Identity authentication method and system, terminal and storage medium
A technology for identity authentication and verification of passwords, applied in the field of network security, can solve problems such as insecurity and cumbersome operations, and achieve the effect of improving security and simplifying the process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
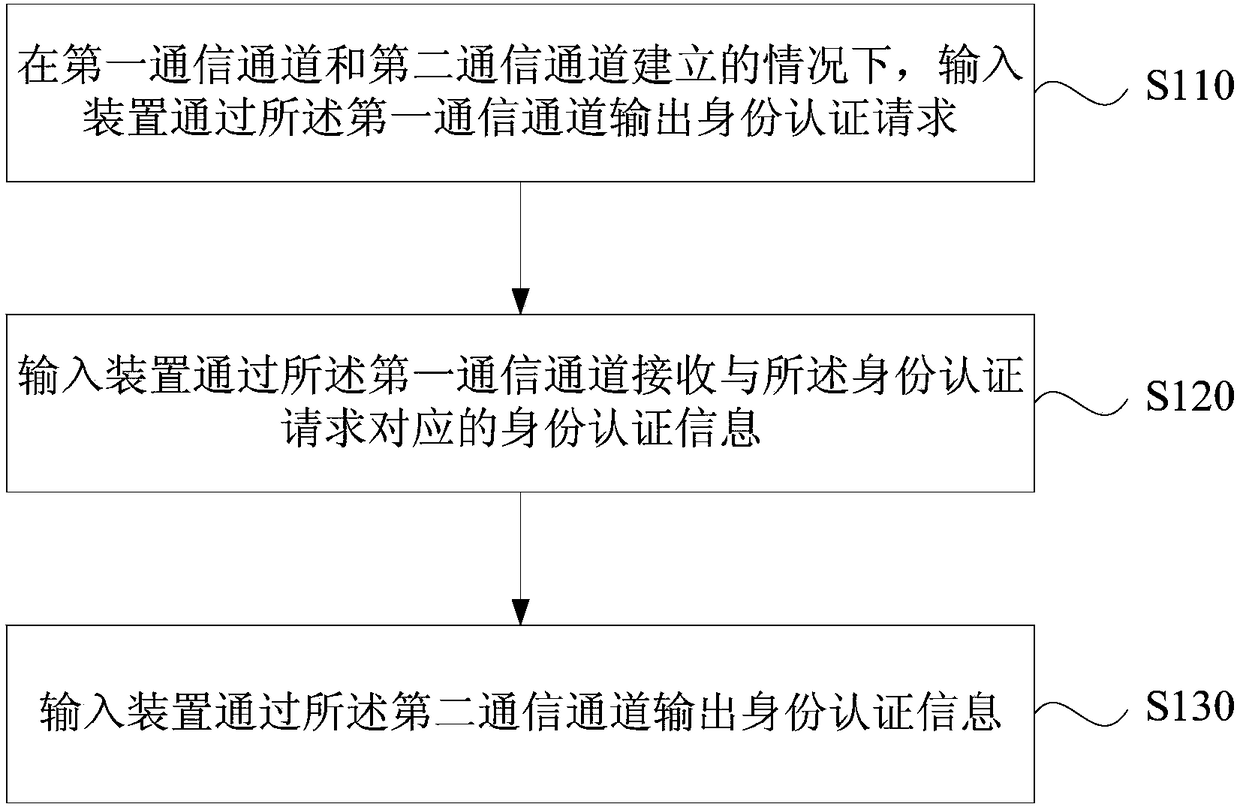
[0046] figure 1 It is a flowchart of an identity authentication method provided in Embodiment 1 of the present invention. The technical solution of this embodiment can be applied to the situation where the input device performs identity authentication. The method can be performed by an identity authentication system provided by an embodiment of the present invention. The system can be implemented in the form of software and / or hardware, and configured for application in a smart terminal with an input device. The smart terminal can be, for example, a smart Mobile phones, computers, tablets, smart watches or smart bracelets, etc. The method specifically includes the following operations:
[0047] S110. When the first communication channel and the second communication channel are established, the input device outputs an identity authentication request through the first communication channel.
[0048] The input device may be, for example, an IMS (Input Method Service, input met...
Embodiment 2
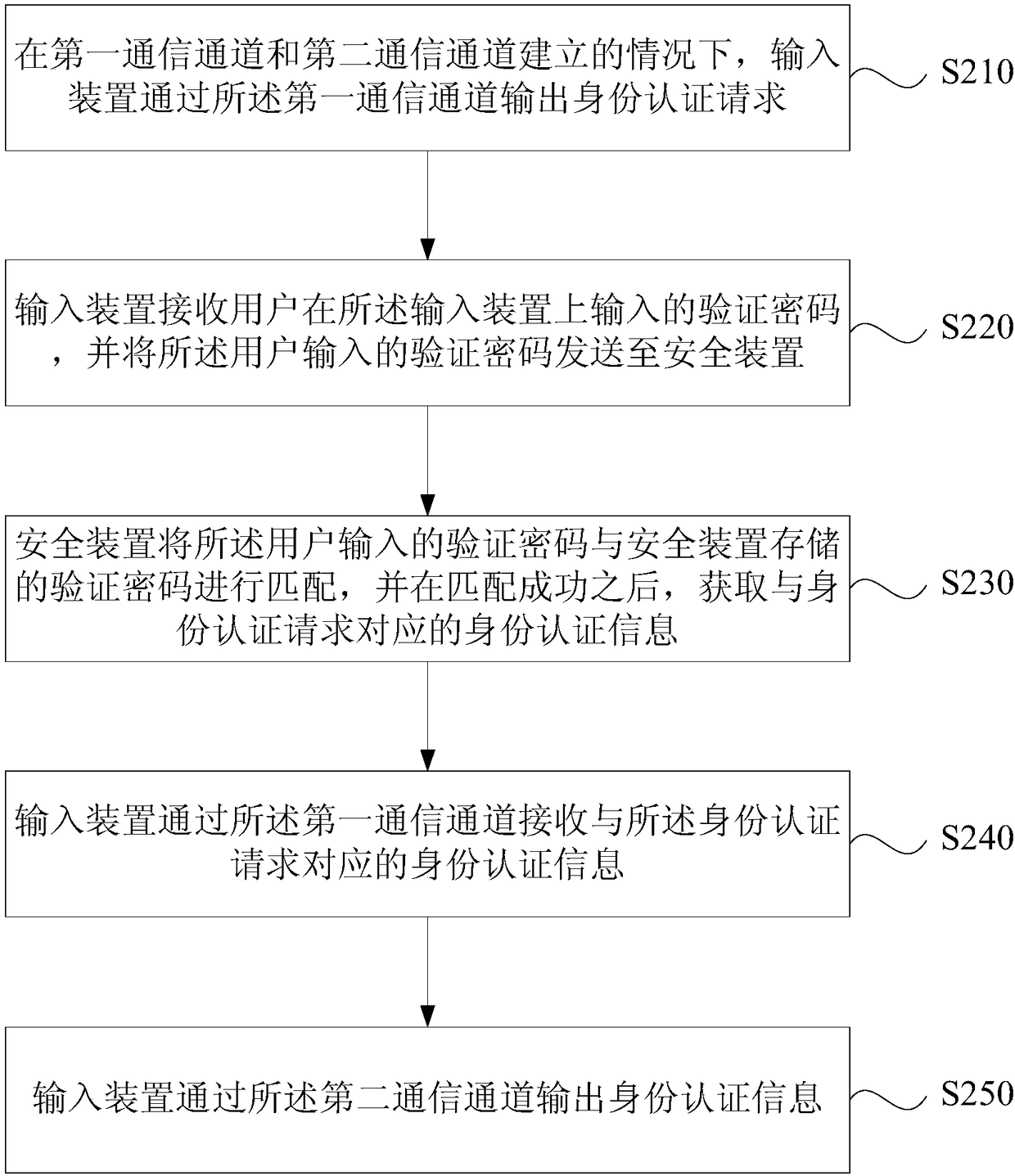
[0063] image 3 It is a flow chart of an identity authentication method provided in Embodiment 2 of the present invention. On the basis of the foregoing embodiments, the embodiment of the present invention adds operations before the input device receives the identity authentication information corresponding to the identity authentication request through the first communication channel. Correspondingly, the method of this embodiment includes:
[0064] S210. When the first communication channel and the second communication channel are established, the input device outputs an identity authentication request through the first communication channel.
[0065] S220. The input device receives the verification password input by the user on the input device, and sends the verification password input by the user to the security device.
[0066] The input device generates an identity authentication request, which is sent to the security device, and the security device retrieves the veri...
Embodiment 3
[0073] Figure 4 It is a flowchart of an identity authentication method provided by Embodiment 3 of the present invention. On the basis of the foregoing embodiments, the embodiment of the present invention adds operations before the input device outputs an identity authentication request through the first communication channel. Correspondingly, the method of this embodiment includes:
[0074] S310. The input device receives trigger information input by the user, where the trigger information is used to trigger the input device to generate an identity authentication request.
[0075] Exemplarily, the trigger information may be transaction-related information, including transaction type, transaction counterparty name, transaction account number, transaction bank, transaction amount, transaction time, electronic contract or electronic signature, and the like. Wherein, the transaction type may include transferring money or sending red envelopes, etc. The user inputs trigger inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com