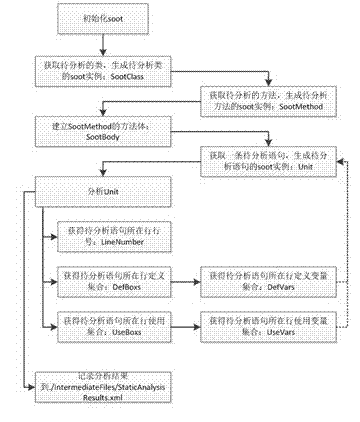
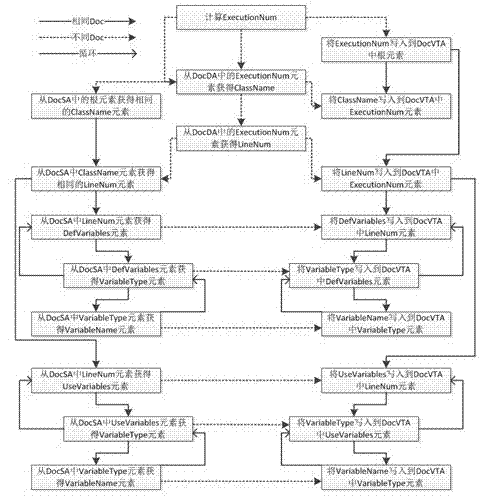
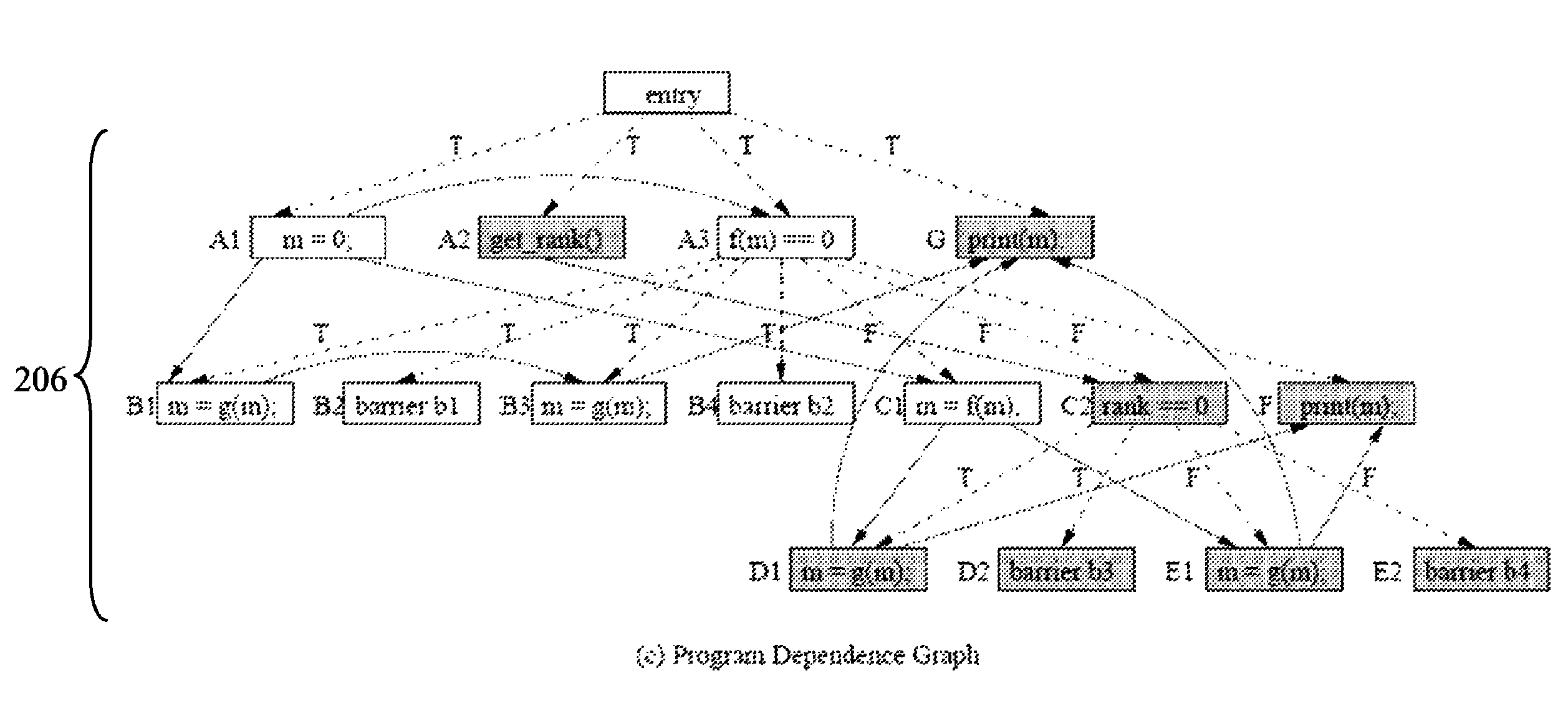
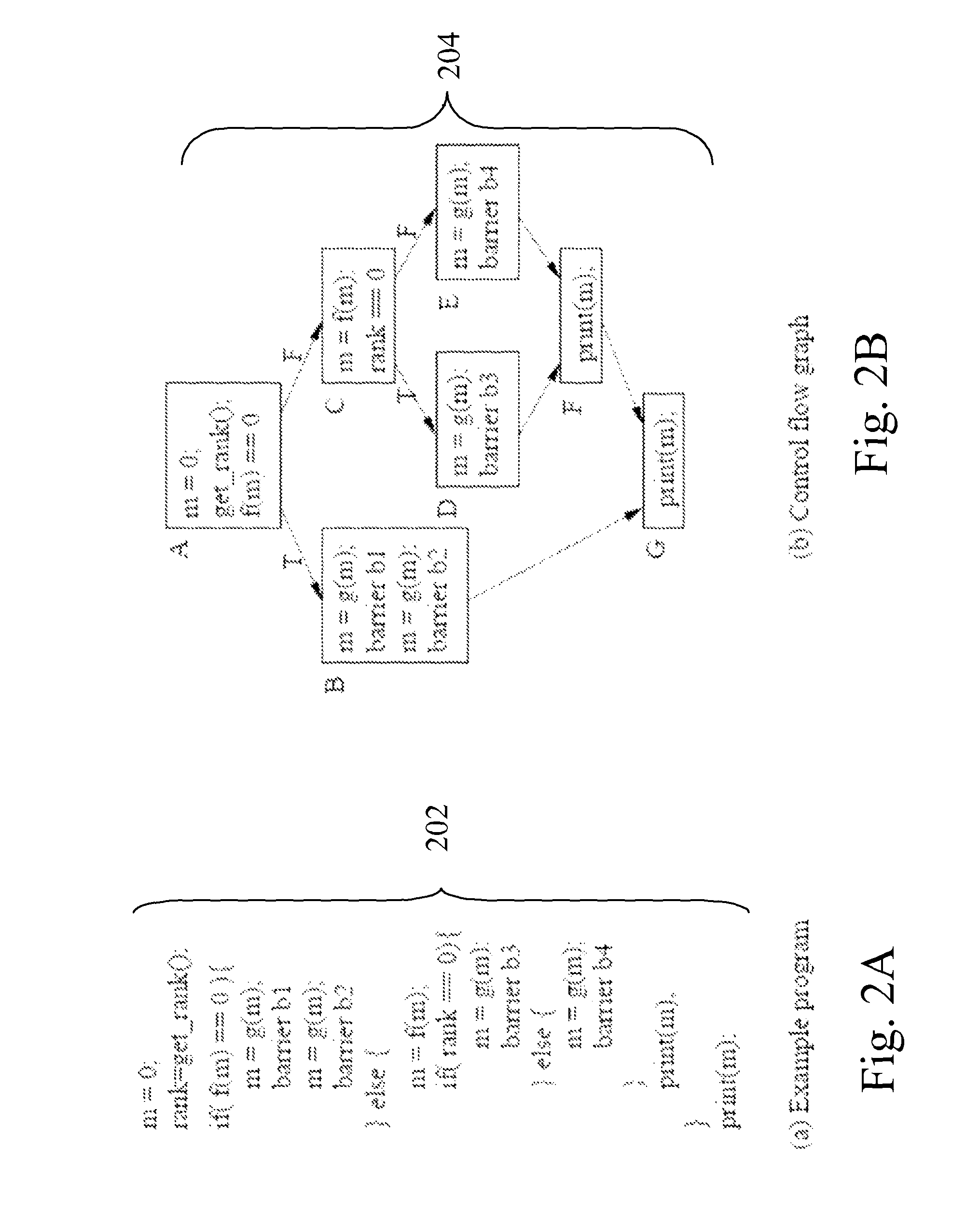
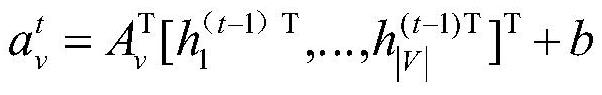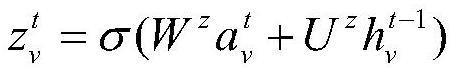Patents
Literature
87 results about "Program slicing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
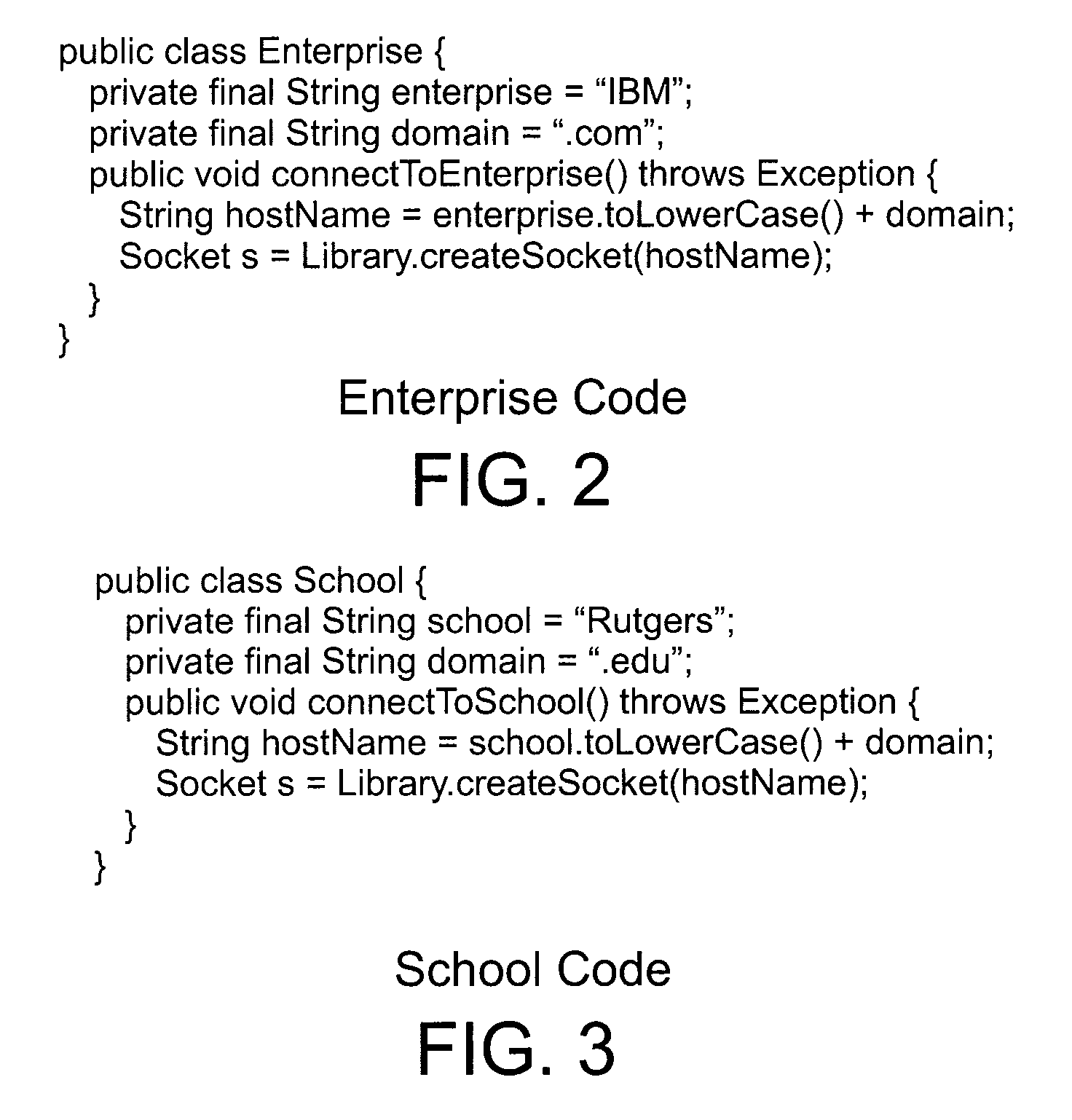
In computer programming, program slicing is the computation of the set of program statements, the program slice, that may affect the values at some point of interest, referred to as a slicing criterion. Program slicing can be used in debugging to locate source of errors more easily. Other applications of slicing include software maintenance, optimization, program analysis, and information flow control.
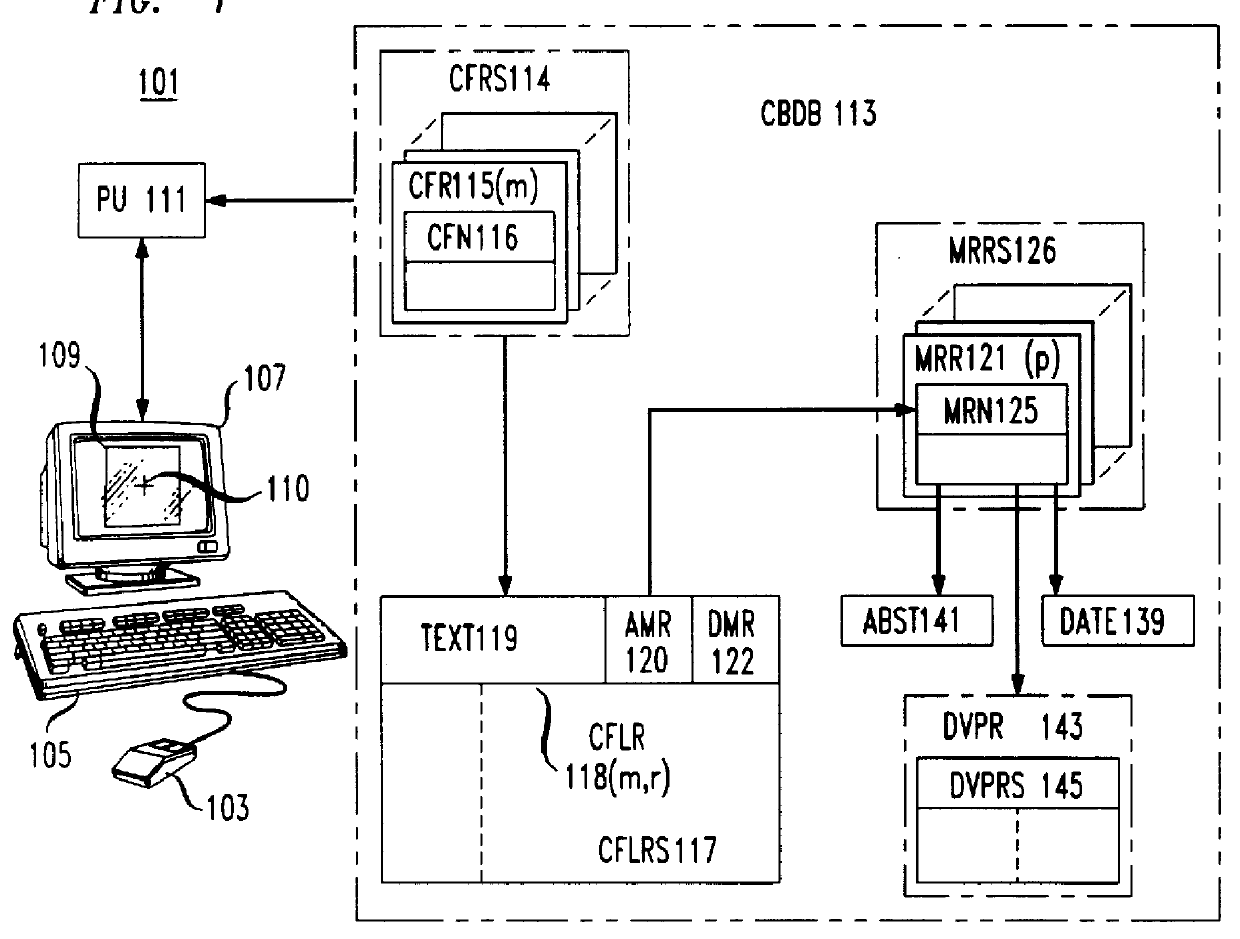
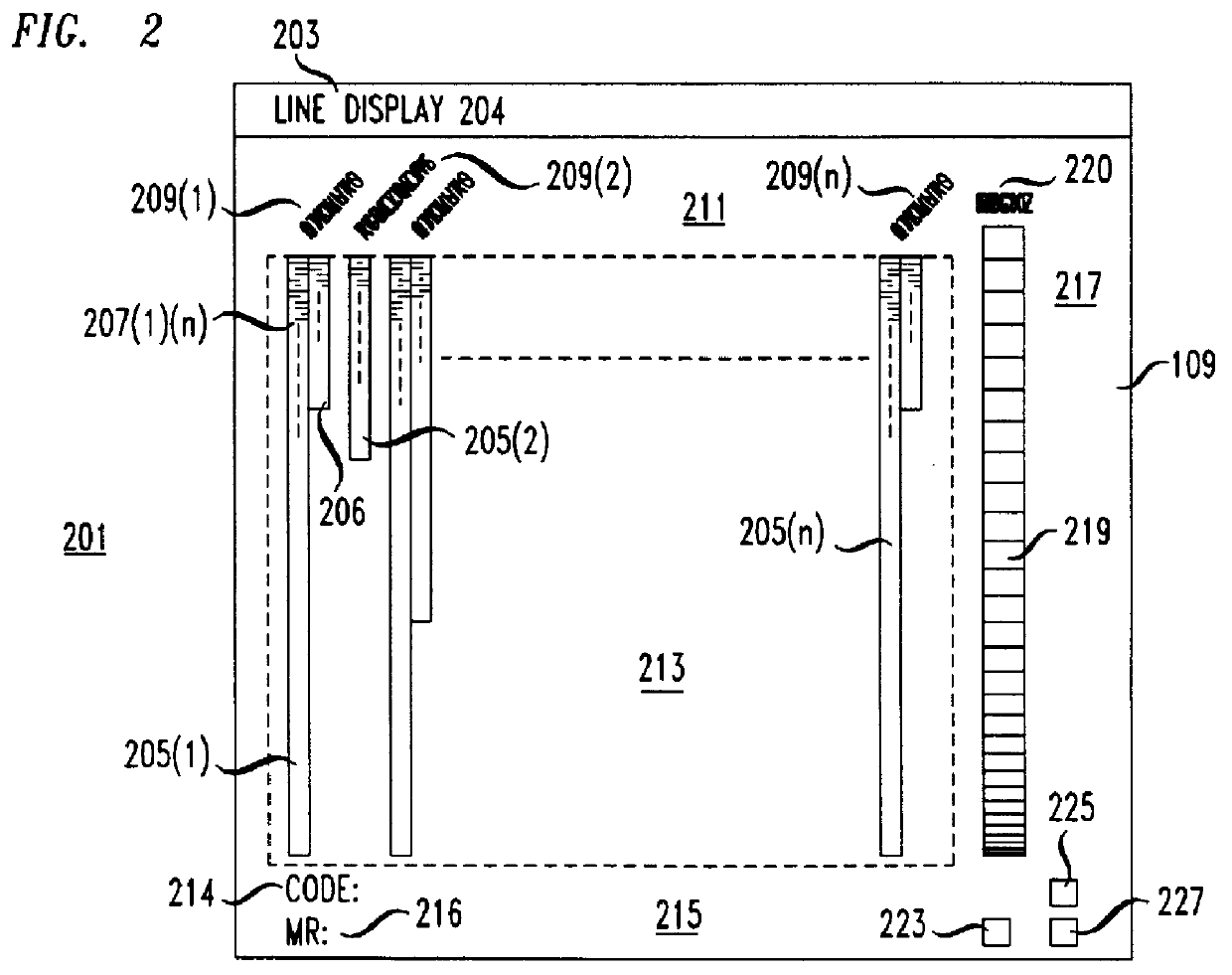
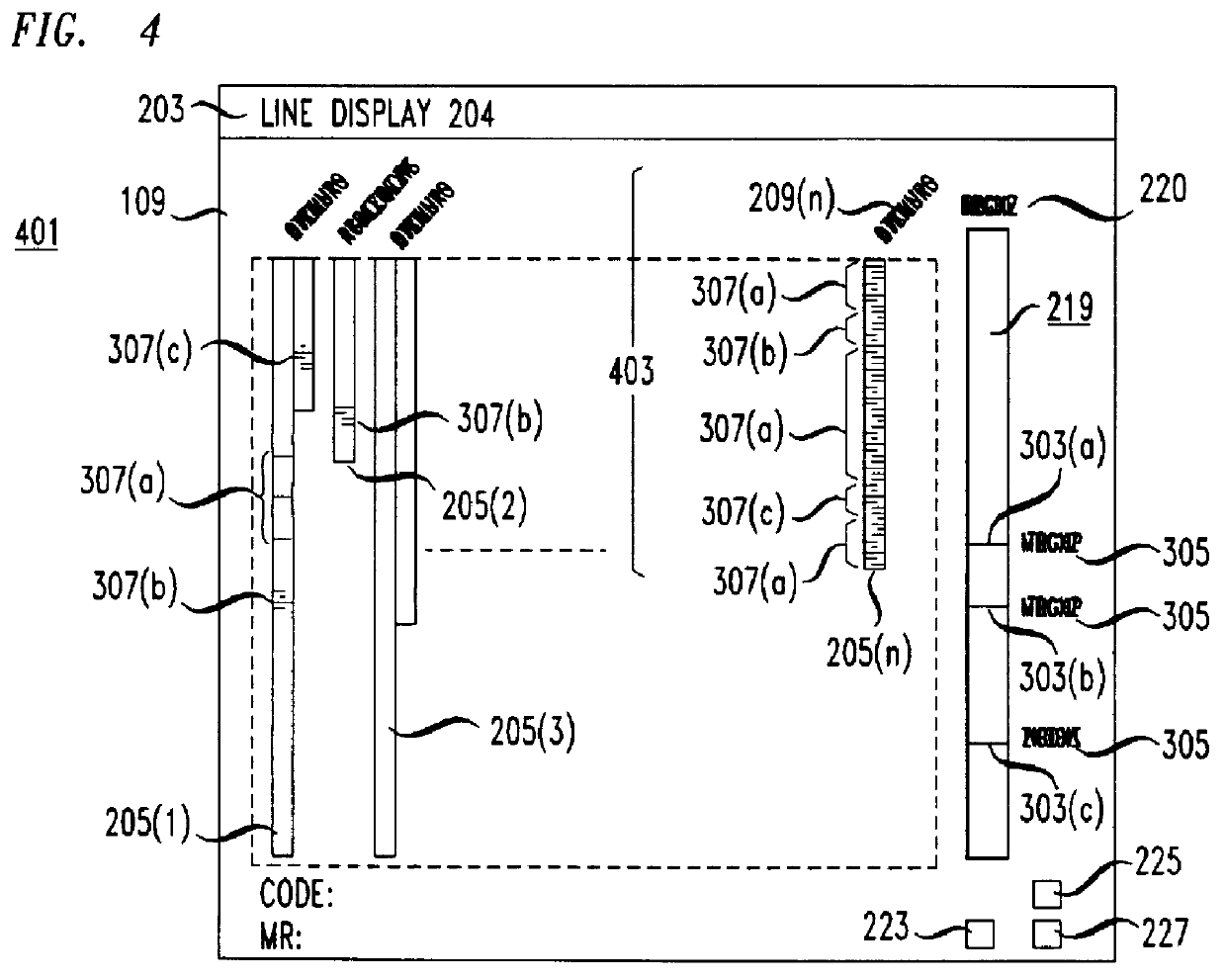
Apparatus for visualizing program slices
Apparatus for visualizing slices of transitive closures of entities having dependence relationships with one another. A preferred embodiment visualizes slices of programs. A display in a computer system includes reduced representations of the files, procedures, and lines making up a program. The user employs a pointing device to interactively select a reduced representation as the slice point and the apparatus computes the slice and changes the color of the reduced representations in the slice. The color of the reduced representation indicates the distance of the entity represented by the reduced representation from the slice point. The display may be rearranged so that files and procedures are ordered by distance from the slice point. Other aspects of the display include scaling the size of the reduced representation of a procedure to indicate the number of lines in the procedure and filling the reduced representation of the procedure according to the number of lines belonging to the slice which are contained in the procedure. A user may select open and closed representations of procedures. The open representation of a procedure contains reduced representations of the lines in the procedure. The apparatus also includes a viewer for viewing the text of lines in the program.
Owner:LUCENT TECH INC
Aggregate structure identification and its application to program analysis
InactiveUS6279149B1Digital data processing detailsReverse engineeringArray data structureSimple component
An efficient program analysis method is provided for lazily decomposing aggregates (such as records and arrays) into simpler components based on the access patterns specific to a given program. This process allows us both to identify implicit aggregate structure not evident from declarative information in the program, and to simplify the representation of declared aggregates when references are made only to a subset of their components. The method can be exploited to yield: (i) a fast type analysis method applicable to program maintenance applications (such as date usage inference for the Year 2000 problem); and (ii) an efficient method for atomization of aggregates. More specifically, aggregate atomization decomposes all of the data that can be manipulated by the program into a set of disjoint atoms such that each data reference can be modeled as one or more references to atoms without loss of semantic information. Aggregate atomization can be used to adapt program analyses and representations designed for scalar data to aggregate data. In particular, atomization can be used to build more precise versions of program representations such as SSA form or PDGs. Such representations can in turn yield more accurate results for problems such as program slicing. Our techniques are especially useful in weakly-typed languages such as Cobol (where a variable need not be declared as an aggregate to store an aggregate value) and in languages where references to statically-defined sub-ranges of data such as arrays or strings are allowed.
Owner:IBM CORP
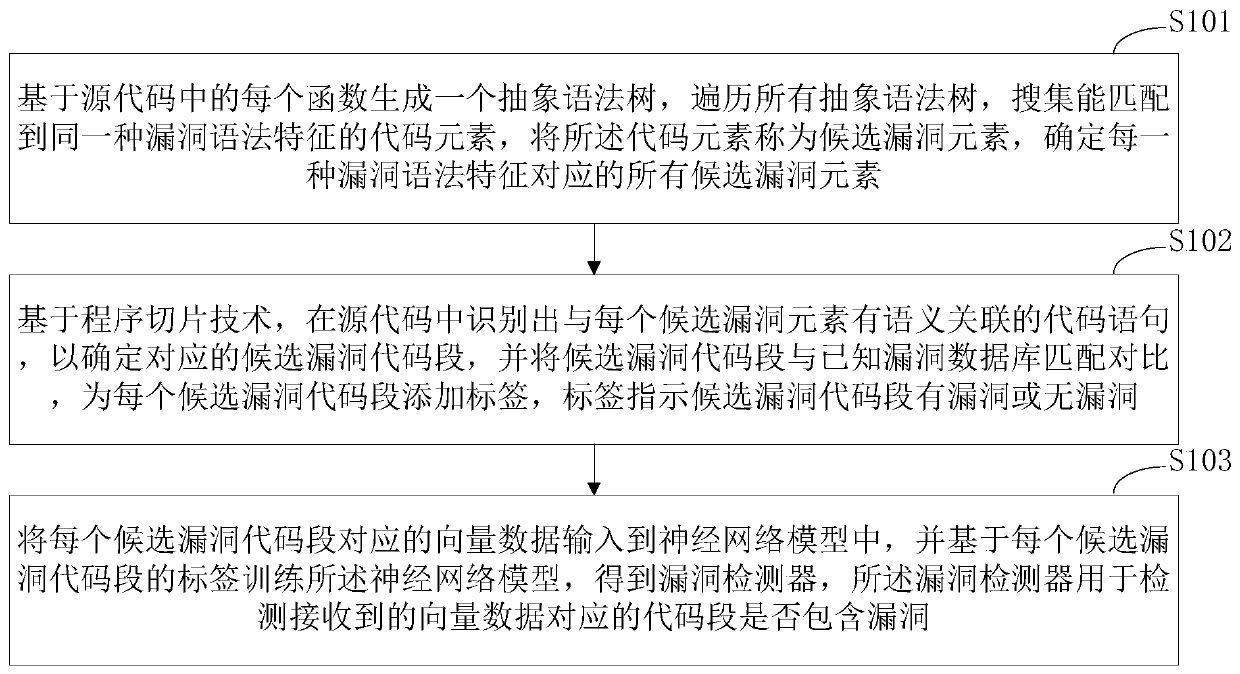
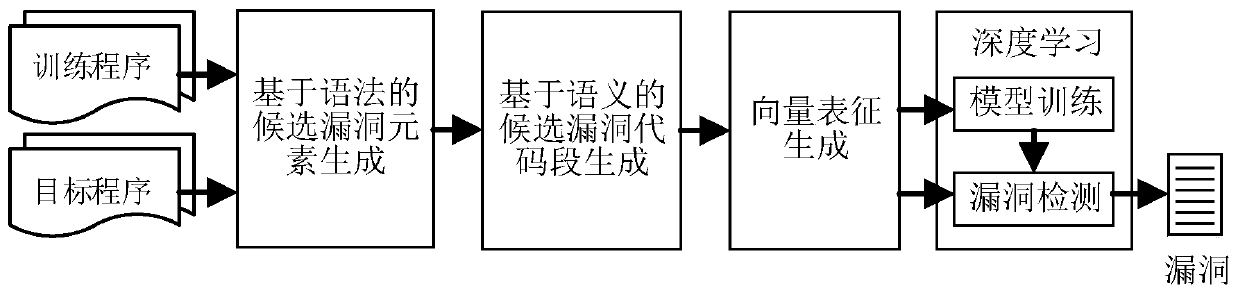
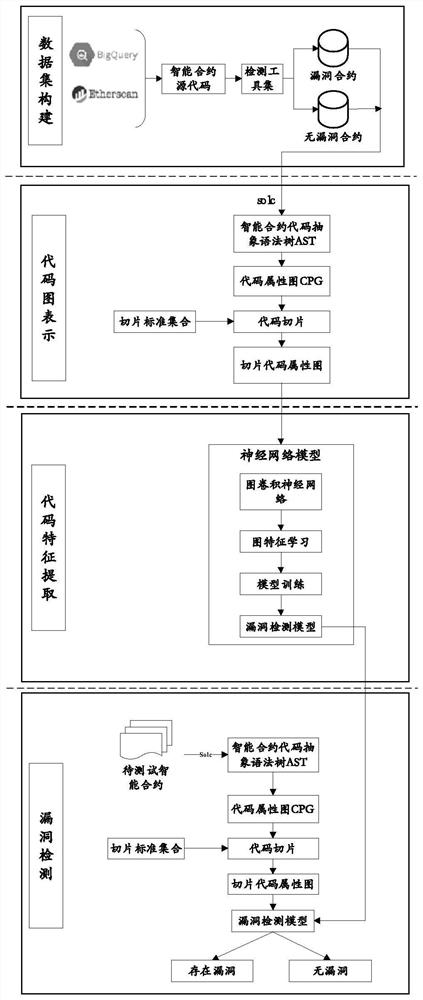
Source code vulnerability detection method, detector and training method and system thereof
ActiveCN110245496ATraining accuratelyImprove classification accuracyCharacter and pattern recognitionPlatform integrity maintainanceNerve networkCoded element
The invention discloses a source code vulnerability detection method, a detector and a training method and system thereof. The method comprises the steps of generating an abstract syntax tree based on each function in a source code, traversing all the abstract syntax trees, searching the code elements capable of being matched with the same vulnerability syntax feature, calling the code elements as the candidate vulnerability elements, and determining all the candidate vulnerability elements; based on a program slicing technology, identifying the code statements in semantic association with each candidate vulnerability element in the source code to determin the corresponding candidate vulnerability code segments, and adding the vulnerability labels to the candidate vulnerability code segments; and inputting the vector data corresponding to each candidate vulnerability code segment into a neural network model, and training the neural network model based on the label of each candidate vulnerability code segment to obtain a vulnerability detector. Based on the deep neural network, the vulnerability syntax features are extracted through a universal framework, the method is not limited to the vulnerability types and is high in expandability.
Owner:HUAZHONG UNIV OF SCI & TECH +1
System, Method, and Apparatus for Modular, String-Sensitive, Access Rights Analysis with Demand-Driven Precision
InactiveUS20100043048A1Reduce in quantityGood precisionPlatform integrity maintainanceTransmissionProgram slicingSoftware engineering
A static analysis for identification of permission-requirements on stack-inspection authorization systems is provided. The analysis employs functional modularity for improved scalability. To enhance precision, the analysis utilizes program slicing to detect the origin of each parameter passed to a security-sensitive function. Furthermore, since strings are essential when defining permissions, the analysis integrates a sophisticated string analysis that models string computations.
Owner:IBM CORP
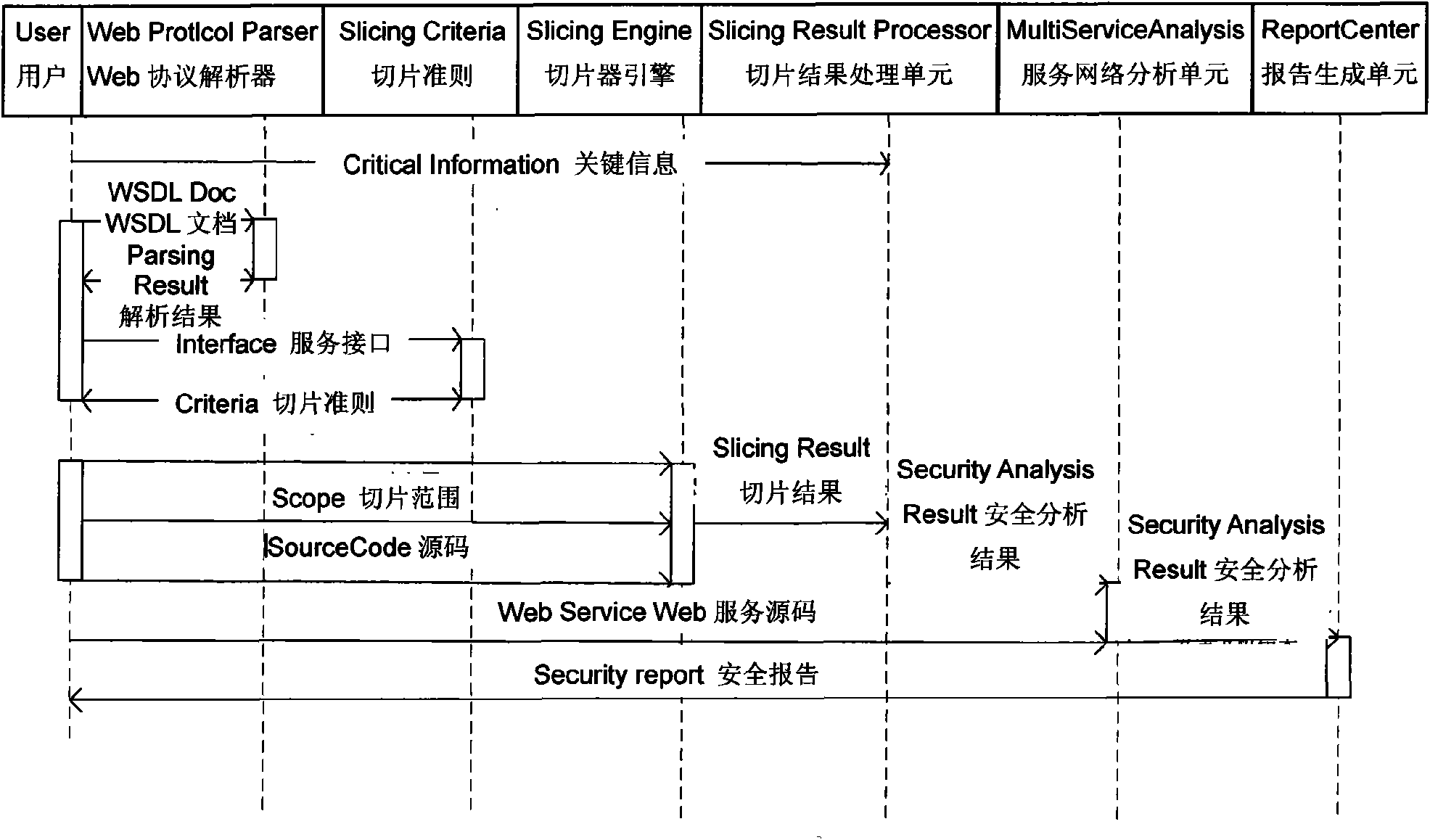
Web service security analysis method based on program slicing technique
InactiveCN102622556AImprove comprehensivenessReduce missed detectionPlatform integrity maintainanceResearch ObjectProgram slicing
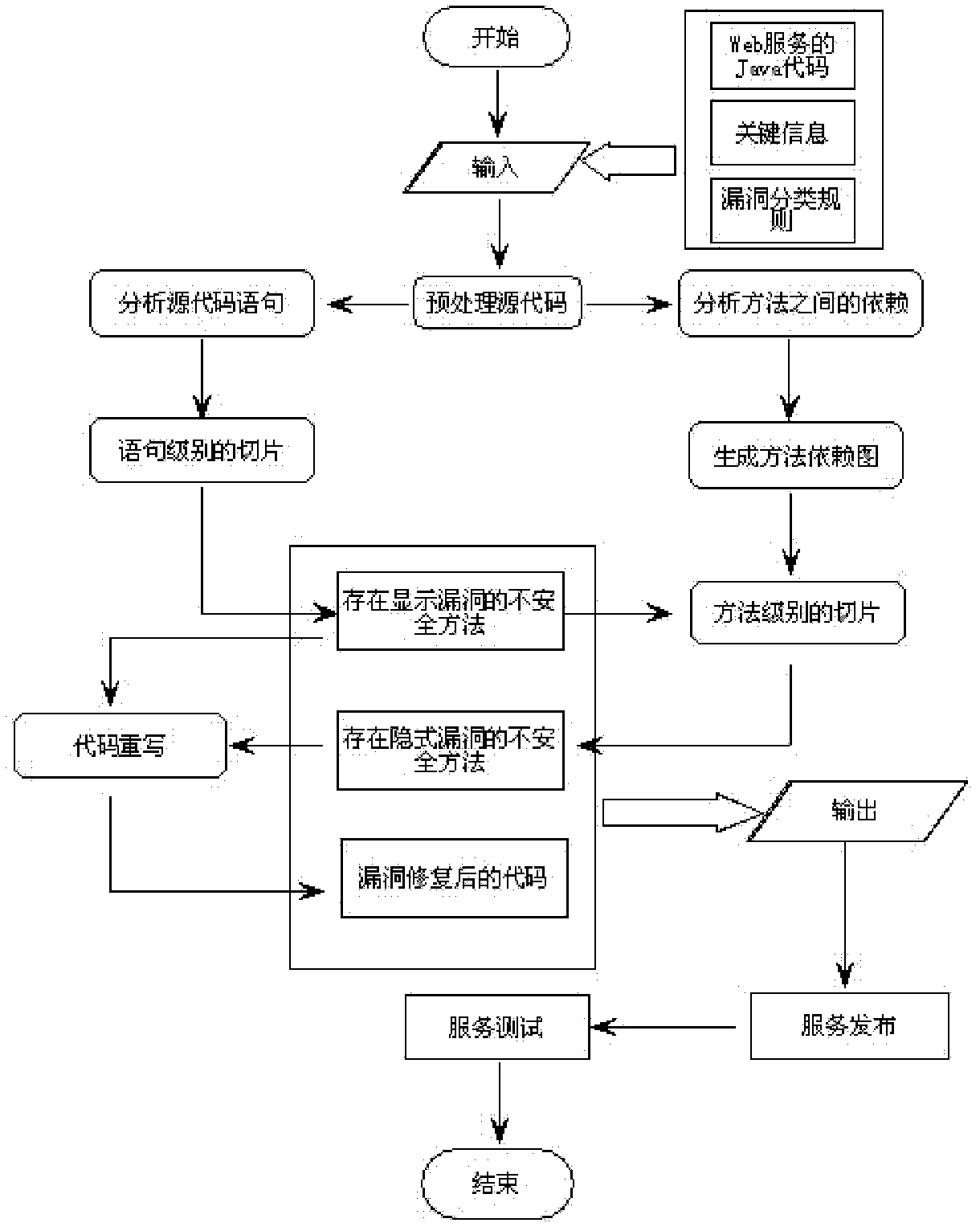
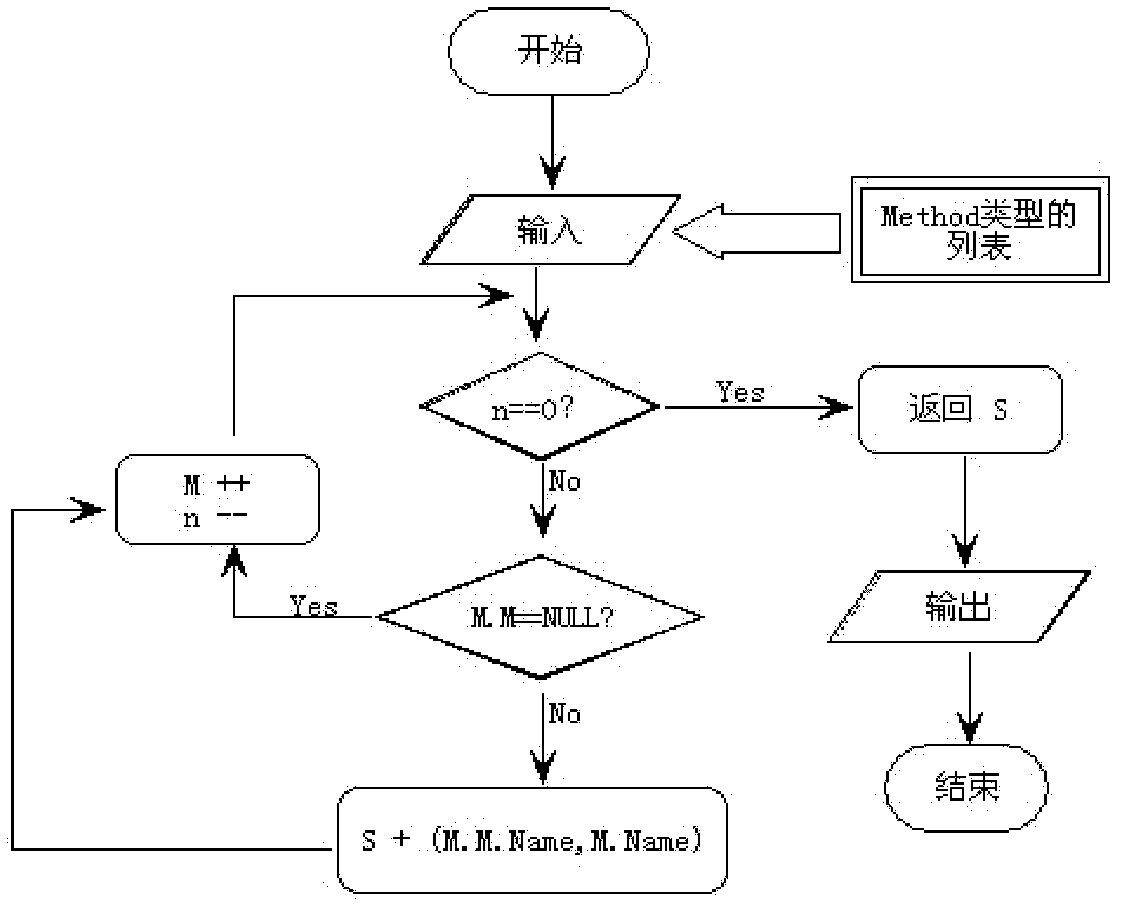
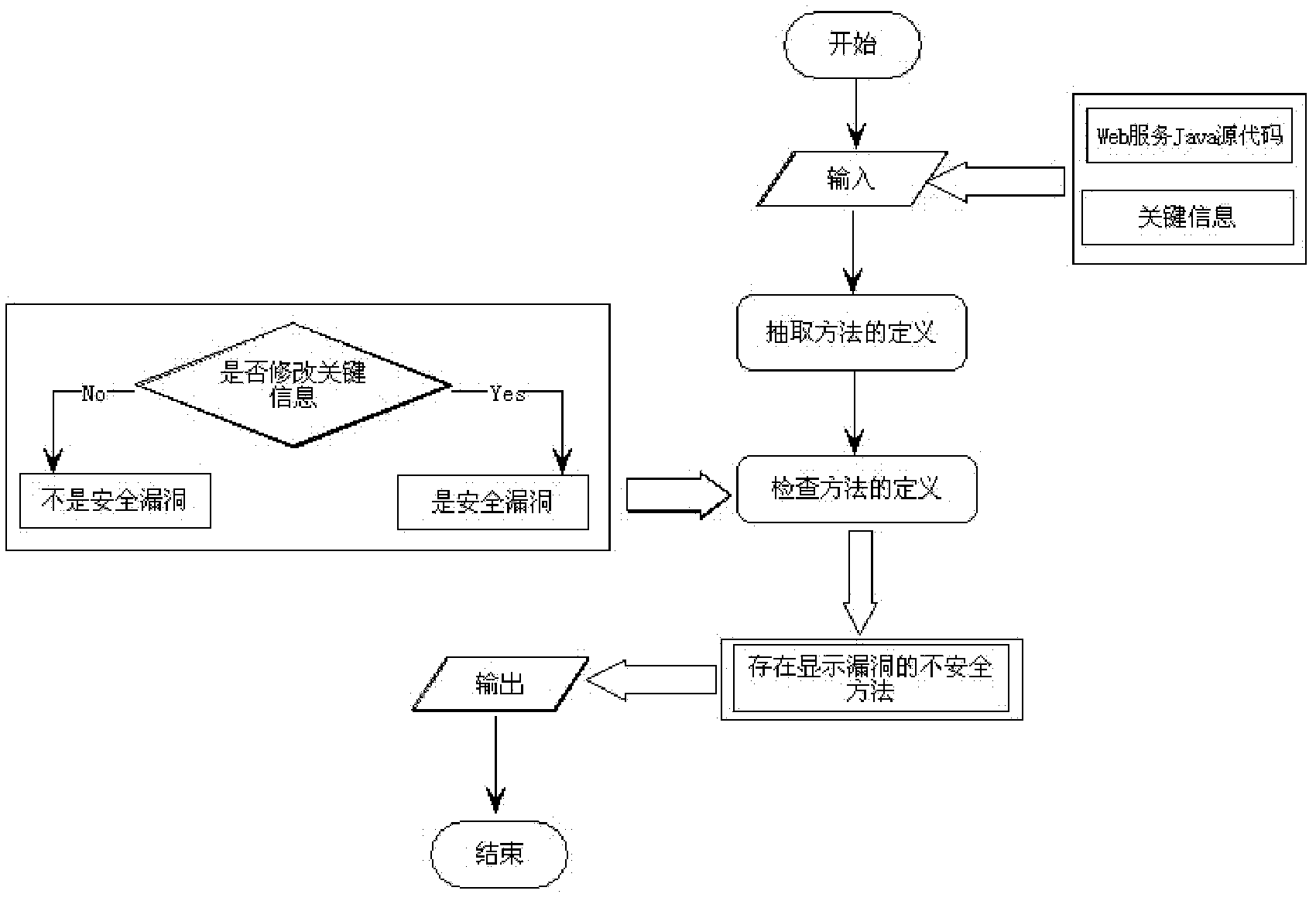
The invention provides a web service security analysis method based on a program slicing technique. Starting from key information in a Java source code, the method mainly researches on web services developed based on Java, and vulnerabilities in the Java source code include explicit vulnerabilities and implicit vulnerabilities. For the explicit vulnerabilities, the source code can be analyzed and extracted through traditional statement-level slices to obtain an explicit vulnerability analysis result. For the implicit vulnerabilities, dependency of methods in the source code is analyzed first to generate a method dependency graph, and method-level slices are used to slice the method dependency graph to obtain an implicit vulnerability analysis result. According to analysis on the explicit and implicit vulnerabilities, a vulnerability fixing module is used to fix the vulnerabilities and a service issuing module is used to issue fixed web services.
Owner:NANJING UNIV OF POSTS & TELECOMM
Static defect detection method of application program slicing technology
InactiveCN102110051AMeet the conservatismImprove defect detection efficiencySoftware testing/debuggingPathPingProgram slicing
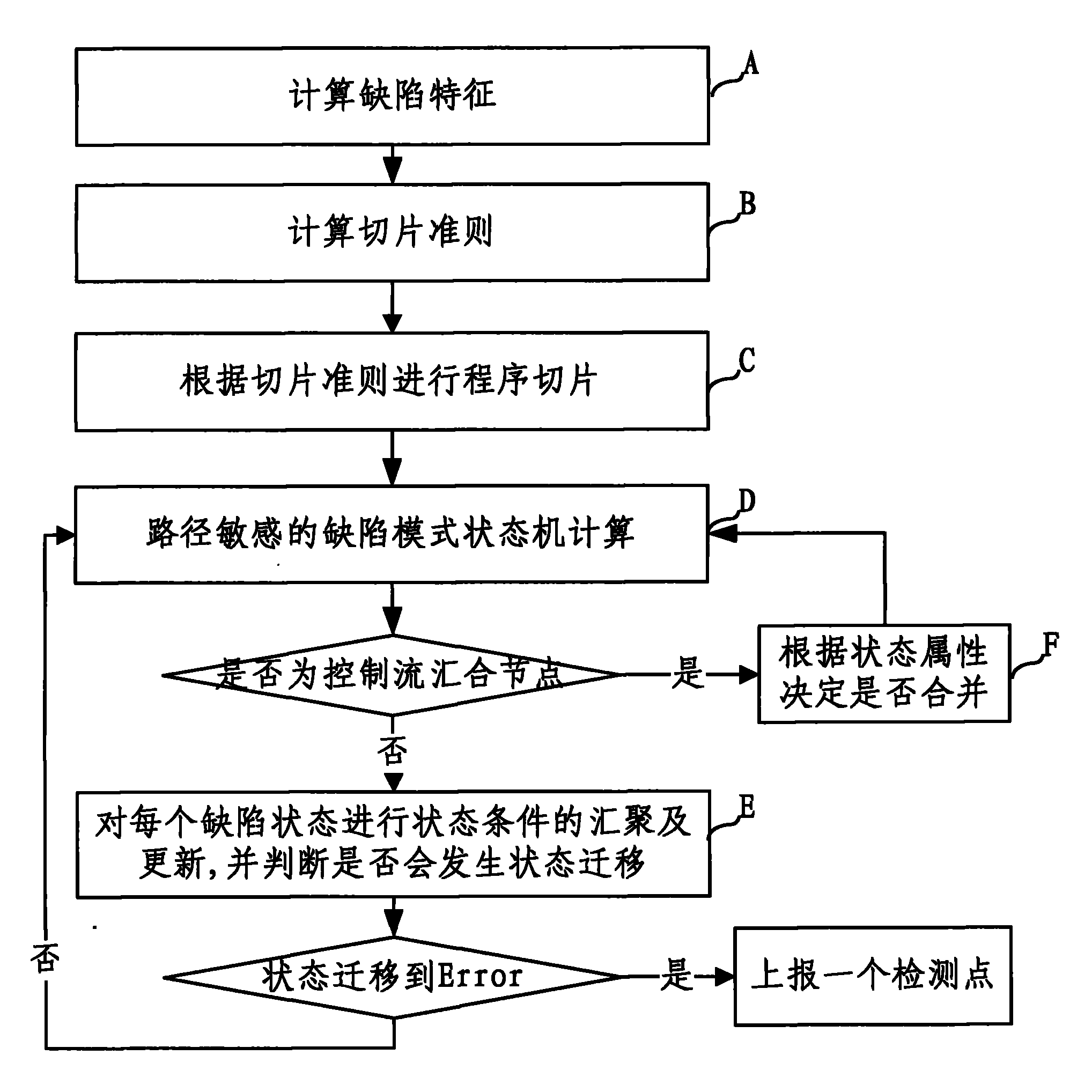
The invention discloses a static defect detection method of an application program slicing technology, which comprises the following steps of: A, acquiring defect characteristics of a defect mode to be detected; B, calculating path conditions of all branch nodes according to the defect characteristics, and generating slicing criteria; C, traversing a control flow graph according to the slicing criteria to perform program slicing, and reconstructing the control flow graph to obtain a reconstructed control flow graph; D, performing defect mode state machine calculation by using the reconstructed control flow graph and using a defect state iterative algorithm; E, if the current control flow graph node is a non-convergence node, converging and updating the state conditions in all defect states; and F, if the current control flow graph node is a convergence node, merging the states according to the state condition of the current defect state. By adopting the method, the defect detection efficiency can be improved to certain degree, and misinformation of a path merging strategy-based path sensitivity detection method is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Function-level code vulnerability detection method based on slice attribute graph representation learning
ActiveCN112699377AIncrease coverageReduce false positivesPlatform integrity maintainanceRelation graphProgram slicing
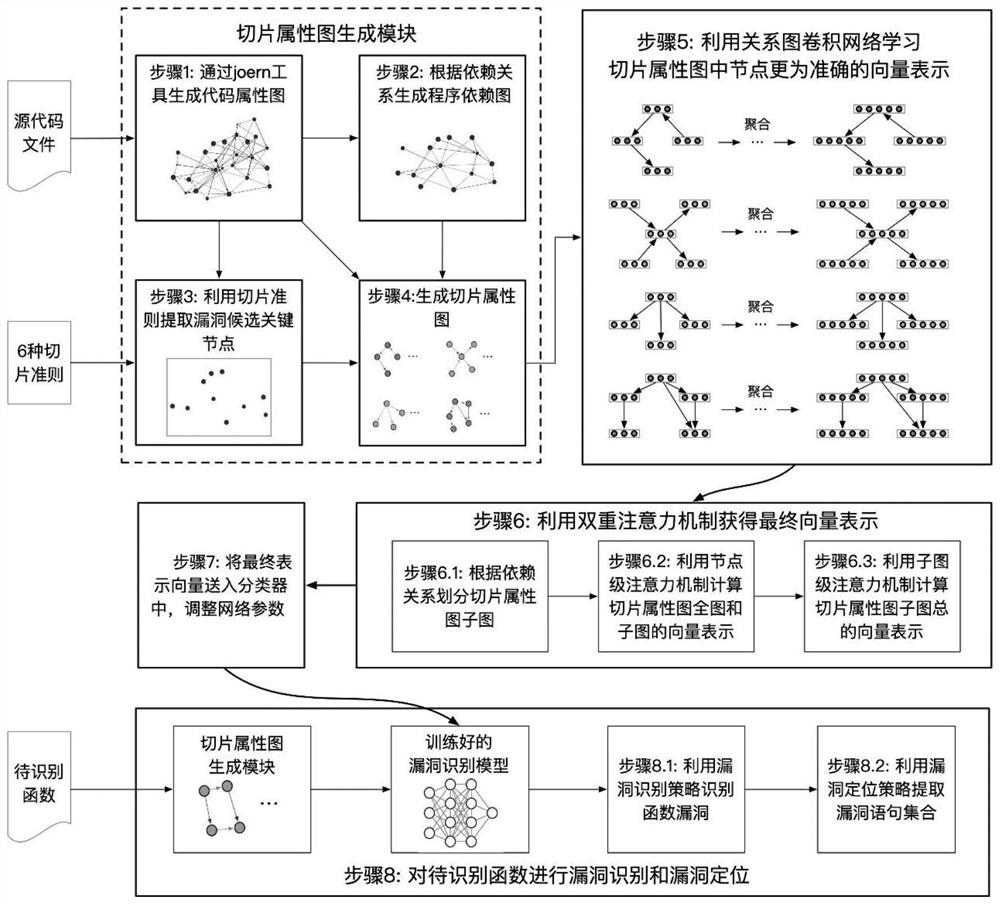
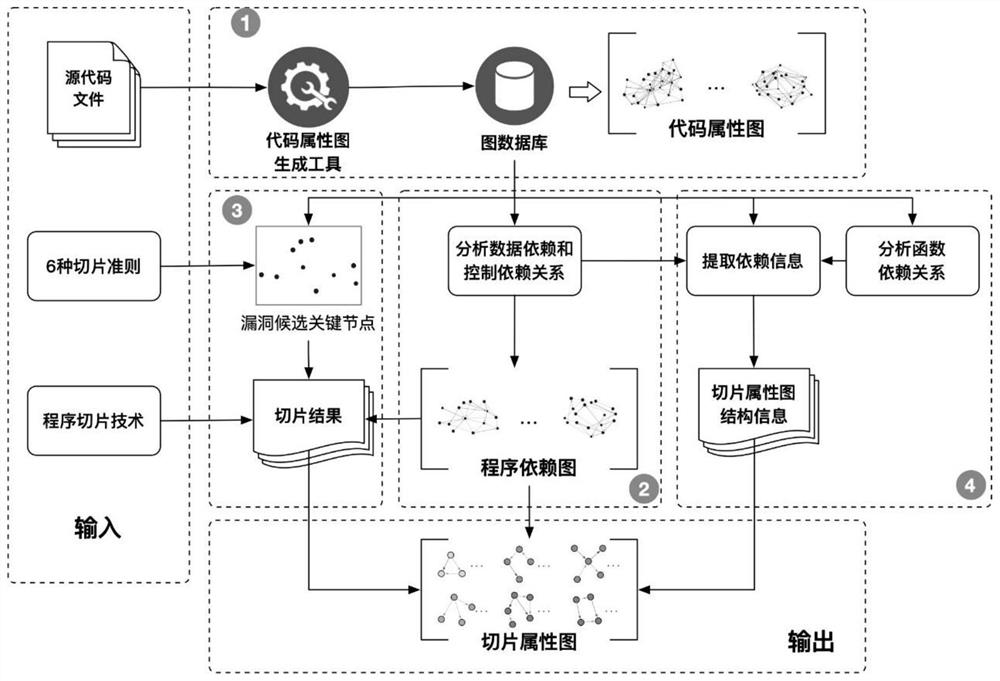
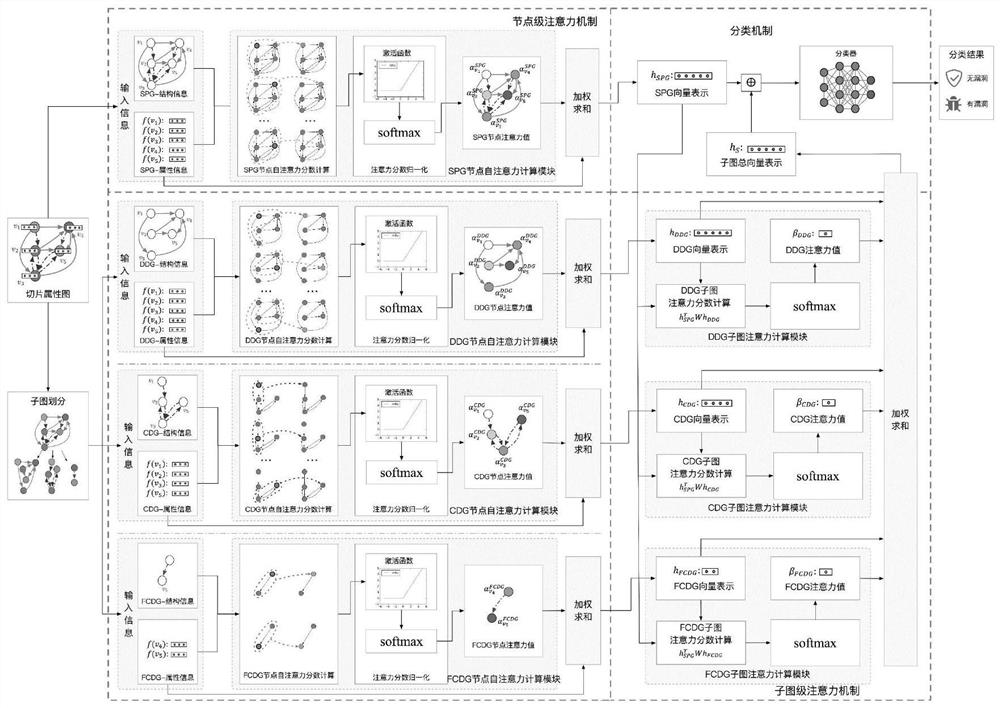
The invention discloses a function-level code vulnerability detection method based on slice attribute graph representation learning, and the method comprises the steps: firstly introducing a new slice criterion, proposing the concept of a slice attribute graph, and generating a slice attribute graph of a code based on the slice criterion and a program slice technology; extracting graph structure information, node attribute information and code context information which have a dependency relationship with the vulnerability candidate key points; then, performing representation learning on the slice attribute graph by utilizing a relation graph convolutional neural network and combining a dual attention mechanism based on nodes and sub-graphs so as to learn a more comprehensive and accurate vulnerability mode; and finally, fusing the vulnerability identification results of the slice attribute graphs to realize function-level vulnerability detection, and determining a set of vulnerability candidate statements and grammatical elements associated with vulnerabilities. More vulnerability candidate key points can be covered, structures, attributes and context information related to vulnerabilities are fully learned and expressed, and the vulnerability detection accuracy is improved.
Owner:HARBIN INST OF TECH
Method and system for detecting synchronization errors in programs
InactiveUS20080201629A1Error detection/correctionSpecific program execution arrangementsProgram slicingPath expression
A method and system for error detection in programs with collective synchronization and / or procedures are provided. In one aspect, the method and system may use interprocedural analysis for matching synchronizations in a program in order to detect synchronization errors, and, if no such errors exist, may determine the synchronization phases of the program. The method and system in one aspect may use a combination of path expressions and interprocedural program slicing to match the synchronization statements that may execute along each program path. If the synchronization matching succeeds, the method and system in one aspect may determine the sets of synchronization statements that synchronize together. A matching failure may indicate the presence of a synchronization error and the method and system in one aspect may construct a counter example to illustrate the error.
Owner:GLOBALFOUNDRIES INC
Method for optimizing integrated circuit device design and service
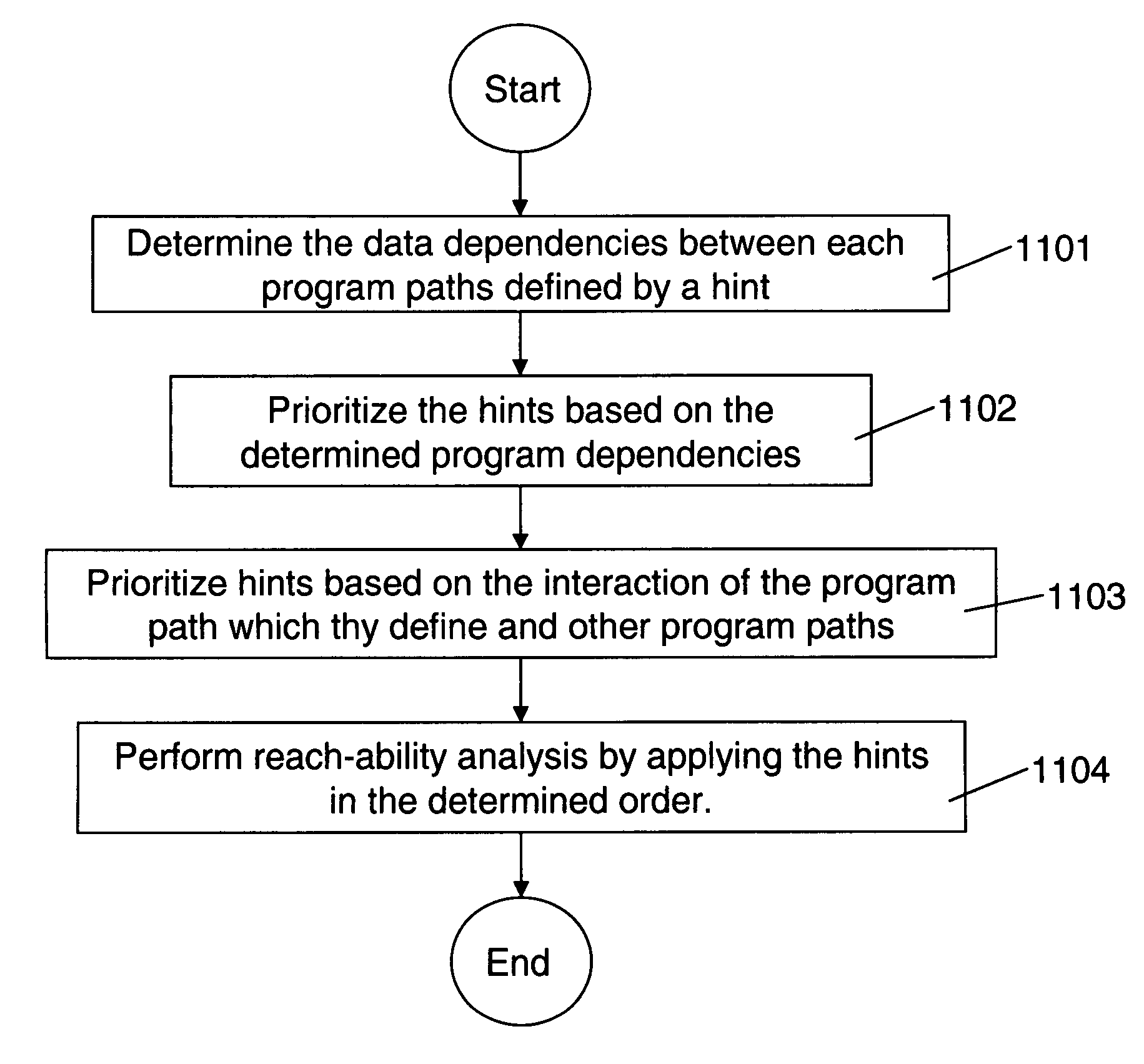
InactiveUS20070089075A1Computer aided designSoftware simulation/interpretation/emulationComputer architectureProgram slicing
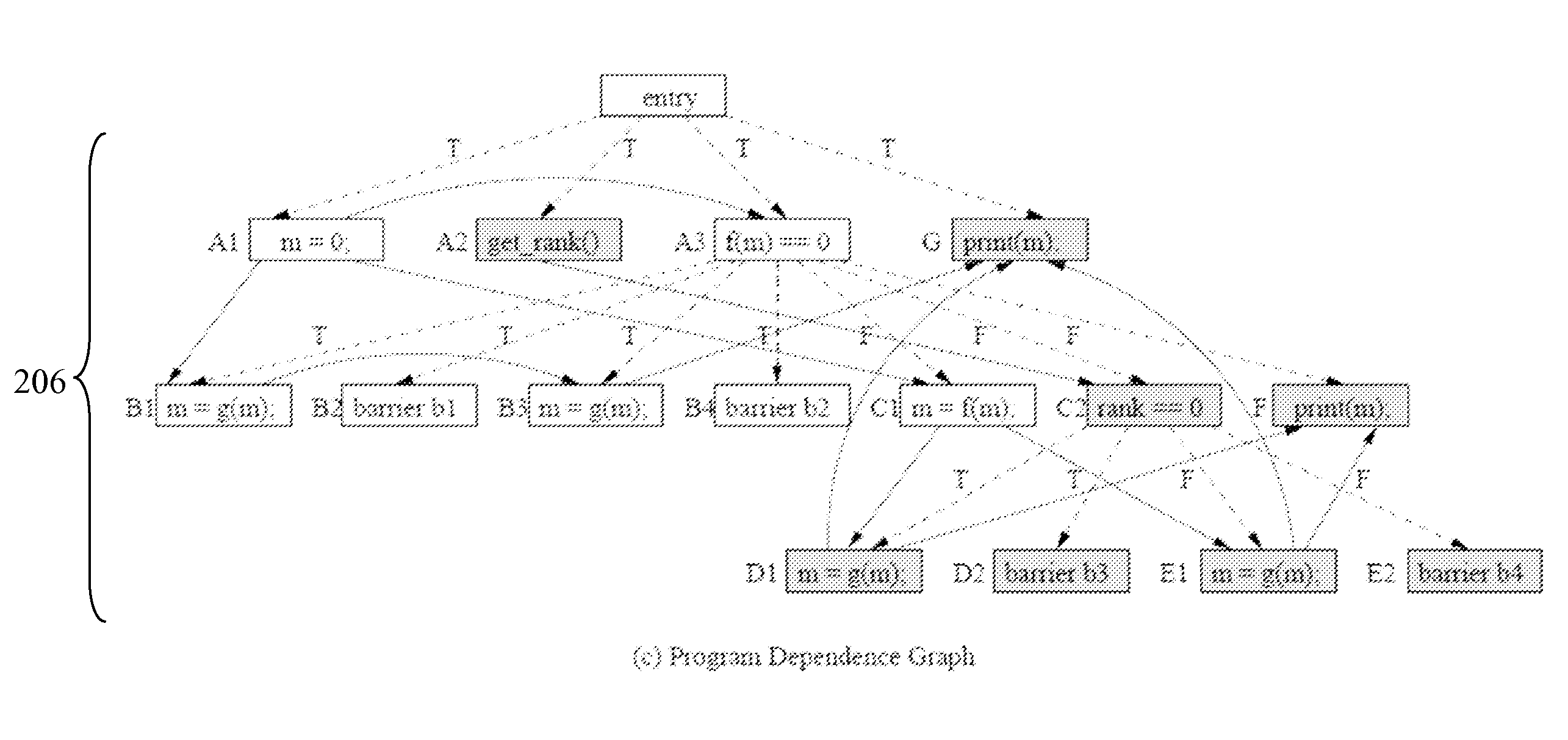
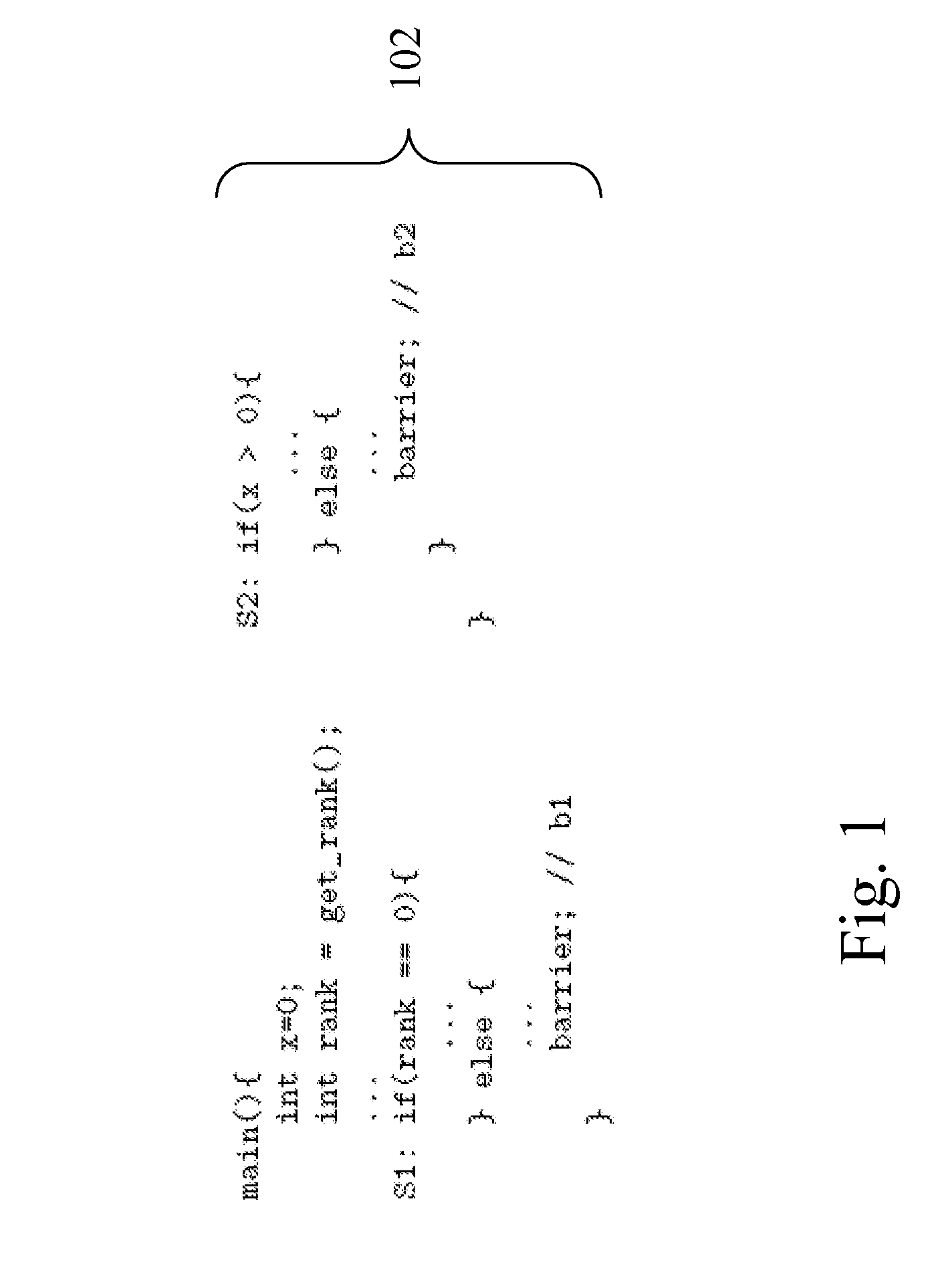
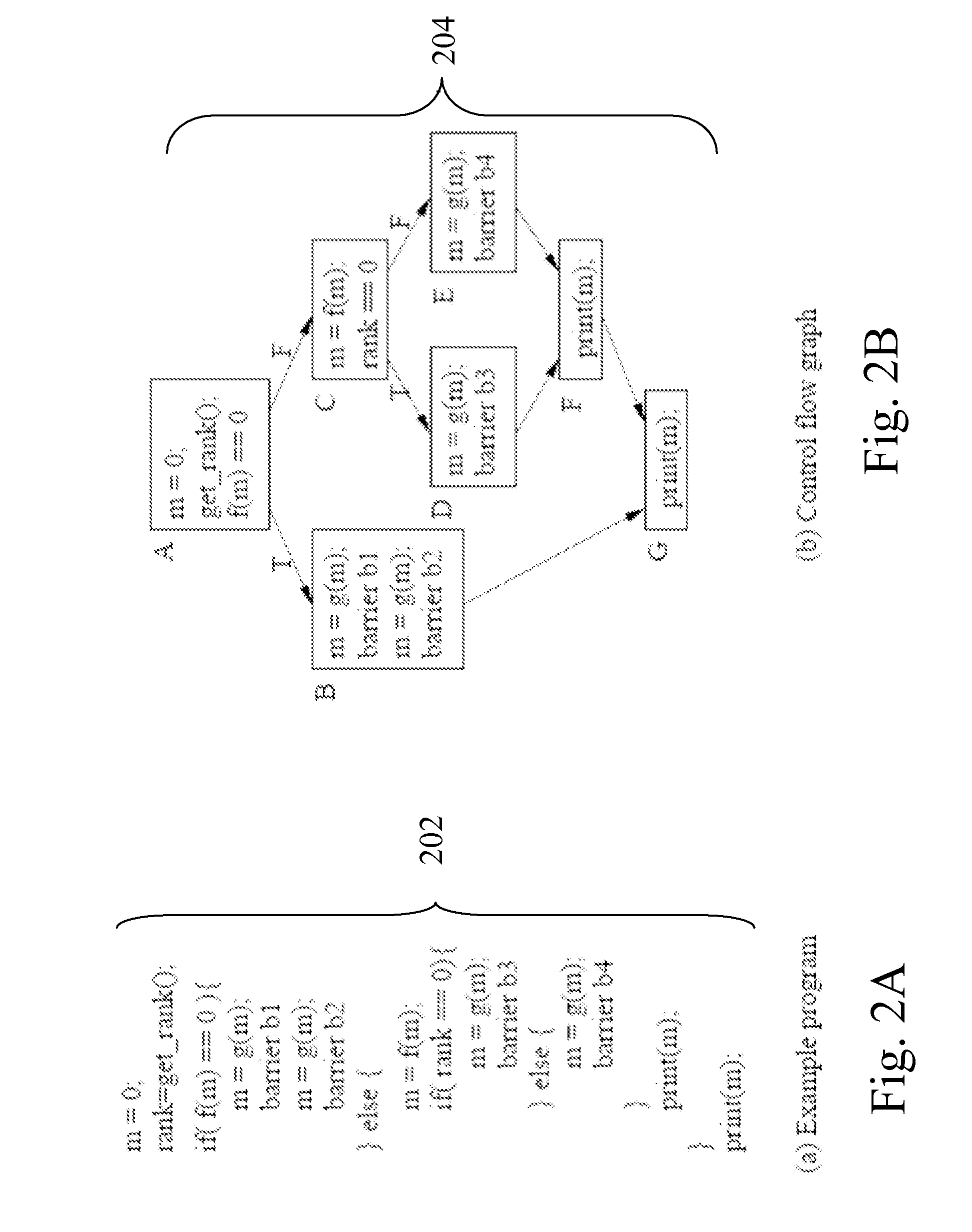
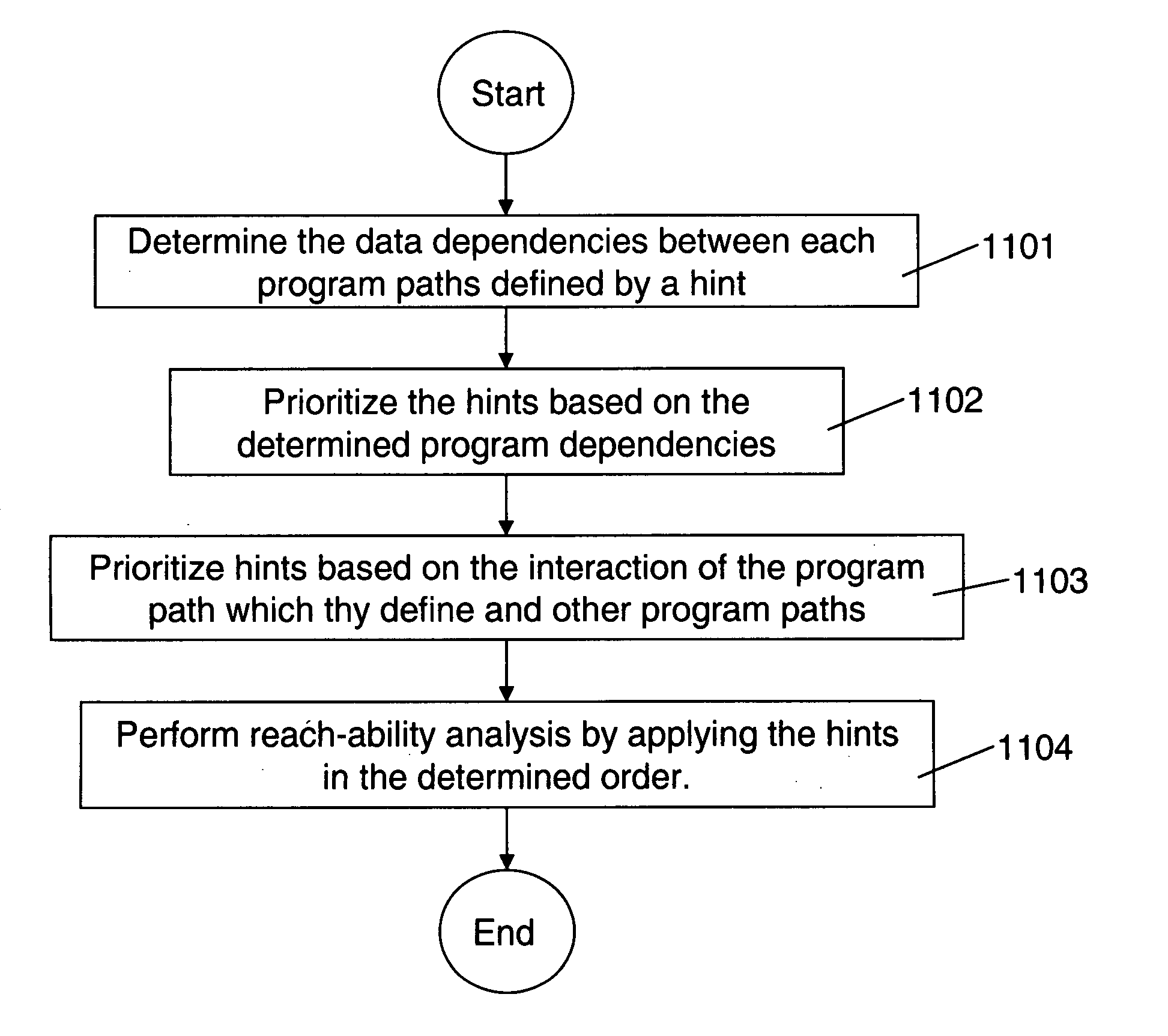
Improved analysis and refinement of integrated circuit device design and other programs is facilitated by methods in reach-ability analysis is performed using hints which define a particular path through a program. To ensure that a reasonable number of states are reached during reach-ability analysis a order to apply the hints is determined. The ordering prioritizes hints which define program paths which set a given variable over hints which define program slice which use the given variable.
Owner:IBM CORP
Software safety testing method based on program slicing
ActiveCN104572476ADoesn't hurt debuggabilityOptimize compile timeSoftware testing/debuggingTest efficiencyProgram slicing
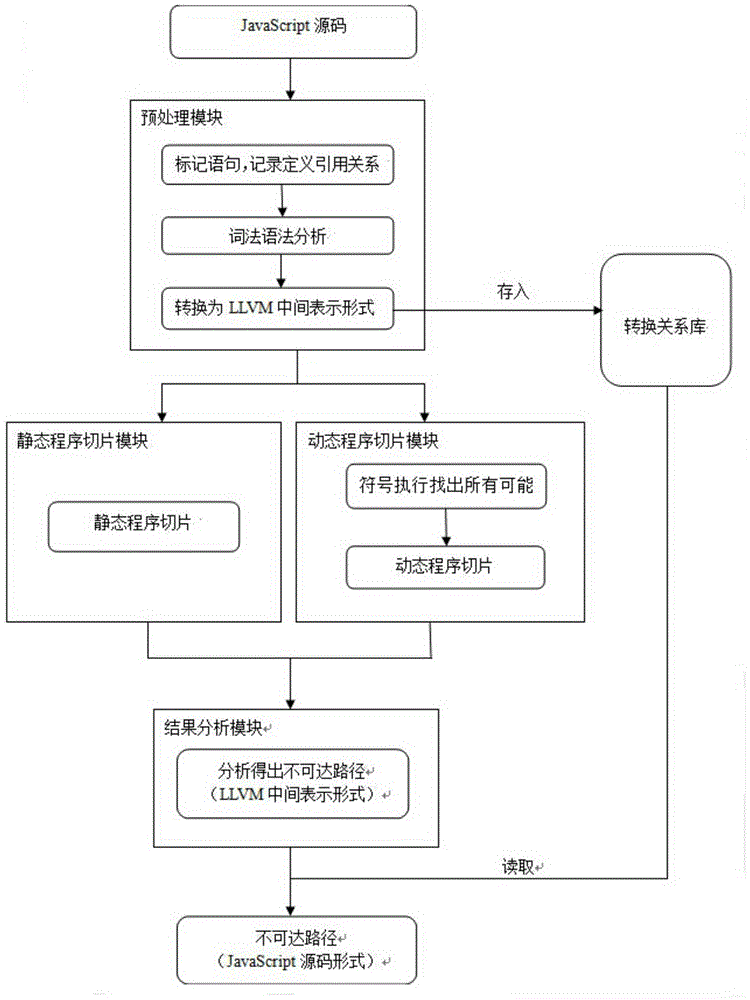
The invention provides a software safety testing method based on program slicing. By the method, a program slicing technology is discussed, and an unreachable path detecting scheme based on program slicing is raised. The software safety testing method comprises the following steps of inputting JavaScript language codes extracted from a webpage; converting the JavaScript language codes into LLVM (low level virtual machine) intermediate representation; and respectively performing static program slicing and dynamic program slicing on the LLVM intermediate representation. Inputting of programs is not assumed during static program slicing, analysis is based on static information of the programs completely, and a slicing result contains an unreachable path. In dynamic program slicing, a path behavior carried out under certain specific inputting is concerned, and path behaviors caused by all possible inputting of variables are not concerned, so that a dynamic slicing result does not contain the unreachable path. By the combination of the static program slicing and the dynamic program slicing, the unreachable path in the program can be detected, so that the testing efficiency of software is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method of tracing software abnormal behaviors based on software functional layer
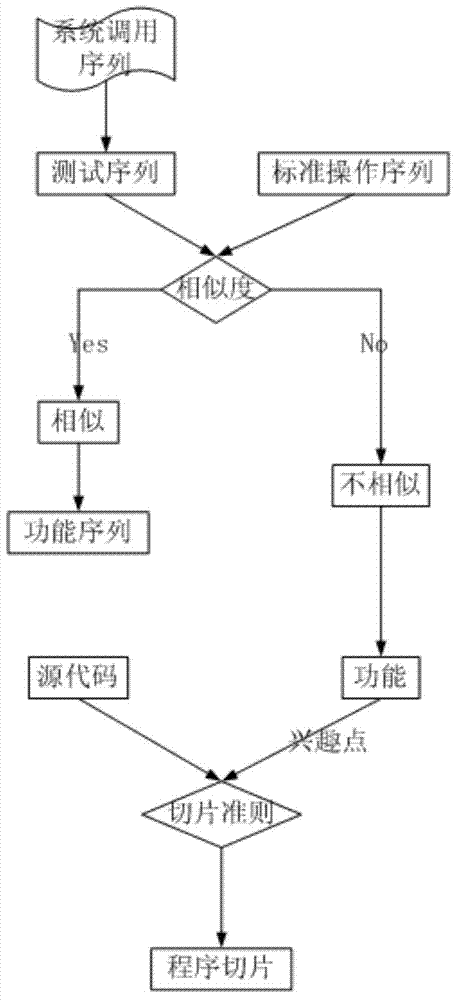
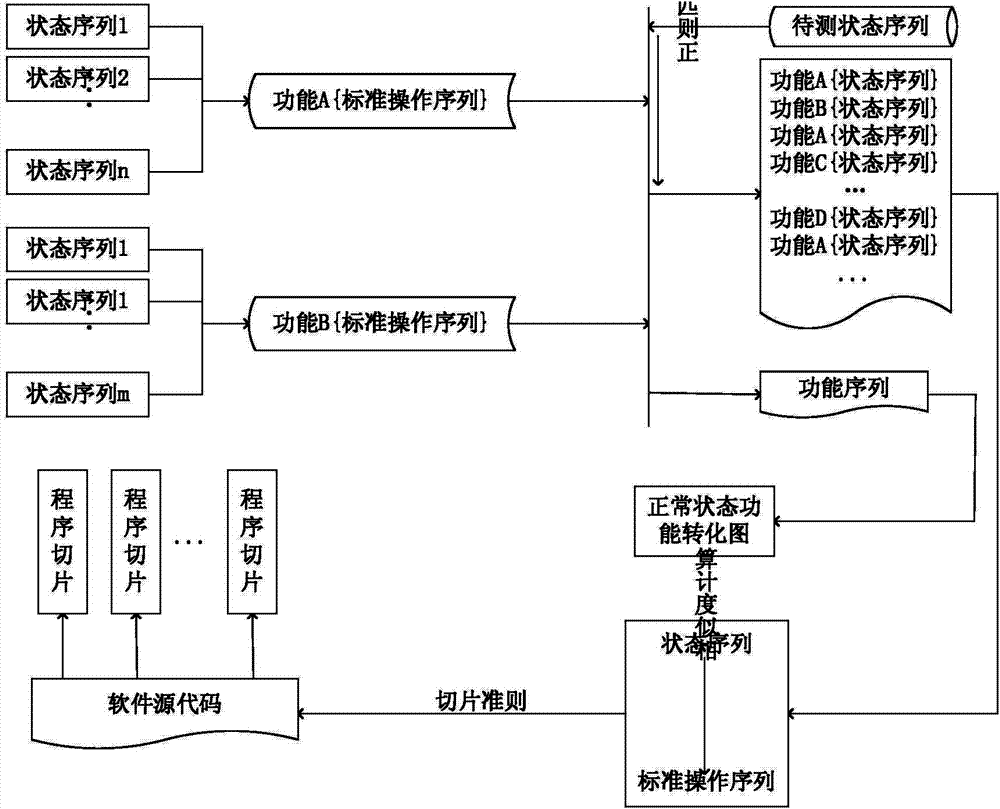
InactiveCN103744786AAbnormal Behavior ResolutionSoftware testing/debuggingProgram slicingState model
Owner:BEIJING UNIV OF TECH
Method for optimizing integrated circuit device design and service
InactiveUS7788646B2Computer aided designSoftware simulation/interpretation/emulationProgram slicingComputer architecture
Improved analysis and refinement of integrated circuit device design and other programs is facilitated by methods in reach-ability analysis is performed using hints which define a particular path through a program. To ensure that a reasonable number of states are reached during reach-ability analysis a order to apply the hints is determined. The ordering prioritizes hints which define program paths which set a given variable over hints which define program slice which use the given variable.
Owner:INT BUSINESS MASCH CORP
Method for test case reduction based on program behavior slices
InactiveUS20150363305A1Ensuring validityReduce in quantitySoftware testing/debuggingSpecific program execution arrangementsControl flowProgram slicing
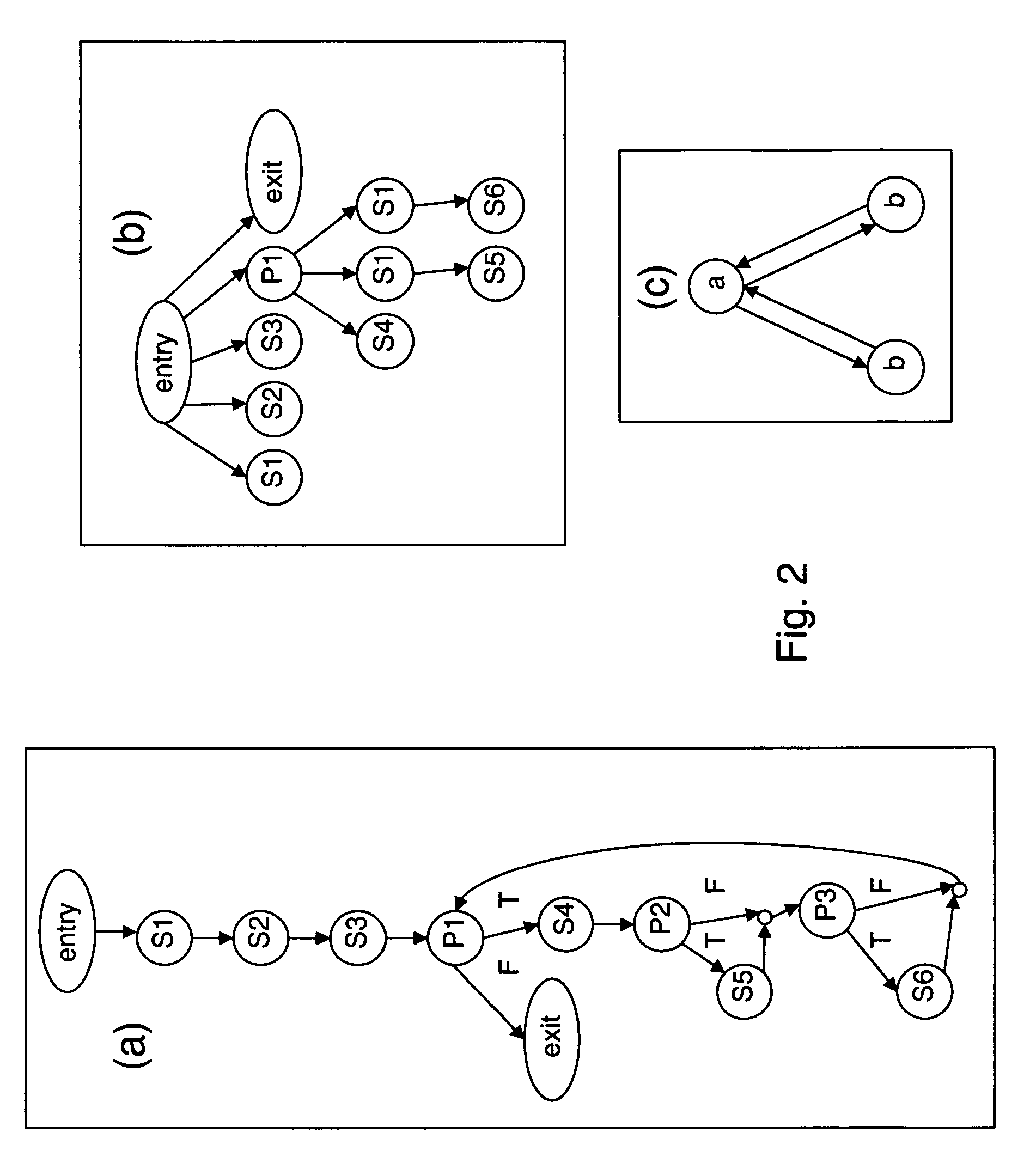
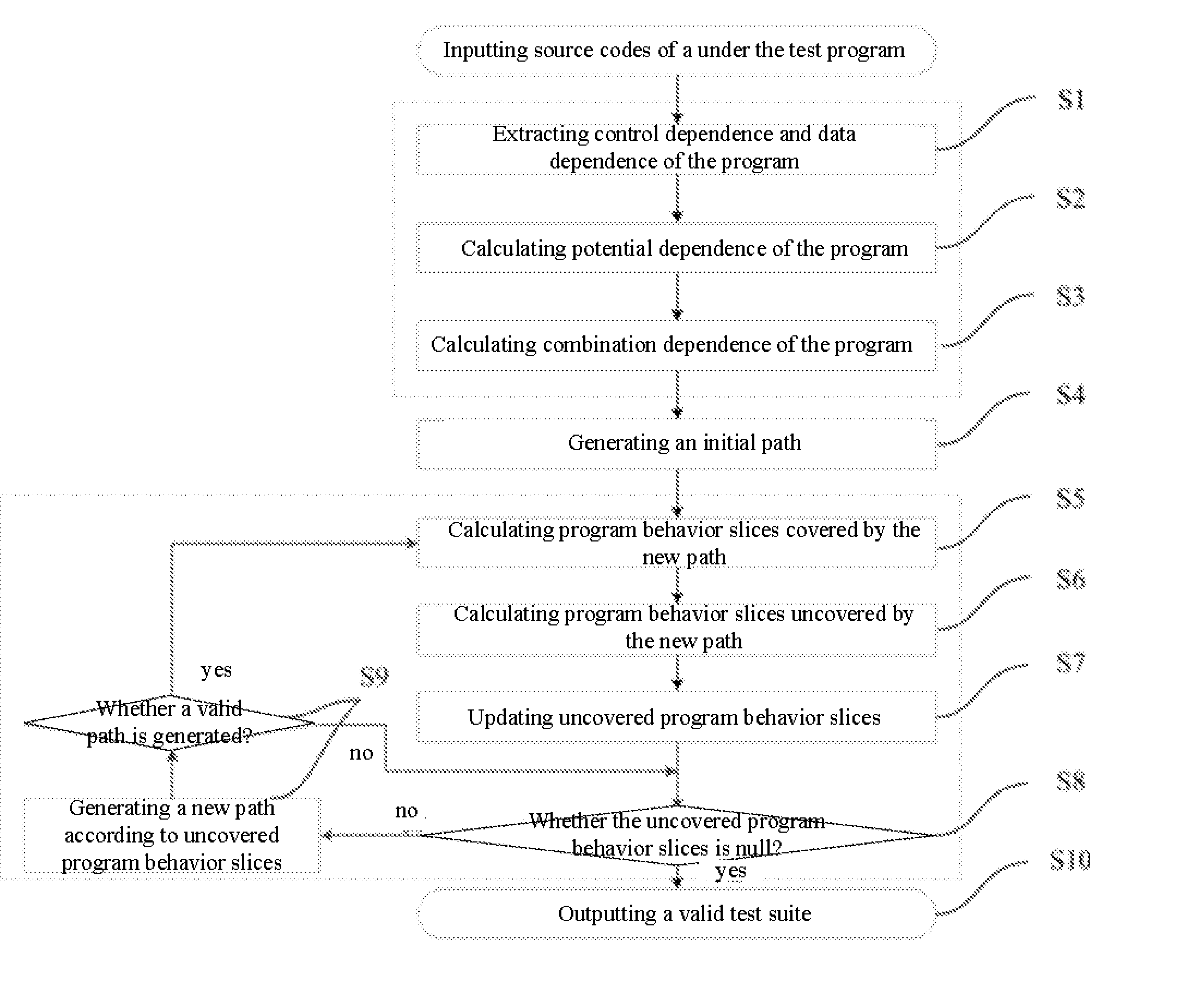
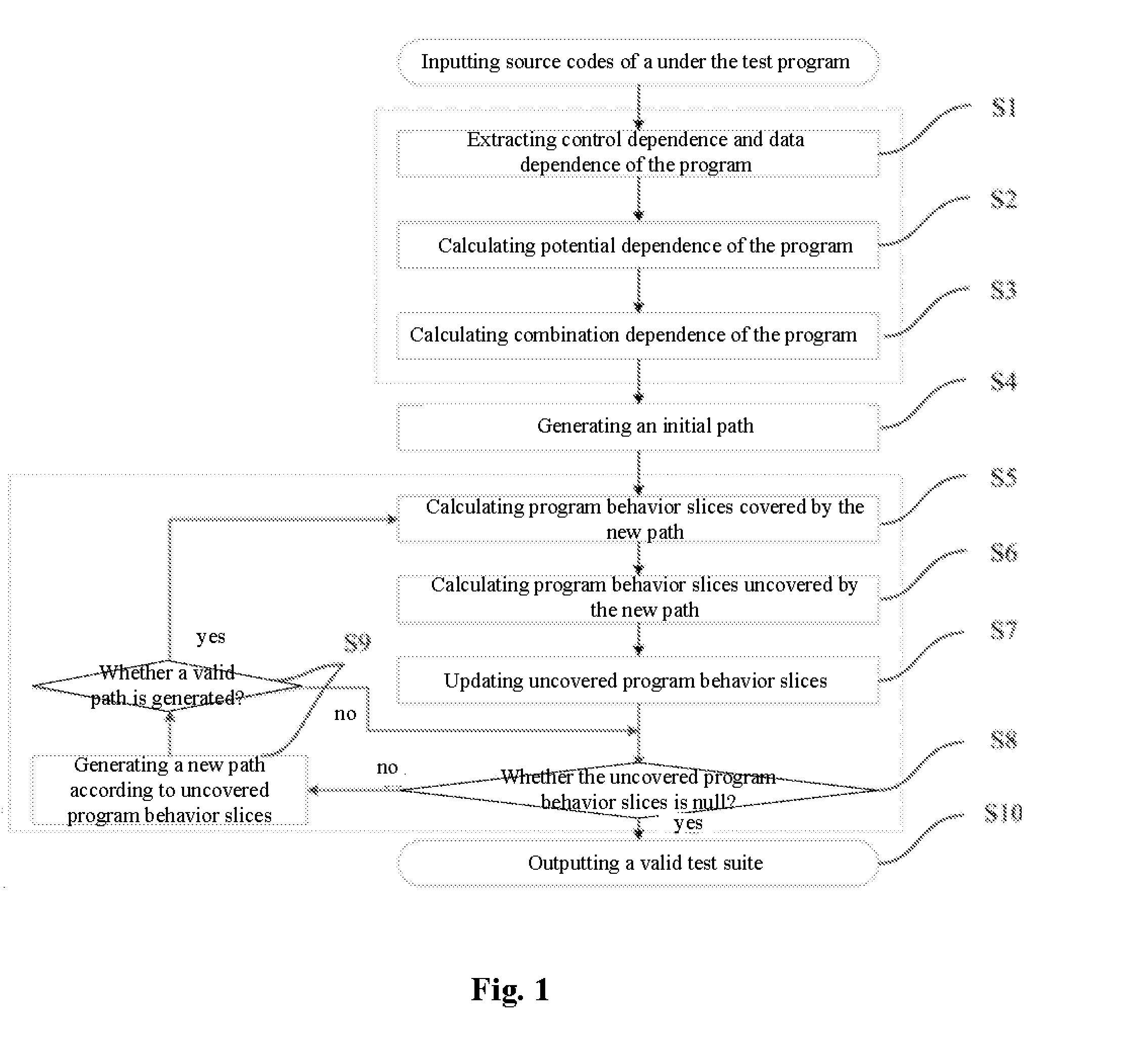
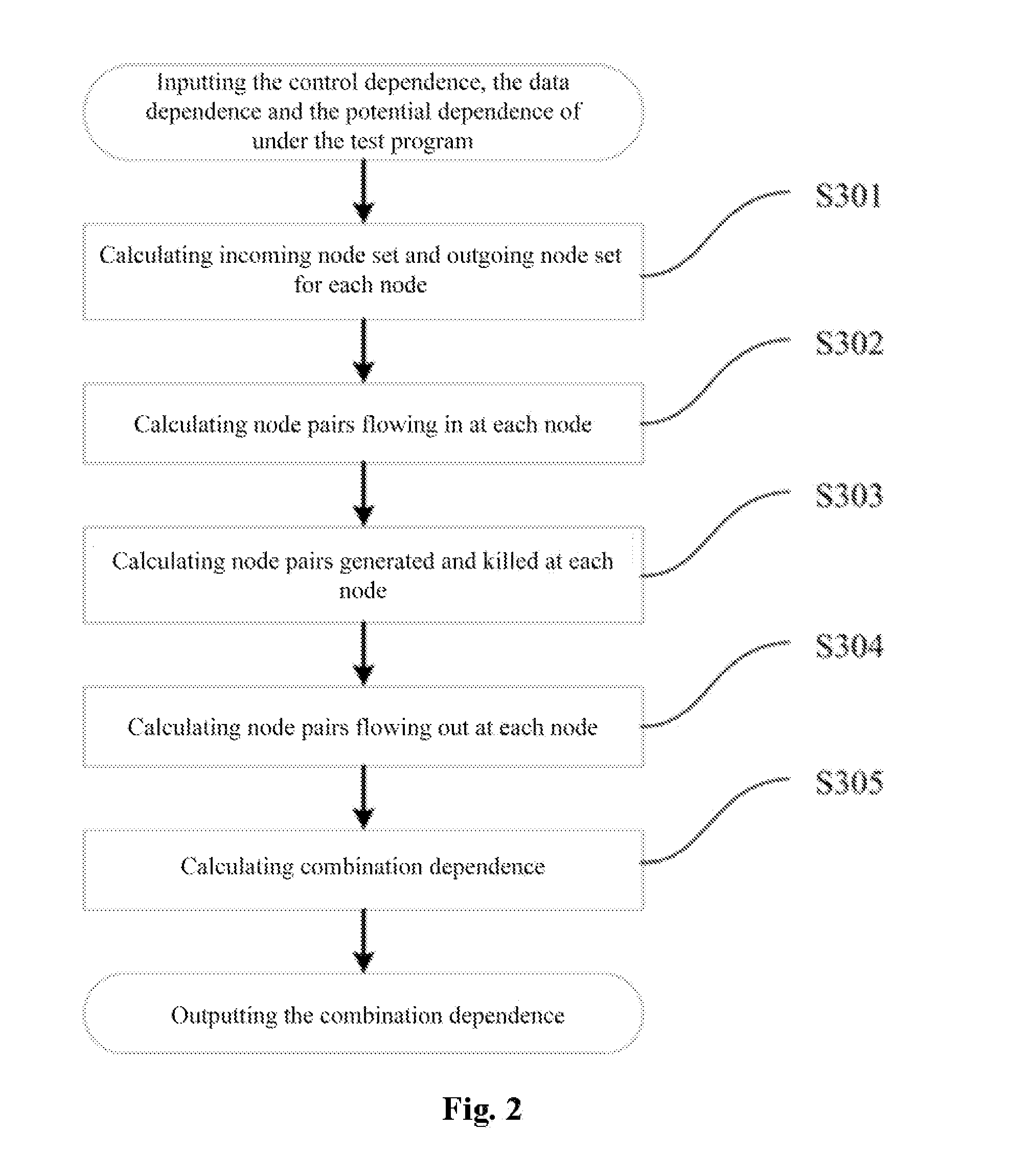
The present invention provides a method of test cases reduction based on program behavior slices. In the case that there is no need to scan all program paths, a test suite capable of covering all program behaviors is generated to relieve the state-space explosion problem confronted by program tests. In the present invention, during a static analysis stage, analyzing a control flow and an information flow of a program according to input program codes, extracting control dependence and data dependence of the program; calculating potential dependence of the program according to the control dependence and the data dependence of the program; on the basis of the control dependence, the data dependence and the potential dependence, constructing combination dependence of the program; during a dynamic execution stage, according to an execution path and the dependence relation, calculating program behavior slices covered by the path and program behavior slices uncovered by the path, and guiding symbolic execution to generate a path capable of covering new program slices according to the uncovered program behavior slices. Compared with the existing symbolic execution technique, the present invention can ensure the validity of the test suite, while at the same time reducing the number of the generated test cases remarkably.
Owner:XI AN JIAOTONG UNIV
Software vulnerability intelligent detection and positioning method and system based on intermediate language
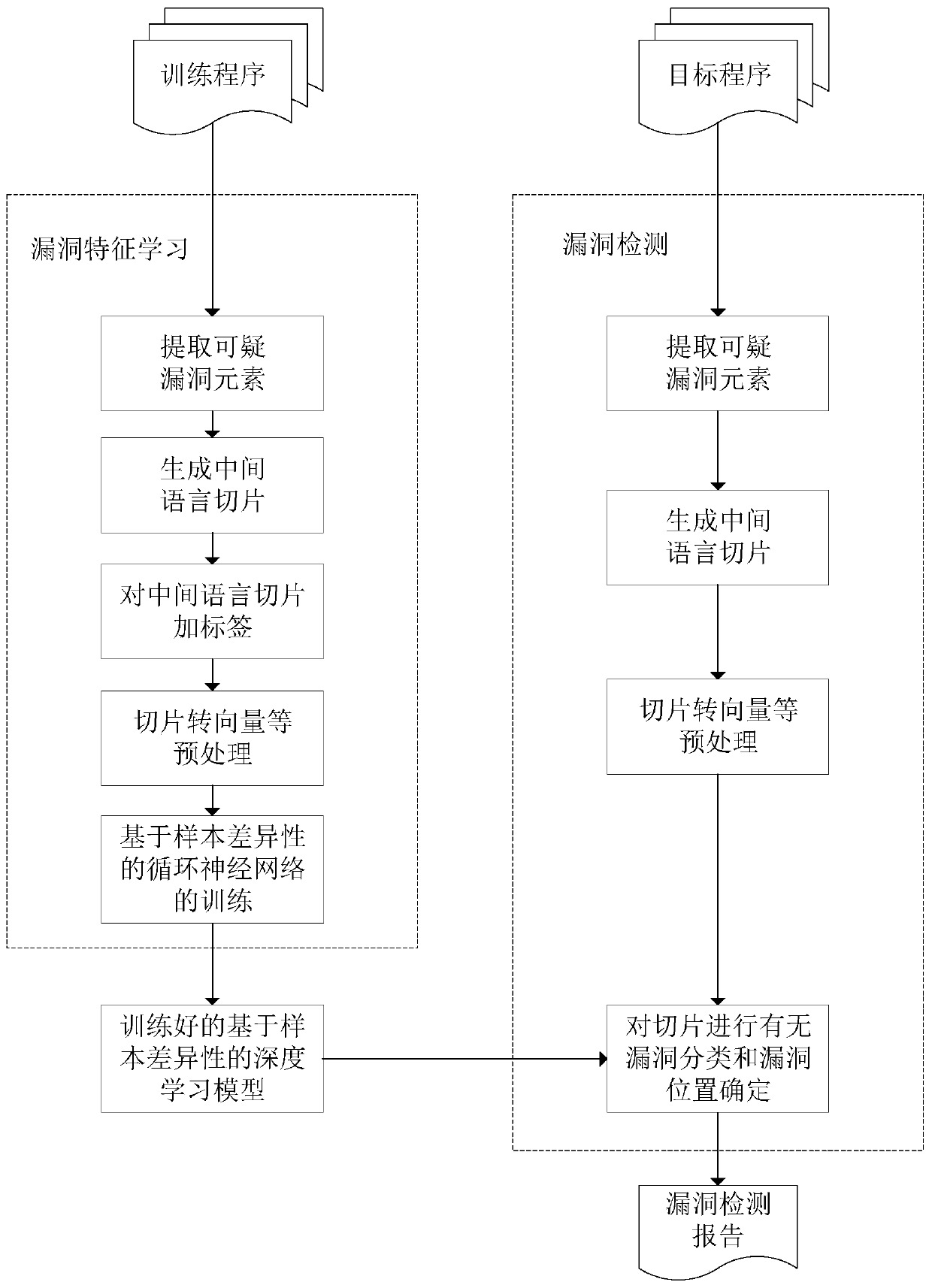
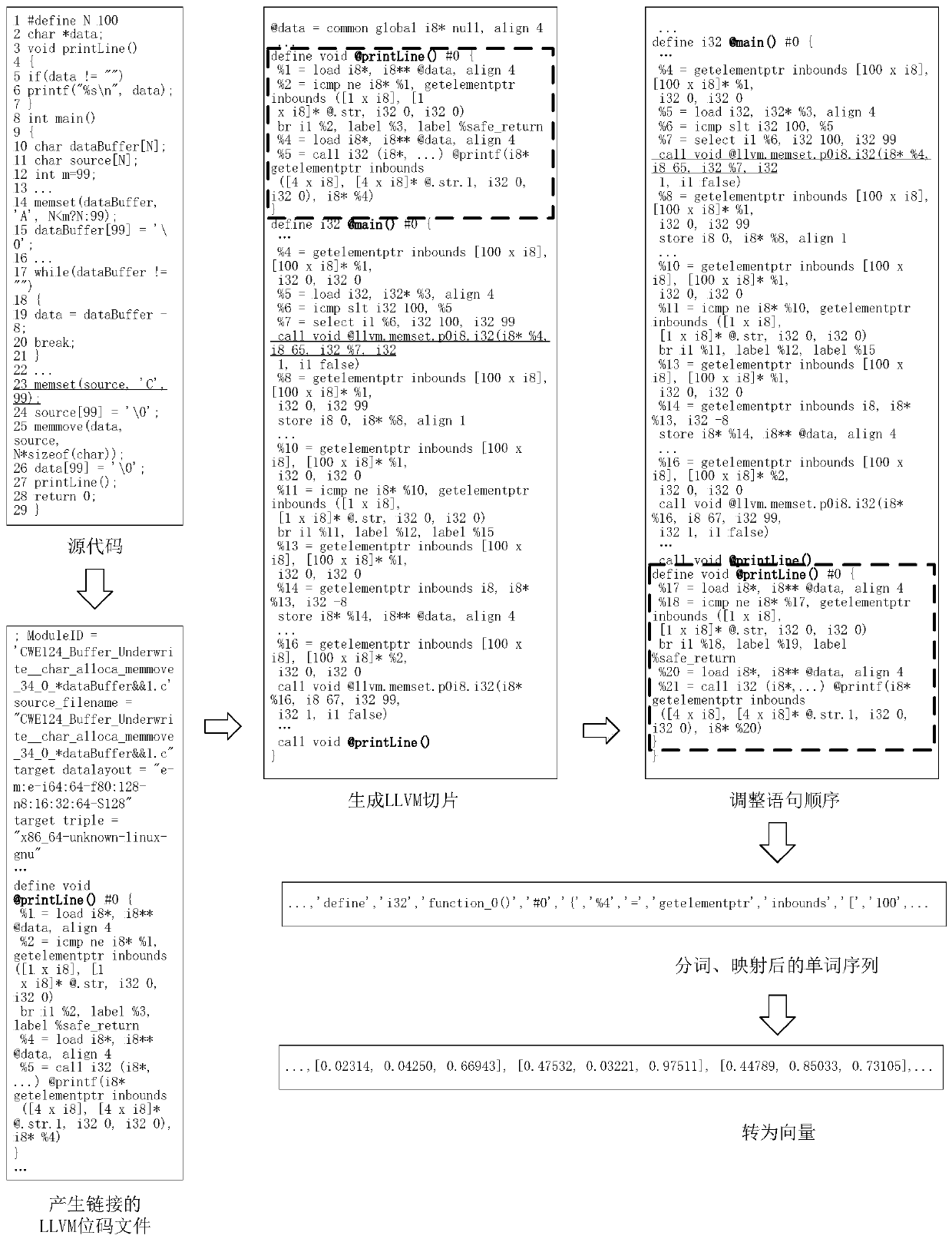
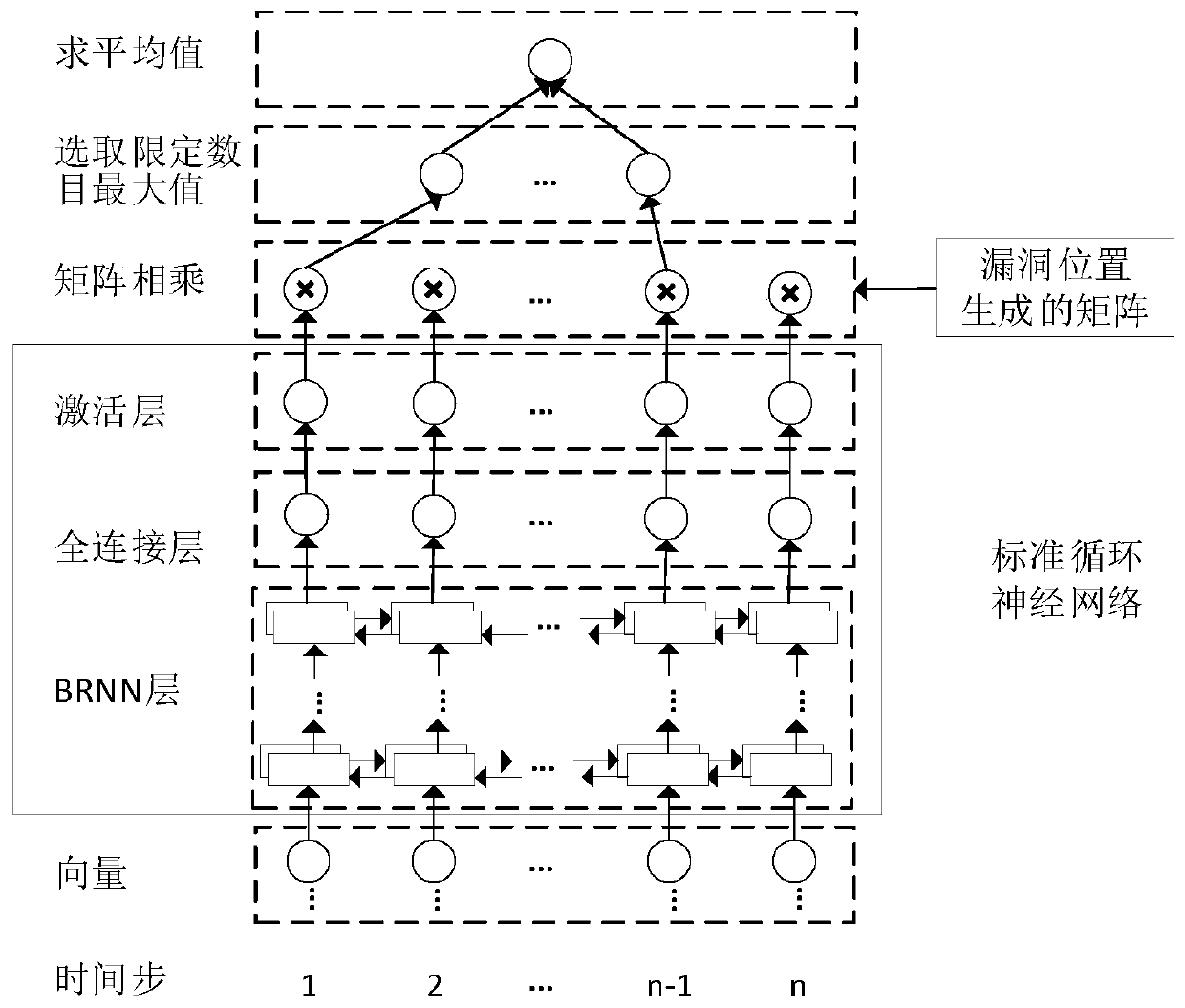
ActiveCN110222512AClear structureImprove accuracyPlatform integrity maintainanceNeural architecturesProgram slicingForward propagation
The invention discloses a software vulnerability intelligent detection and positioning method and system based on an intermediate language, and belongs to the field of vulnerability detection. The method comprises the steps of converting a training program source code and a target source code into the intermediate language program slices, wherein the intermediate language program slices comprise the codes related to the suspicious vulnerability elements; if the intermediate language program slice corresponding to the training program source code contains the known vulnerability code, adding avulnerability tag to the intermediate language program slice and recording the position of the intermediate language program slice in the slice; if not, adding a vulnerability-free label to the targetobject; training a recurrent neural network based on the sample difference; and performing vulnerability intelligent detection and positioning on the intermediate language program slice correspondingto the target program source code by using the trained sample difference-based recurrent neural network. According to the present invention, the intermediate language slice is used as a unit of vulnerability detection, and the detection accuracy is improved. And only the data corresponding to the known vulnerability rows is selected from the output sequence of the recurrent neural network to participate in forward propagation, so that the trained model can identify the vulnerability rows.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Storage system reference evaluation program generating method and apparatus
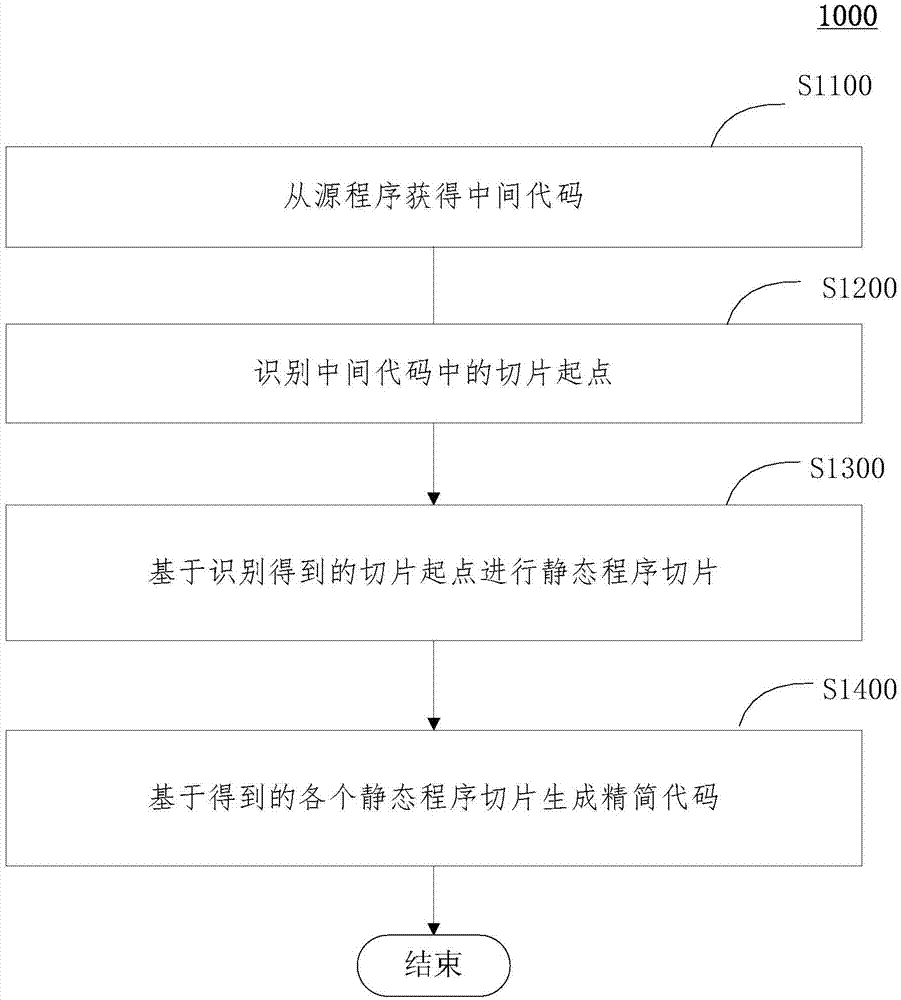
ActiveCN104850411AAutomated Execution Process StreamliningNo human intervention requiredSpecific program execution arrangementsAnalysis dataSystems design
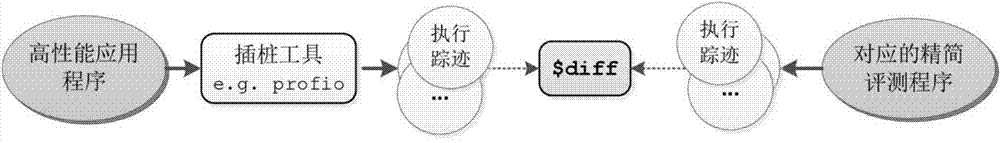
The invention relates to a storage system reference evaluation program generating method and apparatus and belongs to the high-performance computing performance evaluation field. The storage system reference evaluation program generating method includes the following steps that: intermediate codes are obtained from a standardized source program; slicing starting points of the intermediate codes are identified; static program slicing is carried out based on identified slicing starting points; and simplified codes can be generated based on obtained static program slices. The method is based program slicing technology; data dependence, control dependence and communication dependence are analyzed in a compiler; all statement operation related to input and output is automatically extracted so as to form the compilable, executable, manually-readable and transplantable simplified program codes; the simplified program can faithfully reflect input and output load characteristics of an original application program, and less time and fewer resources are needed to execute the simplified program, and therefore, rapid evaluation can be facilitated. The simplified program generating method is very effective in fast evaluation of the performance of a high-performance storage system and design assistance of the storage system.
Owner:TSINGHUA UNIV
Extraction method of parallel program communication mode and system
ActiveCN101661409ALess computing resourcesLow memory resourcesInterprogram communicationProgram slicingData stream
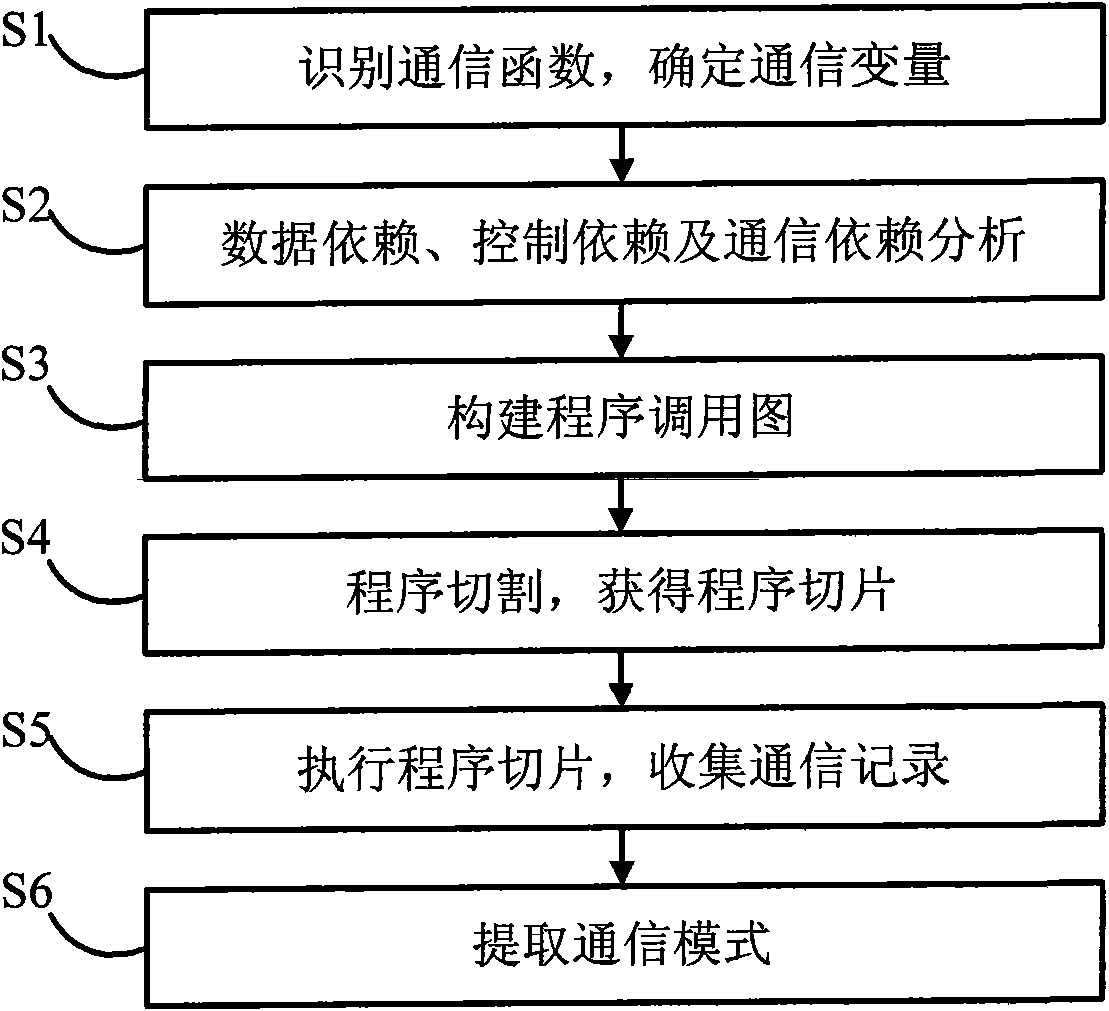
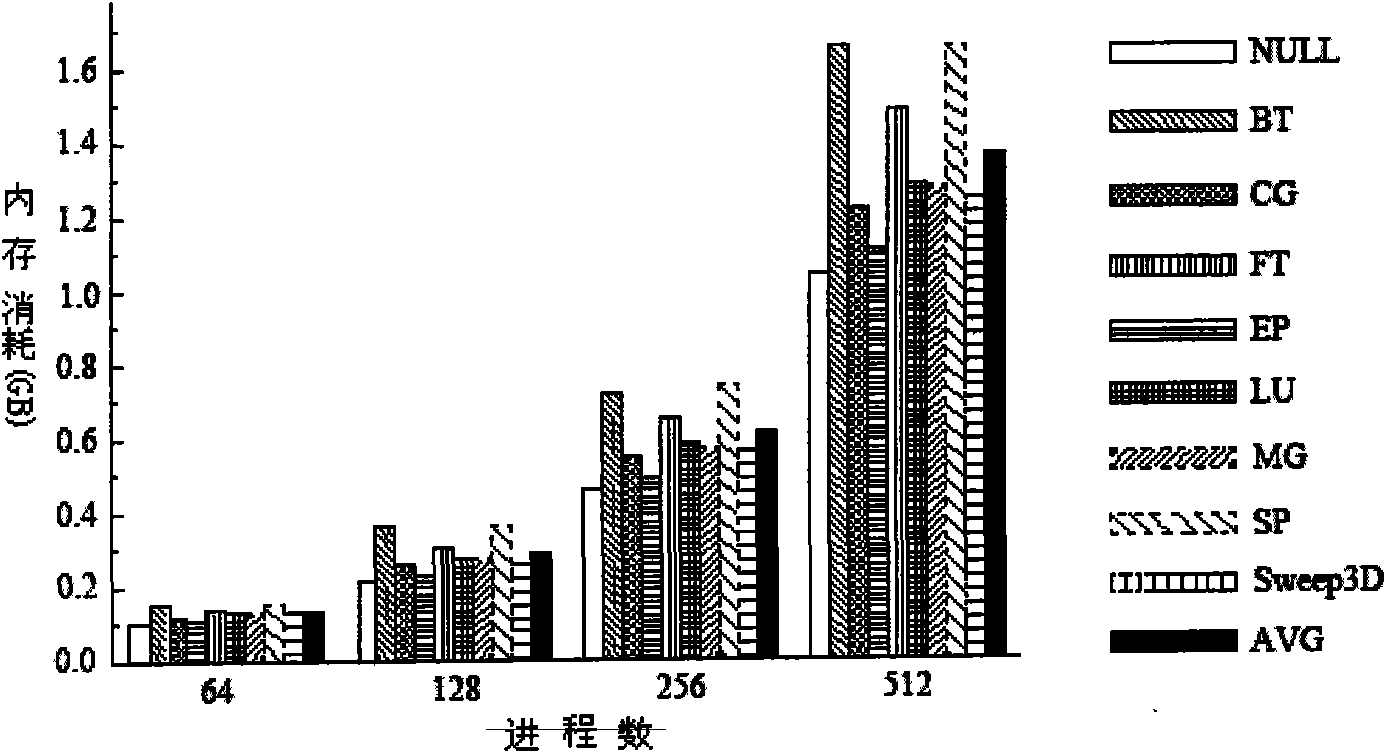
The invention relates to an extraction method of parallel program communication mode and a system. The method includes the following steps of: analyzing a parallel program source code, identifying thecommunication function call in the parallel program, determining the communication variable in the communication function and putting the communication variable in a setting set; analyzing the control stream and data stream of the parallel program and collecting the information of data dependence, control dependence and communication dependence of the parallel program; collecting the call information in the parallel program and constructing a program call graph; conducting program cut on the parallel program through a cut algorithm based on LIVE variable transmission to obtain the program slice of the parallel program; executing the program slice and collecting and outputting communication records; and according to the communication records, acquiring the communication mode of the parallel program according to set objectives. The method and the system can reduce the resource requirement and time cost in collecting large-scale parallel program communication mode and realize the objectof collecting the large-scale parallel program communication mode on a small-scale system.
Owner:TSINGHUA UNIV
Intelligent contract multi-vulnerability detection method and system based on source code graph representation learning
PendingCN113360915AAvoid loss of structural featuresImprove accuracySoftware testing/debuggingPlatform integrity maintainanceAlgorithmTheoretical computer science
The invention discloses an intelligent contract multi-vulnerability detection method and system based on source code graph representation learning, and the method comprises the steps: carrying out representation of an intelligent contract source code through a function granularity code attribute graph in combination with an abstract syntax tree and semantic information of an intelligent contract; and according to grammatical features of different types of vulnerabilities of the intelligent contract, defining a slicing criterion, using a program slicing technology to carry out noise reduction on the intelligent contract graph representation, carrying out feature extraction in combination with a gated graph neural network, and carrying out vulnerability prediction based on the extracted features. The method has the advantages that the intelligent contract source code is represented by combining multiple graph structures, and grammar and semantic information and a context structure of the code are fully reserved; noise codes irrelevant to vulnerability detection are removed by using a program slicing technology, so that the detection accuracy is improved; the features of various vulnerabilities are automatically learned based on the gated graph neural network, the application range and the detection efficiency of vulnerability detection are improved, and the detection cost is reduced.
Owner:YANGZHOU UNIV
Guided slicing system for obtaining histological samples and methods thereof
ActiveUS20140030757A1Withdrawing sample devicesPreparing sample for investigationPattern recognitionProgram slicing
Systems and methods for providing guided slicing of histological samples. The samples are acquired, spacially labeled with a fiducial marker, and imaged with a scanning system. The images are analyzed, either manually, semi-automatically or automatically, and likely locations of pathologies are identified. A slicing program is then generated and the sample sliced according to the slicing program, thereby ensuring that likely locations of pathologies are analyzed.
Owner:ASPECT IMAGING
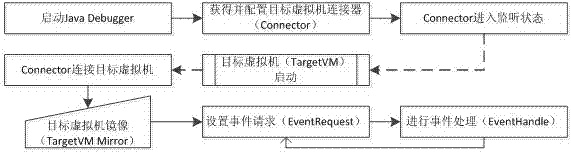
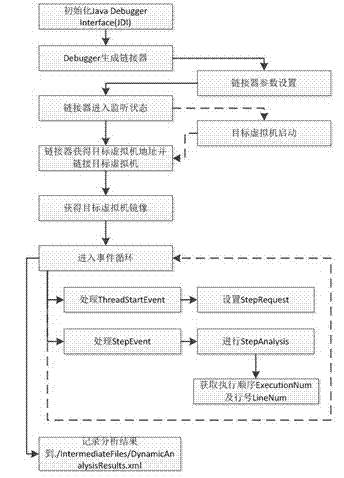
Program debugging system with program analysis function
InactiveCN102968372AReduce focusImprove efficiencySoftware testing/debuggingProgram slicingSoftware engineering
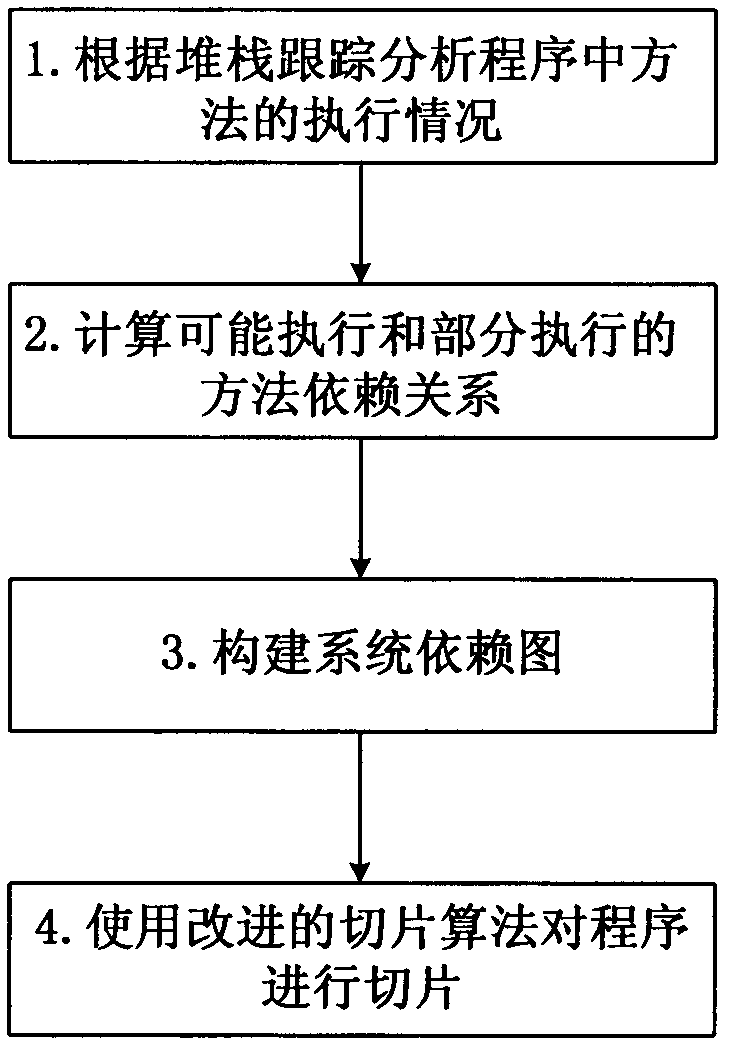
The invention relates to a program debugging system with a program analysis function. The program debugging system comprises debugging steps as follows; establishing connection with a target virtual machine, conducting standard debugging and conducting expansion debugging. The program debugging system is not limited to the traditional program debugging mode any longer; debugging is not to only analyze the current running status of a program any longer; debugging personnel can check a complete executing process of the program; debugging is convenient; and the program can be understood conveniently; the program debugging system can record application classes and application methods in one execution of the program and reduce attention ranges of the debugging personnel. When the system conducts dynamic program slicing, the program is not required to be traced and control dependence analysis is only conducted on methods concerned in the program executing process; the algorithm efficiency can be improved; and the precision of slicing can be improved according to stack information and control dependence relationship.
Owner:CHINA UNIV OF MINING & TECH
Defending method based on virtual function table hijacking
InactiveCN105868641AHigh speedReduce overheadPlatform integrity maintainanceProgram slicingSemantics
The invention provides a defense method based on virtual function table hijacking, which can determine the utilization and further attack of potential use-after-free type loopholes in binary executable files. Step 1. Use the static instruction fragmentation and extraction framework to disassemble an executable file as input and generate a control flow graph and assembly language; Step 2. Compress and simplify the assembly language obtained in Step 1; Step 3. vEXTRACTOR in Step 2 Execute backward program slicing on the obtained intermediate language; step 4, extract all low-level semantics satisfying virtual function scheduling from the first three steps, and take out the virtual function scheduling part; step 5, rewrite and configure ID; All reference parameters of the function table are changed to new addresses of vtables, and VRewriter equips each virtual function with a security check to verify the integrity of the target virtual table; step 7, put the execution code equipped with security check into a new The code segment, to ensure that most of the original code department intact.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
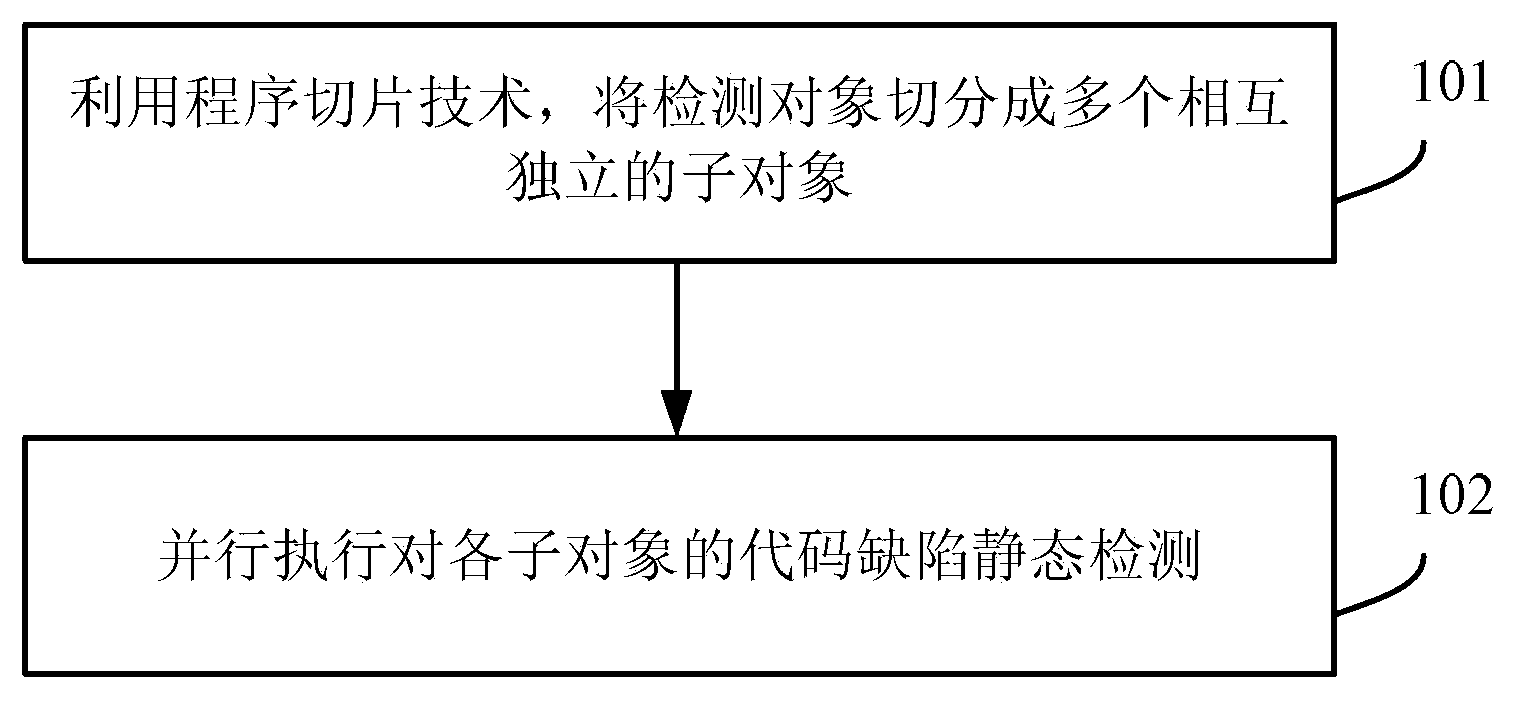
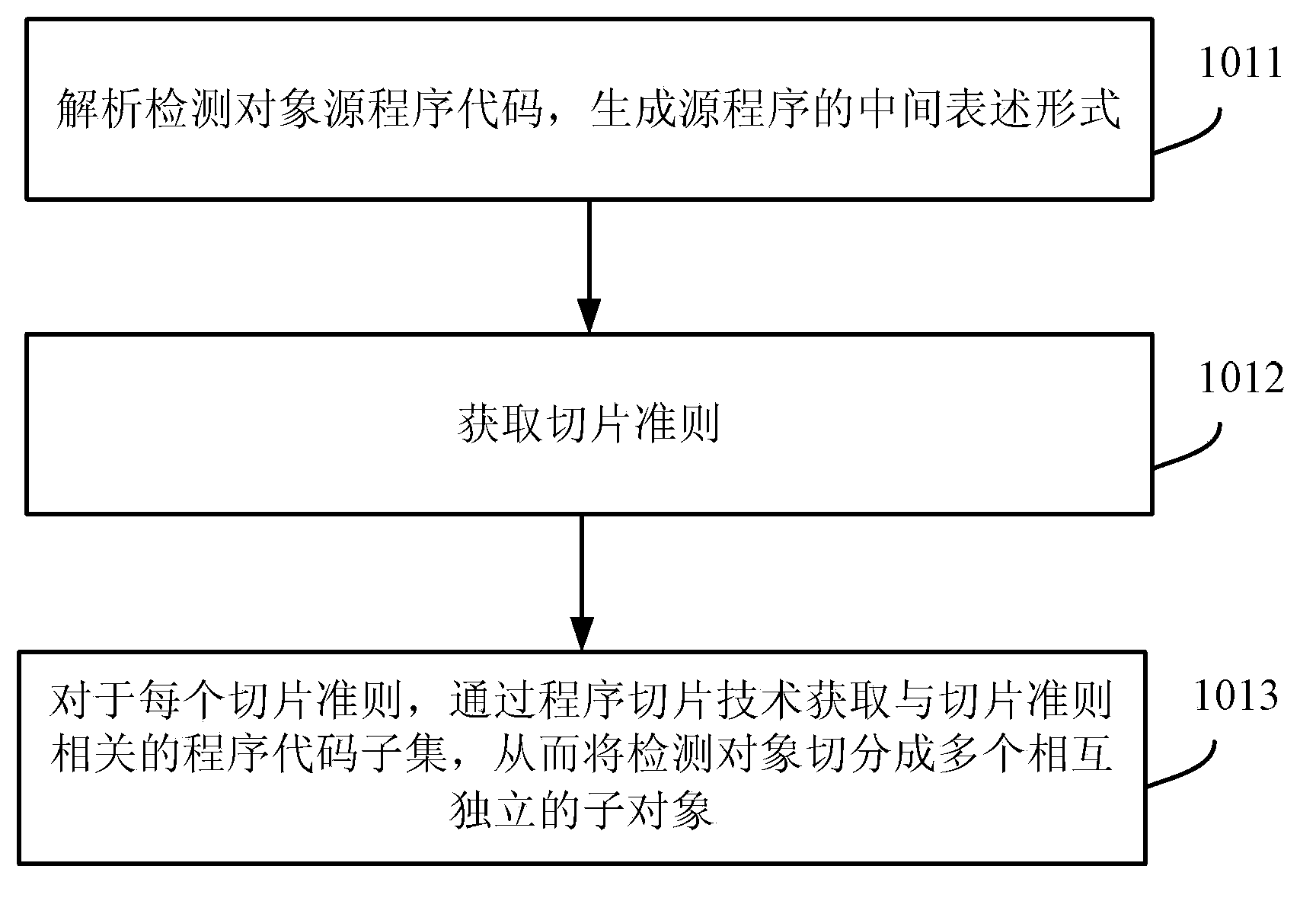
Program slicing based parallelization method and device of code defect static detection
InactiveCN103914372AImprove efficiencyHigh precisionSoftware testing/debuggingProgramming languageProgram slicing
The invention provides a program slicing based parallelization method and device of code defect static detection. The program slicing based parallelization method comprises splitting a detection object into a plurality of sub-objects which are mutually independent by a program slicing technology and executing the code defect static detection of every sub-object in a parallel mode. According to the program slicing based parallelization method and device of the code defect static detection, the object to be detected is divided into the plurality of sub-objects which are mutually independent by the program slicing technology, the detection processes of the sub-objects are not interfered with each other, the code defect static detection of every sub-object can be executed in a parallel mode, and accordingly the efficiency and the accuracy of the static detection are improved.
Owner:BEIJING VENUS INFORMATION TECH +1
Dynamic slicing system based on execution tract of program
The invention relates to a dynamic slicing system based on the execution tract of a program, which comprises functions as follows: acquiring execution path information of the program, statically analyzing a class file of the Java, analyzing the attached variable set of each sentence of each sequence in the execution track of the program, acquiring a direct control dependence junction point of each sentence in a source program, executing additional control dependence of each sentence of each sequence in the execution tract of the program and dynamically slicing the process internal program of the Java. Retrospection of the program is not required during program slicing; efficiency of algorithm is greatly improved; and precision of the program slicing is advanced according to a control dependence relationship and definition reference information of variable.
Owner:CHINA UNIV OF MINING & TECH
Method and system for detecting synchronization errors in programs
InactiveUS7865778B2Software testing/debuggingSpecific program execution arrangementsProgram slicingPath expression
A method and system for error detection in programs with collective synchronization and / or procedures are provided. In one aspect, the method and system may use interprocedural analysis for matching synchronizations in a program in order to detect synchronization errors, and, if no such errors exist, may determine the synchronization phases of the program. The method and system in one aspect may use a combination of path expressions and interprocedural program slicing to match the synchronization statements that may execute along each program path. If the synchronization matching succeeds, the method and system in one aspect may determine the sets of synchronization statements that synchronize together. A matching failure may indicate the presence of a synchronization error and the method and system in one aspect may construct a counter example to illustrate the error.
Owner:GLOBALFOUNDRIES INC
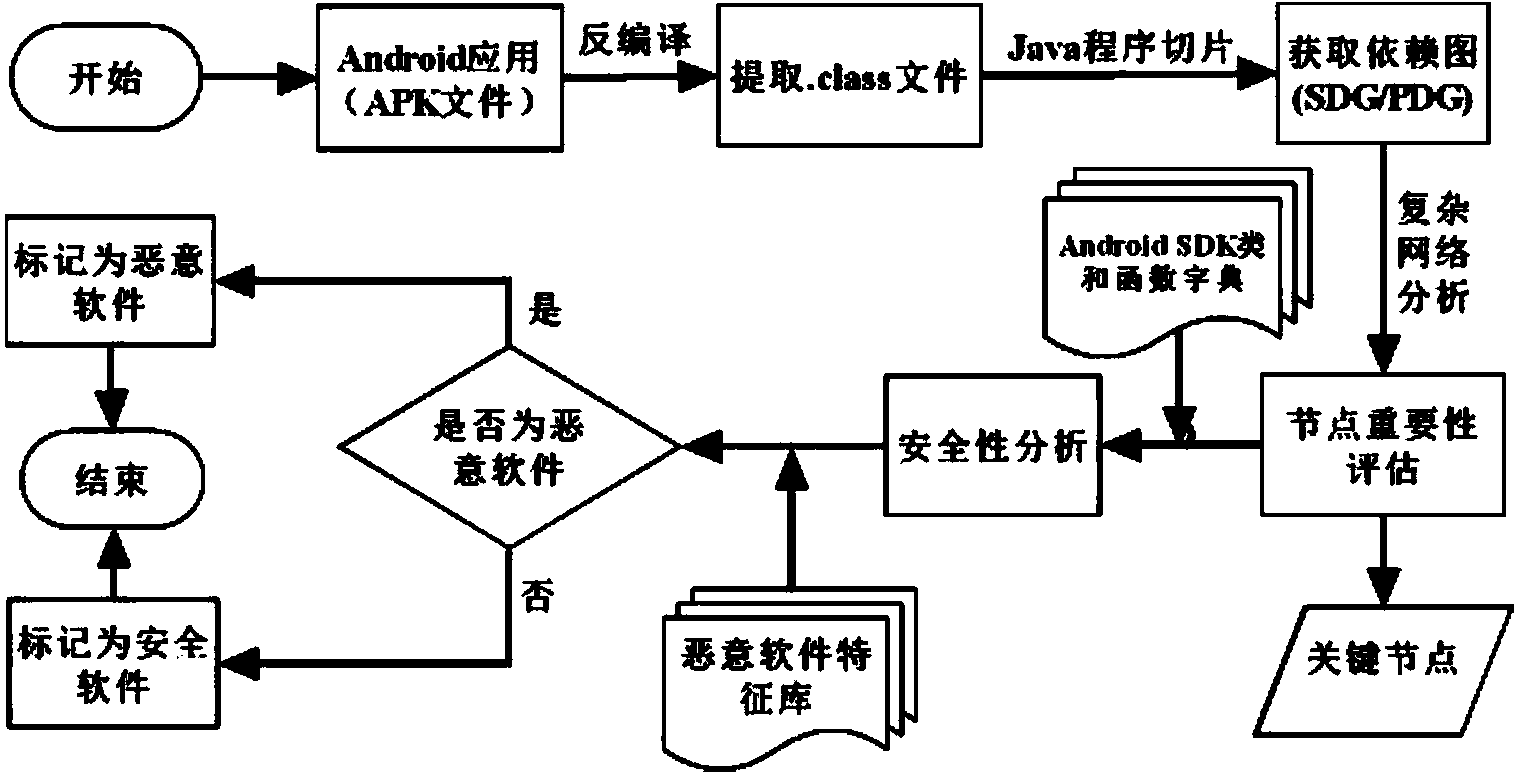
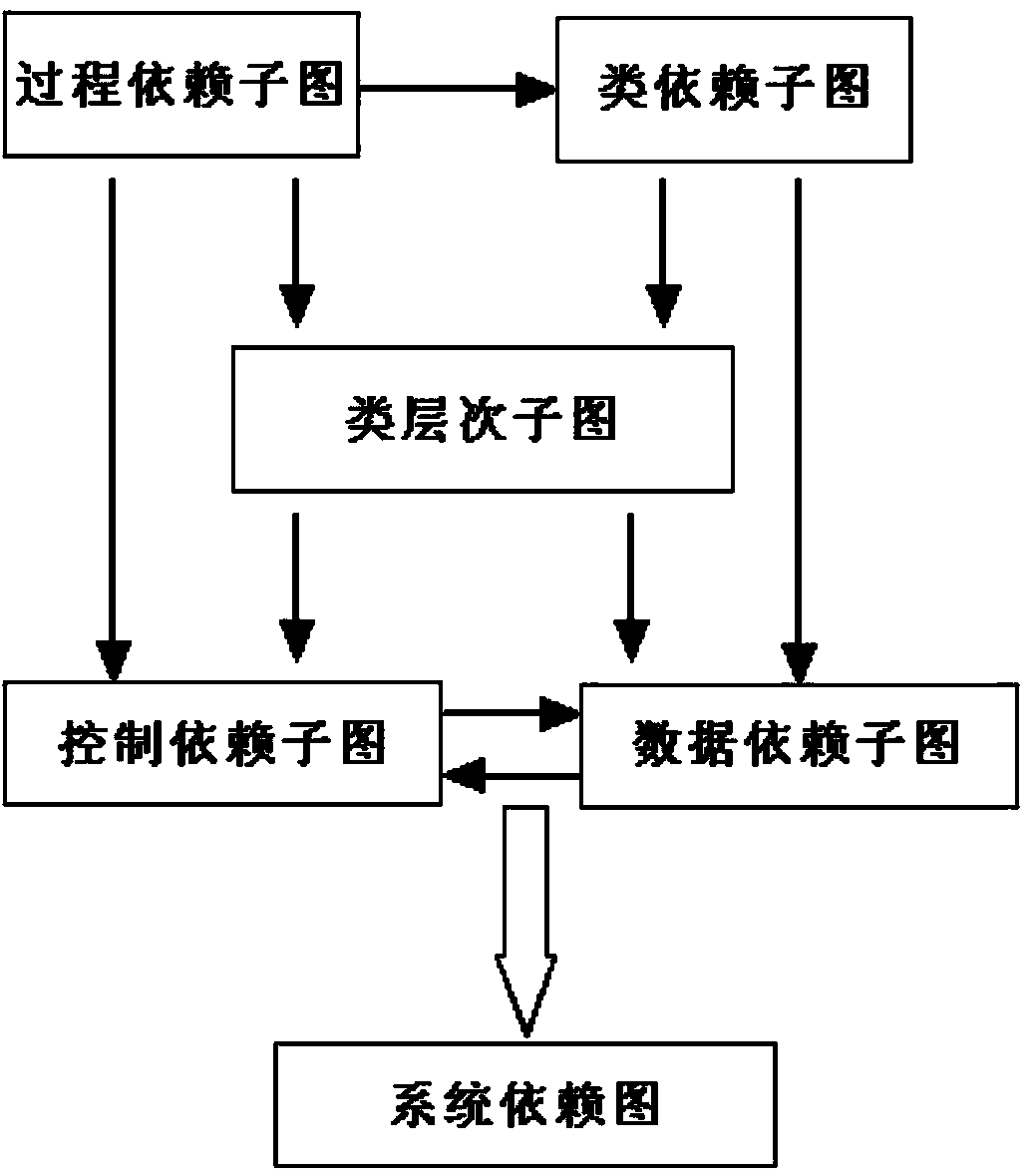
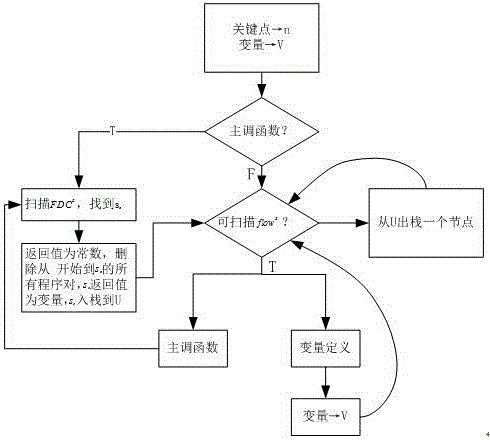
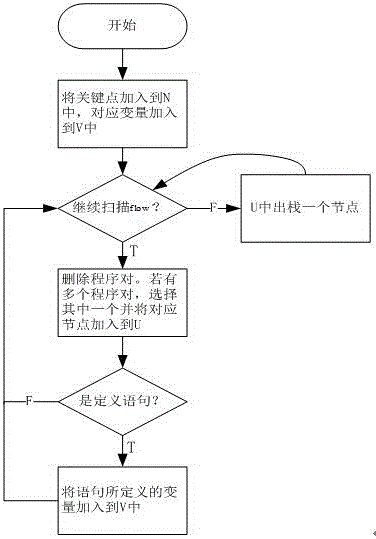
Android malicious software detection method based on program slicing technology
InactiveCN103971055ASolve semantic understandingSolve reverse analysisPlatform integrity maintainanceProgram slicingSoftware engineering
The invention provides the design scheme of an Android malicious software detection method based on a program slicing technology. According to the scheme, starting from an installation file APK of an installation application, source codes of the application are analyzed through the program slicing technology, key nodes affecting the safety of the application are found out, Android malicious software is detected, and the purpose of reducing manual operation is achieved. The test result shows that the Android malicious software detection method based on the program slicing technology can reliably detect the Android malicious software; the method based on the program slicing is more accurate than a traditional detection method; the Android malicious software is analyzed from the angle of the source codes, and flexibility is higher for continuously updated viruses and Trojan variants.
Owner:NANJING UNIV OF POSTS & TELECOMM
Test case set reduction method based on program slice
InactiveCN106095662ATest case set reductionSmall time complexitySoftware testing/debuggingProgram slicingTested time
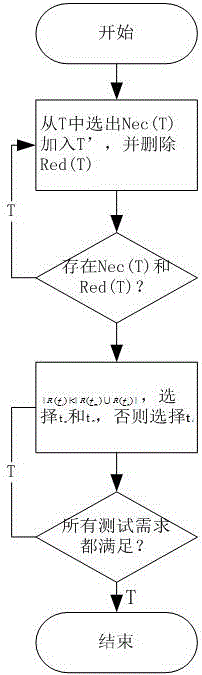
The invention discloses a test case set reduction method based on a program slice, and relates to the field of software testing. The test case set reduction method is based on a program slice algorithm and a GRE algorithm and is recorded as a GRE-R-T algorithm. Test requirement reduction and test case set reduction are combined. Firstly, test requirements are subjected to slice calculation, an obtained slice and a program associated with the test requirements are combined to generate a test case set corresponding to statements in the slice, and finally, the test case set is subjected to reduction according to the GRE-R-T method. Compared with a traditional algorithm, the GRE-R-T algorithm is characterized in that the test case set is effectively subjected to the reduction, an amount of detected bugs is not lowered, and test time and workloads are greatly saved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Real-time stack-based program slicing method
InactiveCN102214141AShorten the timeImprove real-time performanceSoftware testing/debuggingProgramming languageProgram slicing
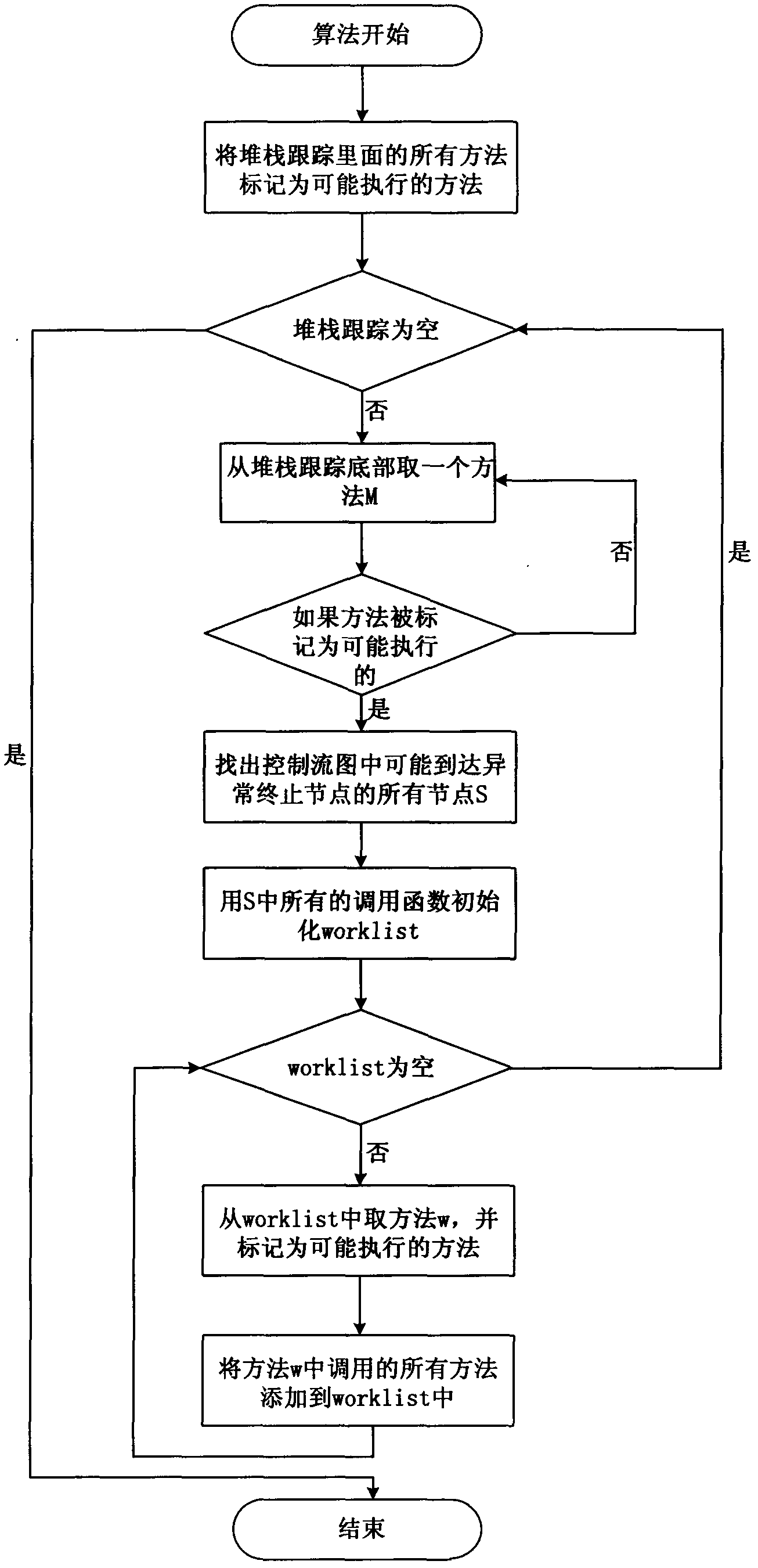
The invention relates to a real-time stack-based program slicing method which speculates the execution track of a program by utilizing stack tracing information saved when the program is thrown abnormally. By using the program slicing method, the real time performance of static program slicing in software development is greatly improved, the accuracy of the static program slicing is improved, the number of sentences contained in slicing results is reduced, and the time for developing and maintaining the program is effectively shortened.
Owner:CHINA UNIV OF MINING & TECH
Method for estabilishing Web service security analysis model based on program slice
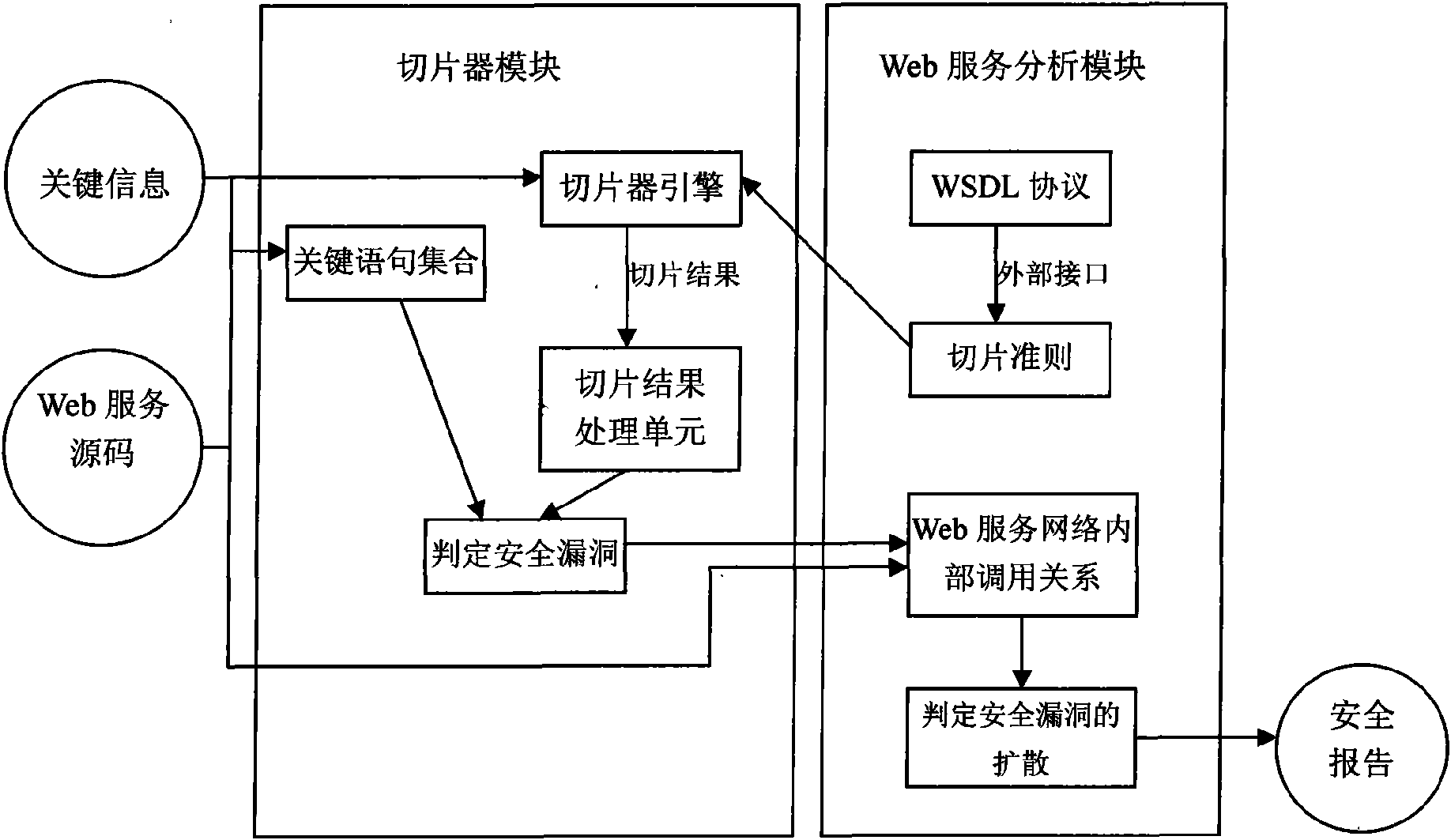
ActiveCN101588363AReduce security breachesQuality improvementSecuring communicationProgram slicingWeb service
The present invention relates to a software establishing technique and network security, and specifically to a method for establishing the Web service security analysis model based on the program slice. The invention provides a method for establishing Web service security analysis model based on program slice for protecting the key information and the common information in the network service from the inside and the outside and increasing the network service security. The method of the invention adopts the following technical solutions: 1) establishing a slicer module for obtaining the abstract of the information flow in the Web service realizing code; 2) establishing a network service analysis module for discovering the safety breaking state that the key information is leaked to the Internet user through the current service interface, wherein the step comprises the safety analysis of the independent network service and the safety analysis of the network service network; and 3) establishing a safety reporting module for analyzing the result based on the module, and combining the safety measures presented in the existing Web service security specification and process for generating a corresponding security report. The method of the invention is mainly used for providing the Web service security.
Owner:江苏永达电力电信安装工程有限公司
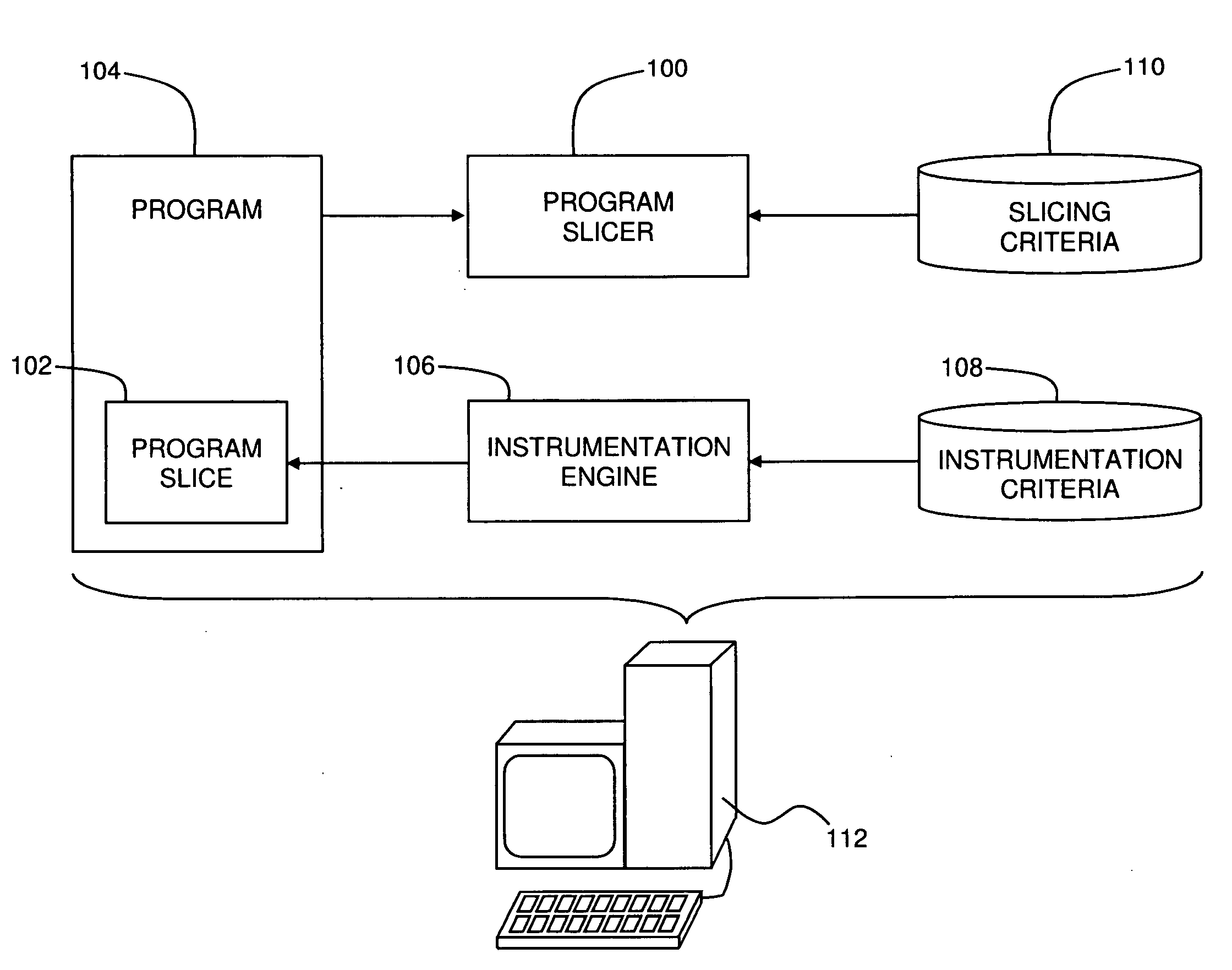
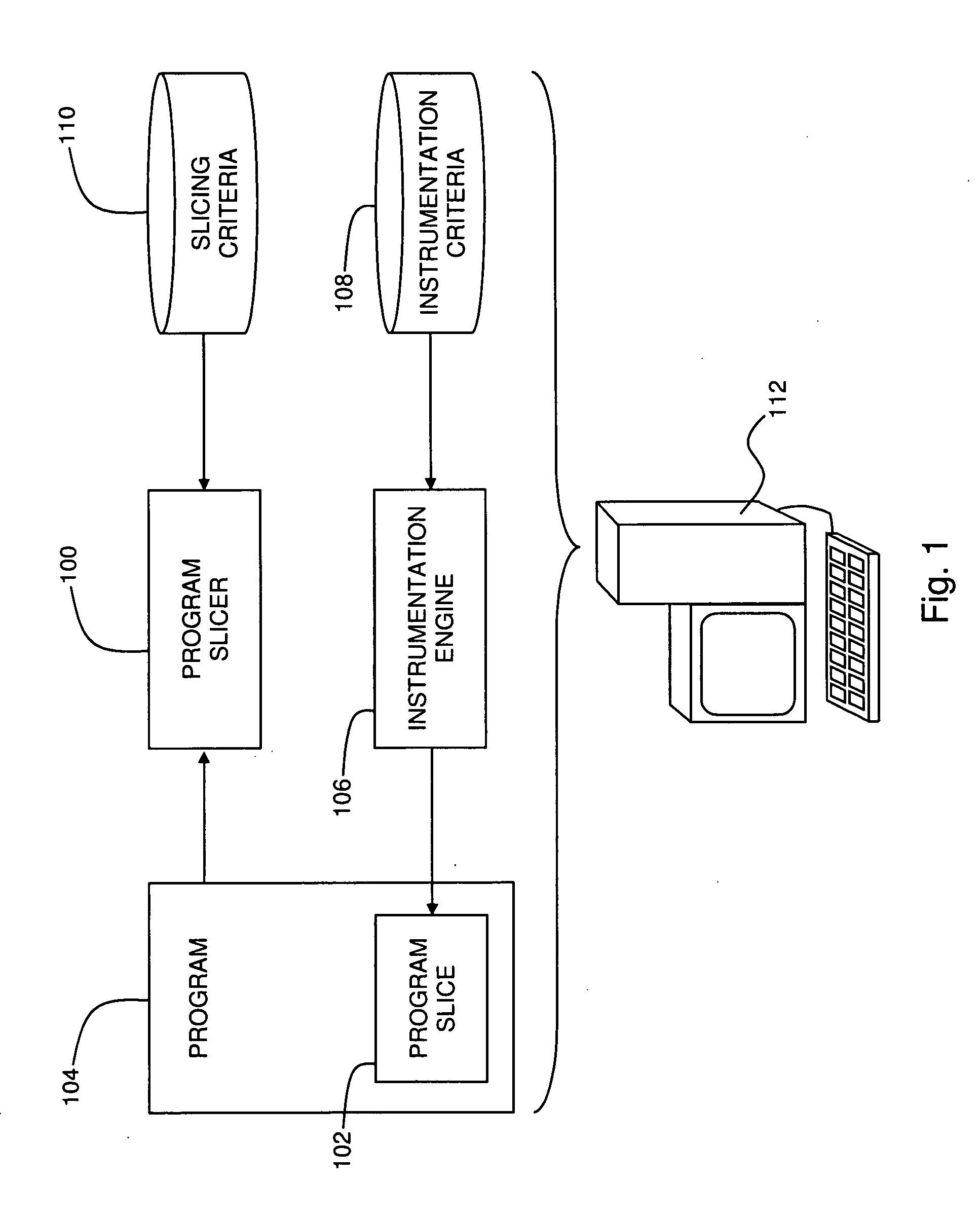
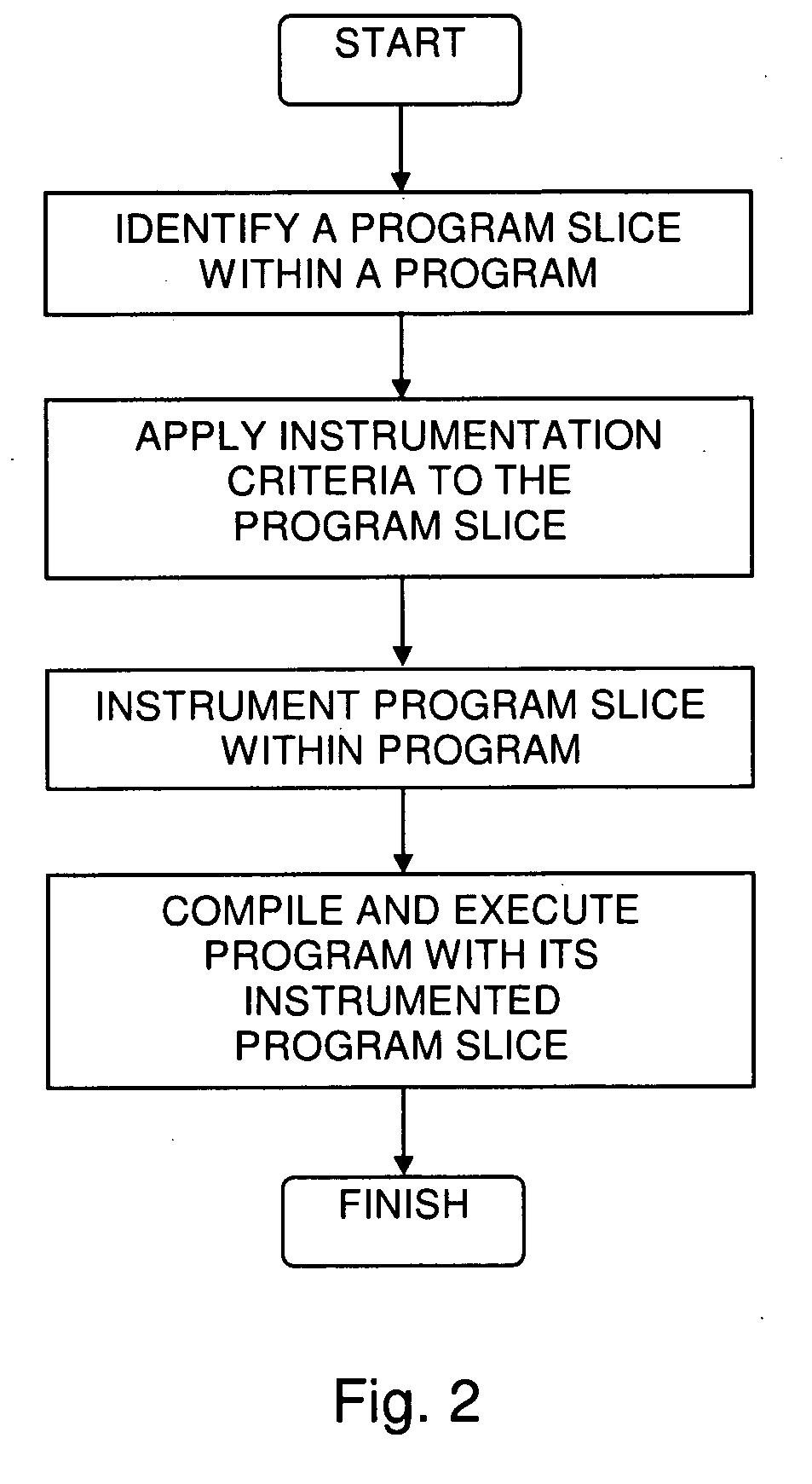
Efficient Code Instrumentation
InactiveUS20100306745A1Software testing/debuggingSpecific program execution arrangementsProgram slicingComputer science
A method for instrumenting a computer program, the method including identifying a program slice within a computer program, and instrumenting the program slice within the program.
Owner:IBM CORP
System, method, and apparatus for modular, string-sensitive, access rights analysis with demand-driven precision
InactiveUS8572674B2Reduce in quantityGood precisionPlatform integrity maintainanceTransmissionProgram slicingModularity
A static analysis for identification of permission-requirements on stack-inspection authorization systems is provided. The analysis employs functional modularity for improved scalability. To enhance precision, the analysis utilizes program slicing to detect the origin of each parameter passed to a security-sensitive function. Furthermore, since strings are essential when defining permissions, the analysis integrates a sophisticated string analysis that models string computations.
Owner:INT BUSINESS MASCH CORP
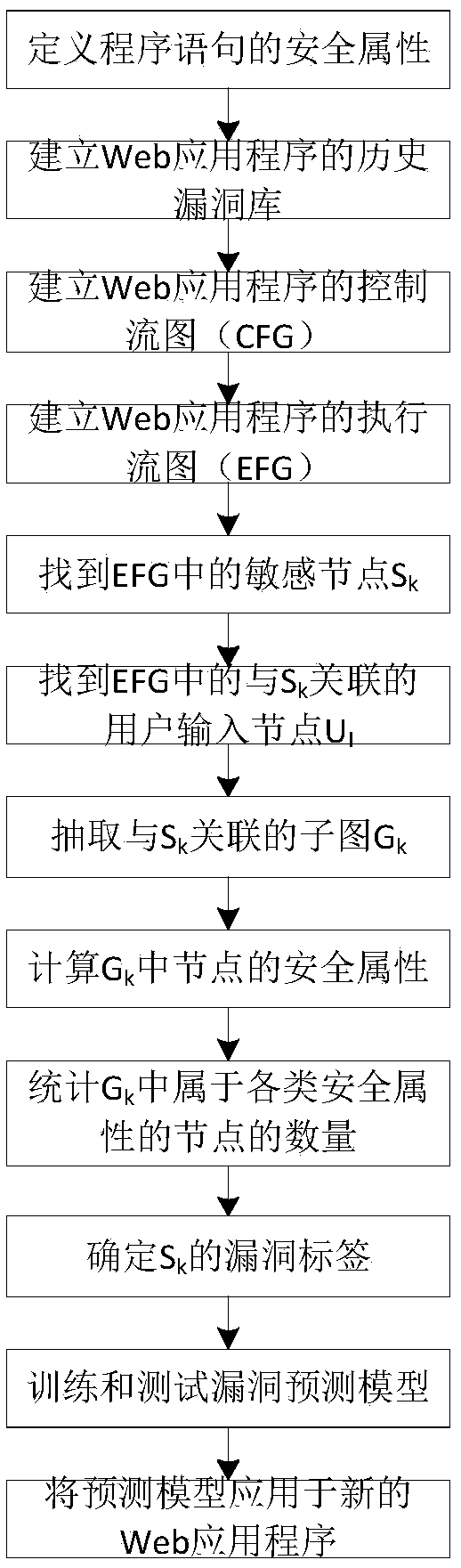
A Web application security vulnerability prediction method based on execution flow graph
ActiveCN109101820APredicting Vulnerability LocationsPlatform integrity maintainanceNODALProgram slicing
The invention discloses a Web application security vulnerability prediction method based on an execution flow graph. The execution flow graph EFG is constructed according to the data dependency relationship and the control dependency relationship of the Web application; a sub-graph is extracted from the EFG with the node Sk where the security sensitive statement is located as an end point and theuser inputs node UI associated with the Sk as a starting point, and a metric element is extracted for each sub-graph; the concrete value of the metric element of the sub-graph is taken as the input and the Sk vulnerability of the corresponding sub-graph is taken as the output, the vulnerability prediction model is constructed, so as to realize the security vulnerability prediction of Web application. The invention comprises a judging node on the extraction of the metric element, and the workload is greatly reduced compared with the analysis of the program slice directly.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com