Patents
Literature
1343 results about "Rule sets" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
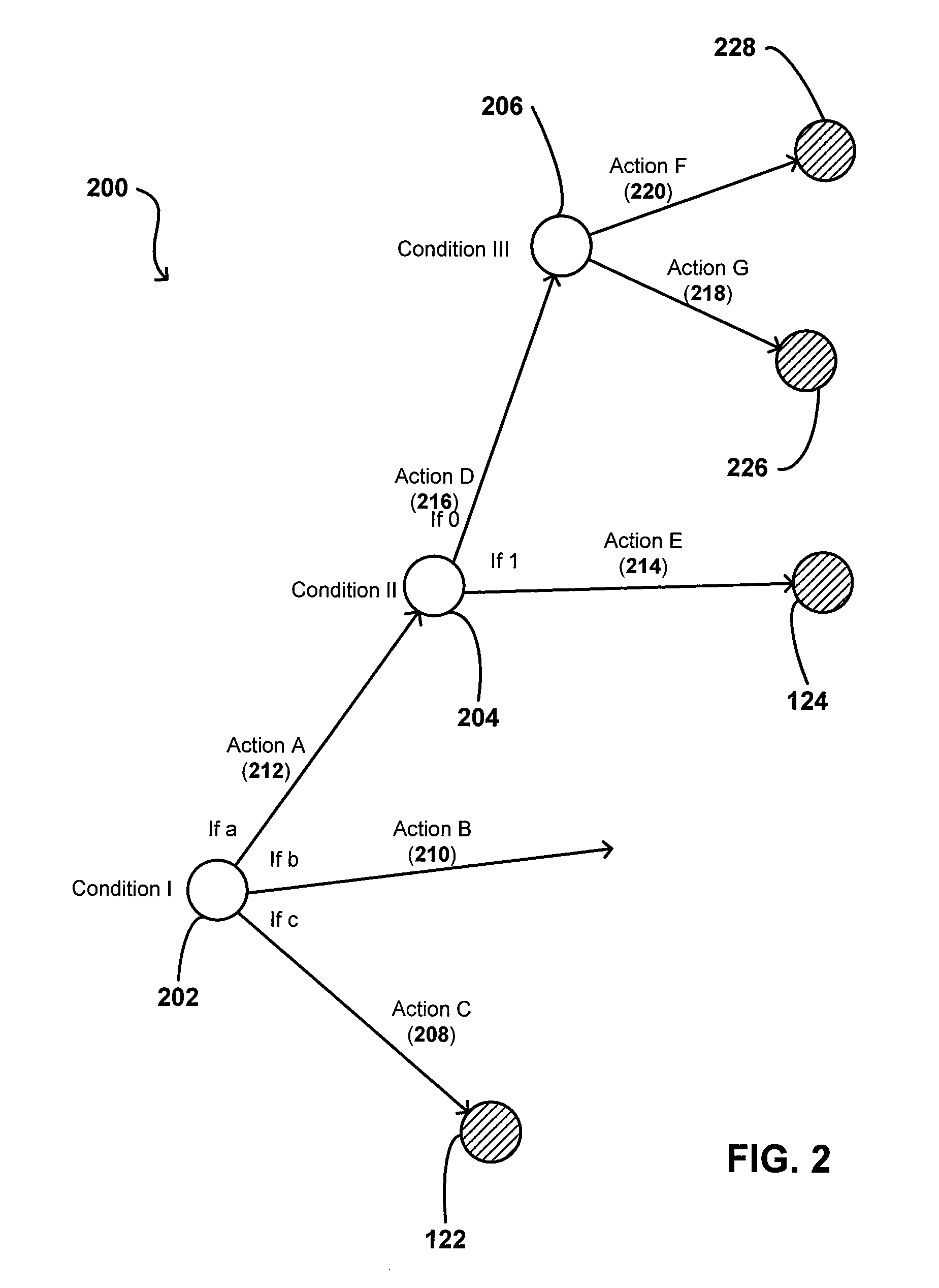
The rule set evaluates to true or false based on the evaluation of each rule it contains and the evaluation type ( All True or Any True ). A rule within a rule set is a PL/SQL expression that evaluates to true or false. You can create a rule and add the rule to multiple rule sets.
Methods and apparatus for controlling access to a resource
InactiveUS7185192B1Limit staff employee accessVerification of the security policy more straightforwardData processing applicationsDigital data processing detailsProgramming languageDecision taking
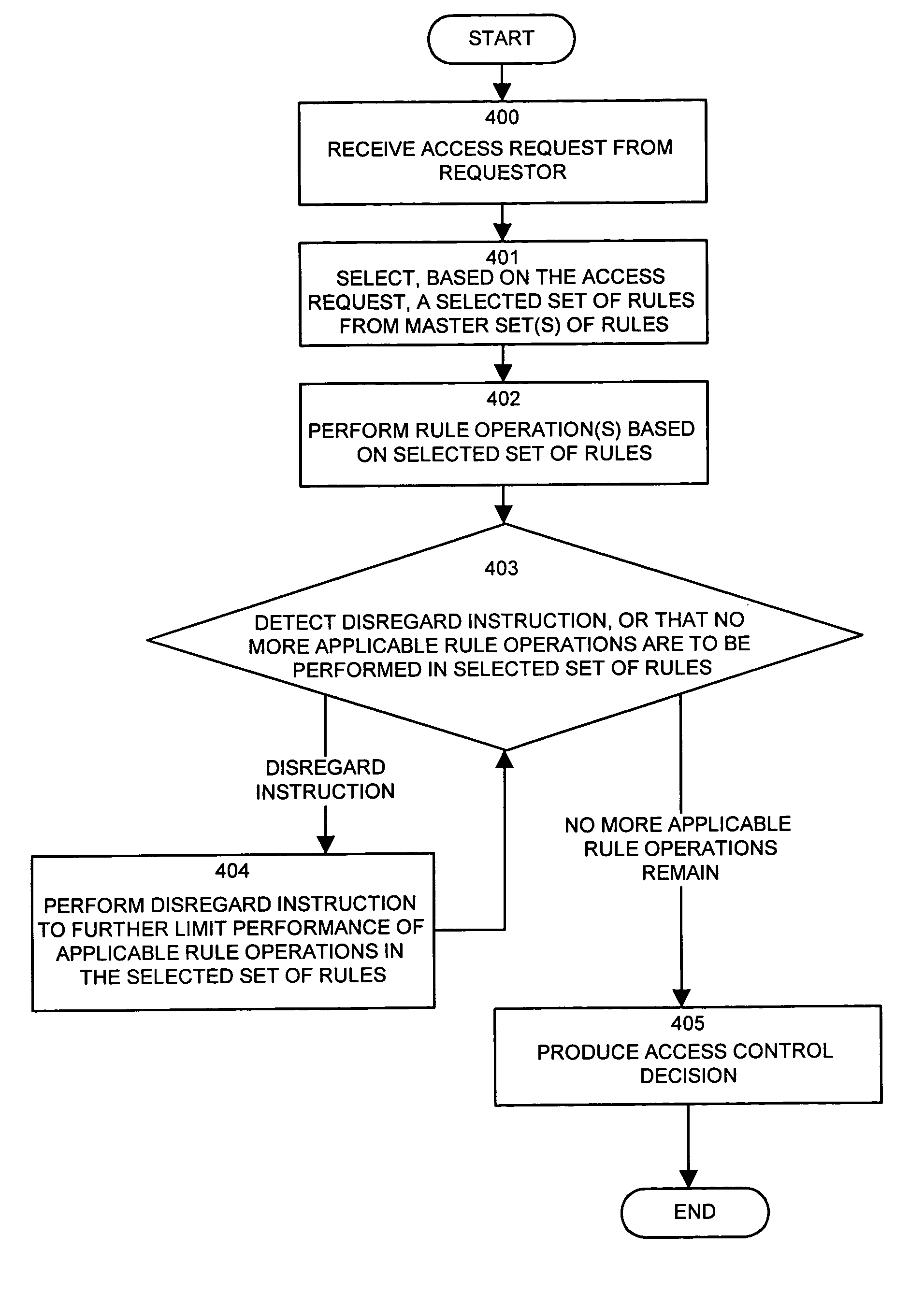
An input / output interface receives an access request from a requester. A processor associated with the input / output interface applies a filter operation to select a subset of rules from a master set of rules maintained within an authorization database. Rules can be selected in this manner using filter operations so that all rules in the rule set need not be processed. A rule may include a disregard instruction. The processor further performs at least one rule operation based on the subset of rules to produce an access control decision in the memory system until either a rule operation including a disregard instruction is performed to limit performance of rule operations in the selected set of rules or until all rule operations in the selected set of rules that are applicable to the access control decision are performed.
Owner:EMC IP HLDG CO LLC
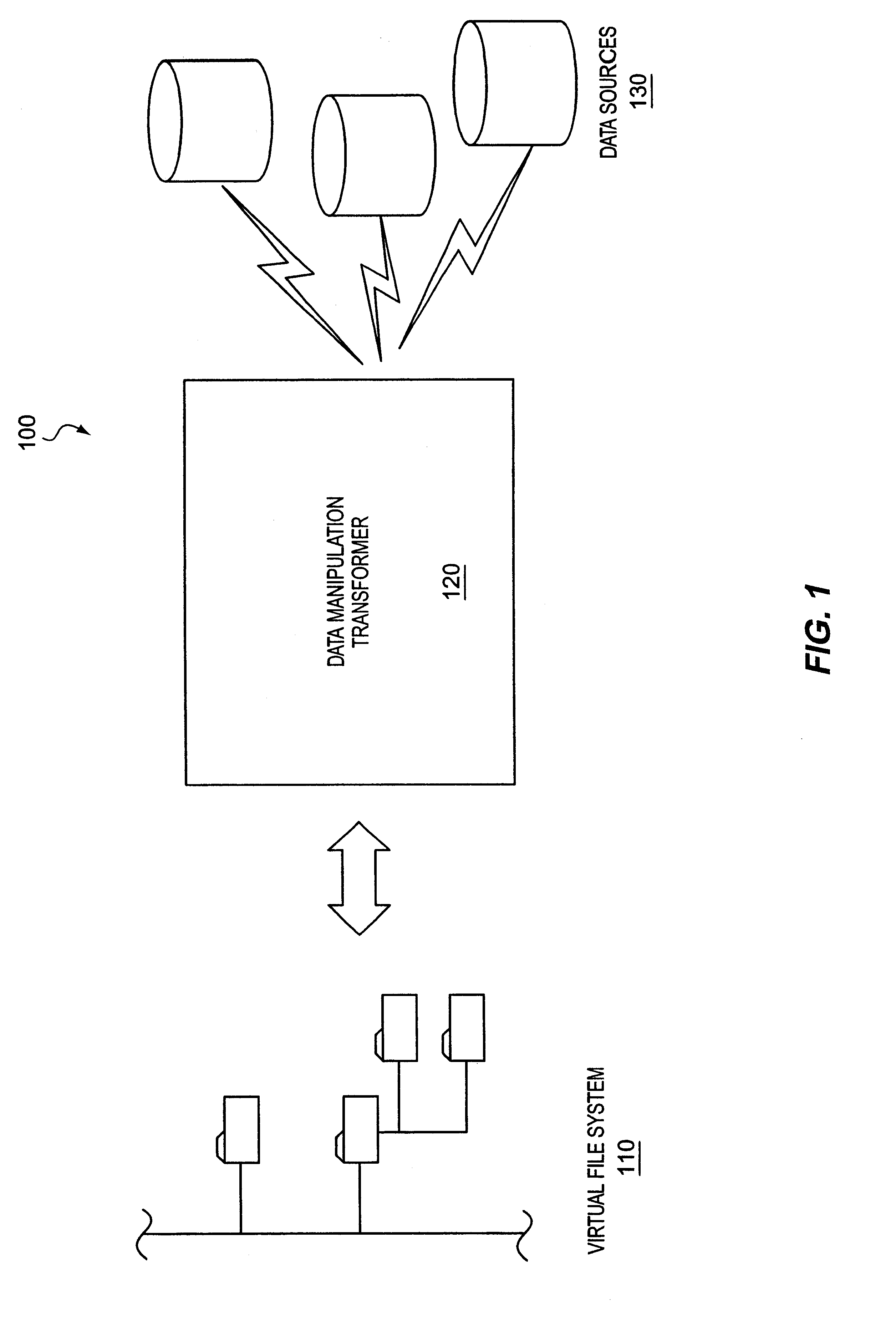
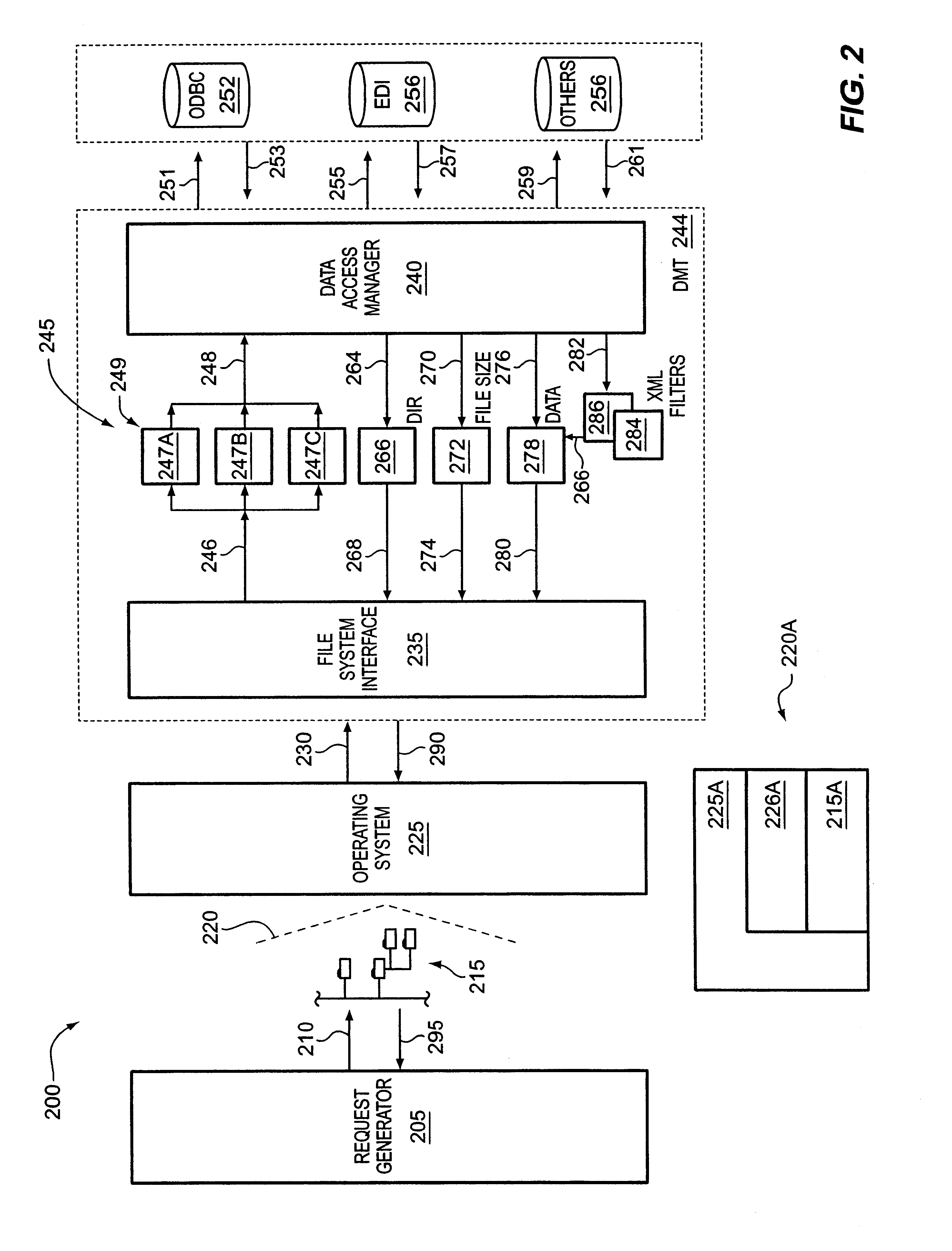
XML presentation of general-purpose data sources
InactiveUS6901403B1Data processing applicationsDigital data processing detailsGeneral purposeVirtual file system
A system and method for presenting one or more general-purpose application-accessible data sources as an XML representation is discussed. Information that describes the way data is structured or organized in the data source is accessed from the data source. A virtual file system representation comprising a plurality of hierarchical folders is provided to represent the structural information. Optionally, the virtual file system representation may be modified, either manually or according to rules sets. After any desired modification, the XML representation is generated based on the virtual file system representation.
Owner:ROGUE WAVE SOFTWARE
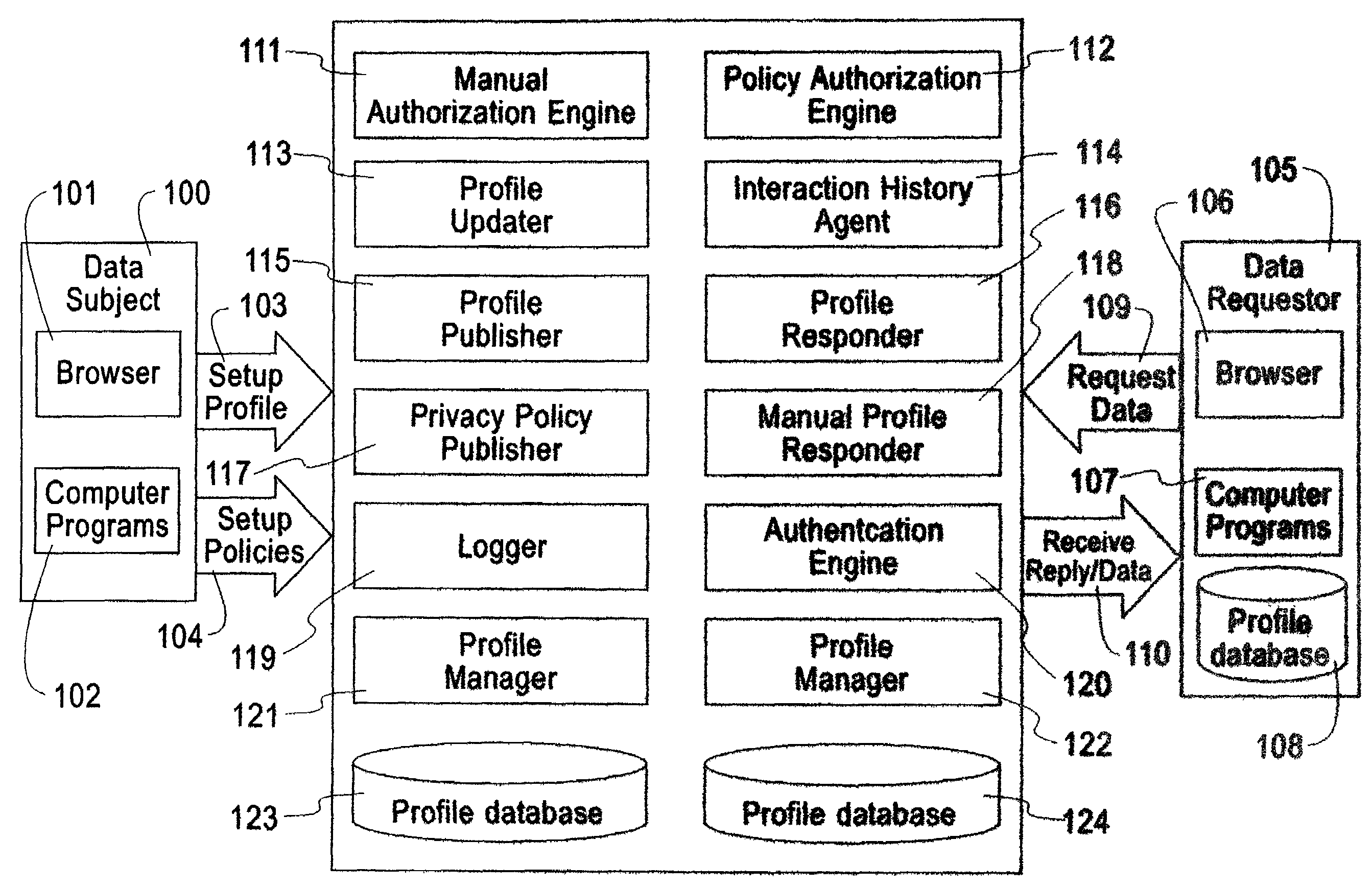
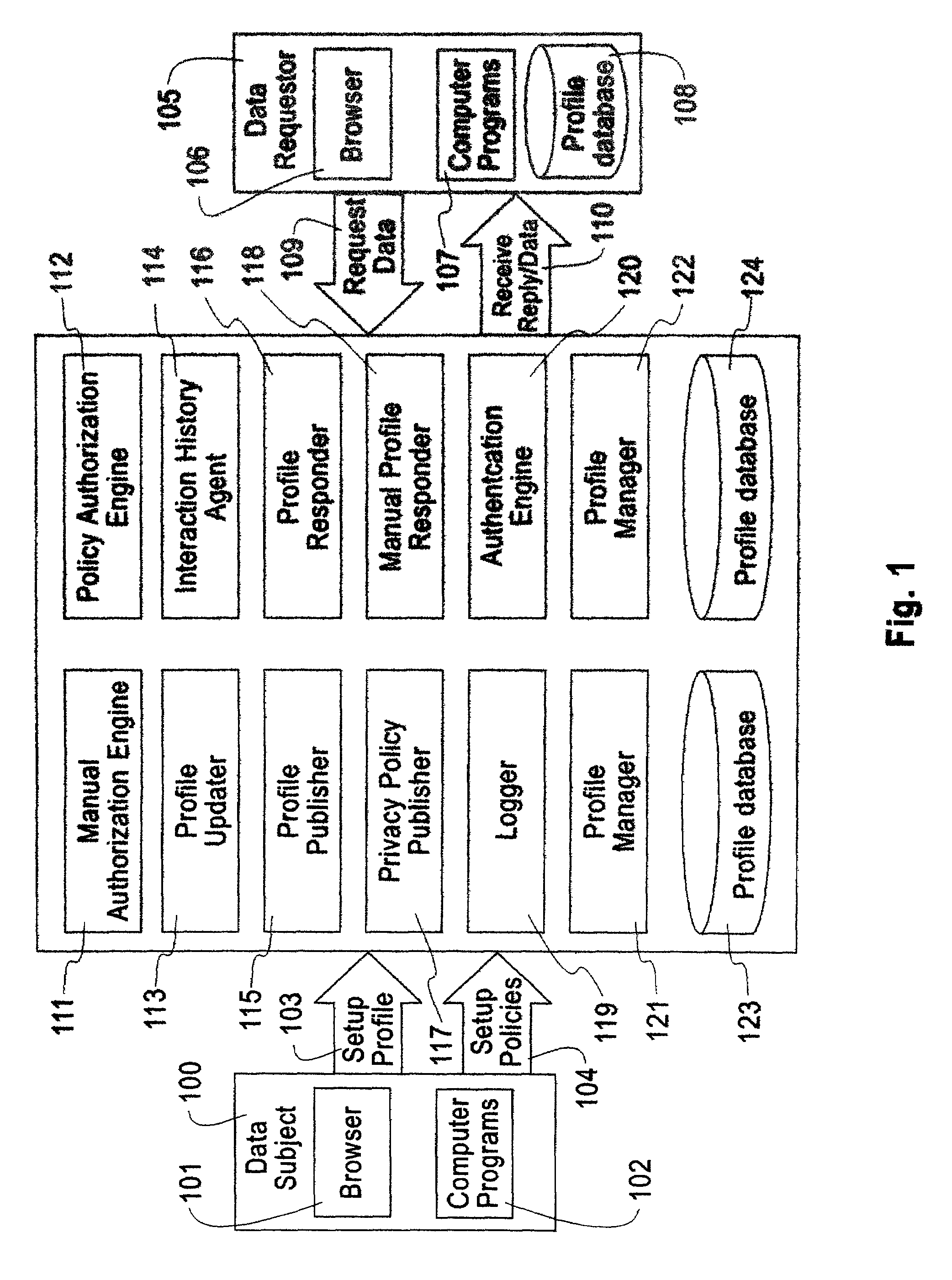
System, method, and business methods for enforcing privacy preferences on personal-data exchanges across a network
ActiveUS7478157B2Digital data processing detailsDigital computer detailsInternet privacyData exchange
An exemplary embodiment of the present invention includes a method to enforce privacy preferences on exchanges of personal data of a data-subject. The method comprises the steps of: specifying data-subject authorization rule sets having subject constraints, receiving a request message from a requester and a requester privacy statement, comparing the requester privacy statement to the subject constraints, and releasing the data-subject data in a response message to the requester only if the subject constraints are satisfied. The requester privacy statement includes purpose, retention, recipient, and access information, wherein the purpose information specifies the purpose for which the requested data is acquired, the retention information specifies a retention policy for the requested data, the recipient information specifies the recipients of the requested data, and the access information specifies whether the requested data should be accessing to the data-subject after the data has been released.
Owner:IBM CORP
Method and apparatus for training a multilingual speech model set
InactiveUS6912499B1Reduce development costsShorten development timeSpeech recognitionSpecial data processing applicationsMore languageSpeech identification
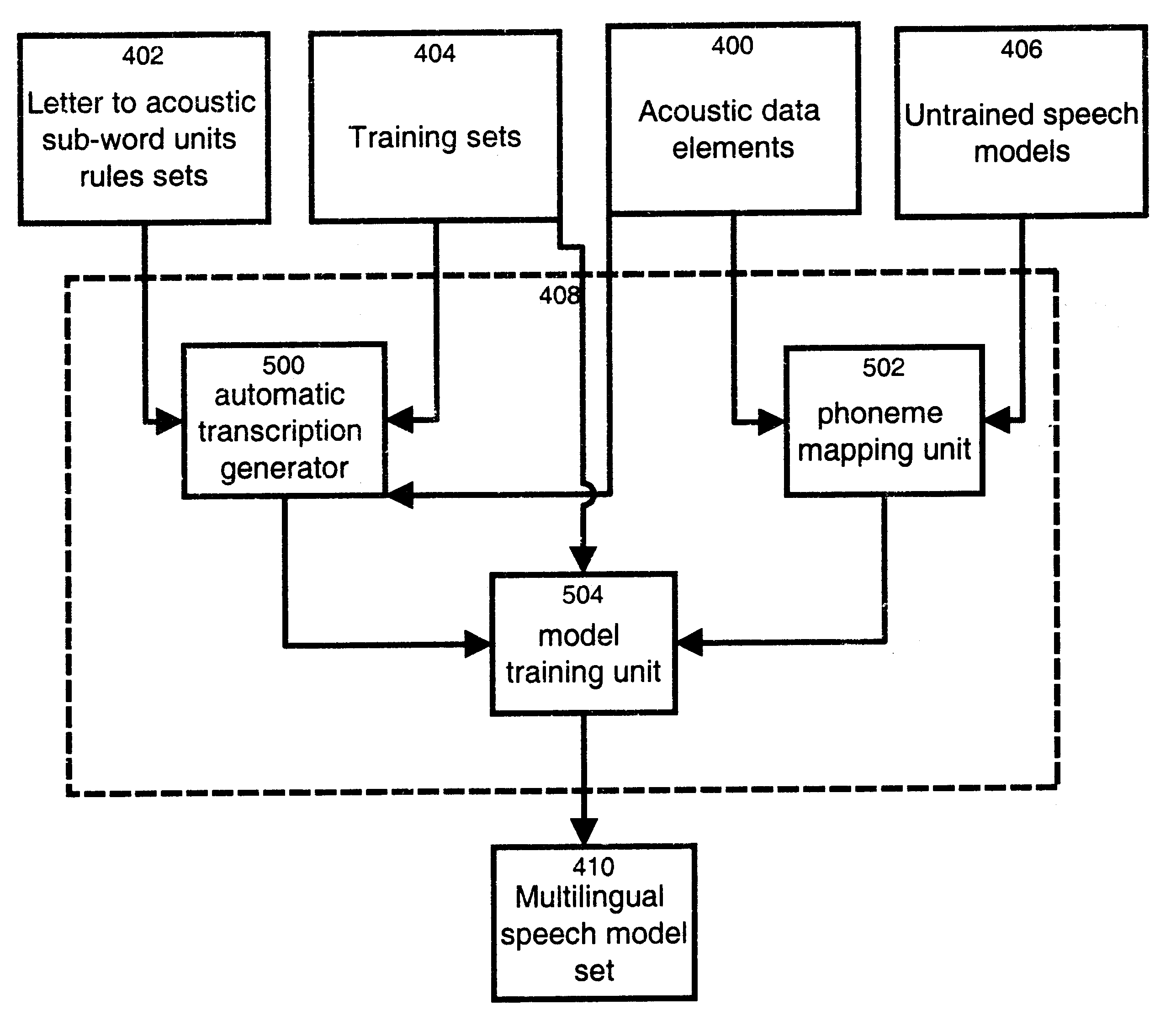
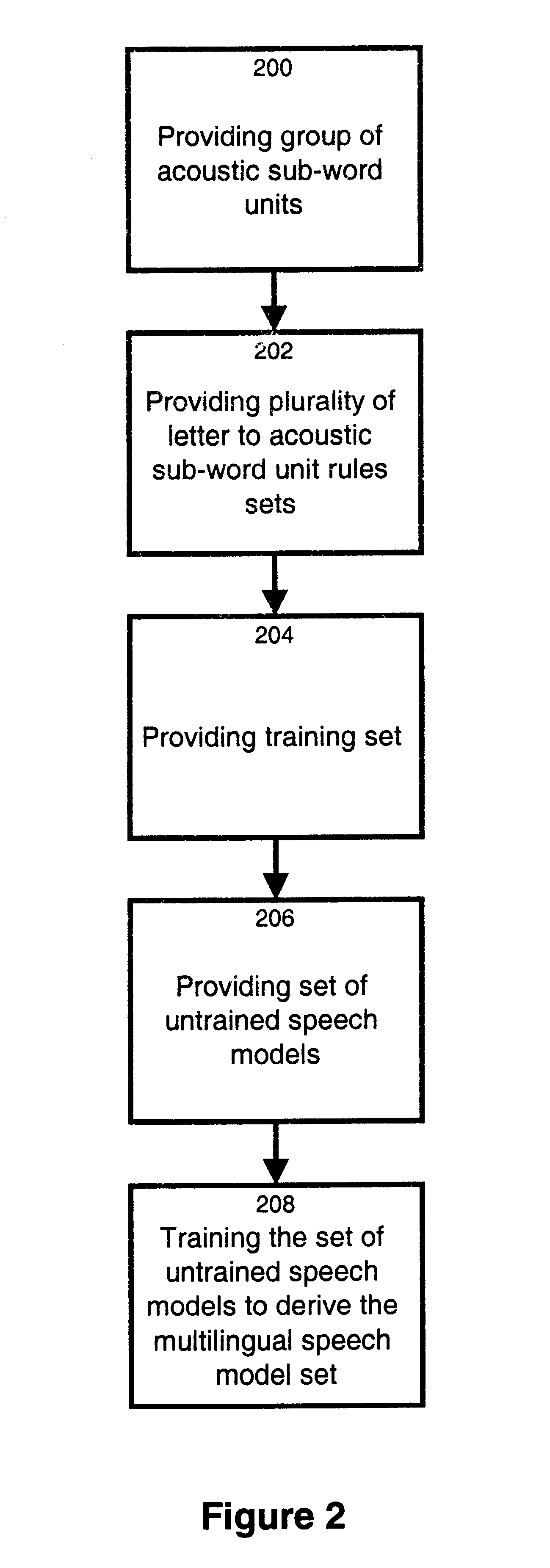
The invention relates to a method and apparatus for training a multilingual speech model set. The multilingual speech model set generated is suitable for use by a speech recognition system for recognizing spoken utterances for at least two different languages. The invention allows using a single speech recognition unit with a single speech model set to perform speech recognition on utterances from two or more languages. The method and apparatus make use of a group of a group of acoustic sub-word units comprised of a first subgroup of acoustic sub-word units associated to a first language and a second subgroup of acoustic sub-word units associated to a second language where the first subgroup and the second subgroup share at least one common acoustic sub-word unit. The method and apparatus also make use of a plurality of letter to acoustic sub-word unit rules sets, each letter to acoustic sub-word unit rules set being associated to a different language. A set of untrained speech models is trained on the basis of a training set comprising speech tokens and their associated labels in combination with the group of acoustic sub-word units and the plurality of letter to acoustic sub-word unit rules sets. The invention also provides a computer readable storage medium comprising a program element for implementing the method for training a multilingual speech model set.
Owner:RPX CLEARINGHOUSE
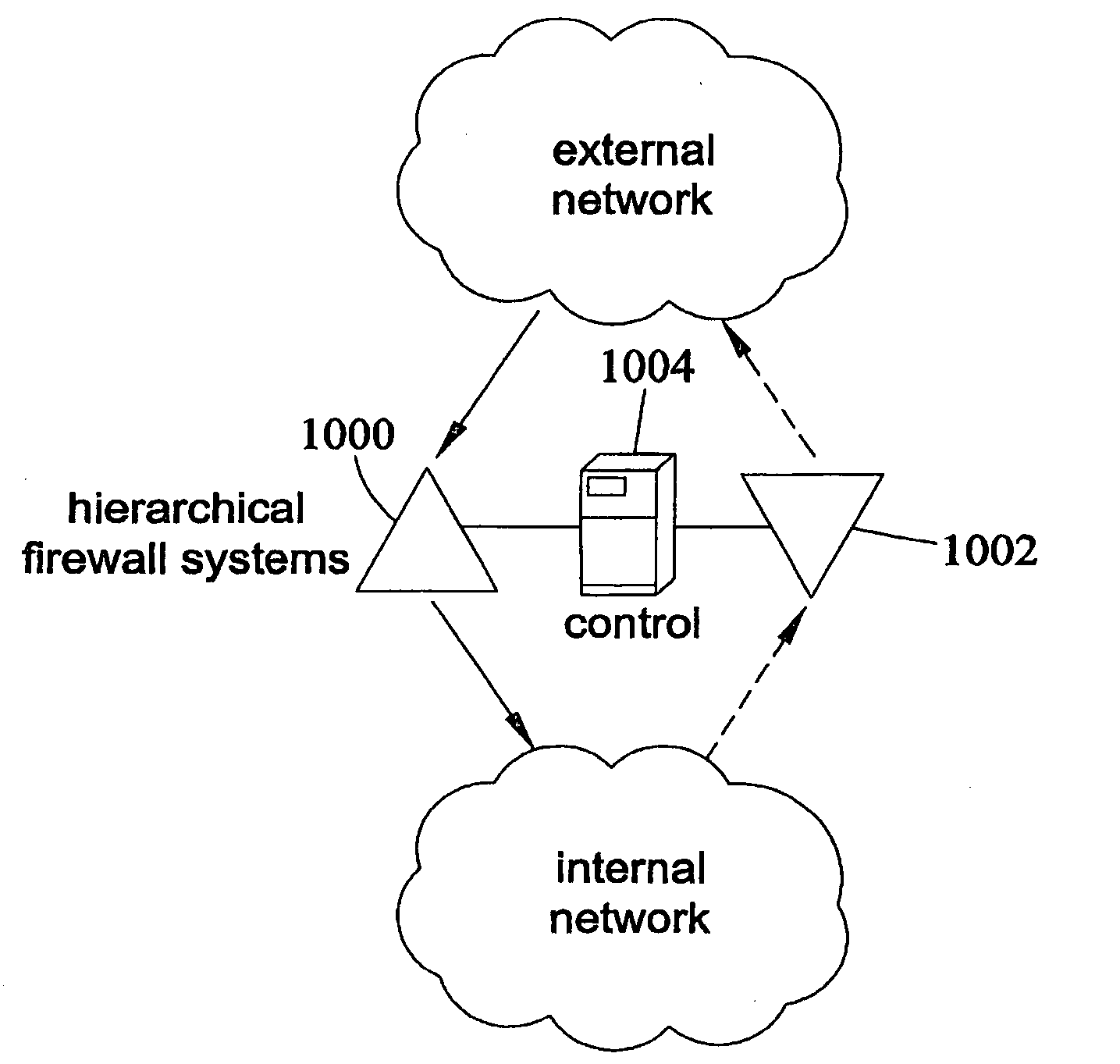
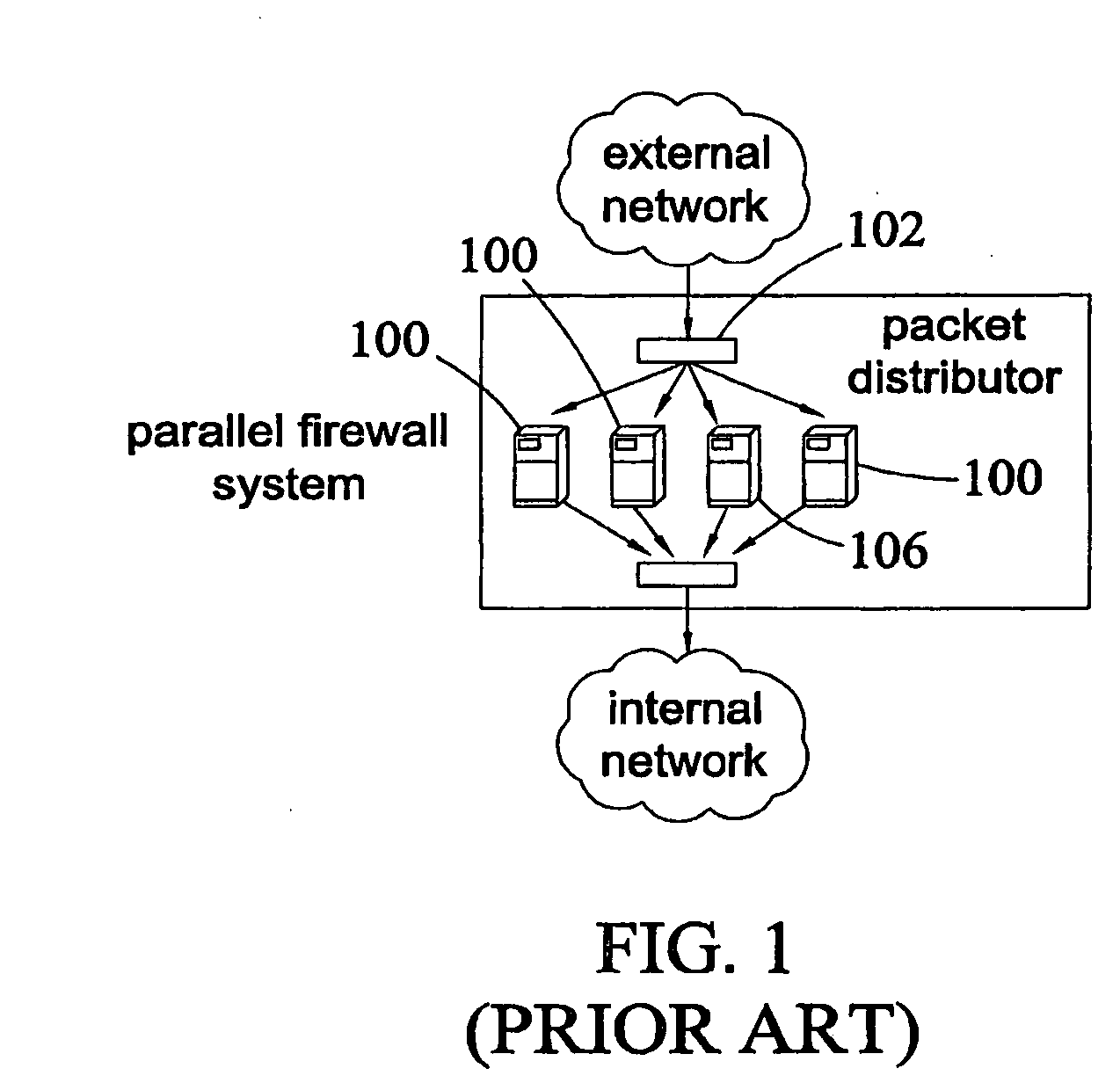
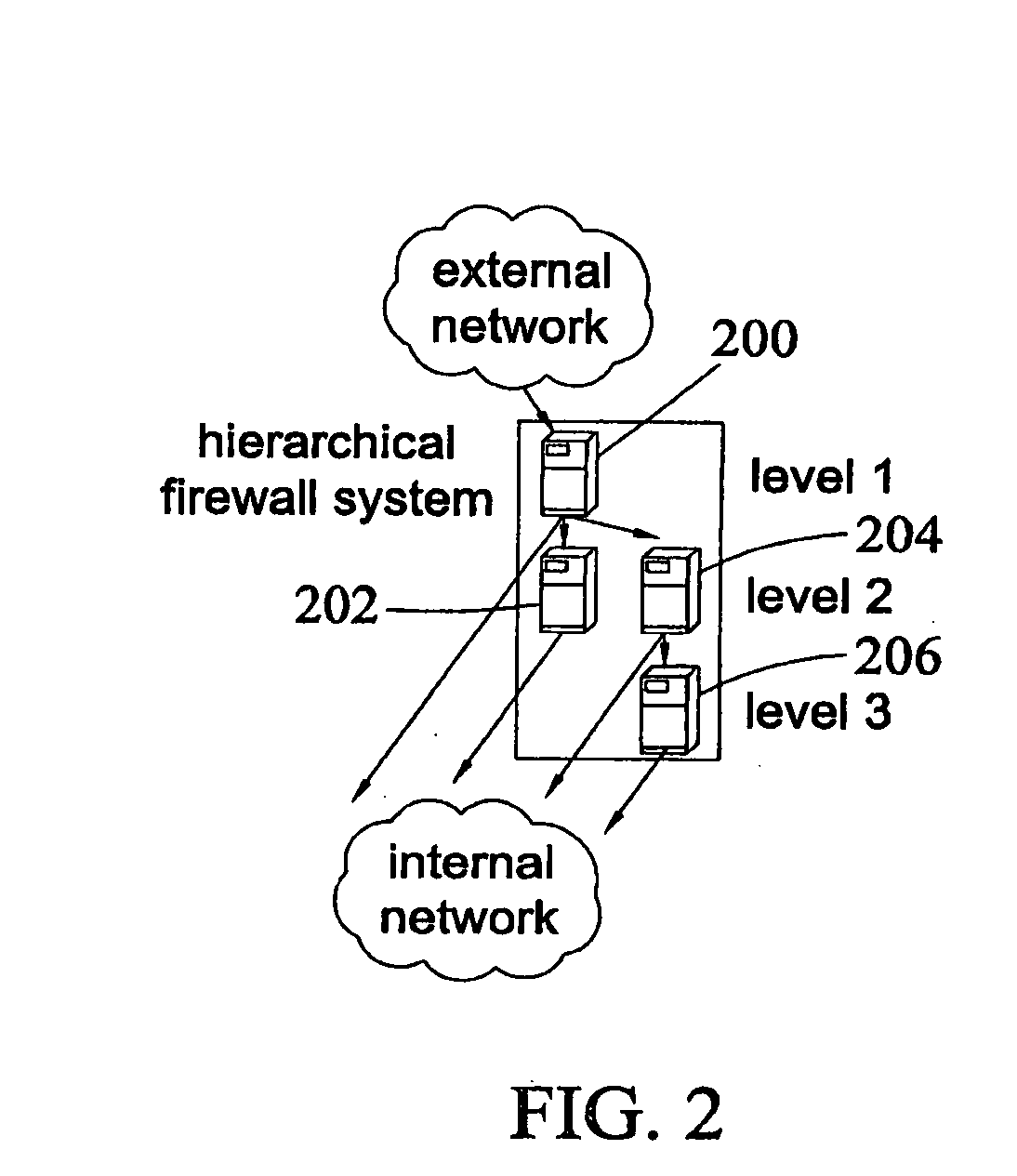
Method, systems, and computer program products for implementing function-parallel network firewall
ActiveUS20060195896A1Reduce impactMinimum delayMemory loss protectionError detection/correctionData packRule sets
Methods, systems, and computer program products for providing function-parallel firewalls are disclosed. According to one aspect, a function-parallel firewall includes a first firewall node for filtering received packets using a first portion of a rule set including a plurality of rules. The first portion includes less than all of the rules in the rule set. At least one second firewall node filters packets using a second portion of the rule set. The second portion includes at least one rule in the rule set that is not present in the first portion. The first and second portions together include all of the rules in the rule set.
Owner:WAKE FOREST UNIV
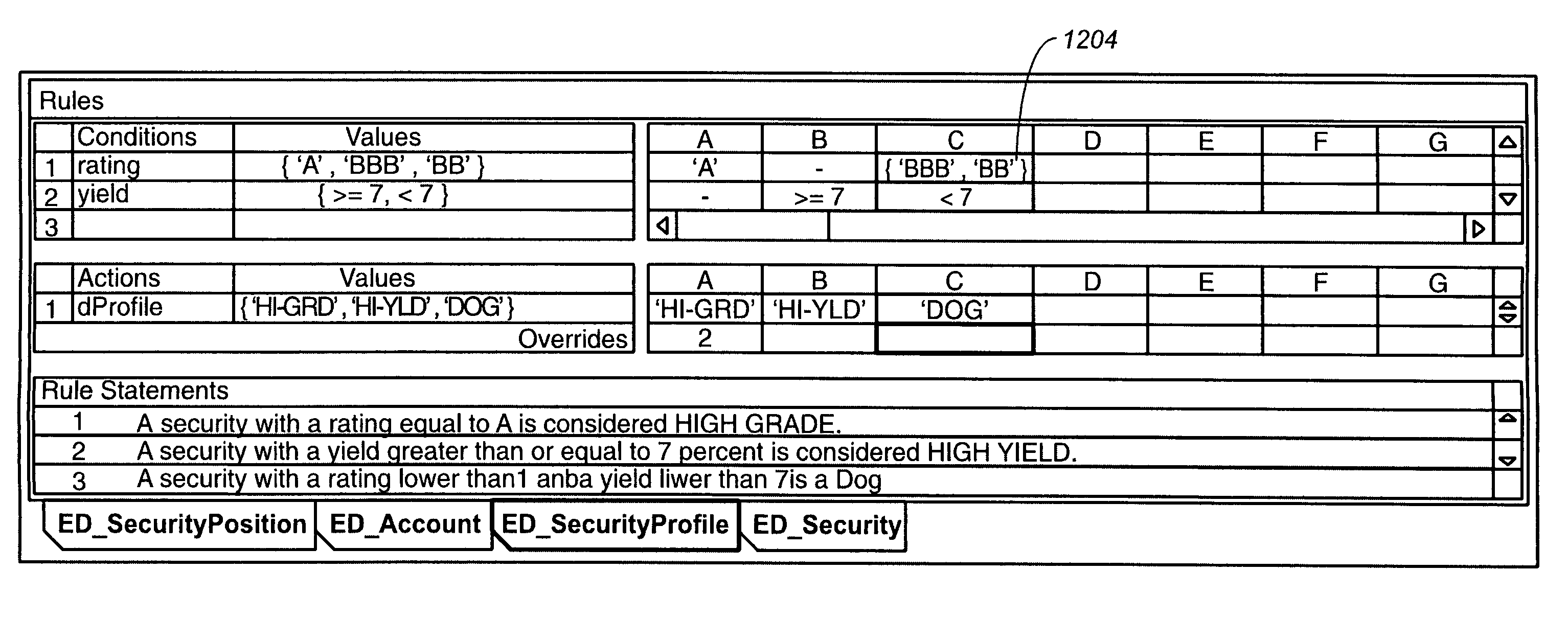
Business rules user interface for development of adaptable enterprise applications
ActiveUS7020869B2Reduce complexityMinimization requirementsTechnology managementVisual/graphical programmingApplication softwareDisplay list
Methods and apparatus, including computer program products, for interacting with a user to define business rules in a declarative manner. The invention operates to display a rule set as an editable list of conditions and an editable list of actions, the conditions and actions being linked to each other by the combination of an editable list of if-values and an editable list of then-values, wherein if-values and then-values are explicitly linked to each other, conditions and if-values are explicitly linked to each other, and then-values and actions are explicitly linked to each other in the displayed lists.
Owner:PROGRESS SOFTWARE
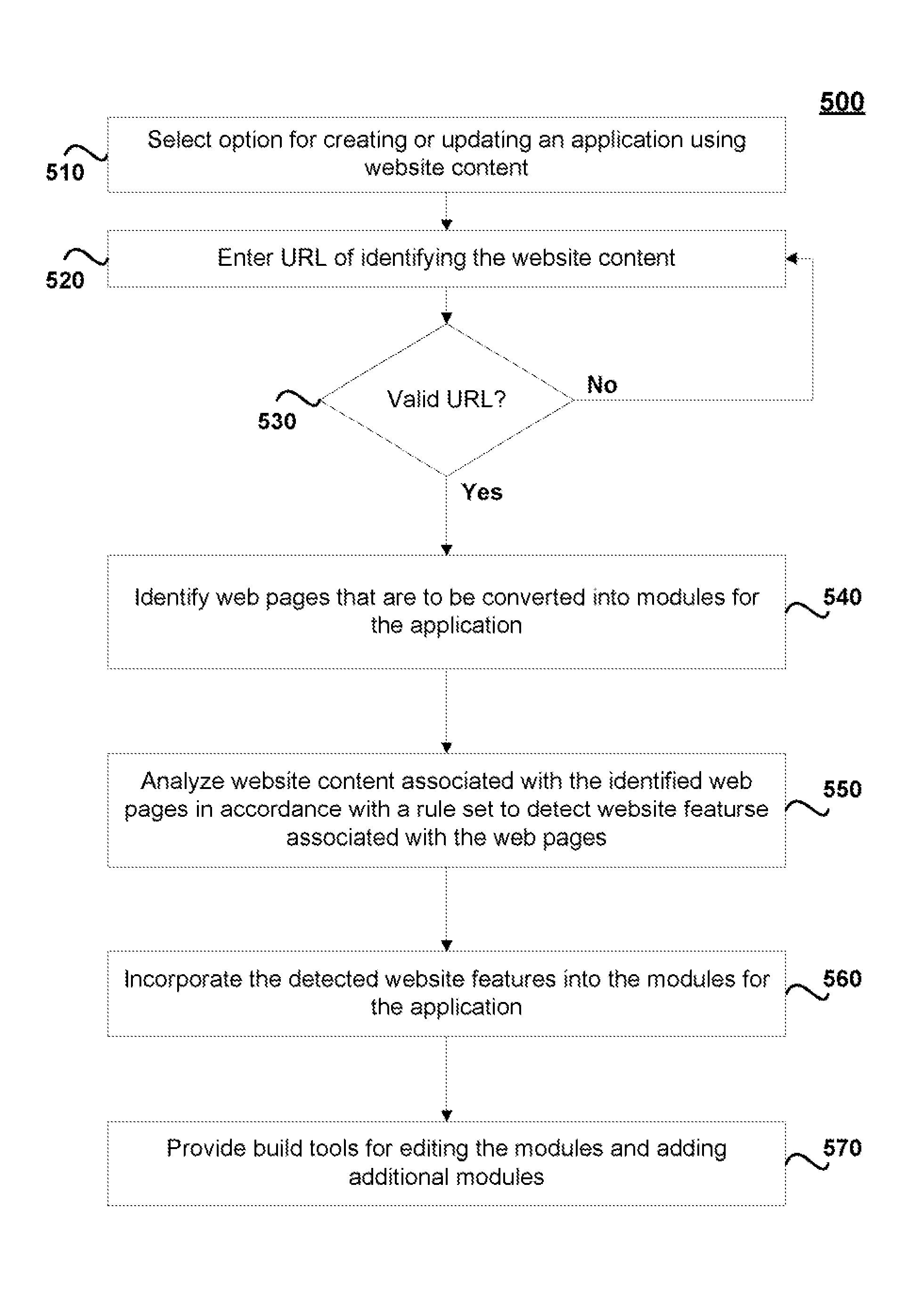
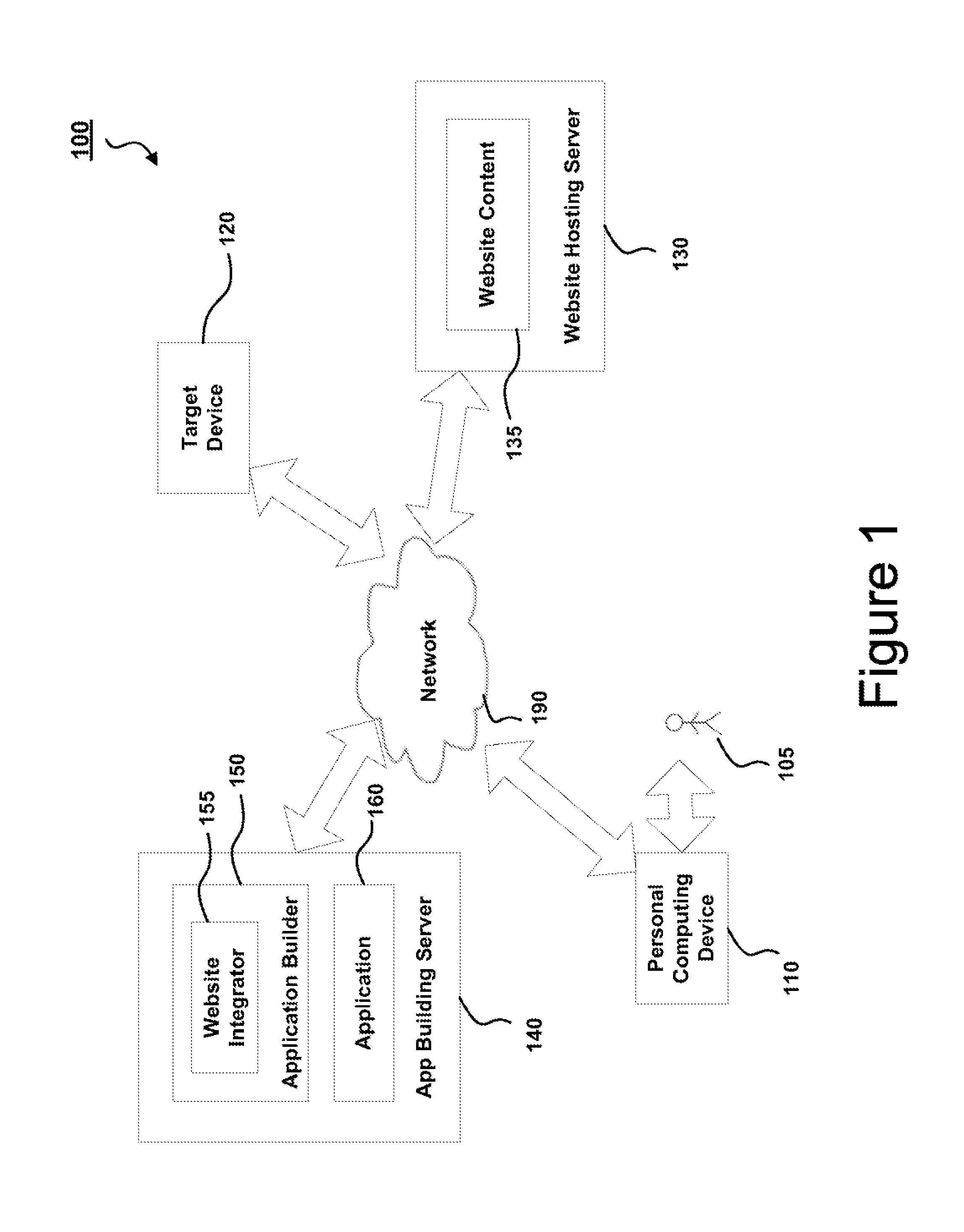
Systems and methods for creating or updating an application using website content
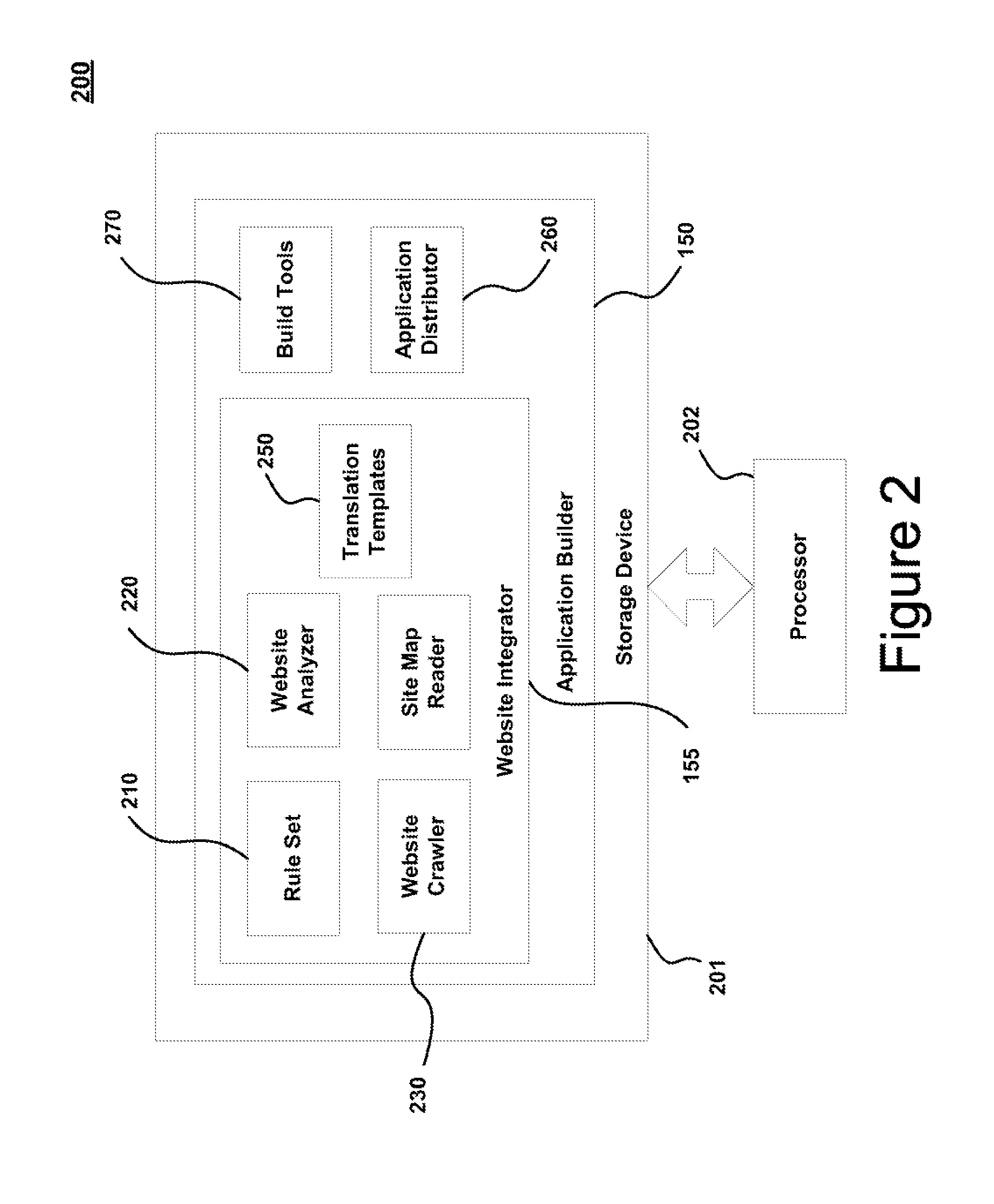
ActiveUS8788935B1Promote generationVersion controlNatural language data processingWeb siteApplication module
The disclosure herein relates to systems and methods for creating or updating applications using website content. An input may be received that identifies website content to be utilized in creating or updating an application. One or more application modules may to be derived from the website content. The website content may be analyzed in accordance with a rule set to detect website features associated with the website. The website features may be incorporated into the one or more application modules. The application modules may then be compiled into an application such as a mobile application or HTML 5 application.
Owner:MEDIA DIRECT
System and method for controlling manipulation of tiles within a sidebar
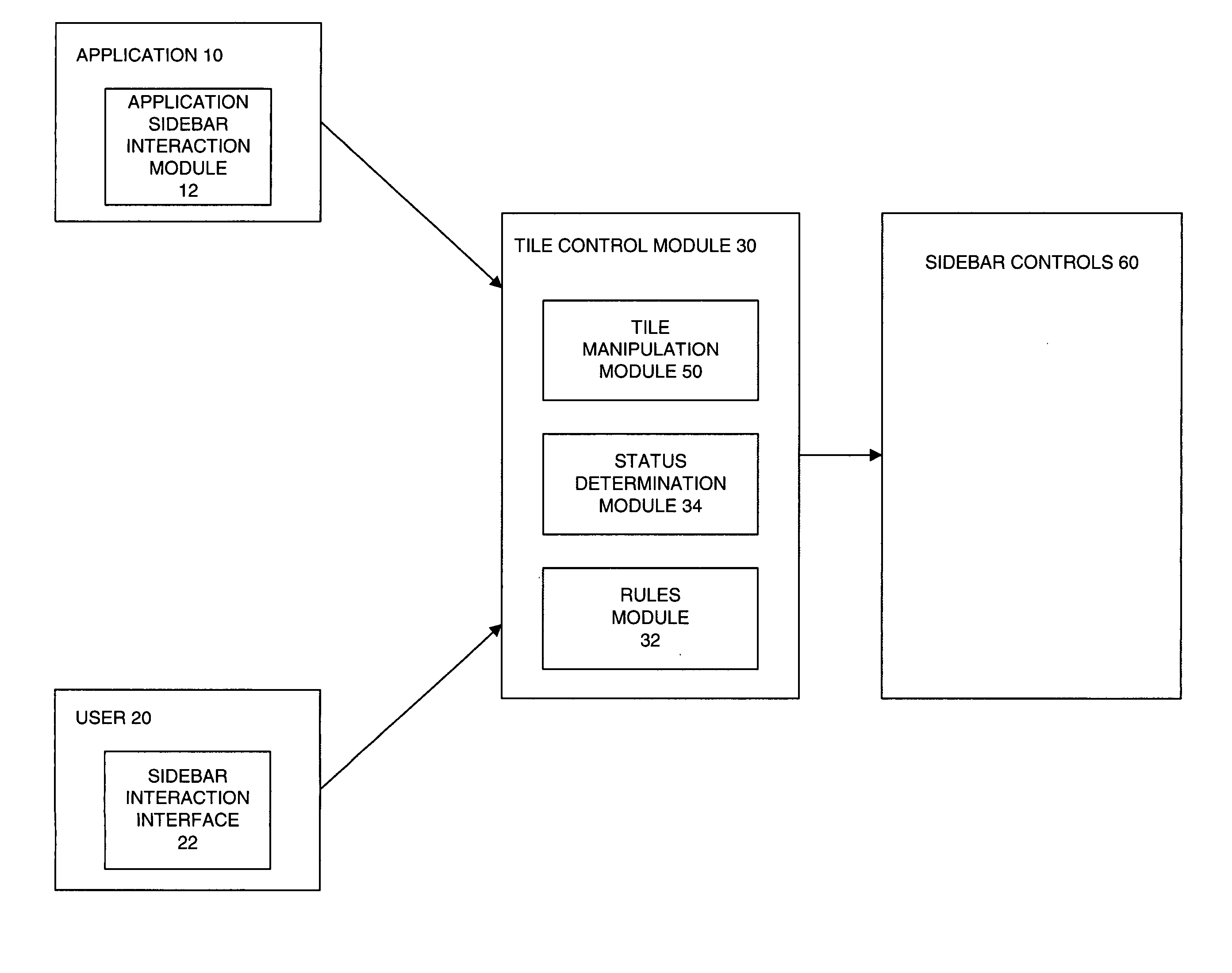
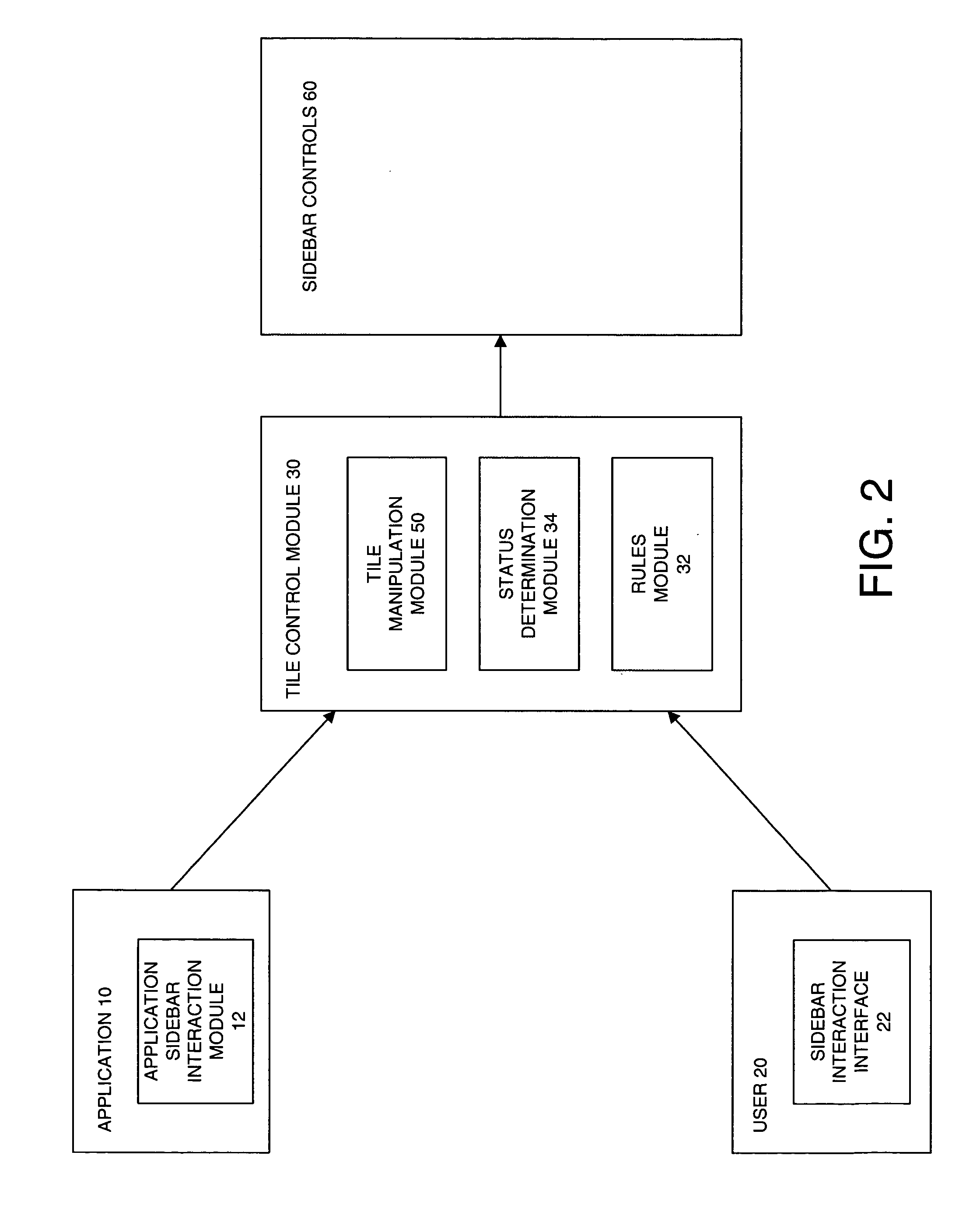
InactiveUS20050198584A1Execution for user interfacesInput/output processes for data processingGraphicsRule sets
The present invention is directed to a method and system for allowing a user to control the user interface environment and specifically a sidebar within the user interface environment. The method controls tiles within a sidebar to respond to a manipulation request by a system user or by an application to manipulate a selected tile. The method includes determining a current status of the selected tile and selecting an appropriate rule for manipulating the tile based on the status of the tile and an identity of the manipulation requestor. One rule set is provided for the application and another rule set is provided for the user. The method further includes manipulating the selected tile in accordance with the appropriate rule. The user rules allow insertion of the tile in most, if not all cases, whereas the application rules may prohibit insertion of the selected tile.
Owner:MICROSOFT TECH LICENSING LLC
Systems and/or methods for enabling cooperatively-completed rules-based data analytics of potentially sensitive data
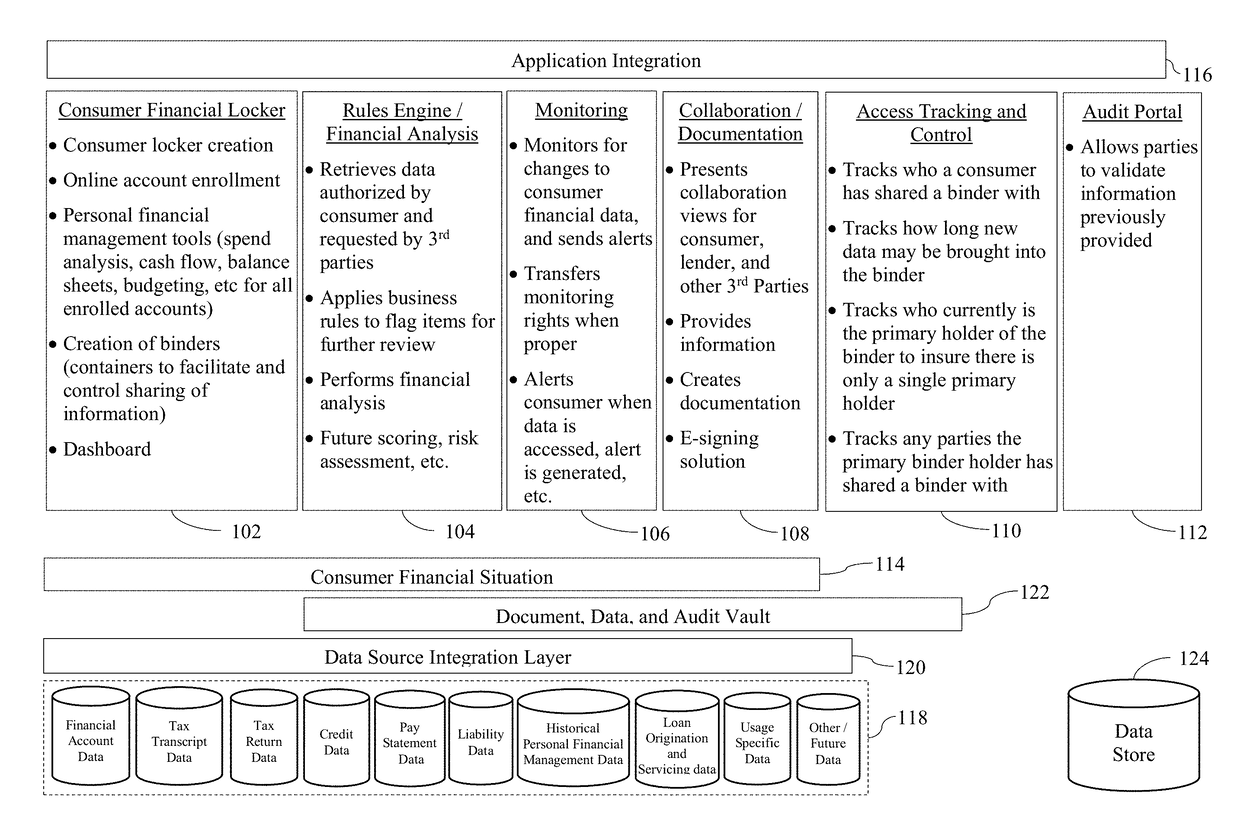
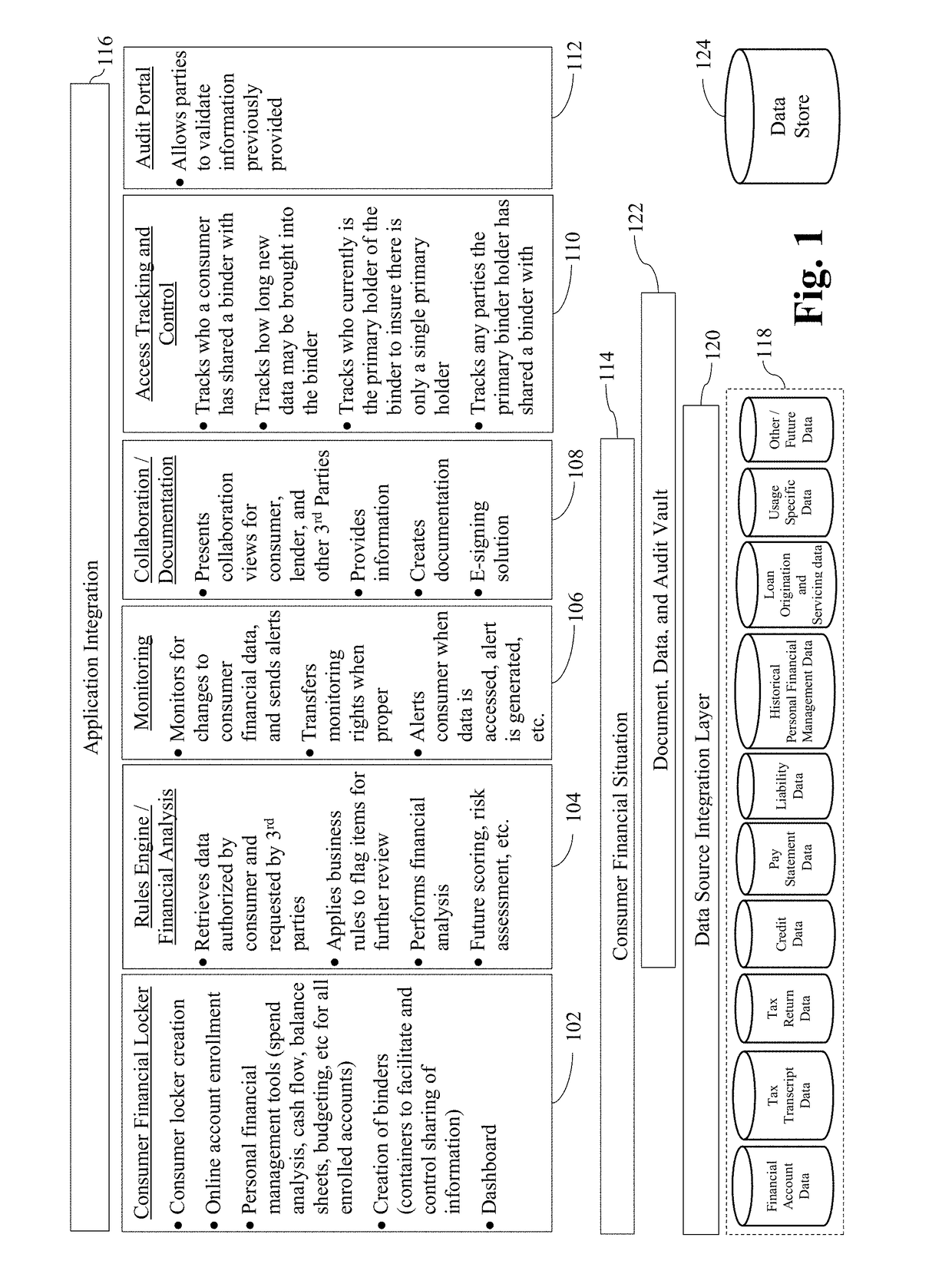
Certain example embodiments relate to systems and / or methods for providing enhanced control over potentially sensitive data sharable among and / or between different parties. For example, certain example embodiments provide views into computer-enabled workflows managed by external parties, including views into what sensitive data has been accessed, who has accessed it, etc., e.g., throughout the lifecycle of a product granted on the basis of an analysis of such data. A computer-enabled system for automatically assessing received sensitive data in accordance with one or more digitized rule sets also is provided in certain example embodiments, as are computer-mediated tools for helping to automatically, semi-automatically, and / or manually resolve issues detected in the assessments, e.g., via enhanced communication and collaboration, among and / or between parties to a transaction, as well as third-parties who indirectly are involved in the transaction. The data remains secure and traceable, e.g., in accordance with its provider's specifications.
Owner:FINLOCKER LLC
System and method for multi-tiered rule filtering
ActiveUS7027463B2Interconnection arrangementsData switching by path configurationRule setsTemporary storage
A system is described for processing messages and calls comprising: a plurality of filtering modules to apply a corresponding plurality of rule sets in succession to filter incoming and / or outgoing electronic messages and to apply the highest priority rule from among a plurality of rule sets to calls; and a pre-inbox for temporarily storing the calls and / or electronic messages as each of the plurality of rule sets are applied, the calls and / or electronic messages being removed from the pre-inbox and disposed of only after each of the plurality of rule sets have been applied to the calls and / or electronic messages.
Owner:CATALYSTWEB
Multi-application IC card with secure management of application
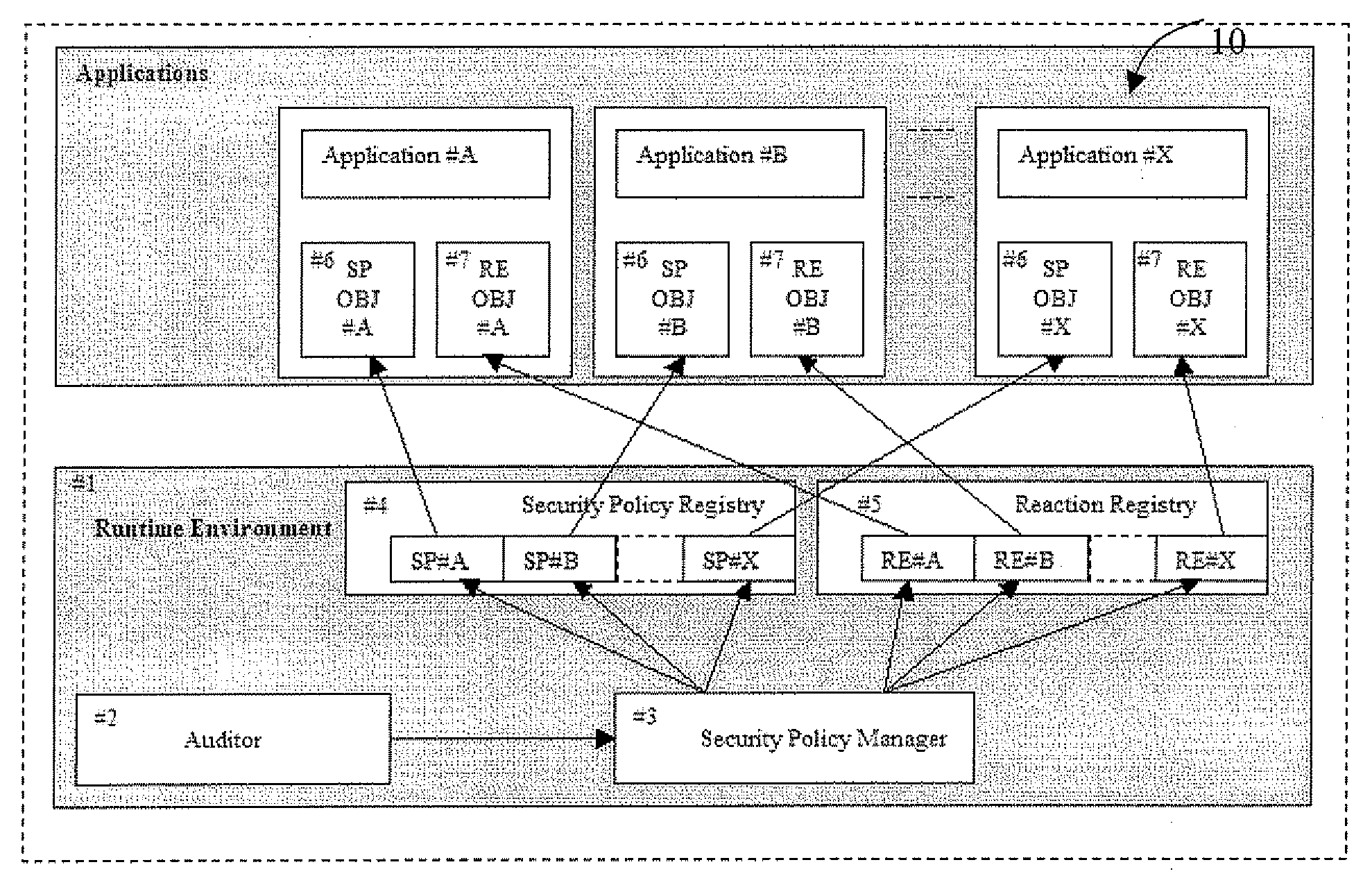
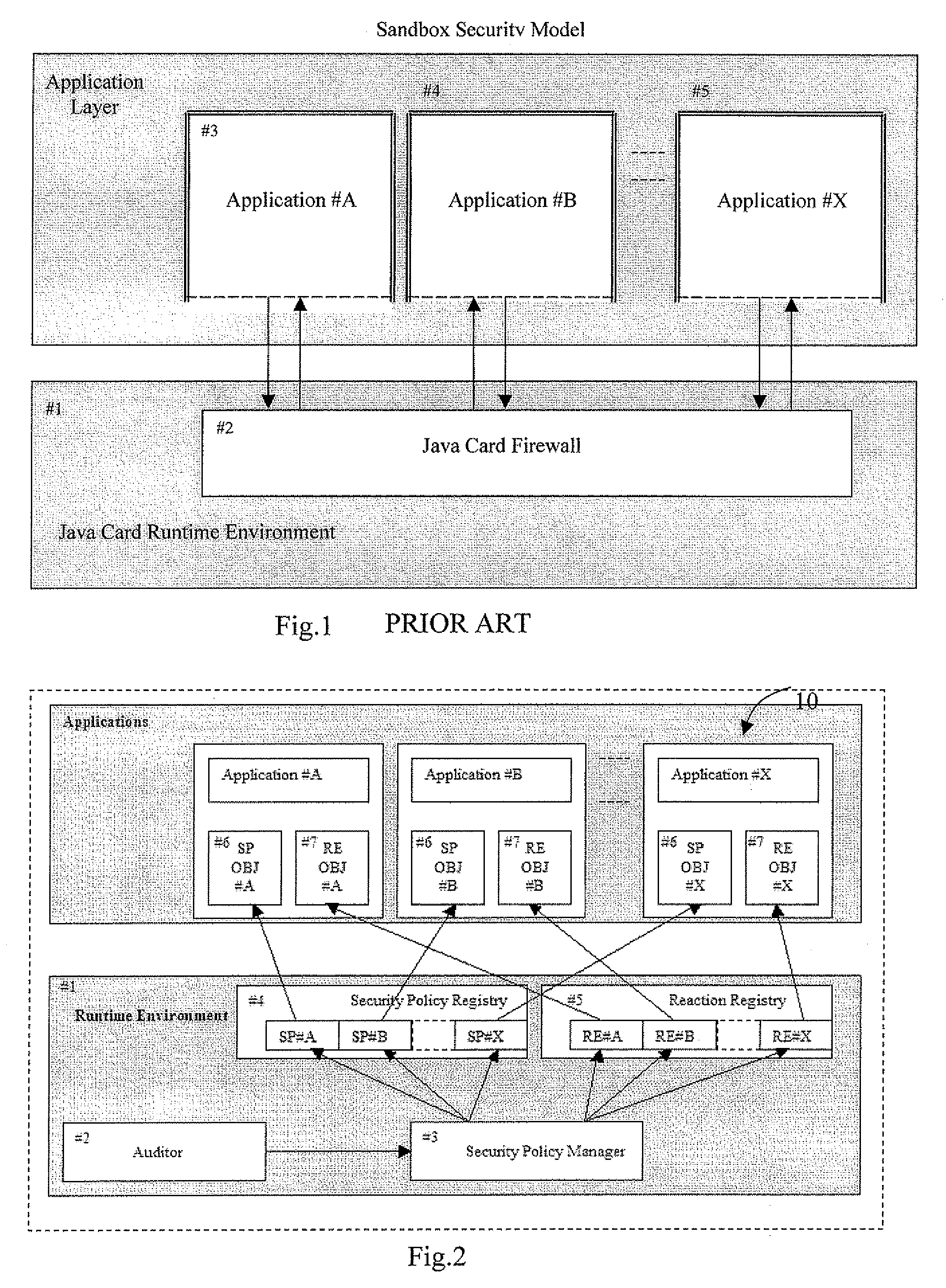
ActiveUS20080128515A1Avoid spreadingAcutation objectsPayment architectureProcessor registerSecurity policy management
A multi-application IC card may include a runtime environment for managing executions of a plurality of stored application. Each application may include a set of rules, to be satisfied by their execution, and a corresponding set of reactions, to be taken if the rules are not satisfied. The runtime environment may include security and reaction registers to reference, respectively, the set of rules and reactions associated with the applications. A security policy manager may initialize, for each application, a reference between the security registers and the rules set between the reactions register and the reactions set. Checking the rules set and / or an activation of the reactions set is controlled by the security policy manager through the security registers and reaction registers. The security policy manager may include a registration function for initializing the security and reaction registers. The registration function may be called from the applications or an administrative user.
Owner:STMICROELECTRONICS INT NV
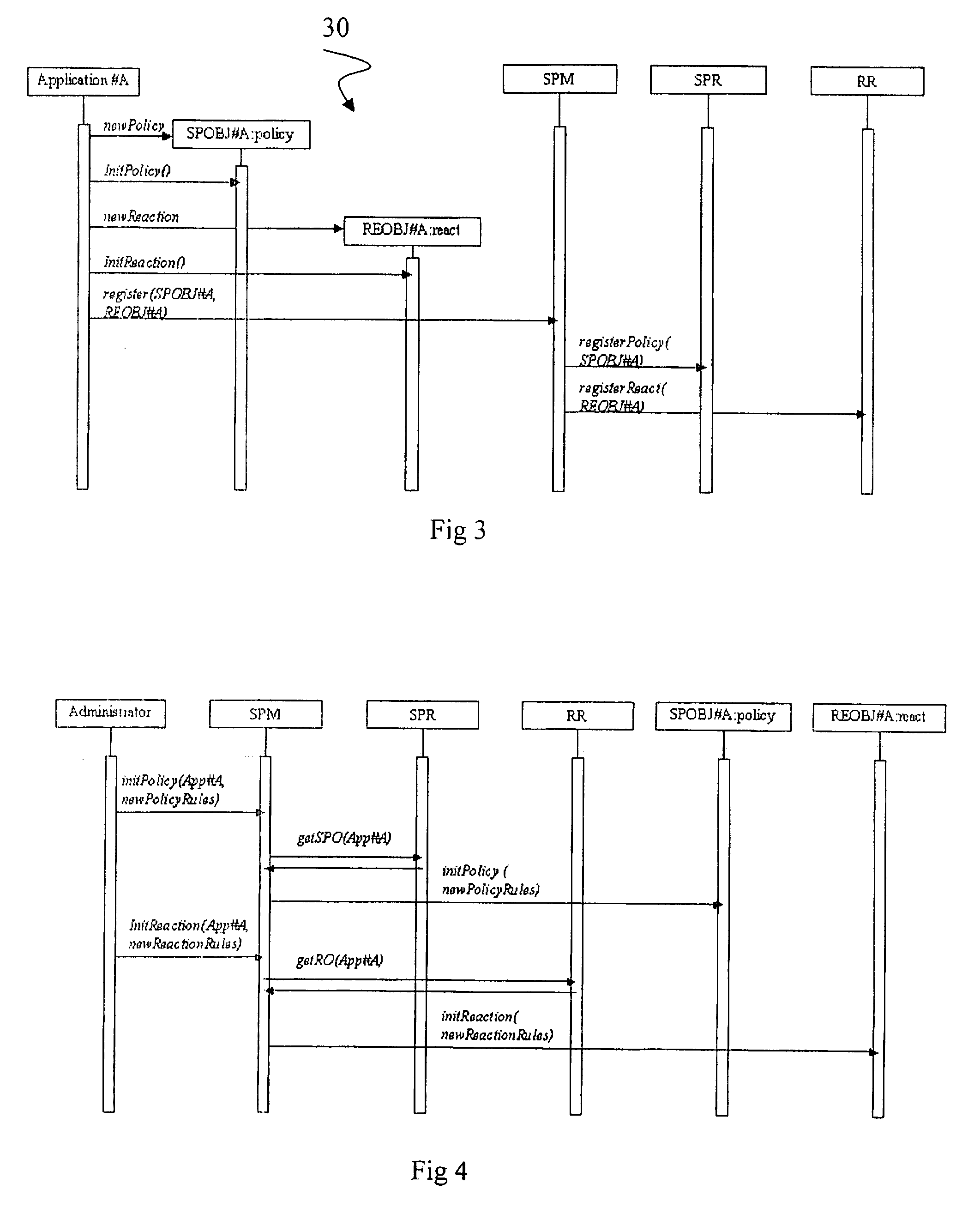
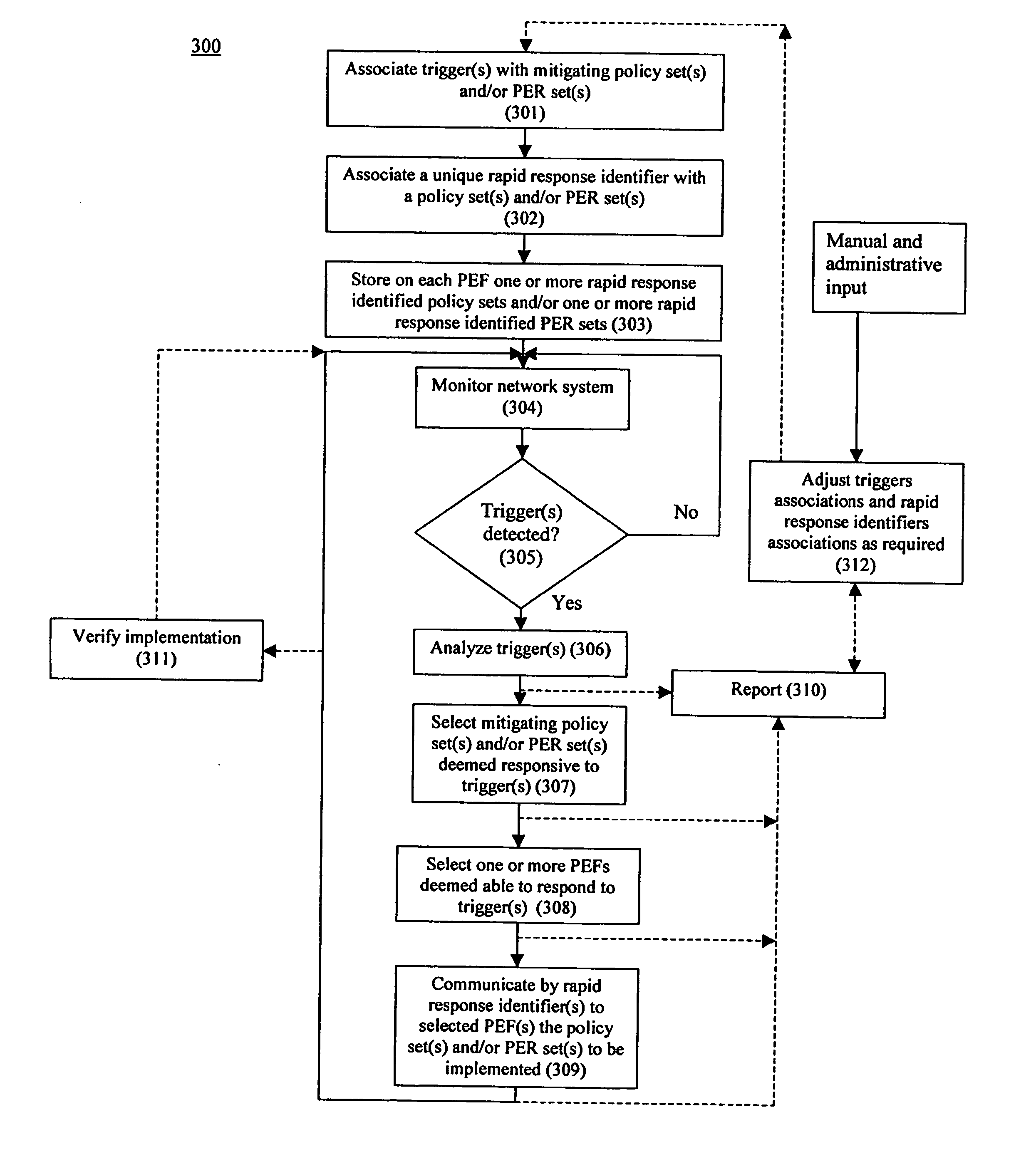
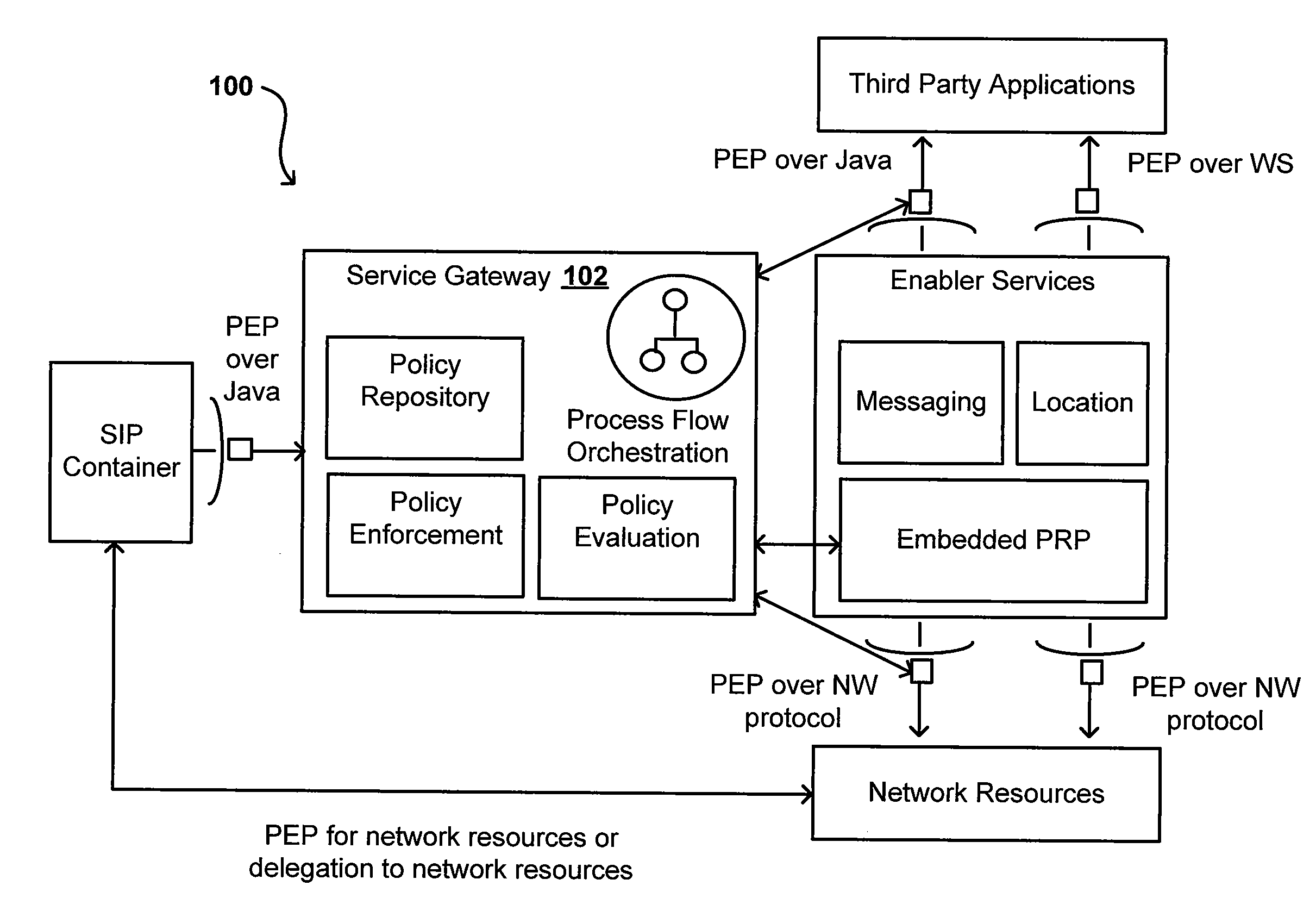
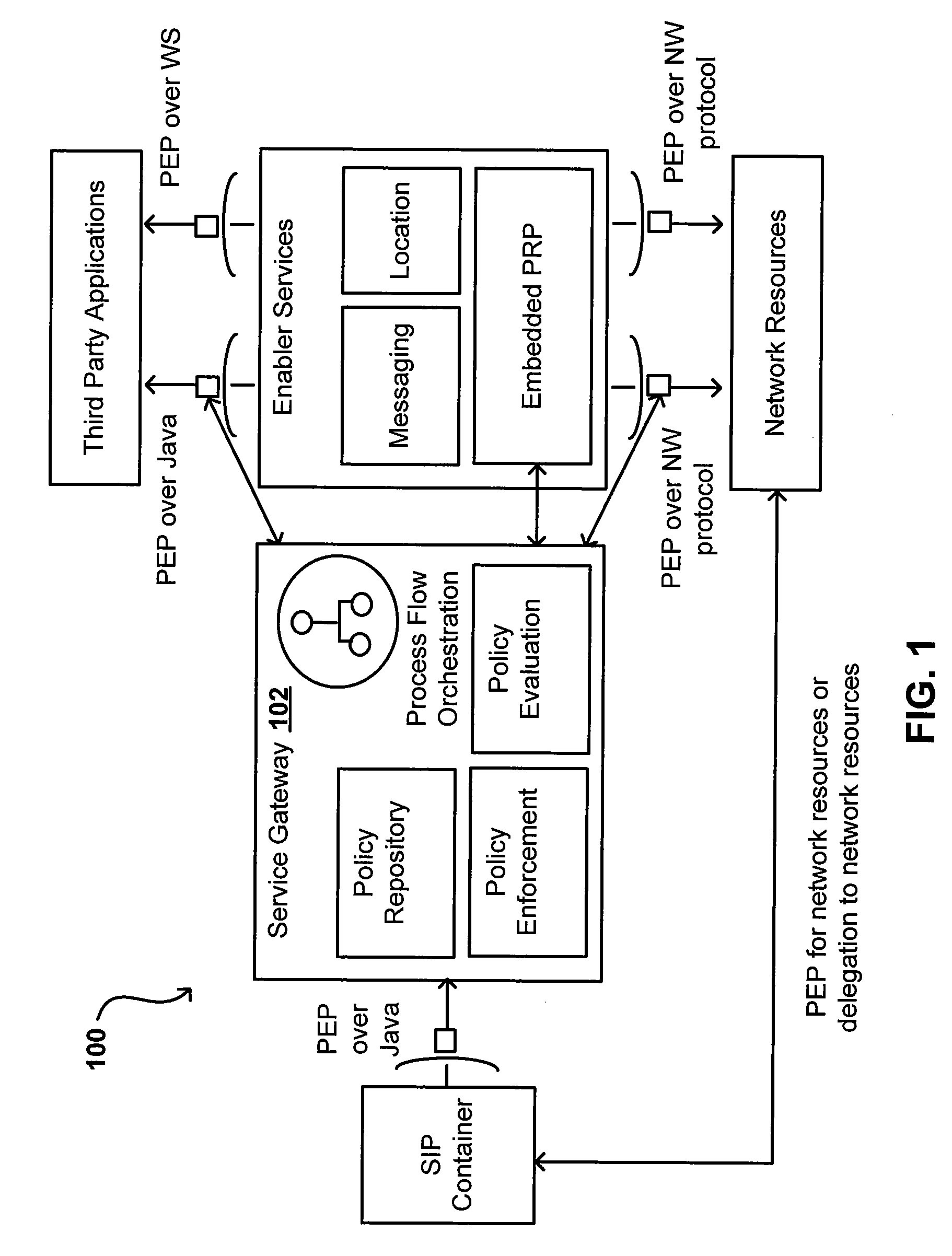
System and method for rapid response network policy implementation
A system and method for rapidly responding to triggering events or activities in a network system. The system includes a policy enforcement function, a policy manager function, and one or more network devices of the network system. The policy enforcement function includes one or more installed policy sets and / or policy enforcement rule sets suitably responsive to triggering events or activities. Upon detection of a trigger, the policy manager function analyzes the trigger and selects one or more appropriate policy sets and / or policy enforcement rule sets deemed to be responsive to the trigger. Each set has a unique rapid response identifier. The policy manager function signals for implementation of the one or more policy and / or rule sets, based on one or more rapid response identifiers, which are enforced through the policy enforcement function. The policy enforcement function may be a part of one or more of the one or more network infrastructure devices for implementing the policy change. The system and method enable rapid response to a detected trigger (which might be a manual input) by pre-installing responsive policy and / or rule sets first and then generating and transmitting the unique rapid response identifier(s) corresponding to one or more selected policy and / or rule sets for implementation. That is, the network device is already configured with a response through the pre-installed policy and / or rule sets. Responses may be implemented and / or removed gradually, and different network devices may be instructed to implement different policies in response to the same trigger and the same policy may be implemented with different policy enforcement rules on different devices, ports, or interfaces.
Owner:ENTERASYS NETWORKS
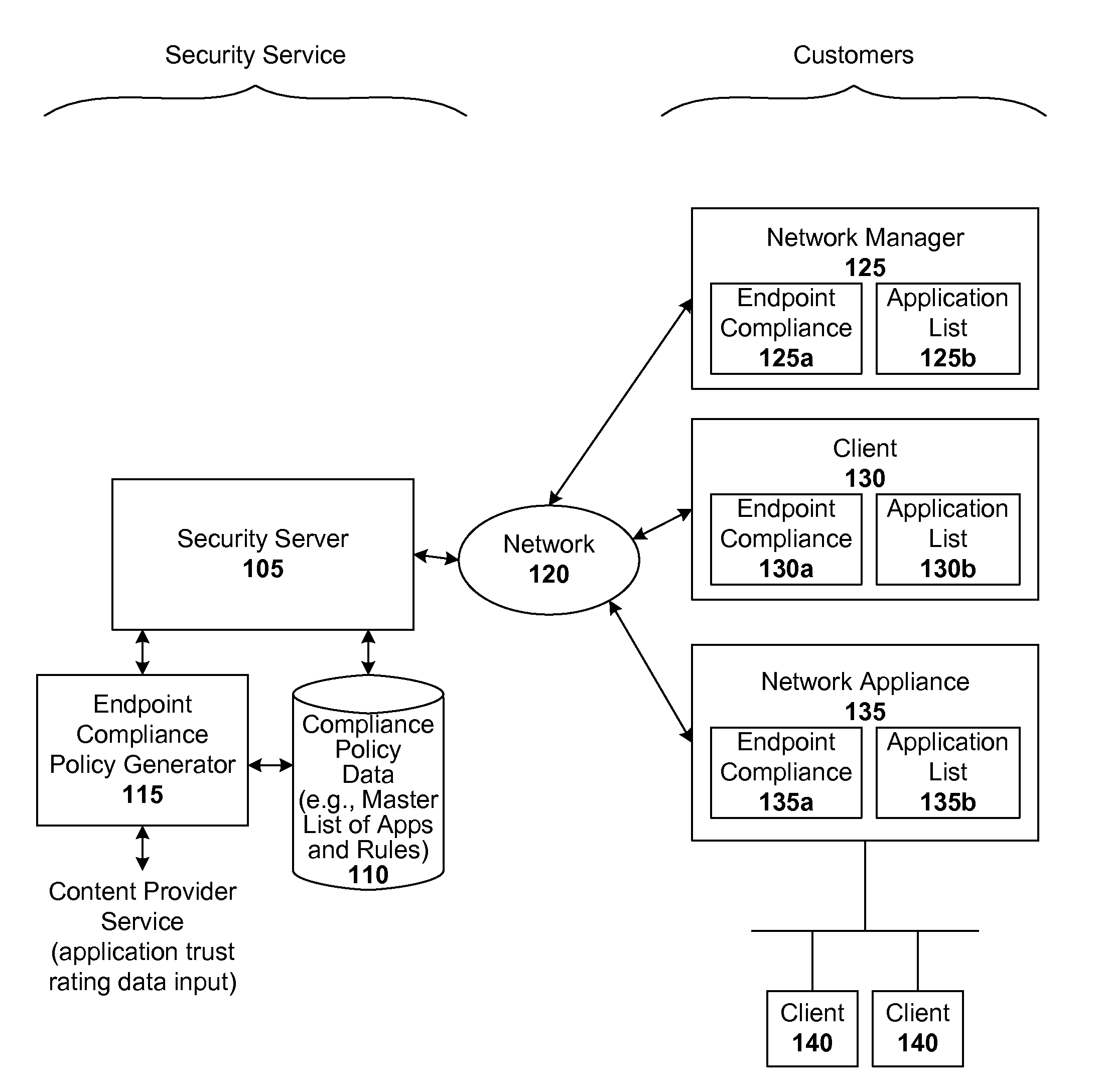
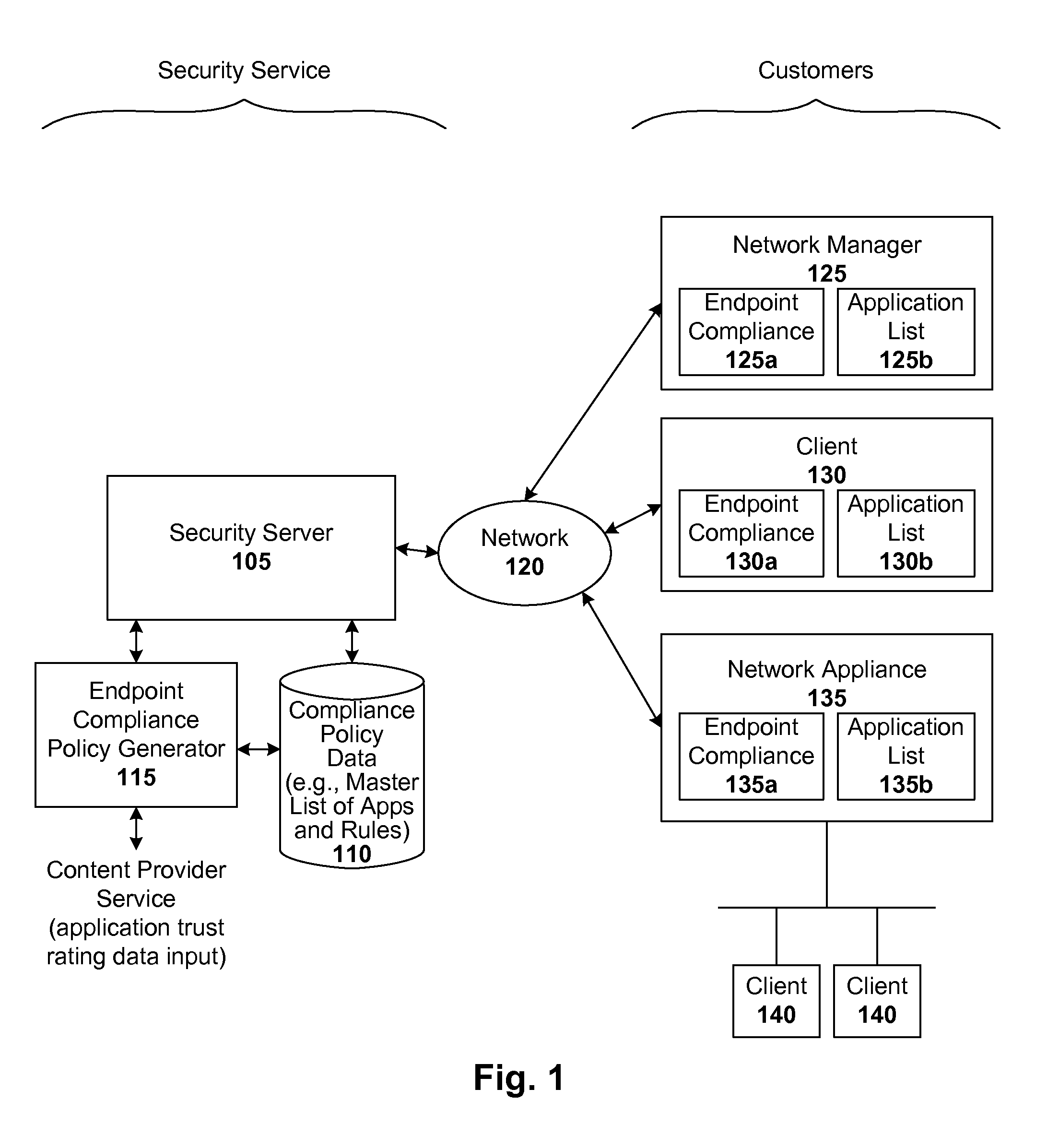
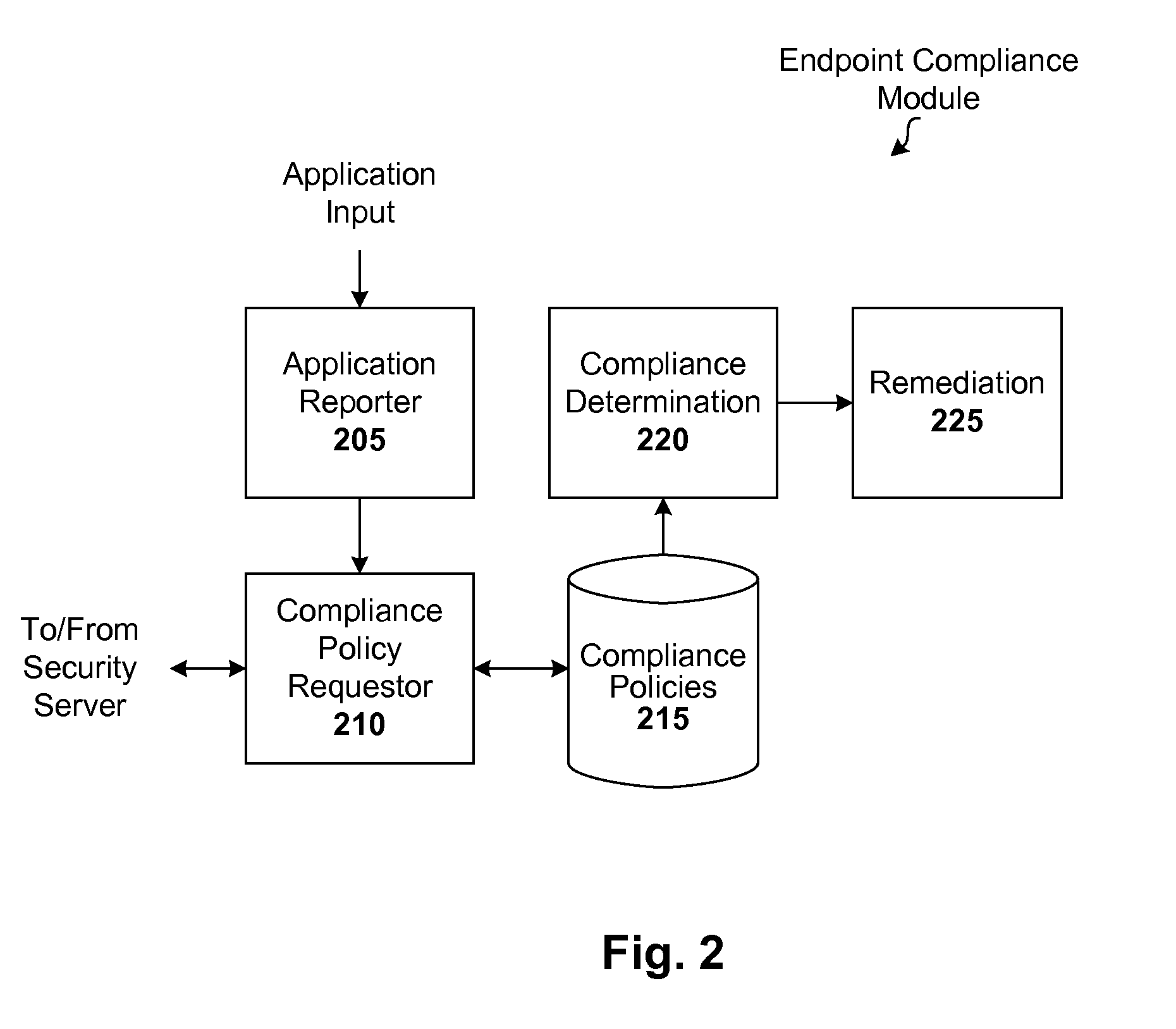
Endpoint management using trust rating data
ActiveUS8239915B1Digital data processing detailsComputer security arrangementsApplication softwareApplication security
Techniques are disclosed for implementing dynamic endpoint management. In accordance with one embodiment, whenever an endpoint joins a managed network for the first time, or rejoins that network, a local security module submits a list of applications (e.g., all or incremental) to a security server. The server validates the list and sends back a rule set (e.g., allow / block rules and / or required application security settings) for those applications. If the server has no information for a given application, it may further subscribe to content from a content provider or service. When the server is queried regarding an unknown application, the server sends a query to the service provider to obtain a trust rating for that unknown application. The trust rating can then be used to generate a rule set for the unknown application. Functionality can be shifted from server to client, and vice-versa if so desired.
Owner:CA TECH INC
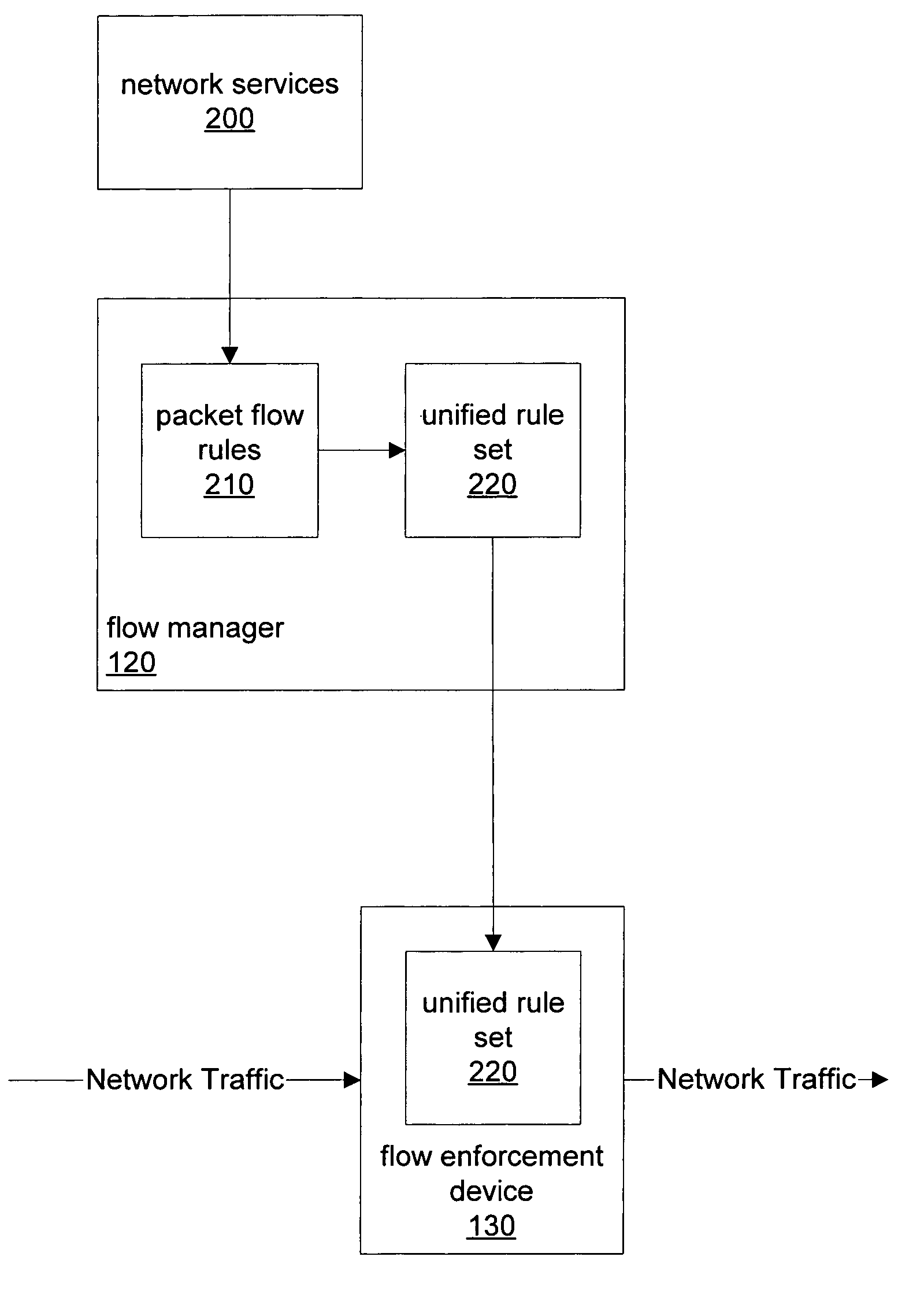
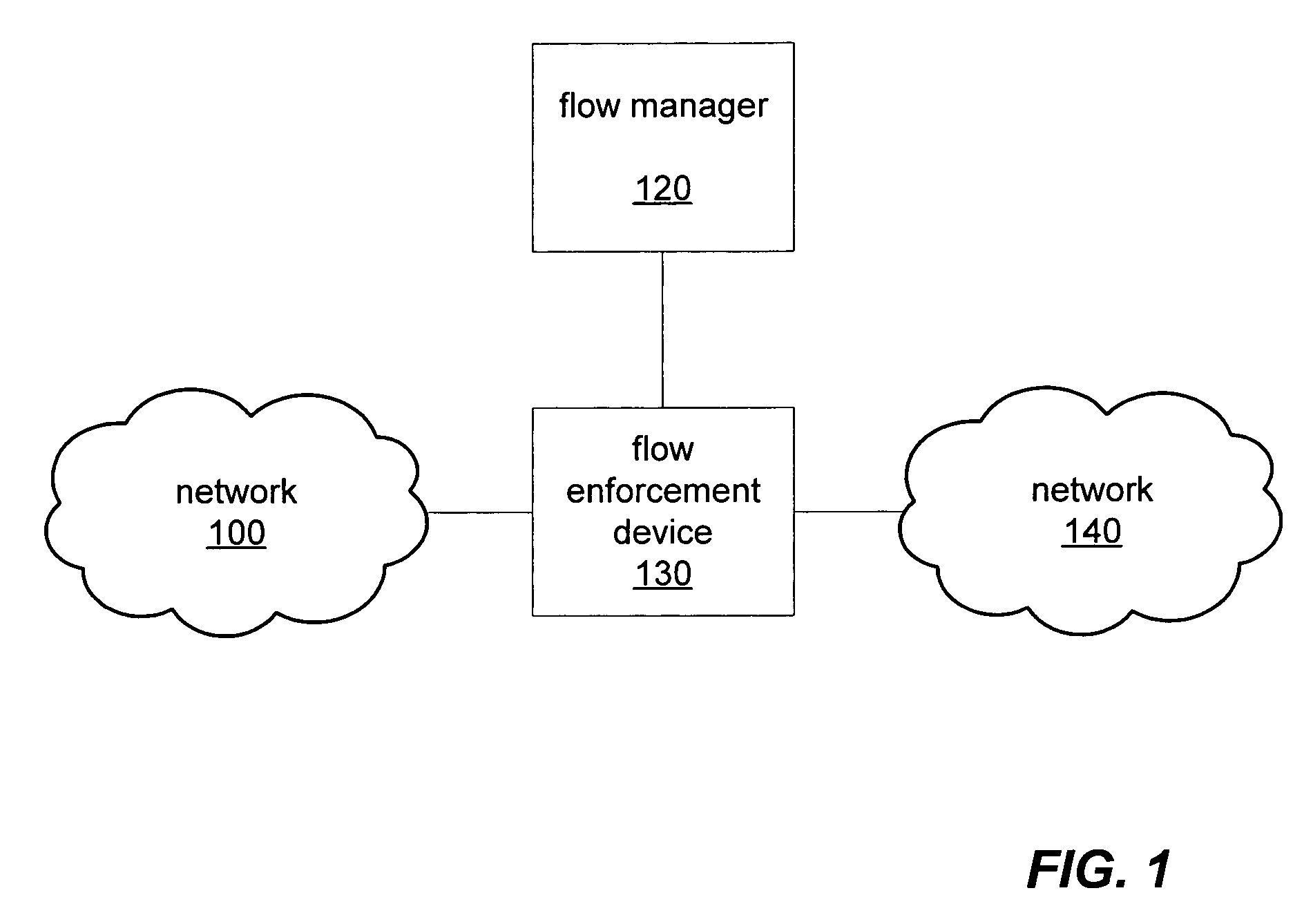
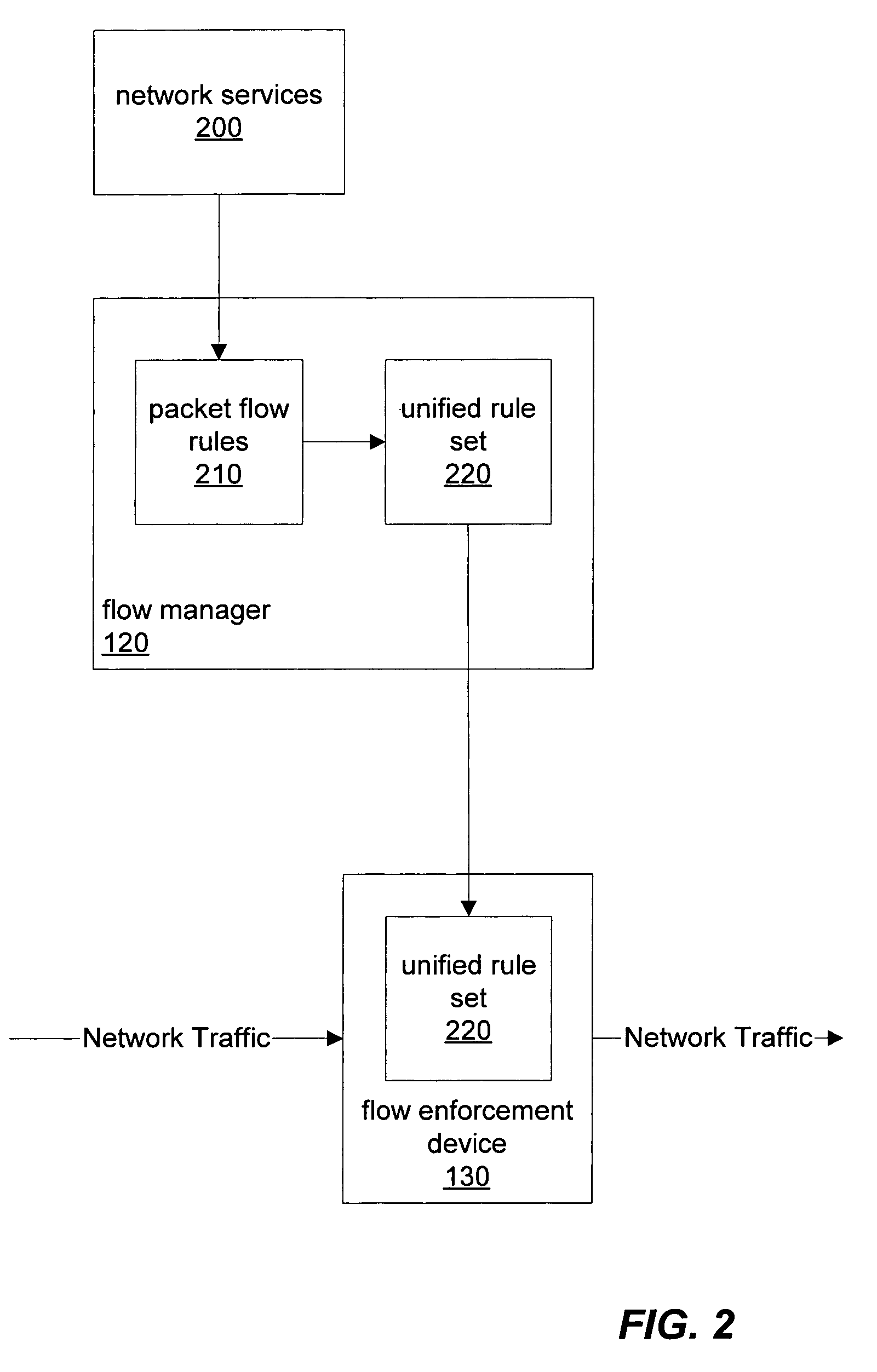
Rule set conflict resolution
ActiveUS7505463B2Data switching by path configurationMultiple digital computer combinationsNetwork serviceDistributed computing
A flow manager may receive prioritized packet flow rules from multiple prioritized network services where each flow rule may comprise a packet filter and a prioritized action list. The priority for the flow rules from each network service may be expressed as either longest prefix or ordered precedence. The flow manager may generate a unified rule set according to the received packet flow rules by identifying conflict between pairs of rules and resolving the identified conflicts according the priority relationship two rules of each pair. When resolving conflicts between rules, the flow manager may append the action list of one rule to the action list of another rule, and may also create a new rule by combining the packet filters and actions lists of the conflicting rules.
Owner:ORACLE INT CORP
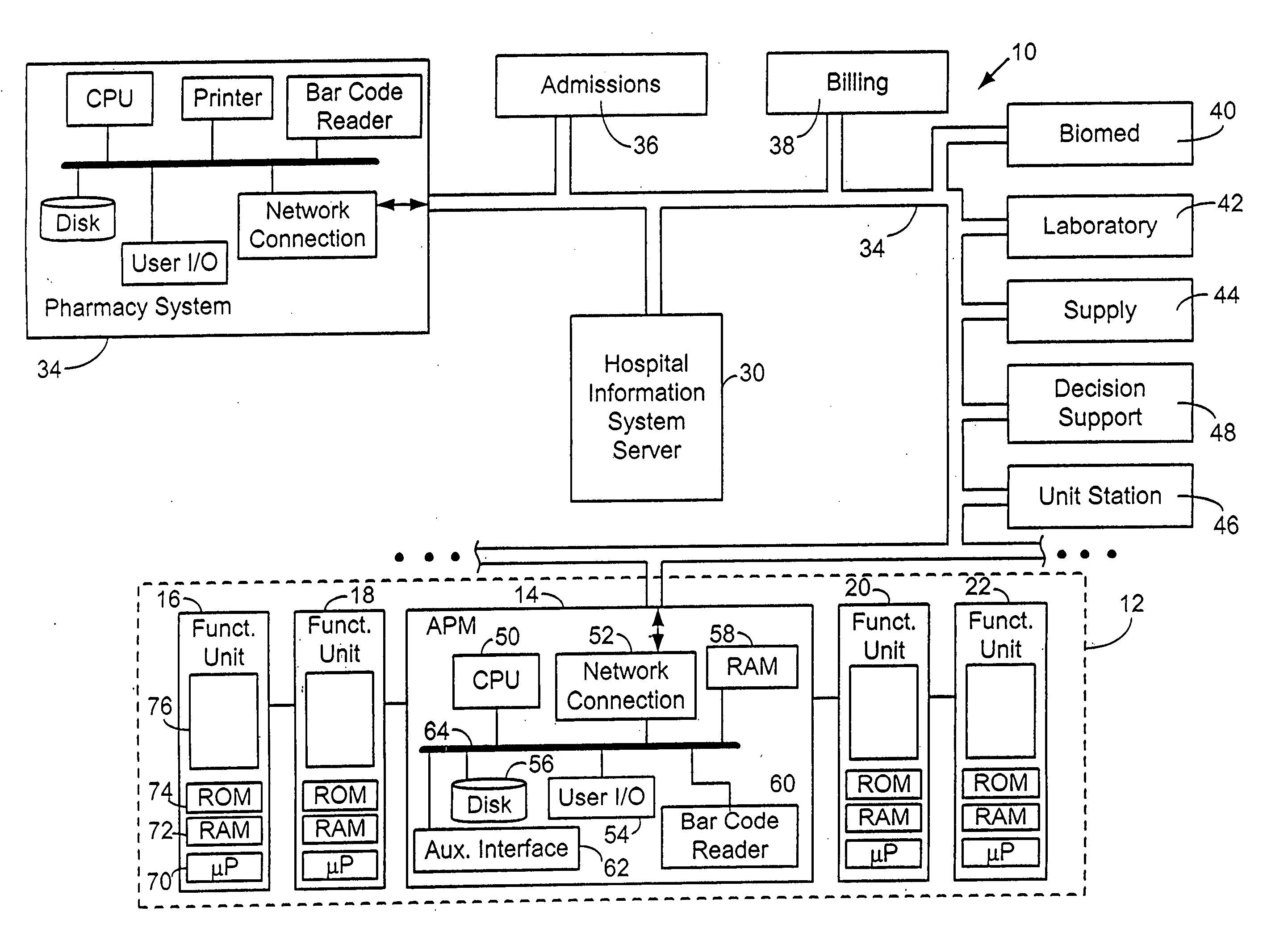
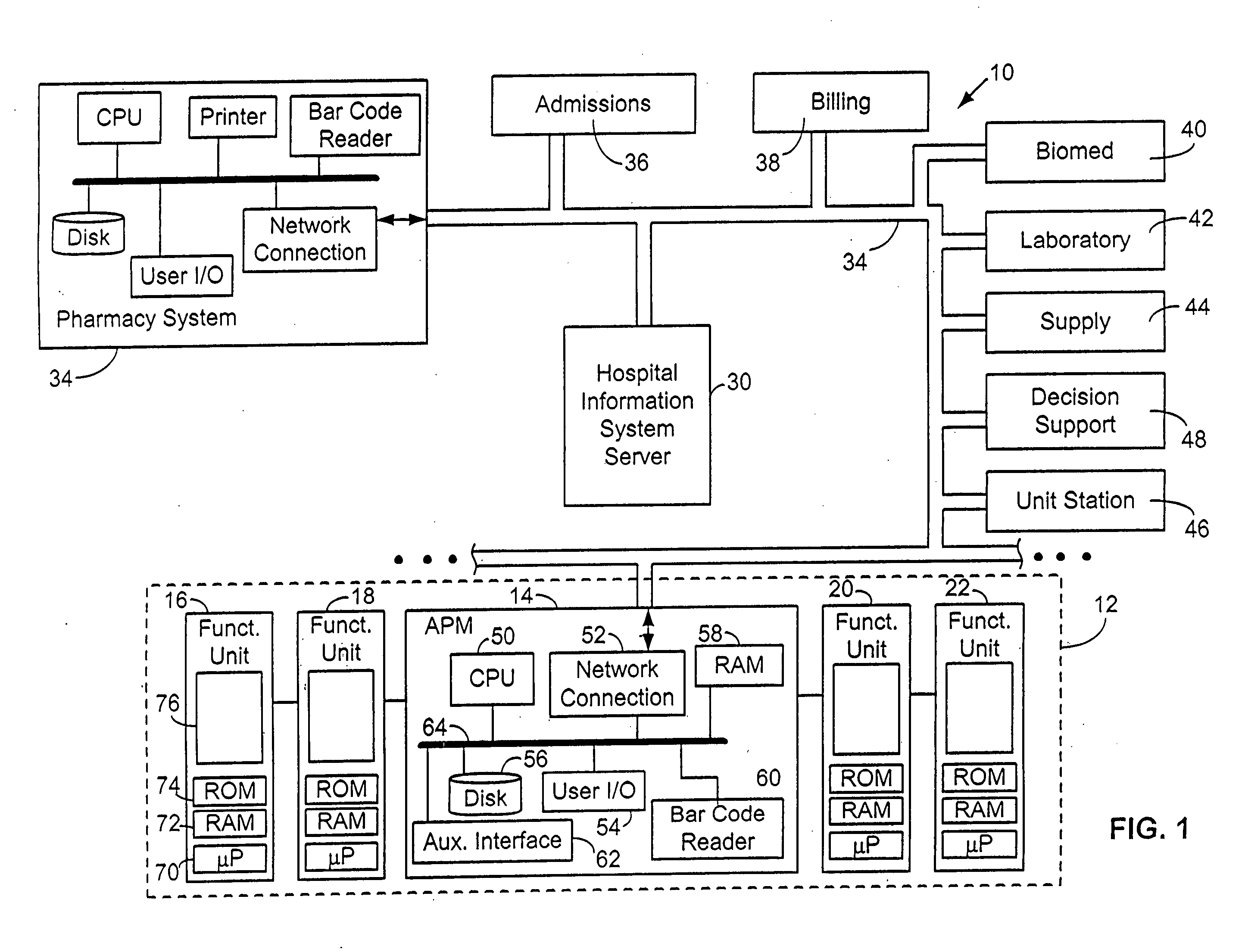
Method for programming a patient care device
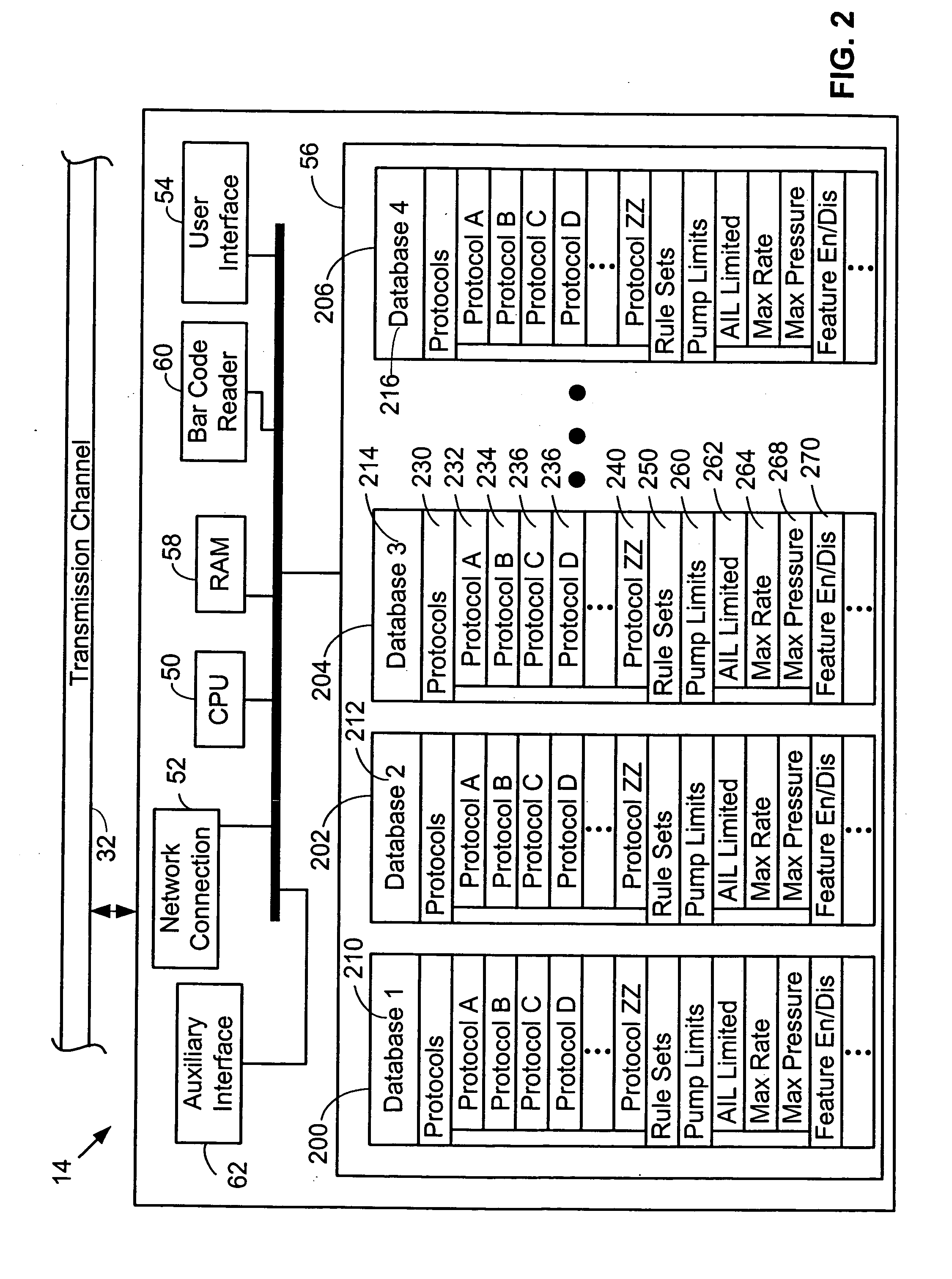
InactiveUS20060106649A1Improve quality of careReduce labor costsCoupling device connectionsDrug and medicationsDrugs labelHospital network
The present invention is directed to a system and method for providing care to a patient, comprising a patient care device having a number of configuration databases stored in a memory in the device. Each configuration database preferably includes protocols, operating limits, rule sets and / or operating features that collectively define an operating environment, or personality, of the device. Selection of a specific configuration database preferably is based at least in part upon patient-specific information obtained from any location in a distributed hospital network. Examples of such patient-specific information include patient age or size, patient medical characteristics, a location of the patient or a location of the care device. In a preferred embodiment, programming a patient care device to deliver a drug to a patient entails activating a configuration database and scanning a machine-readable drug label identifying a particular protocol stored in the activated database. The selected protocol includes default parameters for delivering the drug, and the label optionally includes instructions for deviating from the default protocol.
Owner:CAREFUSION 303 INC
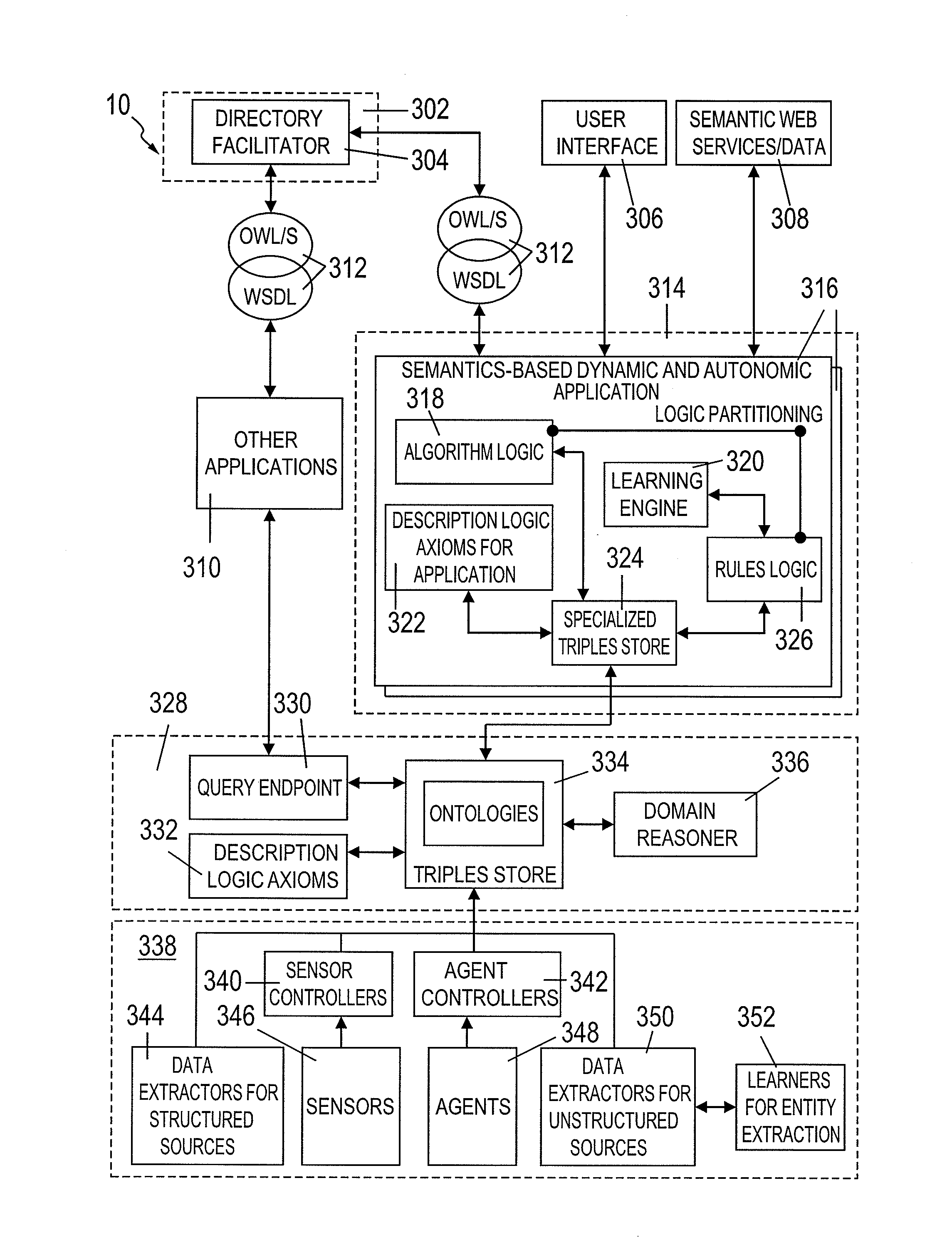
System for supporting coordination of resources for events in an organization
A system and method for supporting coordination of resources for events in an organization includes a knowledge component storing a resource-utilization model, the resource-utilization model comprising at least one ontology, each ontology comprising a respective schema and data stored according to the schema; a knowledge acquisition component adapting the resource-utilization model in real-time in response to receiving data from various sources about resource utilization in the organization; a domain reasoner adapting the resource-utilization model based on contents of a modifiable set of rules applied by the organization; and a query endpoint receiving queries about resources for events and responding to the queries based on the resource-utilization model.
Owner:SMART TECH INC (CA)
Overload protection for SIP servers
InactiveUS7522581B2Data switching by path configurationNetwork connectionsComputer scienceDistributed computing
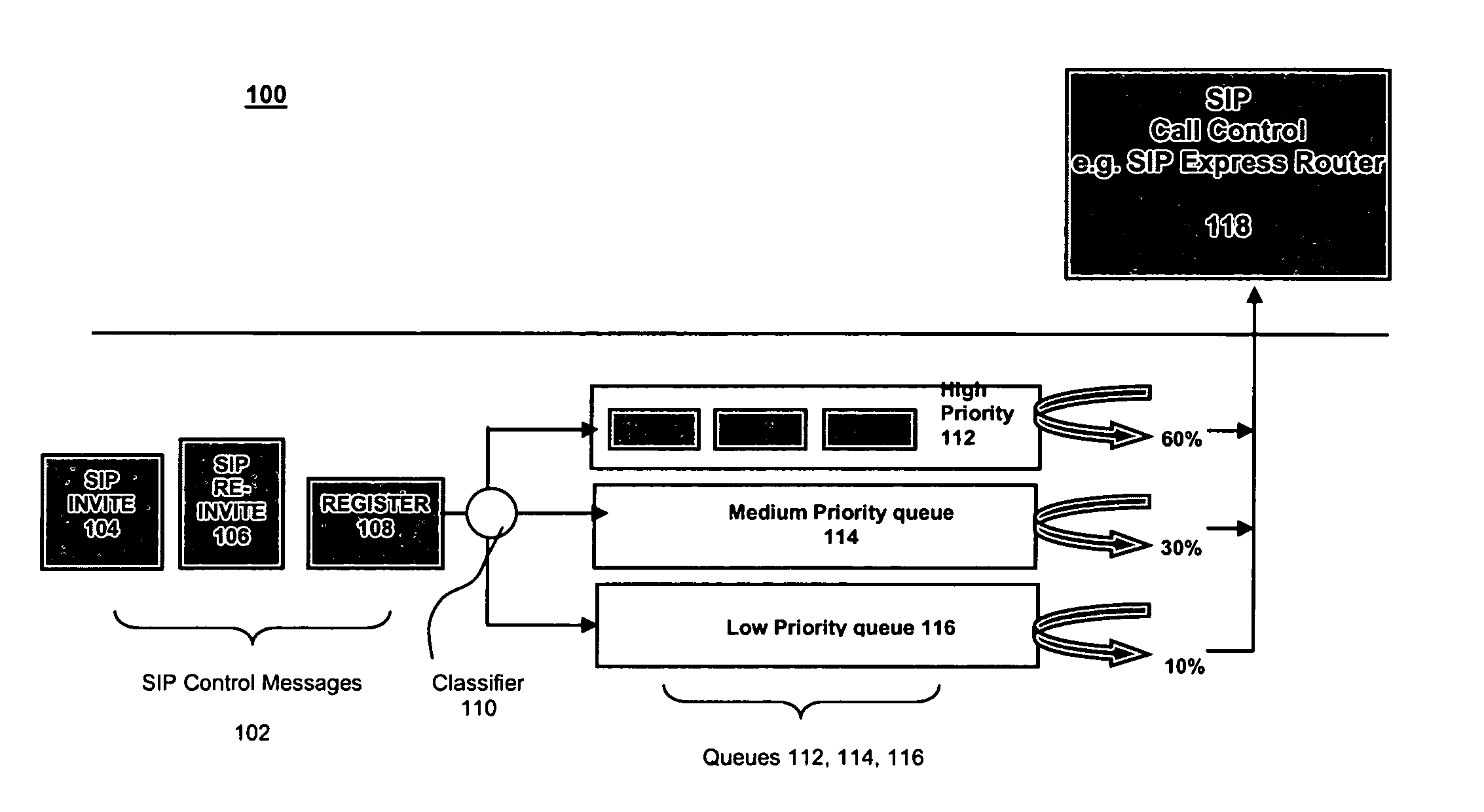
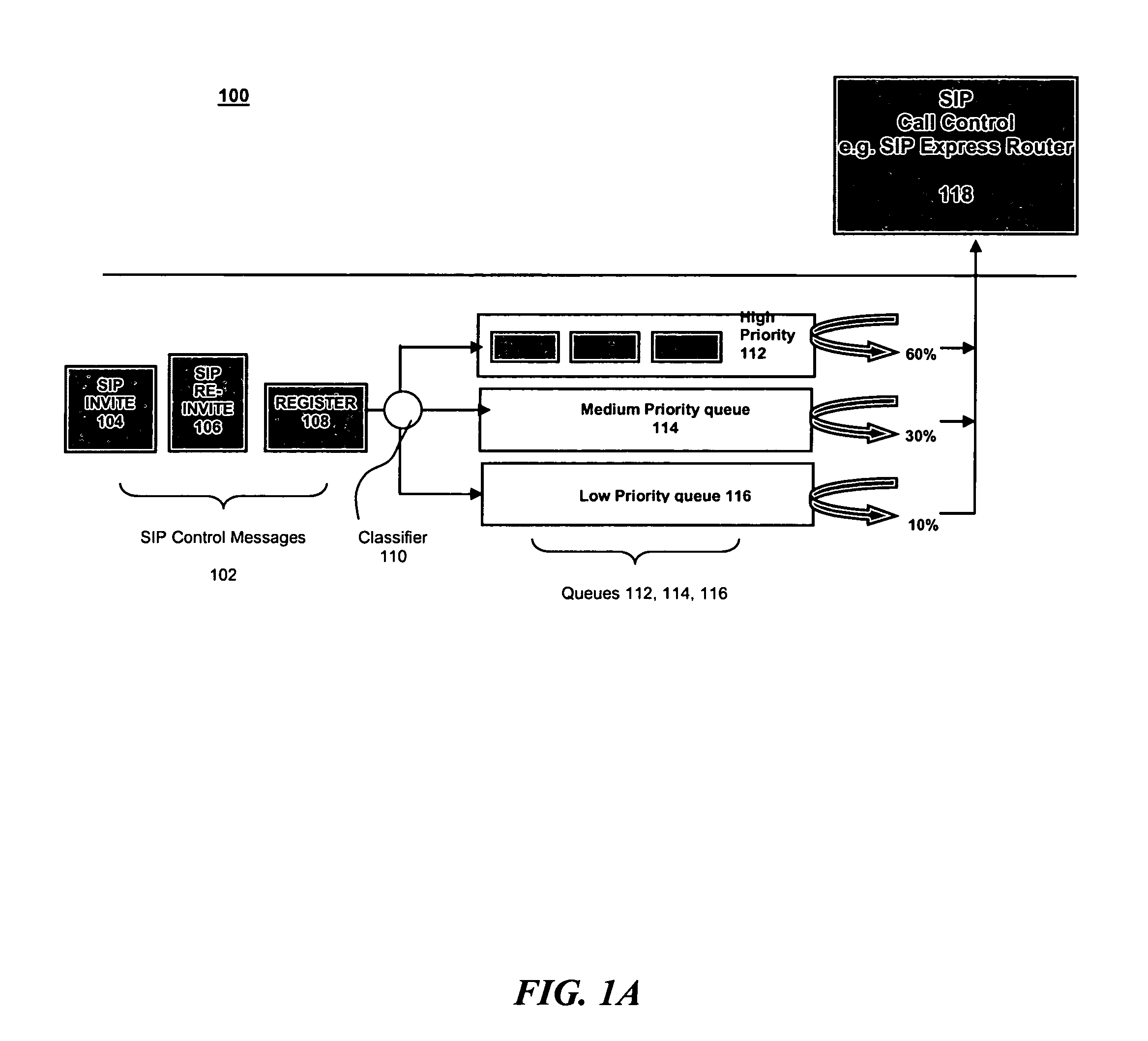
A method for operating a server having a maximum capacity for servicing requests comprises the following steps: receiving a plurality of requests; classifying each request according to a value; determining a priority for handling the request according to the value, such that requests with higher values are assigned higher priorities; placing each request in one of multiple queues according to its priority value; and dropping the requests with the lowest priority when the plurality of requests are received at a rate that exceeds the maximum capacity. The server operates according to a session initiation protocol.Classifying each request comprises running a classification algorithm. The classification algorithm comprising steps of: receiving a rule set, each rule comprising headers and conditions; creating a condition table by taking a union of all conditions in the rules; creating a header table by extracting a common set of headers from the condition table; extracting the relevant headers from the header table; determining a matching rule; creating a bit vector table; selecting the matching rule according to data in the bit vector table; and applying the rule to place the message in the appropriate queue.
Owner:INT BUSINESS MASCH CORP
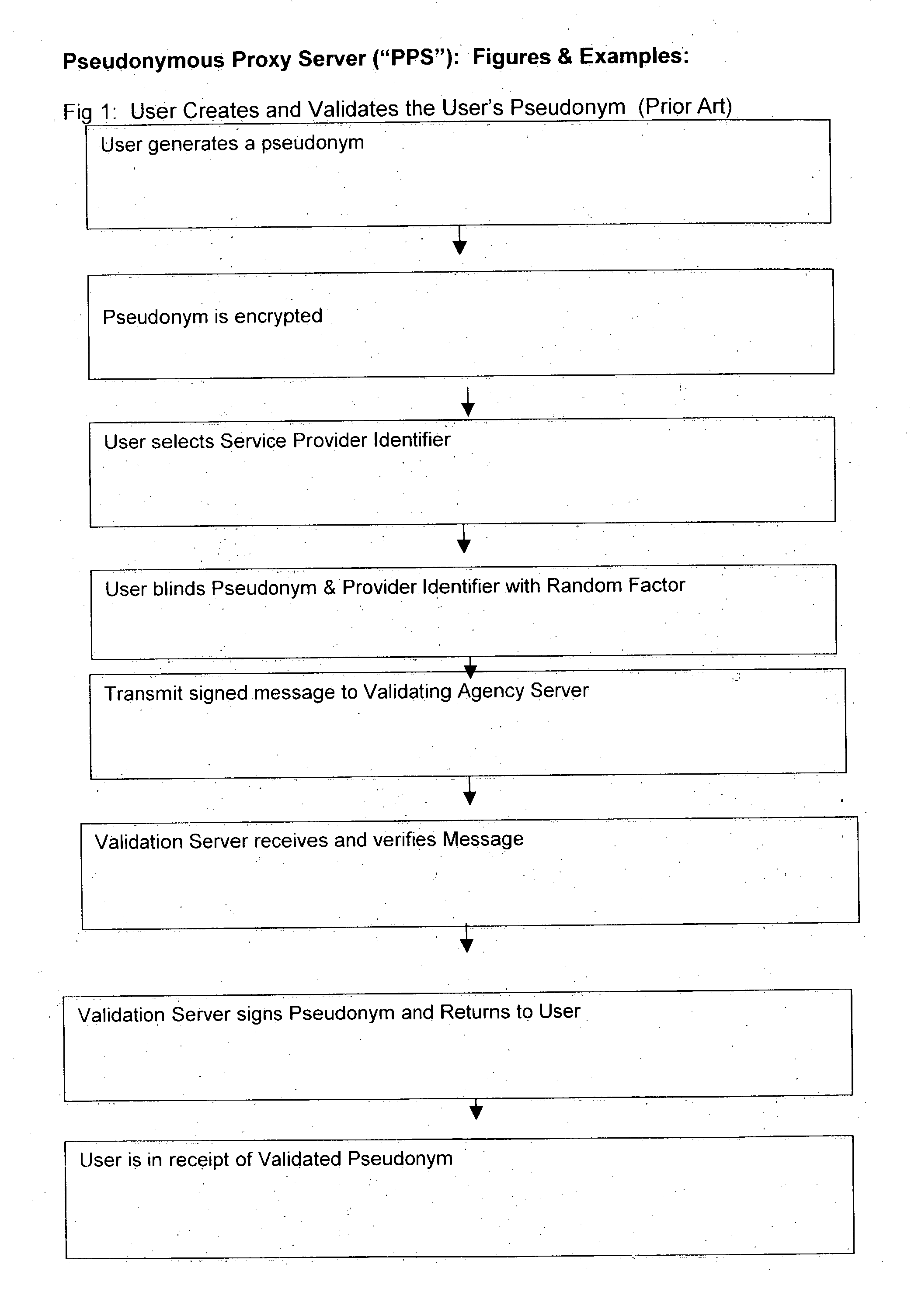
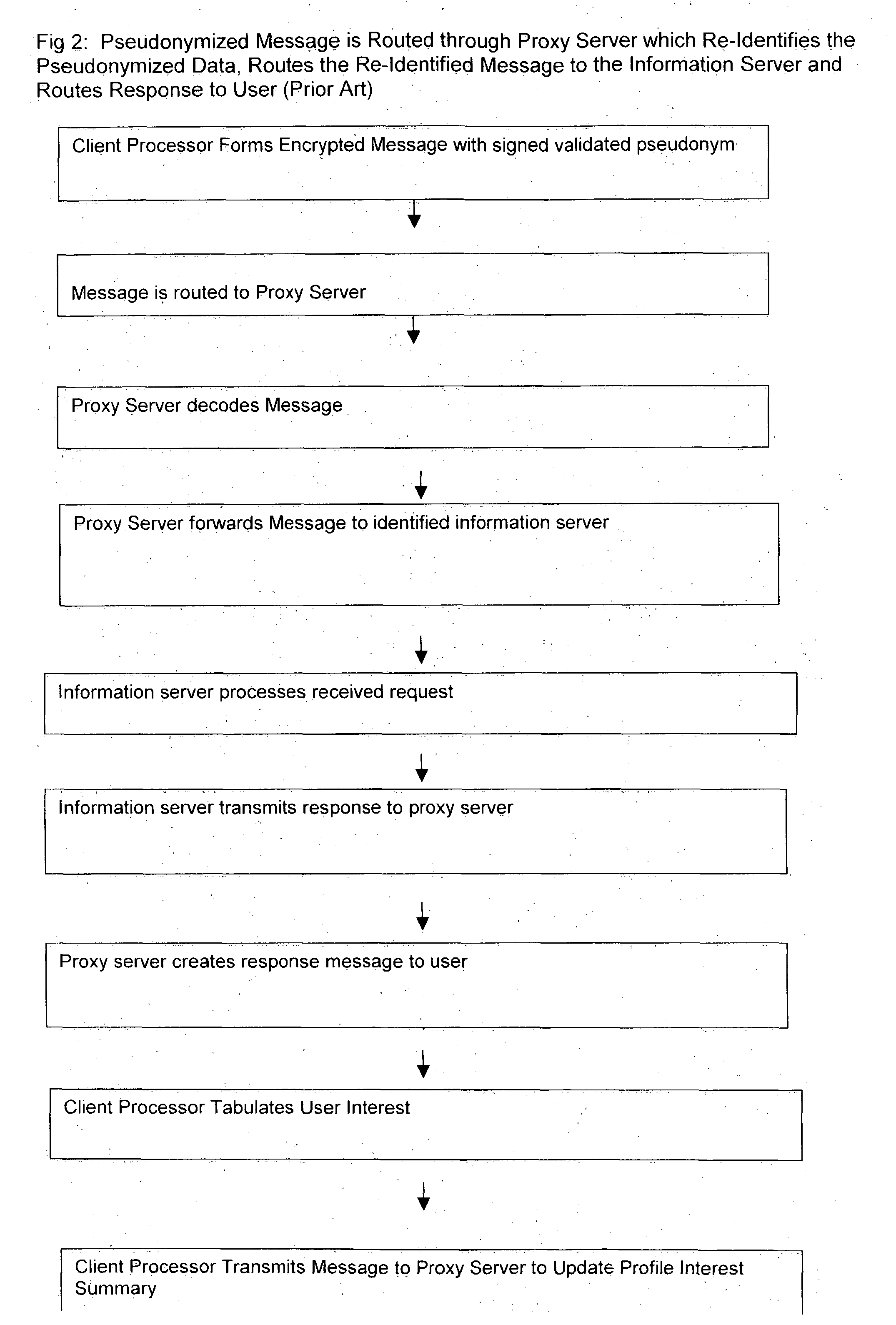
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
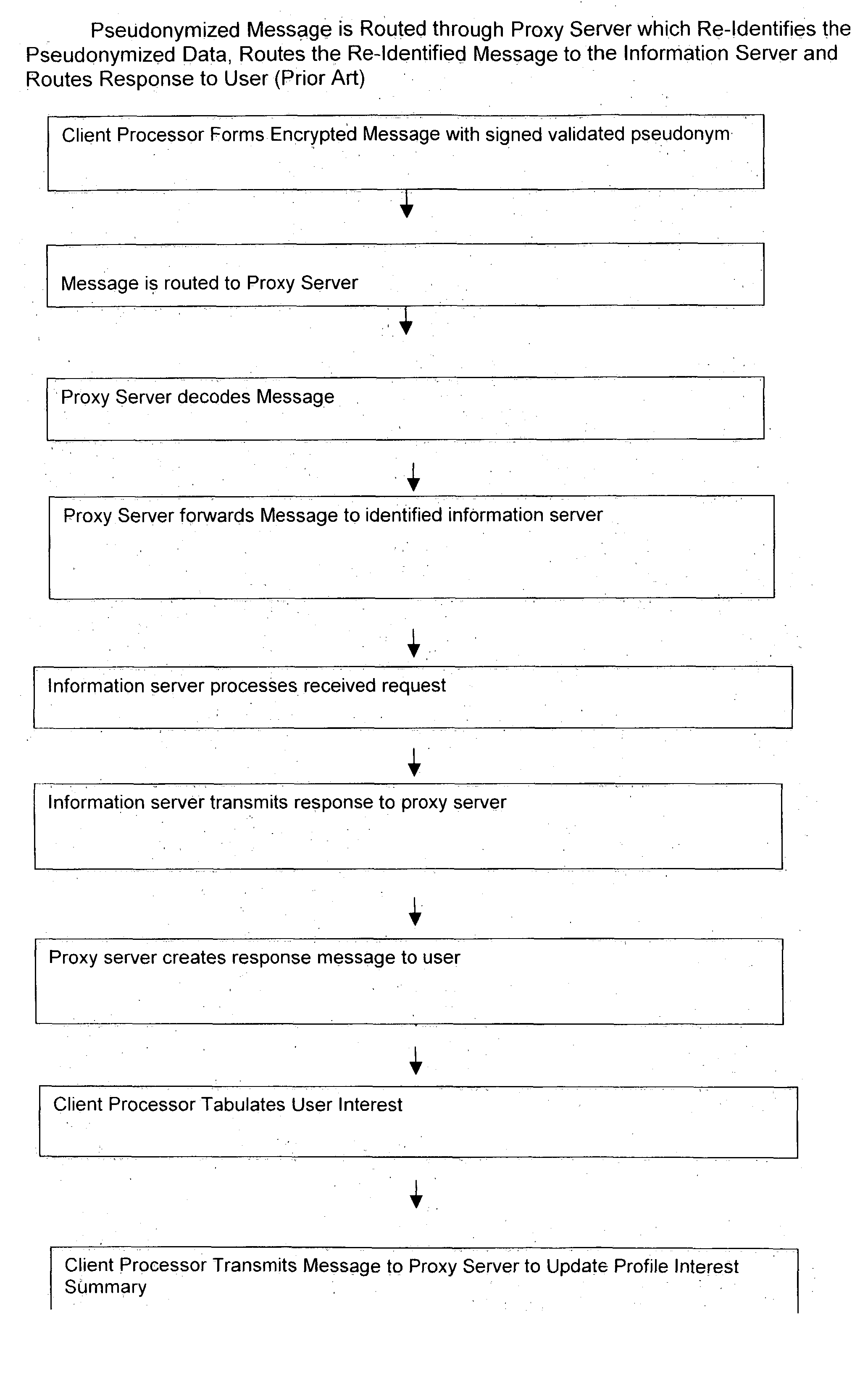
InactiveUS20060031301A1Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsInternet privacyData access
A system is provided that preserves data privacy for the Individual—I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User—U, Individual—I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
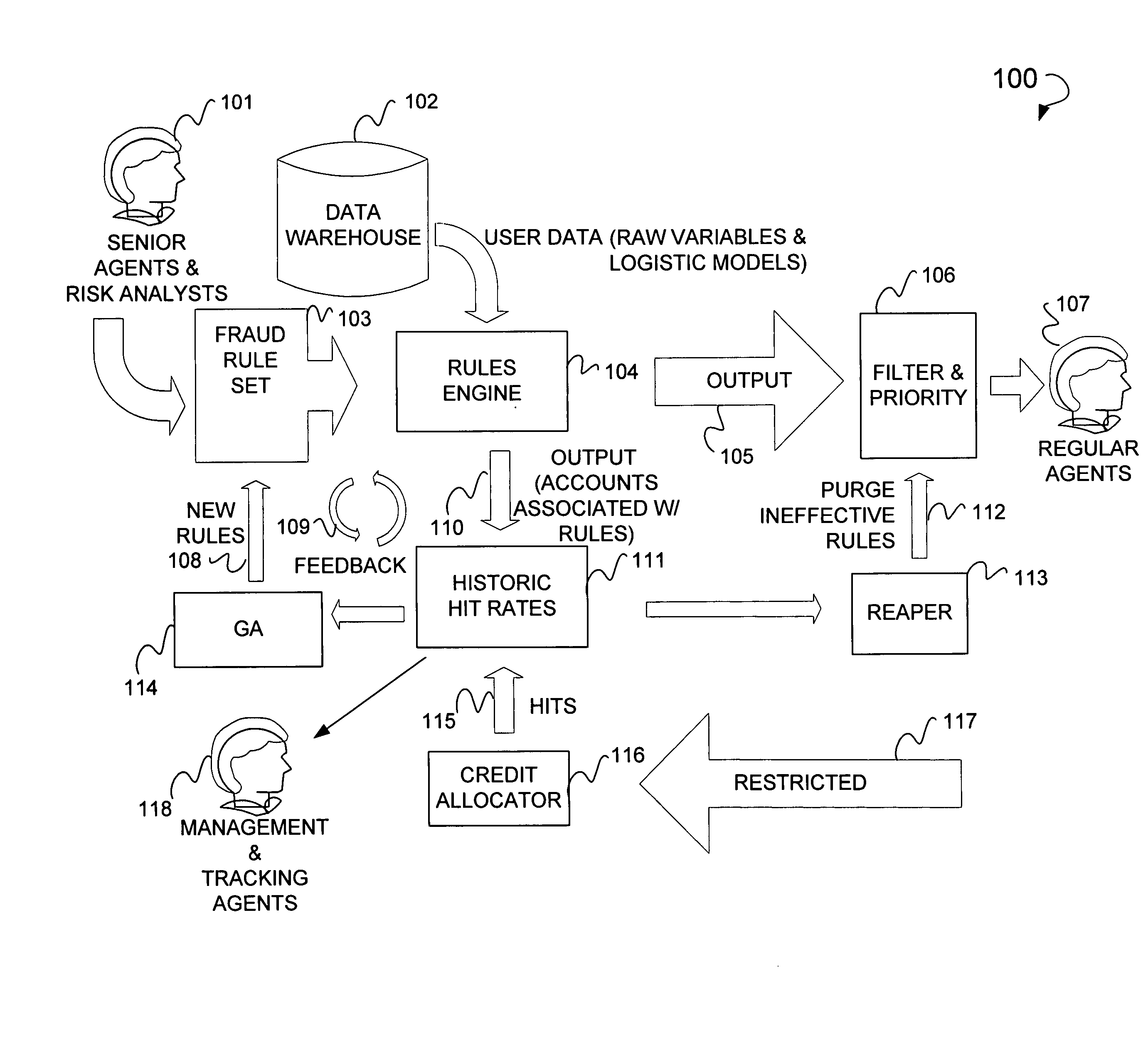
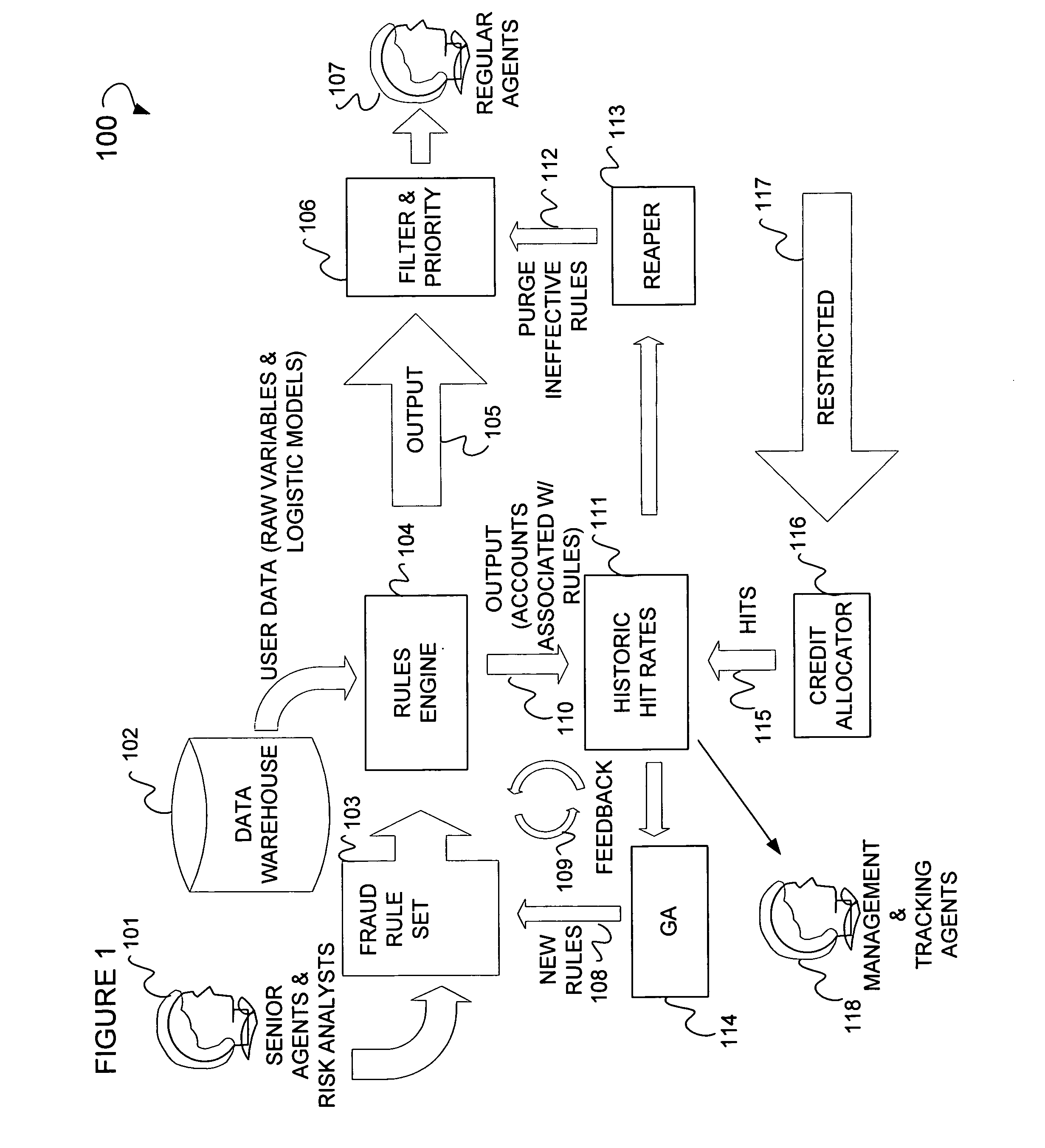
Online fraud prevention using genetic algorithm solution
Online fraud prevention including receiving a rules set to detect fraud, mapping the rules set to a data set, mapping success data to members of the rules set, filtering the members of the rules set, and ordering members of the data set by giving priority to those members of the data set with a greater probability for being fraudulent based upon the success data of each member of the rule set in detecting fraud. Further, a receiver coupled to an application server to receive a rules set to detect fraud, and a server coupled to the application server, to map the rules set to a data set, and to map the success data to each members of the rules set. The server is used to order the various members of the data set by giving priority to those members of the data set with a greatest probability for being fraudulent.
Owner:PAYPAL INC
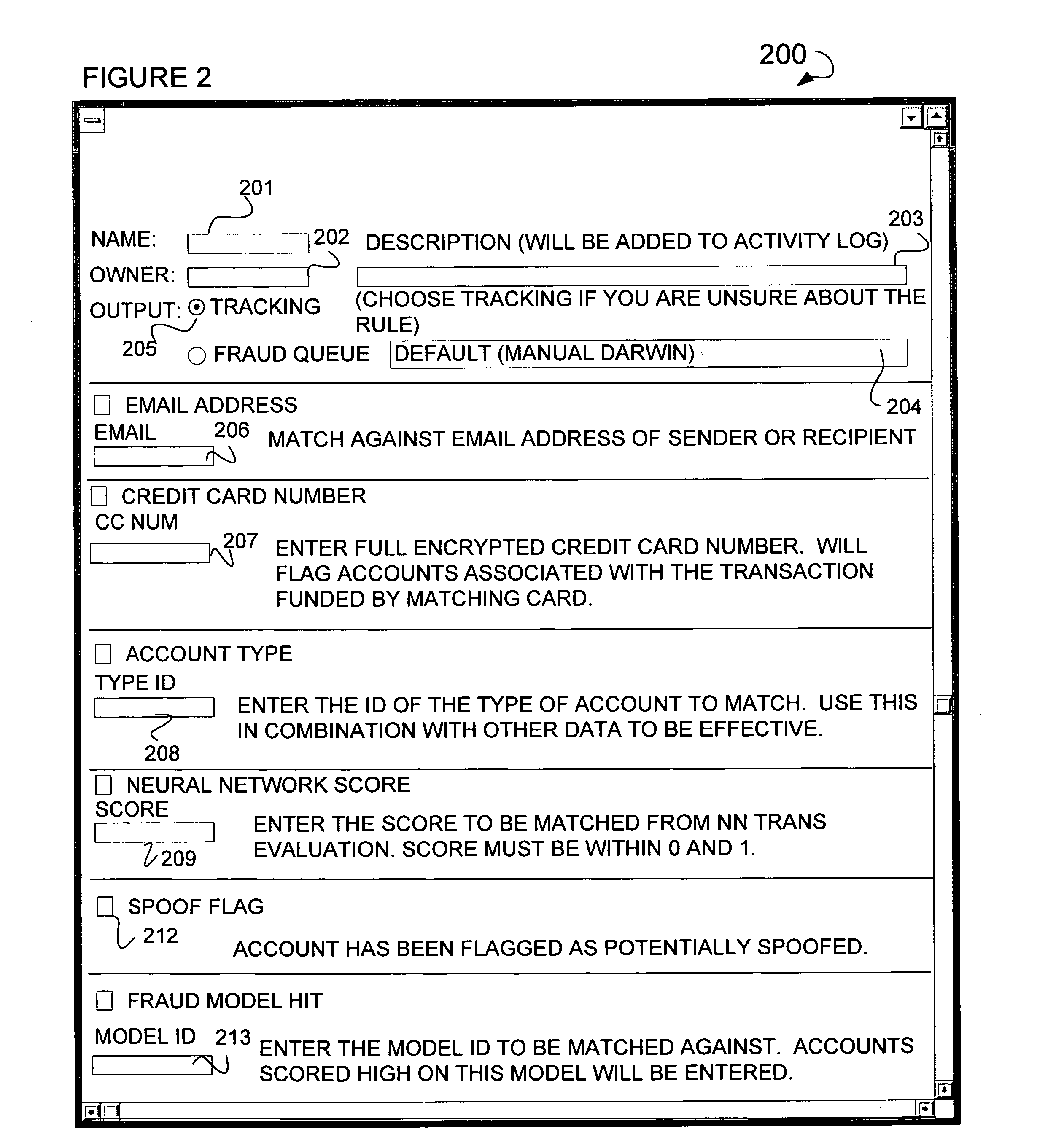
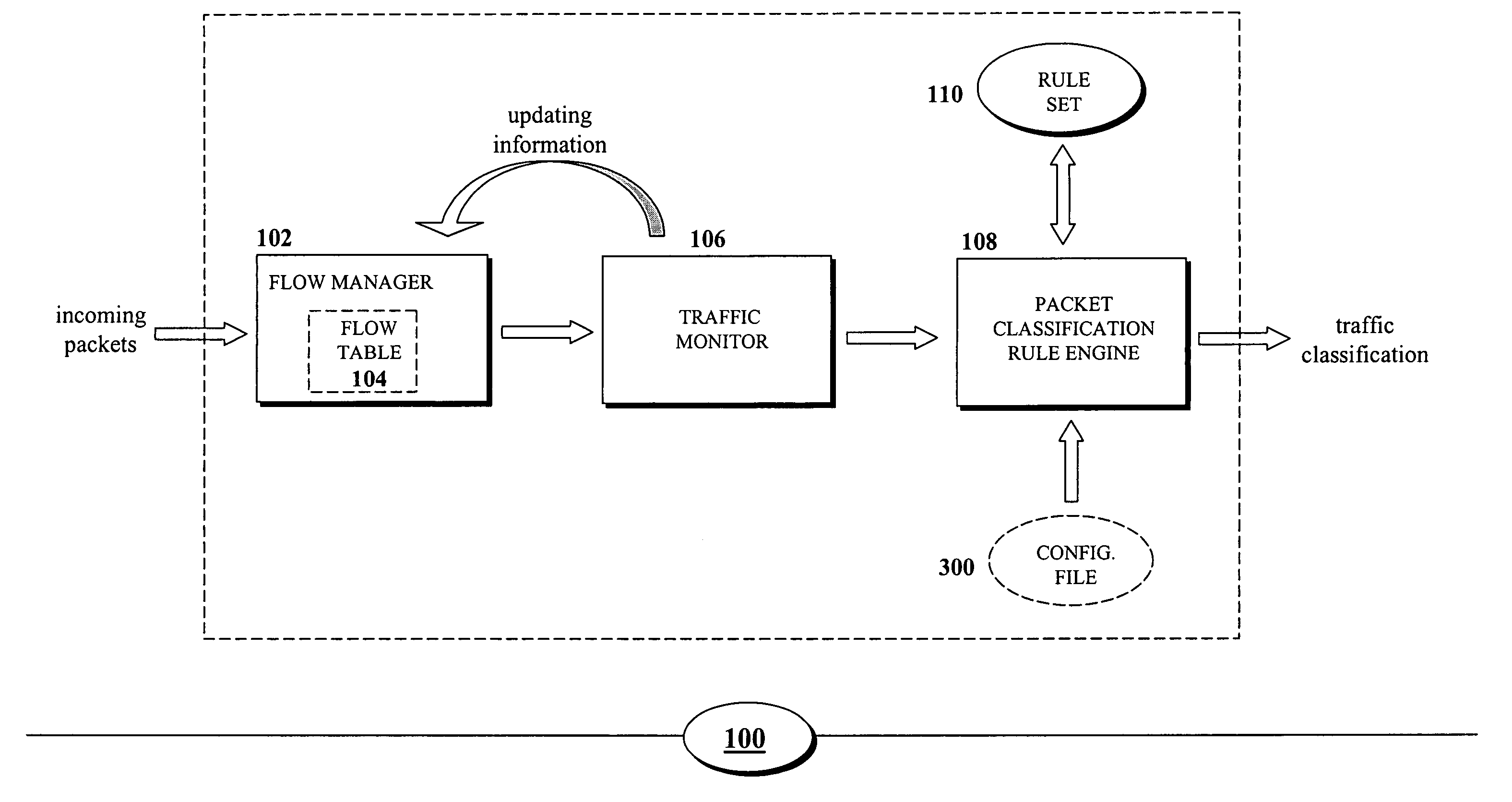
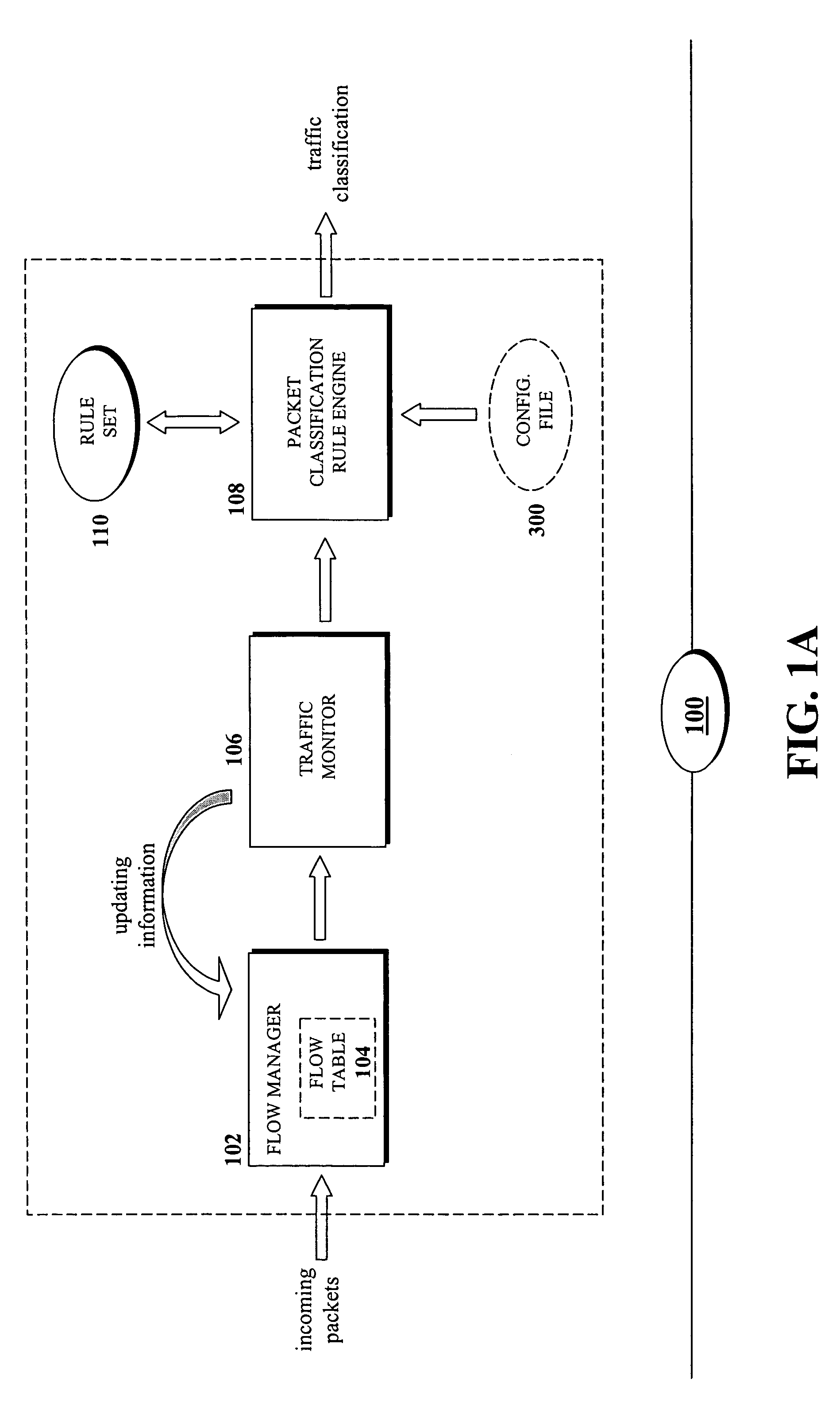
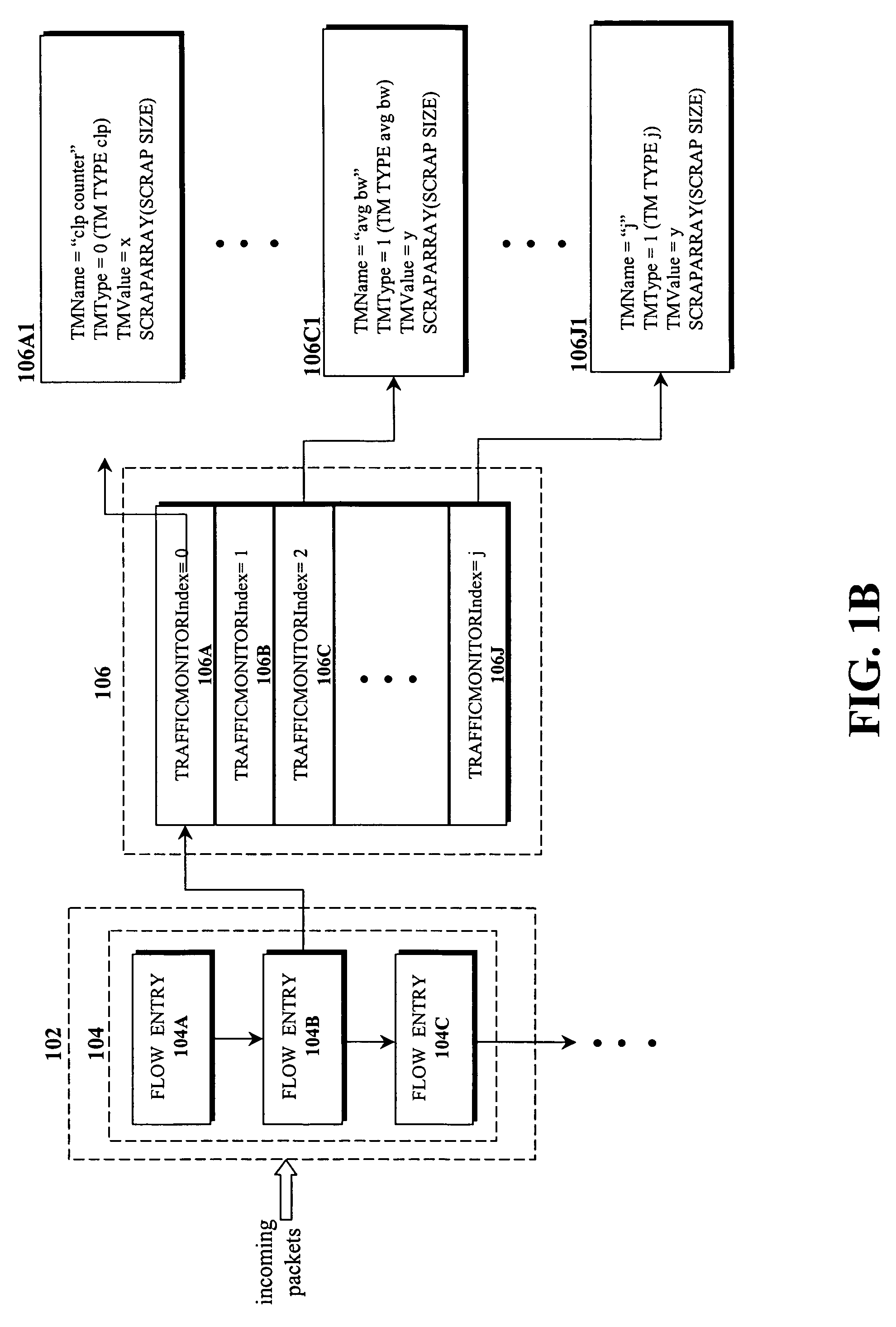
Configurable rule-engine for layer-7 and traffic characteristic-based classification
A system and method for data flow classification based on a configurable rule-engine, is presented herein. In accordance with an embodiment of the invention, the system includes a data flow managing mechanism configured to identify, track, and manage the data flows and a rule set, which includes a plurality of rules for comparing information contained within data flow with pre-specified values. The system also includes a configurable classification rule engine for classifying the data flows into one of a plurality of traffic classes based on results of the comparisons. The configurable classification rule engine is configured via a configuration file that specifies and allows for the modification and reconfiguration of the pre-specified values and information regarding the data flows, the rule set, and the traffic classes.
Owner:RPX CLEARINGHOUSE
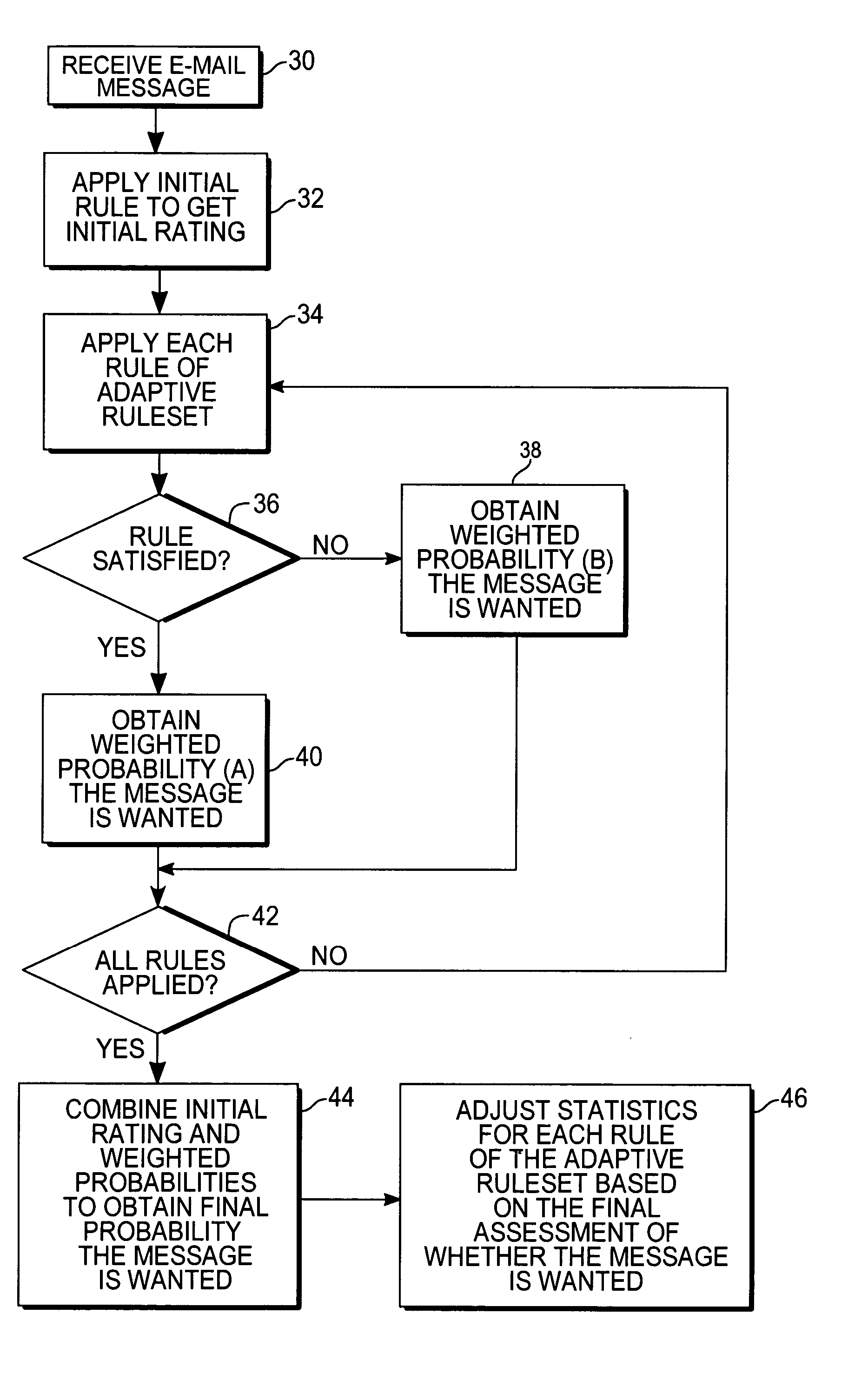
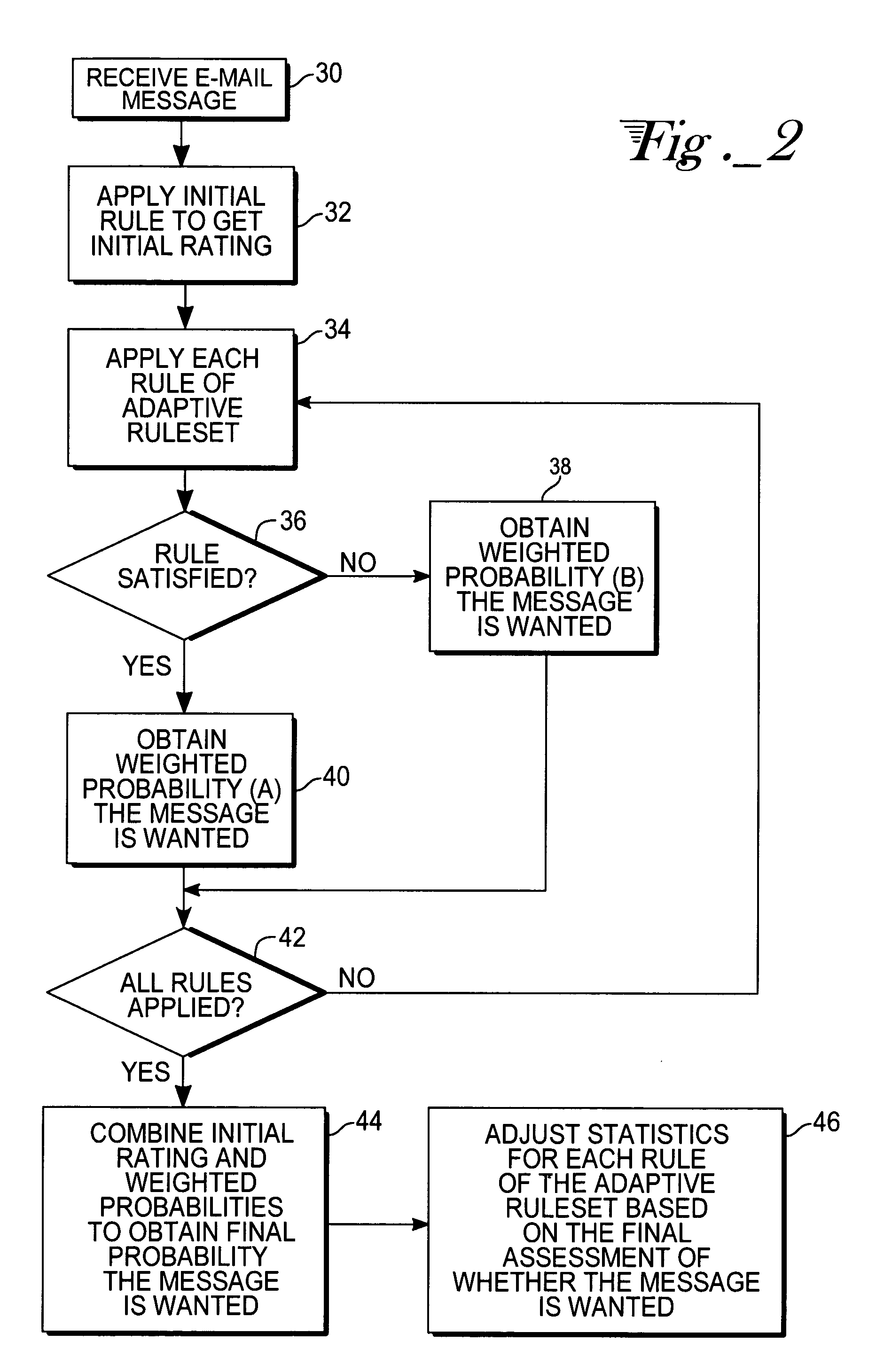
E-mail filter employing adaptive ruleset
InactiveUS20050102366A1Accurate initial rating of the messageMultiple digital computer combinationsElectric digital data processingUser inputSelf adaptive
An e-mail filter employing an adaptive ruleset for classifying received e-mail messages. The individual rules of the ruleset are applied to all or some received e-mail messages, depending on the configuration of the filter. In some embodiments, an initial rule or filter is applied to the message to obtain an initial rating indicating whether the recipient would want the message. Statistics collected for each rule in the ruleset are used to determine a weighted probability the message is wanted. A different weighted probability is obtained if the rule is satisfied or if the rule is not satisfied. A final probability the message is wanted is obtained after applying the filter's adaptive ruleset and using a weighted average to combine that score with any other rules and the message is processed accordingly. Statistics are updated using the machine-generated final probability, so the adaptive ruleset of the filter is constantly updated without requiring user input.
Owner:ABACA TECH CORP
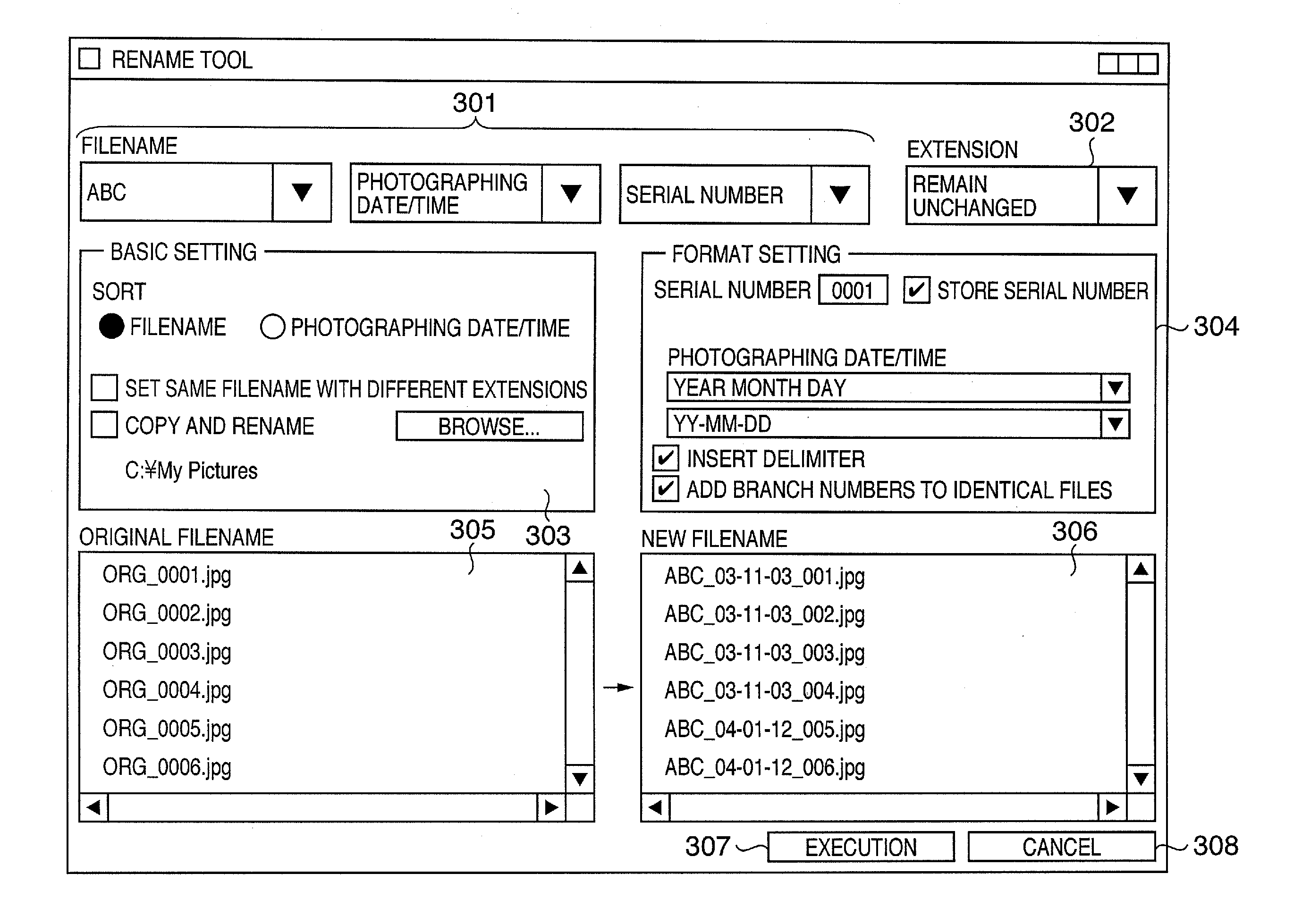
File Management Apparatus and Its Control Method
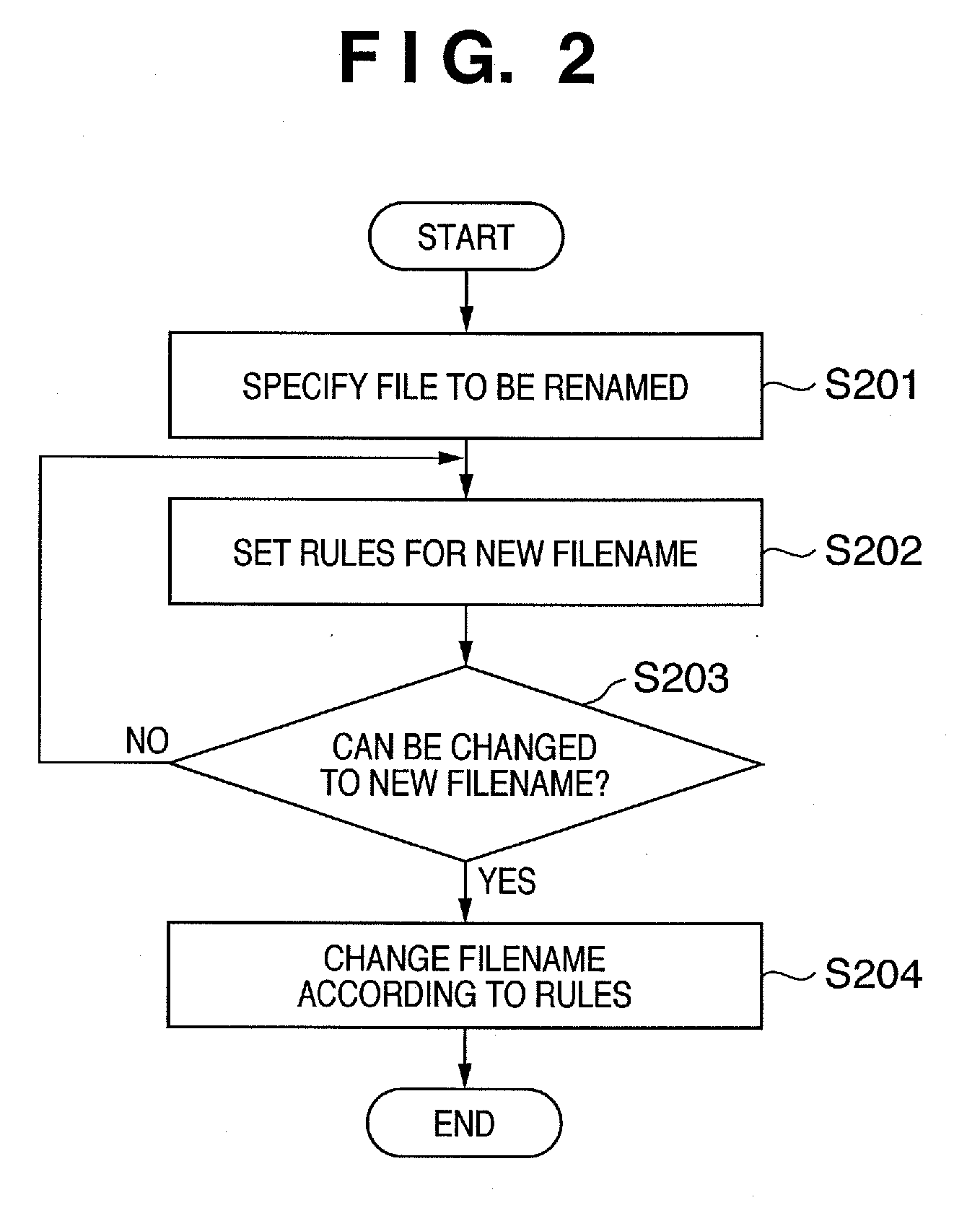
InactiveUS20060174054A1Digital data information retrievalUnauthorized memory use protectionHuman–computer interactionRule sets
A new filename after change is generated based on rules set using a filename setting menu (301), extension format selection menu (302), basic setting menu (303), and format setting menu (304), and is displayed on a new filename list display window (306). In this case, if the new filename is unusable, it is displayed in distinction from other filenames, thus informing the user of it. A file management apparatus can detect in advance whether or not an error may occur upon changing the filename and can notify the user of such error.
Owner:CANON KK
XML patterns language
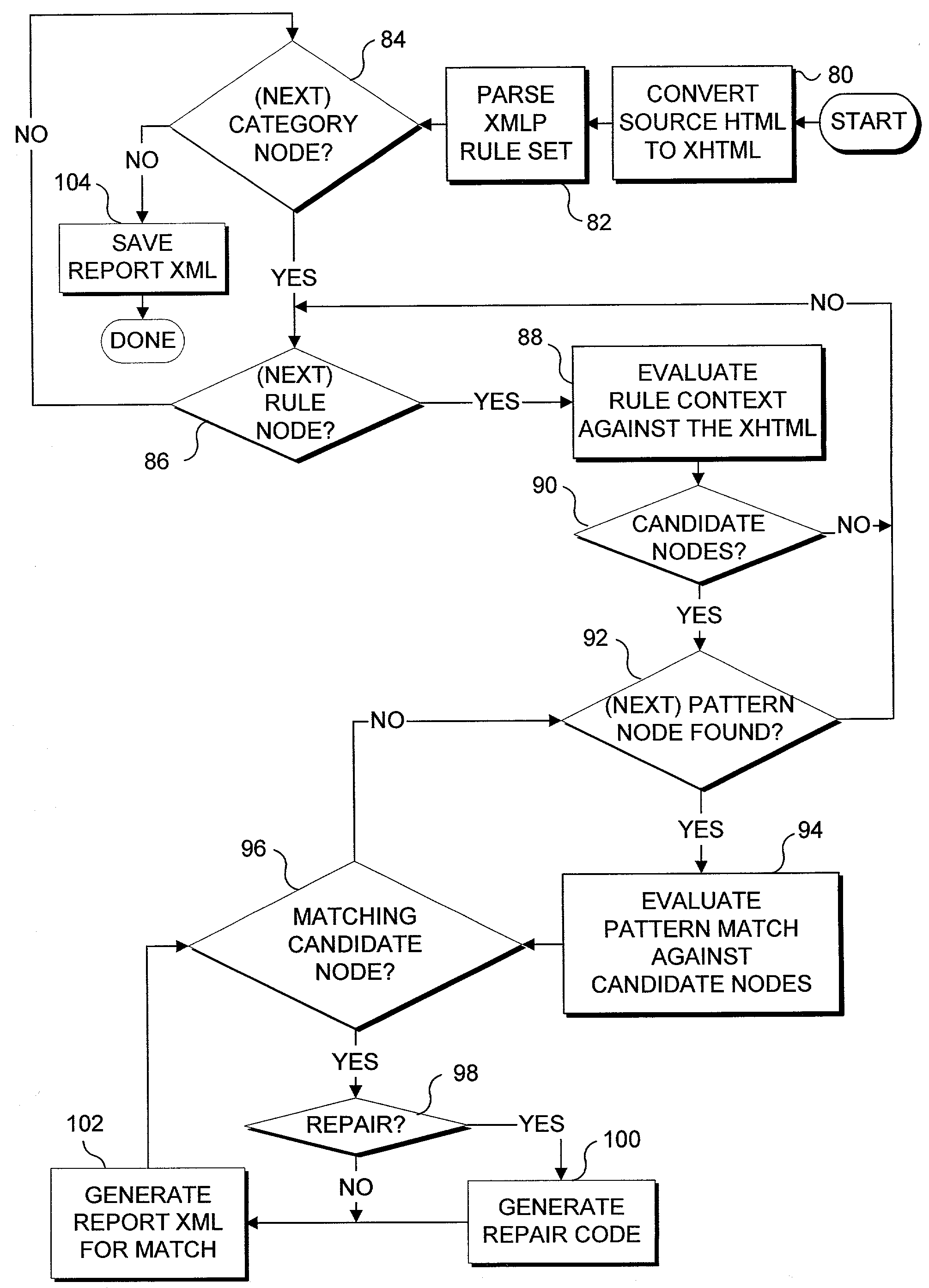
InactiveUS7240279B1Digital data processing detailsNatural language data processingGuidelinePattern matching
Evaluating a source document for compliance with a rule set that represents contextual guidelines to which the source document must conform. The rule set comprises a rule node that includes a context that is compared to the source document to identify candidate nodes for further evaluation. Each rule node also includes a descendant pattern node that includes a pattern matching expression representing at least one aspect of the contextual guidelines to which the source document must conform. Preferably a match between a candidate node and the pattern matching expression indicates a nonconformance to the contextual guideline(s), and a predefined action is initiated. Predefined actions include reporting the nonconformance, and automatically repairing the nonconformance through script code.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for automated data storage and retrieval
InactiveUS7013298B1Low costMaximize end-user accessibilityDigital data information retrievalFinanceSystem identificationData store
A system and method for creating links between first records stored on a database and references to the first records within a second record, the system including a data reference list including keywords or phrases which may be used in the second record to reference the first records, the system also including address formats corresponding to each data reference which indicate the form of a first record address corresponding to the data reference, the system also including record rule sets for gleaning information from the second record for populating the address format, when a data reference is identified, the system identifying the corresponding address format, gleaning address information from the second record, forming the record address and linking the first record reference to the first record via the record address.
Owner:HYPERPHRASE TECH
Method and apparatus for interactive real time distributed gaming
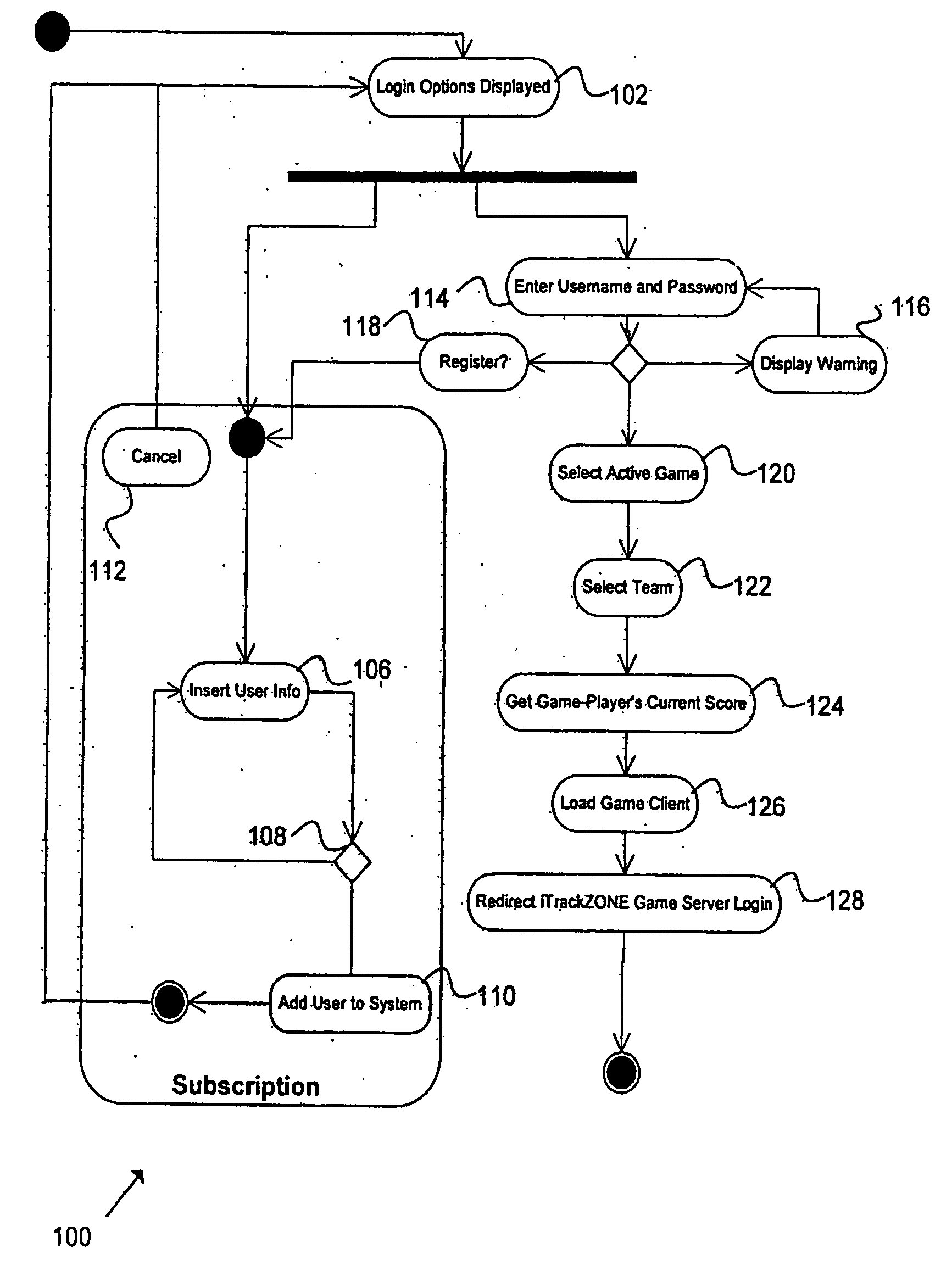
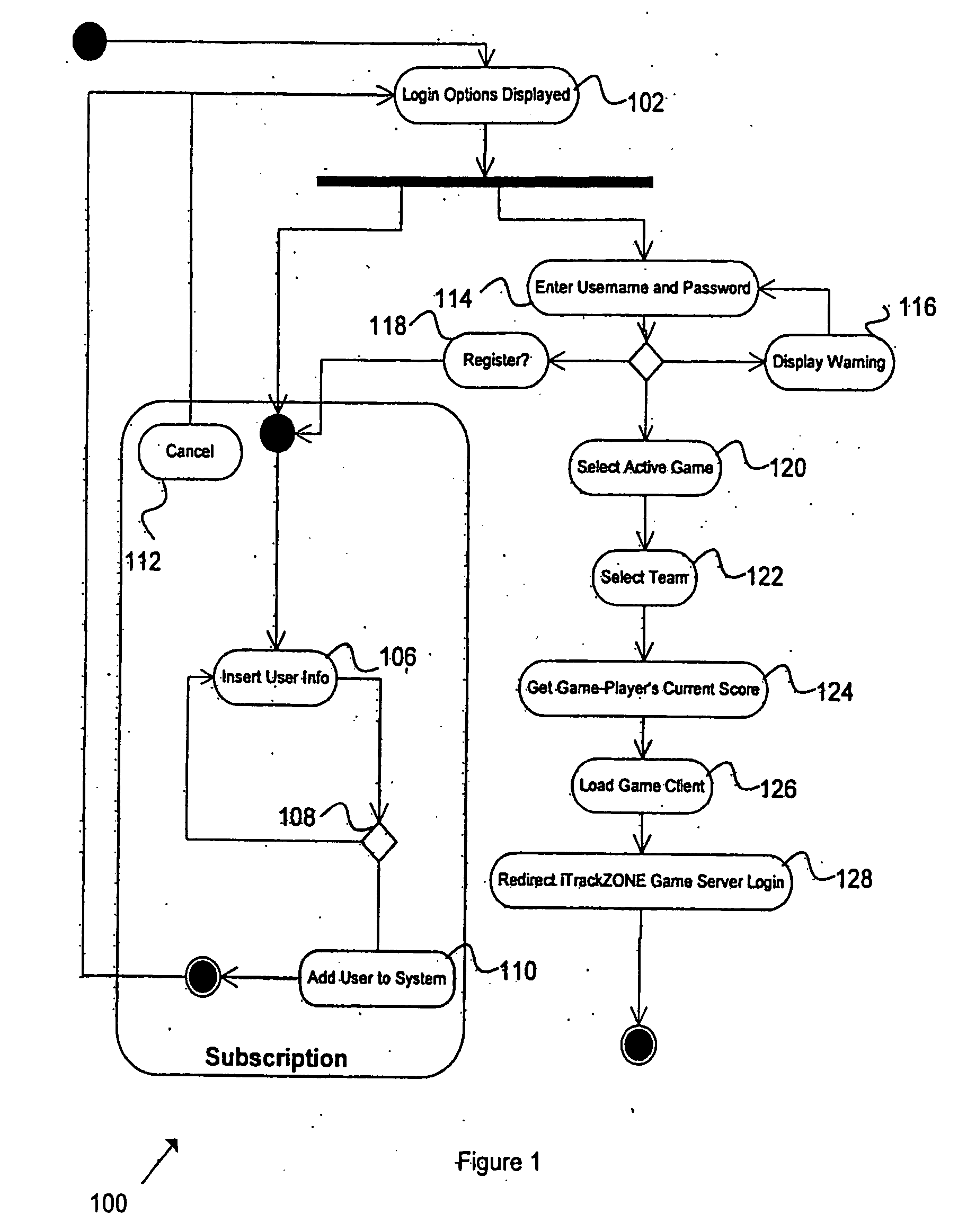
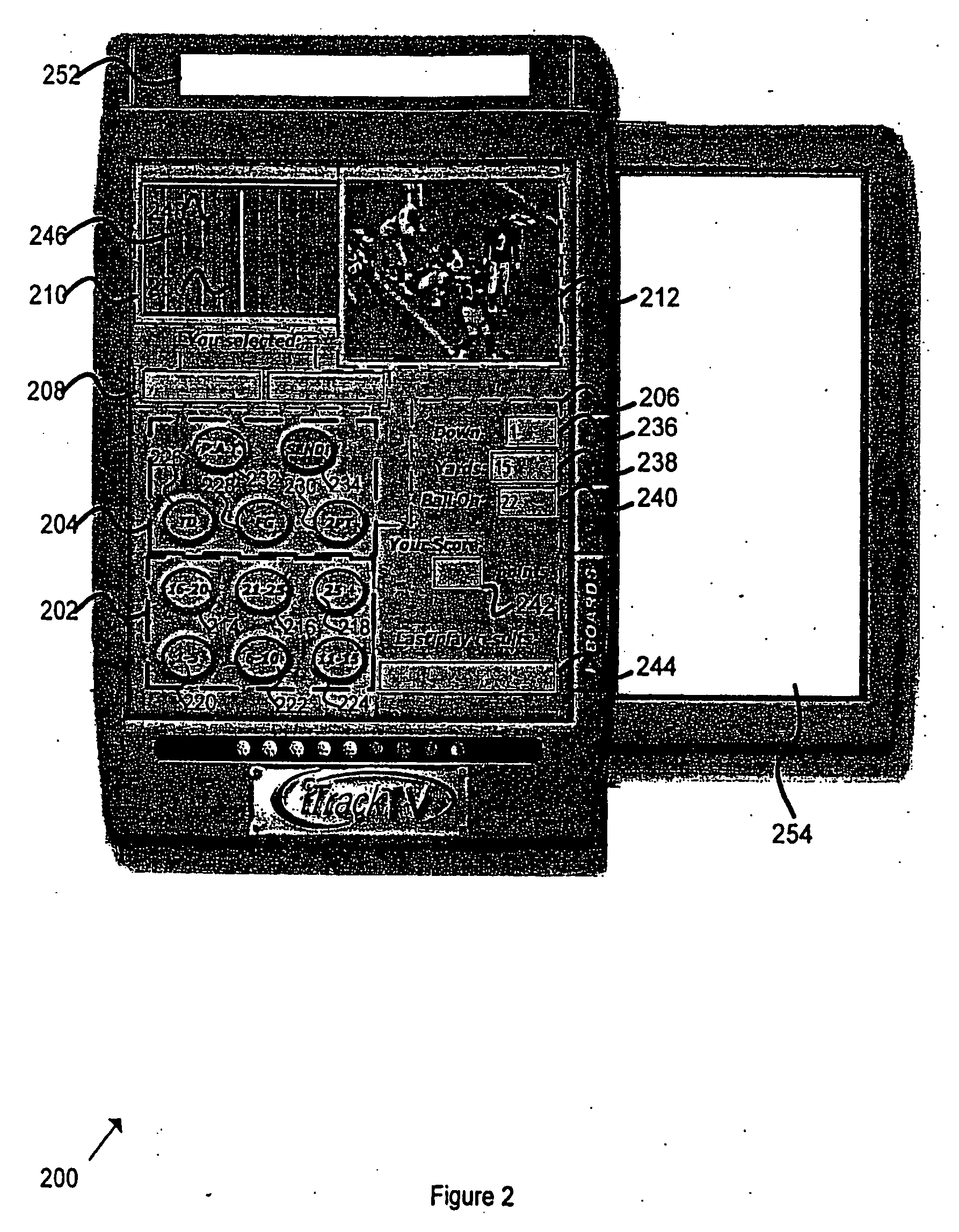
The present invention relates to an apparatus, system and method for playing interactive distributed gaming. One embodiment of the method comprises transmitting a performance prediction to a scoring database on a game server and determining an actual performance outcome. The actual performance outcome representation is transmitted to a remote terminal. The performance prediction is scored based on the actual performance outcome. In at least one embodiment, a predetermined ruleset is used to score the performance prediction based on the actual performance outcome.
Owner:JORDAN KENT WILCOXSON +1
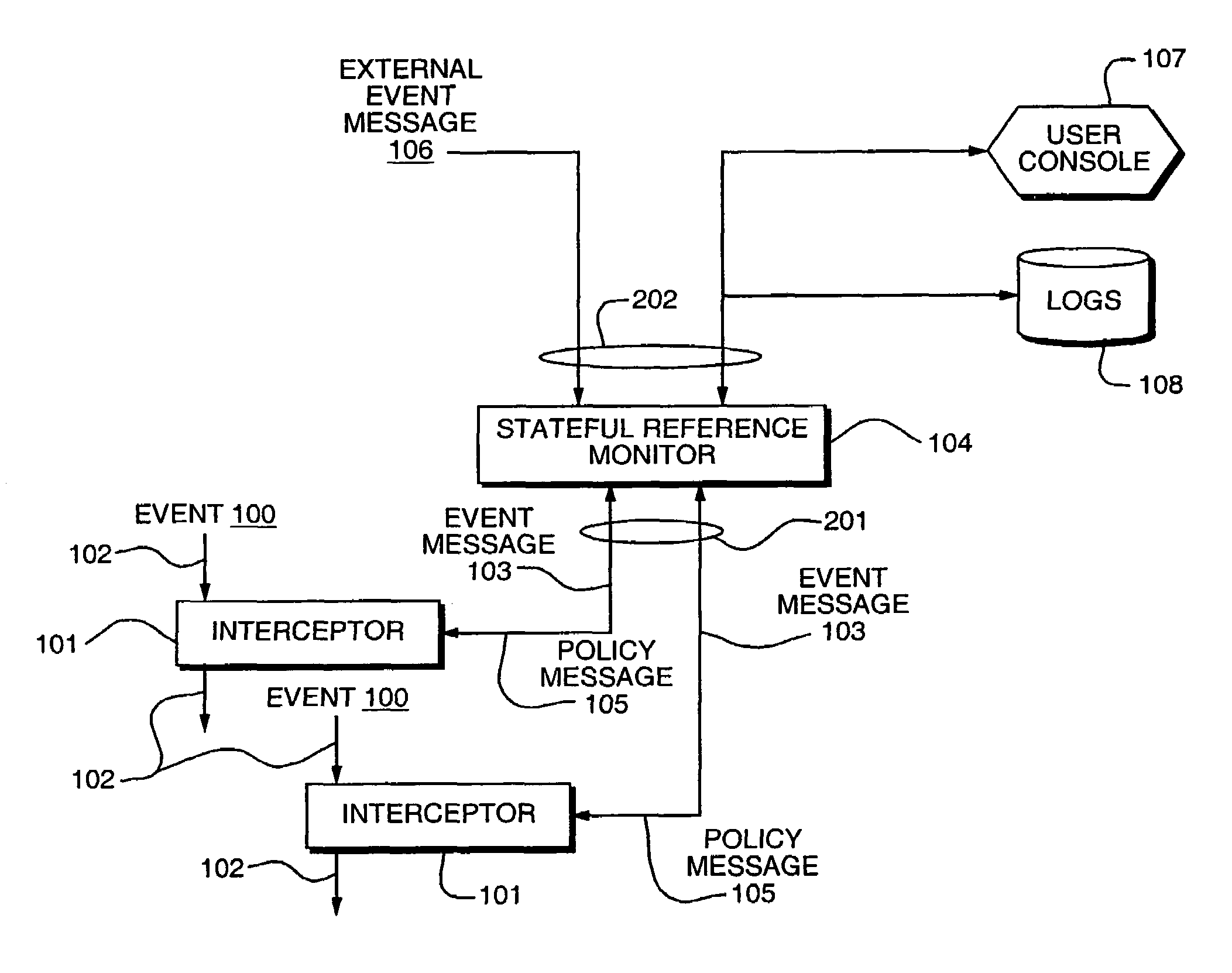
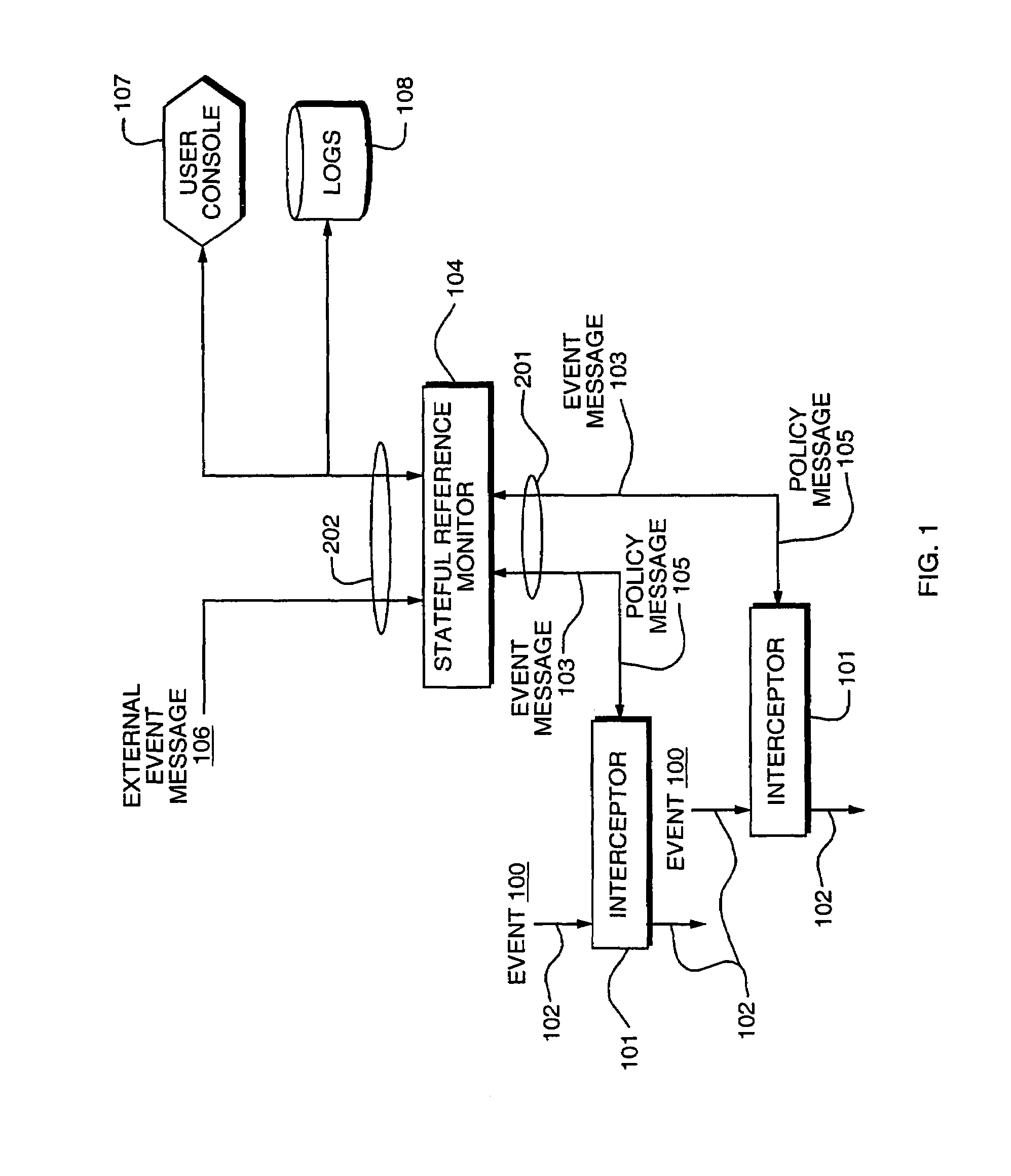
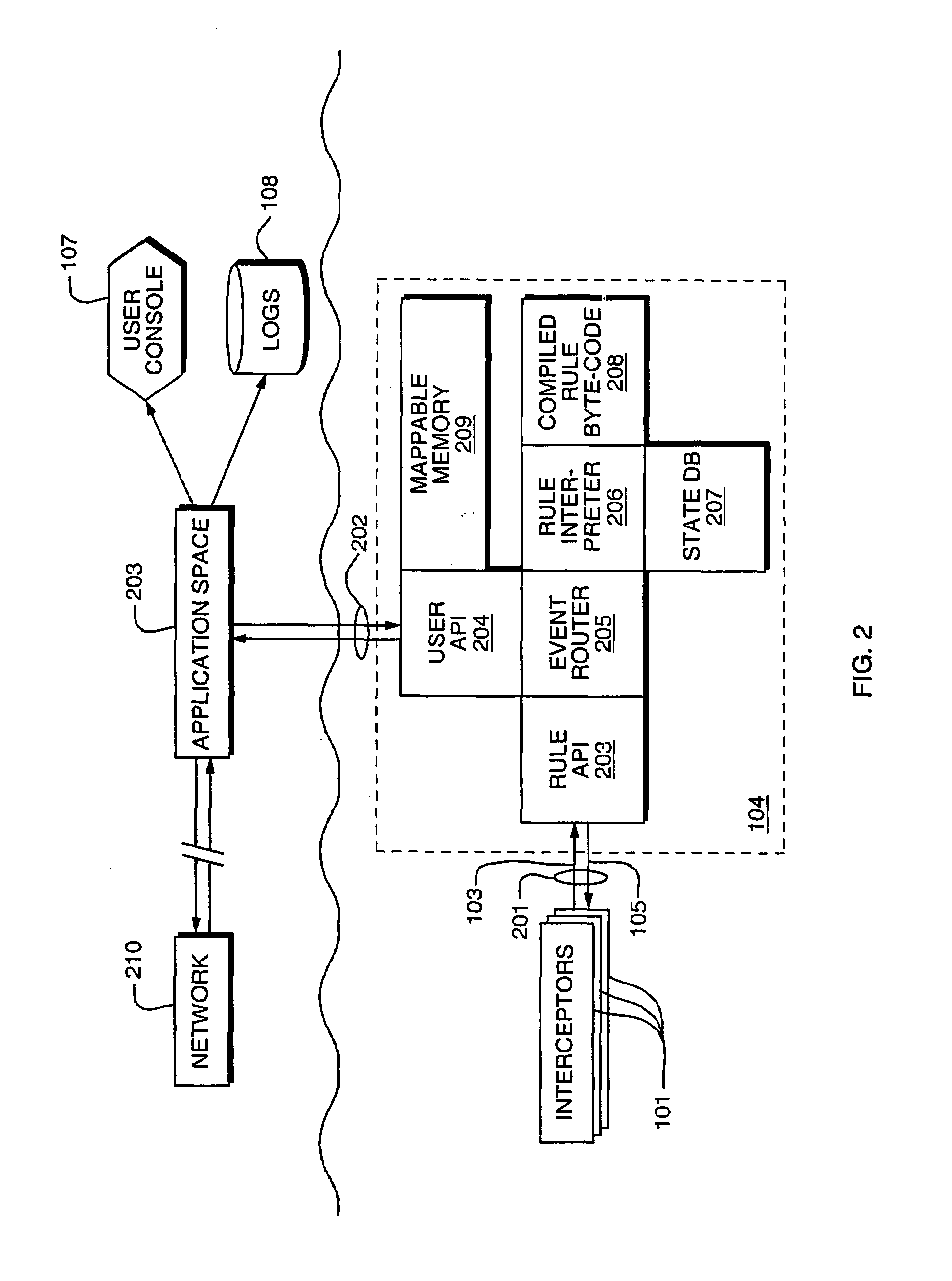
Access control by a real-time stateful reference monitor with a state collection training mode and a lockdown mode for detecting predetermined patterns of events indicative of requests for operating system resources resulting in a decision to allow or block activity identified in a sequence of events based on a rule set defining a processing policy
ActiveUS7290266B2Access control difficultSpecific access rightsDigital data processing detailsOperational systemRule sets
A Stateful Reference Monitor can be loaded into an existing commercial operating system, and then can regulate access to many different types of resources. The reference monitor maintains an updateable storage area whose contents can be used to affect access decisions, and access decisions can be based on arbitrary properties of the request.
Owner:CISCO TECH INC
Orchestration of policy engines and format technologies
ActiveUS20070150936A1Efficient mergeOptimize topologyChaos modelsNon-linear system modelsSoftware engineeringOrchestration
Policies can combine the efficiency of rule sets with the flexible expression power of workflow engines, as well as advantages of other programming languages and engines. Consistent modelling of policy rules is provided across different levels, such as network, control, and service levels. In one system, a policy module can orchestrate rule set and workflow engines in order to evaluate different conditions of a policy. In another embodiment, a hybrid language can be used that allows rule set and other variables to be used in a business process container, workflow and other variables to be used in a rule set container, rule set and business process variables to be used in other containers. In this way, a subset of conditions in a policy can be evaluated using multiple languages and / or engines in order to enforce or evaluate a policy.
Owner:ORACLE INT CORP
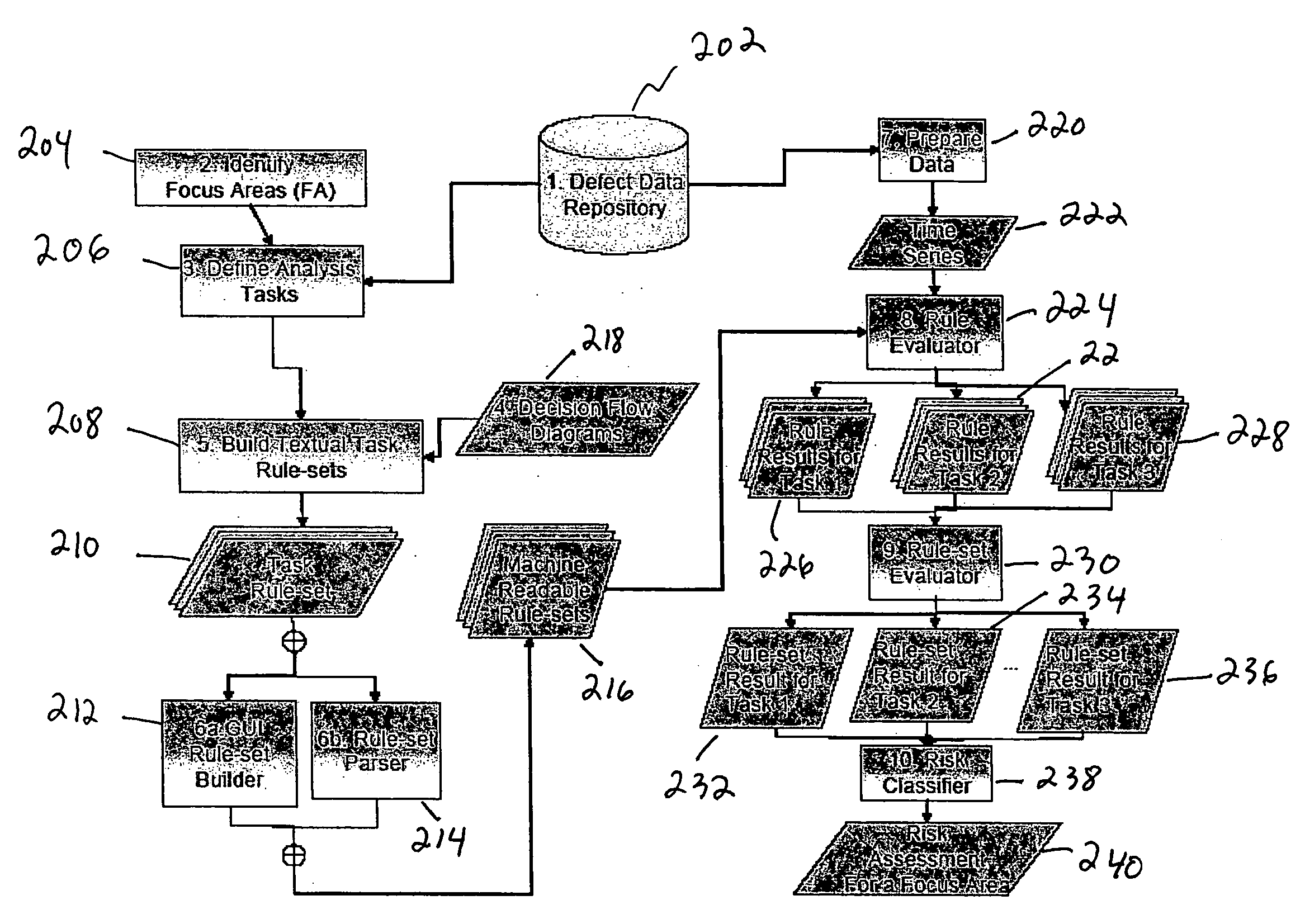
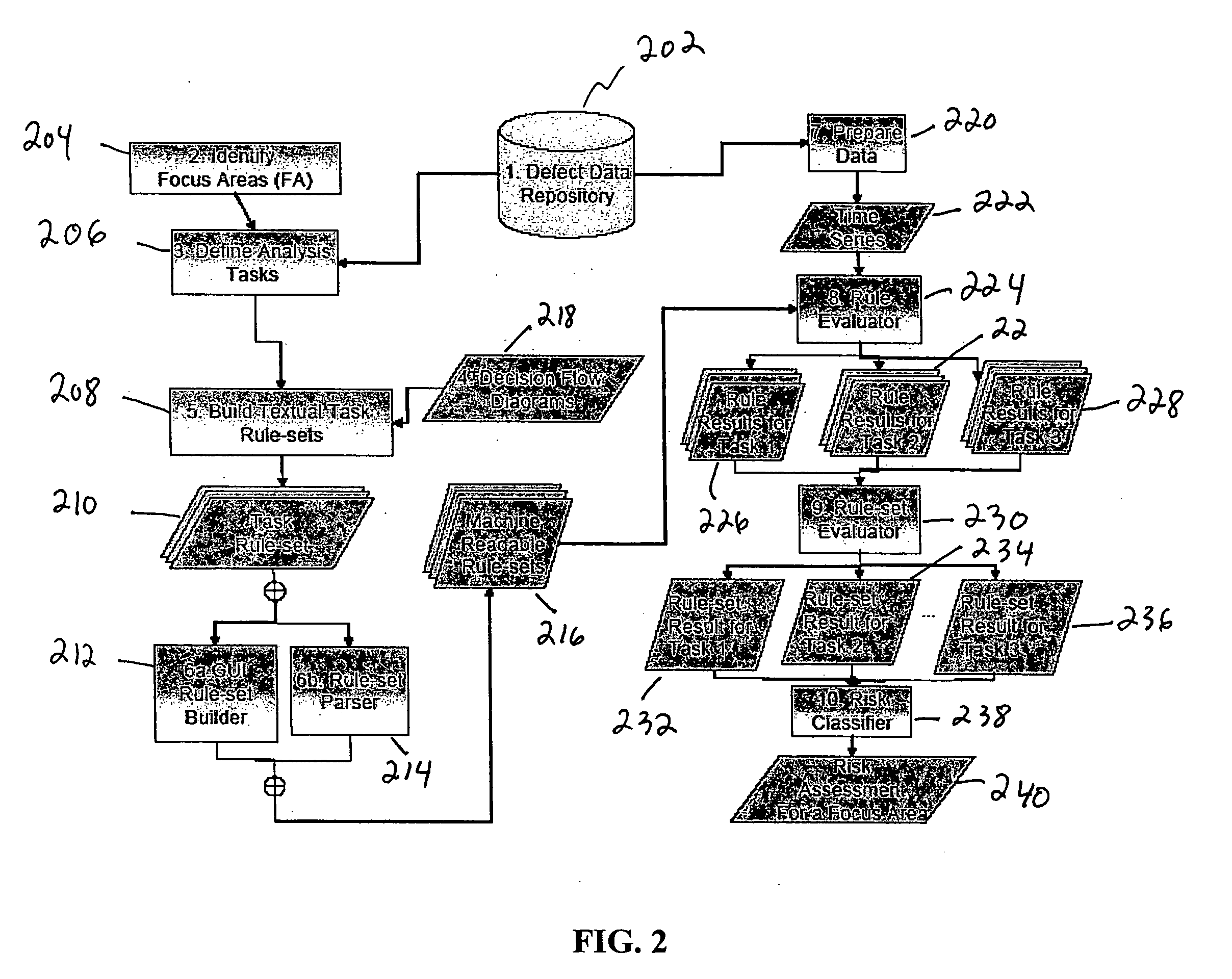
Method and apparatus for automated risk assessment in software projects
A method, information processing system and computer readable medium for assessing risk in a software development project. The method includes receiving software project data for assessing risks in a software development project and identifying a plurality of focus areas for analysis. The method further includes defining a set of analysis tasks for each focus area and creating one or more rule sets for each analysis task, each rule set comprising one or more rules including software project data. The method further includes evaluating each rule set against the software project data summarizing results of evaluating each rule set corresponding to an analysis task. The method further includes providing a risk assessment value for each analysis task using the results of the summarizing element.
Owner:TWITTER INC
Rules based custom catalogs generated from a central catalog database for multiple entities
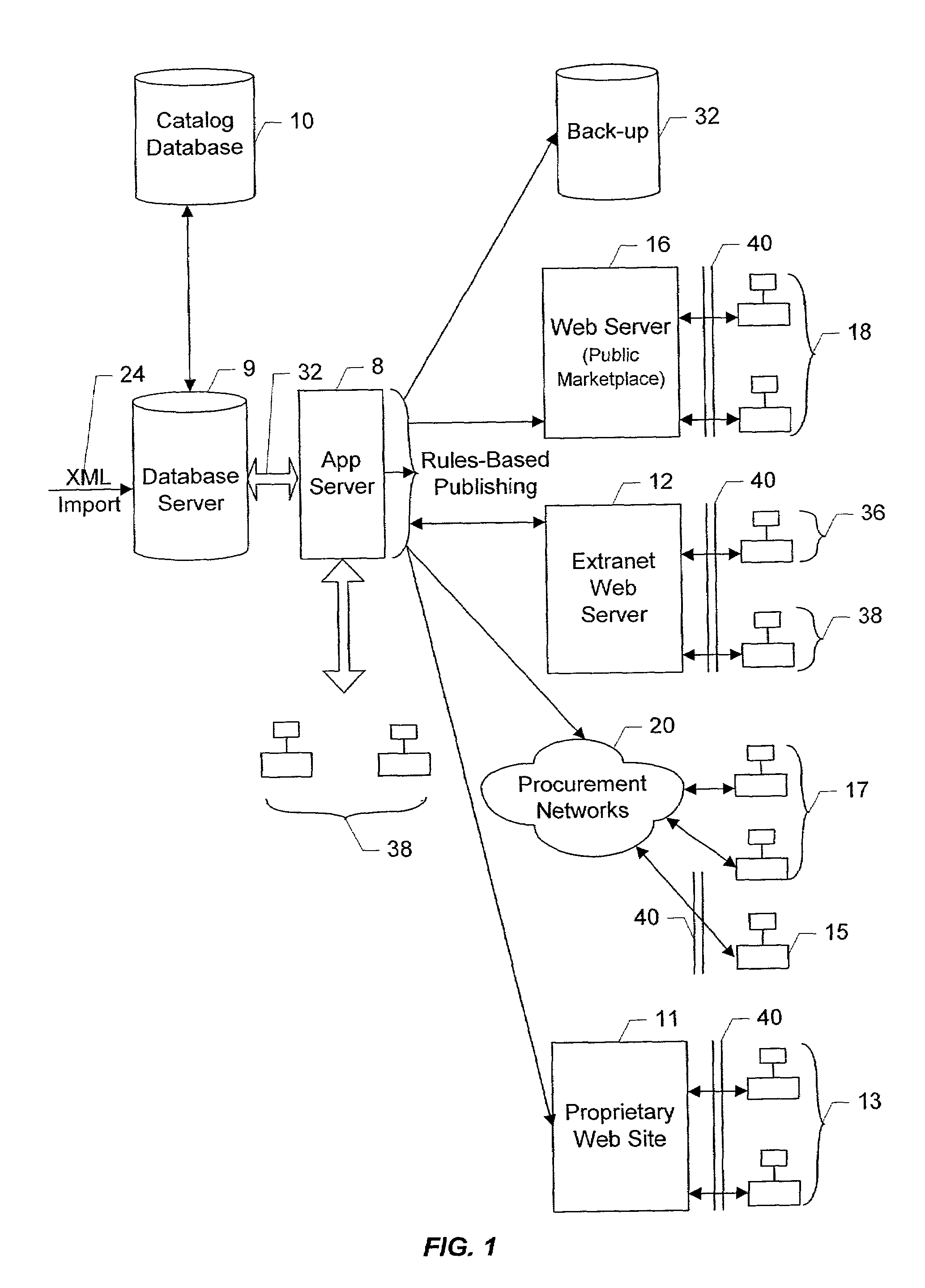
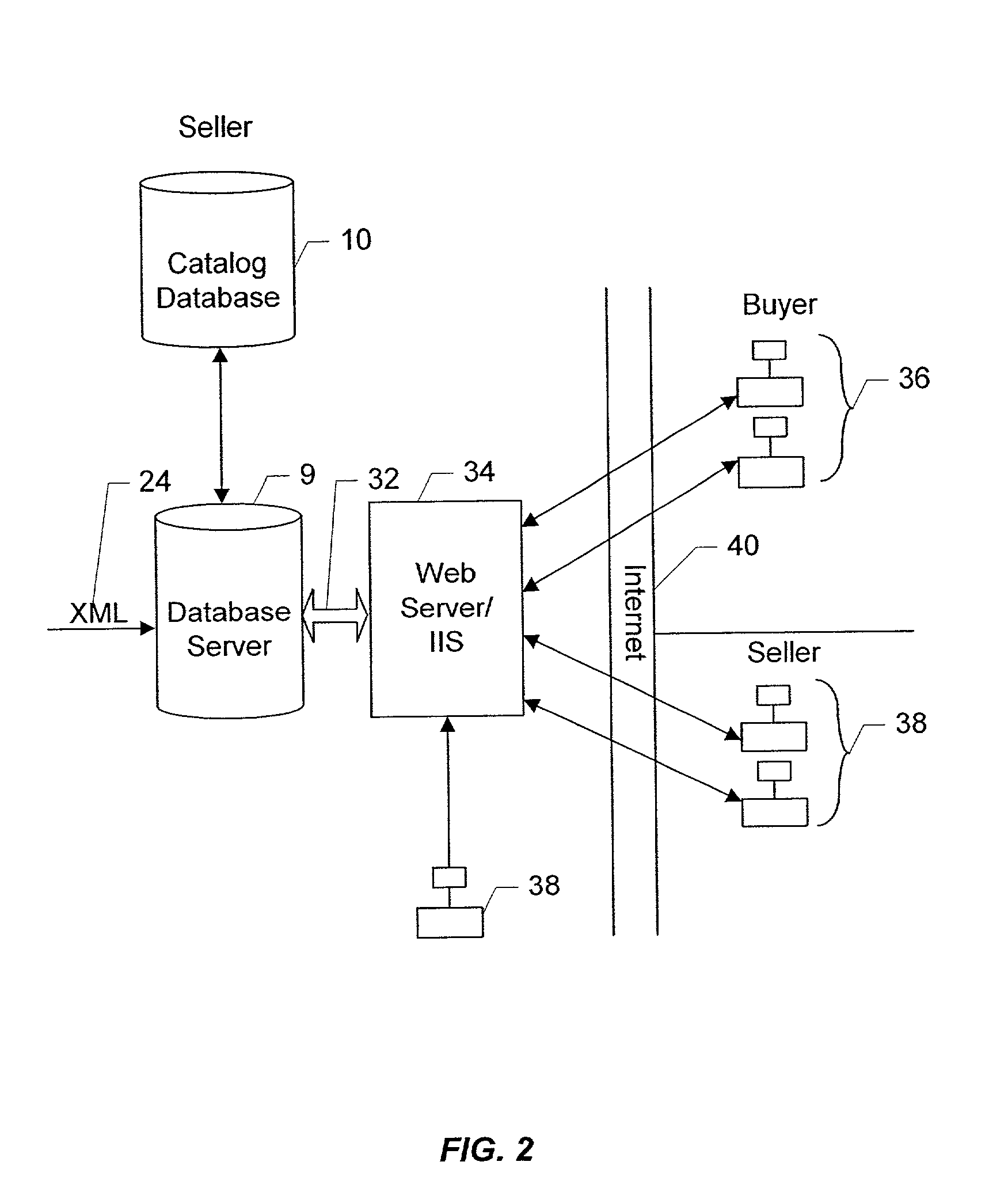
An arbitrary number of custom catalogs for an arbitrary number of customers can be published from a centrally maintained database of seller catalog data. The custom catalogs are subsets of the catalog database, and are generated in accordance with a set of rules that defines the scope of the content of the custom catalog. The rule sets define a series of sequential searches by which a subset of the item SKUs contained in the database are returned. For extranet buyers, the subsets for each rule set are maintained in a subset table. Whenever a user authorized by a particular buyer wishes to browse the unique catalog subset assigned to that buyer, any queries regarding the catalog will result first in a search of the full catalog database, and the results from the full search are pared down to only those items the SKUs for which have entries in the subset table associated with the buyer's assigned subset. A buyer-authorized user browses the catalog using a standard PC and browser, and SKUs returned to the user based on the user's query will include descriptive information such as descriptive text, pictures etc., which are displayed by the browser. Buyers who are not coupled to the seller via an extranet connection can have customized subsets of the total catalog database produced in accordance with their own rule sets, and formatted and delivered off-line for incorporation into their web sites and procurement networks.
Owner:VERSATA DEV GROUP
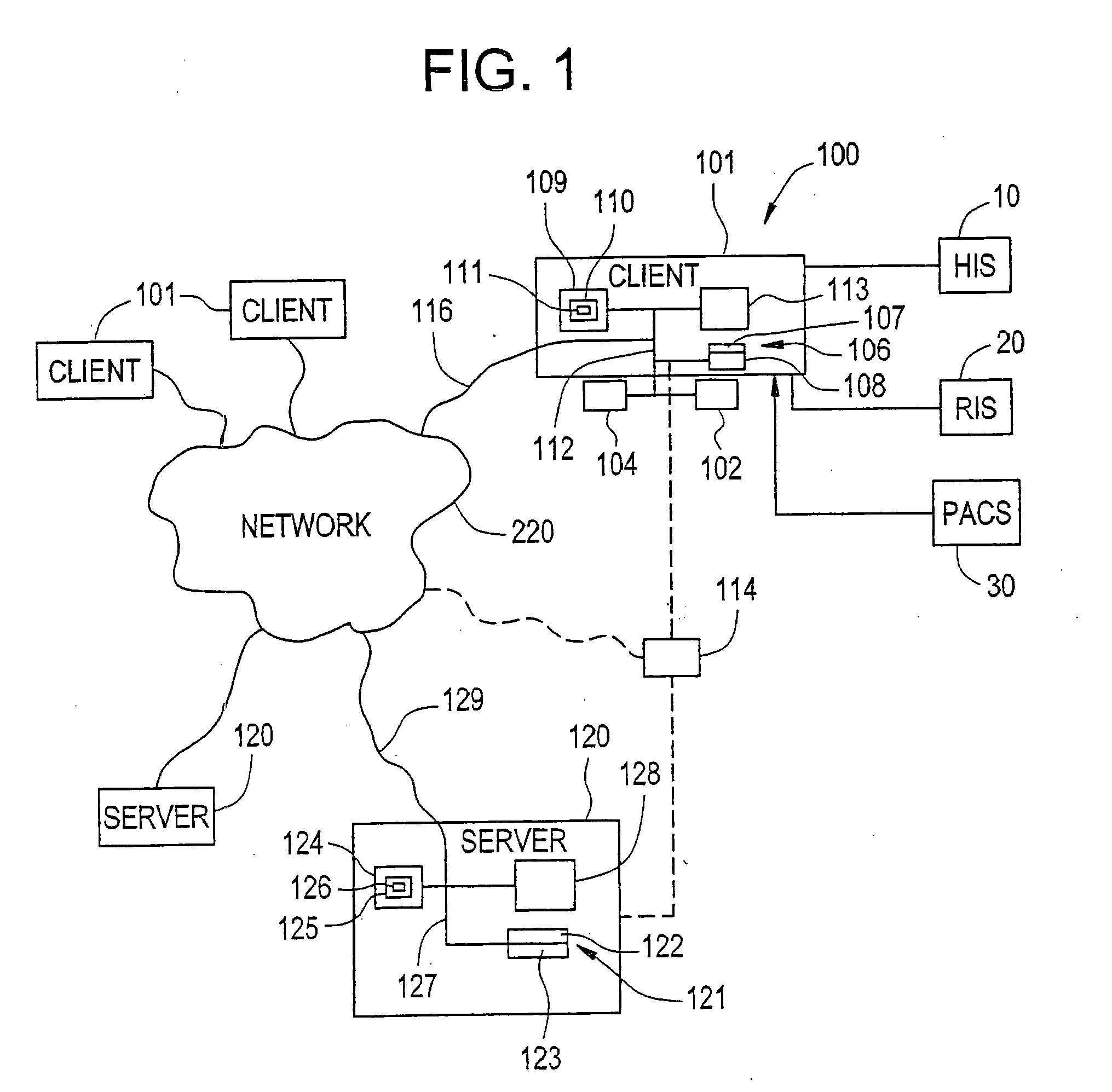
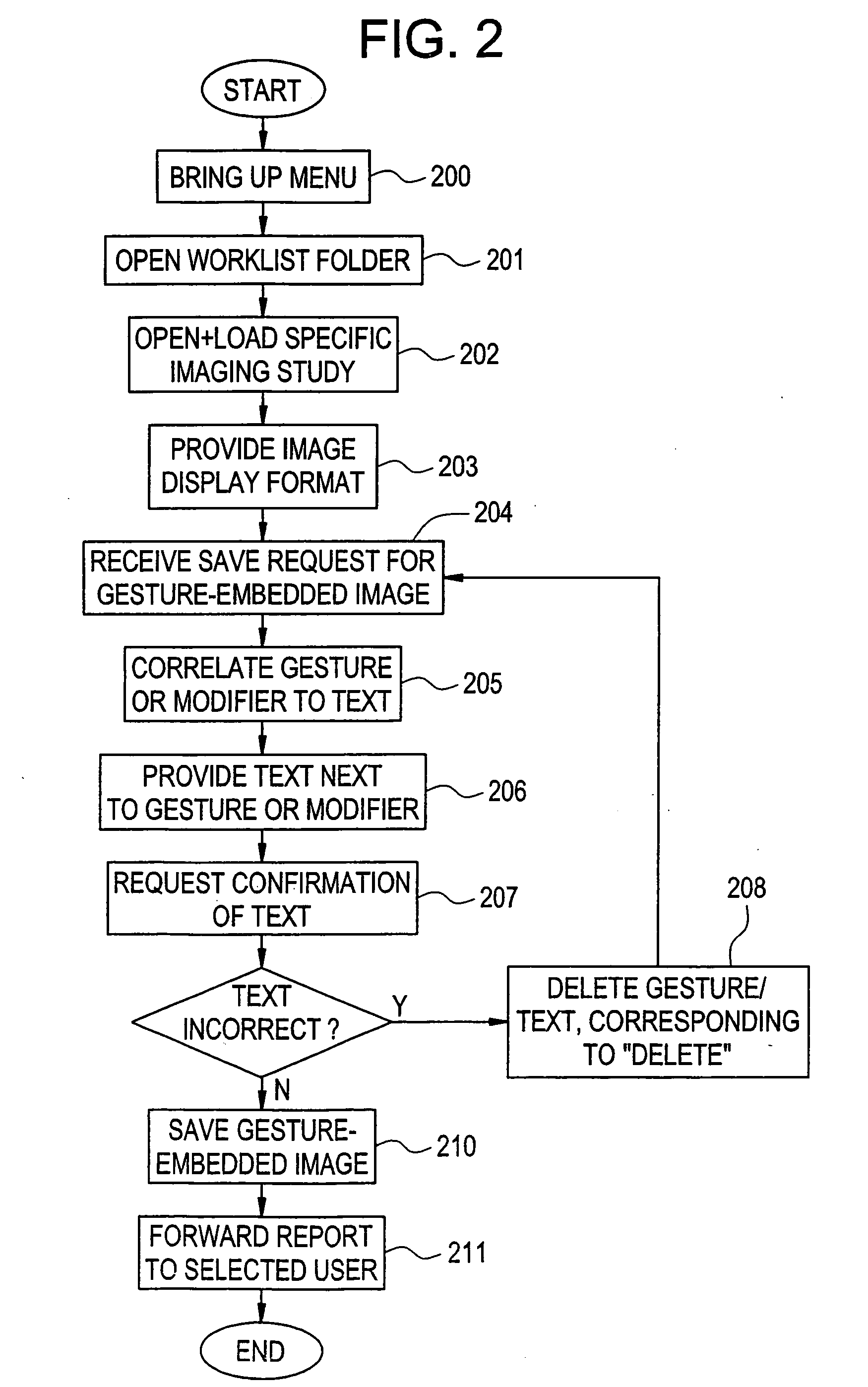
Gesture-based communication and reporting system
ActiveUS20090018867A1Avoid mistakesFacilitate communicationData processing applicationsMechanical/radiation/invasive therapiesData dredgingImaging quality
The present invention relates to a gesture-based reporting method and system, including a critical results reporting pathway, which is used to communicate critical findings to users according to predetermined methods (i.e., e-mail, facsimile, etc.), and create an electronic auditing trail to document receipt, understanding, bi-directional queries, and track clinical outcomes. Based on a predetermined rule set, predetermined data elements within the structured database could trigger the critical results reporting pathway. There is a quality assurance component to the invention, such that technical deficiencies in an imaging quality can be noted, analyzed, and tracked. There is a workflow and data analysis portion to the invention, wherein workflow is enhanced, and structured data is mapped to a standardized lexicon, such that data mining can be performed. Thus, the present invention extends beyond reporting alone and is a tool to facilitate electronic communication, consultation, education / training, and data mining for quality assurance.
Owner:IMPRIVATA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com