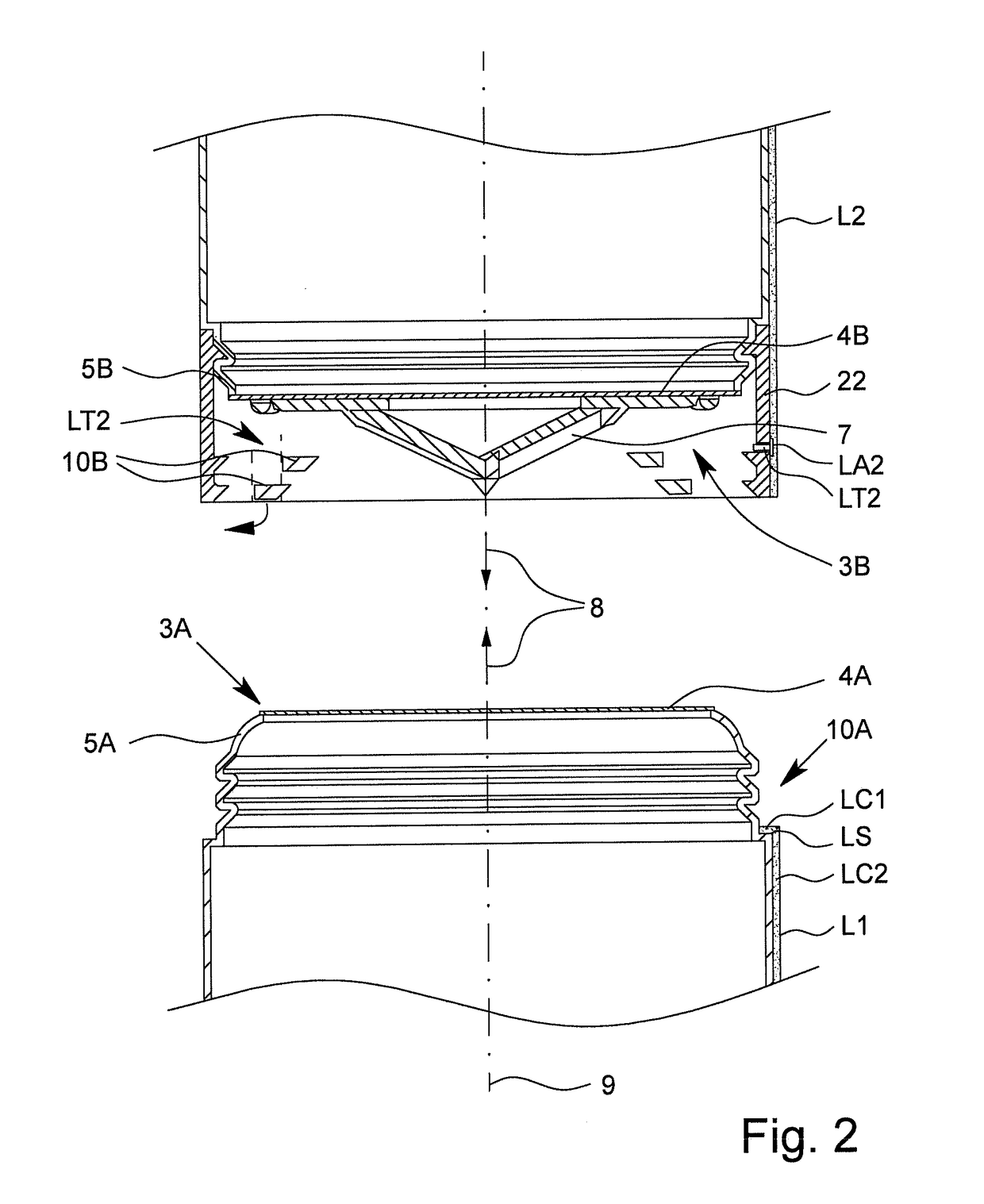
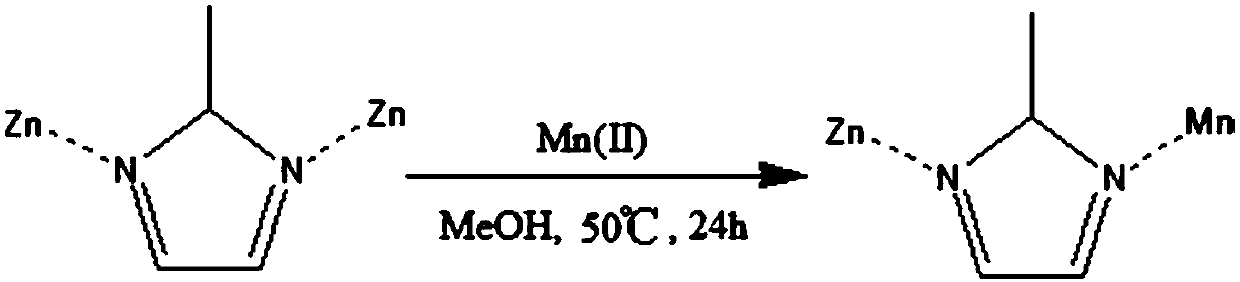Patents
Literature
121results about How to "Improve application security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Enhanced security using service provider authentication
ActiveUS20060031941A1Improve application securityAccess is deniedDigital data processing detailsUser identity/authority verificationService providerService provision
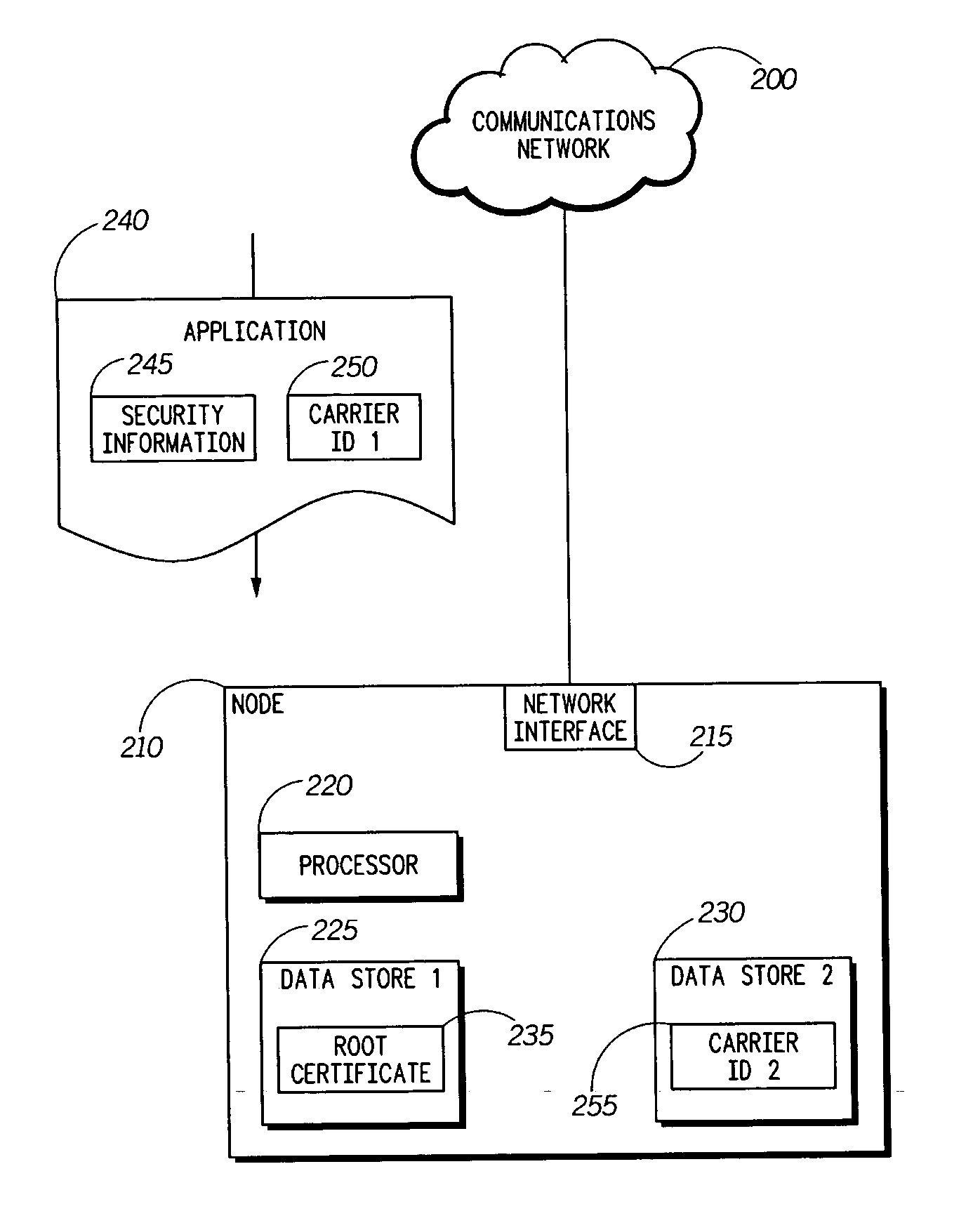
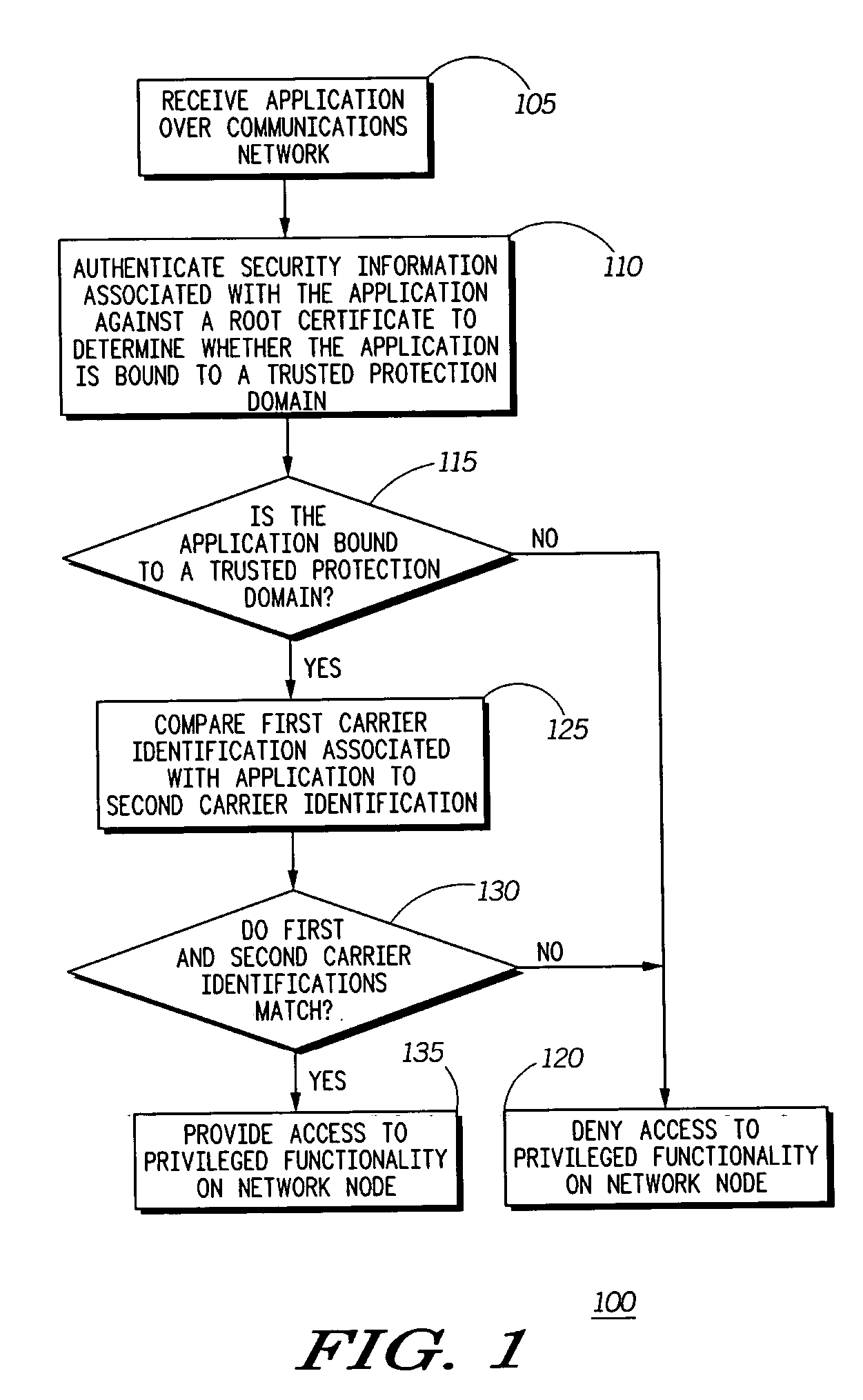
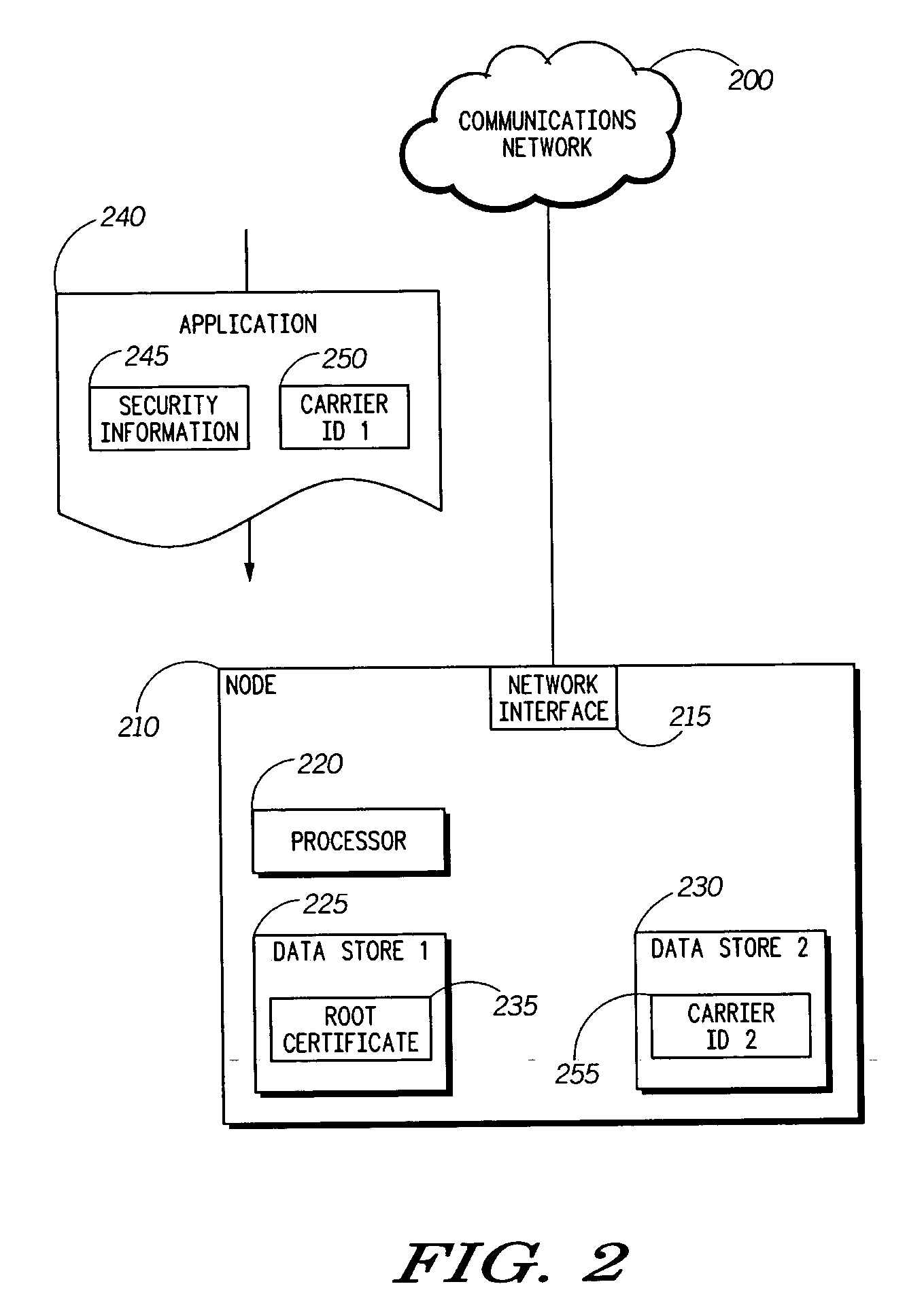
A method (100) and an apparatus (210) for providing enhanced security using service provider authentication. In addition to authenticating an application signature (245) against a root certificate (235) stored on the network node (210), a first carrier identification (250) associated with the application (240) is compared to a second carrier identification (255). If the first and second carrier identifications match, then the application can be assigned to a trusted protection domain and granted permissions which provide privileged access to the network node. For example, the application can be granted permission to be installed and / or executed on the network node. Otherwise the application can be denied privileged access. Accordingly, a carrier's applications will be only installed onto network nodes that are intended recipients of the applications.
Owner:GOOGLE TECH HLDG LLC
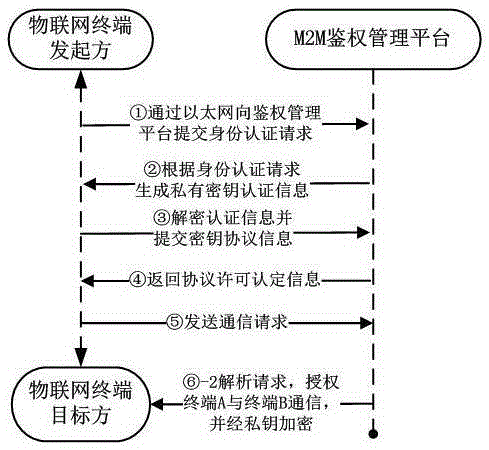
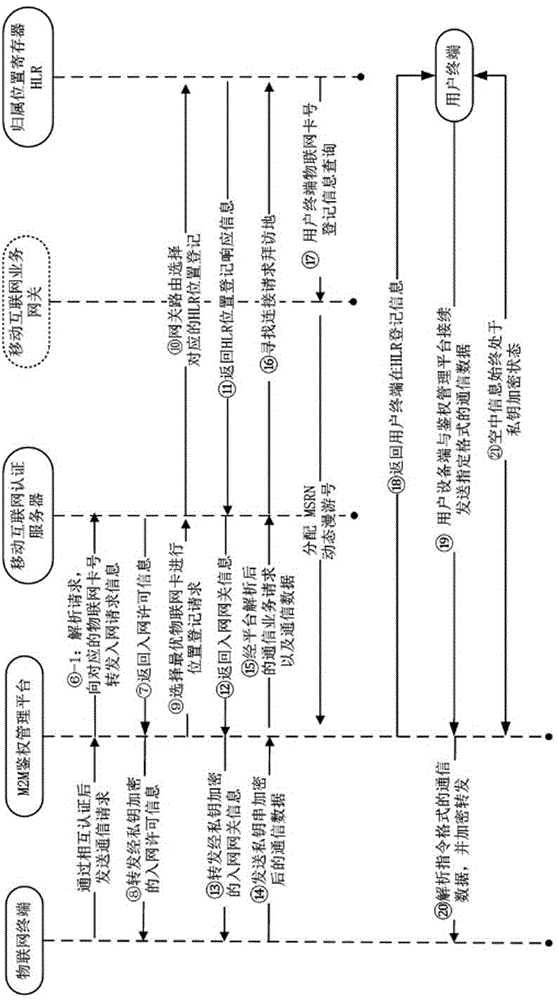
Internet of things information interactive communication method and system
ActiveCN105307108AImprove securityImprove application securityWireless commuication servicesTransmissionThe InternetMedia access control
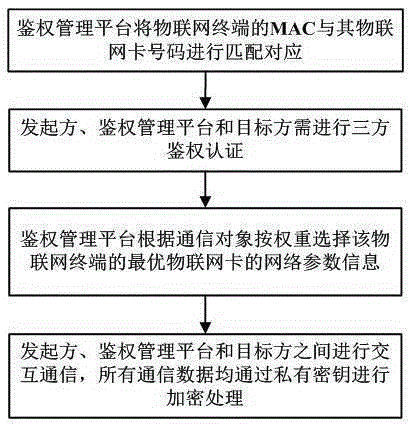
The invention discloses an Internet of things information interactive communication method and system. The method comprises the following steps that: a cloud authentication management platform correspondingly matches MAC (Media Access Control) of an Internet of things terminal with an Internet of things card number of the Internet of things terminal; when an initiator makes a request of performing interactive communication with a target party to the authentication management platform, the initiator, the authentication management platform and the target party need to perform three-party authentication certification; during authentication of the Internet of things terminal, the authentication management platform selects network parameter information of an optimal Internet of things card of the Internet of things terminal according to a communication object on the basis of weights in order to realize registration and access in a mobile communication network; and when the initiator, the authentication management platform and the target party perform a communication, all communication data is encrypted through a private key, wherein the private key is a dynamic random key string code and is relevant to the Internet of things card number in order that the transmitted communication data can only be resolved and read by the initiator, the authentication management platform and the target party.
Owner:成都工百利自动化设备有限公司
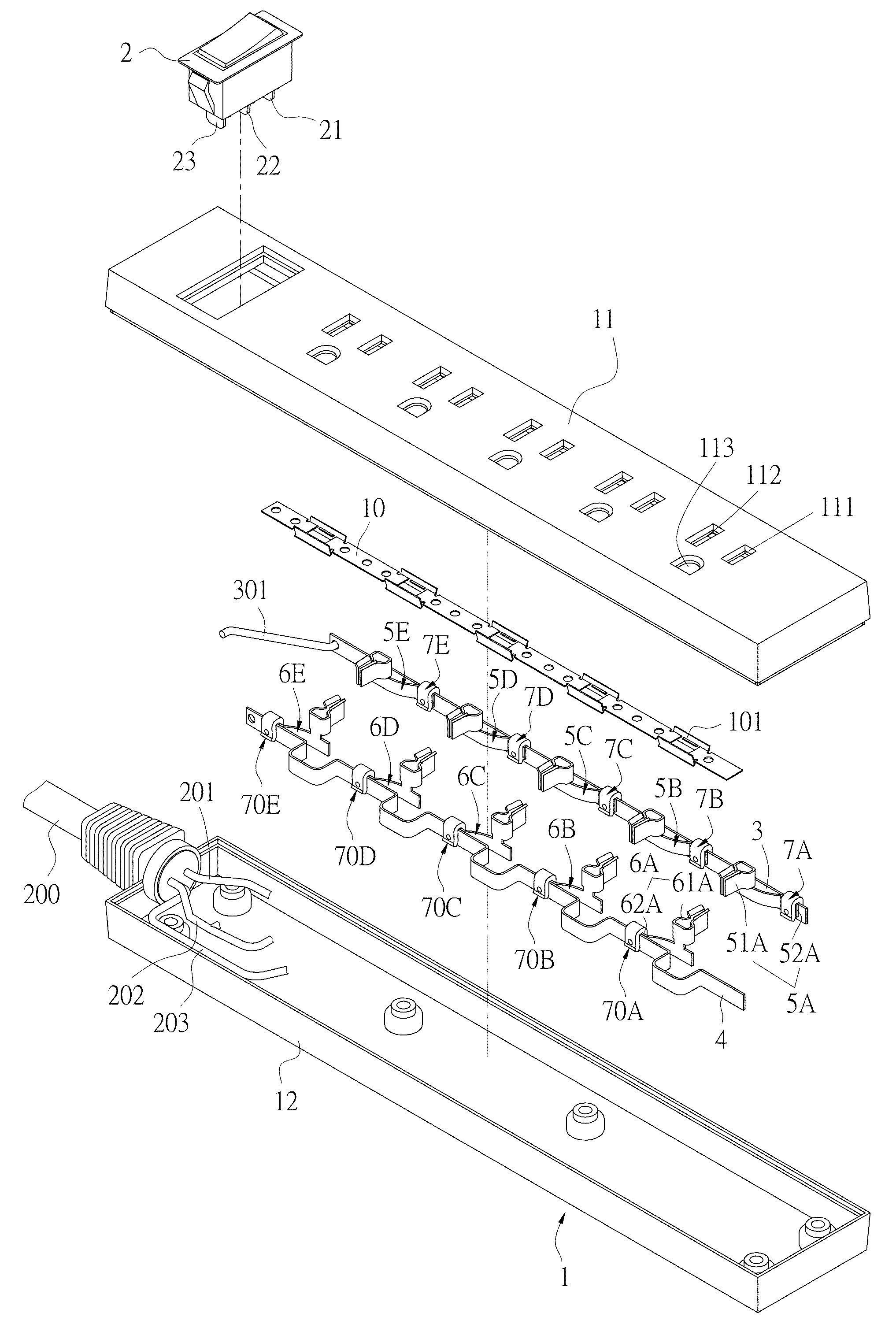
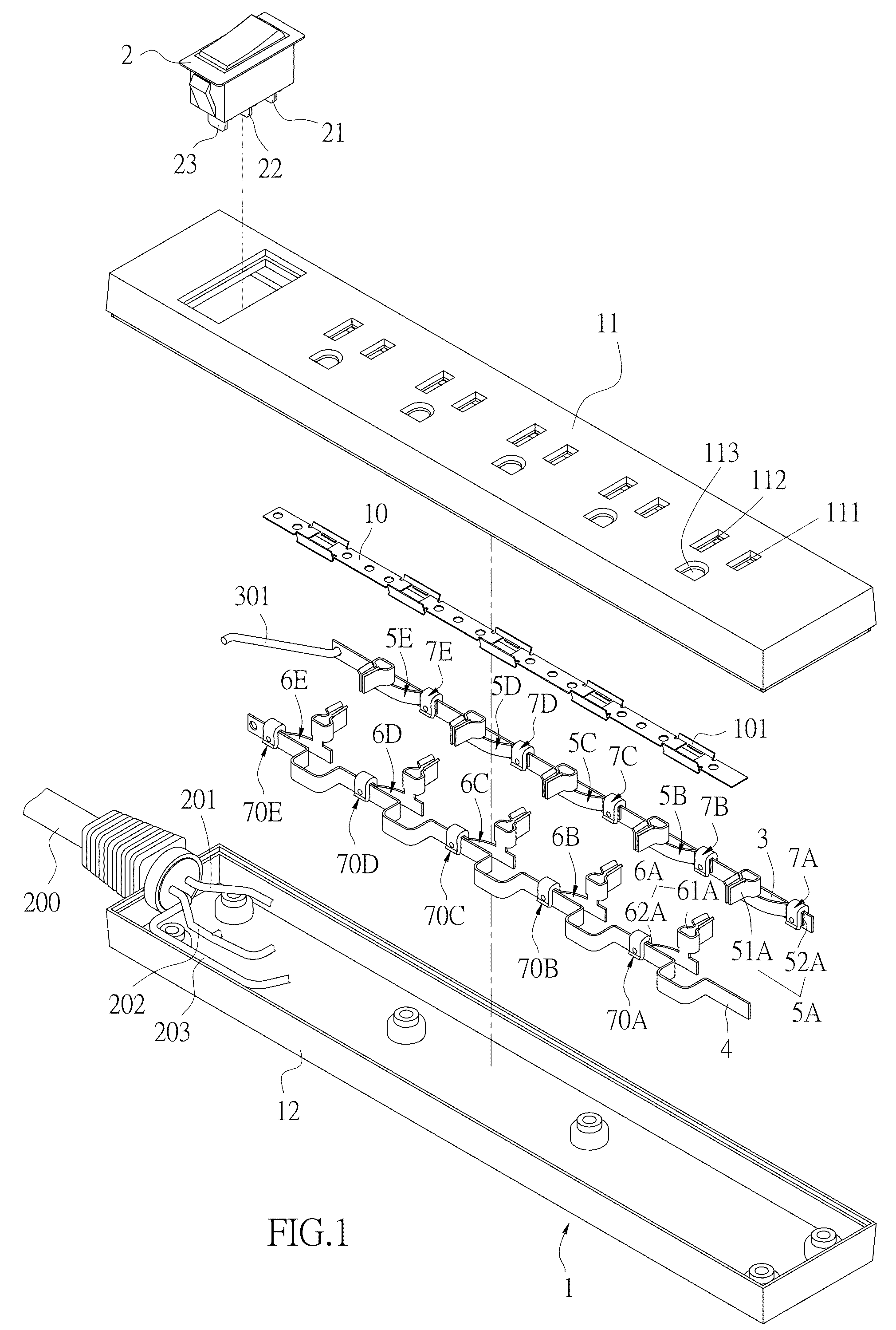
Socket having overheating destructive limiting element
ActiveUS9257798B2Improve application securityOvercomes drawbackSpark gap detailsCoupling device detailsOperating temperatureEngineering
A socket having an overheating destructive limiting element includes a housing, a live wire conductive plate, a neutral wire conductive plate, at least one live wire terminal, at least one neutral wire terminal, and at least one limiting element. The live wire terminal includes a live wire contact portion in contact with the live wire conductive plate. The neutral wire terminal includes a neutral wire contact portion in contact with the neutral wire conductive plate. The limiting element is an insulating body, and is placed at contact parts of the live wire conductive plate and the live wire contact portion, and / or at contact parts of the neutral wire conductive plate and the neutral wire contact portion. When an operating temperature becomes excessively high, the limiting element becomes deformed and destructed to form a turn-off position.
Owner:GREEN IDEA TECH INC
Preparation method of gel containing stem cell exosomes for repairing skin wounds
InactiveCN111420117AImprove application securityHigh clinical safetyCulture processSkeletal/connective tissue cellsMesenchymal stem cellEngineering
The invention relates to a preparation method of a gel containing stem cell exosomes for repairing skin wounds. The method comprises the following steps: 1) primary extraction and culture of human umbilical cord mesenchymal stem cells: 1.1) primary extraction of human umbilical cord mesenchymal stem cells, 1.2) subculture, and 1.3) collection of the culture supernatant; 2) extraction of human umbilical cord mesenchymal stem cell exosomes: 2.1) primary centrifugation, 2.2) secondary centrifugation, 2.3) removal of organelles by centrifugation, 2.4) coarse extraction of exosomes, and 2.5) finalextraction of exosomes; 3) preparation of a gel material: 3.1) preparation of chitosan, 3.2) configuration of beta-glycerol phosphate (beta-GP), and 3.3) preparation of the gel material; and 4) gel loading of the exosomes. The gel containing stem cell exosomes can promote repair of skin wounds, shorten the healing time of wounds and reduce scar formation.
Owner:陕西朗泰生物科技有限公司
Inorganic modified polyurethane grouting material and preparation method thereof
The invention discloses an inorganic modified polyurethane grouting material. The inorganic modified polyurethane grouting material comprises a component A and a component B, wherein the component A comprises the following components in parts by weight: 85-98 parts of sodium silicate solution, 0.5-3 parts of catalyst, 1-5 parts of chain extender and 0-8 parts of water; and the component B comprises the following components in parts by weight: 10-80 parts of modified polymeric MDI-PU2101, 10-75 parts of modified polymeric MDI-PU2102, 5-20 parts of viscosity reducing agent and 5-15 parts of plasticizer. A preparation method of the material disclosed by the invention is simple, and the material is injected into a coal-rock mass through a dual-liquid grouting pump and can achieve the function of reinforcing the coal-rock mass after fast curing; compared with the conventional polyurethane grouting material, the material has the advantages of lower highest reaction temperature, excellent flame resistance, lower cost, capability of keeping the mechanical properties at a higher level, capability of still keeping the higher strength in a water environment and the like; and the material does not contain toxic, volatile and corrosive substances and can meet underground safety and environmental protection requirements of the material.
Owner:SHANDONG ANLENG NEW MATERIAL TECH CO LTD
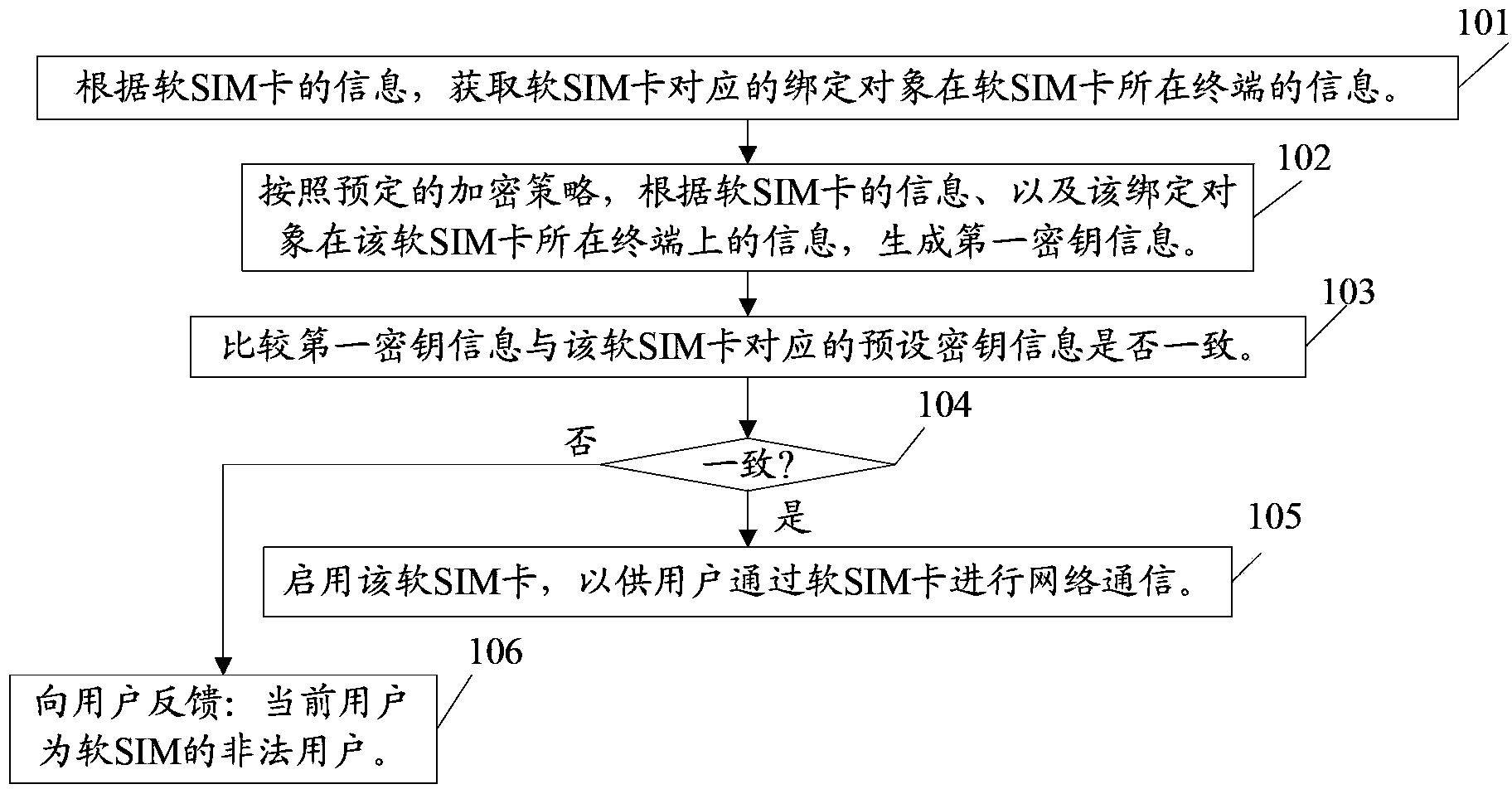
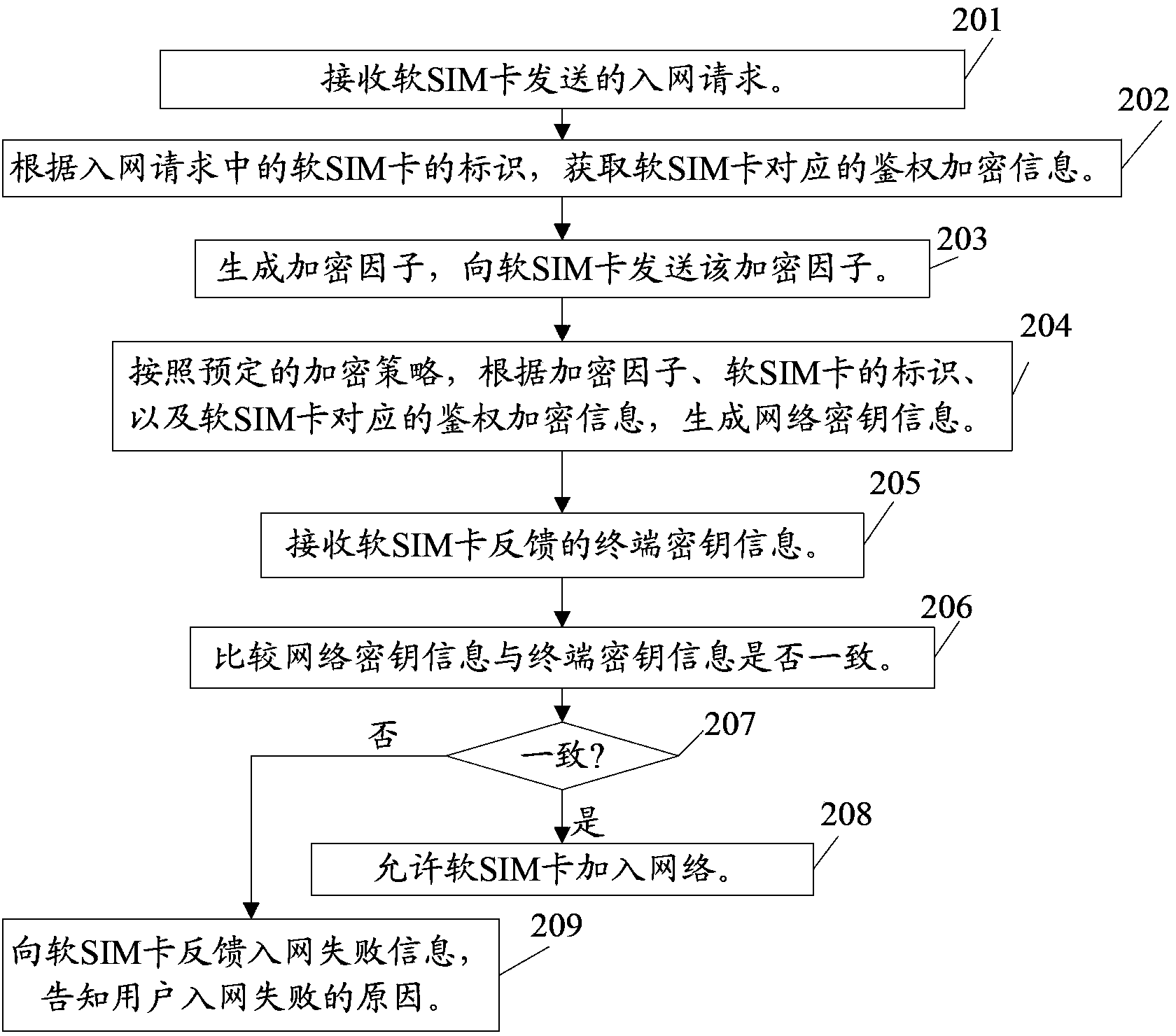
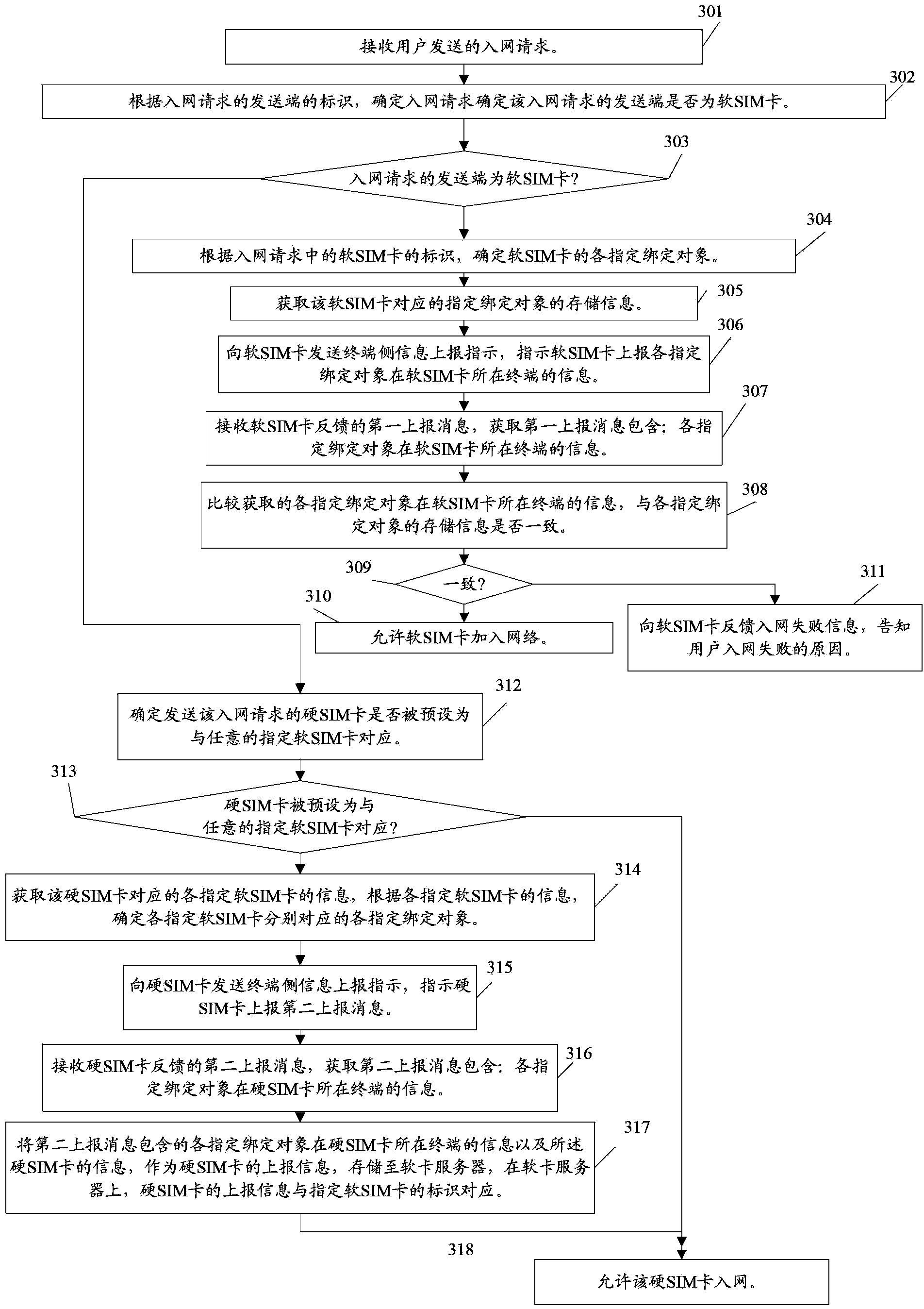
Soft SIM card enabling method and network access method, terminal, and network access device
ActiveCN103813314AImprove application securitySecurity arrangementNetwork data managementComputer hardwareAccess method
The invention relates to the field of communication, and discloses a soft SIM card enabling method and network access method, a terminal, and a network access device. The enabling method comprises the following steps: information of a bound object corresponding to the soft SIM card at the terminal at which the soft SIM card is located is acquired according to information of the soft SIM card; according to a predetermined encryption policy and according to the information of the soft SIM card and the information of the bound object at the terminal at which the soft SIM card is located, a first key information is generated, the first key information is compared with default key information corresponding to the soft SIM card, if the first key information is consistent with default key information corresponding to the soft SIM card, then the soft SIM card is allowed to be enabled for a user to perform network communication through the soft SIM card; and the default key information corresponding to the soft SIM card is that the soft SIM card operator generate and provide key information for the user according to the predetermined encryption policy and according to the information of the soft SIM card and the default information of the bound object. By applying the technical scheme, the application safety of the soft SIM card can be improved.
Owner:HUAWEI TECH CO LTD
High polymer composite electrothermal film and preparation method thereof
ActiveCN106183239AImprove heat resistanceHigh strengthPolyureas/polyurethane adhesivesChemical industryCarbon nanotubeHeat generation
The invention discloses a high polymer composite electrothermal film. The film comprises a carbon-nano-tube polyurethane resin thermal film and an electrode, and is characterized in that the carbon-nano-tube polyurethane resin thermal film is composed of a thermosetting polyurethane resin conductive heating layer and a polyurethane resin insulating layer by hot-pressing. Compared with the existing thermosetting polyurethane resin electrothermal film, the electrothermal film disclosed by the invention is high in heat resistance and strength, is not softened within the temperature range of 160 DEG C, can maintain the strength, meets the halogen-free flame-retardant and environmental-friendly requirements and reaches the level UL 94V-0; the application safety performance is high, the heat generation efficiency is improved by 10%, the heat transfer efficiency of the electrothermal film is improved by 20-30%, and temperature rise is rapid.
Owner:江苏康尼纺织品有限公司
Container system and method
ActiveUS20180168930A1Improve reliabilityImprove application securityCannulasPharmaceutical containersEngineeringElectrical and Electronics engineering
A container system having at least two containers, wherein the container system comprises a light member which is configured to provide information through the emission of light, wherein the container system is configured to provide or trigger the light member to provide the information through the emission of light when a step related to preparing a mixture of contents of the containers is performed. In particular, triggering occurs when the containers are separated from one another and / or when a fluidic connection is created between the containers.
Owner:BOEHRINGER LNGELHEIM VETMEDICA GMBH
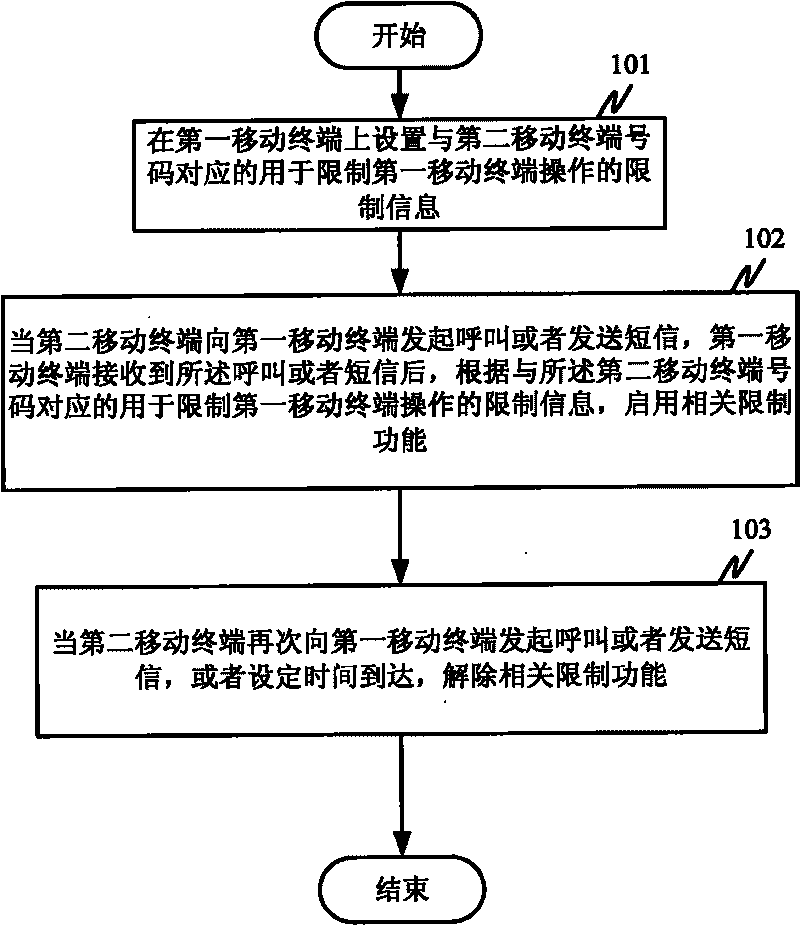
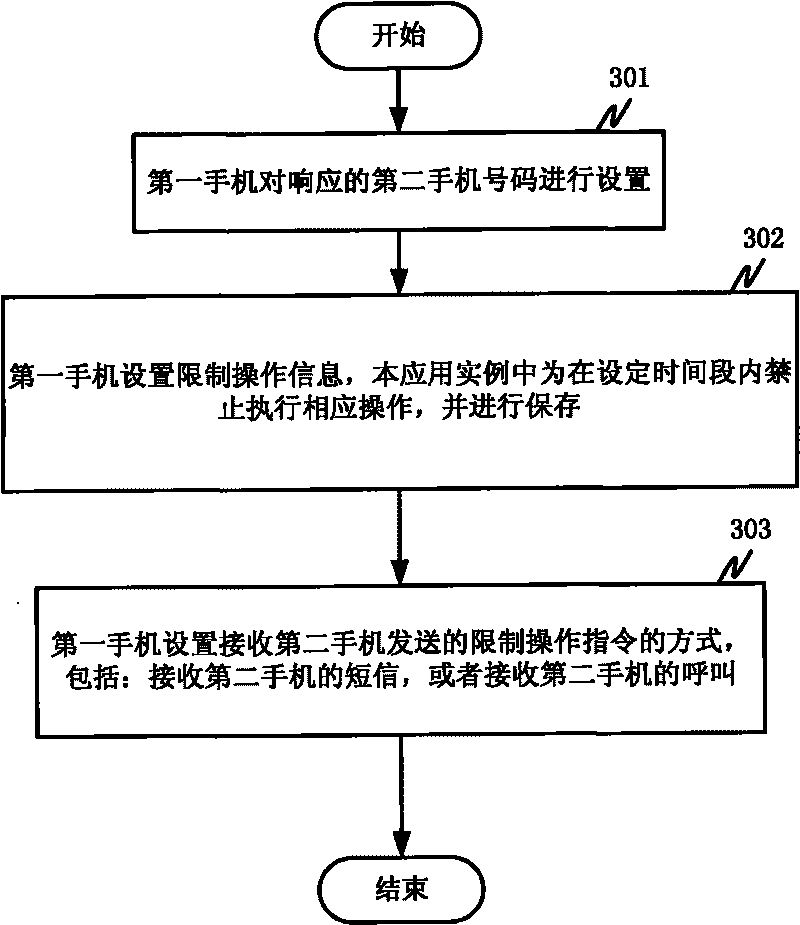
Controlled mobile terminal response method, device and mobile terminal
InactiveCN101765241AImprove application securityImprove protectionWireless communicationResponse methodApplication security
The invention discloses a controlled mobile terminal response method, a controlled mobile terminal response device and a mobile terminal. The method comprises that: a first mobile terminal sets restriction information which corresponds to the number of a second terminal or an equipment identifier and is used for restricting the operation of the first mobile terminal; and after the second terminal sends an instruction for starting the restriction function which contains the number of the second terminal or the equipment identifier to the first mobile terminal and the first mobile terminal receives the instruction for starting the restriction function, the related restriction function is started according to the restriction information which corresponds to the number of the second terminal and is used for restricting the operation of the first mobile terminal. By setting on the mobile terminal, the method and the mobile terminal can make one terminal restrict the operation of another mobile terminal so as to improve the application security of a mobile phone and meet the requirement in a specified field, such as the protection on juvenile students.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for extracting fucoidan for brown seaweed
The invention relates to a fucoidan extract method, in particular to a method for extracting fucoidan for brown seaweed, comprising the following steps: 1. desalting: adopting fresh brown seaweed or unfreezed frozen brown seaweed to soak in pure water to remove salt; 2. enzymolysis: adding enzyme in the desalted brown seaweed to perform enzymolysis at 40-60 DEG C for 1-3h; 3. abstraction: adding calcium chloride in enzymatic hydrolyzate obtained by enzymolysis, and heating the solution to 90-100 DEG C for 1-4h to obtain the fucoidan extract. The invention is characterized of simple operation, high application security, high extraction efficiency, high extraction purity and the like and the extraction process is applicable to factory mass production.
Owner:大连海宝生物技术有限公司
Device for fixing drainage tube
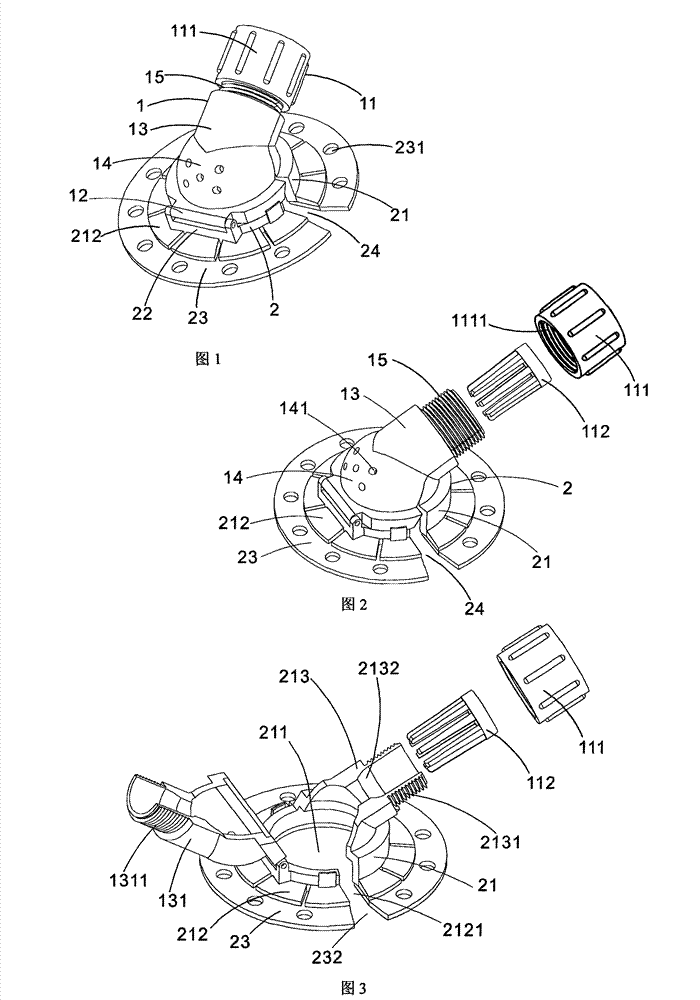
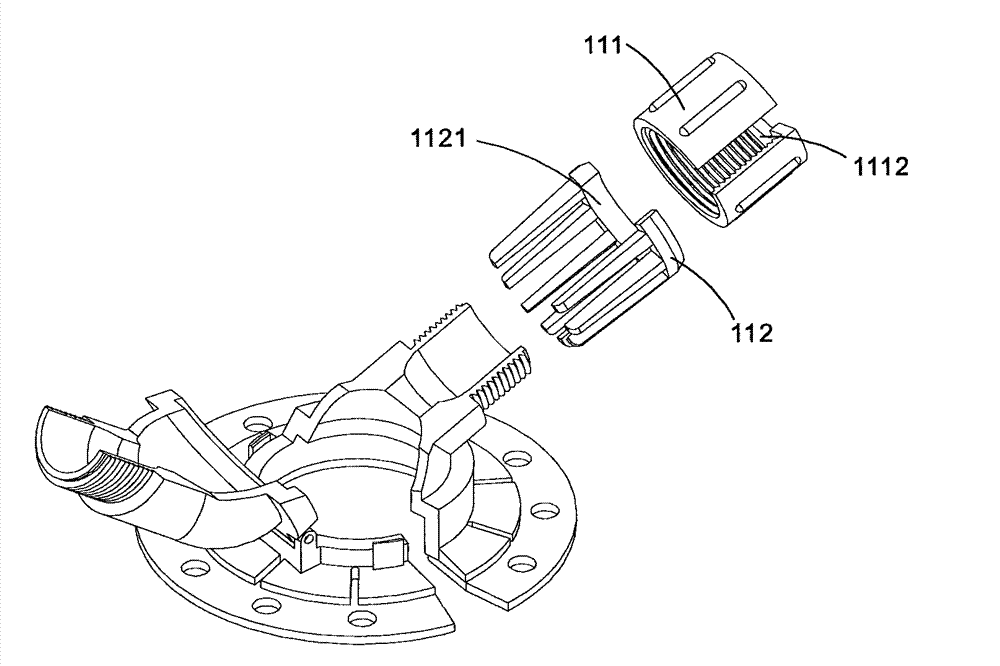
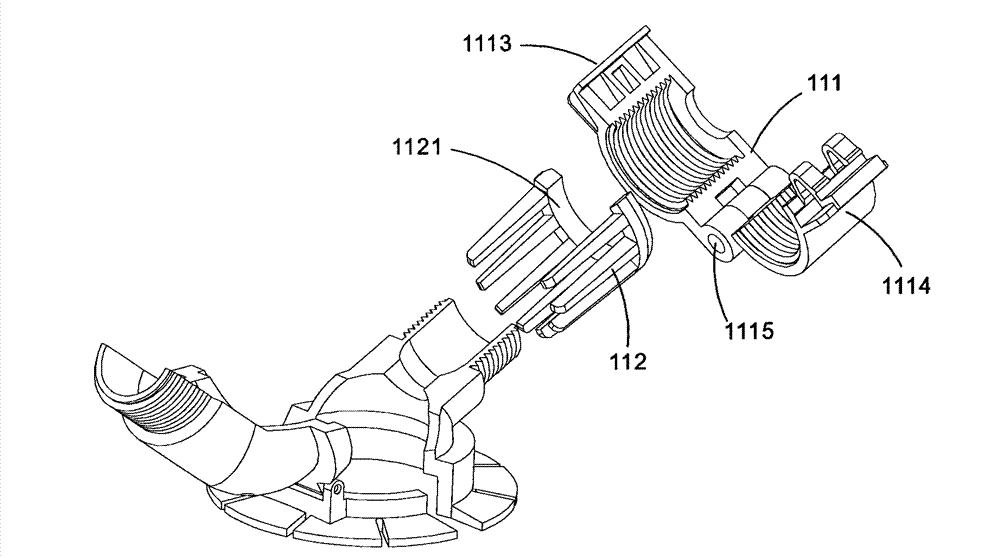
A drainage tube fixing assembly which is used for supporting and fixing a drainage tube and a body surface fixing component are connected and the flip-type structure which can be opened and locked is combined with the integrated design of a tube imbedding opening and a screwing ring, thus the drainage tube is easy to imbed without pressing peripheral muscle of the wound, the drainage tube is prevented from bending and winding and the wound can be observed and nursed at any time.
Owner:李林风
Vulnerability detection method and device
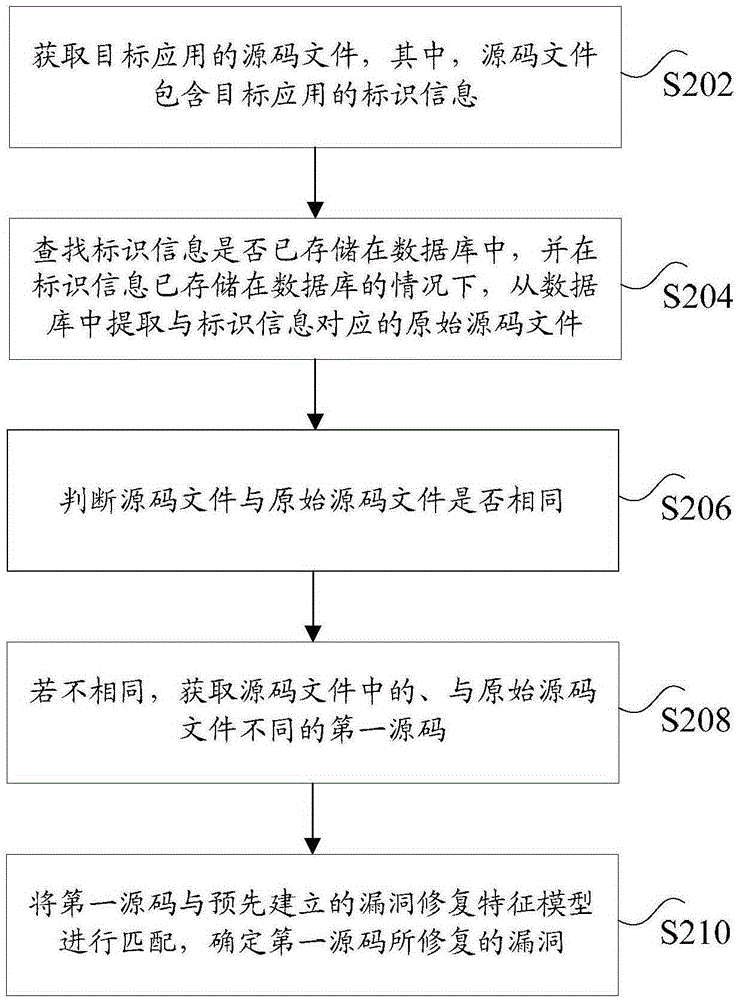
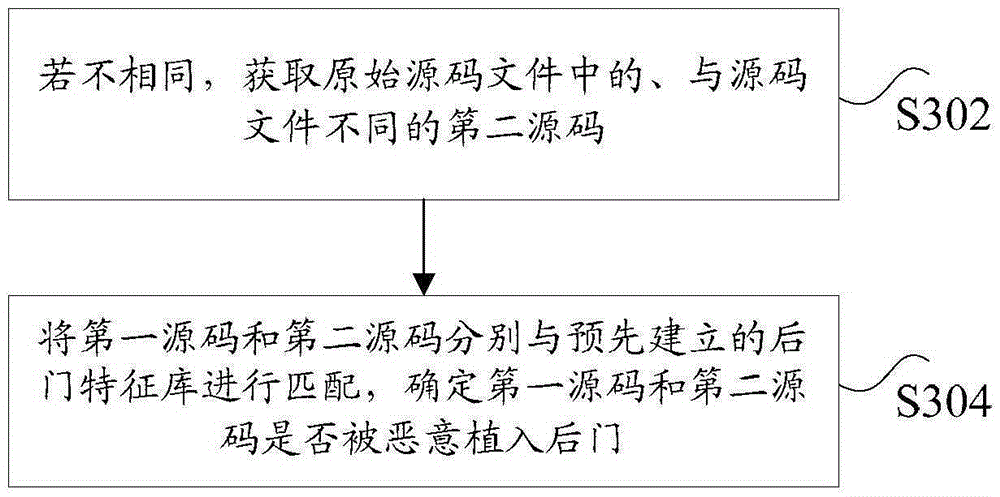
ActiveCN106815135AAccurate analysisImprove application securitySoftware testing/debuggingSource code fileData mining
The invention discloses a vulnerability detection method and device. The method comprises the steps that a source-code file of a target application is obtained, wherein the source-code file contains identification information of the target application; whether the identification information is stored in a database or not is found, and under the condition that the identification information is stored in the database, an original source-code file corresponding to the identification information is extracted from the database; whether the source-code file is identical to the original source-code file or not is judged, and if not, first source codes, different from those of the original source-code file, in the source-code file are obtained; the first source codes are matched with a prebuilt vulnerability fixing characteristic model, and vulnerabilities fixed by the first source codes are determined. By means of the vulnerability detection method and device, the technical problems that in the prior art, the vulnerability position and fixed vulnerability parameters cannot be effectively recognized, and accordingly more labor needs to be consumed for vulnerability analysis are solved.
Owner:ALIBABA GRP HLDG LTD
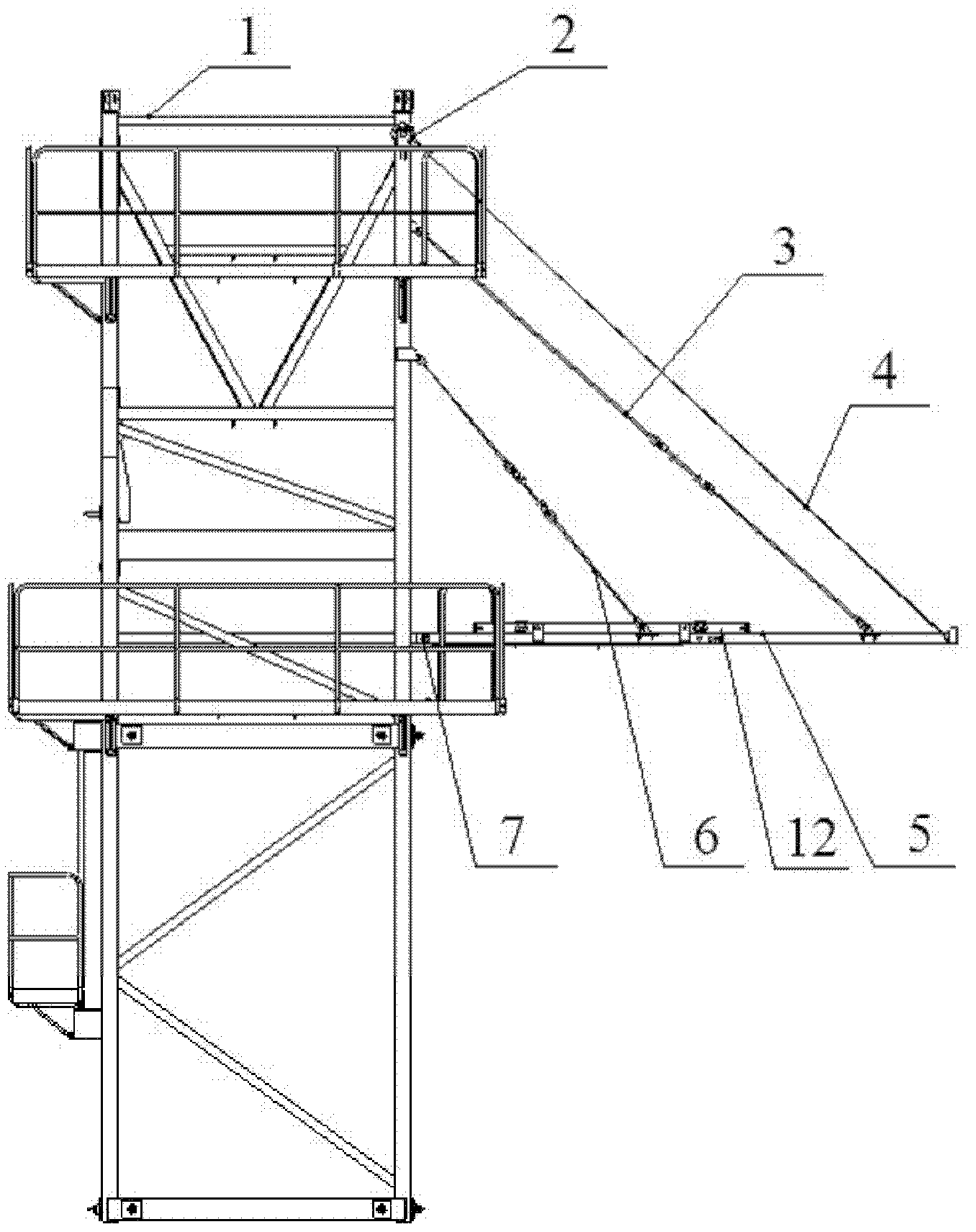
Tower crane introducing platform structure
The invention provides a tower crane introducing platform structure, which comprises an introducing platform, a pull rod and a turning lifting mechanism, wherein the introducing platform has a hinge part which is hinged with the main body of the tower crane; the first end of the pull rod is connected to the main body of the tower crane, while the second end of the pull rod is connected to the introducing platform; and the turning lifting mechanism drives and is connected to the introducing platform, so as to ensure the introducing platform to turn around the hinge part. The tower crane introducing platform structure provided by the invention can prevent the interference of a hook and the platform and reduce potential safety hazard, meanwhile the structure can reduce the introducing platform size, so that the structure is convenient for use and transportation.
Owner:ZOOMLION HEAVY IND CO LTD
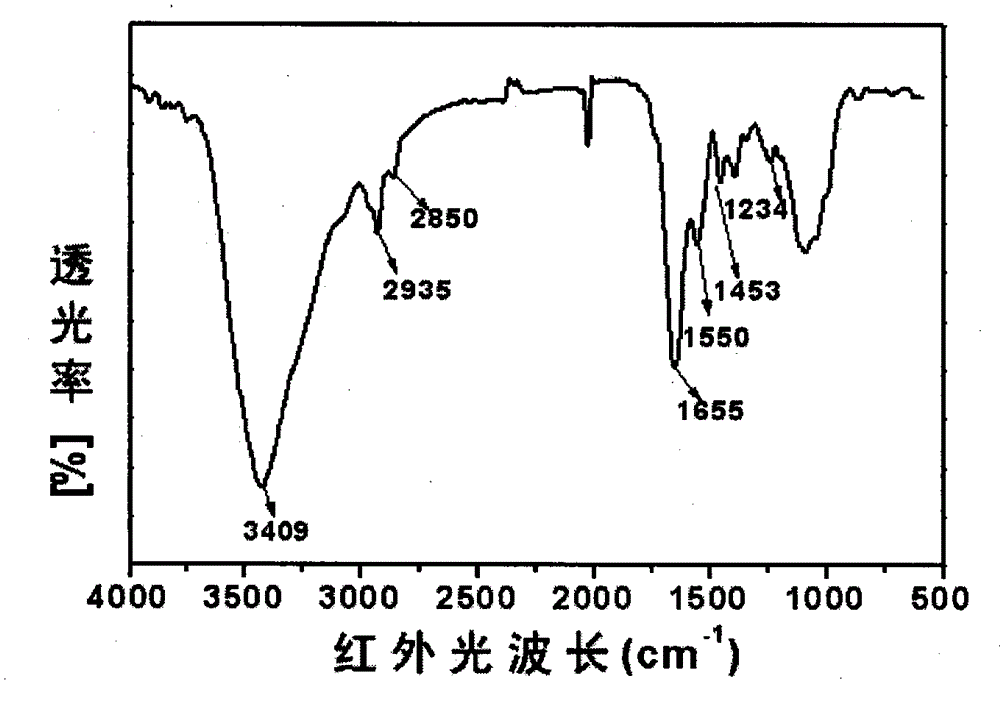
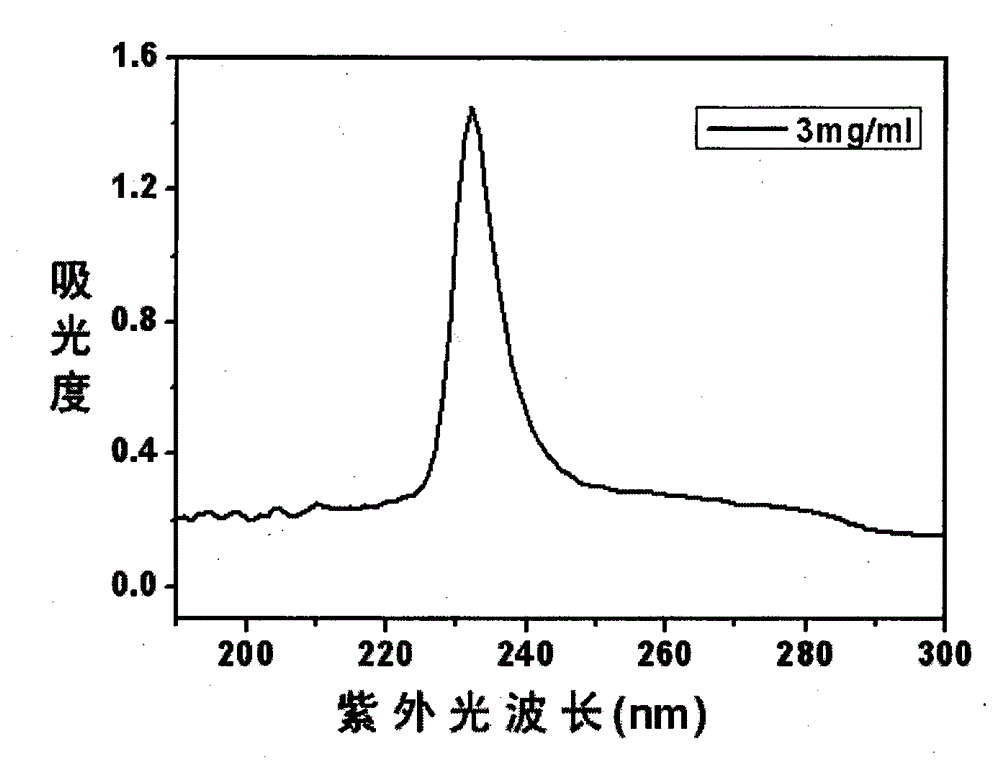
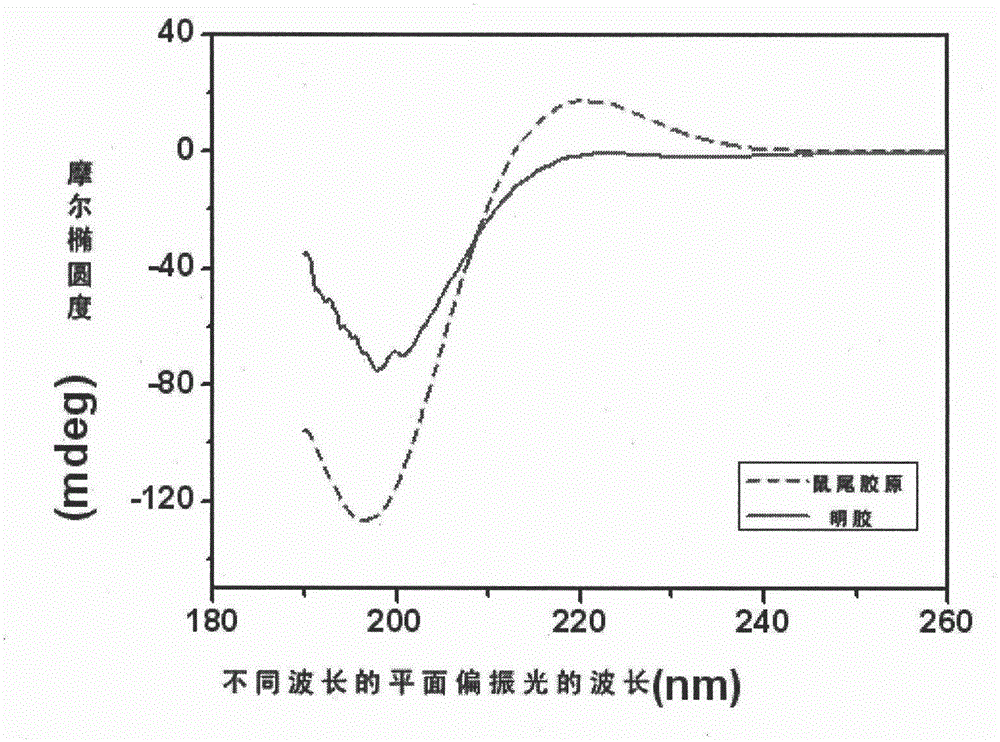
Biomedical mouse tail collagen extraction method
ActiveCN104788559ALow antigenicityImprove application securityConnective tissue peptidesPeptide preparation methodsWater contentChemistry
The invention discloses a biomedical mouse tail collagen extraction method. A process combining an acid method with an enzymic method is adopted, a constant low-temperature aseptic environment is kept, a salt solution at the same concentration is used for twice salting out and centrifugation, so that purification steps are simplified. Adopted acid is a low-concentration acid solution, and citric acid is used for purification instead of acetic acid. From raw material extraction to sample generation, vacuum freeze drying is performed for many times, collagen micro powder with water content of lower than 3 percent is obtained by further treatment, and is finally sterilized and aseptically packaged, and the purity of a collagen powder finished product is over 98 percent. According to the method, the immunogenicity of the collagen is reduced, yield and biocompatibility are improved, the cost is reduced, the method is applied to a biomedical material, and a peculiar triple helix structure of the obtained collagen can be completely preserved.
Owner:HEILONGJIANG LIHAIXIN BIOTECH CO LTD
Integrated floor-heating flexible ceramic tile and production method thereof
ActiveCN106433096AHigh hardnessImprove heat resistanceHeating fuelNon-macromolecular adhesive additivesElastomerEpoxy
The invention relates to an integrated floor-heating flexible ceramic tile and a production method thereof. The integrated floor-heating flexible ceramic tile combined by a flexible ceramic layer and a polymer composite electric-heating film is good in flexibility, high in tear resistance, high in elongation at break, high in heat resistance, high in heat efficiency, fast in heating, and the like. The flexible ceramic layer is produced by inorganic powder and polymer materials, and the polymer materials are water-borne epoxy resin emulsion, water-soluble epoxy resin curing agent, rubber elastomer and fluorine-containing polyacrylate elastic emulsion. The polymer composite electric-heating film comprises a polyurethane resin heat-conducting insulating layer, a carbon nanotube polyurethane resin heating layer, a polyurethane resin insulating layer and electrodes. The polymer composite electric-heating film is formed by the heat-conducting insulating layer semi-cured by polyurethane resin, the heating layer semi-cured by carbon nanotube polyurethane resin and the insulating layer semi-cured by polyurethane resin through hot pressing. The soft ceramic layer is integrally connected with the polymer composite electric-heating film through the polyurethane resin heat-conducting insulating layer to form the integrated floor-heating flexible ceramic tile.
Owner:万卓(江苏)新材料有限公司
Method and system for improving payment terminal application security
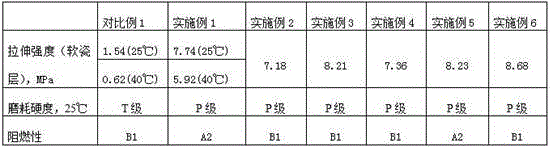
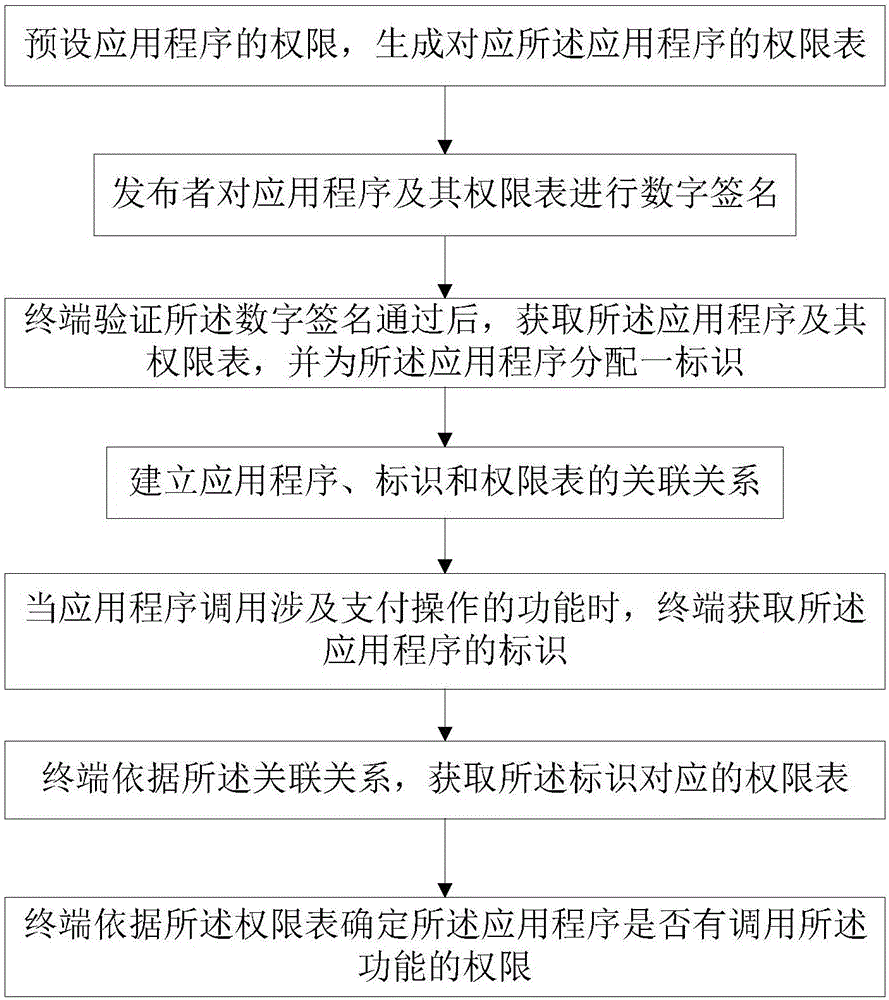
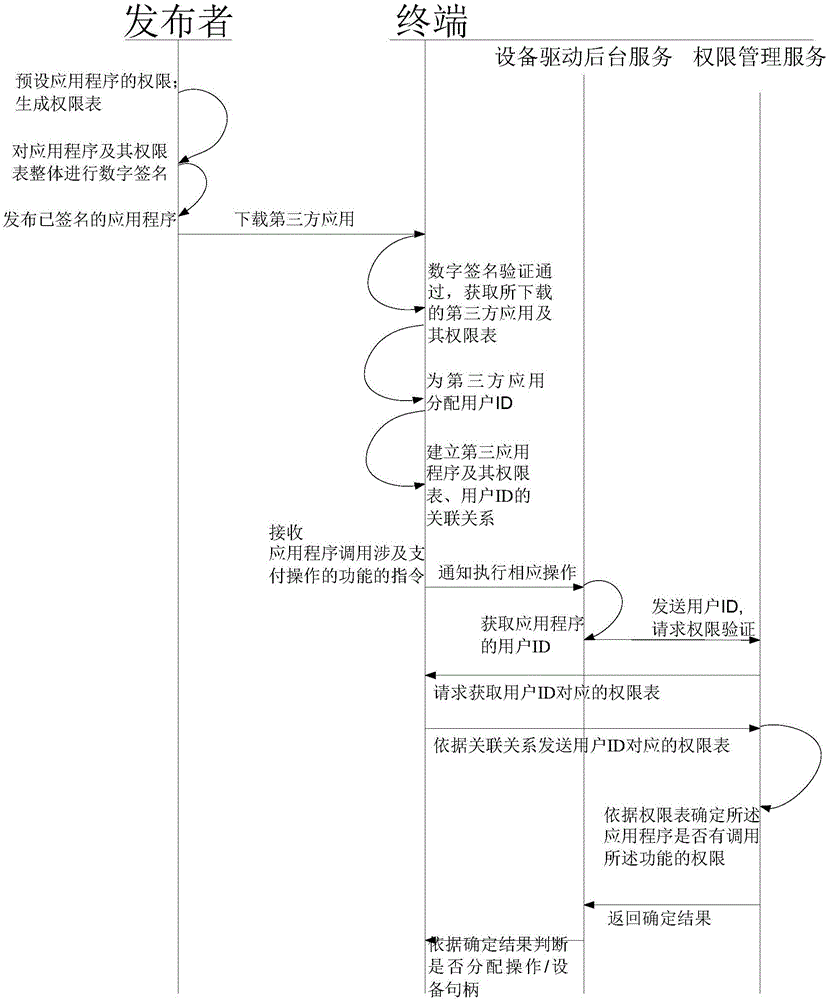
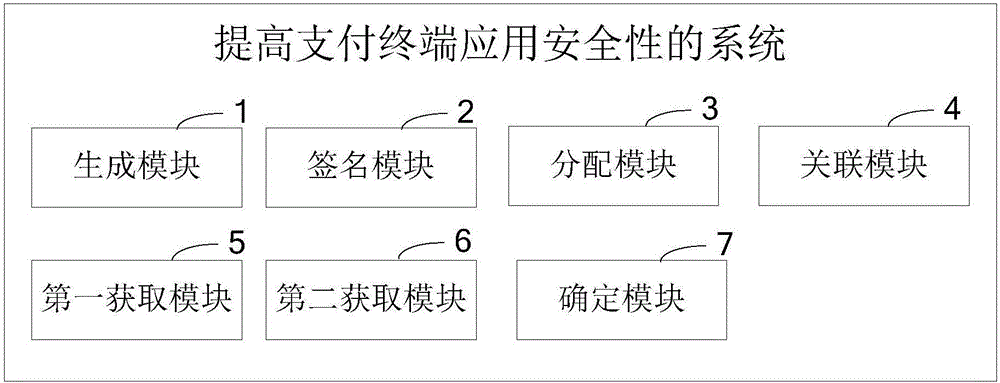
InactiveCN106372496AImprove application securityEnsure application securityPayment protocolsPlatform integrity maintainanceRights managementThird party
The invention provides a method for improving the payment terminal application security and a device thereof. The method comprises the following steps of presetting the authority of an application program; generating an authority table corresponding to the application program; performing digital signature on the application program and the authority table by a publisher; after the digital signature passes through terminal verification, obtaining the application program and the authority table; allocating a mark for the application program; building the association relationship of the application program, the mark and the authority table; when the application program calls a function involving the payment operation, obtaining the mark of the application program by a terminal; obtaining the authority table corresponding to the mark by the terminal according to the association relationship; determining whether the application program has the authority for calling the function or not by the terminal according to the authority table. The method and the device provided by the embodiment of the invention are based on the cooperated matching among a signature tool, an authority management service and equipment driver background service; an authority management mechanism aiming at the third party application program is built; the authority management on the third-party application is realized; the terminal payment security is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Method for realizing APK unified signature by using three-level certificate authentication
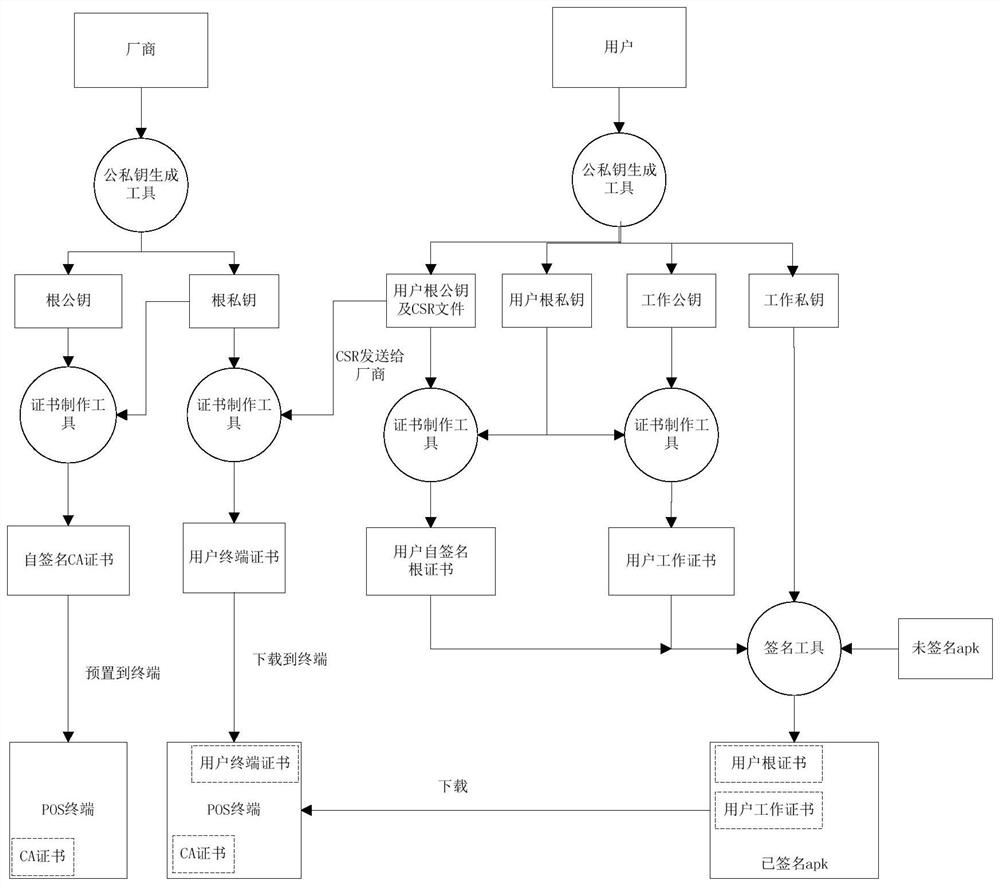
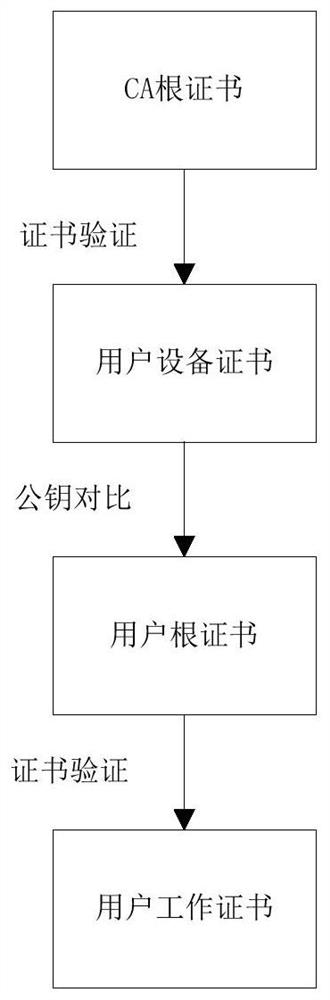
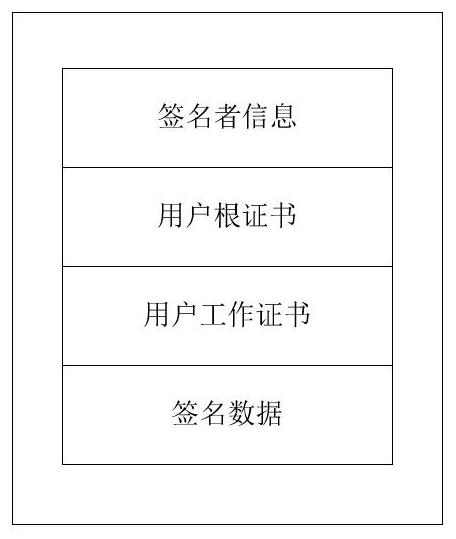
ActiveCN112560017AAdd a custom signatureImprove application securityComputer security arrangementsRoot certificateUser equipment
The invention relates to a method for realizing APK unified signature by using three-level certificate authentication, which adopts a three-level certificate chain including a CA certificate, a user equipment certificate, a user root certificate and a user working certificate to carry out CA authentication, the CA certificate is integrated into firmware, and the user equipment certificate is preset into equipment when the equipment leaves a factory. The POS terminal integrated with the scheme can download different user terminal certificates to support diversified application signature verification requirements of users, such as SM3WithSM2, SHA3-256WITHRSA and the like, manufacturers do not need to customize versions for clients due to the signature verification scheme, version managementis facilitated, and development cost is reduced.
Owner:FUJIAN NEWLAND PAYMENT TECH
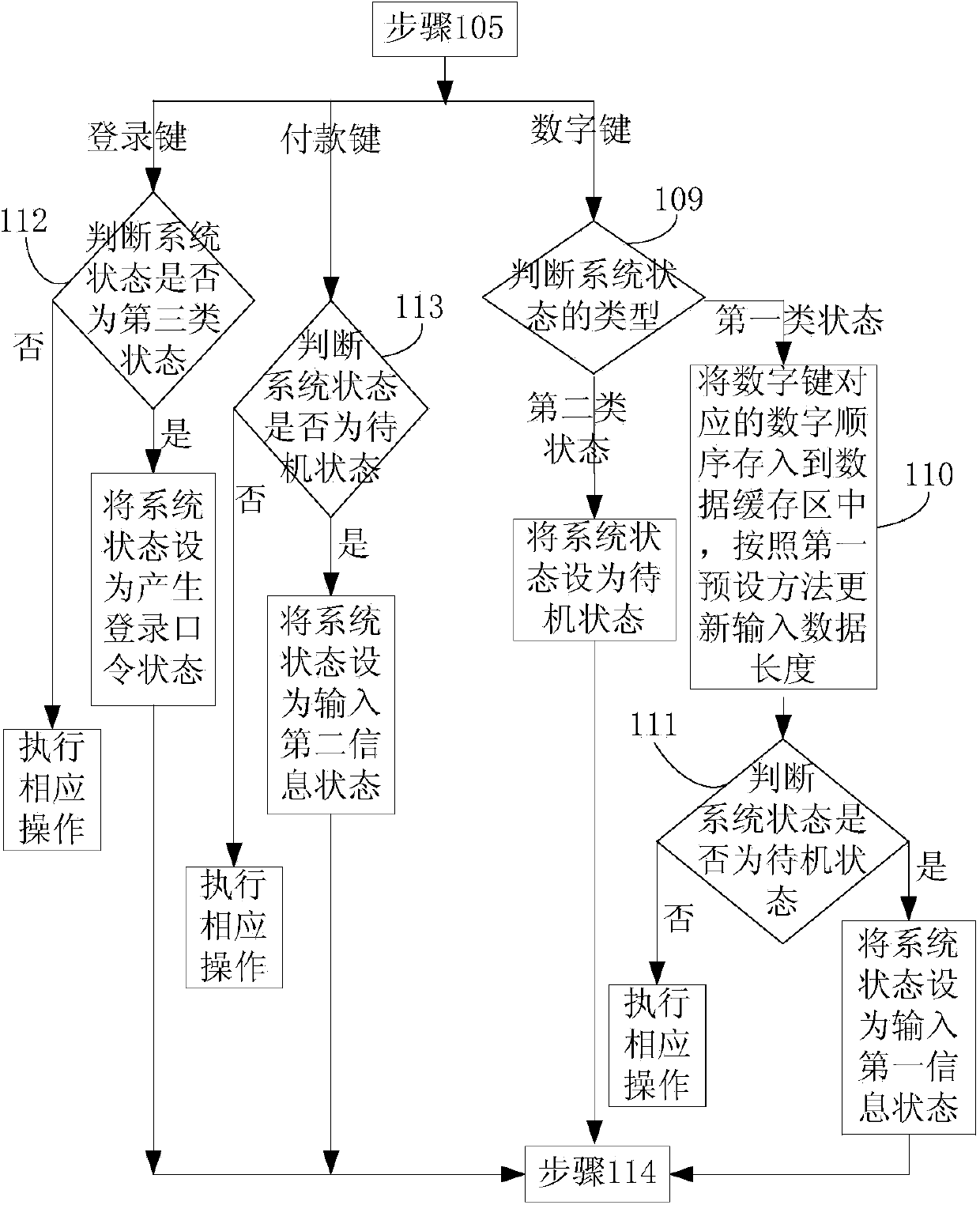
Working method for dynamic token
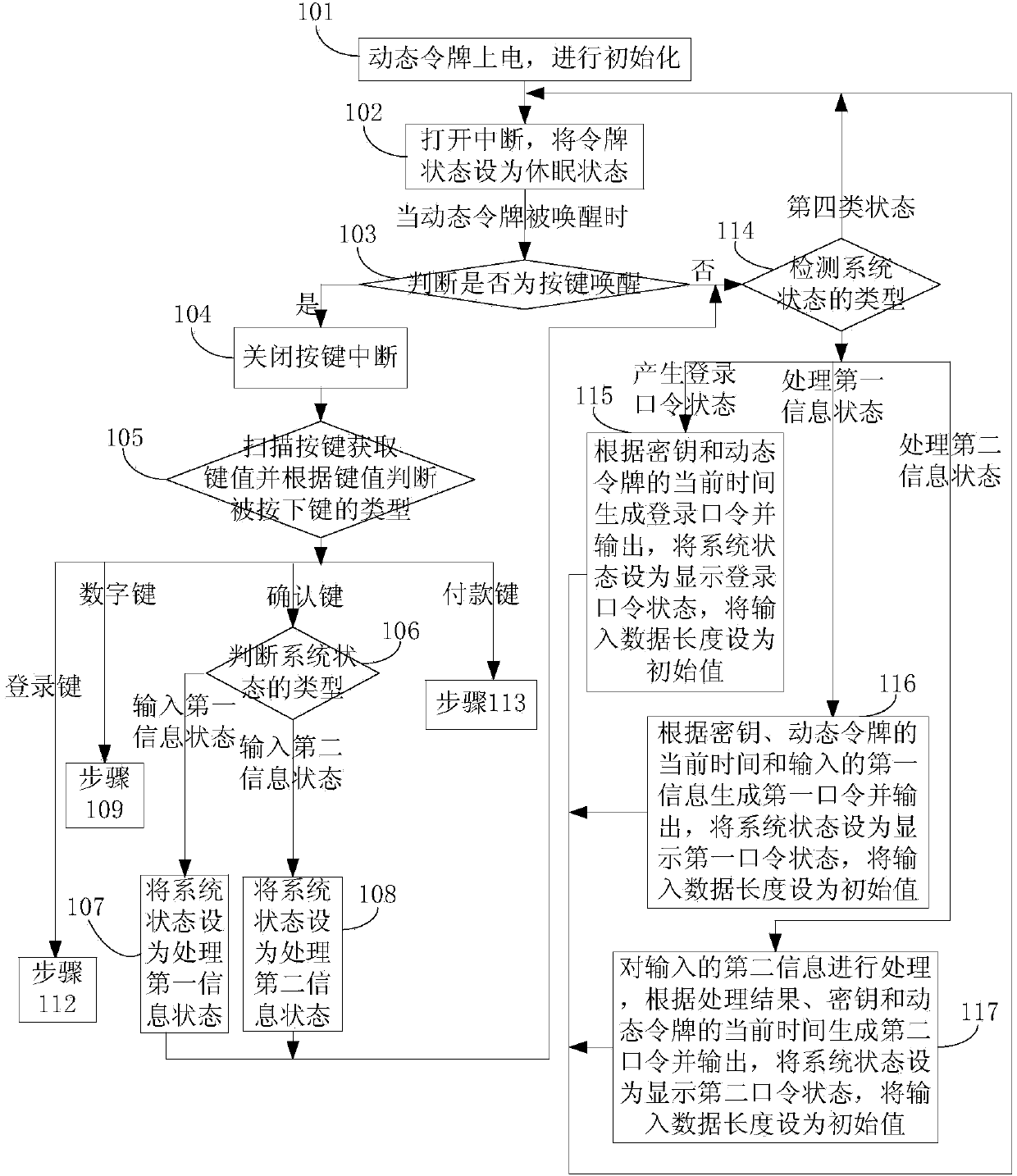
ActiveCN103391195AImprove application securityAvoid illegal operationUser identity/authority verificationCurrent timeComputer hardware
The invention discloses a working method for a dynamic token and relates to the field of information safety. The working method comprises the steps of judging a wake-up type when the dynamic token is waken up, and if the wake-up type is key wake-up, enabling a system state to be set as a corresponding state according to the type of a pressed key; if the wake-up type is other wake-up, judging a system state type; if the system state type is a login password generating state, generating a login password according to a secret key and current time and outputting the login password, enabling the system state to be set as a login password display state, and enabling the input data lengths to be set as initial values; if the system state type is a first information processing state, generating a first password according to the secret key, the current time and the input first information and outputting the first password, enabling the system state to be set as a first password display state, and enabling the input data lengths to be set as the initial values; if the system state type is a second information processing state, processing input second information, generating a second password according to processing results, the secret key and the current time and outputting the second password, enabling the system state to be set as a second password display state, and enabling the input data lengths to be set as the initial values.
Owner:FEITIAN TECHNOLOGIES
Preparation method of zeolite imidazole framework structure material
The invention discloses a preparation method of a zeolite imidazole framework structure material. According to the method, a zeolite imidazole framework structure is subjected to ion exchange to become a composite of two metal ions, wherein post-exchanged particles have a nuclear magnetic resonance effect. The method is mild in reaction condition, easy to operate and low in raw material cost and comprises simple steps. The zeolite imidazole framework structure contrast medium prepared with the method has good water solubility, improved application safety, small toxicity to normal cells and efficient contrast effects.
Owner:NINGBO INST OF MATERIALS TECH & ENG CHINESE ACADEMY OF SCI
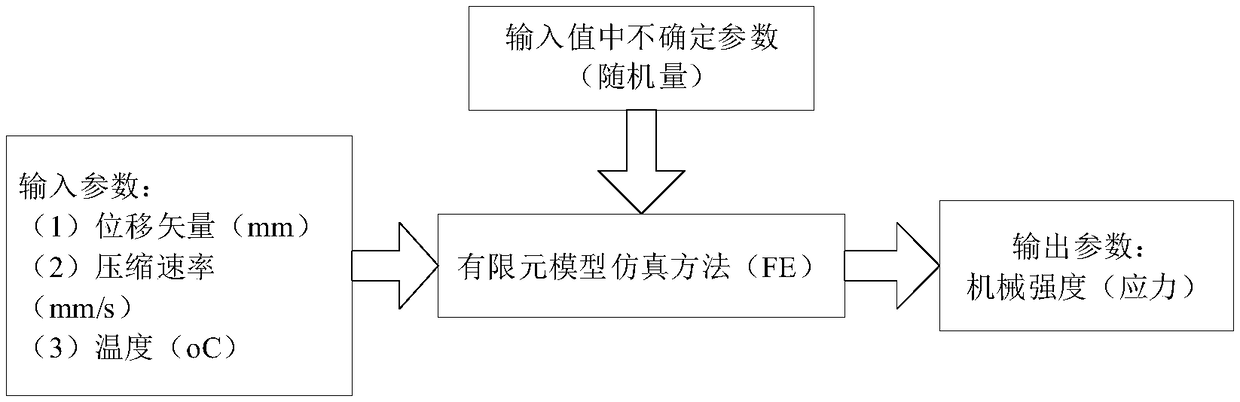
Hybrid simulation method based lithium battery mechanical strength probability model
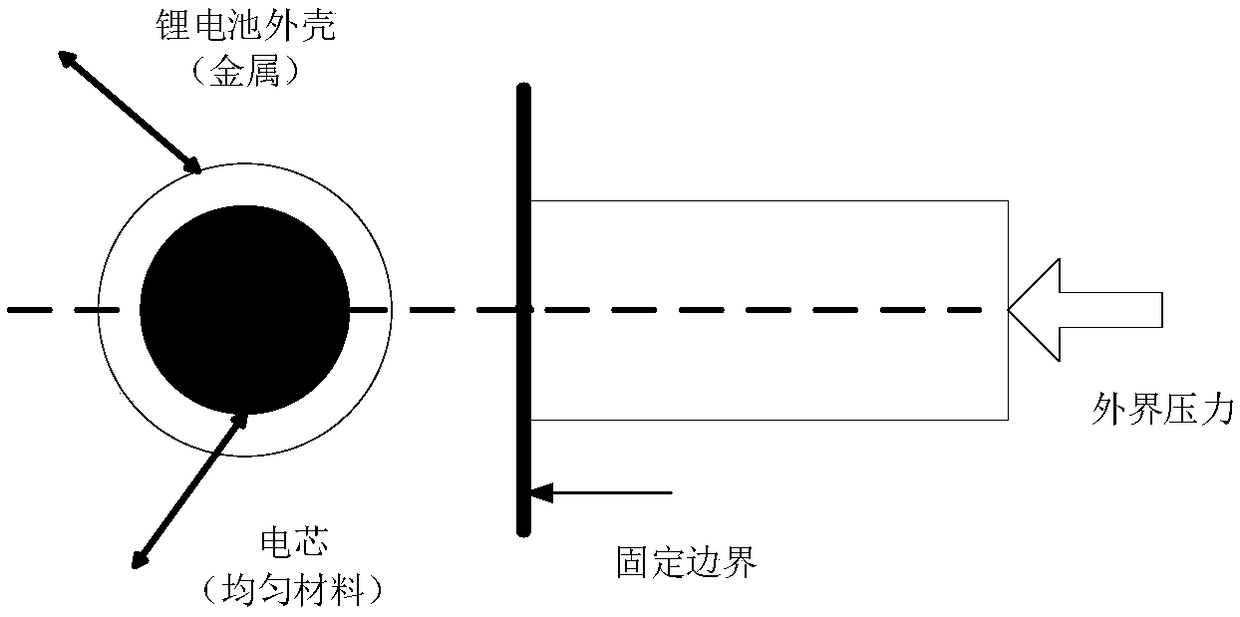
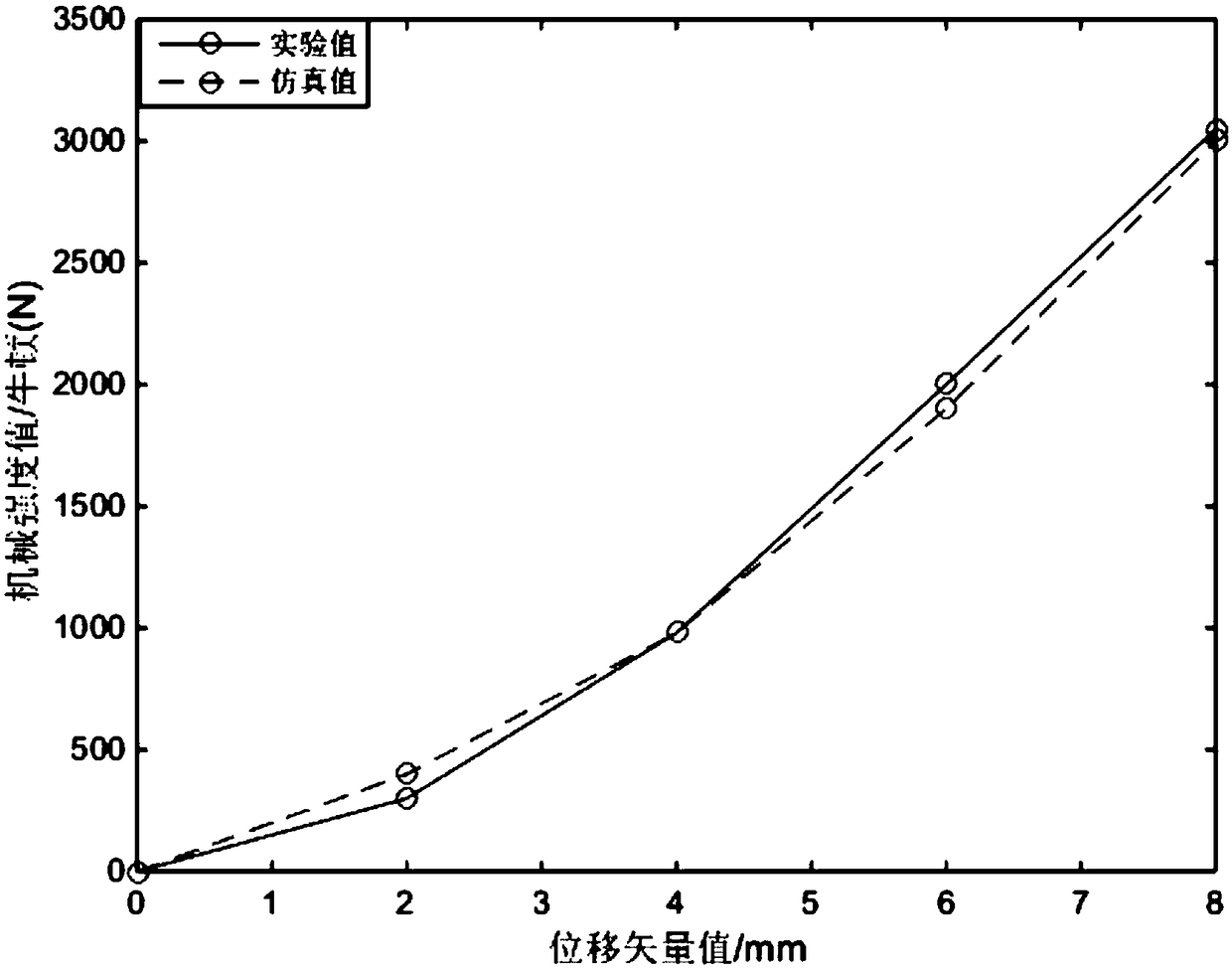
ActiveCN108717475AAccurate calculation of distribution dataPrecise calculation of distribution curvesDesign optimisation/simulationSpecial data processing applicationsElement modelEngineering
The invention relates to a hybrid simulation method based lithium battery mechanical strength probability model. The model is established through the following steps: (1) a step of establishment of alithium battery mechanical strength boundary condition model, namely a step of determining boundary conditions of mechanical strength response based on materials of a lithium battery; (2) a step of establishment of a lithium battery finite element model, namely a step of establishing the lithium battery finite element model according to the mechanical strength boundary condition model and a displacement-mechanical strength relation curve; and (3) a step of establishment of a lithium battery mechanical strength estimation hybrid simulation model, namely a step of establishing the hybrid simulation model by introducing an artificial neural network (ANN) and an uncertainty estimation theory (MUET). the beneficial effects of the lithium battery mechanical strength probability model are as follows: the model combines the artificial neural network and the matrix based uncertainty estimation theory and evaluates the internal mechanical strength of the lithium battery by using the lithium battery finite element model, and the probability model and research results help lithium battery manufacturers to improve the application safety of electric vehicles and traffic road safety.
Owner:ZHEJIANG UNIV CITY COLLEGE
Wear-resistant electrostatic-resistant flame-resistant ultrahigh molecular weight polyethylene composite material
InactiveCN103772780AImprove mechanical propertiesImprove wear resistanceWear resistantFire retardant
The invention discloses a wear-resistant electrostatic-resistant flame-resistant ultrahigh molecular weight polyethylene composite material. The composite material is prepared by performing mixing on ultrahigh molecular weight polyethylene with a viscosity-average molecular weight of 3-3.5 million and an electronic-resistant material by an open mill to form a mixture, then adding a filling material, a novel bromine-based compounded fire retardant, and proper amount of flow modifier, coupling agent, compatibilizer and anti-oxidant, and processing by a double screw extruder, wherein ultrahigh molecular weight polyethylene accounts for 40-60 parts, the filling material accounts for 15-20 parts, the novel bromine-based compounded fire retardant accounts for 20-25 parts, the electronic-resistant material accounts for 5-15 parts, the flow modifier accounts for 5-8 parts, the coupling agent accounts for 0.2-0.5 part, the anti-oxidant accounts for 0.2-0.5 part, and the compatibilizer accounts for 0.2-0.5 part. The above raw materials are weighed according to the above ratio and are mixed by the open mill for forming the mixture, and the mixture and the raw materials weighed according to the above ratio are extruded by the double screw extruder for preparation of the composite material. The composite material is widely applicable to fields of mines, ships, coal and the like. The preparation technology provided by the invention is easy to control, high in production efficiency and stable in quality.
Owner:HEILONGJIANG XINDA ENTERPRISE GRP
Internet-of-Things security gateway with data aggregation and one-way transmission functions and implementation method thereof
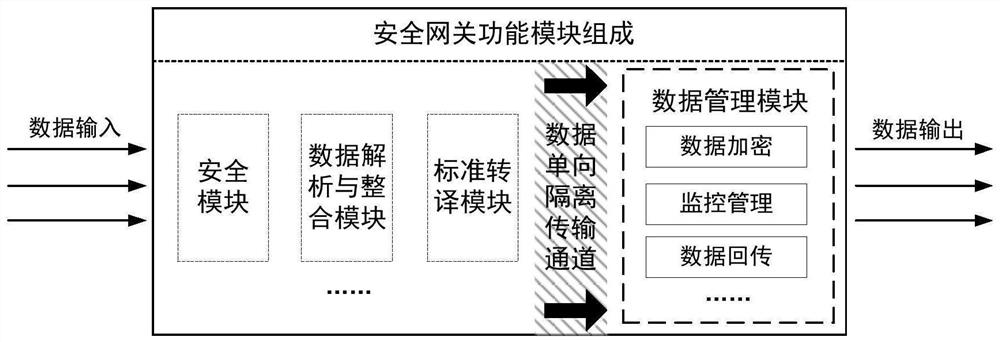
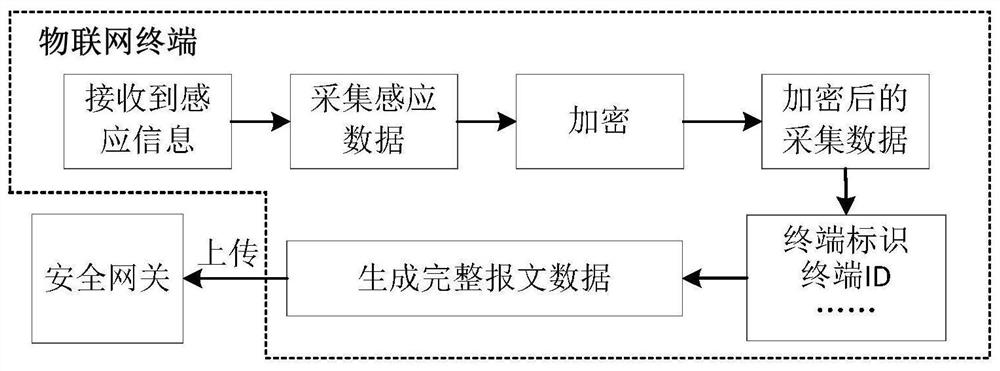
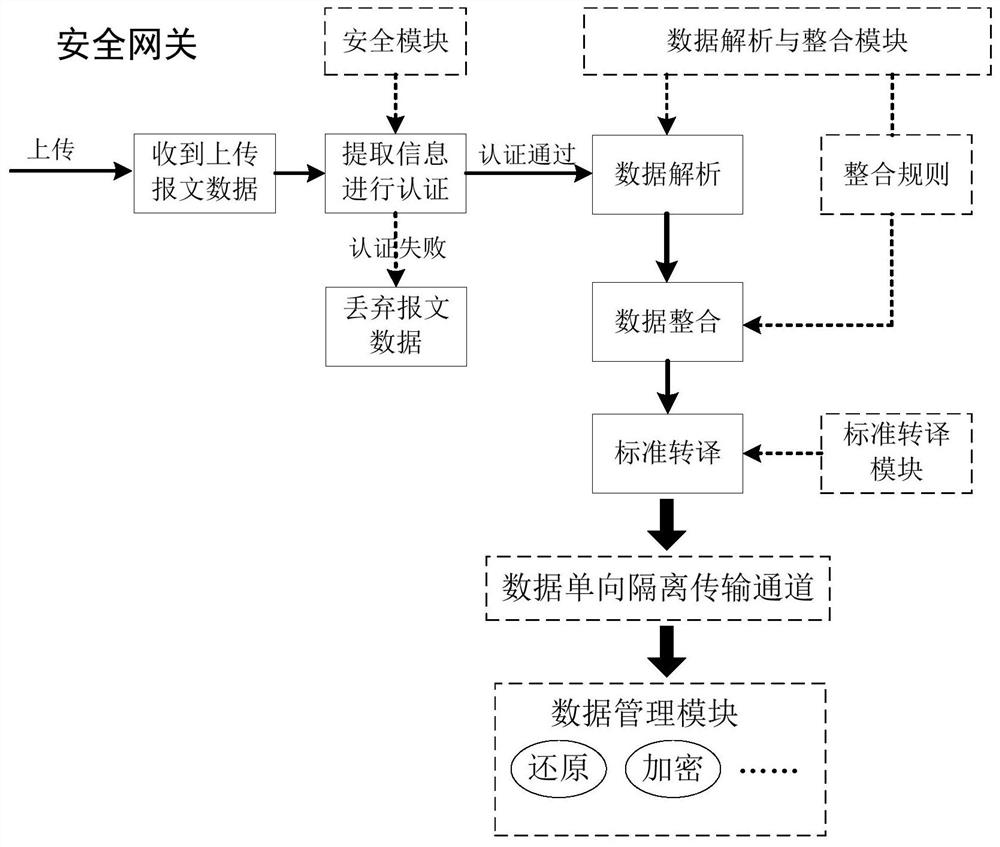
ActiveCN112968908AImprove forwarding efficiencySimplify the interaction processTransmissionData packEncapsulated data
The invention discloses an Internet-of-Things security gateway with data aggregation and one-way transmission and an implementation method thereof, and the security gateway comprises: a security module which is used for extracting authentication information in message data uploaded by an Internet-of-Things terminal to carry out security access authentication; a data analysis and integration module which is used for carrying out data analysis on the message data uploaded by the Internet-of-Things terminal passing the security access authentication to obtain corresponding related communication parameters, and carrying out integration according to a set integration rule to form integrated data; a standard translation module which is used for carrying out compression coding on the integrated data according to a set standard to form a standard data packet, and packaging the standard data packet by using a special protocol; and a data one-way isolation transmission channel and a data management module which are respectively used for carrying out one-way transmission and subsequent operation on the packaged standard data packet. According to the invention, lightweight access authentication of the terminal, convergence and unification of data acquired by various types of transmitters and unidirectional transmission of data information in the gateway can be realized at the same time.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method for preparing wild rosa SOD complex enzyme
The invention discloses a method for preparing a wild rosa SOD complex enzyme. According to the technical scheme, the method comprises the following steps: cleaning and washing rosa fruits; breaking cell walls with high pressure; preparing SOD-containing stock juice; centrifugally separating at a high speed; performing ultra-filtration; performing reverse osmosis concentration; stabilizing an SOD crude enzyme; concentrating in vacuum; and lyophilizing to obtain the rosa SOD complex enzyme. The method has a reasonable process flow, easily selected processing equipment, an easily controlled production control point and an easily formulated and implemented industrial scheme, and has good application prospects in medicines, health foods and cosmetics.
Owner:武熙熙
Safety control method and system based on automatic assembly of industrial robot
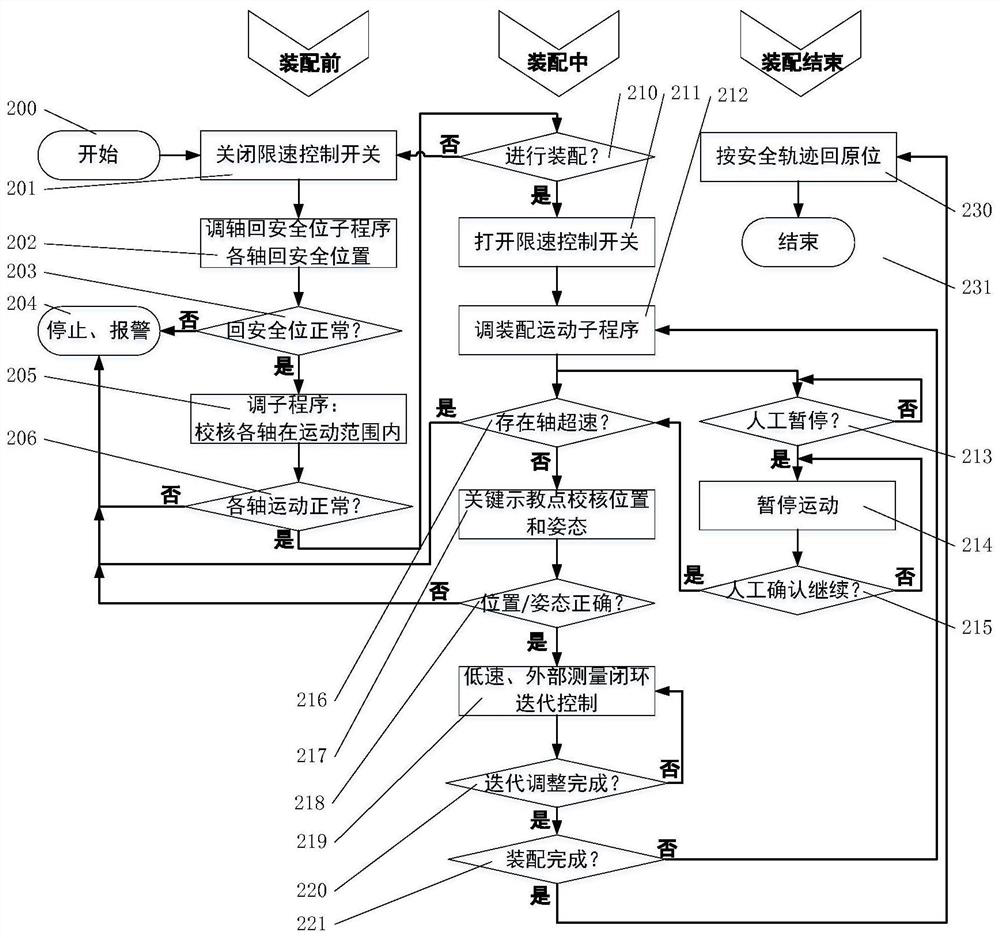
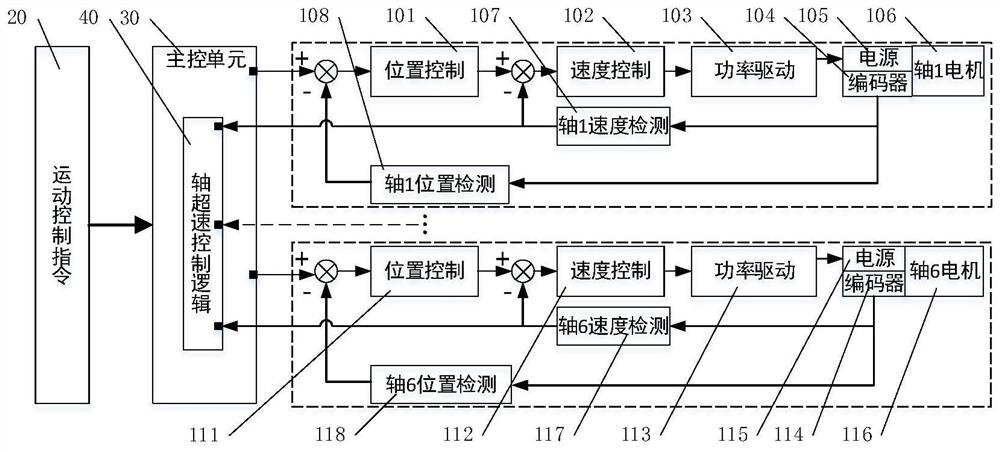
PendingCN113290364ACompensate for lack of motion accuracyAchieving Motion Precision RequirementsProgramme-controlled manipulatorMetal working apparatusControl systemControl engineering
The invention provides a safety control method and system based on automatic assembly of an industrial robot, and the method and system are particularly applied to low-speed, large-load man-machine cooperation, high-precision and high-safety-reliability assembly scenes, and system safety protection control over products and personnel in the automatic assembly process is achieved. Namely, whether the motion function of the industrial robot is normal or not is quickly checked before assembly, product assembly under the condition that a control system has problems is avoided, and safety risks caused by out-of-control motion are prevented; in the assembling process, an over-speed motion limiting strategy is adopted, an operator holds a key by hand to carry out safety confirmation on a key assembling link, and multi-stage safety control protection in the automatic assembling process is achieved; and the position and the posture of the industrial robot are adjusted through external measurement feedback, the problem that the positioning precision of the industrial robot is insufficient is solved, the high-precision sleeving requirement is met, closed-loop monitoring of the position and the posture is achieved in the sleeving process, and it is ensured that the sleeving process meets the assembling precision requirement and does not generate interference collision.
Owner:INST OF MACHINERY MFG TECH CHINA ACAD OF ENG PHYSICS
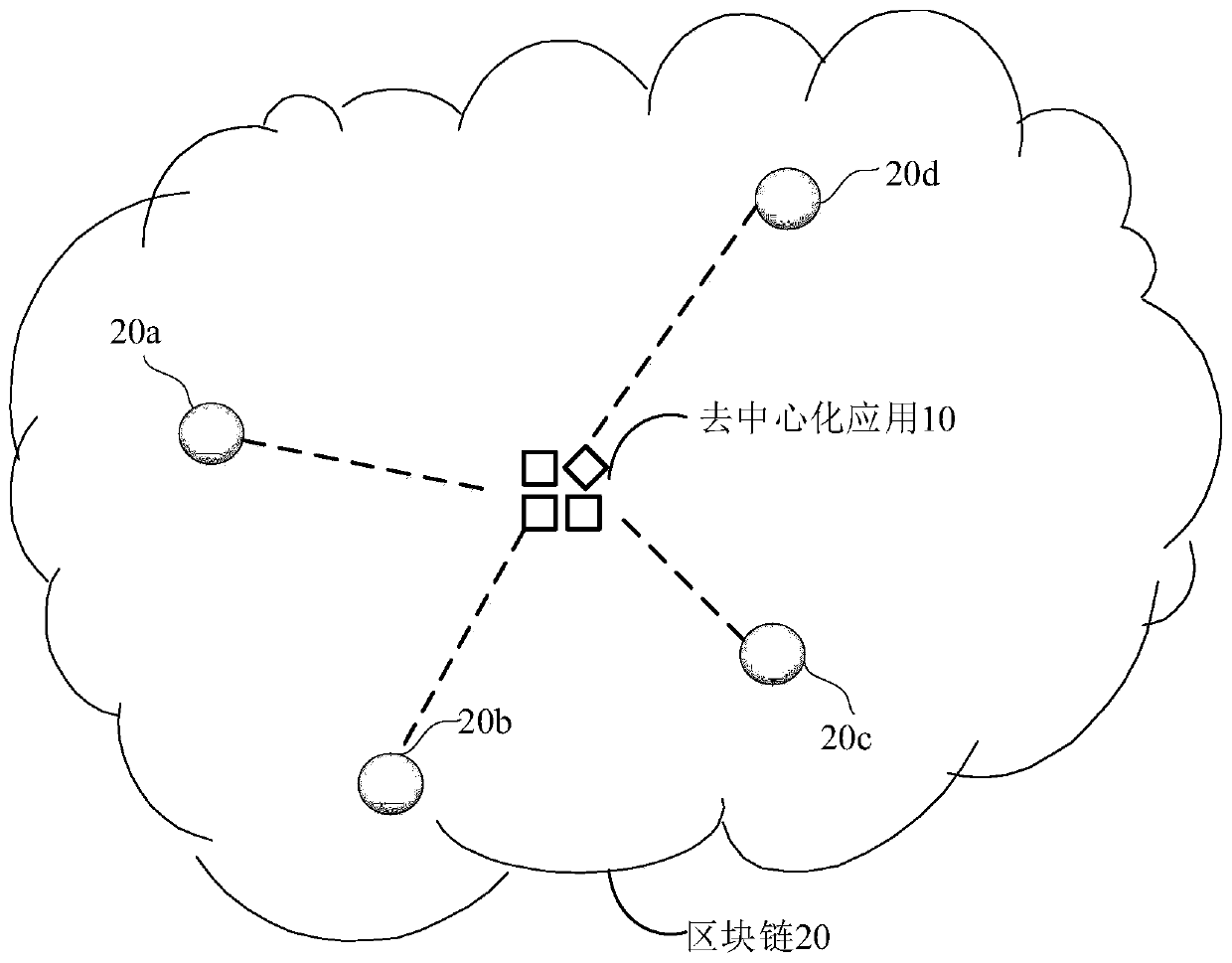
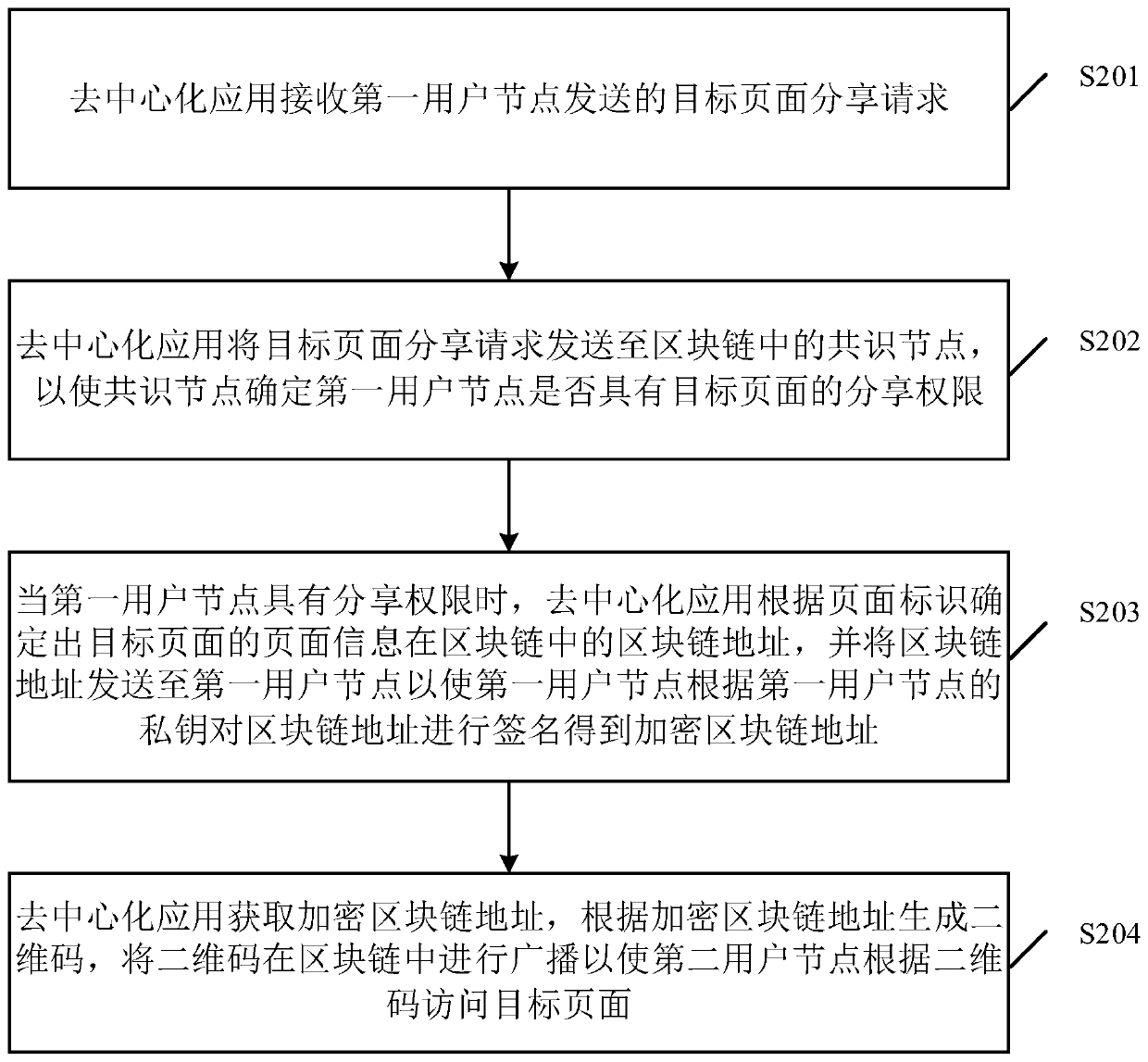
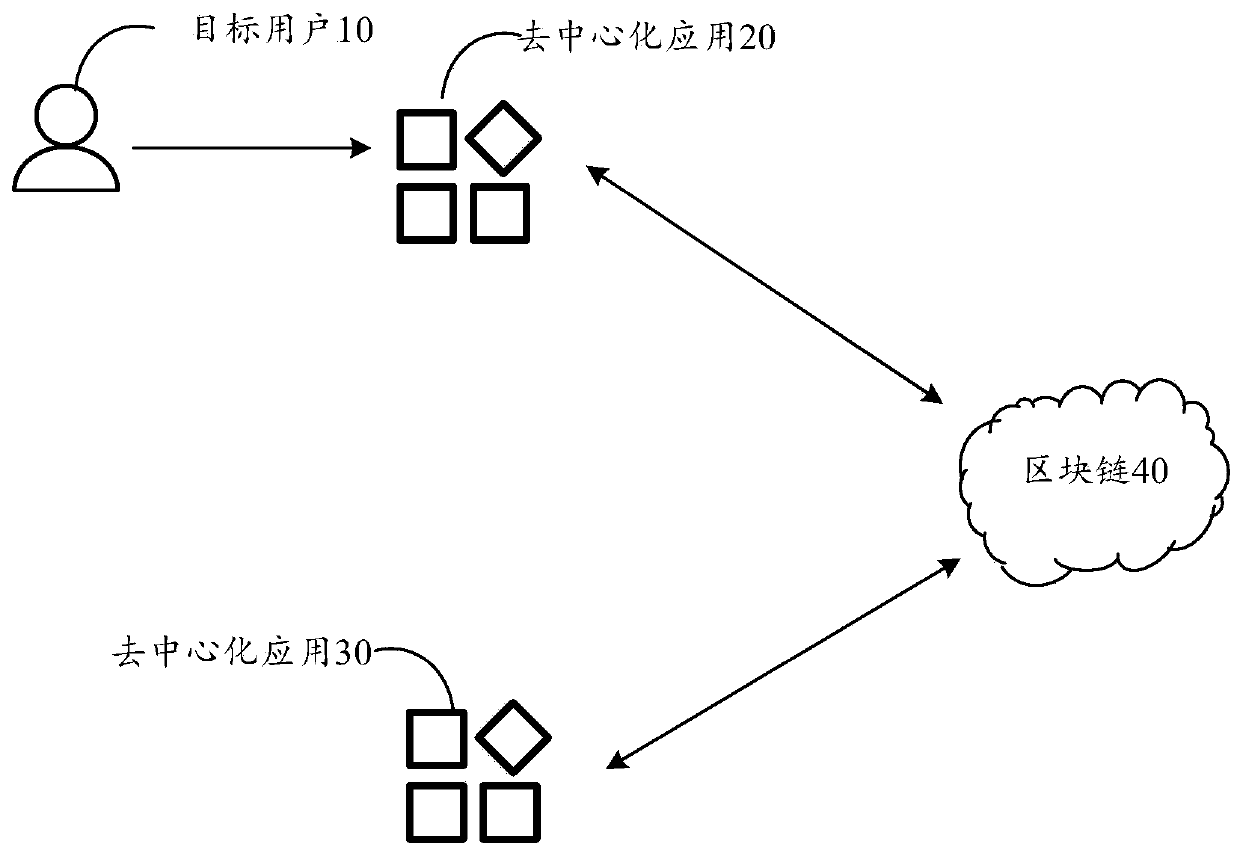
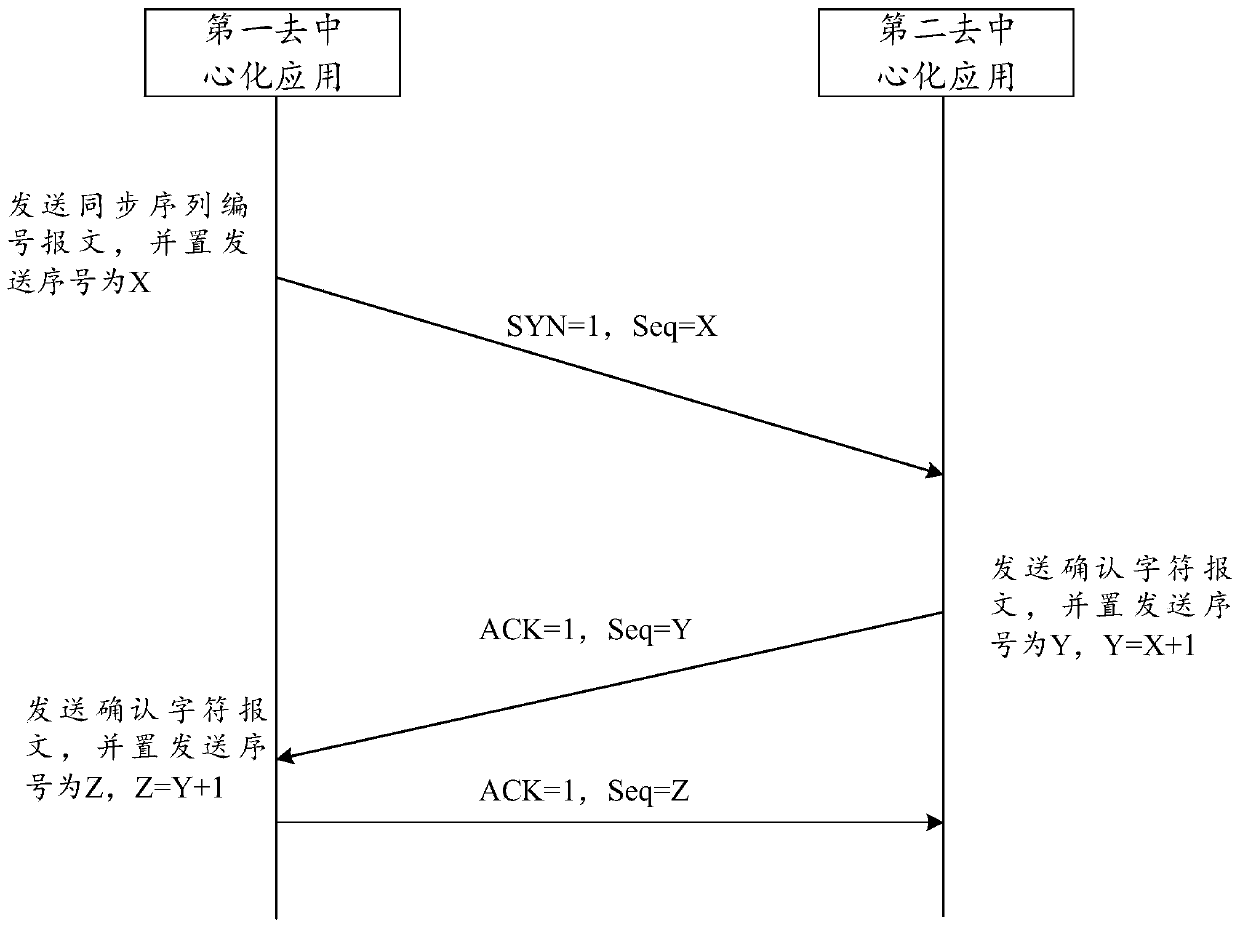
Page access method and device for decentralized application, equipment and storage medium
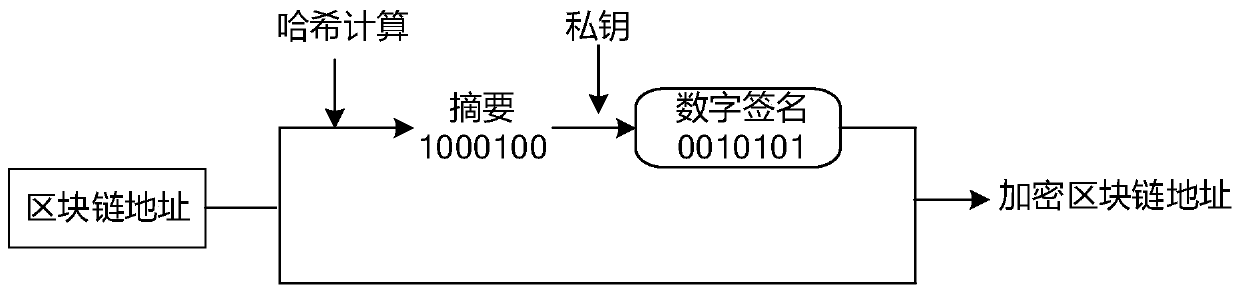
PendingCN111309808AImprove access efficiencyImprove application securityDatabase distribution/replicationDigital data protectionAccess methodEngineering
The embodiment of the invention discloses a page access method and device for a decentralized application, equipment and a storage medium. The method comprises the steps that the decentralized application receives a target page sharing request sent by a first user node; the decentralized application sends the target page sharing request to a consensus node in the blockchain, so that the consensusnode determines whether the first user node has the sharing permission of the target page or not; when the first user node has the sharing permission, the decentralization application determines a block chain address of page information of the target page according to the page identifier, and sends the block chain address to the first user node to obtain an encrypted block chain address; and the decentralized application acquires the encrypted blockchain address, generates a two-dimensional code according to the encrypted blockchain address, and broadcasts the two-dimensional code in the blockchain, so that the second user node accesses the target page according to the two-dimensional code. By adopting the embodiment of the invention, the target page of the decentralized application can bequickly accessed through the two-dimensional code, and the applicability is high.
Owner:TENCENT TECH (SHENZHEN) CO LTD
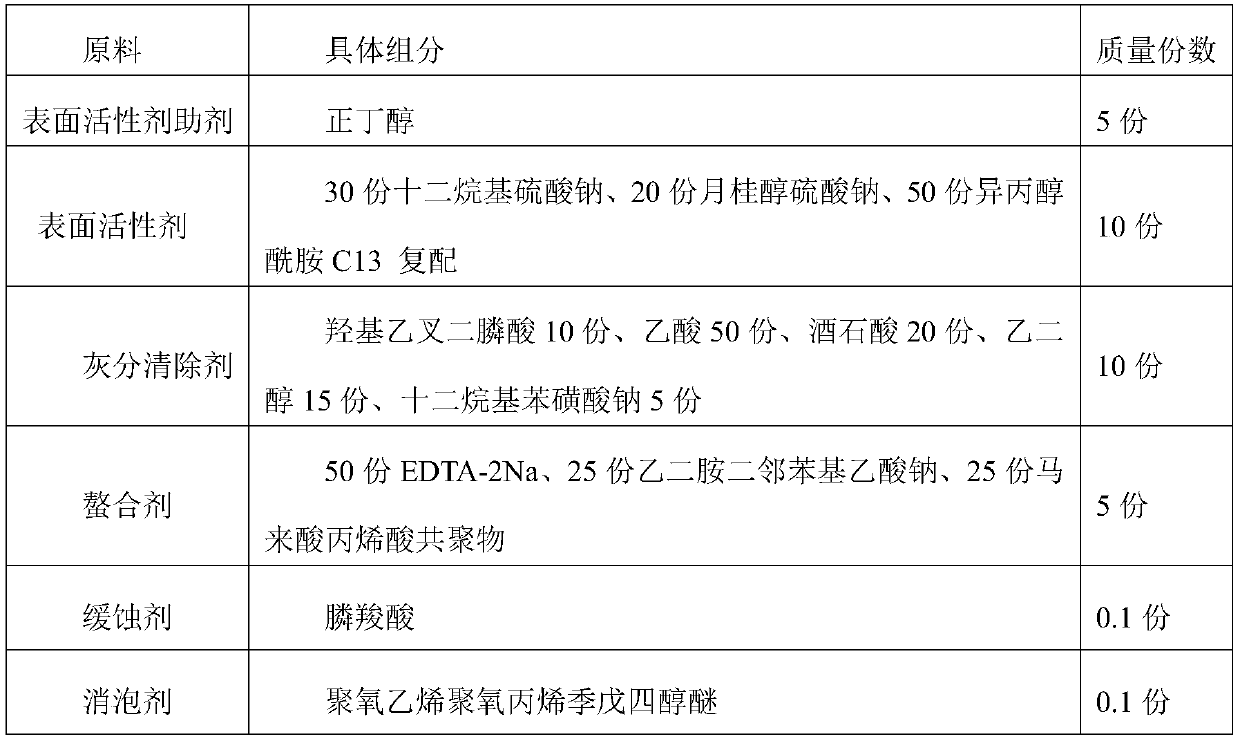
Diesel oil particle capturing device ash cleaning liquid and preparation method thereof
ActiveCN110846144AGood cleaning effectExcellent Application SecurityOrganic detergent compounding agentsNon-ionic surface-active compoundsActive agentSurface-active agents
The invention discloses a diesel oil particle capturing device ash cleaning liquid and a preparation method thereof, wherein the ash cleaning liquid is prepared from the following raw materials by mass: 1-10 parts of a surfactant aid, 5-15 parts of a surfactant, 5-15 parts of an ash scavenger, 1-10 parts of a chelating agent, 0.05-0.15 part of a corrosion inhibitor, 0.05-0.15 part of a defoaming agent, 0.05-0.15 part of a dispersing agent and the balance of water. According to the invention, the diesel oil particle capturing device ash cleaning liquid can rapidly dissolve metal oxides, sulfates, phosphates, silicates and chlorides in DPF ash to make the metal oxides, the sulfates, the phosphates, the silicates and the chlorides react to form water-soluble compounds so as to be taken away by the aqueous solution and discharged, and the compounds formed by the reaction have surface activity, so the dissolving cleaning of soot particles is easily achieved.
Owner:DONGFENG COMML VEHICLE CO LTD
Building curtain wall safety nondestructive testing imaging method based on microwave imaging
PendingCN113689416AAvoid the element of chanceAccurate detectionImage enhancementImage analysisAlgorithmImaging Feature
The invention discloses a building curtain wall safety nondestructive testing imaging method based on microwave imaging, and the method comprises the following steps: respectively imaging defective curtain walls and newly built curtain walls under different working conditions, extracting imaging features of various defects, and taking the imaging features as identification elements of the defects to establish a feature library; setting detection equipment and carrying equipment, and confirming an initial acquisition position; carrying out comprehensive scanning detection on a to-be-detected curtain wall to realize microwave imaging; identifying a microwave imaging result, comparing the microwave imaging result with data in the feature library, marking working conditions with the same features, determining defect types, and reminding a person in charge to further observe and confirm; and determining a defect position and combining a defect type, and recording the defect position, the defect type and a non-conformance condition according to the conformance condition of the drawing, the standard and the feature library. According to the method, comprehensive scanning detection is completed on the premise that the original structure of the curtain wall is not damaged, accidental factors caused by sampling inspection are avoided, detection is more accurate, and the detection effect is good.
Owner:DECORATION CO LTD OF CHINA CONSTR 3RD ENG BUREAU
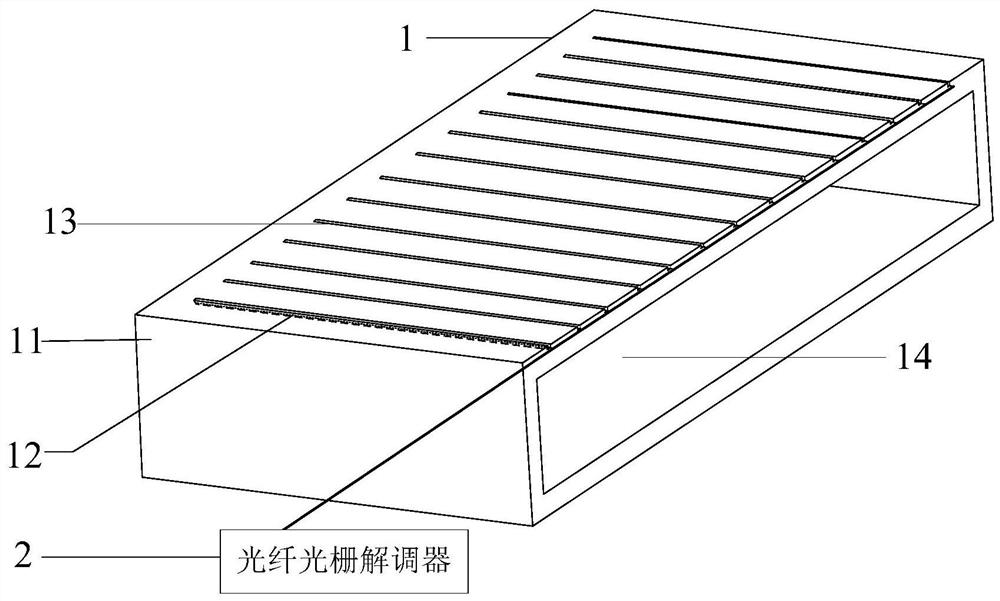
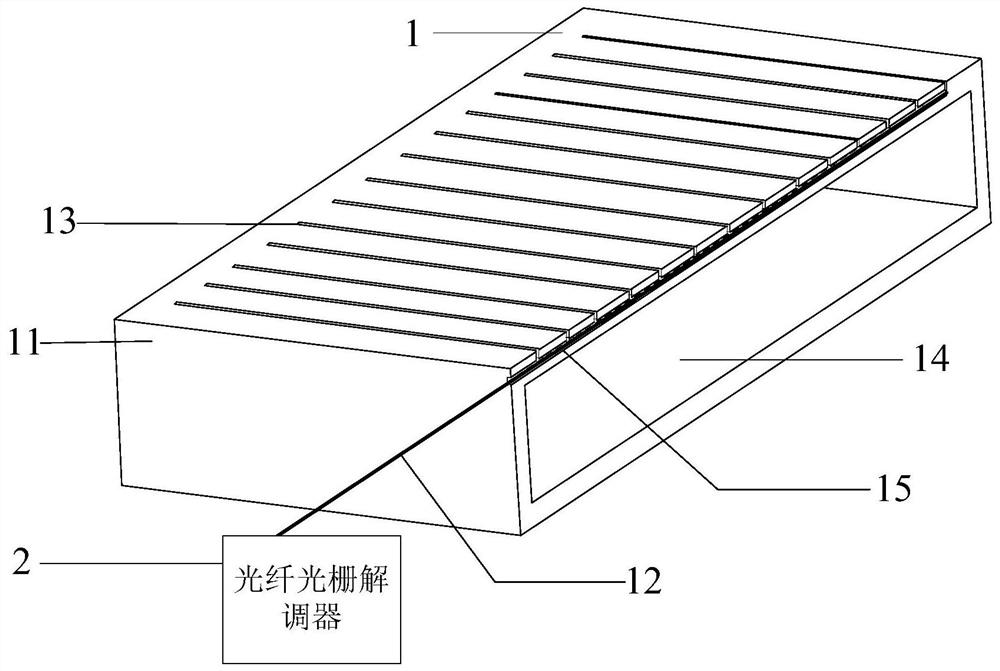
Crystallizer, method for measuring height of liquid level of molten steel in crystallizer and related device
The embodiment of the invention provides a crystallizer, a method for measuring the height of the liquid level of molten steel in the crystallizer and a related device. The crystallizer comprises a crystallizer body and a plurality of optical fibers. A plurality of parallel first grooves are formed in at least one side wall of the crystallizer body, and the same ends of the first grooves in the length direction extend to an upper opening of the crystallizer. One end of each optical fiber is independently arranged in the corresponding first groove, and the other ends of the optical fibers extend out of the corresponding first grooves and are used for being connected with a fiber grating demodulator. The accuracy and stability of crystallizer temperature measurement can be effectively improved, and then the accuracy and efficiency of acquiring the molten steel liquid level fluctuation state in the crystallizer through the crystallizer temperature measurement result can be effectively improved.
Owner:MCC CAPITAL ENGINEERING & RESEARCH +1
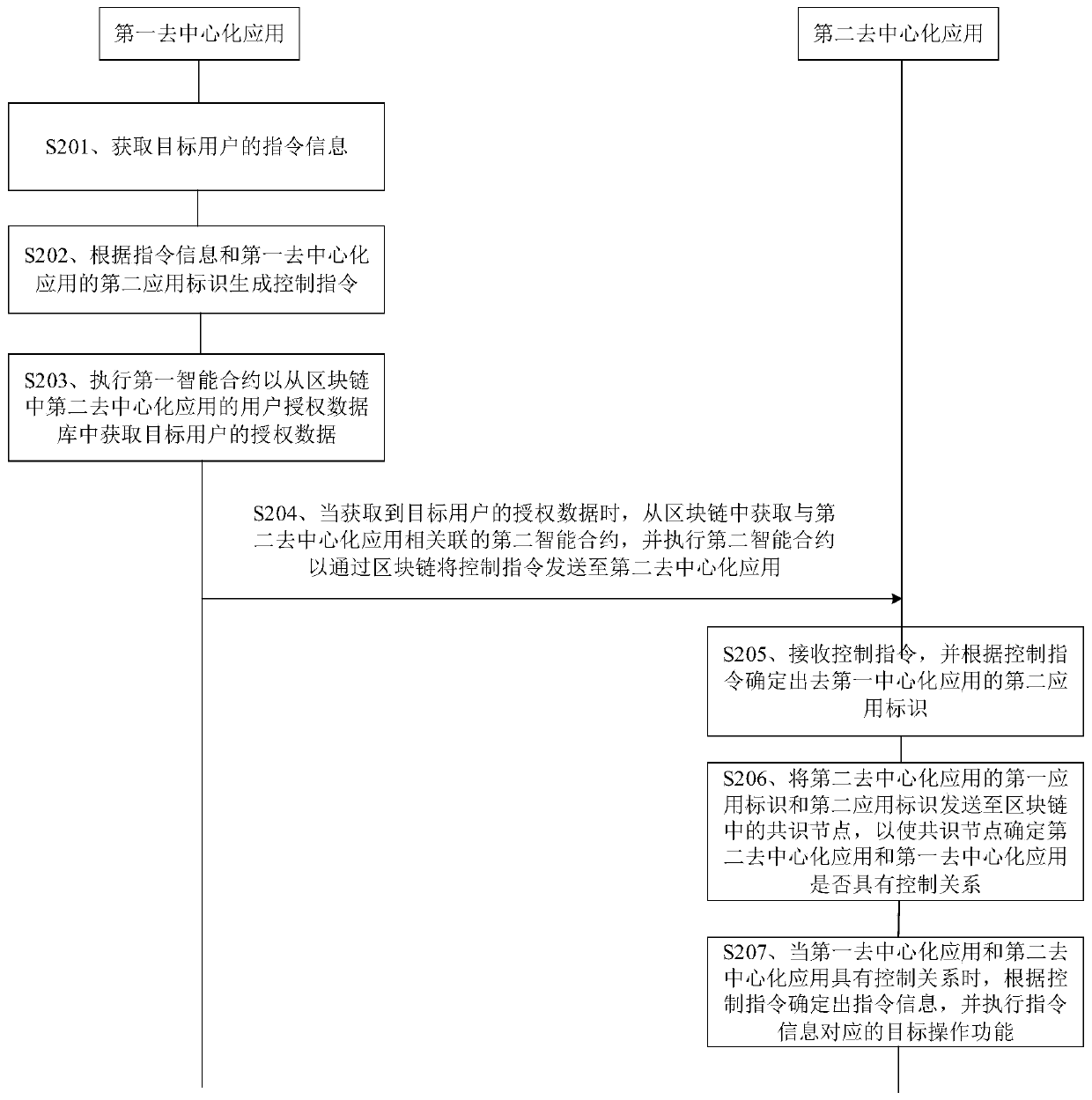
Application control method, device and equipment and storage medium
PendingCN111444496AImprove application securityImprove transmission securityDigital data protectionDigital data authenticationSoftware engineeringSmart contract
The embodiment of the invention discloses an application control method and device, equipment and a storage medium, and the method comprises the steps: obtaining the instruction information of a target user, wherein the instruction information carries a first application identification, the first application identification is used for marking a second decentralized application, and the instructioninformation is used for controlling the second decentralized application to execute a target operation function; generating a control instruction according to the instruction information and a secondapplication identifier of the first decentralized application; executing the first smart contract to obtain authorization data of the target user from a user authorization database of a second decentralized application in the blockchain; and when the authorization data of the target user is obtained, obtaining a second smart contract associated with the second decentralized application from the blockchain, and executing the second smart contract to send the control instruction to the second decentralized application through the blockchain, so that the second decentralized application executesthe target operation function. By adopting the embodiment of the invention, the application can be controlled based on the blockchain, and the applicability is high.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Fish meal additive
InactiveCN104186980APrevent oxidationReduce oxidation activityAnimal feeding stuffButylated hydroxytolueneToluene
The invention provides a fish meal additive, belongs to the field of additives, and solves the problems that fat is easy to rancidify and protein is easy to corrupt and mildew in fish meal of feeds in the prior art. The fish meal additive comprises the following components in parts by weight: 0.2-0.6 part of butylated hydroxytoluene, 0.2-0.6 part of tert-butyl hydroquinone, 2-4 parts of malic acid, 1-2 parts of citric acid, 1-2 parts of silica bauxite, 2-5 parts of zeolite and 0.05-0.1 part of yeast. According to the fish meal additive, by selecting varieties and contents of materials, the possibilities of rancidity of the fat and corruption and mildewing of the protein are reduced, so that the preservation time of the fish meal is prolonged, and the application security of the fish meal in the feeds is improved.
Owner:巨星农牧有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com