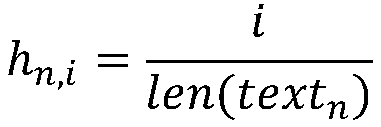Patents
Literature
816 results about "Relation graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Unsupervised ontology-based graph extraction from texts
Owner:XEROX CORP
Video description system and method
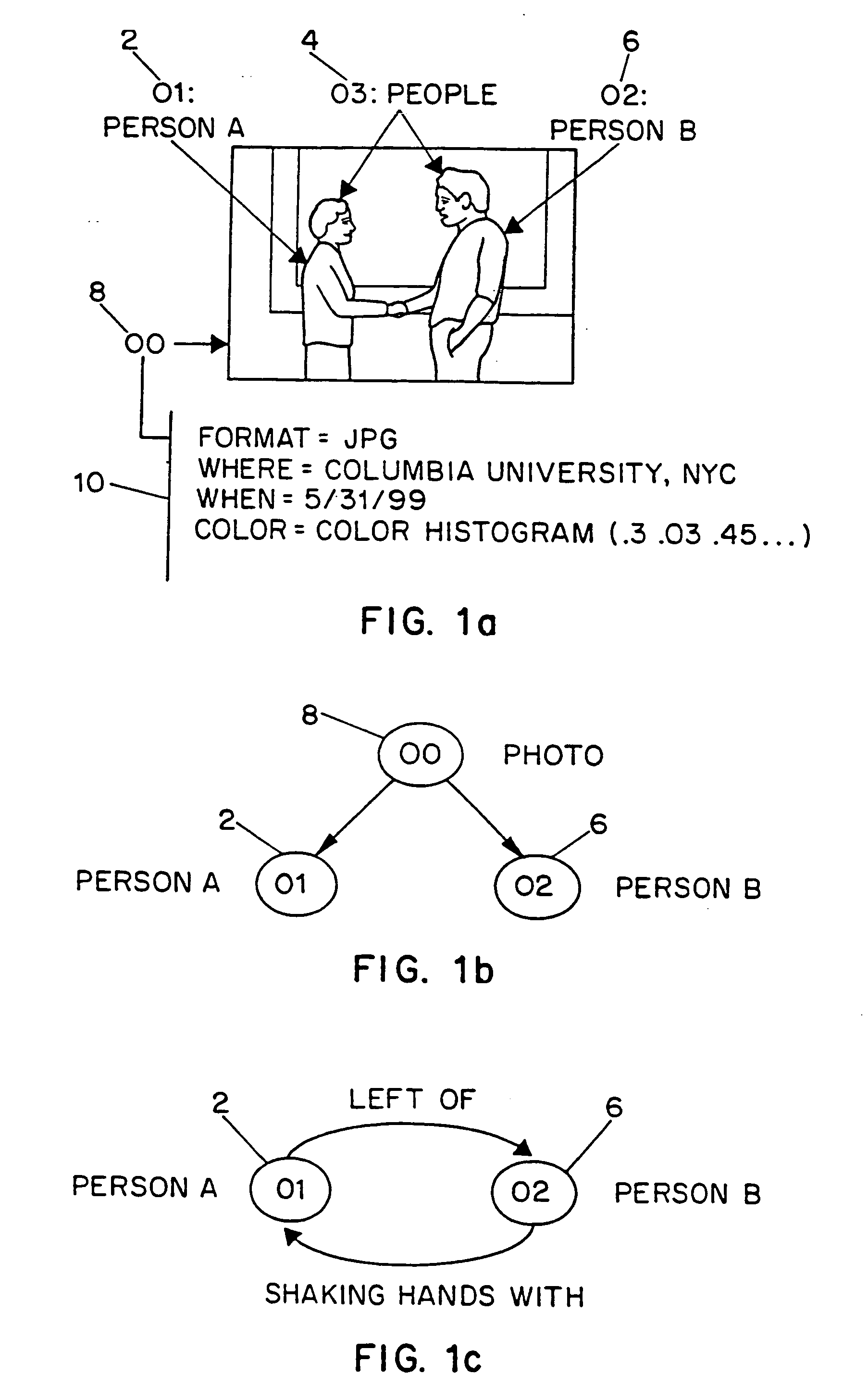
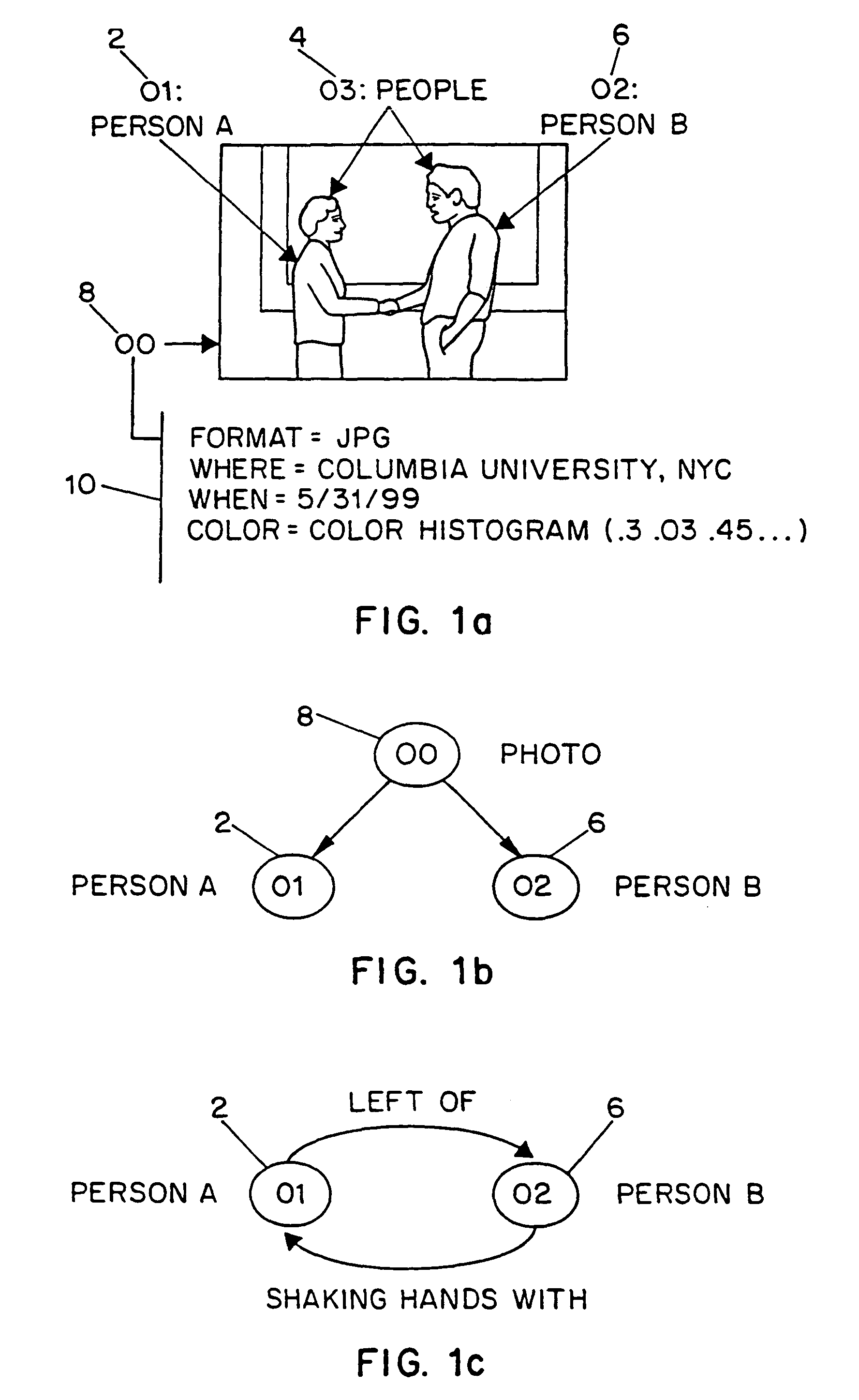
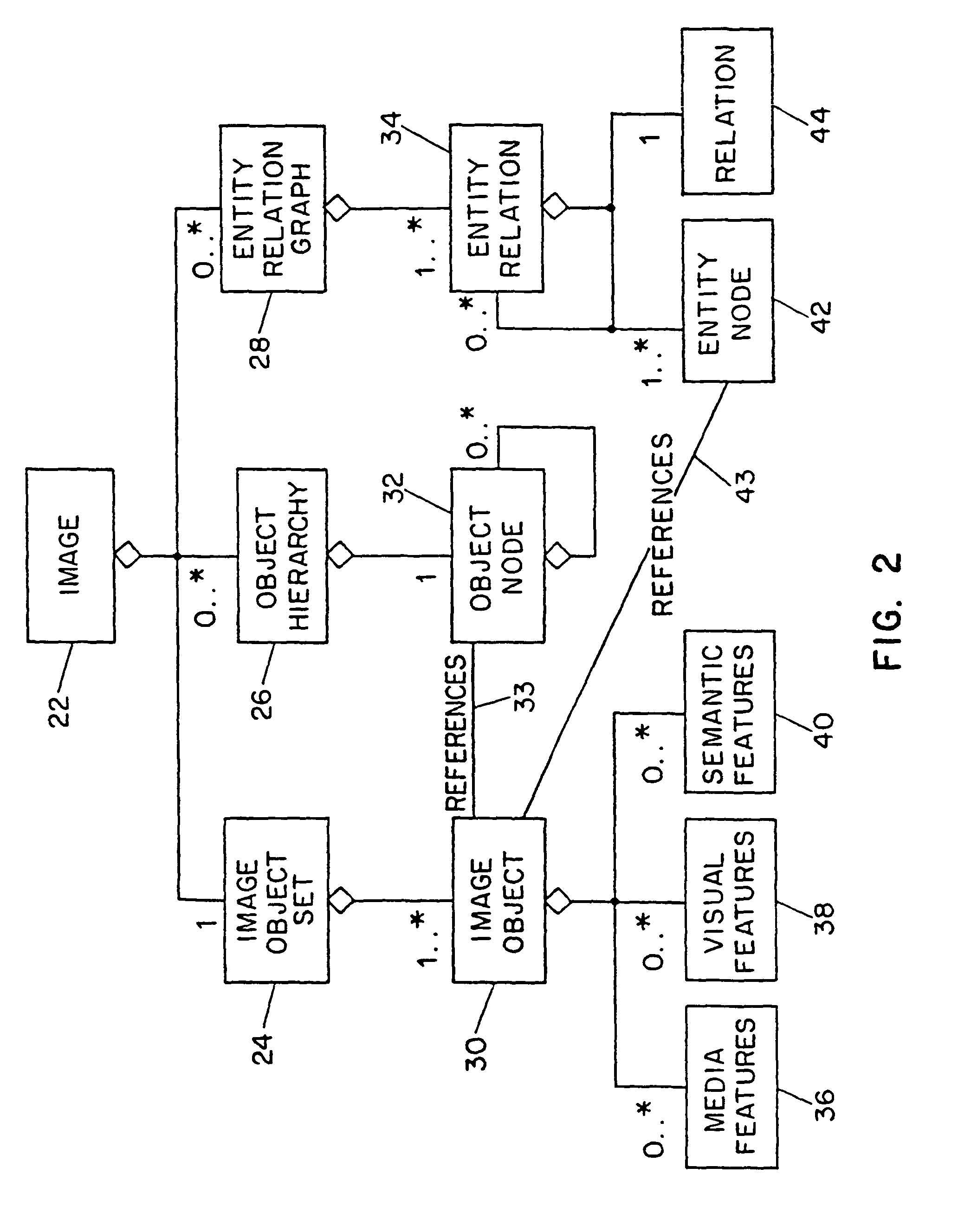
InactiveUS20070245400A1Video data indexingAnalogue secracy/subscription systemsRelation graphEntity relation diagram
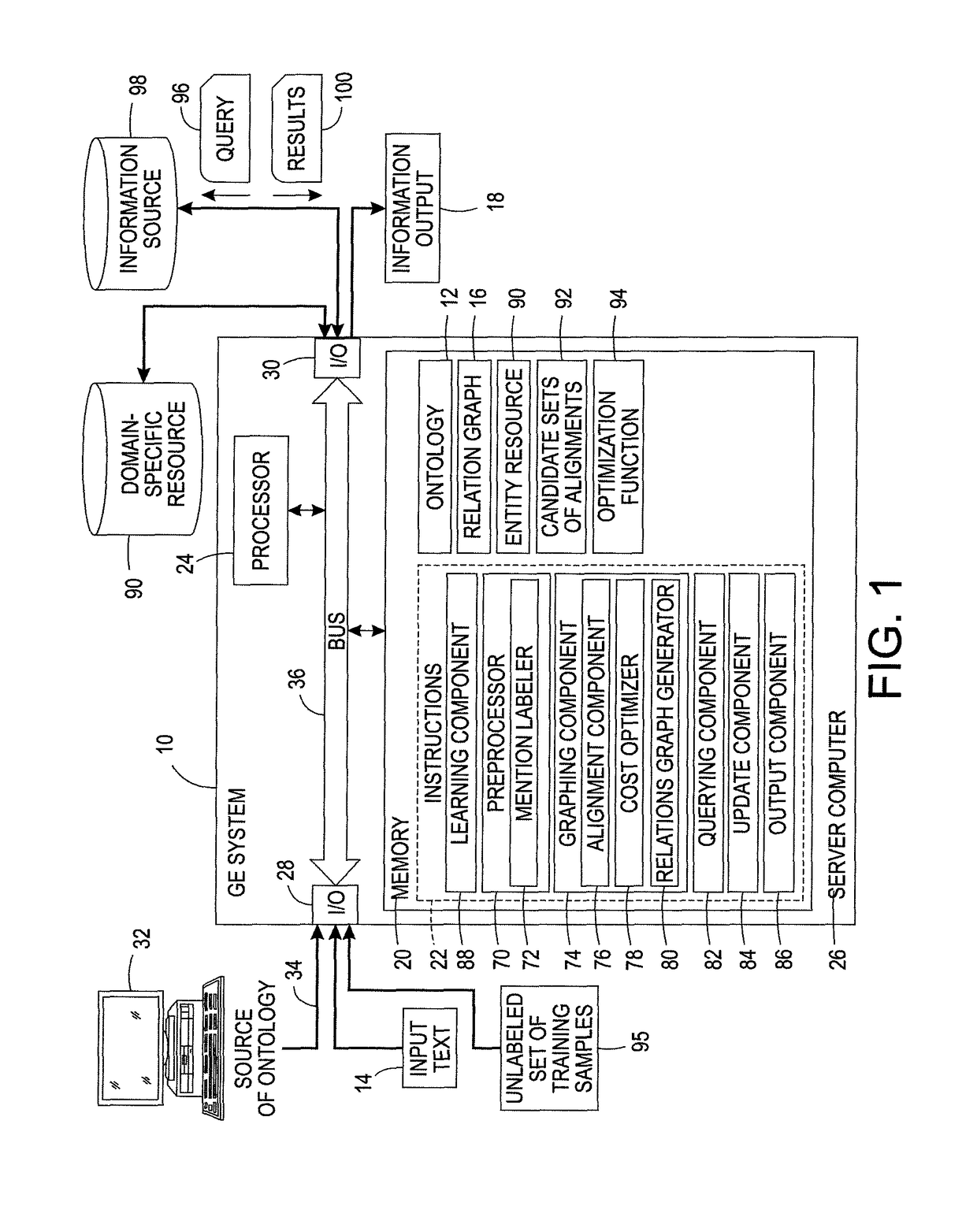
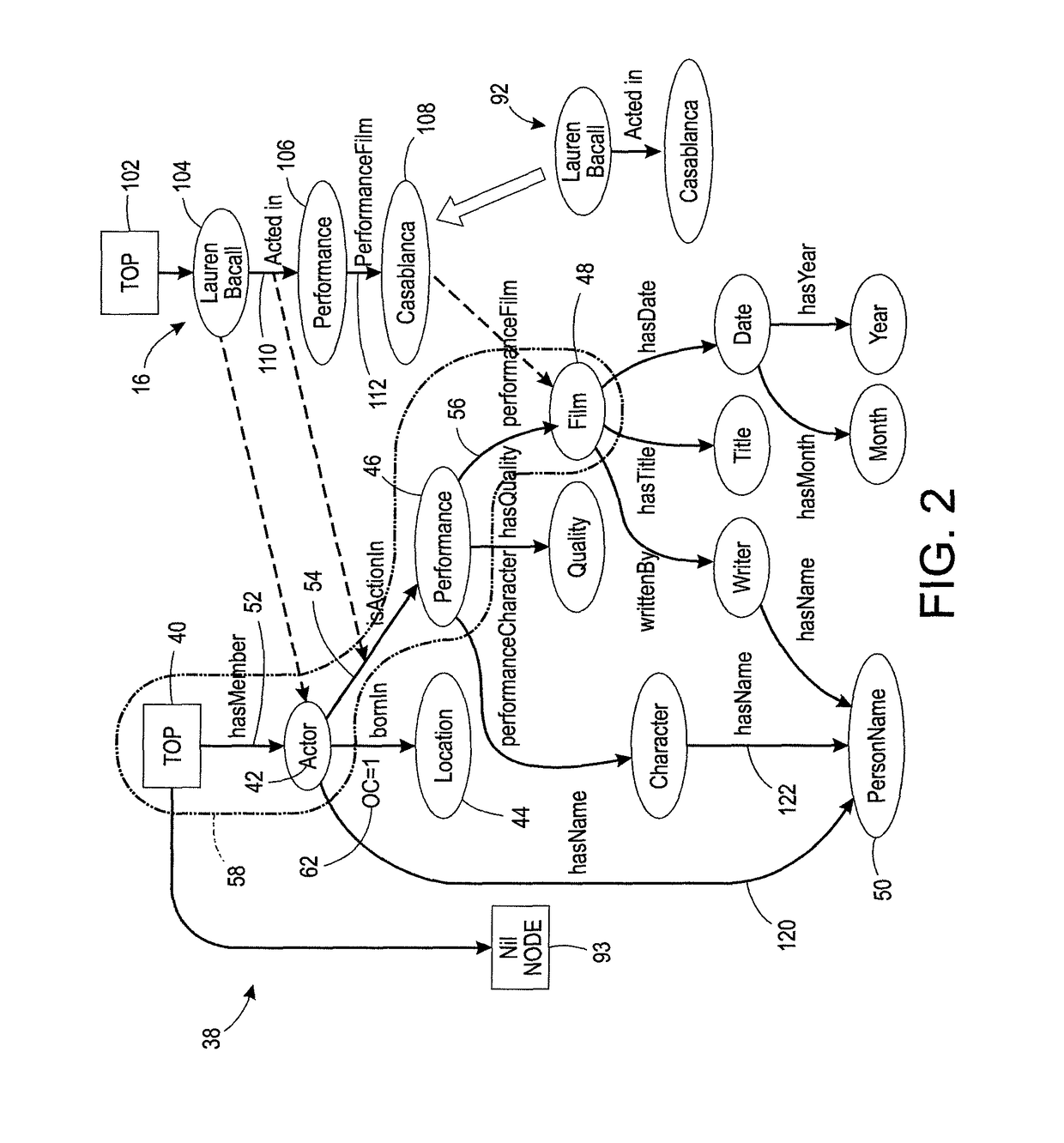
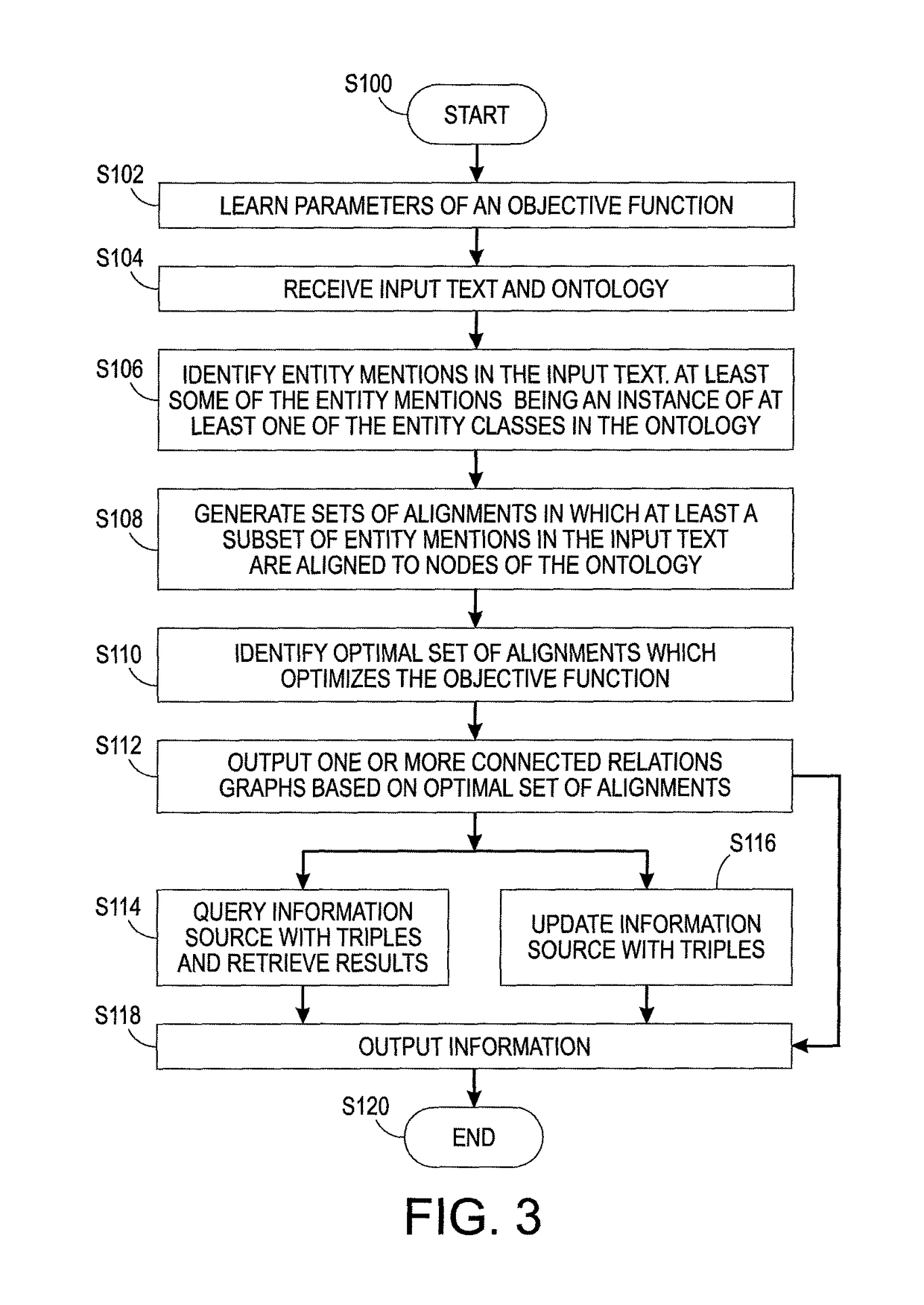
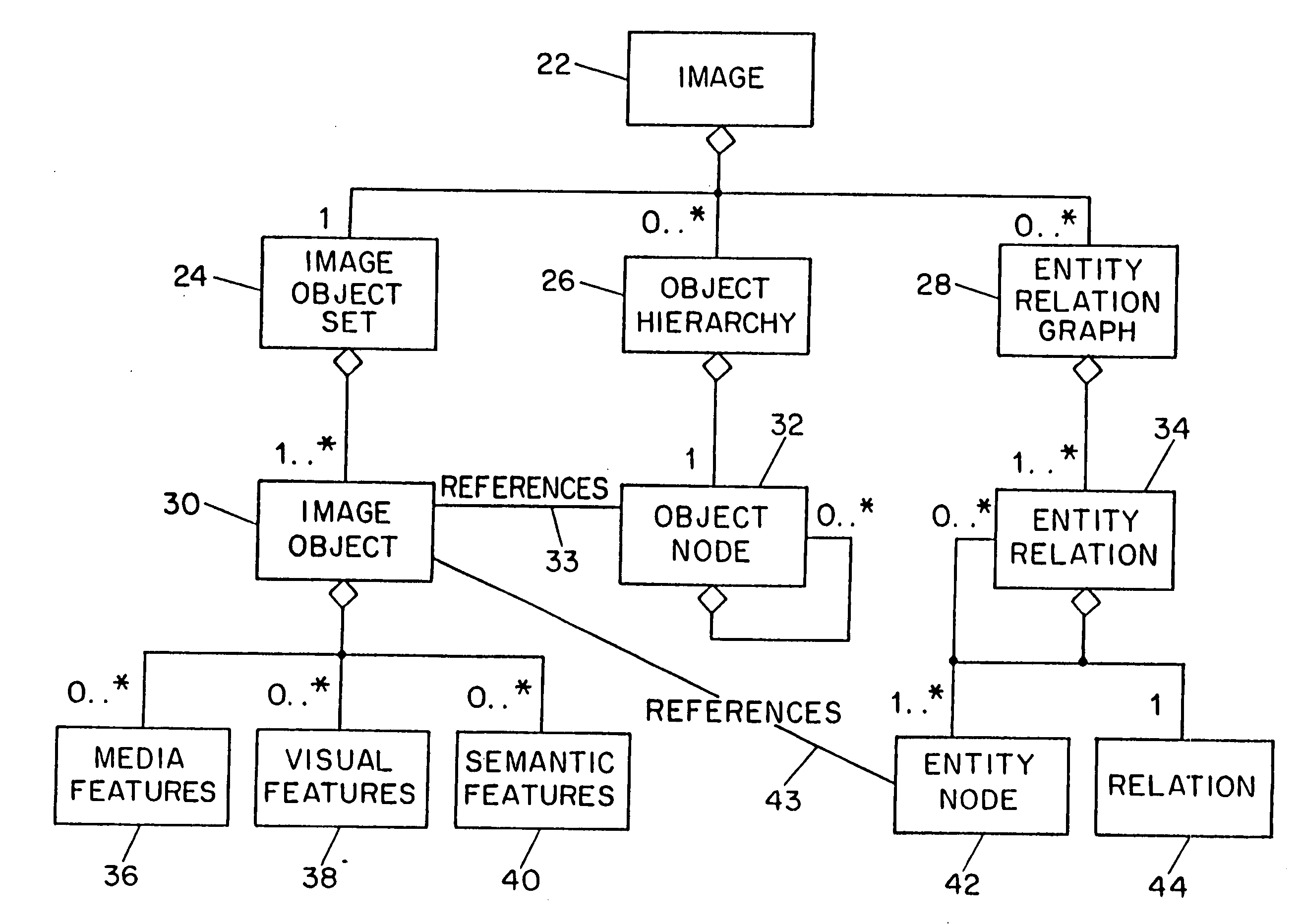
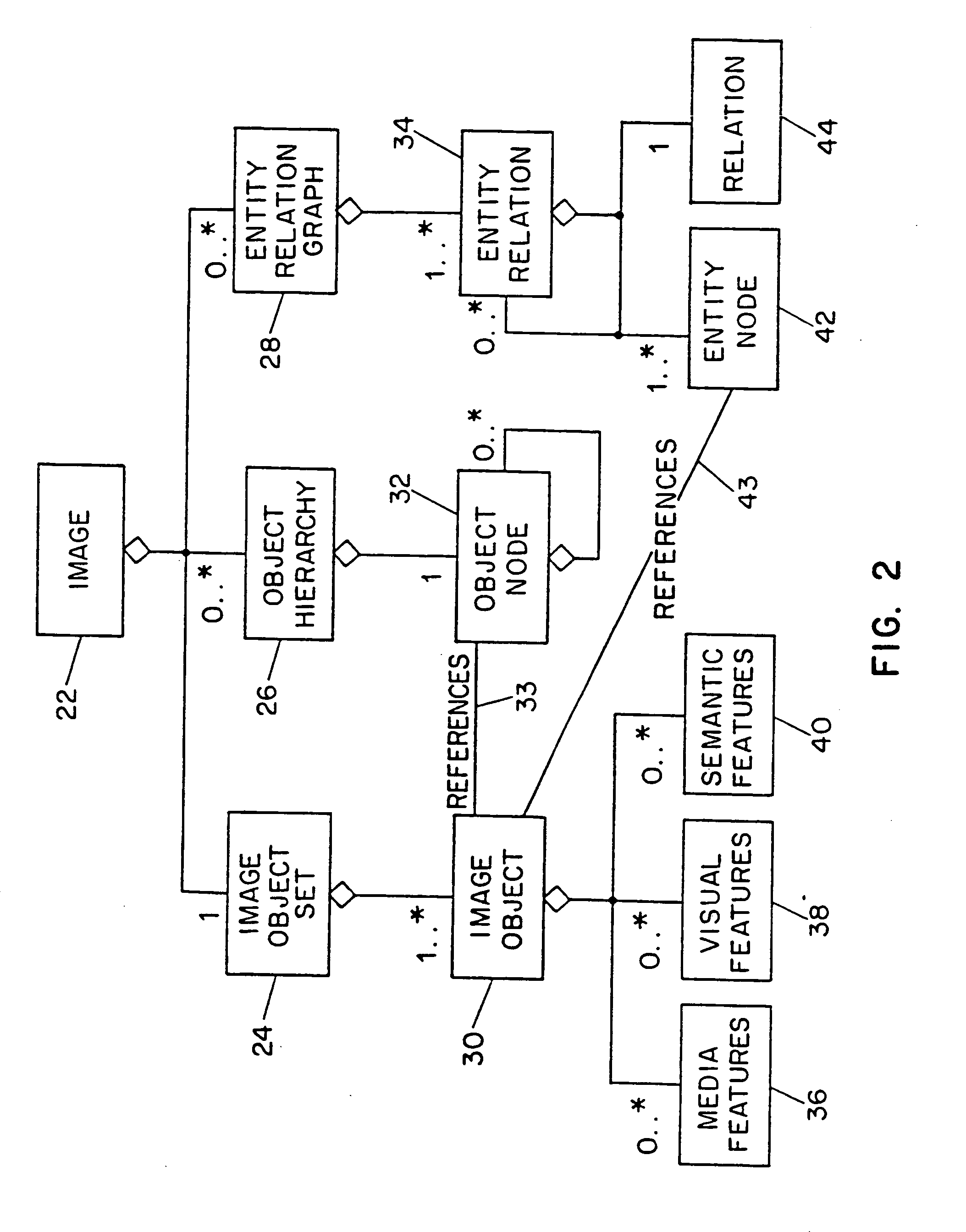
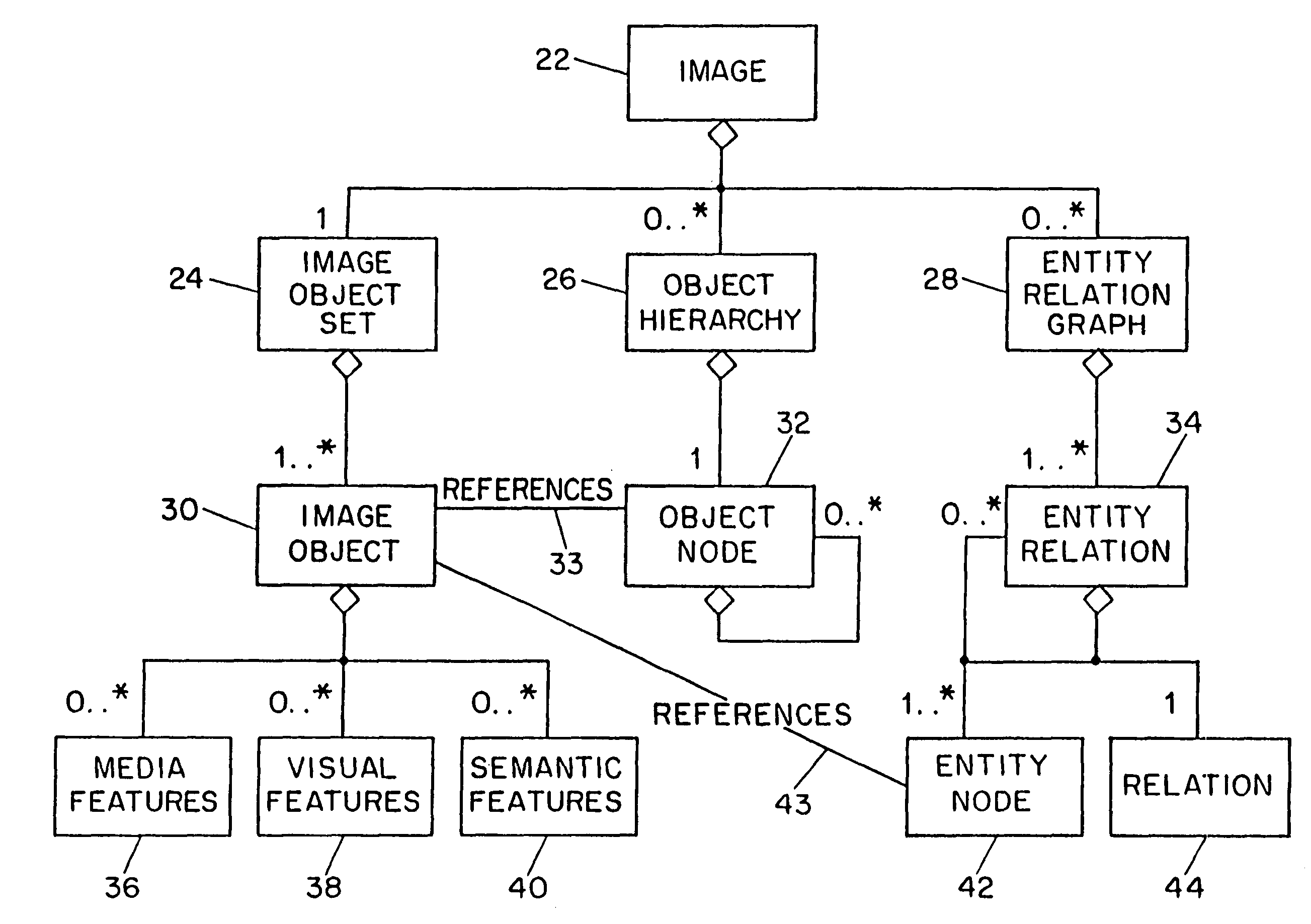
Systems and methods for describing video content establish video description records which include an object set (24), an object hierarchy (26) and entity relation graphs (28). Video objects can include global objects, segment objects and local objects. The video objects are further defined by a number of features organized in classes, which in turn are further defined by a number of feature descriptors (36, 38, and 40). The relationships (44) between and among the objects in the object set (24) are defined by the object hierarchy (26) and entity relation graphs (28). The video description records provide a standard vehicle for describing the content and context of video information for subsequent access and processing by computer applications such as search engines, filters and archive systems.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK +1
Video description system and method
InactiveUS8370869B2Video data indexingAnalogue secracy/subscription systemsRelation graphEntity relation diagram
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK +1
Predictive and descriptive analysis on relations graphs with heterogeneous entities
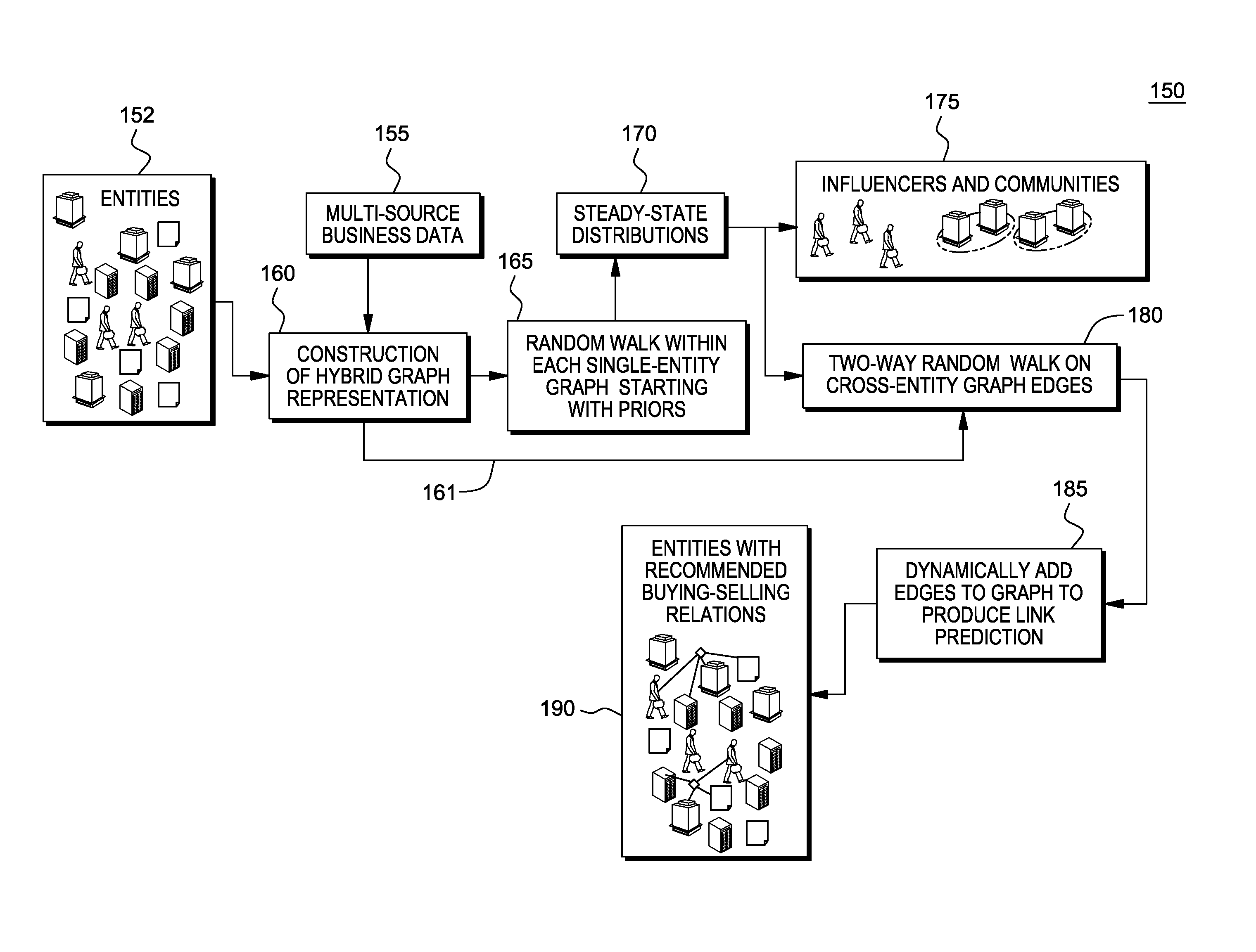
InactiveUS20140317033A1Avoid information lossMathematical modelsDigital computer detailsRelation graphGraphics
A system, method and computer program product provides a random walk model with heterogeneous graphs to leverage multiple source data and accomplish prediction tasks. The system and method components include: 1) A heterogeneous graph formulation including heterogeneous instances of abstract objects as graph nodes and multiple relations as edges connecting those nodes. The different types of relations, such as client-vendor relation and client-product relation, are often quantified as the weights of edges connecting those entities; 2) To accomplish prediction tasks with such information, launching a multi-stage random walk model over the heterogeneous graph. The random walk within a subgraph with homogenous nodes usually produces the relevance between entities of the same type. The random walk across different type of nodes provides the prediction of decisions, such as a client purchasing a product.
Owner:IBM CORP
Method and device for recommending related items
InactiveCN102063433ASolving the problem of maximum term dependenciesSpecial data processing applicationsRelation graphData mining
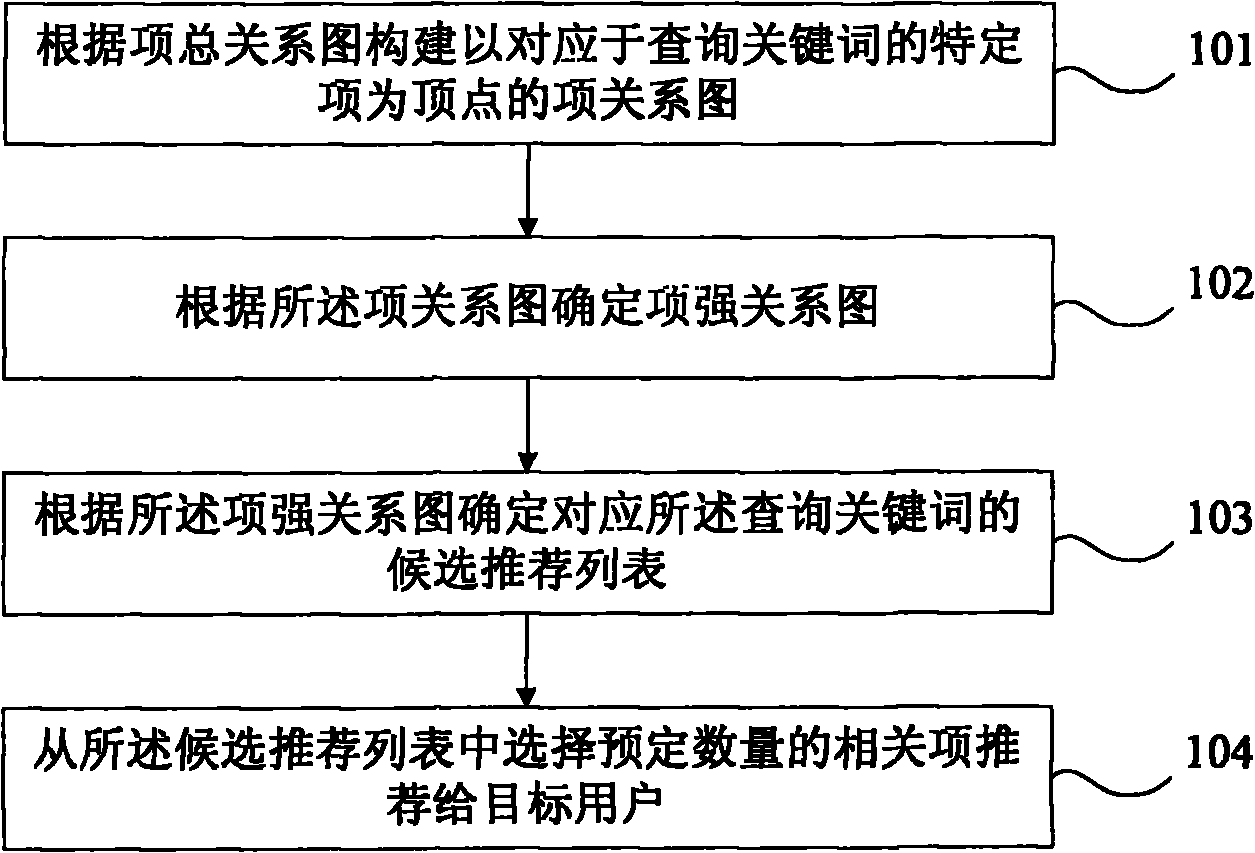
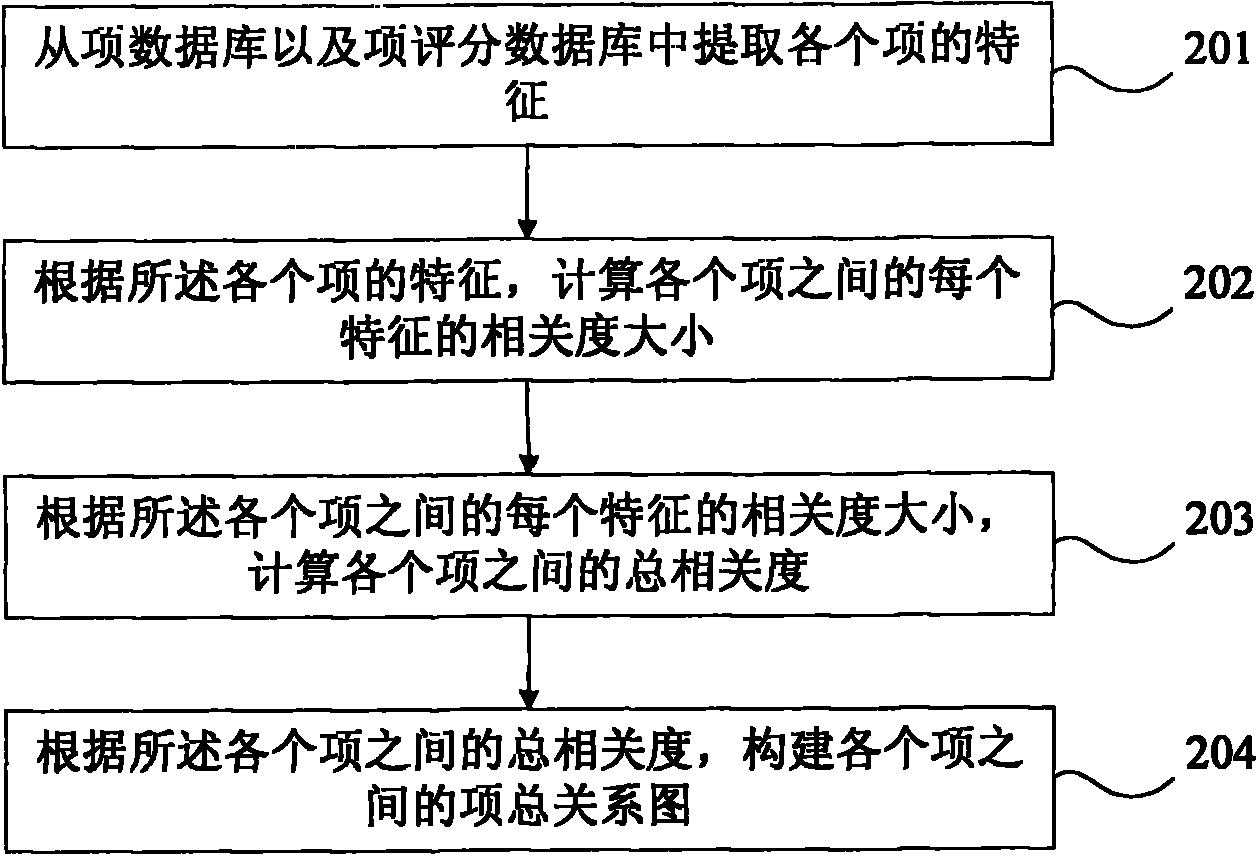
The embodiment of the invention provides a method and a device for recommending related items. The method for recommending related items comprises the following steps: constructing a relation graph of items, which takes a specific item corresponding to a queried key word as a vertex, according to a total relation graph of the items; determining a strong relation graph of the items according to the relation graph of the items; determining a candidate recommendation list which corresponds to the queried key word according to the strong relation graph of the items; and selecting a predetermined number of related items from the candidate recommendation list and recommending the related items to the user. Due to the adoption of the method and the device for recommending related items, the problem on maximum item relevance is effectively solved, and the product really needed by the user can be selected according to the current need of the target user and recommended to the target user.
Owner:HUAWEI TECH CO LTD +1
Method and device based on reverse engineering for automatically generating software documents
InactiveCN103336760ASimple configurationSimple processSpecial data processing applicationsSoftware design descriptionSoftware engineering
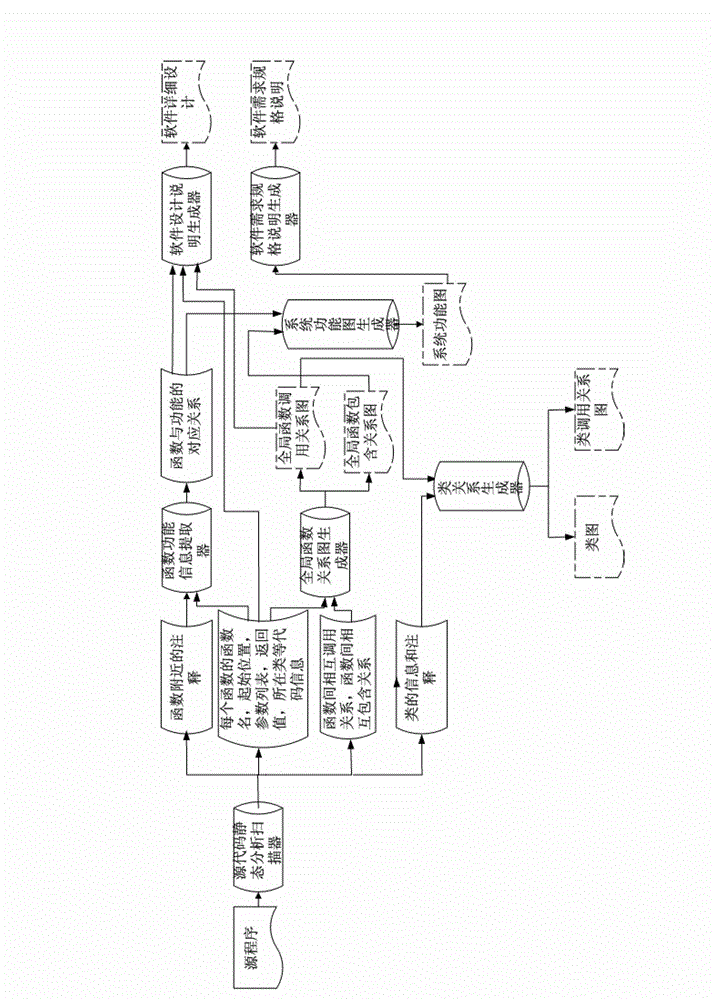
The invention relates to a method and device based on reverse engineering for automatically generating software documents. The method and device based on the reverse engineering for automatically generating the software documents comprises scanning source programs, obtaining function comments, function detail information and a mutual call relation and a mutual inclusion relation among functions, identifying and abstracting function information of functions through a natural language, generating a global function call relation graph and a global function inclusion relation graph respectively based on the function information of the functions and the mutual call relation and mutual inclusion relation among functions, automatically generating software design description documents based on the function information of the functions, the function detail information and the global function call relation graph, generating a system function graph based on the function information of the functions and the global function inclusion relation graph, and generating software requirement specification documents automatically based on the system function graph. According to the method and device based on the reverse engineering for automatically generating the software documents, the software requirement specification documents and the software design description documents are generated automatically, the reverse engineering from codes to documents is achieved, and the method and device based on the reverse engineering for automatically generating the software documents is wide in application and strong in adaptability.
Owner:BEIJING INFORMATION SCI & TECH UNIV +1
Method and system for linking entities
InactiveCN105224648AReduce complexityEntity link is accurateSpecial data processing applicationsText database clustering/classificationEntity linkingRelation graph
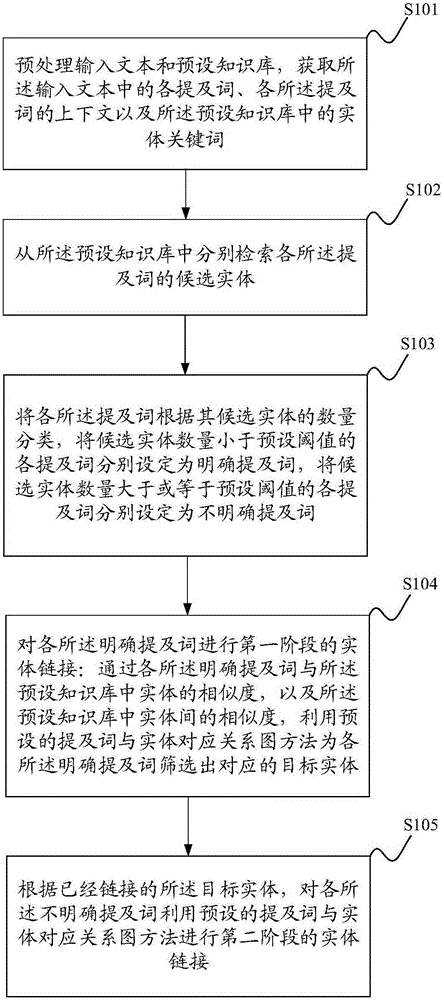
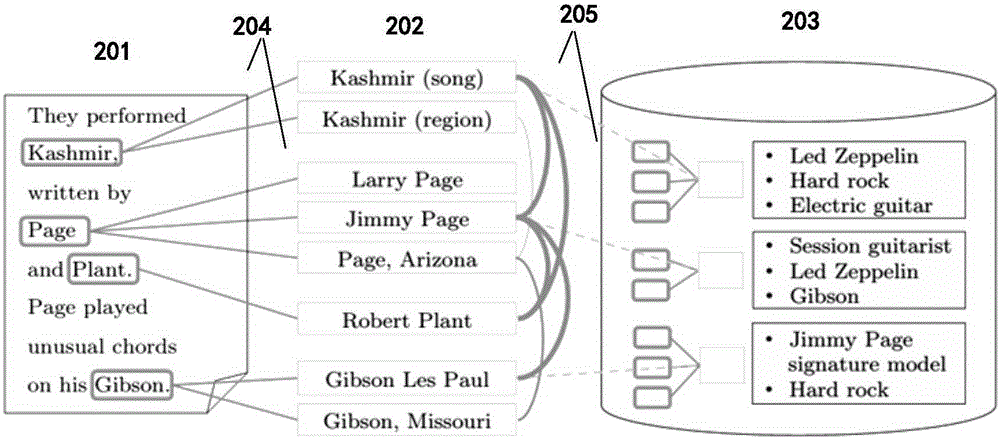
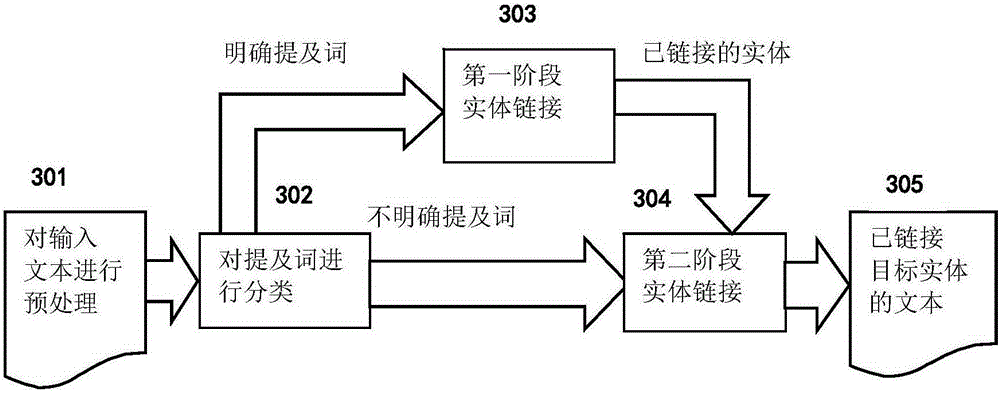
The invention discloses a method and a system for linking entities. The method comprises: pre-processing input texts and a knowledge base, obtaining mentions and contexts thereof, and entity keywords; retrieving candidate entities of each mention; classifying the mentions in two kinds according to the number of candidate entities of the mentions, the mentions whose number of candidate entities is smaller than a preset threshold being clear-cut mentions, and others being undefined mentions; performing first stage entity linking on the clear-cut mentions; through similarity of the mentions and the entities in the knowledge base, and similarity among the entities, using a method of a corresponding relation graph of a preset mention and the entities to complete screening of the candidate entities; and according to linked target entities, performing second stage linking on the undefined mentions. The method respectively performs calculation of entity linking in stages according to whether the mentions are the clear-cut mentions or not, so that complexity of the algorithm is greatly reduced. Through upgrading the contexts of the mentions, for example, the linked entities, entity linking can be performed on the mentions in a text more accurately and rapidly.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method for automatically extracting character relations from text set
InactiveCN103235772AFast recognitionImprove accuracySpecial data processing applicationsRelation graphApplicability domain
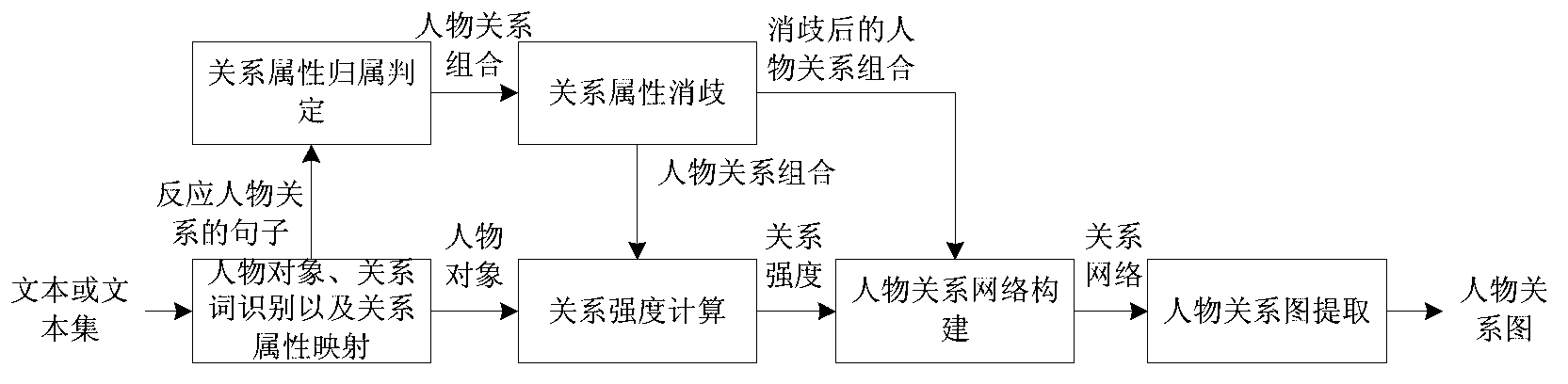
The invention relates to a method for automatically extracting character relations from a Chinese text or a text set, and belongs to the technical field of computer science and information extraction. In the method, by means of sentence meaning model characteristics, the relation attribute affiliation is determined; the character relations scattered in the text or the text set are automatically extracted by combining methods such as relation attribute disambiguation, character relation strength calculation and the like; and the character relations are organized by a character relation network, and the character relations comprising character relation attributes and the relation strength are displayed in a character relation graph manner. According to the method, sentence meaning model characteristics are introduced, so that the accuracy of the method for extracting entity relations is improved, and the method for extracting the character relations is enriched. Besides, as the number of texts about a central character in the text set is increased, the method can extract character relations of the central character more accurately and comprehensively, and the application range is wider.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Automatic multi-document abstract extraction method and automatic multi-document abstract extraction system based on sentence vectors
ActiveCN108090049ANatural language data processingSpecial data processing applicationsNatural language processingRelation graph
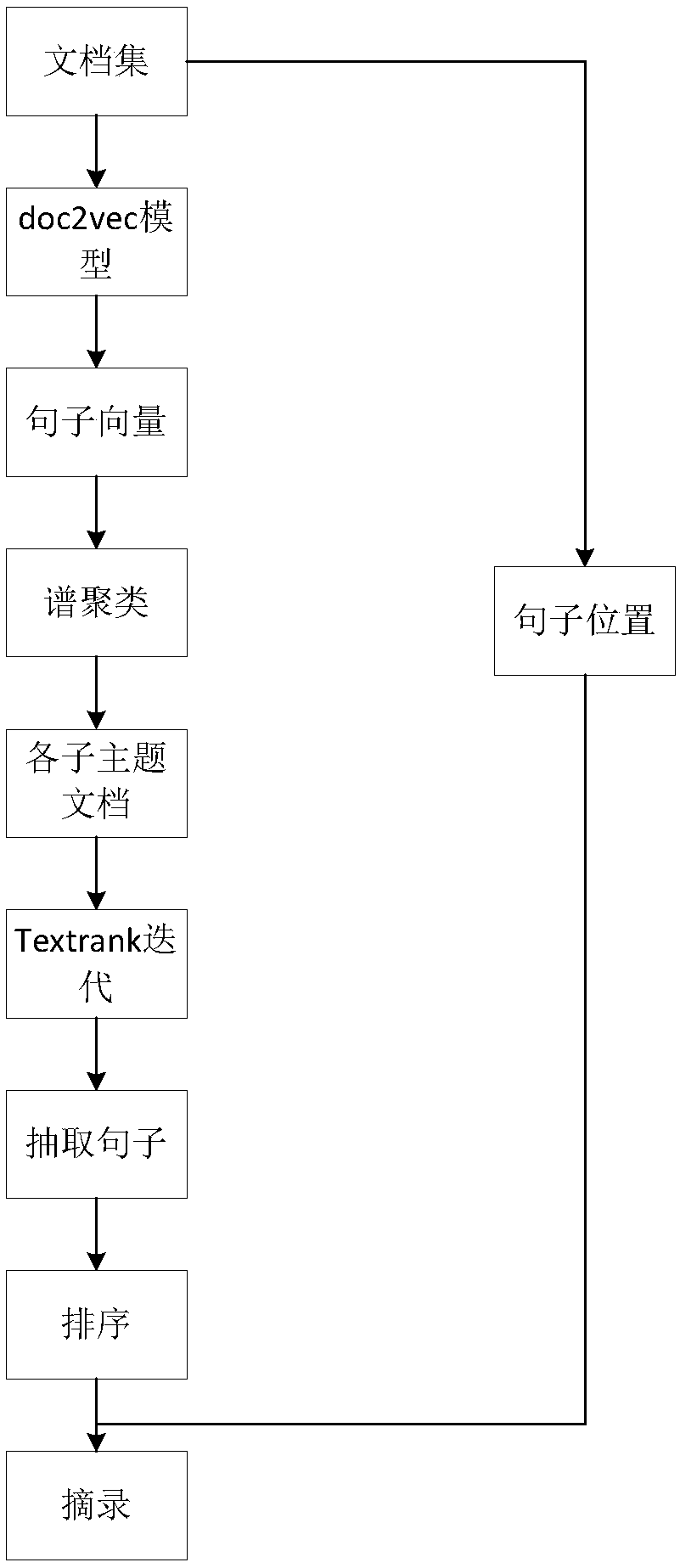
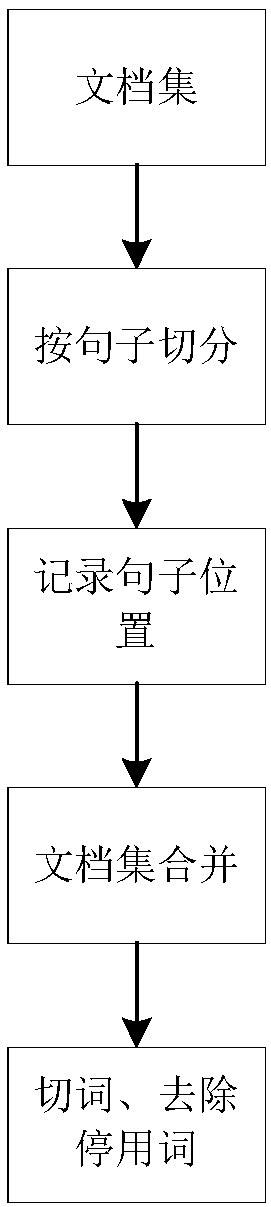
The invention discloses an automatic multi-document abstract extraction method and an automatic multi-document abstract extraction system based on sentence vectors. The automatic multi-document abstract extraction method includes S1, preprocessing document collections; S2, generating the sentence vectors through doc2vec model training; S3, cluttering the sentence vectors into sub-theme documents;S4, creating a sentence relation graph model in each sub-theme document; S5, calculating sentence weights; S6, extracting and sequencing sentences to form abstracts. The automatic multi-document abstract extraction method and the automatic multi-document abstract extraction system have the advantages that all the sentences in the target document collections are expressed by the vectors through thelarge-corpus-set training doc2vec model; sub themes are acquired through spectral clustering, one sentence is extracted from each sub theme, and accordingly, sentence redundancy is avoided; the sentences are sequenced according to positions in original documents to form the abstracts, and coherence of the abstract sentences is improved.
Owner:SHANDONG INST OF BUSINESS & TECH
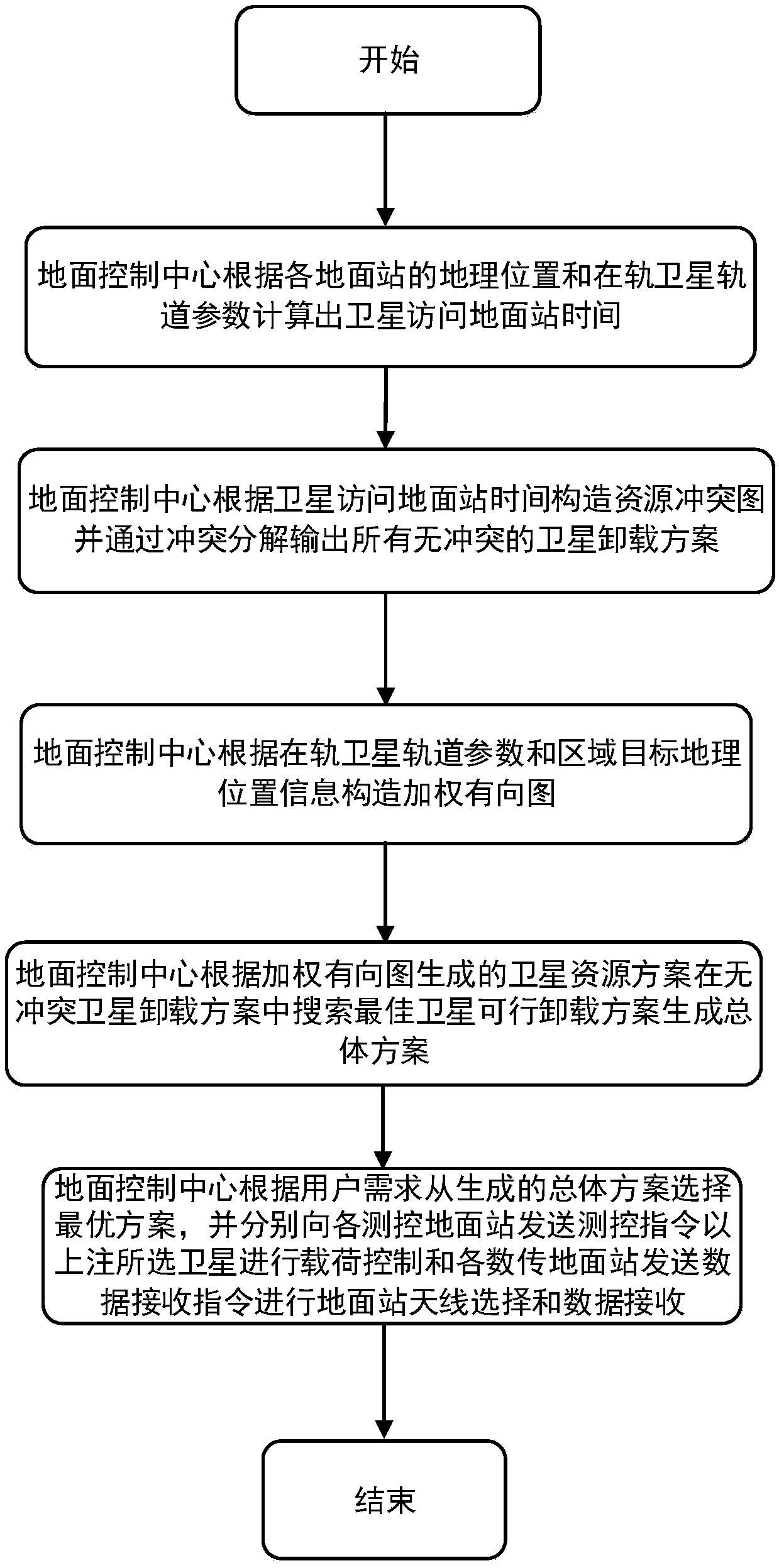
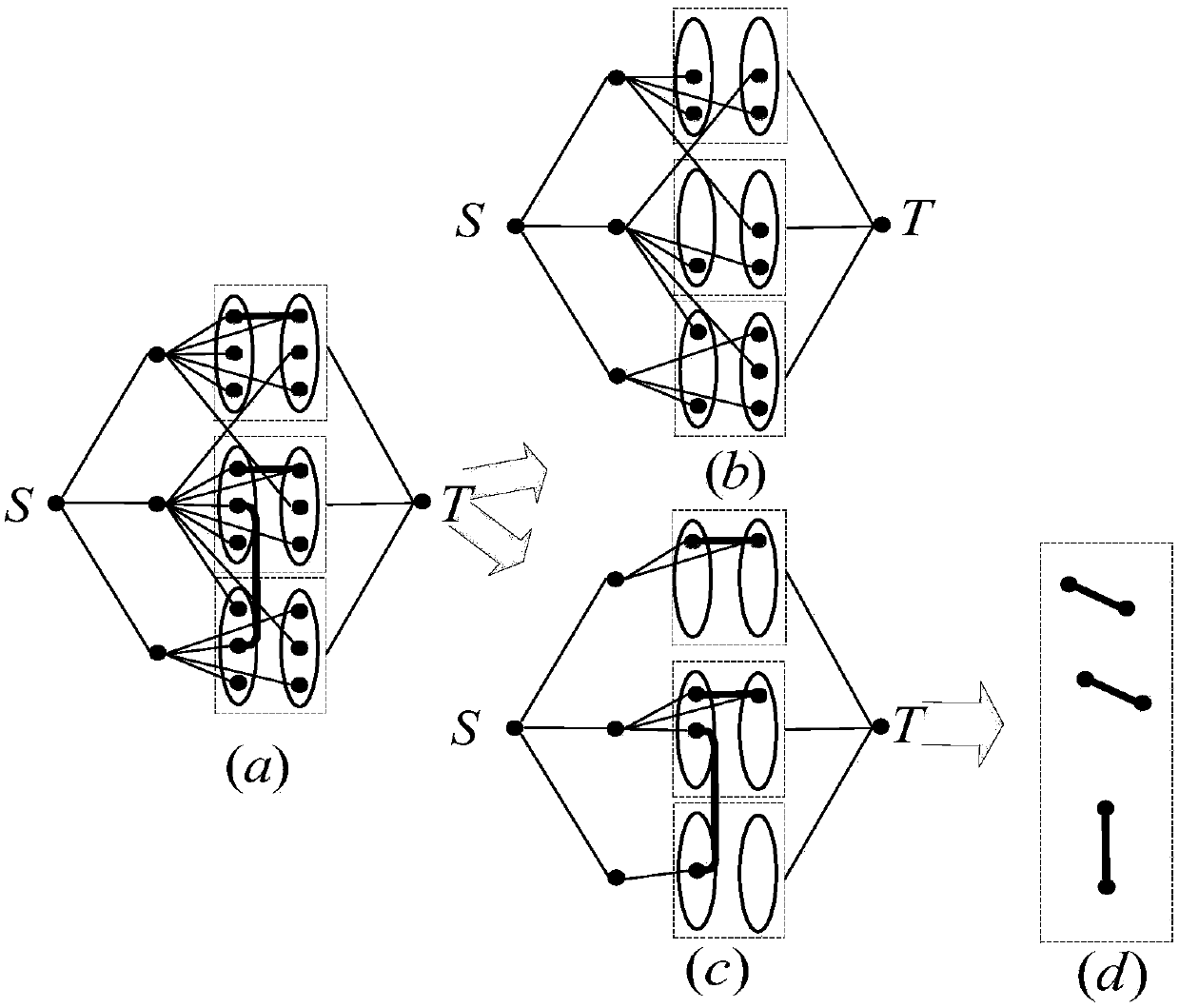
Multi-satellite and multi-ground station resource collaborative allocation management method oriented to region target
ActiveCN107864007AImprove resource utilizationSimplify complexityRadio transmissionRelation graphDirected graph
The invention discloses a multi-satellite and multi-ground station resource collaborative allocation management method oriented to a region target. The multi-satellite and multi-ground station resource collaborative planning problem is solved. The realization process is as follows: respectively constructing resource relation graphs, communication resource conflict-free graphs and communication resource conflict graphs through a ground control center by acquiring the ground station and satellite information, thereby generating a satellite unloading scheme; computing a satellite access region target by using the target region information and the satellite ephemeris, extracting all possible and feasible satellite unloading schemes from the satellite unloading scheme; constructing a weighted directed graph for each feasible satellite unloading scheme, traversing all weighted direction graphs, and finding out a path with large coverage rate and less hop count by using a labelling algorithmand a defined addition, thereby generating a total unloading scheme and annotating a measurement and control instruction. Through the method disclosed by the invention, the resource use ratio and thetask planning efficiency are improved, the complexity of the resource management is reduced, and the method can be used for the resource management of the ground observation satellite system.
Owner:陕西丝路天图卫星科技有限公司
Predictive and descriptive analysis on relations graphs with heterogeneous entities
InactiveUS9195941B2Avoid information lossProbabilistic networksKnowledge representationNODALRelation graph
Owner:IBM CORP
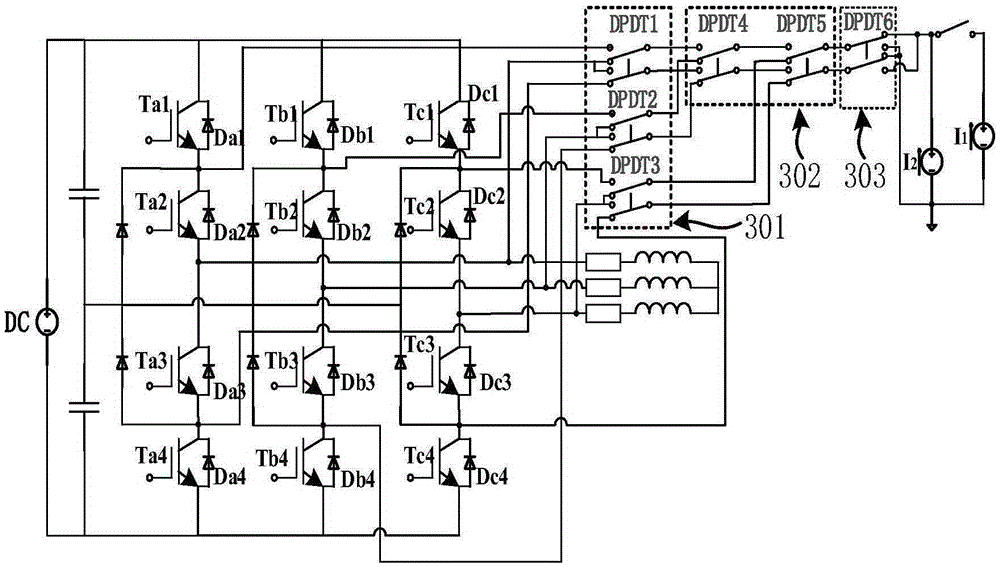
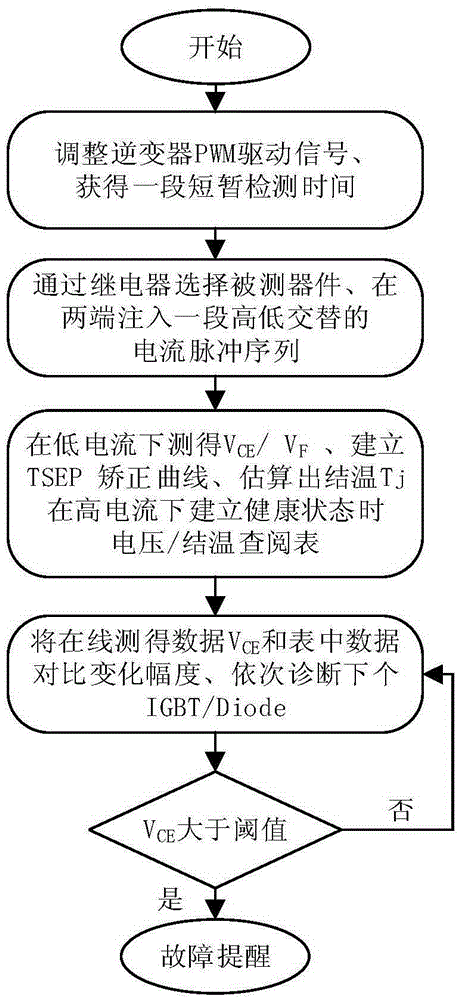
On-line reliability monitoring system of NPC type three-level inverter and method thereof
ActiveCN105337523AEmergency protective circuit arrangementsAc-dc conversionJunction temperatureEngineering
The invention discloses an on-line reliability monitoring system of an NPC type three-level inverter and a method thereof. The method comprises: switching states of twelve power switching devices in a three-phase bridge arm are determined based on a current flowing path of an NPC inverter, micro adjustment of PWM waveforms within each period is carried out to select a proper measurement time period, and detection work is carried out on a normal working condition; an external auxiliary power supply unit injects currents with two kinds of amplitudes into a measured device within the detection period, and a data acquisition unit measures on-state voltage drops of the IGBT power devices and diodes connected with the devices in an anti-parallel mode; and an analysis reliability unit generates a breakover drop and junction temperature relation graph as a calibration curve by using measured voltages as temperature-sensitive parameters, and a reference look-up table is obtained based on the obtained junction temperatures and on-state voltage drops. When amplifications of breakover drops of the devices are monitored to exceed a threshold value under high currents in an on-line mode, occurrence of bonding wire failure phenomena inside the IGBT devices can be determined. And healthy states of all devices are obtained successively to obtain a reliability detection result of the inverter.
Owner:HEFEI UNIV OF TECH
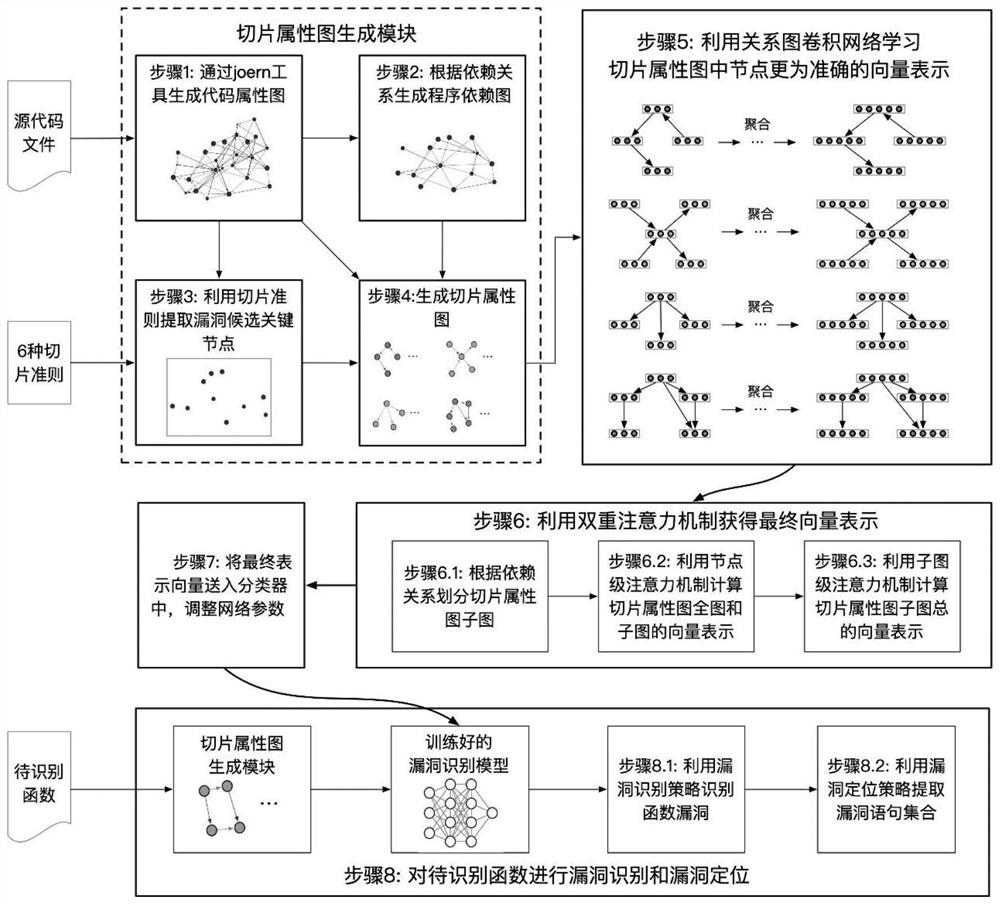
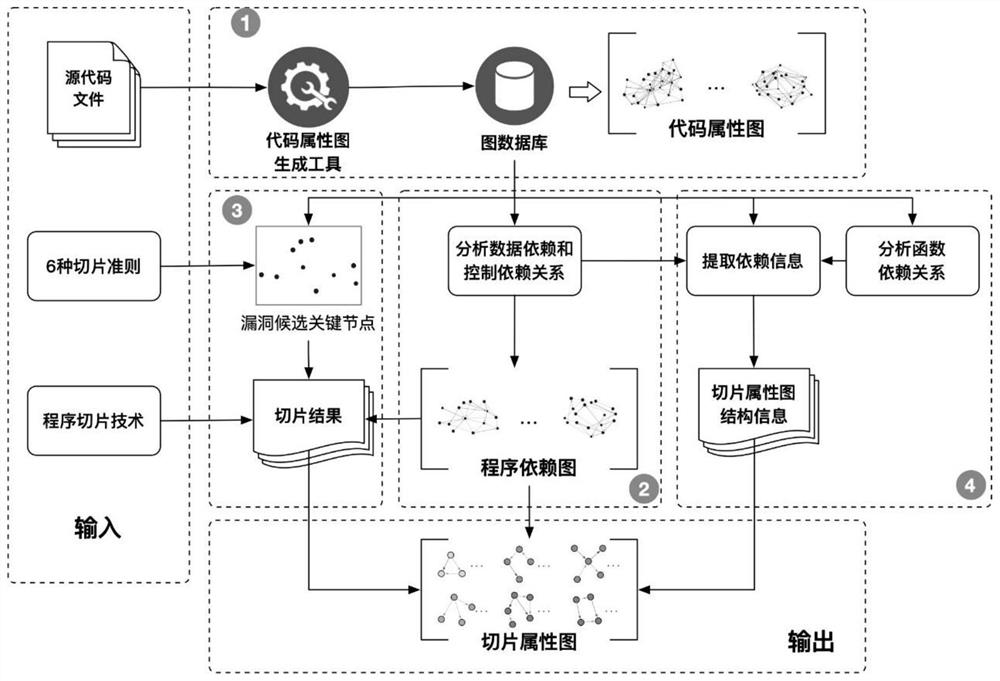
Function-level code vulnerability detection method based on slice attribute graph representation learning
ActiveCN112699377AIncrease coverageReduce false positivesPlatform integrity maintainanceRelation graphProgram slicing
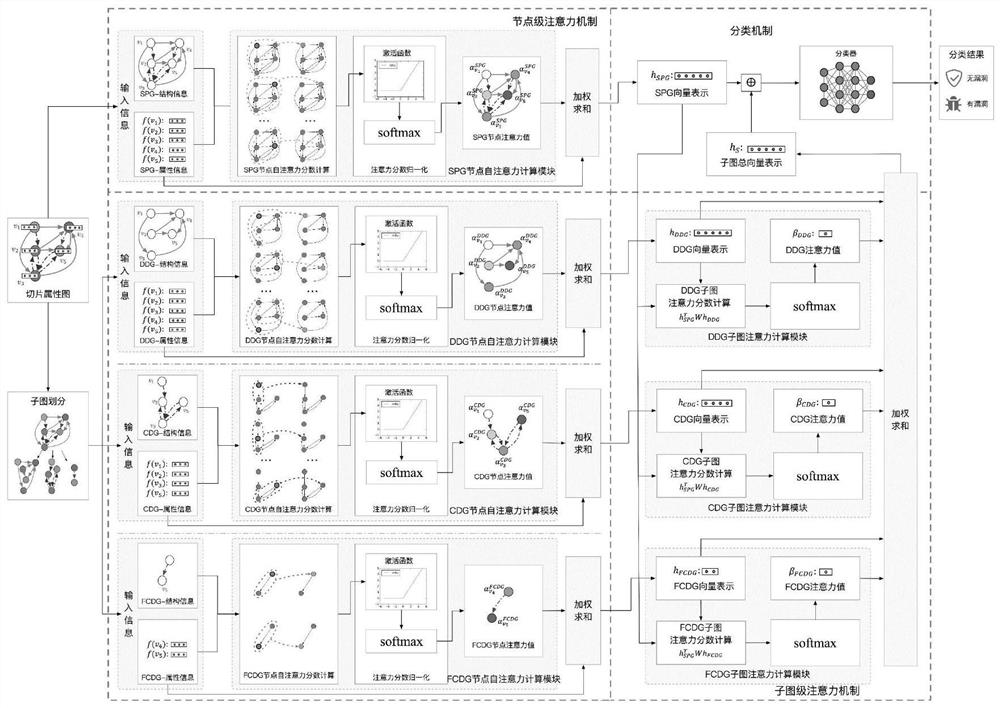
The invention discloses a function-level code vulnerability detection method based on slice attribute graph representation learning, and the method comprises the steps: firstly introducing a new slice criterion, proposing the concept of a slice attribute graph, and generating a slice attribute graph of a code based on the slice criterion and a program slice technology; extracting graph structure information, node attribute information and code context information which have a dependency relationship with the vulnerability candidate key points; then, performing representation learning on the slice attribute graph by utilizing a relation graph convolutional neural network and combining a dual attention mechanism based on nodes and sub-graphs so as to learn a more comprehensive and accurate vulnerability mode; and finally, fusing the vulnerability identification results of the slice attribute graphs to realize function-level vulnerability detection, and determining a set of vulnerability candidate statements and grammatical elements associated with vulnerabilities. More vulnerability candidate key points can be covered, structures, attributes and context information related to vulnerabilities are fully learned and expressed, and the vulnerability detection accuracy is improved.
Owner:HARBIN INST OF TECH
Node relation graph displaying method and system based on HTML5
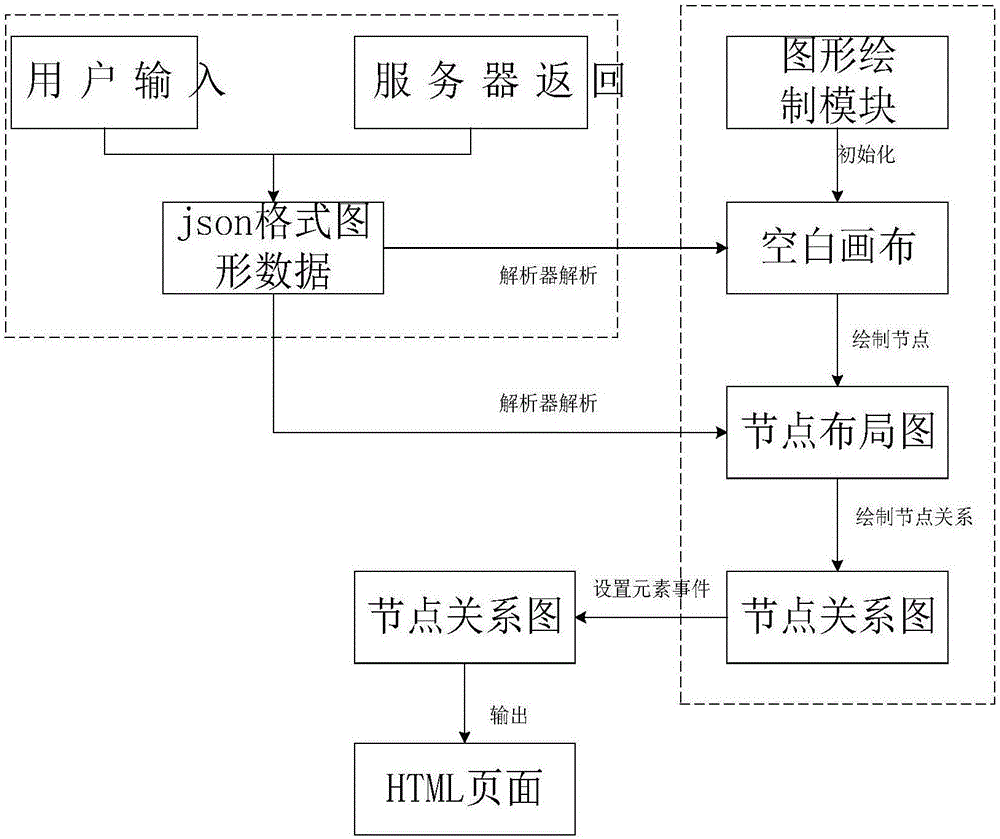
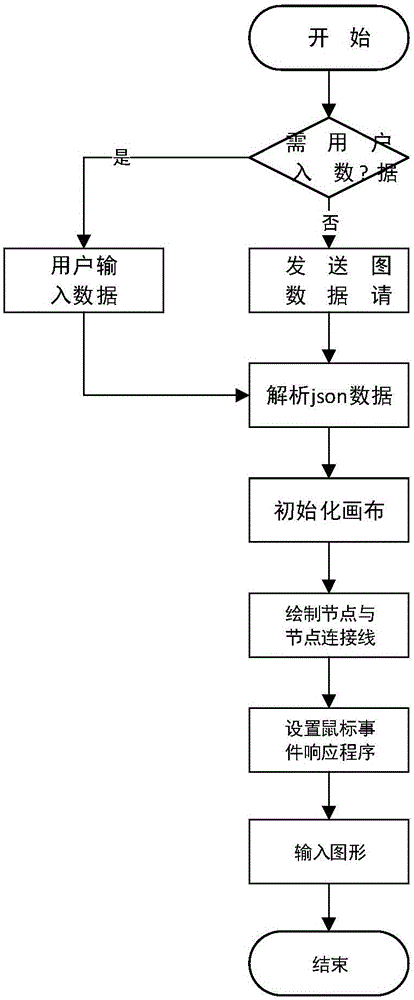
InactiveCN106484408AAvoid crossingRelationship performanceText processingExecution for user interfacesHTML5Relation graph
The invention provides a node relation graph displaying method and system based on an HTML5. The method comprises the steps that a user inputs or a website server background returns graph data of a node relation graph, wherein the graph data is of a specific json format; a data input module obtains corresponding json graph data and stores the data temporarily; through utilization of new features of the HTML5, a graph drawing module is established and initial blank canvas is established; the json graph data is resolved through utilization of a JavaScript program resolver; the graph drawing module sets an initial position of nodes according to the resolved graph data and draws the nodes; the graph drawing module draws corresponding node connecting lines according to the drawn node graph and the corresponding graph data; a graph element event processing module sets mouse events of graph elements according to the graph data; and a graph output module outputs a graph to a webpage, and the node relation graph is displayed to the user. According to the method and the system, through utilization of a canvas function of the HTML5 and the mouse events of various graph elements supported by an html page, the node relation graph is efficiently and clearly displayed on the webpage through the graph data of the specific format.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
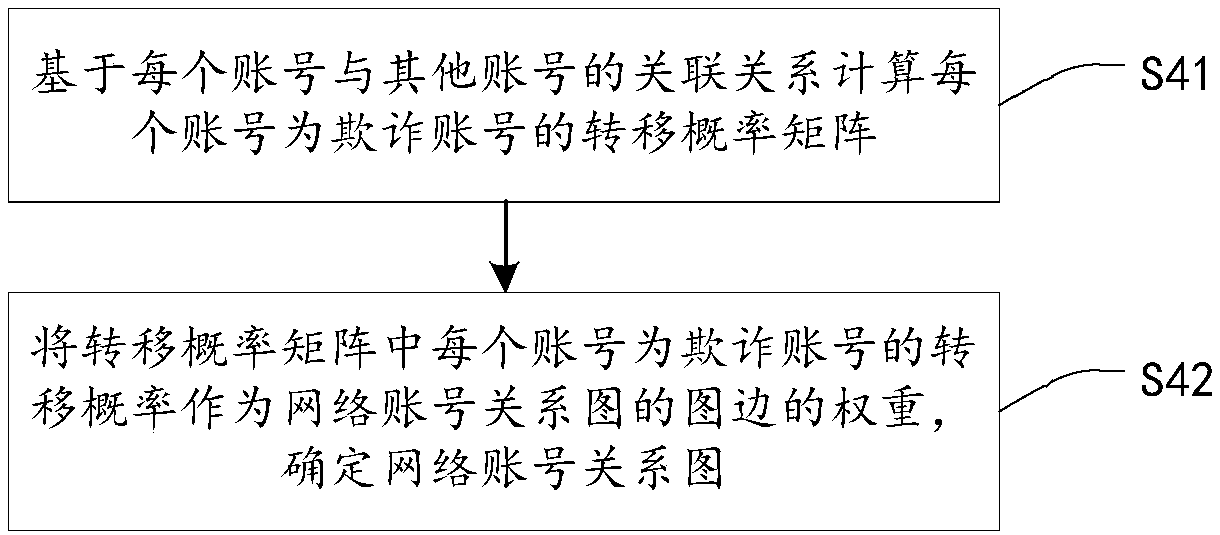
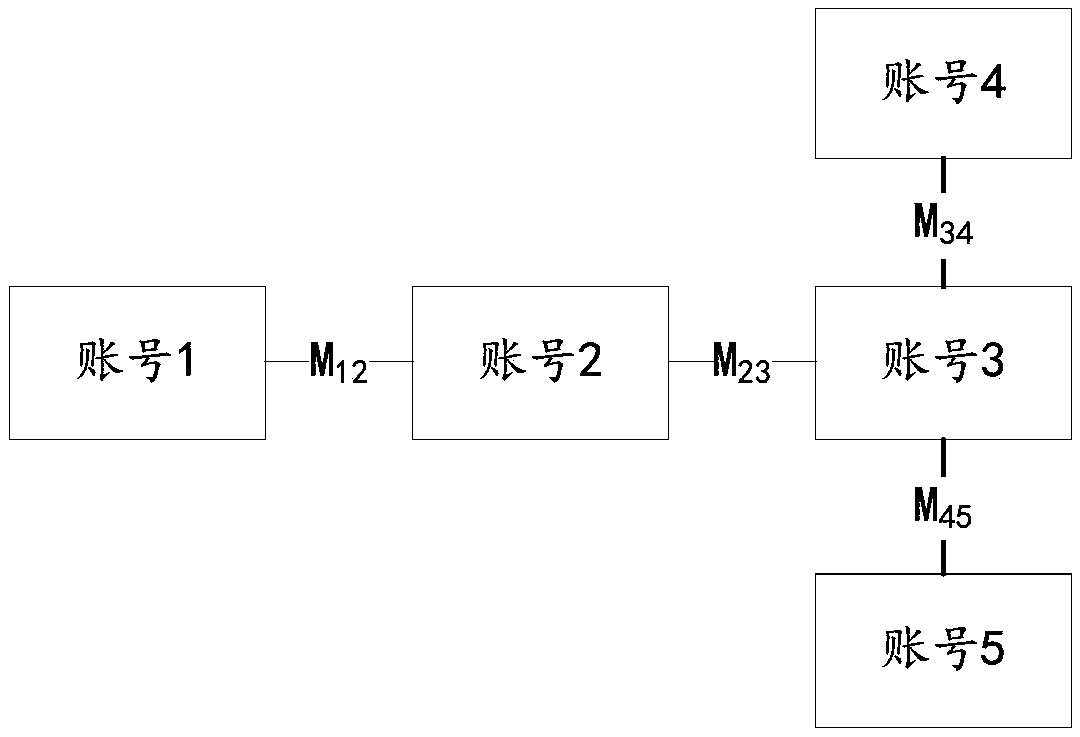
Fraud account detection method and device and storage medium thereof
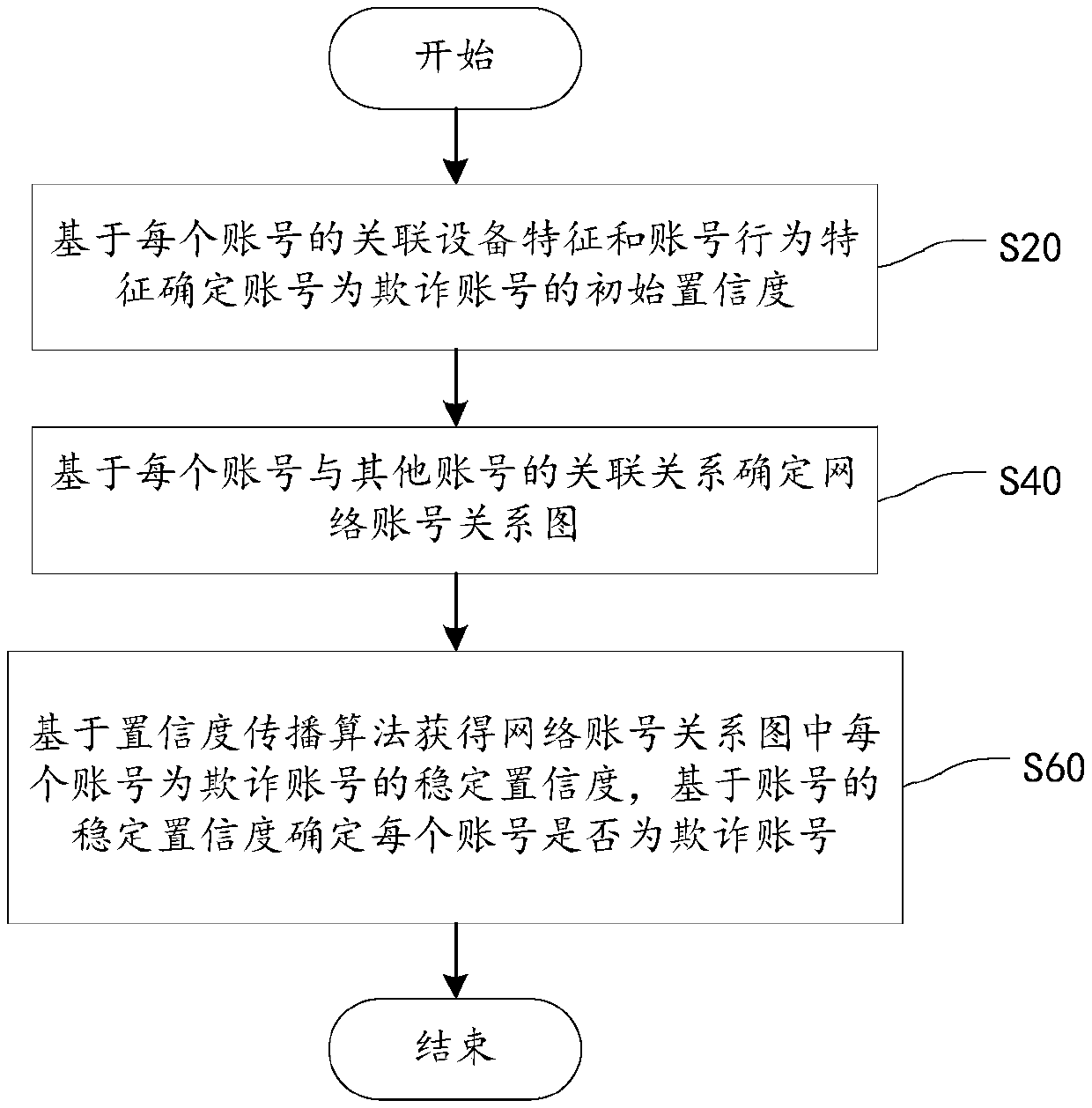
ActiveCN109558951AImprove generalization abilityImprove fraud detection accuracyCharacter and pattern recognitionMachine learningRelation graphData mining
The invention provides a fraud account detection method and device and a storage medium, and relates to the technical field of anti-fraud detection. The fraudulent account detection method comprises the steps of determining an initial confidence coefficient of an account as a fraudulent account based on an associated equipment feature and an account behavior feature of each account; determining anetwork account relation graph based on the association relationship between each account and other accounts, wherein the network account relation graph comprises the transition probability that eachaccount and other accounts are fraudulent accounts under different association relationships; and obtaining a stability confidence coefficient of each account in the network account relation graph asa fraudulent account based on a confidence coefficient propagation algorithm, and determining whether each account is a fraudulent account based on the stability confidence coefficient of the account.According to the method, whether the account is a fraud account or not is judged by combining the inherent characteristics of the account, the login behavior characteristics and the confidence coefficient propagation algorithm, so that the efficiency, the accuracy and the generalization capability of fraud prediction are improved.
Owner:BEIJING KNOWNSEC INFORMATION TECH
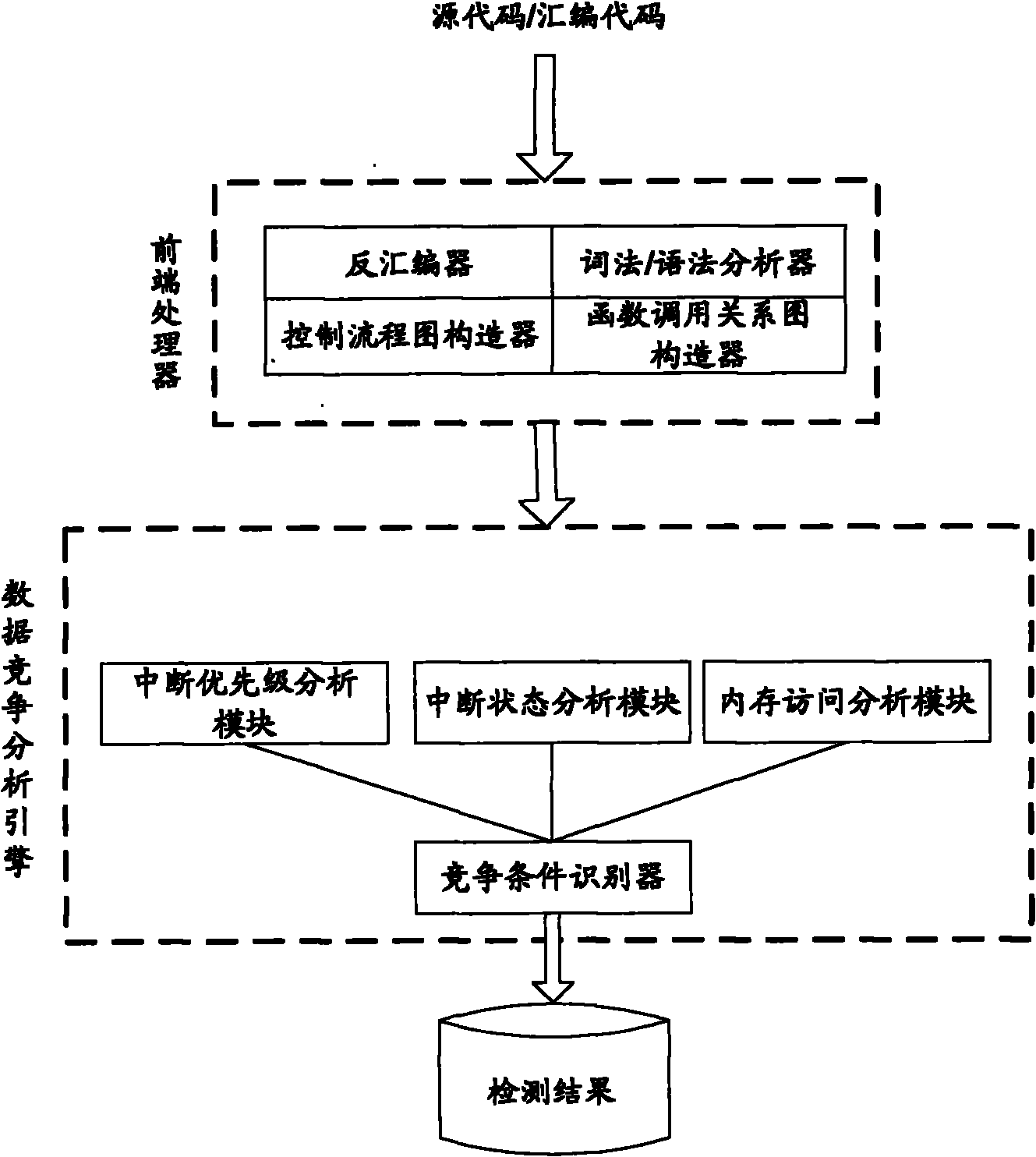
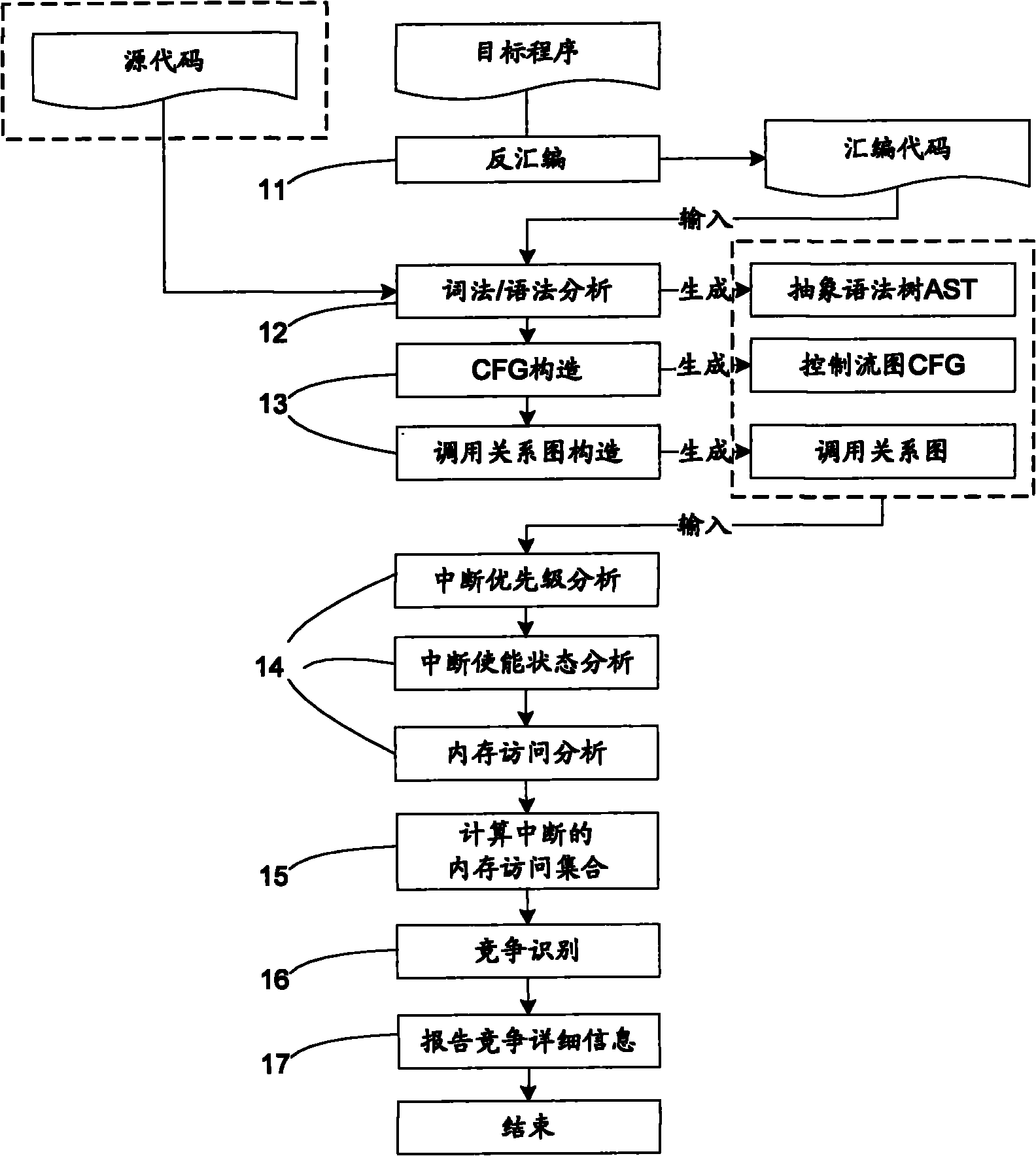
System for detecting interrupt-driven type program data competition
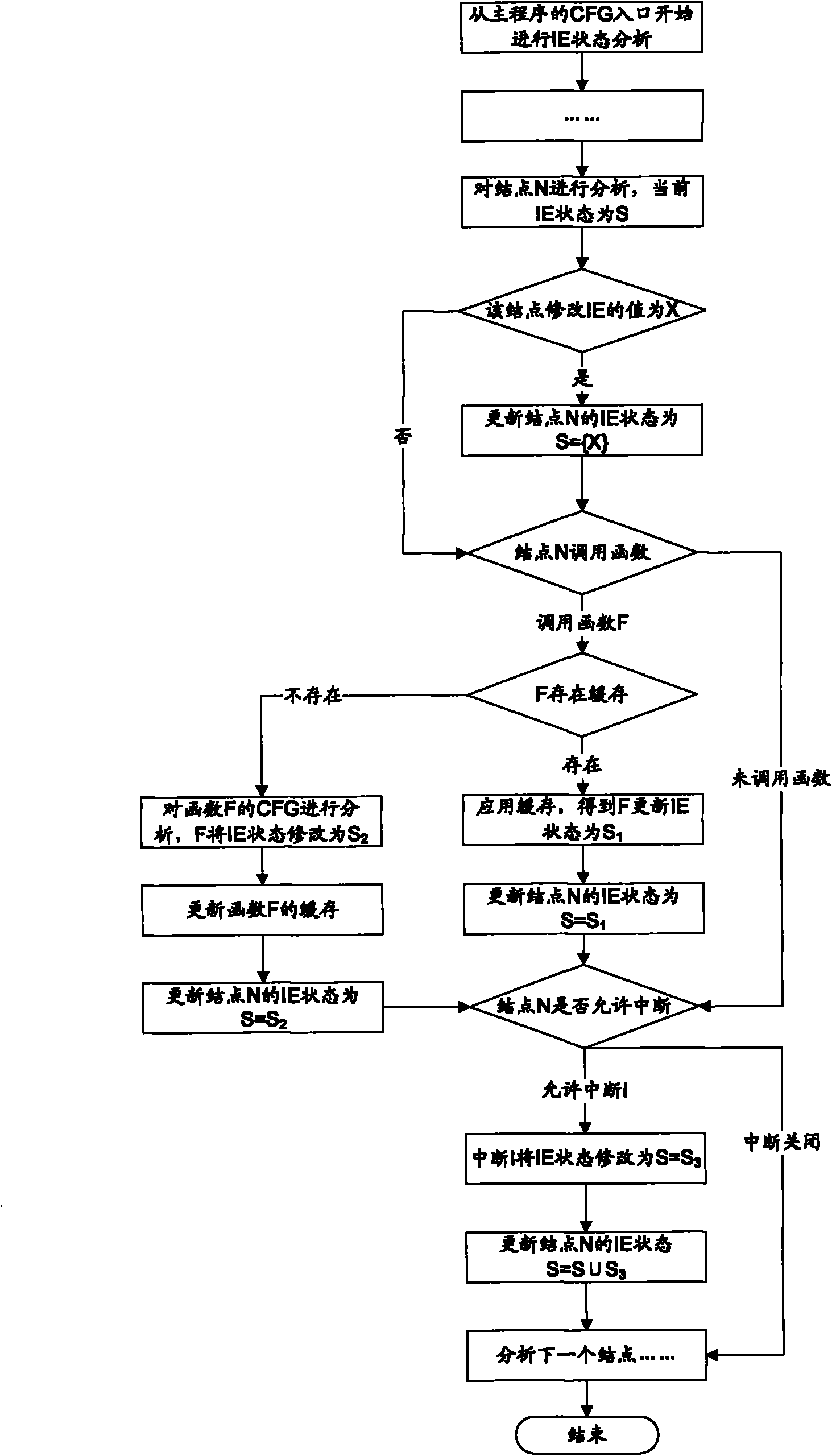
ActiveCN102063328AReduce false positivesHigh degree of automationMultiprogramming arrangementsSoftware developmentSyntax
The invention discloses a system for detecting interrupt-driven type program data competition, which comprises a front-end processor and a data race analysis engine, wherein the front-end processor comprises a disassembler, a morphology / syntax analyzer, a control flow graph constructor and a function call relation graph constructor, and the data race analysis engine comprises an interrupt priority analysis module, an interrupt state analysis module, a memory access analysis module and a race condition identifier. A static detection method is adopted in the invention, wherein a source code or assembly code is input; the detected program does not need to run; the method can be applied in the early stage of software development; the automaticity is high; and the interrupt enabled state is analyzed in iterative inter-process manner; through 'iteration', all the possible interrupt switching conditions can be extremely collected and the failed report of data race detection is reduced; and through 'inter-process', the function call and the influence of the interruption on the program state are regarded and the detection accuracy and the detection efficiency are increased.
Owner:BEIJING INST OF CONTROL ENG
Method and system for predicting power of microgrid group
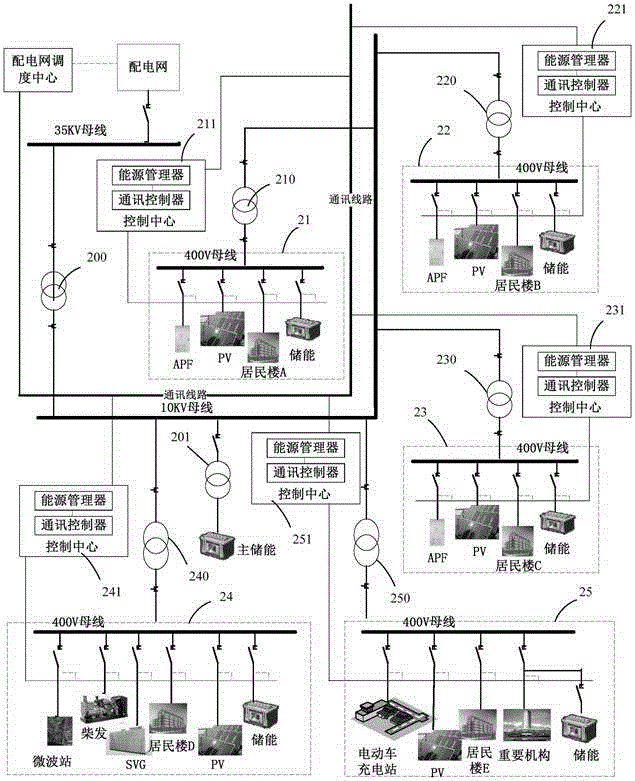
InactiveCN105826944AAvoid the various disadvantages of centralized forecastingGood forecastLoad forecast in ac networkSingle network parallel feeding arrangementsRelation graphPrediction algorithms
The invention discloses a method and a system for predicting power of a microgrid group. The method comprises steps: a microgrid graph theory model is built according to a communication relation between sub microgrids in the microgrid group; according to an intelligent agent node consistency theory and in combination with a micro Calman filter prediction algorithm, a power prediction algorithm for distributed prediction for needed power by a total grid of the microgrid group is determined; on the basis of the already-built communication relation graph theory topology, each sub microgrid in the microgrid group integrates grid needed power information of a local sub microgrid system and an adjacent sub microgrid system and uses a prediction algorithm to distributively perform short-term prediction on the needed power by the total grid of the microgrid group in the local sub microgrid system. Short-term prediction is carried out on the overall grid needed power of the microgrid group formed by multiple microgrids, and strong guarantee is provided for aspects of stable operation and power dispatching for the microgrid group power sharing system.
Owner:SHANGHAI DIANJI UNIV
A method and system for determining fault of heterogeneous system based on machine learning
PendingCN111209131AReduce dependenceImprove securityNon-redundant fault processingRelation graphSystem failure
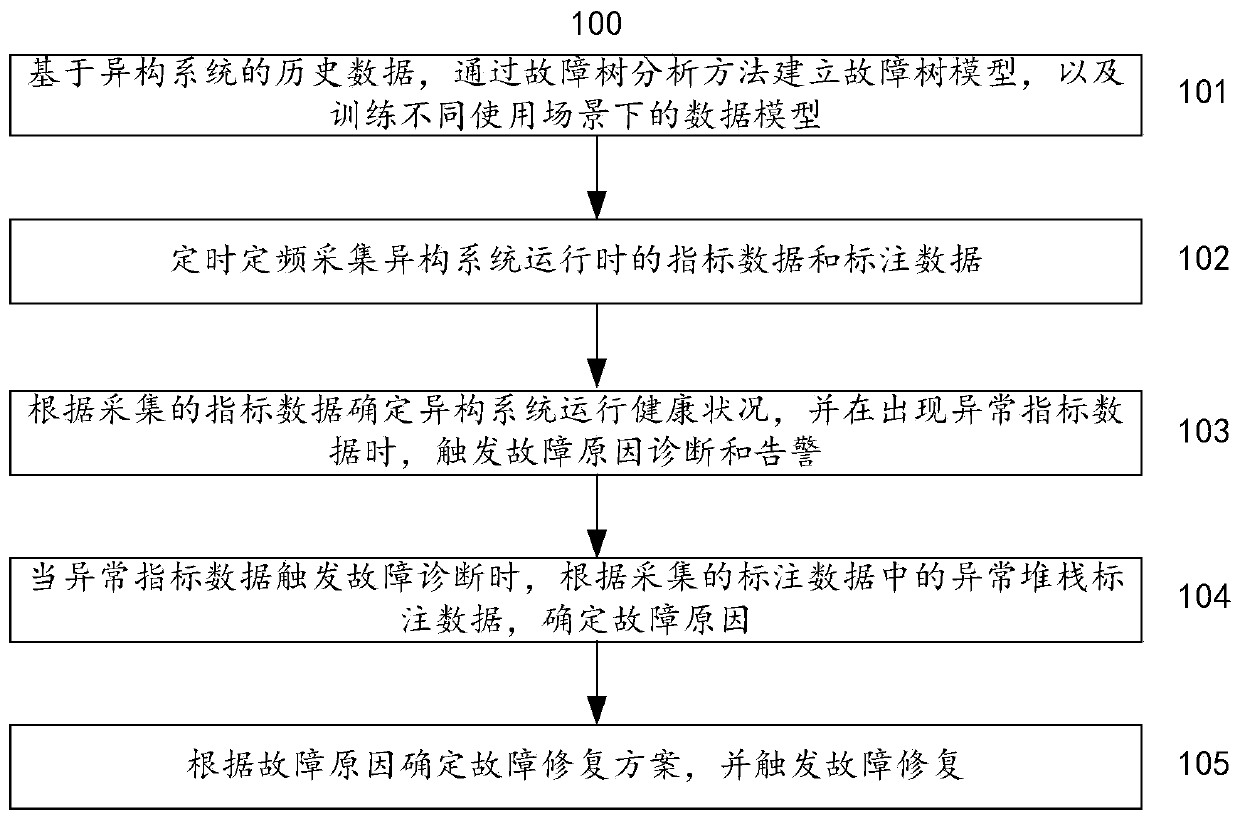
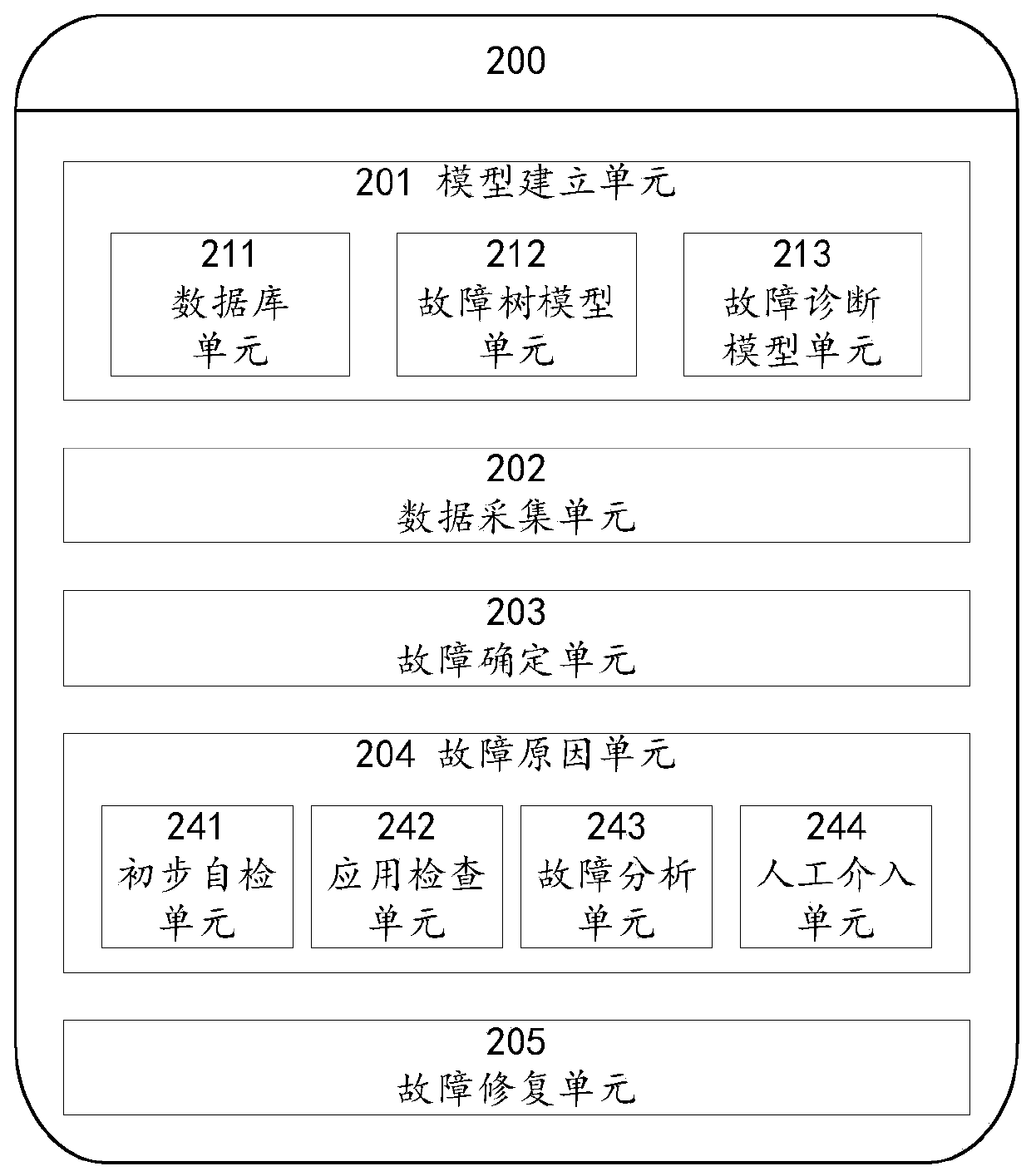
The invention provides a method and system for determining faults of a heterogeneous system based on machine learning, and the method comprises the steps: carrying out the analysis of the safety of historical system faults and major events, preliminarily building case library data and a fault tree model, arranging and analyzing index data and labeling data, and respectively training data models ofdifferent application scenes; according to the collected current index data and the data model, calculating and analyzing the operation health condition of the system, and triggering fault diagnosisand alarm for the grabbed abnormal index data; and automatically diagnosing a fault reason according to a relation graph established by machine learning and the collected abnormal stack annotation data, determining a fault repair scheme according to the fault reason, and triggering fault repair. According to the method and the system, the dependence of operation and maintenance personnel on professional business knowledge is reduced, intelligent and rapid fault discovery and fault generation reason diagnosis are realized through machine learning, self-repair is automatically completed, and theoperation safety and stability of the distributed heterogeneous system are greatly improved.
Owner:AEROSPACE INFORMATION
Business connection system between enterprises based on cloud platform
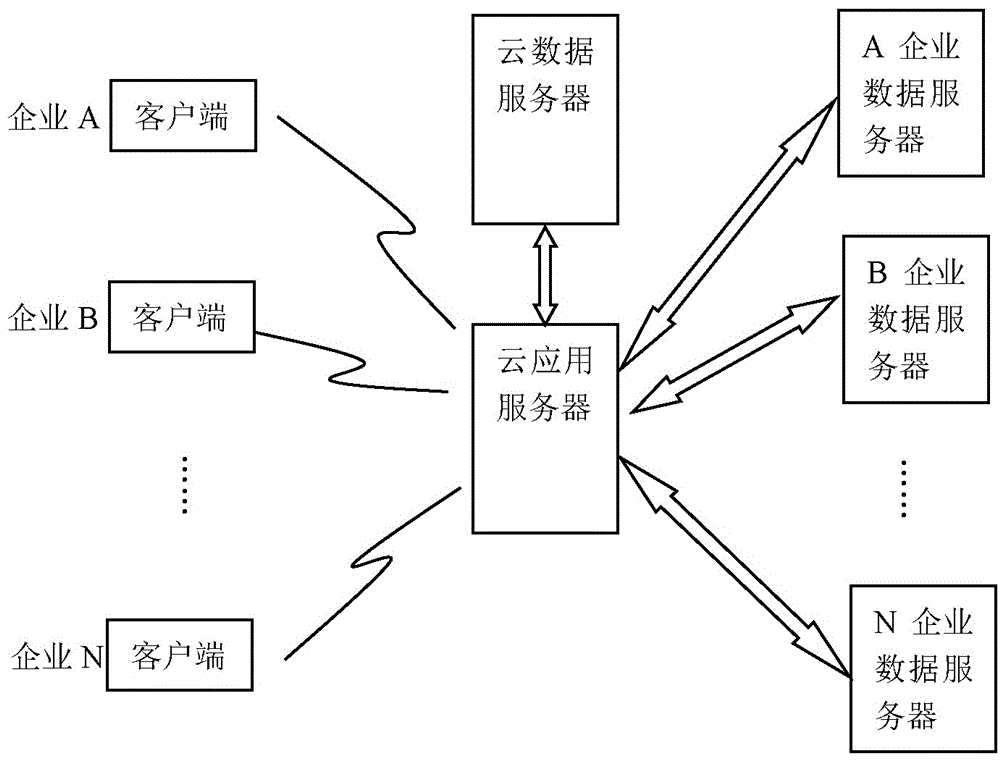
InactiveCN105913179AExcellent adhesionChange the way you workResourcesRelation graphProduction optimization
The invention discloses a business connection system between enterprises based on a cloud platform, comprising a cloud database server for storing all enterprise account basic data, an enterprise database server for storing business data of all enterprises, a cloud application server for visiting the cloud database server, the enterprises database server, providing corresponding business ports to the enterprises and performing processing on the businesses of all enterprises, and a client terminal for visiting the cloud data server and the corresponding enterprise database server to execute the business through the cloud application server according to the authorization conditions of all enterprises. The business connection system between enterprises based on cloud platform combines the business information of the upstream enterprises and the downstream enterprises with the production information and arranges the information into a net mode enterprise relation graph, which benefits the production optimization and cooperation optimization between the enterprises.
Owner:SHENZHEN ELS TECH CO LTD
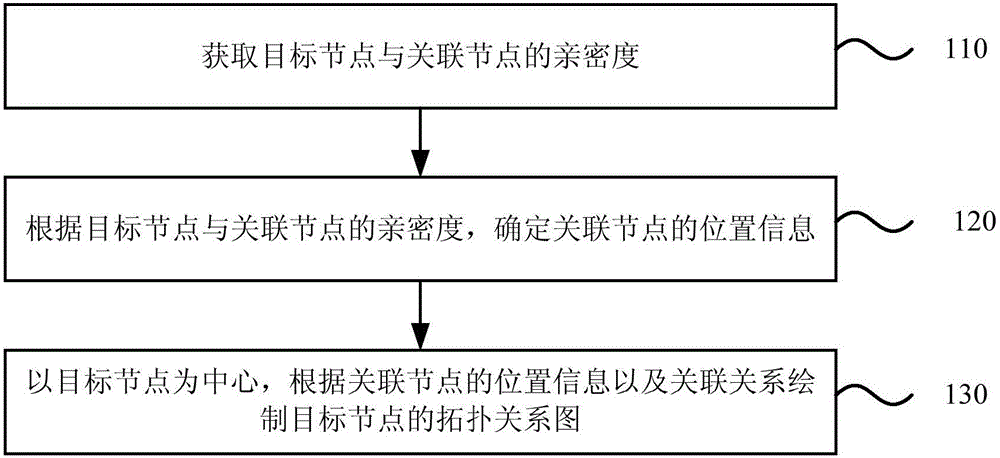
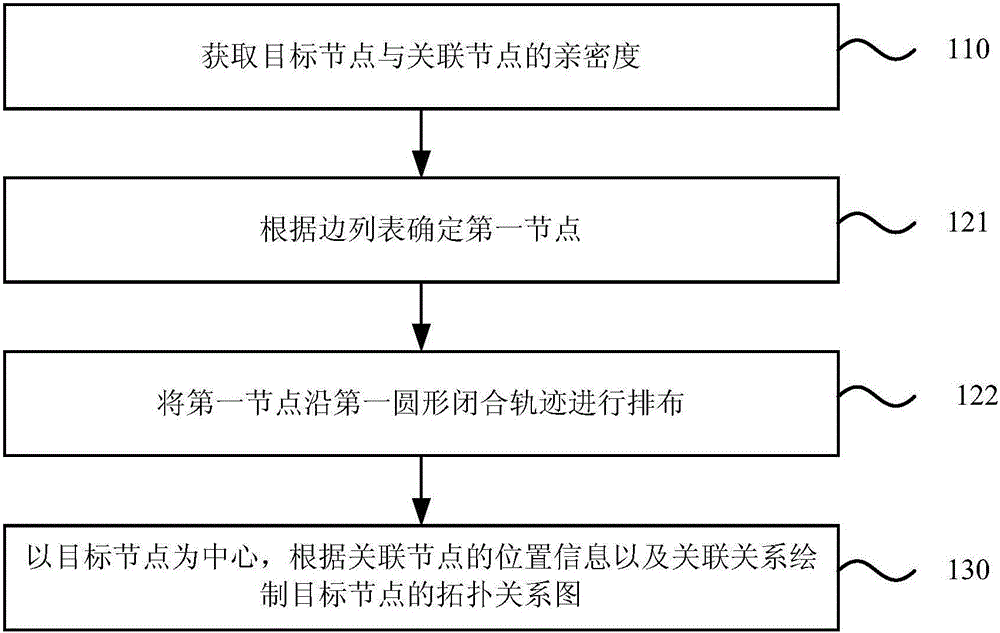
Method and apparatus for displaying topological relations
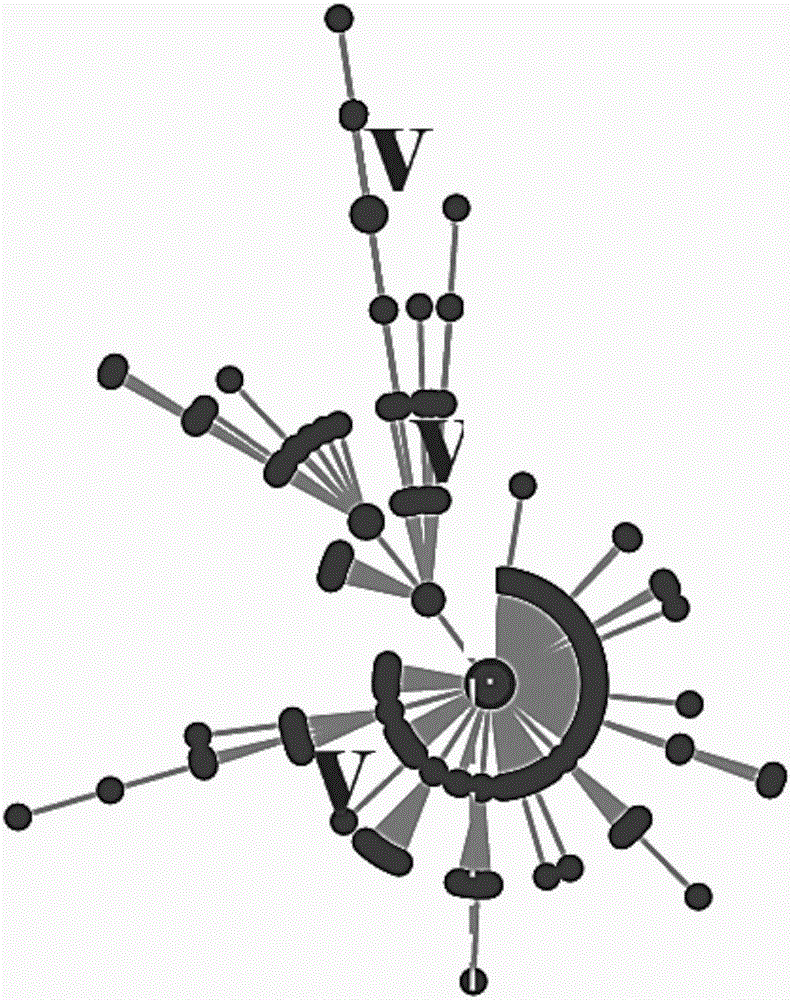
The invention discloses a method and apparatus for displaying topological relations. The method comprises the steps of acquiring the intimacy between a target node and an associated node, the associated node being a node having an association relation with the target node; determining the position information of the associated node according to the intimacy between the target node and the associated node; and drawing a topological relation graph of the target node by taking the target node as the center according to the position information of the associated node and the association relation. In the embodiment of the invention, the topological relation graph of the target node is drawn based on the intimacy between the target node and the associated node. Therefore, the position information of the associated node is determined by the association relation and intimacy between the associated node and the target node, the hierarchy and mesh relation in the social relation can be displayed for a user in the form of a graph, the user is allowed to intuitively obtain the topological relation between the target node and the associated node by reading the topological relation graph, and the readability is improved.
Owner:武汉科讯智安科技有限公司
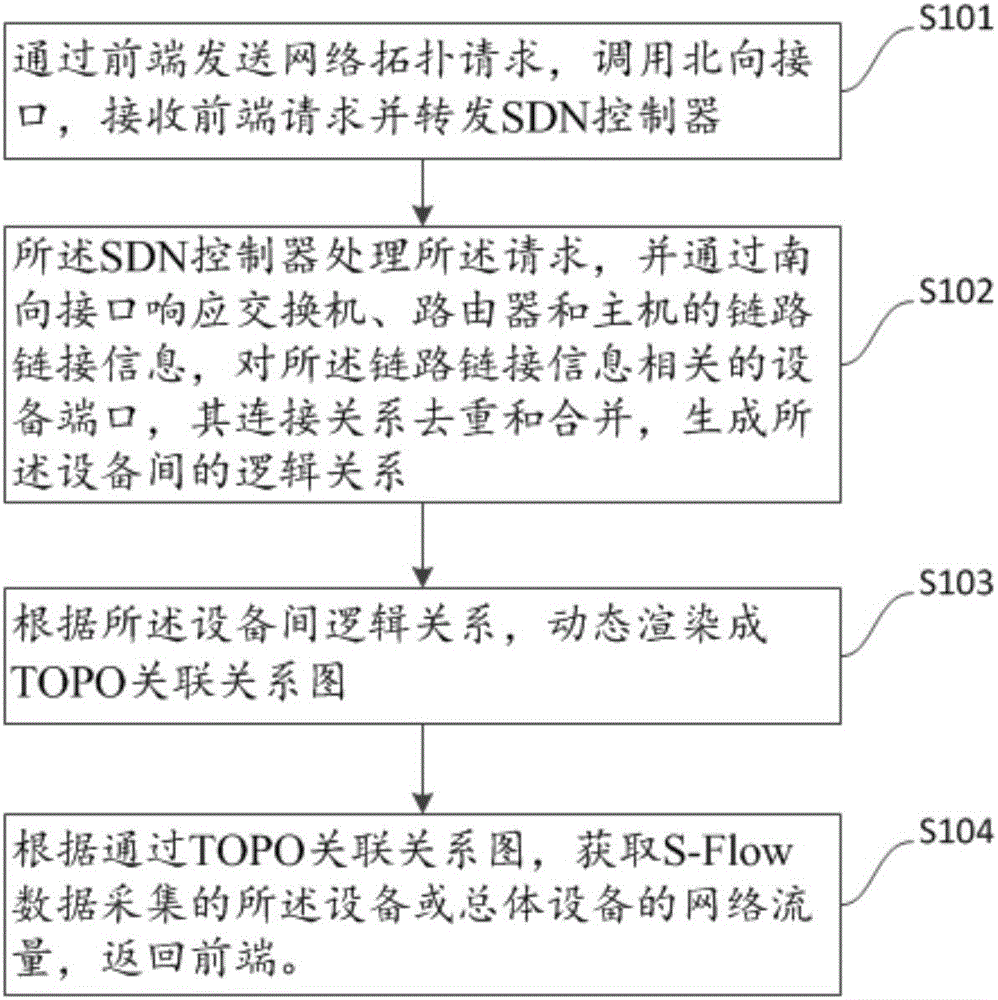
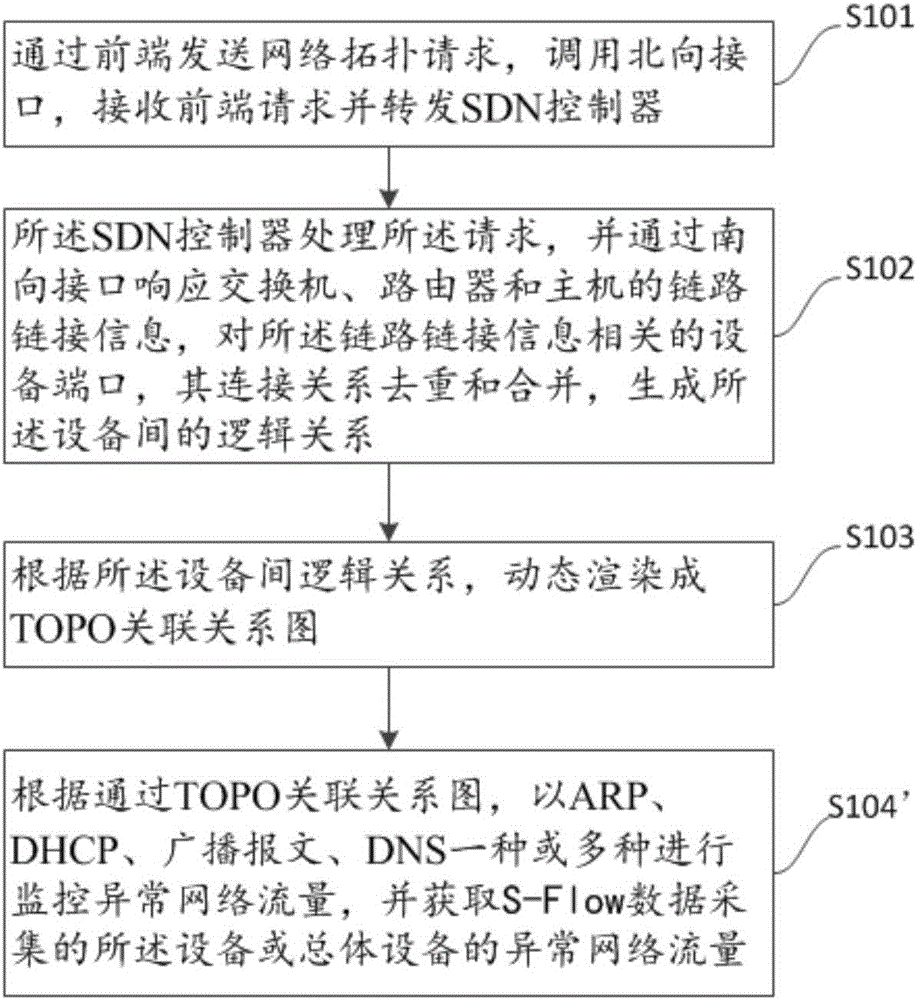
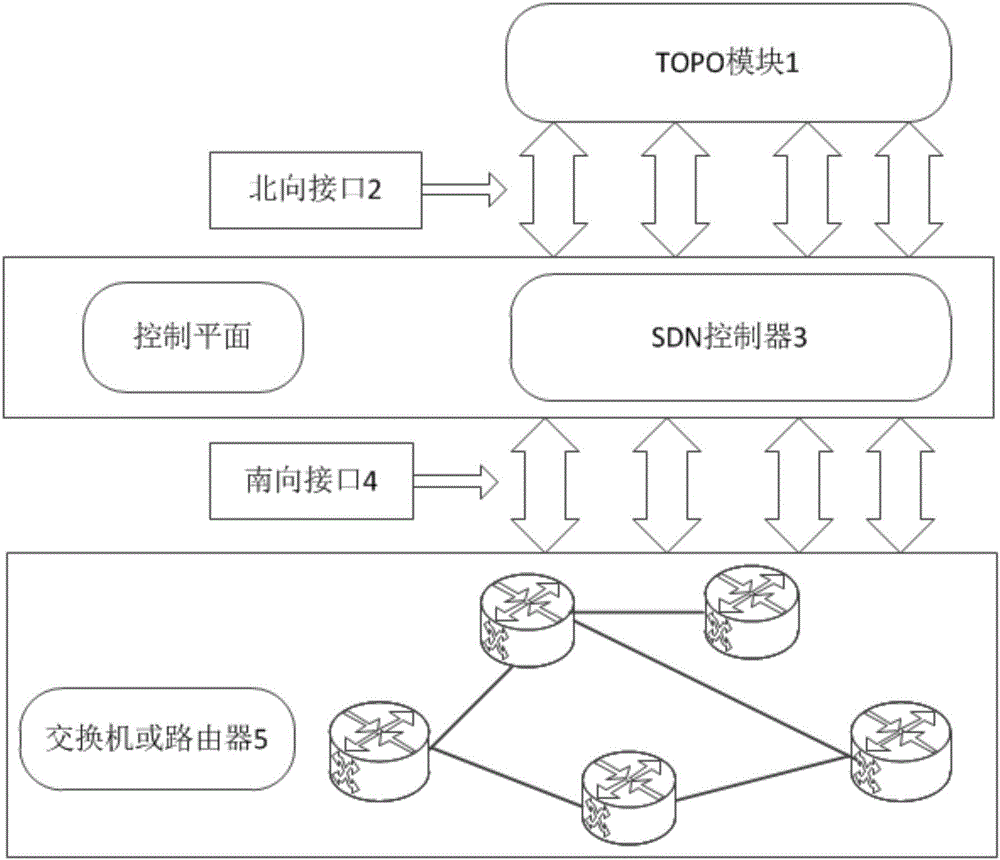
Software defined networking (SDN) network topology flow visual monitoring method and control terminal
ActiveCN106130796AEasy to coordinate and distributeData switching networksRelation graphVisual monitoring
The invention discloses a software defined networking (SDN) network topology flow visual monitoring method comprising the steps of 1, sending a network topology request via a front end, calling a northbound interface, receiving the request of the front end and forwarding the request to an SDN controller; 2, processing the request, responding to link connection information of a switch, a router and a host via a southbound interface, de-weighting and combining connection relations of ports of devices, and generating logic relations between the devices by using the SDN controller; 3, dynamically rendering a TOPO association relation graph according to the logic relations between the devices; and 4, acquiring network flow, collected by S-flow data collection technology, of a device or overall devices according to the TOPO association relation graph, and returning the network flow to the front end, thus being convenient to achieve overall distribution of network resources. The invention also discloses an SDN network topology controller control terminal which can count, analyze and display the overall network flow and the abnormal network flow.
Owner:GUANGZHOU VCMY TECH CO LTD
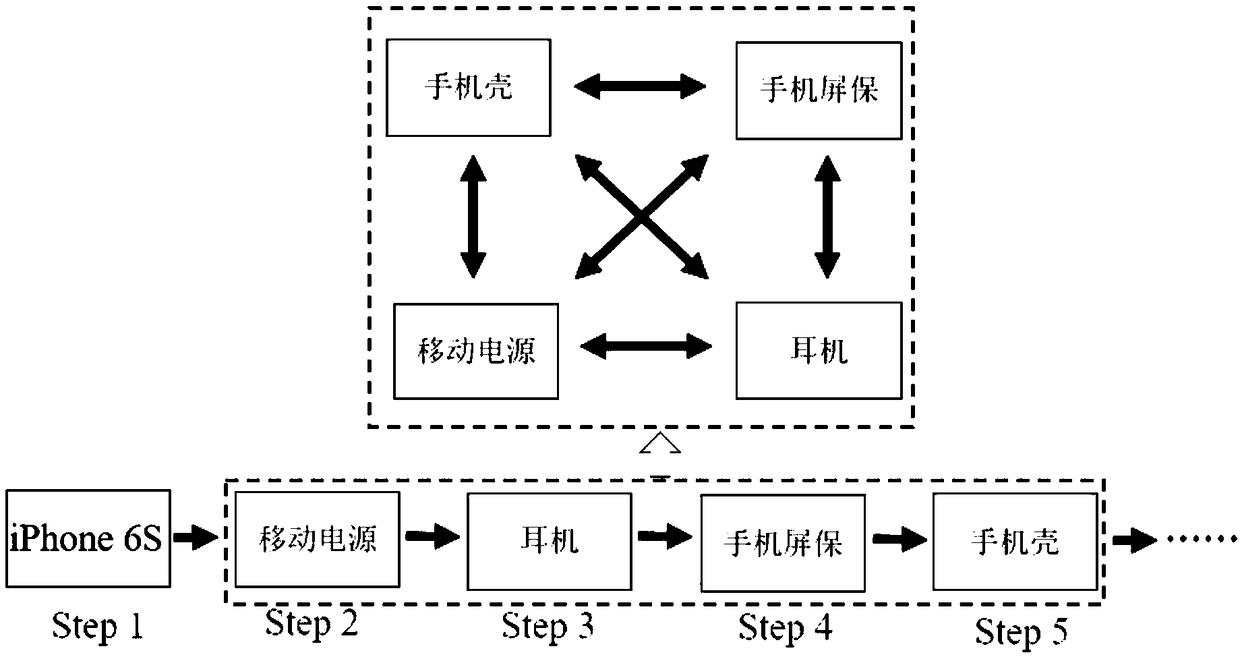
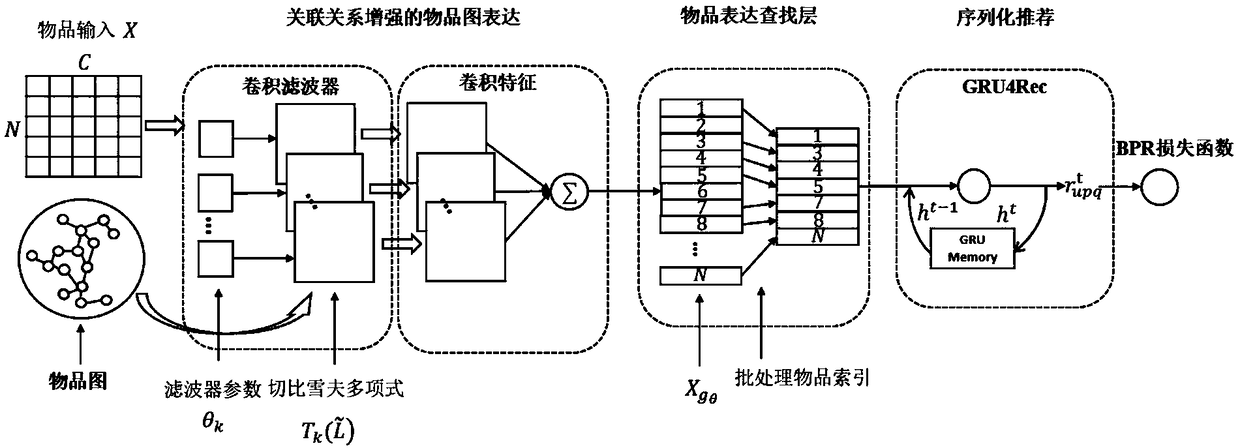
A serialized recommendation method based on item association relationship
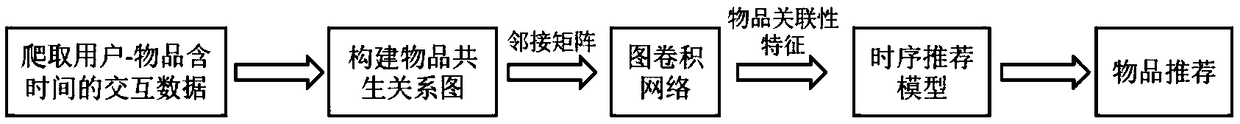
ActiveCN109446413AShow associative featuresDigital data information retrievalBuying/selling/leasing transactionsRelation graphRecommendation model
The invention provides a serialized recommendation method based on an item association relationship, which obtains interaction data between a user and an item from a network end. The interactive datais used to construct a symbiotic relation graph of the article, and the symbiotic relation graph is represented by an association relation graph adjacency matrix. Convolution of the adjacency matrix of the association relation graph is performed to obtain the association characteristics of the object. The relevant features of the object are inputted into the recommendation model for training; Therecommendation model outputs the serialized recommendation. The method can mine the implicit relationship between objects in user's behavior and train it with serialized recommendation model to provide service for user's serialized recommendation, utilizes the interactive data between users and articles to mine the association relationship between articles, and the vectorized representation of theassociation relationship, intuitively and objectively show the association characteristics of each article, uses the European distance to analyze the associated articles, and carries ou the end-to-end training and serialization recommendation model to provide the end-to-end serialization recommendation services for users.
Owner:SHANGHAI JIAO TONG UNIV
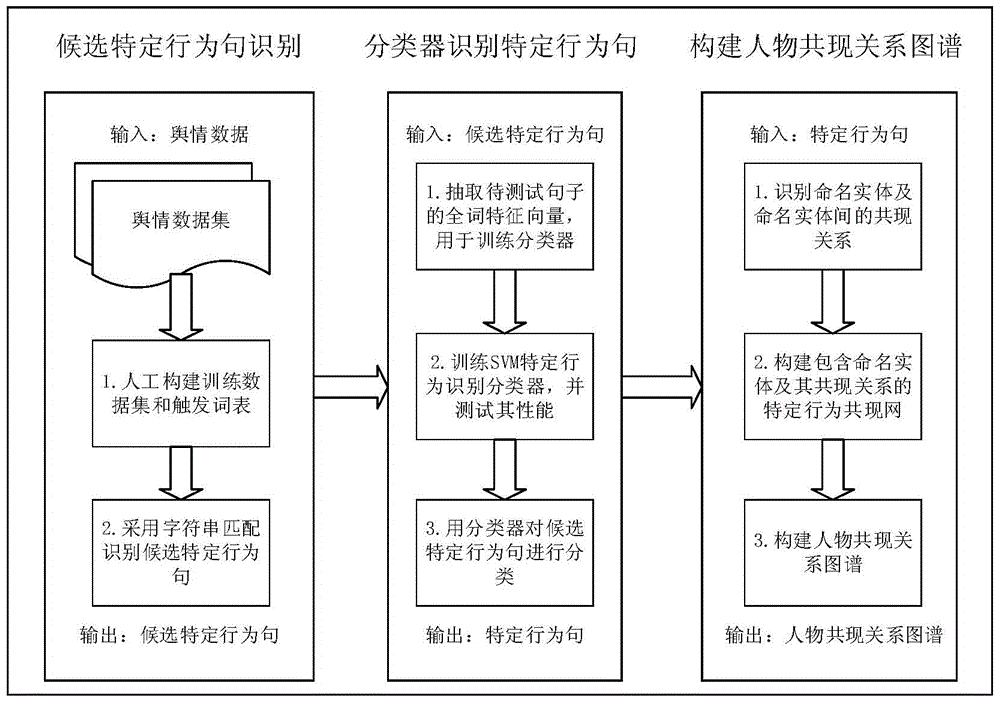
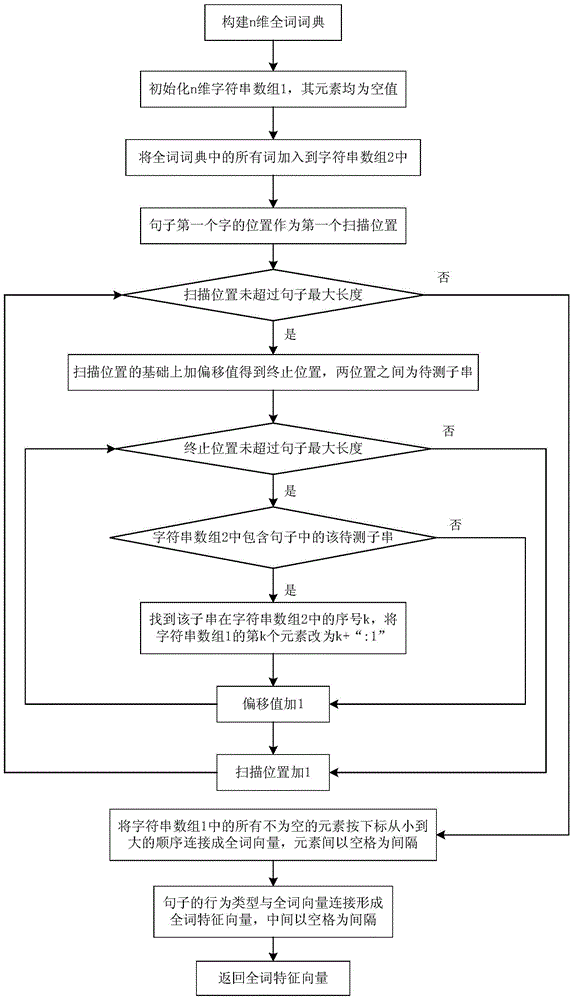
Figure cooccurrence relation graph establishing method based on specific behavior cooccurrence network
ActiveCN105760439AGuaranteed correctnessImprove accuracyWeb data indexingCharacter and pattern recognitionRelation graphFeature vector
The invention discloses a figure cooccurrence relation graph establishing method based on a specific behavior cooccurrence network. The method comprises the steps that firstly, a standard training data set and a triggering vocabulary are established, and all sentences to be tested are filtered with a string matching method to obtain a collection of candidate specific behavior sentences; then, whole word feature vectors of all the sentences in the standard training data set are extracted and used for training an SVM classifier to recognize specific behaviors, the candidate specific behavior sentences are classified with the trained SVM classifier, and specific behavior sentences are recognized; finally, a specific behavior cooccurrence network including named entities and the cooccurrence relation thereof is established, and a figure cooccurrence relation graph is established based on the specific behavior cooccurrence network. By means of the figure cooccurrence relation graph establishing method, the specific behavior sentences can be effectively recognized from a large quantity of real online public opinion data, the specific behavior cooccurrence network and the figure cooccurrence relation graph are established on the base, and a novel visualized analysis method is provided for public opinion analysis.
Owner:XI AN JIAOTONG UNIV
Method for converting ladder diagram into PLC (Programmable Logic Controller) program command
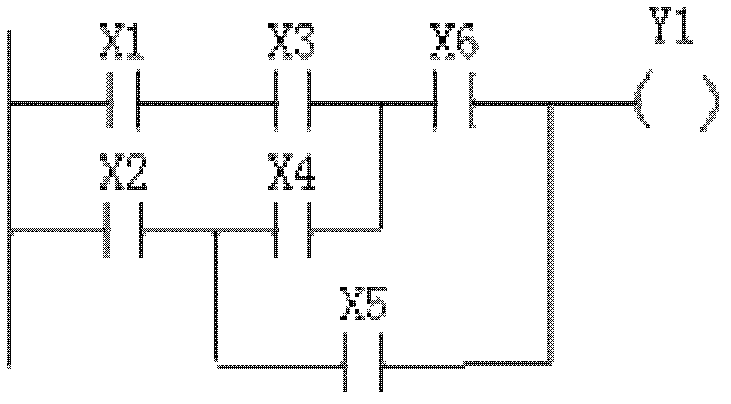
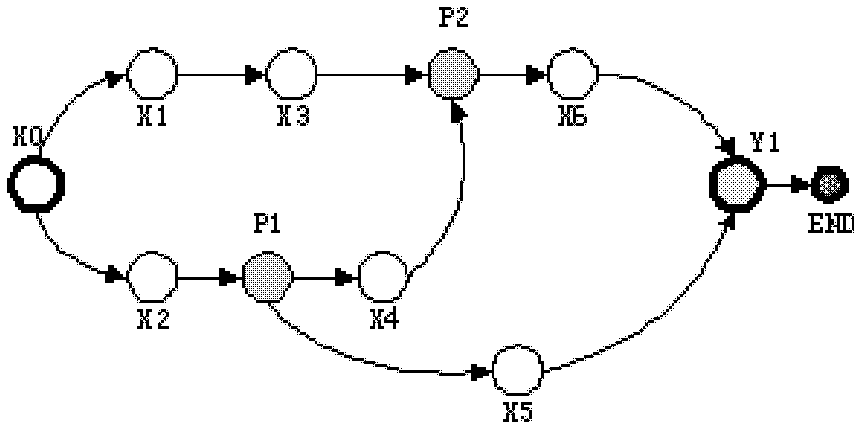
InactiveCN102354144AQuick searchAnalyzing the time complexity of the job is easyProgramme control in sequence/logic controllersRelation graphDepth-first search
The invention relates to a method for converting a ladder diagram into a PLC (Programmable Logic Controller) program command, which comprises the following steps of: 1, presenting a topological structure of a ladder diagram by using a directed graph; 2, traversing a transposed graph GL <T> by using a depth-first search method, storing a topological sorting relation of parallel-connection peaks and coil peaks in a queue Q; 3, carrying out breadth-first search on the parallel-connection peaks according to a connection relation of the directed graph GL, carrying out depth-first search on serial-connection peaks adjacently connected with the parallel-connection peaks, generating an AND expression of the directed graph GL on the whole serial-connection path and an OR expression of the serial-connection peaks; 4, generating a final expression of the maximum combining item of the parallel-connection peaks; 5, carrying out breadth-first search on a connection relation graph Gp by using the Q,figuring out an OR expression of the corresponding parallel-connection peaks and verifying, finally, constructing the maximum combining item into the AND expression to form a final result; 6, judgingwhether a queue Q' is empty; and 7, processing a starting peak. The invention can be widely applied to the process of converting the ladder diagram into the PLC program command.
Owner:BEIJING UNION UNIVERSITY
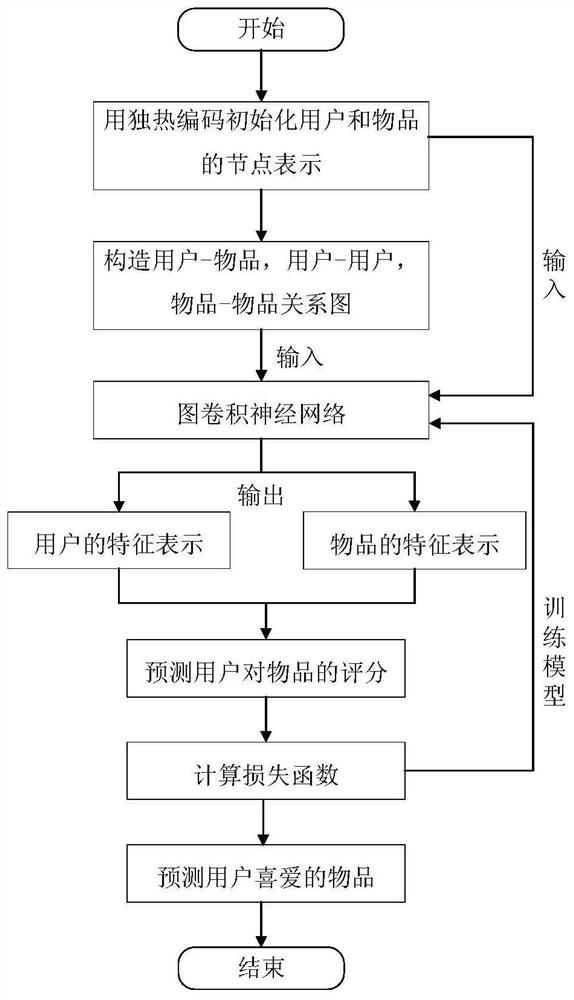
Article score prediction method based on improved graph convolutional neural network
ActiveCN111859166AAchieve scoreImprove accuracyDigital data information retrievalData processing applicationsRelation graphRelational graph
The invention relates to an article score prediction method based on an improved graph convolutional neural network, and belongs to the technical field of information recommendation. The method comprises the following steps: S1, acquiring a historical score of a user on an article, personal information of the user and attribute information of the article; S2, constructing a user-article relationship graph, a user-user relationship graph and an article-article relationship graph; S3, extracting the structure and content features of nodes in the plurality of relational graphs by using an improved graph convolutional neural network; S4, selecting multiple pieces of feature information of fusion nodes of the neural network model; S5, predicting the probability that the user is interested in the article according to the feature representation of the user and the article; S6, training a model by using the training set and the verification set; S7, utilizing the trained model to predict the score of the user on the article. According to the method, the features of the user and article relation graph are effectively extracted through the improved graph convolutional neural network, the score of the user to the article is predicted, and the prediction accuracy is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Display method of network data and apparatus thereof
ActiveCN106341265AOptimize visual display technologyData switching networksTemporal informationRelation graph
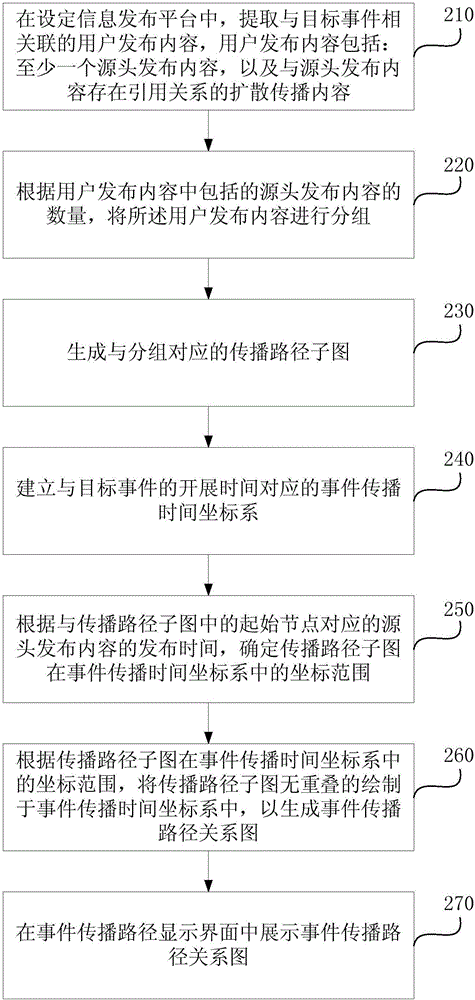
Embodiments of the invention disclose a display method of network data and an apparatus thereof. The method comprises the following steps of in an information issuing platform, extracting a user issuing content associated with a target event, wherein the user issuing content includes at least one source issuing content and a diffusion spreading content which has a reference relationship with the source issuing content; according to issuing time of the user issuing content, drawing an event spreading path relation graph which takes the source issuing content as an initial node and takes the diffusion spreading content as a diffusion node; displaying the event spreading path relation graph in an event spreading path relation graph. In the technical scheme of the invention, the user issuing content is served as a node, a spreading diffusion path of an event and time information are combined and displayed, a technical effect of visually displaying an evolution process of the event along with time is achieved, an existing visualization display technology of network data is optimized and a user can simply, visually and effectively acquire a spreading diffusion condition of an event content.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Customized just-in-time learning support system and method based on constructivist learning theory
ActiveCN104866557AWebsite content managementSpecial data processing applicationsPersonalizationSocial media
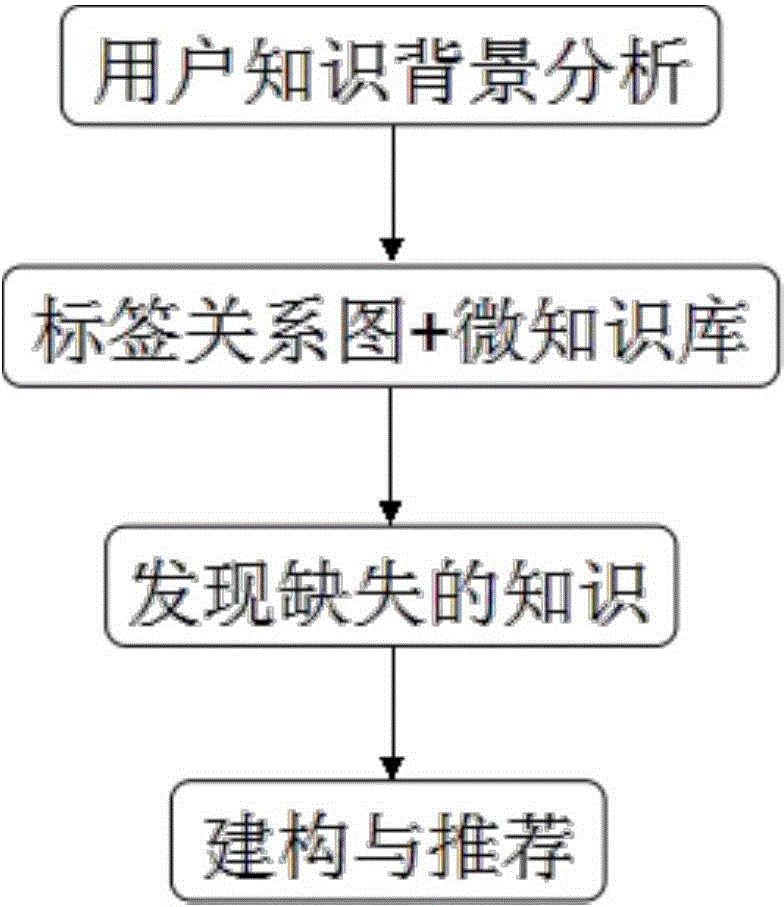
The present invention provides a customized just-in-time learning support system and method based on constructivist learning theory. The system comprises a user knowledge demand behavior analyzing and recording module, a label relation graph micro-knowledge base, a constructivist learning-based micro-knowledge recommendation algorithm module and the like modules. With the system according to the present invention, construction demands of knowledge are analyzed based on social networking media information of a user, and micro-knowledge for customized learning is recommended to the user, thereby quickly making up for the deficiency of knowledge for the user. The method according to the present invention, as important service content in an Internet-based social networking system, efficiently and intelligently helps a user to improve personal knowledge quality, thereby achieving good economical and social benefits.
Owner:江苏国基科技有限公司
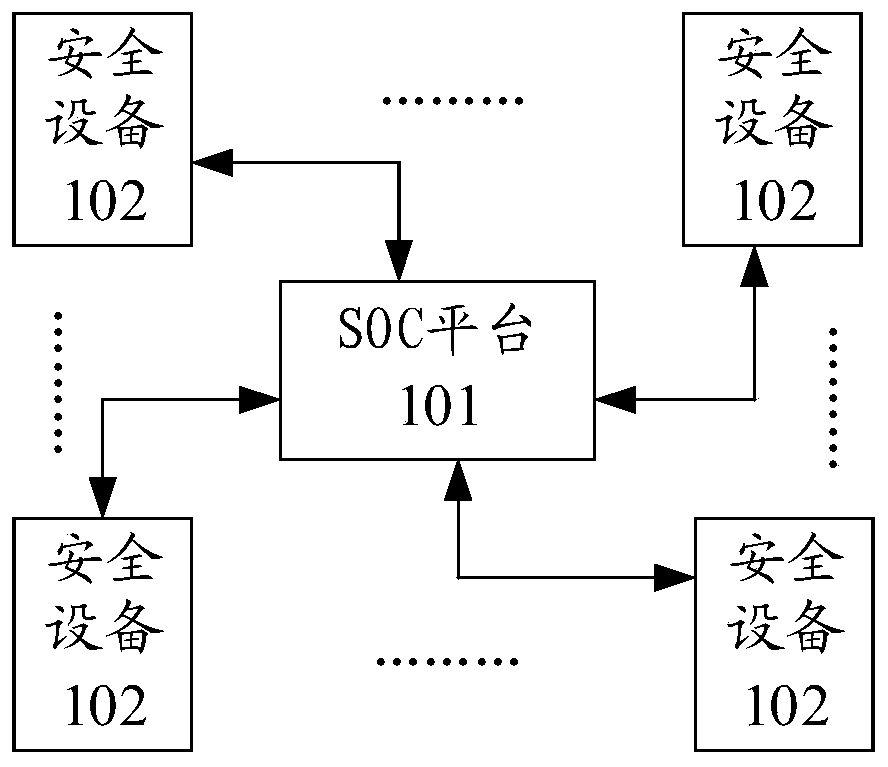
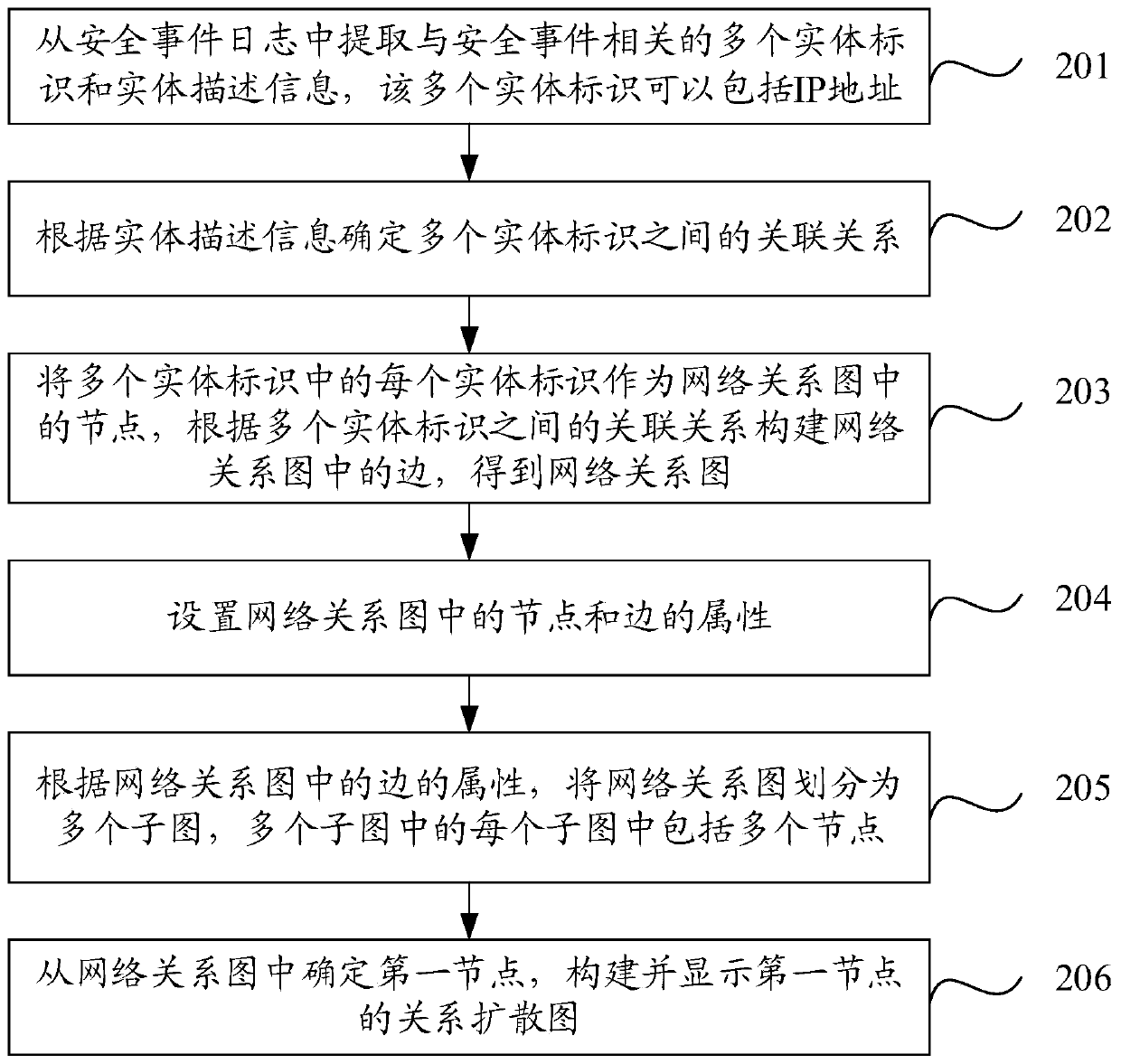
Security event log processing method and device and storage medium
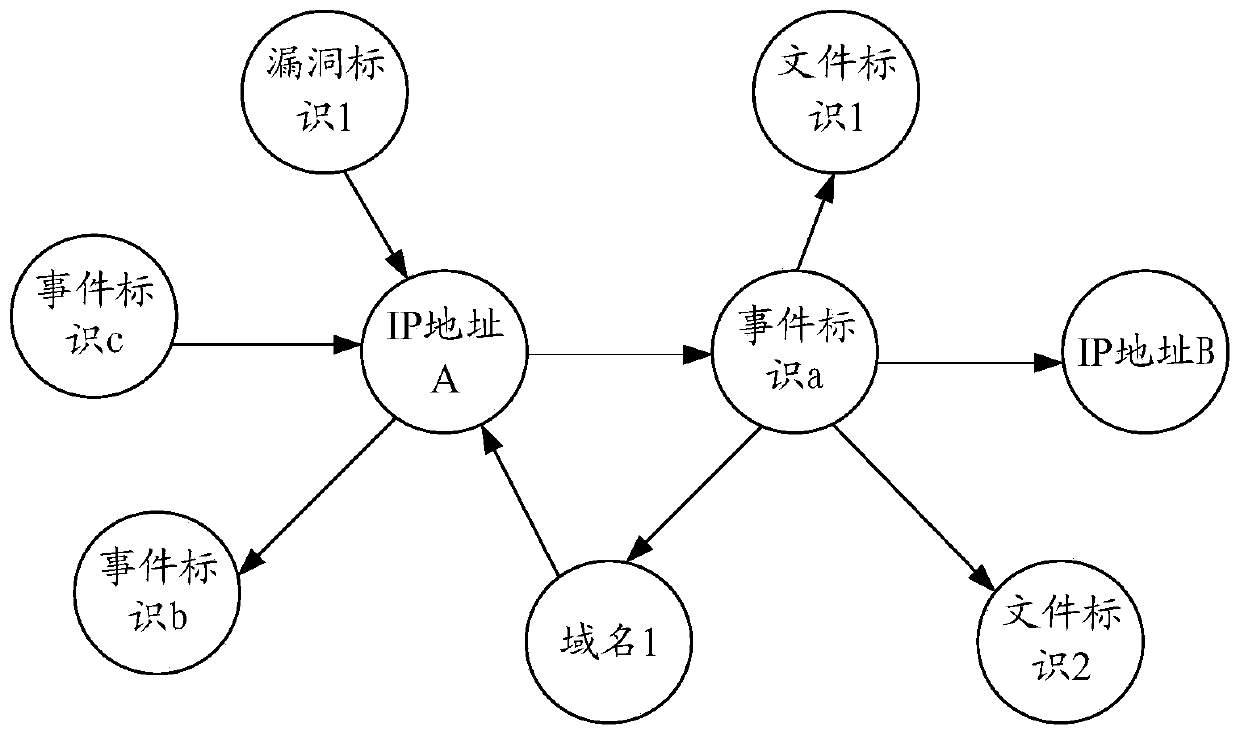
ActiveCN110933101AQuick discoveryImprove Security Operational EfficiencyTransmissionRelation graphEntity identifier
The invention discloses a security event log processing method and device and a storage medium, and belongs to the technical field of network security. The method comprises the following steps: extracting a plurality of entity identifiers and entity description information related to a security event from a security event log, wherein the plurality of entity identifiers comprise internet protocolIP addresses; determining an association relationship among the plurality of entity identifiers according to the entity description information; and taking each entity identifier in the plurality of entity identifiers as a node in a network relationship graph, and constructing an edge in the network relationship graph according to an association relationship among the plurality of entity identifiers to obtain the network relationship graph. In this way, the incidence relation between the nodes corresponding to the entity identifiers can be visually displayed in the obtained network relation graph, that is, comprehensive analysis is conducted on the basis of global information, so that technicians can conveniently and rapidly find entities needing to be highly concerned, and the safety operation efficiency can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data mining system and data mining method
ActiveCN103699550AReusable extension serviceWeb data indexingSpecial data processing applicationsData dredgingRelation graph
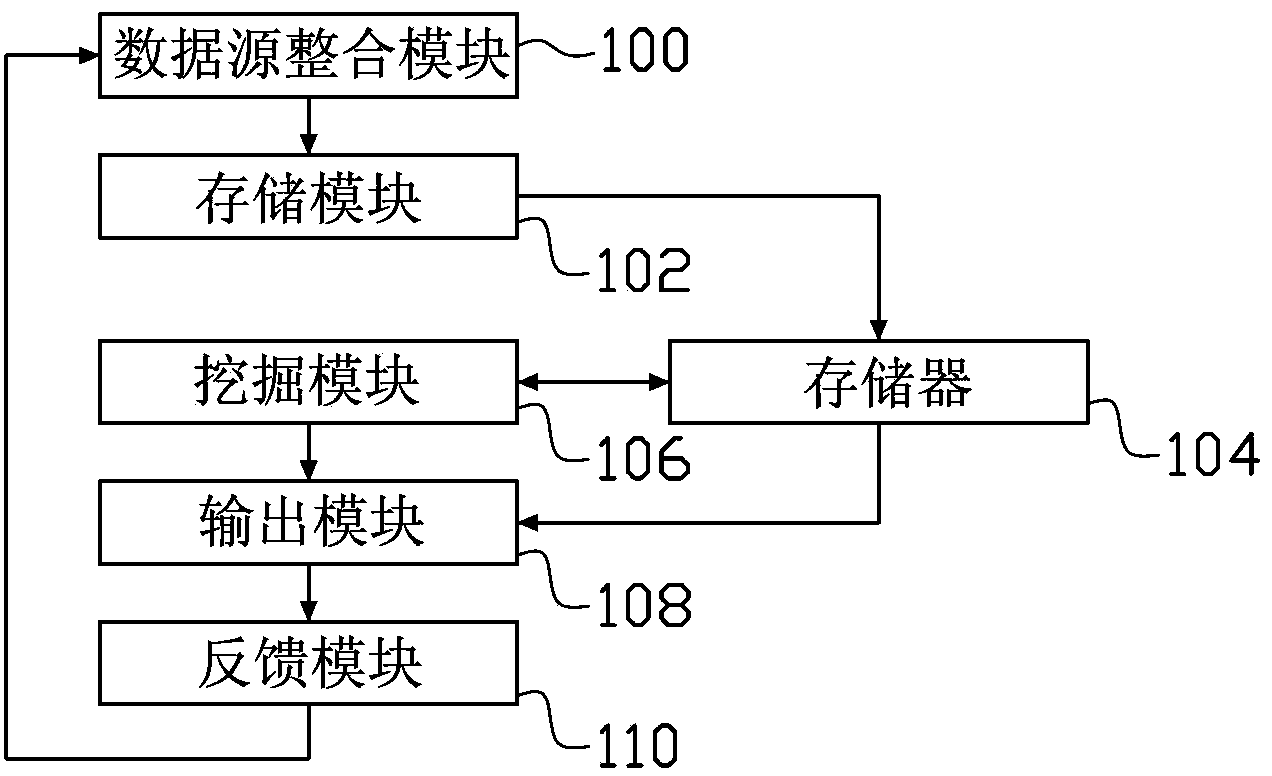
The invention relates to a data mining system and a data mining method. The data mining system comprises a data source integration module, a storage module, a mining module and an output module, wherein the data source integration module is used for performing correlation matching on query words submitted by a user to a searching engine and buying words which are pre-stored, so as to form at least one data source corresponding to a correlation between the query words and the buying words; the storage module is used for establishing a graph storage structure between the query words and the buying words by using the correlation between the query words and the buying words of each data source; the mining module is used for establishing a network topological relation graph based on the graph storage structure and performing data mining based on graphs; the output module is used for outputting results of data mining according to different application demands input by users to enable the users to select the output results to trigger the display of output information. The data mining system and the data mining method can be used for analyzing business data from multiple views and multiple granularities.
Owner:TENCENT TECH (SHENZHEN) CO LTD
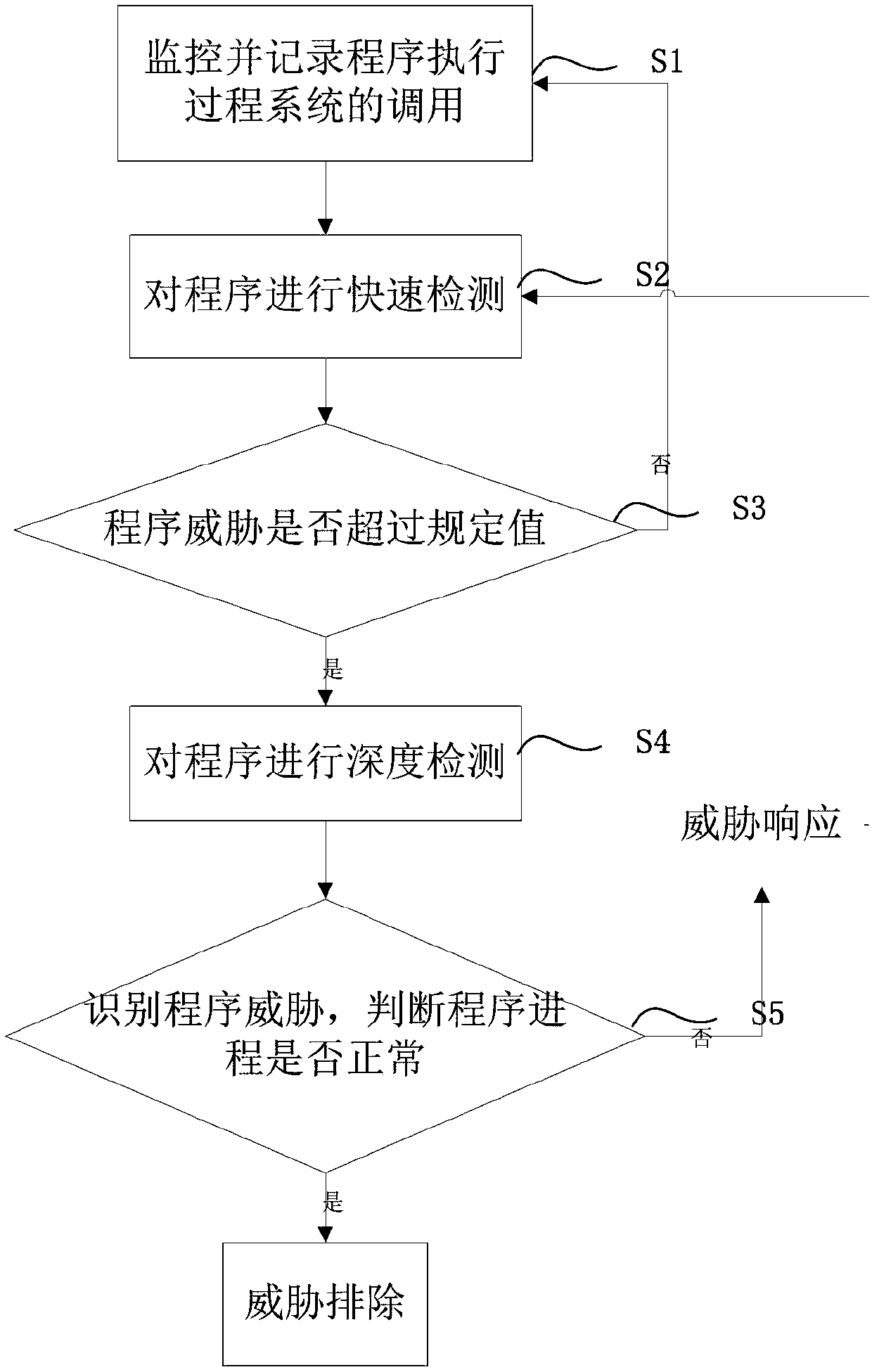
Real-time threat detection method
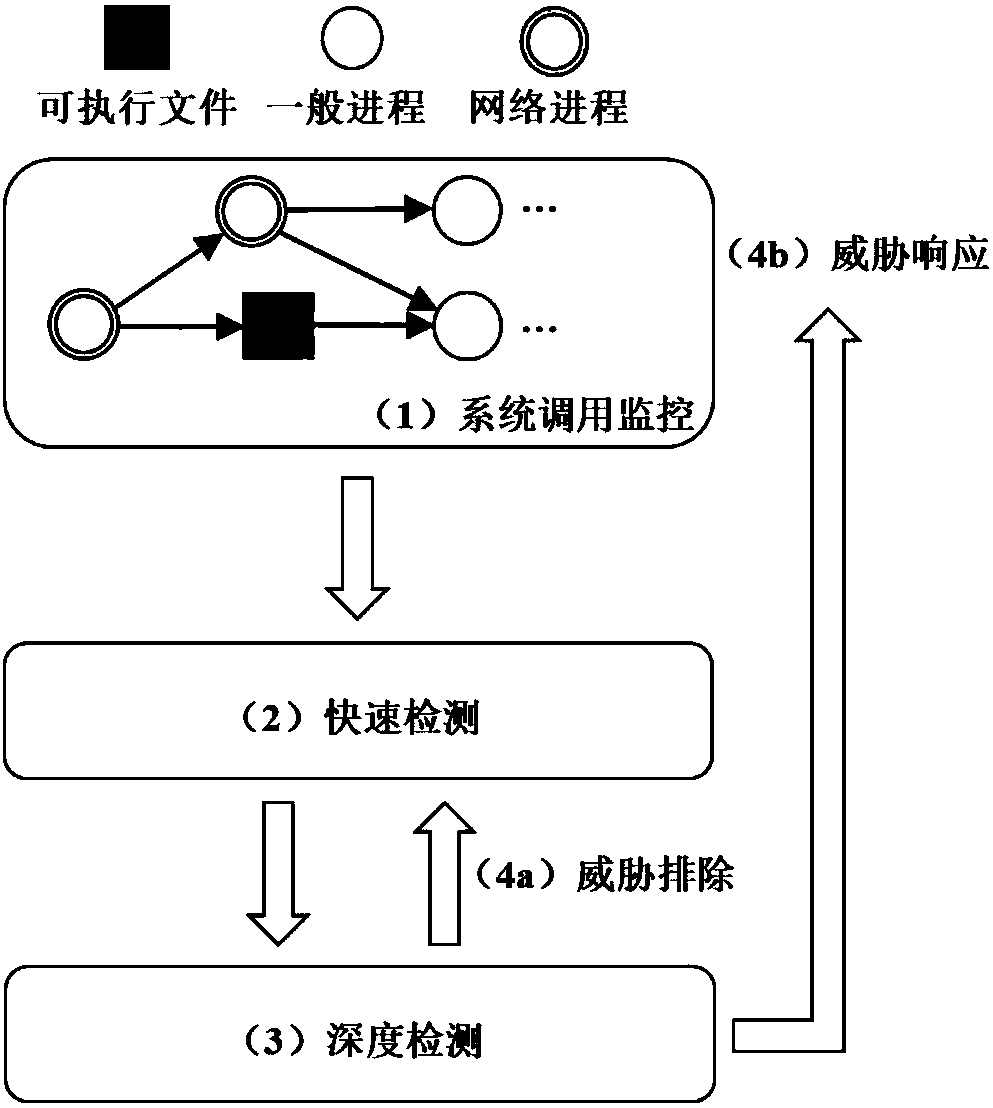
InactiveCN108038374AAvoid damageImprove securityCharacter and pattern recognitionPlatform integrity maintainanceProcess systemsRelation graph
The embodiment of the invention discloses a real-time threat detection method. According to the method, a chain relation graph of specific processes and executable file objects is formed by tracking an information stream on a system level, system calling monitoring is performed according to the objects involved in the relation graph, and the objects are detected. The method comprises the specificsteps that system calling in the program execution process is monitored and recorded; quick detection is performed on a program; whether program threat exceeds a stipulated value is judged, if yes, next operation is performed, and otherwise monitoring continues to be executed; deep detection is performed on the program; and the program threat is recognized, if the program process is normal, the threat is eliminated, and quick detection is continued, and otherwise threat response is performed. Through the method, security threat, such as file viruses, Trojan horses and ransomware, running in ahost can be recognized effectively and accurately; and meanwhile, damage of unknown malicious codes to a host file can be relieved, and the security and availability of a terminal host system are remarkably improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com