Patents
Literature
1793 results about "Web system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Social network systems and methods
InactiveUS20100306249A1Digital data processing detailsSpecial data processing applicationsInternet privacySocial web
Embodiments of computer-implemented methods and systems are described, including: in a computer network system, providing a user page region viewable by a user; providing to the user, in the user page region, indicators of each of three categories, the categories consisting essentially of: (i) what the user has, (ii) what the user wants, and (c) what the user has thought or is thinking; wherein the user page region accepts a post by the user; after the post by the user, displaying the post in a group page region, viewable by a set of one of more persons other than the user, the set of persons being separated from the user at locations on a network; before the displaying, requiring the user to select one of the three categories to be associated with the post; and displaying the category selected by the user, with the post, in the group page region.
Owner:FOSTER JOHN C
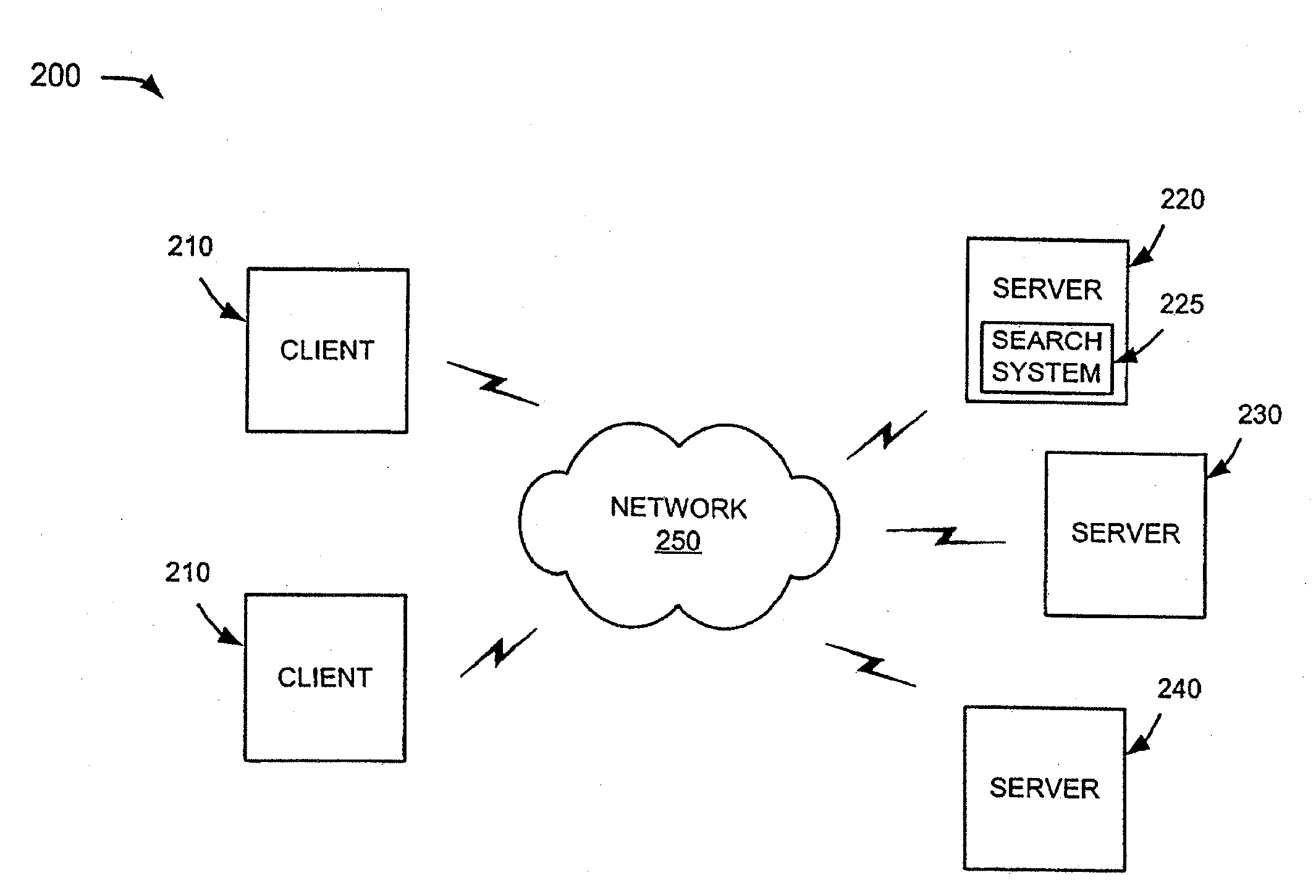
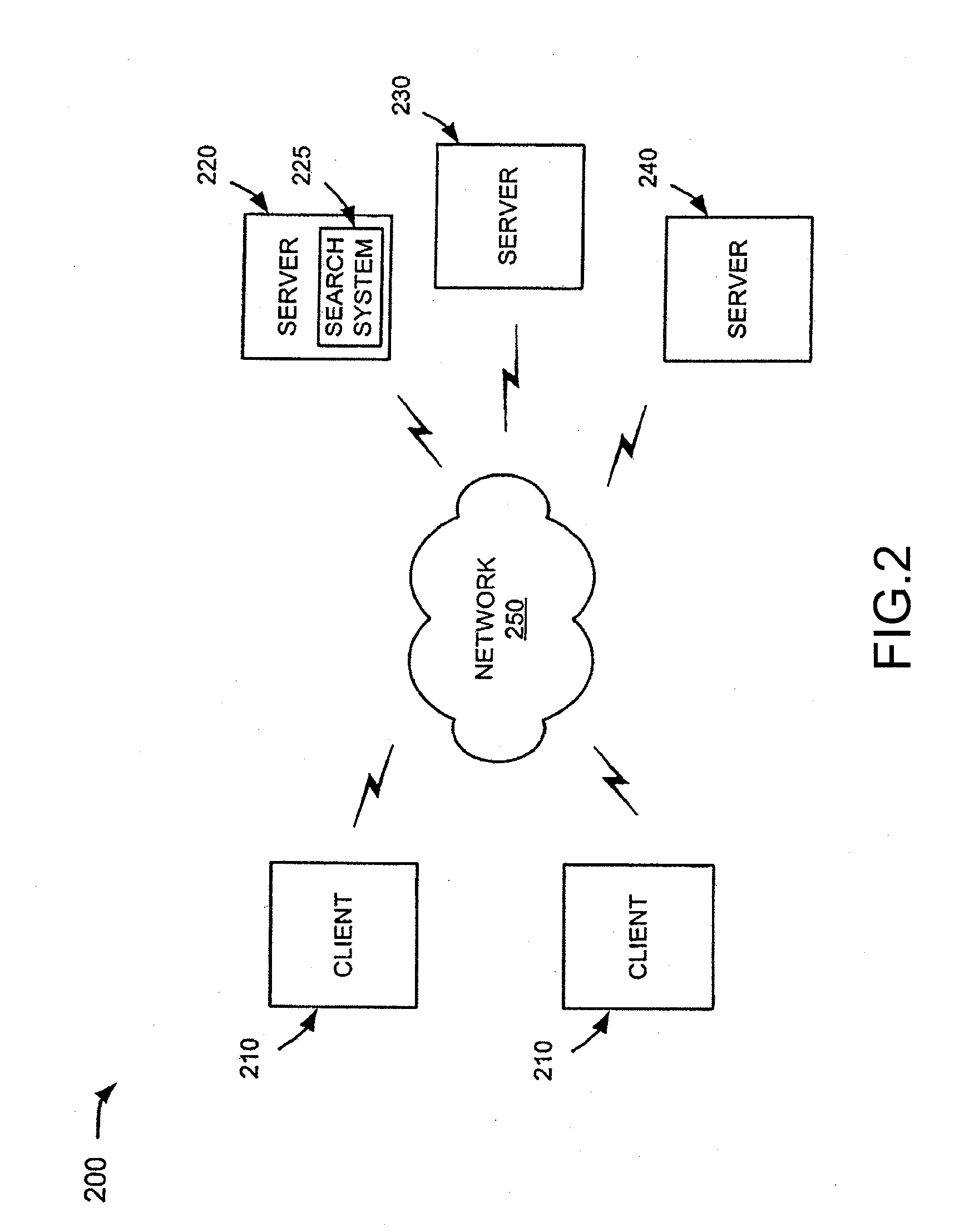
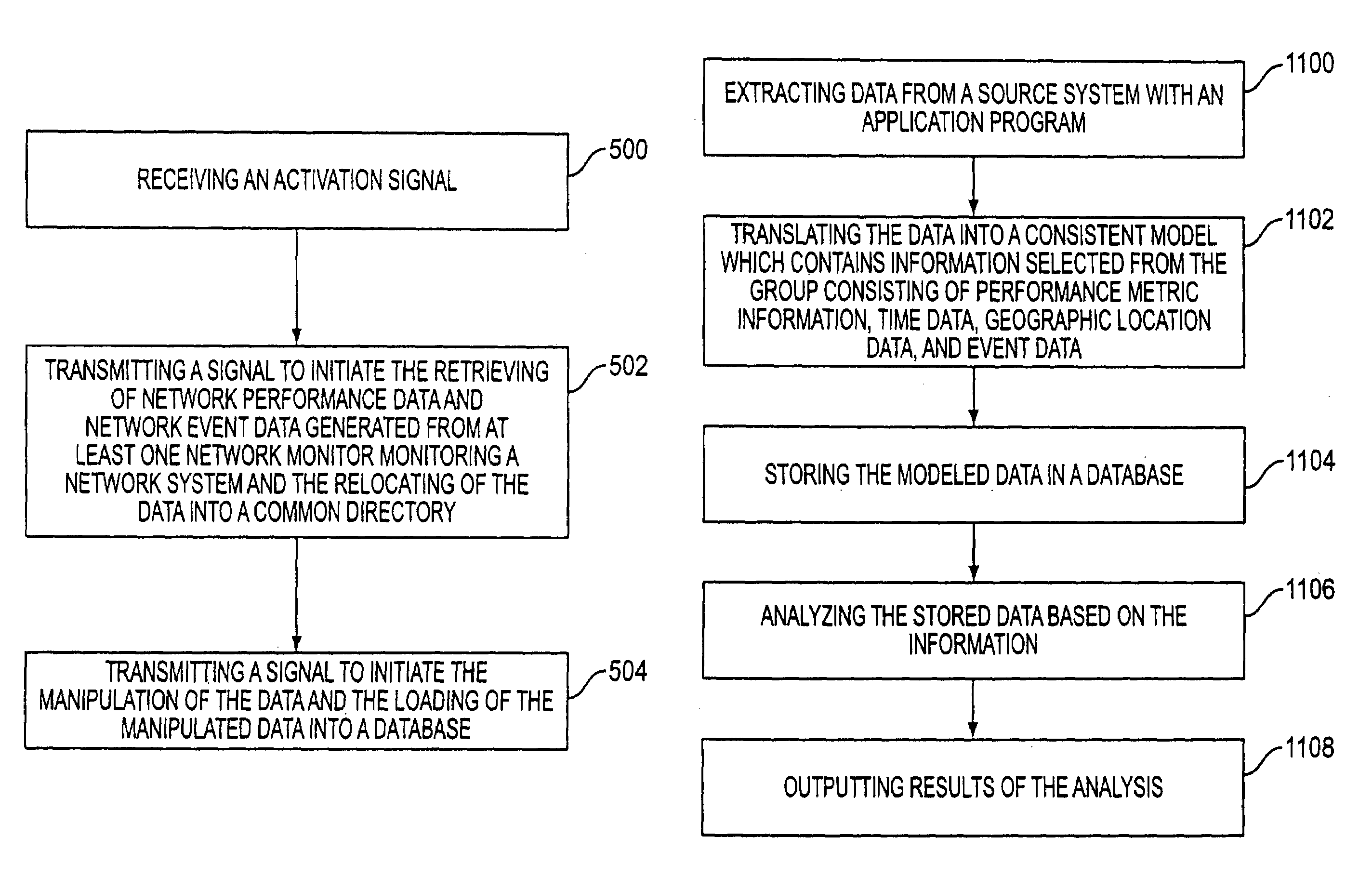
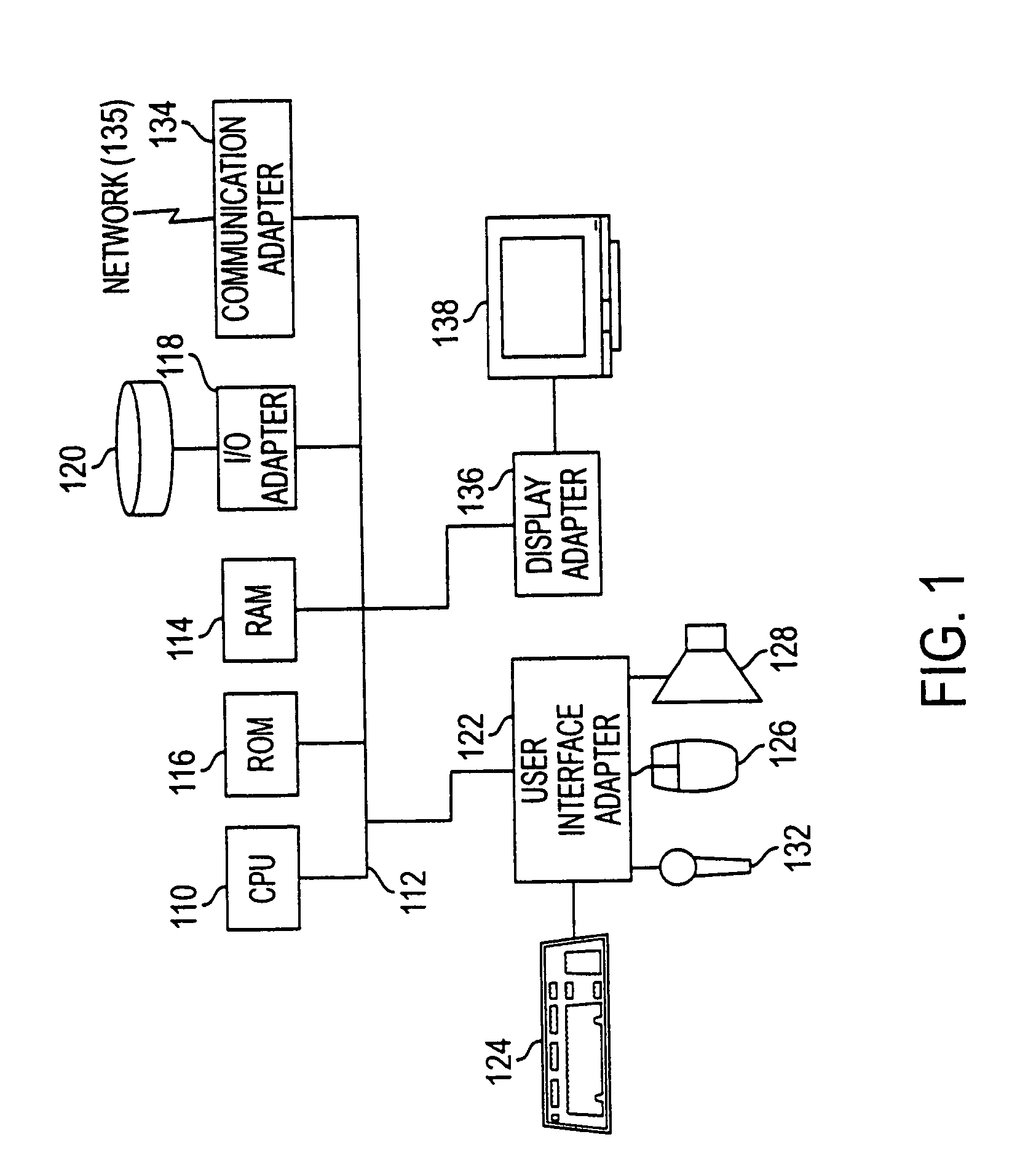
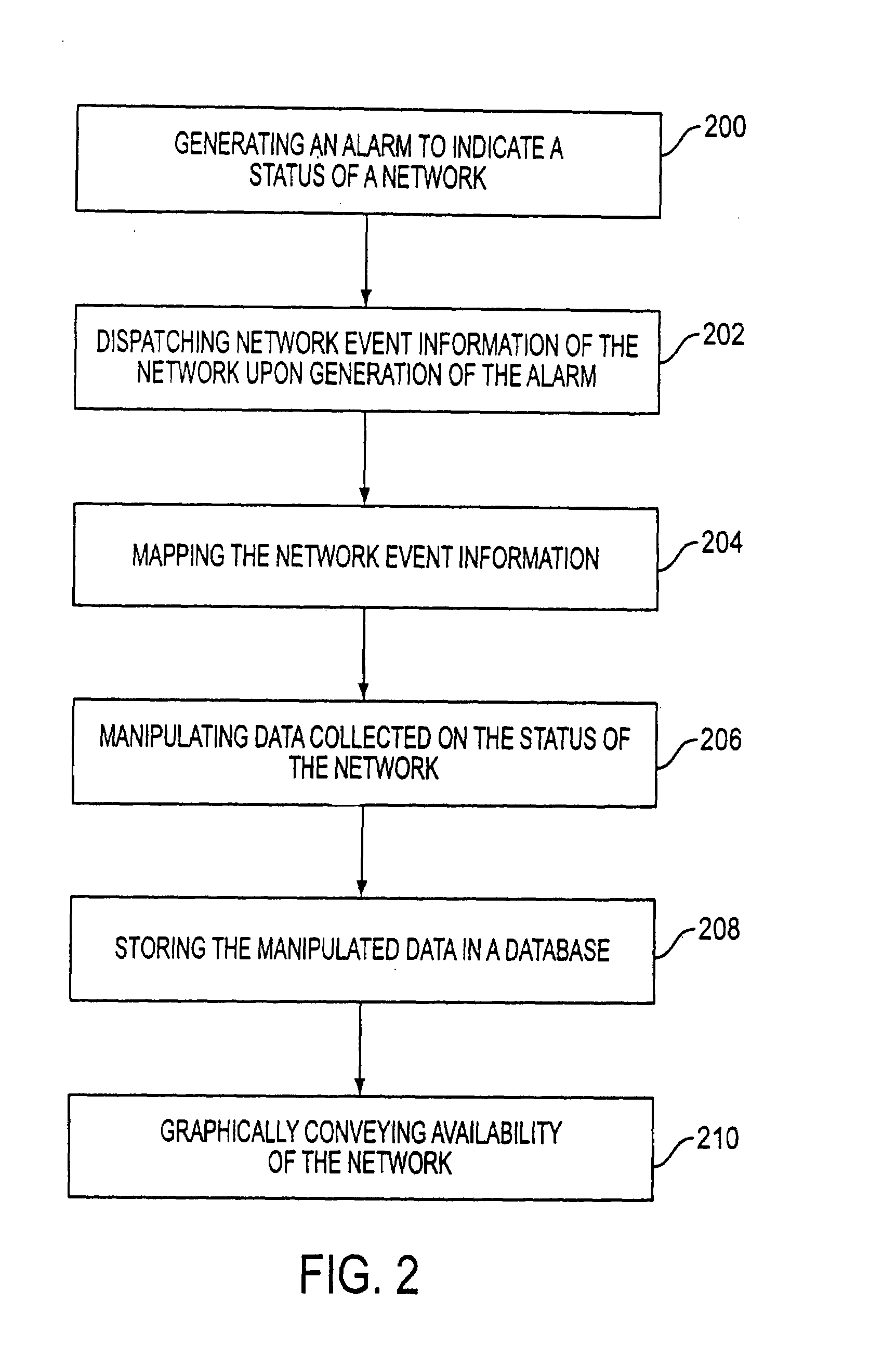
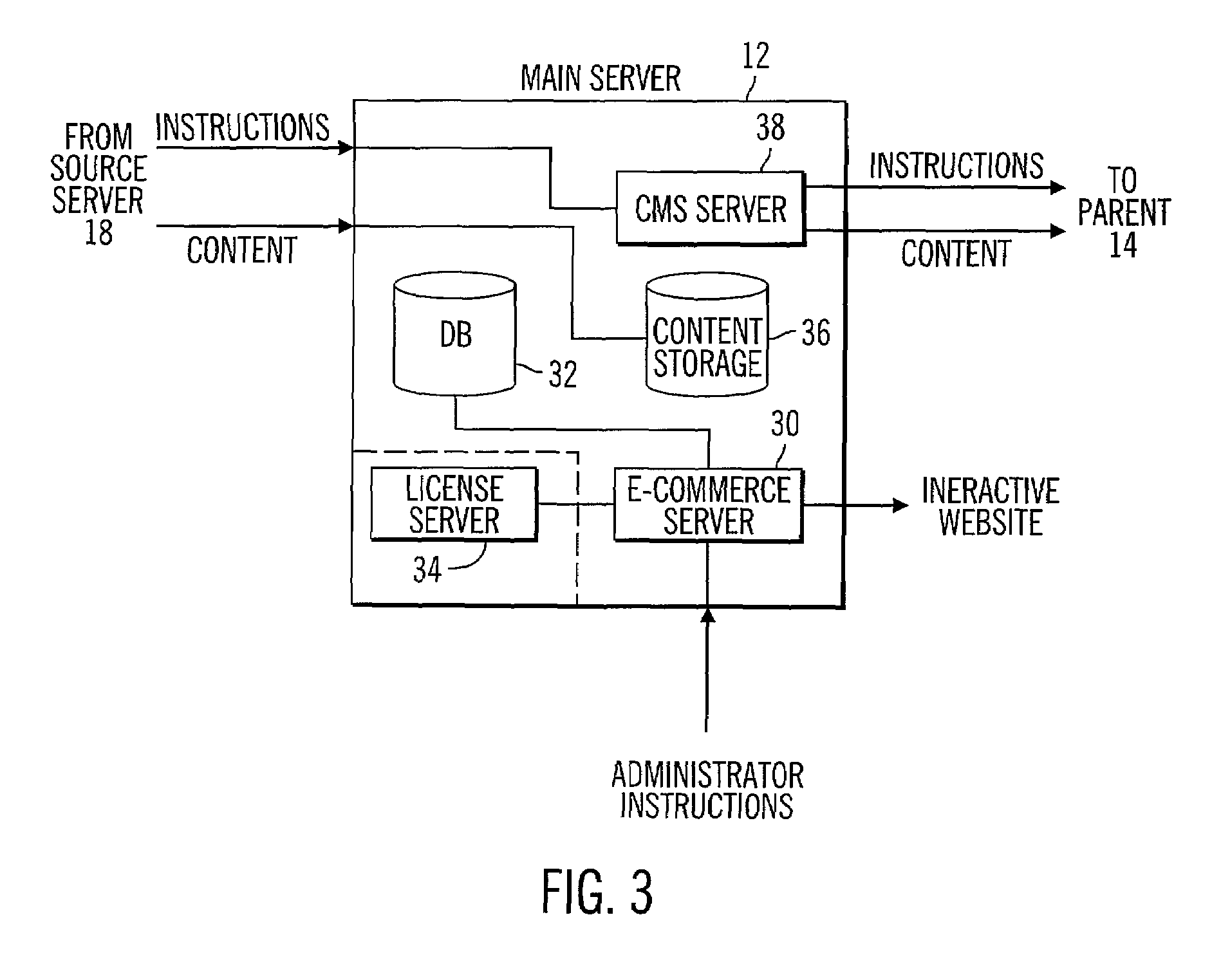
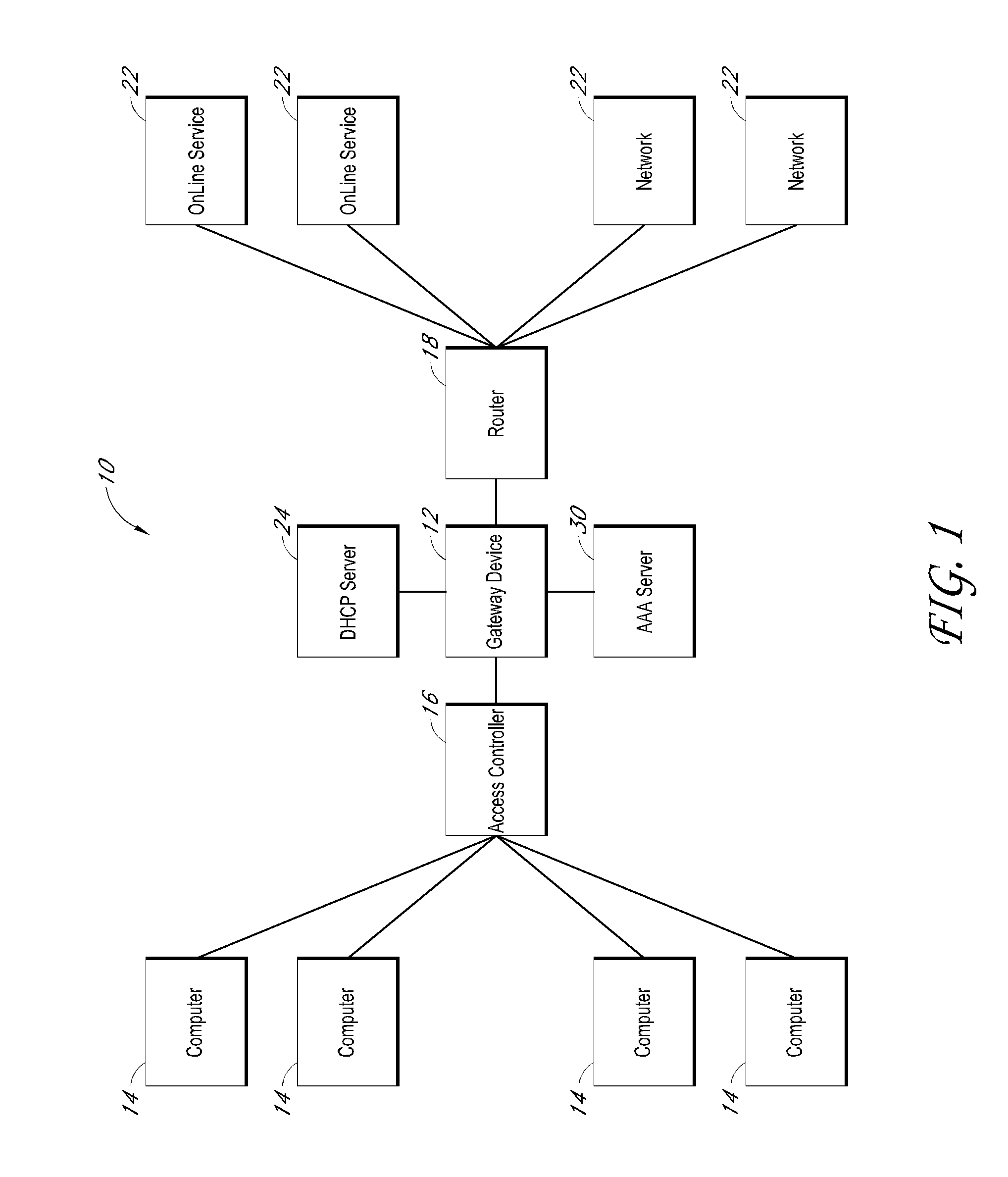
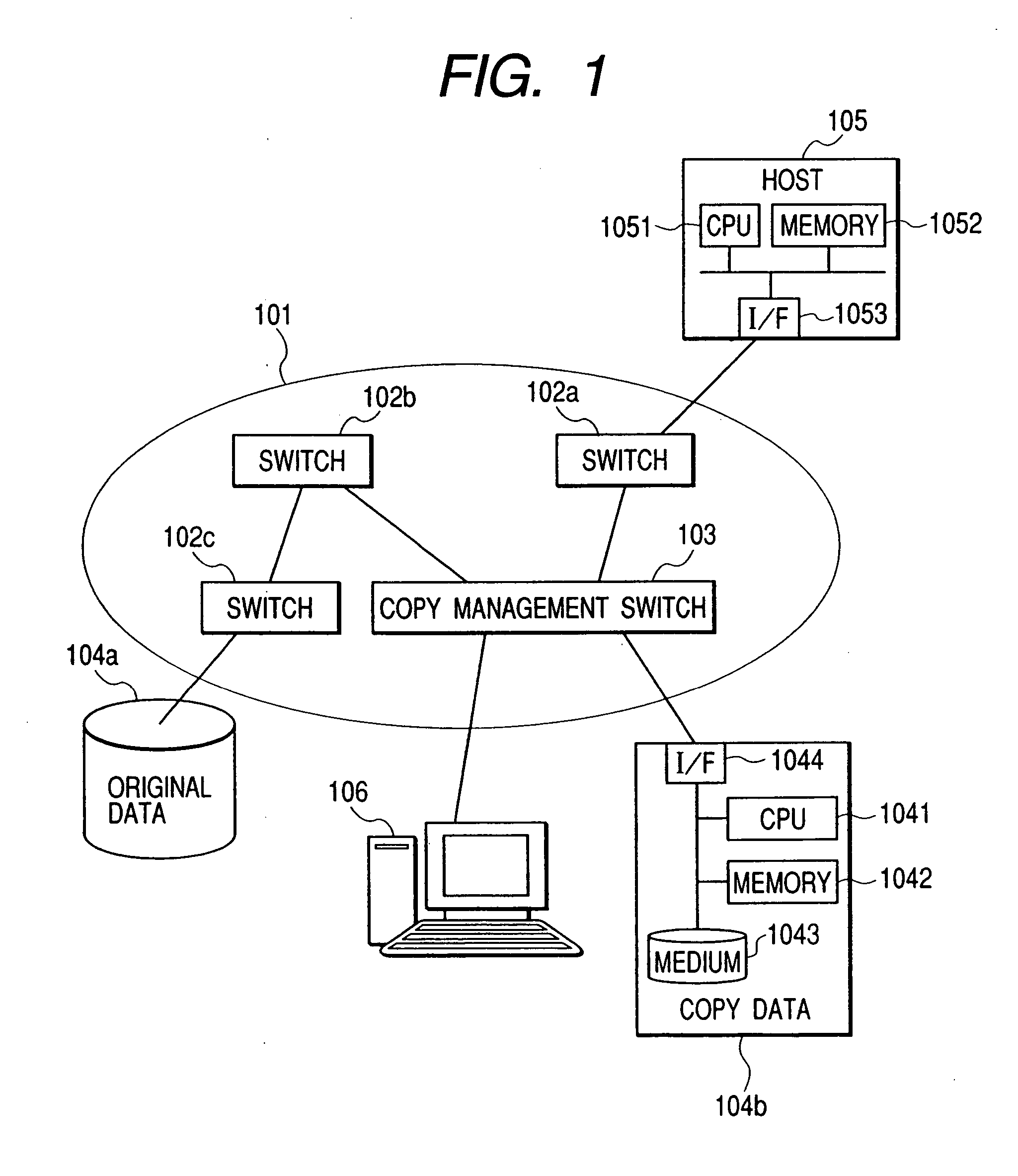
Controlling data collection, manipulation and storage on a network with service assurance capabilities
InactiveUS6985901B1Data processing applicationsDigital computer detailsEvent dataBiological activation
The present disclosure provides for controlling the collection, manipulation and storage of network performance data and network even data of a network with service assurance capabilities. Upon the receipt of an activation signal, a signal is transmitted to initiate the retrieving of network performance data and network event data generated from at least one network monitor. Such network monitor is adapted for monitoring a network system and the relocating of the data into a common directory. A signal is then transmitted to initiate the manipulation of the data and the loading of the manipulated data into a database.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method and apparatus for the management of data files
InactiveUS6263330B1Easy retrievalEasy accessData processing applicationsTelemedicineMedical recordData file
The present invention provides a network system for storage of medical records. The records are stored in a database on a server. Each record includes two main parts, namely a collection of data elements containing information of medical nature for the certain individual, and a plurality of pointers providing addresses or remote locations where reside other medical data for that particular individual. Each record also includes a data element indicative of the basic type of medical data found at the location pointed to by a particular pointer. This arrangement permits a client workstation to download the record along with the set of pointers which link the client to the remotely stored files. The identification of the basic type of information that each pointer points to allows the physician to select the ones of interest and thus avoid downloading massive amounts of data where only part of that data is needed at that time. In addition, this record structure allows statistical queries to be effected without the necessity of accessing the data behind the pointers. For instance, a query can be built based on keys, one of which is the type of data that a pointer points to. The query can thus be performed solely on the basis of the pointers and the remaining information held in the record.
Owner:BESSETTE LUC
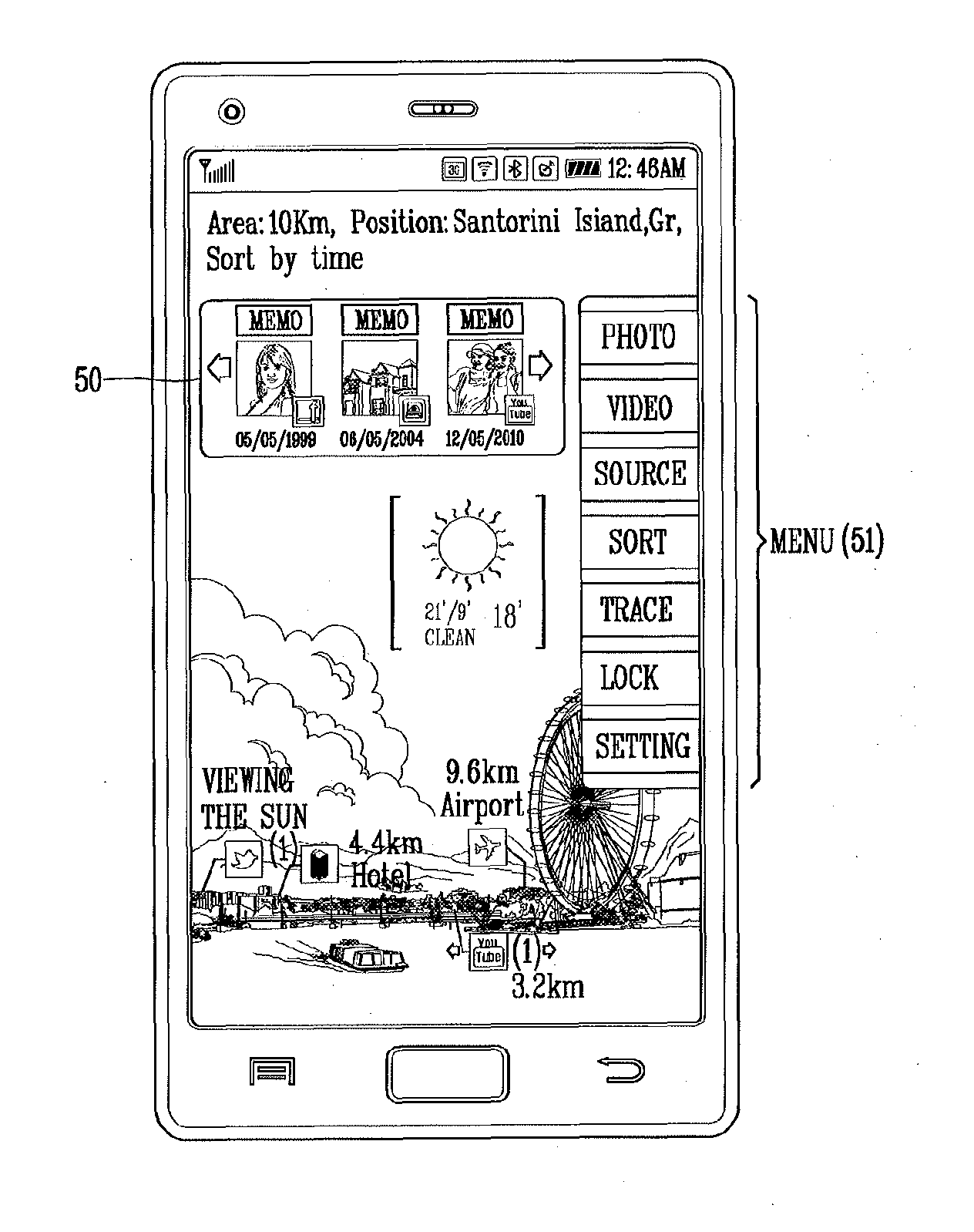
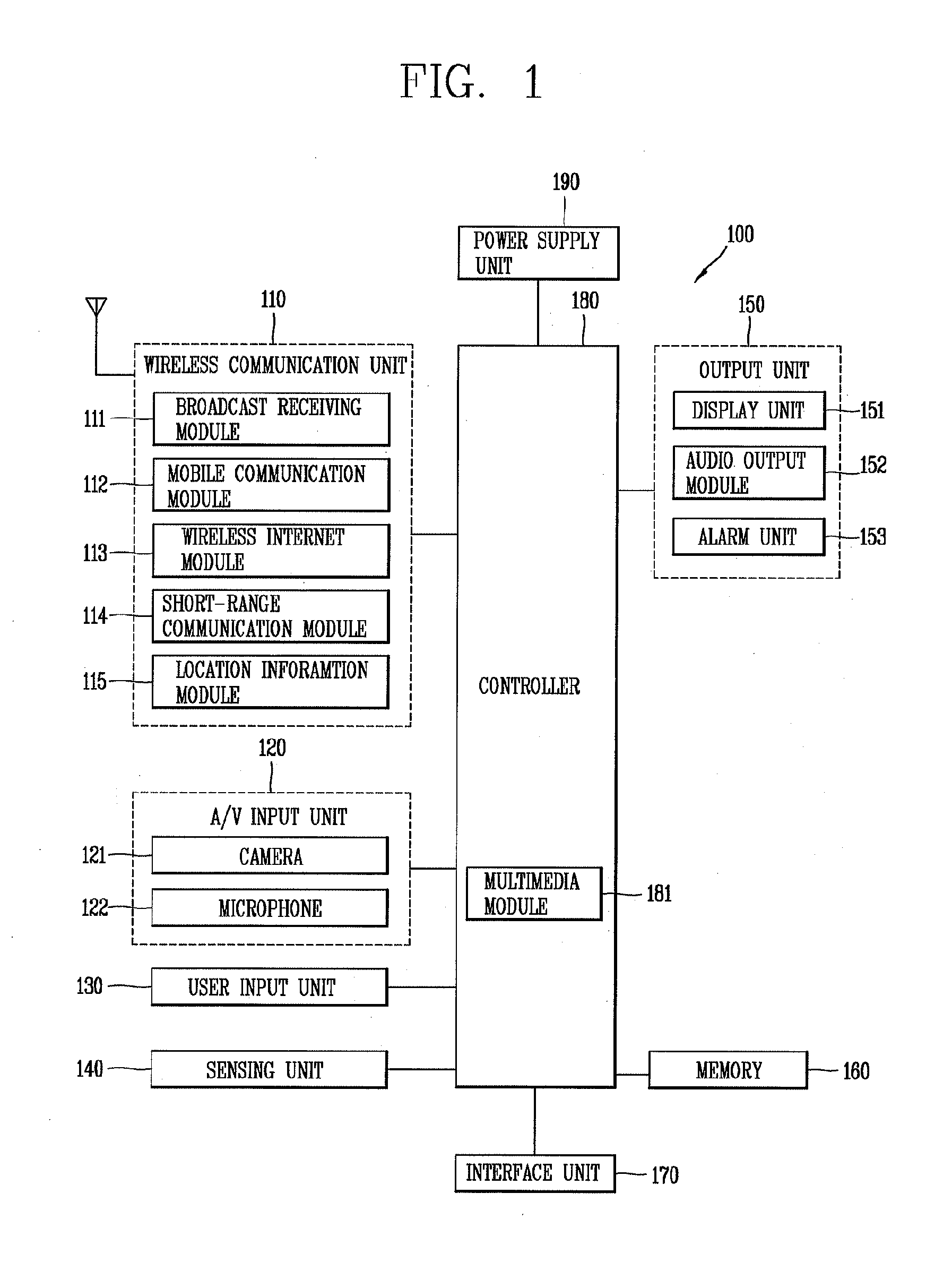
Mobile terminal and photo searching method thereof
InactiveUS20130198176A1Digital data processing detailsMetadata still image retrievalPosition dependentAugmented reality
The present disclosure relates to a mobile terminal and a photo search method thereof capable of searching and displaying photos shared by the cloud and SNS systems in connection with a specific location on a camera view using augmented reality. To this end, according to the present disclosure, when a photo search function is selected on an augmented reality based camera view, photo information associated with at least one location on which the focus of the camera view is placed is searched from a network system to sort and display the searched photo information on the camera view, thereby allowing the user to conveniently search photos associated with old memories.
Owner:LG ELECTRONICS INC
Facilitating annotation creation and notification via electronic mail
InactiveUS6917965B2Metadata multimedia retrievalCathode-ray tube indicatorsClient-sideClient machine
Owner:MICROSOFT TECH LICENSING LLC
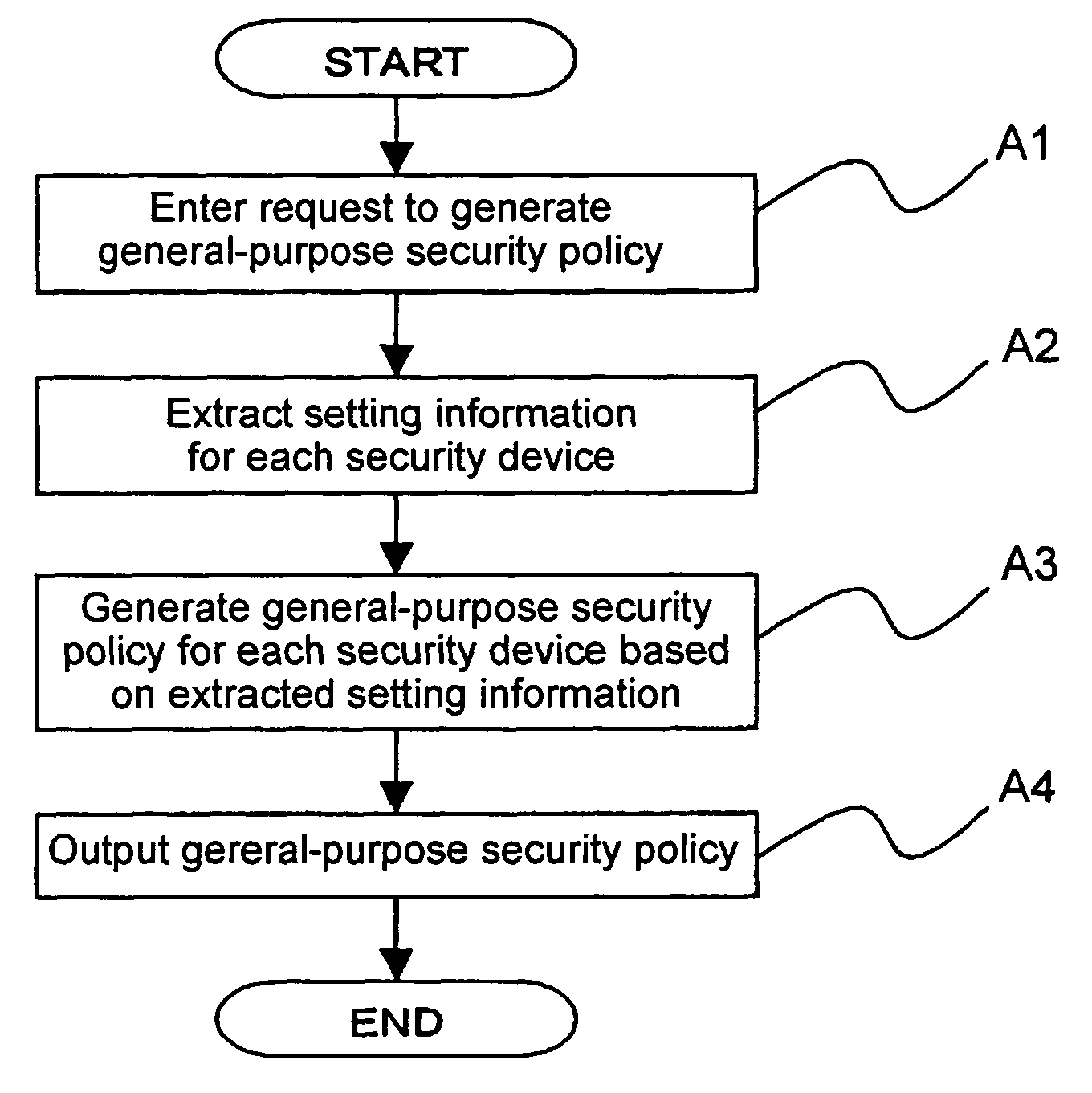
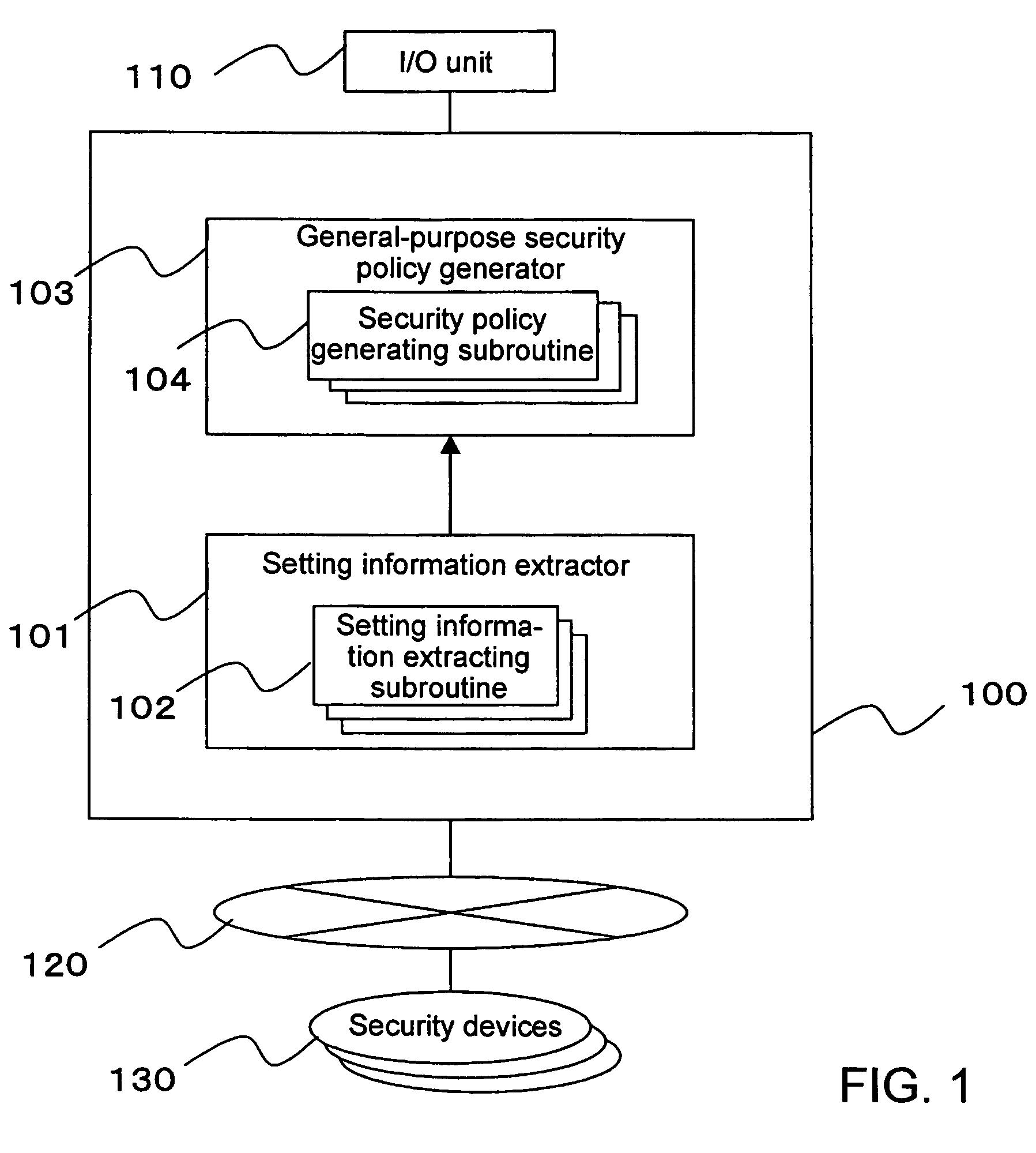
Method and apparatus for security policy management
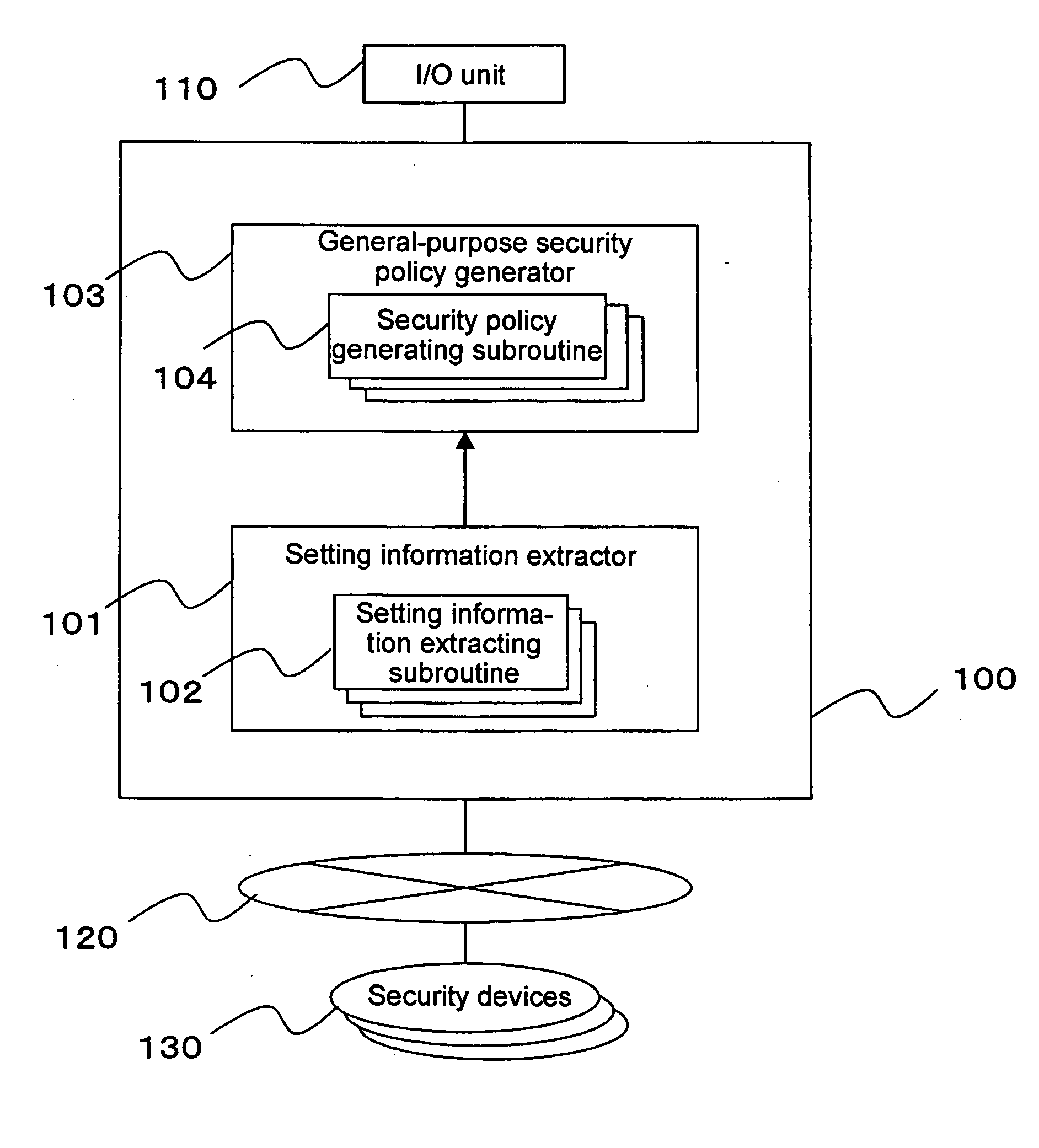
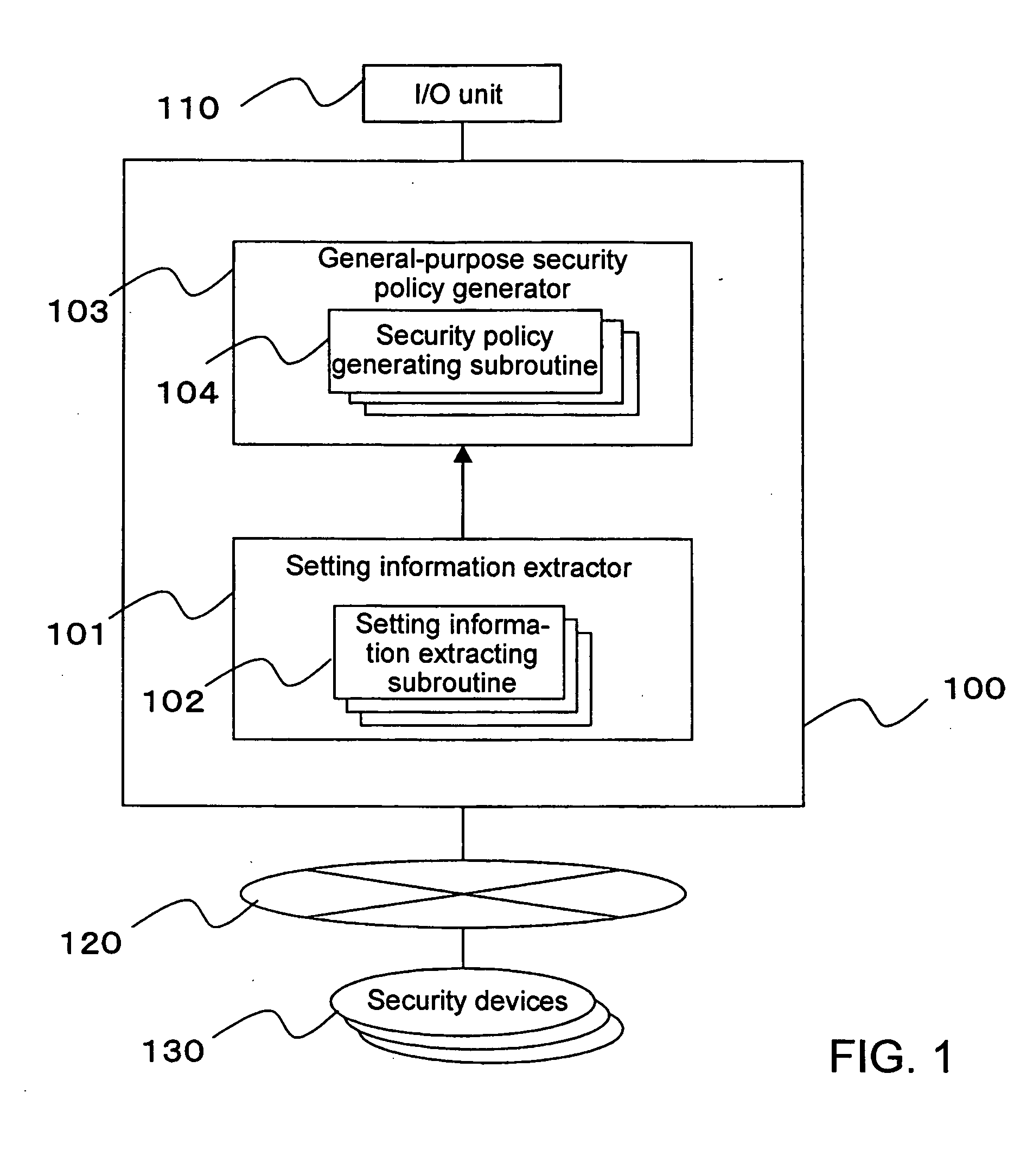
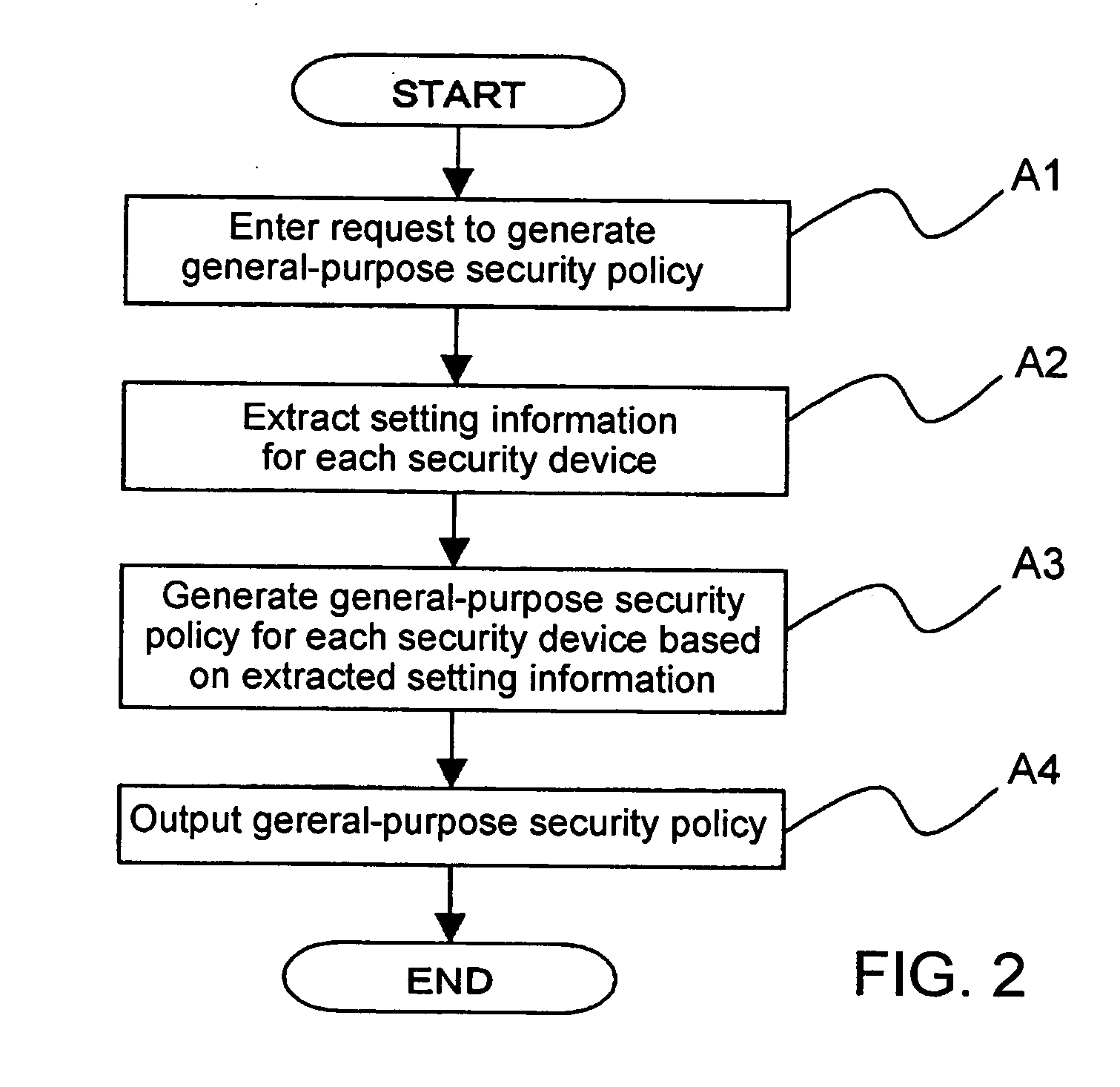
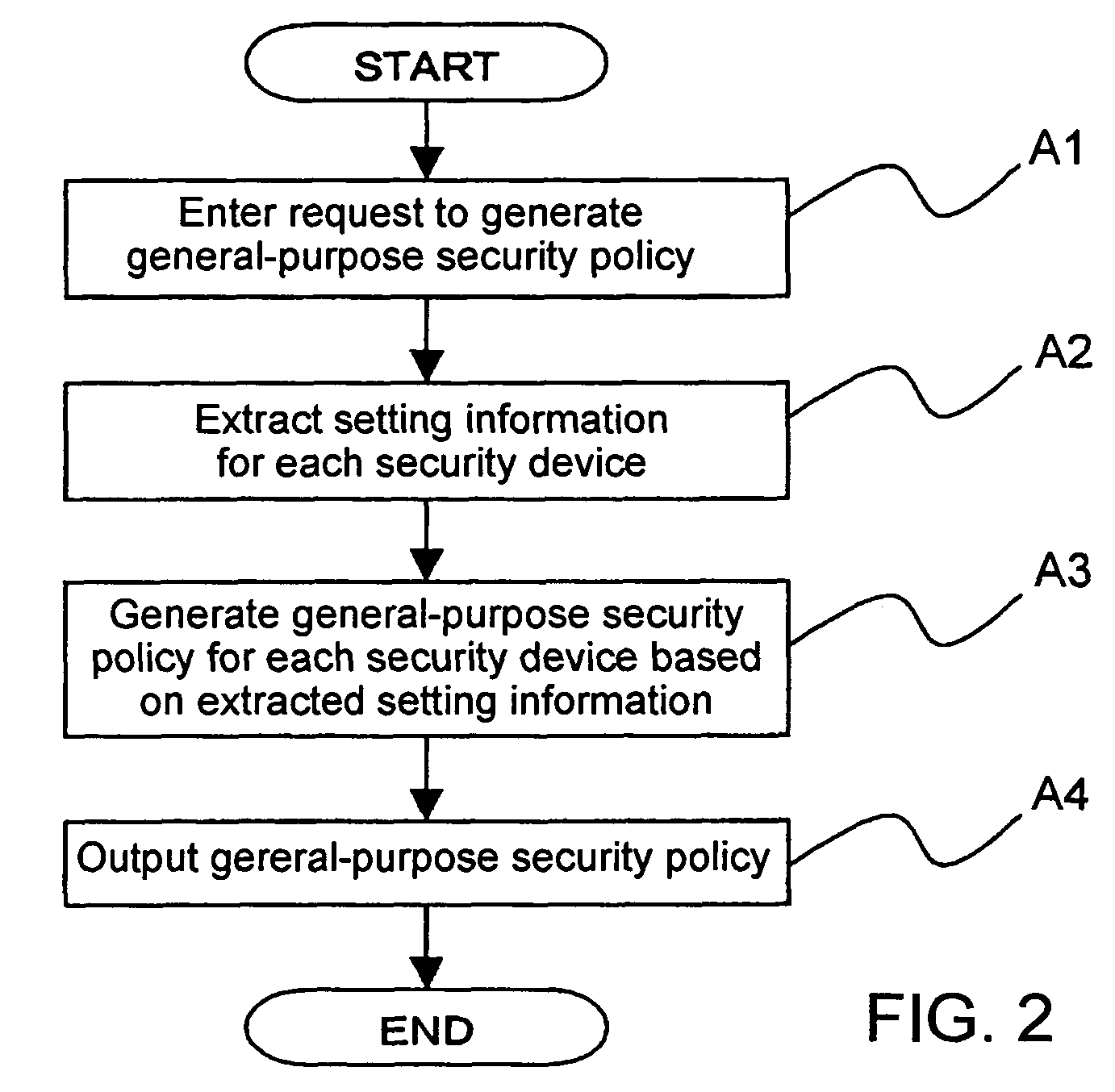
InactiveUS20050283823A1Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
Dynamic content conversion
ActiveUS20090083369A1The process is simple and fastDigital data information retrievalMultiple digital computer combinationsDisplay deviceClient-side
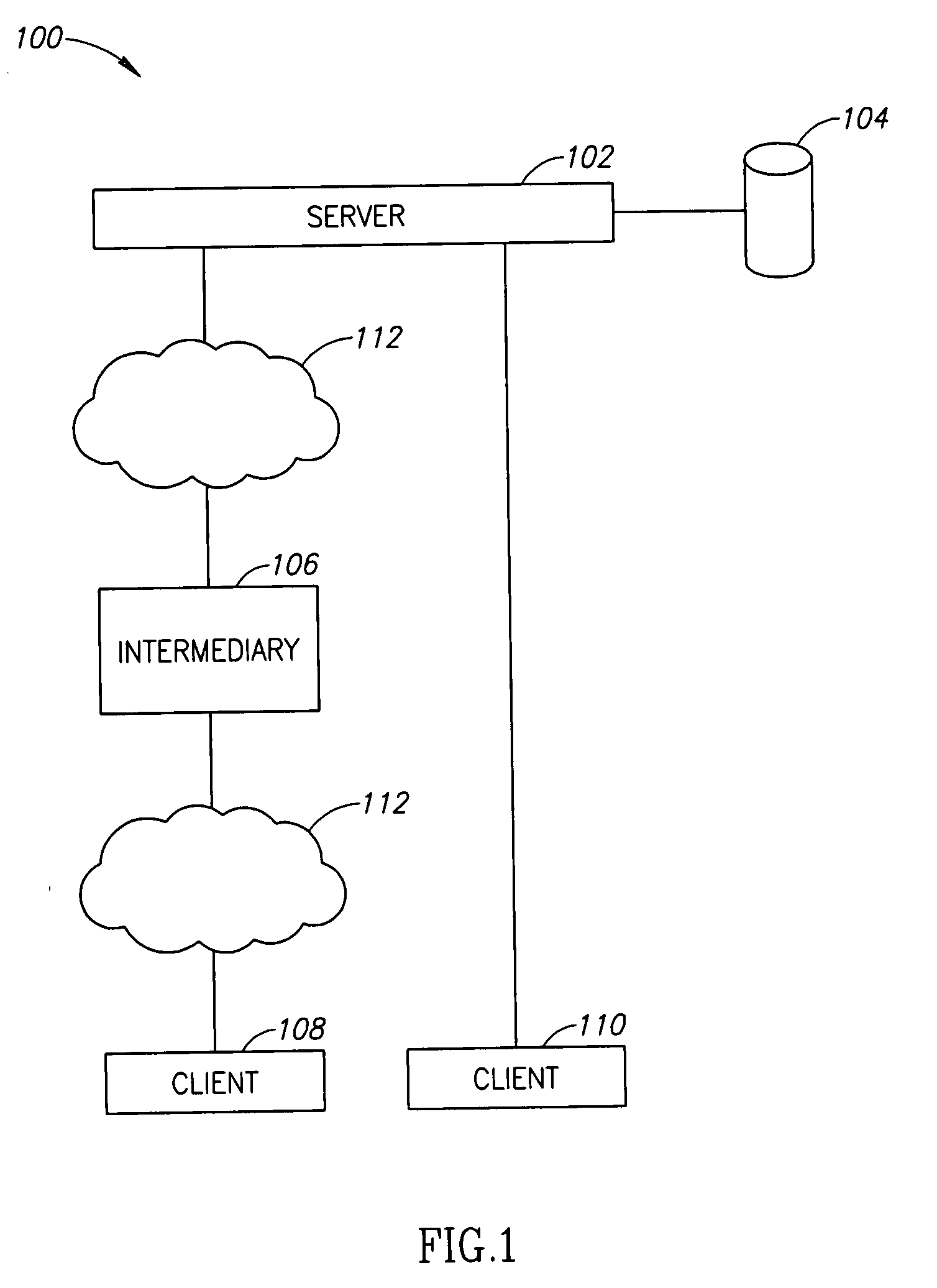
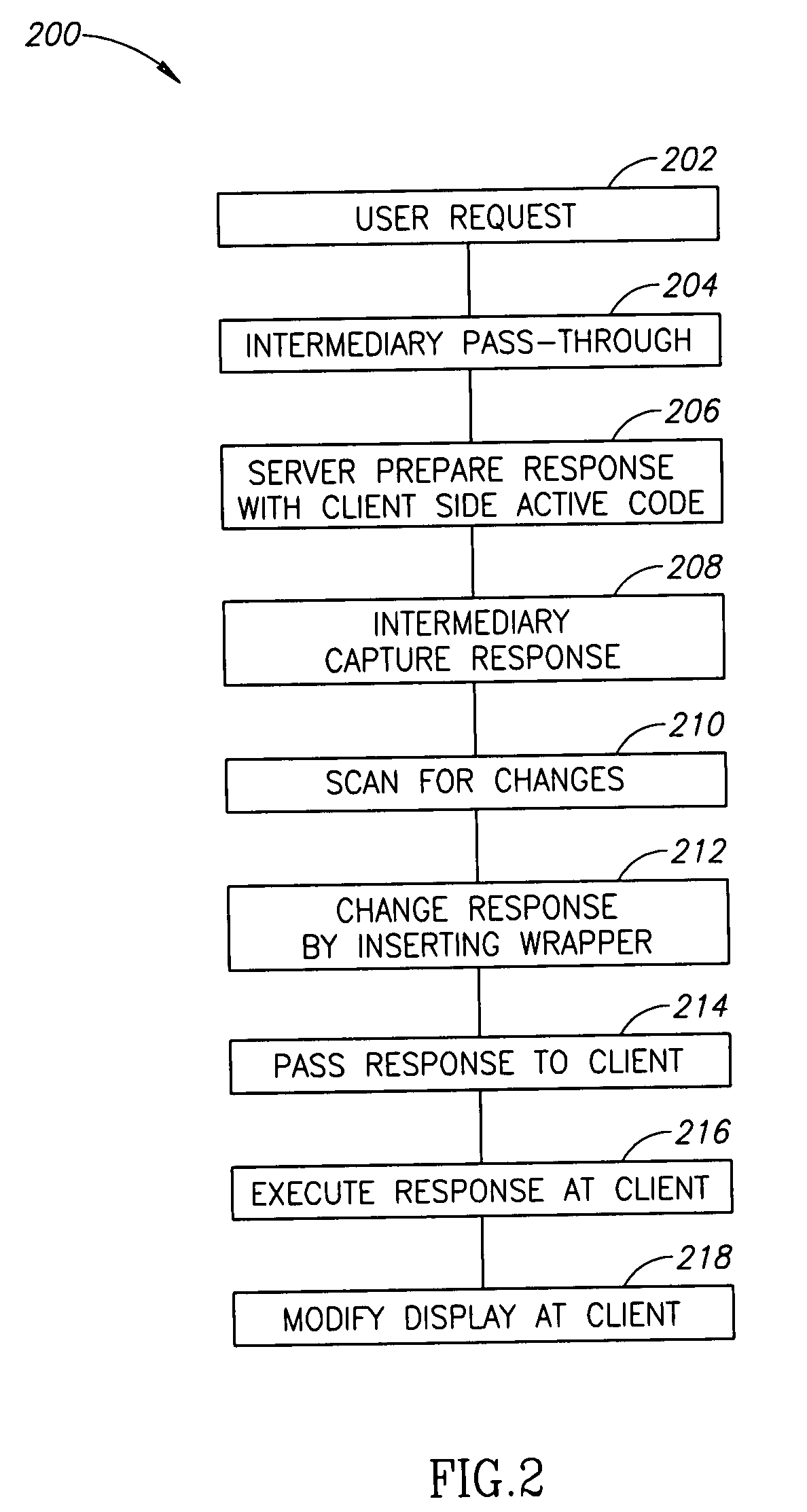
A method of display modification in a client server web system, comprising, intercepting, by a web intermediary, a response to a client request, sent by a server in response to the request, the response including client side active content adapted to execute at a browsing software on a client computer; replacing at least one display-related code section in said response by a wrapper section that includes code for modification of at least one display element and code for executing the original display-related code section; and executing said wrapper section as client side active content at said client to generate a display, modified from a display that would have been generated by executing the response.
Owner:GOOGLE LLC
Network configured for delivery of content for download to a recipient
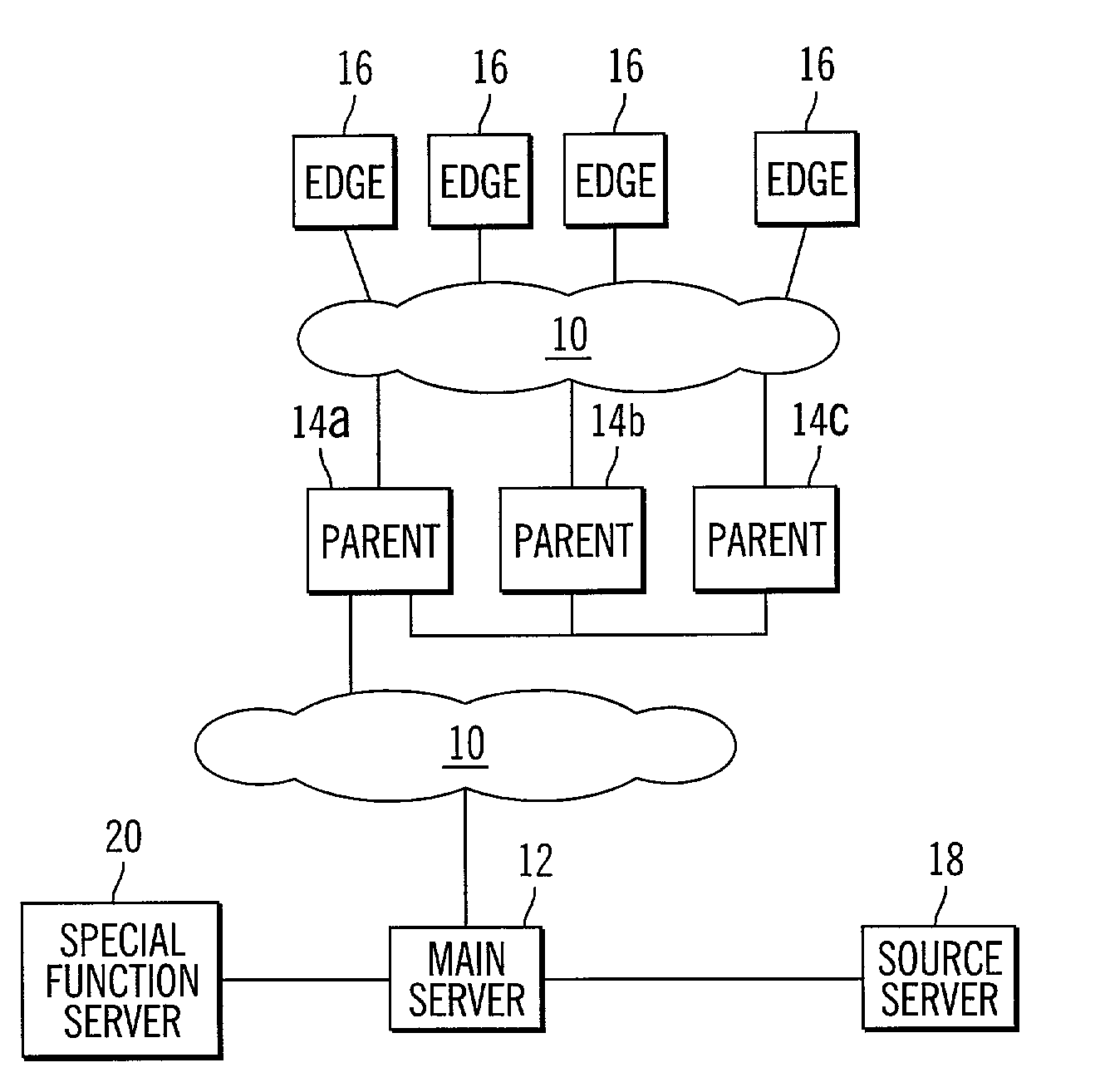
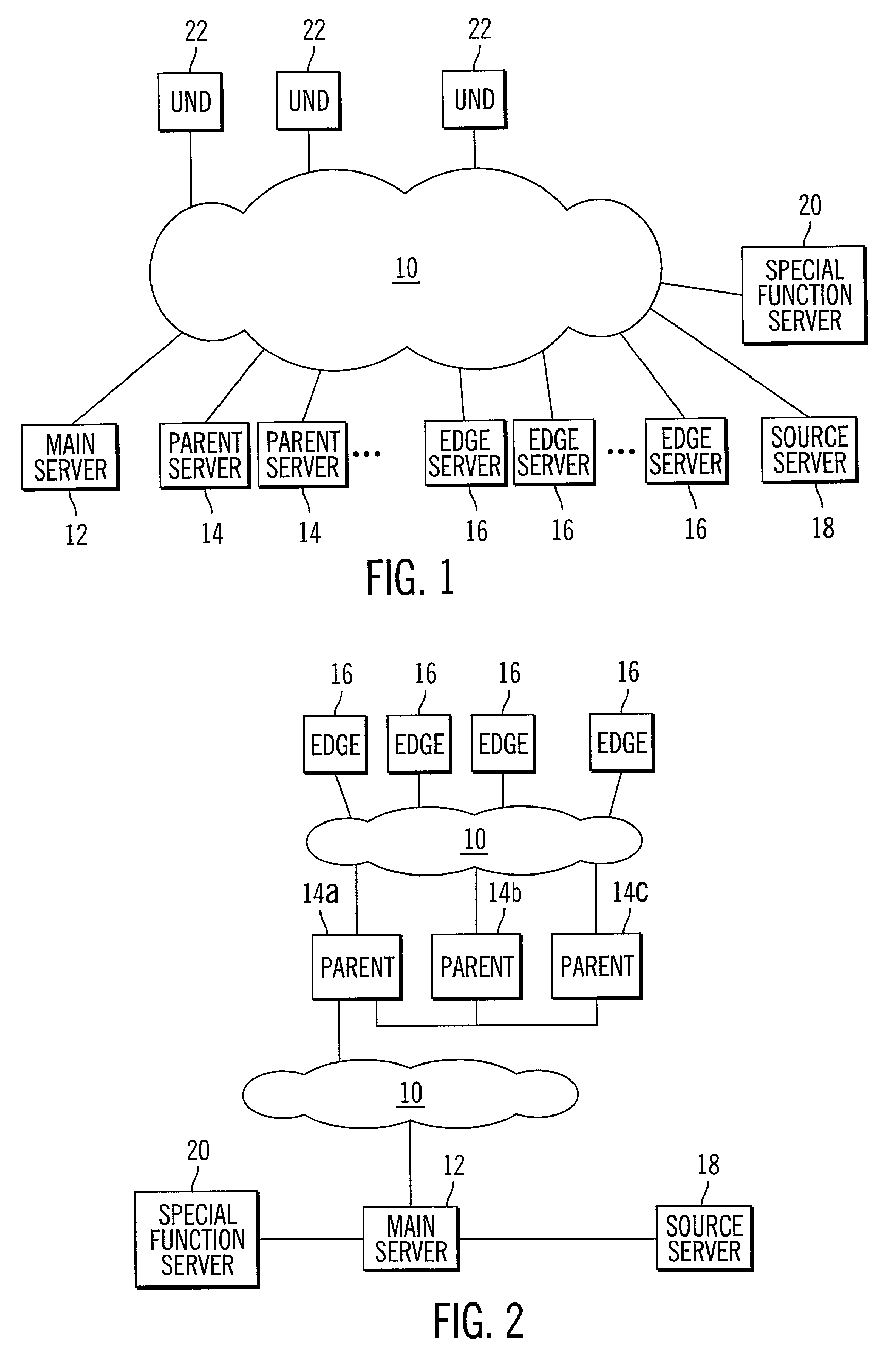
InactiveUS7024466B2Increase speed and efficiencyEffective controlMultiprogramming arrangementsMultiple digital computer combinationsEdge serverNetwork architecture
Owner:BLOCKBUSTER LLC
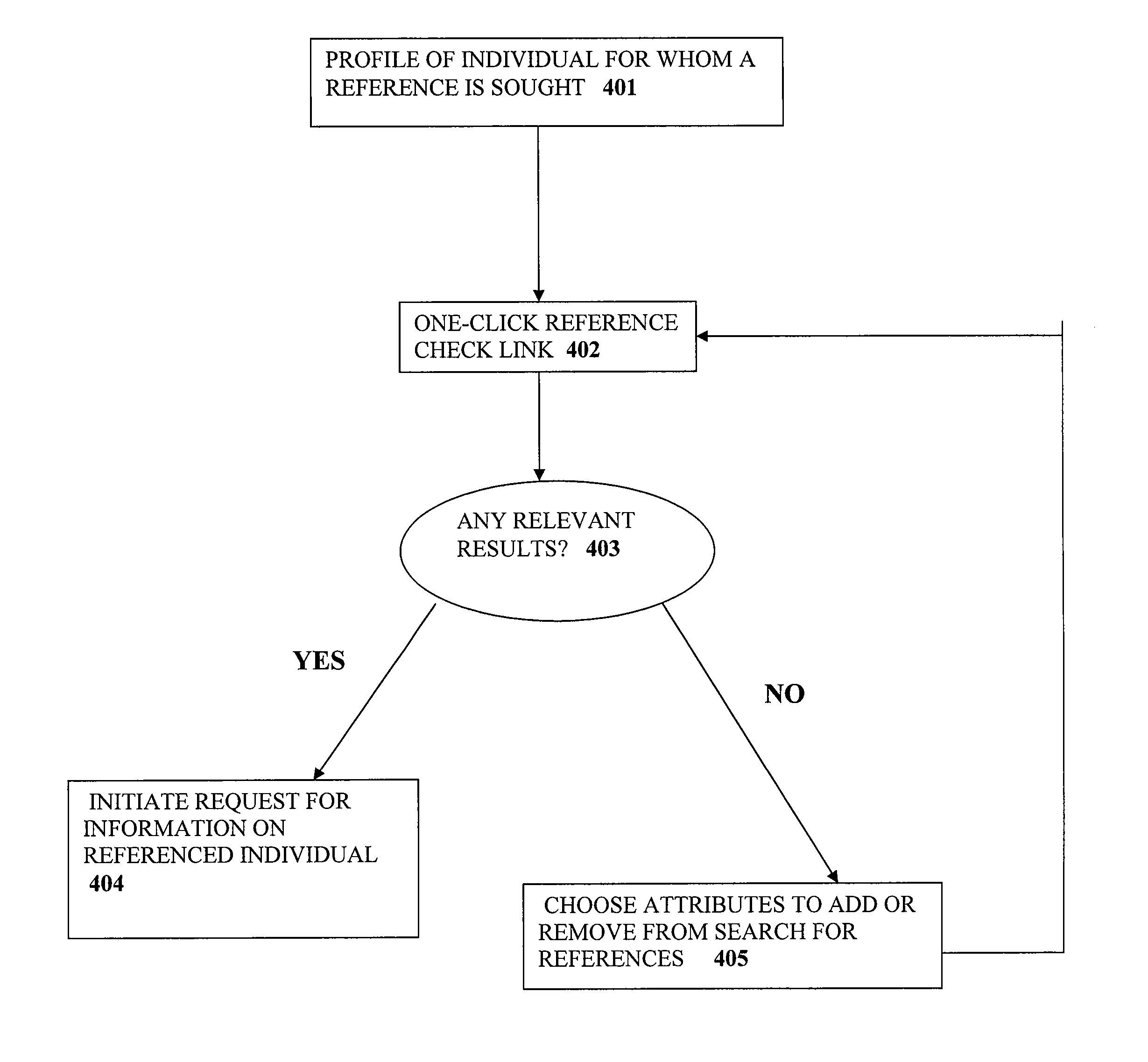
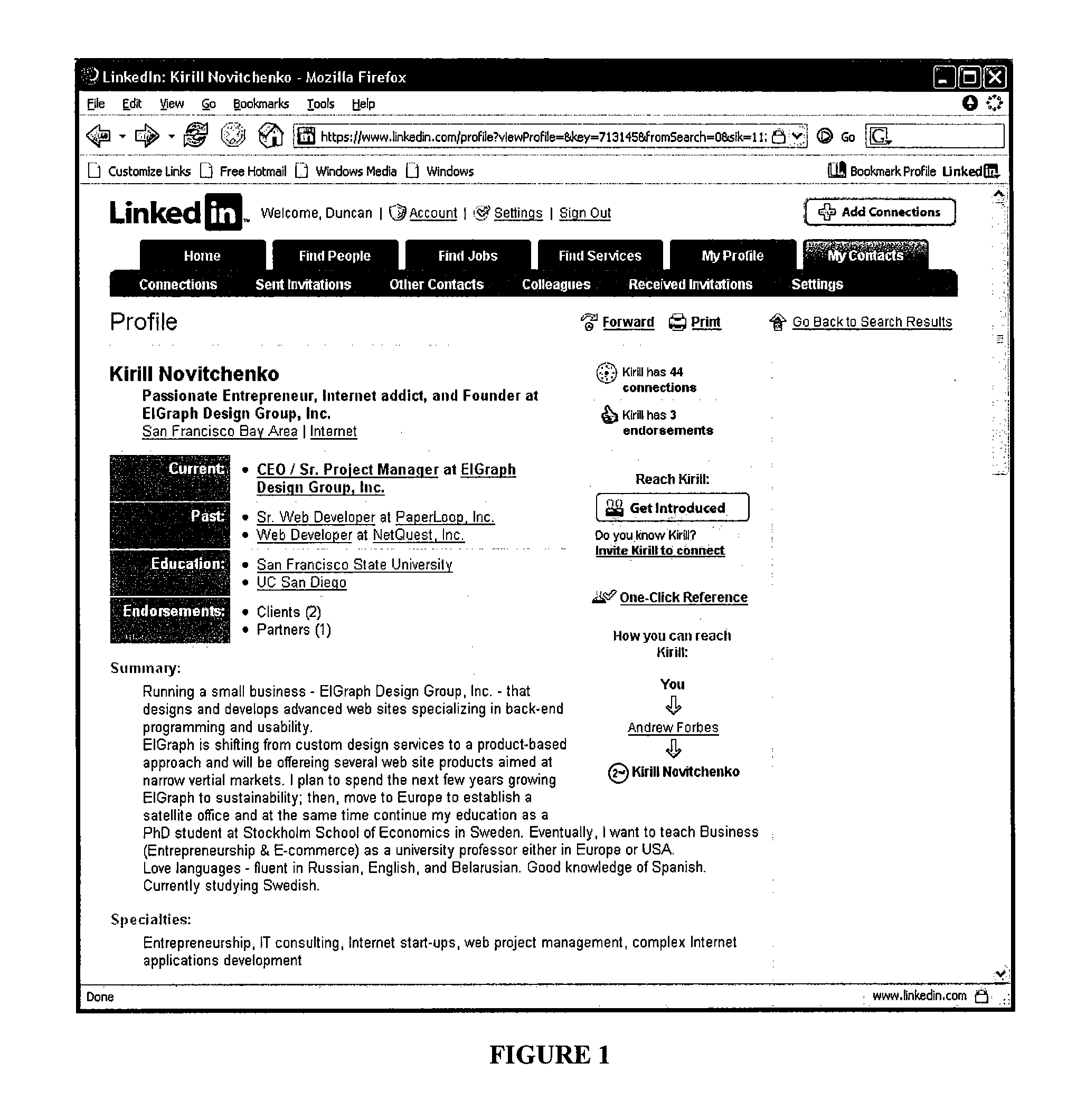
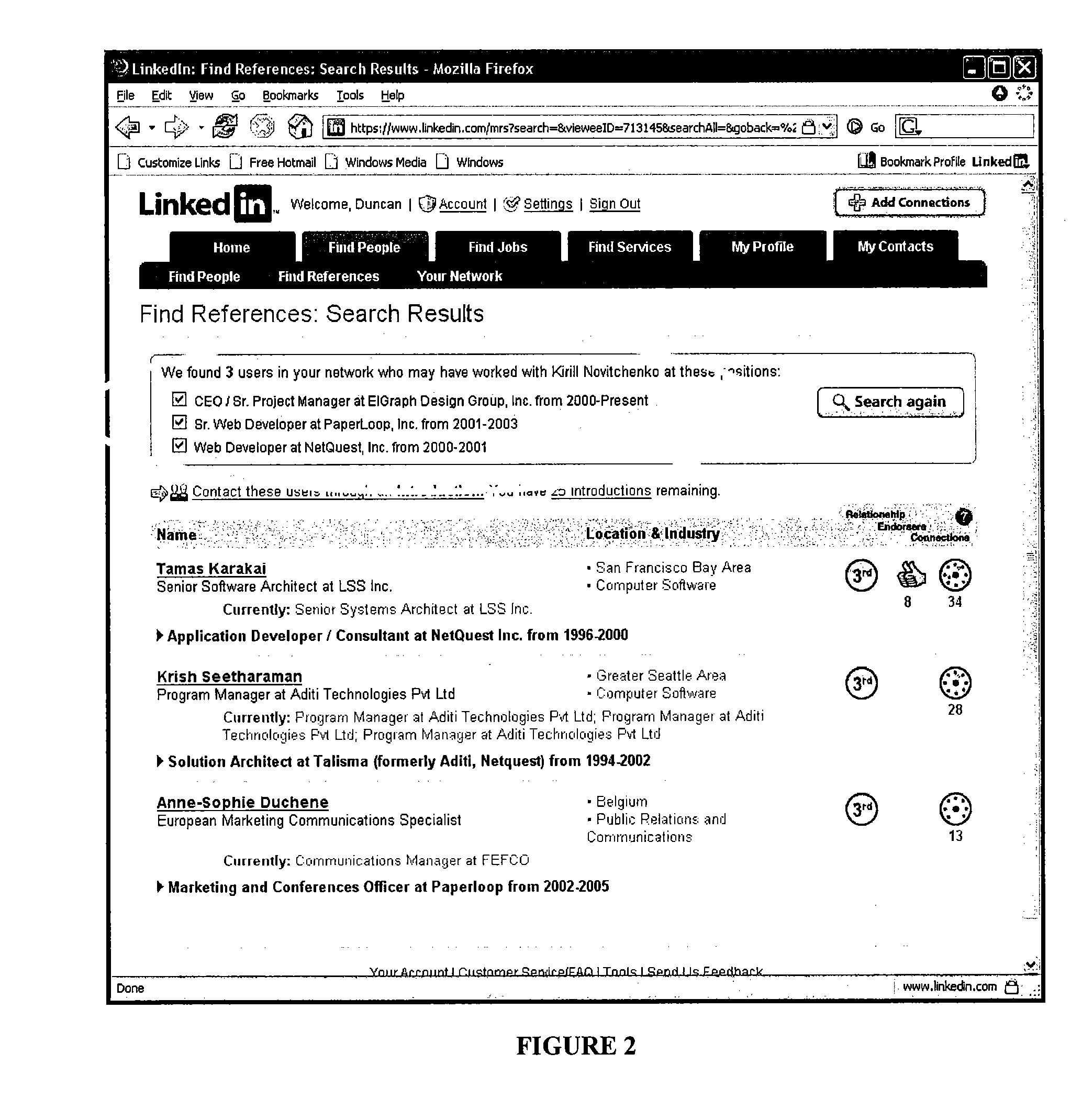
Searching and reference checking within social networks
A computer-implemented method for identifying a potential reference is disclosed. In one embodiment, a user interface (UI) object (e.g., a one-click reference search button) is provided, for example, on a web page displayed at a user's client device. When selected, the UI object causes a reference search query to be generated. The search query identifies the user performing the search, and a target person for whom the user would like a reference. The search query is communicated to, and processed by, a social networking system (e.g., through an API function call). In turn, the social networking system returns information about potential references to the client.
Owner:MICROSOFT TECH LICENSING LLC
Virtual world avatar control, interactivity and communication interactive messaging
Methods and systems for rendering an interactive virtual environment for communication is provided. The interactive virtual environment is depicted from images to be displayed on a display and the interactive virtual environment is generated by a computer program that is executed on at least one computer of a computer network system. The interactive virtual environment includes one or more virtual user avatars controlled by real-world users. The method further includes controlling a virtual user avatar to move about a virtual space and generating an interface for composing a message to be displayed as a virtual message within the virtual space. The virtual message is posted to an interactive space within the virtual space. The method further includes associating permissions to the virtual message, such that the permissions define which of the one more virtual user avatars are able to view the virtual message that is posted to the interactive space. The virtual message is one of a plurality of virtual message posted to the interactive space, and the permissions prevent viewing of the virtual message by virtual user avatars that do not have permission to view the virtual message. The permissions may be based on one of buddy lists, game familiarity relative to other real-world users, skill level of other real-world users, and combinations thereof. In some embodiments, the avatars can be computer controlled bots, thus not requiring a real-world user to dictate control.
Owner:SONY INTERACTIVE ENTERTAINMENT AMERICA LLC +1
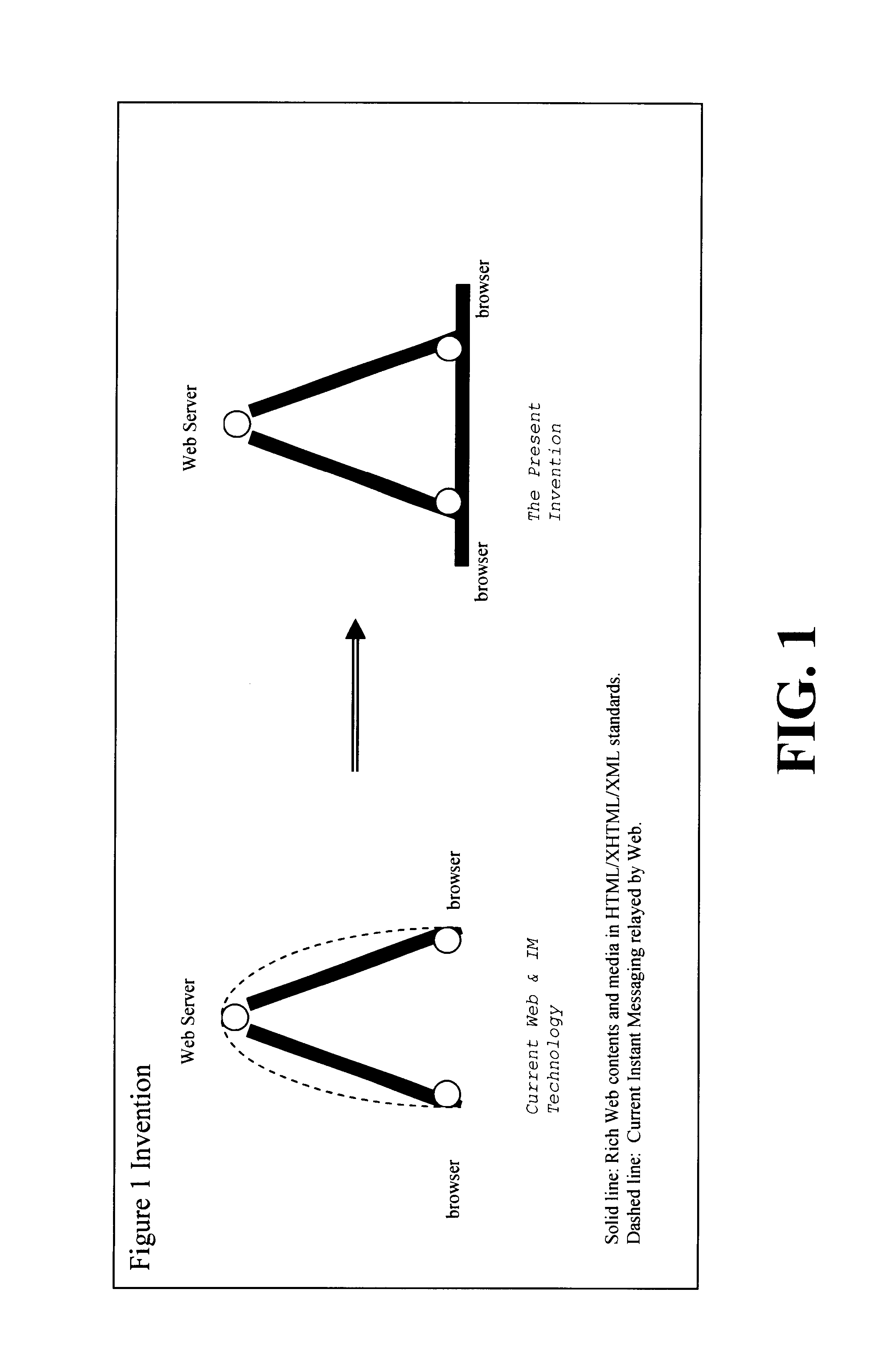
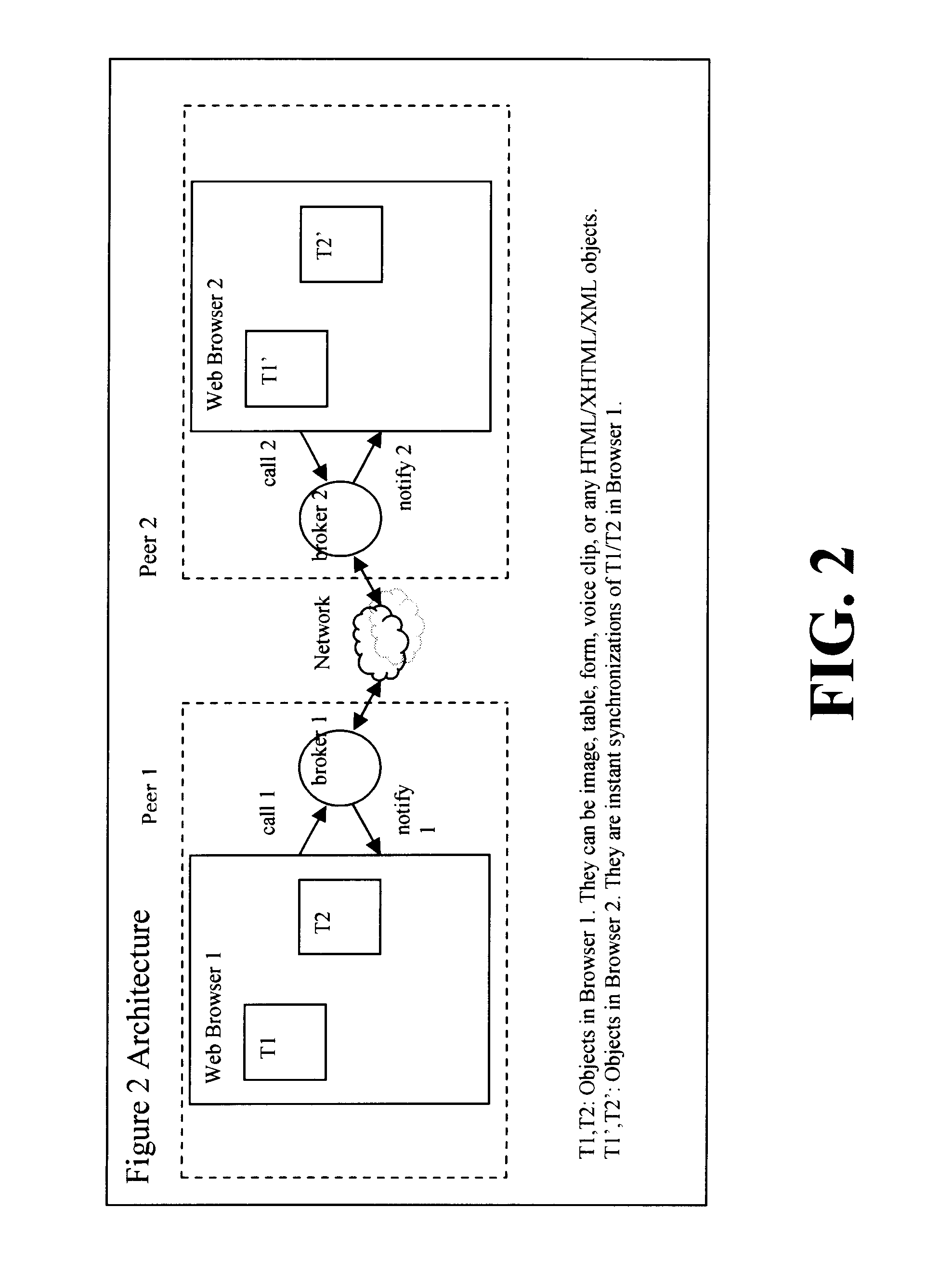
Browser-to-browser, dom-based, peer-to-peer communication with delta synchronization
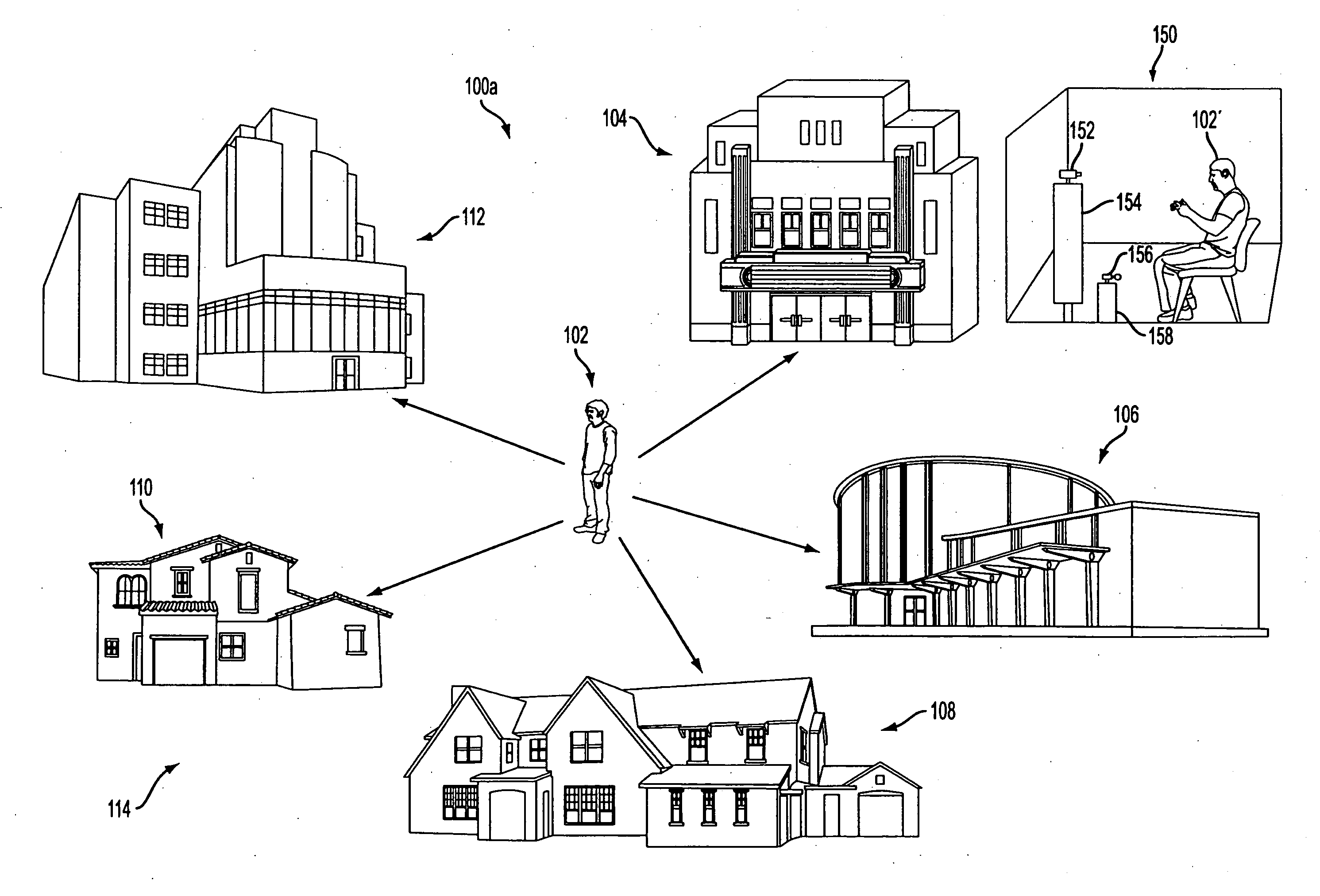
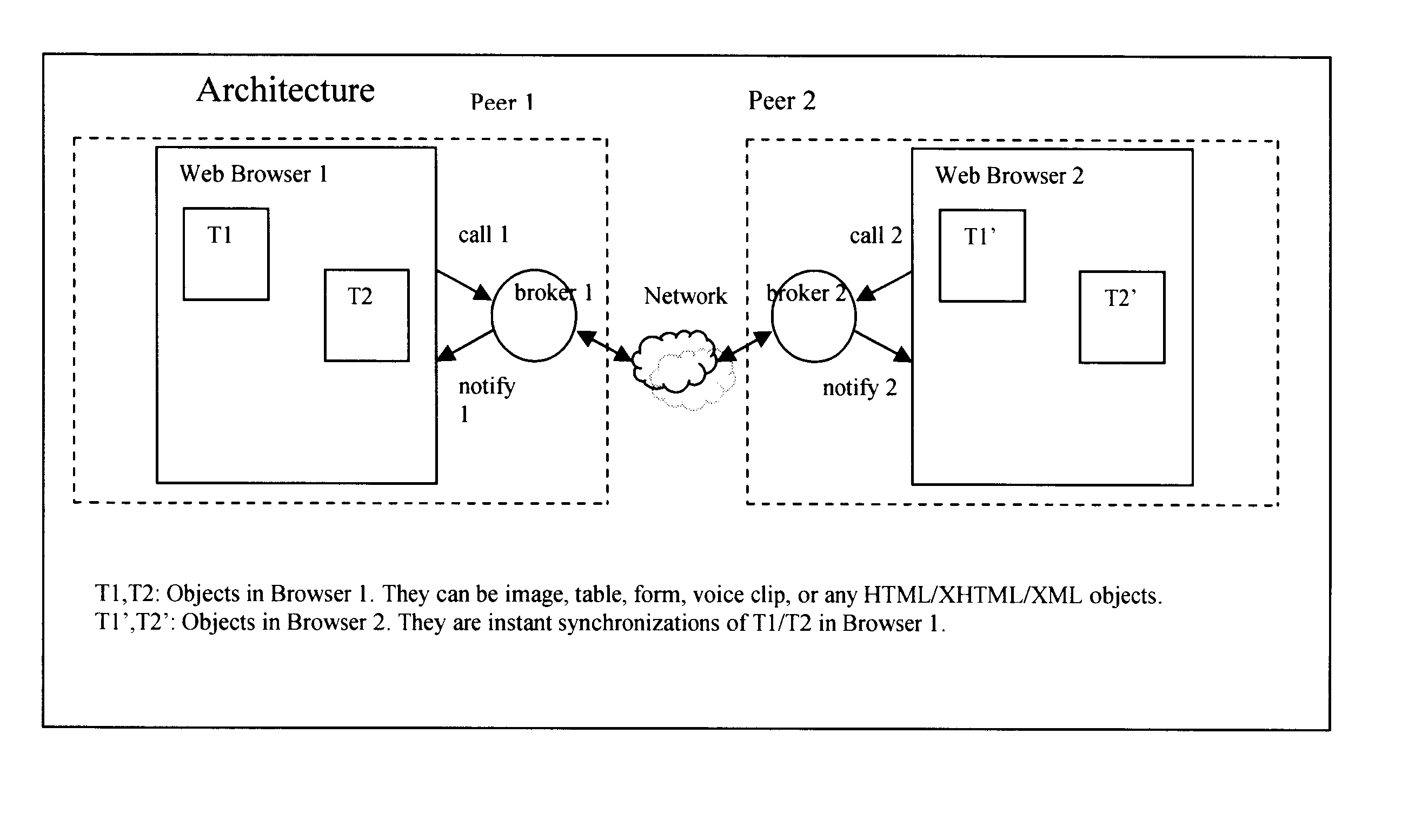
InactiveUS6865599B2Multiple digital computer combinationsData switching networksWeb browserEngineering
A peer-to-peer communication system for use over an underlying computer network system, the peer-to-peer communication system comprising: a web browser; and a broker interposed between the browser and the underlying computer network system, with the broker being adapted to (1) monitor a first event taking place within the browser, encode the first event and associated changes in a first event message, and push the first event message to the at least one other peer over the underlying computer network system.
Owner:ZHANG CHENGLIN
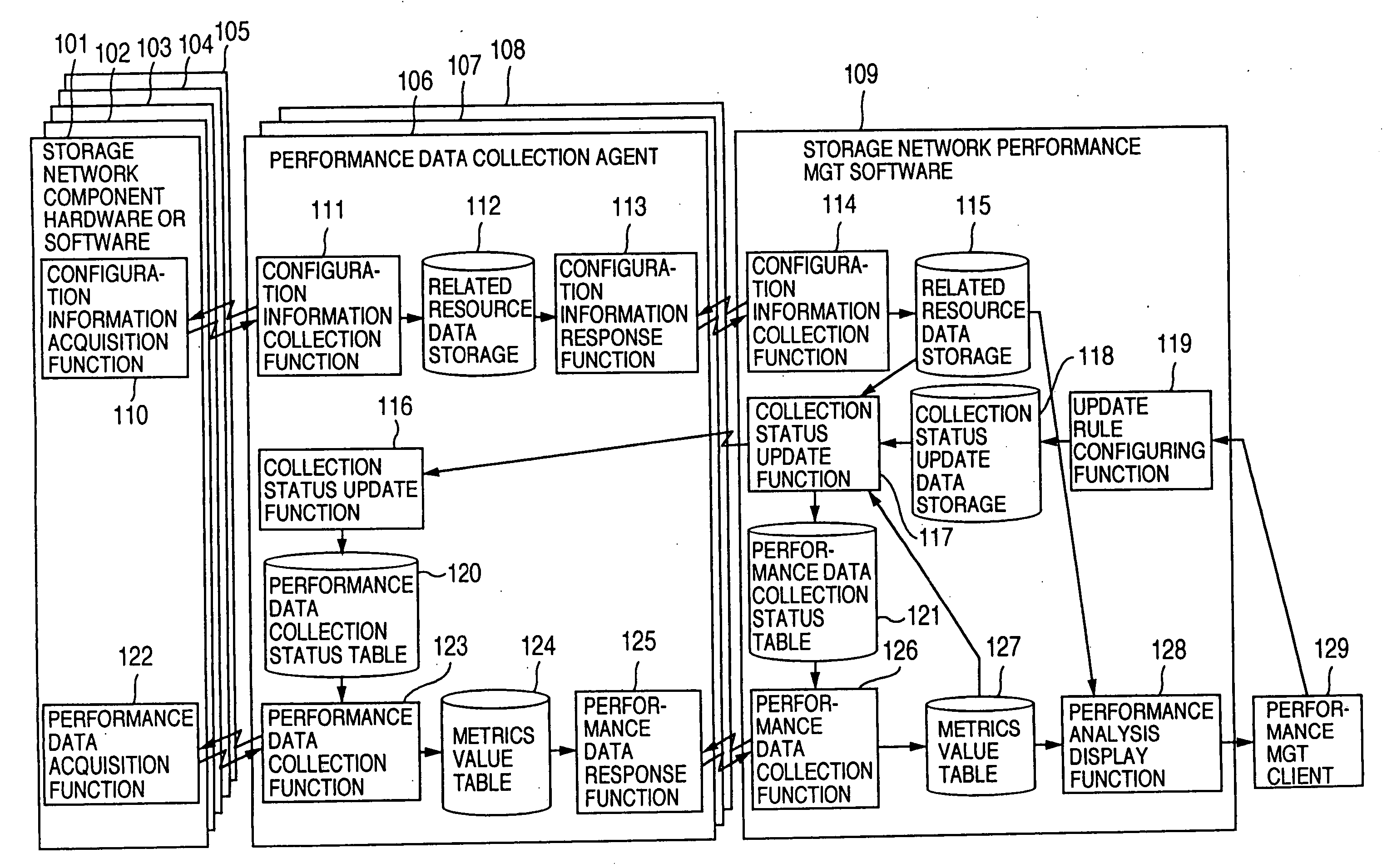
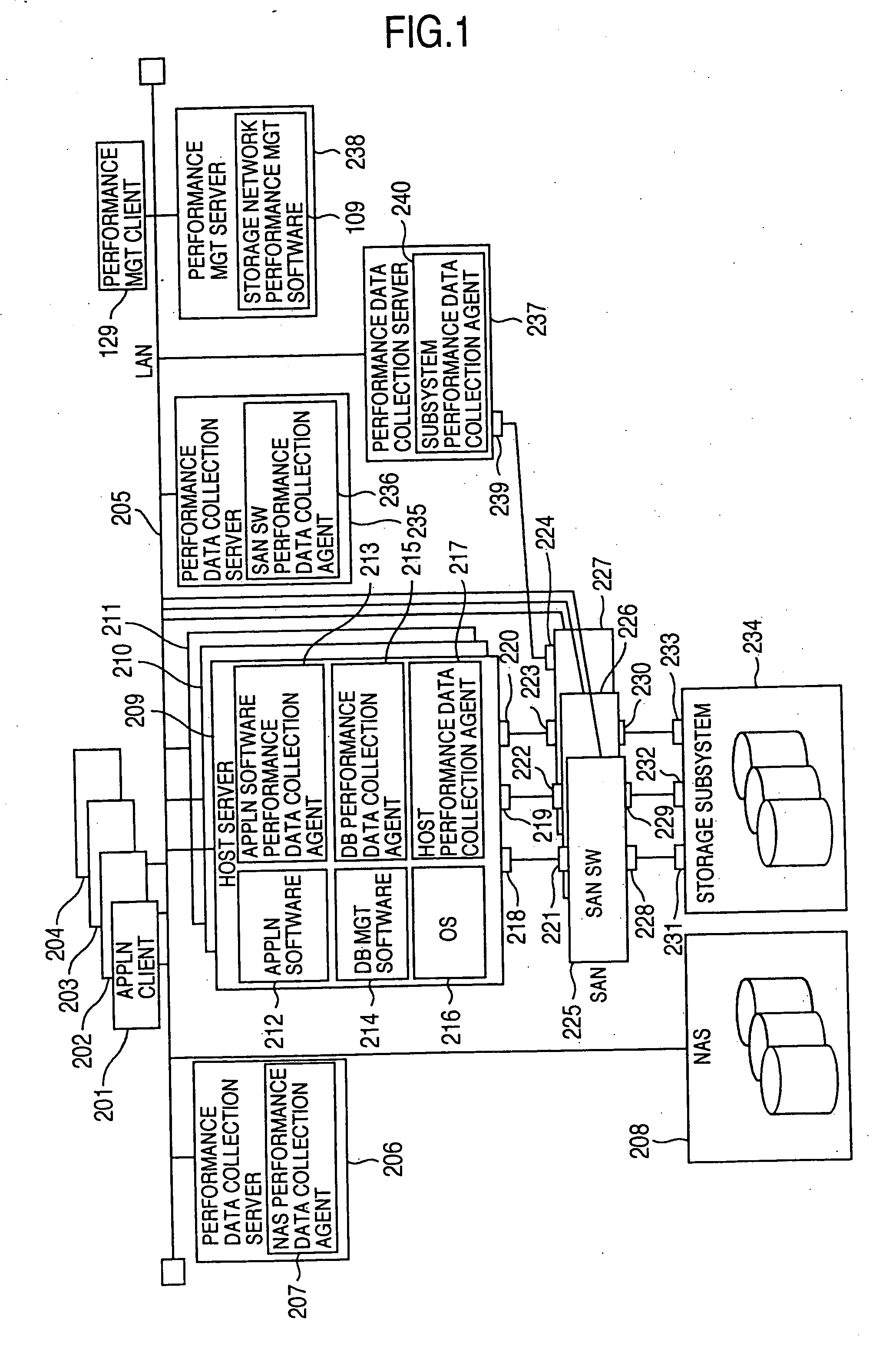
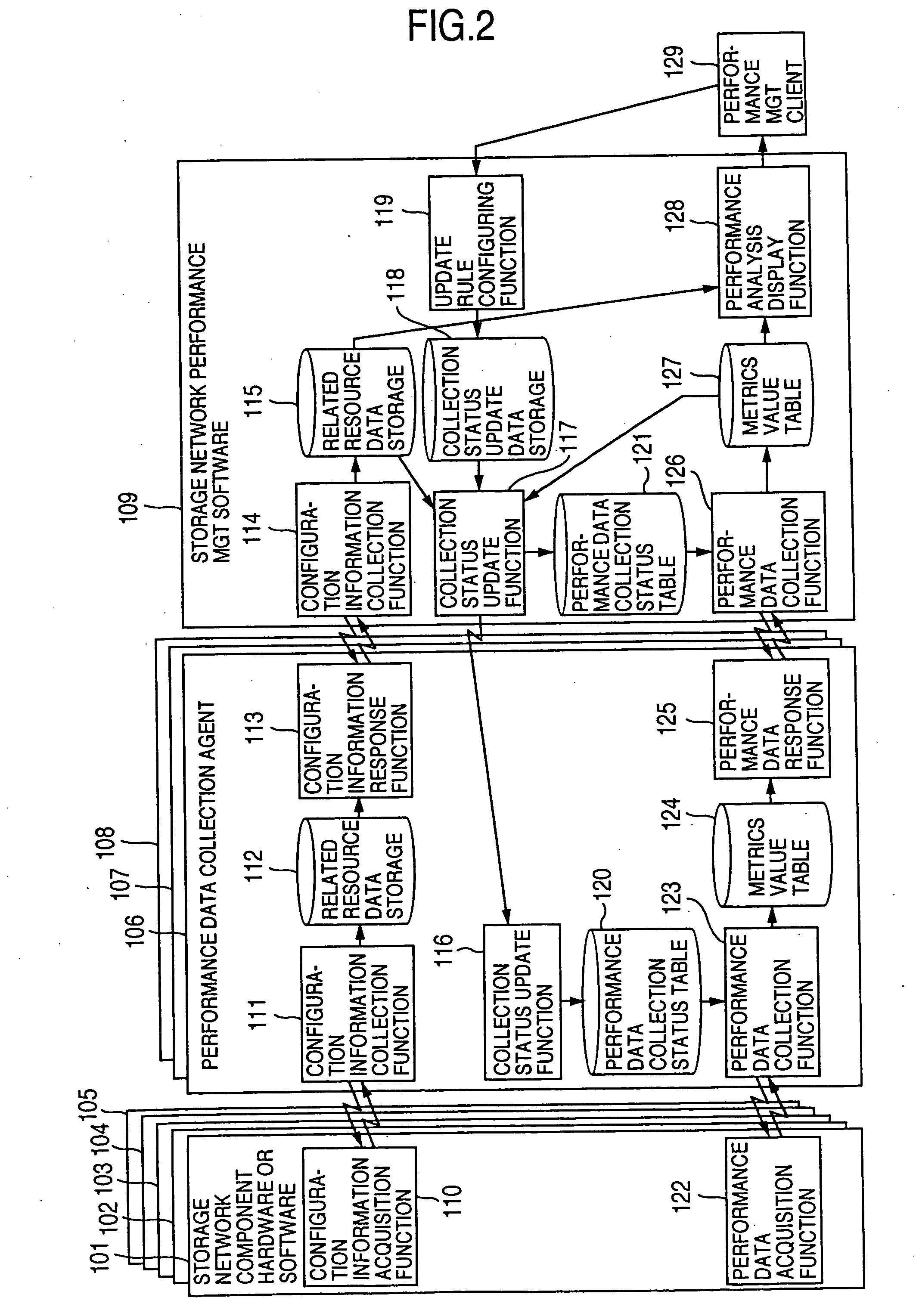
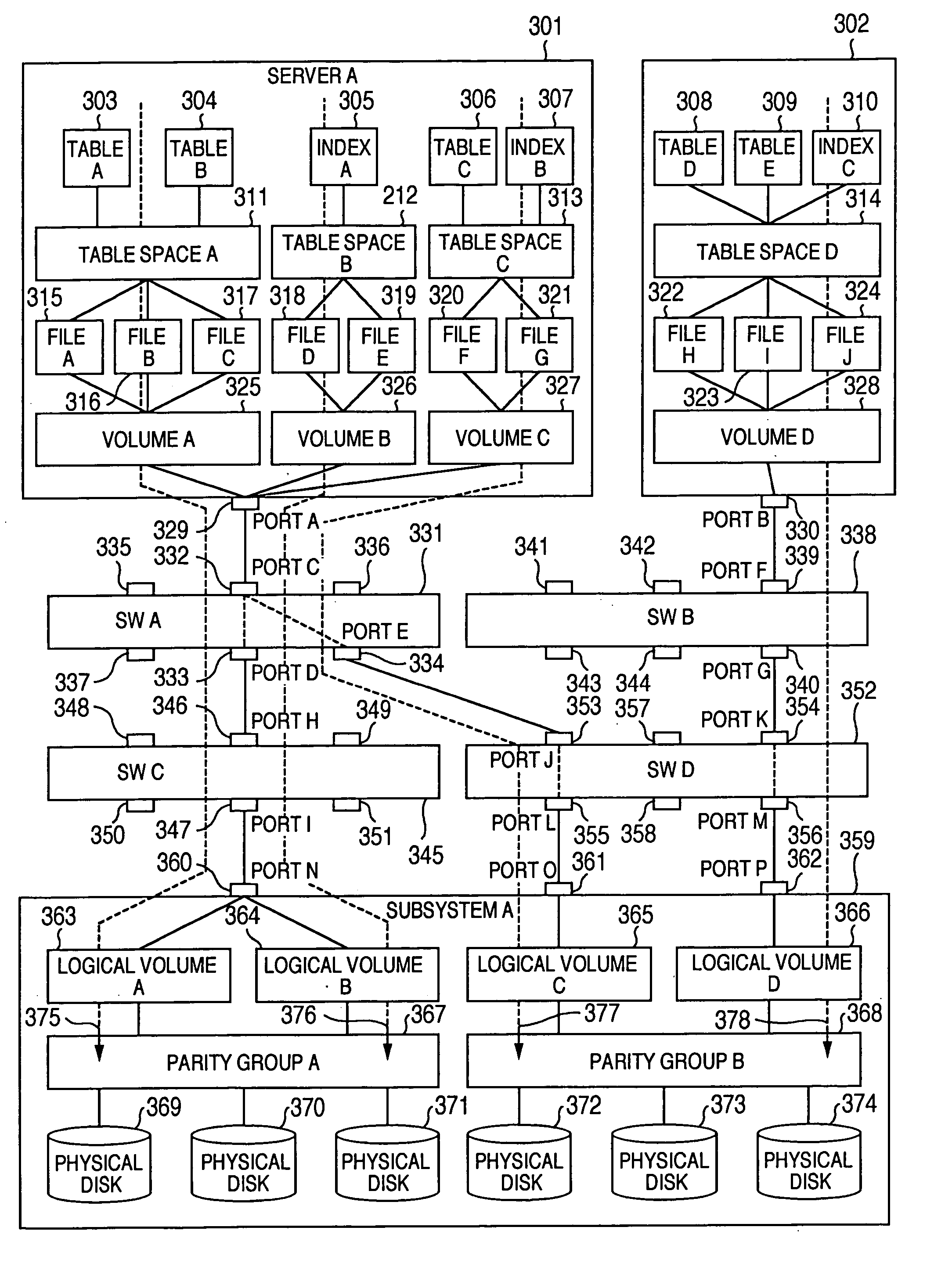
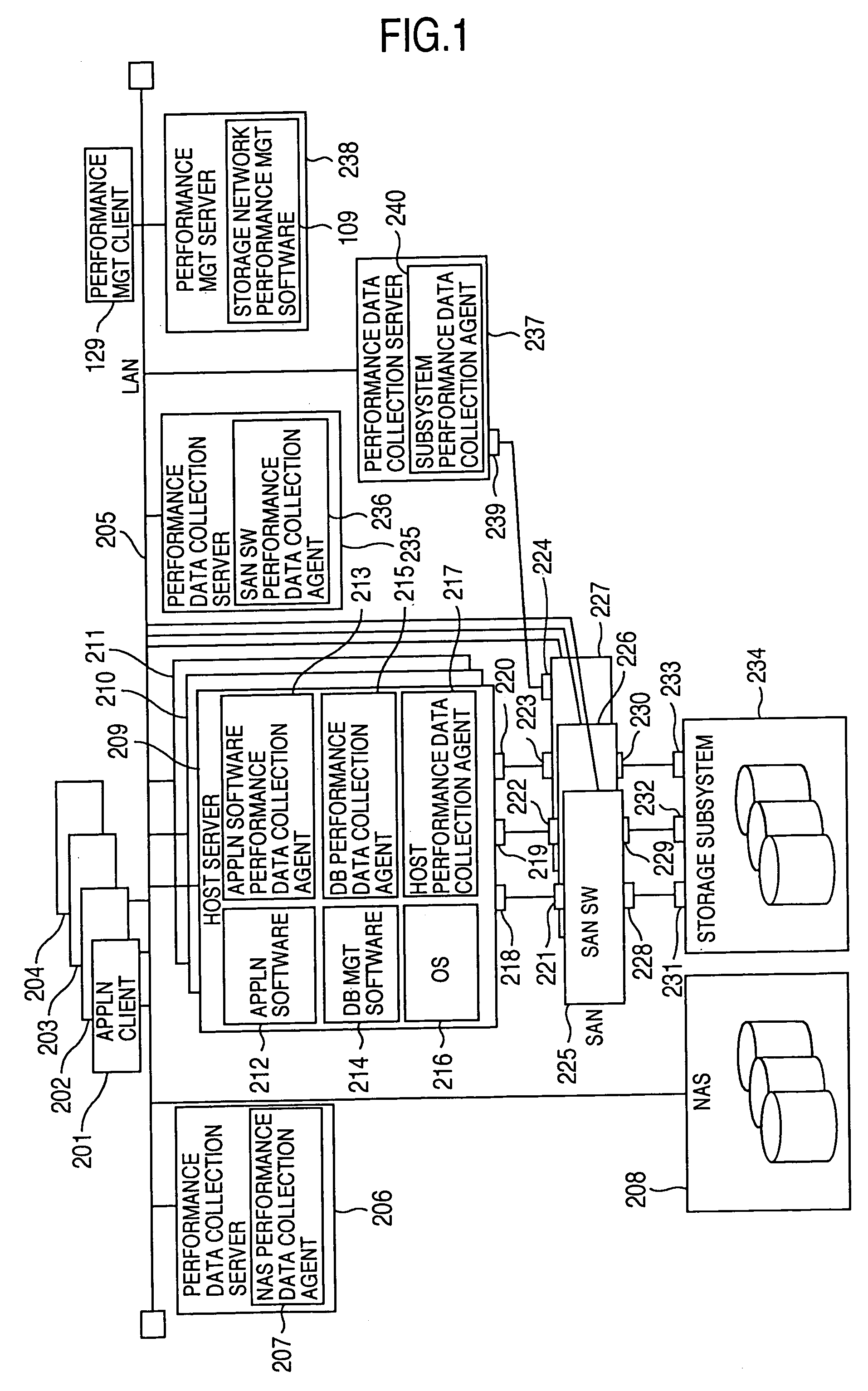
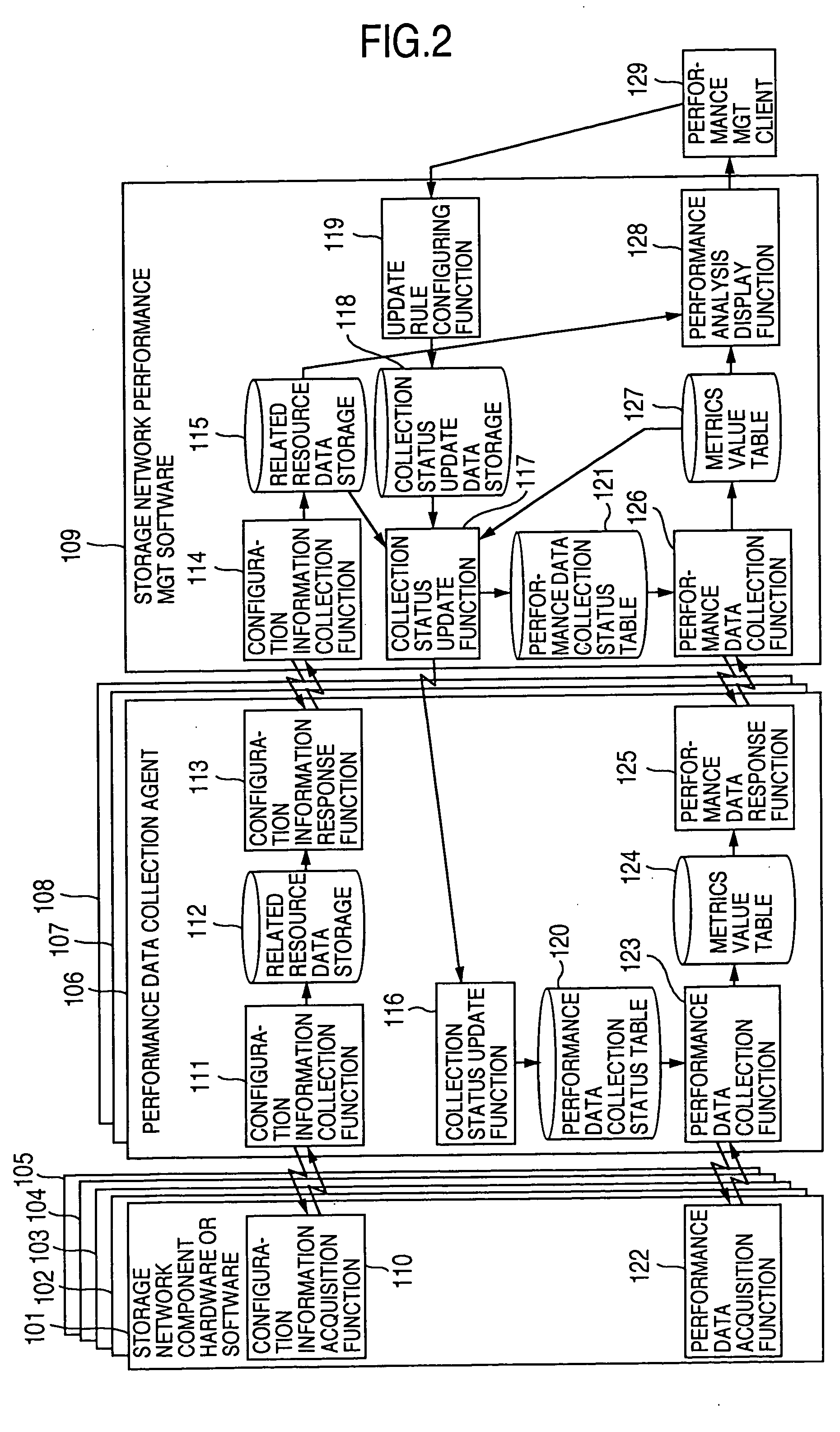
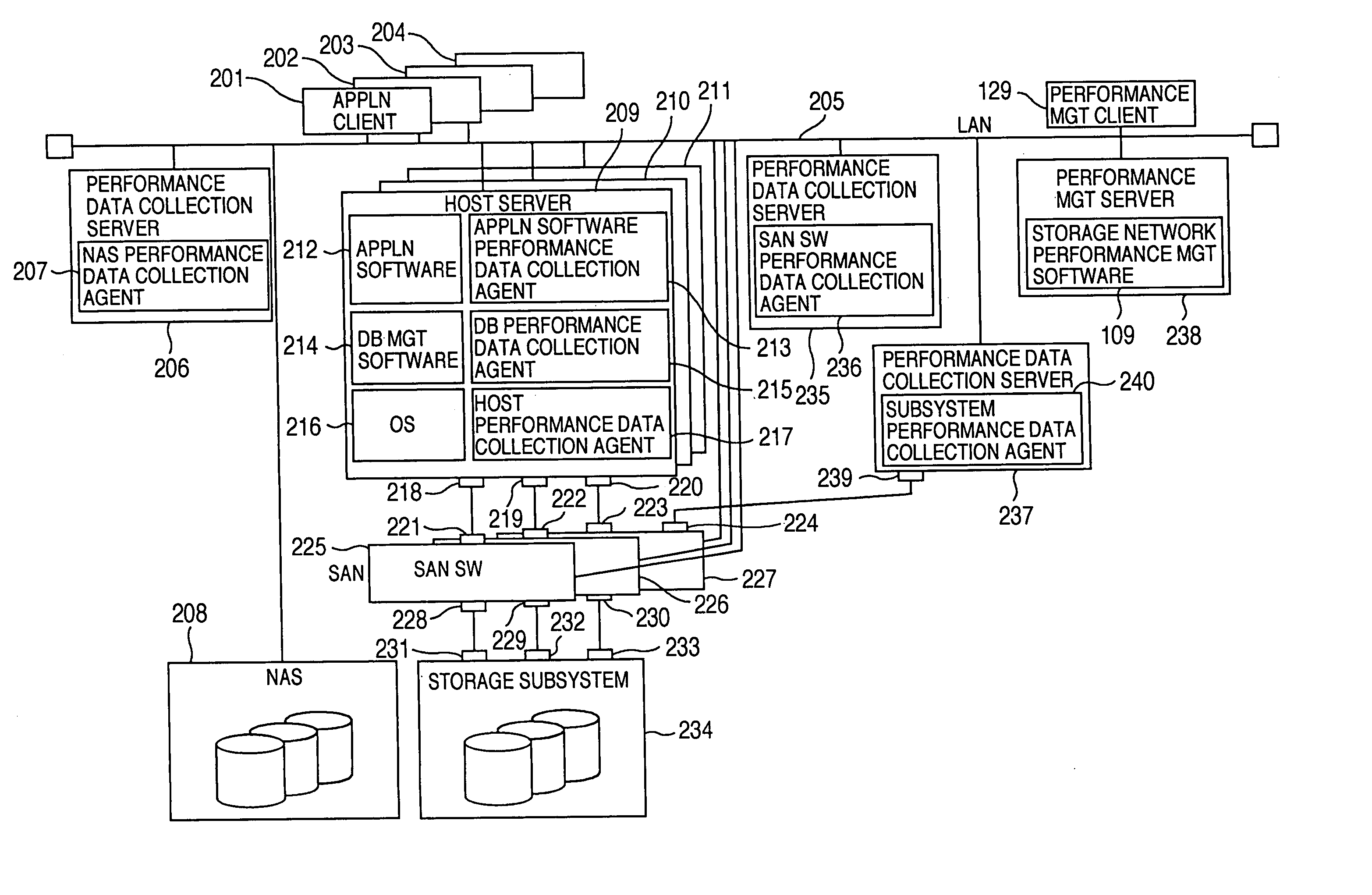
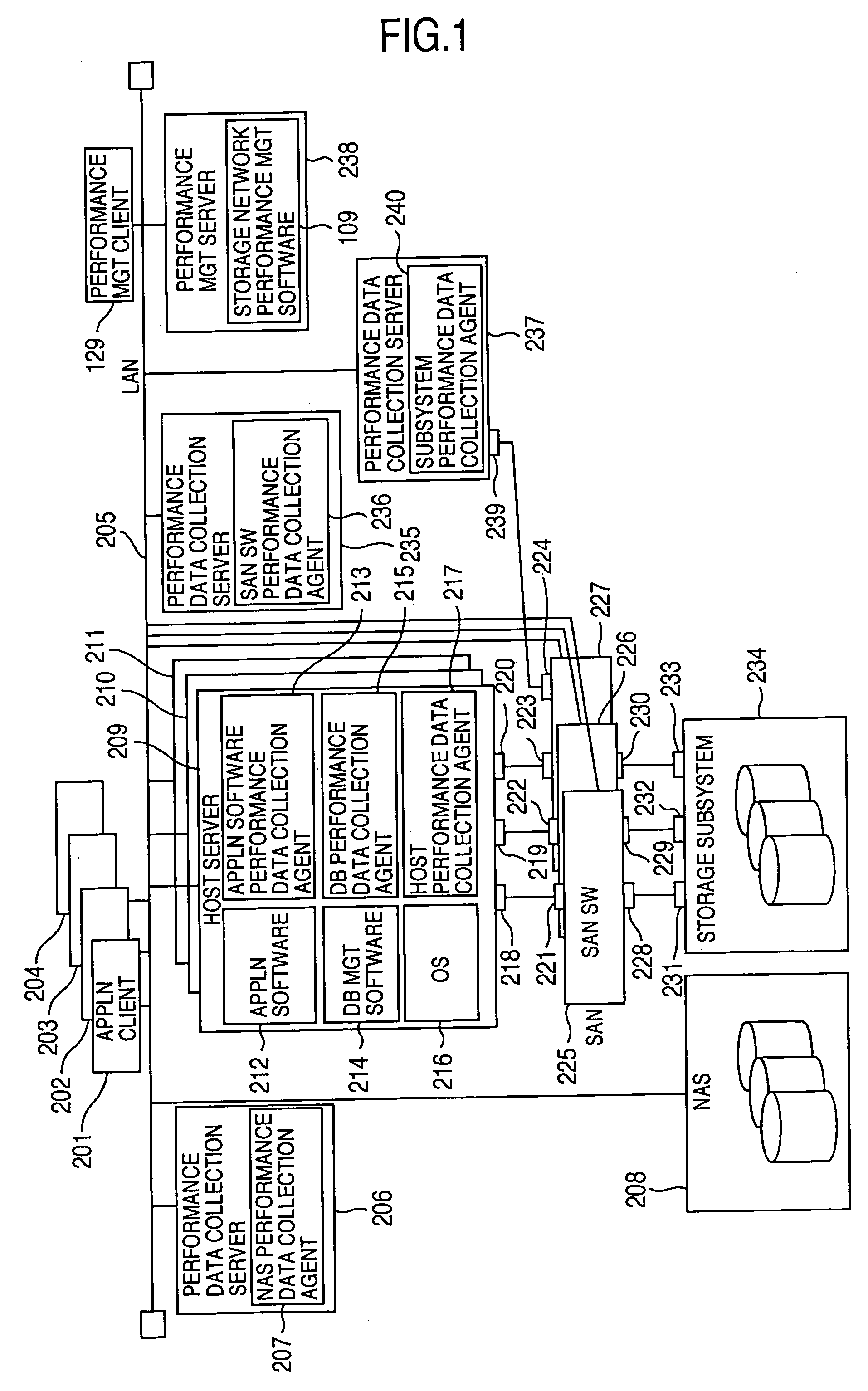
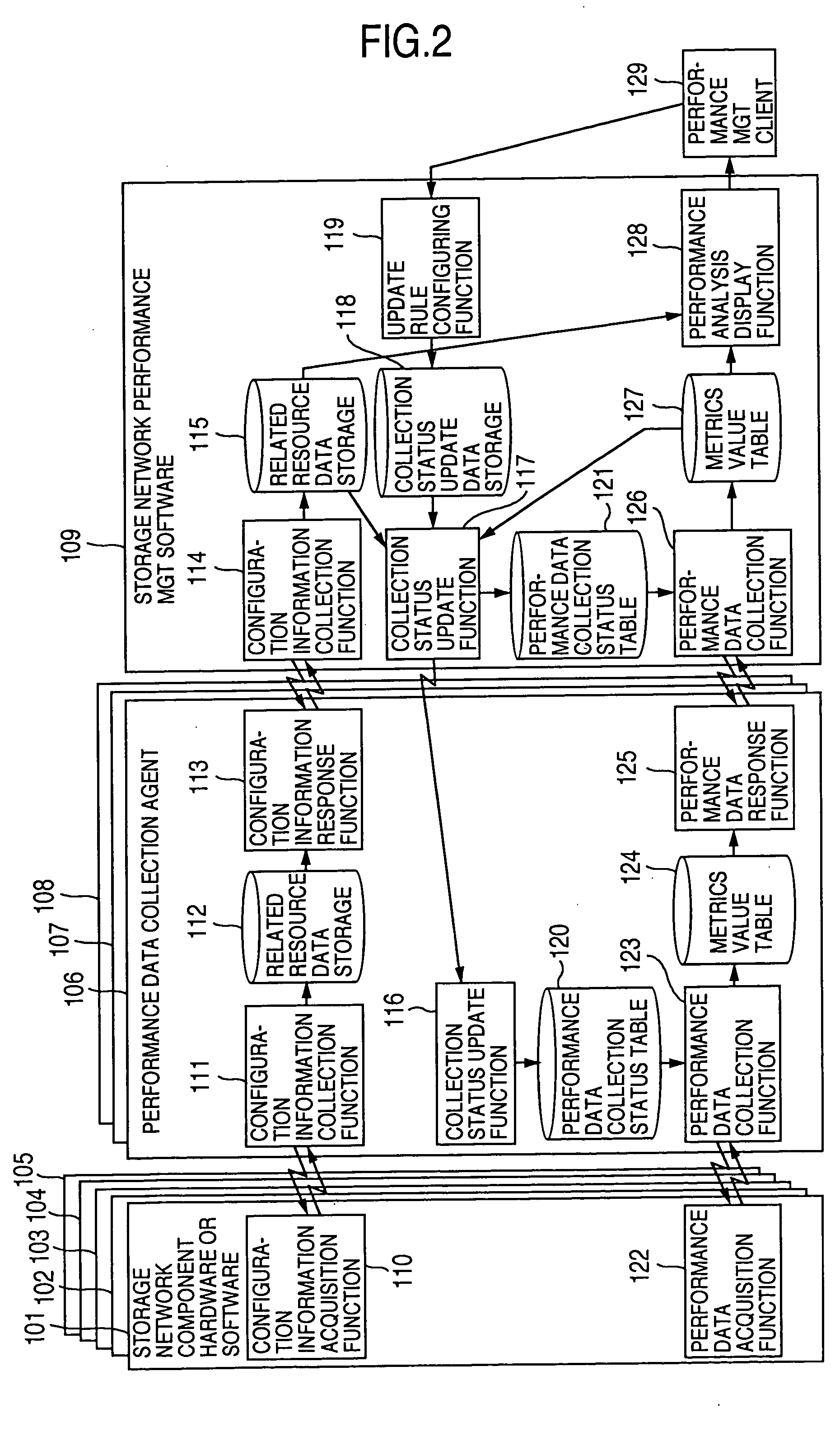
Method and program of collecting performance data for storage network
InactiveUS20060265497A1Input/output to record carriersDigital data processing detailsExternal storageCollections data
In a storage network including at least a computer system, at least an external storage and at least a network system for communication of input / output data between the computer system and the external storage, a method of collecting the performance data on the network system and the software operated on the network system, in which the range or degree of data collection is automatically adjusted as required based on the performance data collected.
Owner:HITACHI LTD
Distributed network system which transmits information to users based on past transactions of the users
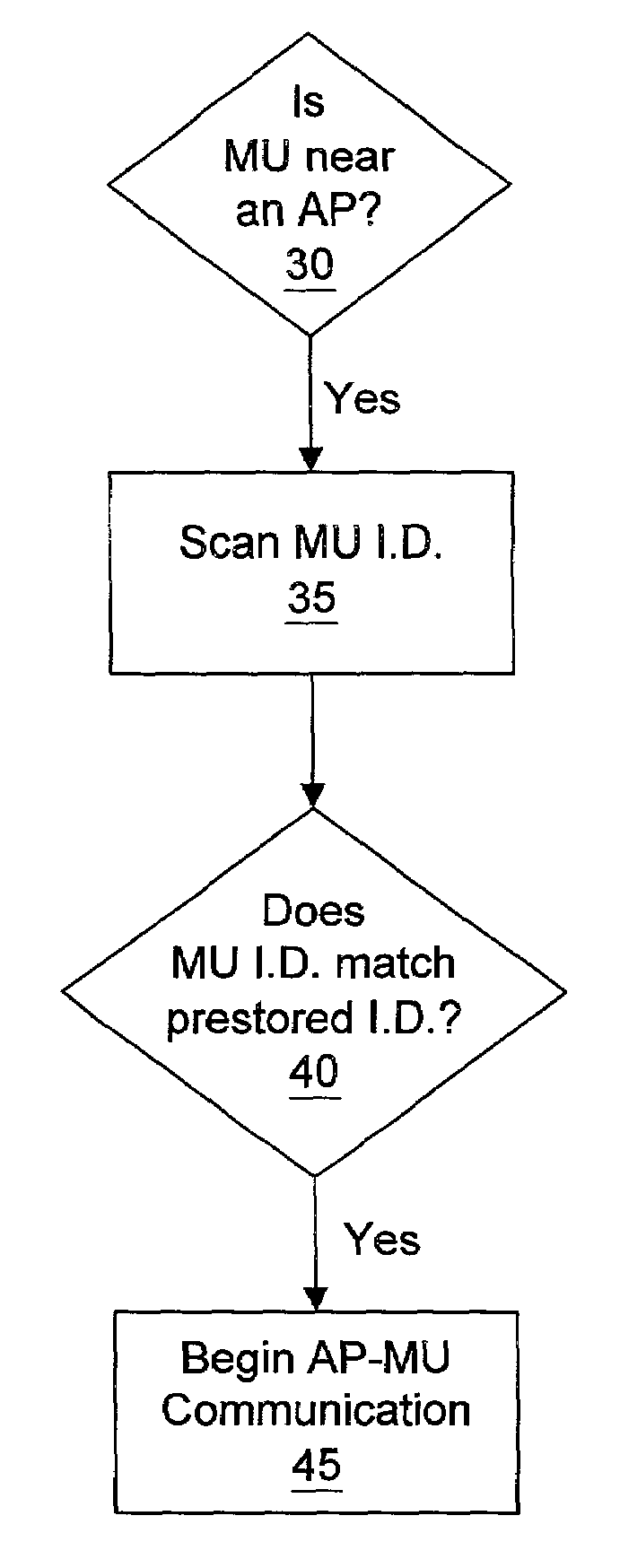
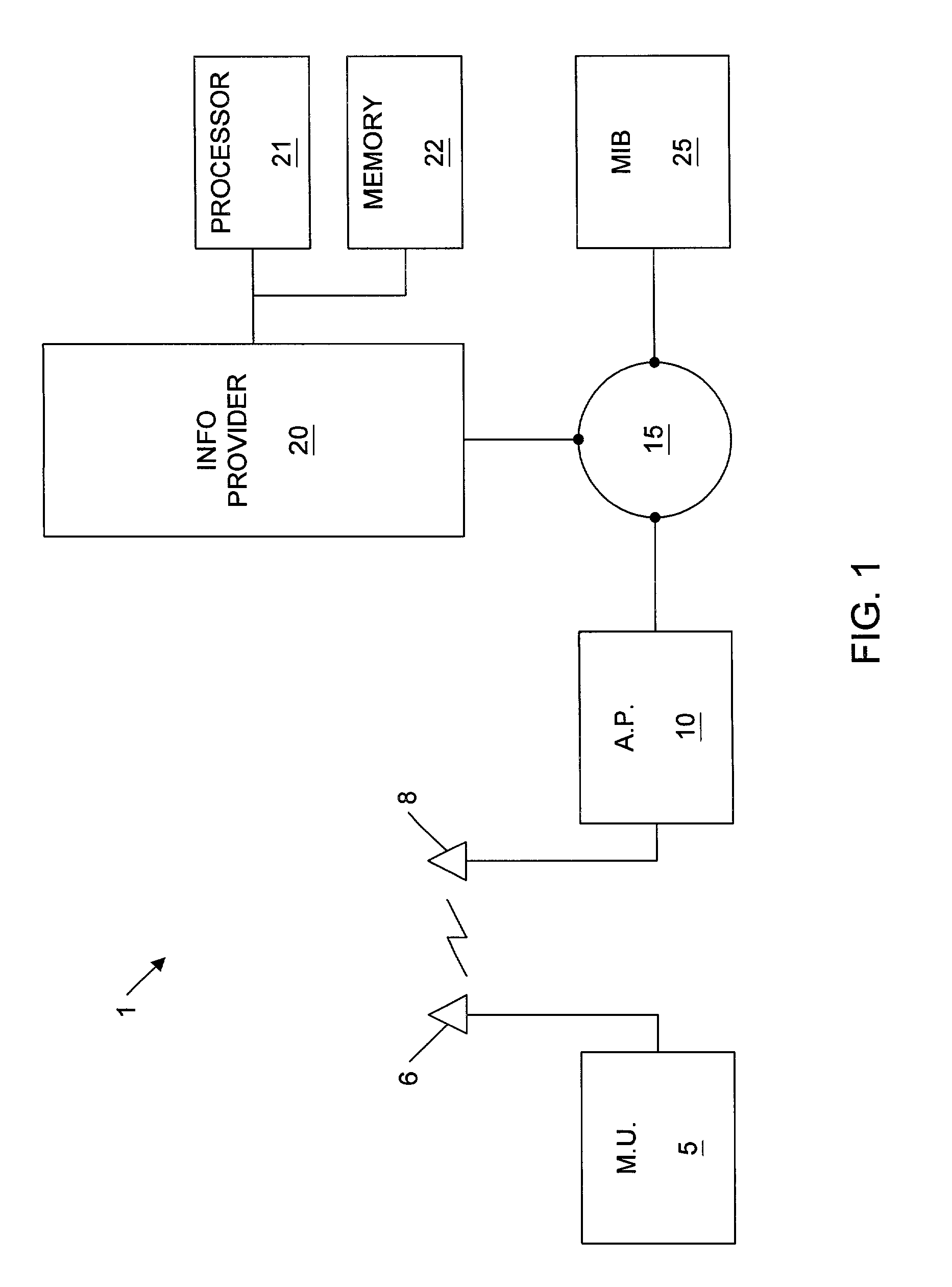
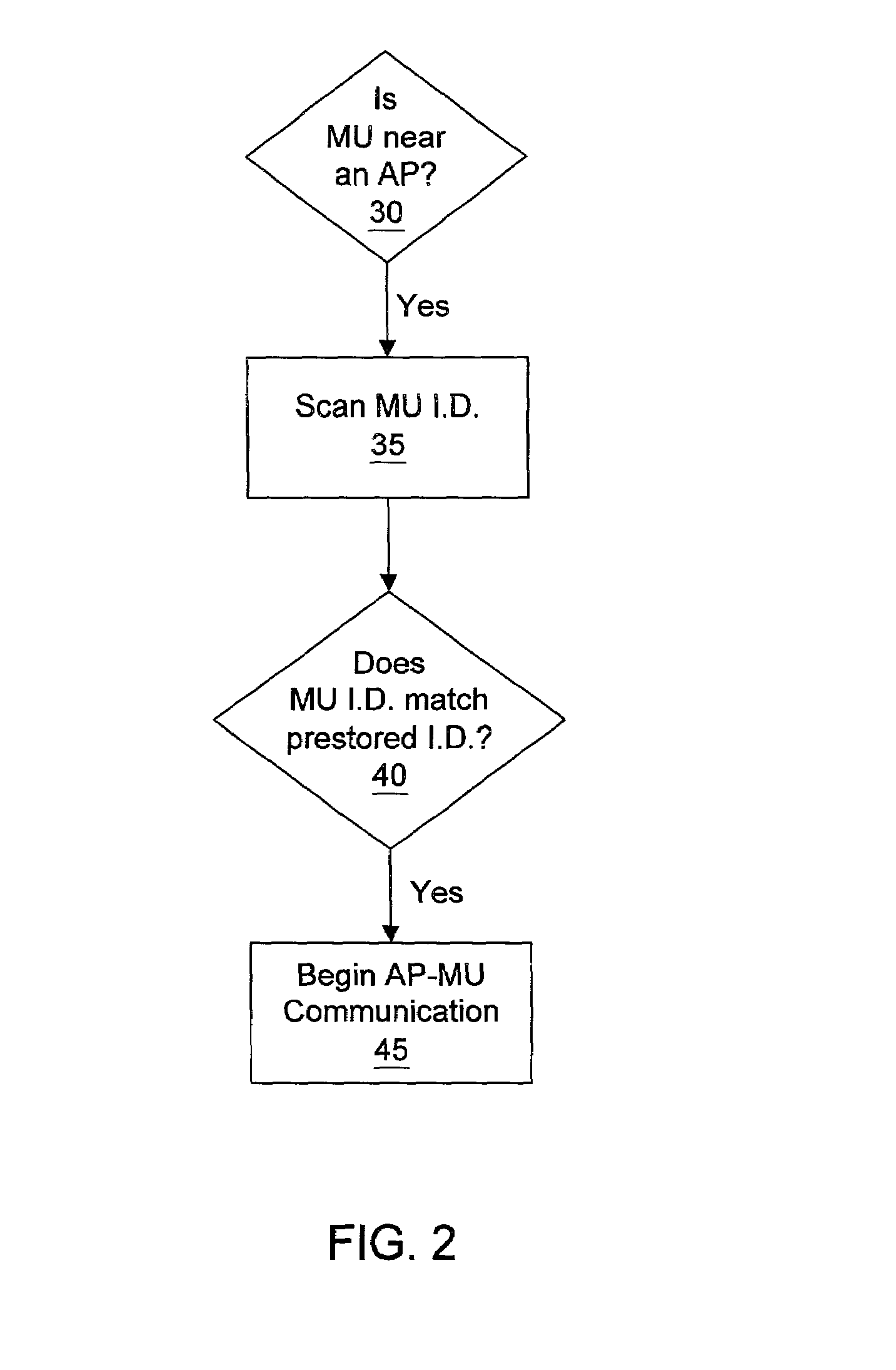
InactiveUS7058594B2Good precisionAccomplished more efficientlyDirection finders using radio wavesBeacon systems using radio wavesTelecommunicationsGeolocation
Owner:WAYPORT
Payment system and method
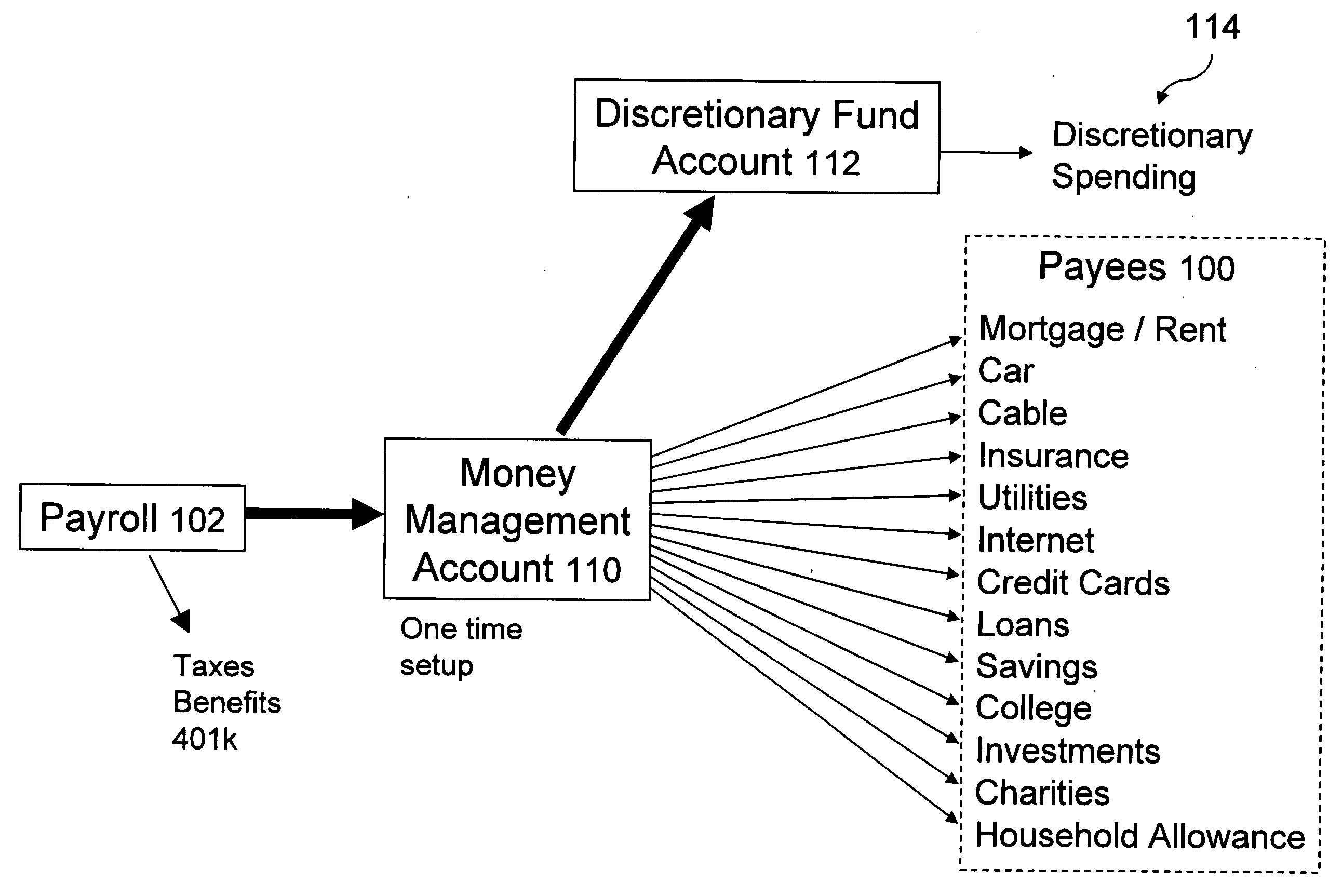
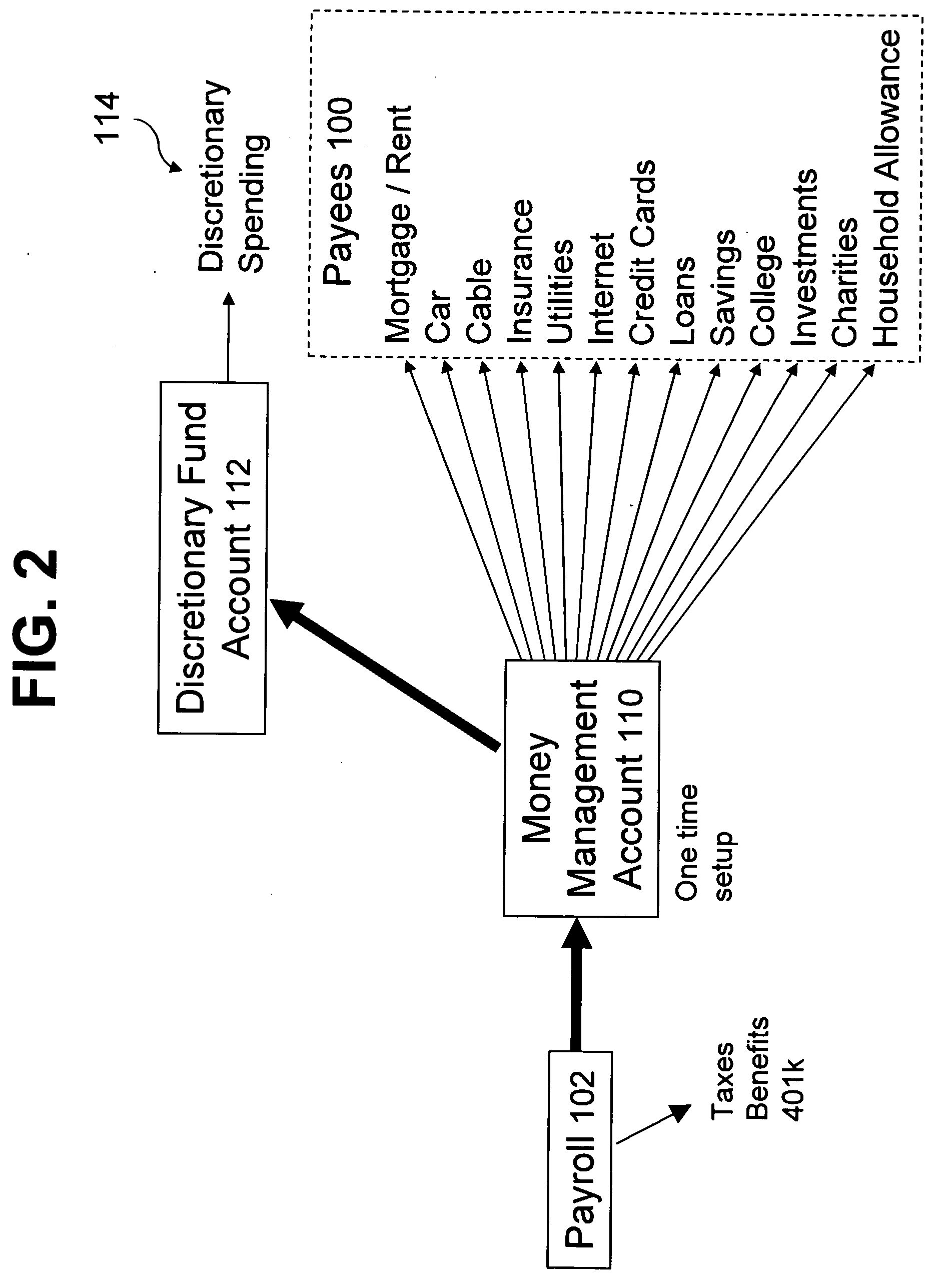
Using a single source money management system customers may automate their committed spending. A money management account and a discretionary fund account are established in response to a customer's request to participate in the system. A financial institution receives money on a periodic basis from a customer's predictable payment system. The money is then deposited / transferred to the money management account, retained in the money management account as required for bill payment, and / or deposited / transferred into the discretionary fund account if it is “excess.” Bills are paid on a customer determined schedule directly from the money management account using the money retained in the money management account. A loan account may also be established in response to a customer's application for a loan account. A financial institution grants a loan for a loan purchase in response to a customer's application for a loan purchase. The system and / or the financial institution handles payment for the loan purchase and repayment of the loan from the loan account from the money management account. The present invention may include a secure internet shopping system that includes a vendor web system and a financial institution web system. Each vendor offers goods and / or services. The financial institution web system permits customer authorization of payment to a selected vendor.
Owner:LINDSAY BROWN NICHOLAS ANTHONY
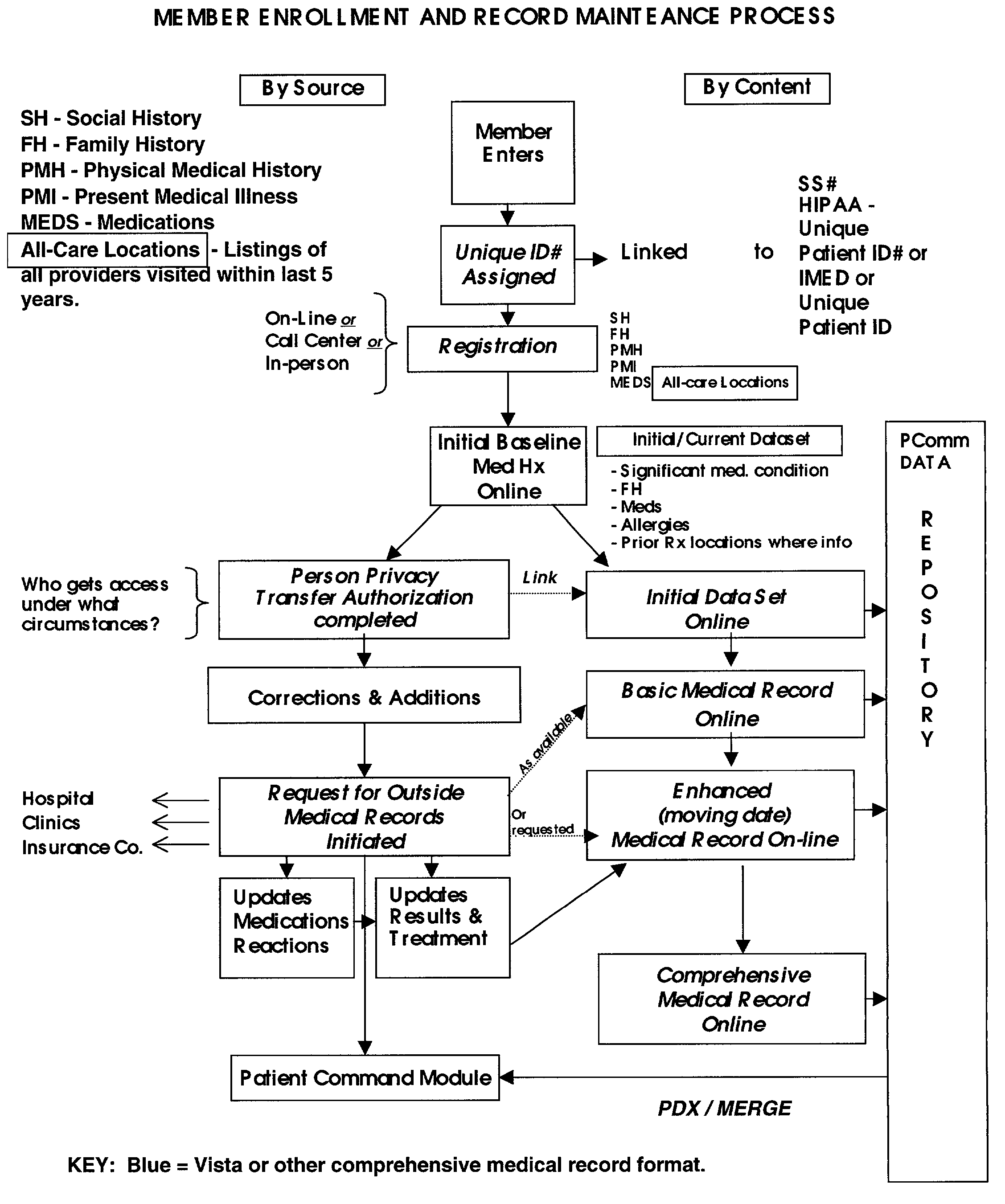
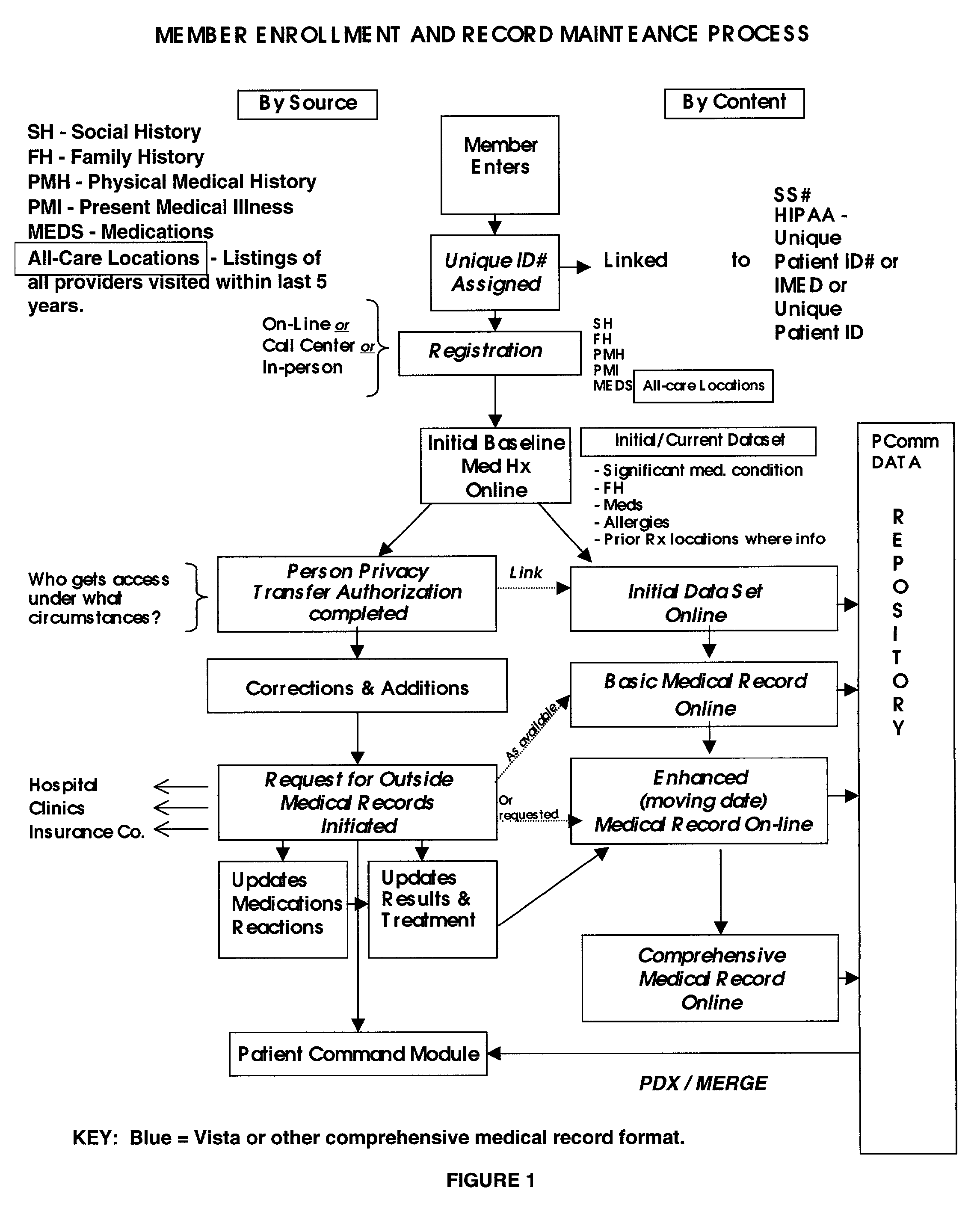
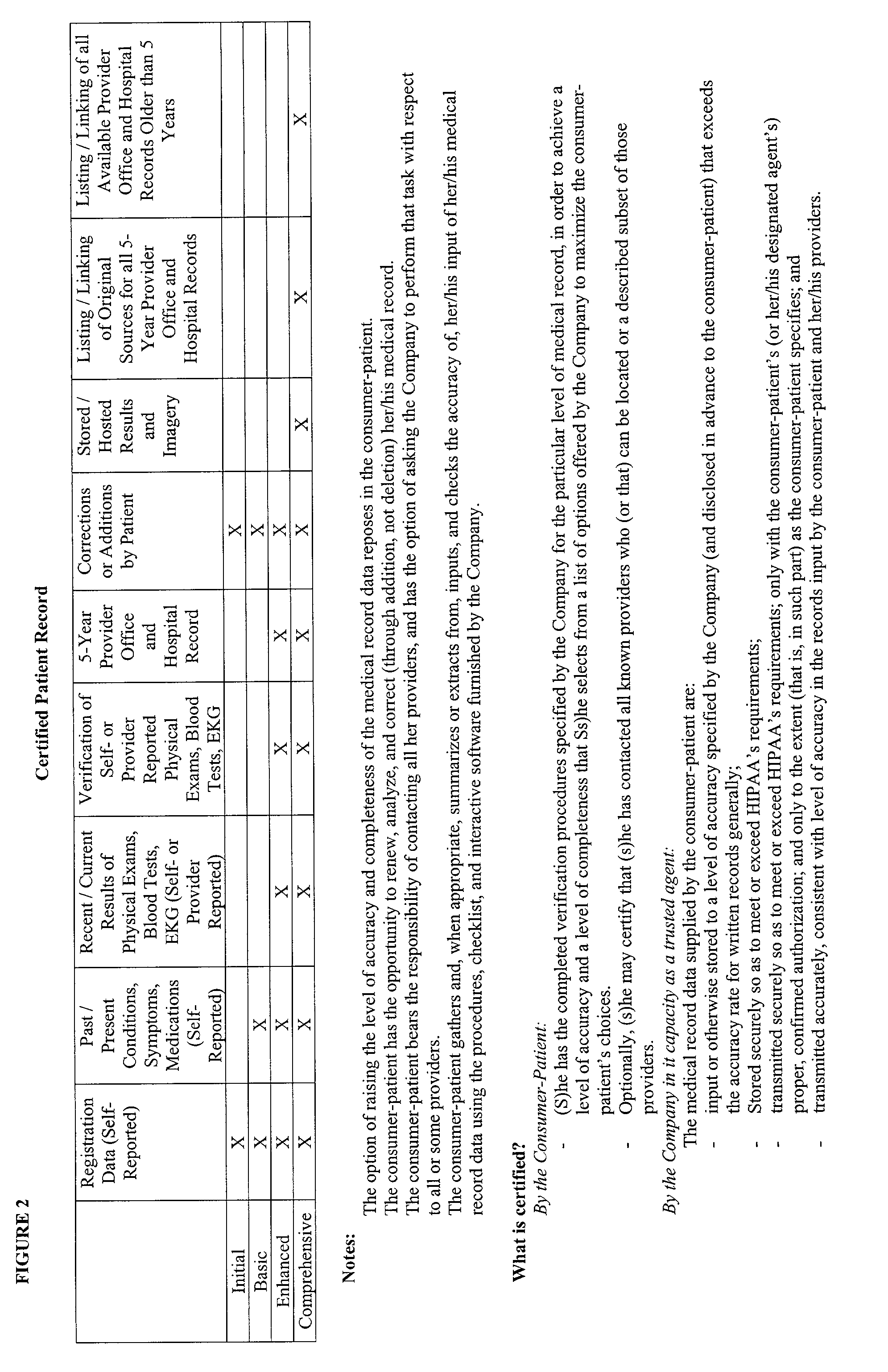
Broadband computer-based networked systems for control and management of medical records
This invention relates to an Internet or other broadband computer-based networked system, operated by a service provider that enables members of the system provider network, which may be patients, family members, employees or others, to assemble, update, enhance, analyze, correct, broker, securely store and transmit, certify and otherwise manage the medical records and, under appropriate circumstances, the medical records of family, friends, clients or customers and integrates those medical records and their updating around the patient.
Owner:KNAUS WILLIAM A +1
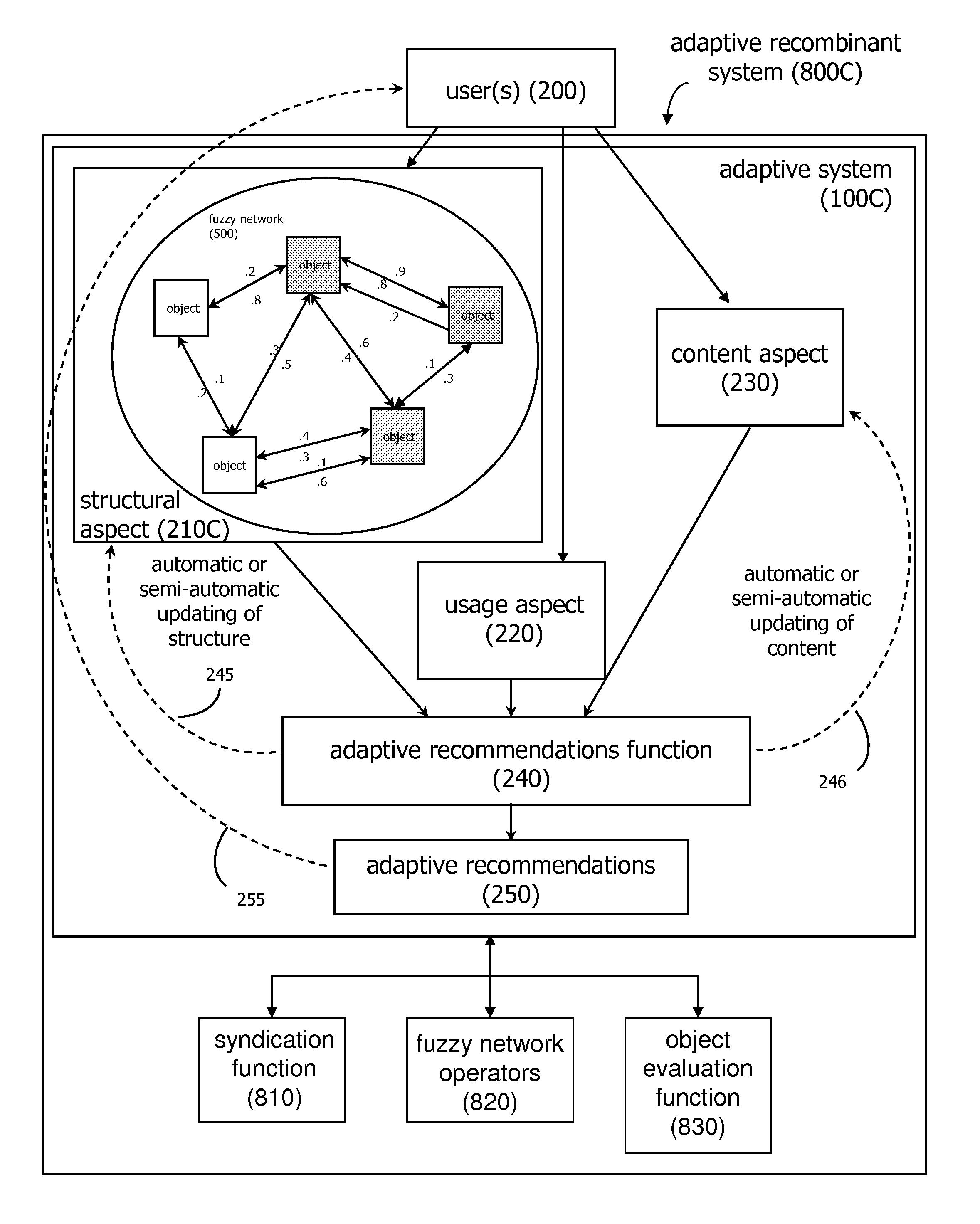
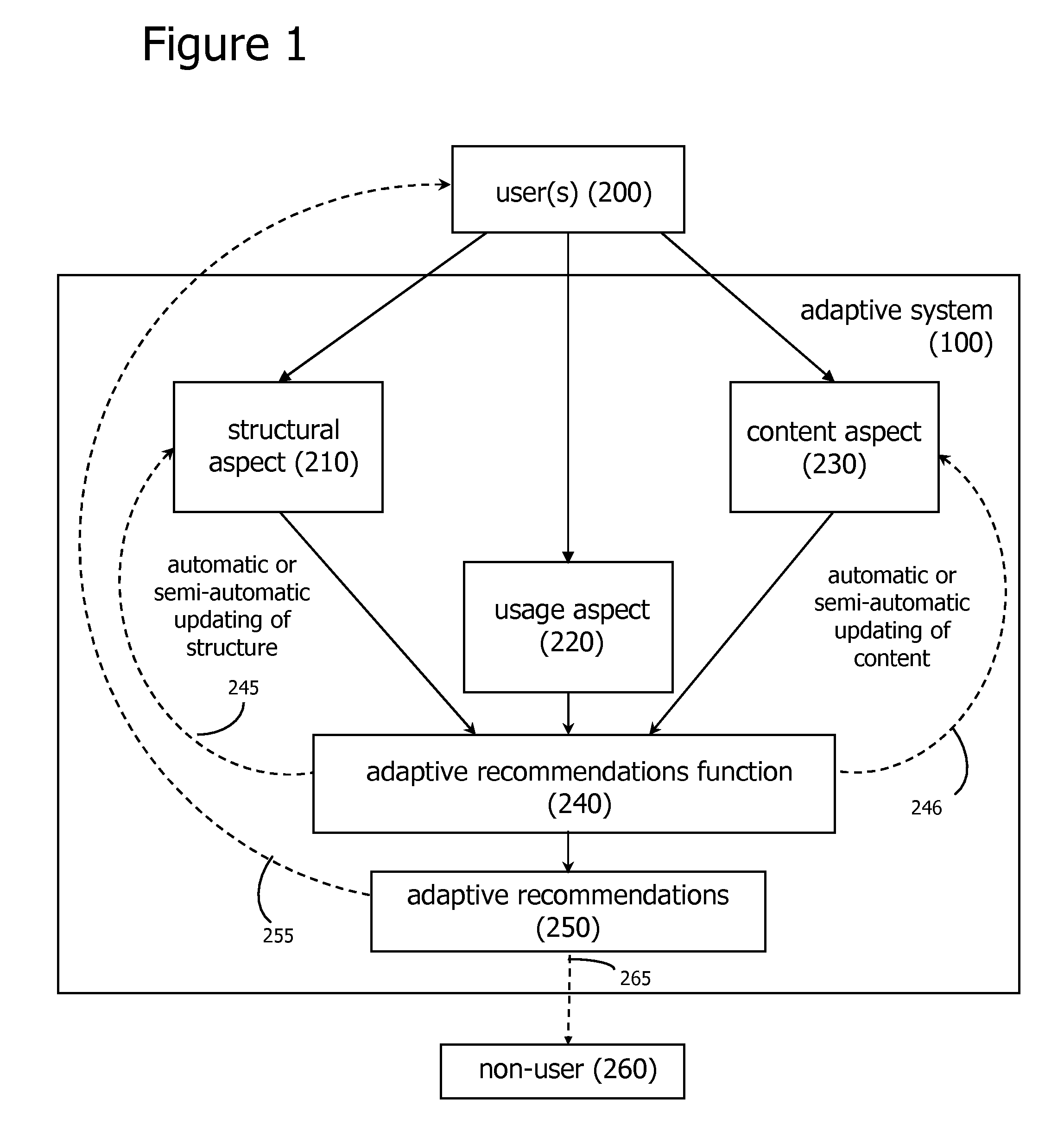
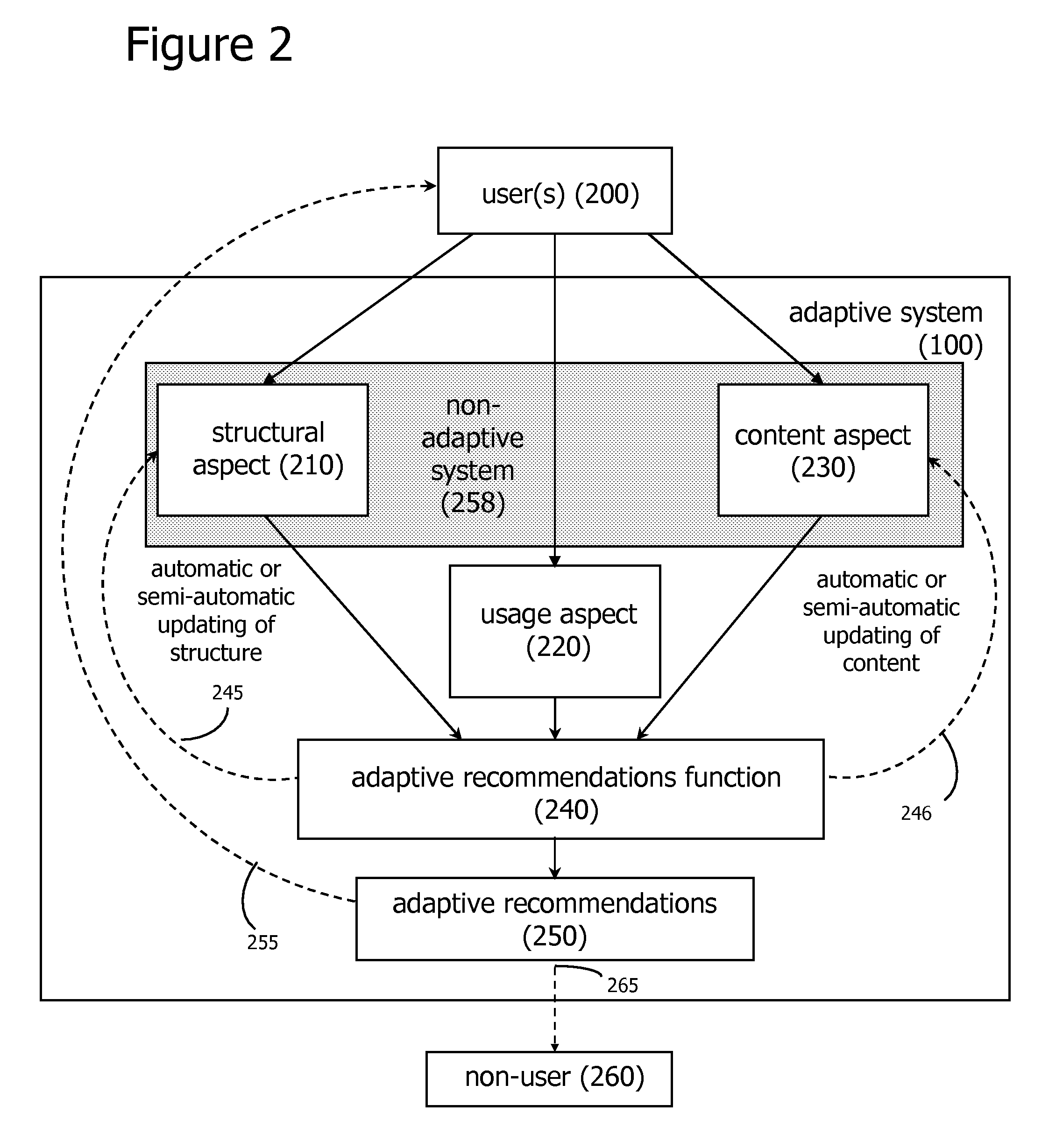
Adaptive Social and Process Network Systems
ActiveUS20060200434A1Easy to adaptEfficiently navigateAdvertisementsDigital computer detailsSelf adaptiveNetwork application
An adaptive system applied to social network and process network applications is disclosed. These adaptive social networking and tagging systems, and adaptive process network systems, apply algorithms for monitoring user usage behaviors across a plurality of usage behavior categories associated with a computer-based system, and generating recommendations based on inferences on user preferences and interests based, at least in part, on usage behaviors. Additional functions for effectively and efficiently managing social and process networks, such as social network measurement and analysis features, community tagging functions, and process network recombination functions are also described.
Owner:WORLD ASSETS CONSULTING AG
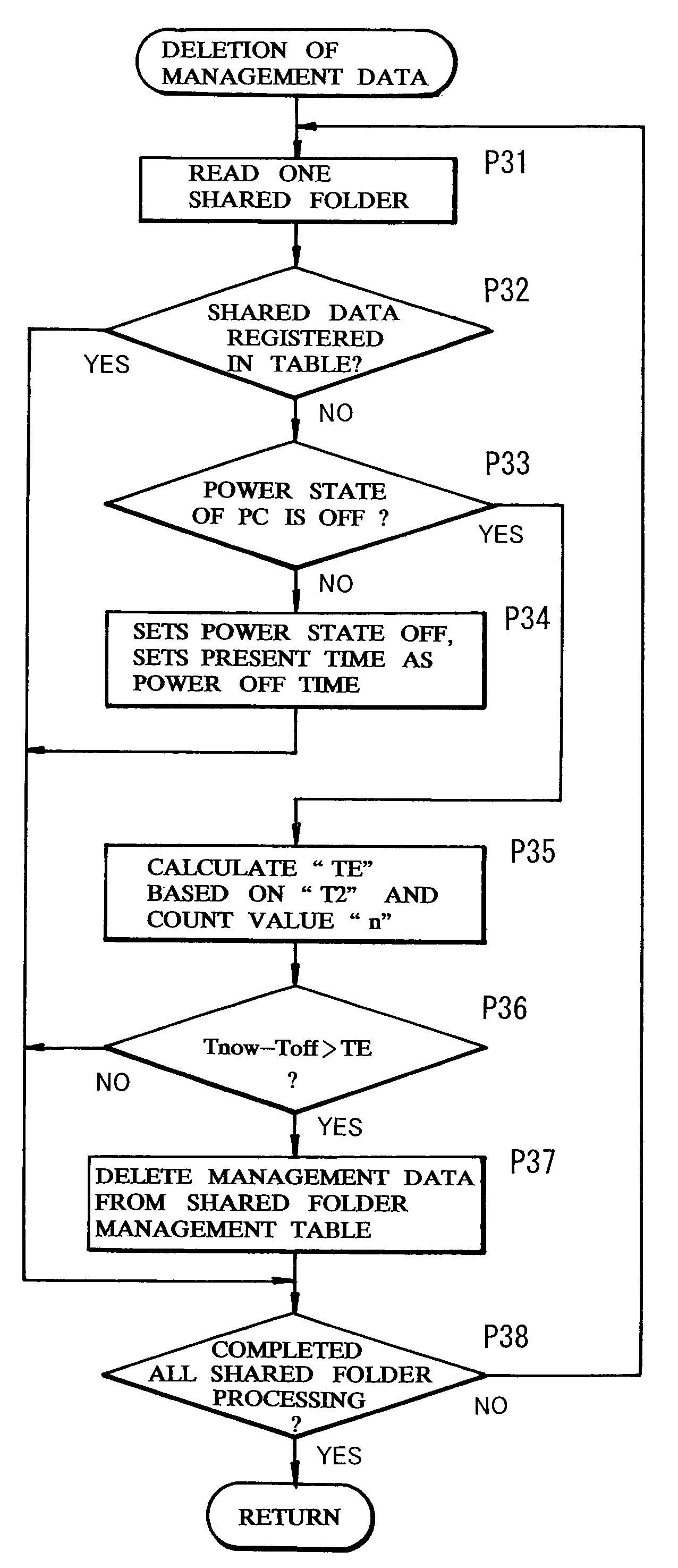
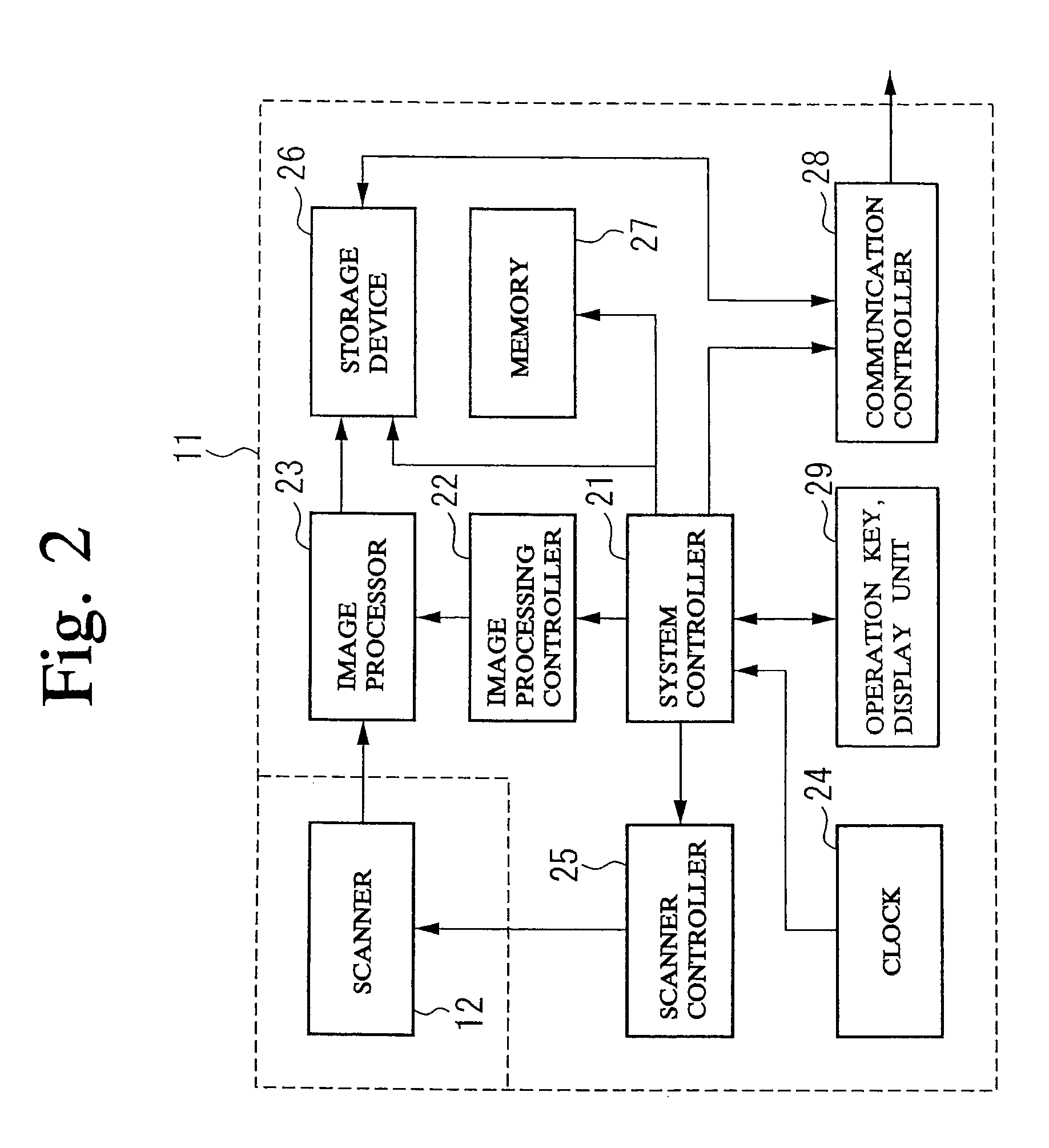
Apparatus and method for information processing in network system
InactiveUS7725474B2Digital data processing detailsSpecial data processing applicationsInformation processingIp address
An apparatus and method for information processing in a network system providing shared folders across a plurality of information processing apparatuses (personal computers) via network. A shared folder management table contains the IP addresses, identifiers of the personal computers, the names of shared folders, and the number of times or attempts to transmit data, etc. Searching of the shared folders is performed at given intervals of time and a search result is compared with the last search result. Based on the search result, a new management data founded is registered in the management table. If a destination personal computer remains inaccessible longer than predetermined time, management data of such personal computers are deleted from the management table.
Owner:KONICA MINOLTA BUSINESS TECH INC
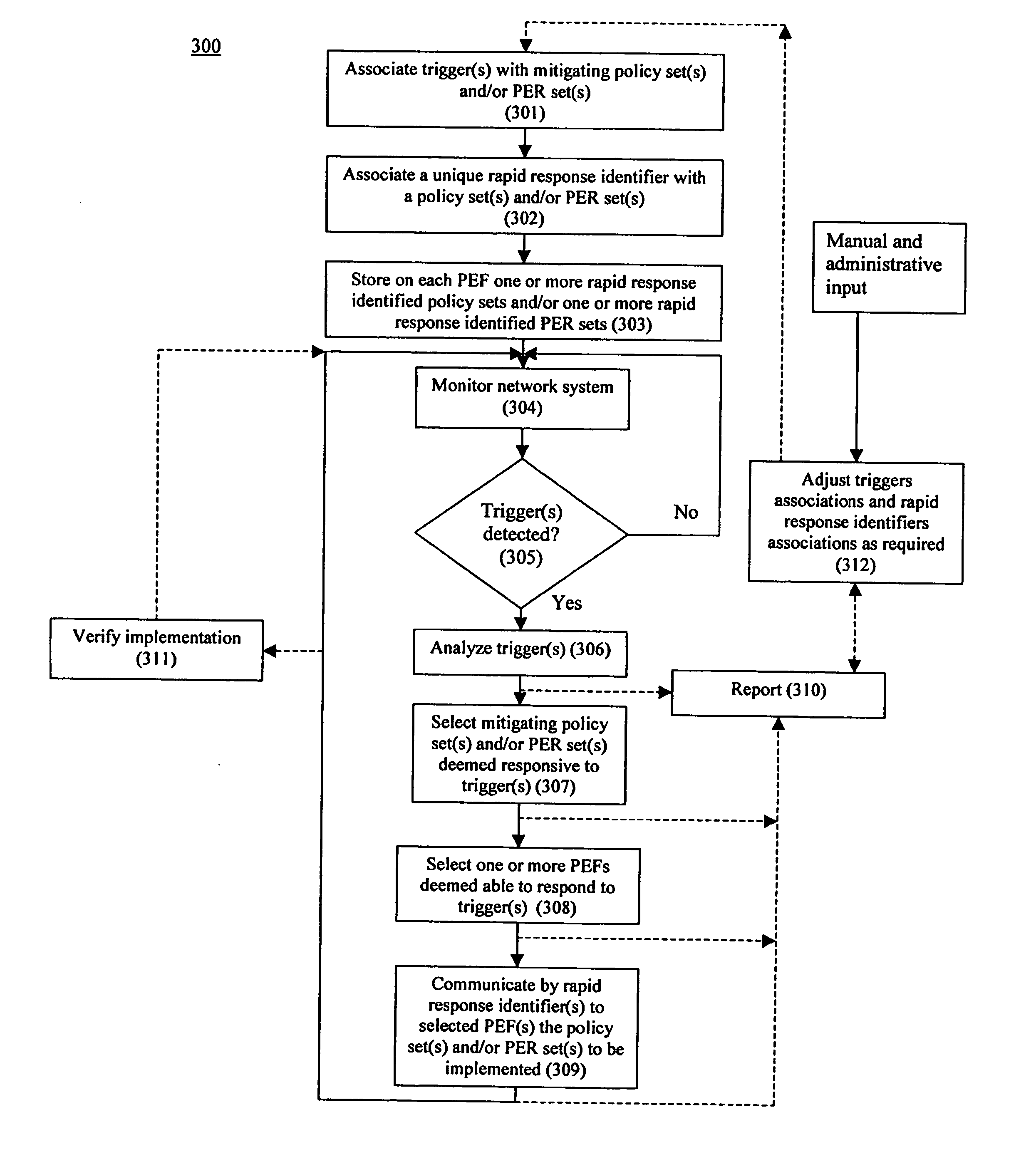
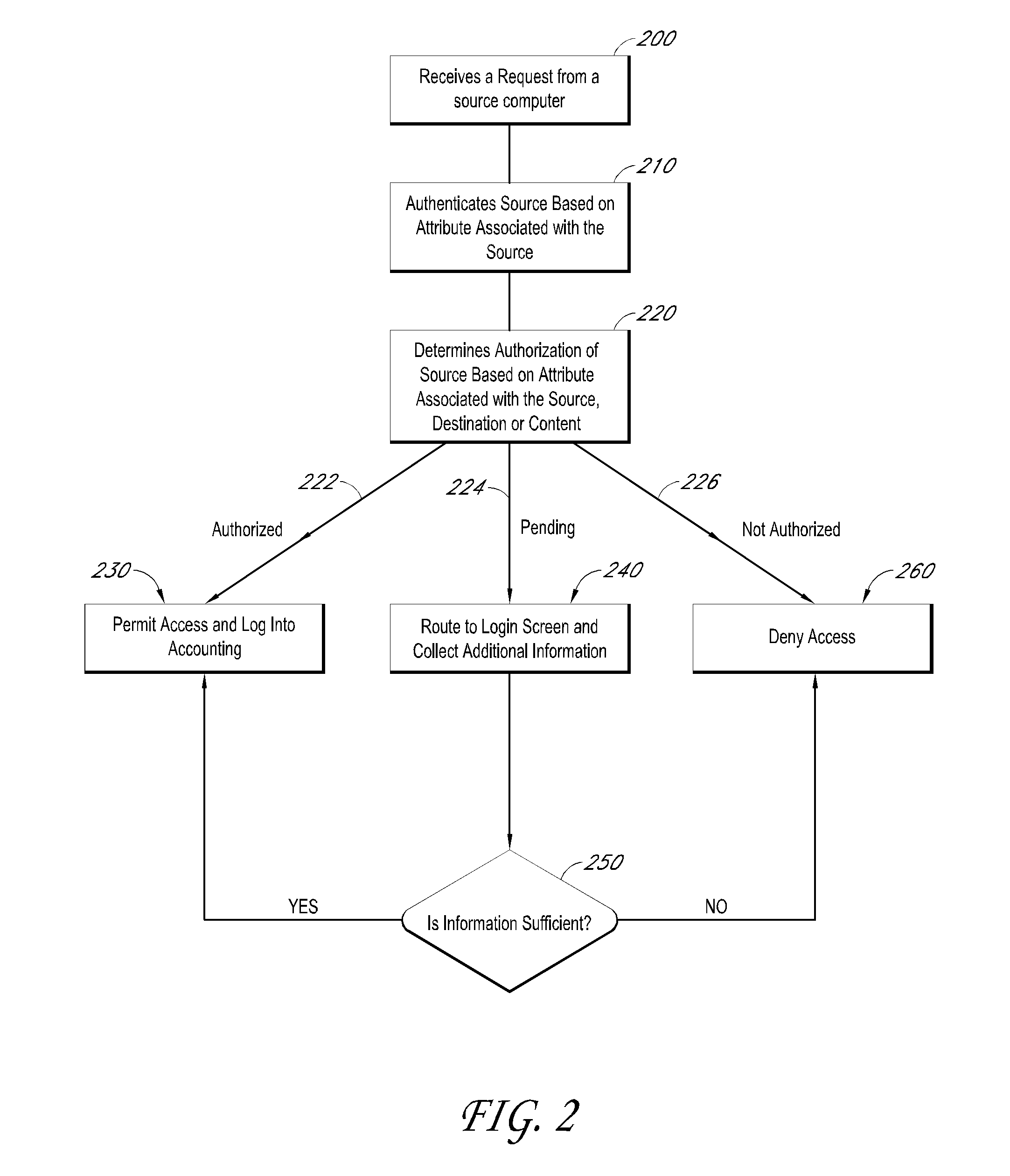
System and method for rapid response network policy implementation
A system and method for rapidly responding to triggering events or activities in a network system. The system includes a policy enforcement function, a policy manager function, and one or more network devices of the network system. The policy enforcement function includes one or more installed policy sets and / or policy enforcement rule sets suitably responsive to triggering events or activities. Upon detection of a trigger, the policy manager function analyzes the trigger and selects one or more appropriate policy sets and / or policy enforcement rule sets deemed to be responsive to the trigger. Each set has a unique rapid response identifier. The policy manager function signals for implementation of the one or more policy and / or rule sets, based on one or more rapid response identifiers, which are enforced through the policy enforcement function. The policy enforcement function may be a part of one or more of the one or more network infrastructure devices for implementing the policy change. The system and method enable rapid response to a detected trigger (which might be a manual input) by pre-installing responsive policy and / or rule sets first and then generating and transmitting the unique rapid response identifier(s) corresponding to one or more selected policy and / or rule sets for implementation. That is, the network device is already configured with a response through the pre-installed policy and / or rule sets. Responses may be implemented and / or removed gradually, and different network devices may be instructed to implement different policies in response to the same trigger and the same policy may be implemented with different policy enforcement rules on different devices, ports, or interfaces.
Owner:ENTERASYS NETWORKS
Systems and methods for providing content and services on a network system
InactiveUS20100332615A1Metering/charging/biilling arrangementsData taking preventionNetwork File SystemClient-side
Owner:NOMADIX INC
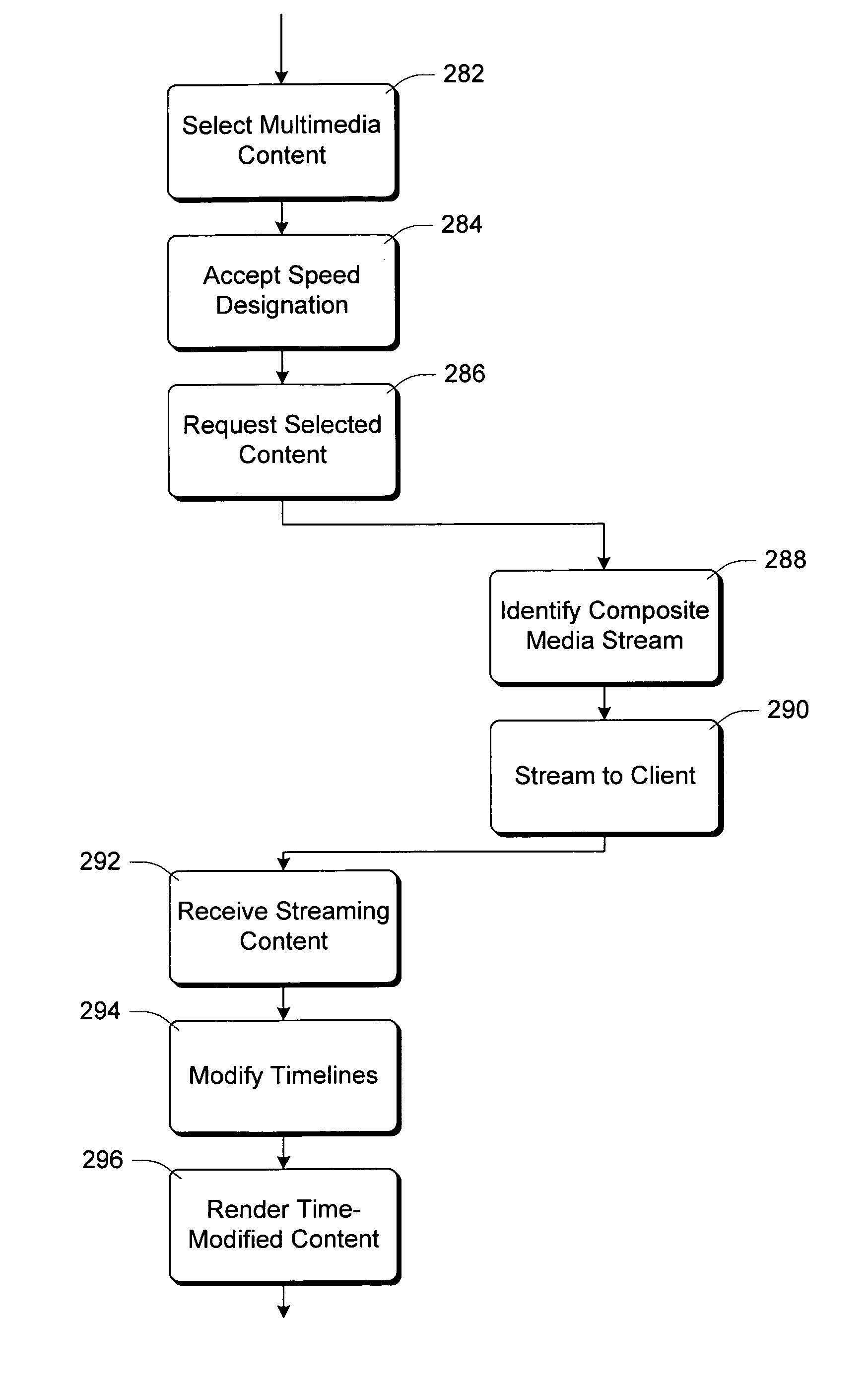
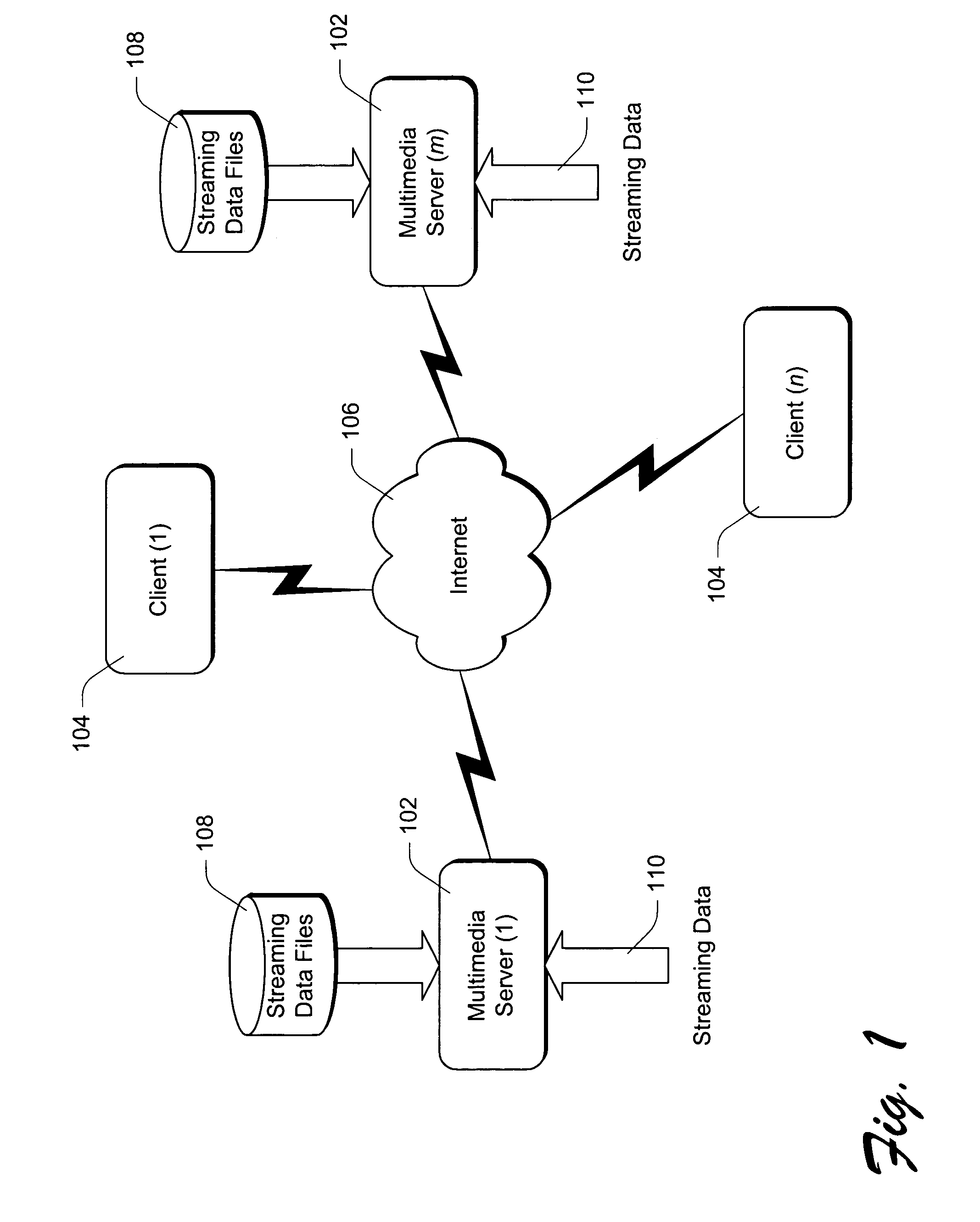
Managing timeline modification and synchronization of multiple media streams in networked client/server systems
InactiveUS7096271B1Quality improvementAvoid OverloadingMultiple digital computer combinationsTransmissionClient-sideMultiple media
In a client / server network system, multimedia content is streamed from one or more servers to the client. The multimedia content includes multiple media streams that can be streamed to the client from the same server or from different servers. The user is able to modify the playback speed of the multimedia content, allowing the playback to be either speeded up or slowed down.
Owner:MICROSOFT TECH LICENSING LLC
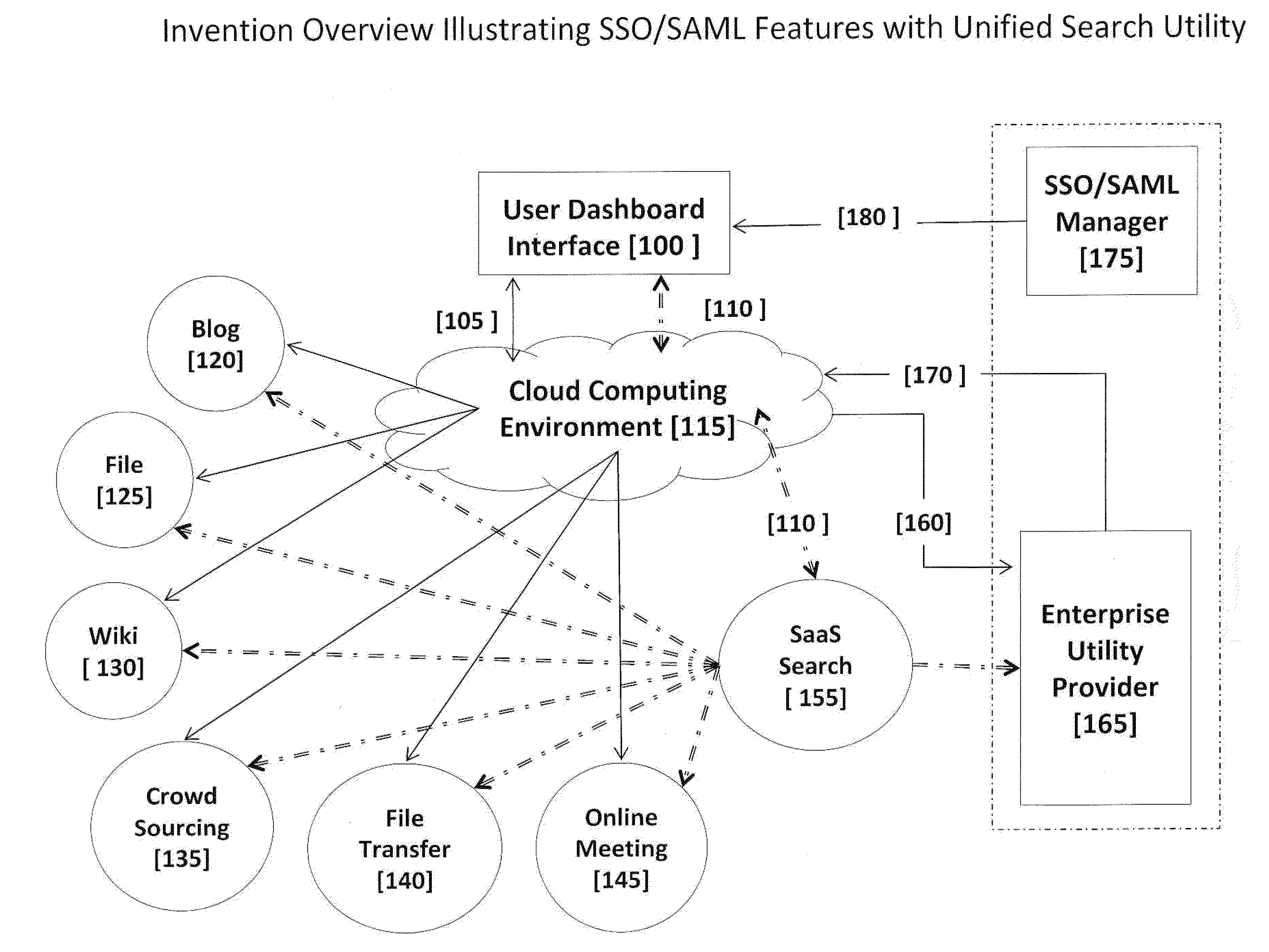
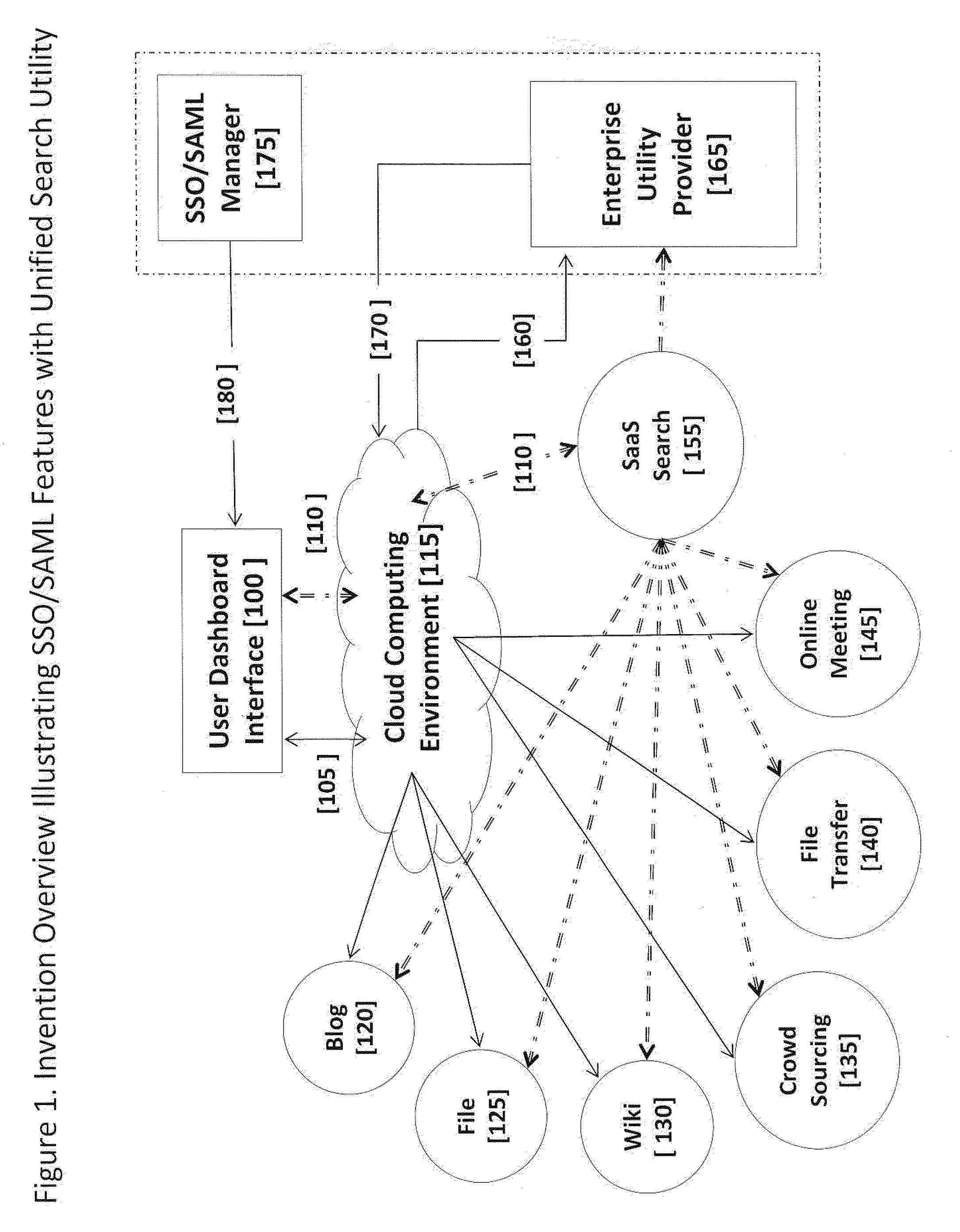
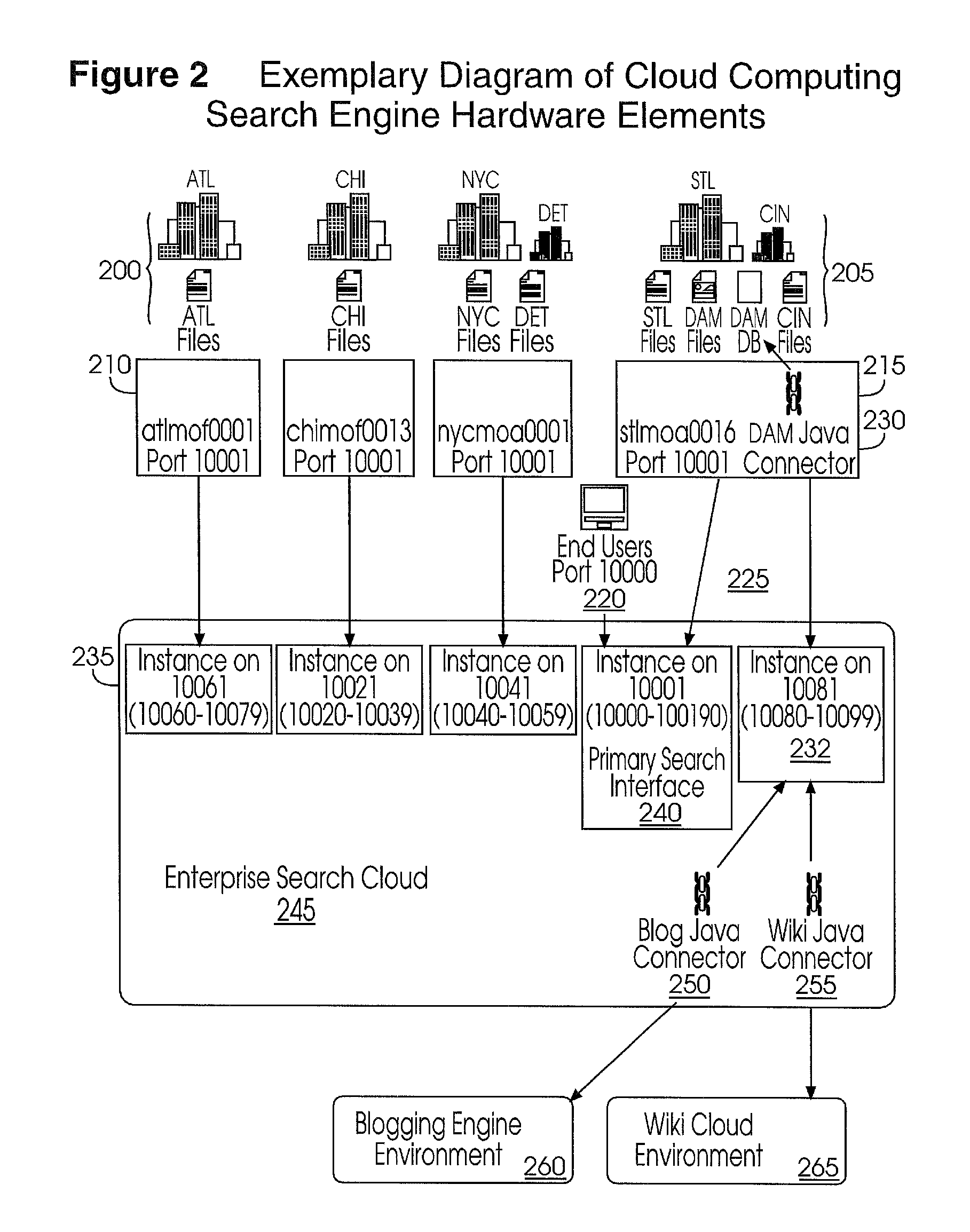
Integrated Enterprise Software and Social Network System User Interfaces Utilizing Cloud Computing Infrastructures and Single Secure Portal Access
InactiveUS20120216125A1Reduced revenue opportunityInput/output for user-computer interactionMultiple digital computer combinationsDashboardCommunications system
A software-based method and system to provide a secure user interface on multiple and diverse electronic computing devices with a customized and secure dashboard feature. The systems and methods simultaneously integrate internally generated software utilities of an enterprise with externally accessed software operating in a ‘cloud computing’ environment. The systems and methods can be used in management and operations that use computer based software, data management, creative processes and communication systems. The systems and methods reduce the requirement for additional programming to integrate or interchange equivalent and independently developed software for use within an enterprise. The systems and methods permit social network communications between members of an enterprise and an external community. The security features of the user interface portal permit collaborations between parties in an external community and enterprise members that can develop new processes that remain proprietary to the enterprise and parties of an external community.
Owner:ZAMA INNOVATIONS LLC
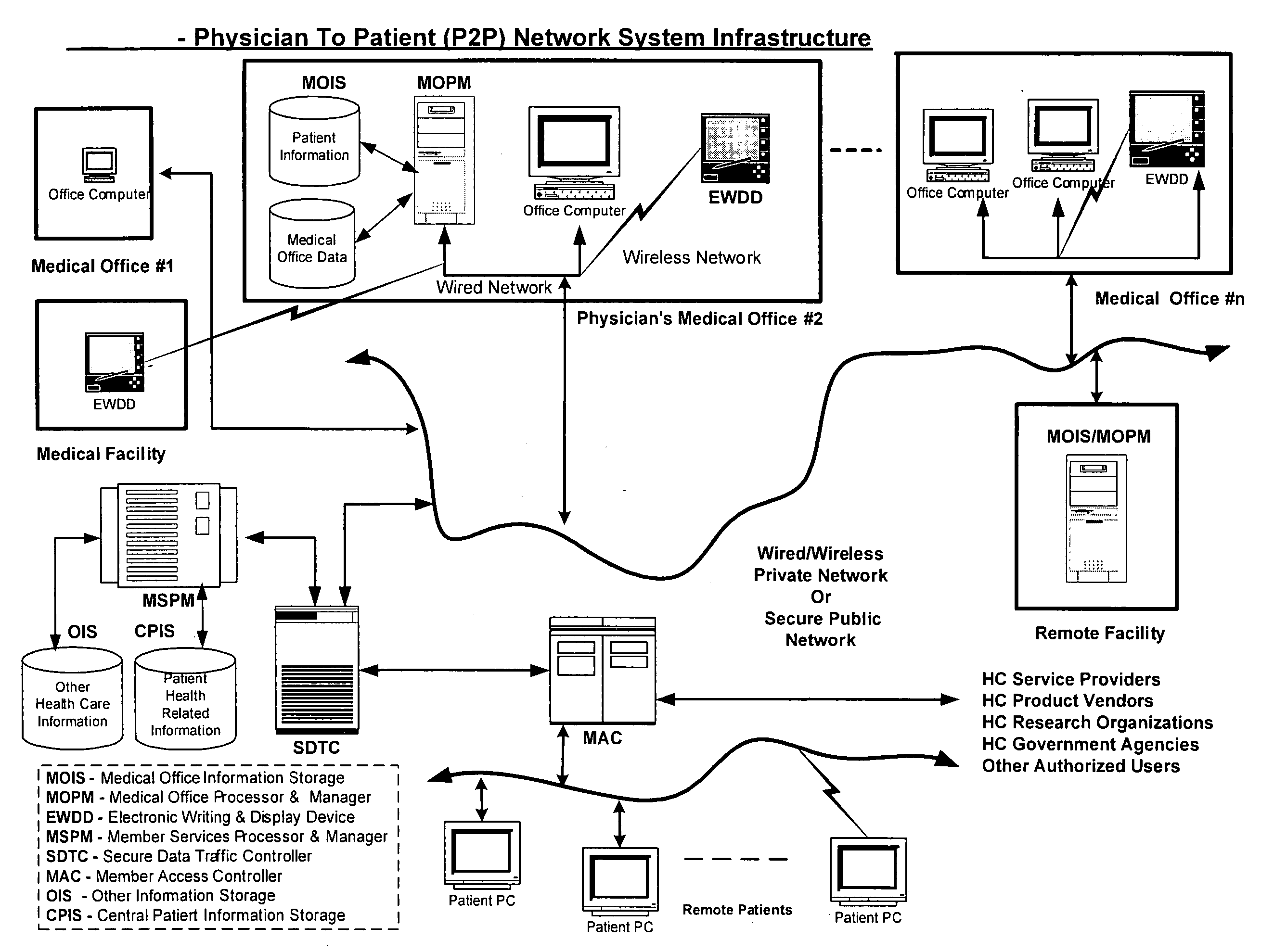
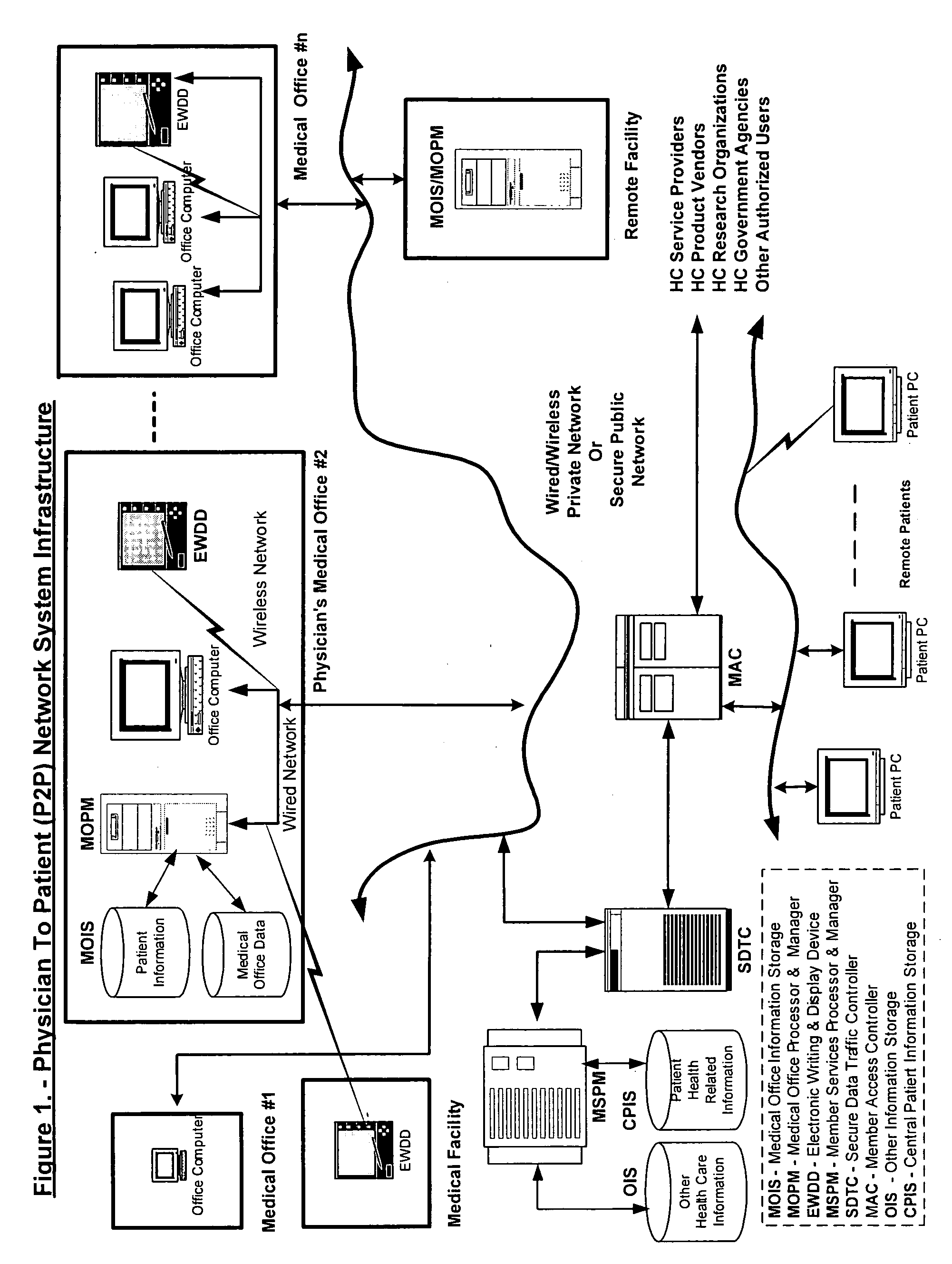
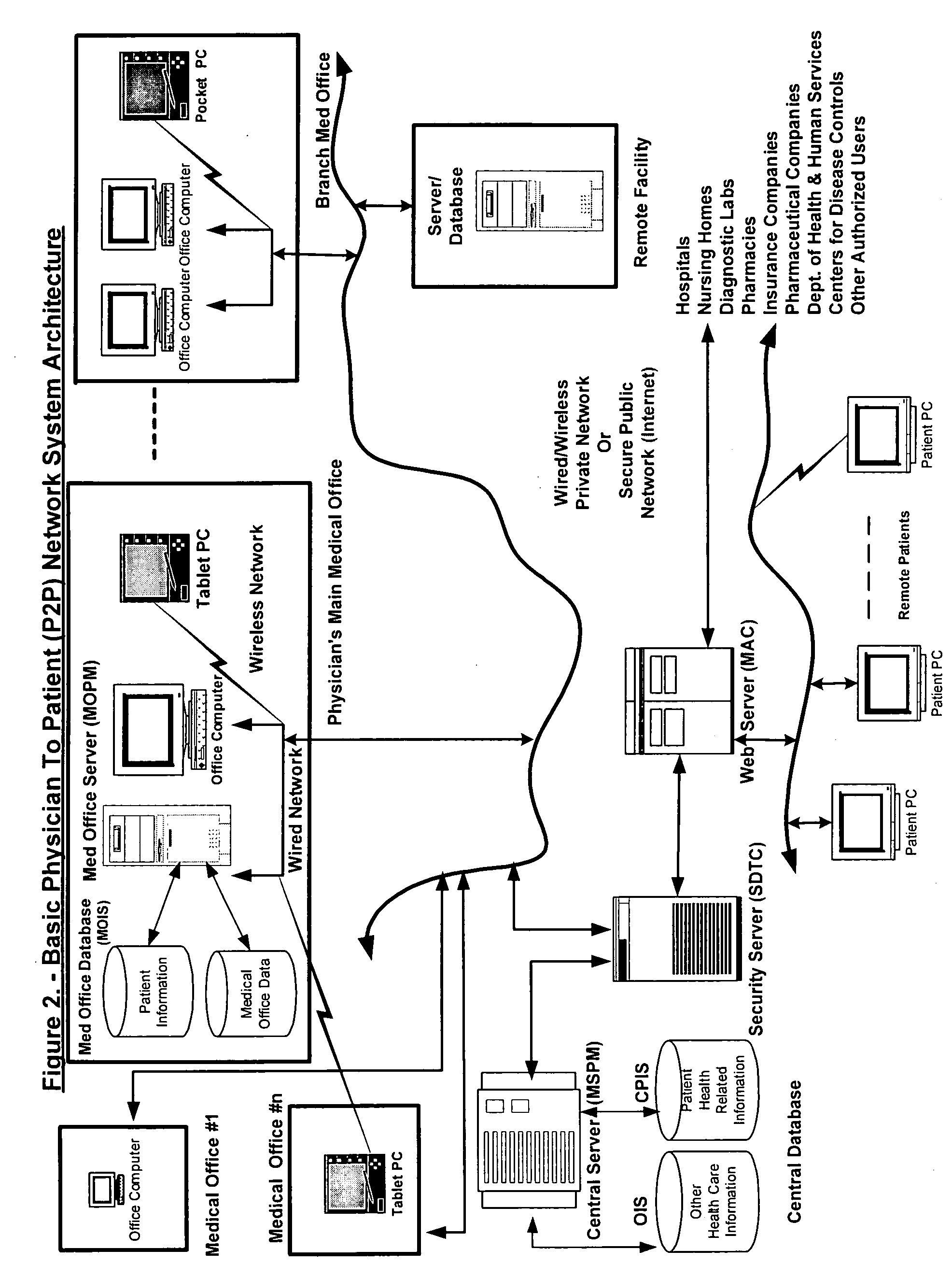
Physician to patient network system for real-time electronic communications & transfer of patient health information
InactiveUS20060277075A1Eliminating paper recordsDrug and medicationsDiagnostic recording/measuringHandwritingMedical record
The Physician To Patient (P2P) network system, a private & secure infrastructure for independently practicing physicians and patients for real-time electronic communication & transfer of patient health information is disclosed by the invention. The invention also discloses an efficient and natural method for creation of Electronic Medical Records by physicians in their own handwriting. The P2P network system utilizes a plurality of devices and components defined by the invention, and custom programming to integrate all equipment, devices and components of the network system. The invention also discloses a highly targeted method of advertising, the One2One Advertising, for healthcare product manufacturers to reach physicians and patients. A number of healthcare related business processes, currently executed manually are performed automatically by P2P network system software. The invention will improve the quality of services to patients, and reduce the overhead cost of the medical offices, and the healthcare industry.
Owner:SALWAN ANGADBIR SINGH
Network system and its switches
InactiveUS20060187908A1SpeedSave network bandwidthMultiplex system selection arrangementsDigital data information retrievalNetwork connectionData transmission
Owner:HITACHI LTD
Method and apparatus for security policy management
InactiveUS7882537B2Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
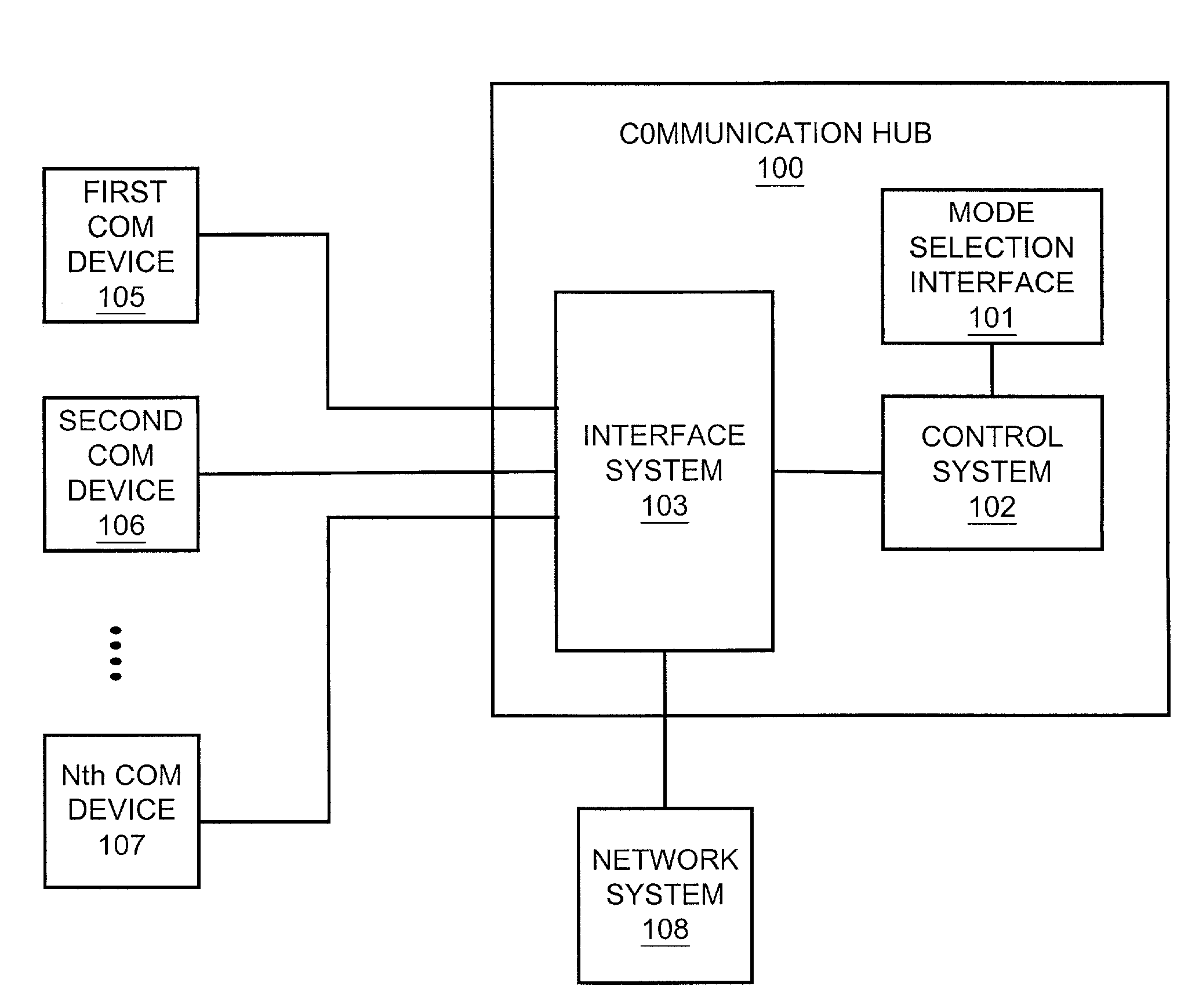
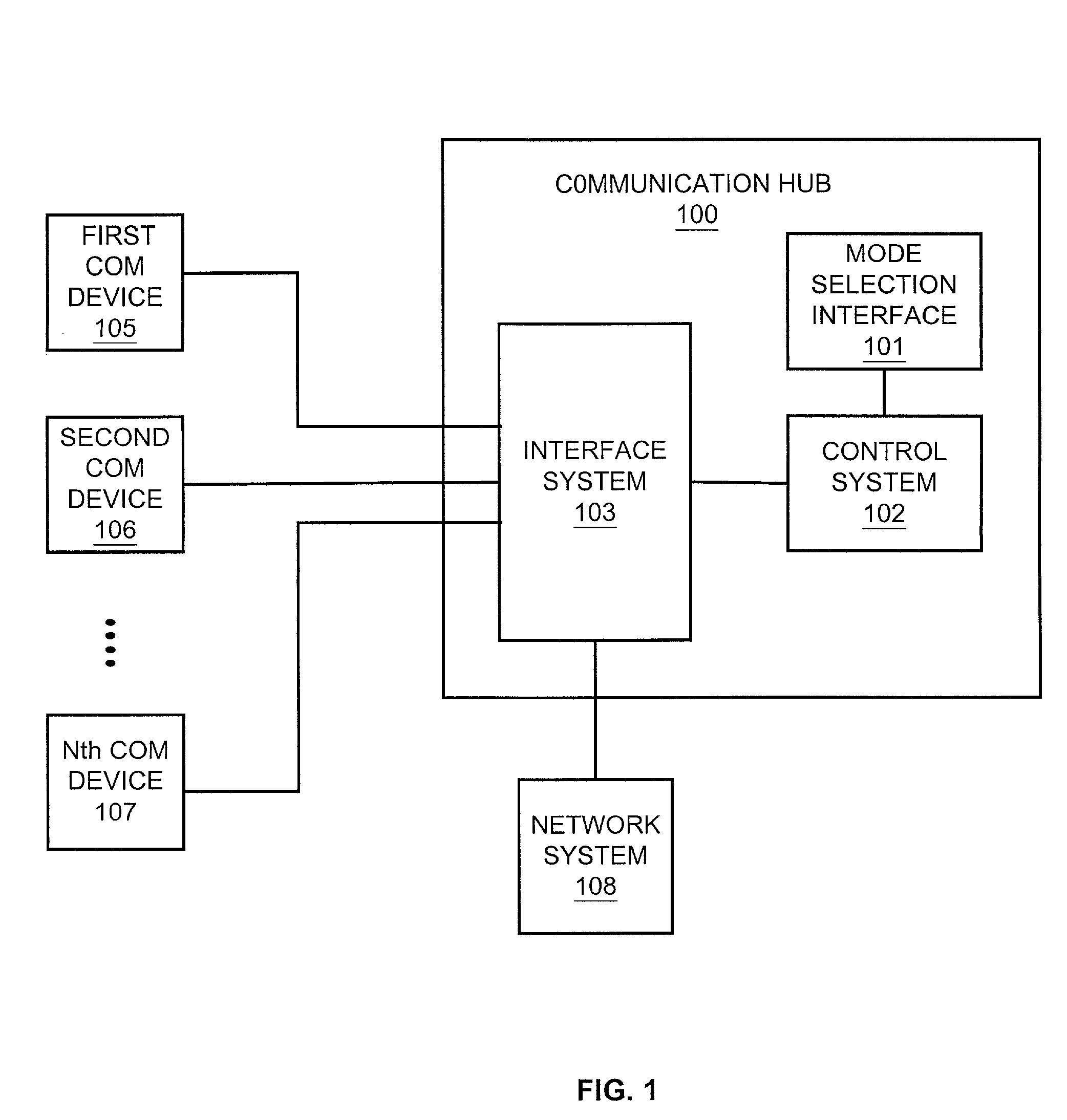
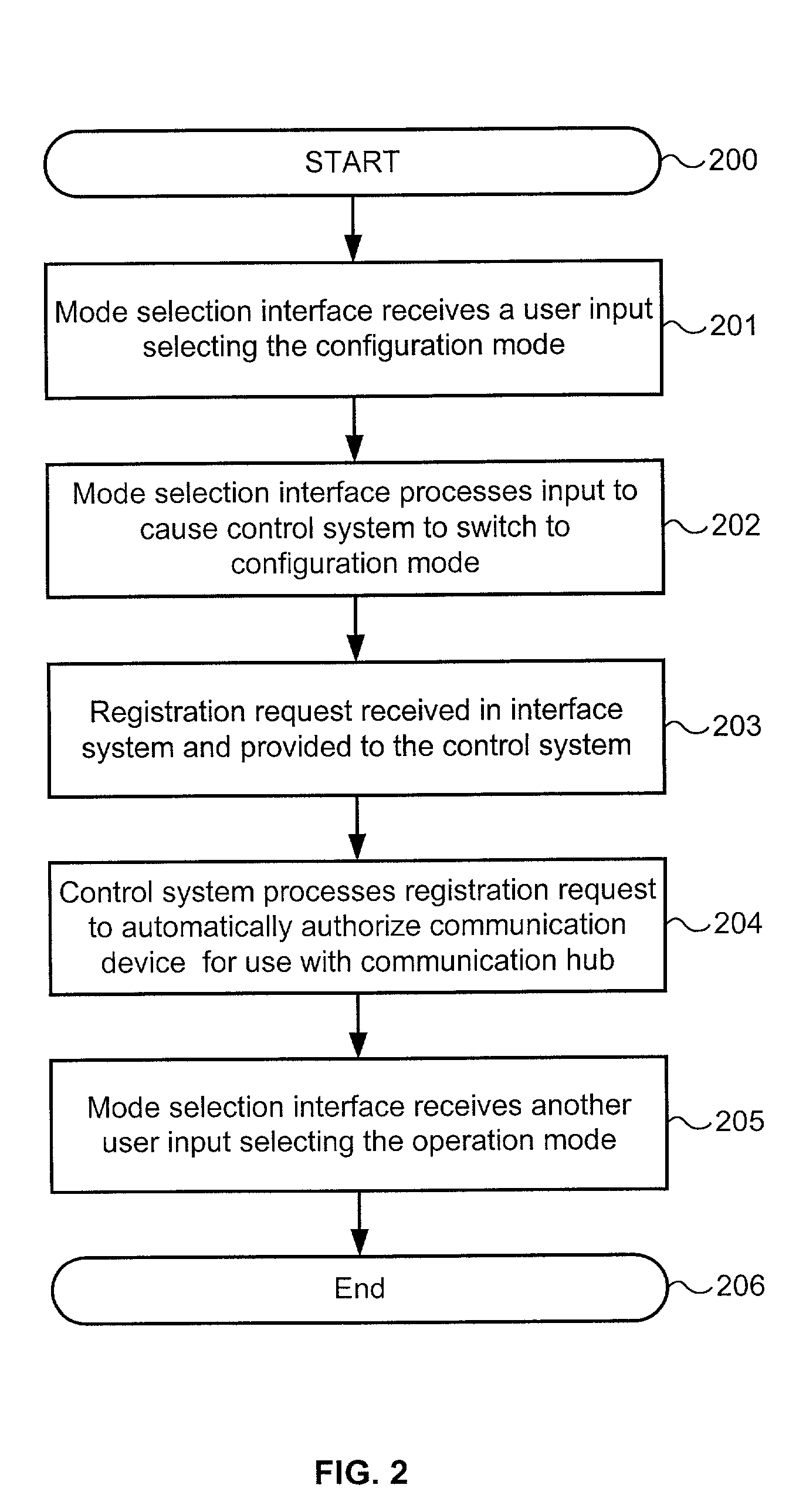
Communication hub with automatic device registration
ActiveUS7260616B1Multiple digital computer combinationsRadio transmissionComputer hardwareControl system
A communication hub that includes a control system, a mode selection interface, and an interface system. The control system is configured to switch between a configuration mode and an operation mode. In response to switching to the configuration mode, the control system receives a registration request from unauthorized communication device. The control system processes the registration request to automatically authorize the communication device for use with the communication hub. In response to switching to the operation mode, the control system controls the exchange of communications between a plurality of previously authorized communication devices, the newly authorized communication device, and a network system. The mode selection interface is configured to receive a user input that selects one of the configuration mode or the operation mode and cause the control system to enter the selected one of the configuration mode or the operation mode. The interface system is configured to exchange communications with the network system, receive the registration request from the communication device and provide the registration request to the control system.
Owner:T MOBILE INNOVATIONS LLC
Method and program of collecting performance data for storage network
InactiveUS7107273B2Input/output to record carriersMemory loss protectionExternal storageStorage area network
In a storage network including at least a computer system, at least an external storage and at least a network system for communication of input / output data between the computer system and the external storage, a method of collecting the performance data on the network system and the software operated on the network system, in which the range or degree of data collection is automatically adjusted as required based on the performance data collected.
Owner:HITACHI LTD
Method and program of collecting performance data for storage network
InactiveUS20050119996A1Input/output to record carriersDigital data processing detailsExternal storageCollections data
In a storage network including at least a computer system, at least an external storage and at least a network system for communication of input / output data between the computer system and the external storage, a method of collecting the performance data on the network system and the software operated on the network system is disclosed, in which the range or degree of data collection is automatically adjusted as required based on the performance data collected.
Owner:HITACHI LTD
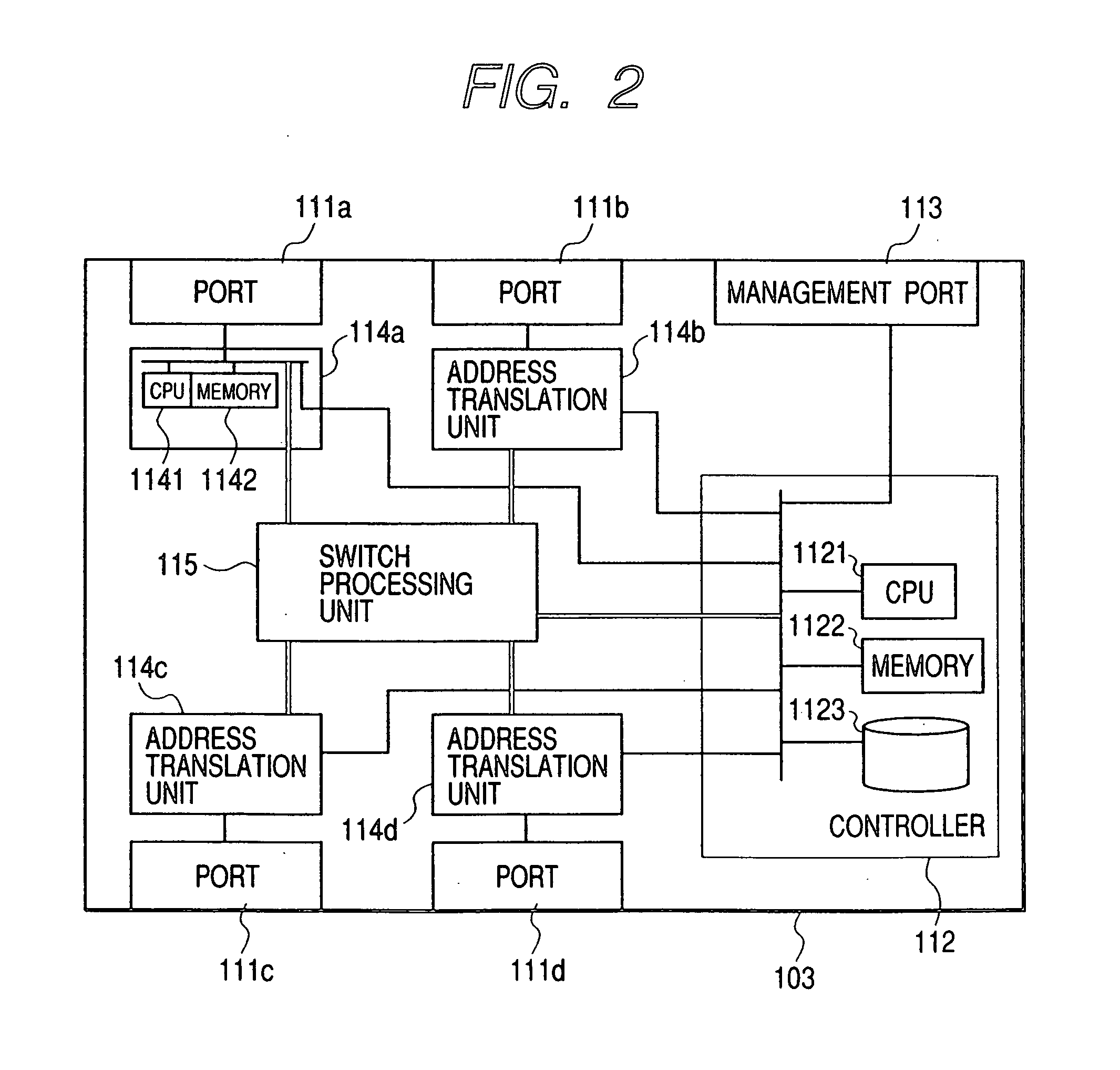
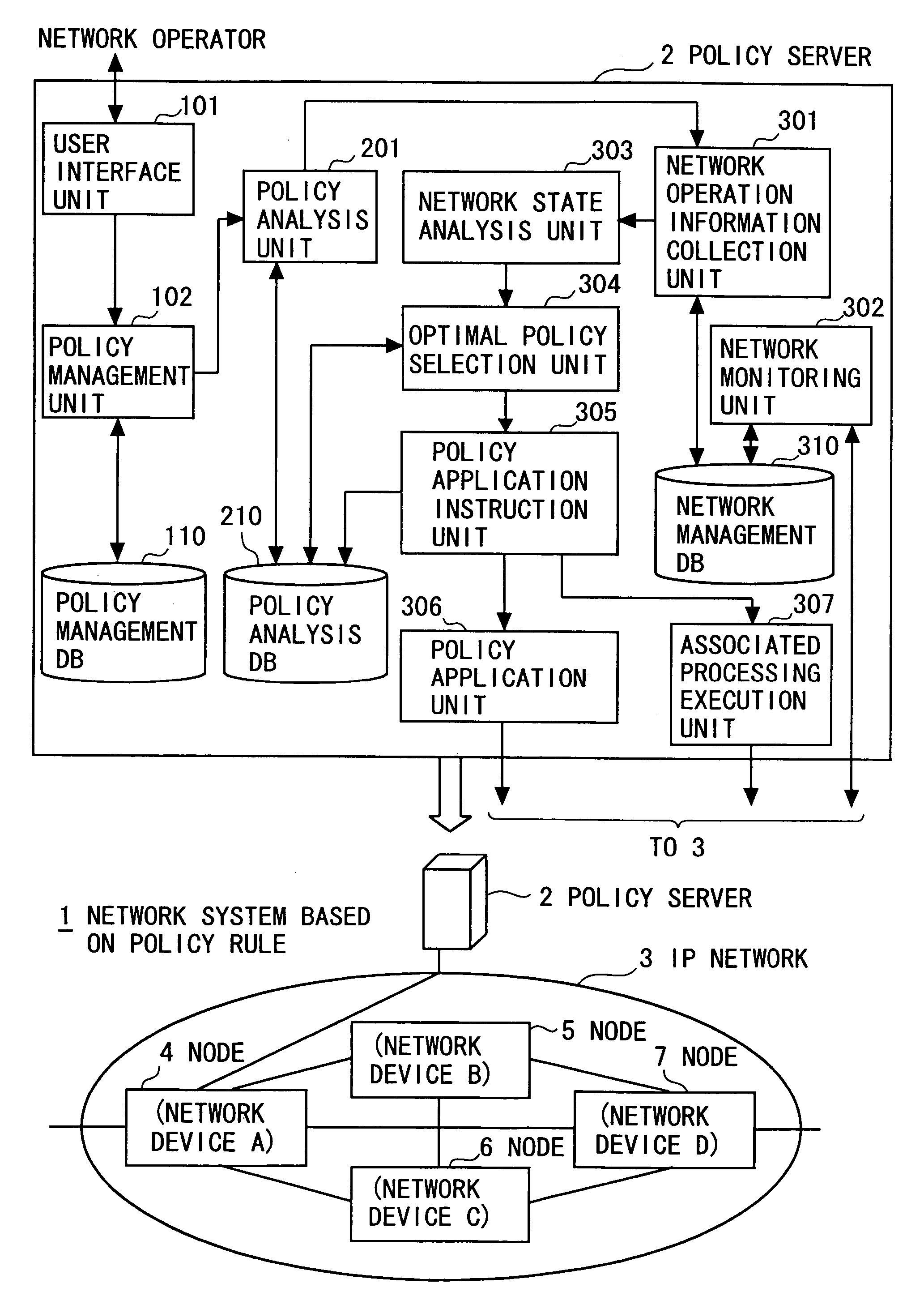
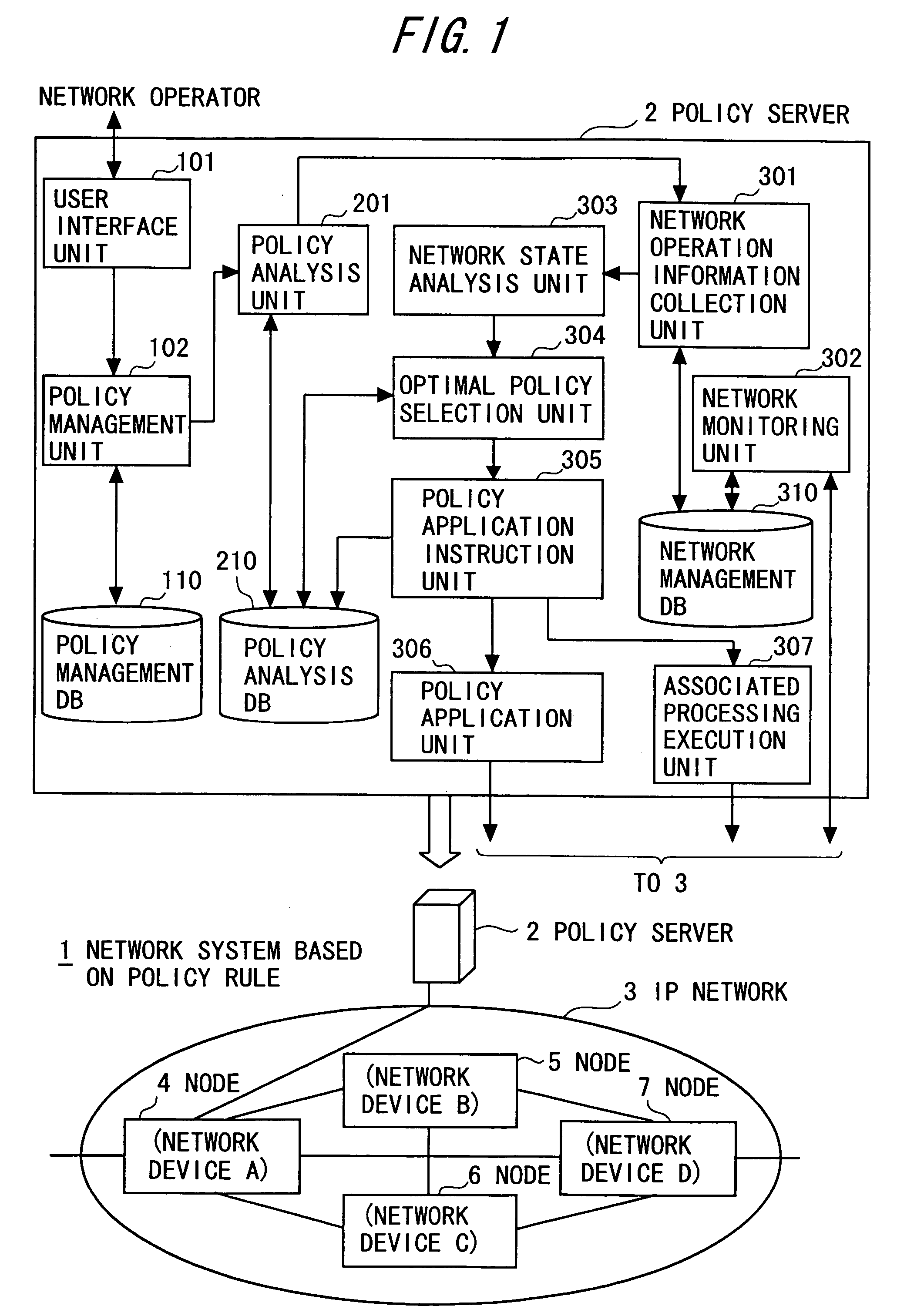
Network system based on policy rule
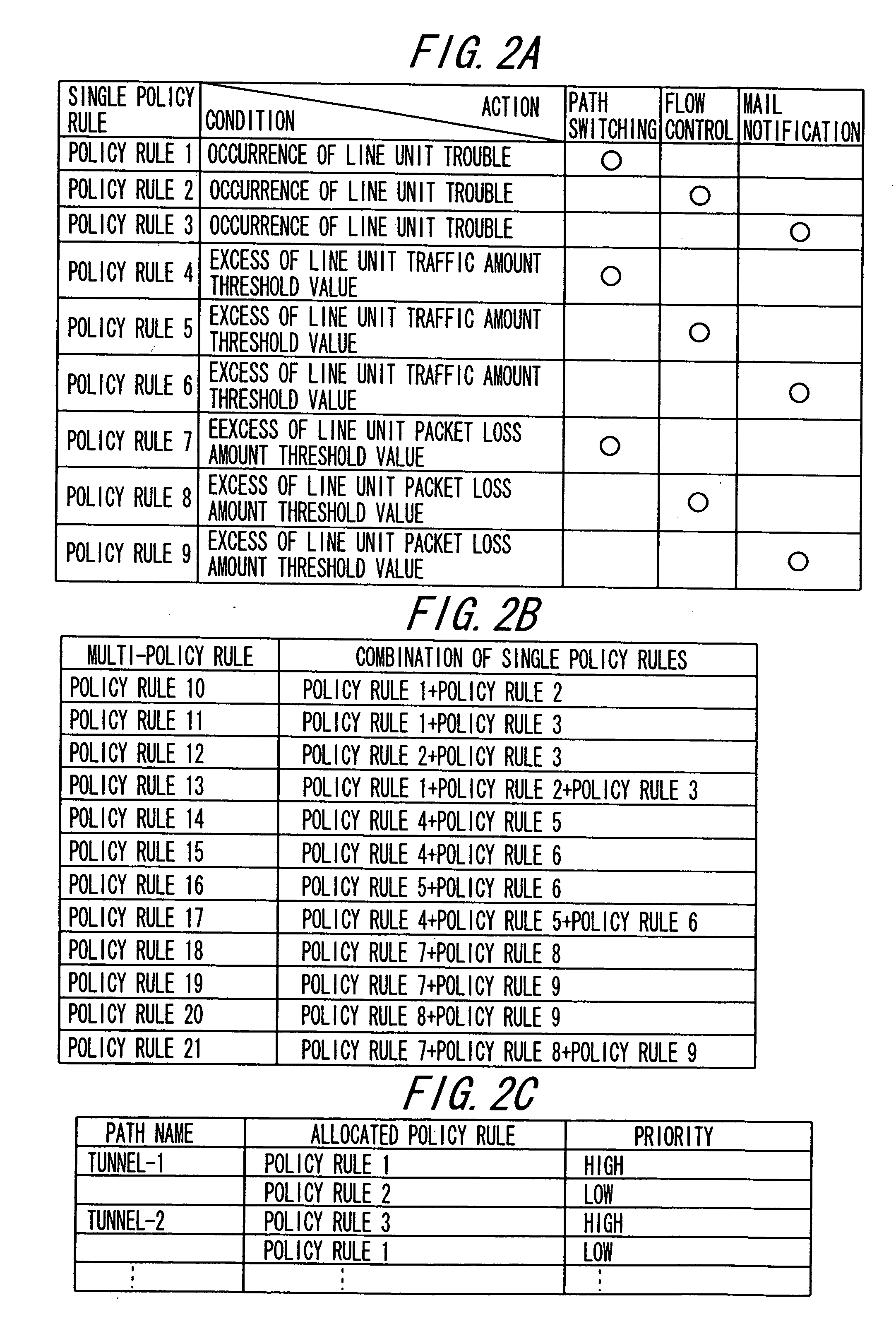
InactiveUS20060294219A1Suppressing a monotonous increase in single policy rulesReduce loadDigital computer detailsData switching networksControl equipmentStorage cell
A policy control device for reflecting a policy rule defined by a condition and an action corresponding to the condition for operation setting of respective network devices present in a network to be managed, according to a transition of operation states of the network, including a storage unit for storing a plurality of multi-policy rules generated in units of combination of at least two single policy rules having different actions on the same condition, together with particular information of a network device to be applied, in such a manner that the plurality of multi-policy rules and the particular information can be updated; and a control unit for applying one of the plurality of multi-policy rules stored in the storage unit for the operation setting of the network device identified, based on the particular information.
Owner:FUJITSU LTD
System for actively updating a cryptography module in a security gateway and related method
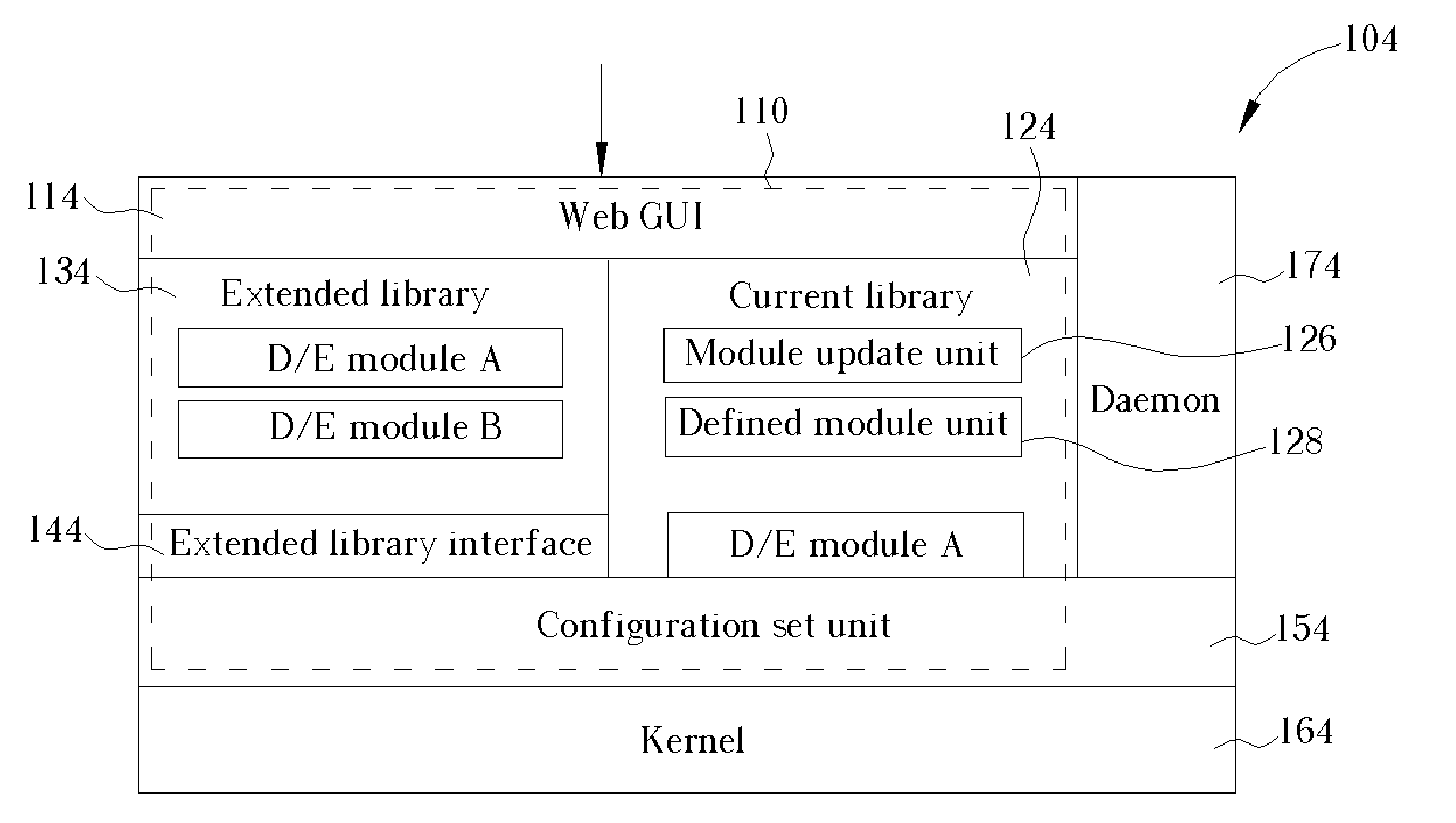
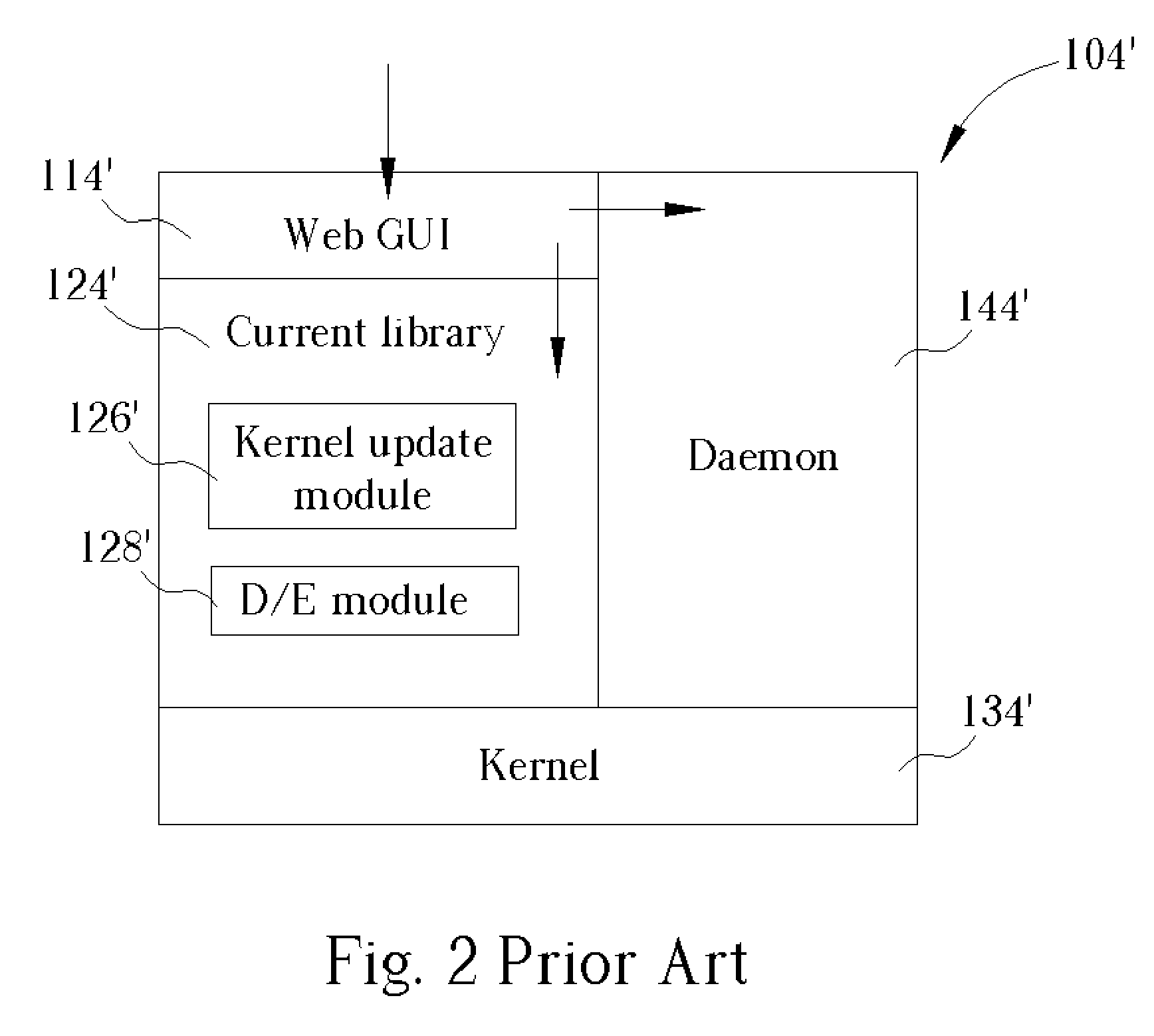
InactiveUS20050149746A1Time expendedImprove operational efficiencyDigital data processing detailsUser identity/authority verificationComputer scienceIpsec protocol
A system for actively updating a cryptography module in a security gateway and related method is used in a security gateway, such as a VPN gateway according to an IPSEC protocol, which is connected between at least one user computer system and a network system. The system includes a Web GUI, a module update unit, a defined module unit, and an extended library. A user can easily update or add decryption / encryption modules into the extended library of the gateway through the Web GUI and the module update unit instead of updating the decryption / encryption modules along with the entire kernel firmware. This can reduce the setting time, increase the efficiency of operation, reduce the maintenance cost, and promote the expansion of decryption / encryption modules of the gateway so that network transmission can become much safer.
Owner:ICP ELECTRONICS
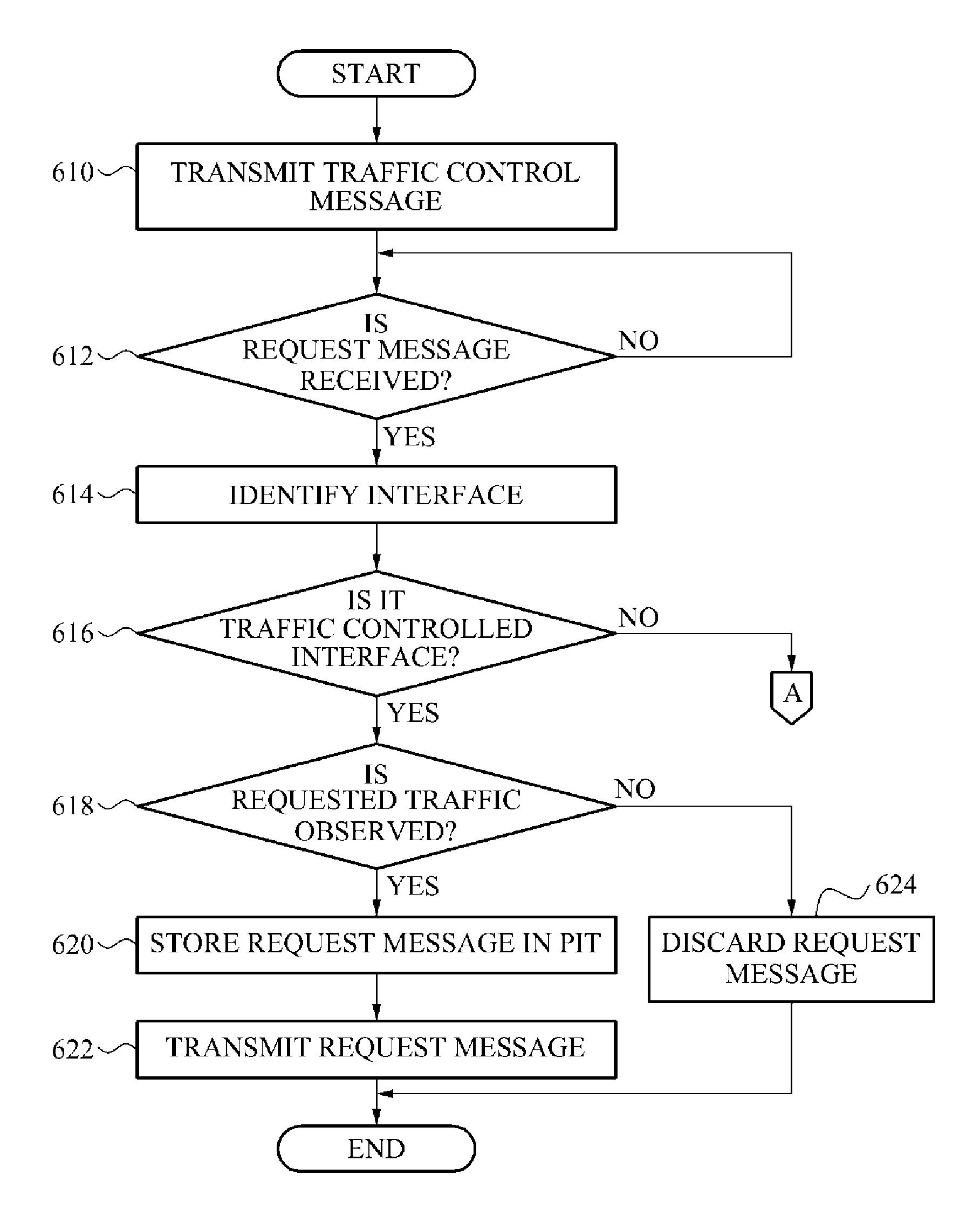
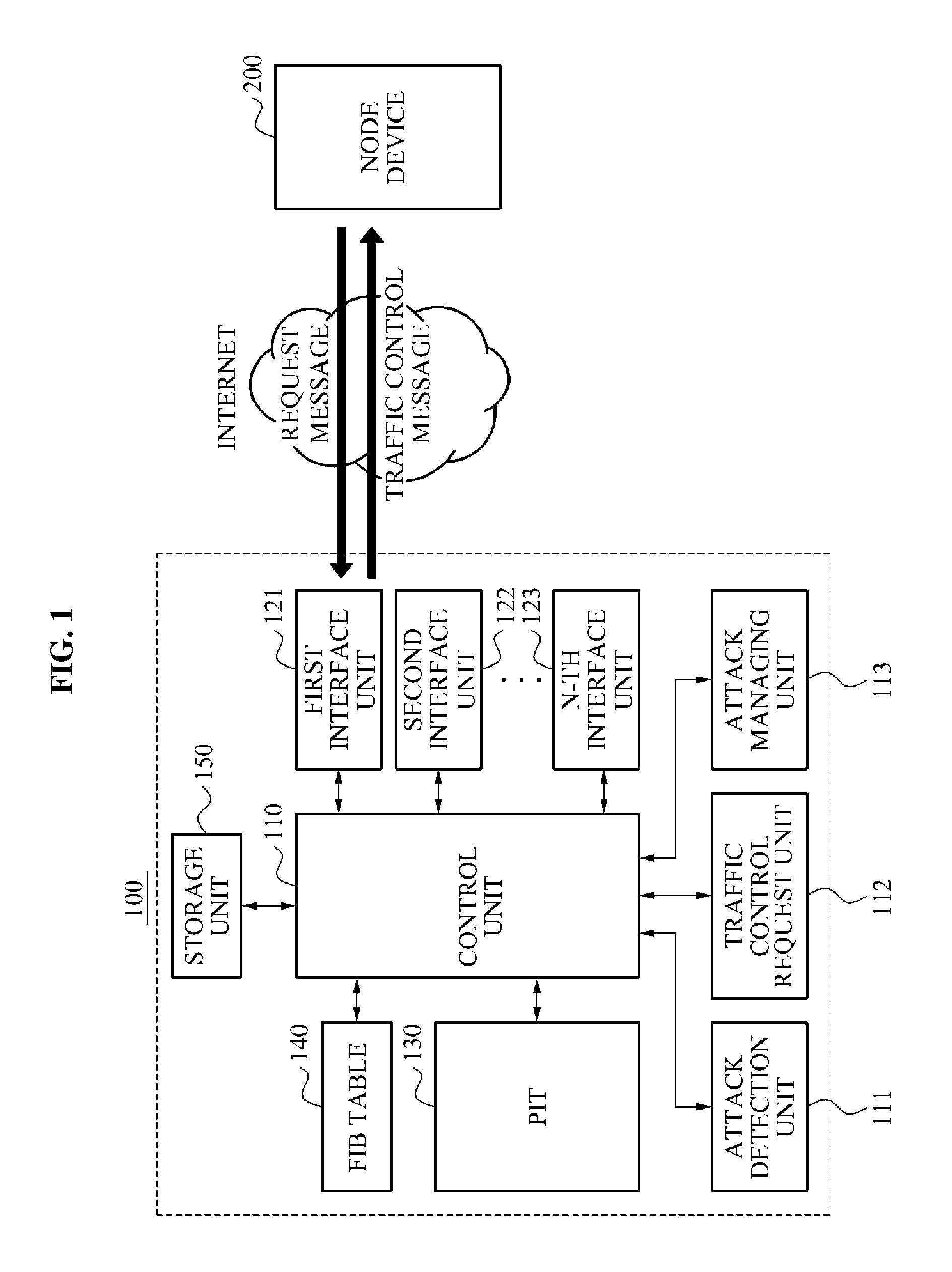
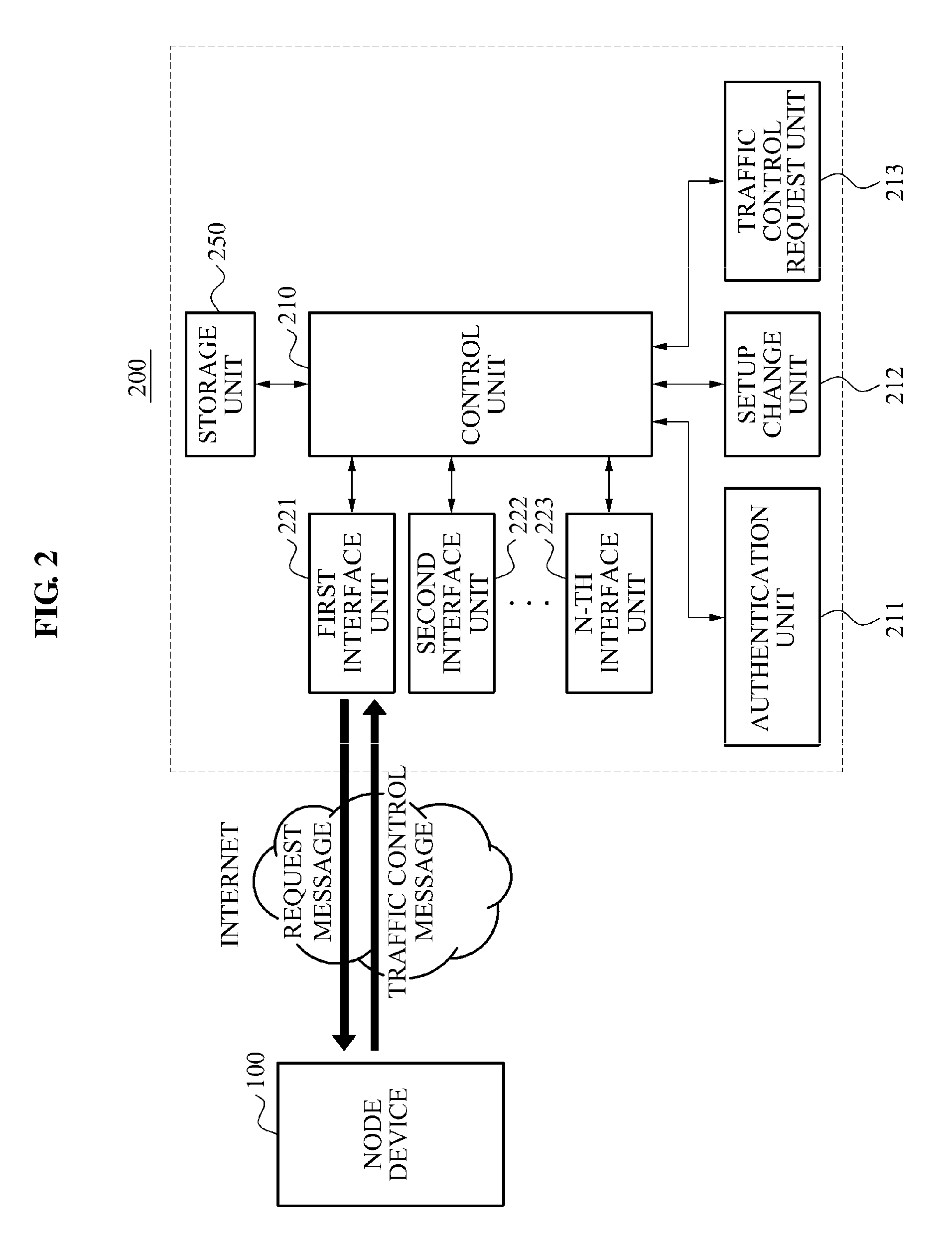
Node device and method to prevent overflow of pending interest table in name based network system
ActiveUS8826381B2Prevent overflowMemory loss protectionData taking preventionTraffic capacityReal-time computing
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com