Patents
Literature
1945results about How to "Avoid connection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
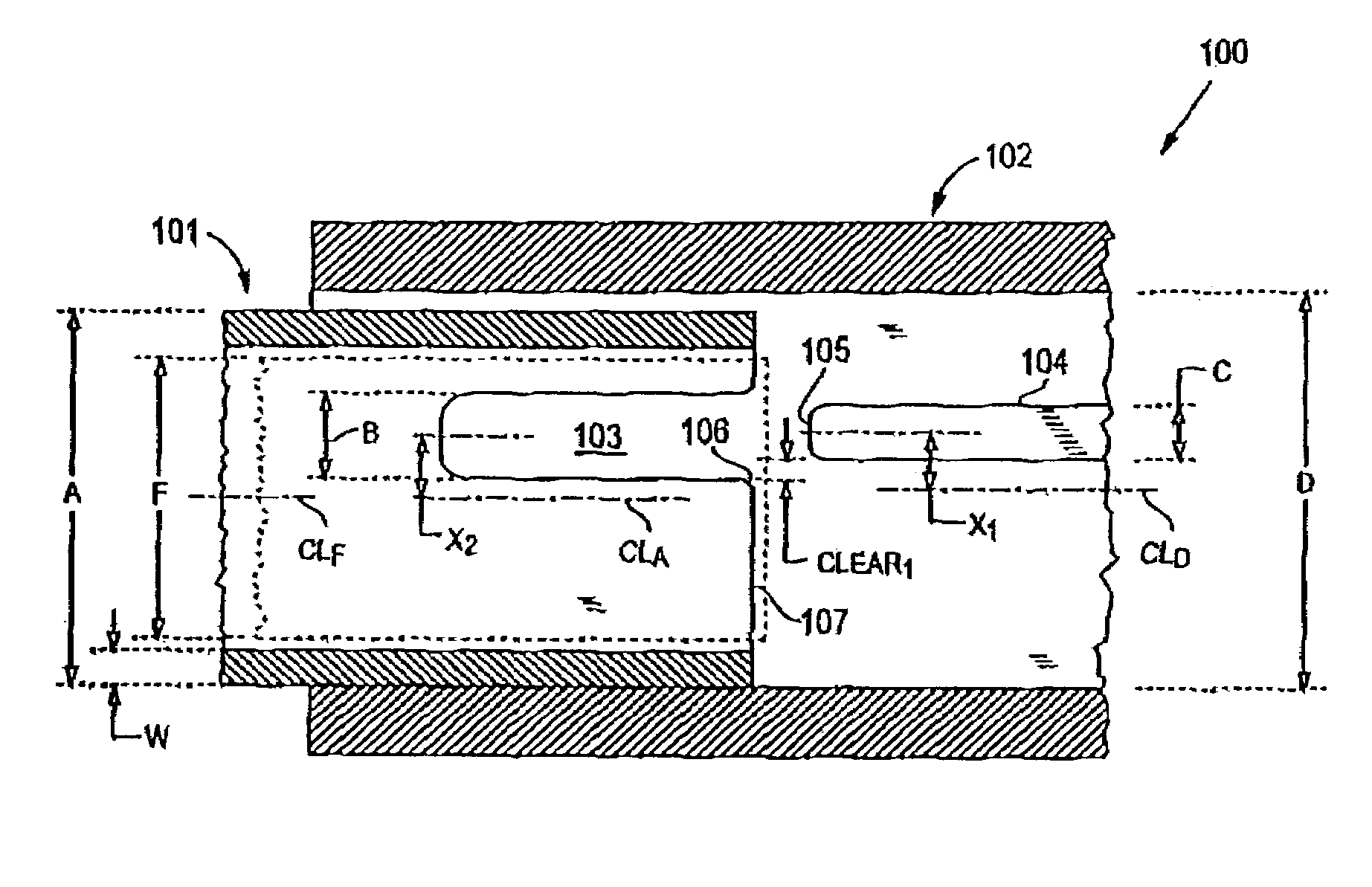
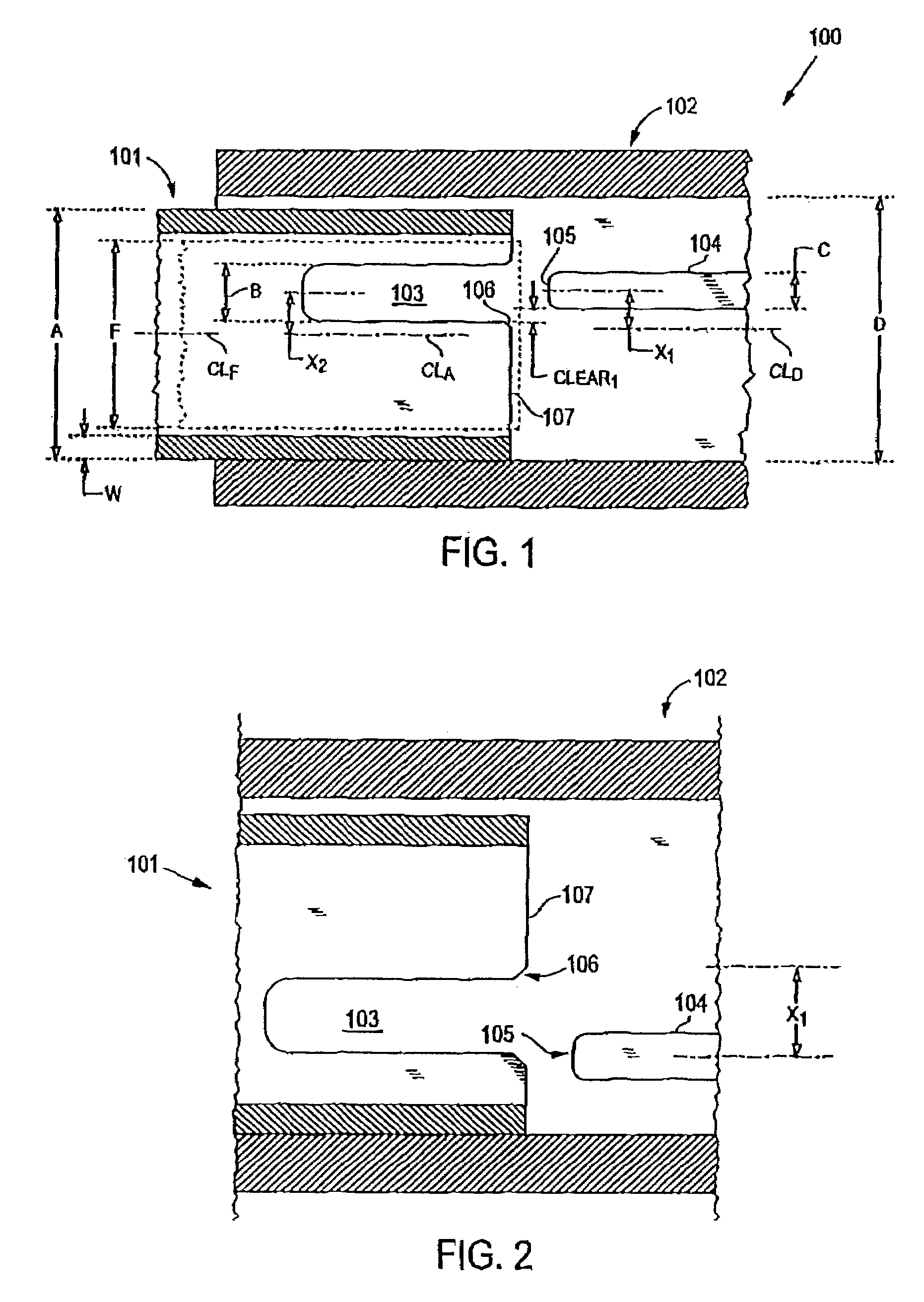
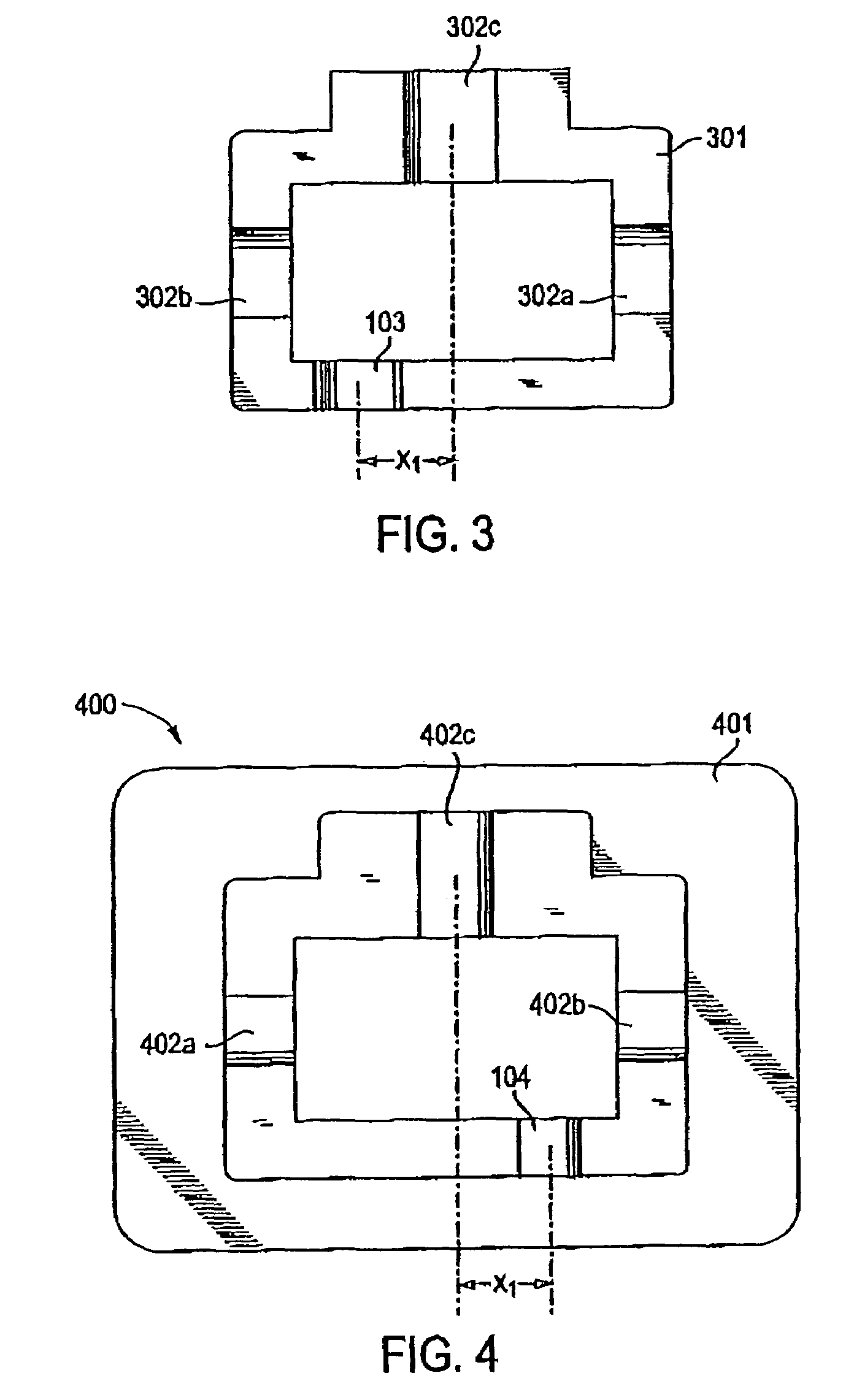
System for treating a wound with suction and method of detecting loss of suction
InactiveUS7438705B2Minimize the possibilityReduce the possibilityWound drainsMedical devicesMonitoring systemCatheter
A system for applying suction to a wound uses a reference airflow for monitoring system operation. A reference airflow (or “controlled leak”) to the suction source is provided when the system is in operation, such that deviation from the reference airflow can be monitored as an indication of a change in operation, such as a leak in the seal of the wound cover, a blockage of airflow from crimping of the suction conduit or overfill of the waste collector, or an inadvertent turn off or disconnect from the suction source.
Owner:PAUL HARTMANN AG
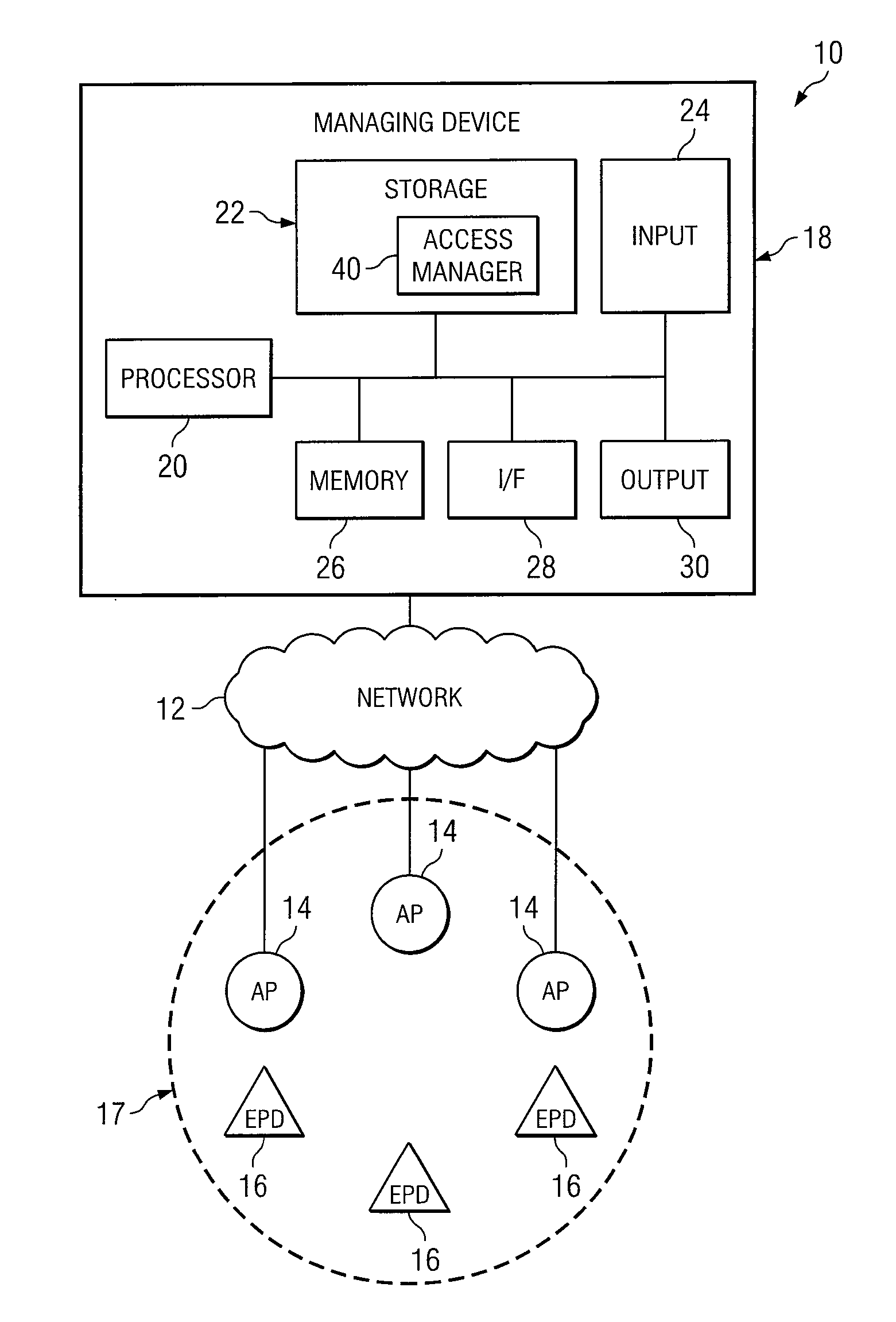
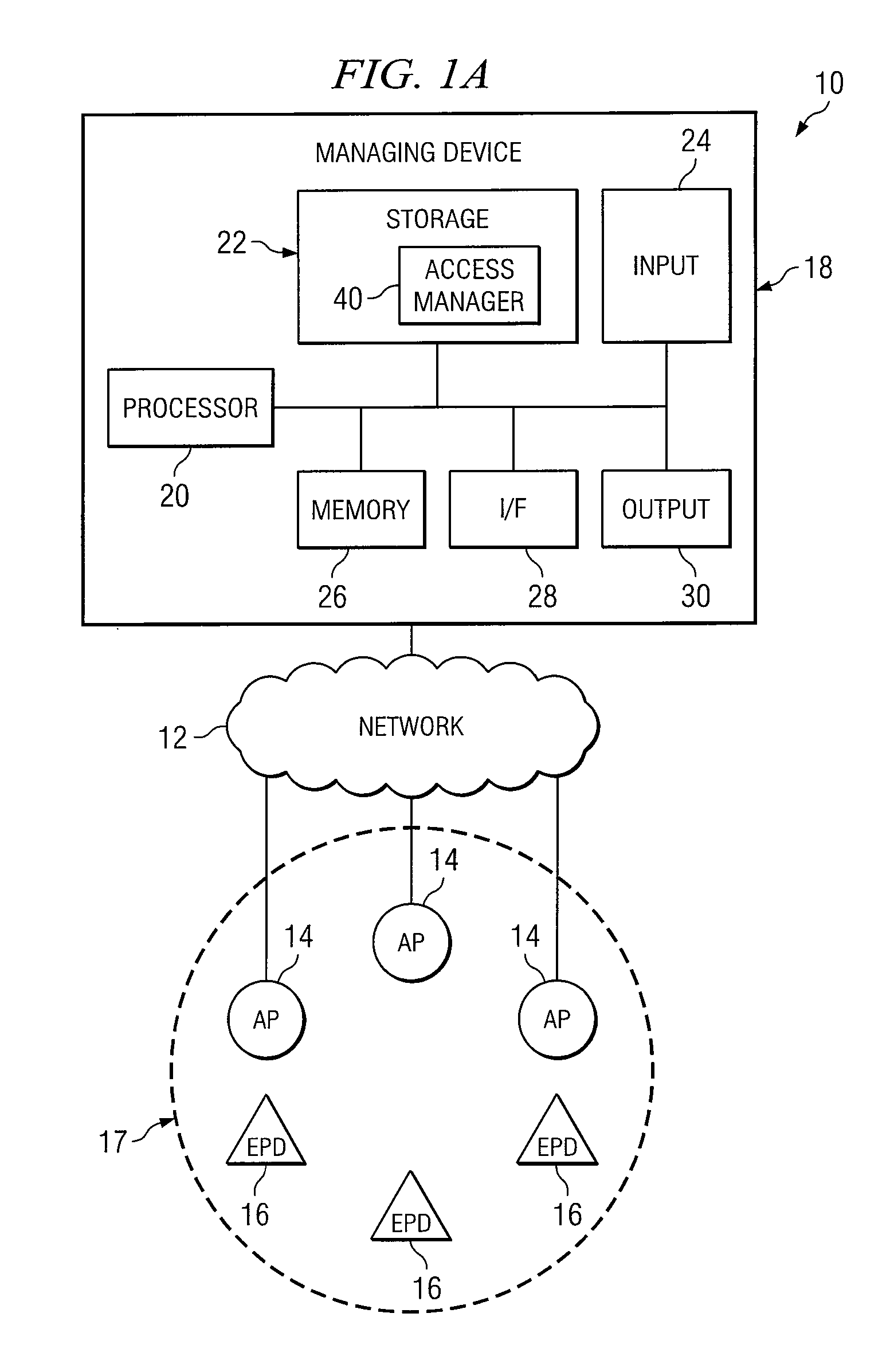
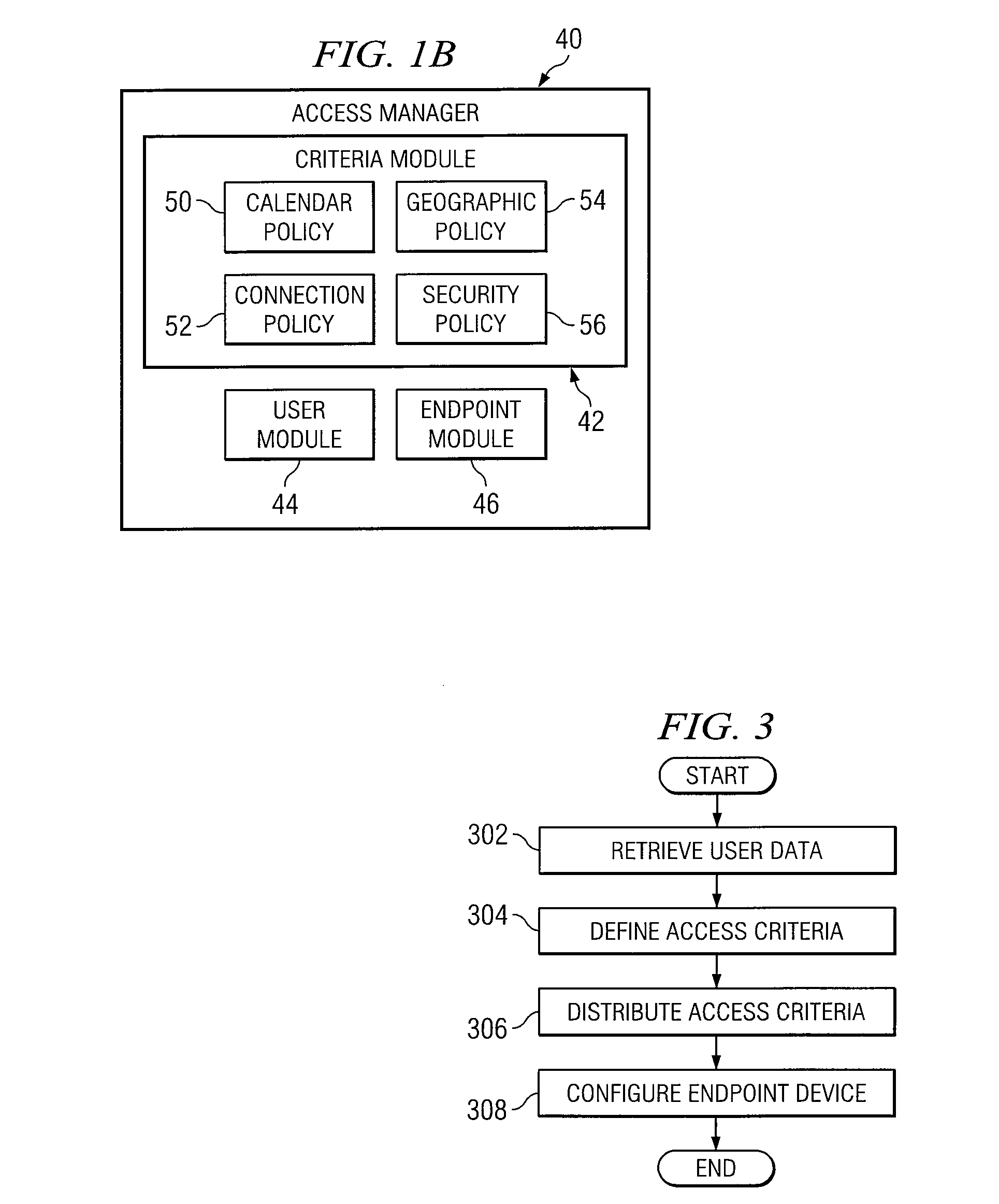
Method and System for Managing Access to a Wireless Network
InactiveUS20070109983A1Avoid connectionRadio transmissionSecurity arrangementComputer networkWireless network
According to one embodiment of the invention, a method for managing access to a wireless network includes defining access criteria for a plurality of endpoint devices in the wireless network. The access criteria includes a group of access policies controlling access to specific access points in the wireless network. The group of access policies are associated with respective access points and an identifier associated with a user. The method further includes configuring at least one endpoint device of the group of endpoint devices in the wireless network with the access criteria.
Owner:COMP ASSOC THINK INC
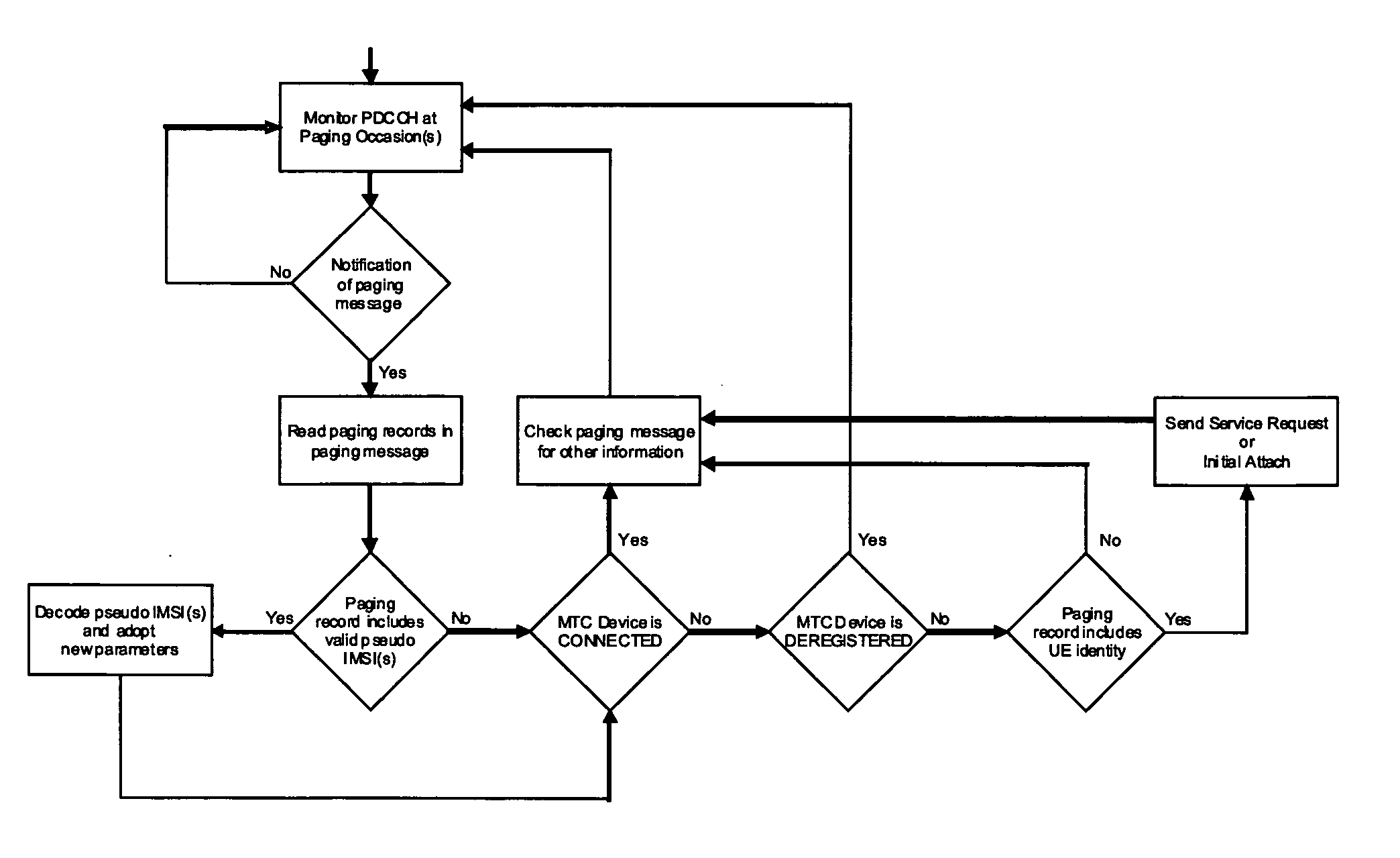
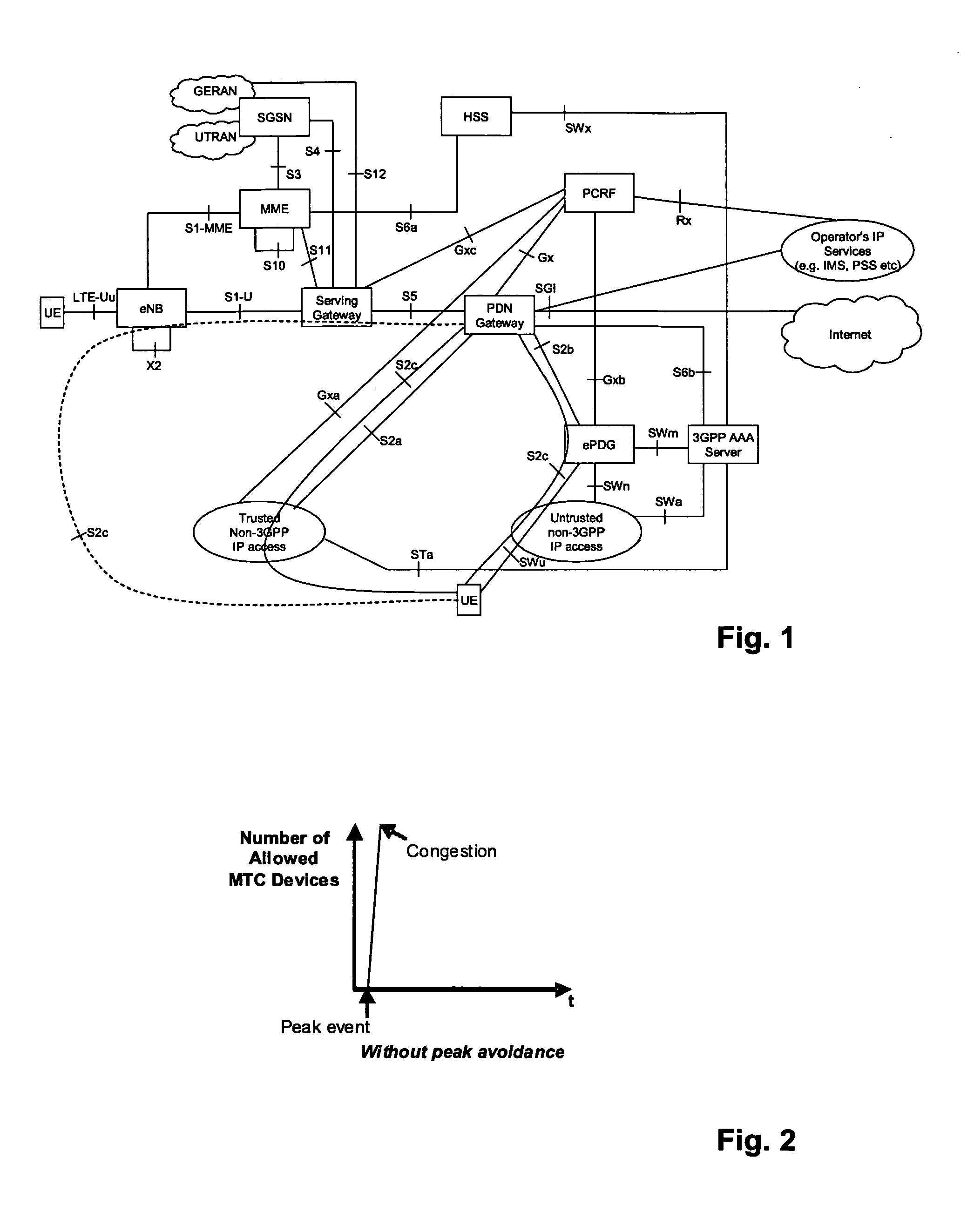
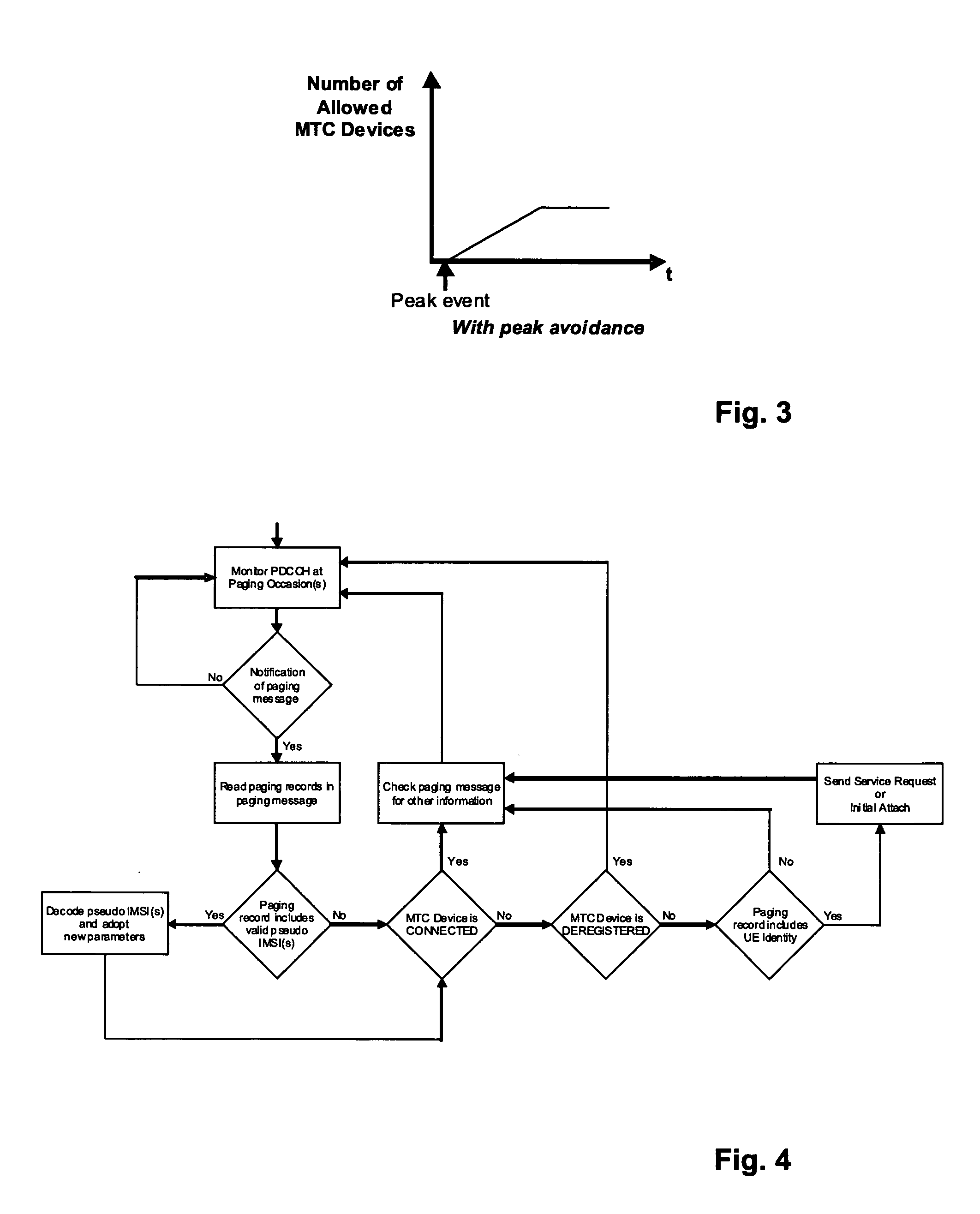
Group-based paging for machine-type-communication (MTC) devices
ActiveUS20130136072A1Avoid confusionLittle trafficBroadcast service distributionWireless commuication servicesTelecommunicationsChannel resource
The invention relates to a method for paging a group of MTC devices, and for transmitting parameter information to the MTC devices using the paging mechanism. MTC devices are grouped together and a different group ID per group to which the MTC device belongs is assigned to the MTC device. A specific group paging resource indication is determined for each group wherein each MTC device is assigned one of the group paging resource indications. The network pages MTC devices of a group by transmitting a paging message at the corresponding channel resources and including the corresponding group ID. Additionally, the group paging resource indications of several groups of MTC devices can be aligned in such a way with the transmissions and re-transmissions by the network, that the different groups respectively receive the transmission and re-transmissions of the paging message.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
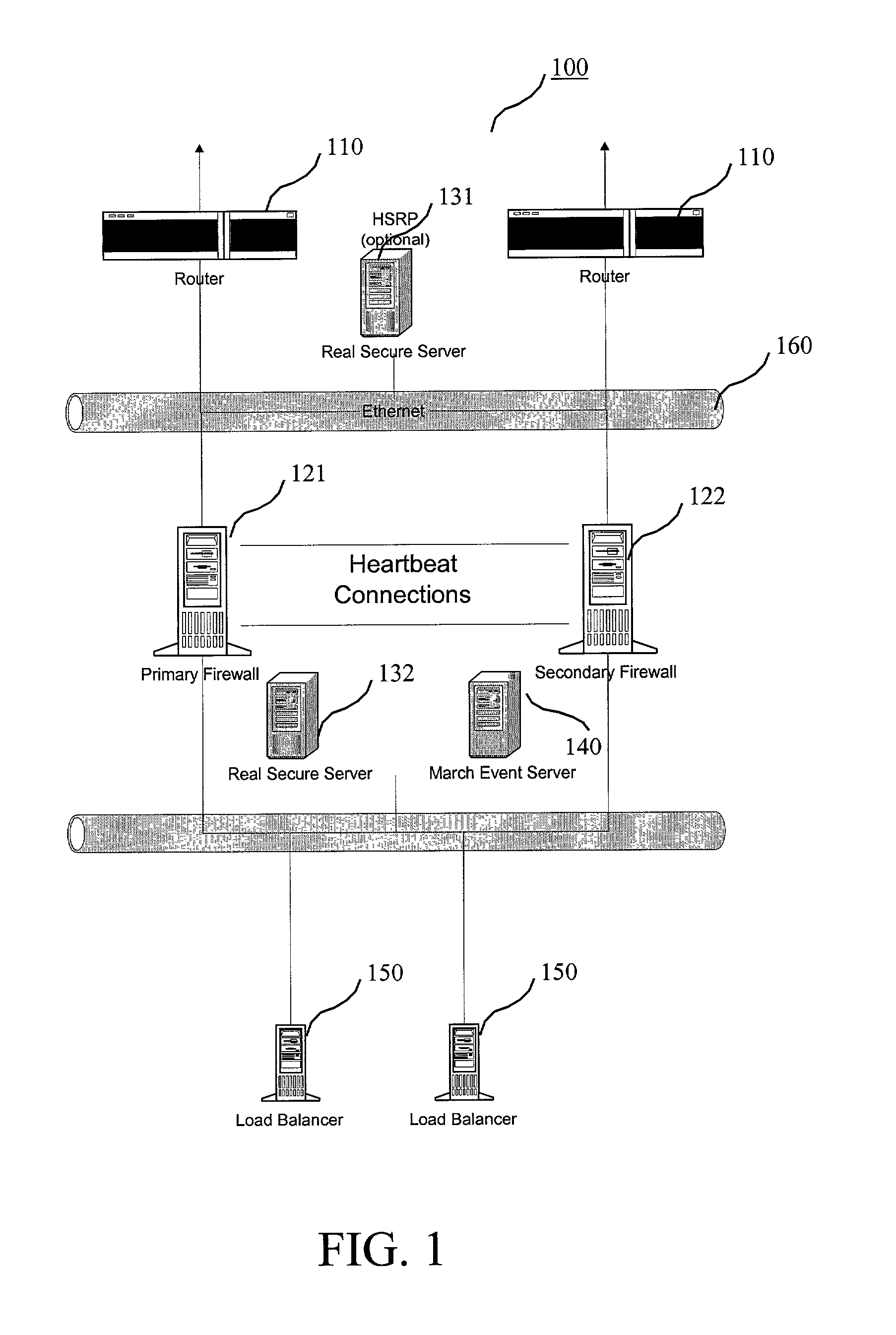
Network security and fraud detection system and method
ActiveUS7272728B2Avoid connectionAccess is deniedUser identity/authority verificationUnauthorized memory use protectionNetwork security policyNetwork service
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
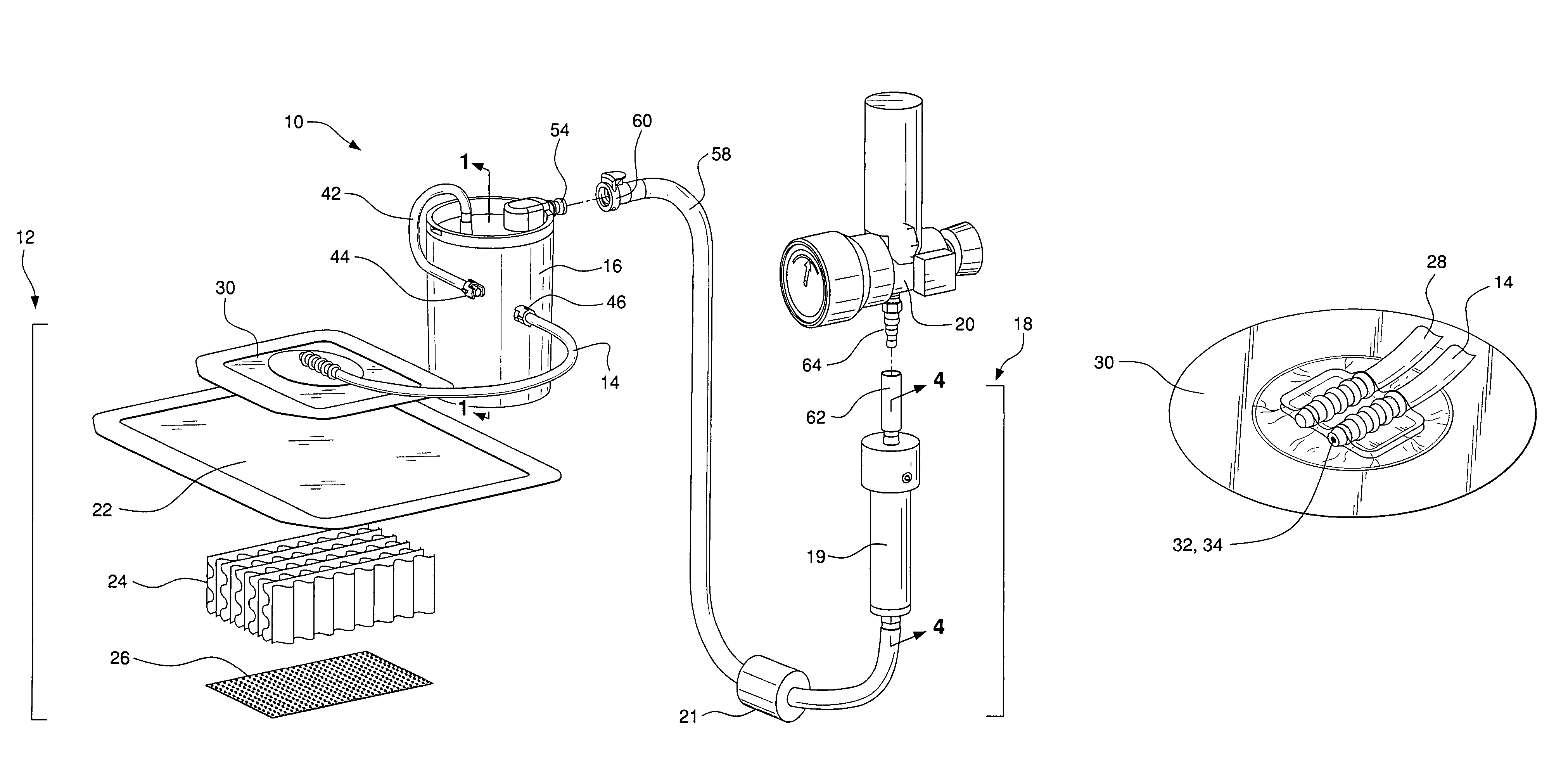
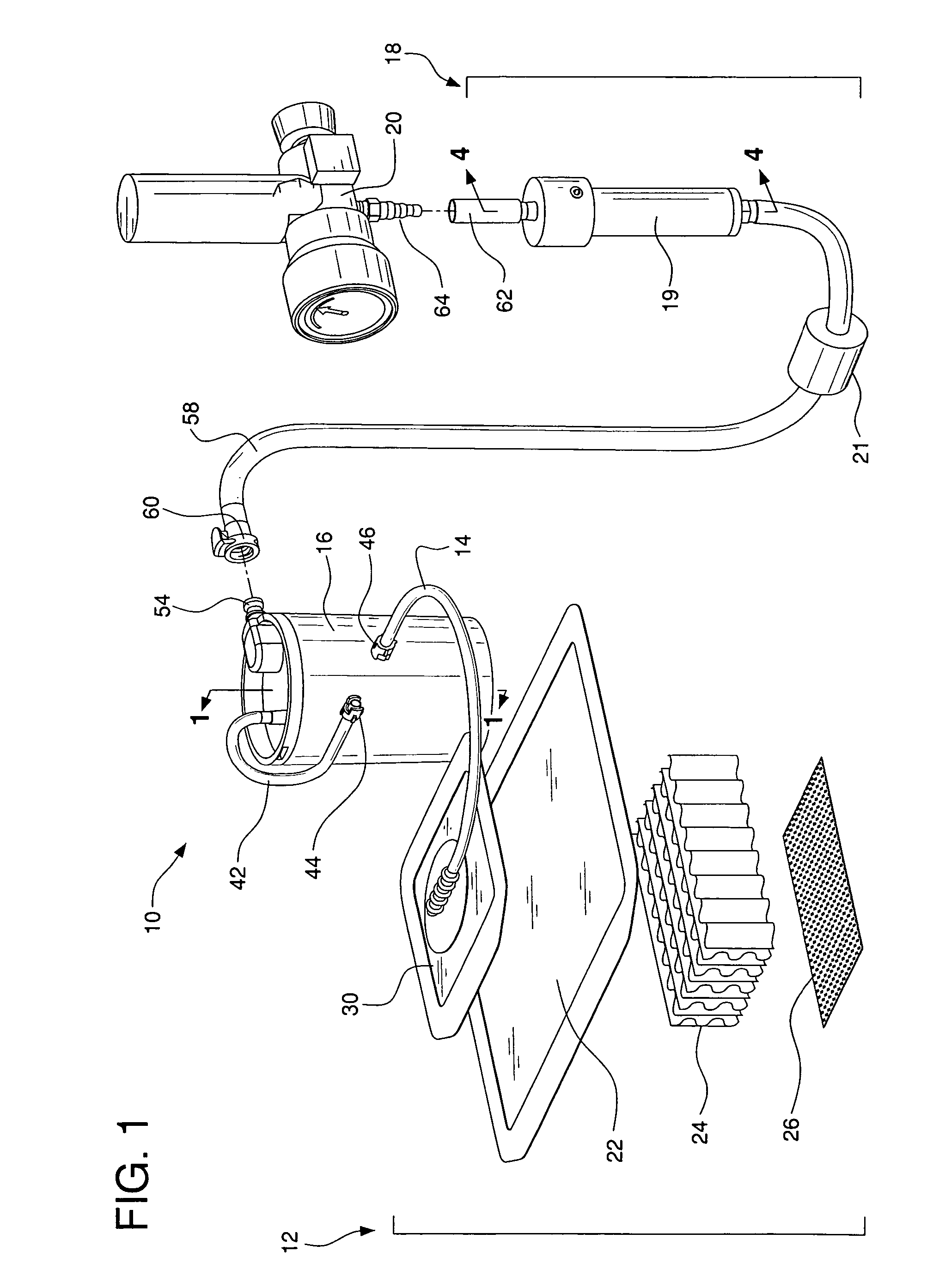
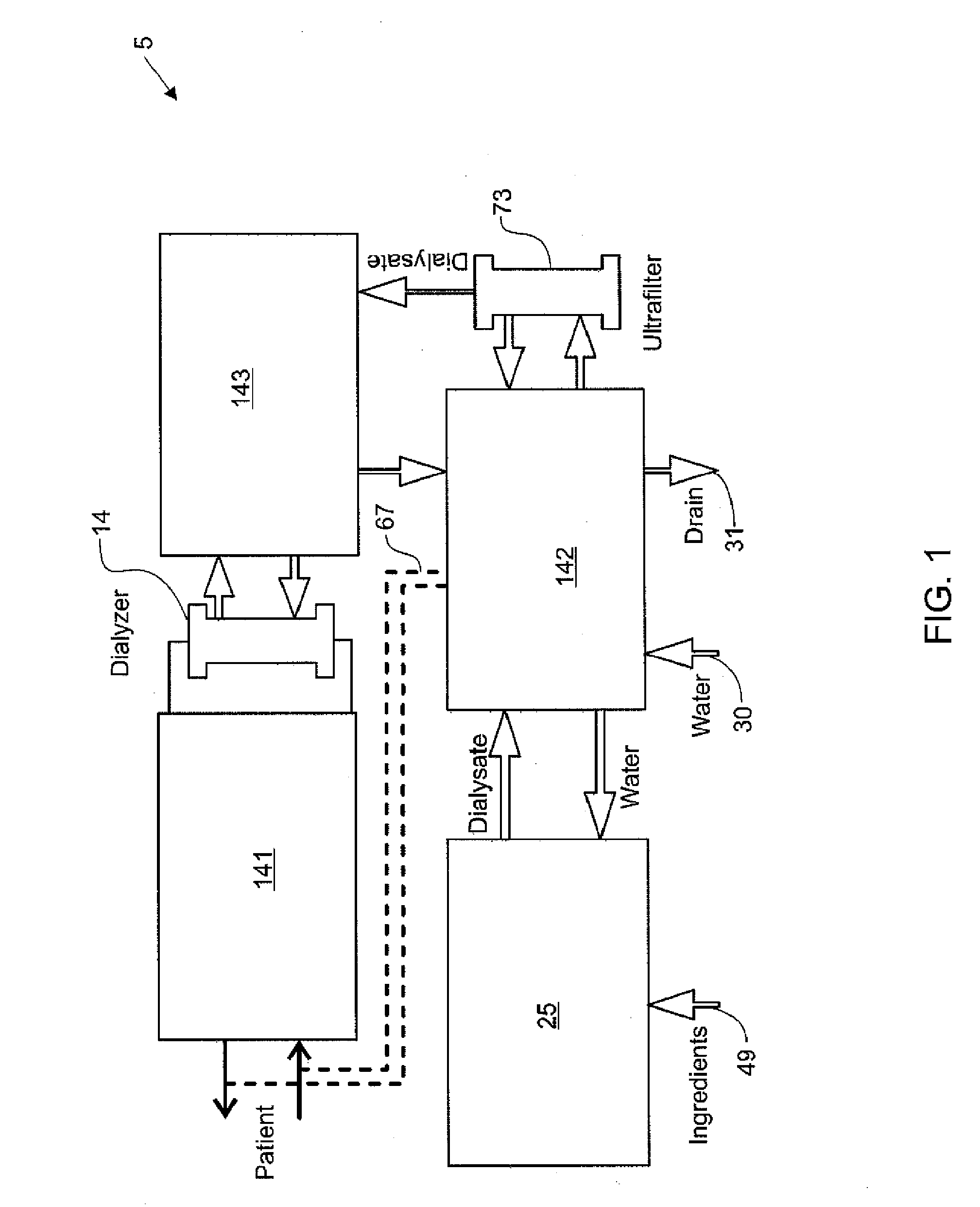
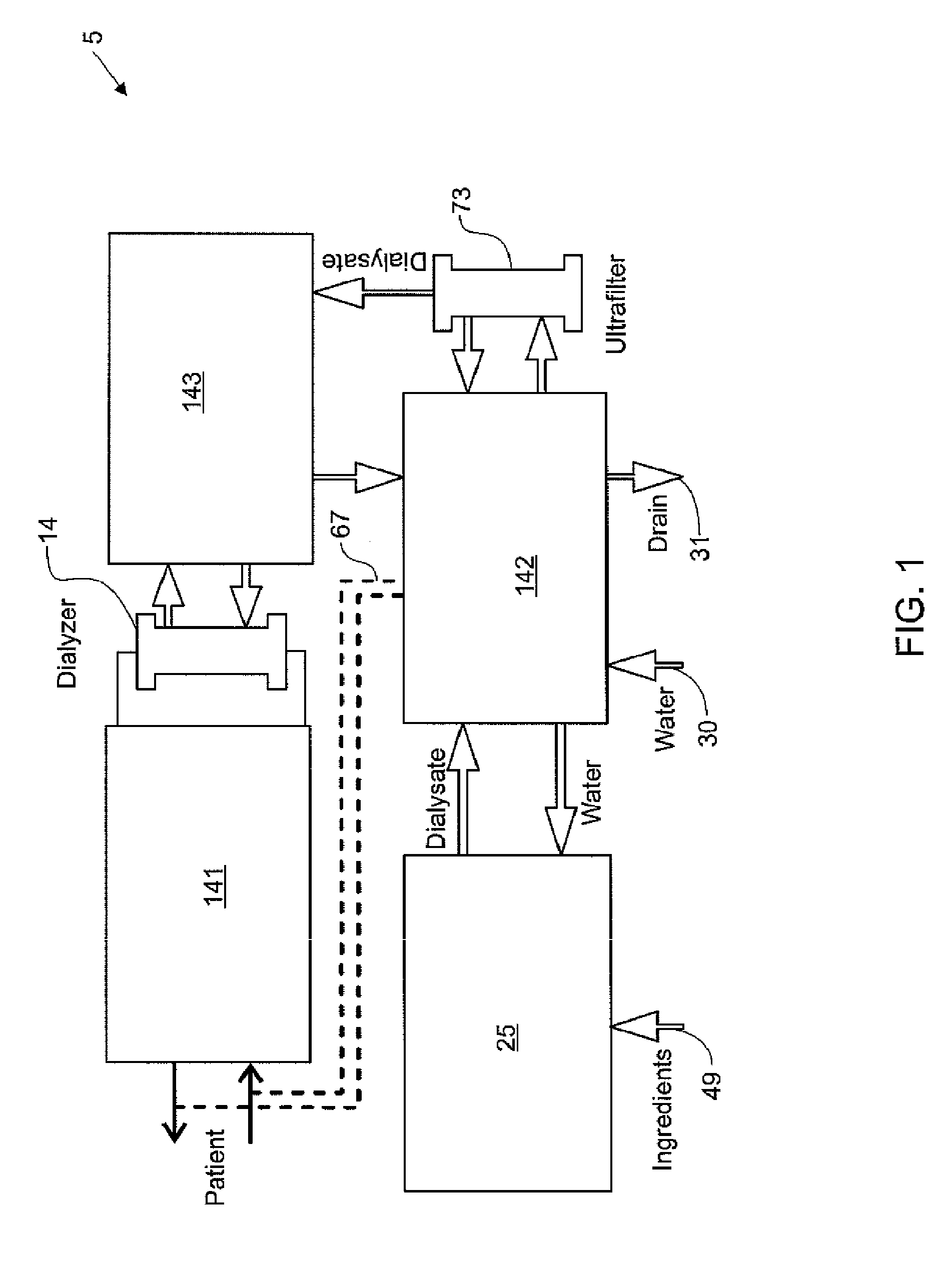
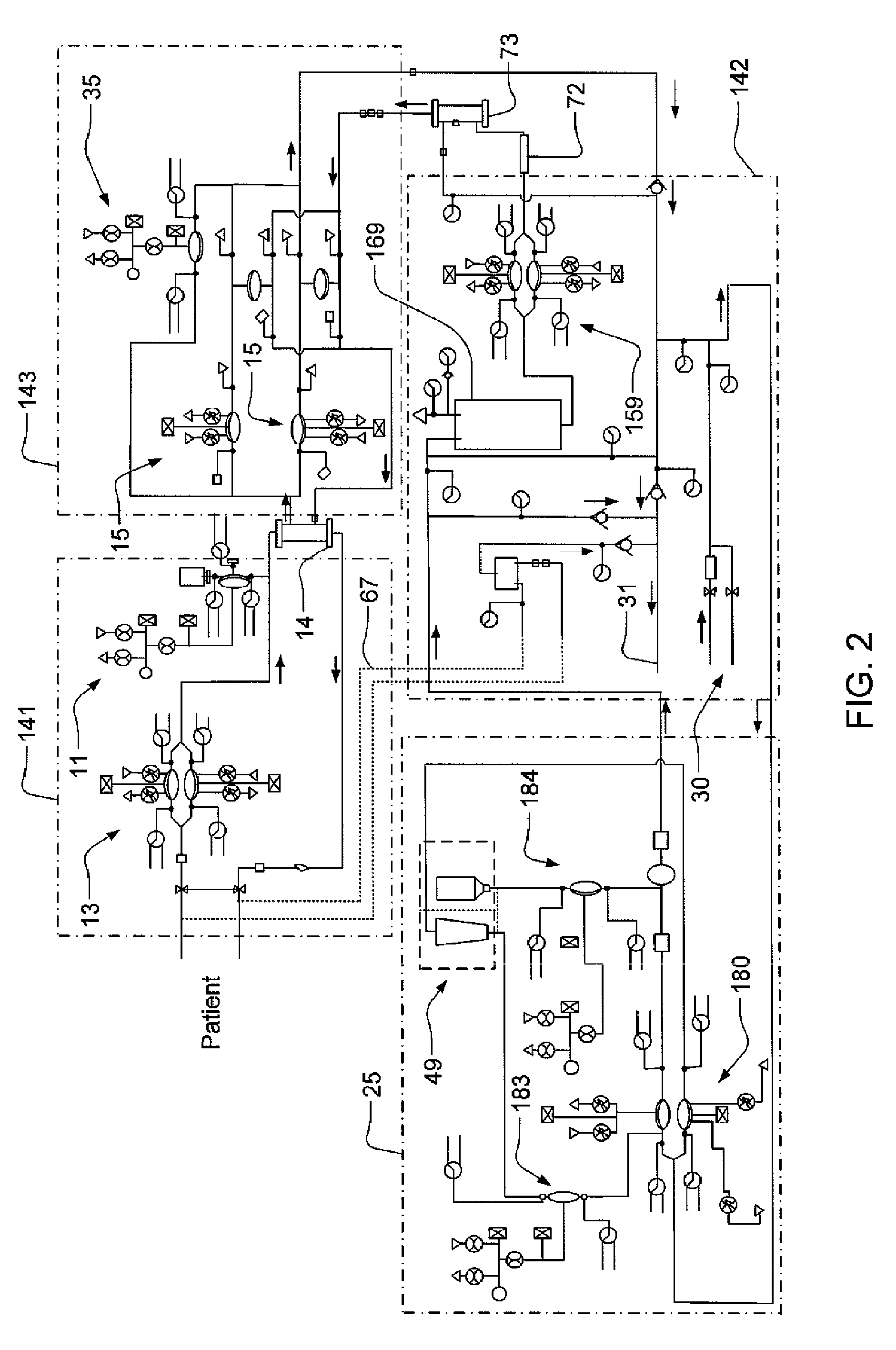
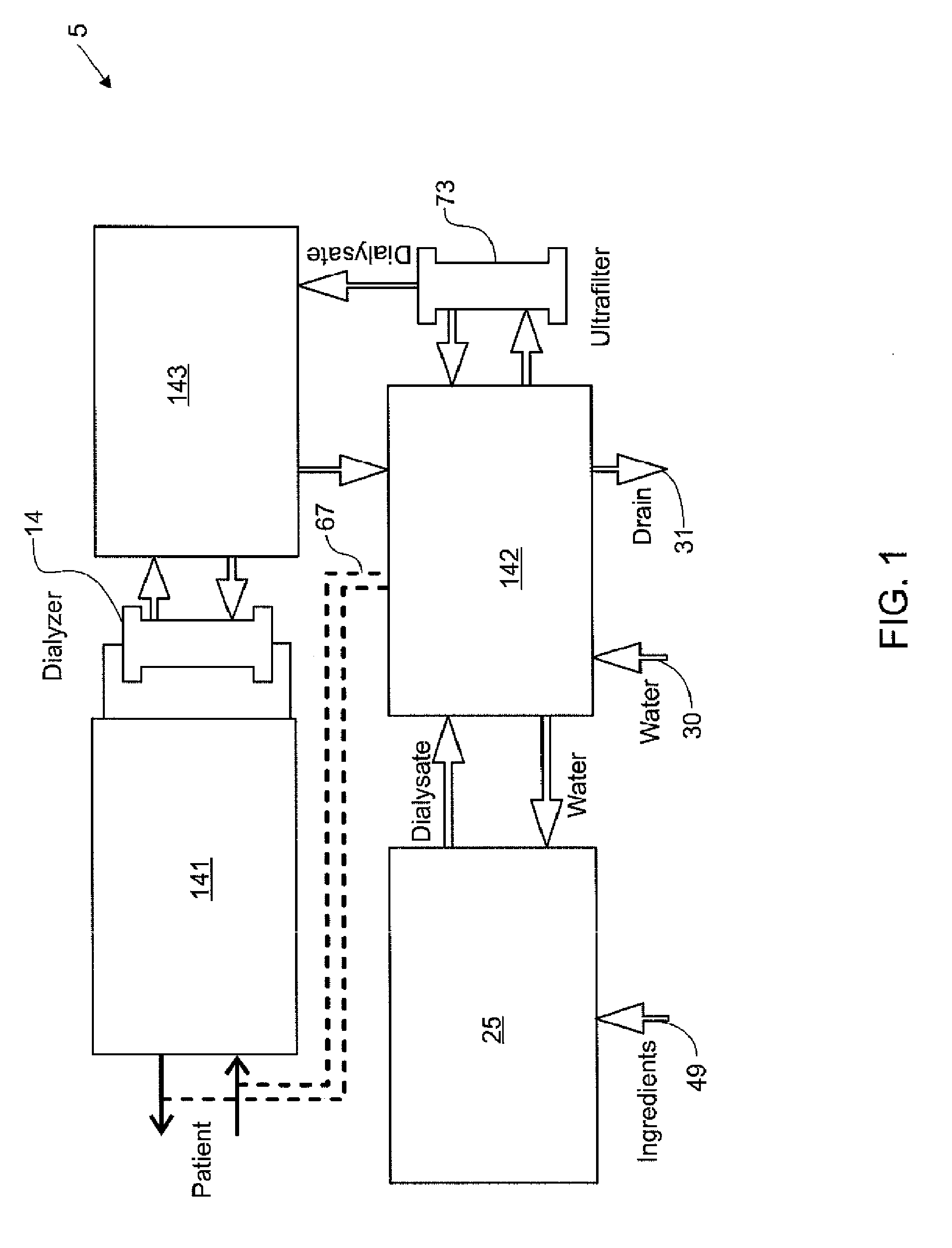
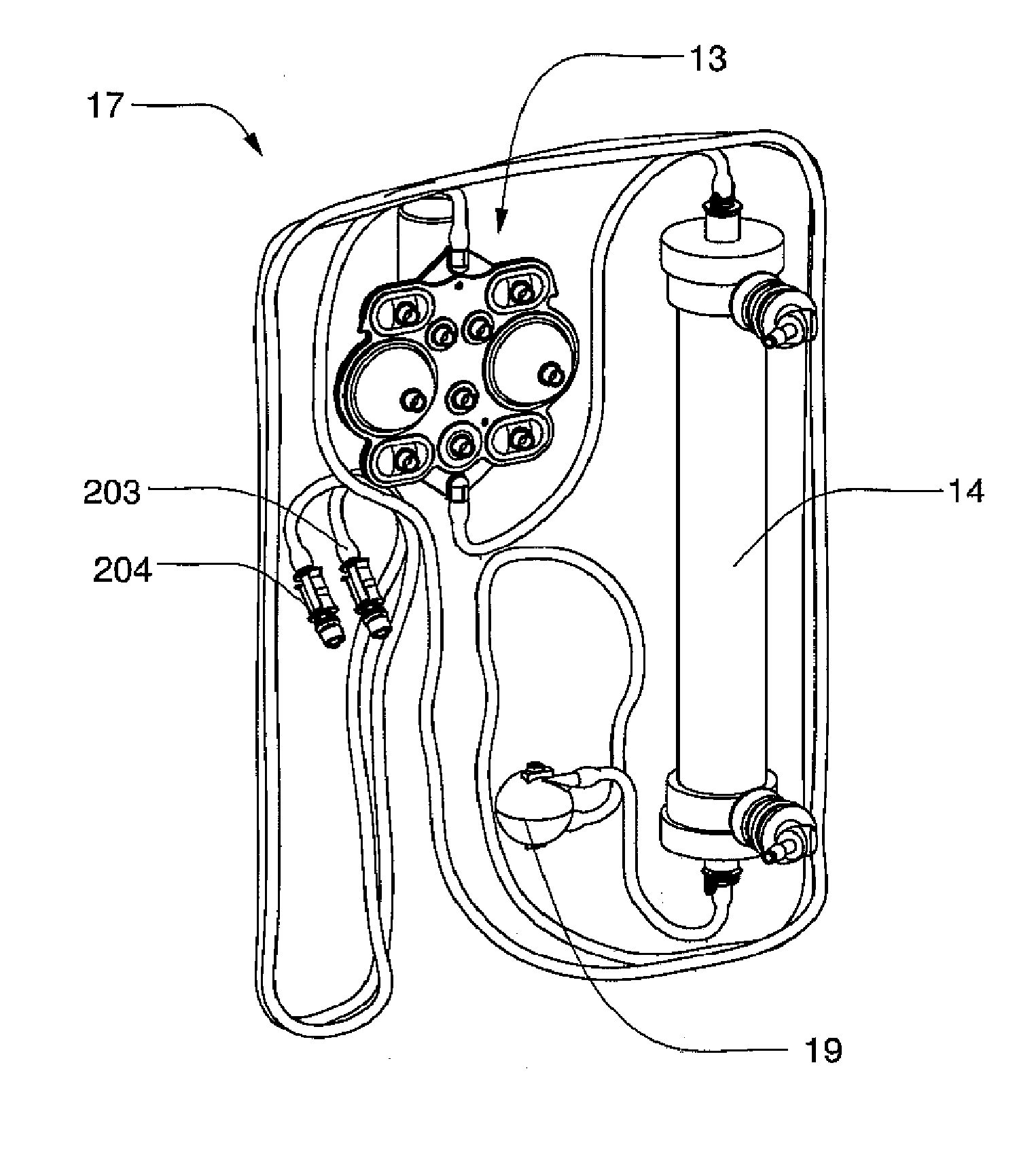
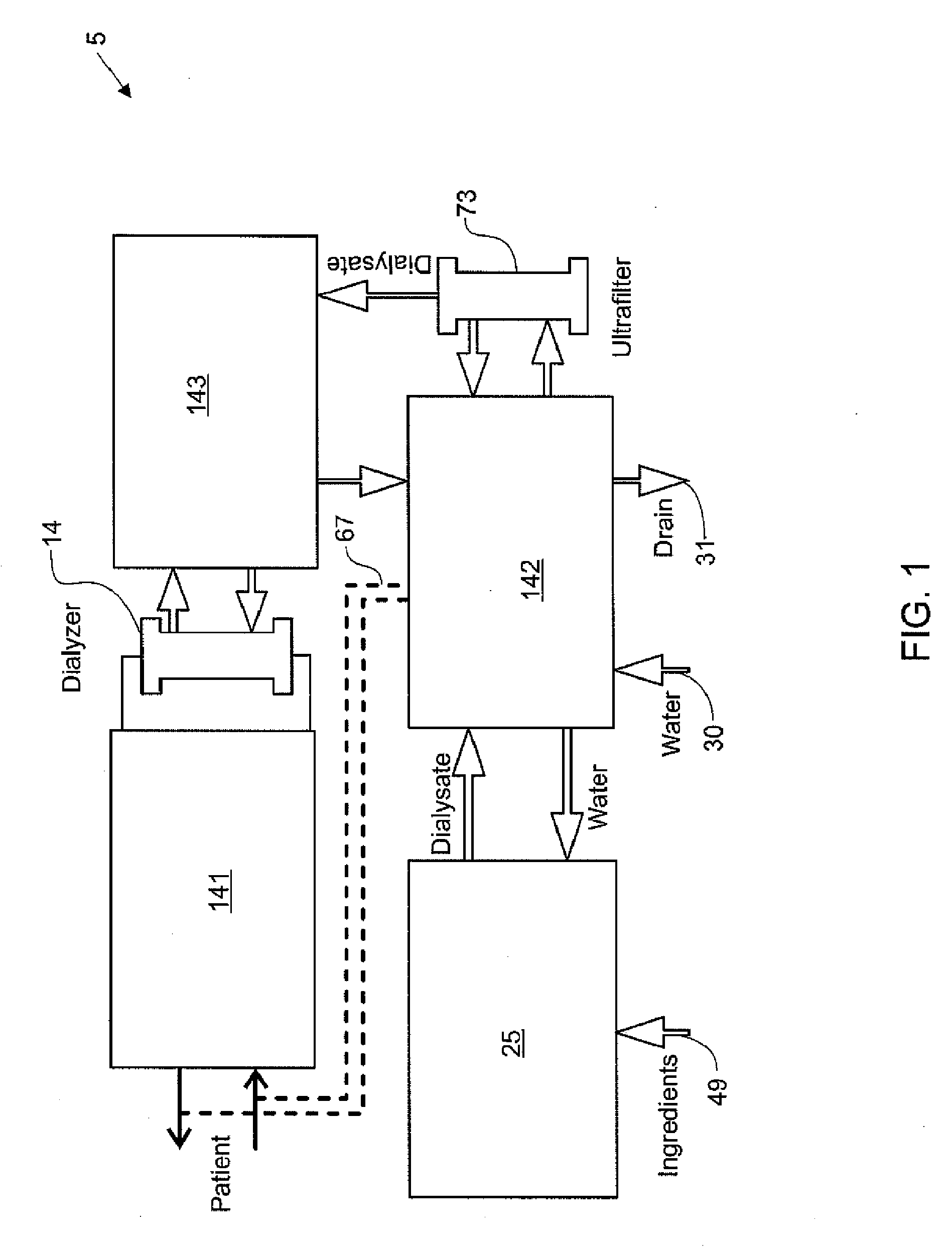
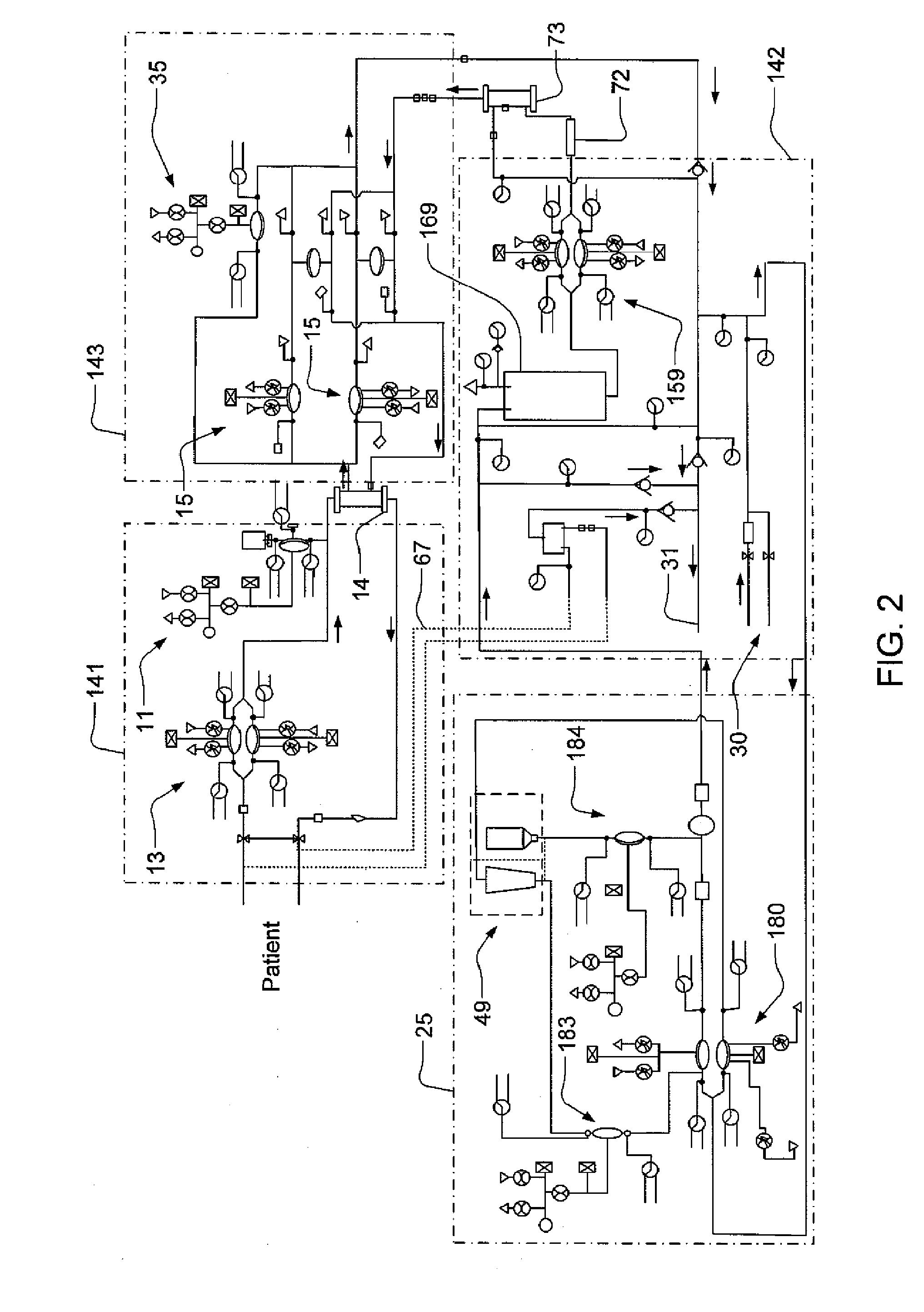
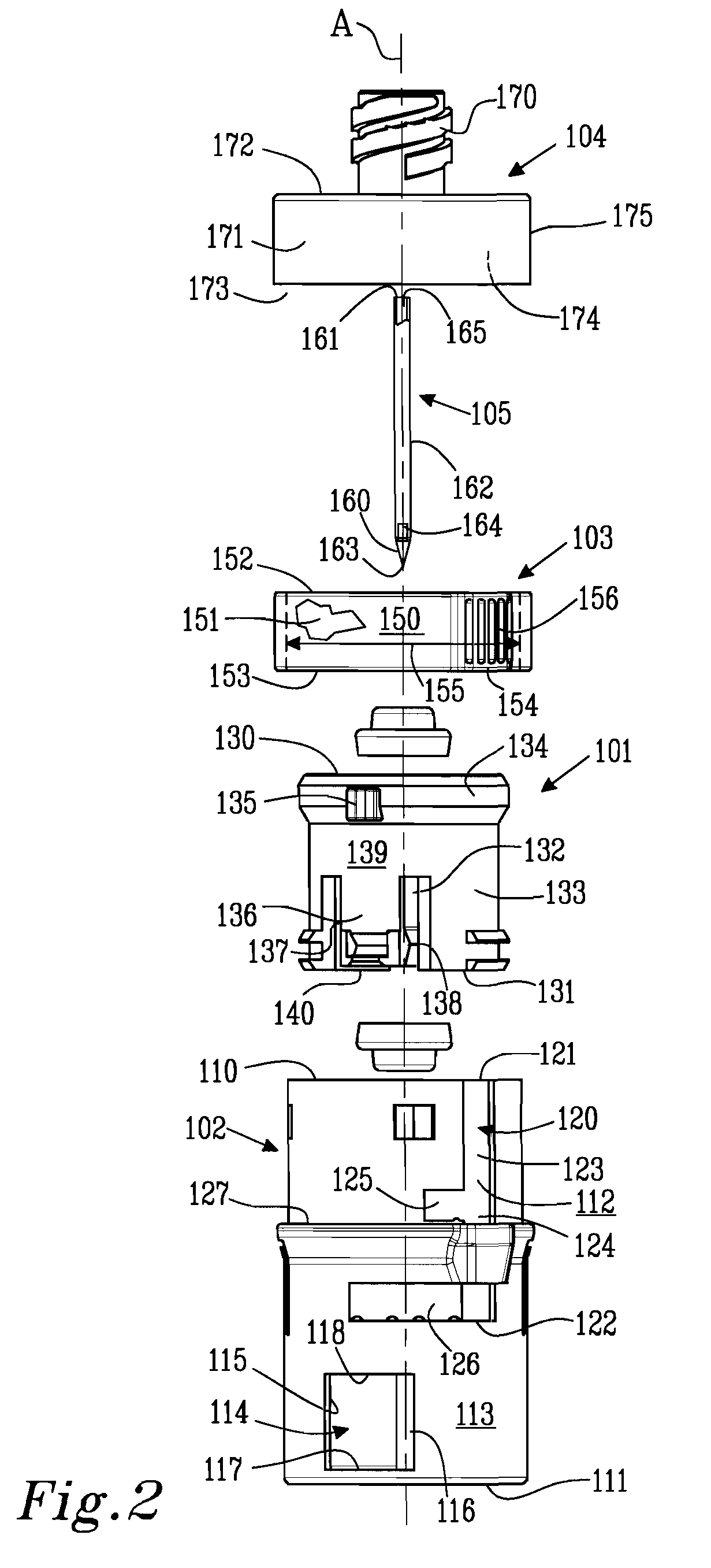
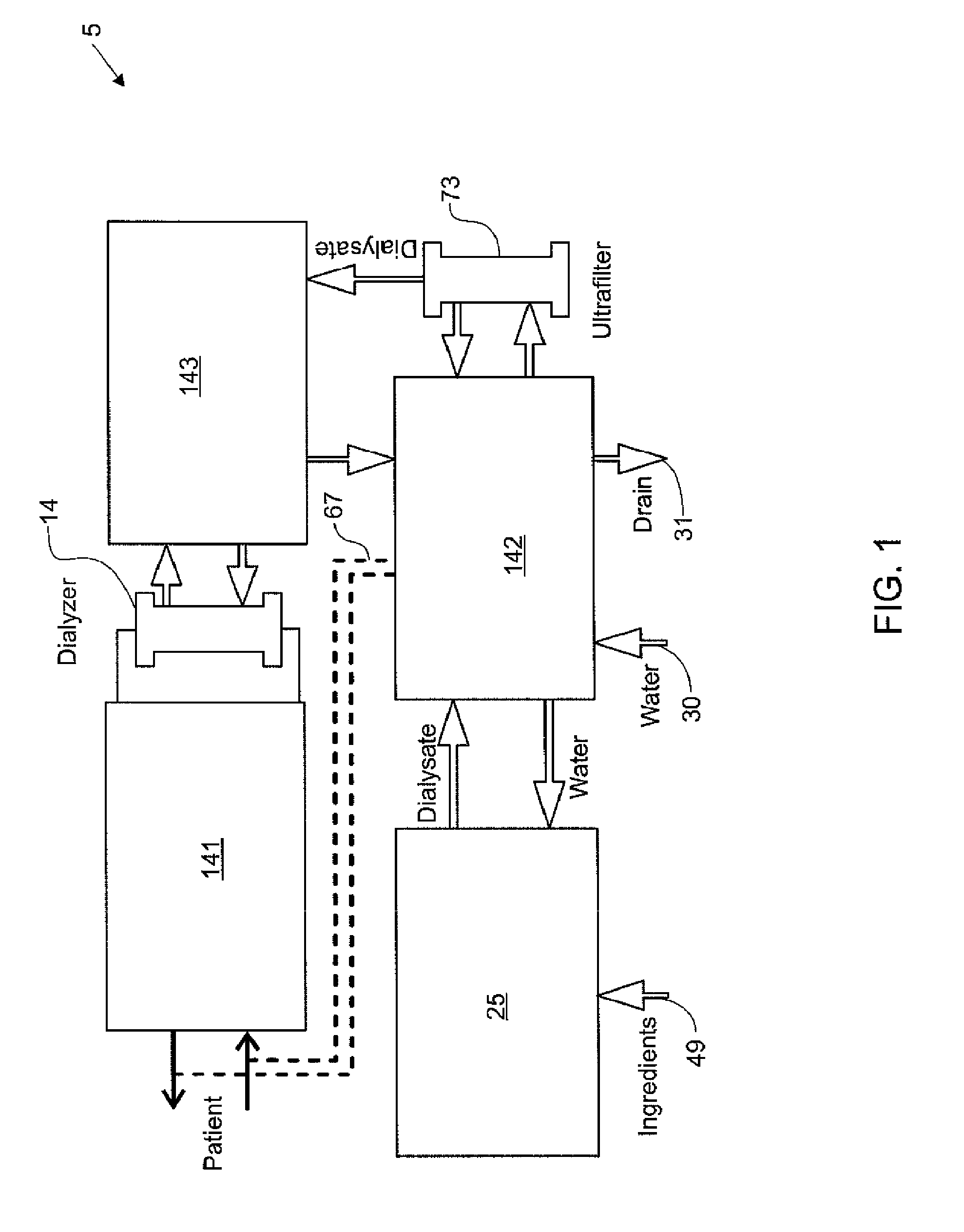
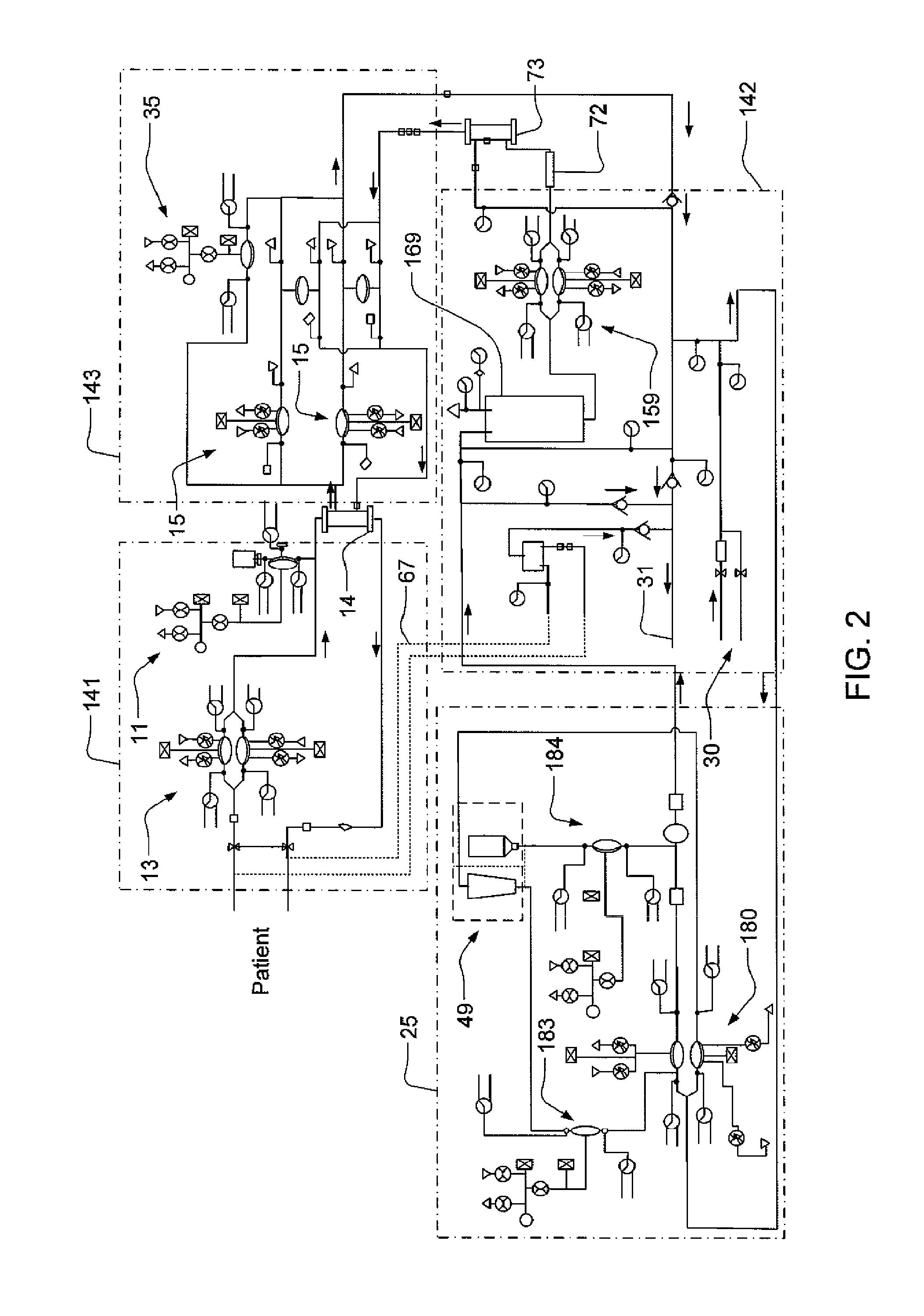
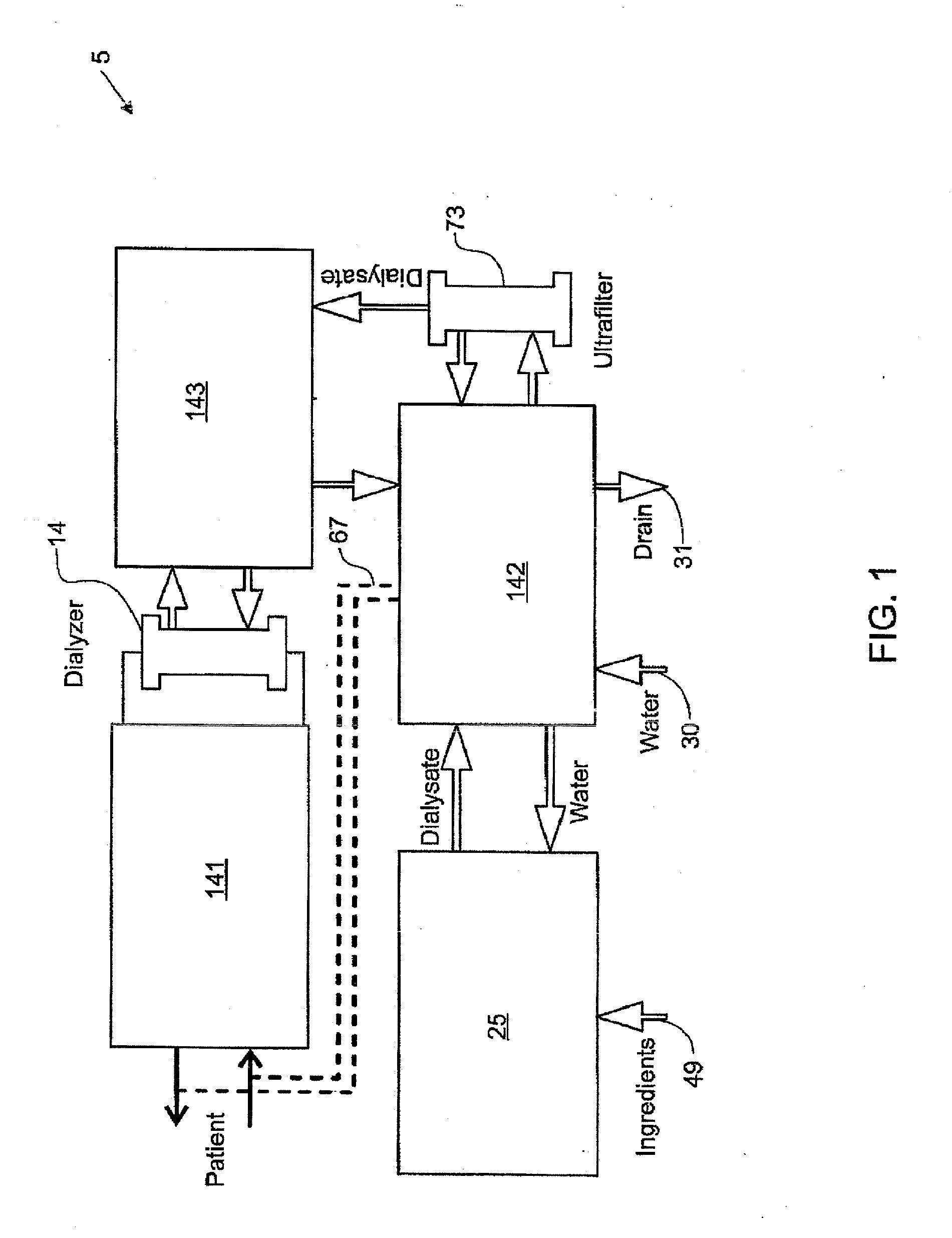
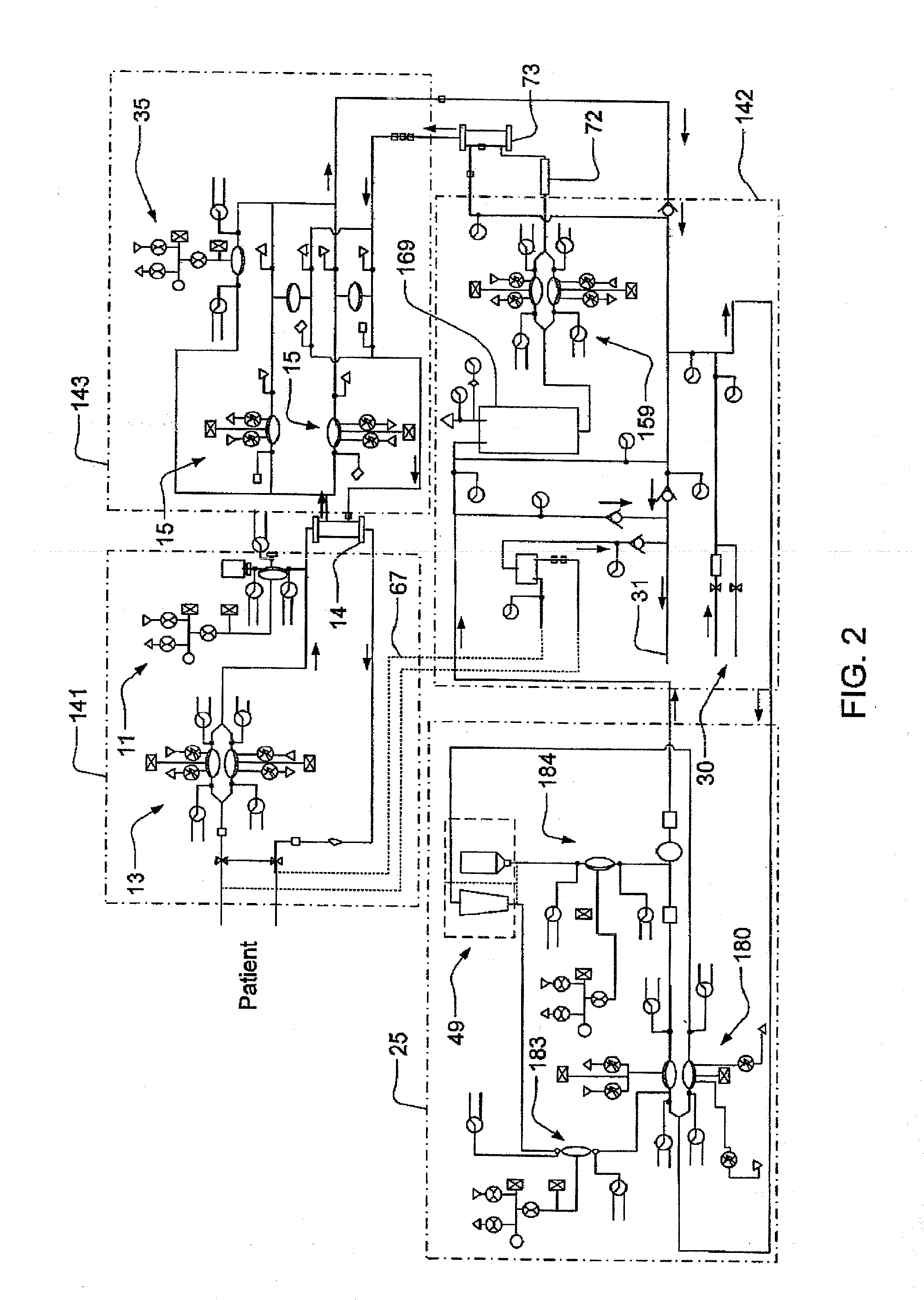
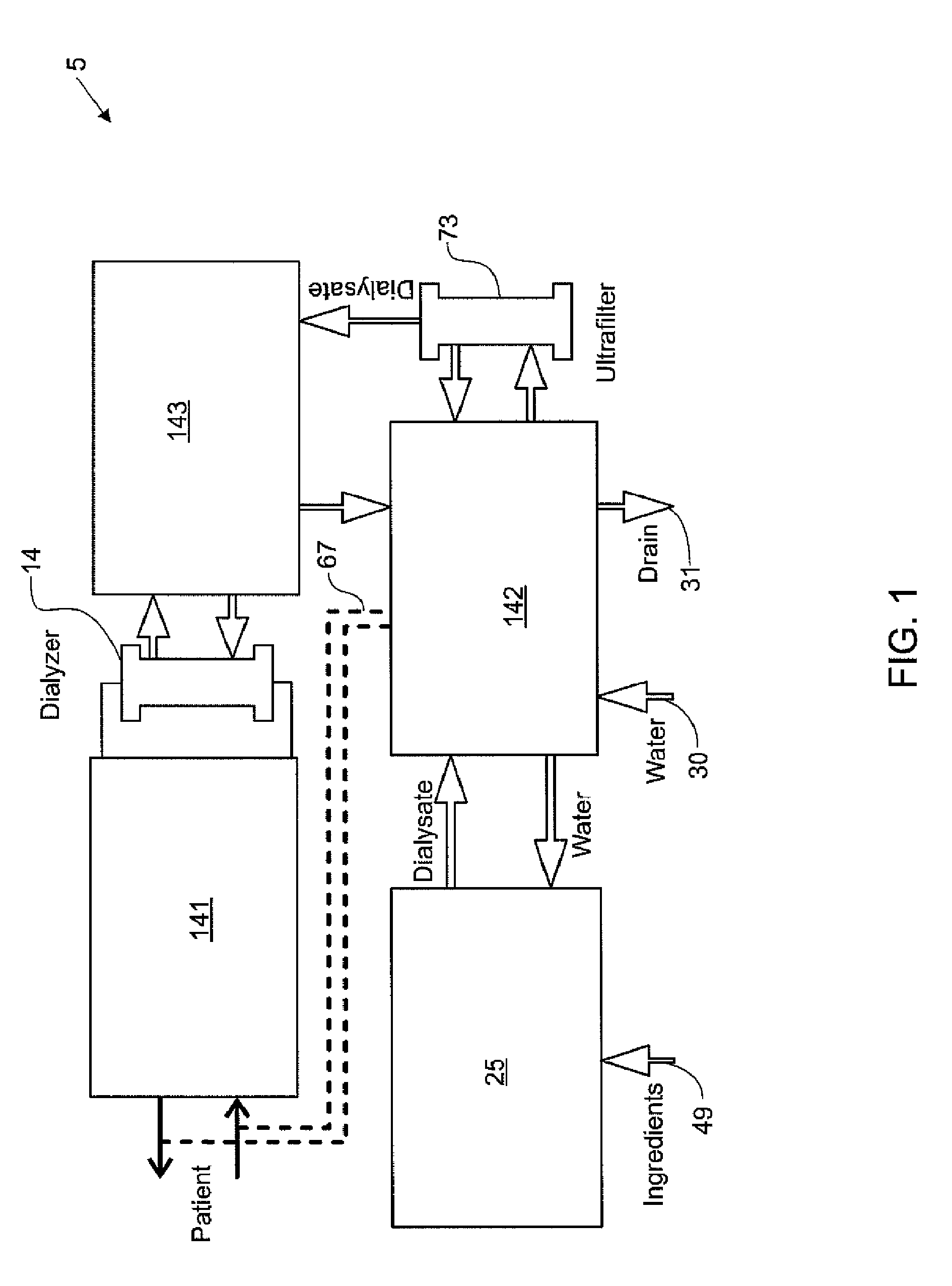
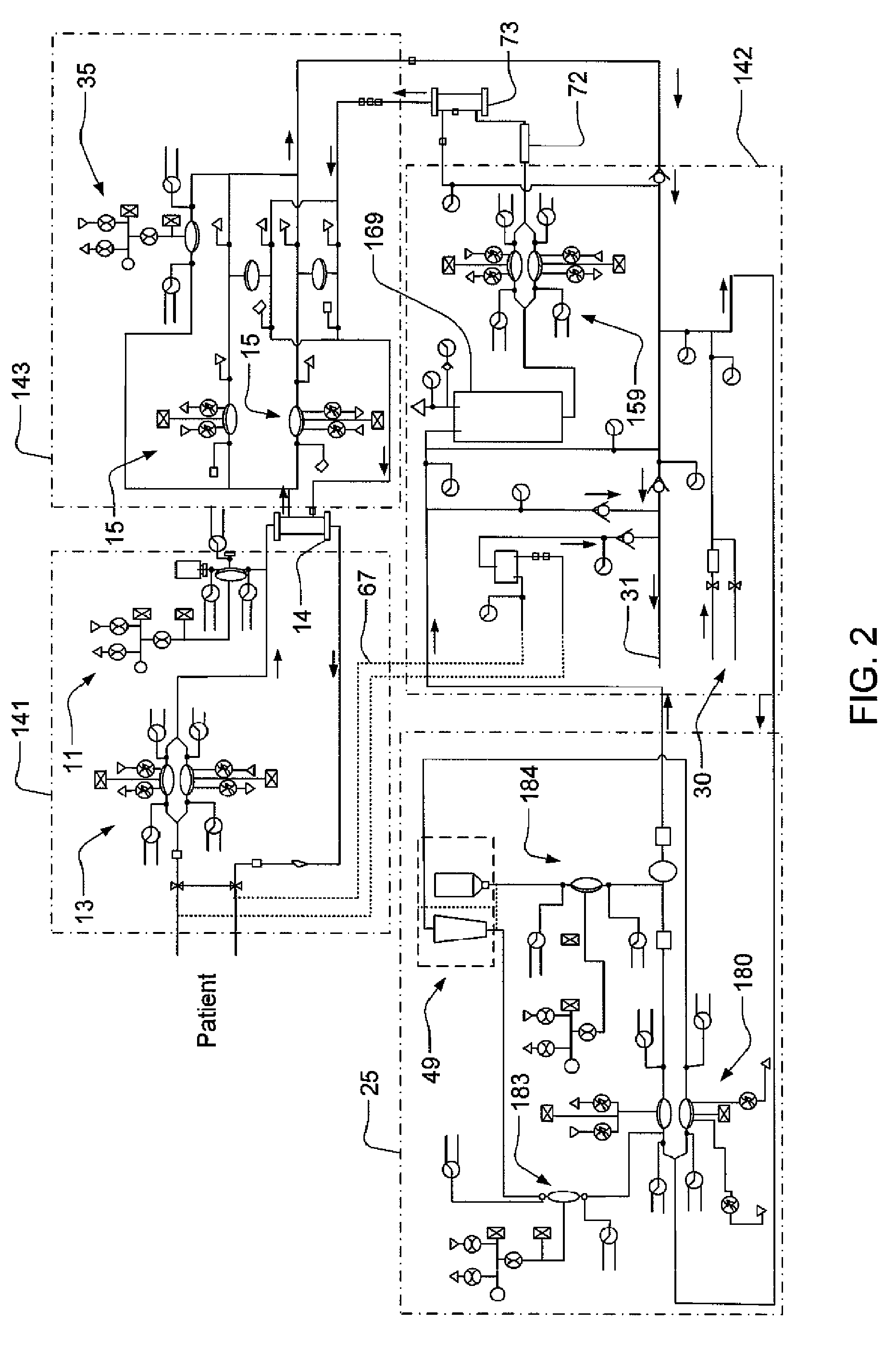
Modular assembly for a portable hemodialysis system
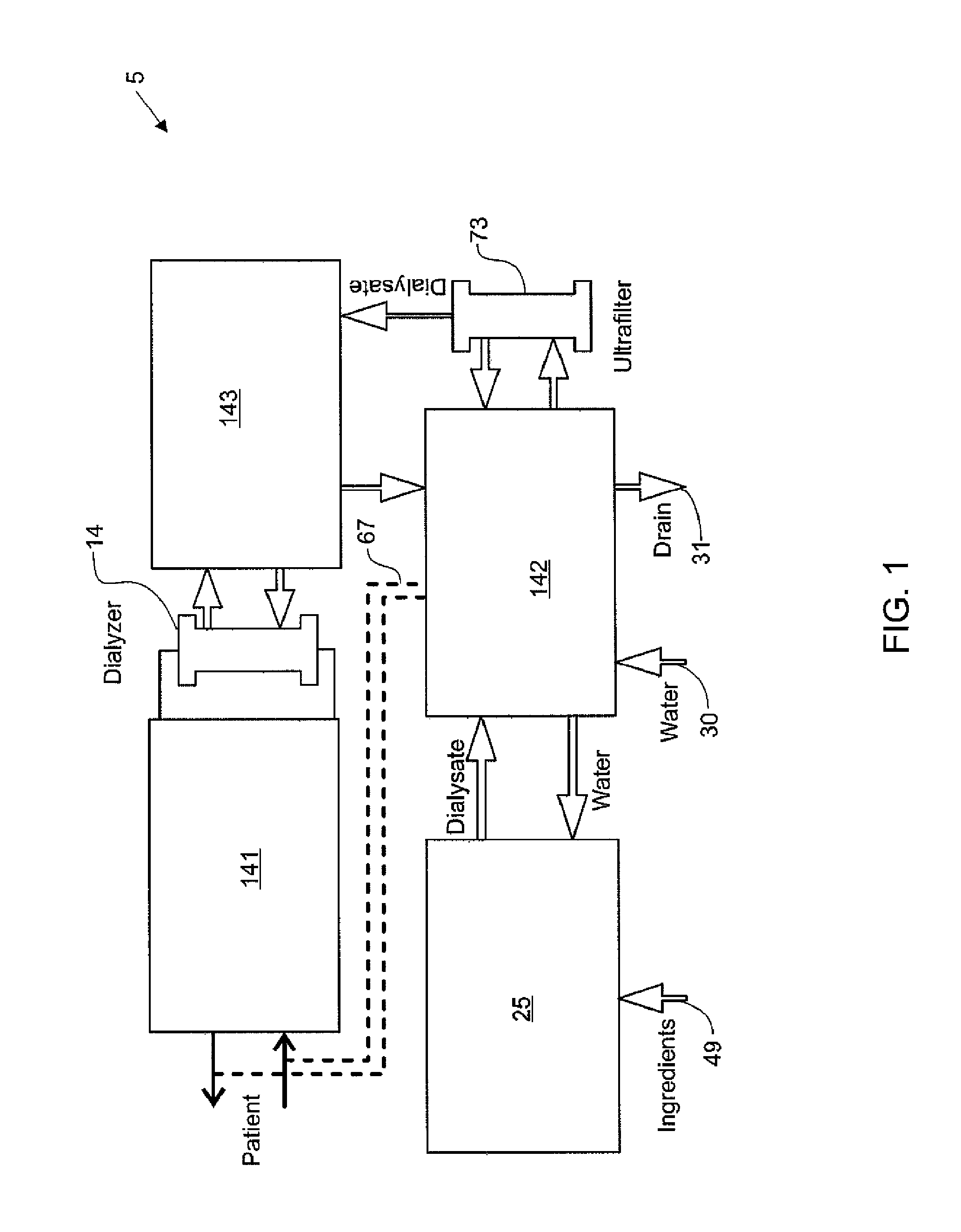
ActiveUS20090101549A1Easy to useOptimize locationMechanical/radiation/invasive therapiesOther blood circulation devicesHaemodialysis machineModularity
A modular assembly for a portable hemodialysis system may include a dialysis unit, e.g., that contains suitable components for performing hemodialysis, such as a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer, and a power unit having a housing that contains suitable components for providing operating power to the pumps of the dialysis unit. The power unit may be selectively connected to the dialysis unit and provide power (e.g., pneumatic power in the form of pressure and / or vacuum) to the dialysis unit for the pumps when connected to the dialysis unit, but may be incapable of providing power to the dialysis unit when disconnected from the dialysis unit. The dialysis unit and the power unit are sized and weighted to each be carried by hand by a human.
Owner:DEKA PROD LLP
Blood line connector for a medical infusion device
InactiveUS20100056975A1Easy to useOptimize locationDialysis systemsMedical devicesLine tubingDialysis fluid
A blood line connector for a blood circuit of a hemodialysis unit with an ability to make two different types of fluid tight connections, e.g., a screw-type connection with a luer connector at a patient access and a press-in type connection with a dialysate circuit. The blood line connector may include a tube connection end arranged to sealingly engage with a blood circuit tube, and a patient access connection end with a frustoconical member having an internally threaded portion arranged to engage with an externally threaded patient access, and a pair of locking arms extending rearwardly from the frustoconical member. The locking arms may each have a finger depression portion and a barbed portion, and may be arranged to engage with a mating connector on the dialysis unit at the barbed portions to lock the frustoconical member in sealing engagement with the mating connector when making a press-in type connection.
Owner:DEKA PROD LLP
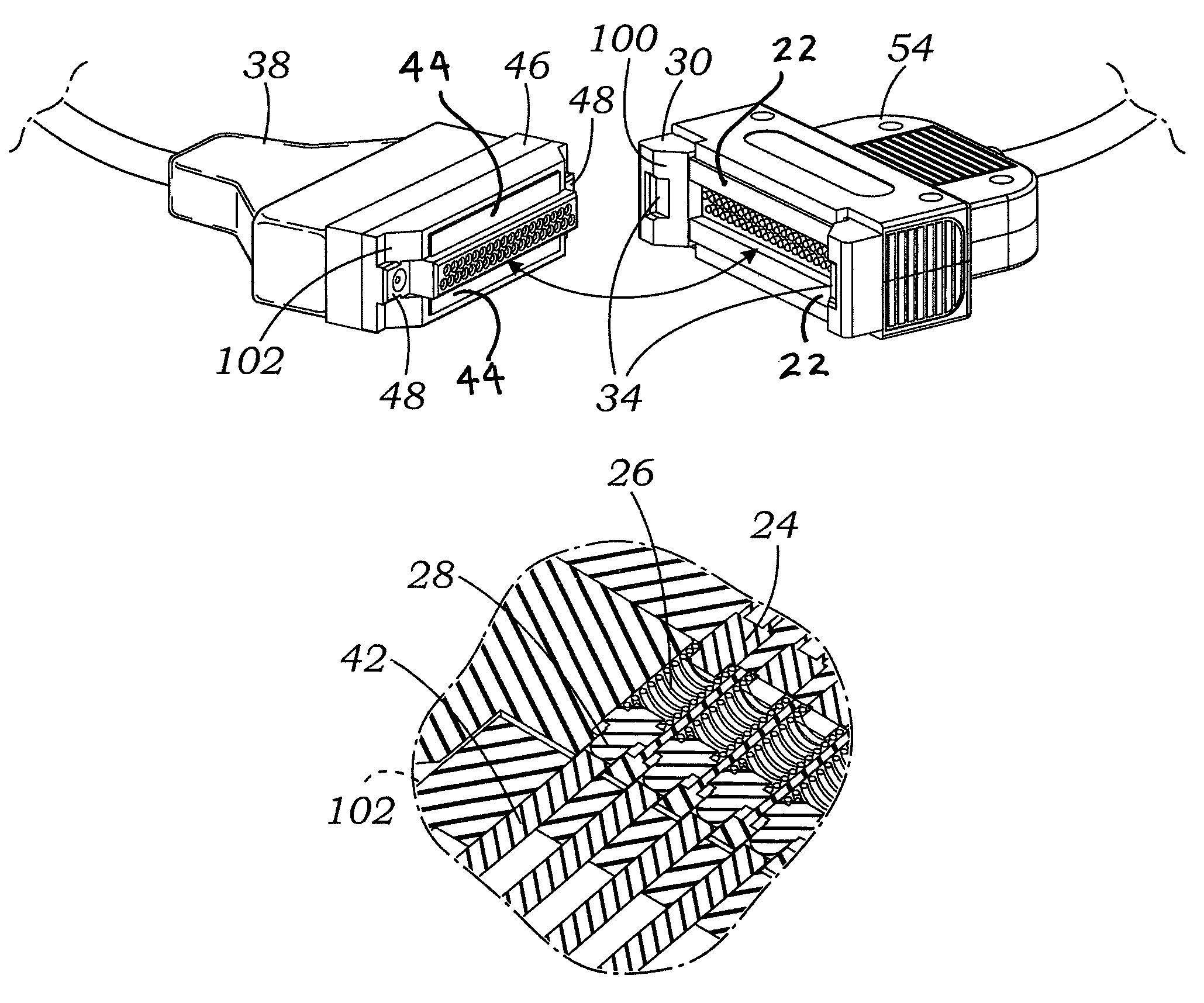
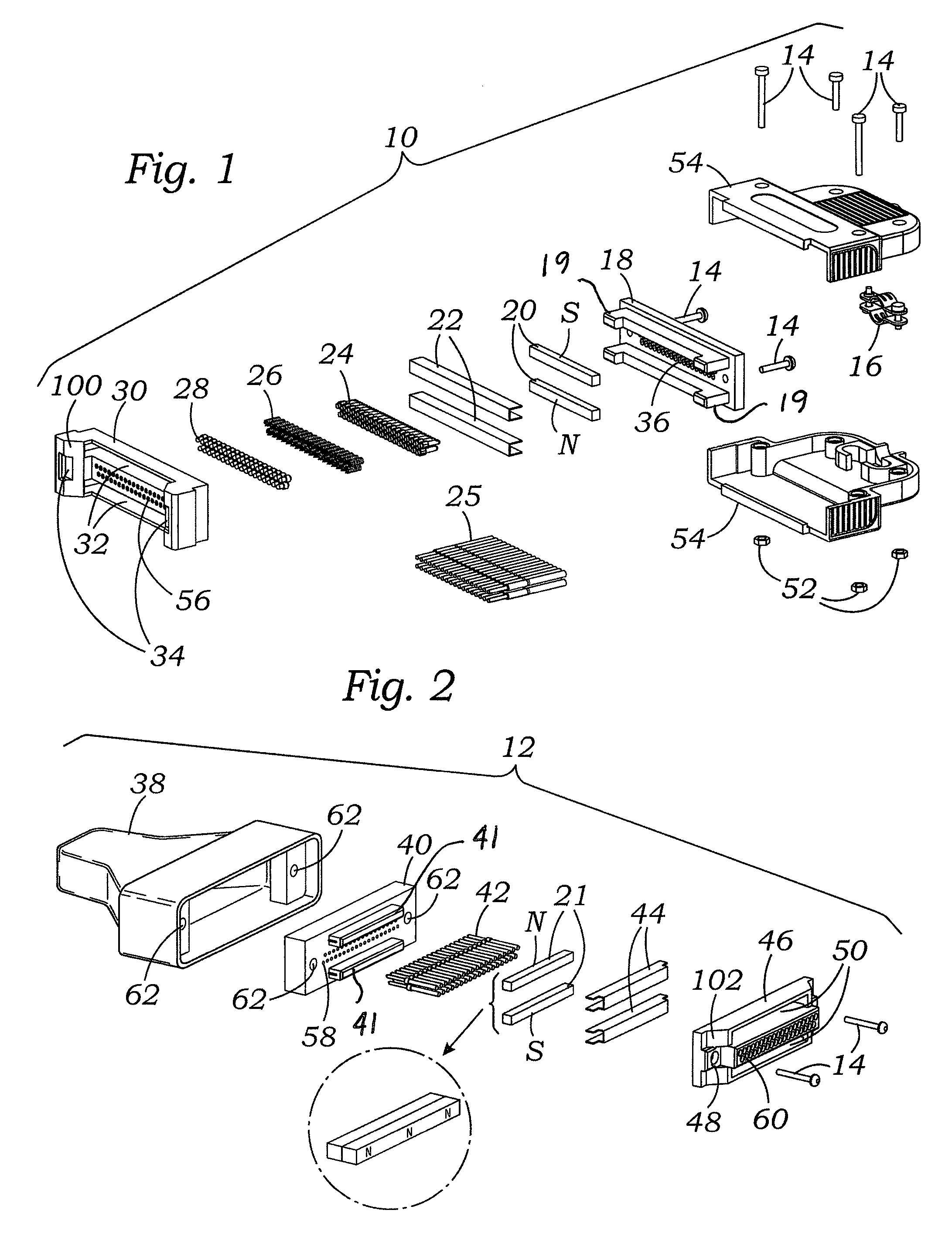
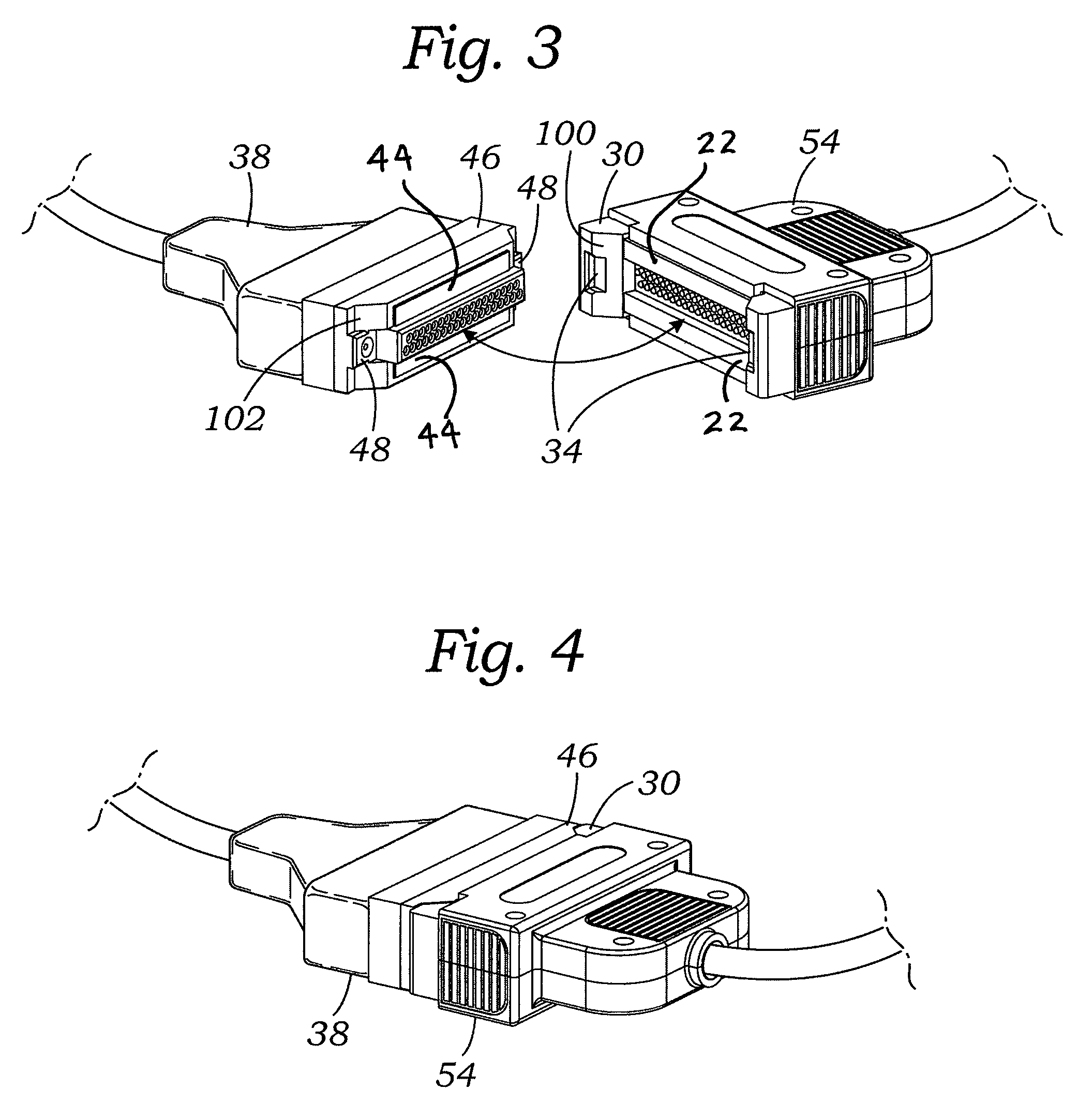
Magnetic-enabled connector device
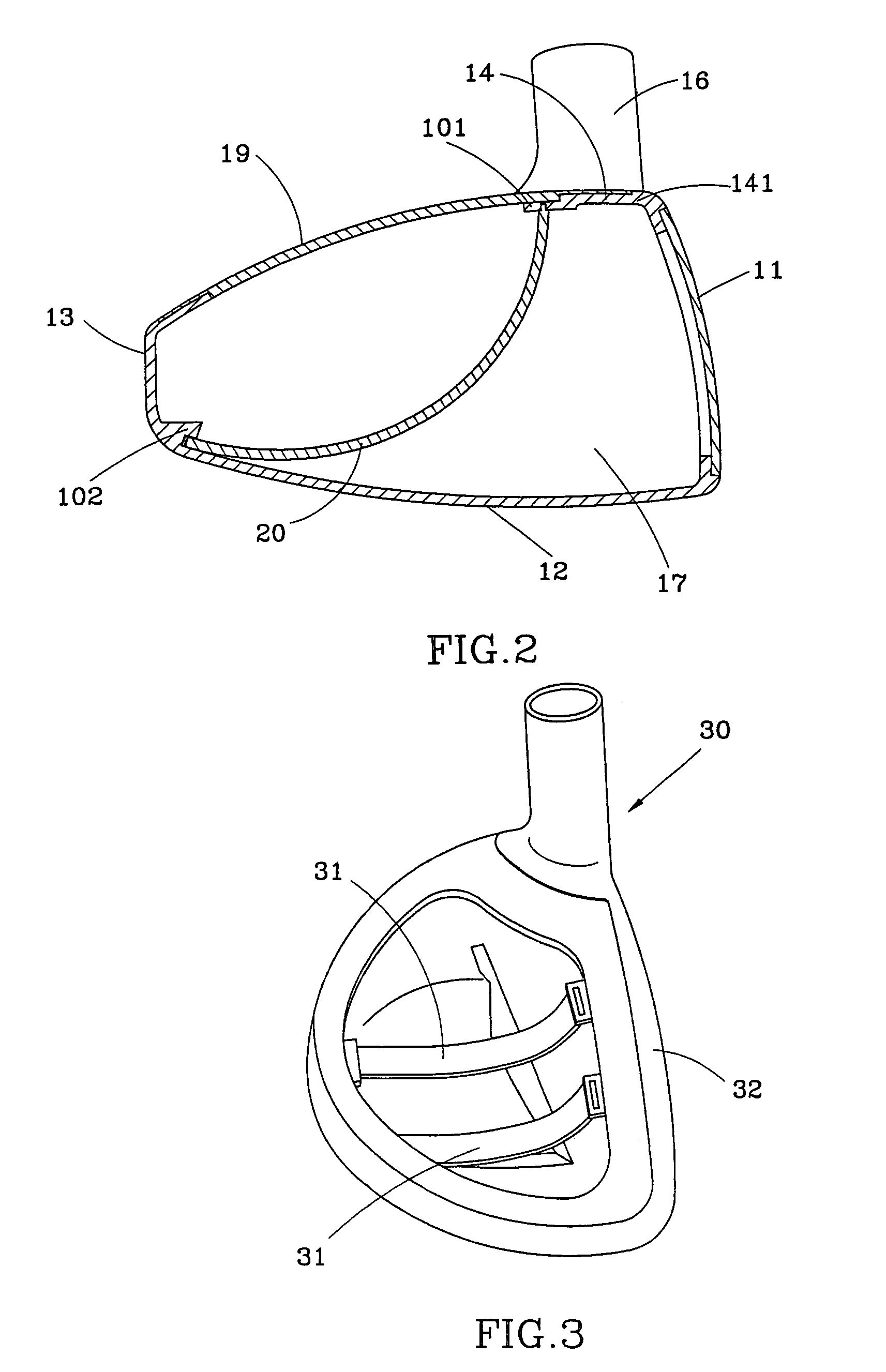
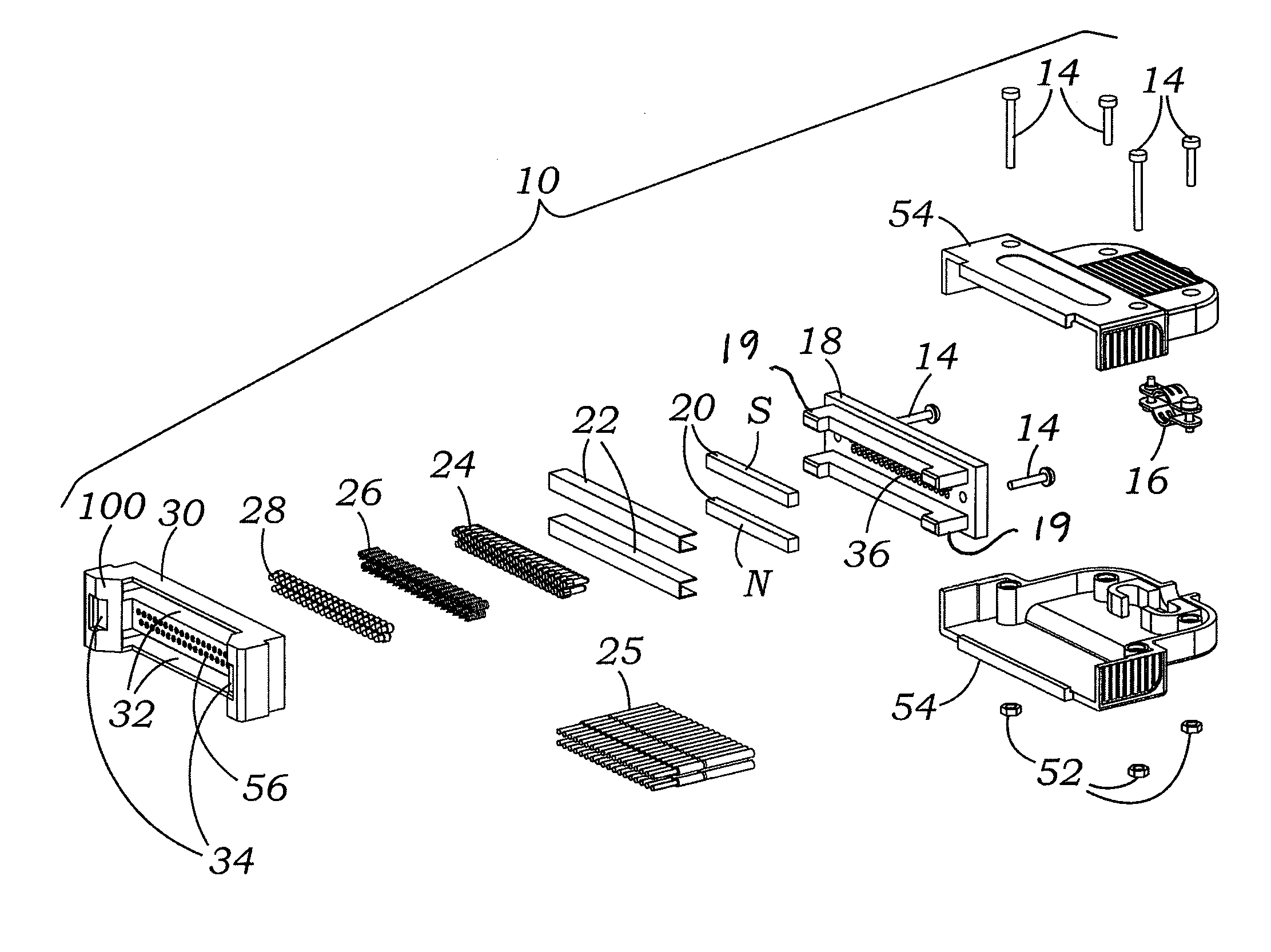
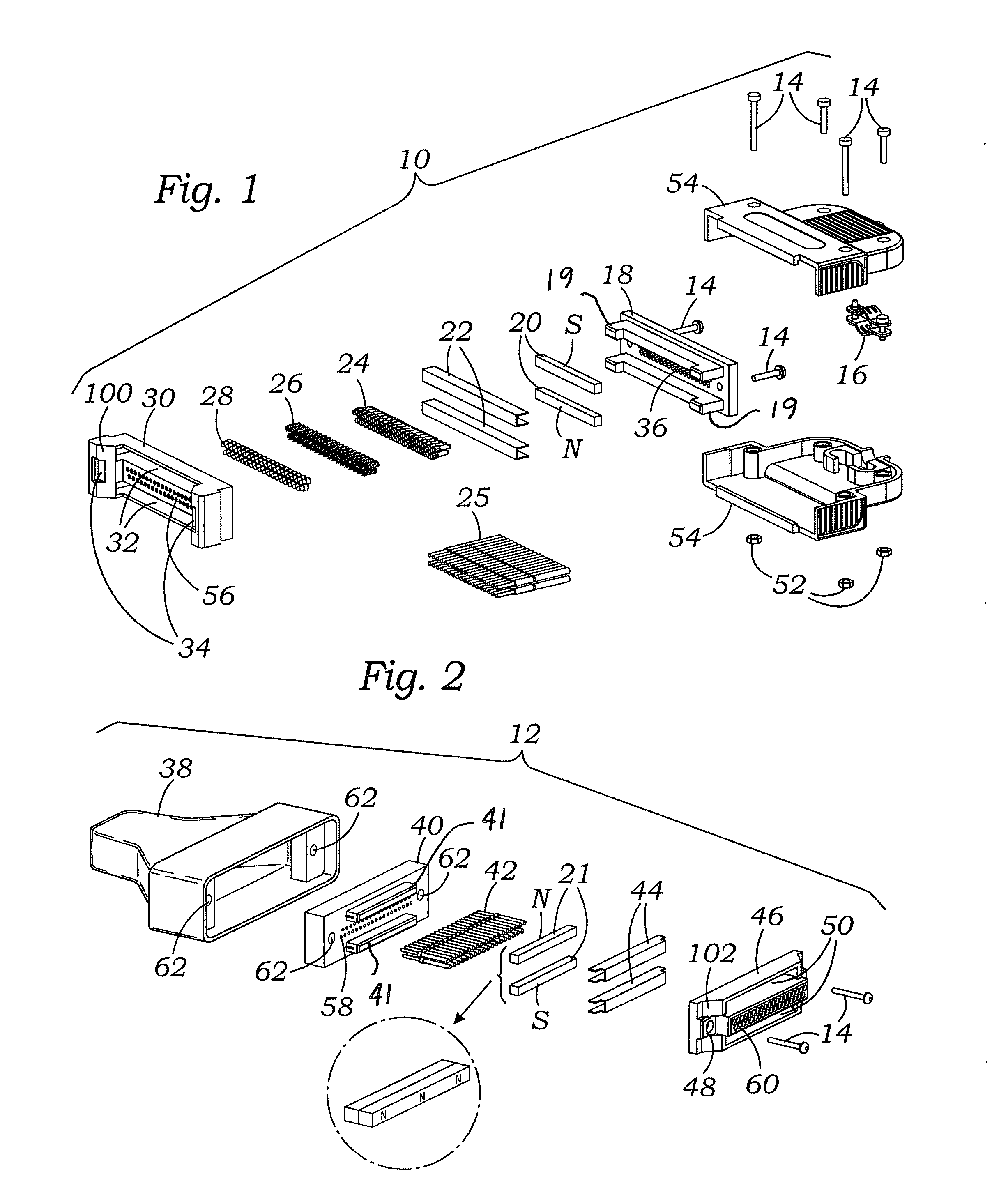
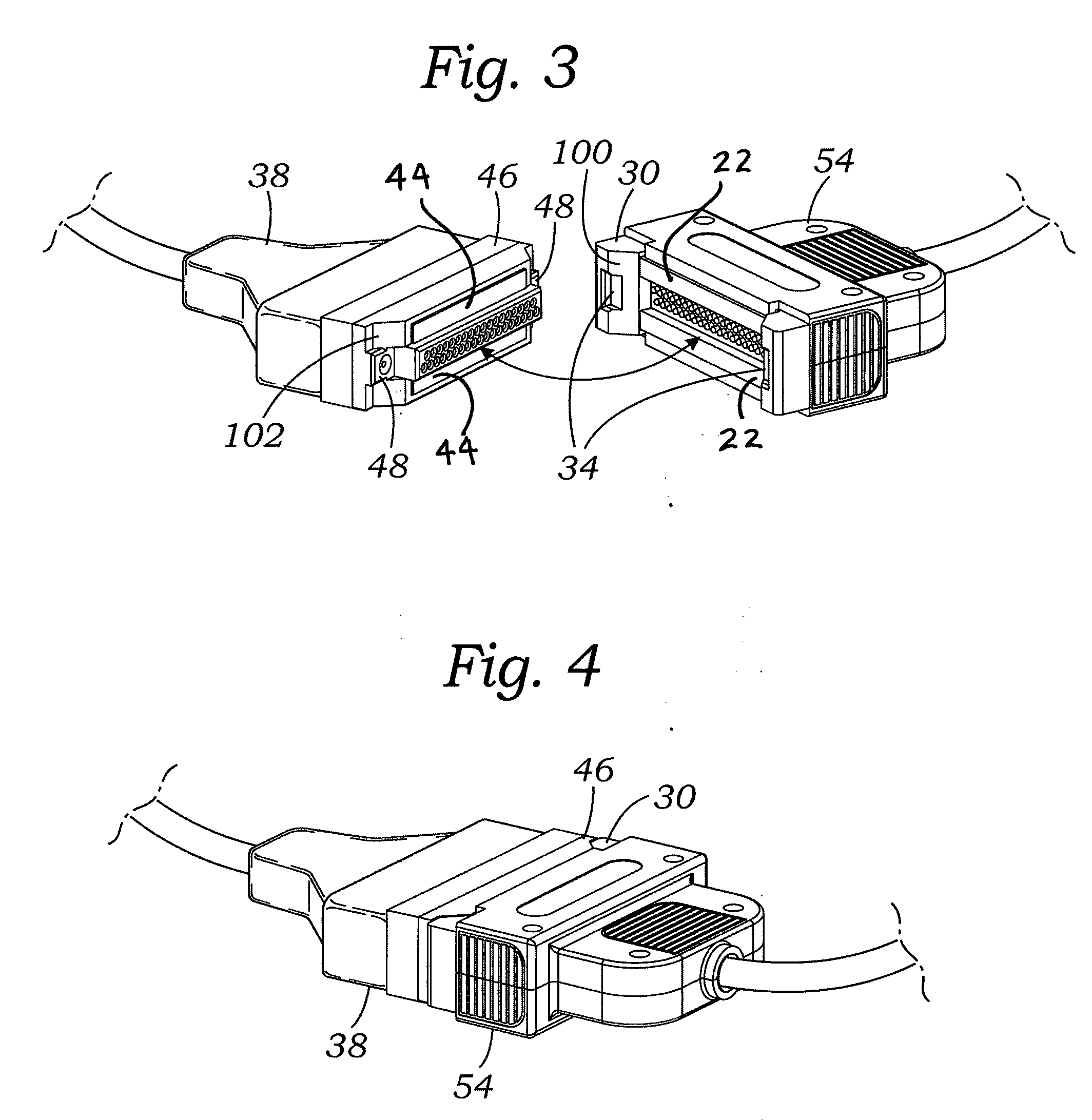
ActiveUS9147965B2Connected quickly and preciselyAvoid connectionEngagement/disengagement of coupling partsCoupling contact membersElectricityNon magnetic
An electrical connector, which may be a multi-pin connector, includes magnetic elements and mechanical alignment elements which provide connective forces and precision alignment and orientation. The magnetic elements permit a user to bring male and female connector portions only into “rough” alignment before magnetic forces bring the portions into the correct position. Pin contacts on the connector portions extend only a small amount beyond respective protective annular openings and are thereby protected. Spring-biased pin elements may be included on one of the connector portions to bias the contact pins into engagement and create conductive paths when the portions are in a connected position. Paramagnetic or non-magnetic sheaths may surround the magnetic elements to focus, or distribute, magnetic forces.
Owner:KC MAGCON
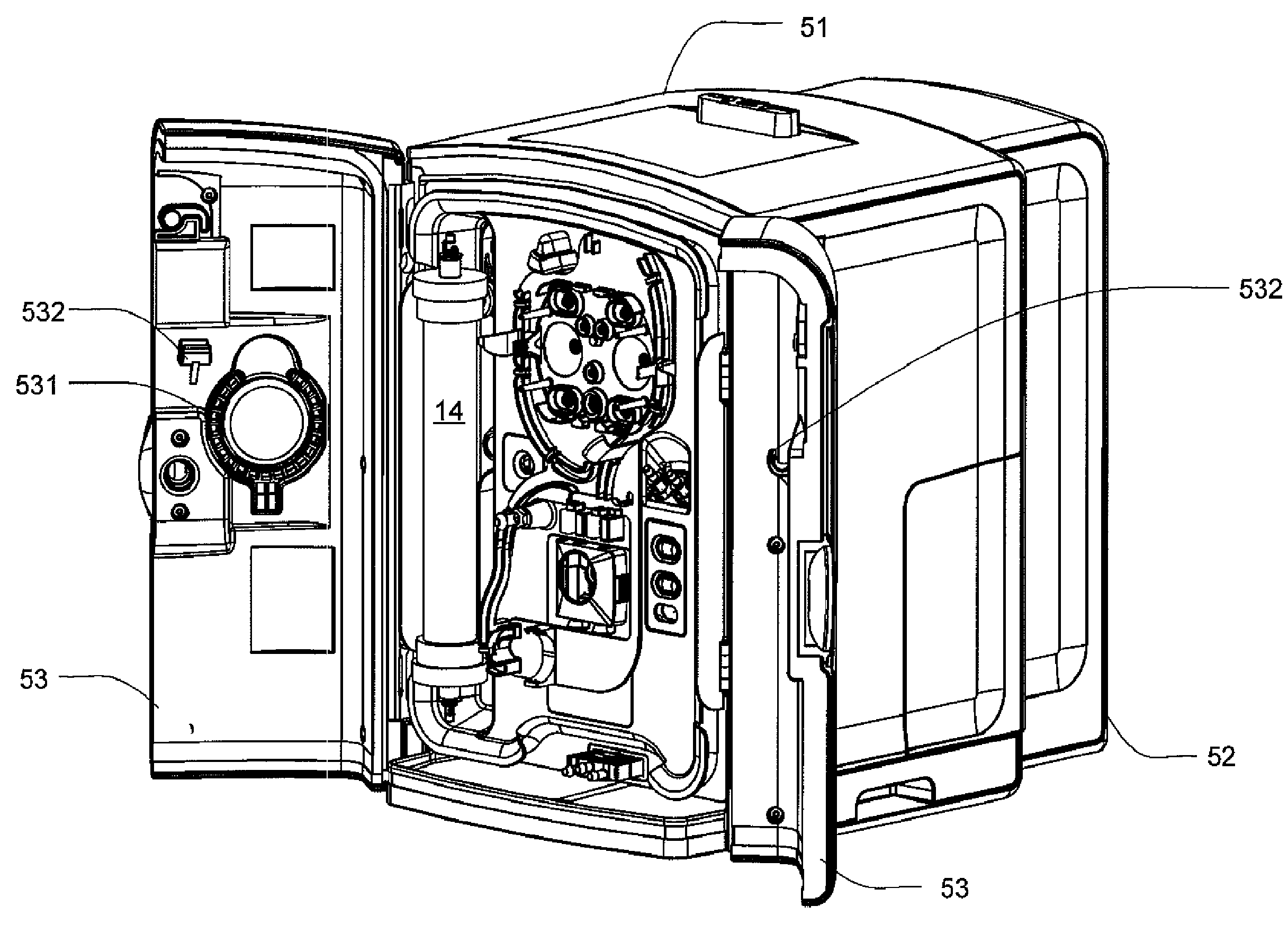
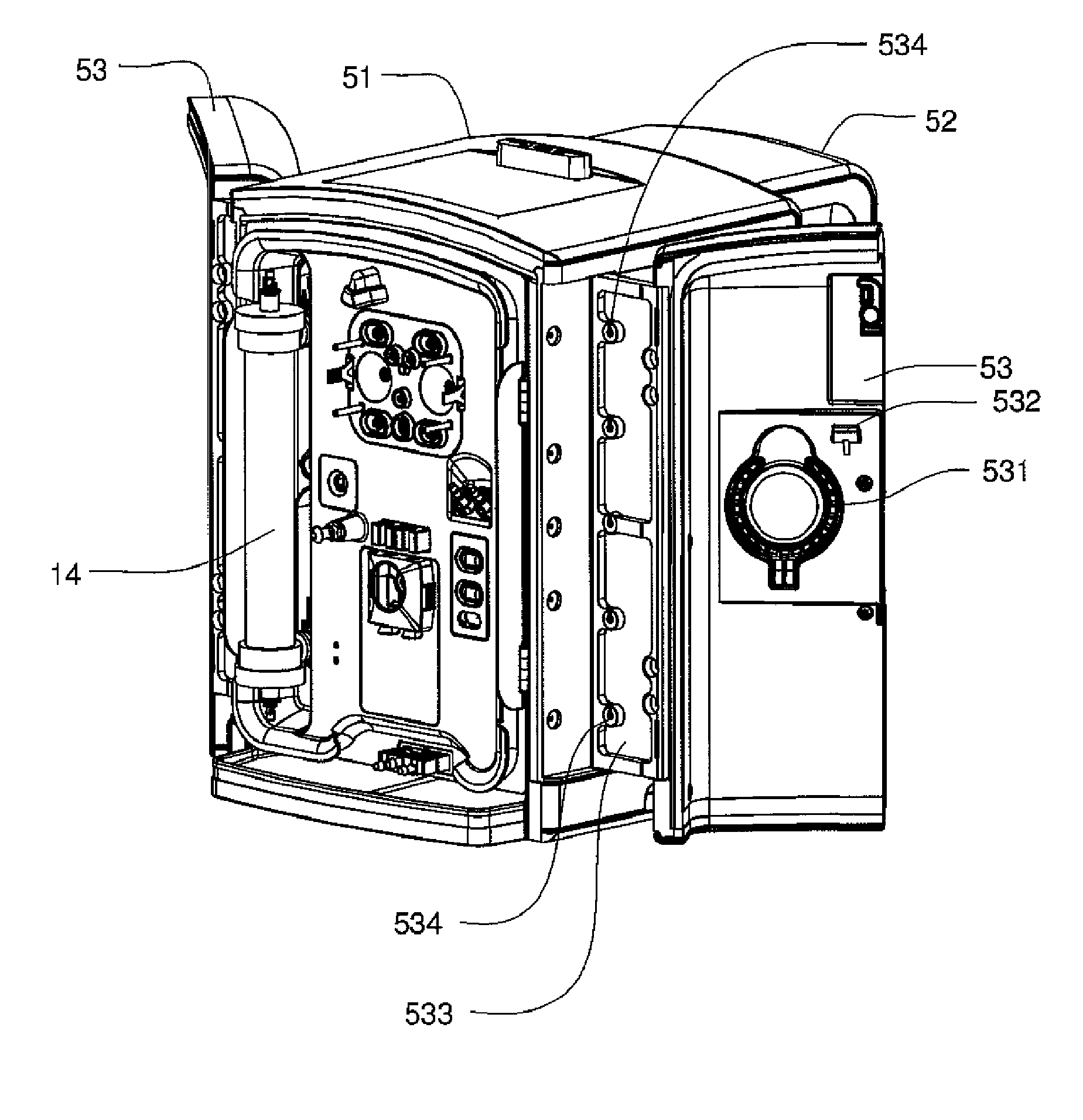
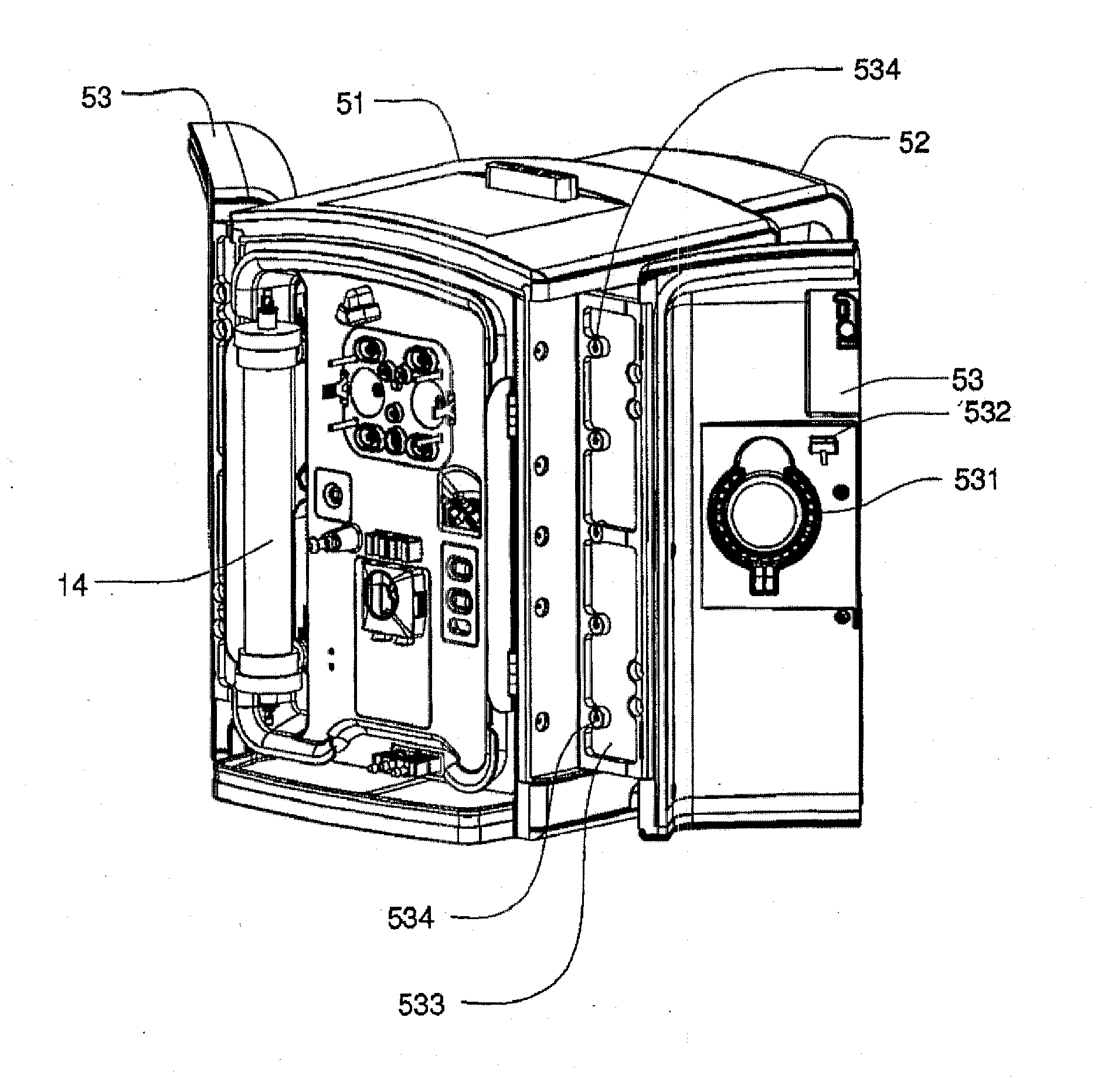
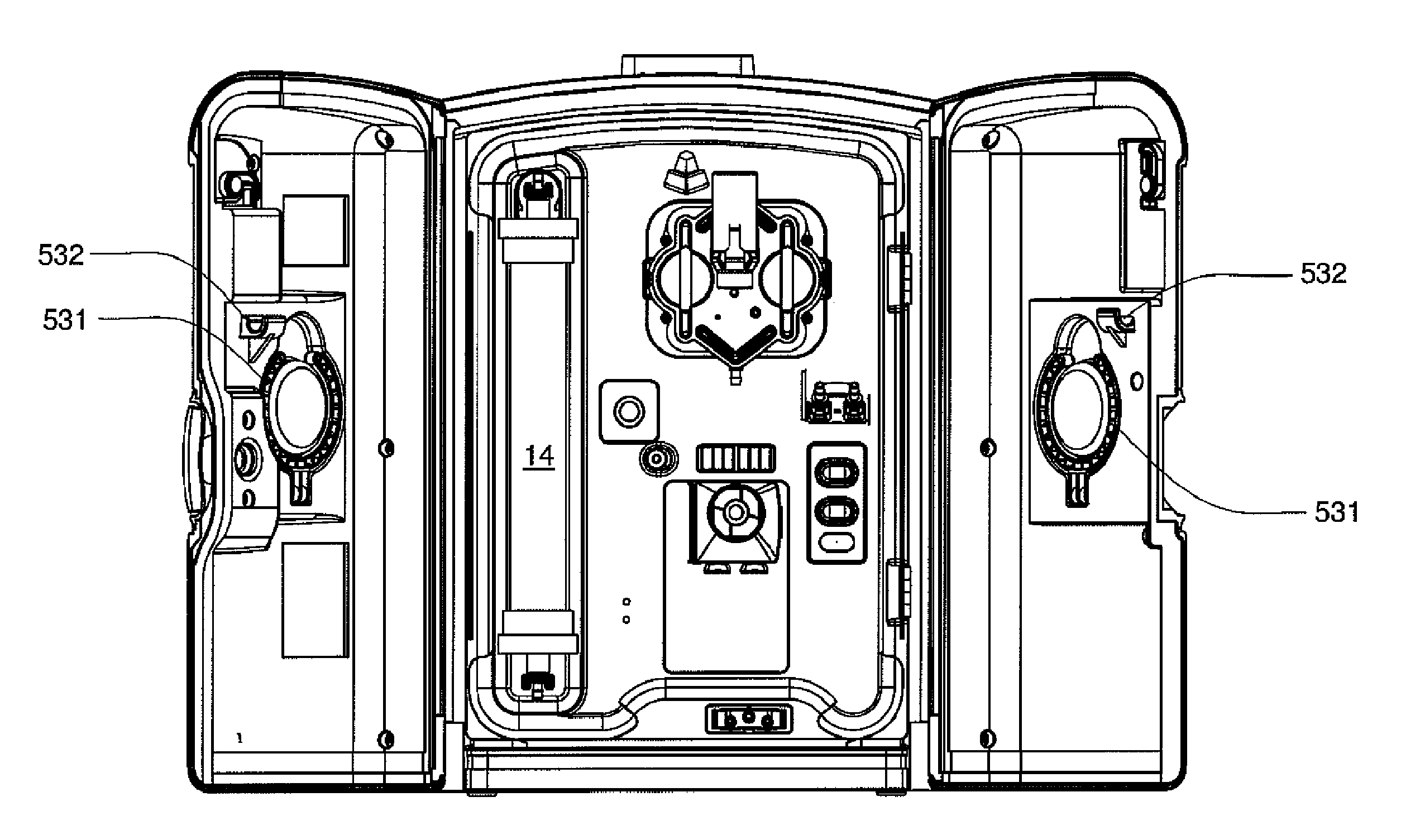
Enclosure for a portable hemodialysis system
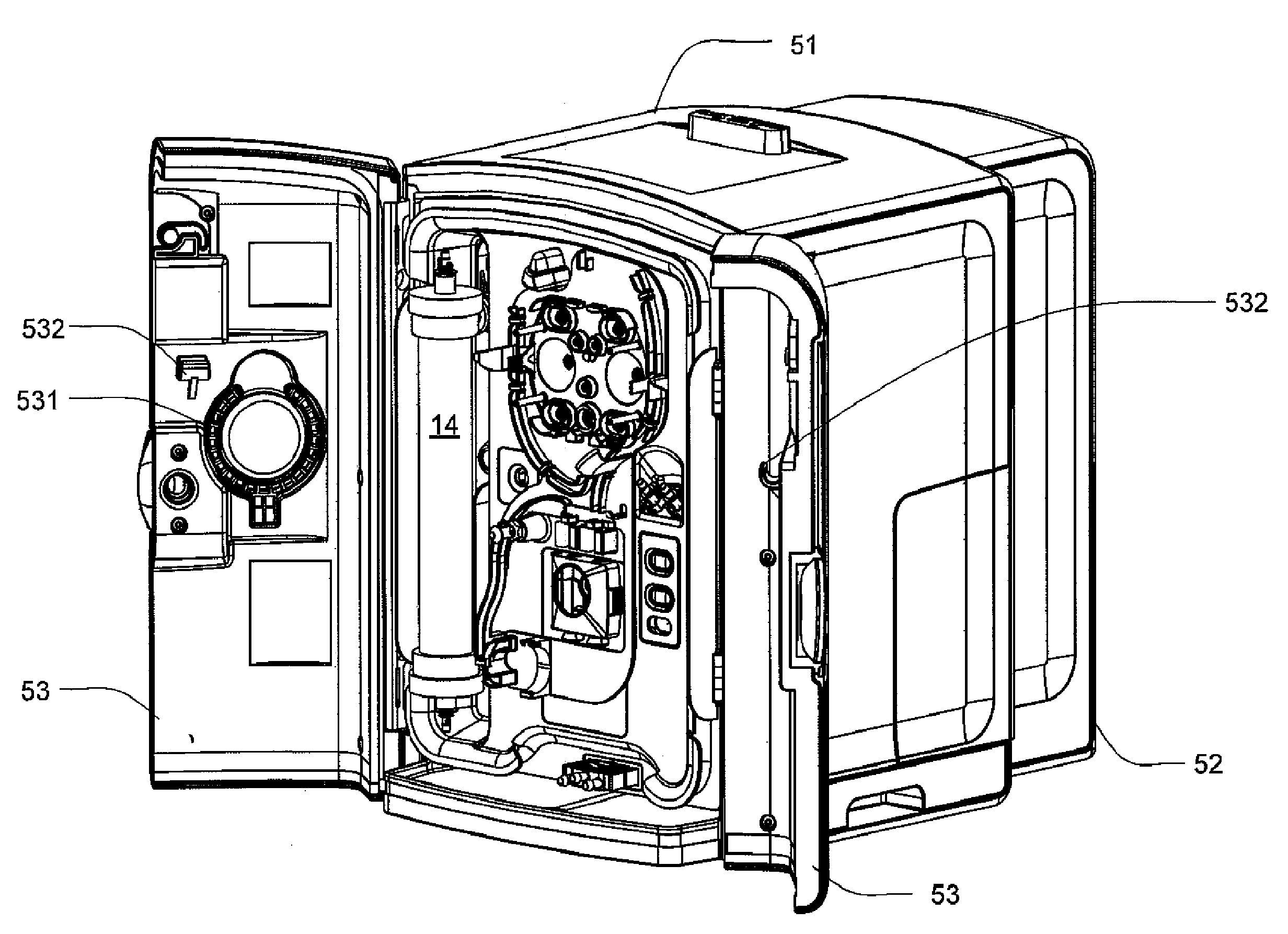
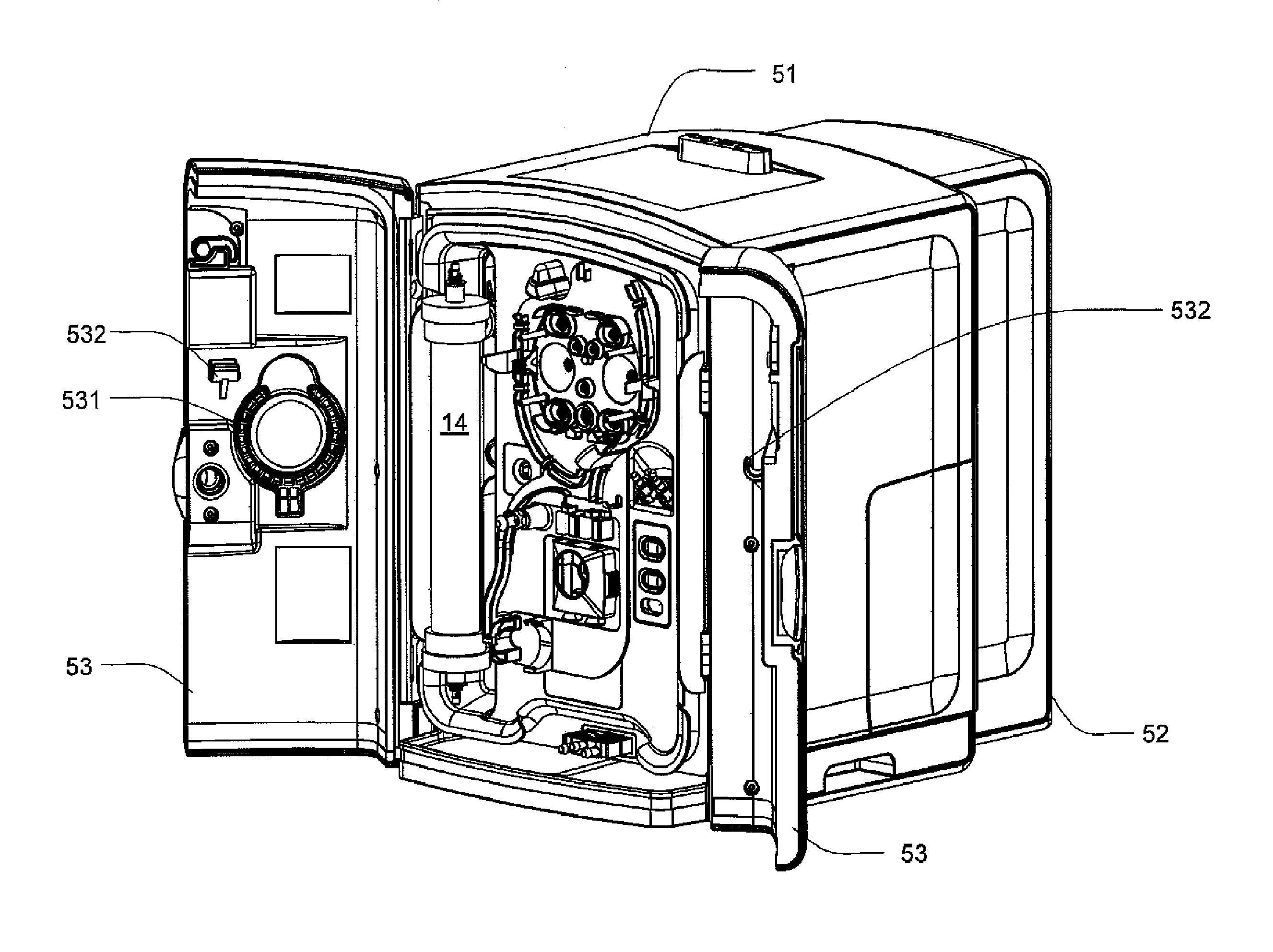
ActiveUS20090114582A1Easy to useResist entry of dustSolvent extractionHaemofiltrationDialysis fluidBlood circulation
An enclosure for containing a portable hemodialysis unit includes a housing suitable to support components for performing hemodialysis including a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer. The housing may have a front panel at which blood circuit connections and dialysate fluidic connections are located, e.g., blood line connections for patient blood access, connections for a reagent supply, dialyzer connections for both blood flow and dialysate, etc. The enclosure may also include a pair of vertical, side-by-side doors hingedly mounted to the housing. With the doors in the closed position, access to the patient access and dialysate fluidic connections may be blocked, and the doors may allow for the retention of heat in the housing suitable for disinfection during a disinfection cycle.
Owner:DEKA PROD LLP
Connector and receptacle containing a physical security feature
InactiveUS7325976B2Imparts physical securityFacilitates discriminationIncorrect coupling preventionCoupling light guidesPhysical securityInformation networks
A network comprising: (a) a plurality of different receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different receptacle coupled to one and only one different information network, each receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different plugs for coupling with the different receptacles, each plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
Air trap for a medical infusion device
InactiveUS20090107335A1Easy to useOptimize locationLiquid degasificationDialysis systemsEngineeringVertical axis
An air trap for a blood circuit and method for removing air from blood in a dialysis unit. The air trap may include a blood inlet supply line, a blood outlet supply line, and a container having an approximately spherical internal wall, an inlet at a top end of the container connected to the blood inlet supply line, and an outlet at a bottom end of the container connected to the blood outlet supply line. The inlet may be offset from a vertical axis of the approximately spherical internal wall such that blood entering the container is directed to flow in a spiral-like path. The inlet port may be arranged to introduce blood into the container in a direction that is approximately tangential to the approximately spherical inner wall of the container and / or in a direction that is approximately perpendicular to the vertical axis of the container.
Owner:DEKA PROD LLP
Piercing member protection device
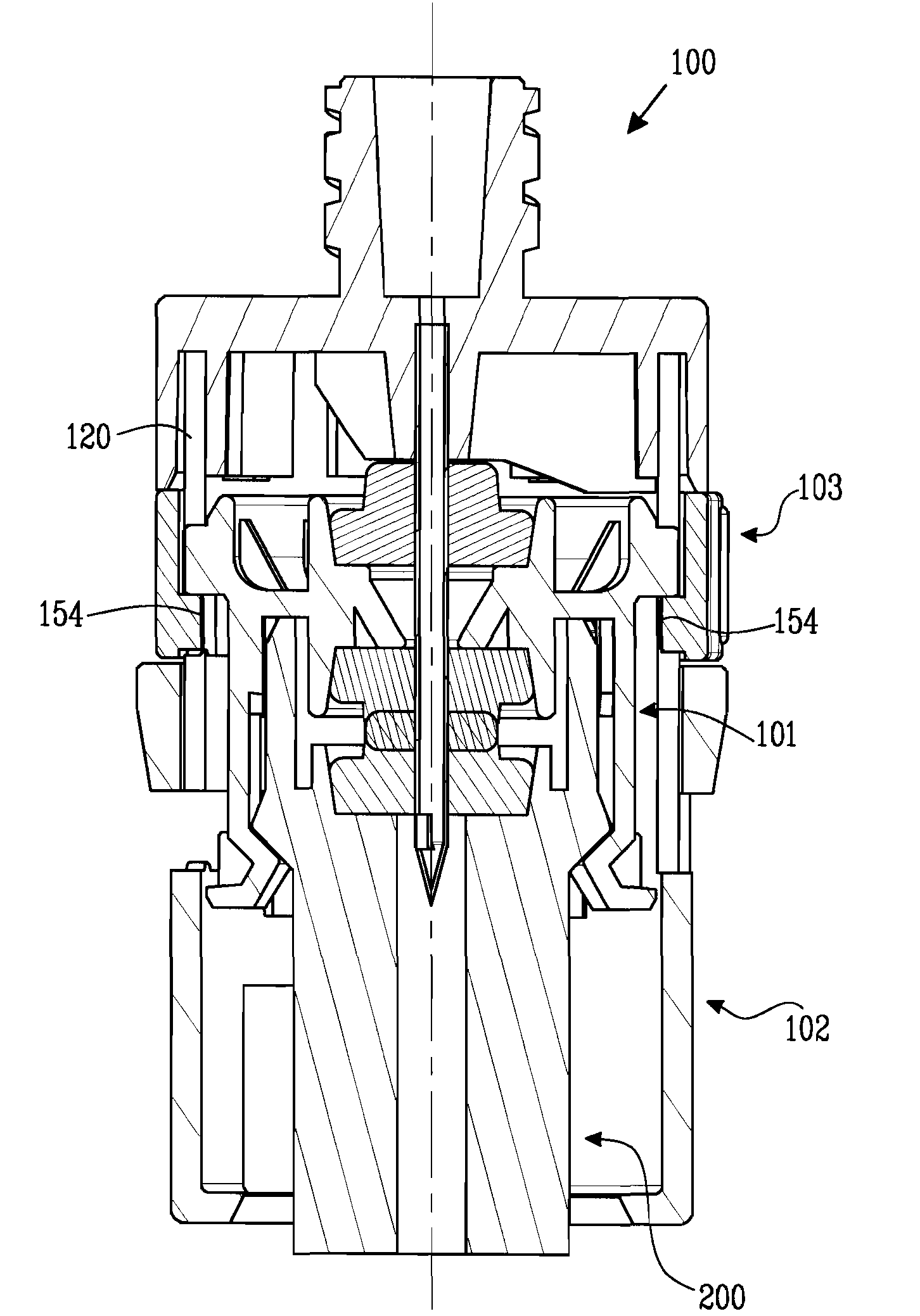
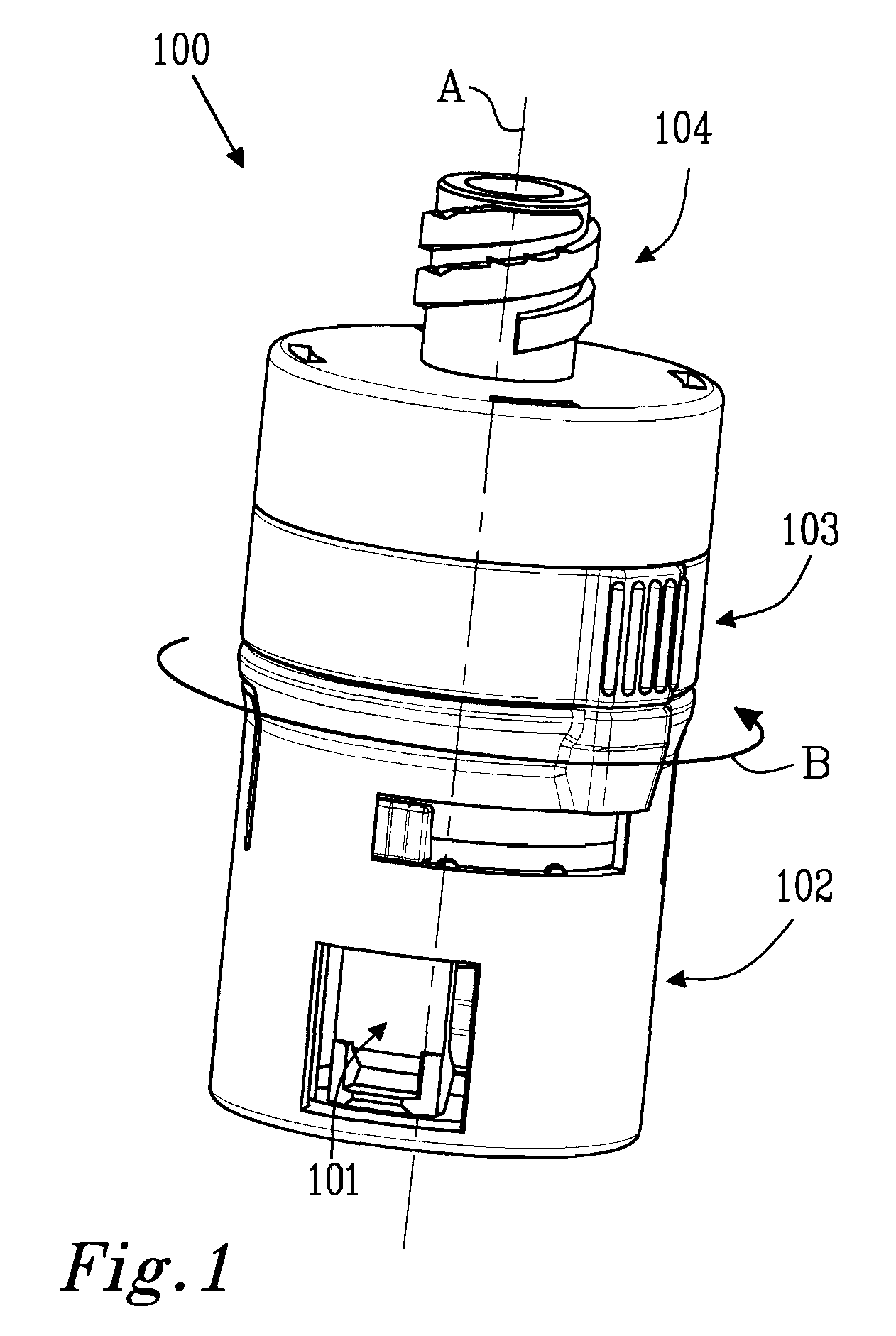
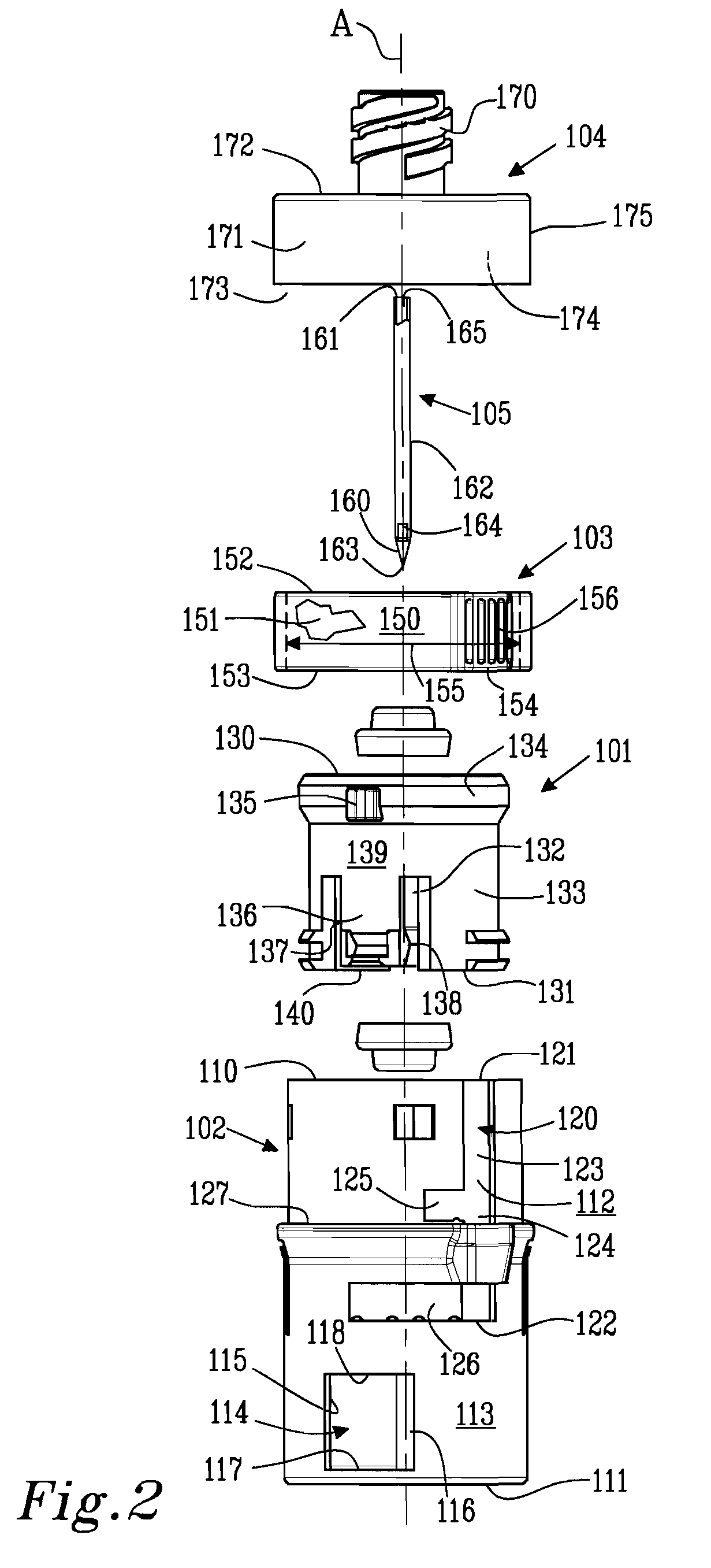
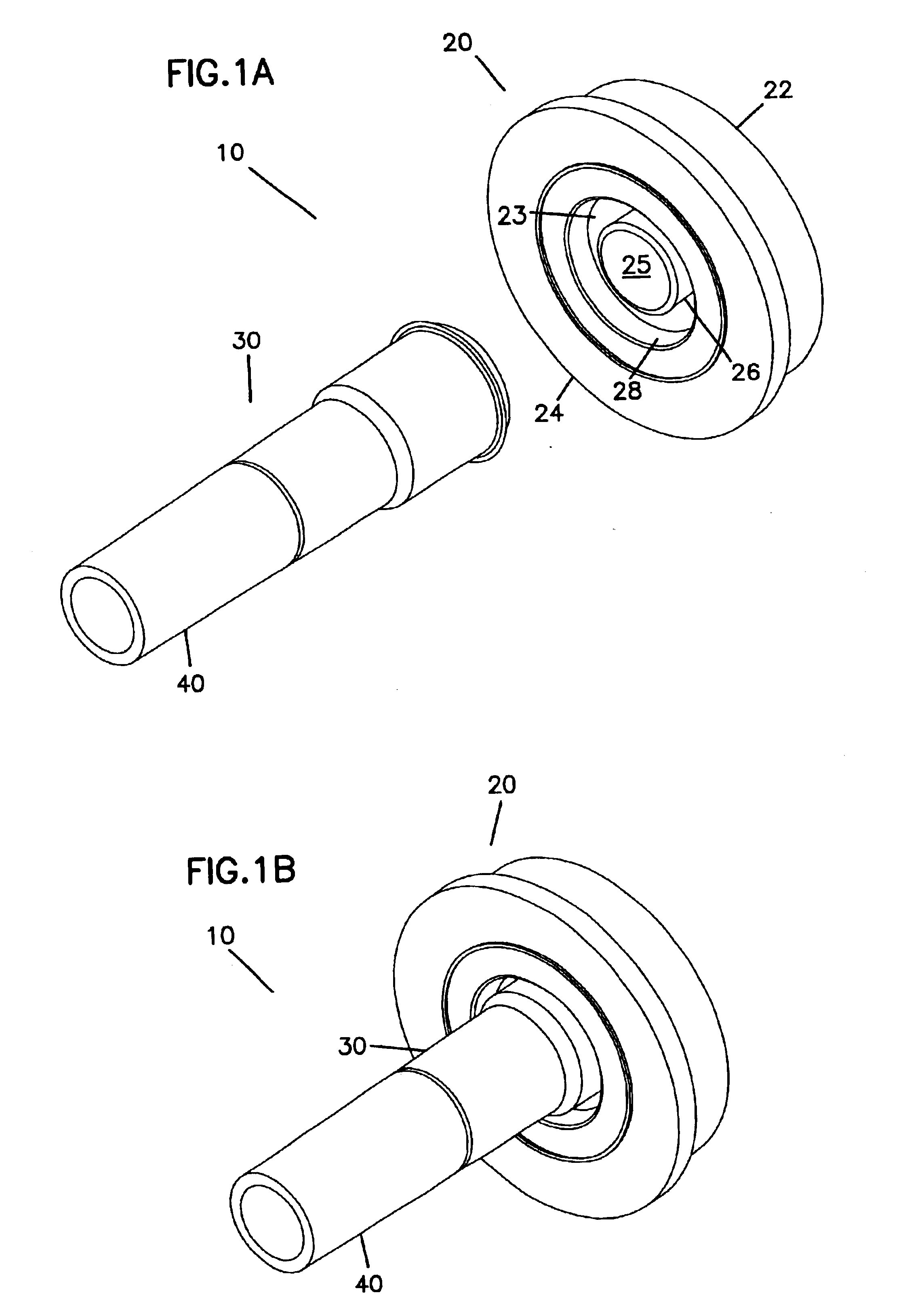
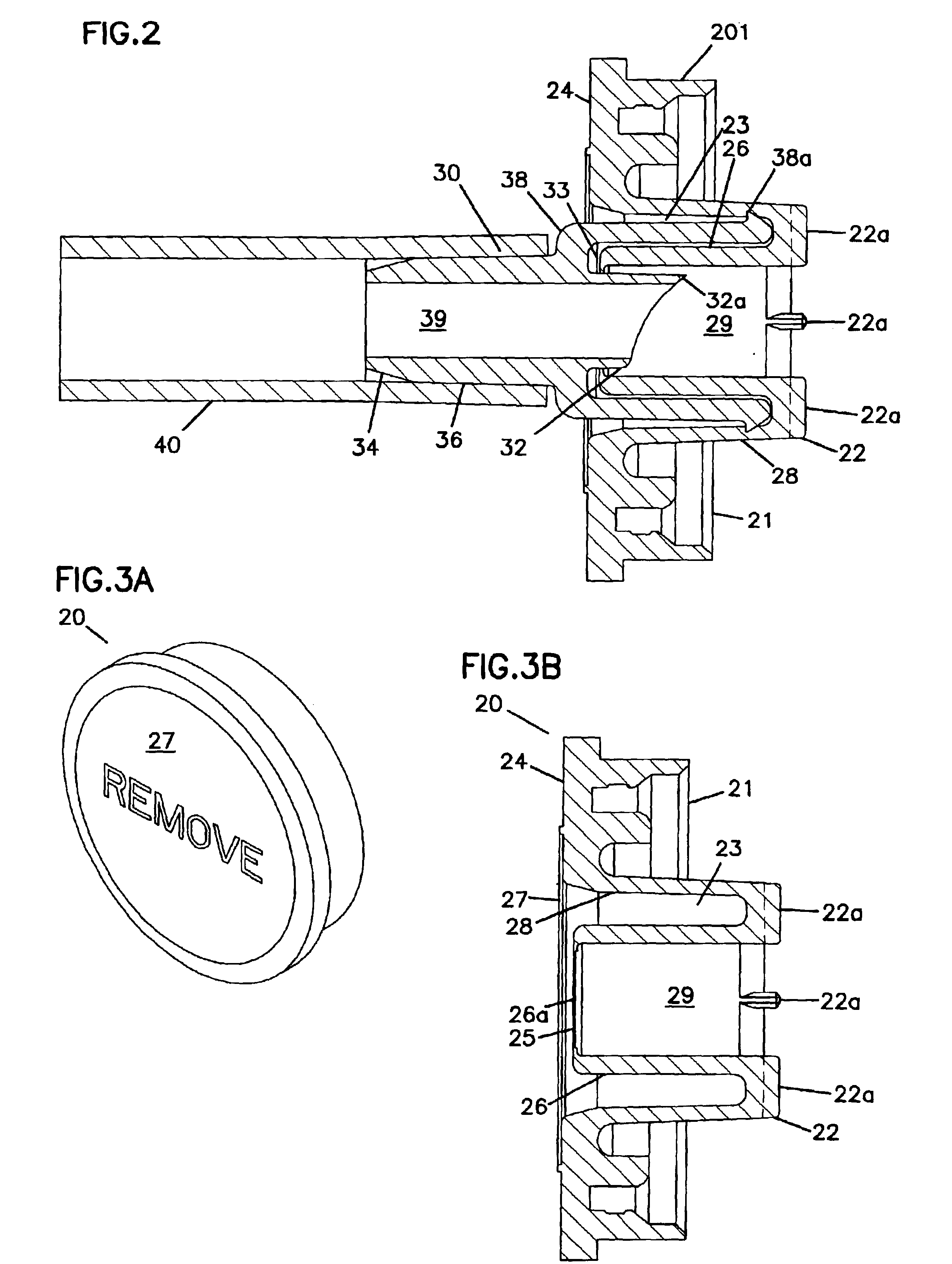
ActiveUS8287513B2Avoid connectionPrevent disengagementCapsLiquid fillingEngineeringElectrical and Electronics engineering
Owner:CARMEL PHARMA
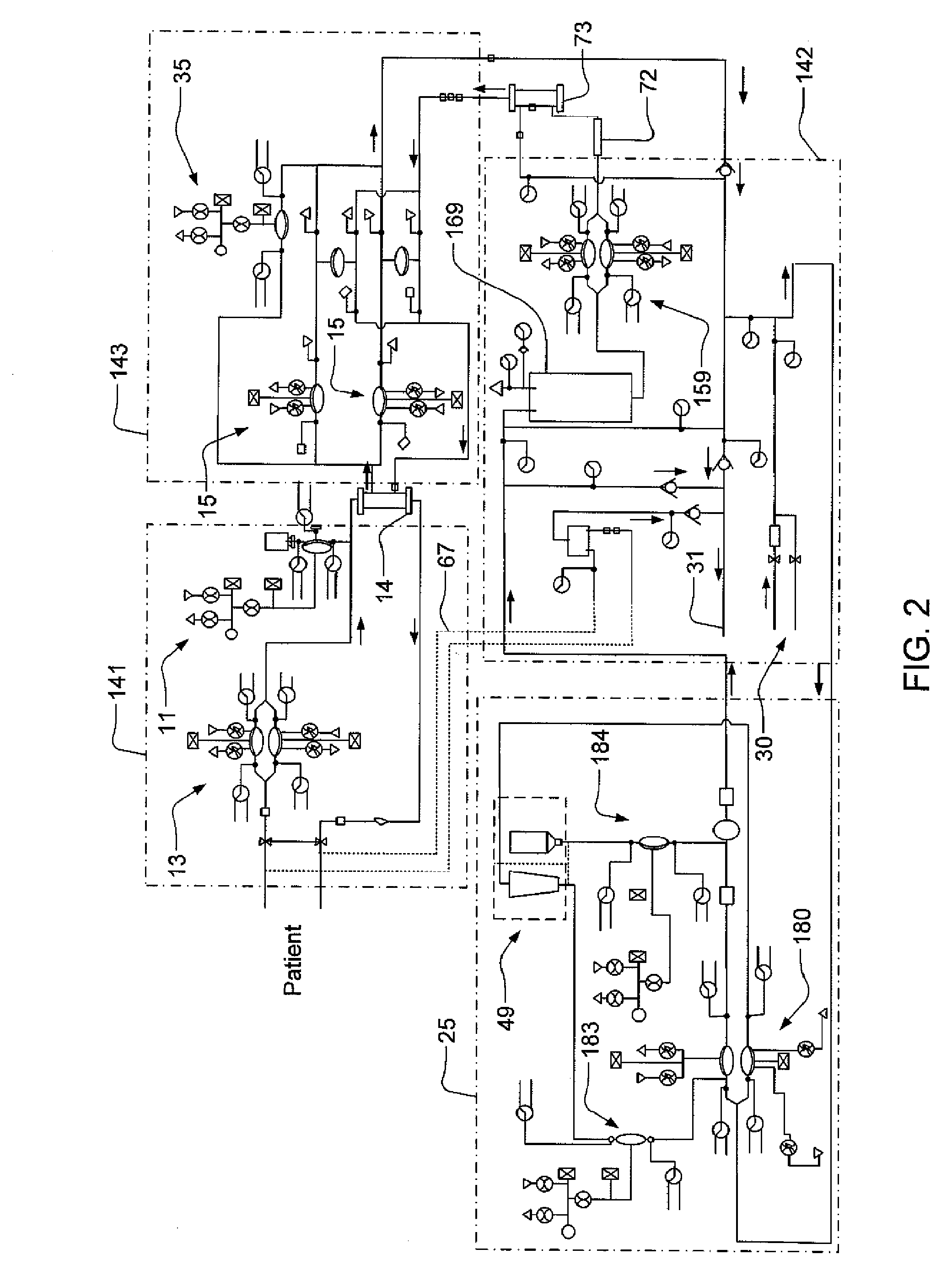
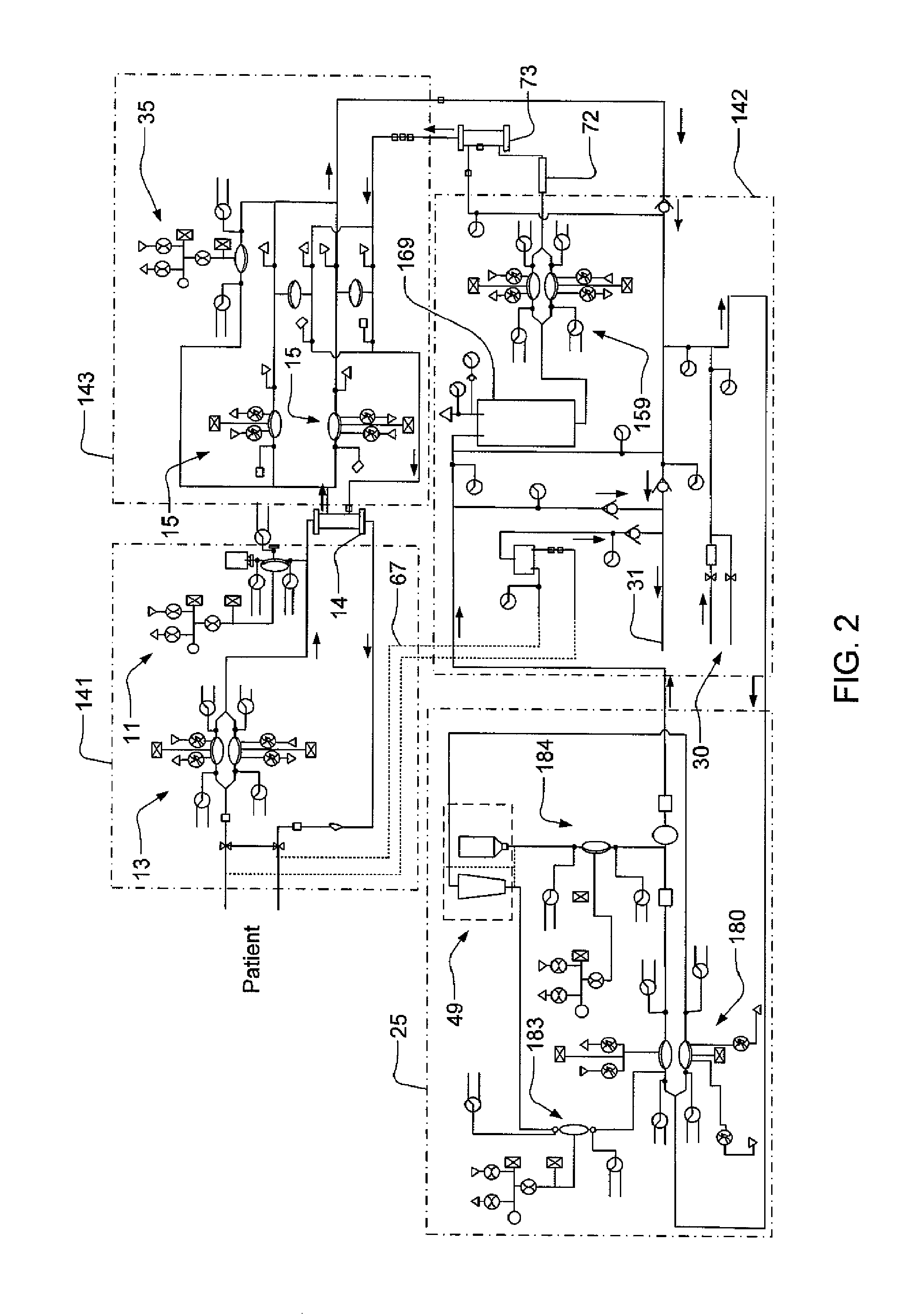
Blood circuit assembly for a hemodialysis system
ActiveUS20090105629A1Easy to useResist entry of dustControl devicesDialysis systemsBiomedical engineeringBlood circulating
A blood circuit assembly for a dialysis unit may include an organizing tray, a pair of pneumatic pumps mounted to the organizing tray for circulating blood received from a patient through a circuit including a dialyzer unit and returned to the patient, an air trap mounted to the organizing tray arranged to remove air from blood circulating in the circuit, a pair of dialyzer connections arranged to connect to the inlet and outlet of a dialyzer unit, and a pair of blood line connectors, one inlet blood line connector for receiving blood from the patient and providing blood to the pneumatic pumps and the other outlet blood line connector for returning blood to the patient.
Owner:DEKA PROD LLP
Hypodermic drug delivery reservoir and apparatus
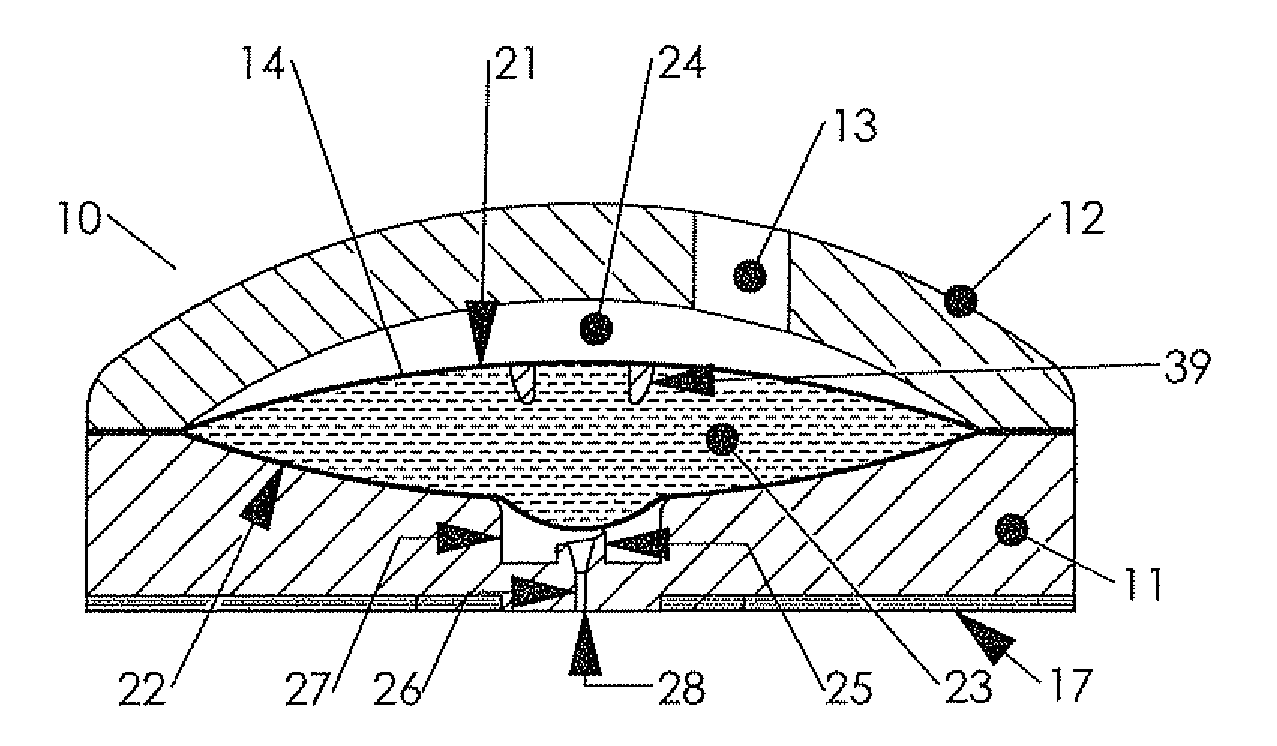
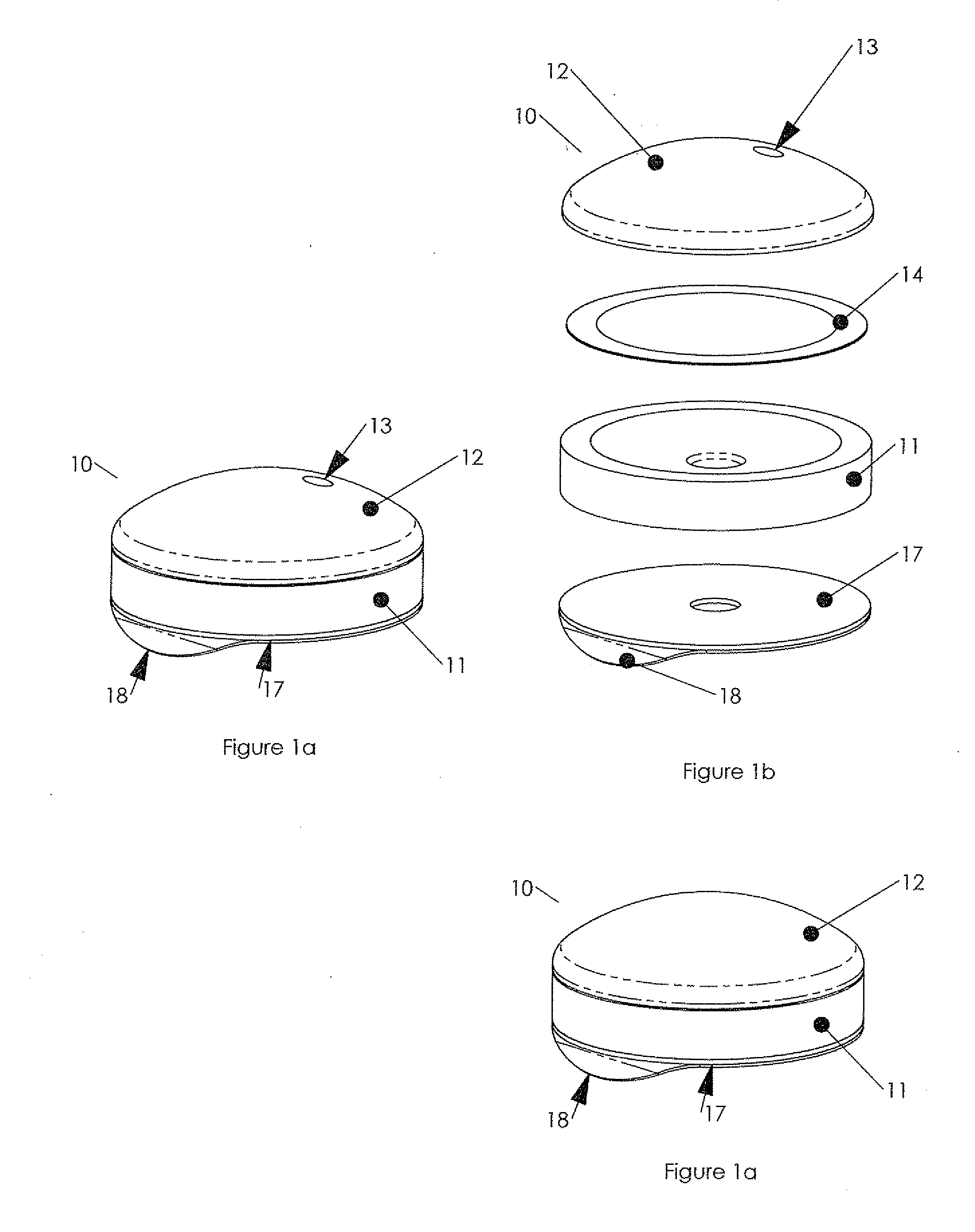
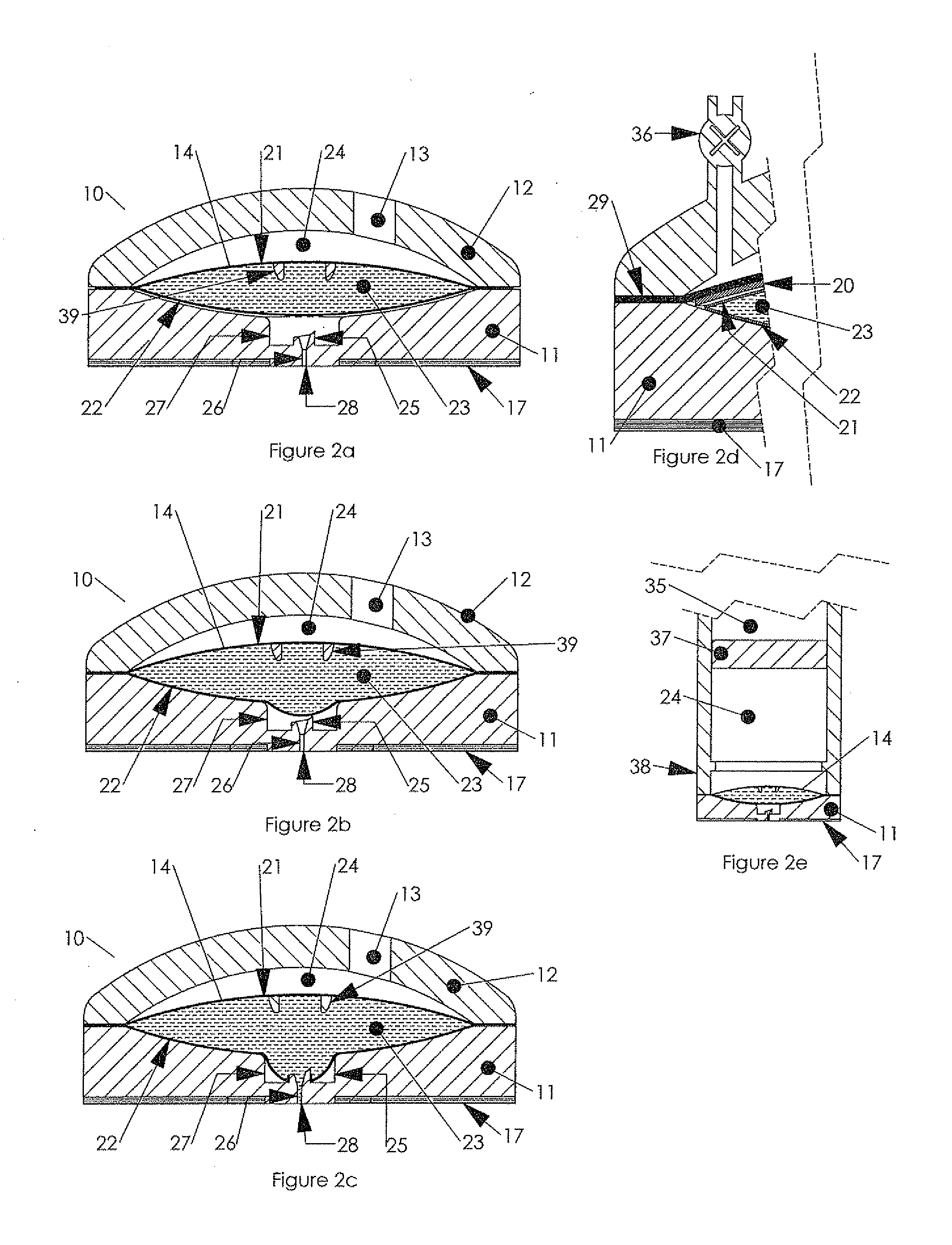
ActiveUS20100179473A1Preventing fluid connectionSeals be limitedJet injection syringesMicroneedlesHypodermoclysisDrug delivery reservoir
A hypodermic drug delivery apparatus (10) for delivering a pressurized medication fluid (23) comprising a reservoir (14) containing at least one deliverable fluid (23) and a rupturing member (25) the reservoir (14) having at least one portion of at least one wall (22) rupturable by the rupturing member (25).
Owner:AKTIVAX INC
Enclosure for a portable hemodialysis system
ActiveUS8393690B2Resist entry of dustAvoid accessSolvent extractionHaemofiltrationHaemodialysis machineBlood circulating
An enclosure for containing a portable hemodialysis unit includes a housing suitable to support components for performing hemodialysis including a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer. The housing may have a front panel at which blood circuit connections and dialysate fluidic connections are located, e.g., blood line connections for patient blood access, connections for a reagent supply, dialyzer connections for both blood flow and dialysate, etc. The enclosure may also include a pair of vertical, side-by-side doors hingedly mounted to the housing. With the doors in the closed position, access to the patient access and dialysate fluidic connections may be blocked, and the doors may allow for the retention of heat in the housing suitable for disinfection during a disinfection cycle.
Owner:DEKA PROD LLP
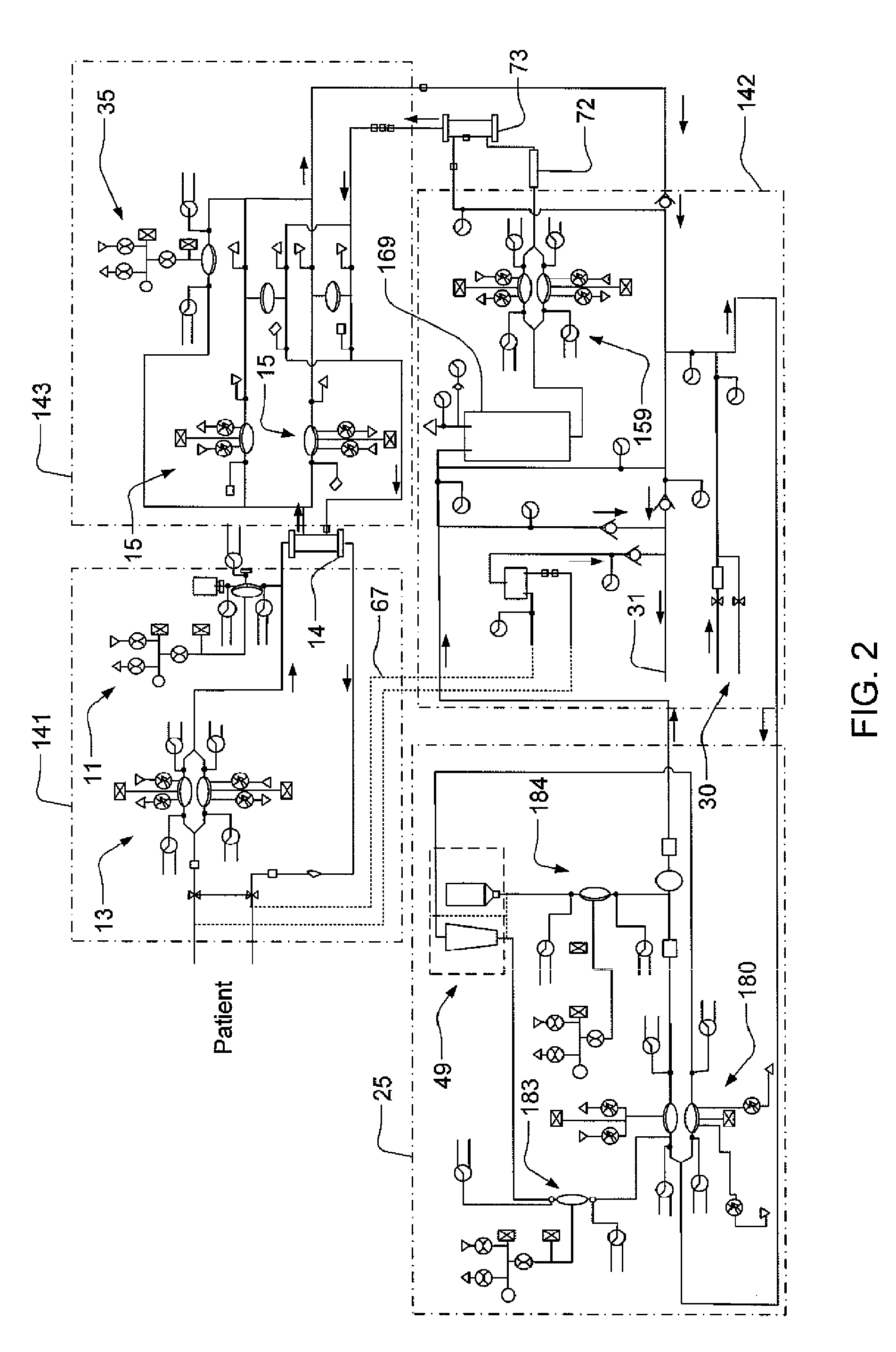
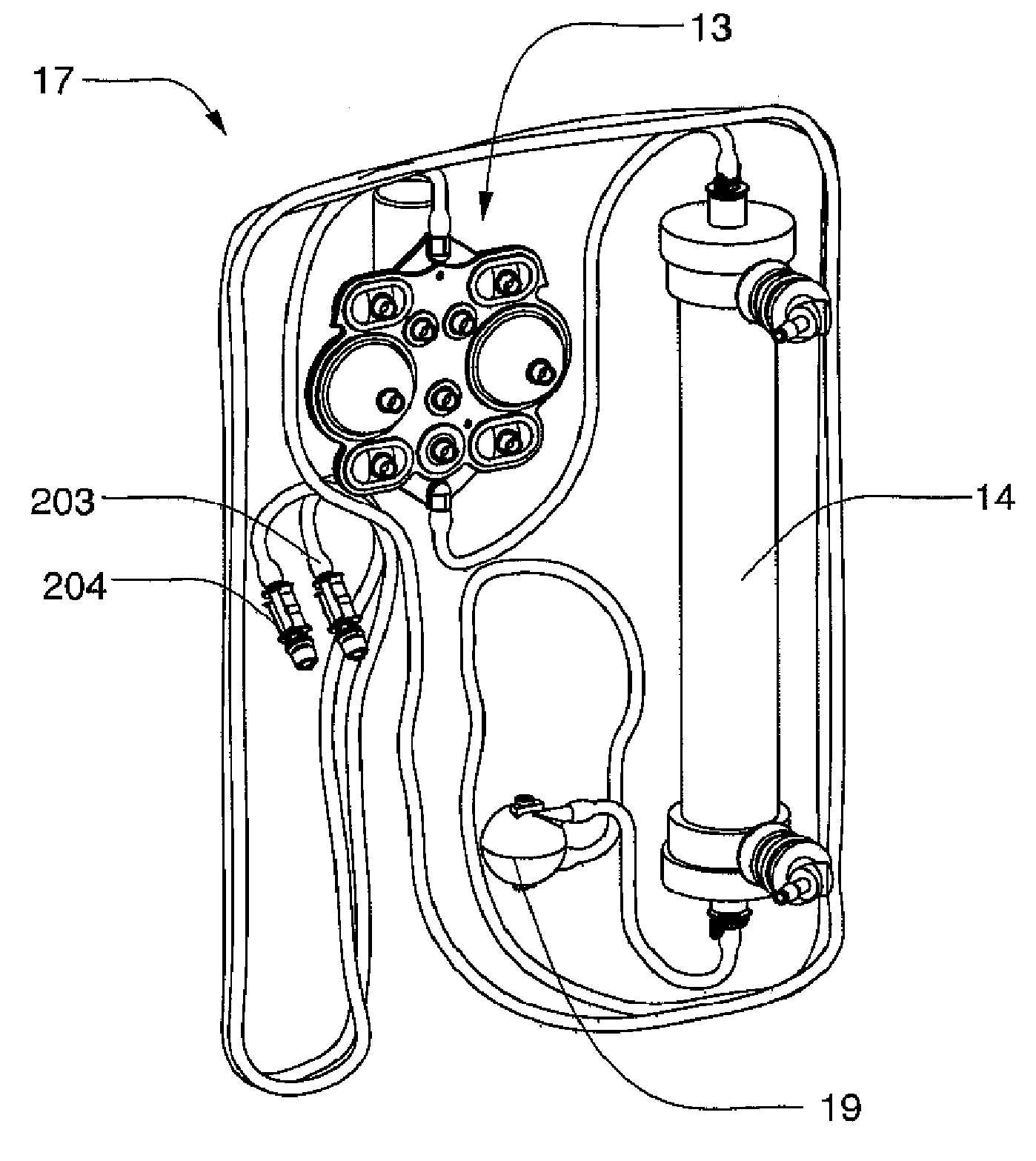
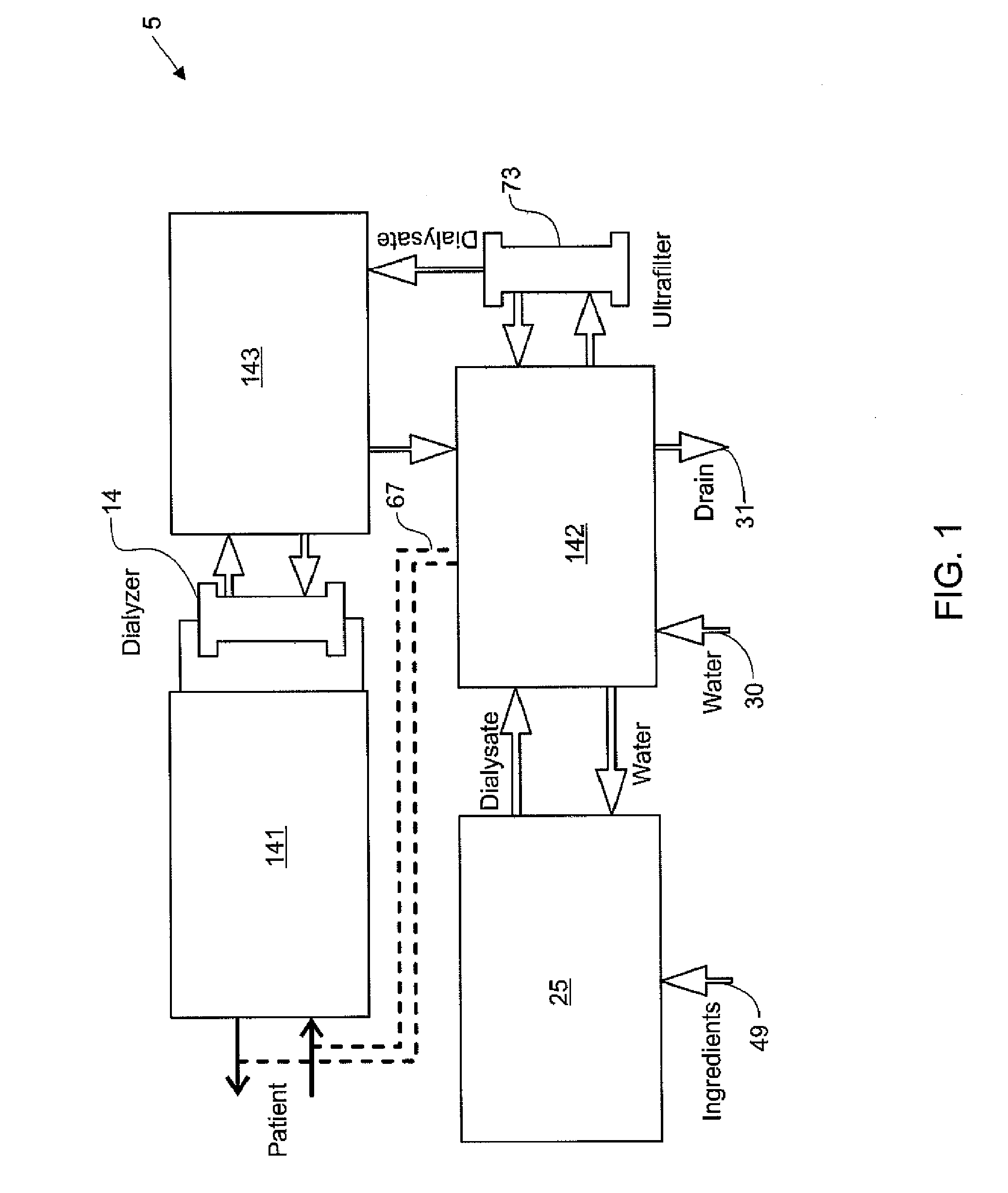
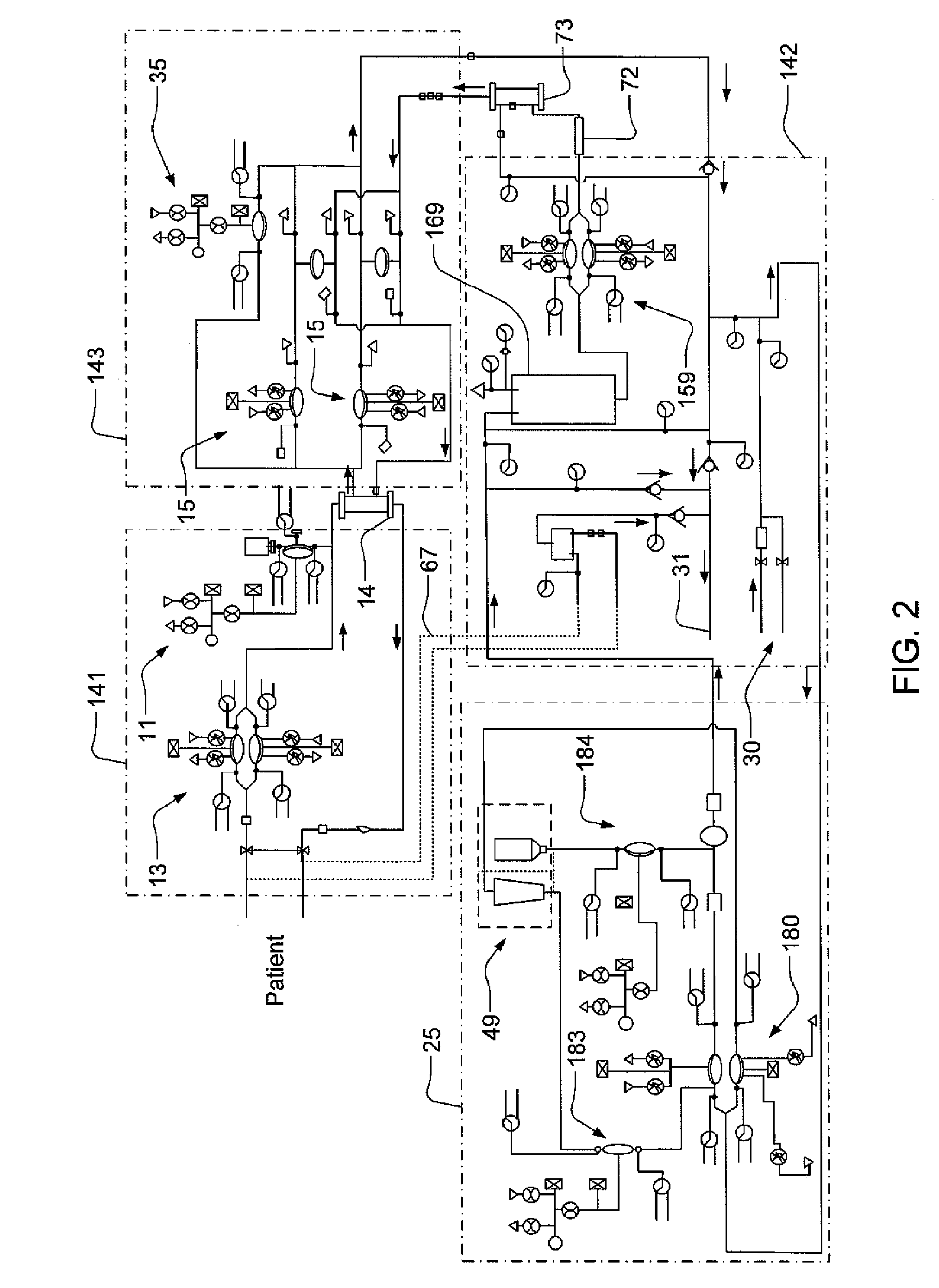
Hemodialysis system
ActiveUS20140112828A1Easy to useOptimize locationOther blood circulation devicesServomotor componentsHaemodialysis machineBlood pump
A drain cassette for a dialysis unit has a fluid channel between venous and arterial connection ports, and a valve may controllably open and close fluid communication between a drain outlet port and the venous connection port or the arterial connection port. A blood circuit assembly and drain cassette may be removable from the dialysis unit, e.g., by hand and without the use of tools. A blood circuit assembly may include a single, unitary member that defines portions of a pair of blood pumps, control valves, channels to accurately position flexible tubing for an occluder, an air trap support, and / or other portions of the assembly. A blood circuit assembly engagement device may assist with retaining a blood circuit assembly on the dialysis unit, and / or with removal of the assembly. An actuator may operate a retainer element and an ejector element that interact with the assembly.
Owner:DEKA PROD LLP
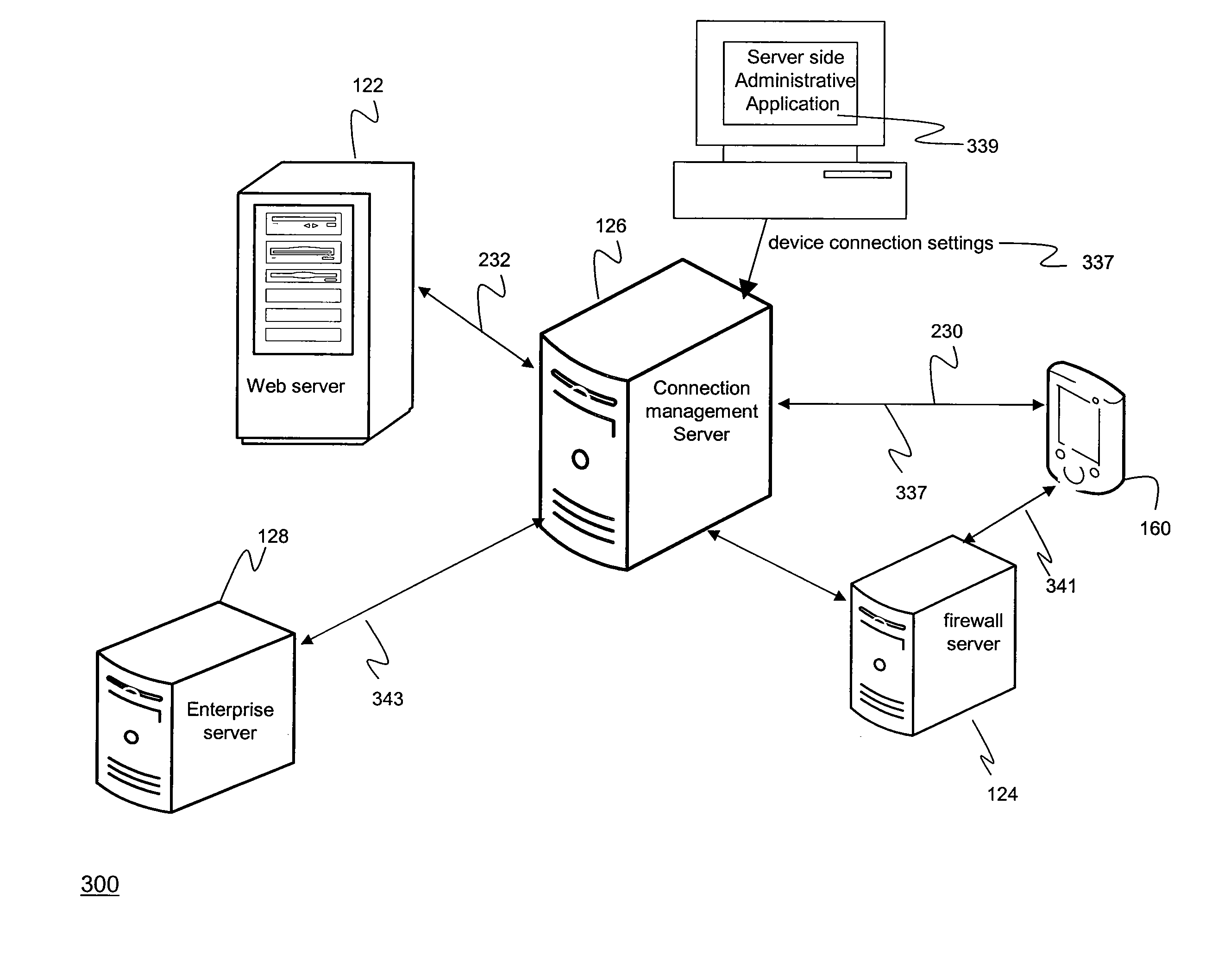
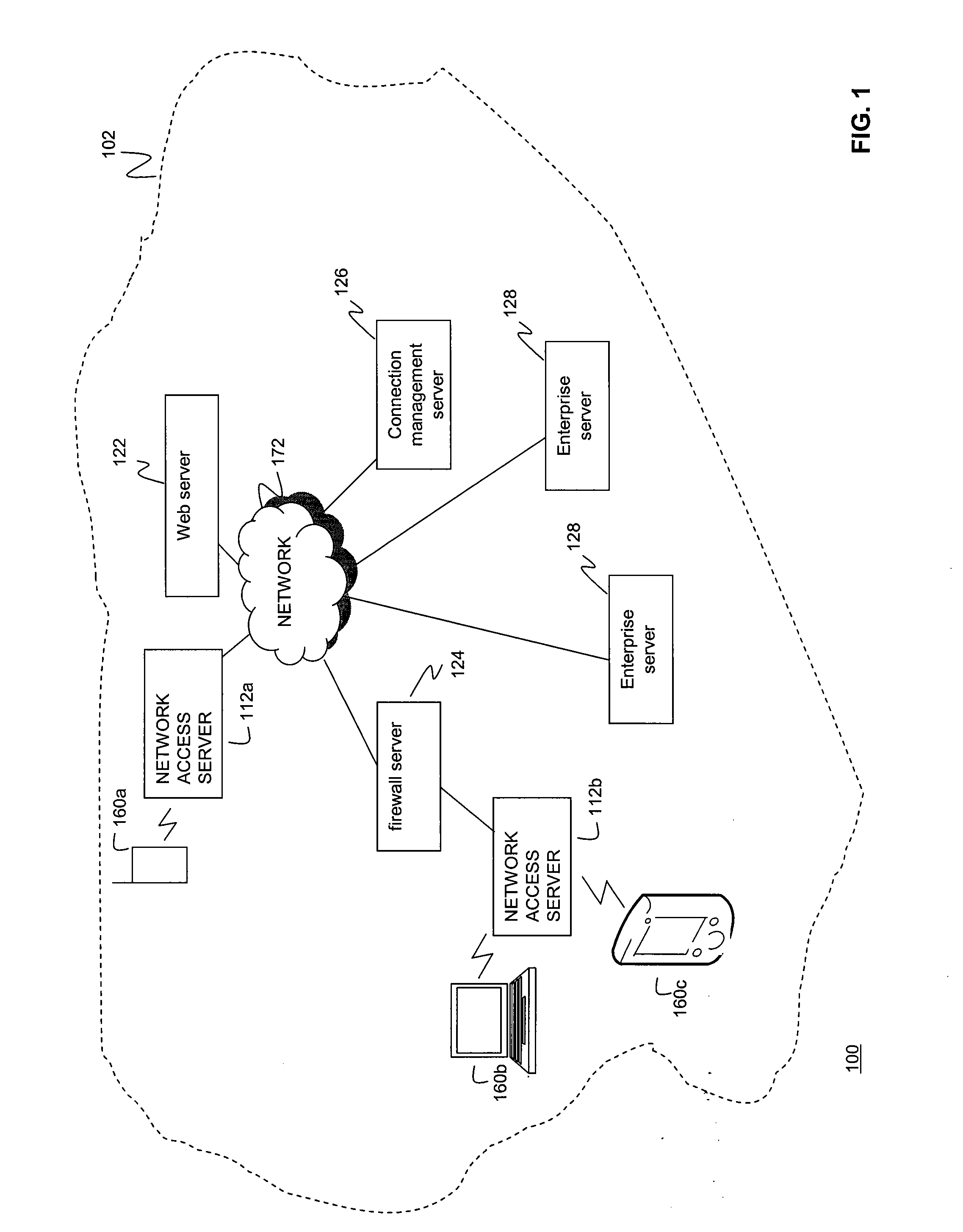
Maintaining Connections Between Mobile Devices and Servers
ActiveUS20100281118A1Avoid connectionAssess restrictionConnection managementActive messageMobile device
A system, method, and computer-readable medium having computer-executable instructions for maintaining connections between a mobile device and a server are described herein. In an embodiment, the method operates by receiving a data request from the mobile device, the data request identifying at least a timeout interval. The method comprises sending the data request to a data server and then determining whether the timeout interval has passed. The method also comprises sending a keep alive message to the mobile device indicating that the request has timed out if it is determined that the timeout interval has passed. The method then receives a re post request from the mobile device, the re post request identifying a timeout interval. The method further comprises receiving a response from the data server, the response including at least data requested by the mobile device and then sends the response to the mobile device.
Owner:IANYWHERE SOLUTIONS
Piercing member protection device
ActiveUS20090069783A1Safely connectedIncrease turning frictionCapsLiquid fillingElectrical and Electronics engineering
Owner:CARMEL PHARMA
System and Method for Detecting and Mitigating Dns Spoofing Trojans
ActiveUS20080147837A1Avoid connectionMultiple digital computer combinationsTransmissionDomain nameLocation detection
Embodiments of the present invention relate to a method and system for detecting and / or mitigating domain name system (DNS) spoofing Trojan horse (or Trojan) code. Trojan code (sometimes called malware or malicious software) is a common computer security problem. Some Trojans modify the DNS resolution mechanism employed by the infected computer, such that the computer traffic, when browsing the Internet, is routed to a location not intended by the rightful owner of the computer. The present invention can detect this phenomenon from a remote device or location and may take action to mitigate its effects.
Owner:EMC IP HLDG CO LLC
Wood golf club head
A golf club head includes a housing and a reinforced elastic supporting member. The housing has a front portion on which a face is disposed, a sole portion, a rear portion, a crown portion, a toe portion, a heel portion, a neck, and a chamber inside. The reinforced elastic supporting member has an end bonded to the sole portion or the rear portion of the housing, the other end bonded to the front portion or the crown portion of the housing, and a middle portion suspended in the chamber of the housing.
Owner:CHEN ARCHER C C
Magnetic-enabled connector device
ActiveUS20140087569A1Reduce risk of damageNot to damageEngagement/disengagement of coupling partsCoupling contact membersElectricityEngineering
An electrical connector, which may be a multi-pin connector, includes magnetic elements and mechanical alignment elements which provide connective forces and precision alignment and orientation. The magnetic elements permit a user to bring male and female connector portions only into “rough” alignment before magnetic forces bring the portions into the correct position. Pin contacts on the connector portions extend only a small amount beyond respective protective annular openings and are thereby protected. Spring-biased pin elements may be included on one of the connector portions to bias the contact pins into engagement and create conductive paths when the portions are in a connected position. Paramagnetic or non-magnetic sheaths may surround the magnetic elements to focus, or distribute, magnetic forces.
Owner:KC MAGCON
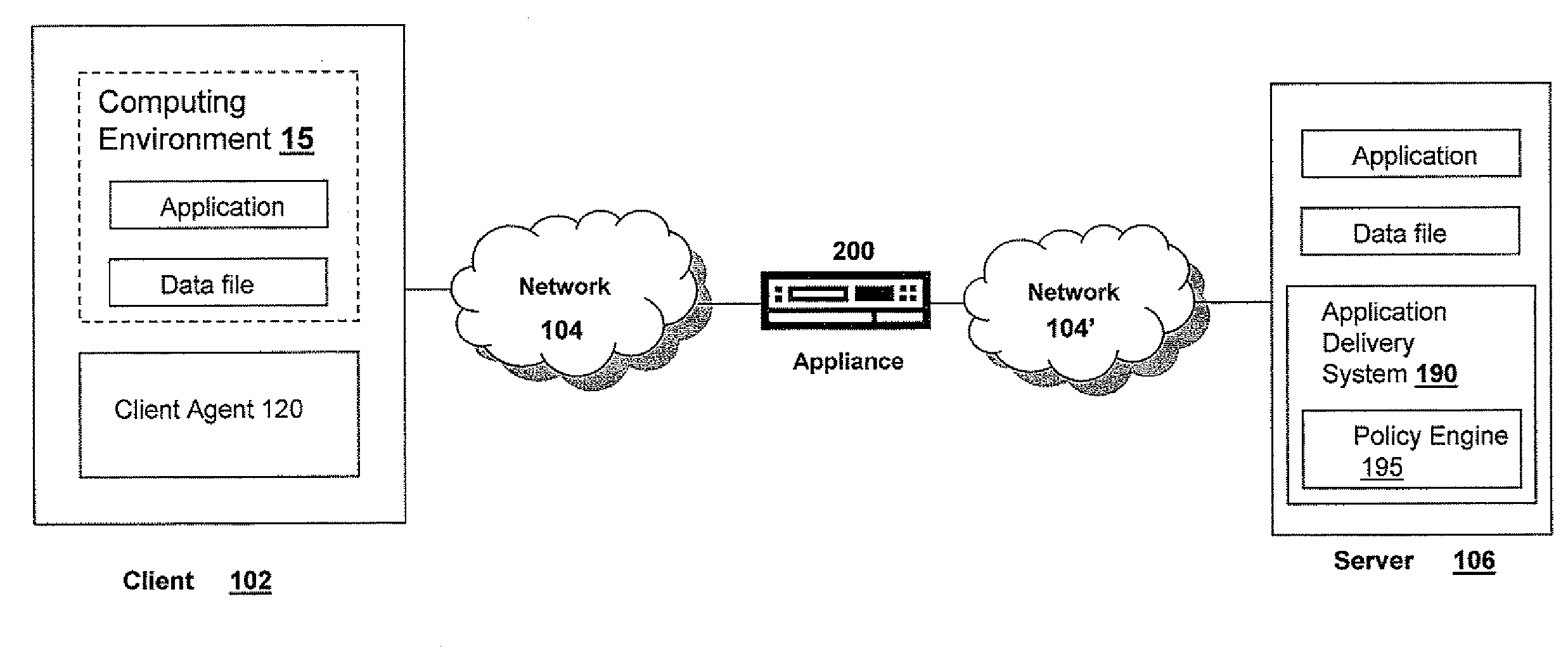
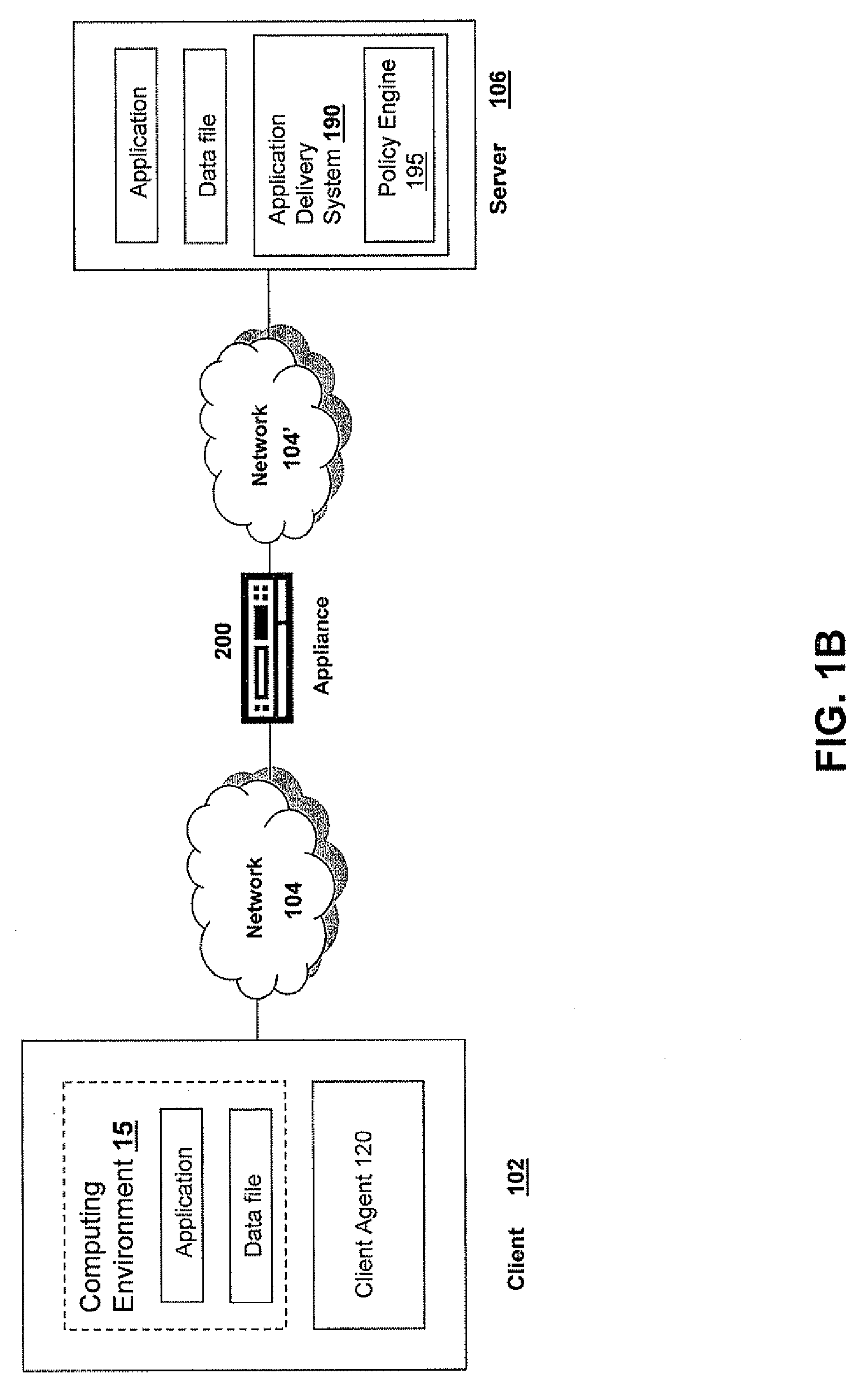
Systems and Methods for Policy Based Triggering of Client-Authentication at Directory Level Granularity
ActiveUS20080034410A1Easy to controlAvoid connectionRandom number generatorsUser identity/authority verificationGranularityPrivate network
Systems and methods are disclosed for an appliance to authenticate access of a client to a protected directory on a server via a connection, such as a secure SSL connection, established by the appliance. A method comprises the steps of: receiving, by an appliance, a first request from a client on a first network to access a server on a second network, the appliance providing the client a virtual private network connection from the first network to the second network; determining, by the appliance, the first request comprises access to a protected directory of the server; associating, by the appliance, an authentication policy with the protected directory, the authentication policy specifying an action to authenticate the client's access to the protected directory; and transmitting, by the appliance in response to the authentication policy, a second request to the client for an authentication certificate. Corresponding systems are also disclosed.
Owner:CITRIX SYST INC
System and method for intrusion prevention in a communications network
InactiveUS20050160289A1Prevents unwanted connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsDatabase accessWeb resource
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
Multilevel security server framework
InactiveUS20120151209A1Avoid connectionUser identity/authority verificationService frameworkSecurity policy
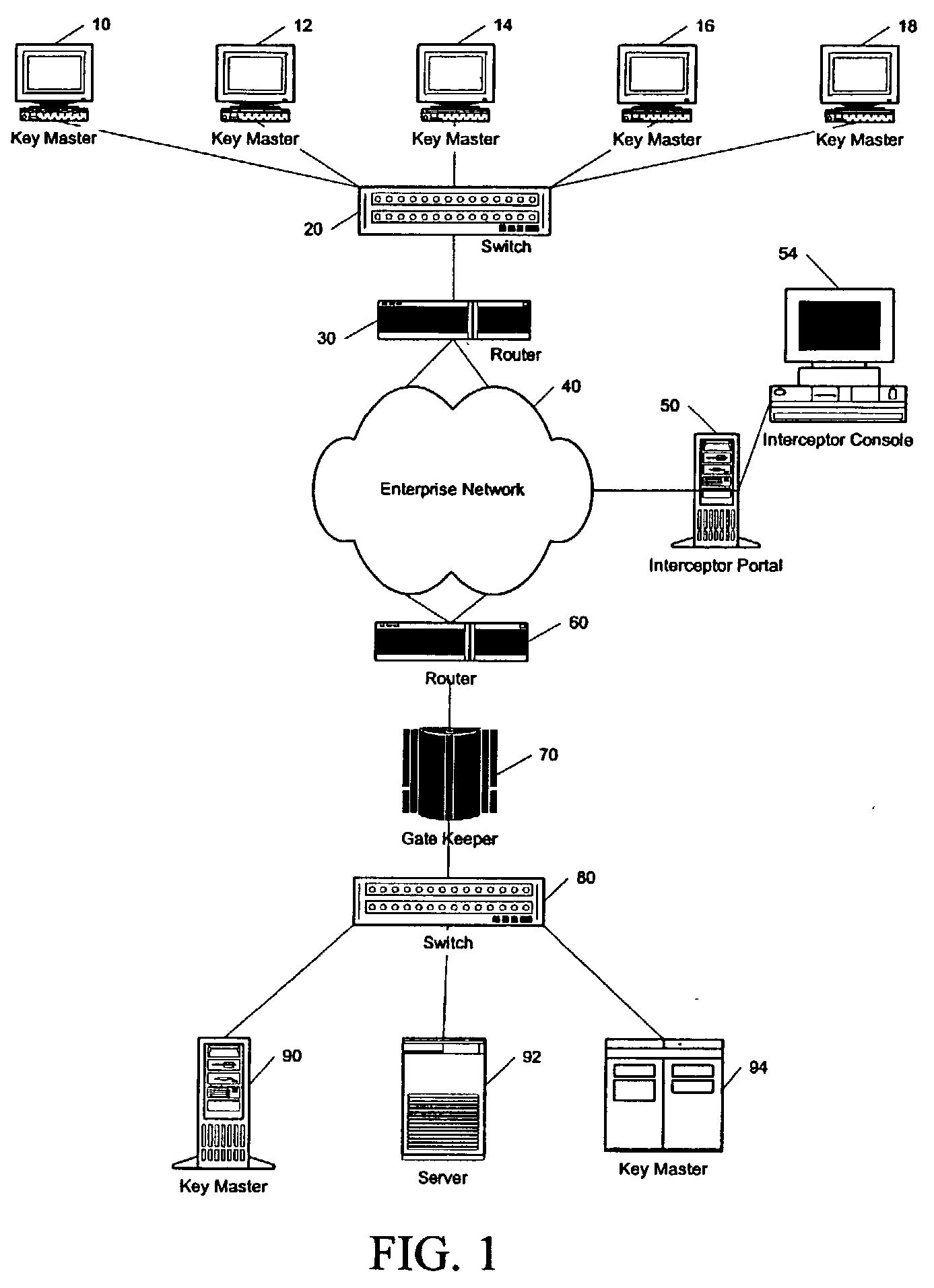
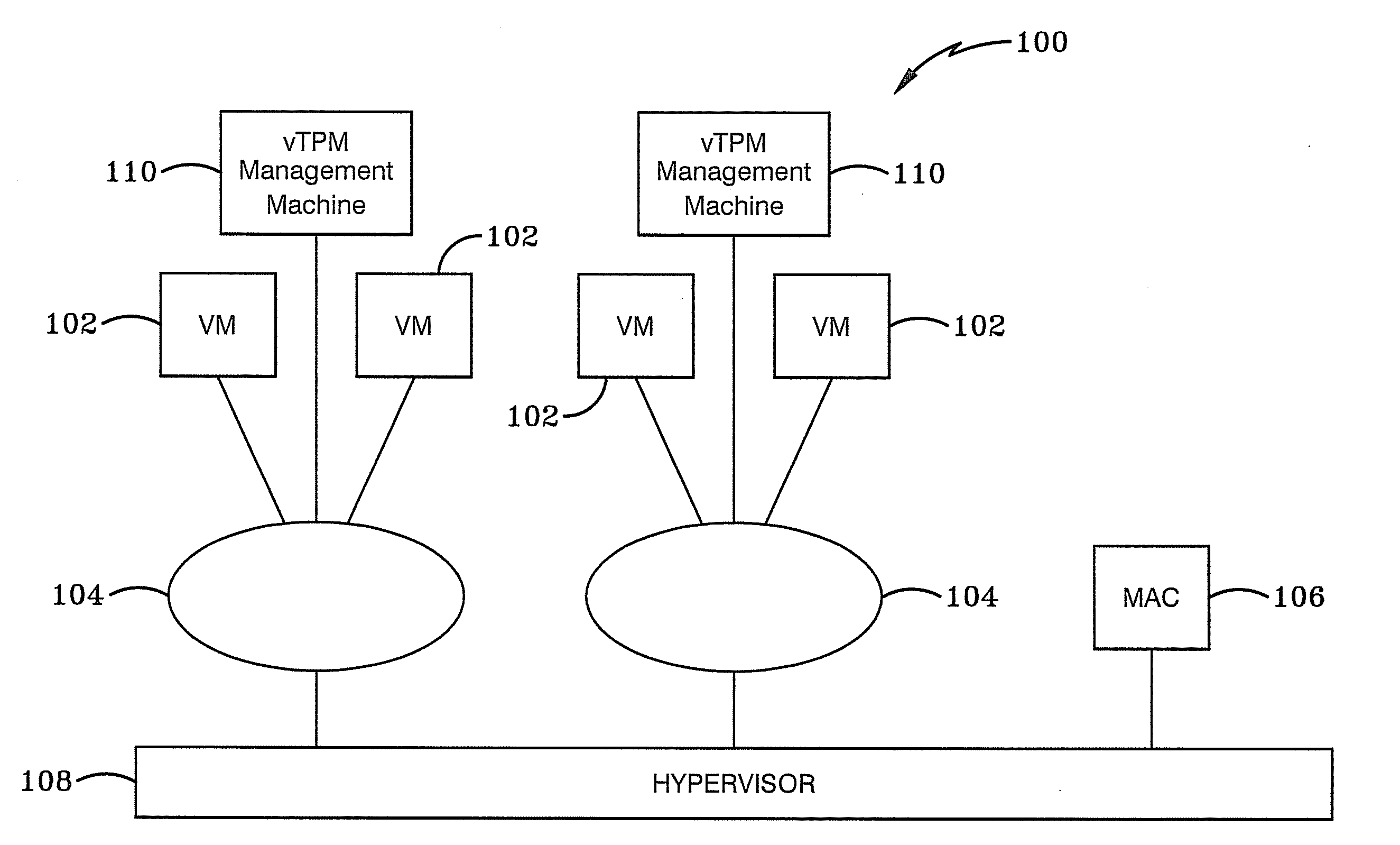
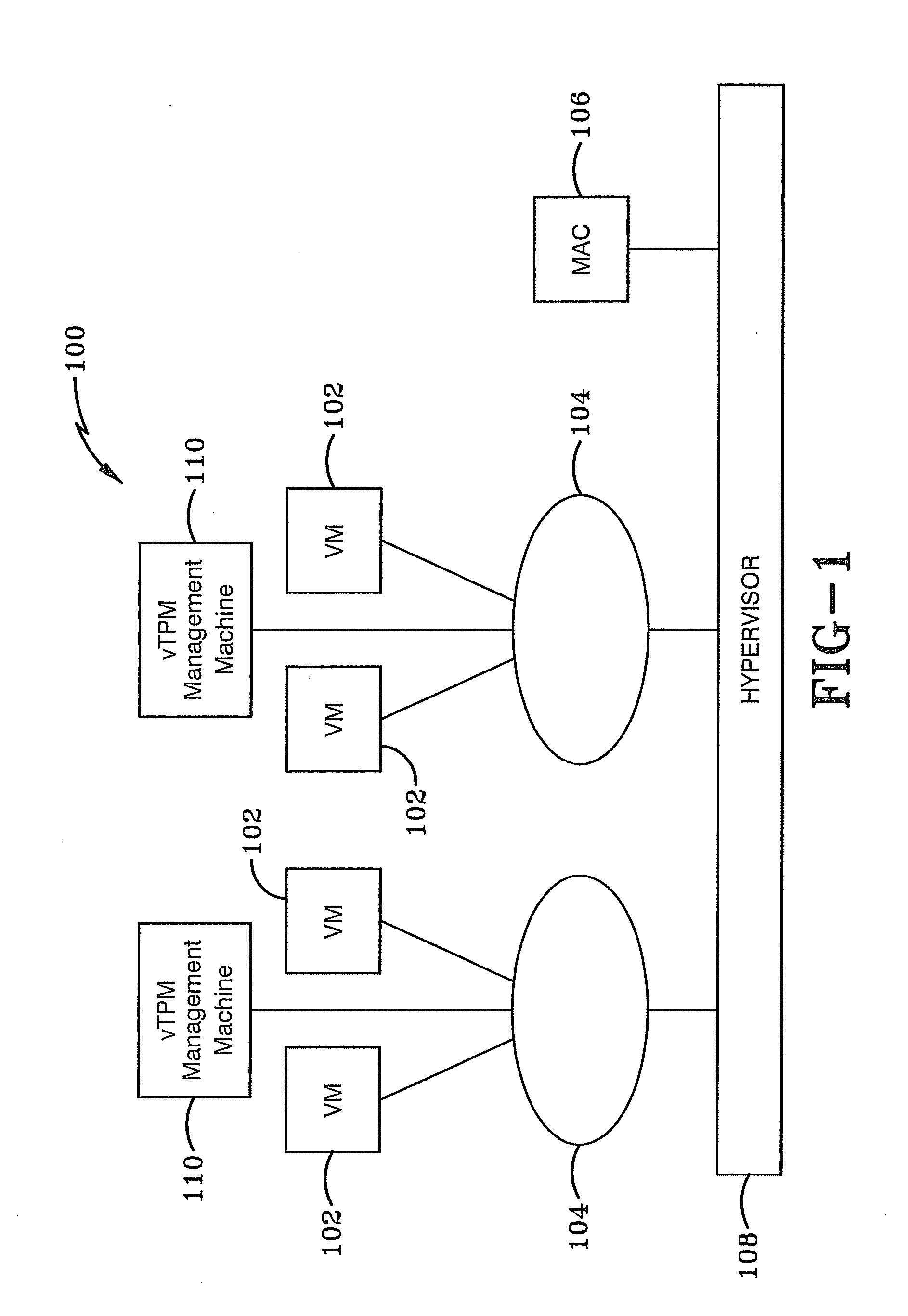
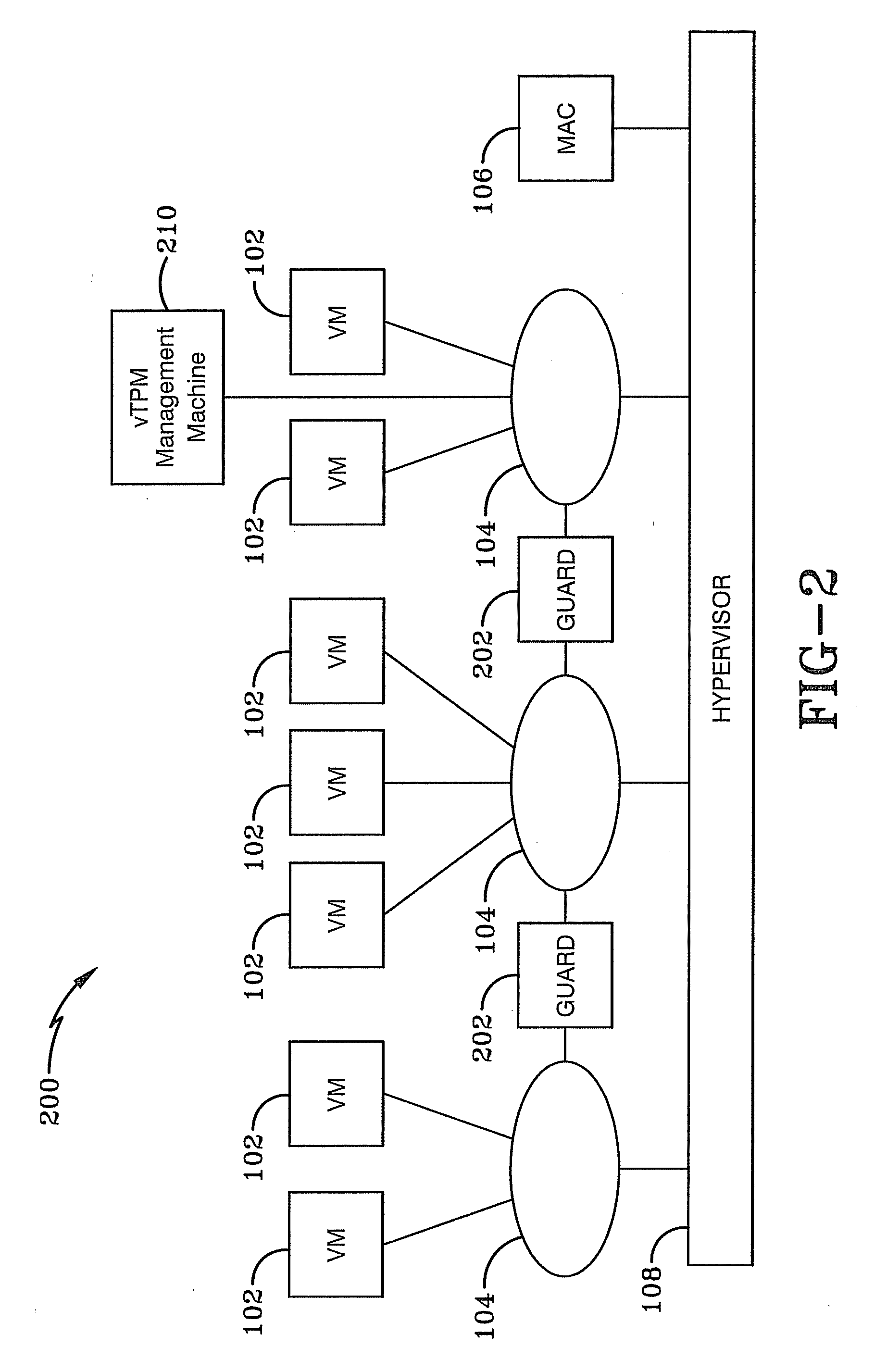
Systems, apparatus and other embodiments associated with a multi-level security (MLS) server framework are presented. An MLS server framework provides a trusted virtual environment to host multiple tenants, categories, classification enclaves and security enclaves. The MLS server framework includes virtual machines, virtual networks, a mandatory access control (MAC), a hypervisor and a virtual trusted platform module (vTPM) management machine. The virtual networks are connected to the virtual machines and the hypervisor is connected to the MAC and the virtual networks. The MAC sets security policies and the hypervisor enforces the security policies and classifies virtual components within a trusted virtual environment formed by the MLS server framework. The vTPM management machine provides attestation of each virtual machine to ensure the MLS server framework is in a secure state.
Owner:BAE SYST NAT SECURITY SOLUTIONS
Modular assembly for a portable hemodialysis system
ActiveUS8562834B2Resist entry of dustAvoid accessSludge treatmentMechanical/radiation/invasive therapiesHaemodialysis machineModularity
A modular assembly for a portable hemodialysis system may include a dialysis unit, e.g., that contains suitable components for performing hemodialysis, such as a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer, and a power unit having a housing that contains suitable components for providing operating power to the pumps of the dialysis unit. The power unit may be selectively connected to the dialysis unit and provide power (e.g., pneumatic power in the form of pressure and / or vacuum) to the dialysis unit for the pumps when connected to the dialysis unit, but may be incapable of providing power to the dialysis unit when disconnected from the dialysis unit. The dialysis unit and the power unit are sized and weighted to each be carried by hand by a human.
Owner:DEKA PROD LLP
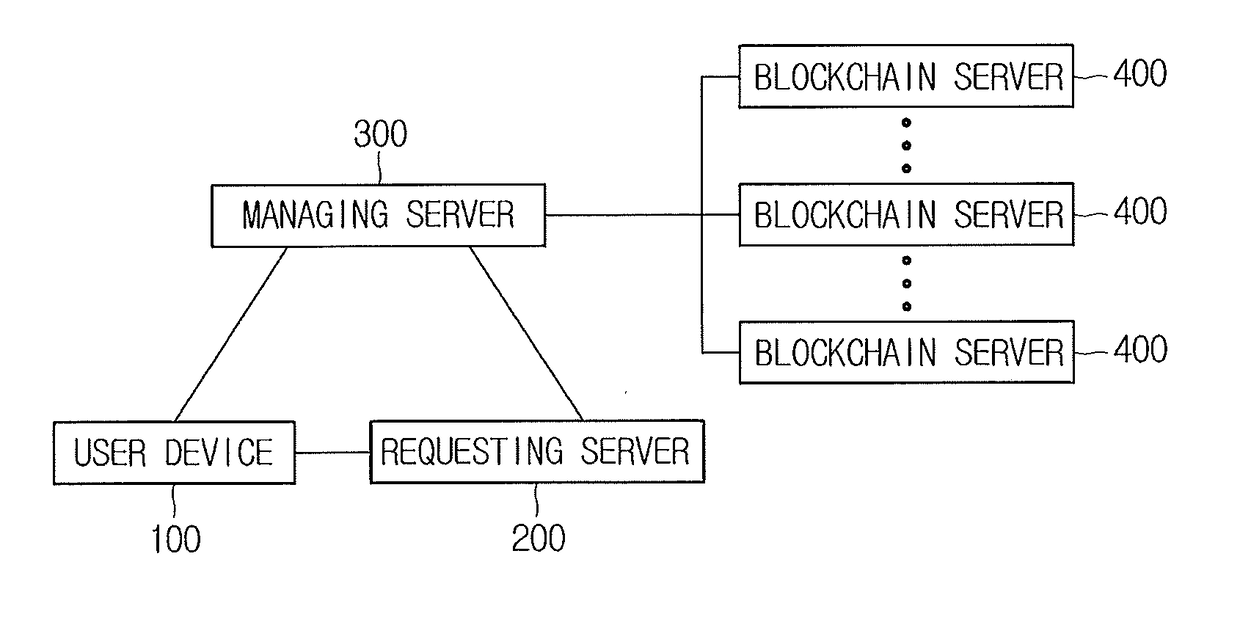
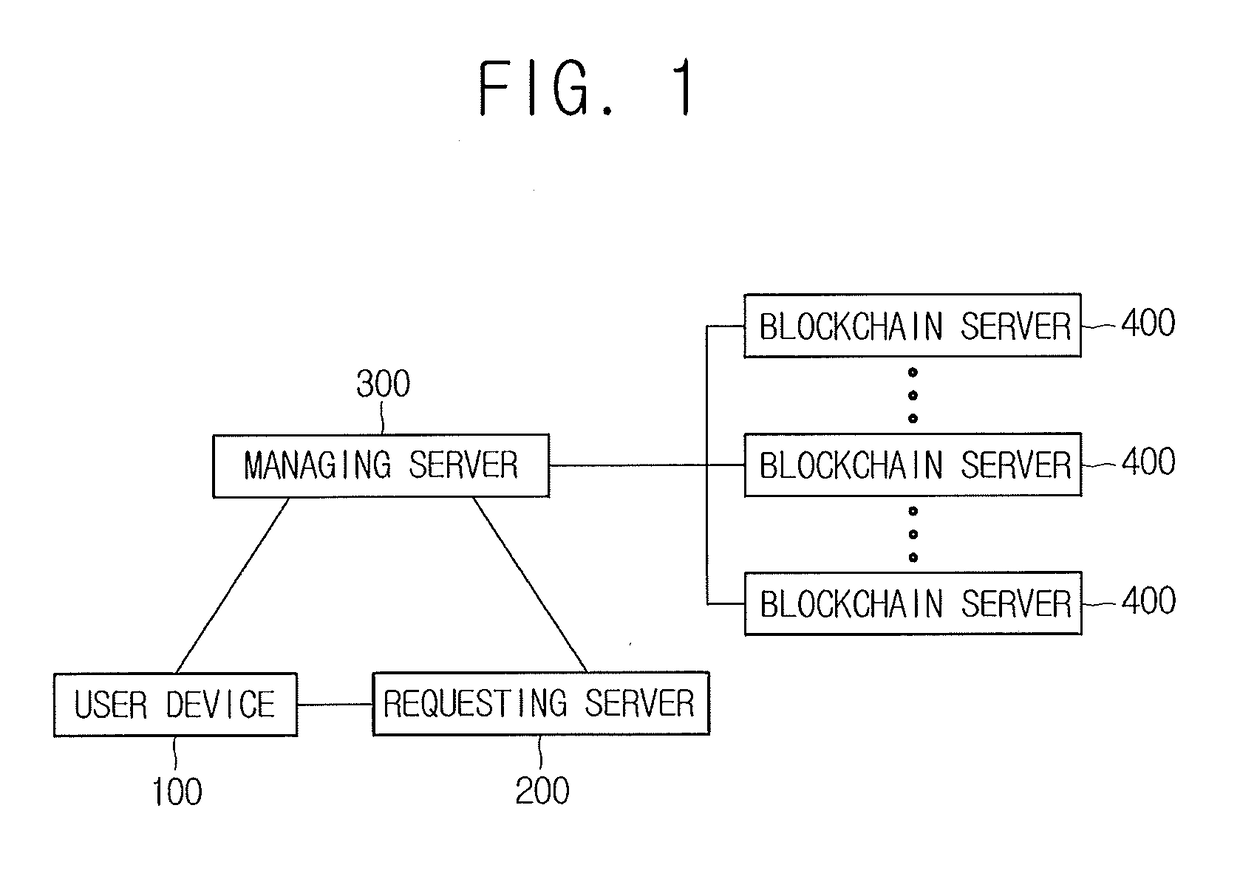
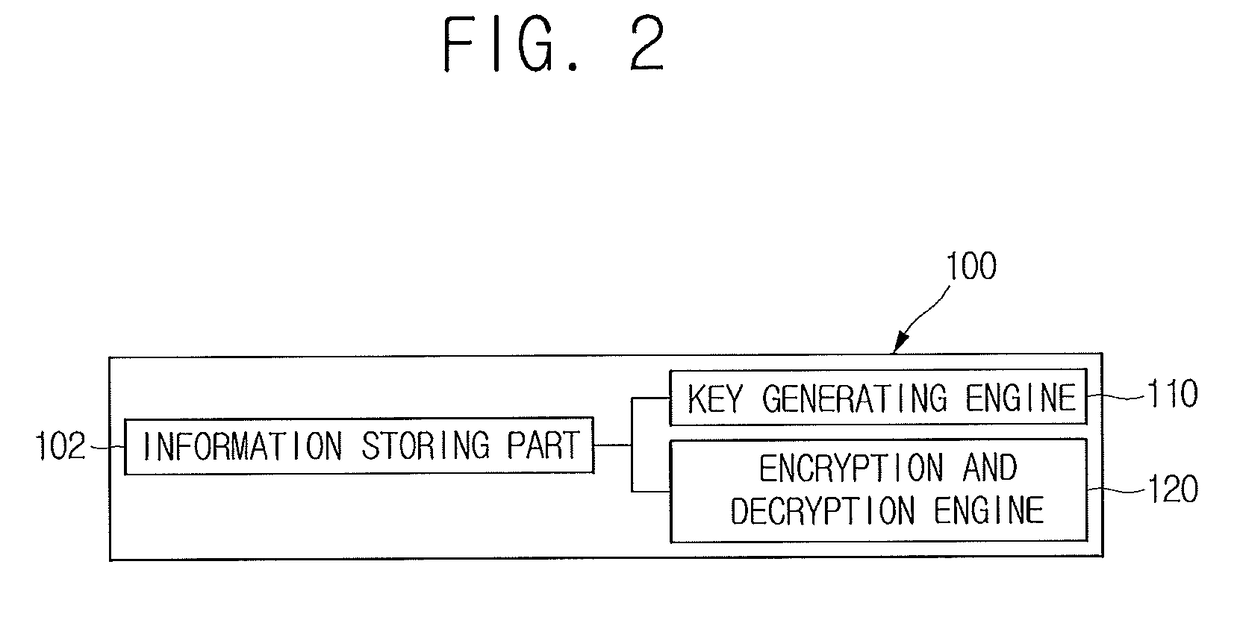
Method for issuing authentication information and blockchain-based server using the same
ActiveUS20170330179A1Avoid connectionNo costPayment protocolsPayment circuitsUser deviceInternet privacy
A method for issuing authentication information is provided. The method includes steps of: (a) a managing server, if identification information of a specific user is acquired from a user device in response to a request for issuing the authentication information and the identification information is determined to be registered, creating a transaction whose output includes: (i) the specific user's public key and (ii) a hash value of the identification information or its processed value to thereby record or support other device to record it on a blockchain; and (b) the managing server acquiring a transaction ID representing location information of the transaction recorded on the blockchain.
Owner:COINPLUG LNC
Dialyzer cartridge mounting arrangement for a hemodialysis system
ActiveUS20100051529A1Easy to useOptimize locationOther blood circulation devicesControl devicesHaemodialysis machineTroffer
A dialyzer mount arranged to support a plurality of differently sized and / or shaped dialyzer units and to accommodate different distances between dialysate connections on the dialyzer units. The dialyzer mount, which may be located on a front panel of the dialysis unit, may include a pair of flange portions that are each arranged to engage with a respective dialysate quick-connect fitting connected to a dialysate port of the dialyzer. Each flange portion may be arranged to engage with a groove on the quick connect fitting that is located between a portion of the base of the quick connect fitting and a slide element of the quick connect fitting. One flange portion may include an adjustable support that is moveable, e.g., in a vertical direction.
Owner:DEKA PROD LLP
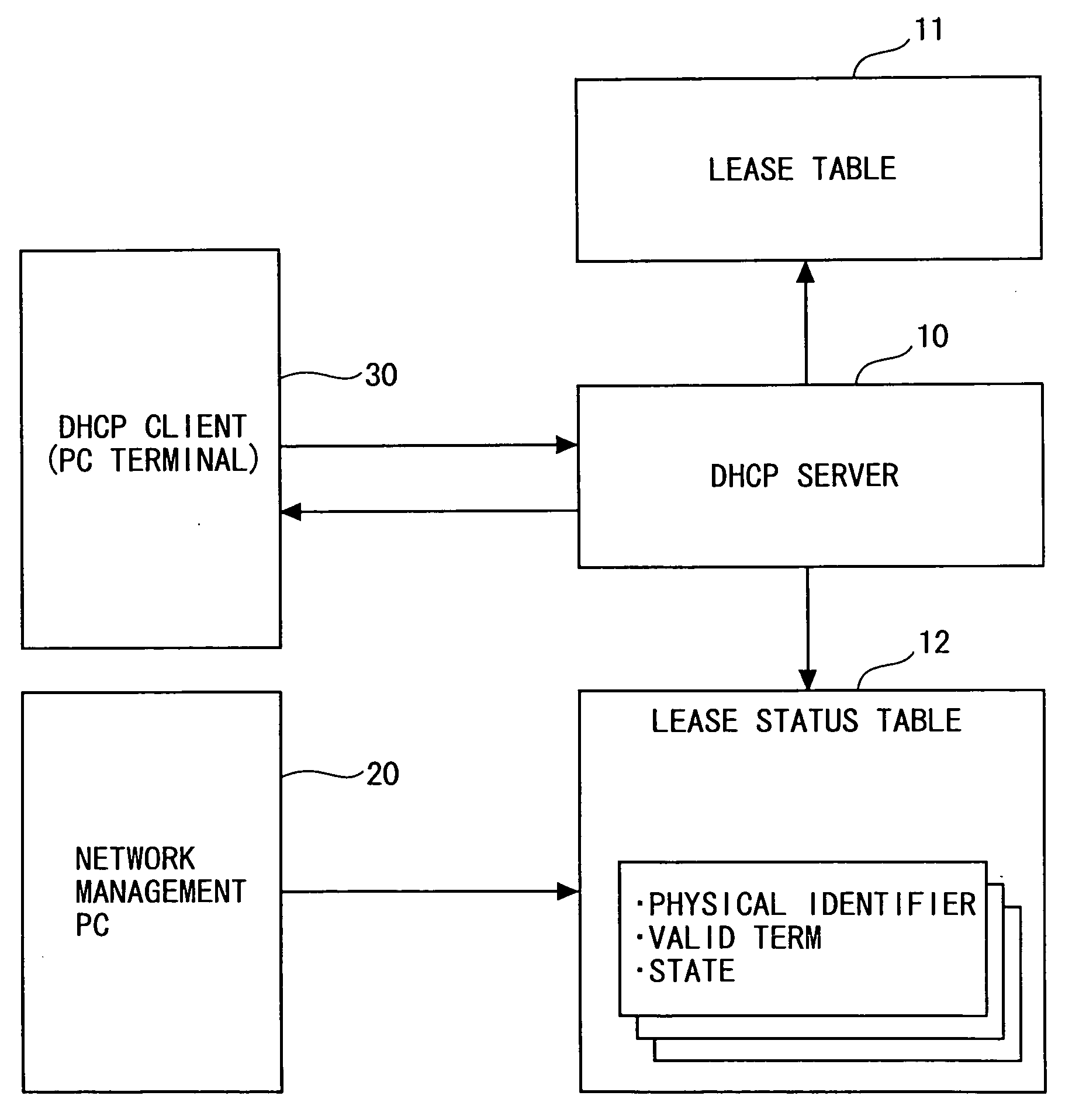
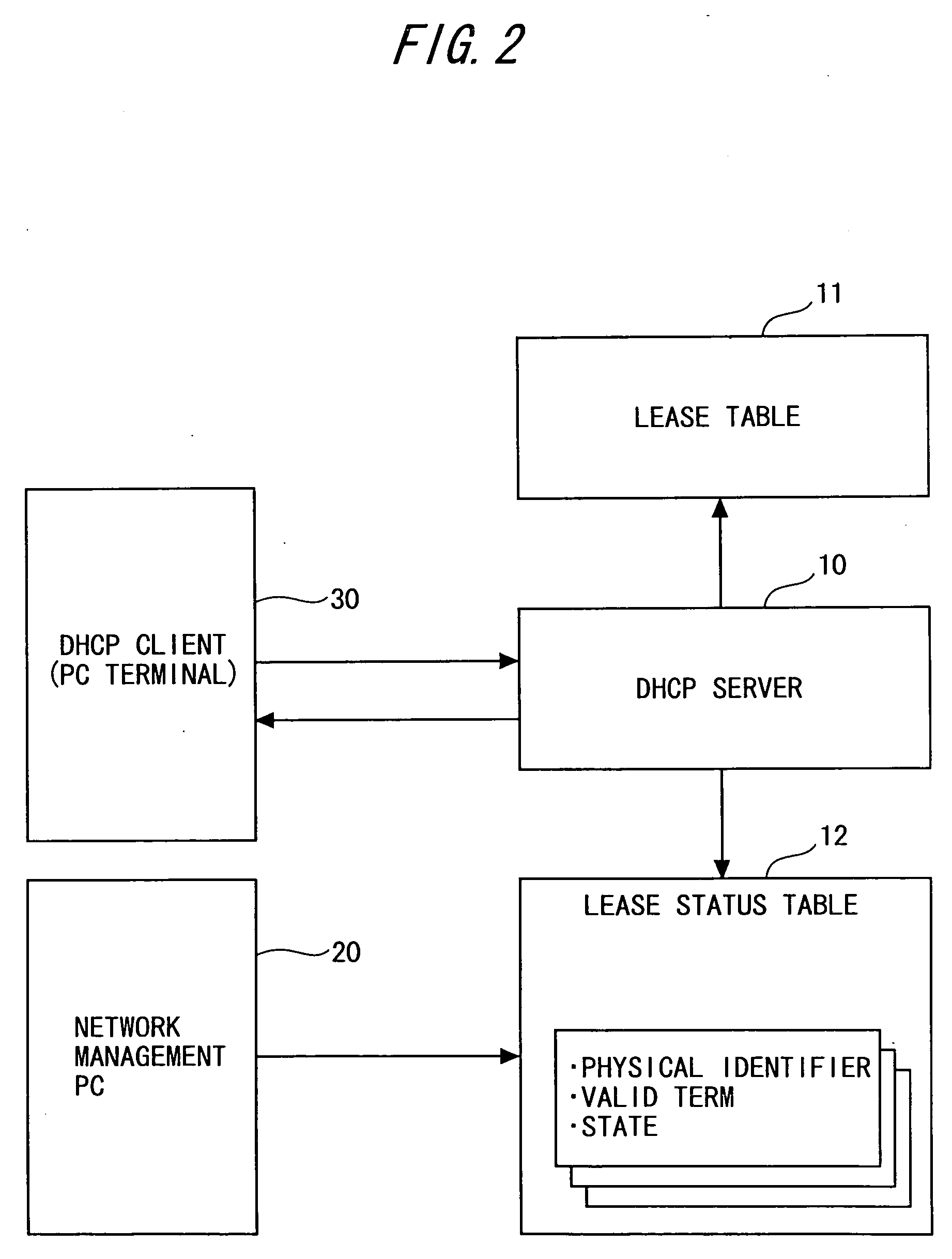
Identifier assignment system, method, and program
InactiveUS20050078681A1Eliminates illegitimate connectionFirmly connectedMultiple digital computer combinationsNetworks interconnectionIp addressDistribution system
An IP address distribution system for distributing an IP address to a client device connected to an IP network based on distribution request information received from the client device, comprises: a lease condition storage unit that stores lease conditions corresponding to the client device indicating conditions relating to approval / prohibition of IP address distribution; an initial control unit that, when the distribution request information is received from the client device, approves the IP address distribution to the client device and stores initial lease conditions corresponding to the client device into lease condition storage unit, if the lease conditions corresponding to the client device are not stored in the lease condition storage unit; a condition modification unit that modifies the lease conditions corresponding to the client device stored in the lease condition storage unit; and an IP address distribution approval / prohibition control unit that controls approval / prohibition of IP address distribution to the client device as a transmission source of the distribution request information, based on the lease conditions corresponding to the client device stored in the lease condition storage unit.
Owner:FUJITSU LTD
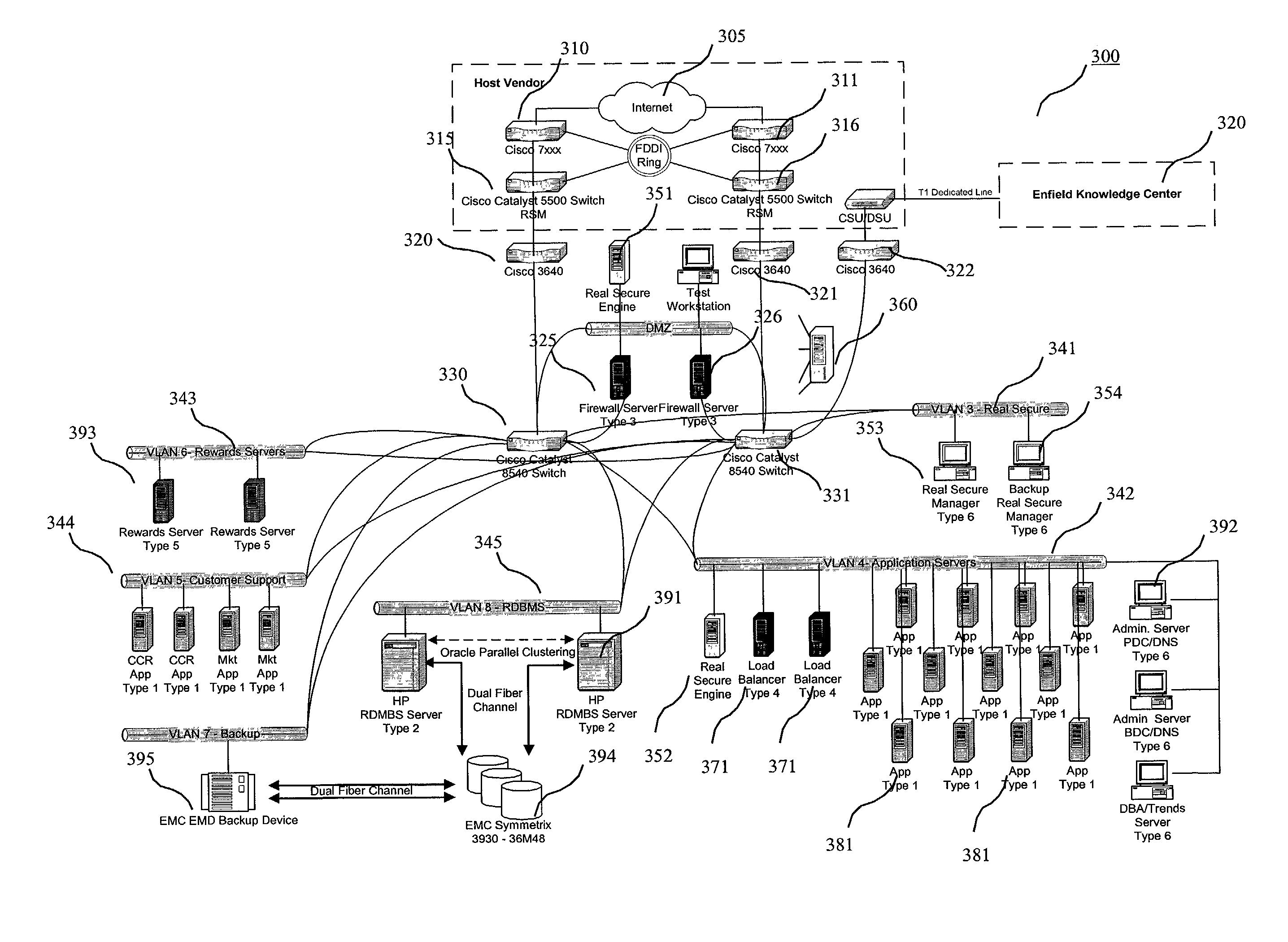
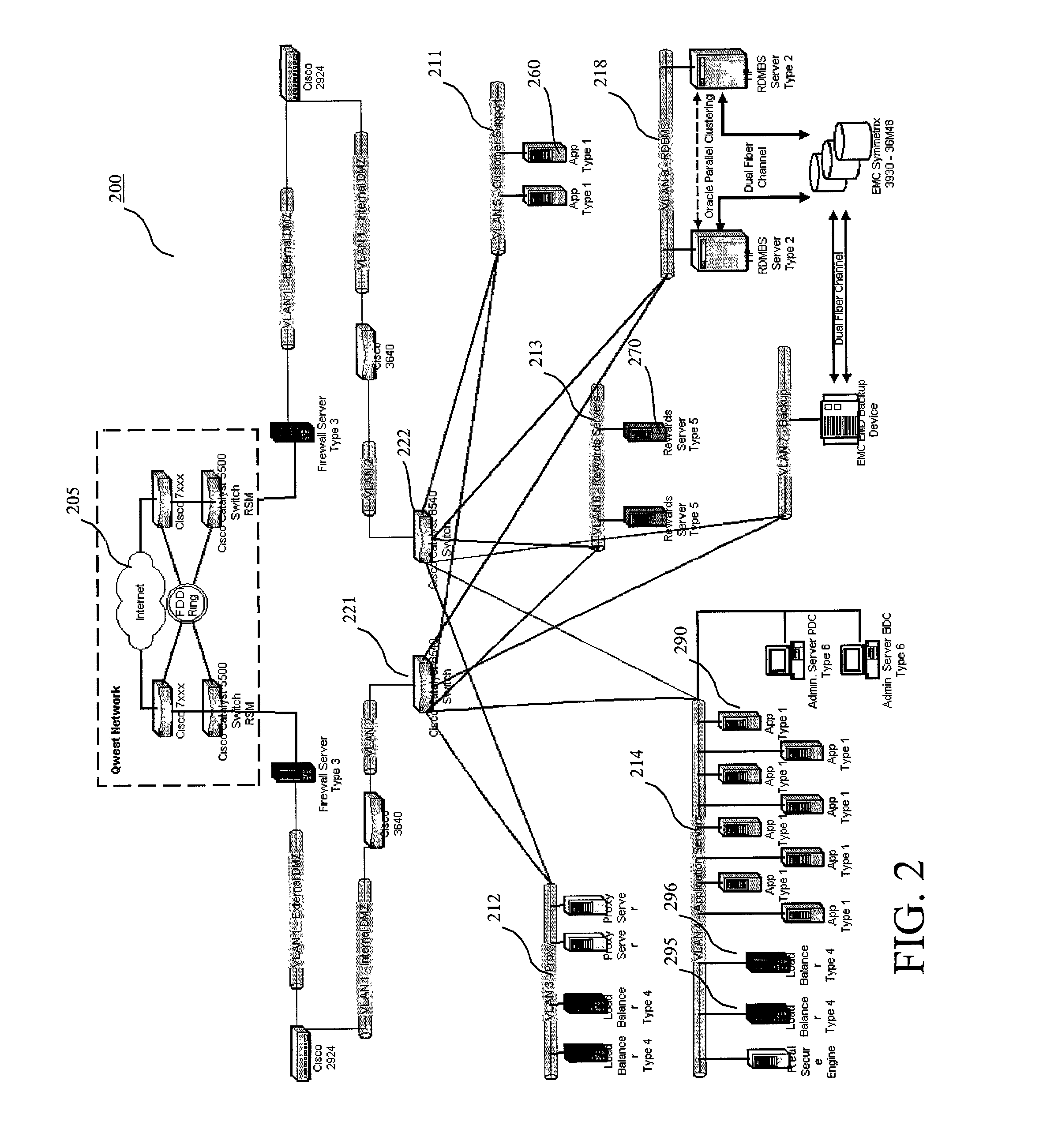
Method and system for internet hosting and security
InactiveUS7007299B2Reduce riskAvoid connectionMemory loss protectionError detection/correctionWeb siteGeolocation
The present invention relates to a system and method for providing security to Internet hosting sites and mitigating electronic attacks against such sites. The system and method of the present invention provide: adequate Internet connections to the site to prevent connection floodings from intruders; implementation of different types of firewalls and an intrusion detection system to monitor and guard the site from electronic attacks; routing protocols to limit access to Internet hosting sites; continuous transfer of a hosting site from one geographic location to another in the event of an electronic attack against the hosting site or a disaster situation.
Owner:CITIBANK
Data transfer error checking
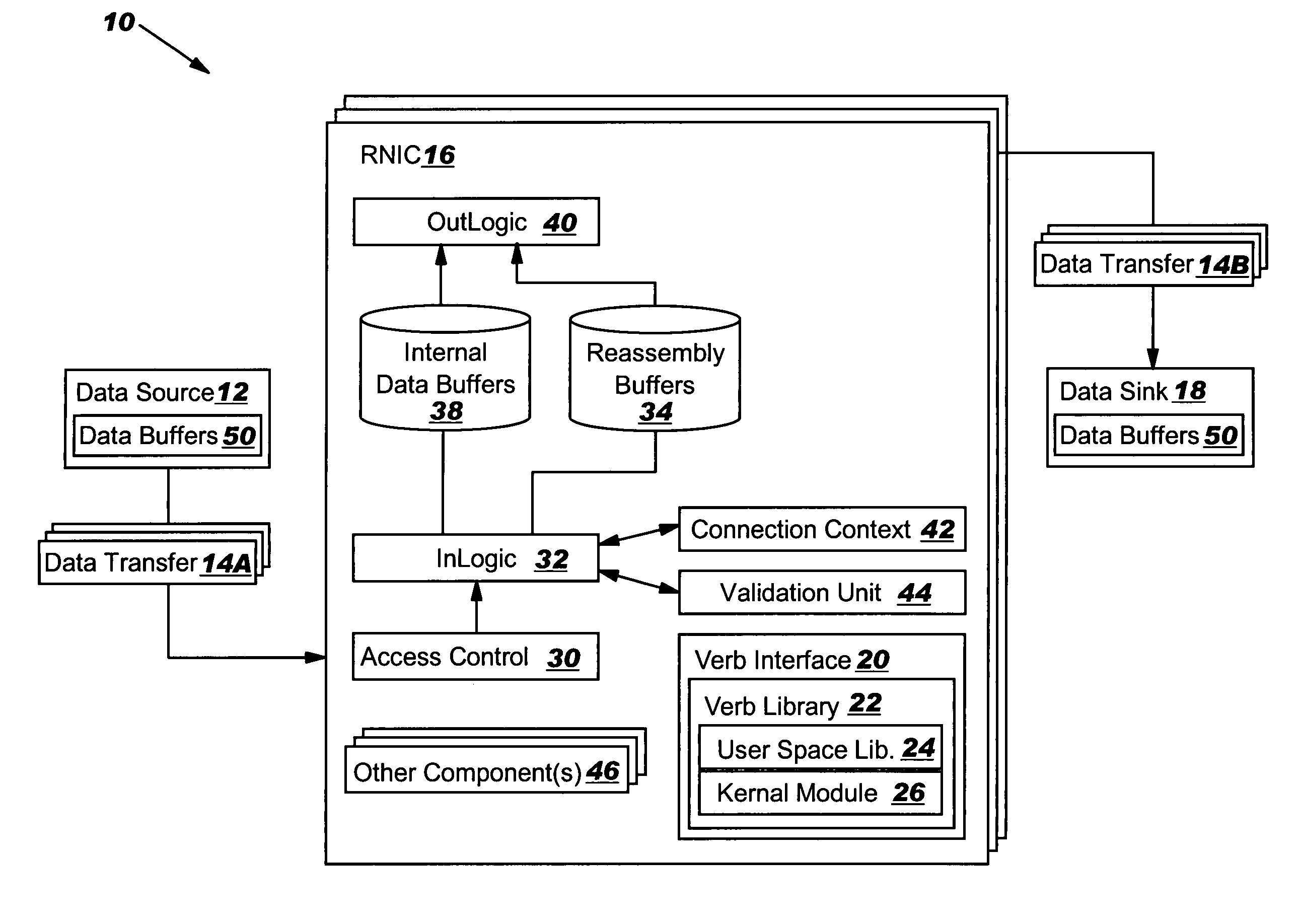
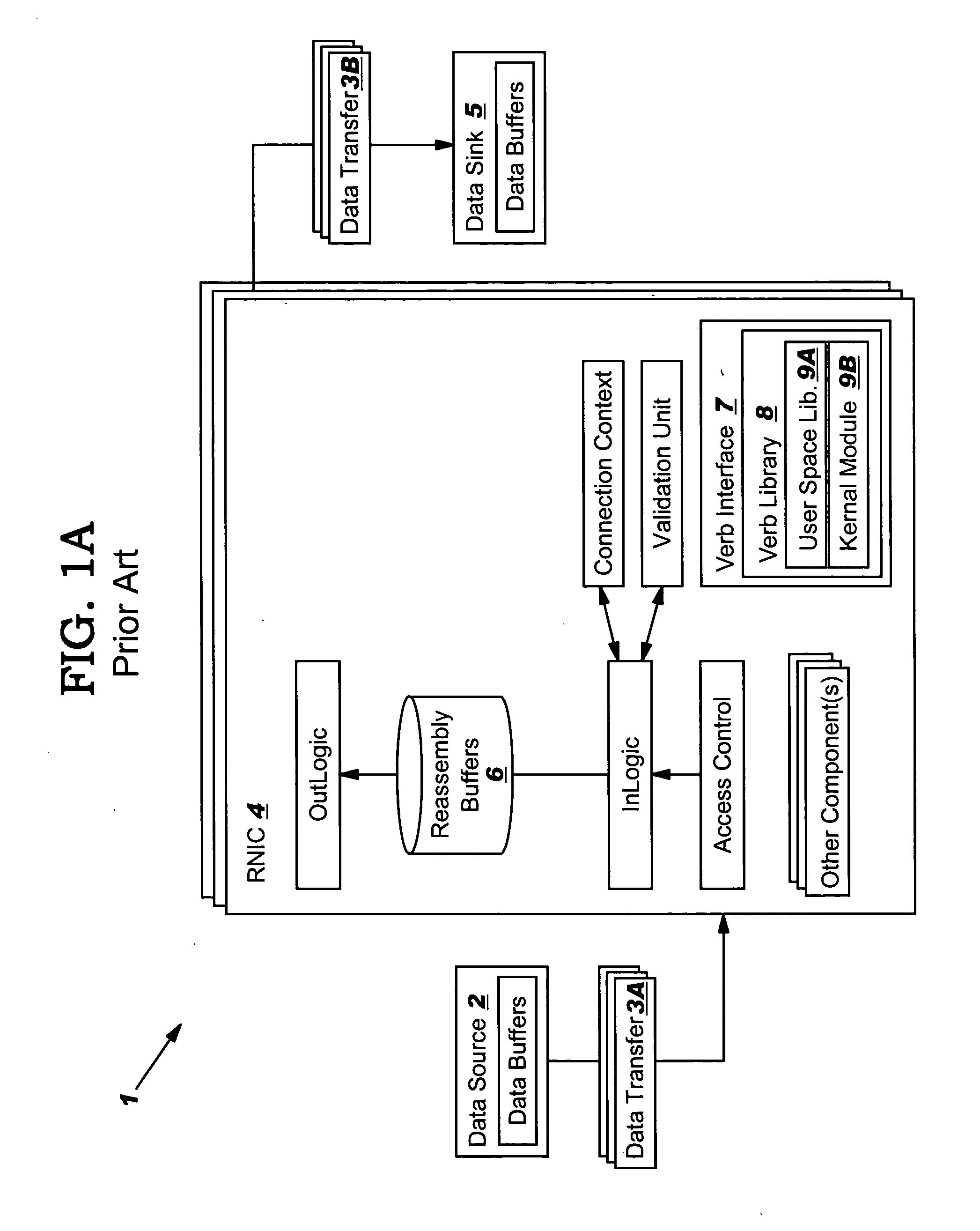
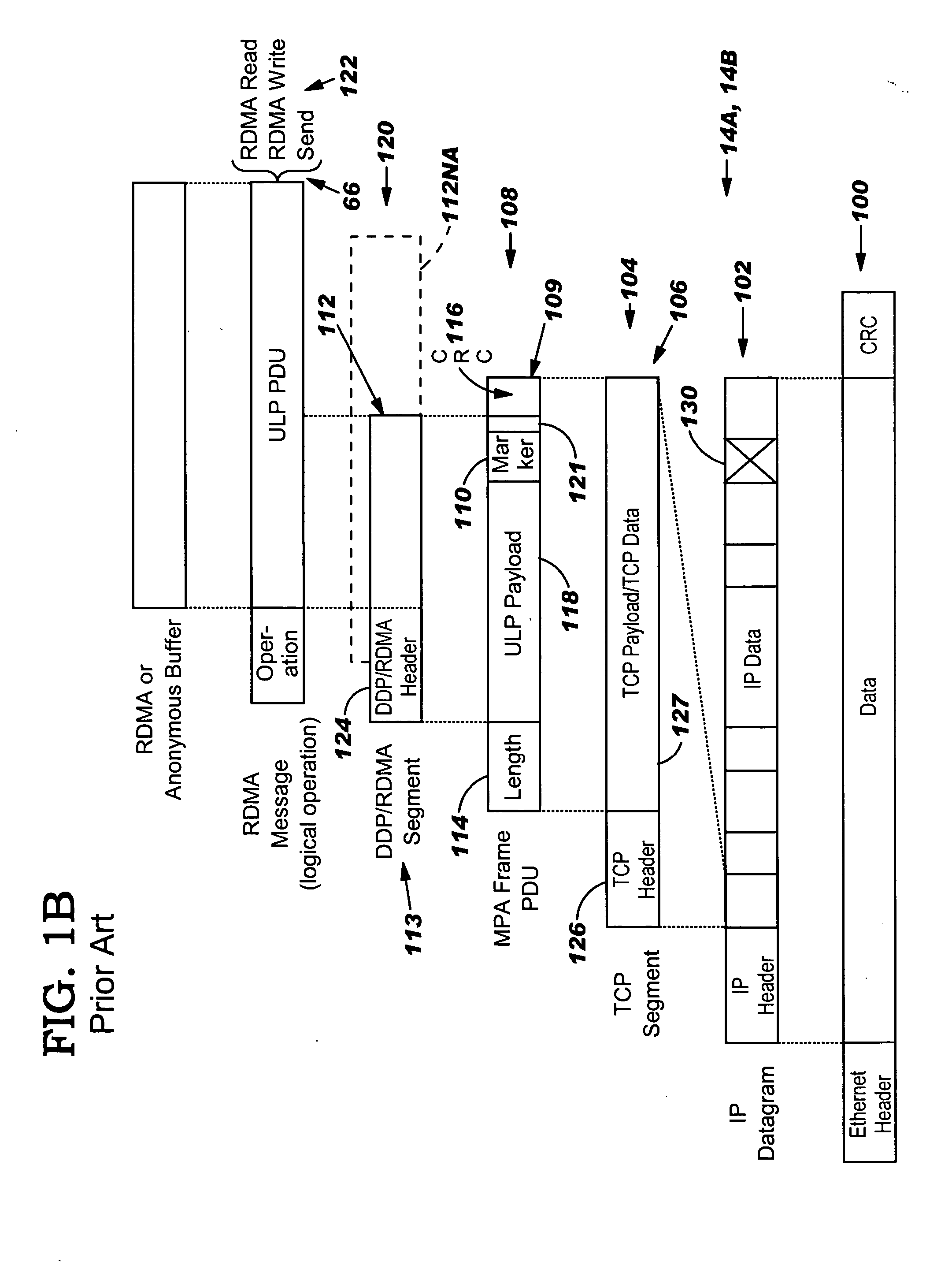
InactiveUS20050149817A1Reduce memory bandwidthReduce latencyCode conversionError detection onlyConnection typeData placement
An RNIC implementation that performs direct data placement to memory where all segments of a particular connection are aligned, or moves data through reassembly buffers where all segments of a particular connection are non-aligned. The type of connection that cuts-through without accessing the reassembly buffers is referred to as a “Fast” connection because it is highly likely to be aligned, while the other type is referred to as a “Slow” connection. When a consumer establishes a connection, it specifies a connection type. The connection type can change from Fast to Slow and back. The invention reduces memory bandwidth, latency, error recovery using TCP retransmit and provides for a “graceful recovery” from an empty receive queue. The implementation also may conduct CRC validation for a majority of inbound DDP segments in the Fast connection before sending a TCP acknowledgement (Ack) confirming segment reception.
Owner:IBM CORP
Fluid coupling with disposable connector body
A coupling apparatus for fluid dispensing with a disposable connector on the fluid line or fluid dispensing system side. The coupling apparatus includes an insert body that is connectable with a disposable connector device. The insert body includes a recess area defined between a first inner sidewall and a second inner sidewall. The second inner sidewall extends coaxially with the first inner sidewall, and has an aperture defining an opening through a first and second end. The connector device includes a connector body connected with an adapter portion. The connector body includes a beveled end that is insertable through the aperture of the second inner sidewall. The adapter portion is disposed proximate and extends past the beveled end, where the beveled end is recessed within the adapter portion. An insertion space is defined between the beveled end and an outer wall defined by the adapter portion. The adapter portion is insertable into the recess area and the insertion space is receivable of the second inner sidewall.
Owner:COLDER PRODS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com