Patents
Literature
2228 results about "File transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
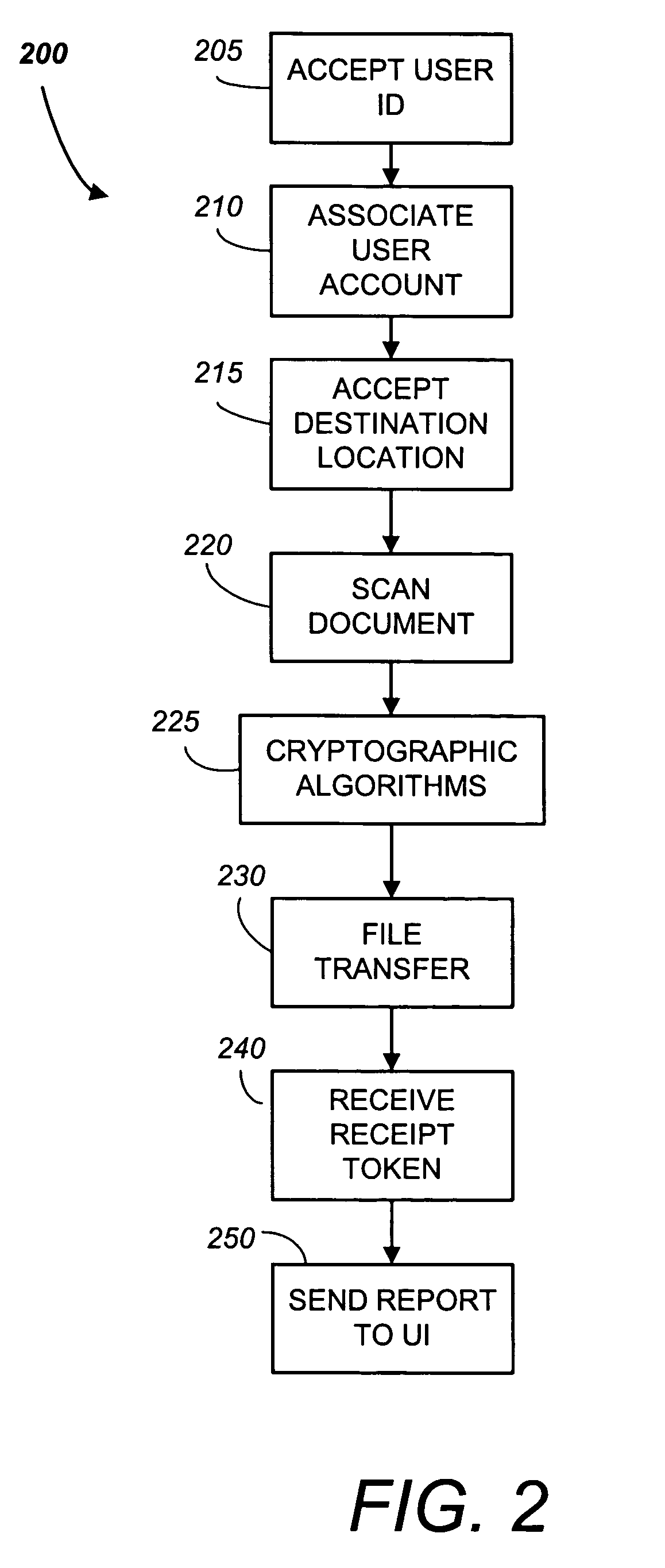
File Transmission. In practice, there are several types of file transmissions most users perform, including the transmission of files through SFTP (secure file transfer protocol), submitting forms by a Web server, and sending e-mail. Transferred data should be encrypted before transmission and during transmission.
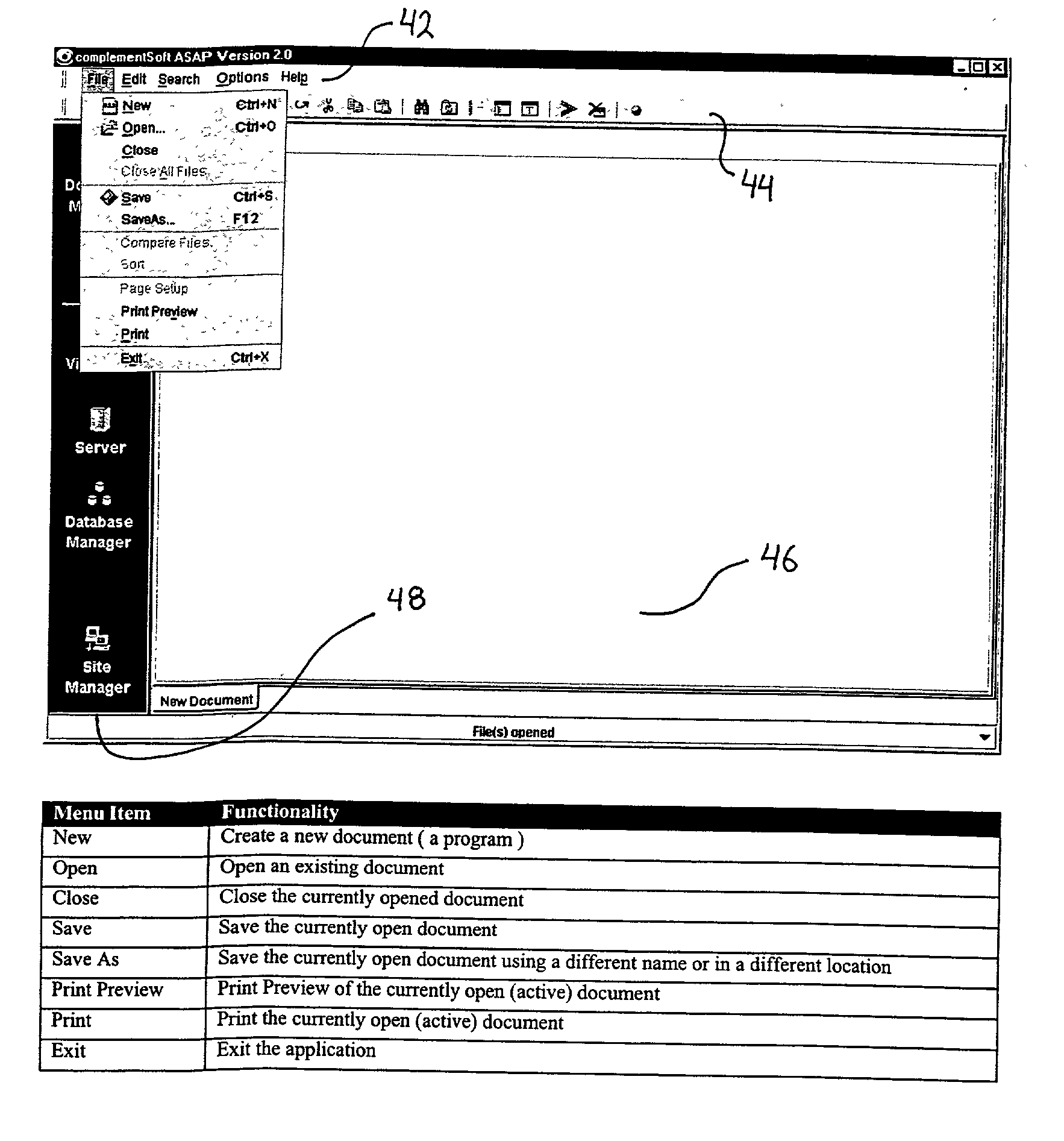
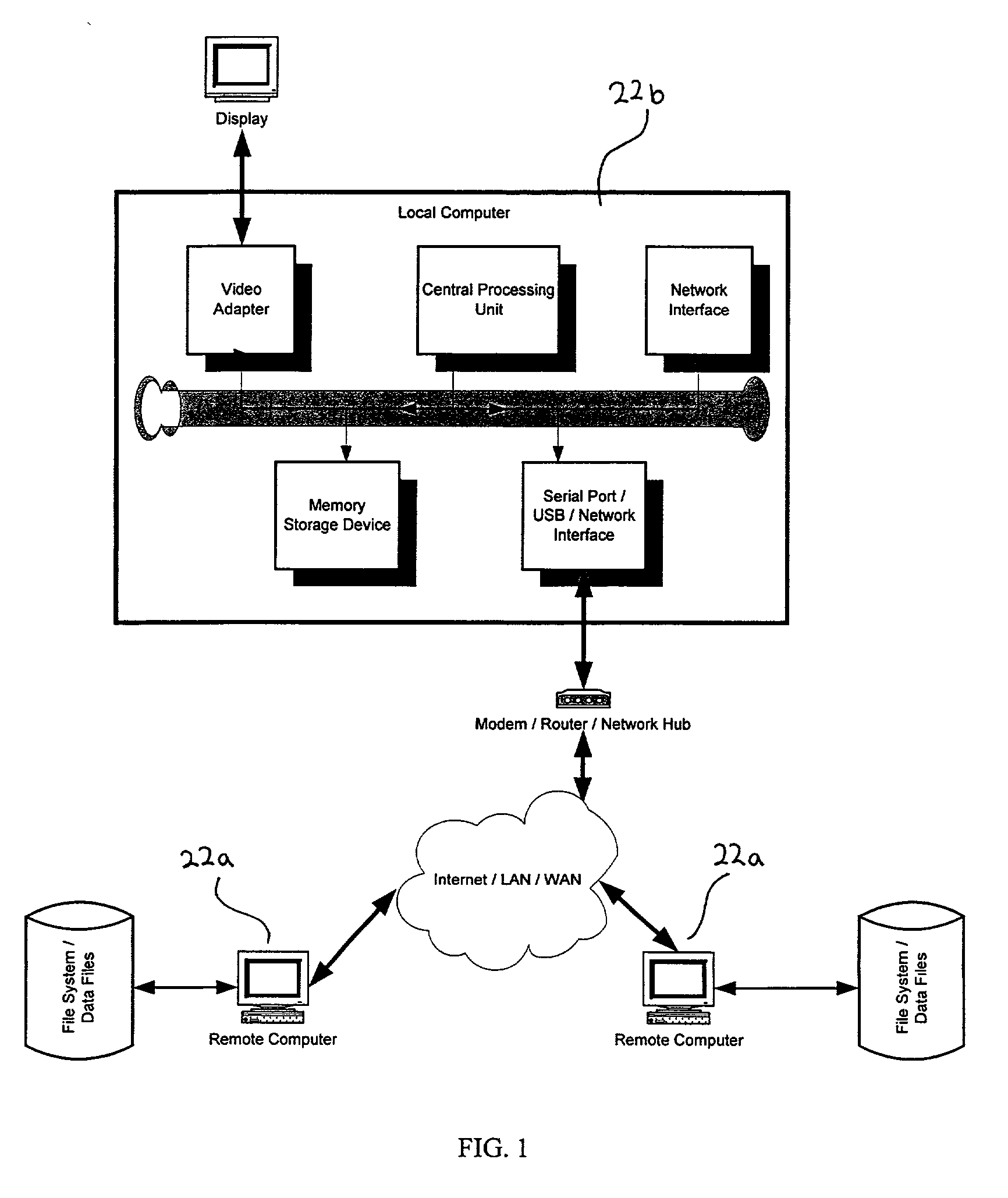
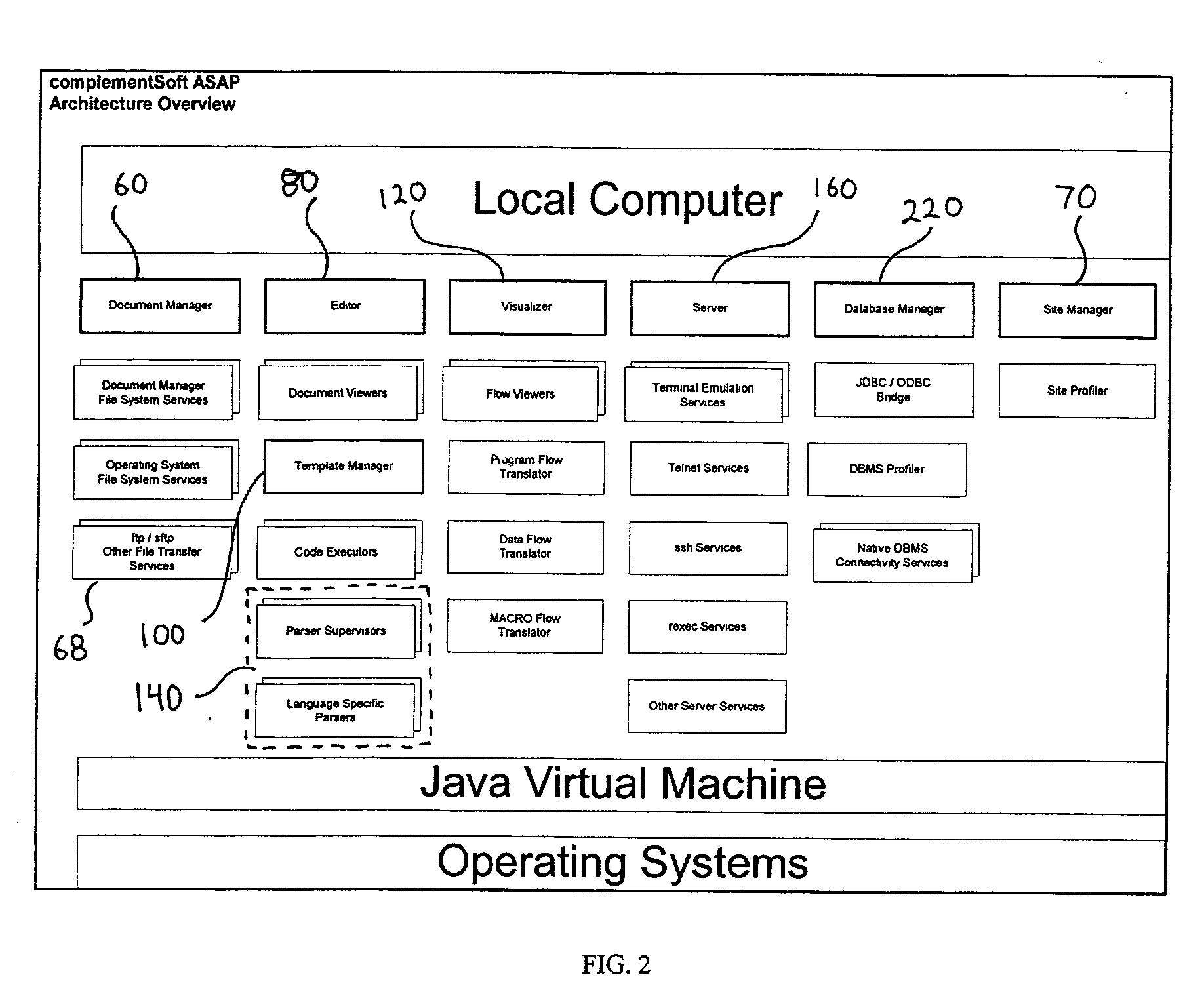
System and method for generating and maintaining software code
ActiveUS20050229154A1Enhanced management functionsVisual/graphical programmingSoftware simulation/interpretation/emulationCode editorData stream
A system and method for intelligently generating computer code. The system being comprised of a local computer, which is connected to a remote computer via a network system or the Internet and which is capable of exchanging files with the remote computer. The local computer is further comprised of a document manager for transferring files between the local computer and the remote computer and for providing enhanced file management functions. The document manager works in connection with the server module, the site manager and the connectivity layer to connect to remote computers, to transparently exchange files with the remote computer and to manage server profiles and connection information that is related to remote computers and transferred files. Once the file is transferred to the local computer, the editor can modify the code associated with the file; the editor is also capable of creating new files. The visualizer is capable of displaying a program flow diagram and a data flow diagram, which are comprised of program flow icons and data flow arrows to depict the code in terms of processing blocks and data blocks. To assist in developing new code or editing existing code, the template manager allows the user to browse through a directory of existing code sections or templates and to copy templates into the selected code for editing. For allowing the editor to process code that is written in different Data Management System programming languages and for creating the program flow icons, the parser layer detects the file type of a selected file and activates the rules and logic that apply to the corresponding Data Management System.
Owner:COMPLEMENTSOFT
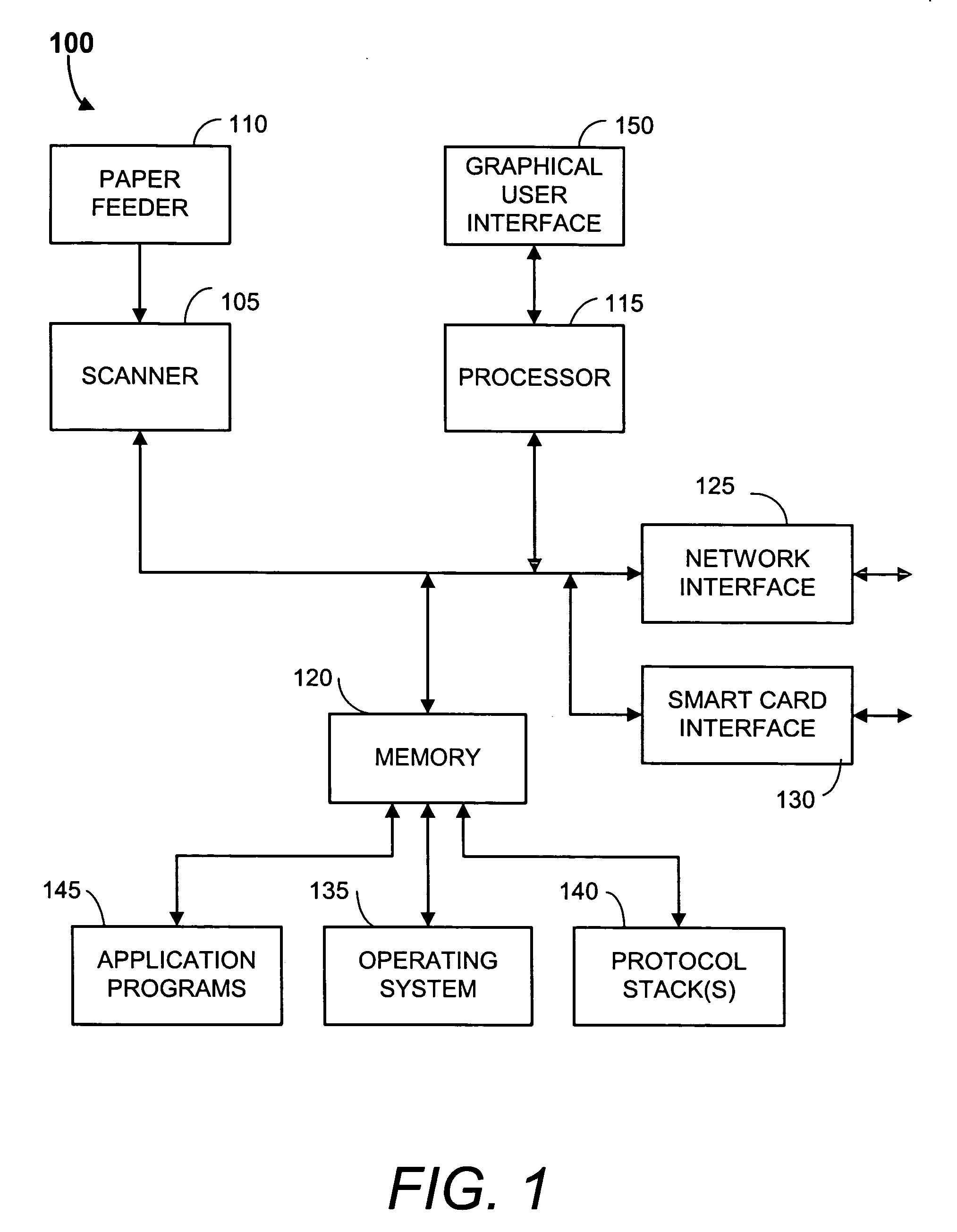
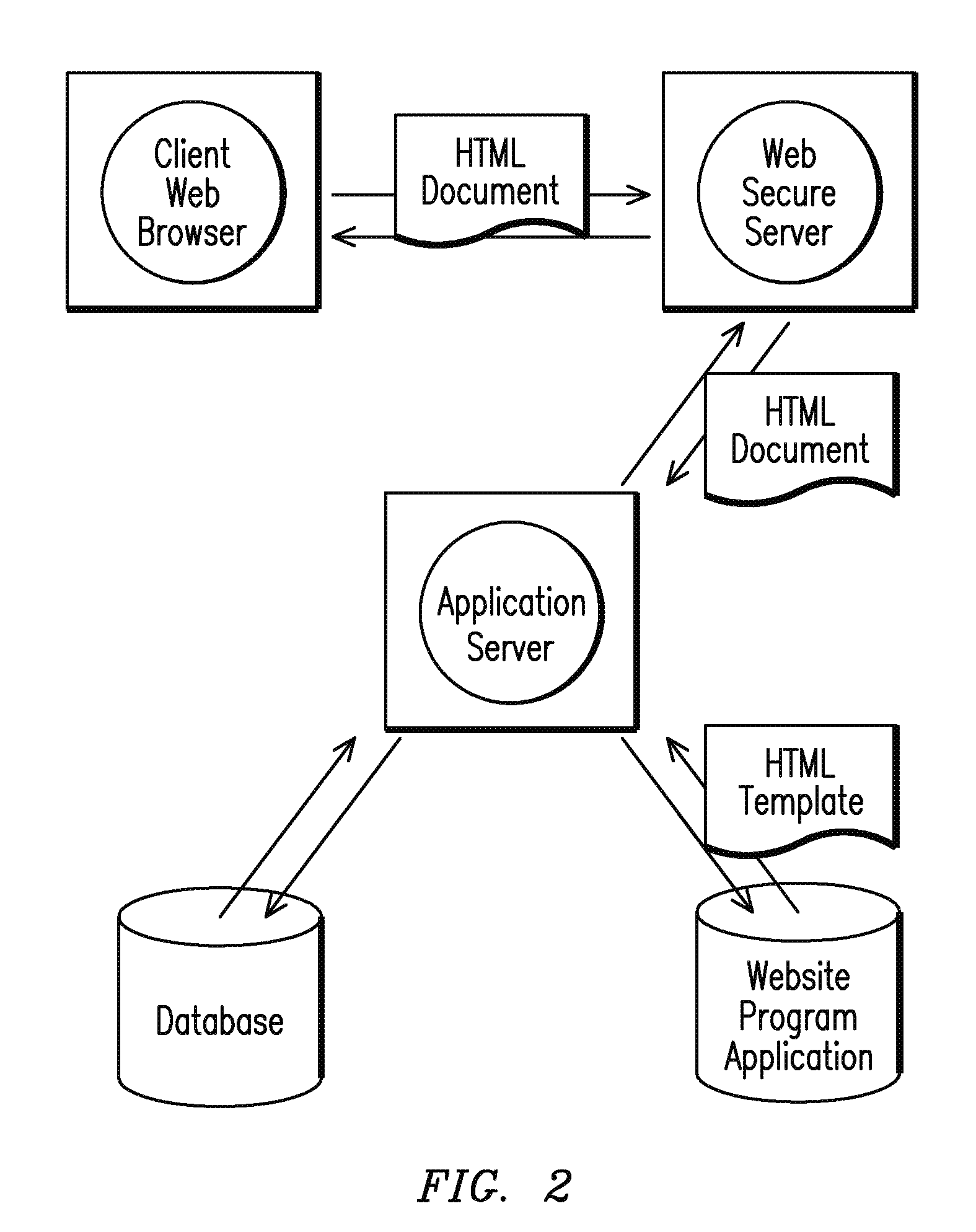
Network scanner for global document creation, transmission and management
InactiveUS20060072144A1Enhanced interactionStrong sender authentication securityTime-division multiplexComputer security arrangementsThe InternetNetwork communication
A network scanner, communication protocols, and client and server programs and are provided which provide an improved way to transmit legally binding documents, obviating the need for outmoded, legacy fax transmissions. Using the network scanner, a document may be scanned and transferred directly into any shared folder inbox residing on any computer attached to the Internet. Enhanced server systems and network communications and messaging protocols are provided that are more practical to use than email for sending documents such as executed legal documents or other documents requiring robust integrity and authenticatability. Similarly, the inventive network scanner, server systems and communication protocols provide improved ways to perform large file transfers and to manage bandwidth to minimize problems associated with uploading / downloading large files as attachments to / from email servers and for enabling user control over VoIP quality during file transmission sessions.
Owner:INTELLECTUAL PROPERTIES I KFT
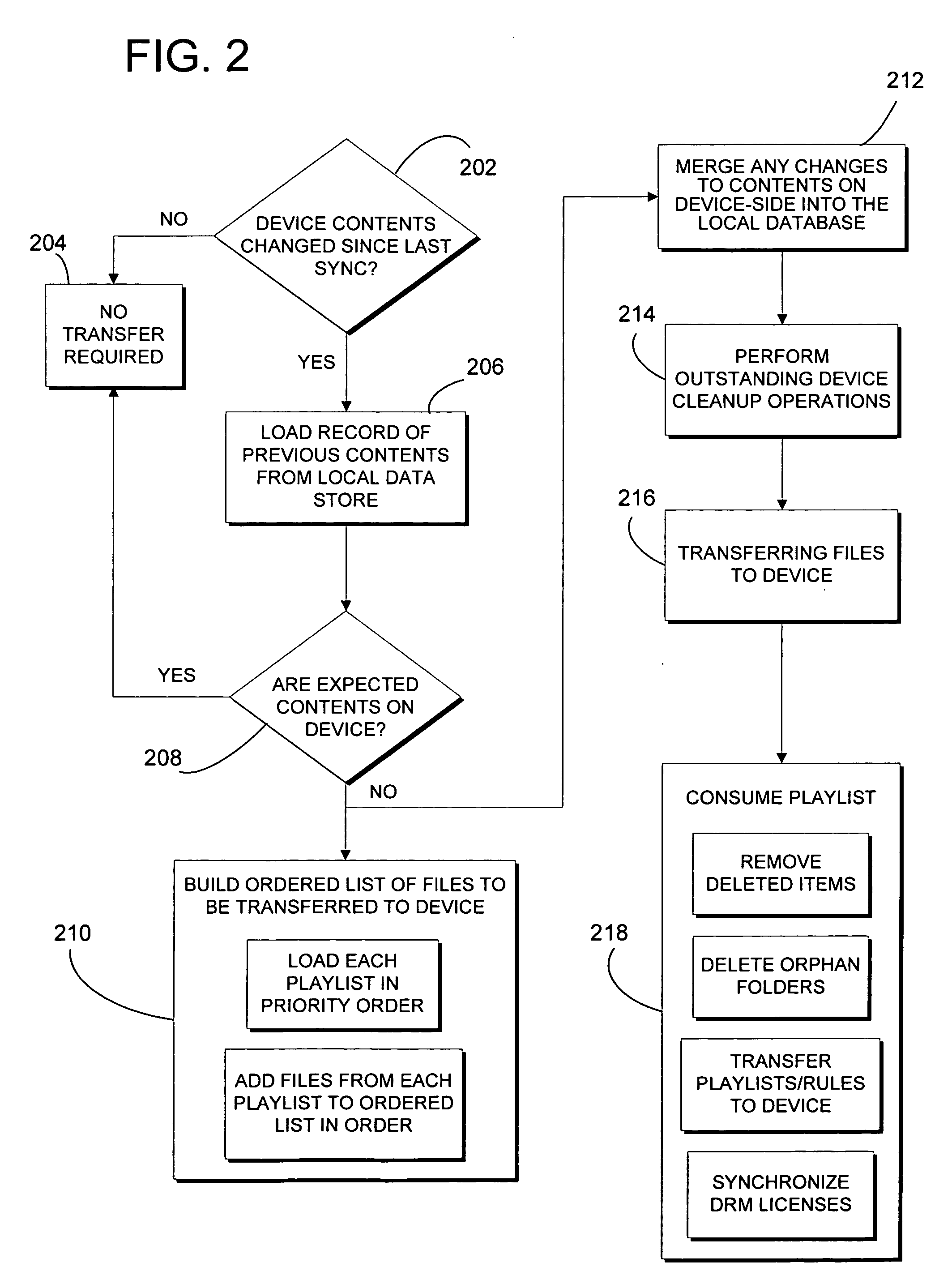
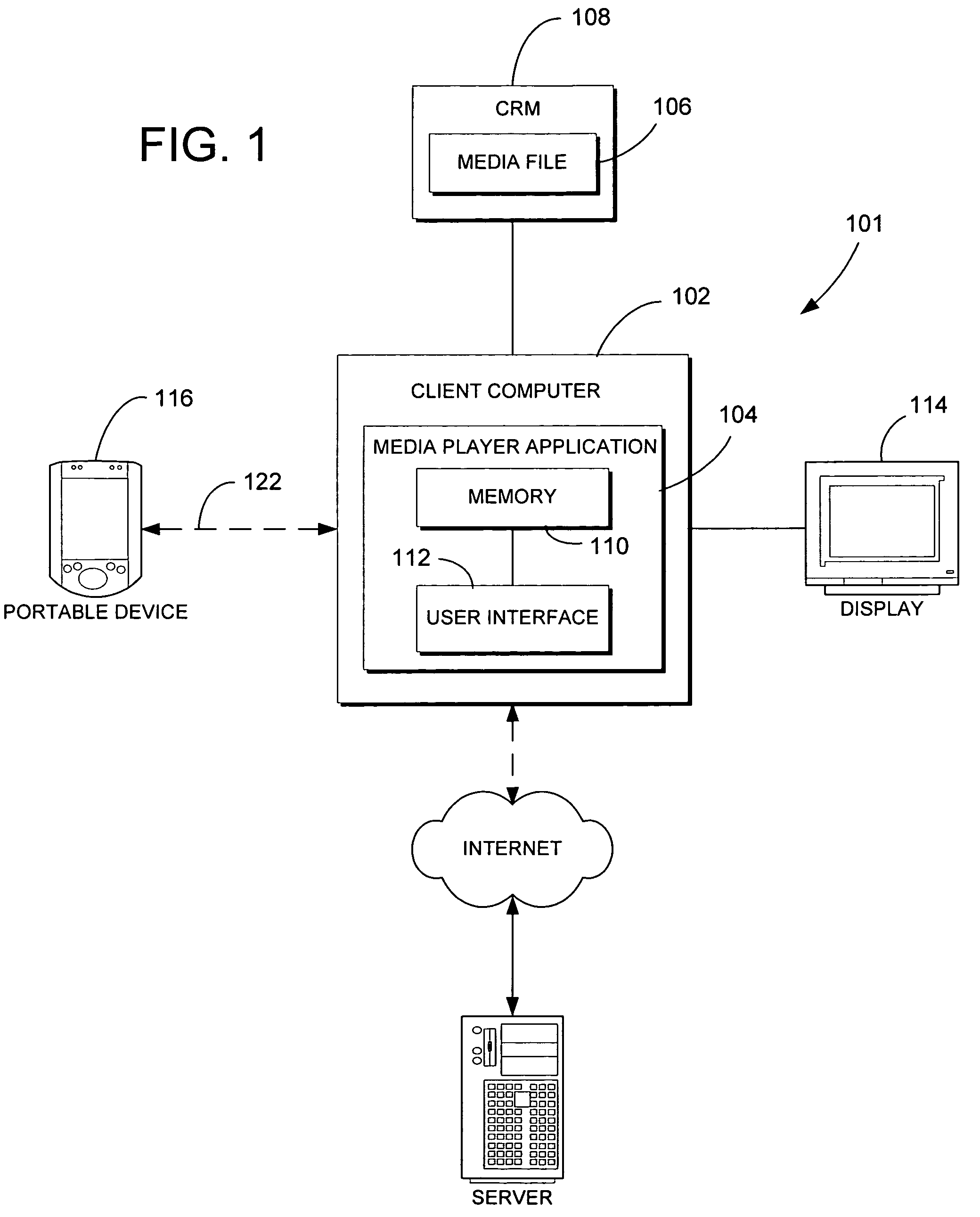
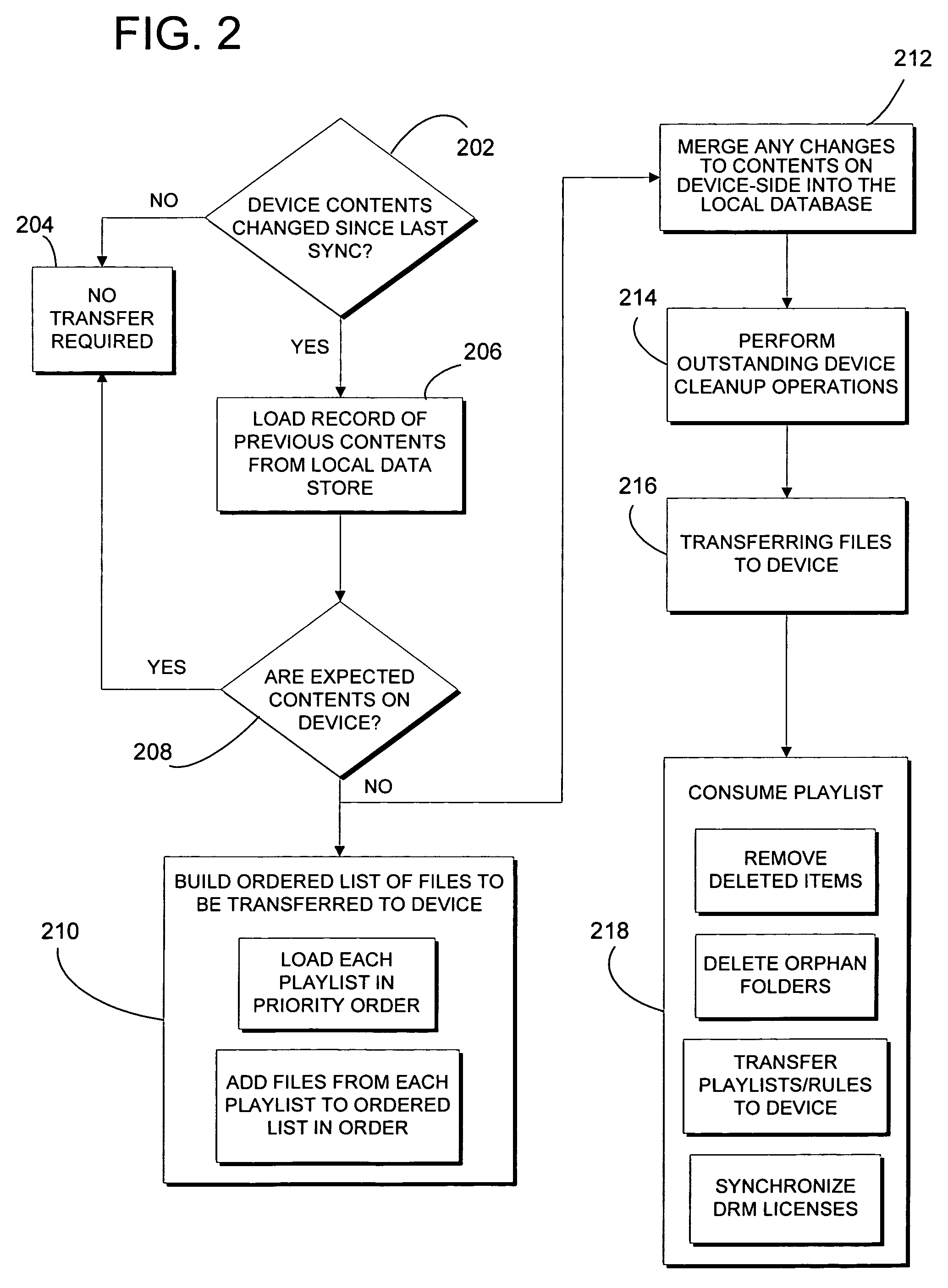
Automatic rules-based device synchronization
ActiveUS20060224620A1Enhances device synchronization experienceImprove experienceData processing applicationsDigital data information retrievalFile transmissionFile allocation
Automatic rules-based synchronization of digital files on a source device and a target device coupled to it. A source computer executes a synchronization engine for managing transfer of files from a source database to a target device coupled to the computer as a function of a defined storage capacity of the device. The synchronization engine is configured to receive user-defined rules for selecting which of the files are to be transferred to the device and assigning priorities to the files. The synchronization engine builds a designated list of the files to be transferred according to the priorities defined by the rules.
Owner:MICROSOFT TECH LICENSING LLC
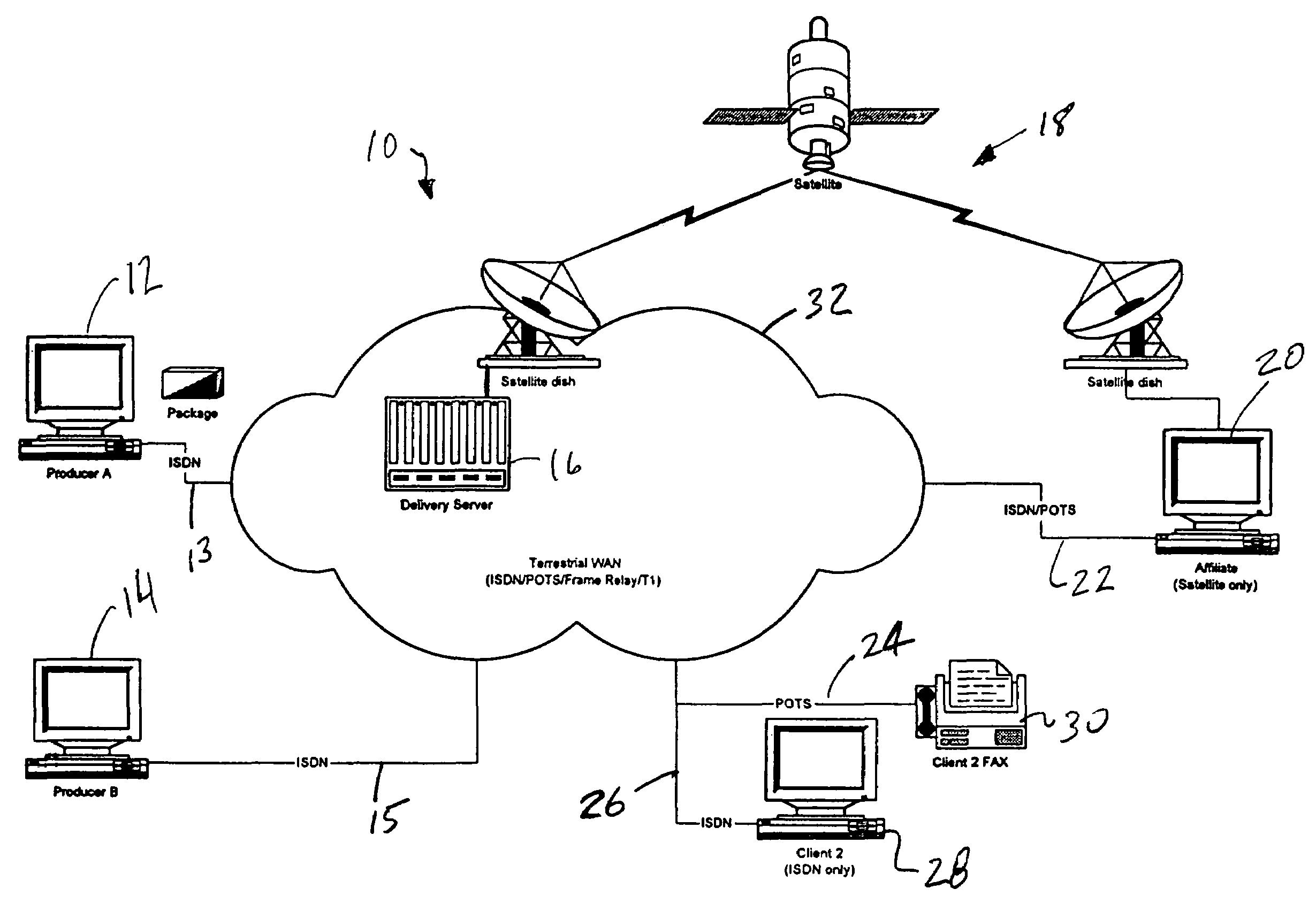
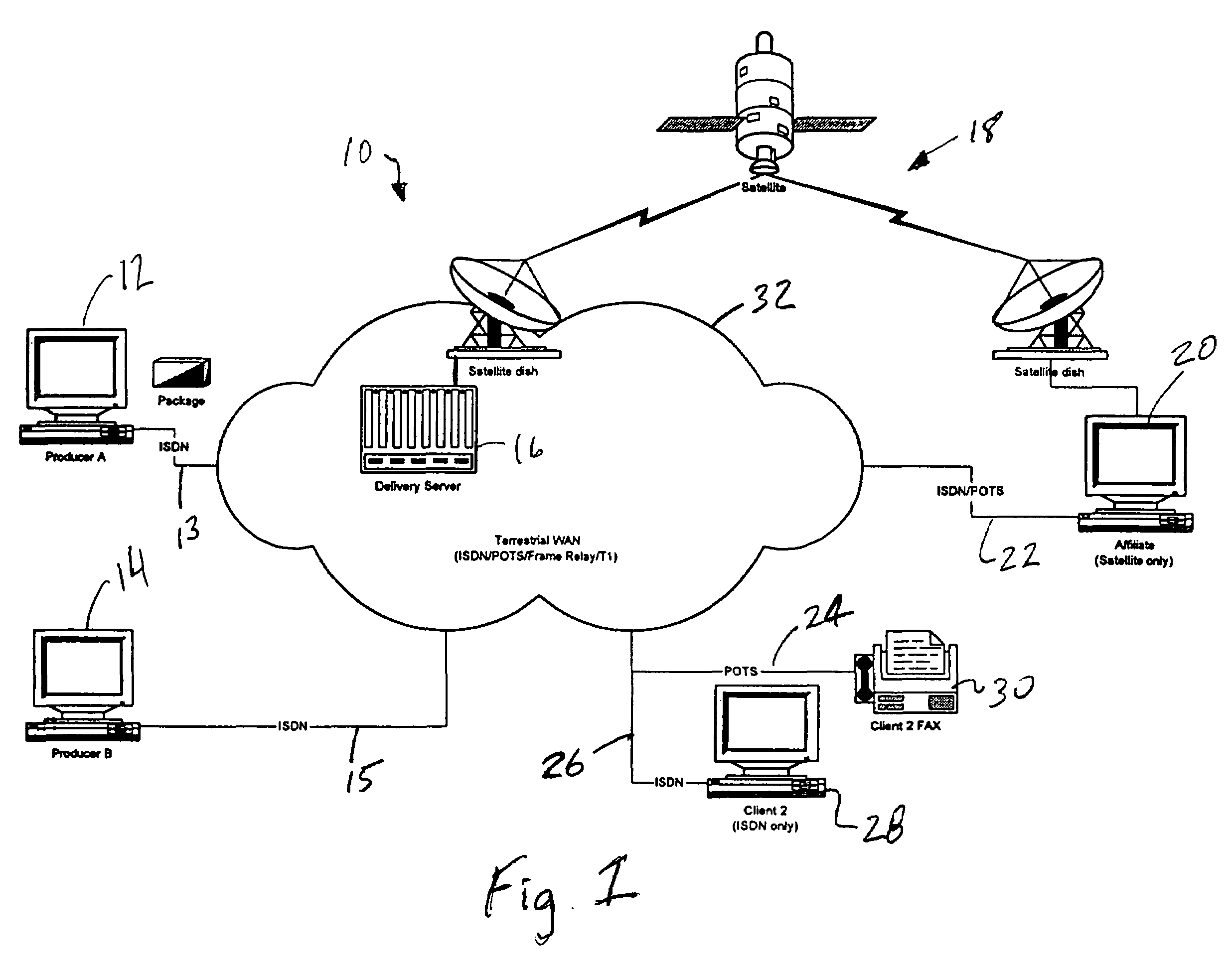
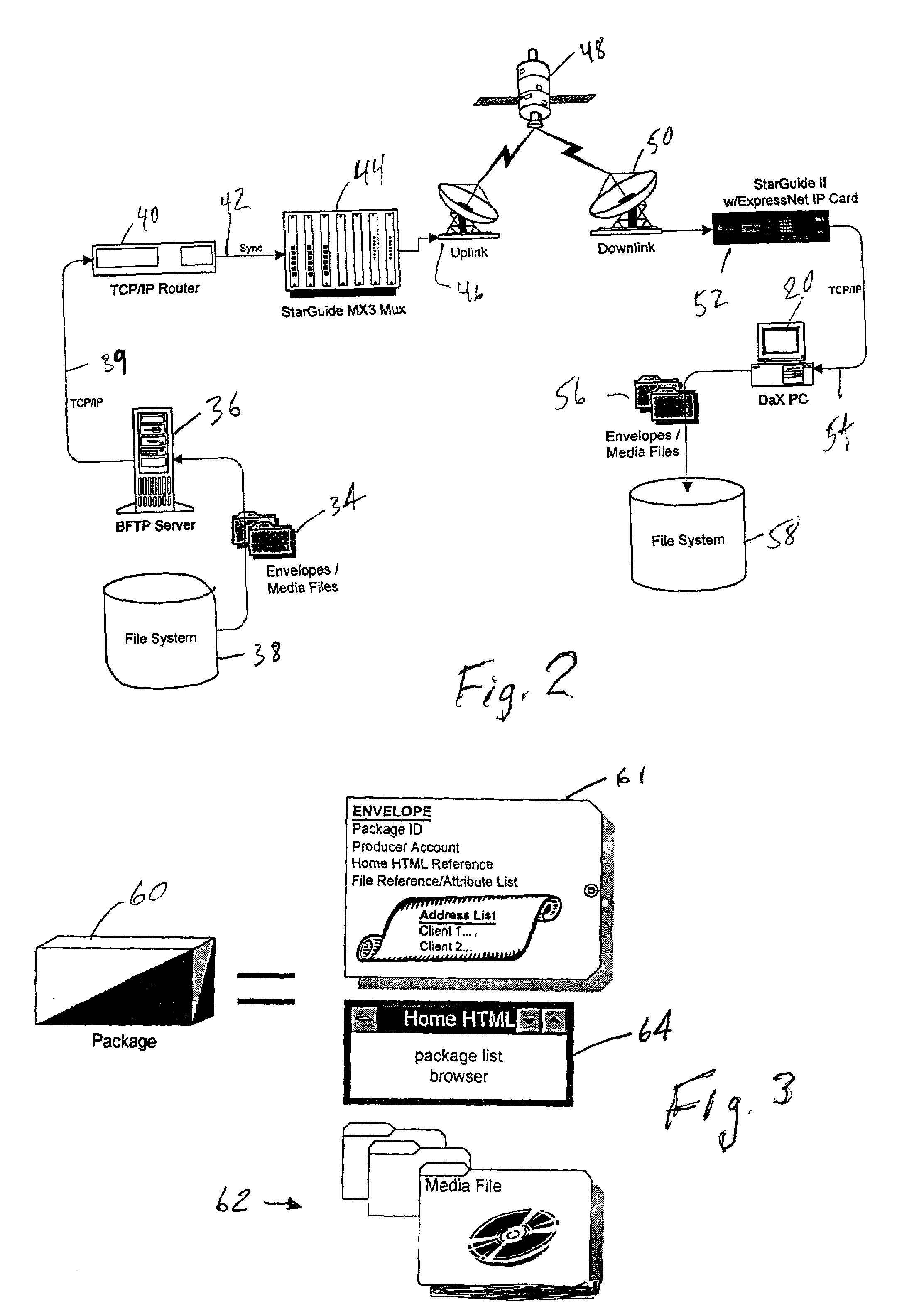
Method and apparatus for push and pull distribution of multimedia
InactiveUS7194757B1Reliable distributionReduce eliminateGHz frequency transmissionOffice automationDistribution systemClient-side
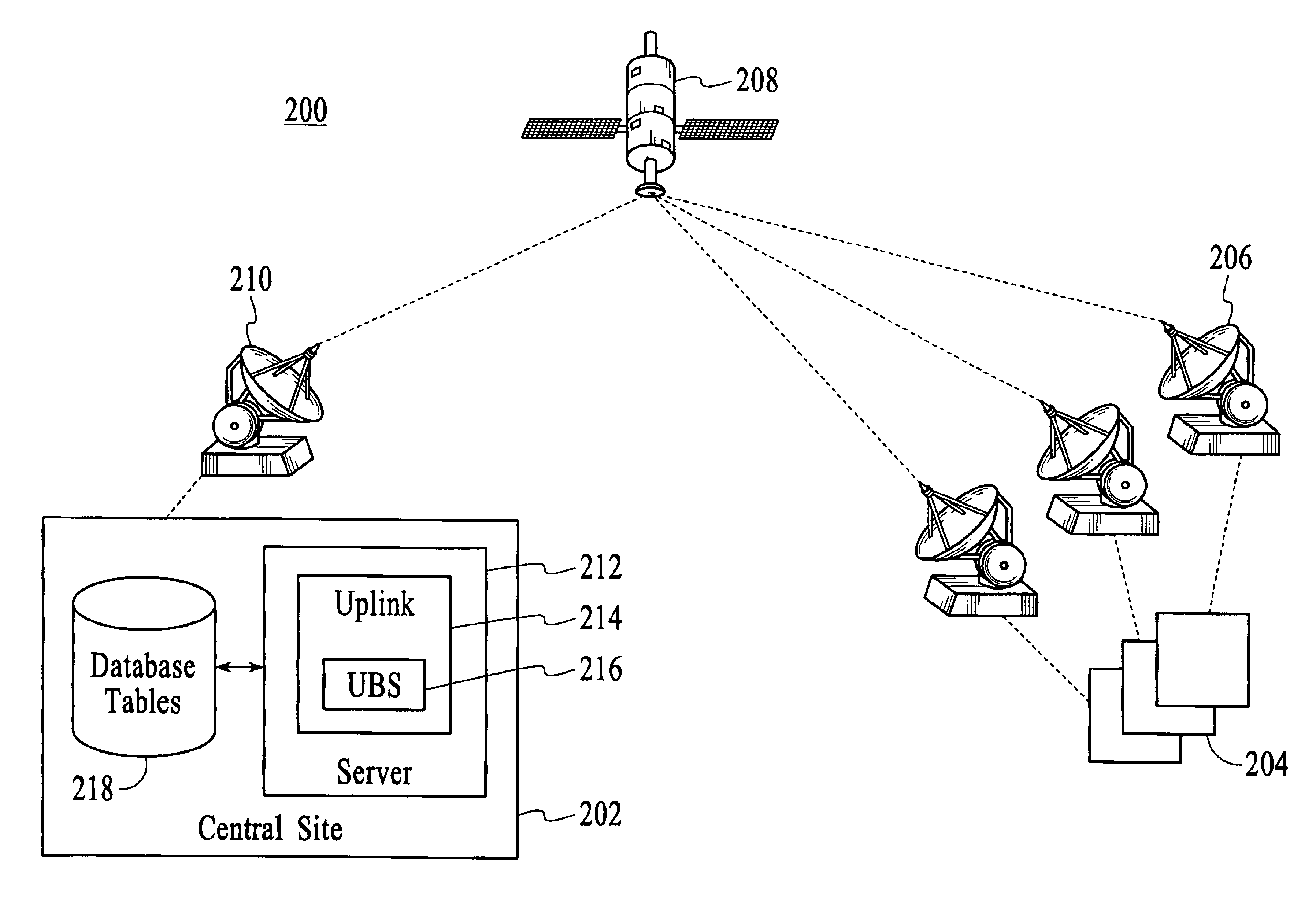
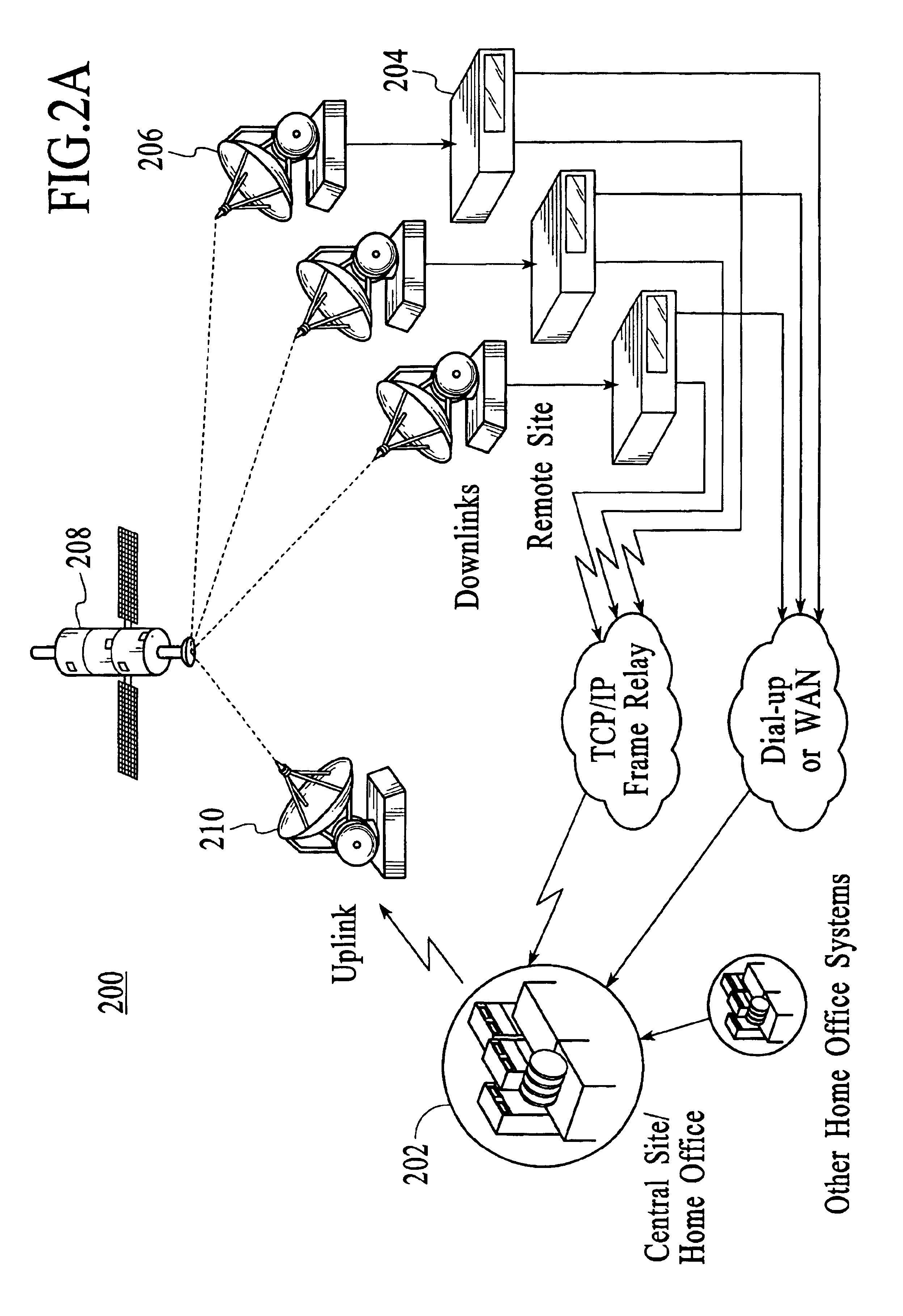
The present specification discloses a multimedia distribution system and method. The system and method has a producer workstation, a delivery server, a high-bandwidth one-way satellite transmission system, a terrestrial two-way communication system (including use of the Internet), a plurality of satellite affiliate workstations, and a plurality of terrestrial client workstations. The delivery server receives digital information (envelopes and associated media files) from the producer workstations for delivery of the information to the affiliate and client workstations addressed in the envelope. The affiliate and client workstations provide the delivery server with confirmation of delivery of each received envelope and its associated files. In the absence of receipt of confirmation of delivery, the delivery server re-sends the unconfirmed envelope and associated files to the non-confirming affiliate or client workstation by a two-way terrestrial connection or by a manual system, such as a dub-and-ship service. The delivery server has the ability to push content to affiliates, push-pull content to affiliate and clients, to conventionally pull content from the delivery server, and push the content to affiliates and clients by manual delivery services. The disclosed system and method utilize a unique envelope and addressing protocol and a unique broadcast file transfer protocol for distribution to affiliate workstations by one-way satellite broadcast. The disclosed system and method also make significant use of the TCP / IP, IGMP, and Ethernet protocols and information distribution techniques.
Owner:RATEZE REMOTE MGMT LLC
System and method for secure file transfer
InactiveUS20090037520A1Digital data protectionMultiple digital computer combinationsFile transmissionData file
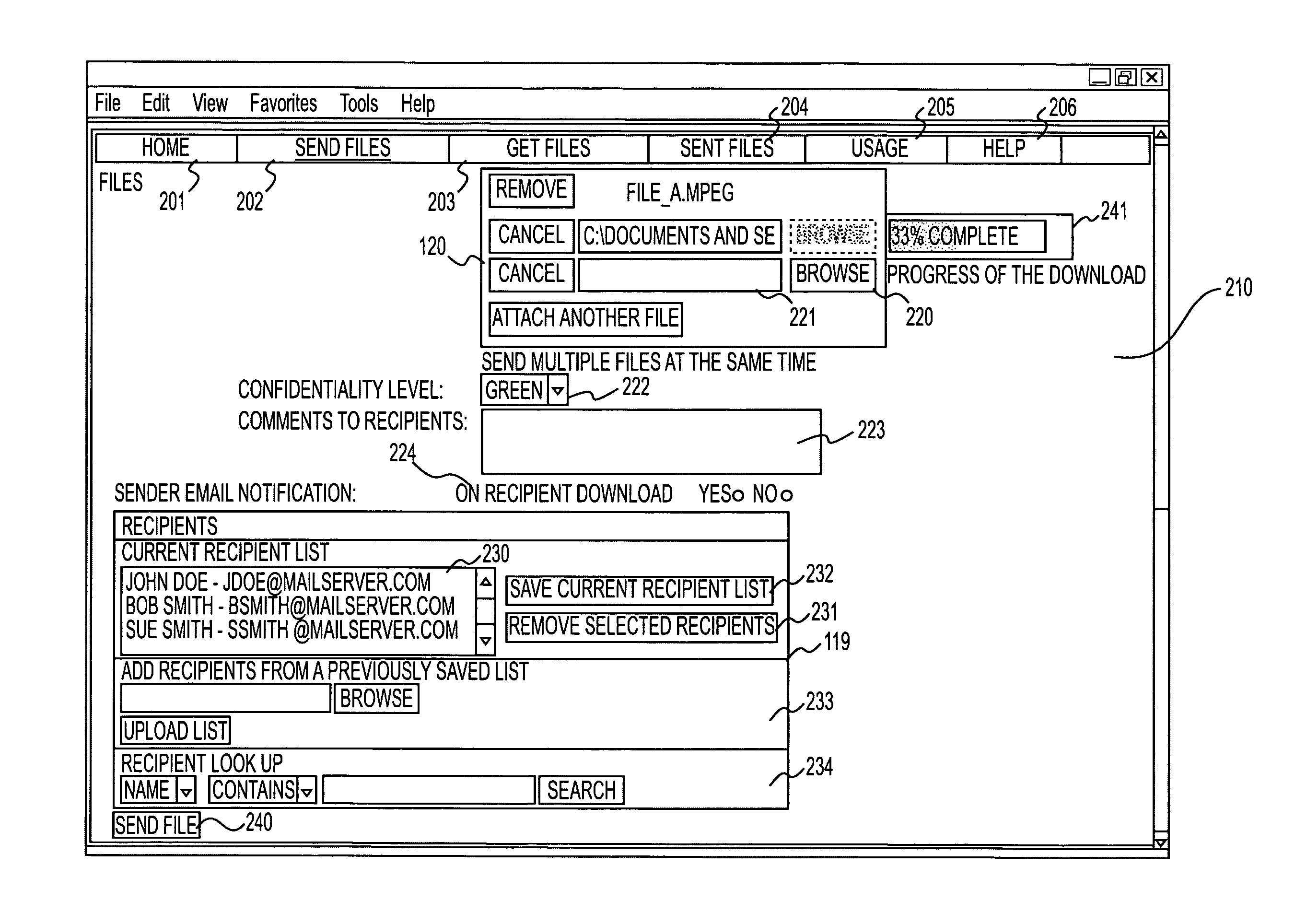
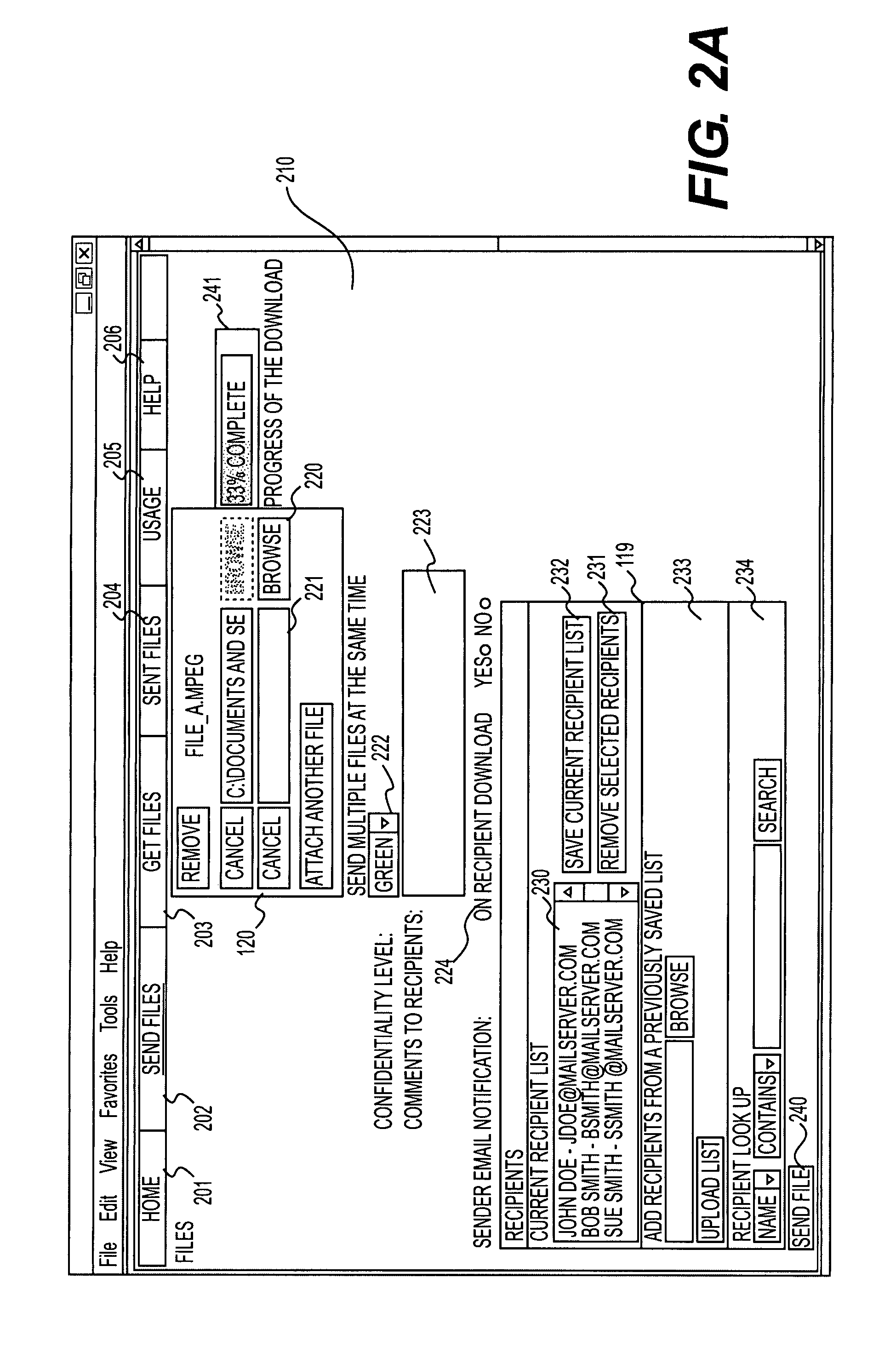
A method for transferring files between a client system and a file server includes receiving a location associated with at least one data file to be uploaded to a file server and a recipient list that includes an electronic address associated with at least one intended recipient of the at least one data file. A communication channel is established between the client system and the file server, and the at least one data file is uploaded to a file transfer account associated with one or more of a sender or the at least one intended recipient. An electronic message is provided to the electronic address, the electronic message including an interactive link to the uploaded file. The user interface modifies the recipient list associated with the at least one data file after the at least one data file has been uploaded to the file transfer server.
Owner:CATERPILLAR INC
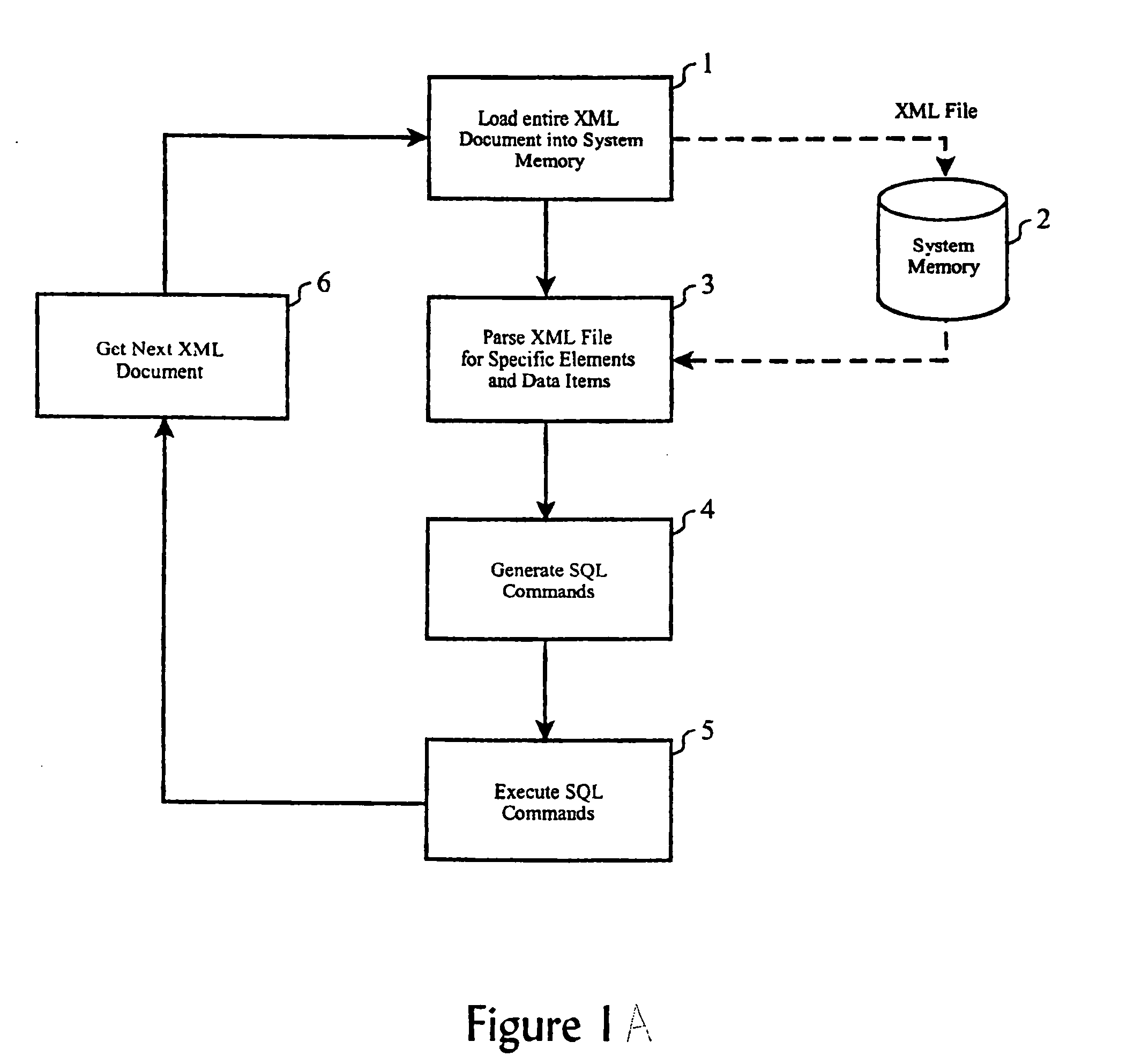
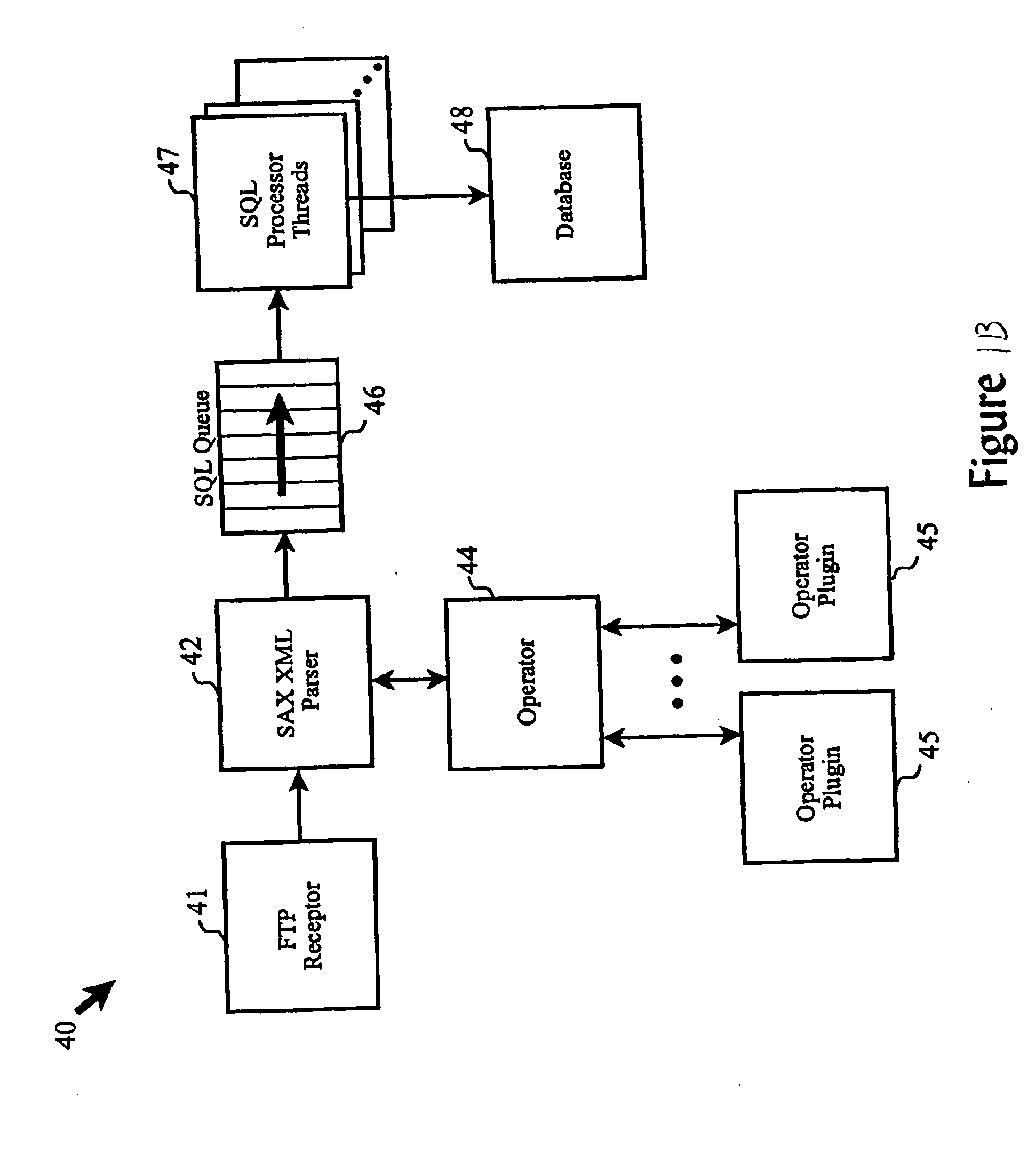
Method for scalable, fast normalization of XML documents for insertion of data into a relational database
InactiveUS20050097128A1Semi-structured data indexingSemi-structured data queryingRelational databaseData file
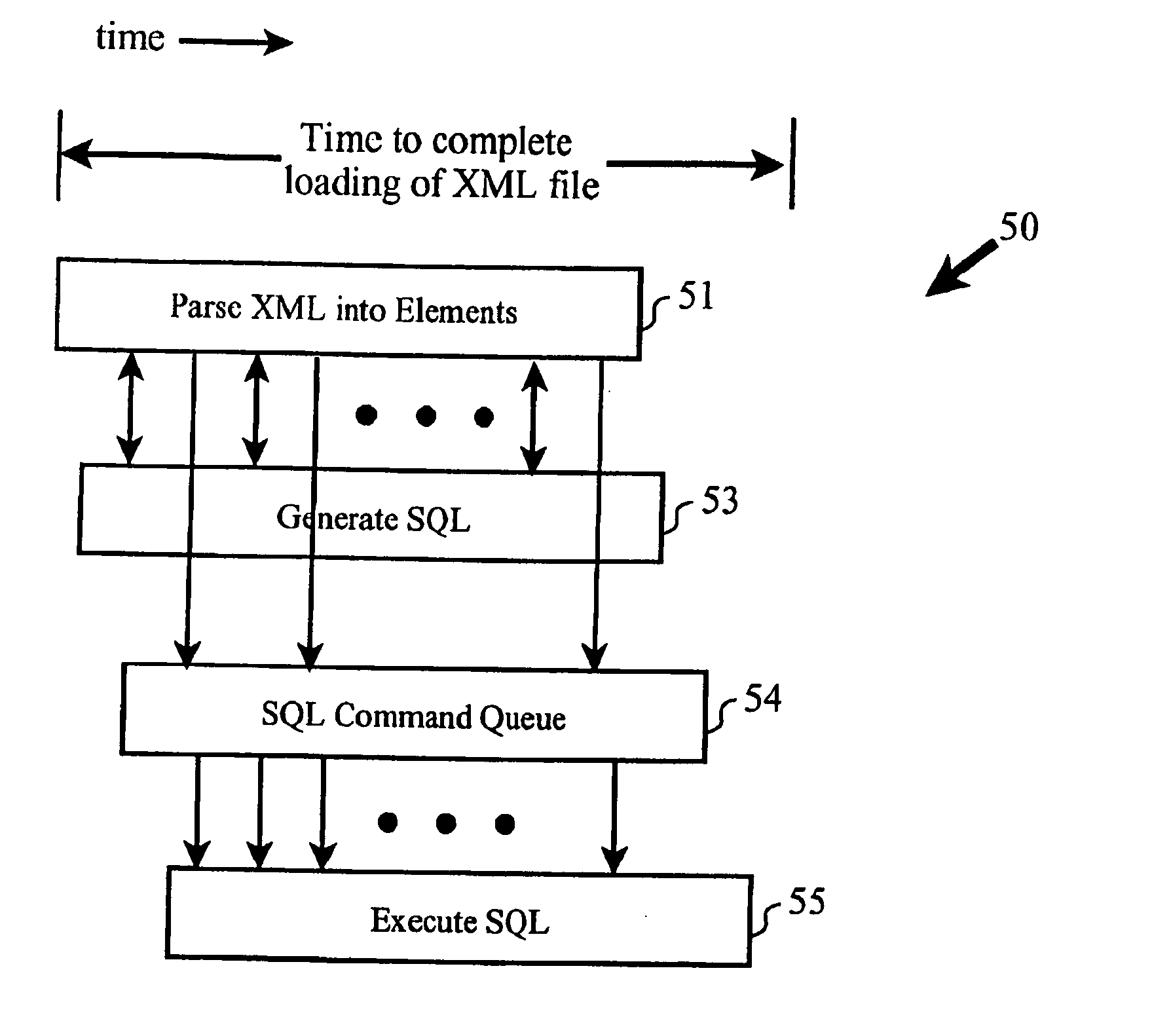
Disclosed is a method of transferring data from a hierarchical file (having a hierarchical structure, e.g., a markup language file) to a relational database structure (made up of columns and rows. Before processing the actual data, the invention first partitions the hierarchical structure into sections, where each section is dedicated to at least one node of the hierarchical structure. The partitioning process is based on the document type definition file, which is separate from, and different than the hierarchical file. After completing the partitioning, the invention then parses the actual data contained in the hierarchical data file to produce a stream of data pairs and end of section indicators. During the data parsing process, the invention loads the data pairs into corresponding “sections” (created prior to the parsing process) as the data pairs are output from the parsing process. The invention also transfers the node data from these sections to the columns and rows of the relational database structure.
Owner:IBM CORP
Method and system for online secure patient referral system
The present invention provides a system and method, relating to the transfer of patient files over a secure, HIPAA compliant, patient file transfer and outpatient order system and a computer site therefore. The method includes obtaining and compiling a patient record pertaining to a patient; electronically inputting the patient record obtained into a secure computer database containing other patient records, allowing physician access to the patient record wherein the access includes allowing the physician to order outpatient services and send part of the patient information, including certain defined fields for a complete record and to send and receive referrals including certain defined fields for a complete record.
Owner:SCHEDULING COM
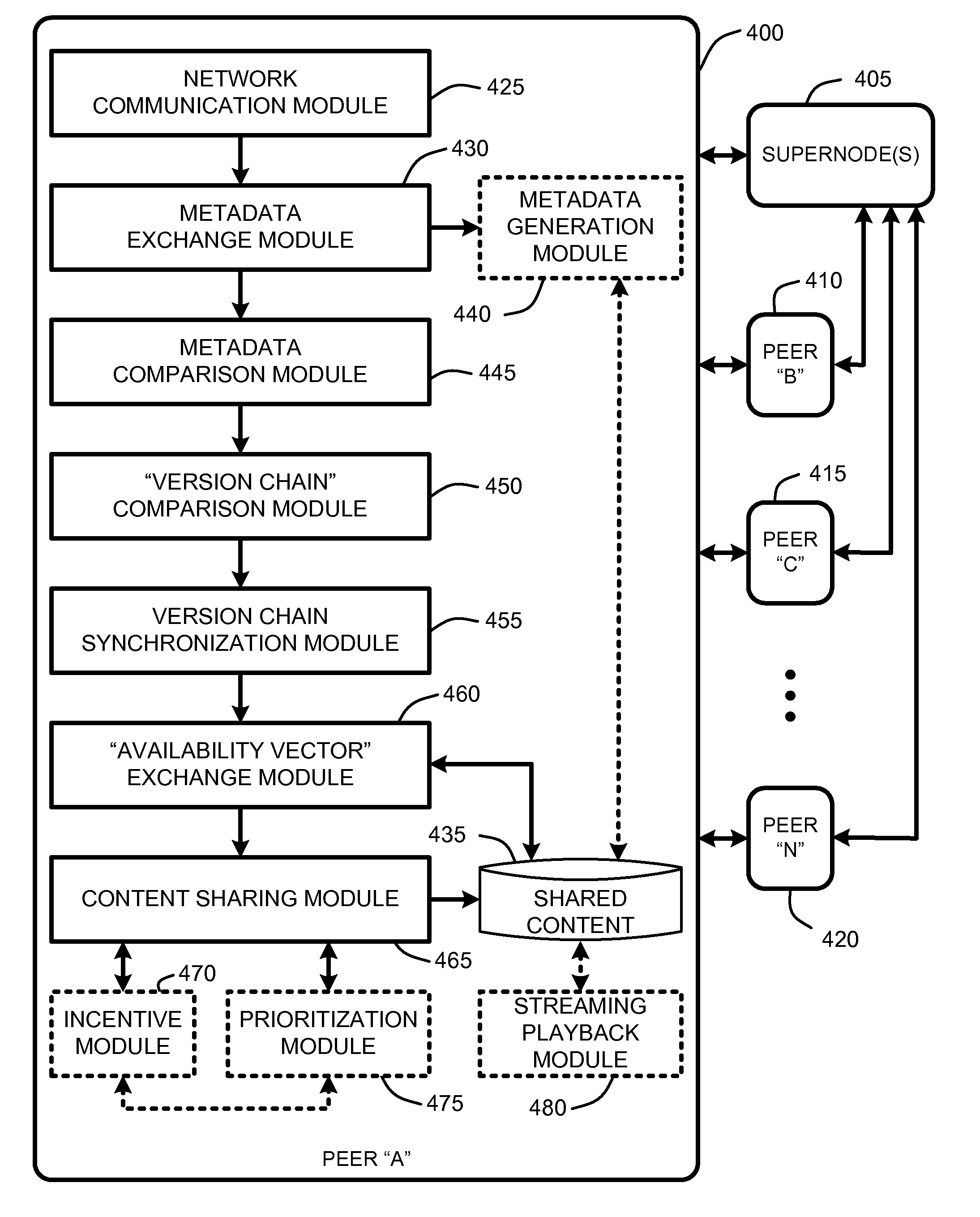
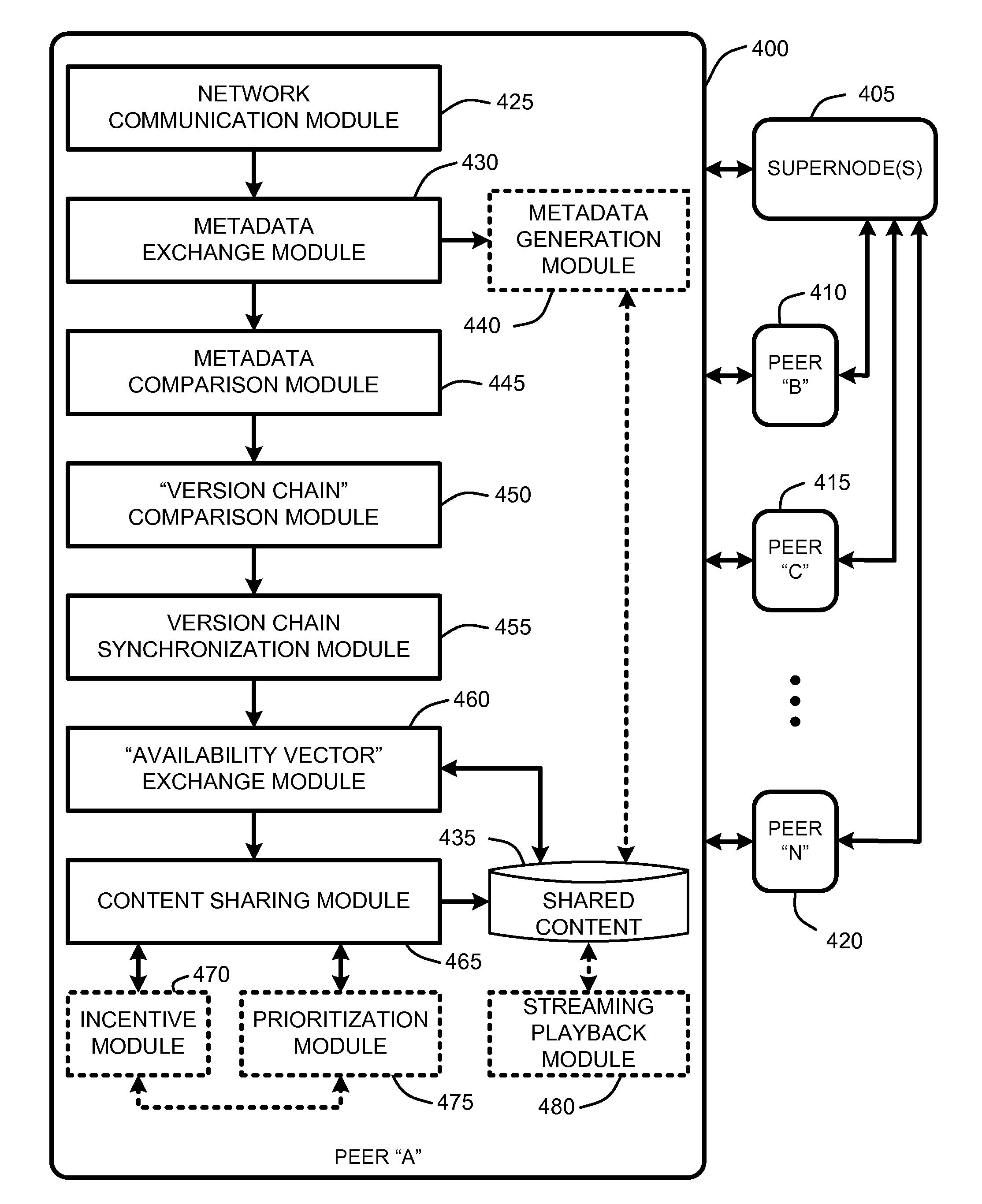
On-demand file transfers for mass p2p file sharing
InactiveUS20080005114A1Digital data information retrievalMultiple digital computer combinationsFile transmissionDirectory structure
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for a real-time bandwidth allocation scheduler for media delivery
InactiveUS6947388B1Reduce wasted bandwidthLow costError preventionTransmission systemsProgram segmentFile transmission
The present invention provides a method and system for providing a bandwidth allocation scheduler for media delivery. The present invention includes determining an available bandwidth for file transmission for a time interval, and allocating at least a portion of the available bandwidth to at least one file transmission task, wherein a different amount of the available bandwidth may be allocated to each of the at least one file transmission tasks. The bandwidth allocation scheduler in accordance with the present invention comprises a set of program segments that provides fast, deterministic real-time scheduling for the allocation of bandwidth for file transmissions. It allows the bandwidth allocated to a delivery to vary according to the amount of bandwidth available. A different amount of bandwidth may be allocated to each individual file transmission task. Higher priority transmissions may be allocated bandwidth before allocation to lower priority file transmissions. The maximum bit rate of the slowest addressed receiver may be considered in allocating the bandwidth. Moreover, the customer can choose between different allocation strategies. Thus, the bandwidth allocation scheduler in accordance with the present invention reduces waste in bandwidth in media delivery, which in turn reduces costs for a customer.
Owner:HULU
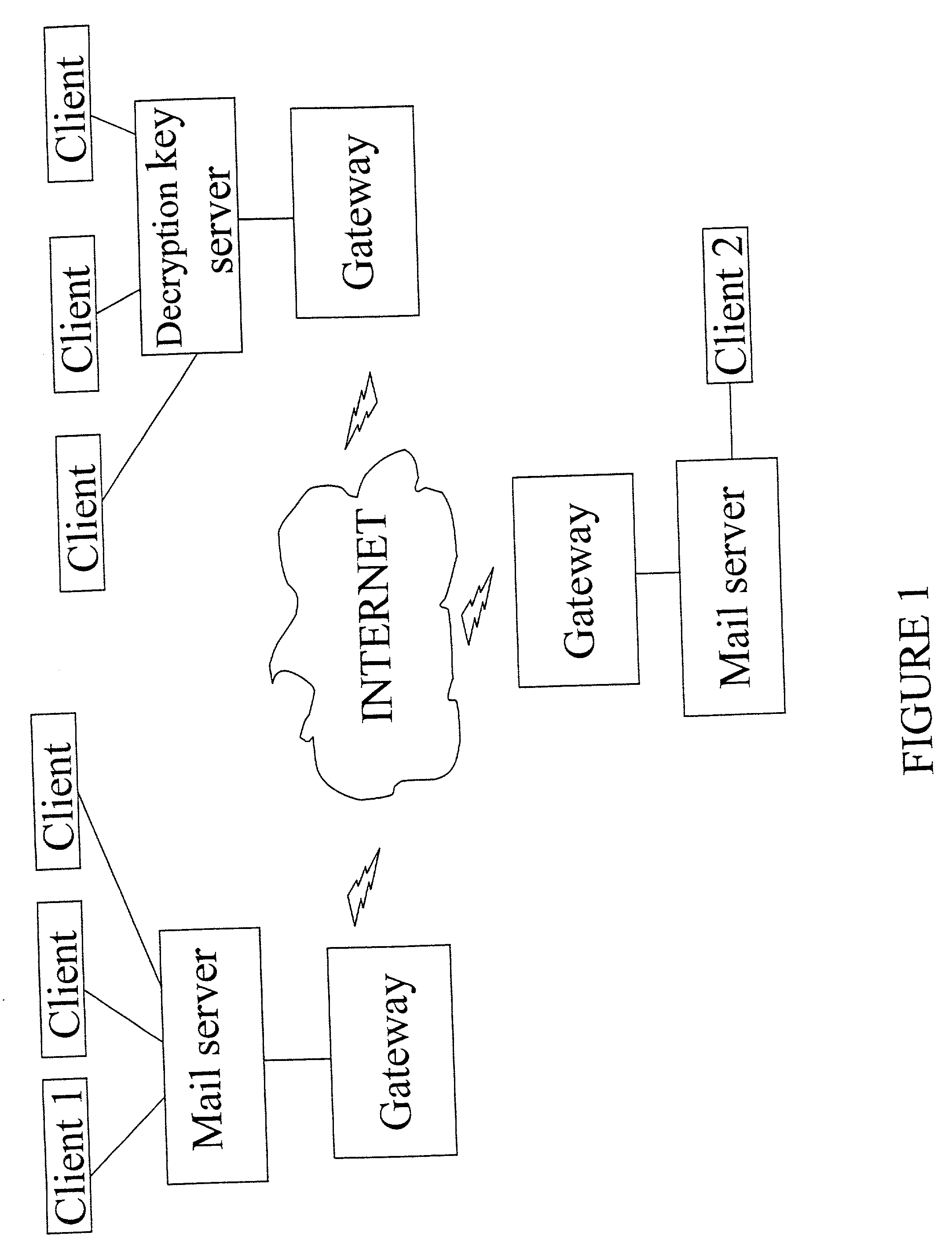
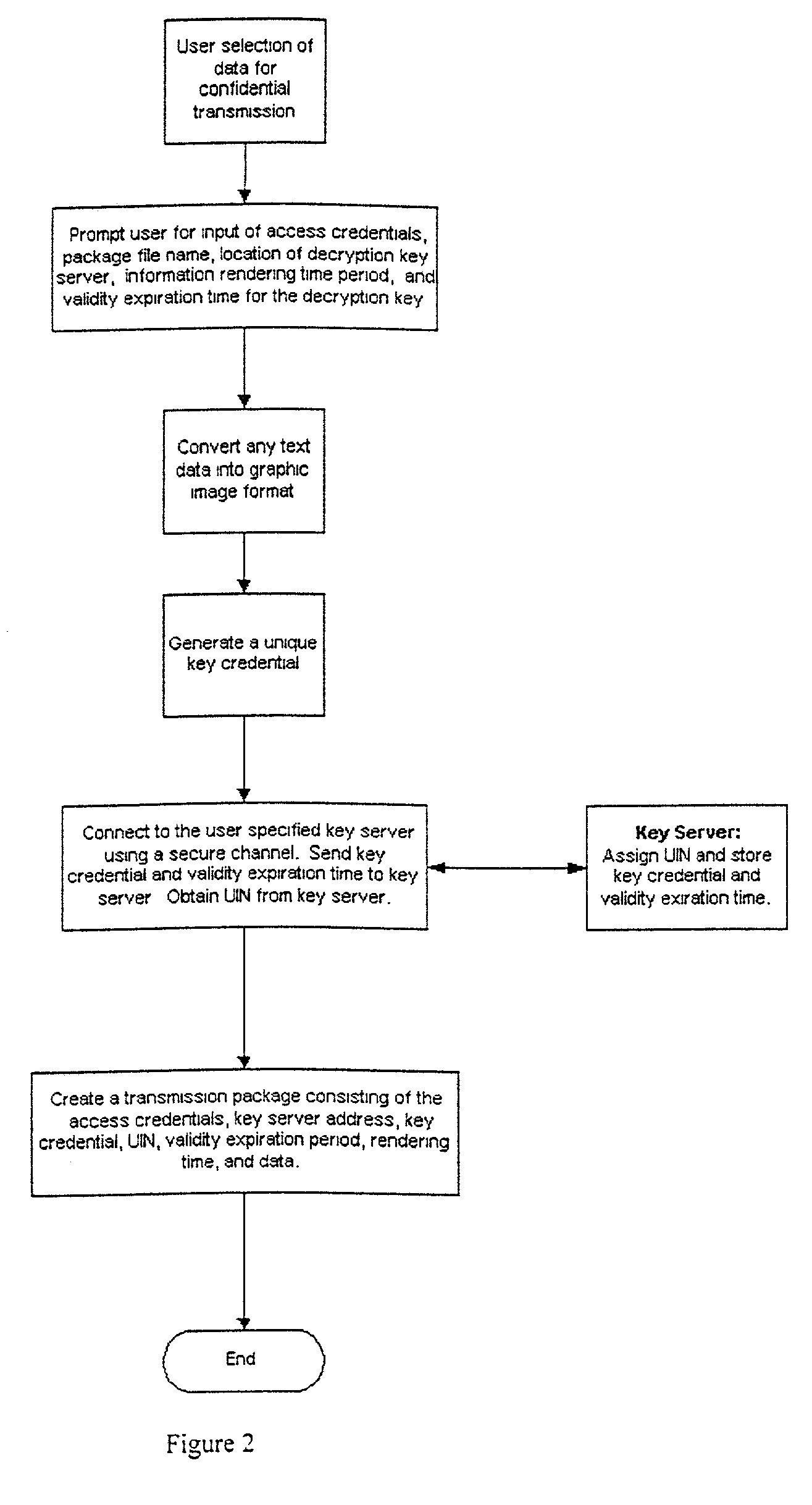
Encrypted data file transmission
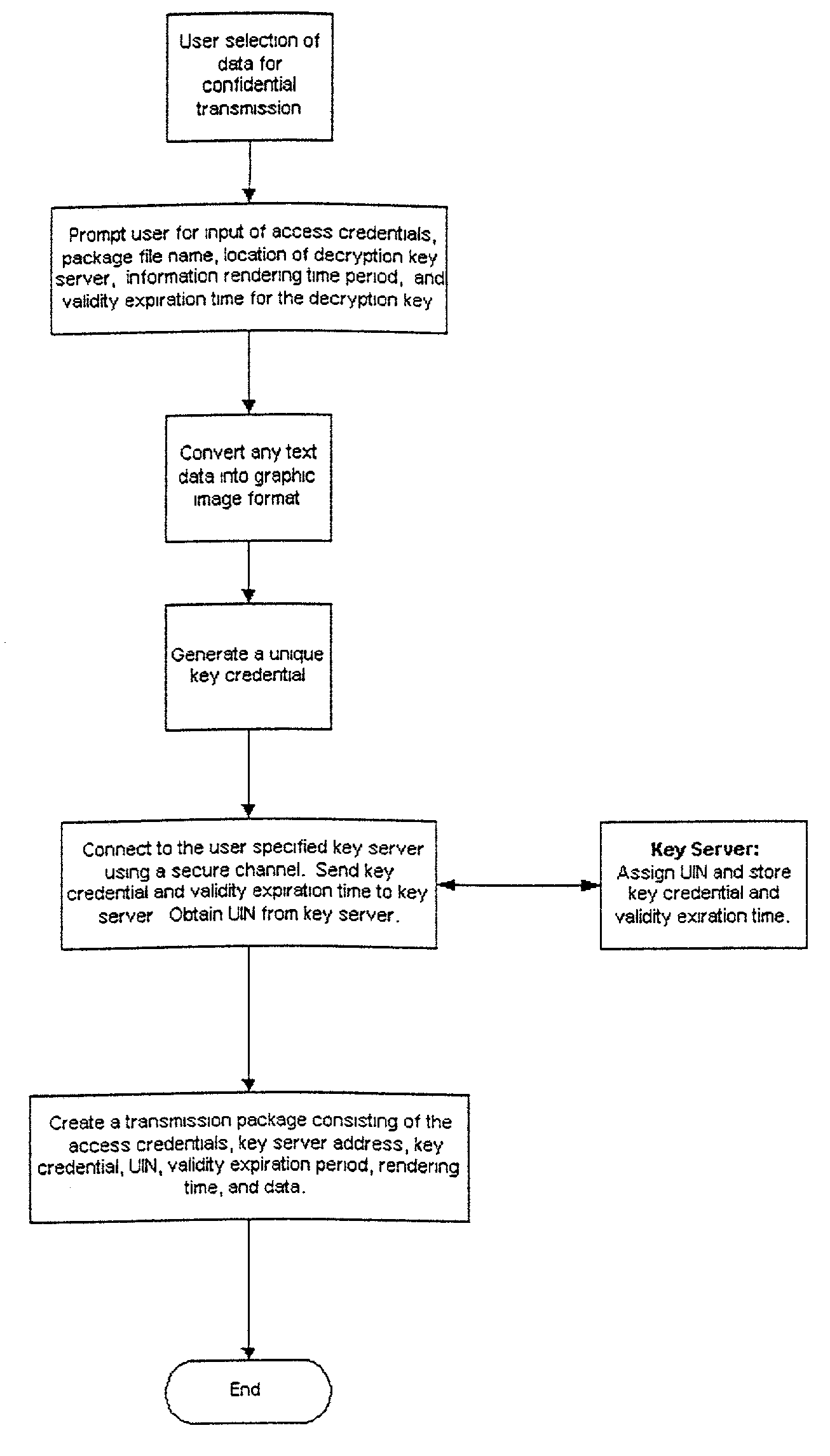
ActiveUS20020194470A1Reduce riskDigital data processing detailsDigital computer detailsComputer hardwareFile transmission
A mechanism for encrypting confidential information, uses a transmission package than can be attached to an electronic message. The transmission package is an executable application and controls the decryption, using a separately stored key, and rendering of the contents. On termination of the rendering of the information the transmission package triggers deletion of the encrypted file, the transmission package, and the separately stored key.
Owner:MCAFEE LLC
Network scanner for global document creation, transmission and management
InactiveUS7672003B2Enhanced interactionRemove uncertaintySpecial service for subscribersTime-division multiplexFile transmissionNetwork Communication Protocols
A network scanner, communication protocols, and client and server programs and are provided which provide an improved way to transmit legally binding documents, obviating the need for outmoded, legacy fax transmissions. Using the network scanner, a document may be scanned and transferred directly into any shared folder inbox residing on any computer attached to the Internet. Enhanced server systems and network communications and messaging protocols are provided that are more practical to use than email for sending documents such as executed legal documents or other documents requiring robust integrity and authenticatability. Similarly, the inventive network scanner, server systems and communication protocols provide improved ways to perform large file transfers and to manage bandwidth to minimize problems associated with uploading / downloading large files as attachments to / from email servers and for enabling user control over VoIP quality during file transmission sessions.
Owner:INTELLECTUAL PROPERTIES I KFT
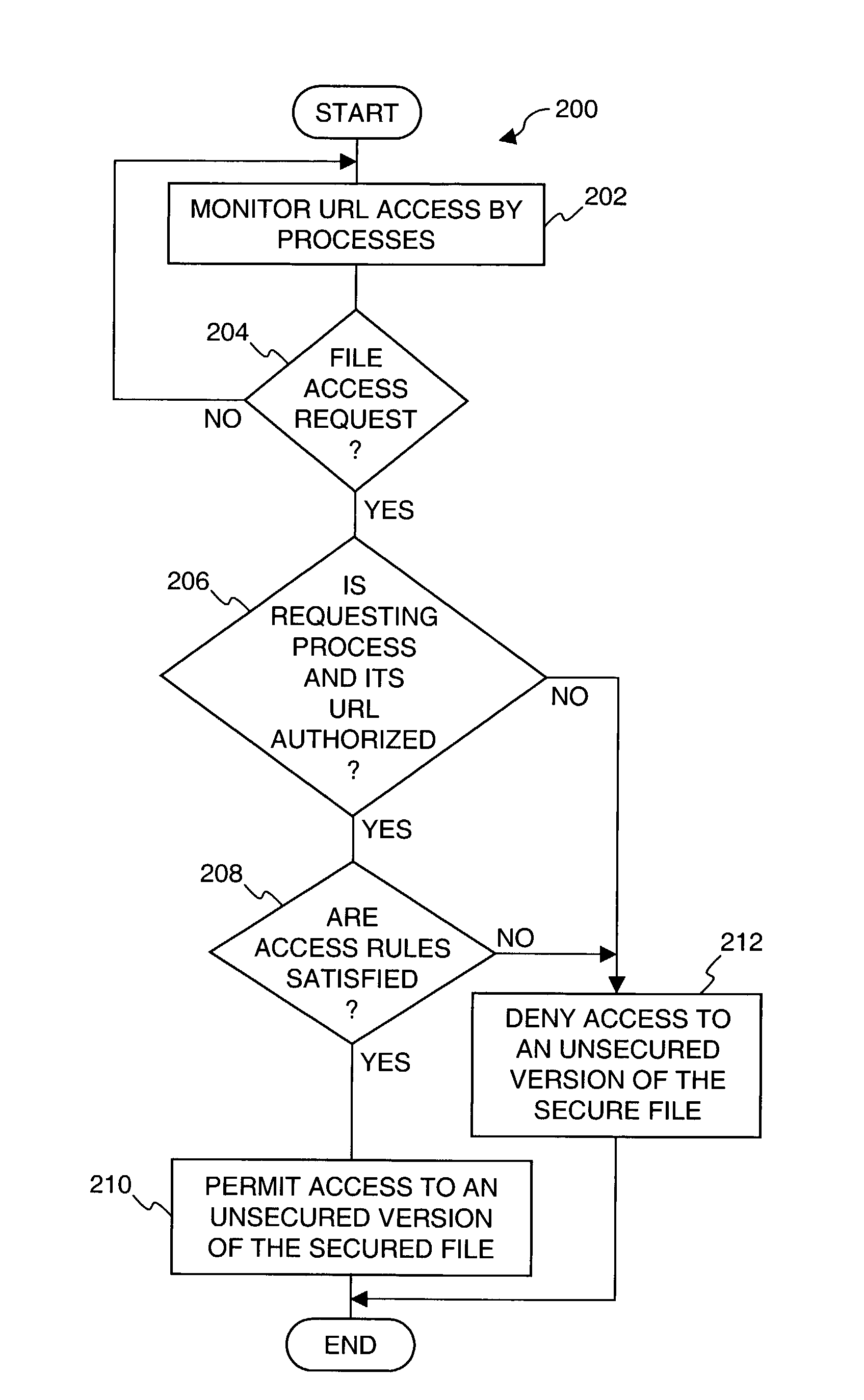
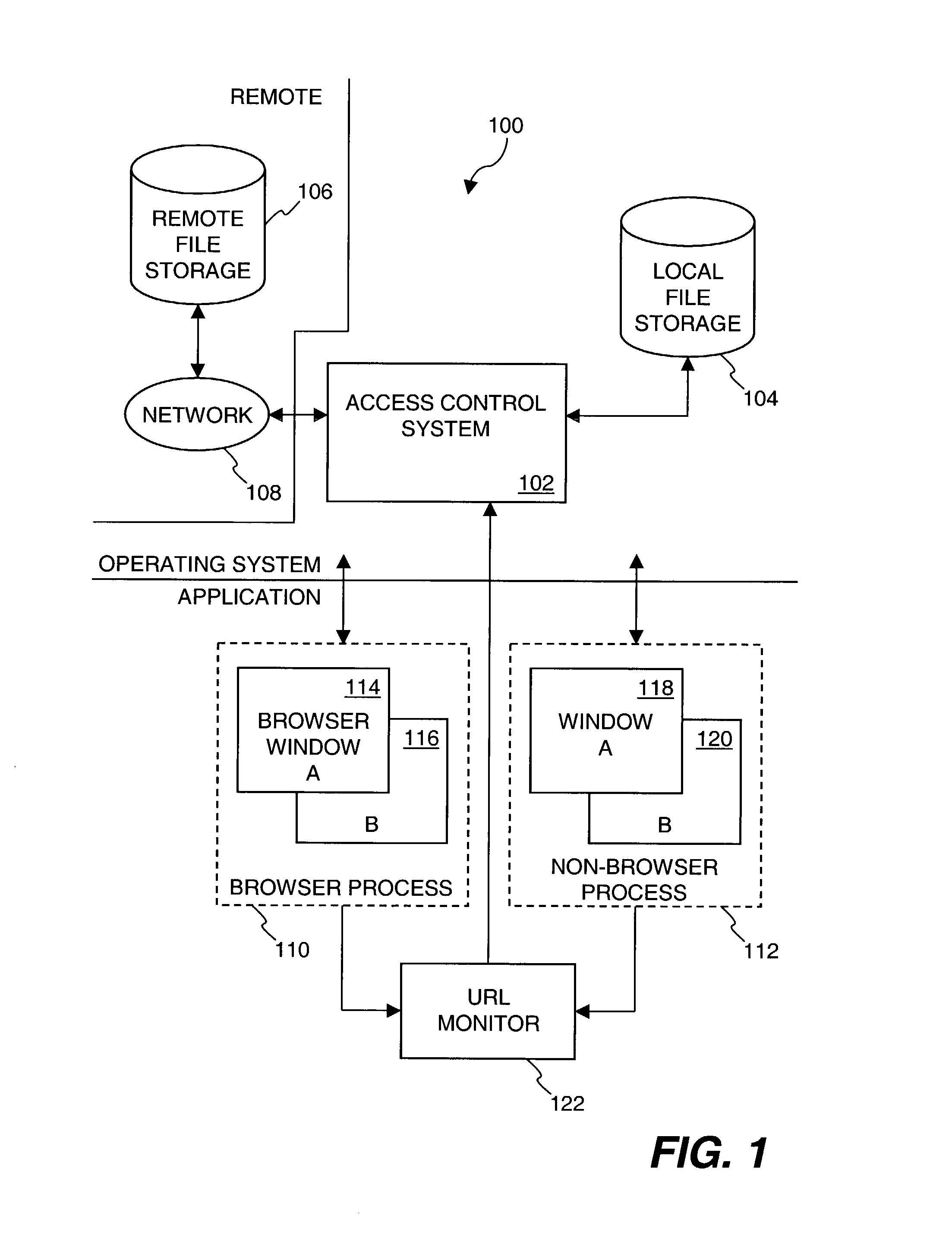
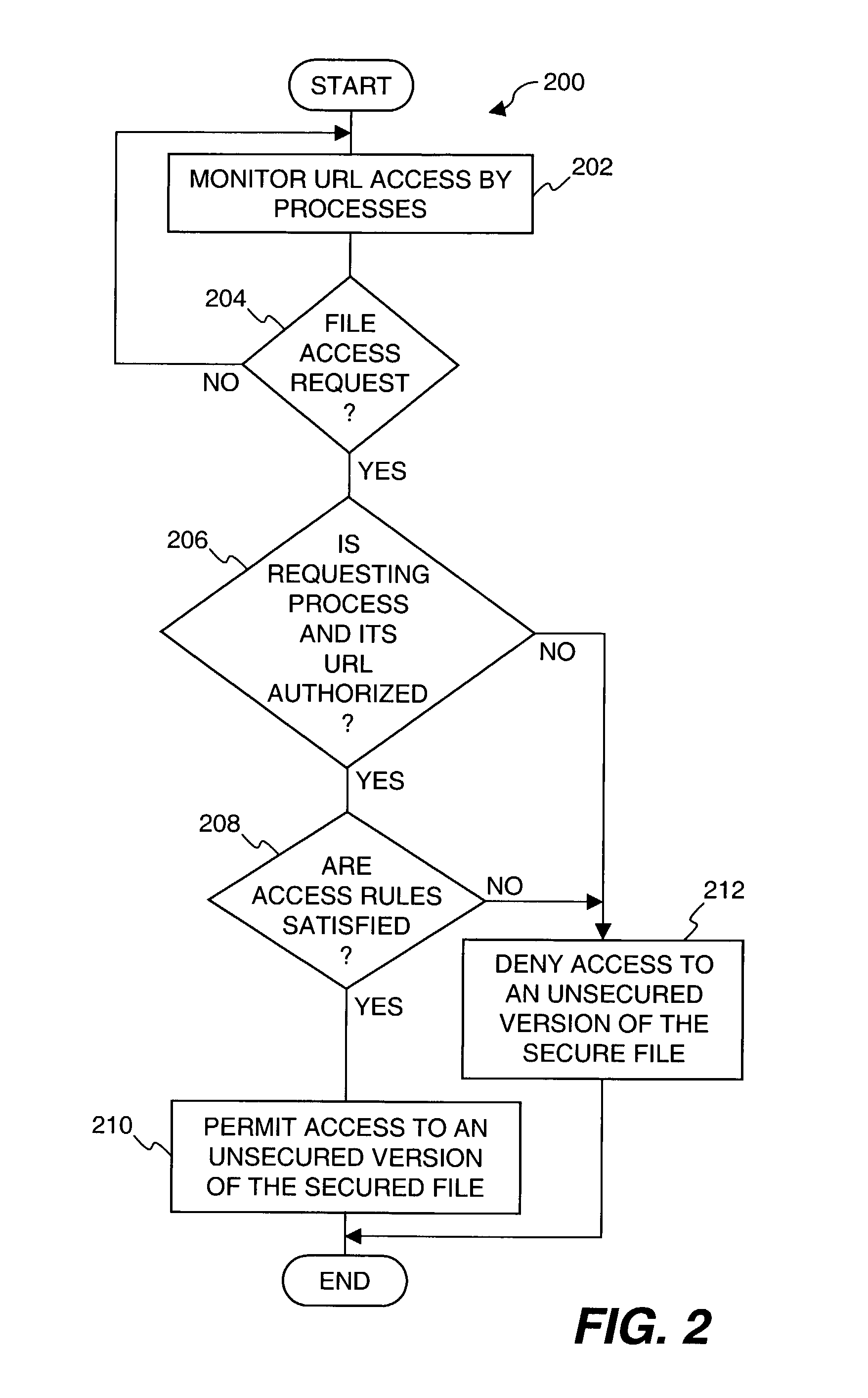
Method and system for protecting encrypted files transmitted over a network
ActiveUS7512810B1Digital data processing detailsUser identity/authority verificationThe InternetComputerized system
An improved system and approaches for protecting secured files when being used by an application (e.g., network browser) that potentially transmits the files over a network to unknown external locations are disclosed. According to one aspect, access to secured files is restricted so that unsecured versions of the secured files are not able to be transmitted over a network (e.g., the Internet) to unauthorized destinations. In one embodiment, in opening a file for use by a network browser, the network browser receives a secured (e.g., encrypted) version of the secured file when the destination location (e.g., destination address) for the network browser is not trusted, but receives an unsecured (e.g., unencrypted) version of the secured file when the destination location for the network browser is trusted. According to another aspect, processes operating on a computer system are monitored to determine destination locations, if any, of said processes, and then using such destination locations to determine whether to permit the processes to open files in a secure or unsecured manner.
Owner:KIOBA PROCESSING LLC
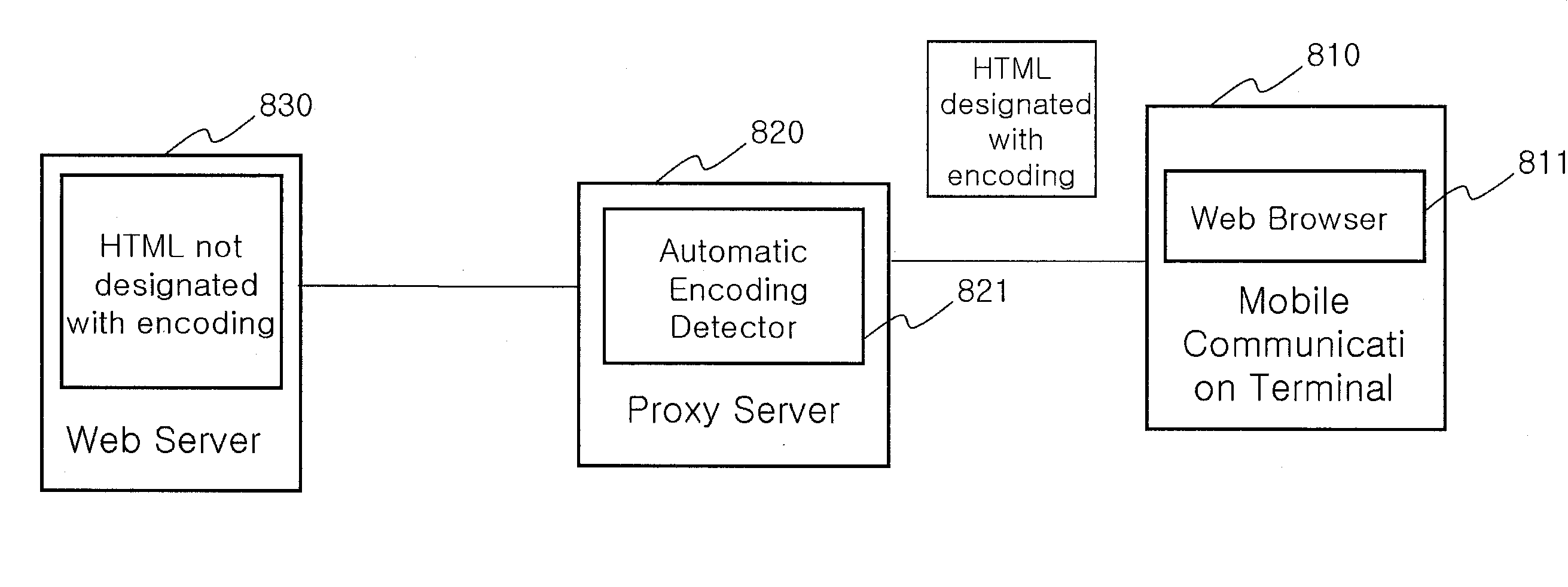
Web browser system of mobile communication terminal, using proxy server
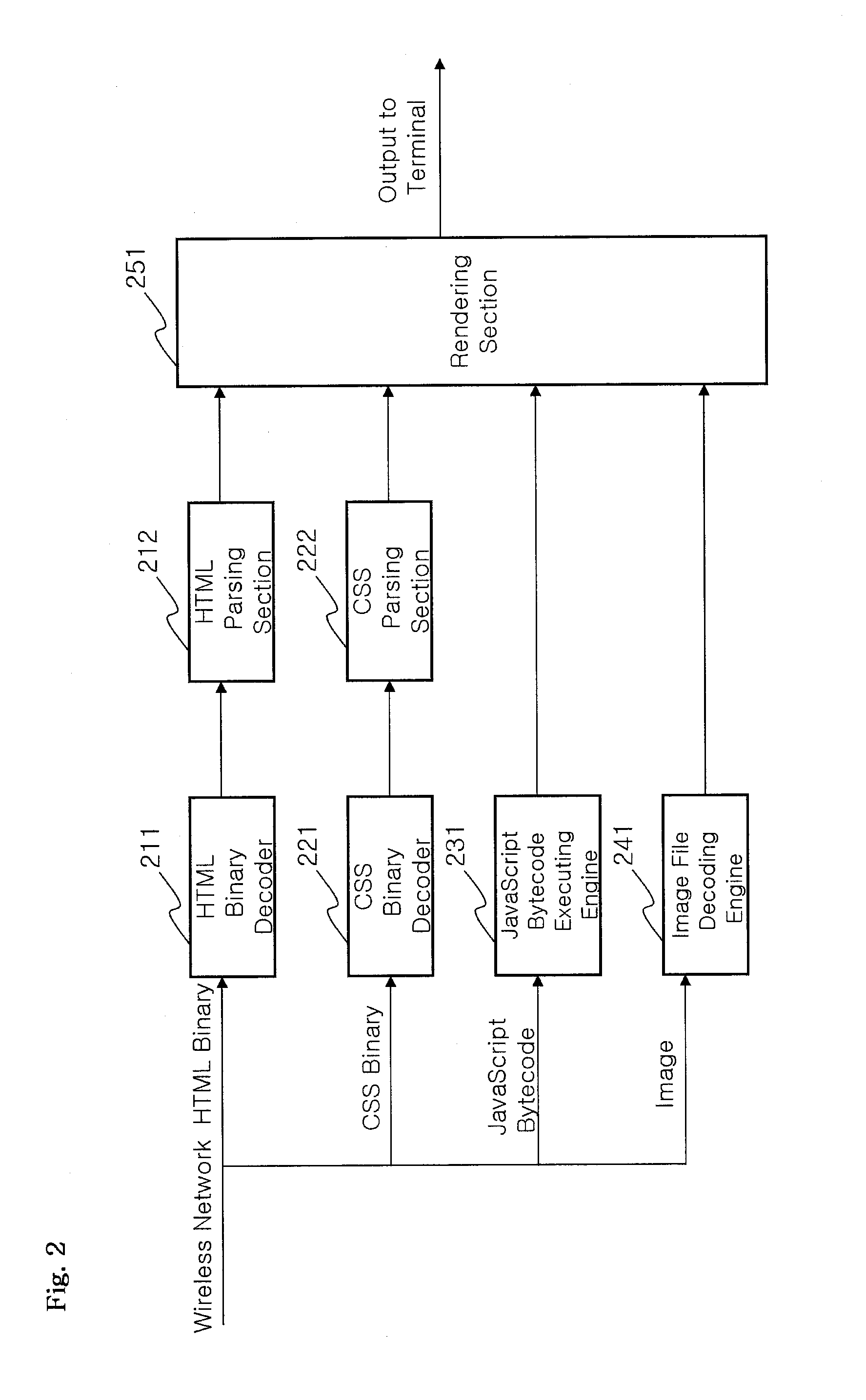
InactiveUS20100050089A1Improve processing speedDecreasing an amount of wireless transmission dataMultiple digital computer combinationsTransmissionFile transmissionWeb browser
A web browser system includes a mobile communication terminal configured to implement decoding and parsing for HTML and CSS binary files, execute a JavaScript bytecode, decode an image file, and implement rendering for respective results, for web browsing of a web browser built therein; a proxy server configured to, in correspondence to a web address transmitted thereto, transmit a page access command to a web server of the corresponding web address via a wired network, implement grammar indentifying binary encoding for HTML and CSS transmitted from the web server to decrease capacity, convert quality for an image file to decrease capacity, compile JavaScript into a bytecode to decrease capacity, and transmit those files to the mobile communication terminal via a wireless network; and a web server configured to transmit files constituting a web page including the HTML, CSS, JavaScript and image files, to the proxy server.
Owner:COMPANY 100 LNC
System and method for uploading files
InactiveUS20070035764A1Fast access timeFast transfer timeStill image data indexingData switching networksFile transmissionAccess time
According to various aspects and examples described herein, systems and methods for uploading / transferring files are provided. In one aspect, an upload manager is provided, the upload manager for coordinating a transfer of an image file to a remote location. In one example, the upload manger includes logic for creating a reduced size image file associated with the image file, the reduced size image file having a smaller data size than the image file, initiating a transfer of the reduced size image file to the remote location, and initiating a transfer of the image file to the remote location subsequent to initiating the transfer of the reduced size image file. Transferring a reduced size image file (e.g., a thumbnailed version) may allow for relatively fast transfer and access times of the reduced size file compared to the full size version image file.
Owner:OATH INC
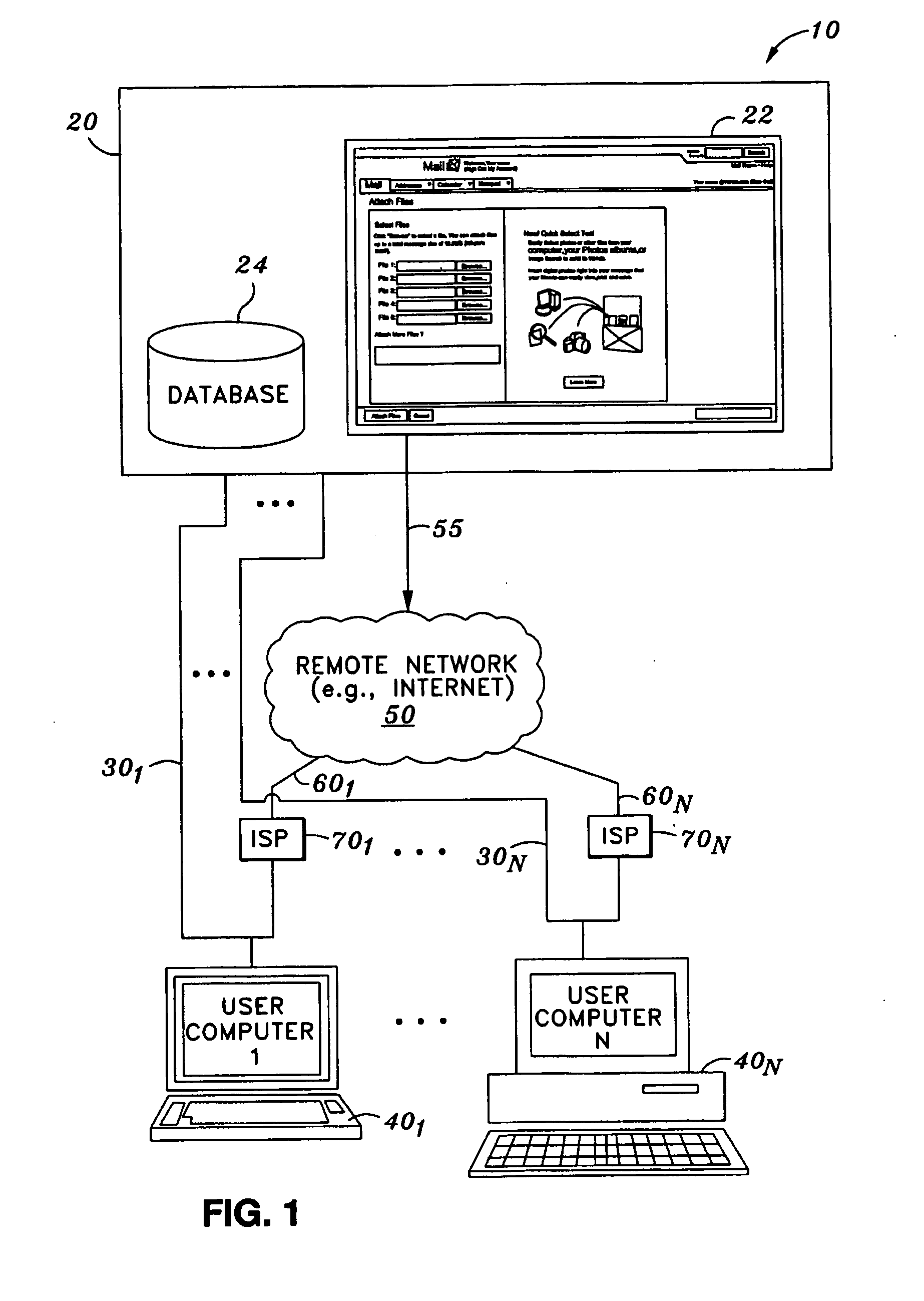
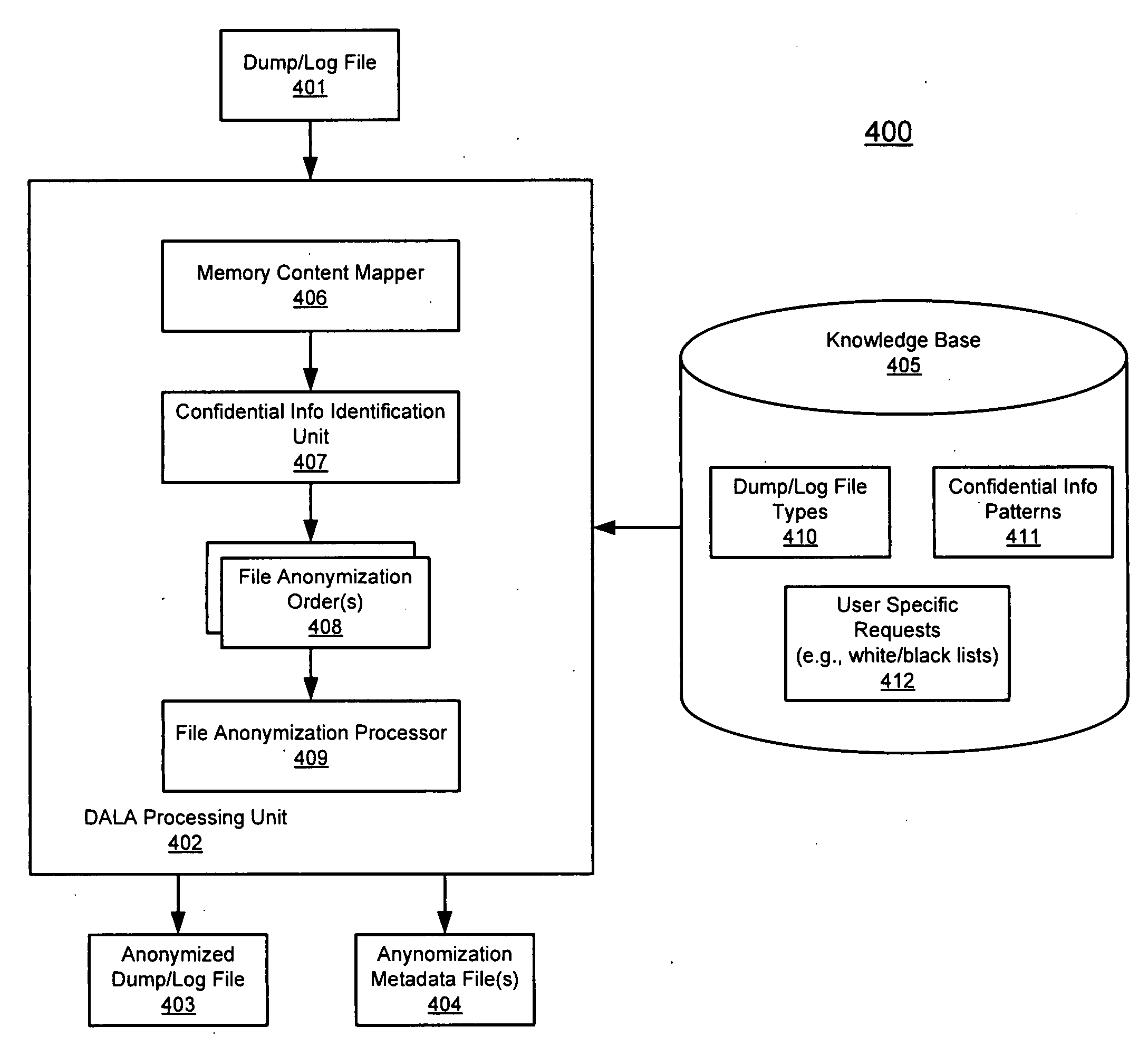
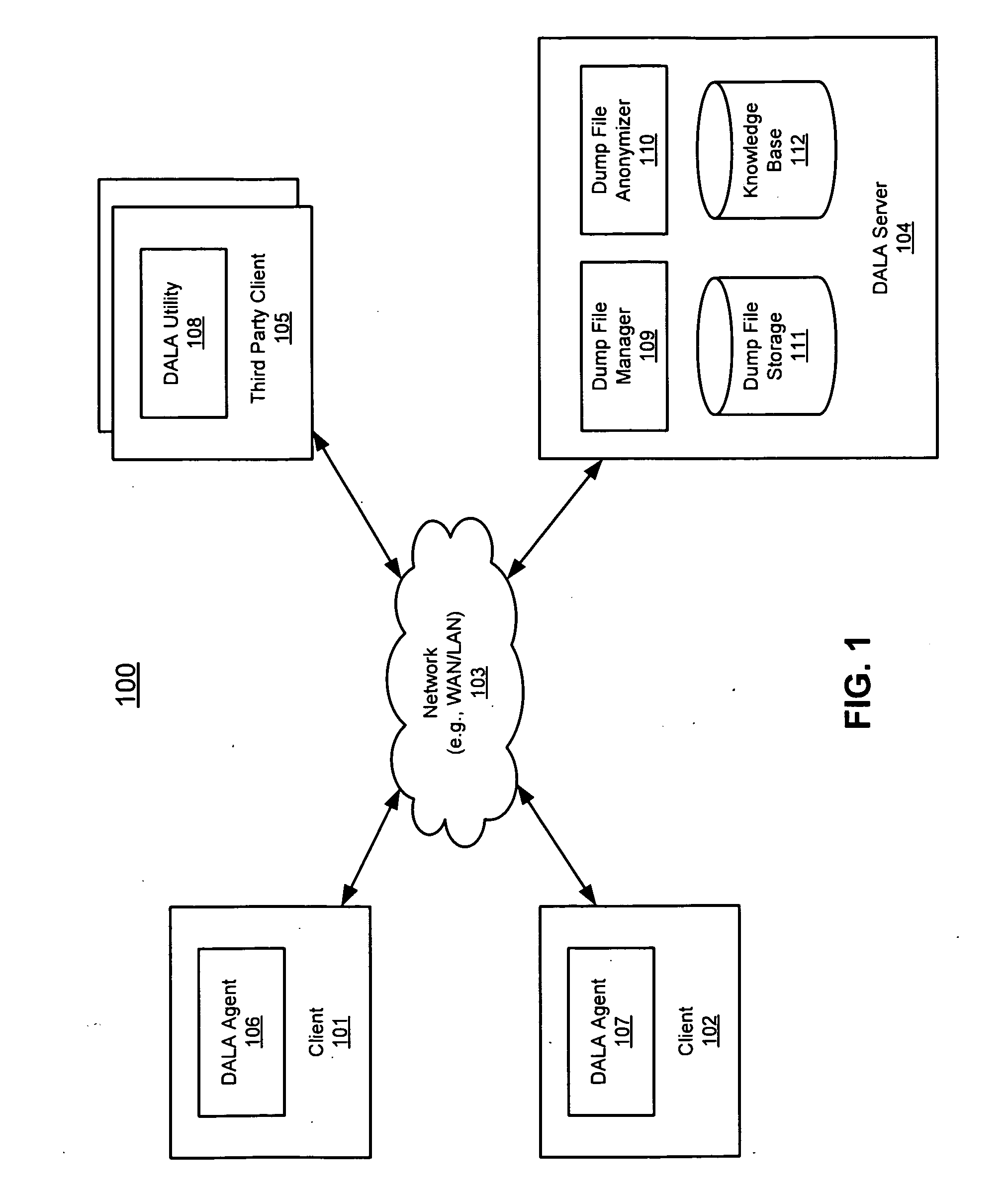
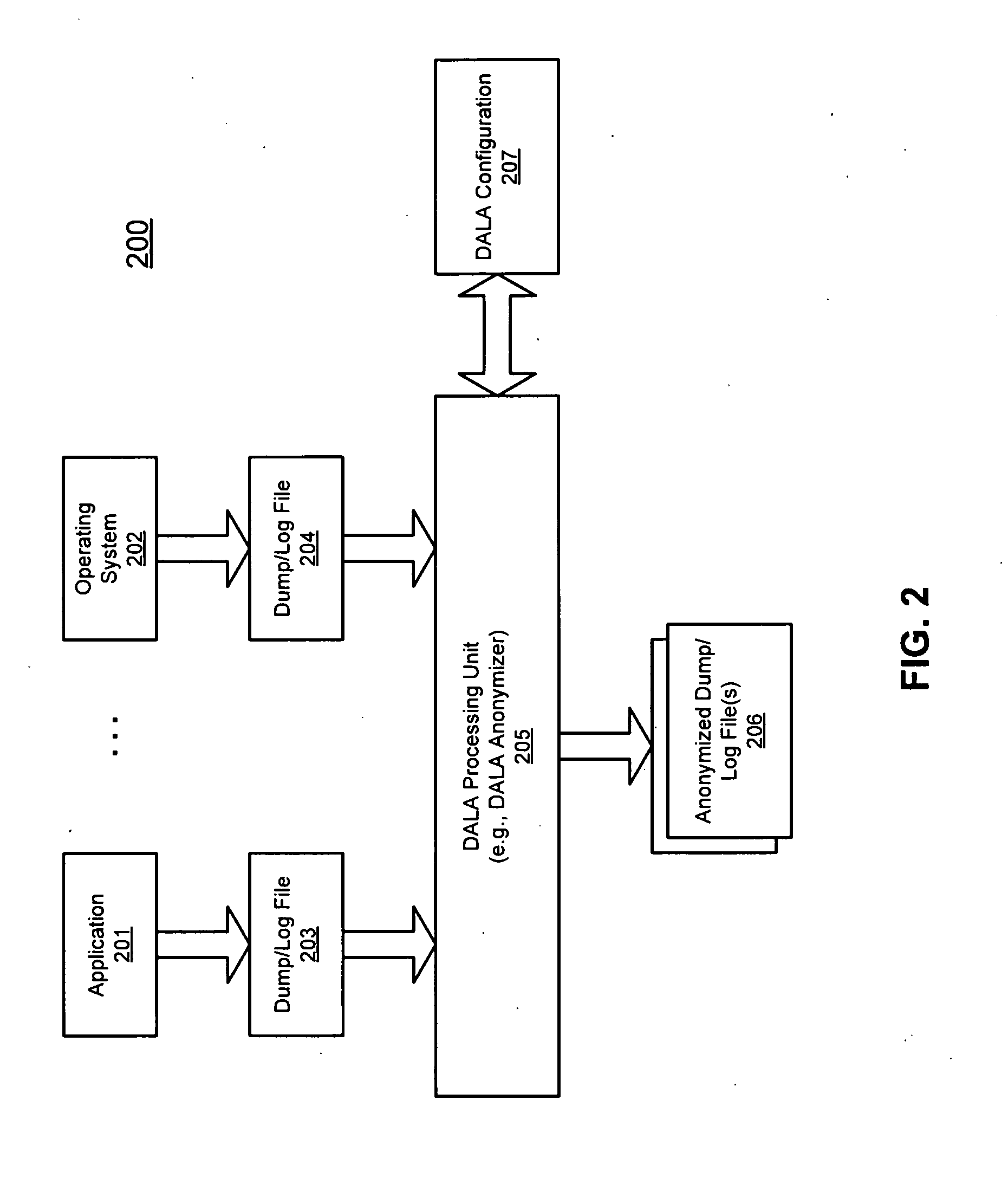
Method and apparatus for dump and log anonymization (DALA)
ActiveUS20090282036A1Digital data processing detailsUnauthorized memory use protectionFile transmissionClient machine
According to one embodiment of the invention, an original dump file is received from a client machine to be forwarded to a dump file recipient. The original dump file is parsed to identify certain content of the original dump file that matches certain data patterns / categories. The original dump file is anonymized by modifying the identified content according to a predetermined algorithm, such that the identified content of the original dump file is no longer exposed, generating an anonymized dump file. The anonymized dump file is then transmitted to the dump file recipient. Technical content and infrastructure of the original dump file is maintained within the anonymized dump file after the anonymization, such that a utility application designed to process the original dump file can still process the anonymized dump file without exposing the identified content of the original dump file to the dump file recipient. Other methods and apparatuses are also described.
Owner:FEDTKE STEPHEN U
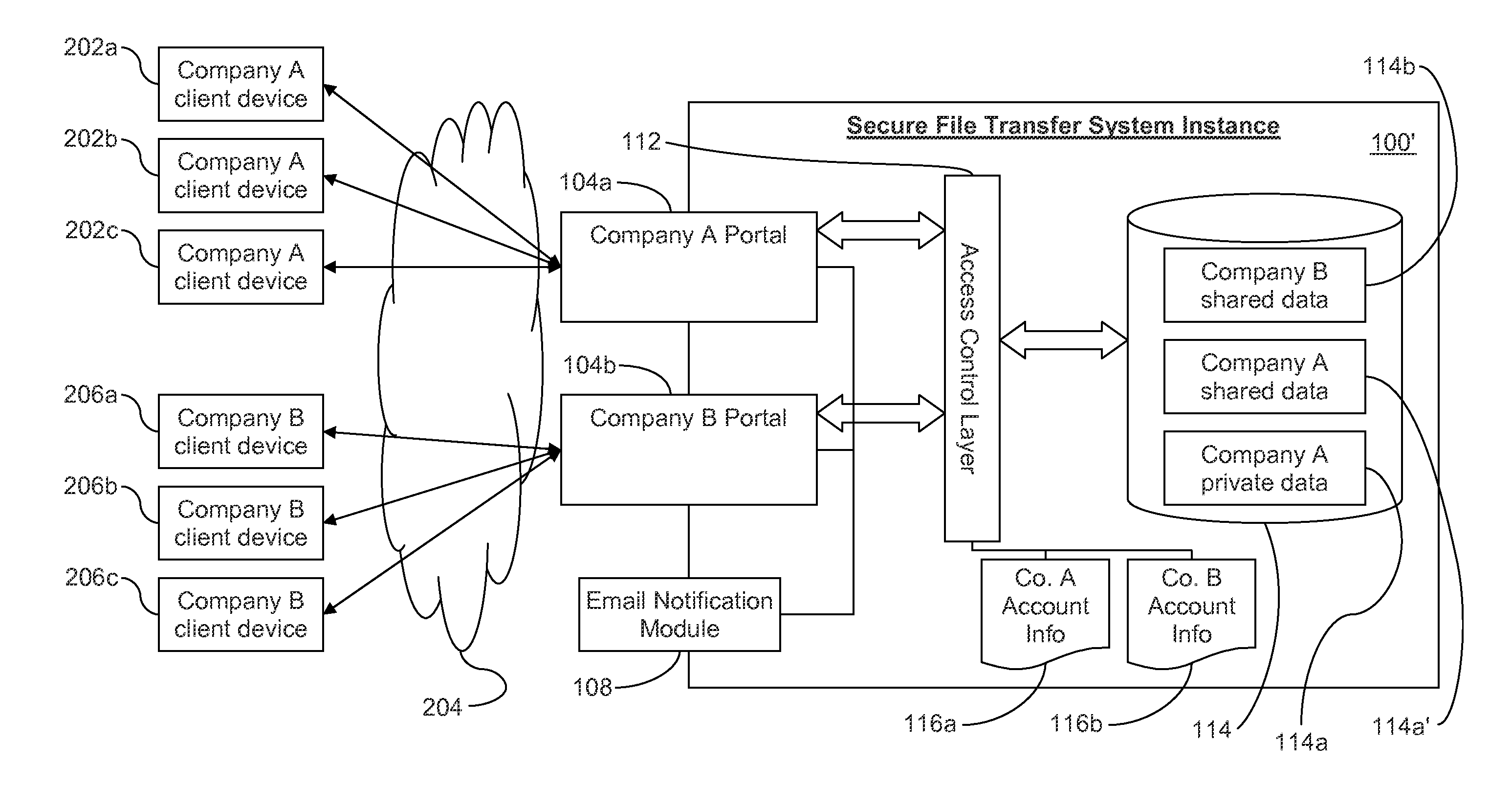
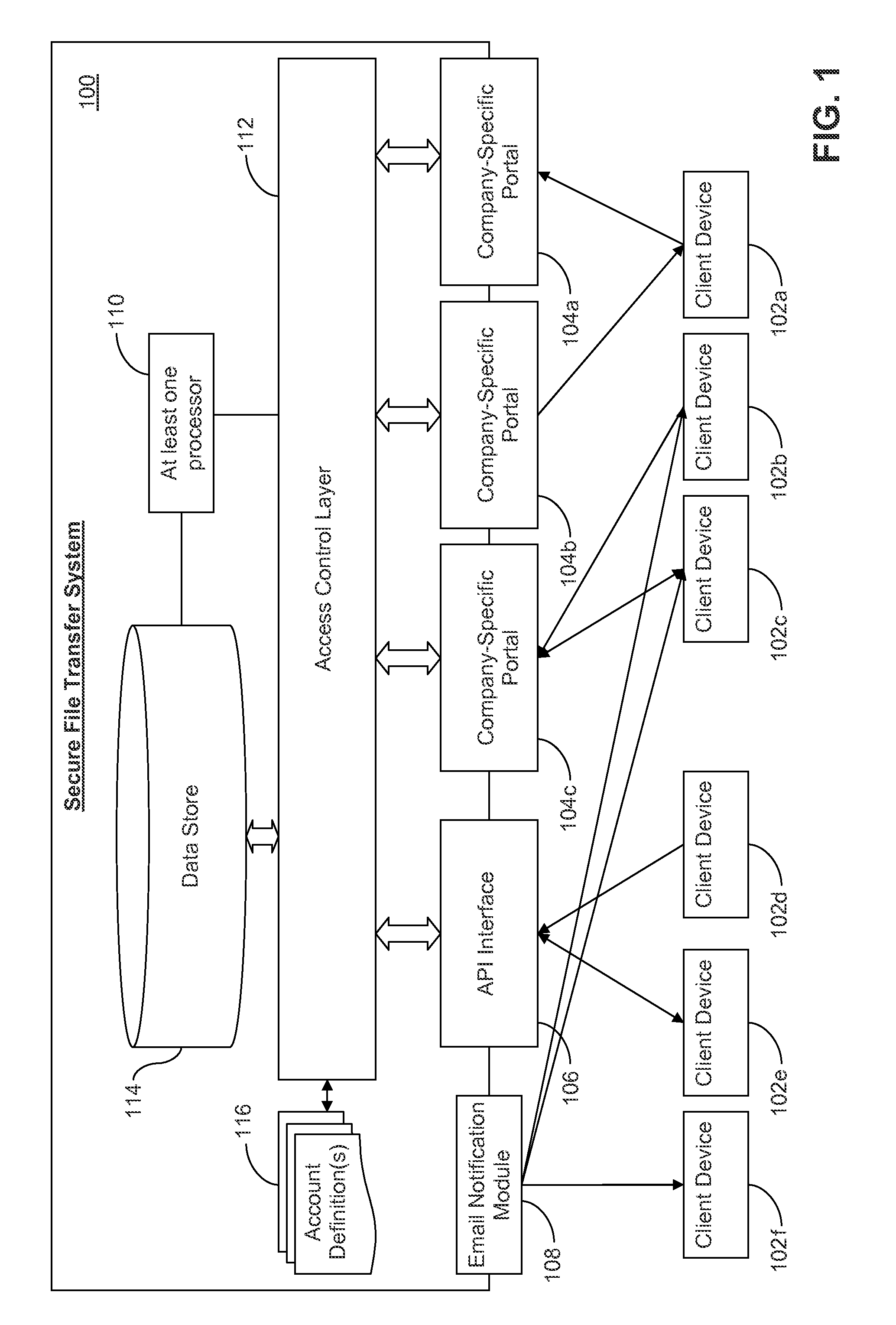
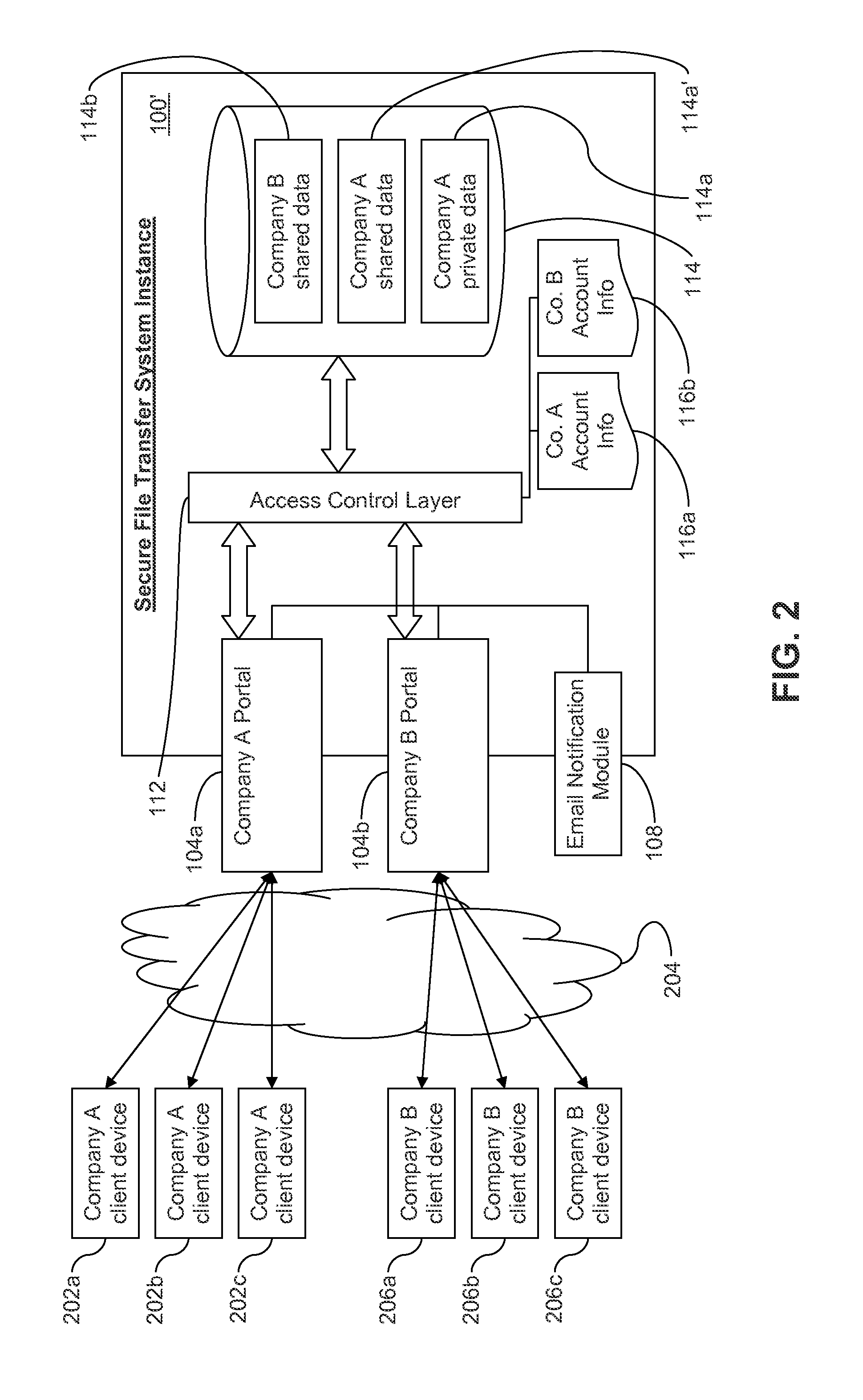
Secure file transfer systems and methods
ActiveUS20150242643A1Environmental impactNew efficiencyDigital data processing detailsAnalogue secracy/subscription systemsFile transmissionDeployment time
Certain example embodiments relate to file transfer systems and / or methods that enable a single provider to offer to different customers customizable file transfer solutions that are secure, scalable to handle enterprise-level amounts of data, and able to meet customer-specific needs even though such needs are not necessarily known in advance. Once initially set up, the file transfer solution of certain example embodiments delegates management of the customer-specific instances of the solution, optionally in a sub-delegatable manner and, thus, the single provider need not be consulted after specific initial instance deployment time (e.g., for security management and / or other routine maintenance issues).
Owner:AITHERAS +1
On-demand file transfers for mass P2P file sharing
InactiveUS7613770B2Digital data information retrievalMultiple digital computer combinationsFile transmissionDirectory structure
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
Automatic rules-based device synchronization
ActiveUS7647346B2Improve experienceDigital data information retrievalData processing applicationsData synchronizationFile synchronization
Owner:MICROSOFT TECH LICENSING LLC
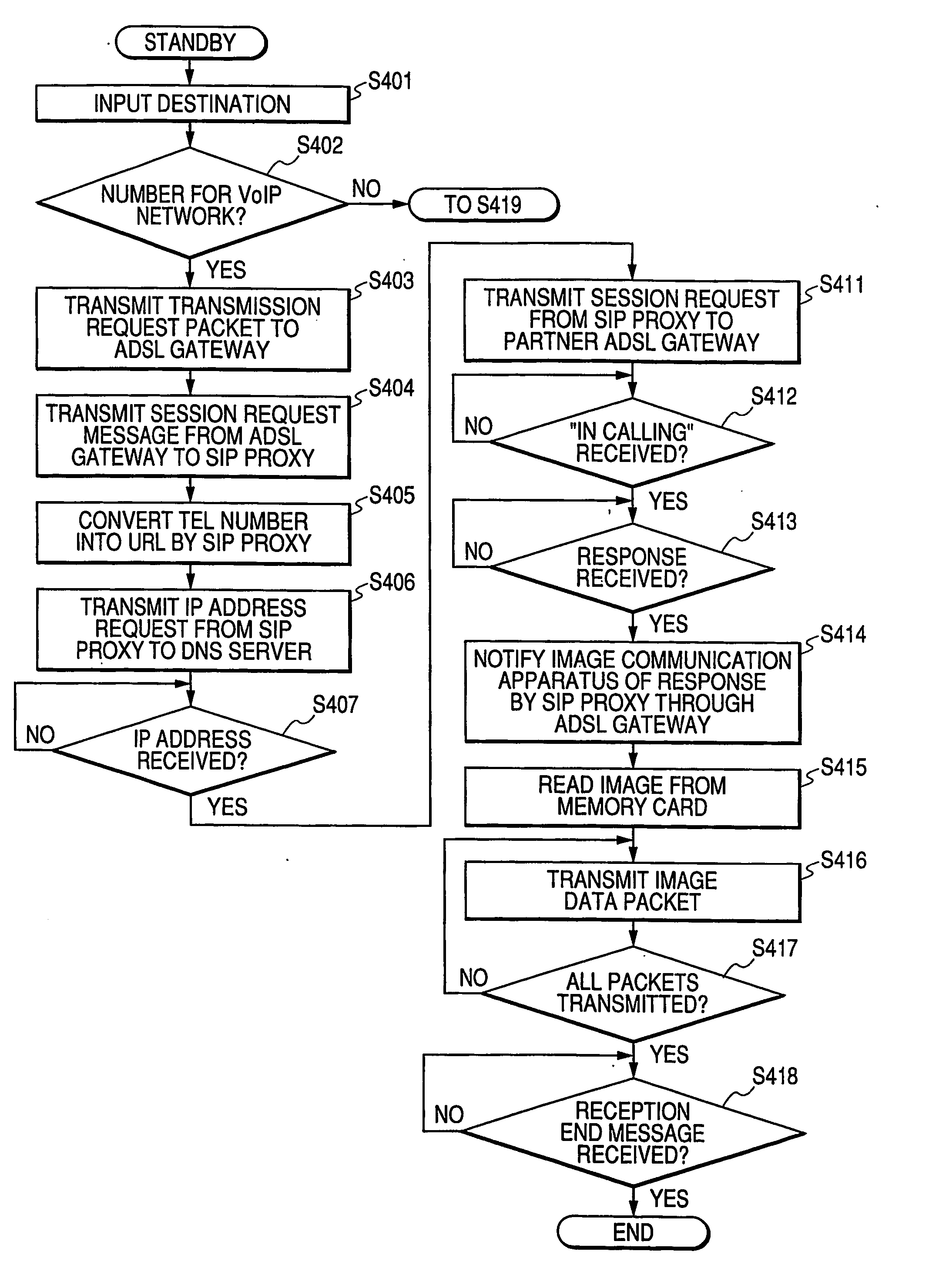
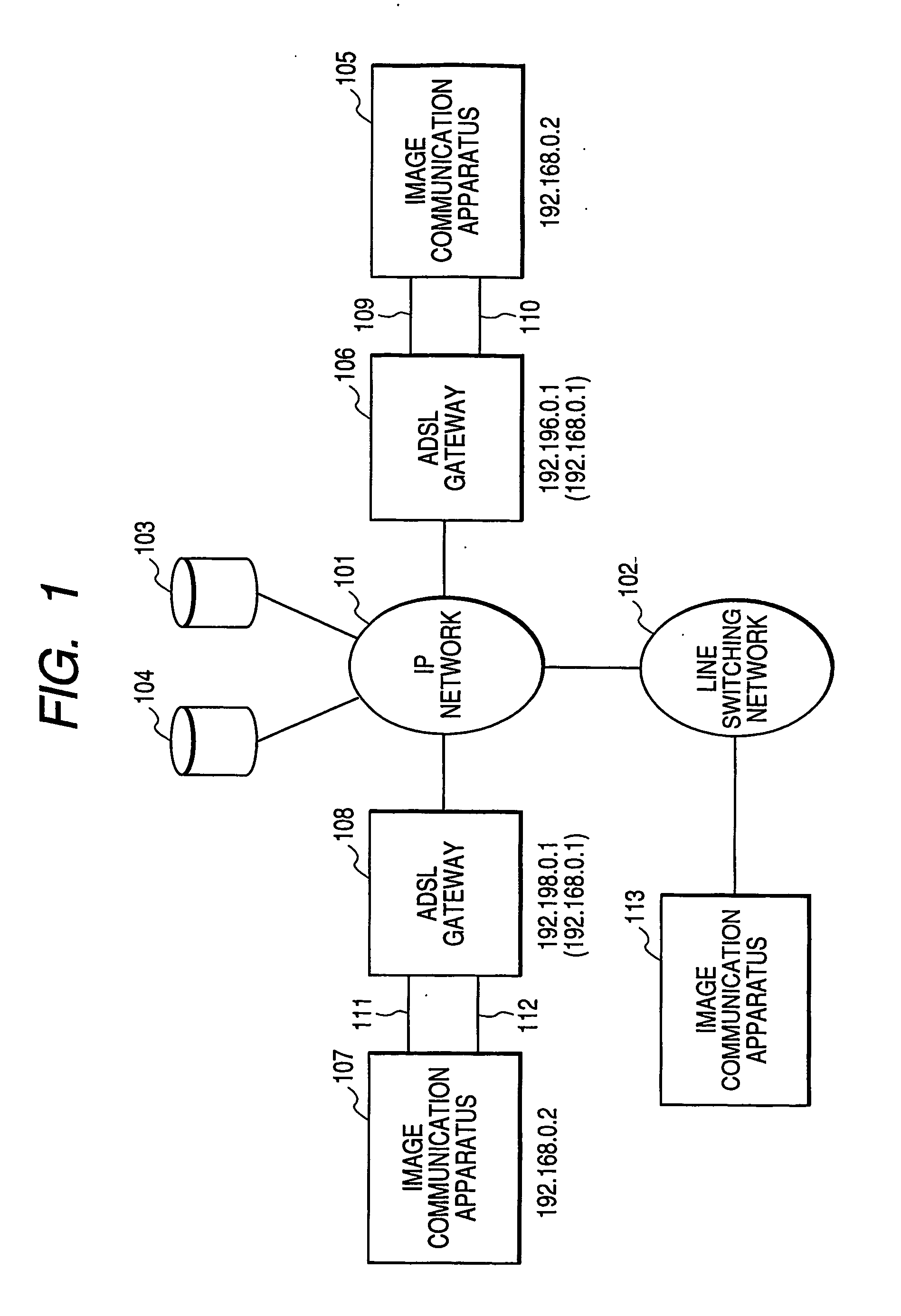
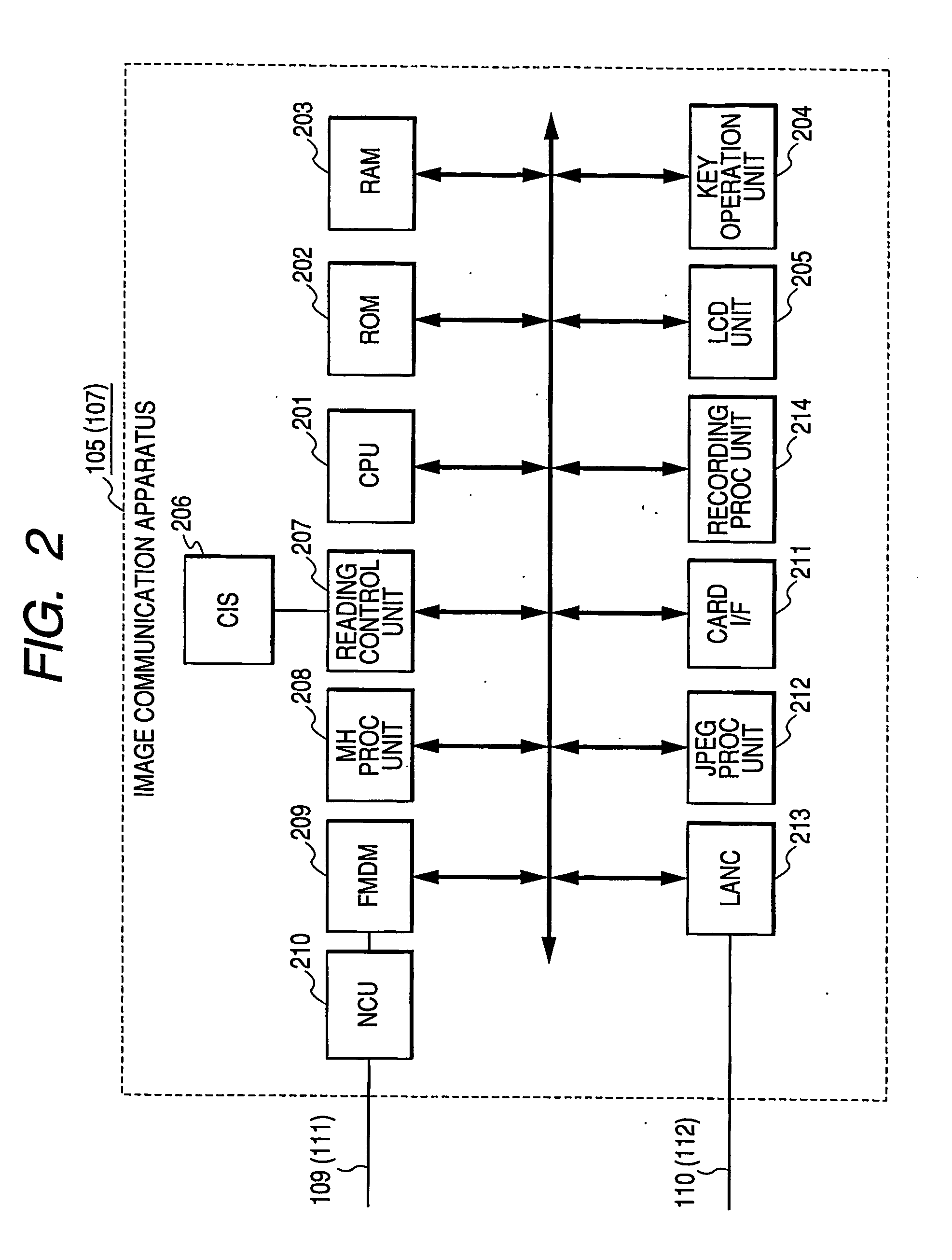
Communication apparatus, control method of communication apparatus, and control program of communication apparatus
InactiveUS20060136596A1Telephonic communicationData switching by path configurationFile transmissionIp address
In a communication apparatus corresponding to a voice-band analog communication path and a network communication path, high-speed and high-reliability data communication is achieved by selecting the appropriate communication path without any complicated user operation. The communication apparatus which performs IP communication and analog communication through an ADSL gateway obtains a communication partner IP address from an SIP proxy when a communication partner telephone number corresponds to a VoIP network, and transmits / receives communication data to / from the communication partner on an IP network based on a file transmission / reception protocol such as FTP, HTTP, or the like. The communication apparatus performs analog facsimile communication on a line switching network when the communication partner telephone number does not correspond to the VoIP network, and performs the analog facsimile communication when the communication partner corresponds to the VoIP network but does not have any digital communication means.
Owner:CANON KK
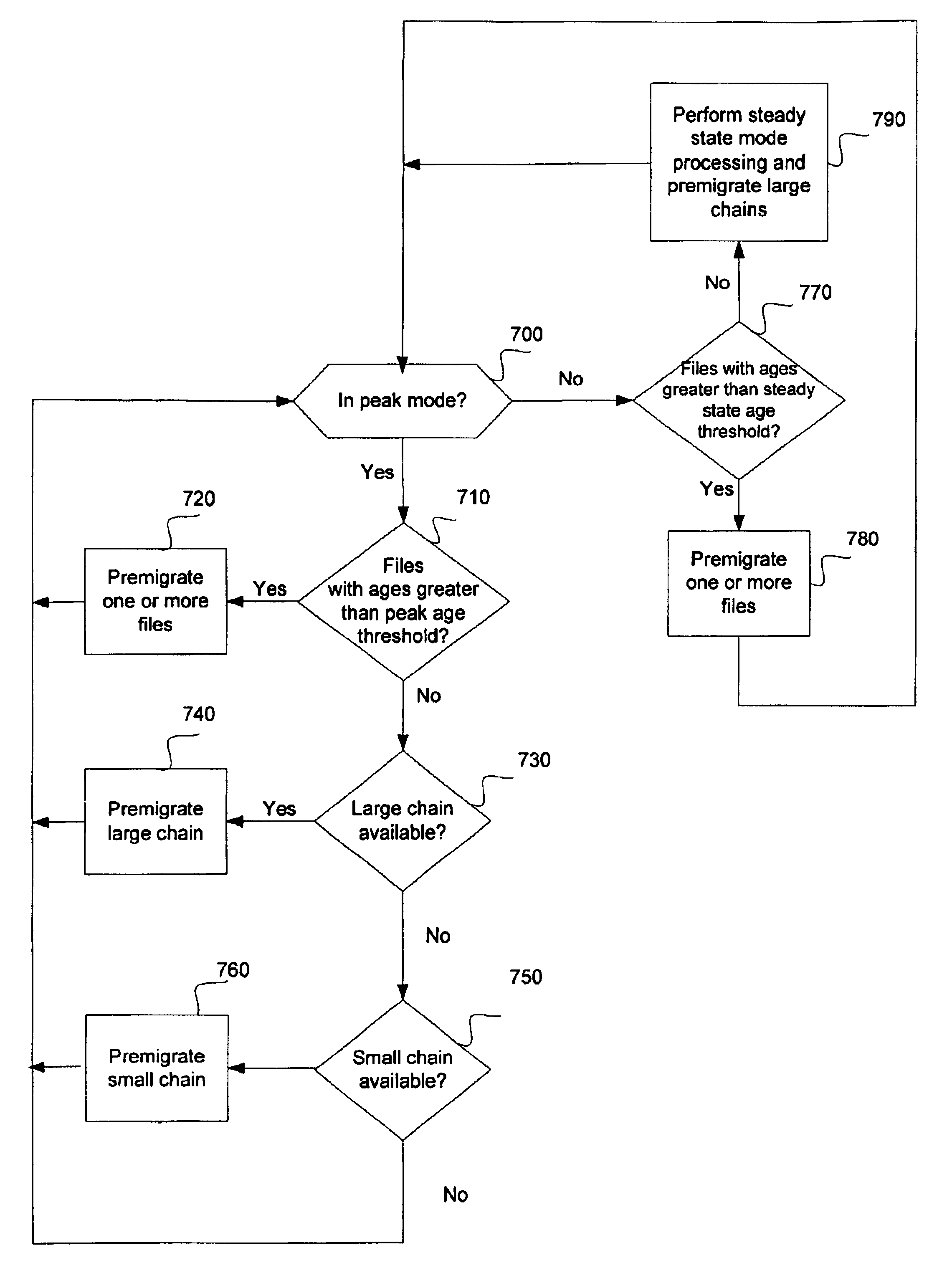
Transferring data in virtual tape server, involves determining availability of small chain of data, if large chain is not available while transferring data to physical volumes in peak mode
ActiveUS6978325B2Input/output to record carriersMemory adressing/allocation/relocationComputer hardwareFile transmission
Disclosed is a system, method, and program for transferring data. Whether data is being transferred to physical volumes in peak mode is identified. If the data is being transferred in peak mode, whether a large chain of data is available for transfer to physical volumes is determined. If the large chain of data is not available, whether a small chain of data is available for transfer to physical volumes is determined. If the small chain of data is available, the small chain of data is transferred to physical volumes. Additionally, if one or more files that have ages greater than a steady state age threshold are available, the one or more files are transferred to the one or more physical volumes. If one or more files that have ages greater than a peak age threshold are available, the one or more files are transferred to the one or more physical volumes.
Owner:IBM CORP
System and method providing a binary representation of a web page
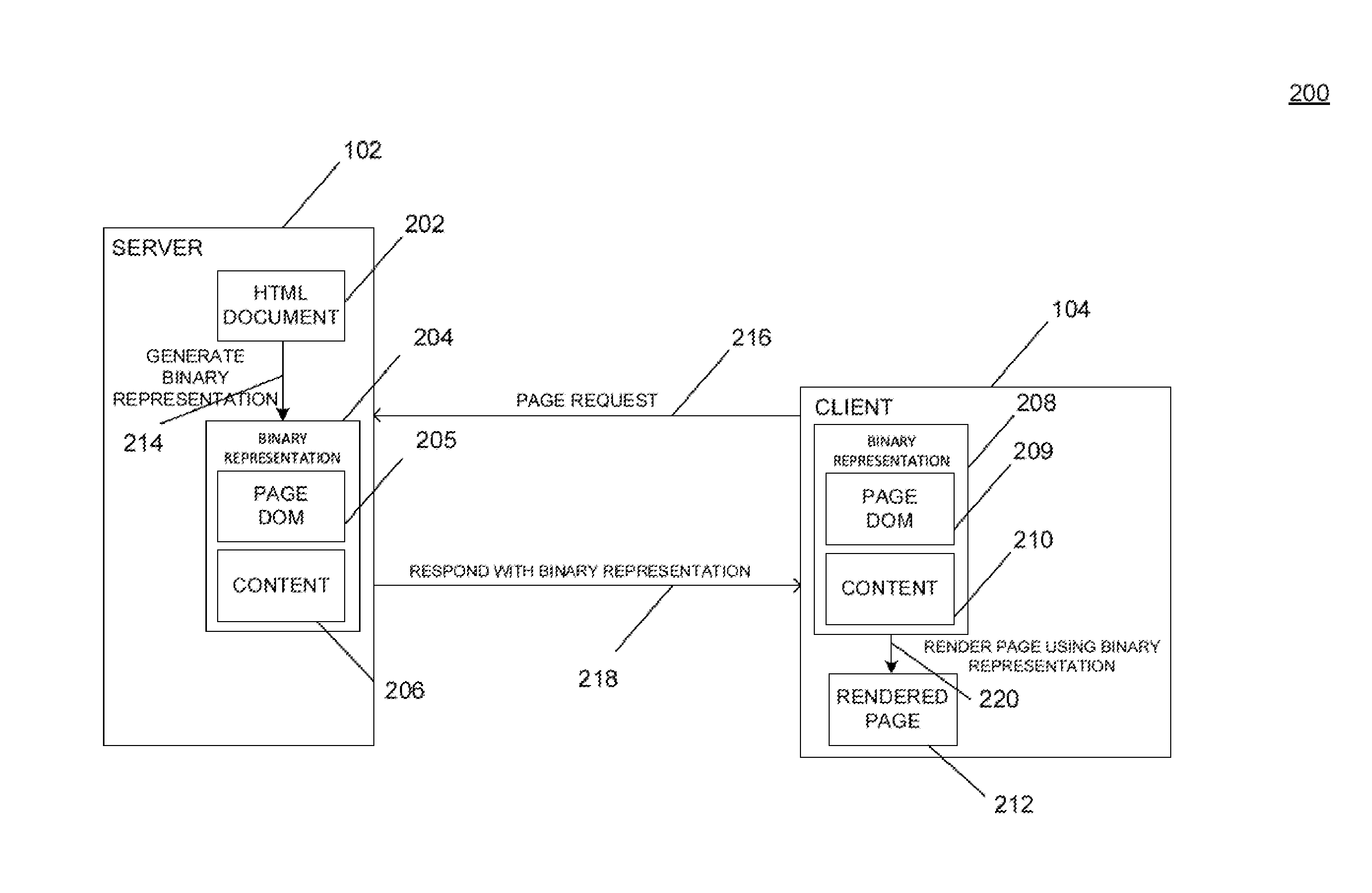
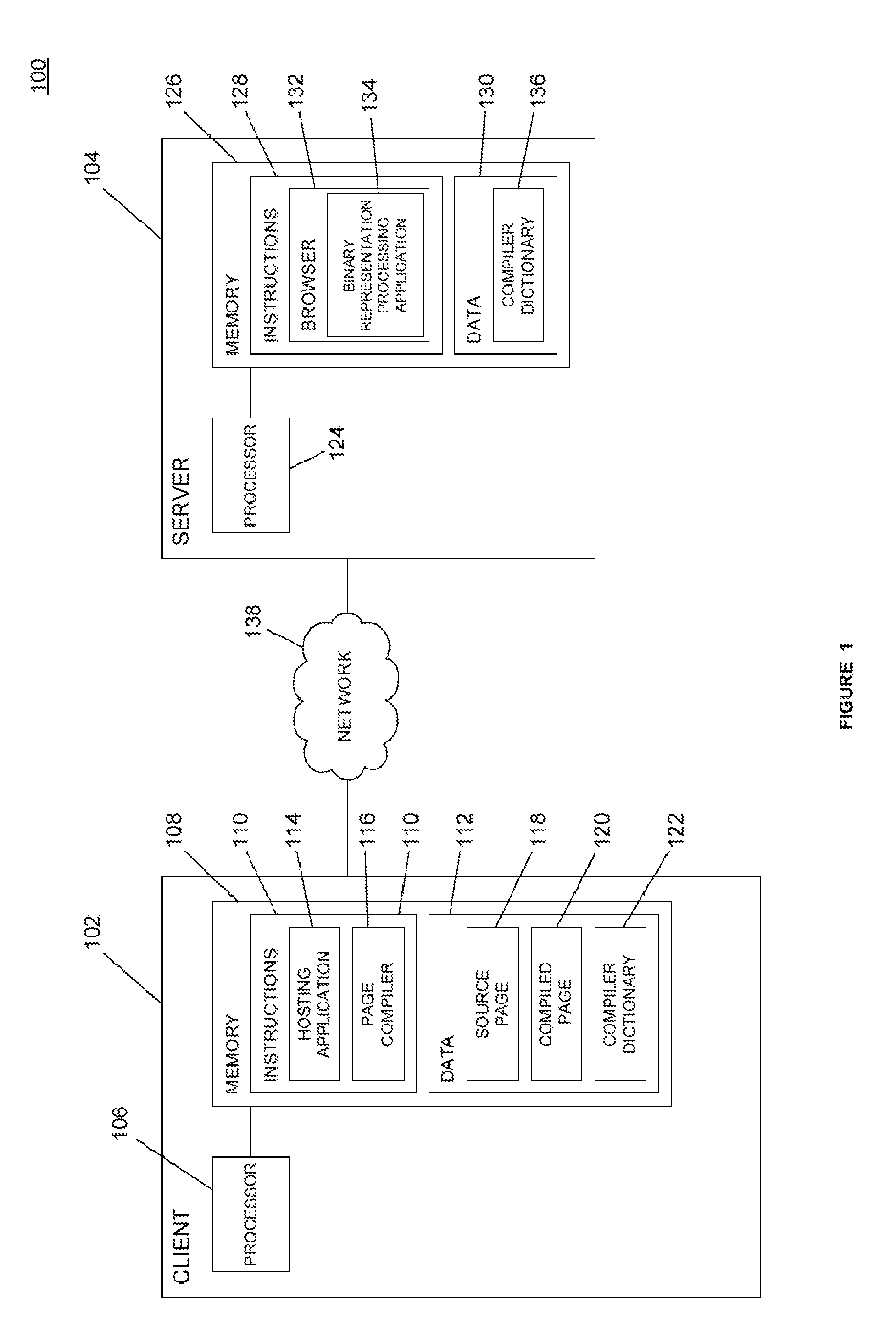
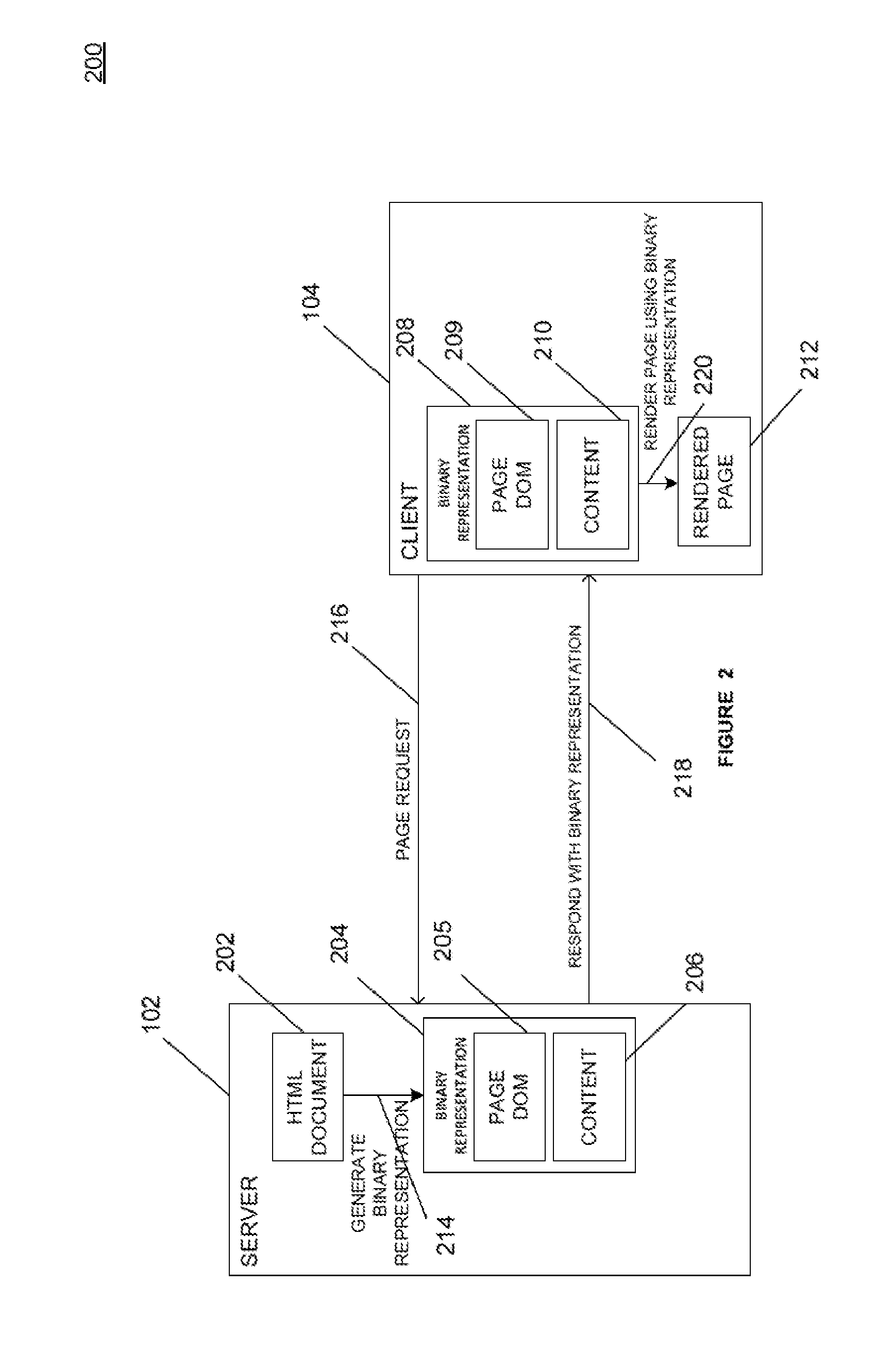
ActiveUS20130246906A1Software engineeringNatural language data processingDocument Object ModelText string
Systems and methods for providing a binary representation of a web page. A server may compile a source page, such as a hypertext markup language (“HTML”) document, to create a compiled representation of the source page. Creation of a compiled representation may include generating a document object model (“DOM”) for the content associated with the source page. The compiled page may be transmitted to a client as a random-access file or flat file, where the data is encoded in one or more data types other than a string representation. The client may receive the compiled page and load the compiled page directly as a DOM for the page without the need to parse HTML text strings. The server and client may reconcile the data format of the compiled page, such as by exchanging or verifying a compiler dictionary associated with the page.
Owner:GOOGLE LLC
Five-axis linkage numerical control (NC) machining post processor and processing method thereof
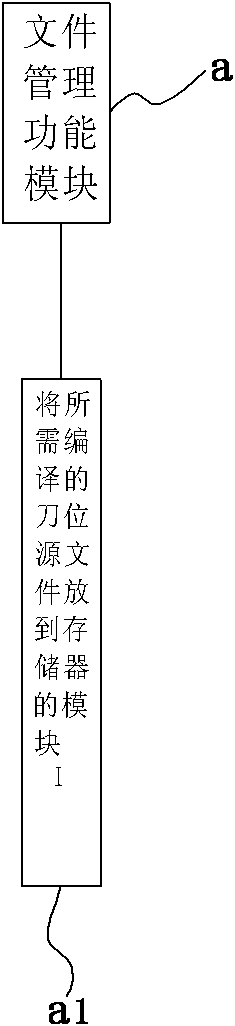
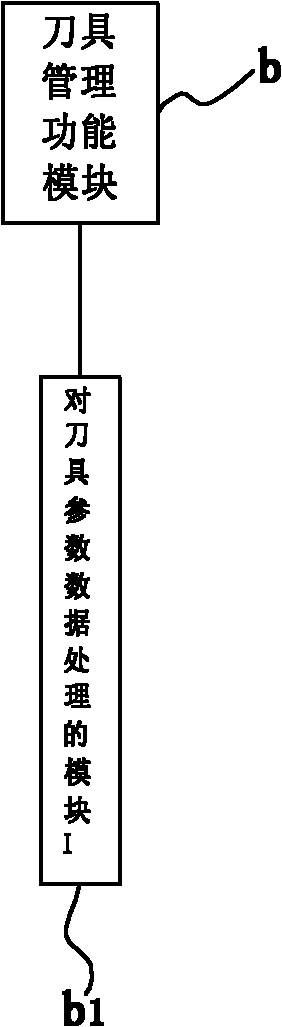
InactiveCN102023613ARealize simulationRealize serial communicationProgramme controlComputer controlPost processorManagement functions
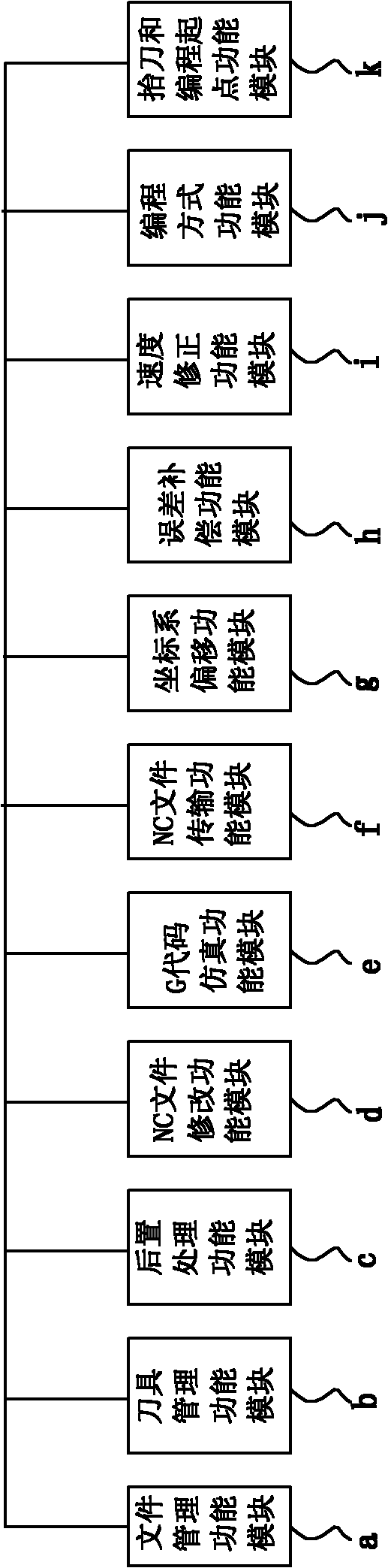
The invention discloses a five-axis linkage numerical control (NC) machining post processor and a processing method thereof, and relates to a post processor for an NC machining program and a processing method. The processor comprises computer program software which is used for processing a cutter location source file generated by a workpiece shape characteristic and a machining process, wherein the computer program software comprises a file management function module, a cutter management function module, a postprocessing function module, an NC file modification function module, a G code simulation function module, an NC file transmission function module, a coordinate system offset function module, an error compensation function module, a speed modification function module, a programming mode function module and a cutter-lifting and programming staring point function module. The processing method comprises the steps of setting a file, arranging a cutter, processing a programming mode, processing data of machine tool motion parameters, processing data of cutter dynamic cutting speed, outputting a G code file and the like. By the processor and the processing method, machining dynamic speed, speed compensation, non-linear error compensation and analog simulation of G code five-axis linkage can be realized.
Owner:GUANGXI UNIVERSITY OF TECHNOLOGY +1
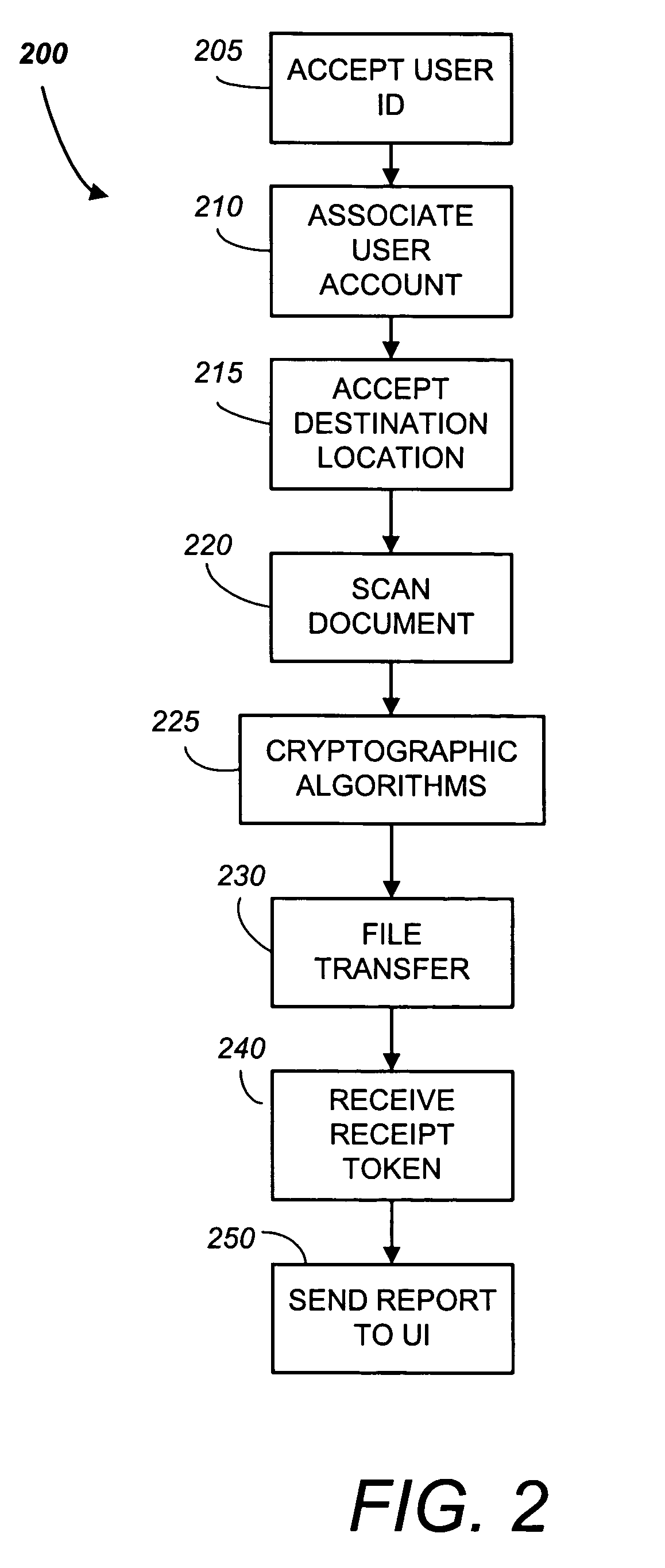
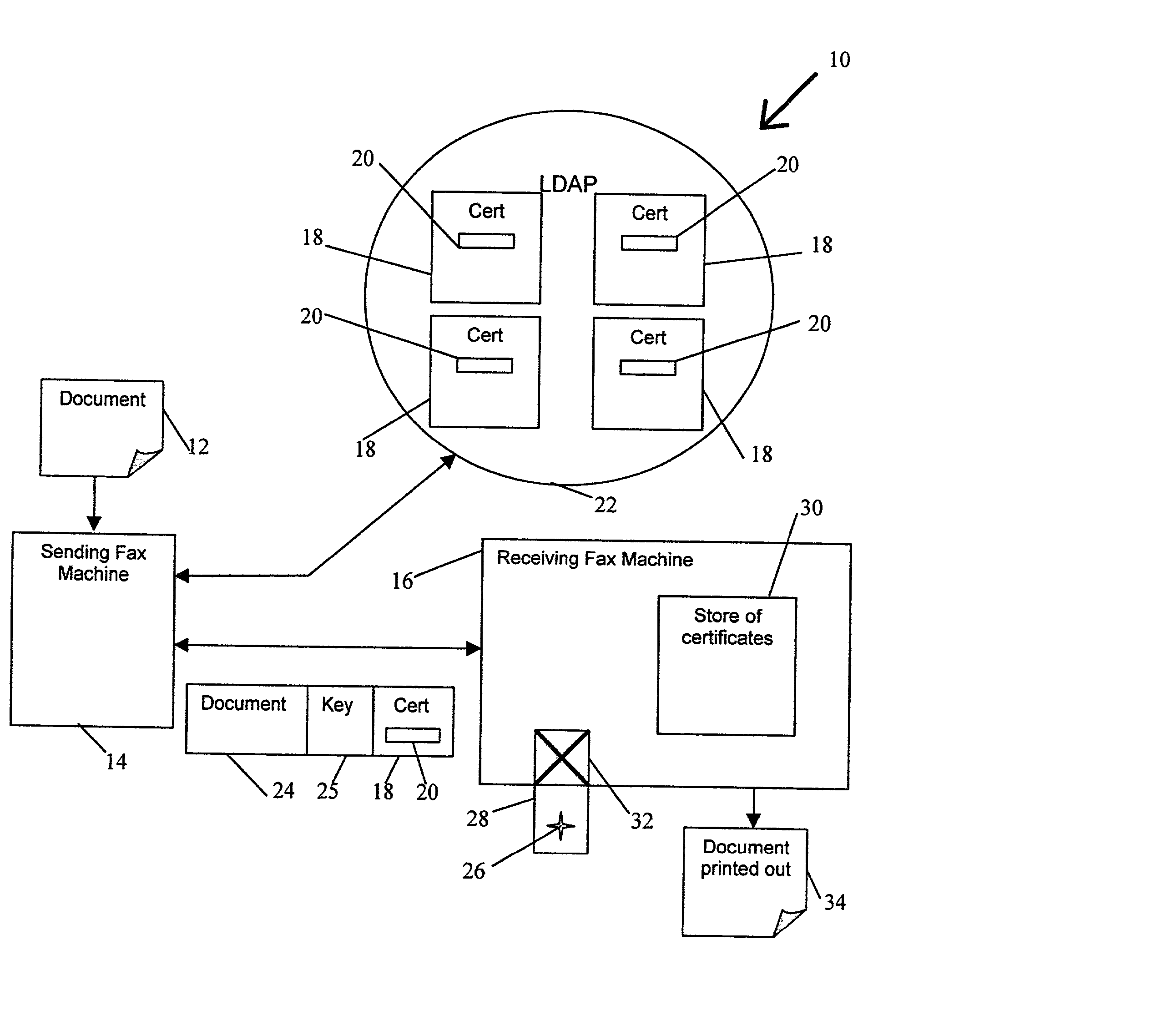
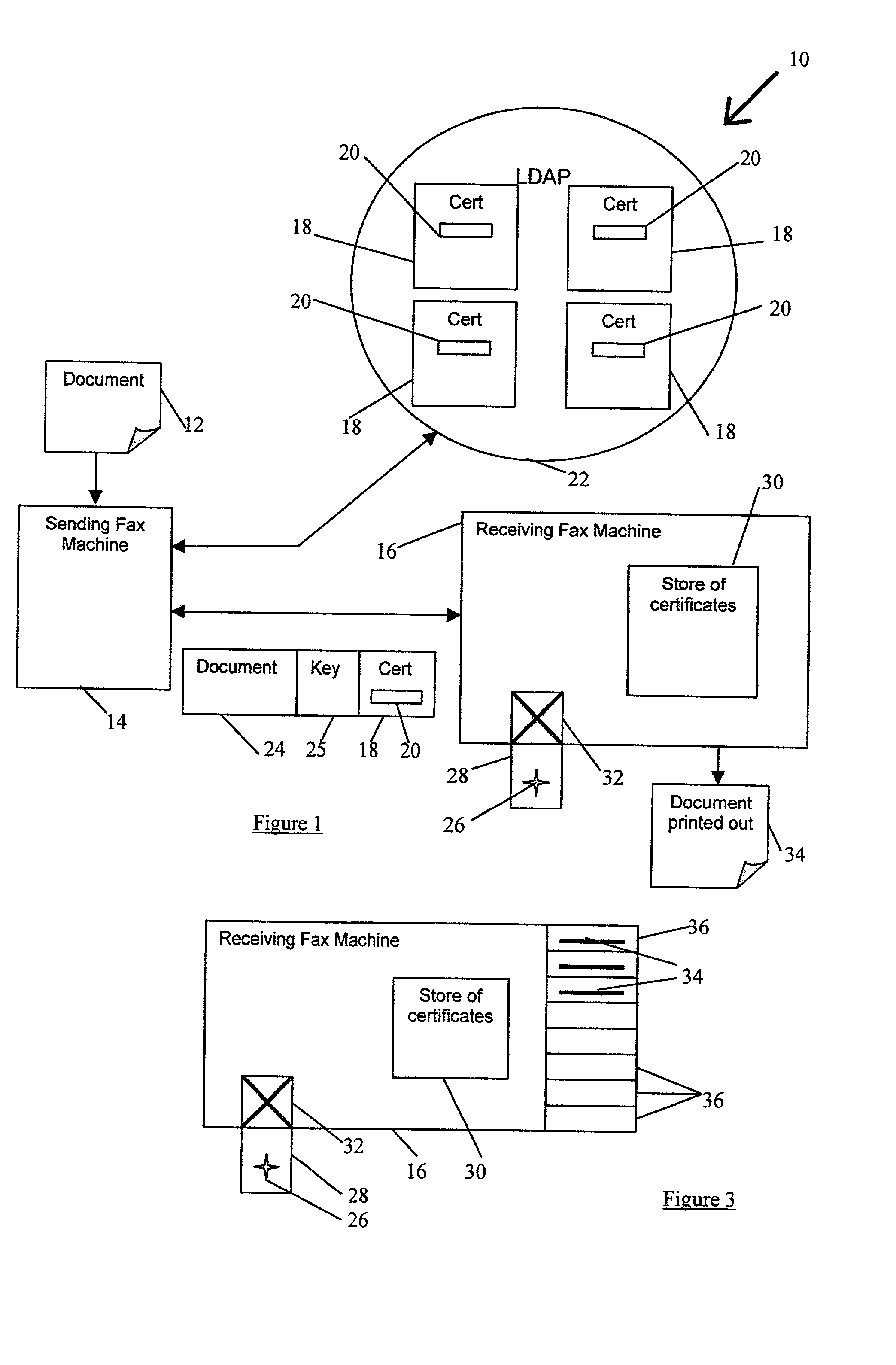
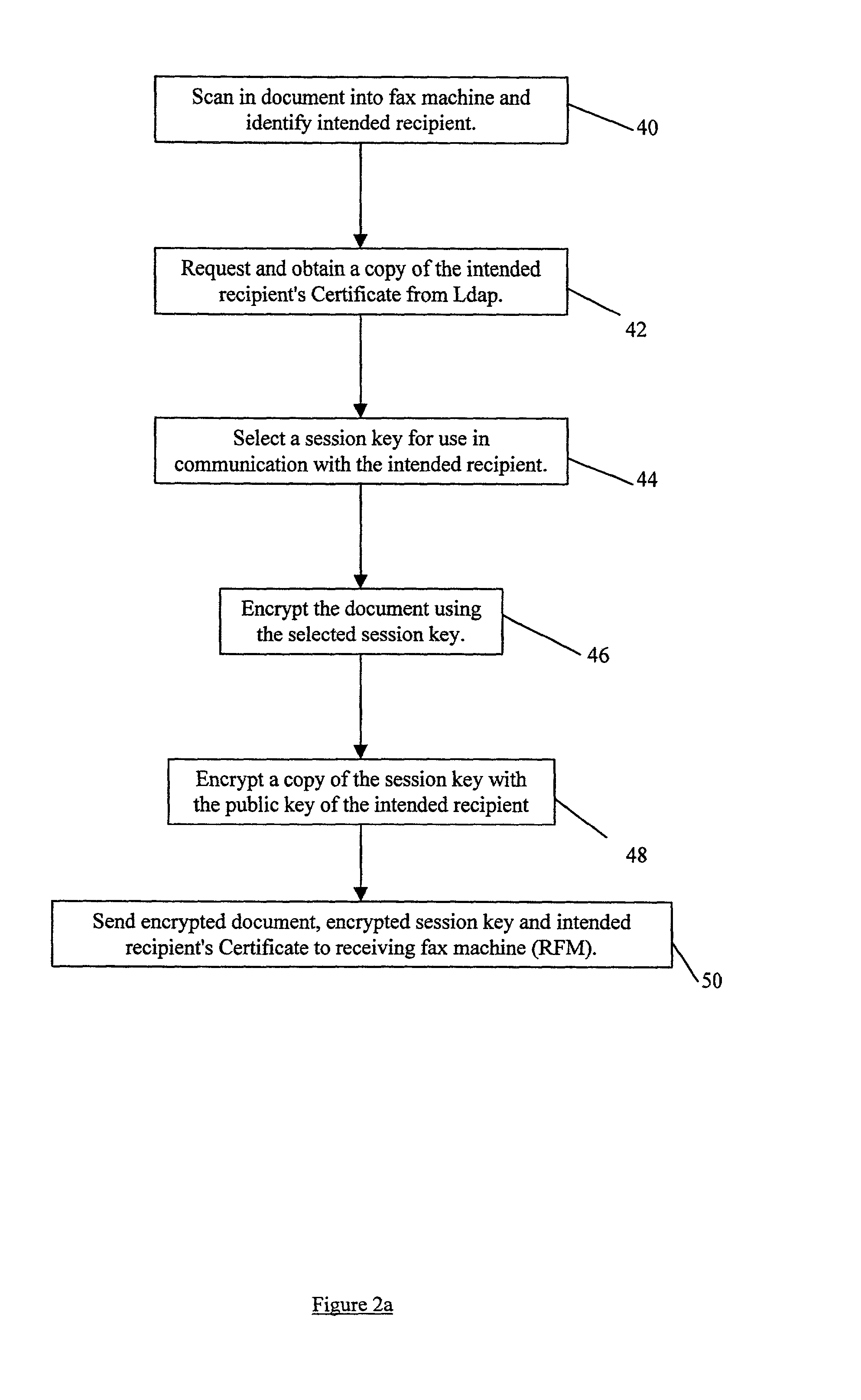
Document transmission Techniques I
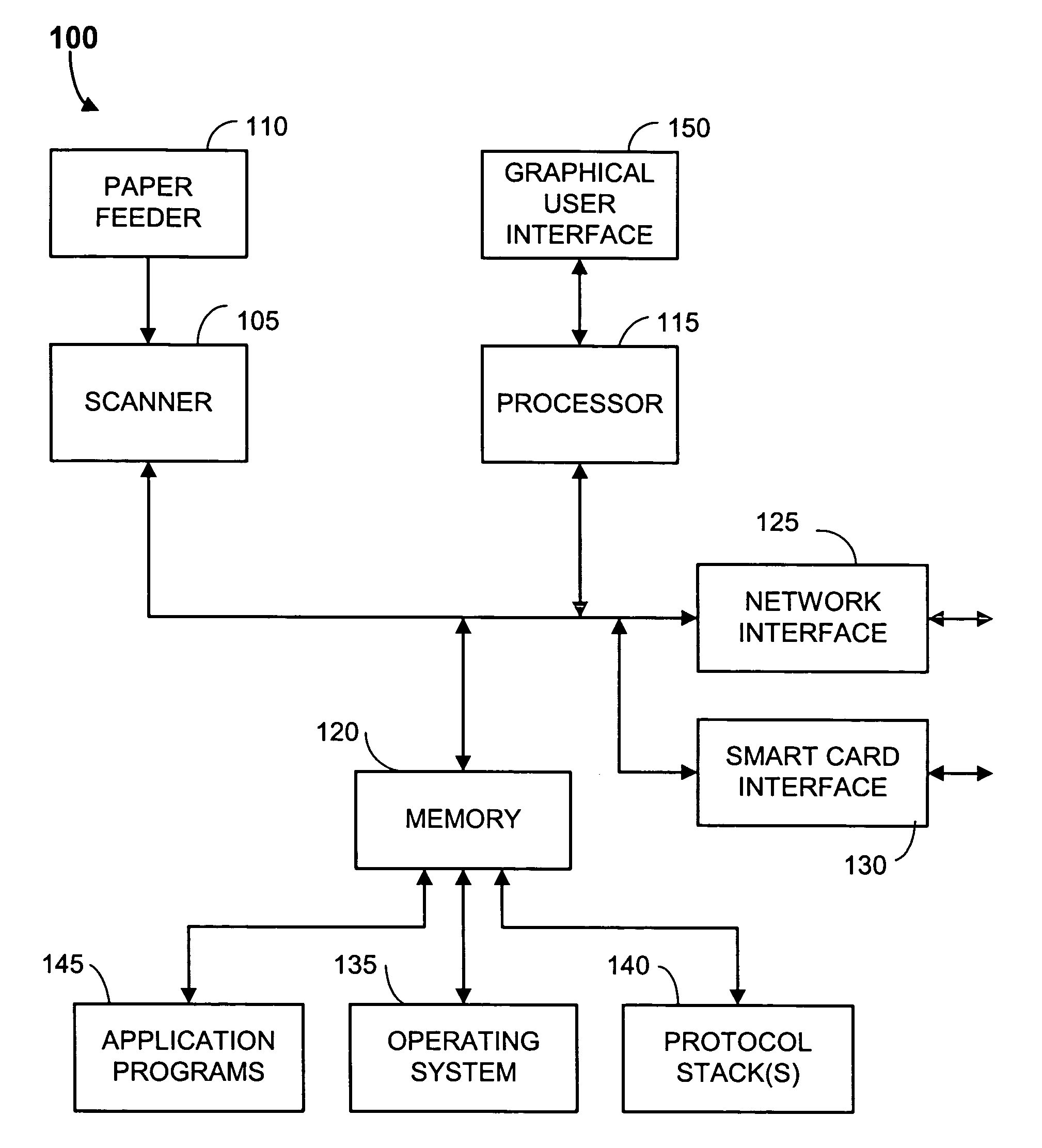
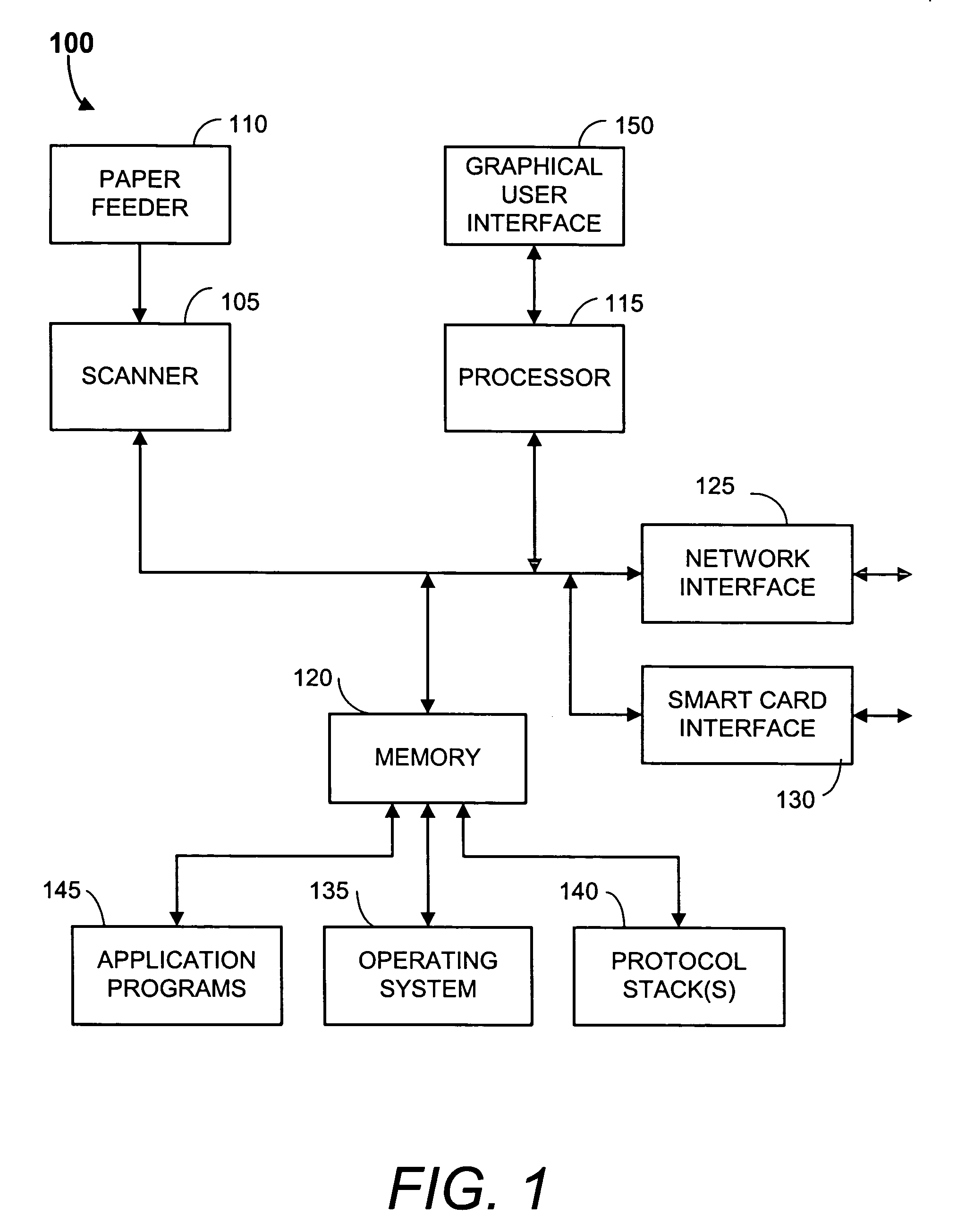
InactiveUS20020054334A1None of methods is secureConfidenceUser identity/authority verificationDigital computer detailsFile transmissionSmart card
A method of delivering a digital document to an intended recipient at a printout station, such as a fax machine. The method comprises receiving and securely retaining a transmitted document and a transmitted independently verifiable data record such as a digital certificate of the intended recipient at the printout station. A first token, such as a public key, of the intended recipient is obtained, usually from the transmitted information. The method includes requesting proof of the intended recipient's identity at the receiving fax machine using data in the digital certificate of the intended recipient and releasing the document when the intended recipient has proved their identity by use of a second token, such as a private key, that is uniquely related to the first token. The private key may be provided on a portable smart card. Also envelope data encryption techniques may be used to add security to the transmission of the document.
Owner:HEWLETT PACKARD DEV CO LP
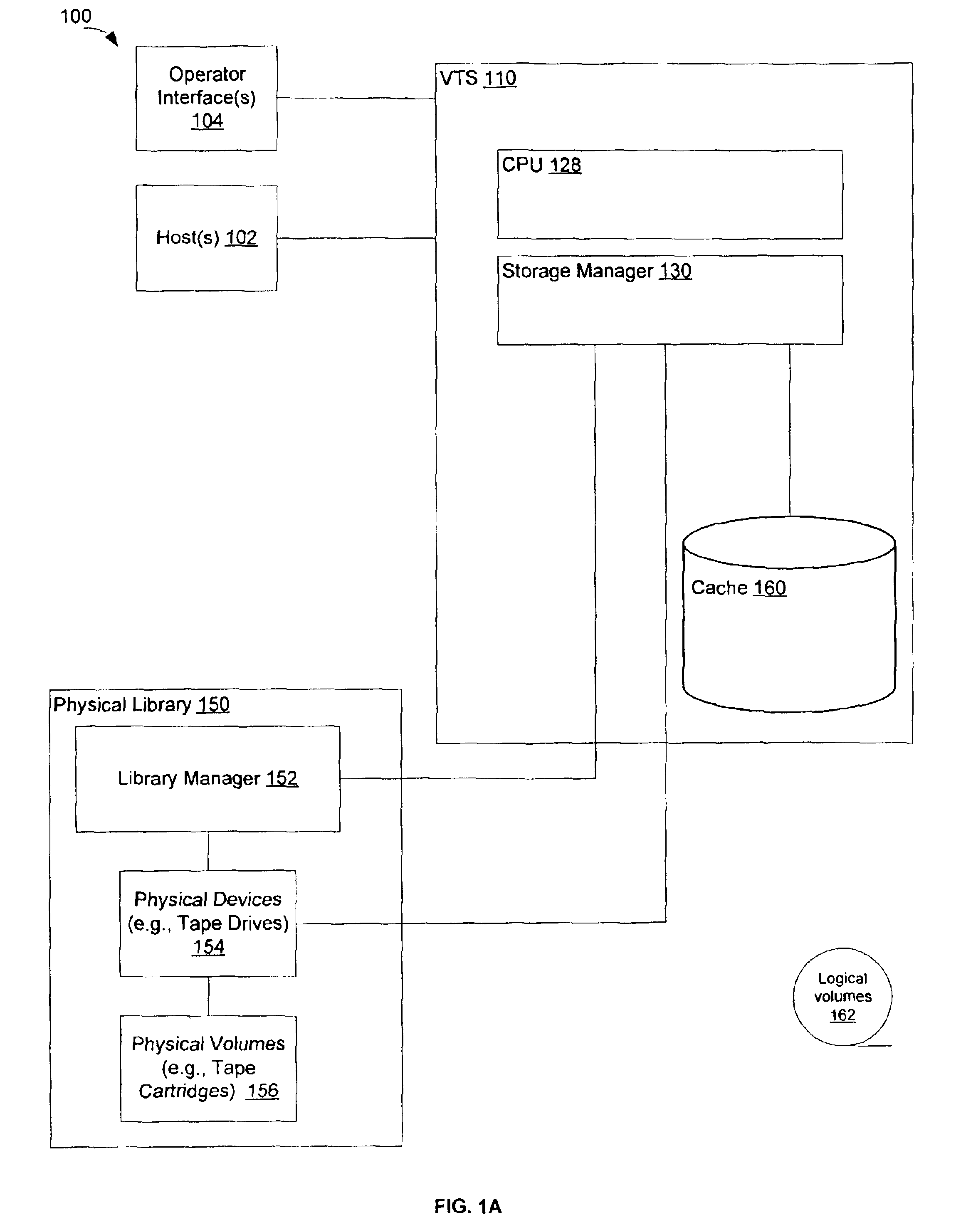
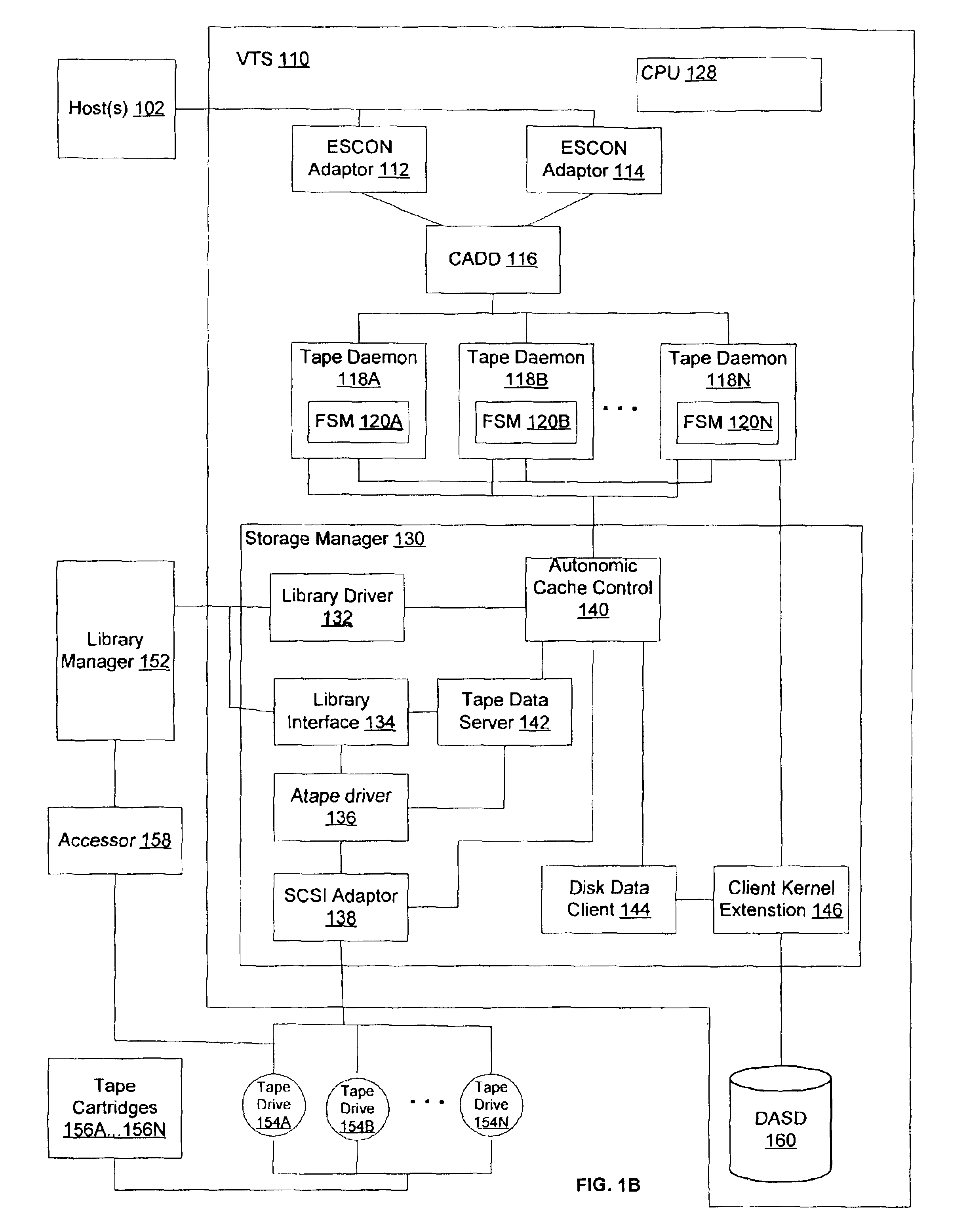
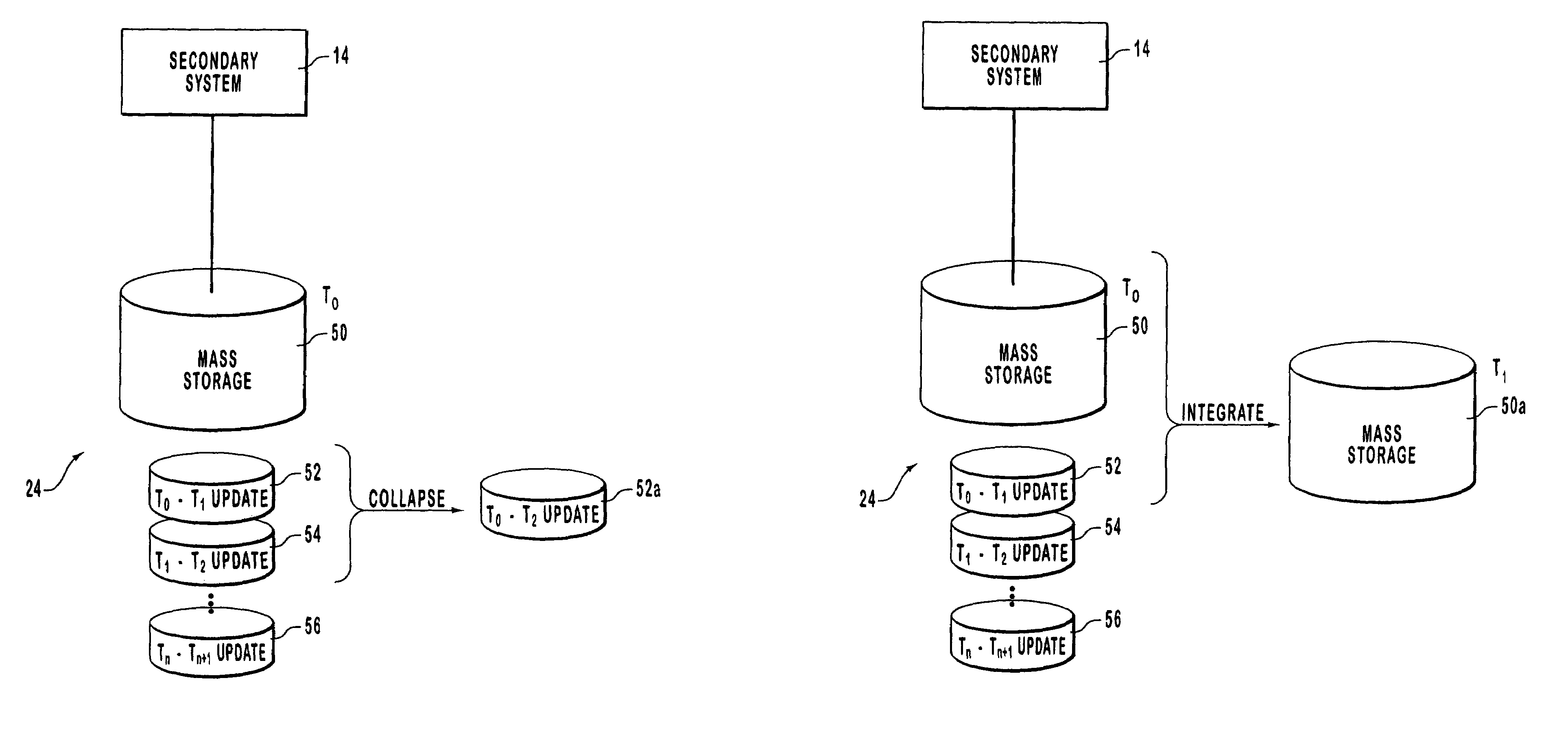
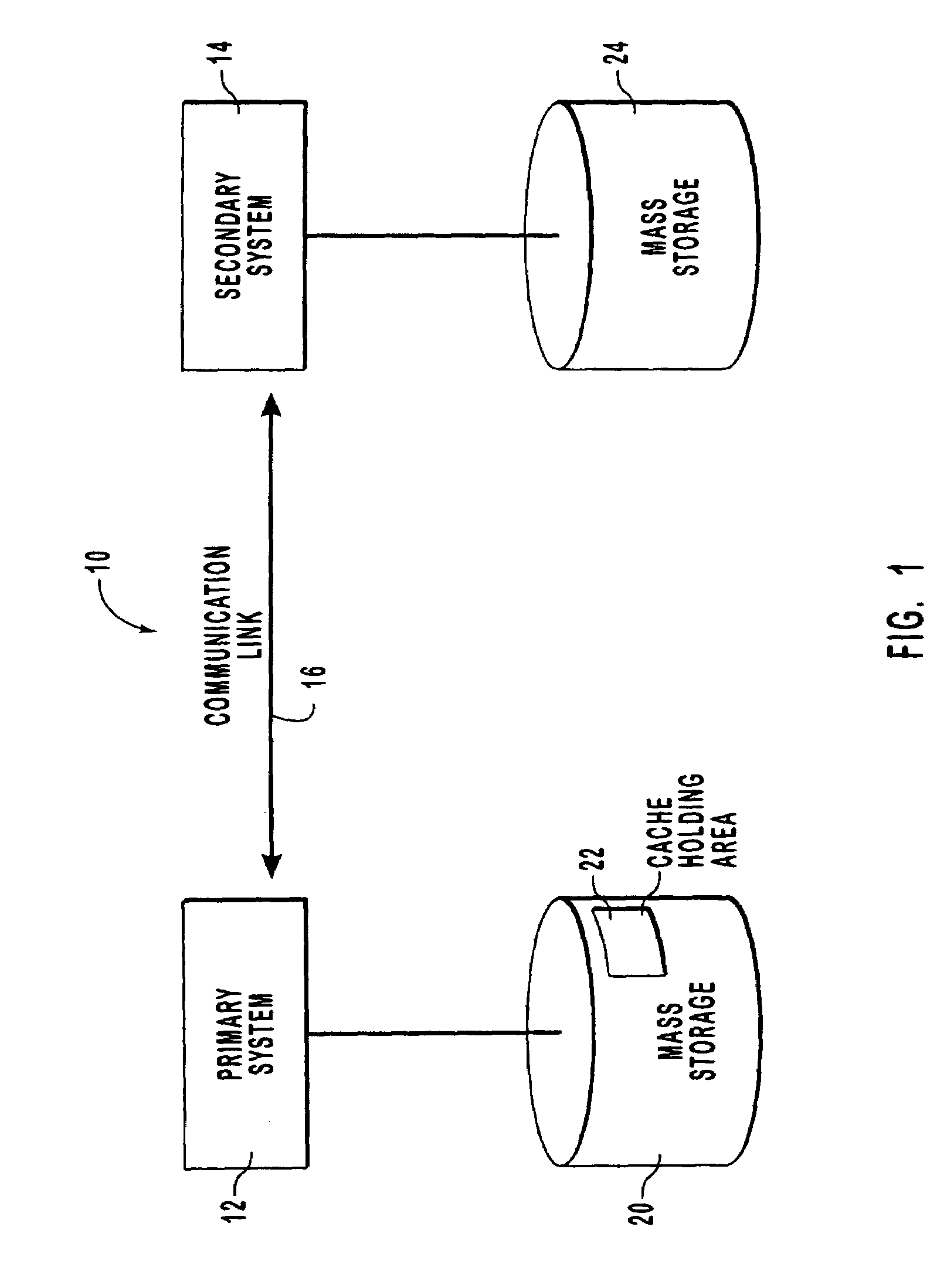
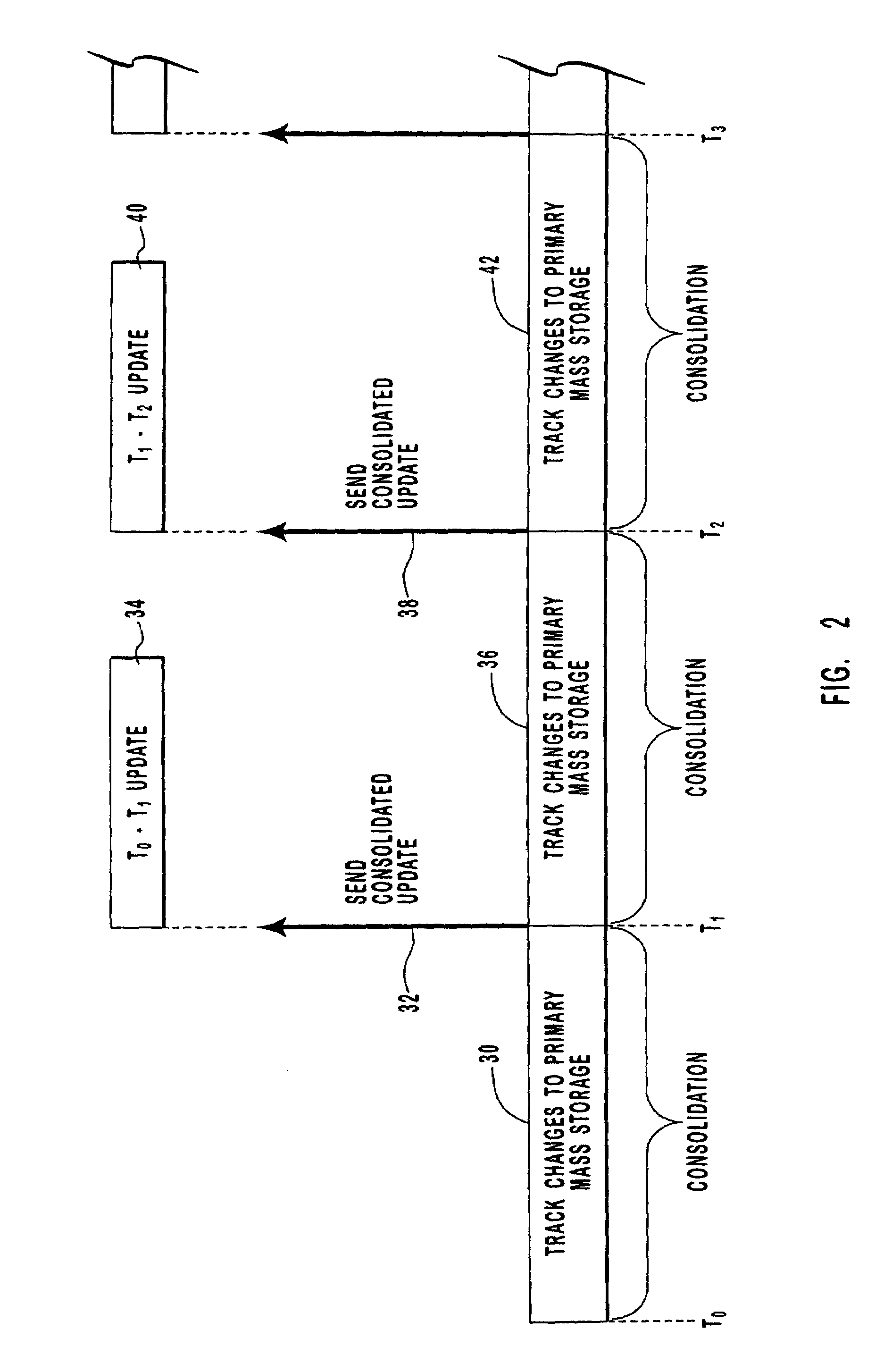
Method and system for mirroring and archiving mass storage
InactiveUS7107418B2Reduce data volumeMinimizing amount of dataData processing applicationsRedundant operation error correctionMass storageFile transmission
A method and system for mirroring and archiving mass storage. A primary mass storage and a secondary mass storage are synchronized to contain the same data. Thereafter, a primary system tracks changes made to the primary mass storage. These changes are consolidated periodically into update files, the consolidations representing changes made to the primary mass storage during a time interval that ends when the primary mass storage is in a logically consistent state. These update files contain only those changes necessary to represent the modified state of the primary mass storage at the time of the update. The primary system then transfers the update files to a secondary system to bring the secondary mass storage current with the primary mass storage. The consolidation minimizes the amount of information that must be transferred and therefore allows for a relatively low band width communication channel. In addition, update files may be cached by the primary system so that requests for mirrored or archived data may be fulfilled by the primary system cache rather than requiring access to the secondary system.
Owner:EMC IP HLDG CO LLC
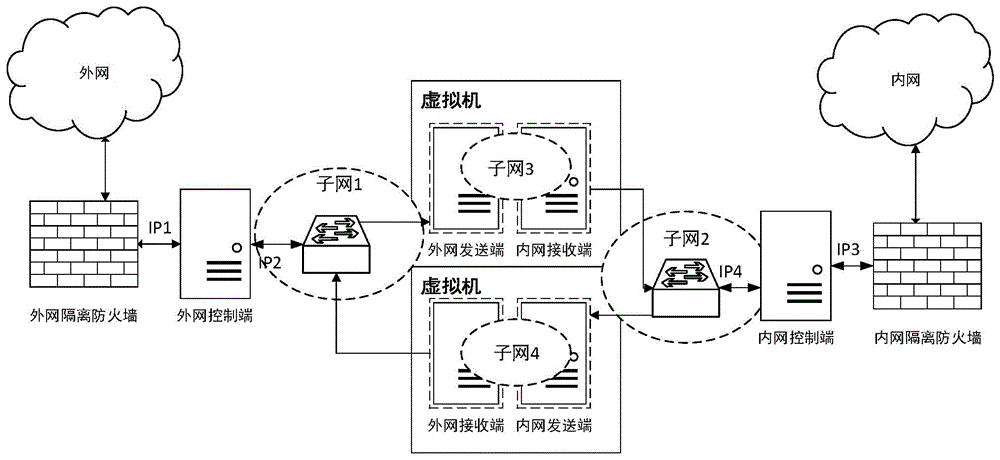
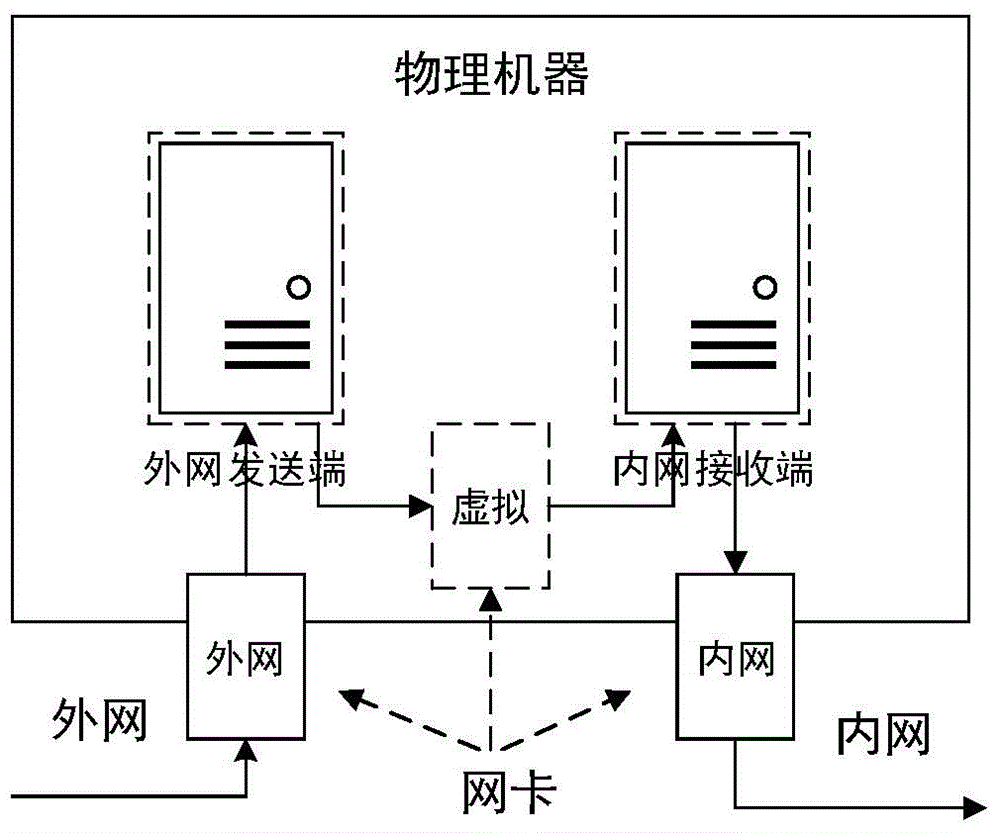
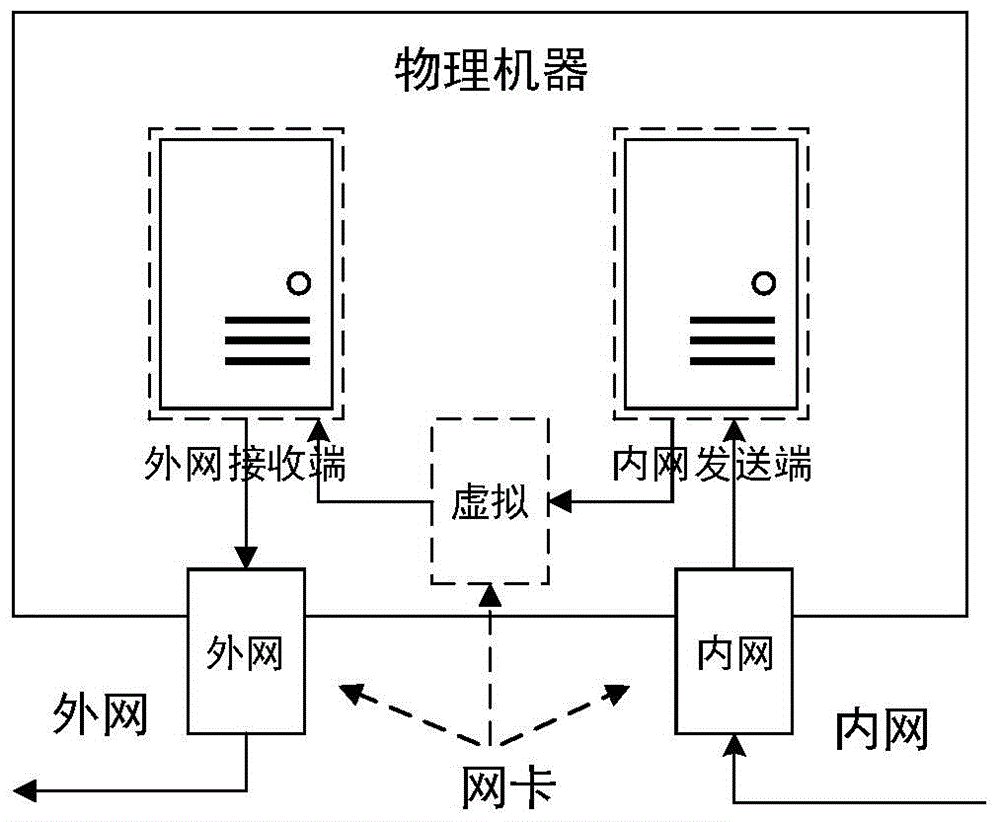
Network safety isolation file transmission control method
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
System and method for transferring a file in advance of its use
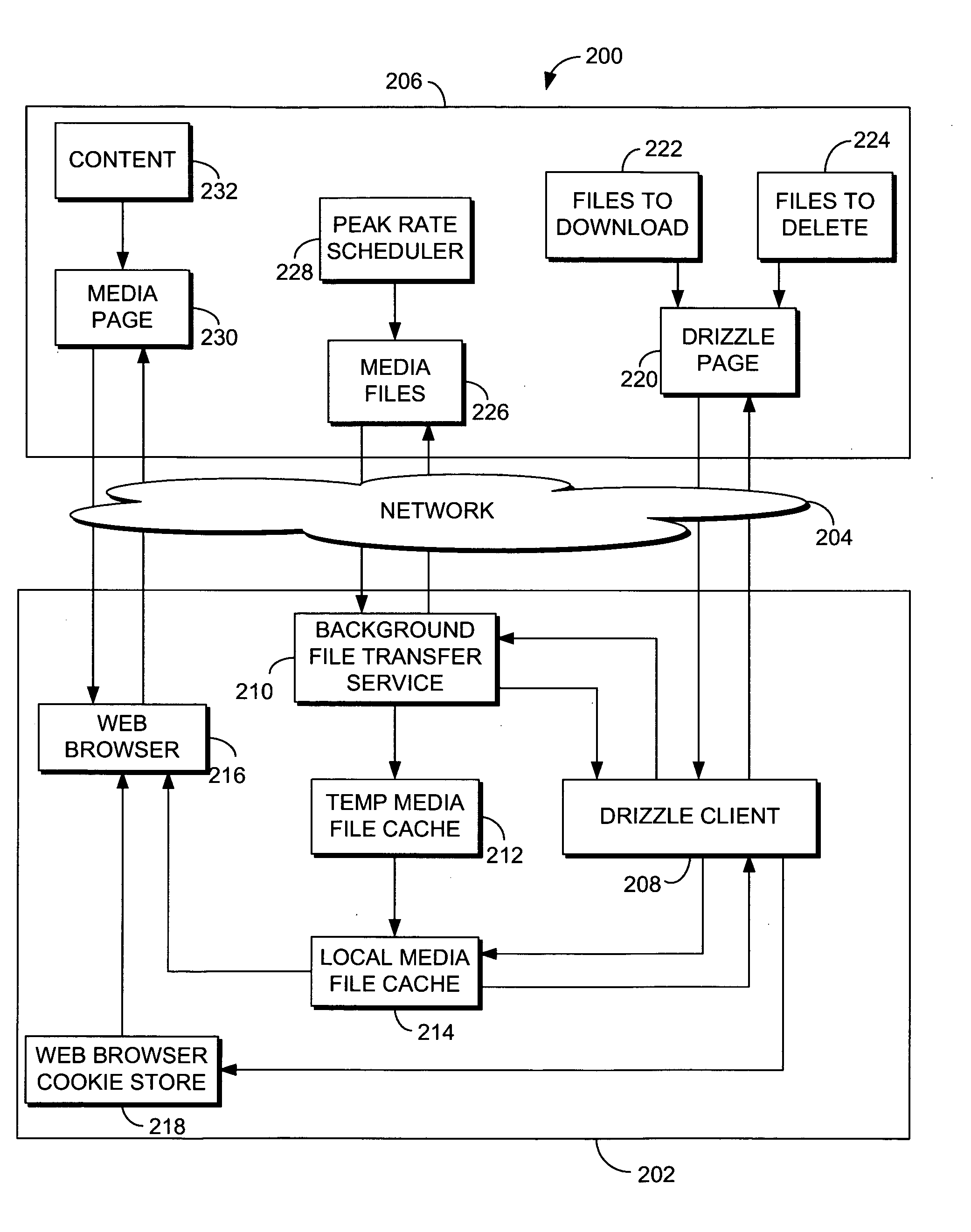
InactiveUS20060106807A1Digital data information retrievalDigital data processing detailsFile transmissionWeb page
The invention relates to a system, methods, and computer-readable media for transferring one or more files to a computer in advance of their use by the computer. In accordance with one method of the invention, the computer sends a request for instructions to acquire at least one predetermined file. The request includes information regarding the location of a cache on the computer. The computer receives the instructions to acquire the file, as well as at least one cookie, which includes information regarding the file and the location of the cache. Based on the instructions, the computer obtains the file and stores it in the cache in advance of its use by the computer. If a web page that includes the file is requested, the request for the web page includes the cookie. The computer then receives data that represents that web page and includes a reference to the file stored in the cache at the computer. The reference may be used to open the file stored in the cache.
Owner:MICROSOFT TECH LICENSING LLC
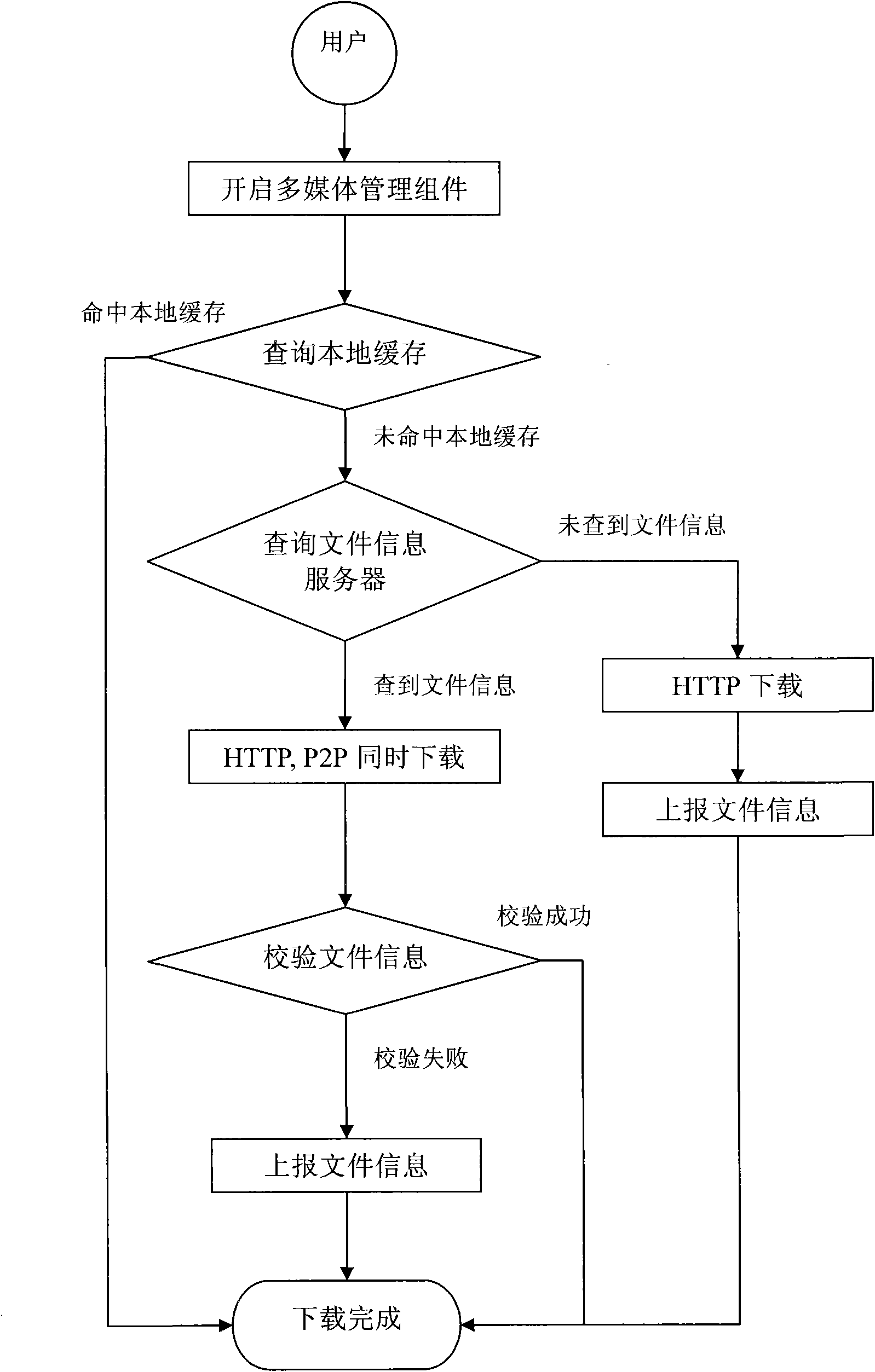
Multi-media transmission system and method in IM (Instant Messaging)
InactiveCN101854278AReasonable useRealize the transmission methodData switching by path configurationWeb serviceMultimedia management
The invention provides a multi-media transmission system in IM (Instant Messaging), which is characterized by comprising a client, a P2SP server and a P2P coupling end, wherein the client is connected with an internet and is provided with an external interface used for connecting with the P2SP server and the P2P coupling end through the network and transmitting data; the client also comprises a multi-media management assembly obtaining multi-media data source through the external interface; the P2SP server is provided with a web server and a file information server, and the web server is directly connected with the client 100 through the network; the file information server and the web server are directly connected and carry out data interaction mutually; and the P2P coupling end is provided with corresponding P2P downloading port and P2P uploading port which are respectively used for downloading and uploading multi-media files by the client. The invention provides a quick-speed and effective network multi-media file transmission system and can be used for simultaneous action of multiple transport protocols to reasonable utilize the network resources.
Owner:升东网络科技发展(上海)有限公司
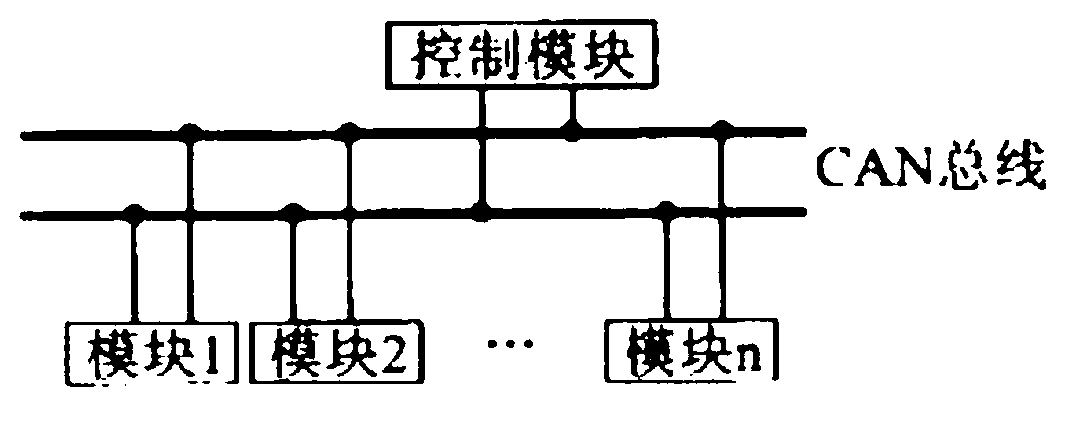
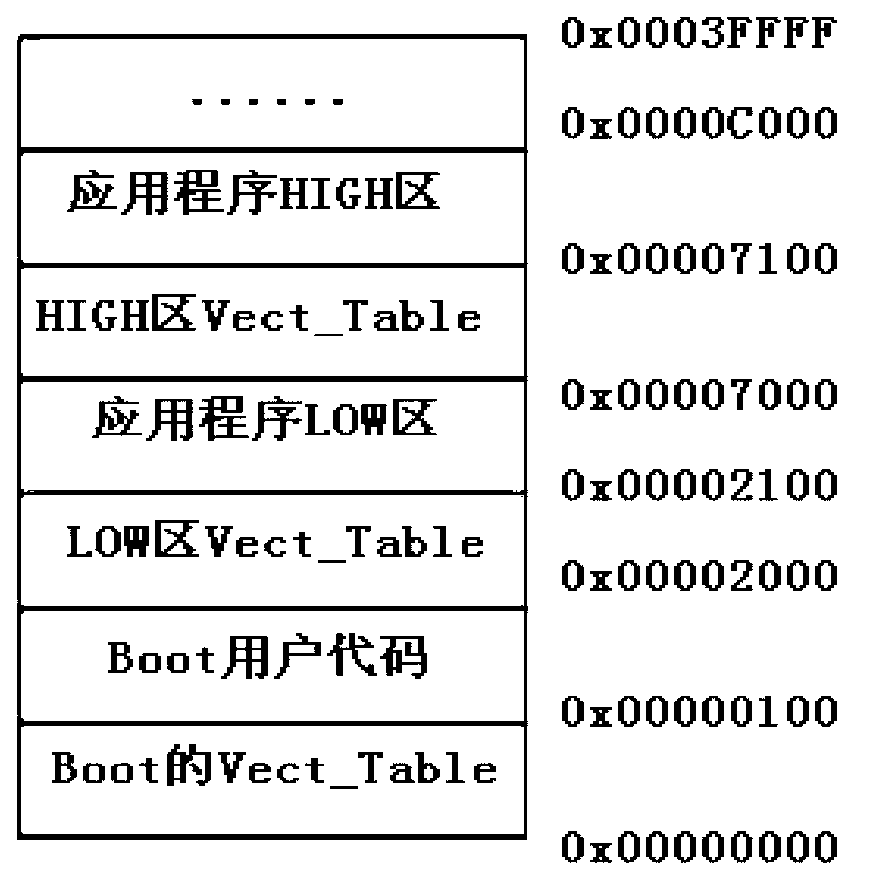
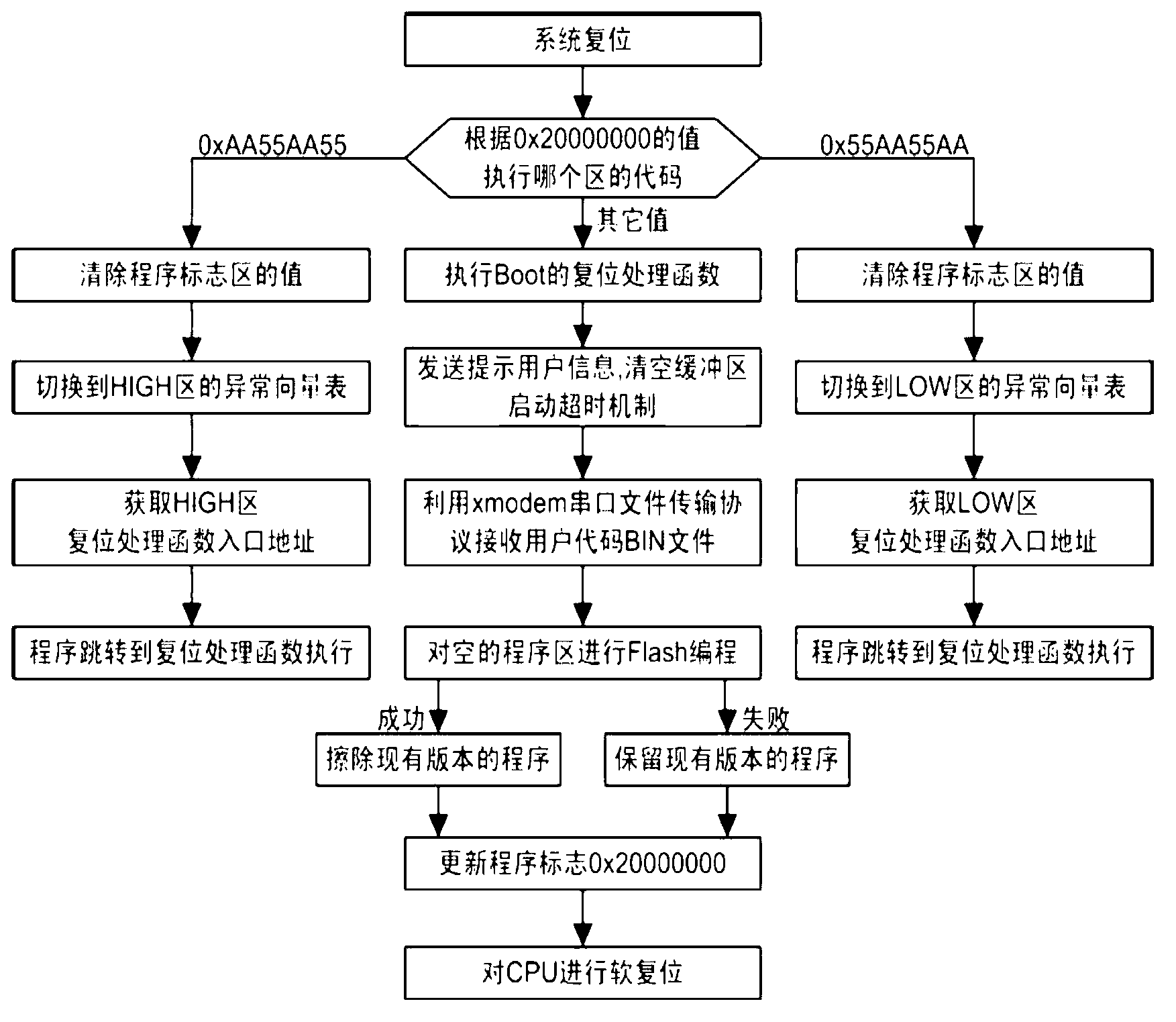
Remote online upgrading method based on CAN (Controller Area Network) bus
InactiveCN103019788AAvoid lossGood for developmentProgram loading/initiatingFile transmissionArea network
The invention discloses a remote online upgrading method based on a CAN (Controller Area Network) bus. The remote online upgrading method is based on a CAN bus system; the system comprises a plurality of embedded functional modules which work independently and a control module for upgrading the system; each functional module is provided with a cured guiding program; the guiding program supports a CAN bus protocol; the control module is used for sending an upgrading command to a functional module which is required to be upgraded; and each functional module is used for skipping to the guiding program after receiving the upgrading command, waiting for the control module to transmit an upgrading data packet, transmitting the received upgrading data packet through a serial file transmission protocol Xmodem, programming the received upgrading data packet to Flash to realize online upgrading, performing software resetting operation after the completion of upgrading, and starting to run an upgraded application.
Owner:SHANGHAI RES INST OF CHINA POST GROUP
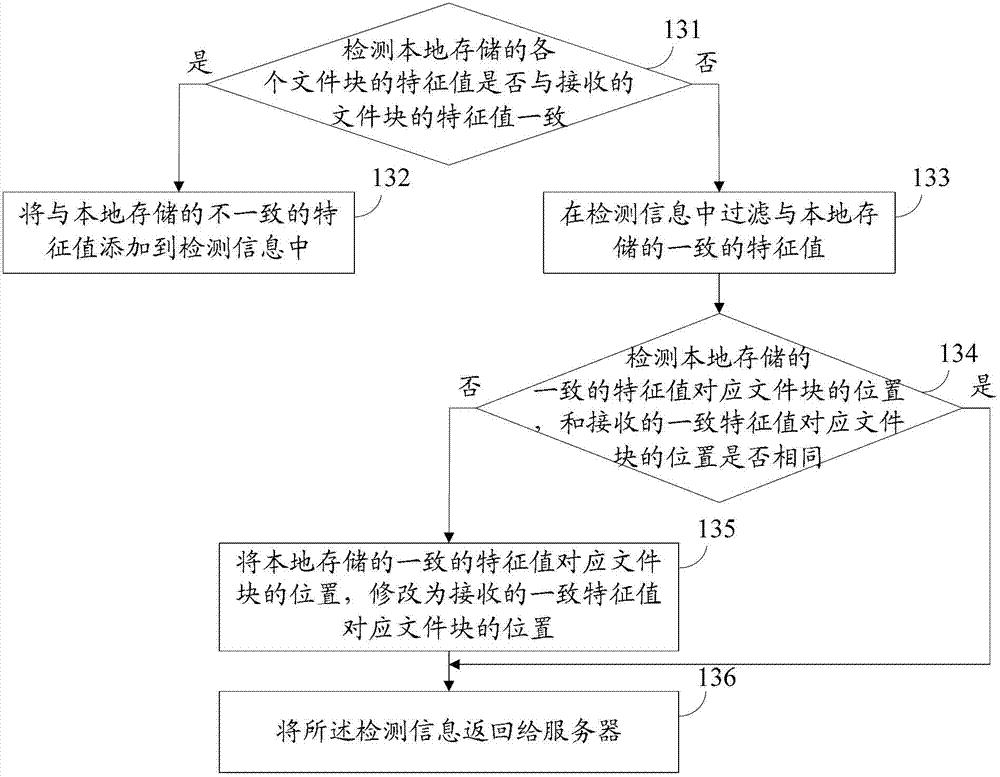
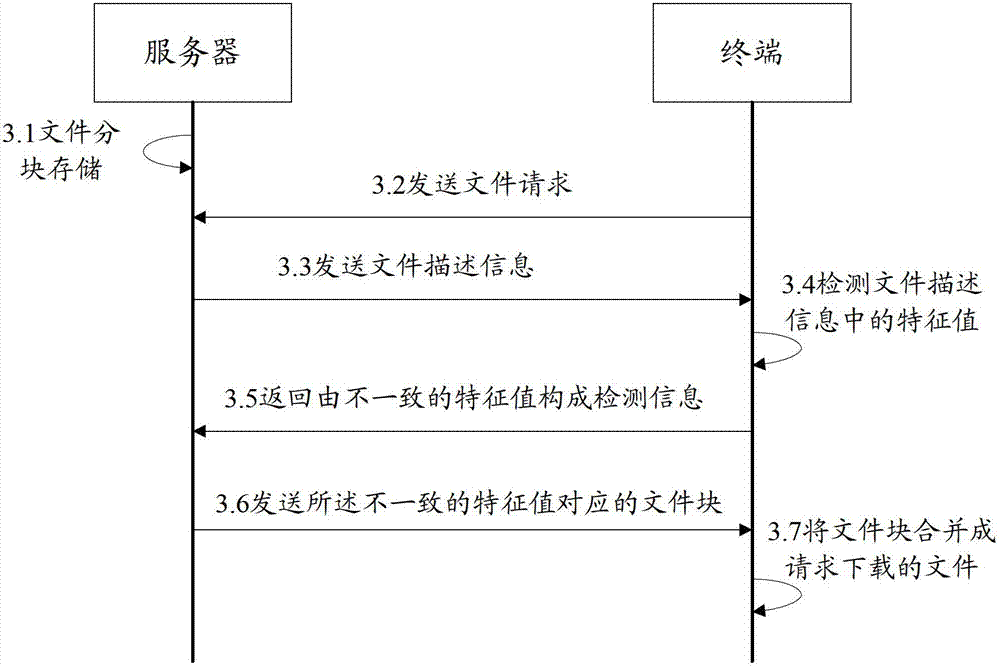
File downloading and uploading method and device
The invention provides a file downloading and uploading method and device, which aims at solving the problems of the prior art that the file transmission time is long and file transmission wastes network resources. The downloading method comprises the steps of: sending a file request to a server, wherein the file request includes a name of the file requesting downloading; receiving file description information sent by the server, wherein the file description information includes the characteristic values of file blocks formed by dividing the file requesting downloading; detecting whether the characteristic values of the file blocks stored locally are consistent with those of the received file blocks, and adding the inconsistent characteristic values into detection information to return to the server; and receiving the file blocks corresponding to the inconsistent characteristic values, sent by the server. According to the file downloading and uploading method and device provided by the invention, the file blocks corresponding to inconsistent characteristic values stored locally can only be downloaded, thus, the file transmission time is shortened and resource waste is reduced.
Owner:360 TECH GRP CO LTD
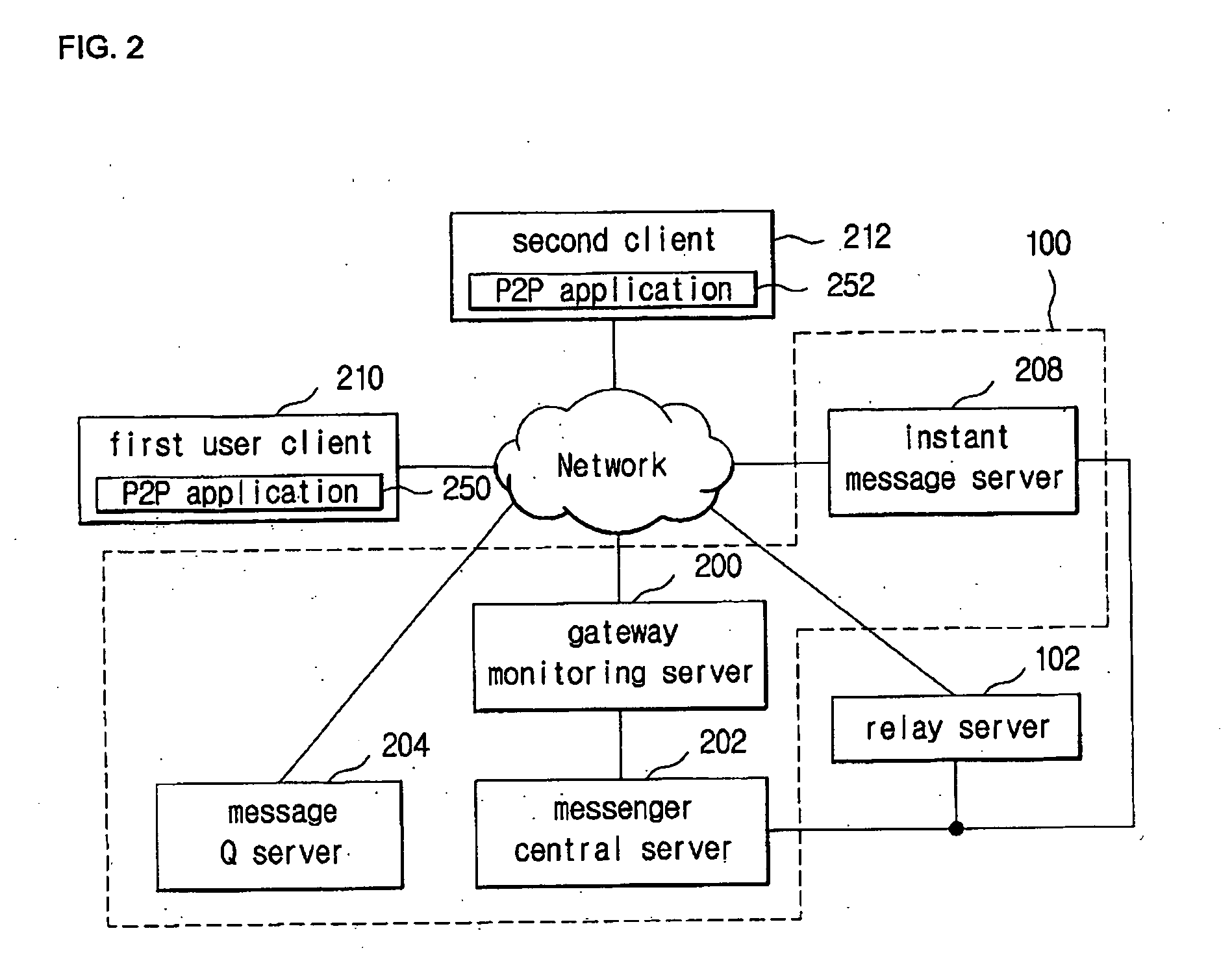
P2p file transmission system and method
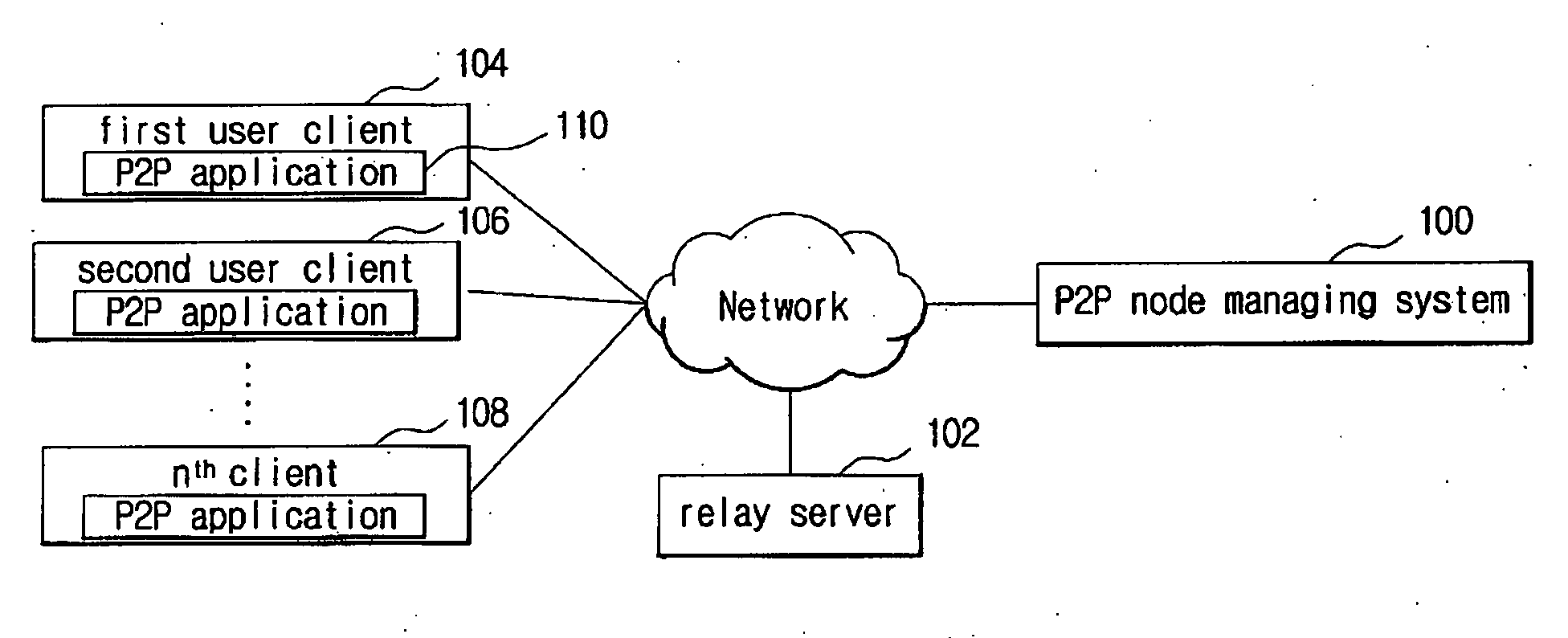
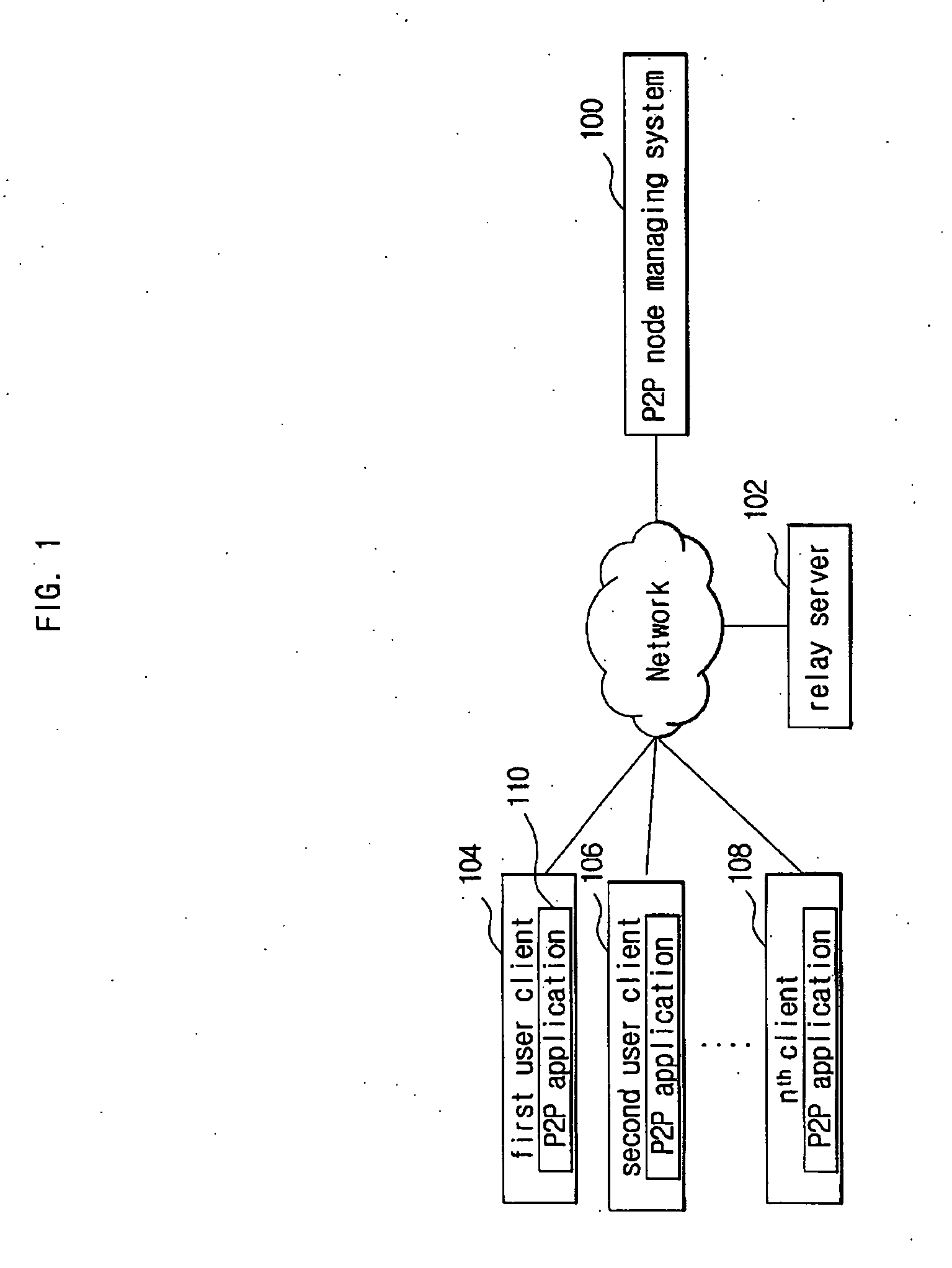
ActiveUS20080301233A1Smooth transmissionConnection managementMultiple digital computer combinationsTransport systemFile transmission
The present disclosure is related to a P2P file transmission system and method, the system according to the present disclosure may include a P2P node managing system managing users connected to the system, and managing P2P file transmissions between the users; and a relay server relaying the file transmitted to the file receiver from the file sender when the P2P file transmission by the direct connection between the file sender and the file receiver fails. According to an embodiment of the present disclosure, the present disclosure provides more stable file transmissions under an unstable environment for the P2P file transmission such as NAT and the P2P file transmission system may be applied to various network places.
Owner:NHN CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com