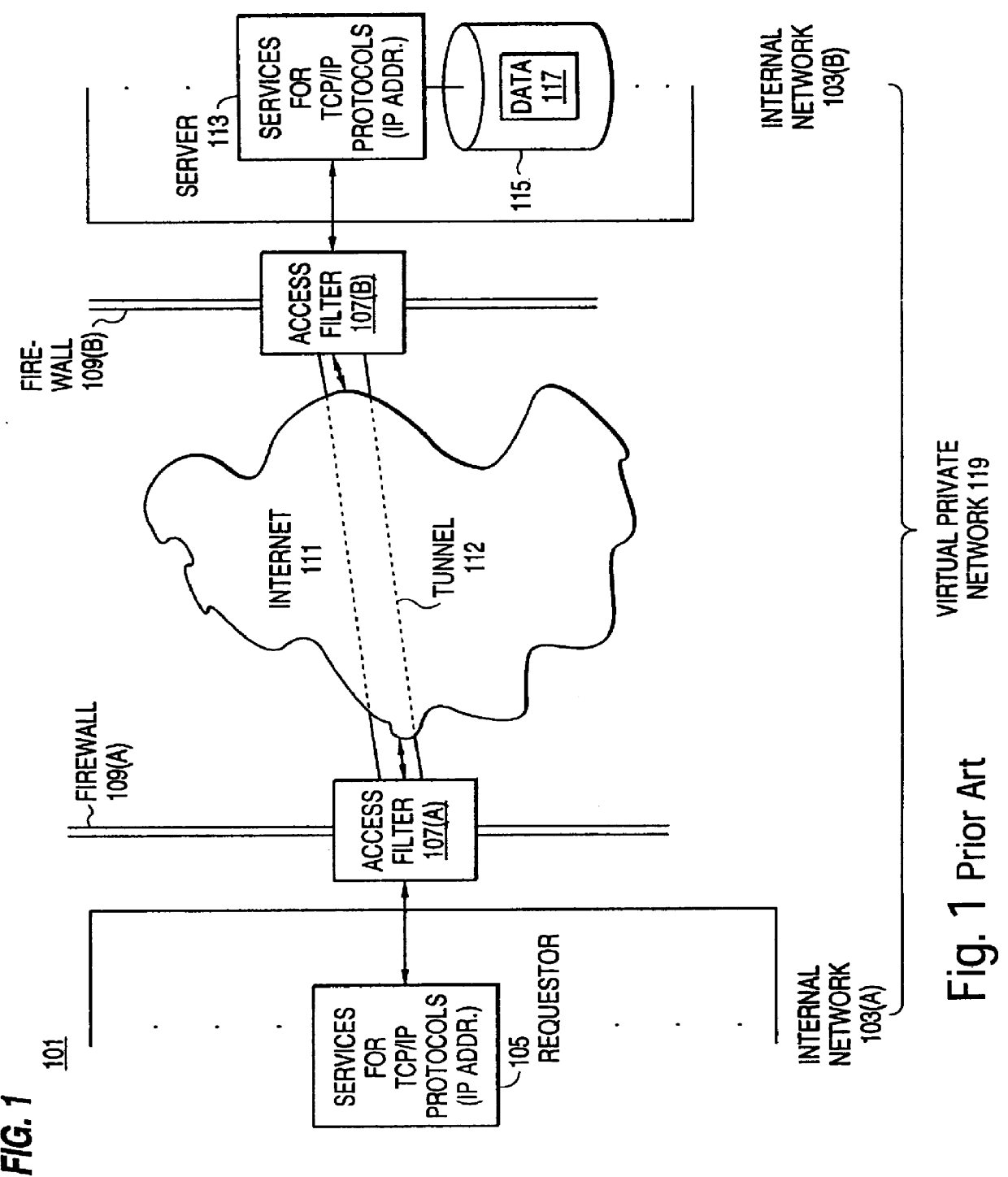
Patents
Literature
5926 results about "User group" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A users' group (also user's group or user group) is a type of club focused on the use of a particular technology, usually (but not always) computer -related. Users' groups started in the early days of mainframe computers, as a way to share sometimes hard-won knowledge and useful software,...
Internet profiling
InactiveUS6839680B1Quick applicationEasy to shareMarket predictionsSpecial data processing applicationsWeb serviceStandardization
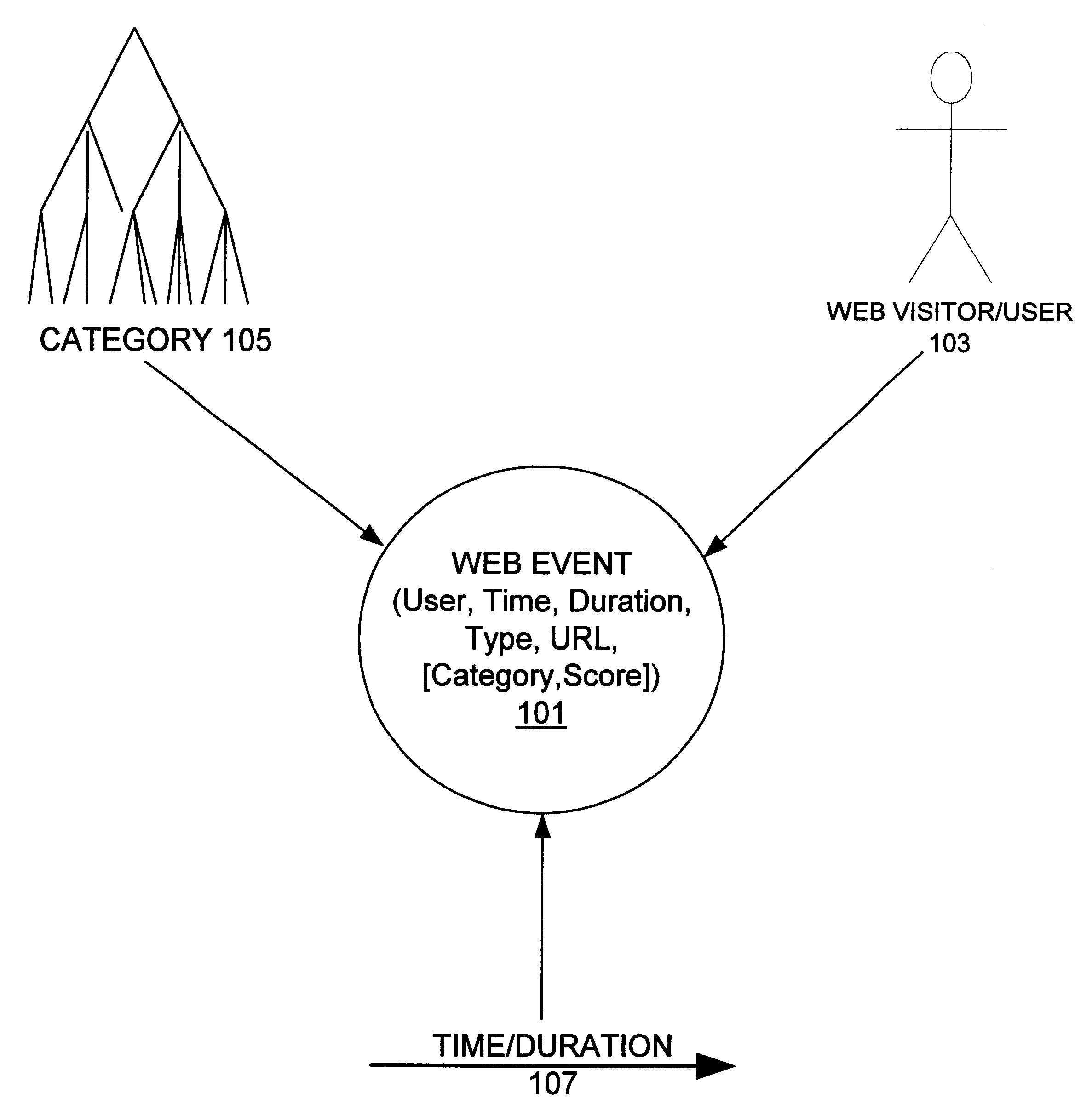
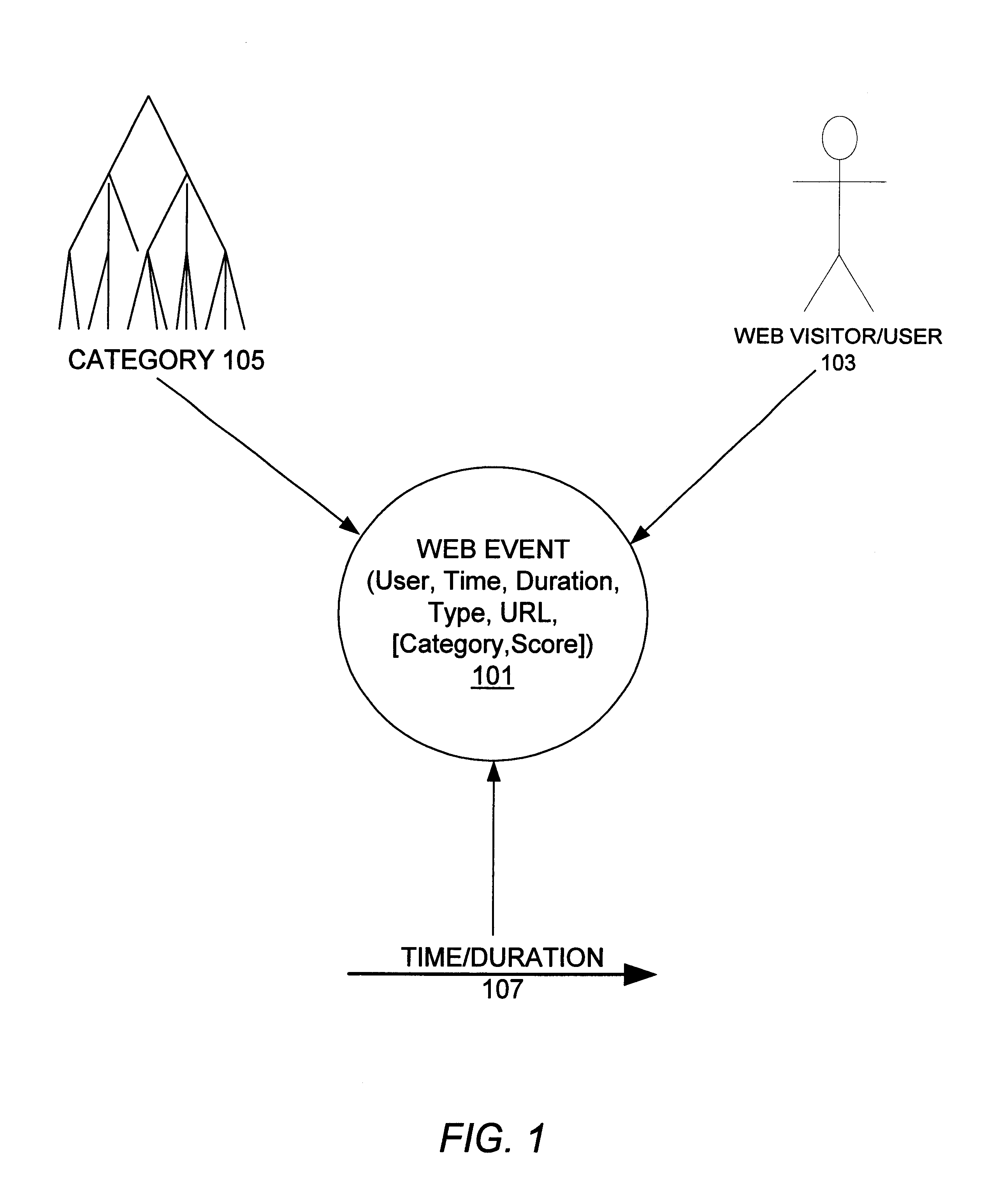
A system, method, and various software products provide for consistent identification of web users across multiple web sites, servers and domains, monitoring and capture of data describing the users' web activities, categorization of the web activity data, aggregation of the data into time dependent models describing interest of users and groups over time. Categorization is made with respect to a category tree which may be standardized or customized for each web site. User groups may be defined based on membership rules for category interest information and demographics. Individual user profiles are then created for users automatically based on satisfaction of the user group membership rules. As new data is collected on a user over time, the category interest information extracted from the user's web activity is updated to form a current model of the user's interests relative to the various categories. This information is also used to automatically update group membership and user profile information. Identification of users across multiple sites is provided by a global service that recognizes each user and provides a globally unique identifier to a requesting web server, which can use the identifier to accumulate activity data for the user. Client side user identification is provided to track user activity data on web servers that do not communicate with the global service and do not process activity for category information. User profiles may be shared among web sites that form alliances. User activity data may be aggregated along various dimensions including users / user groups, categorization, and time to provide robust models of interest at any desired time scale.
Owner:FUJITSU LTD
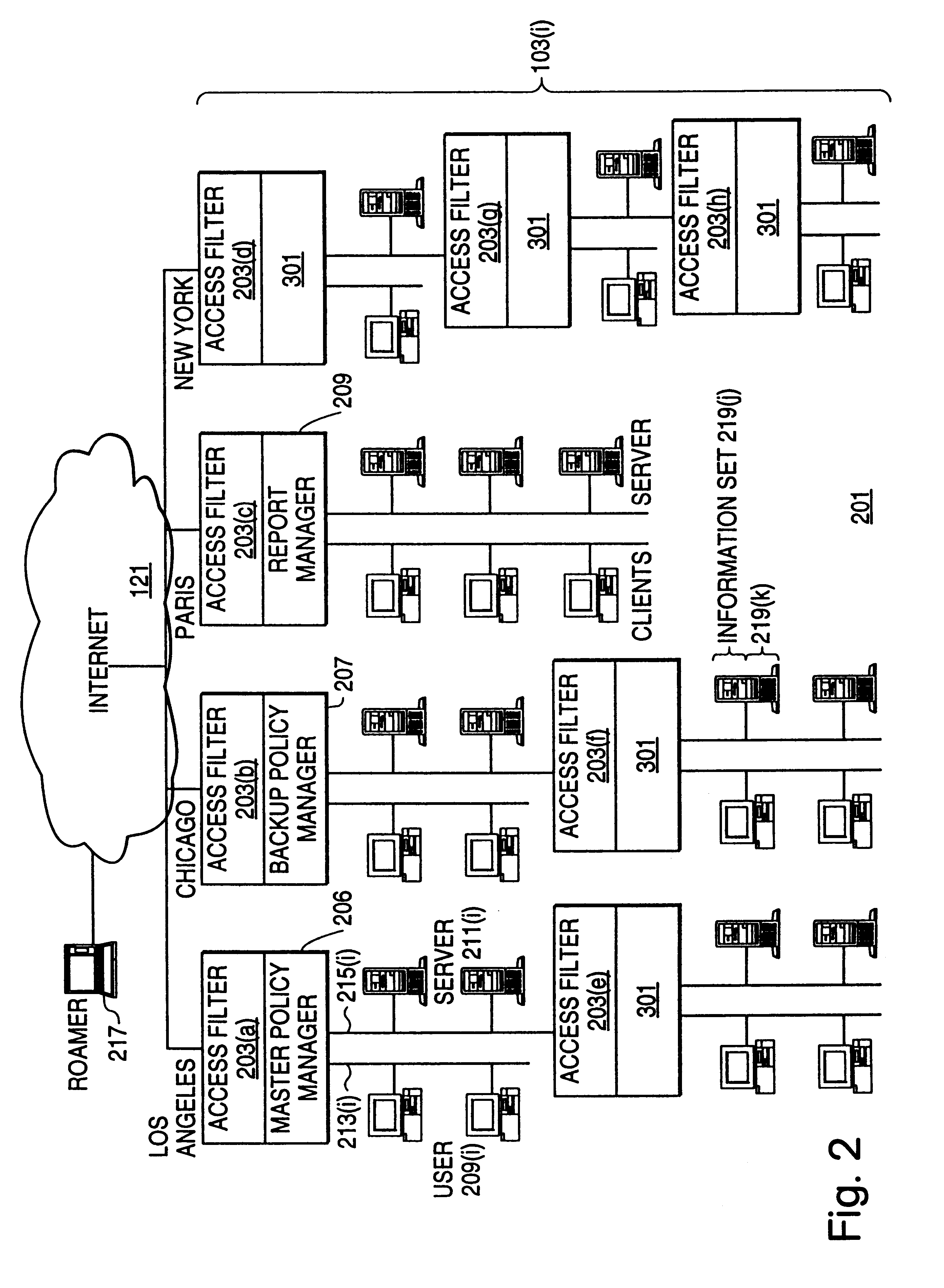
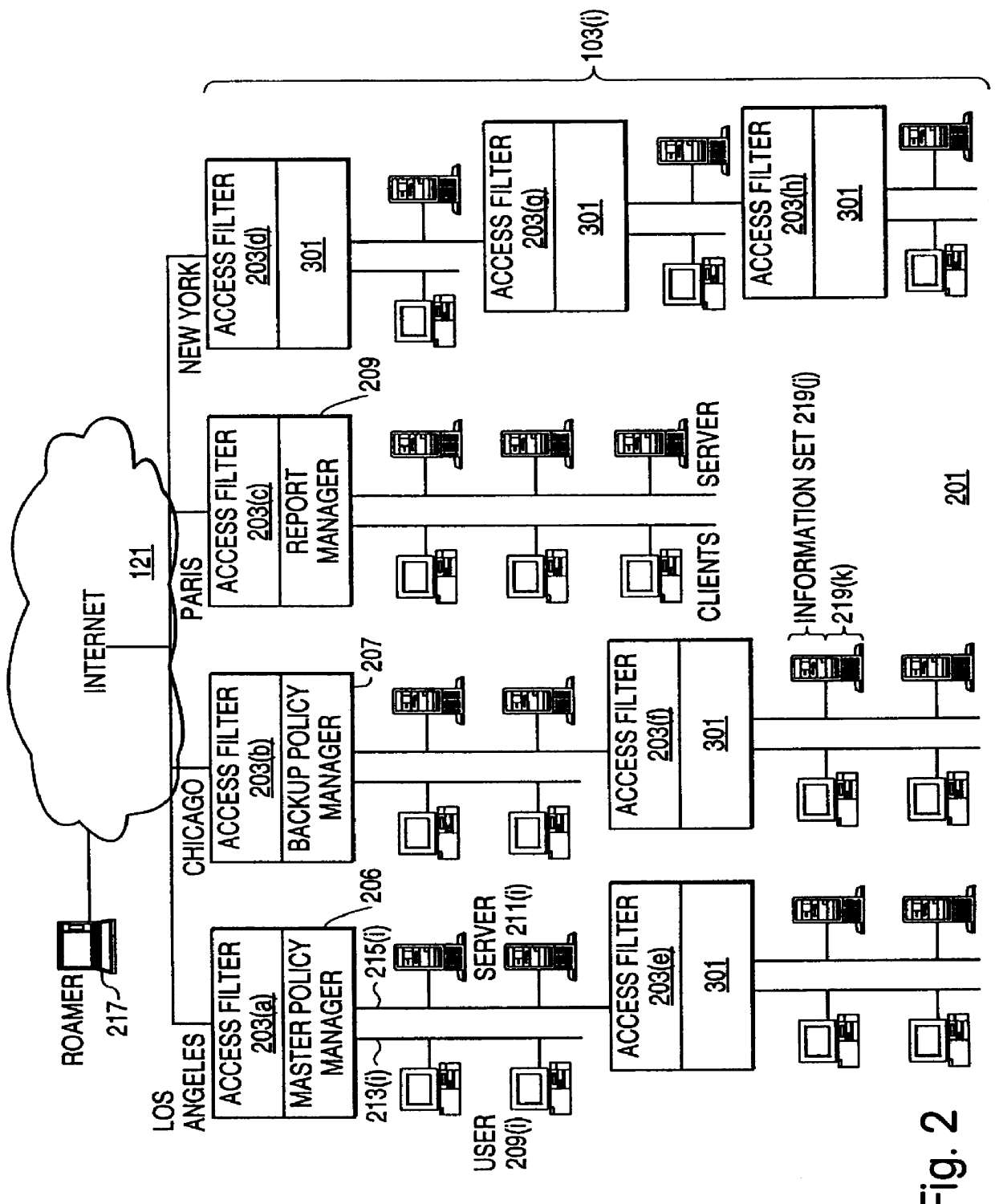
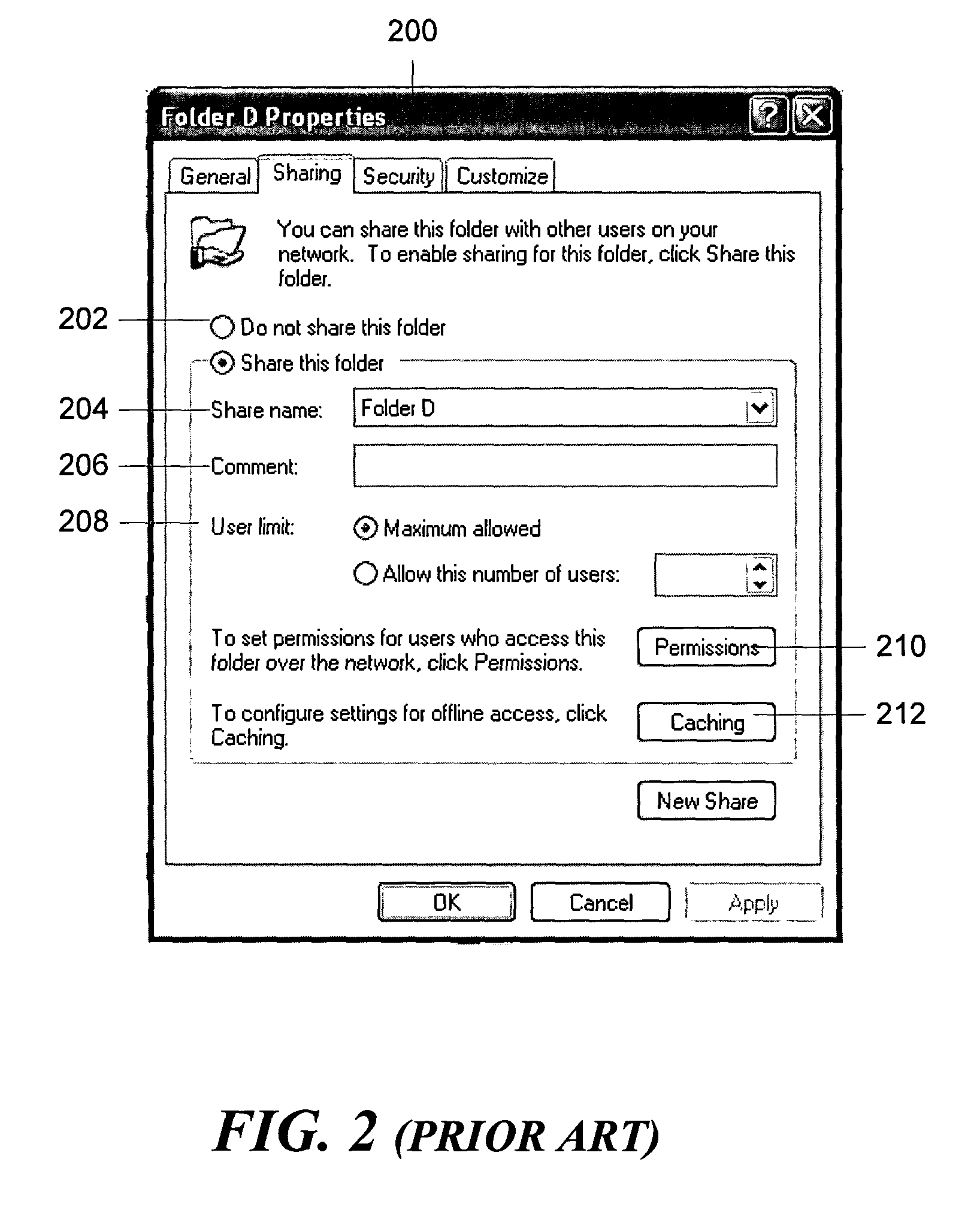
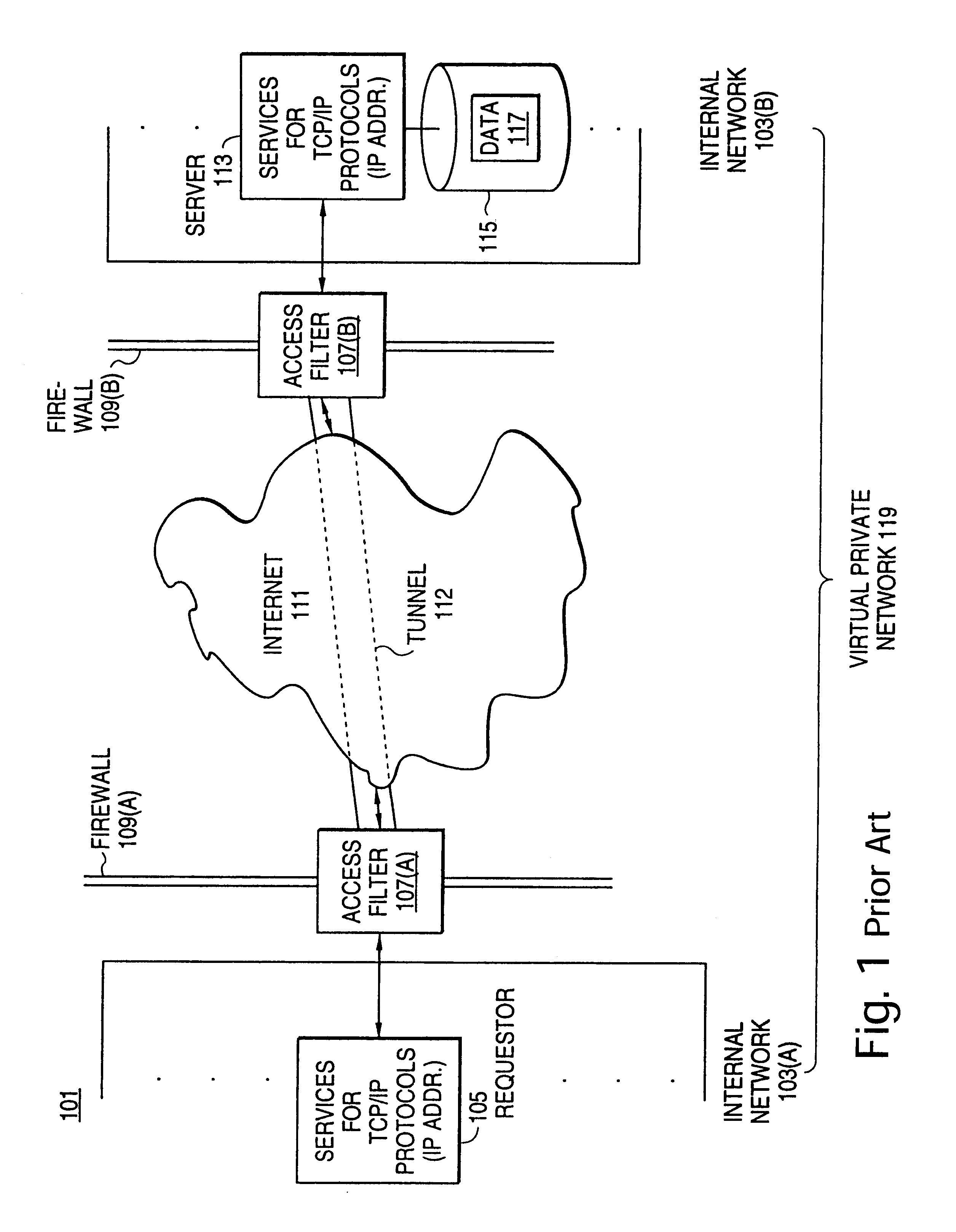
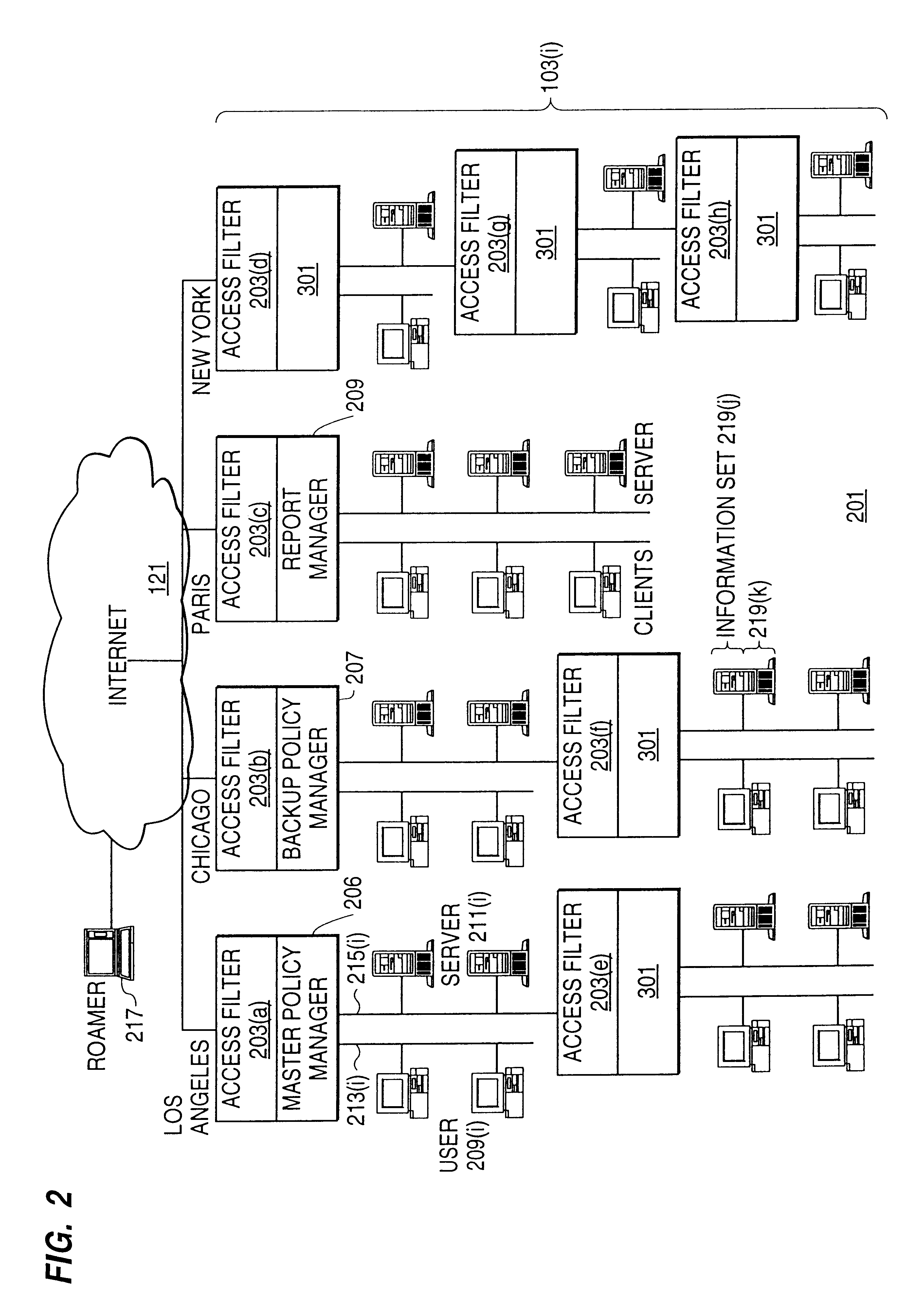
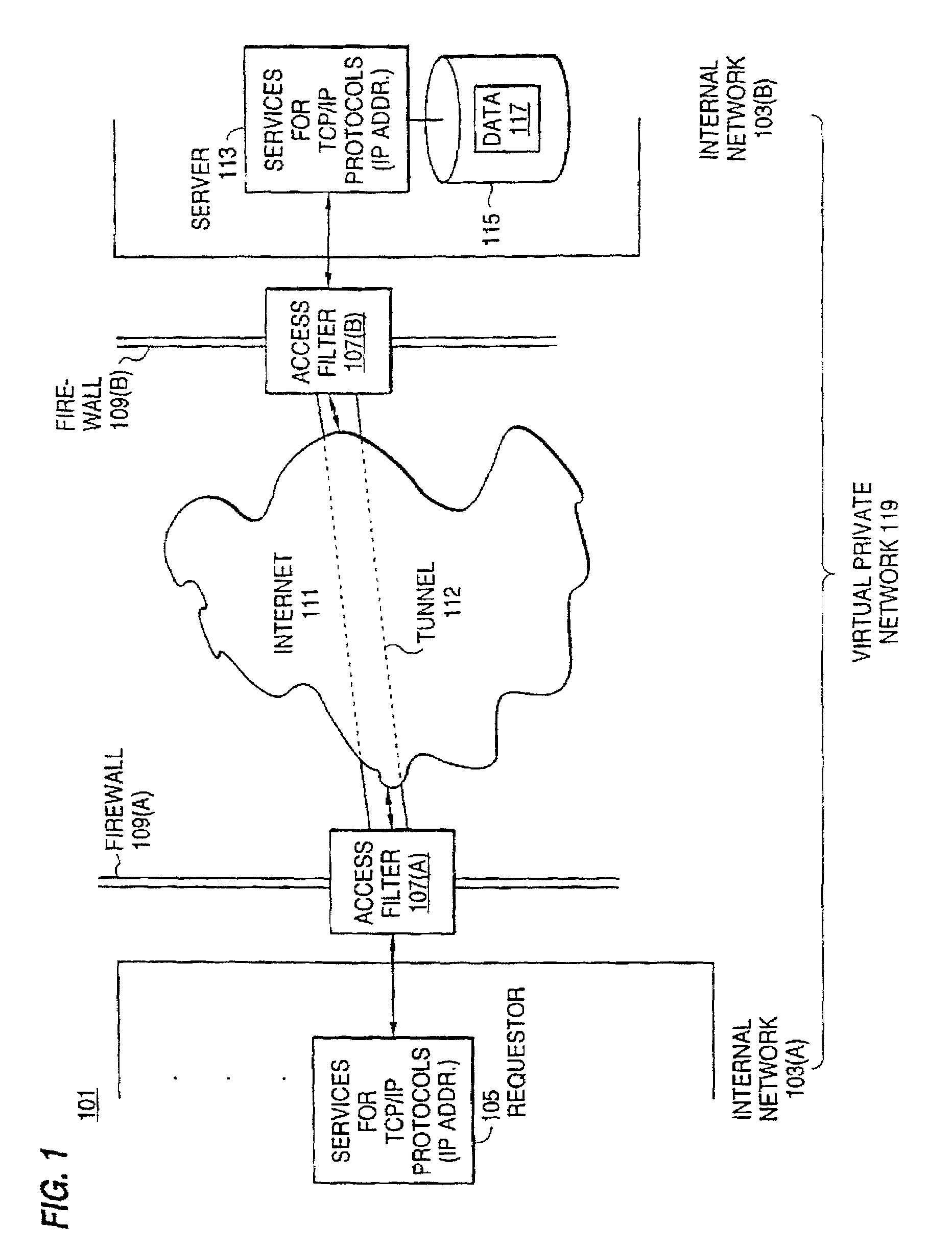
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
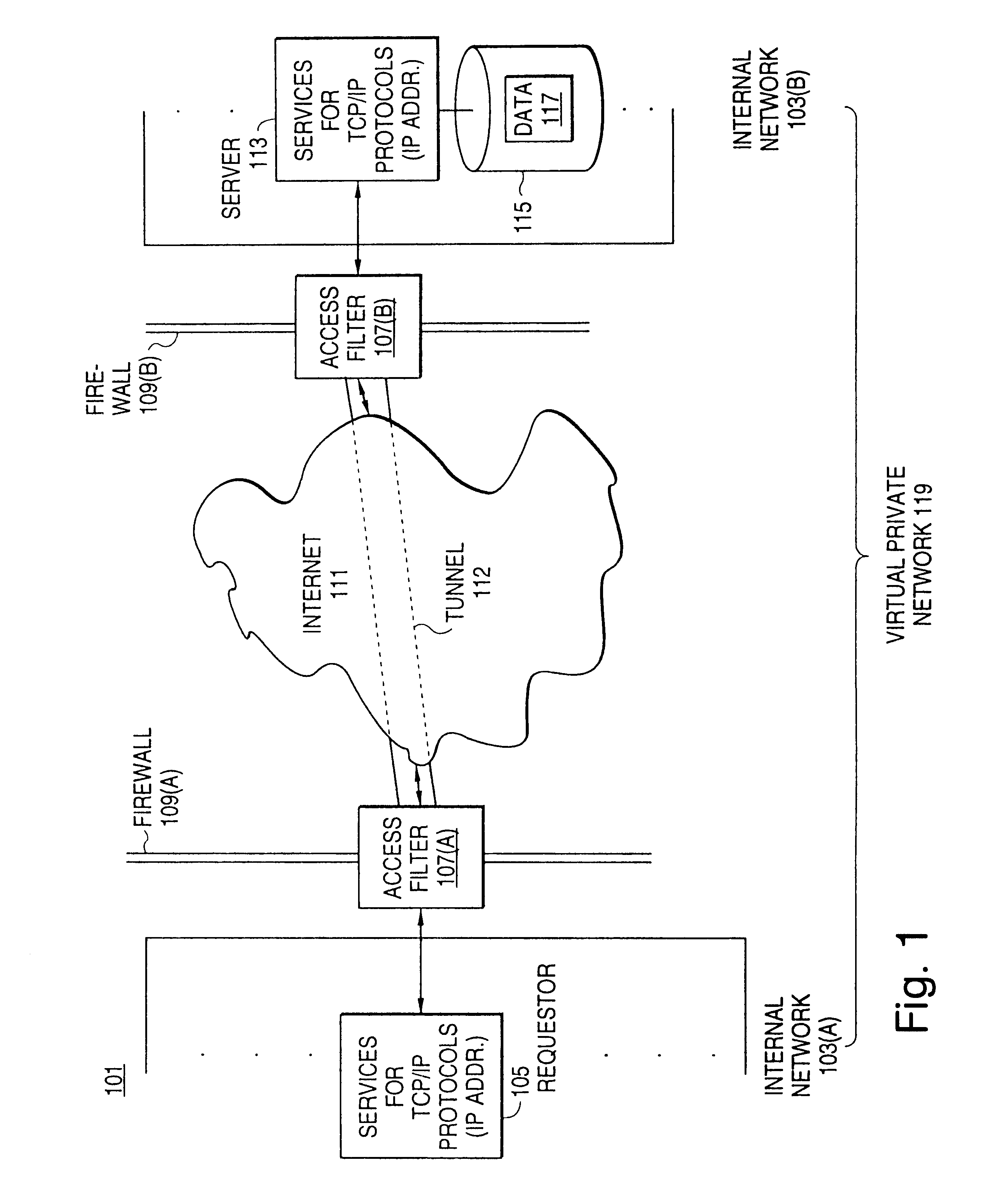
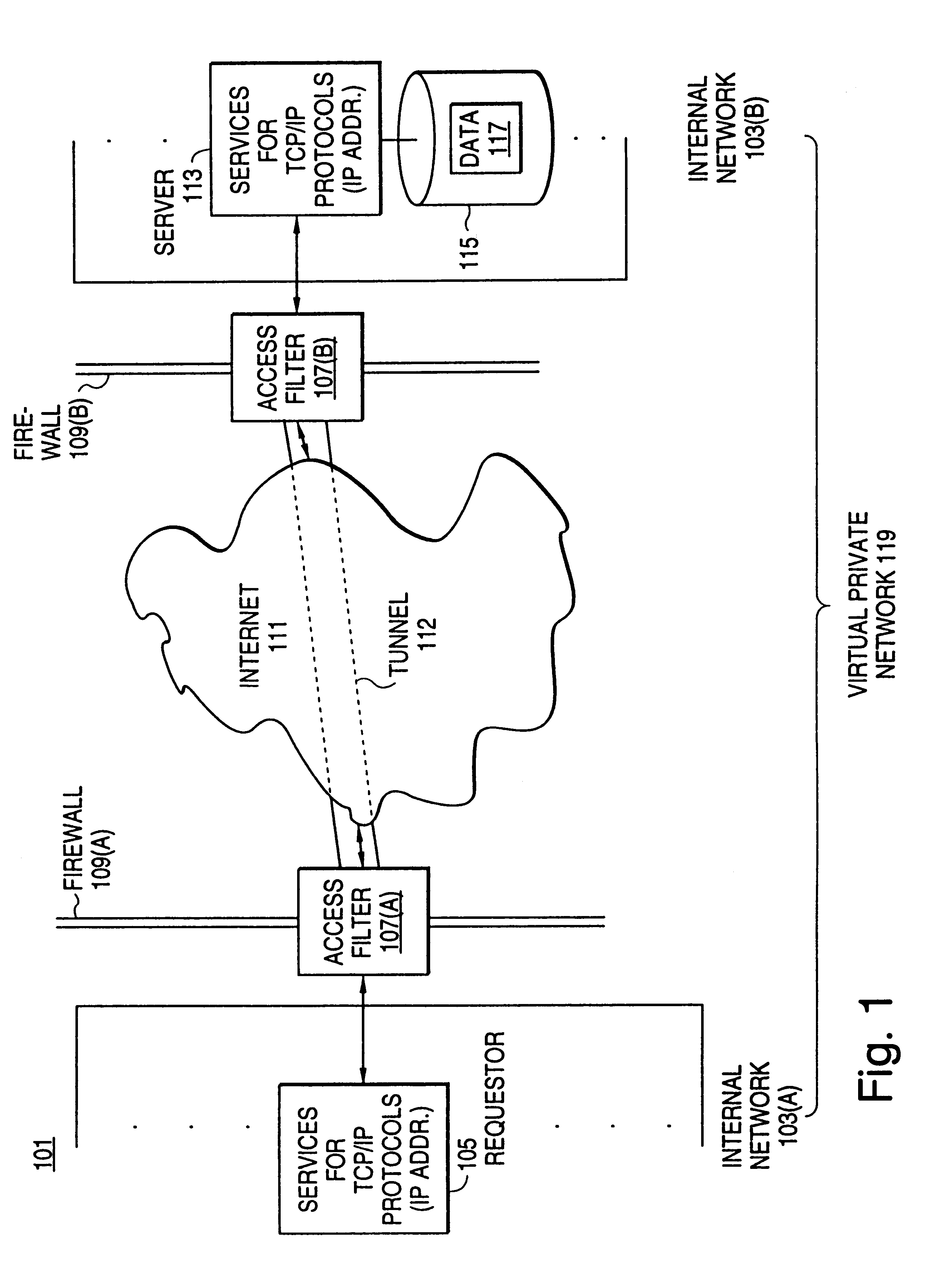
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Secure delivery of information in a network
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Techniques for eliminating redundant access checking by access filters
InactiveUS6105027AData processing applicationsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter uses a local copy of an access control data base to determine whether an access request is made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
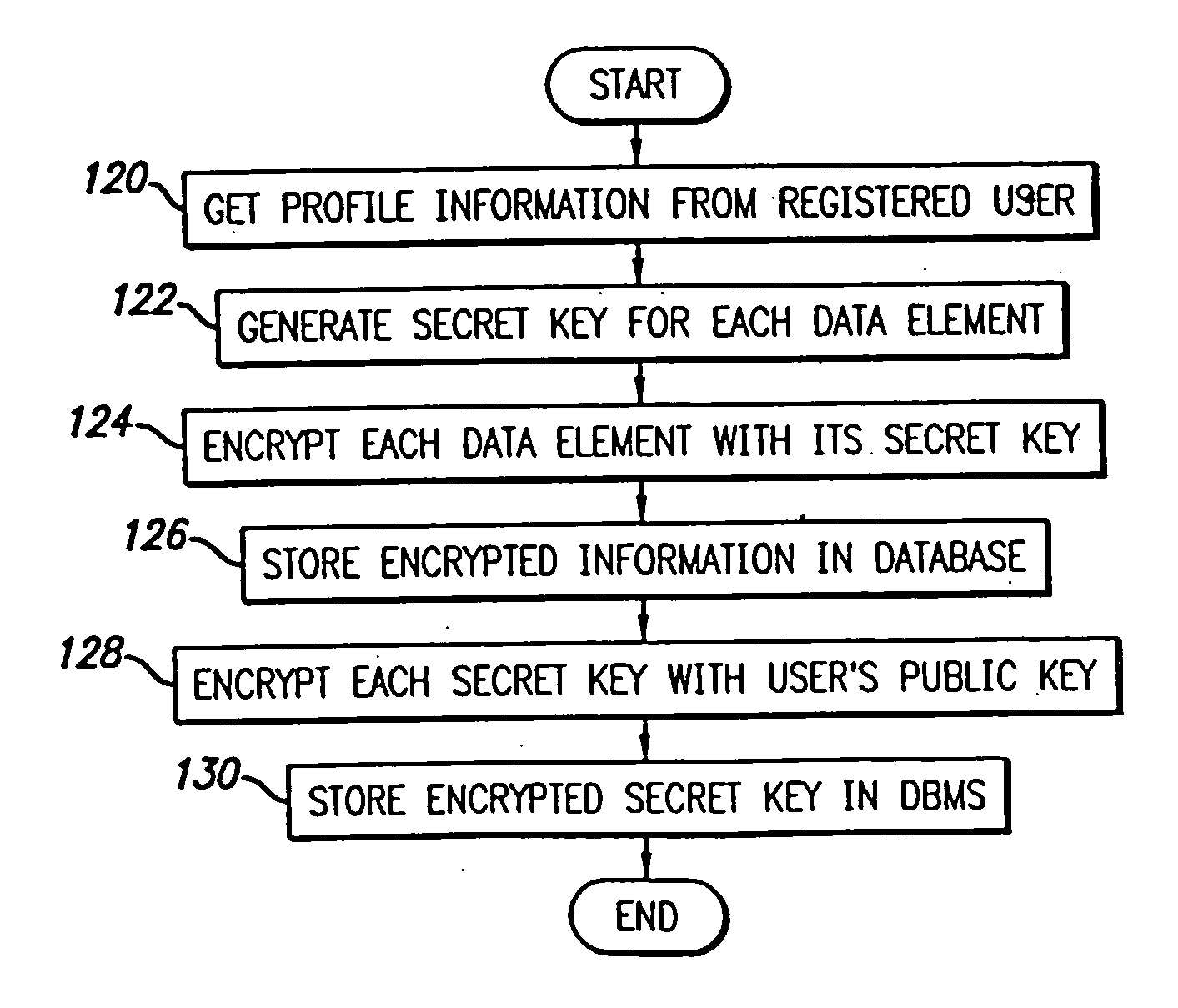
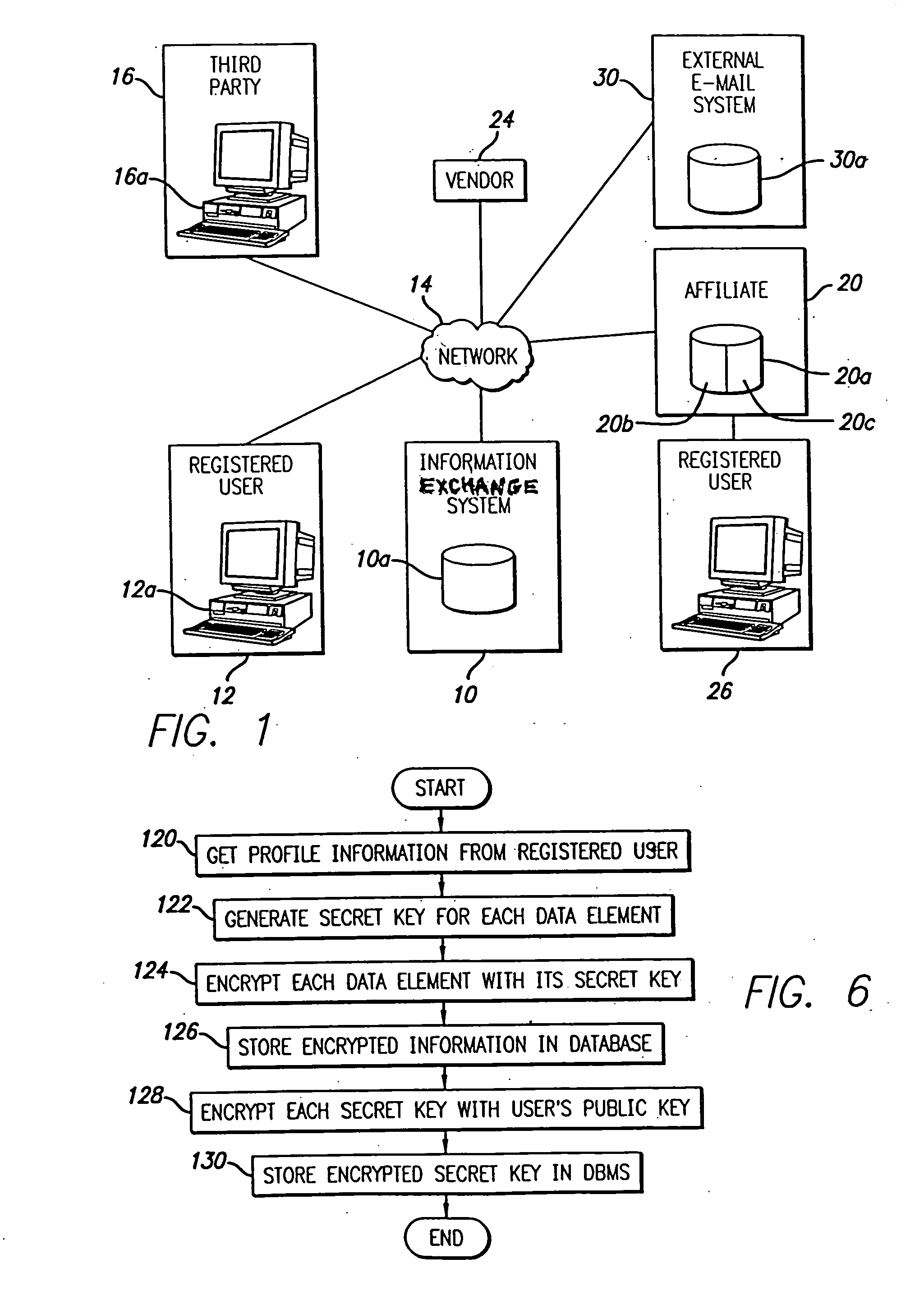
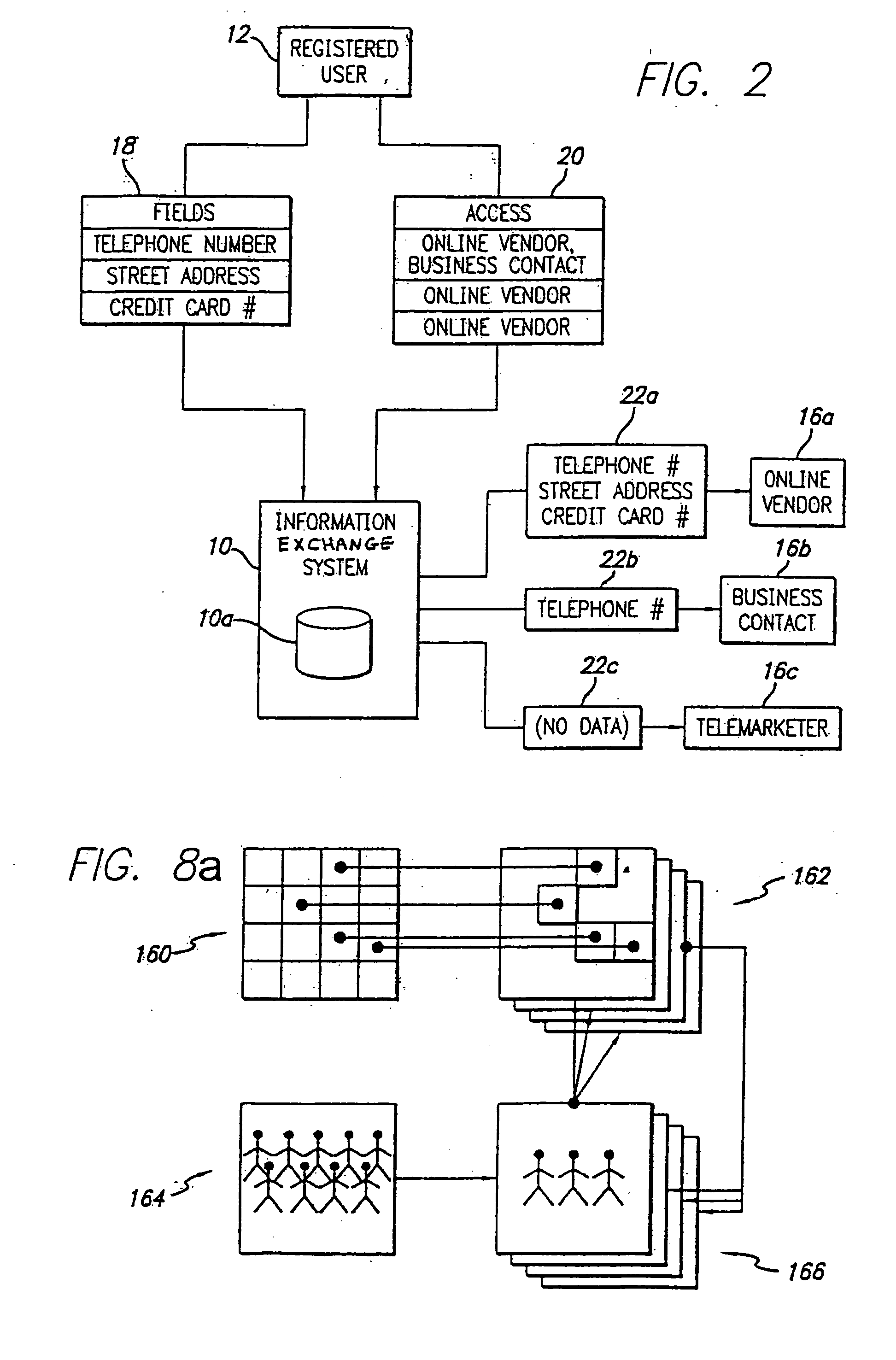
System and method for selective information exchange
InactiveUS20050192008A1Avoid accessComputer security arrangementsRadio/inductive link selection arrangementsTime informationThe Internet
A system and method for providing users with granular control over arbitrary information that allows for selective, real-time information sharing in a communications network such as the Internet is provided. In a network including a plurality of network devices operated by a plurality of users, a real-time information exchange system for sharing user profile information between respective users includes a database management system connected to the network. The database management system, which may be distributed across the network, stores the user profile information for a plurality of registered users of the information exchange system The user profile information includes a plurality of data elements, each data element having an associated one of the plurality of registered users. Each data element has an associated group of users to whom access to the data element has been granted, and users not included in the associated group of users are denied access to the data element. Each registered user may selectively control the granting and denying of access to each of its associated data elements by other respective user, on an element-by-element, and user-by-user basis. Further, each registered user may dynamically create its own data fields.
Owner:DESAI NIMESH +5
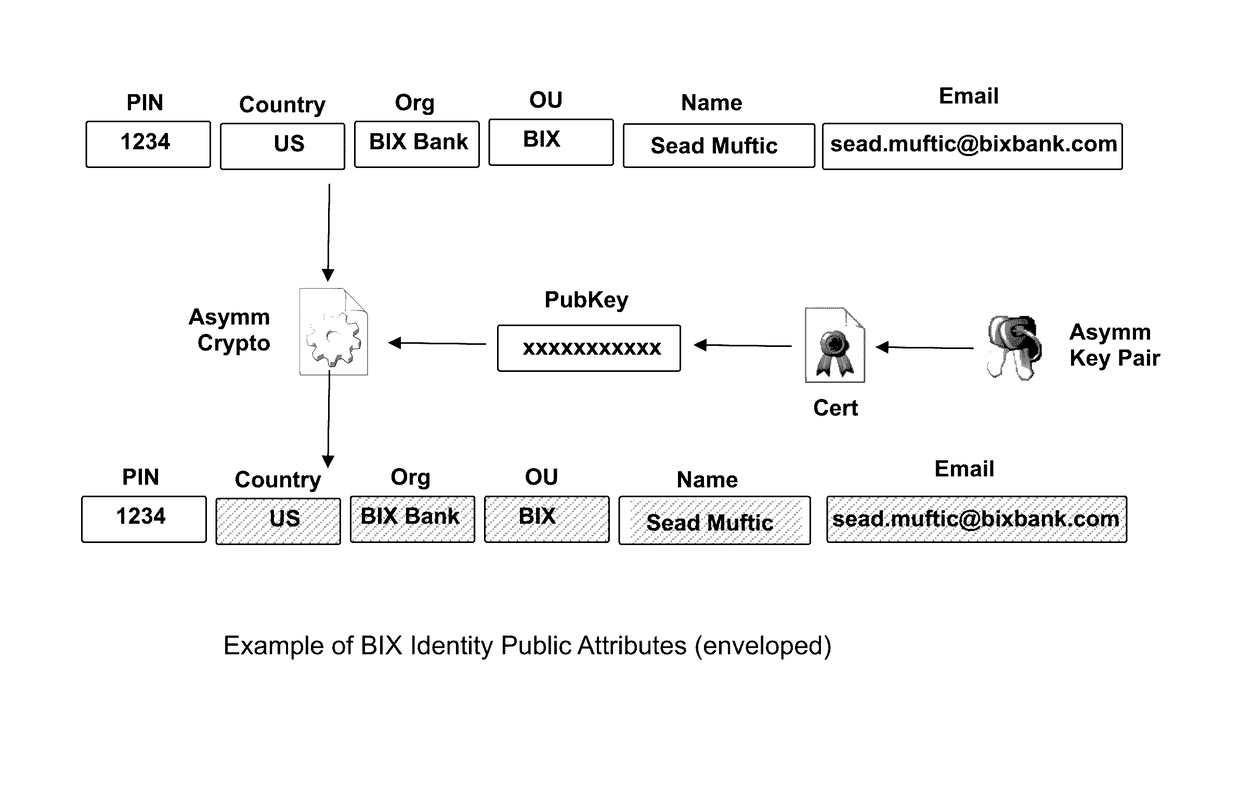
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
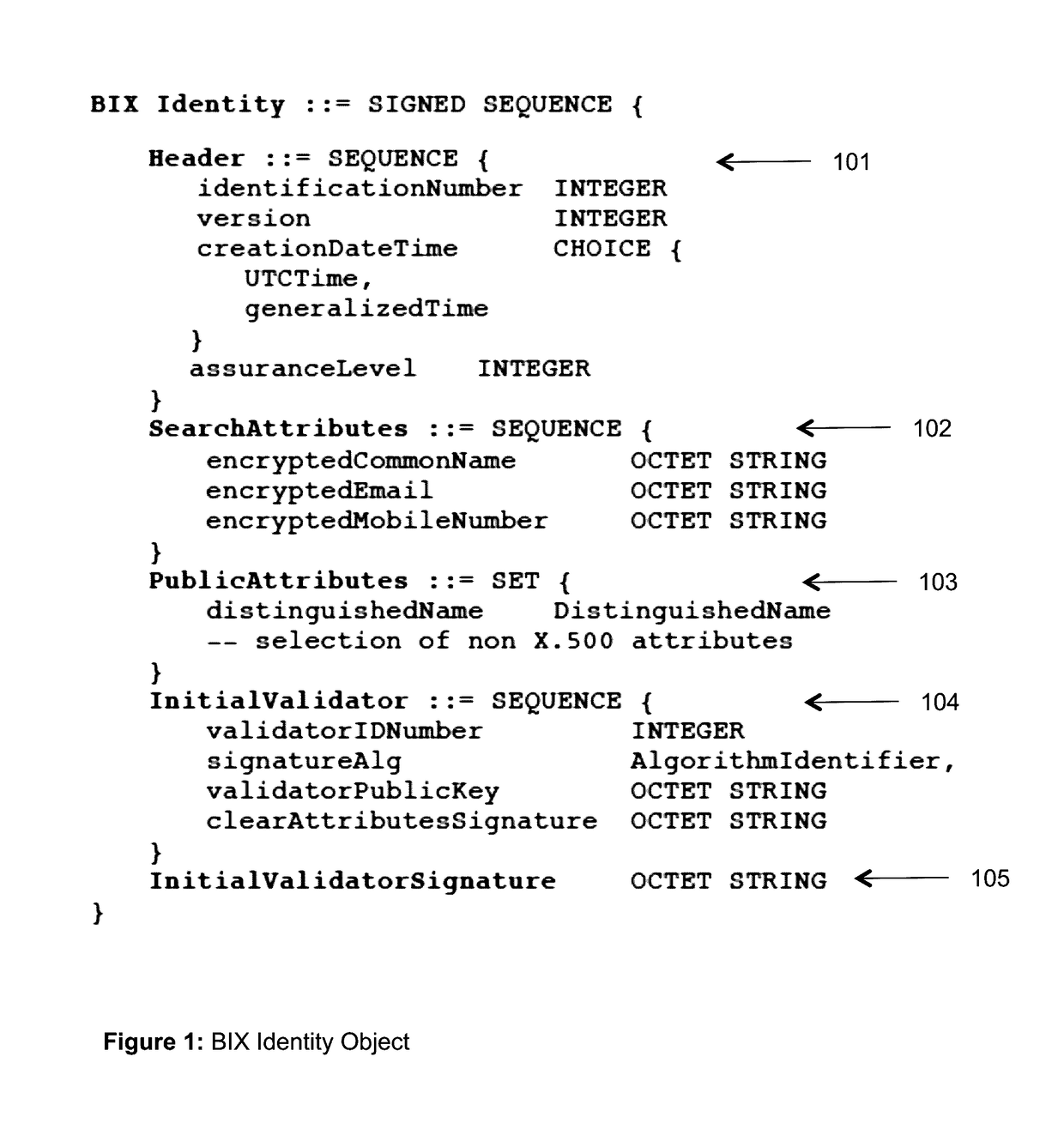
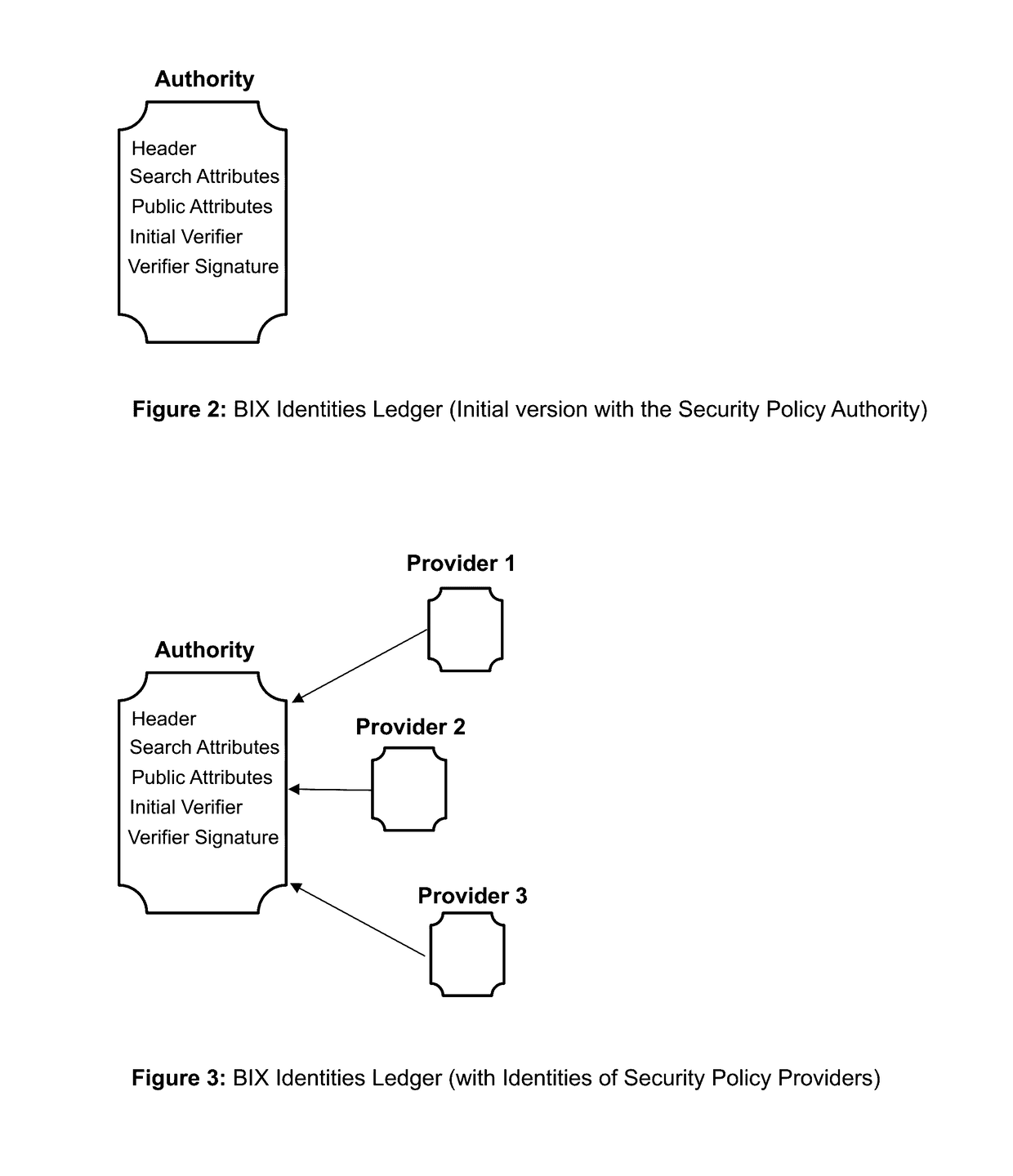
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
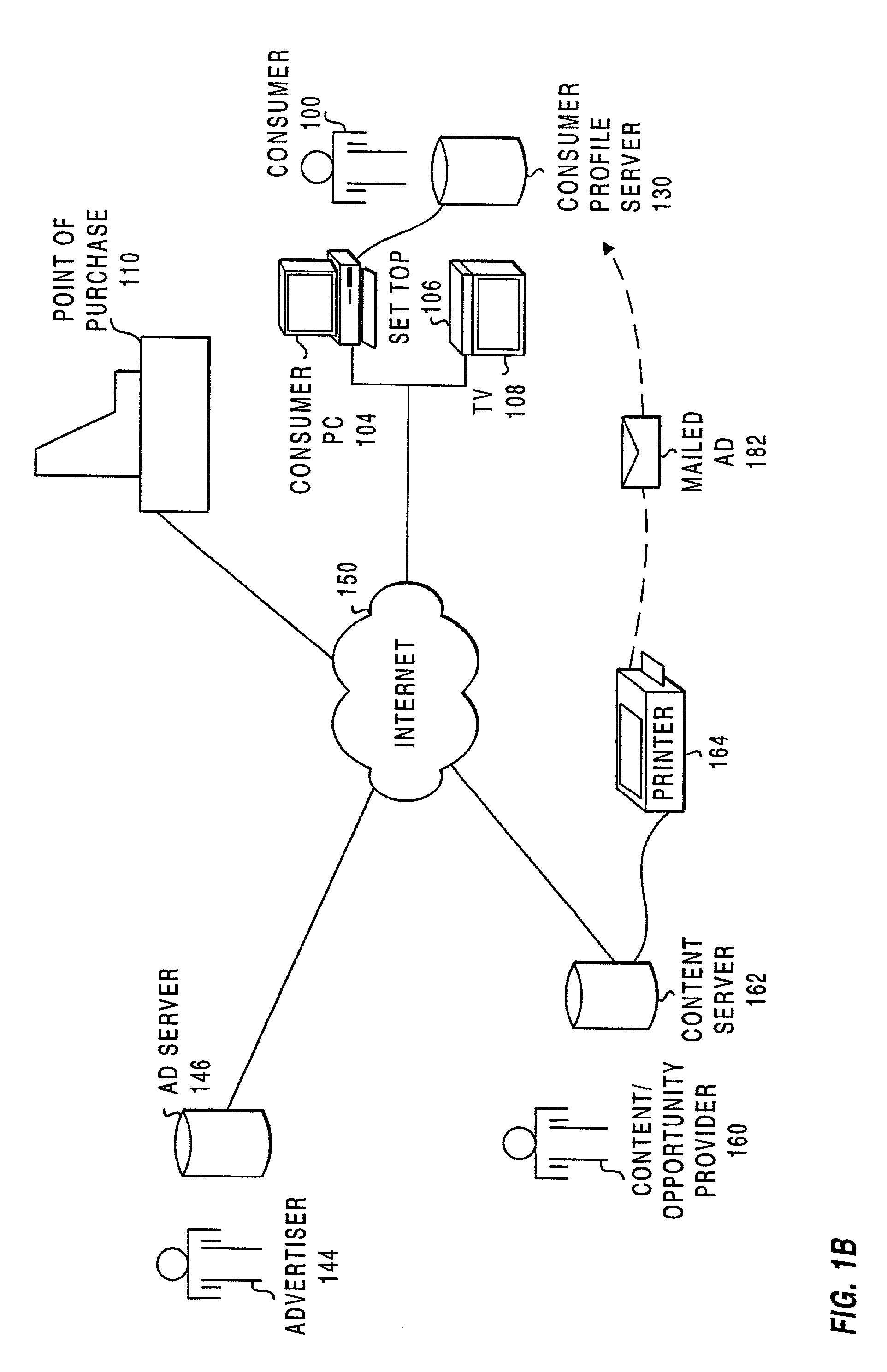
Consumer profiling and advertisement selection system
InactiveUS7062510B1Less chargeHigh priceMarketingSpecial data processing applicationsRegression analysisHabit
Computer network method and apparatus provides targeting of appropriate audience based on psychographic or behavioral profiles of end users. The psychographic profile is formed by recording computer activity and viewing habits of the end user. Content of categories of interest and display format in each category are revealed by the psychographic profile, based on user viewing of agate information. Using the profile (with or without additional user demographics), advertisements are displayed to appropriately selected users. Based on regression analysis of recorded responses of a first set of users viewing the advertisements, the target user profile is refined. Viewing by and regression analysis of recorded responses of subsequent sets of users continually auto-targets and customizes ads for the optimal end user audience.
Owner:PRIME RES ALLIANCE E LLC
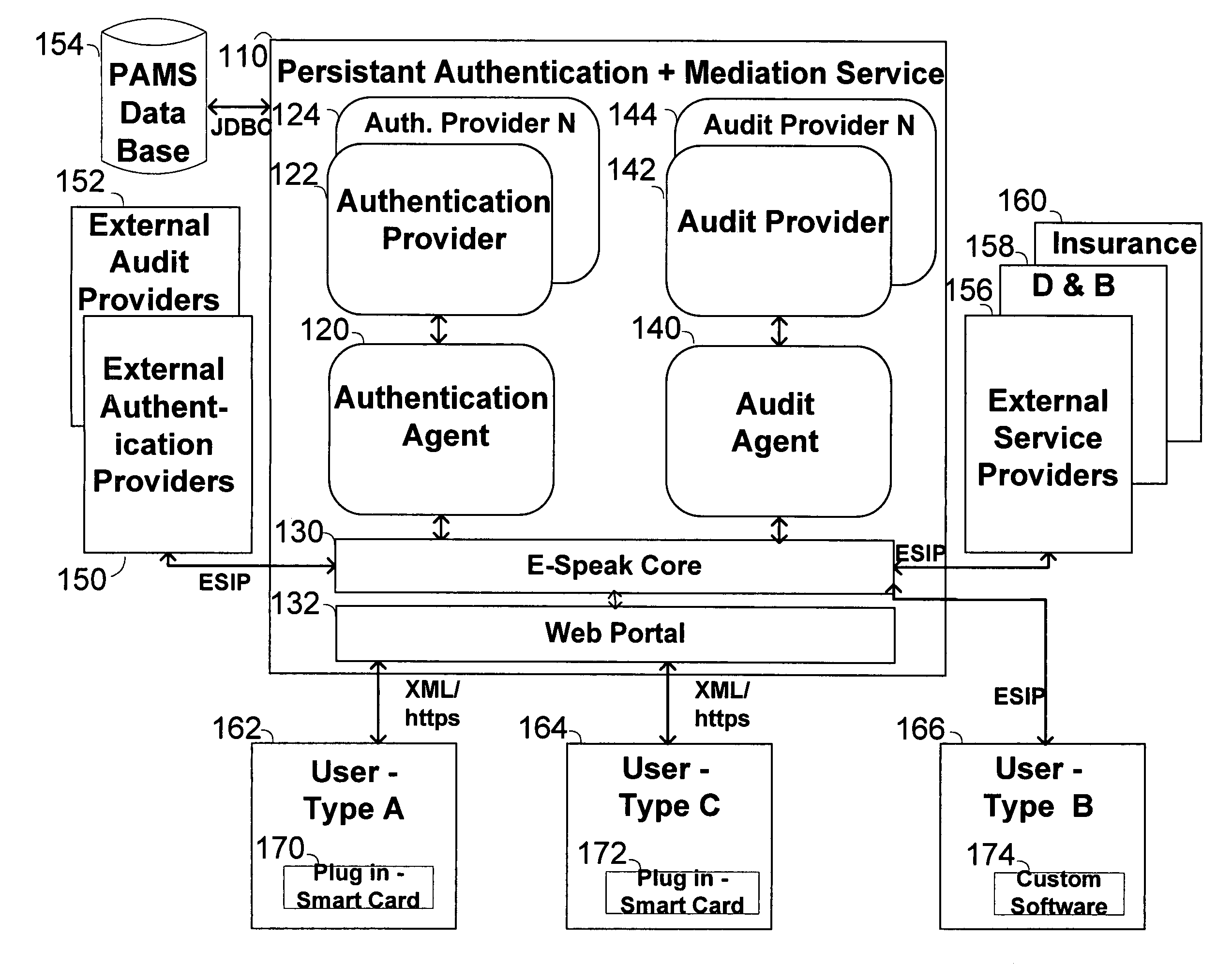
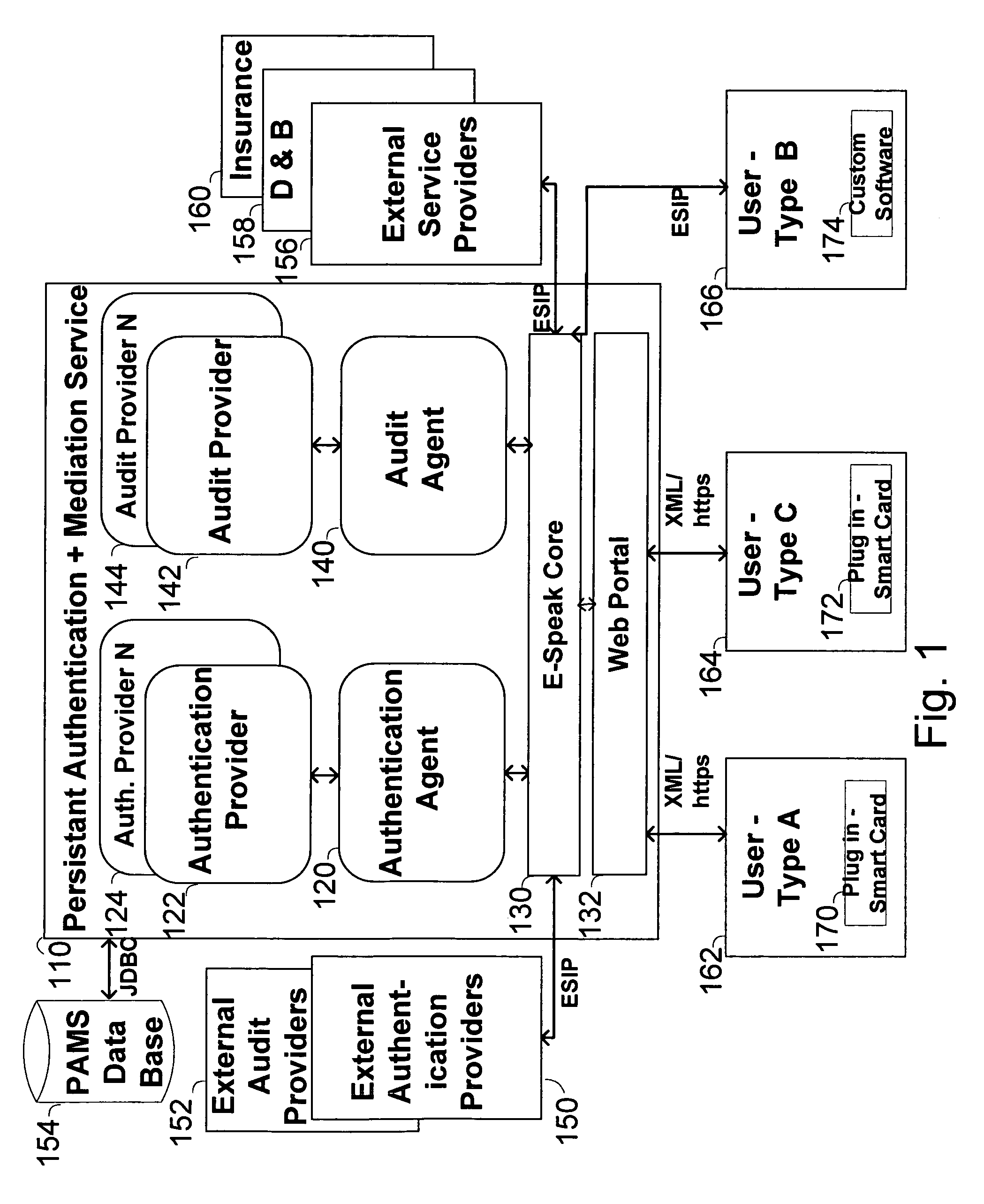
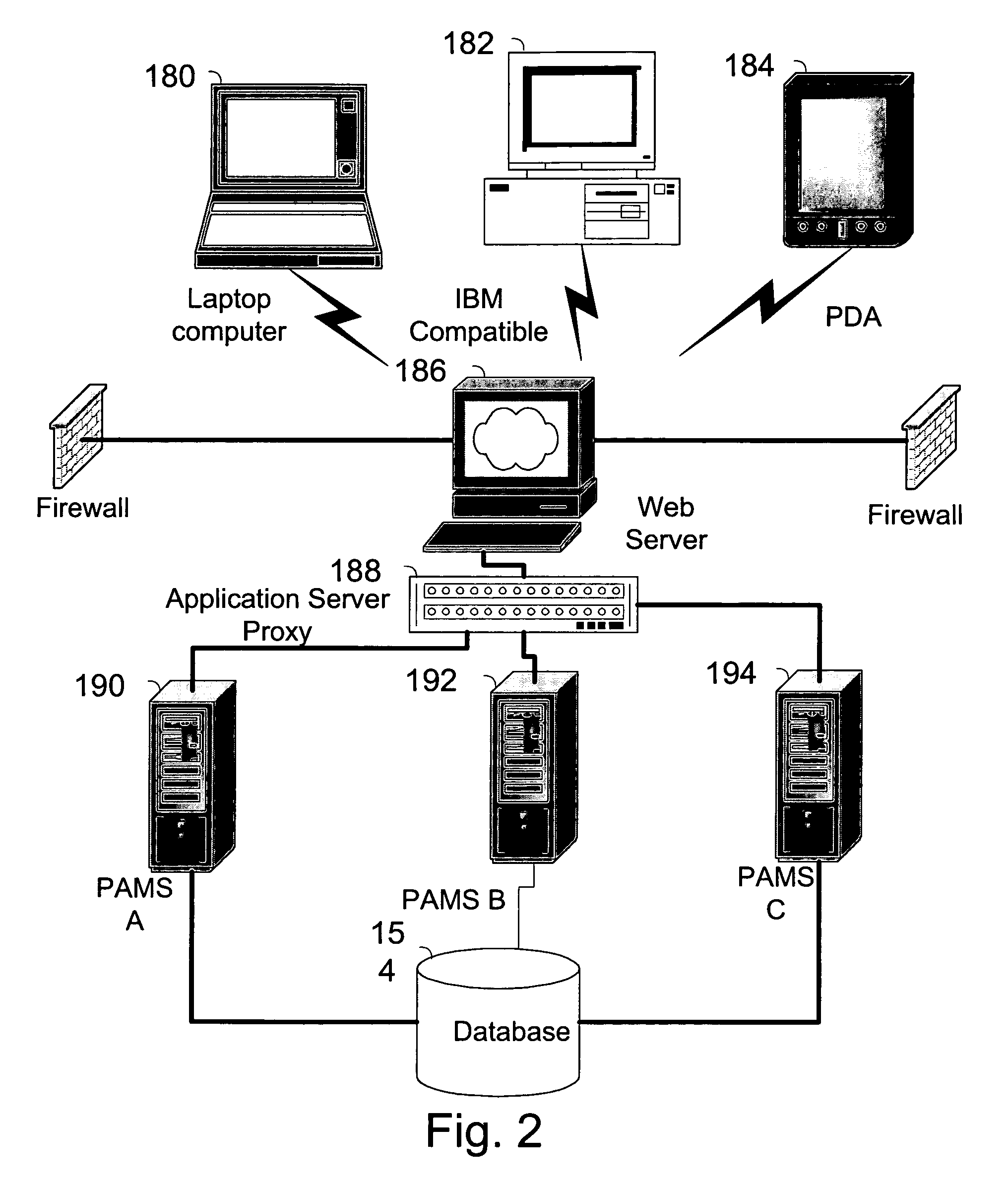
Method, system and service for conducting authenticated business transactions
InactiveUS6957199B1Fast authenticationImprove securityComputer security arrangementsCommerceService provisionThe Internet
The invention pertains to a method, online service, and system, for creating partnerships based on trust relationships over a public network, authenticating trade partners, infrastructure providers and collaborators to each other, and providing users with an environment suitable for conducting transactions requiring a high level of trust. A service according to the invention is a persistent authentication and mediation service (PAMS) which is provided as an on-line service. One embodiment is a method for conducting authenticated business transactions involving microprocessor equipped devices over the Internet comprising:A. providing an on-line authentication service available on the distributed network;B. authenticating a plurality of users to said on-line authentication service using a closed authentication system to produce a plurality of authenticated users; andC. connecting a group of at least two of said plurality of authenticated users under persistent mediation of said on-line authentication service, producing a connected group of authenticated users.
Owner:FISHER DOUGLAS
Selective data encryption using style sheet processing
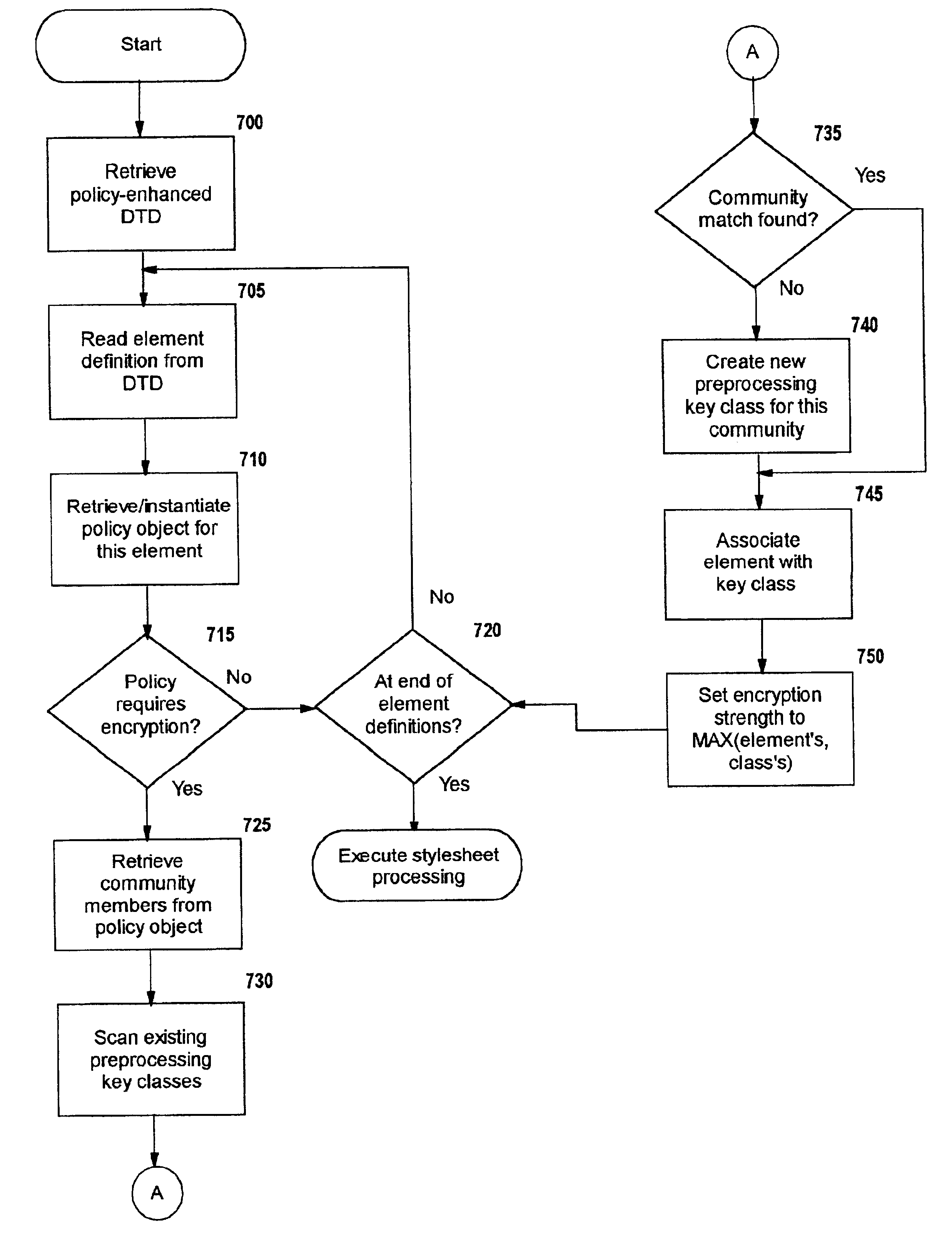
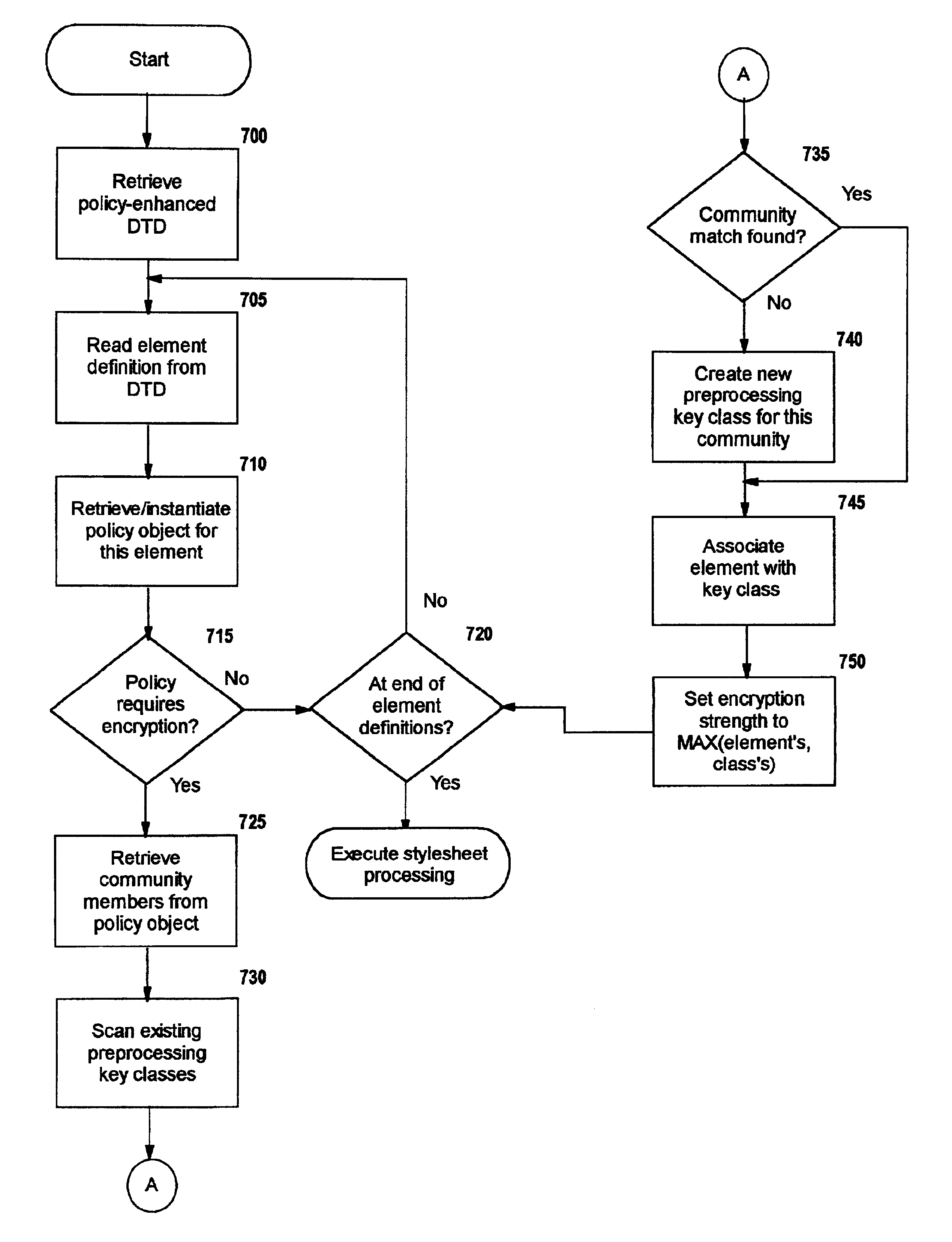
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
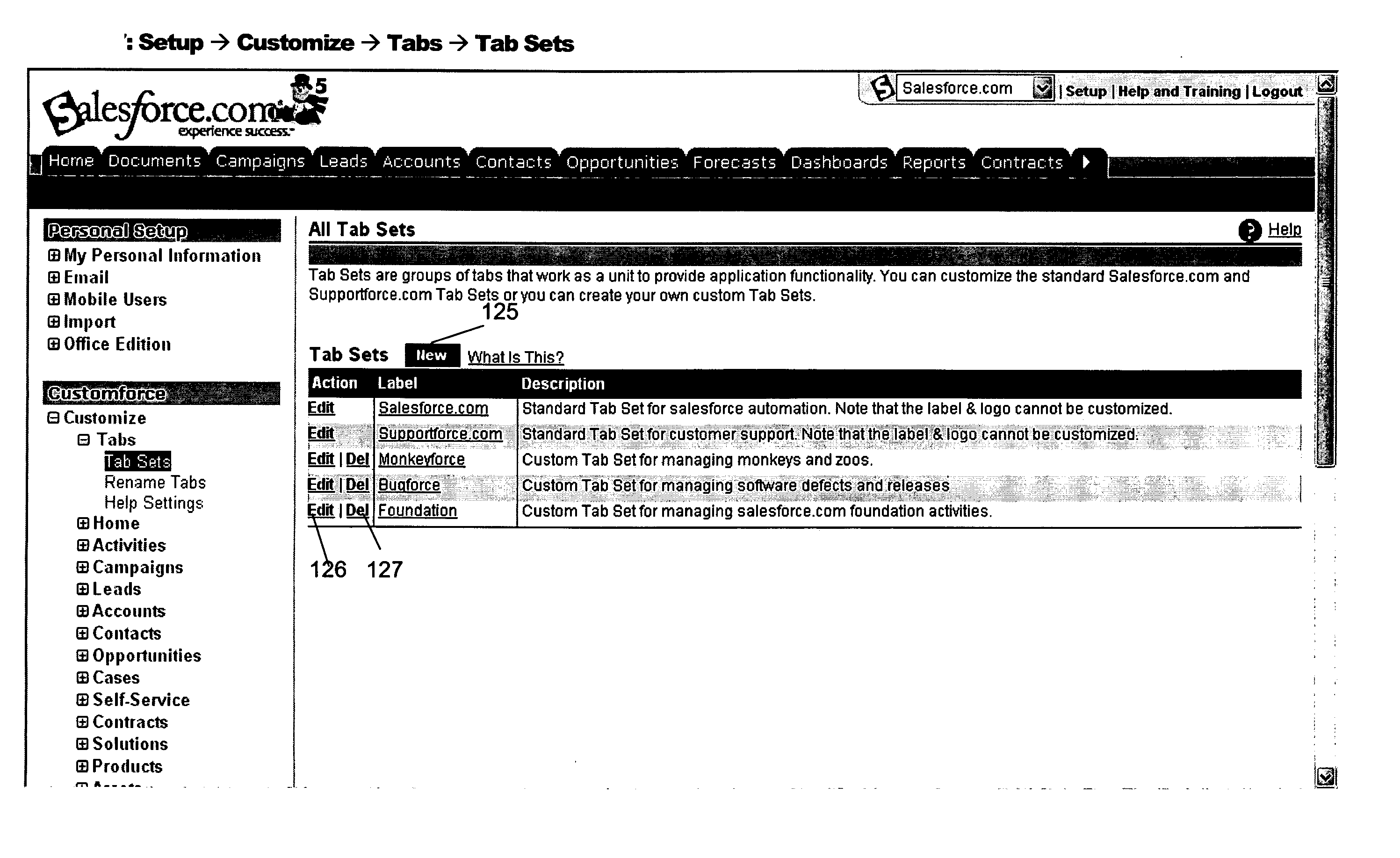
Systems and methods for implementing multi-application tabs and tab sets
ActiveUS20060206834A1Easily and conveniently createEasily and conveniently and shareDigital data processing detailsOther databases browsing/visualisationComputer graphics (images)Application software
A sharing model enables users to easily and conveniently create and share standard and custom database objects, and applications, among users or groups of users. The sharing model includes systems and methods that allow users to conveniently create and customize tabs and tab sets that define relationships between custom objects and fields, standard objects and fields, and applications. A tab visually represents a user interface into an element of an application or into a database object. Selection of a tab provides a user access to the object or element of the application represented by the tab. A tab set is a group of related tabs that work as a unit to provide application functionality. New tabs and tab sets may be defined and tab set views may be customized so that an end user can easily and conveniently switch between the various objects and application elements represented by the displayed tabs and tab set views.
Owner:SALESFORCE COM INC
Method and apparatus for providing attributes of a collaboration system in an operating system folder-based file system
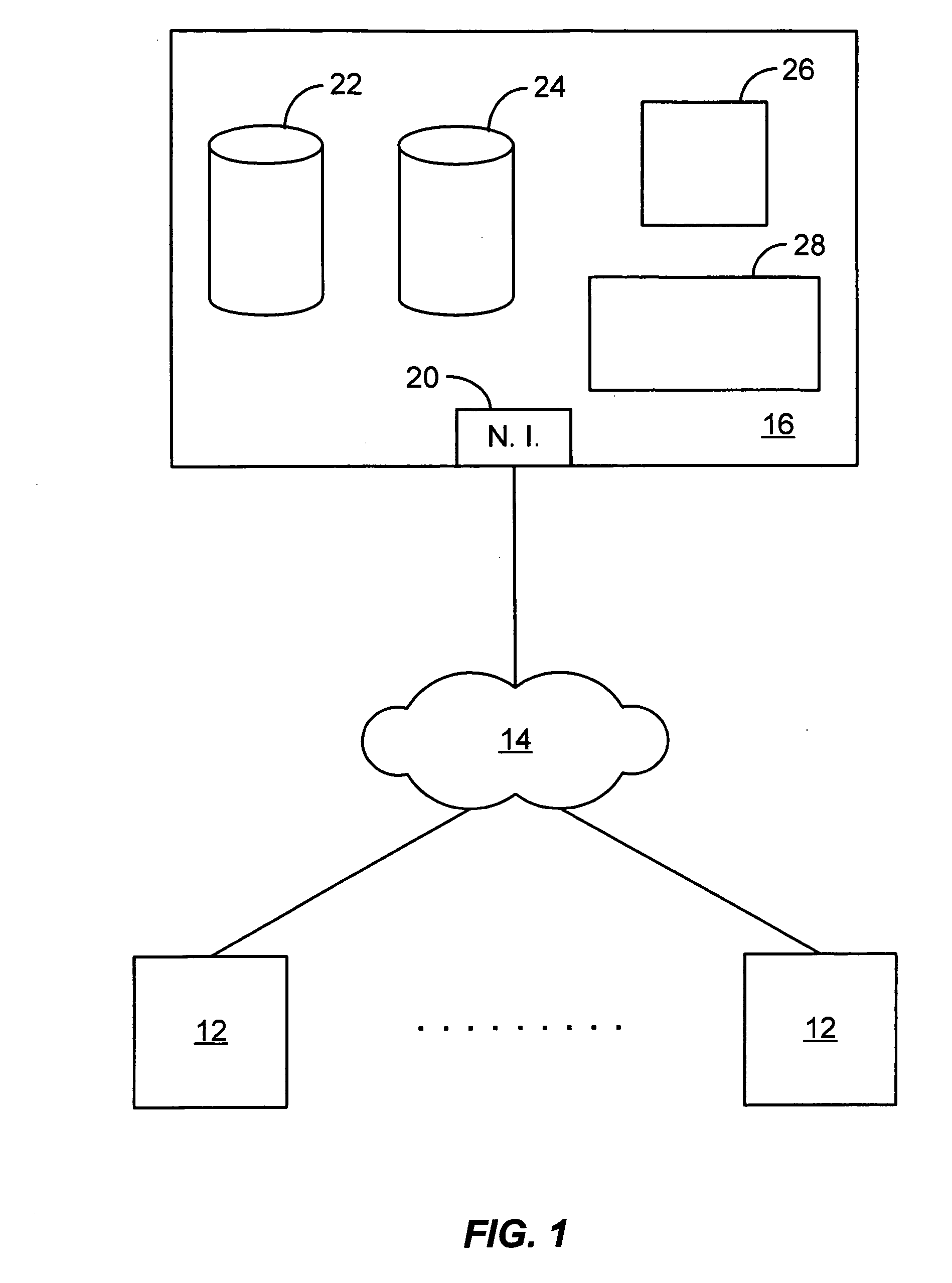
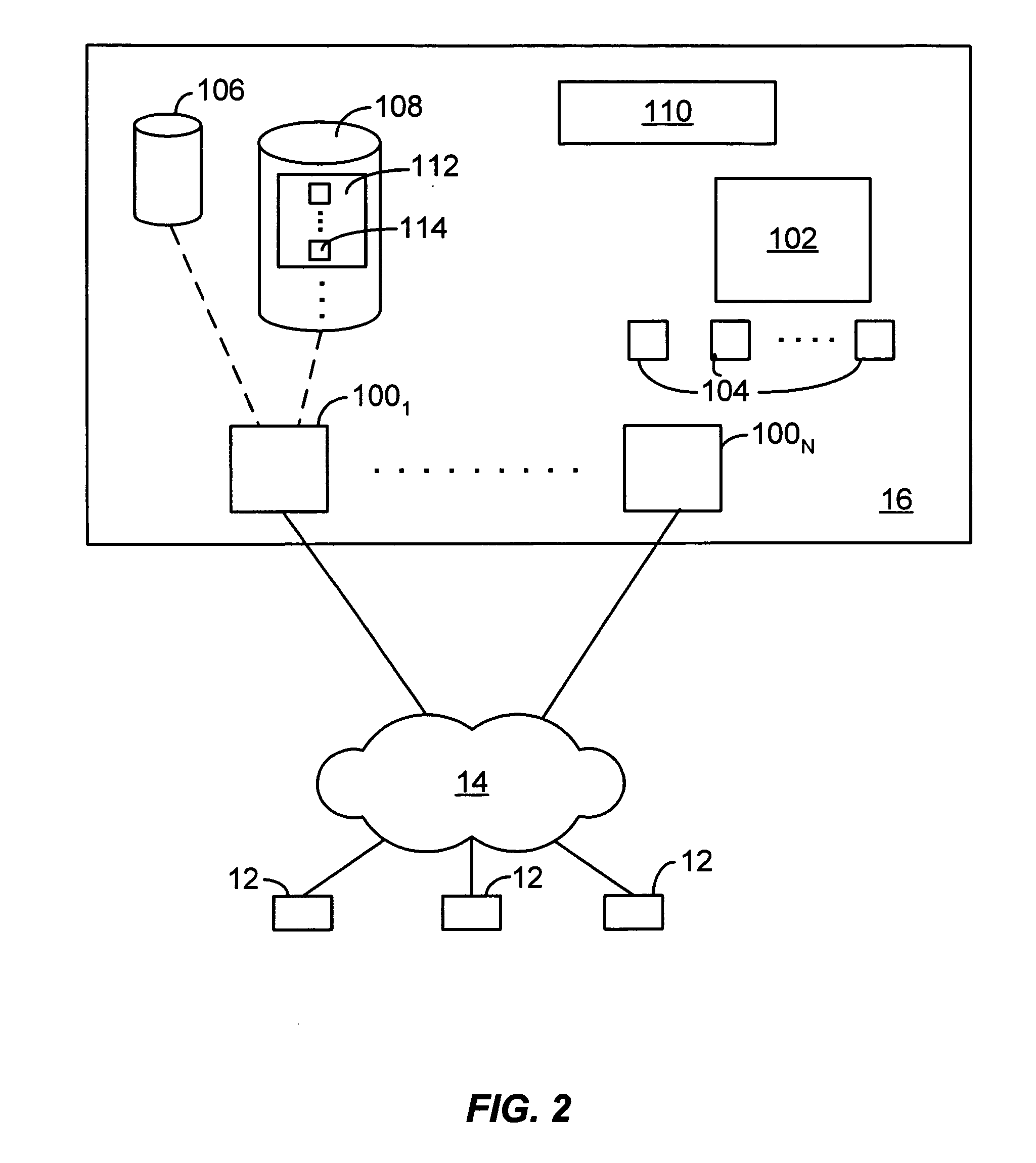
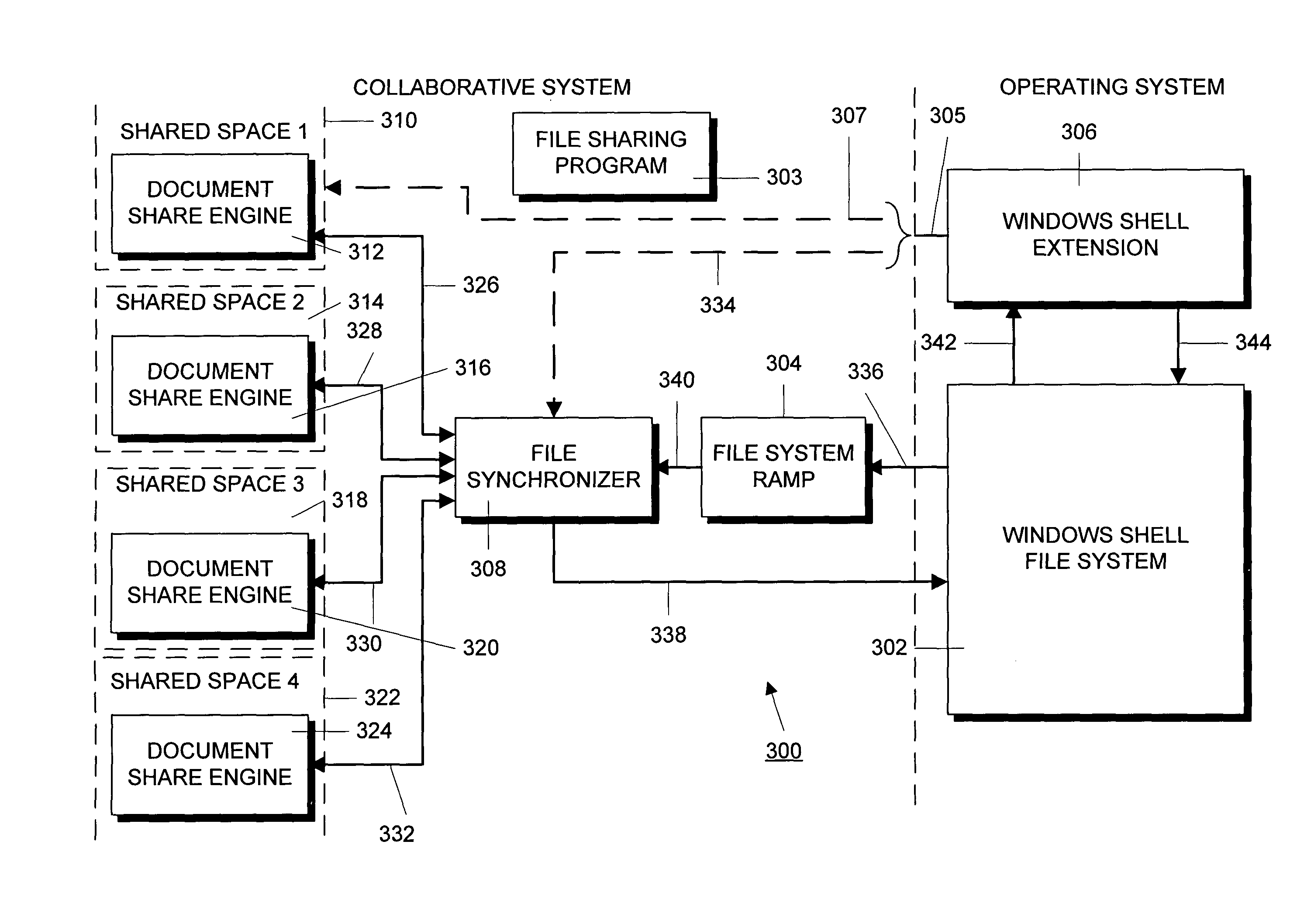
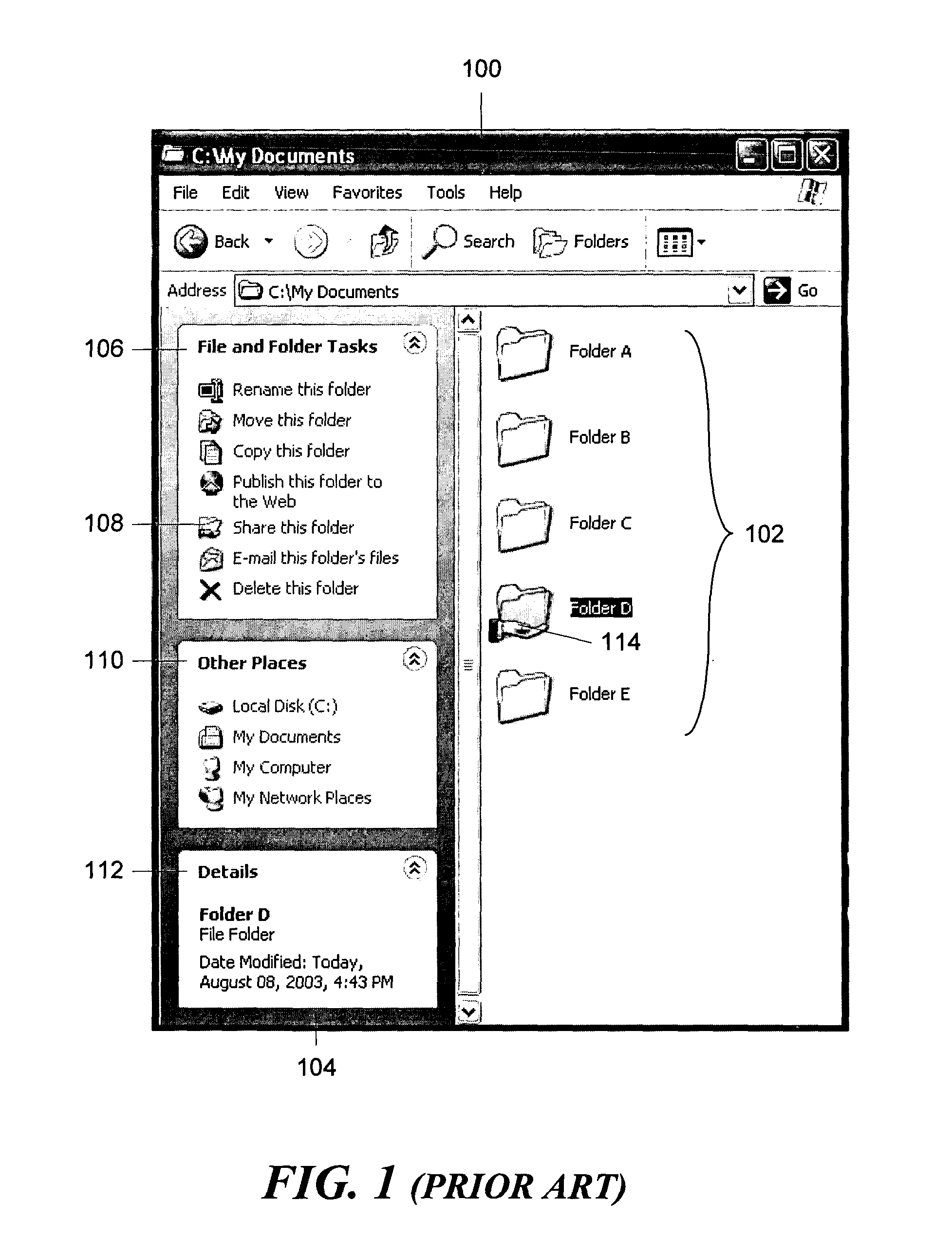
ActiveUS20090138808A1Multiple digital computer combinationsOffice automationOperational systemFile system
A conventional operating system folder or directory based file system is implemented with, or enhanced to provide, attributes of shared collaborative workspaces. In particular, the conventional file system is connected to either a server based or a distributed collaboration system and the user interface of the operating system file system is augmented to allow it to control aspects of the collaboration system. Each folder or directory can be synchronized and treated as a “workspace” that can be viewed and shared with other users or groups of users. Folder can also be provided with “awareness” information that indicates collaborators that are present and those that are sharing the workspace.
Owner:MICROSOFT TECH LICENSING LLC
Distributed administration of access to information
InactiveUS6785728B1Cathode-ray tube indicatorsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Generating audience analytics
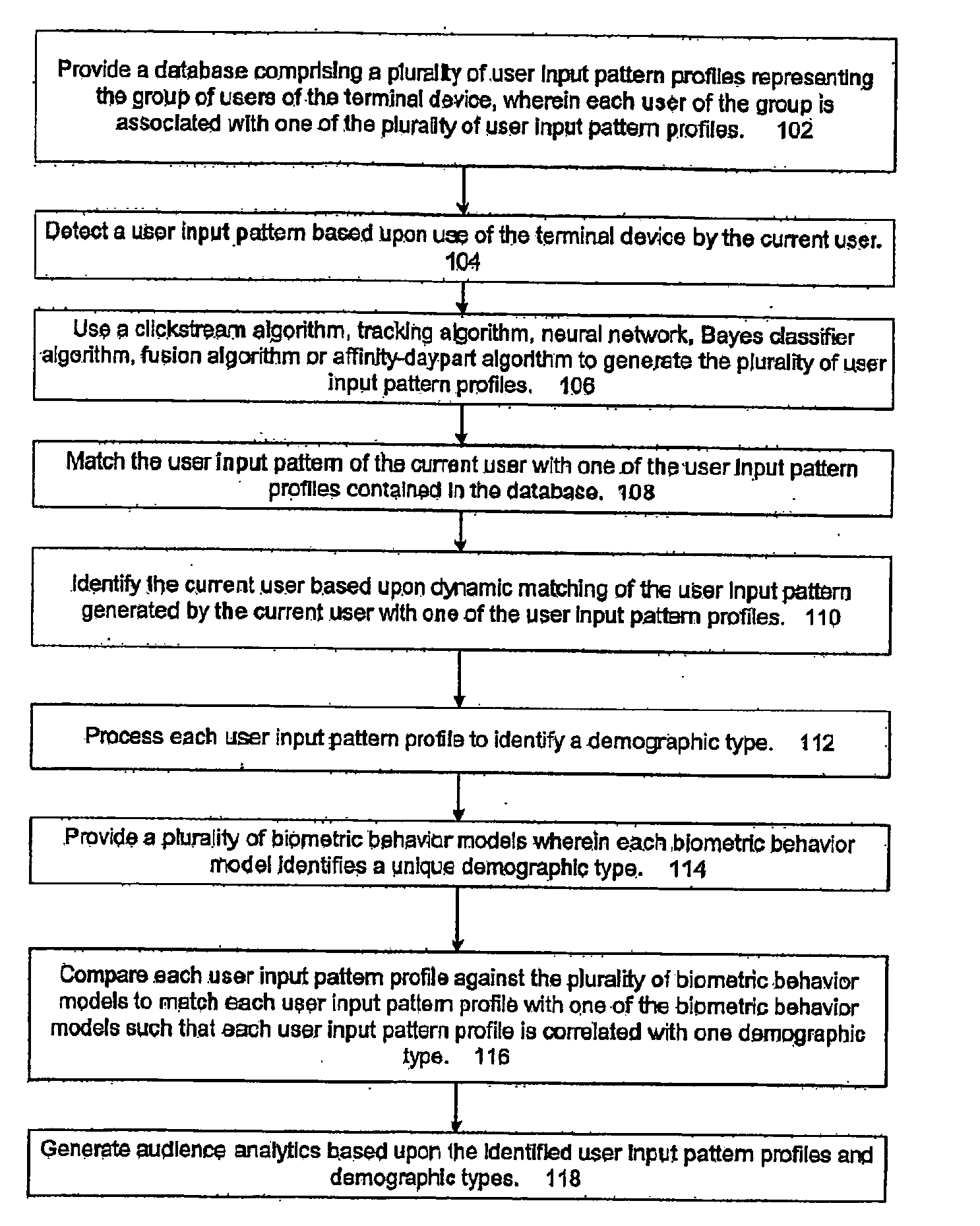
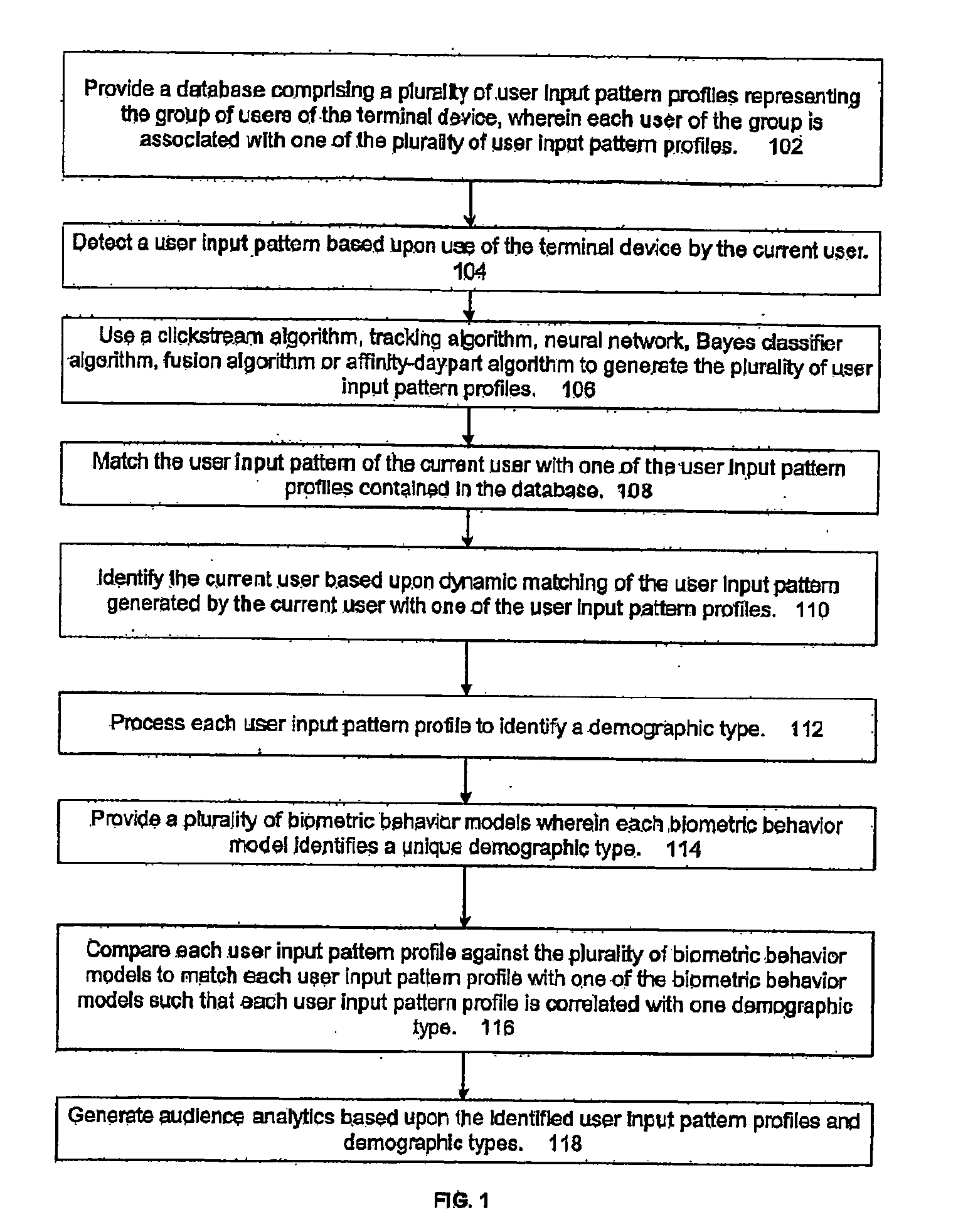
The present invention is directed to generating audience analytics that includes providing a database containing a plurality of user input pattern profiles representing the group of users of terminal device, in which each user of the group is associated with one of the plurality of user input pattern profiles. A clickstream algorithm, tracking algorithm, neural network, Bayes classifier algorithm, or affinity-day part algorithm can be used to generate the user input pattern profiles. A user input pattern is detected based upon use of the terminal device by the current user and the user input pattern of the current user is dynamically matched with one of the user input pattern profiles contained in the database. The current user is identified based upon dynamic matching of the user input pattern generated by the current user with one of the user input pattern profiles. The present invention processes each user input pattern profile to identify a demographic type. A plurality of biometric behavior models are employed to identify a unique demographic type. Each user input pattern profile is compared against the plurality of biometric behavior models to match each user input pattern profile with one of the biometric behavior models such that each user input pattern profile is correlated with one demographic type. Audience analytics are then based upon the identified demographic types.
Owner:COX COMMUNICATIONS
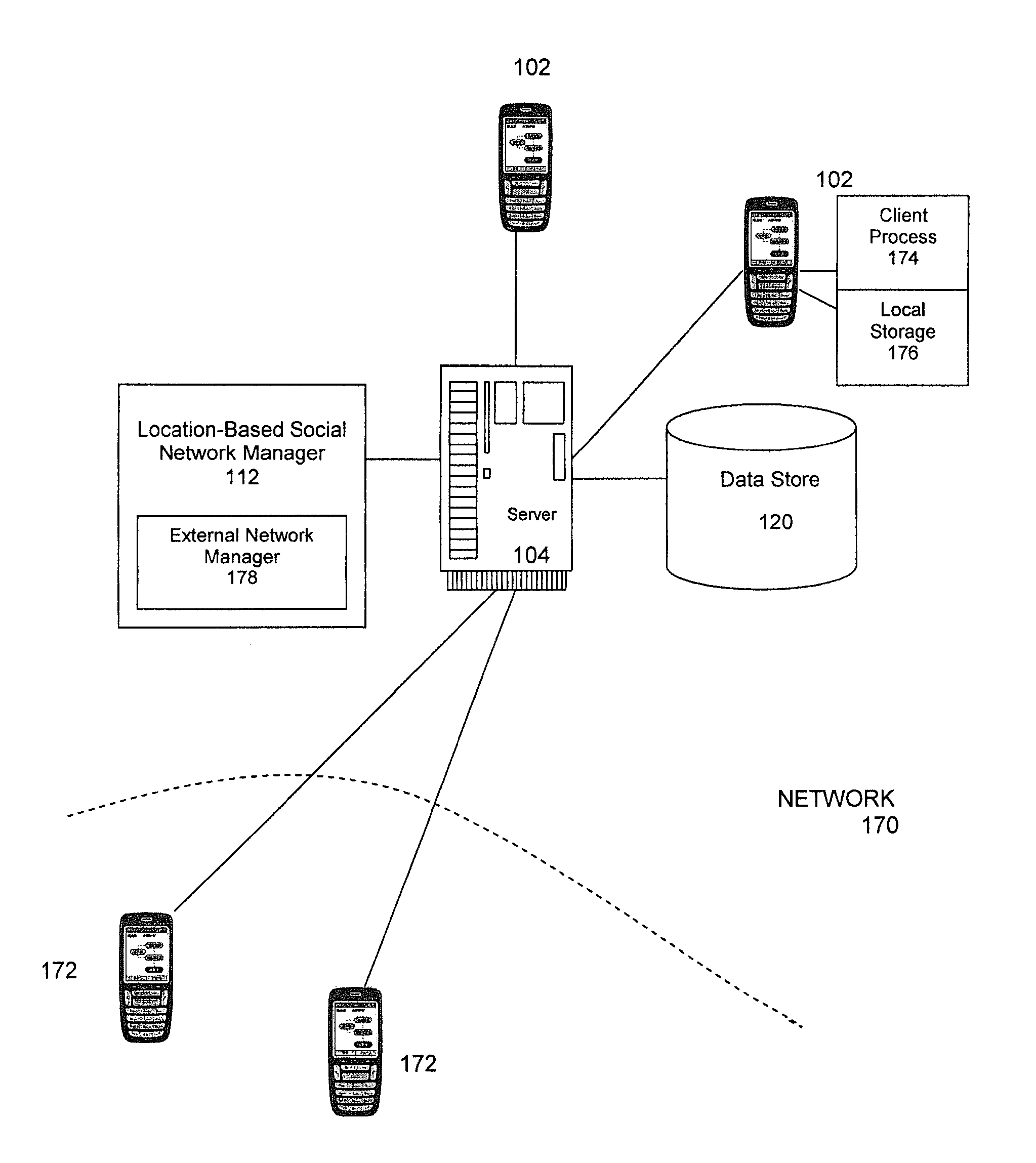
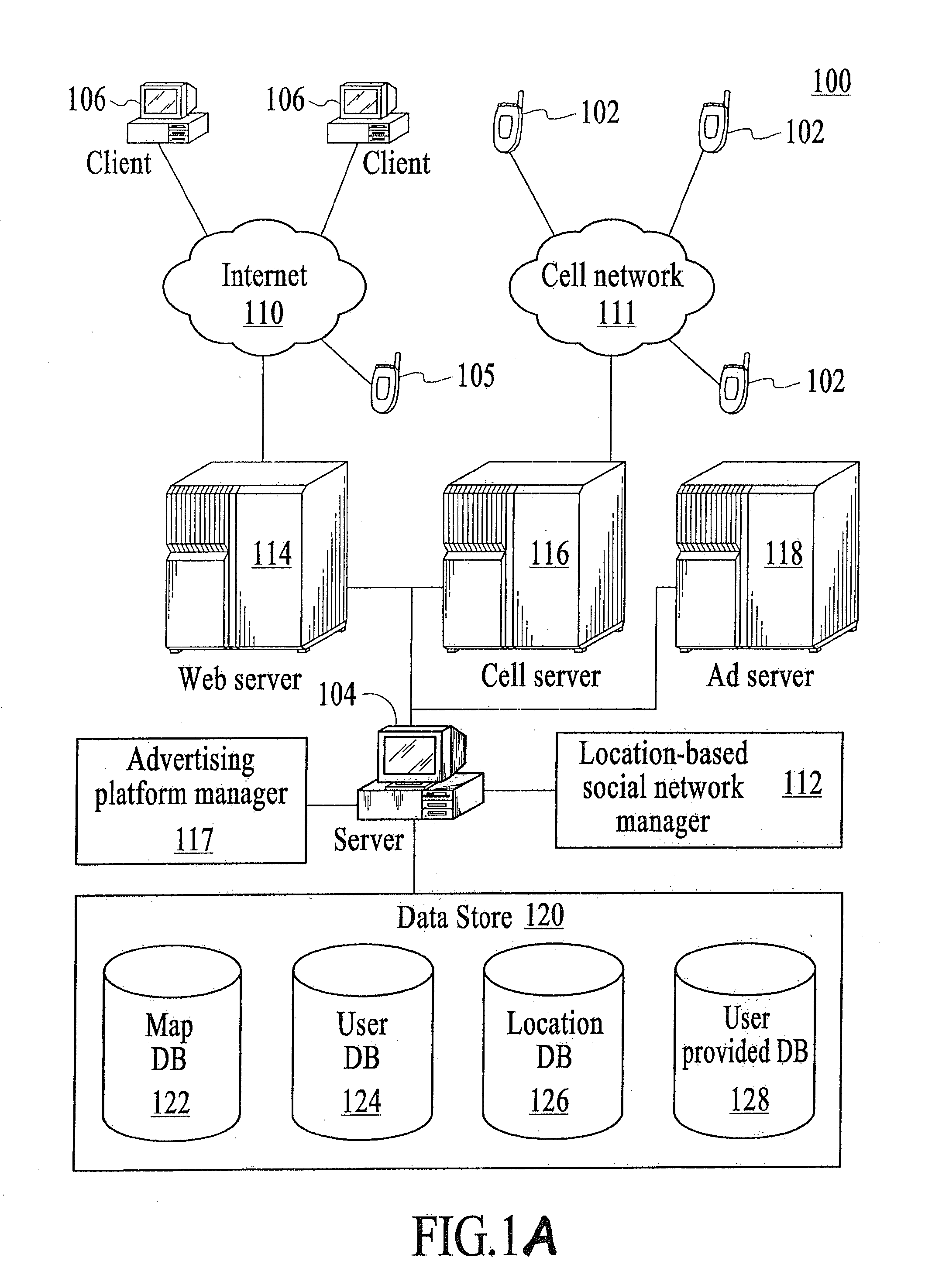
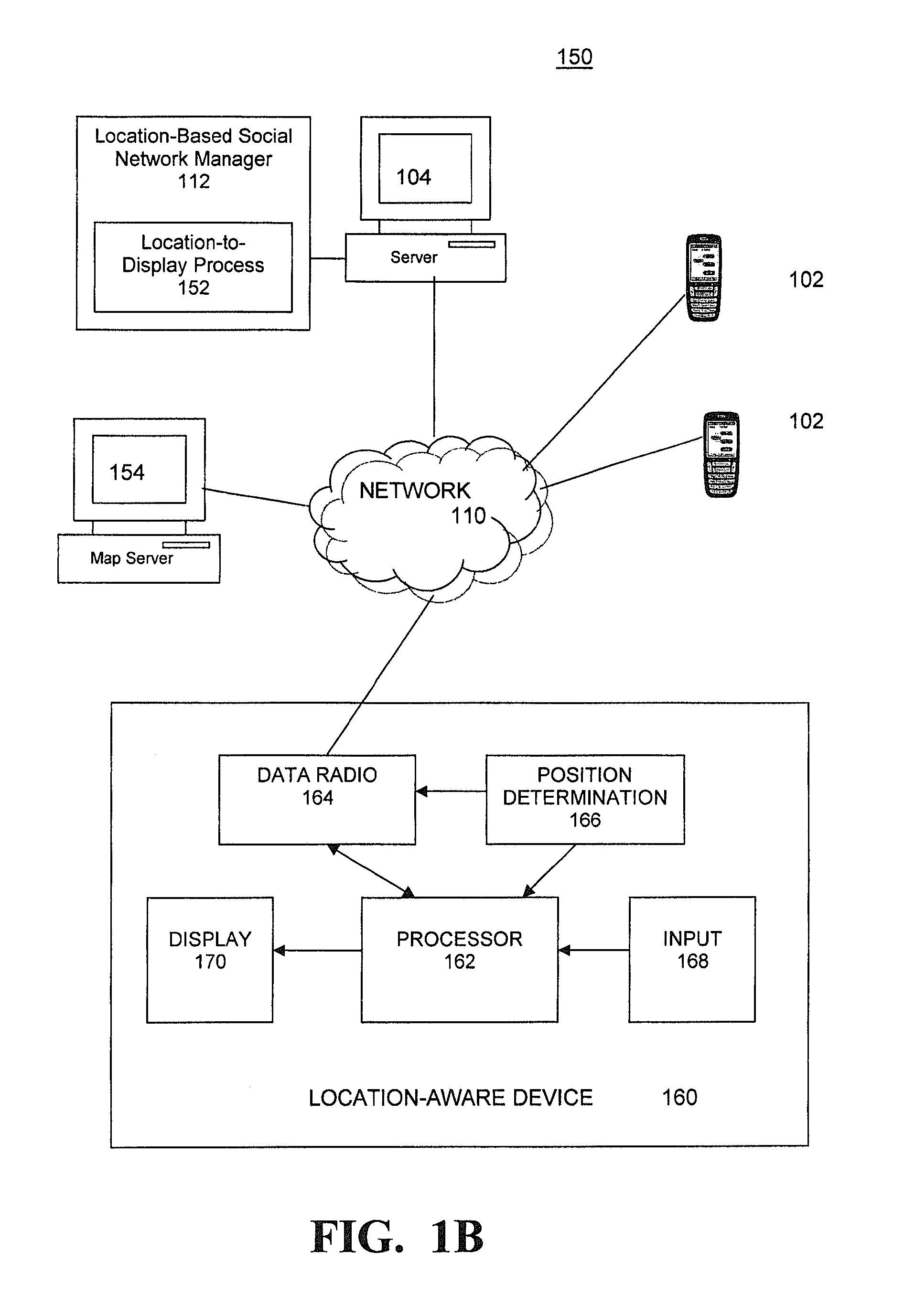
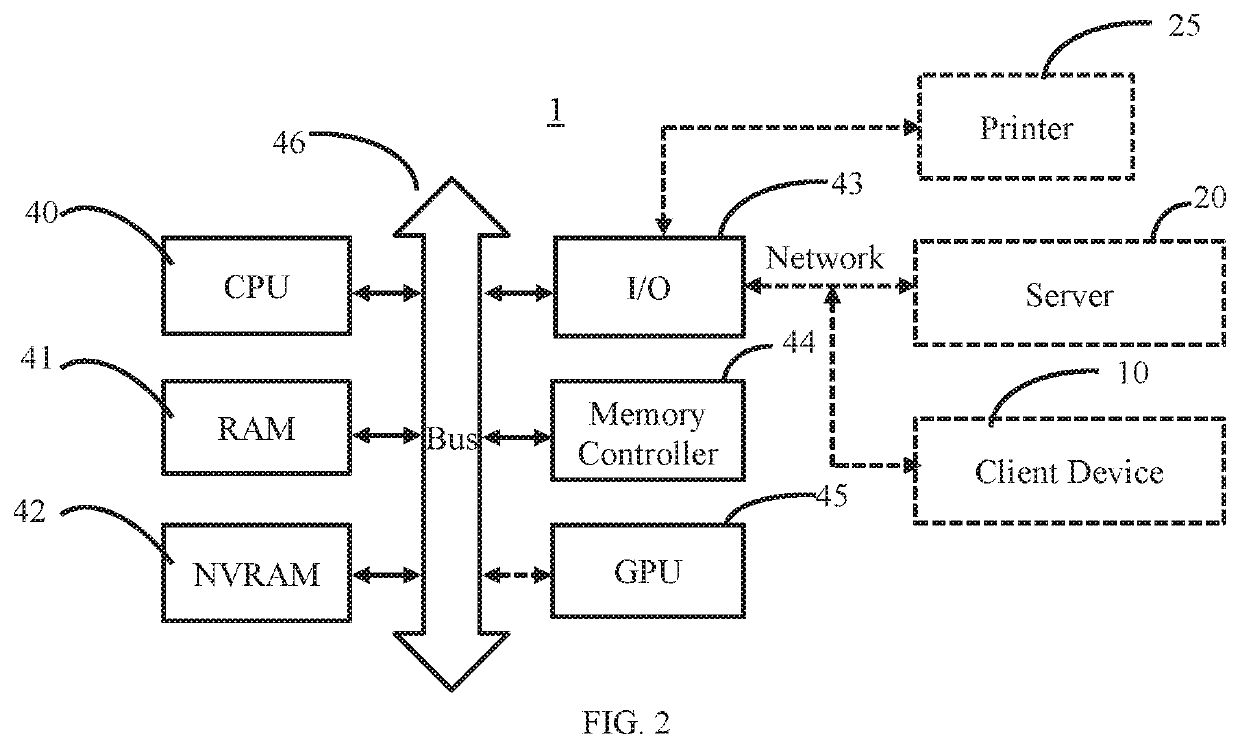
Network manager system for location-aware mobile communication devices
ActiveUS20120172062A1Efficient communicationDiscounts/incentivesNetwork traffic/resource managementGeolocationNetwork management
Embodiments of a location sharing network manager process are described. The process is executed on a server computer coupled to a plurality of mobile communication devices over a wireless network. Each mobile device is a location-aware mobile communication device. The process determines the geographic location of a mobile communication device operated by a user within an area, displays a map representation of the area around the mobile communication device on a graphical user interface of the mobile communication device, and superimposes on the map the respective locations of one or more other trusted users of mobile communication devices coupled to the mobile communication device over the network. A comprehensive network manager process provides management functions to allow communication with mobile phone users outside of the service network and allows for efficient communication with groups of users within the service network.
Owner:GREEN DOT CORPORATION
Generalized policy server
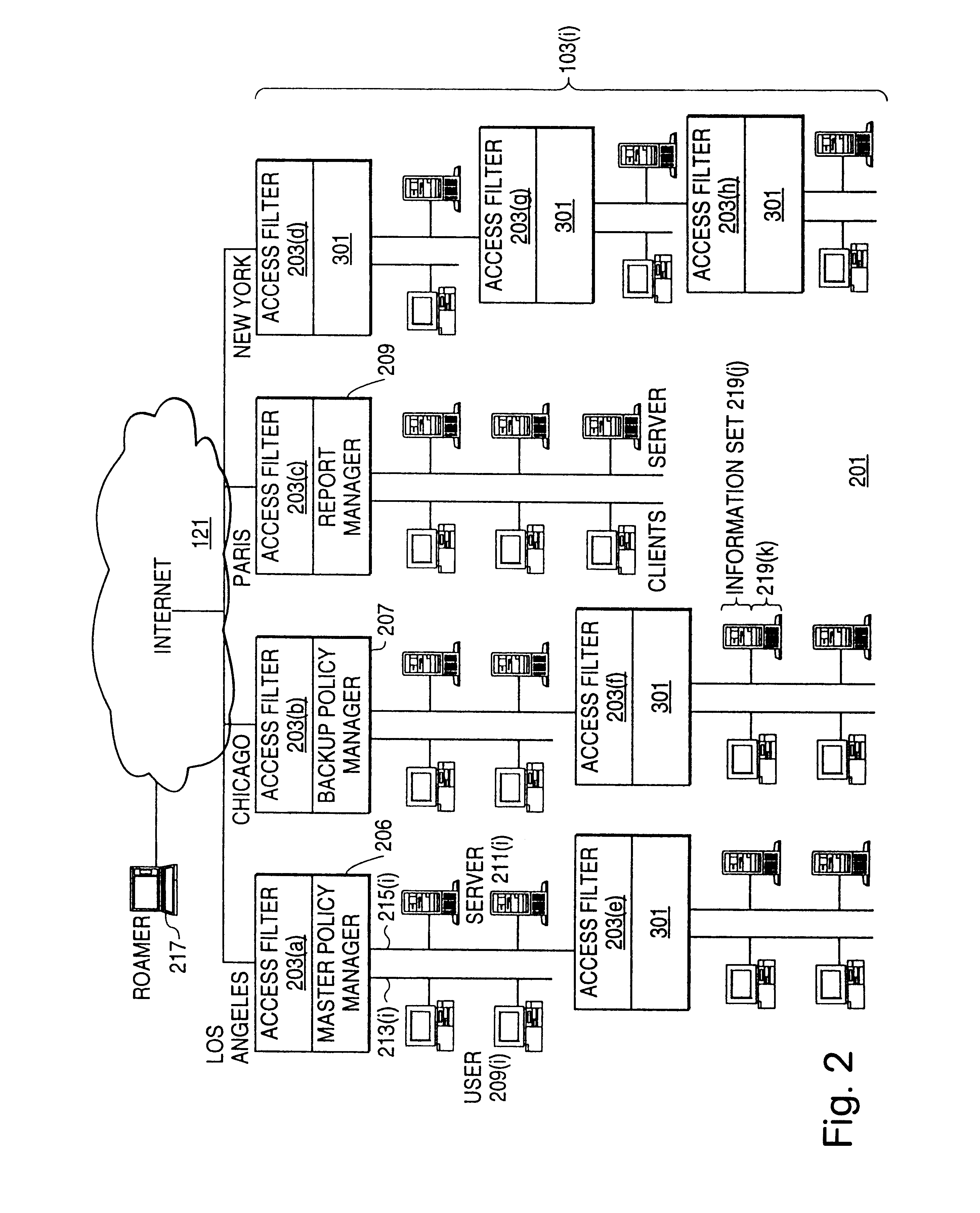
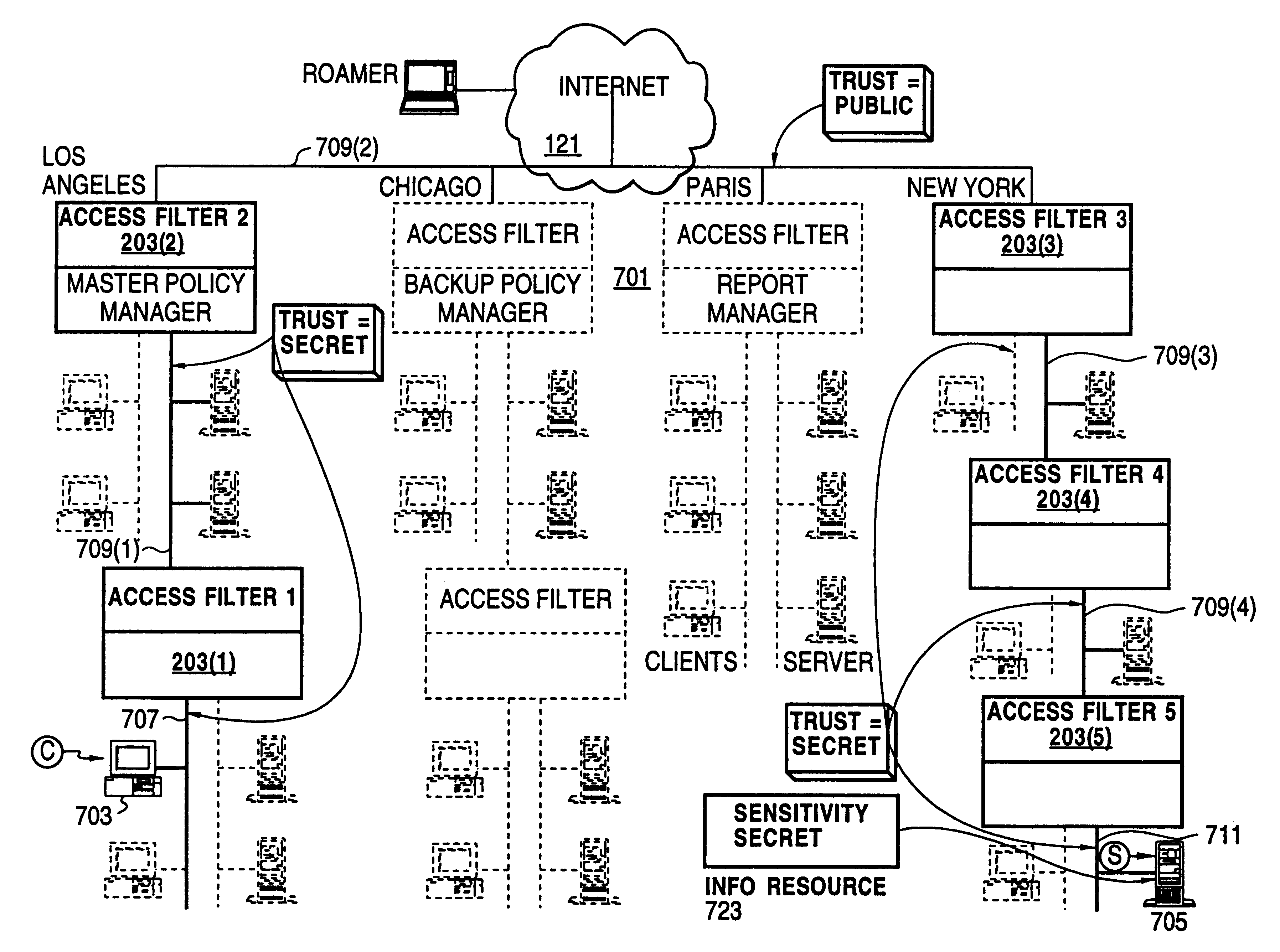
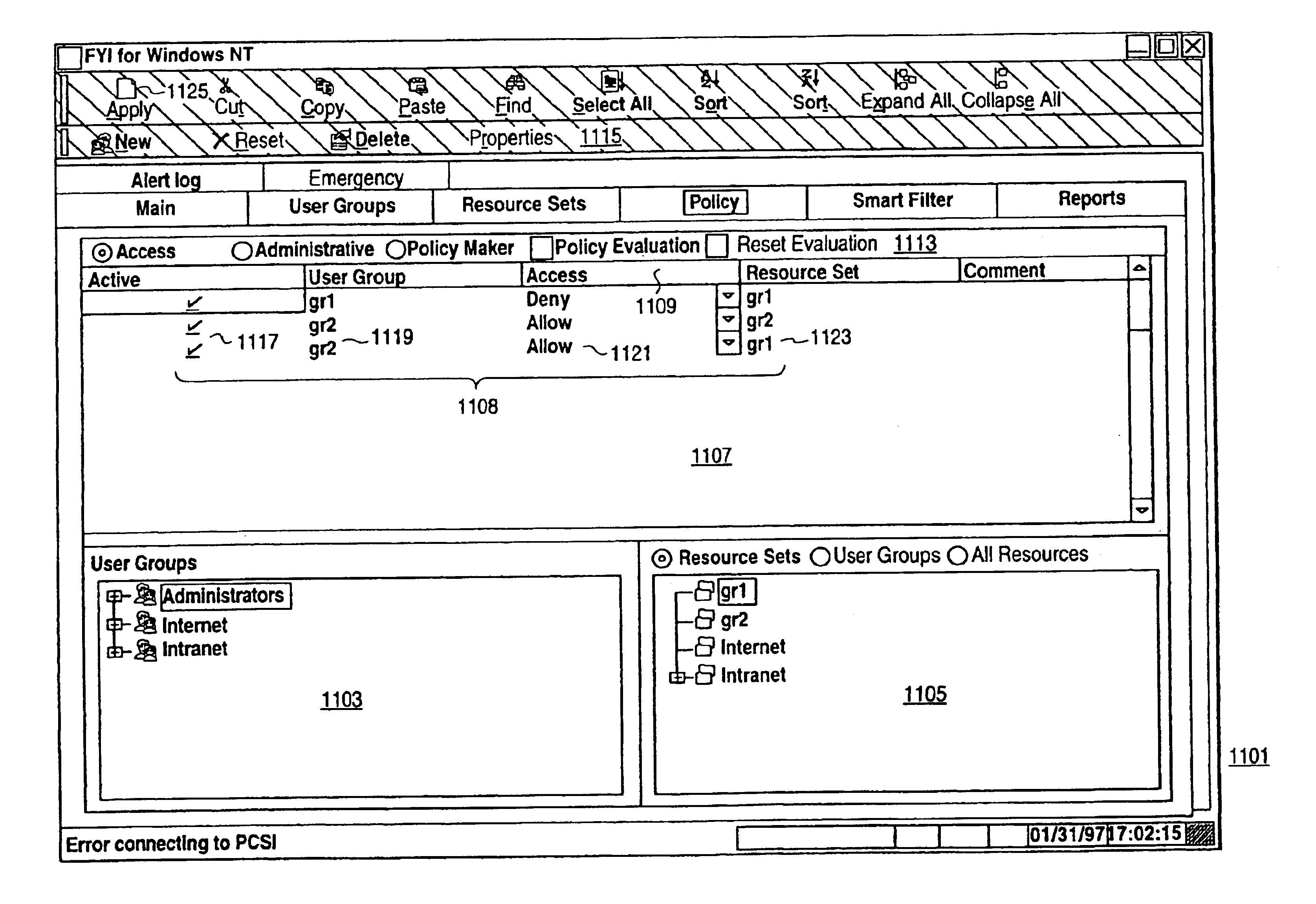
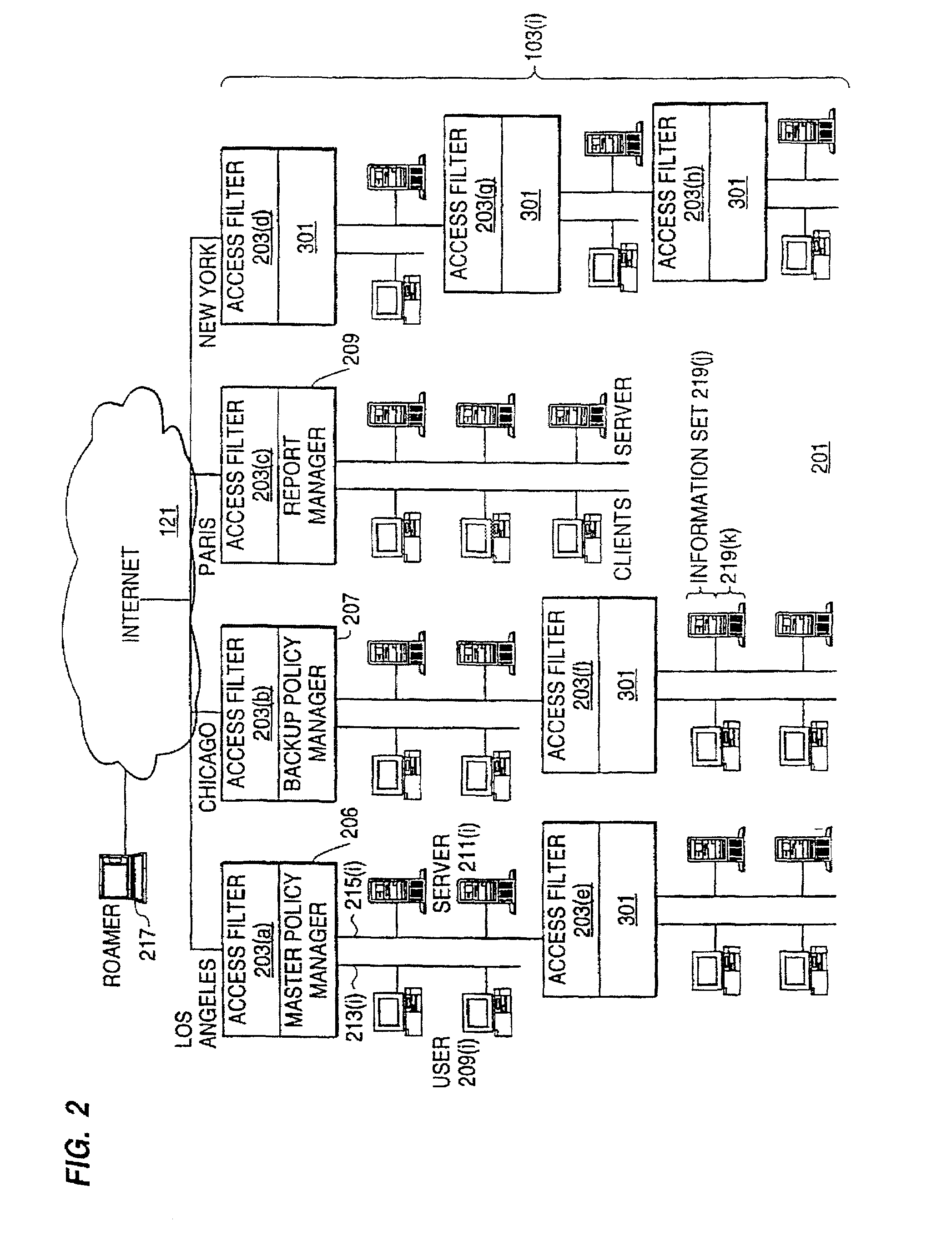
InactiveUS7272625B1Easy to handleMultiple digital computer combinationsTransmissionPolicy decisionTrust level
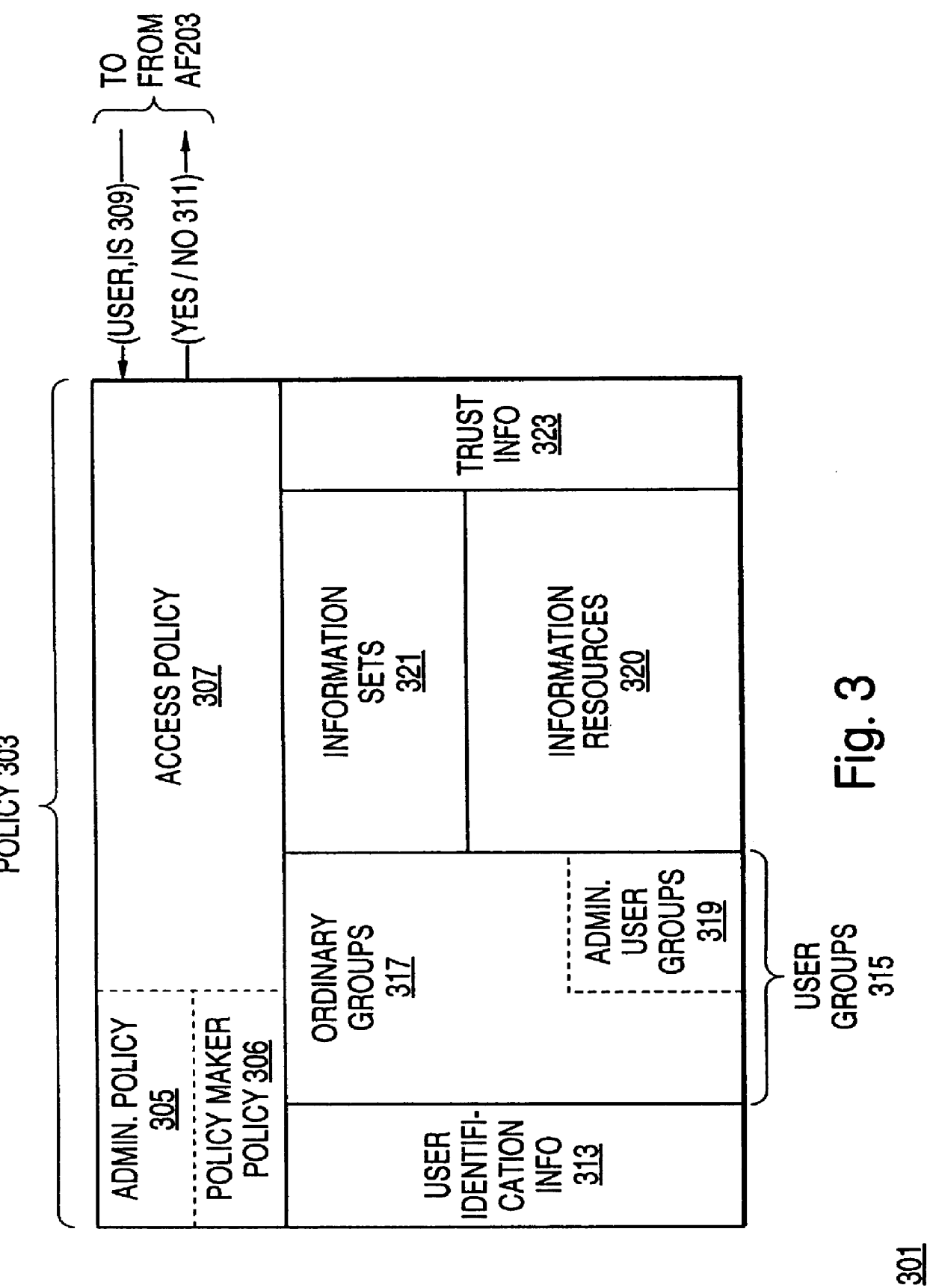
A policy system includes the policy server (2617); a policy database (2619) which located at policy decision point (2723); the access / response entity (2603); resource server (2711); policy message (2725) and policy enforcement point (2721). System connected through public network (2702) or internal network (103). The access filter (107, 203, 403) control access by use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Access is permitted or denied according to of access policies (307) which define access in terms of the user groups (FIGS. 9-12) and information sets (FIGS. 13A-18). The rights of administrators are similarly determined by administrative policies (FIGS. 23A-C). Access is further permitted only if the trust levels of the network by which is made by the sufficient access (FIGS. 25-29). A policy server component of the access filter has been separated from the access filter and the policies have been generalized to permit administrators of the policy server to define new types of actions and new types of entities. Policies may now further have specifications for time intervals during which the policies are in force and the entities may be associated with attributes that specify how the entity is to be used when the policy applies.
Owner:MARSHMAN RES +1
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
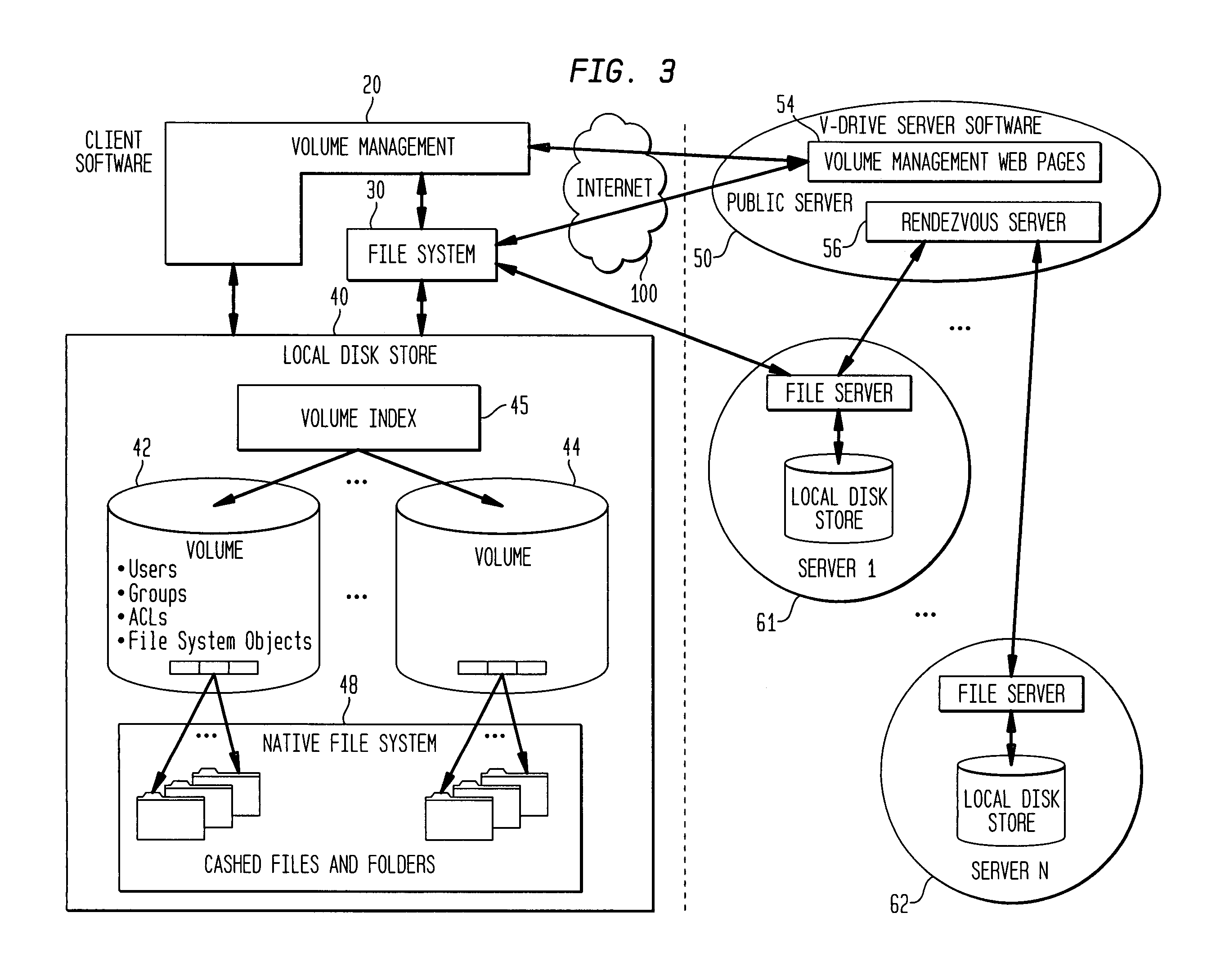
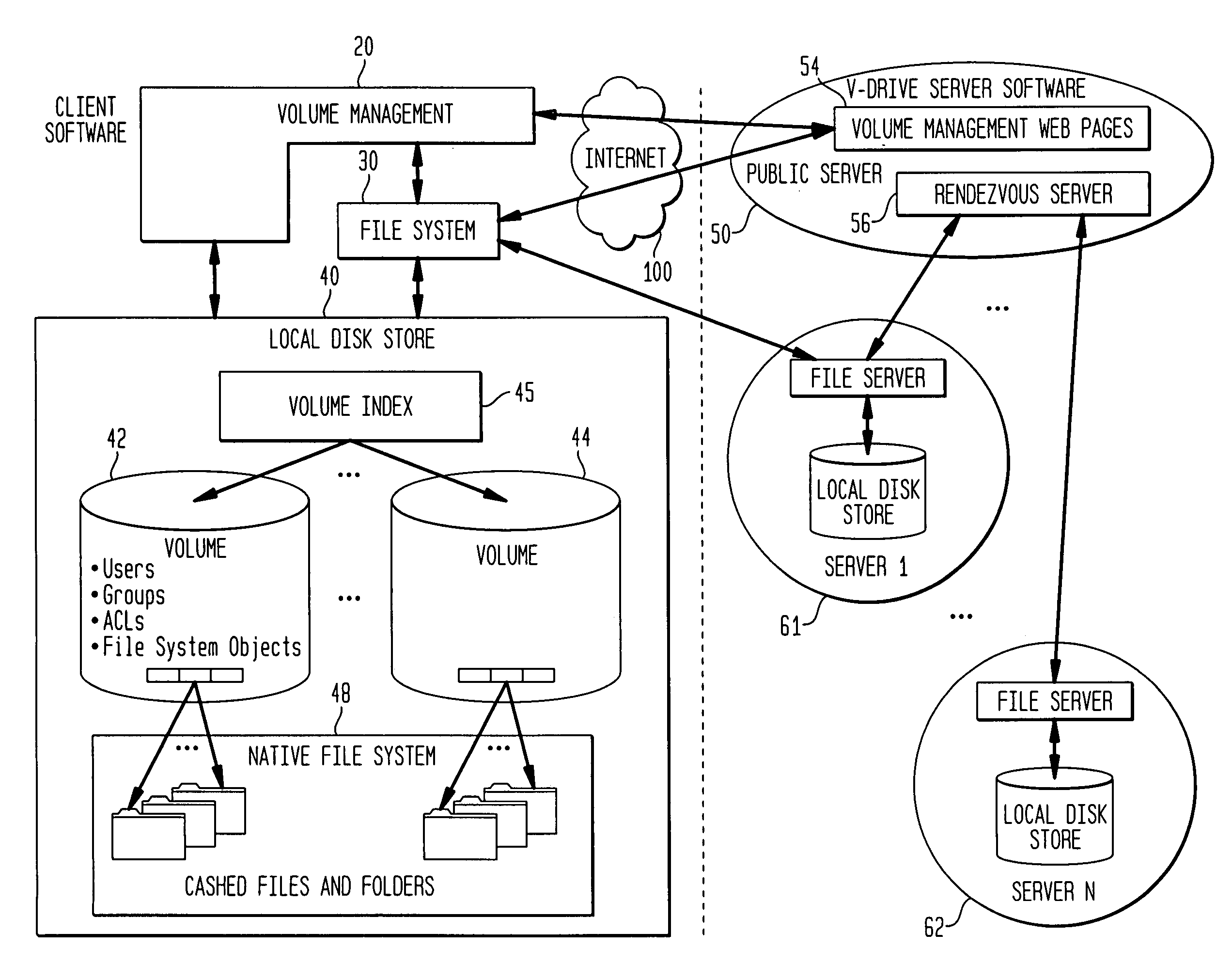
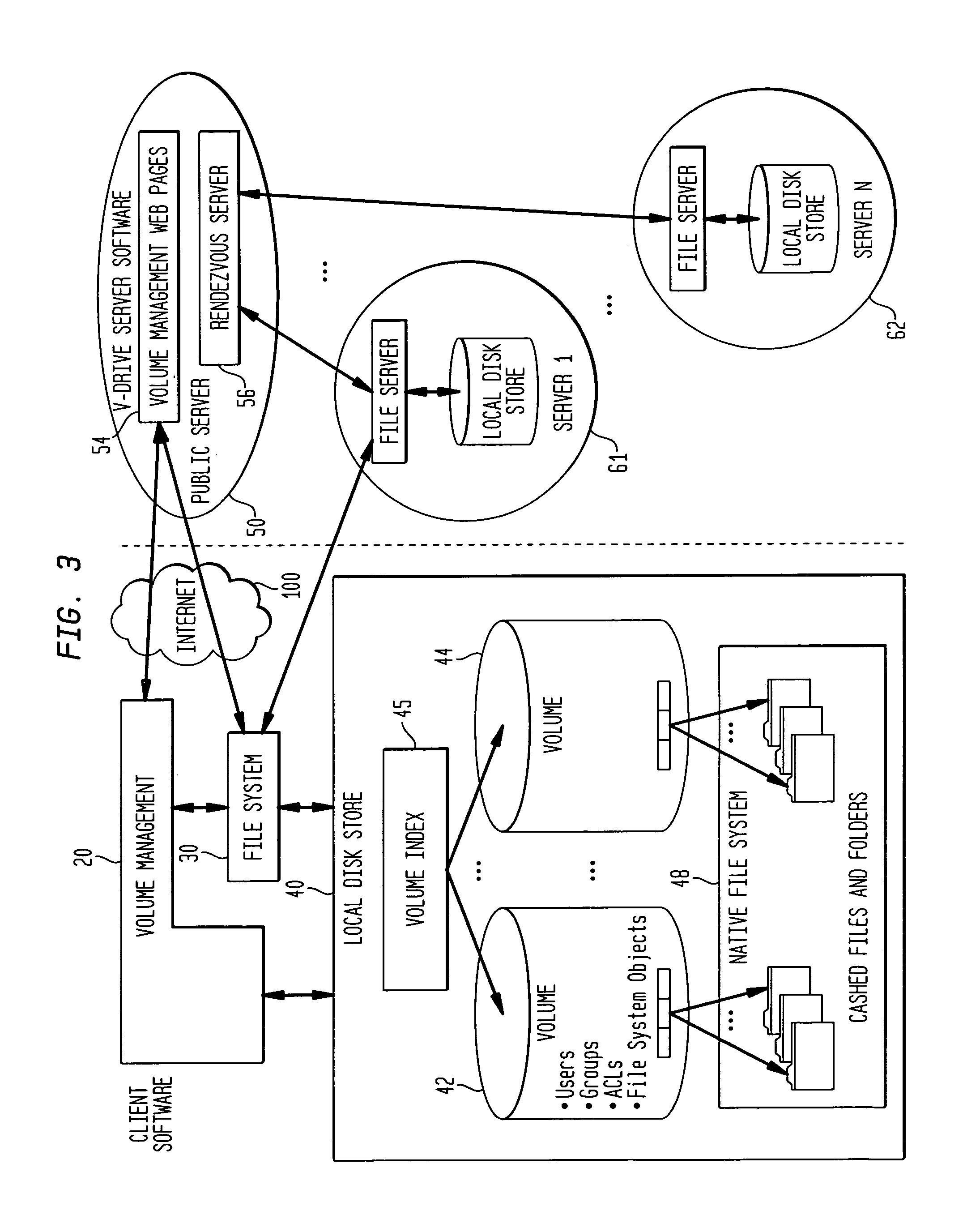
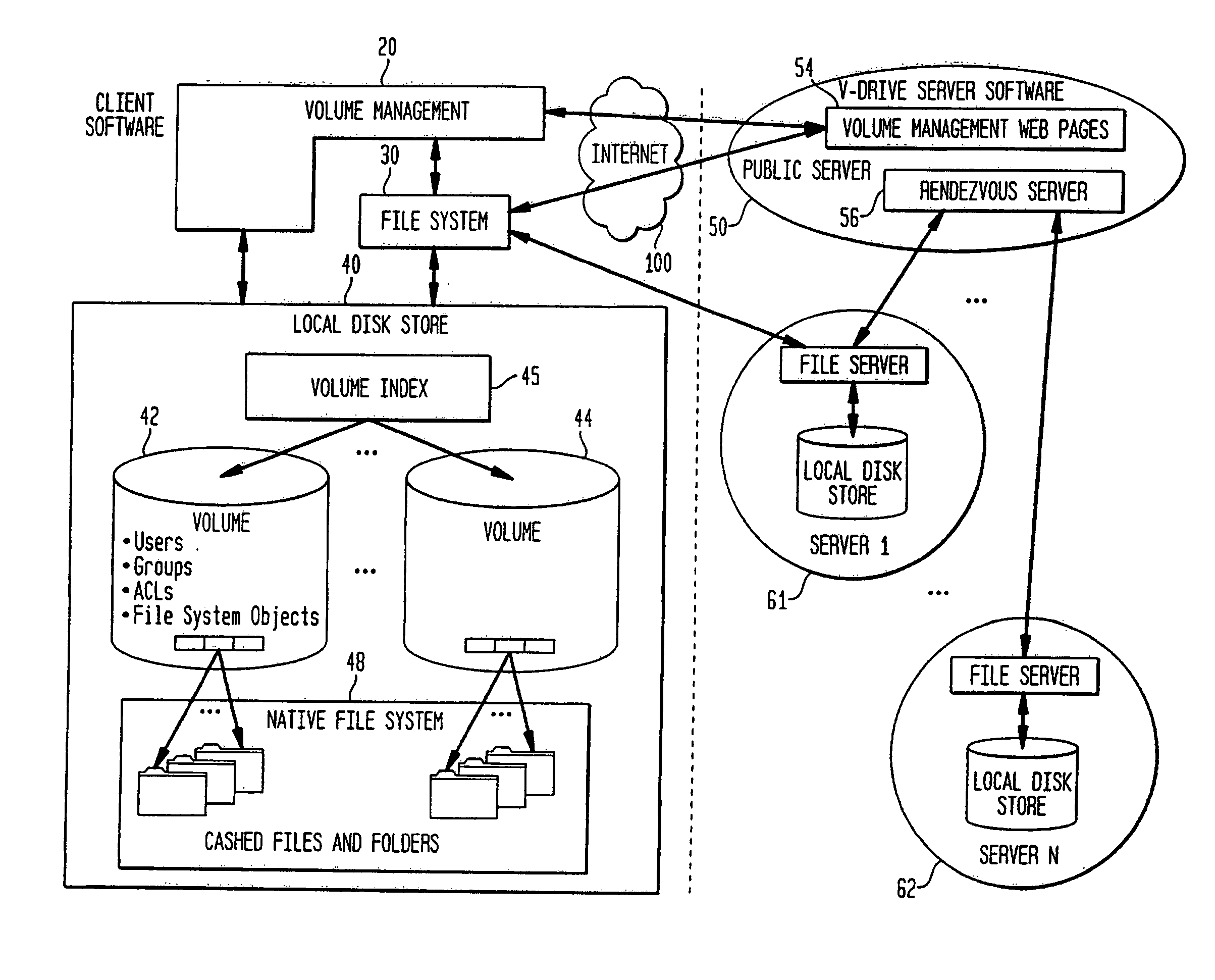
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
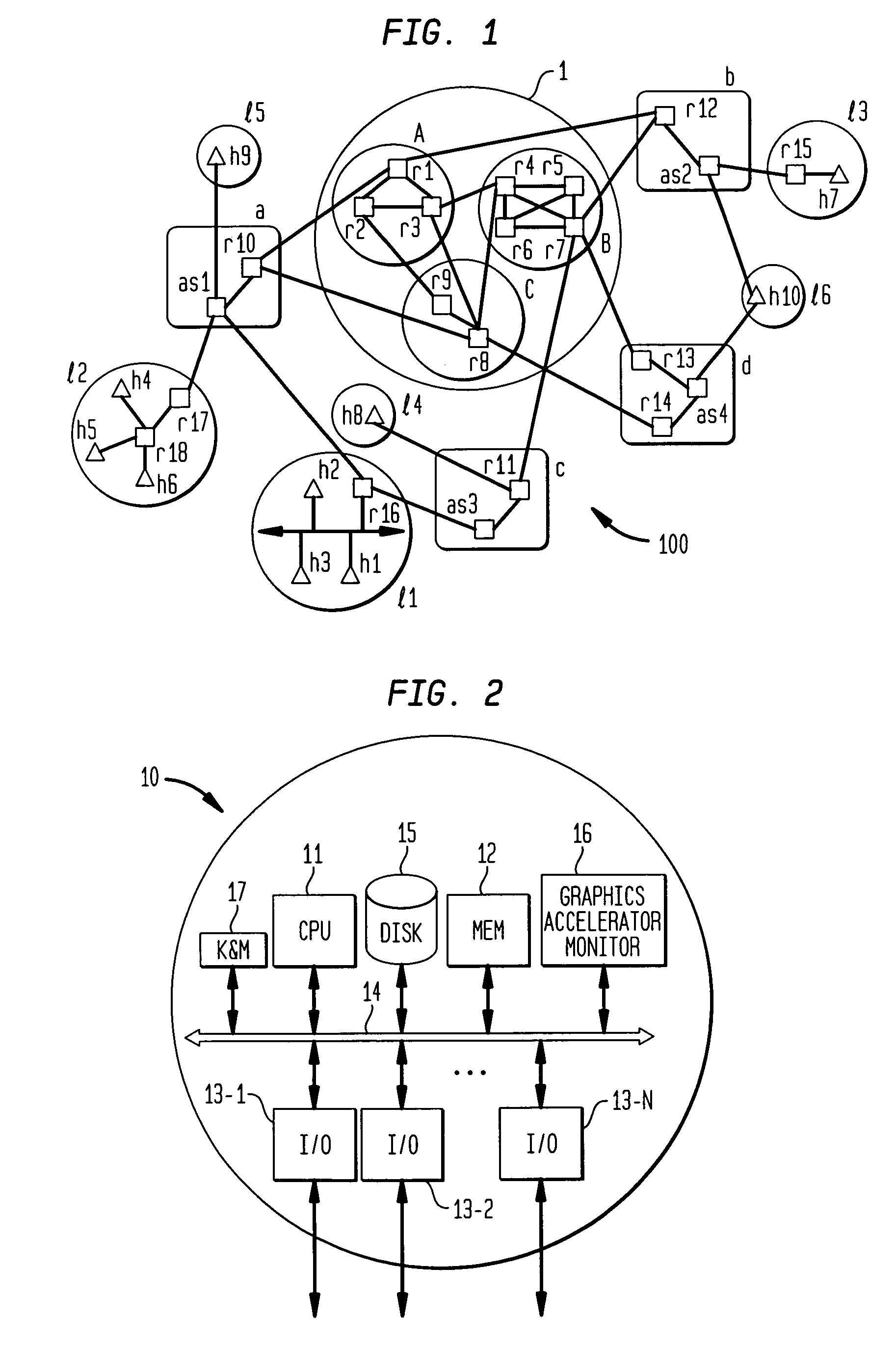
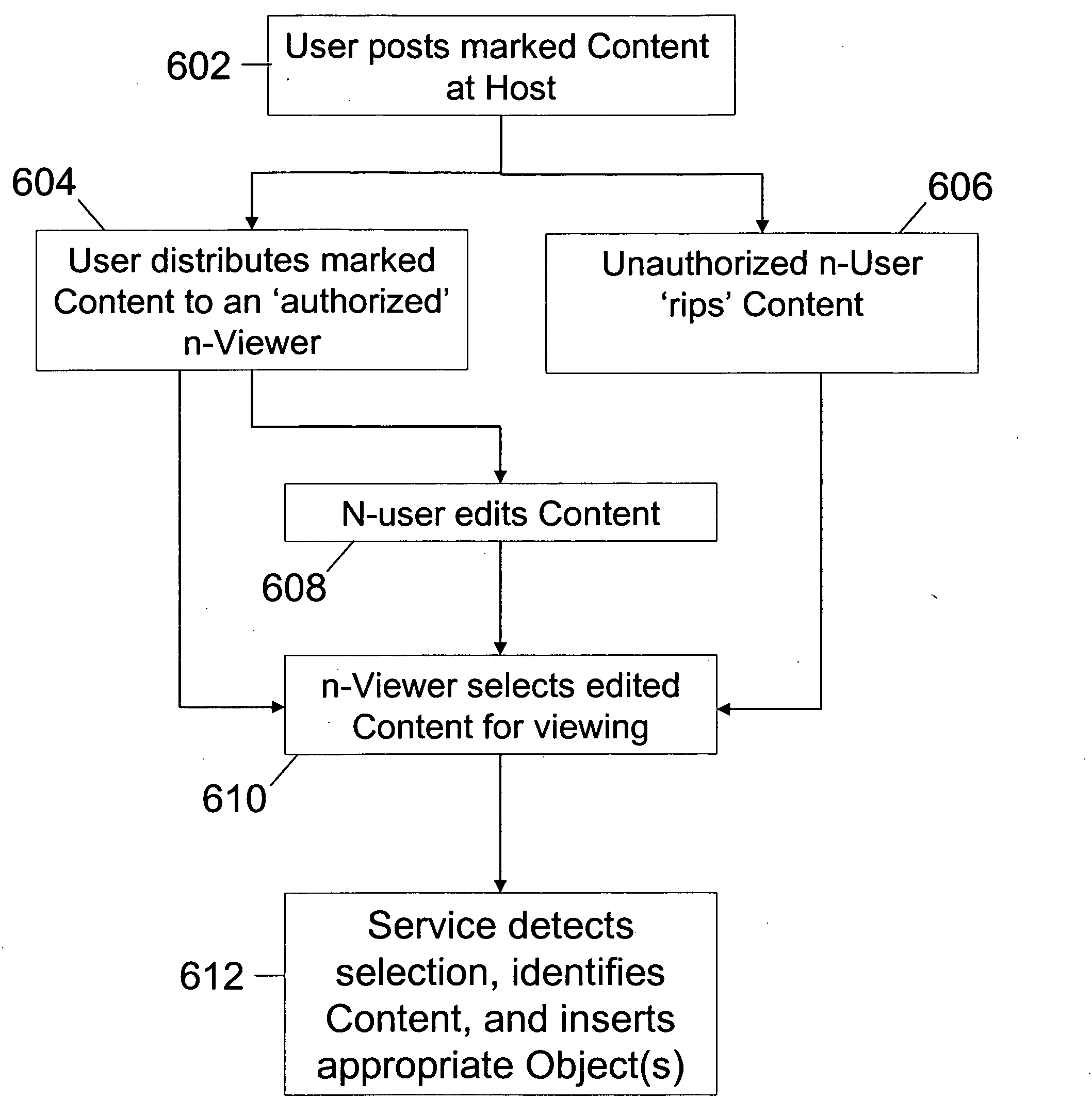
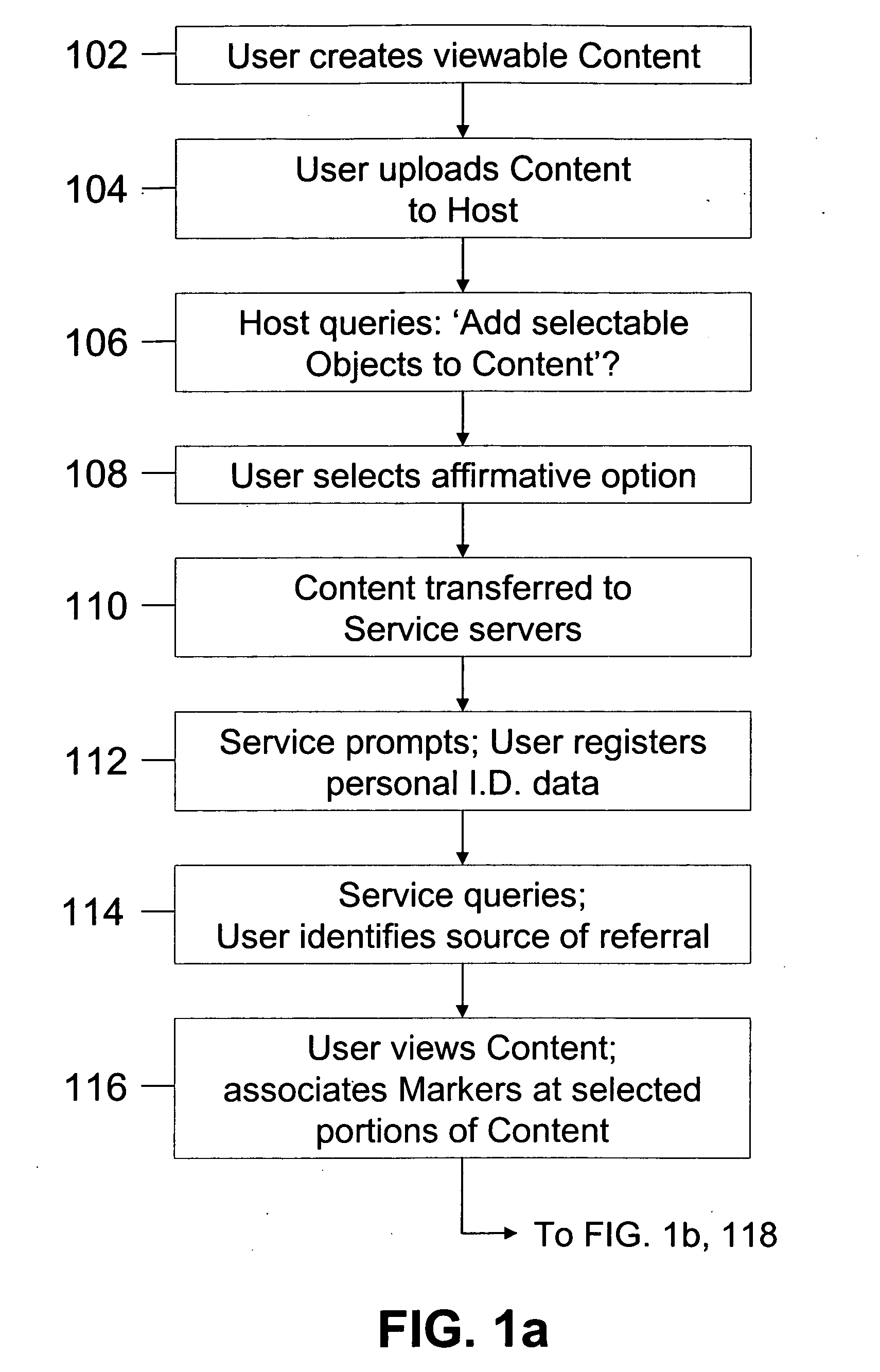
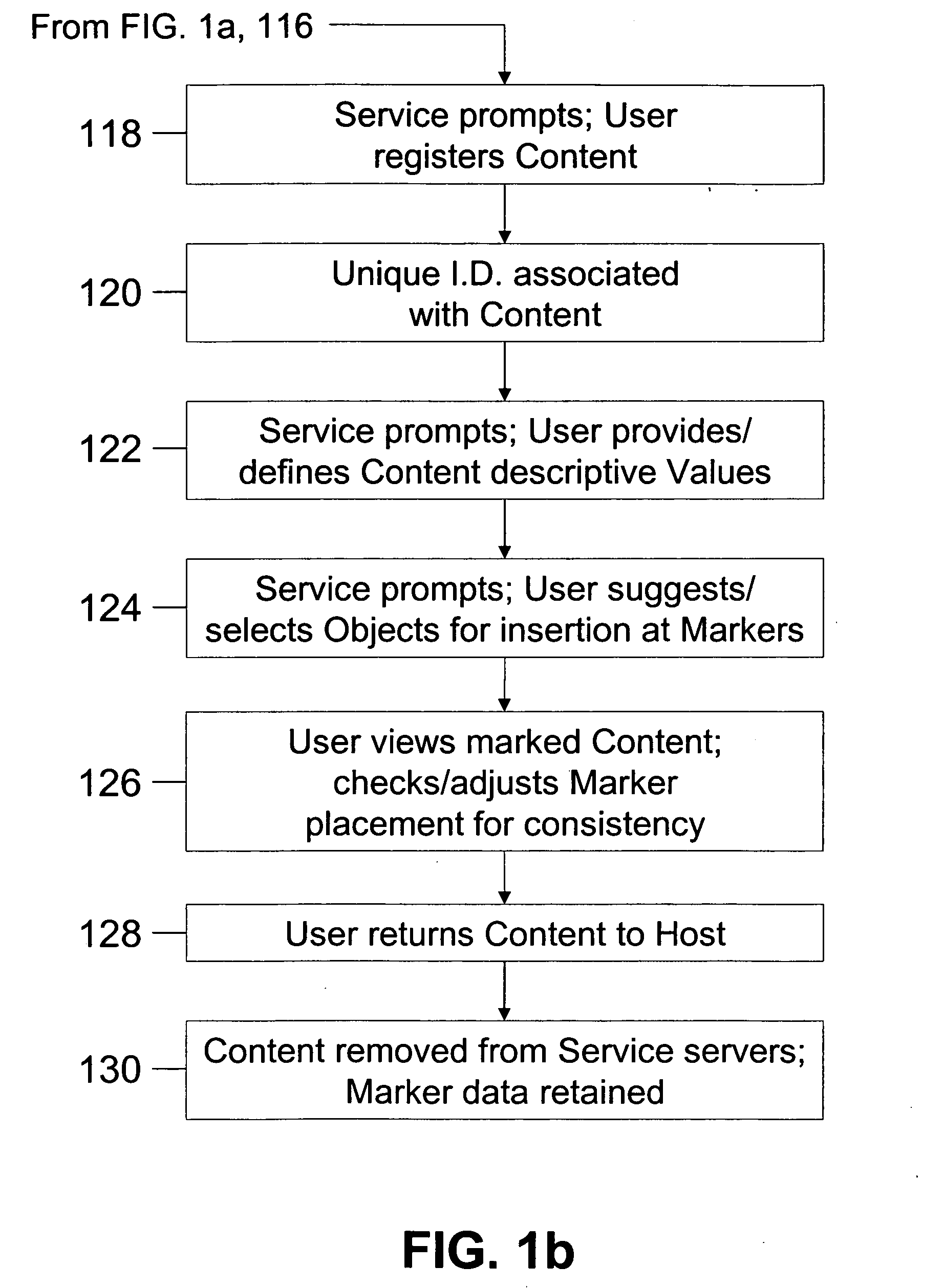
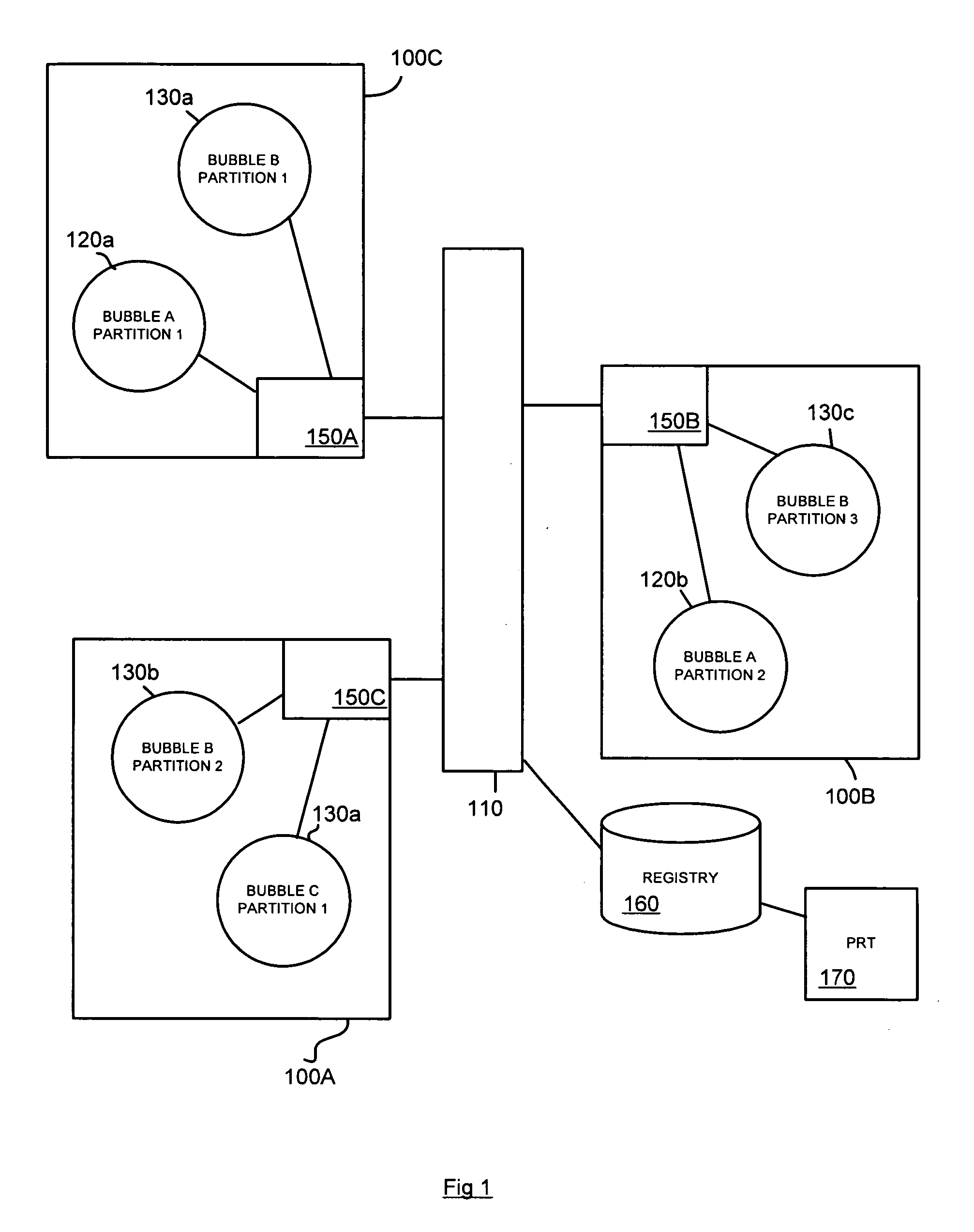
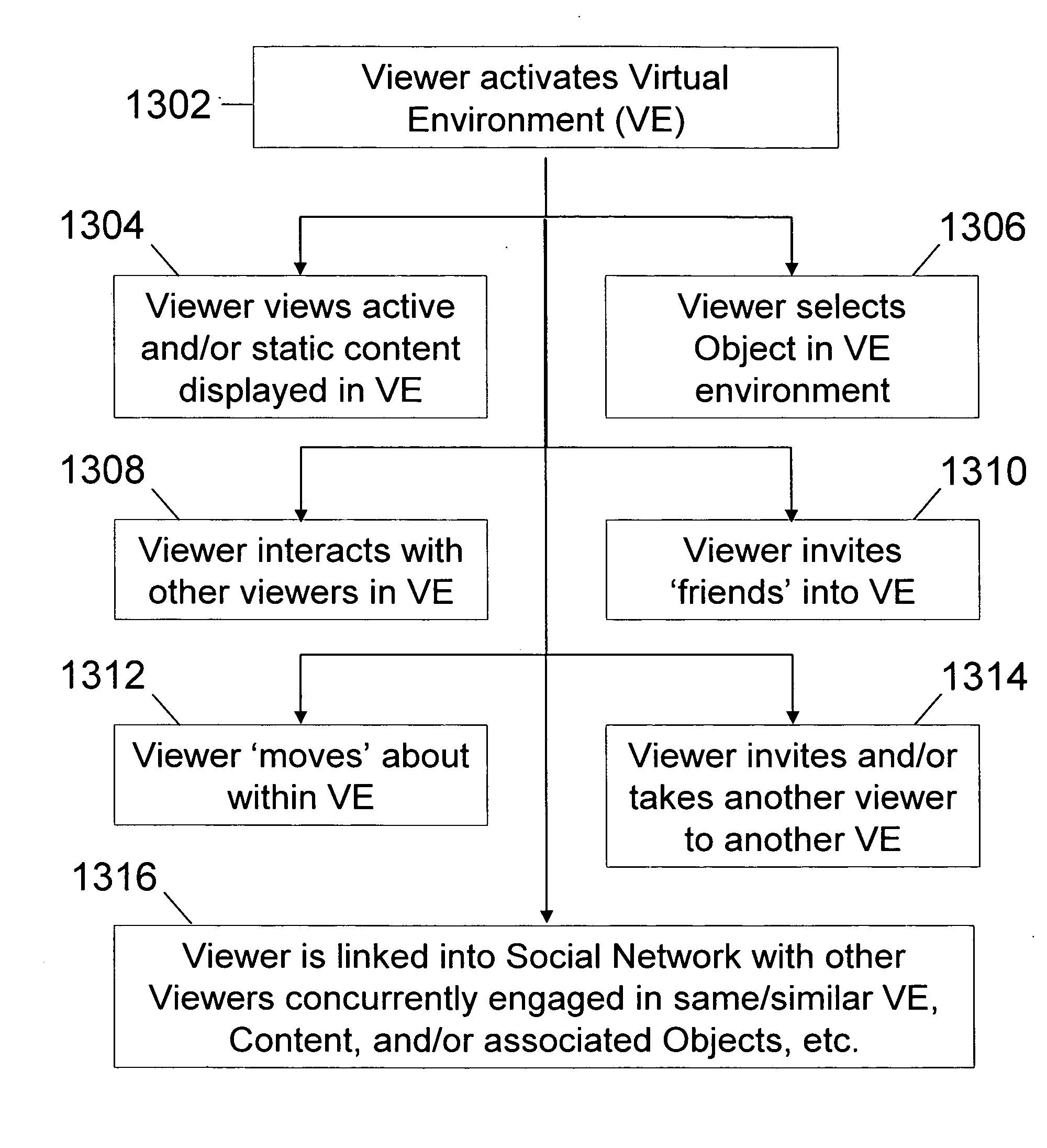
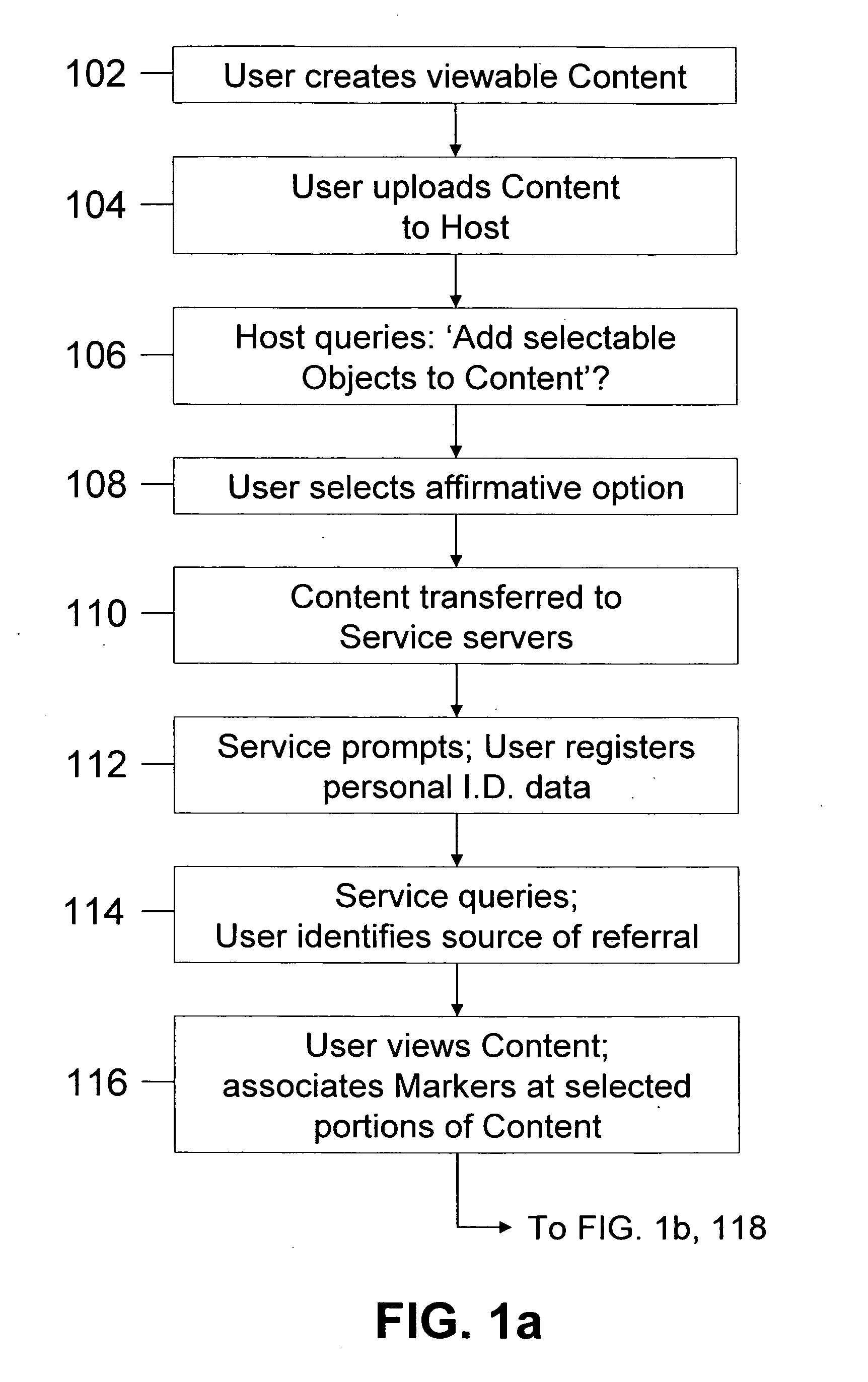
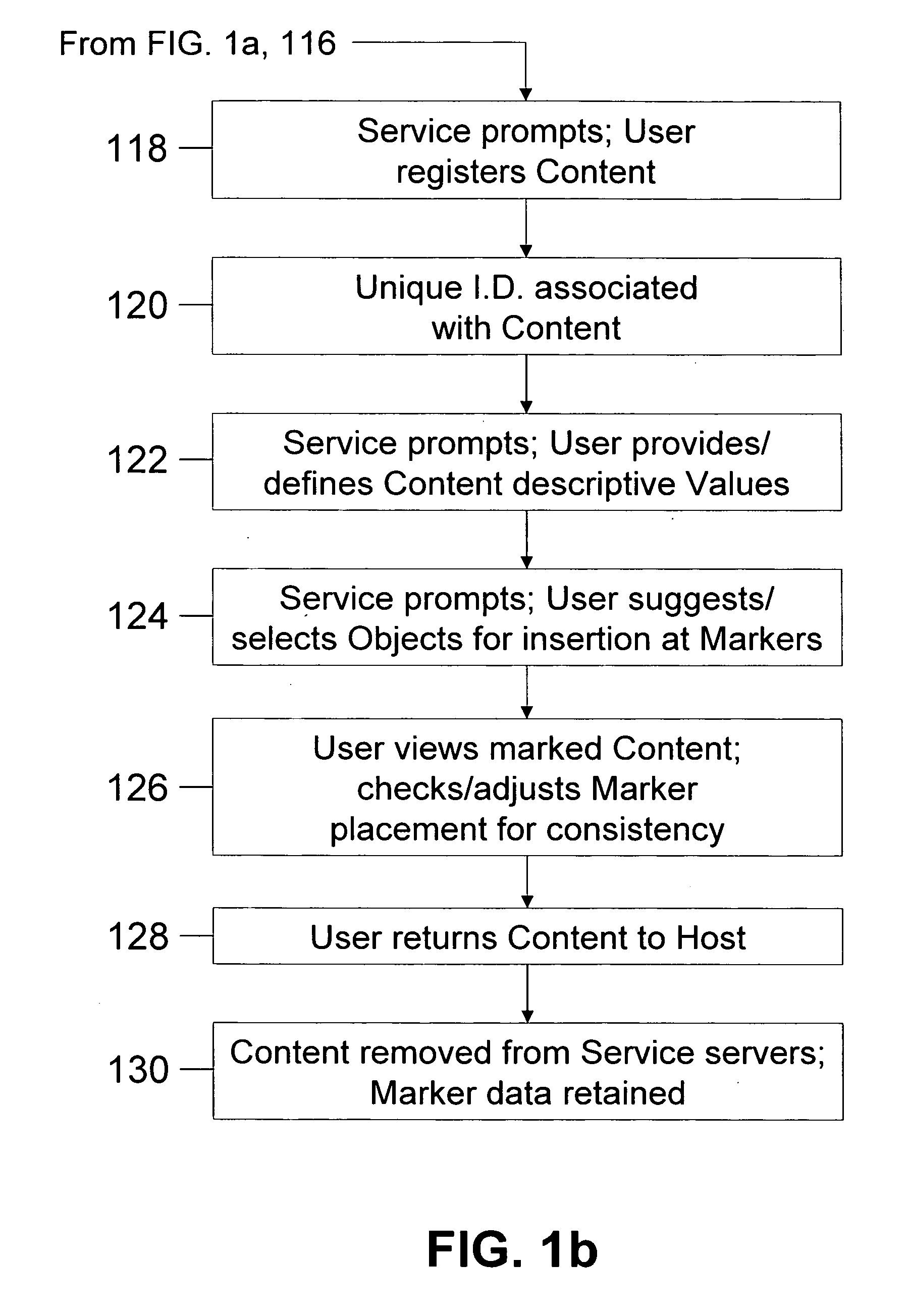
Method of inserting/overlaying markers, data packets and objects relative to viewable content and enabling live social networking, N-dimensional virtual environments and/or other value derivable from the content
ActiveUS20080163379A1Low costReduced flexibilityDigital data processing detailsAnalogue secracy/subscription systemsNetwork packetSocial web
A method by which a User can associate selectable Markers, Data Packets and / or Objects with Content. The Content may generally be distributed electronically, and the Markers allow for insertion and / or overlay of Objects when the Content is selected for viewing by a Viewer. Objects and Data Packets are generally provided by a User, Promoter, Host, Service, or other entity to convey information to a Viewer. A Service provides tools and capabilities to both the User and the Promoter to facilitate their respective actions according to embodiments of the invention, including enabling the creation of live social networks (such as those linked to a specific Service provider, a specific User group, activities by a specific Promoter, and / or to specific Data Packets) and the creation of n-dimensional Virtual Environments.
Owner:NEONEKT LLC
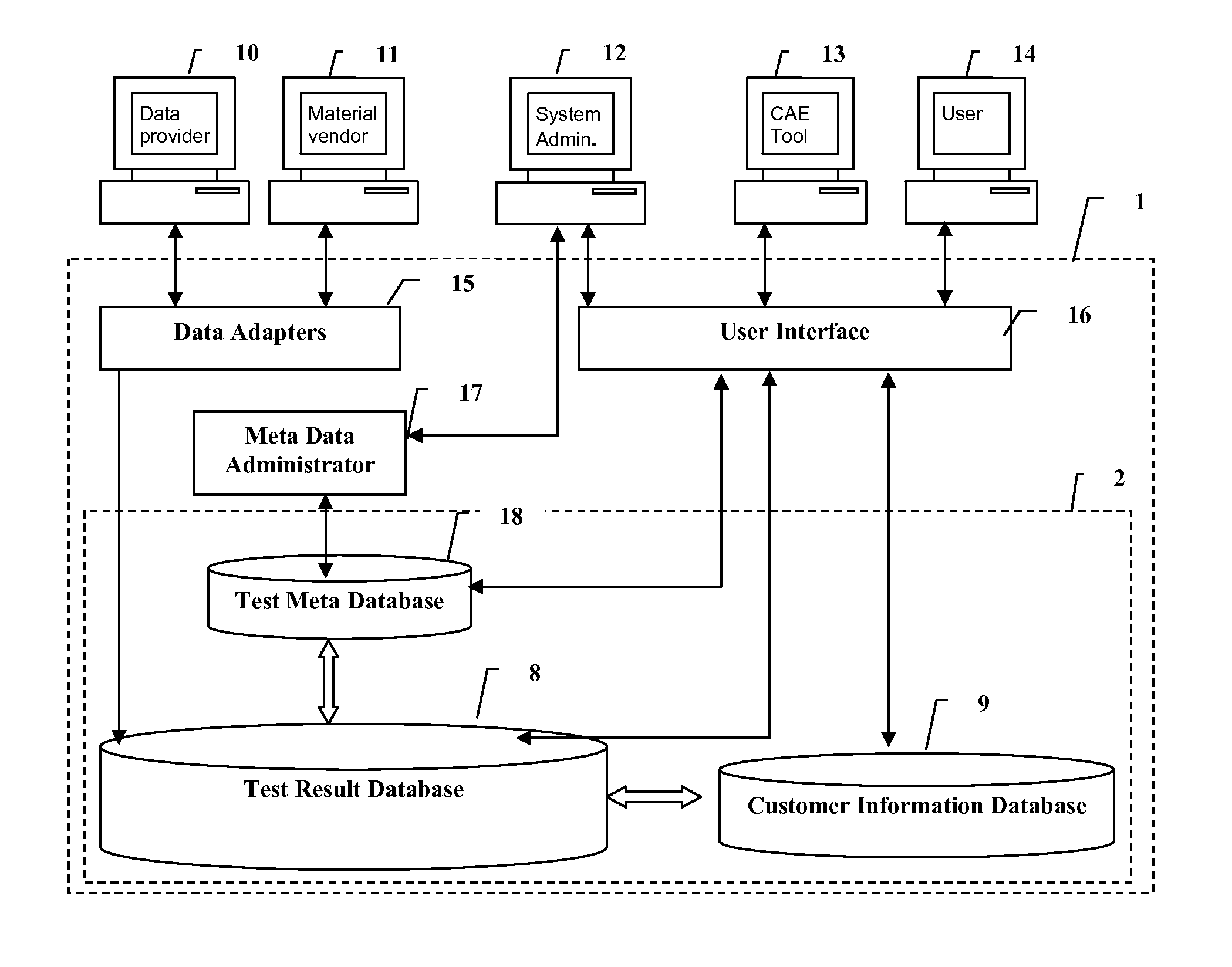
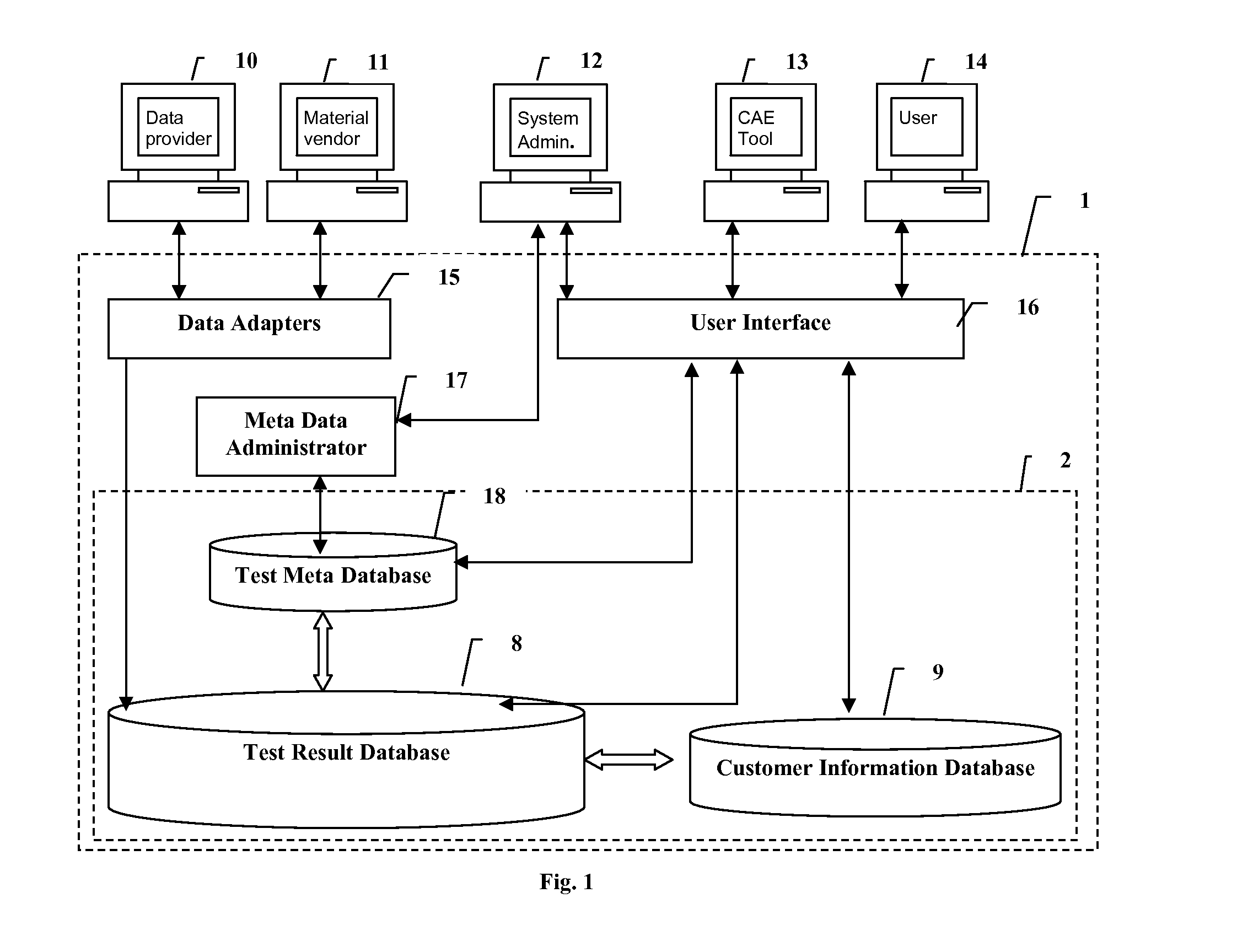
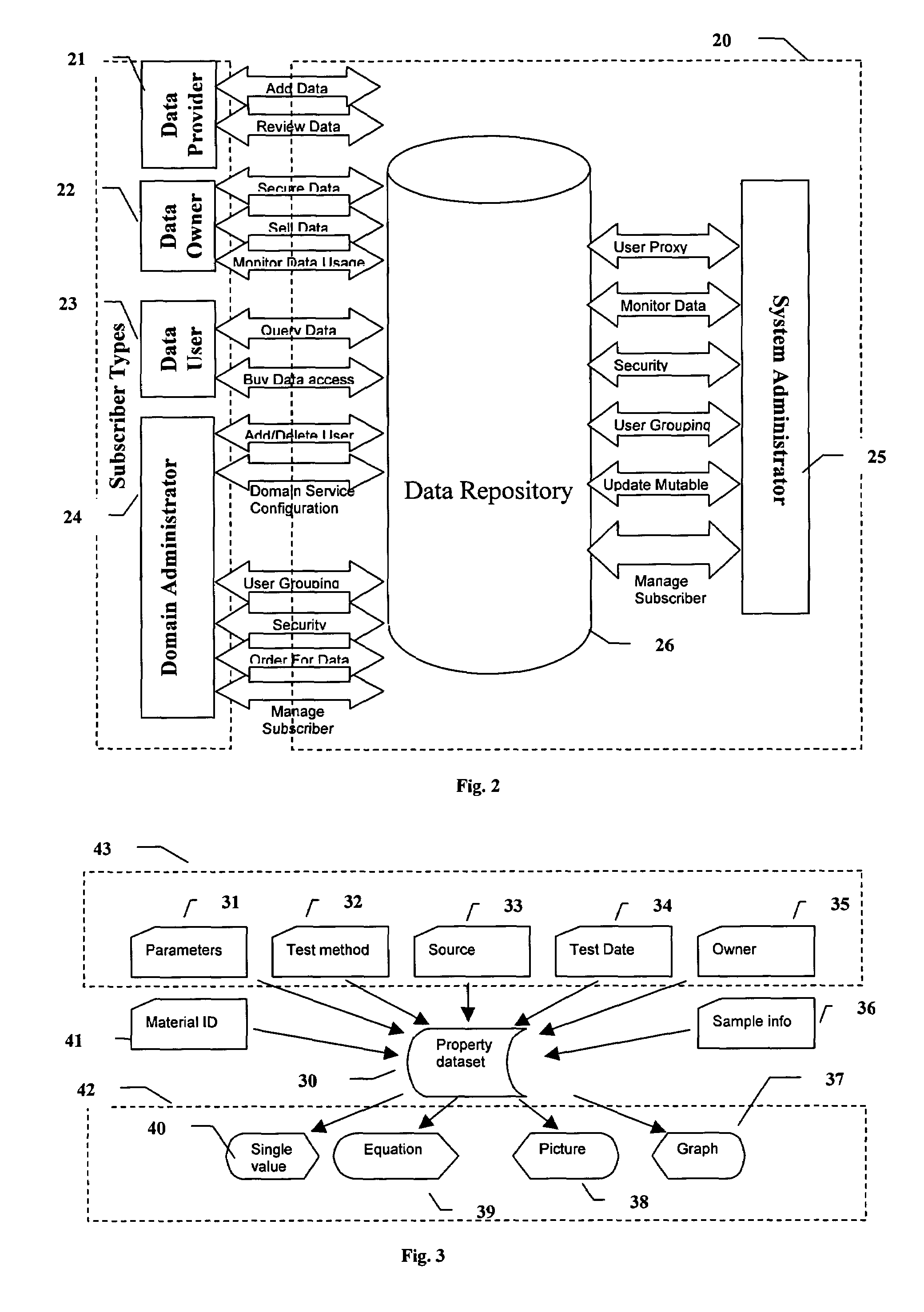
System and method for electronic submission, procurement, and access to highly varied material property data
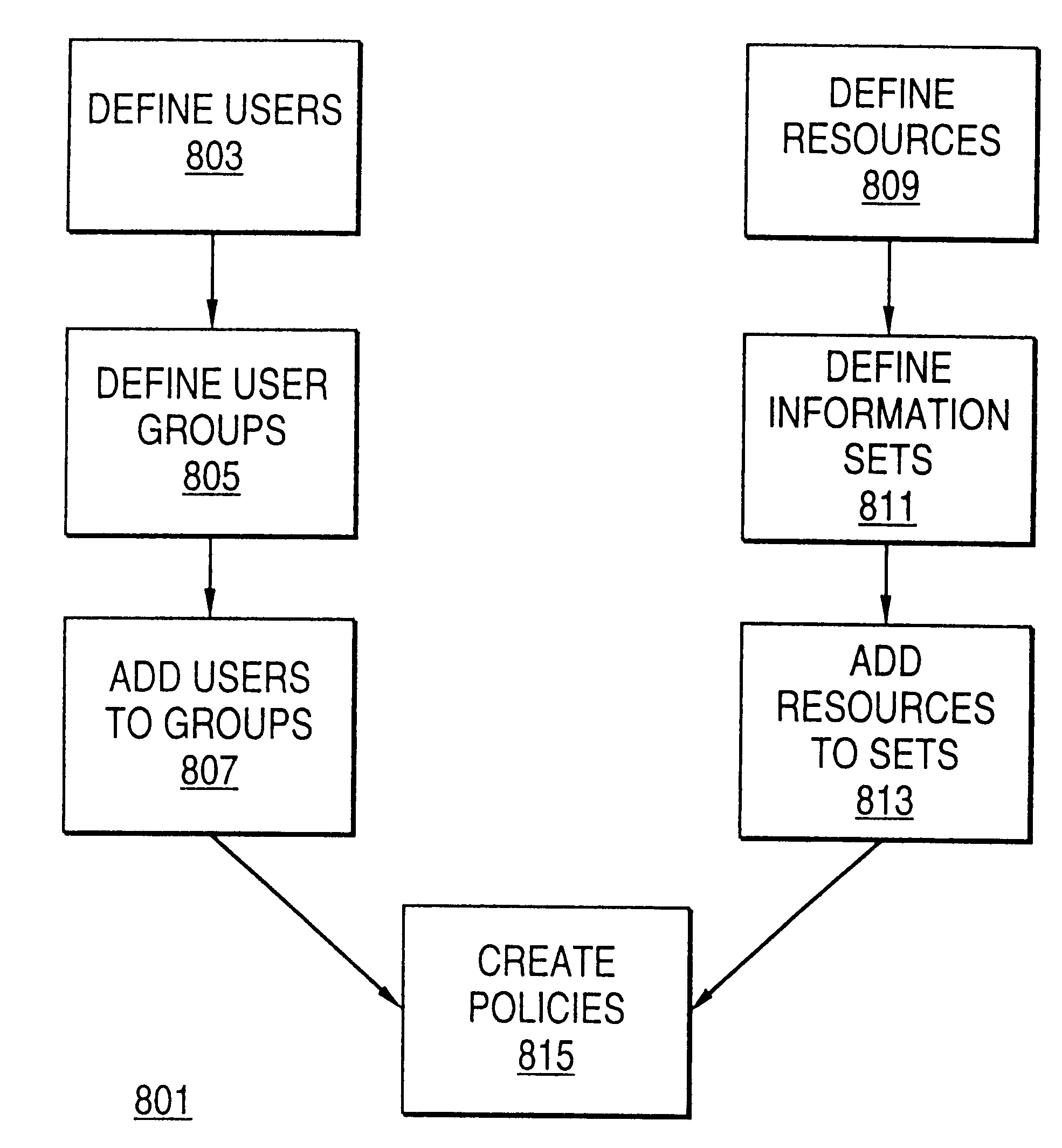
Traceable material property data is maintained in a database and provided to users upon demand. Cohesive and logical definitions of material property datasets are provided that capture the different industry standard facets of a material property. Traceability information includes the manufacturer of the material, the source of the material, the property measuring authority, points of responsibility, facets and constraints of the measurement process. Attributes for dataset ownership and dataset access cost are maintained and only the dataset owner is allowed to update those attributes. The ability to control access to the dataset is provided to the data owner. A dataset's measuring authority is permitted to review and re-grade data. The ability to define groups of users is provided with a designated user having the ability to control group membership and set the group's policies with respect to access of datasets owned by any member of the group. The ability to transfer or trade ownership of data is permitted.
Owner:MATEREALITY
Internet-based shared file service with native PC client access and semantics
A multi-user file storage service and system enables each user of a user group to operate an arbitrary client node at an arbitrary geographic location to communicate with a remote file server node via a wide area network. More than one user of the user group is permitted to access the file group at the remote file server node simultaneously, but the integrity of the files is maintained by controlling access so that each access to one of the files at the remote file server is performed, if at all, on a respective portion of that file as most recently updated at the remote file server node.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
System and method for preference determination
Owner:LOUDDOOR
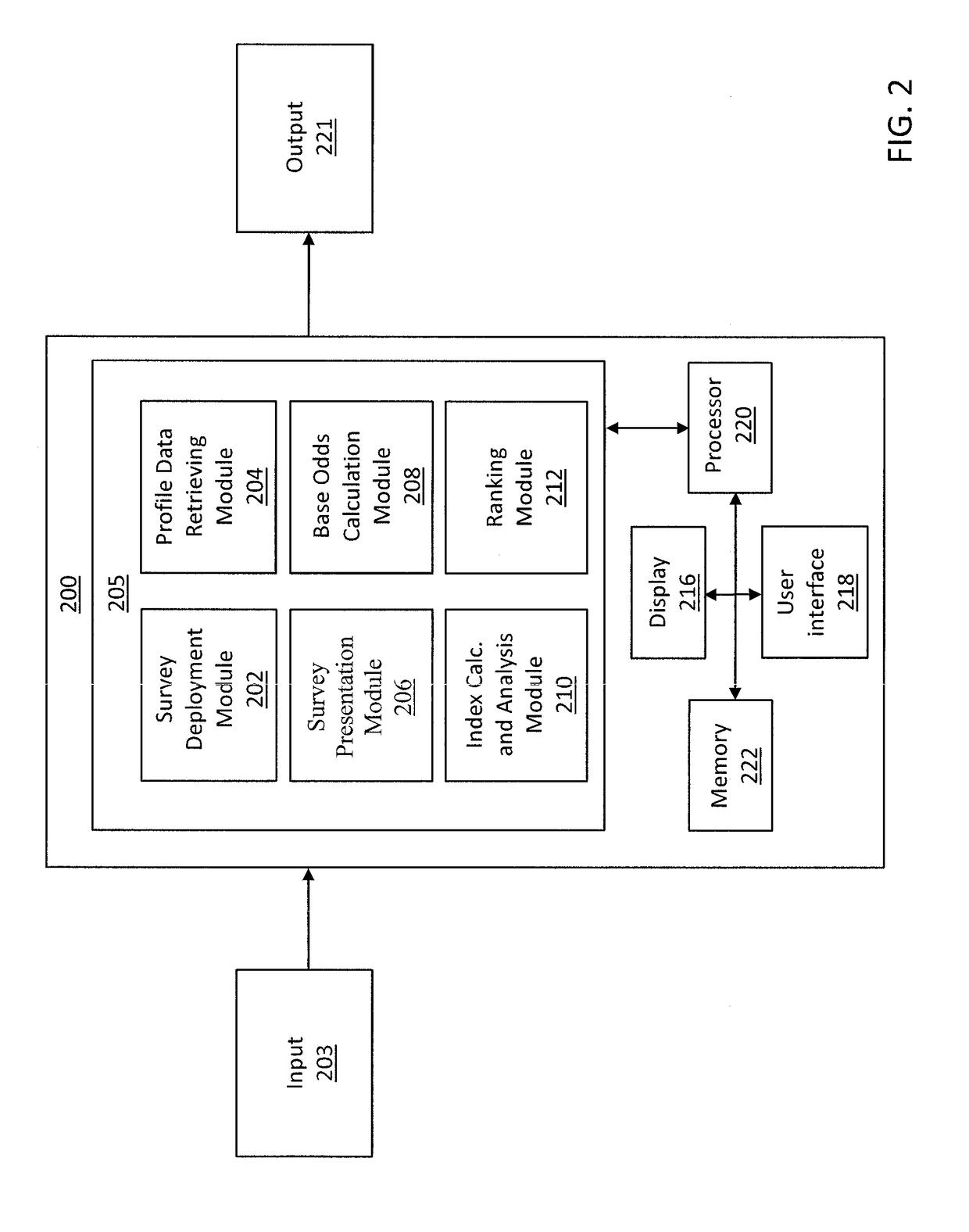
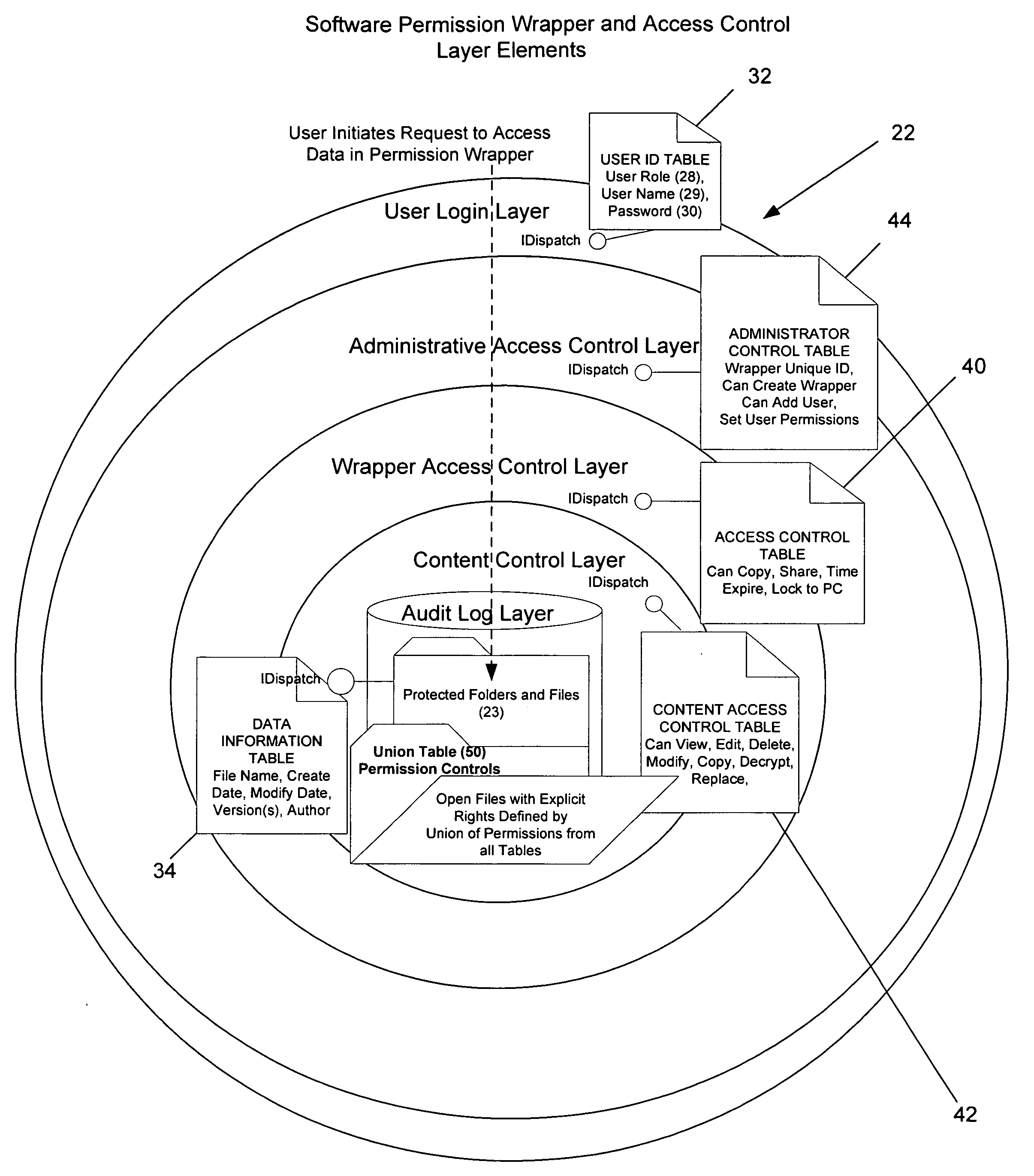
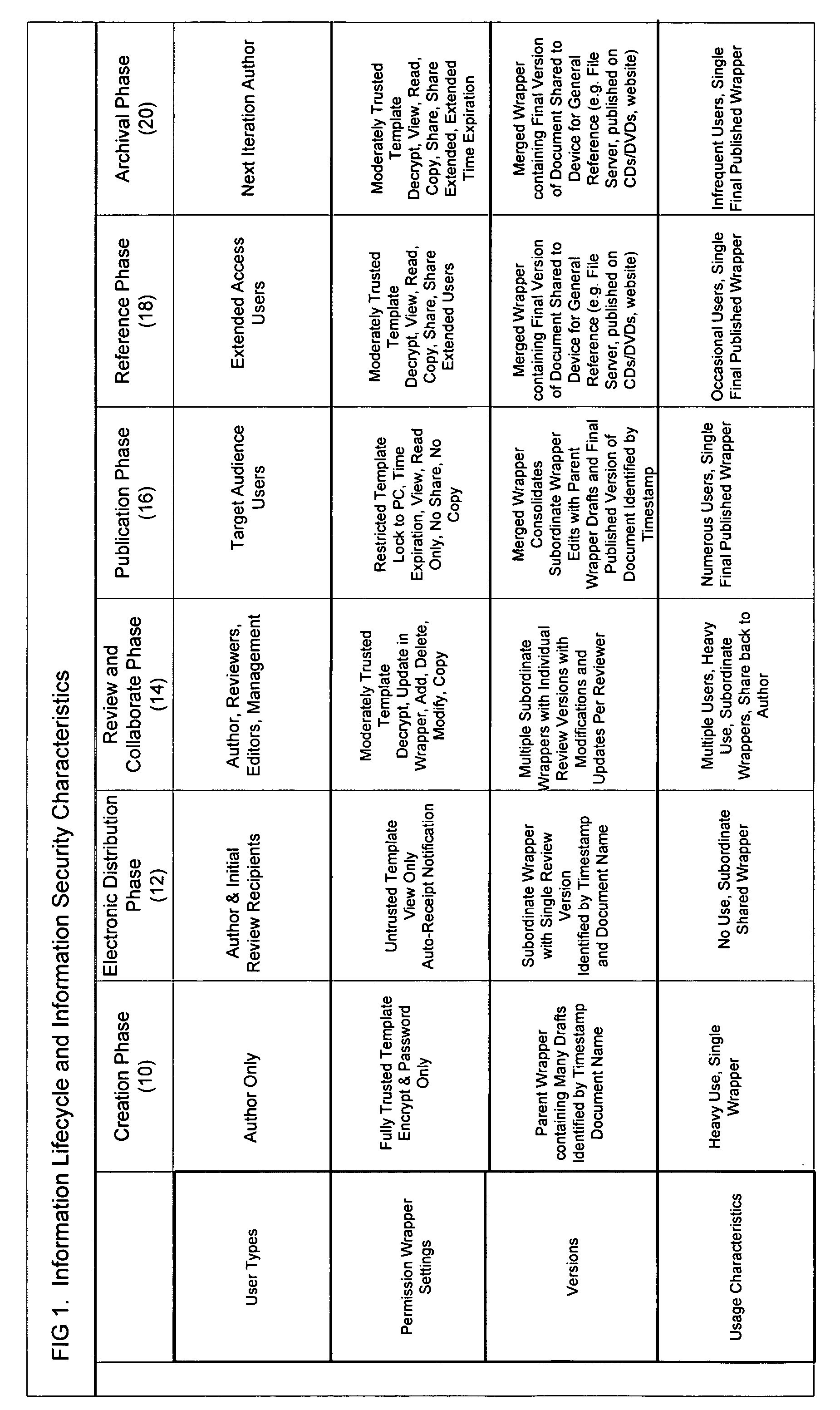
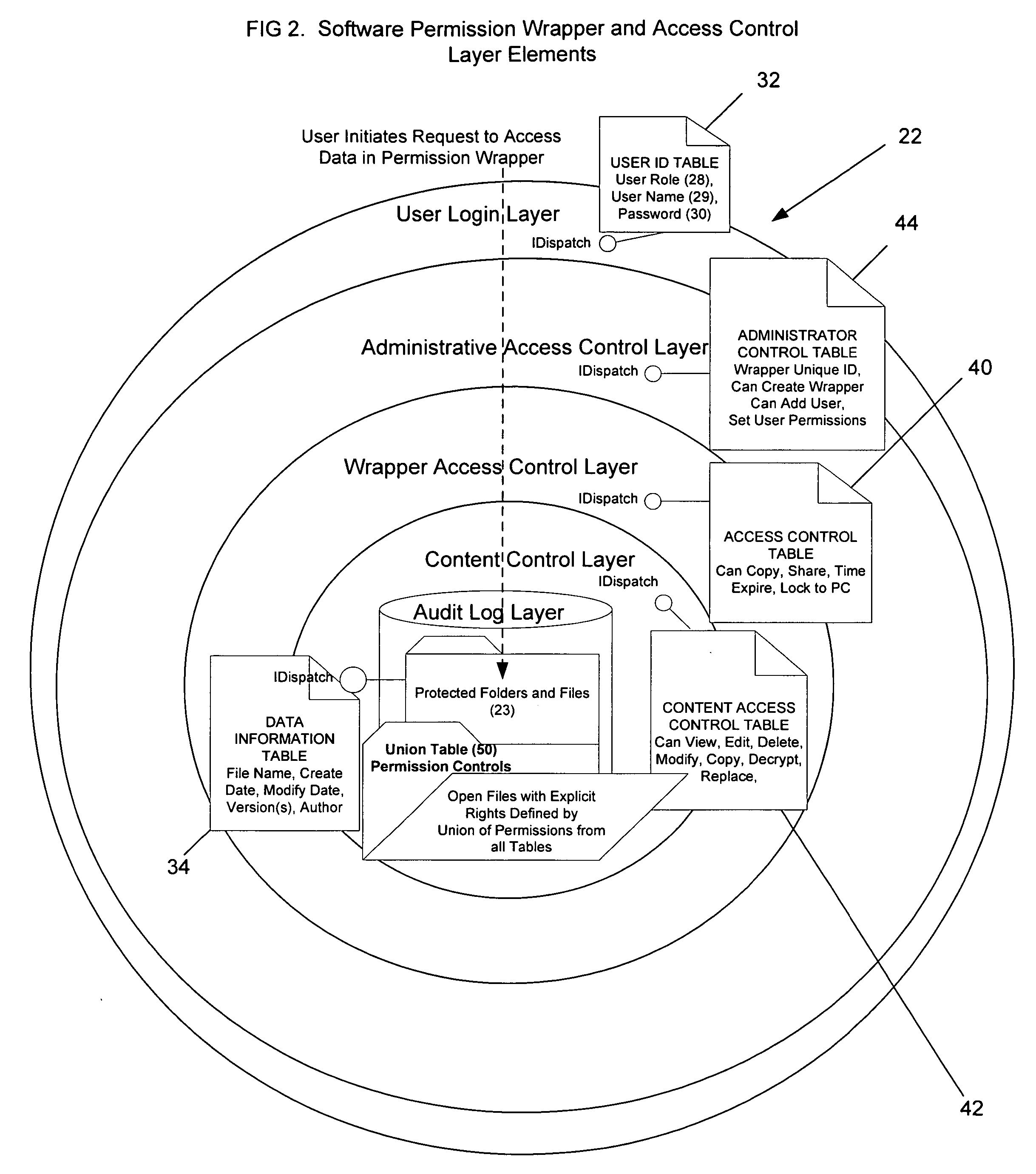
Method and apparatus for automatically detecting sensitive information, applying policies based on a structured taxonomy and dynamically enforcing and reporting on the protection of sensitive data through a software permission wrapper
InactiveUS20060048224A1Reduce spreadMemory loss protectionError detection/correctionInformation controlAutomatic control
The present invention relates to the automatic detection of sensitive digital information, and the identification methods, application and enforcement of information security policies for digital information controlled through a software permission wrapper throughout the useful life of the information. This invention includes a unique taxonomy that defines the policies and rules regarding how the information is controlled automatically throughout its useful lifecycle based on the type of information, the stage of the information lifecycle, the user / group role accessing the information, the locality of the information, and the expected threats to the information. The taxonomy is maintained in a database that associates information security control policies and actions to sensitive data. These policies are enforced through a software permission wrapper that is used to encapsulate sensitive digital information. The software permission wrapper is used to control access and enforce digital rights to the information based on the taxonomy based policies for that information. The permission wrapper can automatically change the protection of the information based on pre-defined protection states that can automatically enforce discretionary access control rights to the sensitive information controlled in the permission wrapper. The changes to the level of protection occur dynamically based on changes in user locality, stage of information lifecycle, and user / group role and the detection of threats. In addition, there is provided an internal audit capability describing what actions the user has performed, where the data is located, with whom and how the data has been shared.
Owner:ENCRYPTX CORP
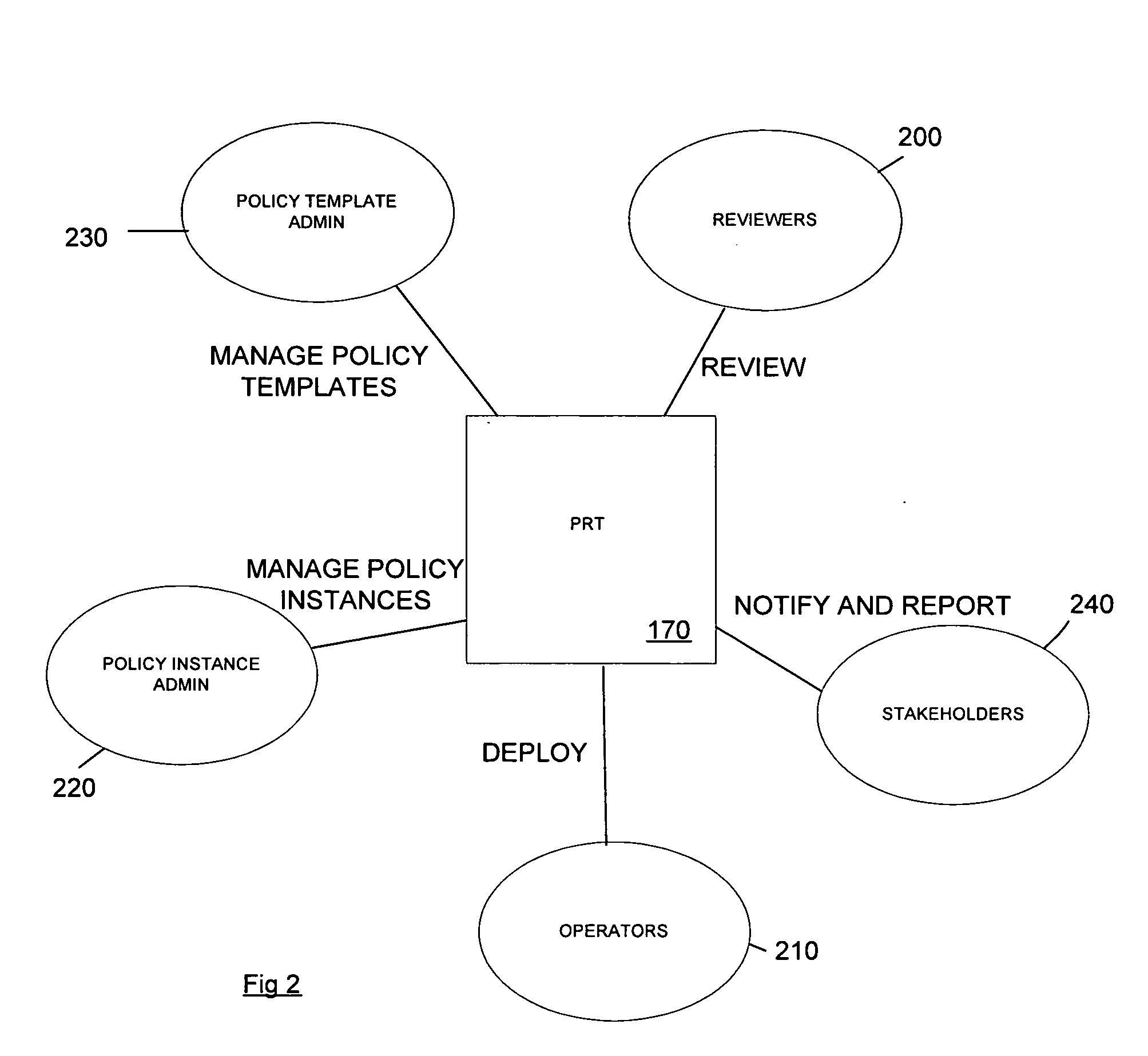
Method and apparatus for role-based security policy management
ActiveUS20050257244A1User identity/authority verificationUnauthorized memory use protectionConfigfsSecurity policy management
A method and corresponding tool are described for security policy management in a network comprising a plurality of hosts and at least one configurable policy enforcement point. The method, comprises creating one or more policy templates representing classes of usage control models within the network that are enforceable by configuration of the policy enforcement points; creating one or more policy instances, each based on one of the templates and instantiating the template for identified sets of hosts within the network to which the usage control model is to be applied, deploying the policy instances by generating and providing one or more configuration files for provisioning corresponding policy enforcement points within the network. Access to the templates and policy instances is controlled so that the policy templates are only modifiable by a first predeterminable user group, the policy instances are only modifiable by the first or a second predeterminable user group and the policy instances are only deployable by a third predeterminable user group.
Owner:VALTRUS INNOVATIONS LTD +1
System for inserting/overlaying markers, data packets and objects relative to viewable content and enabling live social networking, n-dimensional virtual environments and/or other value derivable from the content
InactiveUS20090165140A1Low costReduced flexibilityDigital data processing detailsAnalogue secracy/subscription systemsNetwork packetSocial web
A system by which a User can associate selectable Markers, Data Packets and / or Objects with Content. The Content may generally be distributed electronically, and the Markers allow for insertion and / or overlay of Objects when the Content is selected for viewing by a Viewer. Objects and Data Packets are generally provided by a User, Promoter, Host, Service, or other entity to convey information to a Viewer. A Service provides tools and capabilities to both the User and the Promoter to facilitate their respective actions according to embodiments of the invention, including enabling the creation of live social networks (such as those linked to a specific Service provider, a specific User group, activities by a specific Promoter, and / or to specific Data Packets) and the creation of n-dimensional Virtual Environments.
Owner:ADDNCLICK
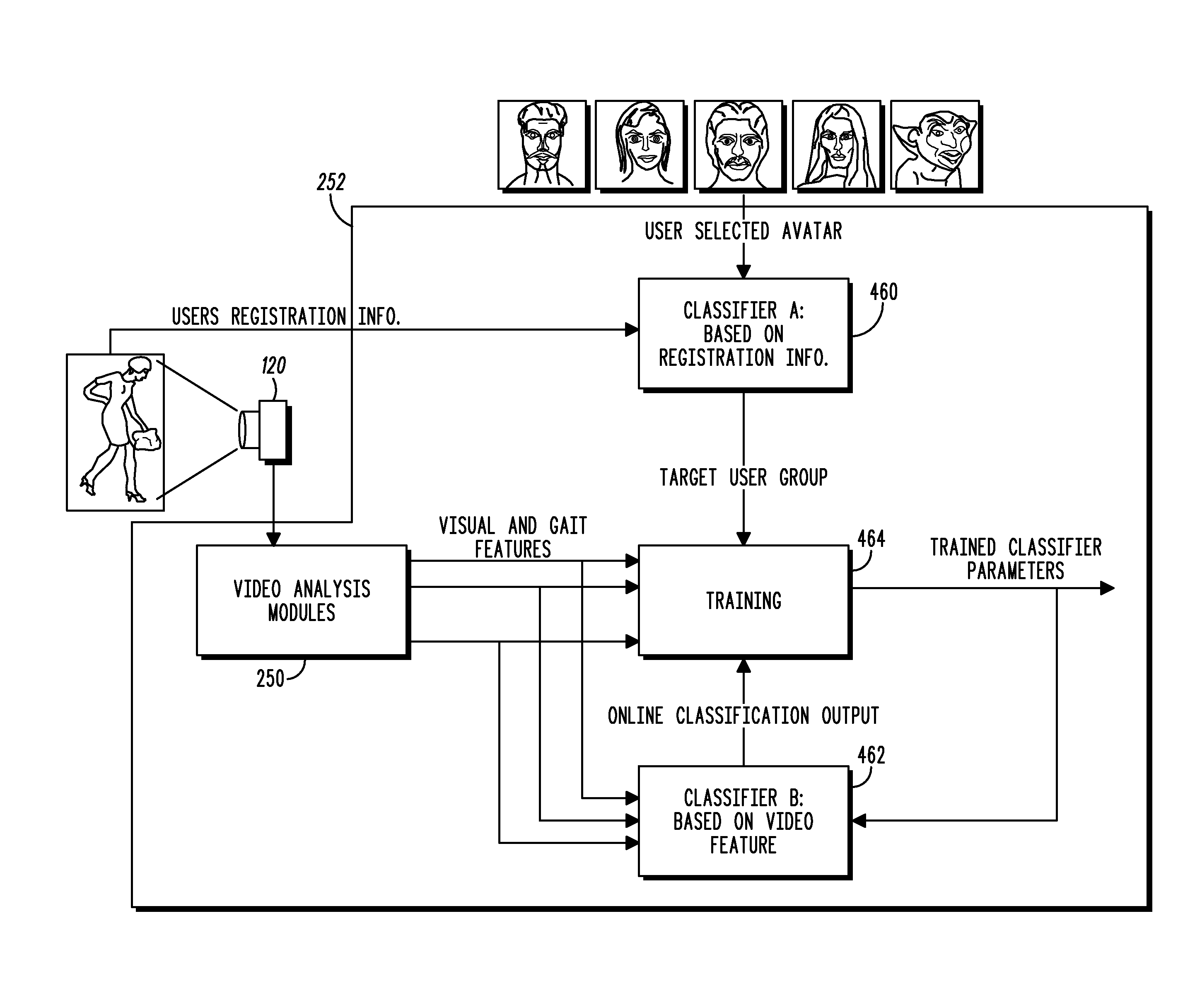
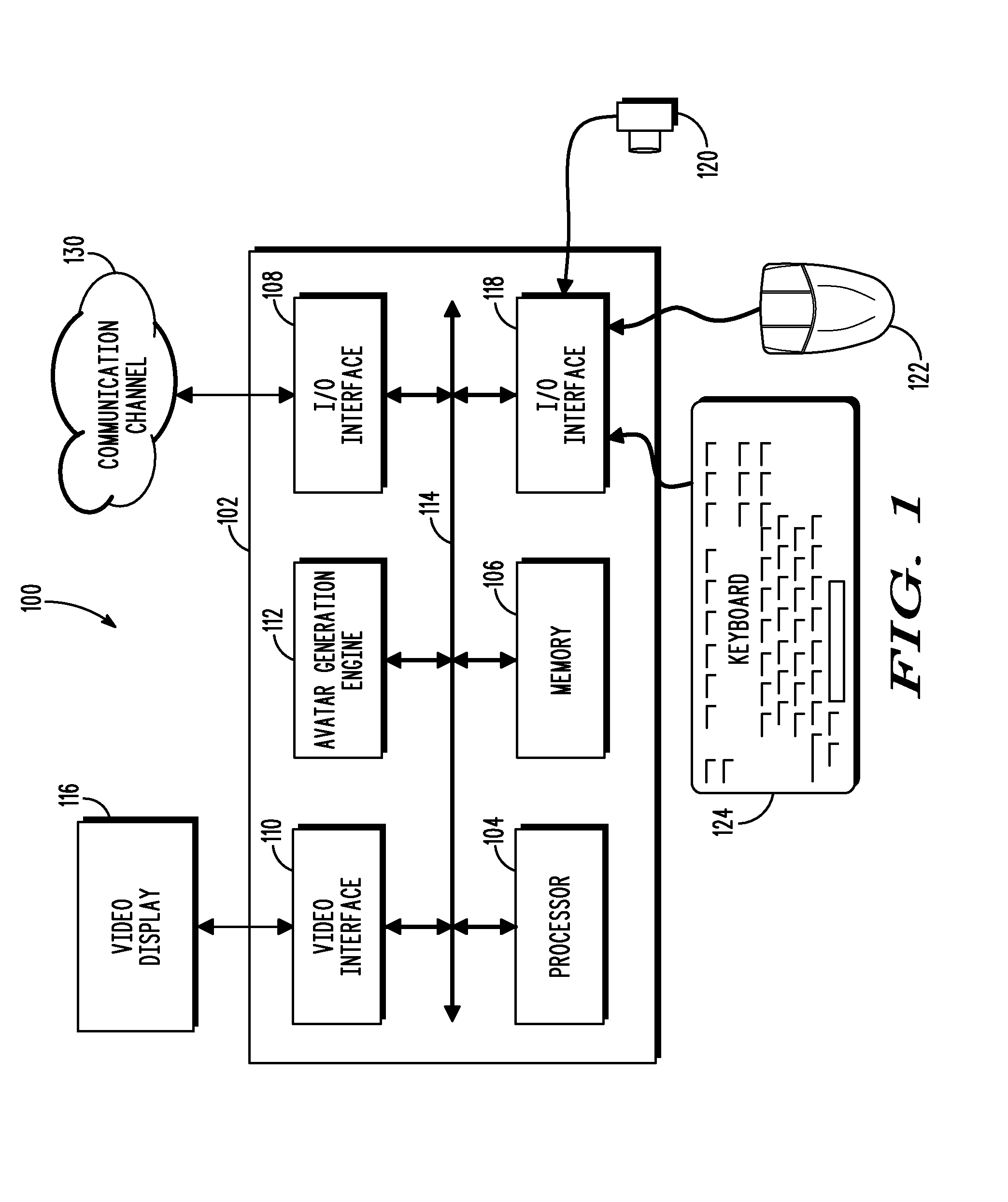
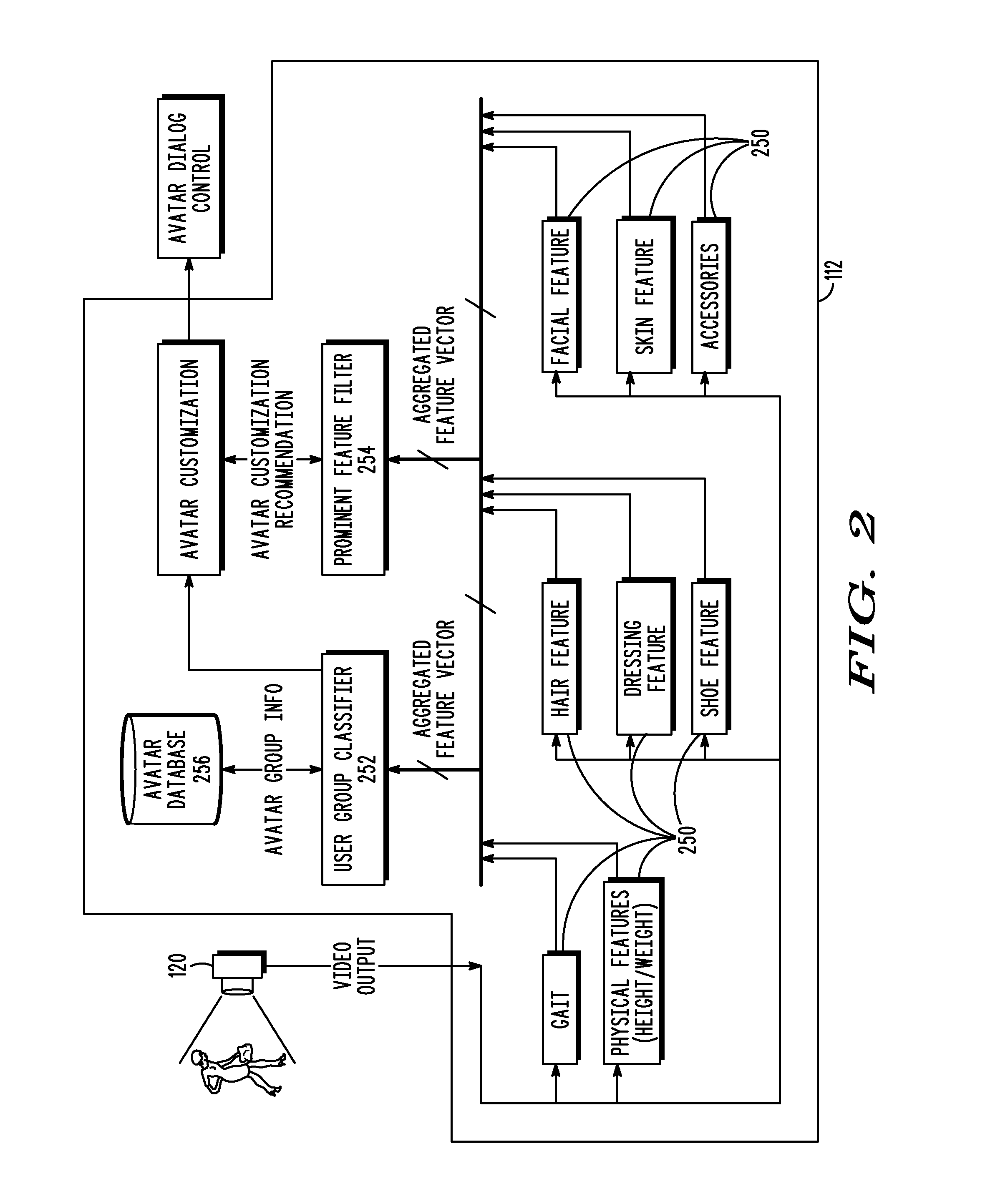
Apparatus and Methods for Selecting and Customizing Avatars for Interactive Kiosks
InactiveUS20080158222A1Digital data information retrievalImage data processing detailsFeature vectorInteractive kiosk
A method of generating an avatar for a user may include receiving image data of a user from a camera, generating feature vectors for a plurality of features of a user, associating the user with a likely user group selected from a number of defined user groups based on the feature vectors, and assigning an avatar based on the associated user group.
Owner:MOTOROLA MOBILITY LLC
Data access control apparatus for limiting data access in accordance with user attribute
InactiveUS6275825B1Reduce loadPrevent setting errorsData processing applicationsDigital data processing detailsData access controlRights management
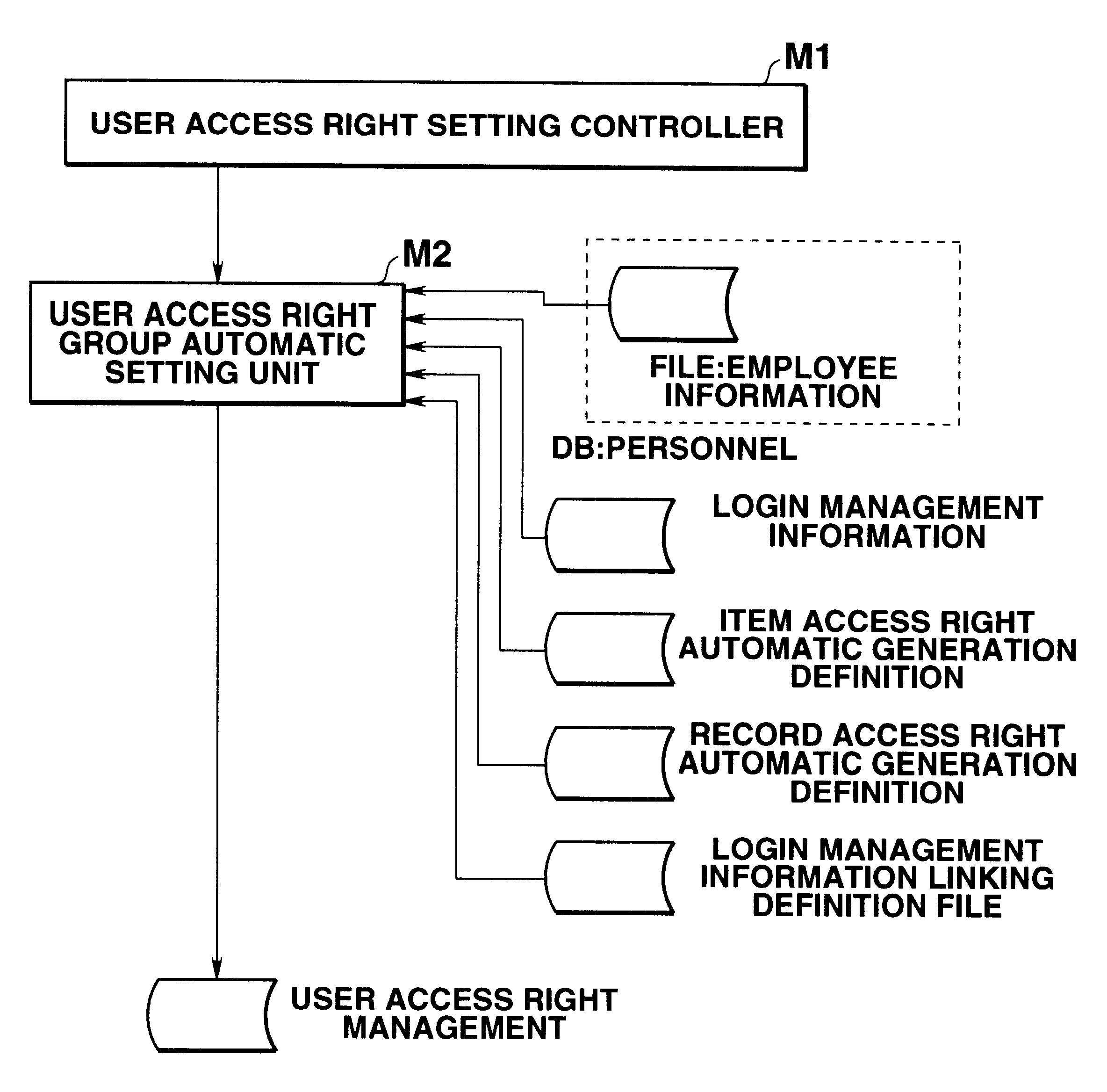
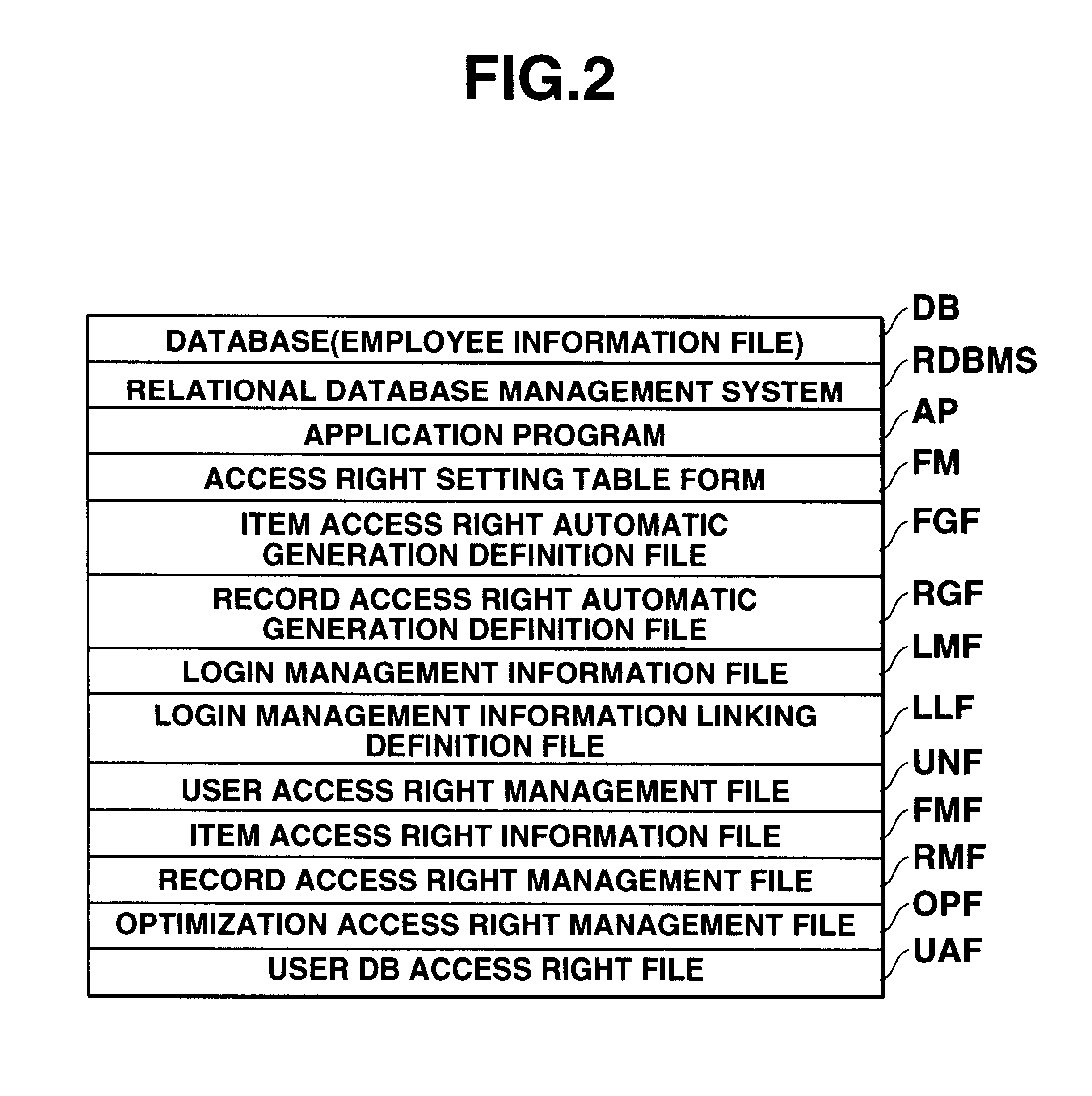
This invention provides a data access control apparatus arranged to automatically set access right information limiting data access, in accordance with a user attribute when a user accesses a database. In setting, for a plurality of users, access right information corresponding to each user, the load on an operator can be reduced, and access right information setting errors can be prevented. An automatic setting unit reads out information from a login management information file and an employee information file on the basis of definition information of a definition files to automatically generate a user access right management file which stores a login ID, an item access right, and a record access right group code for each user. When a login ID is input in accessing the employee information file, a setting controller refers to the management file to determine a user group to which the user belongs and an access enabled / disabled state of the data on the basis of the access right made to correspond to this user group.
Owner:CASIO COMPUTER CO LTD
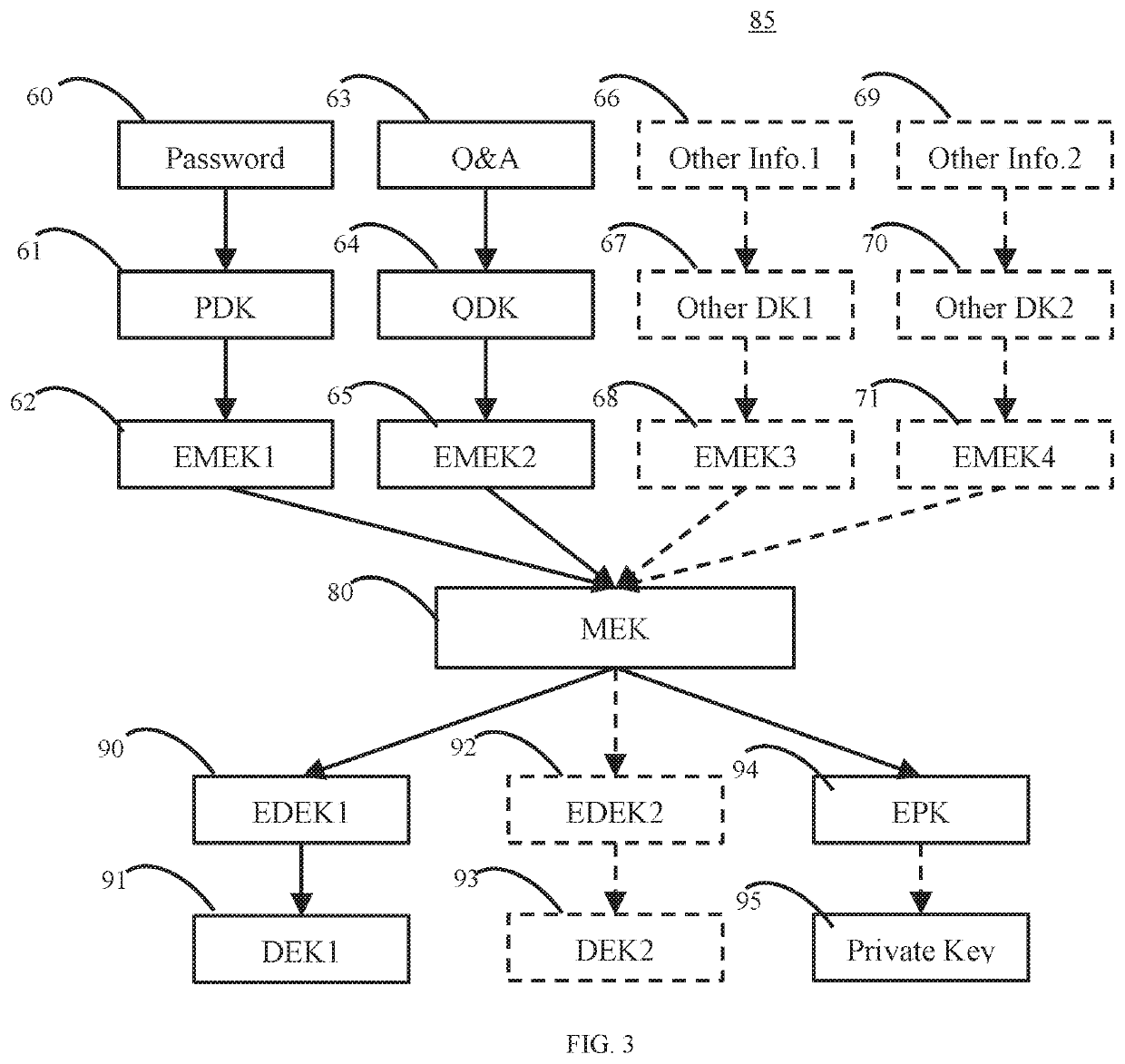
Secure and zero knowledge data sharing for cloud applications
ActiveUS10608817B2Key distribution for secure communicationMultiple keys/algorithms usageData setInternet privacy
Disclosed is a zero-knowledge distributed application configured to securely share information among groups of users having various roles, such as doctors and patients. Confidential information may be encrypted client-side, with private keys that reside solely client side. Encrypted collections of data may be uploaded to, and hosted by, a server that does not have access to keys suitable to decrypt the data. Other users may retrieve encrypted data from the server and decrypt some or all of the data with keys suitable to gain access to at least part of the encrypted data. The system includes a key hierarchy with multiple entry points to a top layer by which access is selectively granted to various users and keys may be recovered.
Owner:MASIMO CORP
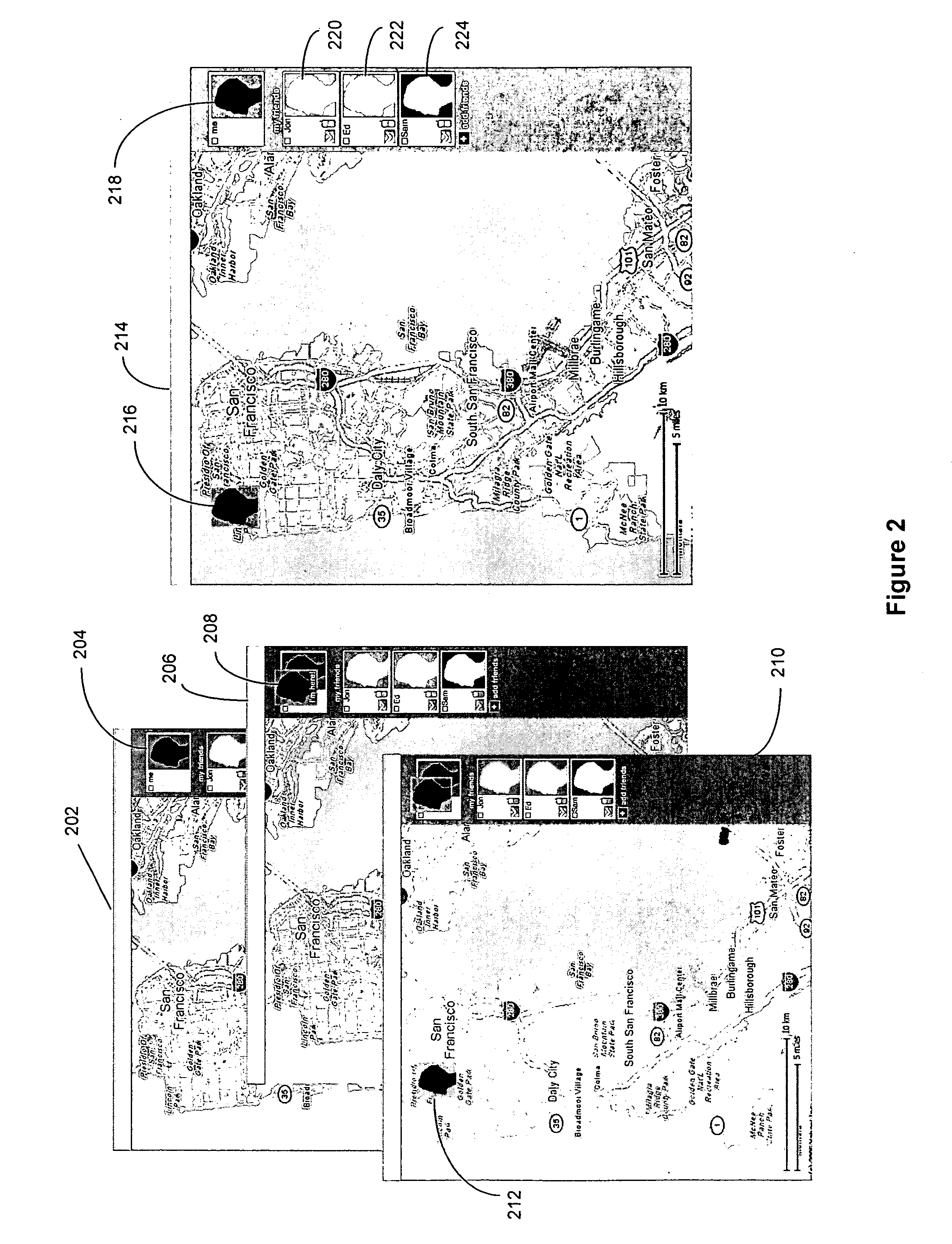
Method and system for communicating with multiple users via a map over the internet
A method, device, and system for communicating with multiple users via a map over the Internet are disclosed. The device includes a processor for executing computer programs, a memory for storing data, an input module for entering user commands, a communication module for transmitting and receiving data, and a display for showing information on a screen. The device further includes logic for selecting a group of users, logic for creating a map to share among the group of users, logic for displaying locations of the group of users on the map, and logic for broadcasting changes of a user's location to the group over the Internet.
Owner:R2 SOLUTIONS
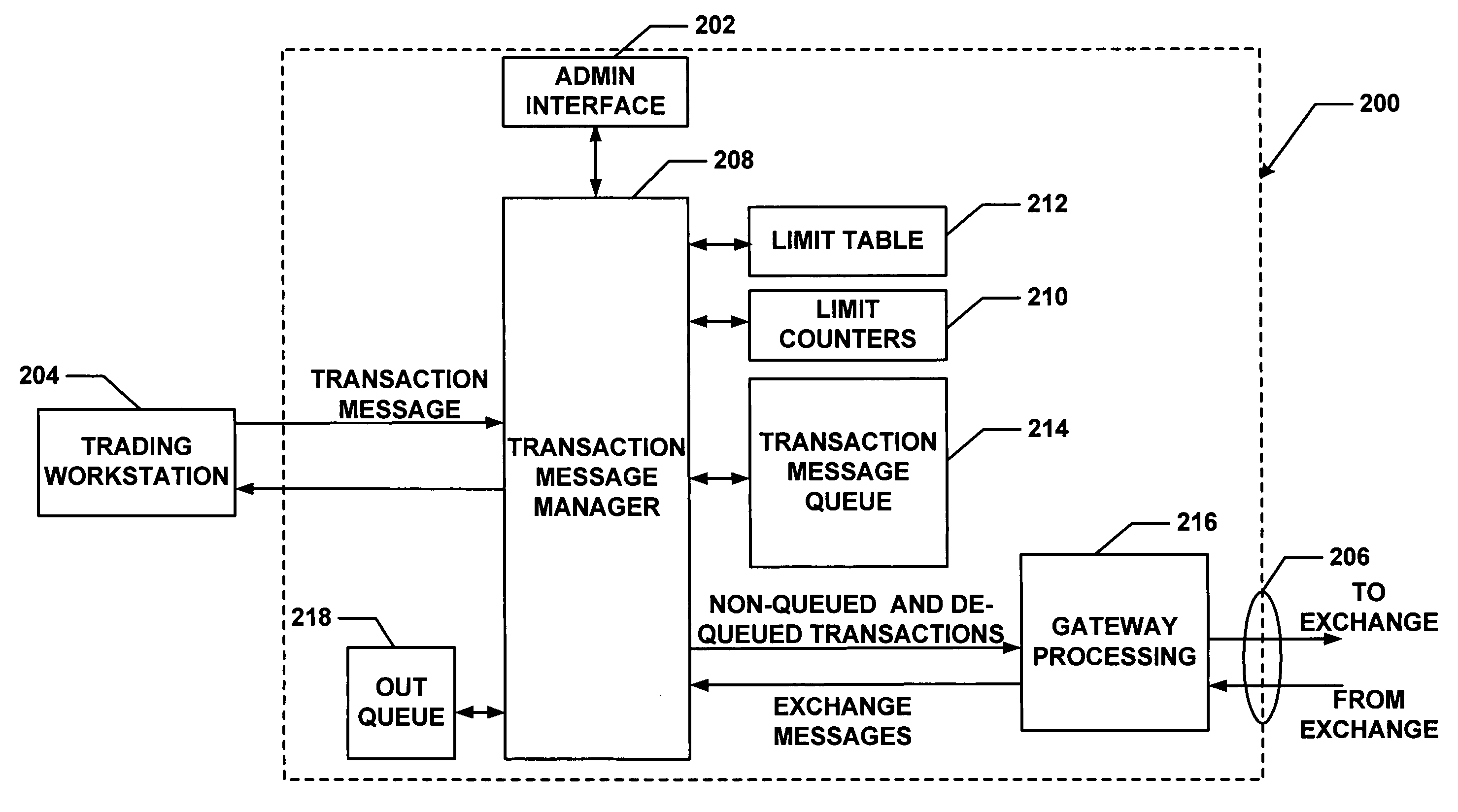
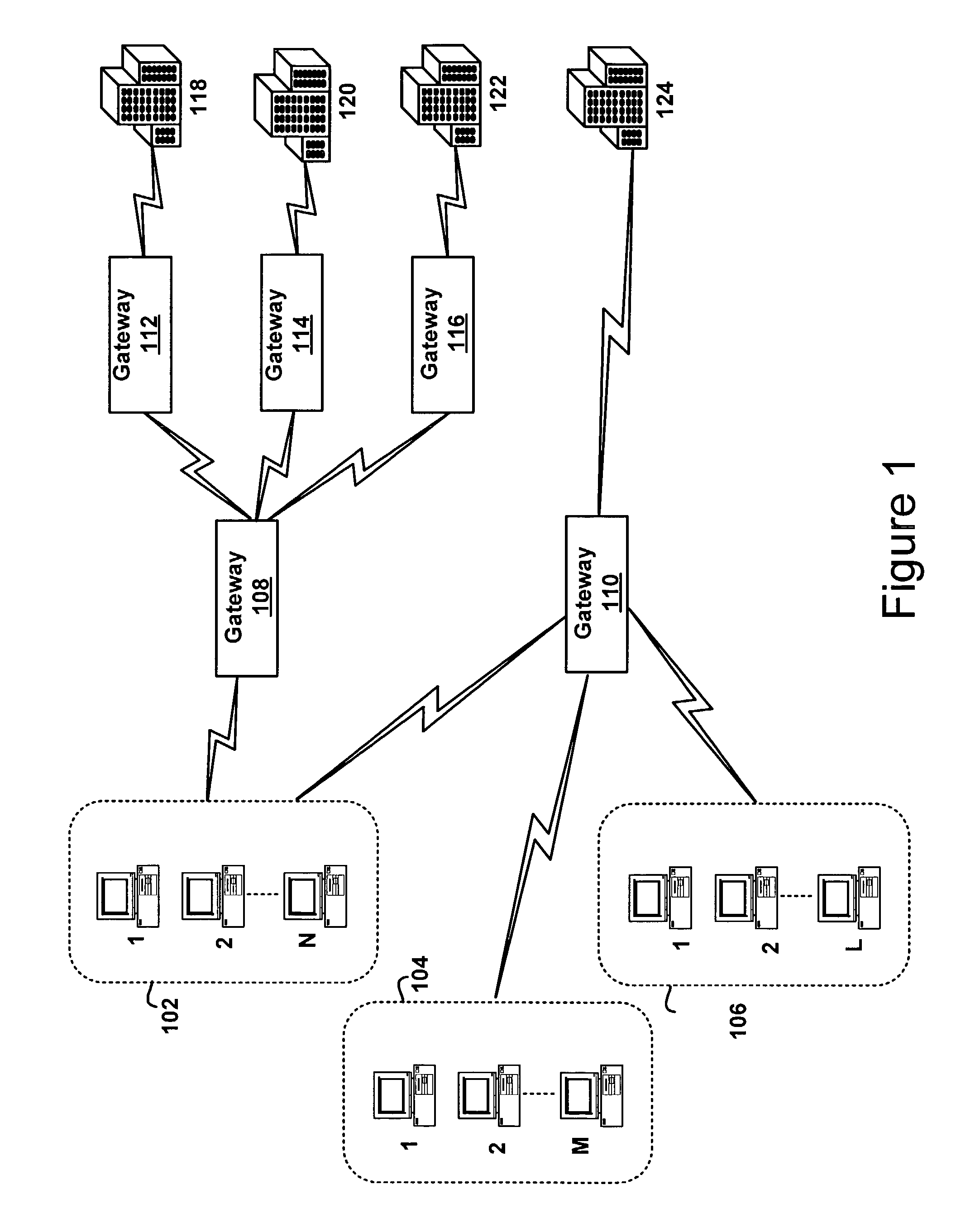
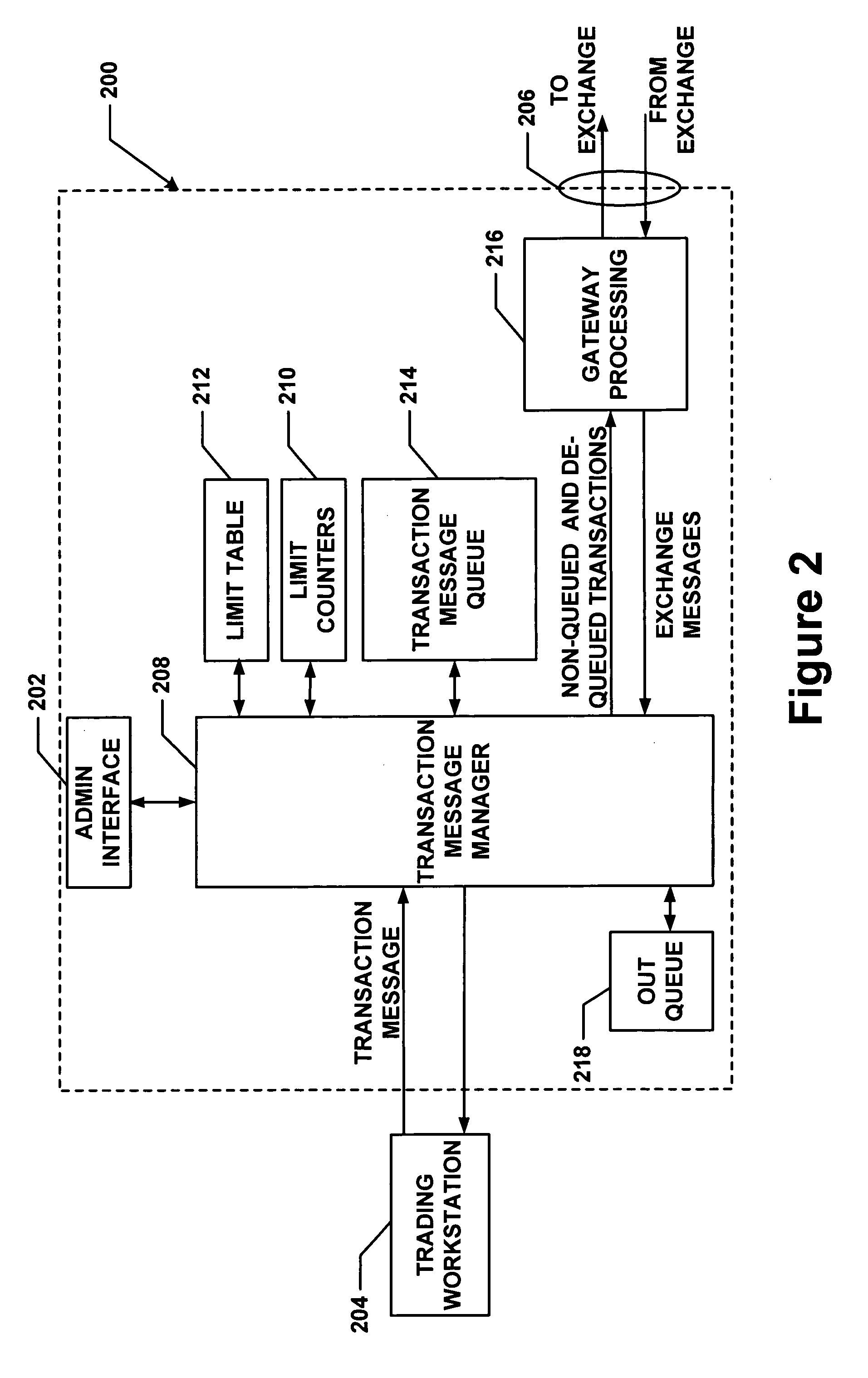
Method and apparatus for message flow and transaction queue management
Management of transaction message flow utilizing a transaction message queue. The system and method are for use in financial transaction messaging systems. The system is designed to enable an administrator to monitor, distribute, control and receive alerts on the use and status of limited network and exchange resources. Users are grouped in a hierarchical manner, preferably including user level and group level, as well as possible additional levels such as account, tradable object, membership, and gateway levels. The message thresholds may be specified for each level to ensure that transmission of a given transaction does not exceed the number of messages permitted for the user, group, account, etc.
Owner:TRADING TECH INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com