Patents
Literature
46 results about "String representation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
String representation in Java. A String is represented as objects in Java. Accordingly, an object contains values stored in instance variables within the object. An object also contains bodies of code that operate upon the object. These bodies of code are called methods.
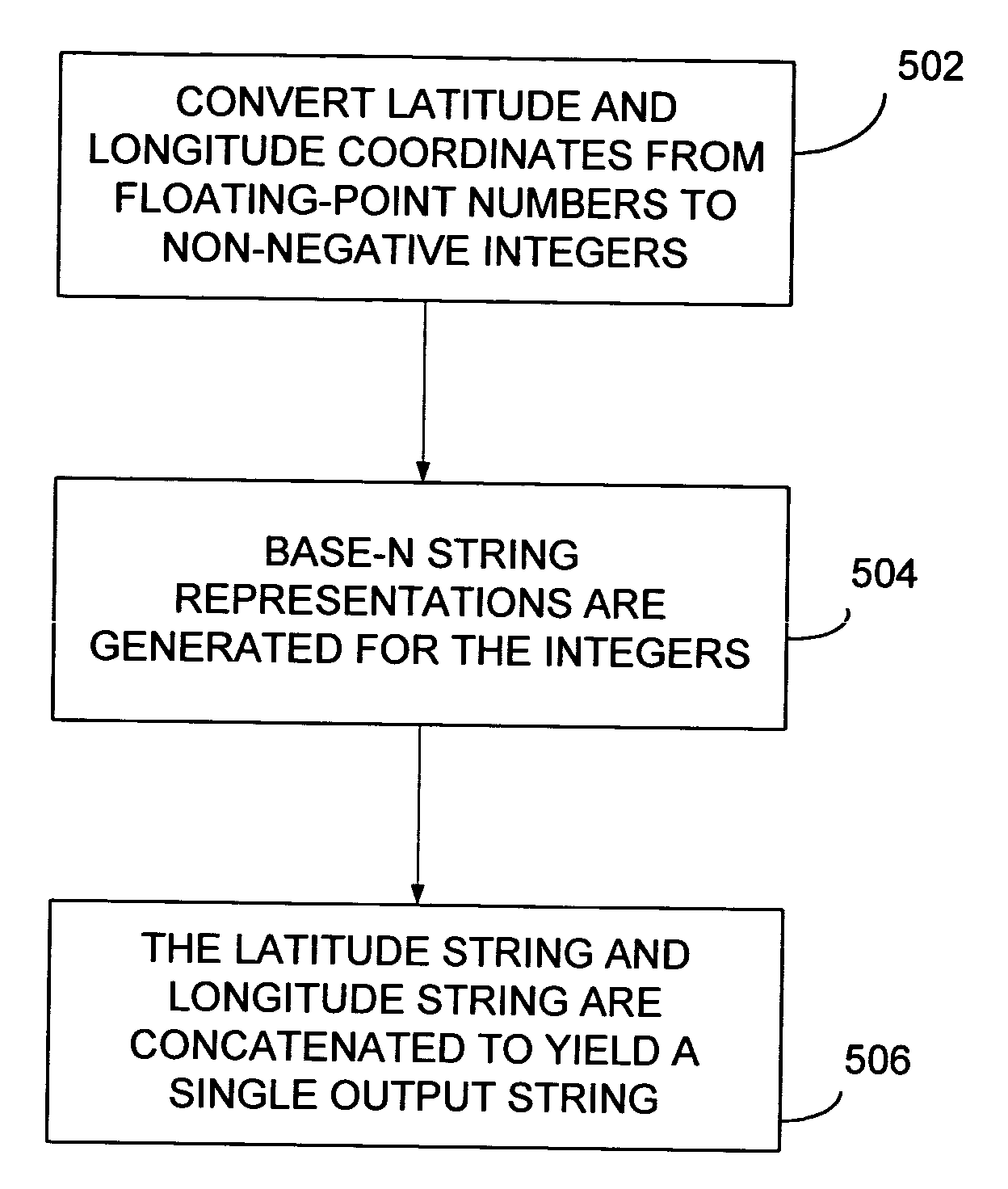
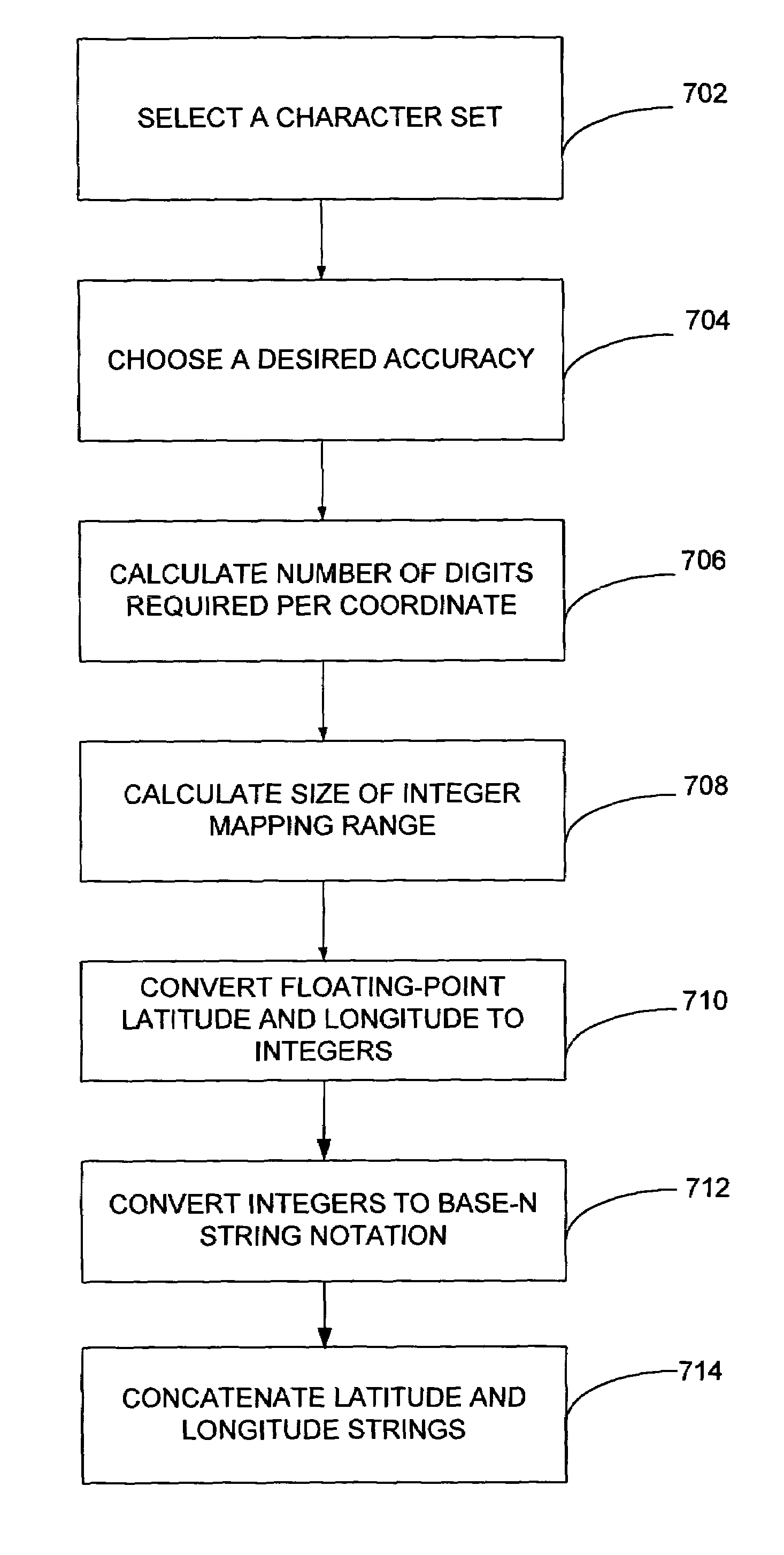
Compact text encoding of latitude/longitude coordinates
InactiveUS20050023524A1Data processing applicationsDigital data information retrievalTheoretical computer scienceLongitude
Methods are disclosed for encoding latitude / longitude coordinates within a URL in a relatively compact form. The method includes converting latitude and longitude coordinates from floating-point numbers to non-negative integers. A set of base-N string representations are generated for the integers (N represents the number of characters in an implementation-defined character set being utilized). The latitude string and longitude string are then concatenated to yield a single output string. The output string is utilized as a geographic indicator with a URL.
Owner:MICROSOFT TECH LICENSING LLC
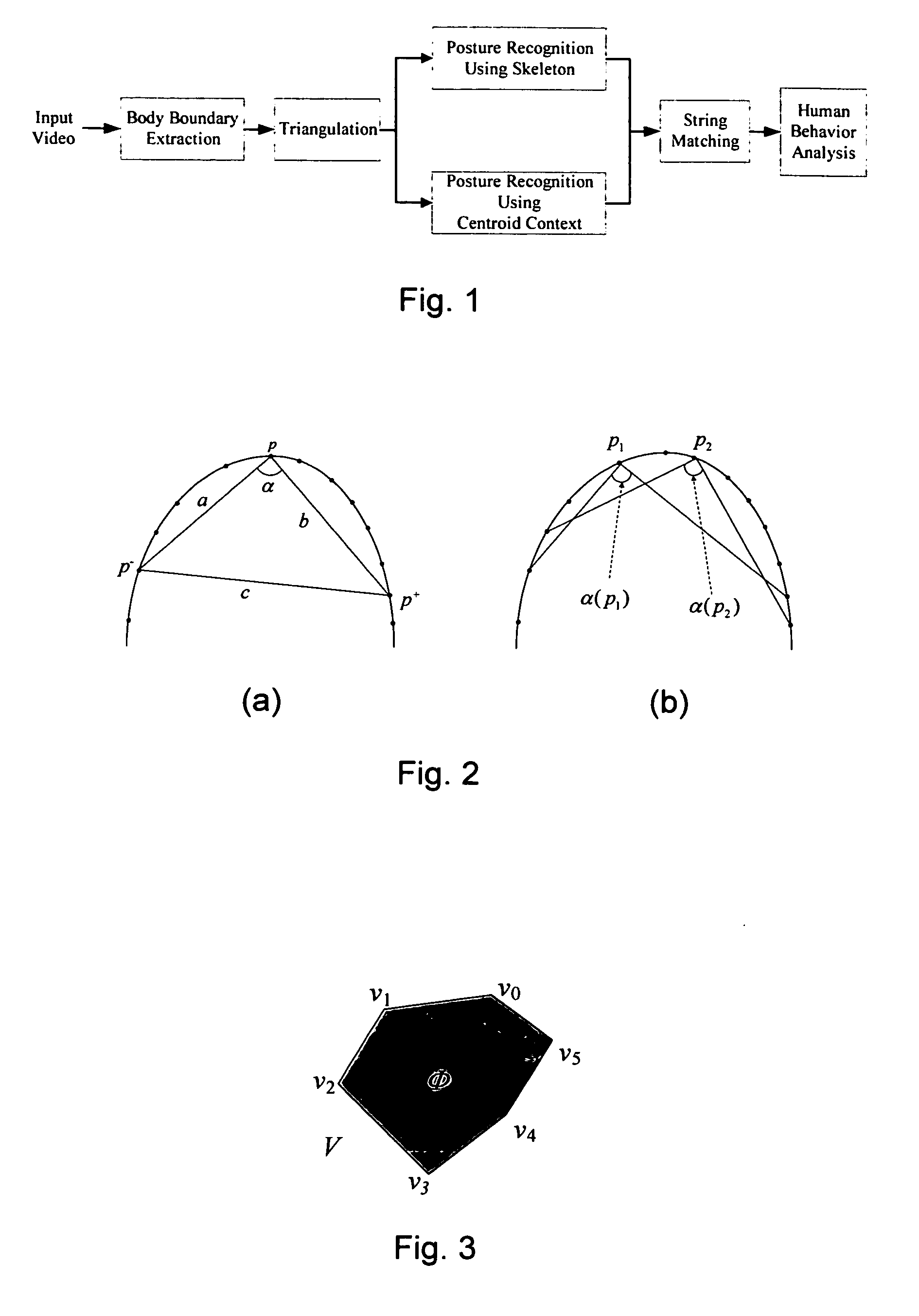
Apparatus for behavior analysis and method thereof
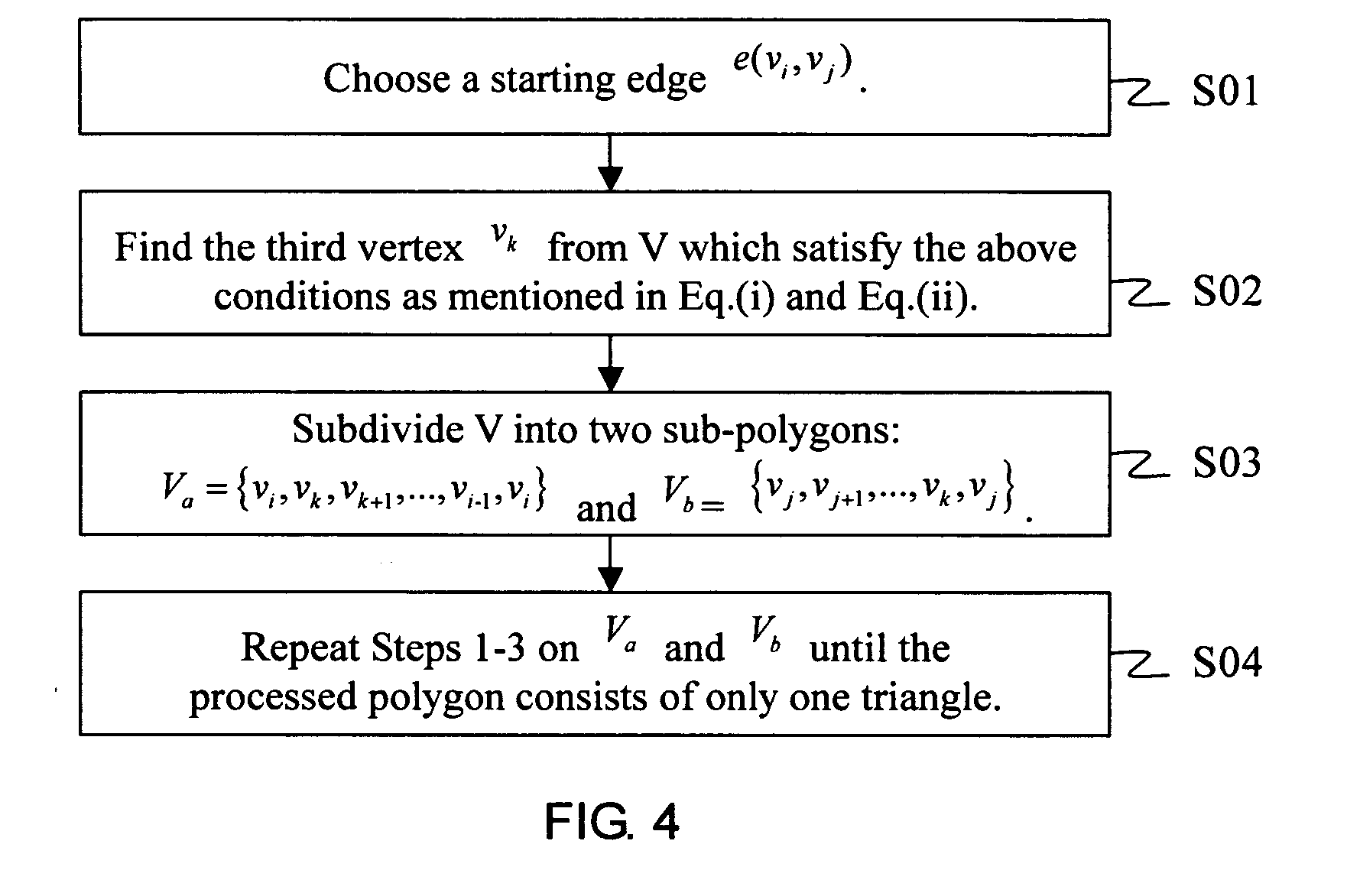
InactiveUS20100278391A1Easy to analyzeEasy to compareImage analysisMedical automated diagnosisHuman behaviorTriangulation
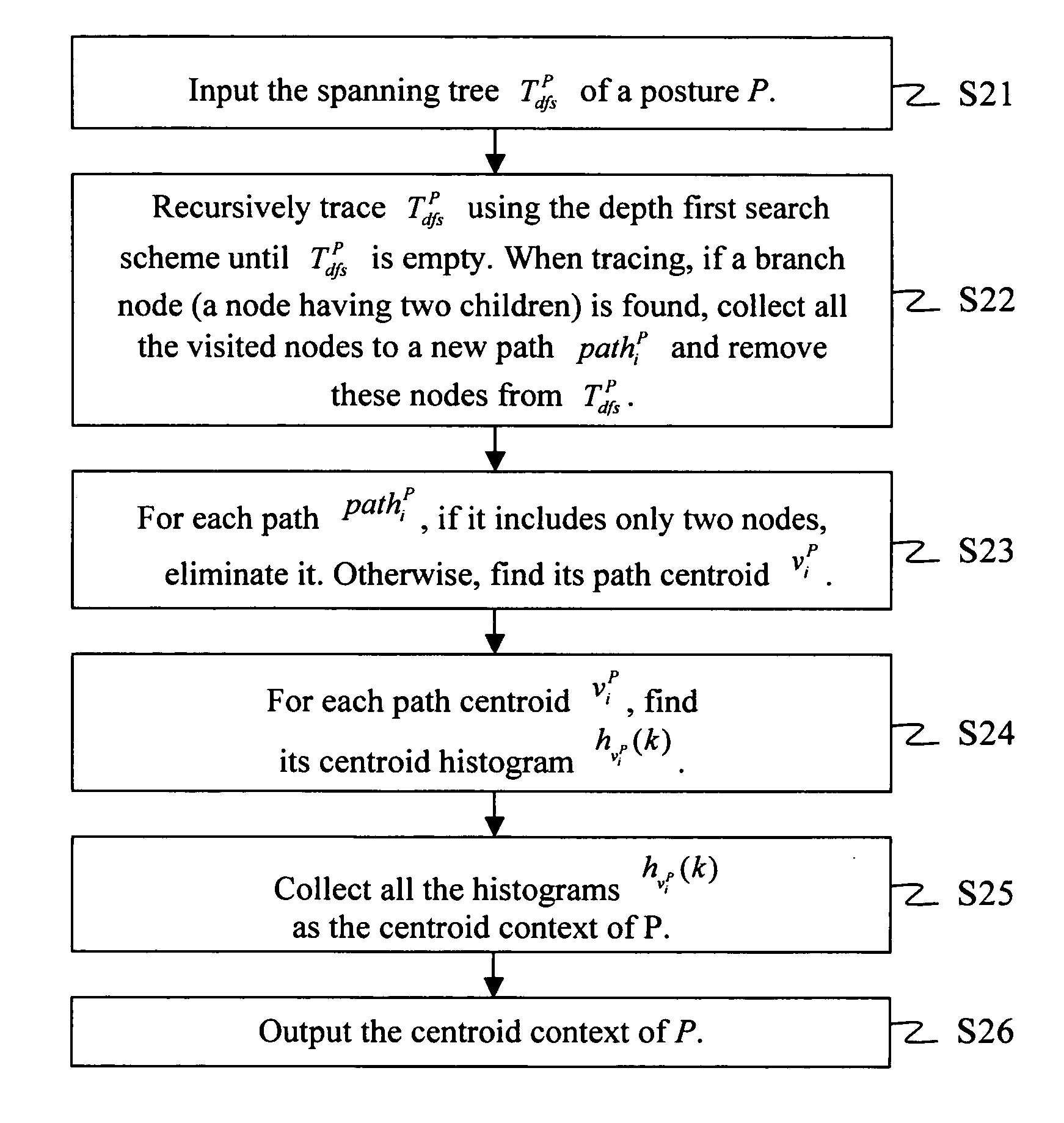
In the present invention, an apparatus for behavior analysis and method thereof is provided. In this apparatus, each behavior is analyzed and has its corresponding posture sequence through a triangulation-based method of triangulating the different triangle meshes. The two important posture features, the skeleton feature and the centroid context, are extracted and complementary to each other. The outstanding ability of posture classification can generate a set of key postures for coding a behavior sequence to a set of symbols. Then, based on the string representation, a novel string matching scheme is proposed to analyze different human behaviors even though they have different scaling changes. The proposed method of the present invention has been proved robust, accurate, and powerful especially in human behavior analysis.
Owner:NAT CHIAO TUNG UNIV
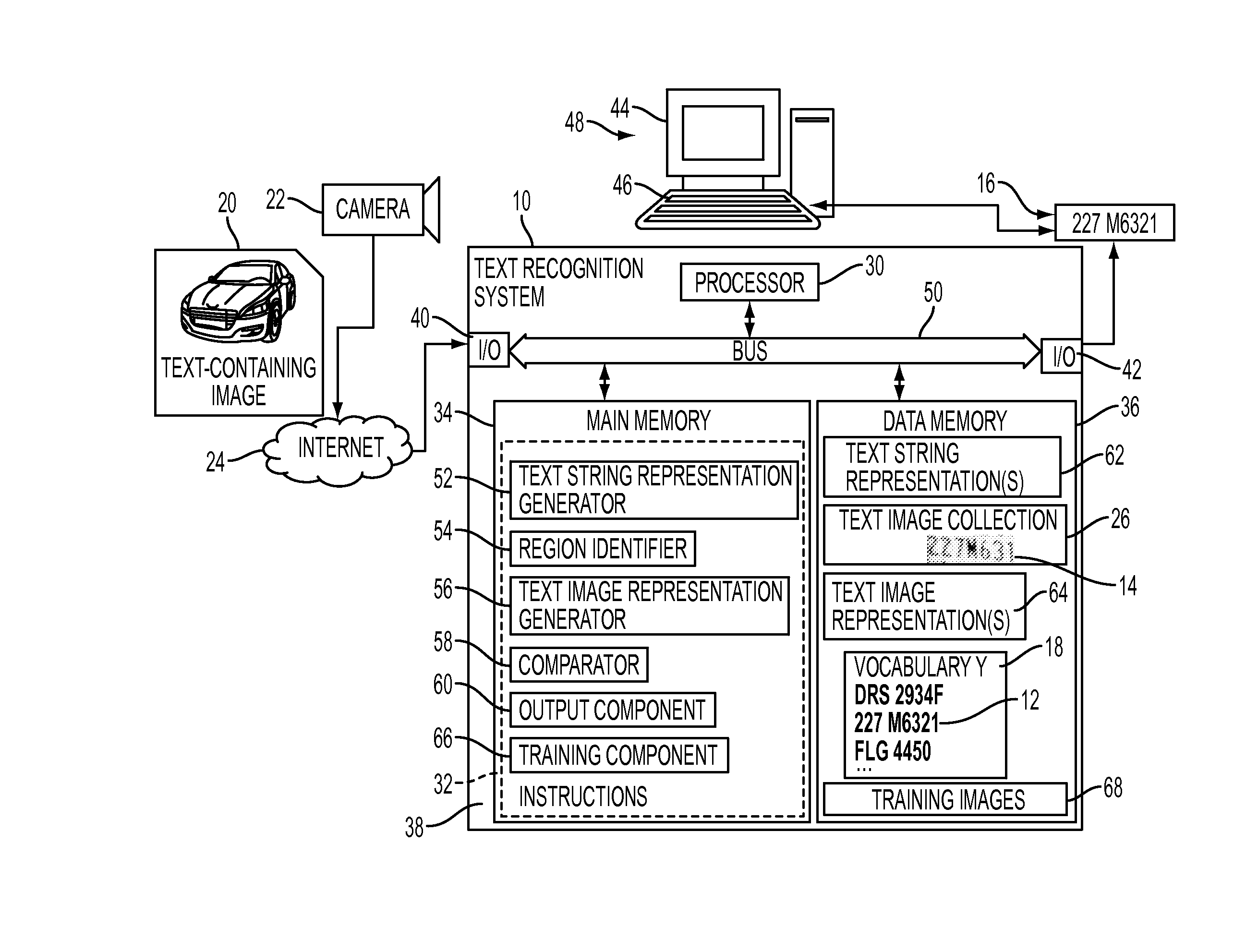
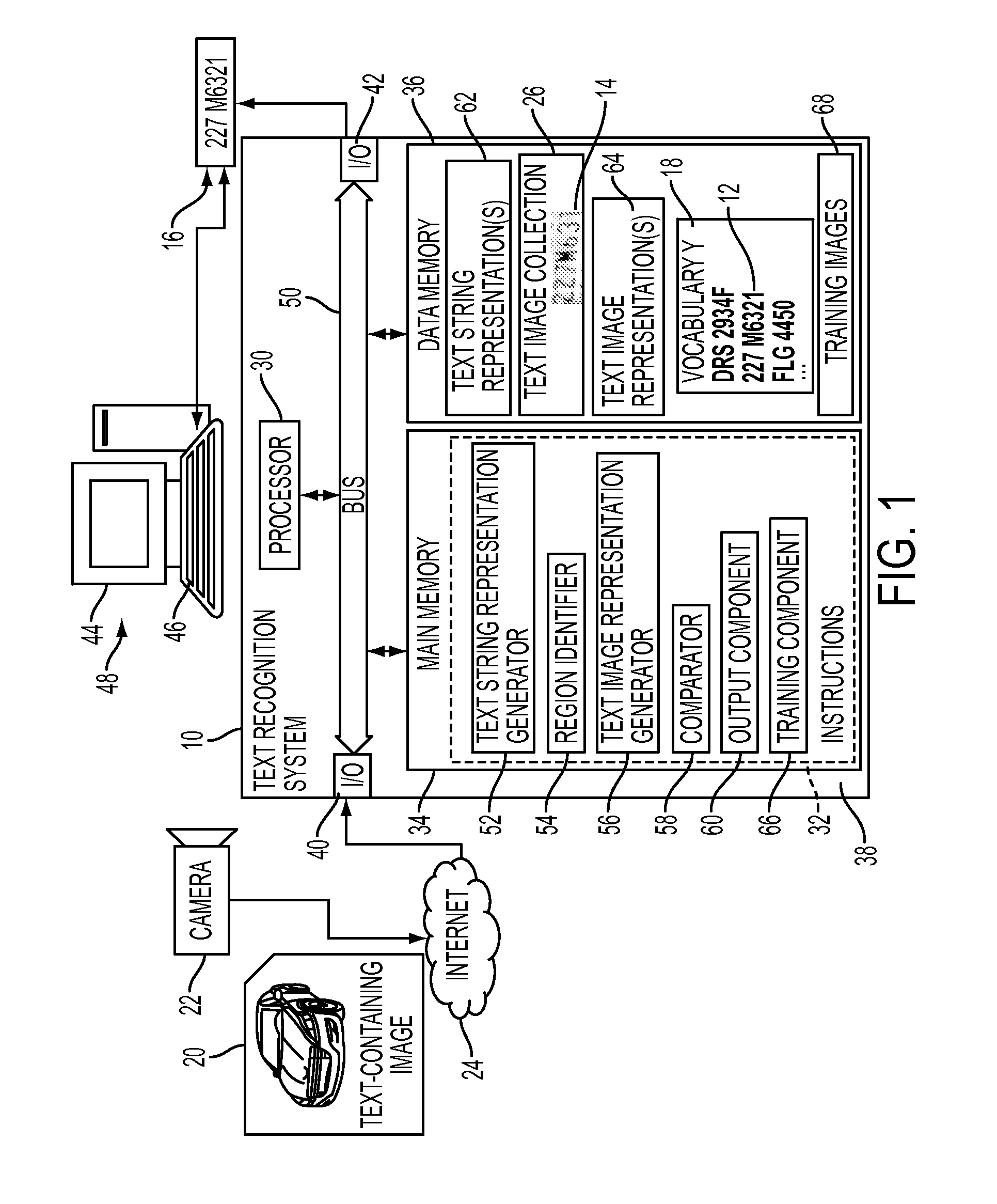
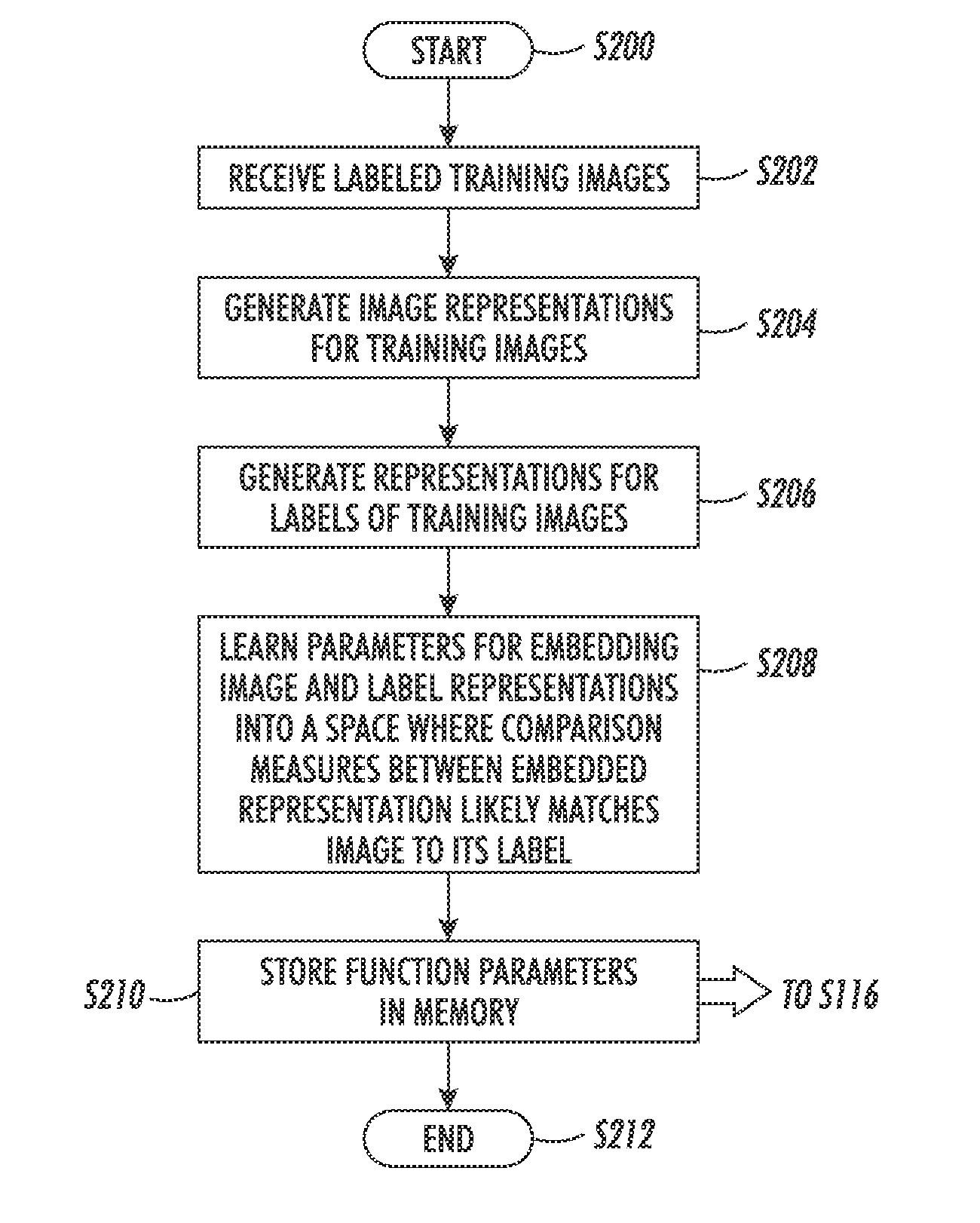
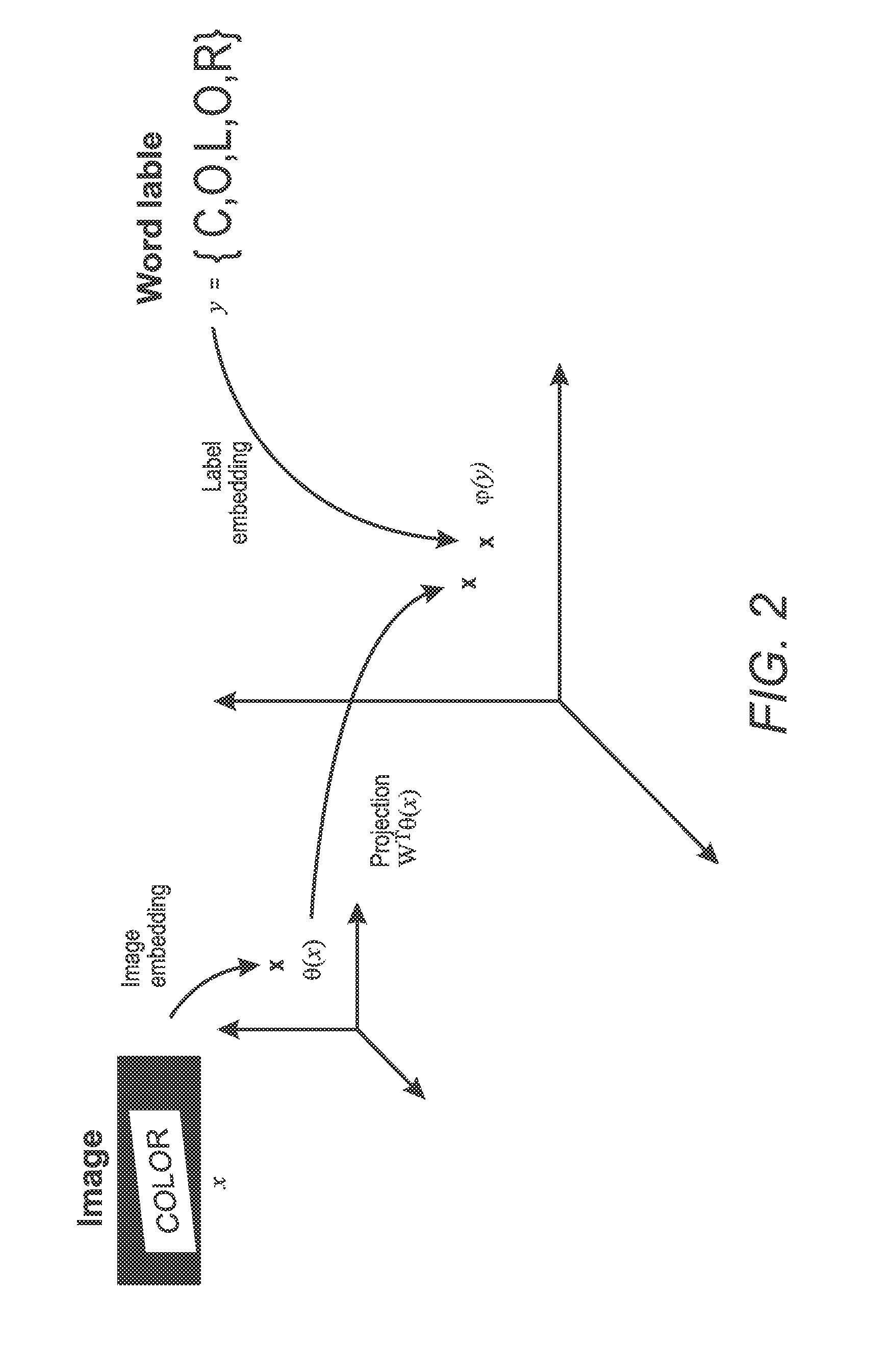
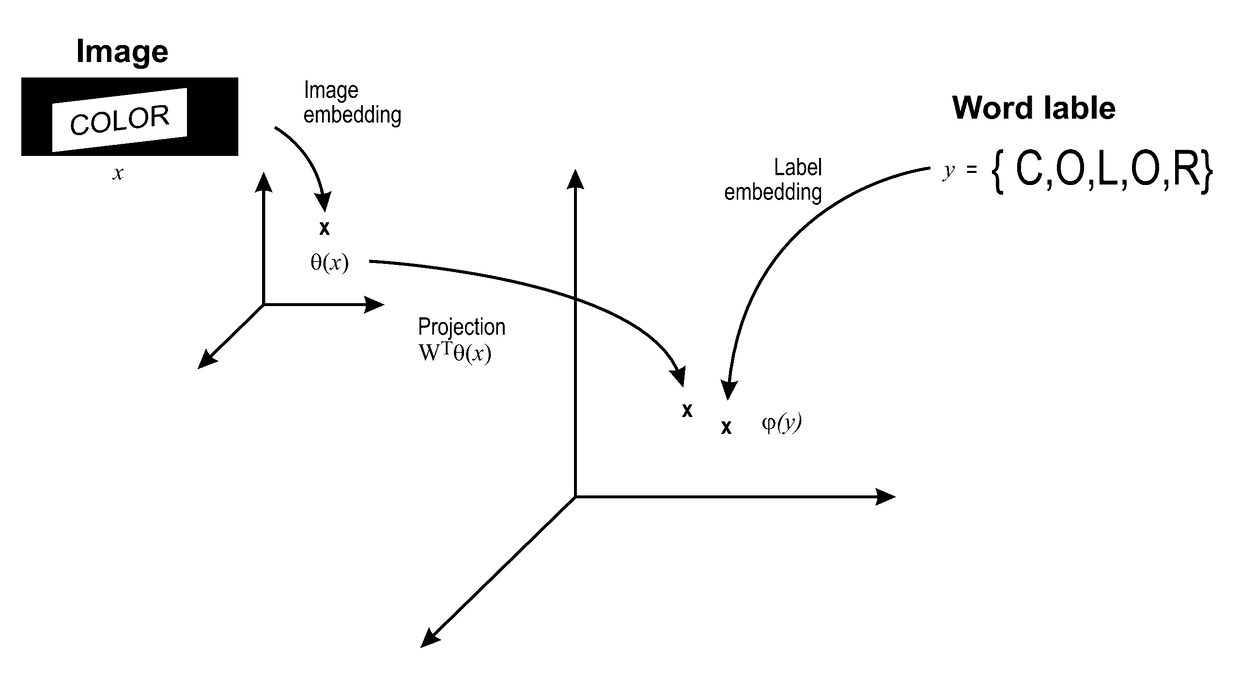
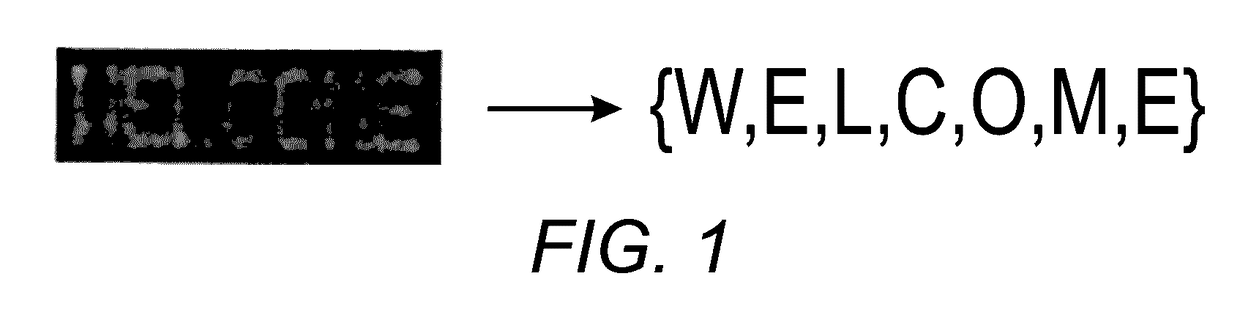
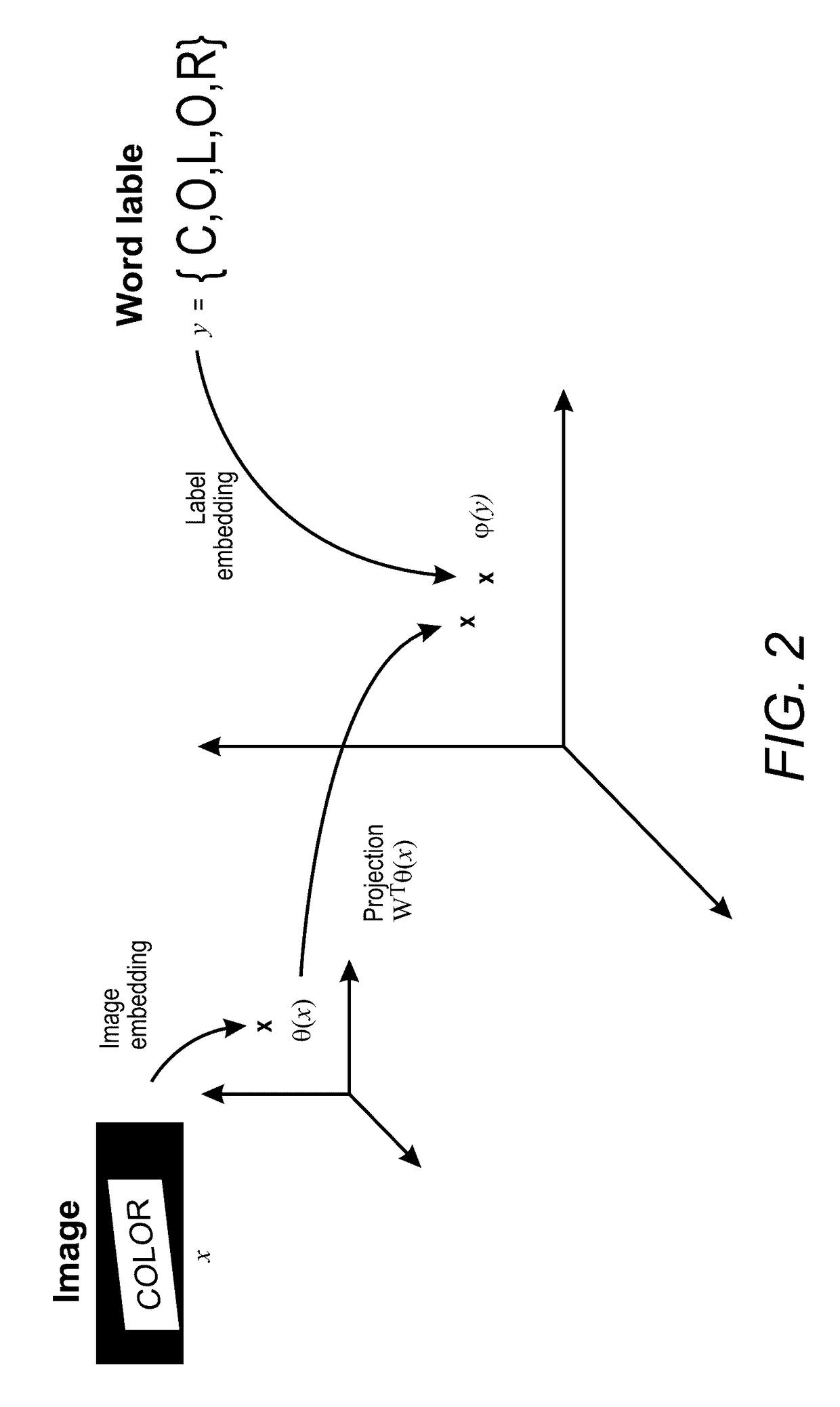
Label-embedding for text recognition
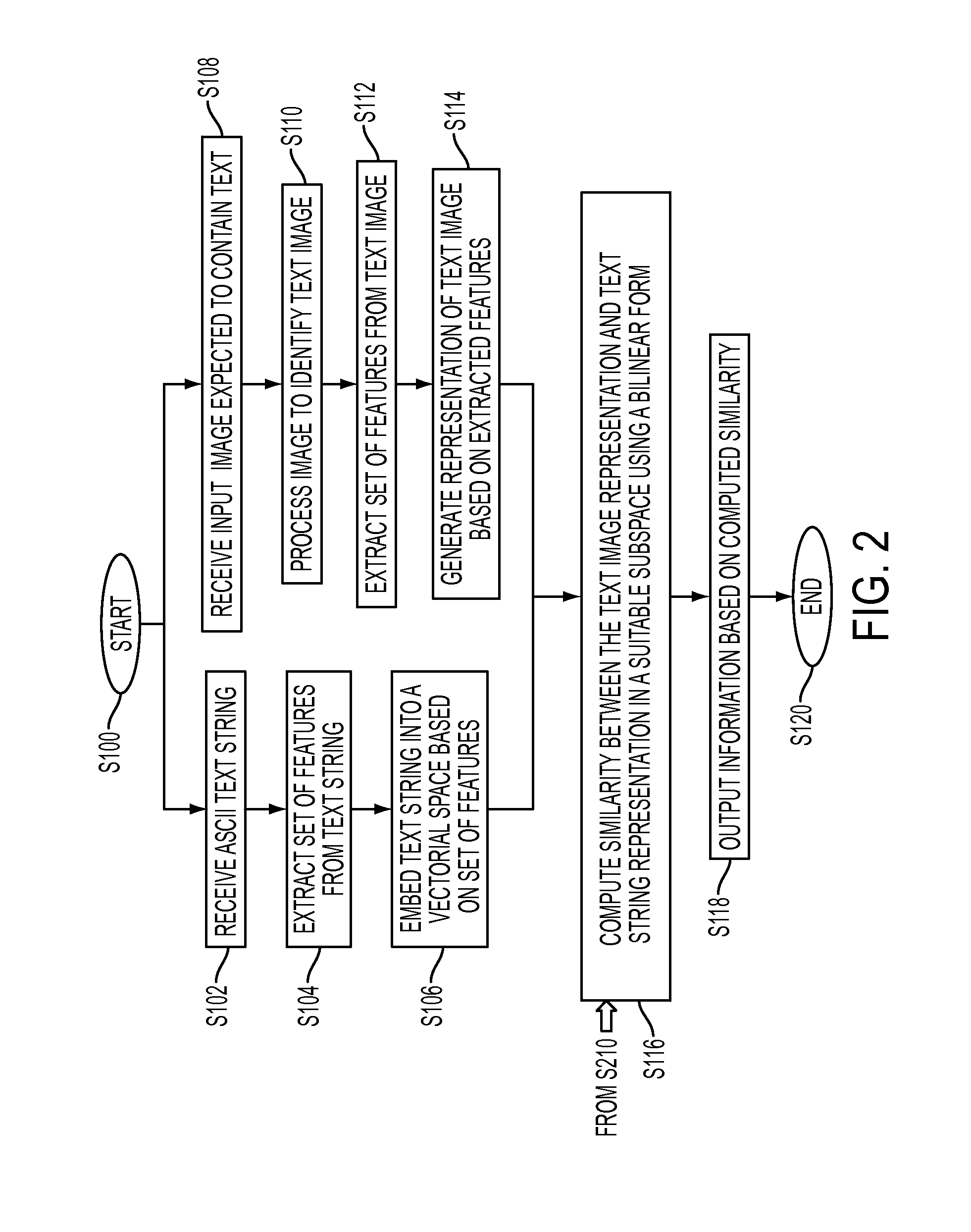
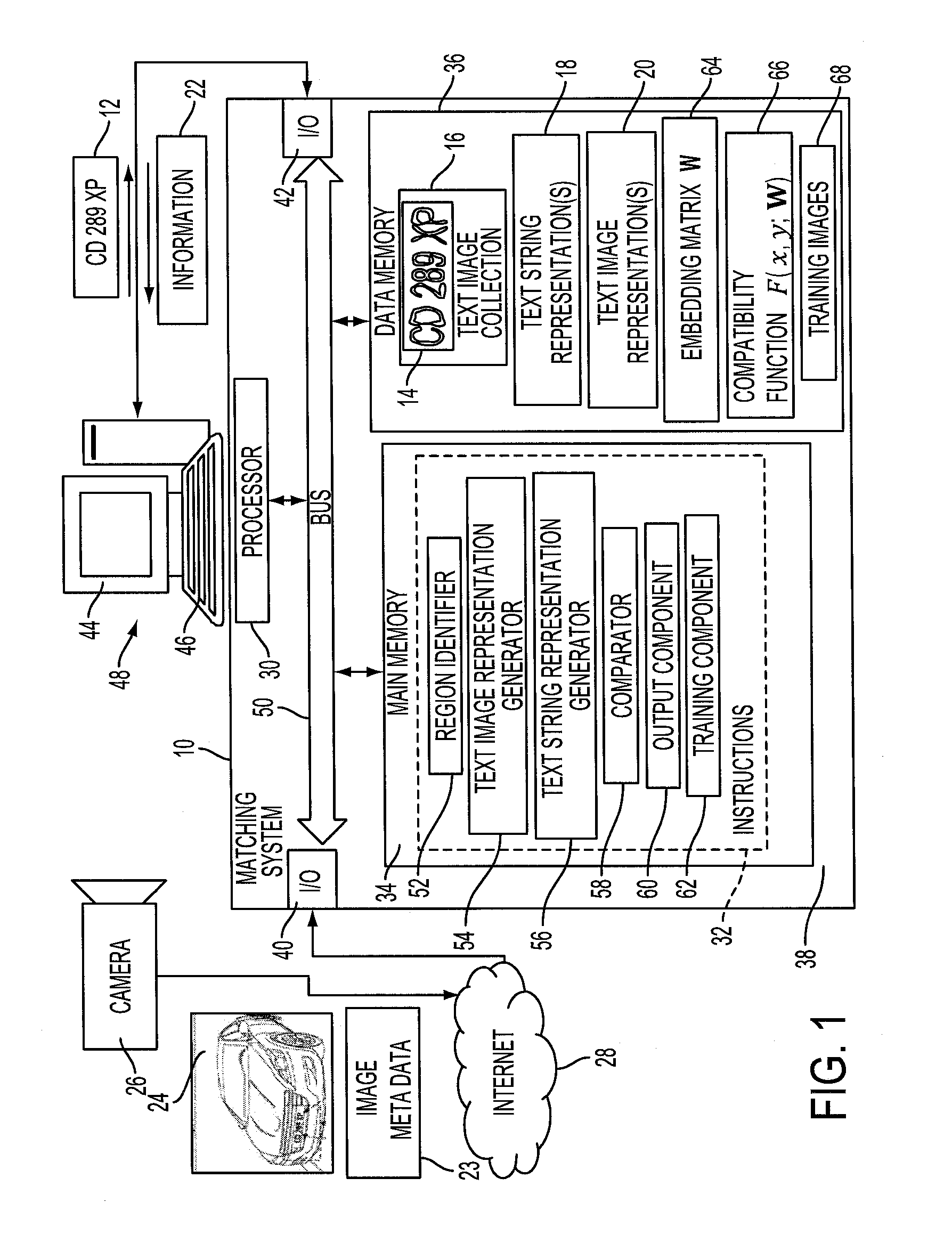
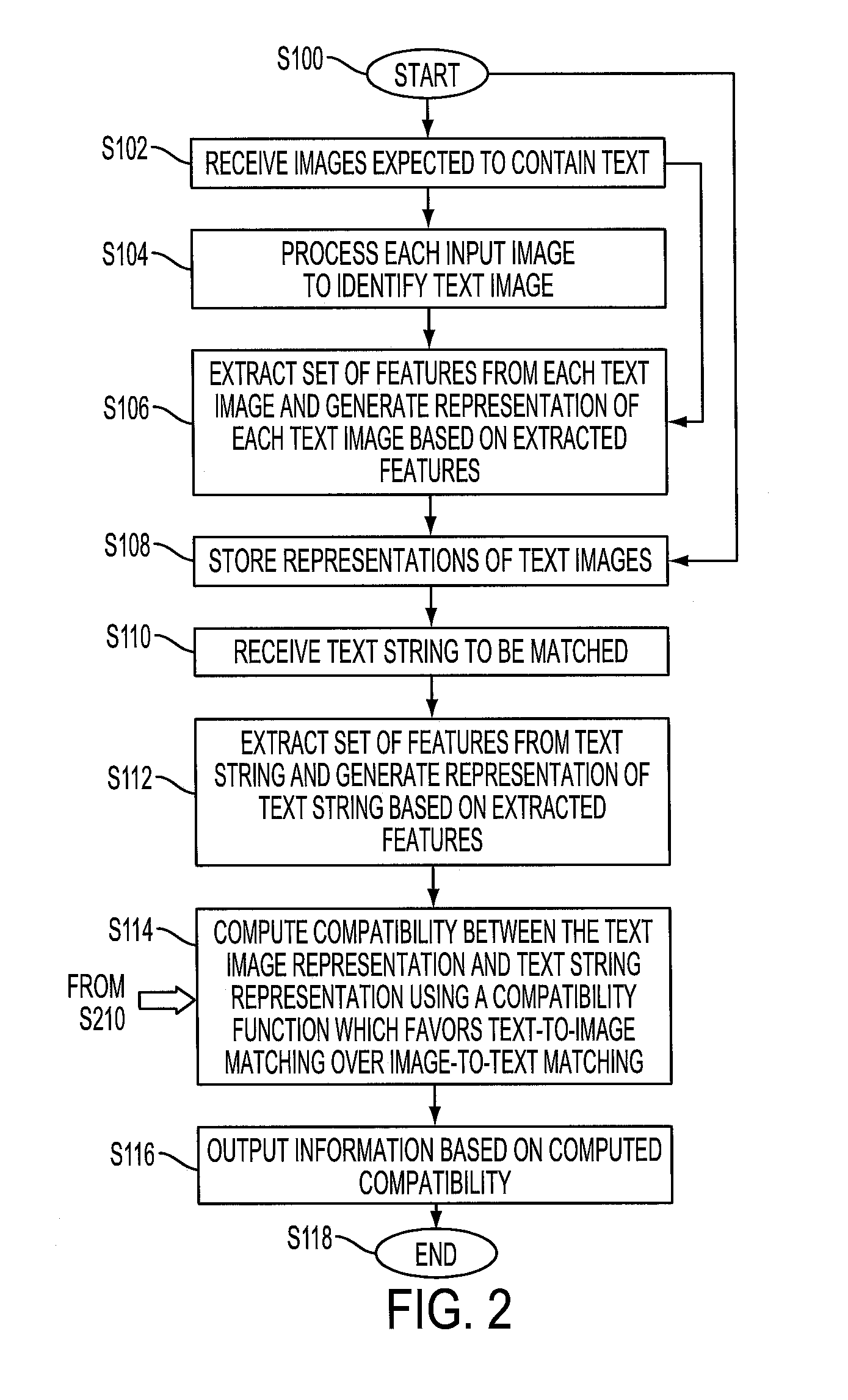
A system and method for comparing a text image and a character string are provided. The method includes embedding a character string into a vectorial space by extracting a set of features from the character string and generating a character string representation based on the extracted features, such as a spatial pyramid bag of characters (SPBOC) representation. A text image is embedded into a vectorial space by extracting a set of features from the text image and generating a text image representation based on the text image extracted features. A compatibility between the text image representation and the character string representation is computed, which includes computing a function of the text image representation and character string representation.
Owner:XEROX CORP
System and method providing a binary representation of a web page
ActiveUS20130246906A1Software engineeringNatural language data processingDocument Object ModelText string
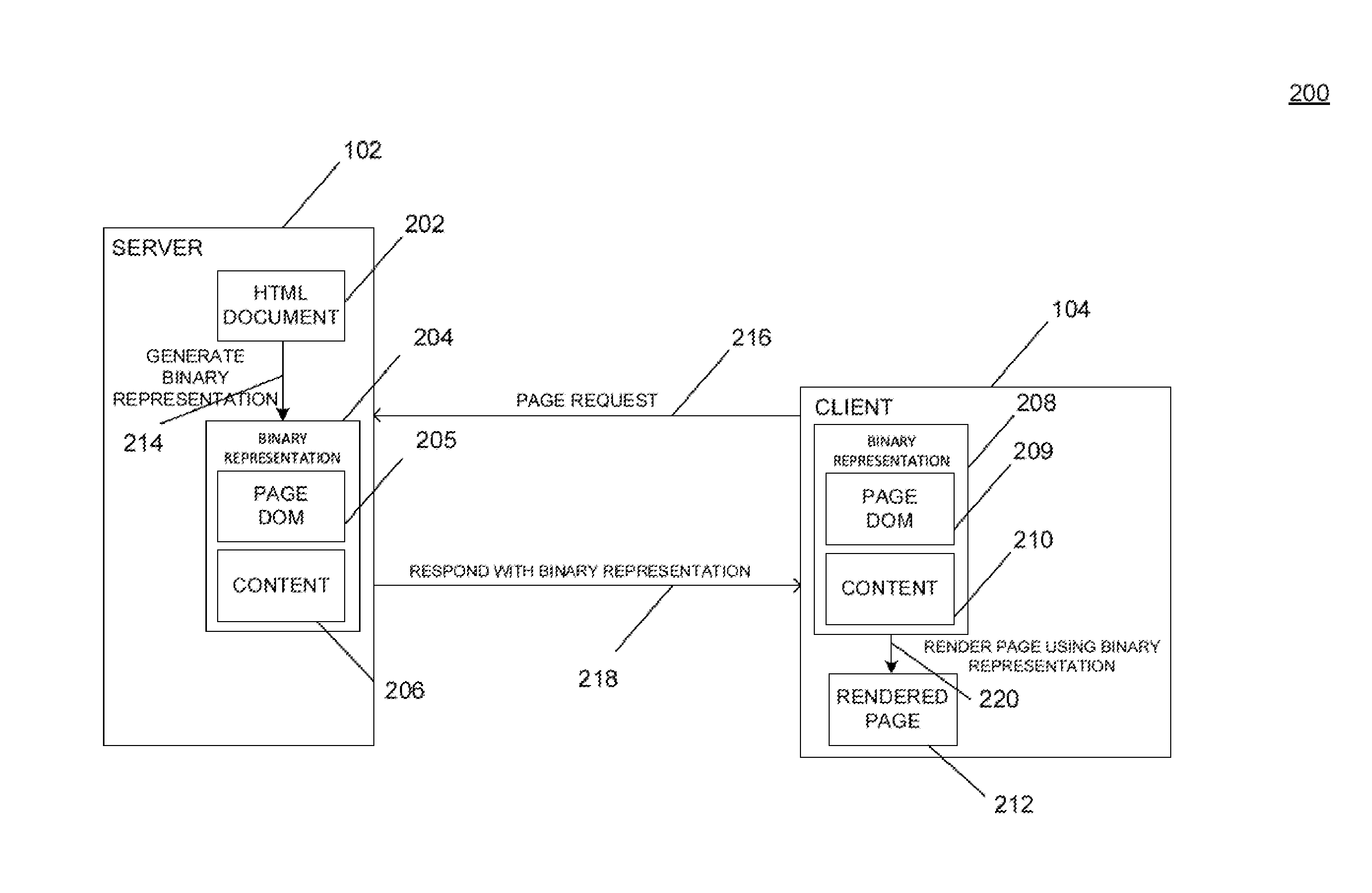
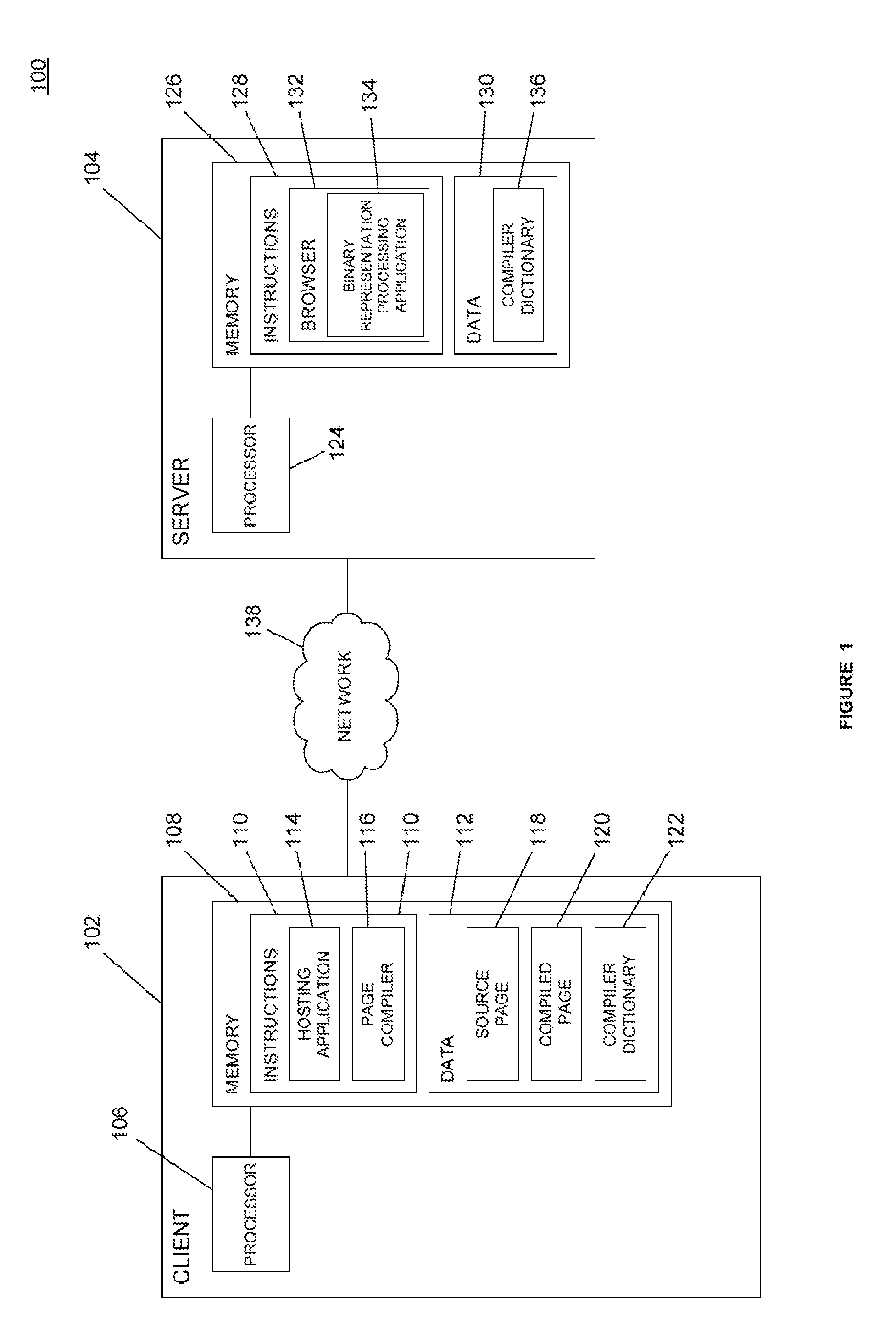
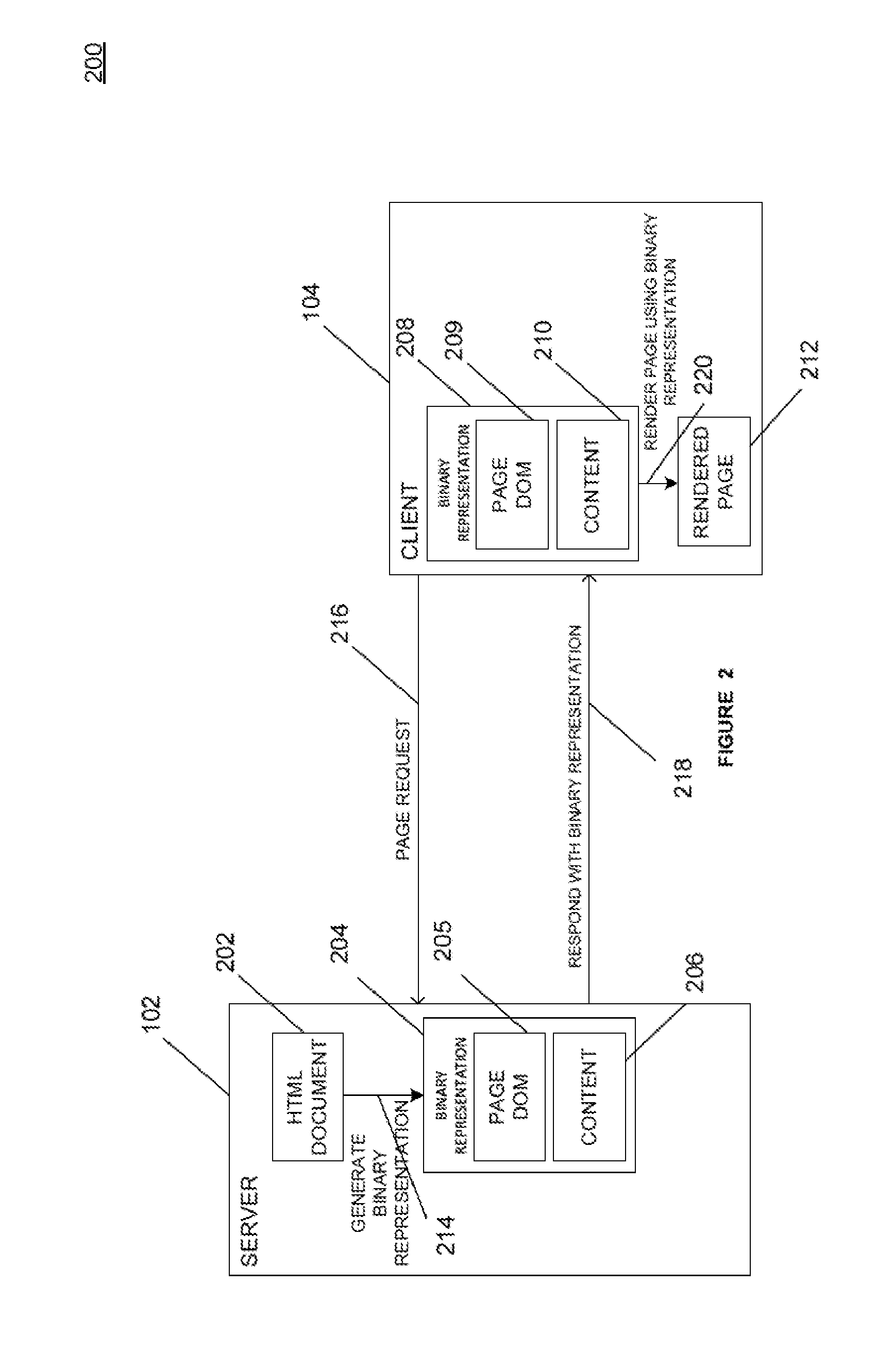
Systems and methods for providing a binary representation of a web page. A server may compile a source page, such as a hypertext markup language (“HTML”) document, to create a compiled representation of the source page. Creation of a compiled representation may include generating a document object model (“DOM”) for the content associated with the source page. The compiled page may be transmitted to a client as a random-access file or flat file, where the data is encoded in one or more data types other than a string representation. The client may receive the compiled page and load the compiled page directly as a DOM for the page without the need to parse HTML text strings. The server and client may reconcile the data format of the compiled page, such as by exchanging or verifying a compiler dictionary associated with the page.
Owner:GOOGLE LLC
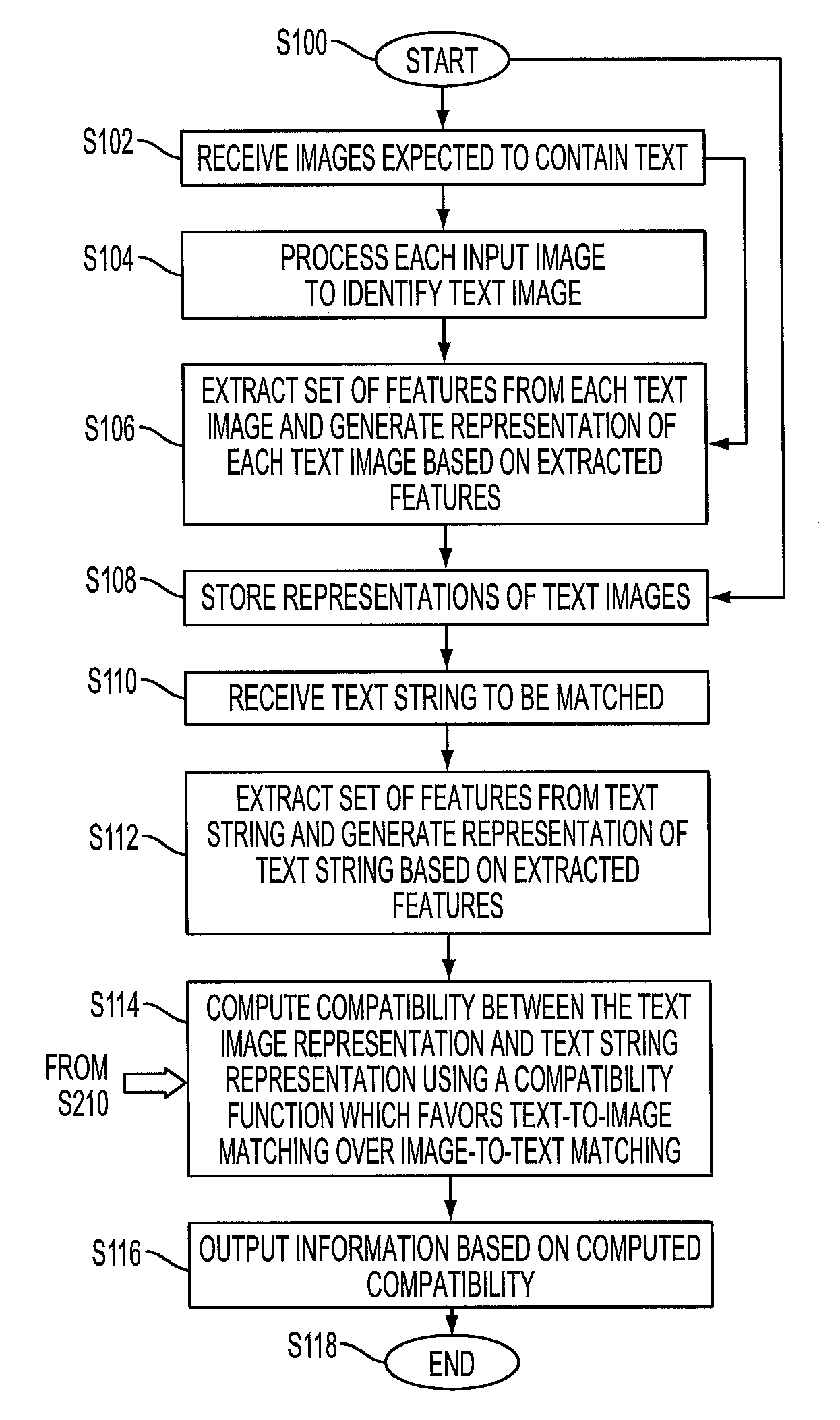
Method and system to perform text-to-image queries with wildcards
A system and method for comparing a text image with or without a wildcard character and a character string are provided. The method includes embedding a character string into a vectorial space by extracting a set of features from the character string and generating a character string representation based on the extracted features, such as a spatial pyramid bag of characters (SPBOC) representation. A text image is embedded into a vectorial space by extracting a set of features from the text image and generating a text image representation based on the text image extracted features. A similarity between the text image representation and the character string representation is computed, which includes computing a function of the text image representation and character string representation.
Owner:CONDUENT BUSINESS SERVICES LLC
Privacy-preserving text to image matching
ActiveUS9367763B1Still image data retrievalCharacter and pattern recognitionPrivacy preservingImage matching
A method for text-to-image matching includes generating representations of text images, such as license plate images, by embedding each text image into a first vectorial space with a first embedding function. With a second embedding function, a character string, such as a license plate number to be matched, is embedded into a second vectorial space to generate a character string representation. A compatibility is computed between the character string representation and one or more of the text image representations to identify a matching one. The compatibility is computed with a function that uses a transformation which is learned on a training set of labeled images. The learning uses a loss function that aggregates a text-to-image-loss and an image-to-text loss over the training set. The image-to-text loss penalizes the transformation when it correctly ranks a pair of character string representations, given an image representation corresponding to one of them.
Owner:CONDUENT BUSINESS SERVICES LLC
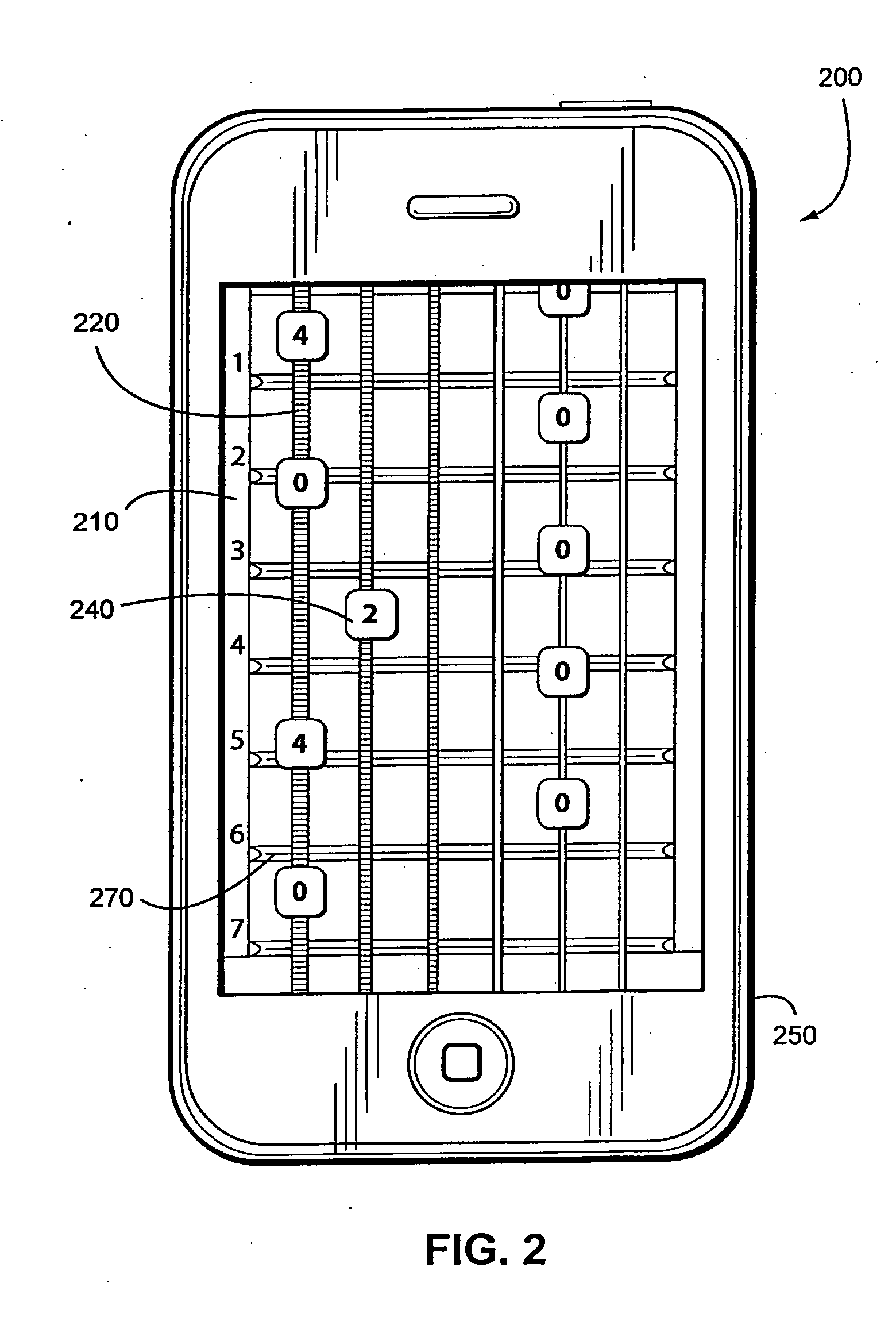
String instrument educational device
InactiveUS20110146477A1Accurate locationElectrophonic musical instrumentsMusicMusical toneHuman–computer interaction
A string instrument educational device implemented on a computer having a touch screen (100) that causes a note representation of a musical note (140) to appear and travel along a string representation (having locations to depress to cause the string representation to play a corresponding plurality of notes) to a target area (150) a time interval before the note is to be played. The note representation (140) preferably reacts when the musical note has been correctly played by the user touching the touch screen (100) at the correct location when the note representation reaches the target area (150). The note representation preferably reflects which location must be touched to correctly play the note.
Owner:MISO MEDIA
Compact text encoding of latitude/longitude coordinates
InactiveUS7302343B2Digital data information retrievalData processing applicationsLongitudeTheoretical computer science
Methods are disclosed for encoding latitude / longitude coordinates within a URL in a relatively compact form. The method includes converting latitude and longitude coordinates from floating-point numbers to non-negative integers. A set of base-N string representations are generated for the integers (N represents the number of characters in an implementation-defined character set being utilized). The latitude string and longitude string are then concatenated to yield a single output string. The output string is utilized as a geographic indicator with a URL.
Owner:MICROSOFT TECH LICENSING LLC
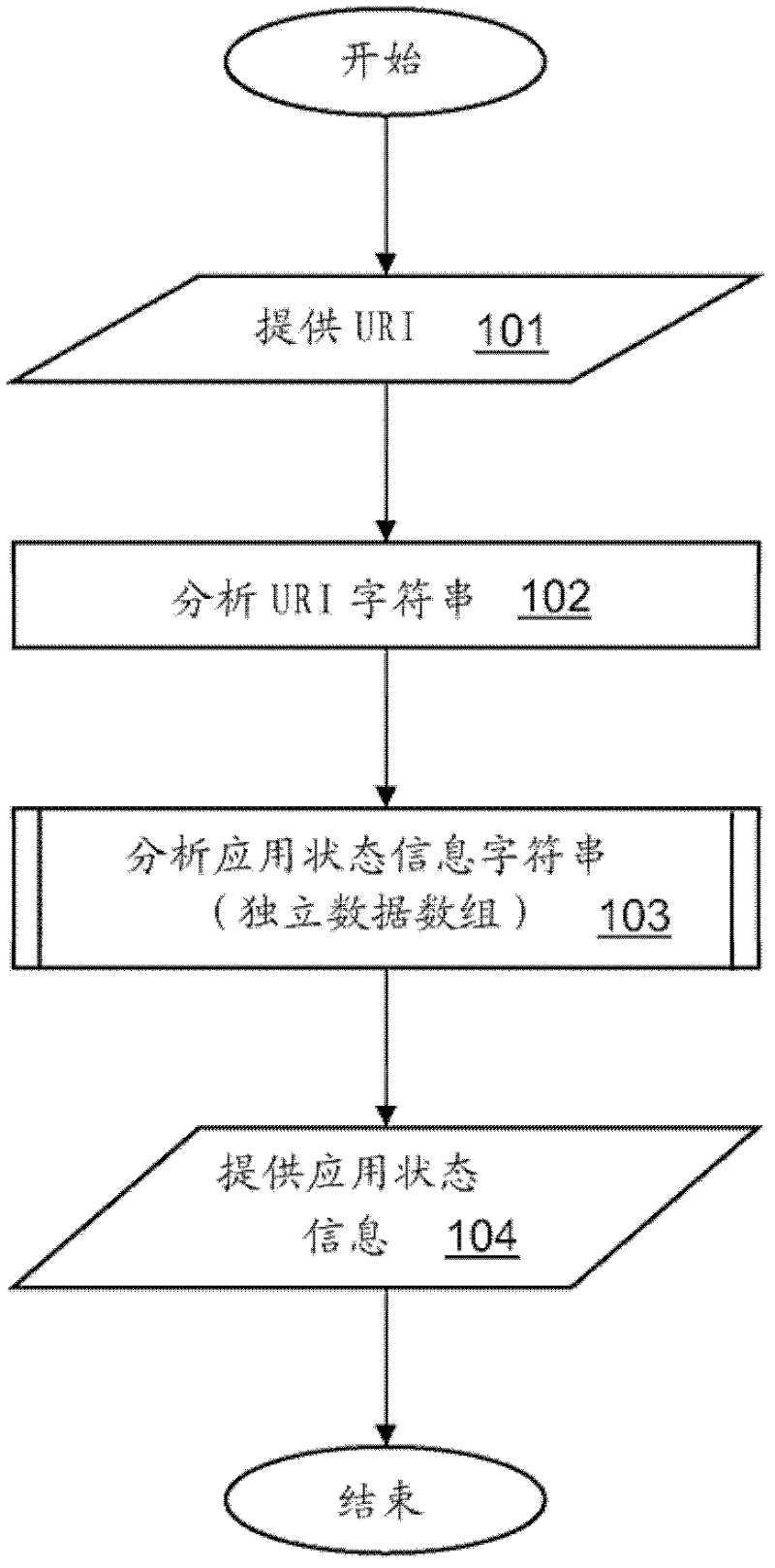
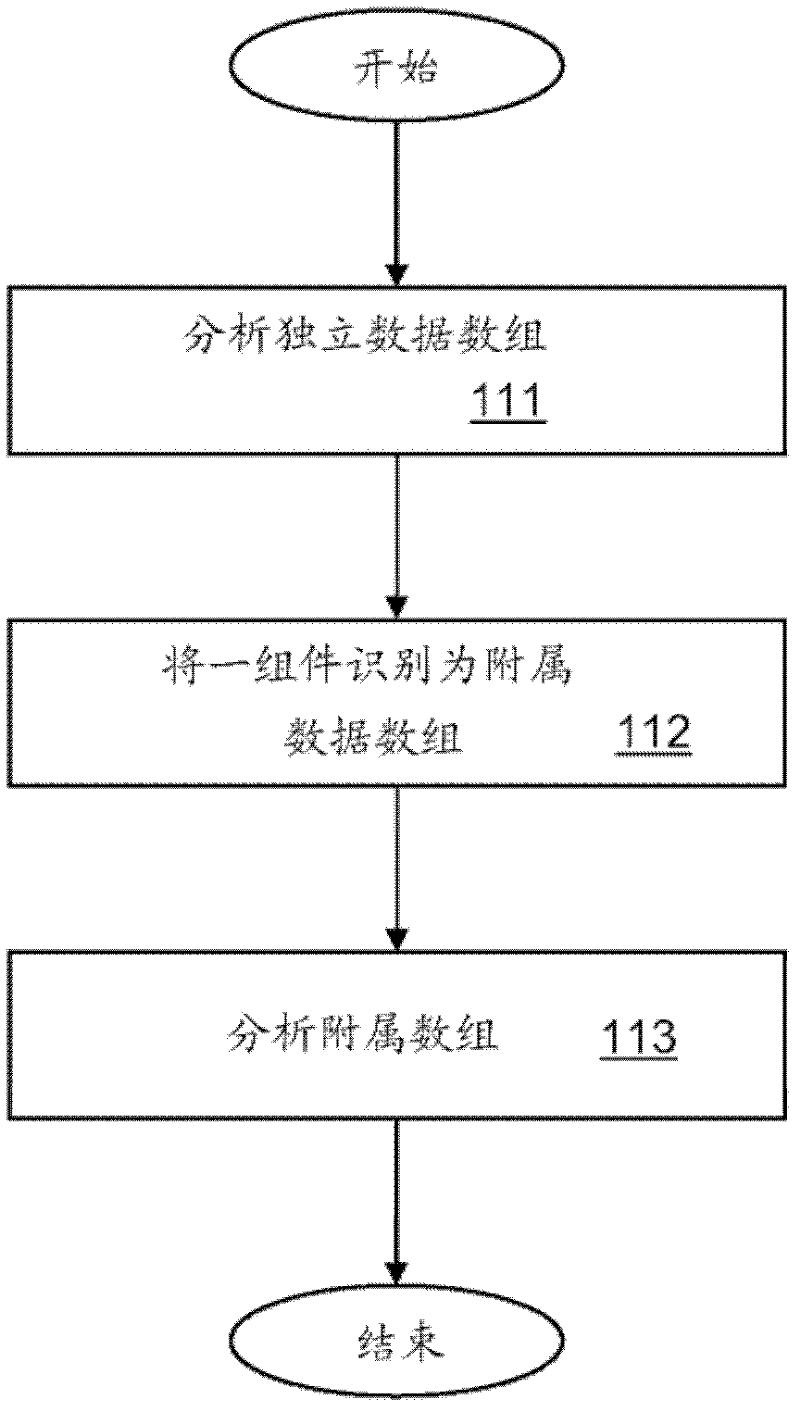
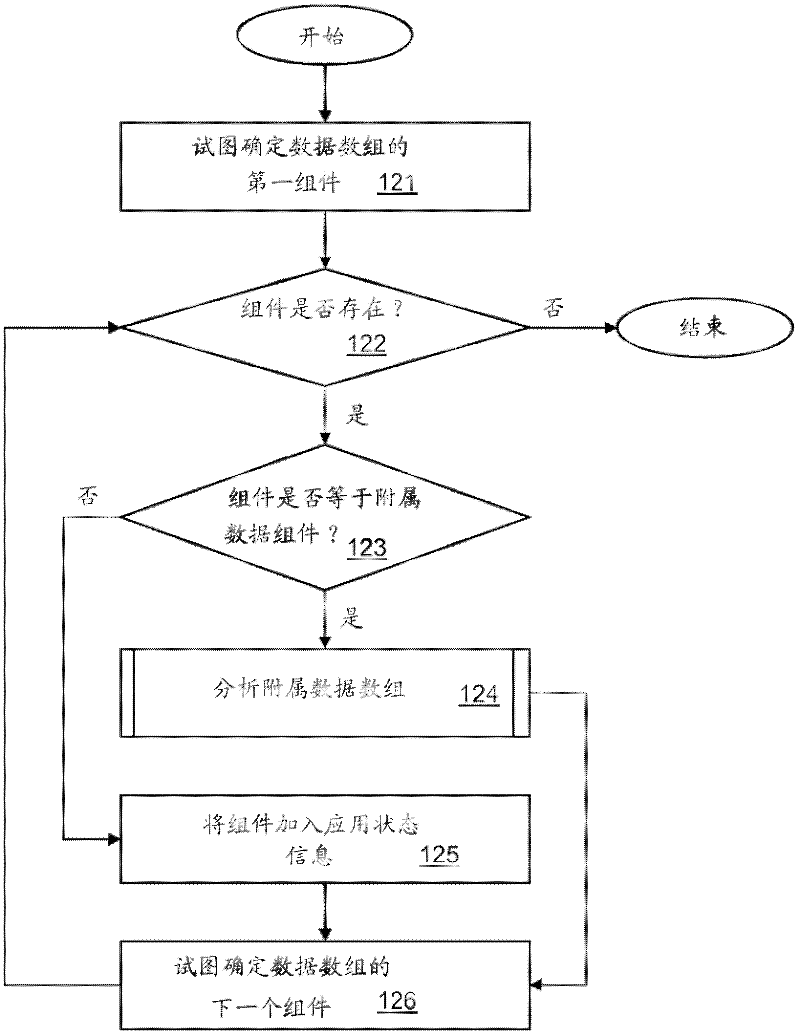
Managing application state information by means of a uniform resource identifier (uri)
InactiveCN102597993ADigital data information retrievalData switching networksJSONString representation
An embodiment provides a method and system for managing application state information, which is represented by a substring of a Uniform Resource Identifier (URI), which identifies a resource in a network. The substring comprises a plurality of nested data arrays. A URI parser and a URI generator convert the application state information between an object representation and a URI string representation. Preferably, the URI is a Uniform Resource Locator (URL), the application state information is provided by a web application, and the URI string representation uses a JavaScript Object Notation (JSON).
Owner:IBM CORP
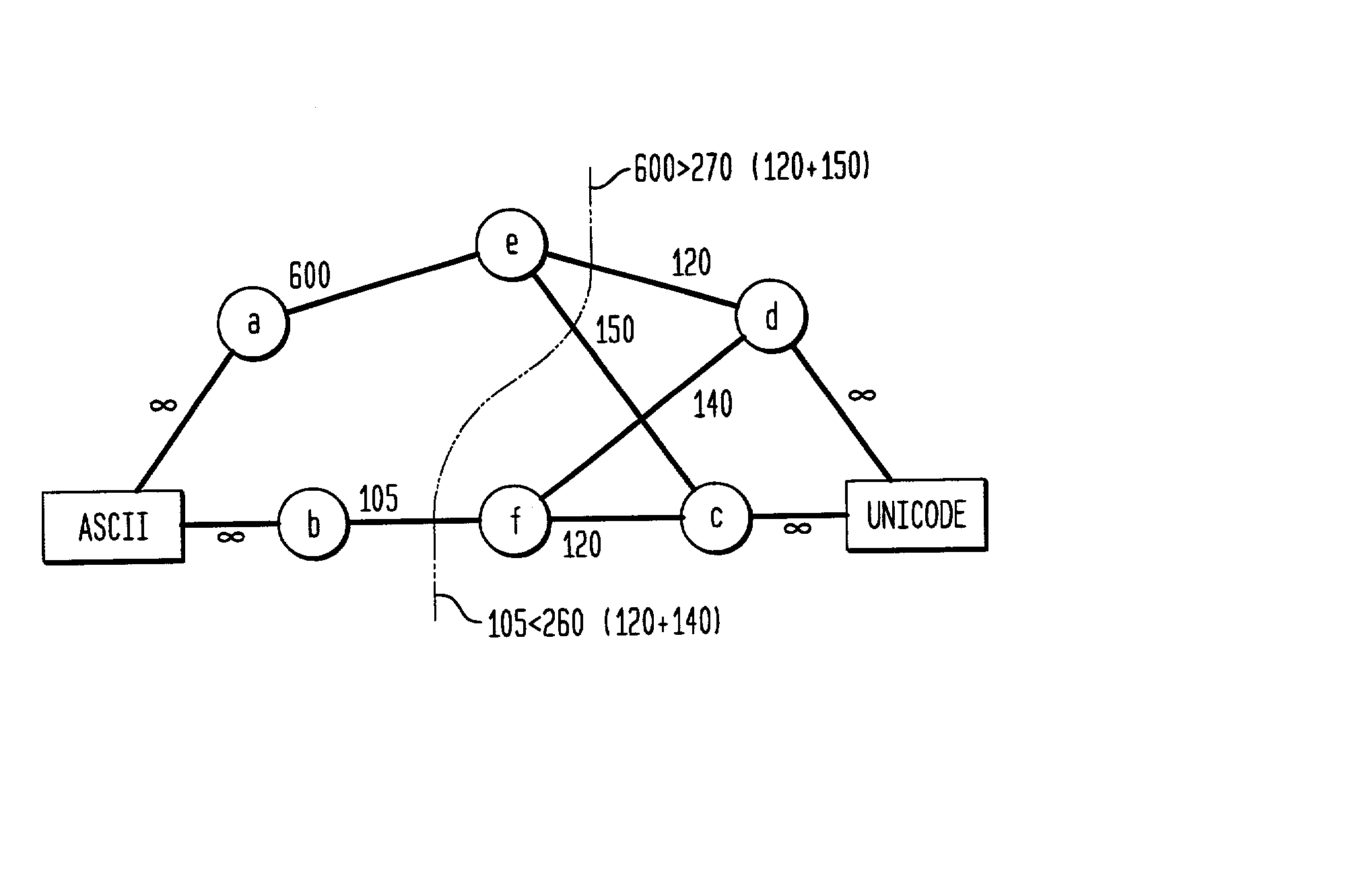
Minimizing interaction costs among components of computer programs
InactiveUS20020111697A1Low costMultiprogramming arrangementsMultiple digital computer combinationsString representationUnicode
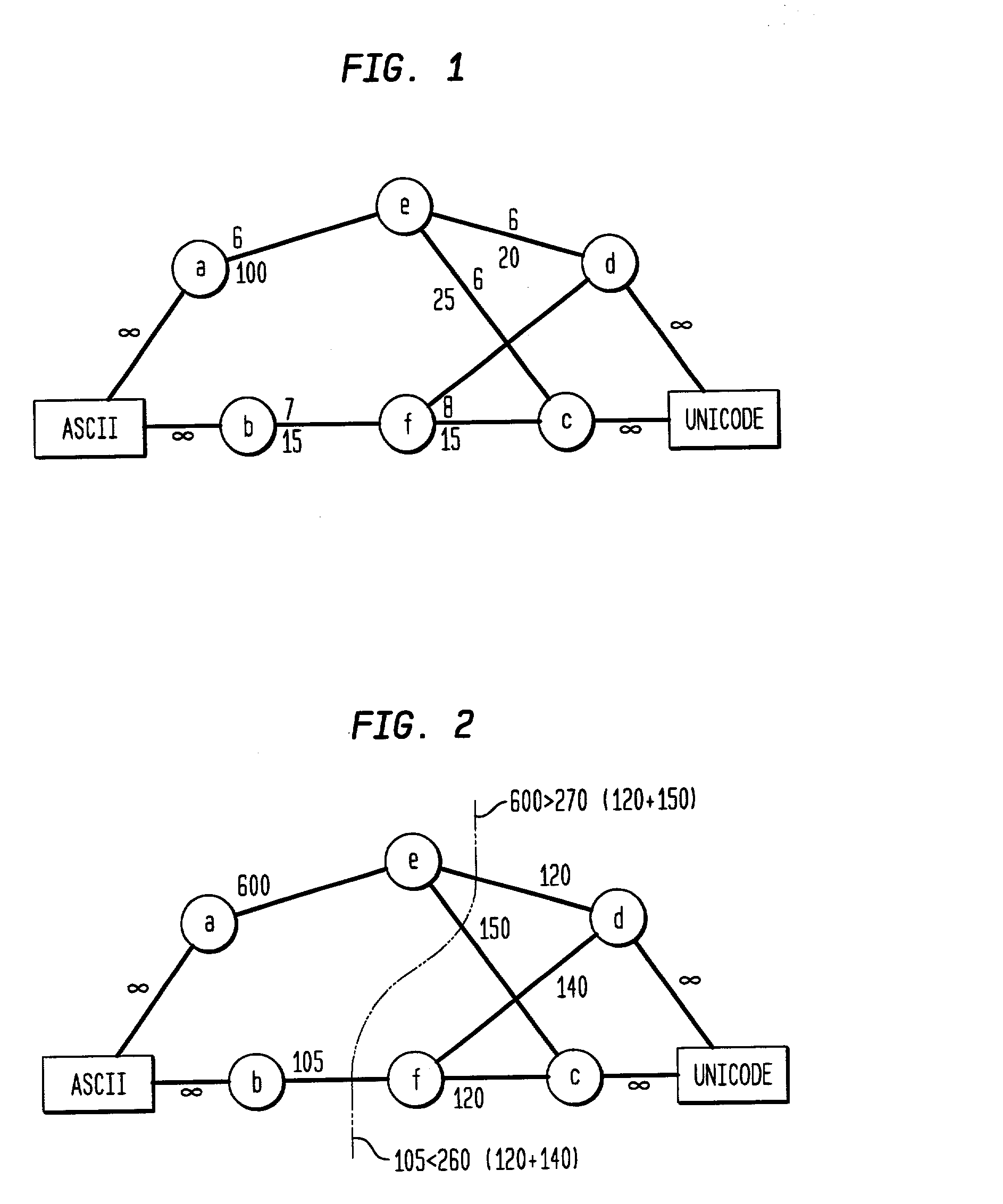
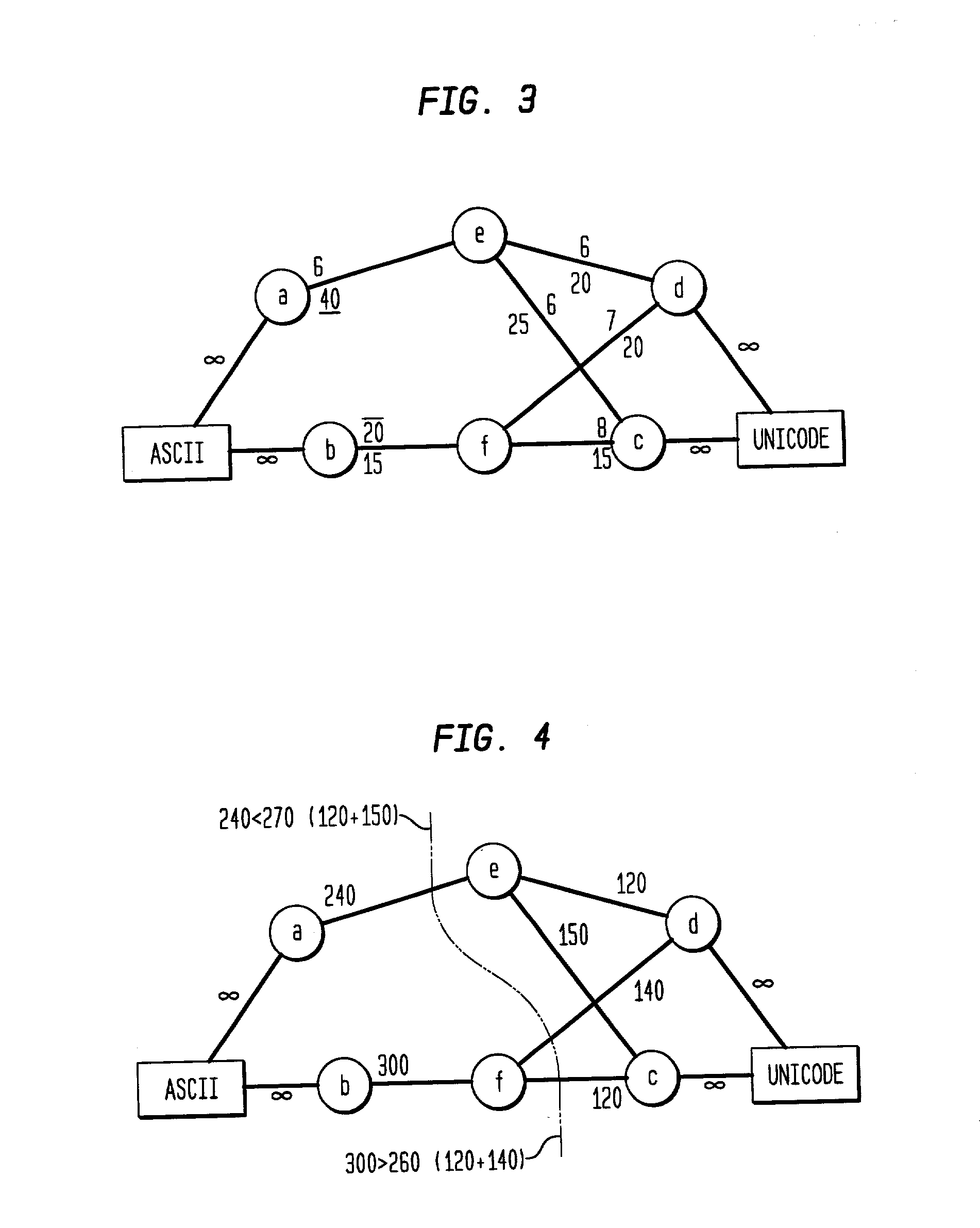
A system and method for minimizing total cost of interaction among components of a computer program which are each characterized by at least one implementation property. A implementation property may, for example, be a choice of string representation (e.g. ASCII, UNICODE, EBCDIC or choice of data structure (e.g. hash, tree, compressed). The method comprises the steps of: carrying out a run of the program; monitoring that run to measure an amount of interaction between each pair of components; determining a cost of interaction between each pair of interacting components; determining a choice of implementation properties which minimizes total cost of the run; and assigning choices of implementation properties to said components for a future run of the program.
Owner:IBM CORP
Behavior segmentation method based on human body motion capture data character string representation
ActiveCN105046720AImprove accuracyAddressing Behavioral Segmentation NeedsImage analysisSpecial data processing applicationsHuman bodyHigh dimensionality
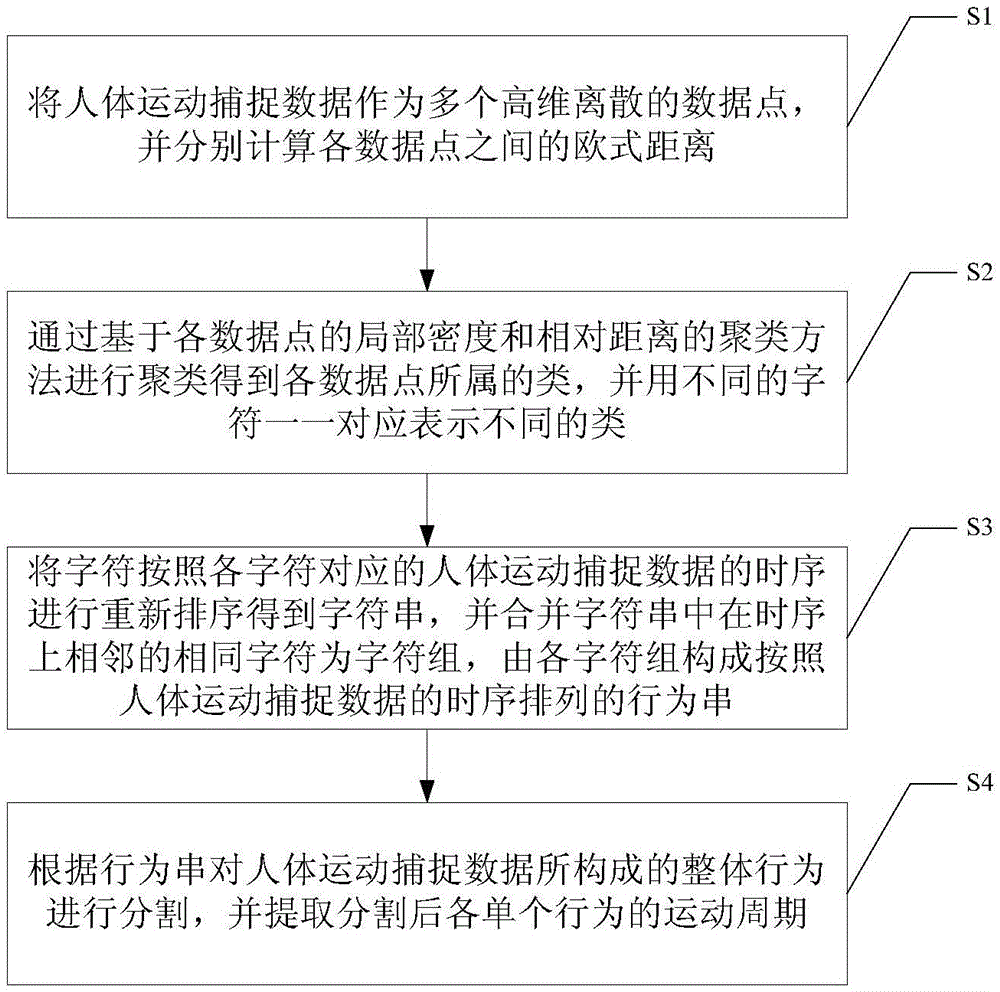
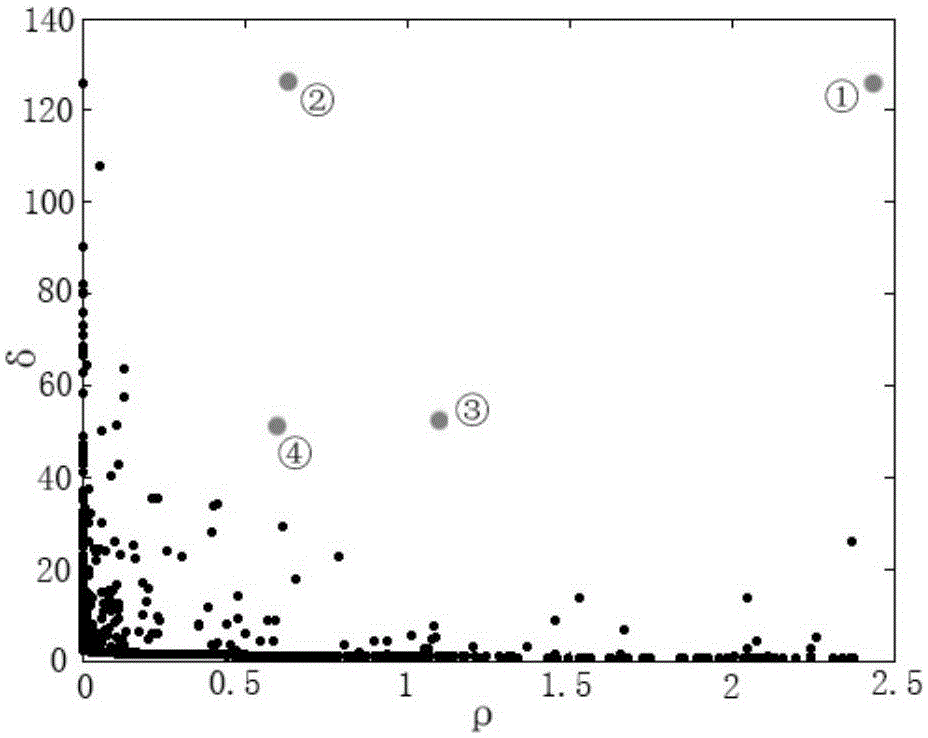
The invention discloses a behavior segmentation method based on human body motion capture data character string representation. The method comprises steps of S1, taking human body motion capture data as multiple high dimension discrete data points, and calculating each Euclidean distance between data points; S2, performing clustering through a cluster method based on the local density and the relative distance of each data point to obtain a category to which the data point belongs, and using different characters for representing different categories; S3, reordering the characters according to time sequences of data corresponding to the characters to obtain character strings, and merging the same characters adjacent in time sequence of the character strings to form character groups, wherein each character group forms a behavior string; and S4, segmenting a whole behavior formed by the human body motion capture data according to the behavior strings, and extracting the motion period of each single behavior after segmentation. The technical scheme of the invention is good in accuracy, and excellent in applicability, validity and non-supervision.
Owner:北交智轨(北京)科技有限公司
Label-embedding for text recognition
A system and method for comparing a text image and a character string are provided. The method includes embedding a character string into a vectorial space by extracting a set of features from the character string and generating a character string representation based on the extracted features, such as a spatial pyramid bag of characters (SPBOC) representation. A text image is embedded into a vectorial space by extracting a set of features from the text image and generating a text image representation based on the text image extracted features. A compatibility between the text image representation and the character string representation is computed, which includes computing a function of the text image representation and character string representation.
Owner:XEROX CORP
Multi-byte compressed string representation
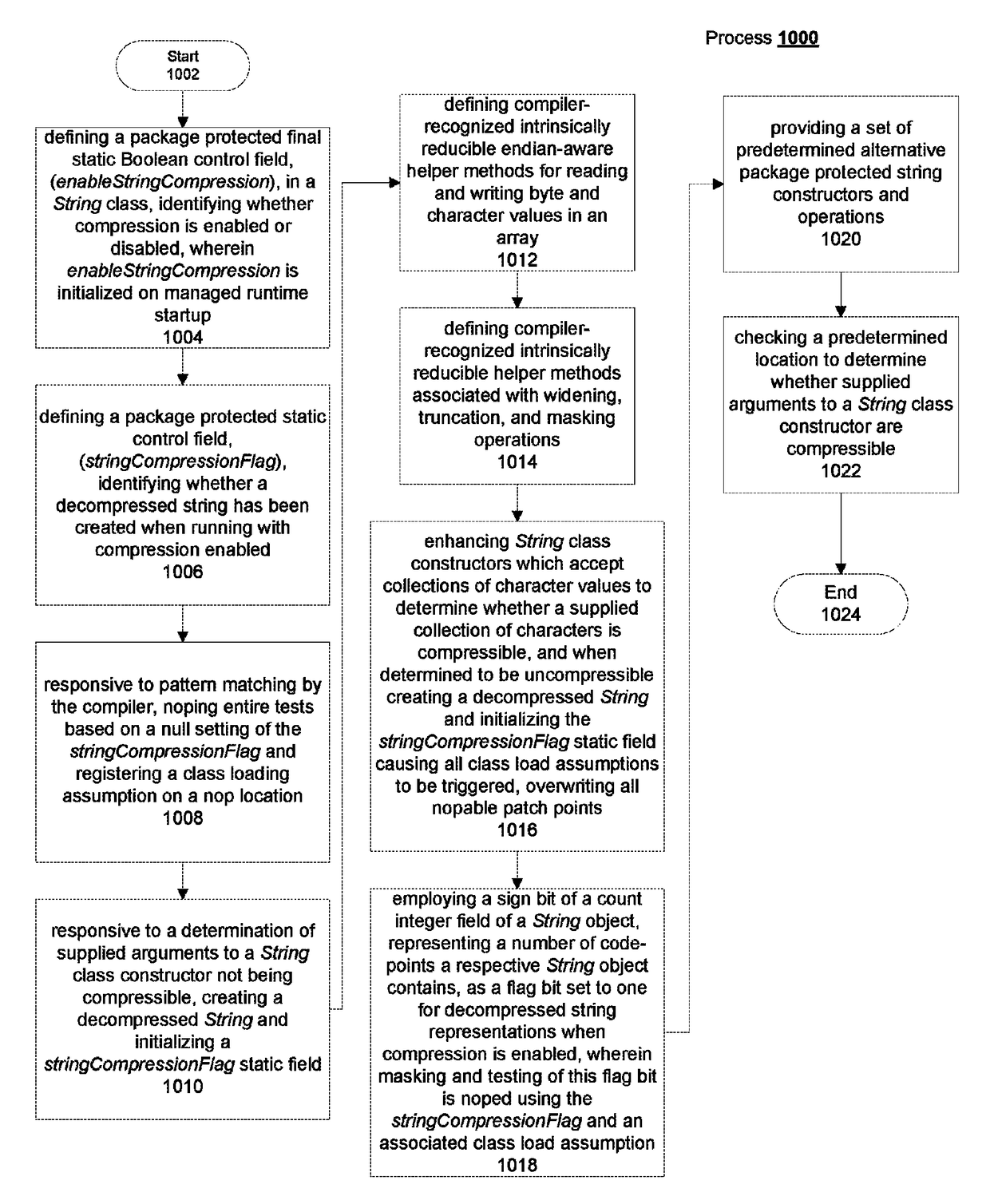
ActiveUS20170329619A1Code conversionSoftware simulation/interpretation/emulationPattern matchingSign bit
Multi-byte compressed string representation embodiments define a String class control field identifying compression as enabled / disabled, and another control field, identifying a decompressed string created when compression enabled. On pattern matching by a compiler, noping tests based on null setting of stringCompressionFlag and registering a class loading assumption on a nop location. When arguments to a String class constructor are not compressible, a decompressed String is created and stringCompressionFlag initialized. Endian-aware helper methods for reading / writing byte and character values and helper methods for widening, narrowing, truncation, conversion and masking are defined. Enhanced String class constructors, when characters are not compressible, create a decompressed String, and initialize stringCompressionFlag triggering class load assumptions, overwriting all nopable patch points. A String object sign bit is set to one for decompressed strings when compression enabled, and masking / testing this flag bit is noped using stringCompressionFlag and associated class load assumption. Alternative package protected string constructors and operations are provided. Checking a predetermined location to determine whether supplied arguments to a String class constructor are compressible is performed.
Owner:IBM CORP
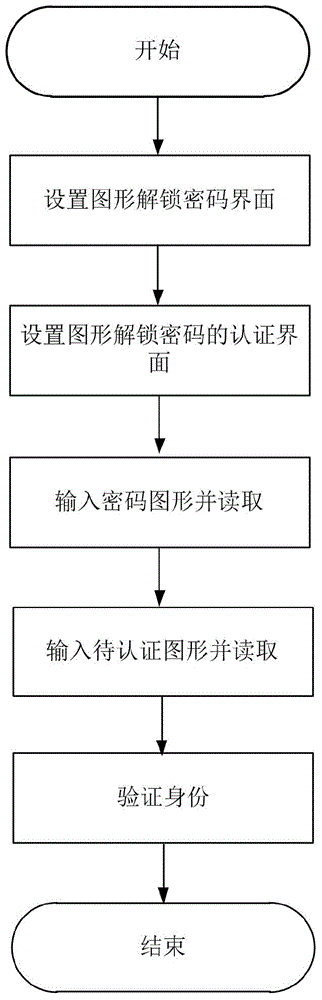
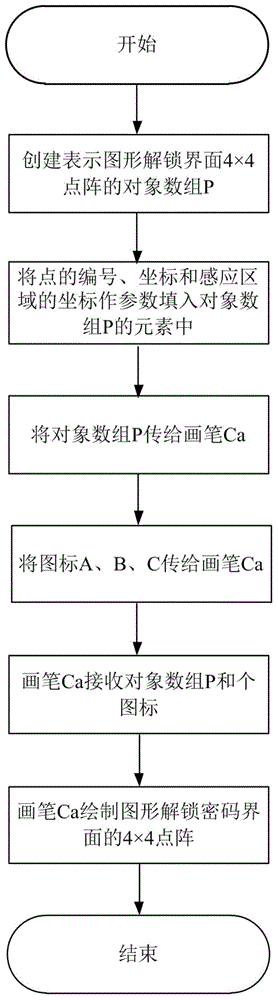
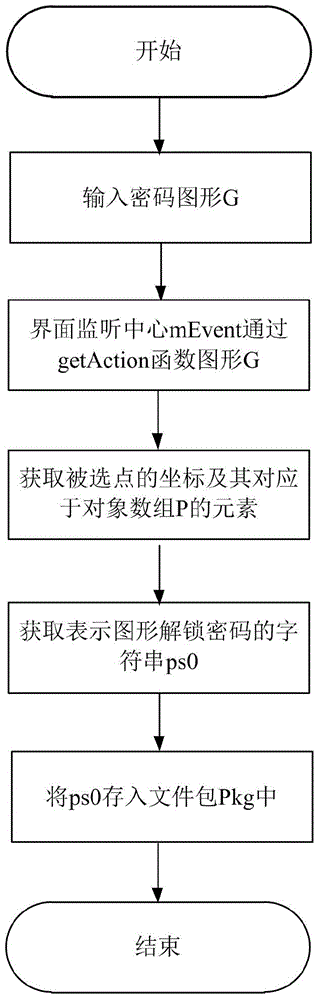
Identity authentication improving method for pattern puzzle password in Android system
ActiveCN104917773ALarge password spaceImprove securityDigital data authenticationTransmissionGraphicsBrute force
The invention discloses an identity authentication improving method for a pattern puzzle password in an Android system, and mainly aims to solve the problem of potential safety hazard due to revealing of the use habit of a user in practical application of existing Android pattern puzzle. An implementation scheme comprises the following steps: (1) setting a pattern puzzle password interface; (2) setting an authentication interface of the pattern puzzle password; (3) inputting a password pattern on the pattern puzzle password interface, and reading the character string representation form of the password pattern; (4) inputting a pattern to be authenticated on the pattern puzzle password interface or the authentication interface of the pattern puzzle password, and reading the character string representation form of the pattern to be authenticated; and (5) comparing whether or not the character string expression ways of the pattern to be authenticated and the password pattern are consistent in order to verify the identity. Through adoption of the identity authentication improving method, the password space is enlarged on the basis of the existing Android pattern puzzle; the security is enhanced; and the defense capability specific to dictionary attacks and brute force attacks is enhanced. The identity authentication improving method can be applied to identity authentication of graphical equipment such as smart phones.
Owner:XIDIAN UNIV
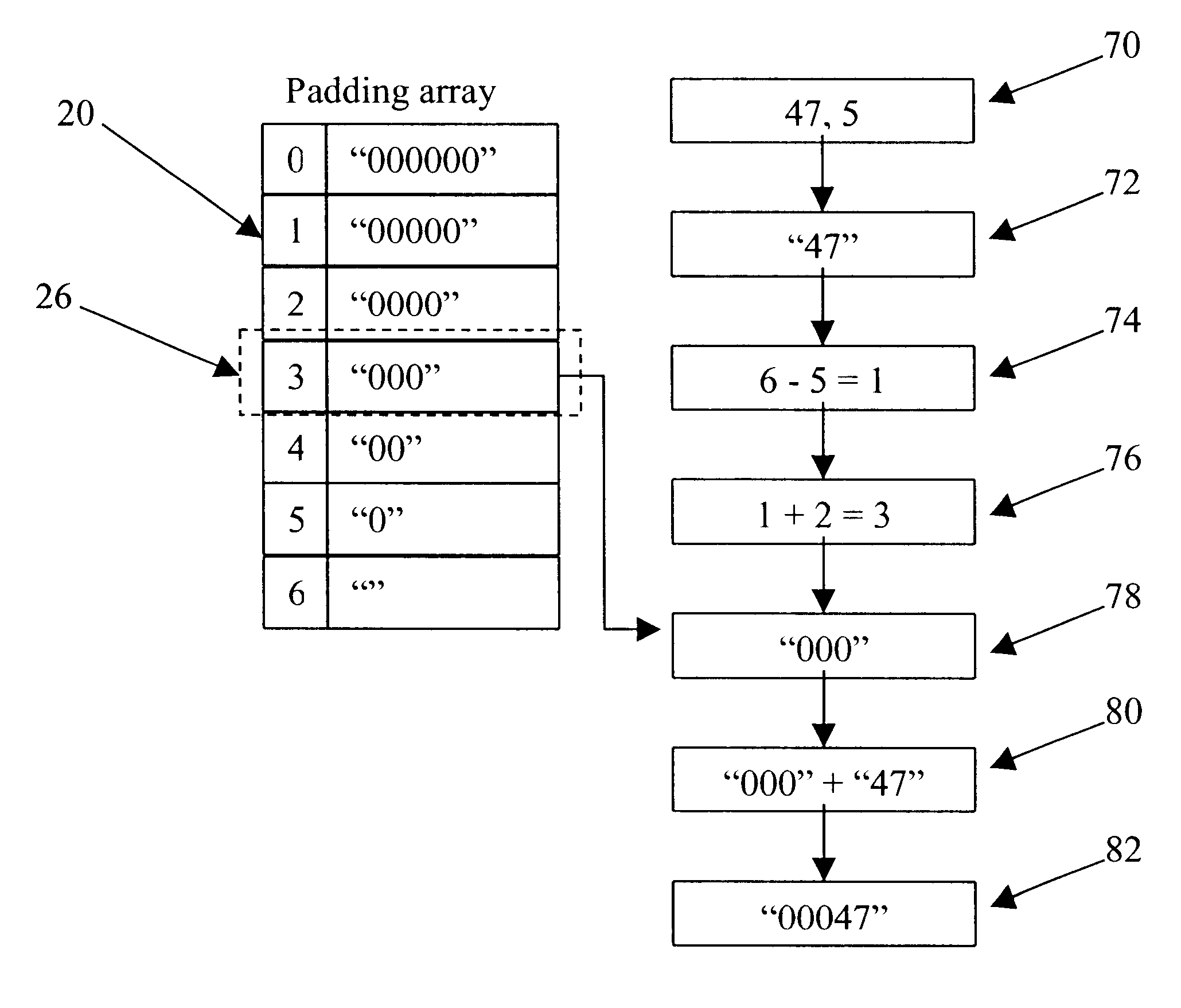
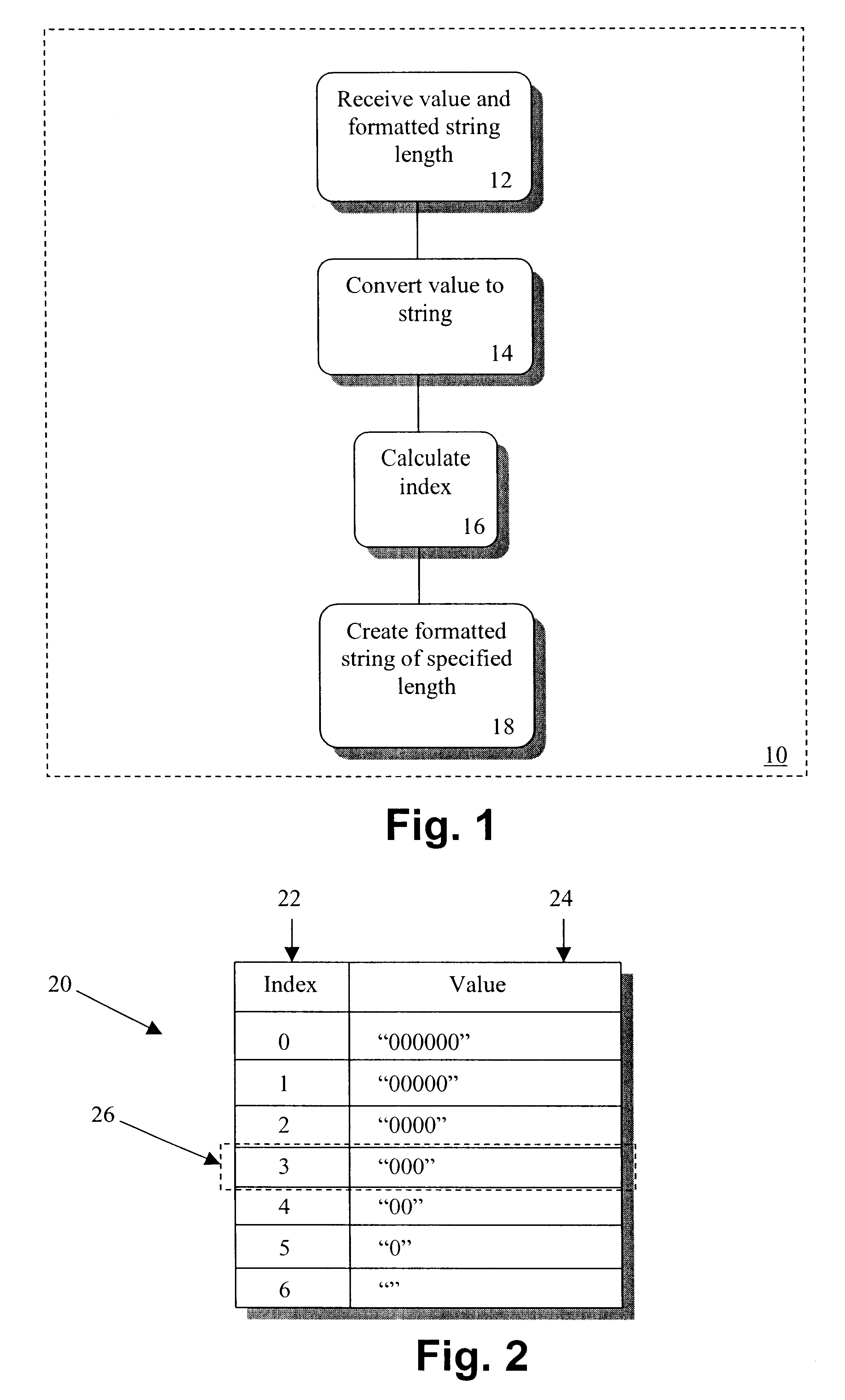
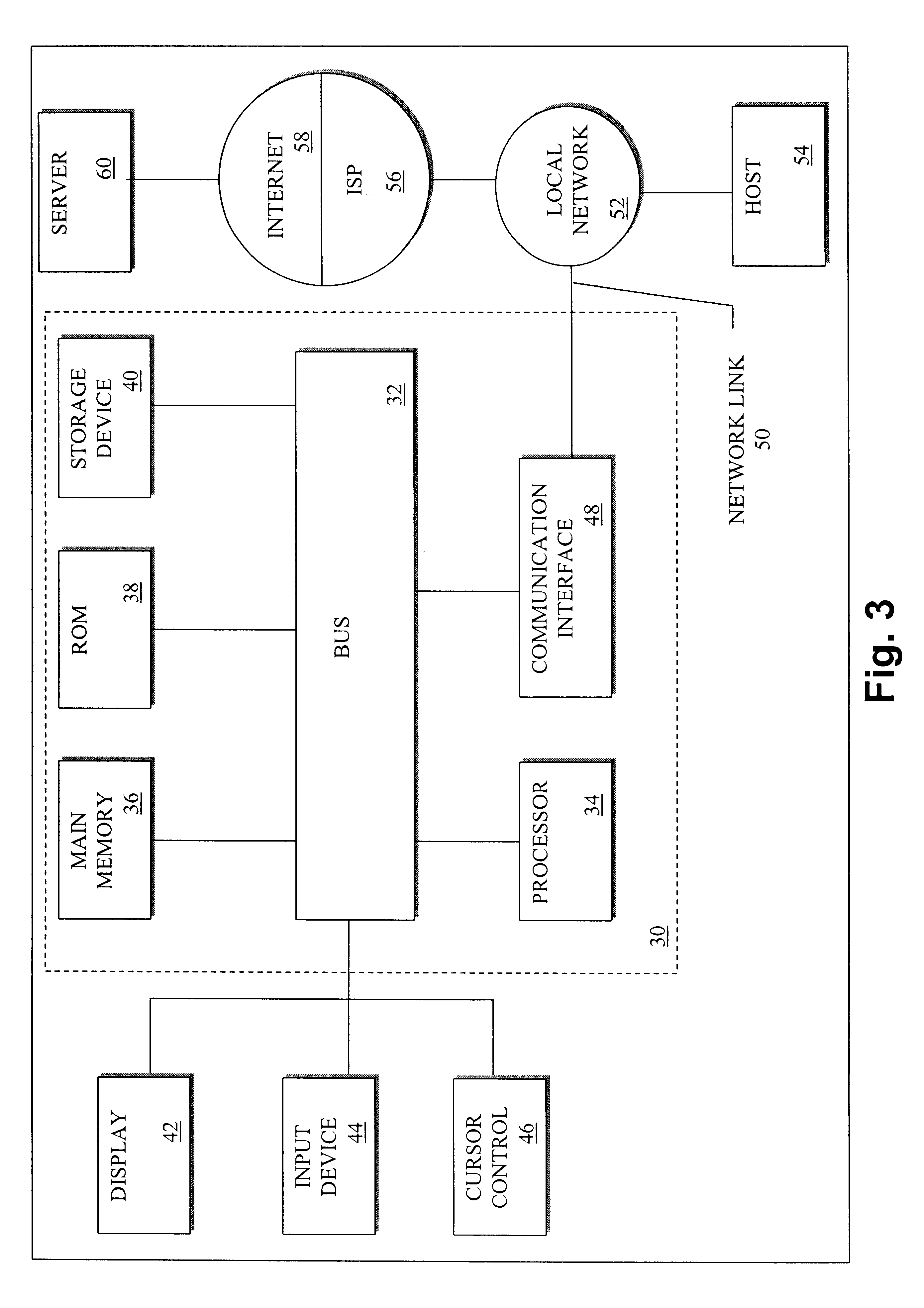
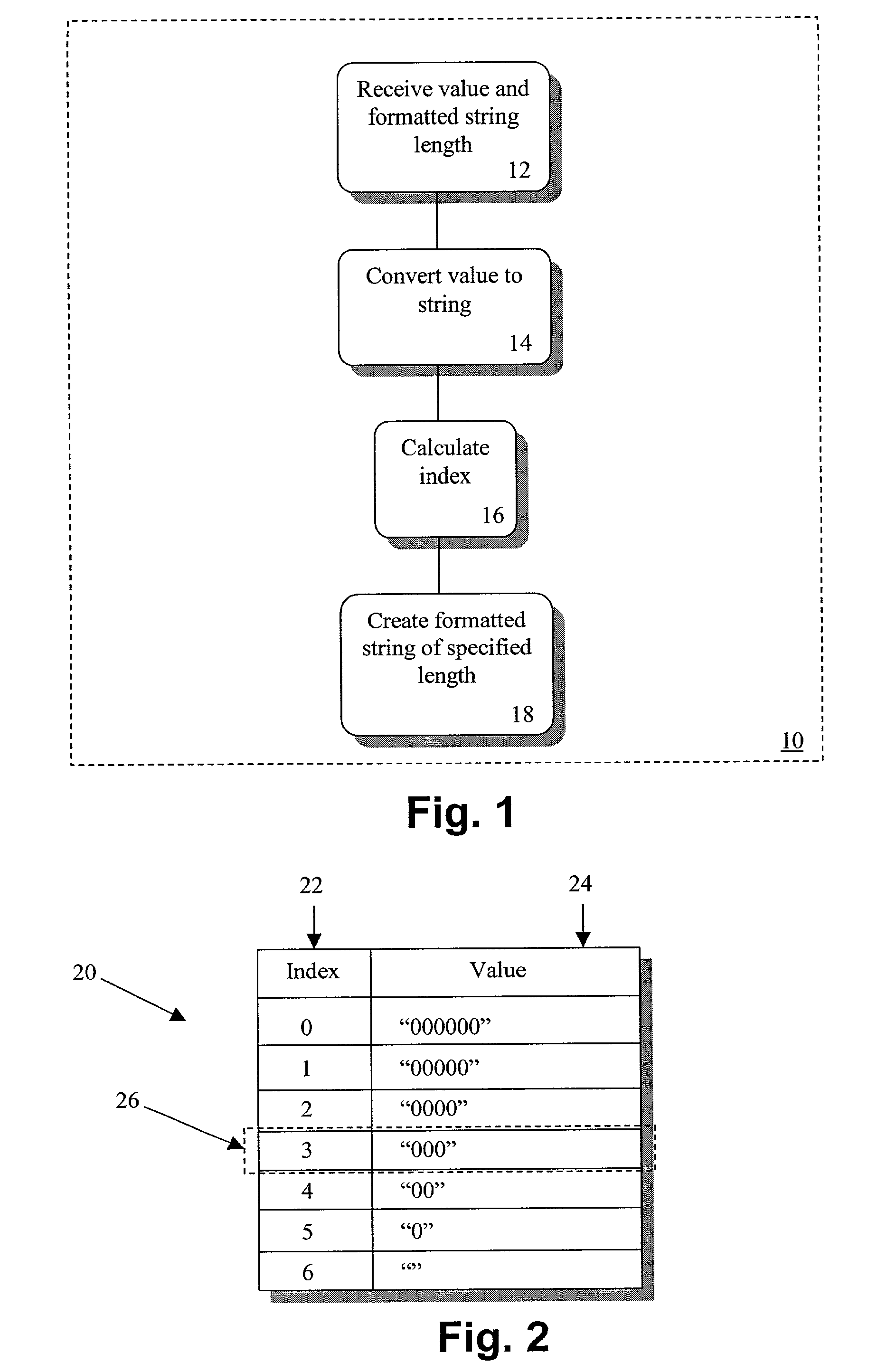
Method of formatting values in a fixed number of spaces using the java programming language
InactiveUS6708177B2Minimal additional processing overheadSpeed up the processData processing applicationsDigital data processing detailsTheoretical computer scienceLookup table
A computer implemented method of and apparatus for printing values in a fixed number of column spaces using Java is described. A value desired to be formatted to a predetermined length string and an indexed lookup table having predetermined formatted string entries are used. An index based on the number of characters needed to represent the value is calculated and then used to locate a desired length formatted string entry in the lookup table. The desired length formatted string entry is then combined with a string representation of the value to form a predetermined length string.
Owner:HEWLETT PACKARD DEV CO LP
Method of formatting values in a fixed number of spaces using the java programming language
InactiveUS20020198879A1Speed up the processMinimal additional processing overheadData processing applicationsDigital data processing detailsTheoretical computer scienceLookup table
A computer implemented method of and apparatus for printing values in a fixed number of column spaces using Java is described. A value desired to be formatted to a predetermined length string and an indexed lookup table having predetermined formatted string entries are used. An index based on the number of characters needed to represent the value is calculated and then used to locate a desired length formatted string entry in the lookup table. The desired length formatted string entry is then combined with a string representation of the value to form a predetermined length string.
Owner:HEWLETT PACKARD DEV CO LP
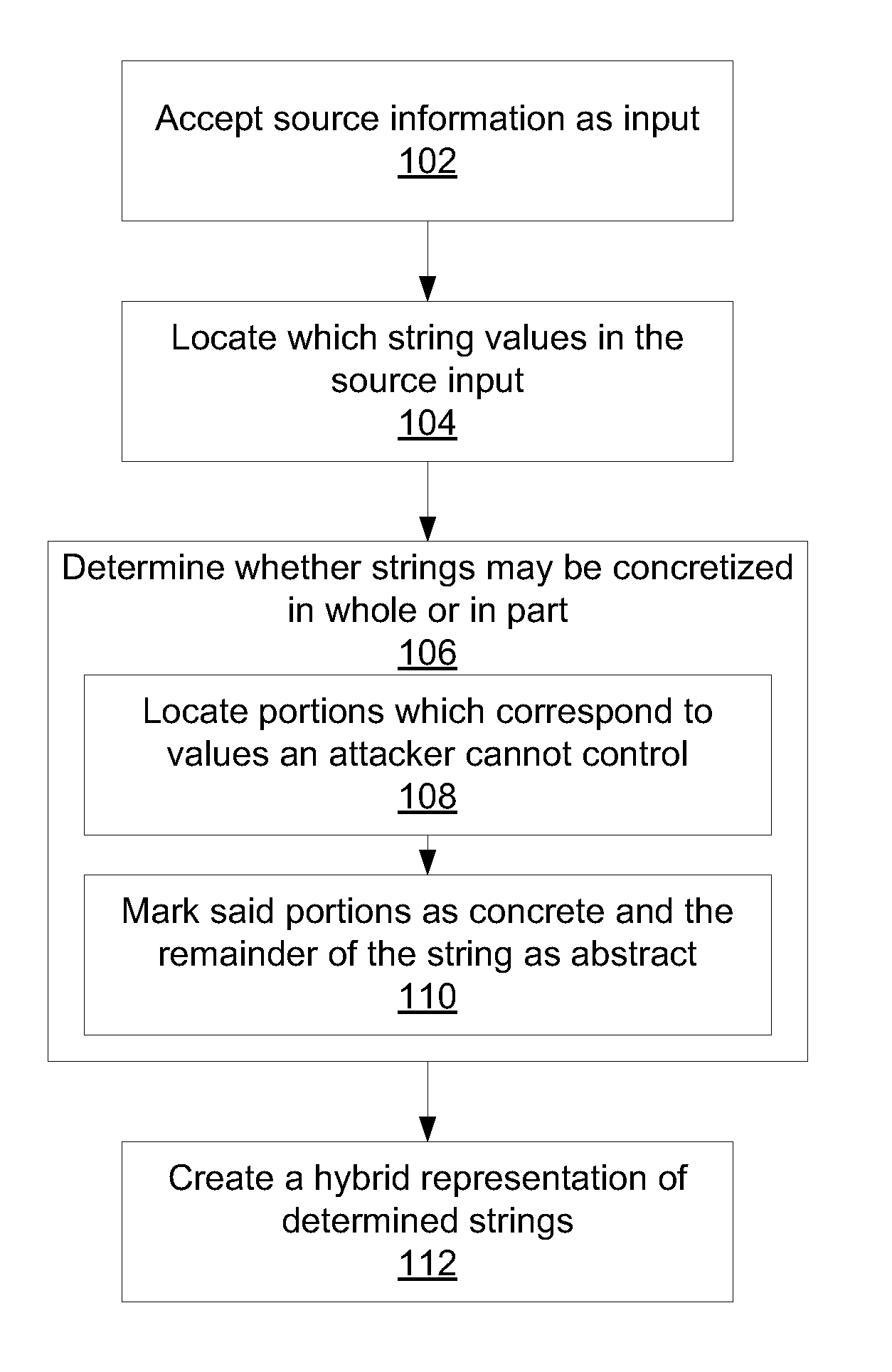
Static security analysis using a hybrid representation of string values
InactiveUS20140075561A1Memory loss protectionError detection/correctionTheoretical computer scienceString group
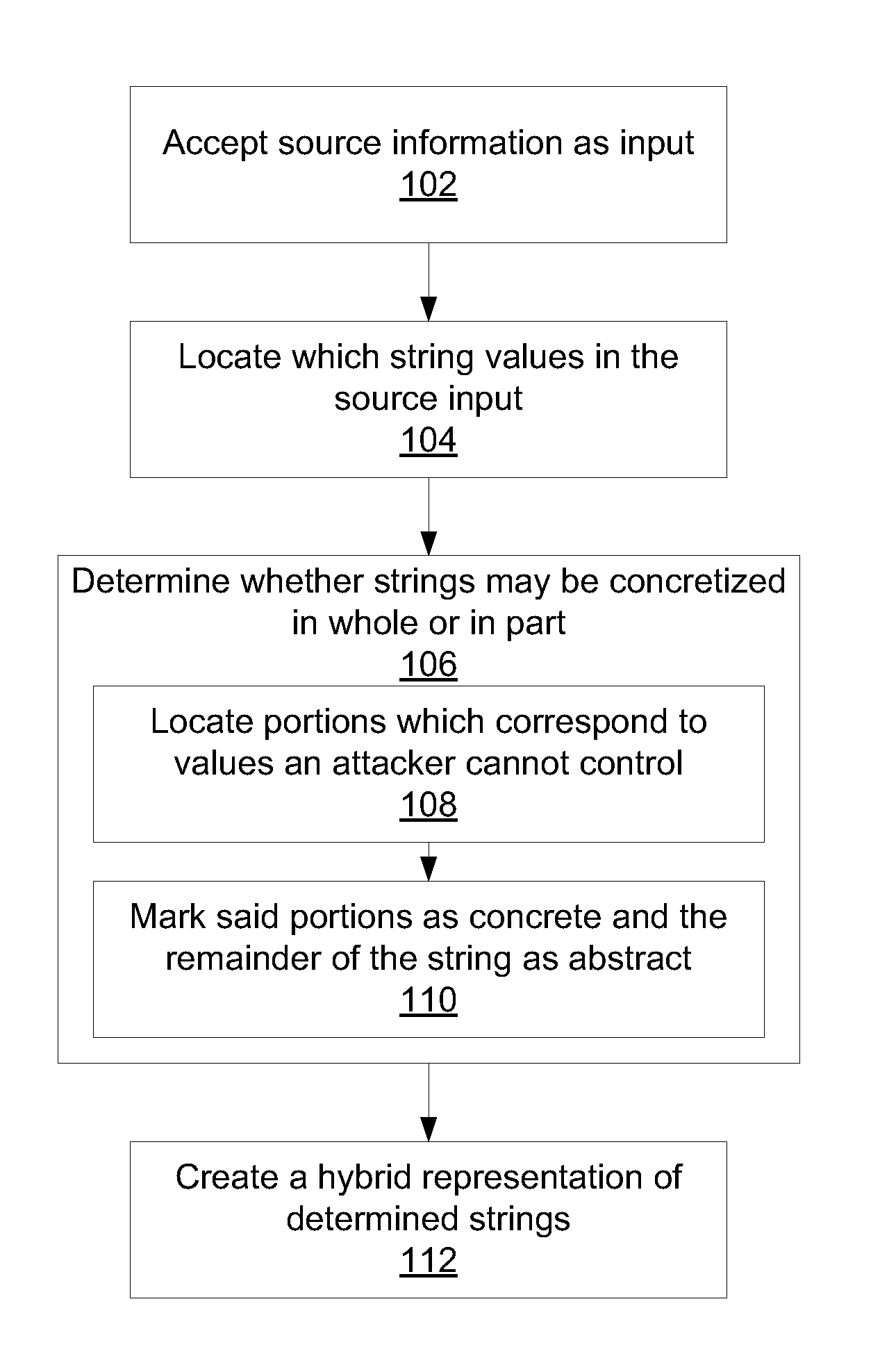
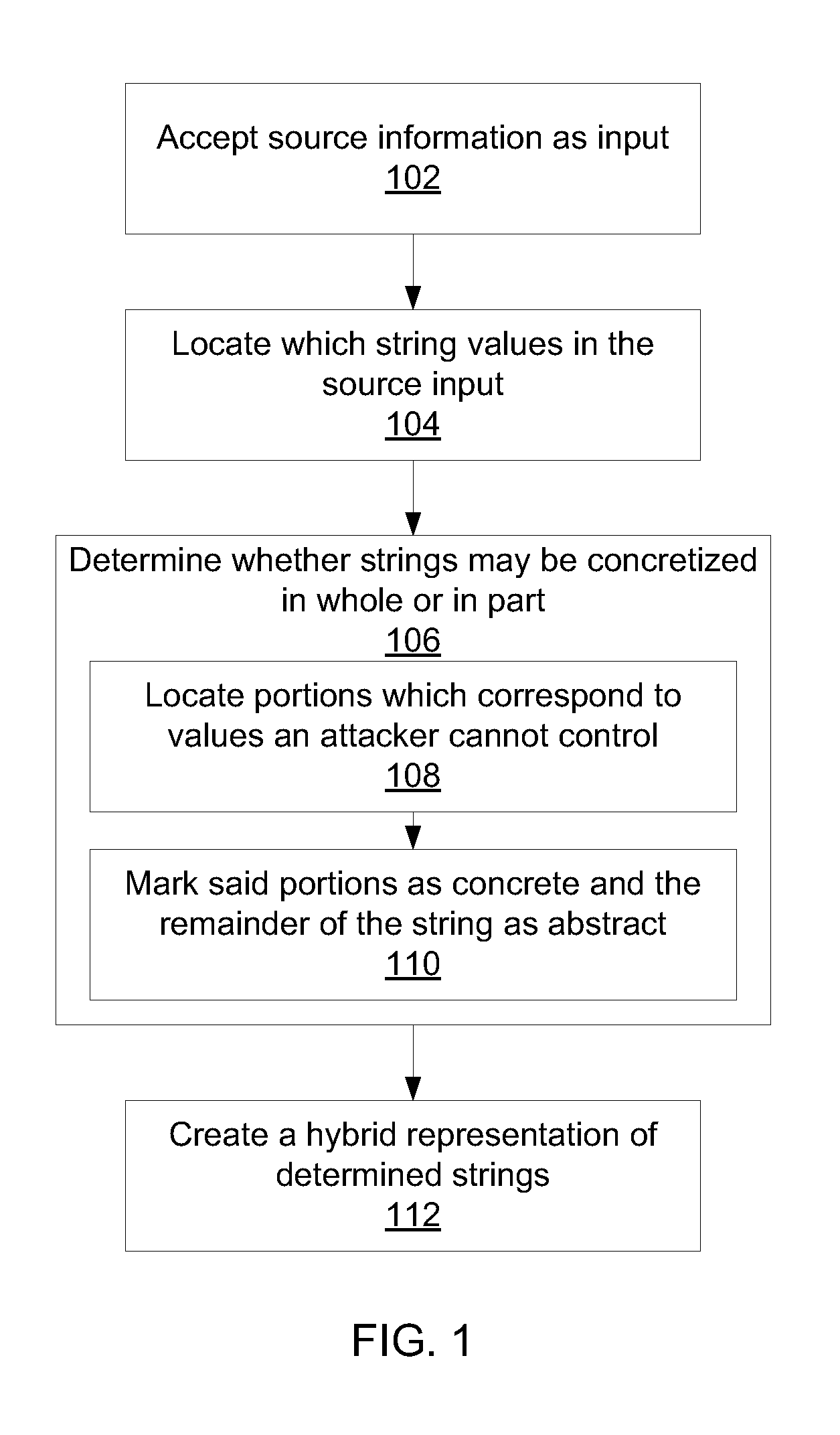
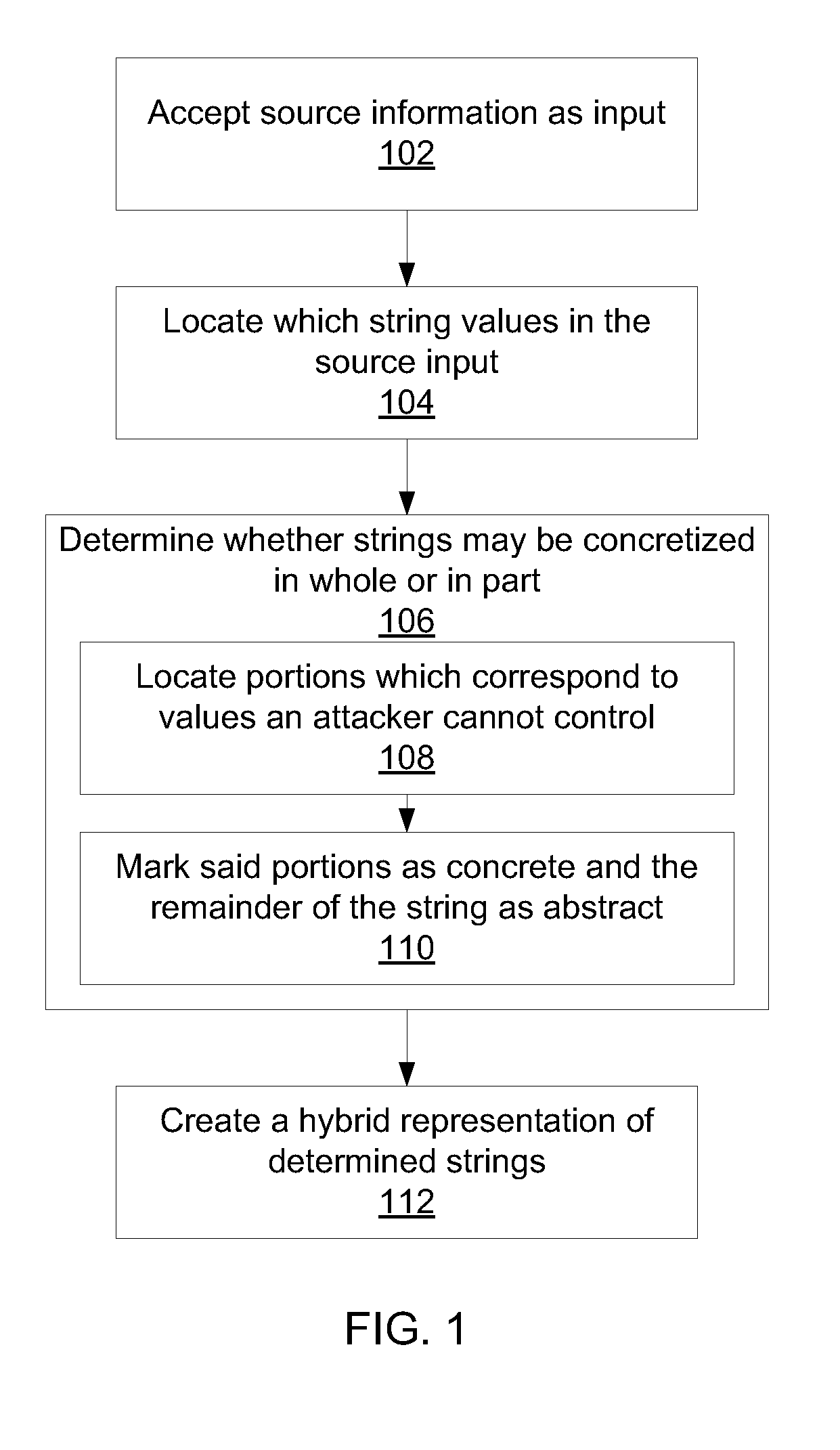
Methods for creating a hybrid string representations include receiving string information as input; parsing the string information to produce one or more string components; determining string components that may be represented concretely by comparing the one or more components to a set of known concretizations; abstracting all string components that could not be represented concretely; and creating a hybrid string representation that includes at least one concrete string component and at least one abstracted string component.
Owner:IBM CORP
Method and system to perform text-to-image queries with wildcards
Owner:CONDUENT BUSINESS SERVICES LLC
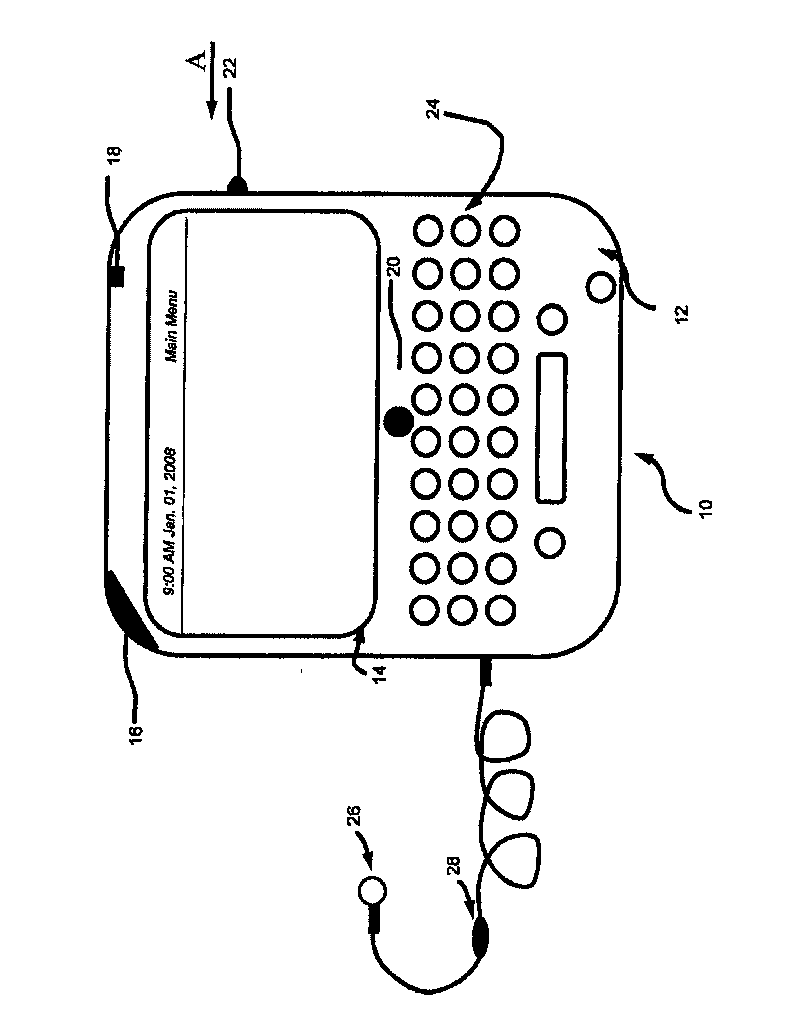
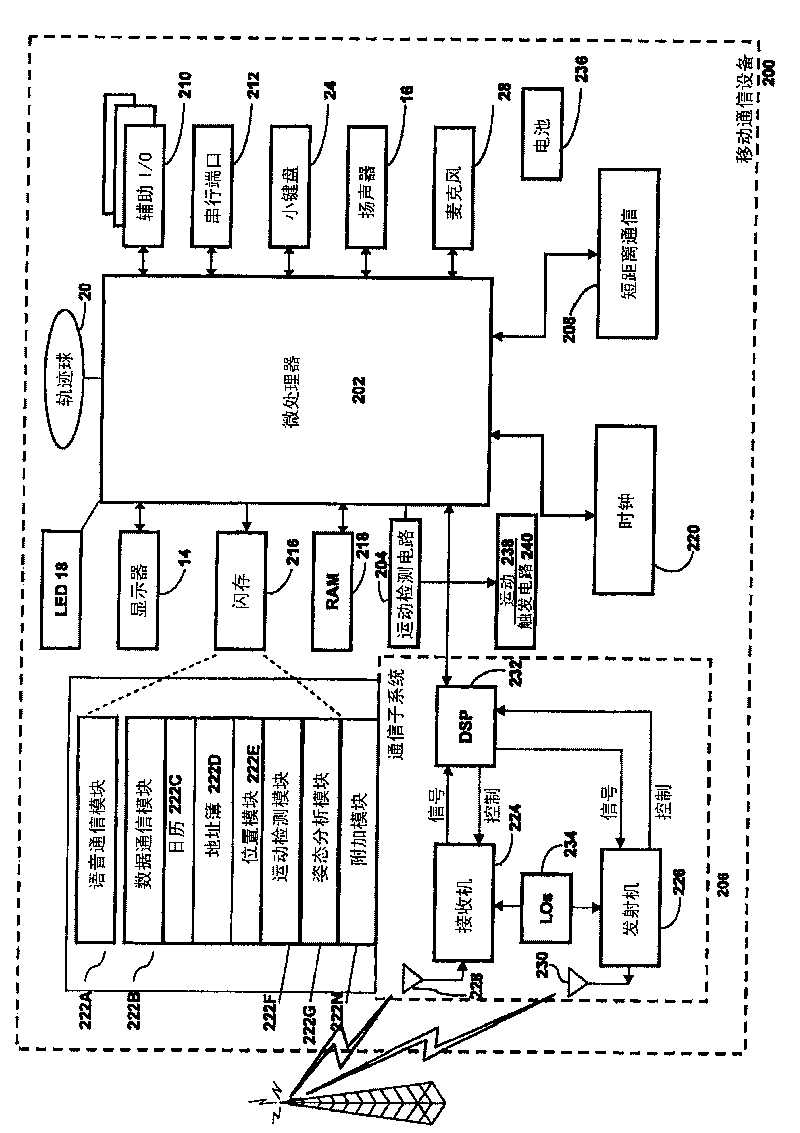
System and method for analyzing movements of an electronic device
InactiveCN101714027AInput/output for user-computer interactionDigital data processing detailsHuman–computer interactionMicroprocessor
The disclosure relates to a system and method for analyzing movements of a handheld electronic device. The system comprises: memory; a microprocessor; a first module to generate movement data responsive to movements of the device; a second module providing instructions to the microprocessor to map the movement data to a string representation relating to symbols in a spatial coordinate system associated with the device and store the string representation in the memory; and a third module. The third module provides instructions to the microprocessor to analyze data relating to the string representation against data relating to a gesture string representing a gesture related to a command for the device to determine if the gesture has been imparted on the device; and if the string representation sufficiently matches the gesture string, executes a command associated with the gesture on the device.
Owner:RES IN MOTION LTD
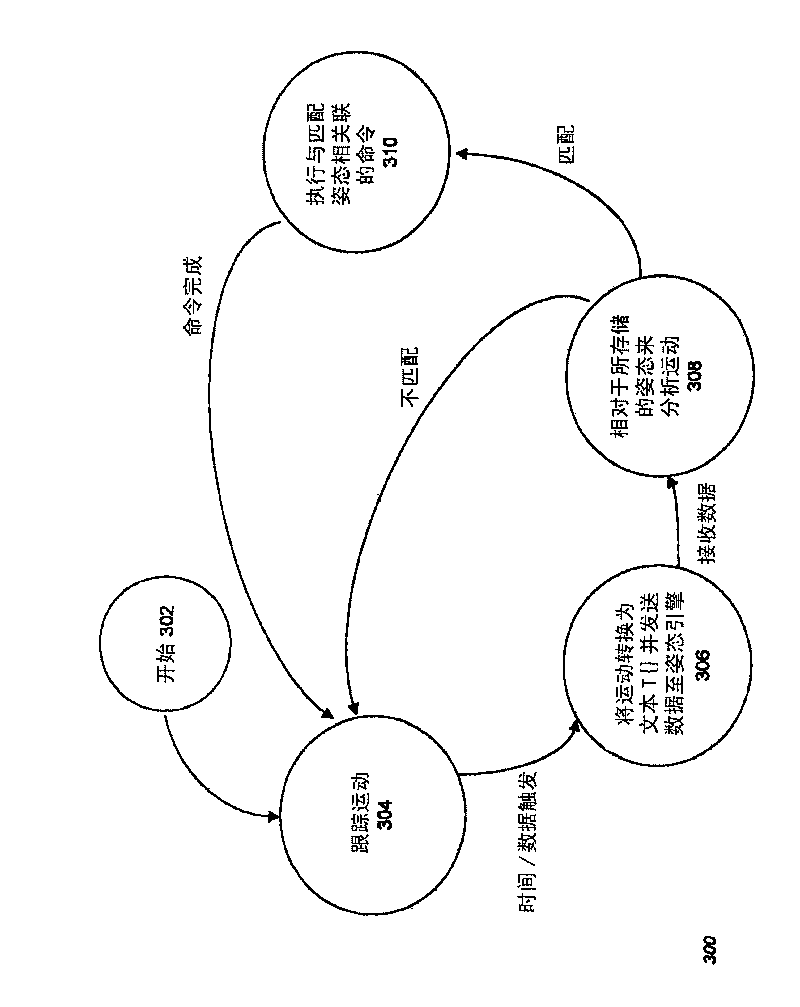
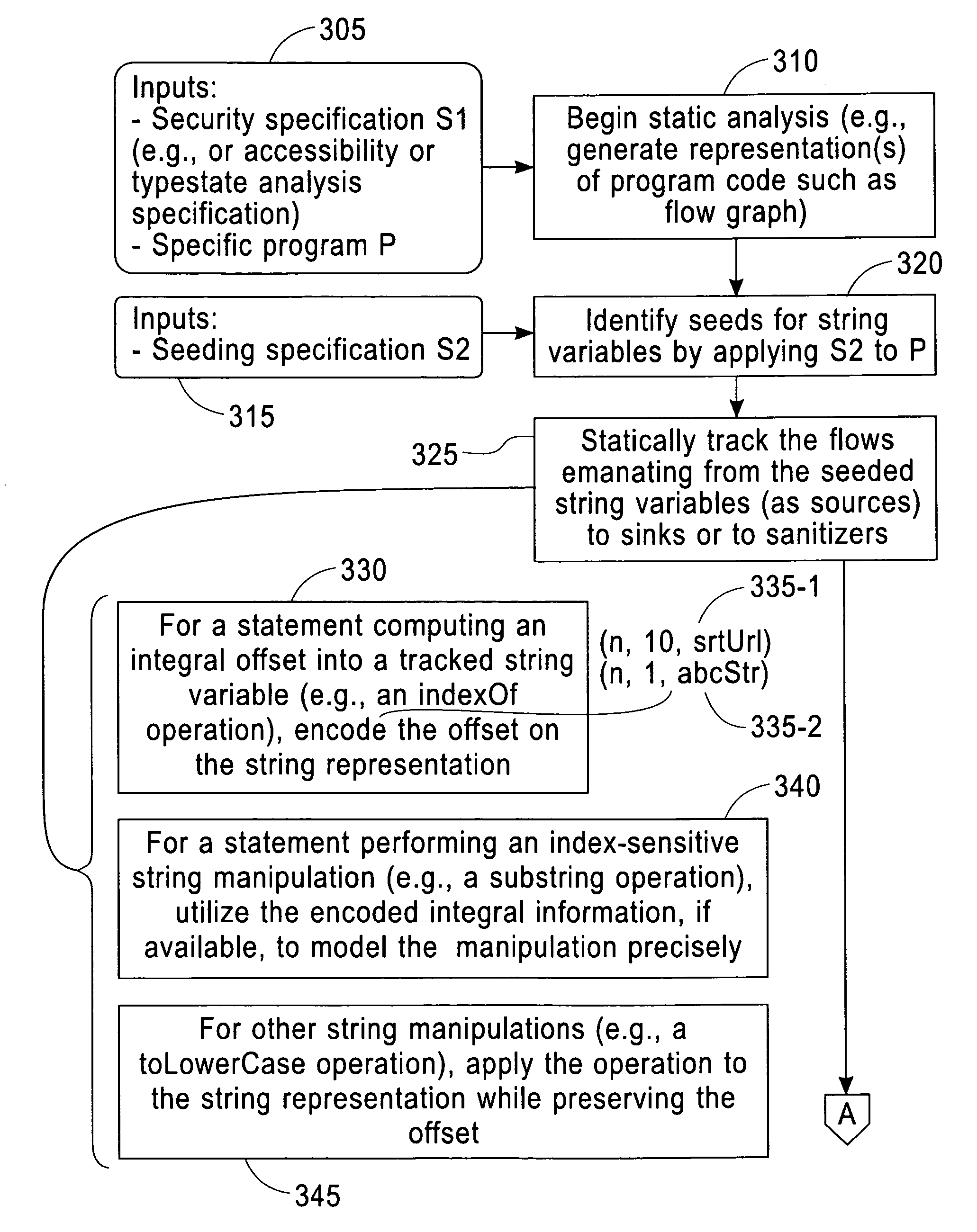
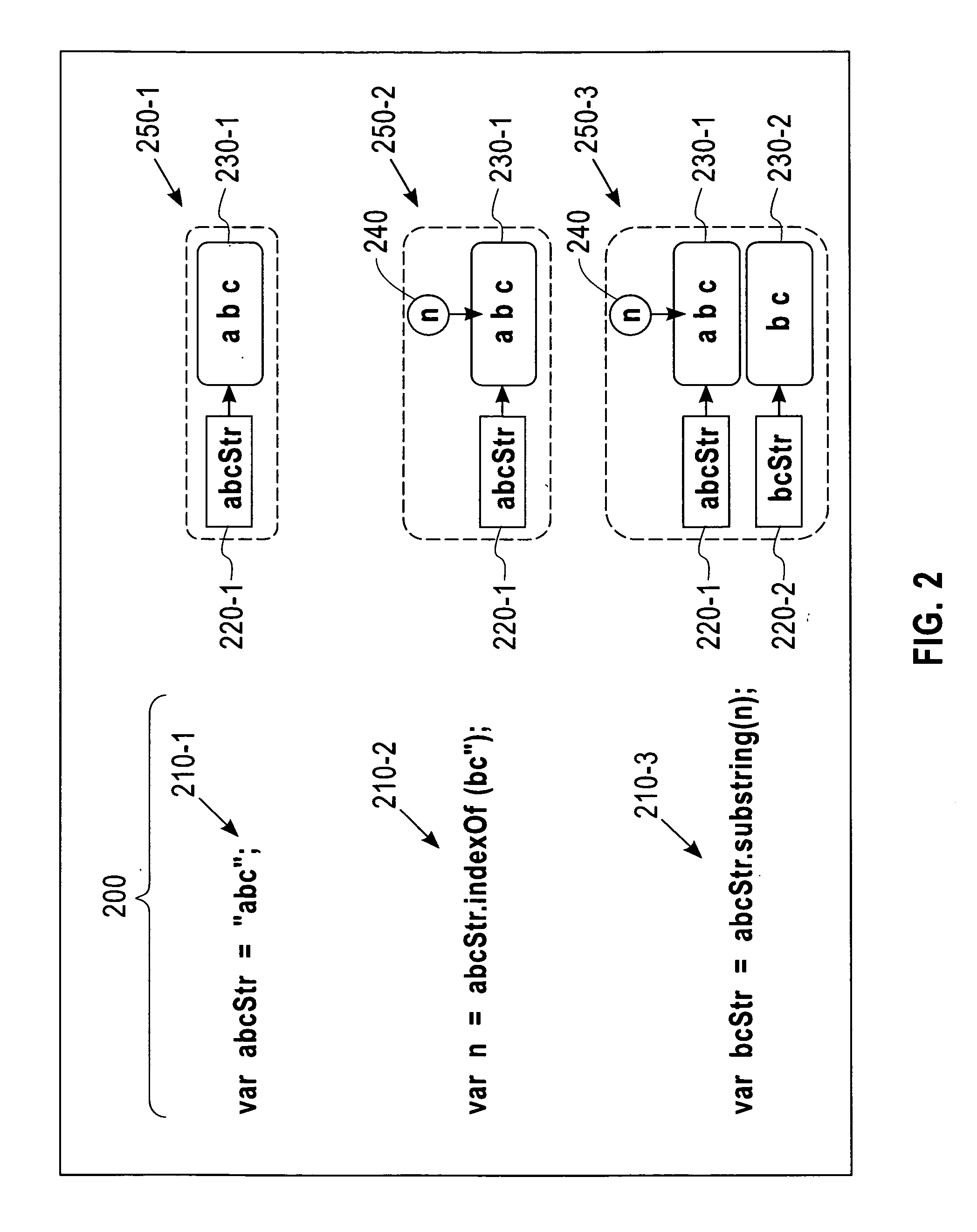
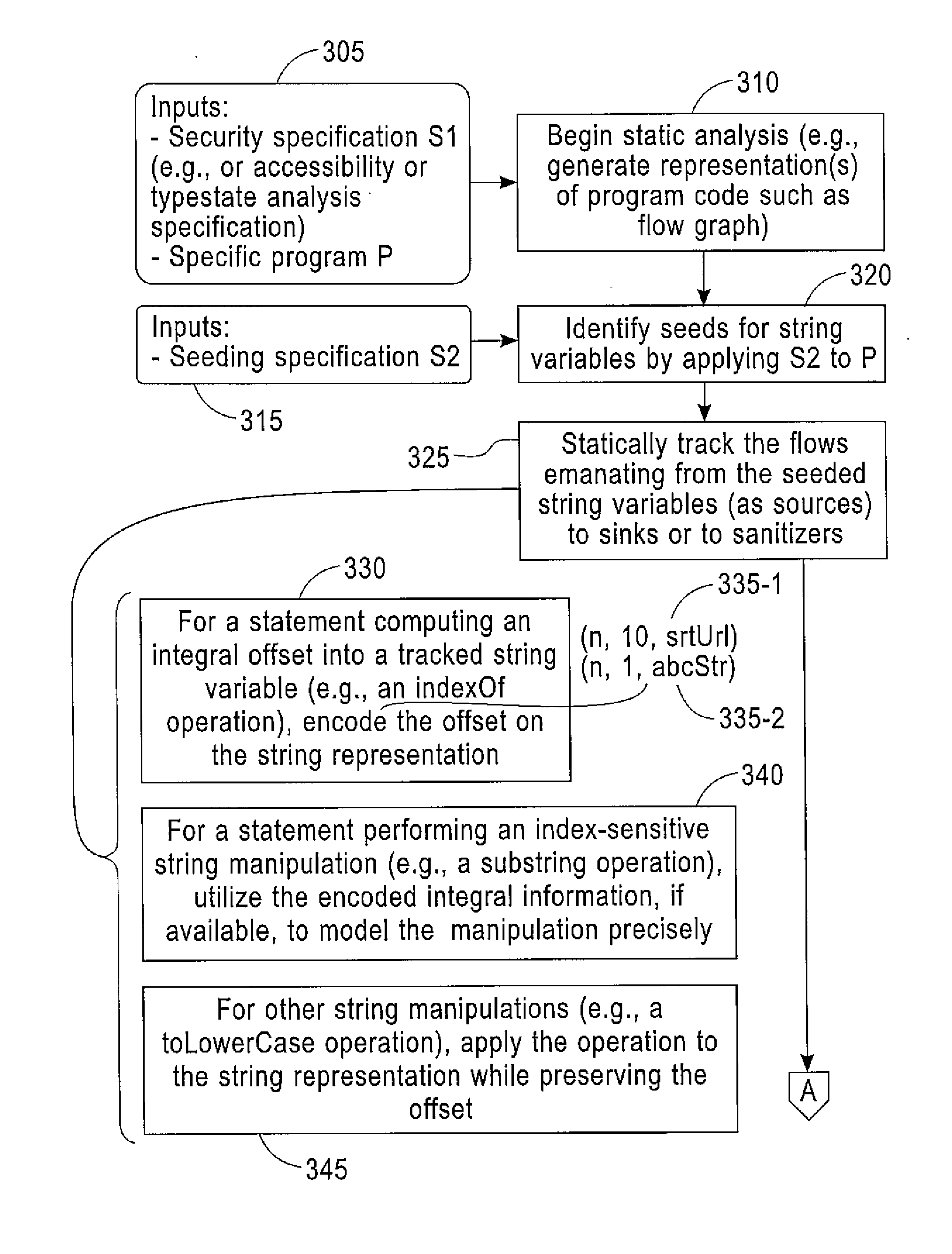
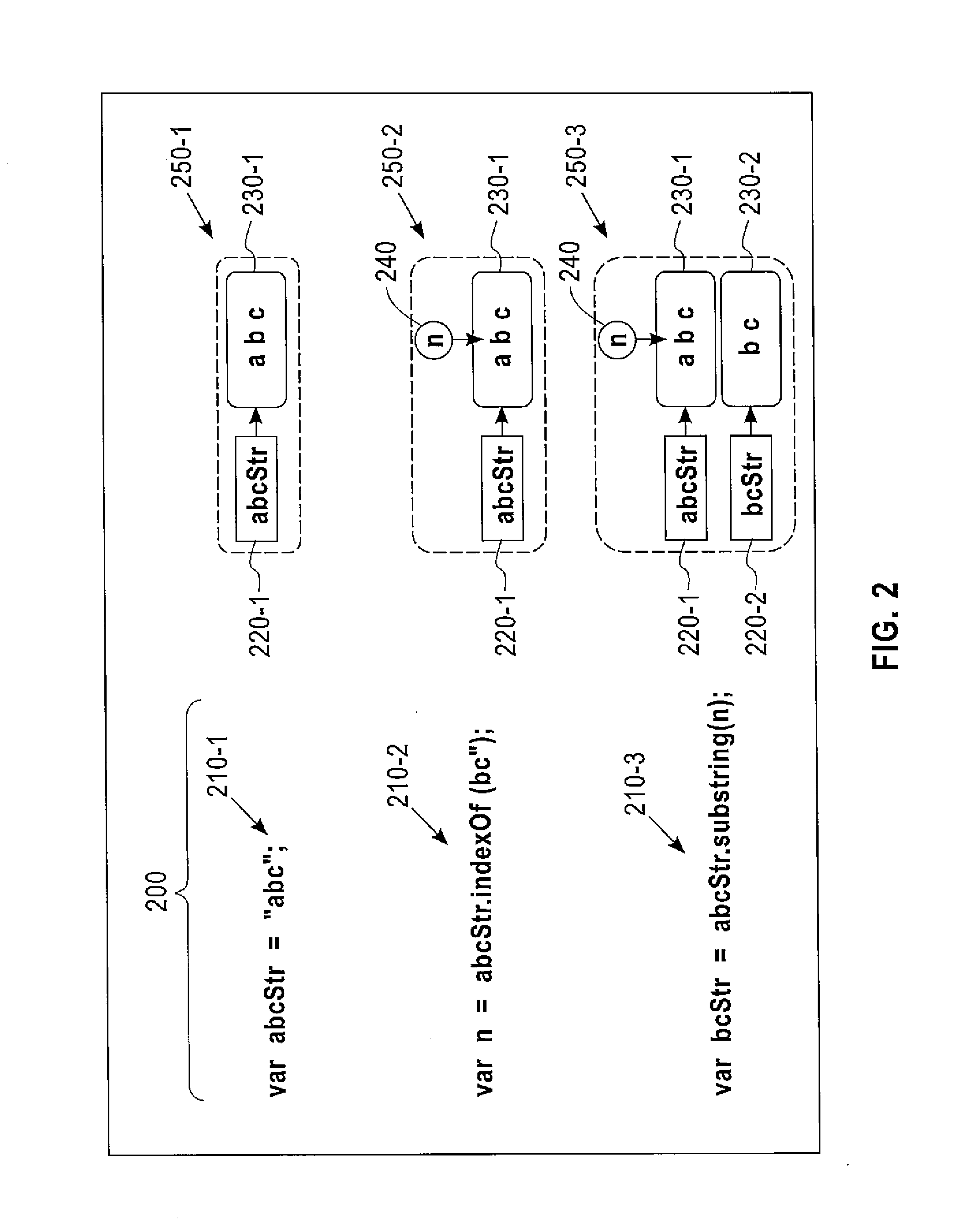
Scalable and Precise String Analysis Using Index-Sensitive Static String Abstractions
InactiveUS20140258992A1Computer security arrangementsSoftware testing/debuggingString analysisString representation
A disclosed method includes accessing one or more seeding specifications and a program including computer-readable code and applying the one or more seeding specifications to the program to identify for analysis seeds including strings for corresponding identified string variables. The method includes tracking flows emanating from the identified seeds. The tracking includes computing an integral offset into a tracked string variable for any statements causing such a computation. The tracking also includes providing a string representation based on the computed integral offset, wherein the provided string representation comprises a value of the integral offset and an indication of the corresponding tracked string variable. The tracking further includes modeling string manipulations of the tracked string variables using the string representations. Apparatus and program products are also disclosed.
Owner:IBM CORP
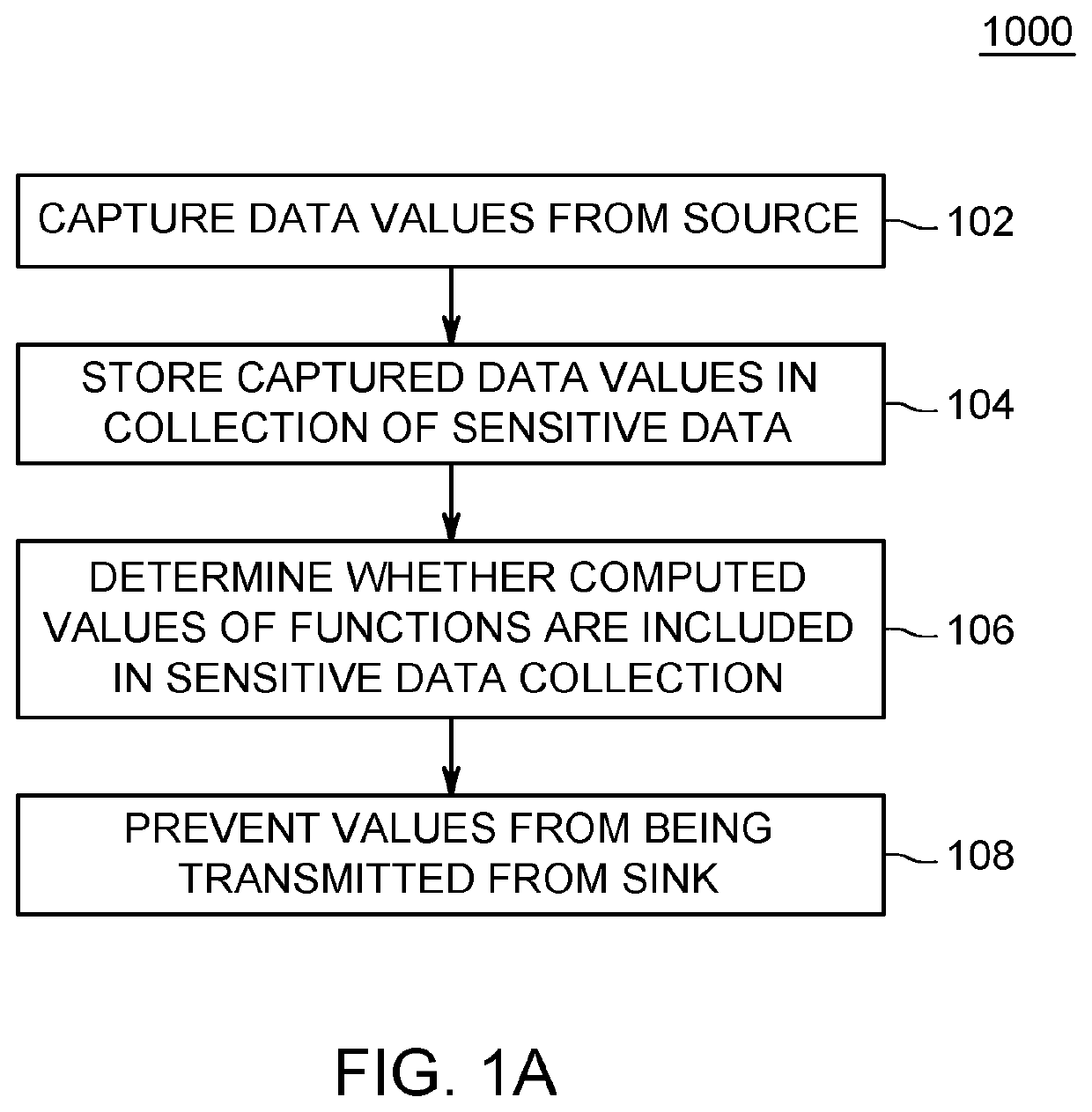
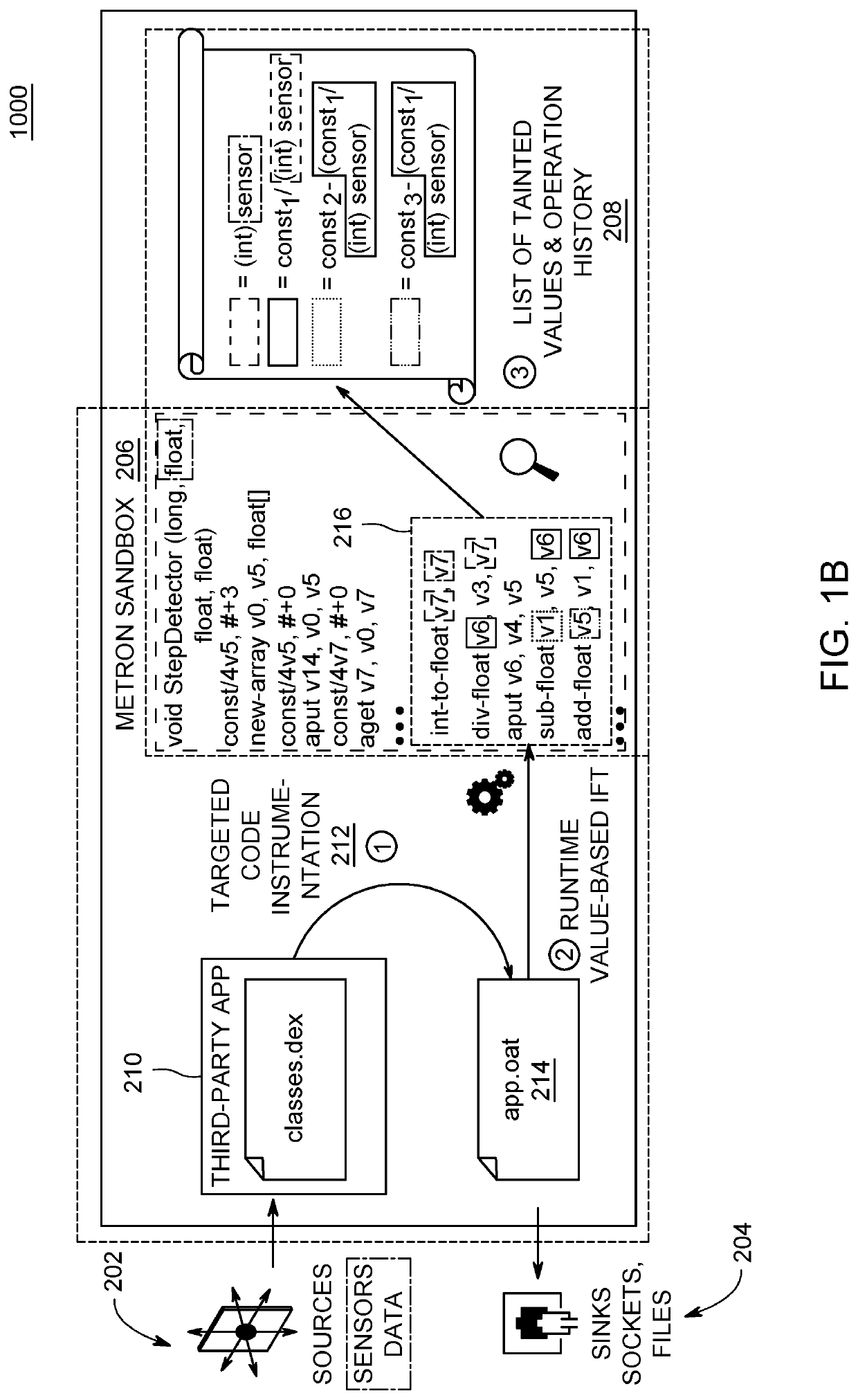
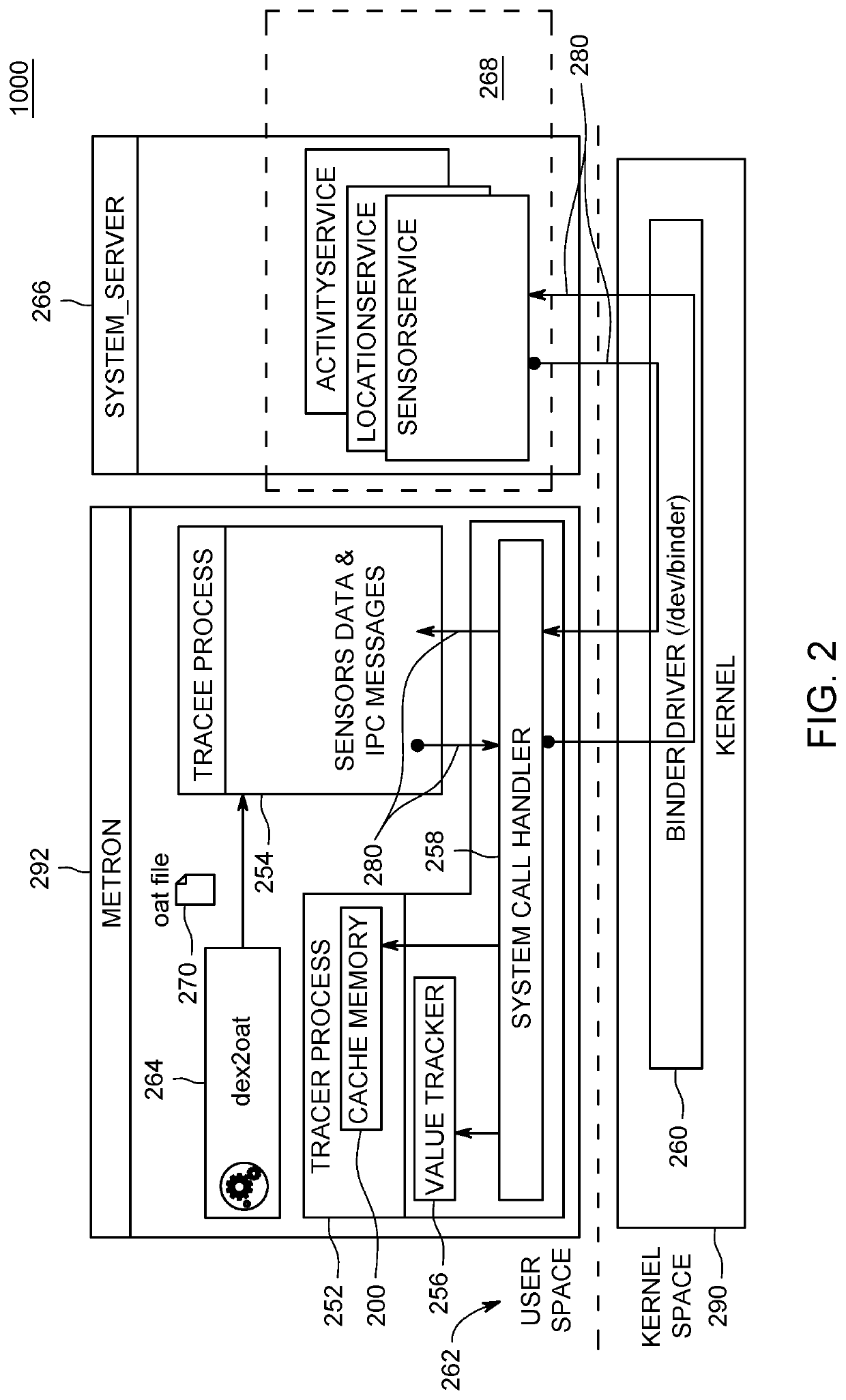
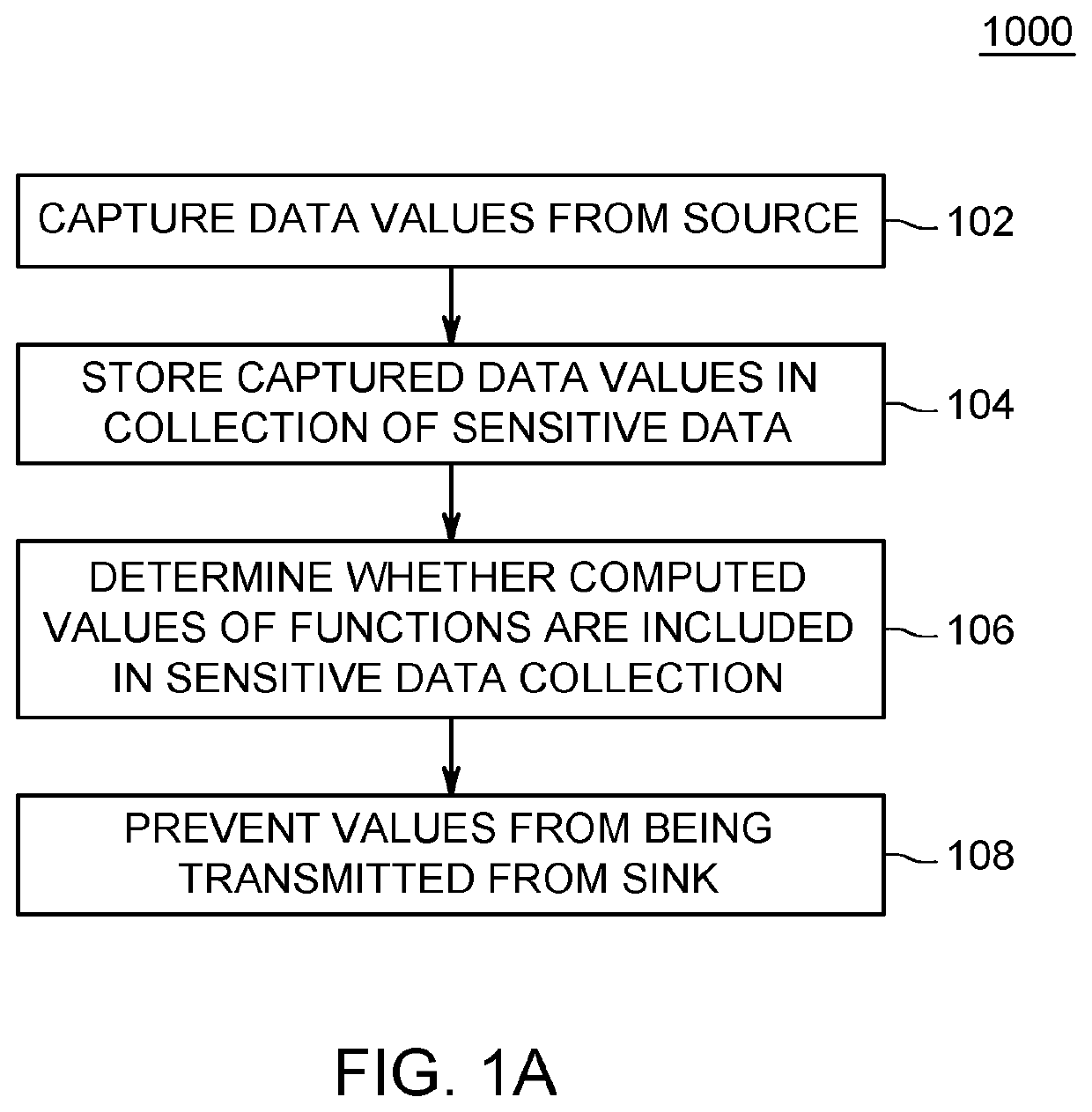
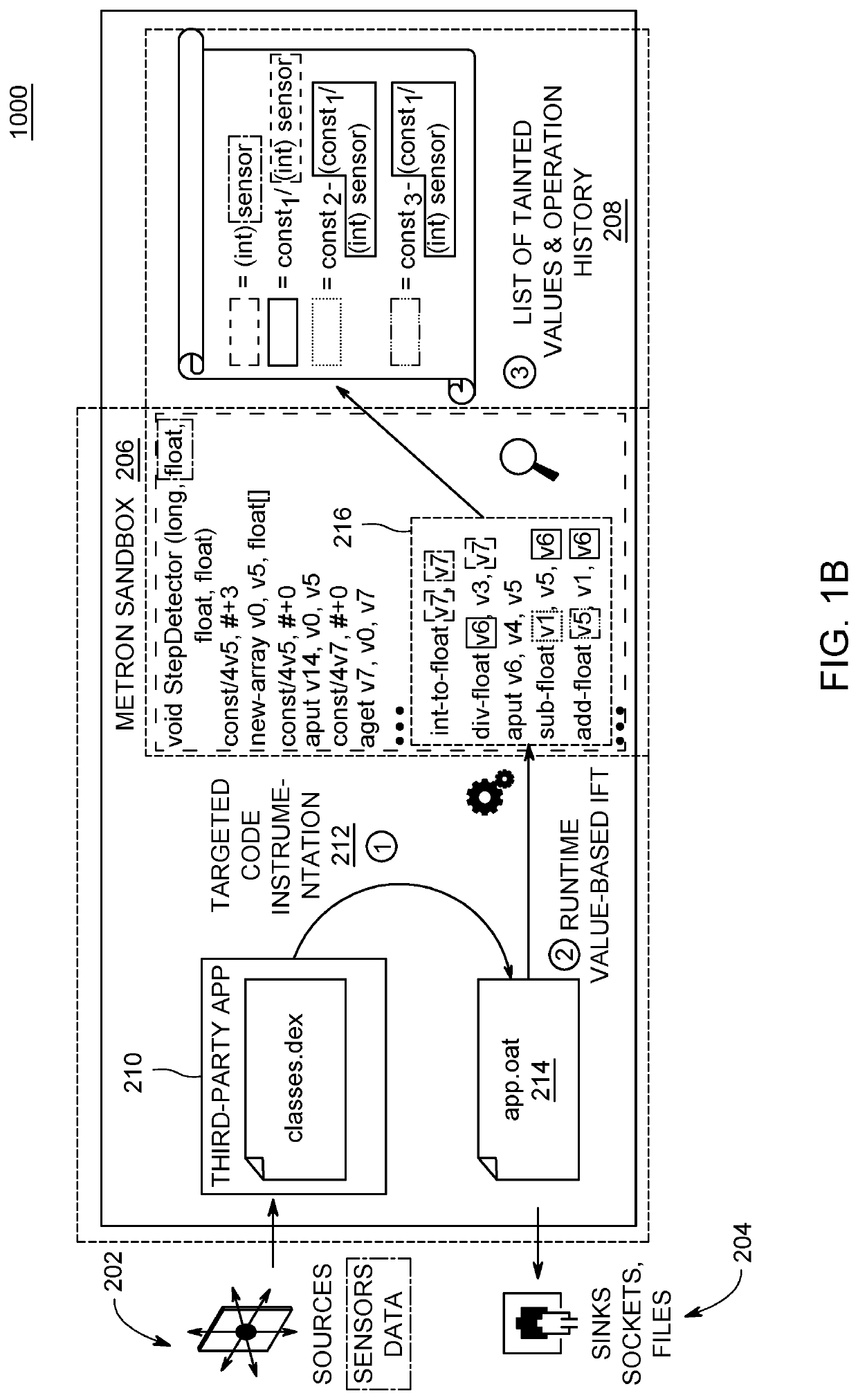
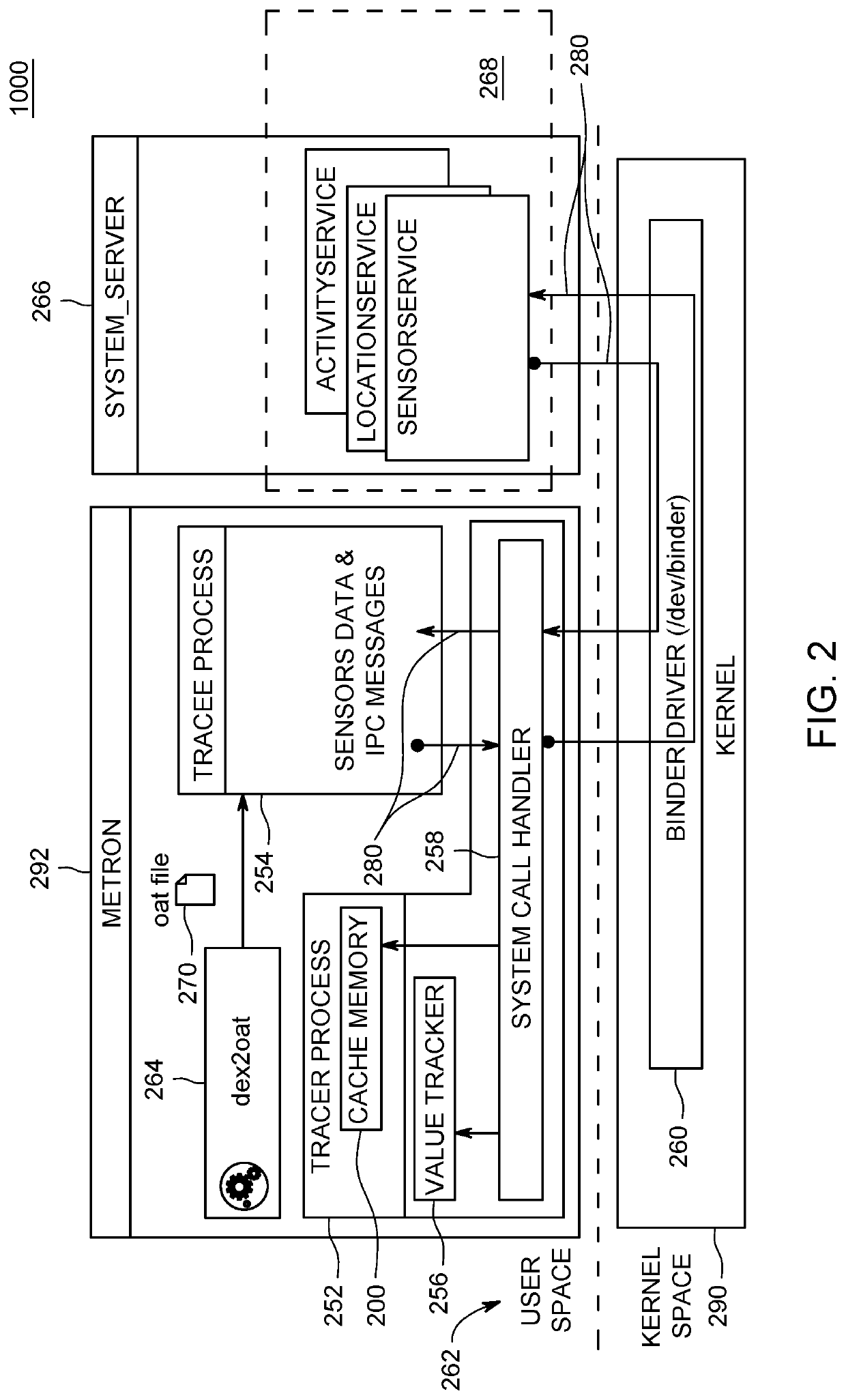
Value-Based Information Flow Tracking In Software Packages
ActiveUS20200293682A1More valueAvoid spreadingDigital data protectionPlatform integrity maintainanceData streamAlgorithm
A computer-implemented method, computer system, and computer program product are directed to improving computer security of a device using value based information flow tracking. Embodiments automatically capture raw data values from a data source of the device and store in memory the captured raw data values in a collection of sensitive data. Embodiments determine whether computed values of functions of a data flow are included in the collection of sensitive data. Based upon the determining, embodiments prevent values of the collection of sensitive data from being transmitted from a sink of the device. Embodiments may determine whether string representations of computed operand and return values of numerical or arithmetic operations of the functions of the data flow are included in the collection of sensitive data.
Owner:RGT UNIV OF CALIFORNIA +1
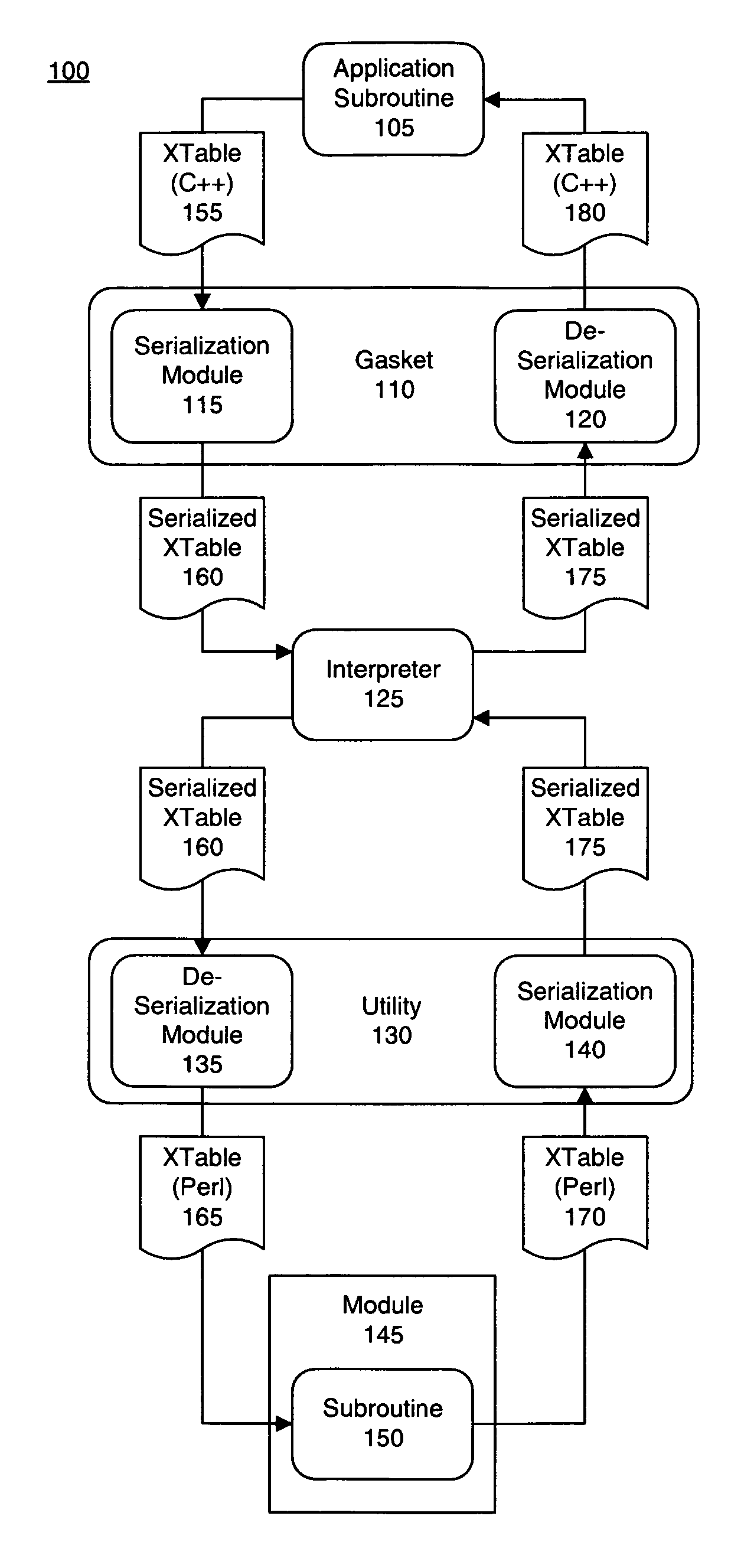
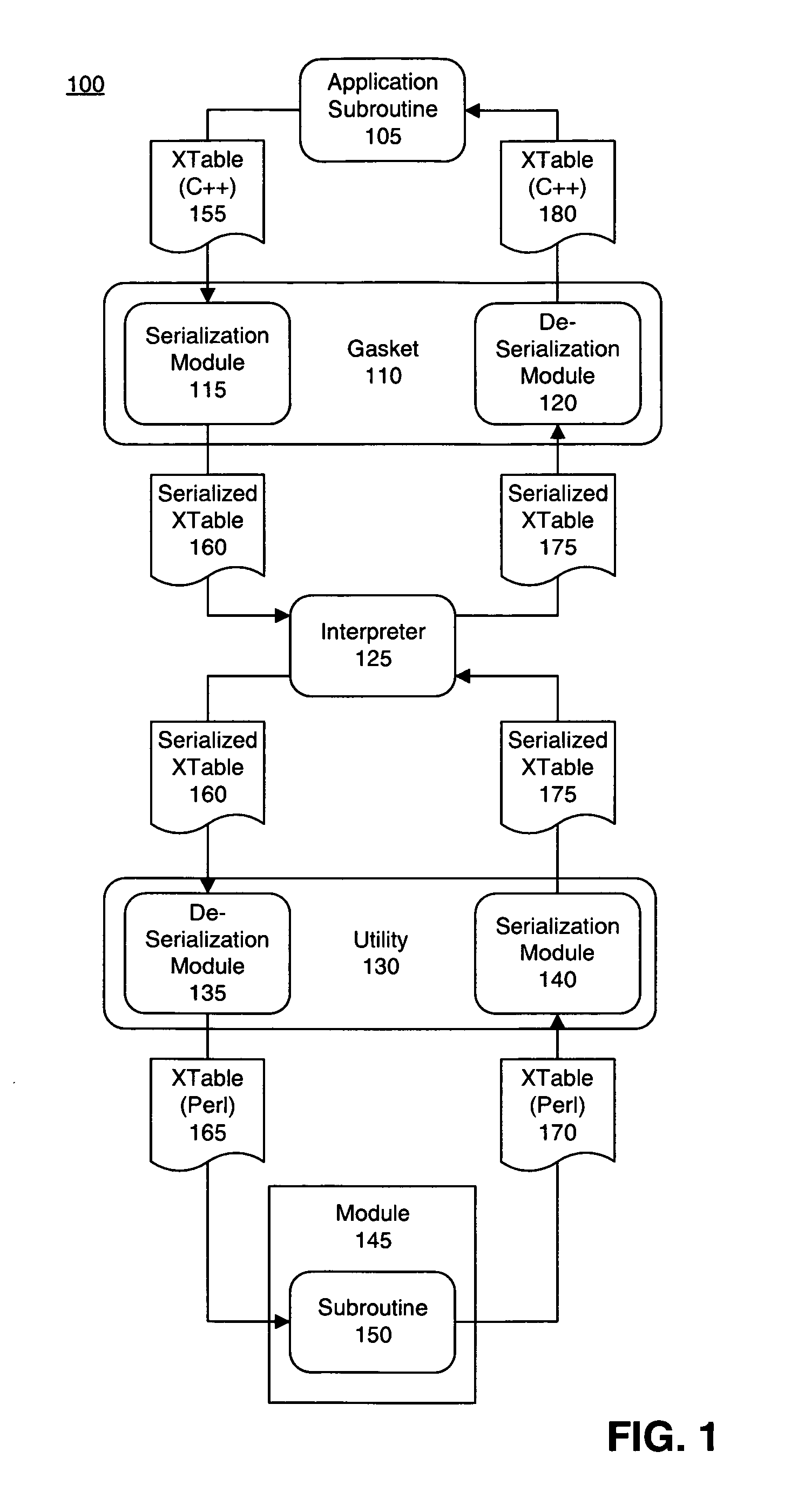
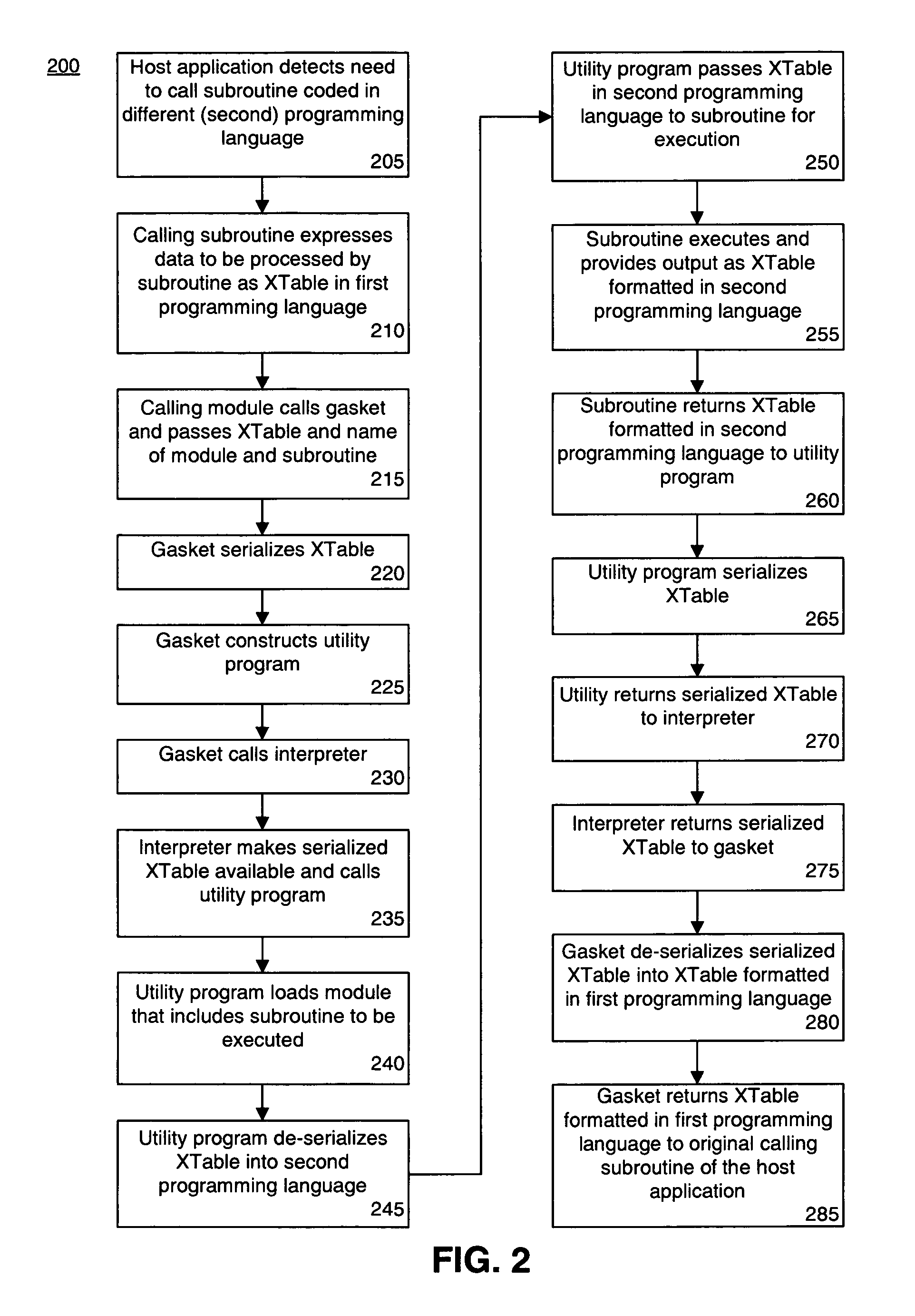
Embedding an interpreter within an application written in a different programming language
ActiveUS7627852B1Specific program execution arrangementsMemory systemsApplication softwareHuman language
A method of accessing, from a host application written in a first programming language, a subroutine written in a second programming language can include serializing input data expressed as an XTable formatted in a first programming language into a string representation of the input data. The method further can include de-serializing the string representation of the input data as an XTable formatted in the second programming language and executing the subroutine, wherein the XTable formatted in the second programming language is processed as input. Output data returned from the subroutine that is expressed as an XTable formatted in the second programming language can be serialized into a string representation of the output data. The string representation of the output data can be de-serialized into an XTable formatted in the first programming language.
Owner:XILINX INC
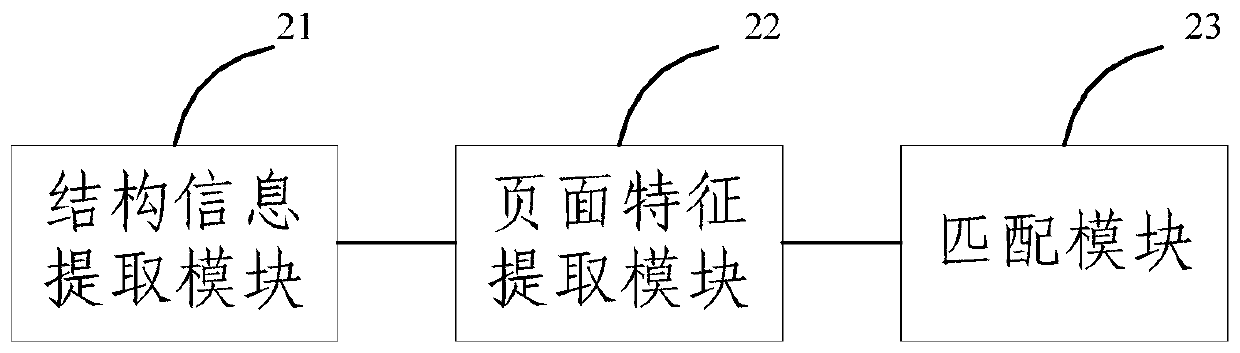
Landing page monitoring method and system
InactiveCN109753790AAlarm in timeReal-time processingWebsite content managementPlatform integrity maintainanceTime processingHTML
The embodiment of the invention provides a landing page monitoring method and system, and the method comprises the steps: carrying out the content extraction of the structure of a landing page after the loading of the landing page is completed, and obtaining the structure information of the landing page; carrying out serialized conversion on the structure information, and obtaining a character string representation of the landing page as a page feature of the landing page; and comparing the page characteristics with characteristics in a preset landing page characteristic depiction library, andjudging that the landing page is an illegal page if the page characteristics are not the same as the characteristics in the preset landing page characteristic depiction library. The embodiment of theinvention provides a method. extracting feature information of a final landing page of an advertisement page put by an advertisement putting person by adopting a js technology with relatively high universality. Compared with the characteristic information of the recorded legal landing page, the method can adaptively monitor various carriers loaded with html advertisement pages in real time, monitors the request of each user in real time, and can realize real-time discovery, real-time alarm and real-time processing of tampering of the advertisement landing page.
Owner:WUHAN JIYI NETWORK TECH CO LTD
Value-based information flow tracking in software packages
ActiveUS11347887B2The result is accurateMore valueDigital data protectionPlatform integrity maintainanceData streamAlgorithm
A computer-implemented method, computer system, and computer program product are directed to improving computer security of a device using value based information flow tracking. Embodiments automatically capture raw data values from a data source of the device and store in memory the captured raw data values in a collection of sensitive data. Embodiments determine whether computed values of functions of a data flow are included in the collection of sensitive data. Based upon the determining, embodiments prevent values of the collection of sensitive data from being transmitted from a sink of the device. Embodiments may determine whether string representations of computed operand and return values of numerical or arithmetic operations of the functions of the data flow are included in the collection of sensitive data.
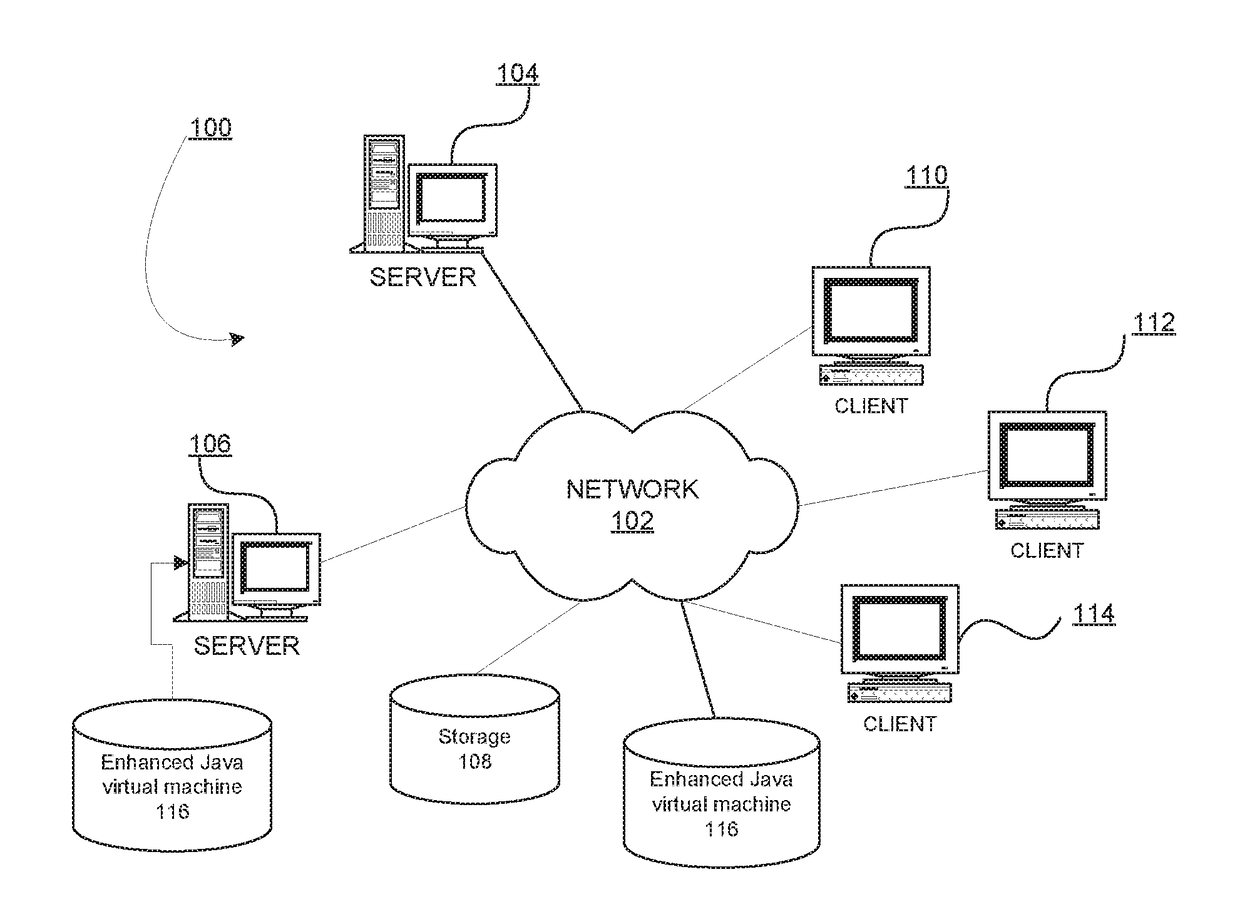
Owner:RGT UNIV OF CALIFORNIA +1
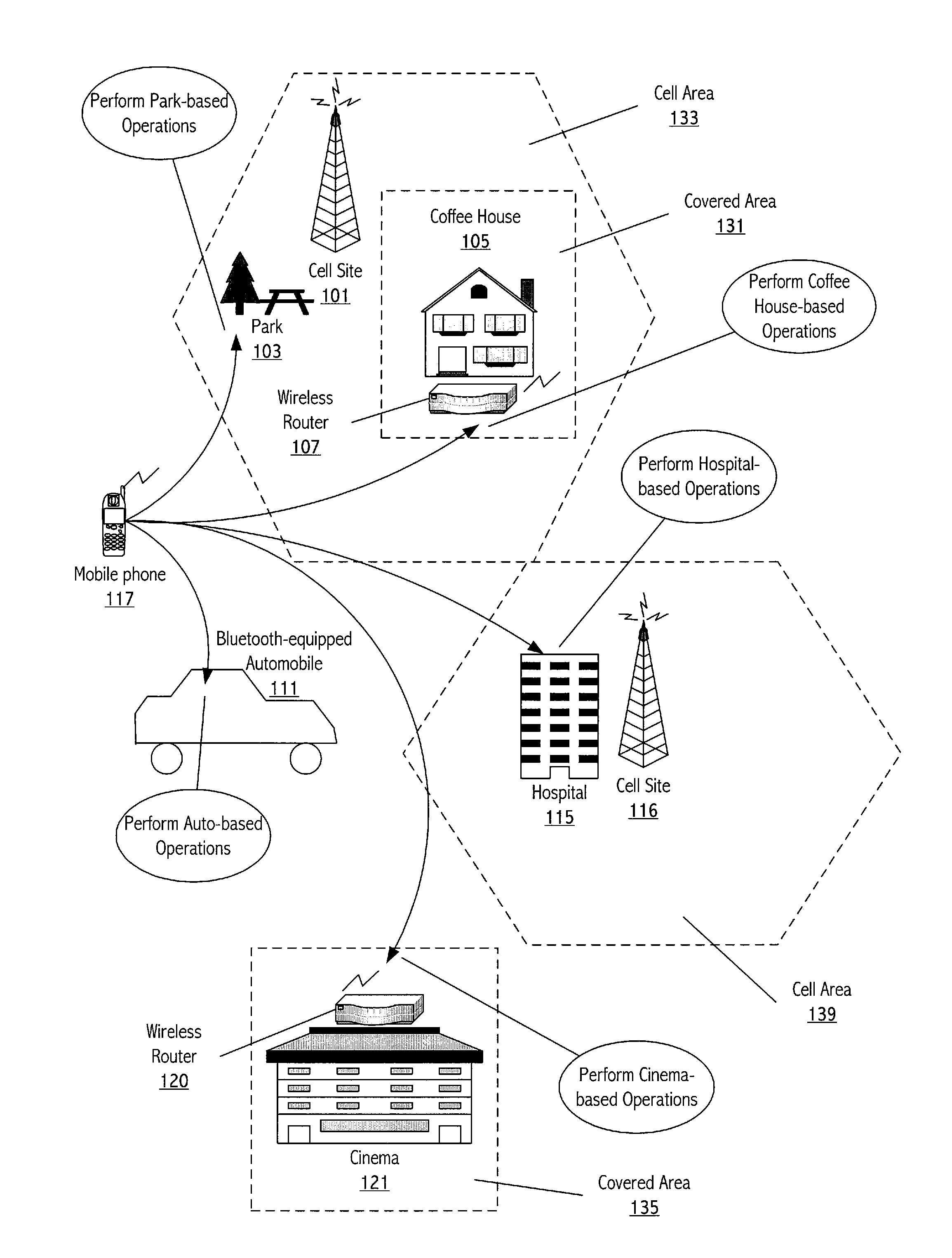
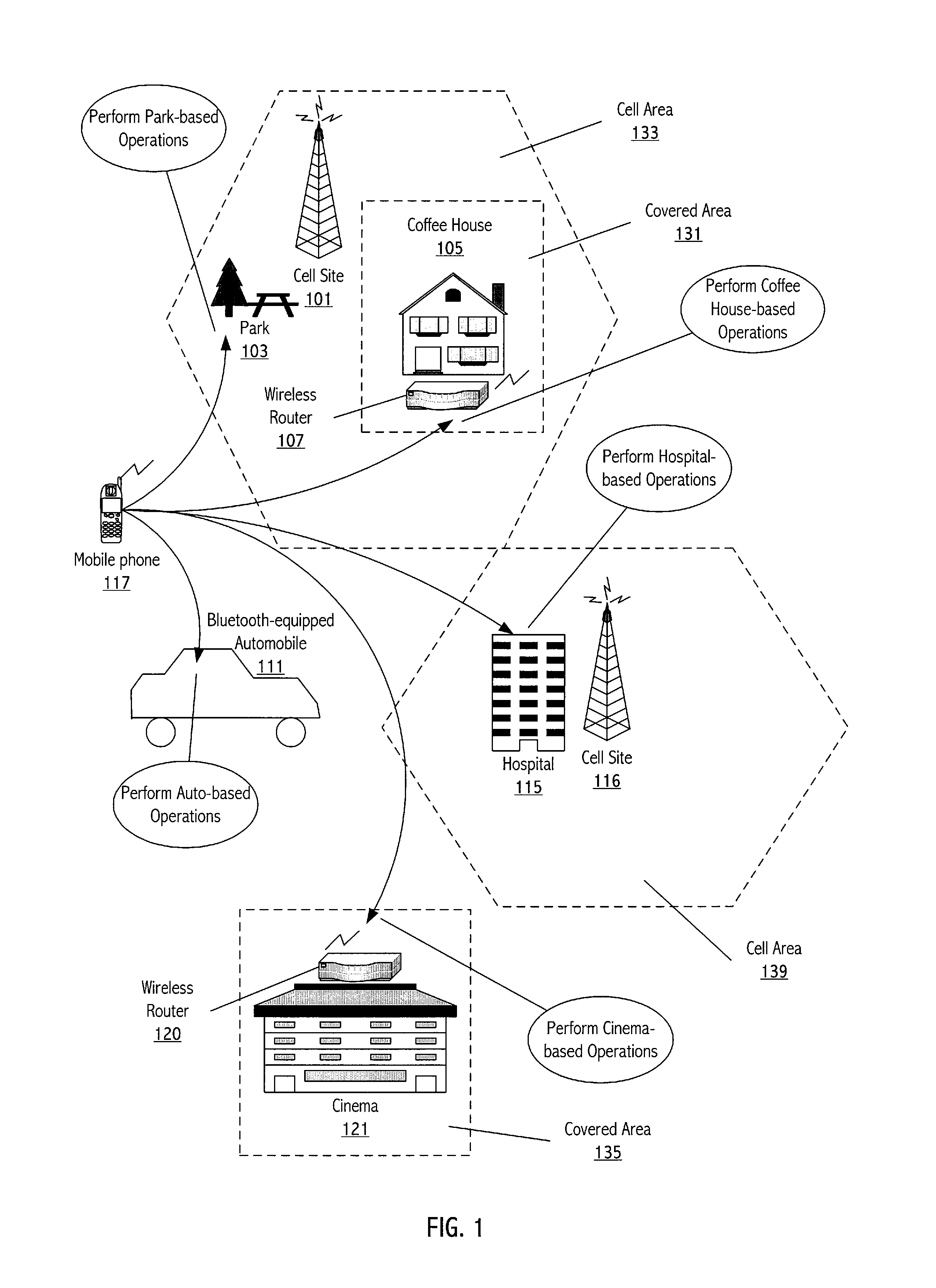
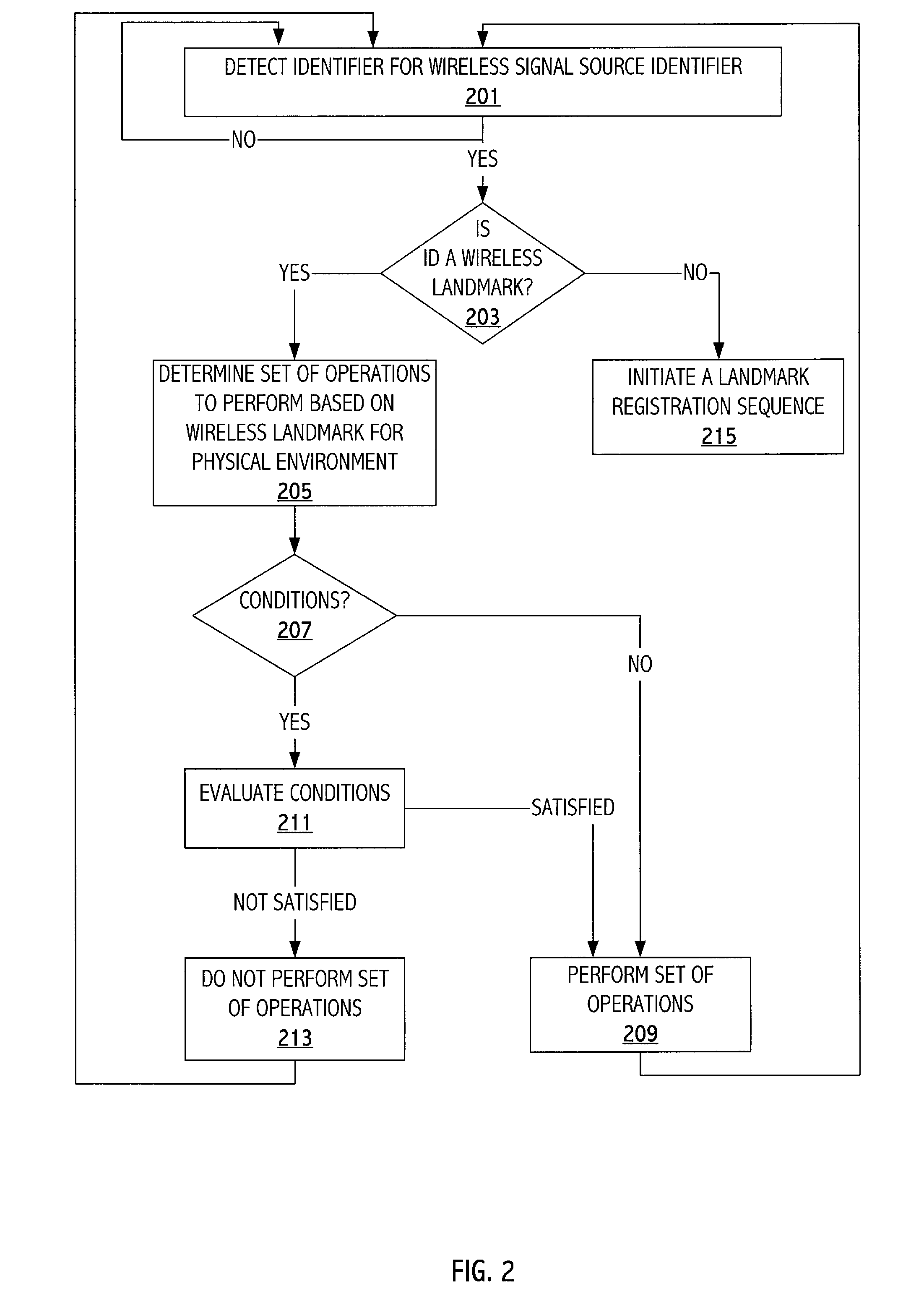
Wireless landmark-based operation of a wireless device
A technique configures a wireless device to perform operations based on the wireless device being within or near a particular physical environment. A wireless signal source identifier (e.g., a cell site identifier) serves as a wireless landmark for the particular physical environment. When the wireless device detects the wireless landmark, the wireless device performs operations previously associated with the wireless landmark. To define a wireless landmark for a particular physical environment, the wireless device detects wireless communications signals and decodes the signals to determine wireless signal source identifiers. A user selects a particular wireless signal source identifier and associates the selected wireless signal source identifier with an indication of the physical environment, such as a character string representation of the physical environment. The user indicates one or more operations for the wireless device to perform in response to subsequent detection of the wireless landmark.
Owner:CINGULAR WIRELESS II LLC
Method and device for encoding chromosome based on intelligent scheduling
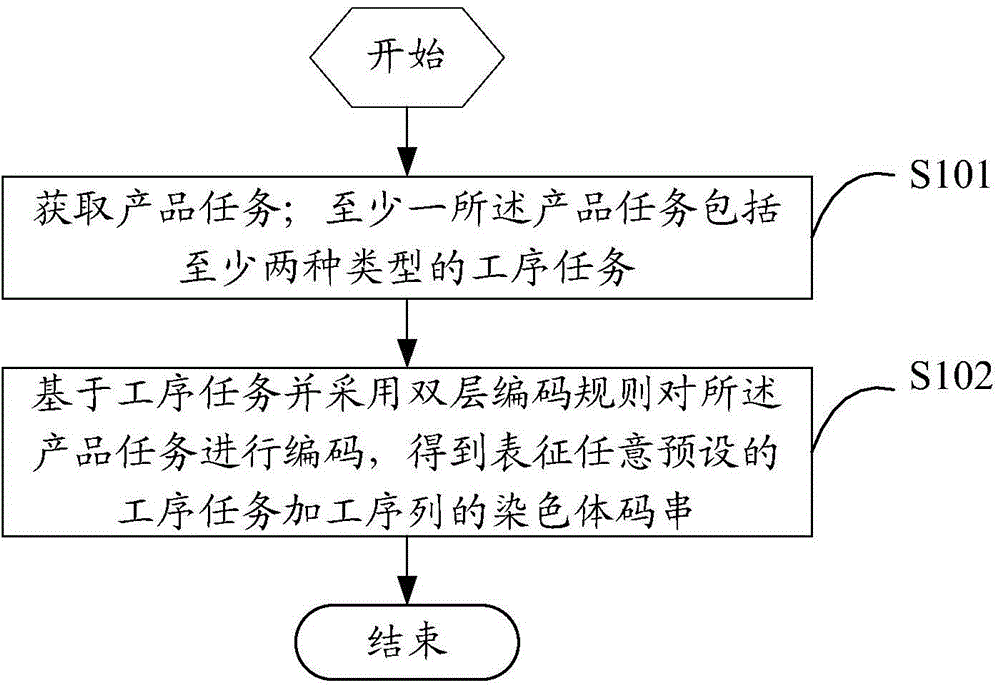
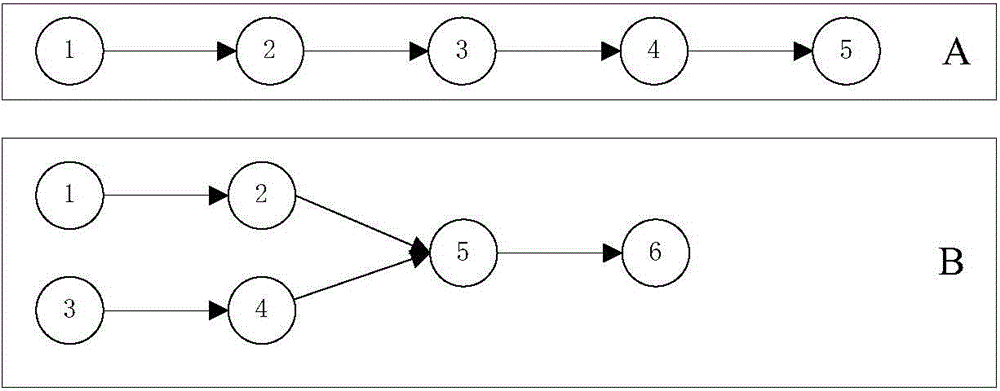
ActiveCN103559544AExpand the scope of insertionImprove search abilityGenetic modelsResourcesChromosome encodingTheoretical computer science
The invention discloses a method and device for encoding a chromosome based on an intelligent scheduling. The method comprises the steps that product tasks are obtained, wherein at least one product task comprises at least two types of working procedure tasks; the product tasks are encoded by adopting a double-layer encoding rule based on the working procedure tasks to obtain a chromosome code string representing any preset working procedure job sequence. Due to the fact that the double-layer encoding is carried out on the chromosome, the chromosome mapping space can completely represent the service solution space when serializability, parallelism, network working procedure tasks and other kinds of working procedure tasks exist in the product tasks, the inserting and searching range of the scheduling algorithm is enlarged, and the problem of deficient code string representation is solved. In addition, the information content contained in the code string can be greatly enlarged through the double-layer encoding, various genetic manipulations based on the double-layer encoding can be extended, and the optimizing performance of the scheduling algorithm can be improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
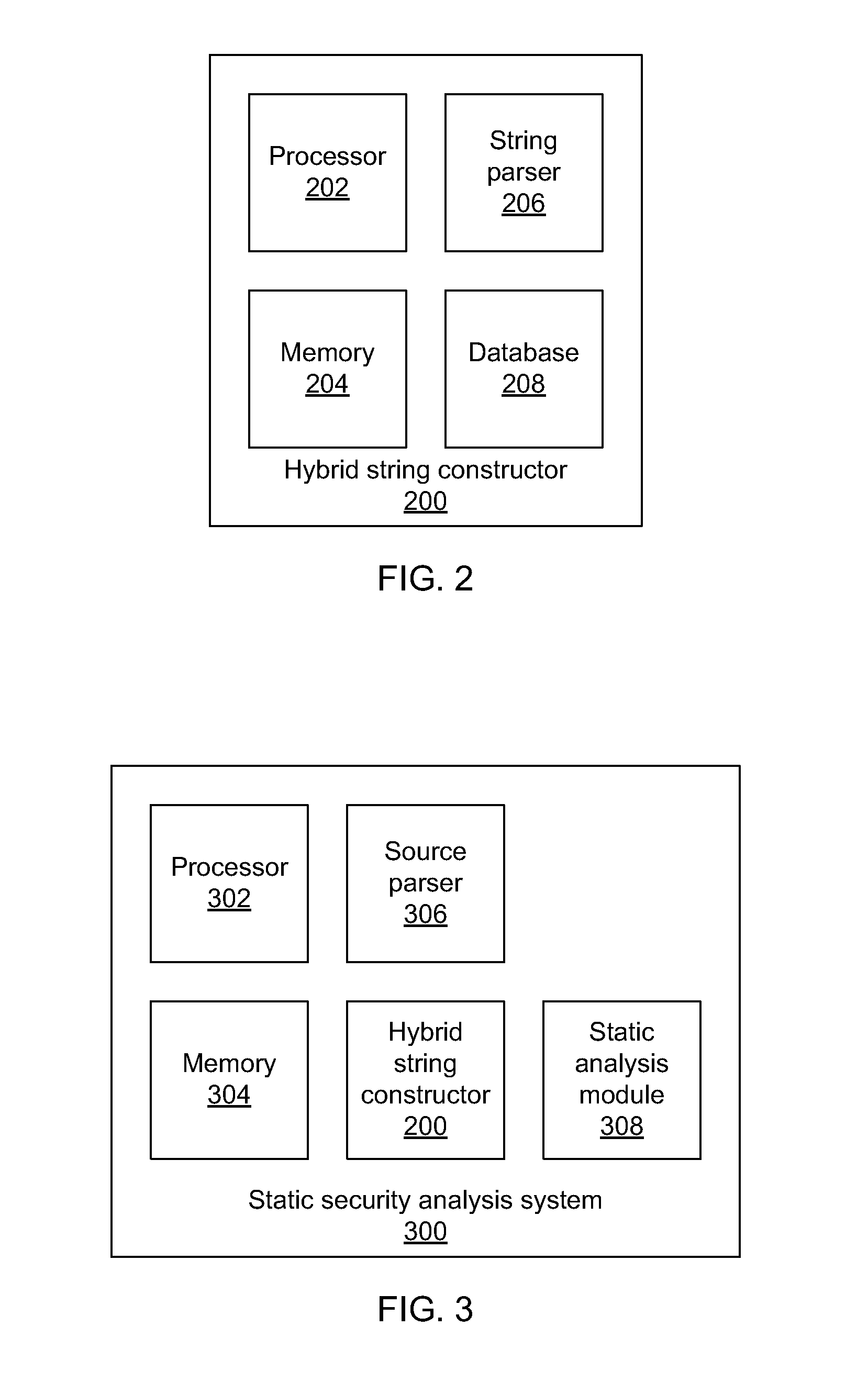
Static security analysis using a hybrid representation of string values
InactiveUS20140075562A1Memory loss protectionError detection/correctionTheoretical computer scienceSecurity analysis
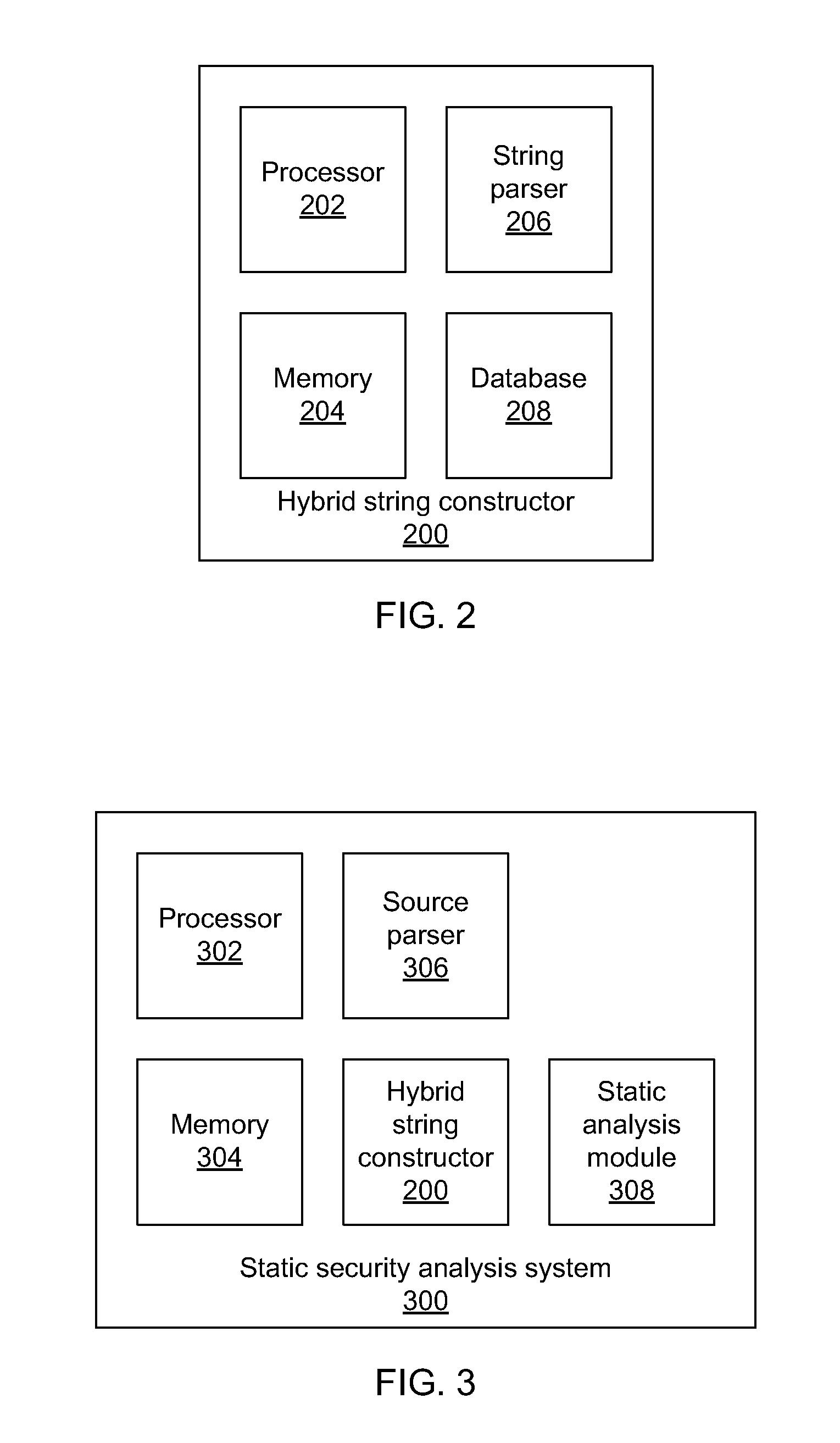
Systems for constructing hybrid string representations include a string parser configured to parse received string information to produce one or more string components, a database configured to store a set of known concretizations, and a processor configured to compare the one or more string components to the set of known concretizations to determine string components that may be represented concretely, to abstract all string components that could not be represented concretely, and to create a hybrid string representation that includes at least one concrete string component and at least one abstracted string component.
Owner:IBM CORP
Multi-byte compressed string representation
ActiveUS10002010B2Code conversionSoftware simulation/interpretation/emulationByteString representation
Multi-byte compressed string representation embodiments define a String class control field identifying compression as enabled / disabled, and another control field, identifying a decompressed string created when compression enabled. Tests are noped based on null setting of the compression flag. When arguments to a String class constructor are not compressible, a decompressed String is created and stringCompressionFlag initialized. Endian-aware helper methods for reading / writing byte and character values are defined. Enhanced String class constructors, when characters are not compressible, create a decompressed String, and initialize stringCompressionFlag triggering class load assumptions, overwriting all nopable patch points. A String object sign bit is set to one for decompressed strings when compression enabled, and masking / testing this flag bit is noped. Alternative package protected string constructors and operations are provided. A predetermined location is checked to determine whether supplied arguments to a String class constructor are compressible is performed.
Owner:IBM CORP
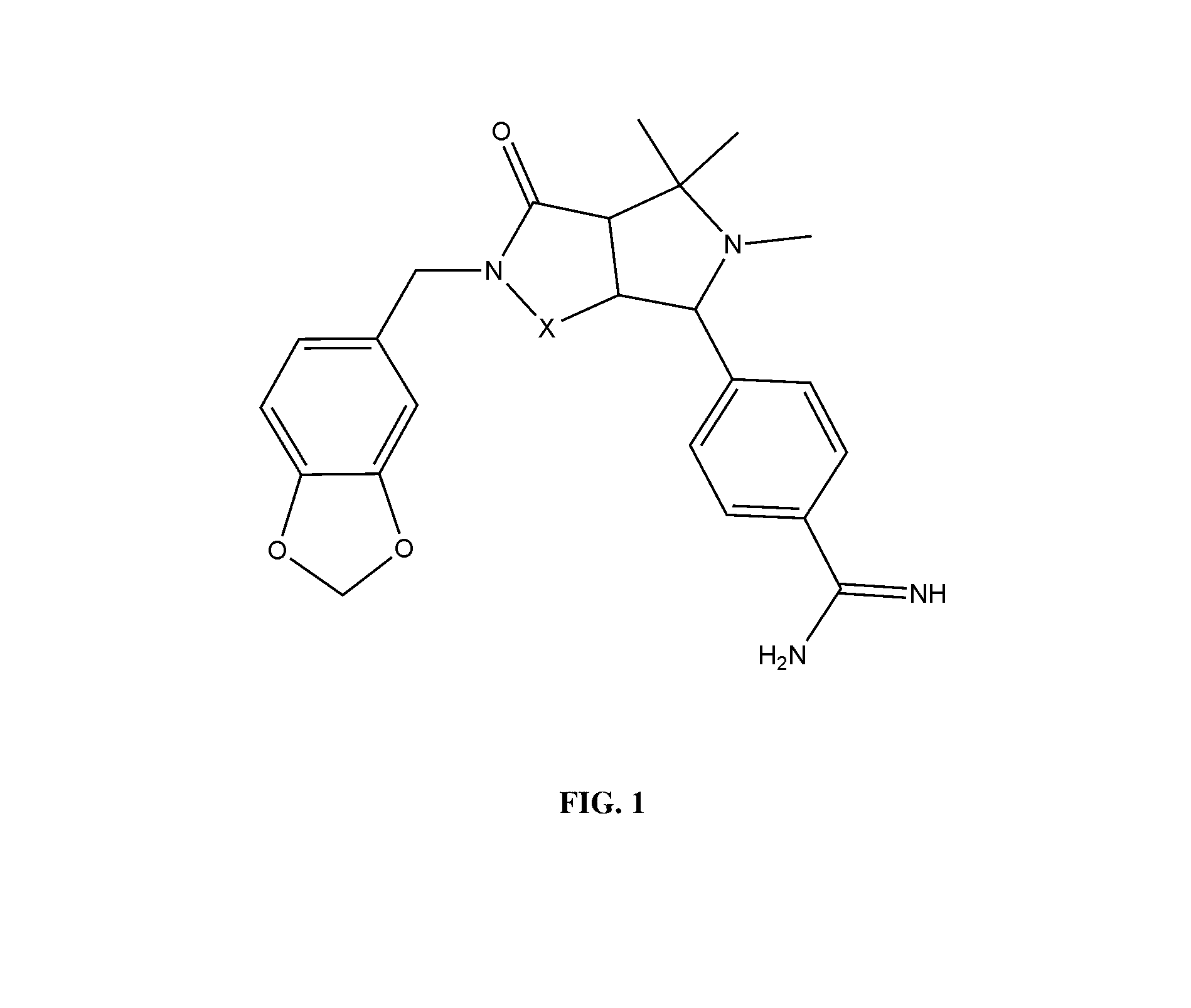
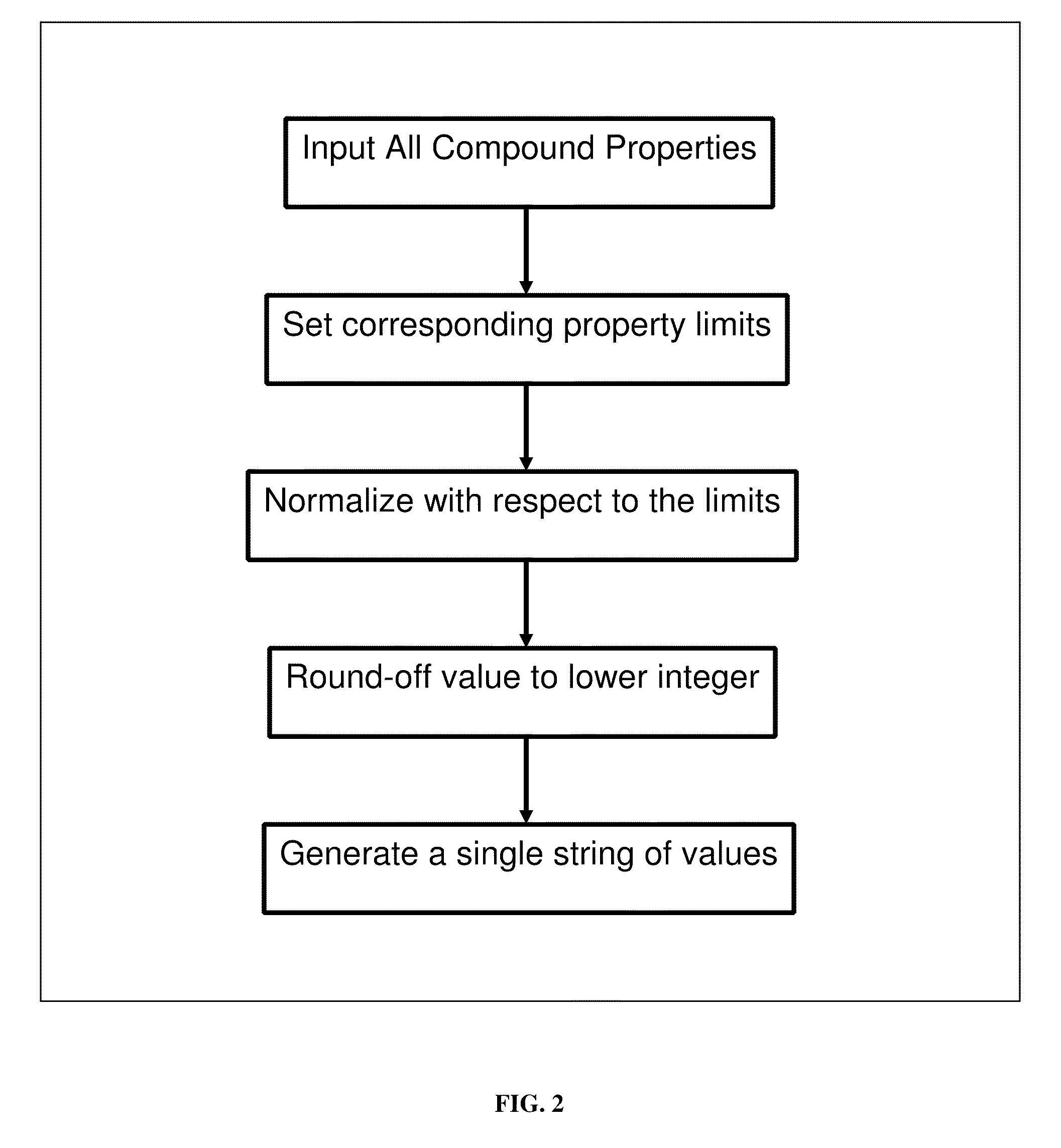
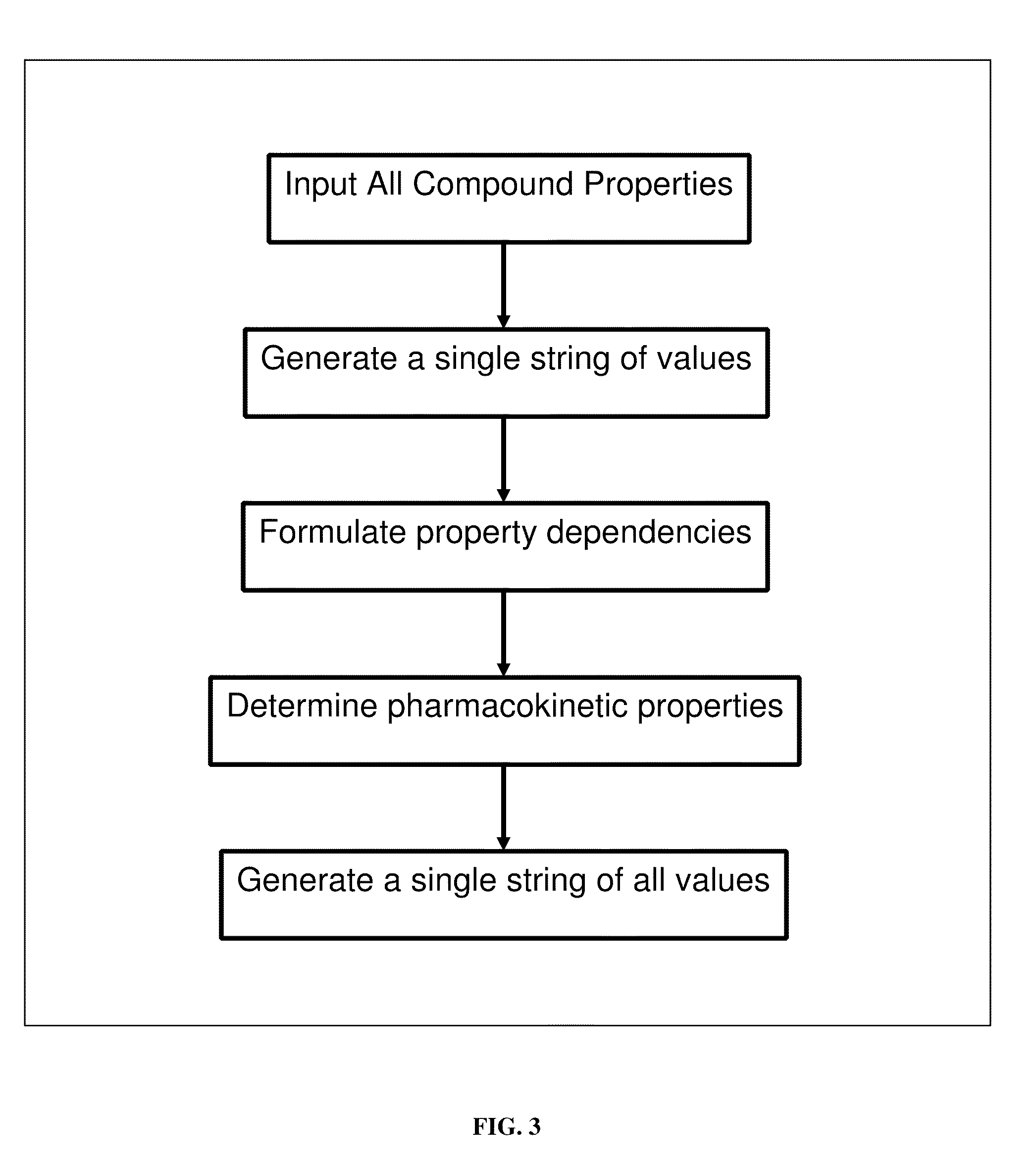
Method for providing a numerical and graphical abbreviated profile of a drug (A-POD)
ActiveUS8392166B2Chemical property predictionAnalogue computers for chemical processesGraphicsRelative Change
A novel numerical and graphical representation has been developed to better comprehend the physicochemical, biological and pharmacokinetic properties of drug-like compounds. Abbreviated profile of drug (A-POD) would help in considering and visualizing the various compound characteristics as one entity. The salient features of A-POD are: a unique way of representing the compound properties, computer friendly numerical string representation making comparison of any properties possible, graphical representation that gives a snapshot of properties and their relative changes, and its usefulness in qualitatively predicting the ADMET properties based on chemical properties alone. This simple yet powerful web-based tool is especially useful in comparing any two compounds at one time. A new therapeutic agent can be compared with the reference compound quickly and easily, by checking which properties are affected and finding out whether it possesses better drug-like properties.
Owner:HIREMATH CHAITANYA N
Scalable And Precise String Analysis Using Index-Sensitive Static String Abstractions
InactiveUS20140259174A1Memory loss protectionError detection/correctionString analysisString representation
A disclosed method includes accessing one or more seeding specifications and a program including computer-readable code and applying the one or more seeding specifications to the program to identify for analysis seeds including strings for corresponding identified string variables. The method includes tracking flows emanating from the identified seeds. The tracking includes computing an integral offset into a tracked string variable for any statements causing such a computation. The tracking also includes providing a string representation based on the computed integral offset, wherein the provided string representation comprises a value of the integral offset and an indication of the corresponding tracked string variable. The tracking further includes modeling string manipulations of the tracked string variables using the string representations. Apparatus and program products are also disclosed.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com