Patents
Literature
55 results about "String analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
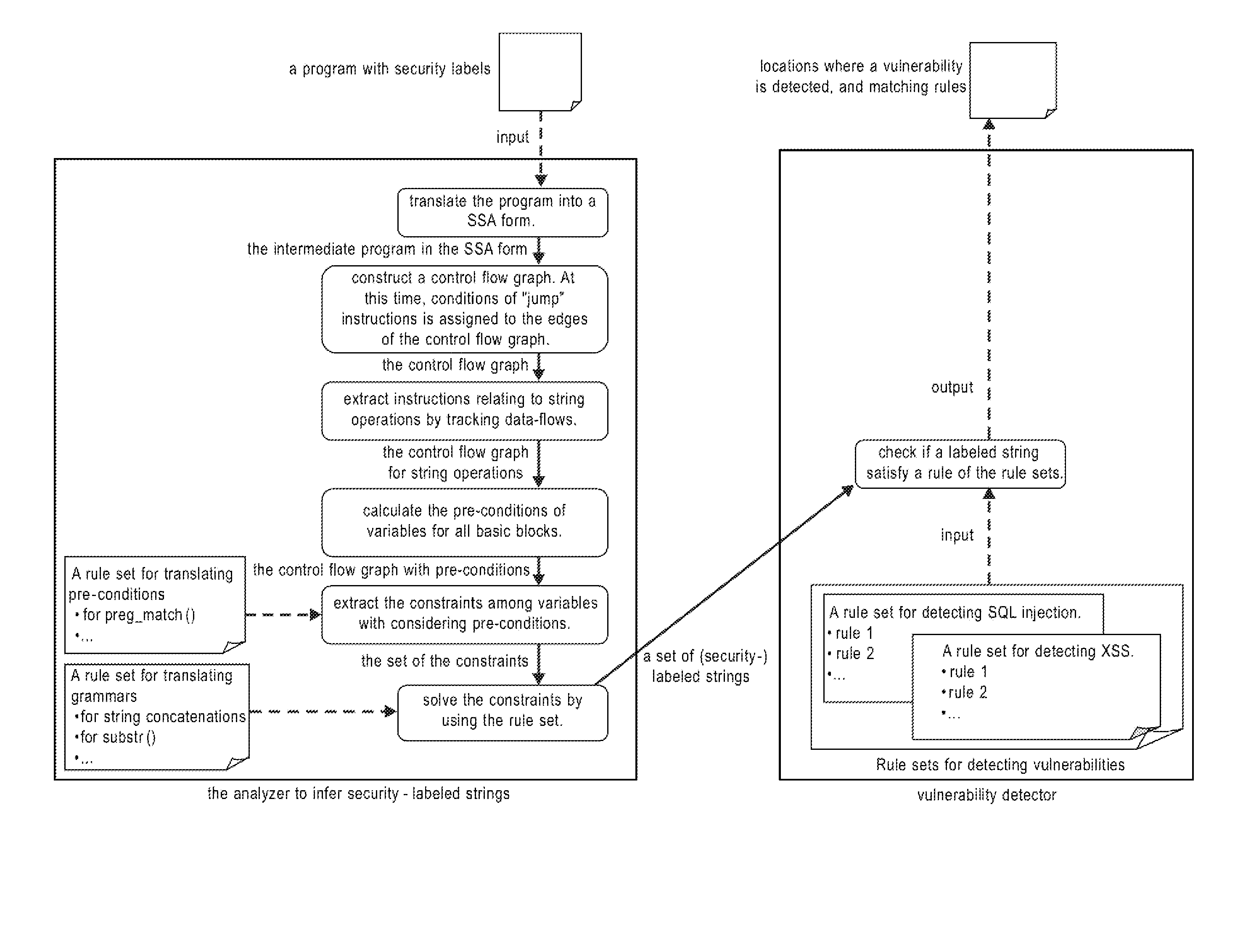
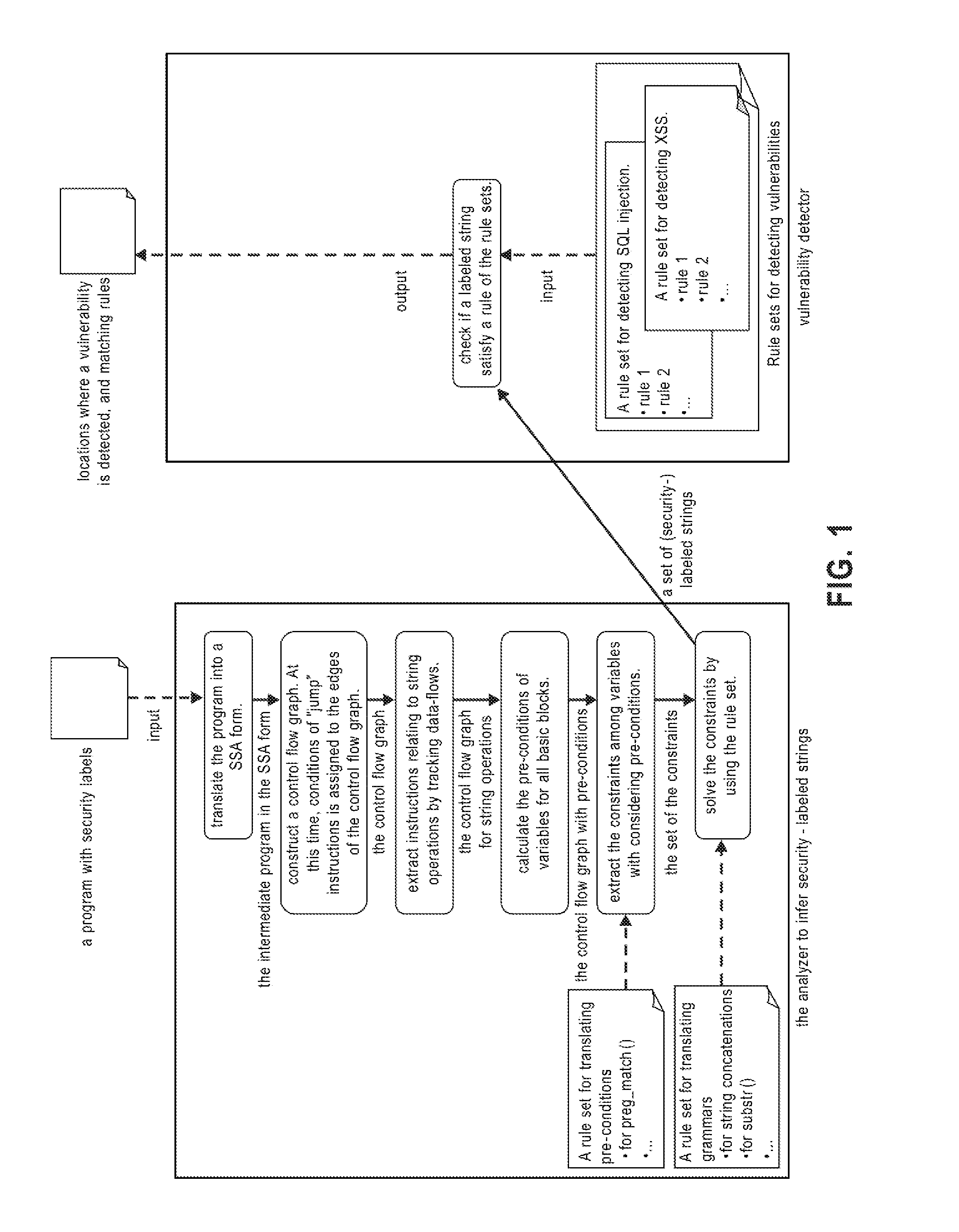
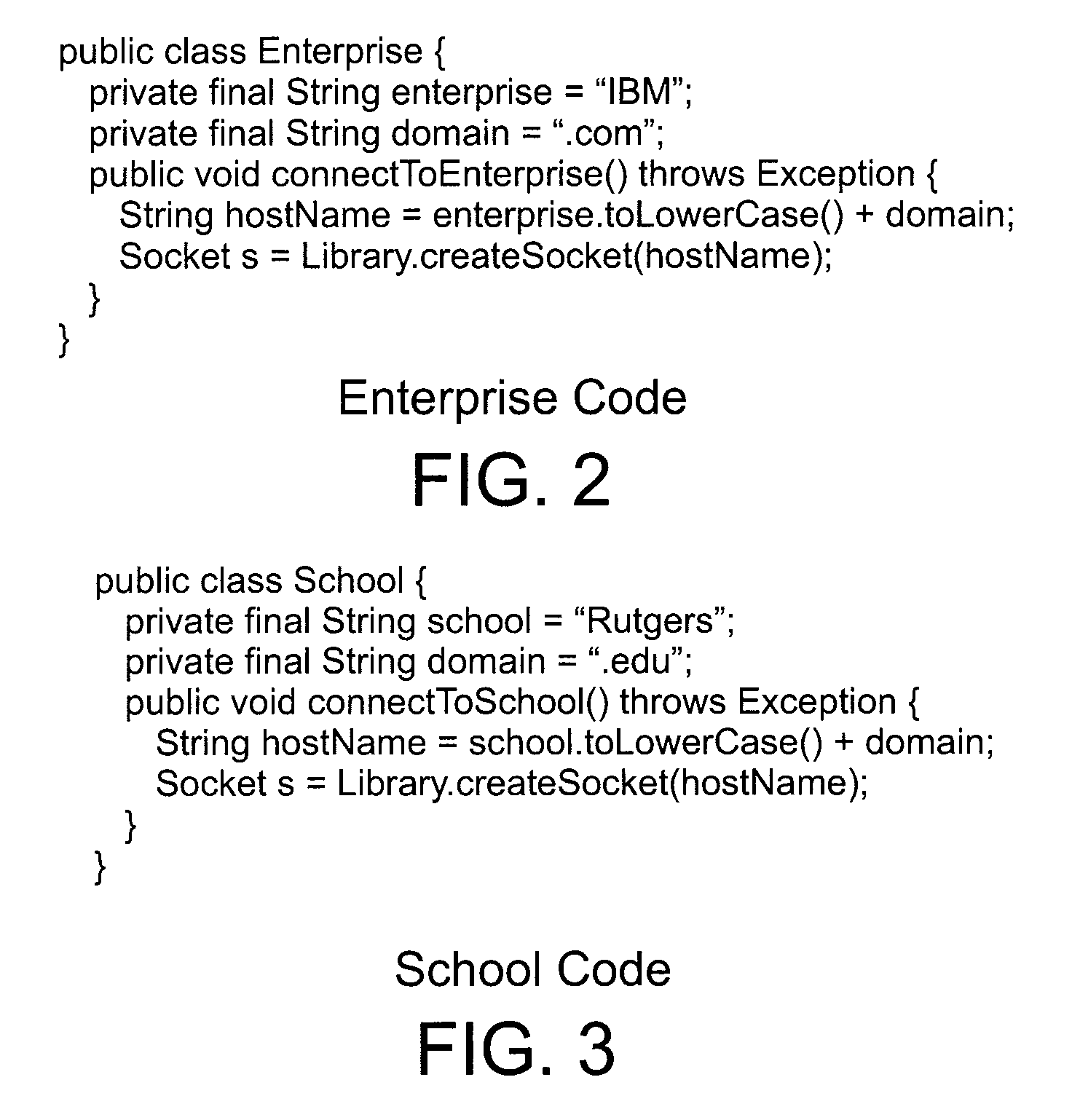
Systems, methods and computer program products for string analysis with security labels for vulnerability detection
InactiveUS7530107B1Suppress false detectionDetailed analysisMemory loss protectionError detection/correctionLocation detectionPre-condition
Systems, methods and computer program products for string analysis with security labels for vulnerability detection. Exemplary embodiments include a method in a computer system configured to analyze security-labeled strings and to detect vulnerability, the method including receiving a program with security labels, translating the program into a static single assignment form, constructing a control flow graph having basic blocks as nodes, extracting instructions relating to string functions and object variables, calculating pre-conditions of variables for the basic blocks, extracting constraints among the variables subject to a rule set for translating pre-conditions, solving the constraints and obtaining a set of strings that he object variables form as a context-free grammar to obtain a set of security-labeled strings, checking if the set of security-labeled strings satisfies a rule of the rule set for translating pre-conditions and identifying locations in the program where a vulnerability is detected.
Owner:IBM CORP
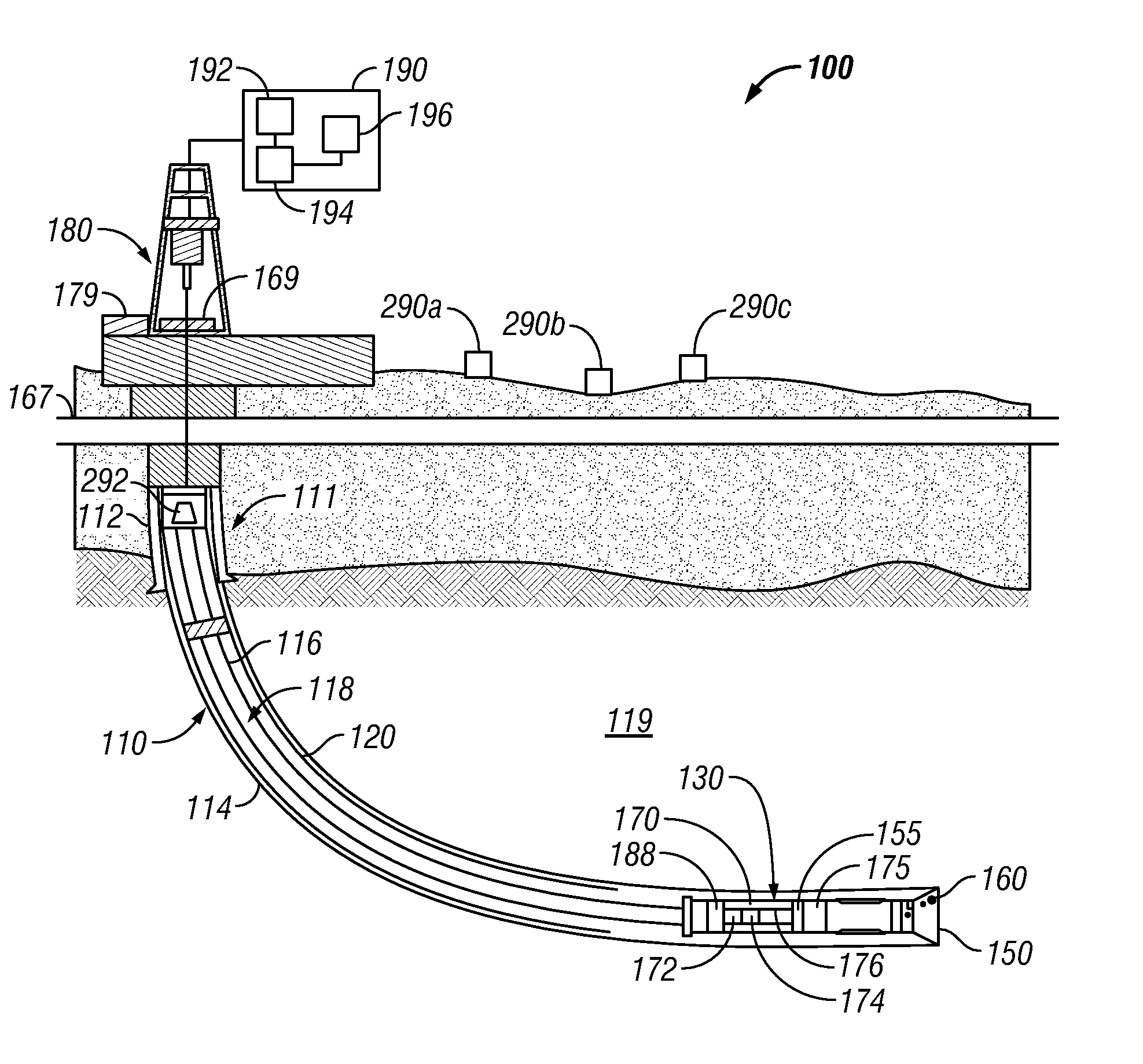
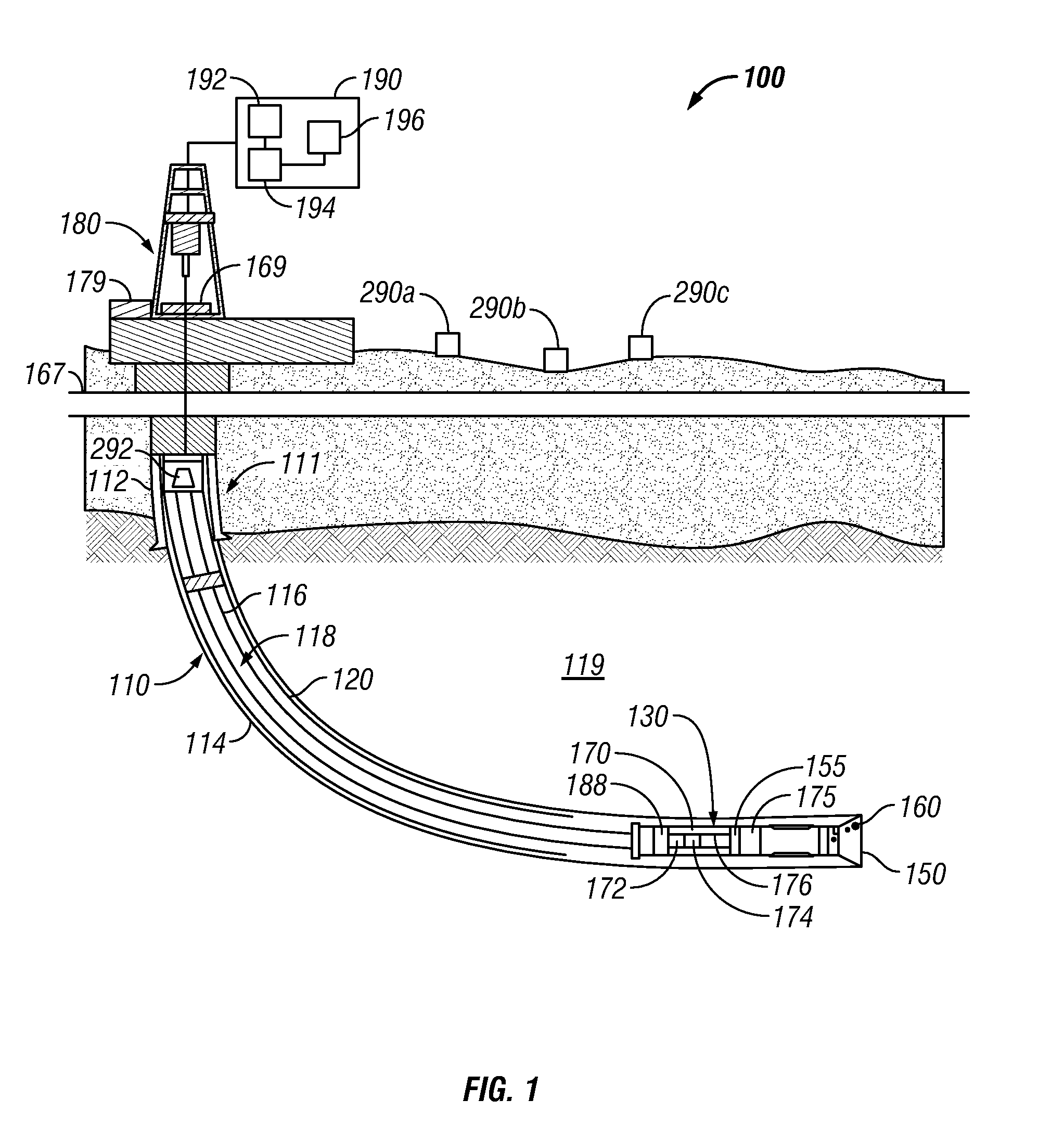
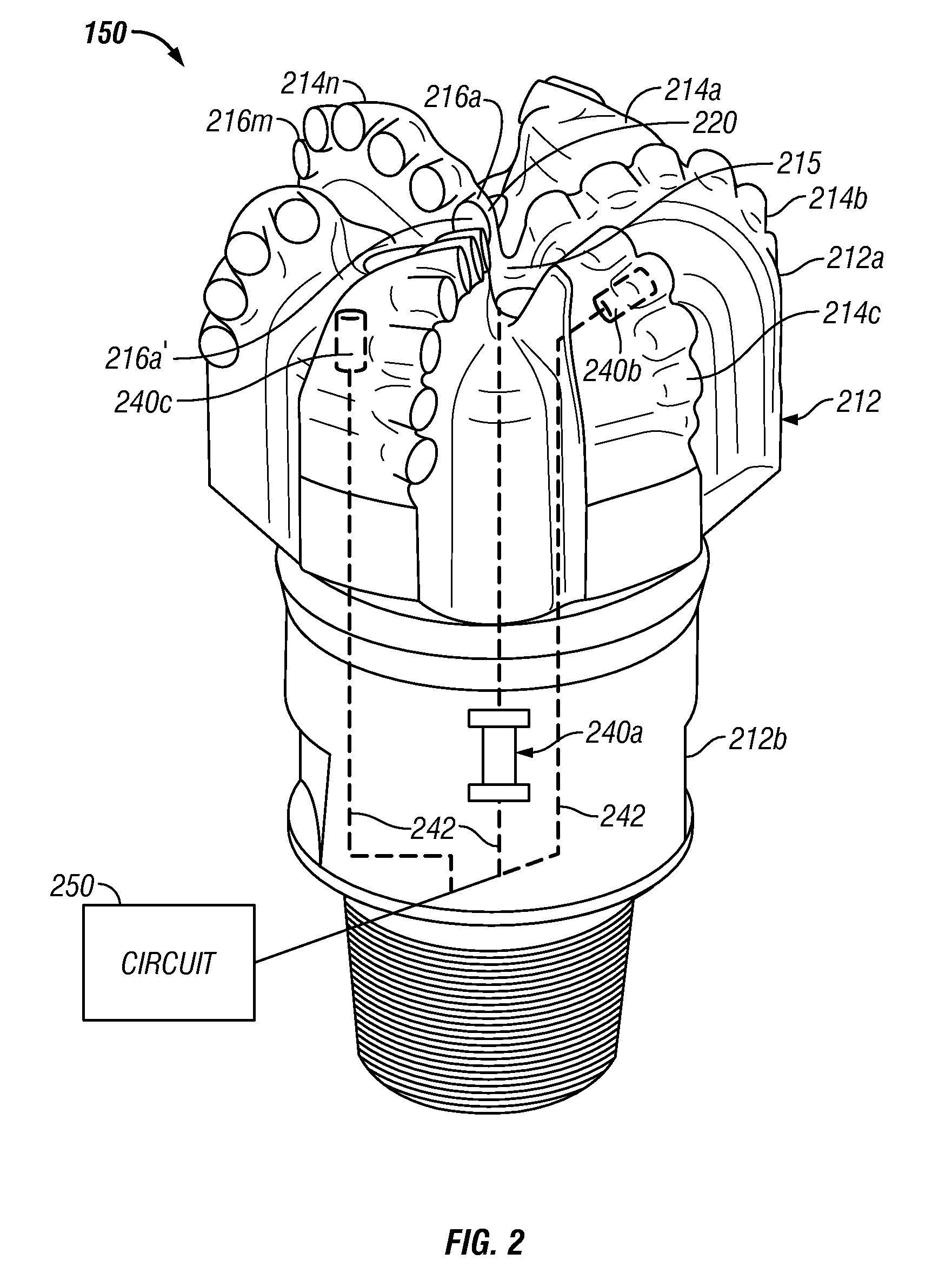
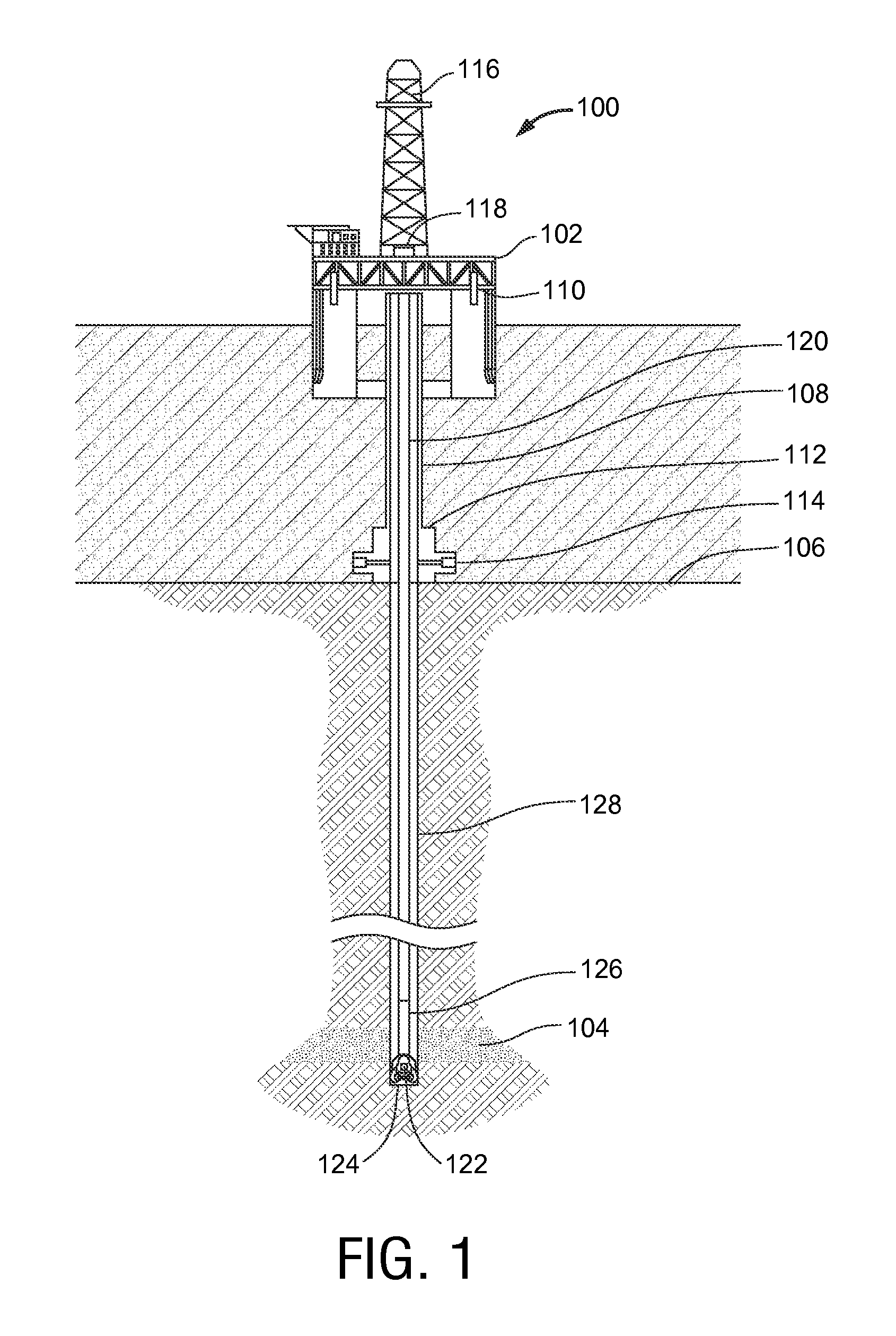
Bit Based Formation Evaluation and Drill Bit and Drill String Analysis Using an Acoustic Sensor
A drill bit having a bit body includes one or more acoustic sensors that are configured to detect elastic waves when the drill bit is used for drilling a wellbore. The acoustic sensor may be configured to detect a sonic signature associated with a failure event. In further arrangements, the acoustic sensors may be configured to receive signals from a controlled acoustic source.
Owner:BAKER HUGHES INC
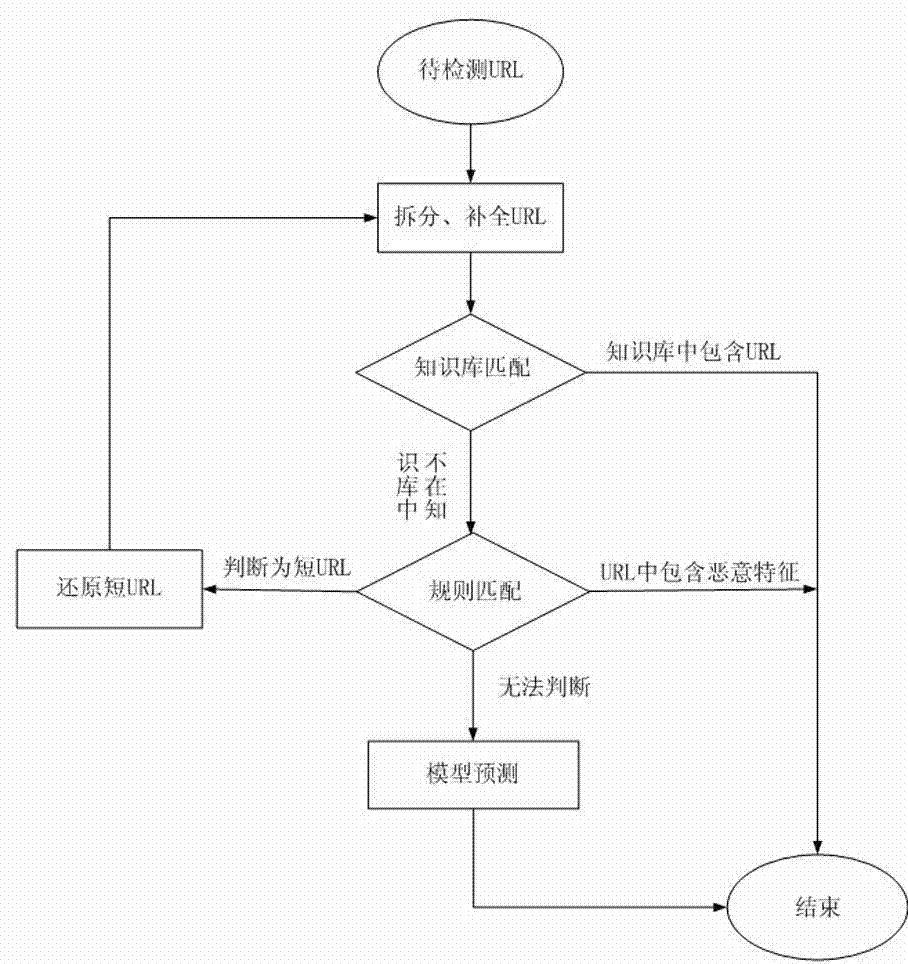
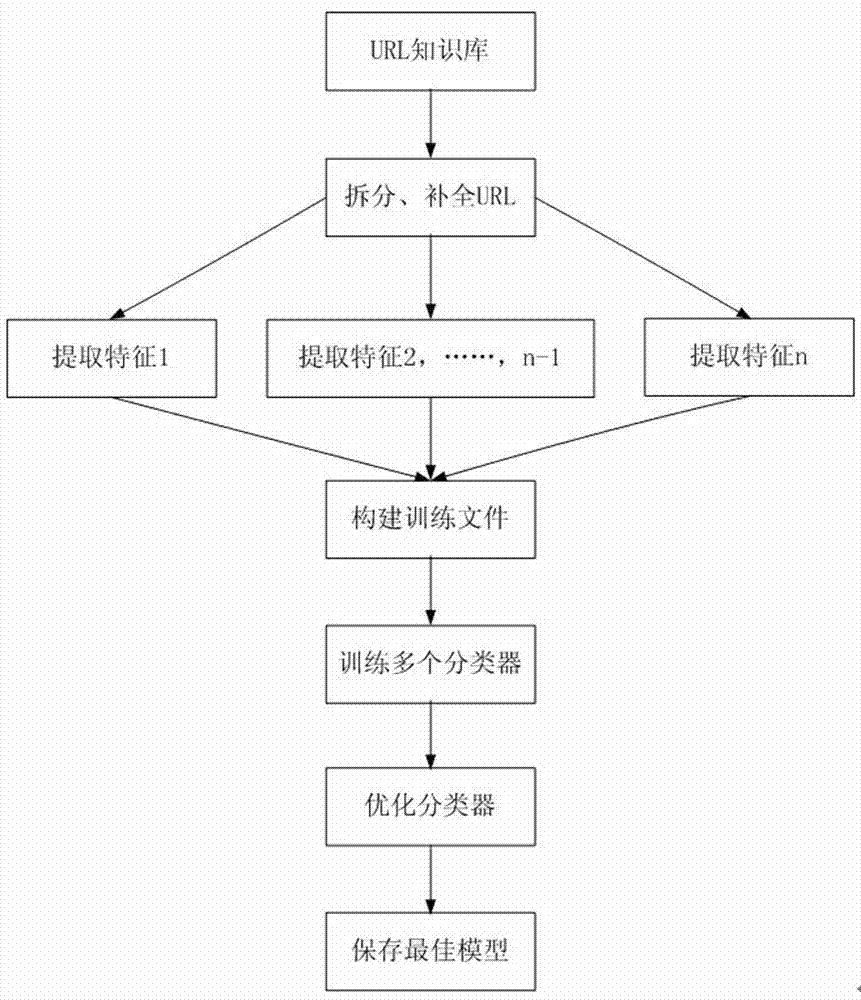
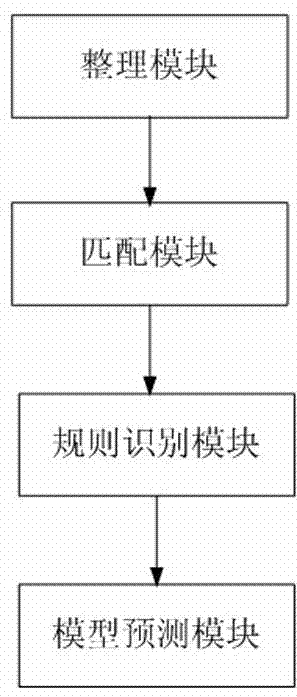
Malicious URL detection method and implement system thereof
The invention discloses a malicious URL detection method and a system. The method comprises the steps of splitting a URL to be detected into character strings according to a URL grammar and a semantic structure in the RFC1738 standard; analyzing, completing and modifying the character strings which are obtained by splitting; aiming at a new URL formed by the processed character strings, traversing and matching a URL knowledge base; judging whether the new URL contains malicious features and belongs to a short URL according to rules, and if the new URL belongs to the short URL, restoring the short URL into a long URL; finally, extracting the features from the URL knowledge base, applying a sorting algorithm training model through machine learning, and predicting the malicious property of the URL. By applying the method and the system, the flexibility and eversporting property of URL forms are solved, a newly-emerging malicious website can be recognized, the harm from the malicious URL can be effectively resisted, and the safety performance of user information can be substantially improved.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
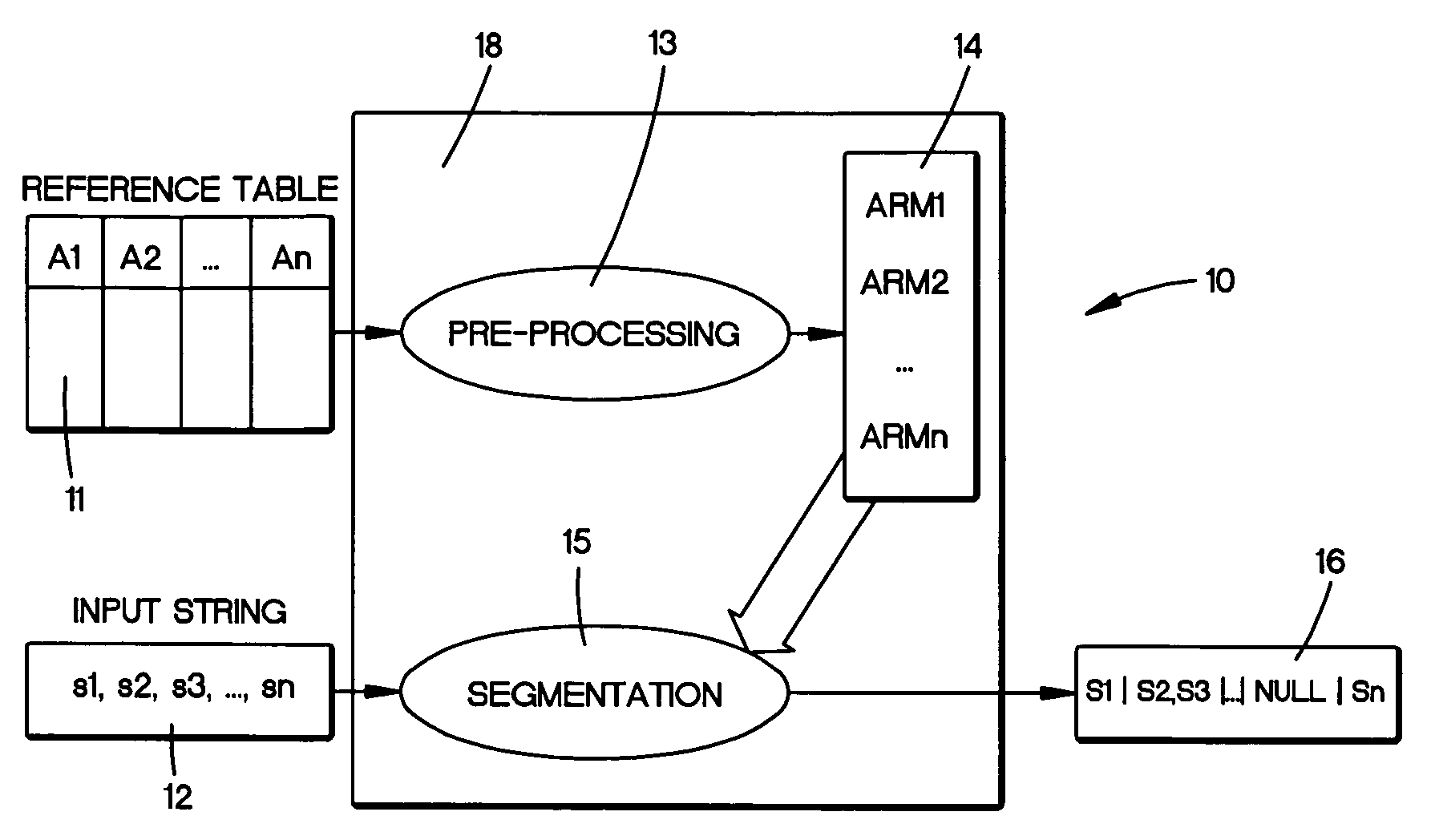
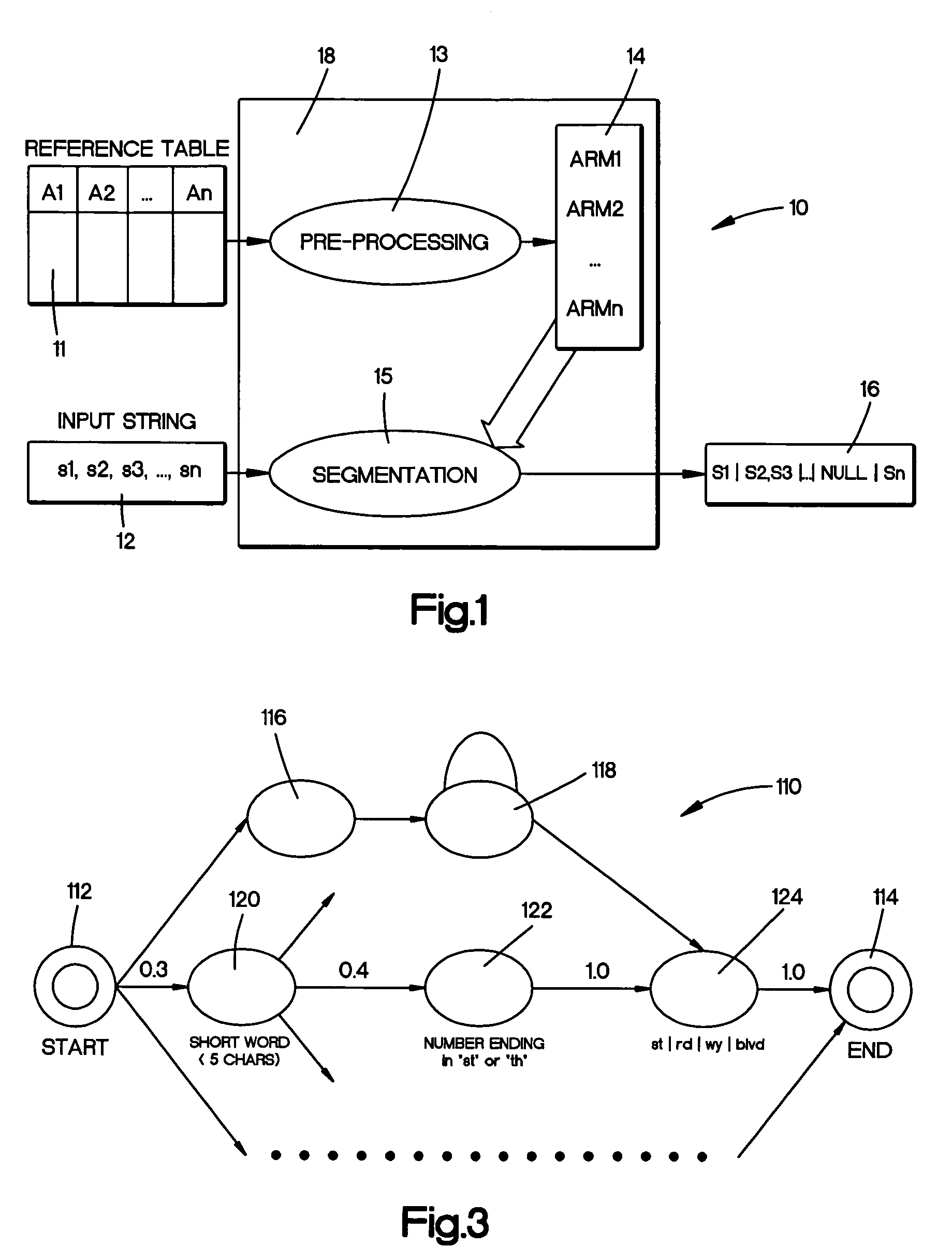
Segmentation of strings into structured records
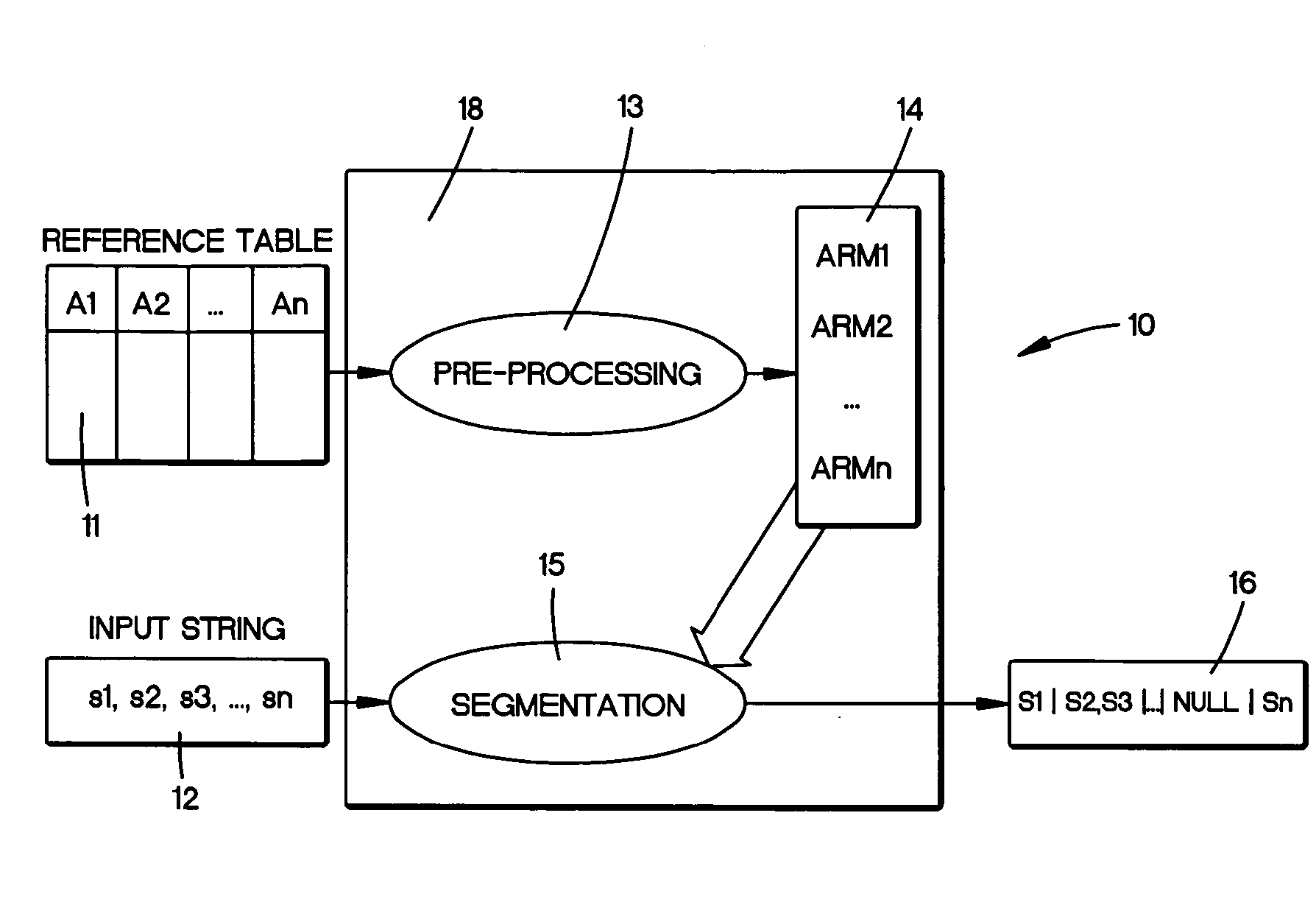
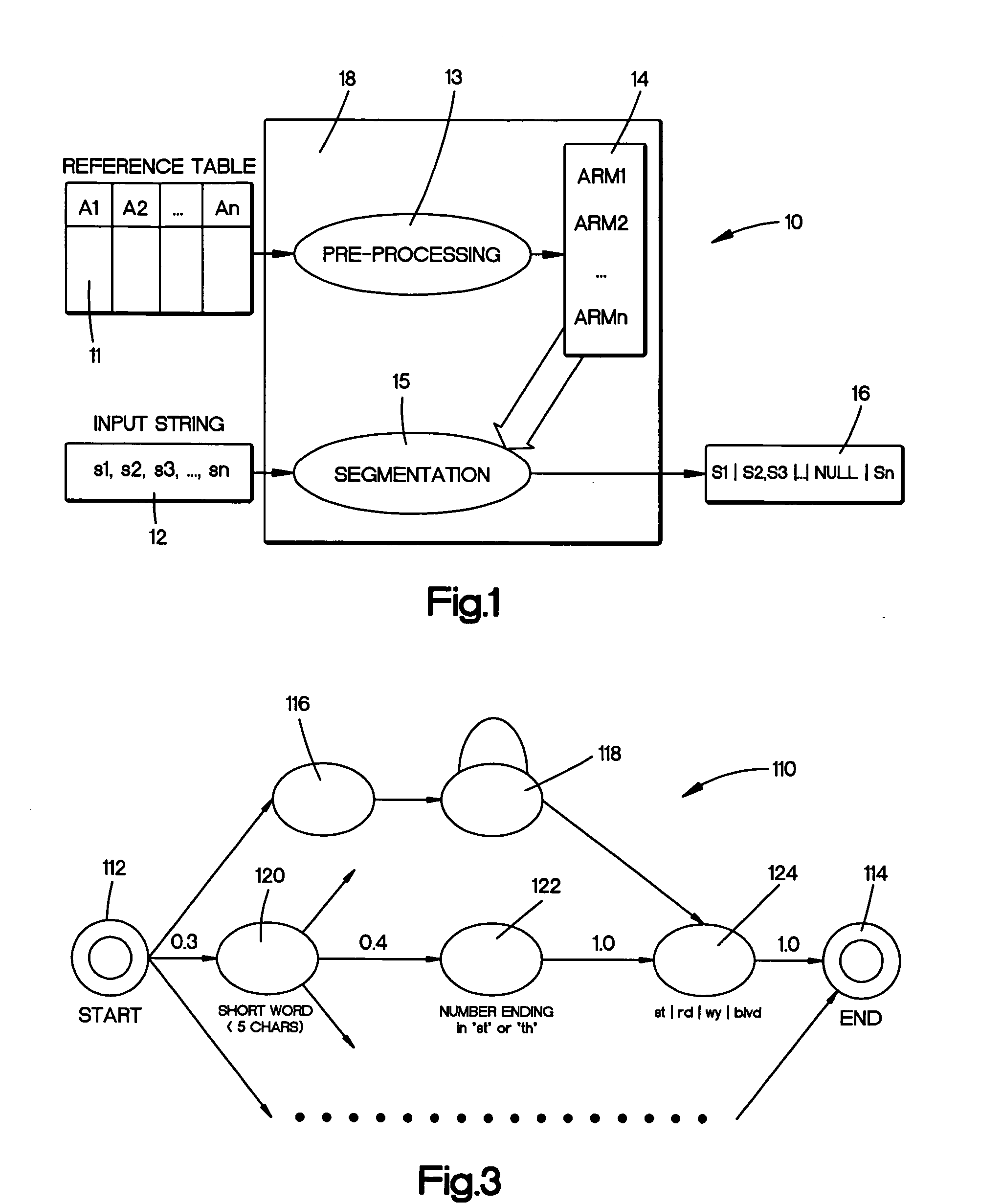
InactiveUS20050234906A1Digital data information retrievalDigital data processing detailsState modelManagement system
An system for segmenting strings into component parts for use with a database management system. A reference table of string records are segmented into multiple substrings corresponding to database attributes. The substrings within an attribute are analyzed to provide a state model that assumes a beginning, a middle and an ending token topology for that attribute. A null token takes into account an empty attribute component and copying of states allows for erroneous token insertions and misordering. Once the model is created from the clean data, the process breaks or parses an input record into a sequence of tokens. The process then determines a most probable segmentation of the input record by comparing the tokens of the input record with a state models derived for attributes from the reference table.
Owner:MICROSOFT TECH LICENSING LLC
System, Method, and Apparatus for Modular, String-Sensitive, Access Rights Analysis with Demand-Driven Precision
InactiveUS20100043048A1Reduce in quantityGood precisionPlatform integrity maintainanceTransmissionProgram slicingSoftware engineering
A static analysis for identification of permission-requirements on stack-inspection authorization systems is provided. The analysis employs functional modularity for improved scalability. To enhance precision, the analysis utilizes program slicing to detect the origin of each parameter passed to a security-sensitive function. Furthermore, since strings are essential when defining permissions, the analysis integrates a sophisticated string analysis that models string computations.
Owner:IBM CORP
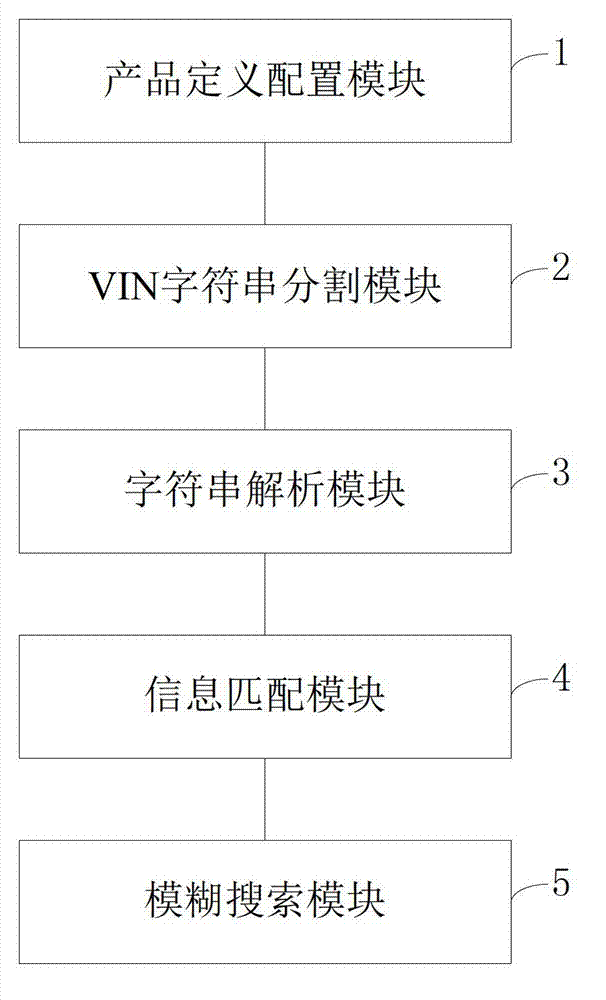
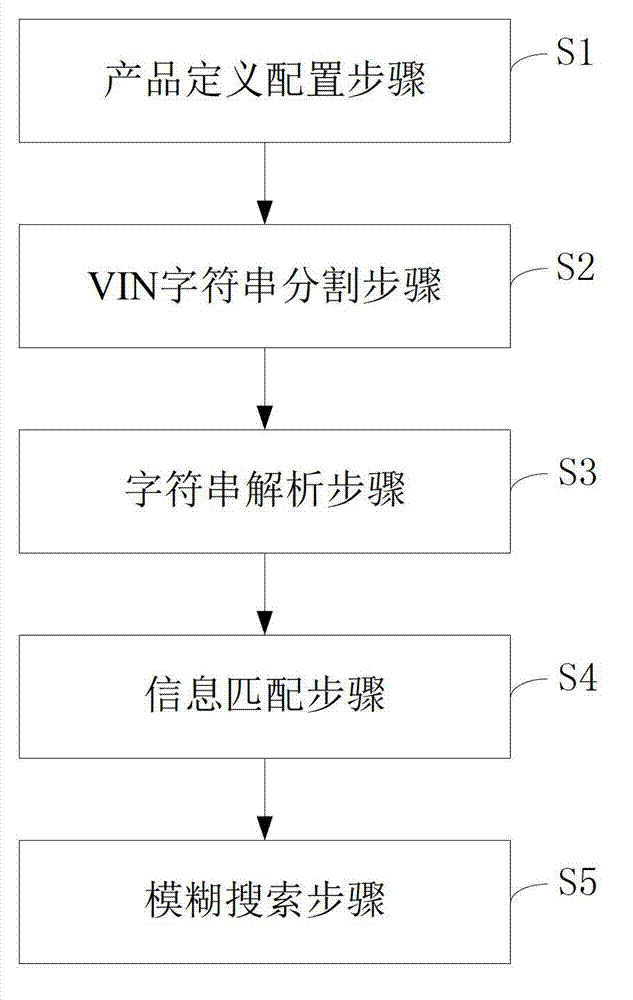
System and method for carrying out searching match on automobile component products by using VIN (Vehicle Identification Number)
InactiveCN102930000AQuick searchExact searchSpecial data processing applicationsSearch wordsDatasheet
The invention discloses a system and a method for carrying out searching match on automobile component products by using a VIN (Vehicle Identification Number). The system comprises a product definition configuration module, a VIN character string division module, a character string analysis module, an information matching module and a fuzzy search module. The product definition configuration module is used for predefining classes and adaptable automobile modes of products in a database; the VIN character string division module is used for intercepting a plurality of character strings from the VIN according to a set rule; the character string analysis module is used for analyzing information corresponding to a vehicle represented by the VIN from the character strings obtained through division; the information matching module is used for carrying out analysis to obtain vehicle information and find out a product matched with the vehicle from a datasheet to be retrieved by virtue of a circular traverse function; and the fuzzy search module is used for finding out the final product needed by a user in combination with keyword fuzzy search specific to the name of the product per se. According to the invention, the specific product needed by the user can be searched quickly and precisely according to search words and the VIN of the vehicle of the user.
Owner:马涛
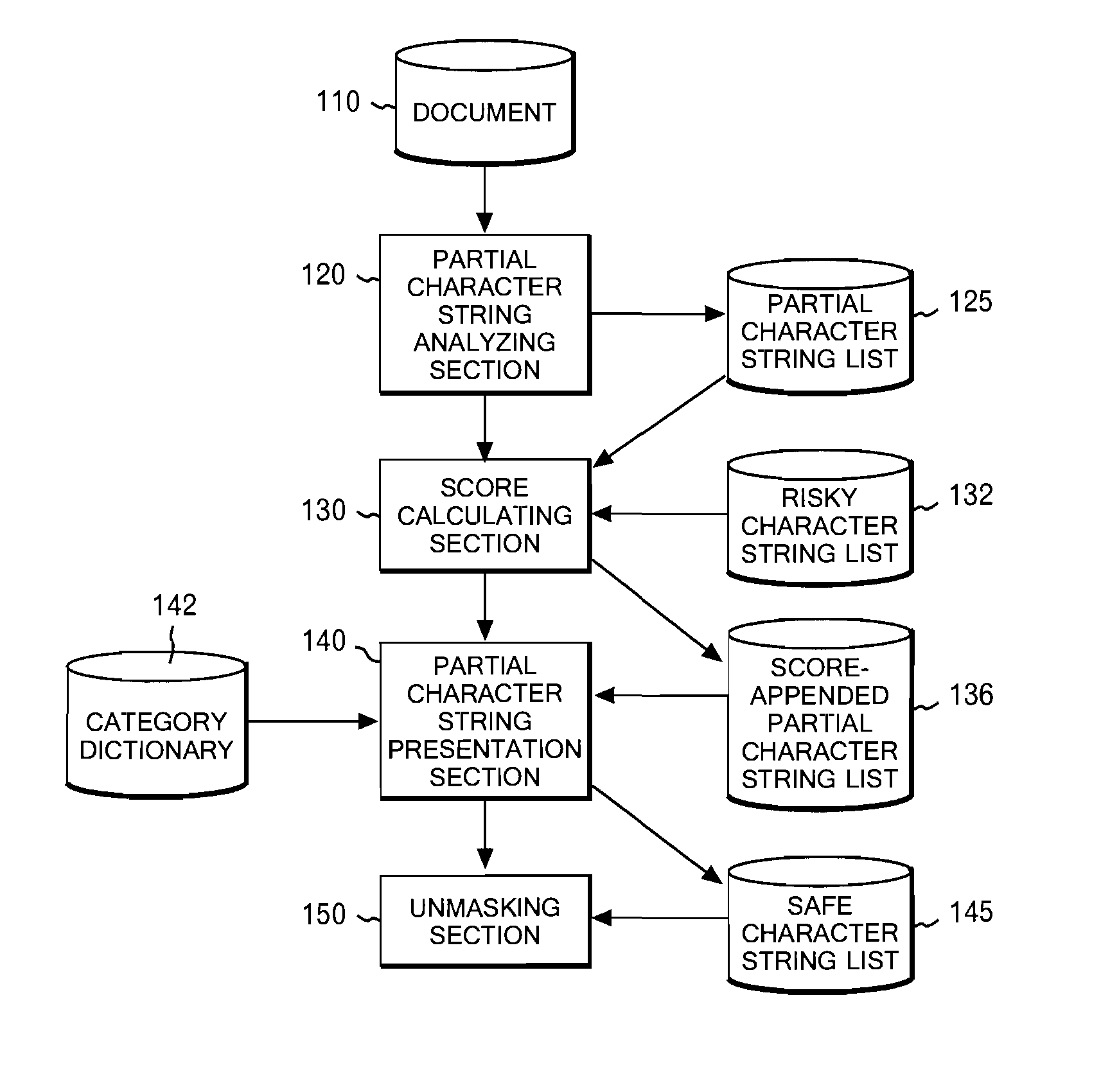
Character string processing method, apparatus, and program
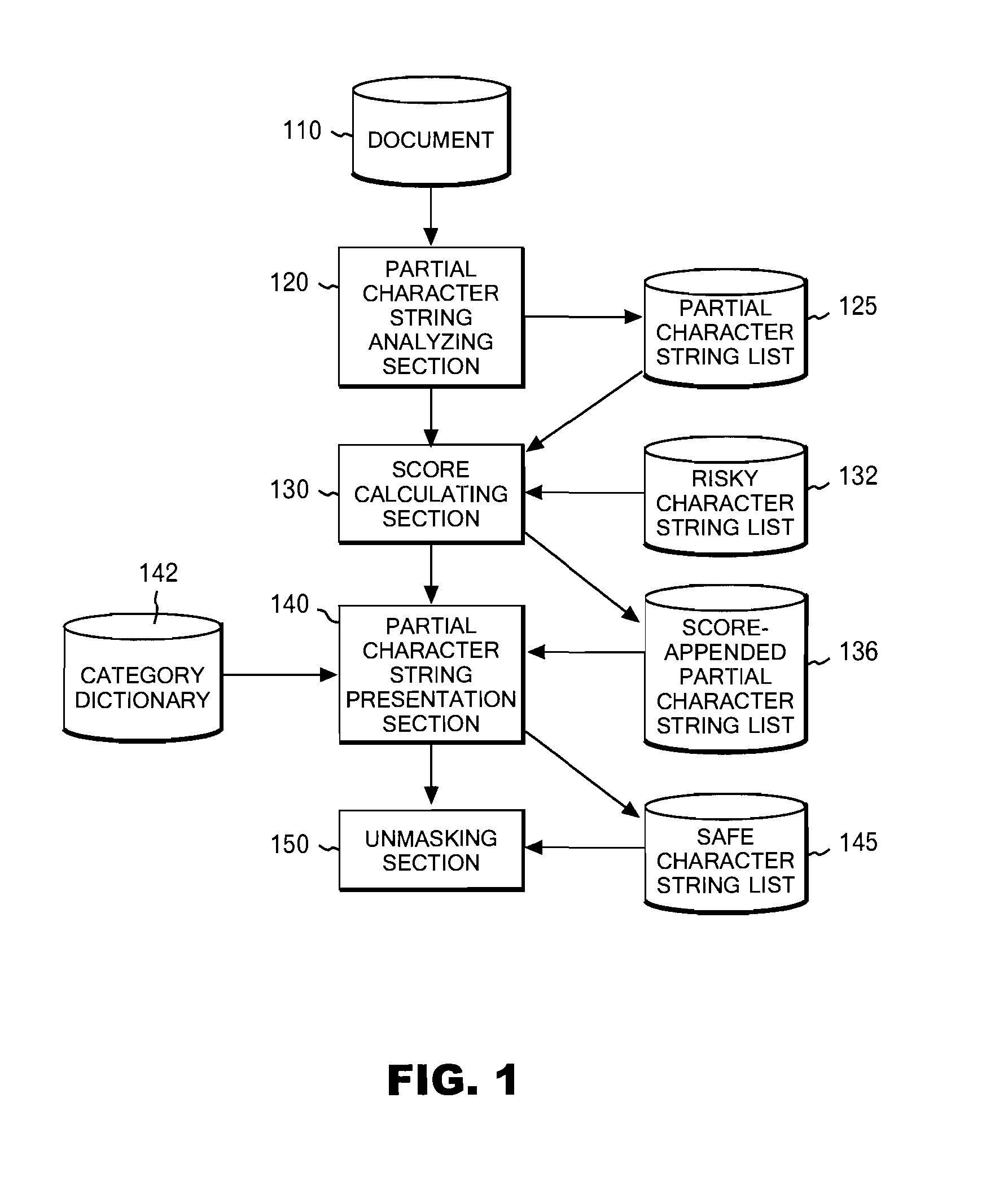
InactiveUS20070157123A1Efficiently maskedShort timeNatural language data processingSpecial data processing applicationsAlgorithmString analysis
In order to solve the above problem, disclosed as a first aspect is a method including the steps of analyzing a character string in a document into partial character strings; calculating, with respect to each of the partial character strings, a score incorporating appearance frequency of the partial character string; presenting the partial character strings and the scores to a user; determining which ones of the partial character strings have been selected by the user; storing the selected partial character strings as a safe partial character string list; and replacing, with predetermined replacement character strings, the partial character strings excluding the partial character strings existing in the safe partial character string list.
Owner:IBM CORP
Automatic testing system and method for command of command line interface of data communication apparatus
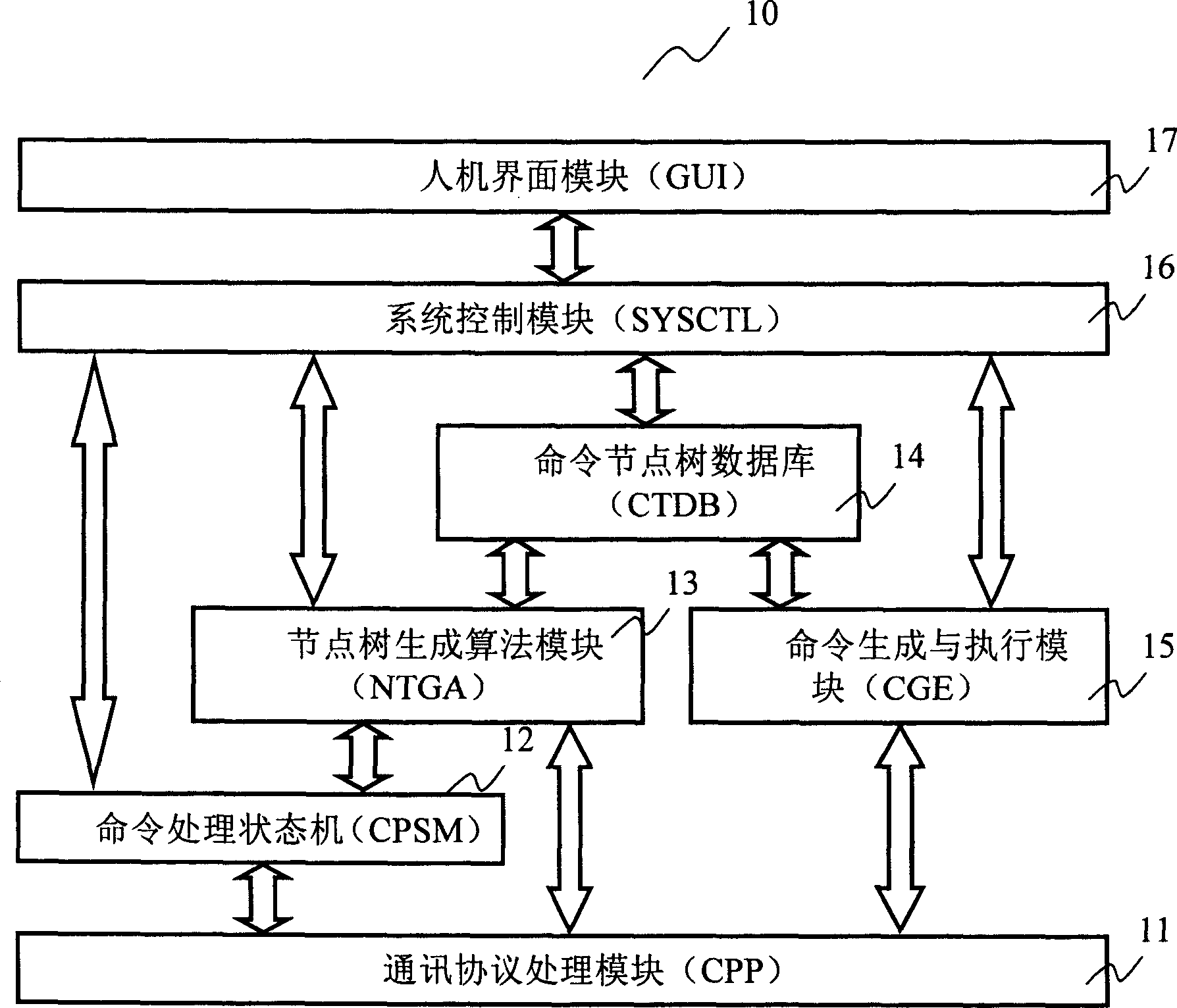
This invention relates to an automatic test system and a method for data communication device command line interface instructions, which constructs a man-machine command character string analysis process software module on a communication protocol software layer of a test host containing a test example automatic generation and executing system and an operation system, automatically generates gateway command node tree data structure and takes it as the basis to utilize software to realize automatic structure, generation and execution of network command test example to realize automatic test of command line interface command to a tested device.
Owner:ZTE CORP
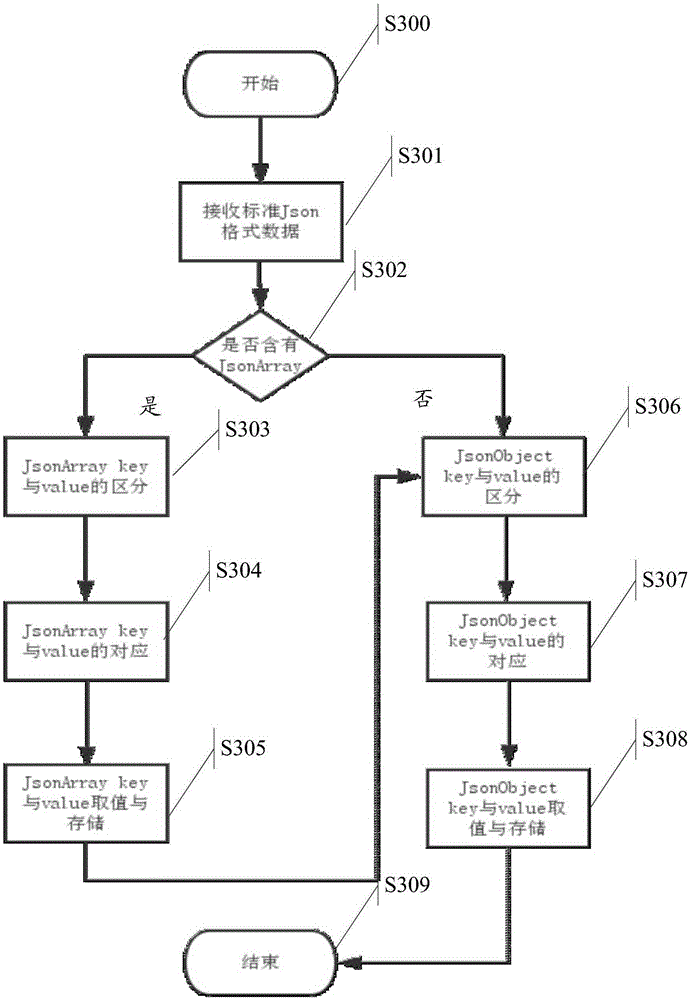
Json format data analytic method and data receiving end
InactiveCN105354020ACorrectly parsedSimplify the development processProgramming languages/paradigmsSpecific program execution arrangementsSoftware designJSON
The present invention relates to the field of software design and discloses a Json format data analytic method and a data receiving end so as to solve the technical problem that in the prior art, a data receiving party cannot correctly receive any data transmitted in a Json format under the condition of not appointing keys. The method comprises: receiving Json format data sent by a data sending end by virtue of the data receiving end ; by character string analysis and a special format character corresponding to a JsonArray, judging whether the Json format data comprises the JsonArray or not; when the Json format data comprises the JsonArray, extracting keys and values of the JsonArray; completing one-to-one correspondence between the keys and the values; the keys and the values are stored into a List and the List is output; completing correspondence between keys and values of a JsonObject; and storing each pair of key and value of the analyzed JsonObject as one element in the List and output the same. The method achieves the technical effect that even though the data receiving party does not know the corresponding relationship between the keys and the values, the data receiving party also can correctly receive and analyze the Json format data.
Owner:WUHAN IRON & STEEL (GROUP) CORP
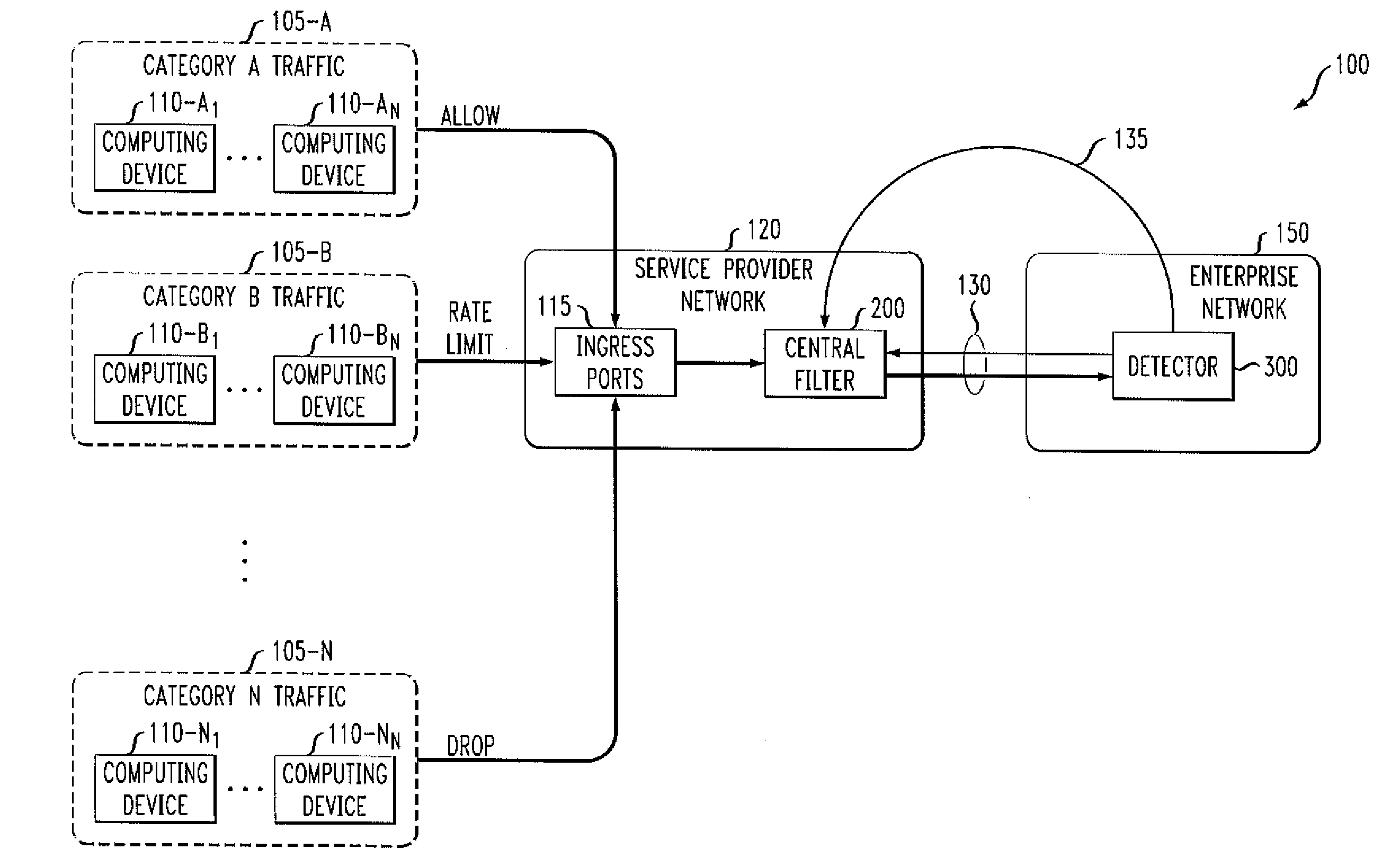
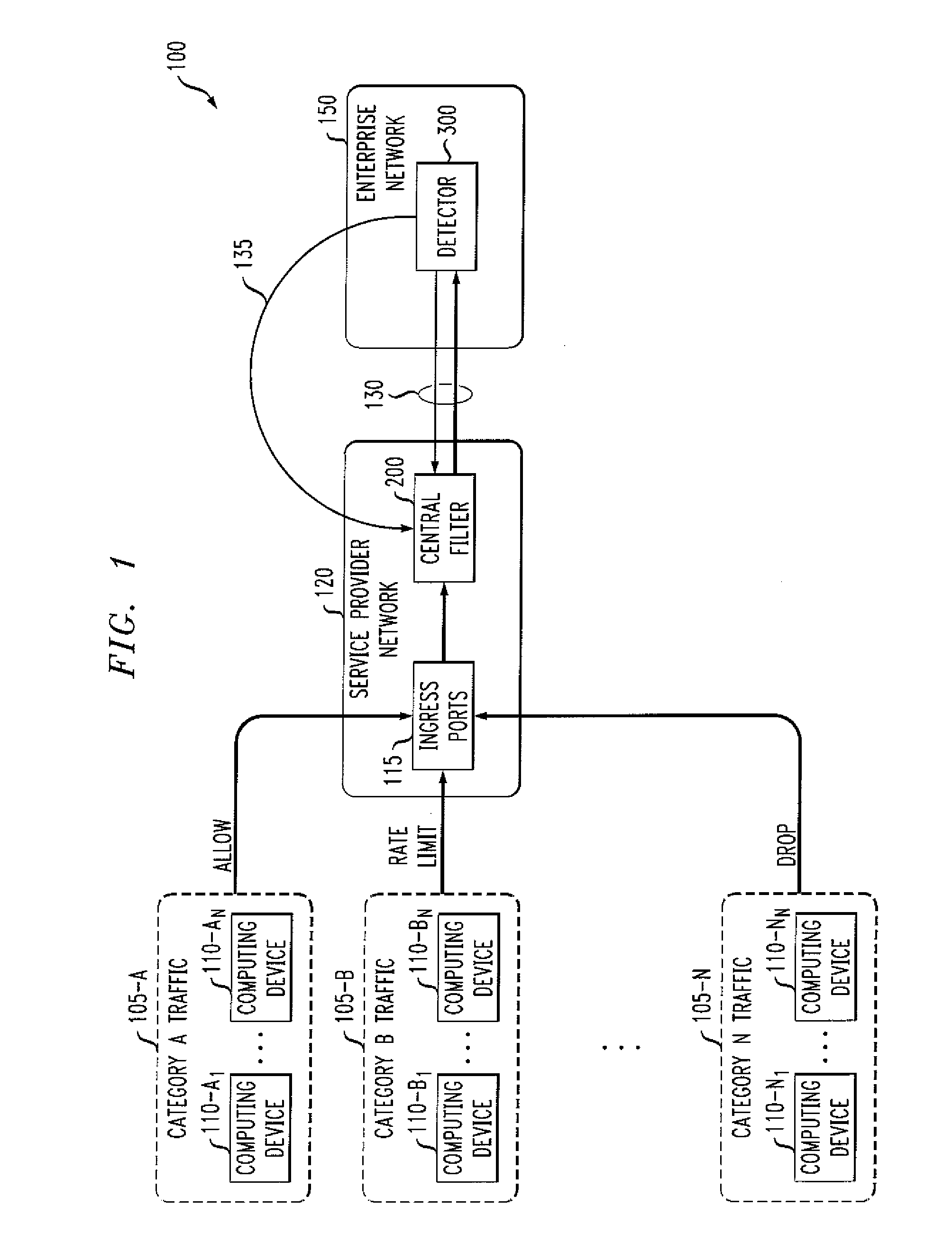
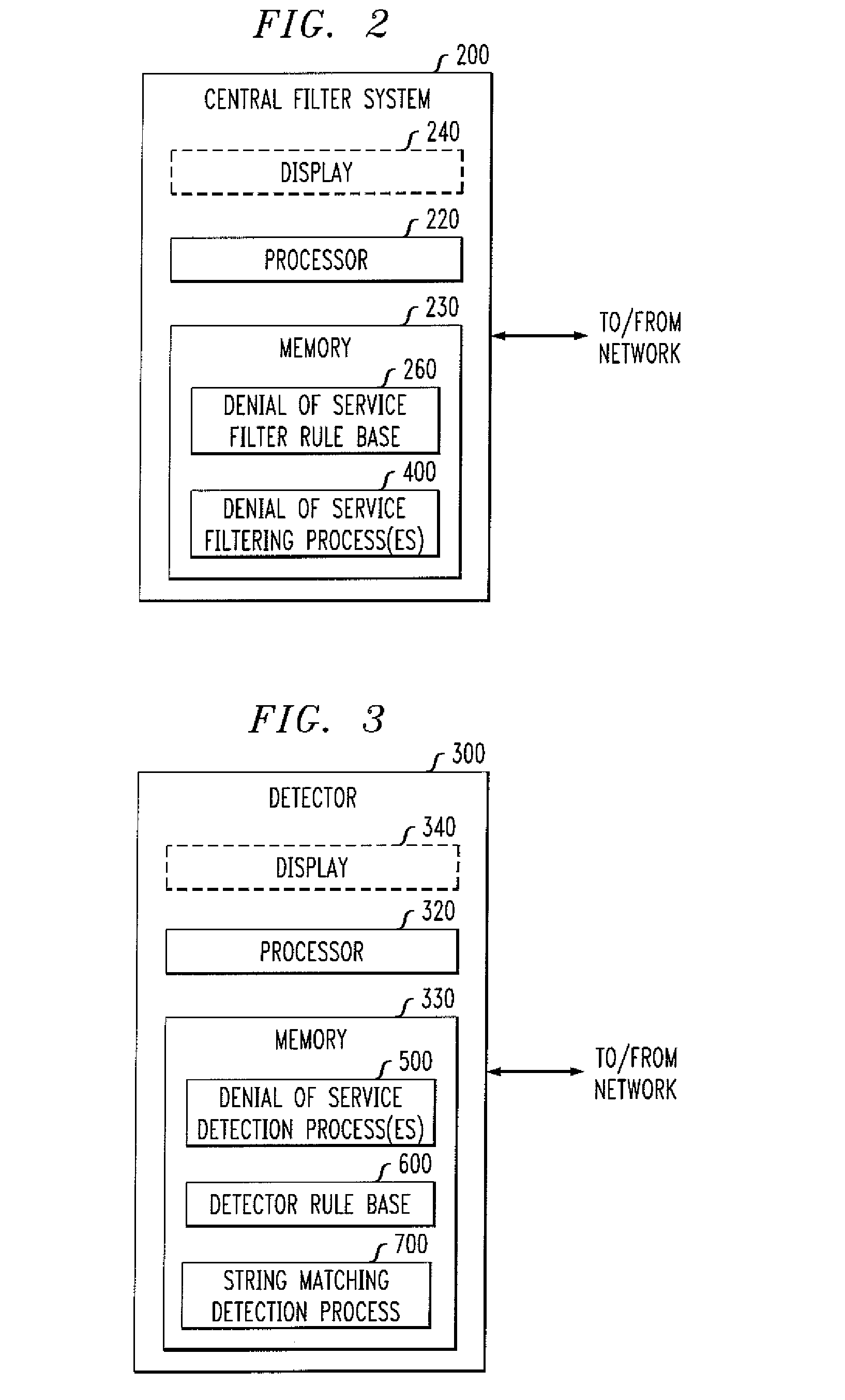
Methods and apparatus for detecting unwanted traffic in one or more packet networks utilizing string analysis
InactiveUS20080109905A1Memory loss protectionData taking preventionTraffic capacityRegular expression
Methods and apparatus are provided for detecting unwanted traffic in one or more packet networks utilizing string analysis. Unwanted traffic received by a target victim, such as a malicious attack, is detected by maintaining a rule base identifying one or more string expressions; analyzing one or more error entries in a log file, the log file comprising one or more requests received by the target victim; determining if the one or more requests include a string that matches one or more of the string expressions in the rule base; and sending a denunciation message to a central filter if the one or more requests include a string that matches one or more of the string expressions in the rule base. The string expressions may comprise, for example, a string or a regular expression and can represent one or more resources that an attacker may attempt to access.
Owner:WSOU INVESTMENTS LLC
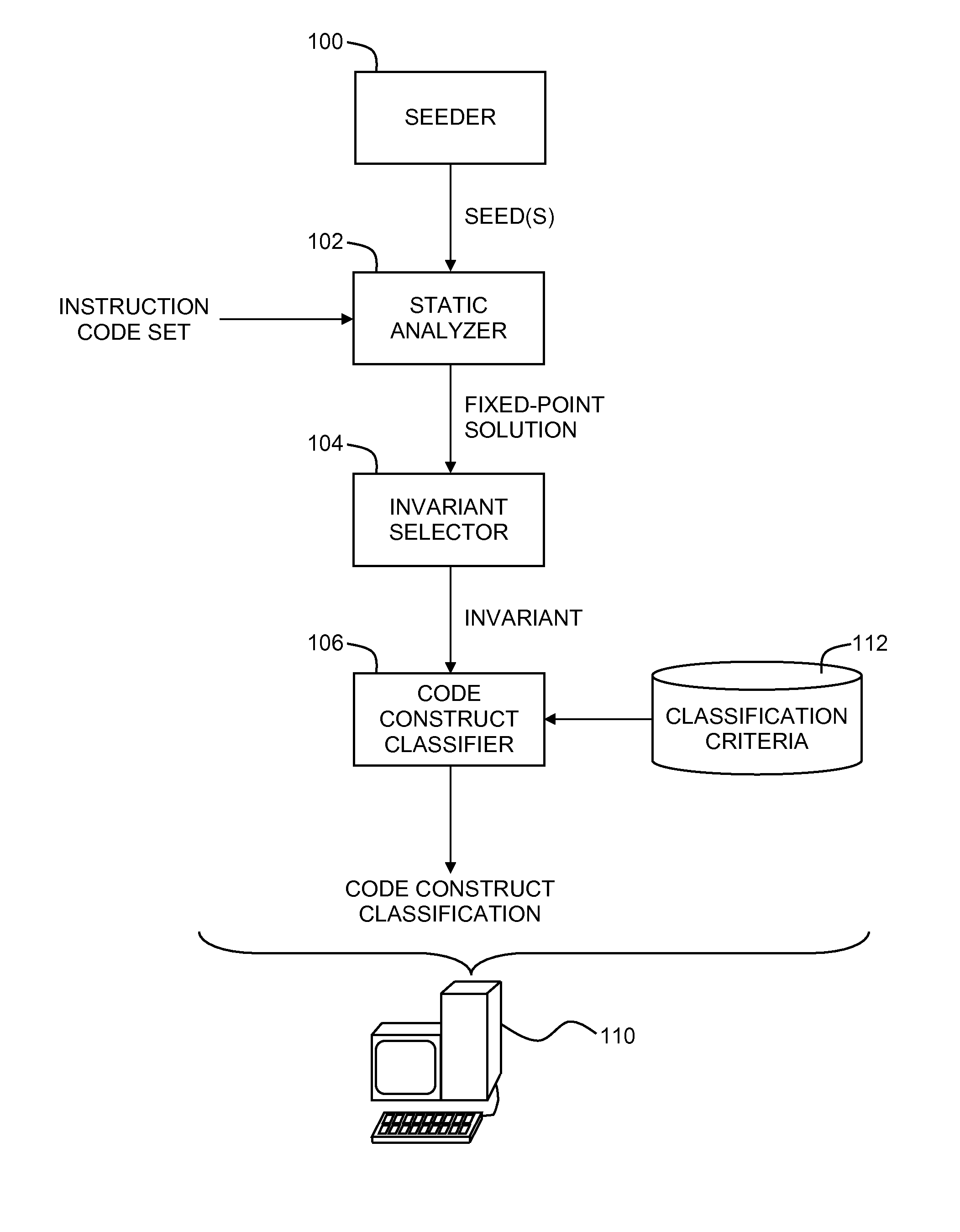
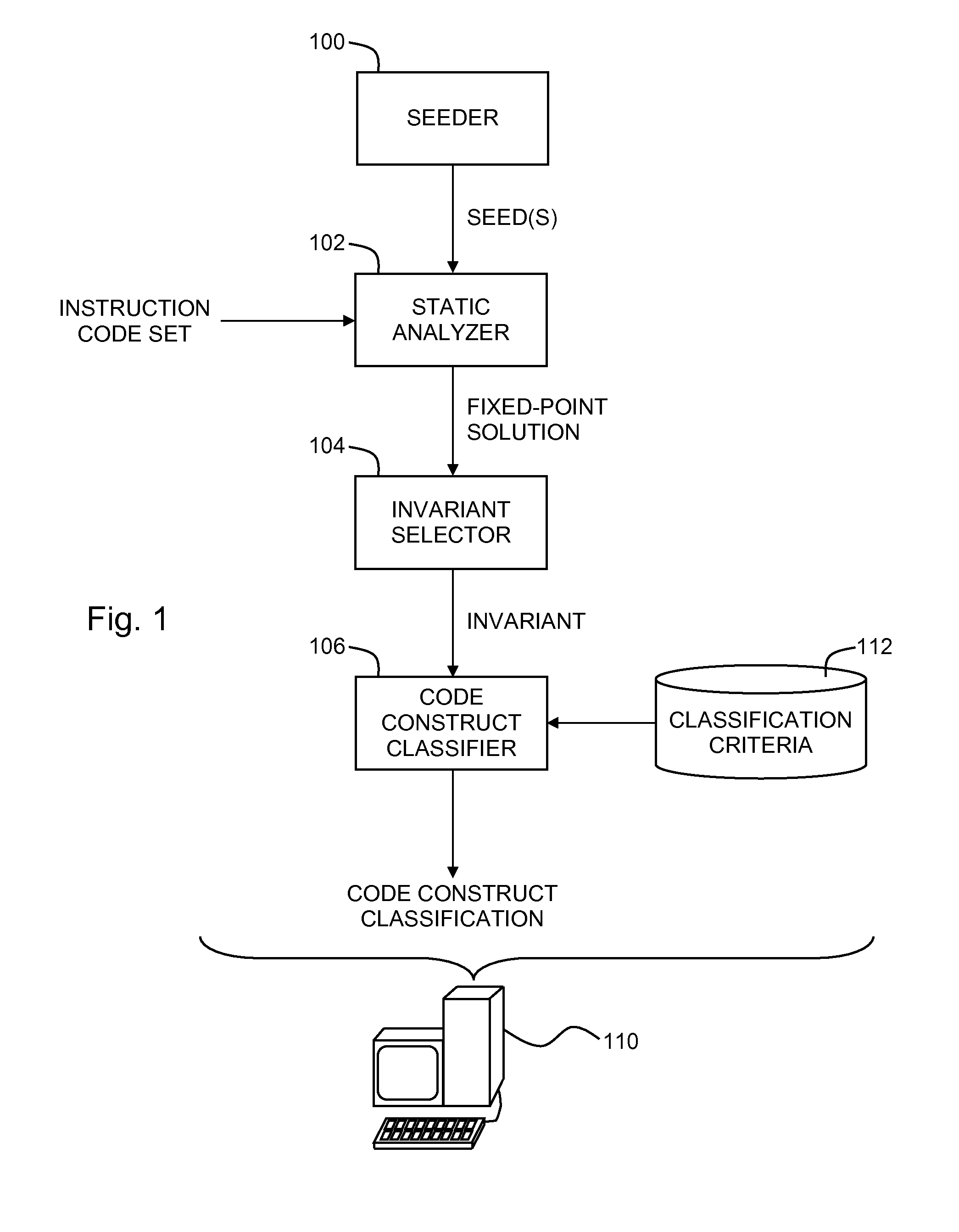
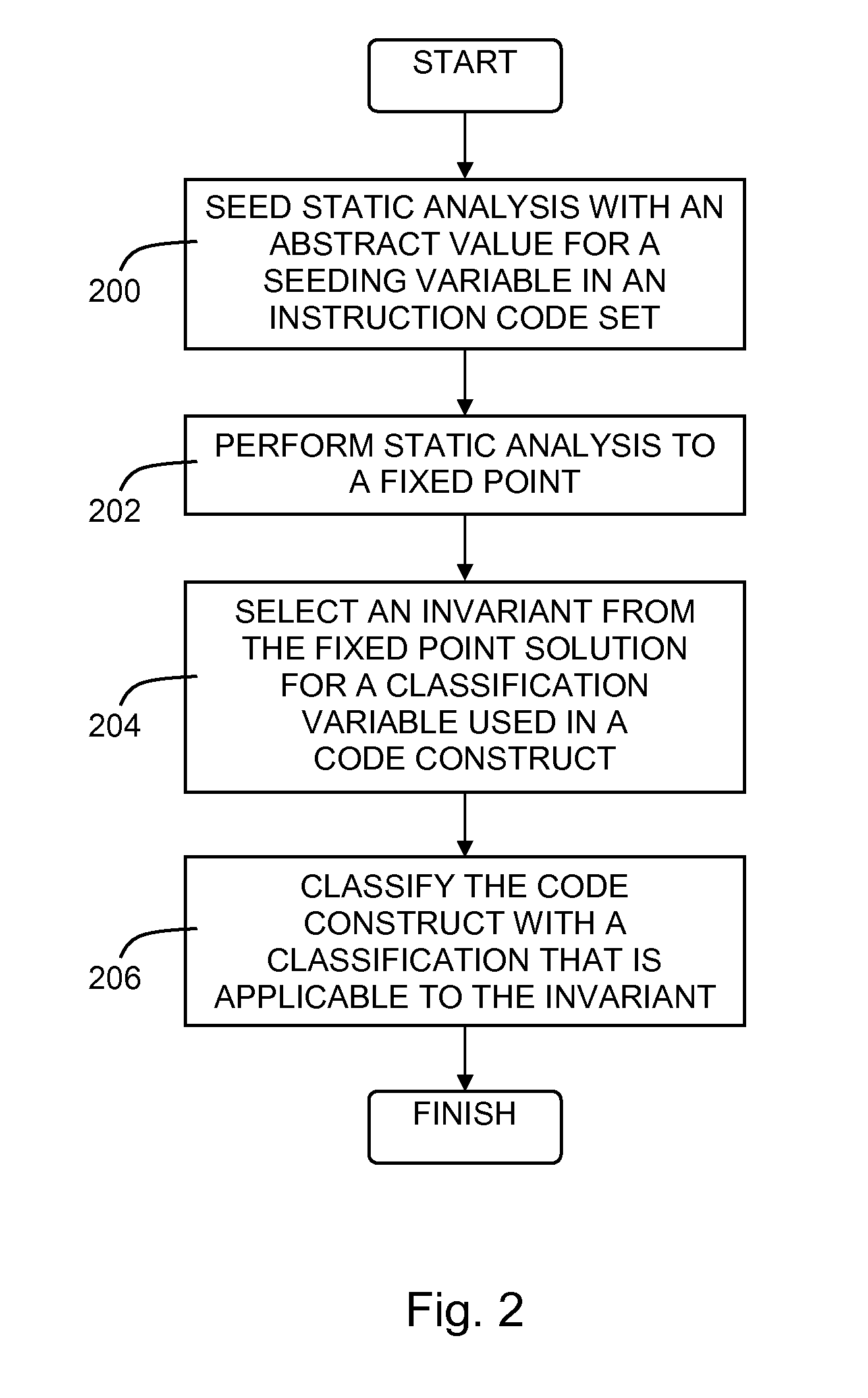
Classification of code constructs using string analysis
A code construct in a computer-based software application is classified by seeding an analysis of an instruction code set of a computer-based software application with a seed for a seeding variable within the instruction code set, wherein the seed is an abstract value representation, performing the analysis to a fixed point, thereby producing a fixed point solution, selecting an invariant from the fixed point solution, wherein the invariant represents at least one value pointed to by a classification variable in a code construct within the instruction code set, and classifying the code construct with a classification that is applicable to the invariant in accordance with an application criterion.
Owner:IBM CORP
Segmentation of strings into structured records
InactiveUS7627567B2Data processing applicationsDigital data information retrievalEngineeringNull (SQL)
An system for segmenting strings into component parts for use with a database management system. A reference table of string records are segmented into multiple substrings corresponding to database attributes. The substrings within an attribute are analyzed to provide a state model that assumes a beginning, a middle and an ending token topology for that attribute. A null token takes into account an empty attribute component and copying of states allows for erroneous token insertions and misordering. Once the model is created from the clean data, the process breaks or parses an input record into a sequence of tokens. The process then determines a most probable segmentation of the input record by comparing the tokens of the input record with a state models derived for attributes from the reference table.
Owner:MICROSOFT TECH LICENSING LLC
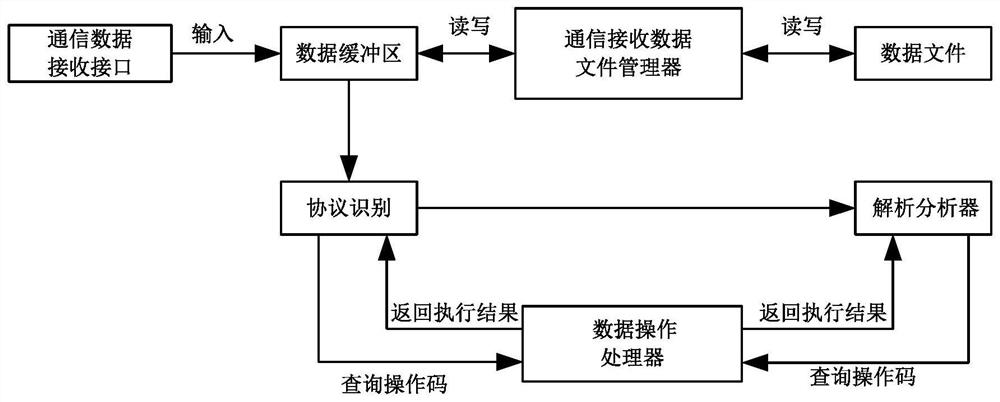
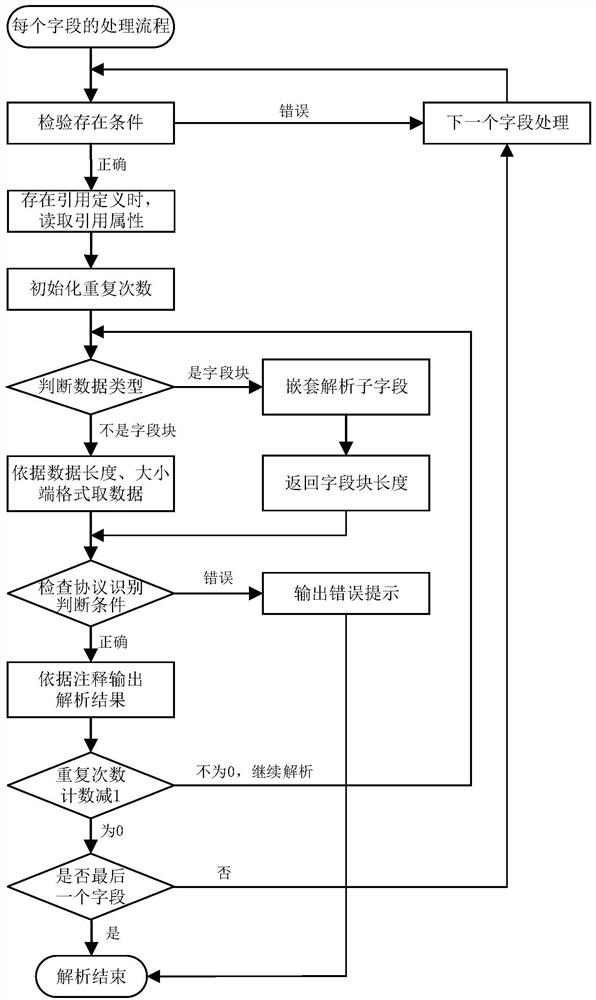
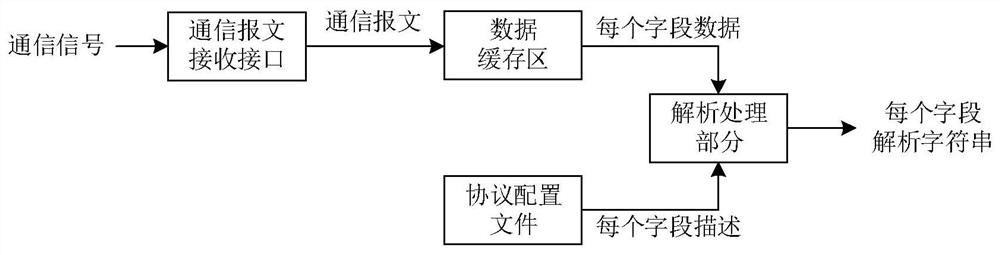
Communication protocol analysis method and system based on field descriptions
The invention provides a communication protocol analysis method and system based on field descriptions. The method comprises: decomposing a communication protocol data frame into a series of field descriptions; on the basis of the field descriptions, analyzing each piece of byte data of an input communication message from front to back according to the field descriptions, wherein anayzling each piece of field data comprises the following steps that firstly, calculating an existence condition judgment formula; acquiring specific attribute parameters of a referenced field according to referencedefinition attributes of the field descriptions; initializing a repetition frequency counter of the current field as a repetition frequency value of the field; determining the data type of the field,and if the data type of the field is a field block type, executing analysis of each sub-field by adopting a nesting mode; if the type is not the field block type, acquiring data in the communication message according to the data length of the field; calculating a formula of a protocol identification judgment condition, and if a result is wrong, outputting an analysis error prompt; if the result iscorrect, executing the next step; and outputting a character string analysis result of the current field.
Owner:常州昊云工控科技有限公司
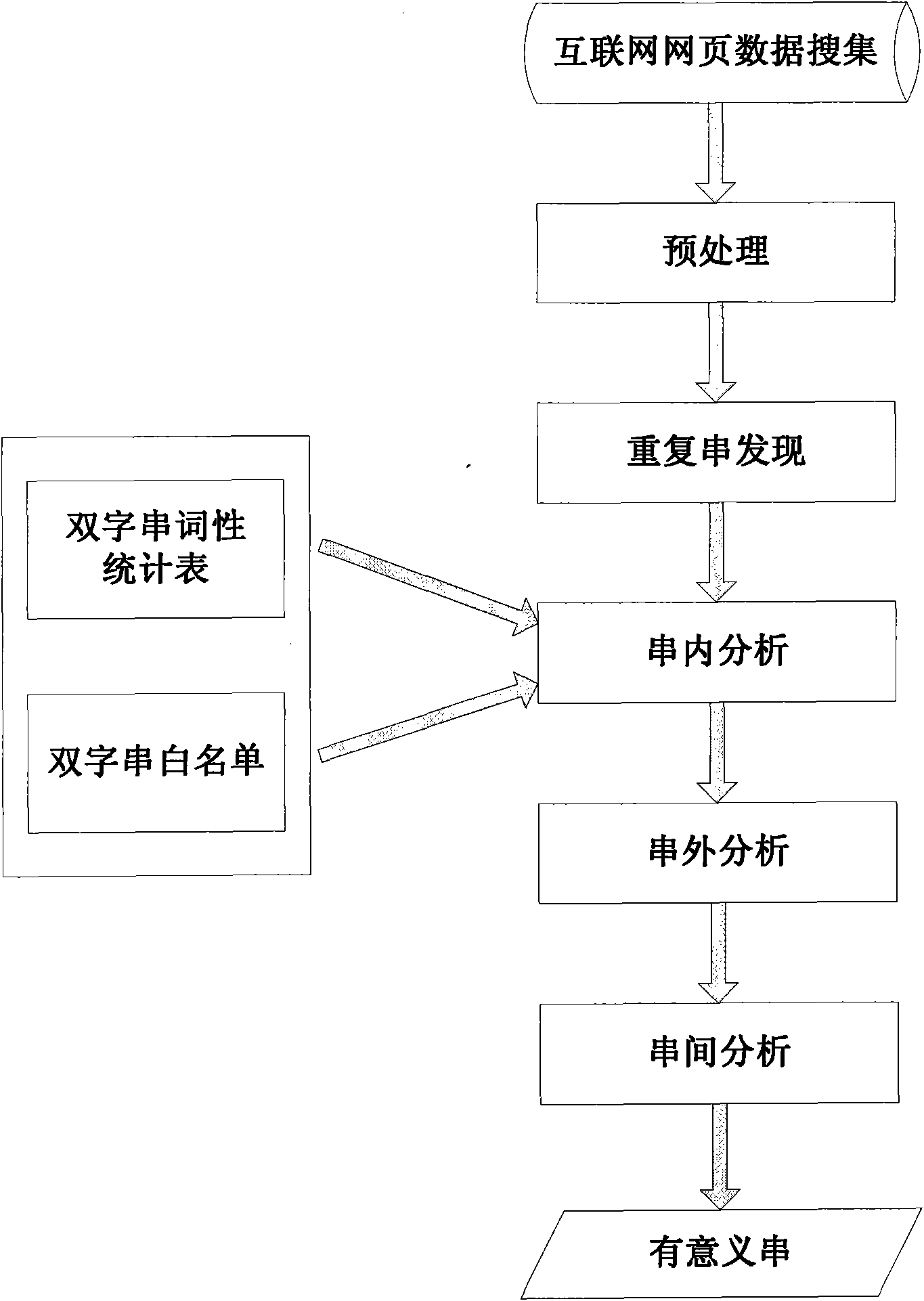
Extraction method and device for Internet-oriented meaningful strings
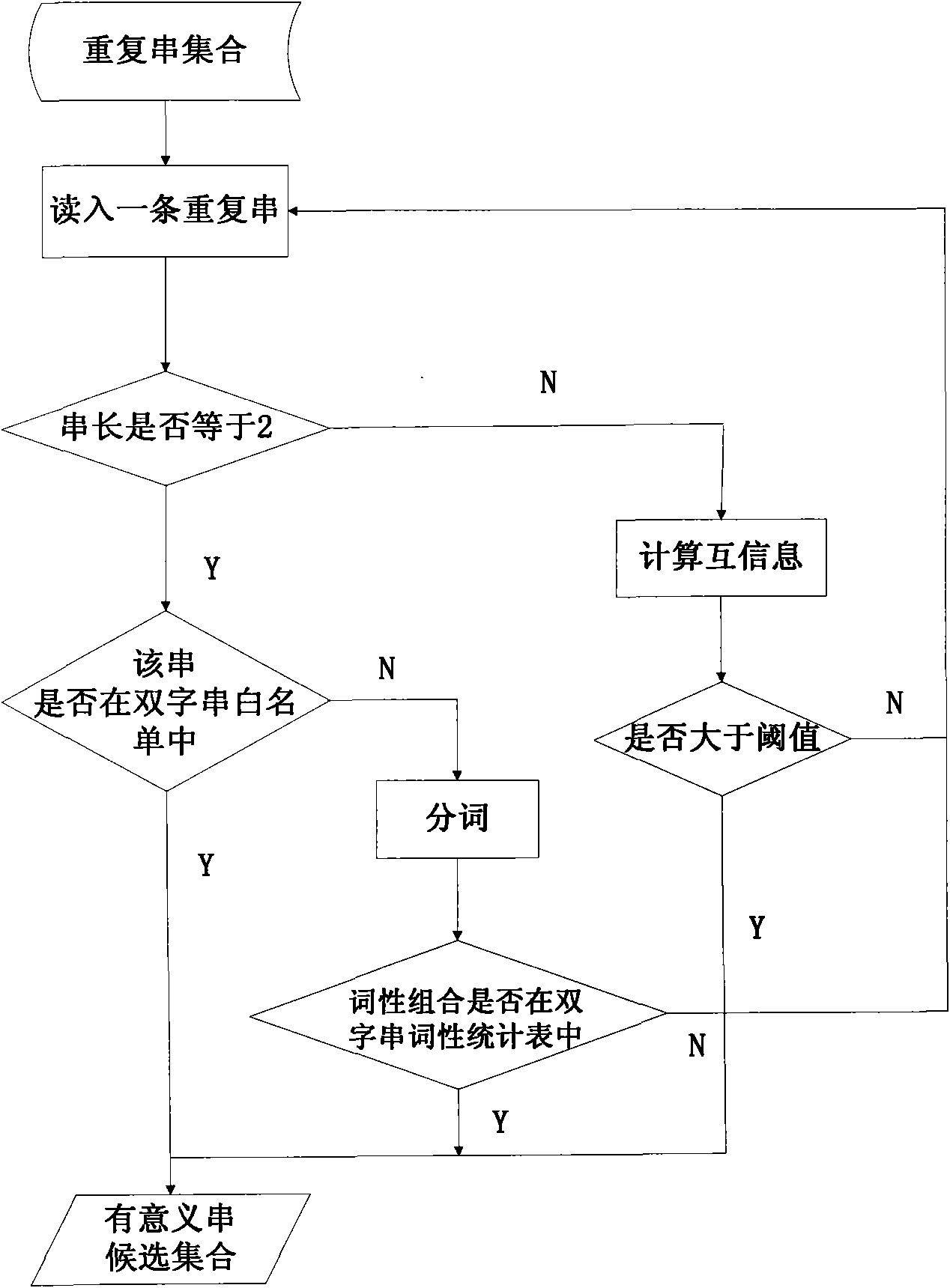
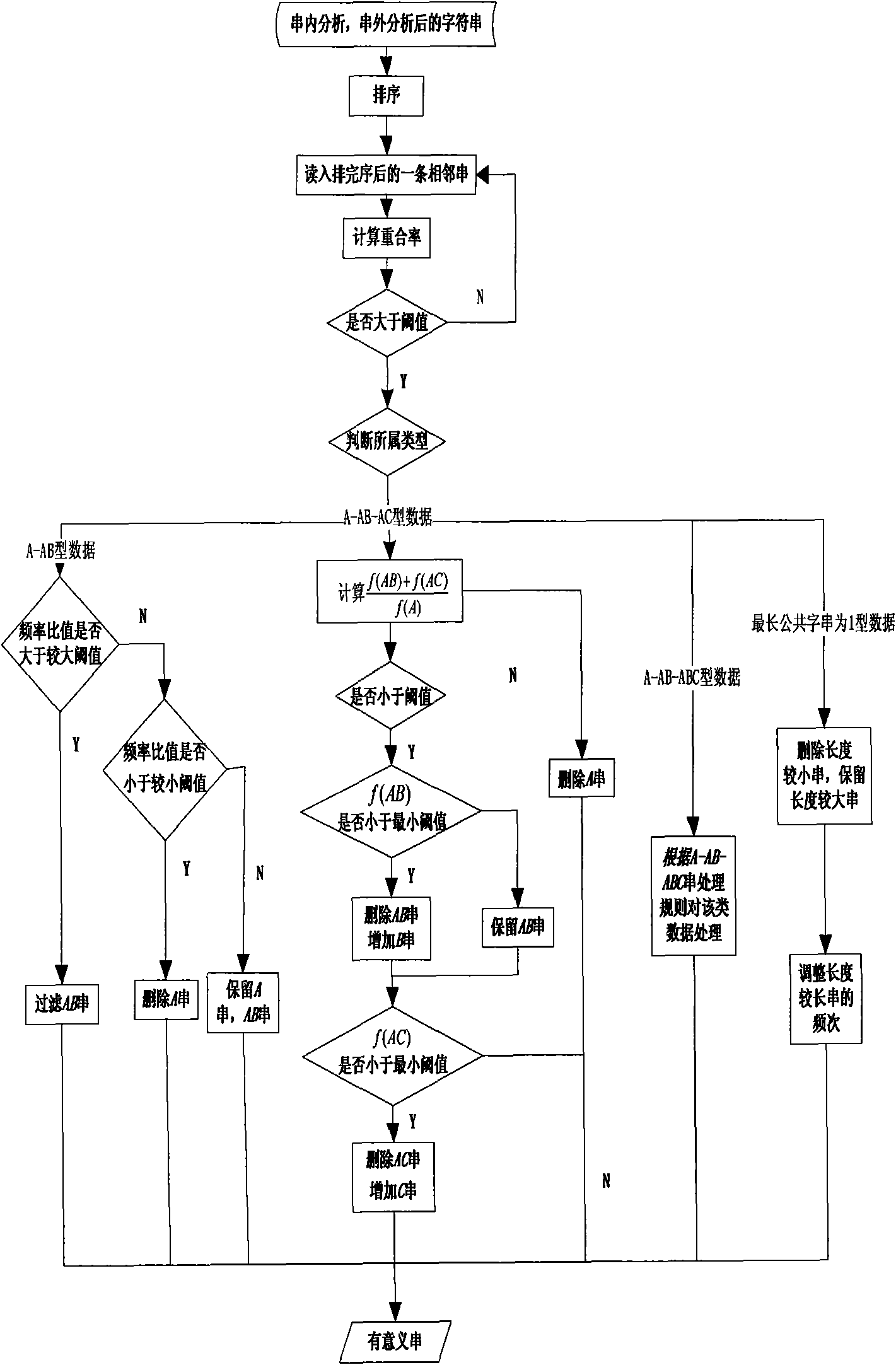
InactiveCN101853284AImprove accuracySemantic independence is goodSpecial data processing applicationsInformation processingThe Internet
Owner:HARBIN ENG UNIV
Search method and device for advertising system
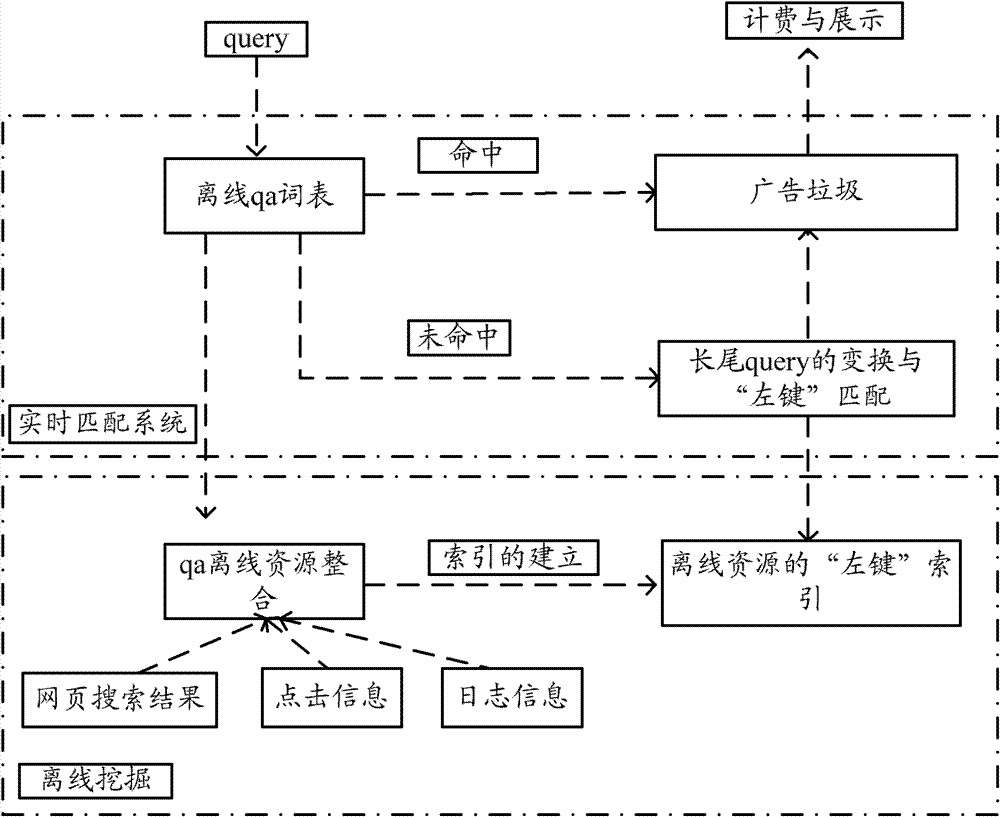
ActiveCN102902671AQuality improvementIncrease the number ofSpecial data processing applicationsMarketingString analysisIndex term
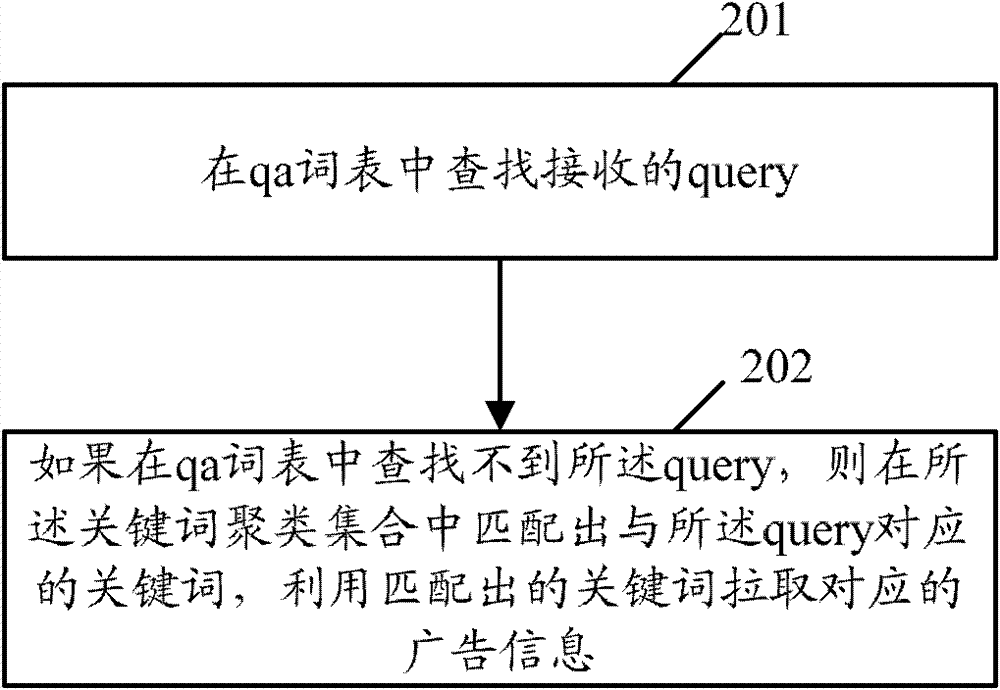
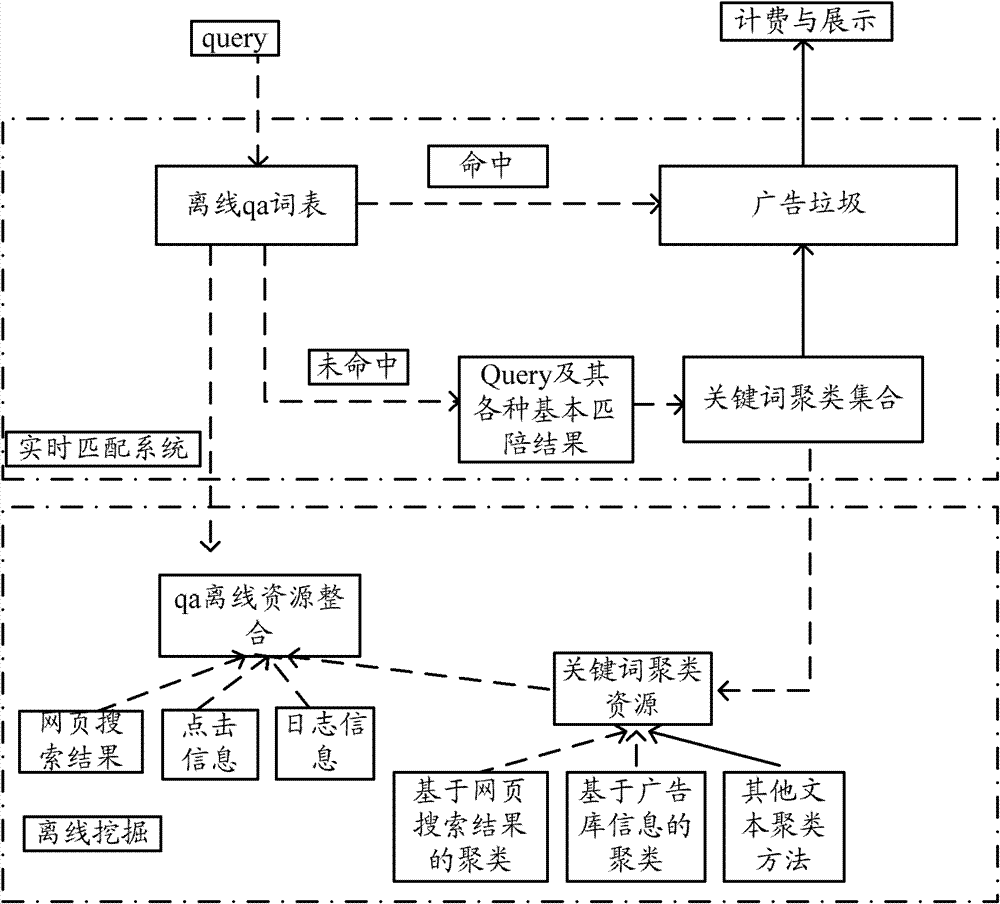
The invention provides search method and device for an advertising system. The search method includes: clustering key words in an advertising library to obtain key word clusters; searching received search strings in a search string analysis QA word list; if the search strings are absent in the QA word list, matching out key words corresponding to the search strings from the key word clusters, and pulling corresponding advertising information by the matched key words.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
Webpage mailbox identification classifying method and system
ActiveCN101937466AAvoid not being able to get webmail contentAvoid the defect that it is impossible to classify and display web mails according to the content of web mailsSpecial data processing applicationsClassification methodsData mining
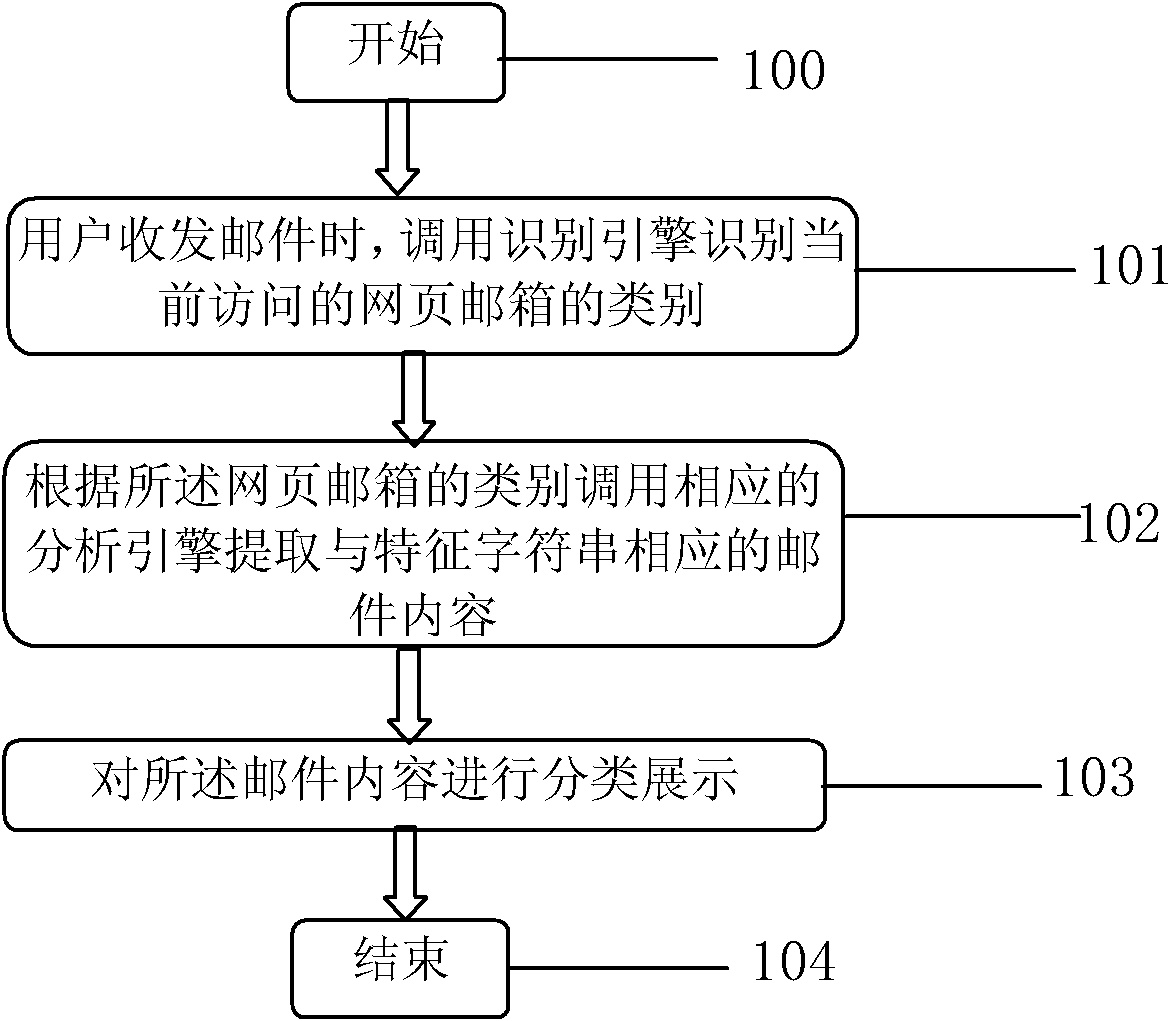
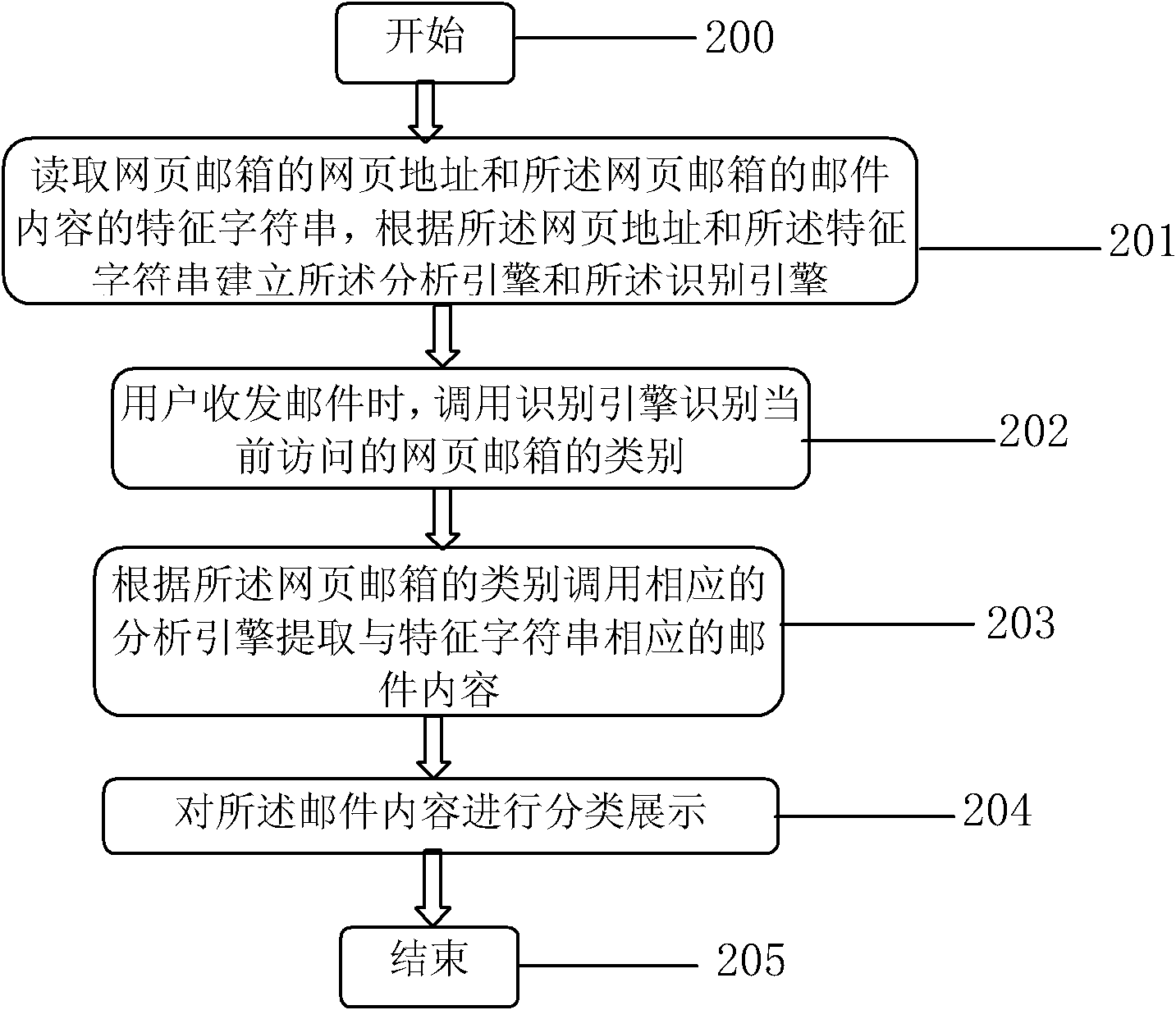
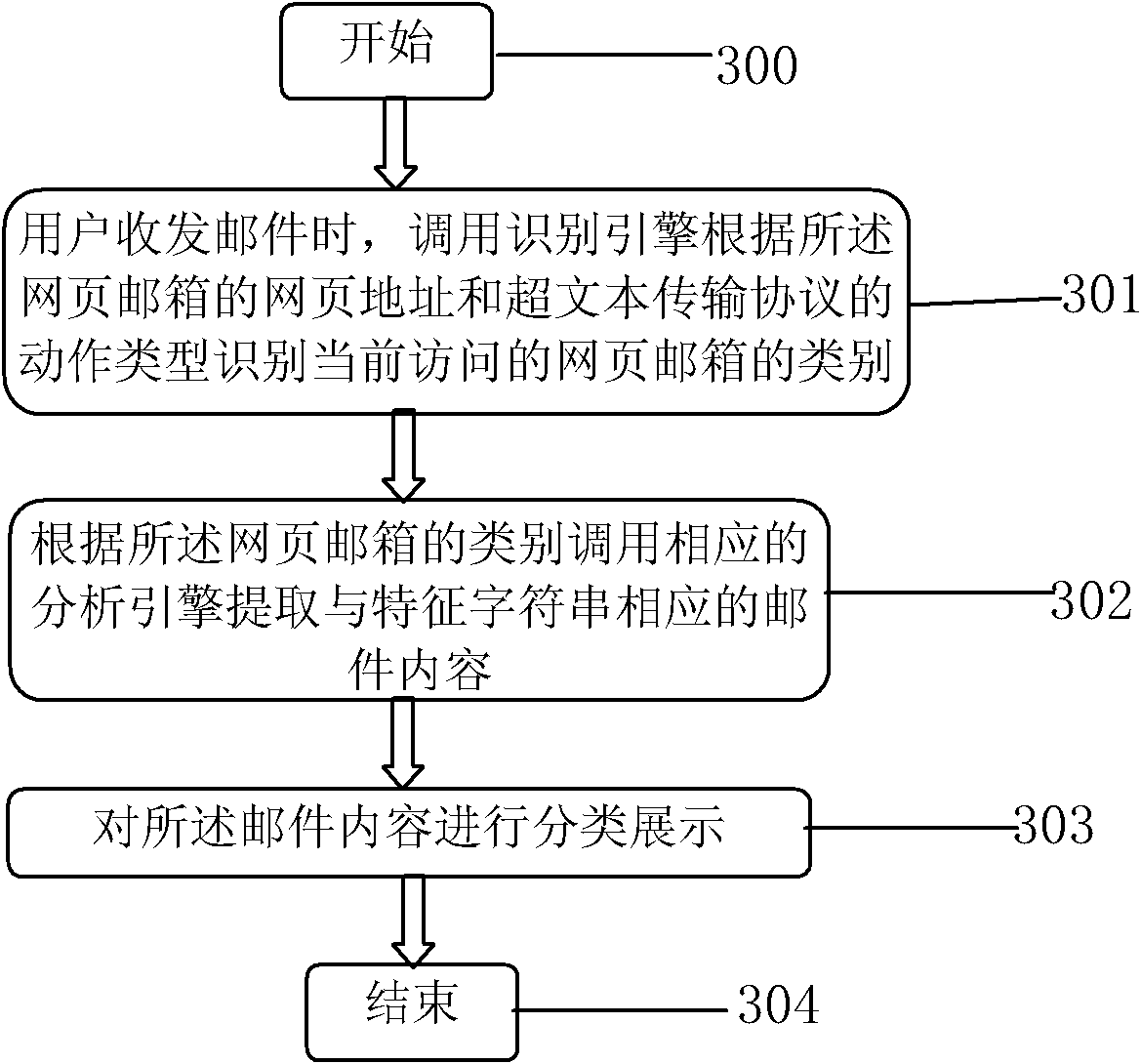
The invention constructs a webpage mailbox identification classifying method. The method comprises the following steps: S0, reading the webpage address of the webpage mailbox and a characteristic string of a mail content in the webpage mailbox, and establishing an identifying engine and an analysis engine according to the webpage address and the characteristic string; S1, calling the identifying engine to identify the type of the currently visiting webpage mailbox when a user receives and sends a mail; S2, calling the corresponding analysis engine to extract the mail content corresponding to the characteristic string according to the class of the webpage mailbox; and S3, presenting the mail content in classes. The invention also constructs a webpage mailbox identification classifying system. The webpage mailbox identification classifying method and system are adopted to establish classification by analyzing the characteristic string in the mail content according to the webpage address of the webpage mailbox and the webpage address of the webpage mail, establish the characteristic string analysis engine according to different classifications, and complete differentiation and content extraction by identifying link of the webpage address when the user receives and sends the mail.
Owner:SURFILTER NETWORK TECH
Electronic translation method and system based on engineering
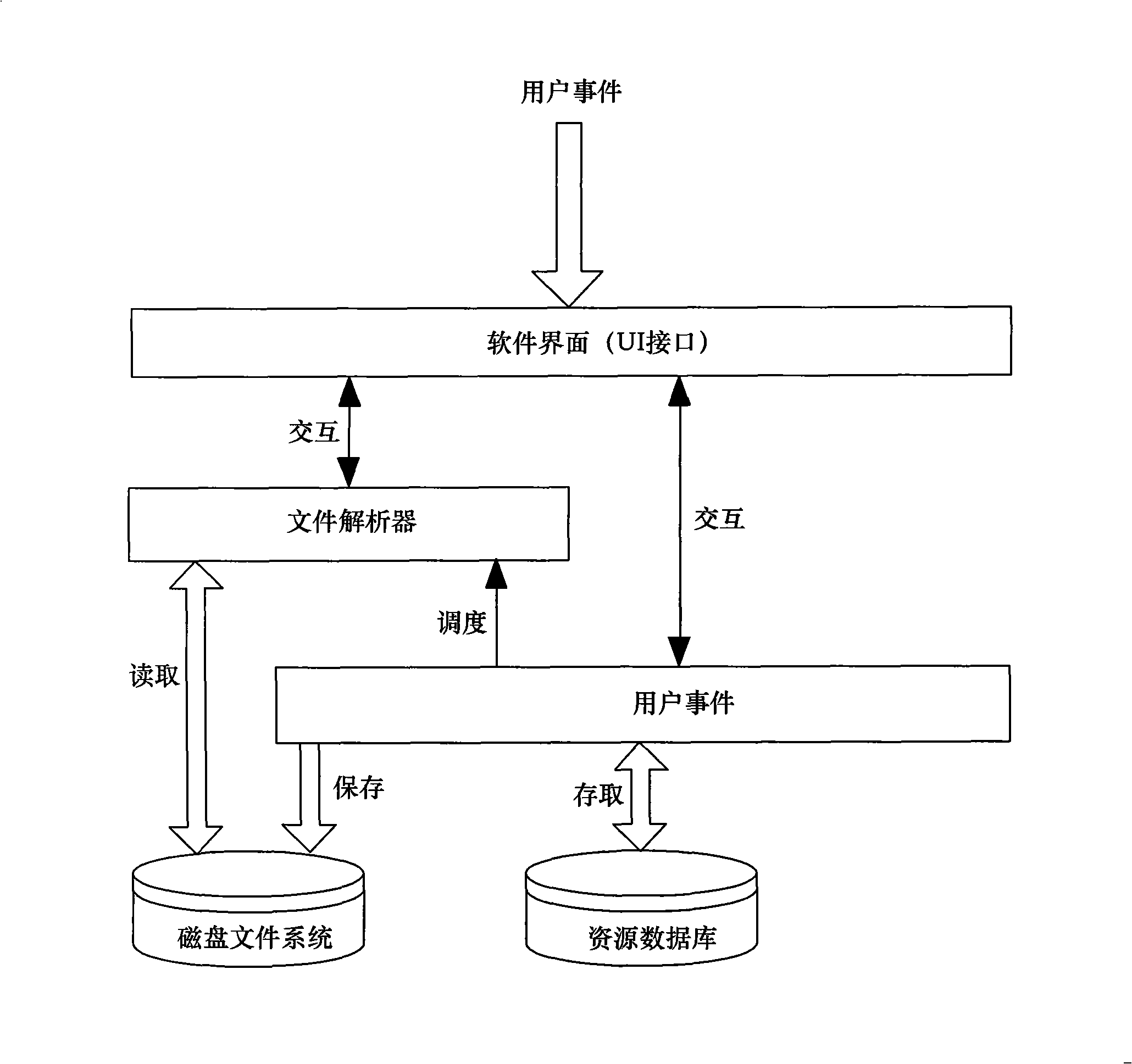
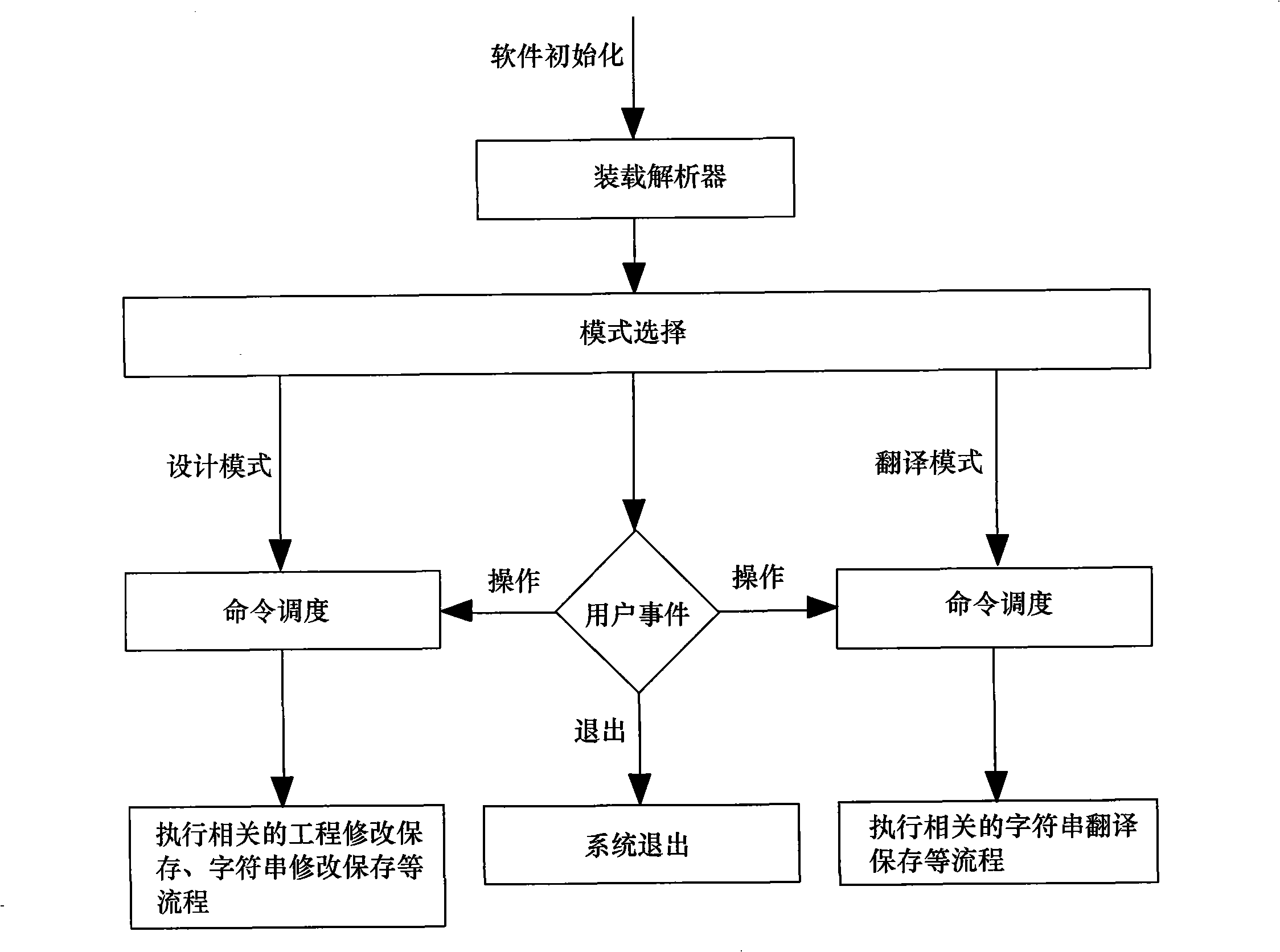
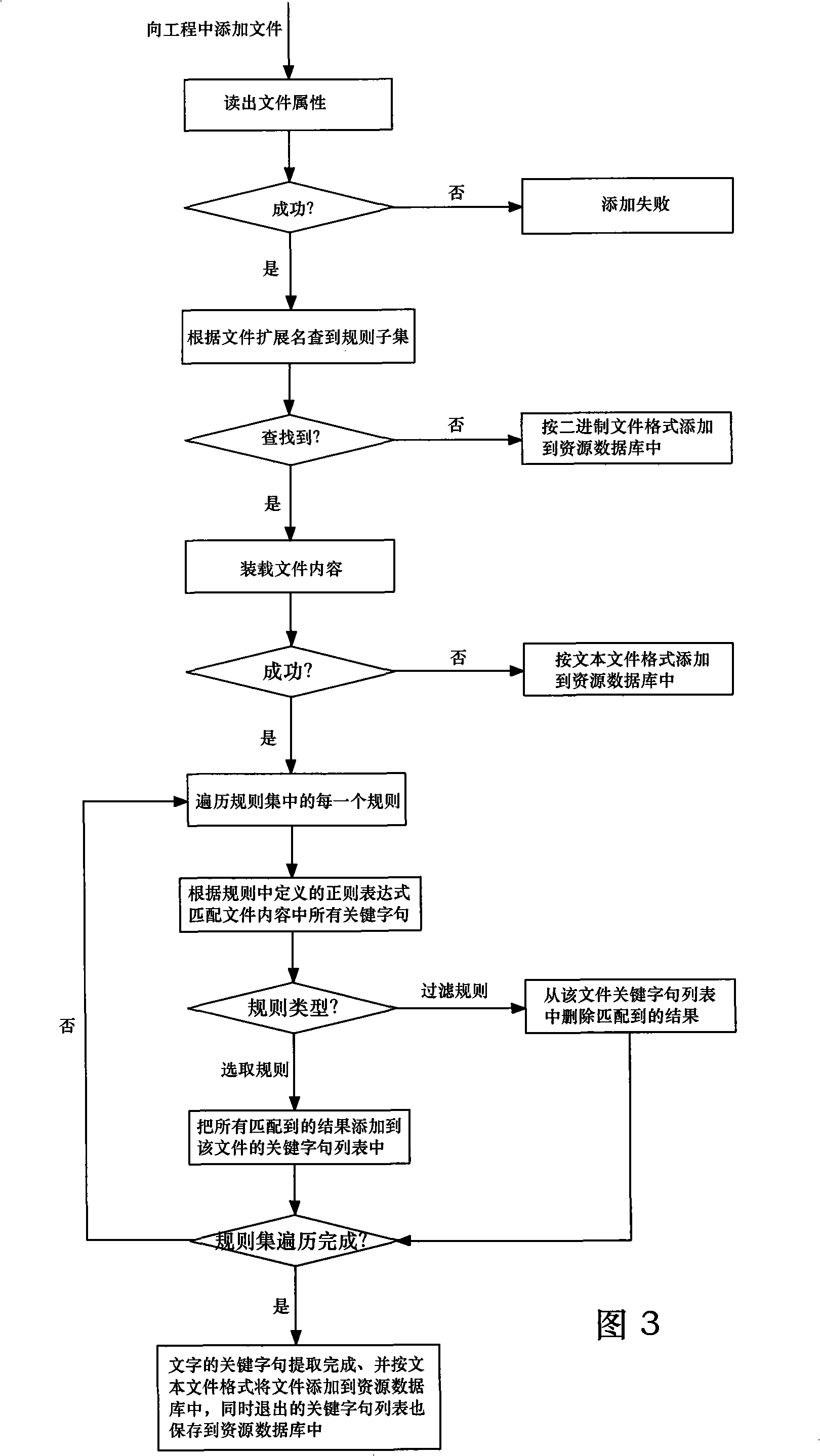
InactiveCN101261633AEfficient managementPromote generationSpecial data processing applicationsDocument analysisDocument preparation
The invention relates to an electronic translation method and a system based on engineering, wherein, the method included the following details: a. a document collection is totally managed in an engineering form; b. keywords in all the documents are automatically extracted according to an expandable rule collection; c. corresponding translation sentences are edited or stored in one edition environment according to different languages; d. a new document collection is generated according to the language appointed by users. The system includes a user interface used for the mutual communication with users; a document parser used for loading various document analysis rules and carrying out string-analysis aiming at various documents; a source databank used for storing all the information required by the engineering and a source engineering management interface used for providing an unified interface for the system so as to lead other parts and courses of the system to operate the source databank. The method of the invention can realize the effective management to a plurality of documents, can expand the keyword extraction rule, can pertinently translate different sentences and store translation results, and also can generate documents corresponding to the appointed language.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
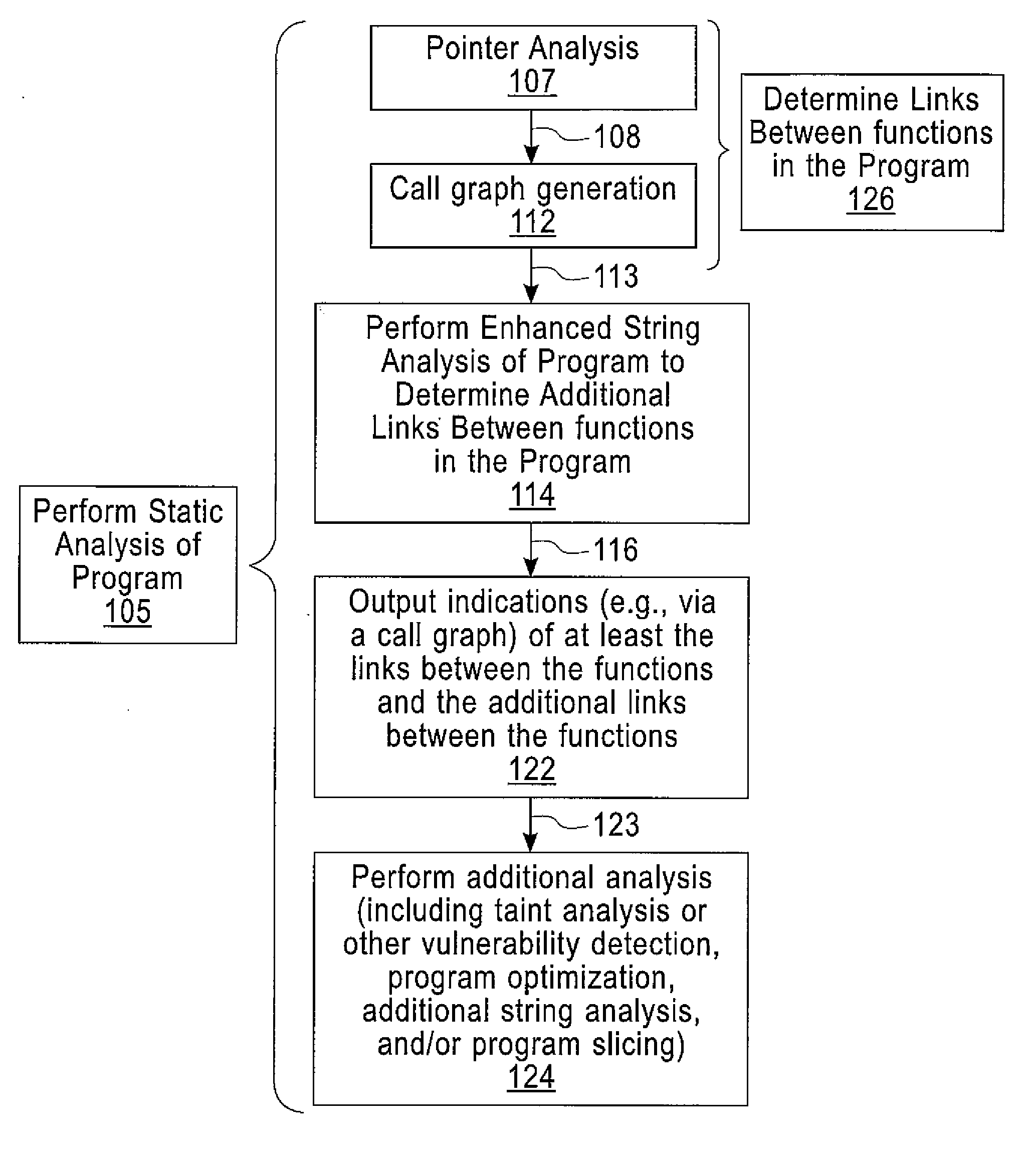
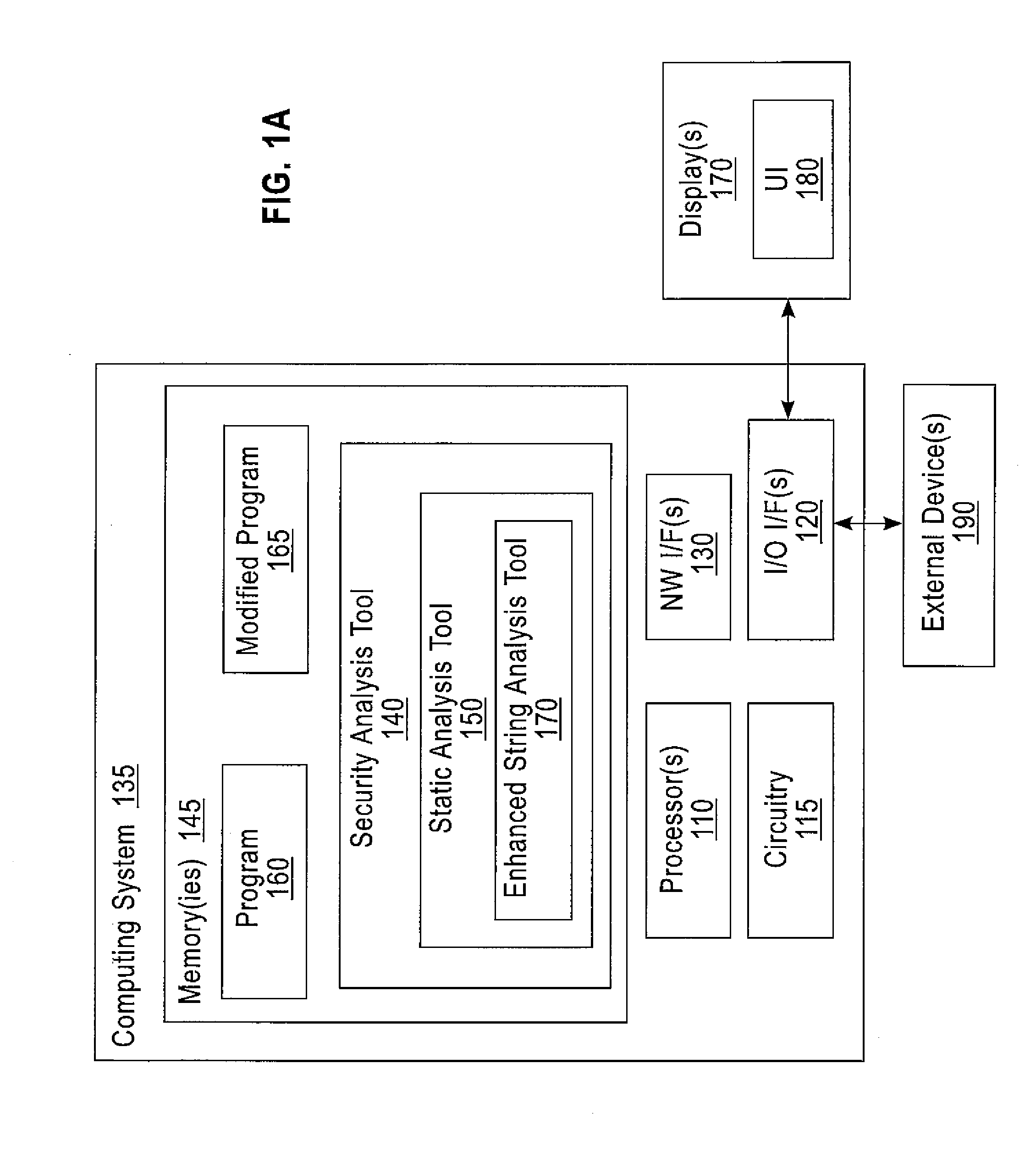
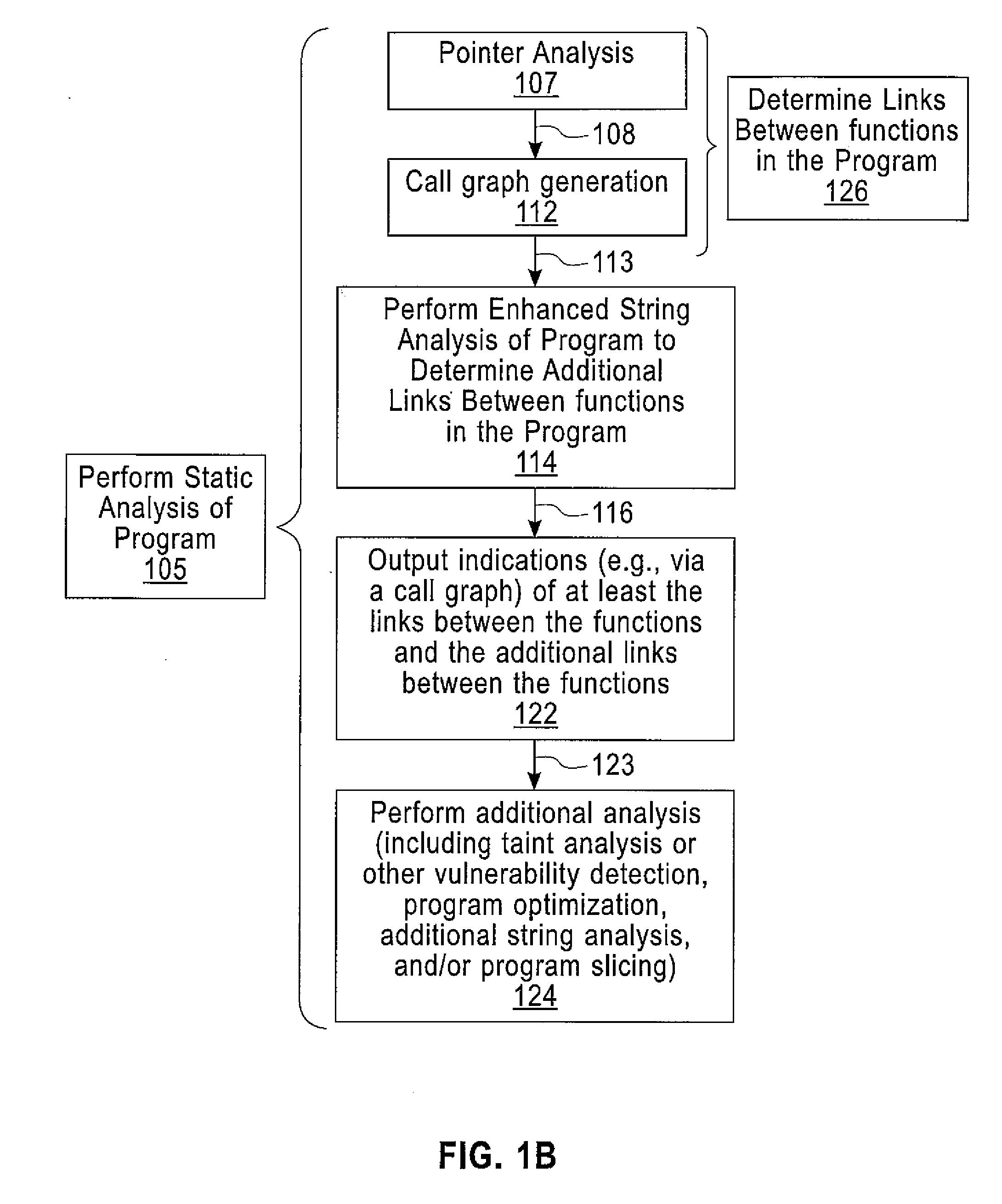
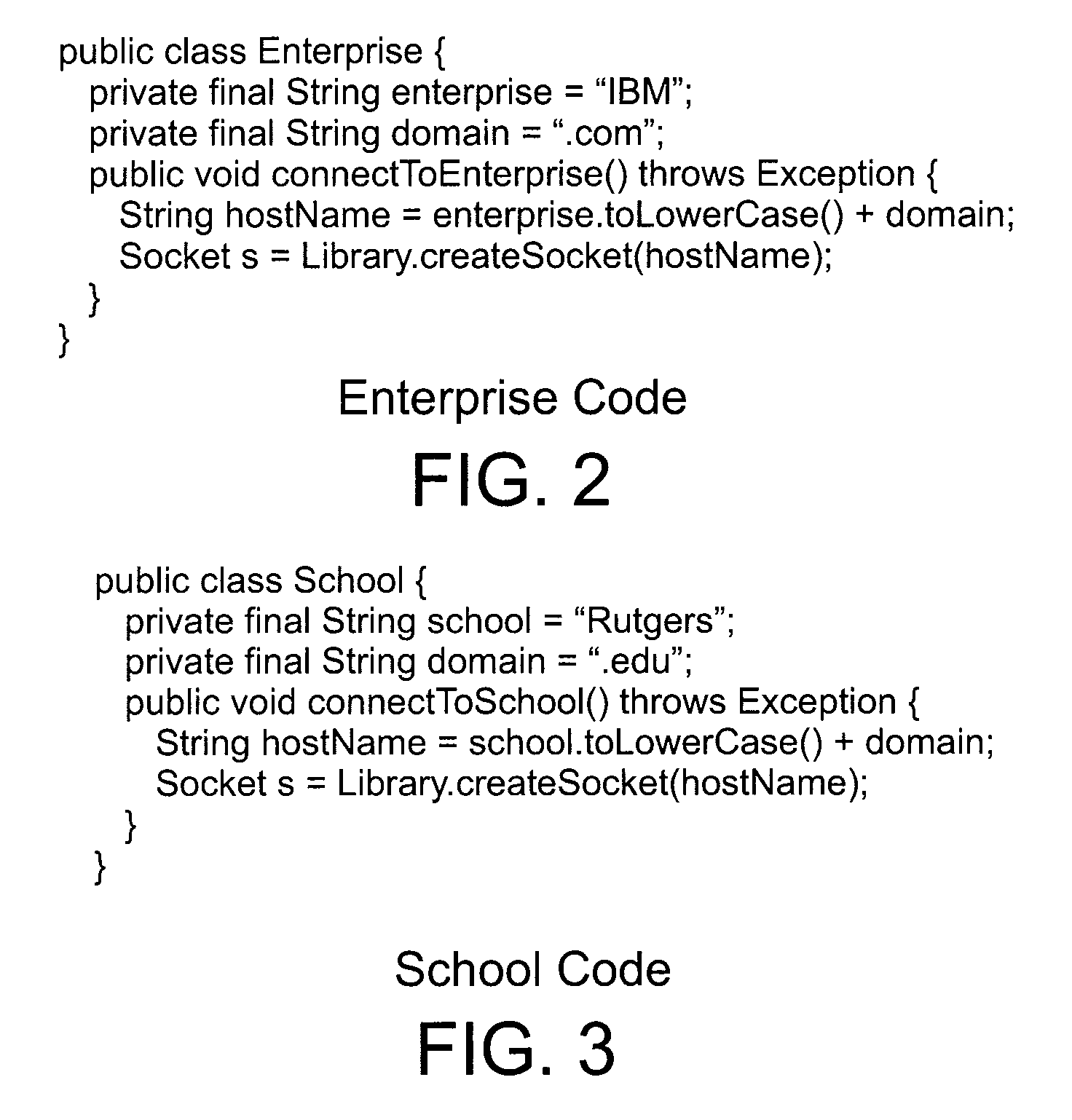
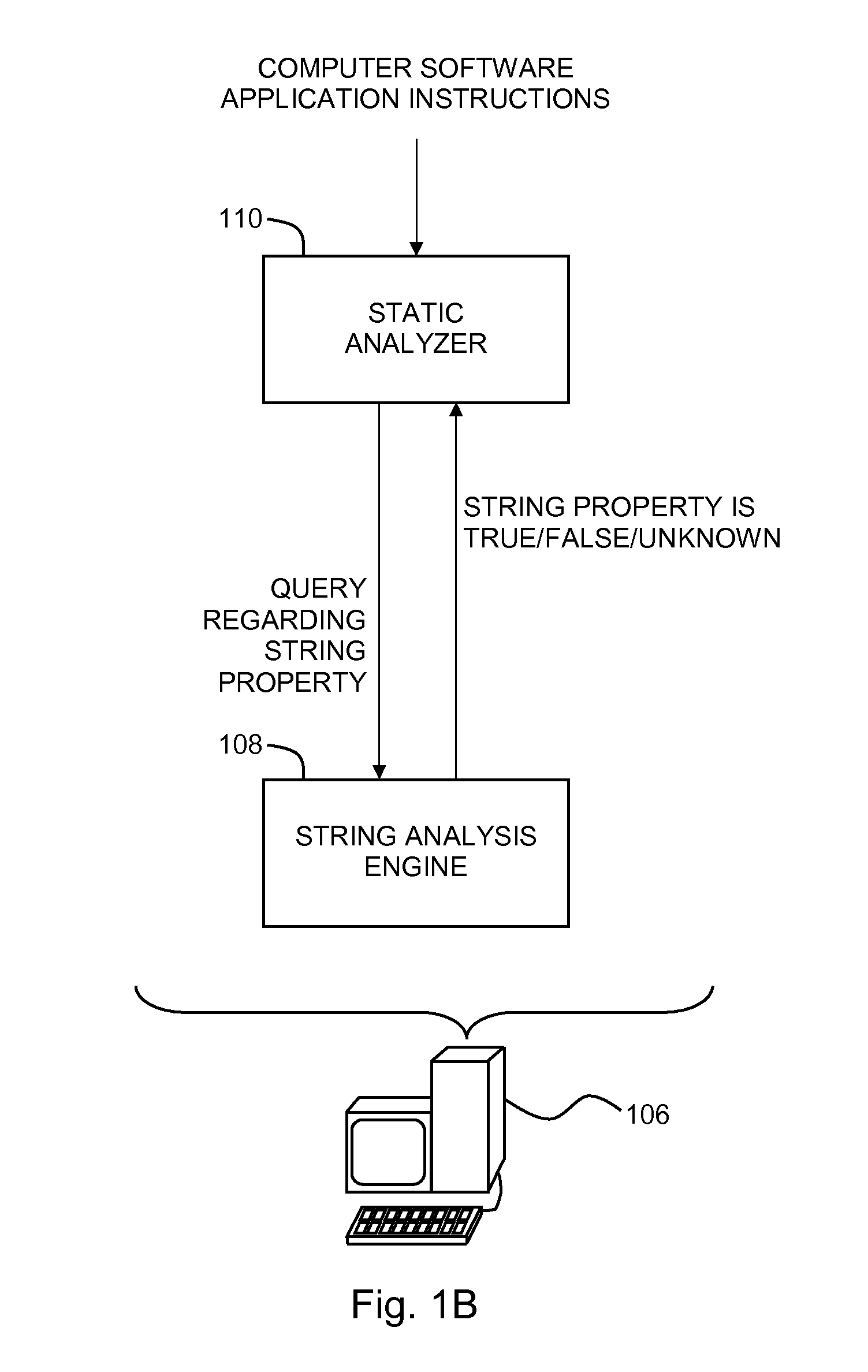
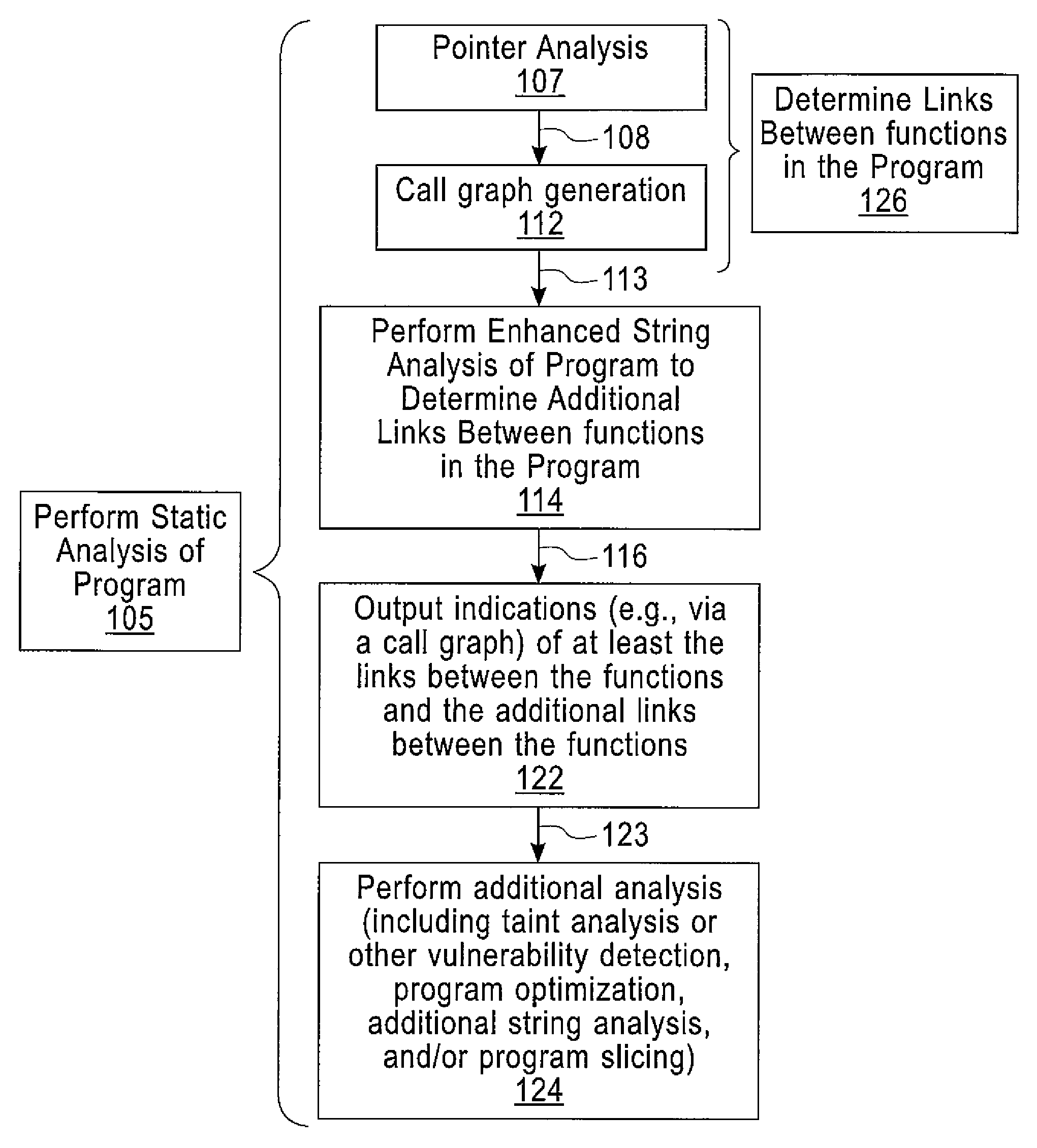
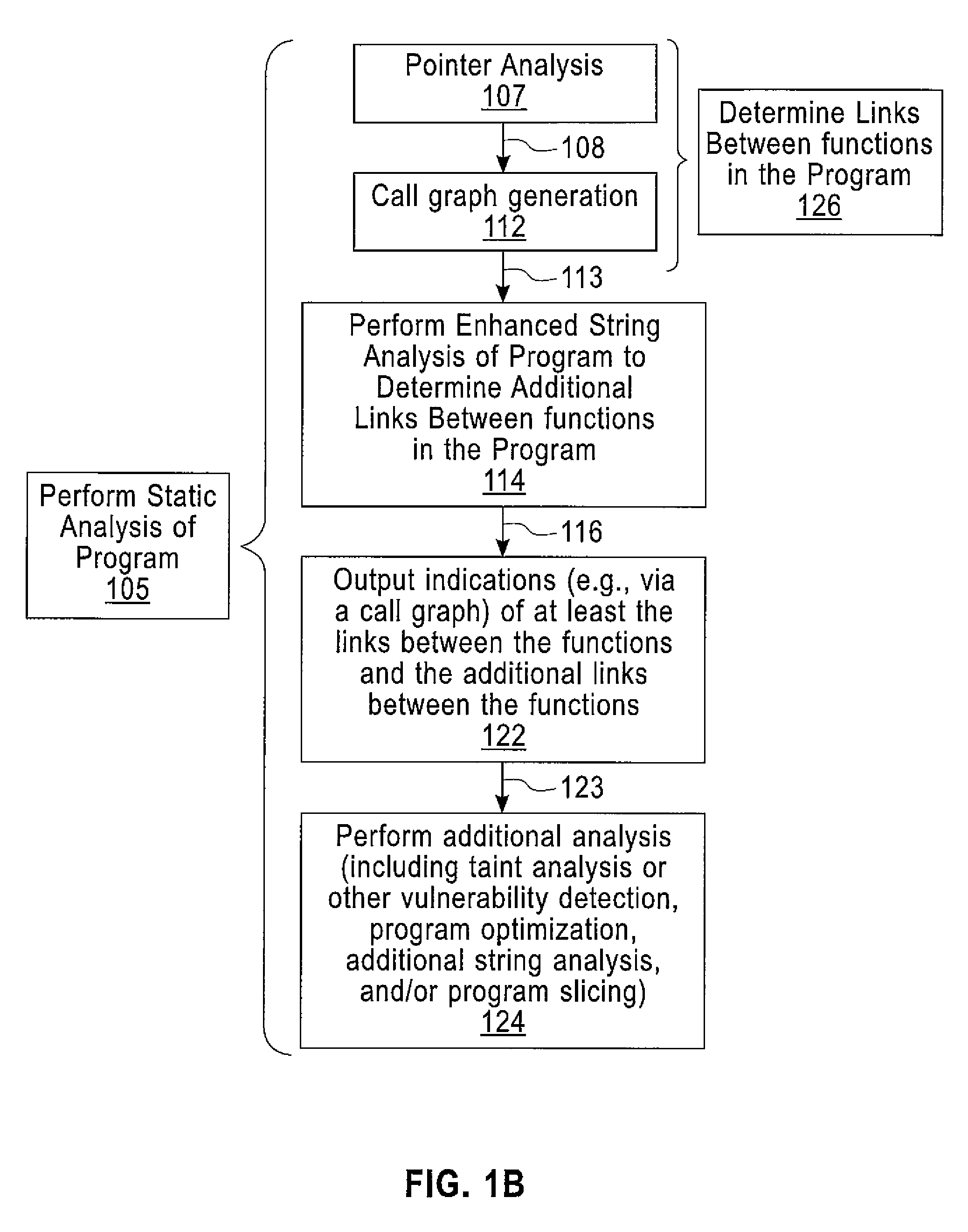
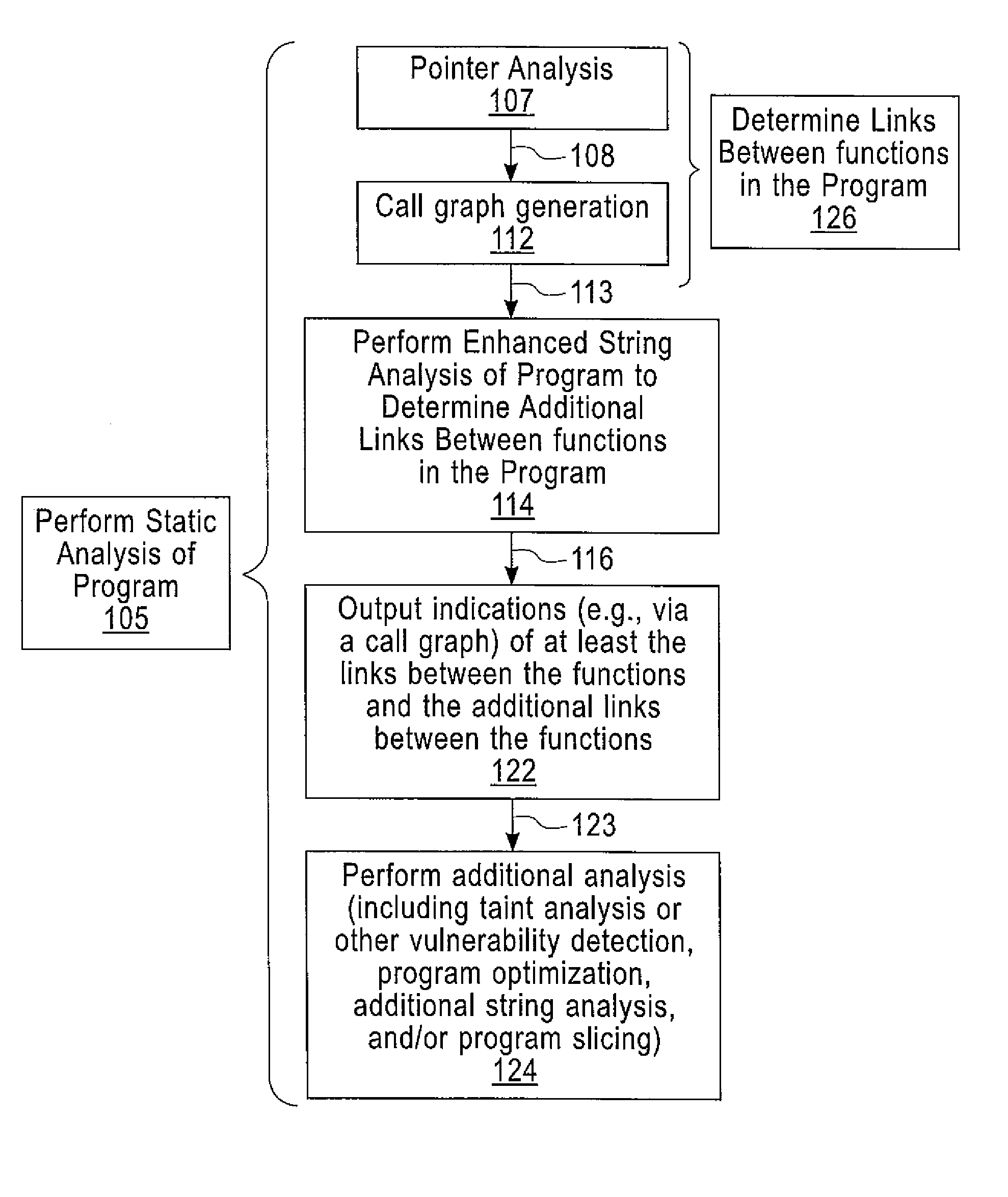
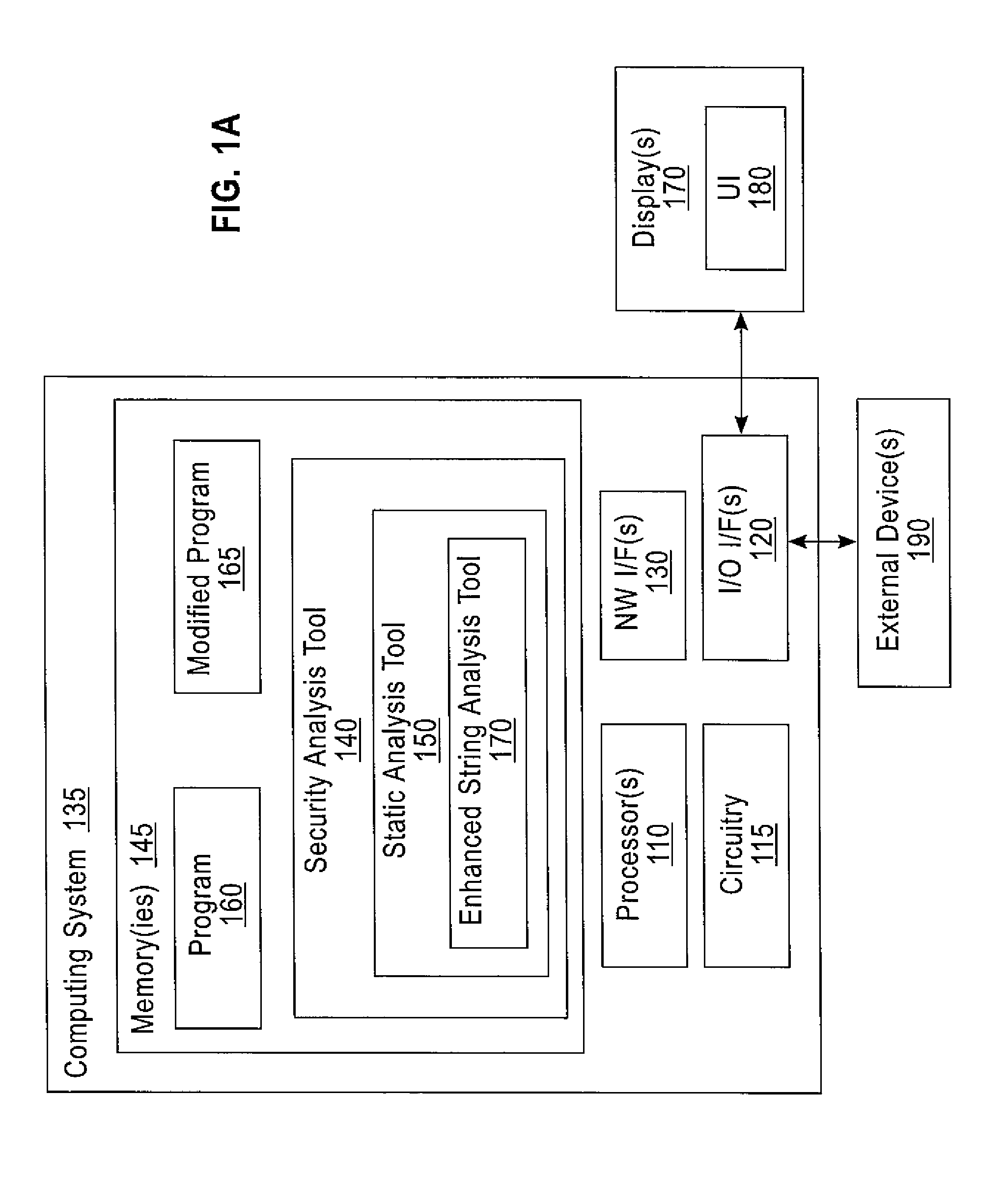
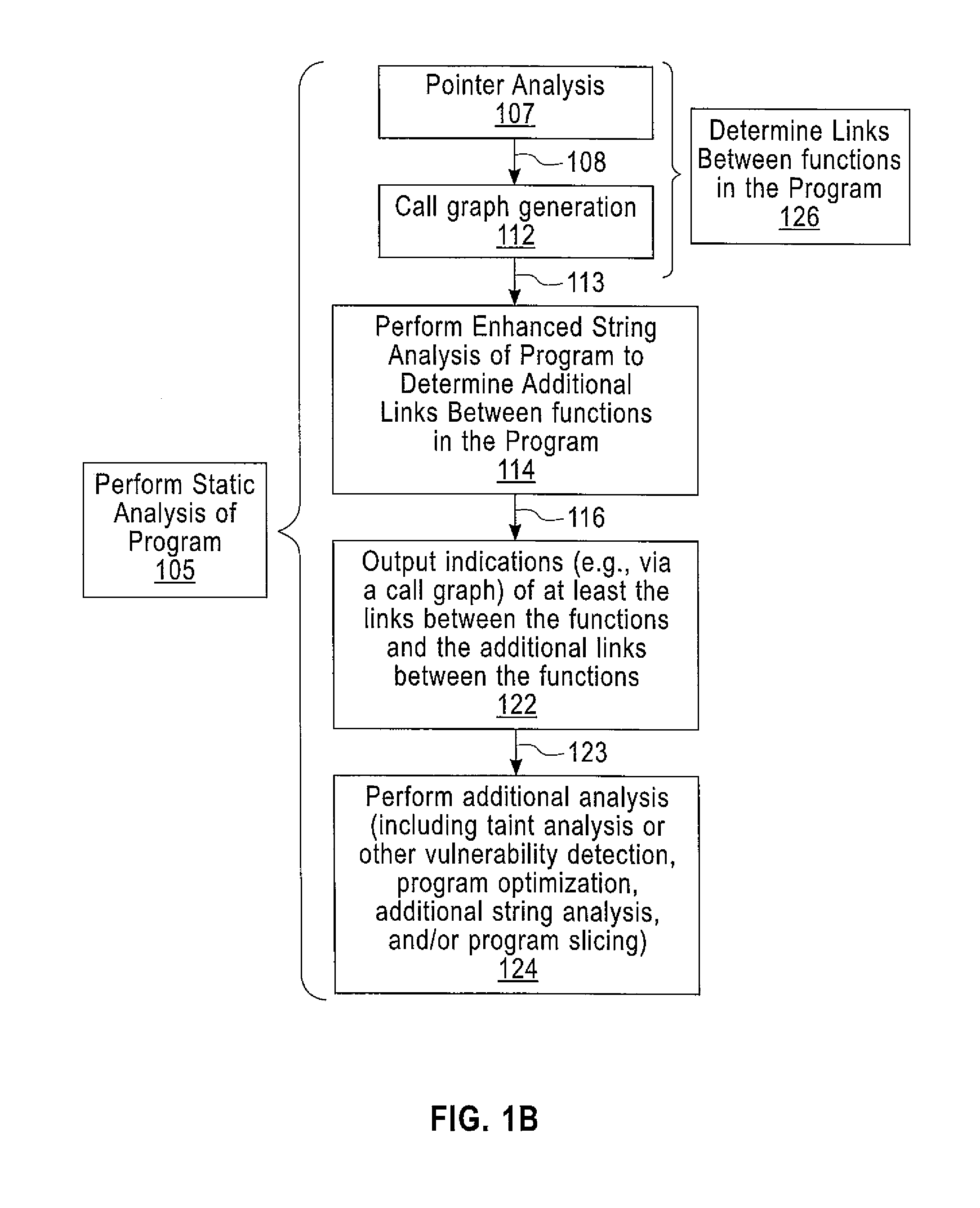
Enhanced String Analysis That Improves Accuracy Of Static Analysis
InactiveUS20140189657A1Software engineeringSoftware testing/debuggingString analysisComputer program
A method includes determining, as part of a static analysis of a program, links between functions in the program and performing, as part of the static analysis, string analysis on strings used in the program to determine additional links between the functions in the program. The method further includes outputting, as part of the static analysis, indications of at least the links between the functions and the additional links between the functions. Apparatus, computer programs, and program products are also disclosed.
Owner:IBM CORP
System, method, and apparatus for modular, string-sensitive, access rights analysis with demand-driven precision
InactiveUS8572674B2Reduce in quantityGood precisionPlatform integrity maintainanceTransmissionProgram slicingModularity
A static analysis for identification of permission-requirements on stack-inspection authorization systems is provided. The analysis employs functional modularity for improved scalability. To enhance precision, the analysis utilizes program slicing to detect the origin of each parameter passed to a security-sensitive function. Furthermore, since strings are essential when defining permissions, the analysis integrates a sophisticated string analysis that models string computations.
Owner:INT BUSINESS MASCH CORP
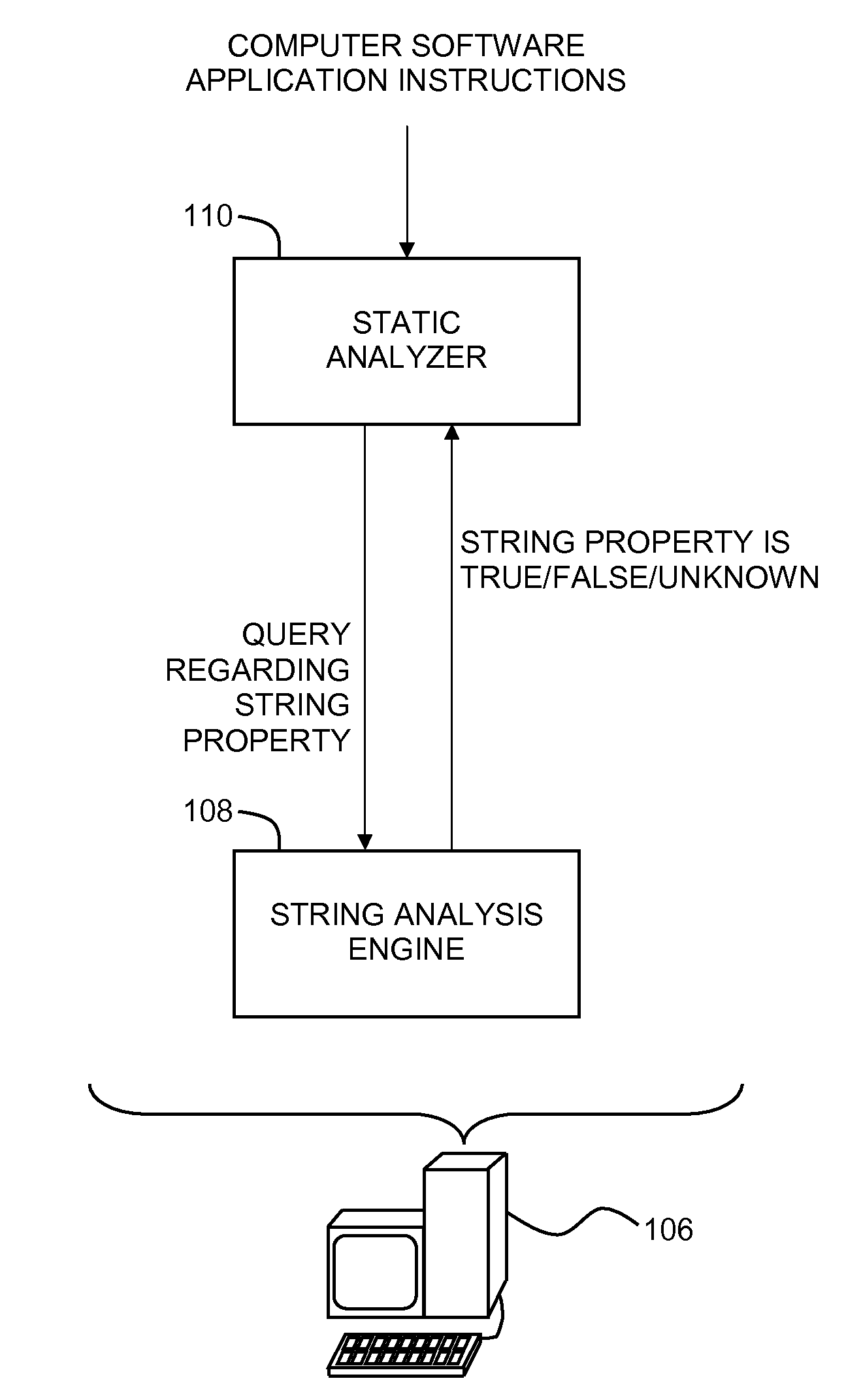
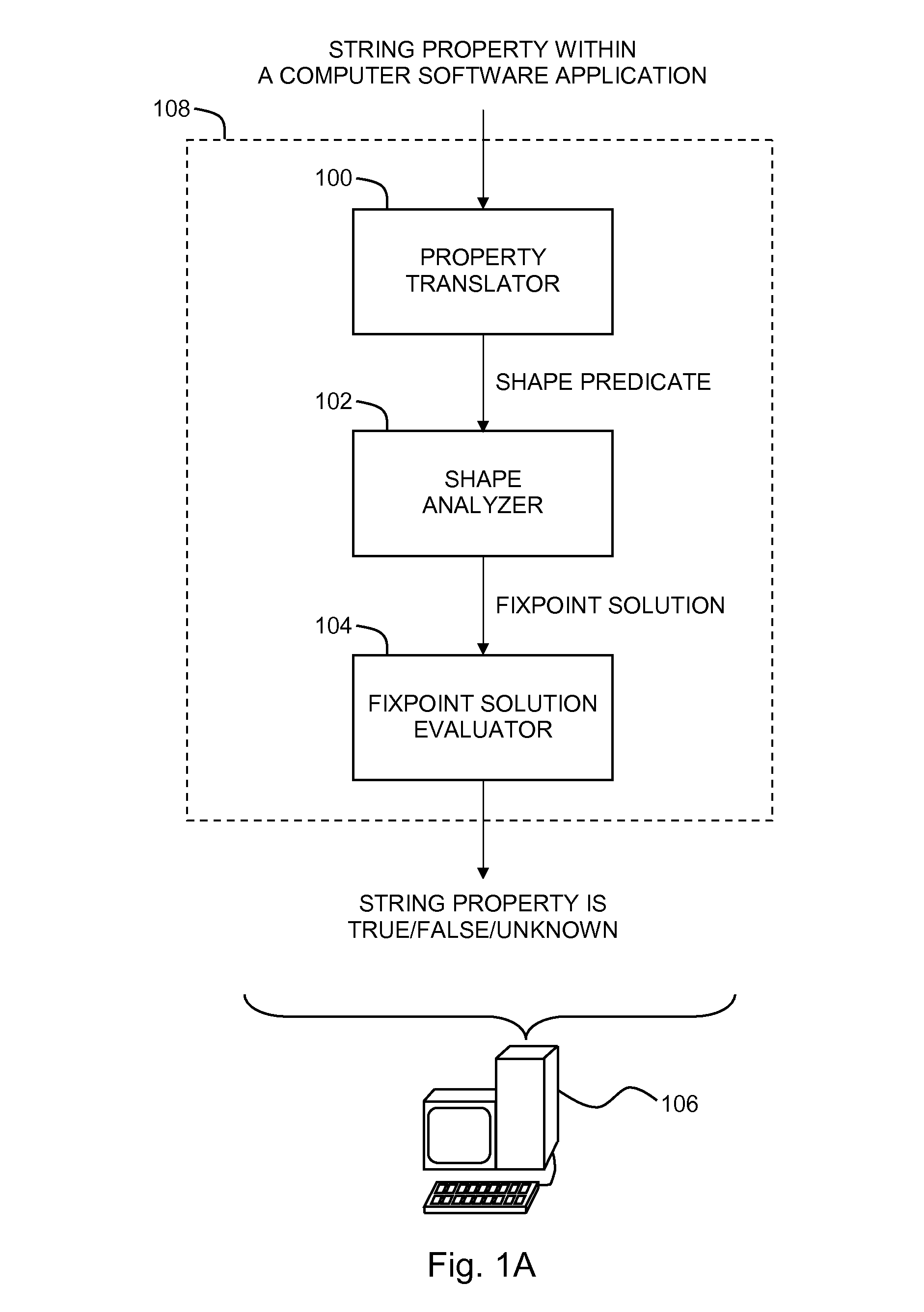
String analysis based on three-valued logic
Performing string analysis based on three-valued logic by including expressing a property of a string in a computer software application as a three-valued logic shape predicate, performing a three-valued logic shape analysis using the shape predicate to reach a fixpoint solution, and evaluating the fixpoint solution to determine a three-valued logic value of the property.
Owner:IBM CORP
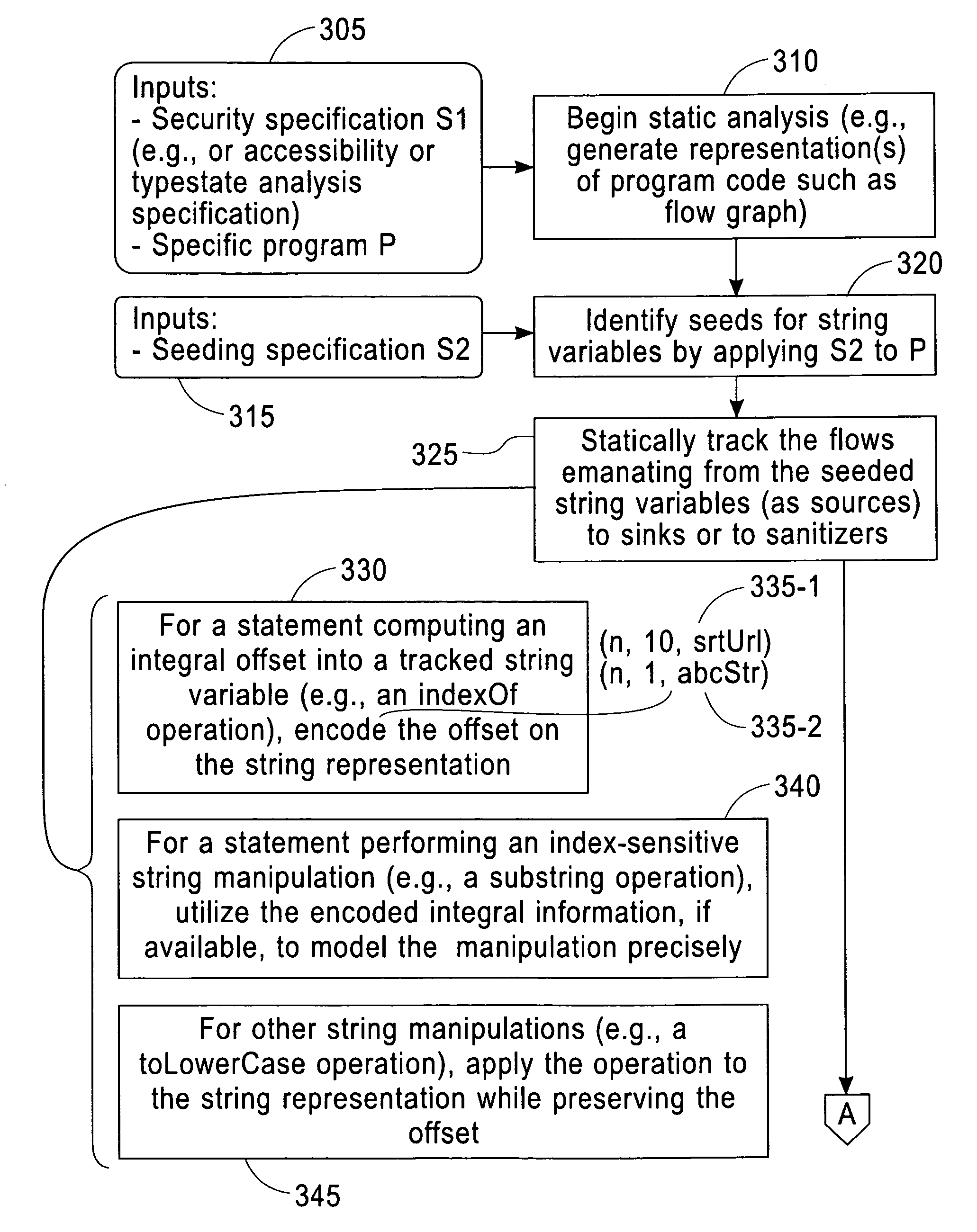
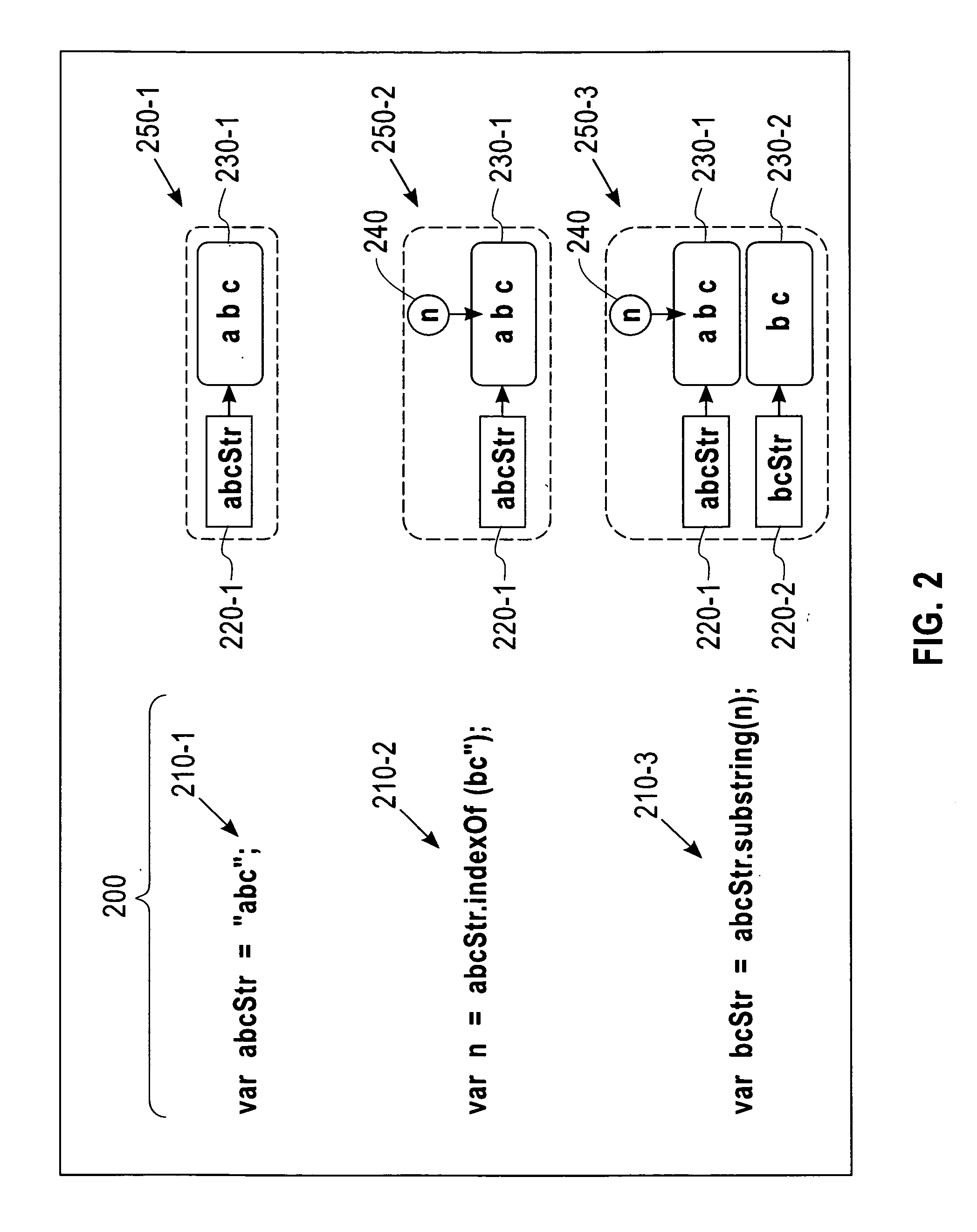
Scalable and Precise String Analysis Using Index-Sensitive Static String Abstractions
InactiveUS20140258992A1Computer security arrangementsSoftware testing/debuggingString analysisString representation
A disclosed method includes accessing one or more seeding specifications and a program including computer-readable code and applying the one or more seeding specifications to the program to identify for analysis seeds including strings for corresponding identified string variables. The method includes tracking flows emanating from the identified seeds. The tracking includes computing an integral offset into a tracked string variable for any statements causing such a computation. The tracking also includes providing a string representation based on the computed integral offset, wherein the provided string representation comprises a value of the integral offset and an indication of the corresponding tracked string variable. The tracking further includes modeling string manipulations of the tracked string variables using the string representations. Apparatus and program products are also disclosed.
Owner:IBM CORP
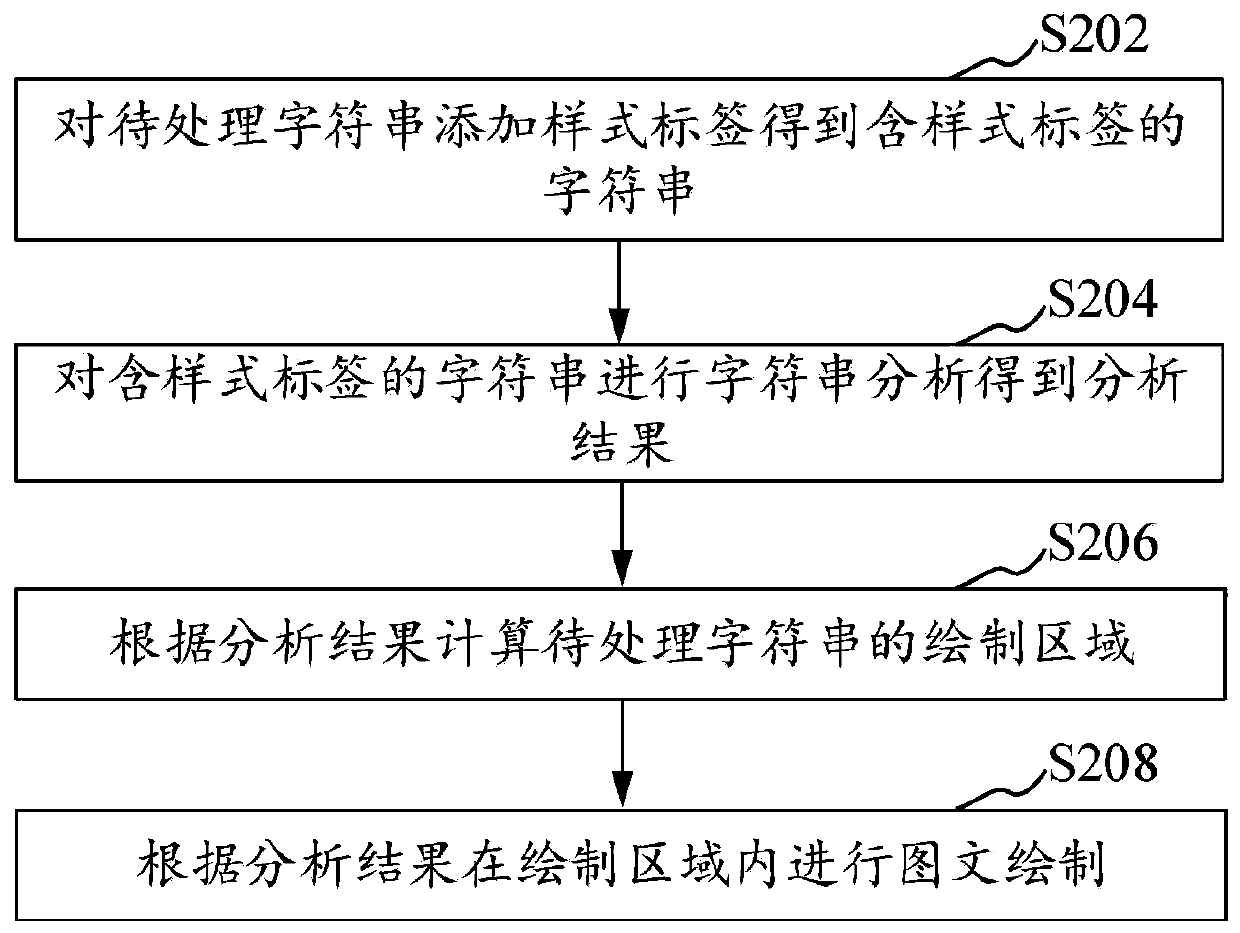
Image-text drawing method and device, computer readable storage medium and computer device
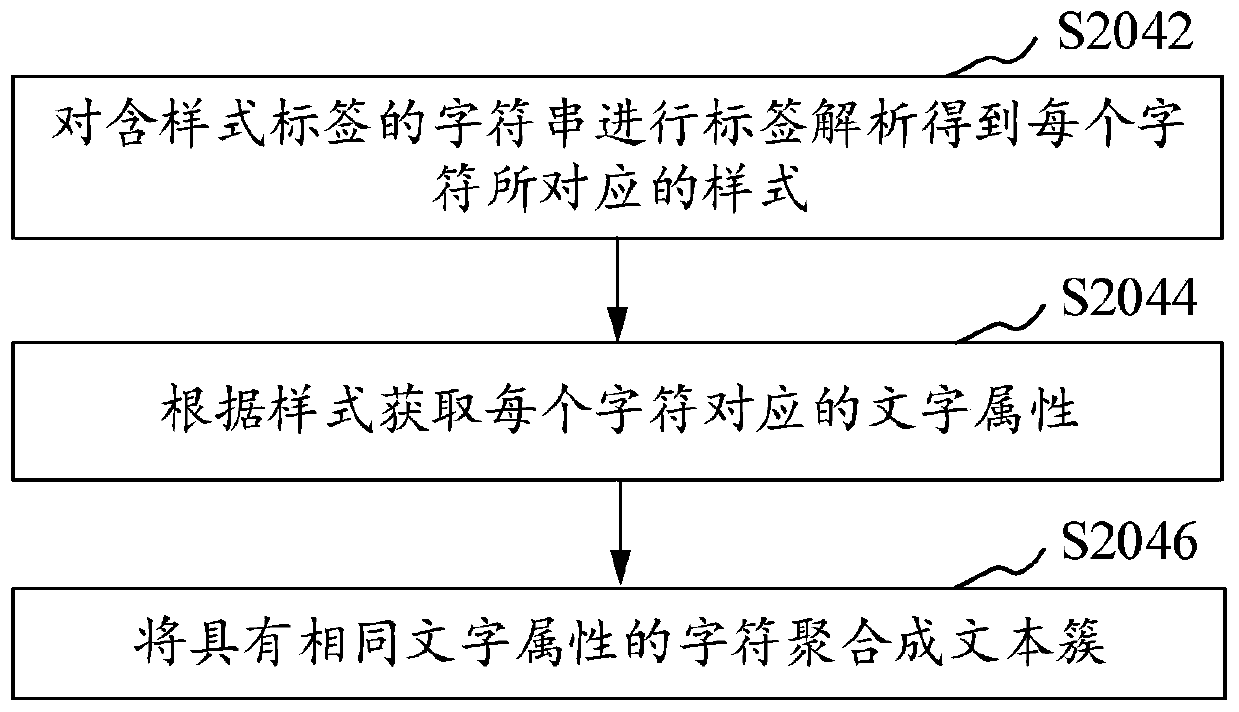
ActiveCN109933751AAvoid code point traversalShorten the timeSpecial data processing applicationsCode pointComputer science
The invention relates to an image-text drawing method and device, a computer readable storage medium and a computer device. The method comprises the following steps: firstly, a style label is added toa to-be-processed character string to obtain a character string containing the style label, then character string analysis is conducted on the character string containing the style label in a unifiedmode to obtain an analysis result, and then a drawing area of the to-be-processed character string can be directly calculated according to the analysis result and image-text drawing is conducted in the drawing area according to the analysis result. Due to the fact that the character string analysis step is added after the style label is added, the analysis result needed by subsequent calculationof the drawing area and the image-text drawing is obtained, and the calculation of the drawing area and the image-text drawing can be achieved by directly using the analysis result. Therefore, code point traversal of the character string containing the style label each time when the drawing area and the image-text are calculated in a traditional method is avoided, time and resources are saved, andthe drawing efficiency is greatly improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for extracting keywords in page
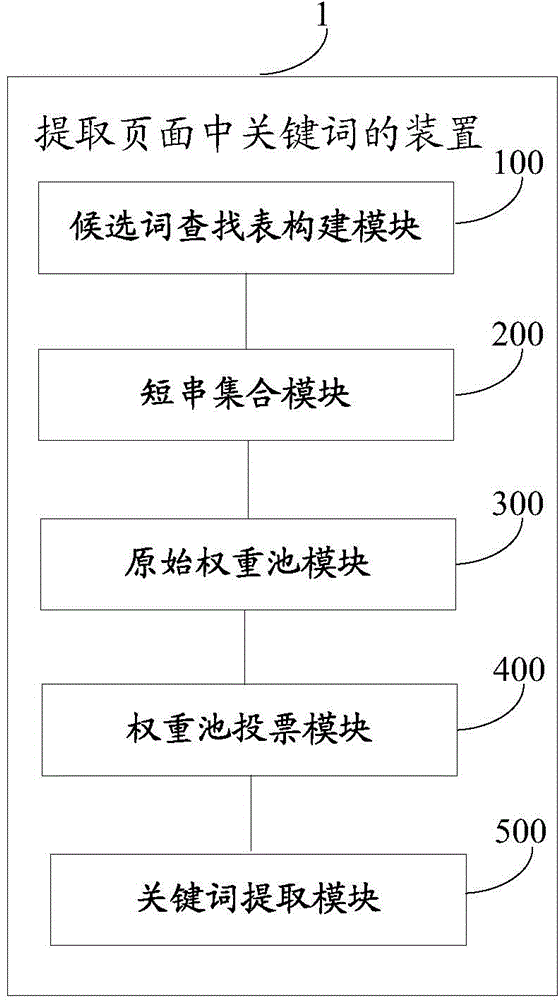
ActiveCN104679731AFix not workingImprove versatilitySpecial data processing applicationsShort stringWord search
The invention discloses a method and a device for extracting keywords in a page. The method comprises the following steps: performing character string analysis on the title content of the page to obtain candidate words, and constructing a candidate word search table by the obtained candidate words; performing page analysis on the page to obtain a character combination, and constructing a short string set by the obtained character combination; performing character string analysis on the short string set to obtain character strings, and constructing an original weight pool by the obtained character strings; performing weighted voting on the candidate words in the candidate word search table through the character strings according to the sequence of the quantities of words included in each character string in the original weight pool, and increasing the weight values of the candidate words if the character strings are consistent with the candidate words in the candidate word search table; sequencing according to the weighted values of the candidate words from large to small, and extracting a preset quantity of candidate words in the front as keywords according to the sequence. By adopting the method and the device, the universality of a keyword extraction technology can be enhanced, and a way for extracting the keywords is more intelligent and efficient.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Enhanced string analysis that improves accuracy of static analysis
Owner:INT BUSINESS MASCH CORP
Depth range manager for drill string analysis
A depth range manager provide users with a way to run and retain multiple depth range analyses for a drill string operation, including the operational parameters for each analysis. This allows users easily to view and compare the analyses at the different drilling depth ranges. In some embodiments, instead of drilling depth ranges, users may also urn and retain multiple different models and analyses using multiple different drilling times. The operational parameters for the multiple different models and analyses may be defined and stored using a flexible one-to-many database structure that accommodates the different sets of operational parameters as well as any existing single-analysis parameters associated with legacy analyses. A graphical interface allows users easily to define and store the operational parameters in the flexible one-to-many database structure.
Owner:LANDMARK GRAPHICS
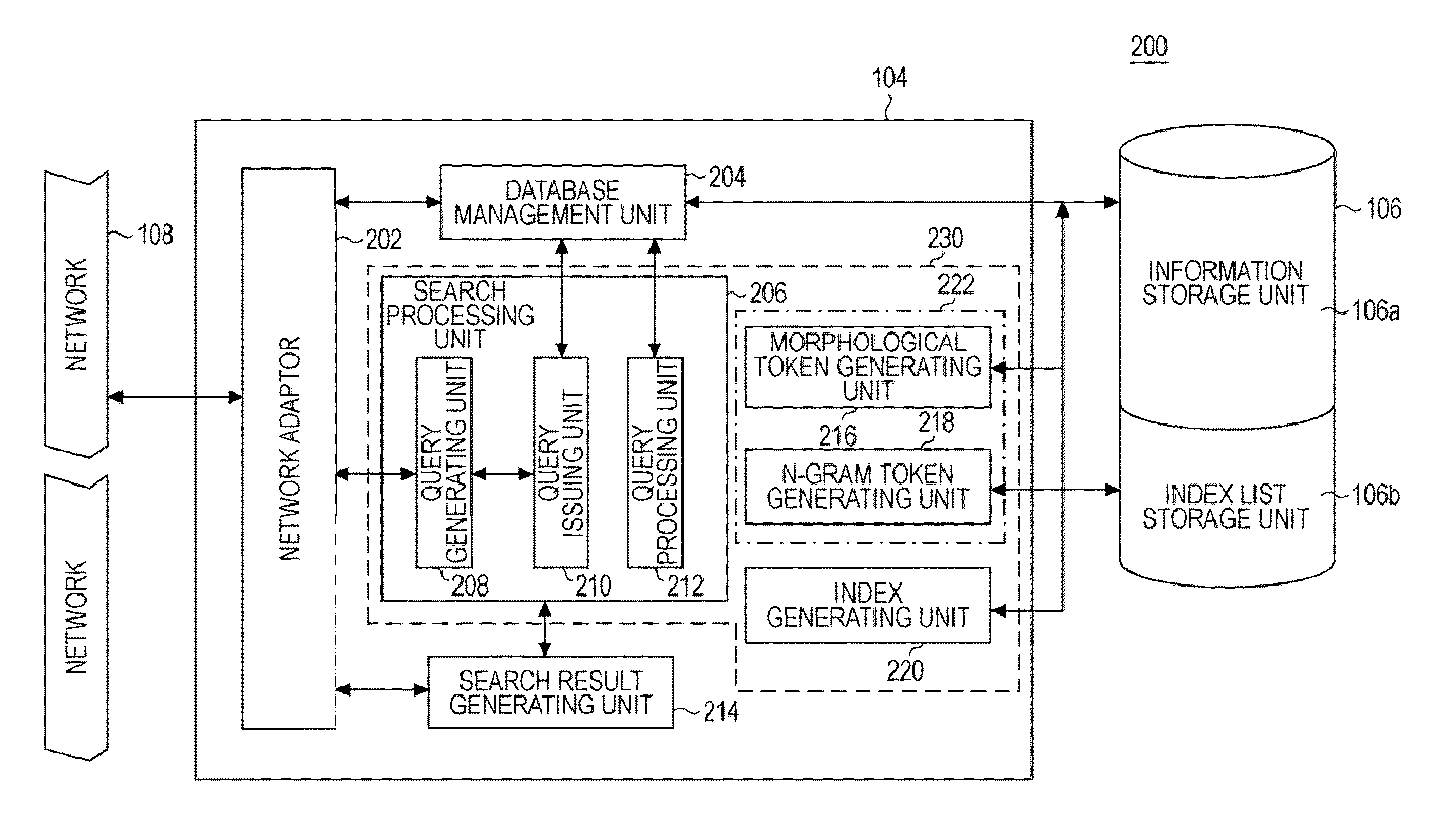
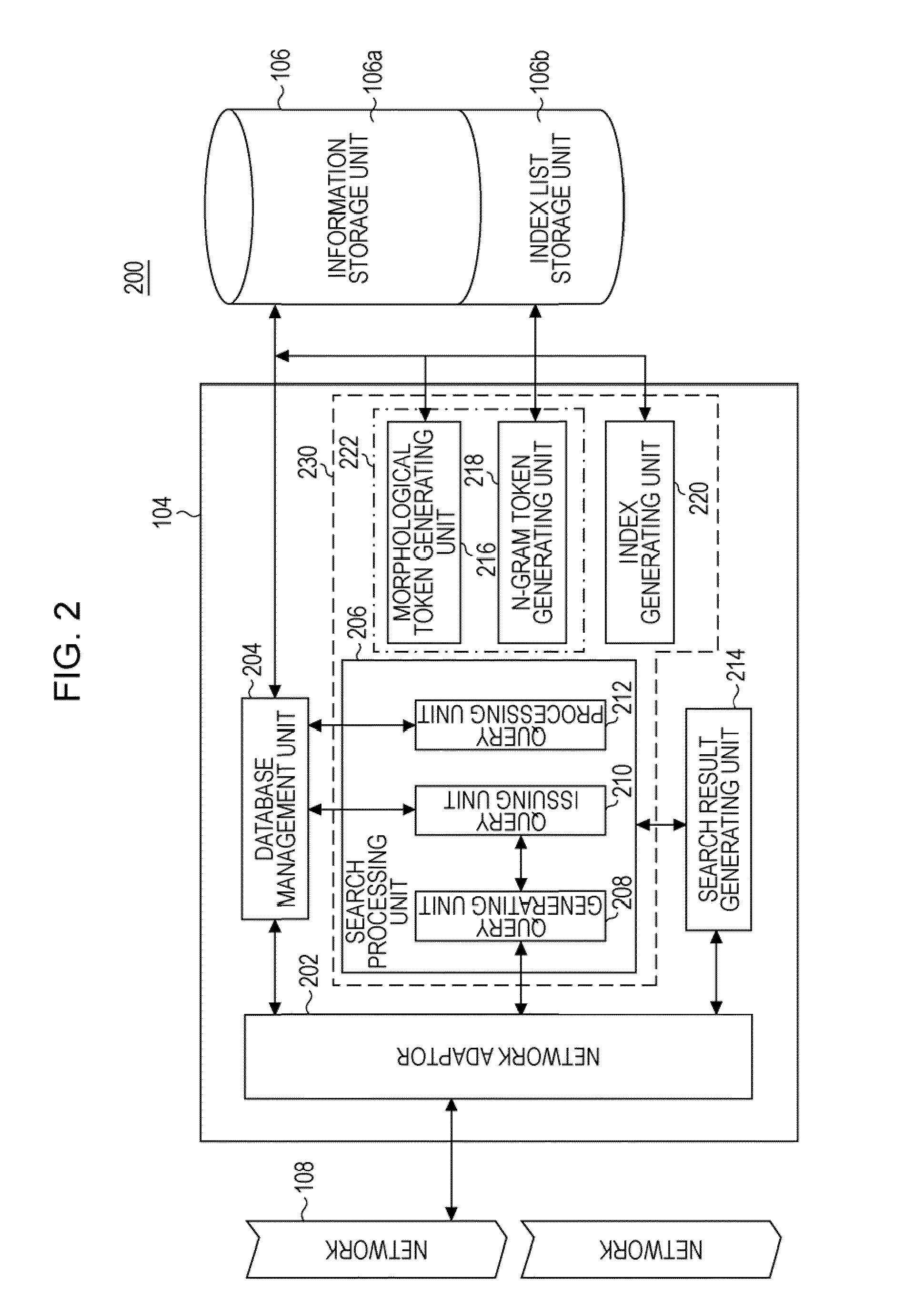
Search engine, search system, search method, and search program product
InactiveUS8930372B2Improve search accuracyImprove fidelityDigital data processing detailsNatural language data processingSearch wordsSearch procedure
A search system can include a server, a token assignment unit for assigning types of tokens based on different kinds of character string analysis methods, an index generating unit for generating an index list that associates the tokens assigned with the token assignment unit, a type identification value for identifying a type of the character string analysis, and information, a search unit that receives a search word for referencing the information to combine types of search tokens generated from the search word to generate a single search command for parallel inquiry of the information to search for the information, and a search result generating unit for displaying information extracted in relation to the search word through parallel inquiry with the search unit and search tokens so as to identify the tokens.
Owner:INT BUSINESS MASCH CORP
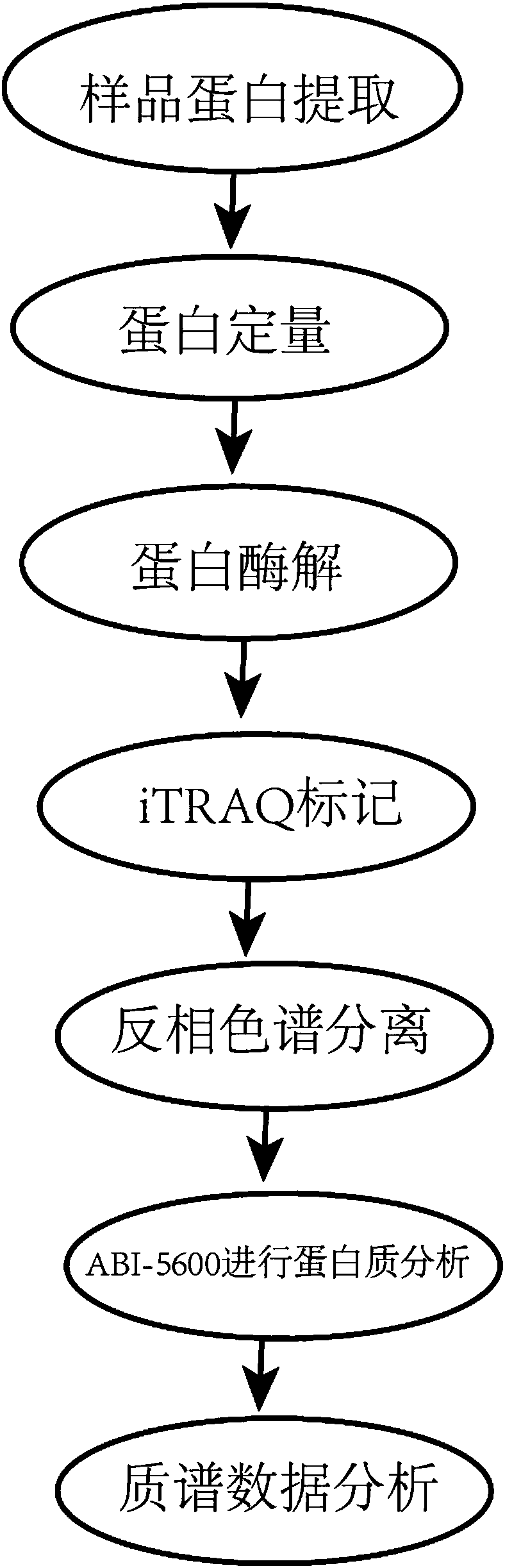
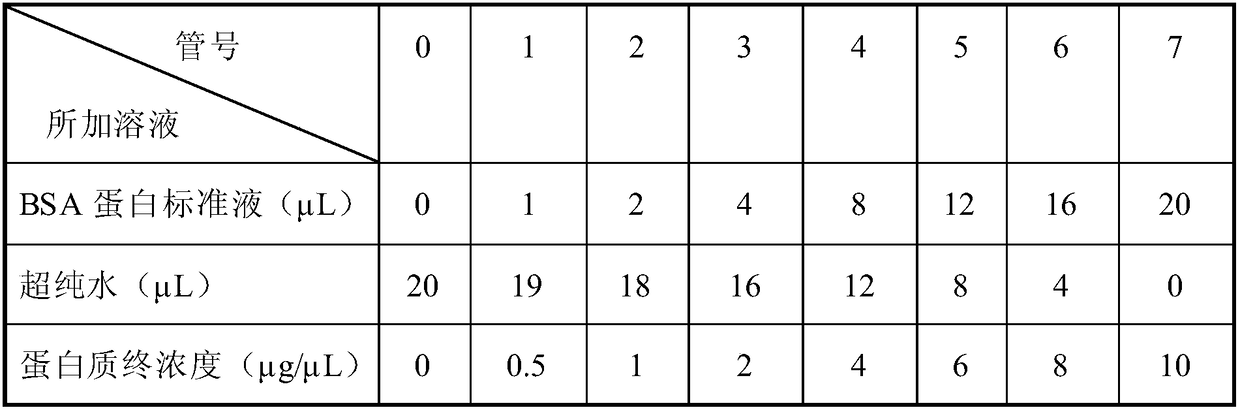
Screening method of non-invasive gastric cancer saliva biomarker
InactiveCN108152508ANon-invasive detection and evaluation meansSimple detection and evaluation meansBiological testingLymphatic SpreadFreeze-drying
The invention discloses a screening method of a non-invasive gastric cancer saliva biomarker. The screening method specifically comprises the following steps: protein sample preparation, protein quantification, proteolysis and freeze-drying, labeling a sample by iTRAQ, C18 desalting, liquid-phase separation and mass spectrum identification, and data analysis; the GO function enrichment including biology progress, the molecule function and the cell component is performed on the screened differential protein by using the Panther Classification System in the data analysis; and then the protein mutual effect analysis is performed on the differential protein by using the STRING analysis software; and then the KEGG signal path analysis is performed on the differential protein. Through the screening method disclosed by the invention, the specificity protein marker in the gastric cancer can be discovered through a fast and reliable proteomics technical program, thereby establishing a non-invasive, simple and convenient, fast and practical detection evaluation measure for the early diagnosis, the postoperative recurrence, metastasis, and prognosis observation of the gastric cancer.
Owner:SHENZHEN ELDERLY MEDICAL RES INST +1
Enhanced String Analysis That Improves Accuracy Of Static Analysis
InactiveUS20140189658A1Software engineeringSoftware testing/debuggingString analysisComputer program
An apparatus and computer program product which are configured for determining, as part of a static analysis of a program, links between functions in the program and performing, as part of the static analysis, string analysis on strings used in the program to determine additional links between the functions in the program. The apparatus and computer program product are further configured for outputting, as part of the static analysis, indications of at least the links between the functions and the additional links between the functions.
Owner:IBM CORP
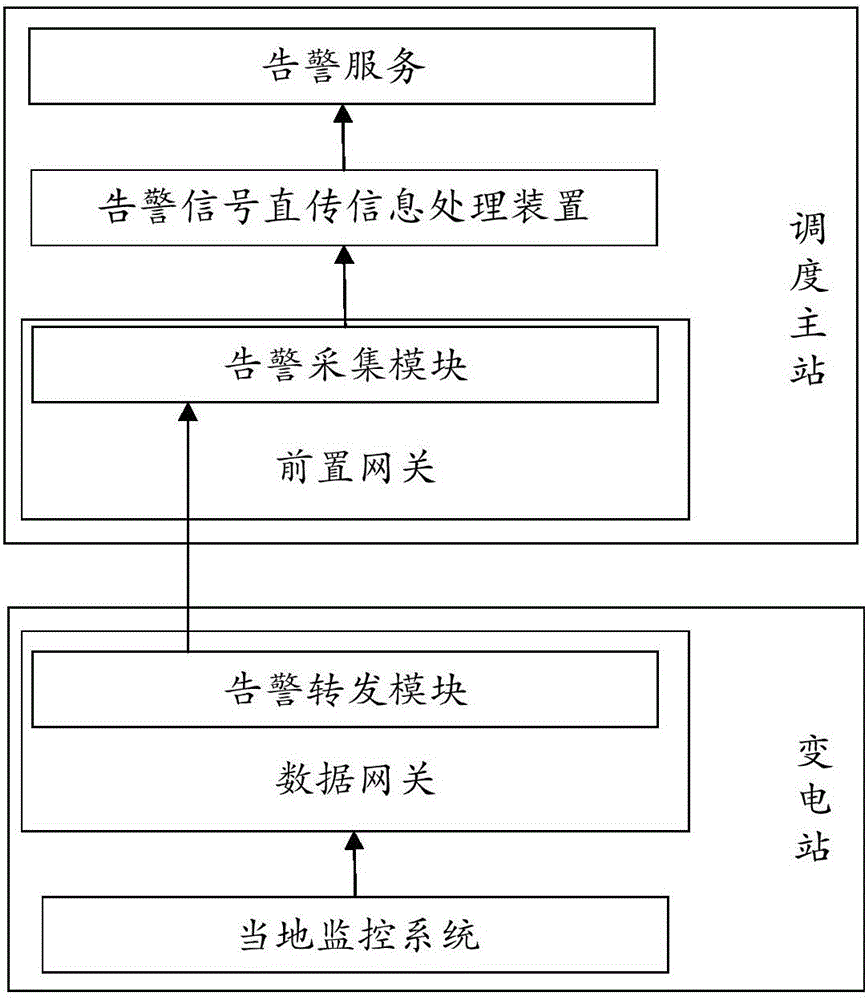
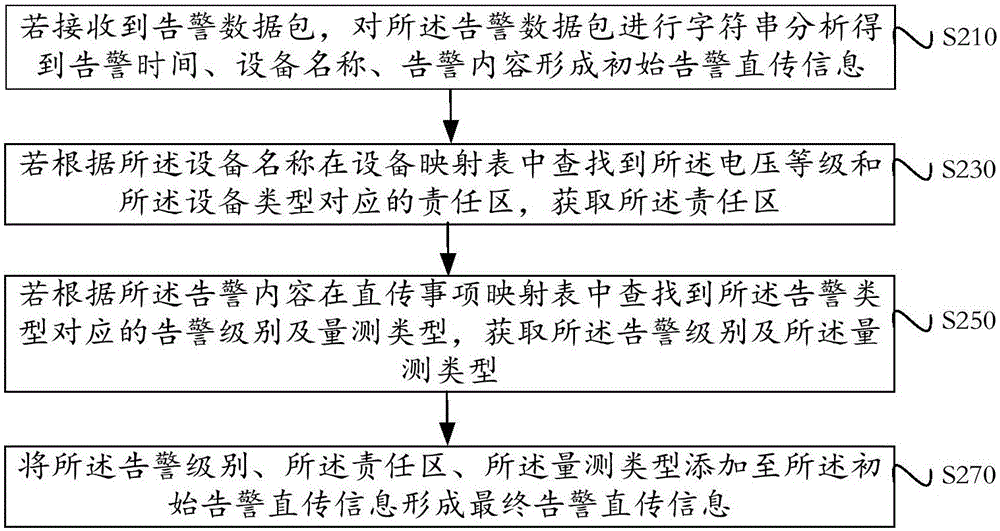
Method and device for processing direct transmission information of alarm signal
ActiveCN106528818AImprove applicabilitySpecial data processing applicationsDevice typeNetwork packet
The invention provides a method and device for processing direct transmission information of an alarm signal. The method comprises the following steps: if an alarm data packet is received, performing character string analysis on the alarm data packet to obtain alarm time, an equipment name and an alarm content, and forming initial alarm direct transmission information; if a responsibility area corresponding to a voltage level and an equipment type is found in an equipment mapping table according to the equipment name, then acquiring the responsibility area; if an alarm level and a measurement type corresponding to an alarm type are found in a direct transmission item mapping table according to the alarm content, then acquiring the alarm level and the measurement type; and adding the alarm level, the responsibility area and the measurement type to the initial alarm direct transmission information, and forming final alarm direct transmission information. Since the final alarm direct transmission information obtained by the method and the device provided by the invention can be conveniently applied, therefore, the method and the device provided by the invention are high in applicability.
Owner:JIANGMEN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID
Access control system and control method thereof
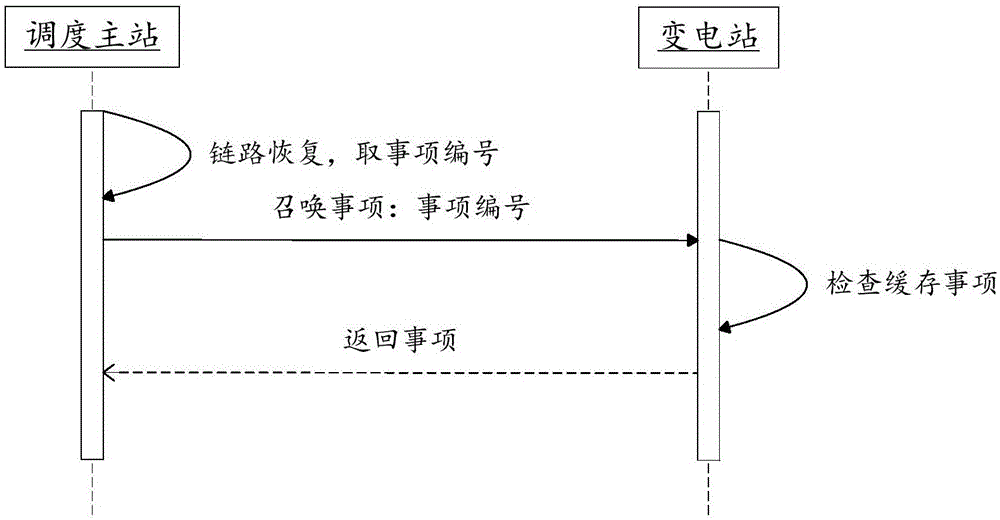
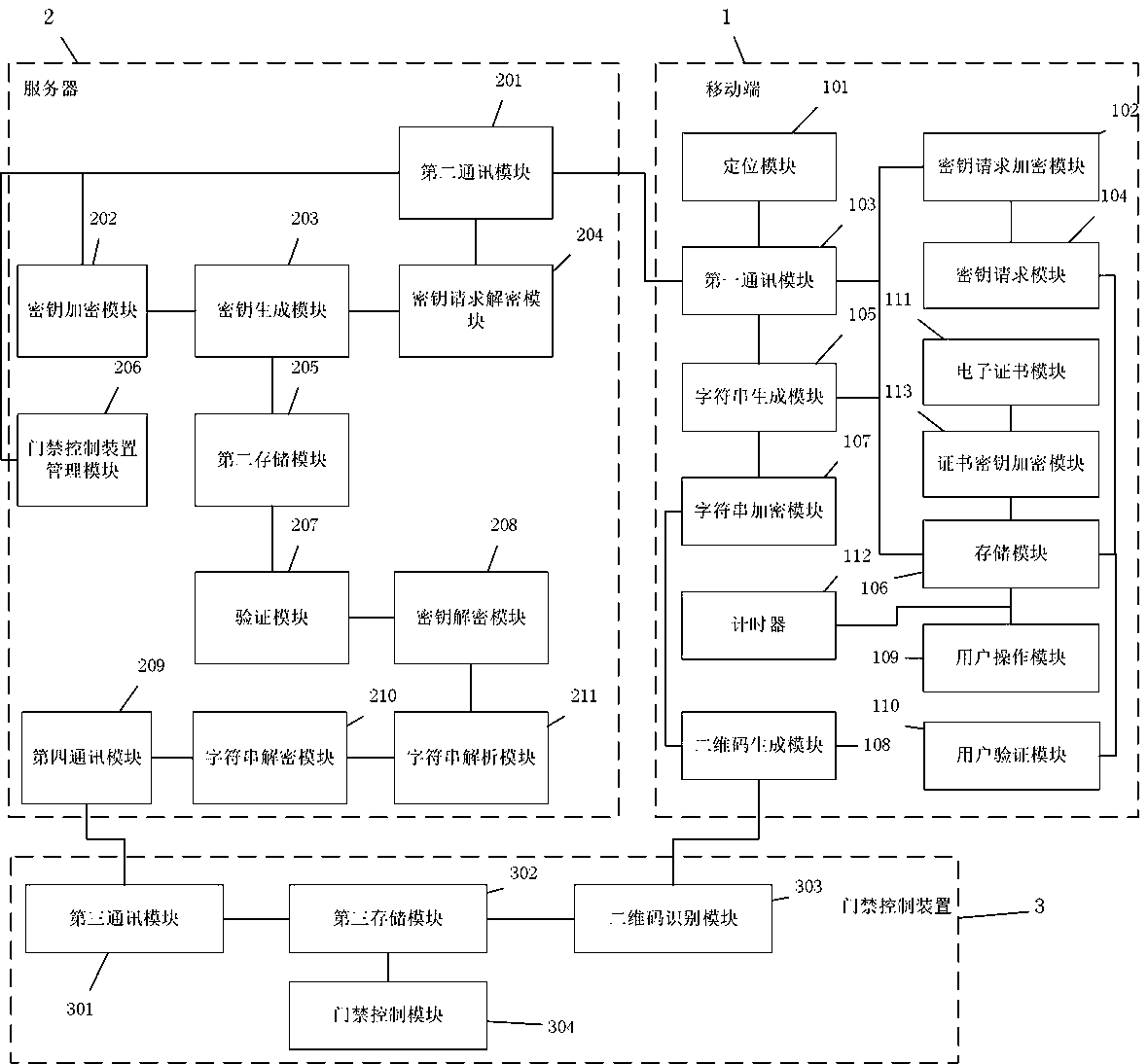
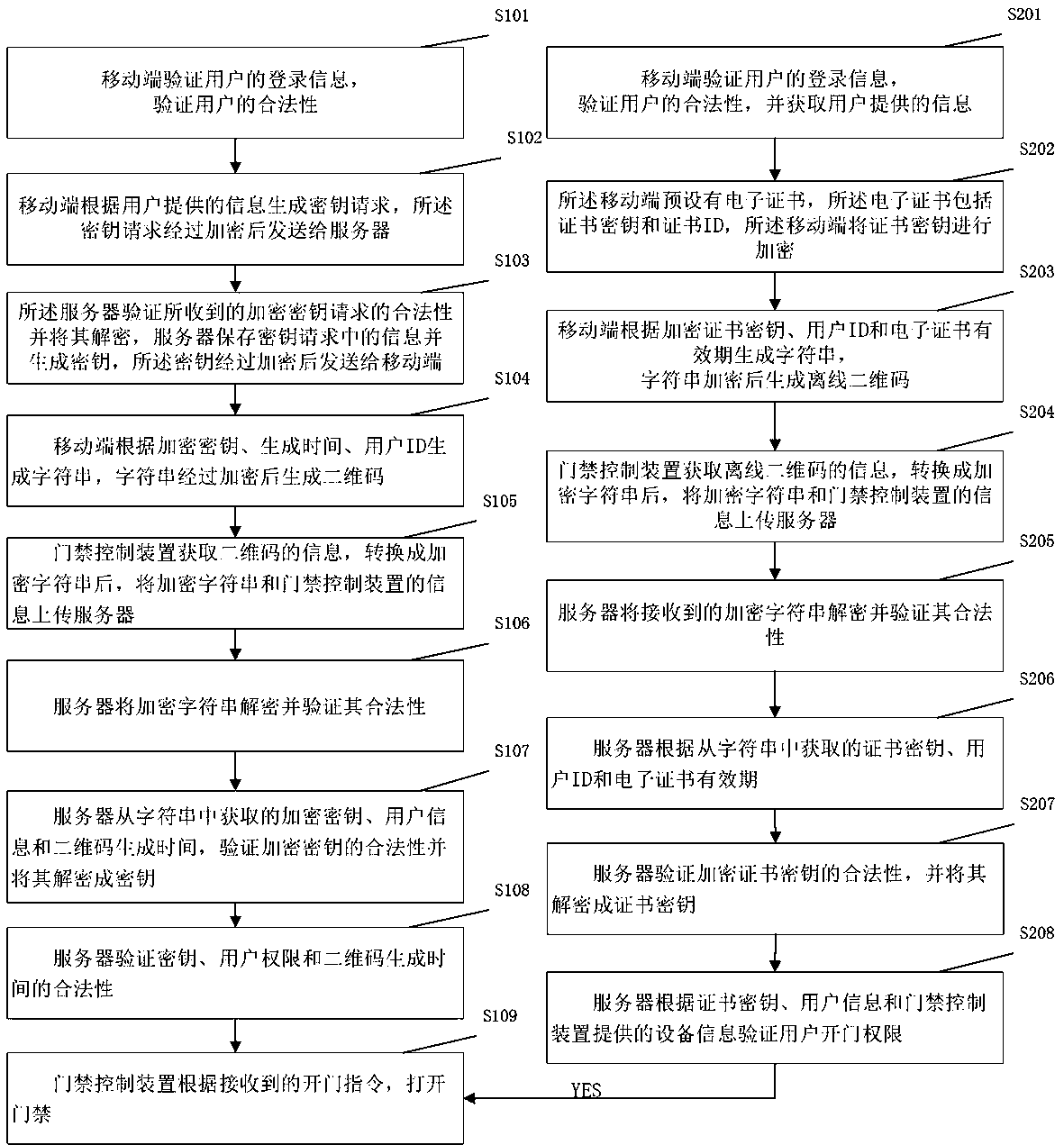
InactiveCN111540093APrevent eavesdroppingPrevent tamperingIndividual entry/exit registersSecurity arrangementMultiple encryptionThird party
The invention provides an access control system and a control method thereof. The access control system comprises a server, a mobile terminal and an access control device. Multiple encryption is carried out in a secret key or two-dimensional code transmission link, so that the secret key is prevented from being eavesdropped or tampered; propagation and tampering of the two-dimensional code are prevented; security of transmissions is enhanced, and eavesdropping or tampering in a verification information transmission process is prevented; the door opening permission of the user is verified according to the time difference of application time, the secret key, the UUID of the access control device and the user permission information; the security is improved, the character string analysis iscarried out in the server, the generation algorithm of the character string is prevented from being acquired by a third party at a mobile phone terminal, and the secret key is carried out in ae generation algorithm and an encryption algorithm in the server, so that the security is improved.
Owner:三仟(杭州)数字科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com