Vulnerability detection method and device
A vulnerability detection and vulnerability technology, which is applied in the field of information security, can solve the problems of vulnerability parameter consumption, manpower, and inability to effectively identify the location of vulnerabilities, and achieve the effect of improving application security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0021] According to the embodiments of the present application, a method embodiment of a vulnerability detection method is also provided. It should be noted that the steps shown in the flowchart of the accompanying drawings can be executed in a computer system such as a set of computer executable instructions, and Although the logical sequence is shown in the flowchart, in some cases, the steps shown or described may be performed in a different order than here.
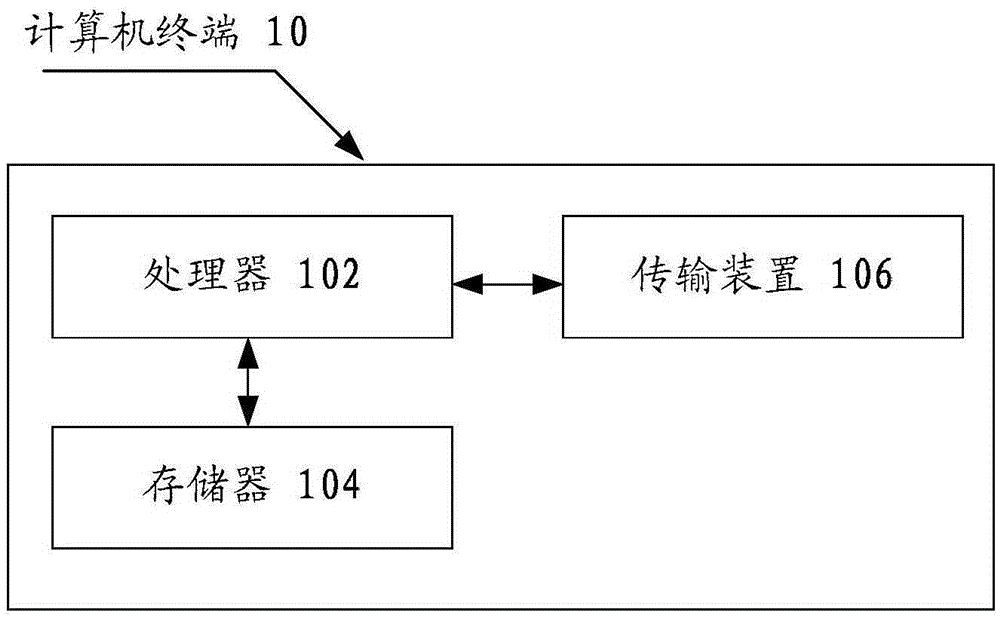
[0022] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a hardware structure block diagram of a computer terminal of a vulnerability detection method in an embodiment of the present application. Such as figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processor 102 (the processor 102 may inc...
Embodiment 2
[0067] According to the embodiment of the present application, an apparatus embodiment for implementing the above method embodiment is also provided. The apparatus provided in the above embodiment of the present application can run on a computer terminal.
[0068] Figure 4 It is a schematic structural diagram of a vulnerability detection device according to an embodiment of the present application.
[0069] Such as Figure 4 As shown, the vulnerability detection device may include a first acquisition unit 402, a search unit 404, a judgment unit 406, a second acquisition unit 408, and a detection unit 410.
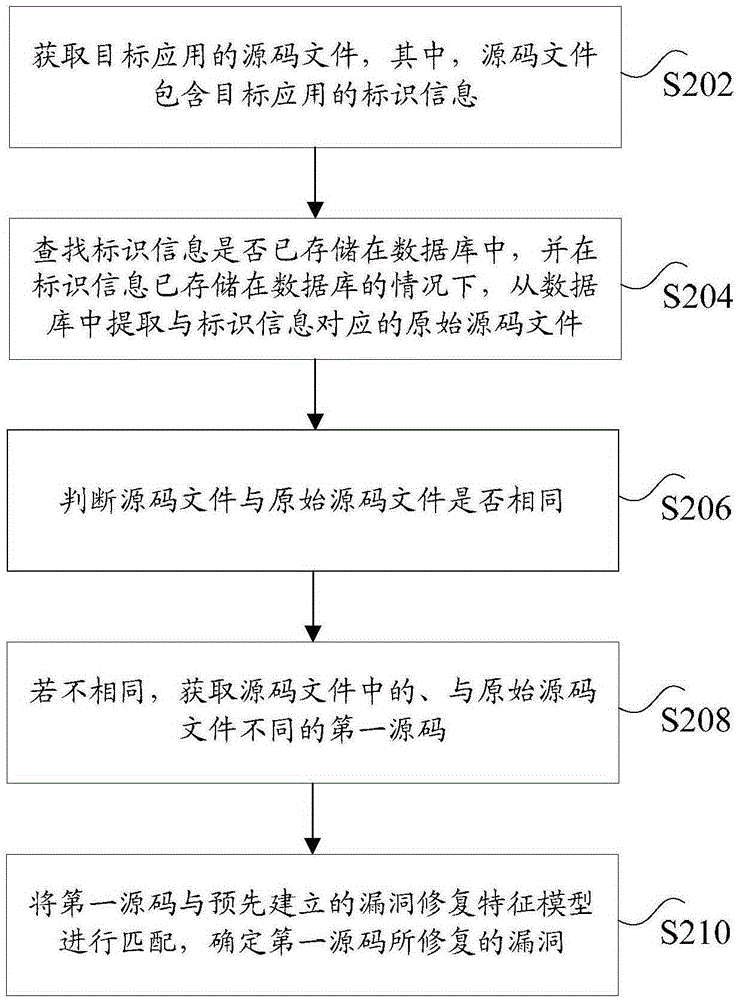
[0070] Wherein, the first obtaining unit 402 is used to obtain the source code file of the target application, where the source code file contains the identification information of the target application; the searching unit 404 is used to search whether the identification information has been stored in the database, And when the identification information has been stored in the d...
Embodiment 3
[0085] According to the embodiment of the present application, an apparatus embodiment for implementing the above method embodiment is also provided. The apparatus provided in the above embodiment of the present application can run on a computer terminal.
[0086] Figure 8 It is a schematic structural diagram of a vulnerability detection device according to an embodiment of the present application.
[0087] Such as Figure 8 As shown, the vulnerability detection device may include an open source application address crawler engine 802, a resource availability analysis engine 804, a download engine 806, a file decompression engine 808, a file change analysis engine 810, and a core vulnerability analysis engine 812.
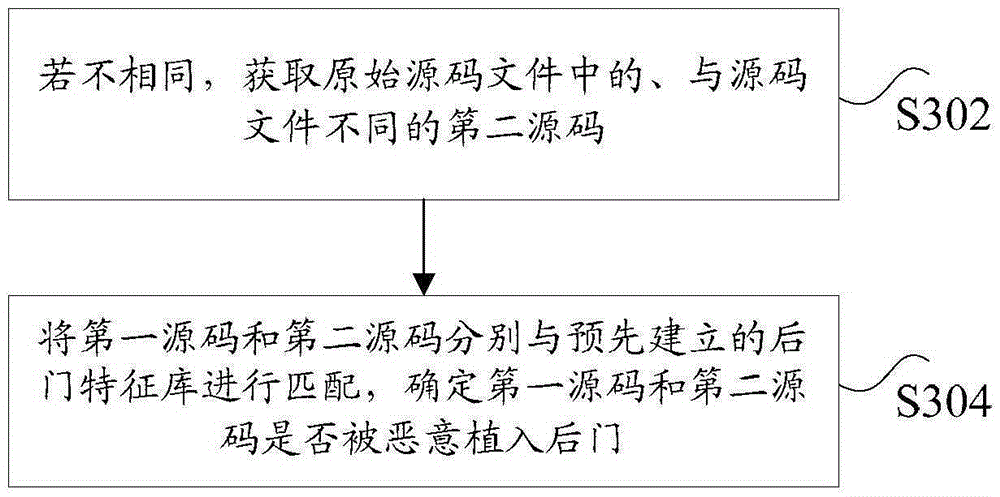
[0088] The first part is the timely monitoring of source code changes and analysis of vulnerability files.
[0089] For a large number of Internet applications that have special situations such as randomization of file names and randomization of download links during applic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com