Patents
Literature
105 results about "Security policy management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
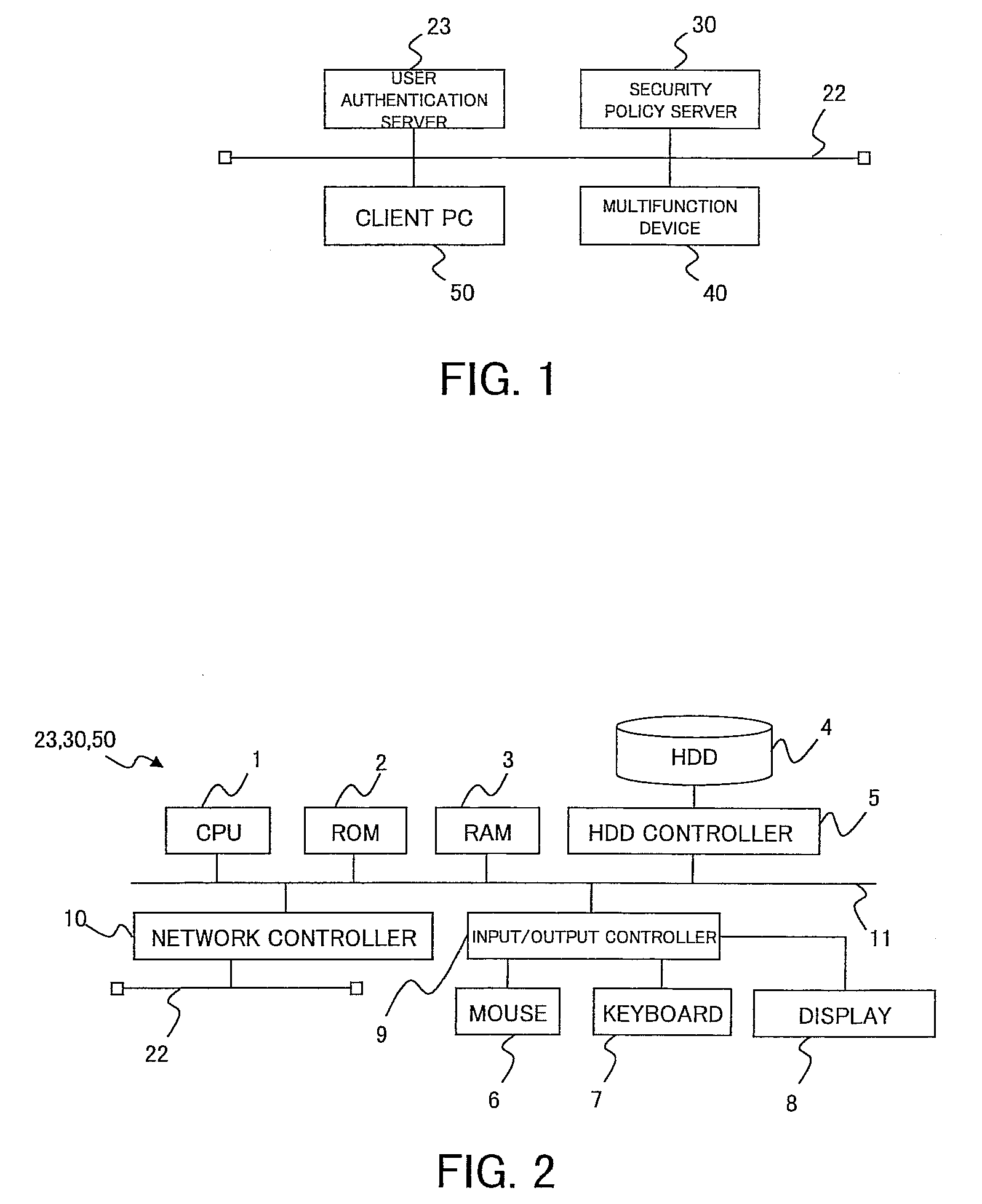
A security policy management program is associated with the management of security policies within an environment. The goal of this program is to keep security policies updated, relevant, and standardized within an environment. The following elements and processes are generally associated with security policy management.
Method and apparatus for security policy management
InactiveUS20050283823A1Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
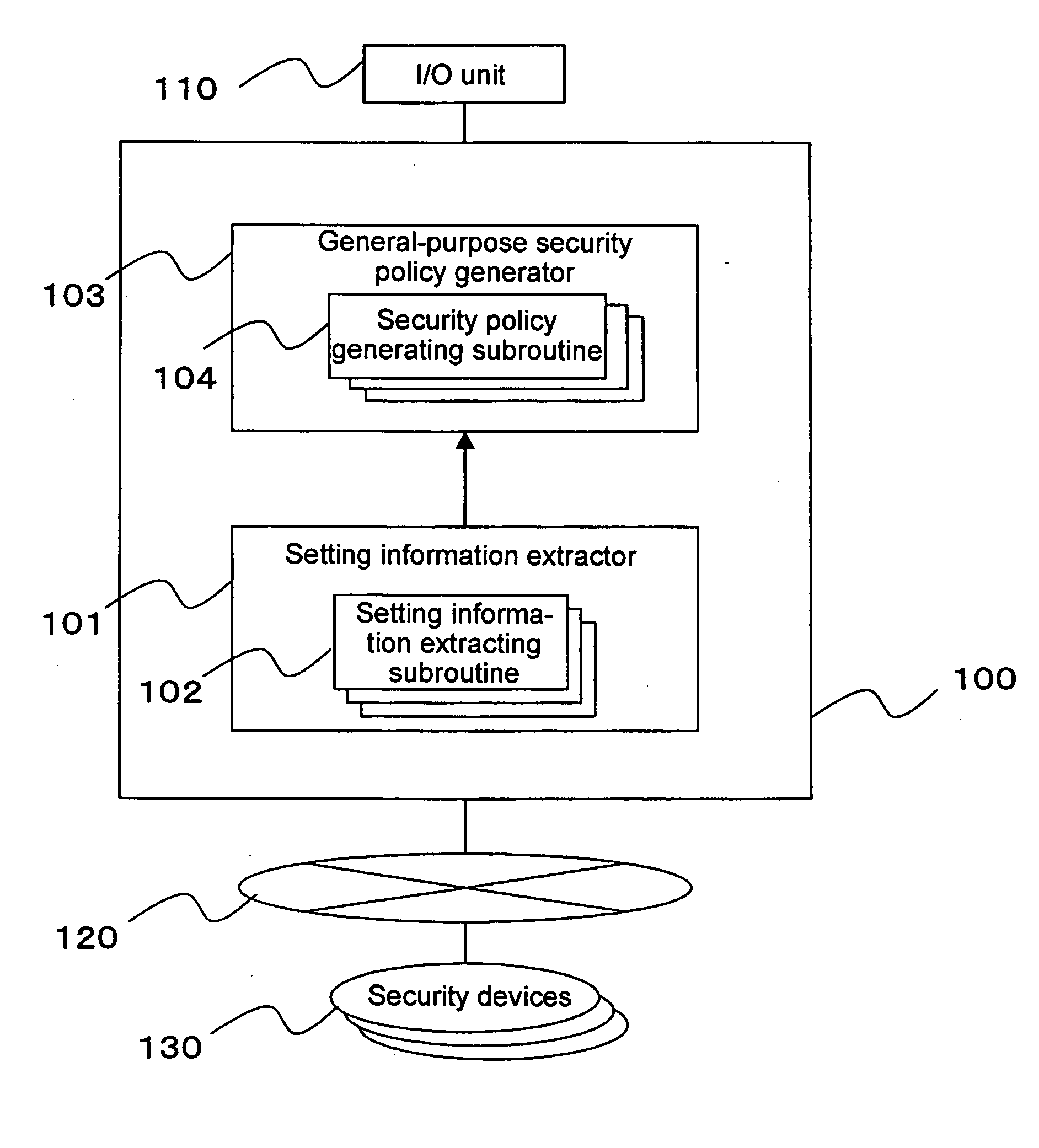
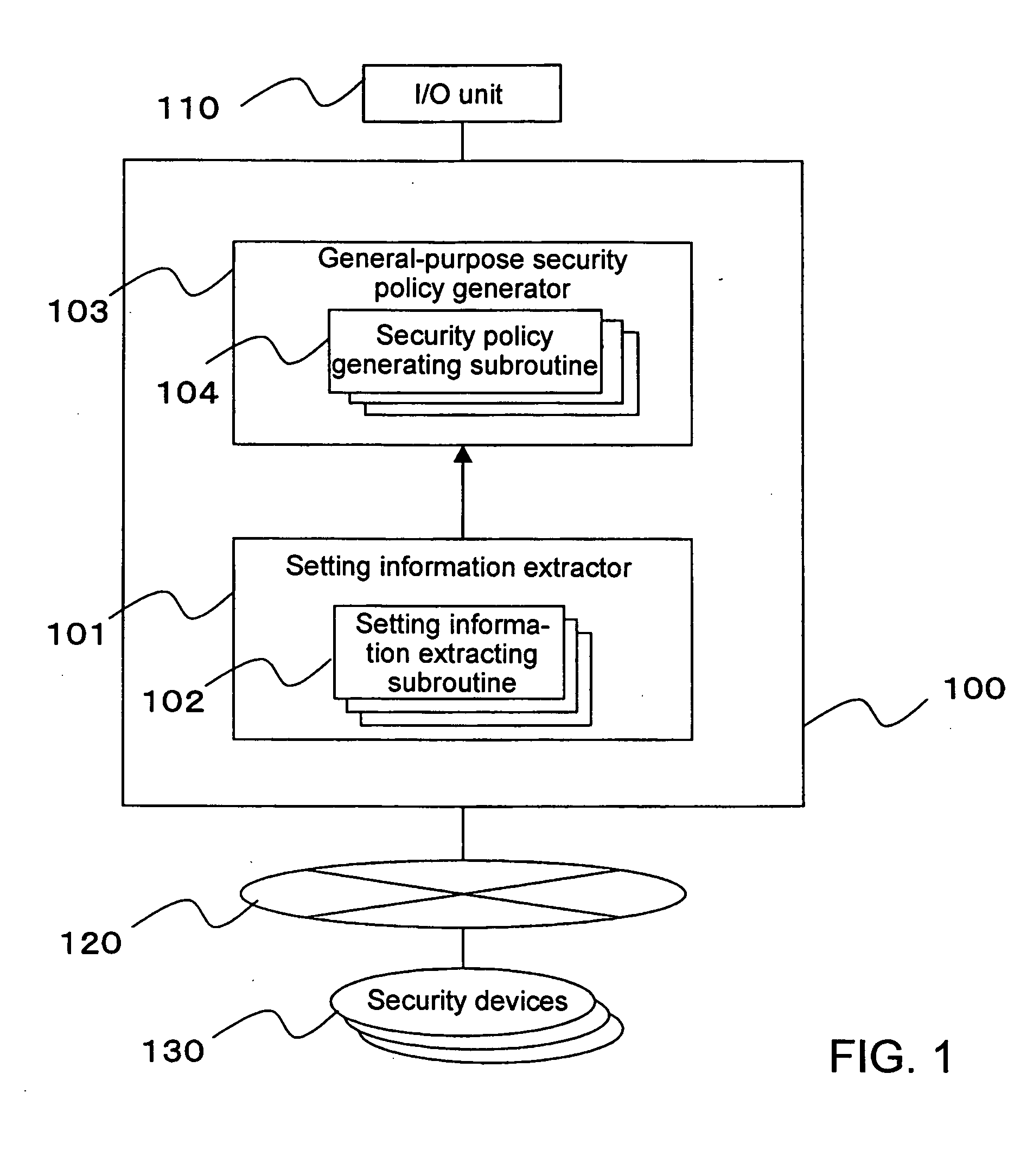
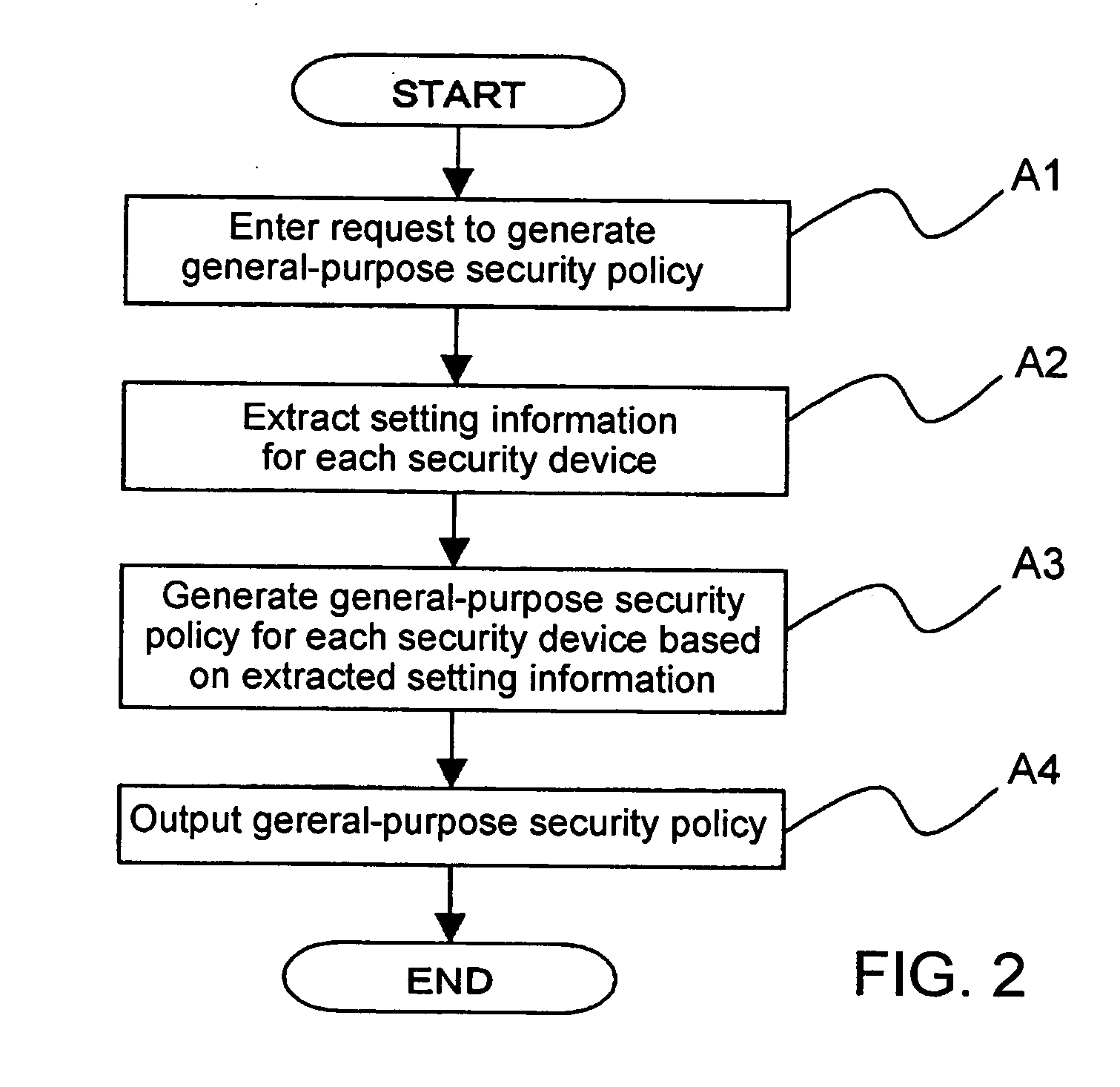
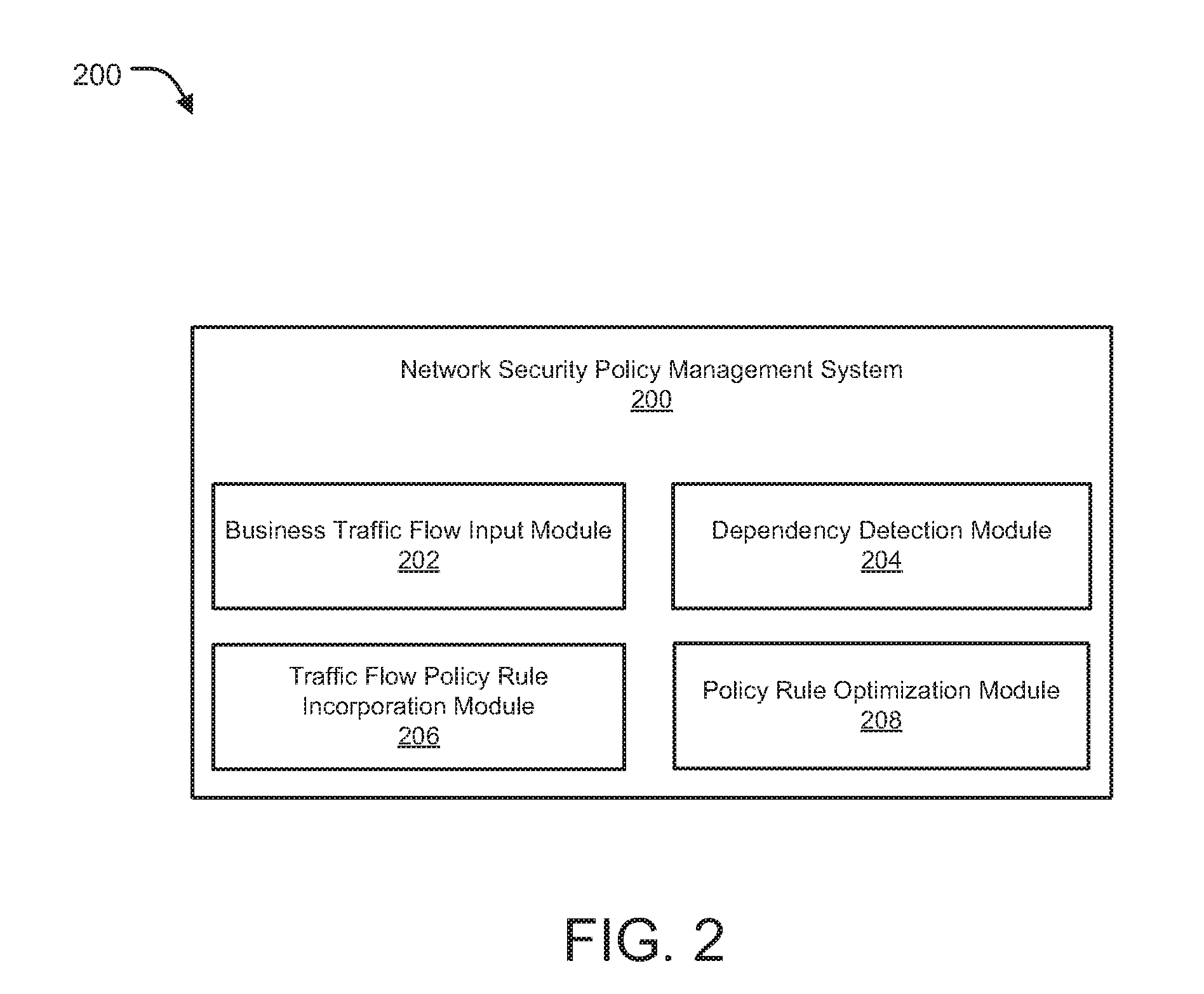
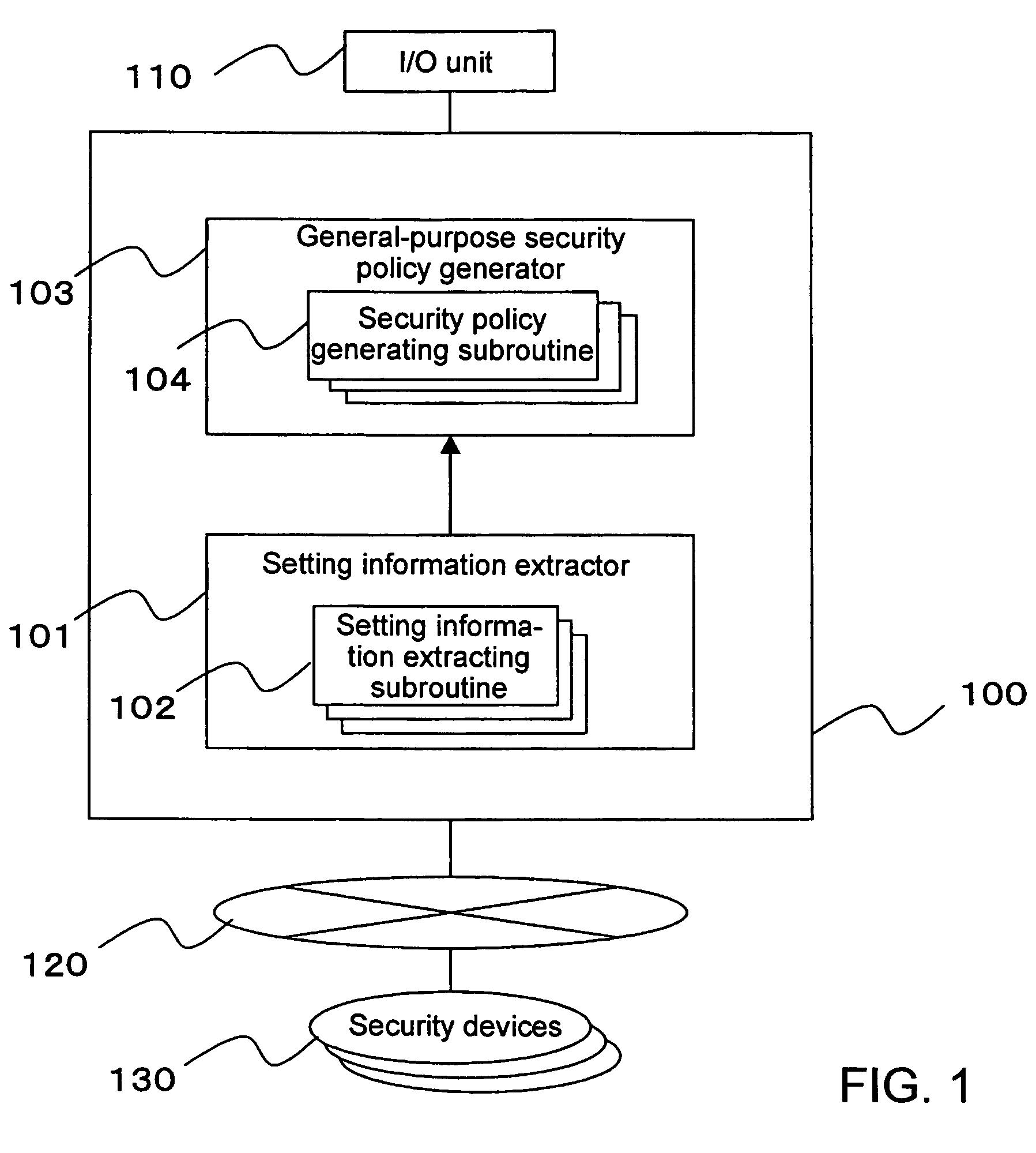
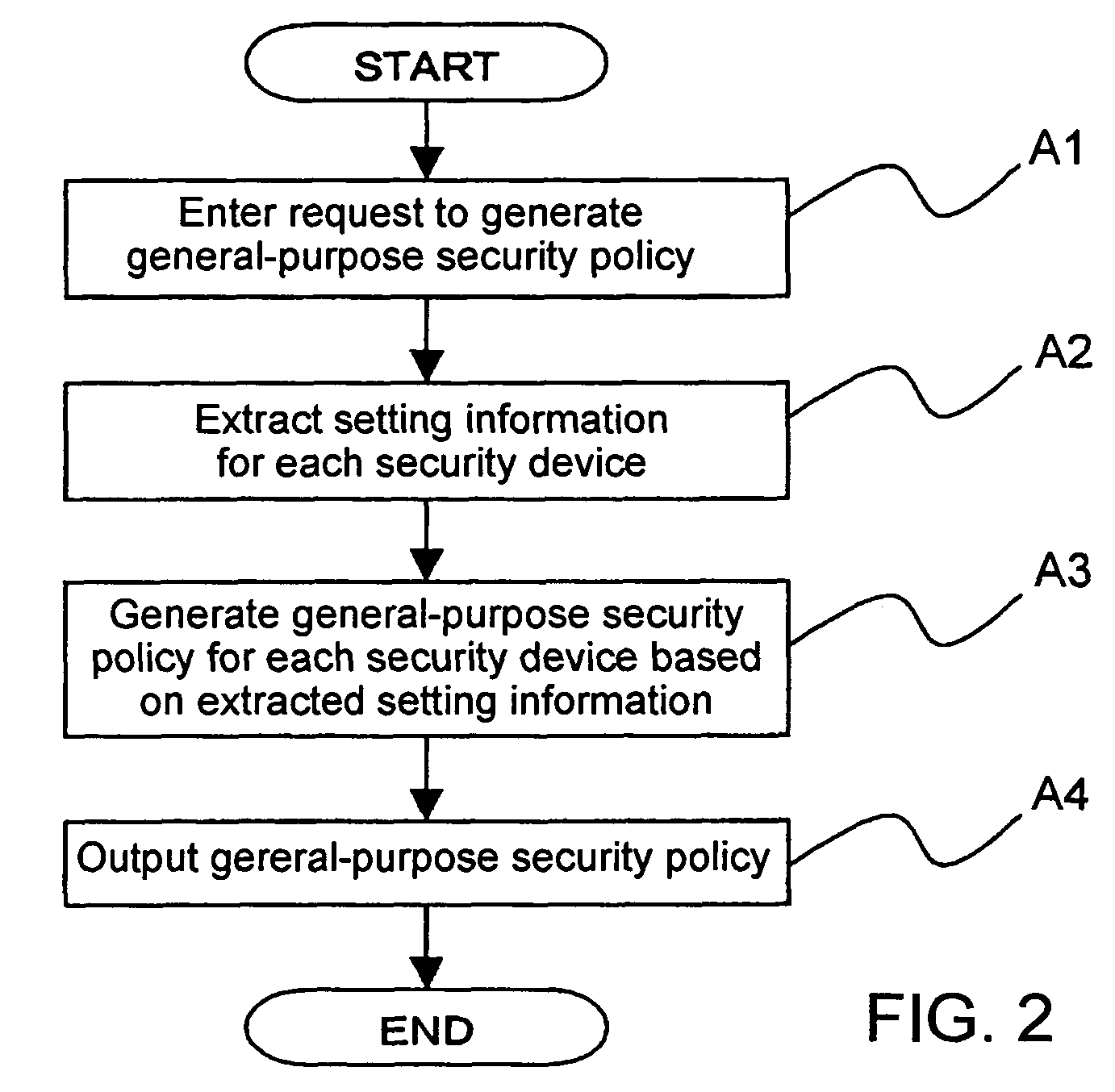
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
Method and apparatus for role-based security policy management
ActiveUS20050257244A1User identity/authority verificationUnauthorized memory use protectionConfigfsSecurity policy management
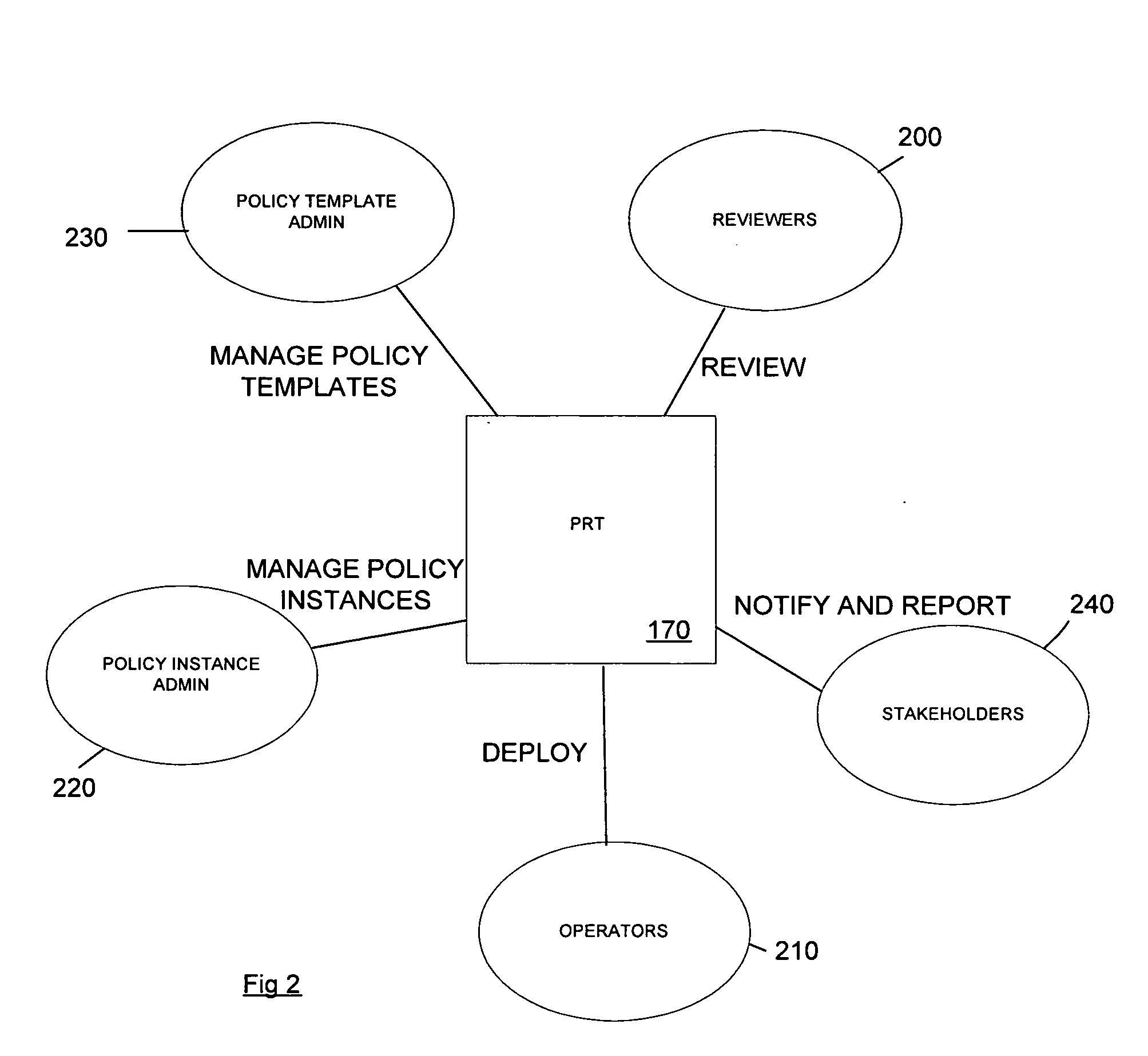
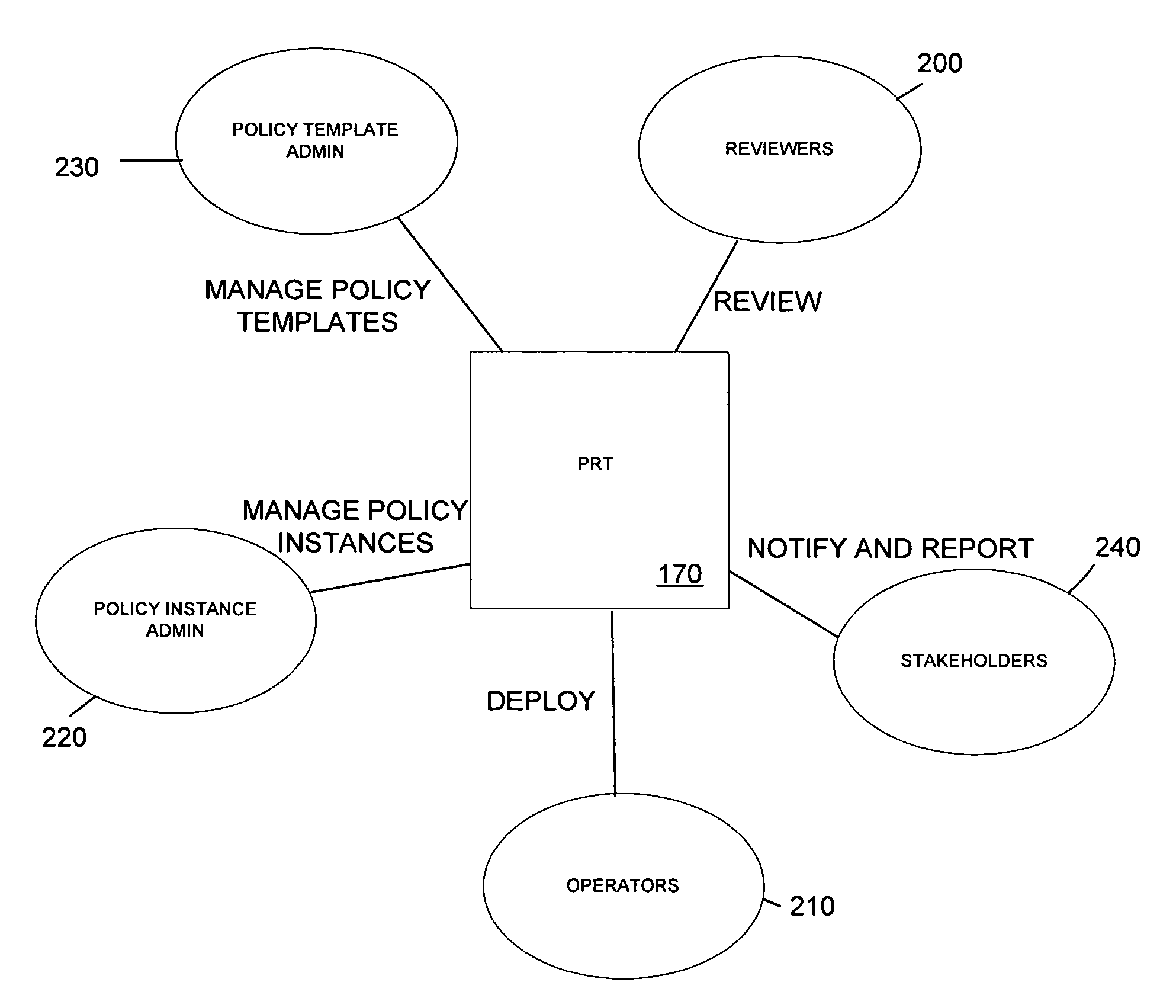
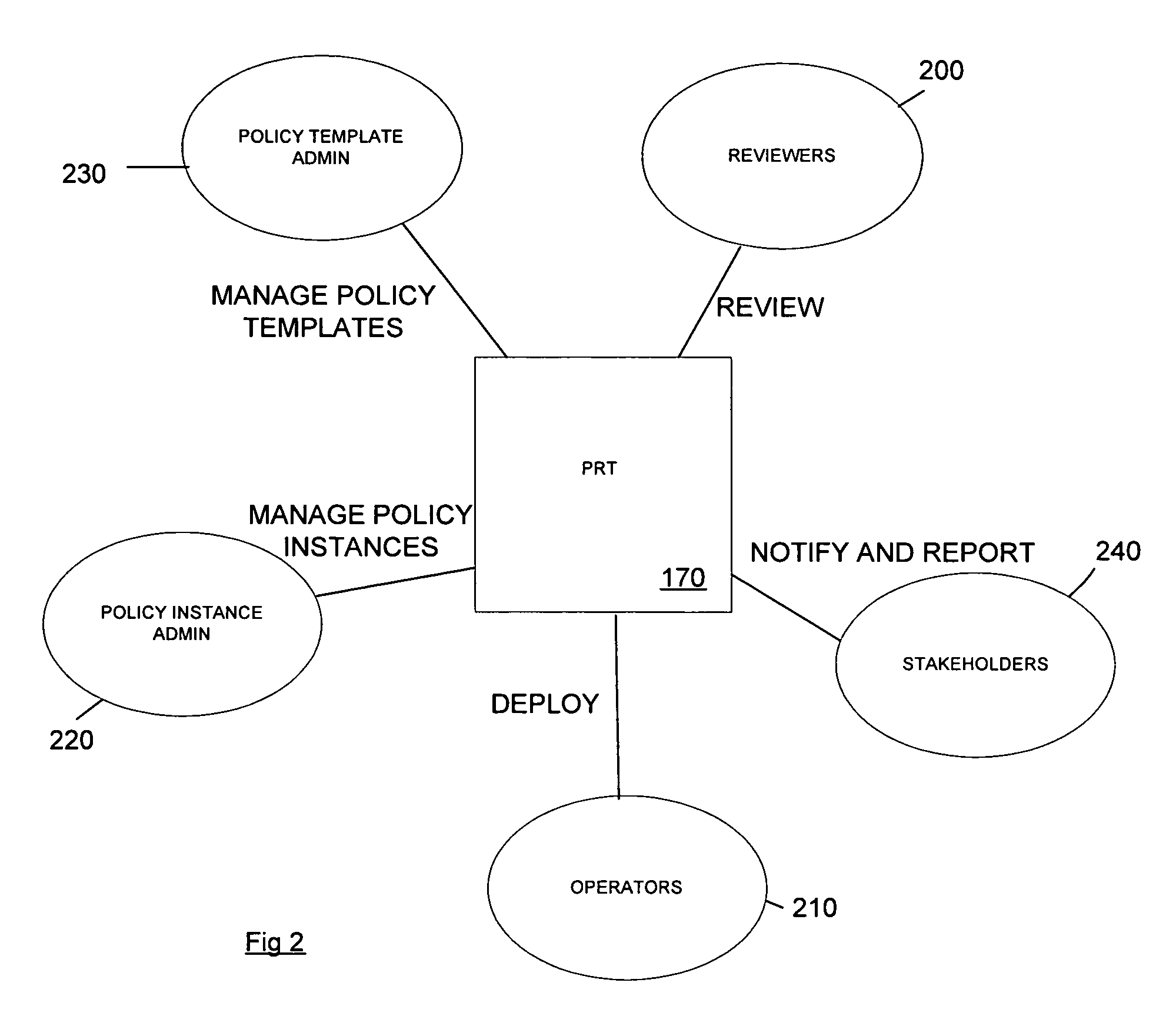
A method and corresponding tool are described for security policy management in a network comprising a plurality of hosts and at least one configurable policy enforcement point. The method, comprises creating one or more policy templates representing classes of usage control models within the network that are enforceable by configuration of the policy enforcement points; creating one or more policy instances, each based on one of the templates and instantiating the template for identified sets of hosts within the network to which the usage control model is to be applied, deploying the policy instances by generating and providing one or more configuration files for provisioning corresponding policy enforcement points within the network. Access to the templates and policy instances is controlled so that the policy templates are only modifiable by a first predeterminable user group, the policy instances are only modifiable by the first or a second predeterminable user group and the policy instances are only deployable by a third predeterminable user group.
Owner:VALTRUS INNOVATIONS LTD +1
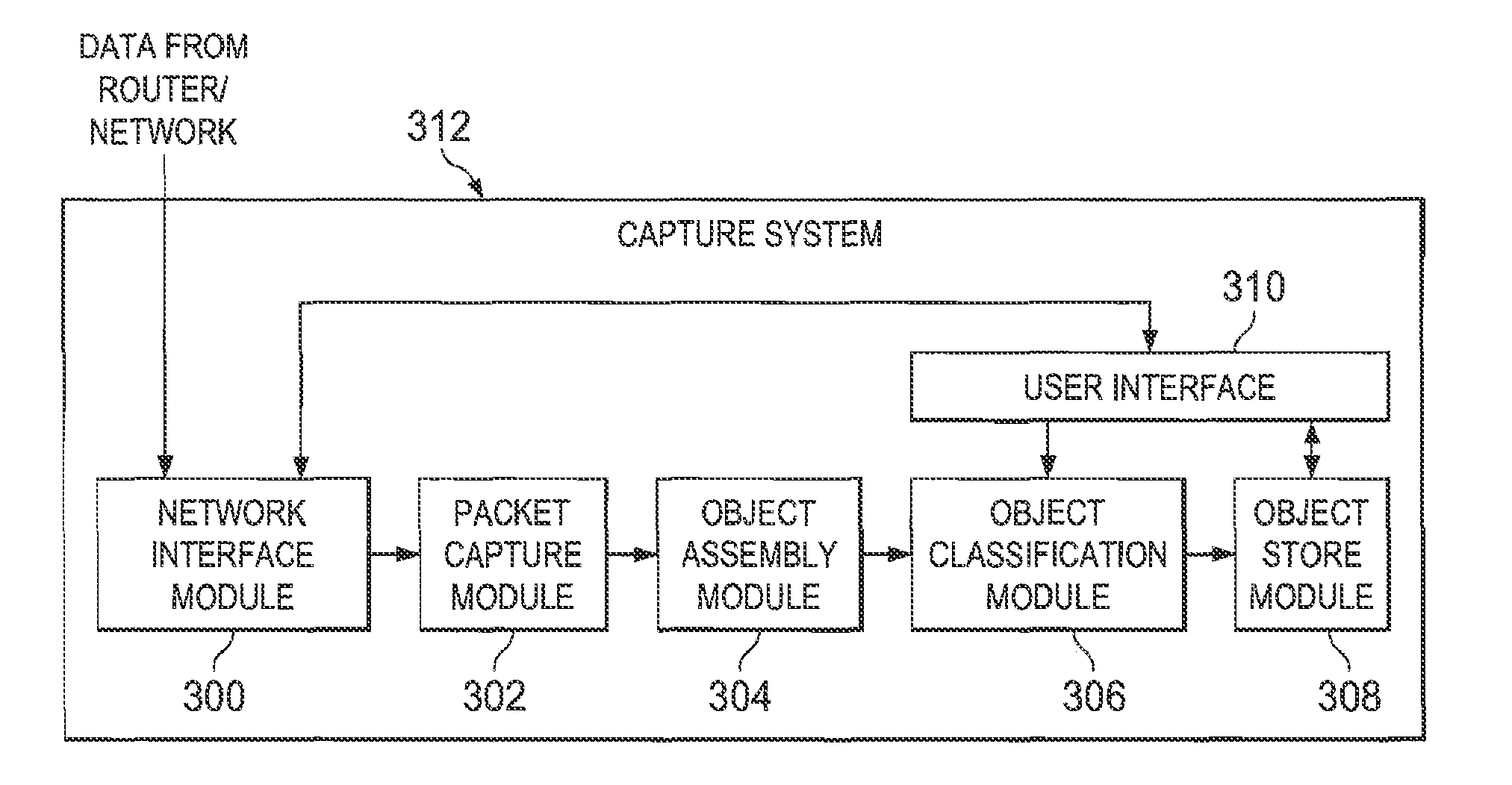
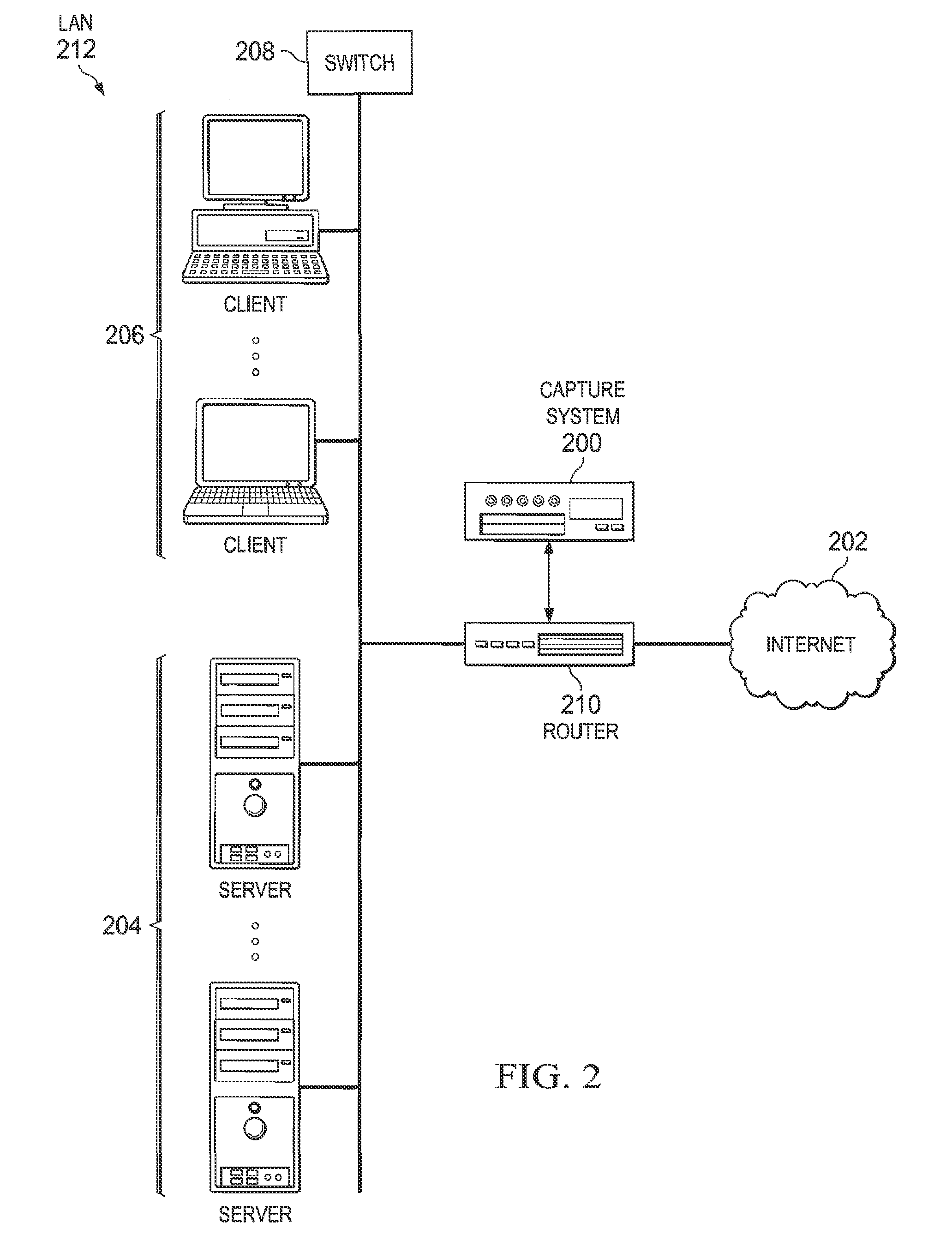
System and method for data mining and security policy management
ActiveUS8447722B1Digital data processing detailsComputer security arrangementsData managementSecurity policy management
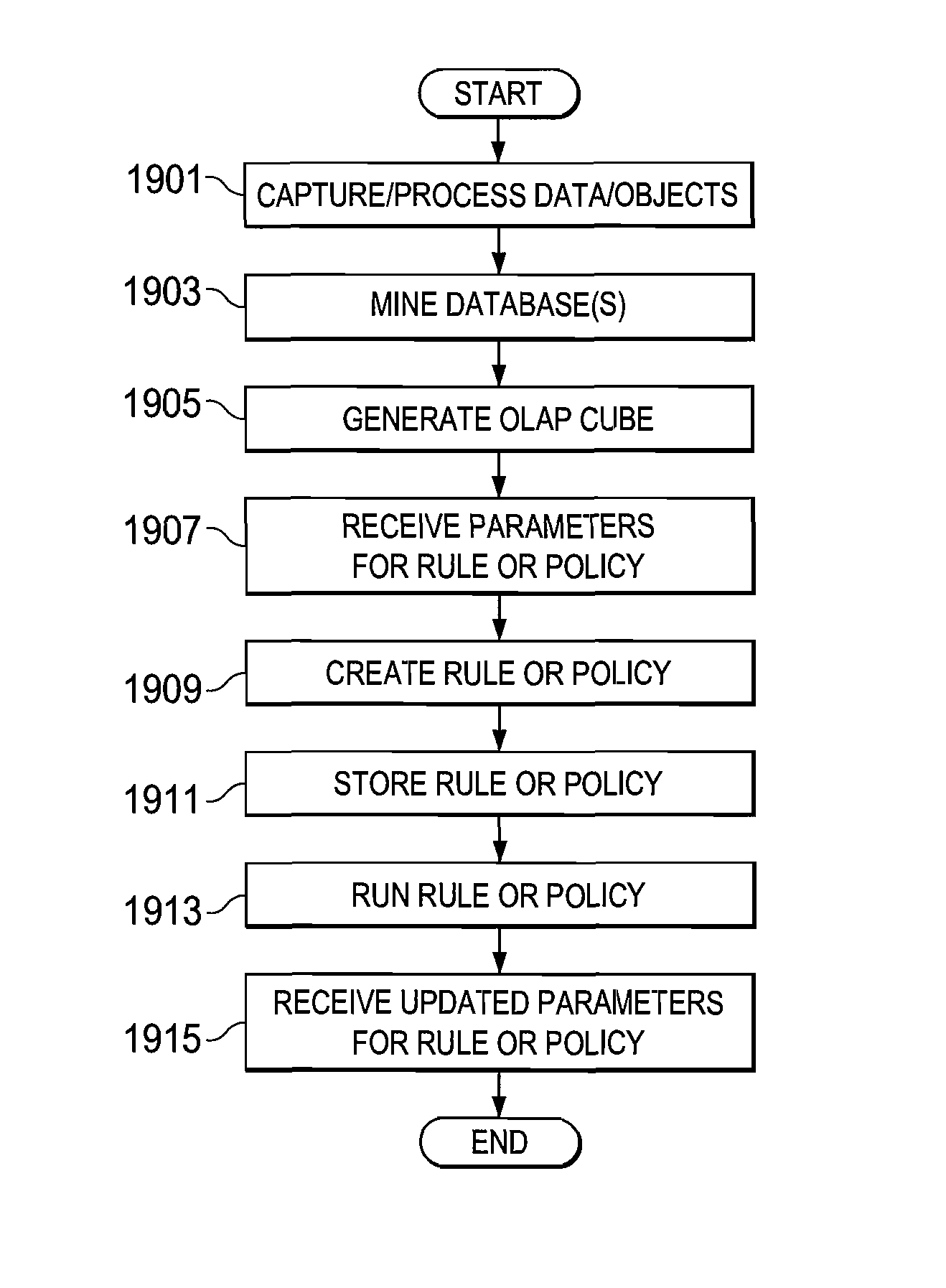
A method is provided in one example and includes generating a query for a database for information stored in the database. The information relates to data discovered through a capture system. The method further includes generating an Online Analytical Processing (OLAP) element to represent information received from the query. A rule based on the OLAP element is generated and the rule affects data management for one or more documents that satisfy the rule. In more specific embodiments, the method further includes generating a capture rule that defines items the capture system should capture. The method also includes generating a discovery rule that defines objects the capture system should register. In still other embodiments, the method includes developing a policy based on the rule, where the policy identifies how one or more documents are permitted to traverse a network.
Owner:MCAFEE LLC
Multi-application IC card with secure management of application
ActiveUS20080128515A1Avoid spreadingAcutation objectsPayment architectureProcessor registerSecurity policy management
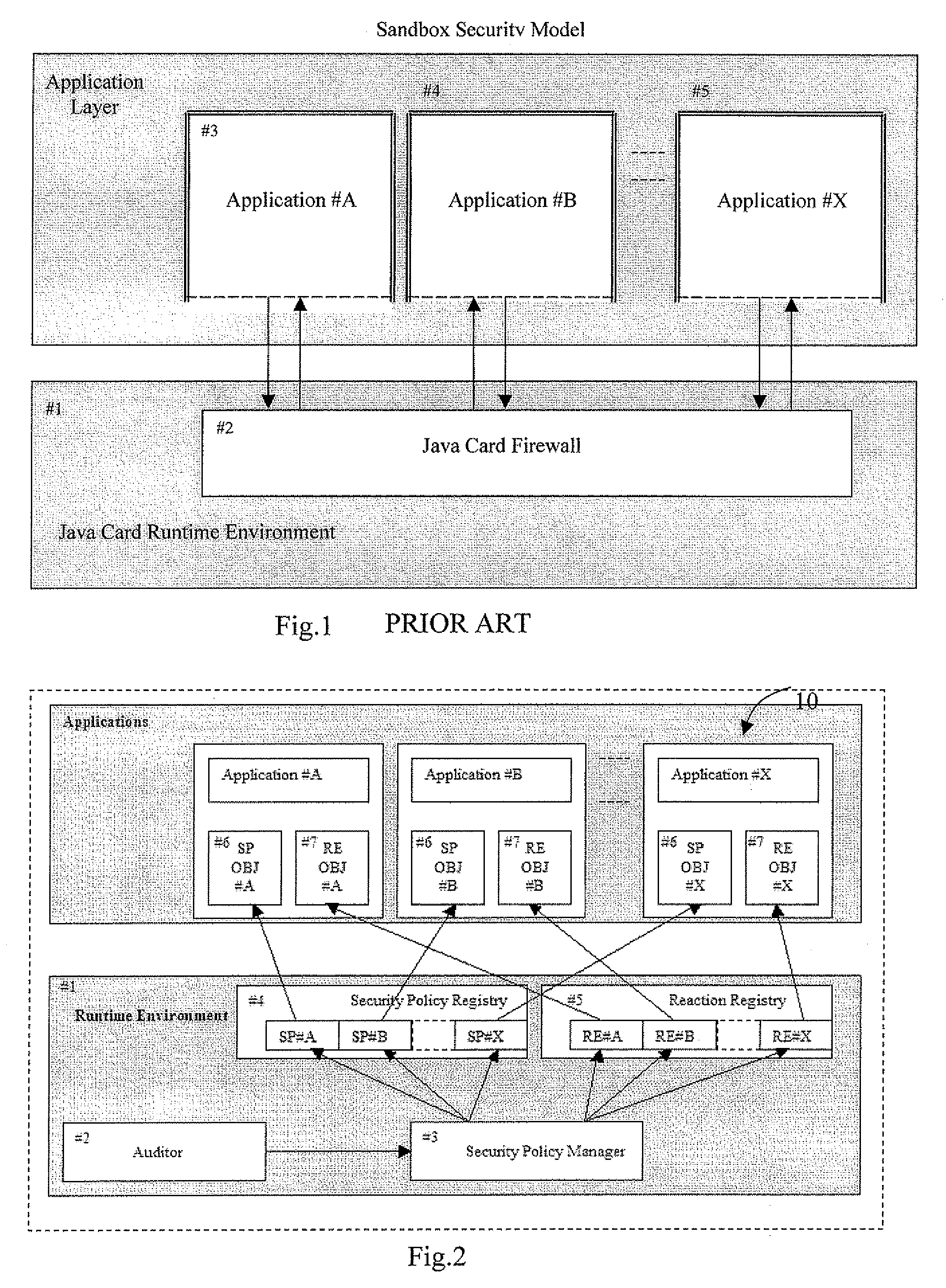
A multi-application IC card may include a runtime environment for managing executions of a plurality of stored application. Each application may include a set of rules, to be satisfied by their execution, and a corresponding set of reactions, to be taken if the rules are not satisfied. The runtime environment may include security and reaction registers to reference, respectively, the set of rules and reactions associated with the applications. A security policy manager may initialize, for each application, a reference between the security registers and the rules set between the reactions register and the reactions set. Checking the rules set and / or an activation of the reactions set is controlled by the security policy manager through the security registers and reaction registers. The security policy manager may include a registration function for initializing the security and reaction registers. The registration function may be called from the applications or an administrative user.
Owner:STMICROELECTRONICS INT NV
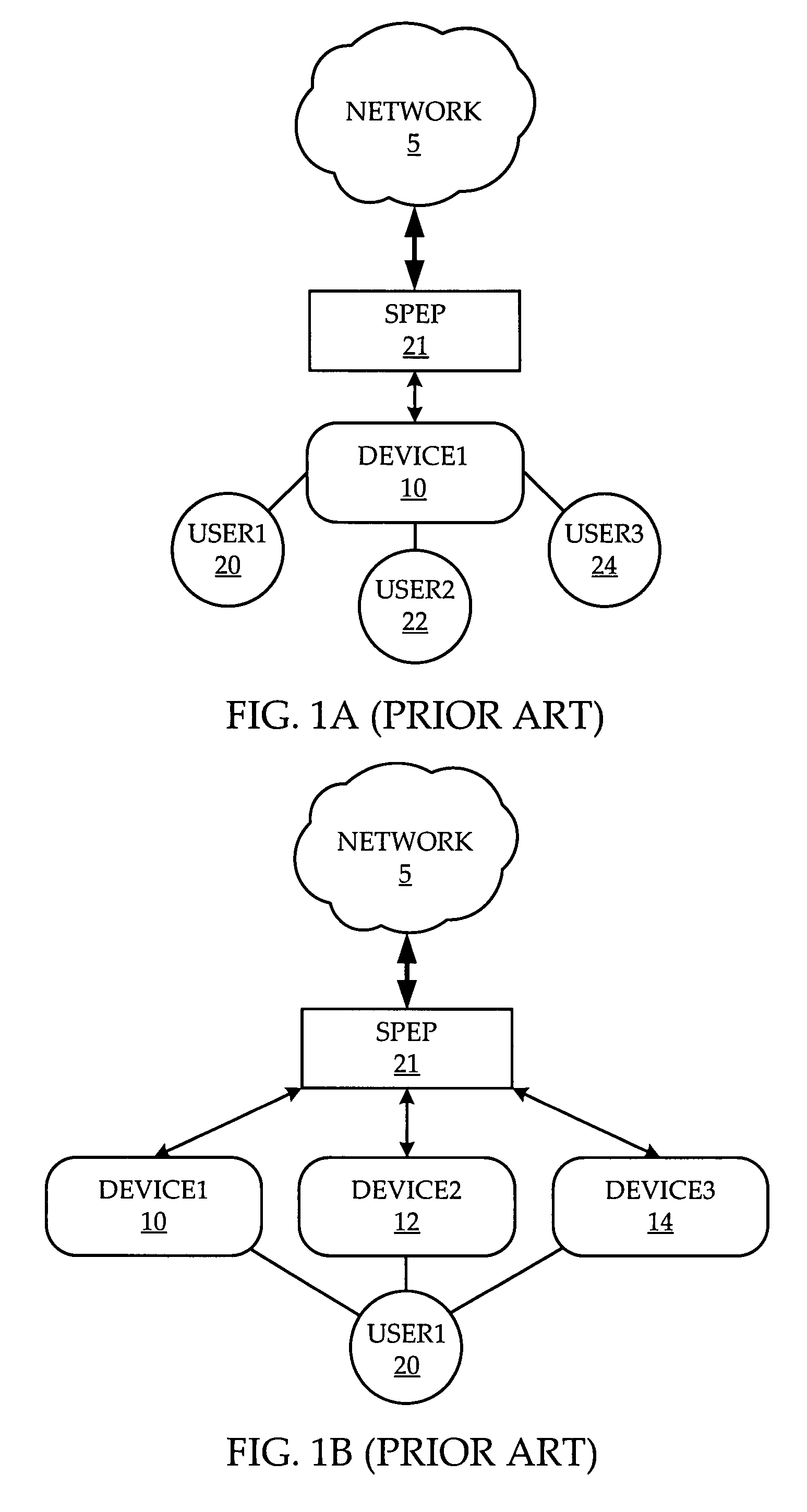
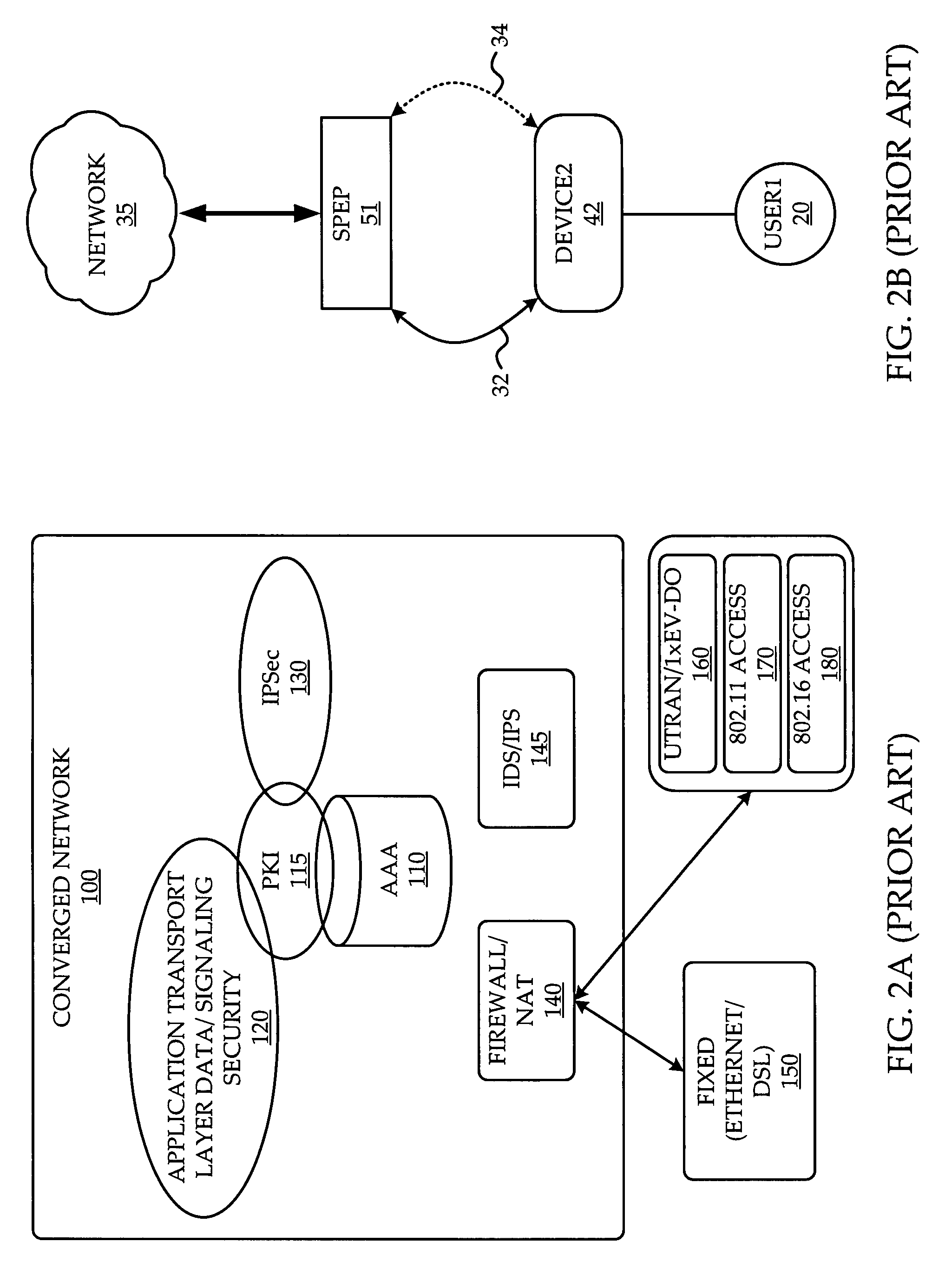
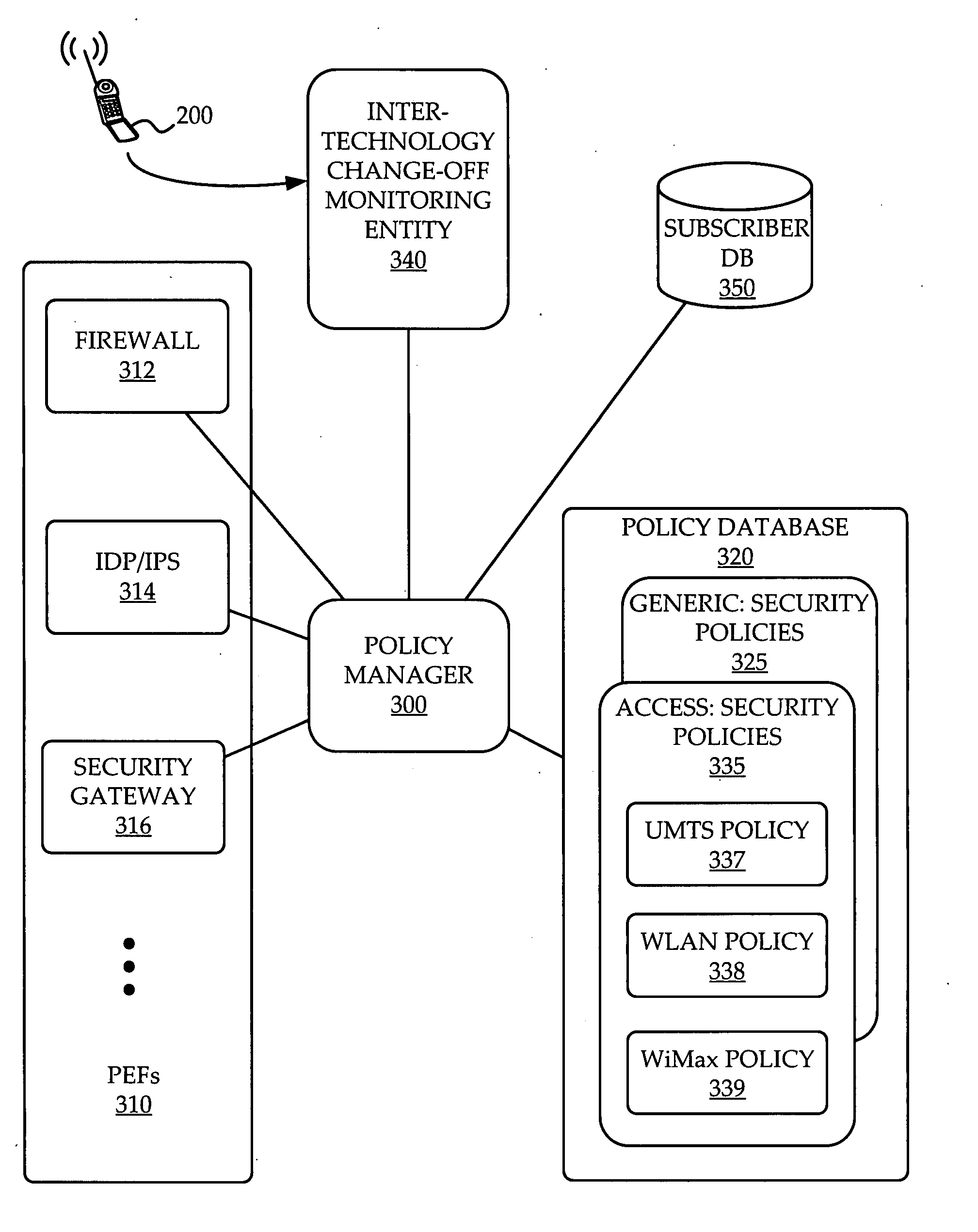
System and method of network access security policy management for multimodal device
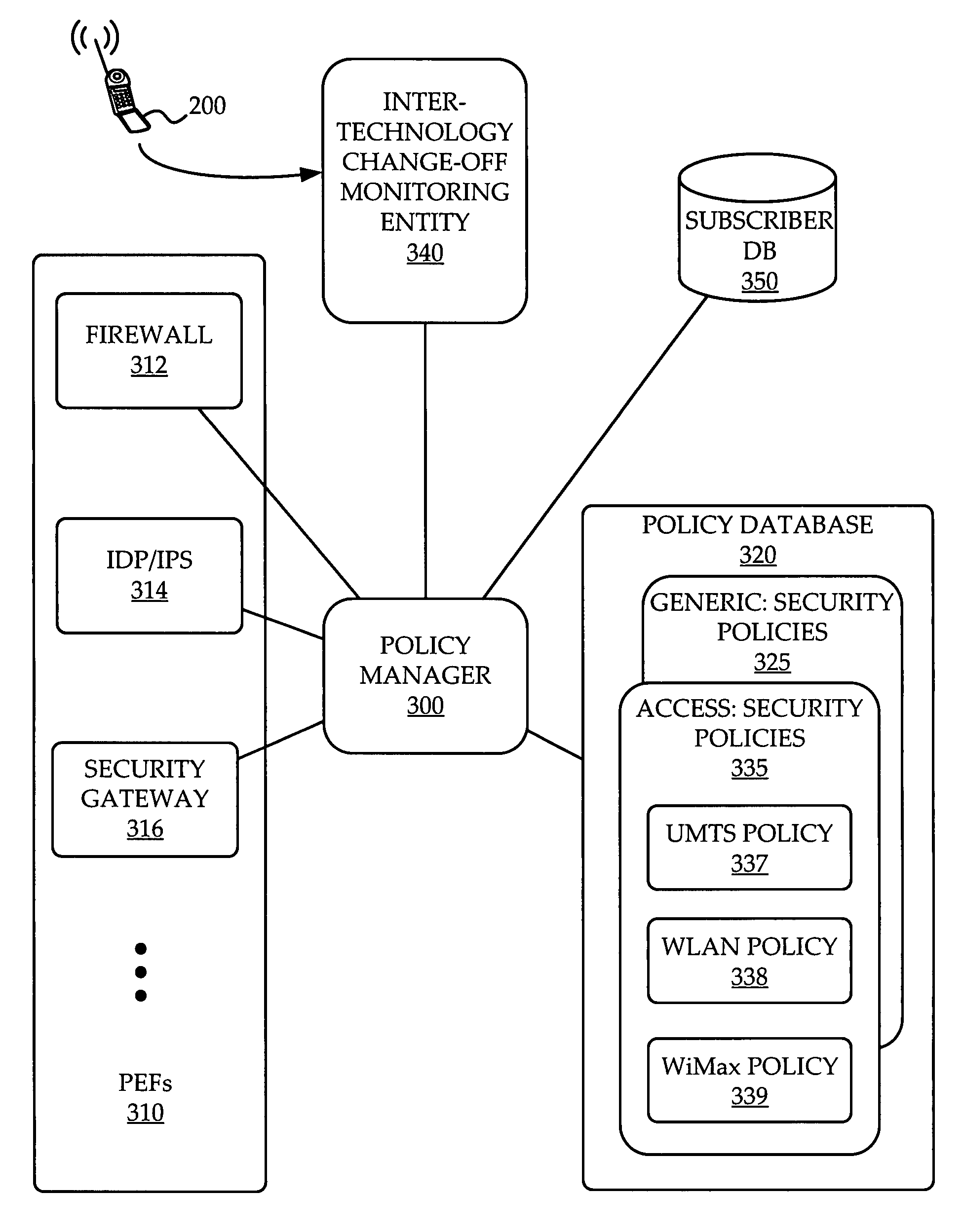
A system and method are provided for management of access security for access by a multimodal device to a converged fixed / mobile network. An inter-technology change-off monitoring entity (ICME) is provided to monitor an inter-technology change-off of the multimodal device and to notify a policy manager of the inter-technology change-off. The policy manager looks up in a policy database, security policies applicable to the user of the multimodal device and the particular technology being used by the multimodal device. The policy manager conveys to various policy enforcement points throughout the converged fixed / mobile network the applicable security policies which take into account the user's identity and the access technology being used.
Owner:WSOU INVESTMENTS LLC
Dynamically optimized security policy management
ActiveUS20160191466A1TransmissionSpecial data processing applicationsTraffic characteristicPriority setting
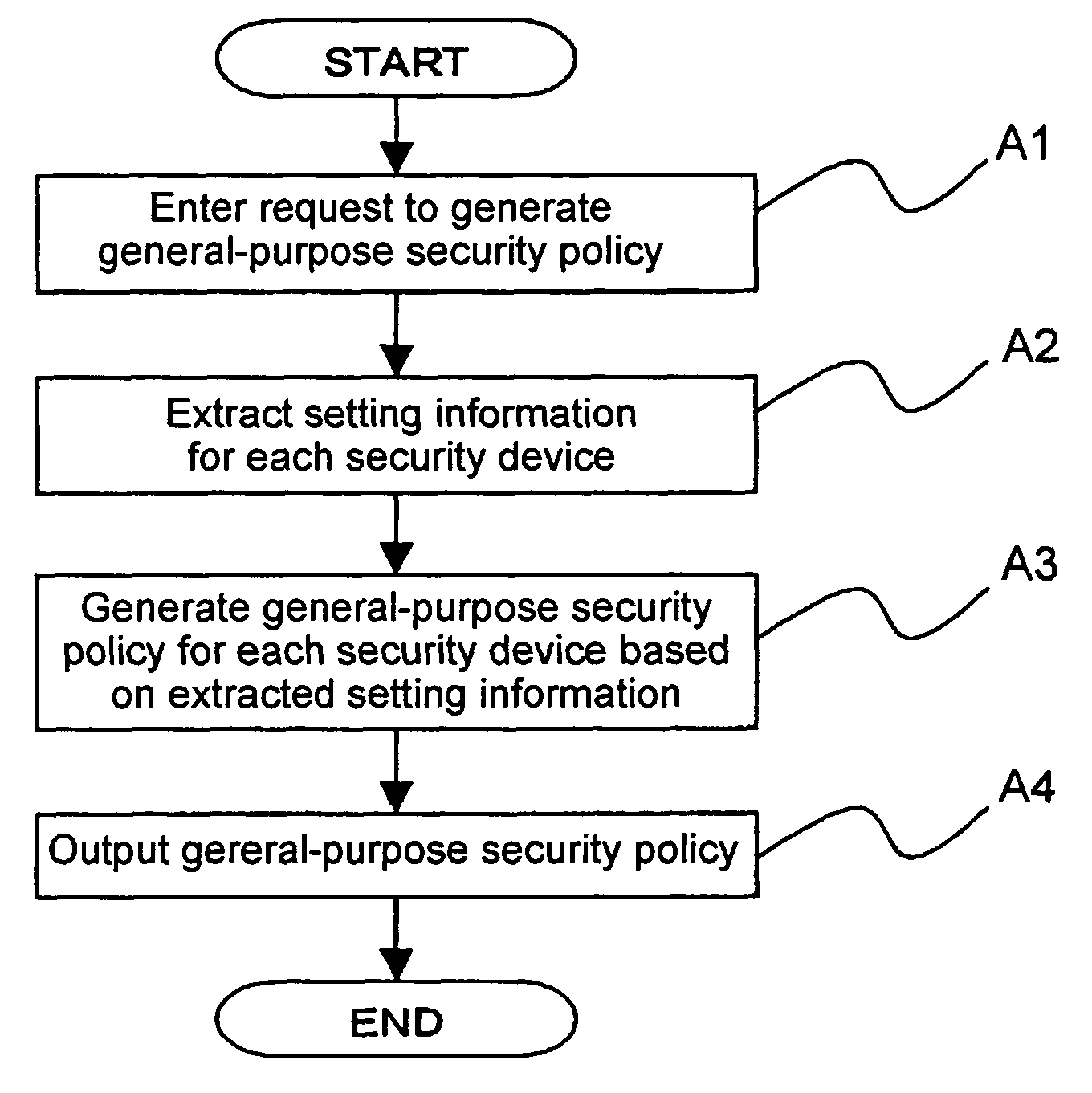
Methods and systems for dynamically optimized rule-based security policy management are provided. A request is received by a network security management device to add a new traffic flow policy rule to multiple existing policy rules managed by the network security management device. Dependencies of the new traffic flow policy rule on the existing policy rules are automatically determined. An updated set of policy rules is formed by incorporating the new traffic flow policy rule within the existing policy rules based on the dependencies. The updated set of policy rules is then optimized by grouping, reordering and / or deleting a sub-set of policy rules of the updated set of policy rules based on one or more of weights assigned to particular types of traffic, preference settings, priority settings, network traffic characteristics and usage statistics for each policy rule of the updated set of policy rules.
Owner:FORTINET
Method and apparatus for security policy management
InactiveUS7882537B2Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
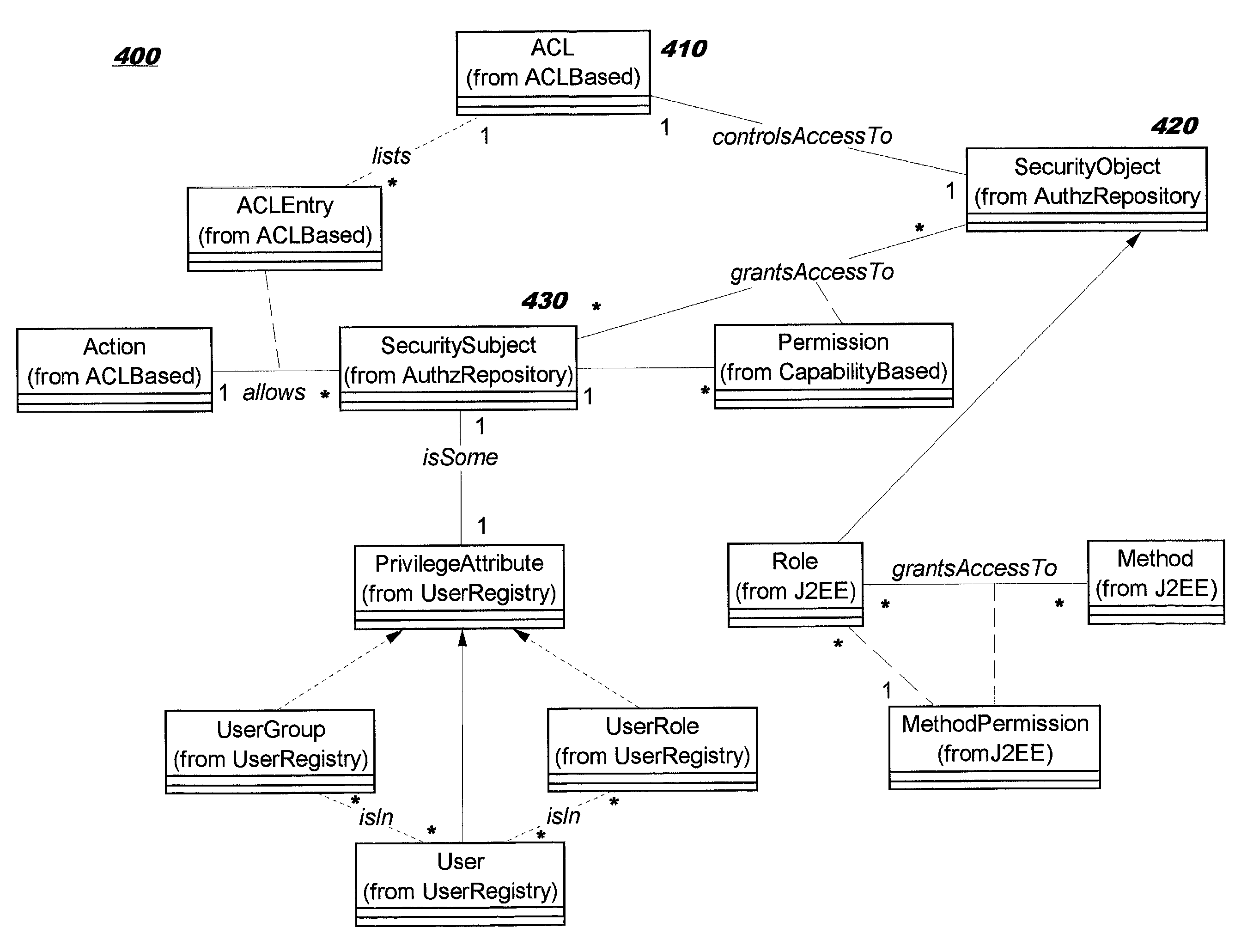
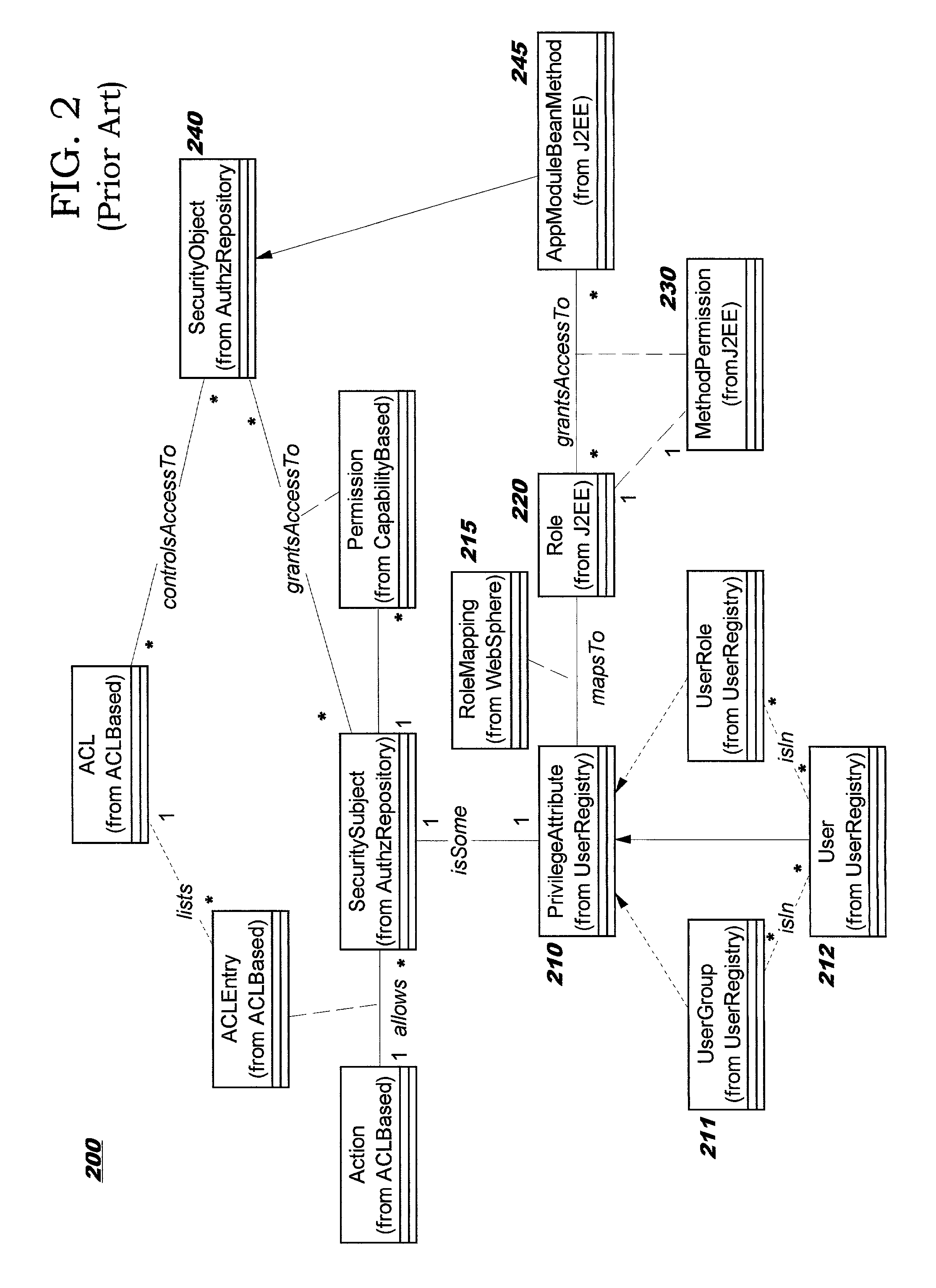
Role-permission model for security policy administration and enforcement
InactiveUS20030046576A1Efficient and more manageableData processing applicationsMultiple digital computer combinationsDistributed Computing EnvironmentInternet privacy
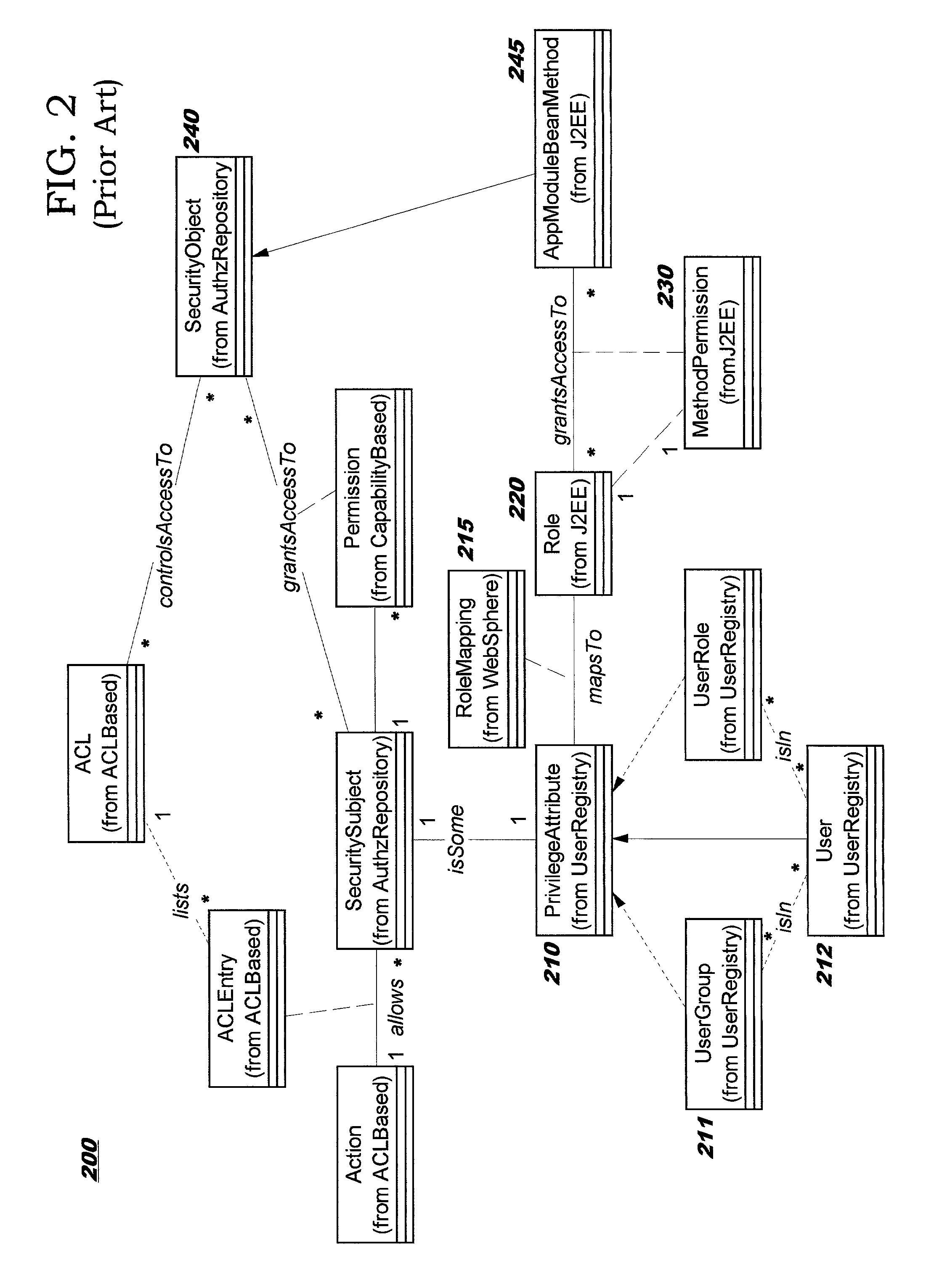
Methods, systems, and computer program products are disclosed for protecting the security of resources in distributed computing environments. The disclosed techniques improve administration and enforcement of security policies. Allowed actions on resources, also called permissions, (such as invocations of particular methods, read or write access of a particular row or perhaps a particular column in a database table, and so forth) are grouped, and each group of permissions is associated with a role name. A particular action on a particular resource may be specified in more than one group, and therefore may be associated with more than one role. Each role is administered as a security object. Users and / or user groups may be associated with one or more roles. At run-time, access to a resource is protected by determining whether the invoking user has been associated with (granted) at least one of the roles required for this type of access on this resource.
Owner:IBM CORP
Method and system for security policy management
InactiveUS20030014644A1Computer security arrangementsSecret communicationNetwork packetSecurity policy management
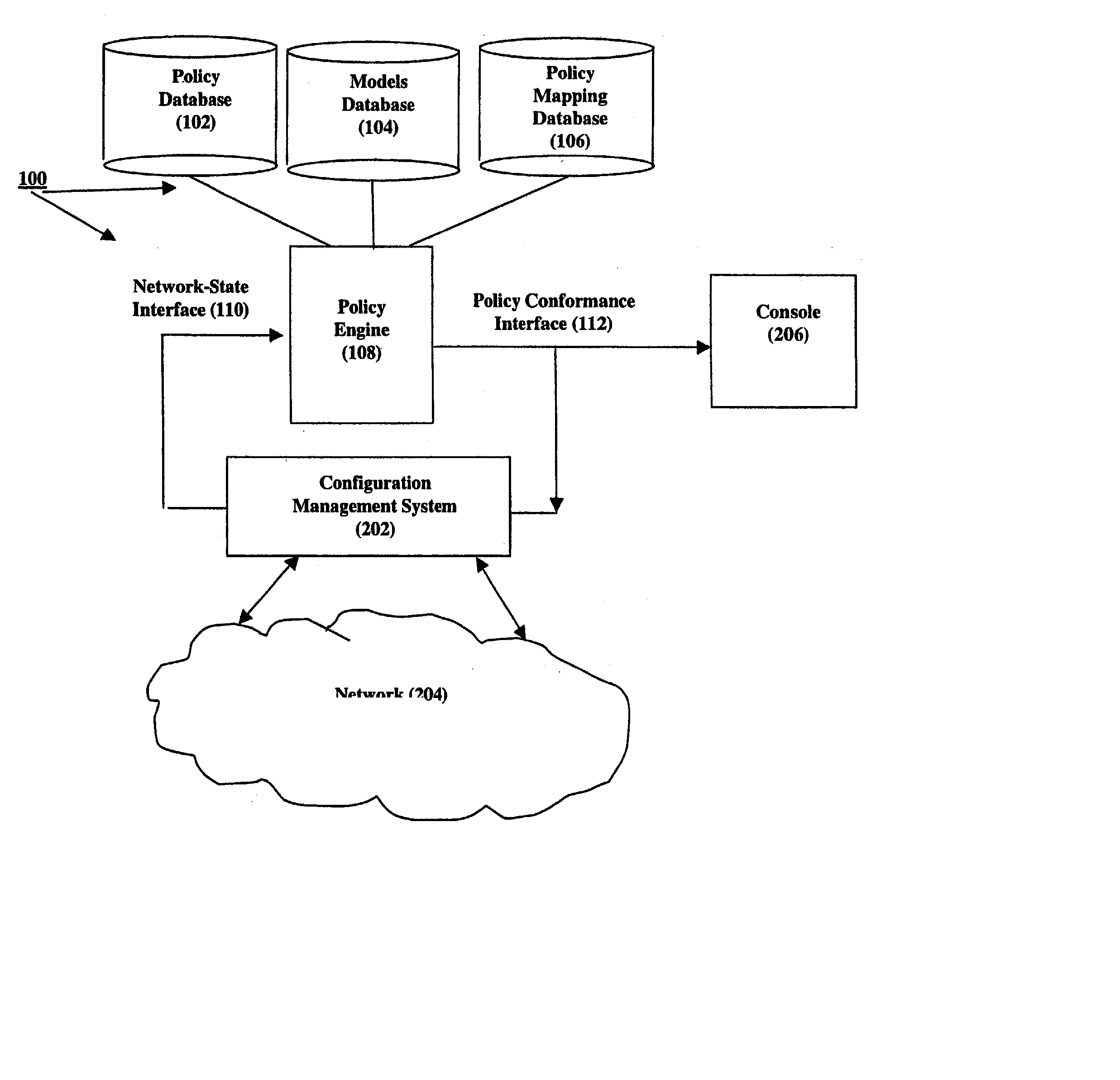
The conformance of a network to a set of security policy statements is determined by attempting to violate the policies by routing packets through models of network elements. Policy statements specify whether a set of clients is granted or denied access to a network service offered by a set of servers. Network element models are in accordance to the element's configurable parameters and supported services, which together indicate how the element will treat packets when the element's current configuration is applied to the model. Conformance to a policy statement is determined by building a packet in accordance with the network service and a representative network-element client and server, and by attempting to move the packet from the client to the server by applying the packet to the network element models. Policy conformance is based on whether the packet reaches the service on the server. Network reconfigurations are determined for non-conformant policies.
Owner:TELCORDIA TECHNOLOGIES INC
Role-permission model for security policy administration and enforcement
InactiveUS7124192B2Efficient and more manageableData processing applicationsDigital data processing detailsDistributed Computing EnvironmentSecurity policy management
Methods, systems, and computer program products are disclosed for protecting the security of resources in distributed computing environments. The disclosed techniques improve administration and enforcement of security policies. Allowed actions on resources, also called permissions, (such as invocations of particular methods, read or write access of a particular row or perhaps a particular column in a database table, and so forth) are grouped, and each group of permissions is associated with a role name. A particular action on a particular resource may be specified in more than one group, and therefore may be associated with more than one role. Each role is administered as a security object. Users and / or user groups may be associated with one or more roles. At run-time, access to a resource is protected by determining whether the invoking user has been associated with (granted) at least one of the roles required for this type of access on this resource.
Owner:INT BUSINESS MASCH CORP
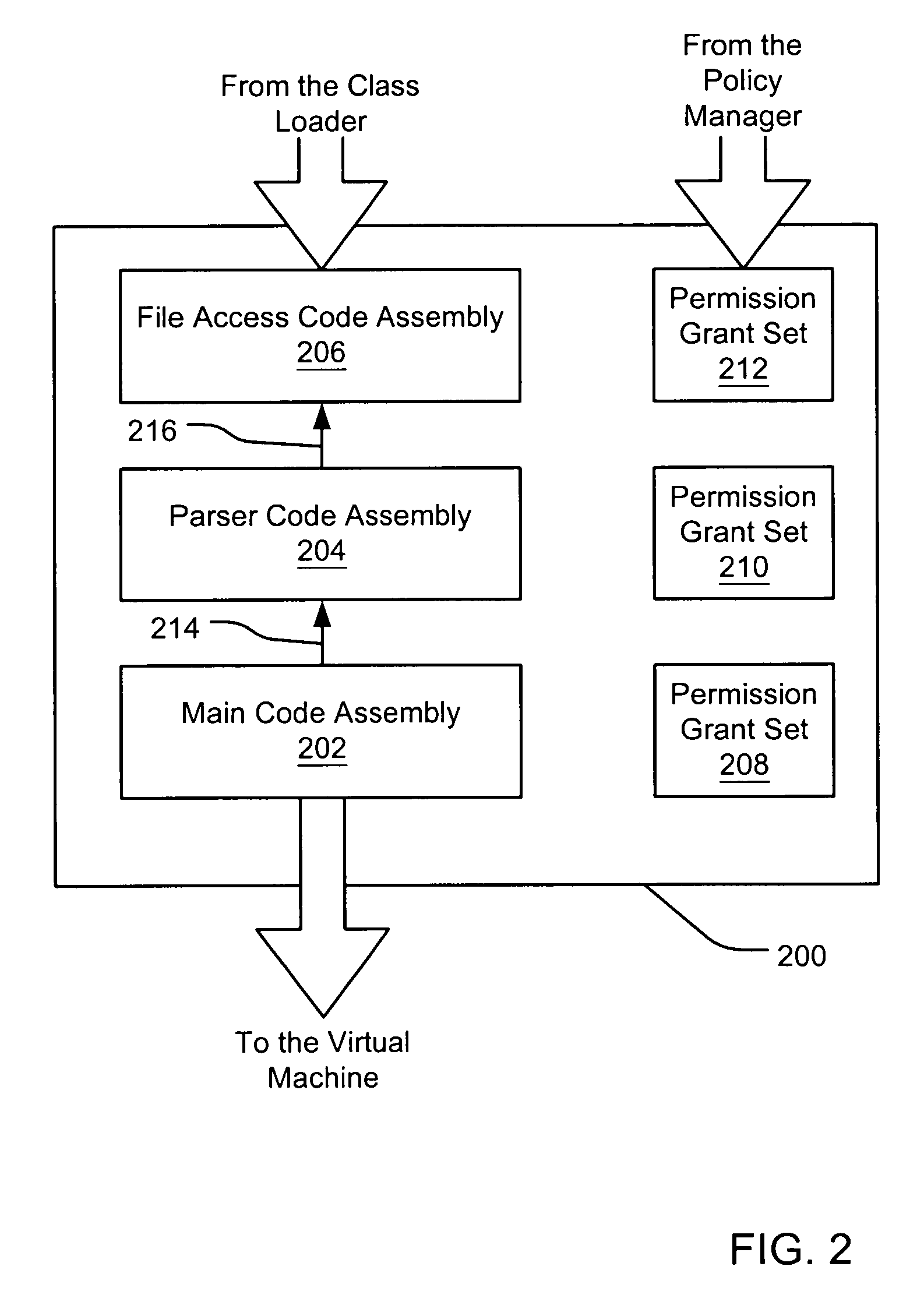
Evaluating initially untrusted evidence in an evidence-based security policy manager
InactiveUS7131143B1Digital data processing detailsAnalogue secracy/subscription systemsCall stackTrust level
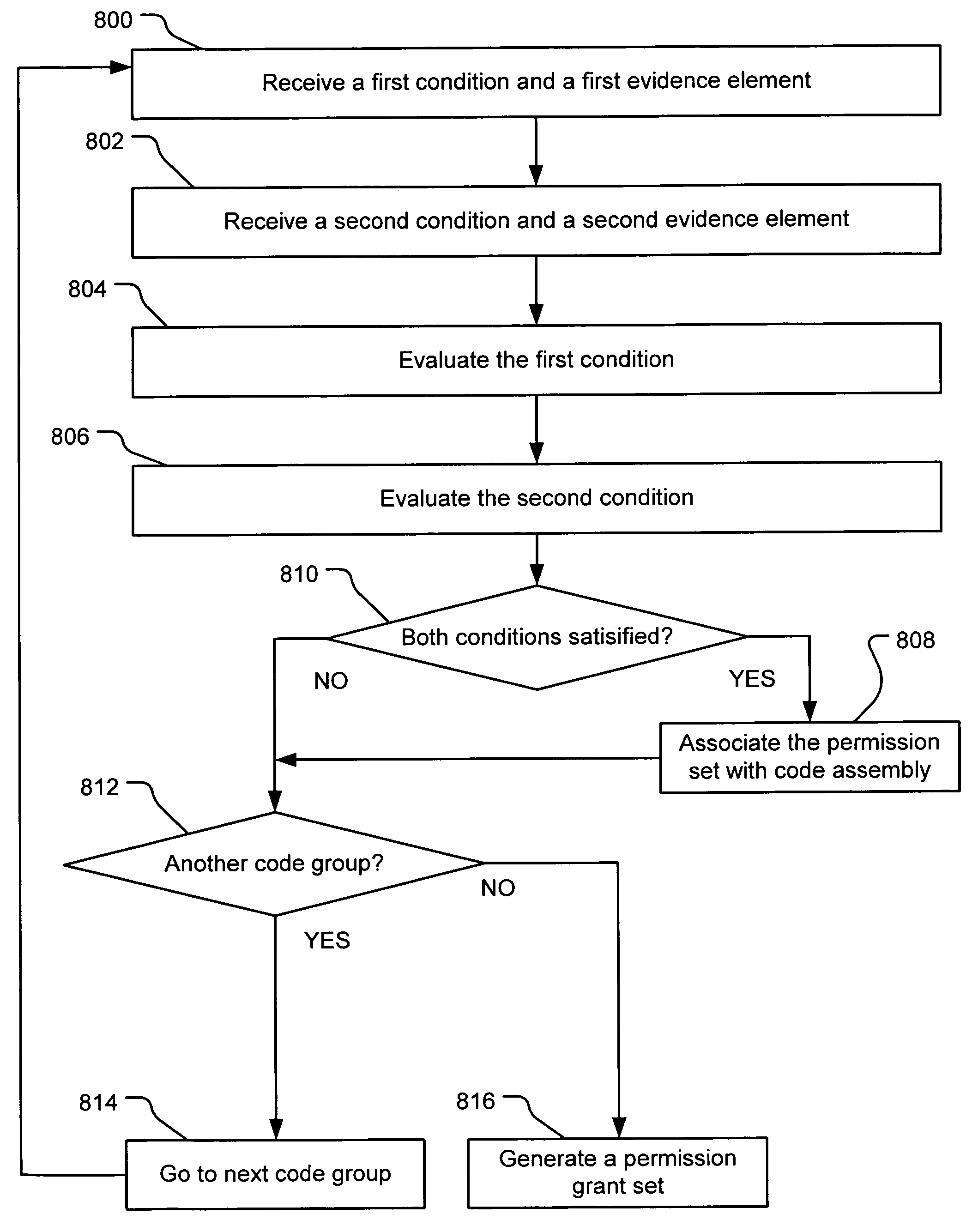
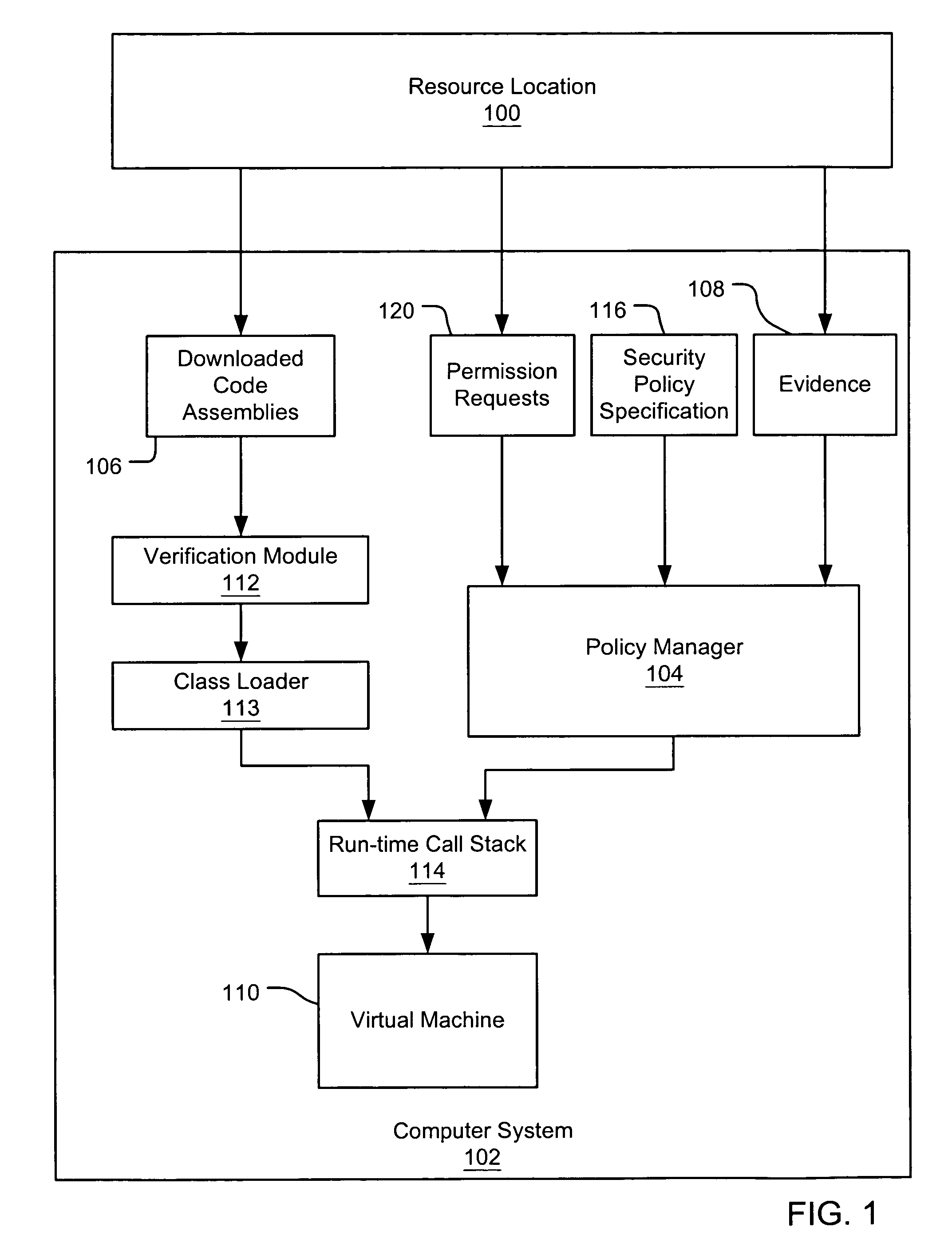
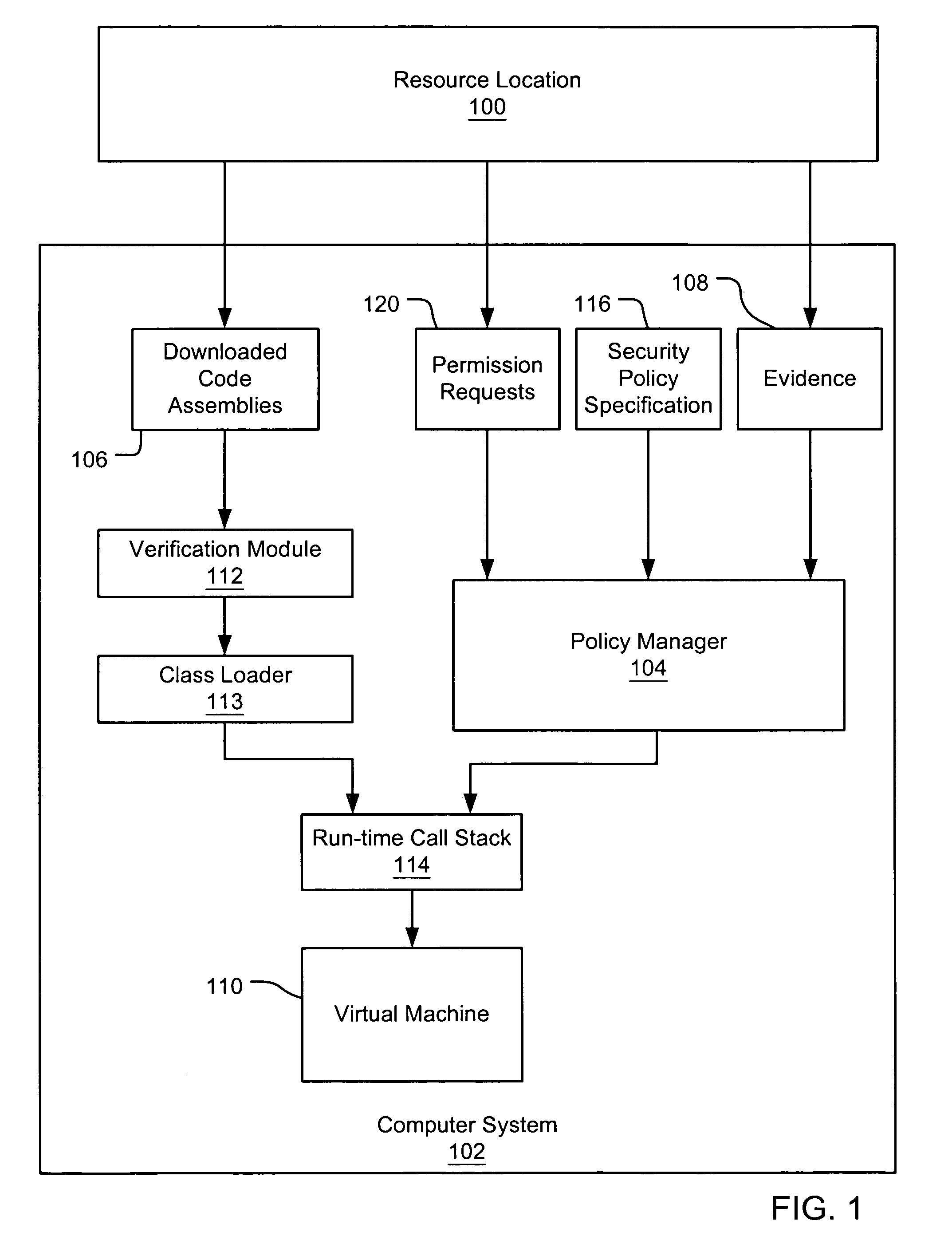
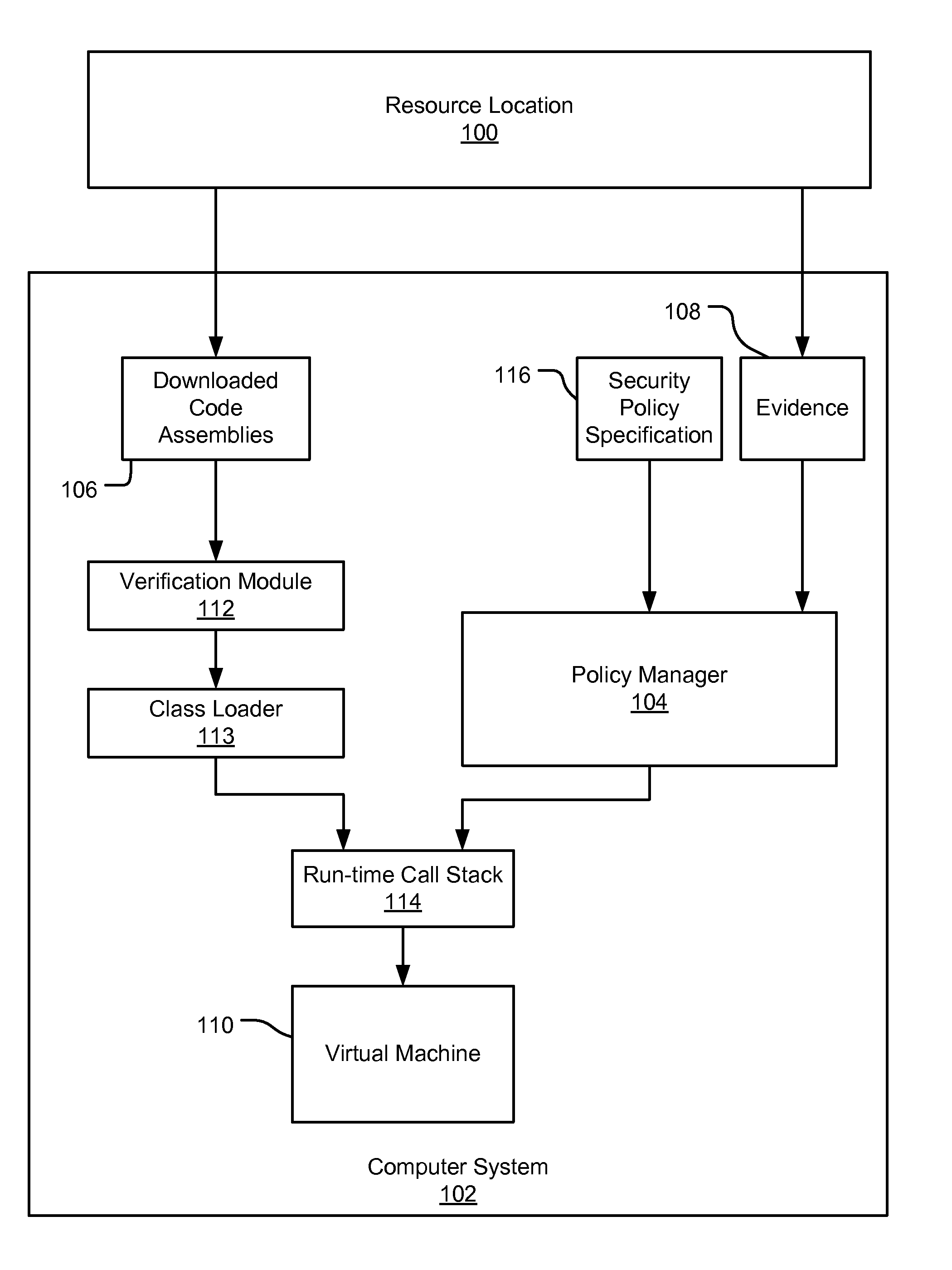
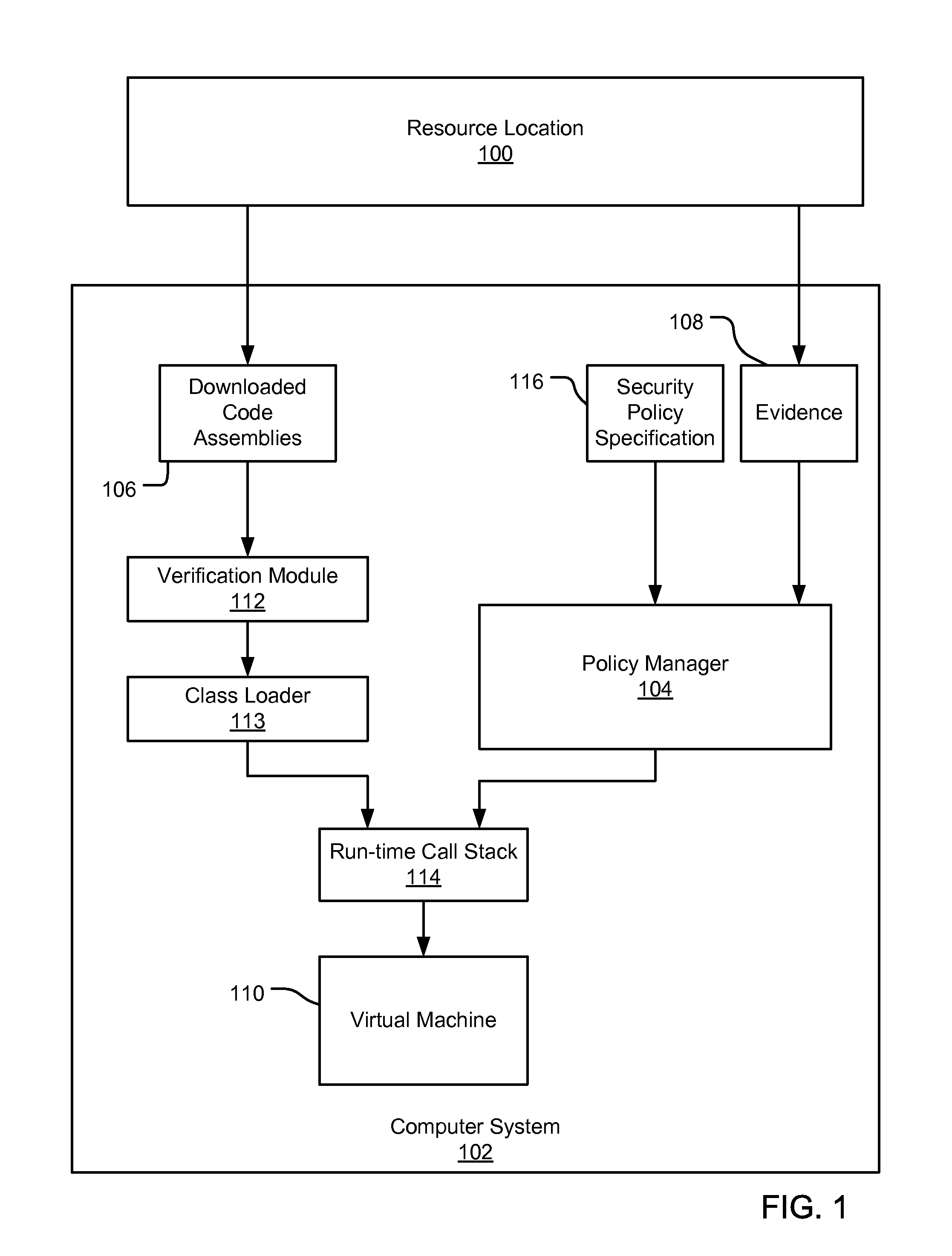
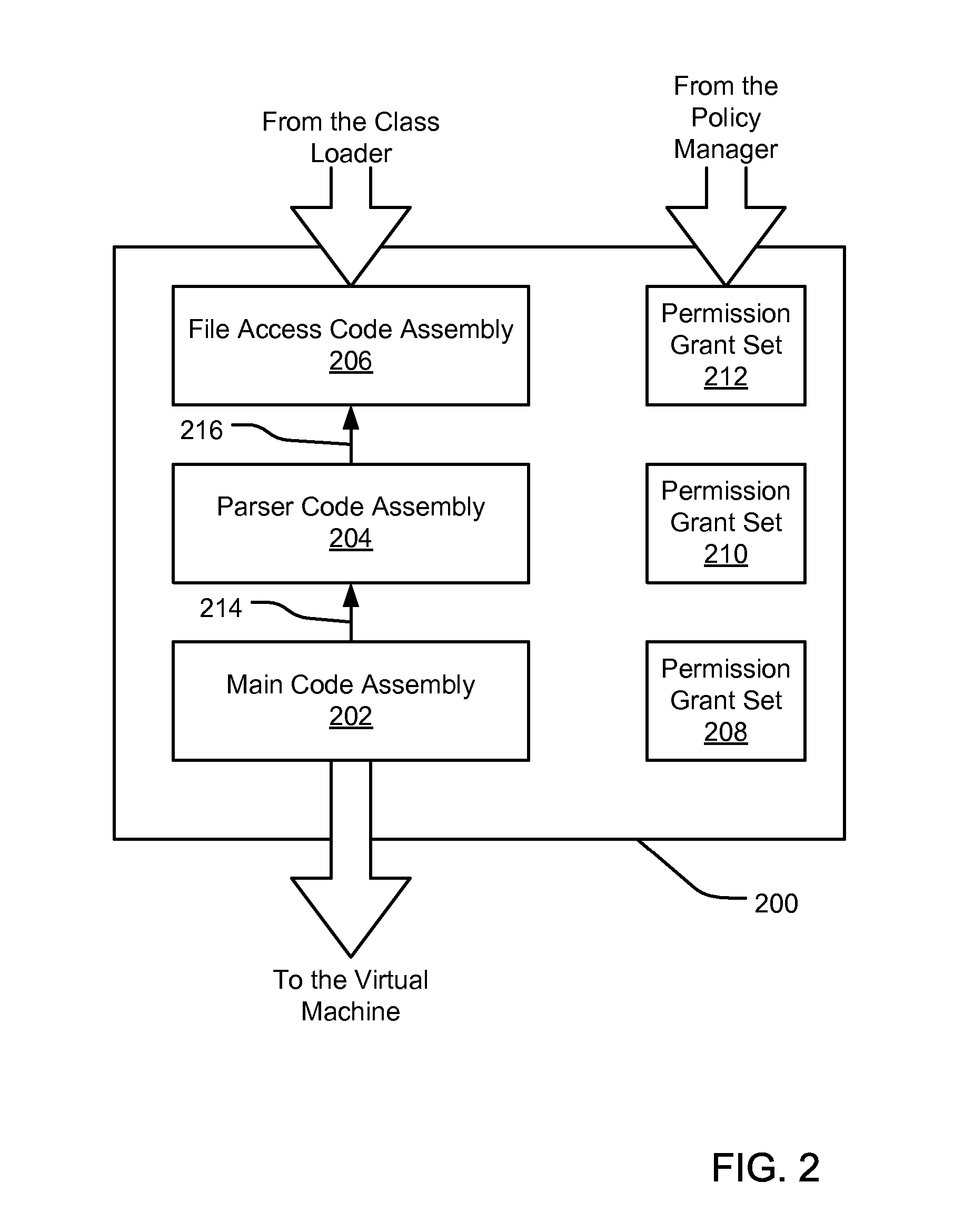
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. Both code assemblies and evidence may be received from a local origin or from a remote resource location via a network (e.g., the Internet). Evidence having different levels of trust may be evaluated in combination so that a permission grant set is associated only with trusted code assemblies. The policy manager may comprise execution modules for parsing a security policy specification, generating one or more code hierarchies, evaluating membership of the received code assembly in one or more code groups, and generating a permission grant set based upon this membership evaluation.
Owner:MICROSOFT TECH LICENSING LLC
System and method of network access security policy management for multimodal device
ActiveUS20080307487A1Wireless network protocolsSpecial data processing applicationsSecurity policy managementAccess technology
A system and method are provided for management of access security for access by a multimodal device to a converged fixed / mobile network. An inter-technology change-off monitoring entity (ICME) is provided to monitor an inter-technology change-off of the multimodal device and to notify a policy manager of the inter-technology change-off. The policy manager looks up in a policy database, security policies applicable to the user of the multimodal device and the particular technology being used by the multimodal device. The policy manager conveys to various policy enforcement points throughout the converged fixed / mobile network the applicable security policies which take into account the user's identity and the access technology being used.
Owner:WSOU INVESTMENTS LLC
System and method for using security levels to simplify security policy management
InactiveUS20050278790A1Reduce in quantitySimplifies application developmentDigital data processing detailsUser identity/authority verificationSecurity policy managementSecurity level
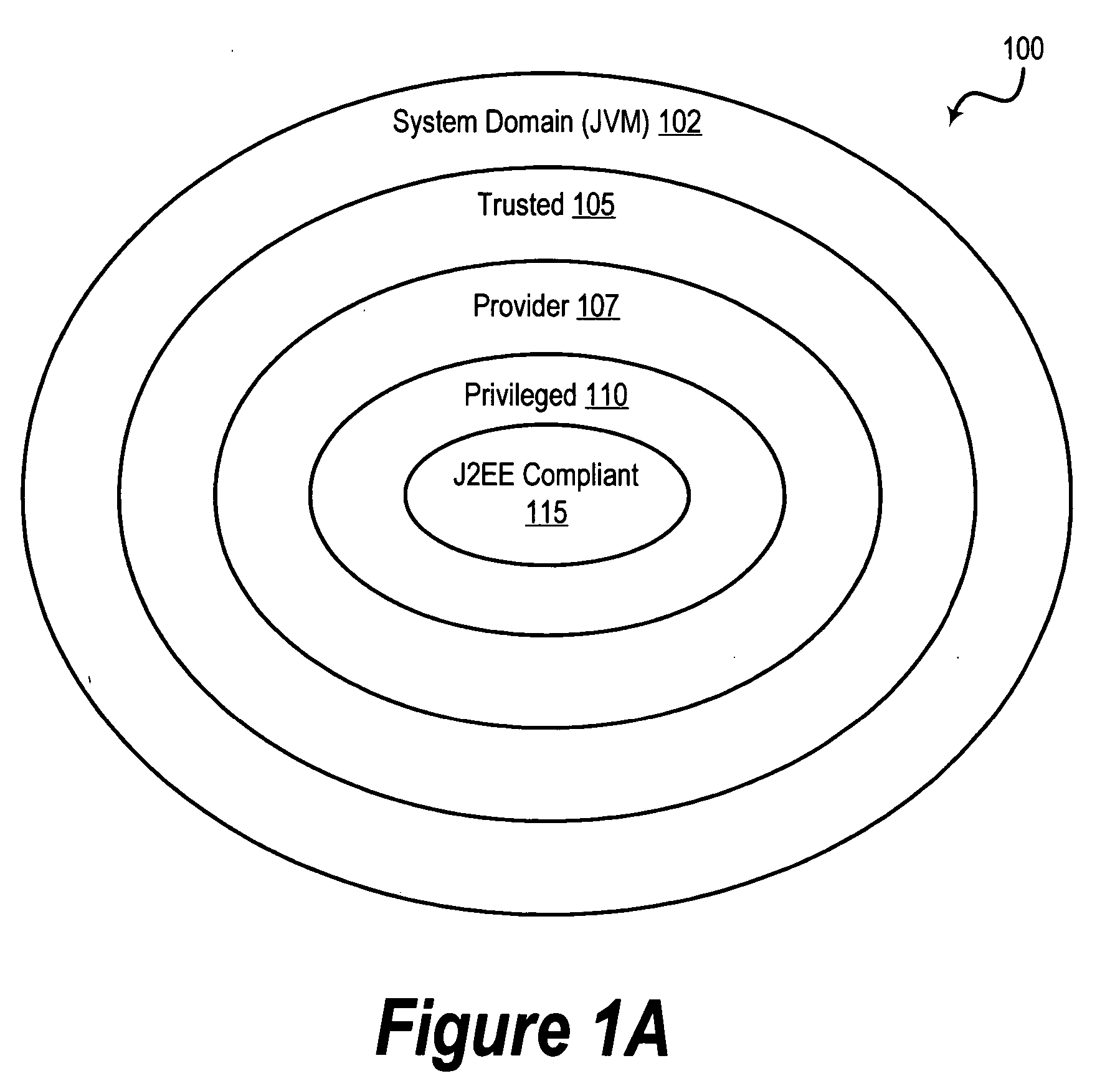
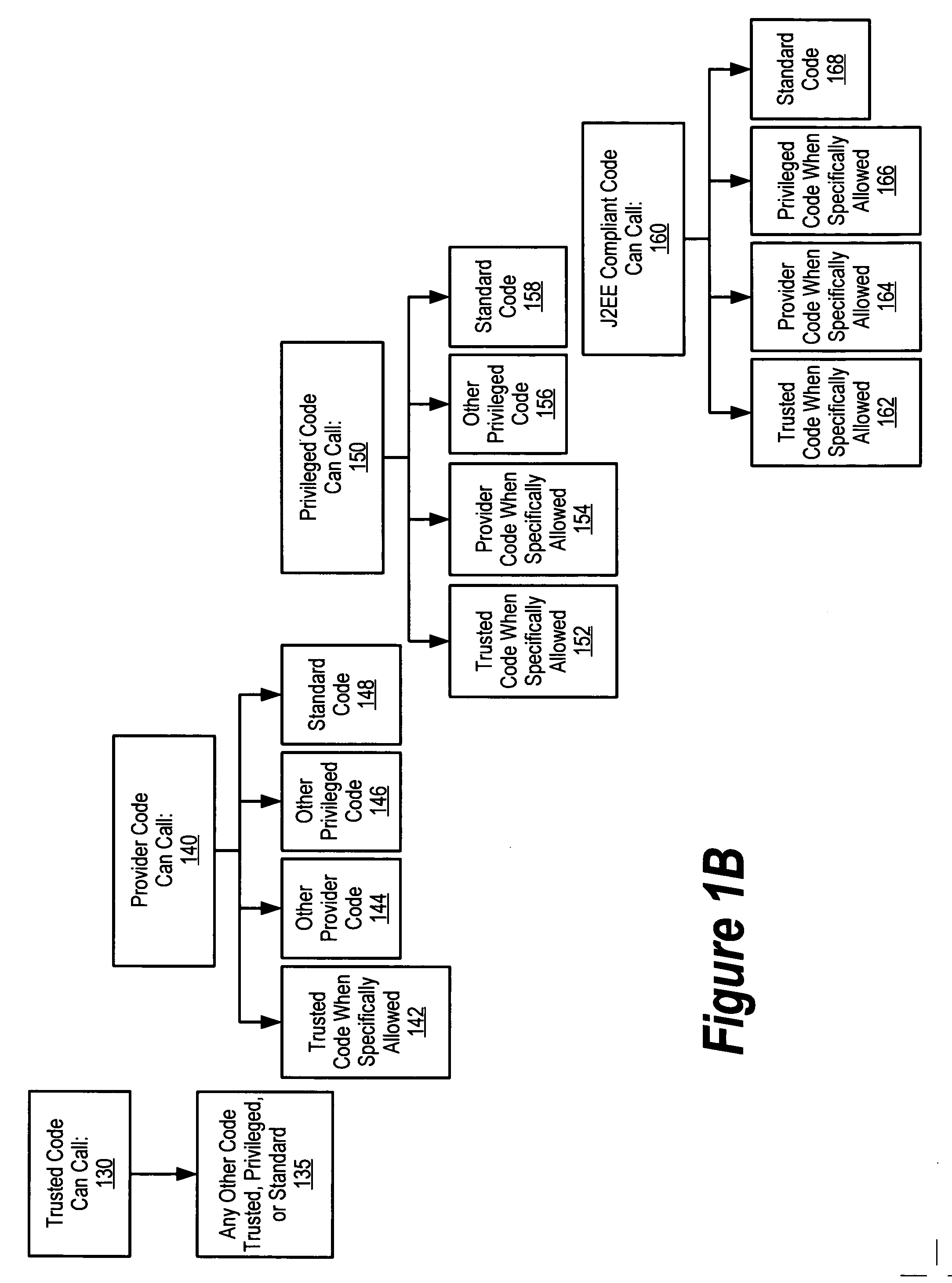
A system and method is provided for reducing the complexity and improving the performance of enforcing security restrictions on the execution of program code in a runtime environment. In a preferred embodiment, units of executable code, such as methods or functions, are classified by “security level.” Code units belonging to a “trusted” security level may call any other code unit in the runtime environment, but other security levels are restricted in the code units they can call. In a preferred embodiment, the security levels are represented by corresponding permission objects. Each permission object that is associated with a particular security level includes a numerical value that denotes that security level. Security policies can be enforced with respect to caller and callee code units by comparing numerical values of corresponding permission objects. This security level scheme also improves runtime performance by making it unnecessary to check individually-defined permissions in many cases.
Owner:IBM CORP
Filtering a permission set using permission requests associated with a code assembly
InactiveUS6981281B1Avoid contactPrevent inadvertent accessDigital data processing detailsUser identity/authority verificationCall stackComputerized system
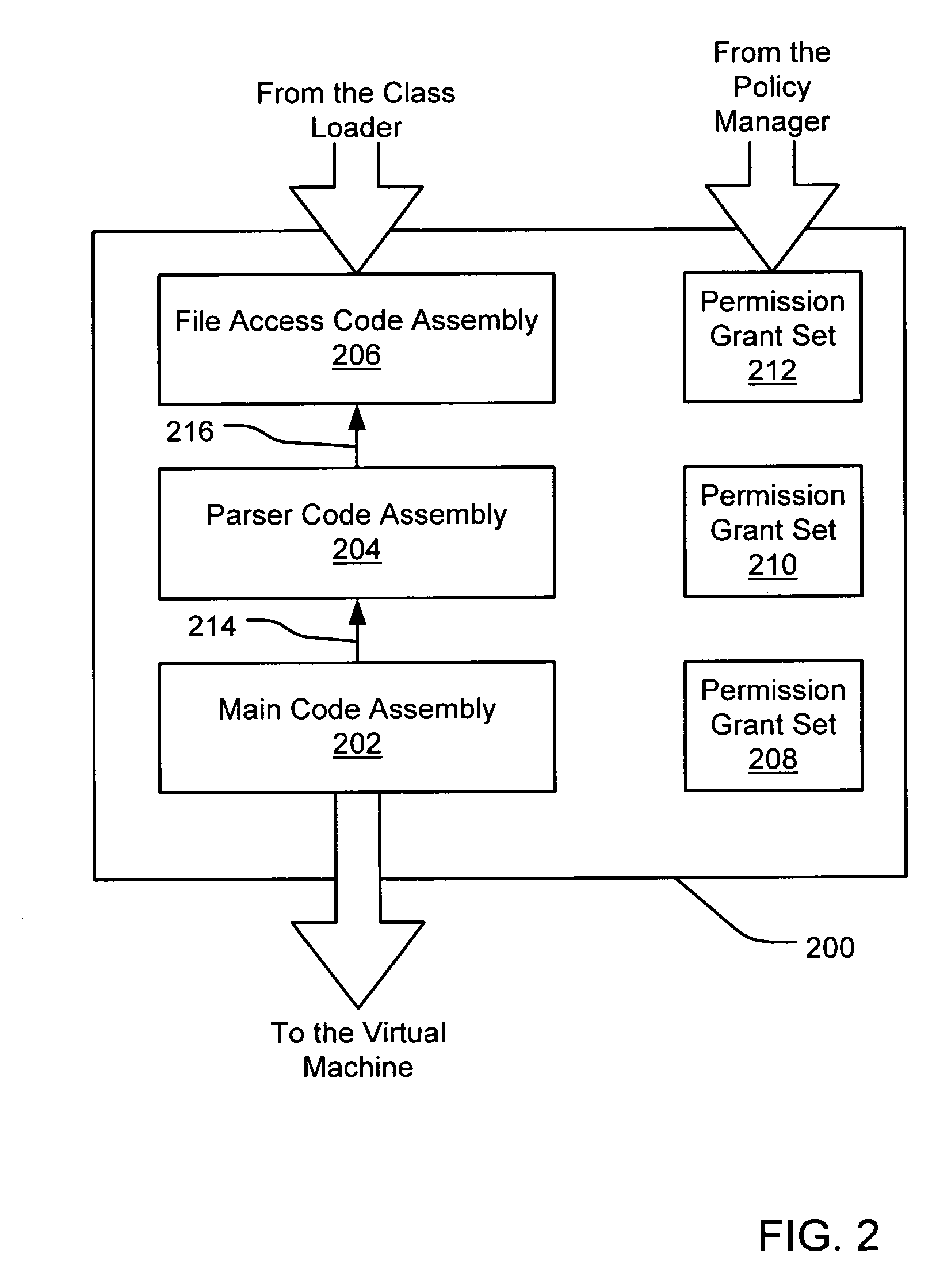
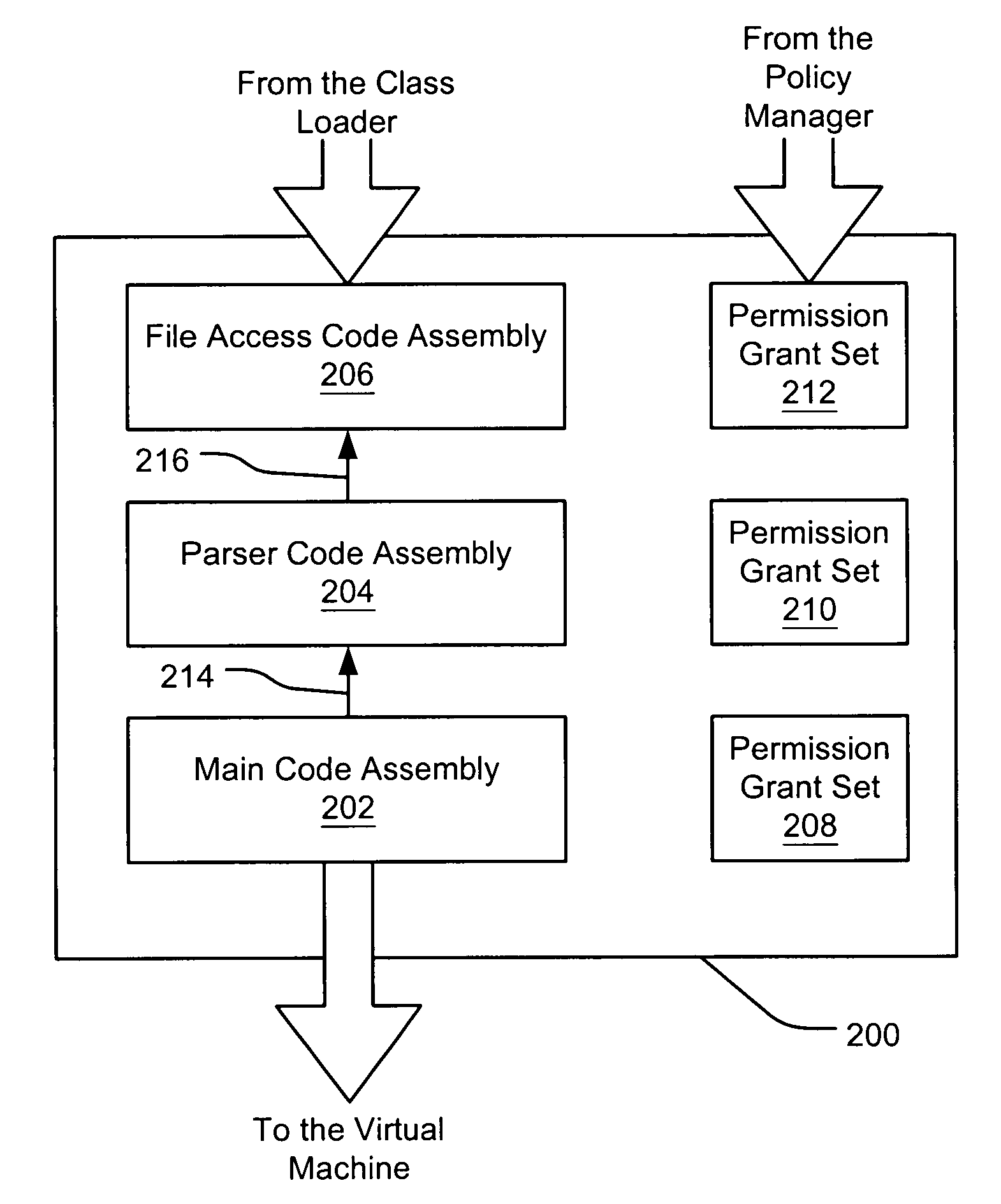
A security policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager can execute in a computer system (e.g., a Web client) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. A permission request set may also be received in association with the code assembly. The permission request set may include a minimum request set, specifying permissions required by the code assembly to run properly. The permission request set may also include an optional request set, specifying permissions requested by the code assembly to provide an alternative level of functionality. In addition, the permission request set may include a refuse request set, specifying permissions that are not to be granted to the code assembly. The permission requests are used to filter a permission set to generate a permission grant set.
Owner:MICROSOFT TECH LICENSING LLC
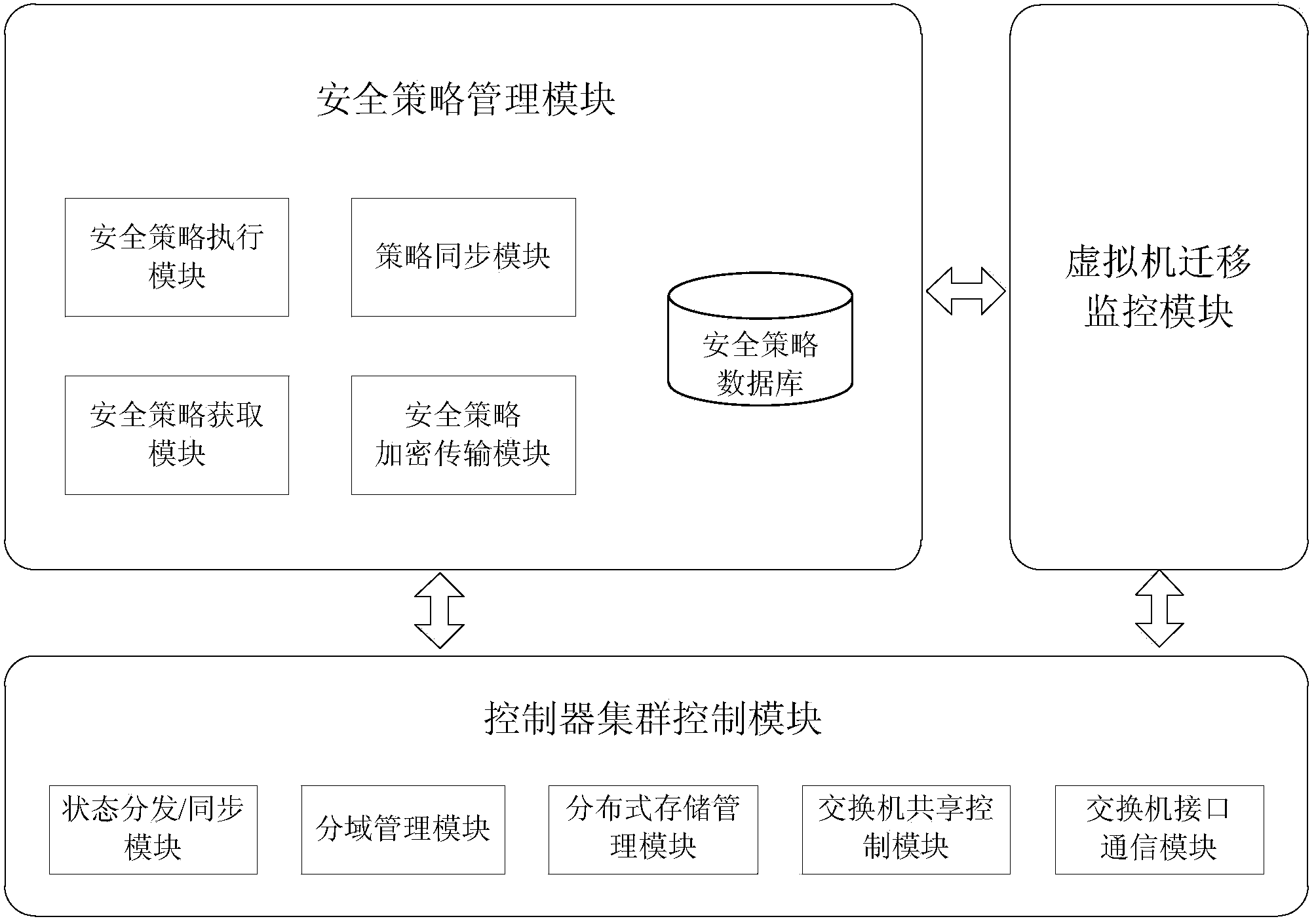
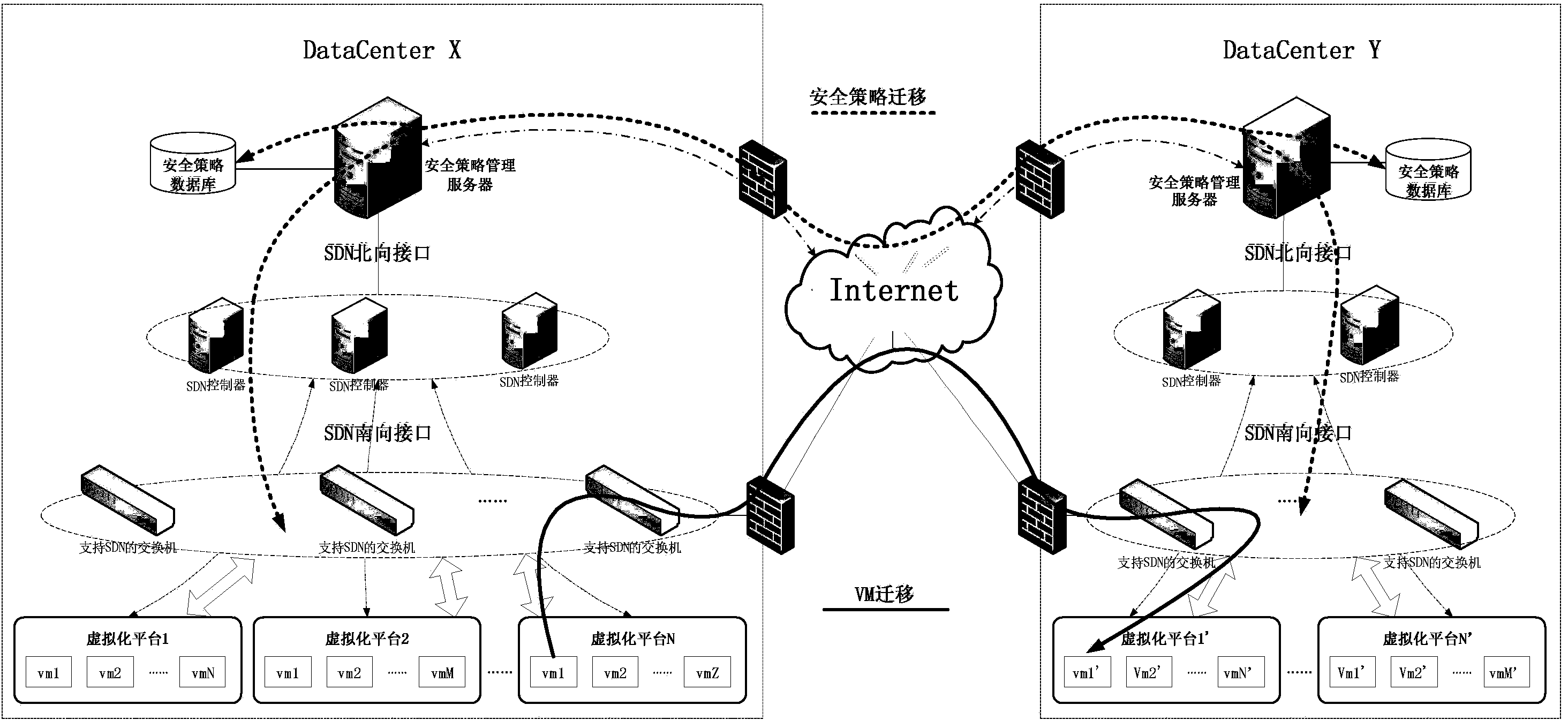
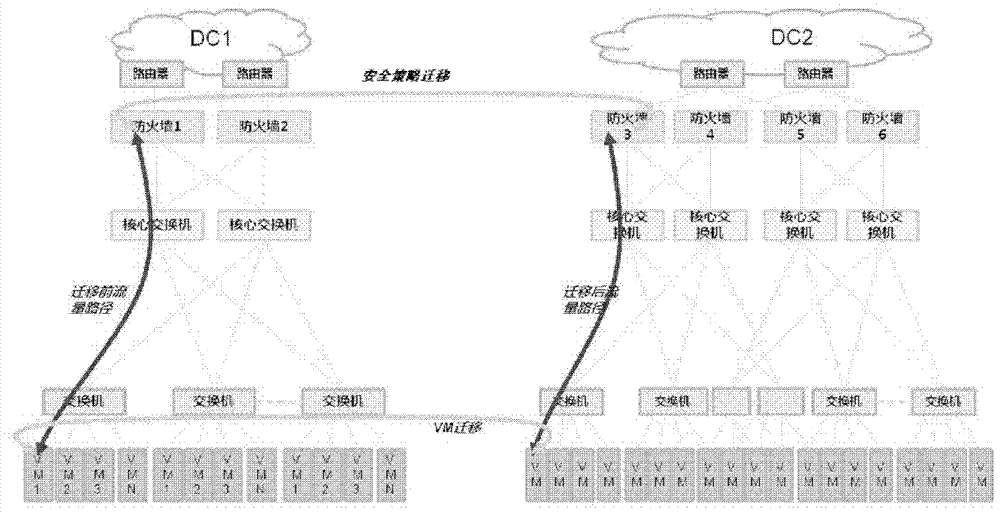
Virtual machine security policy migration system and method based on SDN
InactiveCN103685250AQuick migrationSave resourcesData switching networksSecurity policy managementVirtual machine
The invention discloses a virtual machine security policy migration system based on an SDN. The virtual machine security policy migration system is composed of a security policy management module, a controller cluster control module and a virtual machine migration monitoring module. The invention further discloses a virtual machine security policy migration method based on the SDN. By the adoption of the virtual machine security policy migration system and method based on the SDN, a great number of resources are saved in the whole migration process, and synchronous and flexible transferring of a security policy of a virtual machine is guaranteed automatically, rapidly, easily and conveniently along with the migration of the virtual machine.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
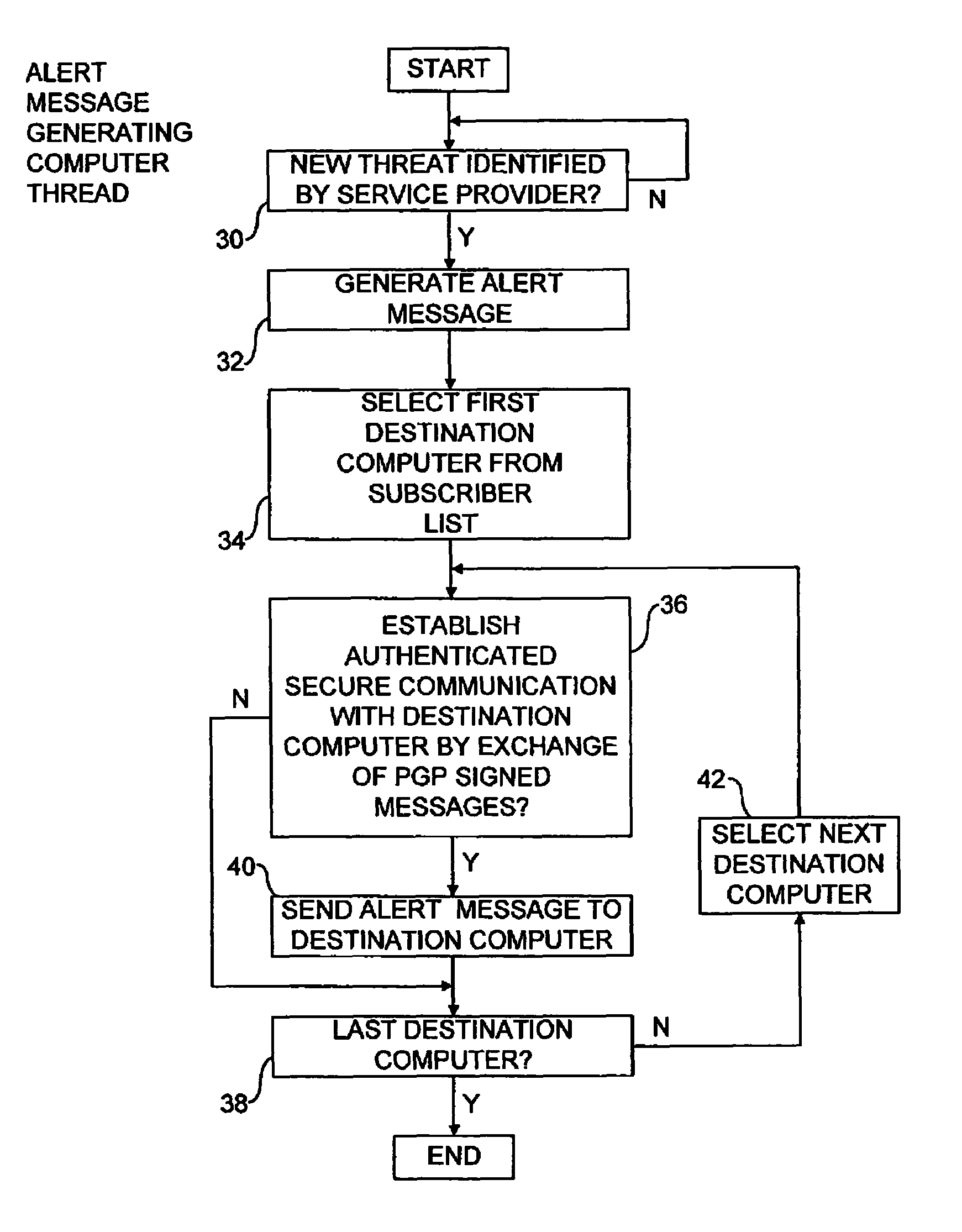
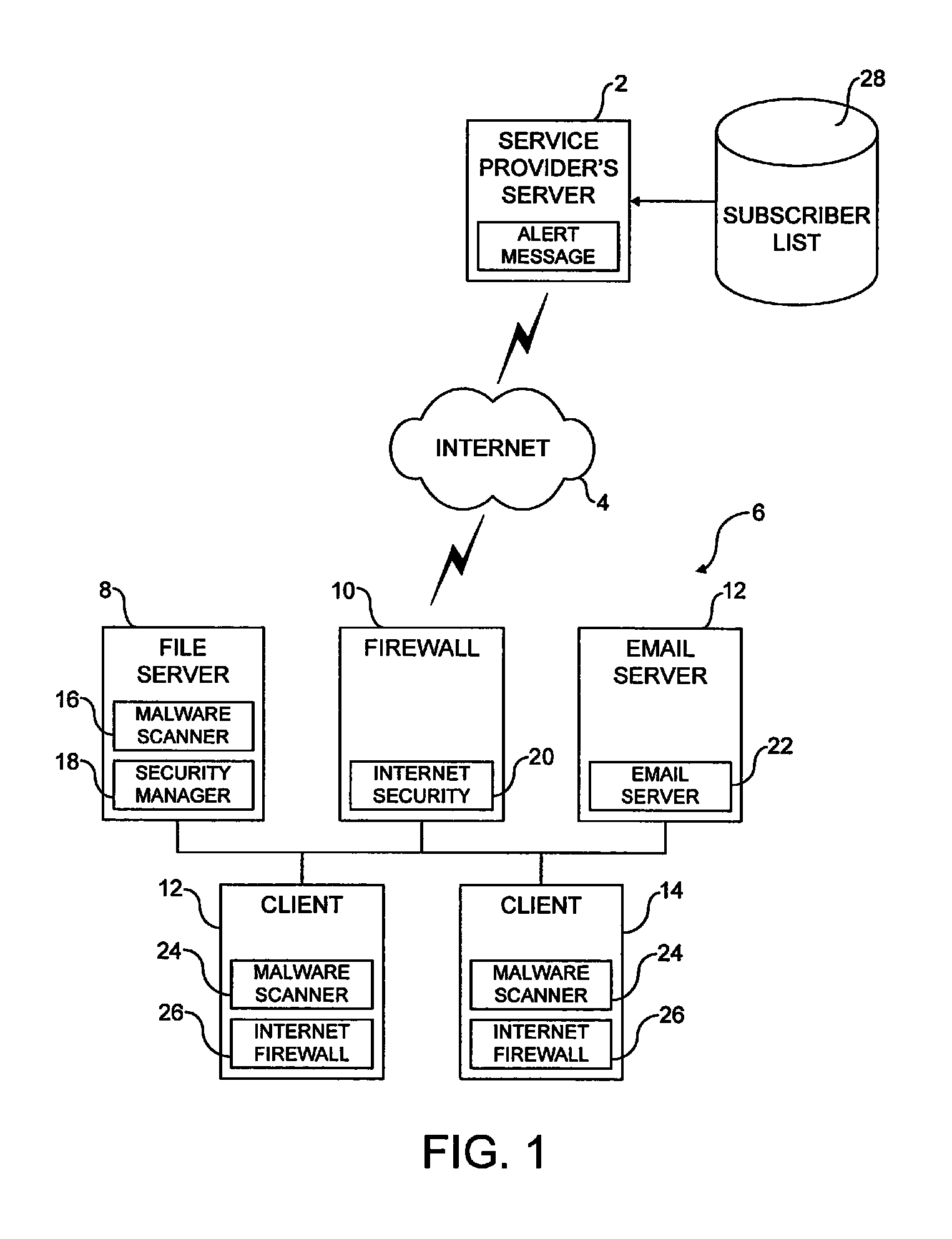
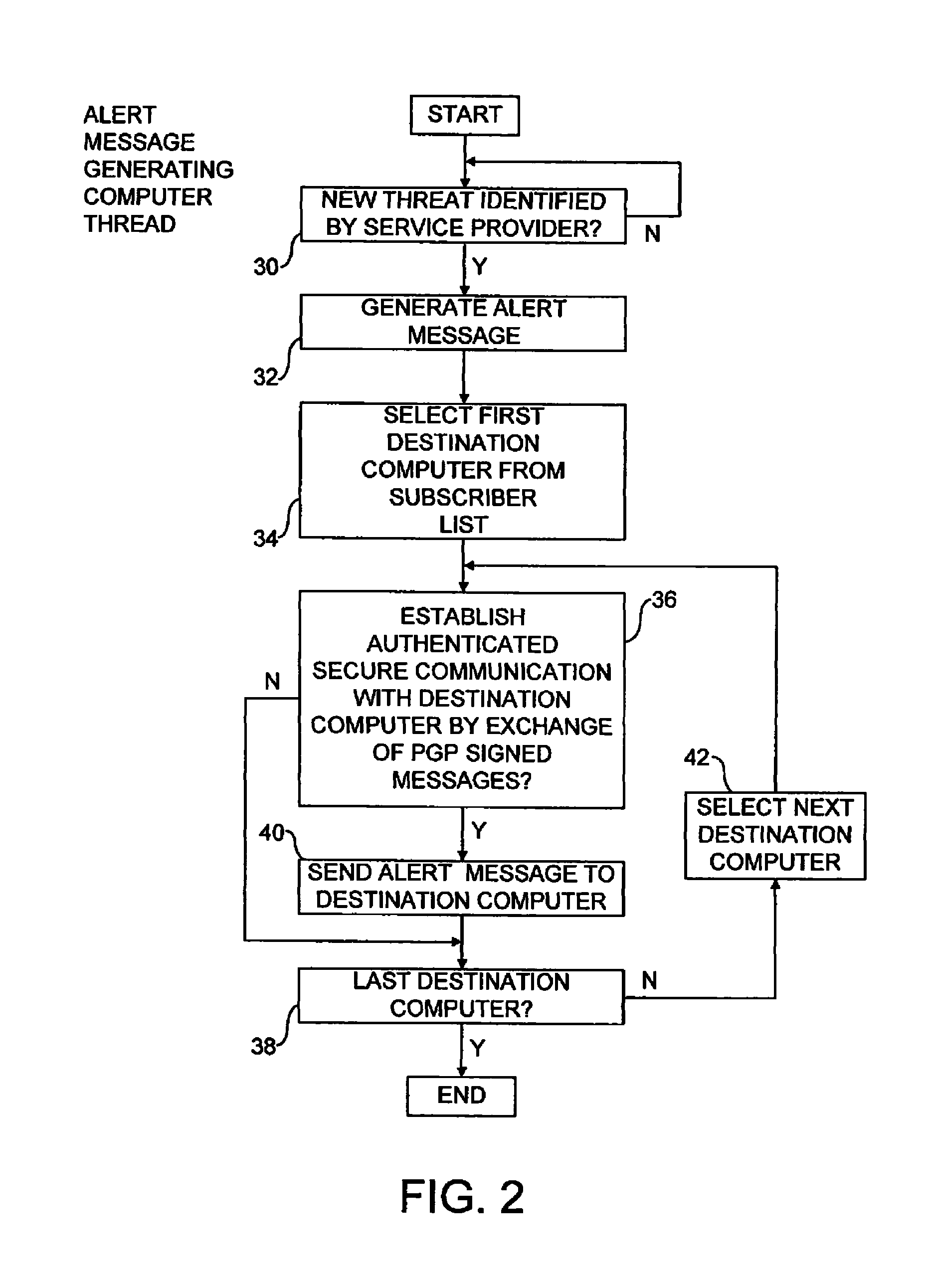
Alert message control of security mechanisms in data processing systems
ActiveUS8042178B1Memory loss protectionError detection/correctionData processing systemCountermeasure
An authenticated secure network communication link is established between an alert message generating computer 2 and a destination data processing system 6. The alert message sent specifies a risk threat level and a suggested countermeasure amongst other data. The destination computer 6 automatically responds to the alert message as controlled by its local response configuration parameters to trigger security actions of one or more security mechanisms, such as malware scanners, firewall scanners, security policy managers and the like.
Owner:MCAFEE LLC
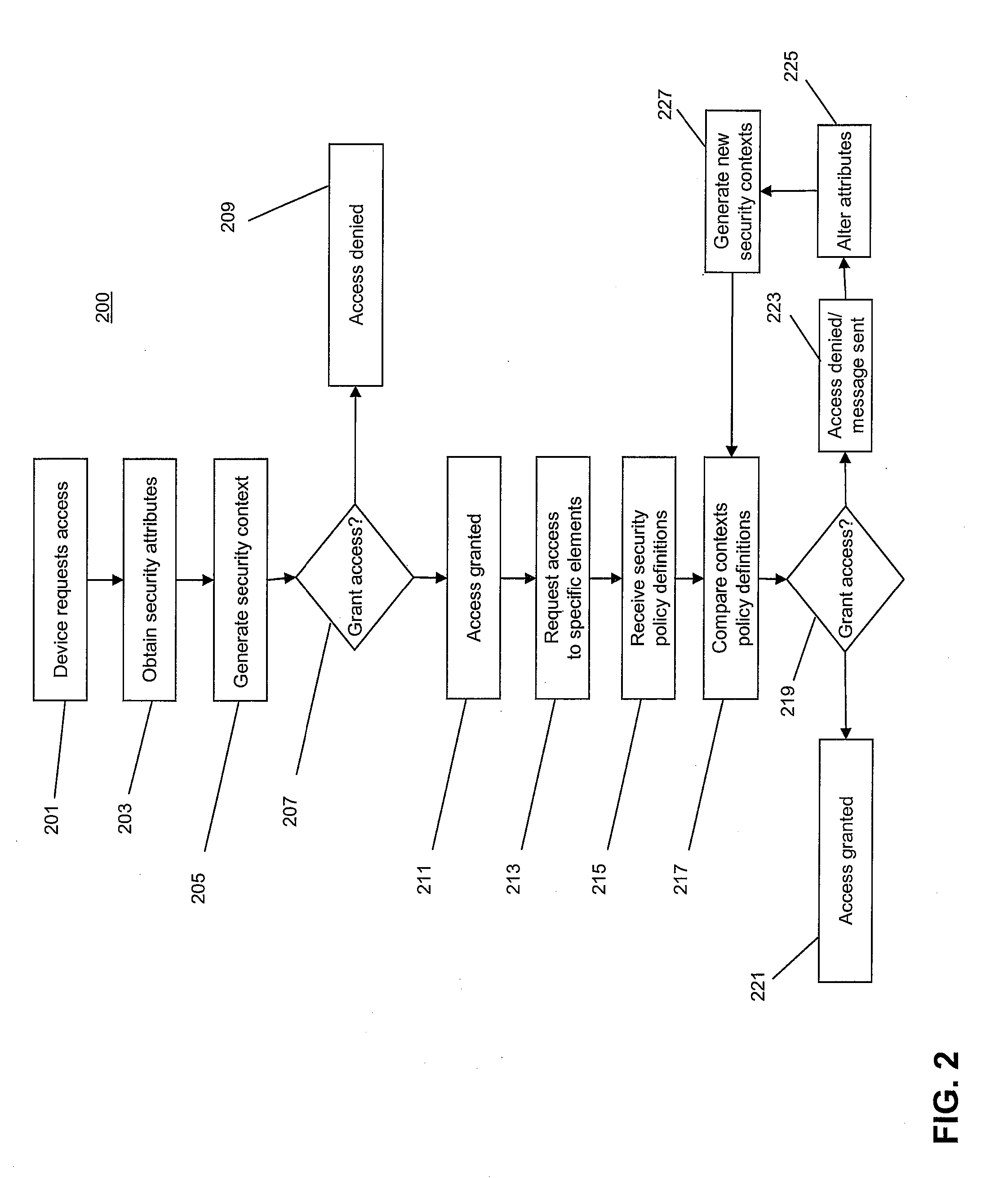
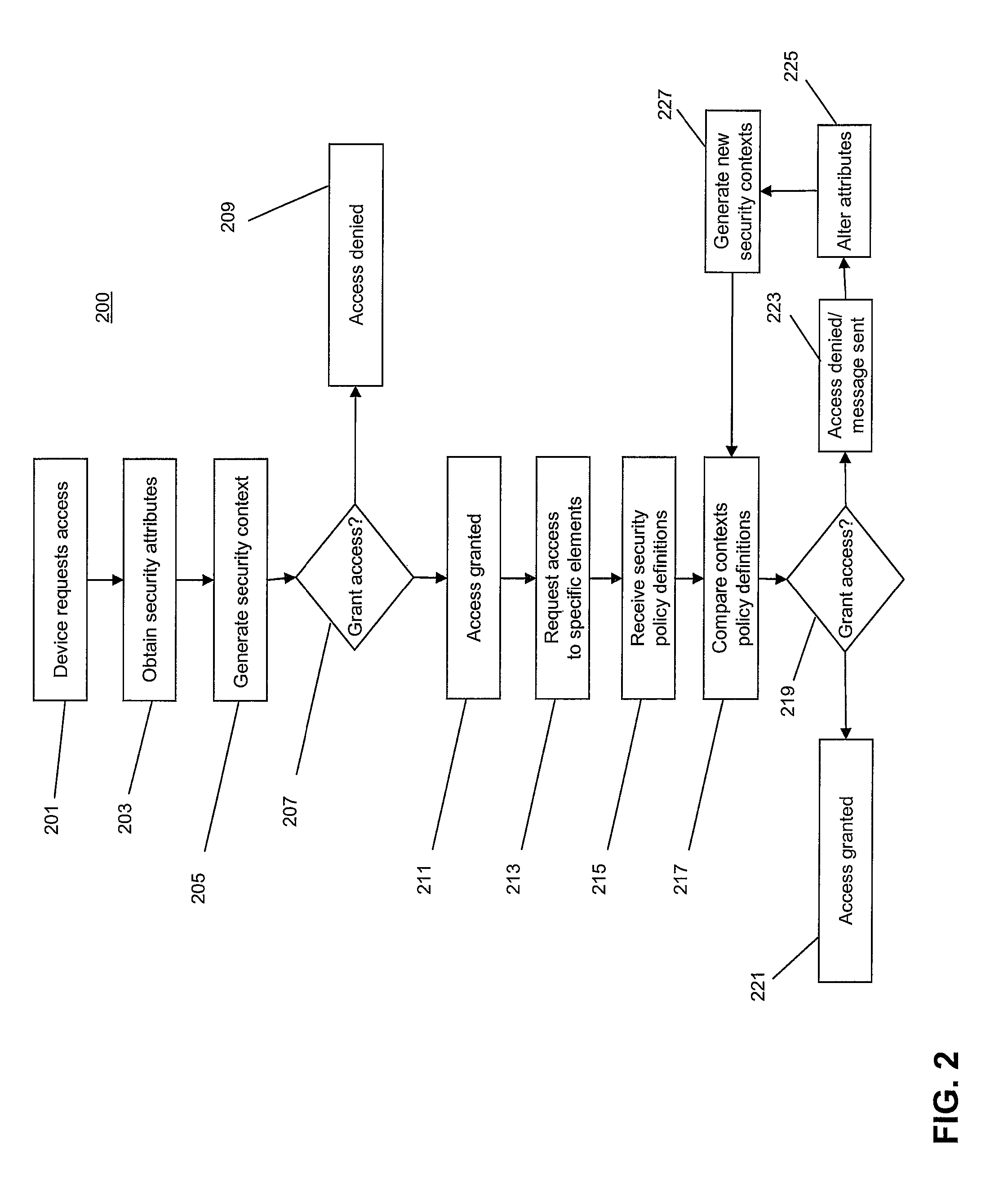
System and method for multi-context policy management
ActiveUS20080155649A1Enhanced Access ControlImprove control configurationComputer security arrangementsTransmissionSecurity policy managementSecurity context
The invention provides systems and methods for multi-context security policy management in a networked computing infrastructure. The invention includes generating a plurality of security contexts regarding different security characteristics of the communication between a computing device and the networked computing infrastructure. The computing device then requests access to at least one specific element of the computing infrastructure. The security policy definitions of the at least one specific element are compared with one or more of the security contexts to determine whether access to the specific elements should be granted.
Owner:COMP ASSOC THINK INC
Risk-based model for security policy management
InactiveUS20130055342A1Impact their effectivenessComputer security arrangementsTransmissionSecurity policy managementTrade offs
A security policy management solution (such as a Data Loss Prevention (DLP) system) is augmented to enable a user to model and visualize how changes in a security policy may impact (positively or negatively) the effectiveness of a policy configuration as well as the risk associated with its deployment. This technique enables a user (e.g., a security policy administrator) to evolve enterprise information technology (IT) security policies and, in particular, to generate and display “what-if” scenarios by which the user can determine trade-offs between, on the one hand, the effectiveness of a proposed change to a policy, and on the other hand, the risk associated with the proposed change.
Owner:IBM CORP
Method and apparatus for role-based security policy management
ActiveUS7484237B2User identity/authority verificationUnauthorized memory use protectionSecurity policy managementPolicy enforcement
A method and corresponding tool are described for security policy management in a network comprising a plurality of hosts and at least one configurable policy enforcement point. The method, comprises creating one or more policy templates representing classes of usage control models within the network that are enforceable by configuration of the policy enforcement points; creating one or more policy instances, each based on one of the templates and instantiating the template for identified sets of hosts within the network to which the usage control model is to be applied, deploying the policy instances by generating and providing one or more configuration files for provisioning corresponding policy enforcement points within the network. Access to the templates and policy instances is controlled so that the policy templates are only modifiable by a first predeterminable user group, the policy instances are only modifiable by the first or a second predeterminable user group and the policy instances are only deployable by a third predeterminable user group.
Owner:VALTRUS INNOVATIONS LTD +1
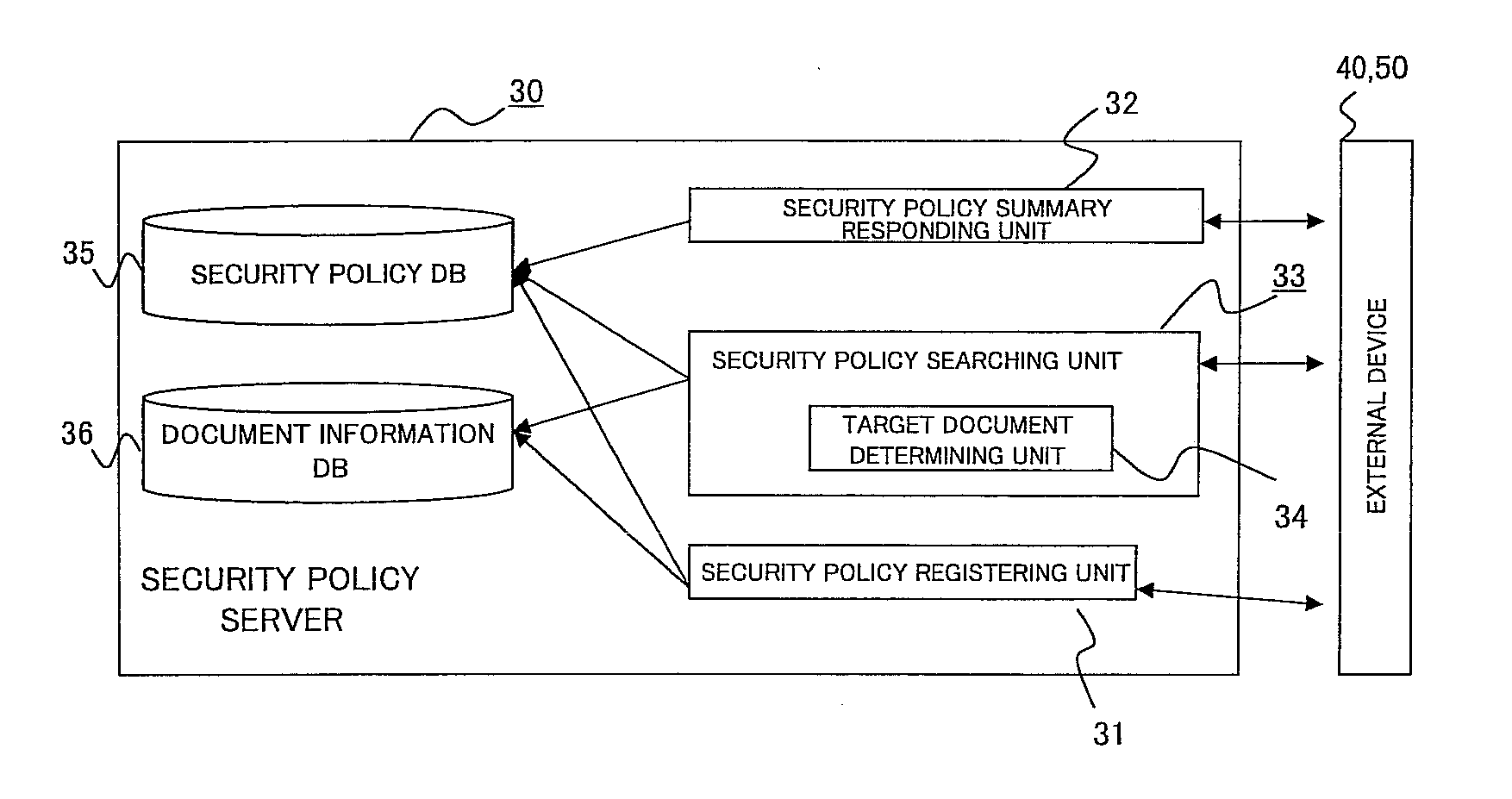
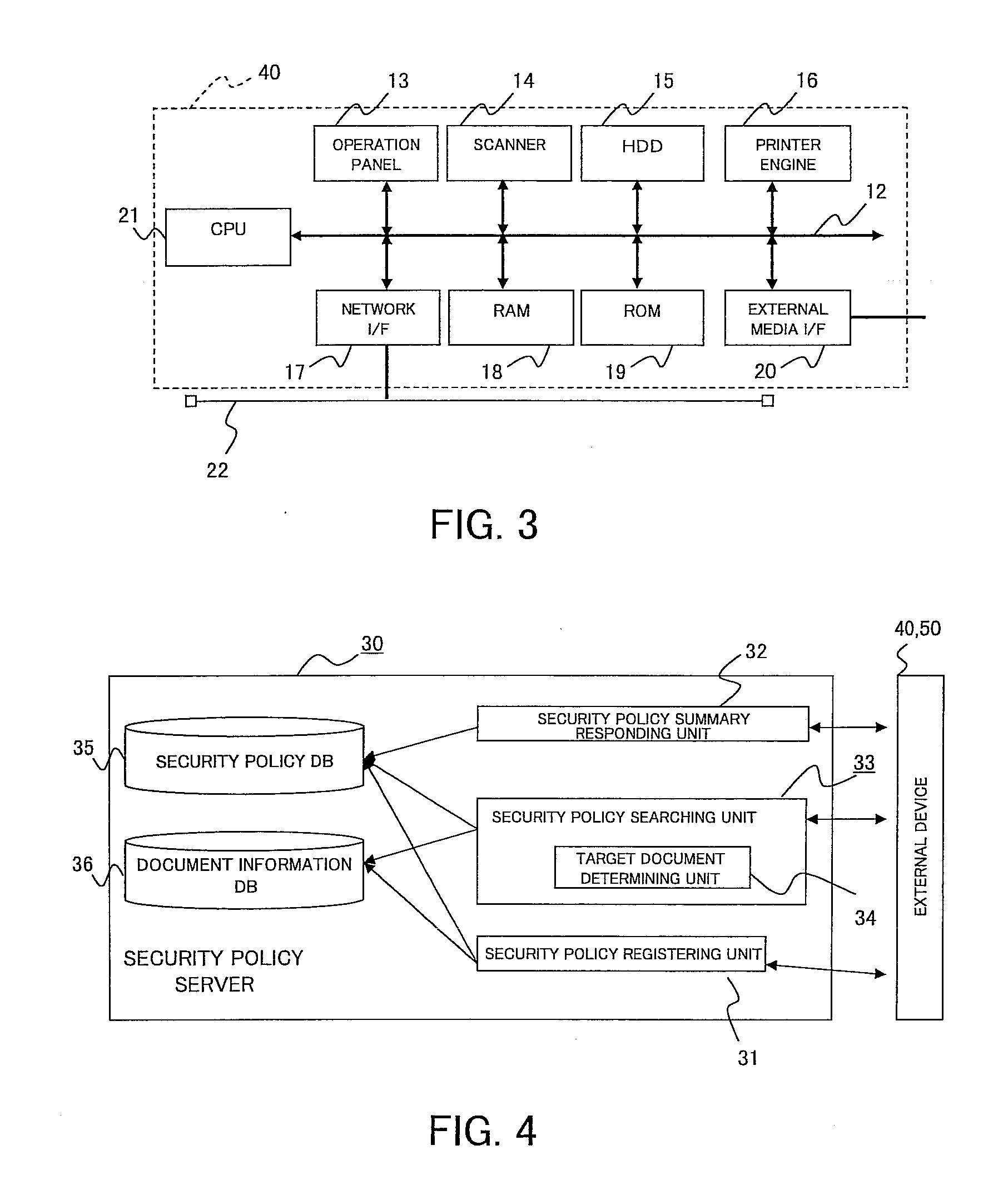
Security policy management device, security policy management system, and storage medium
Policy information stores policy setting information and identification information of a policy in correlation with each other, the policy setting information correlating setting content of the policy with each data type information indicating whether data for which the policy is set is original data or derived data. A data information storage stores identification information of data for which a policy is set in correlation with the data and identification information of the policy attached to the data, and information for identifying that the data is the derived data. A searching unit identifies, in response to a searching request, identification information of a policy correlated to the data whose identification information is designated in the searching request, identifies whether target data of the searching request is the original data or the derived data.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Real time active network compartmentalization
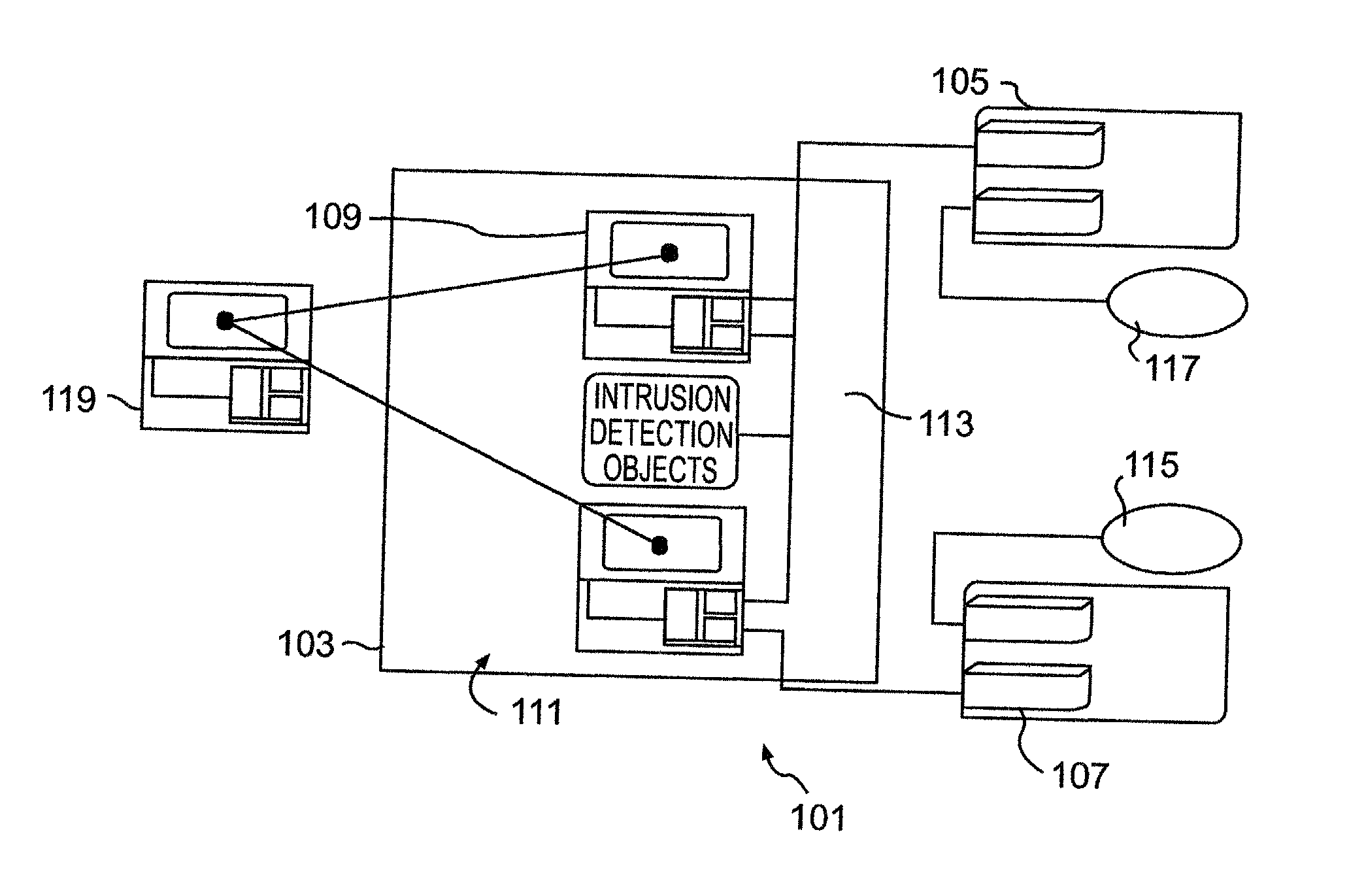
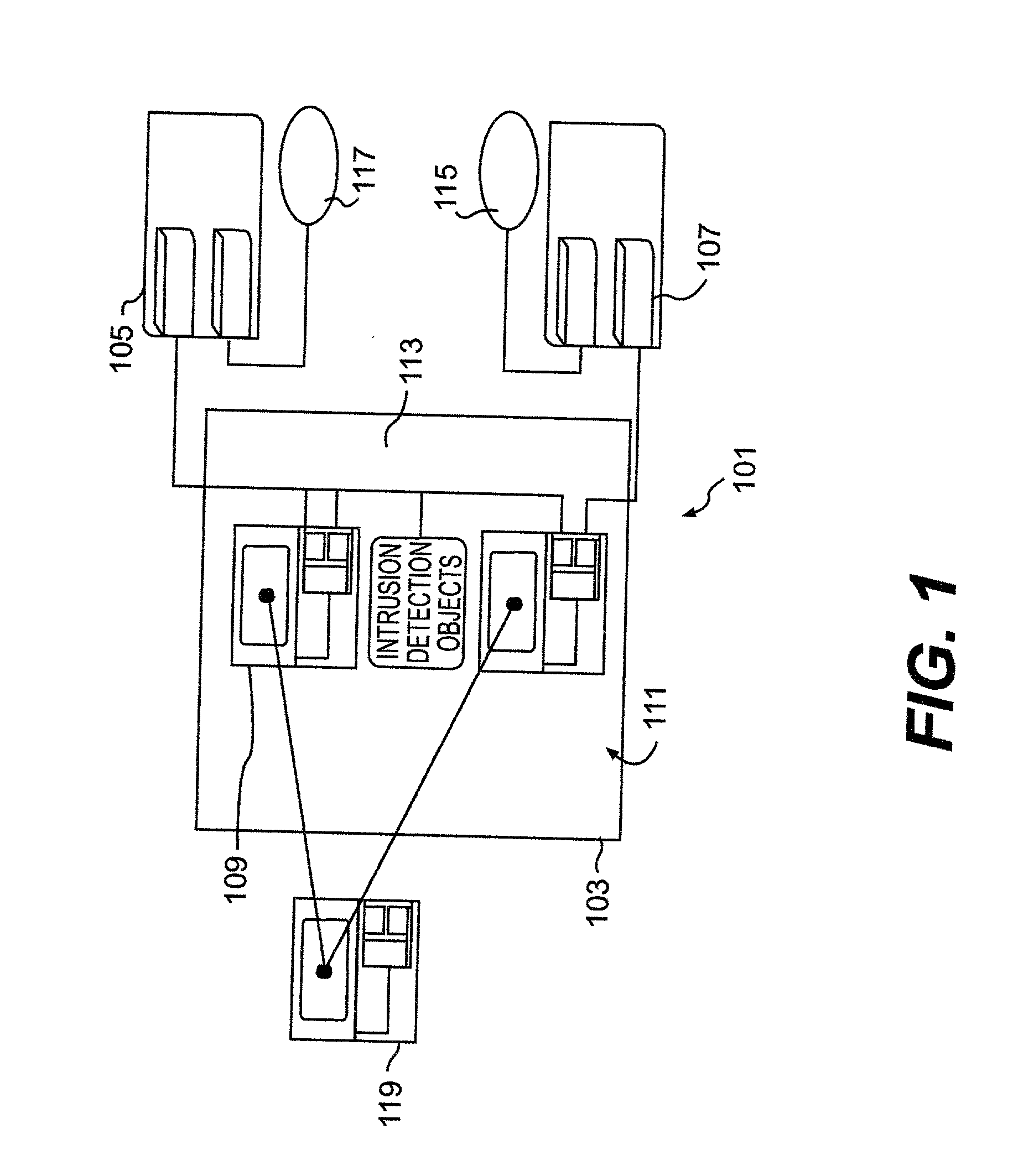
ActiveUS20020059528A1Improve functionalityMinimal disruptionError preventionFrequency-division multiplex detailsInbound communicationSecurity domain
Security policy manager devices are leveraged by manager objects to use highly secure user transparent communications to provide detection of questionable activities at every node, automatic collection of information related to any potential attack, isolation of the offending object with arbitrary flexibility of response (e.g. flexibly determining the level of certainty of an attack for initiation of a response in accordance with the number of nodes to be partitioned that is determined by the collected data concerning the potential attack), changing trust relationships between security domains, limiting the attack and launching offensive information warfare capabilities (e.g. outbound from the compromised node while limiting or eliminating inbound communications) in log time and simultaneously and / or concurrently in different but possibly overlapping sections or segments of a digital network of arbitrary configuration.
Owner:LOCKHEED MARTIN CORP
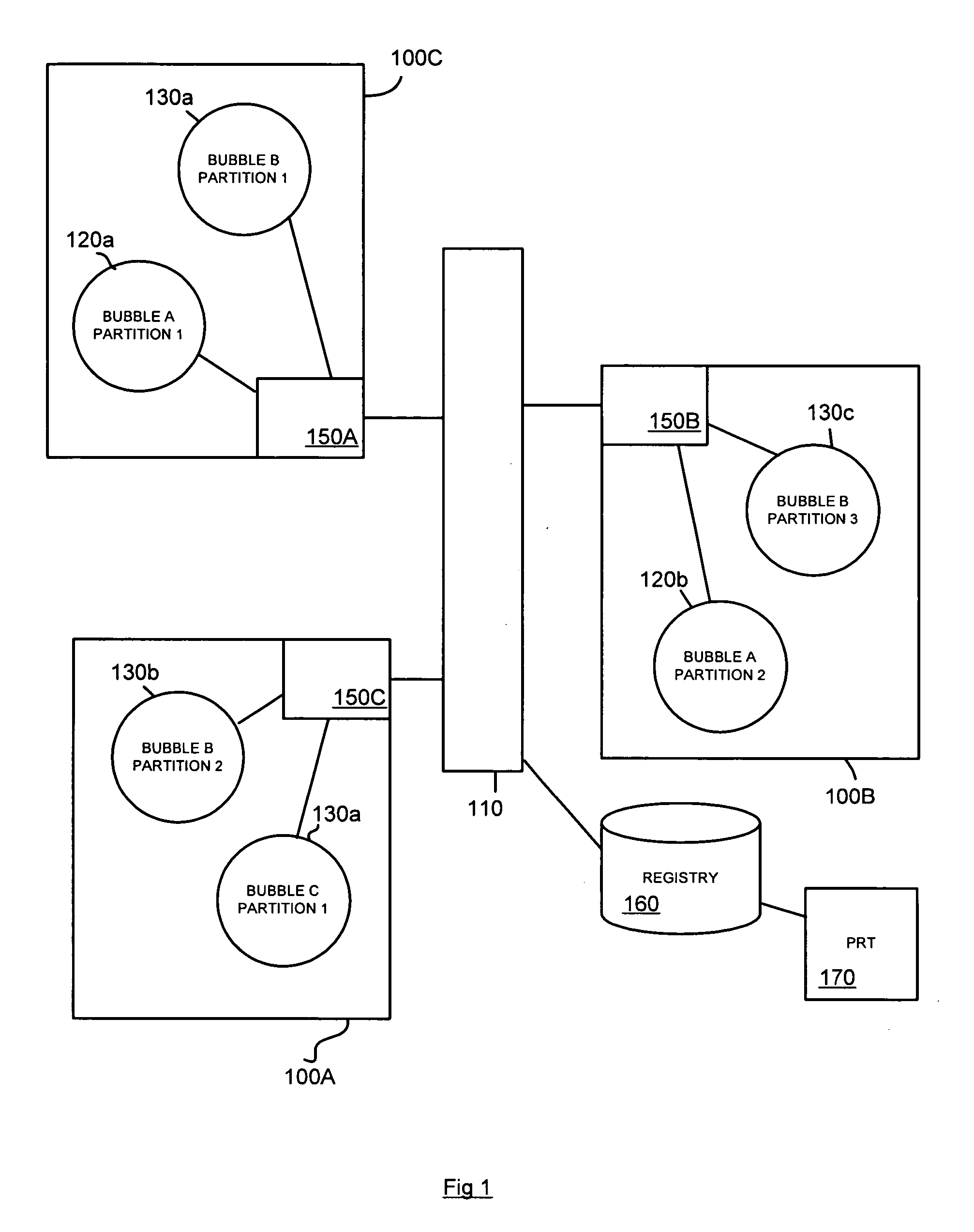
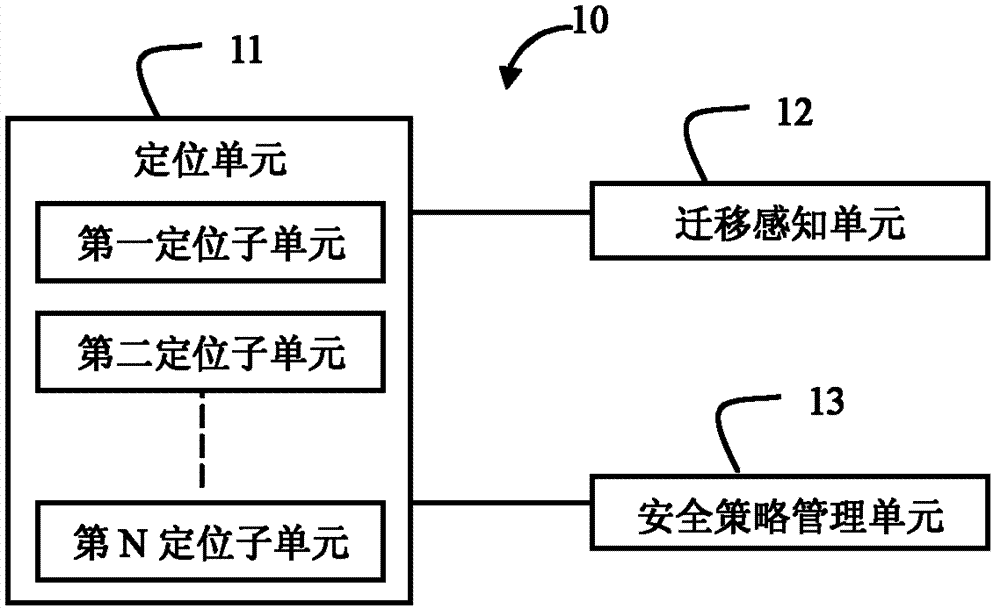
Method and device for migrating virtual machine safety policy
ActiveCN102739645AEliminate manual configuration operationsProgram controlData switching networksManagement unitData center
The invention discloses a virtual machine safety policy migrating device which is applied in a safety management server in a data center and comprises a migration sensing unit, a positioning unit and a safety policy management unit, wherein the migration sensing unit is used for receiving a virtual machine migration report from a virtual machine management device; the report contains location parameters of the virtual machine; the positioning unit is used for determining an original safety device to which the virtual machine belongs before the migration according to the location parameters of the virtual machine, and a new safety device to which the virtual machine belongs after the migration; the safety policy management unit is used for obtaining the safety policy of the virtual machine configured on the original safety device, and transmitting the safety policy to the new safety device. By utilizing the virtual machine safety policy migrating device, the automatic seamless migration of the safety policy of the safety device on the virtual machine along with the migration of the virtual migration is realized; and the manual configuration operation of a manager on the safety device because of the migration of the virtual machine is avoided, which means a lot for a large data center in which the virtual machine migrates often.
Owner:NEW H3C TECH CO LTD
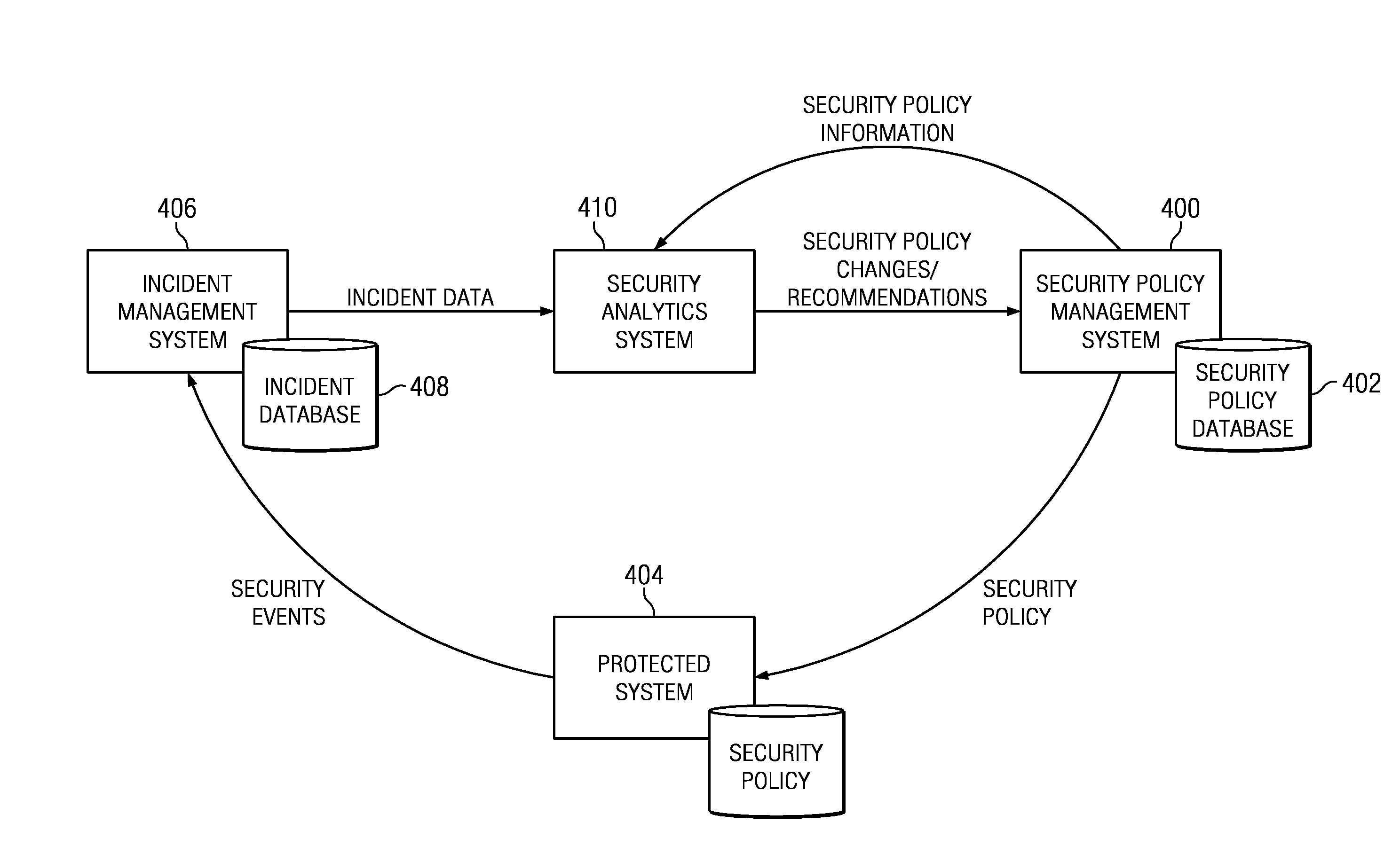
Security policy management using incident analysis
InactiveUS20130179938A1Understand perceived and measured effectiveness and costReduce in quantityError detection/correctionForecastingData setIncident analysis
A security analytics system receives incident data (from an incident management system) and security policy information (from a security policy management system). The security analytics system evaluates these data sets against one another, preferably using a rules-based analysis engine. As a result, the security analytics system determines whether a particular security policy configuration (as established by the security policy management system) needs to be (or should be) changed, e.g., to reduce the number of incidents caused by a misconfiguration, to increase its effectiveness in some manner, or the like. As a result of the evaluation, the security analytics system may cause a policy to be updated automatically, notify an administrator of the need for the change (and the recommendation), or take some other action to evolve one or more security policies being enforced by the security policy management system.
Owner:IBM CORP
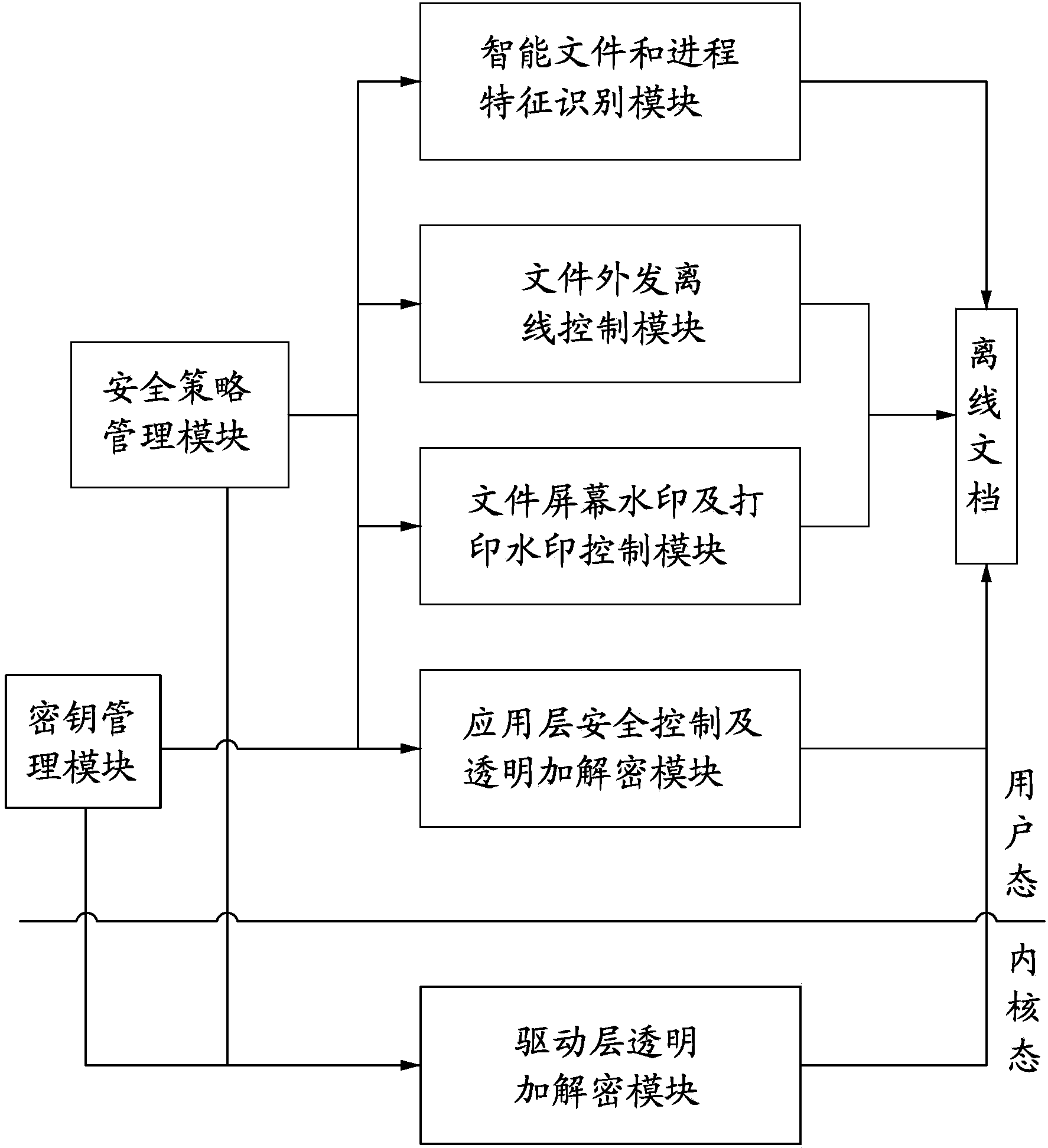
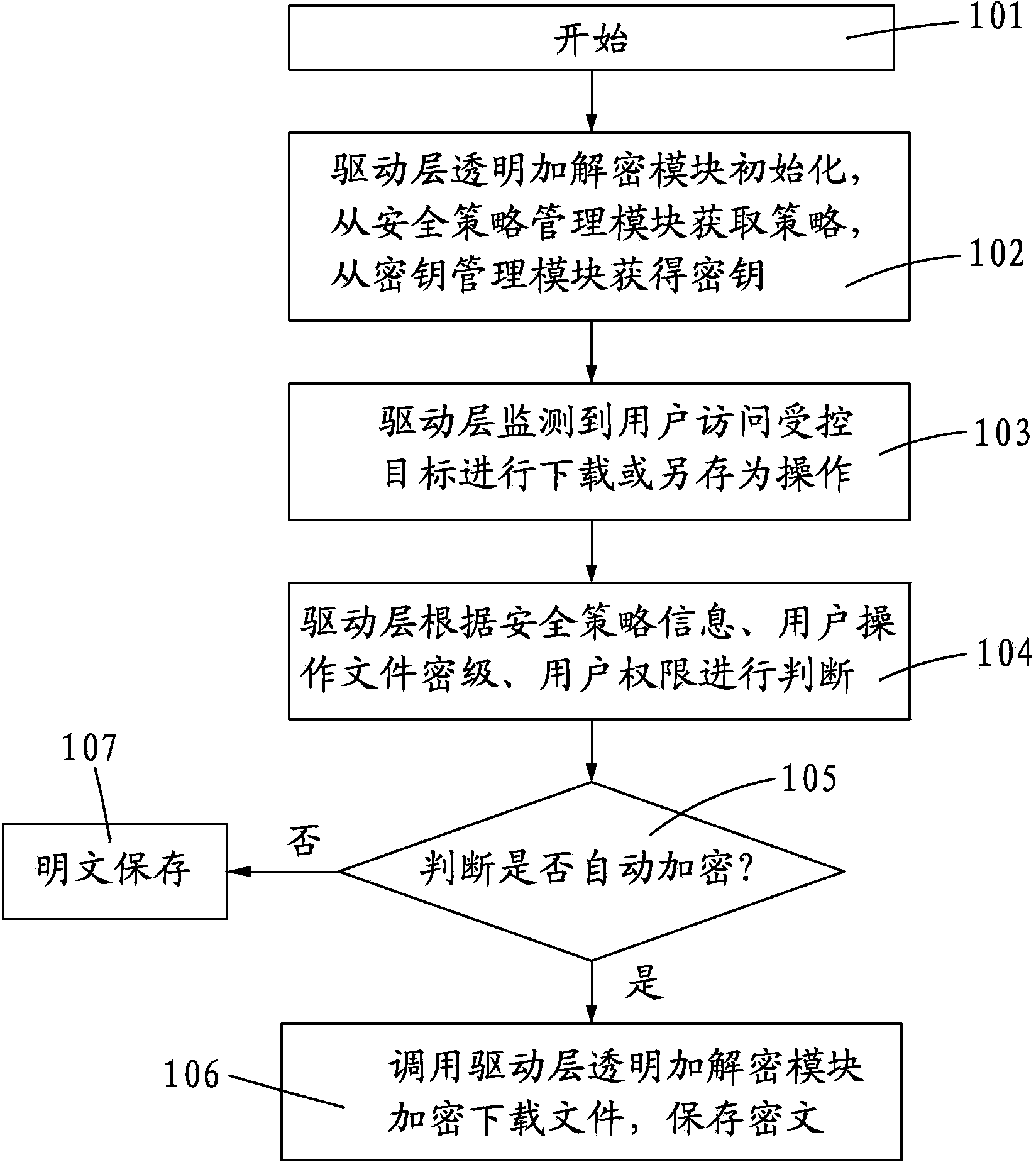
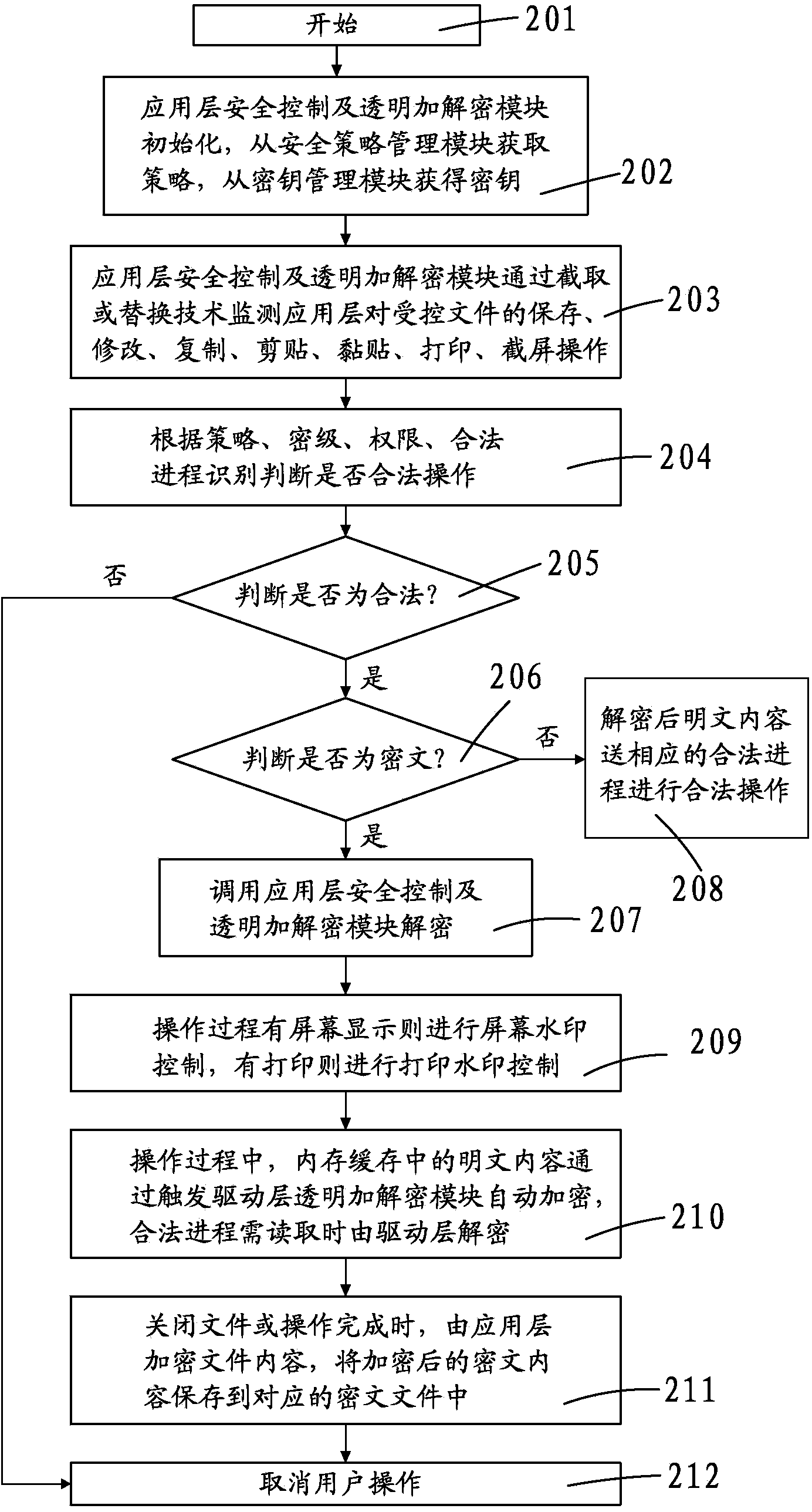
Electronic document safety management system and method
ActiveCN103530570AGuaranteed security controlImprove offline securityDigital data protectionElectronic documentOperational system
The invention discloses an electronic document safety management system and method. The electronic document safety management system comprises a driving layer transparent encryption and decryption module, an application layer safety control and transparent encryption and decryption module, an intelligent file and process characteristic identification module, a file outside issuing off-line control module, a file screen watermark and printing watermark control module, a safety strategy management module and a secret key management module. The core technology of the system is managed in the driver of a client terminal, is operated in the core of the Windows operating system, and is called by an I / O manager to meet the demand of a file system. A data encryption platform of the system will take over the file system of the whole Windows operating system, and is responsible for providing the transparent encryption and decryption data services for the file system in real time. According to the electronic document safety management system and method, due to the fact that the electronic file safety protection measures are improved and the transparent encryption and decryption methods are imported, the off-line high safety and user friendliness of the electronic files are achieved.
Owner:STATE GRID CORP OF CHINA +1
System and method for multi-context policy management
ActiveUS7987495B2Better and more accurate security policy decisions and enforcementImprove configurationComputer security arrangementsSpecial data processing applicationsSecurity policy managementSecurity context
The system and method described herein provides multi-context security policy management in a networked computing infrastructure. The system and method may generate a plurality of security contexts regarding different security characteristics of the communication between a computing device and the networked computing infrastructure. The computing device then requests access to at least one specific element of the computing infrastructure. The security policy definitions of the at least one specific element are compared with one or more of the security contexts to determine whether access to the specific elements should be granted.
Owner:COMP ASSOC THINK INC
System and method for data mining and security policy management
InactiveUS20130254838A1Digital data protectionMulti-dimensional databasesData managementSecurity policy management
Owner:MCAFEE LLC
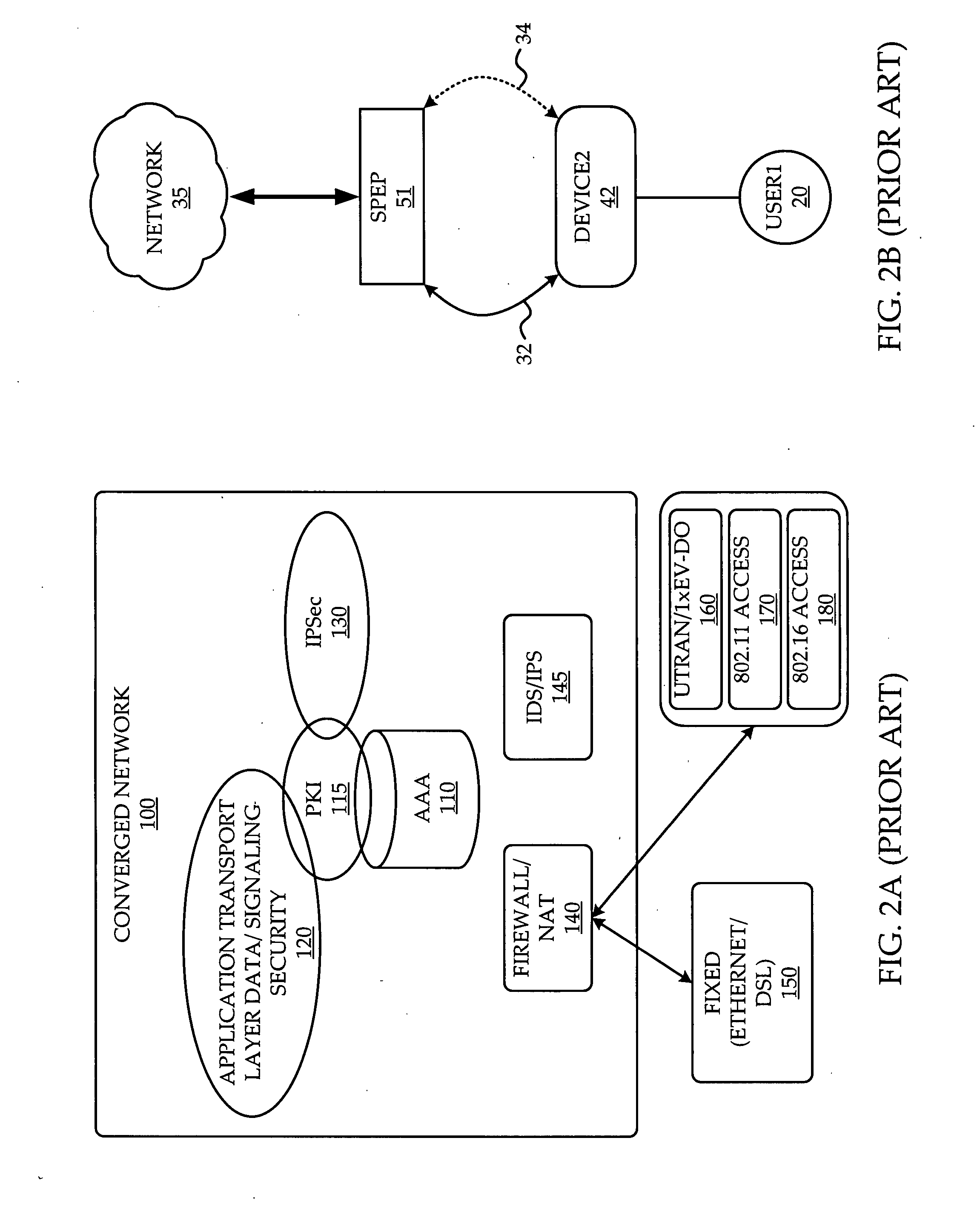
System and method of network access security policy management by user and device
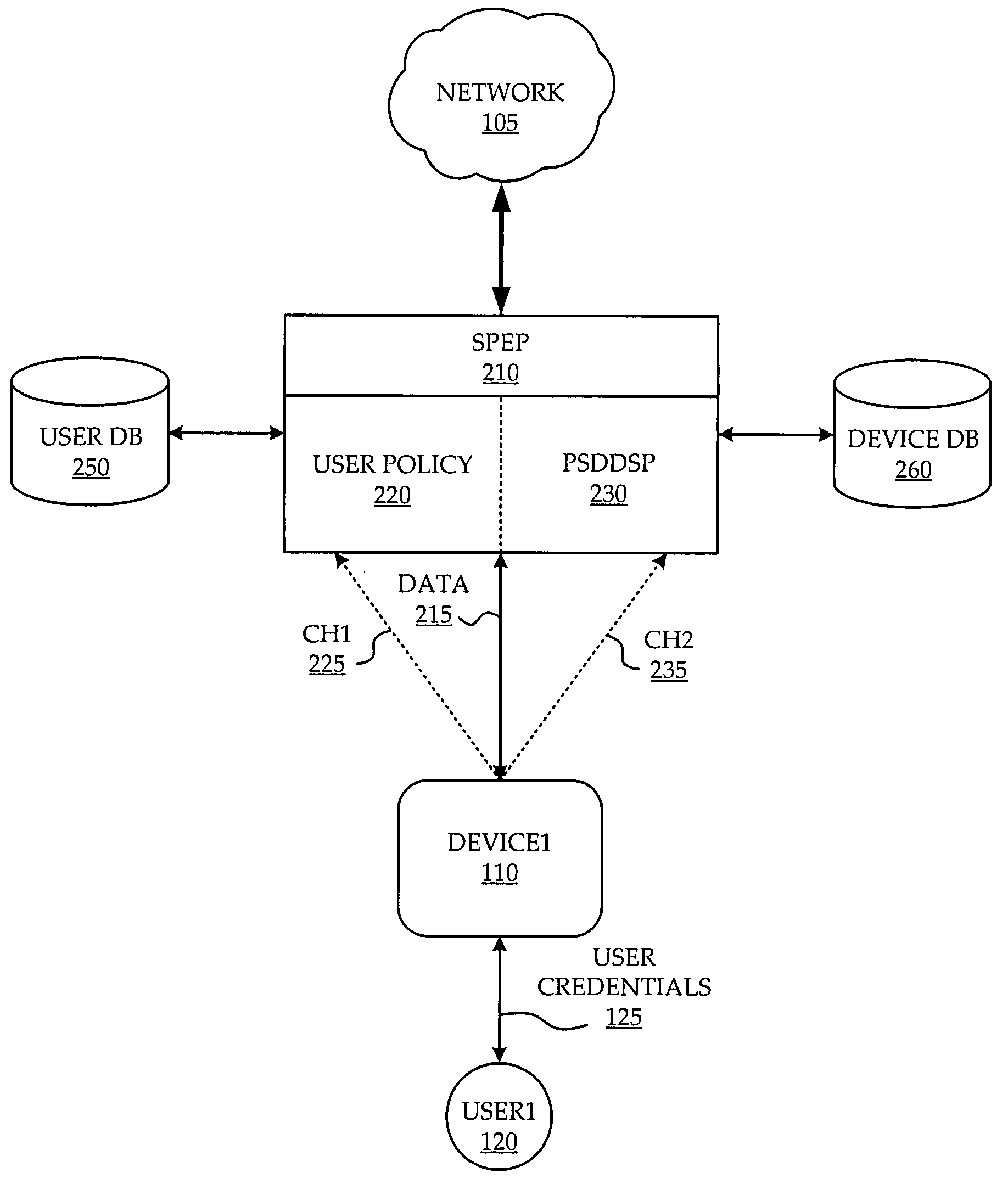
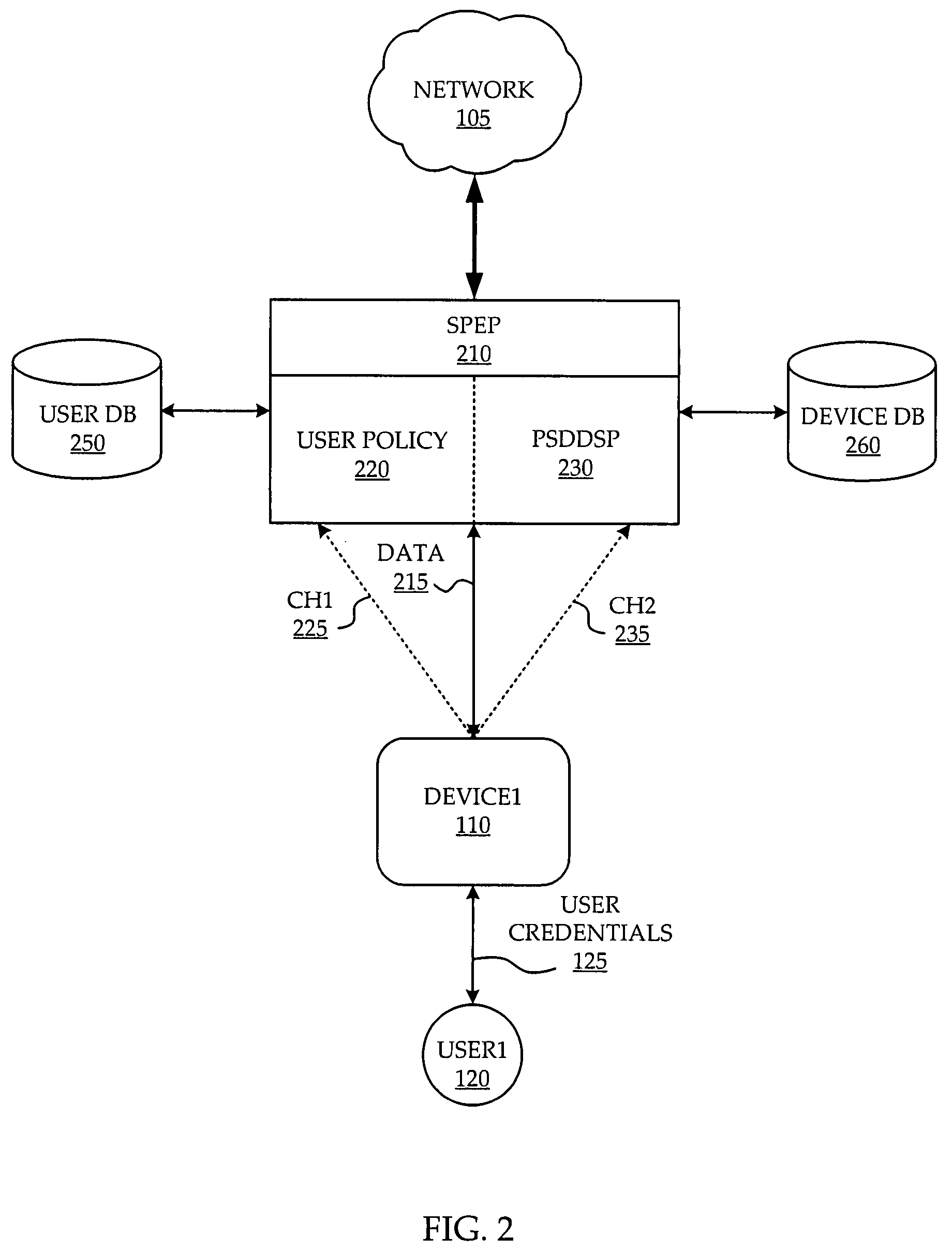
ActiveUS20080196088A1Digital data processing detailsUser identity/authority verificationComputer networkSecurity policy management
A system and method are provided for management of access security by user and device. A security policy enforcement point is provided with a user policy module to receive user credentials from an access device of the user and a point for setting device dependent security policy to receive device credentials from the access device. A user policy is retrieved from a user database with use of the user credentials while a device policy is retrieved from a device database with use of the device credentials. The user policy and device policy are combined and used in the SPEP to enforce a user and device based security policy.
Owner:ALCATEL LUCENT SAS
Method and system for trusted control of operating environment of Android intelligent terminal
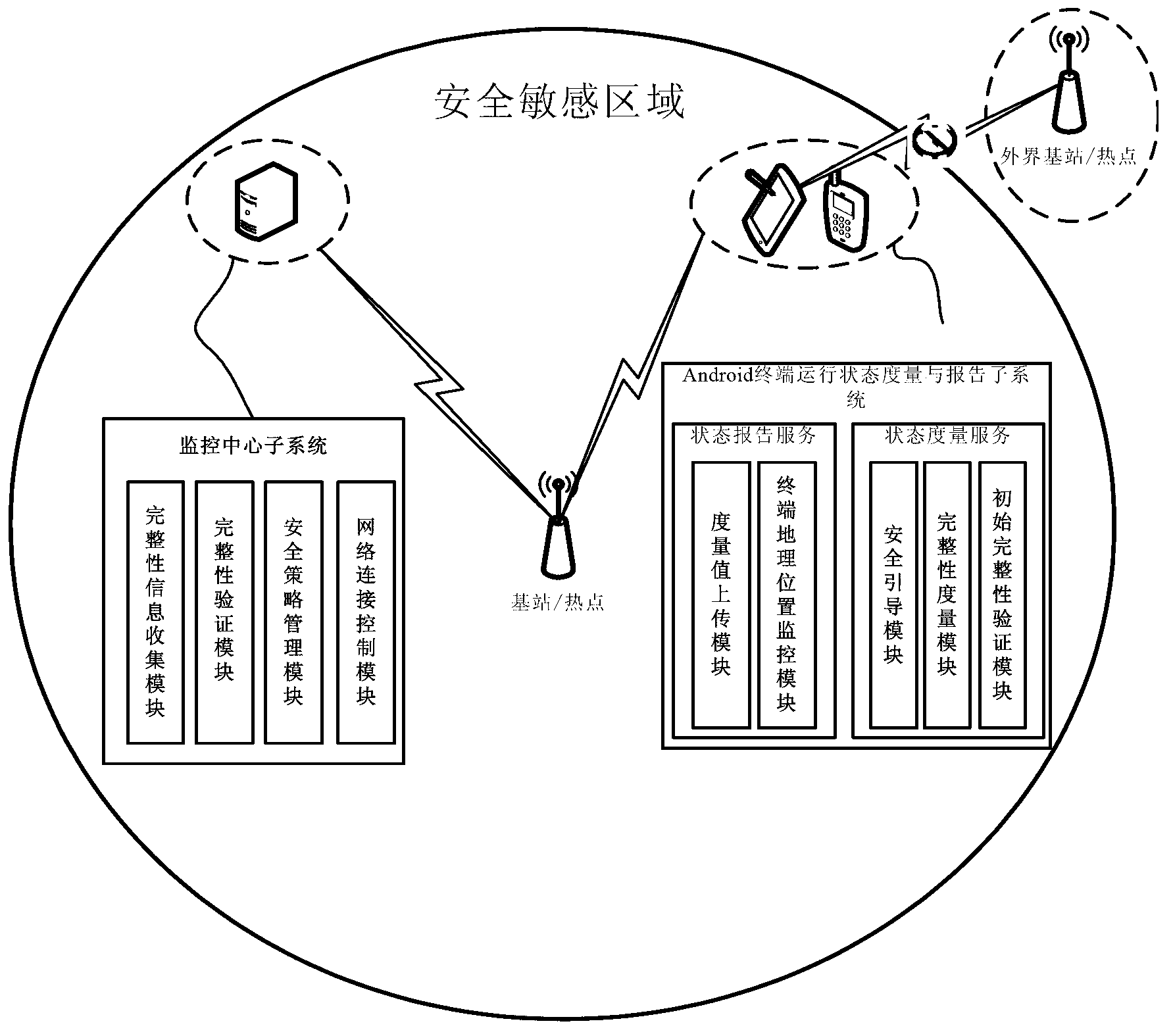
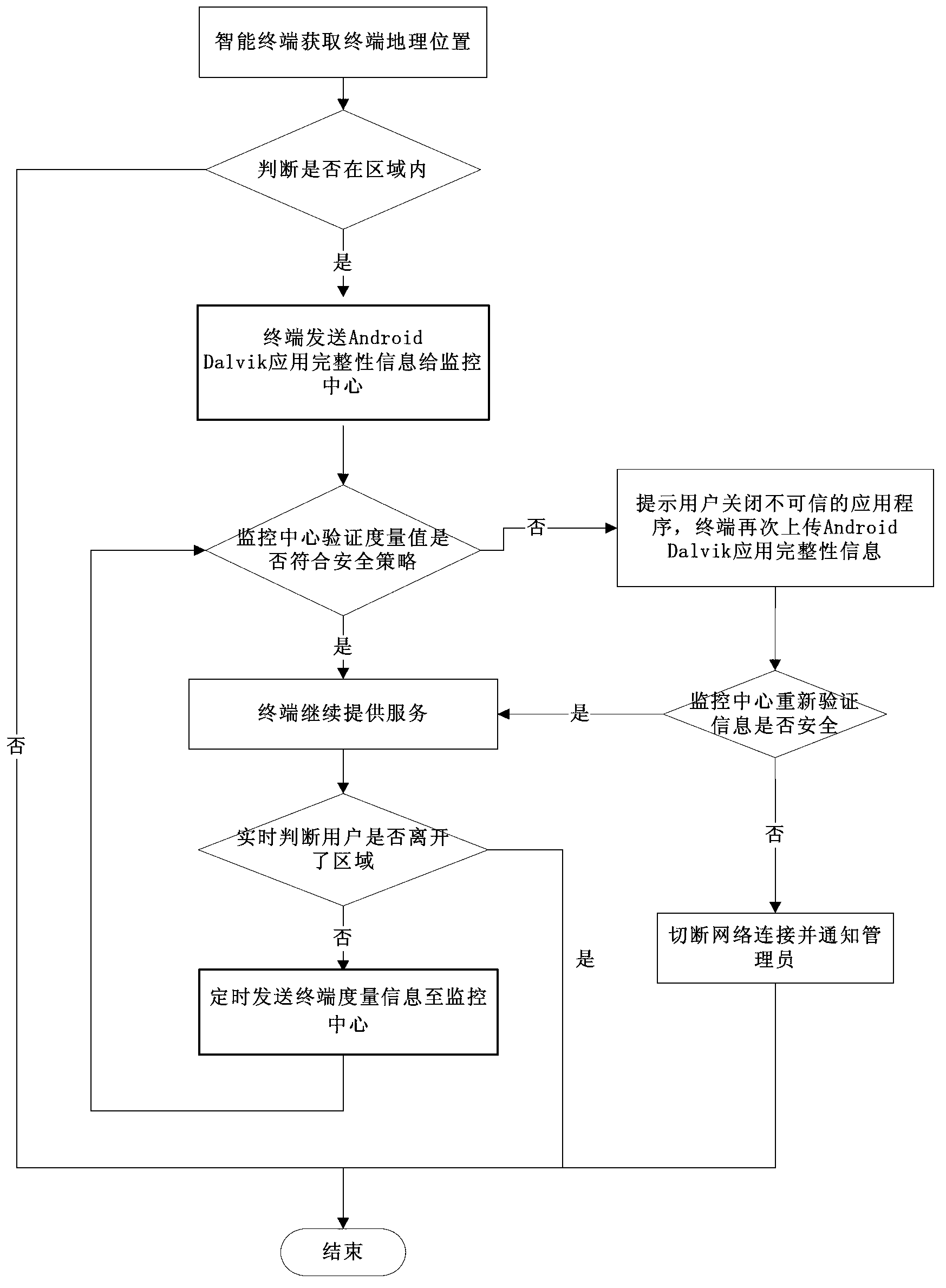
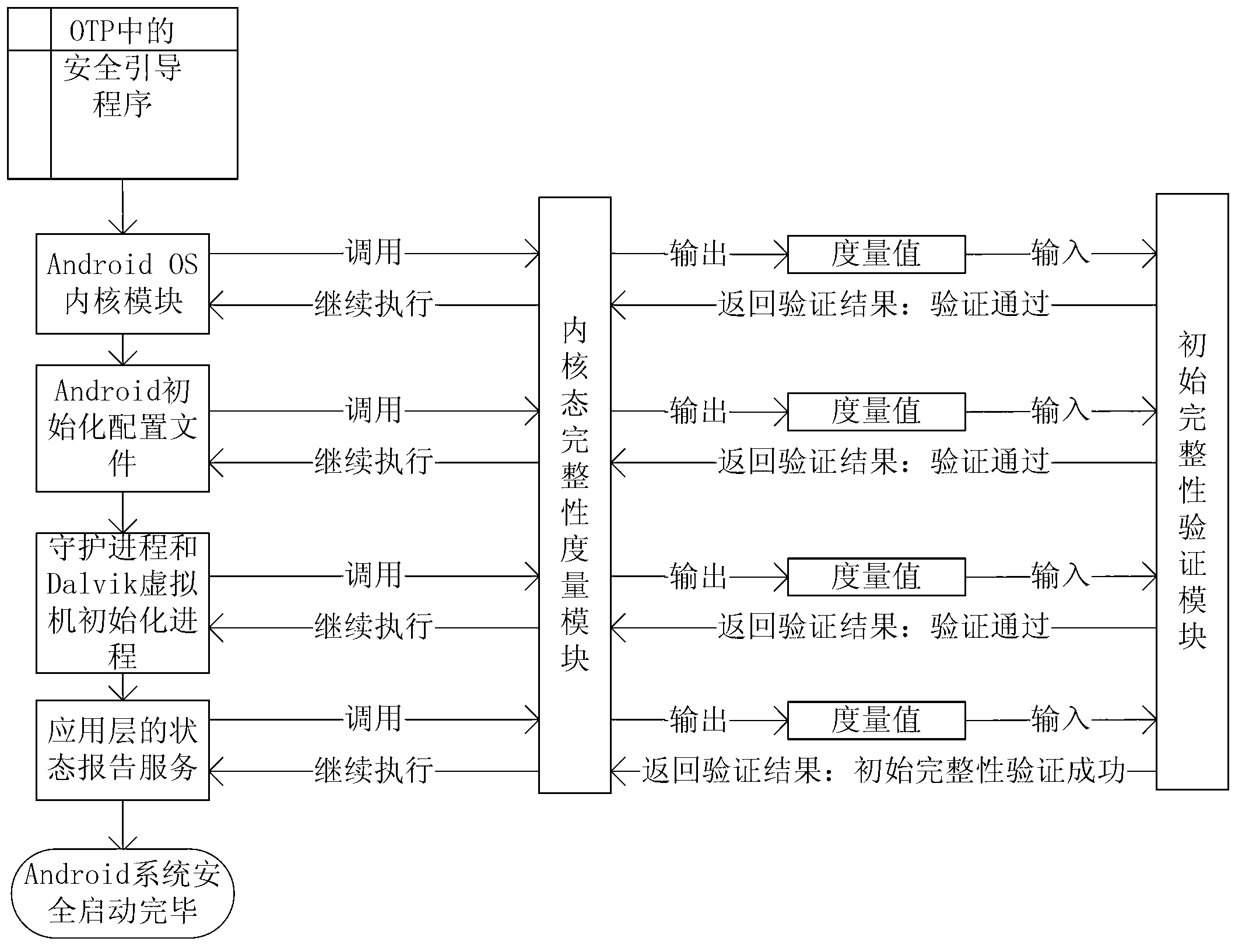
InactiveCN103020531APrevent the spread of stealingGuaranteed confidentialityPlatform integrity maintainanceProgram managementRemote control
The invention relates to a method and a system for trusted control of an operating environment of an Android intelligent terminal. After the Android OS (operating system) of the Android terminal is safety started up, the trusted startup of an Android Dalvik application is conducted, the Android terminal monitors whether the geographical location of the terminal is in a preset sensitive area or not in real time, the Android terminal reports the integrity information of the Android Dalvik application to a monitoring center, the monitoring center sequentially verifies the integrity information of the application according to the security strategies of a security strategy management module, a verification result is fed back to the terminal through the integrity information collection module of the Android terminal, and the terminal executes corresponding operation according to the verification result and then again verifies whether the integrity information of the application is secure or not. By conducting remote control and application program management to a mobile terminal in the sensitive area and cutting off the addressing capability of the terminal, confidential information is prevented from being stolen and diffused.
Owner:HUAWEI TECH CO LTD +1
Partial grant set evaluation from partial evidence in an evidence-based security policy manager
InactiveUS20070192839A1Digital data processing detailsUser identity/authority verificationCall stackEngineering
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. The policy manager may determine a subset of the permission grant set based on a subset of the received code assembly's evidence, in order to expedite processing of the code assembly. When the evidence subset does not yield the desired permission subset, the policy manager may then perform an evaluation of all evidence received.
Owner:MICROSOFT TECH LICENSING LLC
Distributed network security control method of public cloud service
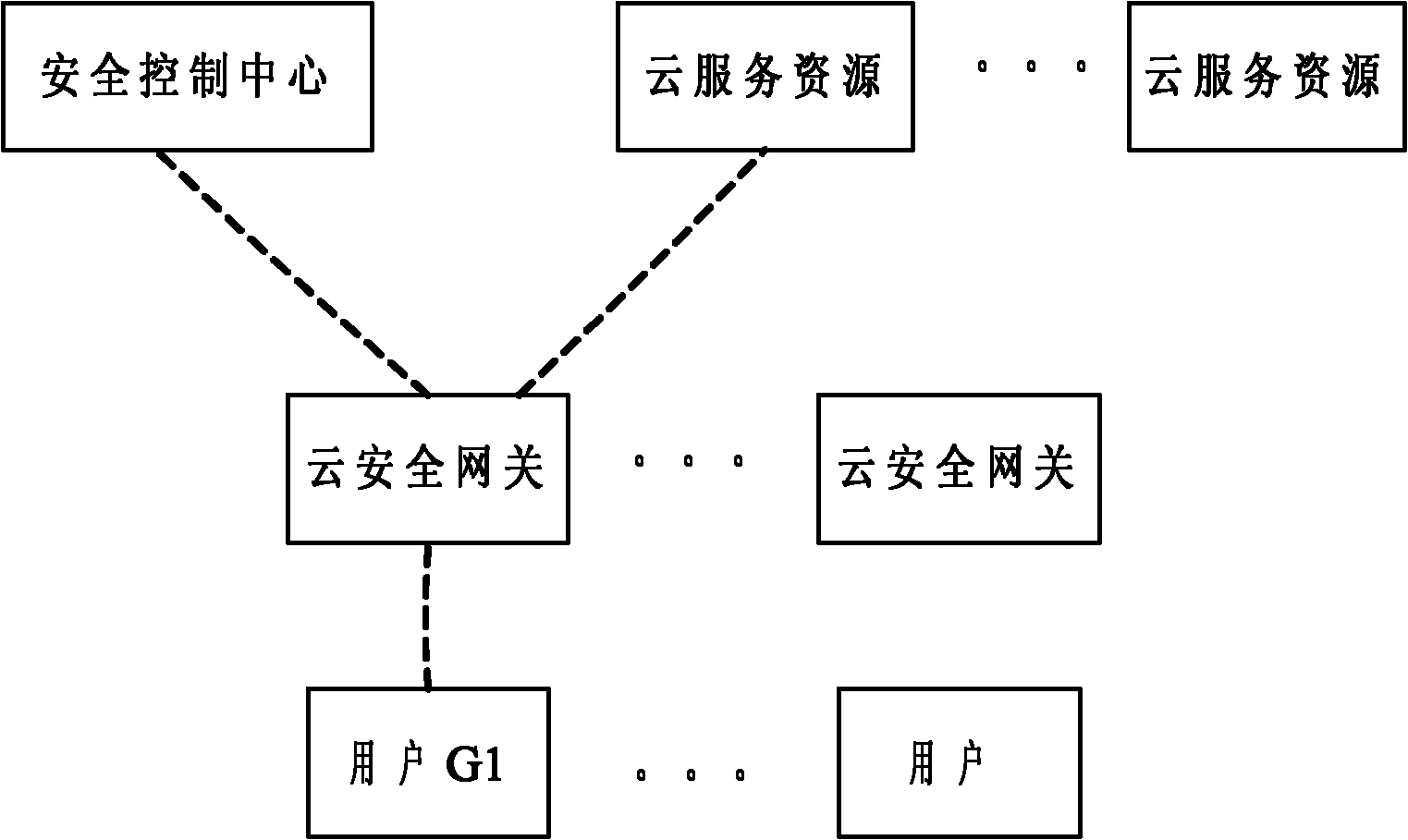
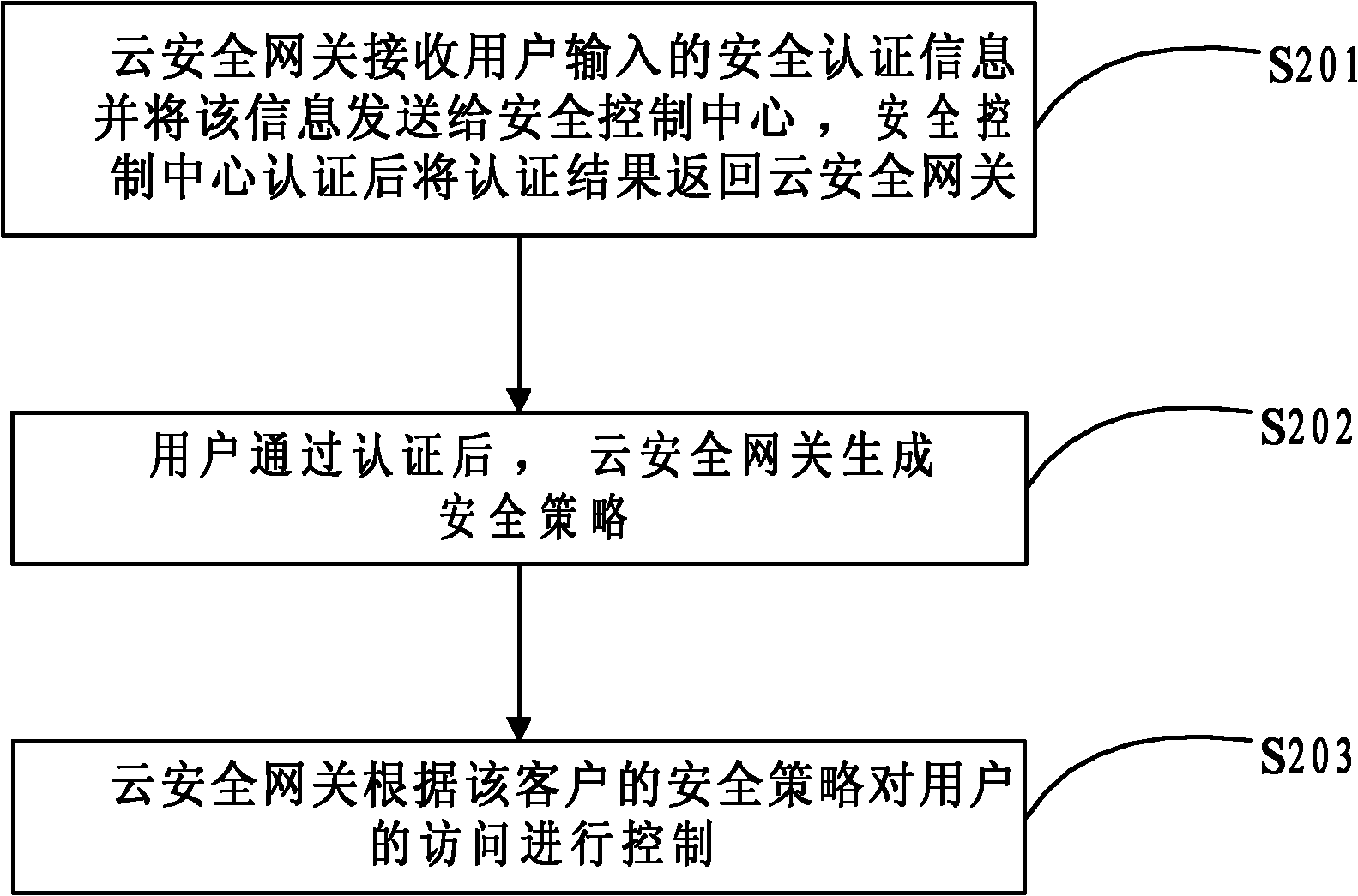
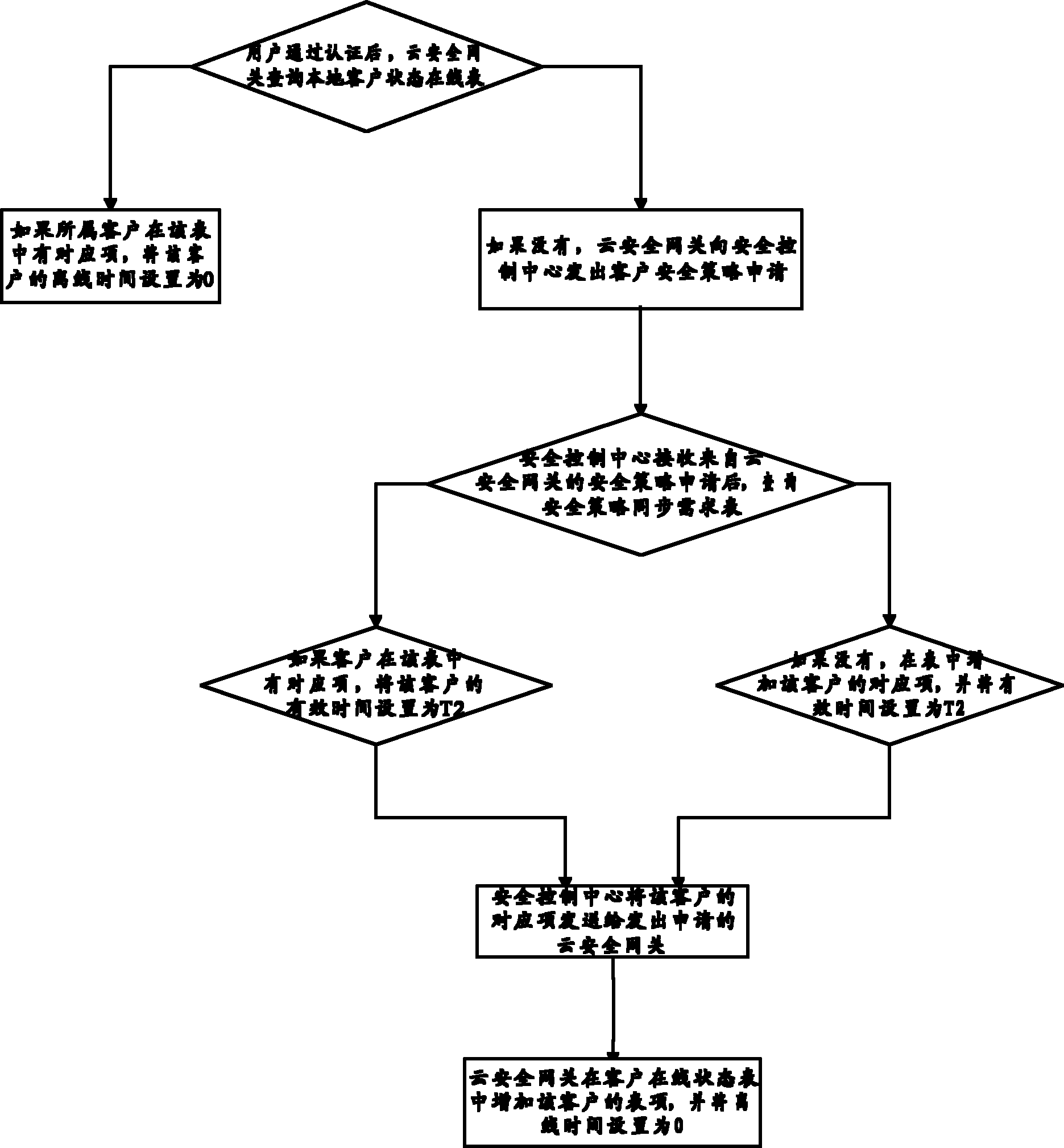
InactiveCN102045353AGuaranteed query performanceOccupancy is minimizedTransmissionSecurity policy managementClient state
The invention discloses a distributed network security control method of a public cloud service, belonging to the technical field of information. The method comprises the following steps of: receiving the authentication information of a user by a cloud security gateway, and after the user passes the authentication, inquiring a local client state on-line table by the cloud security gateway to generate a security policy; if the security policy of the user does not exist in the local client state on-line table, sending a client security apply to a security control center by the cloud security gateway; generating the security policy of the user by the security control center and then sending the security policy of the user to the cloud security gateway; and controlling the access of the user by the cloud security gateway according to the security policy of the user. The invention has the advantages that because the quantity of security policies required to be maintained by the cloud security gateway is small, the security performance is higher; because the system only needs to synchronize update results of the security policies onto the cloud security gateway requiring the security policy update results, the security policy management efficiency is higher; and the occupation of system resources by security policy management is reduced.
Owner:BEIJING JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com