Function-level code vulnerability detection method based on slice attribute graph representation learning
A vulnerability detection and attribute graph technology, applied in the field of vulnerability detection, can solve problems such as affecting model learning efficiency, high model false positive rate, complexity and bulk, and achieve the effect of avoiding adverse effects, improving coverage, and reducing complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
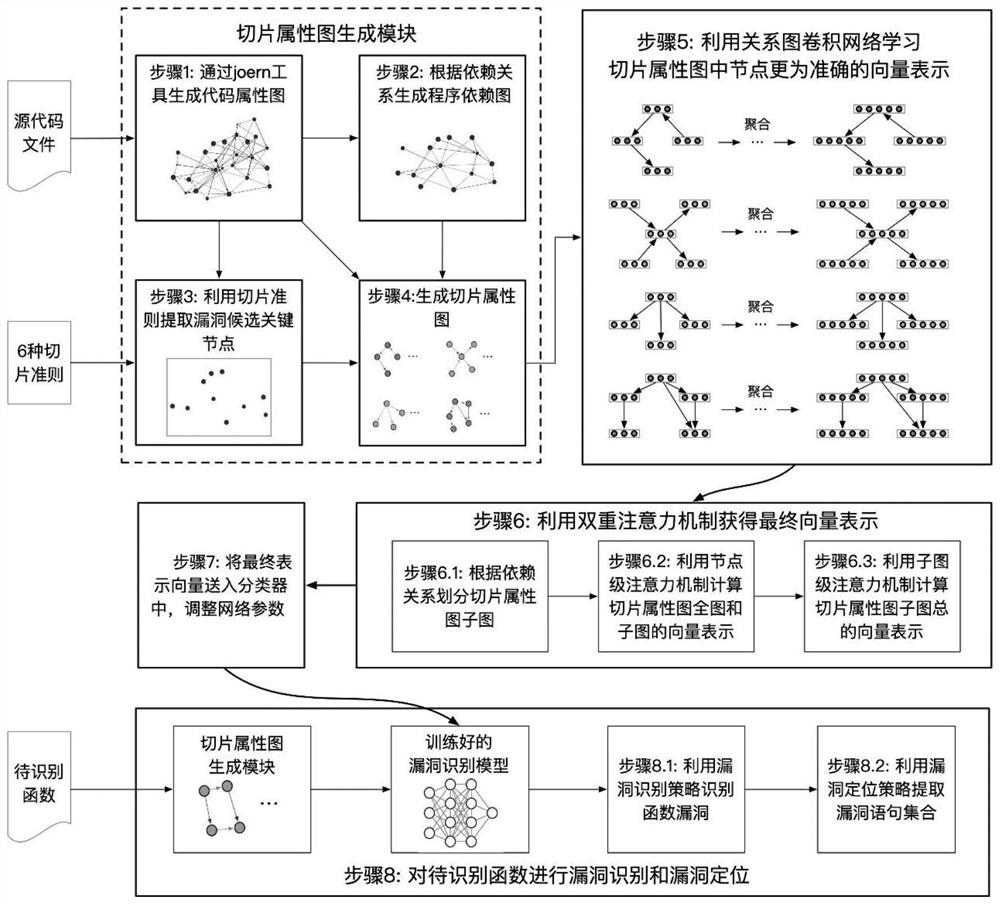
[0065] by Figure 5 Take the vulnerability code shown as an example to illustrate the generation of the slice attribute map and the result of vulnerability identification.
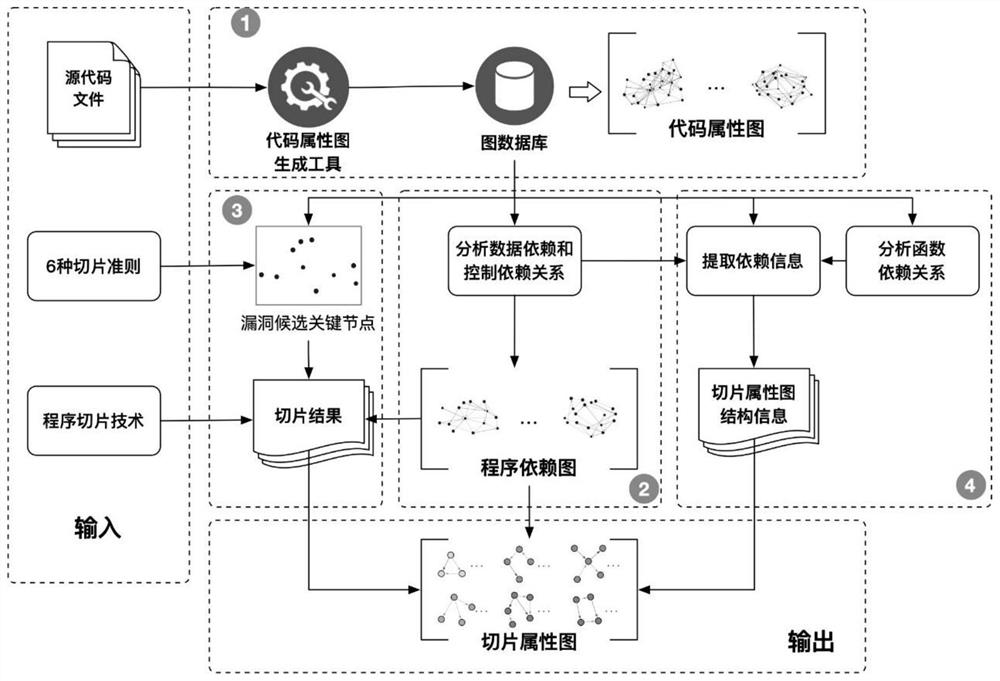
[0066] The source file is the test code with the test ID of 2081 in SARD. The position where the vulnerability statement is framed by a rectangle on line 13 is a buffer overflow vulnerability caused by the strcat function. Use the static analysis tool joern to parse the source file and generate a code property map, such as Image 6 shown. The code attribute graph contains 162 nodes and 290 edges. Extract data dependencies and control dependencies from the code attribute graph, and generate a program dependency graph for each function, such as Figure 7 shown.
[0067] Taking the vulnerability candidate key nodes as the slicing criterion, program slices are generated according to the program dependency graph. Using program slicing, the slice property graph is further generated from the program dependen...
Embodiment 2
[0070] by Figure 9 The vulnerability code shown is taken as an example to illustrate the functions of the newly added vulnerability candidate key points of the present invention and the corresponding vulnerability identification results.
[0071] The source file is part of the code of the matroska_parse_laces function in the real project FFmpeg. The vulnerability statement is in line 1804 of the source file, which is the position of the matrix box in the figure. The slice attribute map generated by the original four slice criteria cannot cover the vulnerability statement, but the newly added slice criterion of the present invention can cover it, and the generated slice attribute map is as follows Figure 10 shown.
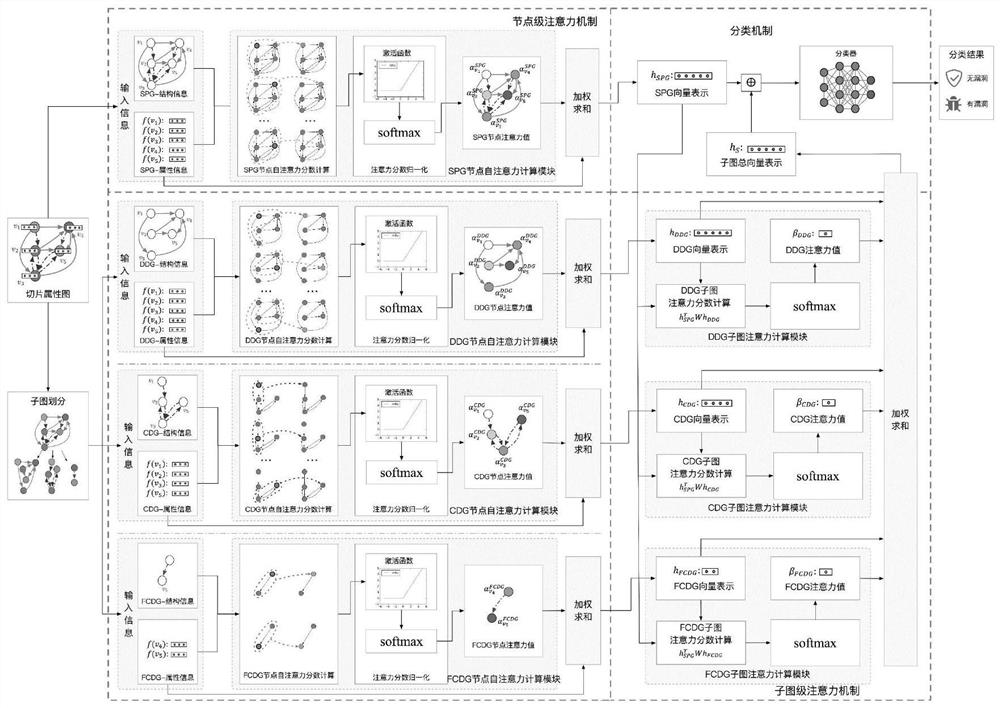
[0072] Similarly, this slice attribute map is fed into the relational graph convolutional neural network with a double attention mechanism, and the vector representation of the splicing of the whole image and the sub-image is obtained, and then passed into the cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com