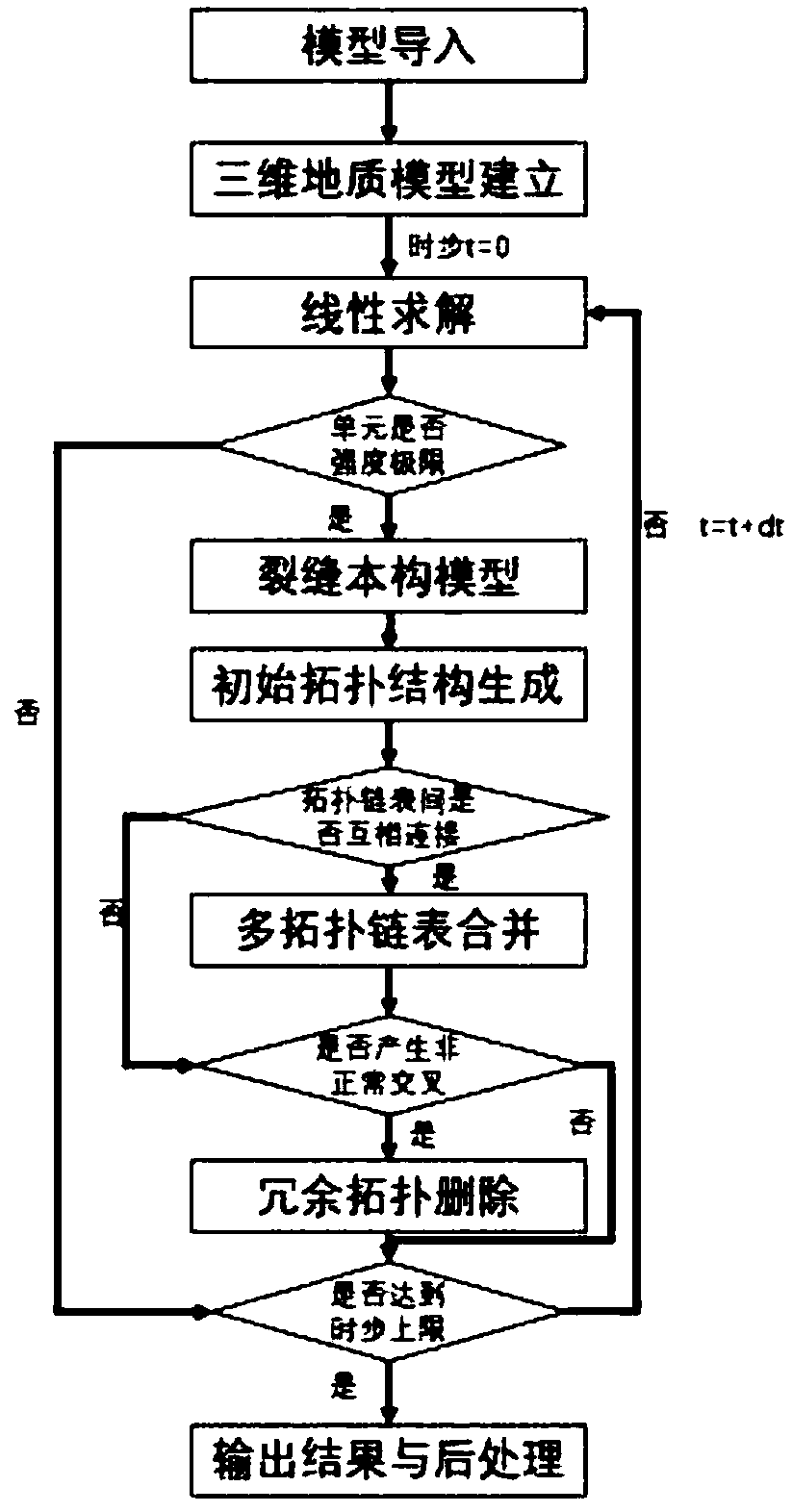
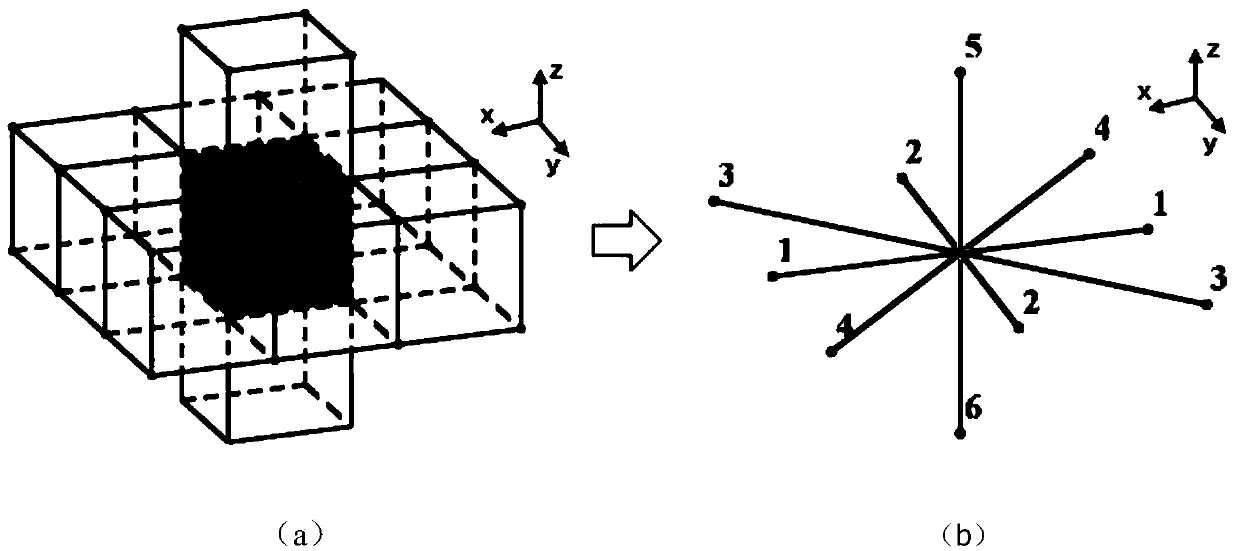
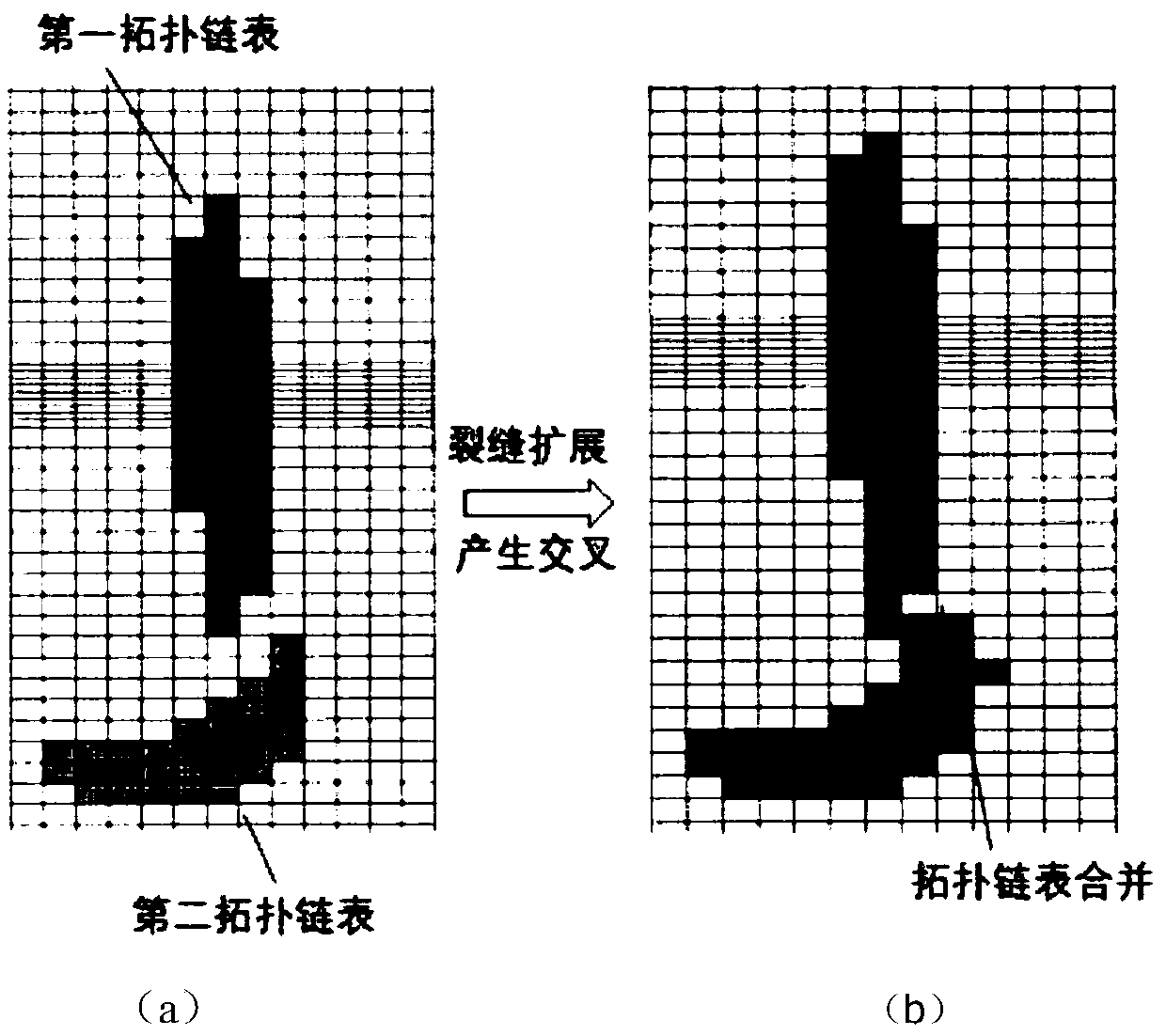
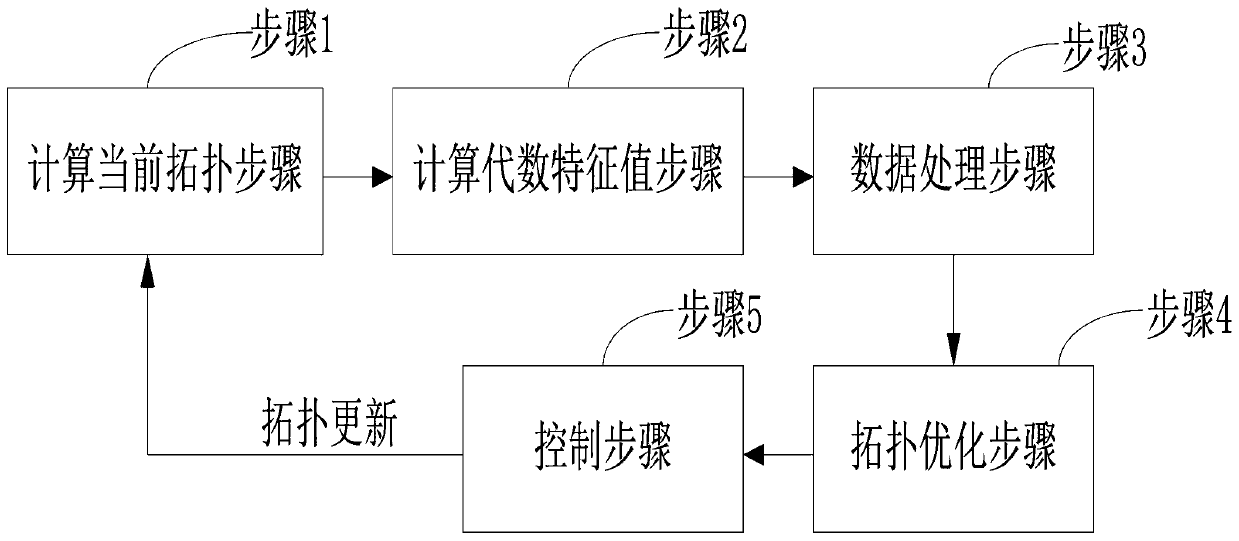
Patents
Literature
133results about How to "Optimize topology" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
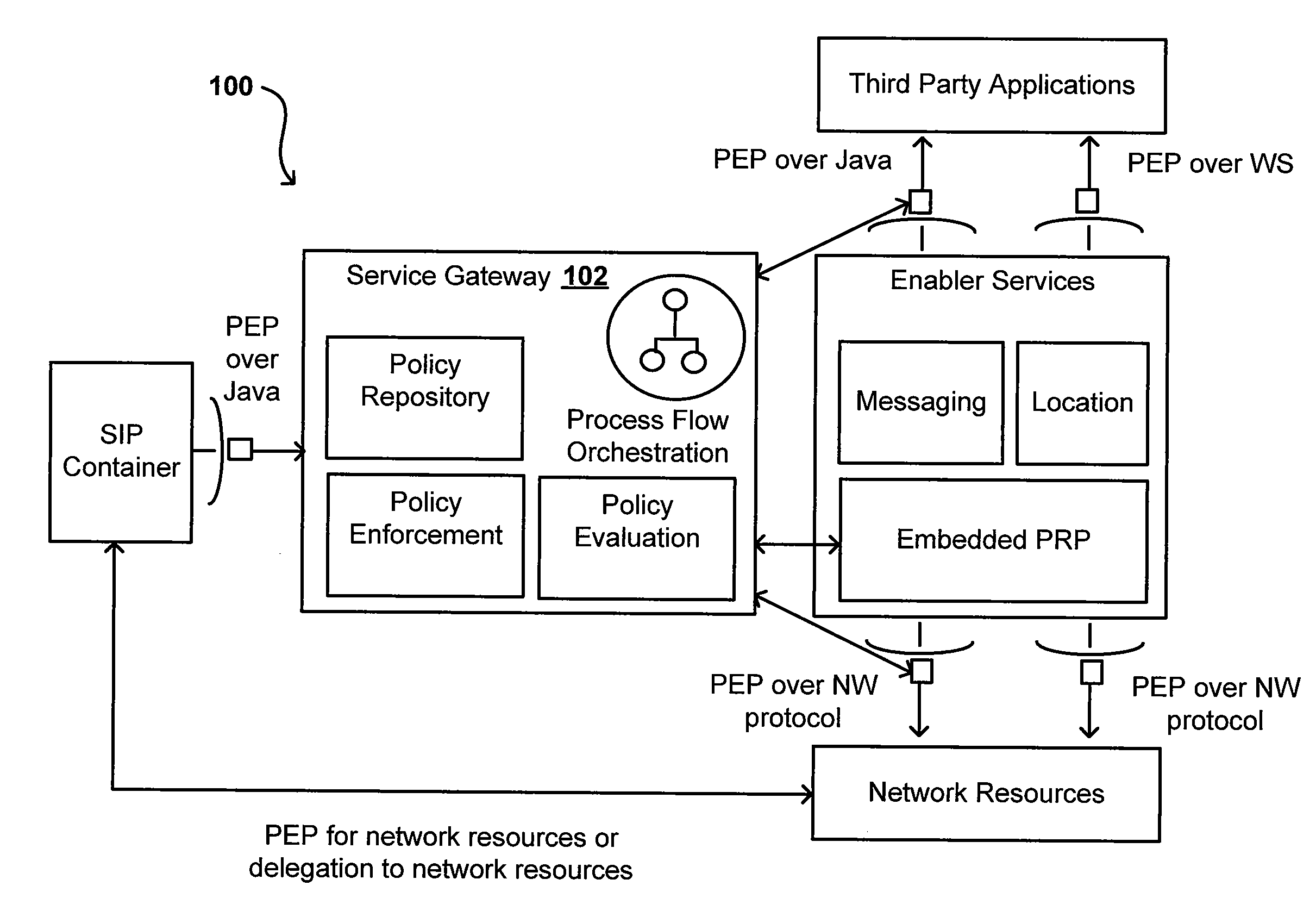
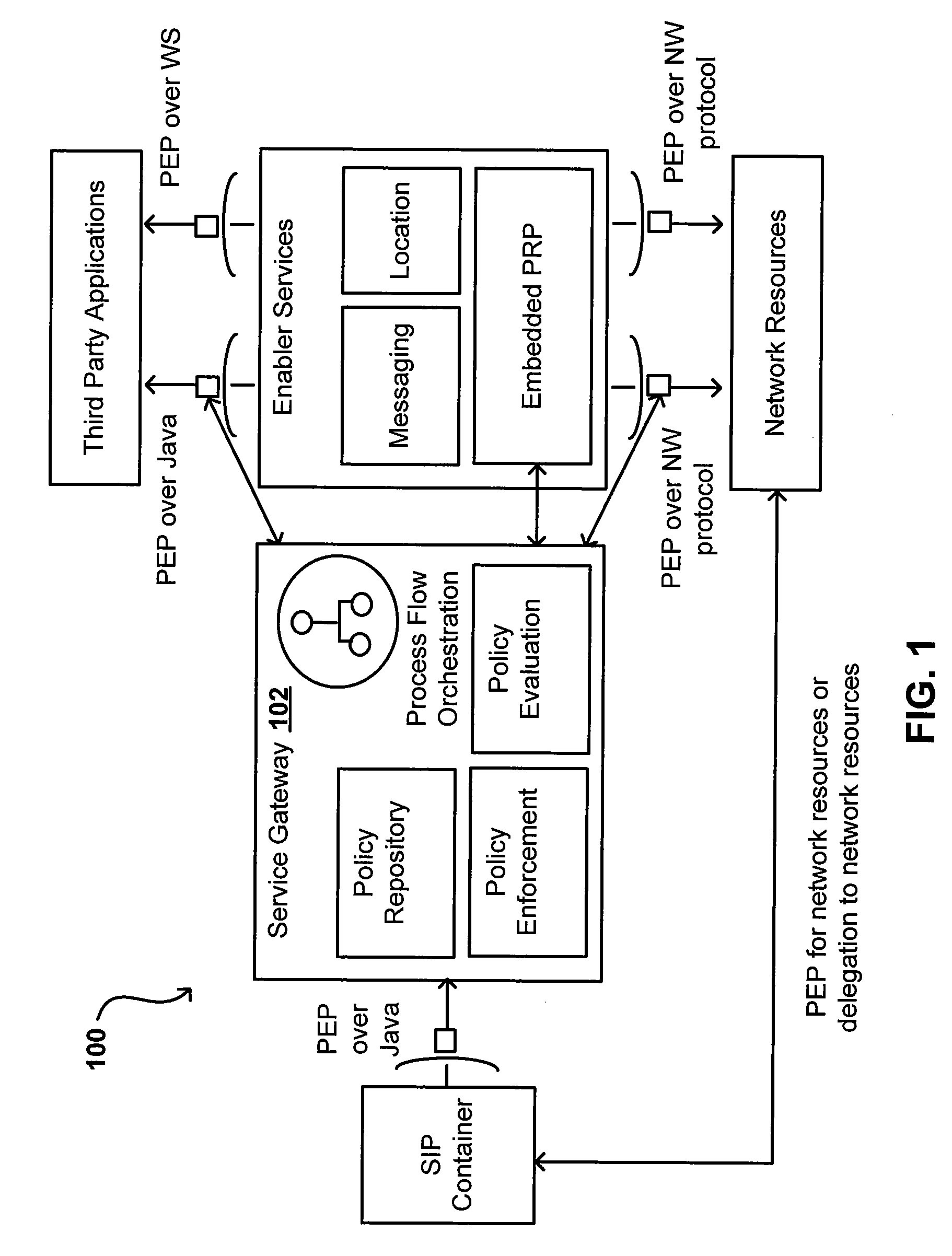
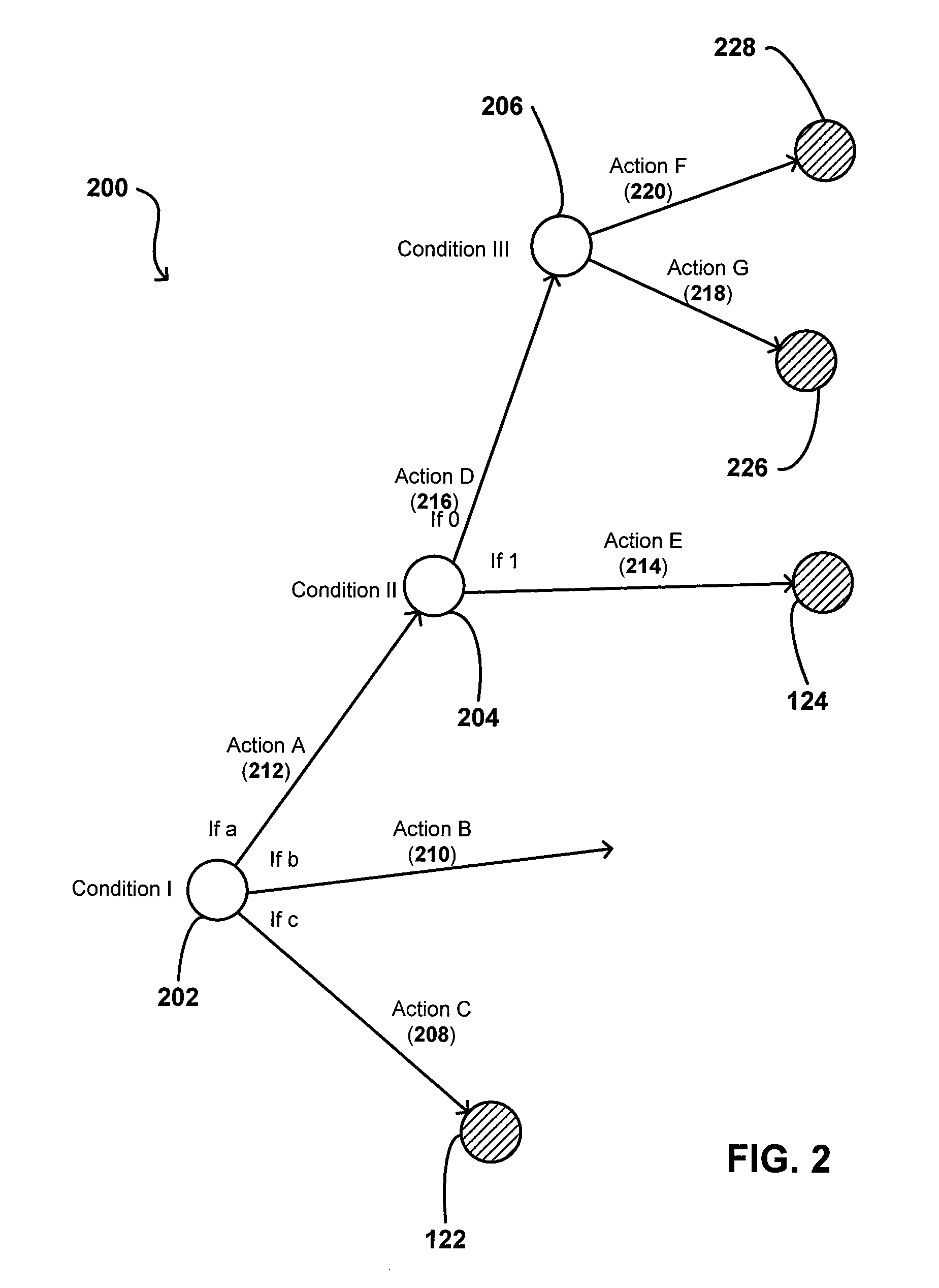
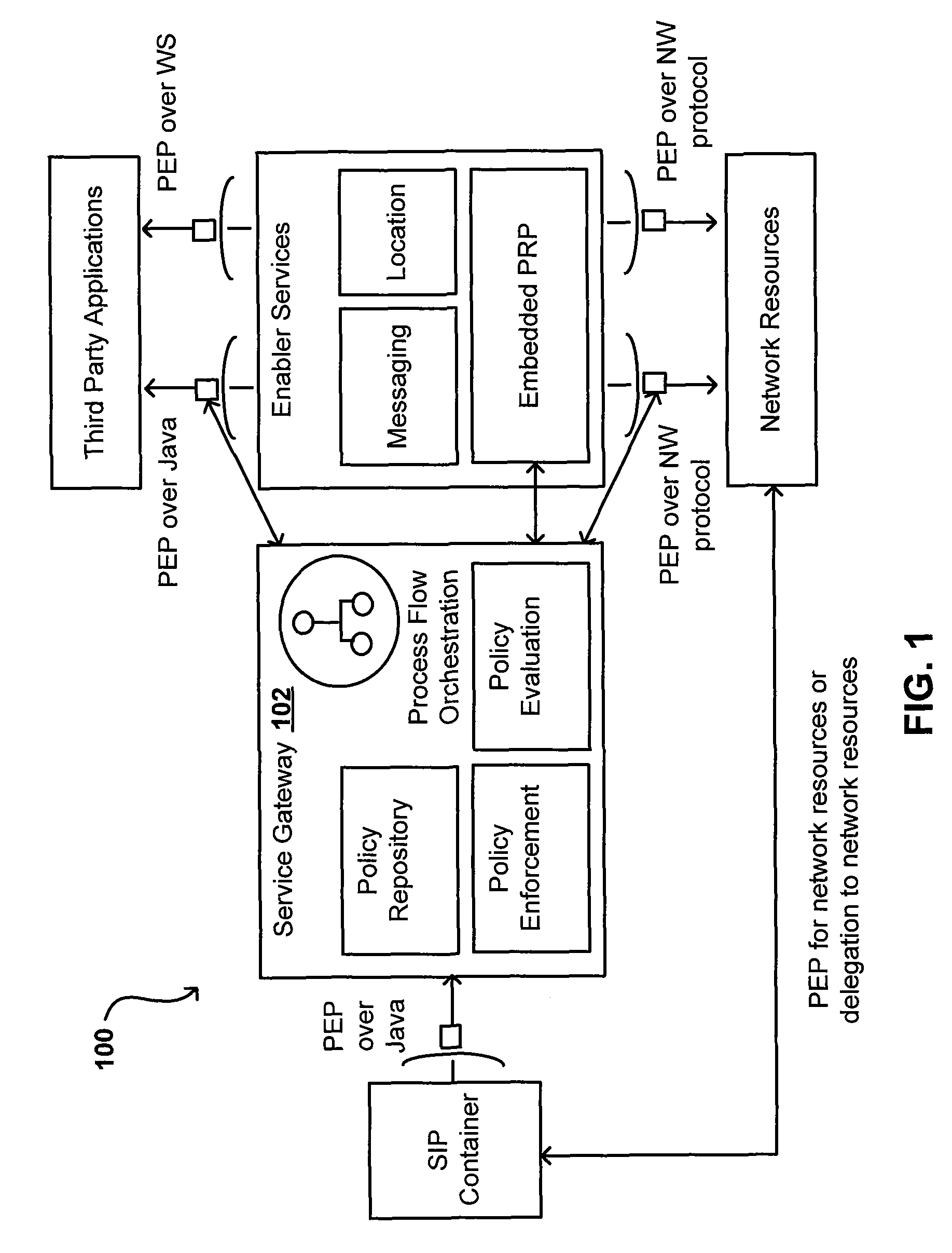
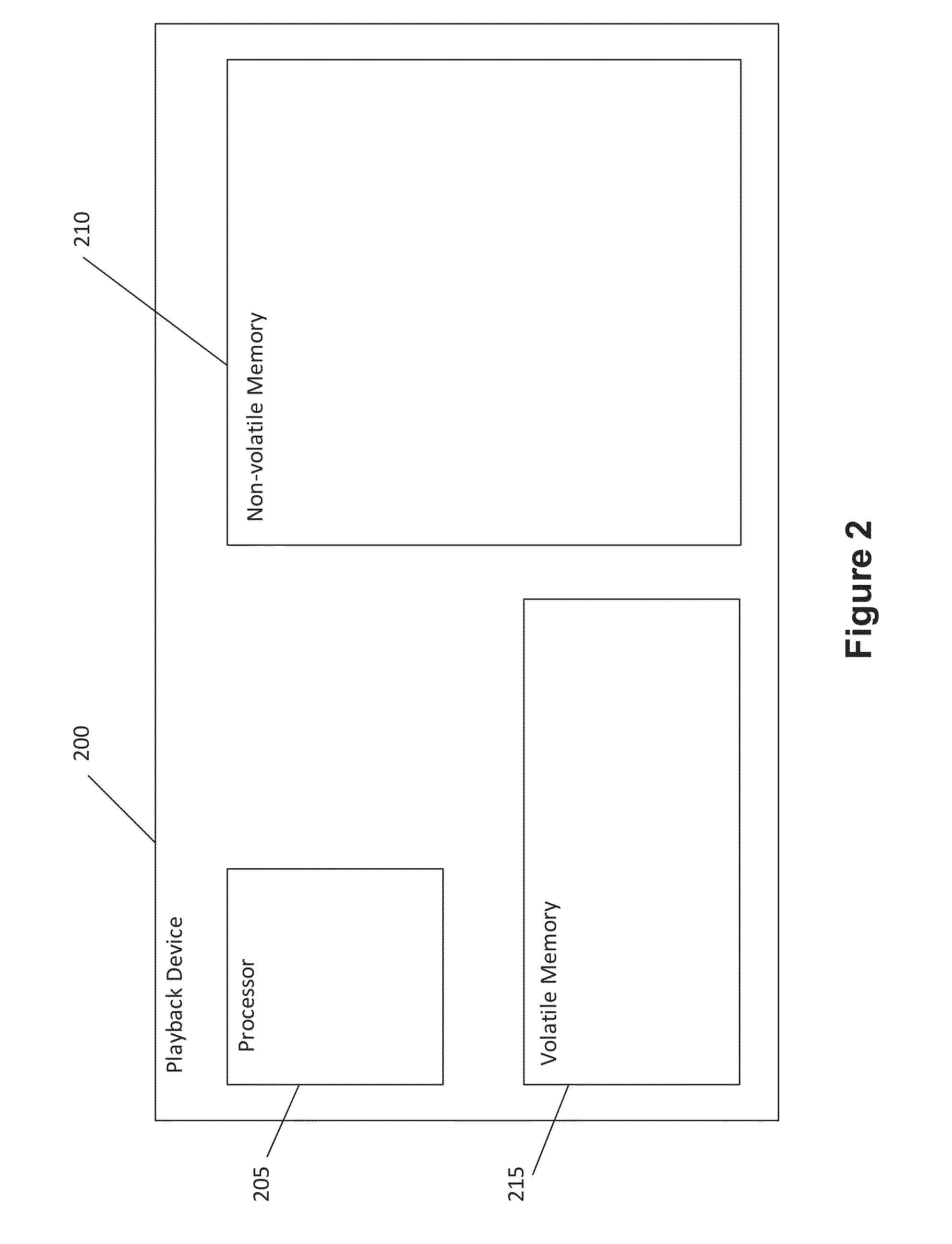
Orchestration of policy engines and format technologies
ActiveUS20070150936A1Efficient mergeOptimize topologyChaos modelsNon-linear system modelsSoftware engineeringOrchestration
Policies can combine the efficiency of rule sets with the flexible expression power of workflow engines, as well as advantages of other programming languages and engines. Consistent modelling of policy rules is provided across different levels, such as network, control, and service levels. In one system, a policy module can orchestrate rule set and workflow engines in order to evaluate different conditions of a policy. In another embodiment, a hybrid language can be used that allows rule set and other variables to be used in a business process container, workflow and other variables to be used in a rule set container, rule set and business process variables to be used in other containers. In this way, a subset of conditions in a policy can be evaluated using multiple languages and / or engines in order to enforce or evaluate a policy.
Owner:ORACLE INT CORP
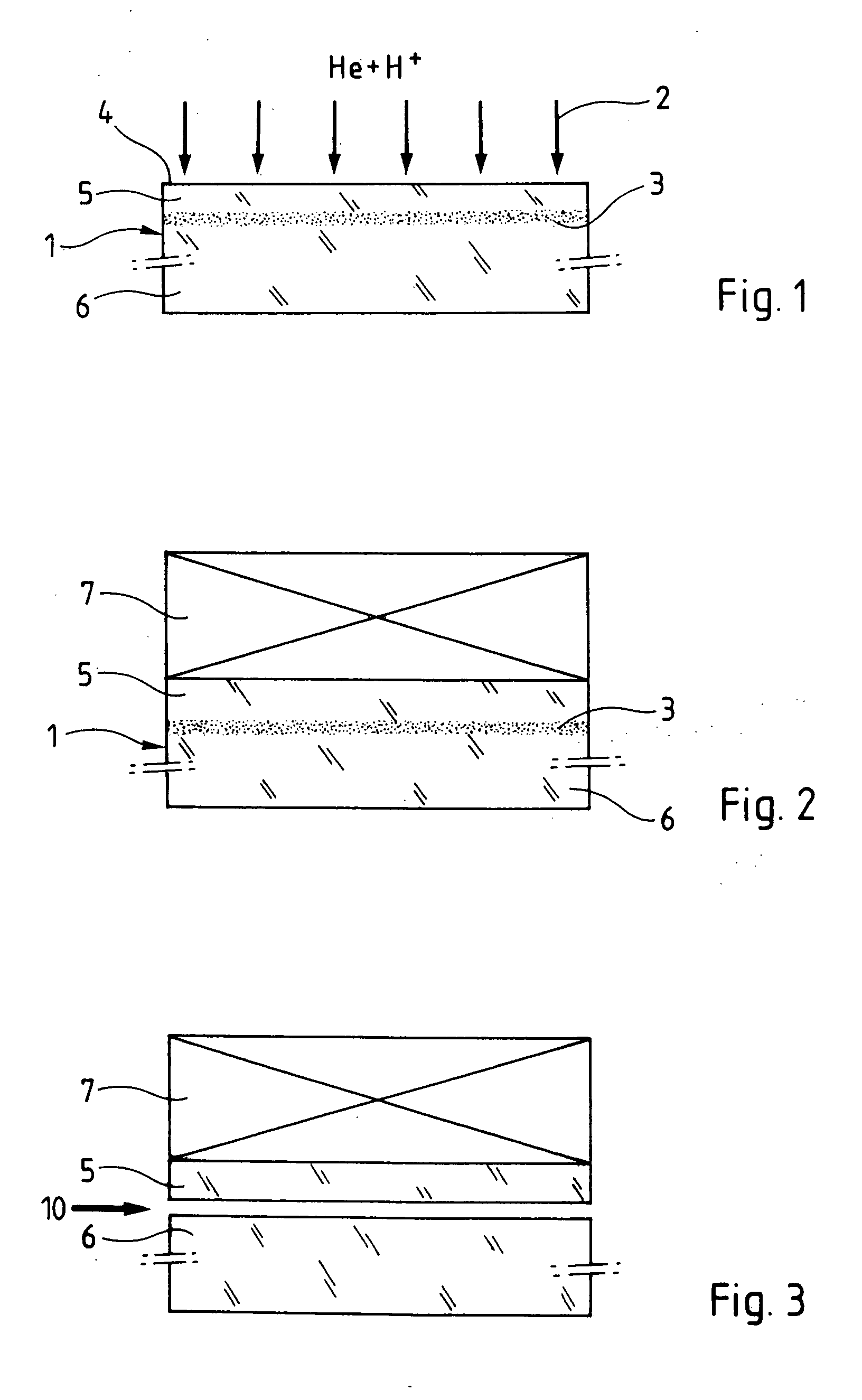
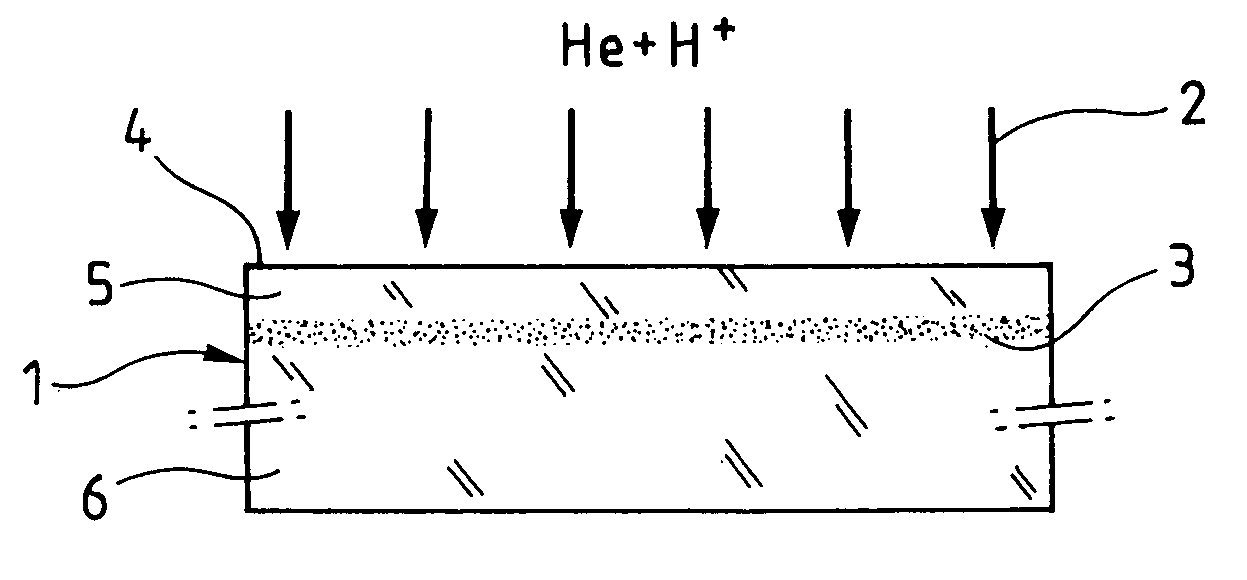
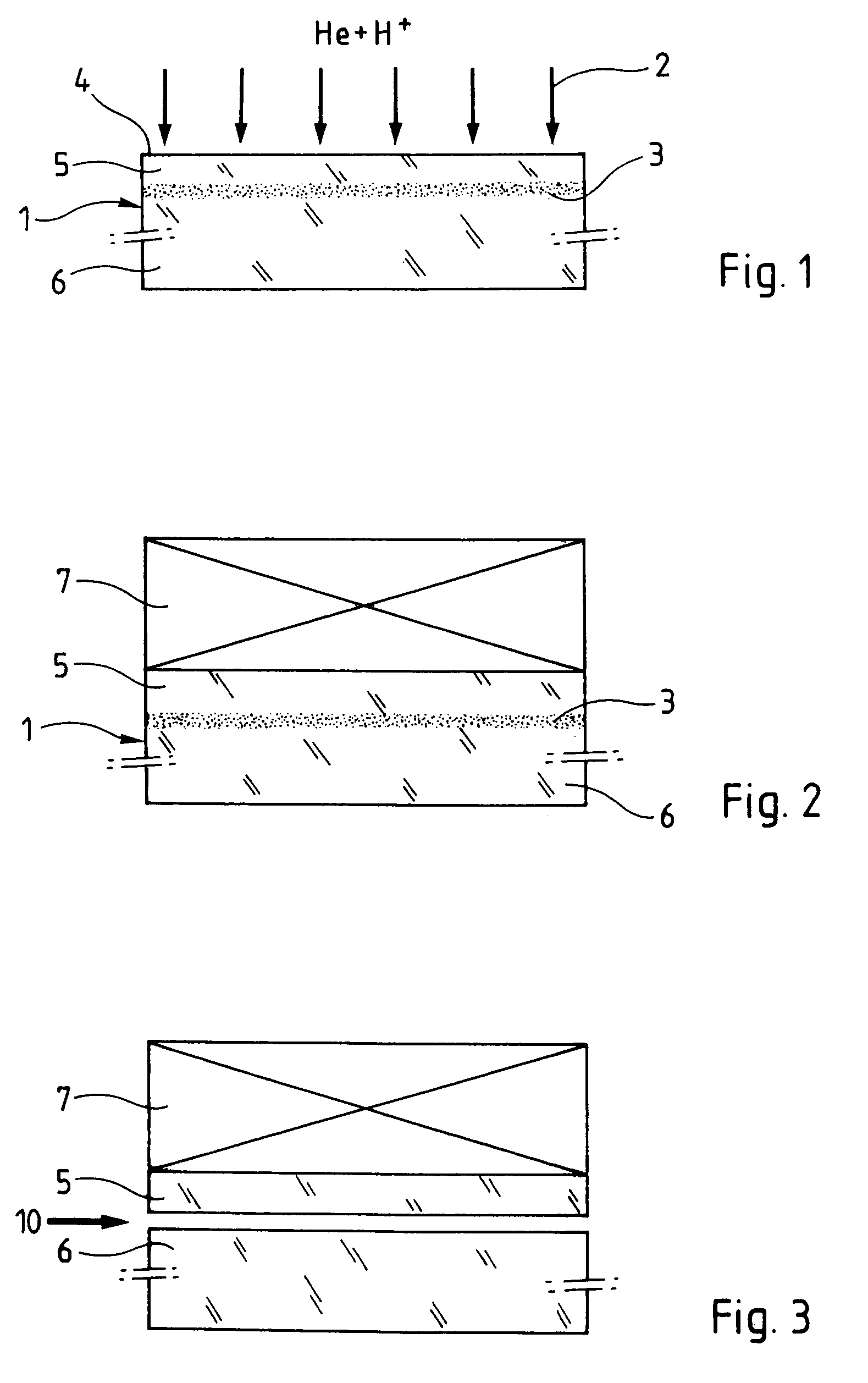
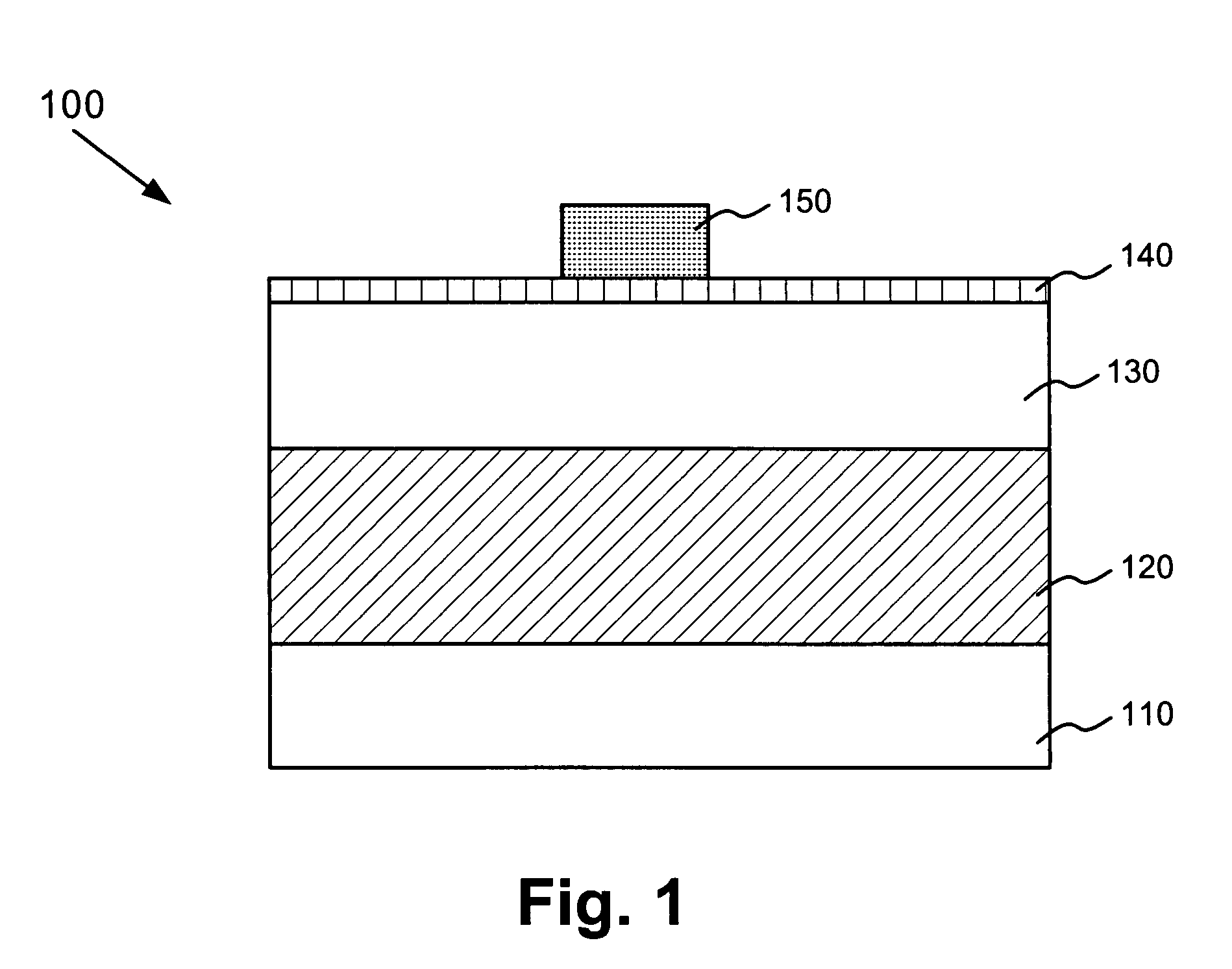
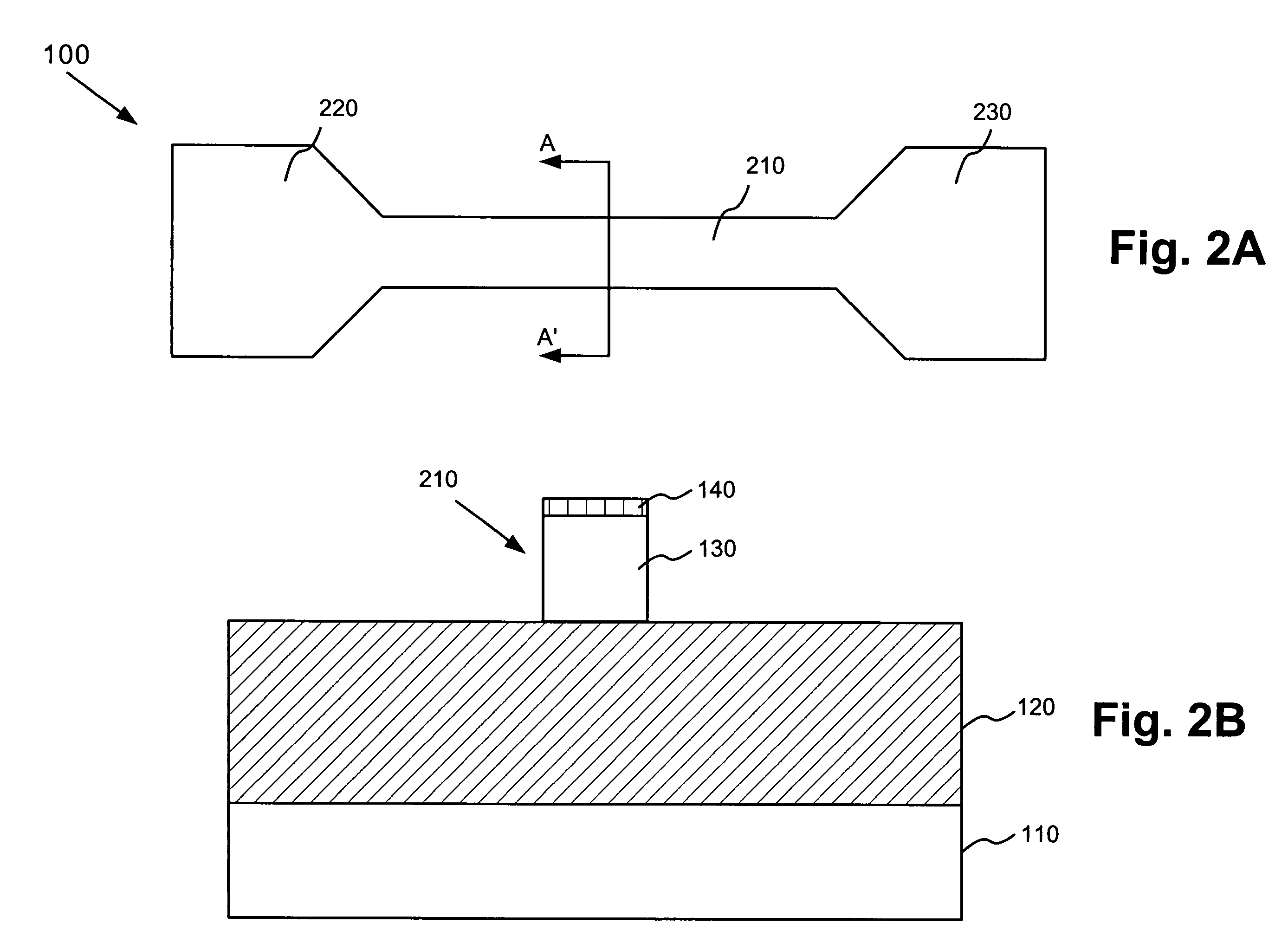
Method of catastrophic transfer of a thin film after co-implantation
ActiveUS20050148163A1Reduce roughnessHigh mechanical stressSemiconductor/solid-state device manufacturingCo implantationAtomic physics
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES +1
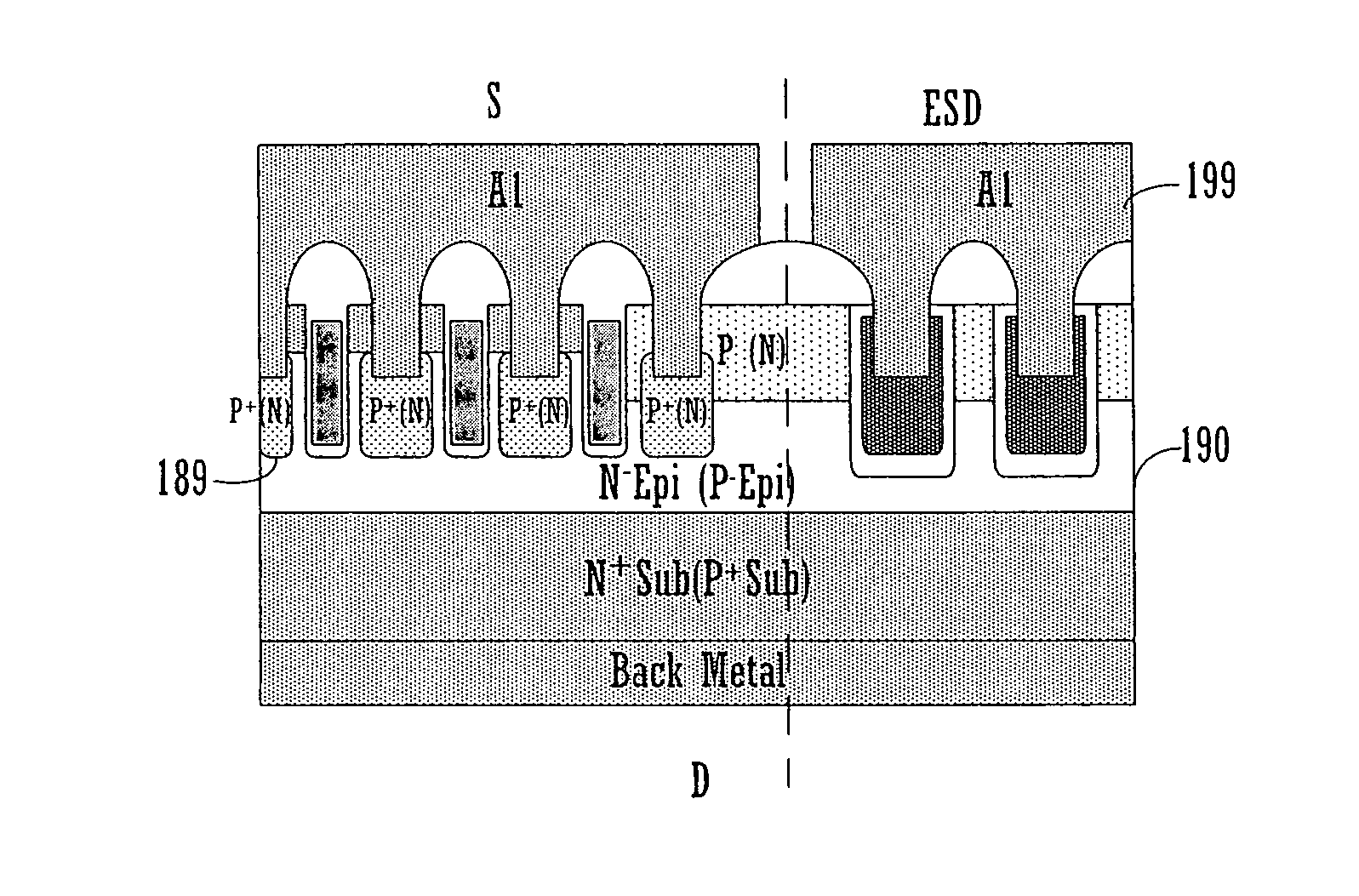
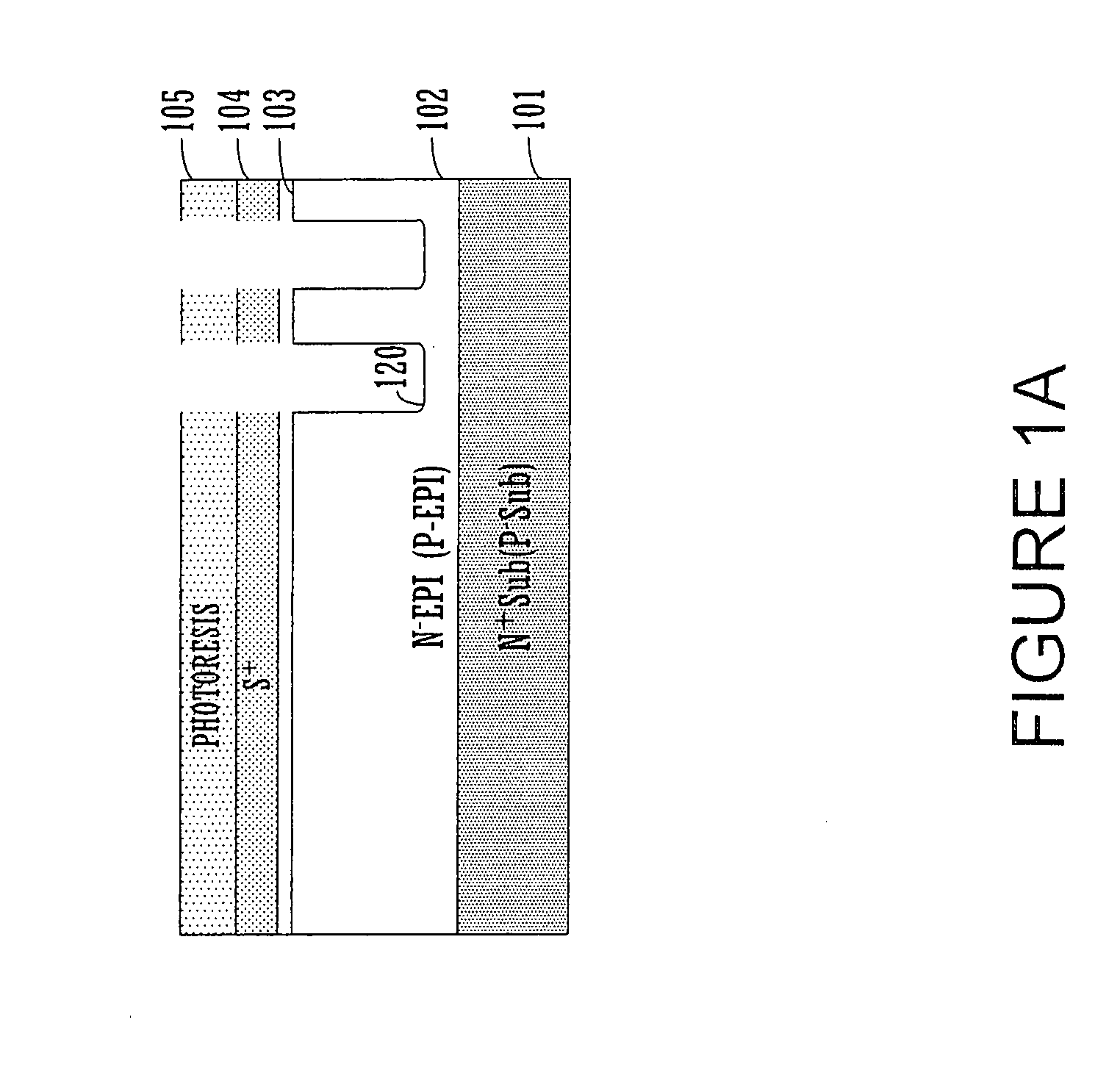
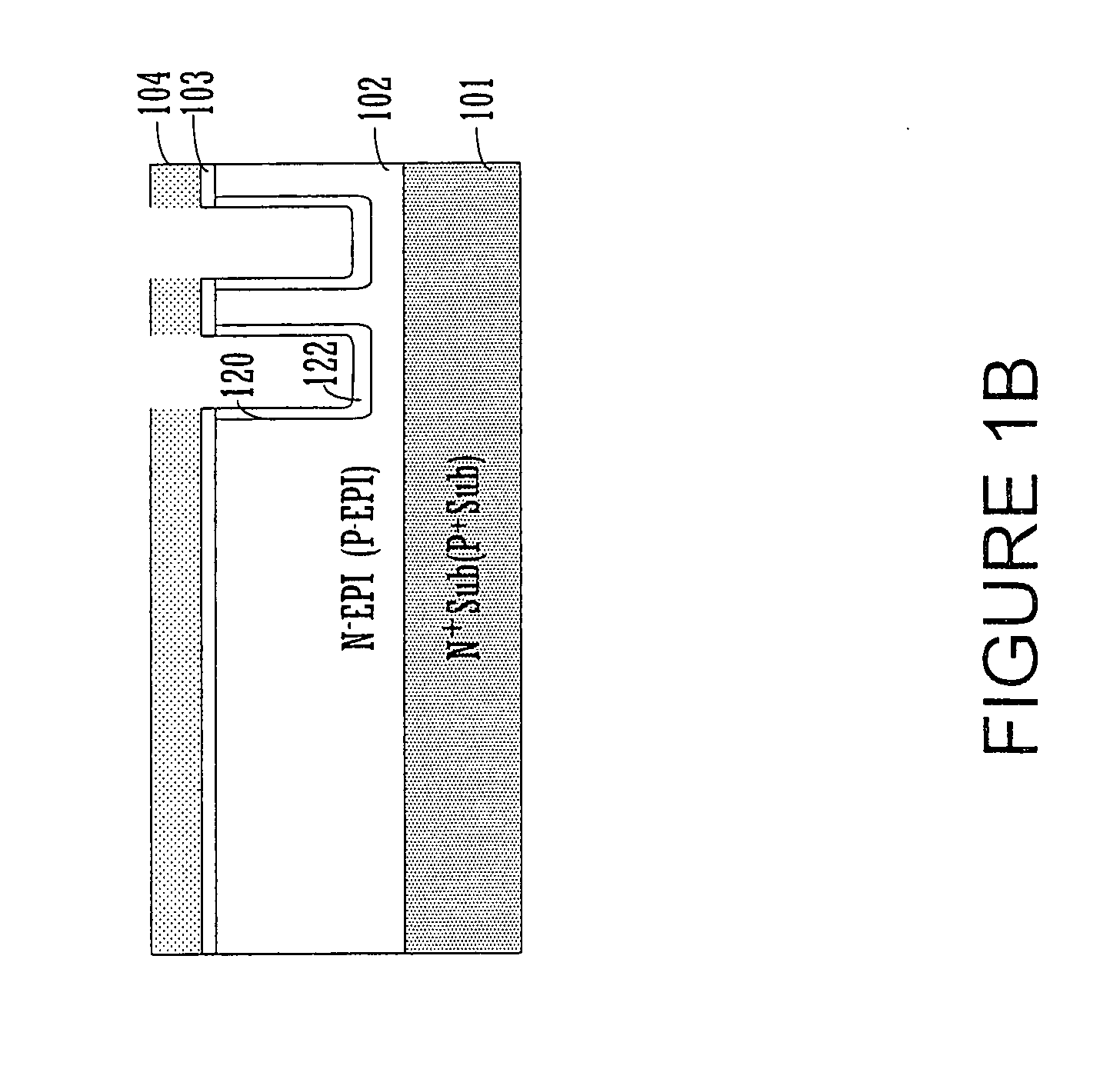
Trench polysilicon diode
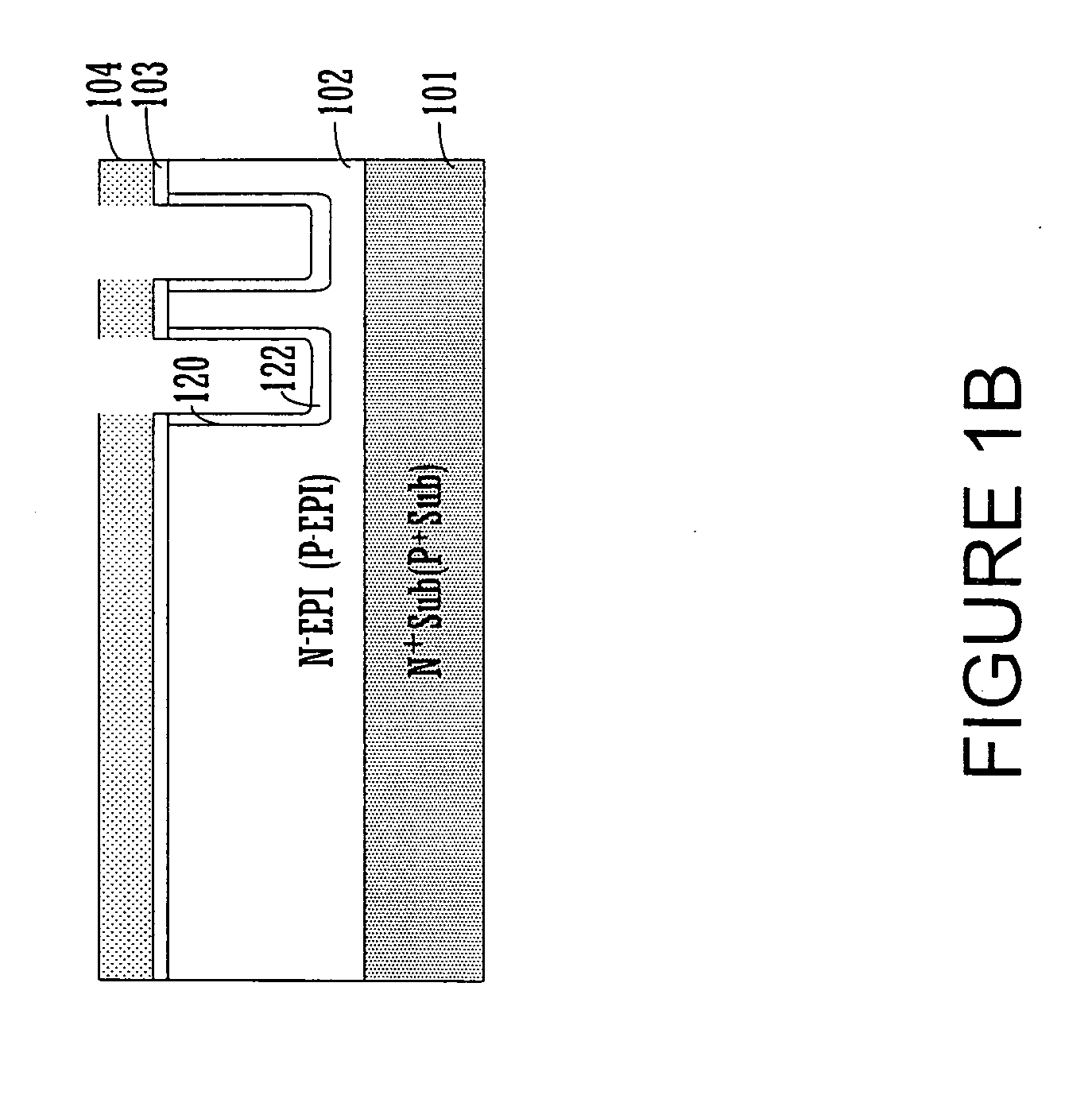
ActiveUS20070145411A1Reduction in topologyOptimize topologyTransistorThyristorEngineeringPolycrystalline silicon
Embodiments of the present invention include a method of manufacturing a trench polysilicon diode. The method includes forming a N− (P−) type epitaxial region on a N+ (P+) type substrate and forming a trench in the N− (P−) type epitaxial region. The method further includes forming a insulating layer in the trench and filling the trench with polysilicon forming a top surface of the trench. The method further includes forming P+ (N+) type doped polysilicon region and N+ (P+) type doped polysilicon region in the trench and forming a diode in the trench wherein a portion of the diode is lower than the top surface of the trench.
Owner:VISHAY SILICONIX LLC
Wireless sensor network topology control method based on non-uniform sections
InactiveCN101267391ABalanced energy consumptionIncrease data transfer volumeEnergy efficient ICTData switching networksWireless transmissionMean square
The invention relates to a topology control method for wireless sensor network based on uneven cluster, belong to sensor technical field, comprising: during the topology generating stage, introducing an uneven minimum mean square subtraction clustering mechanism on a finished cluster in order to reduce energy consumption of in-cluster node; using a strategy based on cluster head energy consumption for setting cluster head changing time, in order to equalize energy consumption on each cluster head node in the network; establishing a cluster head-cluster head energy sensing route, in order to avoid remote wireless transmission; during topology maintenance stage, using a cluster head selection scheme based on node surplus energy and in-cluster node distribution, and using the same strategy to set cluster changing time. With the realization of the method, it can reduce total network energy consumption and equalize energy consumption on each node, in order to prolong cooperative working time of most nodes in the network.
Owner:SHANGHAI JIAO TONG UNIV
Orchestration of policy engines and format technologies
ActiveUS8141125B2Efficient mergeOptimize topologyChaos modelsComputer security arrangementsProgramming languageOrchestration
Policies can combine the efficiency of rule sets with the flexible expression power of workflow engines, as well as advantages of other programming languages and engines. Consistent modelling of policy rules is provided across different levels, such as network, control, and service levels. In one system, a policy module can orchestrate rule set and workflow engines in order to evaluate different conditions of a policy. In another embodiment, a hybrid language can be used that allows rule set and other variables to be used in a business process container, workflow and other variables to be used in a rule set container, rule set and business process variables to be used in other containers. In this way, a subset of conditions in a policy can be evaluated using multiple languages and / or engines in order to enforce or evaluate a policy.
Owner:ORACLE INT CORP
System and method for automatic rigging of three dimensional characters for facial animation
ActiveUS20130127853A1Optimize topologyStay in shapeAnimation3D-image renderingAnimationComputer vision
A system and method for automatic rigging of three dimensional characters for facial animation provide a rigged mesh for an original three dimensional mesh. A representative mesh is generated from the original mesh. Segments, key points, a bone set, and skinning weights are then determined for the representative mesh. The Skinning weights and bone set are placed in the original mesh to generate the rigged mesh.
Owner:ADOBE SYST INC
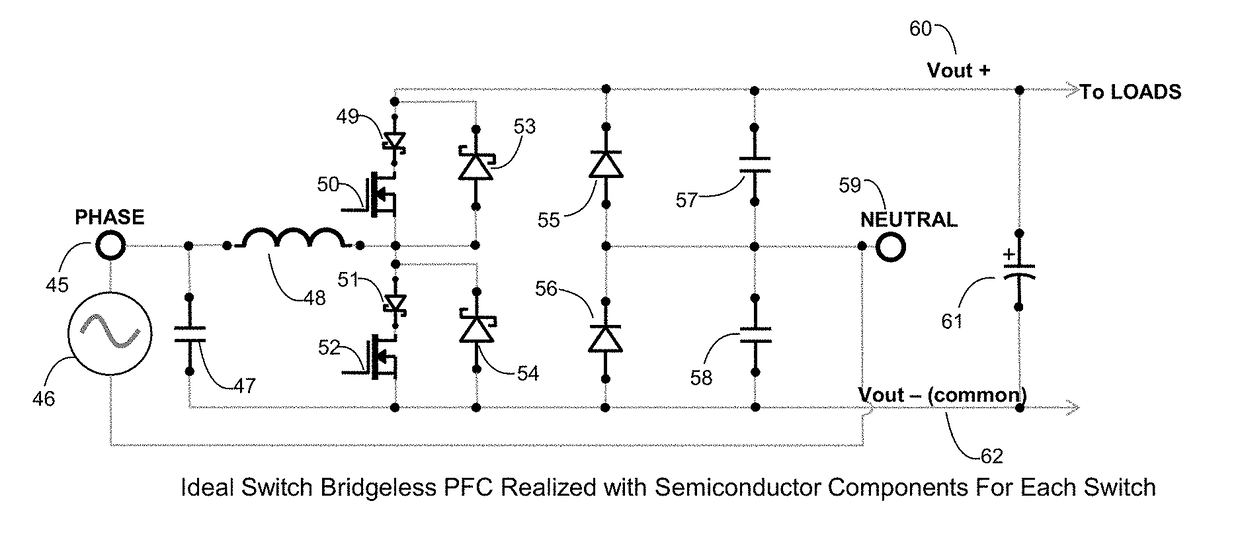
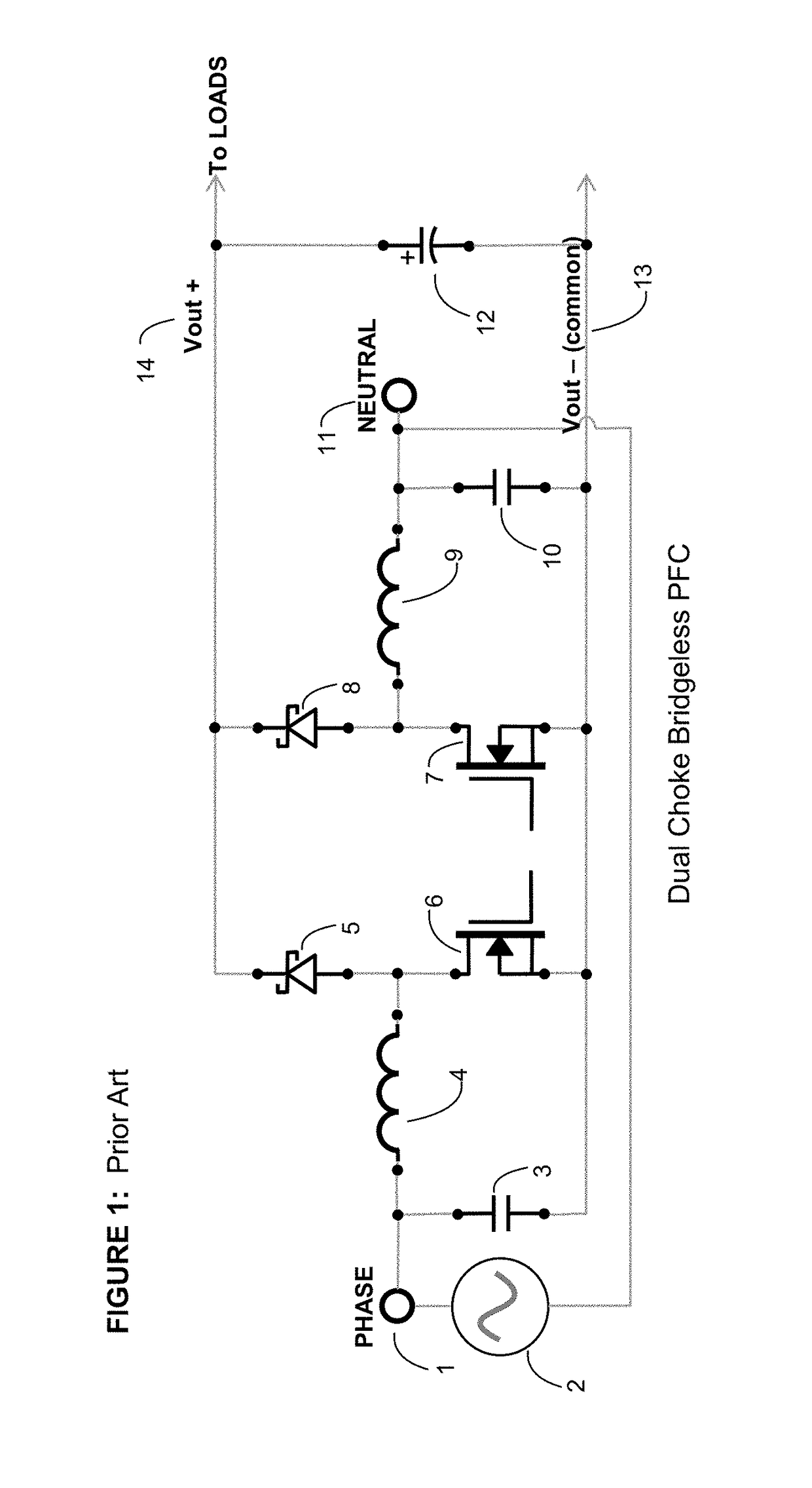
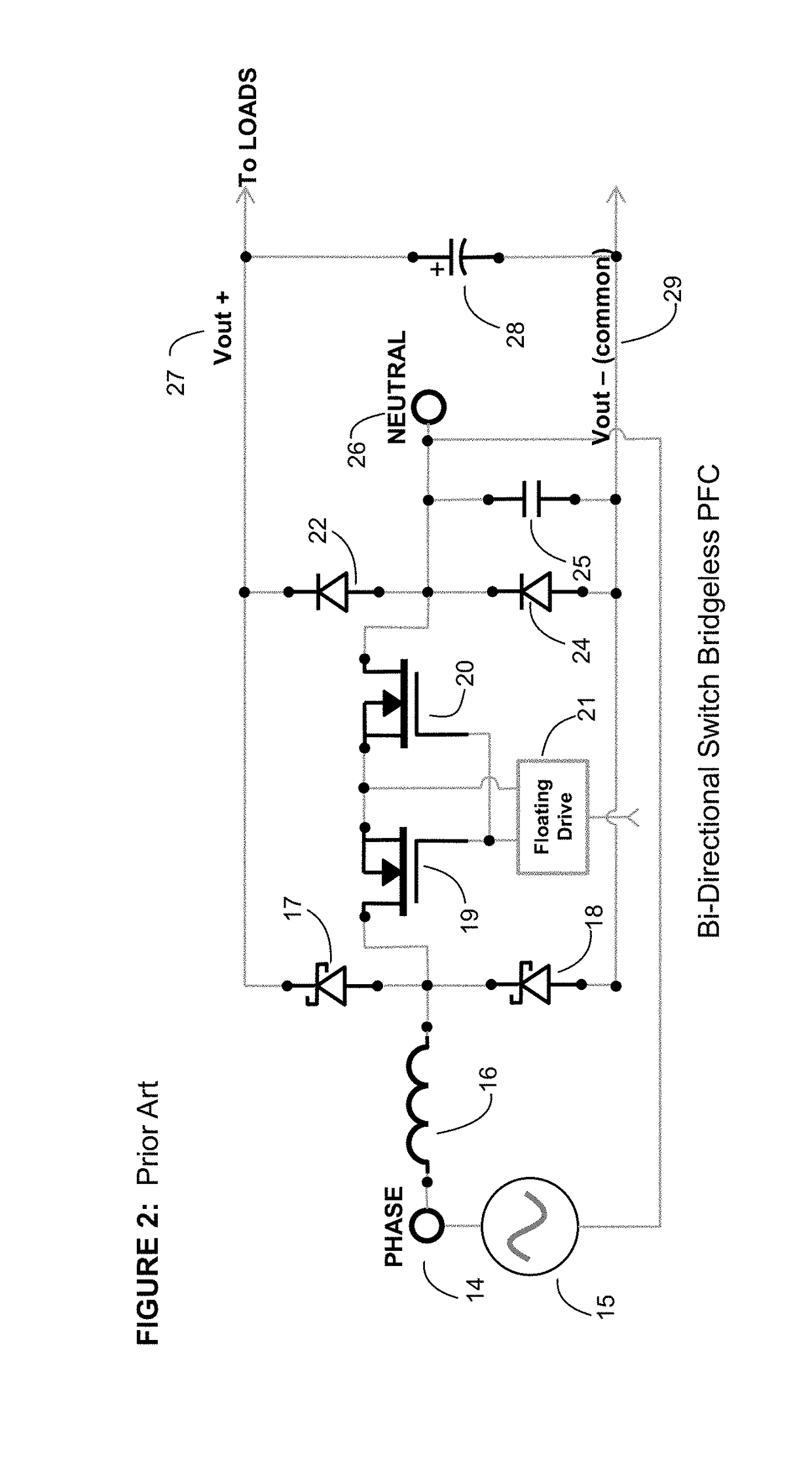
Ideal switch bridgeless pfc
InactiveUS20170214314A1Easy to driveImprove featuresAc-dc conversion without reversalEfficient power electronics conversionPower factor correction circuitsZero crossing distortion
Ideal switch bridgeless PFC topologies are presented with the purpose of increasing the efficiency in power factor correction circuits and inverter applications. The topology also leverages the new GaN switches that are available. This patent offers also a very good solution for the Zero crossing distortion problem improving greatly the THD both in power factor correction and inverter applications.
Owner:ROMPOWER TECH HLDG LLC
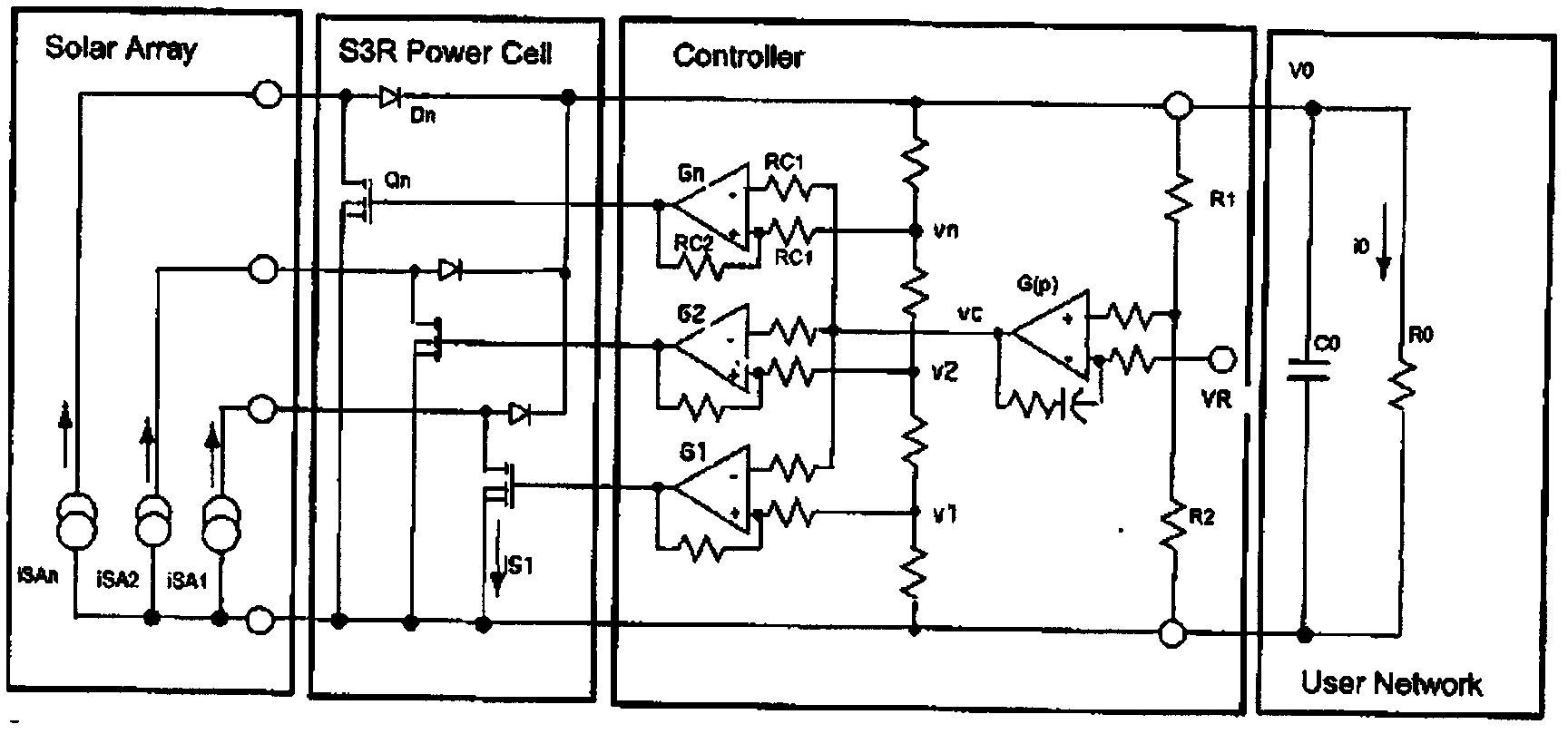
Lithium ion storage battery charging method based on sequential shunt switching regulation (S3R)
ActiveCN102324583AOptimize topologyRealize constant current and constant voltage charging controlSecondary cells charging/dischargingLithiumCharge current
The invention discloses a lithium ion storage battery charging method based on sequential shunt switching regulation (S3R). Based on an original S3R system battery charging control regulator (BCR) constant current charging, the lithium ion storage battery charging method based on S3R improves a constant-pressure charging standard, and can introduce directly a part of solar battery arrays for charging of a storage battery in order to solve the problem of heavy-current charging. When heavy-current charging is needed, the directly introduced solar battery arrays and a BCR are combined to form a heavy and constant-current charging mode, wherein the BCR is utilized for accurate adjustment of charging current intensity. When charging develops to a constant voltage stage, a BEA replaces D / A control to convert the BCR to constant voltage control so that a charging current decreases gradually. When heavy-current charging is not needed, a rapid charging array is switched off by a BEA control signal. When a detection result shows that a solar cell array current is surplus and a charging current is less than a certain value, the storage battery is full and D / A output is stopped so that charging is finished. The lithium ion storage battery charging method based on S3R can satisfy the requirements of heavy-current, constant-current and constant-voltage charging control of Leo satellite lithium ion storage batteries.
Owner:AEROSPACE DONGFANGHONG SATELLITE
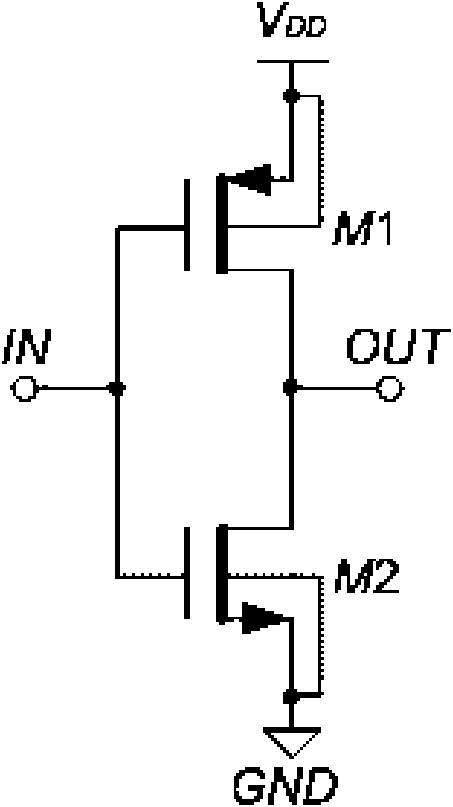
Switch-capacitor integrator
InactiveCN101621292ARelax requirementsOptimize topologyElectric pulse generator detailsLogic circuitsCapacitanceIntegrator
The invention discloses a switch-capacitor integrator adopting novel C-class inverters and a switch-capacitor integrator realizing form of a pseudodifferential structure. The switch-capacitor integrator in a pseudodifferential structure comprises two novel C-class inverters (60) and capacitors such as a sampling capacitor CS, a compensation capacitor CC, an integrating capacitor CI, and the like, switches such as an NMOS switch S2, an NMOS switch S4, an NMOS switch S7, an NMOS switch S8, a CMOS switch S3, a CMOS switch S5, a bootstrap NMOS switch S1, a bootstrap NMOS switch S6, a bootstrap NMOS switch S9, and the like and a common mode feedback circuit (61) in the prior art, wherein the two novel C-class inverters (60) are respectively positioned in a positive branch and a negative branch of the integrator and differentially symmetrized to be in the pseudodifferential structure. The invention overcomes the effects of indexes of working efficiency, establishing time, integrating accuracy, power consumption, and the like on the switch-capacitor integrator by technical deviation through the bulk potential modulation effect of a bulk potential modulator in the novel C-class inverters and greatly improves the stability and the robustness of the integrator without obviously increasing the power consumption.
Owner:ZHEJIANG UNIV
Trench polysilicon diode
Embodiments of the present invention include a method of manufacturing a trench transistor. The method includes forming a substrate of a first conductivity type and implanting a dopant of a second conductivity type, forming a body region of the substrate. The method further includes forming a trench in the body region and depositing an insulating layer in the trench and over the body region wherein the insulating layer lines the trench. The method further includes filling the trench with polysilicon forming a top surface of the trench and forming a diode in the body region wherein a portion of the diode is lower than the top surface of the trench.
Owner:VISHAY SILICONIX LLC
Method of catastrophic transfer of a thin film after co-implantation
ActiveUS7772087B2Reduce roughnessHigh mechanical stressSemiconductor/solid-state device manufacturingCo implantationAtomic physics
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES +1
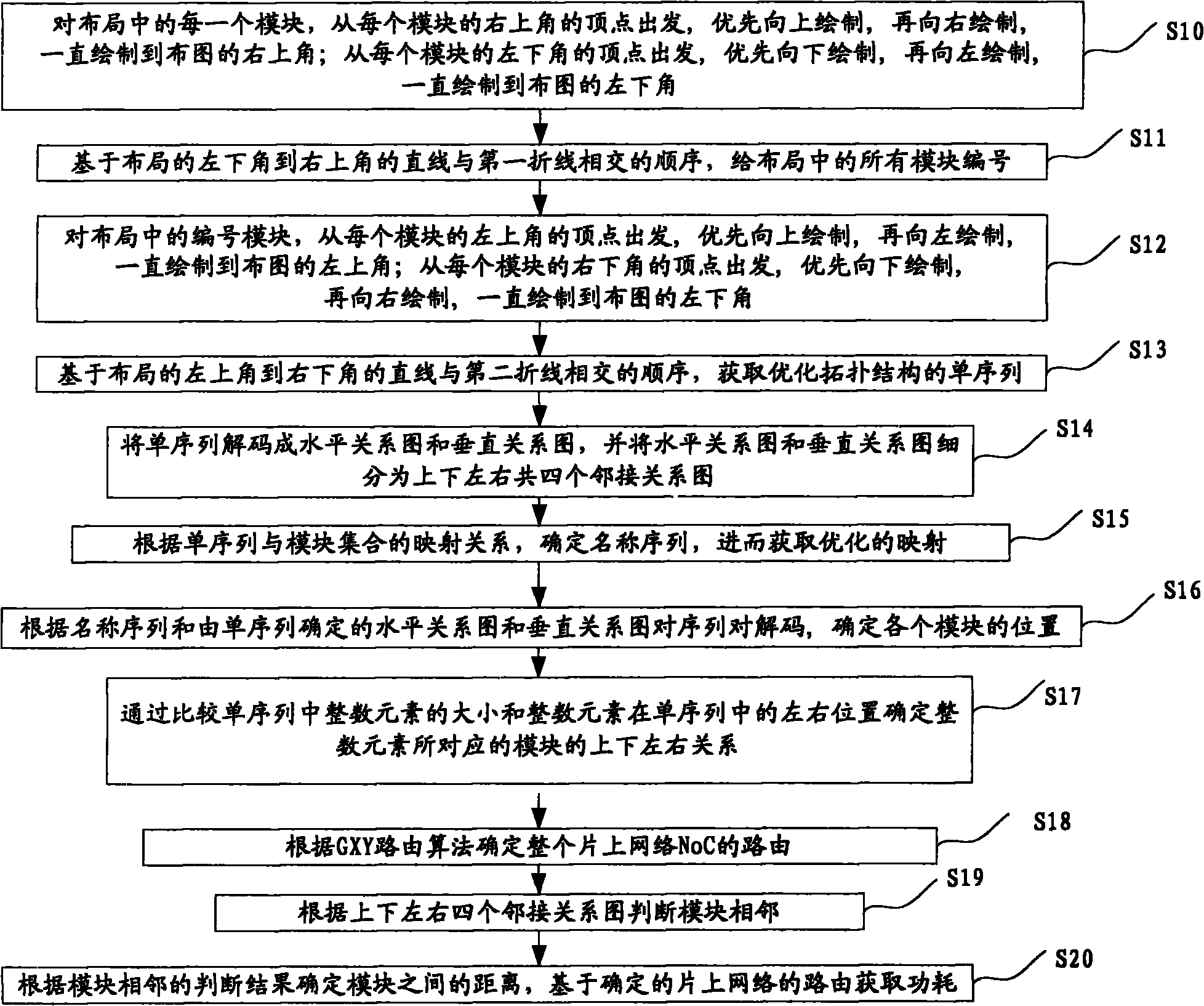
Method for optimizing topological structure and mapping of network on chip
InactiveCN101834780AOptimize topologyEasy mappingData switching networksSpecial data processing applicationsNetwork structureSingle sequence
The invention discloses a method for optimizing a topological structure and mapping of a network on chip (NoC), which comprises the following steps of: determining a single sequence (SS) for optimizing the topological structure through two drawing methods; and acquiring a name sequence for optimizing the mapping through a mapping relation between the single sequence (SS) and a module collection. So, the method can optimize a network structure and the mapping and reduce the power consumption. Besides, the method adopts a GXY routing algorithm to determine the routing of the entire network on chip (NoC), and performs optimization according to a simulated annealing algorithm to obtain a layout result that the power consumption is low and the area is small.
Owner:WUHAN UNIV OF TECH
Security check method for running way of power communication network
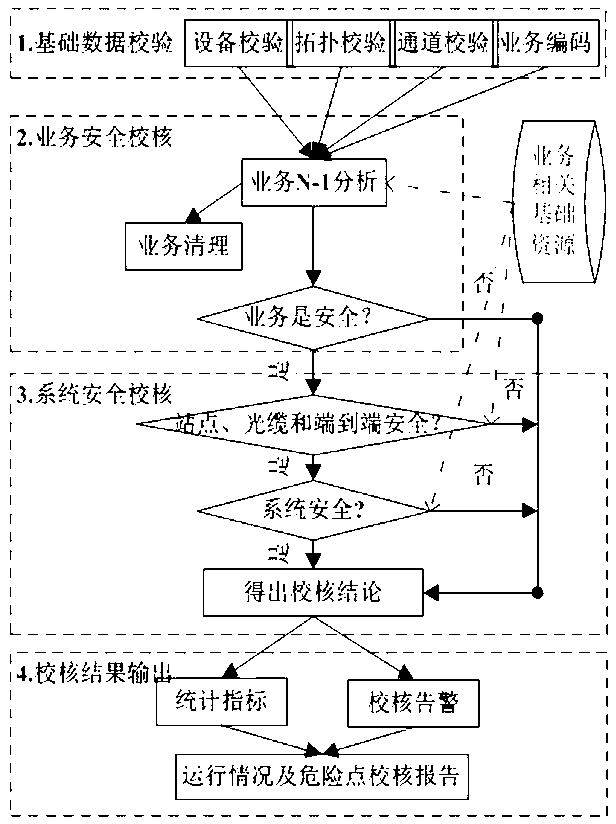
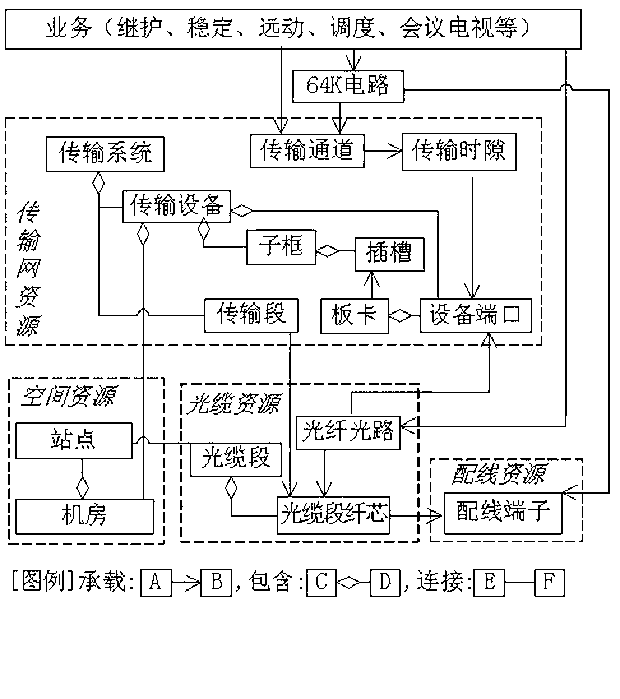
ActiveCN103310387AGuaranteed uptimeOptimize topologyData processing applicationsComputer networkReal time analysis
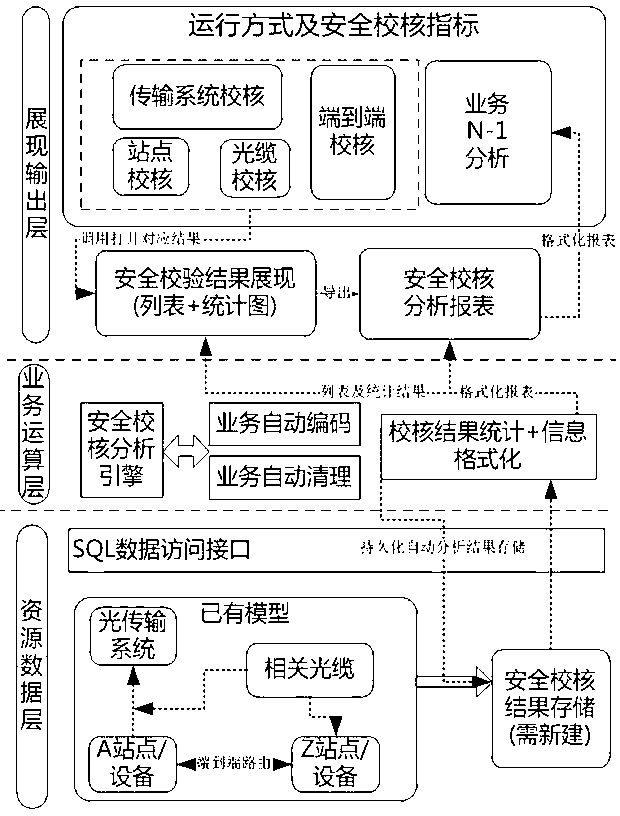
The invention discloses a security check method for the running way of a power communication network. The method comprises the following steps: (1) performing basic data verification: inputting basic data related to the running way, and verifying the uniqueness, rationality and integrity of the basic data; (2) performing service security check: analyzing whether an entire service and each section of route through which the service passes meets an N-1 requirement or not on the basis of a communication service route, and judging whether the service is safe or not during service clearing to make a service security check conclusion; (3) performing system security check to make a security check conclusion of a system; and (4) outputting a check result. According to the method, a relevant service circuit basic encoding rule is put forward on the basis of service N-1 analysis and system security check, and analysis of the service security and system security of the power communication network is realized on the basis of the encoding in combination with N-1 service influence analysis and an effective outlet analysis algorithm, so that a reliable and stable running way security check system can be realized by adopting the design, and online and real-time analysis of the running way of the communication network is realized.
Owner:STATE GRID CORP OF CHINA +2
Multi-time scale heat damage-based improved hybrid MMC operation reliability assessment model and method
ActiveCN108509674AOptimize topologyIncreased level of operational reliabilityDesign optimisation/simulationSpecial data processing applicationsCapacitanceOriginal data
The invention discloses a multi-time scale heat damage-based improved hybrid MMC operation reliability assessment model and method. The method mainly comprises the following steps of: 1) obtaining real-time data of a wind power transmission system, wherein the real-time data mainly comprises a wind speed, an air temperature and equipment electric parameters; 2) establishing a hybrid MMC power device reliability assessment model by utilizing hybrid MMC operation characteristics and a Miner's damage theory according to original data, wherein power devices of the wind power transmission system mainly comprise an insulated gate bipolar transistor IGBT and a crystal diode; 3) establishing a faulted SM voltage sharing-considered capacitor reliability assessment model according to influences, onintact SM capacitors, of faulted SM; and 4) analyzing hybrid MMC device loss distribution so as to establish an SM multi-state-considered improved hybrid MMC operation reliability assessment model. The model and method can be widely applied to operation reliability assessment of hybrid MMC in transmission grid connection of renewable energy sources such as wind power and the like.
Owner:CHONGQING UNIV
Proppant transport simulation method based on three-dimensional pseudo-continuum hydraulic fracturing model
ActiveCN109064561AOptimize topologySolving Migration SimulationsDesign optimisation/simulationSpecial data processing applicationsSimulationModel parameters
The invention discloses a proppant migration simulation method based on a three-dimensional pseudo-continuous medium hydraulic fracturing model, which comprises the following steps of: establishing athree-dimensional pseudo-continuous medium hydraulic fracturing model, introducing model parameters and solving and calculating, and starting to generate new fractures at a certain time; Generating aninitial crack topology; A plurality of topological linked lists represent fracture networks with proppant migration; Automatically merge multiple crack topology links; Remove redundant topology network; Output fracture topology to simulate proppant transport; The simulation of proppant transport based on three-dimensional pseudo-continuum hydraulic fracturing model is realized. The invention effectively solves the proppant migration simulation, optimizes the fracture network topology structure, considers the merging of the topology chain list and the deletion of the redundant topology network, and accelerates the calculation speed of the fracture expansion simulation and the proppant migration simulation.
Owner:北京软能创科技有限公司
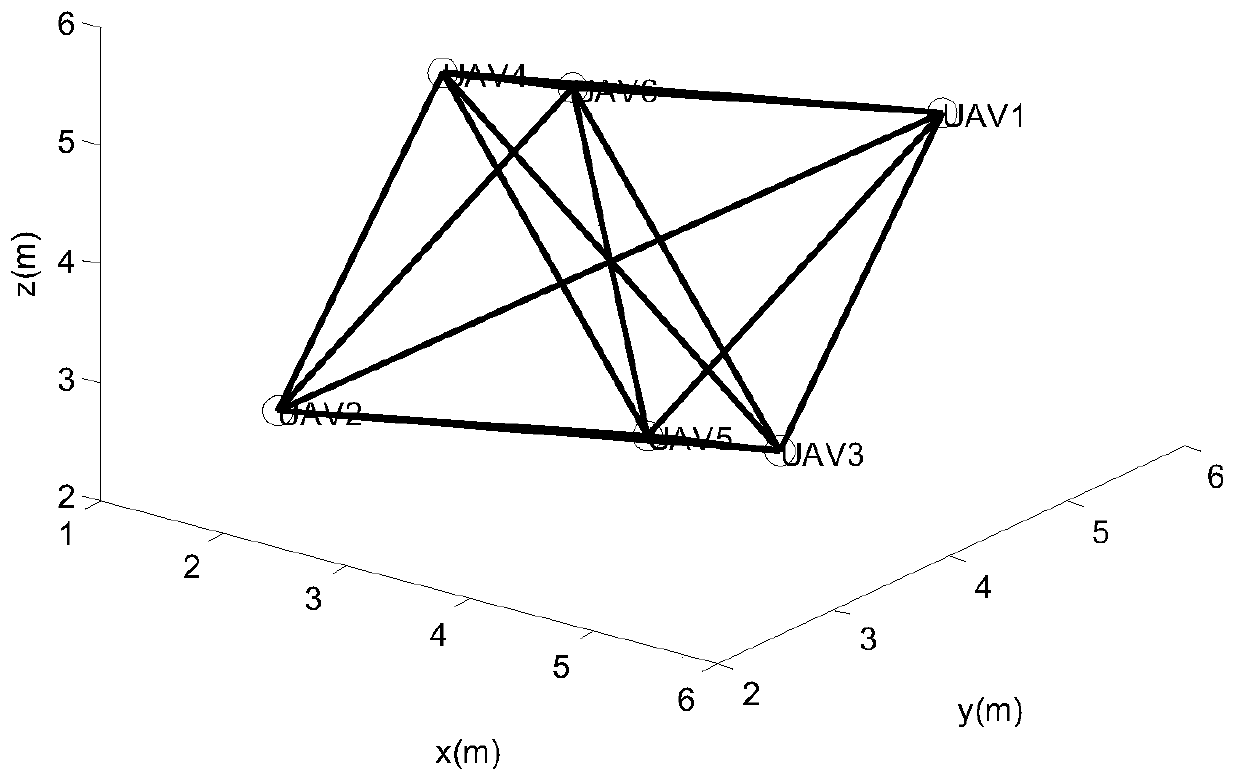
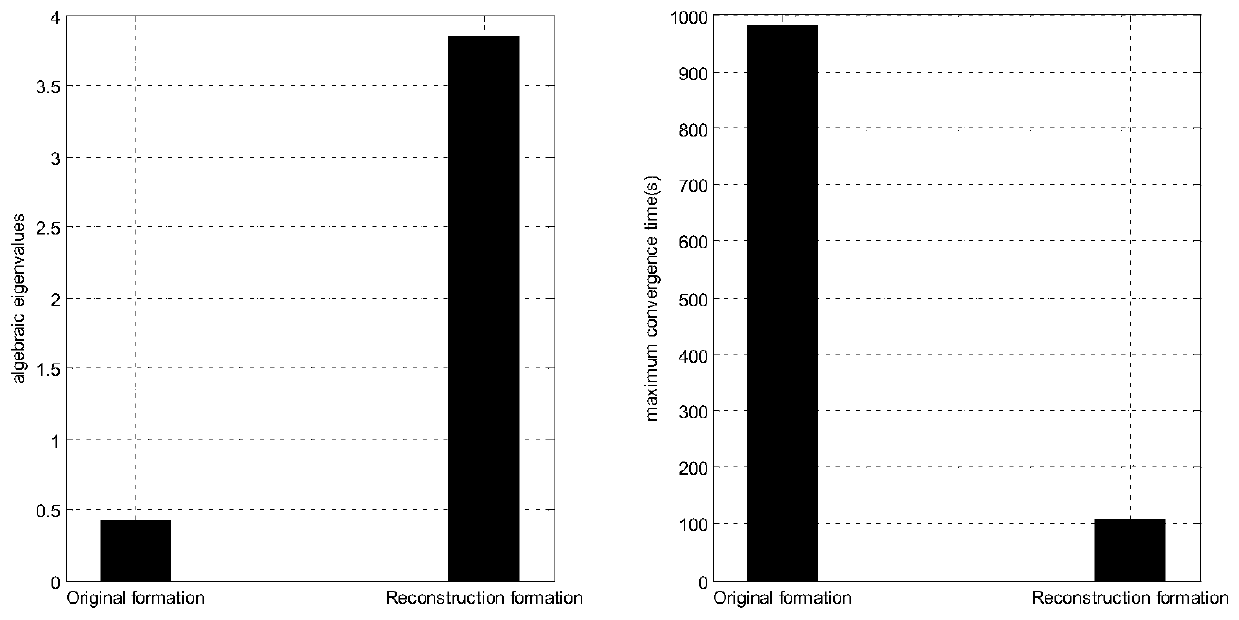
Unmanned aerial vehicle formation consistency control method, system and device under time-varying channel based on topological optimization and storage medium
ActiveCN110673649AOptimize topologyEnhanced formation controlInternal combustion piston enginesPosition/course control in three dimensionsTopology informationAlgorithm
The invention provides an unmanned aerial vehicle formation consistency control method, system and device under a time-varying channel based on topological optimization, and a storage medium. The method comprises the steps: performing distributed data transmission by unmanned aerial vehicles in a formation to obtain a formation topology; selecting a point with the maximum in-degree in the formation topology as a central point of the formation, and calculating an algebraic characteristic value of a topological Laplace matrix by combining the central point with global formation topology information; estimating the maximum convergence time of prediction consistency control according to the relationship between the algebraic characteristic value and the formation consistency control rate; carrying out topology reconstruction and optimization on the formation; and performing consistency control according to the optimized formation topology. The invention has the beneficial effects that thetopological structure can be effectively improved, the formation control under a deteriorated multipath channel is enhanced, the control precision within limited convergence time can be ensured, and avery good technical effect is achieved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
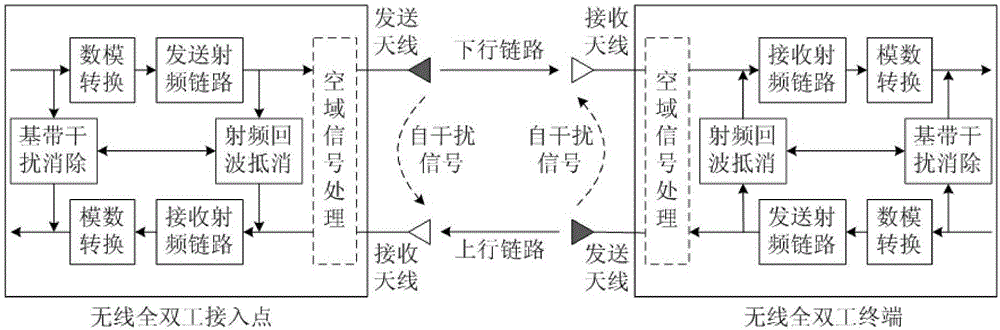
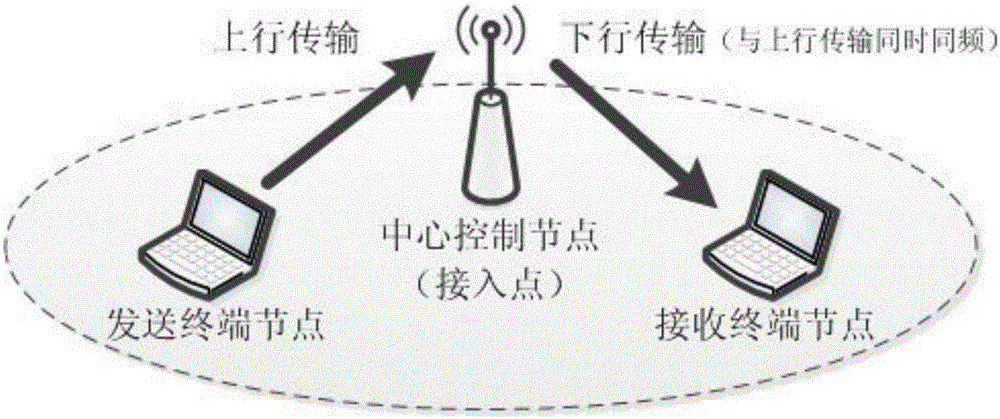
Method for node matching and resource competition in full-duplex wireless network
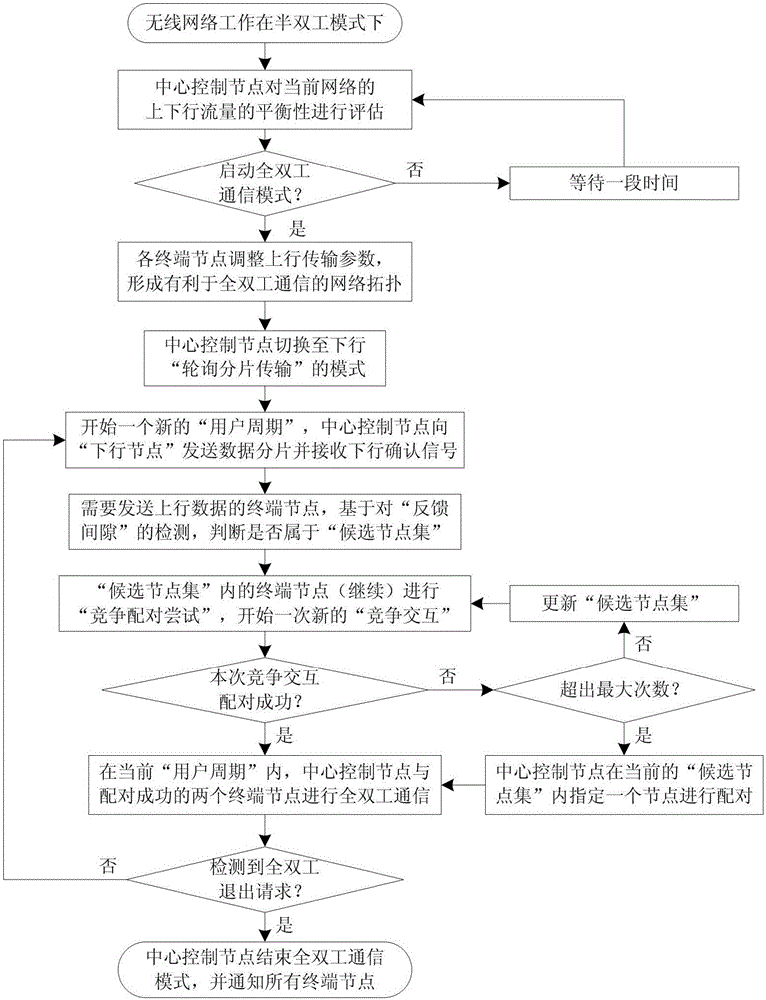
ActiveCN105162568AOptimize topologySolve resource problemsDuplex signal operationComputer networkMulti user environment
The invention relates to a method for node matching and resource competition in a full-duplex wireless network. According to the invention, key problems such as resource competition, flow matching, co-channel interference, node matching, uplink multi-terminal competition access and the like in an existing full-duplex network are effectively solved through comprehensively applying technical means of flow balance evaluation, uplink parameter adaption, polling fragment transmission, feedback gap detection, competition matching attempt and the like, and reliable and efficient co-channel two-way transmission is realized under a multi-user environment.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
A prototype modeling method of network security attack based on industrial control
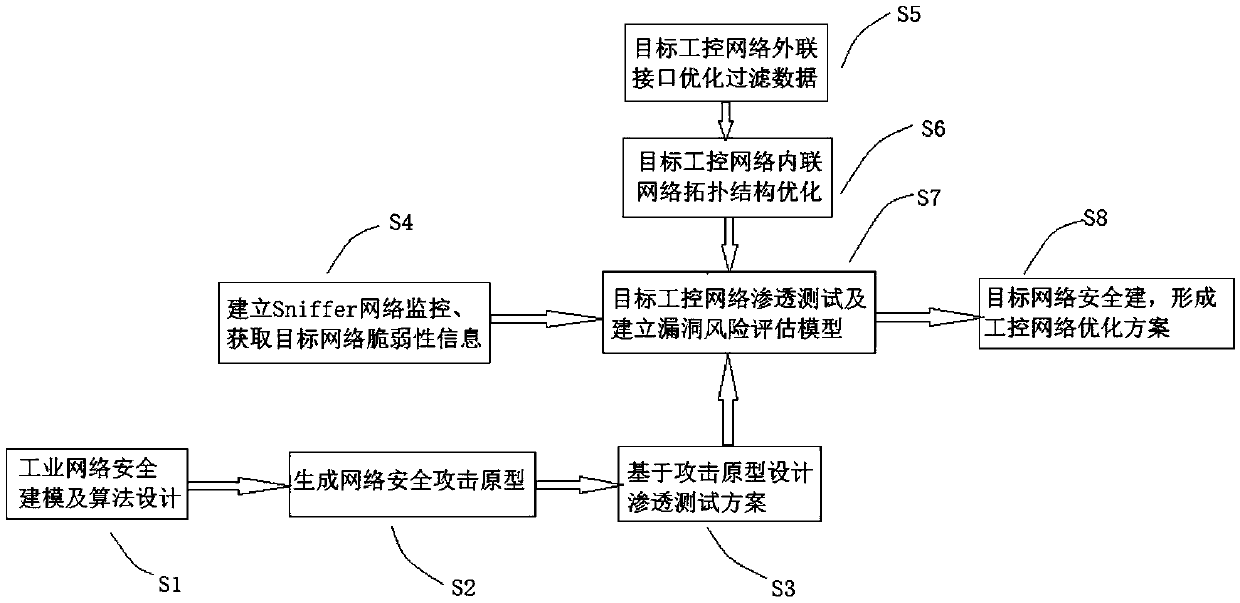
InactiveCN109543301AOptimize topologyDeny illegal intrusionDesign optimisation/simulationTransmissionSecurity solutionVulnerability
The invention discloses an industrial control network security method based on industrial network attack prototype modeling, which comprises the following steps: S1, industrial network security modeling and algorithm design; S2, designing an industrial control network security attack prototype; S3, taking an attack model of an attacker in an algorithm of the attack prototype in S1 as an attack source, and converting the network vulnerability information obtained in S4 into an attack set of an attacker according to attack rules to form an attack prototype; S4: Designing penetration test schemebased on attack prototype; 5, establishing a Sniffer network monitoring system; 6, optimizing and filtering that data through the external interface of the target industrial control network; 7, optimizing that topology structure of the intranet of the target industrial control network; S8: Establishing vulnerability risk assessment and modeling; S9: Forming an industrial network security defense solution. The network optimization and safety solution provided by the invention will effectively solve the safety problem of the industrial control of the enterprise, can timely carry out the risk assessment on the system, reduce the risk factors to the maximum extent, and improve the network operation efficiency and the safety reliability of the production management.
Owner:SUZHOU CHIEN SHIUNG INST OF TECH
Mine surrounding rock monitoring system based on wireless sensor network
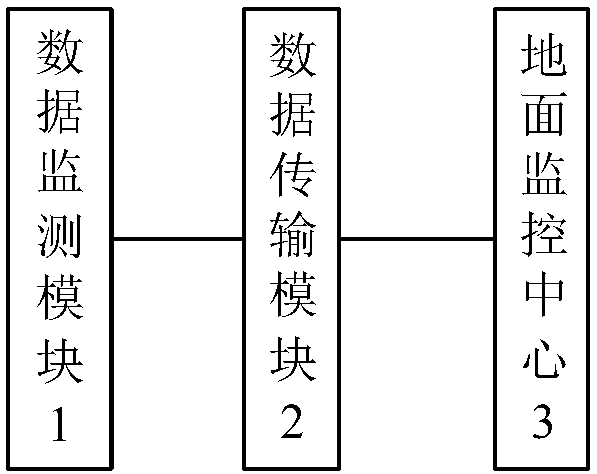
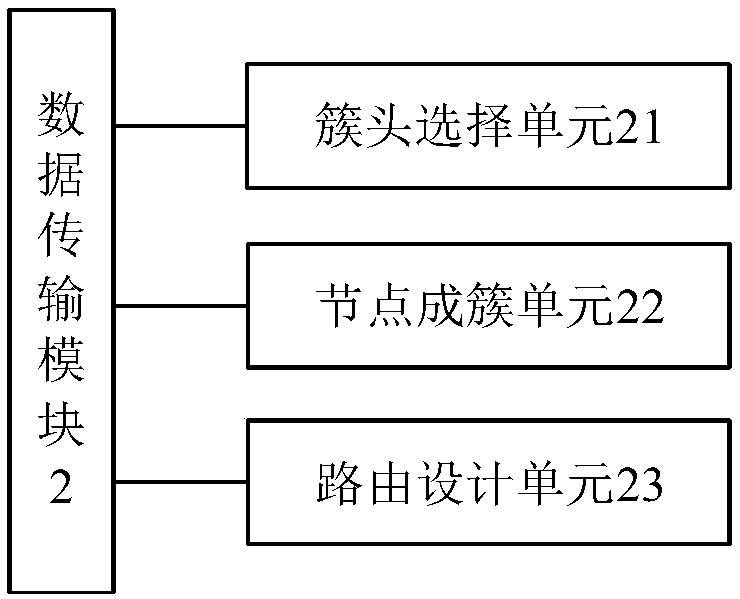
InactiveCN107484222AOptimizing Race ConditionsOptimize topologyPower managementMeasurement devicesLine sensorWireless mesh network
The invention discloses a mine surrounding rock monitoring system based on a wireless sensor network. The system comprises a data monitoring module, a data transmission module and a ground monitoring center. The data monitoring module is used for collecting characteristic changes resulting from surrounding rock stress change in an underground coal mining process, wherein the collection comprises temperature collection, pressure collection and slight vibration signal collection. The data transmission module is used for transmitting collected temperature, pressure and slight vibration signals to the ground monitoring center through adoption of a wireless sensor network technology. The ground monitoring center is used for analyzing geological condition according to the change of received monitoring data when underground mining is carried out and carrying out alarm when an abnormity occurs in the monitoring data. The system has the beneficial effects that through adoption of the wireless sensor technology, the security monitoring of mine surrounding rocks is realized; in the wireless sensor network, a cluster head in the network is selected through adoption of an improved LEACH algorithm; a cluster head competition condition is optimized; and the problem that cluster head nodes are not distributed uniformly is overcome.
Owner:潘金文
EtherCAT-based direct current common bus servo driving apparatus
InactiveCN106849765ATroubleshoot delaysReduce volumeMultiple ac dynamo-electric motors controlIndustrial EthernetPrimary station
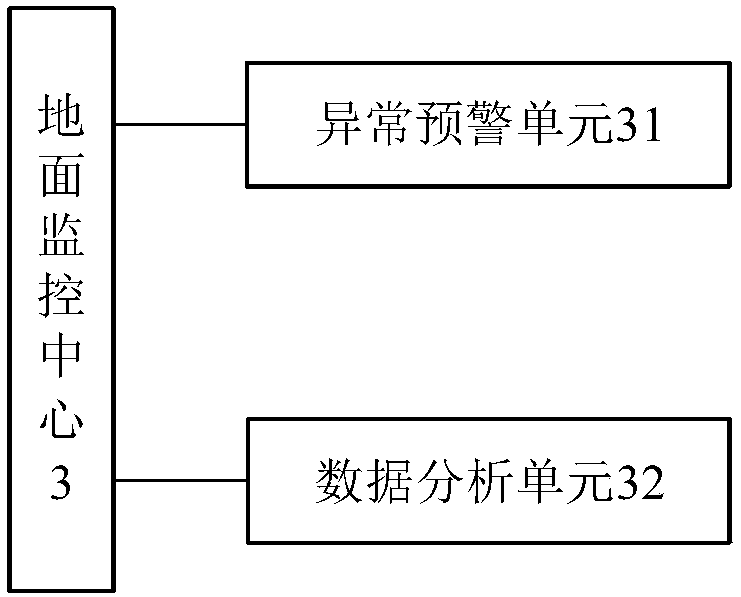
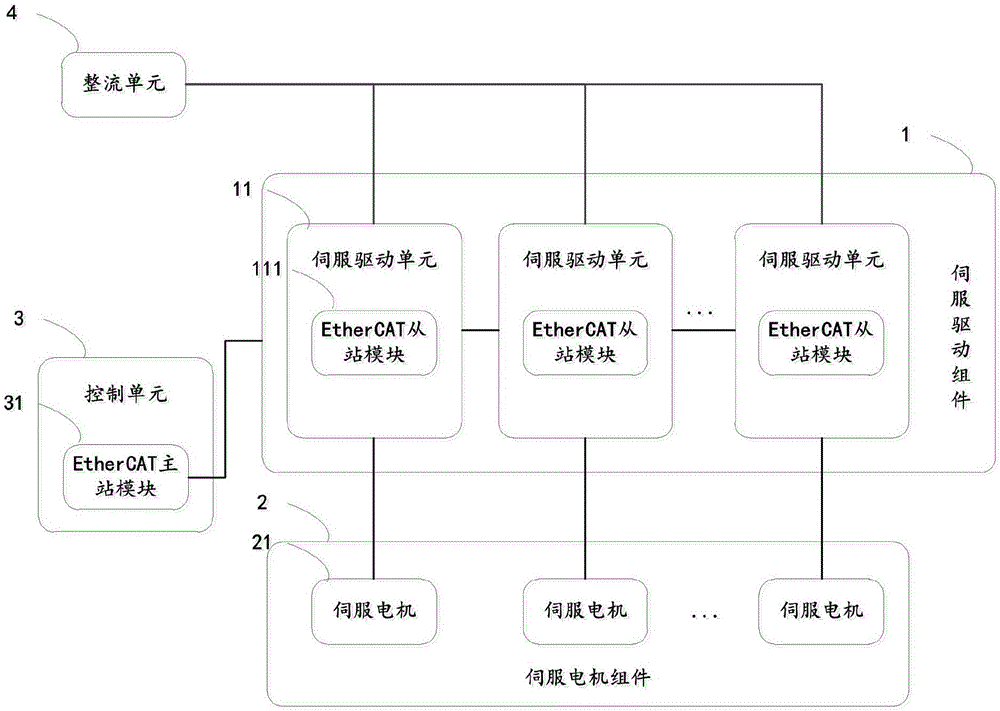
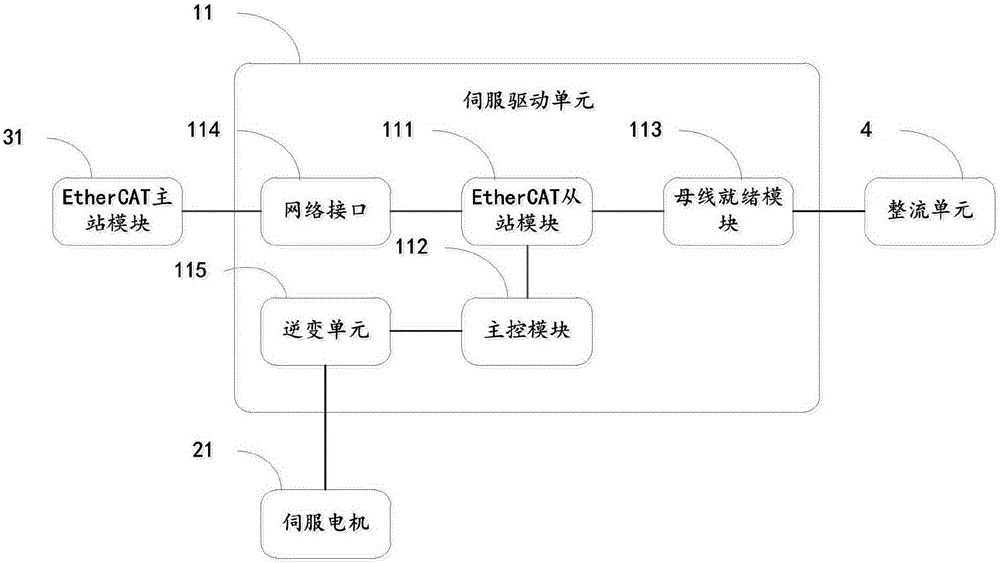
The invention relates to a DC common bus servo drive device based on EtherCAT. The DC common bus servo drive device includes: a servo drive component, a servo motor component, a control unit and a rectifier unit. Both the rectifier unit and the control unit are connected to the servo drive component. The servo drive The components are connected to the servo motor assembly; the control unit includes an EtherCAT master station module; the servo drive assembly includes at least one servo drive unit connected in sequence, the servo motor assembly includes at least one servo motor, and each servo drive unit is connected to a servo motor; each servo drive The units are connected to the rectification unit; each servo drive unit includes an EtherCAT slave module, and each EtherCAT slave module is connected to the EtherCAT master module. The beneficial effects of the invention are: the EtherCAT real-time industrial Ethernet topology structure is convenient, the cost is low, the volume is small, the number of servo drivers can be increased or decreased according to actual application requirements, and the disassembly and assembly are convenient.
Owner:CHONQING HUASHU ROBOT CO LTD +1
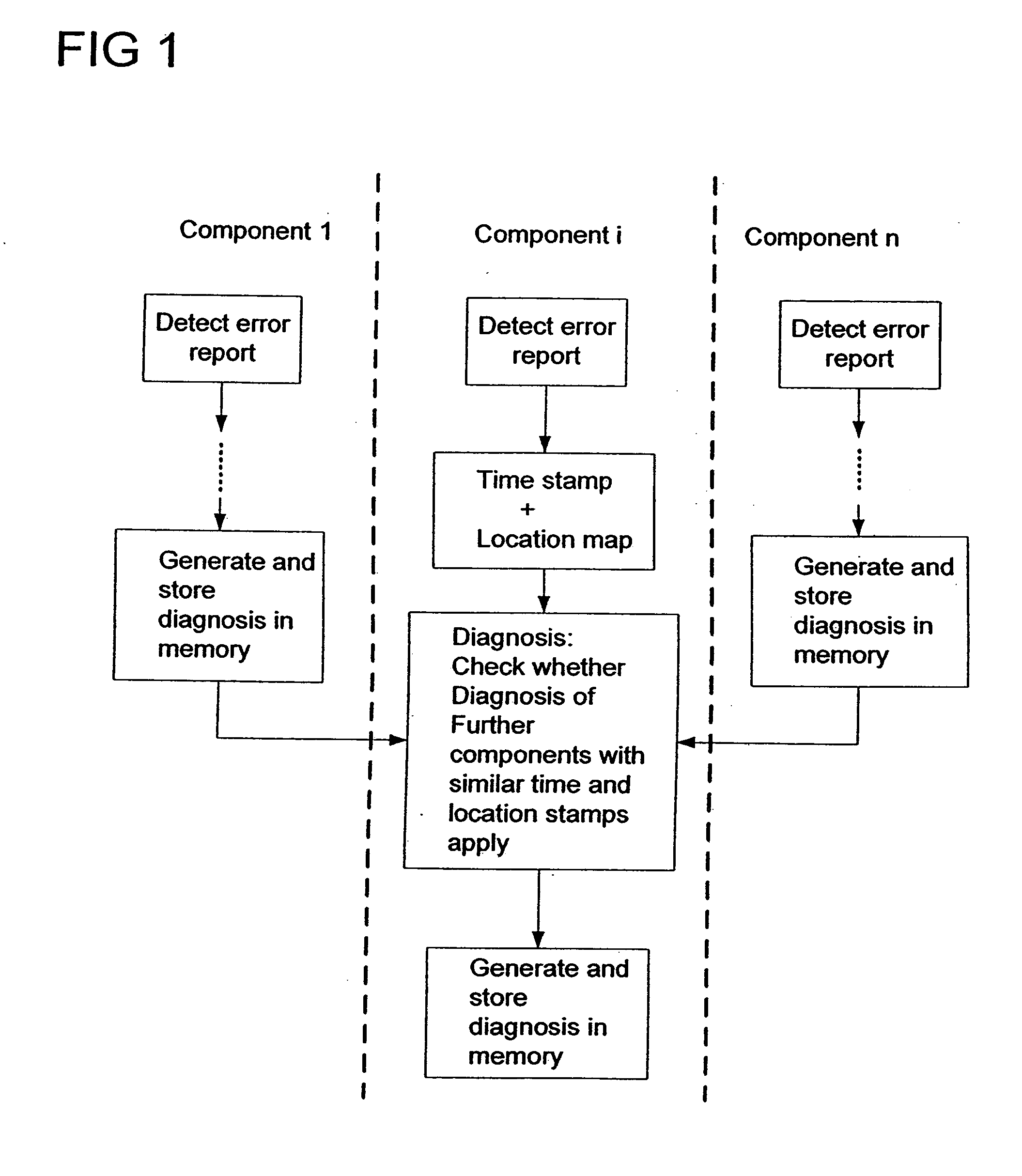
Method and apparatus for diagnosing monitoring systems of technical equipment
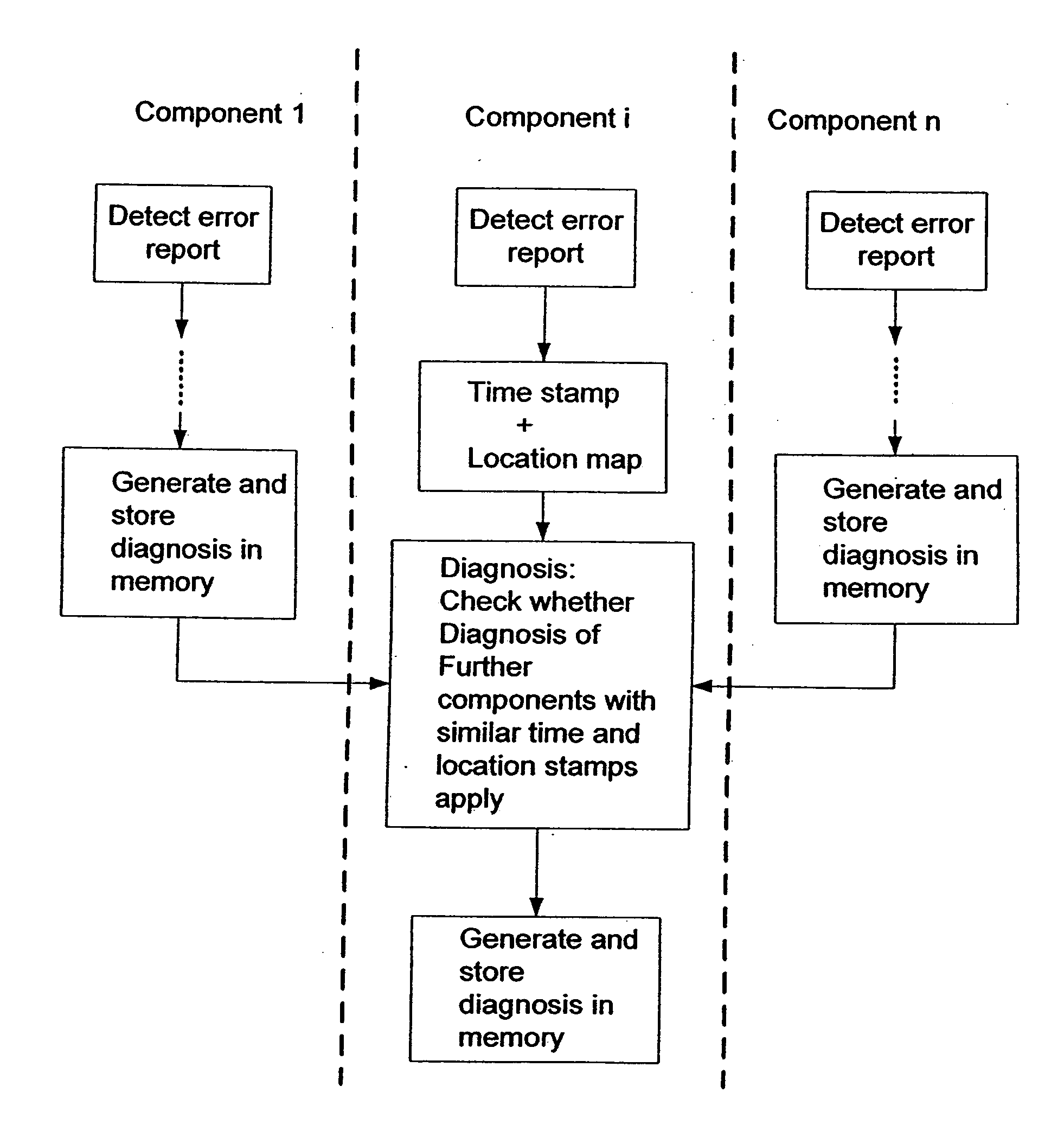
InactiveUS20060047995A1Quality of error diagnosis and searchOptimize topologyError detection/correctionTesting/monitoring control systemsSimilar timeDefective Component
Owner:SIEMENS AG
System-on-chip (SoC) optimization through transformation and generation of a network-on-chip (NoC) topology
InactiveUS10348563B2Improve system efficiencyLower areaCAD circuit designArchitecture with single central processing unitTheoretical computer scienceNetworks on chip
The present disclosure is directed to system-on-chip (SoC) optimization through transformation and generation of a network-on-chip (NoC) topology. The present disclosure enables transformation from physical placement to logical placement to satisfy bandwidth requirements while maintaining lowest area and lowest routing with minimum cost (wiring and buffering) and latency. In an aspect, method according to the present application includes the steps of receiving at least a floor plan description of an System-on-Chips (SoCs), transforming said floor plan description into at least one logical grid layout of one or more rows and one or more columns, optimizing a number of said one or more rows and said one or more columns based at least on any or combination of a power, an area, or a performance to obtain an optimized transformed logical grid layout, and generating said Network-on-Chip (NoC) topology at least from said optimized transformed logical grid layout.
Owner:INTEL CORP
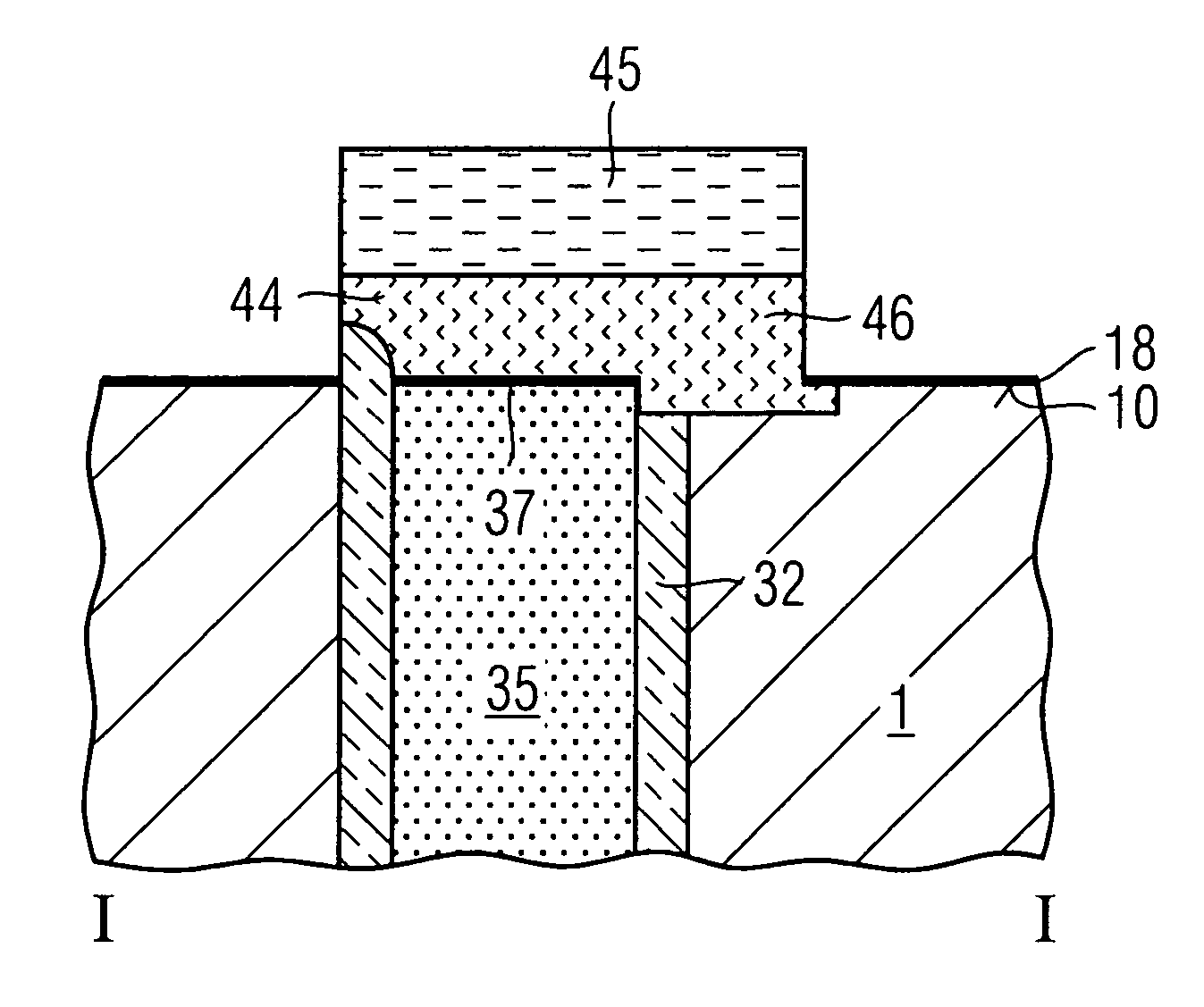
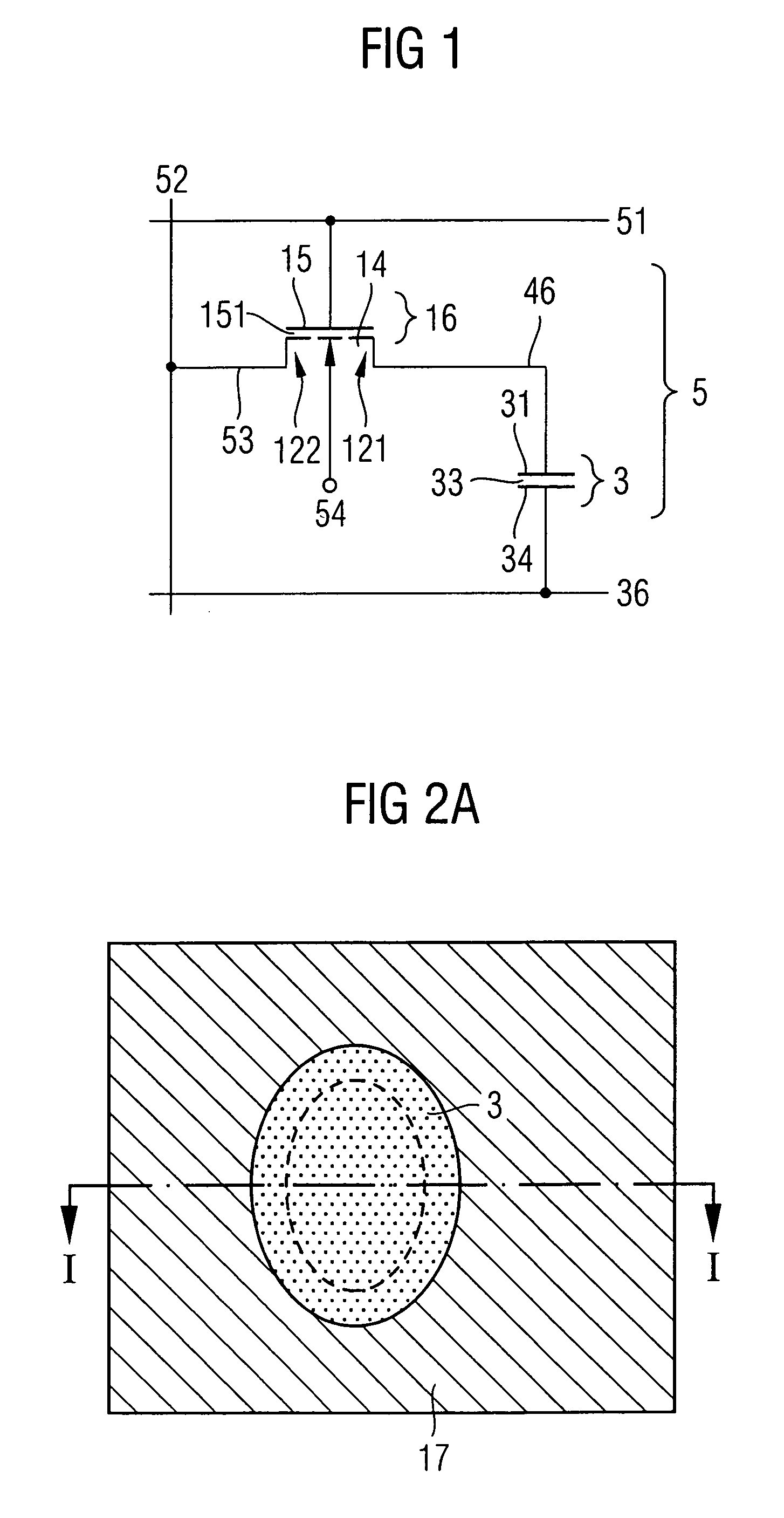
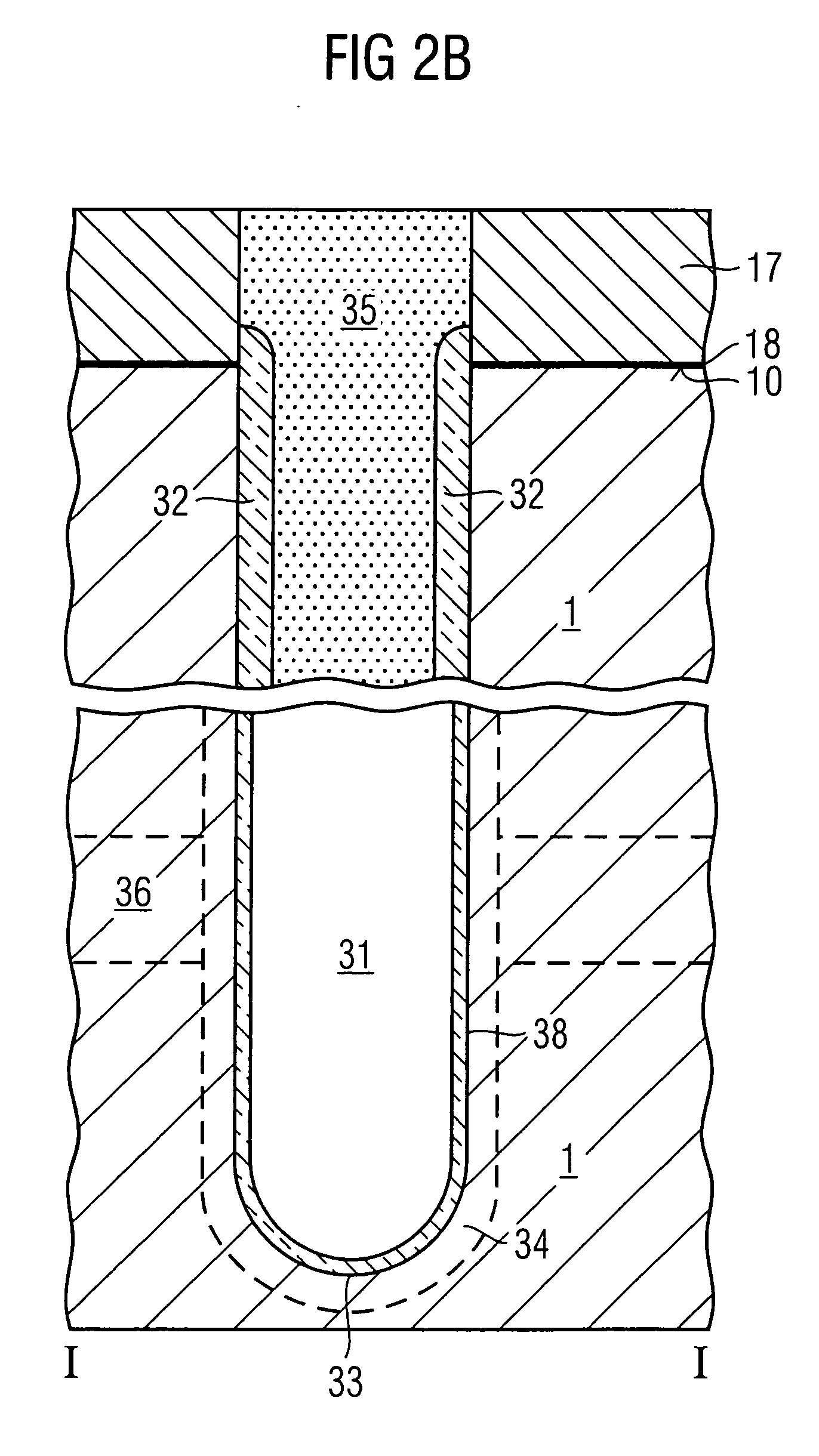
Connecting structure and method for manufacturing the same
InactiveUS20070032032A1Increase channel lengthLarge thicknessSolid-state devicesSemiconductor/solid-state device manufacturingEngineeringCapacitor
A method for manufacturing a surface strap connection between a trench capacitor and a selection transistor includes providing a masking material on a surface of a semiconductor substrate in areas where no trench capacitors have been formed. An undoped semiconductor layer having vertical and horizontal areas is applied. An oblique ion implantation is performed such that a vertical area of the semiconductor layer on which the connecting structure is to be formed is not doped. After removal of the undoped portion of the semiconductor layer, the exposed portion of the masking material is laterally etched, one part of the substrate surface is exposed, and the doped part of the semiconductor layer is removed. An electrically conducting connection material is applied so that an electrical contact exists between the exposed portion of the substrate surface and the storage electrode.
Owner:INFINEON TECH AG
Raster-vector geographic data reversible decryption method based on trigonometric function
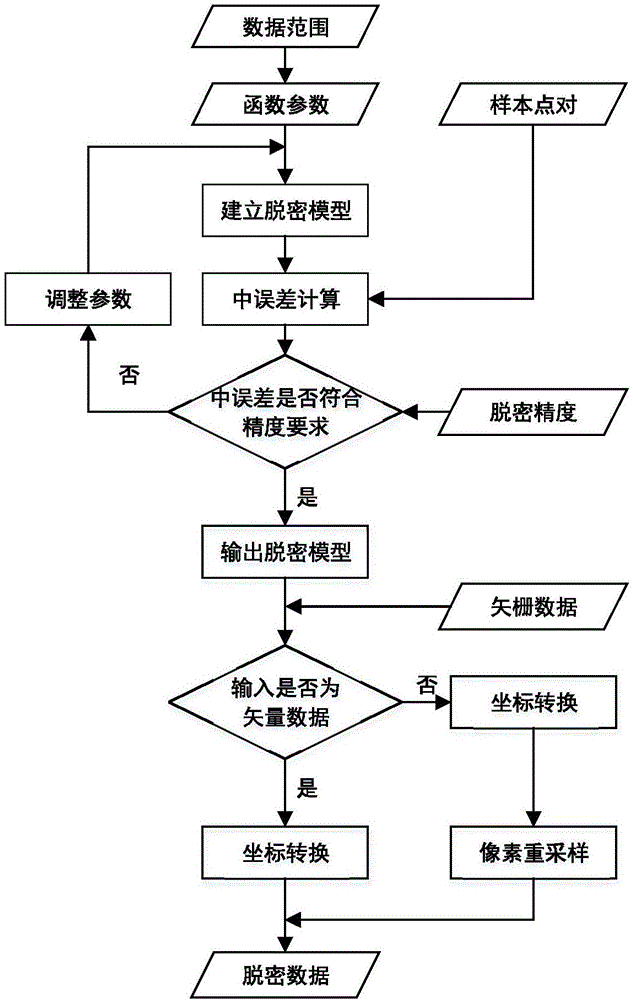
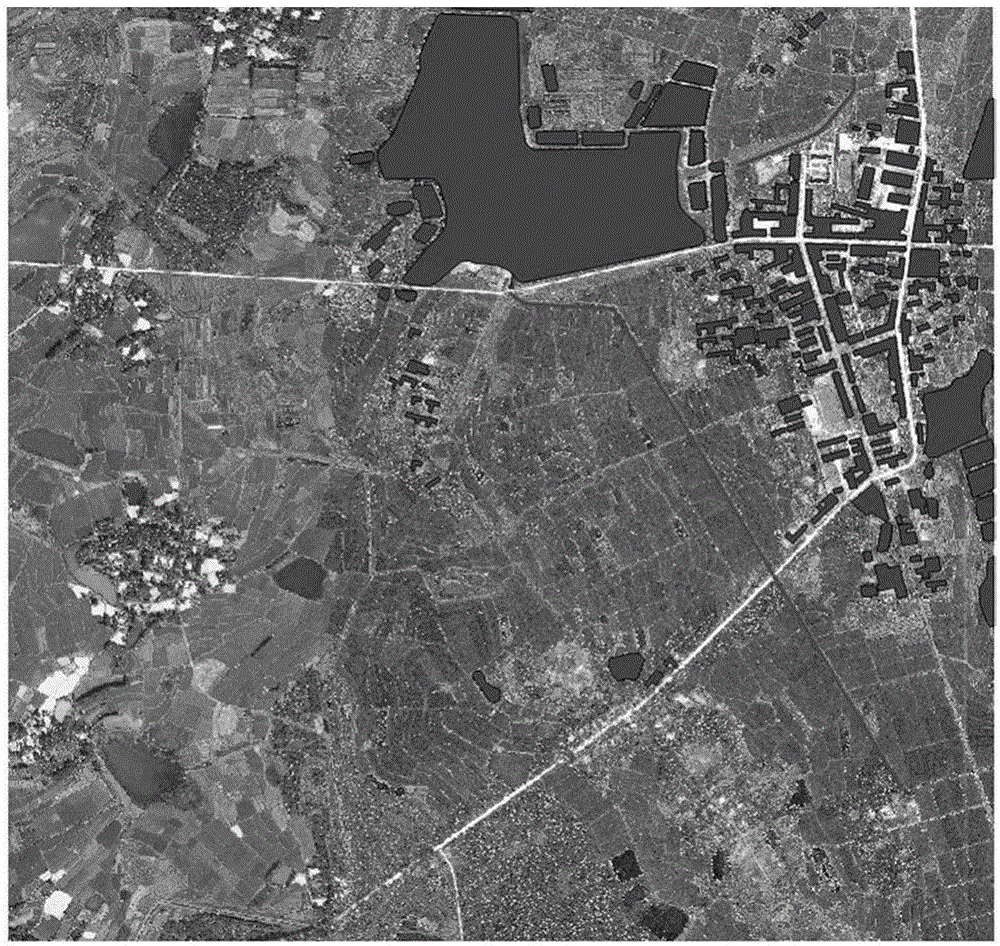
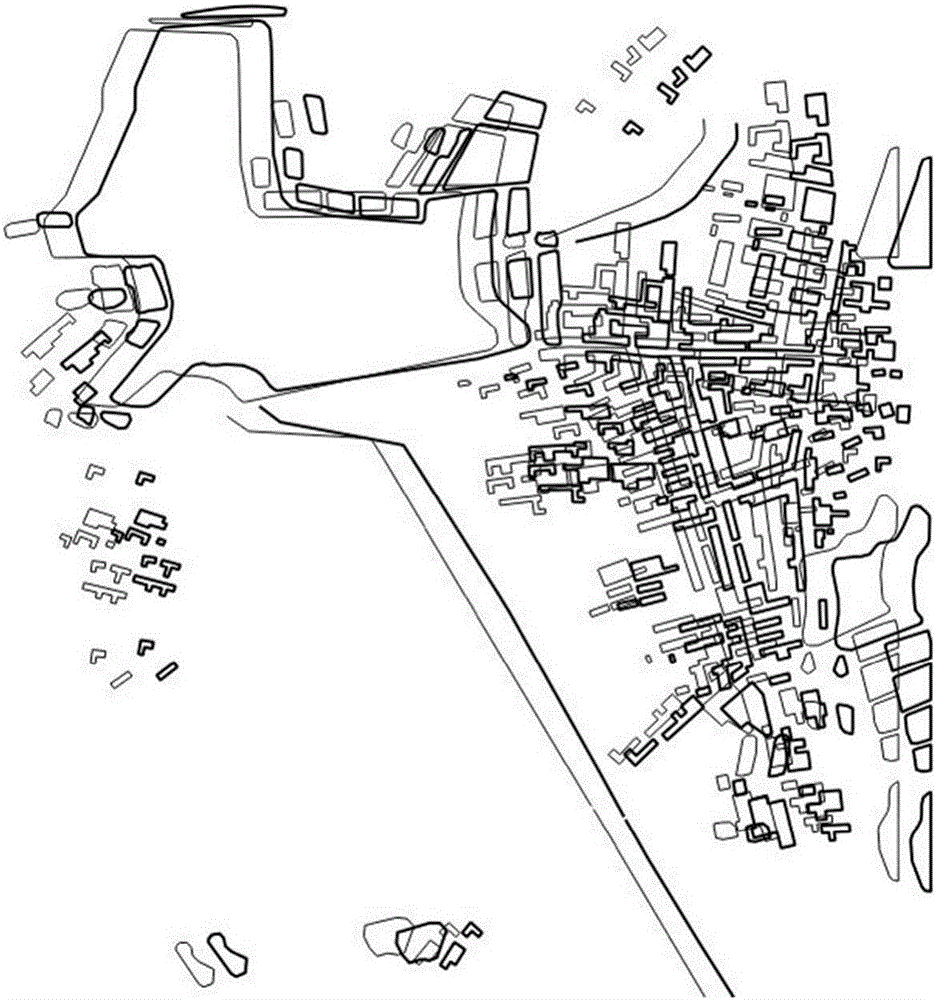
ActiveCN106778347AImprove resistance to attackImprove securityDigital data protectionSpecial data processing applicationsModel parametersComputer science
The invention provides a raster-vector geographic data reversible decryption method based on a trigonometric function. The method comprises the steps of building a trigonometric function model, calculating trigonometric function model parameters and building a decryption model according to original raster-vector geographic data, adopting the decryption model for performing decryption on the raster-vector geographic data, building a recovery model according to decryption model parameters, and adopting the recovery model for recovering the decrypted raster-vector geographic data. On the premise that the vector data topological relation is maintained unchanged, the excellent function characteristics of the trigonometric function are sufficiently utilized, and a decryption error is controlled by adjusting the amplitude; by keeping the model periodicity, and it is ensured that decryption data changes uniformly and the topology is kept good; by maintaining that an arbitrary order is derivable, the decryption effect is smooth and advanced gradually; the model attack resistance is improved, it is ensured that the decrypted data has the high safety, and has the advantages of being reversible and efficient in decryption, and technical supports can be provided for security, secrecy and sharing using of raster-vector geographic data.
Owner:NANJING NORMAL UNIVERSITY
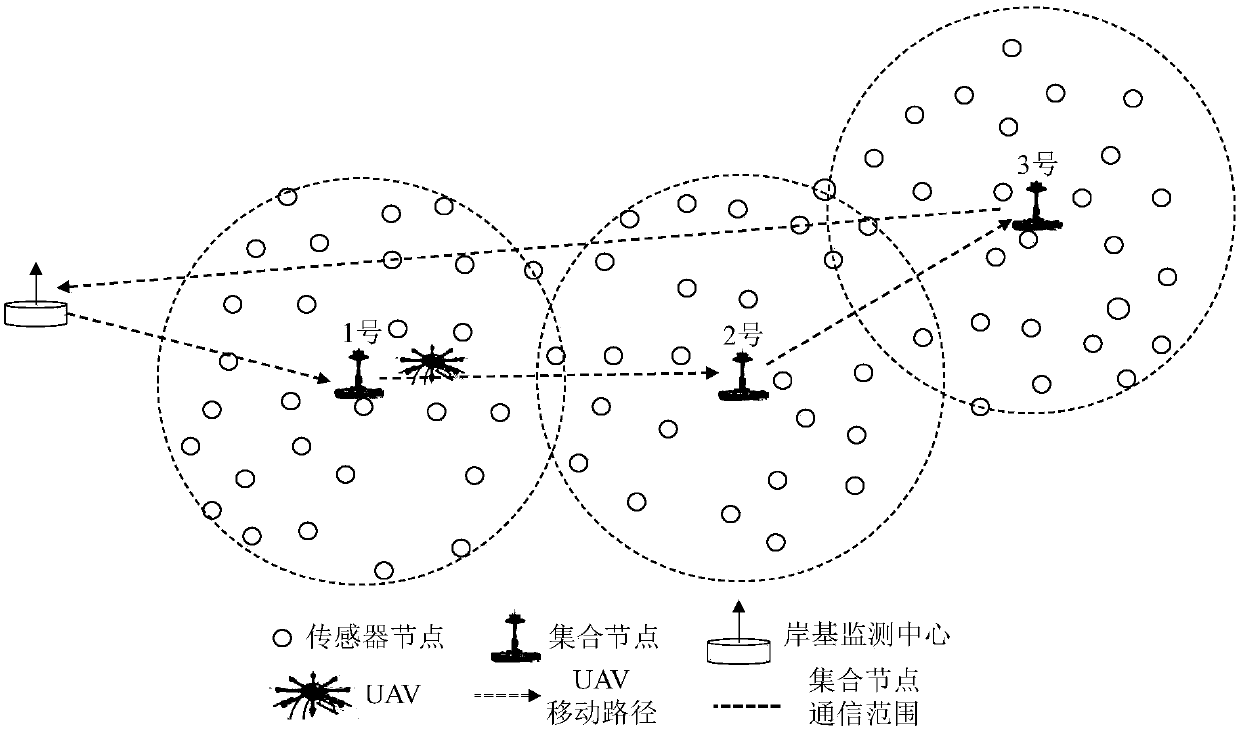
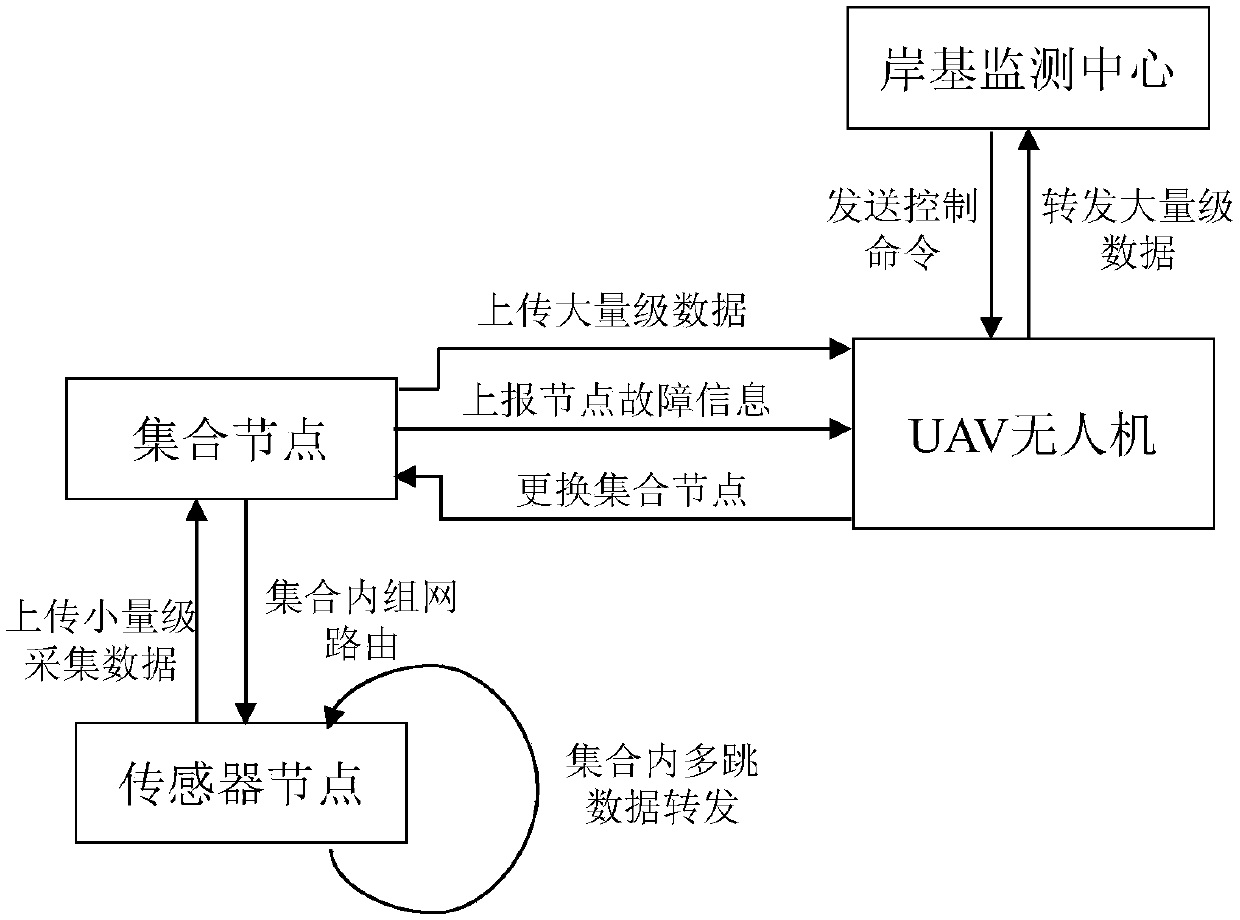
Offshore mobile sensor network routing maintenance method based on cluster ring mechanism
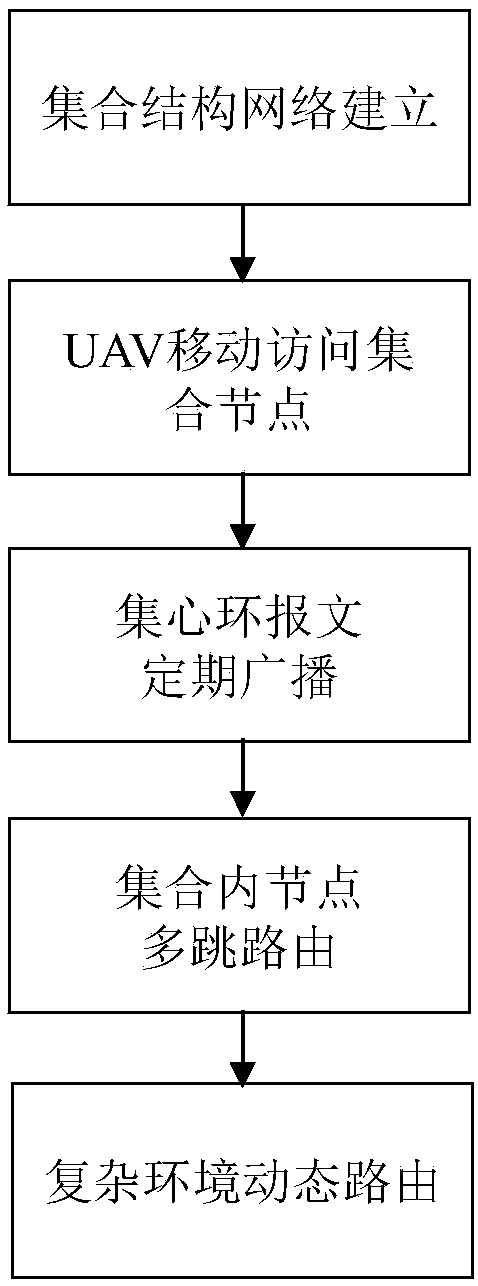
ActiveCN108235273ABalanced energy consumptionShort path distanceParticular environment based servicesNetwork topologiesBalancing networkStructure of Management Information
The invention discloses an offshore mobile sensor network routing maintenance method based on a cluster ring mechanism; the offshore mobile sensor network comprises a sensor node, set nodes and a UAVunmanned aerial vehicle; the offshore mobile sensor network routing maintenance method based on the cluster ring mechanism comprises the following steps: set structure network establishment, UAV mobile access, cluster ring message periodic broadcast, intra-set node multi-hop routing, and dynamic routing in a complex environment. According to the maintenance method, the path distance for multi-hoptransmission of the data to the UAV by each sensor node can be reduced, network energy consumption is balanced, the method is applicable to various network shapes; meanwhile, network topology routingis optimized, and frequent changes of the mobile sensor network topology structure under a severe seaborne environment are self-adapted through the dynamic routing.
Owner:OCEANOGRAPHIC INSTR RES INST SHANDONG ACAD OF SCI
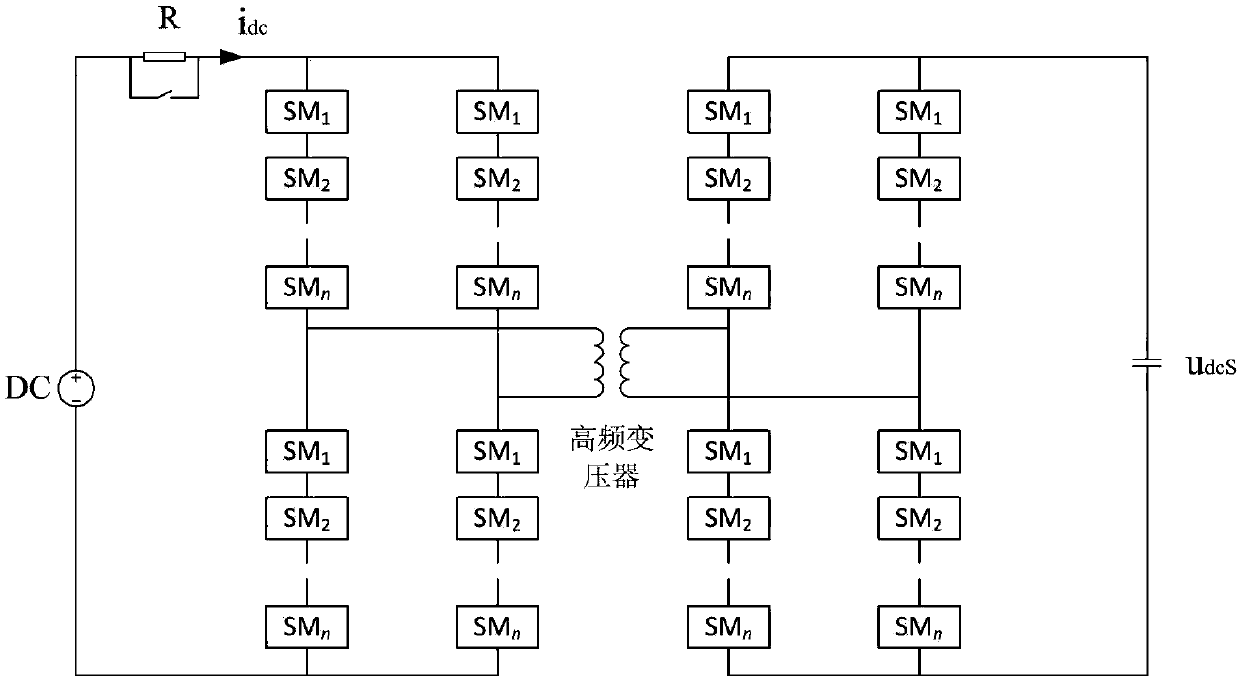
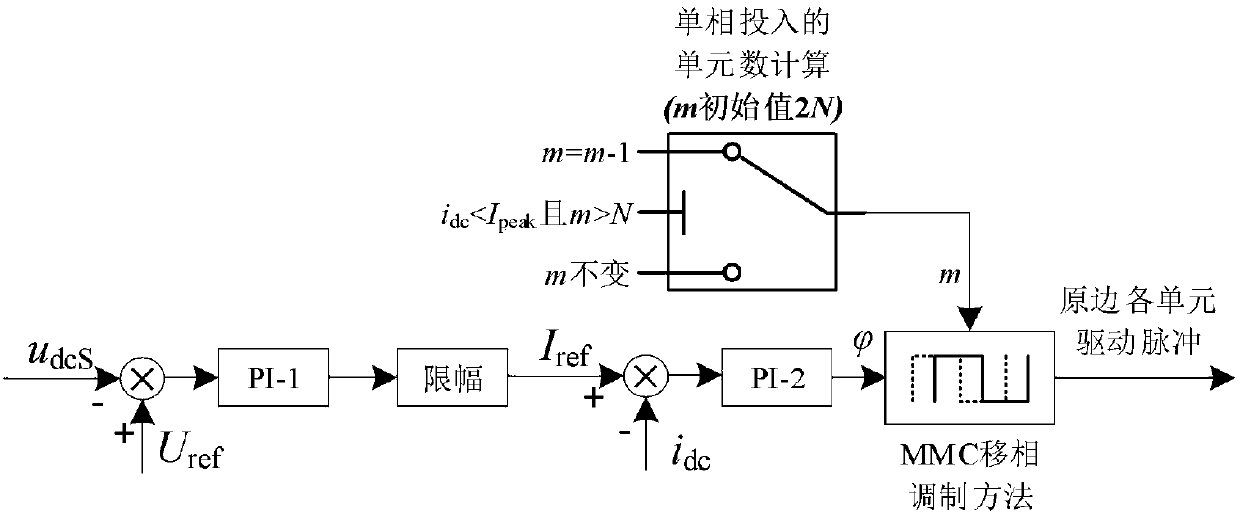
Modular multilevel DC solid state transformer and charging control method thereof
ActiveCN108539987AOptimize topologyReduce charging currentDc-dc conversionDc-ac conversion without reversalPhase shiftedPower flow
The invention discloses a modular multilevel DC solid state transformer and a charging control method thereof. The transformer comprises two groups of MMCs, a high-frequency transformer, a resistor and a switch, wherein one group of MMCs is connected with the primary side of the high-frequency transformer and the other group of MMCs is connected with the secondary side of the high-frequency transformer; the MMCs at the primary side are connected with a DC power supply through a parallel structure of the resistor and the switch; and the MMCs at the secondary side are connected with a load. In the method, all 2N sub modules in each phase of the MMCs at the primary side of the DC transformer are inputted; then, through comparing the primary current value and a limited current value, the inputted number of the primary MMC sub modules is reduced; and finally, the inputted sub modules in each phase are distributed again in an upper bridge arm and a lower bridge arm, a phase-shift angle is combined to determine triggering pulses of the primary MMCs, and soft charging of the DC transformer is realized. the primary DC of the DC transformer and the AC of the high-frequency transformer are reduced, and power sub modules and the high-frequency transformer are protected during the DC transformer charging process.
Owner:NANJING UNIV OF SCI & TECH
Method of high performance distributed Hash table in P2P system
InactiveCN101094244ASmall network topology diameterNode load balancingTransmissionDistributed hash tableNeighbor relation
The method comprises: using the character string whose adjacent bit is different as the resource object ID and the node ID; using the 'ID left shifting' and topological relation invariant to construct regular organization neighboring relation; when node is added or quits, using a 'locally optimizing' dynamical balance mechanism to release the resource object to the node whose node ID is its prefix; when the resource location message is replayed, it is executed according the ' ID left shifting' and 'postfix matching' rule.
Owner:NAT UNIV OF DEFENSE TECH
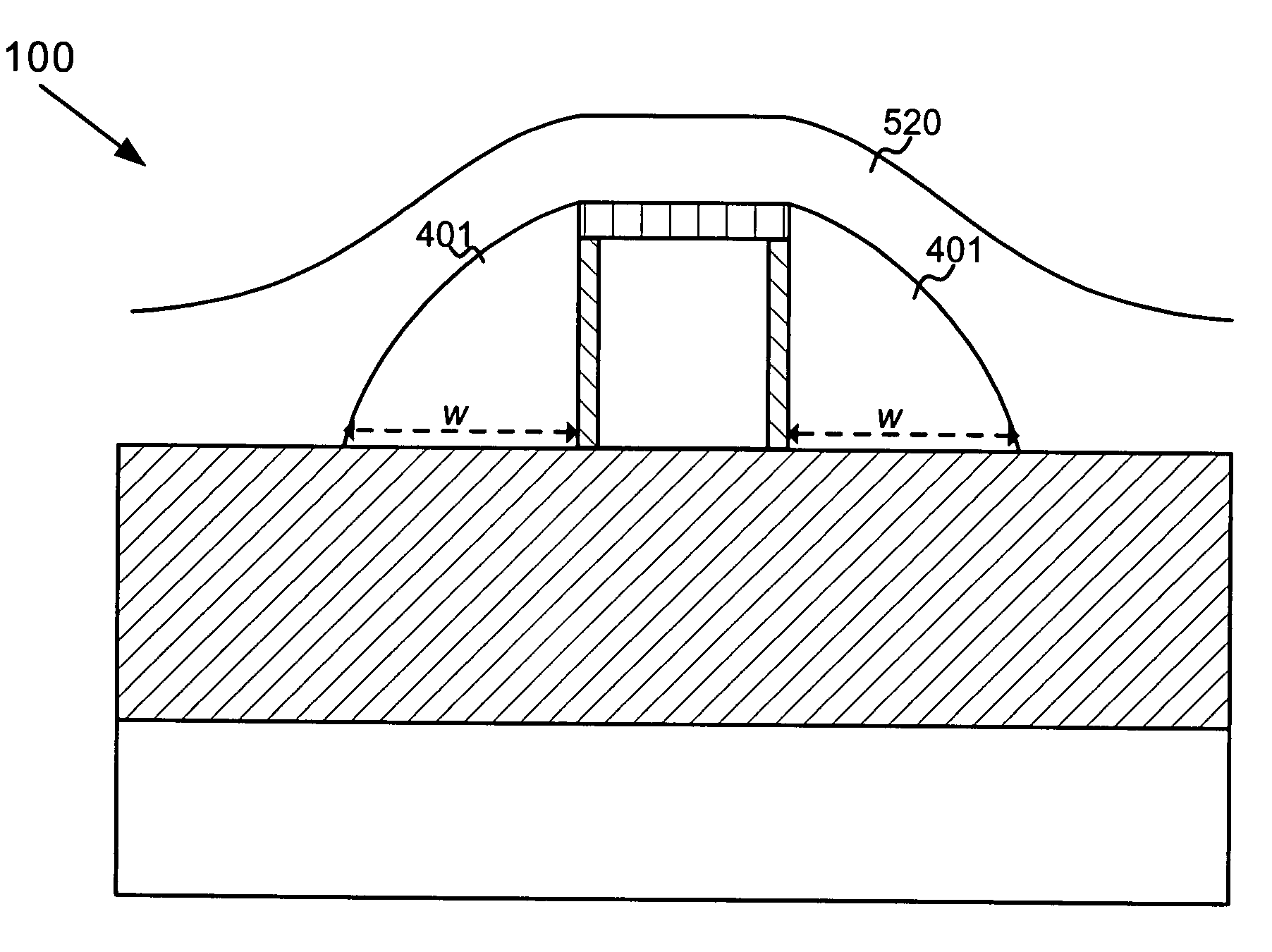
Smooth fin topology in a FinFET device
InactiveUS7112847B1Optimize topologyReduce impactSolid-state devicesSemiconductor/solid-state device manufacturingEngineeringSemiconductor
A semiconductor device includes a semiconductor fin formed on an insulator and sidewall spacers formed adjacent the sides of the fin. A gate material layer is formed over the fin and the sidewall spacers and etched to form a gate. The presence of the sidewall spacers causes a topology of the gate material layer to smoothly transition over the fin and the first and second sidewall spacers.
Owner:ADVANCED MICRO DEVICES INC
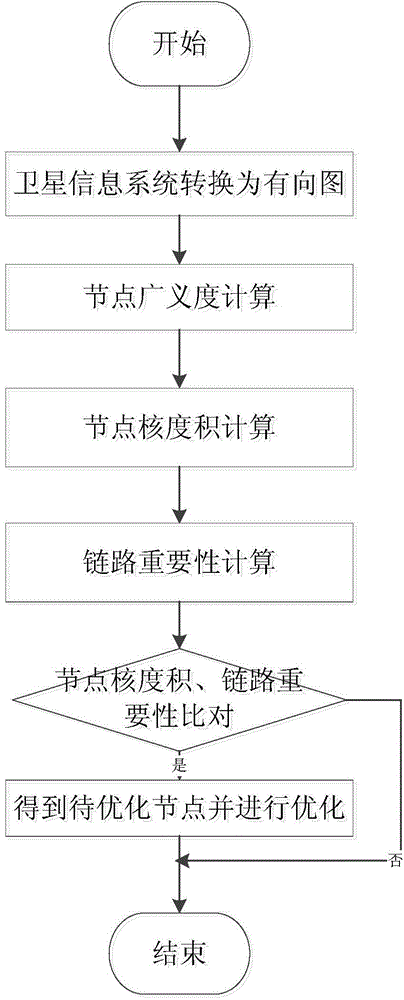
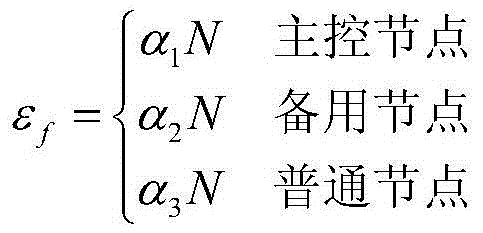
Satellite information system topological structure optimization method based on core-degree product
ActiveCN104869017AComprehensive topologyOptimize topologyRadio transmissionData switching networksSatelliteInformation system
The invention discloses a satellite information system topological structure optimization method based on a core-degree product. The method comprises the following steps: firstly, abstracting a satellite information system to obtain a corresponding directed graph; secondly, introducing a concept of generalized degree and calculating the generalized degree of each node in the directed graph; thirdly, calculating the node core-degree product of each node in the directed graph and the importance of links; and lastly, comparing the node core-degree products of all nodes in the directed graph with a set node core-degree product threshold value as well as the importance of all shortest links between two nodes in the directed graph with a set link importance threshold value in sequence to obtain nodes to be optimized in a topological structure, and optimizing the nodes to be optimized. Compared with the prior art, the method has the advantages that the importance of each node is distinguished through introduction of the generalized degrees, and the degree or betweenness of each node as well as the importance of the nodes and links in the topological structure are considered, so that the whole topological structure can be optimized more accurately and comprehensively.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
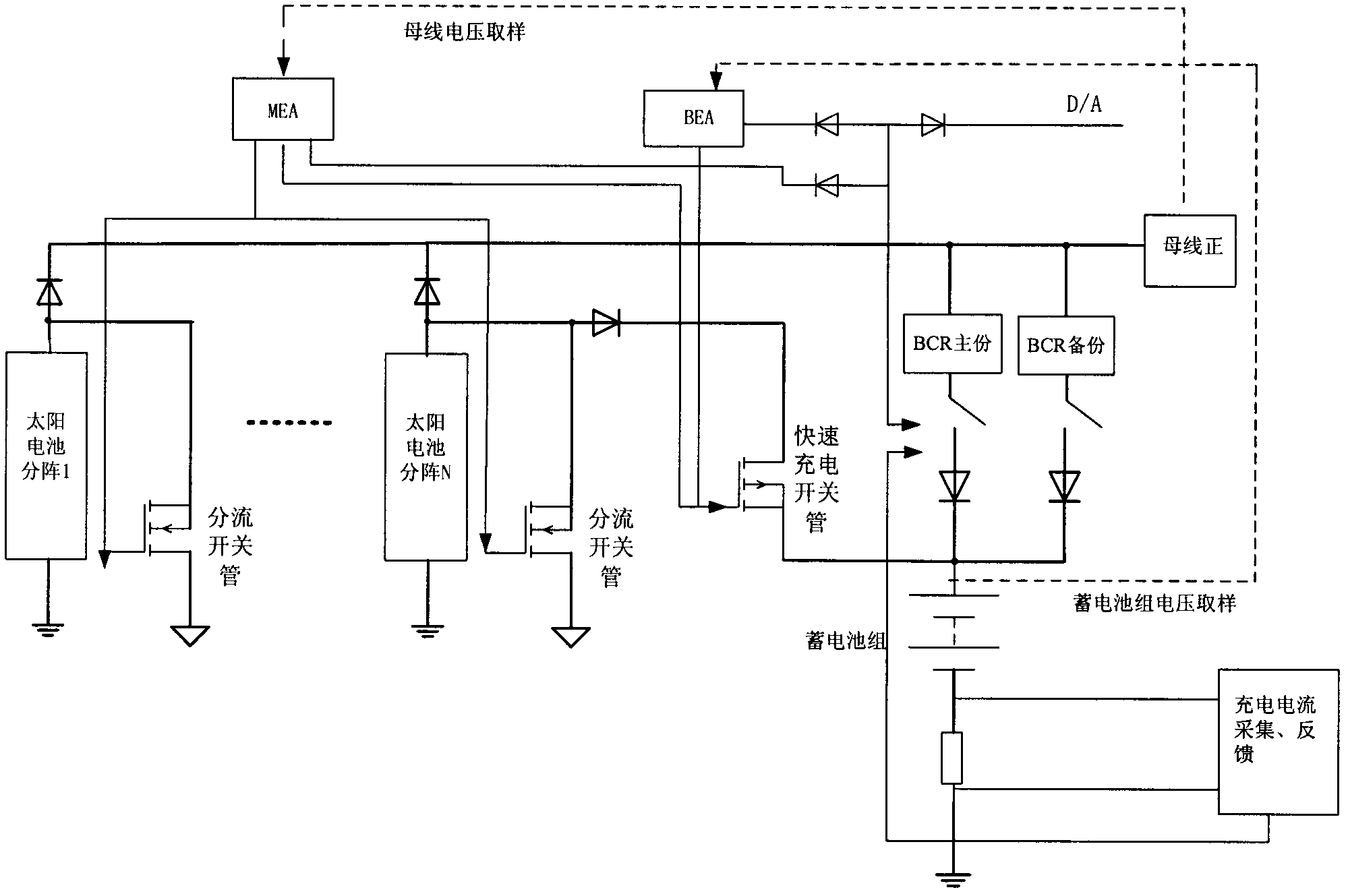
A deep space exploration aircraft power supply system
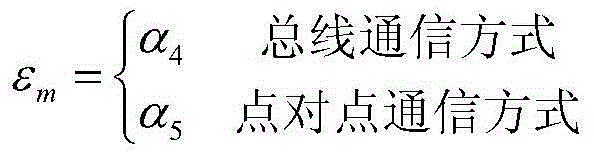
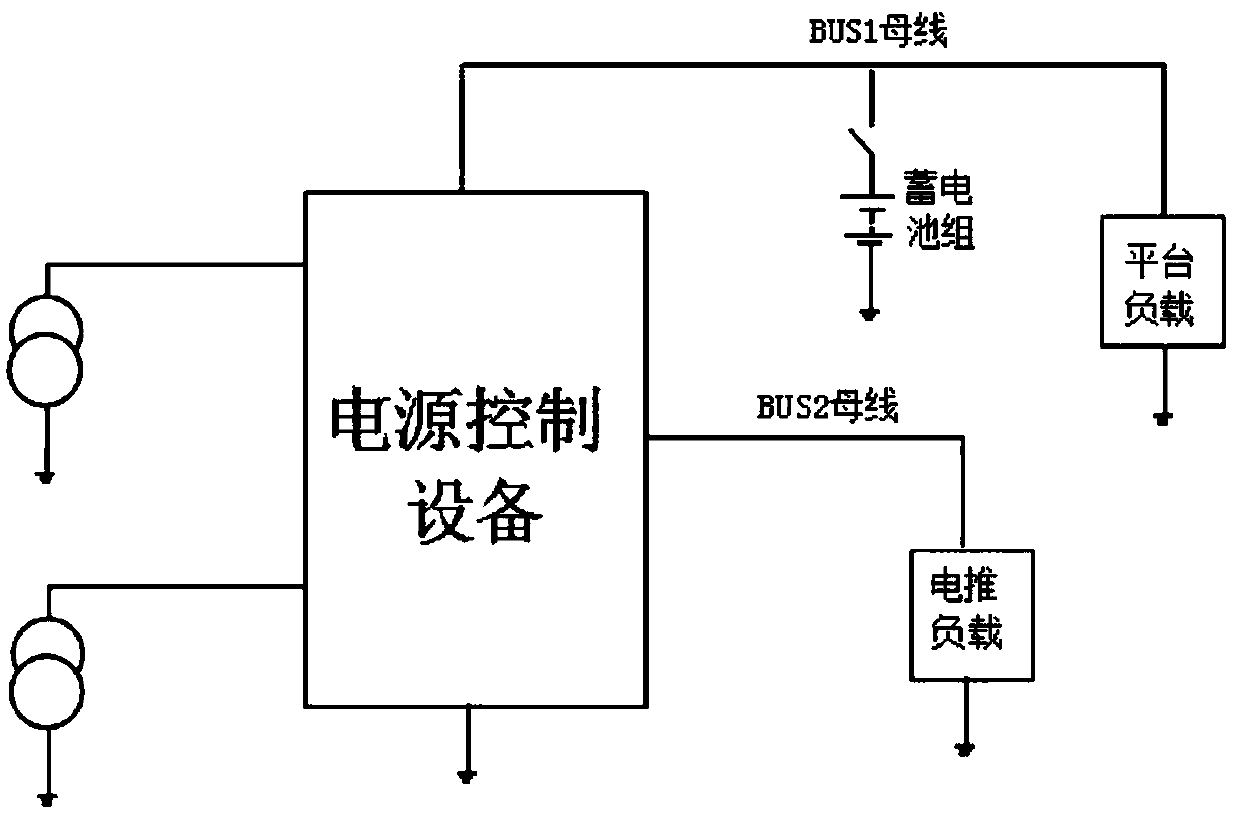
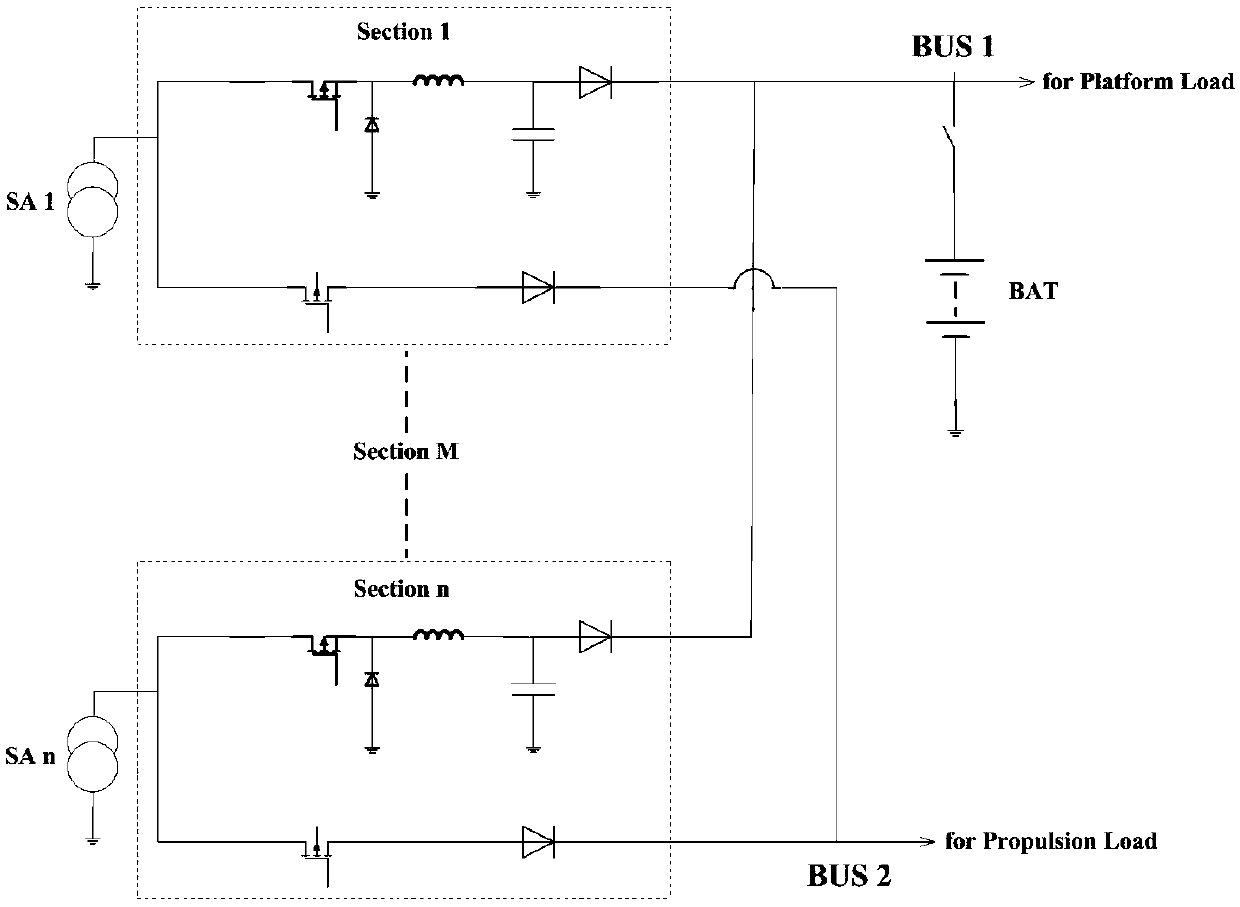
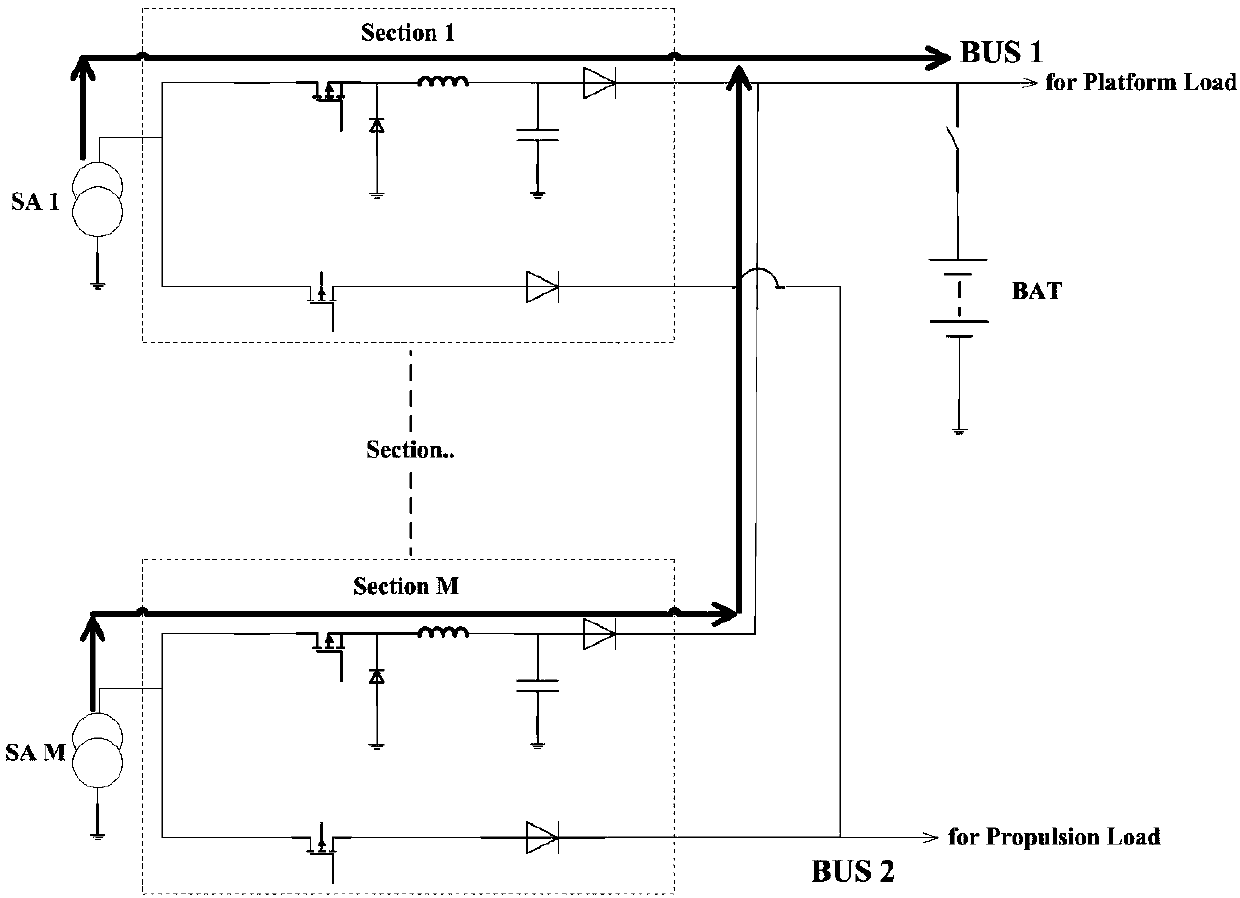
ActiveCN109586391AHigh specific powerOptimize topologyBatteries circuit arrangementsElectric powerElectricitySystems design
A deep space exploration aircraft power supply system includes a solar battery array, an energy storage battery pack and a power supply control device. The output power of the power supply system topology selects from two independent buses: a semi-regulated BUS1 bus and a non-regulated BUS2 bus. The BUS1 bus mainly supplies a platform with electric power. The BUS2 bus mainly supplies an electric propulsion load with electric power. The solar battery array supplies the semi-regulated bus and the non-regulated bus with power sequentially. The system has high current charging capability. The double bus form optimizes the system topology. The power supply system design has high current charging capability. The power utilization of the solar array in the power supply system is raised.
Owner:中电科蓝天科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com