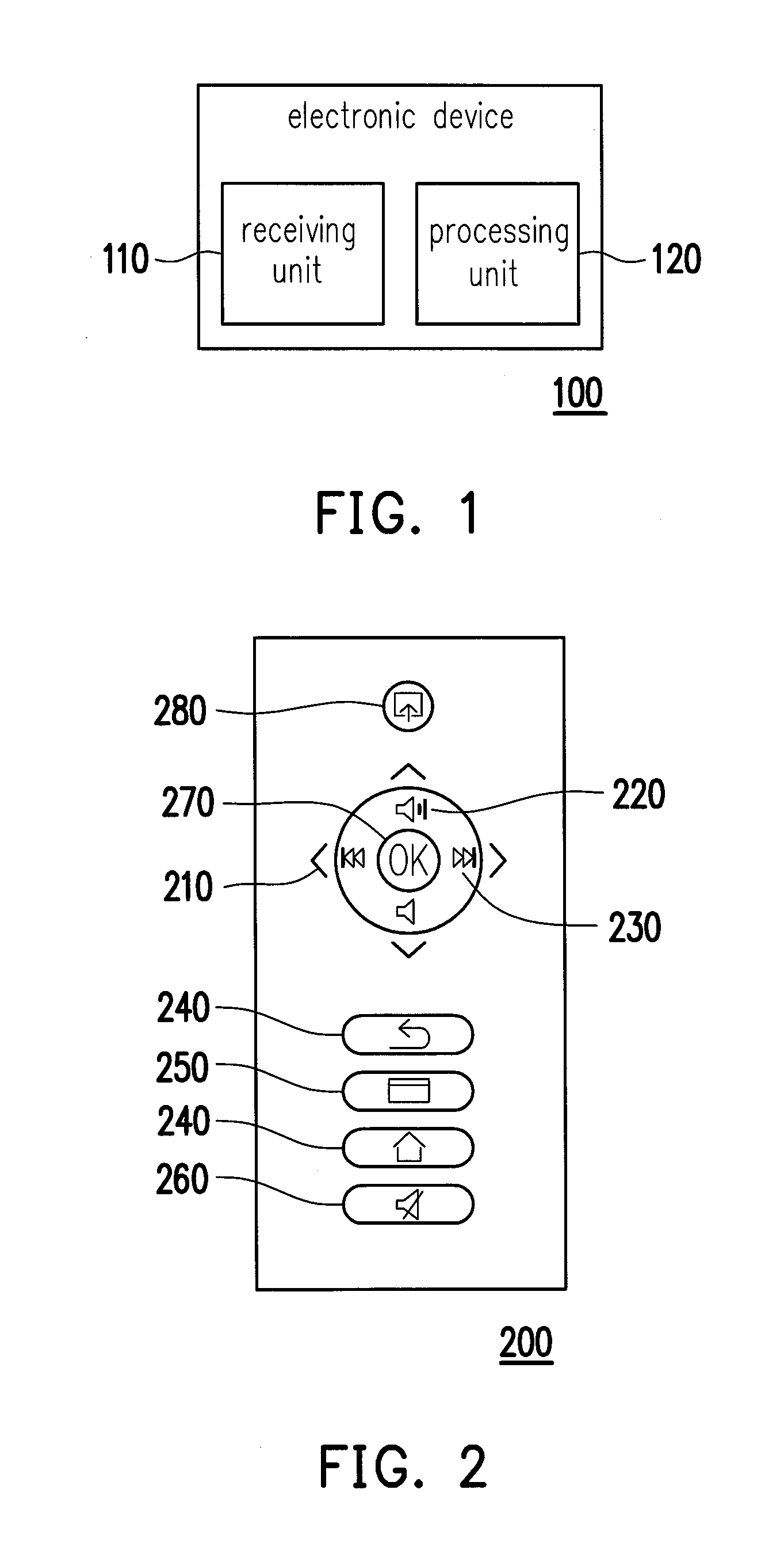
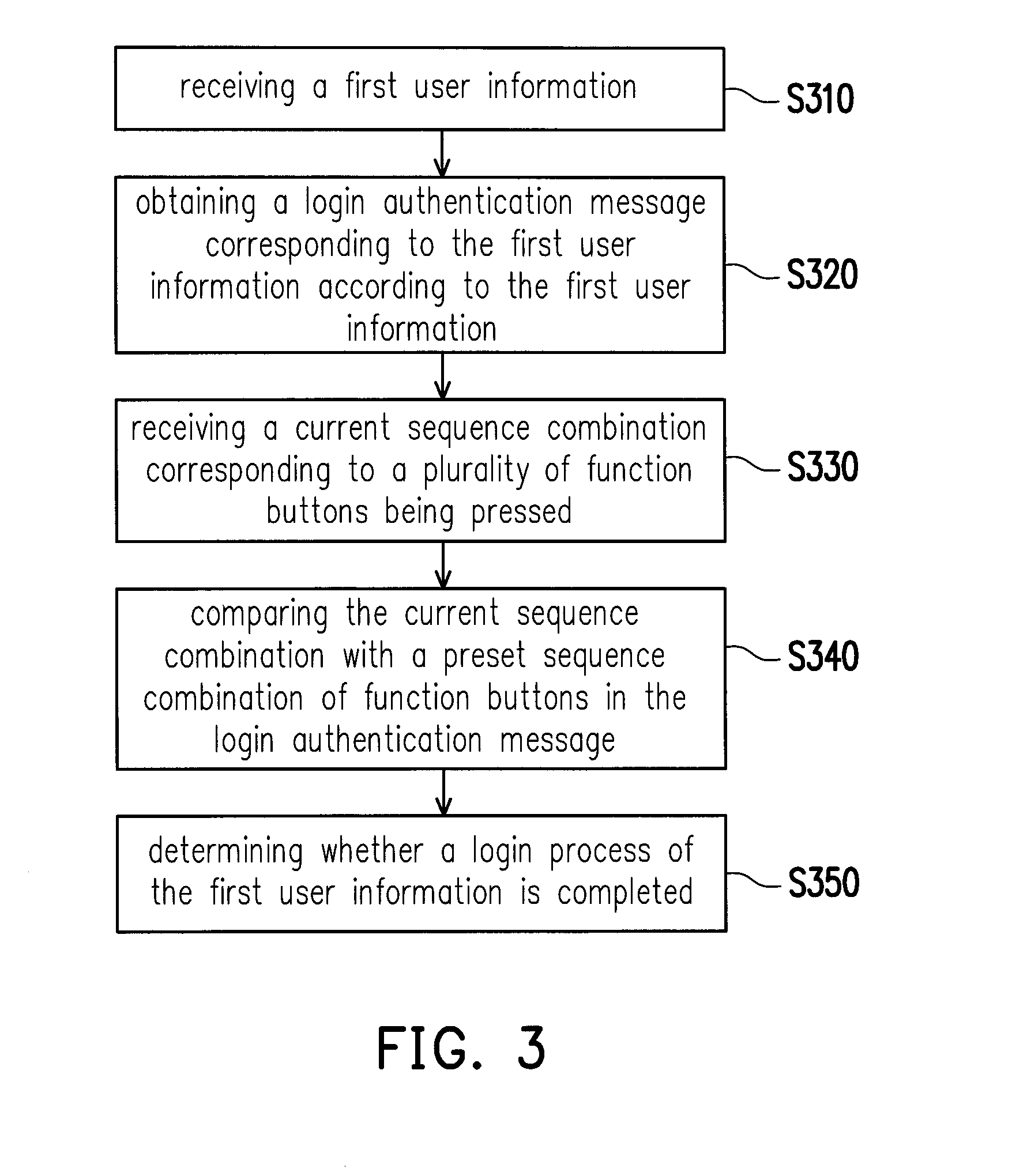
Electronic device and login method thereof
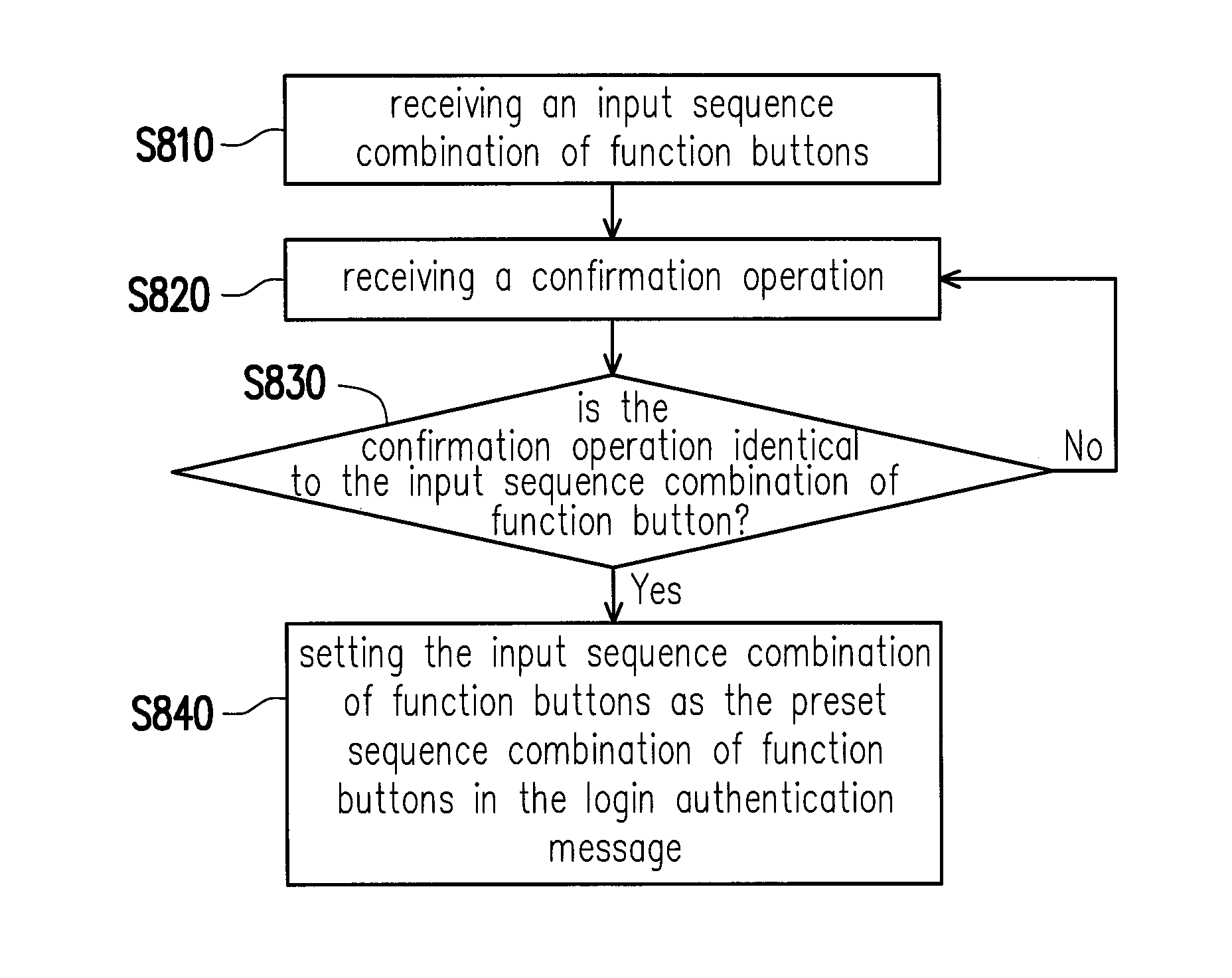
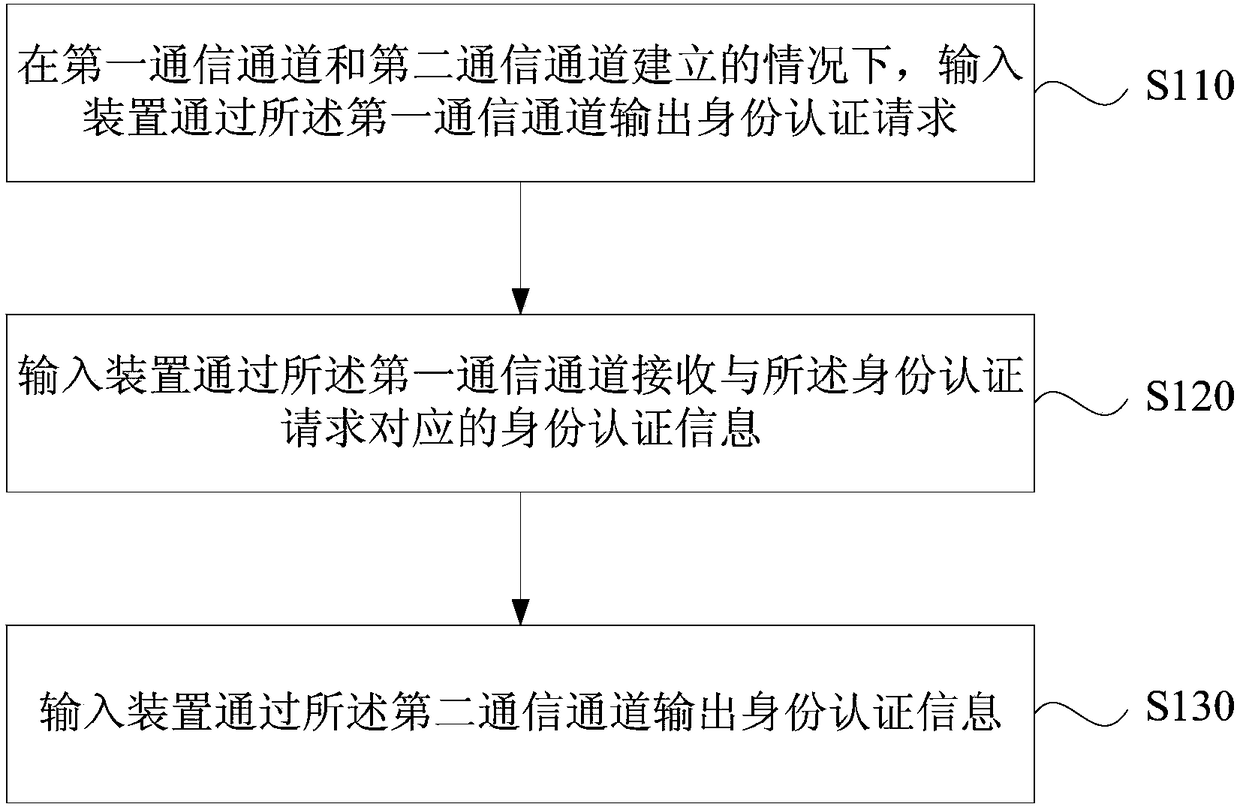
InactiveUS20150143493A1Promote quick completionImprove user experienceDigital data processing detailsMultiple digital computer combinationsComputer hardwarePassword
An electronic device and a login method thereof are provided. The method includes the following steps. A first user information is received. A login authentication message corresponding to the first user information is obtained according to the first user information. A current sequence combination corresponding to a plurality of function buttons being pressed is received, and the function buttons are used for controlling the electronic device to execute a plurality of functions correspondingly. The current sequence combination is compared with a preset sequence combination of function buttons in the login authentication message. Whether a login process of the first user information is completed is determined. Accordingly, difficulties in entering a password may be solved by the function buttons on a remote controller, and an identity authentication may be simplified and quickly completed, so as to provide a better user experience for the user.
Owner:QNAP SYST INC
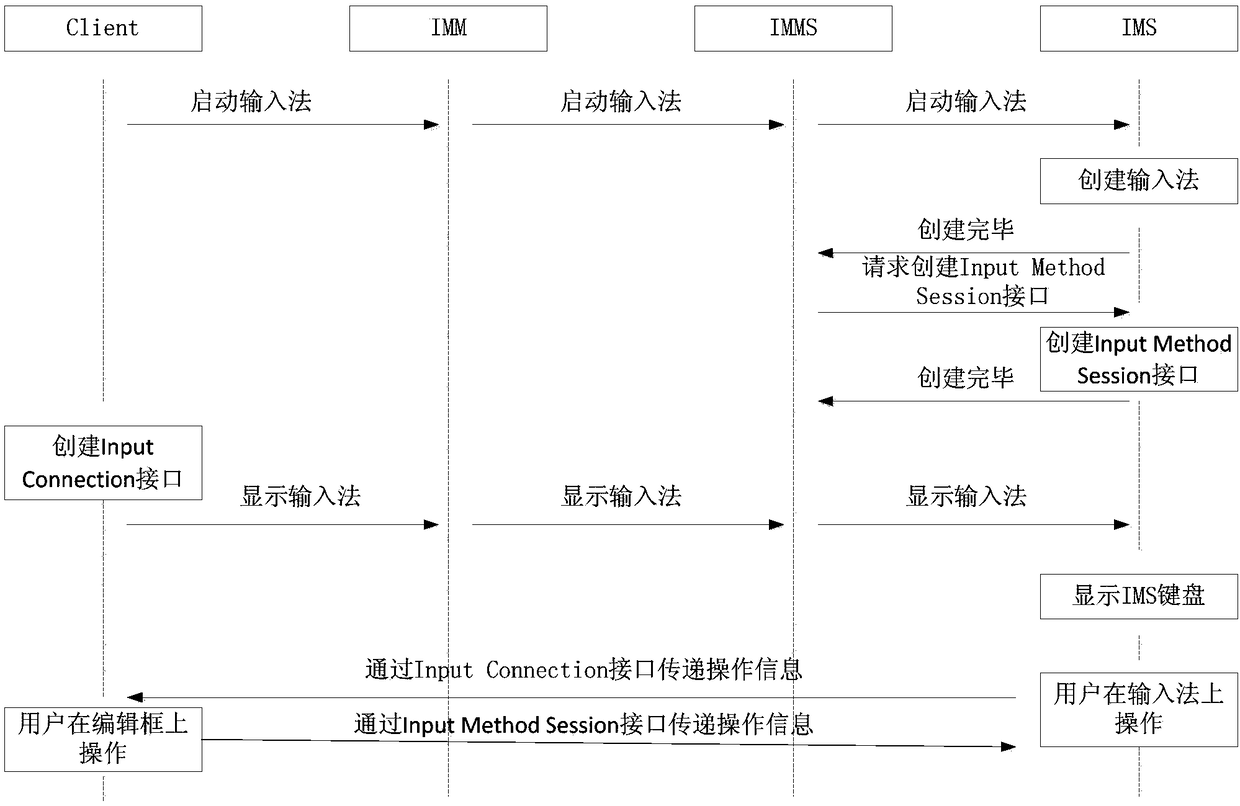
Identity authentication method and system, terminal and storage medium
ActiveCN108200075AImprove securityAvoid connectionTransmissionAuthentication informationInput device
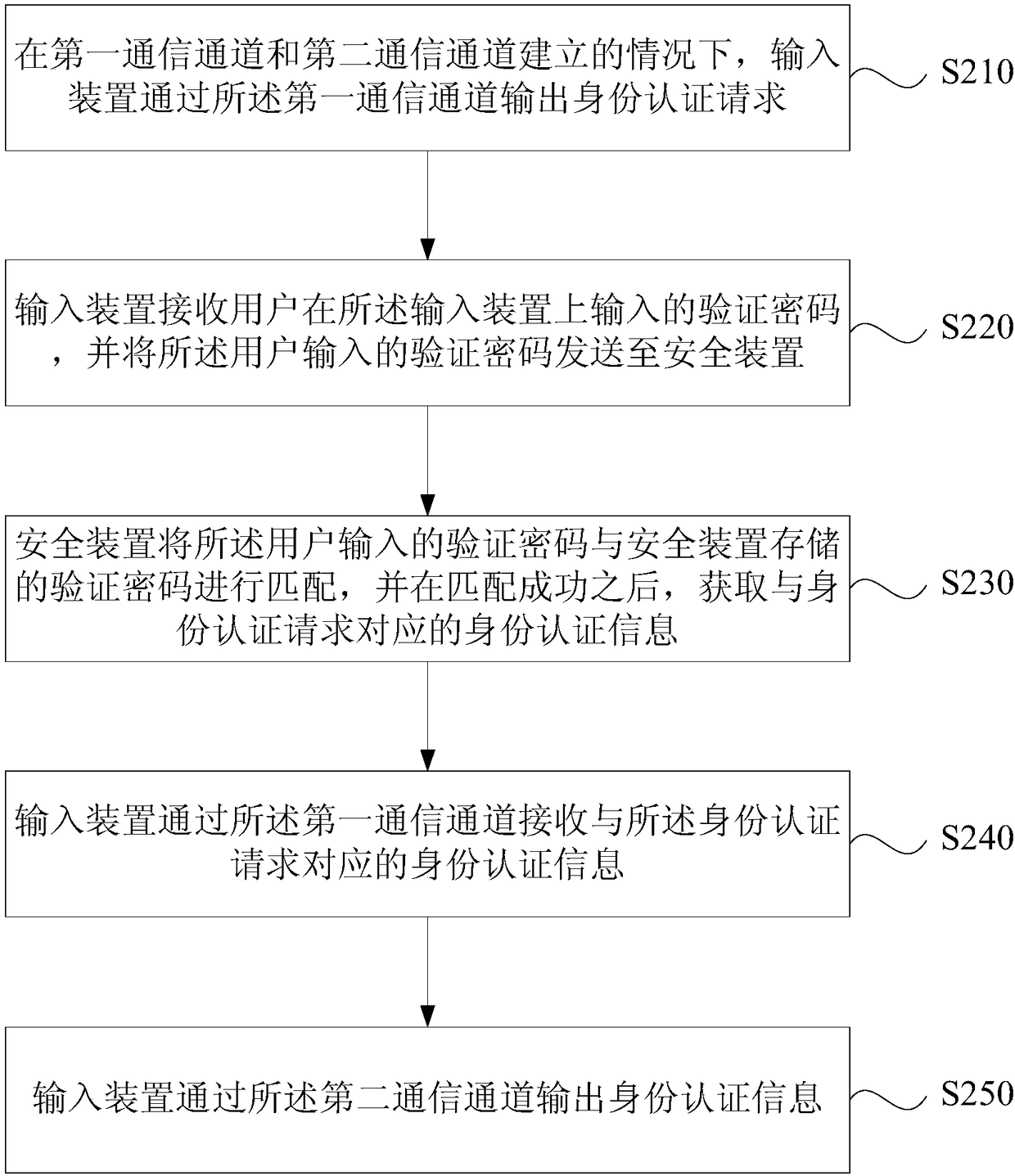
The embodiment of the invention discloses an identity authentication method and system, a terminal and a storage medium. The identity authentication method comprises the following steps: an input device outputs an authentication request through a first communication channel under the circumstance that the first communication channel and a second communication channel are set up; the input device receives the identity authentication information corresponding to the identity authentication request through the first communication channel; and the input device outputs the identity authentication information through the second communication channel. According to the embodiment of the invention, the identity authentication request is received through the input device, and the identity authentication information is output through the input device, therefore, the security of the identity authentication is improved, and the identity authentication process is simplified.
Owner:上海方付通科技服务股份有限公司
Intelligent access control system for transformer substations based on internet of things
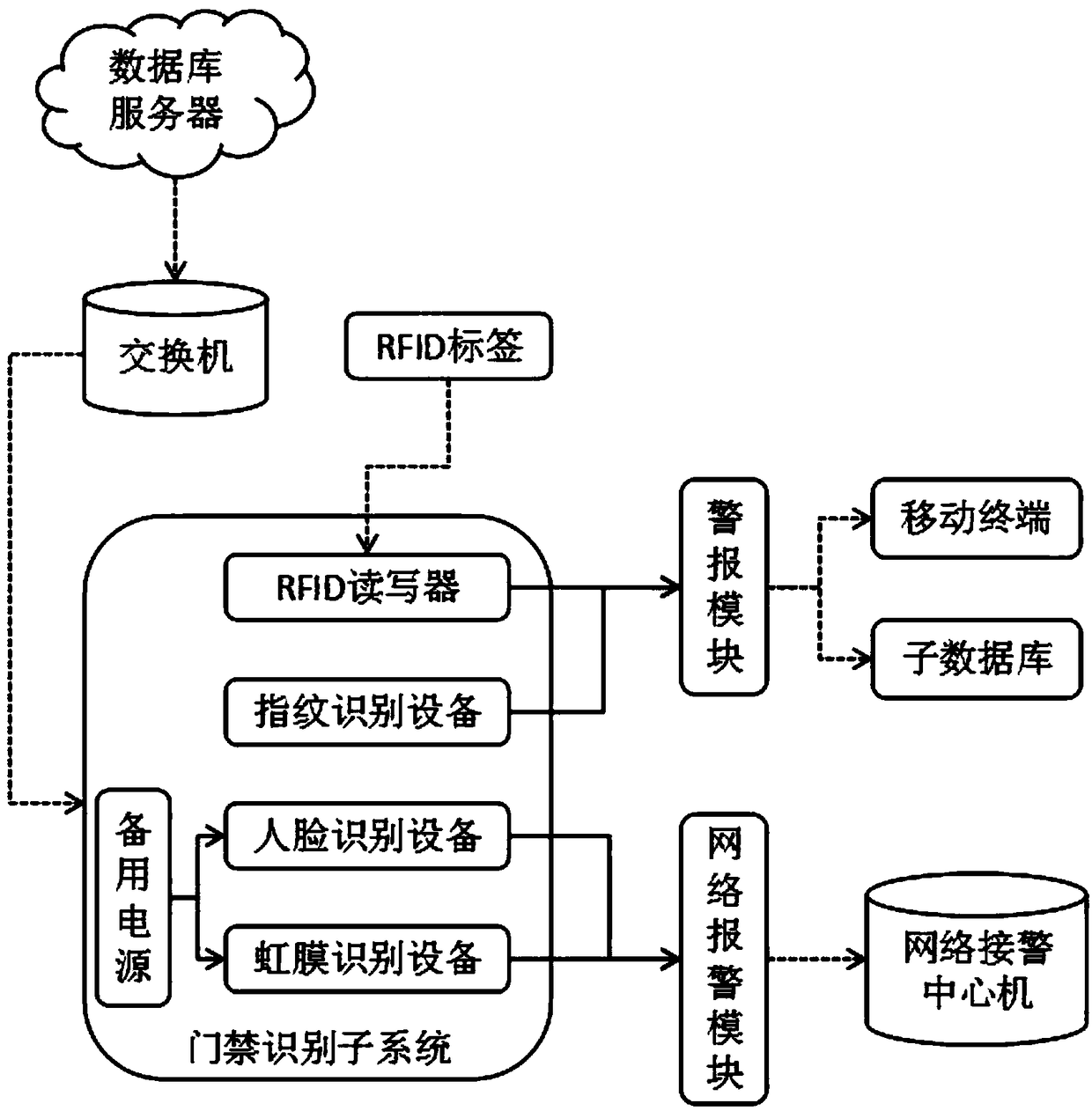
InactiveCN108615279AImprove securitySimplify the authentication processData processing applicationsIndividual entry/exit registersTransformerThe Internet
The invention discloses an intelligent access control system for transformer substations based on the internet of things, belonging to the technical field of access control systems. The intelligent access control system comprises a database server and a switch, wherein the database server is connected with the switch through an Ethernet data transmission module; an access control identification subsystem, which is connected with the switch through an optical fiber data transmission module and comprises an RFID reader-writer, a fingerprint identification device, a face recognition device and aniris recognition device; an alarming module, which is separately connected with the RFID reader-writer and the fingerprint identification device through a data transmission module; and a mobile terminal and a sub-database, wherein the alarming module is separately connected with the mobile terminal and the sub-database through a wireless data transmission module. According to the invention, the identification process of the intelligent access control system is divided into four levels, so the process of staff identity authentication is simplified, and the safety of the access control system for transformer substations is enhanced.
Owner:安徽电科恒钛智能科技有限公司
Methods for dynamic user identity authentication
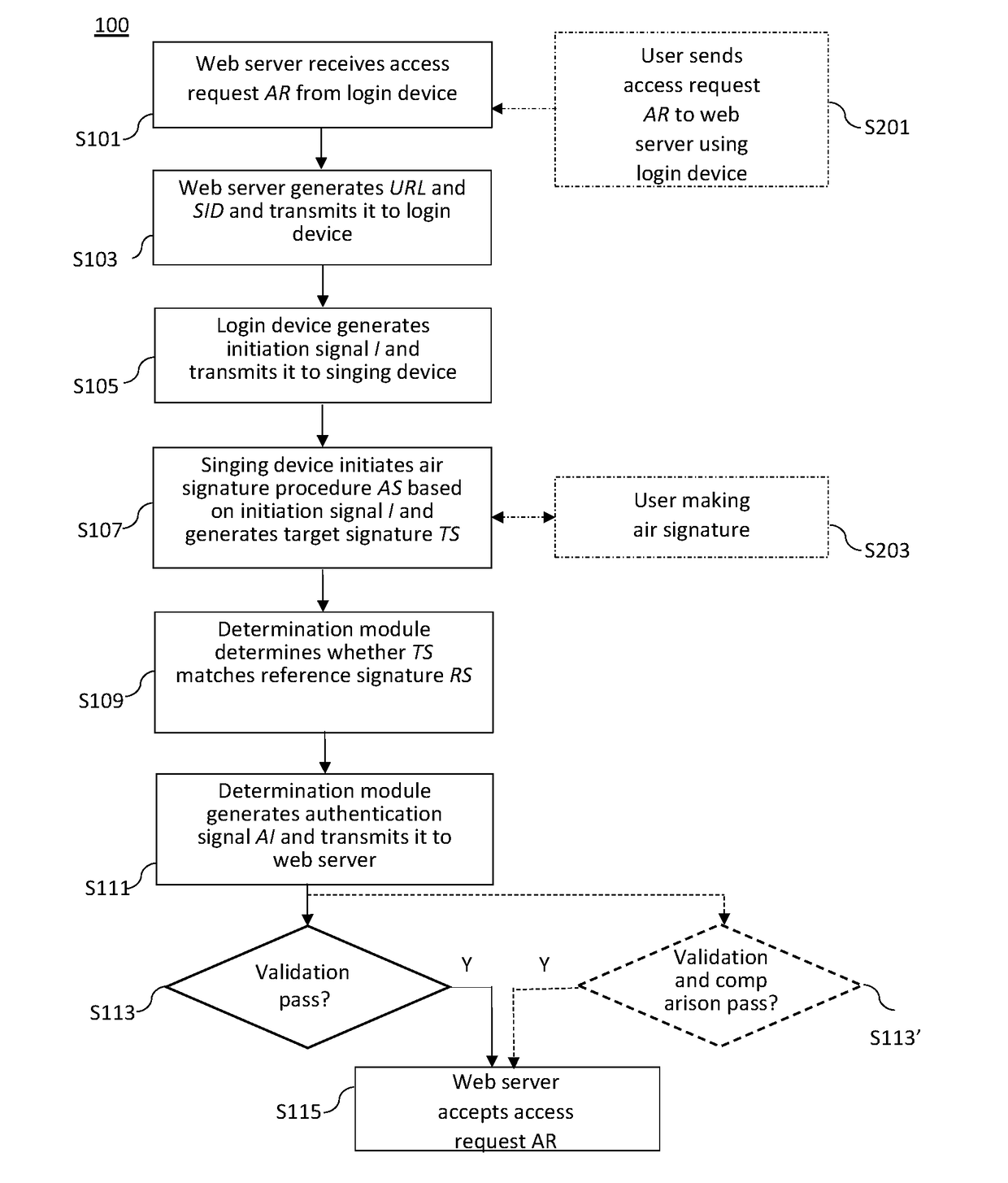
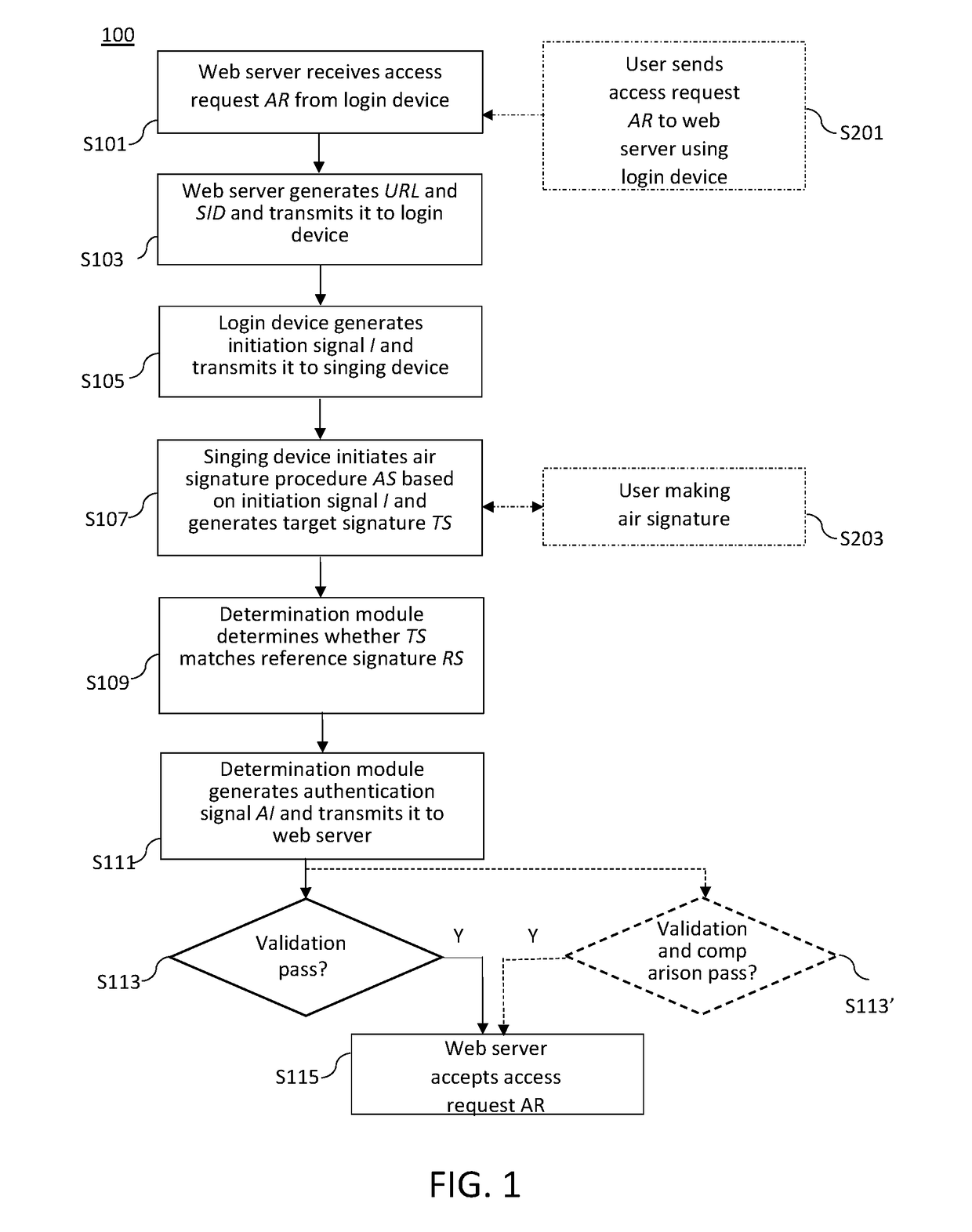
ActiveUS20180212947A1Improve securityConvenient authentication procedureTransmissionRecord carriers used with machinesWeb serviceTarget signature
Disclosed herein are methods for dynamic user Identity authentication for authenticating the identity of a user of a login device. In some embodiments, the method includes the following steps: using a web server to receive an access request from the login device, generate a resource address information and a session identifier, and transmit the same to the login device; using the login device to generate an initiation signal and transmit the same to a signing device thereby initiating an air signature procedure to generate a target signature, wherein the signing device includes a motion sensor configured to sense movement features produced when the user moves the signing device; using a determination module to determine whether the target signature matches a reference signature and generate a authentication information based on the determination; and using the web server to determine whether the access request is granted based on the authentication information.
Owner:CHEN PO KAI
Data packet forwarding method, device and system
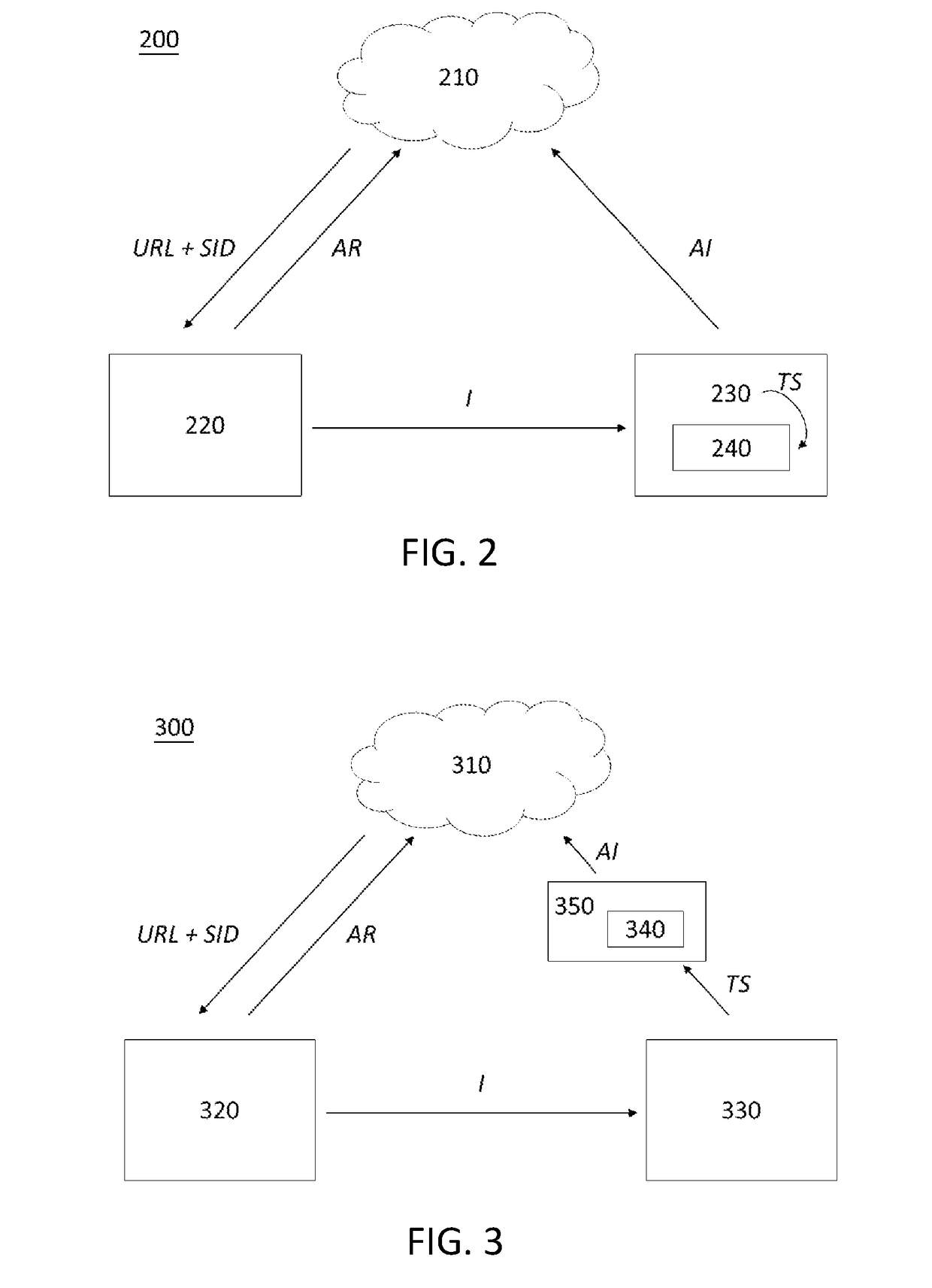
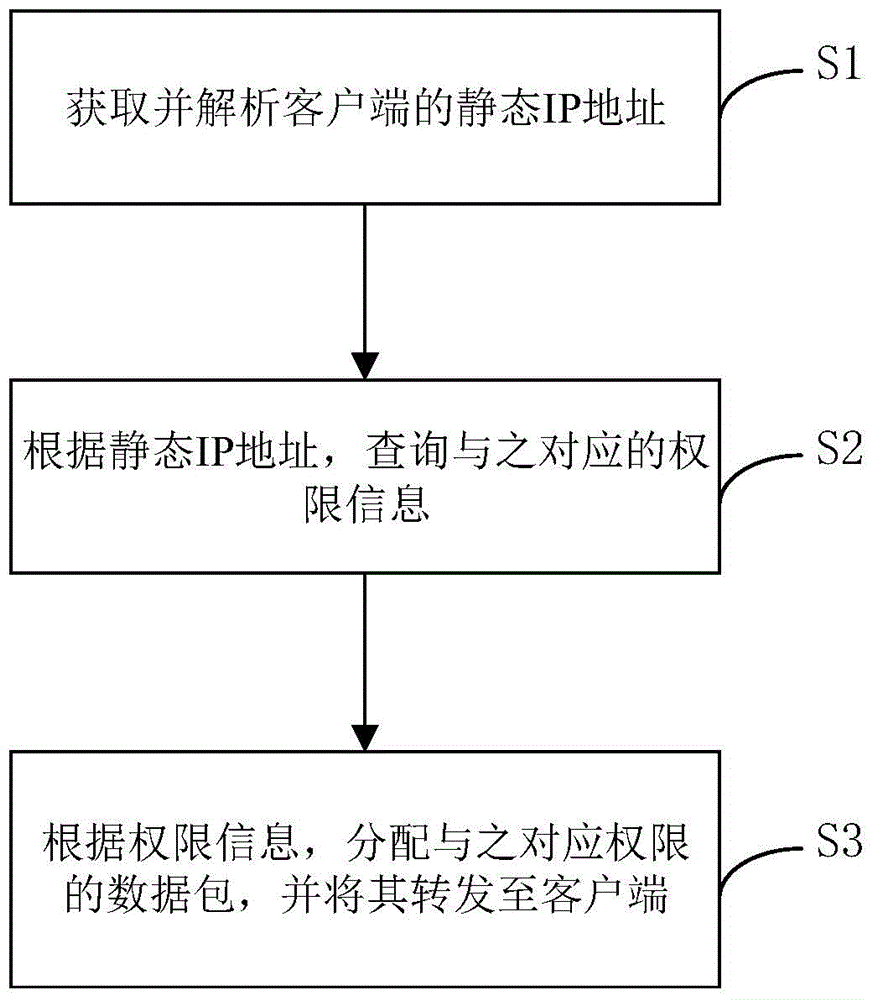
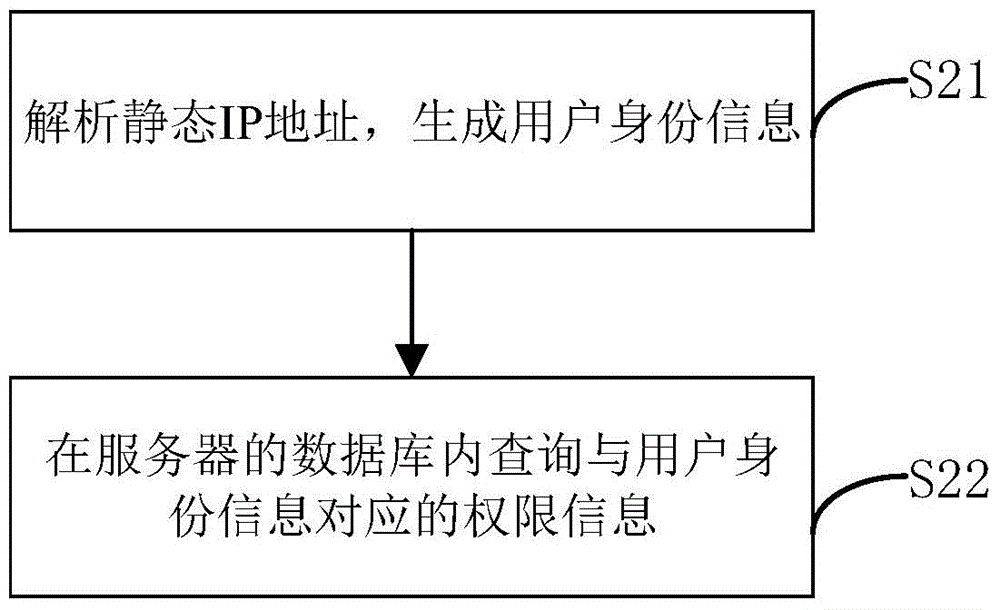
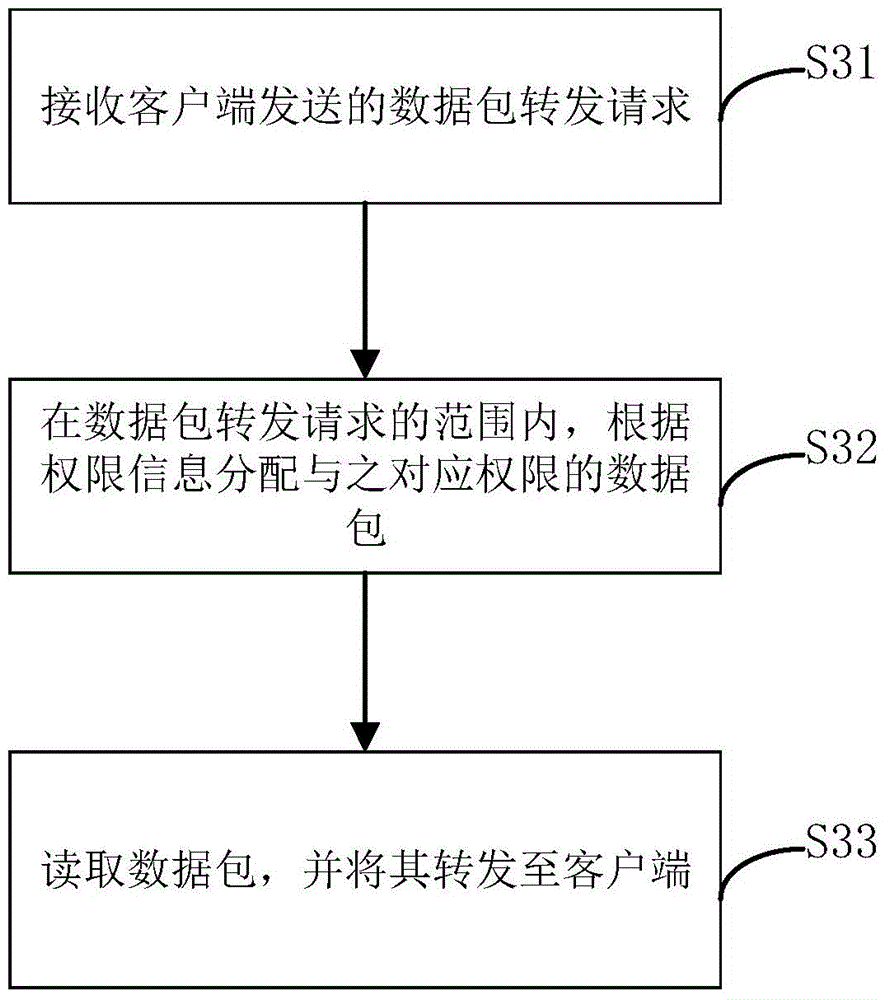
InactiveCN104158817AAvoid dependenceAvoid typingUser identity/authority verificationIp addressPassword
The present invention discloses data packet forwarding method, device and system, the method comprising following steps: obtaining and analyzing a static IP address of a client; querying corresponding authority information according to the static IP address; assigning data packets with corresponding authority according to the authority information, and forwarding the data packets to the client. The implementation of the present invention simulates a hardware based network layer through a virtual network equipment Tun network card, thereby systematically realizing simulation of a forwarding process receiving data packets from a server and avoiding the dependence on hardware in the data packet forwarding process. Meanwhile, by assigning a static IP address to the client, the method directly uses the static IP address as the identification information for a user, simplifies the process of identity verification and authorization, avoids inputting plaintext passwords, enhances safety and improves user experiences.
Owner:NUBIA TECHNOLOGY CO LTD
User authentication method using face recognition and device therefor
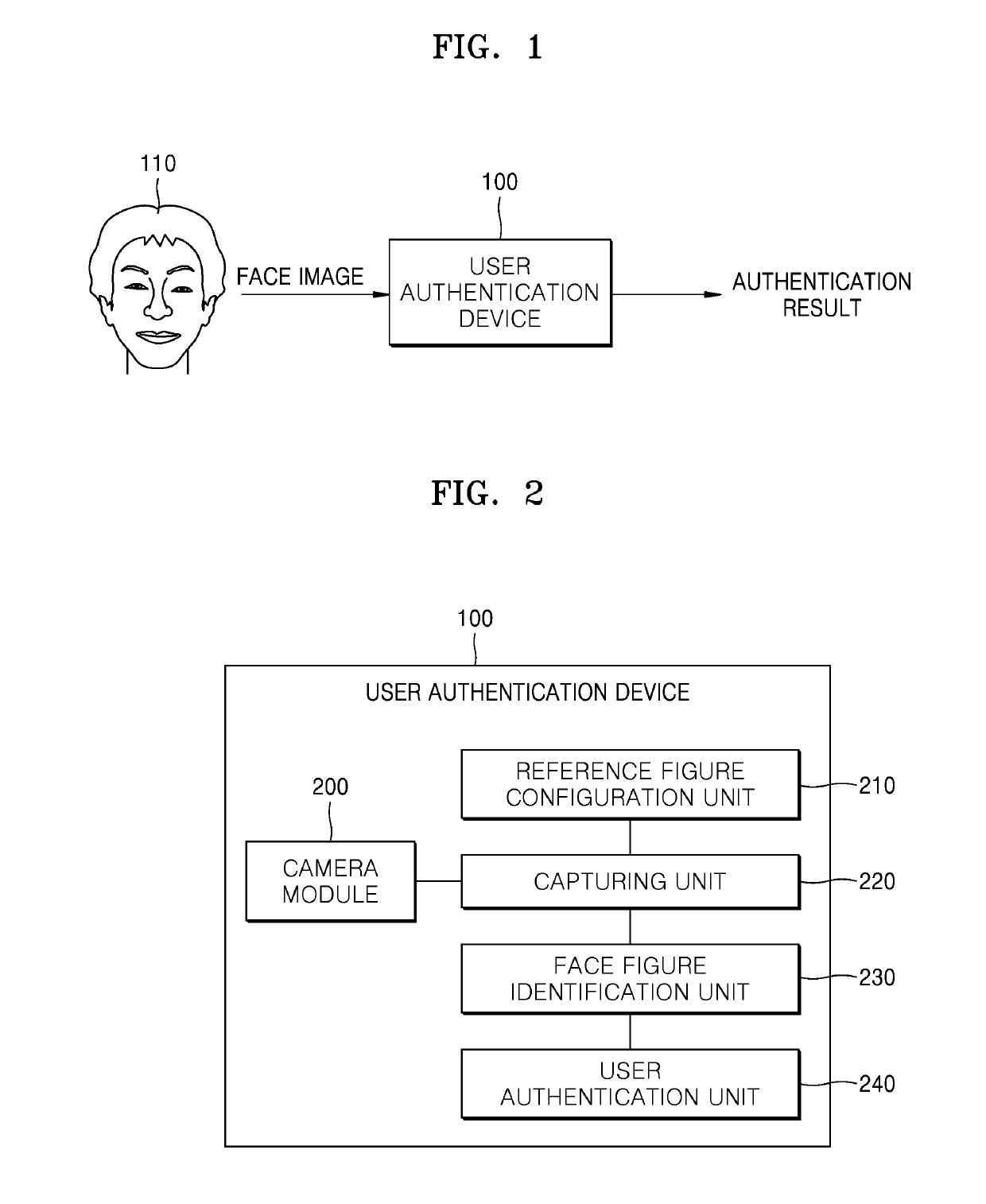
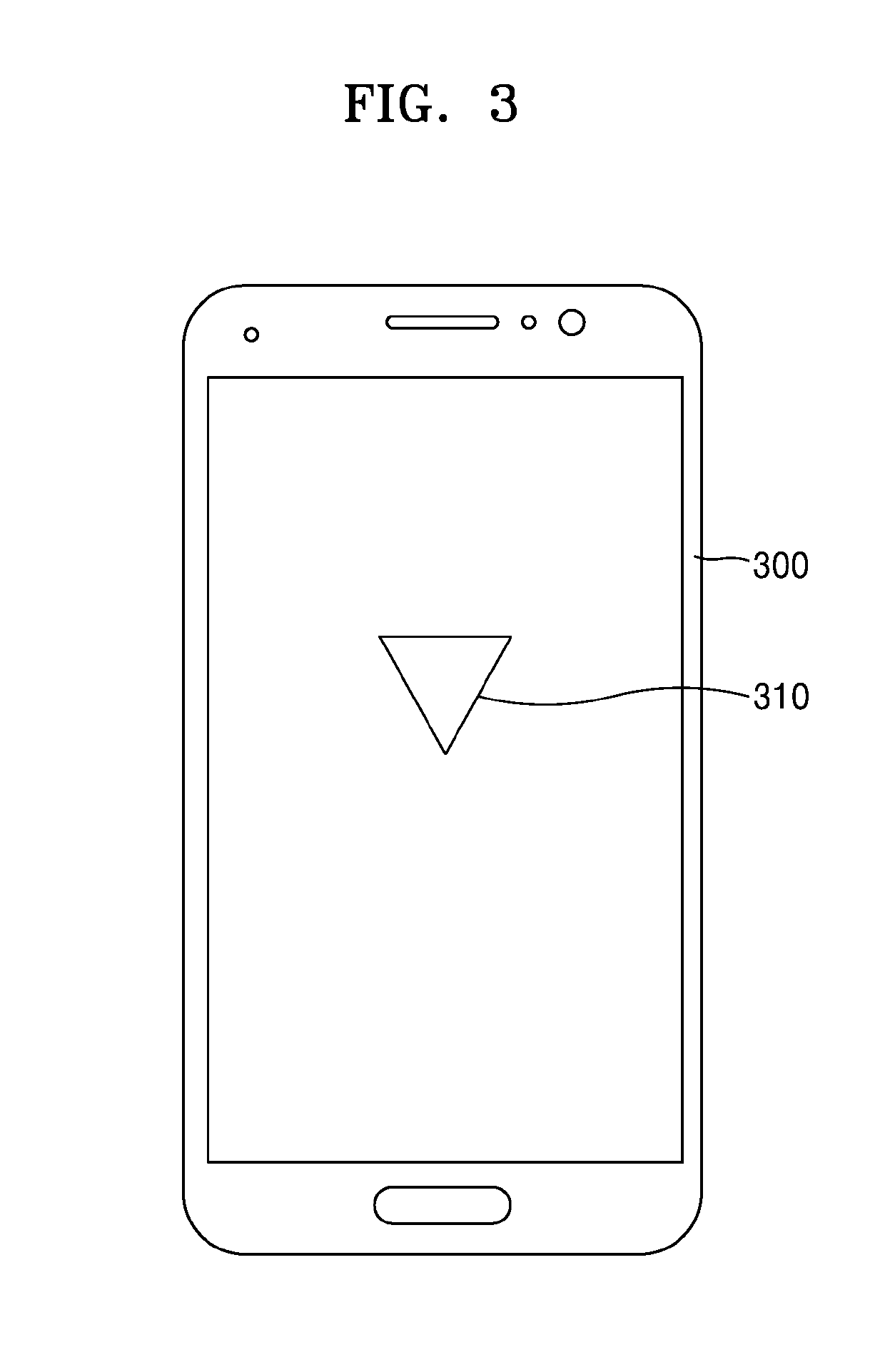
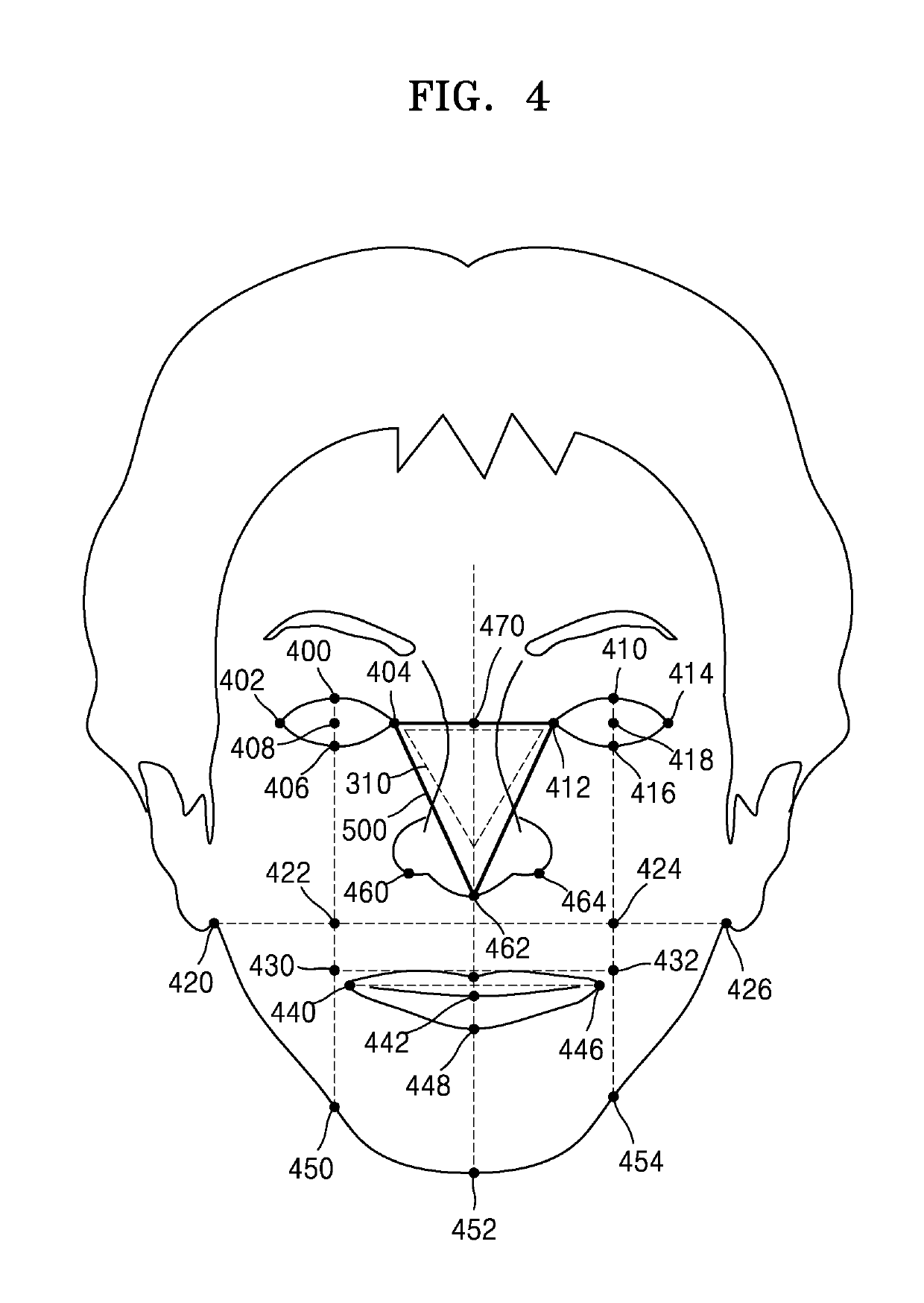
InactiveUS20190286798A1Easy authenticationSimplify the authentication processCharacter and pattern recognitionDigital data authenticationPattern recognitionGraphics
Provided is a user authentication method using face recognition and a device therefor. The user authentication method in a user authentication device includes capturing a face image of a user by using a camera module, identifying a plurality of figures based on positions of an eye, a nose, a mouth or an ear of the face image, and approving user identity based on the plurality of figures.
Owner:KIM YONG SANG
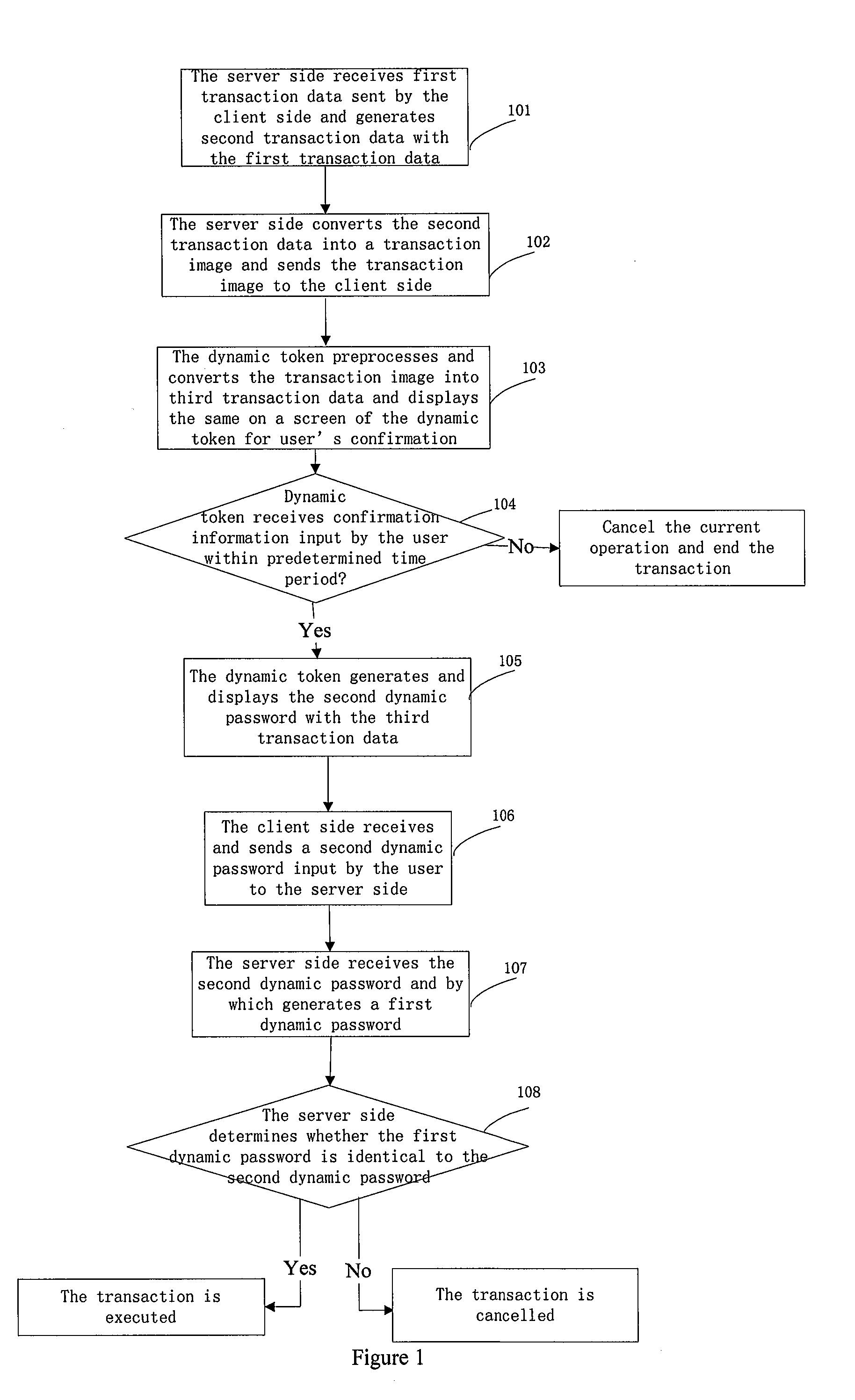
Image collection based information security method and system
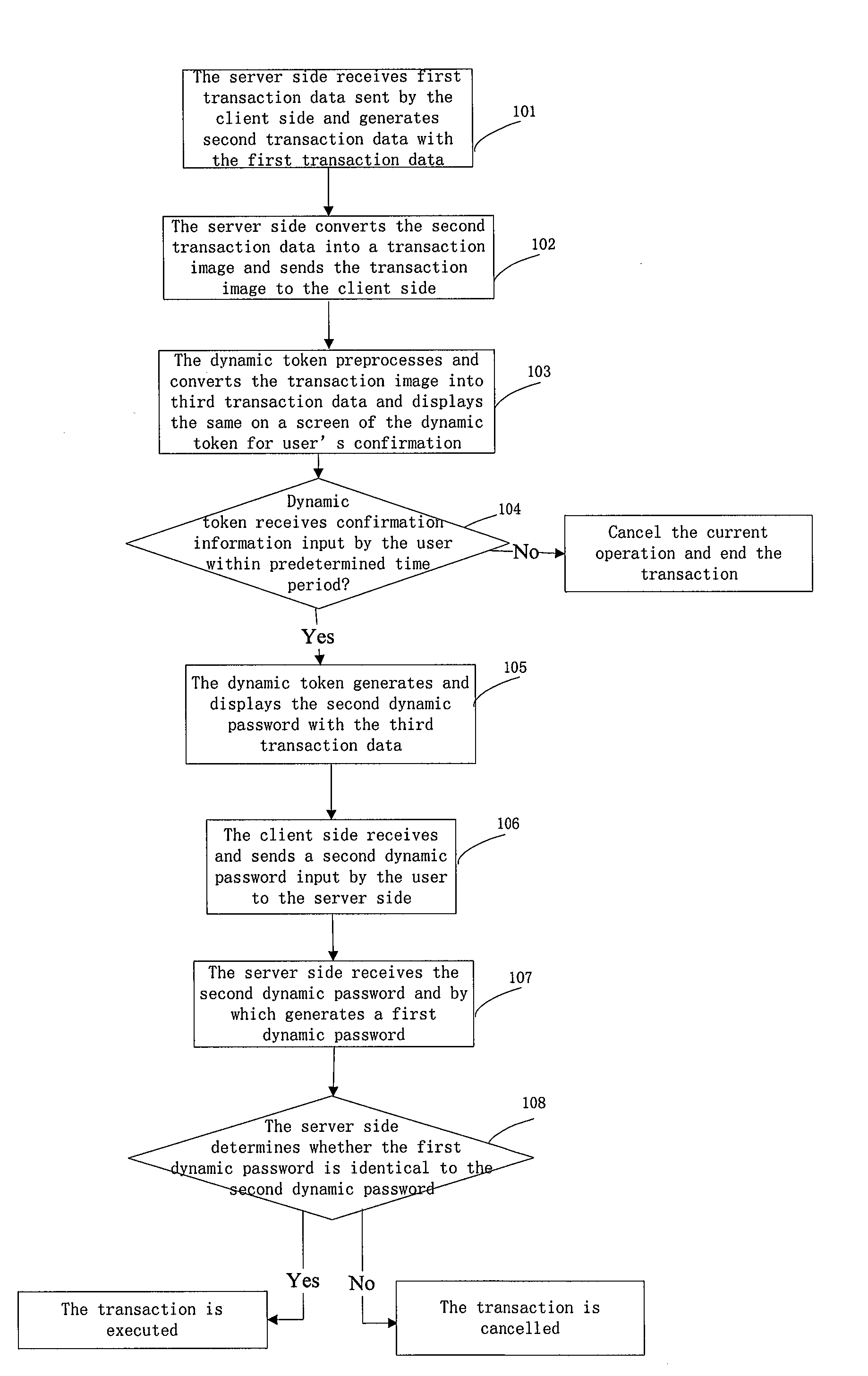
ActiveUS20130160103A1Improve securityReduce error rateDigital data processing detailsMultiple digital computer combinationsUser inputPassword
An image collection based information security method and system is disclosed. The method includes a server side receiving a first transaction data sent by a client side and generating a second transaction data with the first data. The server converts the second data into an image, and sends the image to the client. A dynamic token collects the image, pre-processes, and converts the image into a third transaction data, and displays the third data for user's confirmation. The token generates and displays a second dynamic password according to the third data. The client receives the second password input by a user and sends same to the server. The server receives the second password and generates a first dynamic password, determines whether the first password is identical to the second password; if yes, the authentication is successful and the transaction is executed; if no, the transaction is cancelled.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com