Patents
Literature
35results about How to "Access is denied" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
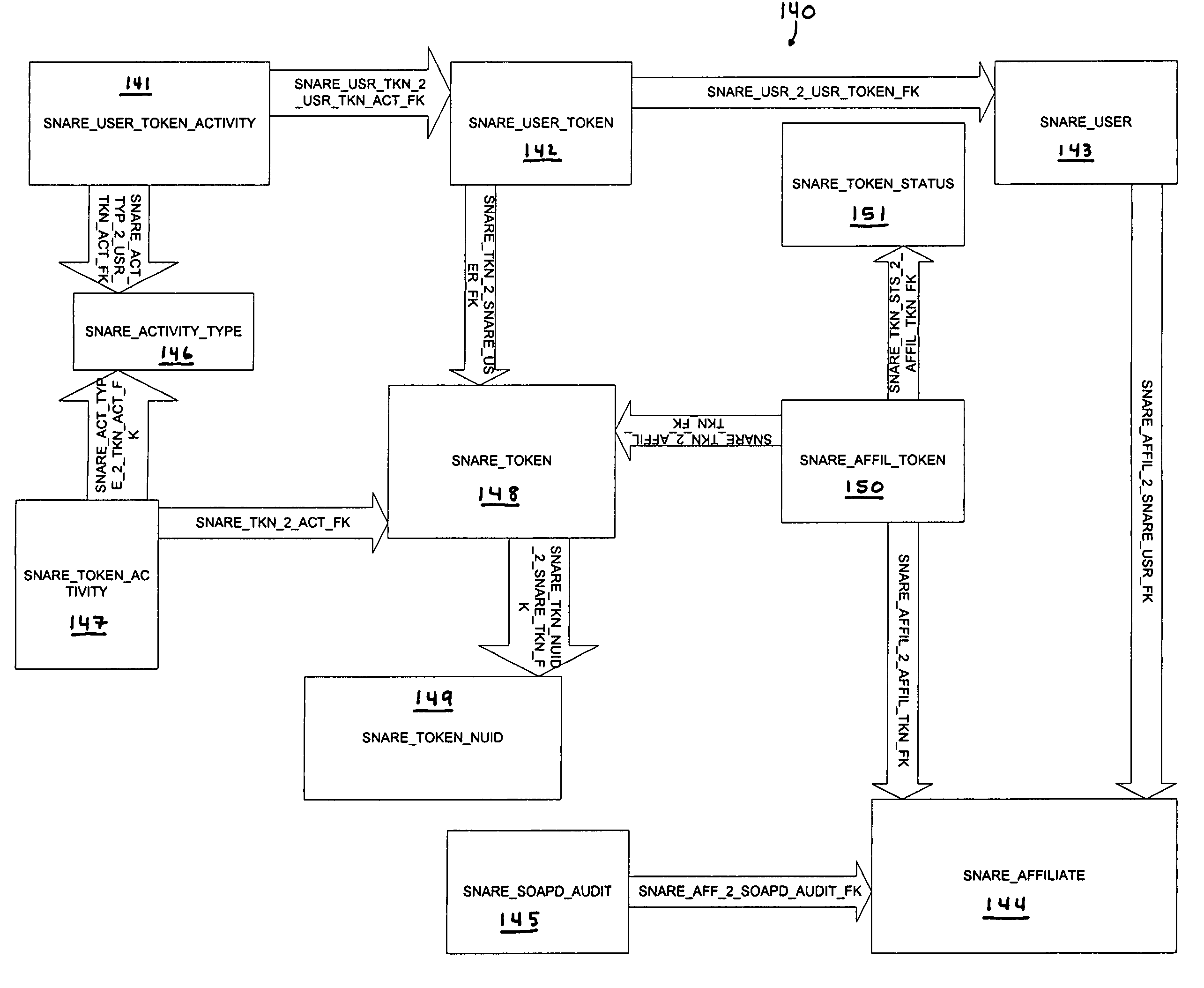
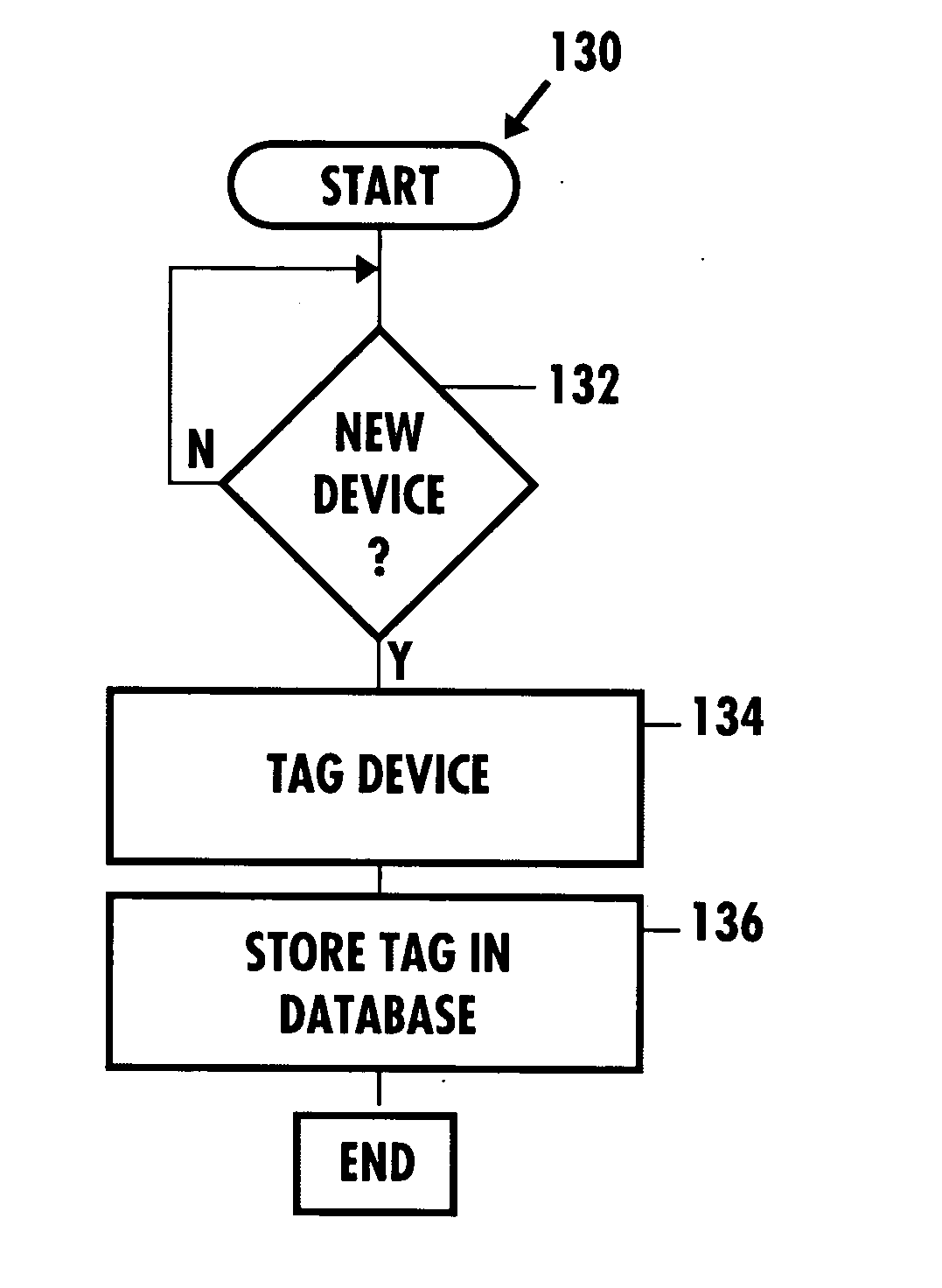
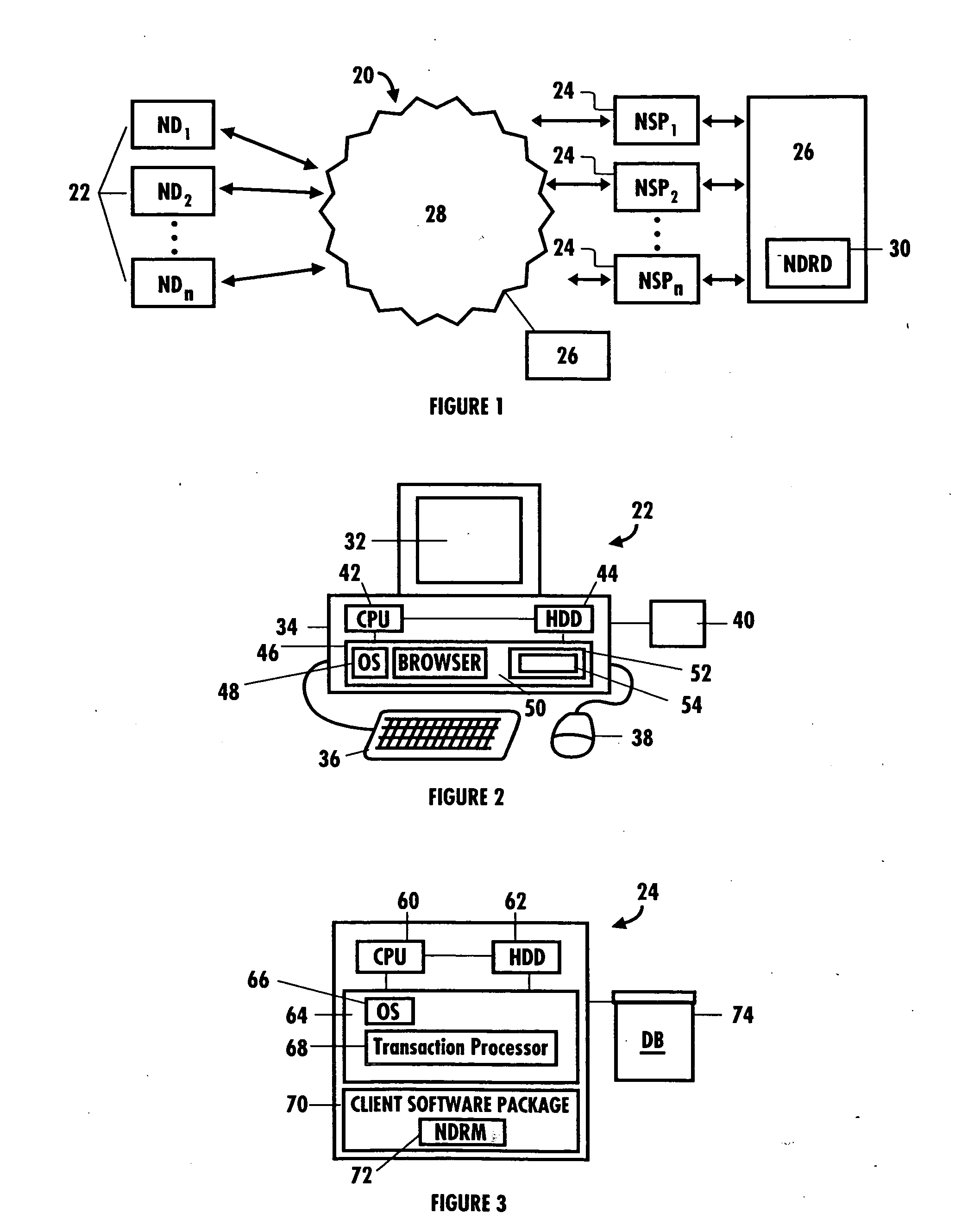
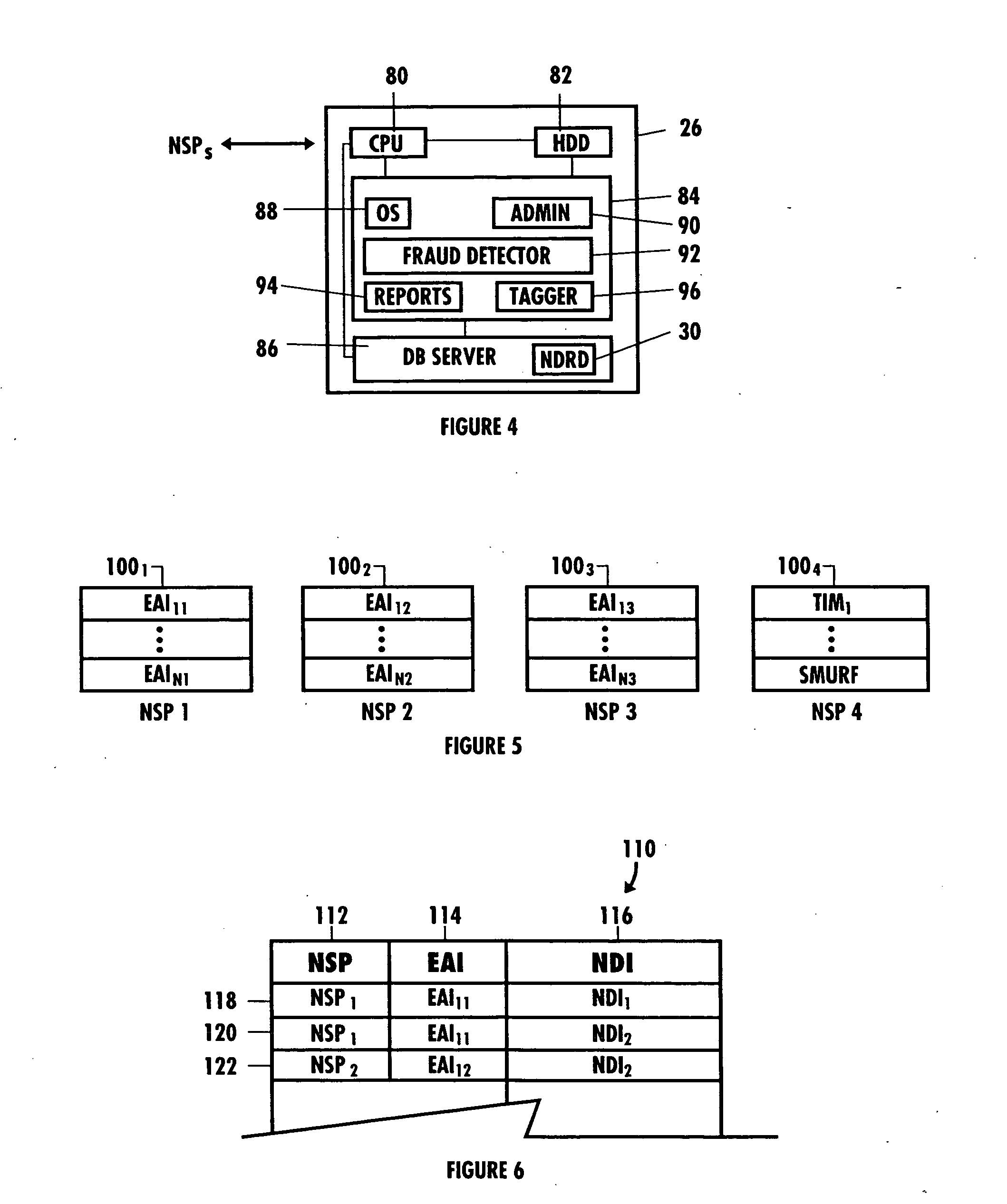
Network security and fraud detection system and method
ActiveUS7272728B2Avoid connectionAccess is deniedUser identity/authority verificationUnauthorized memory use protectionNetwork security policyNetwork service
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
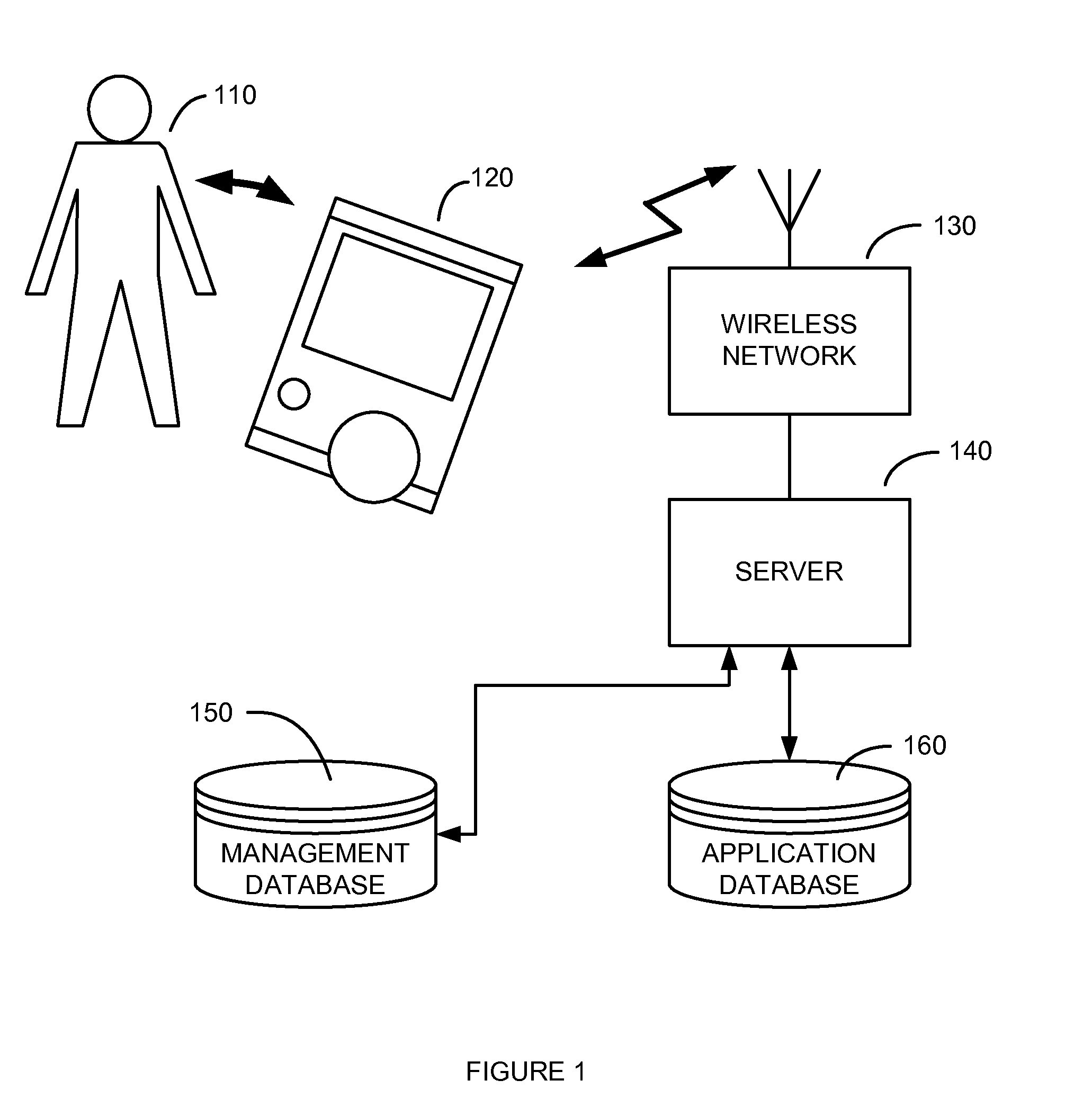
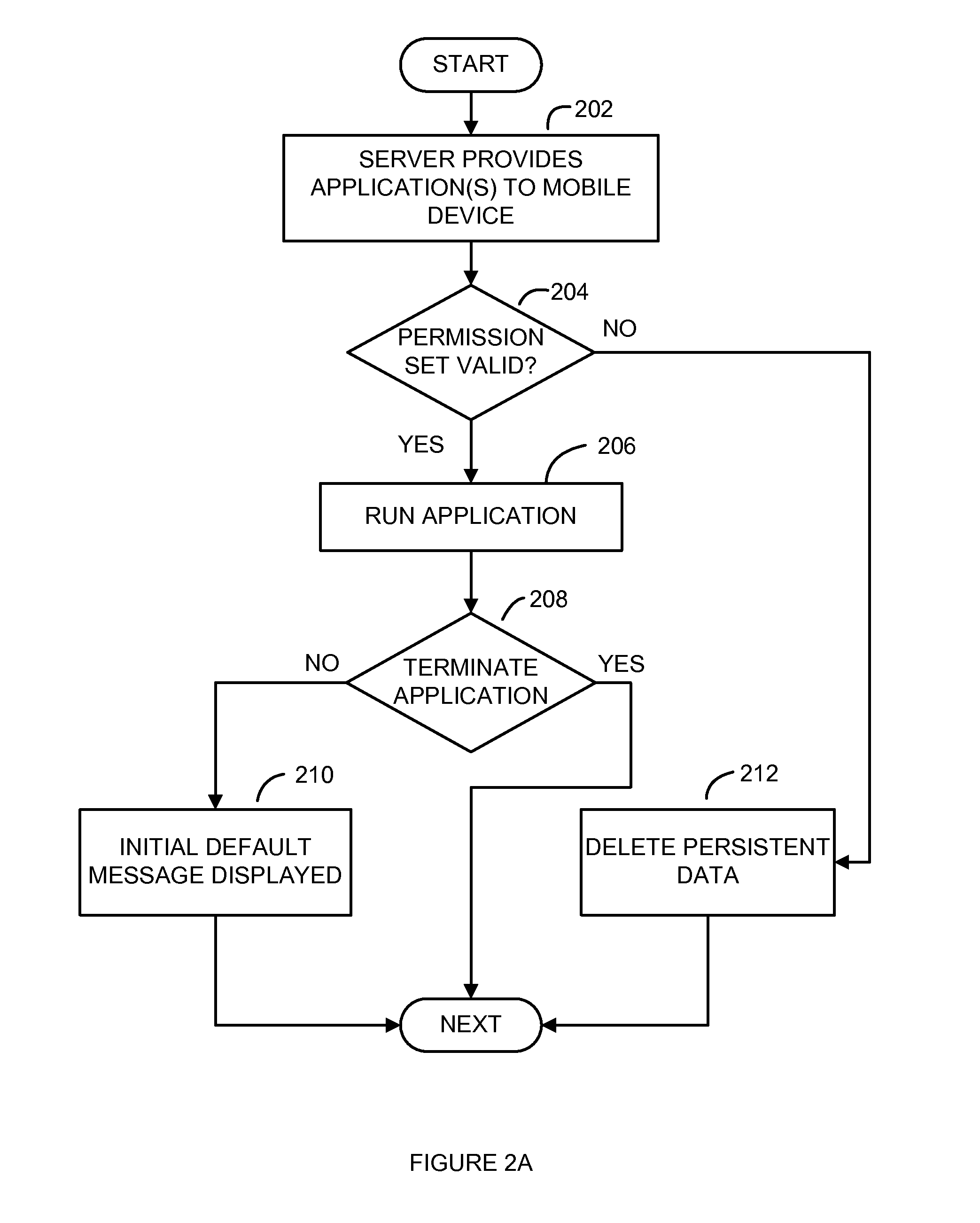
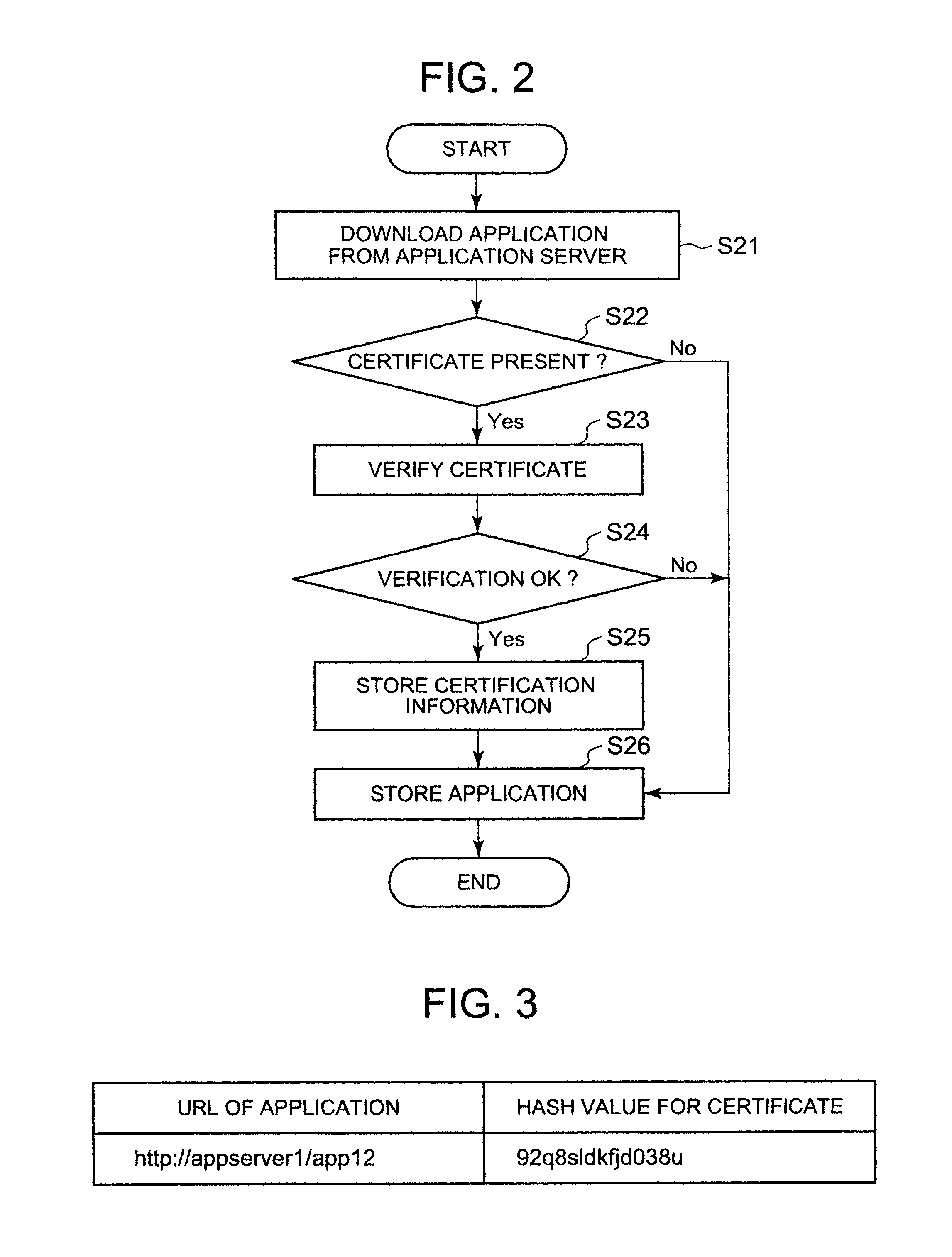
System and Method for Remote Management of Applications Downloaded to a Personal Portable Wireless Appliance
ActiveUS20110145932A1Access is deniedDigital data processing detailsAnalogue secracy/subscription systemsApplication softwareData structure
The present invention relates to a system and method for remote management of applications downloaded to a personal portable appliance. Applications comprising programs and data structures are updated to include a dummy application that can replace the ordinarily executable application and that manipulates the data structure when invoked, so as to limit it. The dummy application is subsequently reduced to have a limited amount of the original functionality and to prompt the user to delete it.
Owner:MALIKIE INNOVATIONS LTD
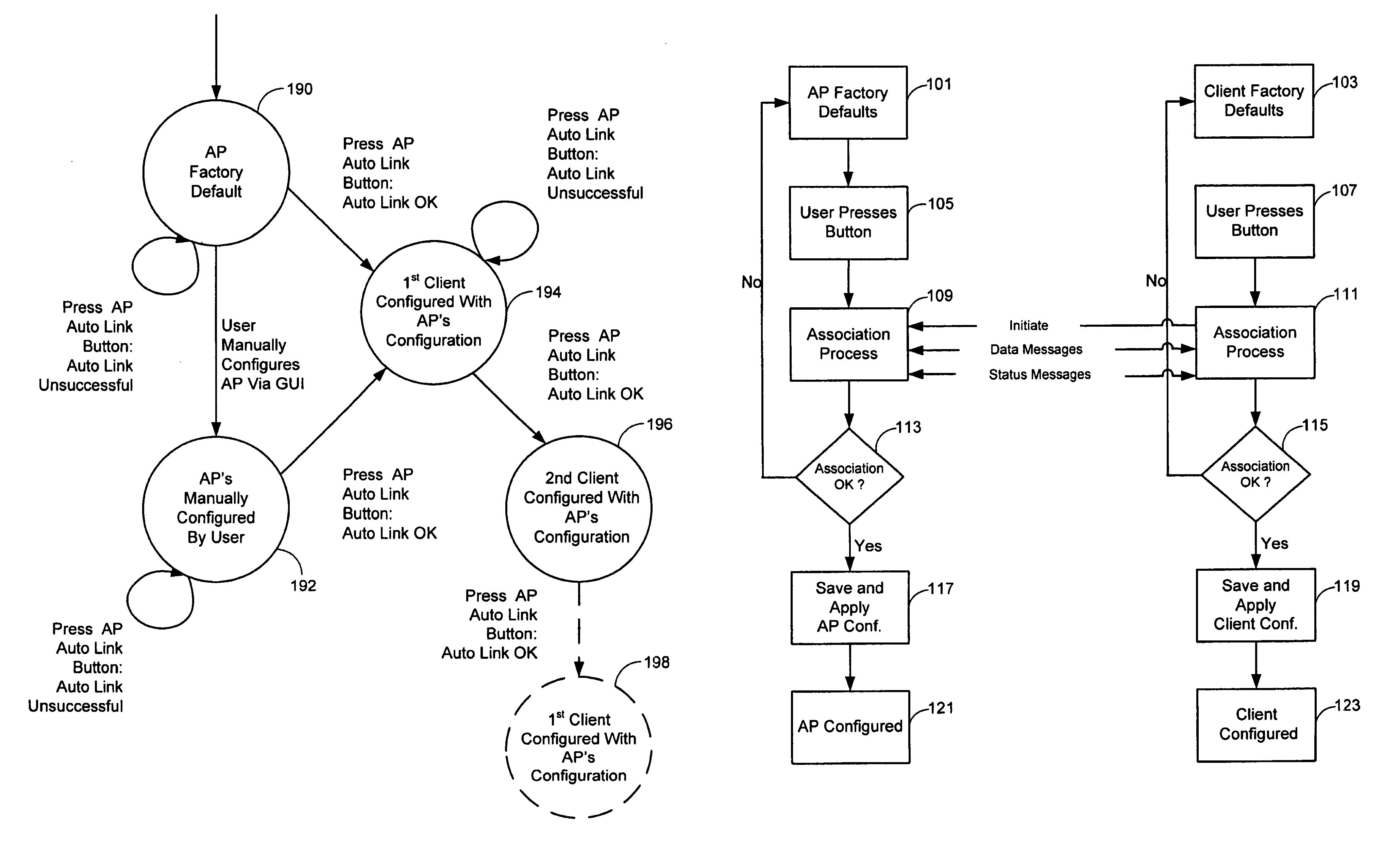
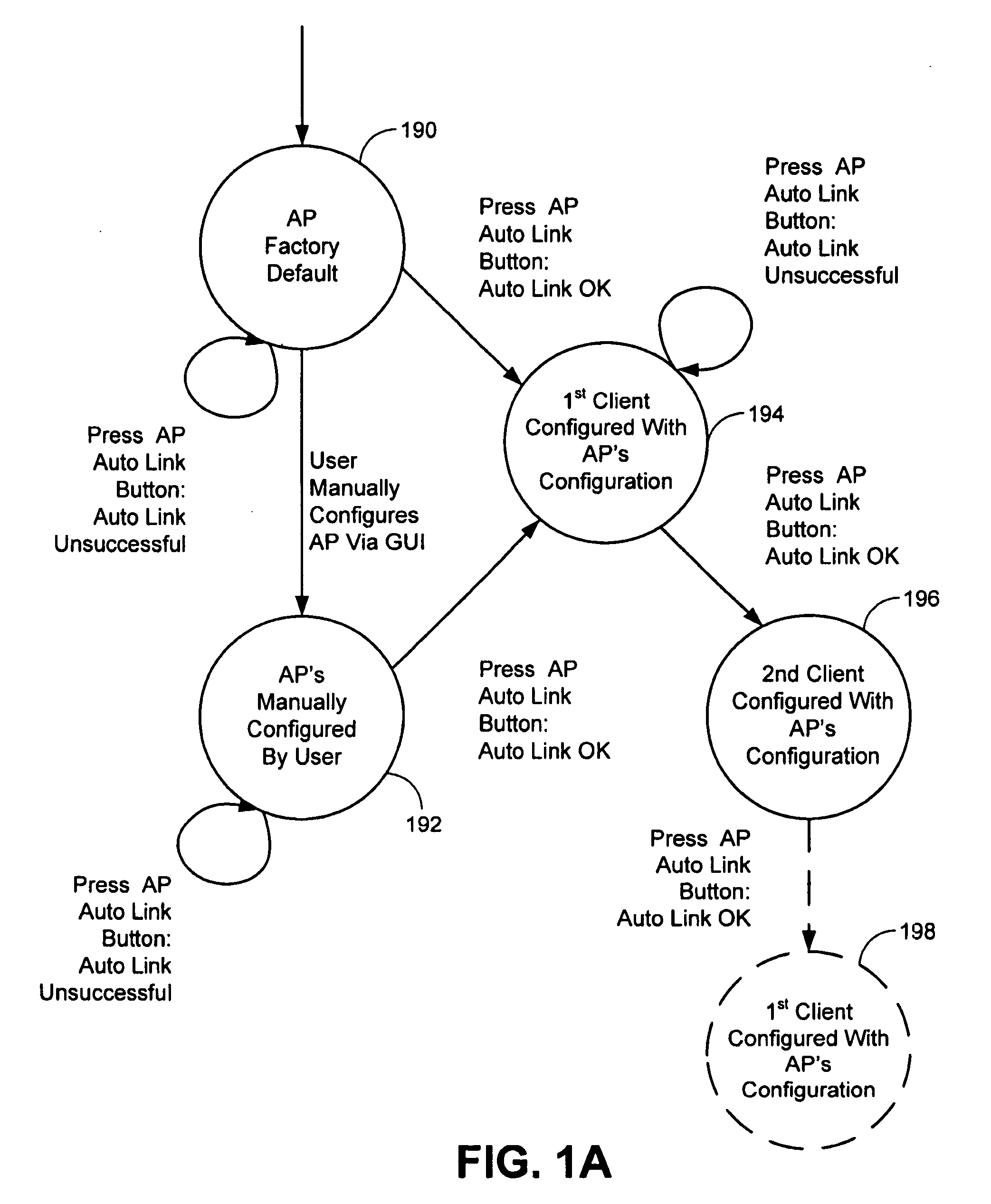
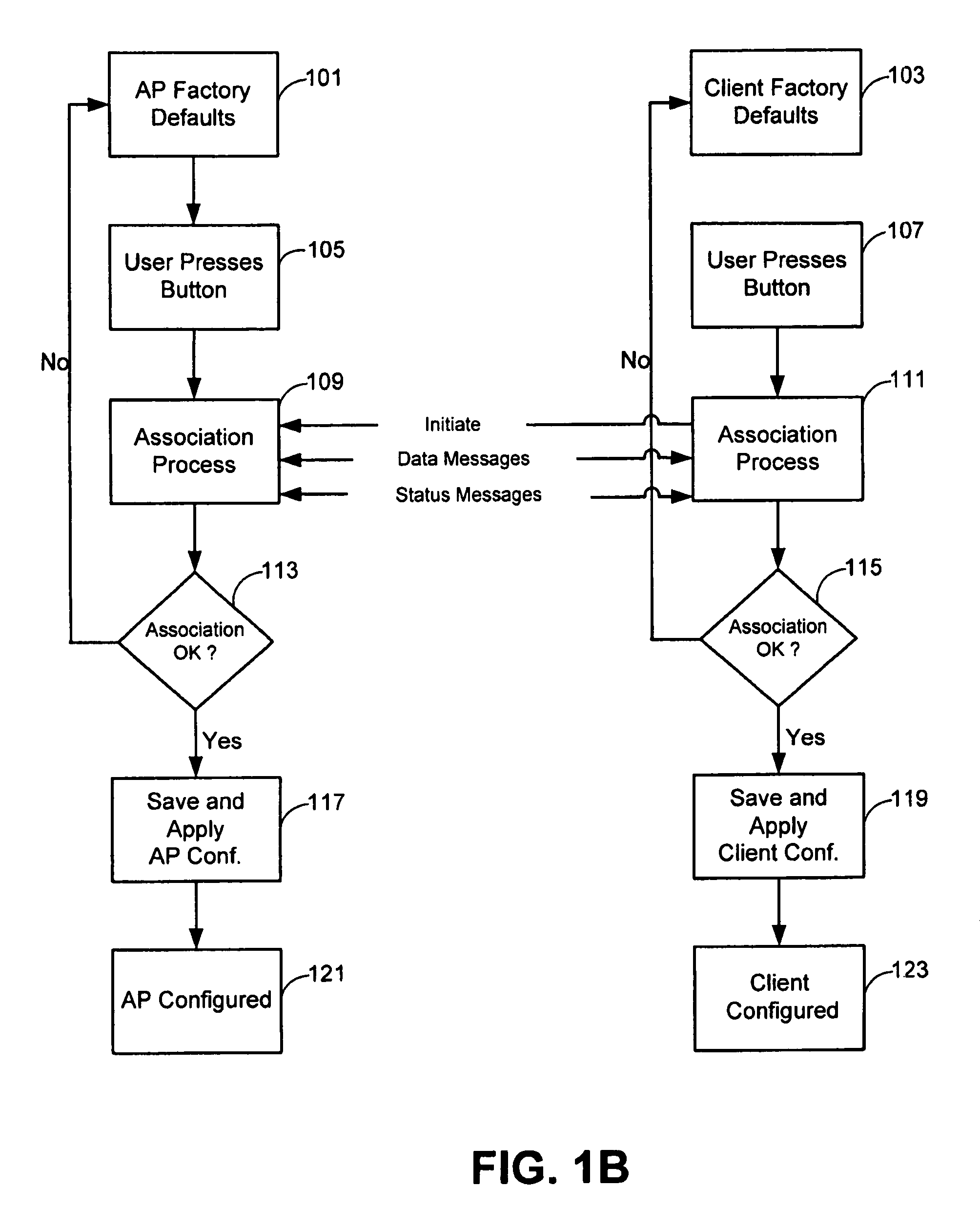
Enhanced association for access points
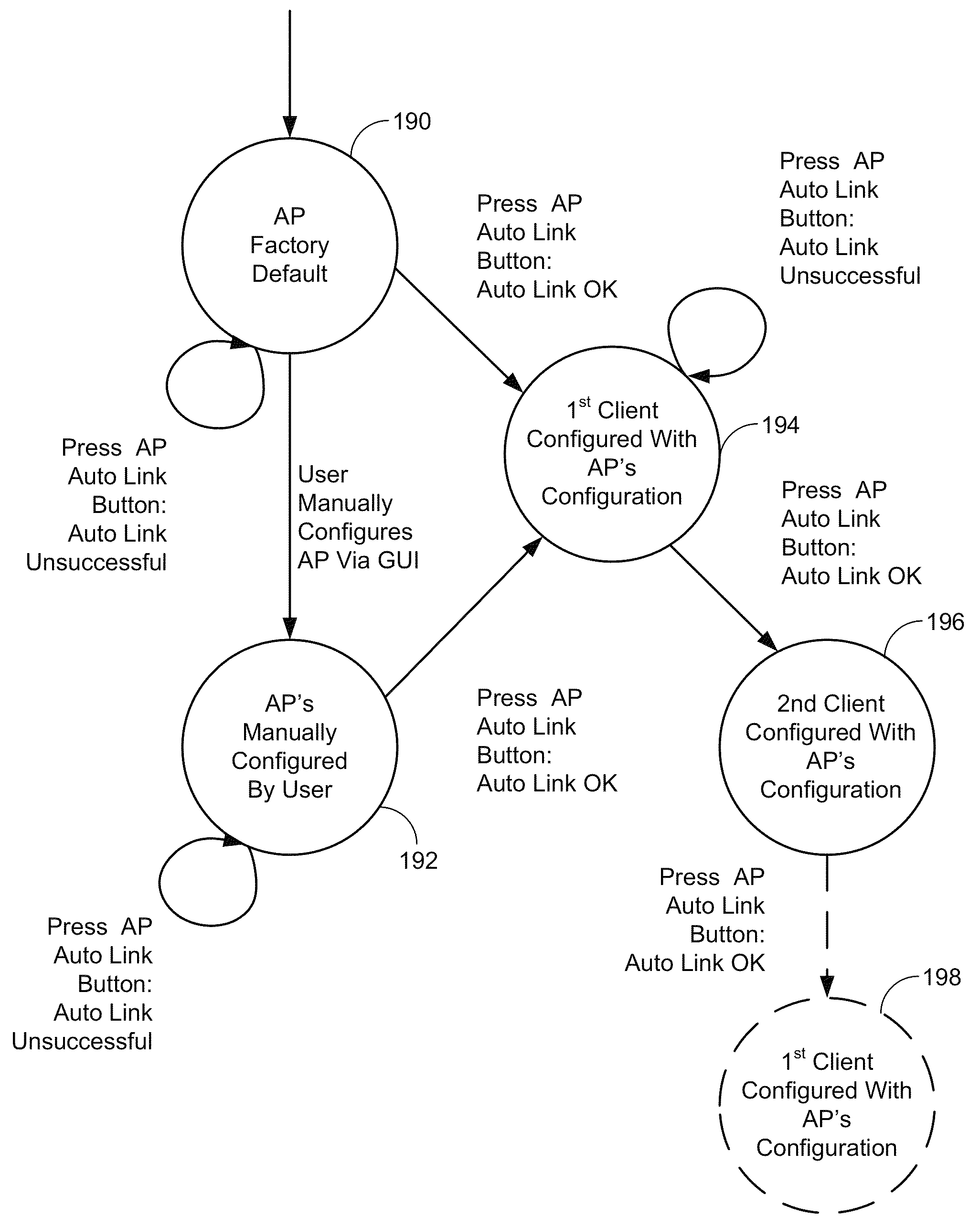
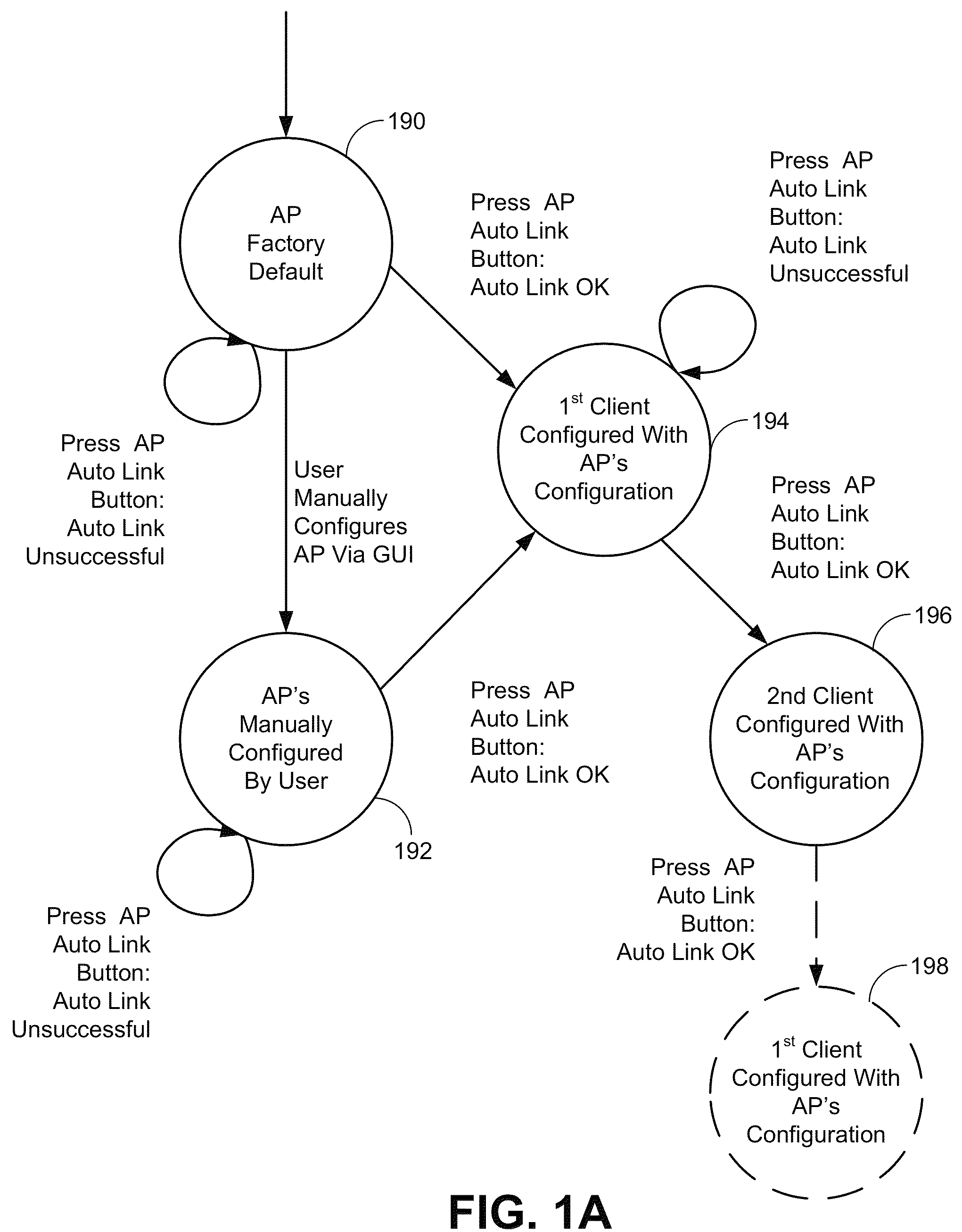
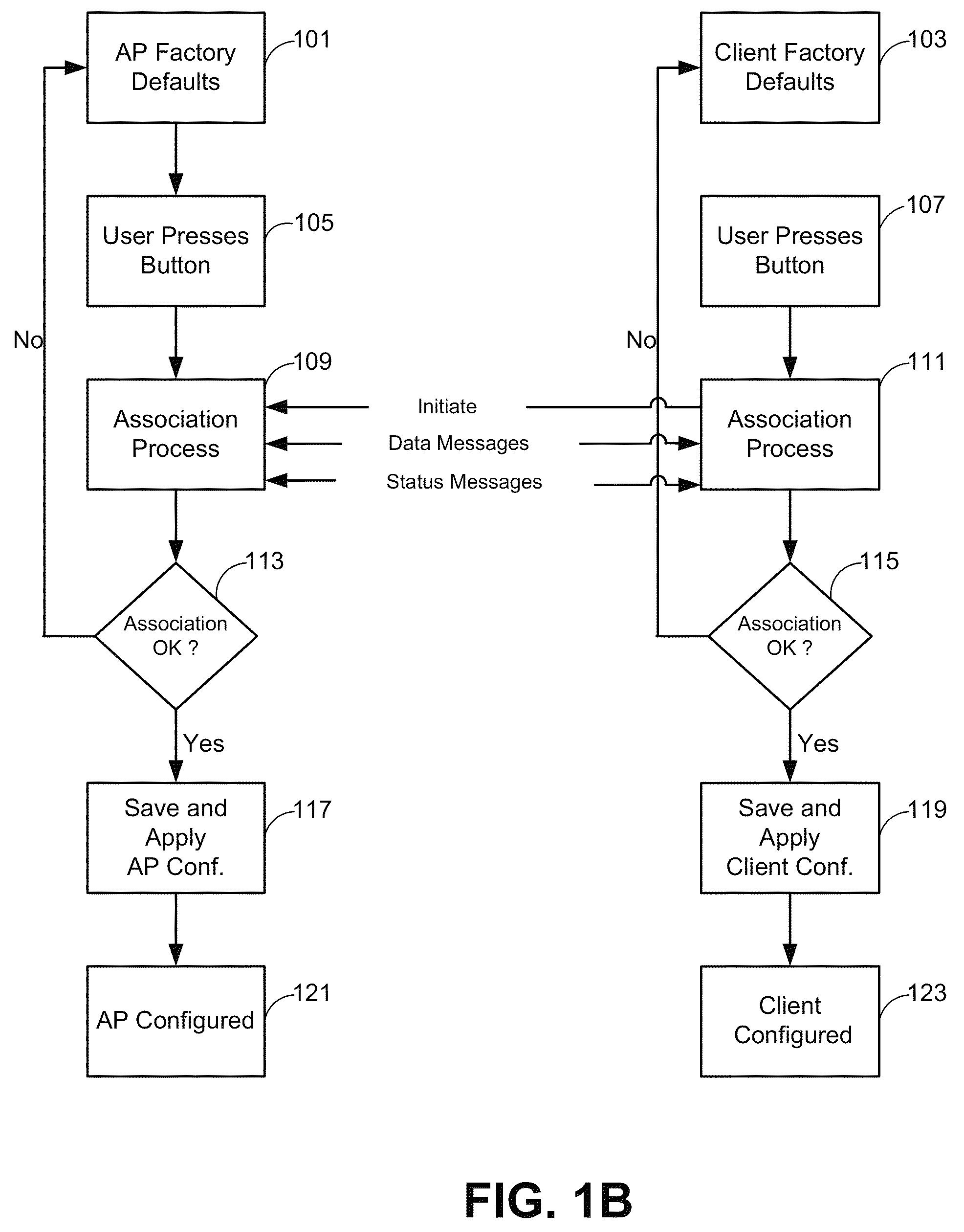
ActiveUS8126145B1Reduce the possibilitySmall rangeData switching by path configurationSecret communicationClient-sideHandshake
The invention relates to a method for associating a client with an access point using a security protocol. The method may include initiating a handshake and exchanging operational information between the access point and the client, establishing an encrypted operational key if the operational information is validated and entering an operational phase using the operational key and an unique service set identifier if valid.
Owner:MARVELL ASIA PTE LTD
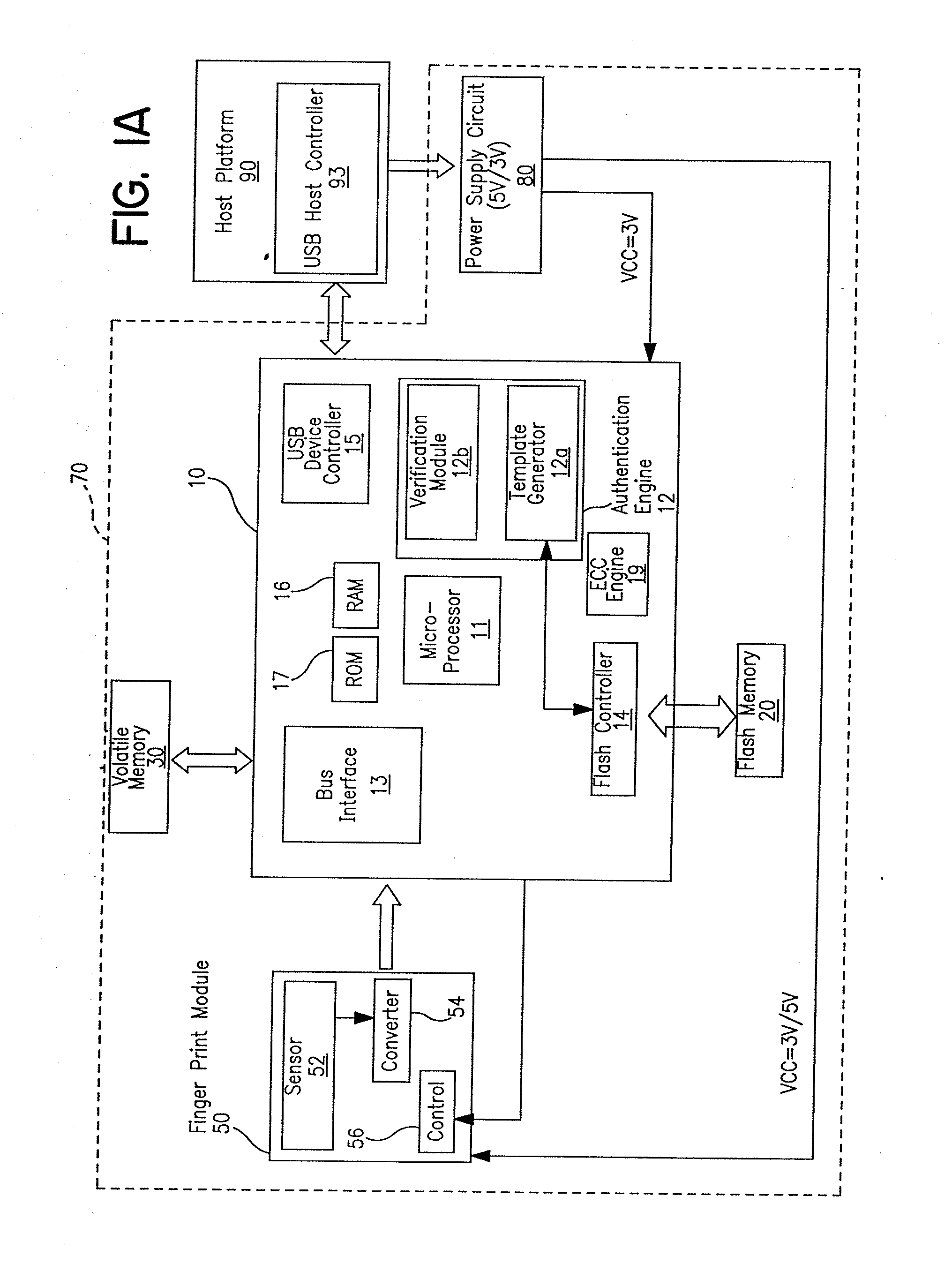
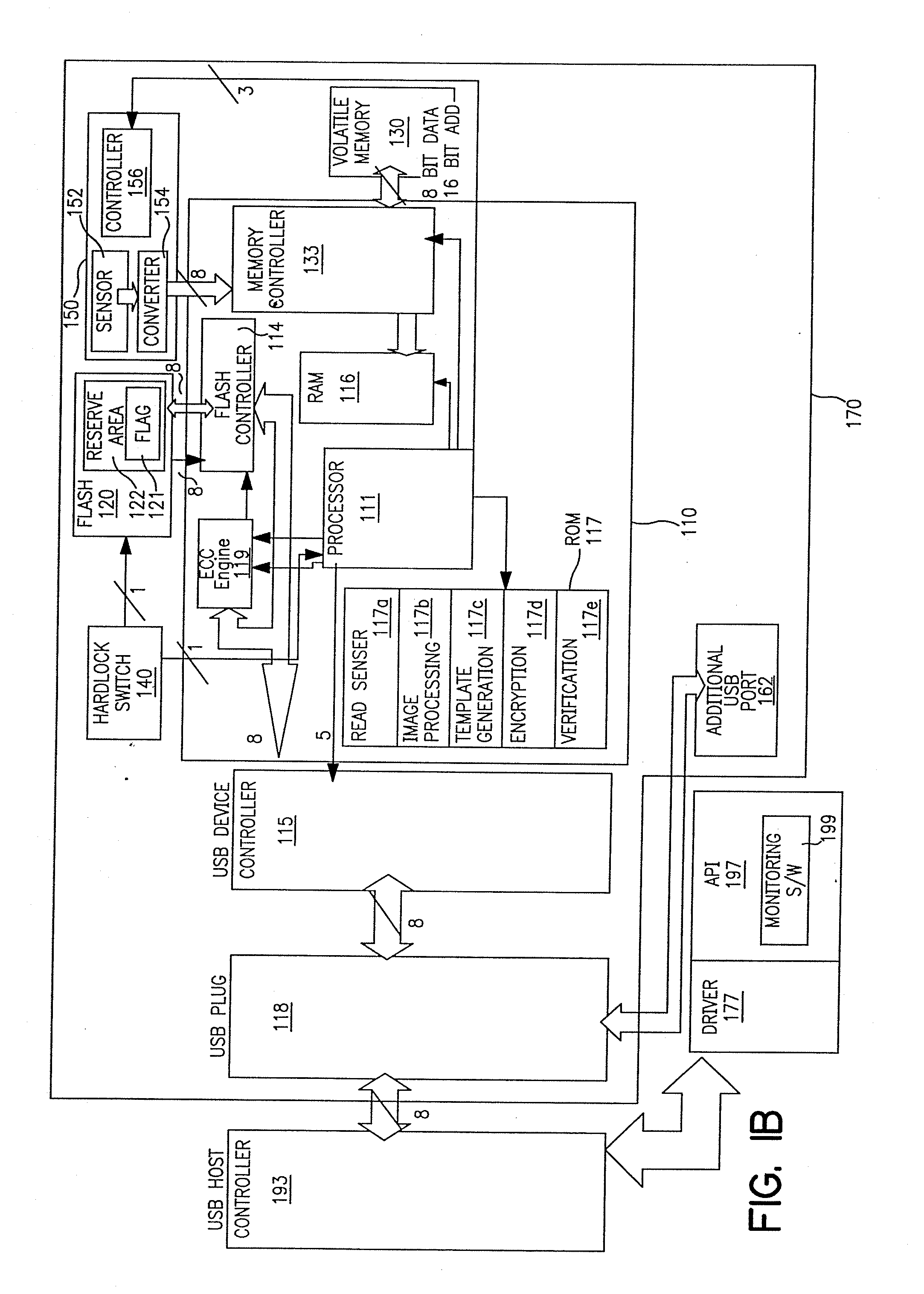
Portable device having biometrics-based authentication capabilities
InactiveUS20080049984A1Access is deniedReliably determinedInput/output to record carriersImage analysisUser authenticationBiometric trait
Apparatus and method for implementing biometrics-based authentication. In a preferred embodiment, the present invention is embodied in a portable device. Specifically, in one embodiment, the portable device includes a microprocessor, a non-volatile memory coupled thereto, and a biometrics-based authentication module controlled by the microprocessor. Preferably, the biometrics technology used is fingerprint authentication technology. The authentication module is capable of registering a fingerprint upon first use of the portable device, storing an encoded version of the fingerprint in the non-volatile memory. Subsequently, the authentication module can read a person's fingerprint and reliably determine whether the fingerprint matches the registered fingerprint stored in the non-volatile memory. If a match is found, access to information in the non-volatile memory is granted to that person; otherwise, access is denied. Embodiments of the present invention thus provide a highly convenient, secured and reliable method and system for user authentication and access control which was not achievable in prior art password-based authentication approaches.
Owner:TREK 2000 INT
Network security and fraud detection system and method
ActiveUS20060048211A1Avoid connectionAccess is deniedDigital data processing detailsUser identity/authority verificationNetwork serviceEnd user
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
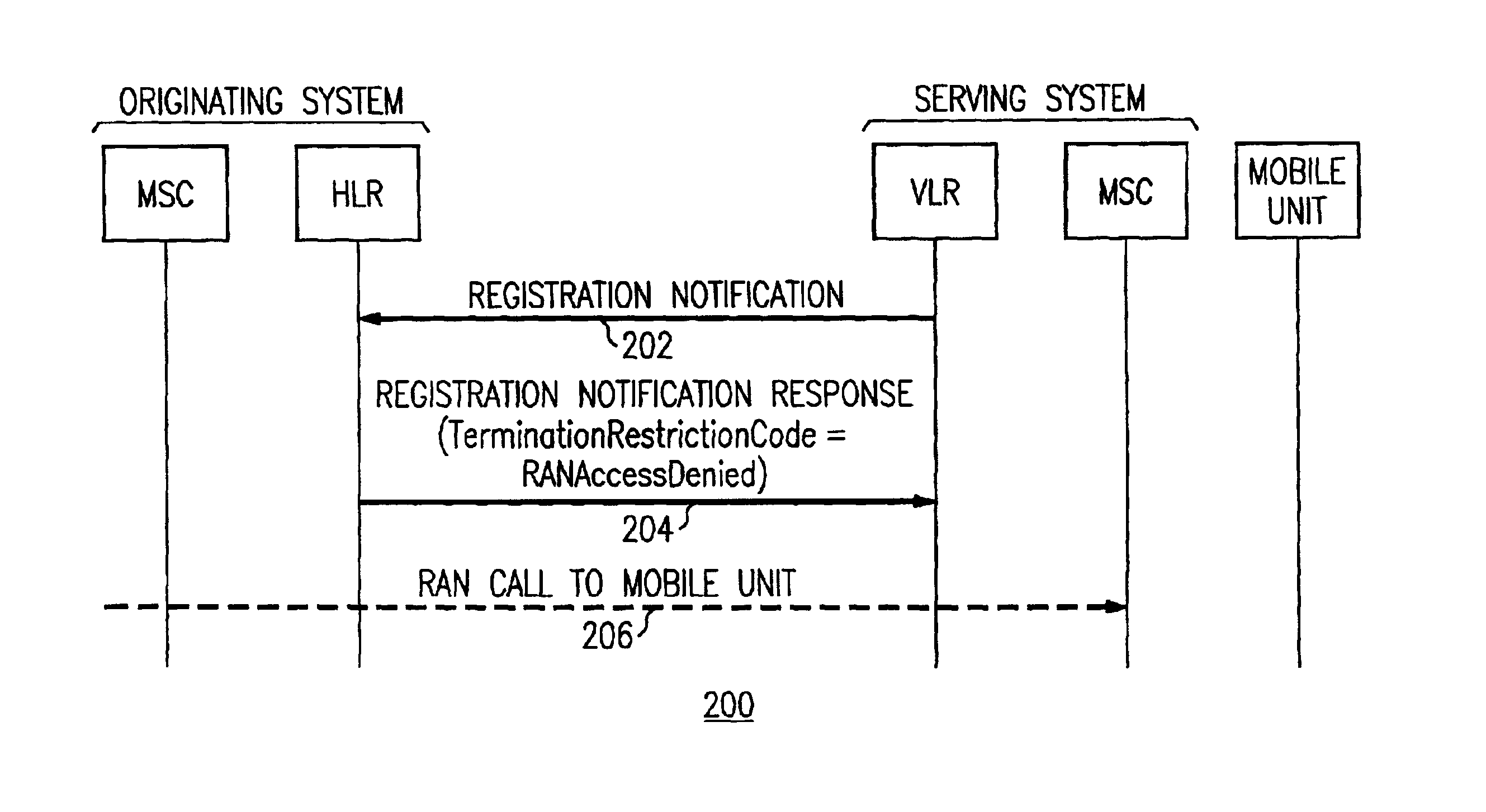
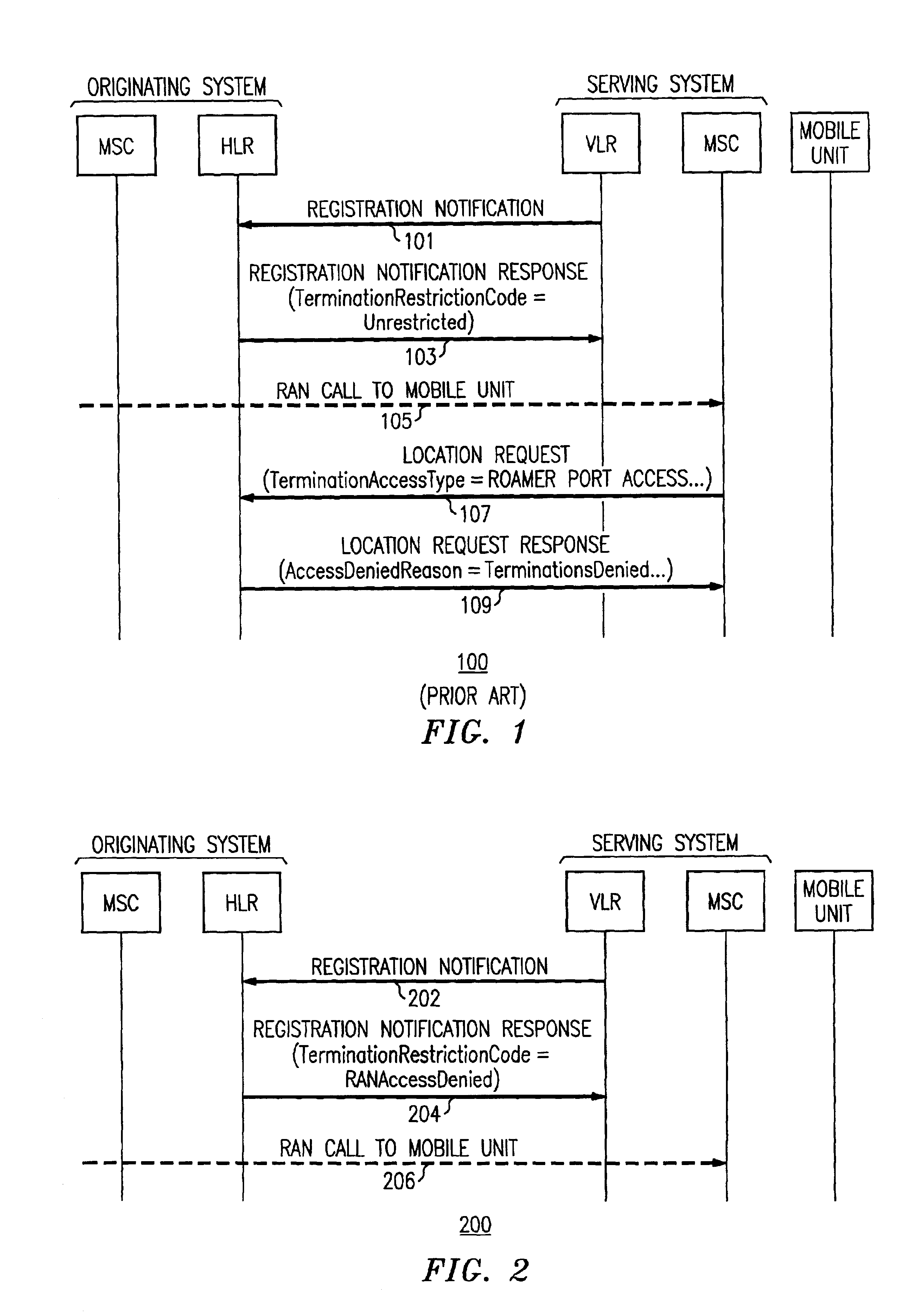
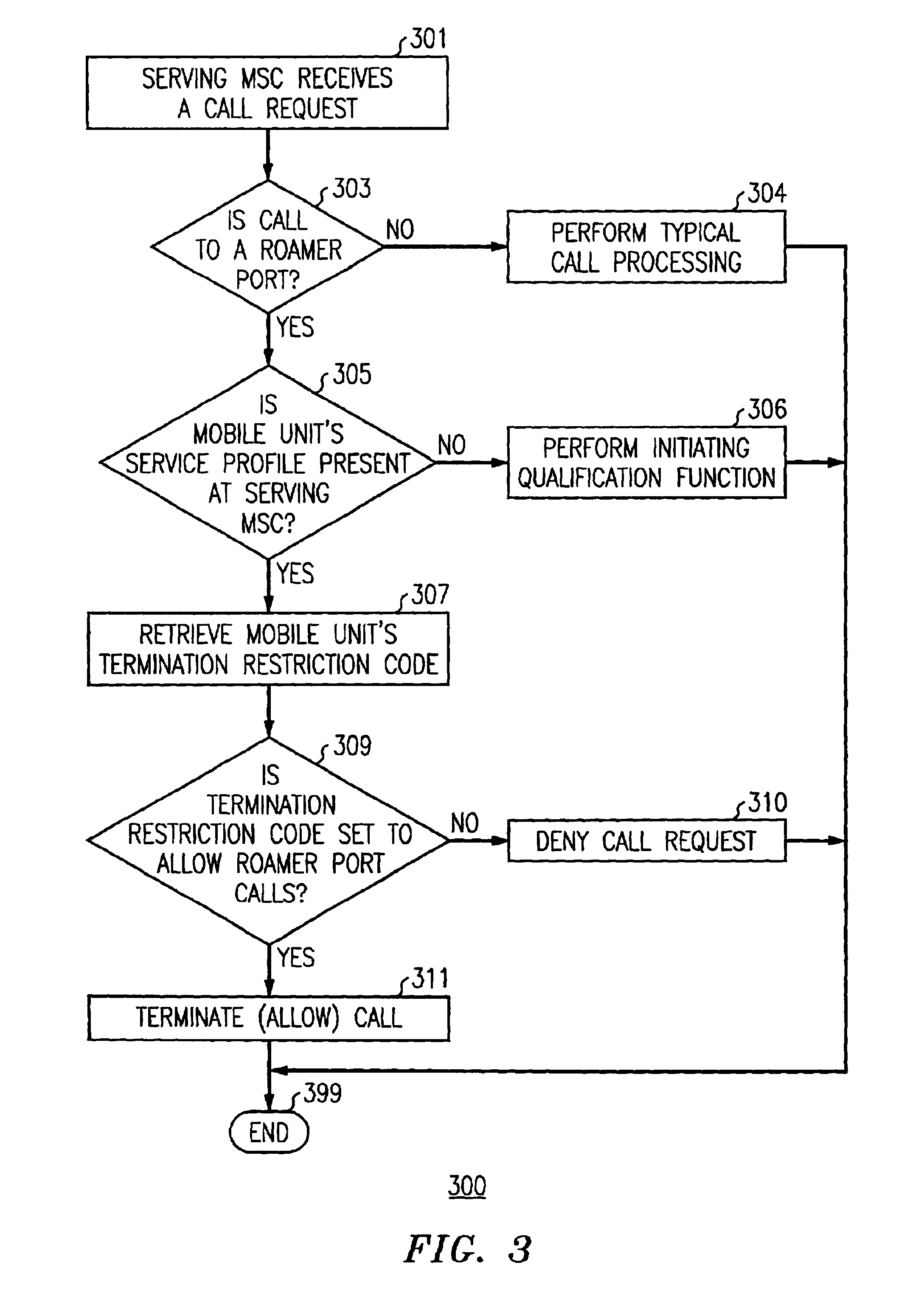
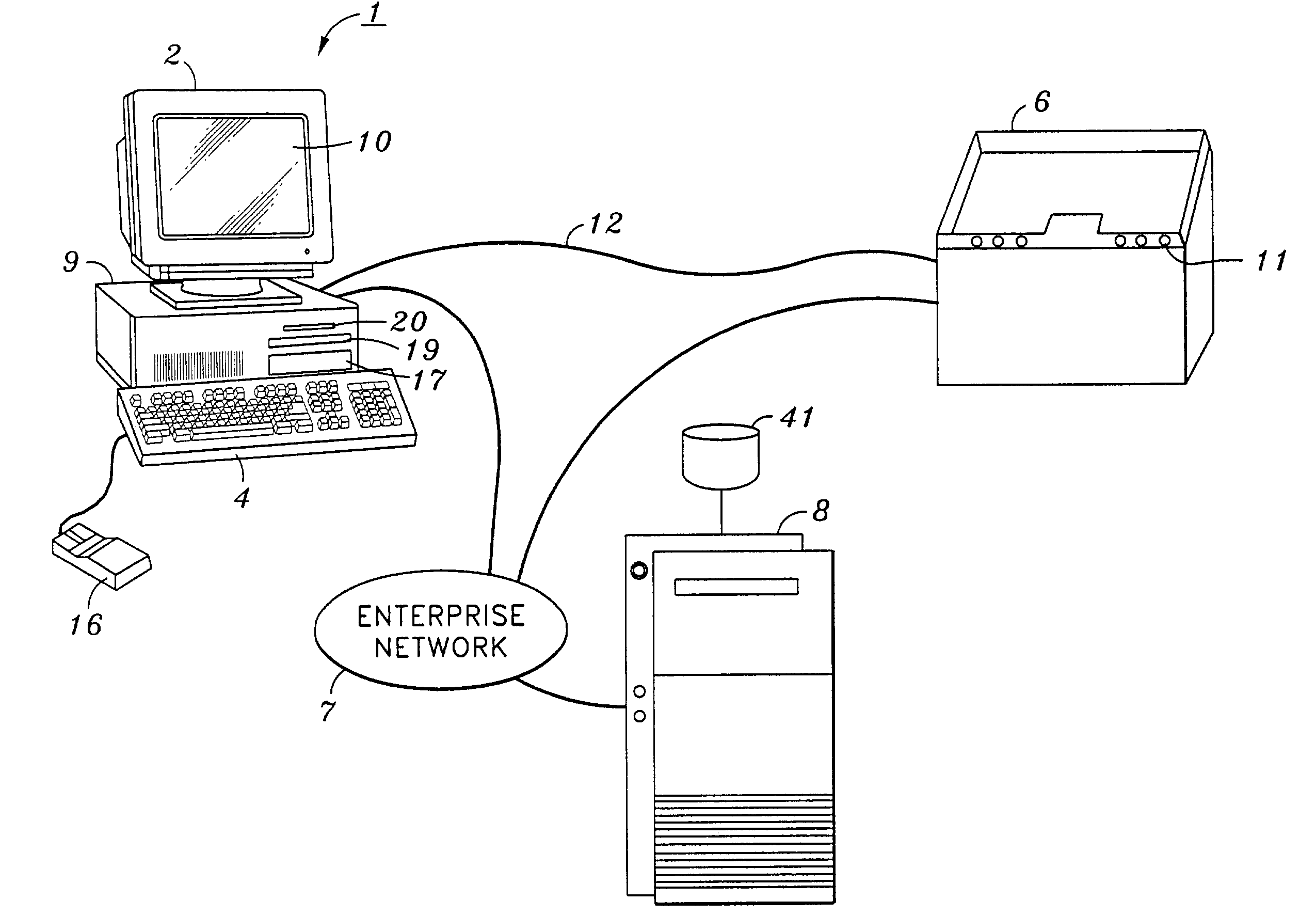
Method and apparatus for restricting call terminations when a mobile unit is roaming
InactiveUS6920326B2Control is terminatedAccess is deniedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCall terminationTelecommunications
The present invention provides a method and apparatus for restricting call terminations for a roaming mobile unit. A serving MSC, which is an MSC providing call processing a mobile unit that is not the home MSC of the mobile unit, sends a registration notification request to the home location register (HLR). The HLR retrieves the termination access code parameter from the HLR and sends it to the serving MSC. The termination access code parameter includes a value that indicates if the mobile unit is allowed to roamer port calls. The parameter is stored at a VLR associated with the serving MSC. When a call request comes in to the serving MSC and requests a roamer port call with the mobile unit, the serving MSC checks the value of the termination restriction code to determine if it should terminate, or complete, the call.
Owner:WSOU INVESTMENTS LLC +1
Two-pass device access management
InactiveUS7167919B2Eliminate needSave computing resourcesMultiple digital computer combinationsInternal/peripheral component protectionAccess managementAuthentication information
Access control to a networked peripheral device by a walk-up user, wherein the networked peripheral device is accessible by both the walk-up user and a remote user, based on centralized access management information. Access control comprises receiving authenticated information for the walk-up user from the networked peripheral device at a centralized location, determining at a server connected to the network a first level of access to the networked peripheral device, determining at the networked peripheral device a second level of access to the networked peripheral device by the walk-up user based on received access management information for the walk-up user, and allowing the walk-up user to access determined user-available features of the networked peripheral device based on the determined first and second levels of access.
Owner:CANON KK
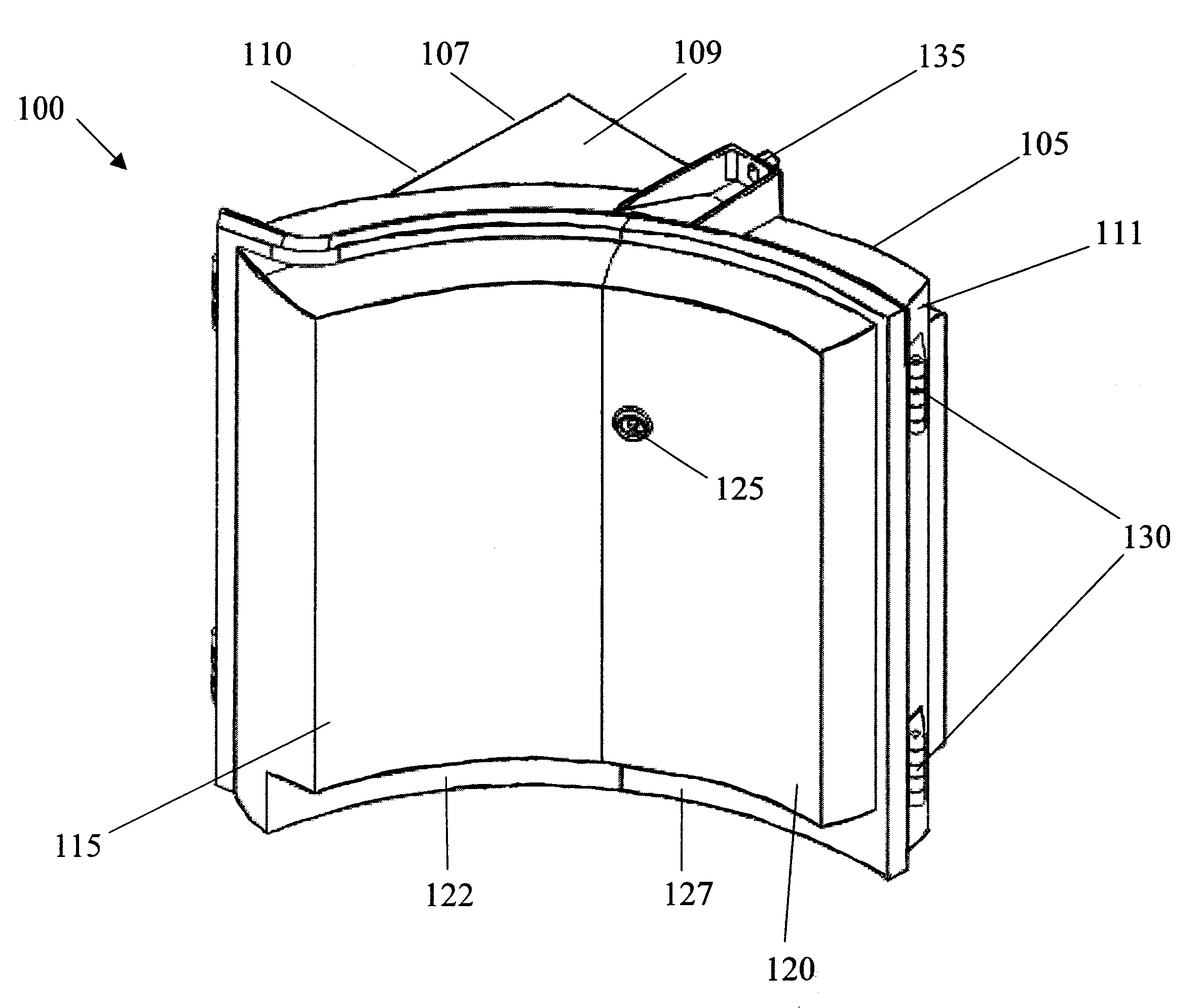
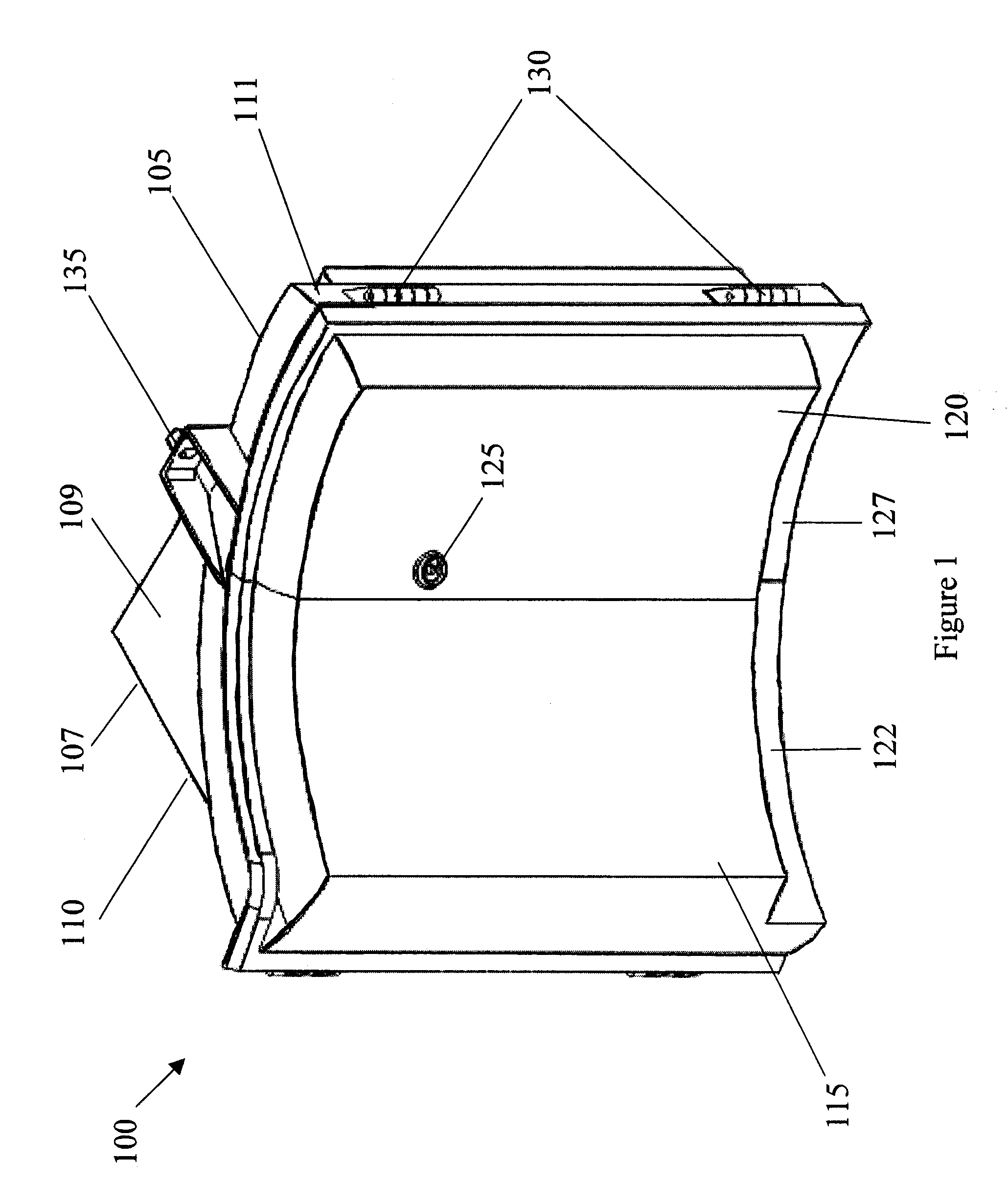
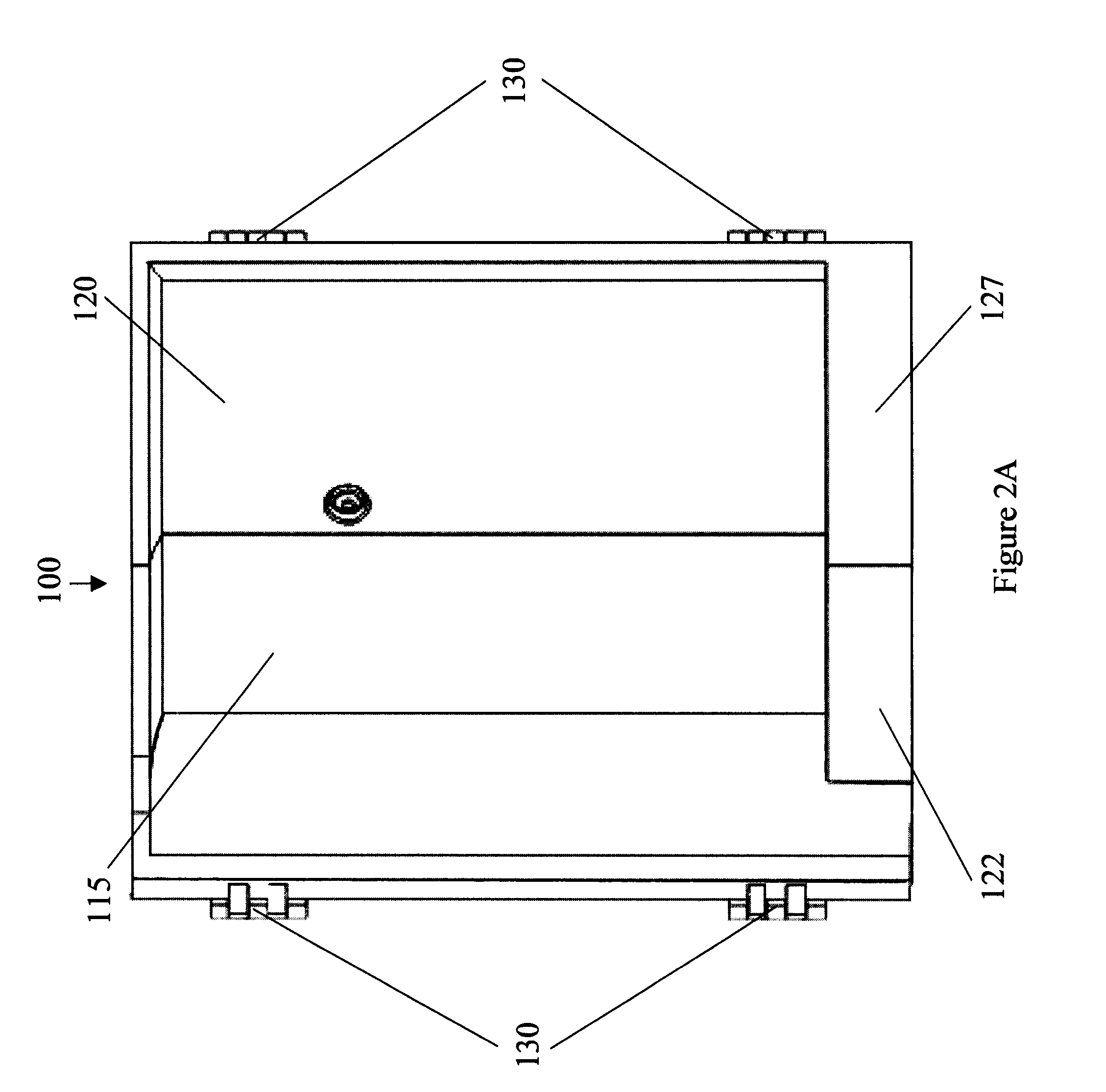
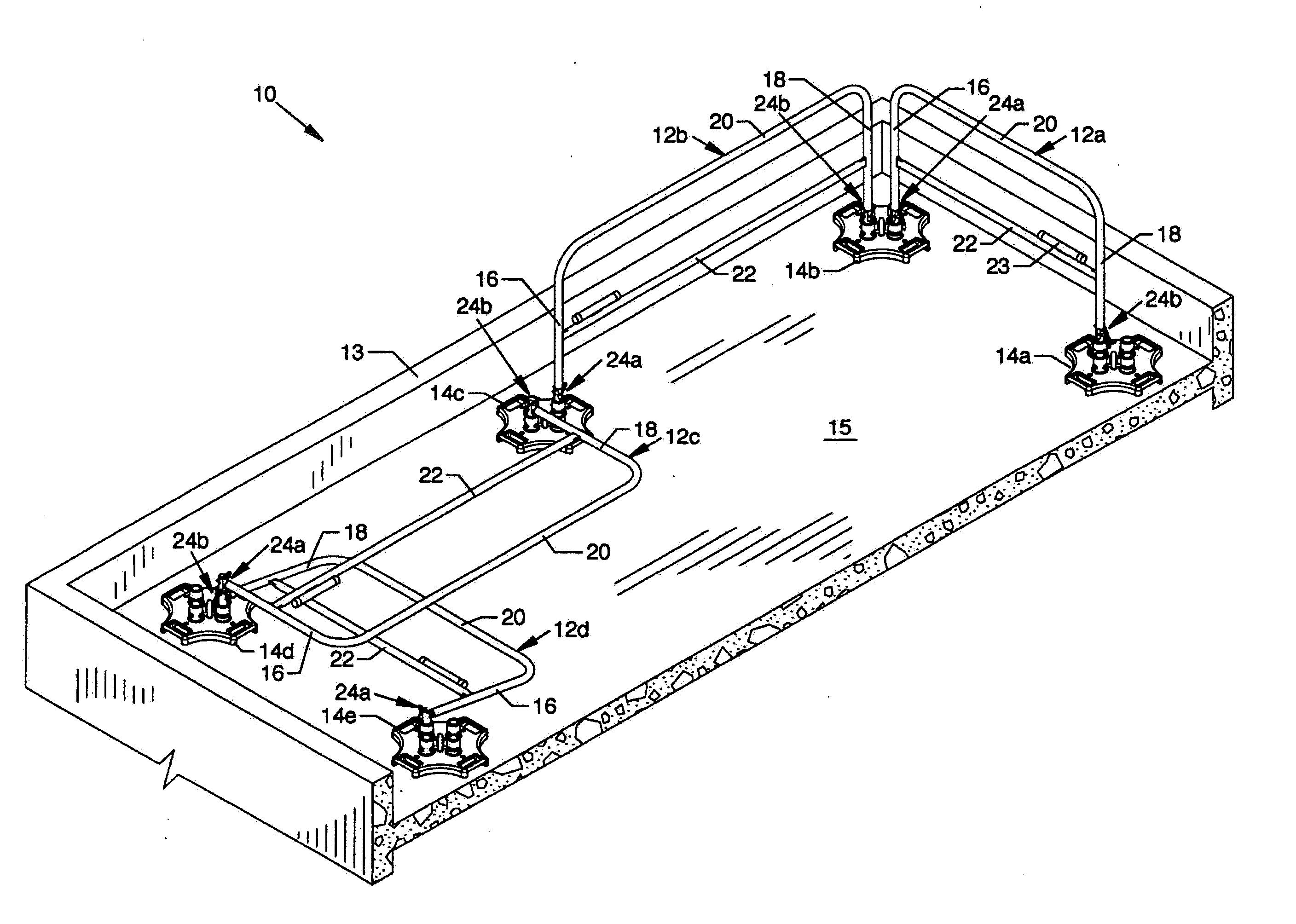
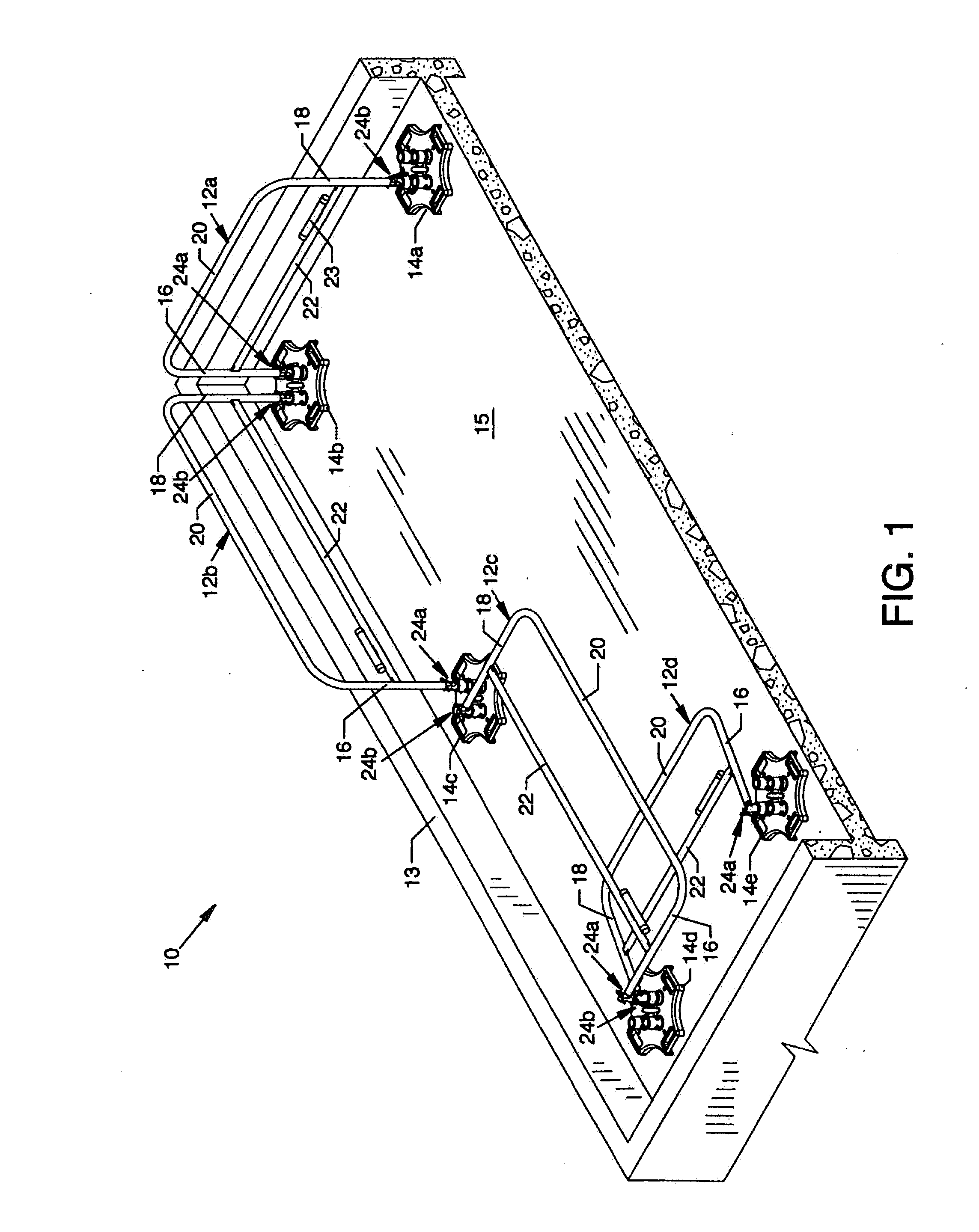
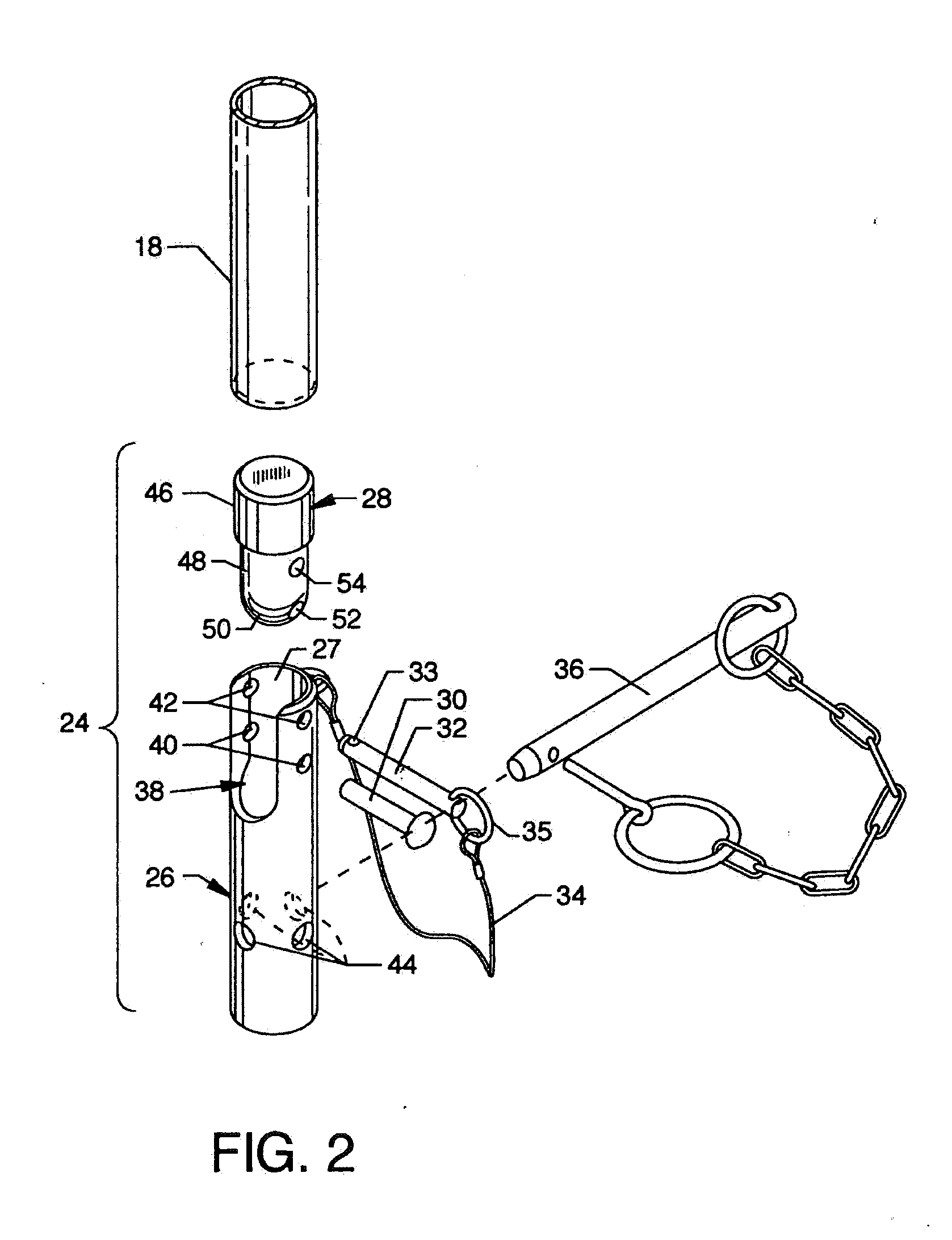
Collapsible safety rail system
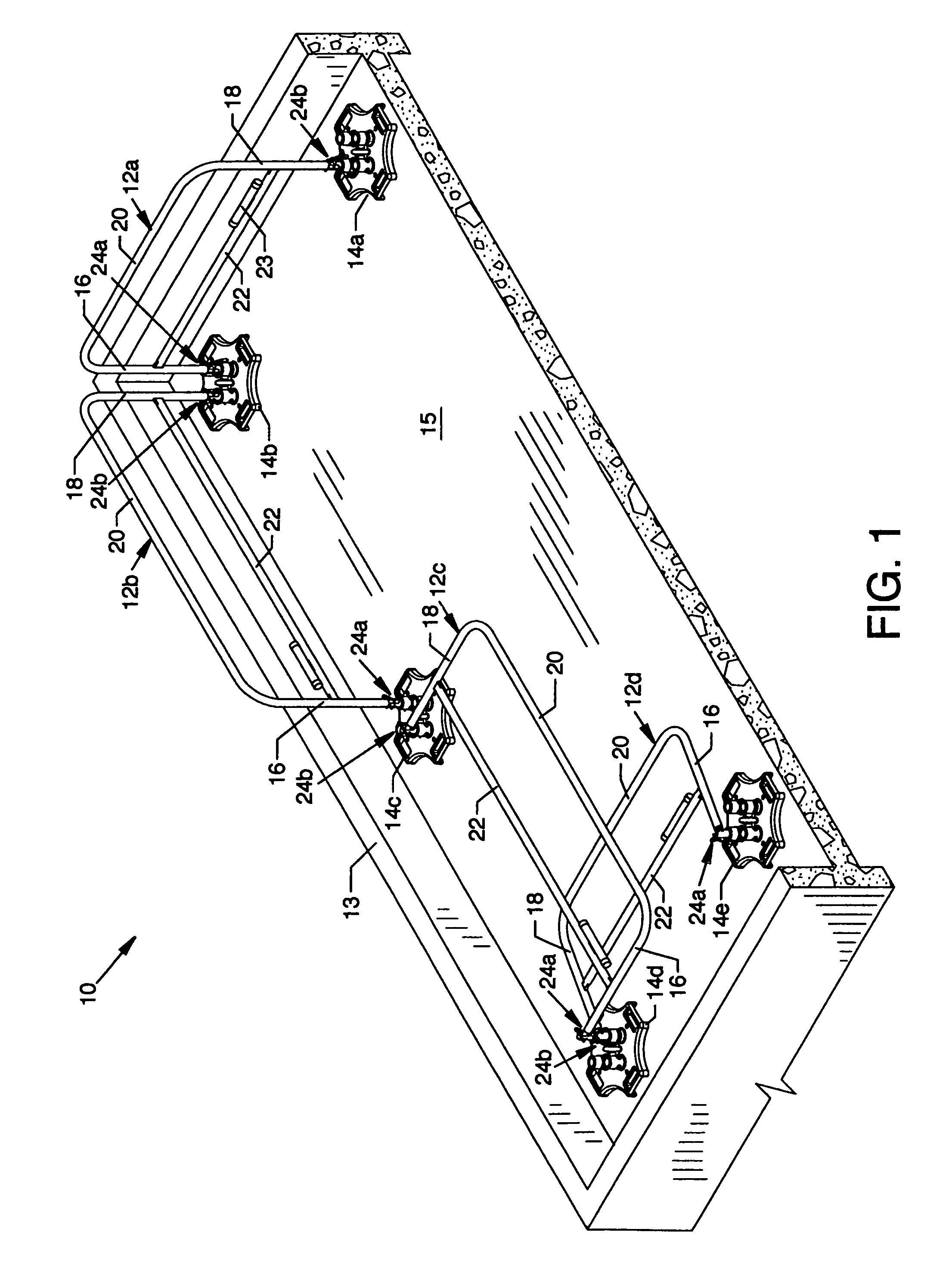
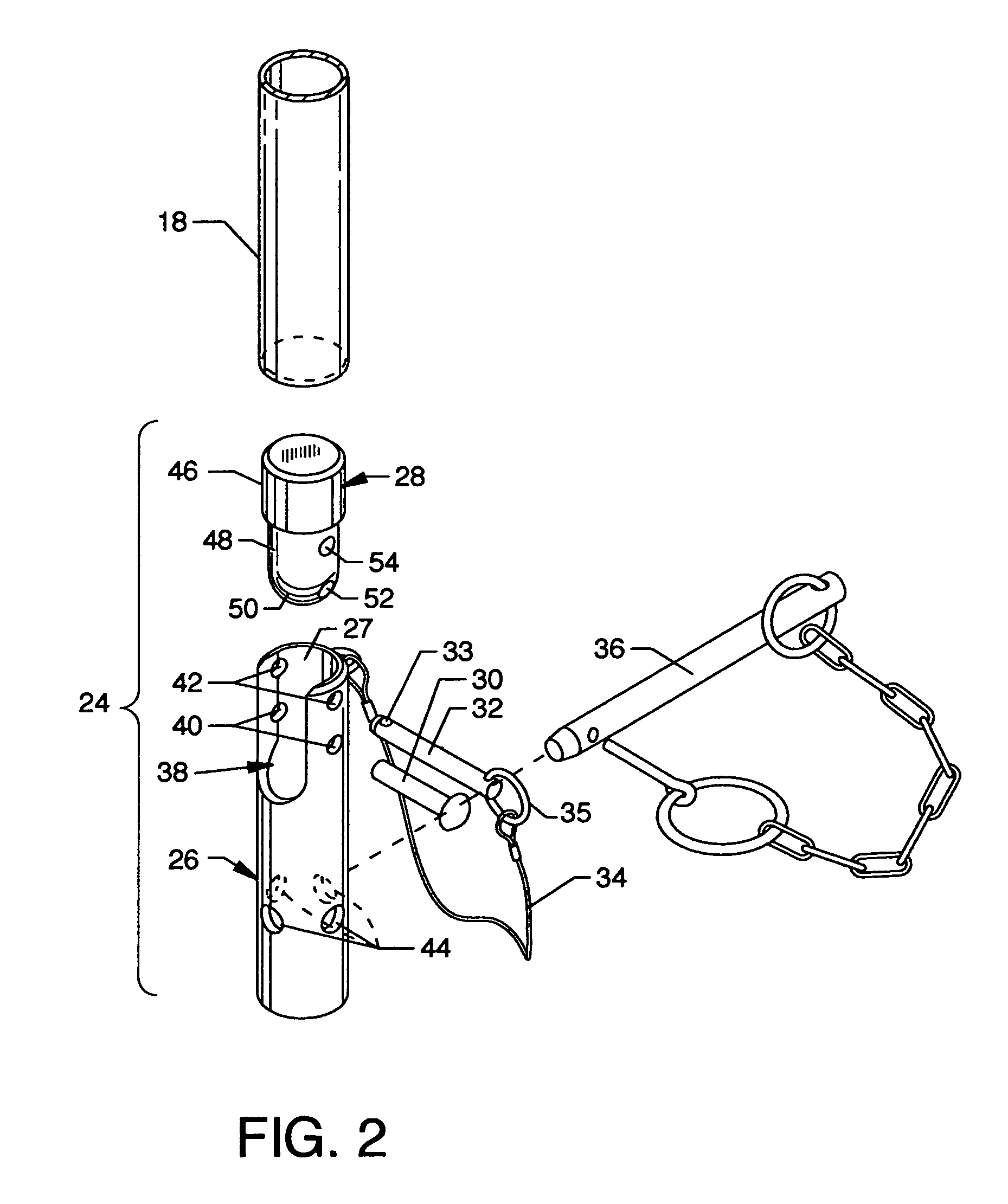
InactiveUS20060278472A1Reducing viewable profileProtection positionDoors/windowsFencingProtective barrierEngineering
A collapsible safety rail system for providing a portable or permanent protective barrier to provide for fall prevention from elevated or other work areas. Lockable pivot assemblies are located between heavy bases and the end posts of collapsible safety rail assemblies. Removable detent pins are utilized to lock the pivot assemblies to maintain the erected position of the collapsible safety rail assemblies in protective vertical orientation or are removed to allow maneuvering of the collapsible safety rail assemblies to a minimum viewable profile position when not required for personnel protection.
Owner:TRACTEL INC
Enhanced security using service provider authentication
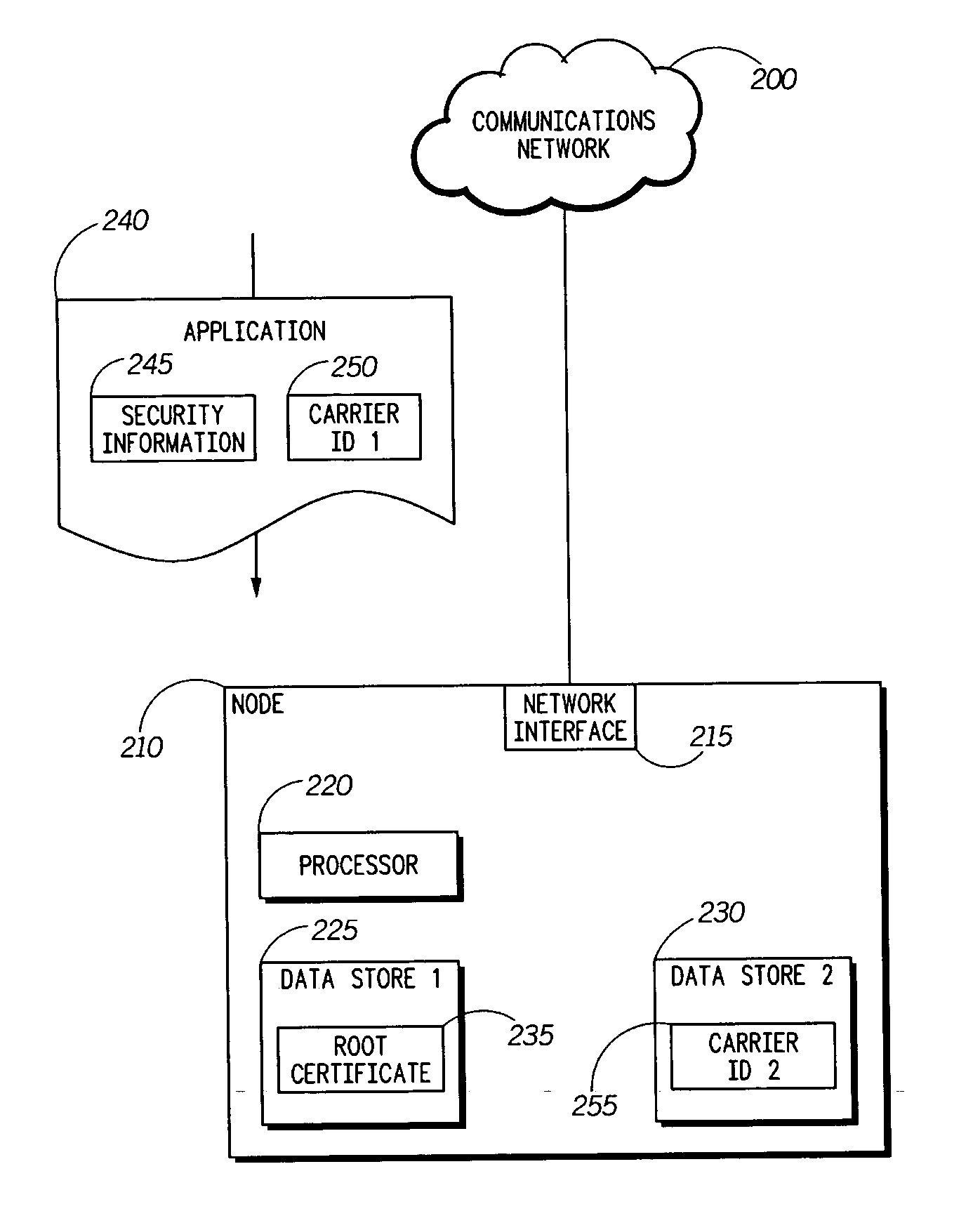
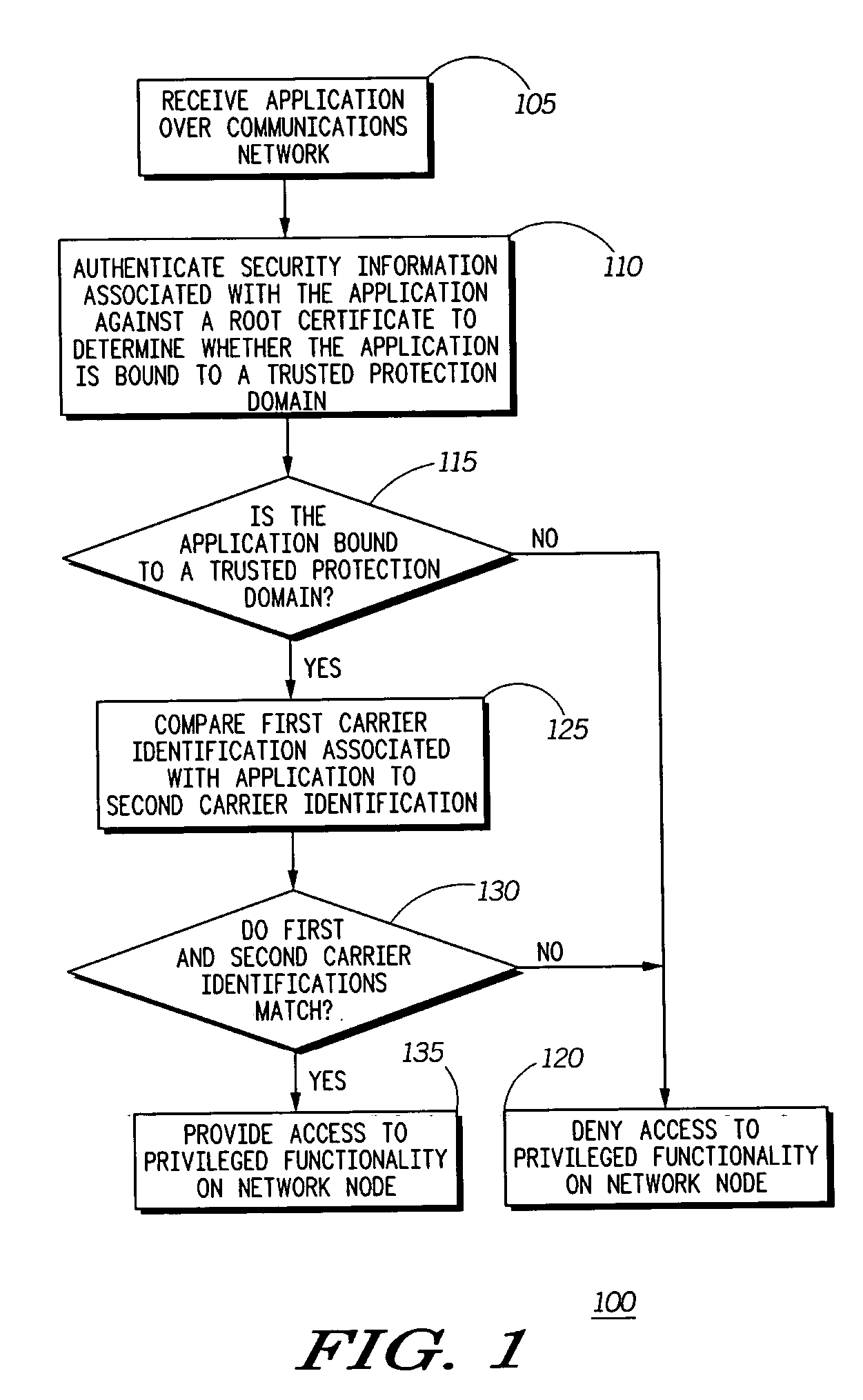
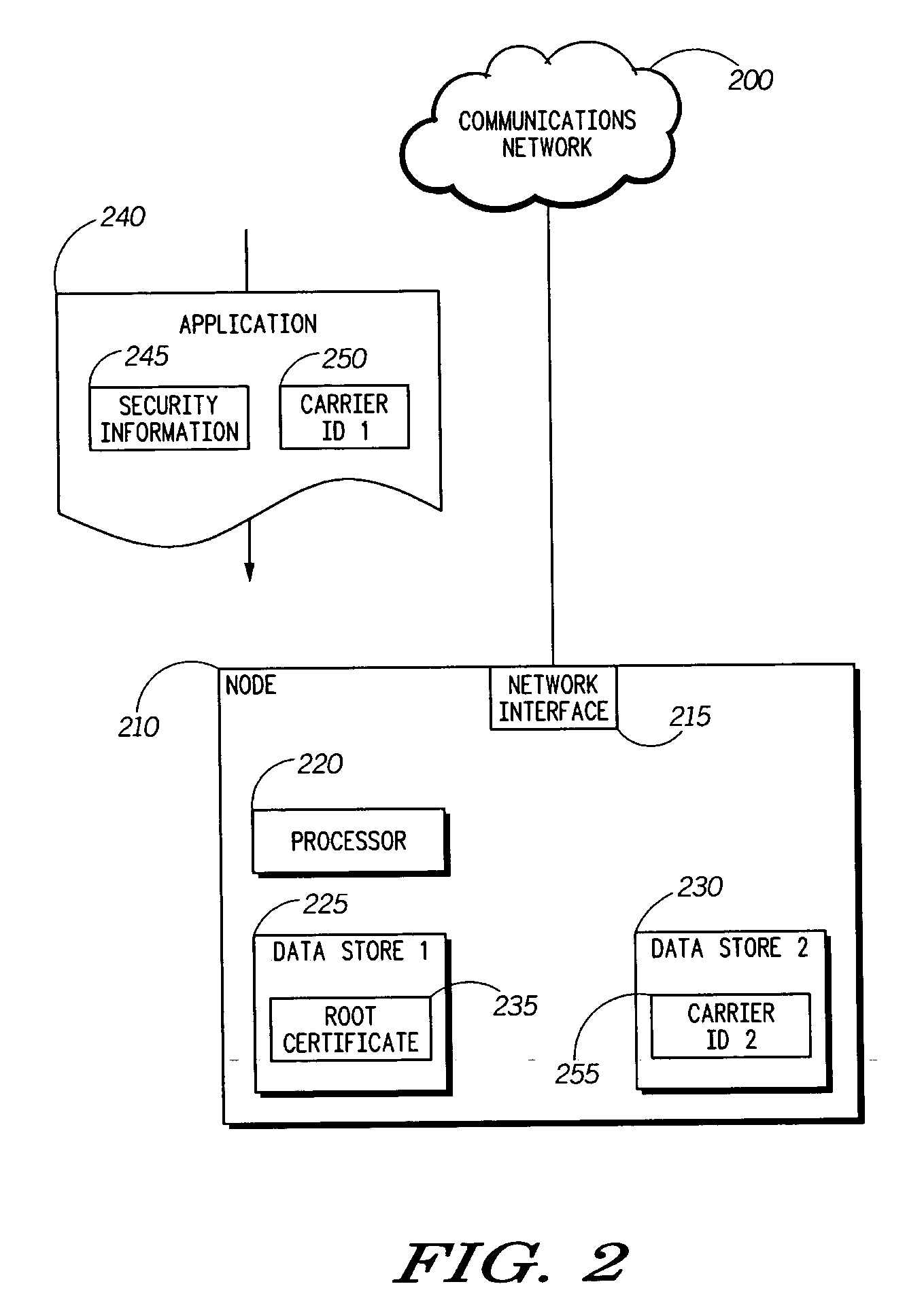
ActiveUS20060031941A1Improve application securityAccess is deniedDigital data processing detailsUser identity/authority verificationService providerService provision
A method (100) and an apparatus (210) for providing enhanced security using service provider authentication. In addition to authenticating an application signature (245) against a root certificate (235) stored on the network node (210), a first carrier identification (250) associated with the application (240) is compared to a second carrier identification (255). If the first and second carrier identifications match, then the application can be assigned to a trusted protection domain and granted permissions which provide privileged access to the network node. For example, the application can be granted permission to be installed and / or executed on the network node. Otherwise the application can be denied privileged access. Accordingly, a carrier's applications will be only installed onto network nodes that are intended recipients of the applications.
Owner:GOOGLE TECH HLDG LLC
Mobile authentication for network access
InactiveUS20060069914A1Improve abilitiesEstablishing connectionUser identity/authority verificationSecurity arrangementService providerWeb authentication
The present invention provides a method for authenticating a user to a network by means of a temporary and / or one-time password. The temporary and / or one-time password being provided by a service provider that can be accessed by means of a mobile telecommunication device. The temporary password is provided on demand, when the user invokes a corresponding access request that is transmitted to the service provider by means of the mobile telecommunication device. The service provider checks and asserts a received access request and generates the temporary password by making use of a dedicated cryptographic method. The generated temporary password is finally displayed to the user by means of the mobile telecommunication device and the user may then manually enter the temporary password into the computing device in order to authenticate to the network.
Owner:ALCATEL LUCENT SAS
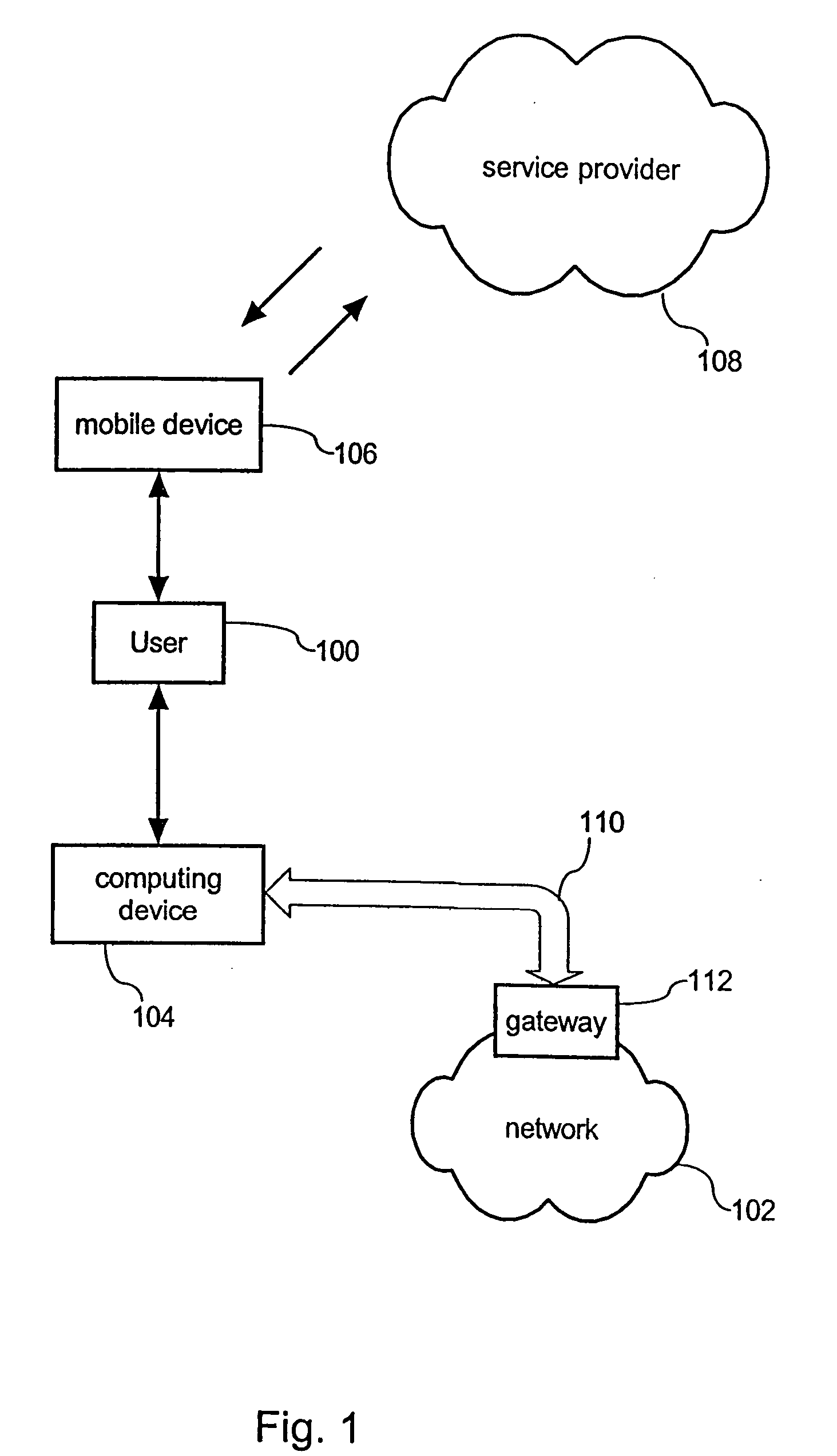
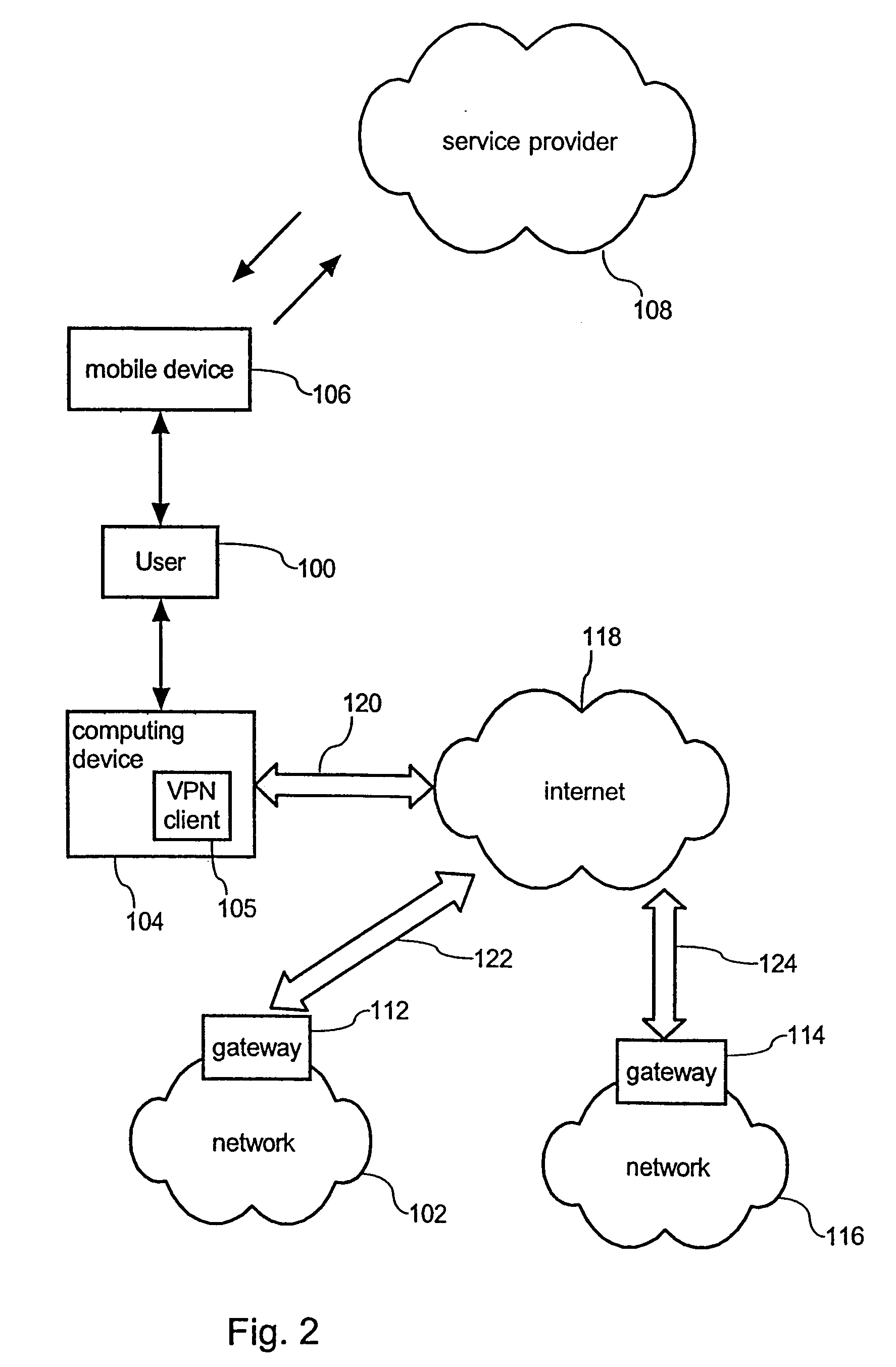
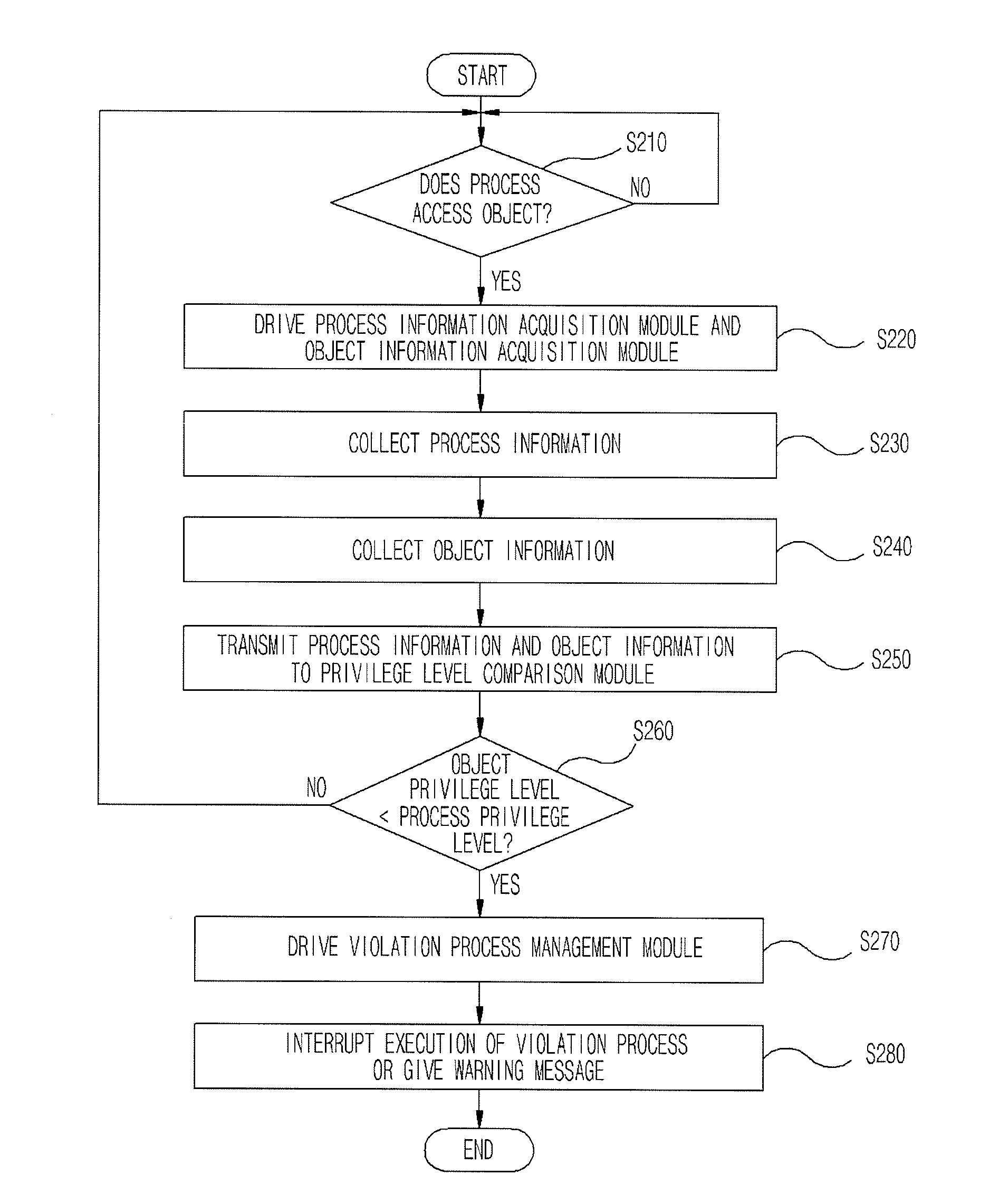
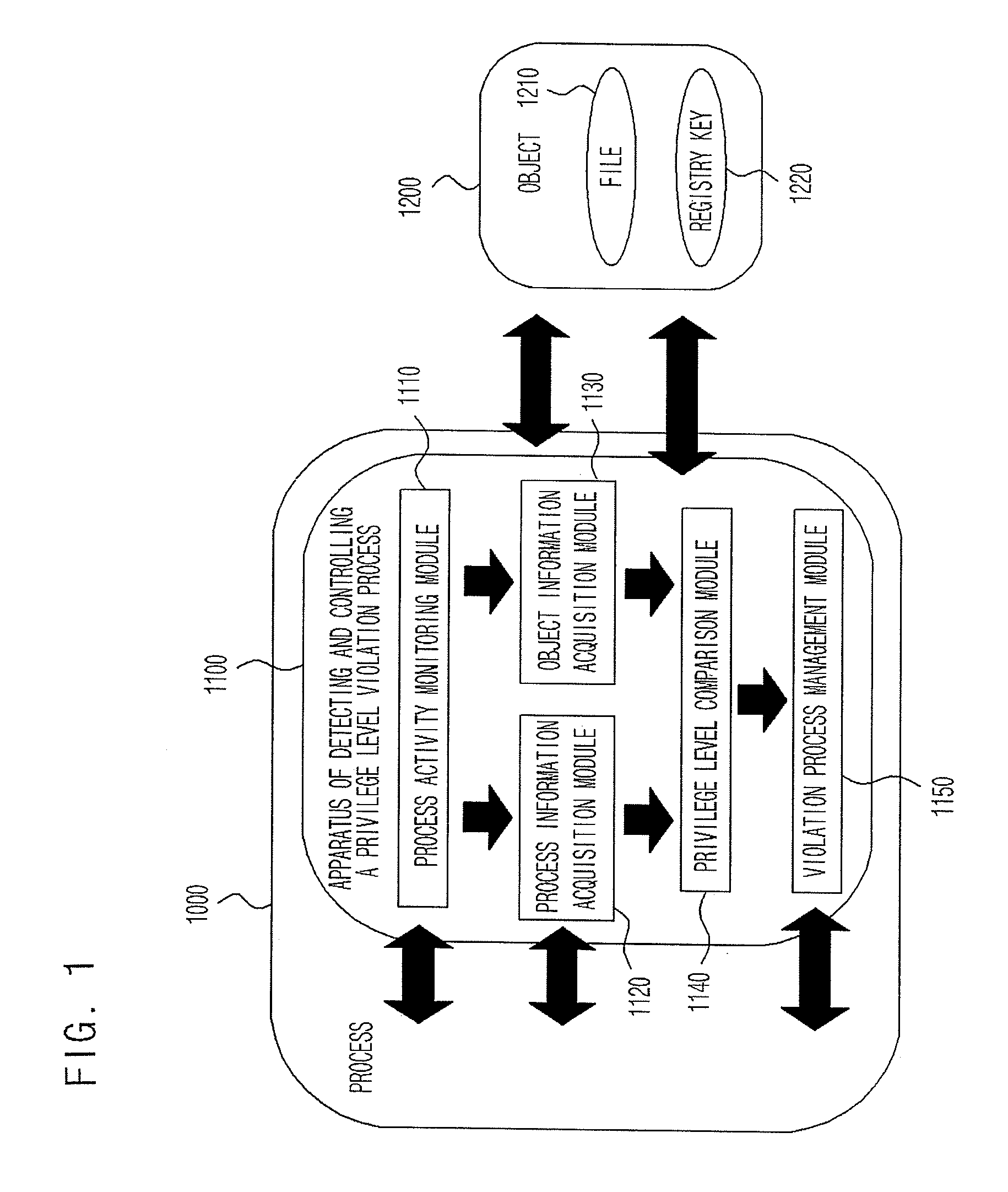
Apparatus and method of detecting and controlling privilege level violation process
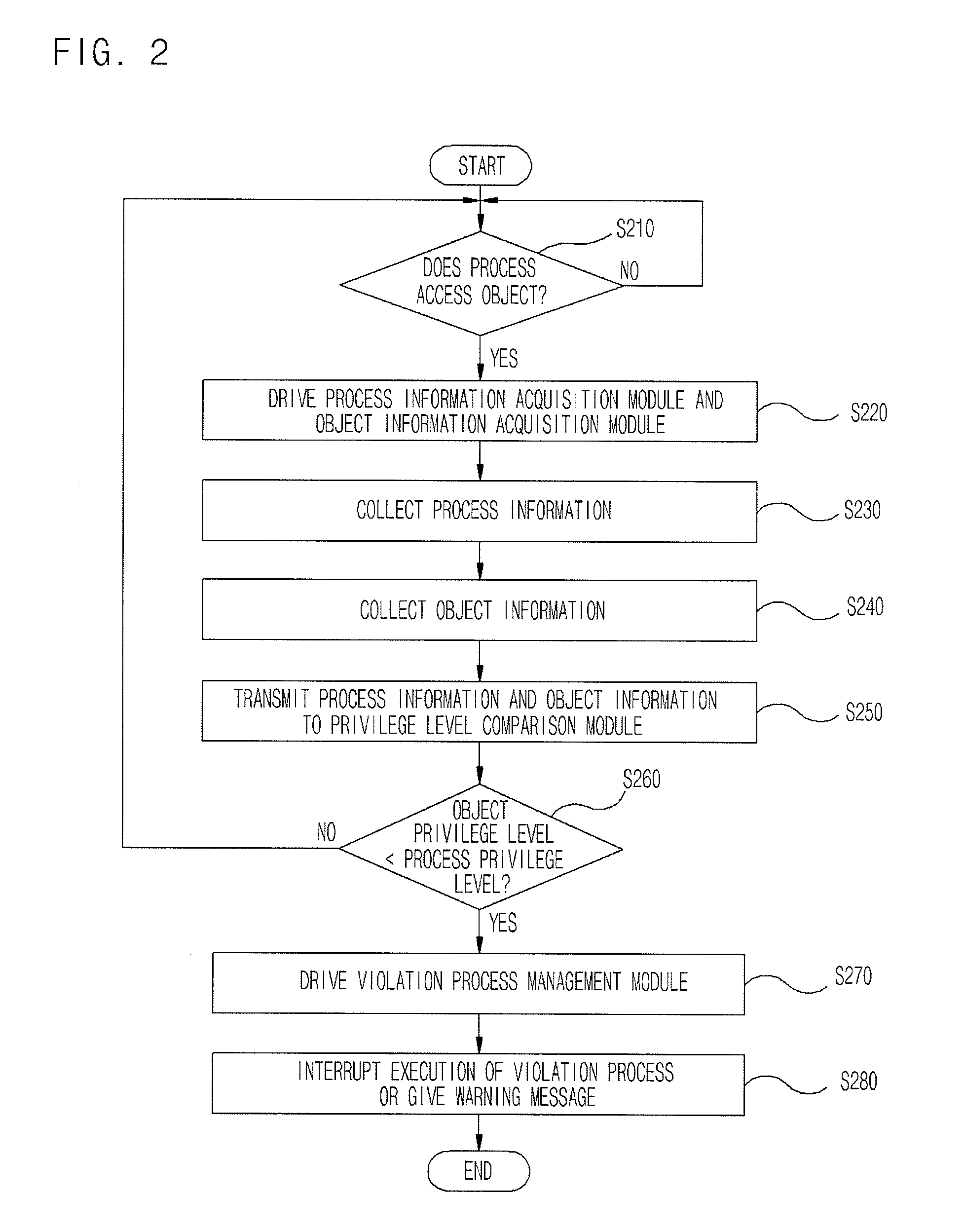
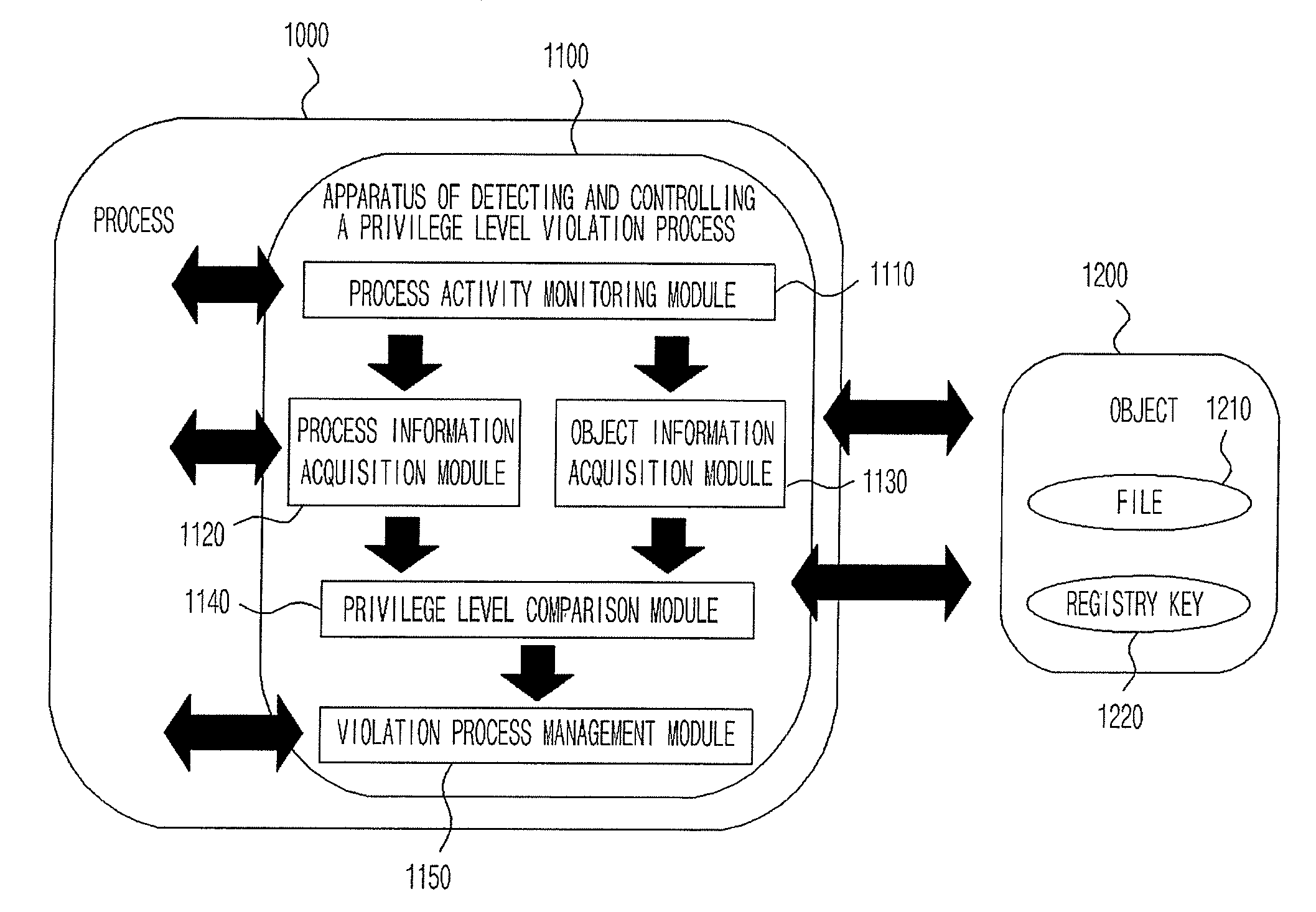
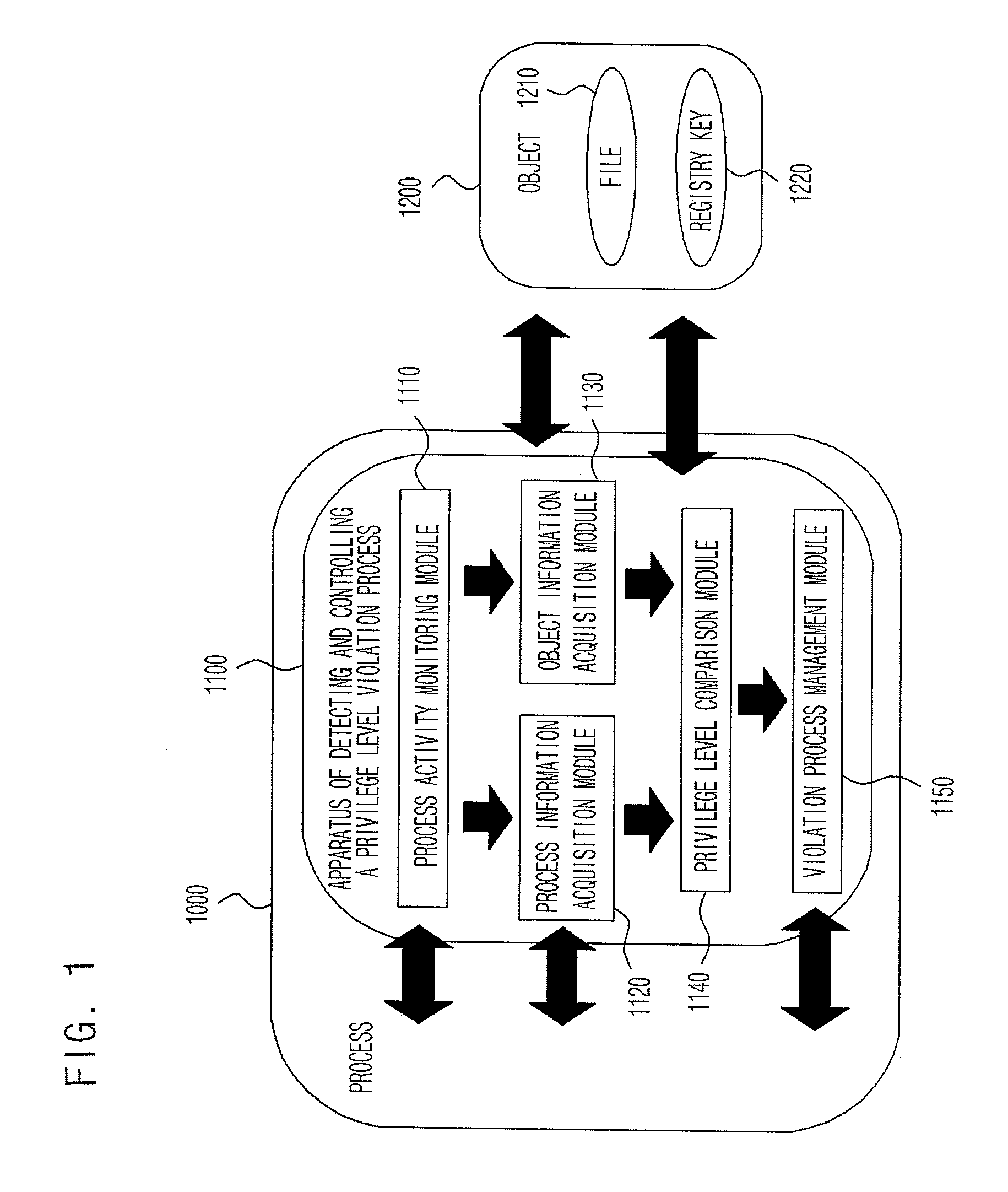
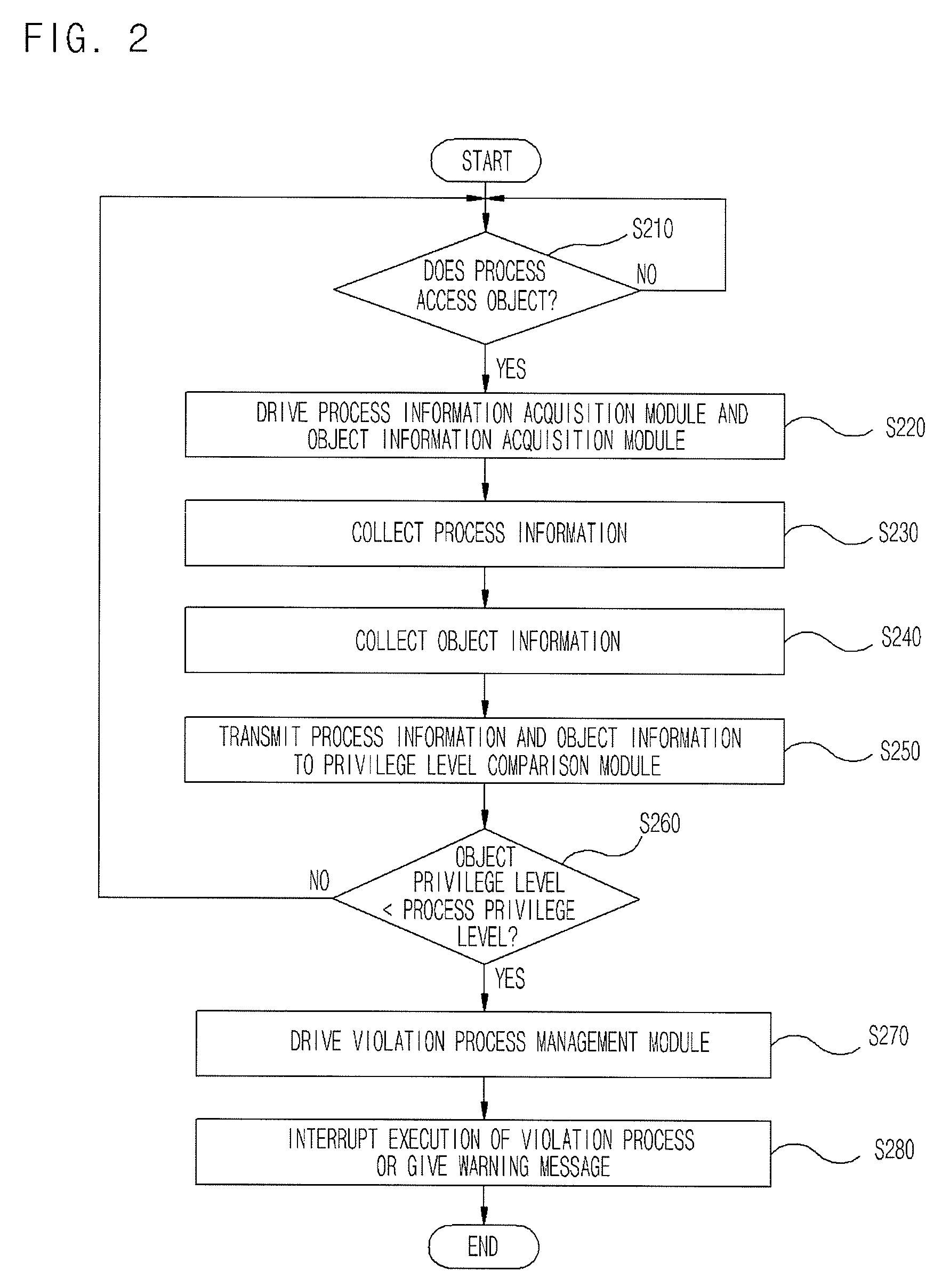
ActiveUS20080313417A1Eliminate riskAccess is deniedDigital data processing detailsDigital computer detailsPrivilege level
Provided are an apparatus and method of detecting and controlling a privilege level violation process. The apparatus monitors whether higher-privileged processes depend on information provided from lower-privileged objects or denies the higher-privileged processes to access the lower-privileged objects. The apparatus is provided in a process, and monitors whether a process accesses to a lower-privileged object. The apparatus gives a warning message or denies an access of the process to the lower-privileged object when it detects that the higher-privileged process access to the lower-privileged object. Therefore, the apparatus of detecting and controlling a privilege level violation process detects weaknesses that may be caused by privilege level violation, thus allowing a system to be safely operated.
Owner:ELECTRONICS & TELECOMM RES INST
Enhanced association for access points
ActiveUS8787572B1Reduce the possibilitySmall rangeData switching by path configurationSecret communicationCryptographic protocolClient-side
Techniques and systems for associating a client with an access point using a security protocol are described. A described technique includes initiating an association request; establishing an association between a first device and a second device different from the first device based on the association request; participating in a handshake including exchanging an operational key between the first device and the second device during the handshake; and entering an operational phase using the operational key when the handshake is successful. Participating in the handshake can include participating in an authenticated handshake when the association request indicates an authenticated access, and participating in an unauthenticated handshake when the association request indicates an unauthenticated access.
Owner:MARVELL ASIA PTE LTD
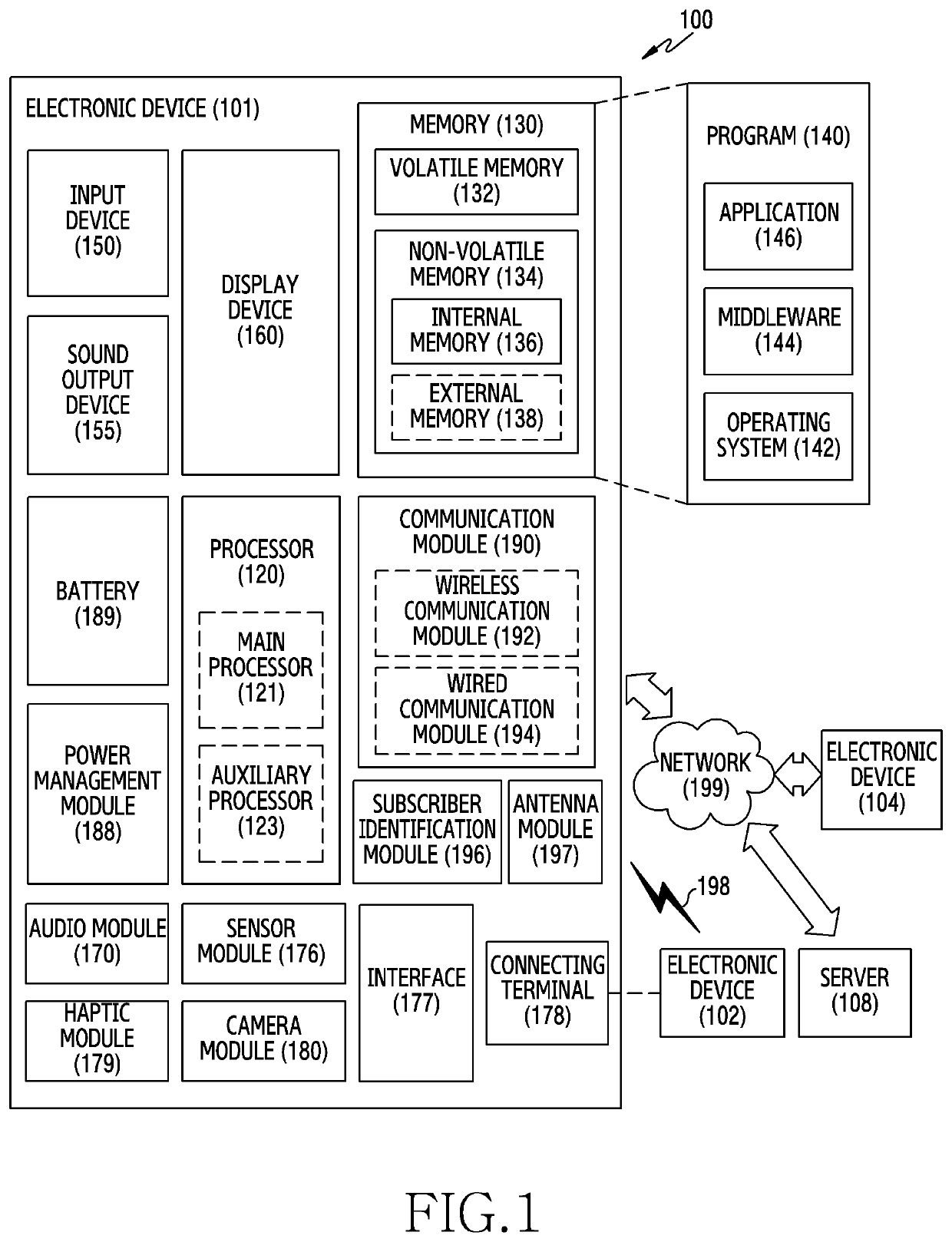
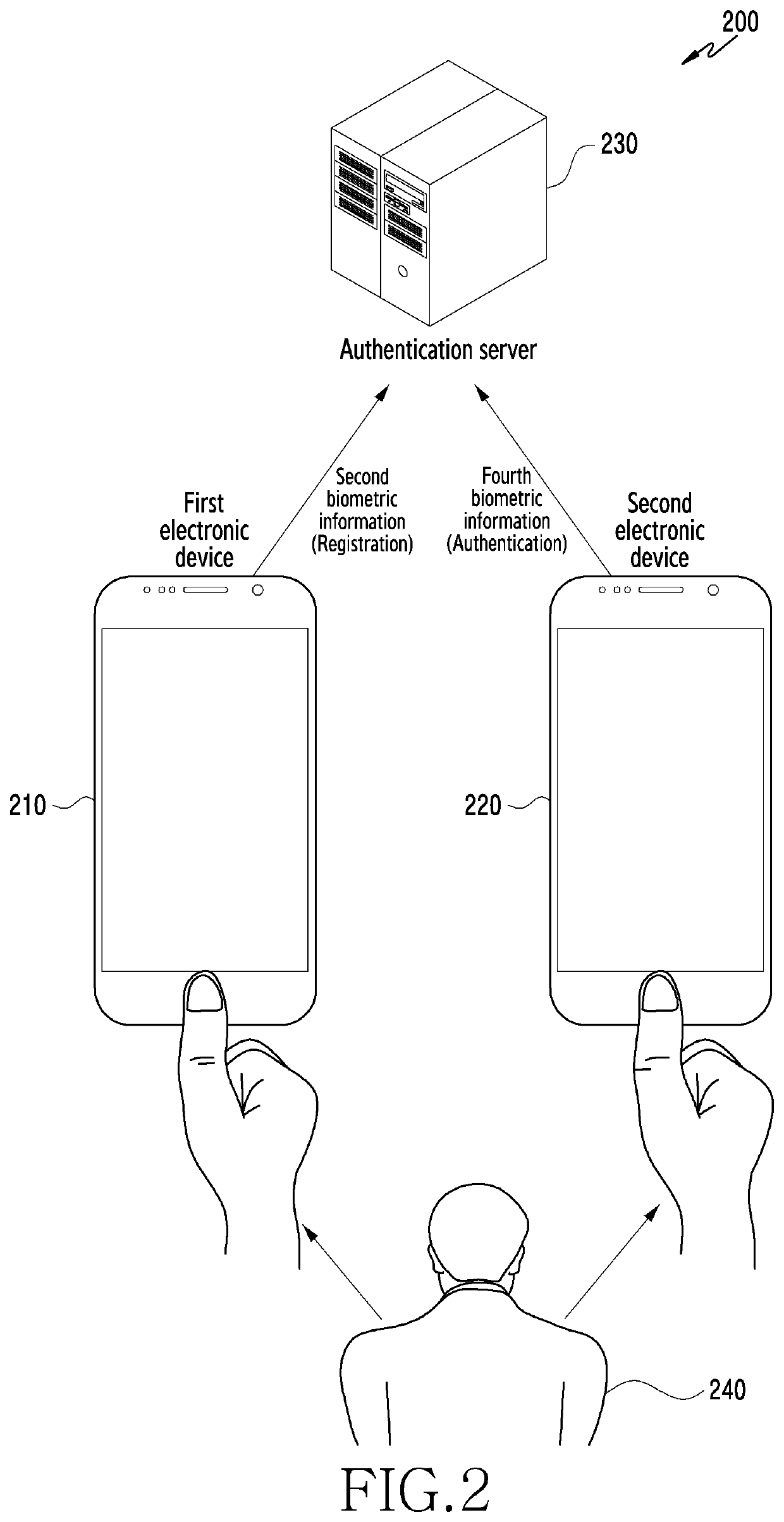
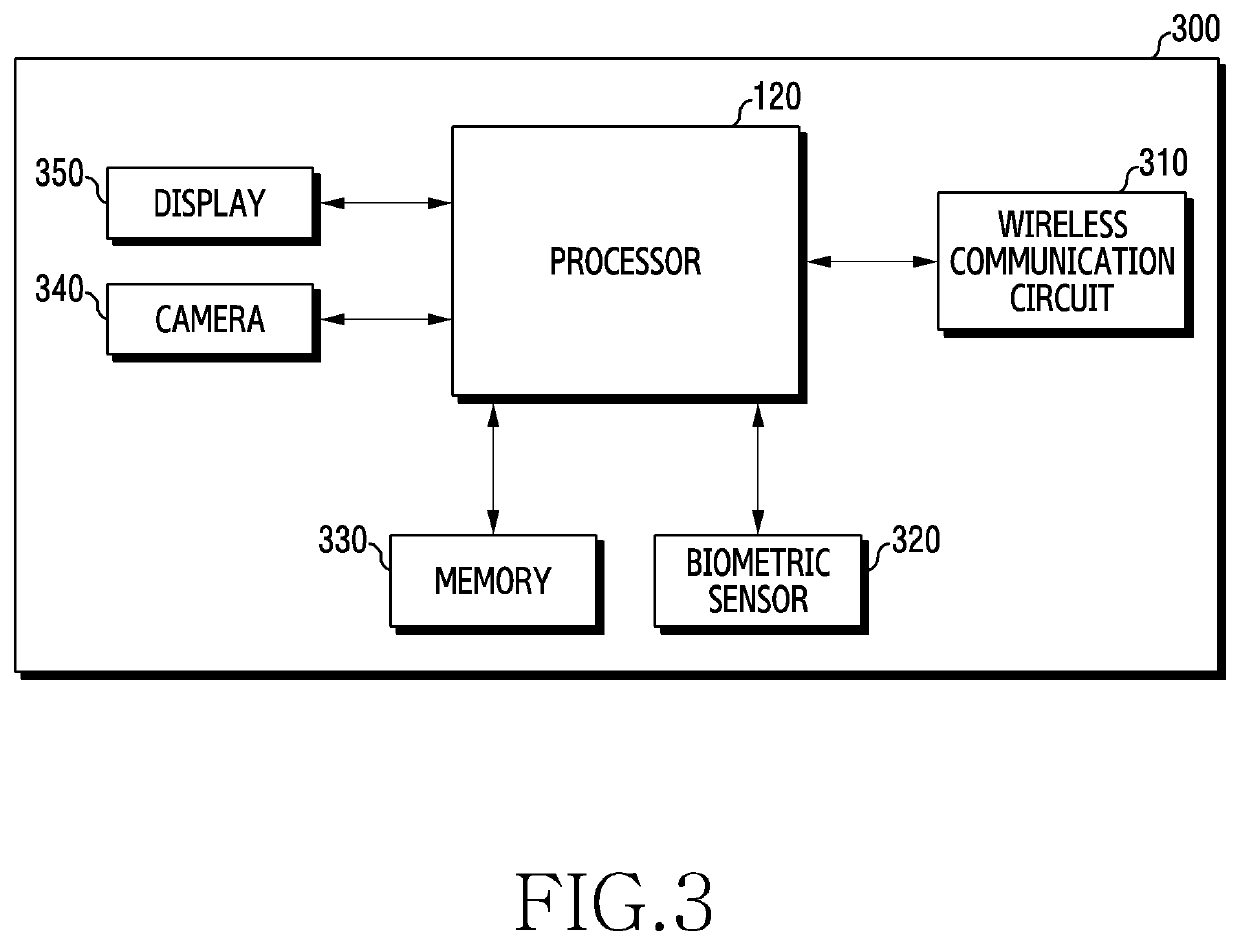
Electronic device for authenticating user and operating method thereof
ActiveUS20190372969A1AccessAccess is deniedTransmissionMultiple biometrics useAuthentication serverConcatenation
Certain embodiments of the disclosure relate to an electronic device for authenticating a user by using user's biometric information, and an operating method thereof. For example, an electronic device according to an embodiment may include: a communication circuit; a biometric sensor; and a processor operatively connected with the communication circuit and the biometric sensor, and the processor is configured to: obtain first biometric information of a user by using the biometric sensor; generate second biometric information for authenticating the user, based on concatenation of the first biometric information and unique information corresponding to the user; and transmit the second biometric information to an authentication server through the communication circuit, where the authentication server authenticates fourth biometric information by comparing the fourth biometric information to the second biometric information, and where the fourth biometric information is generated based on concatenation of third biometric information of the user and the unique information.
Owner:SAMSUNG ELECTRONICS CO LTD
Collapsible safety rail system
InactiveUS8689938B2Reducing viewable profileProtection positionScaffold connectionsDoors/windowsDetentEngineering
A collapsible safety rail system for providing a portable or permanent protective barrier to provide for fall prevention from elevated or other work areas. Lockable pivot assemblies are located between heavy bases and the end posts of collapsible safety rail assemblies. Removable detent pins are utilized to lock the pivot assemblies to maintain the erected position of the collapsible safety rail assemblies in protective vertical orientation or are removed to allow maneuvering of the collapsible safety rail assemblies to a minimum viewable profile position when not required for personnel protection.
Owner:TRACTEL INC
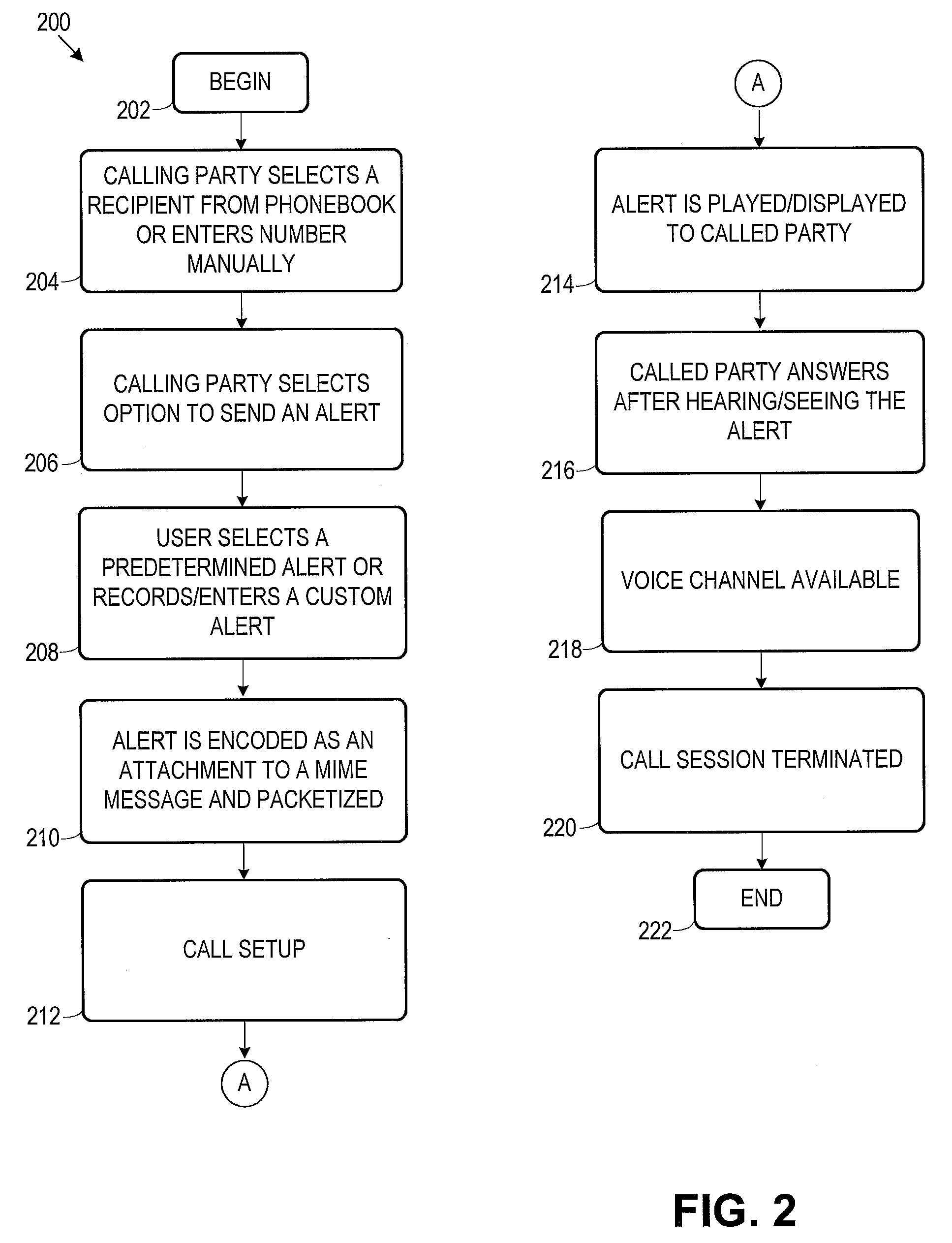
Calling party alert
InactiveUS20080089509A1Access is deniedInterconnection arrangementsSpeech analysisTelecommunicationsCommunication device
Devices, systems, and methods are provided to send an alert to a called party communications device during a call setup phase and to present the alert to a called party during an alert portion of the call setup phase. Other devices, systems, and methods are provided that allow a calling party to remotely and securely access at least one host computer by sending a security phrase during a call setup phase and presenting the security phrase to the host computer to determine if by way of comparison to a voice print if the calling party is a valid user.
Owner:CINGULAR WIRELESS II LLC
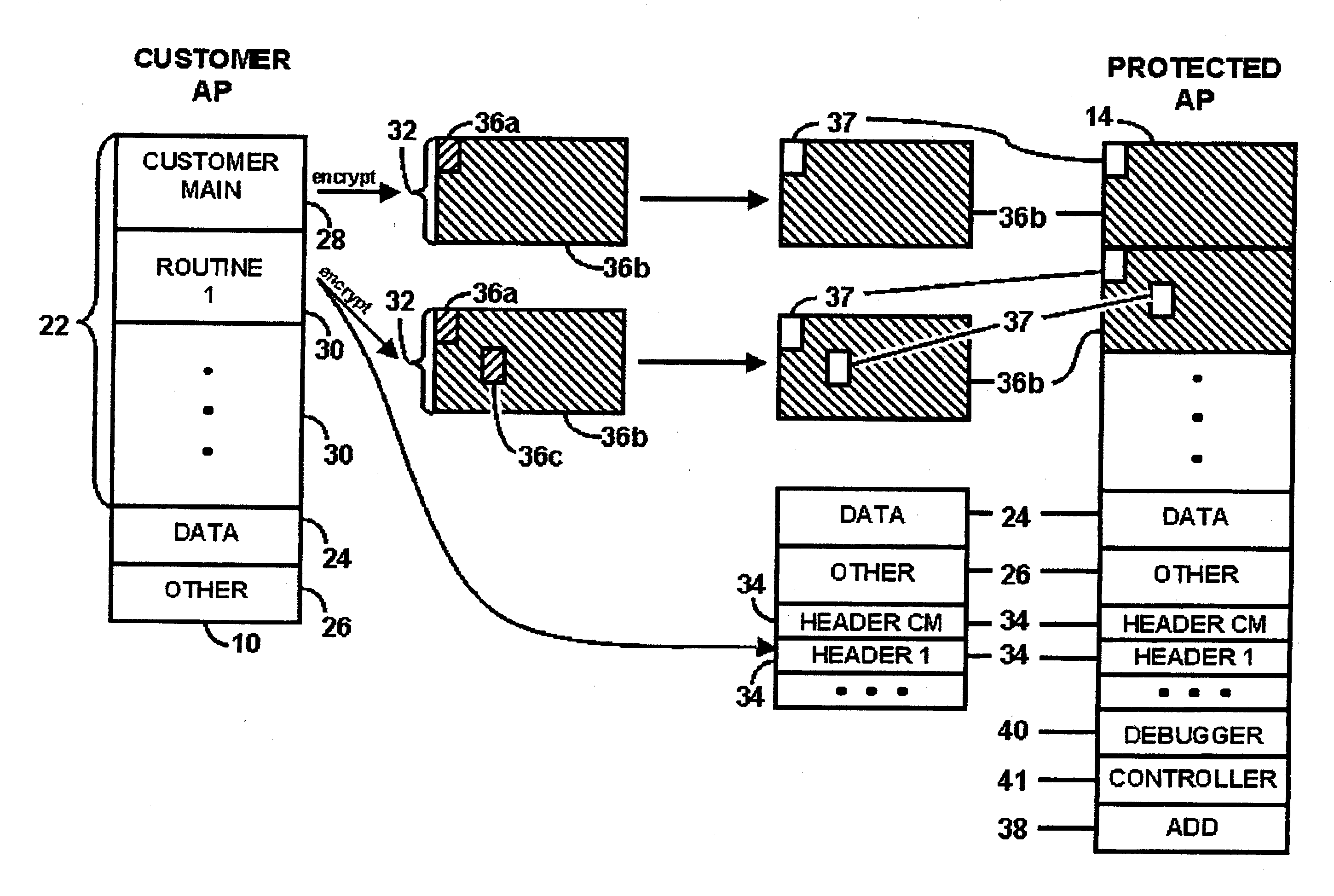
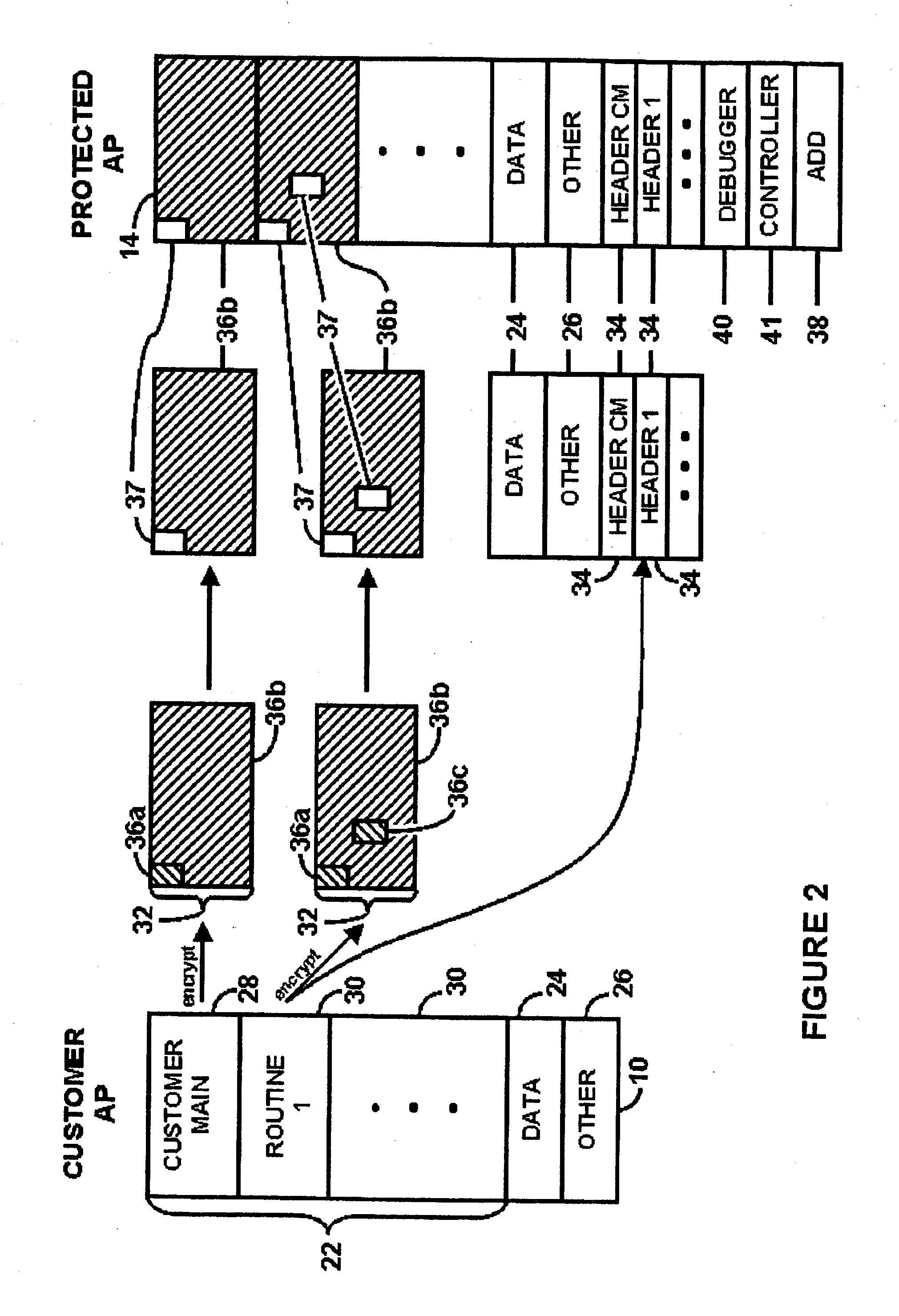
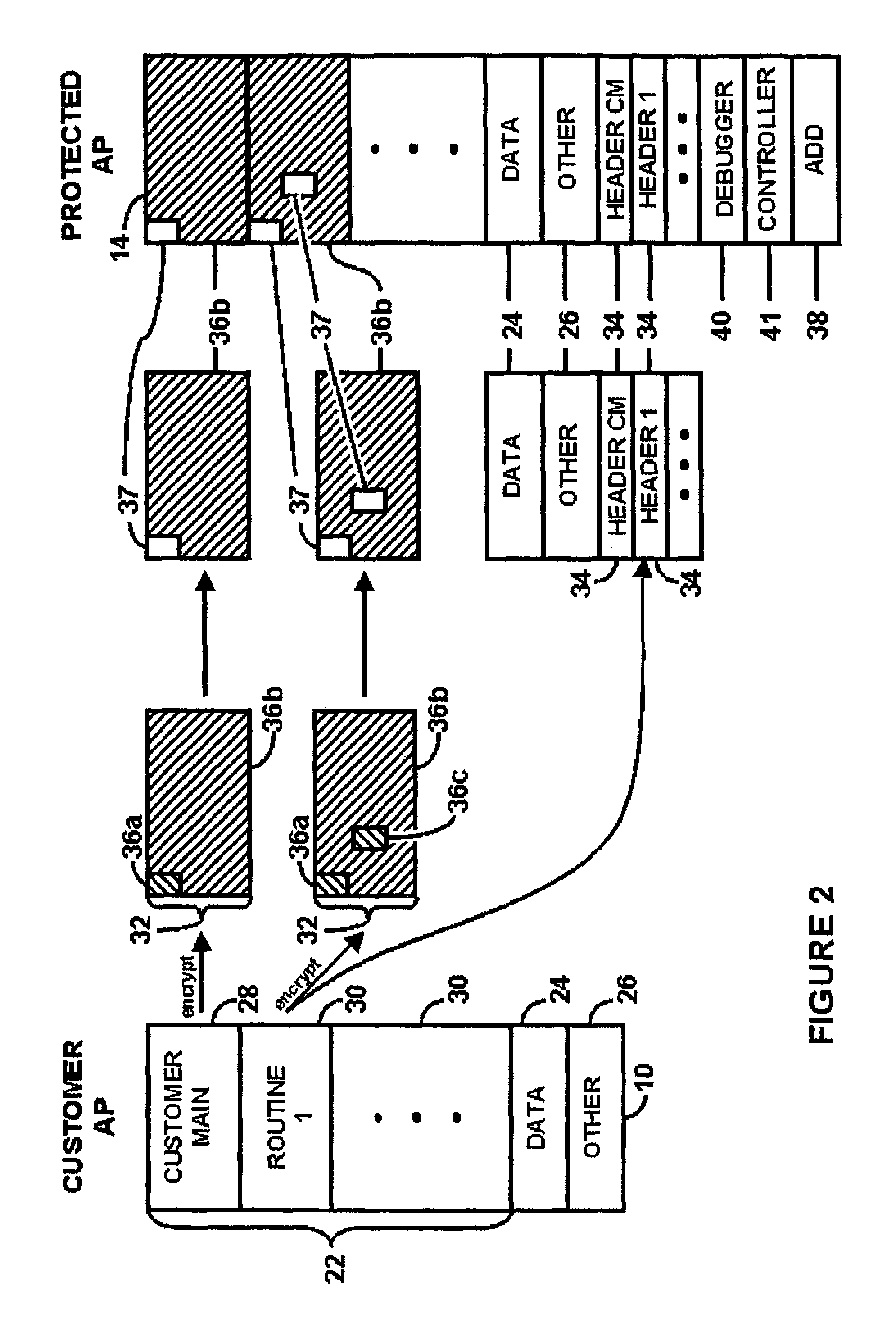
Systems And Methods For Regulating Execution Of Computer Software
InactiveUS20090328003A1Access is deniedSacrificing protectionDigital computer detailsUnauthorized memory use protectionResponse processOperational system
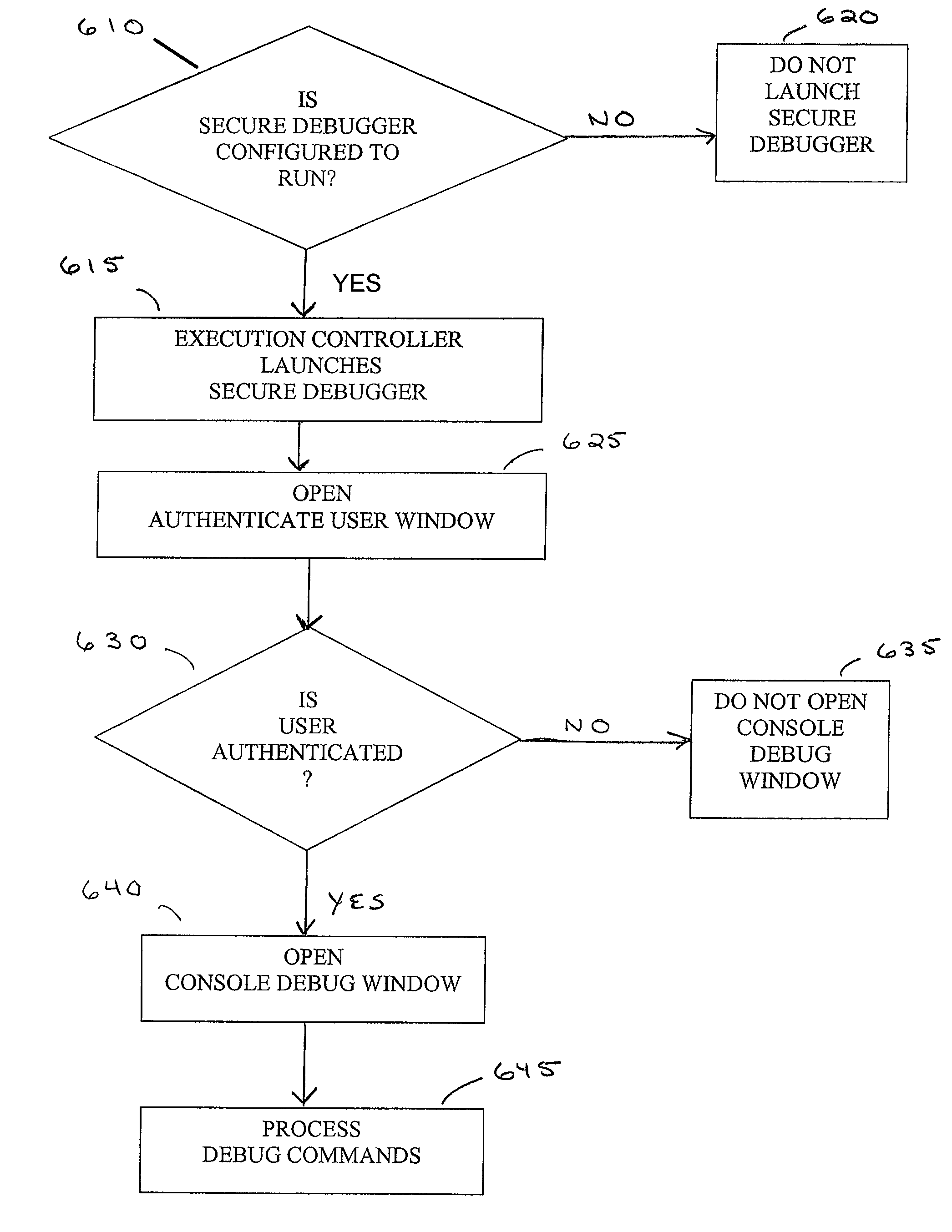
A method for regulating execution of an application program includes a process for preparing the application and a process for executing the application. The preparation process divides the application program into related segments and encrypts instructions of at least one segment. The preparation process positions encrypted instructions in at least two discontiguous regions within an executable file and associates header information with at least one discontiguous region. The header identifies a decryption key and the location of the other discontiguous region. The resulting execution file thus has portions that would not execute and would cause an operating system to call a responsive process. The execution process initiates execution of the protected application when at least a portion of the application instructions are available to the computer only in encrypted form. The user is authenticated, after which the encrypted portions can be decrypted and execution resumed. The processes may also include capability to detect and respond to tampering, or the ability to block execution snooping via a debugger. Also provided are systems and methods to allow debugging of code extensions to protected applications without sacrificing protection of the application. A Secure Debugger allows extension developers to examine memory and set breakpoints in their own extensions, without permitting them to view information in the rest of the protected application.
Owner:REVULYTICS INC
Method and system for secure network service
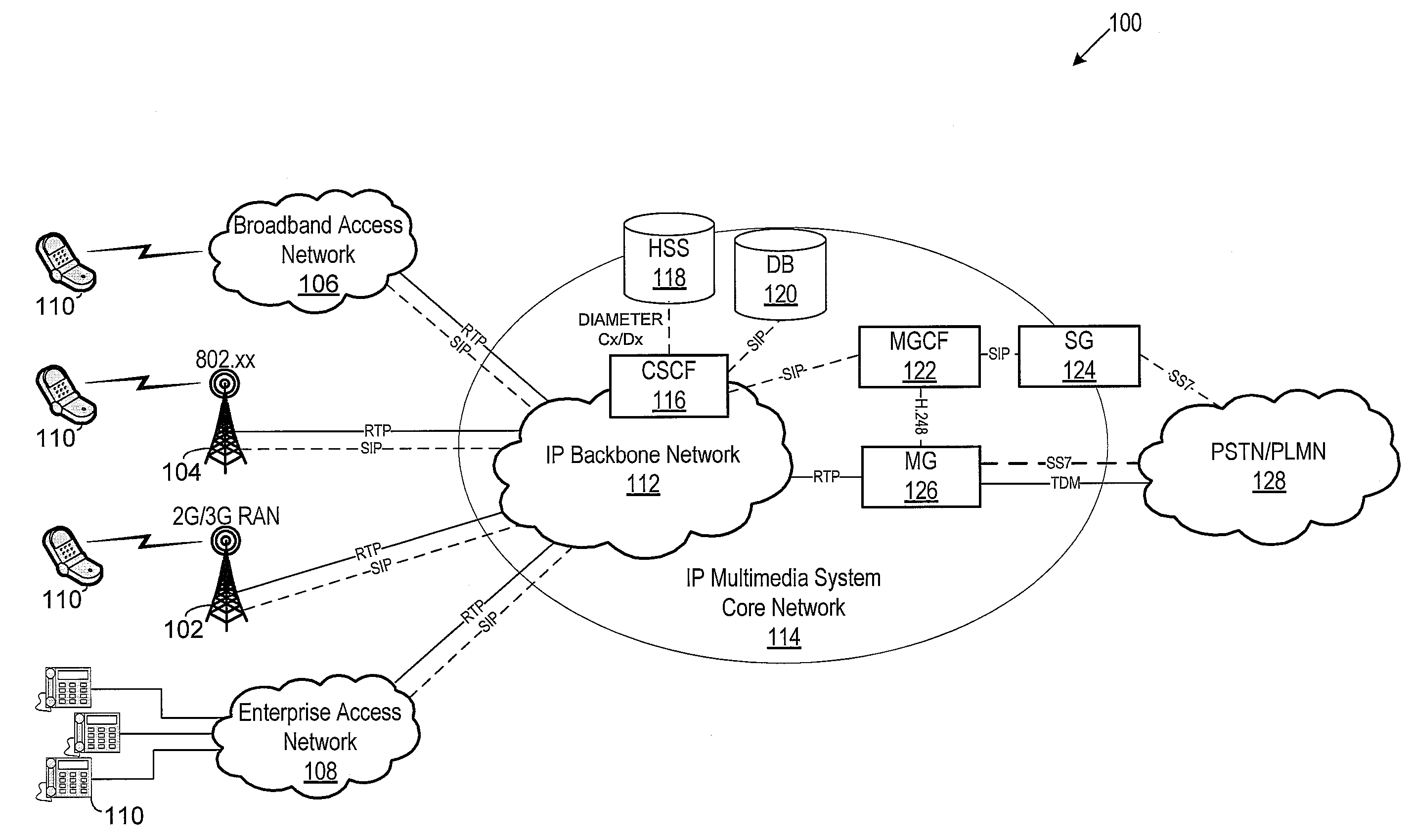
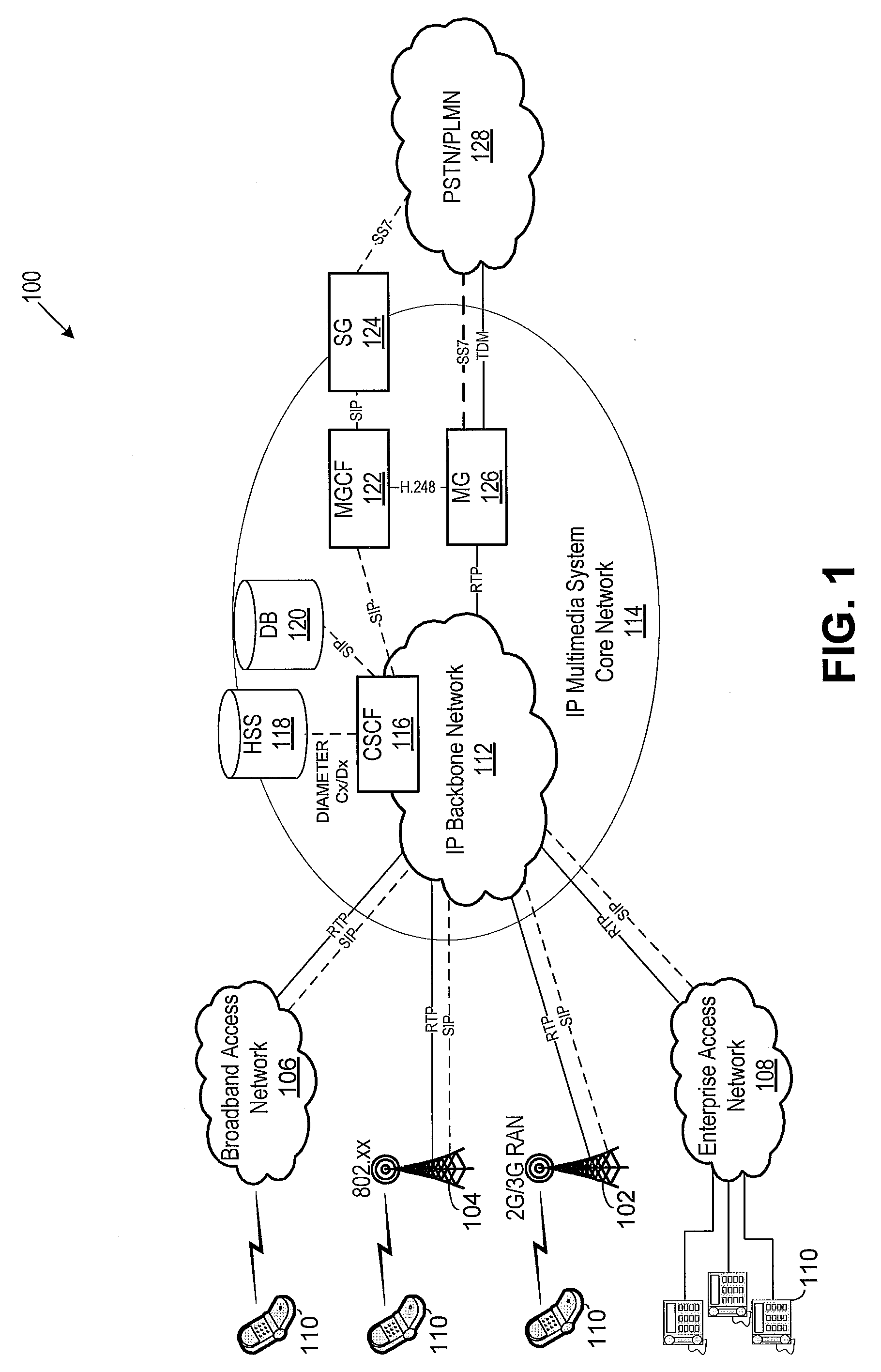
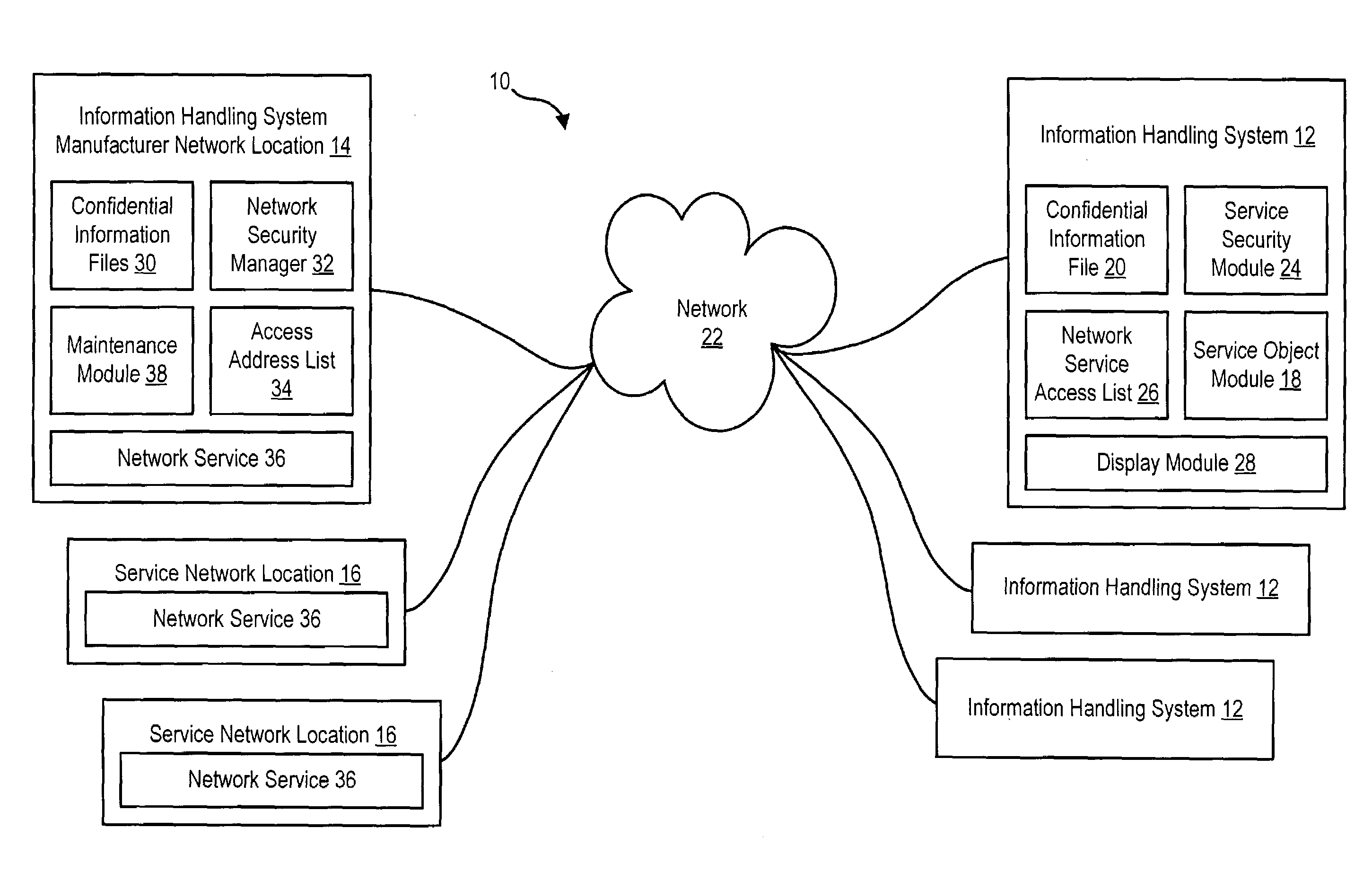
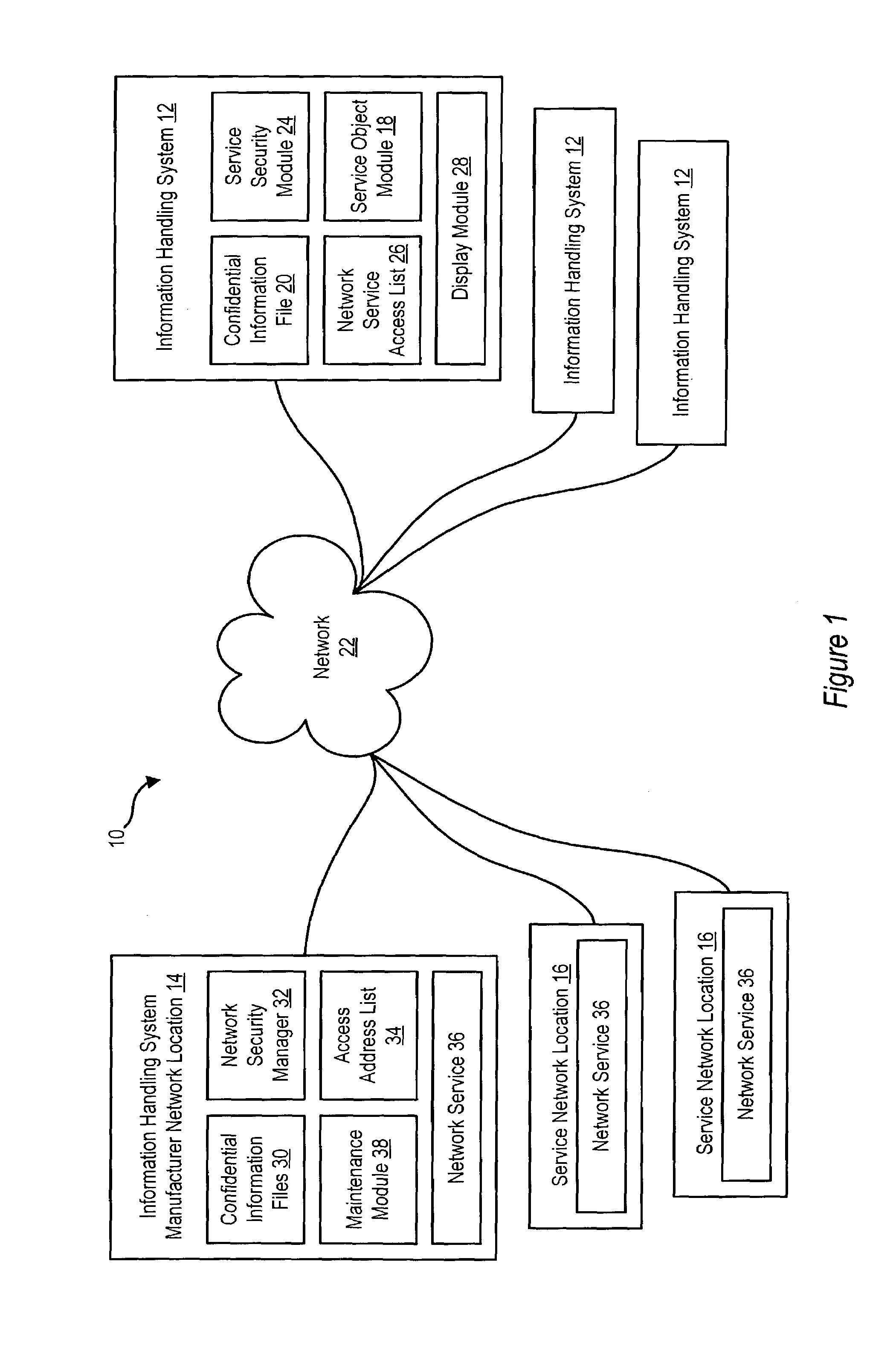
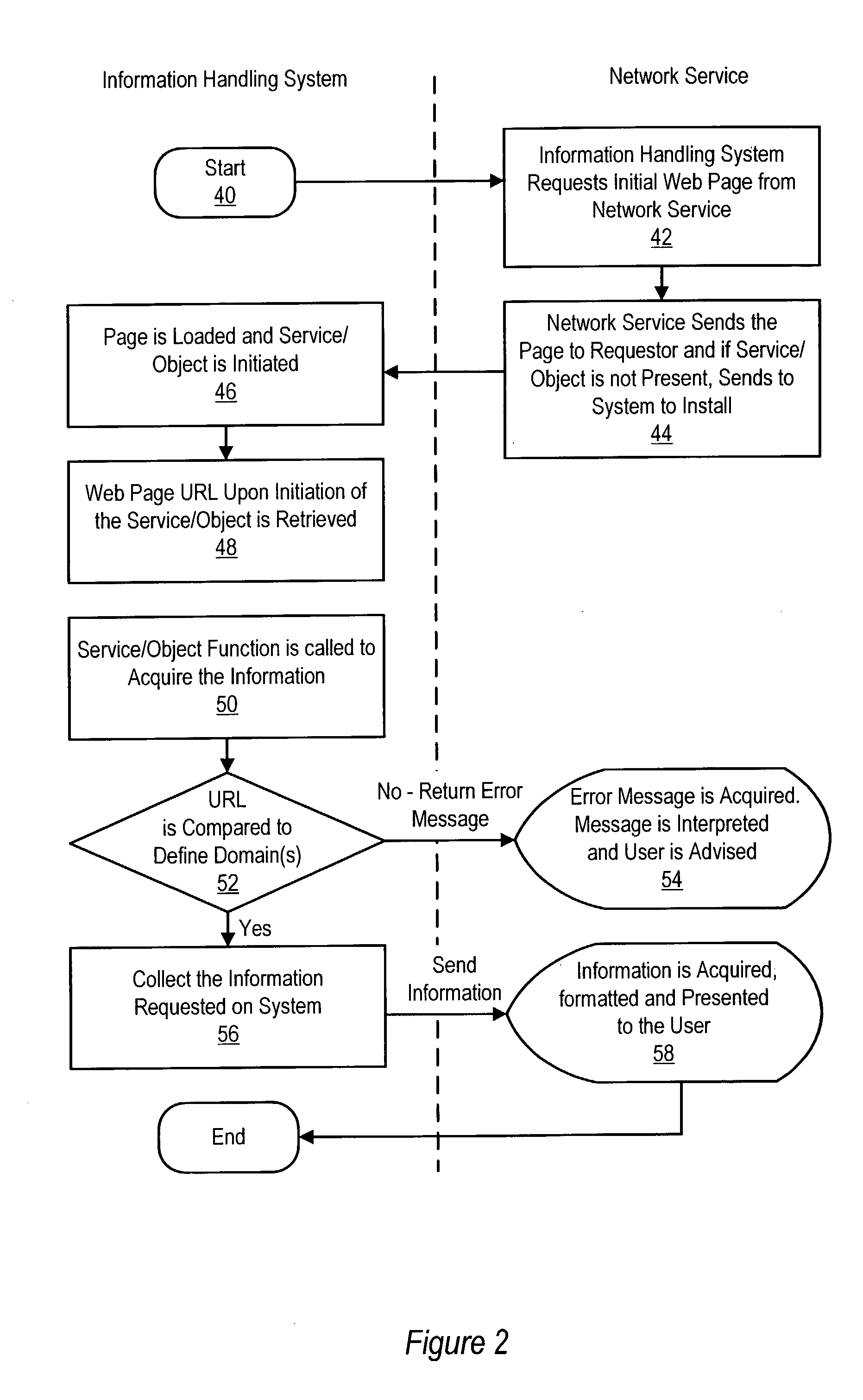
ActiveUS7200860B2Reduce disadvantage and problemReduce riskDigital data processing detailsAnalogue secracy/subscription systemsNetwork addressInformation handling system
A system and method for providing a secure network service to an information handling system compares the detected network address of a service network location that calls a service on the information handling system with a list of authorized network addresses and denies access to confidential information of the information handling system if the detected network address is not authorized to obtain confidential information from the service. For instance, a service security module loaded on the information handling system detects the URL or domain of a service network location and ensures that the URL or domain is on an authorized list of addresses before service functions are allowed to access confidential information associated with the information handling system.
Owner:DELL PROD LP
System providing self-service access to locked merchandise
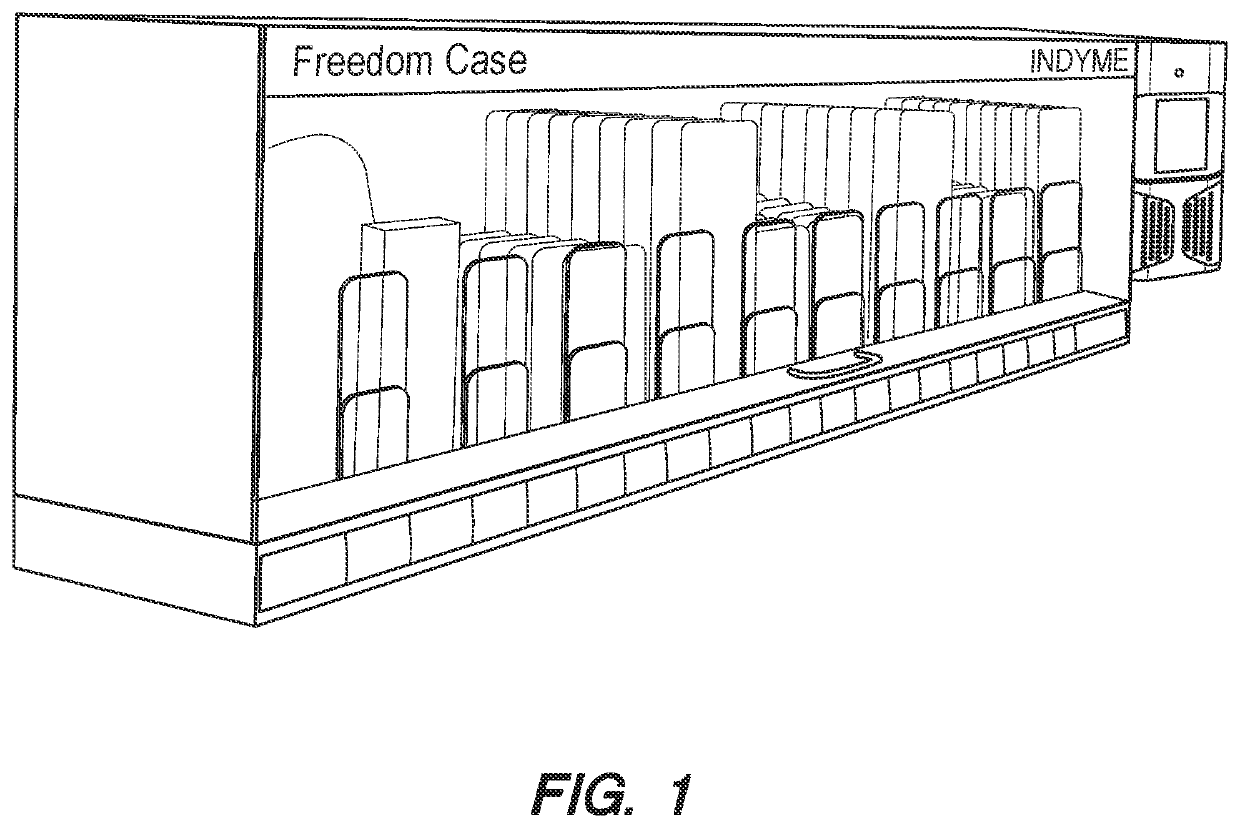
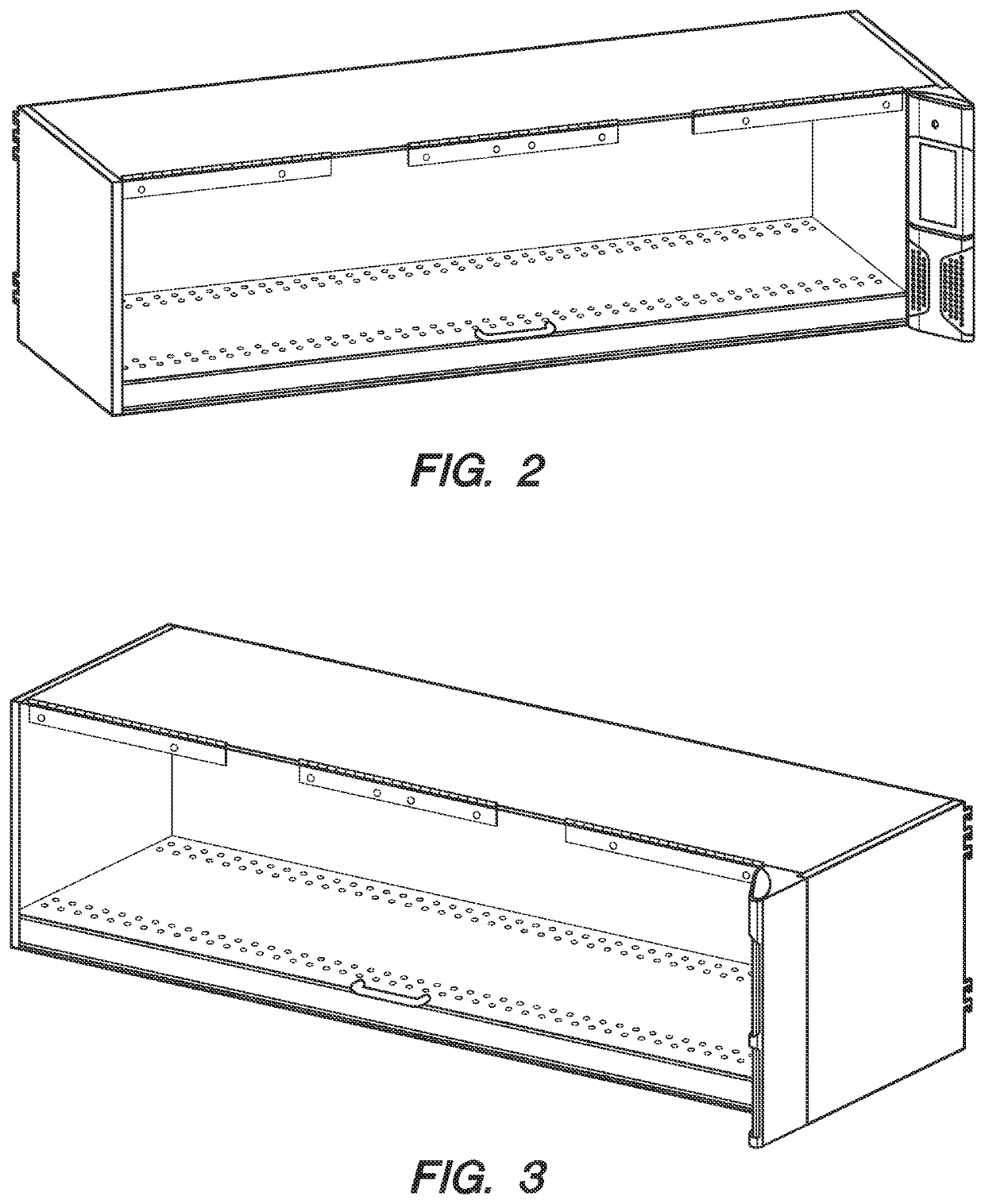
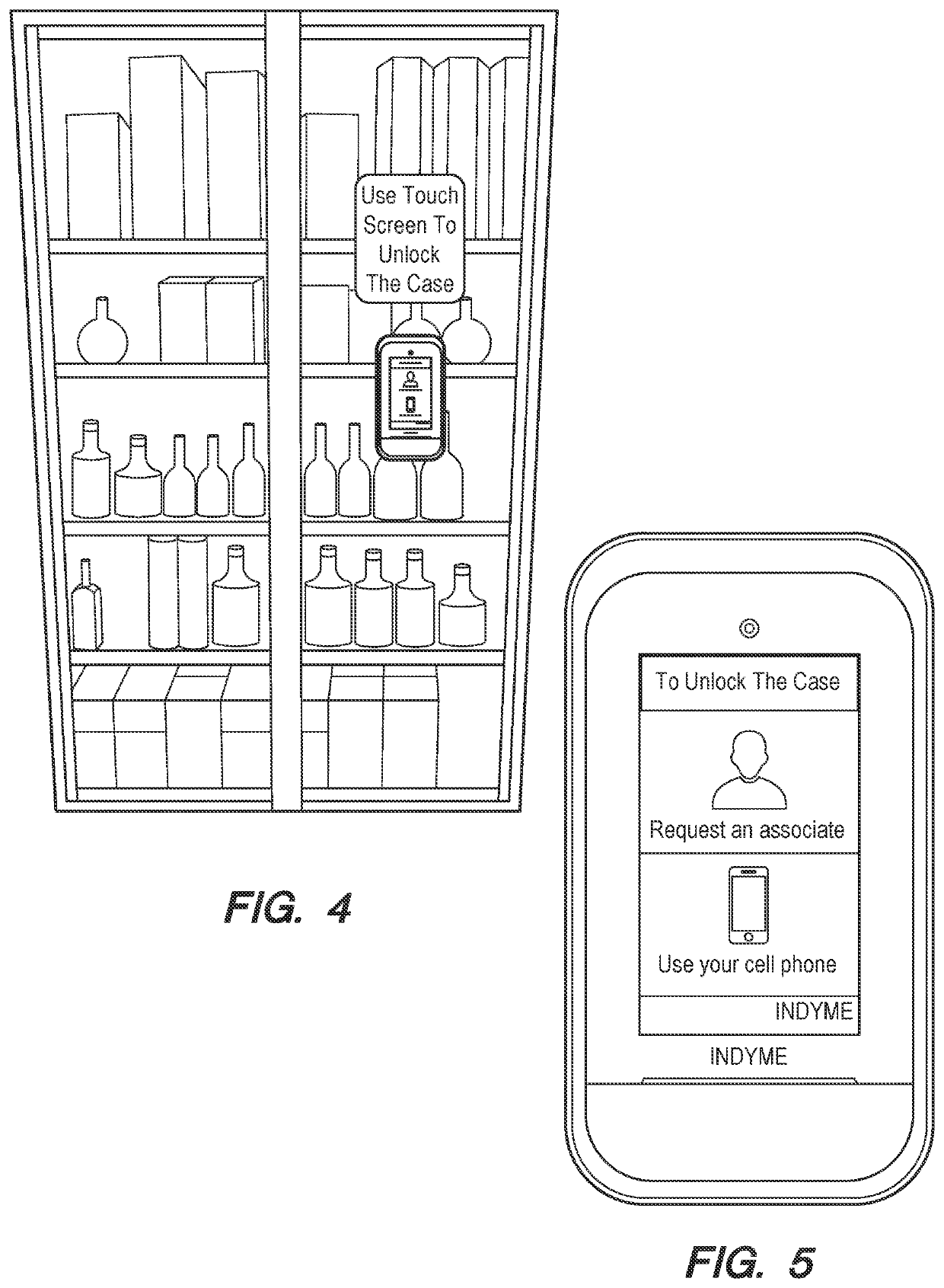
ActiveUS11182803B2Improve shopping experienceMaximize saleVideo data clustering/classificationRelational databasesSoftware engineeringOperating system
A system providing self-service access to locked merchandise comprising: (a) providing a fixture that restricts access to the locked merchandise, wherein the fixture can automatically lock or unlock, allowing or restricting access to the locked merchandise; (b) providing a means of uniquely identifying an individual attempting to access the merchandise; (c) measuring a set of behaviors of the individual during any time the fixture is an open mode; (d) assessing whether the set of behaviors of the individual are suspicious or not relative to a set of suspicious event thresholds; (e) storing the individual and their set of behaviors as accessible records in at least one database; and (f) providing an algorithm which determines future access privileges of the individual to the enclosure based on a set of variables.
Owner:INDYME SOLUTIONS LLC
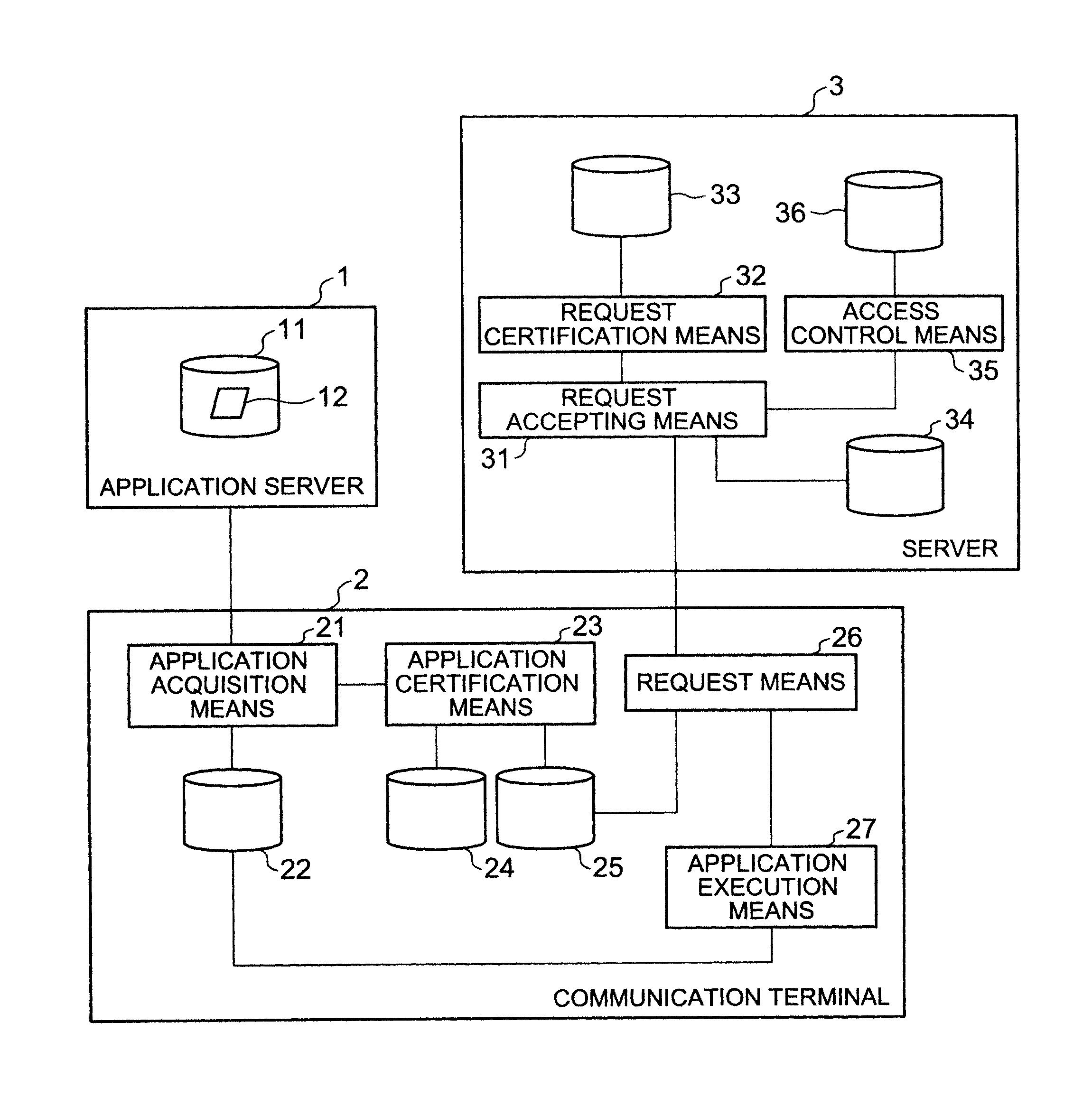
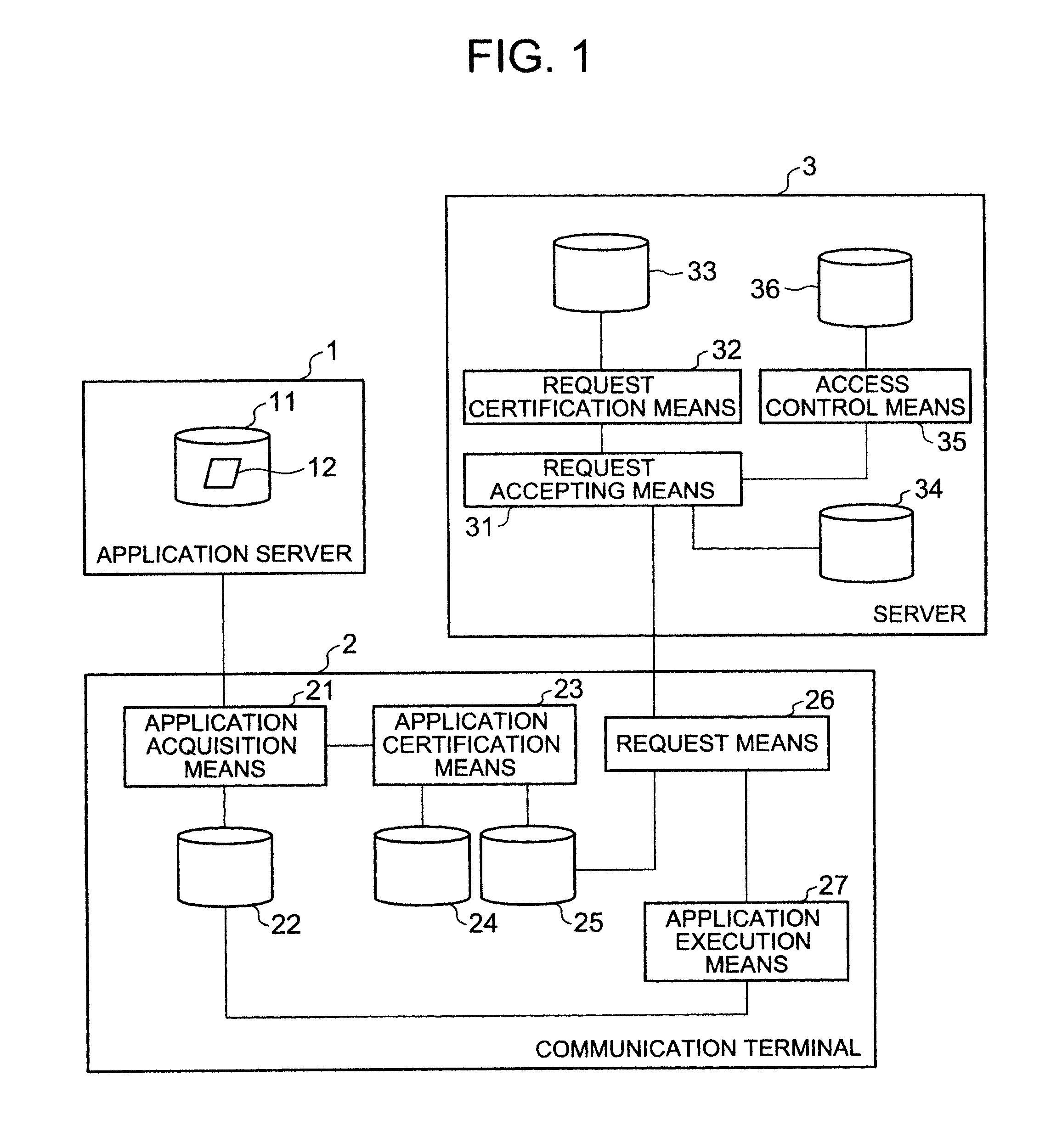
Access control system, communication terminal, server, and access control method
InactiveUS8914905B2Access is deniedDigital data processing detailsUser identity/authority verificationComputer terminalMedia access control
Terminal certification means of a communication terminal manages a content and certification information on the content in association with each other. Upon access to a server associated with the execution of the content, request means sends the server a request including certification information associated with the content. In response to the request from the communication terminal, the server uses server certification means to certify the request. Access control means performs access control based on policy information stored in policy information storage means.
Owner:NEC CORP
Network interface
InactiveUS20090060168A1Durable and flexibleAccess is deniedInterconnection arrangementsSubstation equipmentTamper resistanceNetwork interface device
A network interface device (NID) and associated printed circuit board is provided that includes metallic die cast housing and doors configured so that one of the doors, when closed, physically separates service provider circuitry from the customer premise equipment (CPE) side connections on a circuit card within the NID so that an end-customer may access the CPE side connections while the service provider circuitry remains secured from end-customer access. Moreover, the metallic housing provides increased physical strength and tamper resistance, including improved heat dissipation properties to radiate internal heat build-up more efficiently. The NID may be configured to provide insertable interface cards to permit flexibility in service provisioning and includes options for a type-200 T1 module, a type-400 T1 module, a type-200 high bit rate Digital Subscriber Line (HDSL) module, a type-400 HDSL module or an ISDN module.
Owner:SK COMMUNICATIONS
Passive arc control with sequestered phases in a vertical bus system of a motor control center
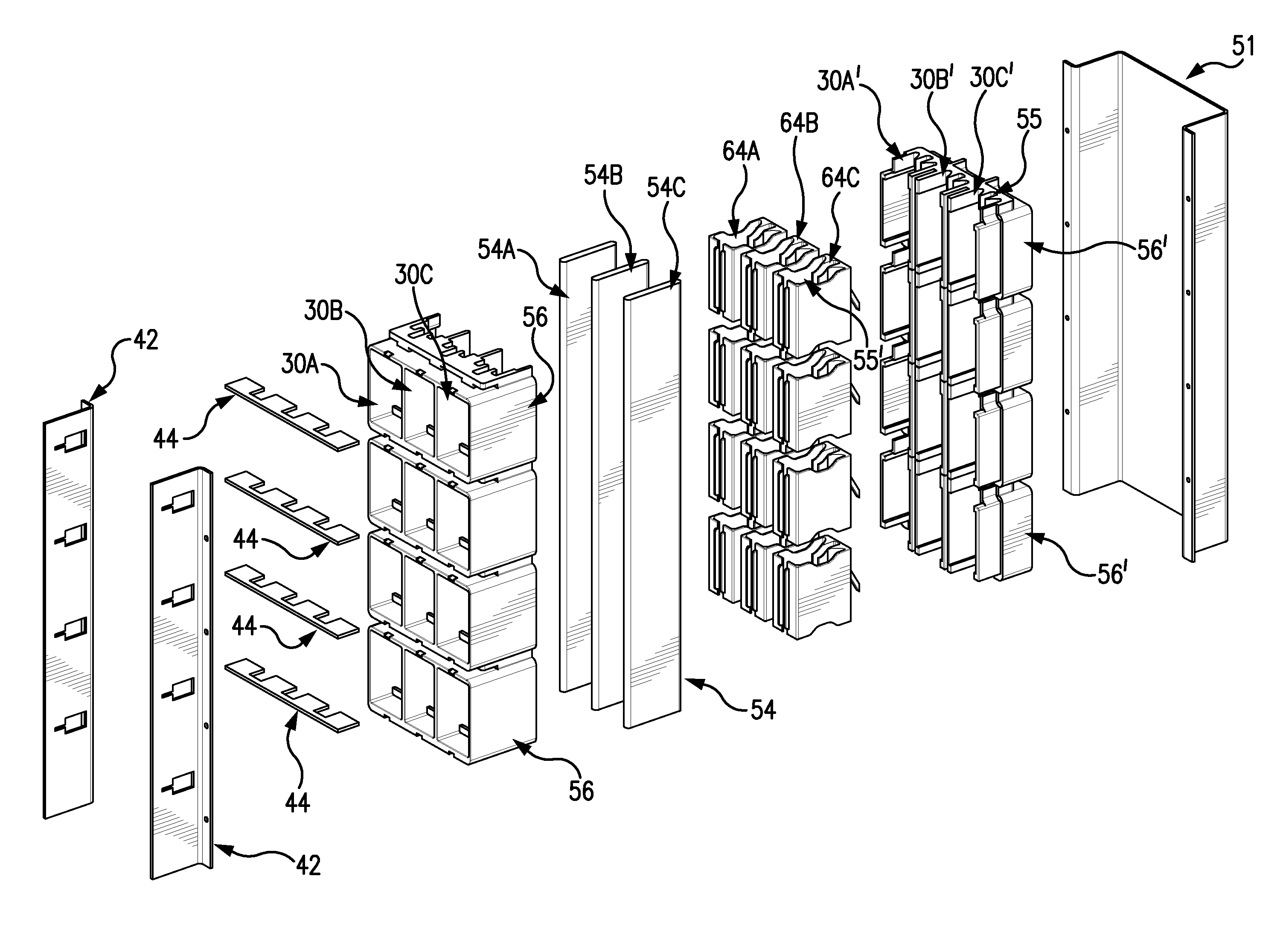
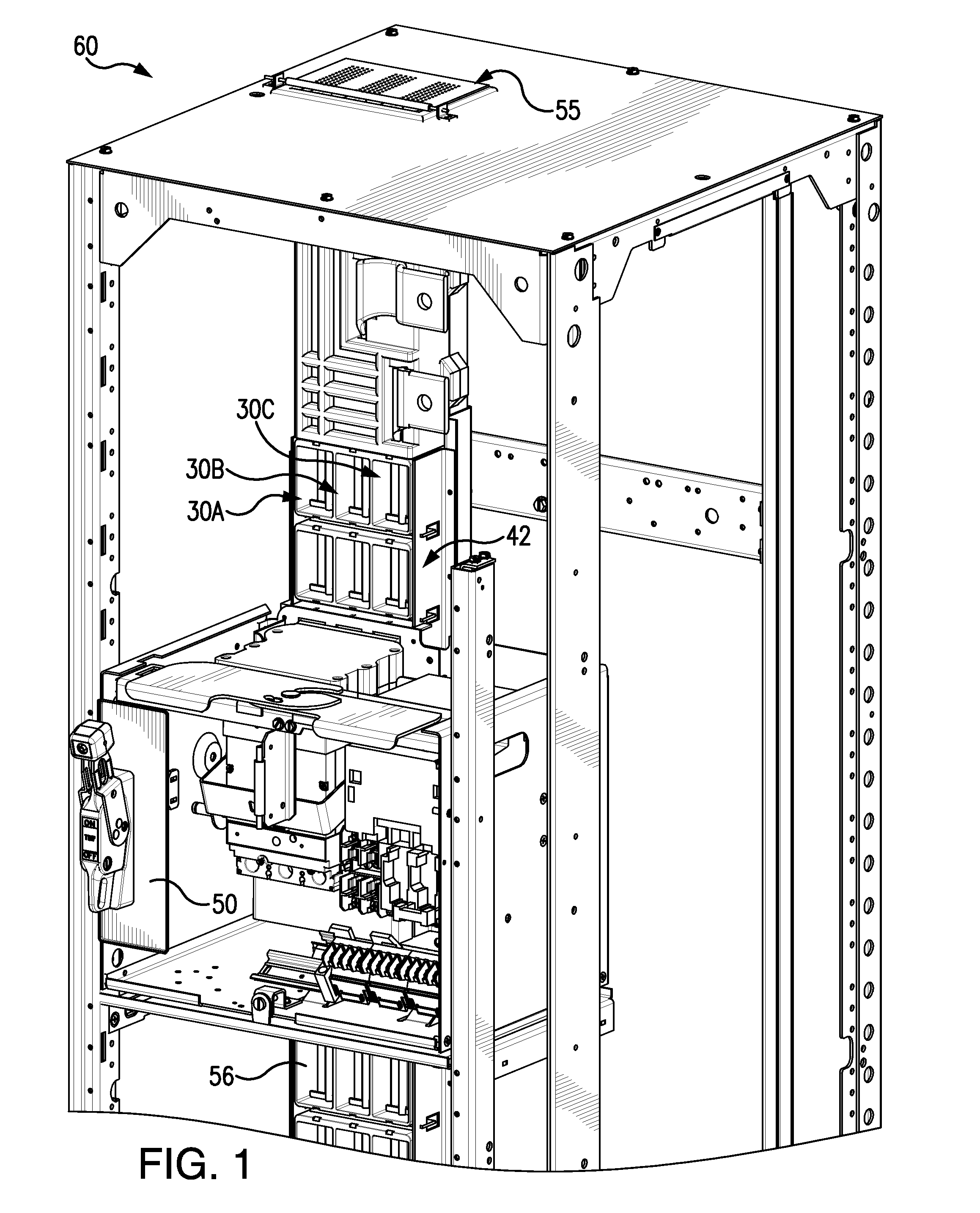
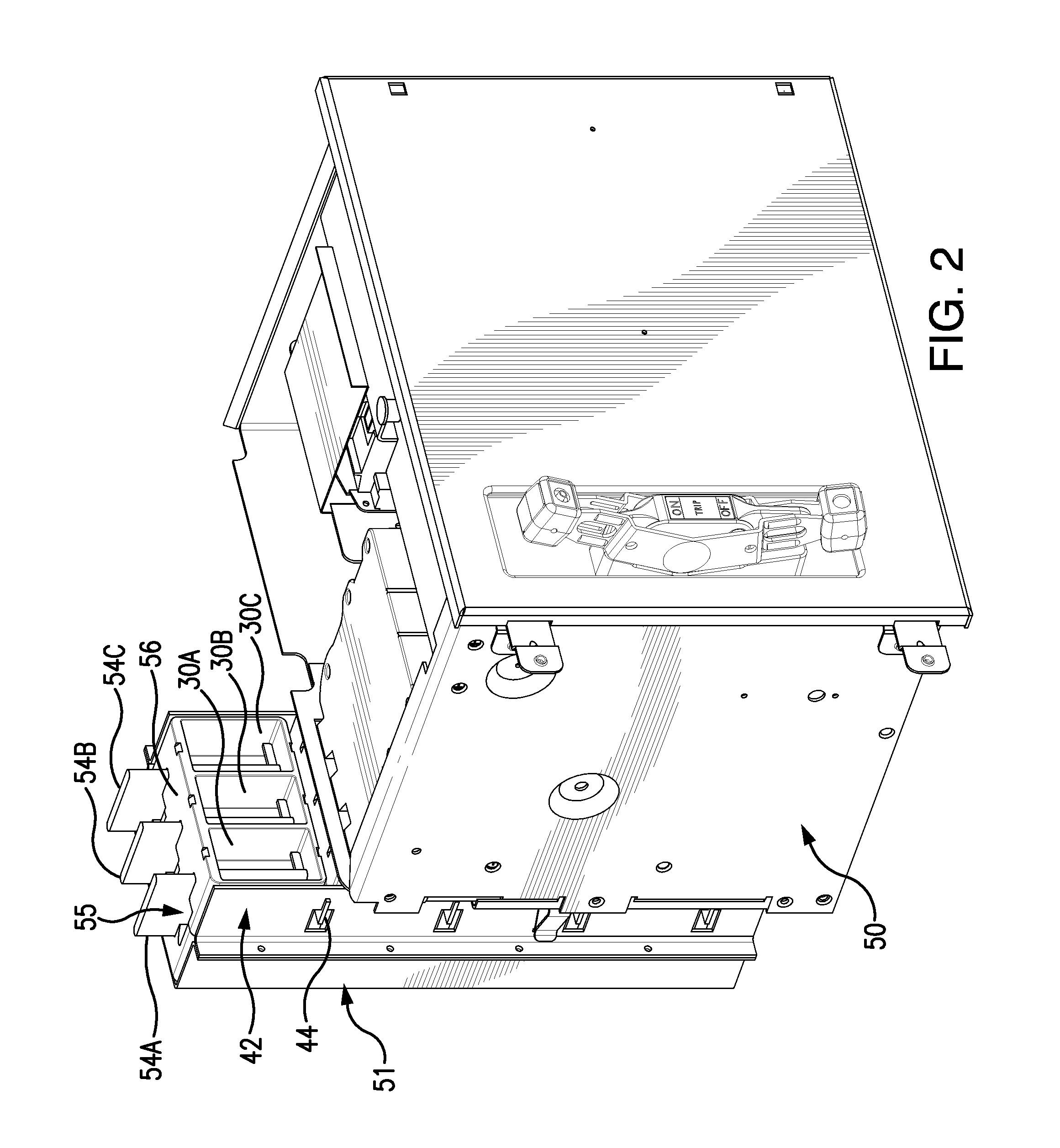
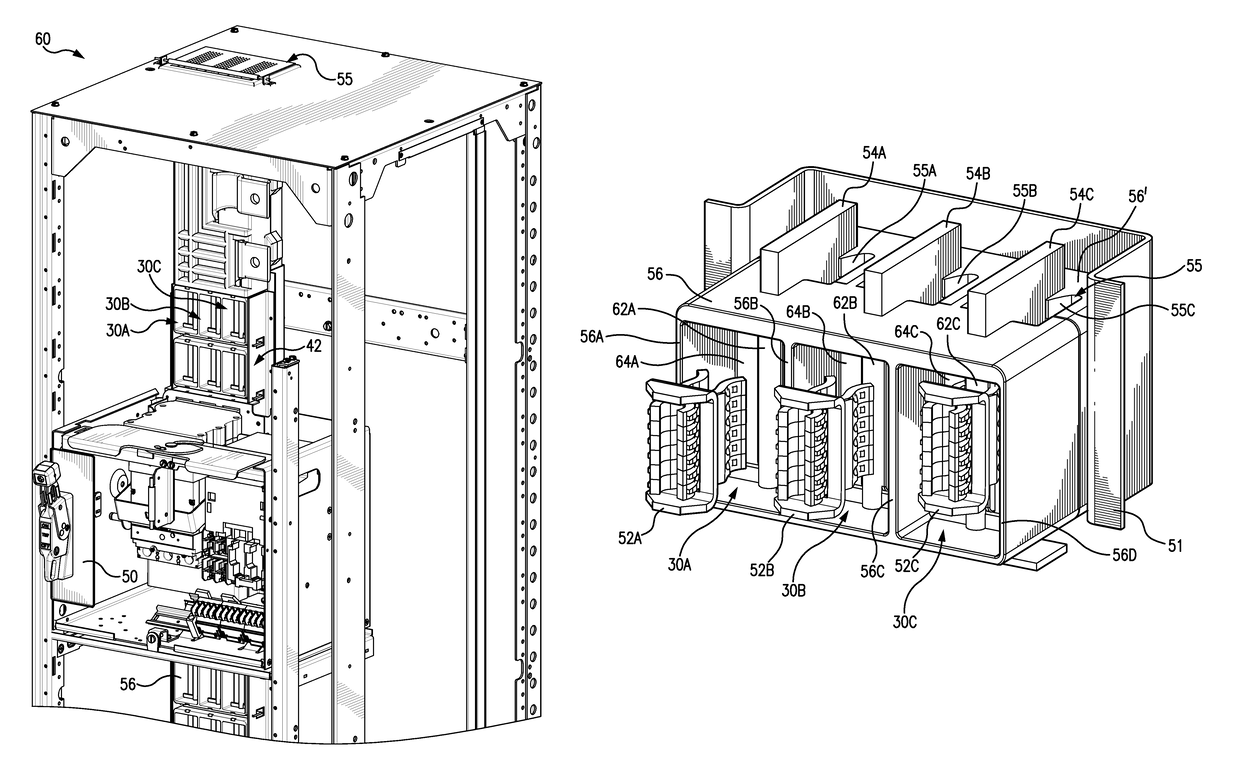
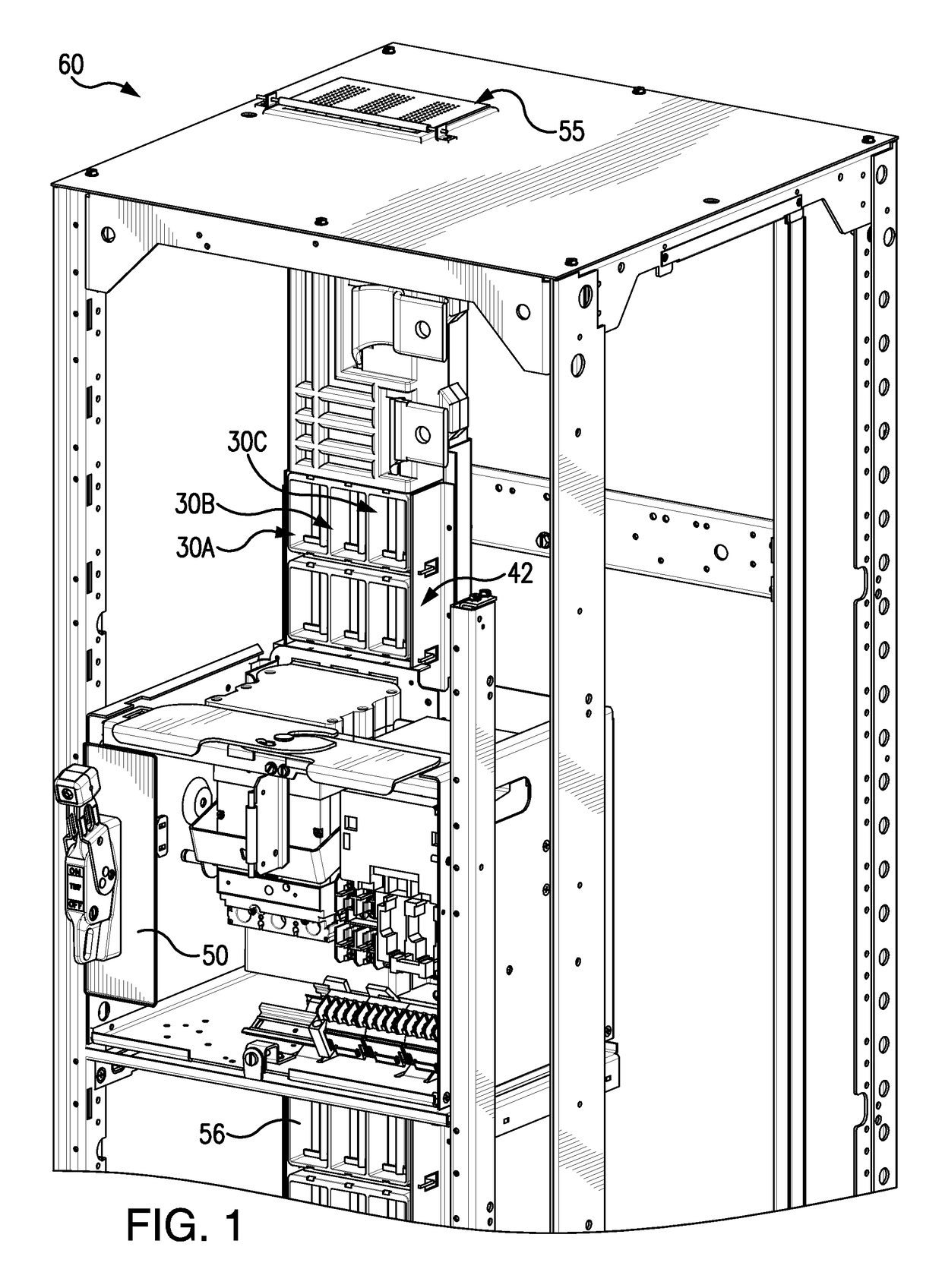
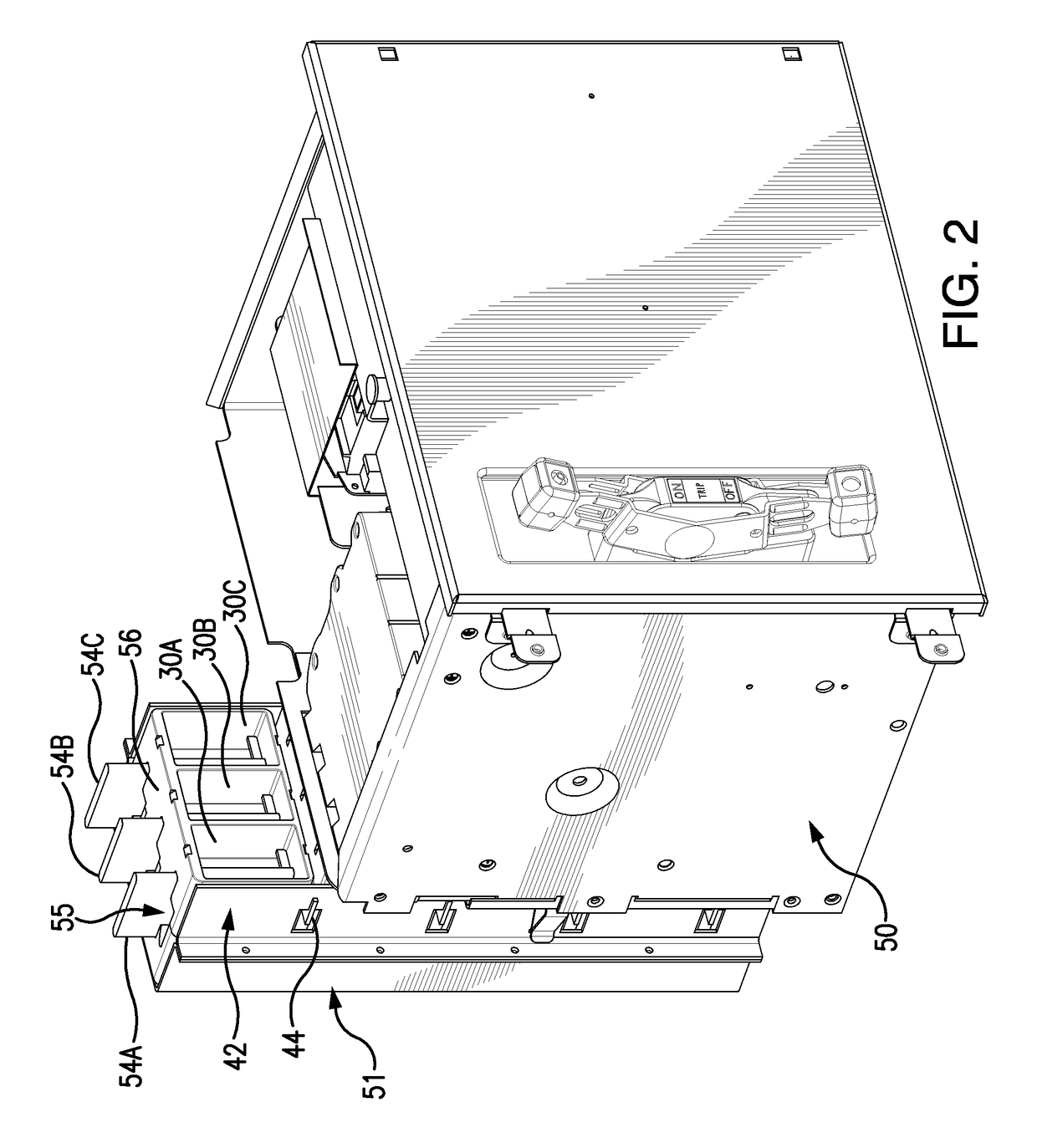
ActiveUS20150372461A1Minimize potential for harmAccess is deniedBus-bar/wiring layoutsSwitchgear detailsArc flashControl system
A passive arc control system for a motor control center 60 includes an arc attenuating box having sides separating adjacent vertical bus bar phases 54, providing a physical barrier to arc flash energy. The box is open at its top and bottom forming a chimney 55. A shutter assembly for each box includes an insulator cap 62 on a free end of the bus bar and an independently moveable, box-shaped shutter 64 that slides along the bus bar away from the insulator cap, when a device is connected to the bus bar. The shutter has an opening 65 through which the bus bar passes when the device is connected to the bus bar and an opening 55′ aligned with the box's chimney. The arc control system provides a high degree of arc protection for personnel working around open motor control centers and is highly modular and easy to construct.
Owner:SCHNEIDER ELECTRIC USA INC
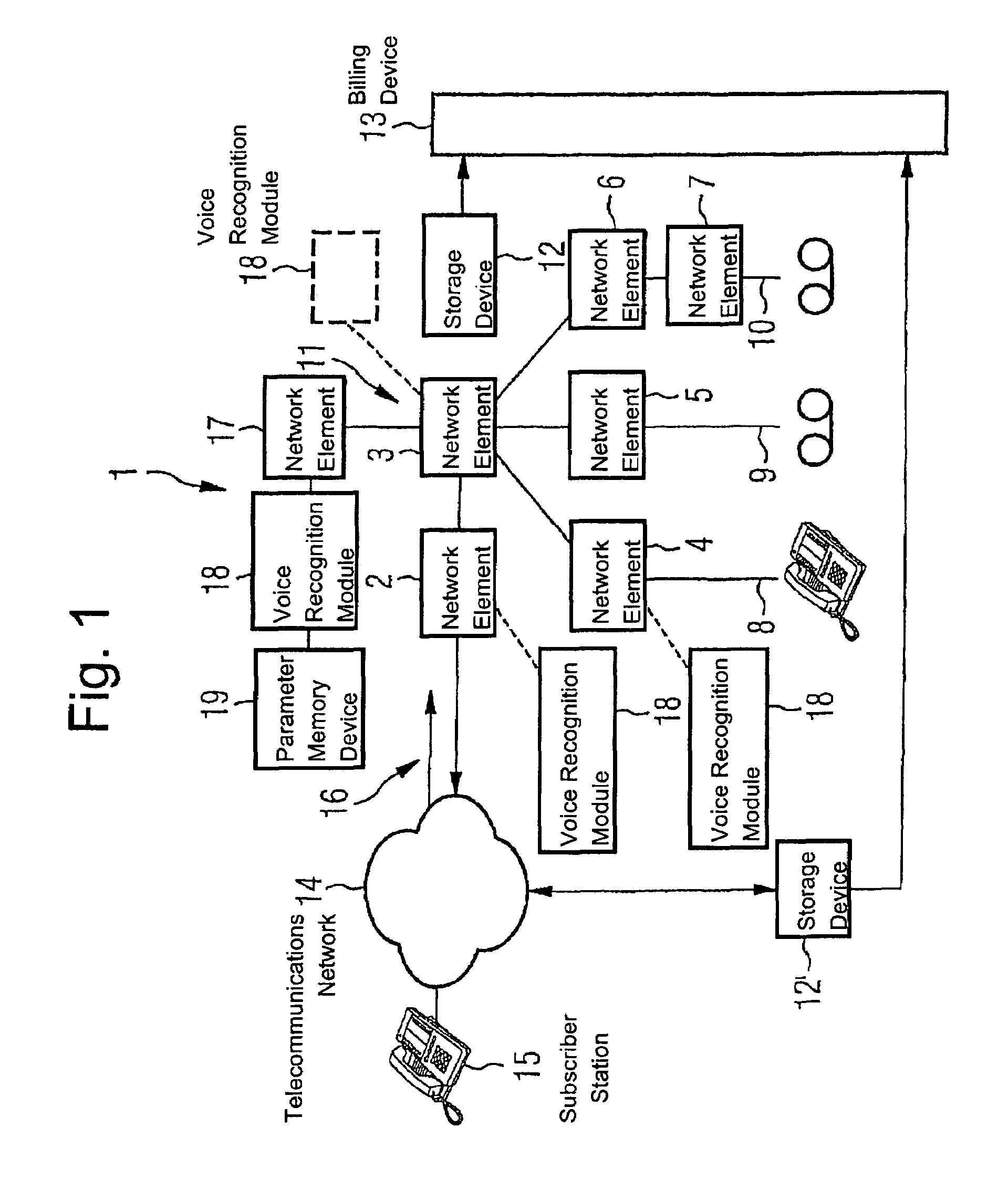
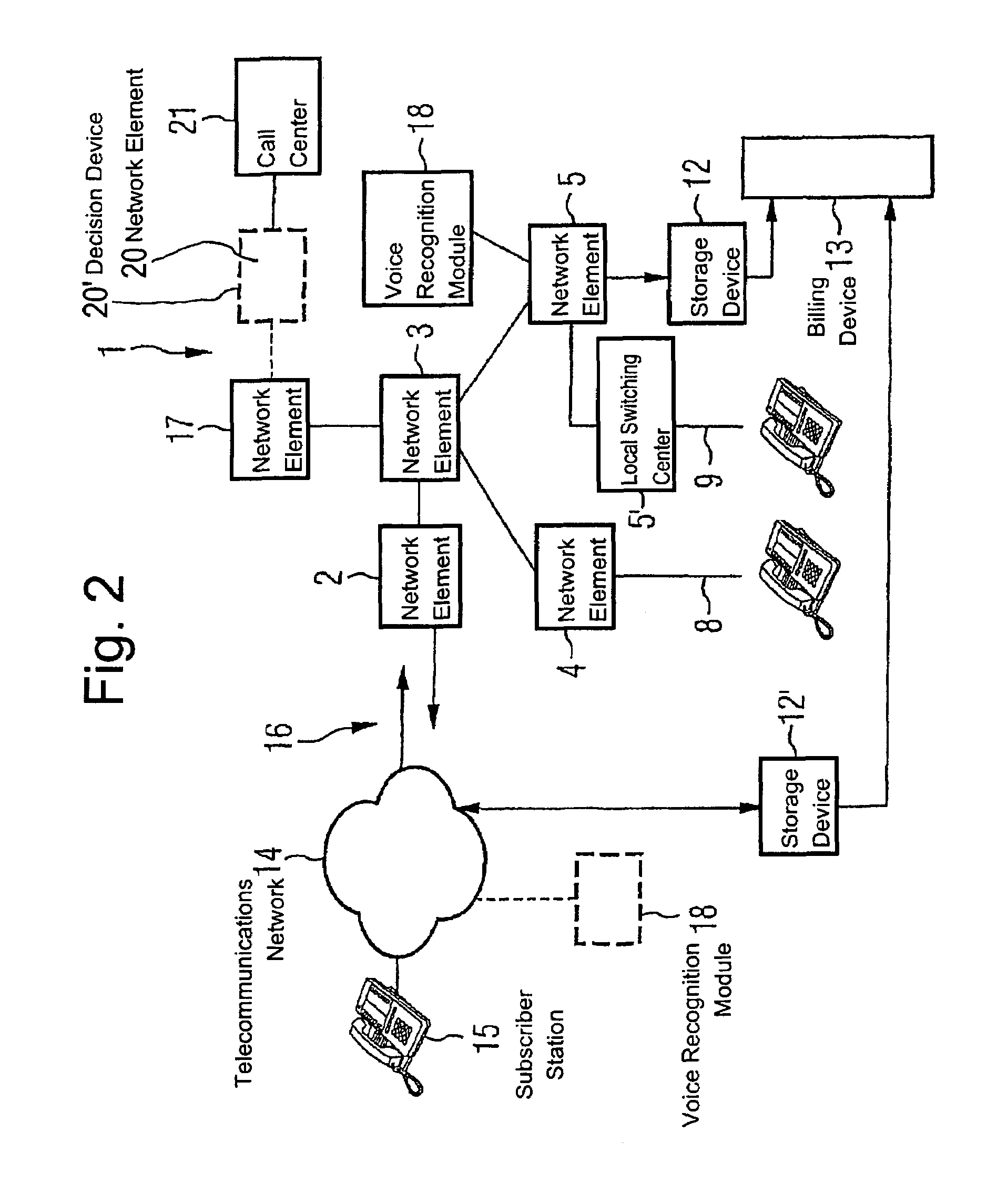
Control of access for telephone service providers using voice recognition
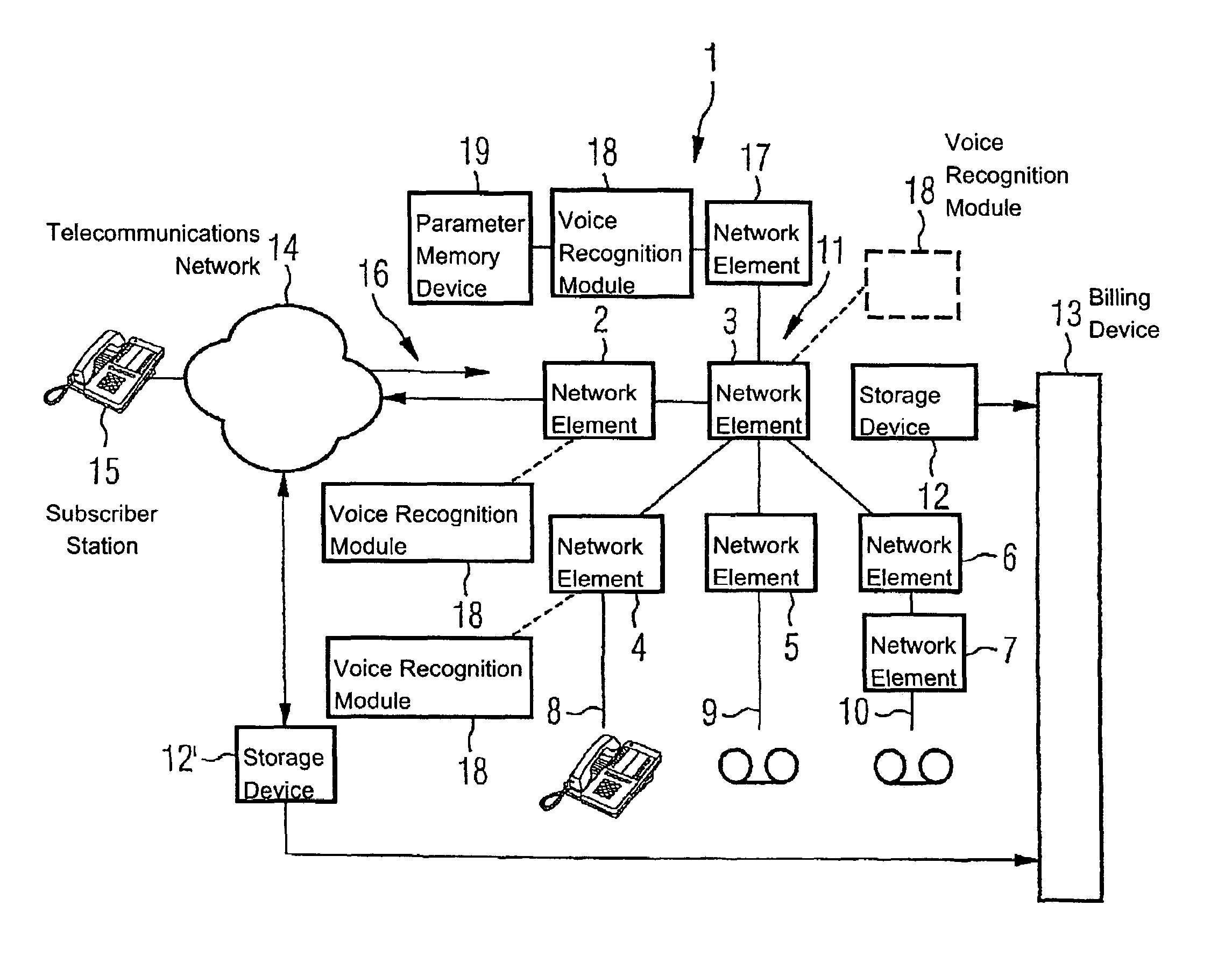
InactiveUS7164754B2Sure easyAvoid problemsElectric signal transmission systemsDigital data processing detailsTelecommunications networkSpeech identification
A telecommunications network includes a plurality of subscriber stations, a plurality of network elements and a voice recognition module. The voice recognition module is associated with a network element and is configured to recognize at least one biometric voice parameter.
Owner:DEUTSCHE TELEKOM AG
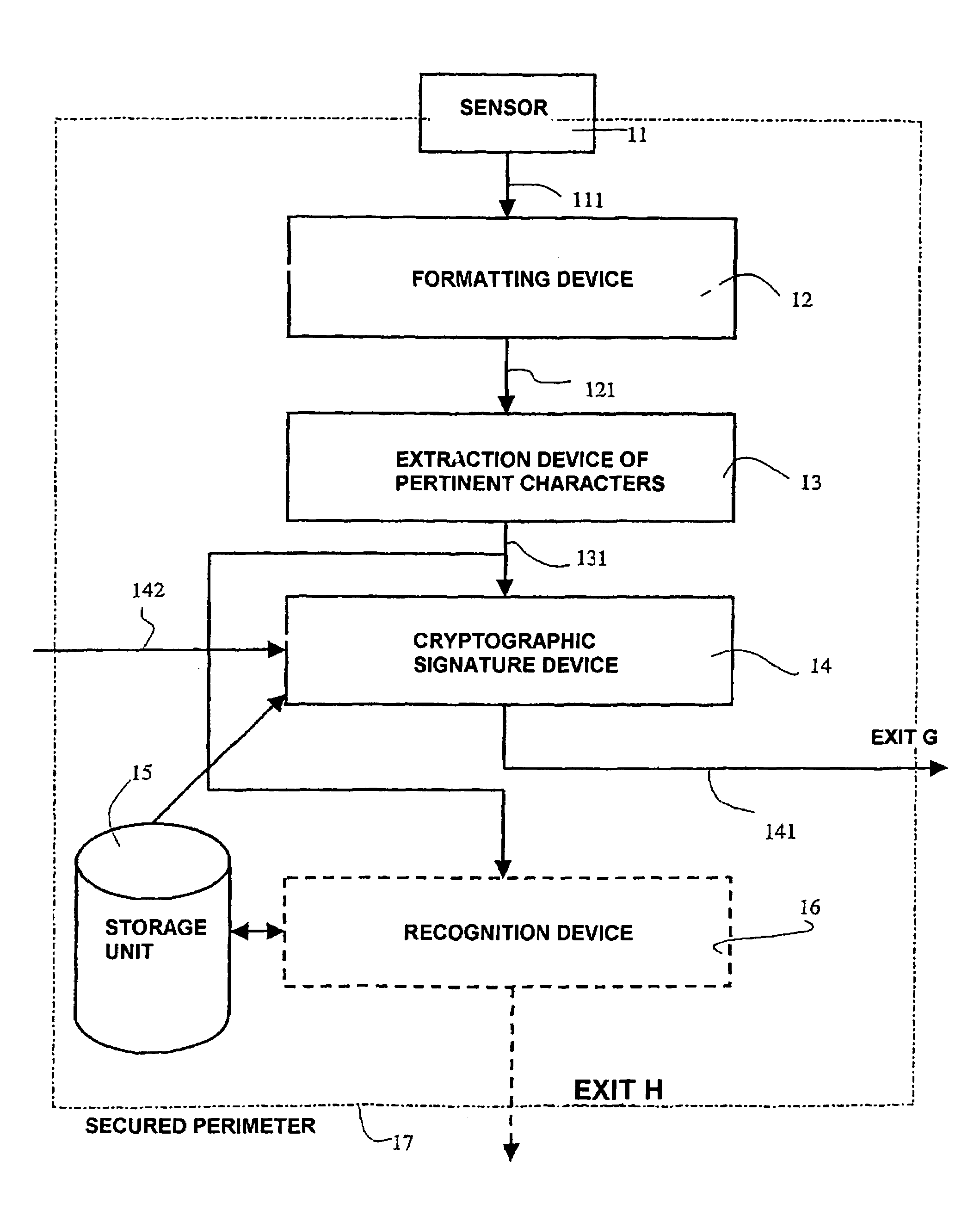
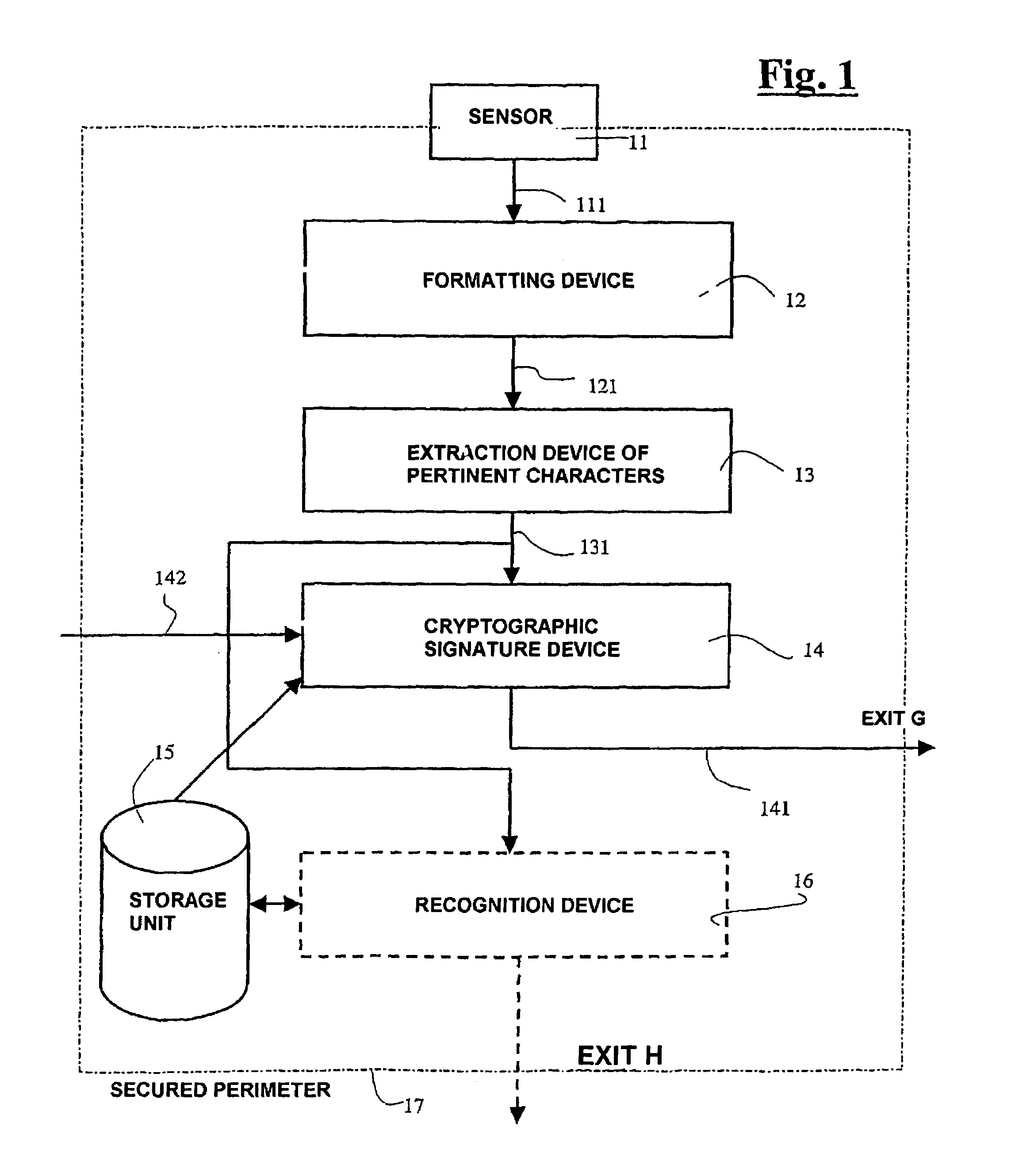
Device and method of recognizing at least one individual, the corresponding access control device and system and applications thereof
InactiveUS7255269B2Guaranteed efficiencyEasy to implementElectric signal transmission systemsDigital data processing detailsIdentification deviceSilicon
The invention relates to a device and method for the recognition of at least one individual and to the corresponding access control device and system and application thereof. The inventive recognition device comprises a one-piece integrated circuit which is produced by integrating the following elements on a silicon substrate: at least one biometric information sensor; means of processing said biometric information; cryptographic means which deliver at least one piece of encrypted data that is representative of at least one part of said biometric information and / or a corresponding piece of recognition information; and protection means that block access to data in transit, stored and / or processed in said one-piece integrated circuit in order to create a secure perimeter. In this way, the data exchanged by said sensor(s), processing means and cryptographic means, and particularly the aforementioned biometric information, are only saved in the one-piece integrated circuit and cannot be accessed from outside. Moreover, only encrypted data are delivered to the outside from said one-piece integrated circuit.
Owner:APPLE INC
Apparatus and method of detecting and controlling privilege level violation process
ActiveUS8082590B2Access is deniedEliminate riskDigital data processing detailsDigital computer detailsWeaknessPrivilege level
Provided are an apparatus and method of detecting and controlling a privilege level violation process. The apparatus monitors whether higher-privileged processes depend on information provided from lower-privileged objects or denies the higher-privileged processes to access the lower-privileged objects. The apparatus is provided in a process, and monitors whether a process accesses to a lower-privileged object. The apparatus gives a warning message or denies an access of the process to the lower-privileged object when it detects that the higher-privileged process access to the lower-privileged object. Therefore, the apparatus of detecting and controlling a privilege level violation process detects weaknesses that may be caused by privilege level violation, thus allowing a system to be safely operated.
Owner:ELECTRONICS & TELECOMM RES INST
Backup service and appliance with single-instance storage of encrypted data
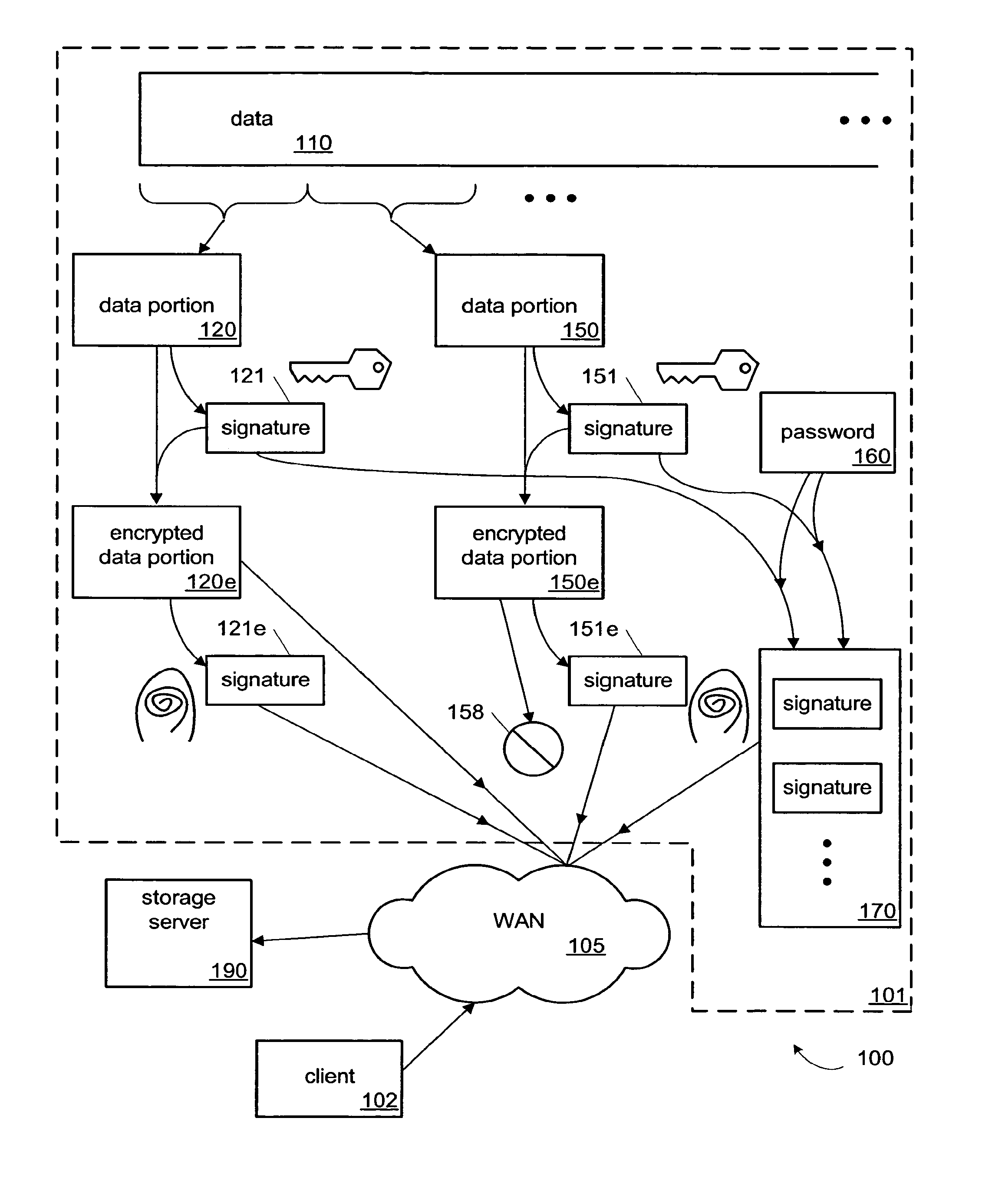
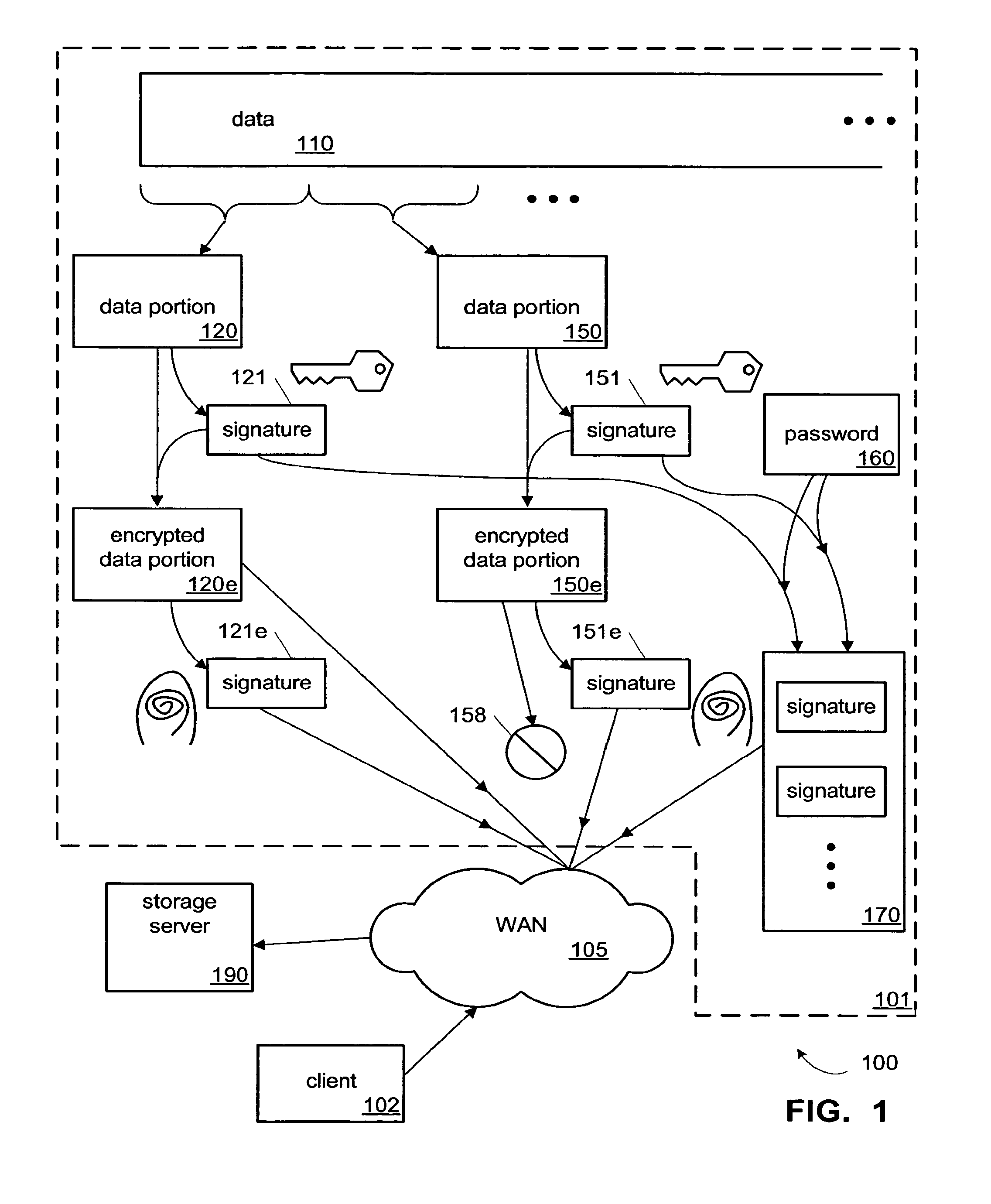
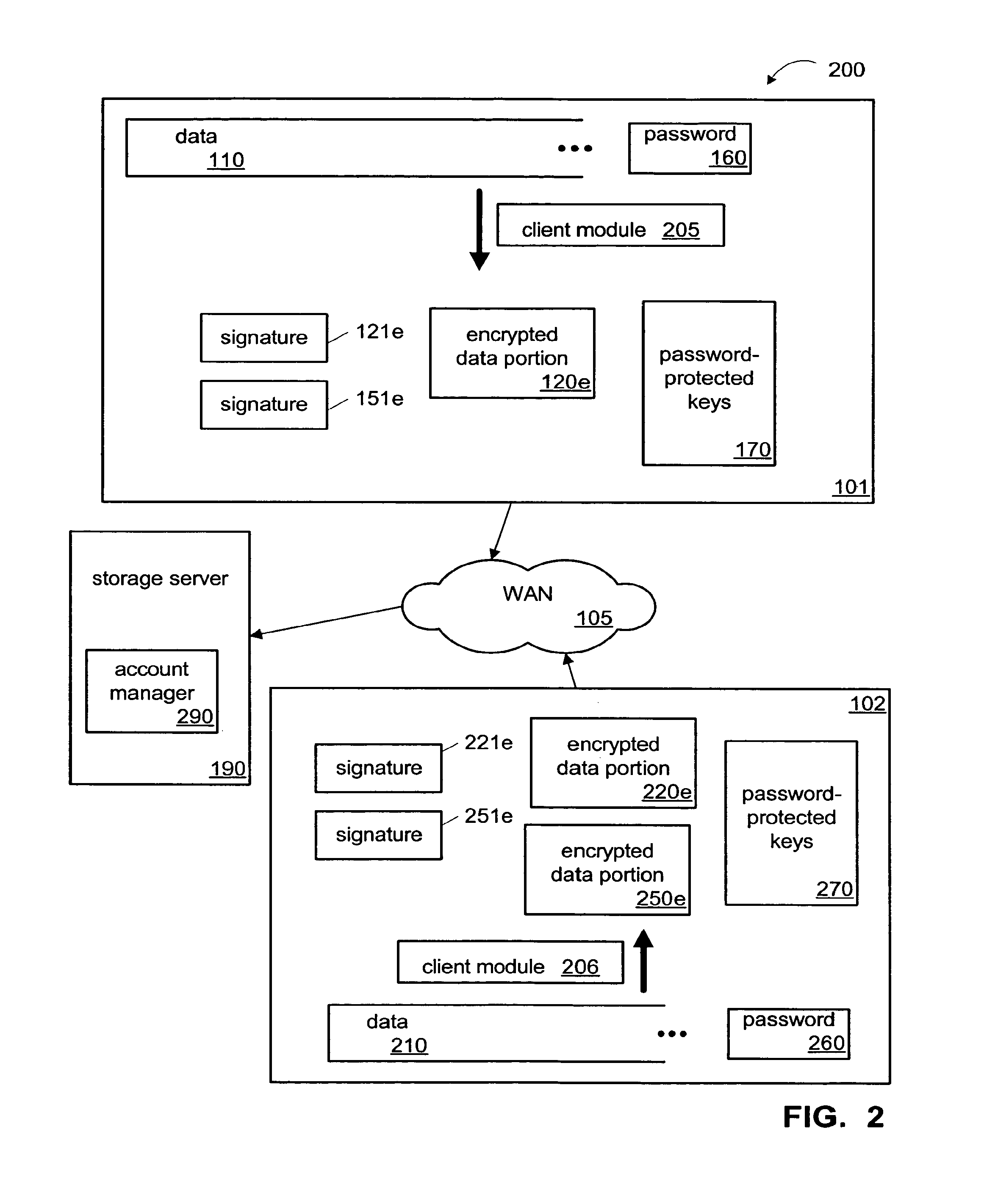
ActiveUS8812442B1Prevent unauthorized accessAccess is deniedDigital data processing detailsError detection/correctionPasswordClient-side
One implementation of a method for providing backup storage services for encrypted data includes receiving signatures of convergently encrypted portions of data from client computers, determining whether the encrypted portions are already present on a backup storage, and obtaining only the needed portions. Users unassociated with a particular user account are denied access to information backed up in that account. The backup storage also stores password protected key files holding signatures of the unencrypted portions of data. One implementation of a system includes a memory, a single-instance storage circuit, a user account management circuit, and a signature index. The memory holds a user-account database and backup copies of convergently encrypted portions of data. The single-instance storage circuit uses the signature index to prevent duplicative backup copies. The user account management circuit responds to download requests after authenticating the user information associated with the requested data.
Owner:VERITAS TECH
Arbitration of data transfer requests
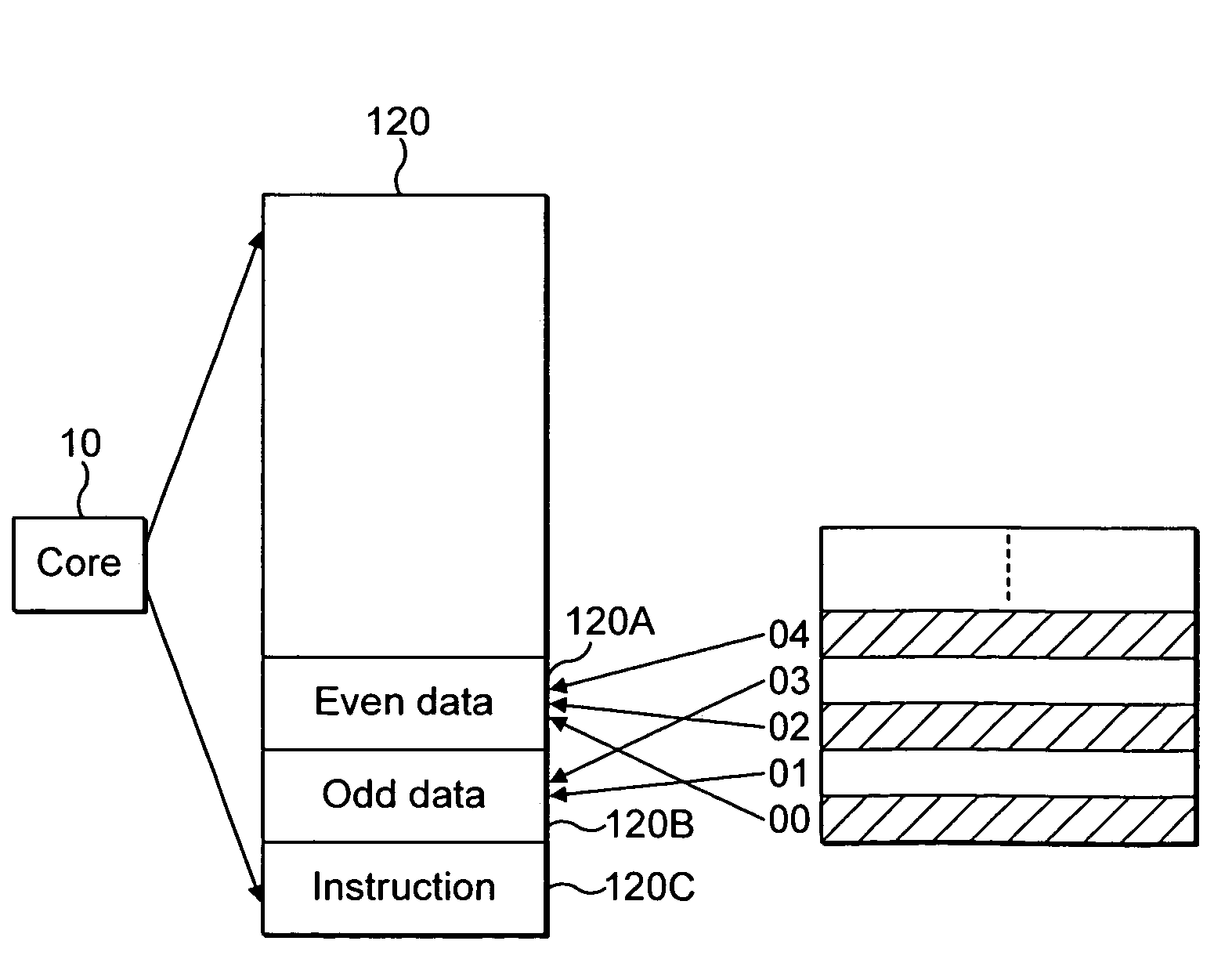
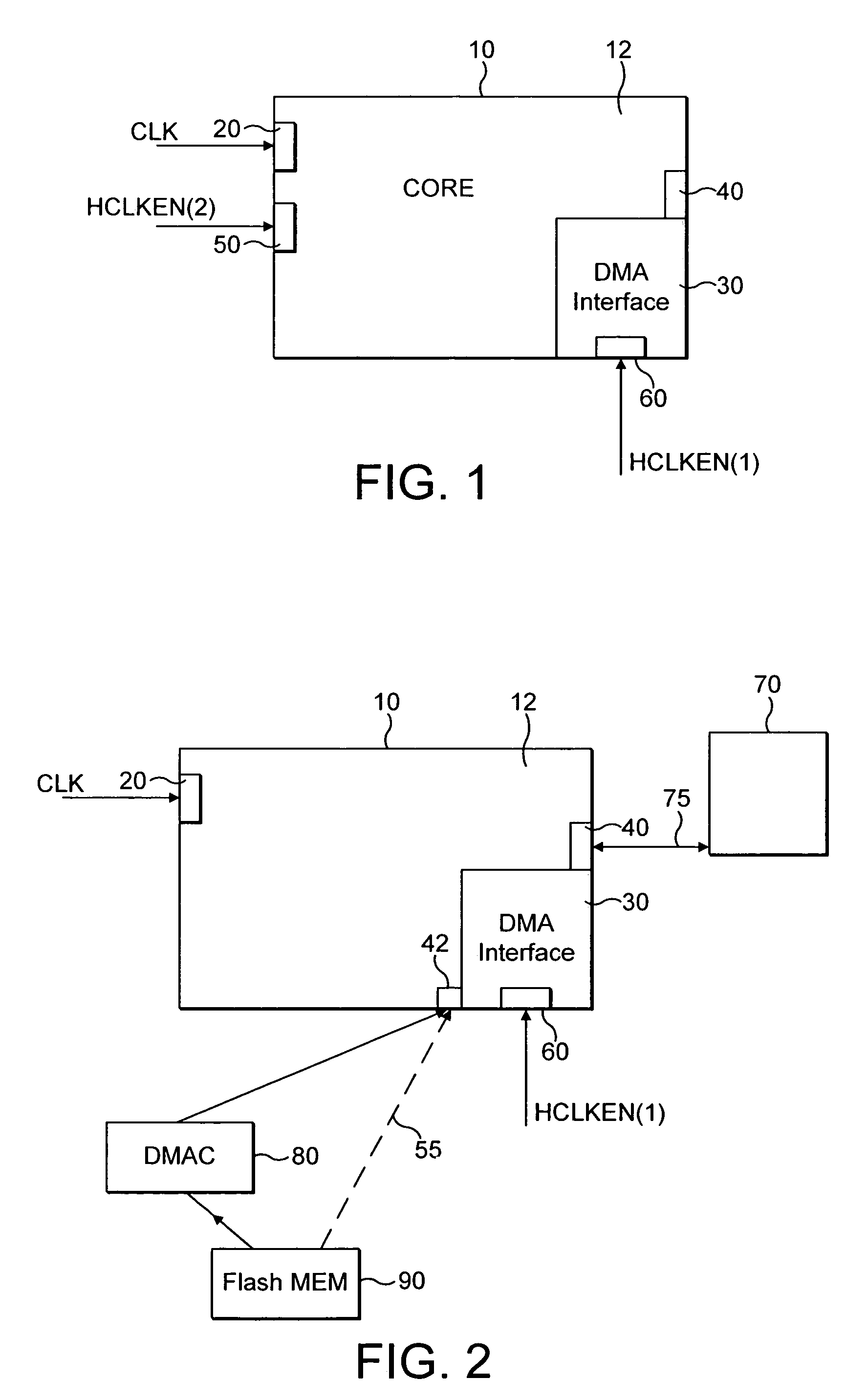
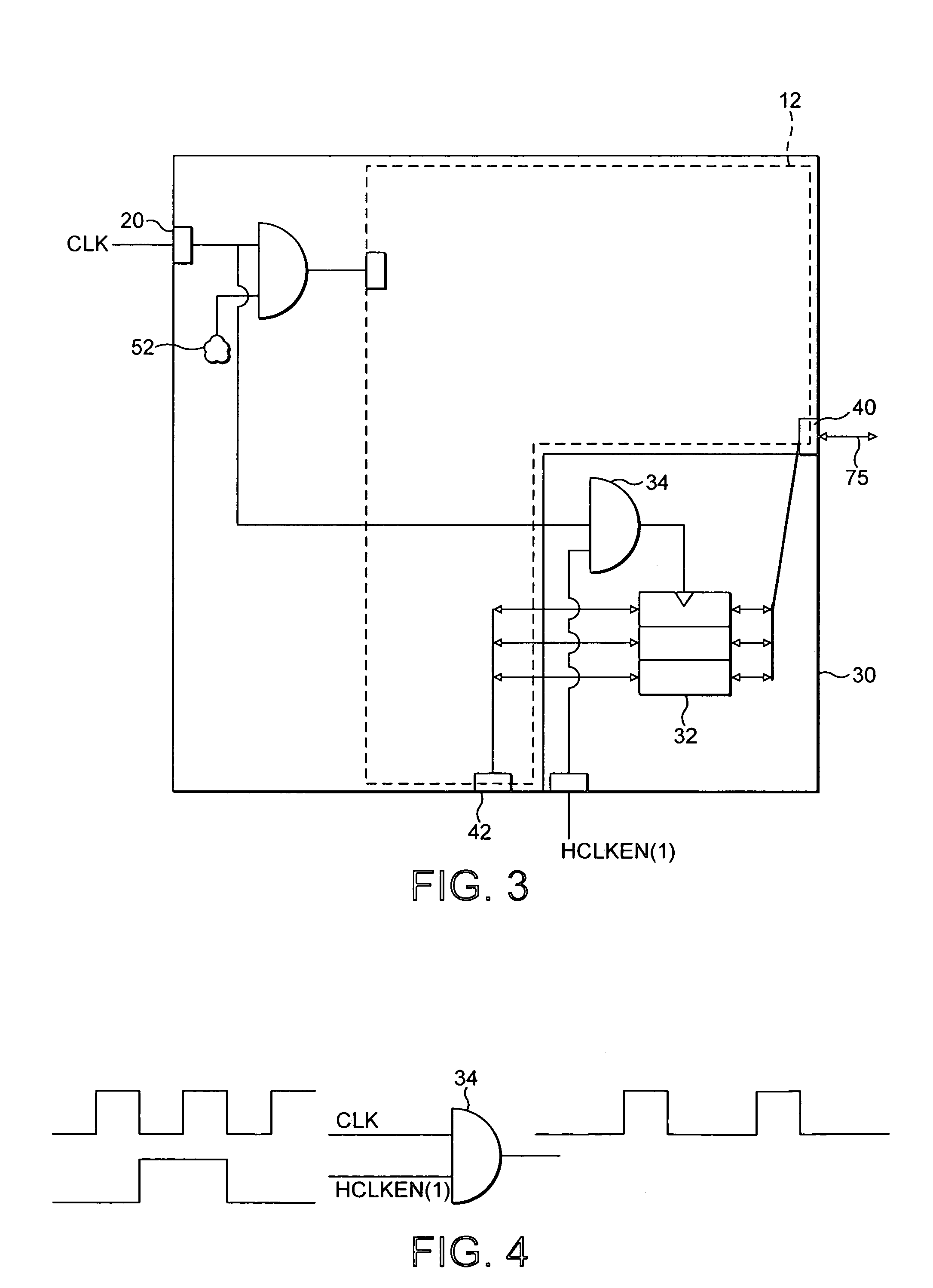
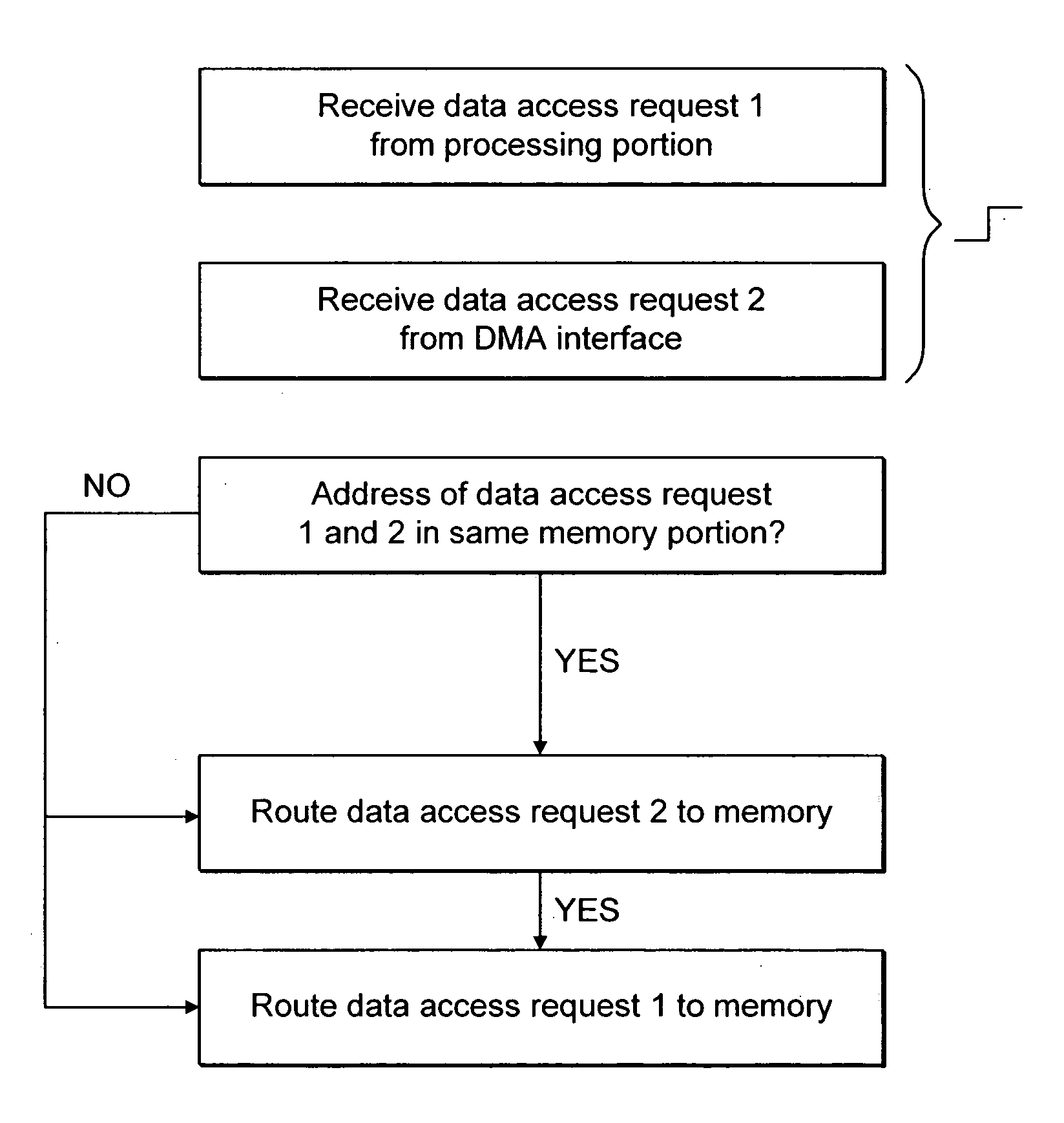
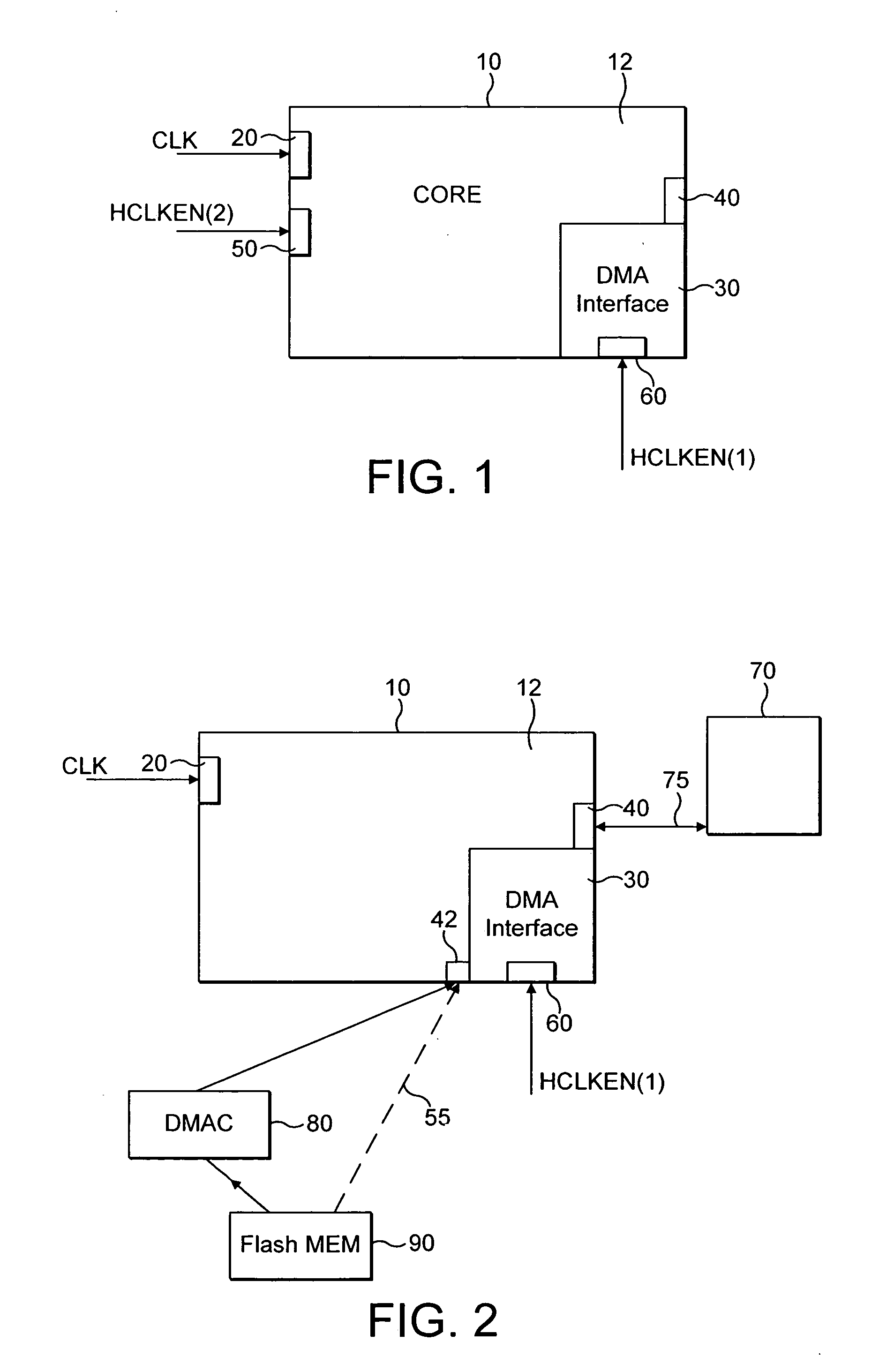
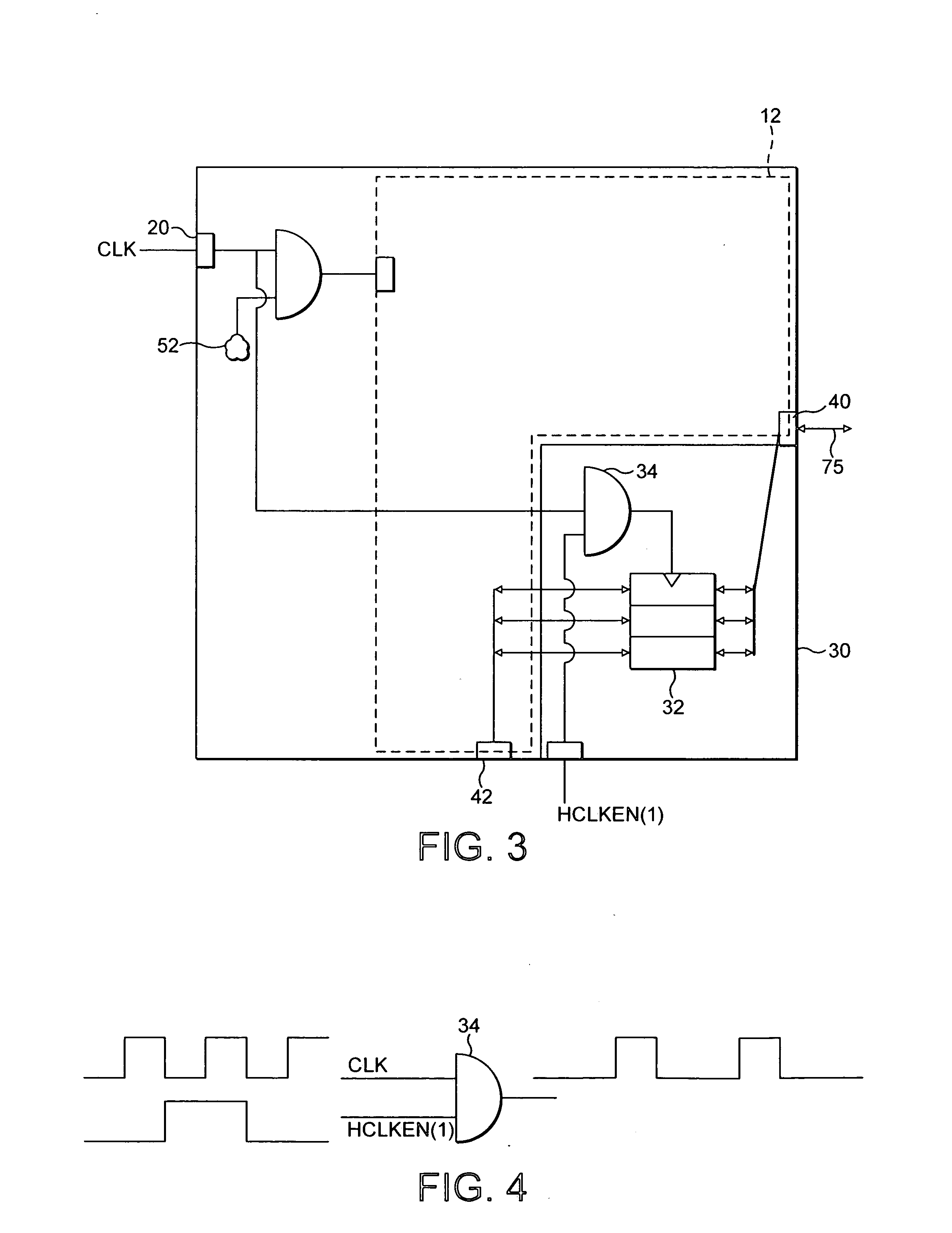
ActiveUS7240144B2Fast transferEasy accessMemory adressing/allocation/relocationDigital computer detailsExternal dataData source
A data processor core 10 comprising: a memory access interface portion 30 operable to perform data transfer operations between an external data source and at least one memory 120 associated with said data processor core; a data processing portion 12 operable to perform data processing operations; a read / write port 40 operable to transfer data from said processor core to at least two buses 75A, 75B said at least two buses being operable to provide data communication between said processor core 10 and said at least one memory 120, said at least one memory 120 comprising at least two portions 120A, 120B, each of said at least two buses 75A, 75B being operable to provide data access to respective ones of said at least two portions 120A, 120B; arbitration logic 110 associated with said read / write port 40; wherein said arbitration logic is operable to route a data access request requesting access of data in one portion of said at least one memory received from said memory access interface to one of said at least two buses providing access to said one portion of said at least one memory and to route a further data access request requesting access of data in a further portion of said at least one memory received from said data processing portion to a further one of said at least two buses providing access to said further portion of said at least one memory, said routing of said data access requests being performed during the same clock cycle.
Owner:ARM LTD
Systems and methods for regulating execution of computer software
InactiveUS8225290B2Preclude obtainingAccess is deniedDigital computer detailsUnauthorized memory use protectionComputer hardwarePartial application
A method for regulating execution of an application program includes a process for preparing the application and a process for executing the application. The preparation process divides the application program into related segments and encrypts instructions of at least one segment, positions encrypted instructions in at least two discontiguous regions within an executable file, and associates header information with at least one discontiguous region. The execution process initiates execution of the protected application when at least a portion of the application instructions are available to the computer only in encrypted form. Also provided are systems and methods to allow debugging of code extensions to protected applications without sacrificing protection of the application. A Secure Debugger allows extension developers to examine memory and set breakpoints in their own extensions, without permitting them to view information in the rest of the protected application.
Owner:REVULYTICS INC
Collapsible safety rail system
InactiveUS20140166955A1Reducing viewable profileProtection positionDoors/windowsFencingDetentEngineering
A collapsible safety rail system for providing a portable or permanent protective barrier to provide for fall prevention from elevated or other work areas. Lockable pivot assemblies are located between heavy bases and the end posts of collapsible safety rail assemblies. Removable detent pins are utilized to lock the pivot assemblies to maintain the erected position of the collapsible safety rail assemblies in protective vertical orientation or are removed to allow maneuvering of the collapsible safety rail assemblies to a minimum viewable profile position when not required for personnel protection.
Owner:BLUEWATER MFG
Passive arc control with sequestered phases in a vertical bus system of a motor control center
ActiveUS9748024B2Minimize potential for harmAccess is deniedBus-bar/wiring layoutsSwitchgear detailsArc flashElectric machine
A passive arc control system for a motor control center 60 includes an arc attenuating box having sides separating adjacent vertical bus bar phases 54, providing a physical barrier to arc flash energy. The box is open at its top and bottom forming a chimney 55. A shutter assembly for each box includes an insulator cap 62 on a free end of the bus bar and an independently moveable, box-shaped shutter 64 that slides along the bus bar away from the insulator cap, when a device is connected to the bus bar. The shutter has an opening 65 through which the bus bar passes when the device is connected to the bus bar and an opening 55′ aligned with the box's chimney. The arc control system provides a high degree of arc protection for personnel working around open motor control centers and is highly modular and easy to construct.
Owner:SCHNEIDER ELECTRIC USA INC
Arbitration of data transfer requests
ActiveUS20050223129A1Data access can be discouragedFast transferMemory adressing/allocation/relocationDigital computer detailsExternal dataData access
A data processor core 10 comprising: a memory access interface portion 30 operable to perform data transfer operations between an external data source and at least one memory 120 associated with said data processor core; a data processing portion 12 operable to perform data processing operations; a read / write port 40 operable to transfer data from said processor core to at least two buses 75A, 75B said at least two buses being operable to provide data communication between said processor core 10 and said at least one memory 120, said at least one memory 120 comprising at least two portions 120A, 120B, each of said at least two buses 75A, 75B being operable to provide data access to respective ones of said at least two portions 120A, 120B; arbitration logic 110 associated with said read / write port 40; wherein said arbitration logic is operable to route a data access request requesting access of data in one portion of said at least one memory received from said memory access interface to one of said at least two buses providing access to said one portion of said at least one memory and to route a further data access request requesting access of data in a further portion of said at least one memory received from said data processing portion to a further one of said at least two buses providing access to said further portion of said at least one memory, said routing of said data access requests being performed during the same clock cycle.
Owner:ARM LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com