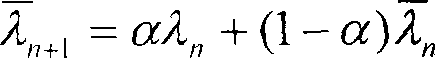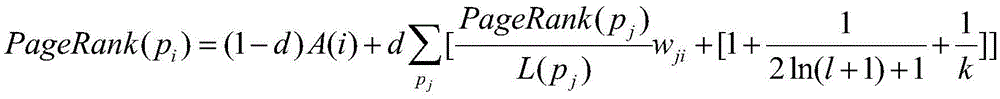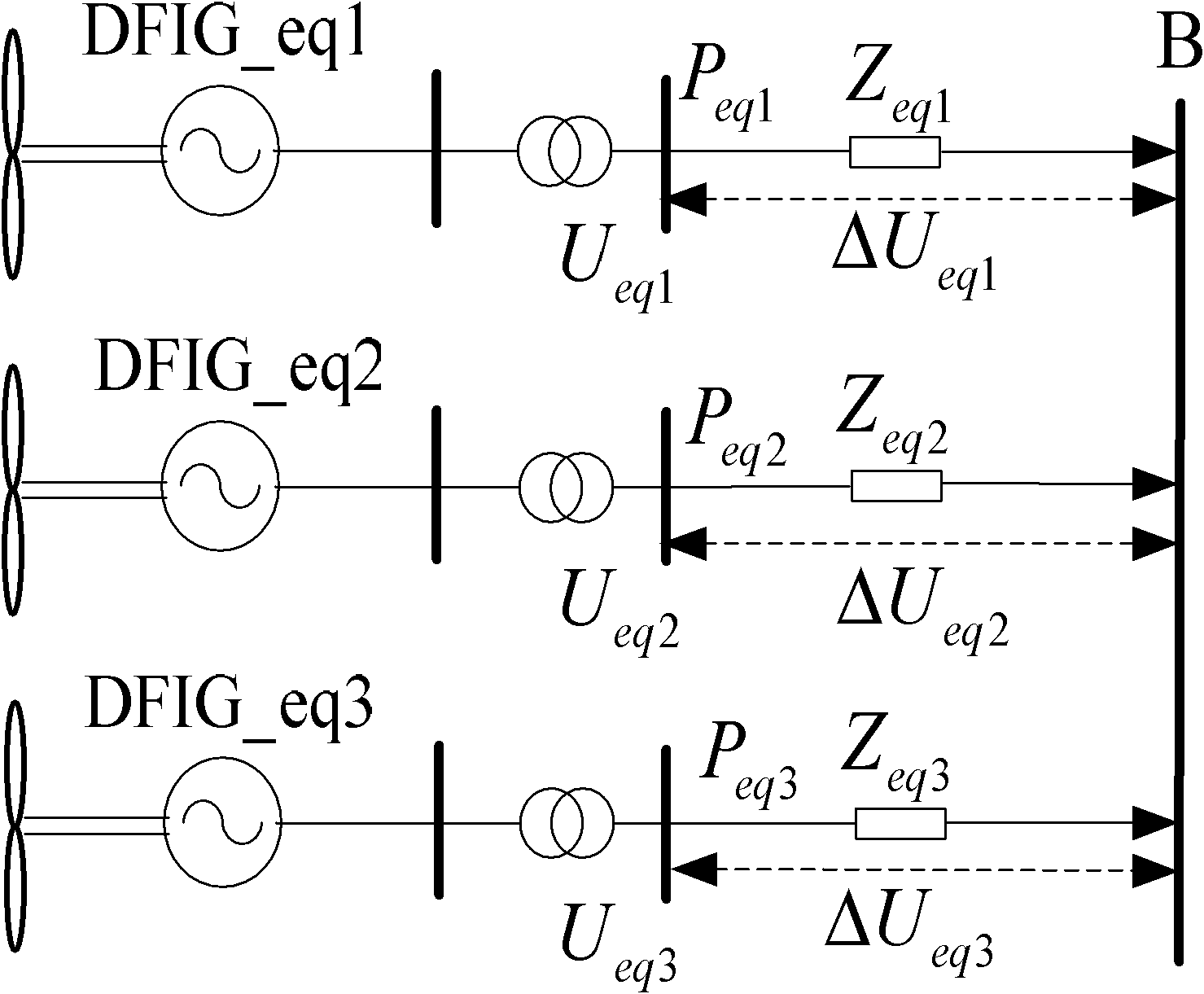Patents
Literature
564 results about "Influence analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
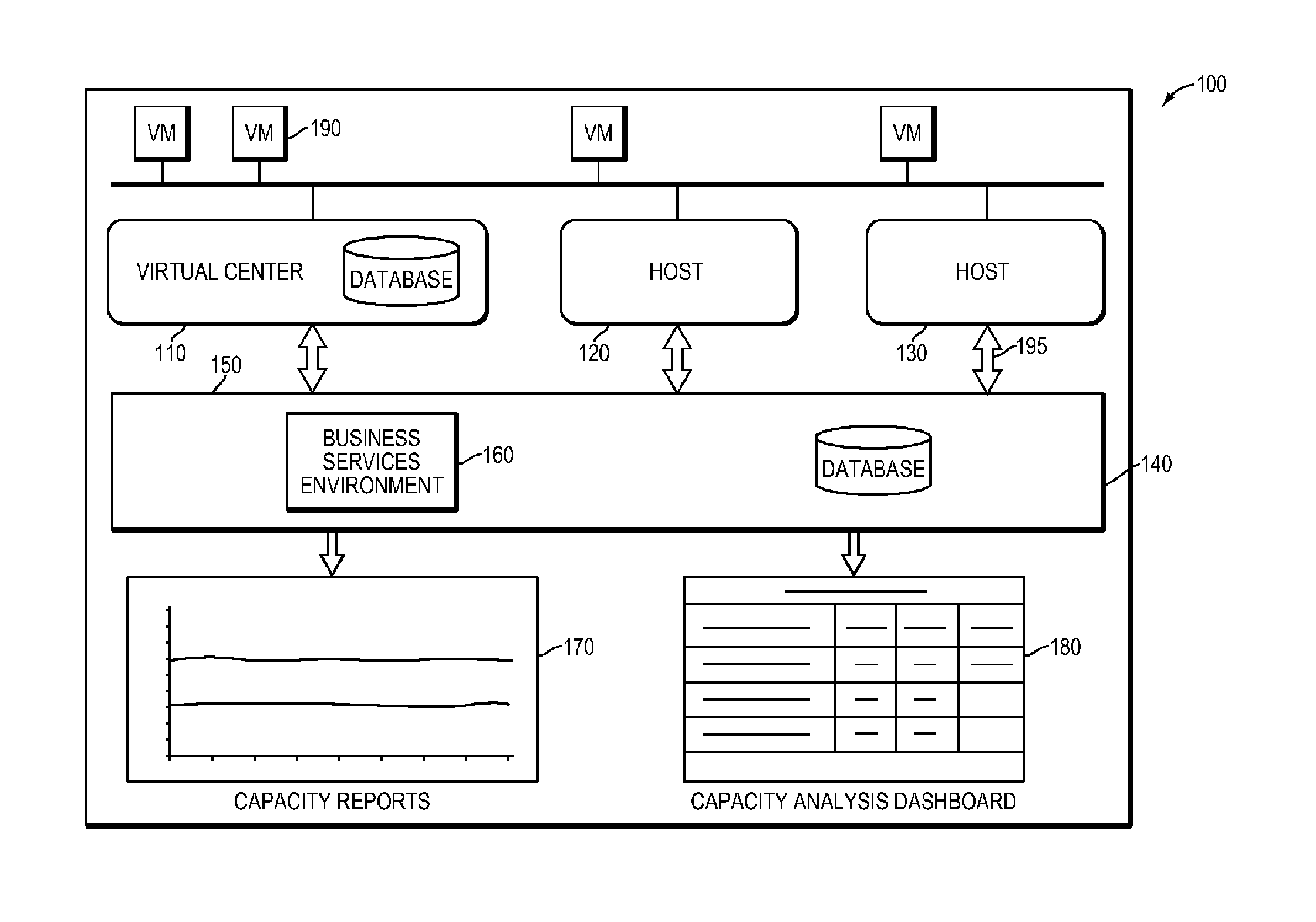
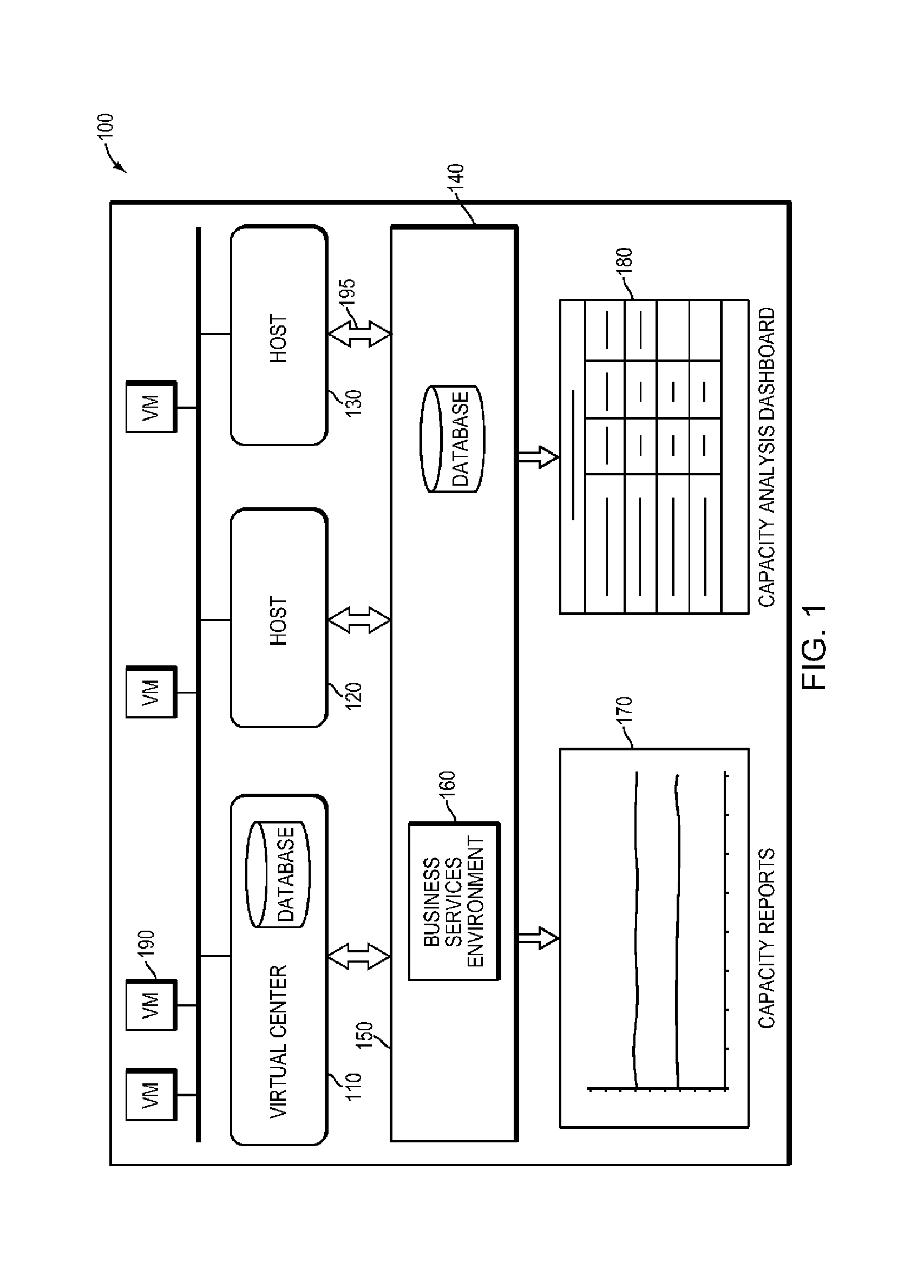
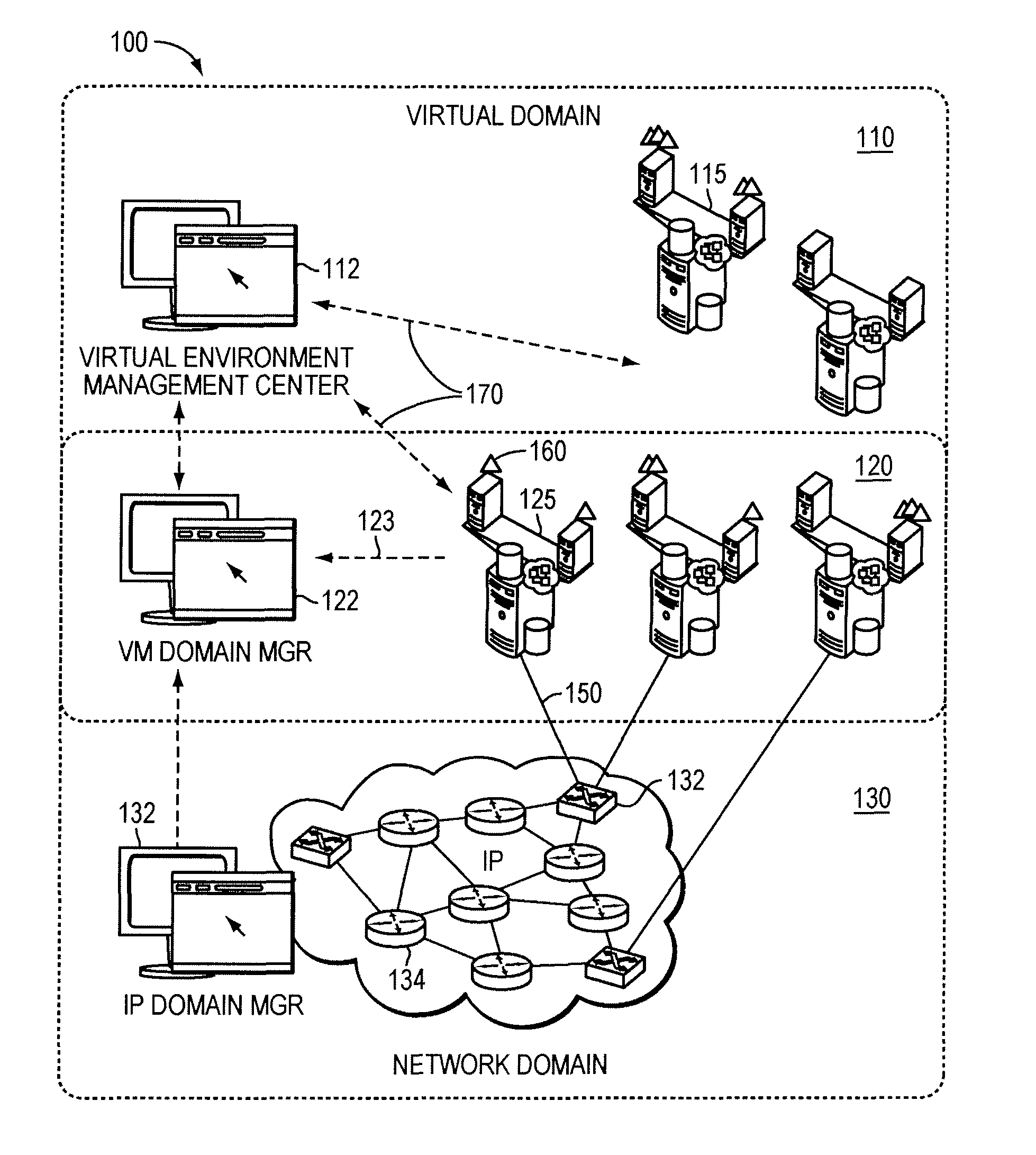
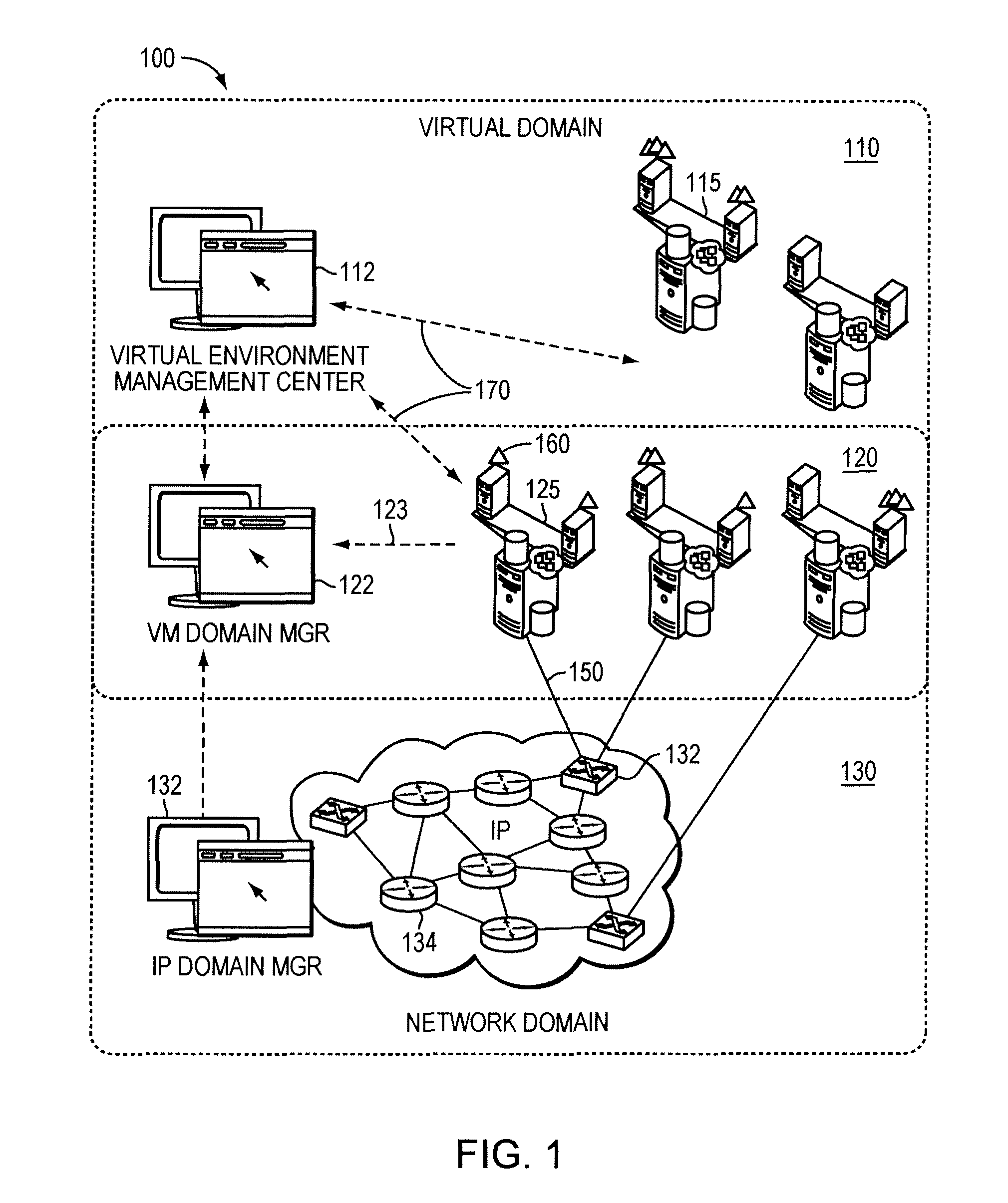
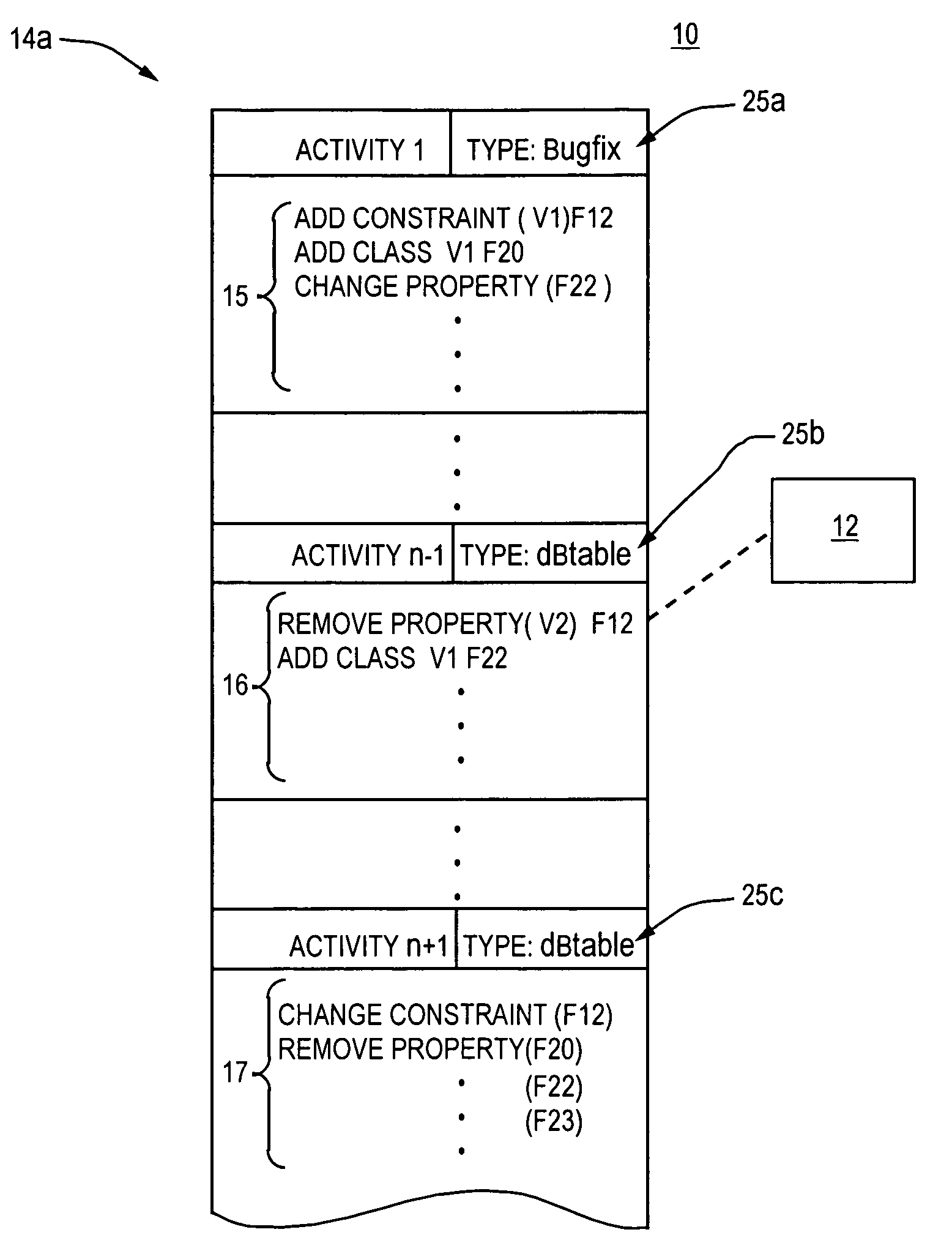
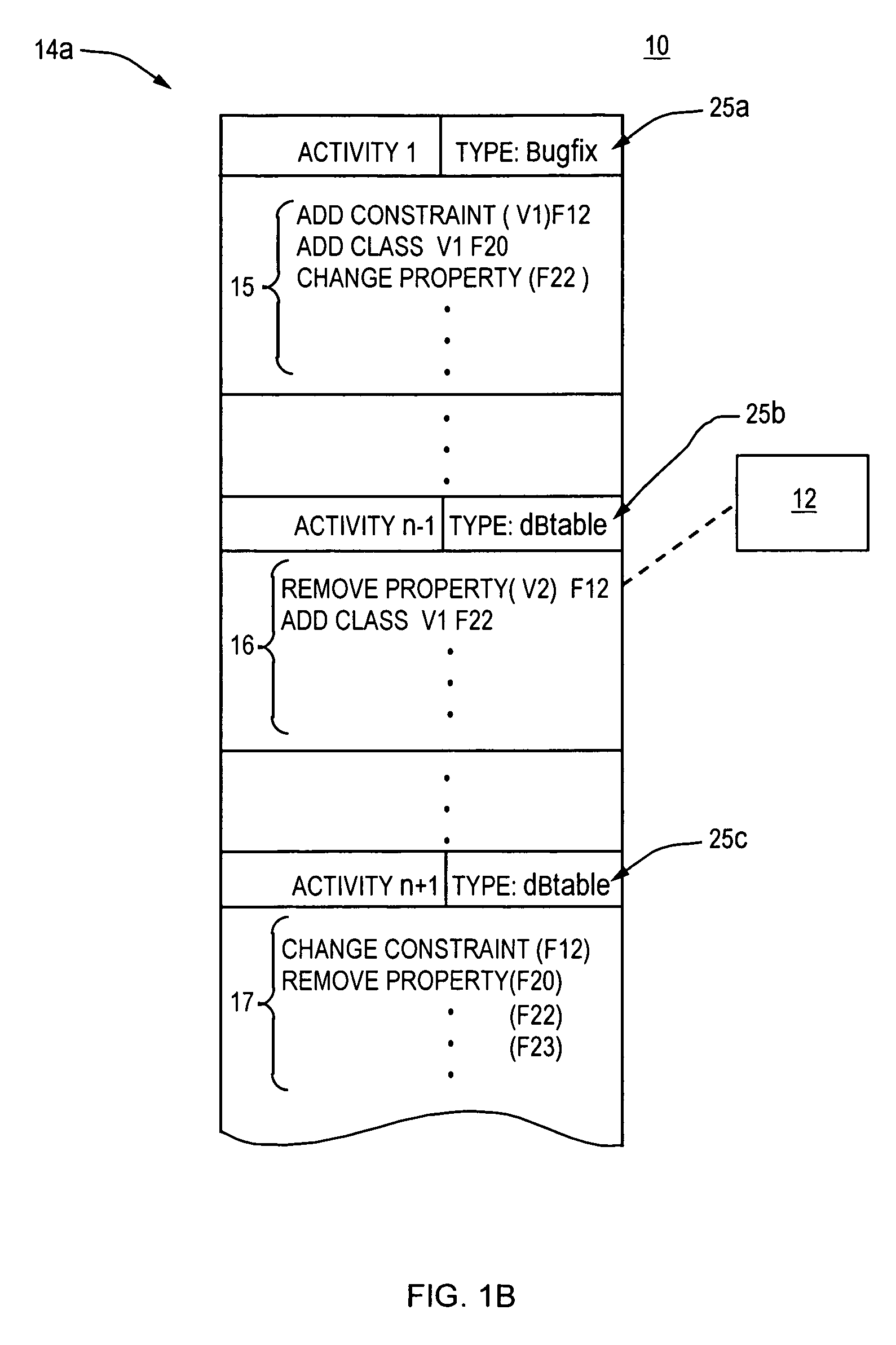
Systems and methods for real-time monitoring of virtualized environments
ActiveUS8738972B1Improve operationImprove performanceError detection/correctionSpecial data processing applicationsVirtualizationRoot cause
A method of root cause analysis in a virtual machine environment includes receiving a plurality of events from a system monitoring the virtualized environment. The events may include alarms or alerts, such as alarms or alerts associated with a resource reaching or exceeding a threshold. The capacity manager consumes these events and performs event correlation to produce a set of correlated events. The capacity manager performs a root cause analysis on the set of correlated events to identify one or more root causes. The capacity manager further performs an impact analysis to determine how the root cause impacts the system, such as other virtual machines, hosts or resource in the virtual environment. Based on the root cause and impact analysis, the capacity manager makes one or more recommendations to address issues with or to improve the operations and / or performance of the virtualized environment.
Owner:QUEST SOFTWARE INC
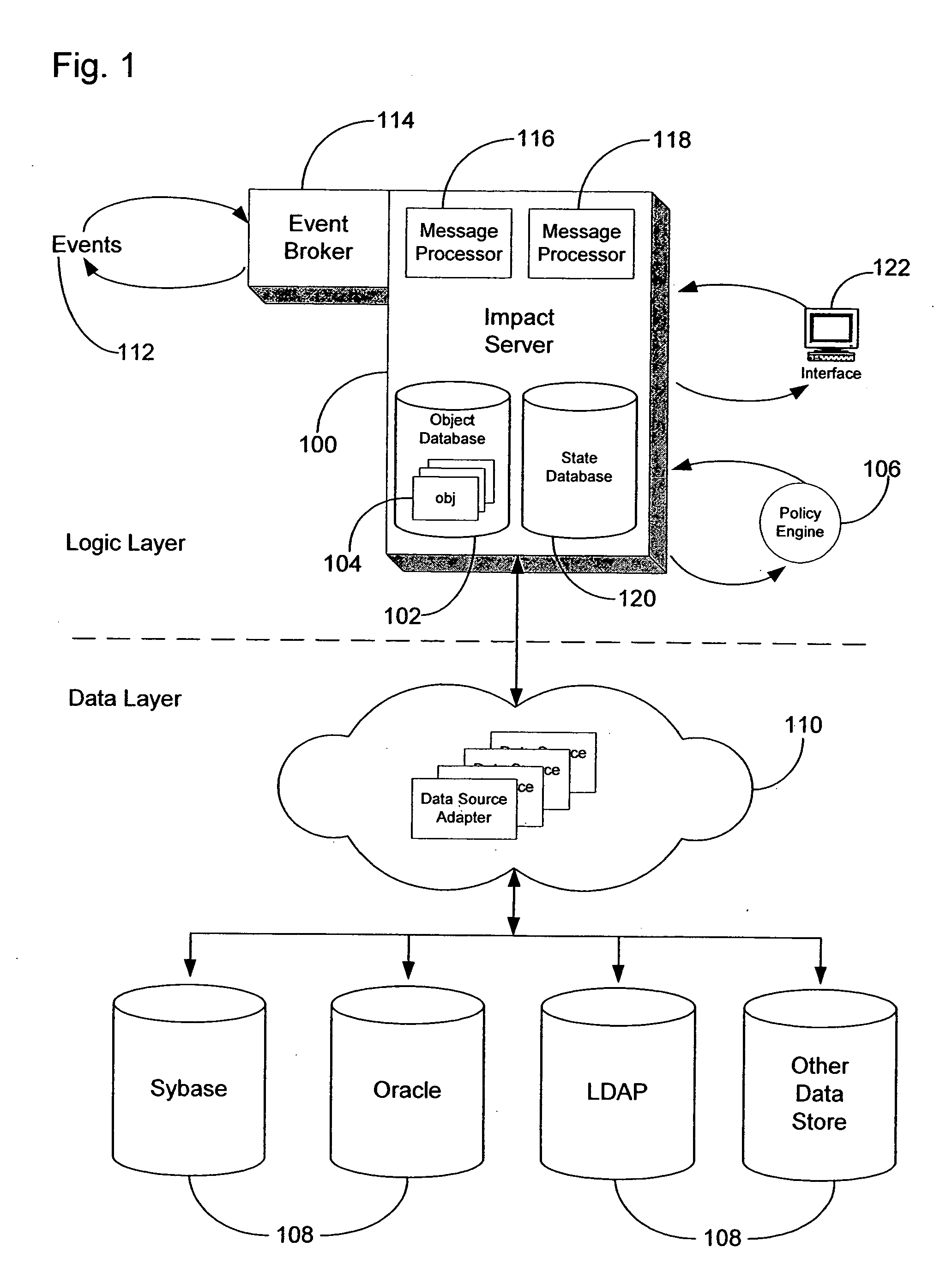
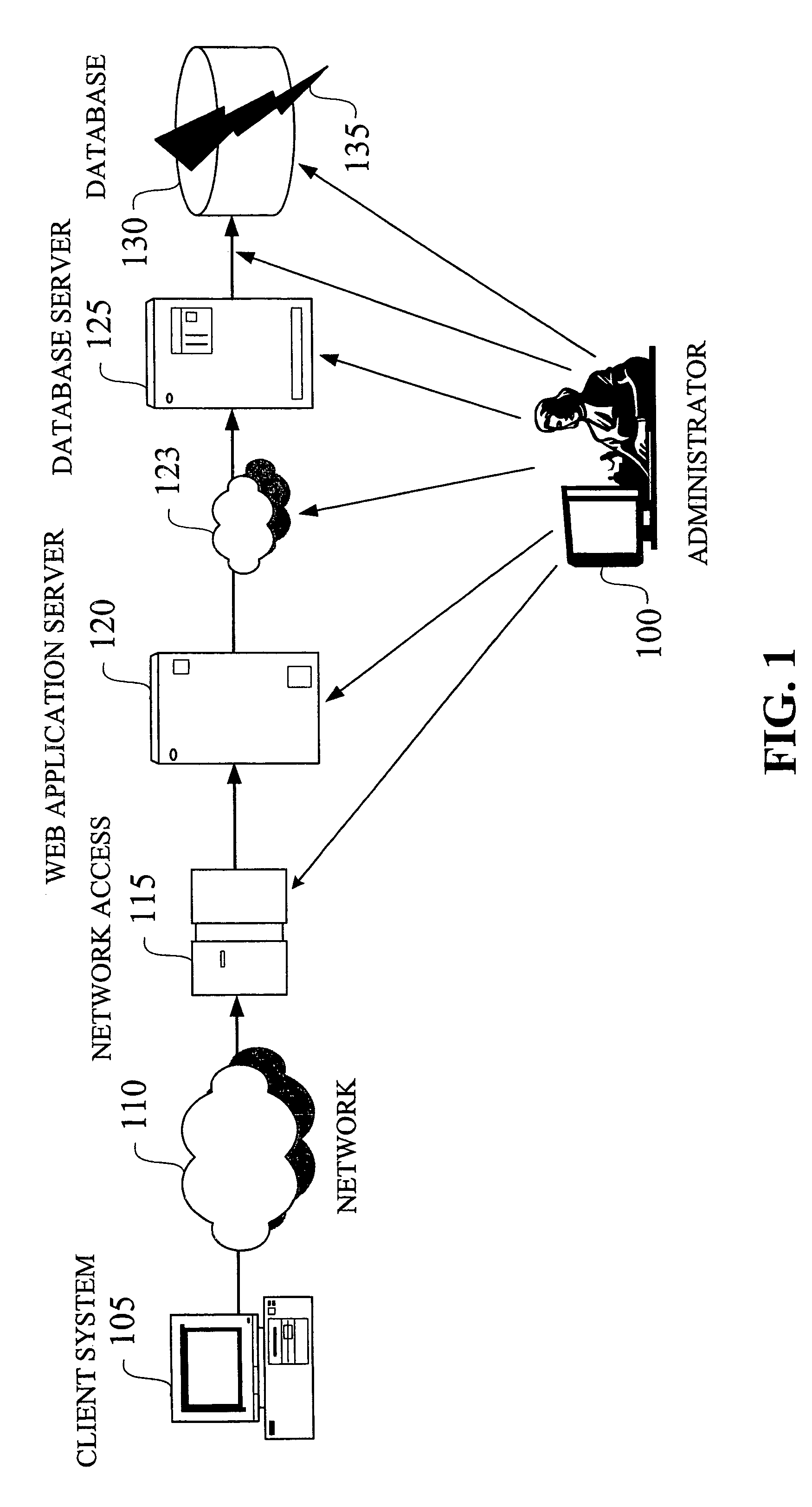
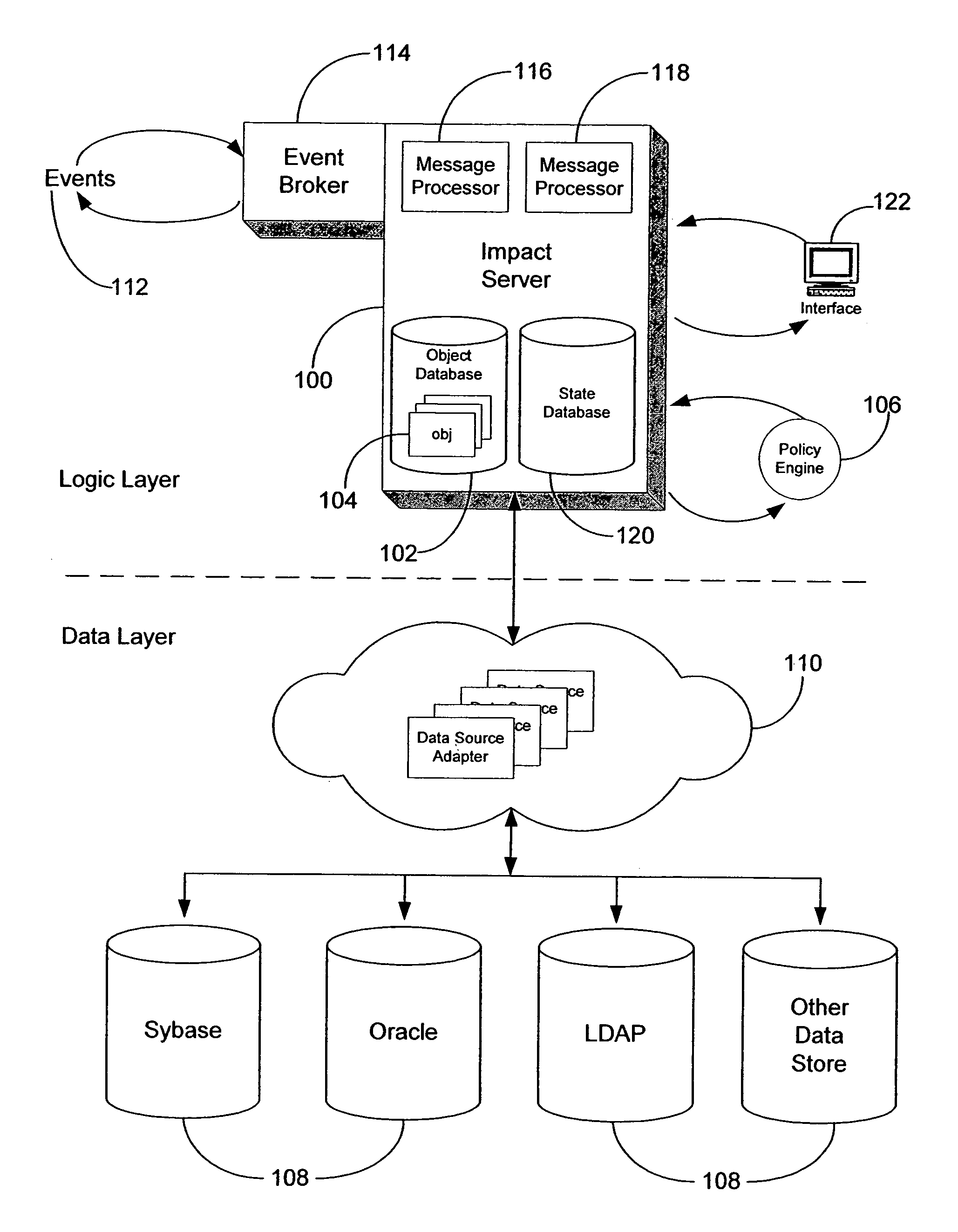
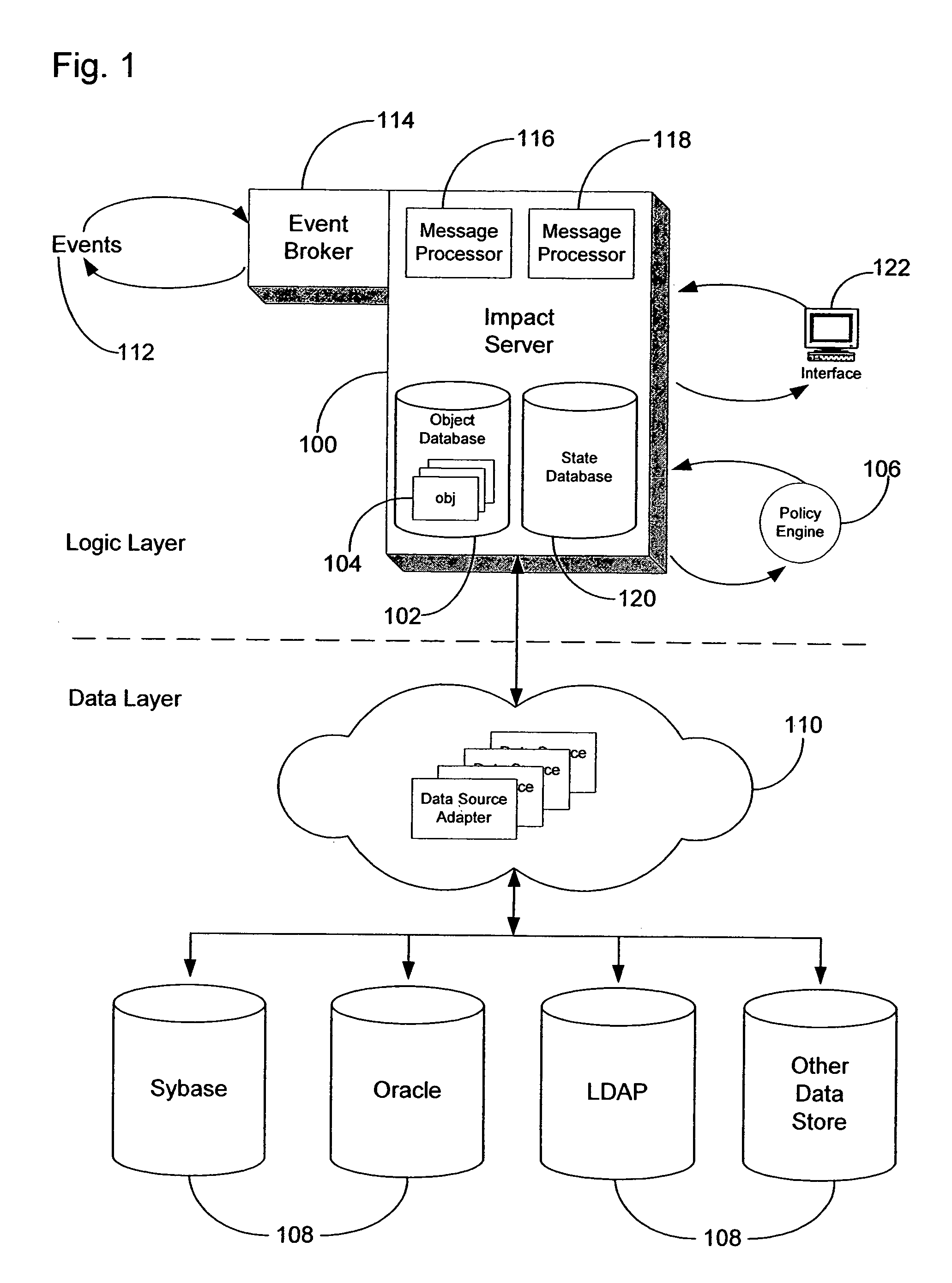
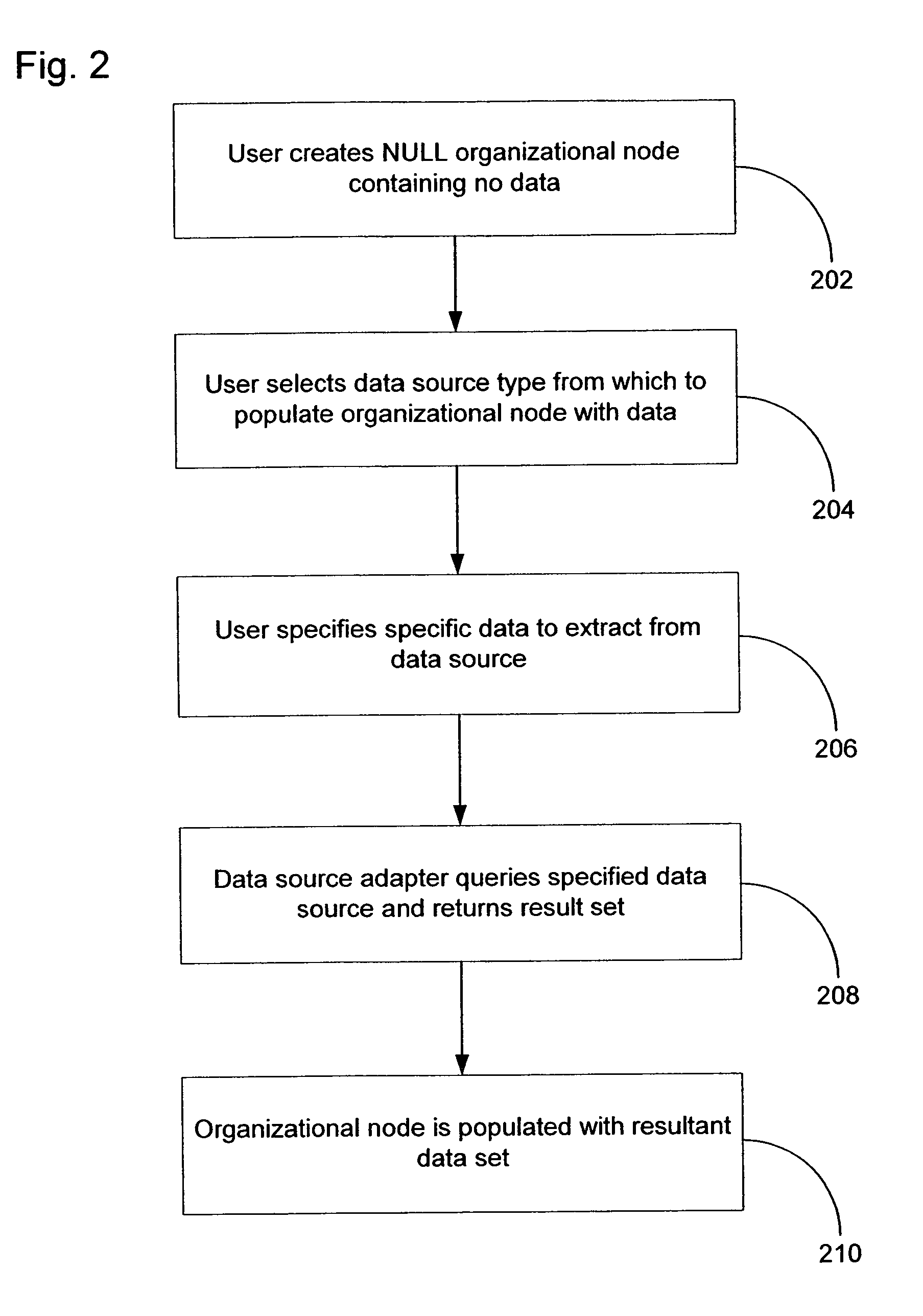
Method and system for event impact analysis
ActiveUS20050027845A1Minimize impactImprove service levelDigital computer detailsData switching networksSystems analysisAnalysis data
An impact analysis software system is described which resides on a computer connected to a network in an enterprise. The system analyzes the impact of network events on the network, and includes a number of modules, including a number of data source adapters for interfacing with external data sources to thereby allow access by the system to enterprise-related data in the external data sources. The system further includes an impact analysis data structure populated with data accessed from the external data sources and defining relationships between the enterprise-related data. One or more action tree data structures comprise a routine which, when executed, acts upon the relationships defined by the impact analysis data structure to handle events. A message processor reads the network events and select one of the action tree data structures to handle each read network event.
Owner:IBM CORP
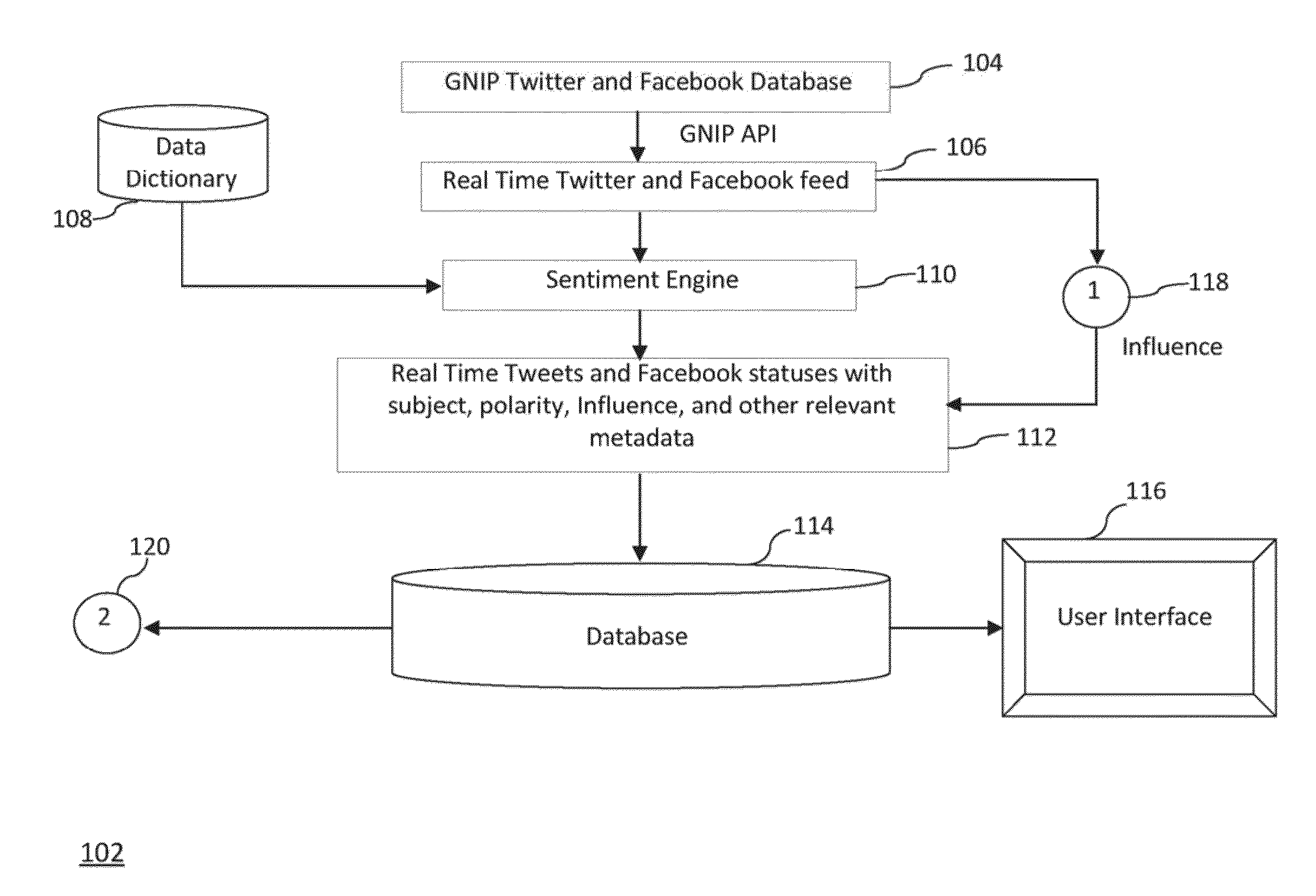
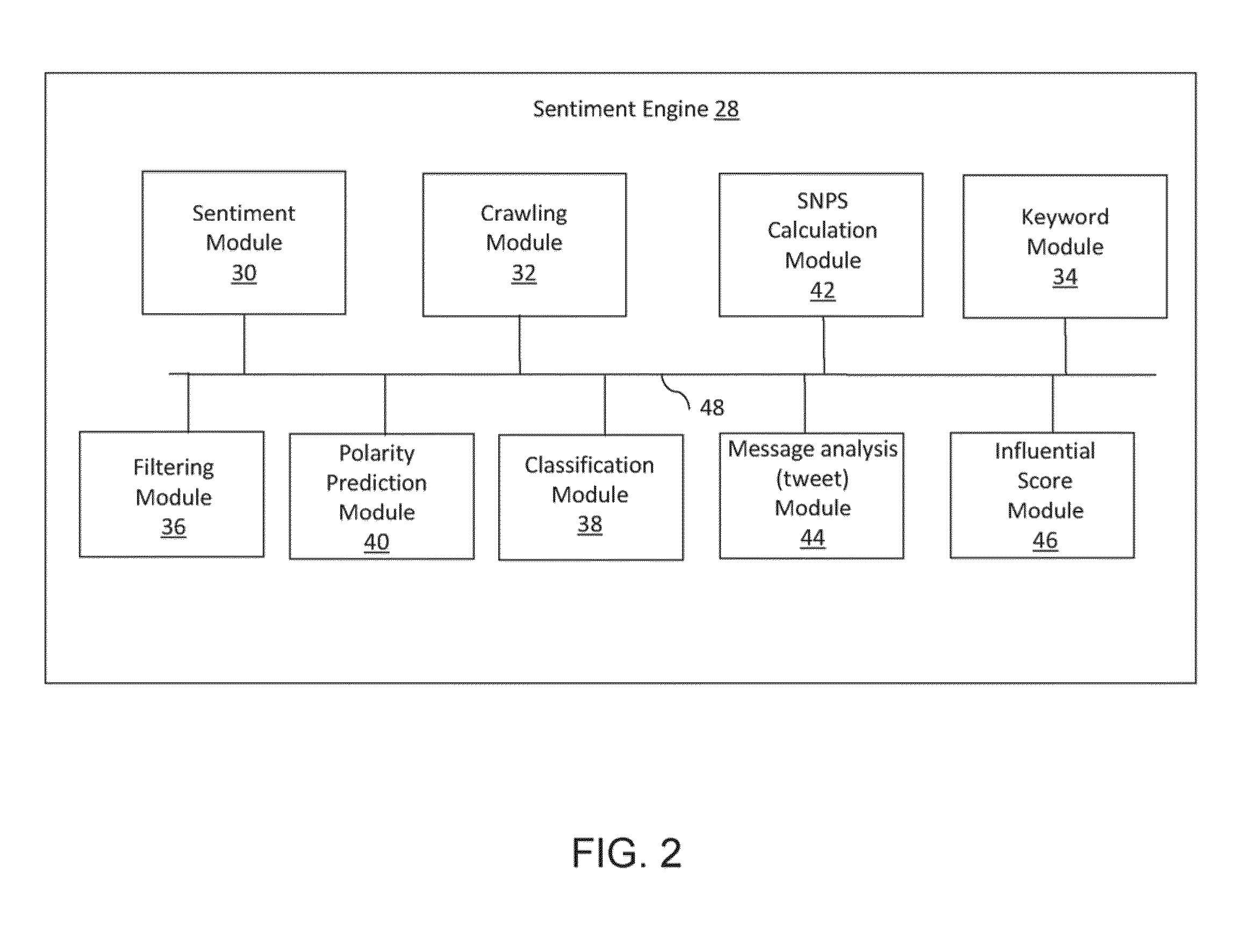
Sentiment and Influence Analysis of Twitter Tweets
The present invention is directed to a system, method, and article of manufacture that employs a sentiment engine for conducting sentiment and influence analysis of various types of messages from the social media hosts or websites to extract opinions on different categories, which includes services, products or hotels, and others, collectively referred to as “the keyword product”. The sentiment engine includes a sentiment module configured to gather opinions or determine sentiment expressed in documents, a crawling module configured to servers of social network websites to obtain at least a subset of the documents or opinions from social media websites, a keyword module configured to extract keywords from documents, a filtering module configured to filter keywords and documents, and a classification module configured to classify documents, sentences, and / or keywords, a polarity prediction module configured to predict the polarity of a sentiment sentence, and a social media net promoter score configured to calculate a loyalty metric of users from social media websites, and a message analysis module configured to conduct analysis of a message from host social media sites, forums, blogs and product / service providers. The message analysis module includes analyzing message from other host social media sites.
Owner:INTEROS INC
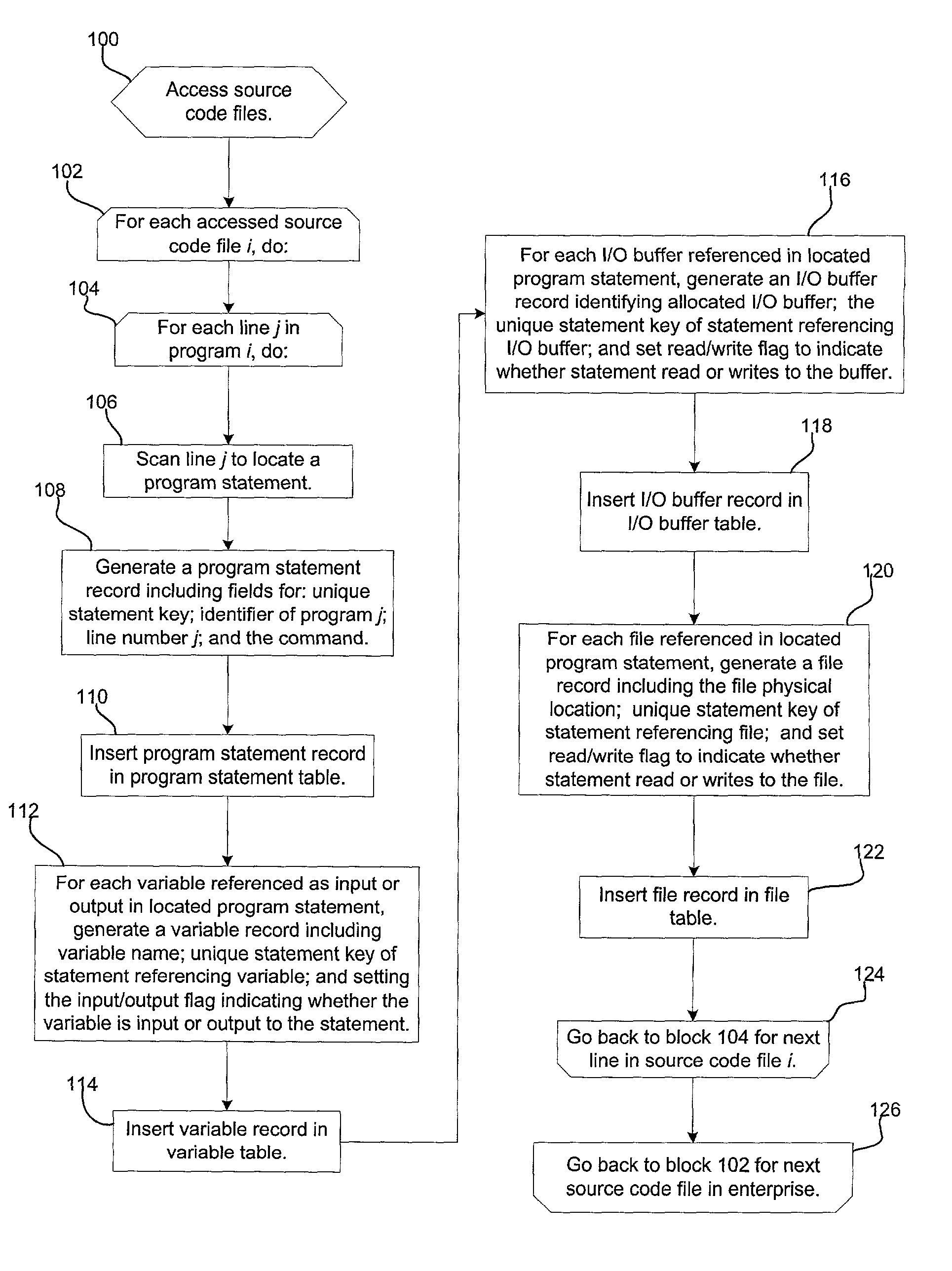
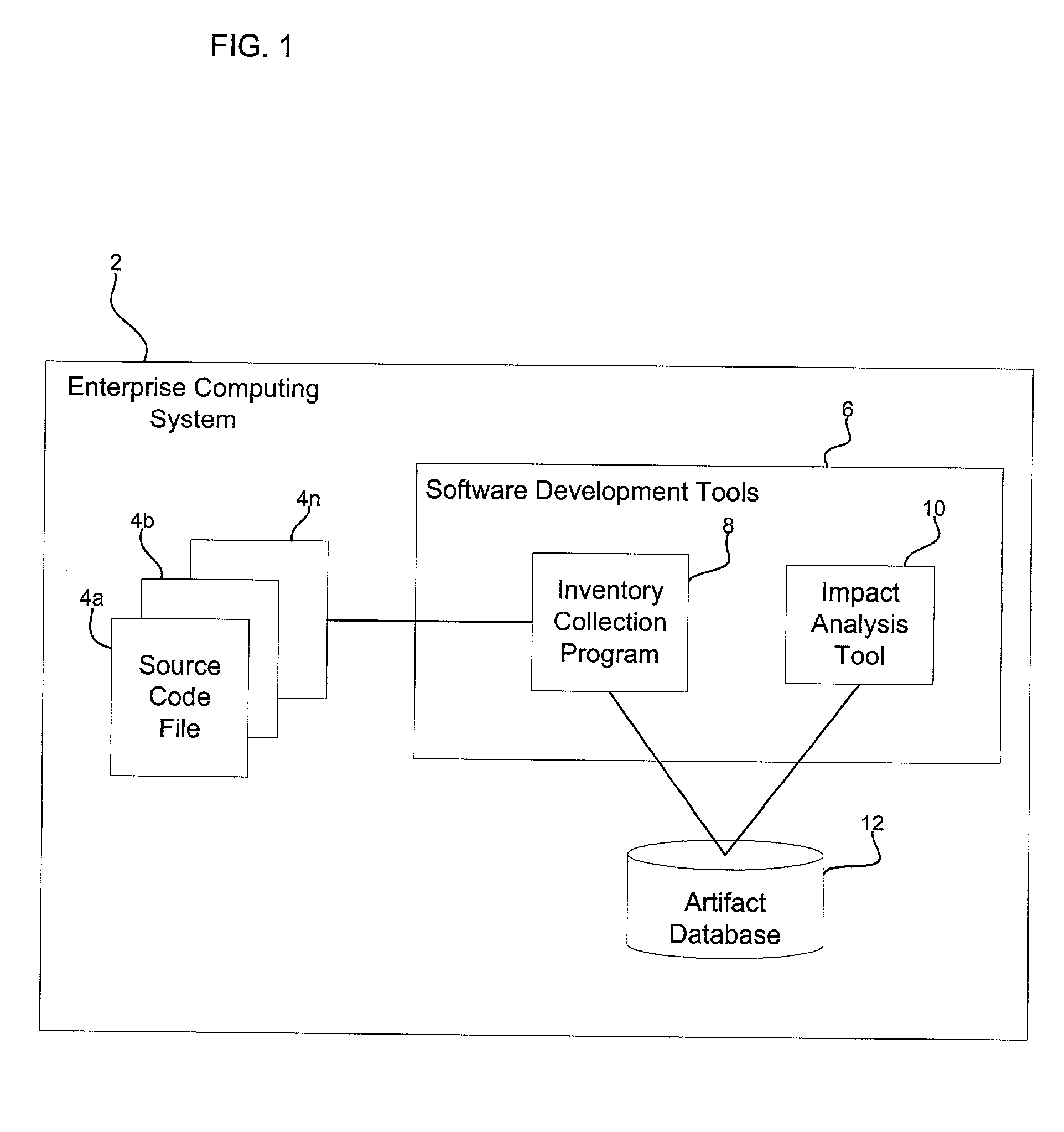
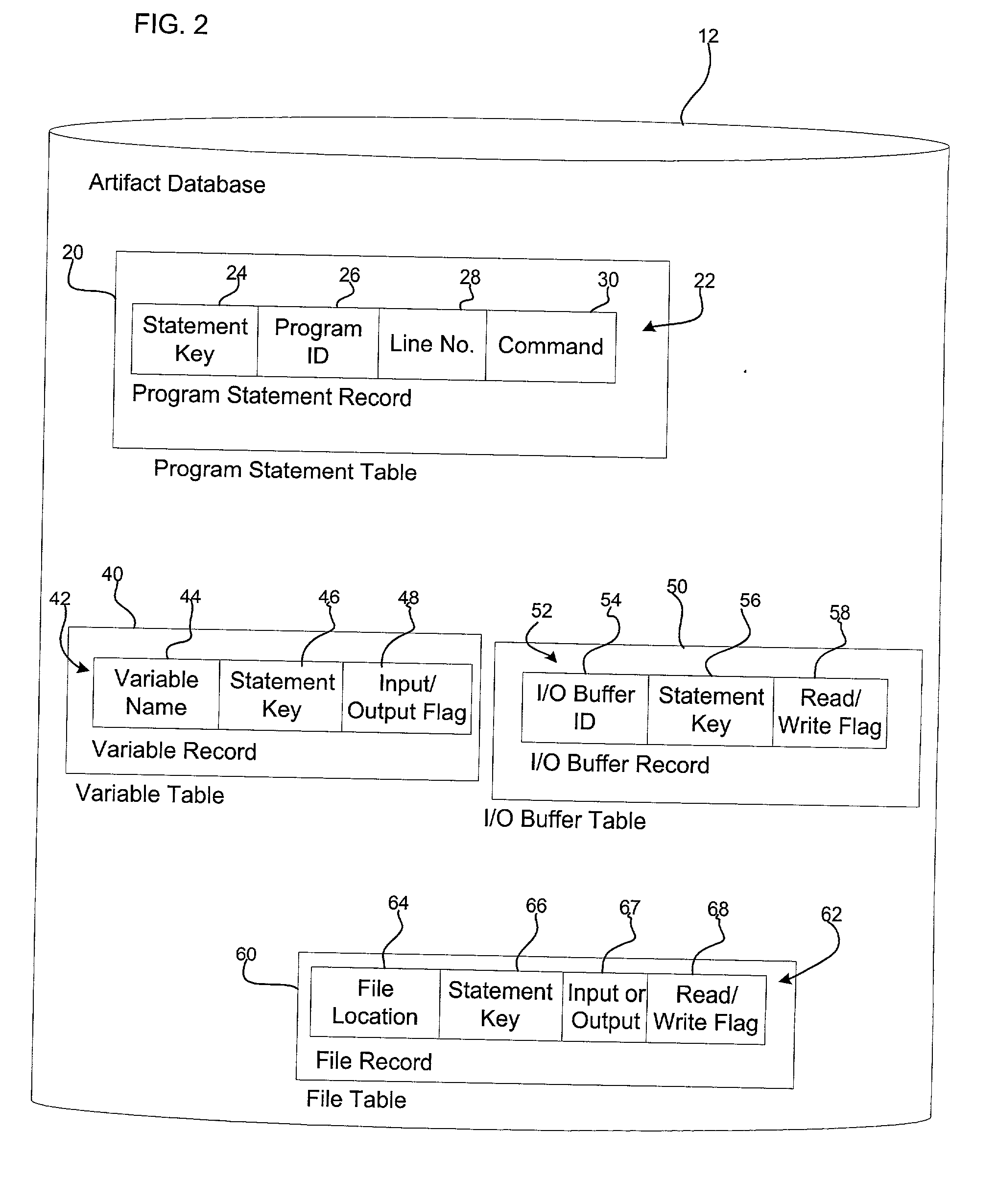
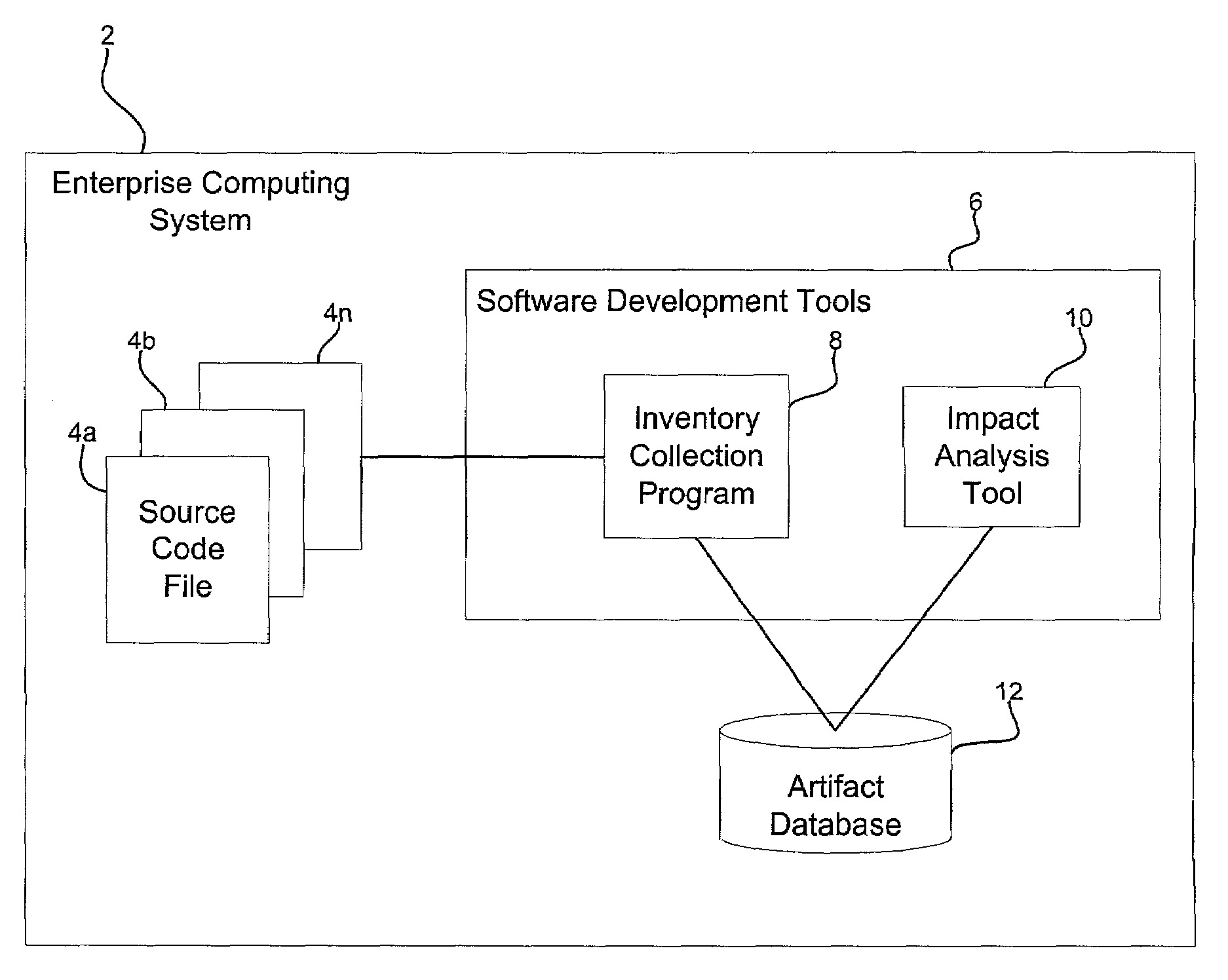
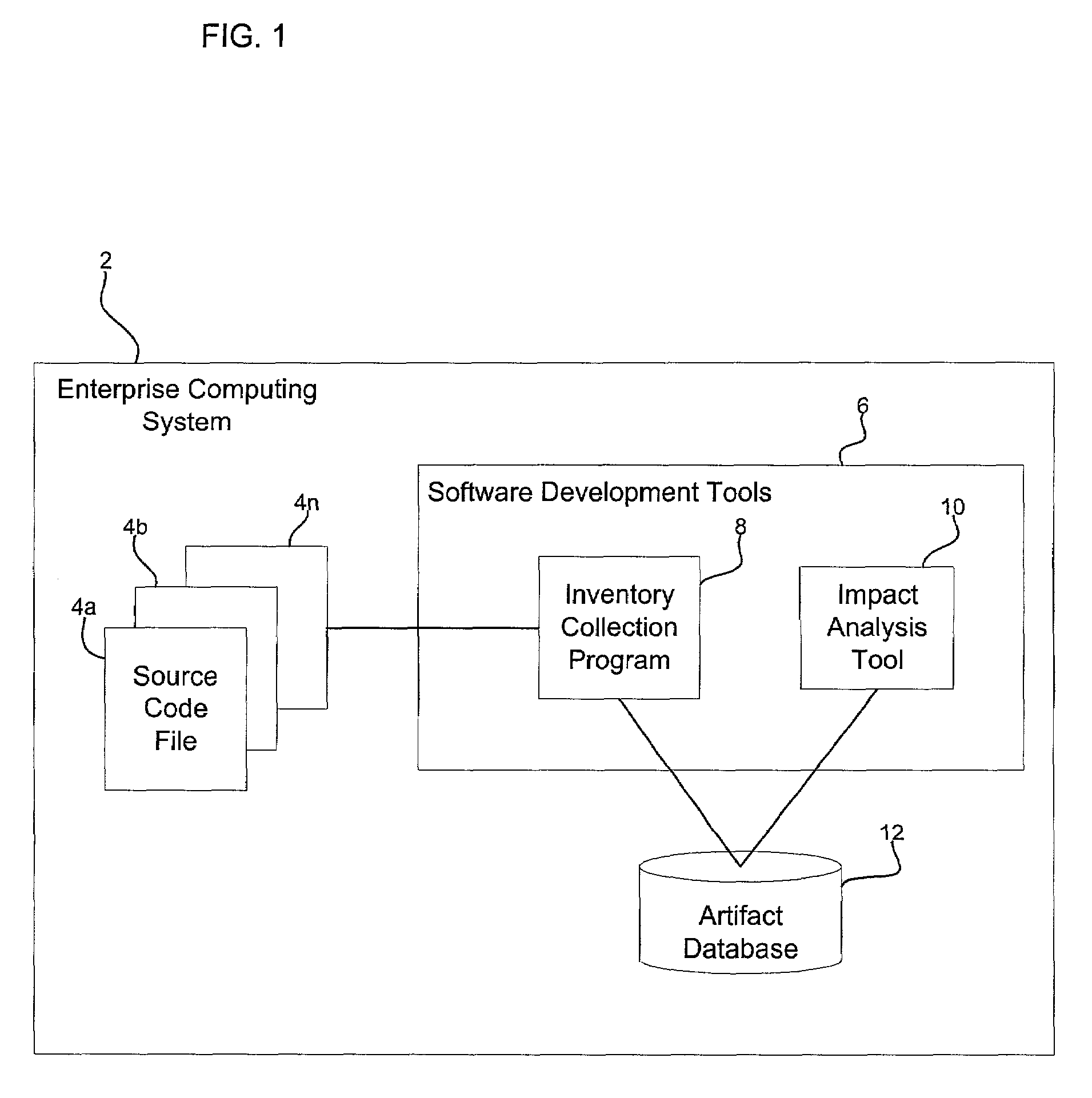
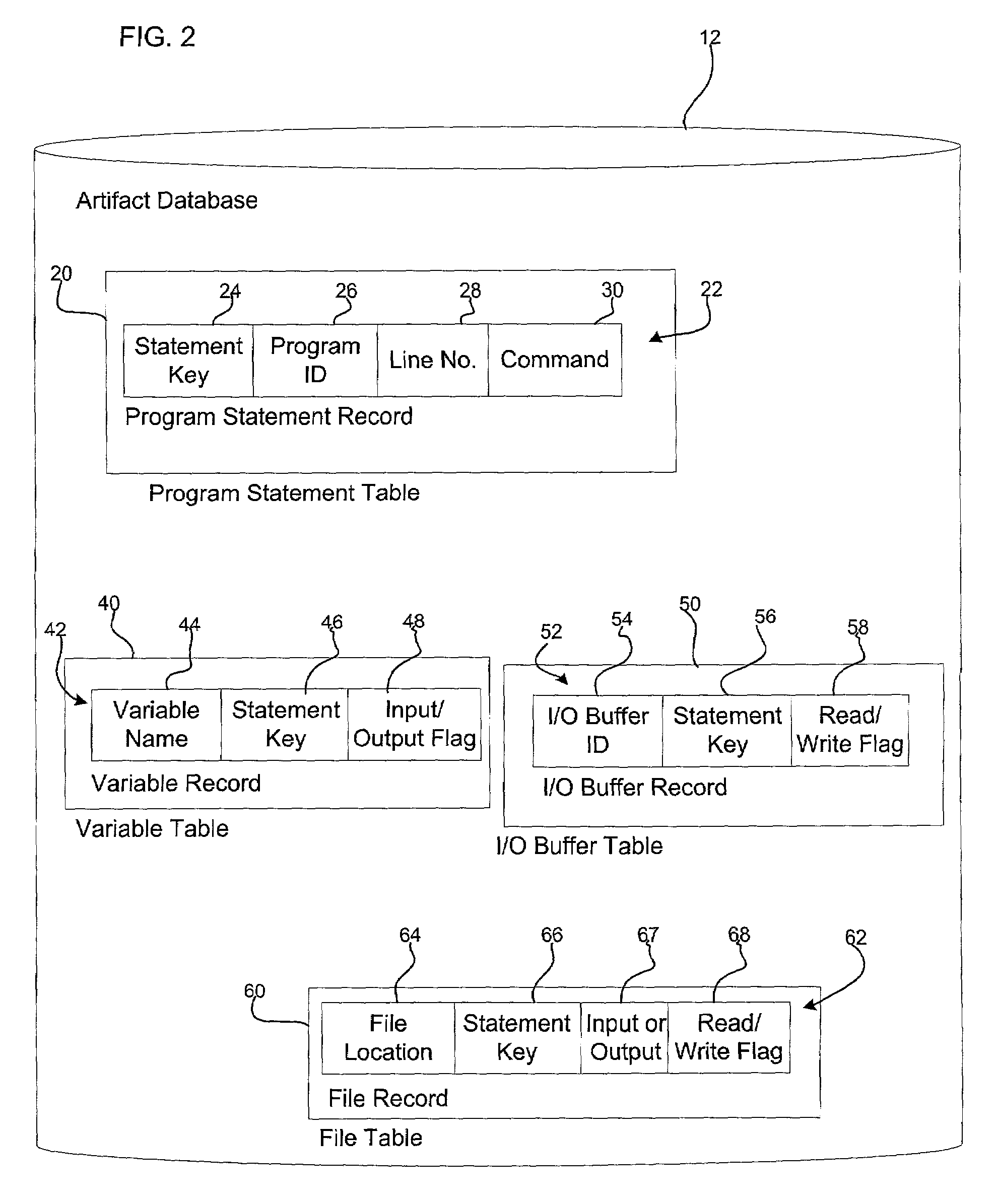
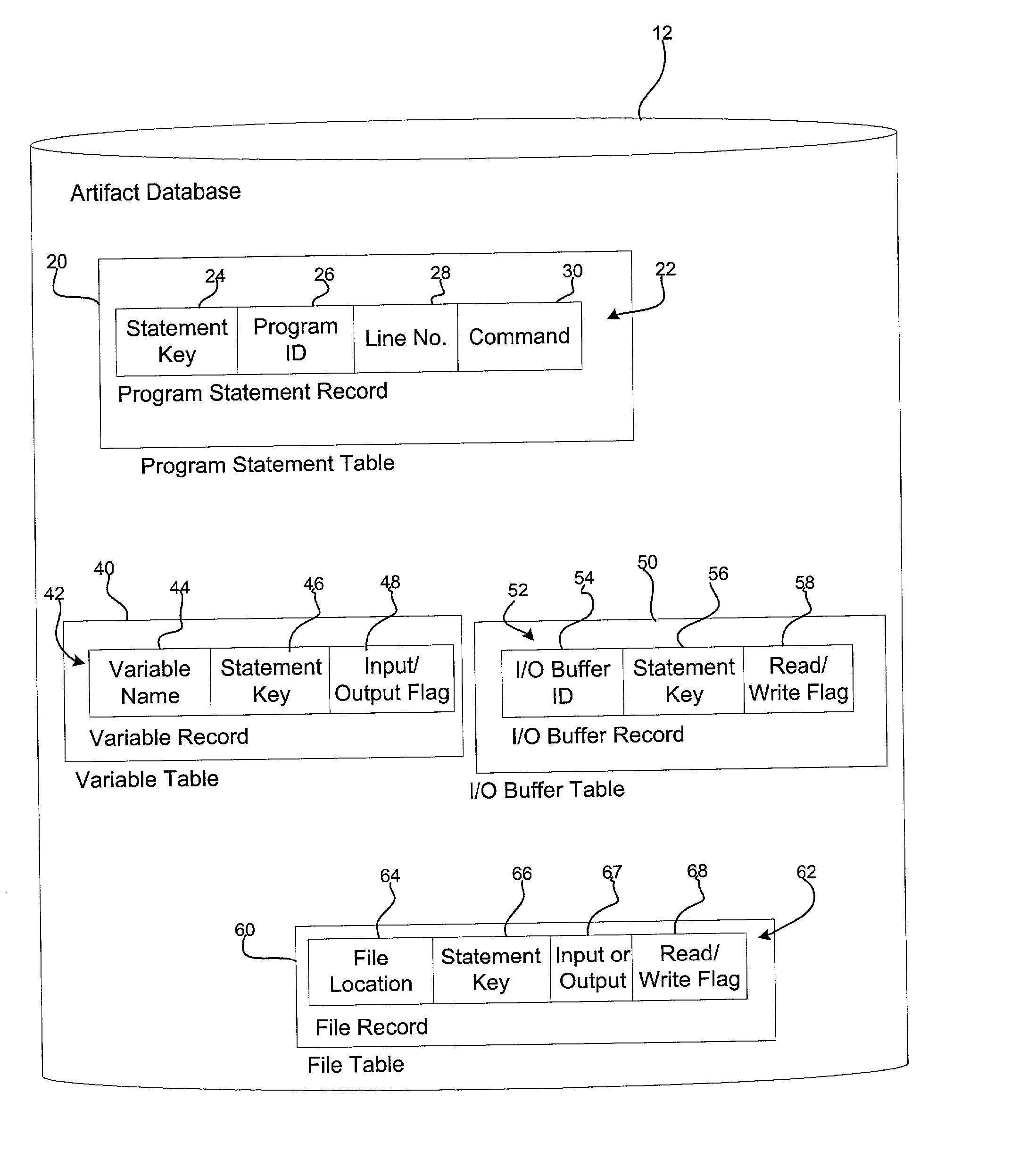
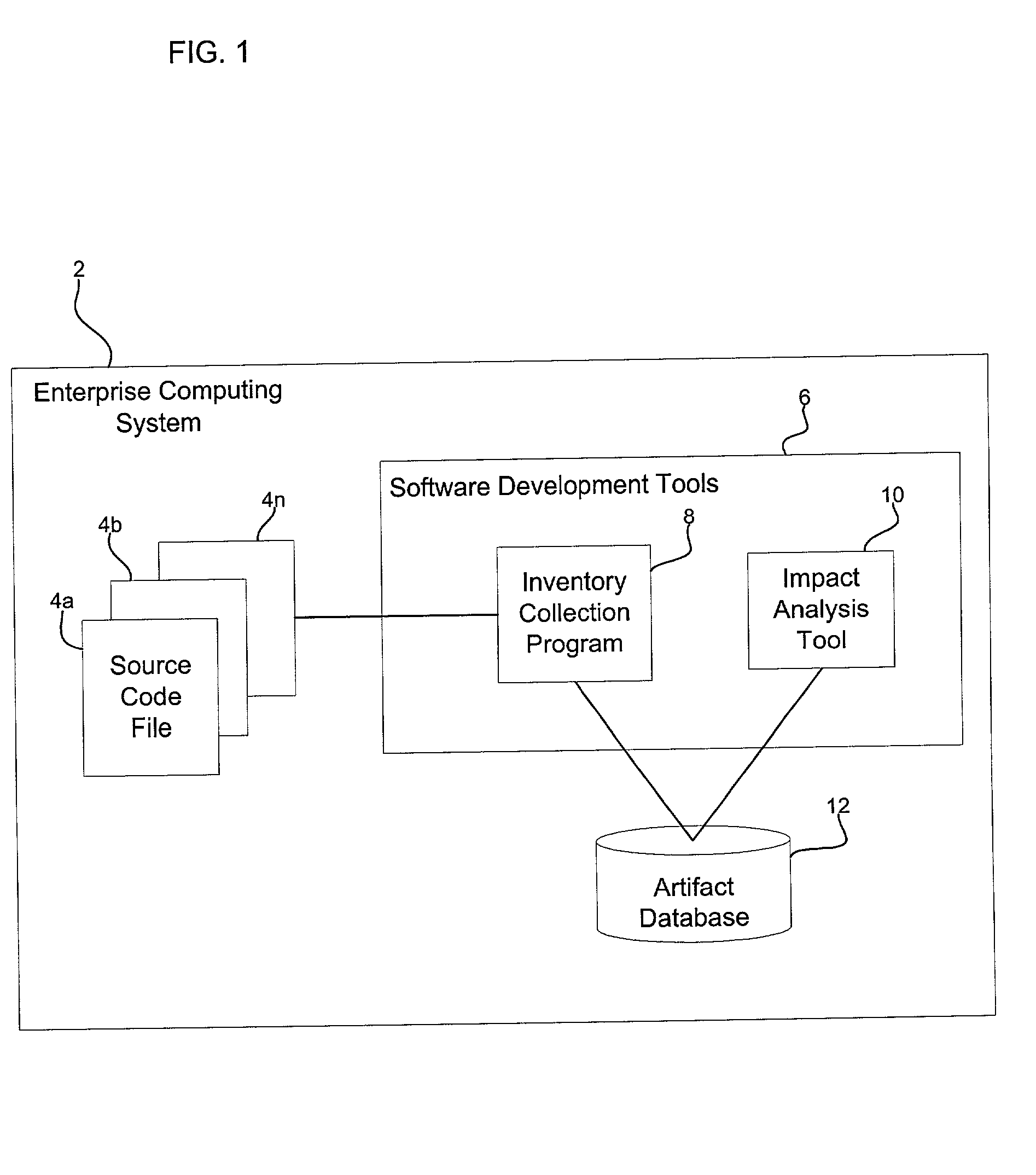
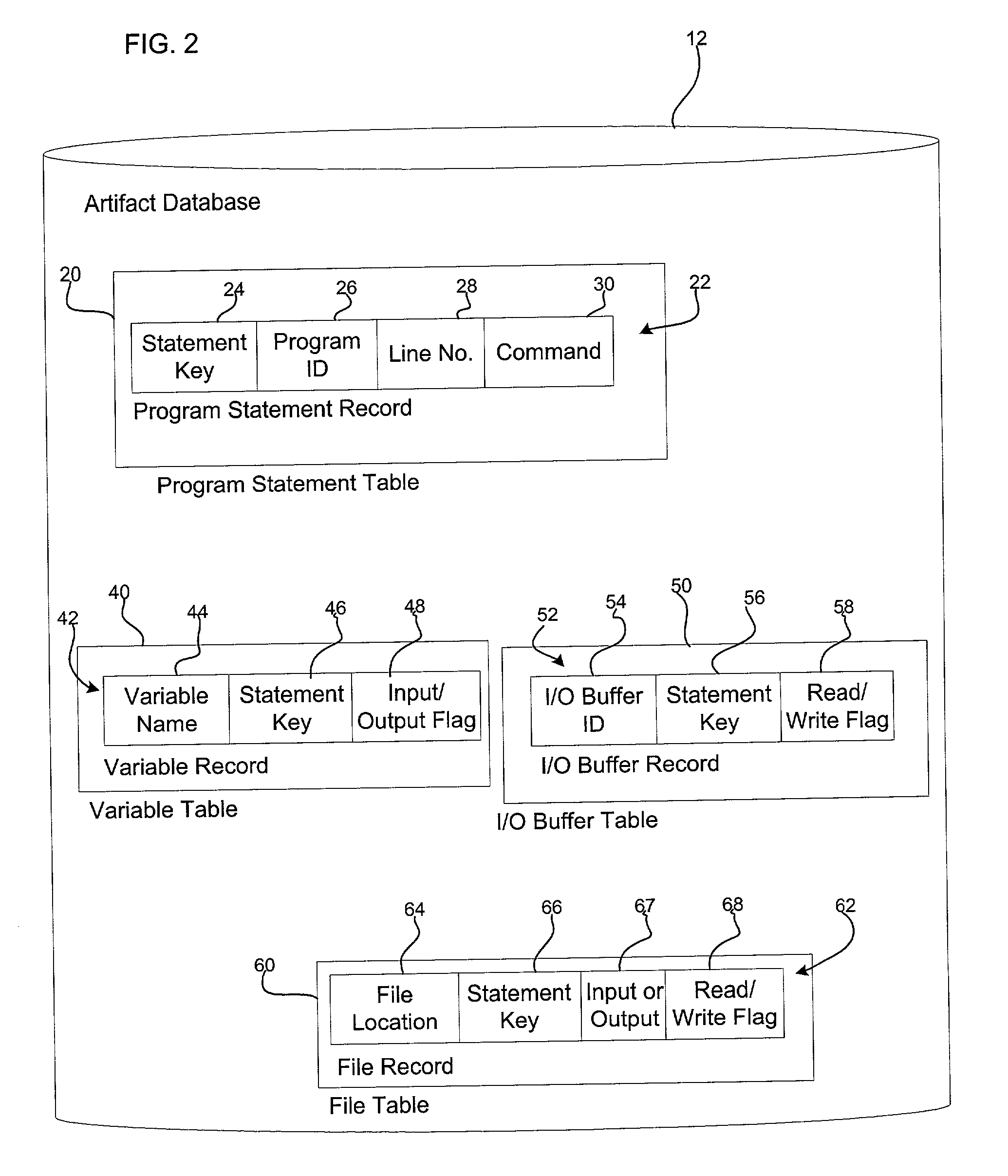
Method, system, and program for utilizing impact analysis metadata of program statements in a development environment
InactiveUS20030084425A1Eliminate errorsData processing applicationsVersion controlSource code fileSoftware development
Provided is a method, system, and program for enabling analysis of proposed changes to program statements in a source code file. A data structure is generated indicating a plurality of program statements affected by one of a plurality of selected program statements to change, wherein the data structure indicates a hierarchical relationship of the effect of program statements on one another resulting from changes to the selected program statements. The data structure is provided to a software development tool to enable a programmer to display information on the hierarchical relationship of the affect of the program statements on one another resulting from changes to the selected program statements.
Owner:IBM CORP
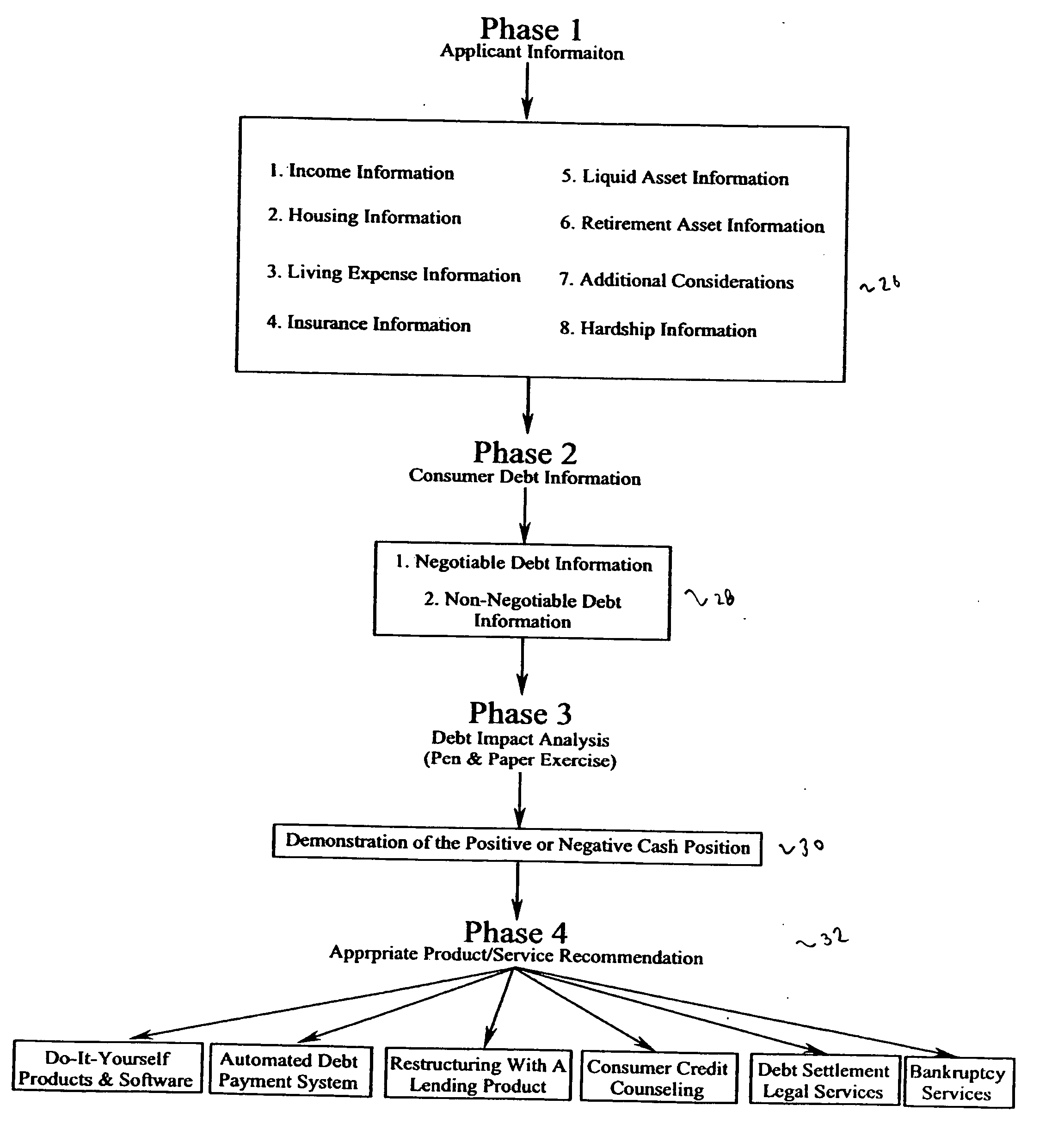
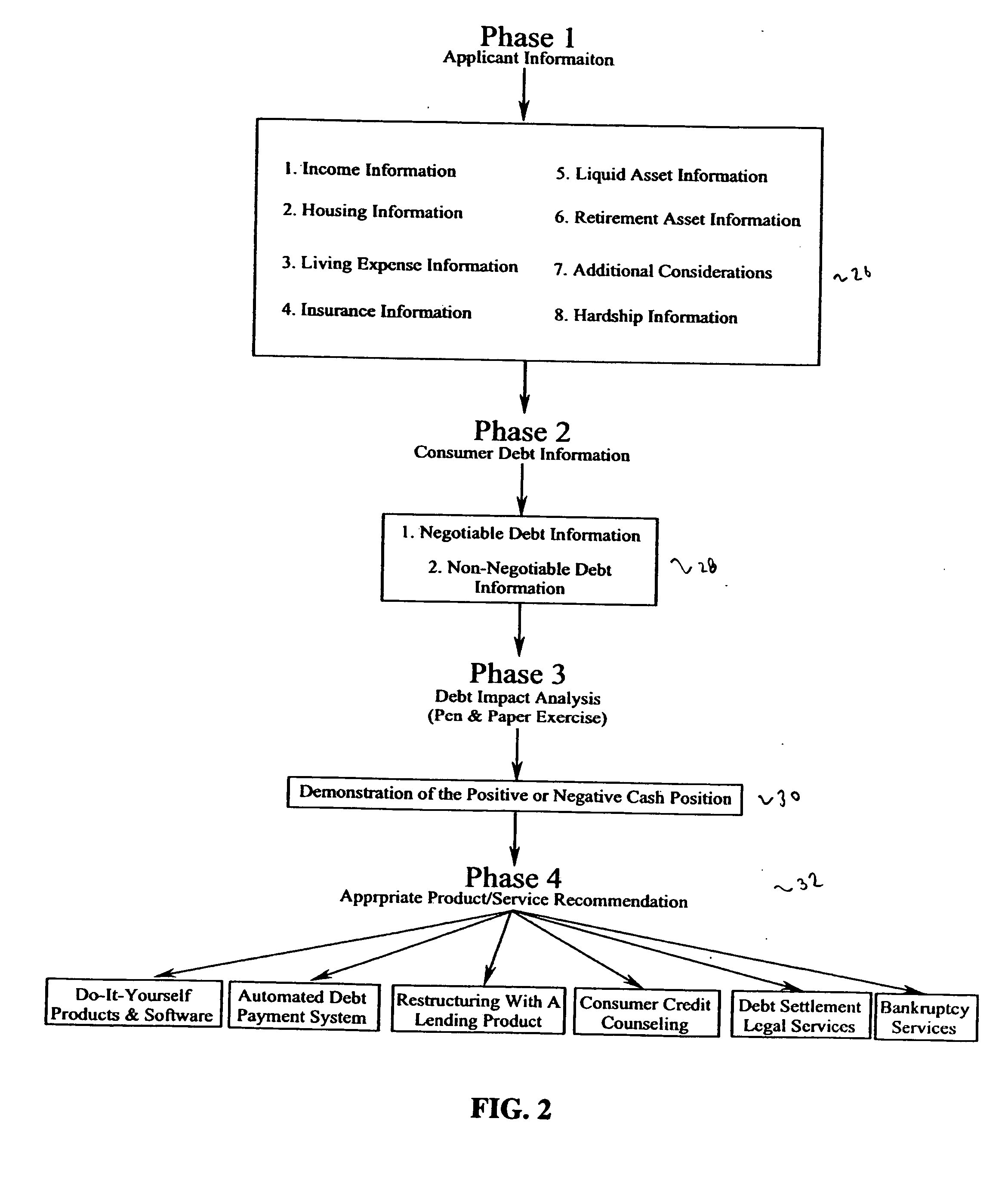
Method and system for debt management
A system and method for debt management is provided, comprising logic for receiving financial information, wherein the financial information comprises debt information. The system further comprises logic for generating a debt impact analysis based on the financial information, and logic for generating a first debt management proposal by analyzing a first impact of the first proposal on the financial information. The system further comprises logic for generating a second debt management proposal by analyzing a second impact of the second proposal on the financial information, and logic for comparing the first and second debt management proposals. The system further comprises logic for generating a user interface comprising one of the first and second debt management proposals, based on the comparison of the first and second proposals.
Owner:MANGANIELLO ANTHONY M
Methods and apparatus for impact analysis and problem determination
ActiveUS7505872B2Digital computer detailsNuclear monitoringDistributed Computing EnvironmentCondition status
A technique for determining an impact of a condition (e.g., service outage) of at least one subject component in a computing environment comprises the following steps / operations. First, one or more components in the computing environment which depend on the at least one subject component (e.g., dependents) are identified. Identification comprises traversing at least a portion of a model representative of an existence of one or more relationships associated with at least a portion of components of the computing environment and which is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Then, one or more procedures are performed in accordance with the one or more identified components to determine a condition status associated with each of the one or more identified components. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:HUAWEI TECH CO LTD
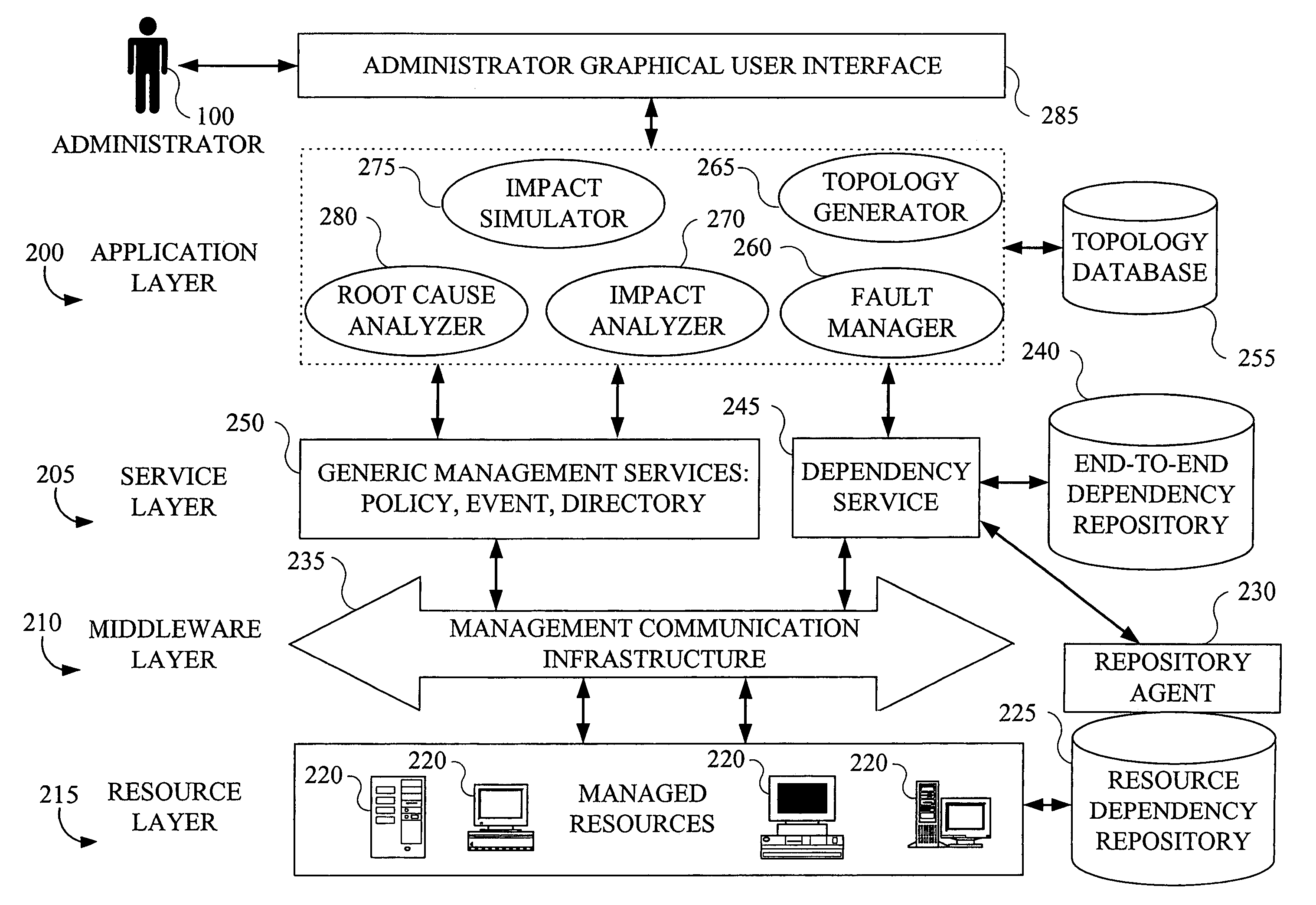
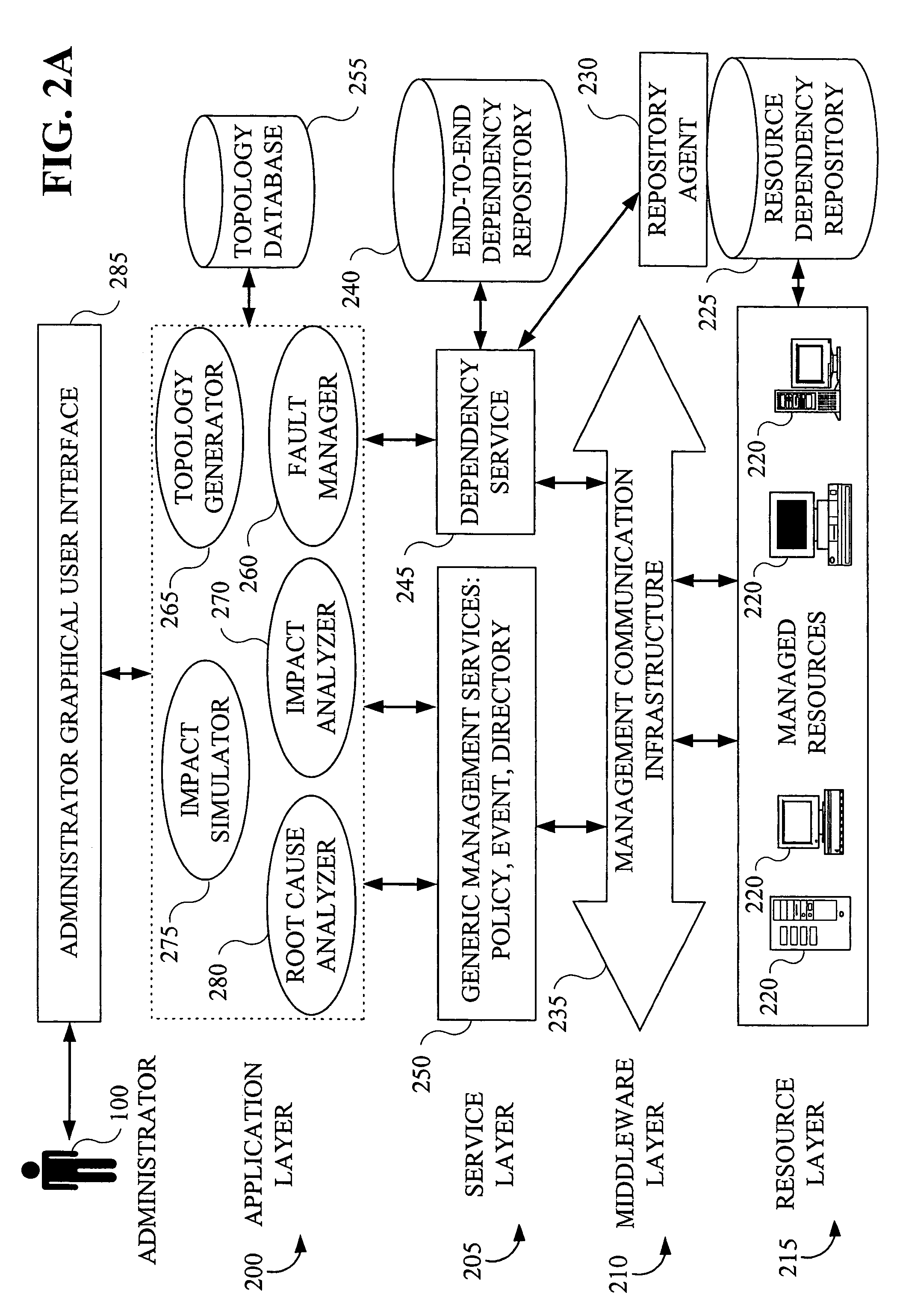
System and method for managing a virtual domain environment to enable root cause and impact analysis
ActiveUS8031634B1Improve intelligenceEasy to analyzeData switching by path configurationRoot causeCausality
A virtual domain management system is provided which associates application, physical and virtual domains to enable propagation of events, symptoms and other information across the domains. The virtual domain manager collects events and symptom information across multiple domains by correlating domain topology models. Using a causality matrix and codebook technology the virtual domain manager uses the information to perform root cause and impact analysis across domains. Information from the analysis may be fed back into the domains to enhance domain management.
Owner:EMC IP HLDG CO LLC
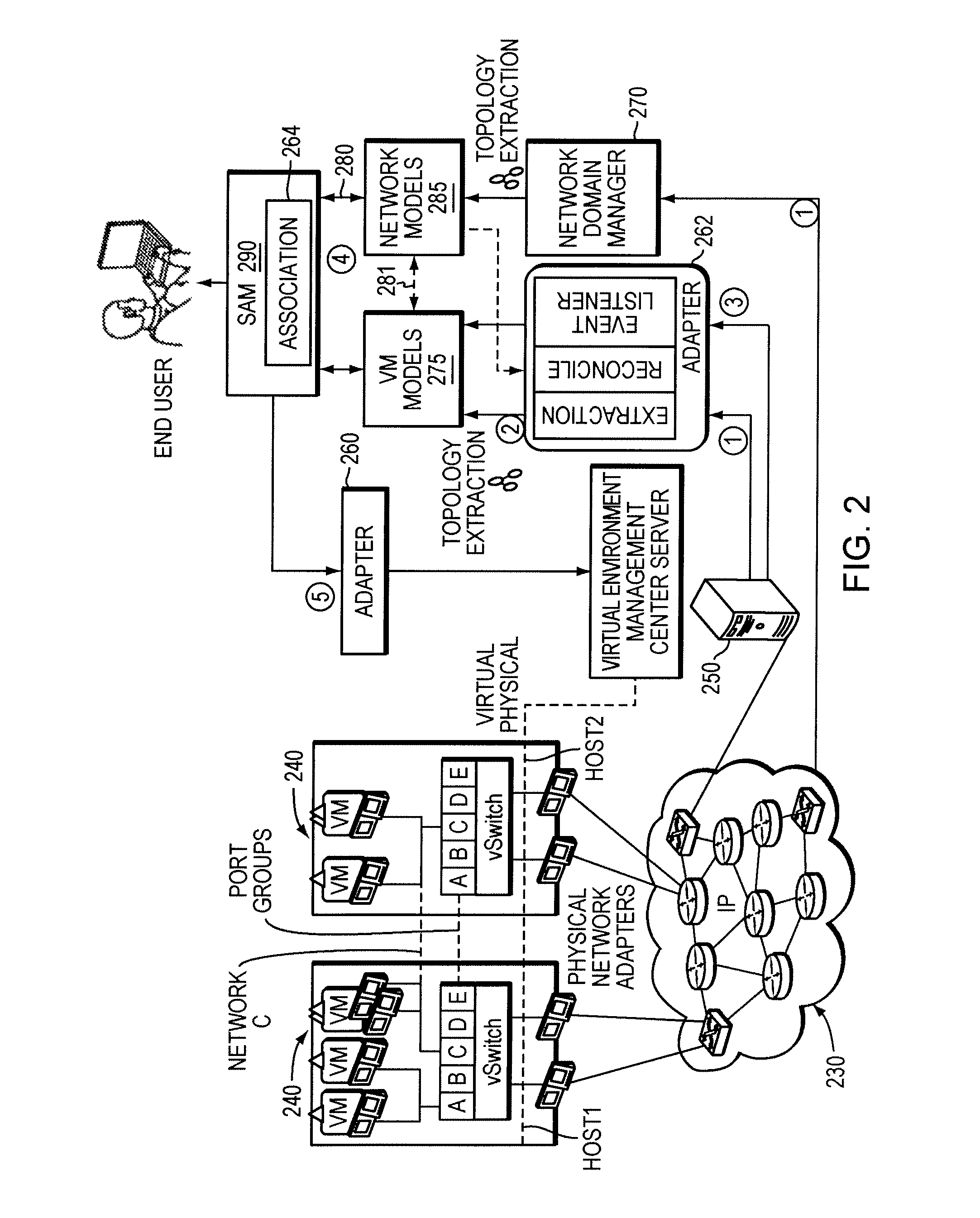
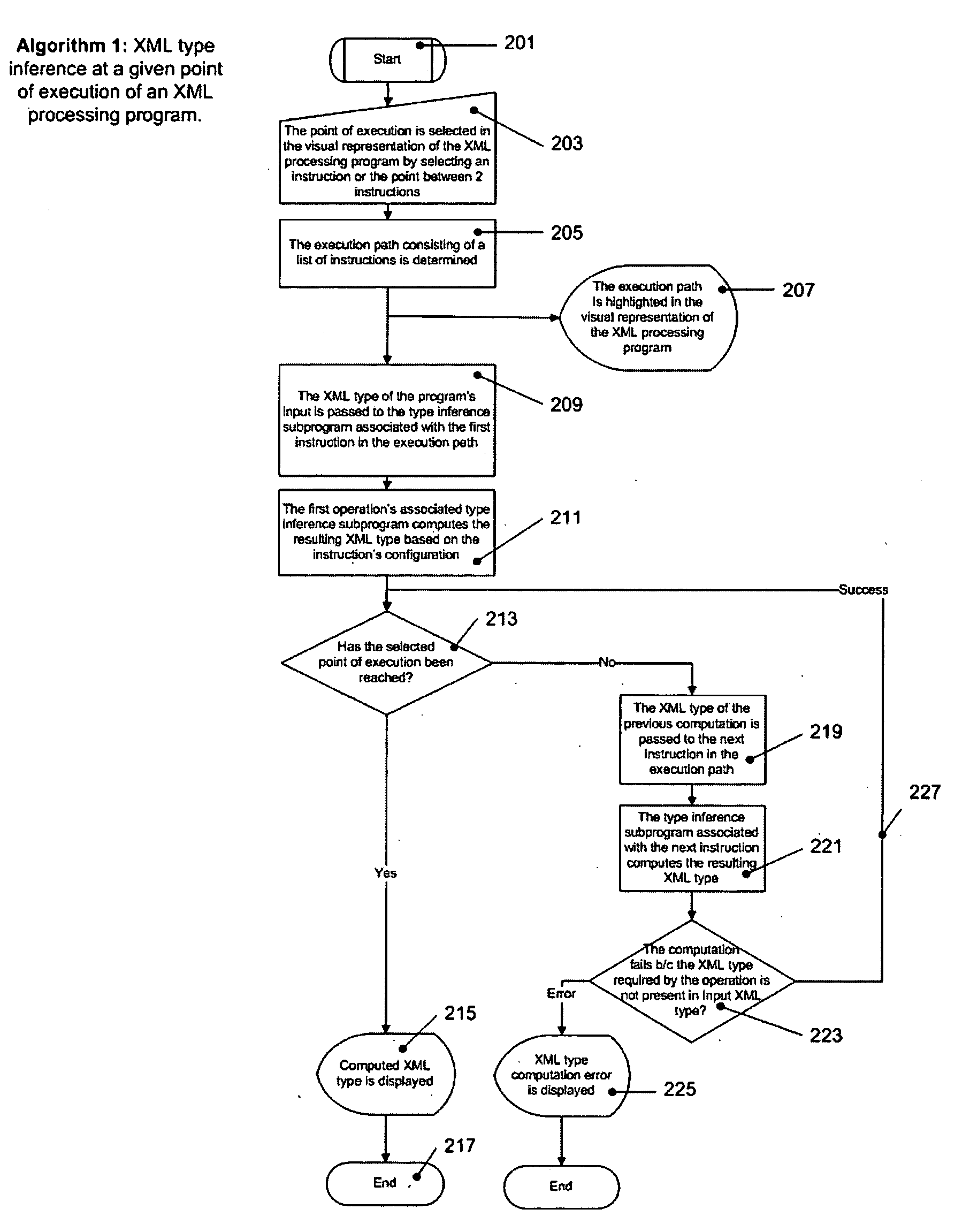
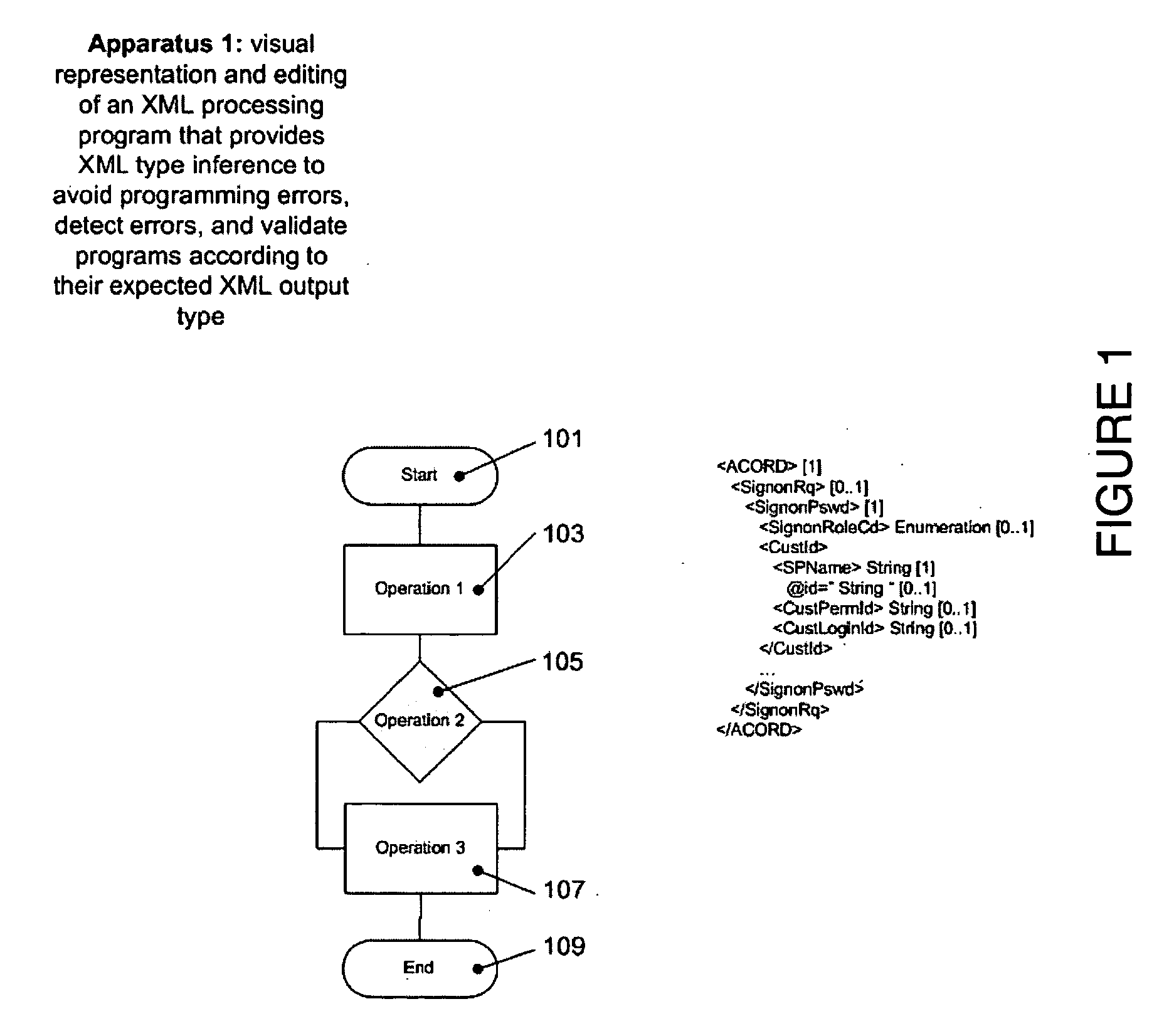
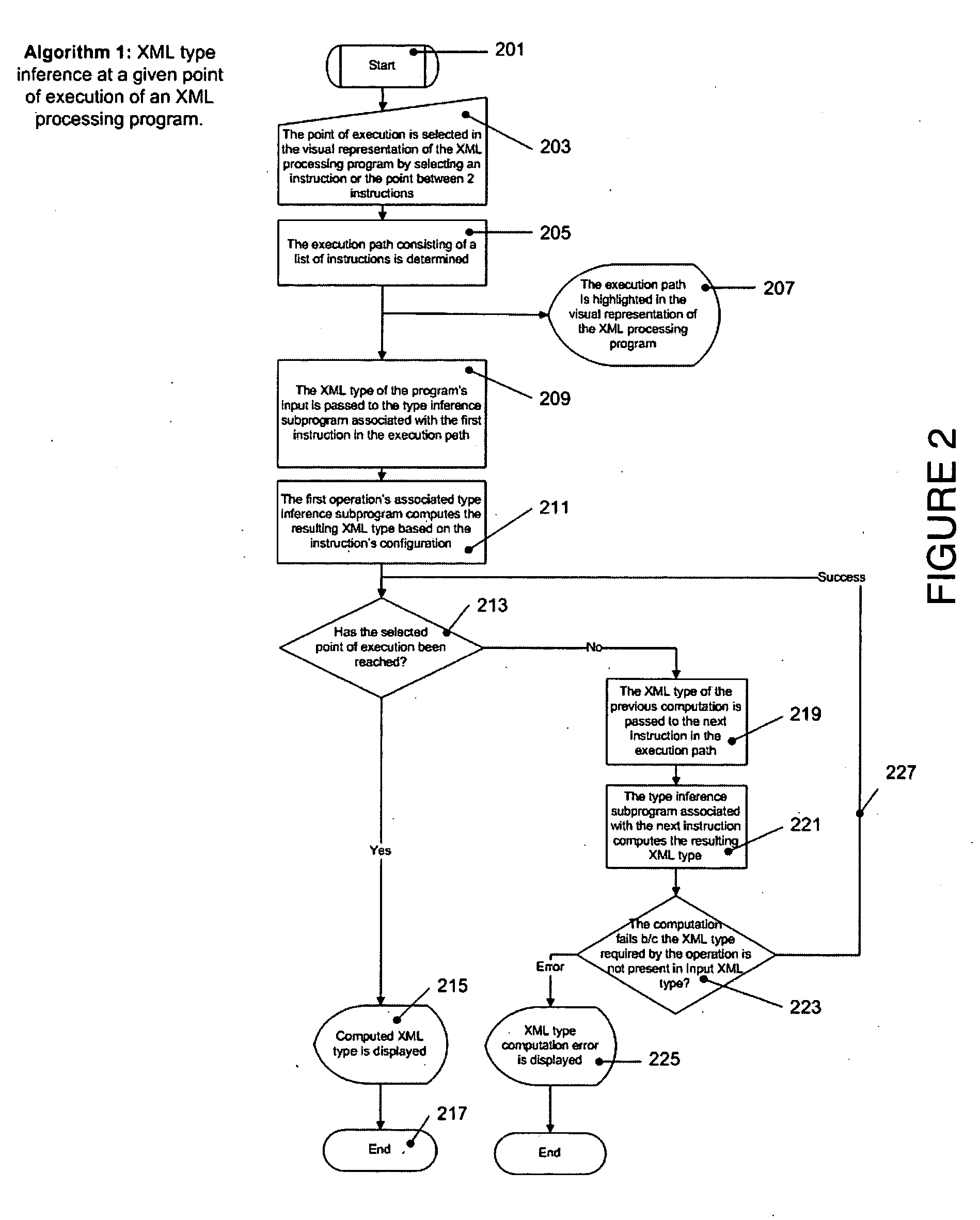
Graphical XML programming system and engine where XML processing programs are built and represented in a graphical fashion
ActiveUS20060075387A1Fix bugsDesign errorNatural language data processingVisual/graphical programmingChange managementWeb service
A system and methods are provided for operating and building graphically XML processing programs, guiding the user in development of the program, preventing and detecting development errors as the program is being designed, ensuring that the program is valid, i.e. satisfies required input and output constraints at all times, i.e. from the time it is developed to when it is deployed in a production environment, ensuring the automated change management if the internal logic of the Web service, or data sources called by the service or the schema that underlies the Web service are modified. The system includes a graphical XML Programming system where XML processing programs are built and represented in a graphical fashion, a real-time metadata computation and visualization method for each selected execution point in the visual program that provides guided programming, error prevention and detection, and change impact analysis and change management, and, an automated execution path exploration method that enables overall program validation and error identification. The system and methods allow a user to reduce by at least a factor of 2 the costs of development and maintenance of reliable XML processing programs such as Web Services.
Owner:DIEBOLD NIXDORF
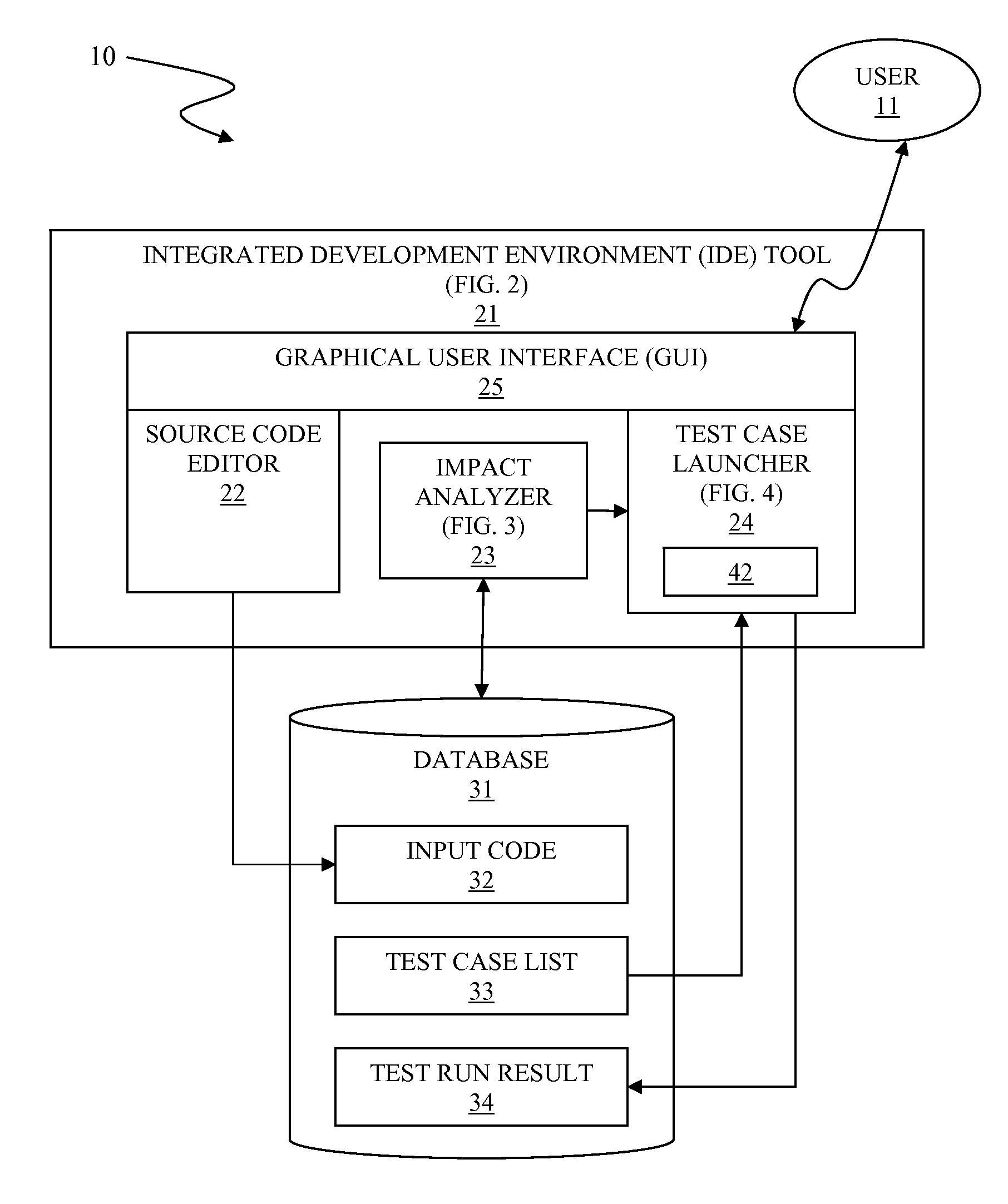
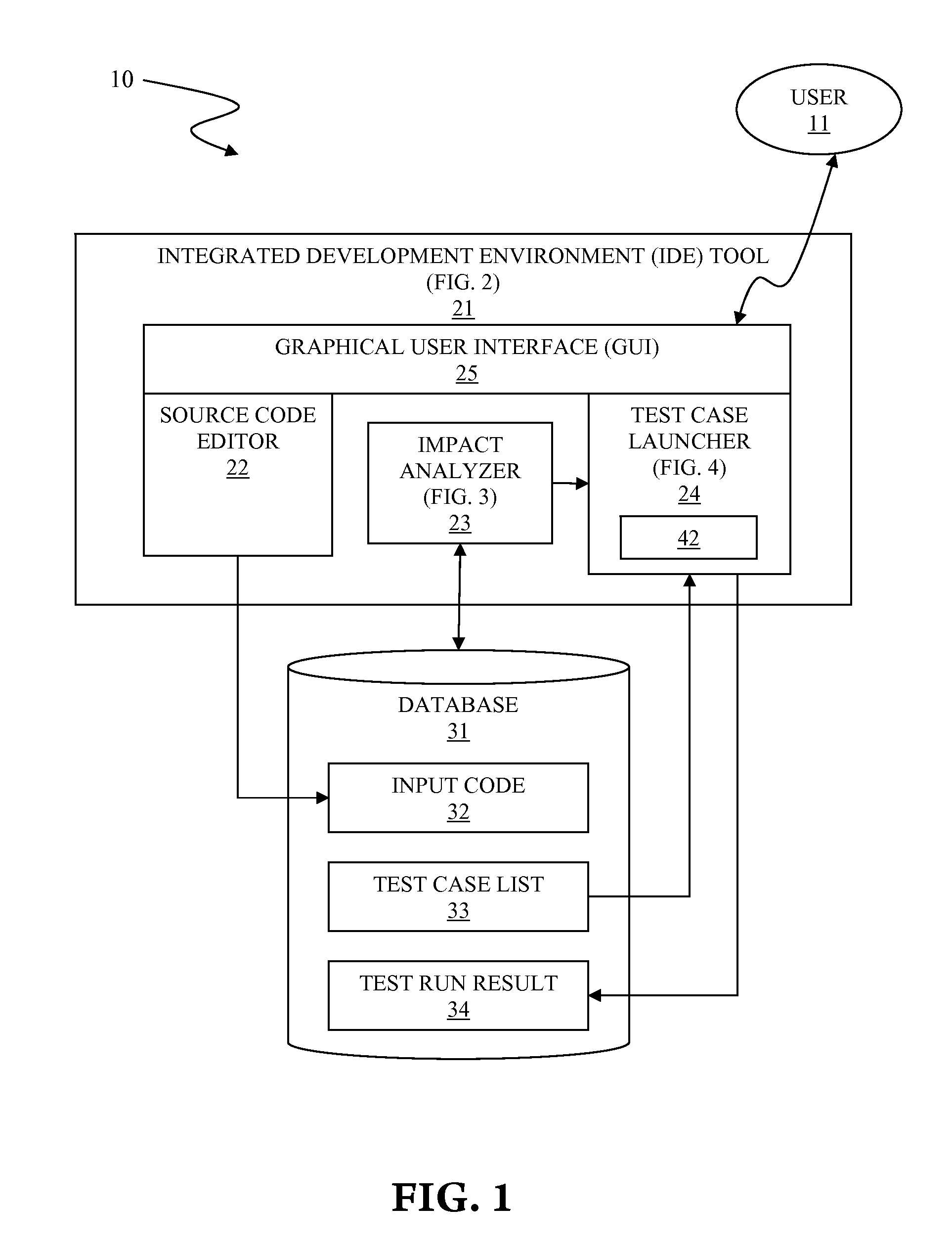
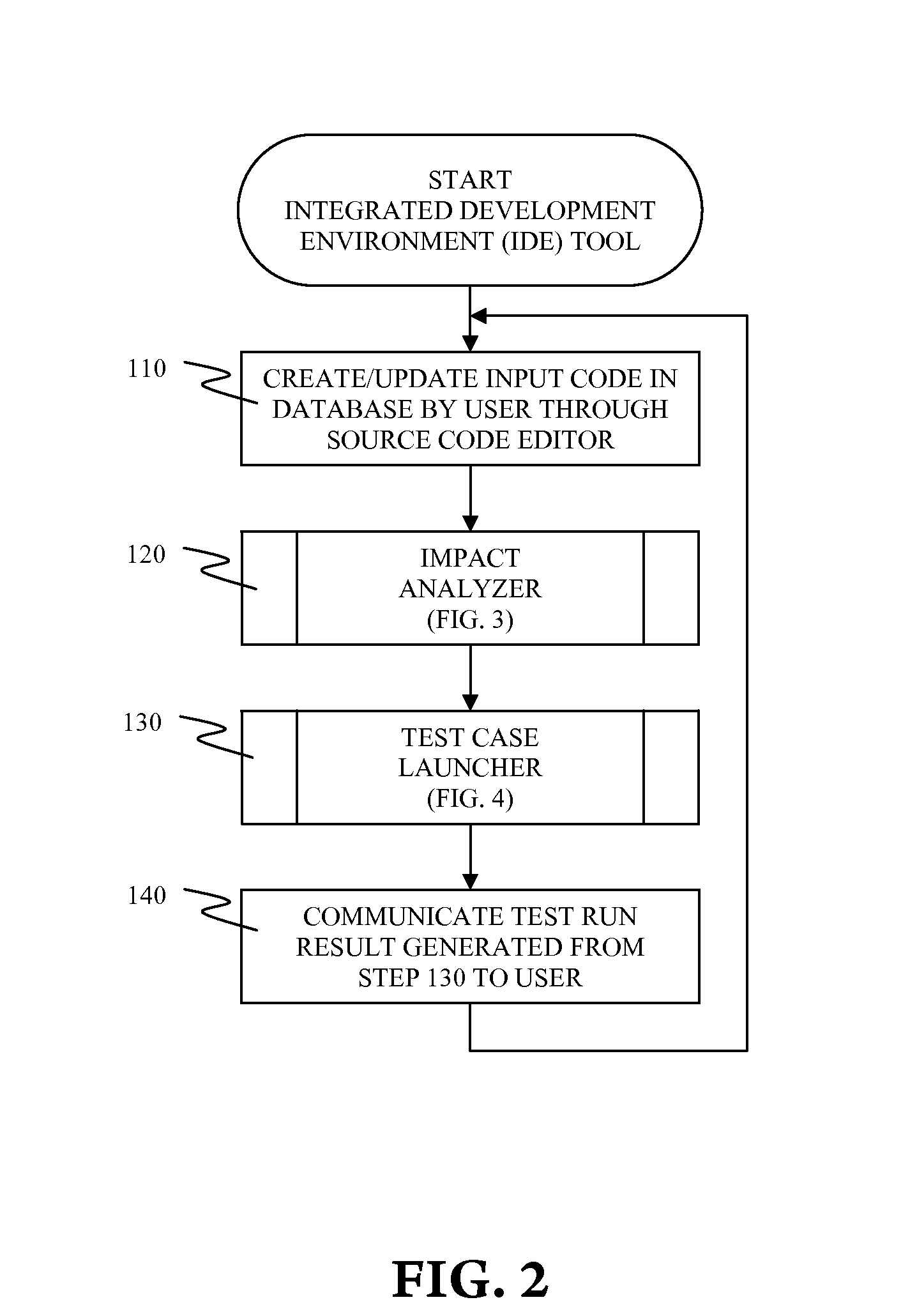
Asynchronous code testing in integrated development environment (IDE)
InactiveUS20120089964A1Error detection/correctionSpecific program execution arrangementsCoding blockGraphical user interface
A system and associated method for asynchronous code testing in an Integrated Development Environment (IDE). The IDE has components of a source code editor, an impact analyzer, a test case launcher, a graphical user interface (GUI), and a database. All components run concurrently for asynchronous and real-time code editing. Upon modification of a code block of an input code, a test case is automatically generated and a launching priority is calculated based on the relationship between the modified code block and each code block affected by the modification. Generated test cases are automatically run by the test case launcher or manually selected by the user to produce a test run result.
Owner:IBM CORP
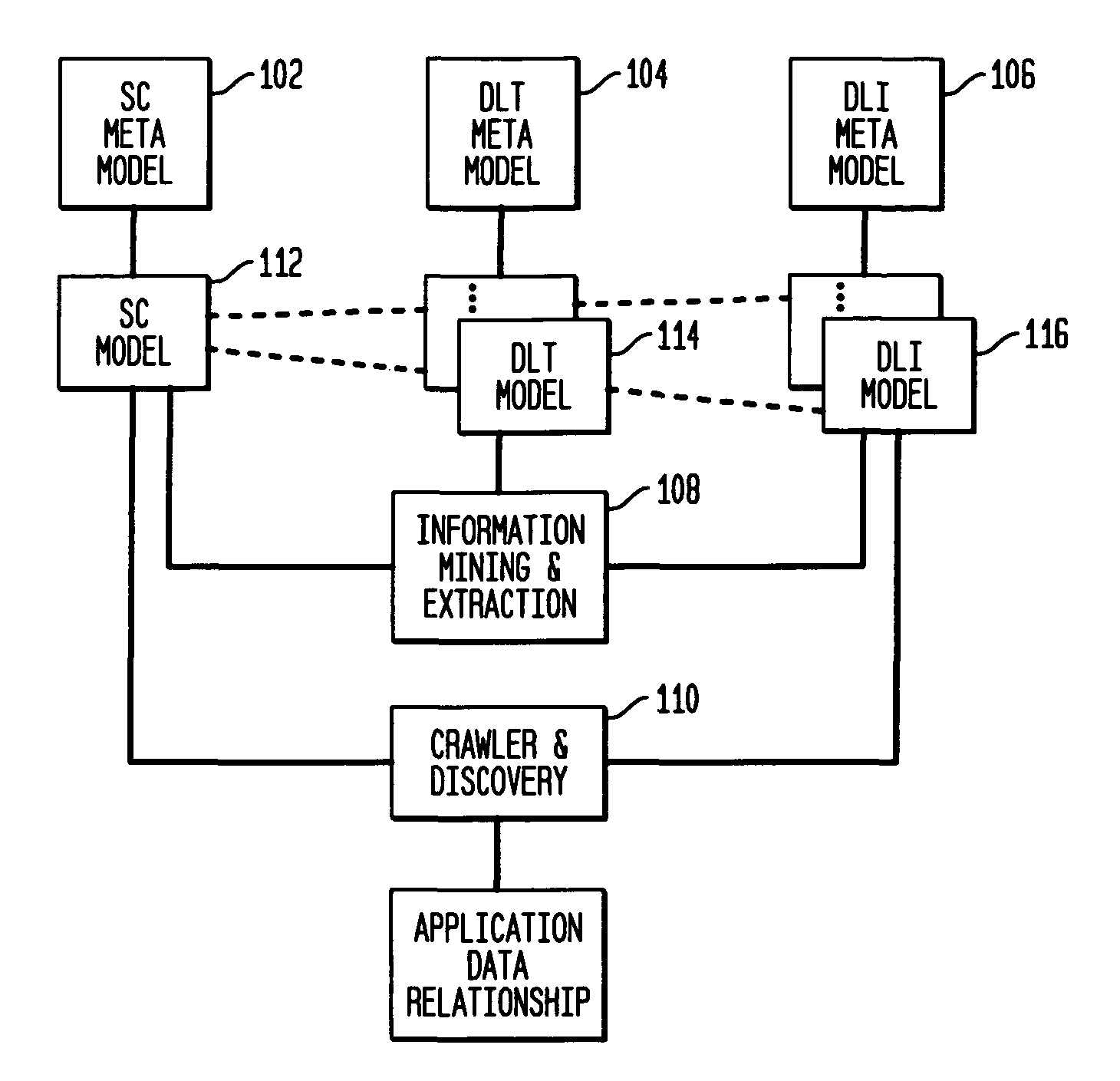
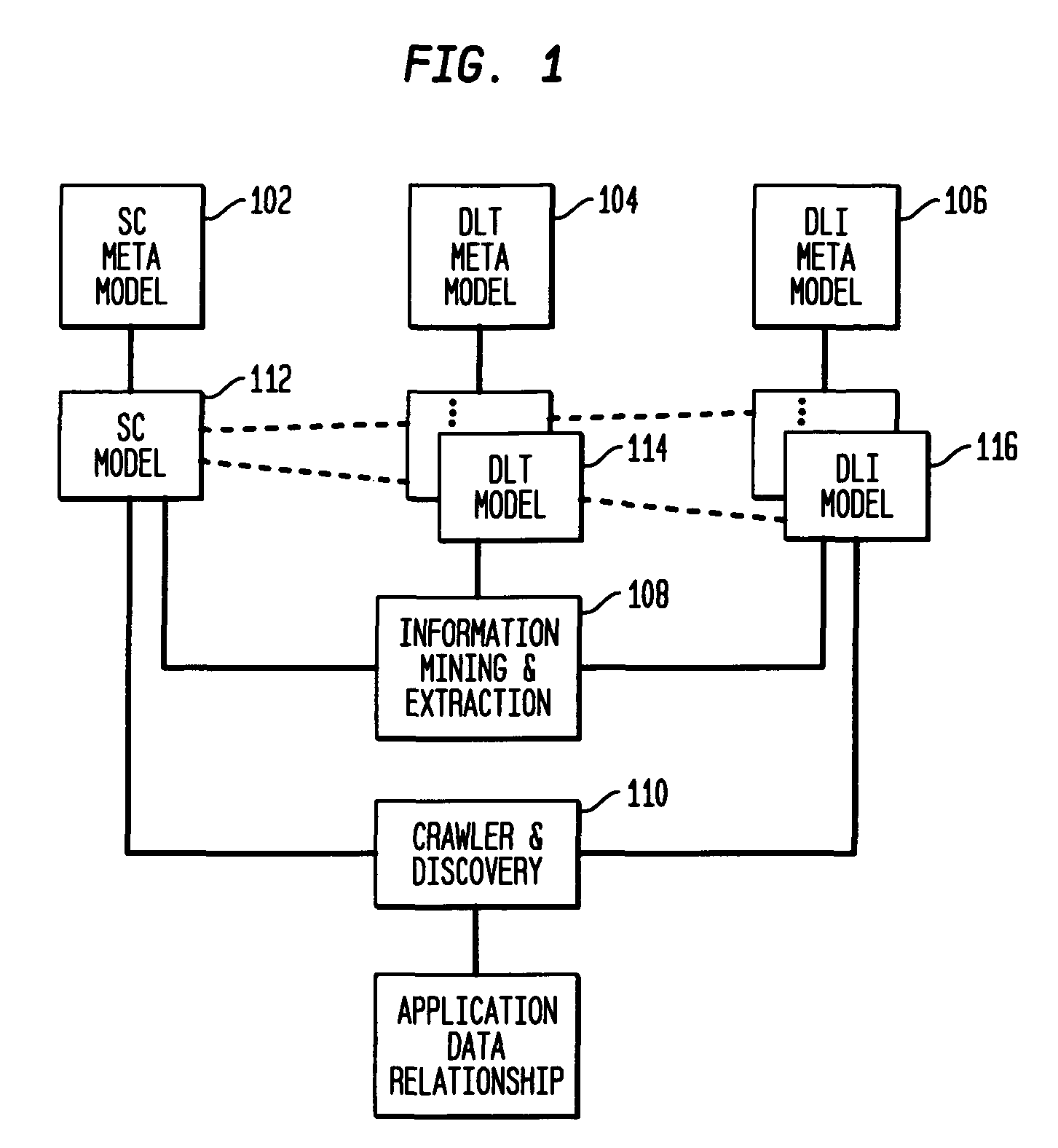
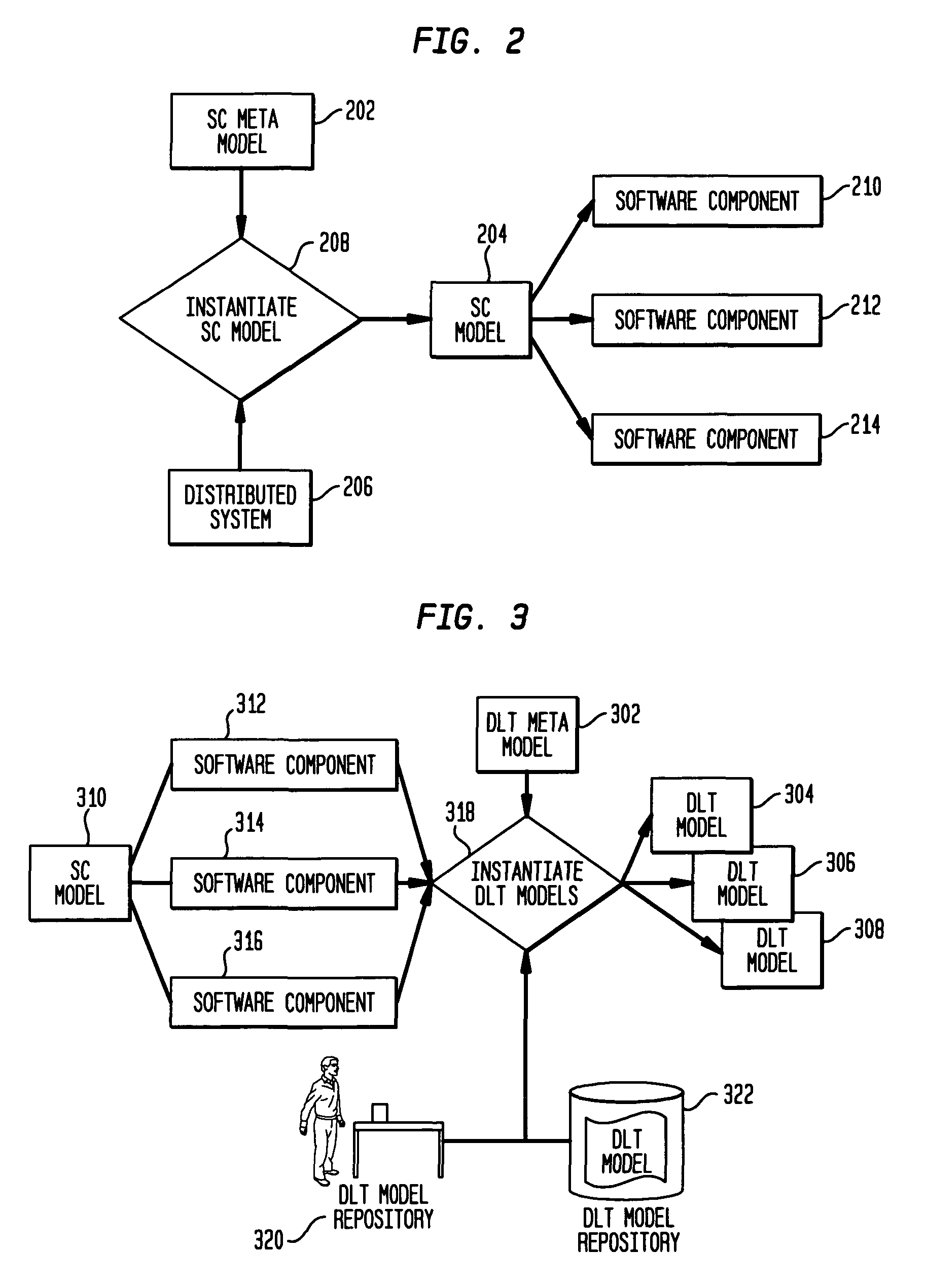
Data locations template based application-data association and its use for policy based management
Method and system are disclosed for automatically discovering associations between applications and data in multi-tiered distributed systems. The method in one aspect uses a machine-readable specification of a model or template that describes use and transformation of data by software components. The method additionally utilizes a model of system configuration and appropriate runtime support to mine information available from systems management software present in enterprise systems. The application-data association discovery process performs a traversal of the distributed system configuration graph with actions taken during this traversal driven by the contents of the templates for the software components present in the system. The results of the application-data association discovery process are stored in a database and may be used to specify application-specific information lifecycle management (ILM) policy or as input to impact analysis tools in access control and antivirus systems.
Owner:INT BUSINESS MASCH CORP
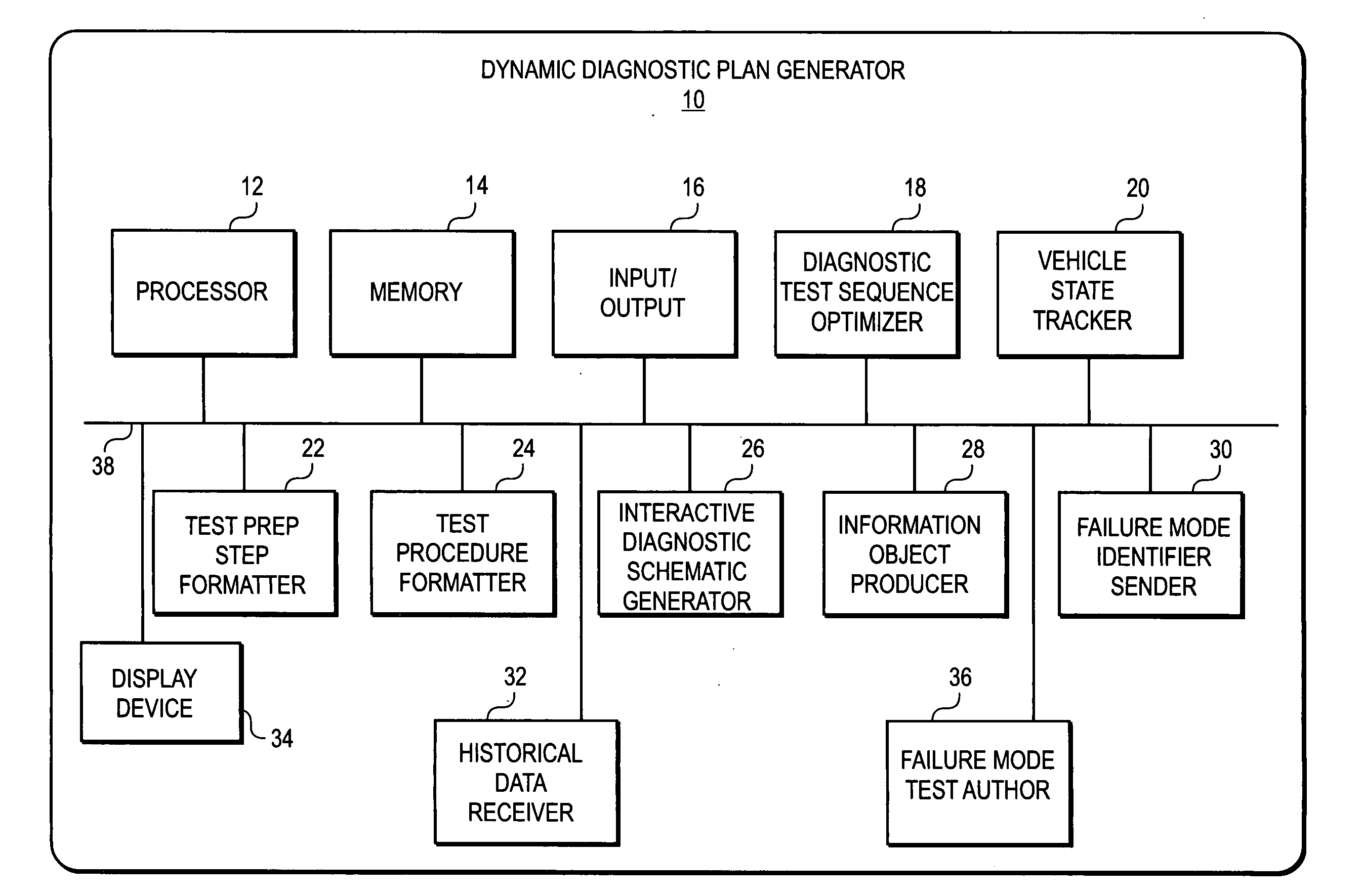
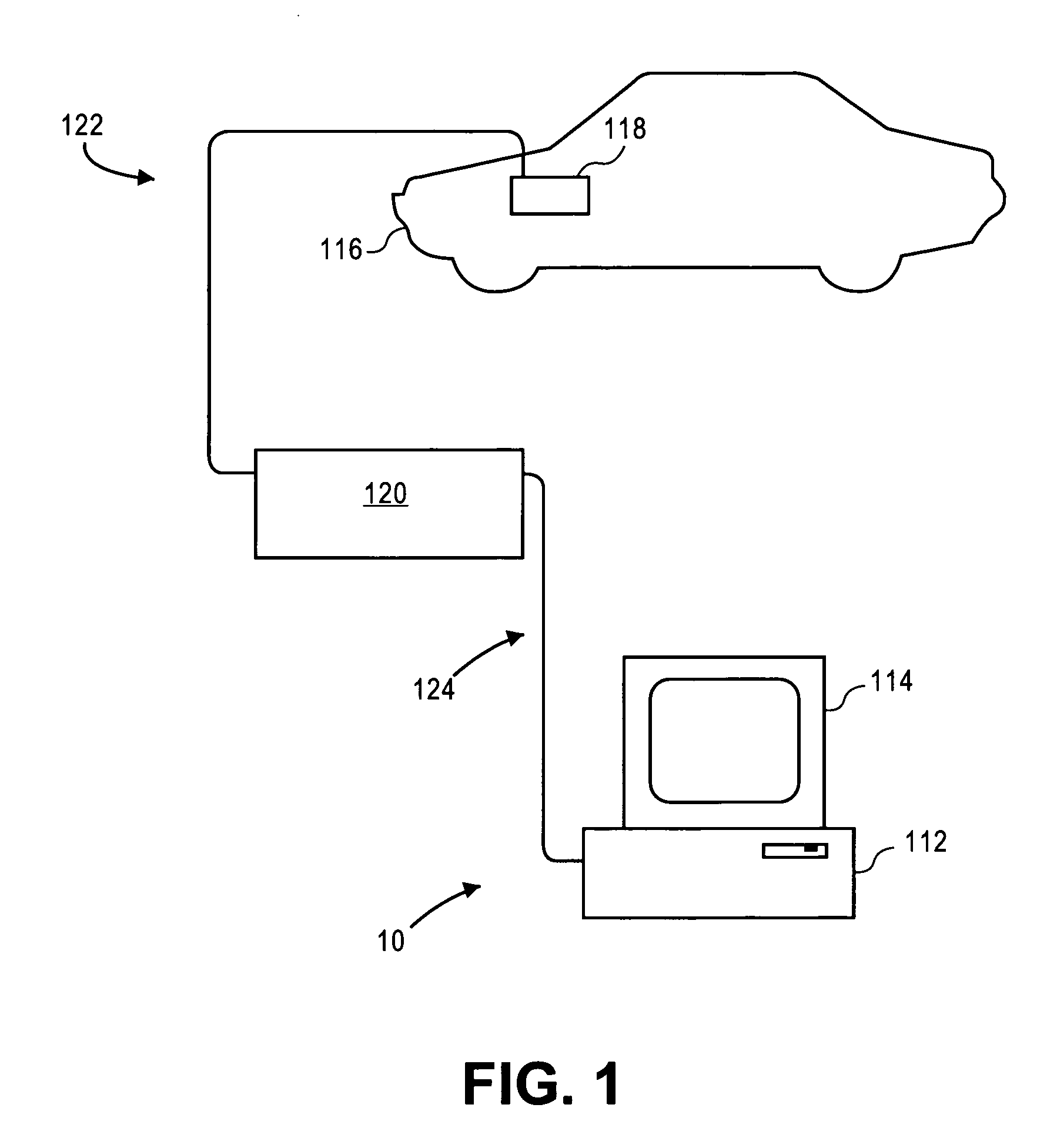
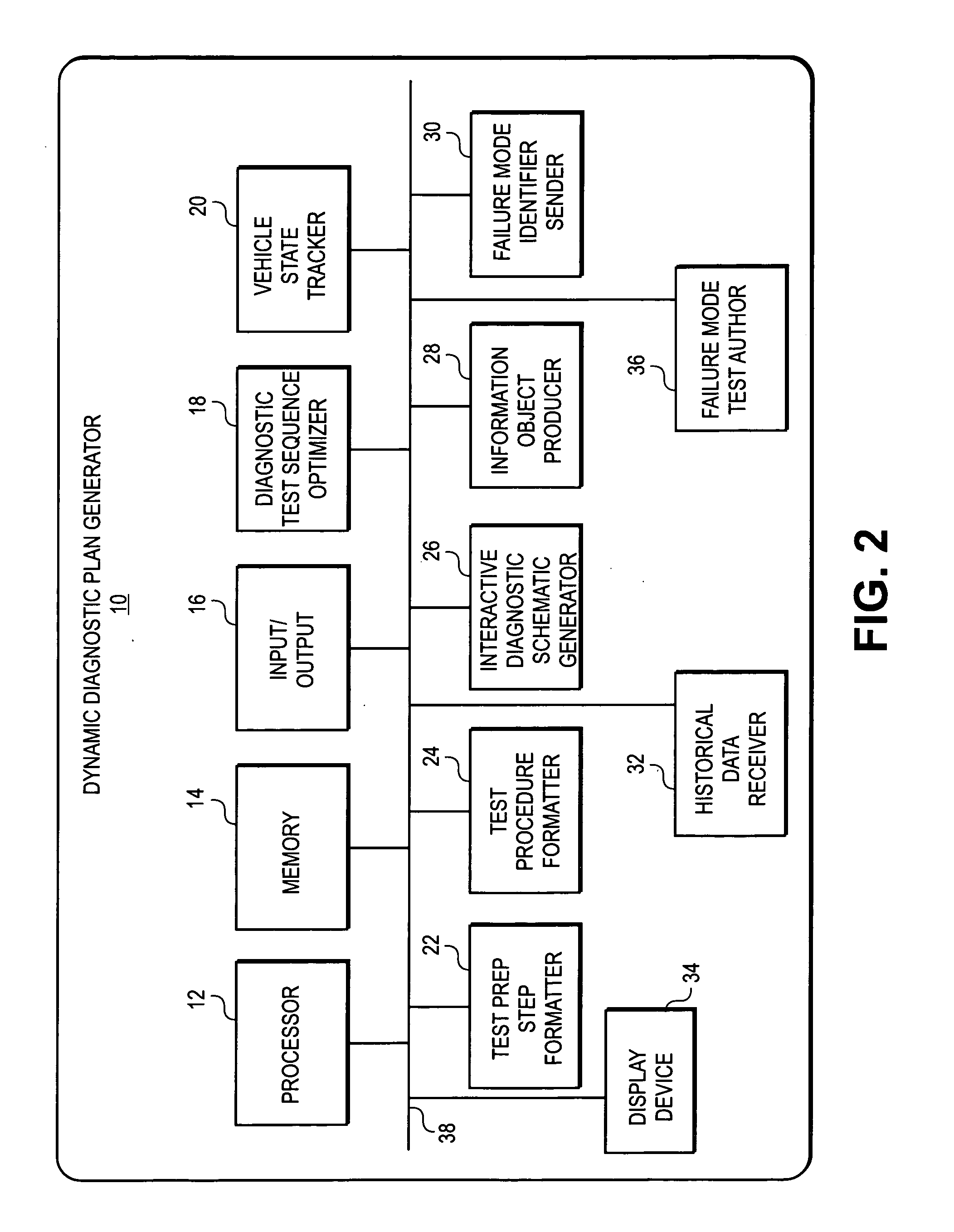
Dynamic decision sequencing method and apparatus for optimizing a diagnostic test plan
ActiveUS20070294001A1Vehicle testingRegistering/indicating working of vehiclesDiagnostic dataProgram planning
A dynamic diagnostic plan generator arranges diagnostic test procedures related to a vehicle symptom or operational problem in a sequence based on a probabilistic Failure Mode and Effects Analysis (FMEA). The diagnostic plan generator also tracks a vehicle state, and provides instructions for test preparation steps and instructions for performing the diagnostic test procedures. The plan generator further generates schematic illustrations of the diagnostic test procedures, and creates a diagnostic data structure containing information related to the diagnostic test procedures. In addition, the diagnostic plan generator sends and receives information regarding actual failure mode occurrences, for example, to and from a central database. Furthermore, the diagnostic plan generator facilitates the creation of failure mode tests by an expert diagnostics author.
Owner:BOSCH AUTOMOTIVE SERVICE SOLUTIONS
Method and system for event impact analysis
ActiveUS8296412B2Minimize impactQuickly and correctlyDigital computer detailsData switching networksAnalysis dataSystems analysis
Owner:INT BUSINESS MASCH CORP
Activity-based software traceability management method and apparatus
Computer method and apparatus for managing traceability of a software program are disclosed. Given a subject software program, the invention method / apparatus provides a respective history log for each artifact of the program. The invention method / apparatus records in the respective history log changes made to an artifact of the subject software program. During a change being made to the artifact, a processor routine determines from the respective history log related artifacts. An indication of the determined related artifacts is displayed to a user as impact analysis results.
Owner:IBM CORP
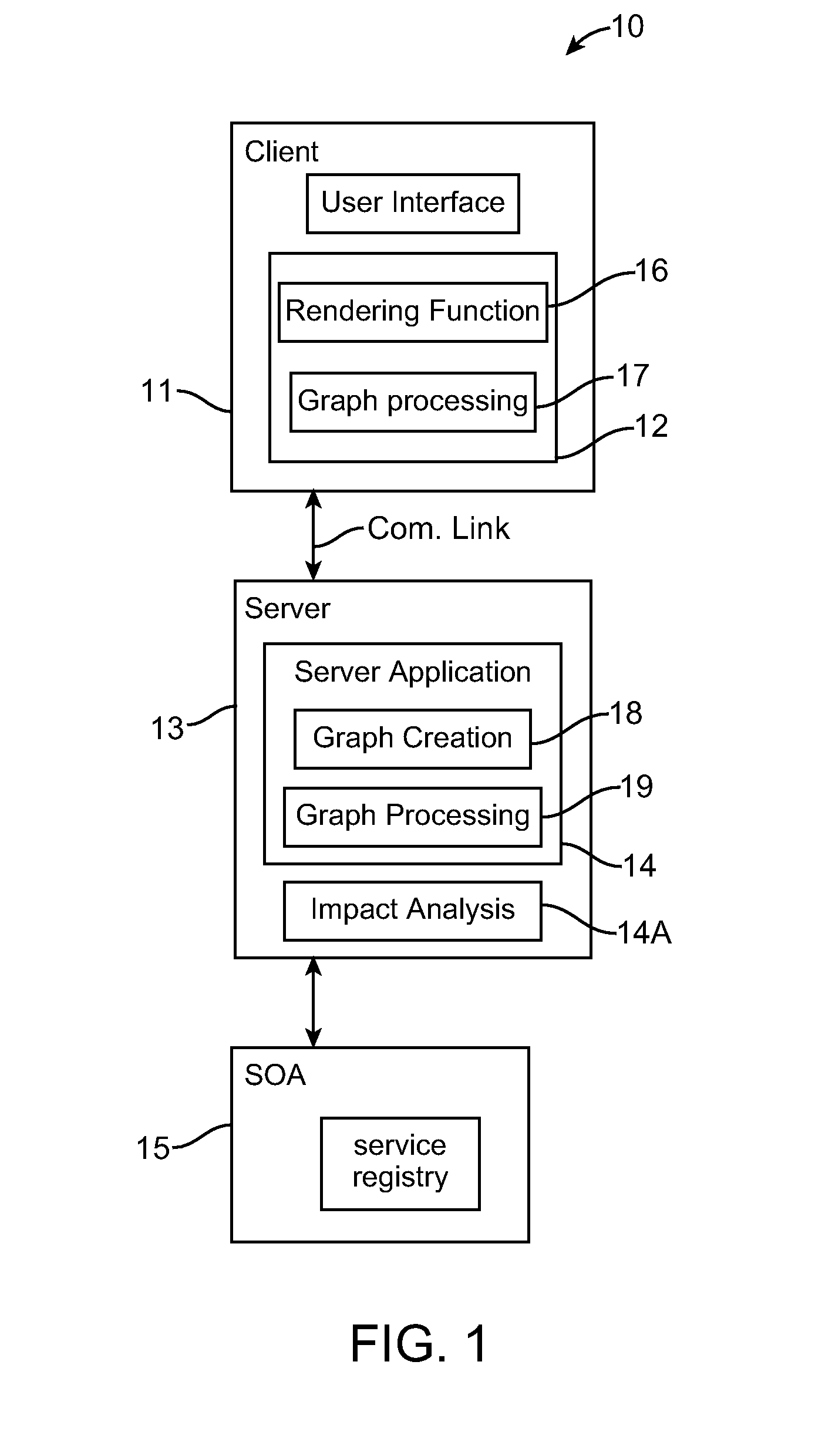
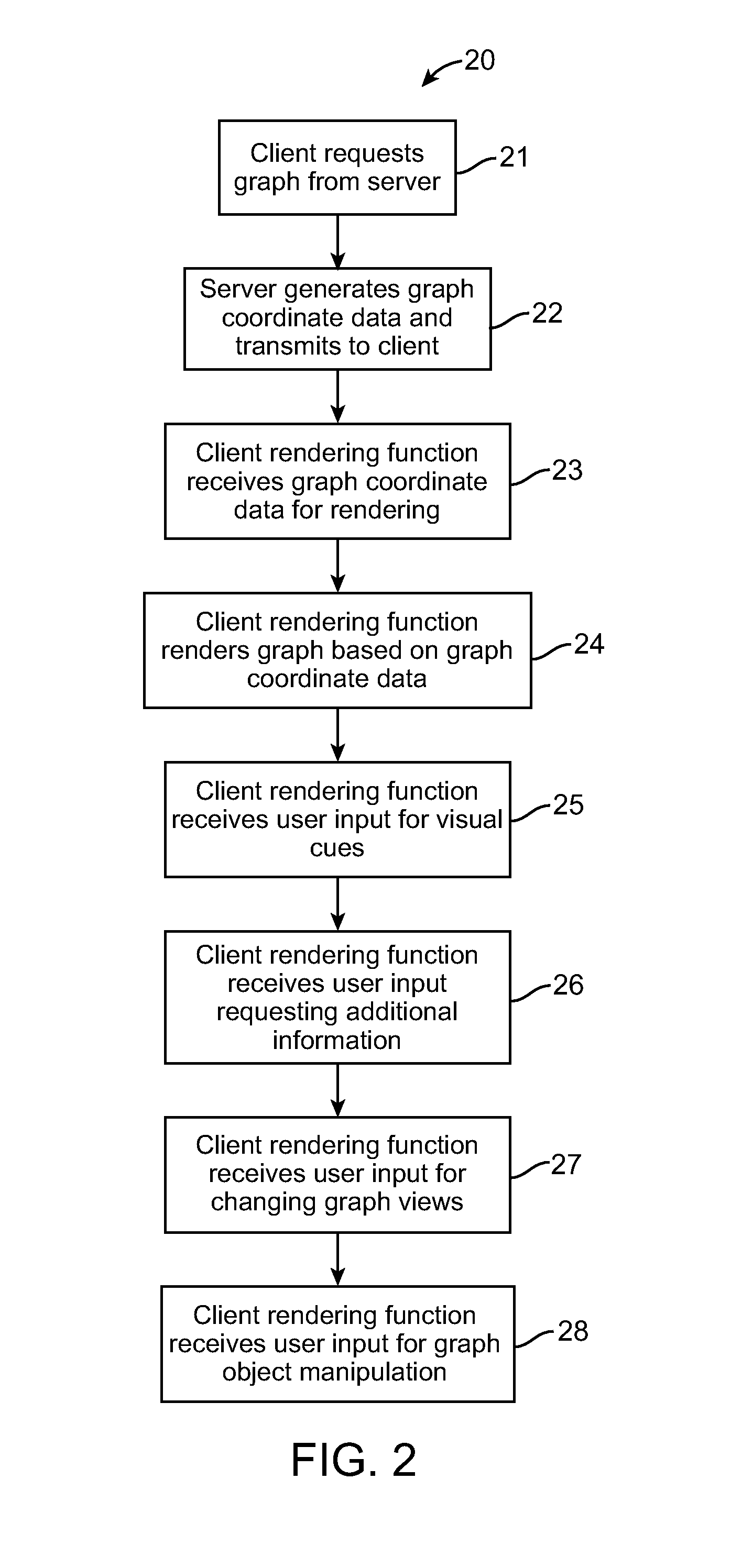
Method and system for generating and displaying an interactive dynamic view of bi-directional impact analysis results for multiply connected objects
A method and system for generating a graph view on a user interface in a computing environment, is provided. One implementation involves, at a server, generating graph coordinate data for a dependency graph view of bi-directional impact analysis results for multiply connected objects in a data source; transmitting the graph coordinate data to a client as lightweight object data; and at the client, based on the lightweight object data rendering an interactive dynamic dependency graph view on a user interface.
Owner:IBM CORP
Method, system, and program for utilizing impact analysis metadata of program statements in a development environment
InactiveUS7069547B2Eliminate errorsData processing applicationsVersion controlSource code fileSoftware development
Provided is a method, system, and program for enabling analysis of proposed changes to program statements in a source code file. A data structure is generated indicating a plurality of program statements affected by one of a plurality of selected program statements to change, wherein the data structure indicates a hierarchical relationship of the effect of program statements on one another resulting from changes to the selected program statements. The data structure is provided to a software development tool to enable a programmer to display information on the hierarchical relationship of the affect of the program statements on one another resulting from changes to the selected program statements.
Owner:INT BUSINESS MASCH CORP
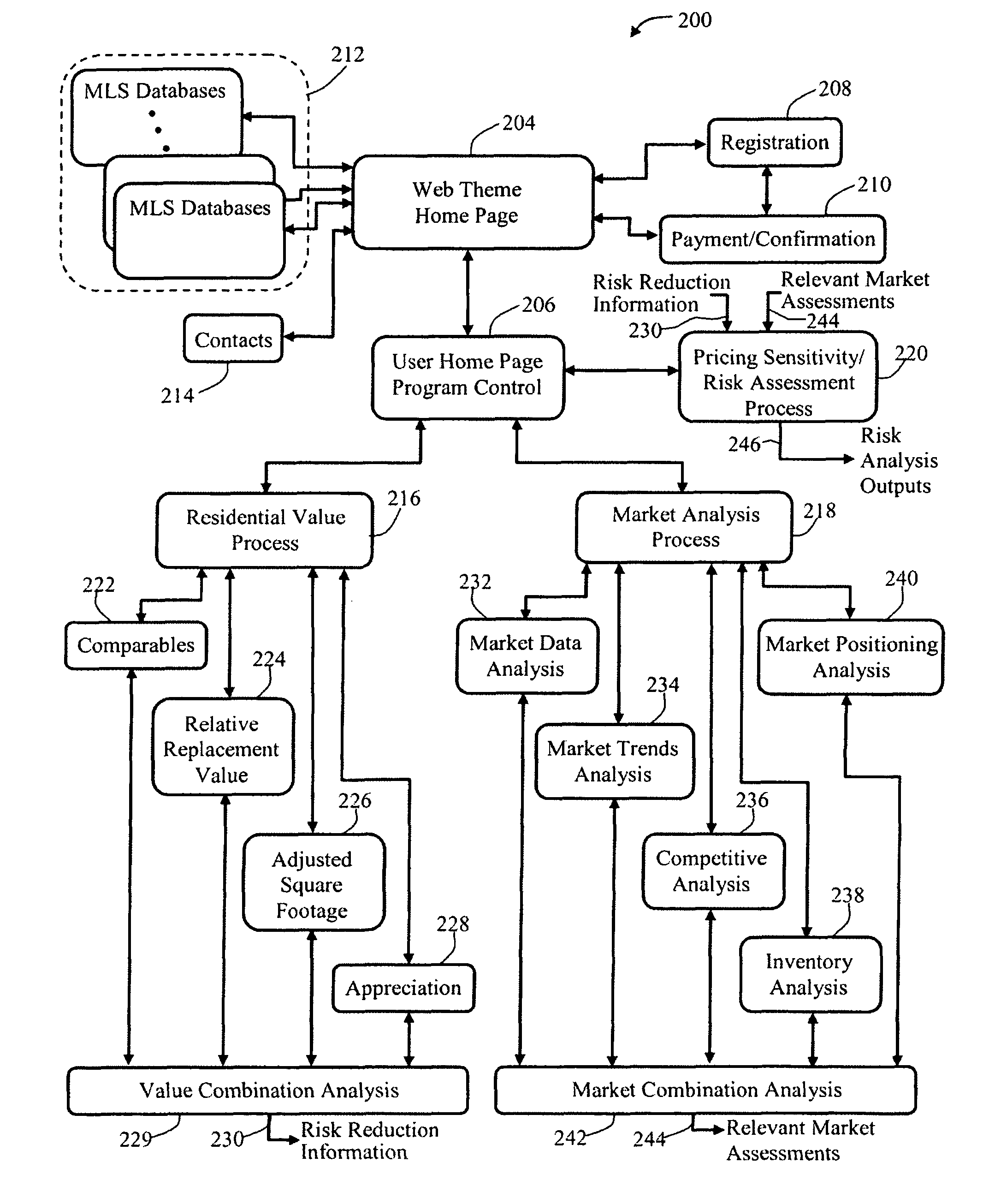
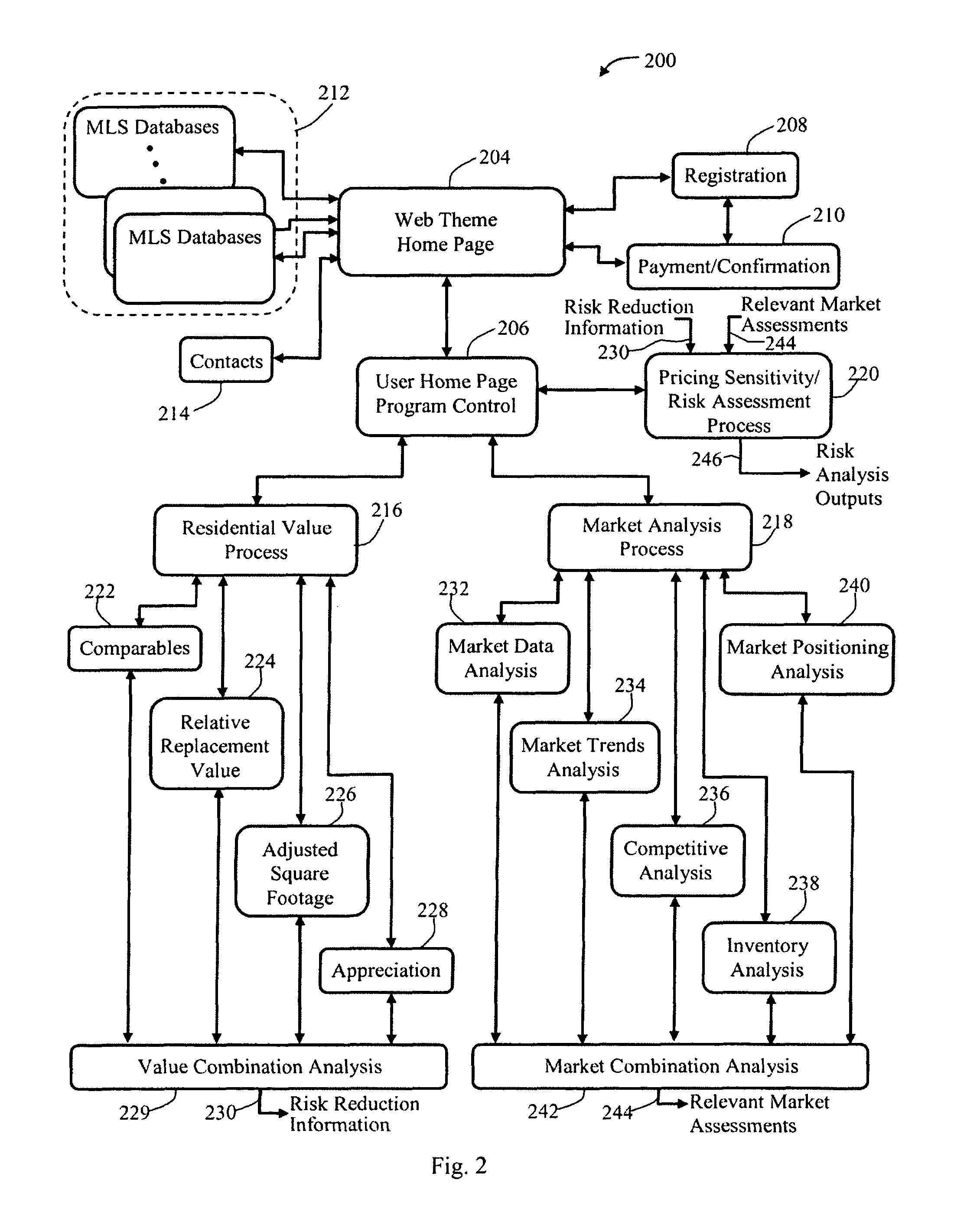
Systems, methods, and computer program product for real estate value analysis
ActiveUS8650067B1Reduce riskAccurate analysisFinanceMarket data gatheringSubject matterAnalysis method
Methods, apparatus, and computer-readable media are described for generating a credible market value that is utilized to produce a listing price for a property with reduced risk of a substantial reduction in the listing price before selling the property and for assessing risk of incorrectly pricing a property. A subject property, selected comparables, and selected comparables having multiple sales are imported from one or more databases for analysis. Information that is imported may include, for example, property features, original listing prices, record of days on the market, and a final listing price and sales price for each property that was sold. A market analysis process is run to produce relative market assessments and a residential value process is run including appreciation calculations based on the comparable properties having multiple sales to produce the credible market value. Graphs are plotted and other computer outputs are provided to identify the risk of incorrectly pricing a property and to illustrate that risk to a potential seller. Additionally, tools are provided to readily illustrate how changes in underlying assumptions affect the analysis.
Owner:MOSS RICHARD
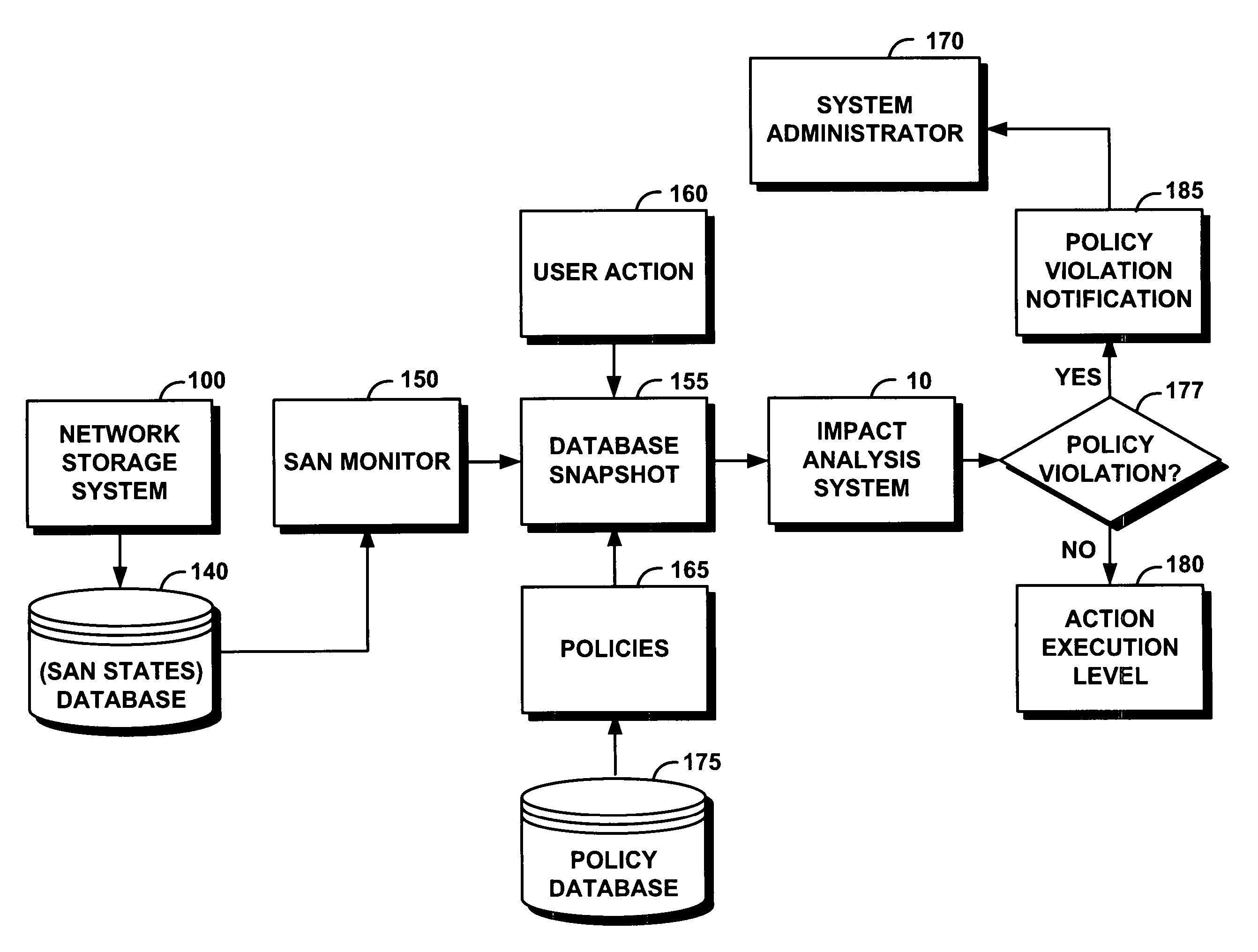
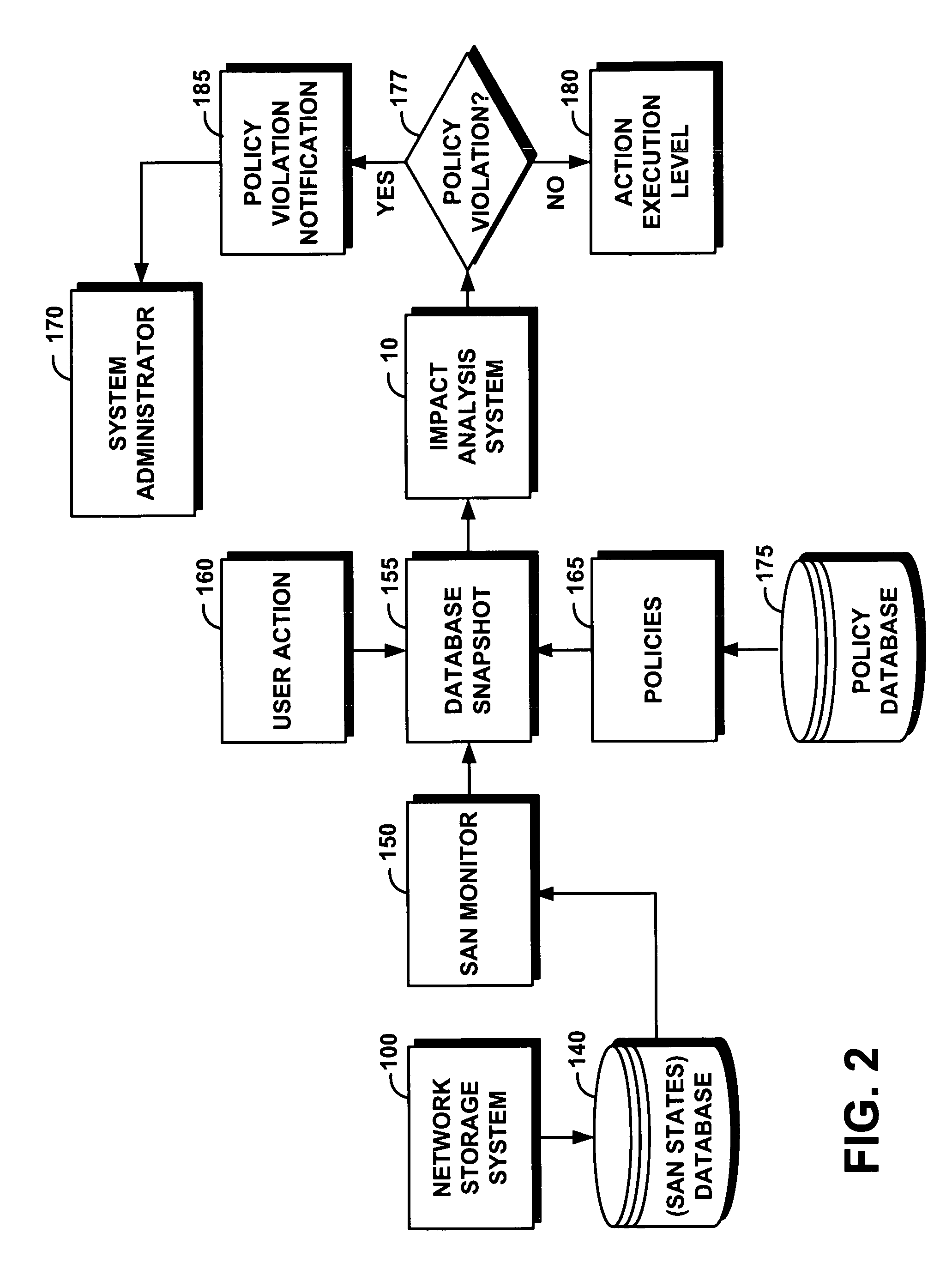
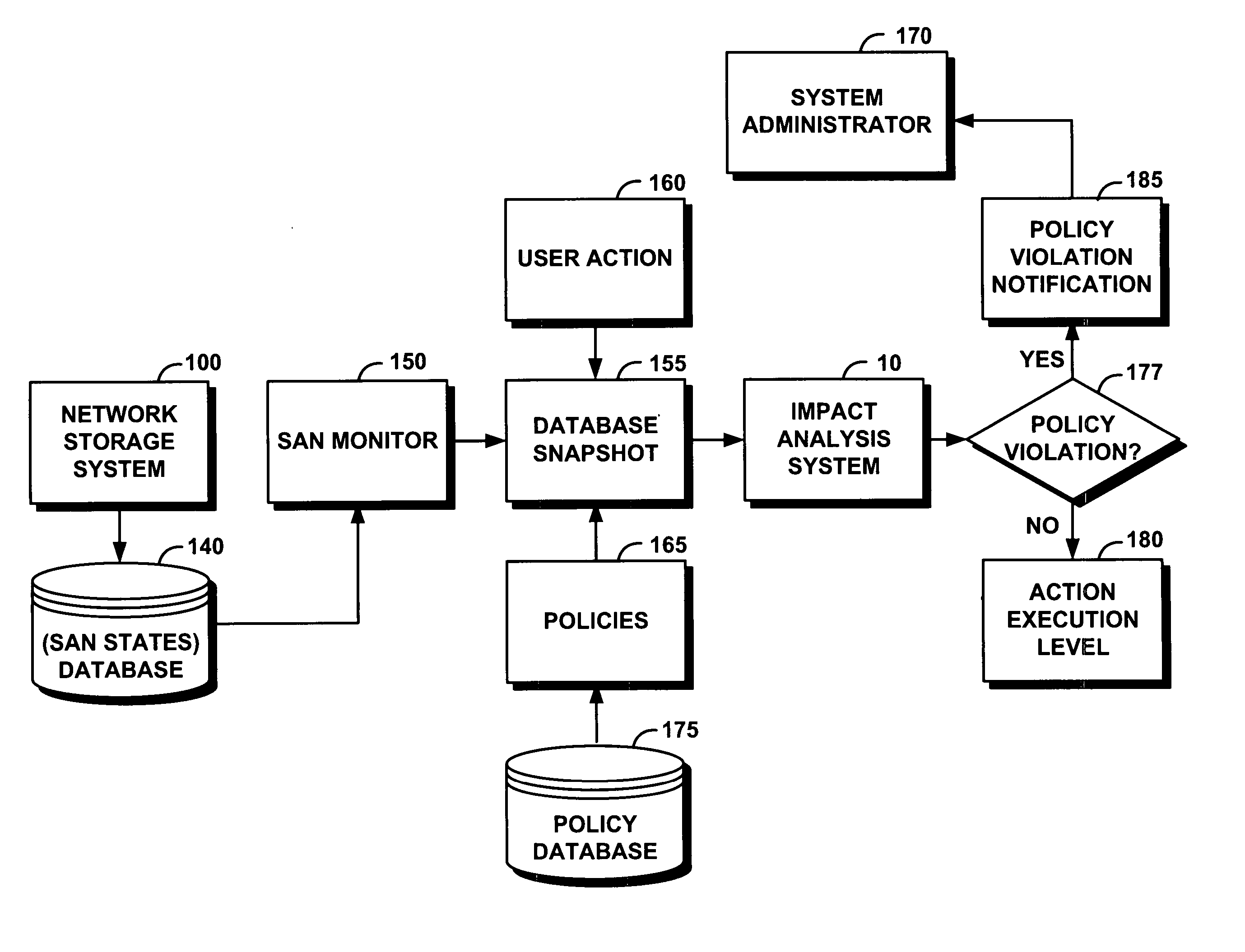
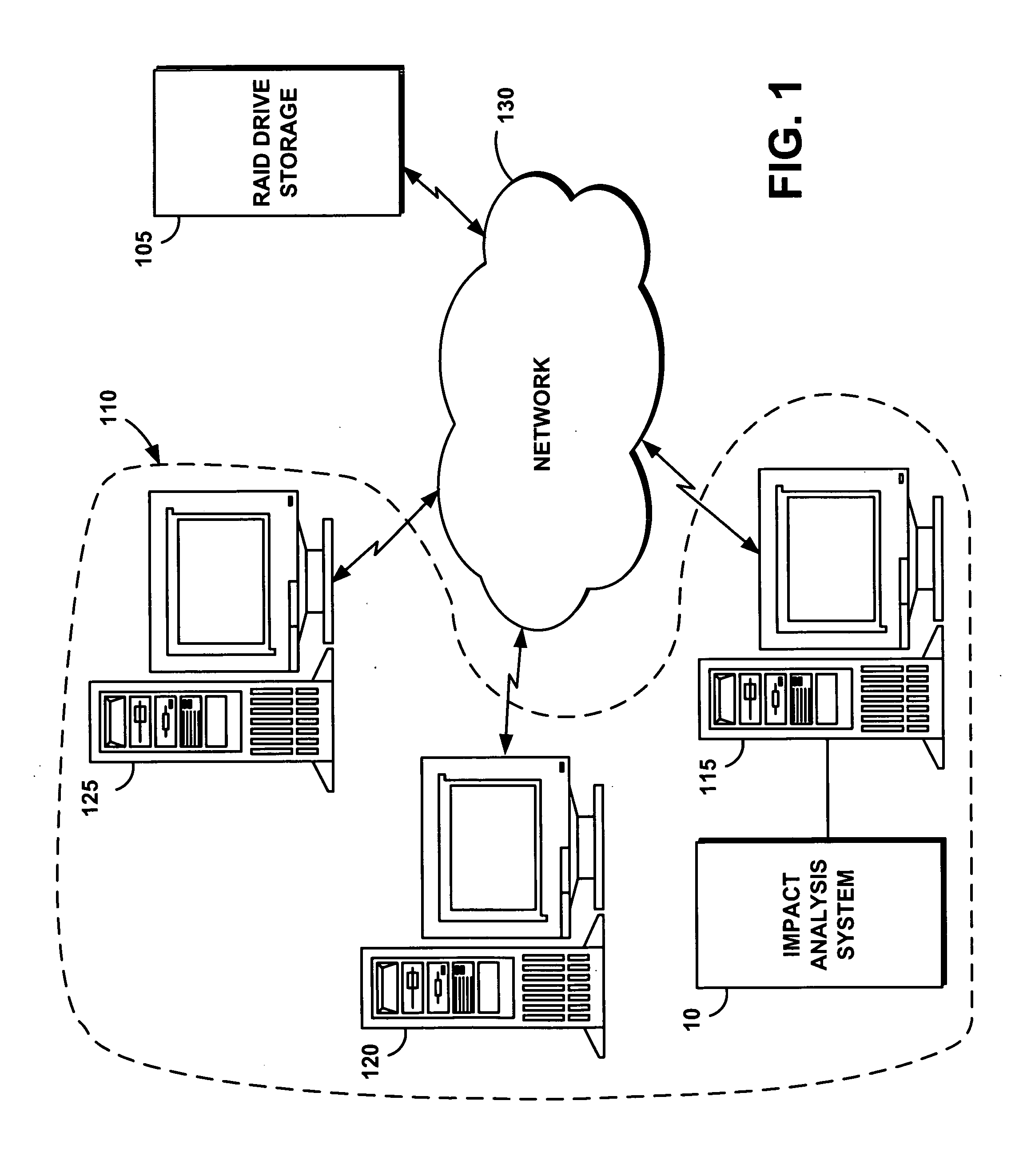
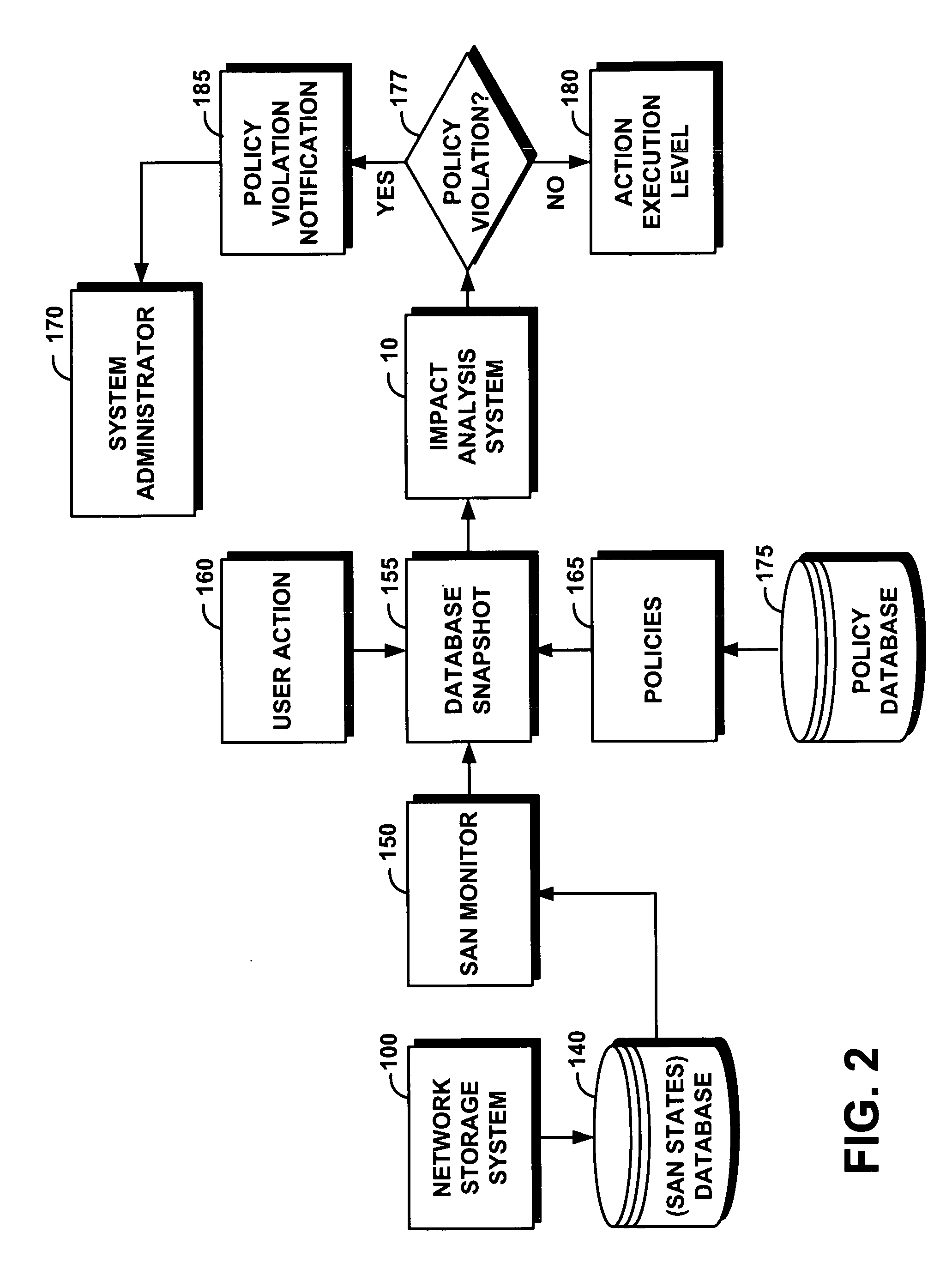
Method for proactive impact analysis of policy-based storage systems
InactiveUS7519624B2Assessing the impact of user's actionsDigital computer detailsSpecial data processing applicationsStorage area networkData mining
Owner:INT BUSINESS MASCH CORP
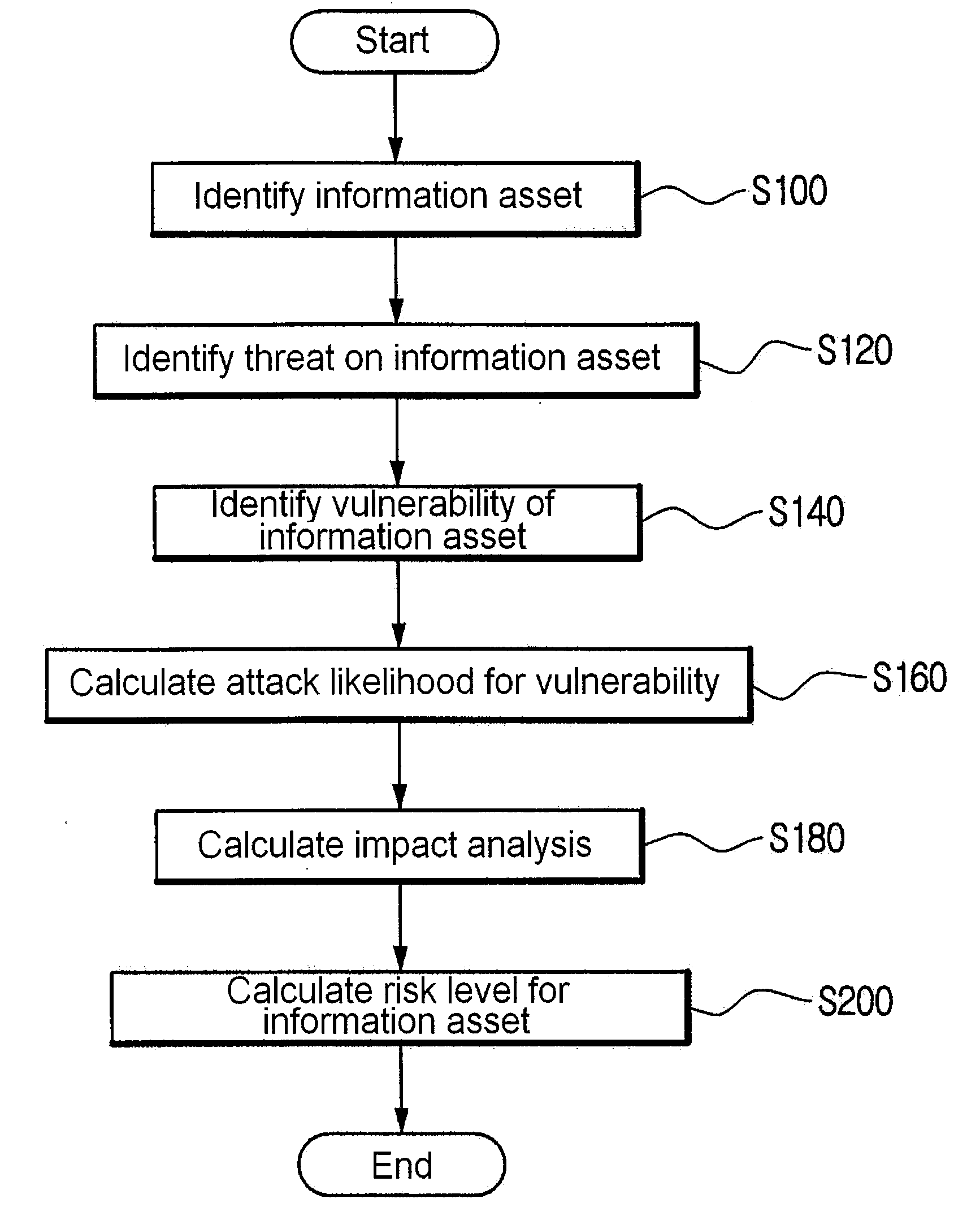
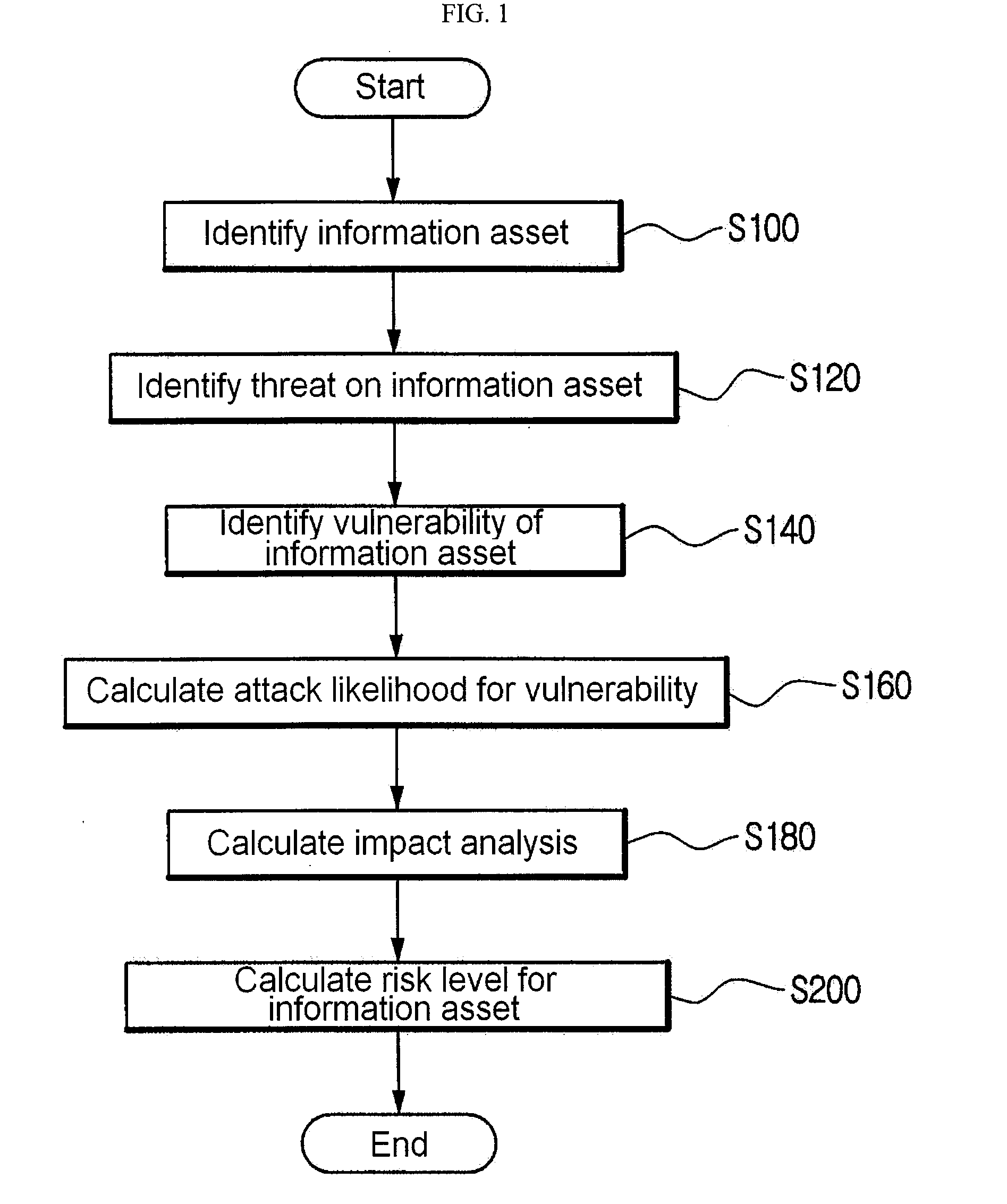
Method for risk analysis using information asset modelling
InactiveUS20090099885A1Minimizing interventionMemory loss protectionError detection/correctionRisk levelNetwork service
A method for risk analysis using information asset modeling. The method has the steps of: (a) identifying an information asset which uses or provides a network service; (b) identifying a threat on the information asset through a computer network; (c) identifying a vulnerability of the information asset; (d) calculating an AL (attack likelihood) by using a CVSS (Common Vulnerability Scoring System) score obtained by converting a severity caused by a success of an attack on the vulnerability into a standardized value; (e) computing the value of the information asset so as to calculate an IM (impact analysis); and (f) multiplying the calculated AL and IM so as to determine an RL (risk level) for the information asset.
Owner:KOREA INTERNET & SECURITY AGENCY
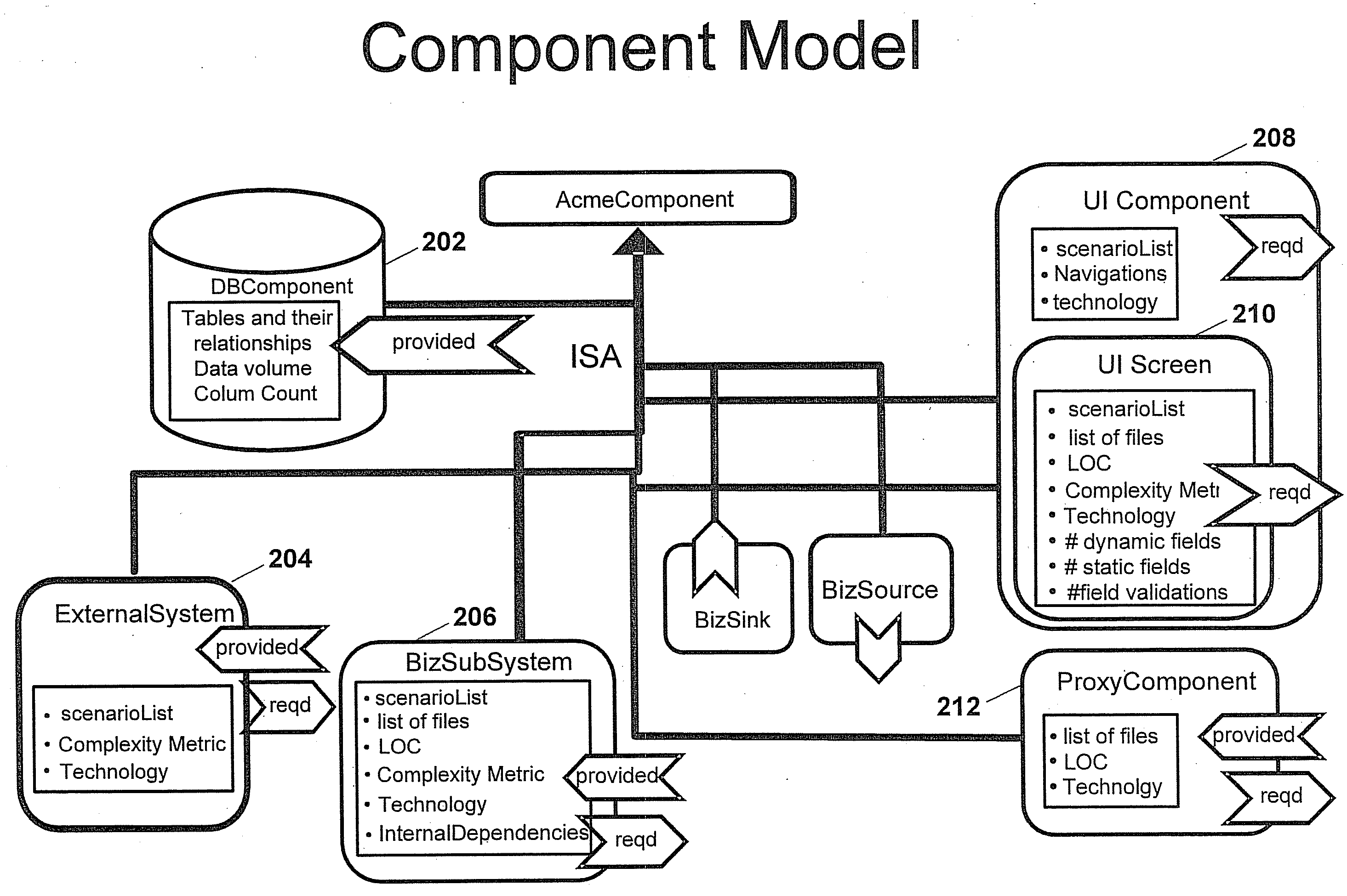
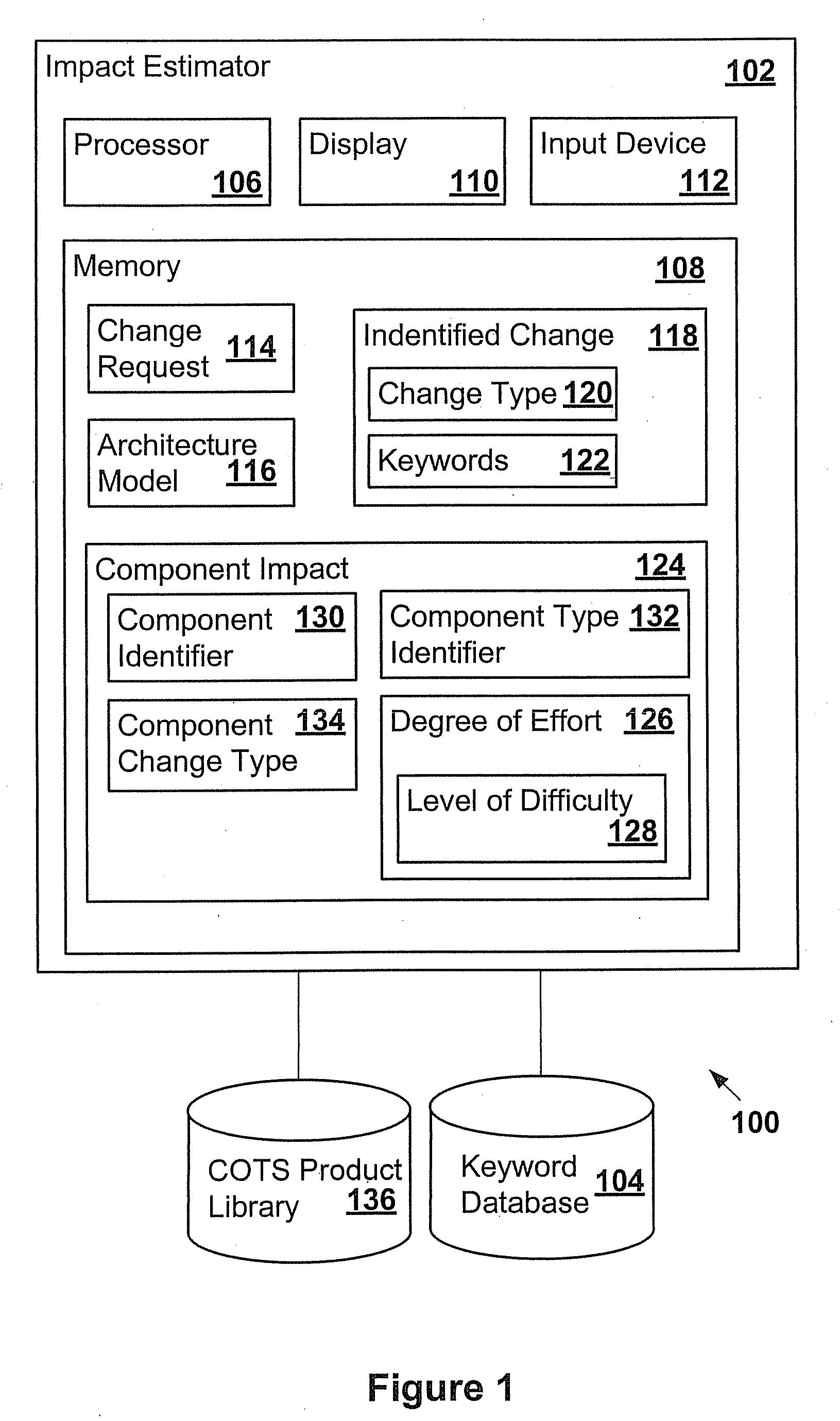
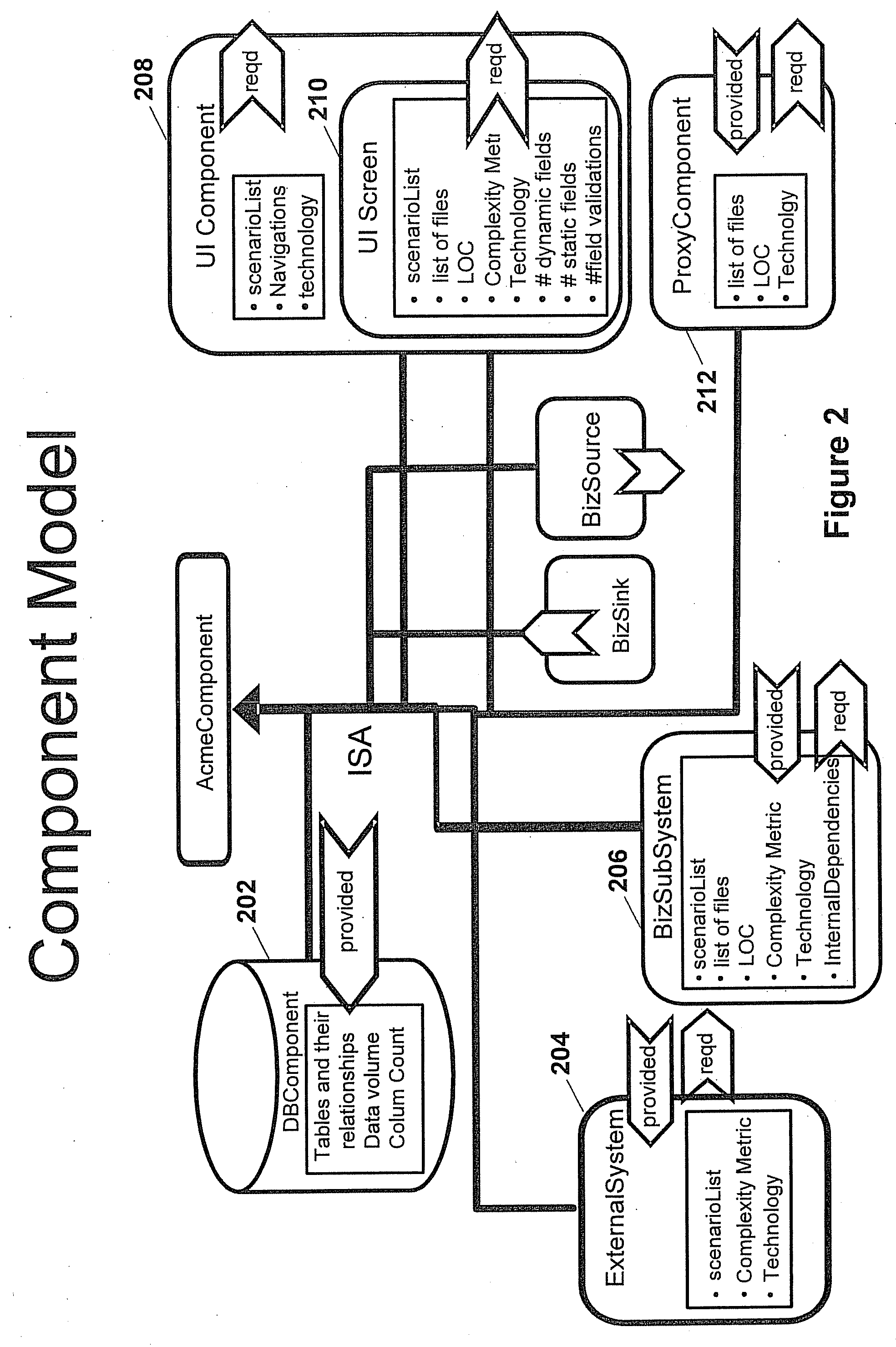
Impact analysis of software change requests
In one example, a system is provided to determine the impact of implementing a change request on a software program. The system may include an architecture model of the software program that includes components. Each of the components may have attributes that may be used by the system to determine a degree of effort to modify each respective one of the components. Components may be associated with keywords. The system may search the change request for the keywords to identify components that may be impacted by the change request. The system may determine the degree of effort to modify any impacted component based on the architecture model. The system may determine the overall impact on the software program based on the degree of effort determined for the impacted components.
Owner:ACCENTURE GLOBAL SERVICES LTD
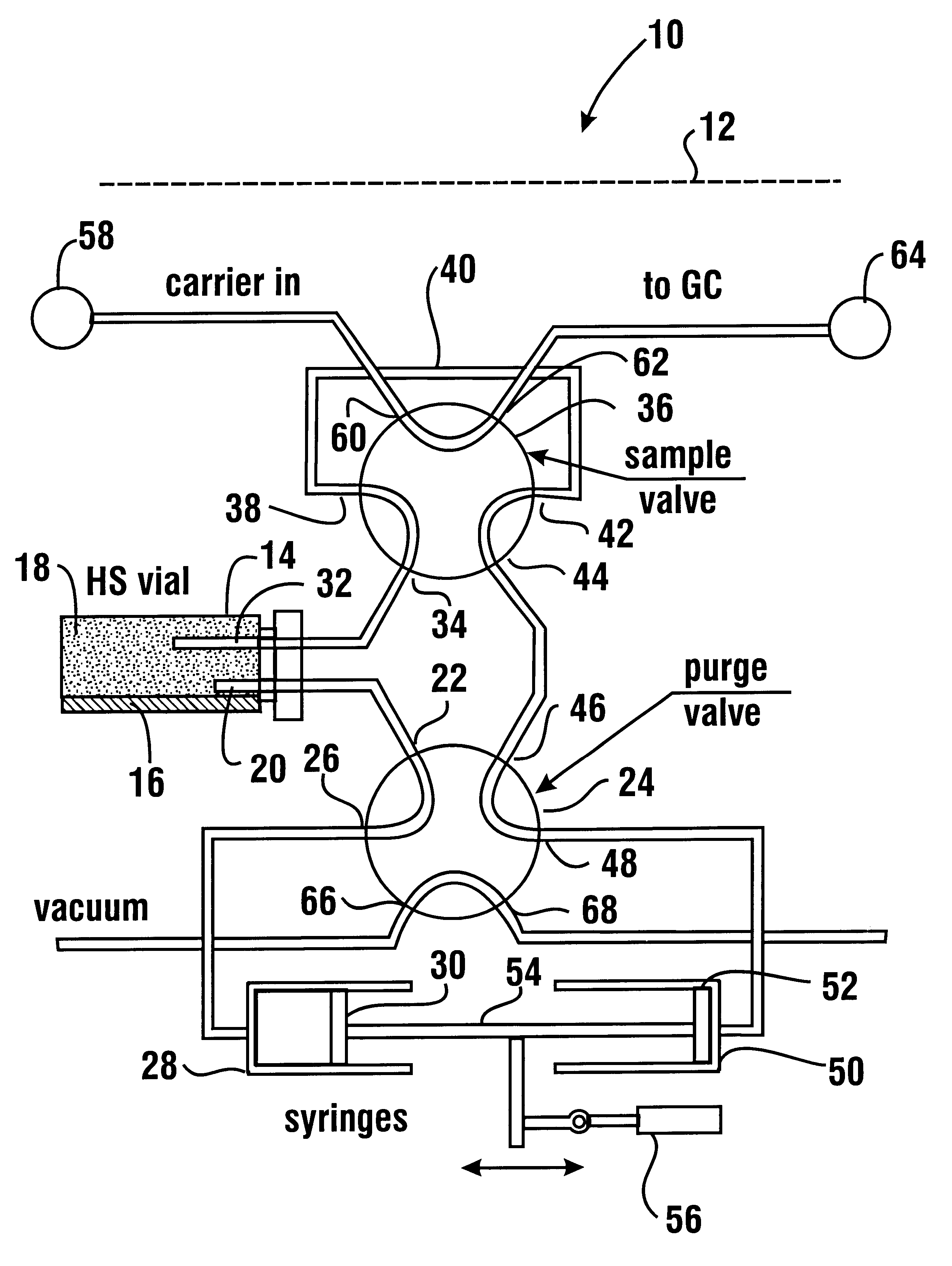
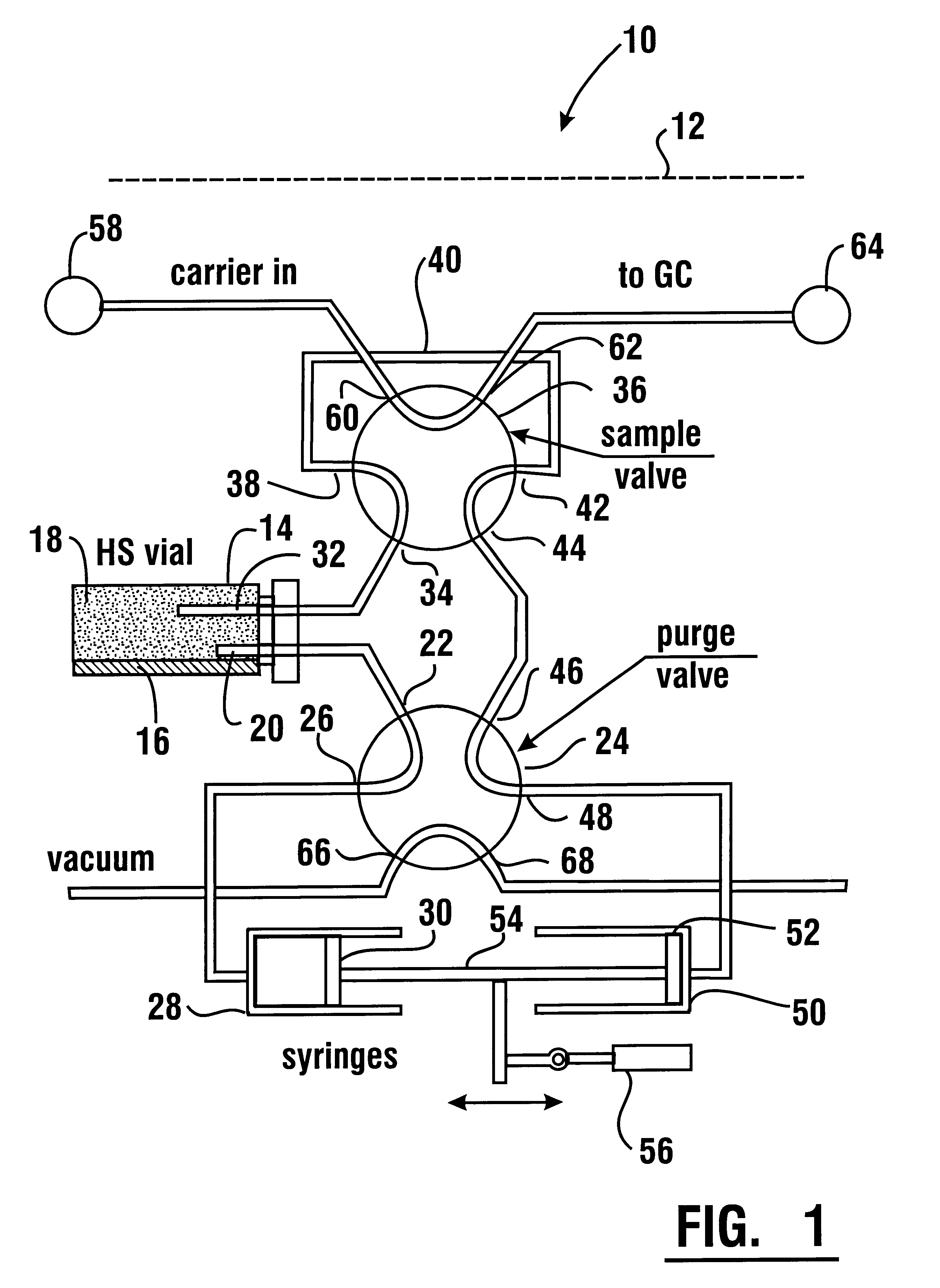
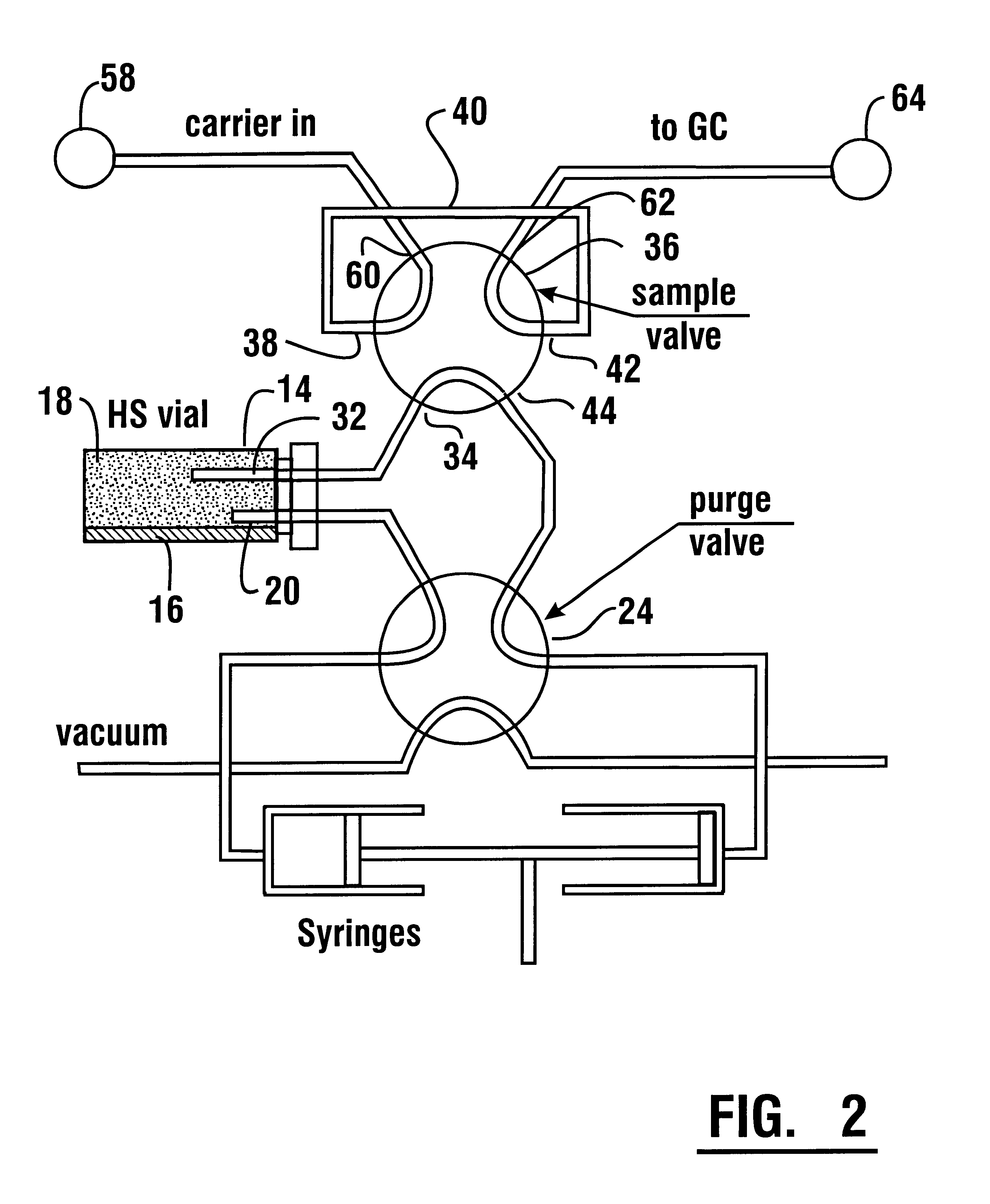
Headspace instrument
InactiveUS6365107B1Minimize disturbanceRisk minimizationChemical analysis using combustionComponent separationDesorptionGas phase
A headspace instrument (10, 70) operates to equilibrate a vapor phase of a headspace sample in a sample loop (40, 74). The sample is equilibrated by flow through the headspace between variable volume chambers (28, 50, 86, 90). The volume of the variable volume chambers are changed in coordinated relation so that a constant total volume is always maintained. An aliquot of the equilibrated sample in the sample loop is delivered to an analytical instrument. The headspace instrument enables delivering a vapor sample from a headspace under conditions which do not disturb the thermodynamic equilibrium between the vapor phase and the non-vapor phase of the sample and avoids having the sampling process impact the results of the analysis. Alternative forms of the headspace instrument enable the conduct of concentration dependent processes and absorption and desorption experiments.
Owner:MARKELOV MICHAEL +1
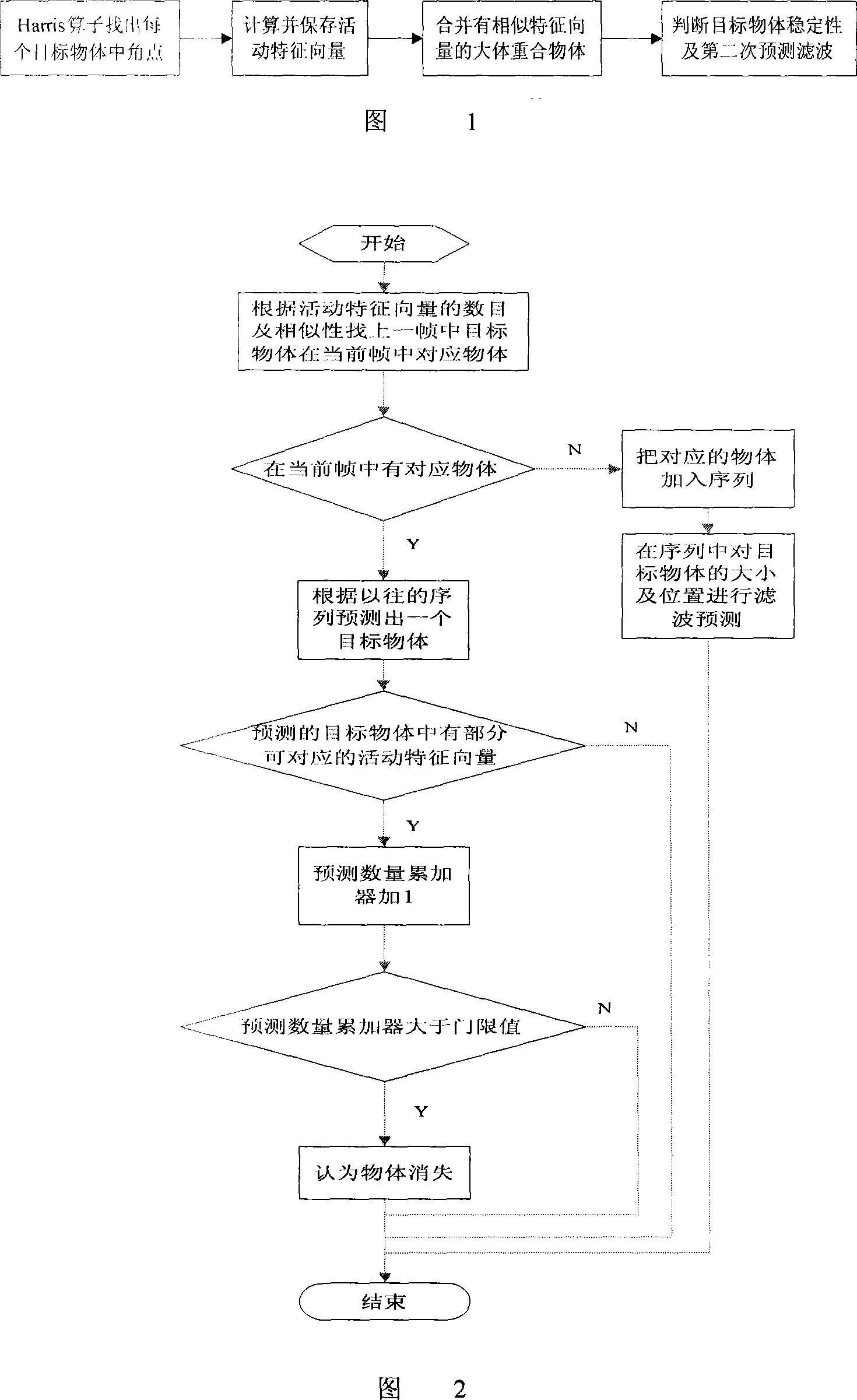
Characteristic point analysis based multi-target separation predicting method
InactiveCN101159855ASolve the problem of mutual interference of multiple moving targetsAchieving identifiabilityImage analysisCharacter and pattern recognitionVideo monitoringImaging processing
The invention relates to a multi-target division prognostication method based on feature analysis and belongs to video monitoring image processing technical field. The method includes extracting background, determining motion detecting threshold, performing clustering on the motion detection and processing into rectangles, performing first matching and wave filtering, determining corner points, forming vectors, and performing second matching. With the invention, no influence on the analysis prognostication results occurs even if the target object is shielded locally; therefore problem of interference among mobile targets which cannot be solved with the prior arts is solved. By applying the invention on a video monitoring system, recognition, tracking and monitoring on adjacent targets can be realized effectively.
Owner:SEU INTELLIGENCE SYST CO LTD
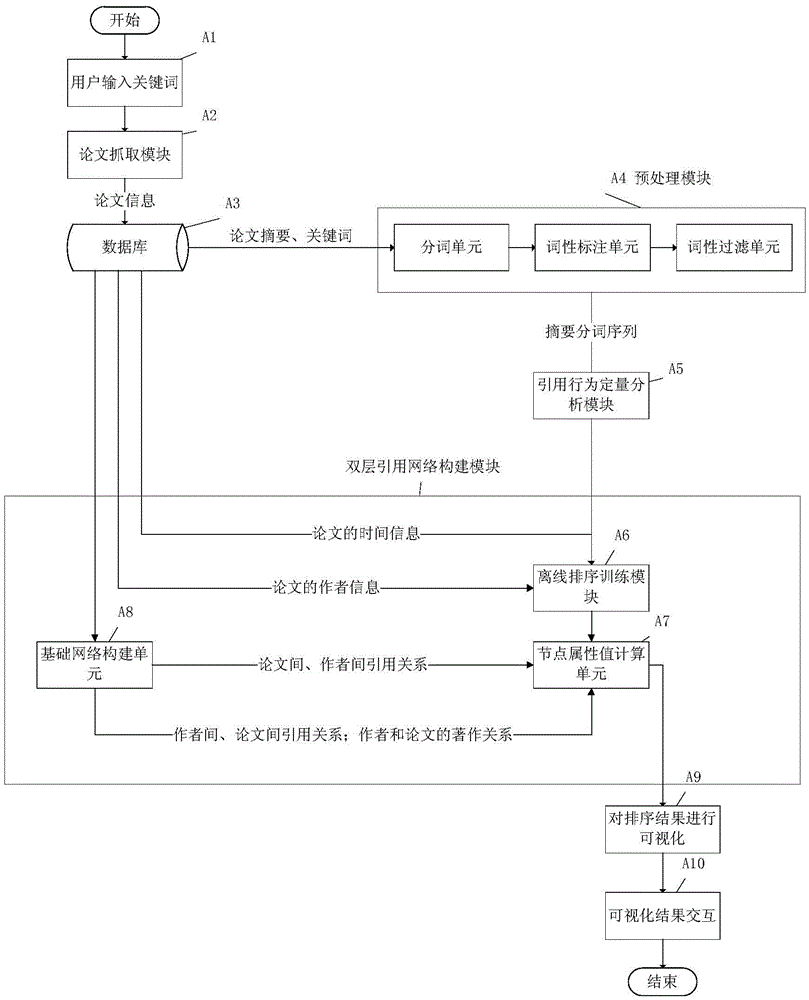
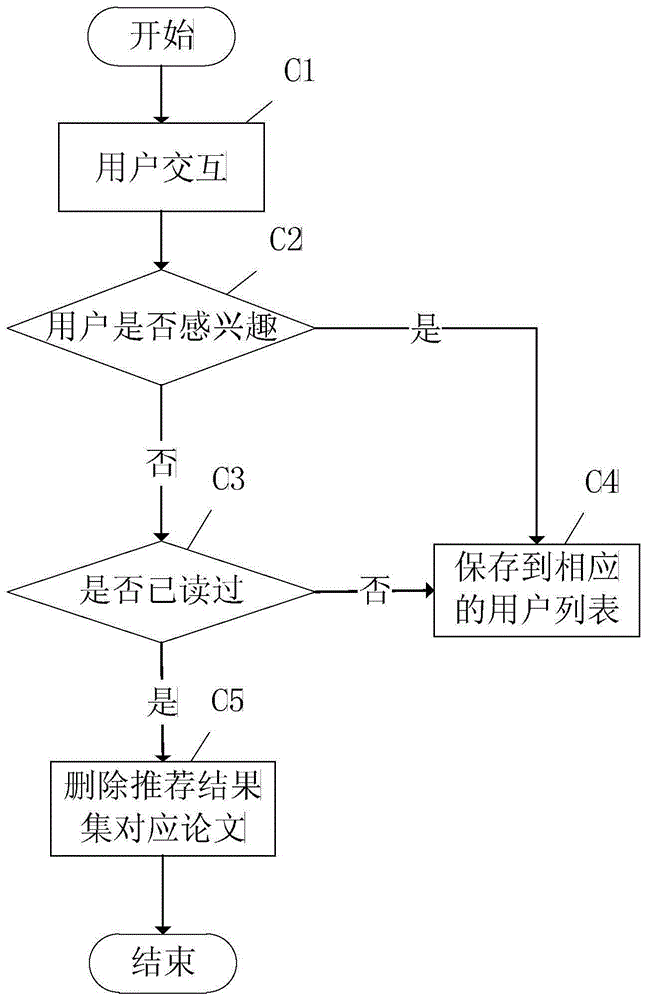
Document citation network visualization and document recommendation method and system
ActiveCN105589948AAvoid the "cold start" problemGuaranteed accuracyWeb data indexingSpecial data processing applicationsTime informationDocument similarity
The invention discloses a document citation network visualization and document recommendation method and system, and relates to the fields of document influence analysis and information visualization. The method comprises the following steps of calculating the importance degree of documents according to authors, time information, citation numbers and other inherent attributes, document similarities and transfer values generated by introducing behavior quantitative analysis, and sorting the documents; then performing clustering on the sorted documents and performing visualization on the clustered result to establish a dual-layer network model, and displaying important documents in a clear manner; and finally, recommending the documents in the center of clustering displayed in the visualization manner to a user. The document citation network visualization and document recommendation method and system are high in usability and can help science researchers to rapidly screen out most authoritative papers.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method, system, and program for performing an impact analysis of program statements in at least one source code file
InactiveUS20030084063A1Data processing applicationsDigital data processing detailsSource code fileInfluence analysis
Provided is a method, system, and program for performing an impact analysis of program statements in a source code file, wherein each program statement has at least one of an input parameter and output parameter. A selection is received of at least one program statement in the source code file. For each selected program statement, a determination is made of program statements in the source code file having as one input parameter one program artifact that is affected by the selected program statement.
Owner:IBM CORP
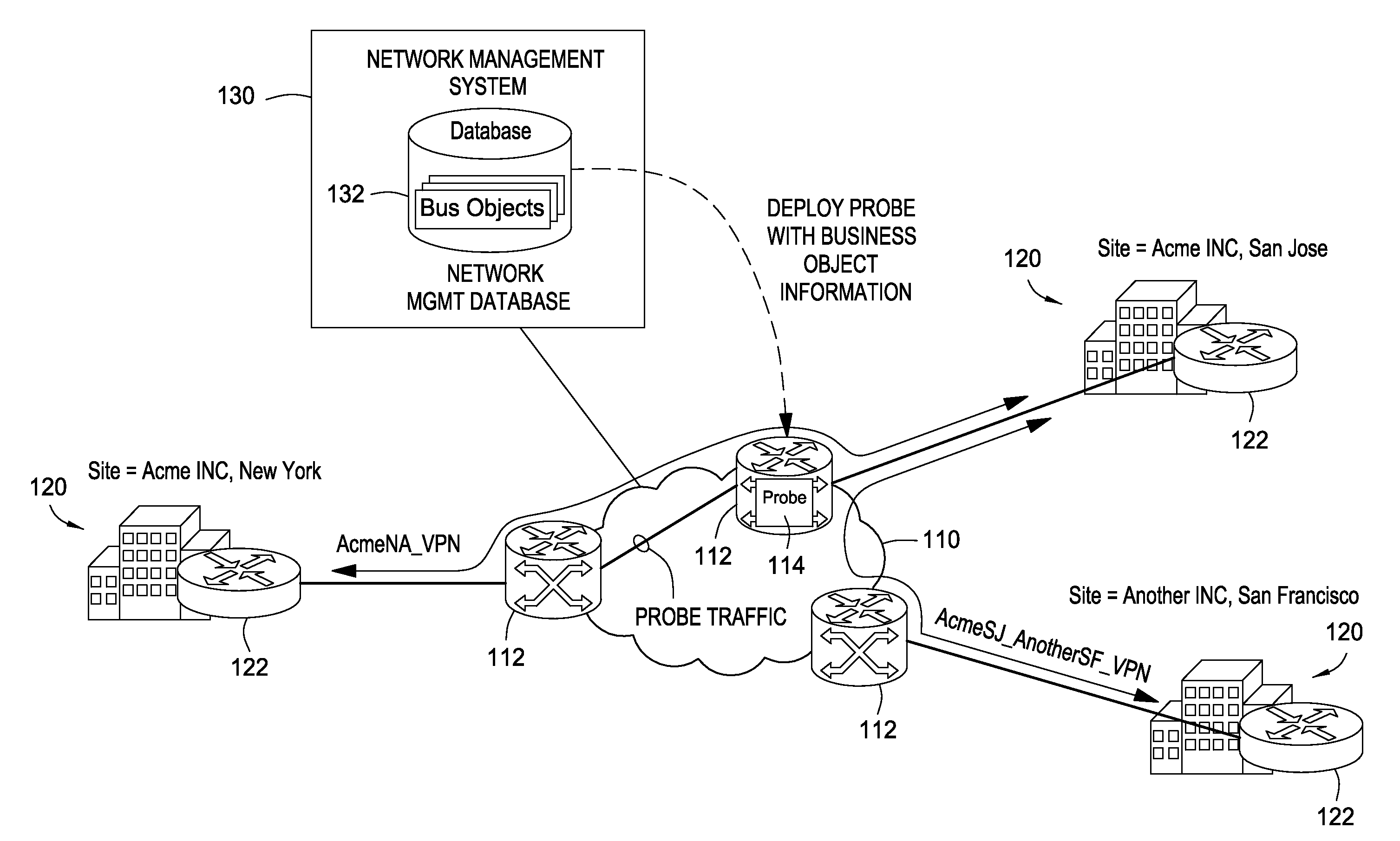
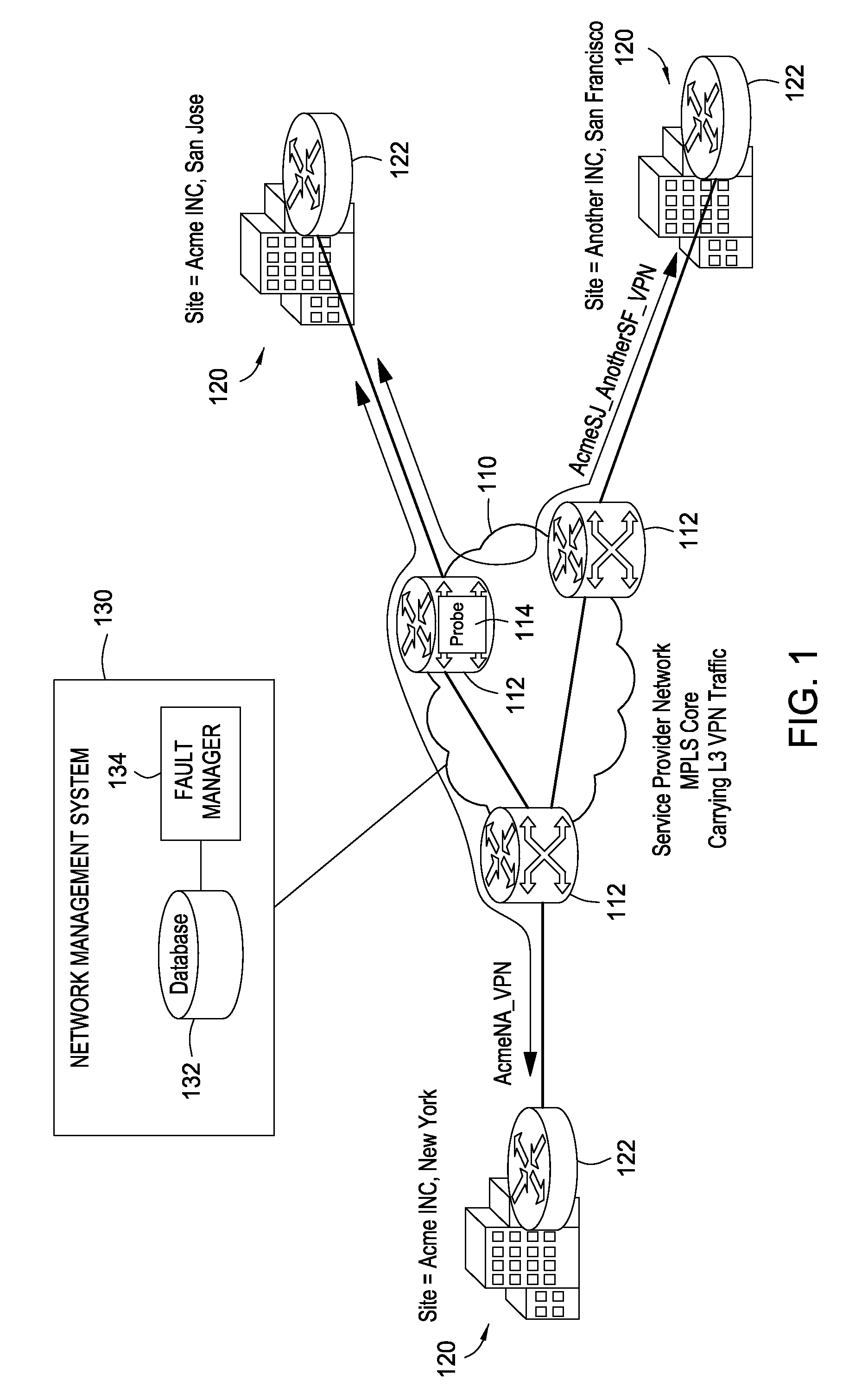
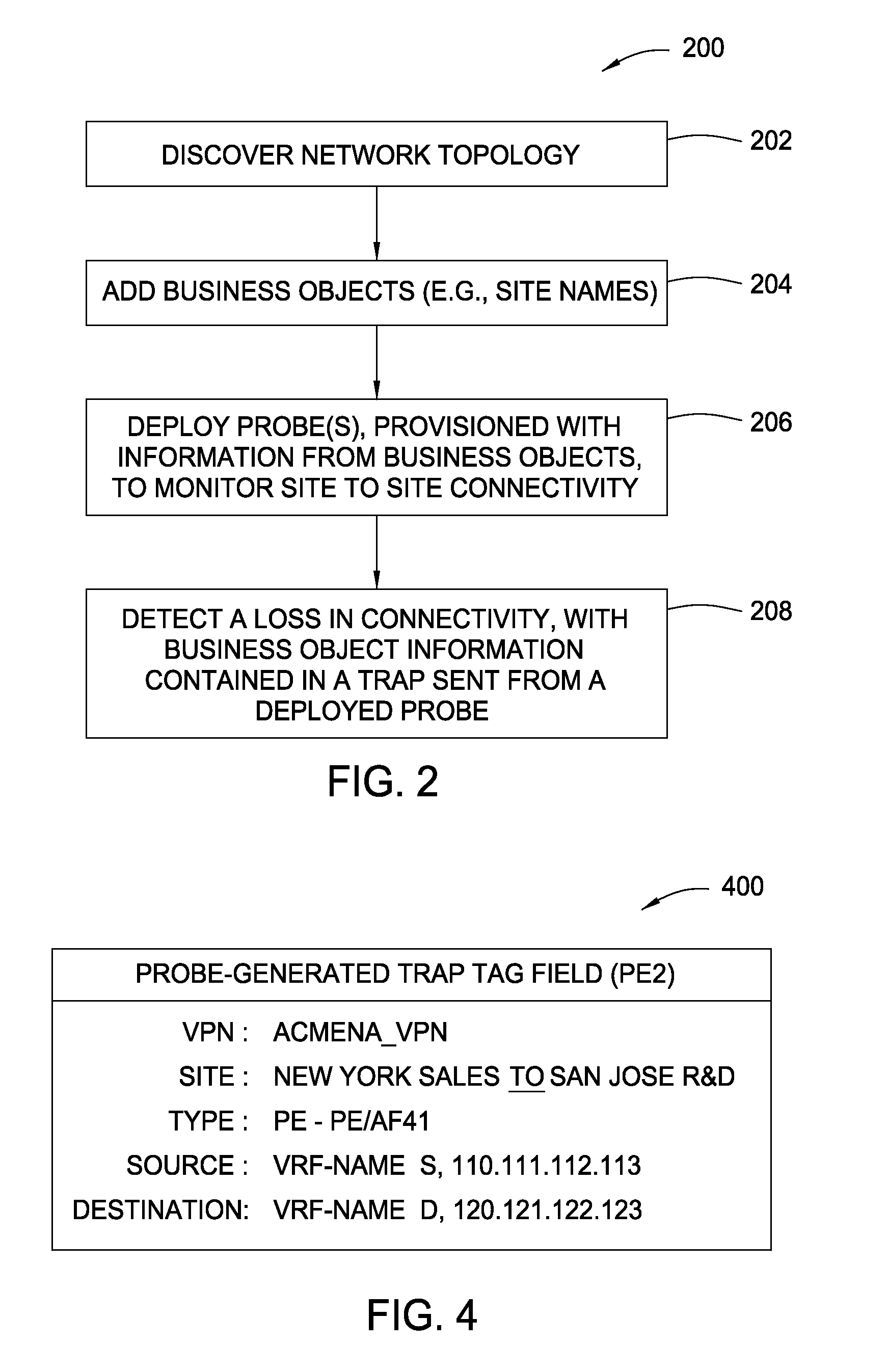
Connectivity outage detection: network/ip sla probes reporting business impact information
InactiveUS20080091822A1Digital computer detailsNetwork connectionsNetwork deploymentOutage detection
Techniques for accurate determination of service impact are provided by provisioning network deployed probes with actual business object information related to business entities, such as VPN sites. Such probes are capable of sending a network trap (or alarm) containing actual business information in response to detecting a loss of connectivity. As a result, service impact caused by the loss of connectivity may be determined accurately by simply parsing the contents of a network trap, thus avoiding the complication and inaccuracy of conventional impact analysis.
Owner:CISCO TECH INC
Dynamic equivalence modeling method for double-fed set wind power station based on action condition of pitch angle
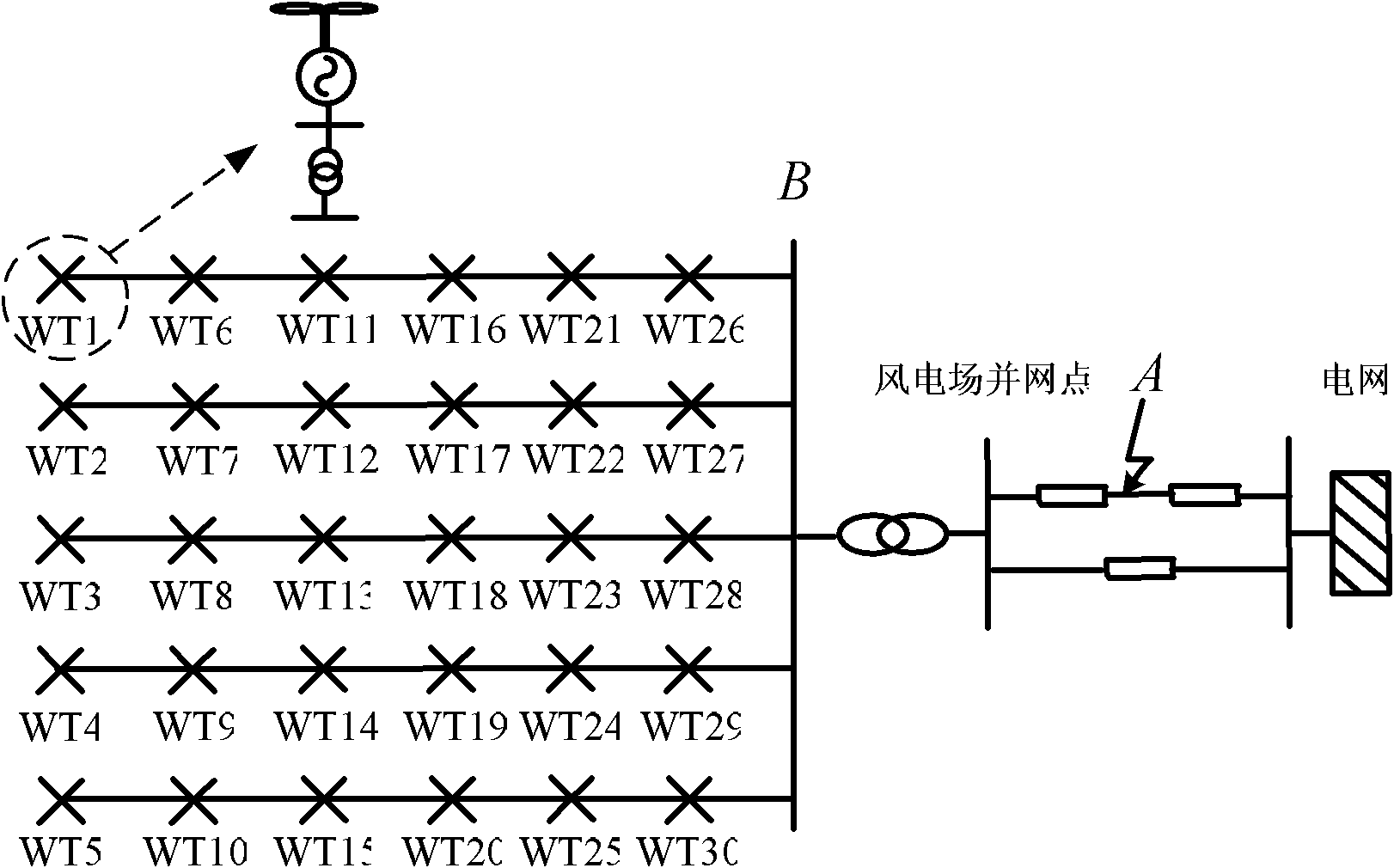
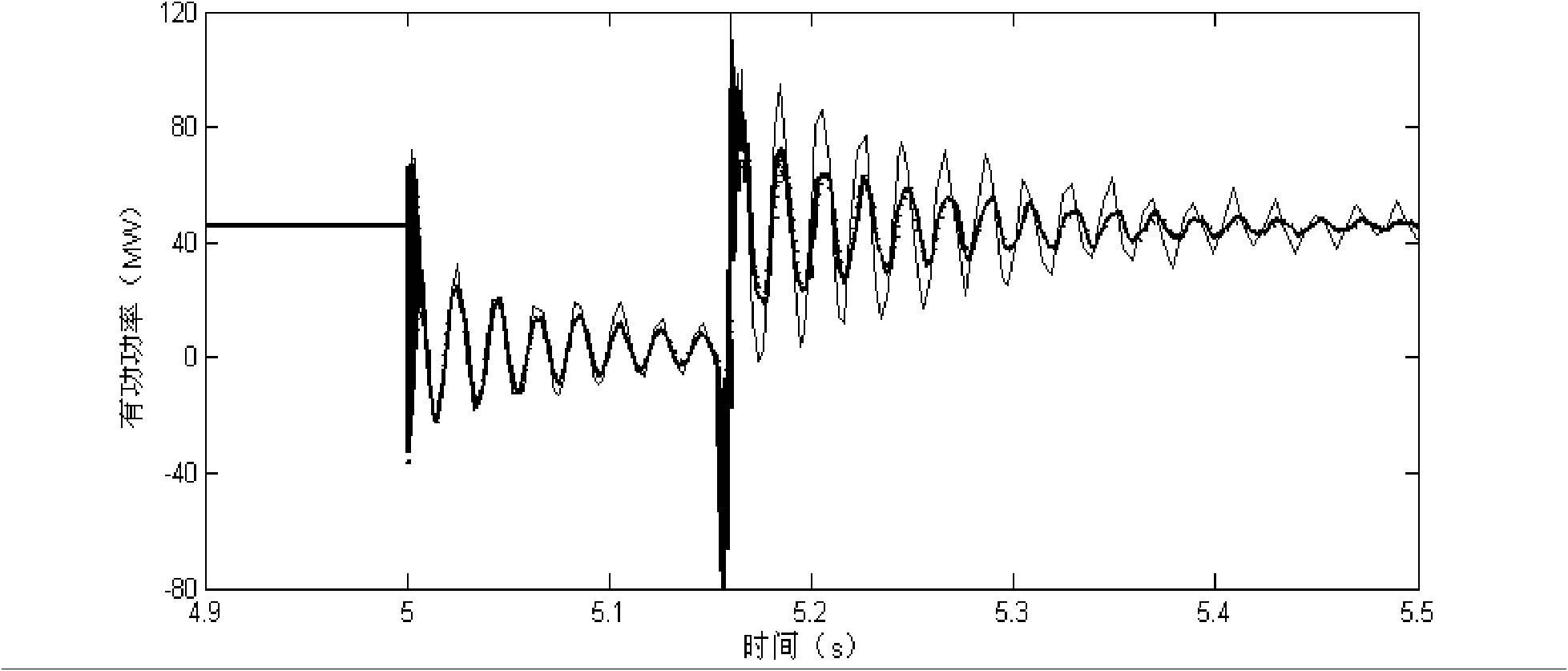
InactiveCN101937483AReduce the numberIncrease reflectionSpecial data processing applicationsInformation technology support systemElectric power systemTerminal voltage
The invention discloses a dynamic equivalence modeling method for a double-fed set wind power station based on the action condition of an pitch angle, relating to the technical field of wind power generation and solving the problem of low accuracy and difficult realization of the existing equivalence modeling method. The method comprises the following steps: firstly, acquiring the active power, generator terminal voltage and wind speed of the double-fed set before the fault of a model to be modeled in the wind power station; according to the parameter, extracting the characteristic vector reflecting the action of the pitch angle, inputting into a support vector machine classifier, and dividing the vector into three cluster; and finally equaling the three clusters into three equivalent double-fed wind power sets respectively and calculating the parameters and the equivalent cable parameter of each set, thereby obtaining a wind power station equivalent model. The modeling method has less number of the equivalent wind power sets, is convenient to use, can more accurately reflect the sychronization point dynamic characteristics of the wind power station, is applied to the dynamic equivalence modeling of the high-capacity wind power station and the impact analysis of the high-capacity wind power station to a power system, and has the important project application value.
Owner:HARBIN INST OF TECH +1
Comprehensive device monitoring system architecture
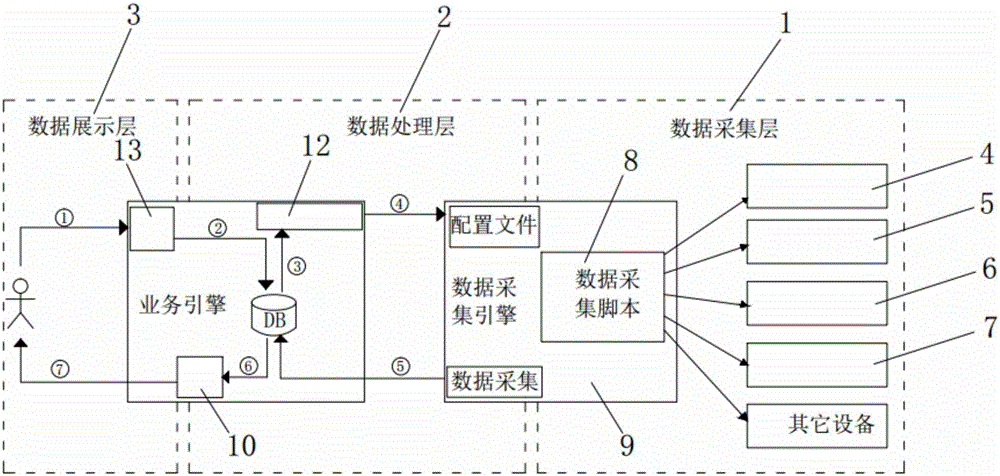
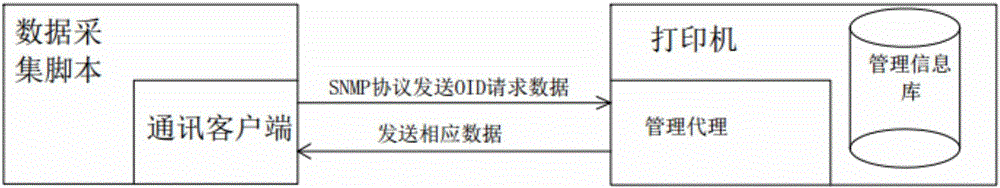
InactiveCN106487585AQuick searchLabor savingData switching networksIntegrated monitoringFile transmission
The invention discloses comprehensive device monitoring system architecture. The comprehensive device monitoring system architecture comprises a data collection layer, a data processing layer and a data presentation layer; the data collection layer comprises a data collection engine and a data collection script and monitors the automatic generation of a configuration file; the data processing layer comprises a CMDB library data processing module, a business engine, a data collection engine monitoring configuration file transmission module, a collected transmission module of a data collection engine and a business engine and an analyzing and processing module of alarm data; the comprehensive device monitoring system architecture disclosed by the invention has a large alarm data size, thereby requiring a good alarm collection processing means to ensure the instantaneity; as the definitions of alarm fields of different industries and manufacturers are different, a large amount of works are required to trim the alarms; a flat management structure collectively processes the alarms in the industries on the basis of standardization of the alarms, thereby requiring an extract alarm association and preprocessing rule; and the incidence relation among the alarms, the IT resources and business is confirmed, and a model of alarm influence analysis is established.
Owner:深圳市思博创科技有限公司
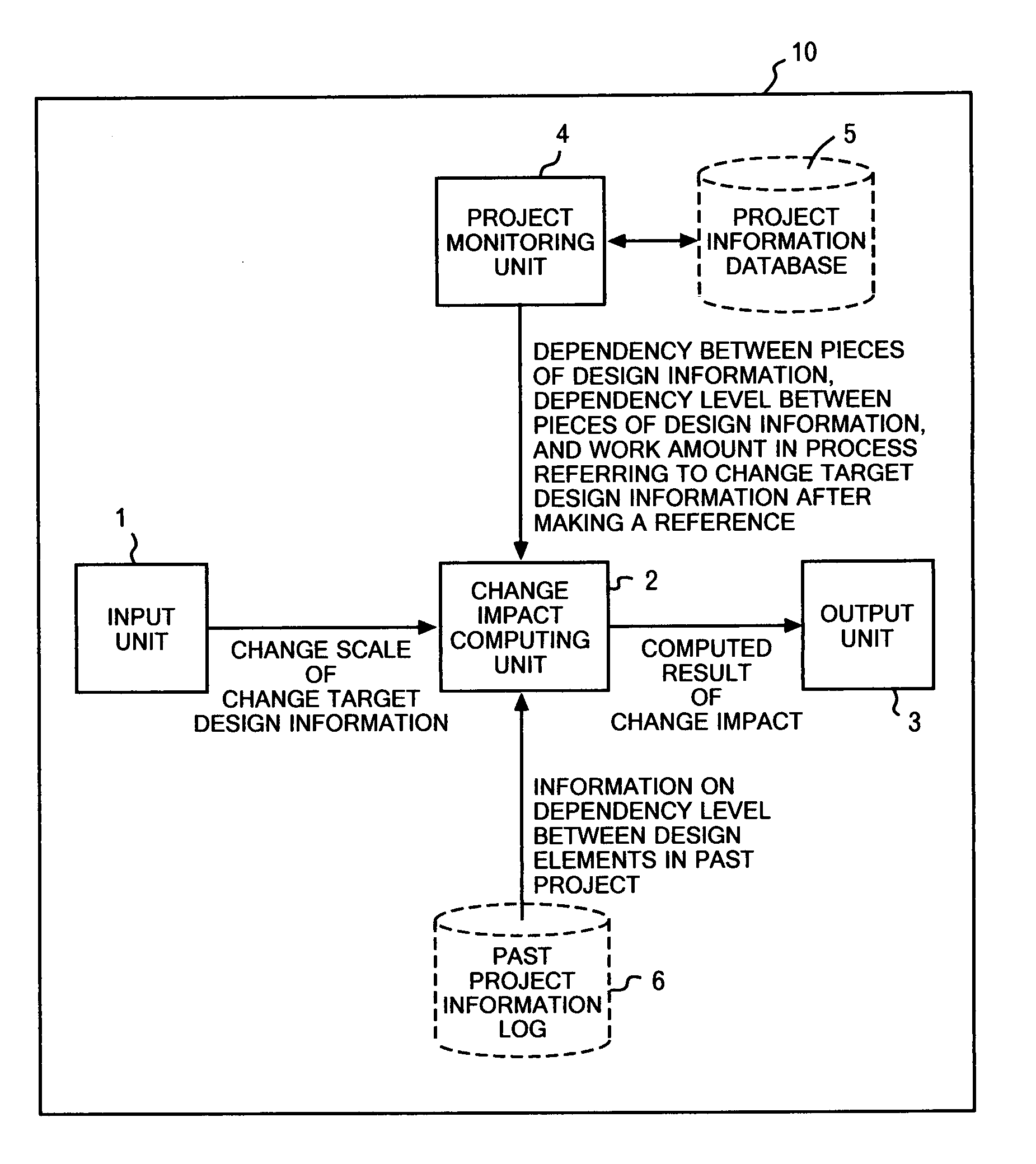
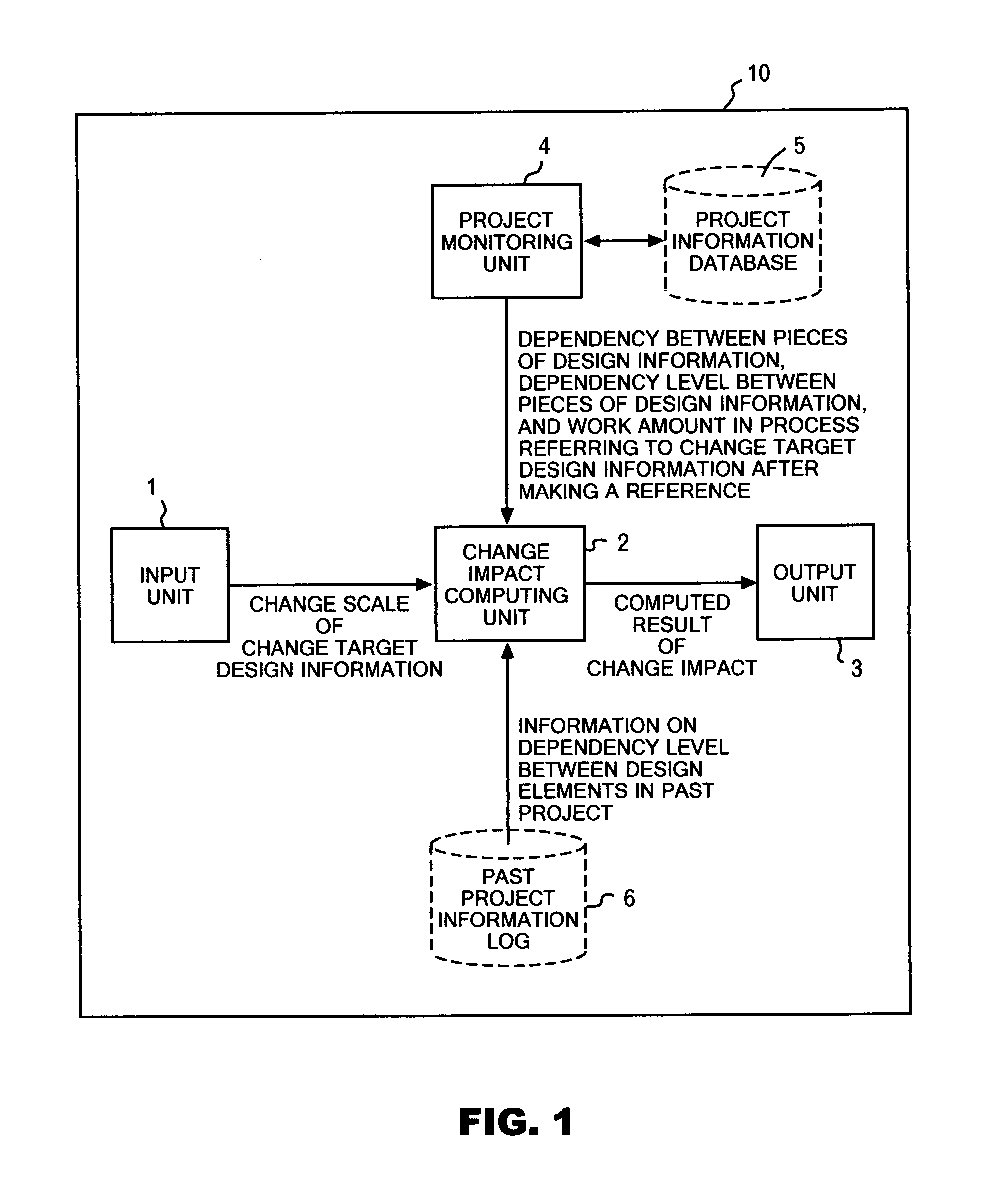
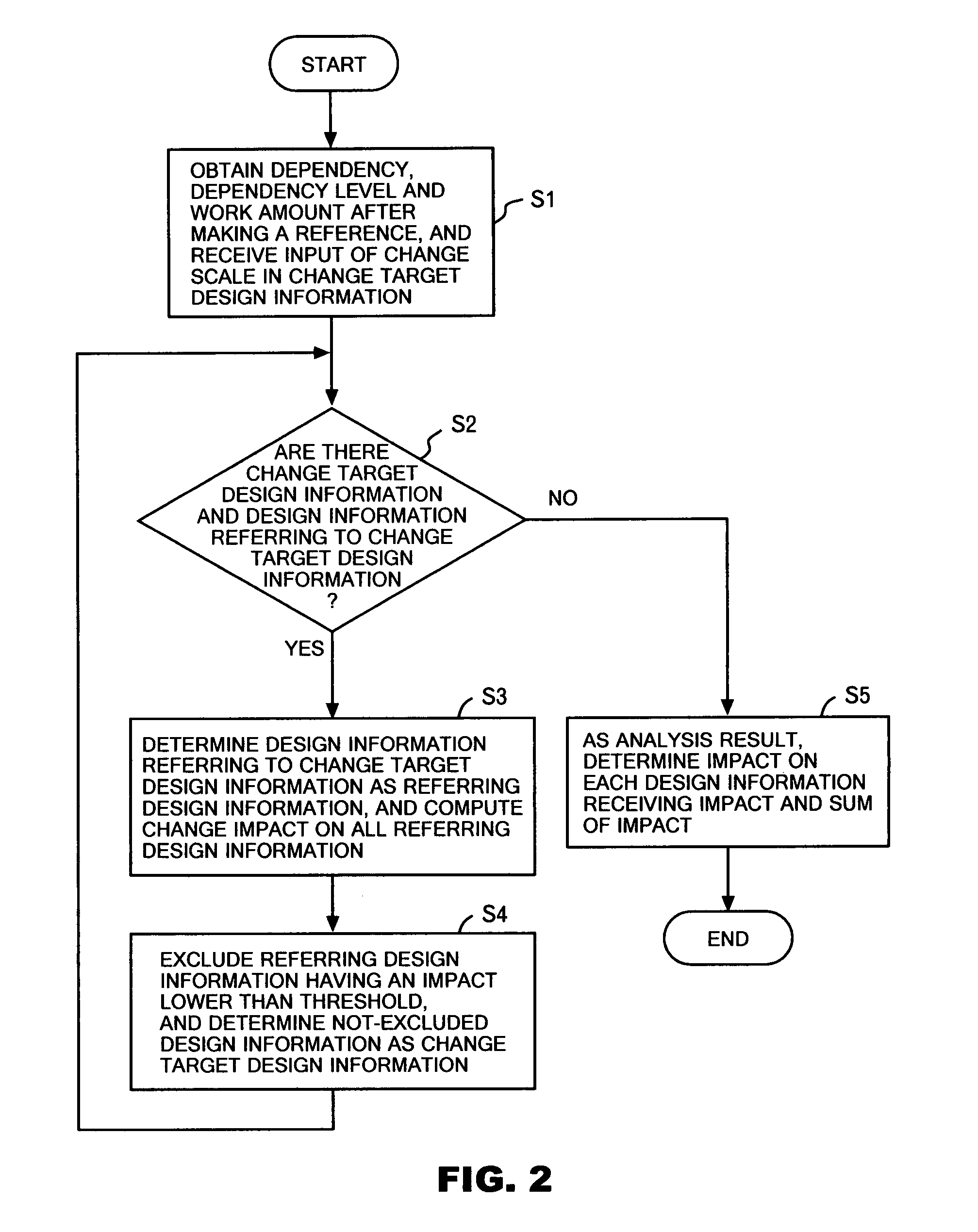
Apparatus and method for analyzing design change impact on product development process
An impact of a change in design information is defined as a sum of an additional work amount that must be reworked in each design process referring to the design information. At a time of requesting an impact analysis of a design change, all processes referring to certain design information to be changed are extracted from a project monitoring unit. An impact of the change in the referred design information on each extracted process is calculated. With respect to design information created on the basis of the referred design information in each extracted process, the maturity levels at a time when the process makes a reference and at a time when the reference design information is changed are obtained. Then, the difference therebetween is determined as the work amount that may possibly become useless.
Owner:IBM CORP
Physics-of-failure-based MOS (metal oxide semiconductor) device reliability simulation evaluation method
InactiveCN103955568ASoftware simulation/interpretation/emulationSpecial data processing applicationsElement analysisFailure mechanism
The invention relates to a physics-of-failure-based MOS (metal oxide semiconductor) device reliability simulation evaluation method. The method comprises the following steps: first, acquiring related parameters of an MOS device; second, analyzing a failure mode, a mechanism and an influence; third, establishing CFD (computational fluid dynamics), FEA (finite element analysis) and failure prediction models; fourth, carrying out the simulation analysis on temperature, vibration and electrical characteristics; fifth, performing stress damage analysis; sixth, performing cumulative damage analysis; seventh, considering deviation and performing parameter randomization simulation; eighth, obtaining a time vector before a failure by utilizing a competition failure mechanism; ninth, estimating the average starting failure time of the device. According to the method, a potential failure mechanism and a corresponding failure physical model of the device are obtained by analyzing, the using stress of the device is determined by simulating and analyzing, and finally, the average starting failure time of the MOS device under using conditions is obtained by calculating from the possible failure reasons of the MOS device on the basis of a failure physical theory. The method belongs to the technical field of MOS device reliability simulation and evaluation.
Owner:BEIHANG UNIV
System and method for proactive impact analysis of policy-based storage systems
InactiveUS20070112870A1Assessing the impact of user's actionsDigital computer detailsSpecial data processing applicationsStorage area networkData mining
A system efficiently and proactively assesses the impact of user's actions on a network storage system. The system generally operates on a storage area network that includes a database represented by states and policies, before the user action is executed. The system comprises a storage monitor that captures a snapshot of the database states. An impact analysis module of the system then applies a user action to the snapshot; and further selectively applies at least some of the policies to the snapshot. The impact analysis module simulates the user action on the snapshot without applying actually changes to the database, and further analyzes whether the simulated user action violates at least one applied policy. The system takes the appropriate action based on the result of the analysis.
Owner:IBM CORP
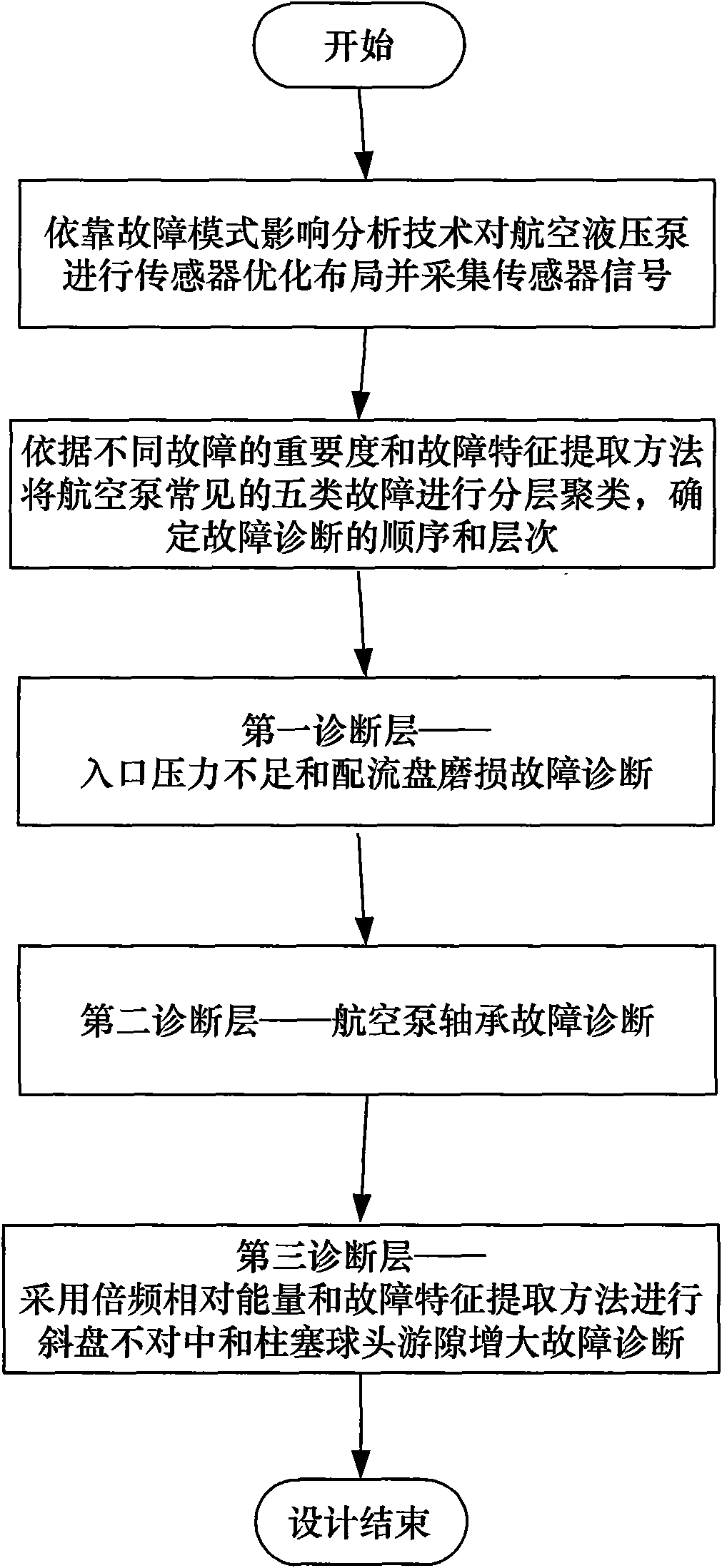
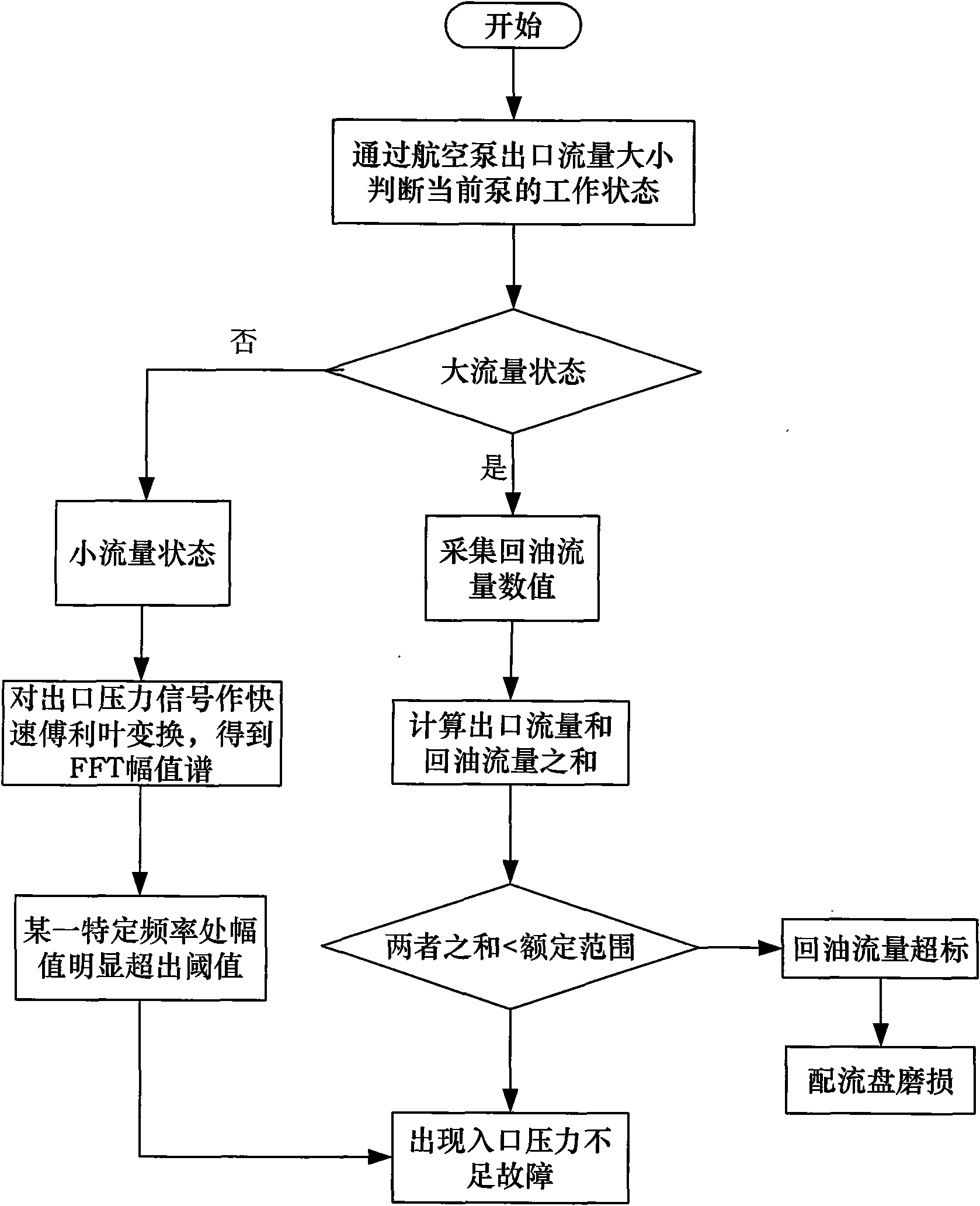
Hierarchical cluster aviation pump multiple fault diagnostic method based on frequency multiplication relative energy sum
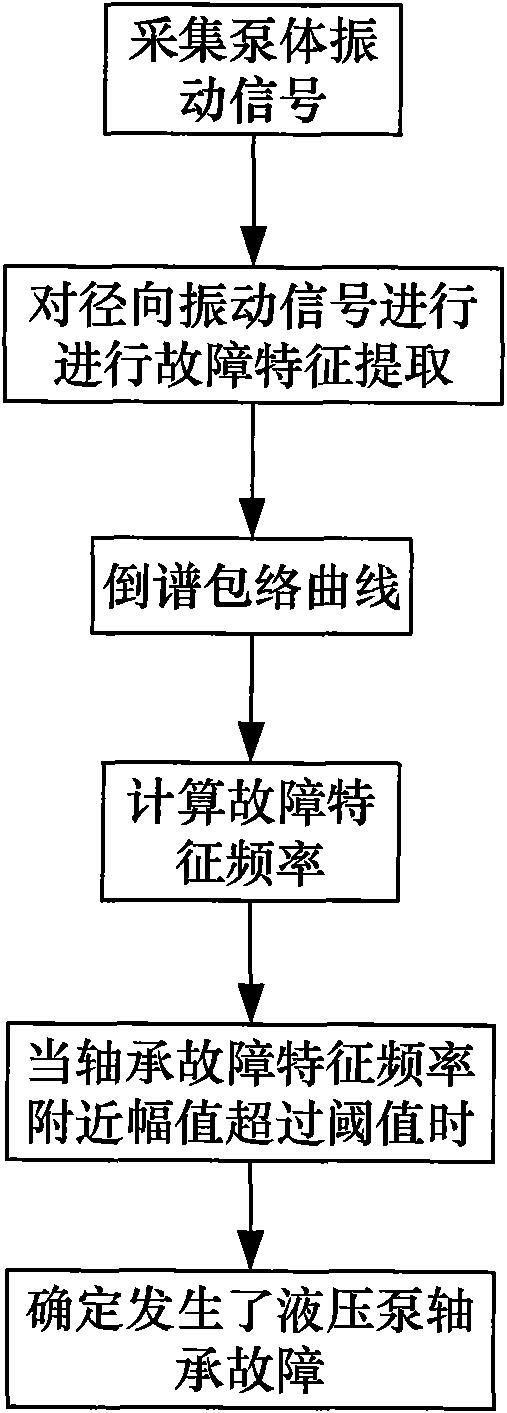
InactiveCN101571120AImplement diagnosticsRealize multi-fault high-precision diagnosisPump testingPositive-displacement liquid enginesAviationRelative energy
The invention discloses a hierarchical cluster aviation pump multiple fault diagnostic method based on frequency multiplication relative energy sum. In the method, firstly fault mode effect influence analysis technology is used for carrying out sensor optimal distribution on an aviation hydraulic pump and acquiring sensor signal; then common faults of the aviation hydraulic pump are classified by hierarchical cluster to determine the sequence and hierarchy of fault diagnosis; and finally fault diagnosis of a first diagnosis layer, a second diagnosis layer and a third diagnosis layer is carried out to complete the multiple fault diagnosis on the aviation pump. The method realizes the multiple fault diagnosis of the aviation pump with high accuracy; a extraction method of fault feature and frequency doubling relative energy sum is designed aiming that typical gradual fault of the aviation hydraulic pump is extremely weak at fault initial signature, the method can effectively realize the fault feature extraction of weak signal, and the method is proved to be accurate and efficient by plenty of experiments.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com