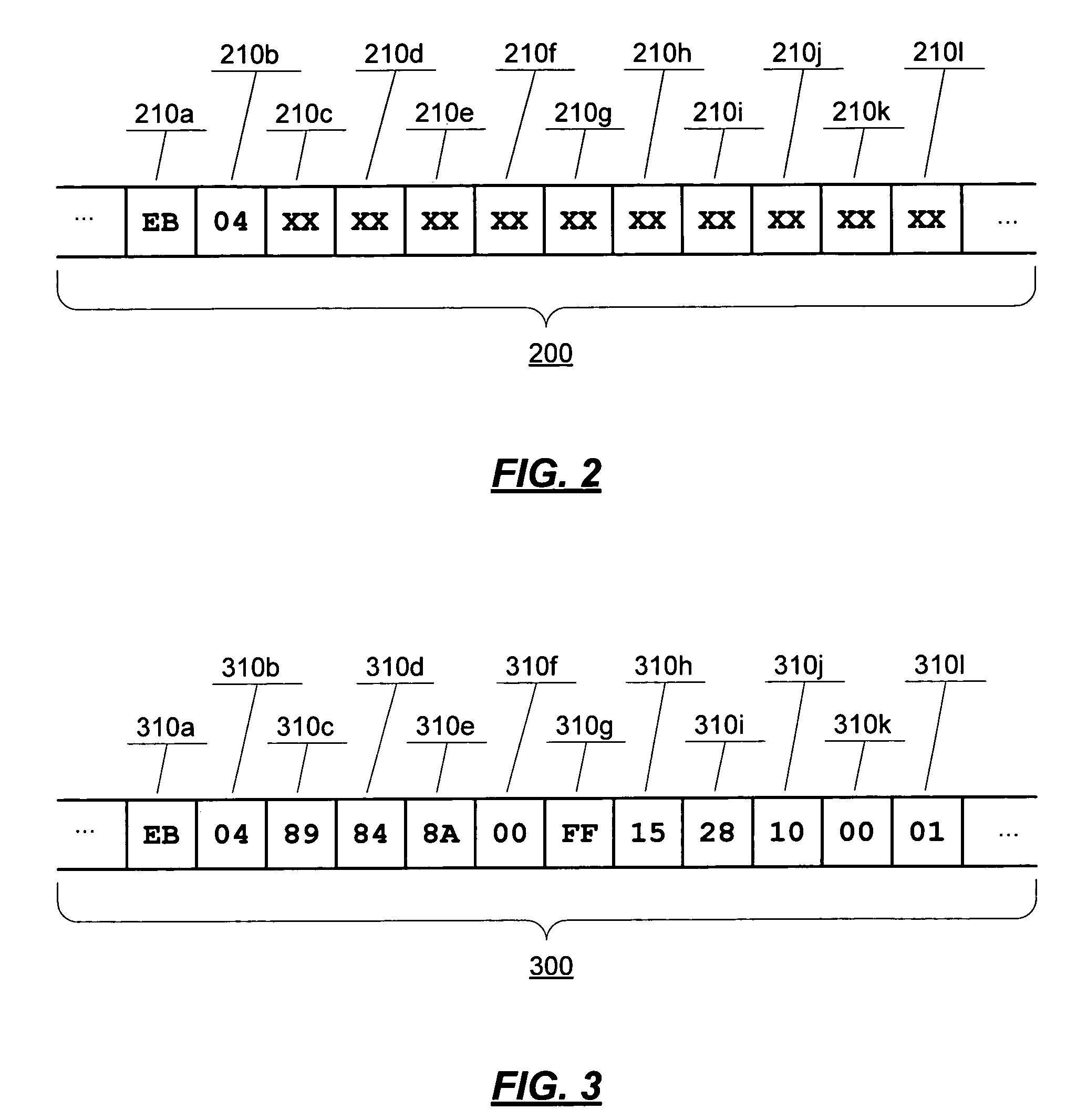
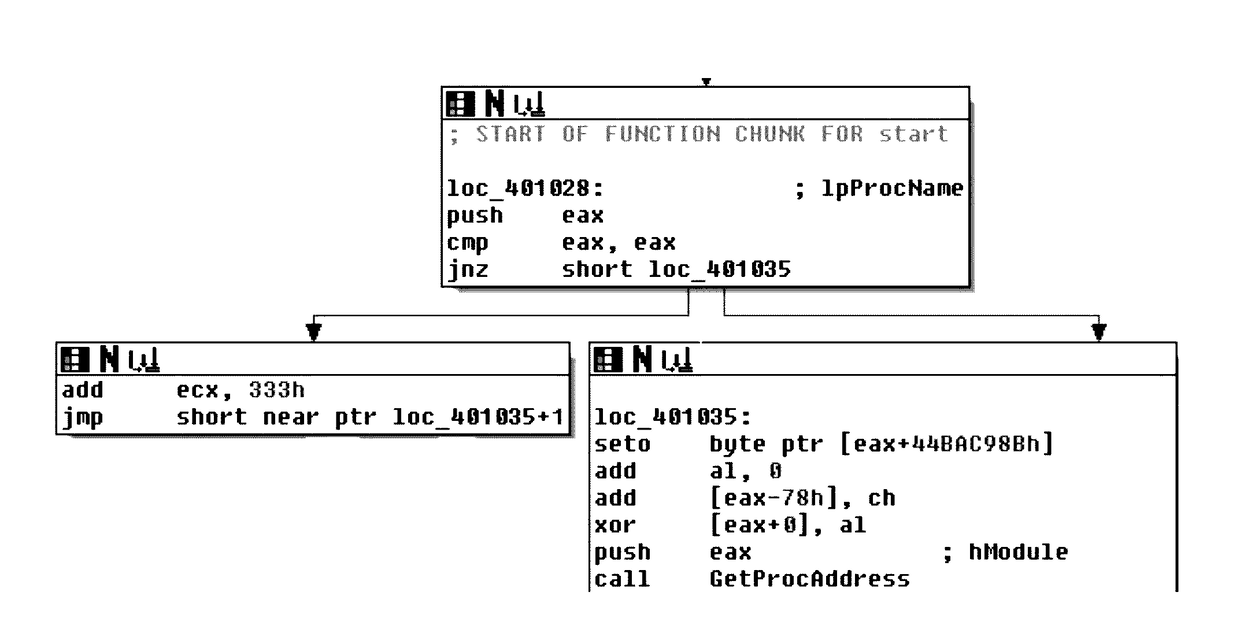
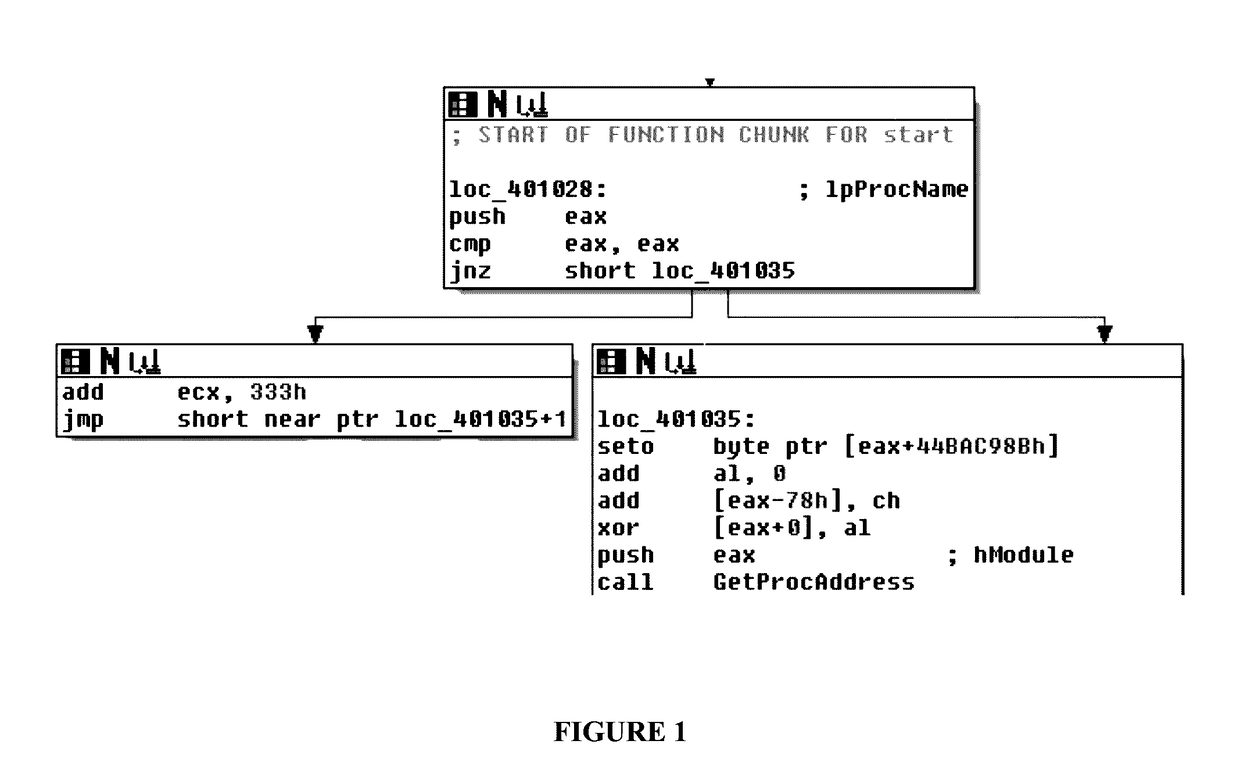
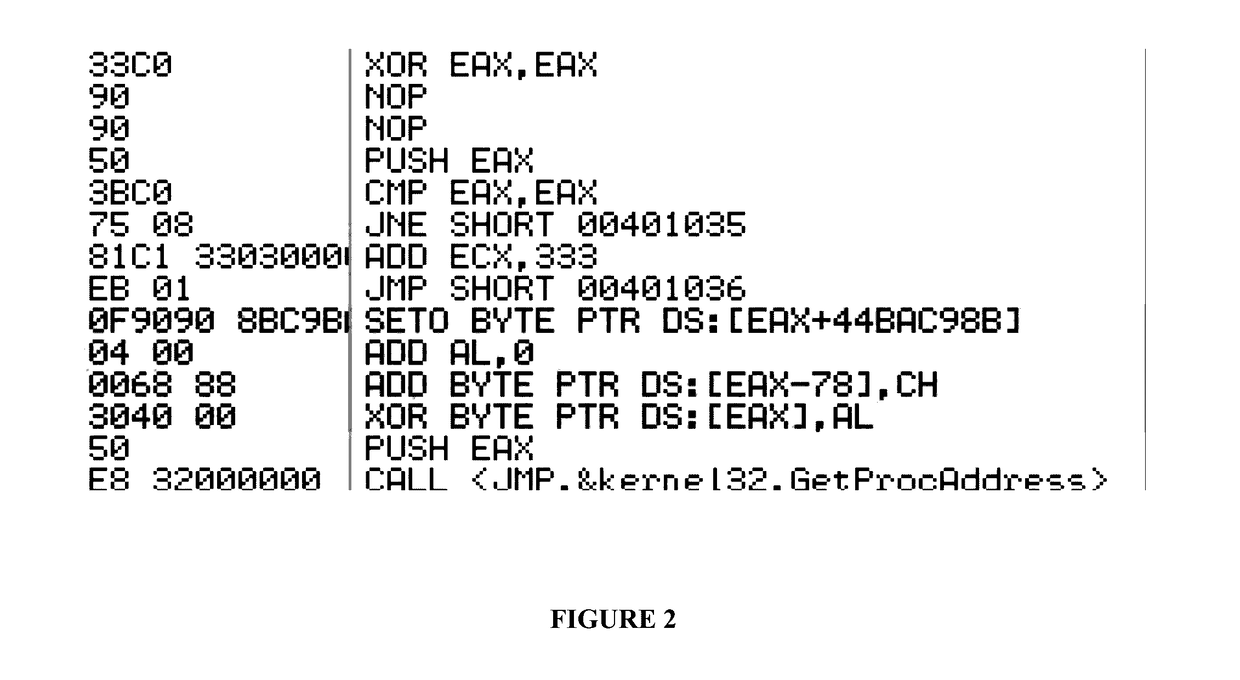
Patents
Literature
66 results about "Disassembler" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
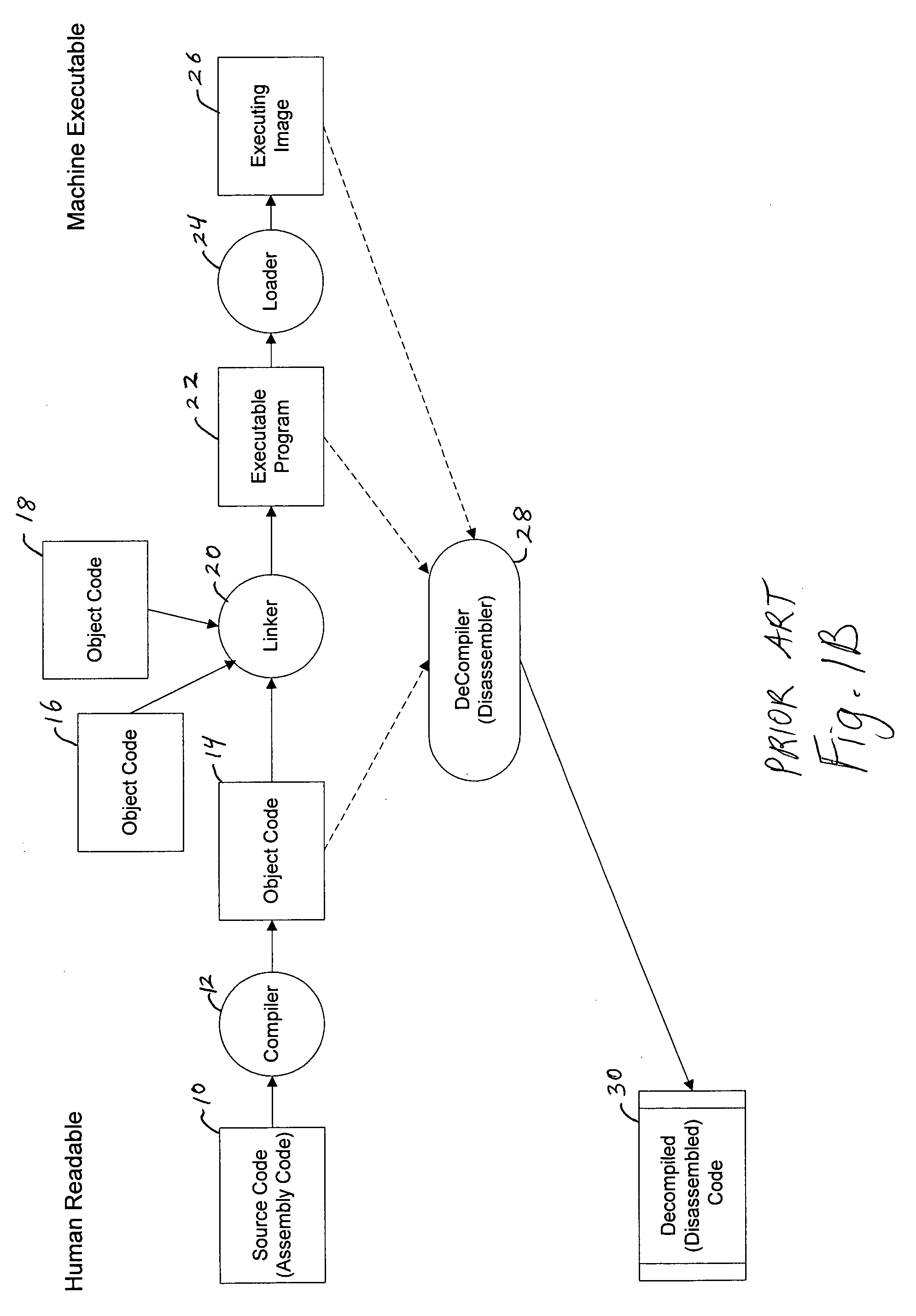
A disassembler is a computer program that translates machine language into assembly language—the inverse operation to that of an assembler. A disassembler differs from a decompiler, which targets a high-level language rather than an assembly language. Disassembly, the output of a disassembler, is often formatted for human creativity in the code writing process.
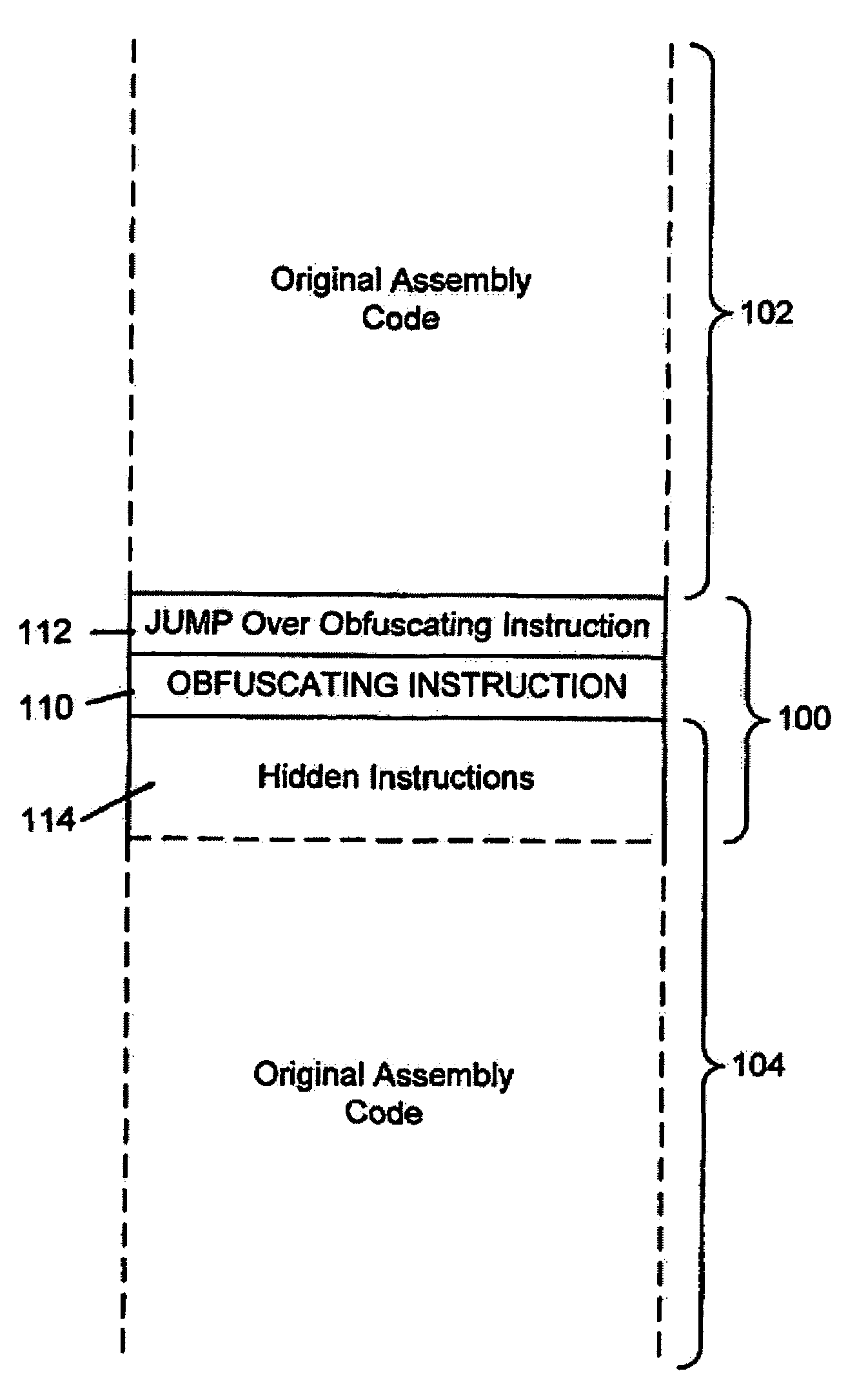
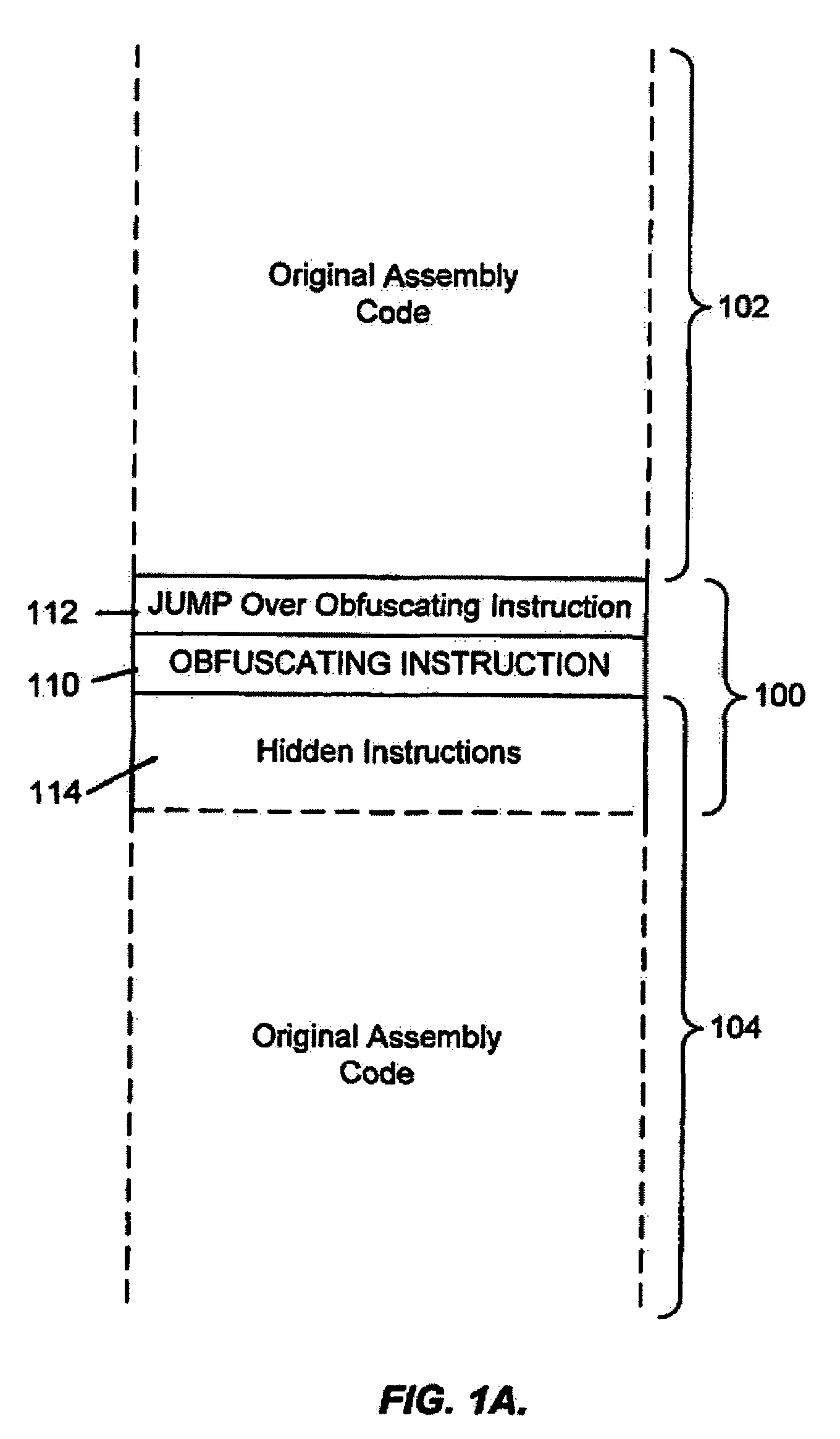
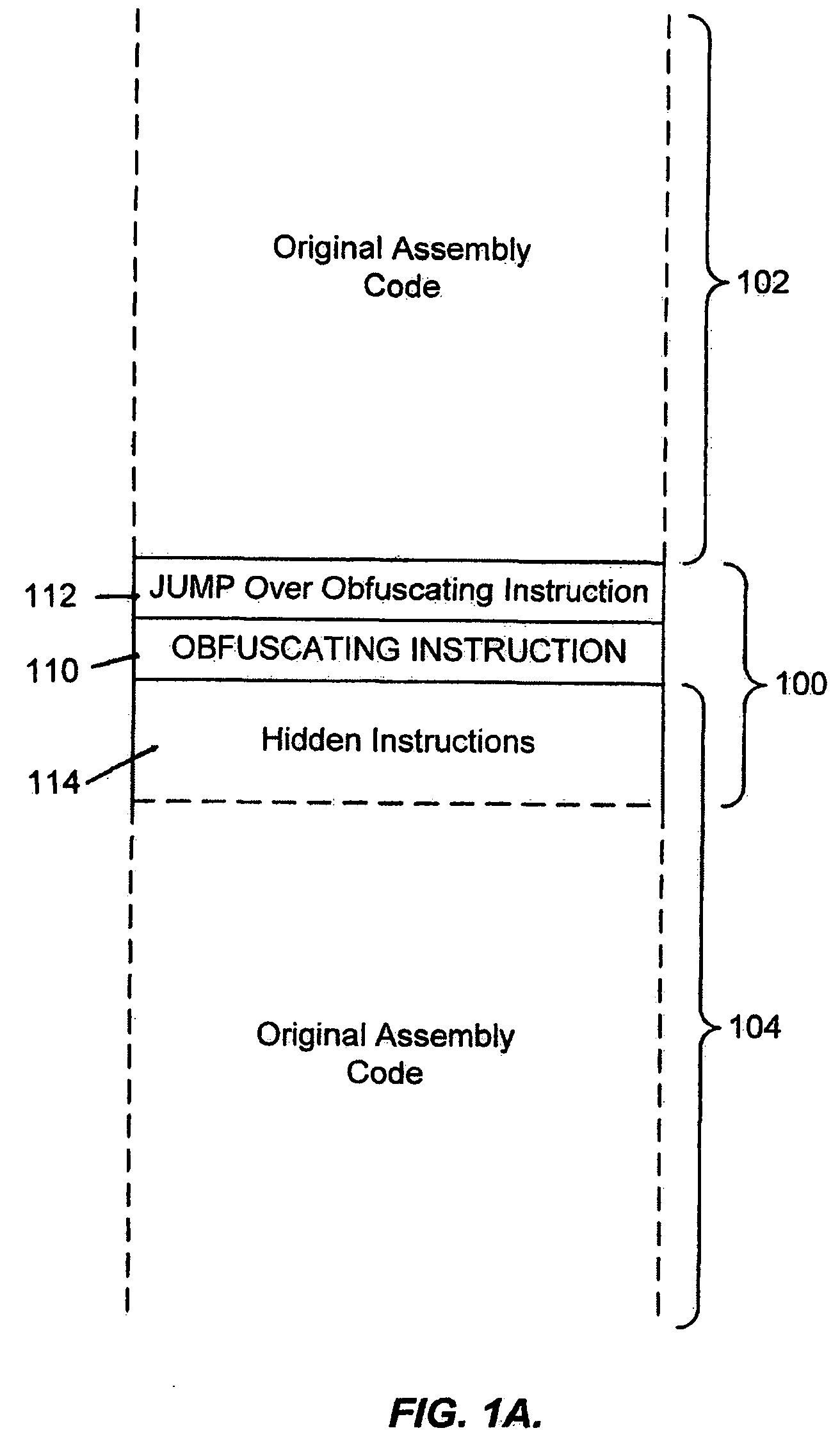
System for obfuscating computer code upon disassembly
InactiveUS7065652B1Avoid disassemblyDigital data processing detailsUser identity/authority verificationObfuscationDerivative work
Owner:SAFENET DATA SECURITY ISRAEL
Data communication system, method and apparatus for communicating a data signal formed of successive data elements
InactiveUS7499500B2Relatively large bandwidthProven electromagnetic compatibilitySynchronisation information channelsModulated-carrier systemsData connectionCommunications system
A data communications system for communicating a data signal formed of successive data elements, said system comprising a transmission node; a reception node; and a link providing a data connection from said transmission node to said reception node; in which: said transmission node comprises a clock signal transmitter for transmitting a synchronisation clocking signal to said reception node via said link, said synchronisation clocking signal having synchronising features occurring at a frequency lower than a data element rate; an assembler for assembling elements of said data signal into data frames, each data frame having a plurality of successive data elements of said data signal, for transmission to said reception node via said link, said assembler being responsive to said synchronisation clocking signal so as to set a synchronisation flag associated with a data element having a first predetermined temporal relationship with a synchronising feature of said synchronisation clocking signal; and said reception node comprises: a detector detecting a synchronising feature of said synchronisation clocking signal received from said transmission node; a disassembler for disassembling received data frames to regenerate said data signal, said disassembler being operable to detect a data element associated with a set synchronisation flag; an output unit for outputting a data element associated with a set synchronisation flag at a second predetermined temporal relationship with respect to said synchronising feature of said received synchronisation clocking signal; said first and second predetermined temporal relationships being arranged so that a predetermined system latency exists between input of a data element to said transmission node and subsequent output of that data element by said reception node.
Owner:SONY UK LTD
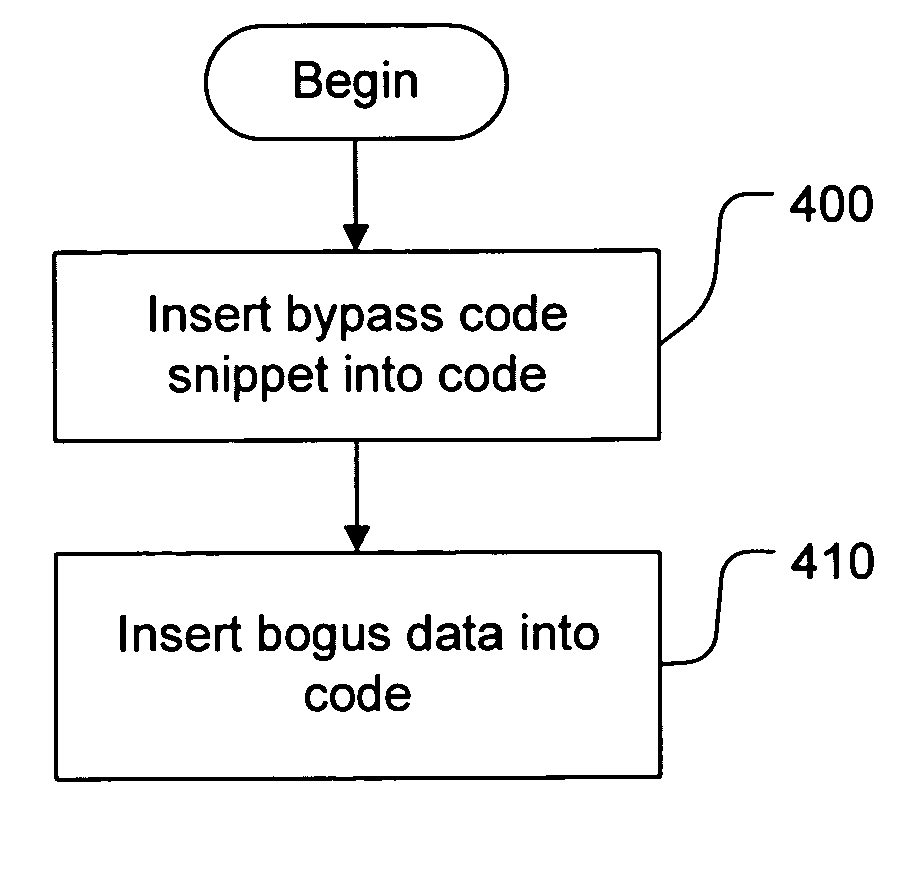
Static and run-time anti-disassembly and anti-debugging
InactiveUS20050198526A1Avoid analysisMemory loss protectionError detection/correctionObfuscationRunning time
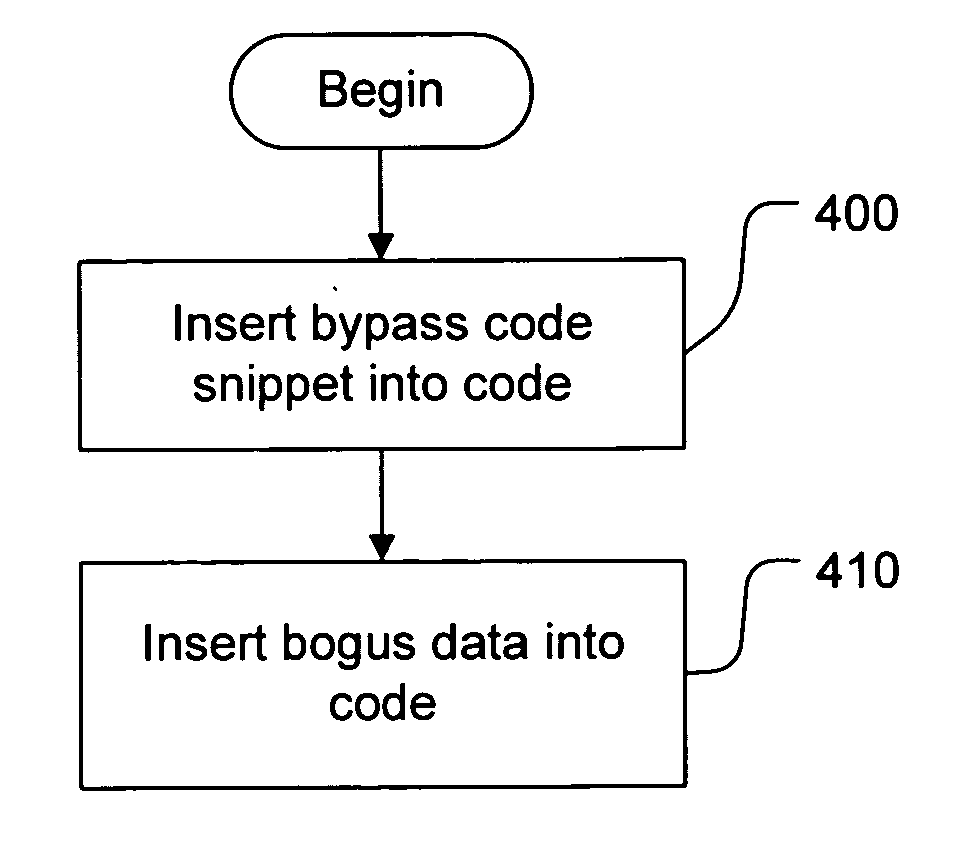
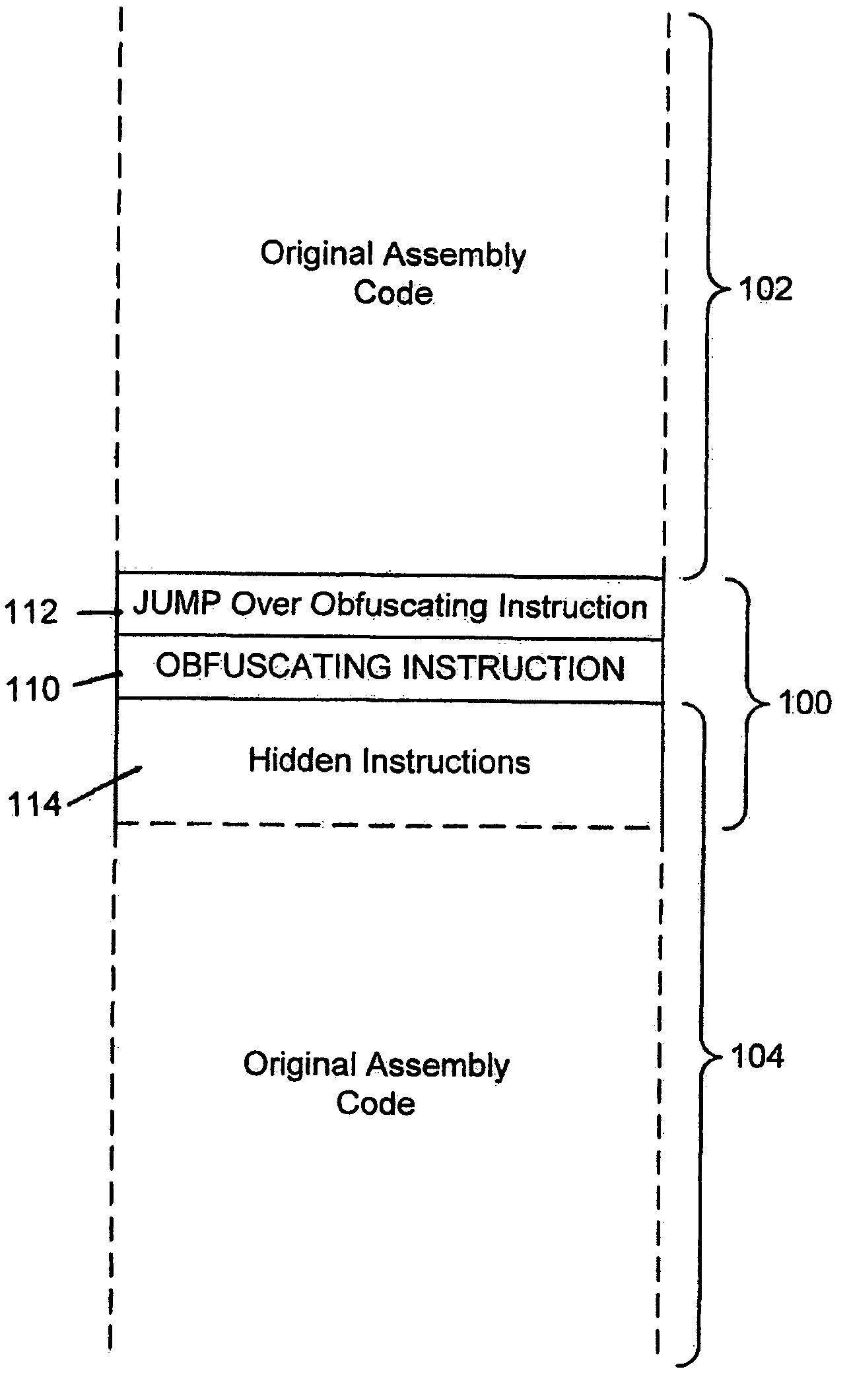
In order to prevent analysis by static and dynamic disassembly techniques, instruction level code obfuscation is performed to induce misalignment and mistaken analysis by disassemblers. Misalignment is induced by including a bypass which leads, during execution, to a legitimate location. During analysis, however, bogus data may be analyzed by the disassembler due to the bypass. Run-time modifications may also be included in code. Code is changed to an invalid state, and instructions inserted into the code which will return the code to a valid state during execution. During analysis, these invalid states may be analyzed by the disassembler as invalid instructions. Induced misalignments and run-time modifications can be chained together to produce sequences of code that will always produce invalid disassembly output from common disassemblers.
Owner:MICROSOFT TECH LICENSING LLC
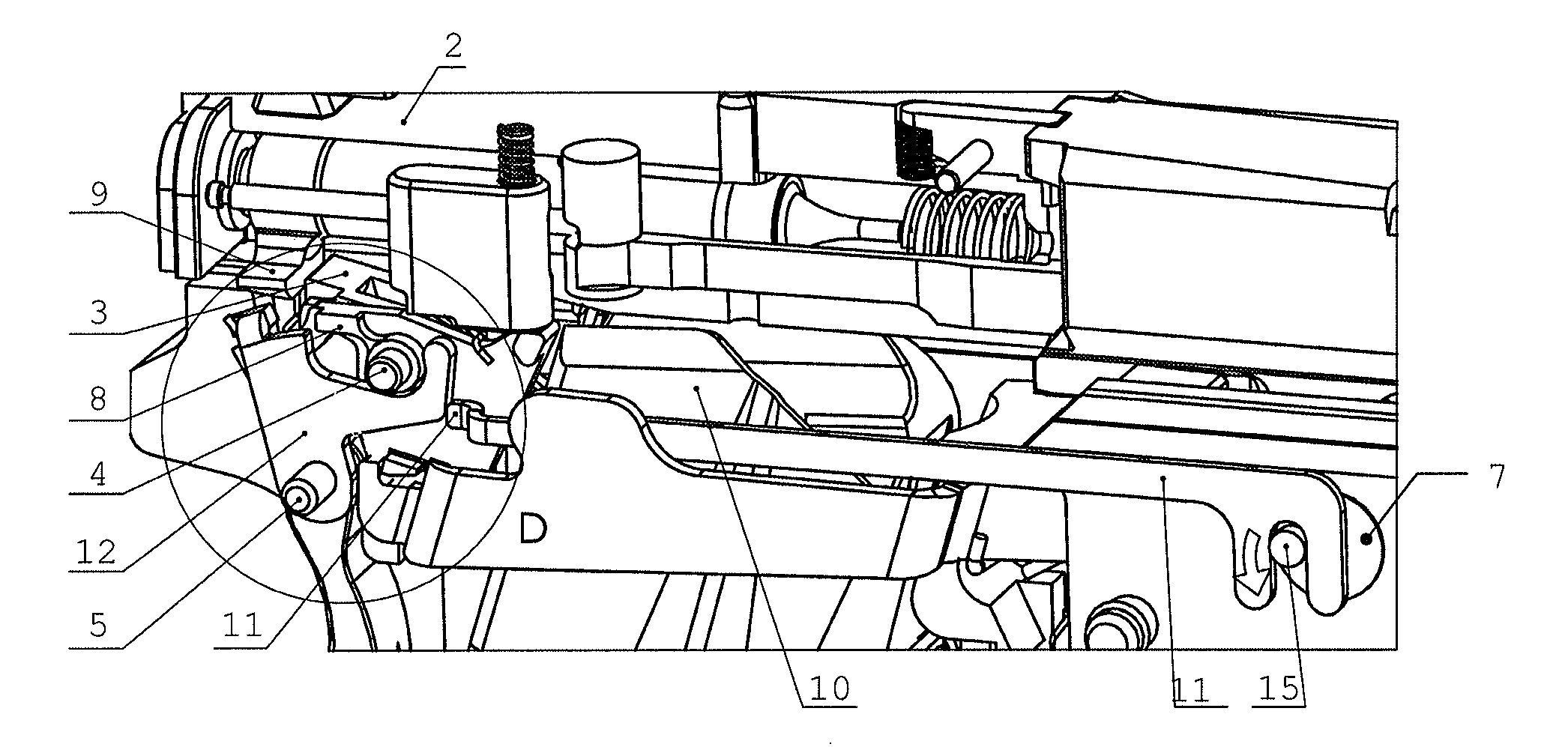
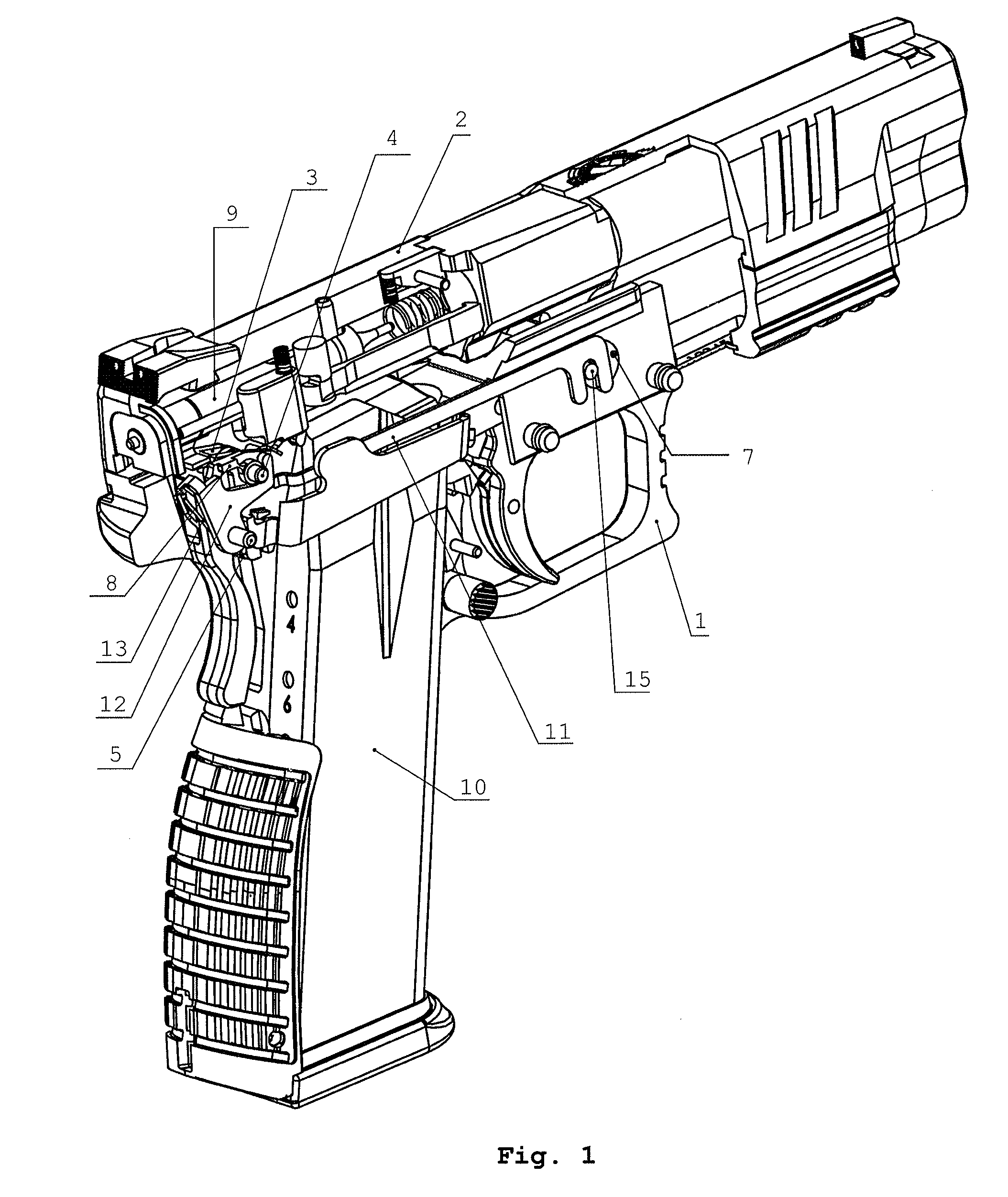
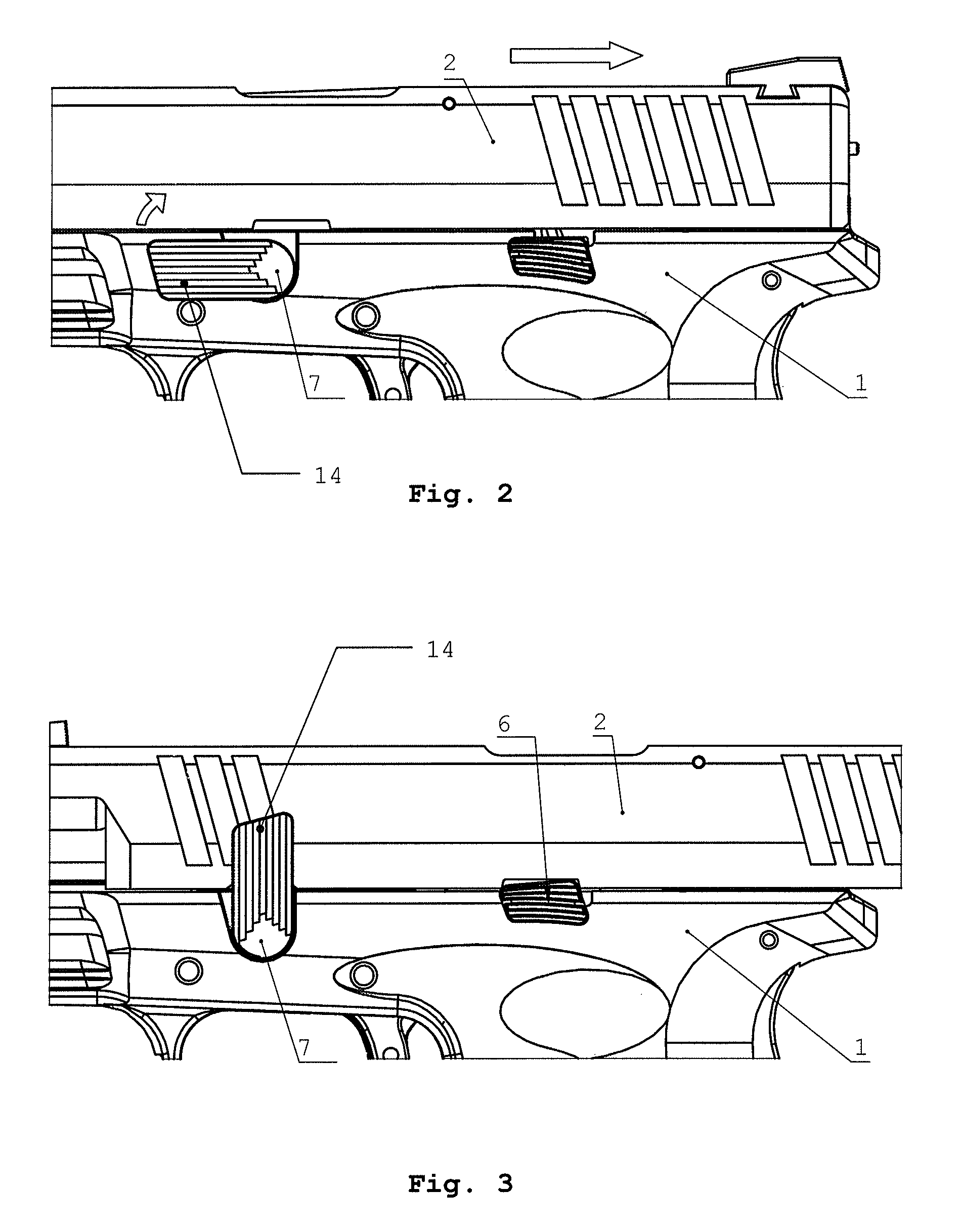
Mechanism for the disassembly of a handgun without triggering
Owner:HS PROD D O O
System for detecting interrupt-driven type program data competition
ActiveCN102063328AReduce false positivesHigh degree of automationMultiprogramming arrangementsSoftware developmentSyntax
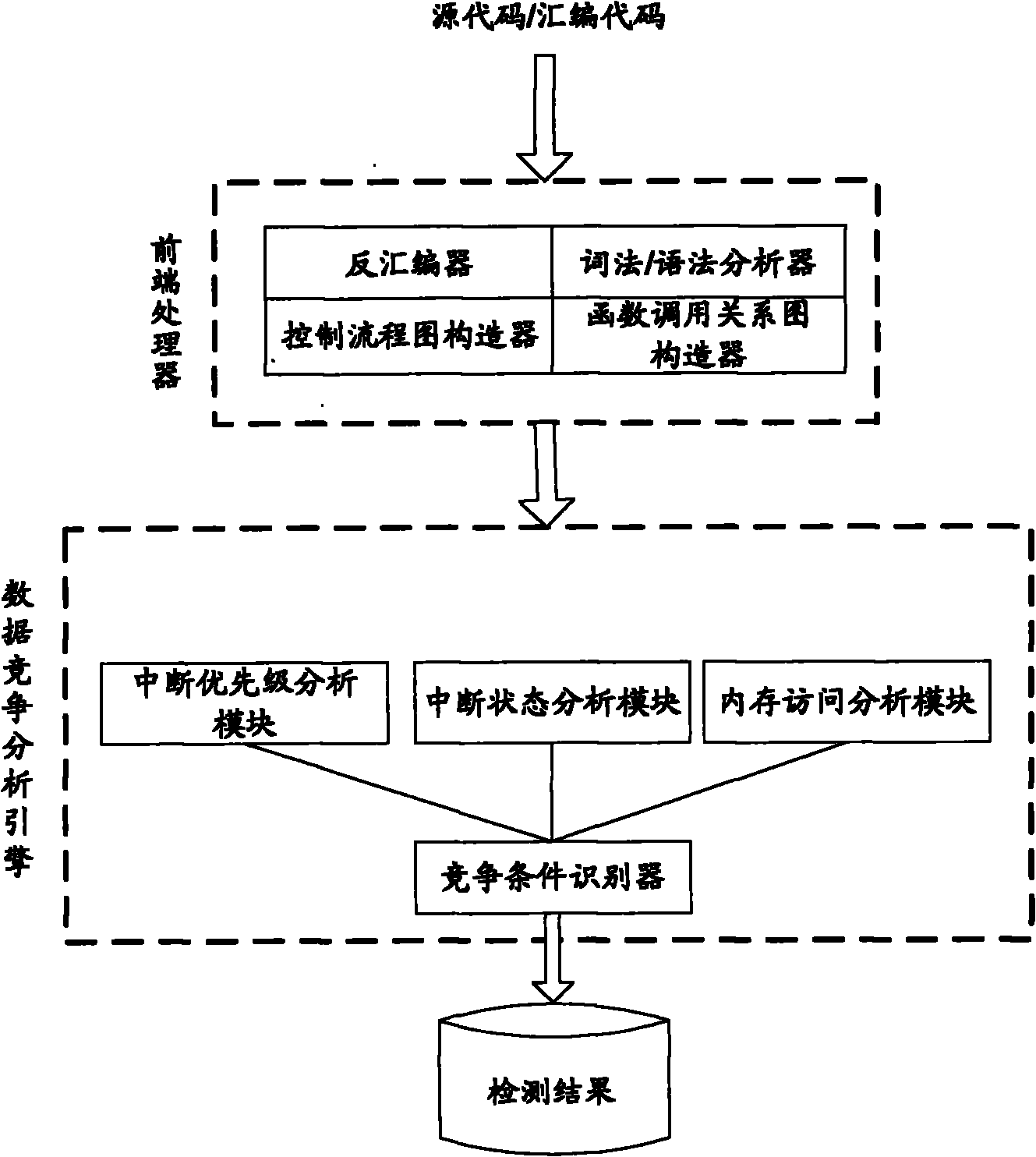
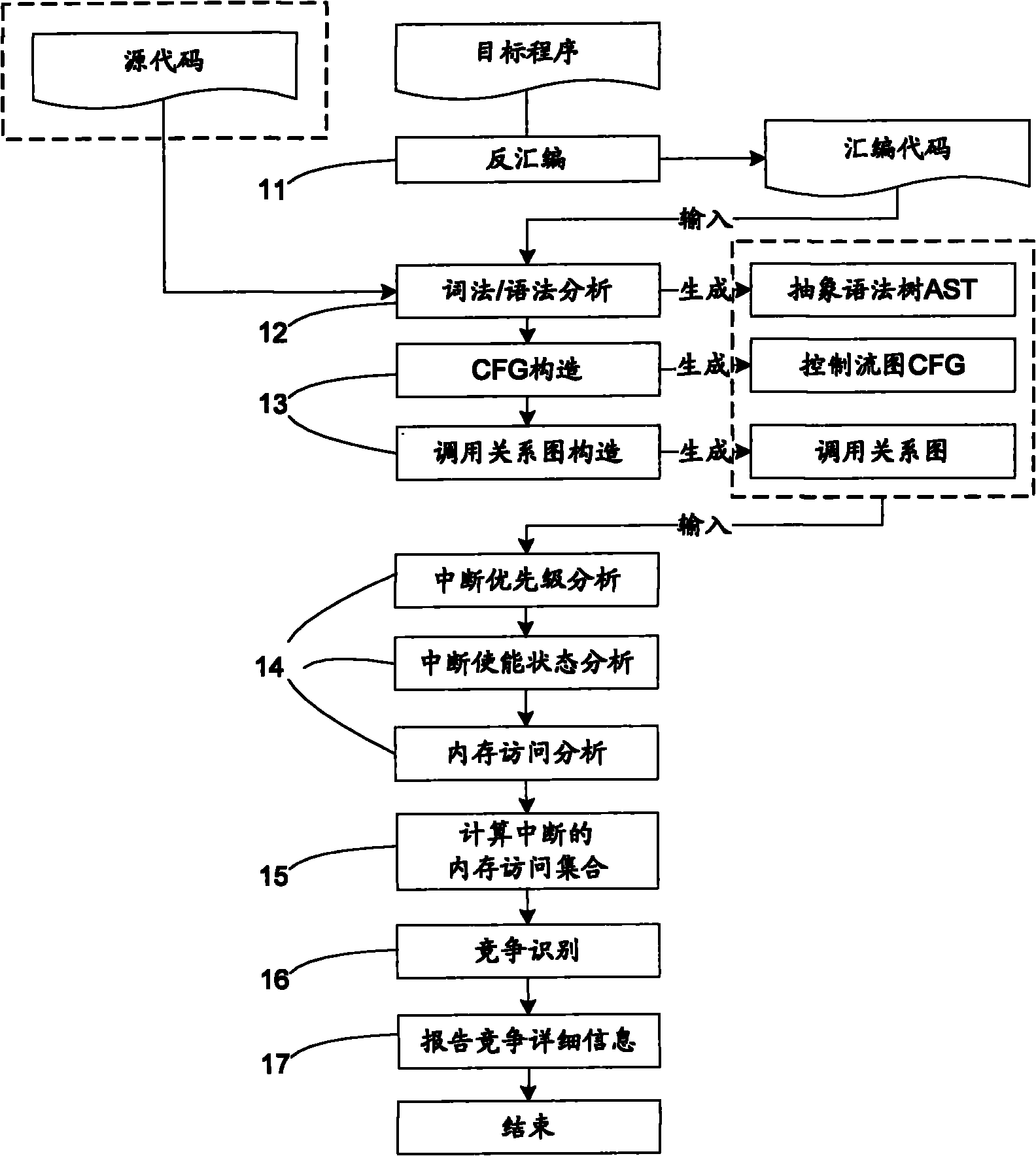
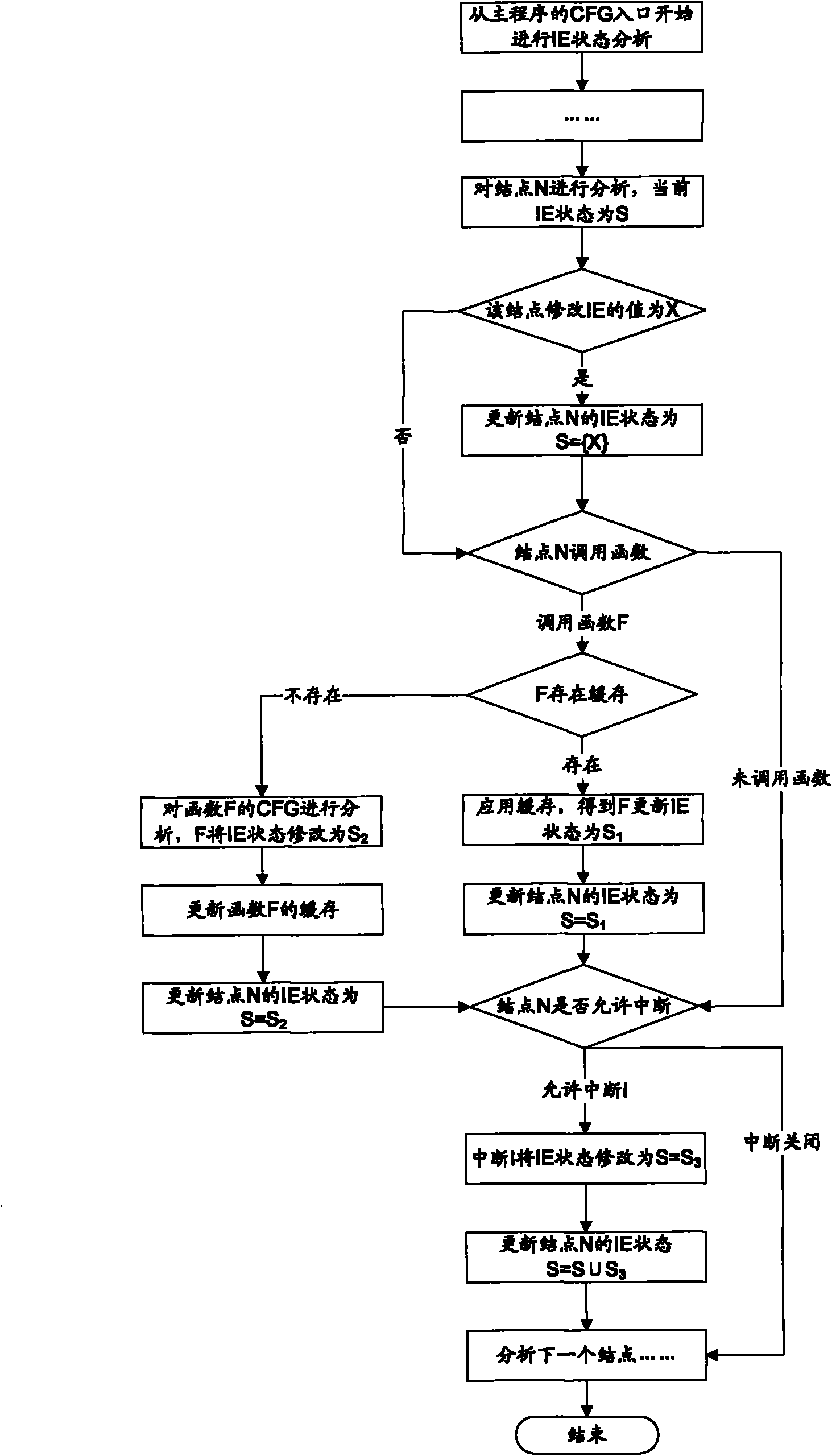
The invention discloses a system for detecting interrupt-driven type program data competition, which comprises a front-end processor and a data race analysis engine, wherein the front-end processor comprises a disassembler, a morphology / syntax analyzer, a control flow graph constructor and a function call relation graph constructor, and the data race analysis engine comprises an interrupt priority analysis module, an interrupt state analysis module, a memory access analysis module and a race condition identifier. A static detection method is adopted in the invention, wherein a source code or assembly code is input; the detected program does not need to run; the method can be applied in the early stage of software development; the automaticity is high; and the interrupt enabled state is analyzed in iterative inter-process manner; through 'iteration', all the possible interrupt switching conditions can be extremely collected and the failed report of data race detection is reduced; and through 'inter-process', the function call and the influence of the interruption on the program state are regarded and the detection accuracy and the detection efficiency are increased.
Owner:BEIJING INST OF CONTROL ENG
System for obfuscating computer code upon disassembly
InactiveUS20060053307A1Avoid disassemblyUnauthorized memory use protectionHardware monitoringObfuscationDerivative work
A system for preventing accurate disassembly of computer code. Such code masking, referred to as “obfuscation,” is useful to prevent unwanted parties from making copies of an original author's software, obtaining valuable information from the software for purposes of breaking into a program, stealing secrets, making derivative works, etc. The present invention uses assembly-language instructions so as to confuse the disassembler to produce results that are not an accurate representation of the original assembly code. In one embodiment, a method is provided where an interrupt, or software exception instruction, is used to mask several subsequent instructions. The instruction used can be any instruction that causes the disassembler to assume that one or more subsequent words, or bytes, are associated with the instruction. The method, instead, jumps directly to the bytes assumed associated with the instruction and executes those bytes for a different purpose. A preferred embodiment works with a popular Microsoft “ASM” assembler language and “DASM” disassembler. The instructions used to achieve the obfuscation include “INT” instructions. Using this approach up to 17 bytes of obfuscation can be achieved with five instructions. Each instruction remains obfuscated until executed and returns to an obfuscated state afterwards.
Owner:ALADDIN KNOWLEDGE SYSTEMS
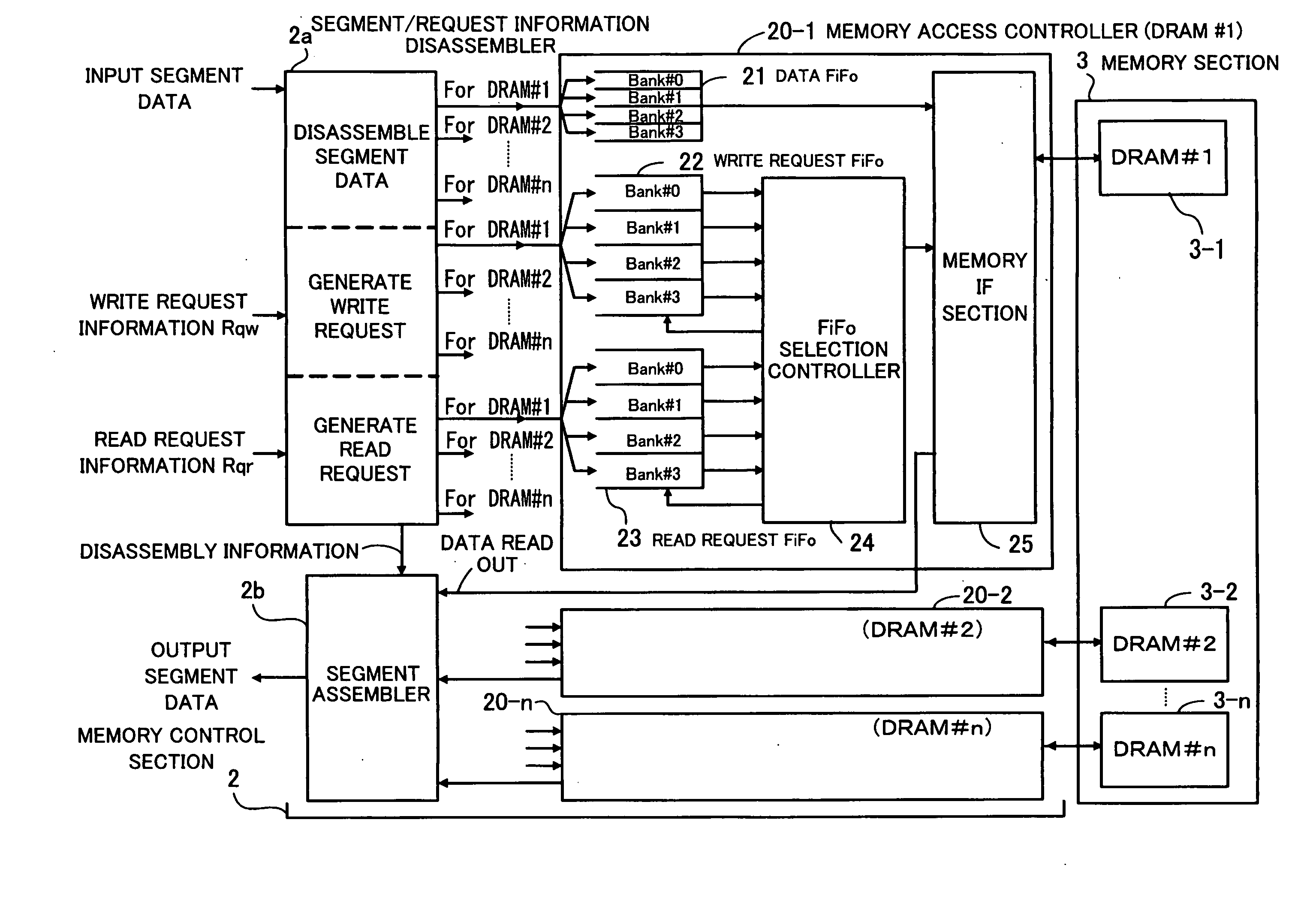
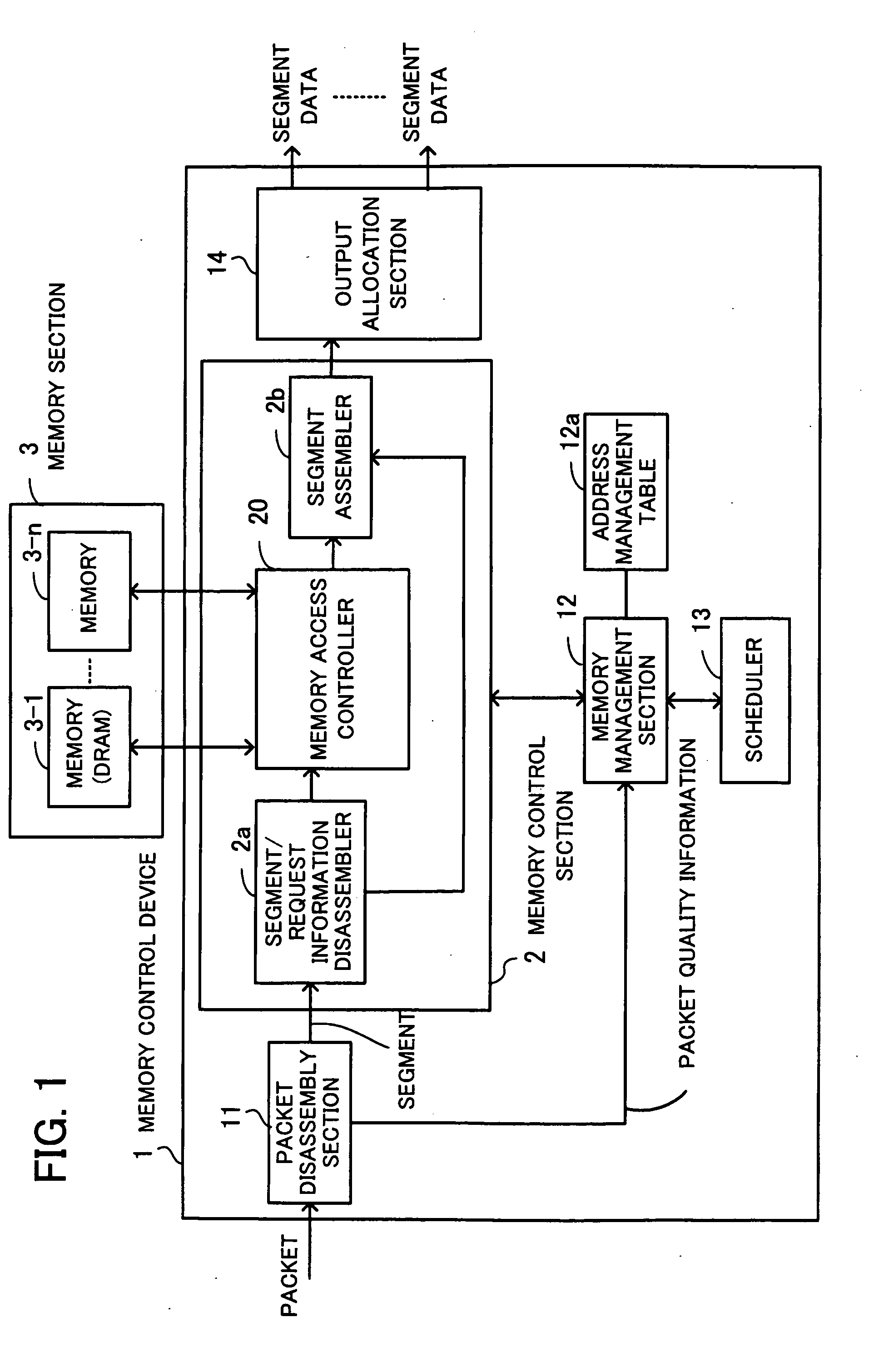
Memory control device
InactiveUS20090172318A1Improve efficiencyReduce in quantityUnauthorized memory use protectionMicro-instruction address formationMemory interfaceMemory controller
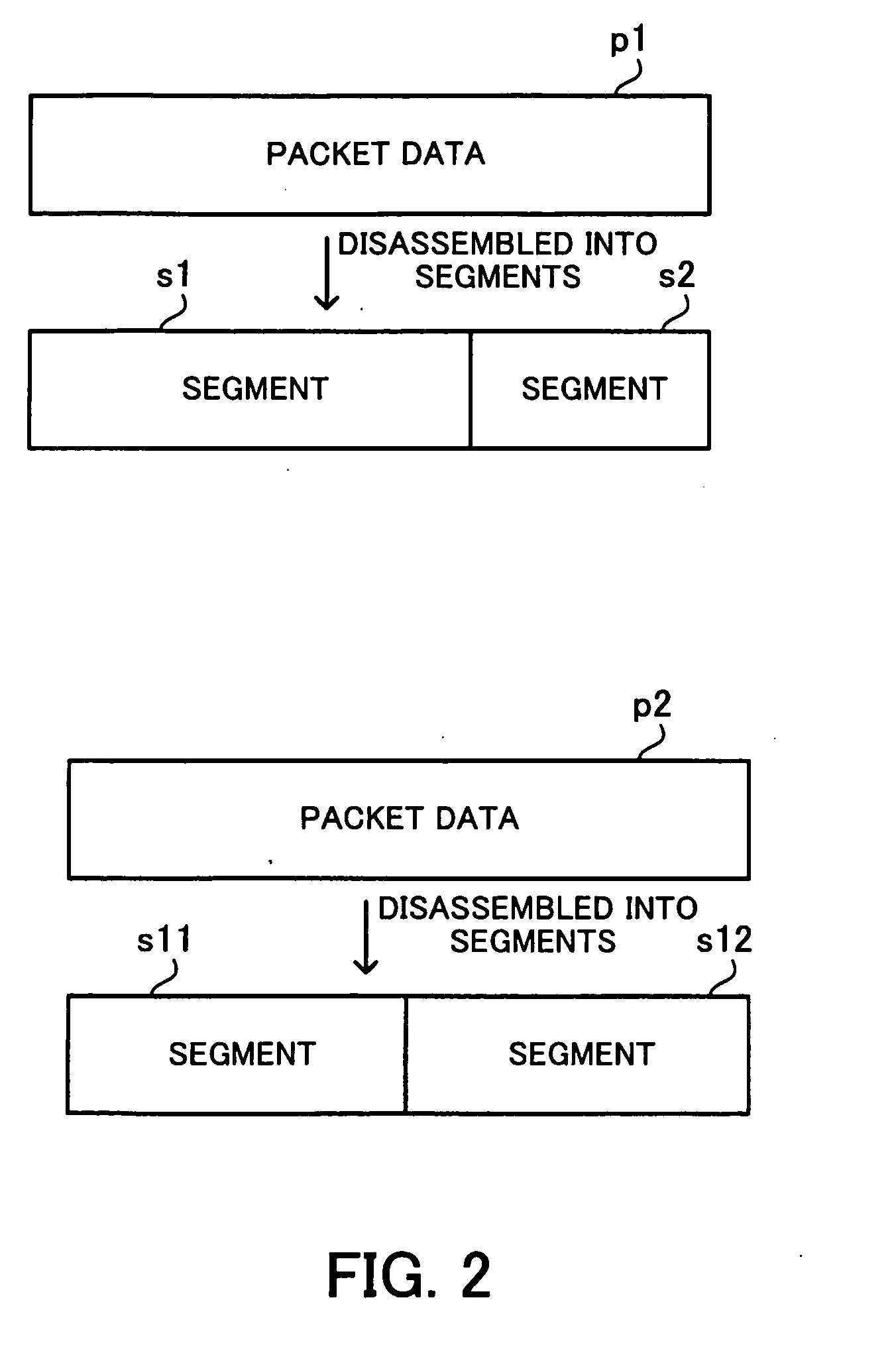
A memory control device that can improve the speed of a memory interface. A packet disassembly section disassembles packet data into segments and detects packet quality information. A memory management section has an address management table and manages a state in which the packet data is stored according to the packet quality information. A segment / request information disassembler disassembles the segments into data by an access unit by which memories can be written / read, and generates write requests and read requests according to the access unit. A memory access controller avoids a bank access to which is prohibited because of a bank constraint, extracts a write request or a read request corresponding to an accessible bank from the write requests or the read requests generated, and gains write / read access to the memories.
Owner:FUJITSU LTD
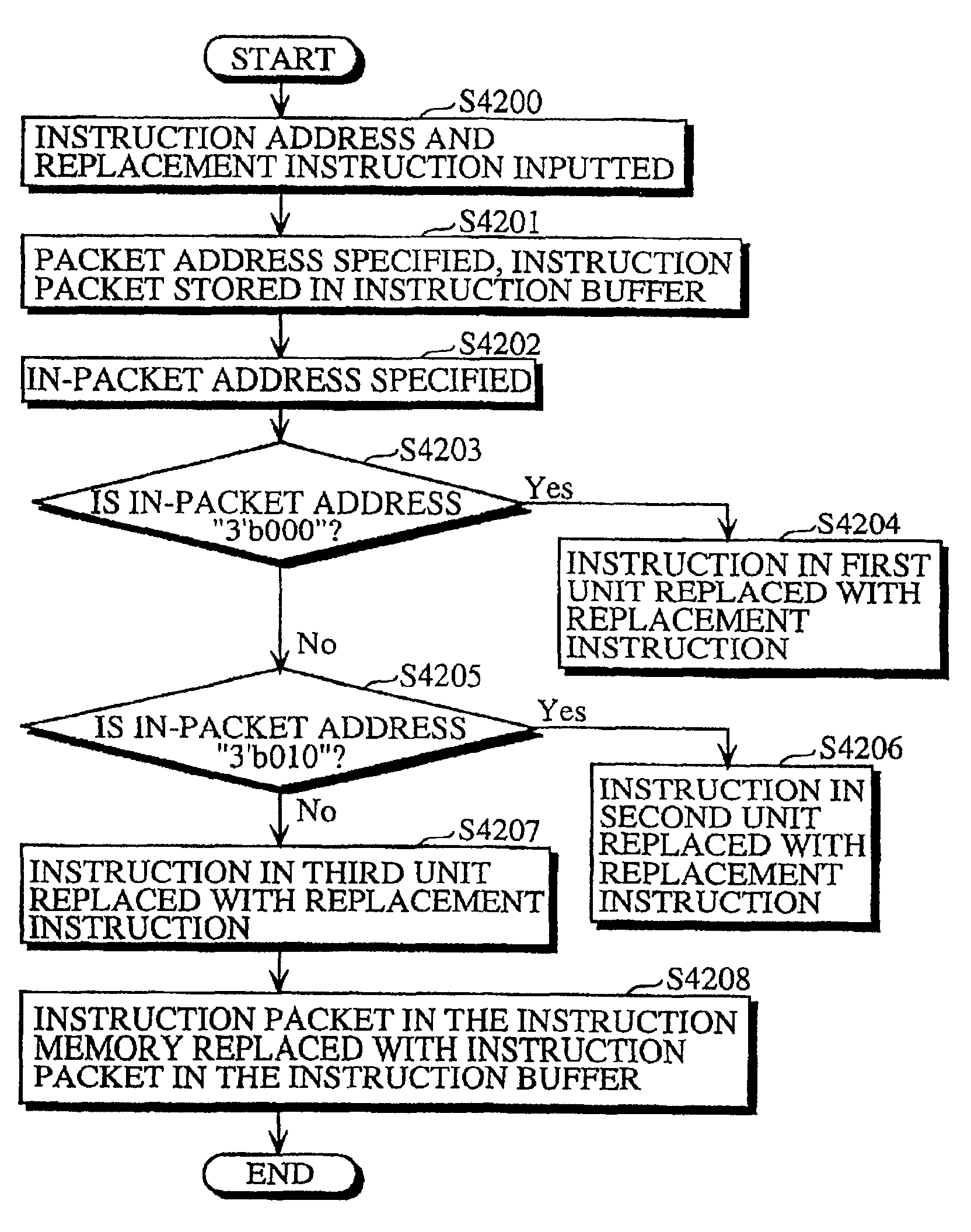
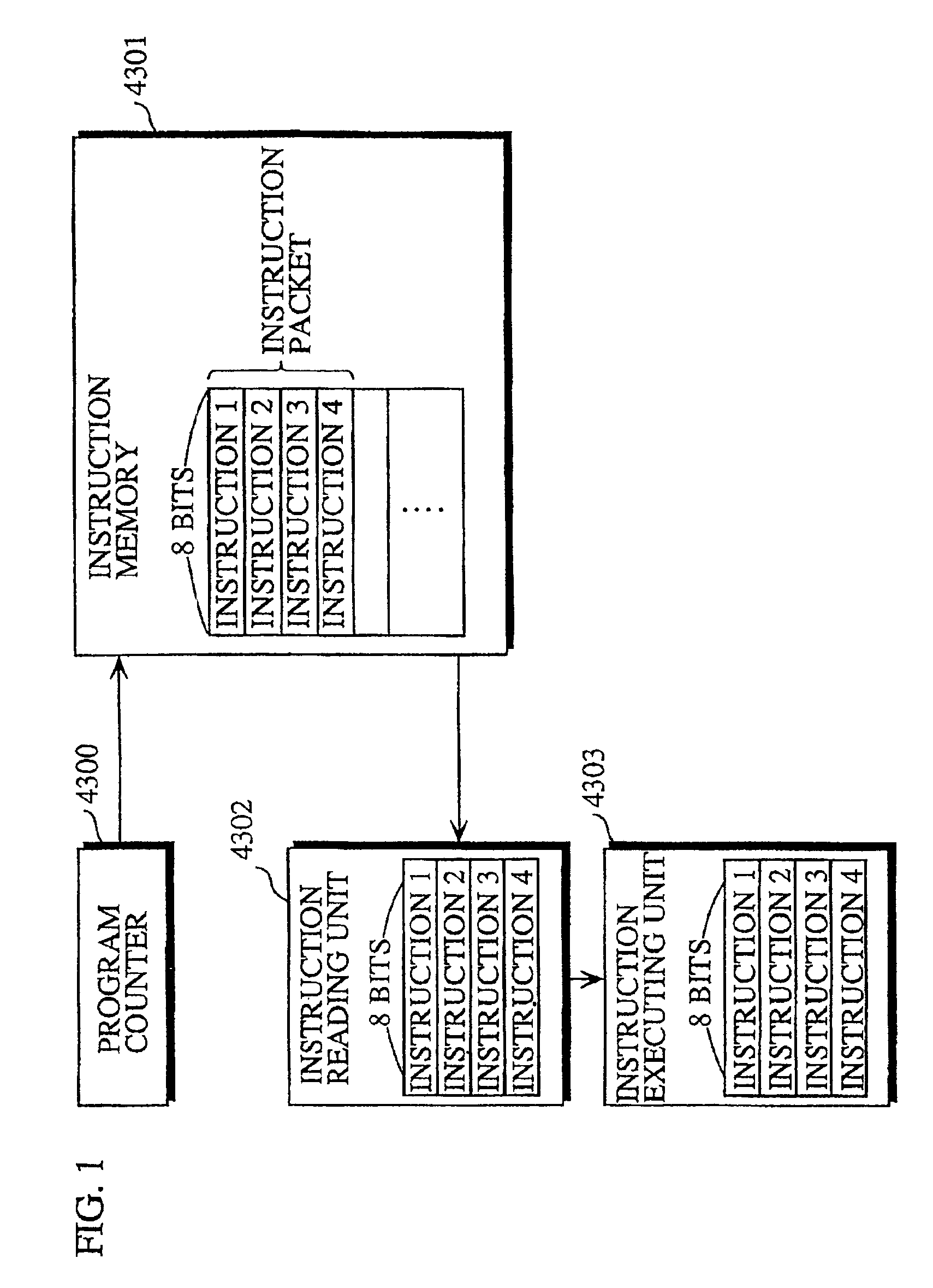
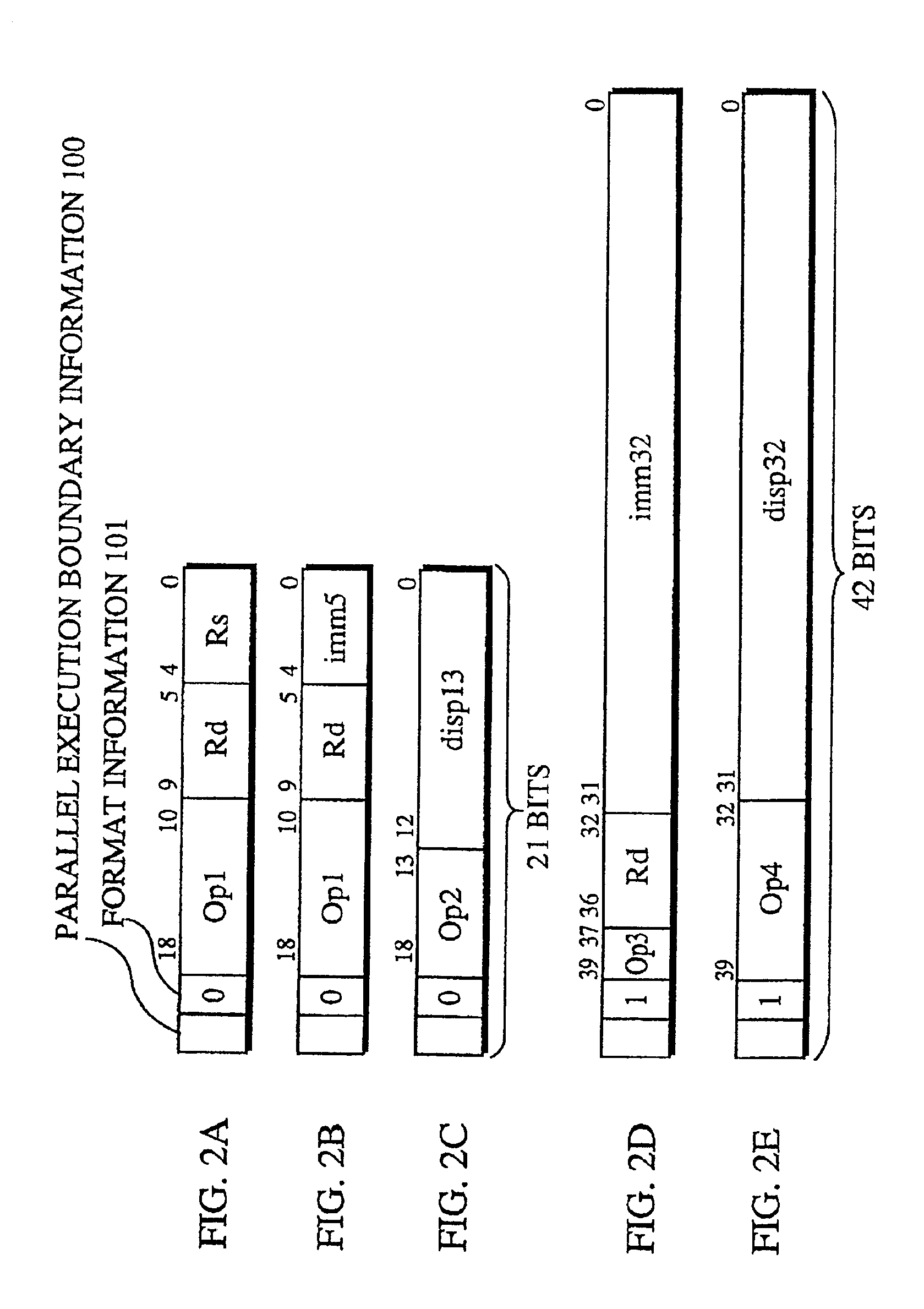
Processor for executing instructions in units that are unrelated to the units in which instructions are read, and a compiler, an optimization apparatus, an assembler, a linker, a debugger and a disassembler for such processor
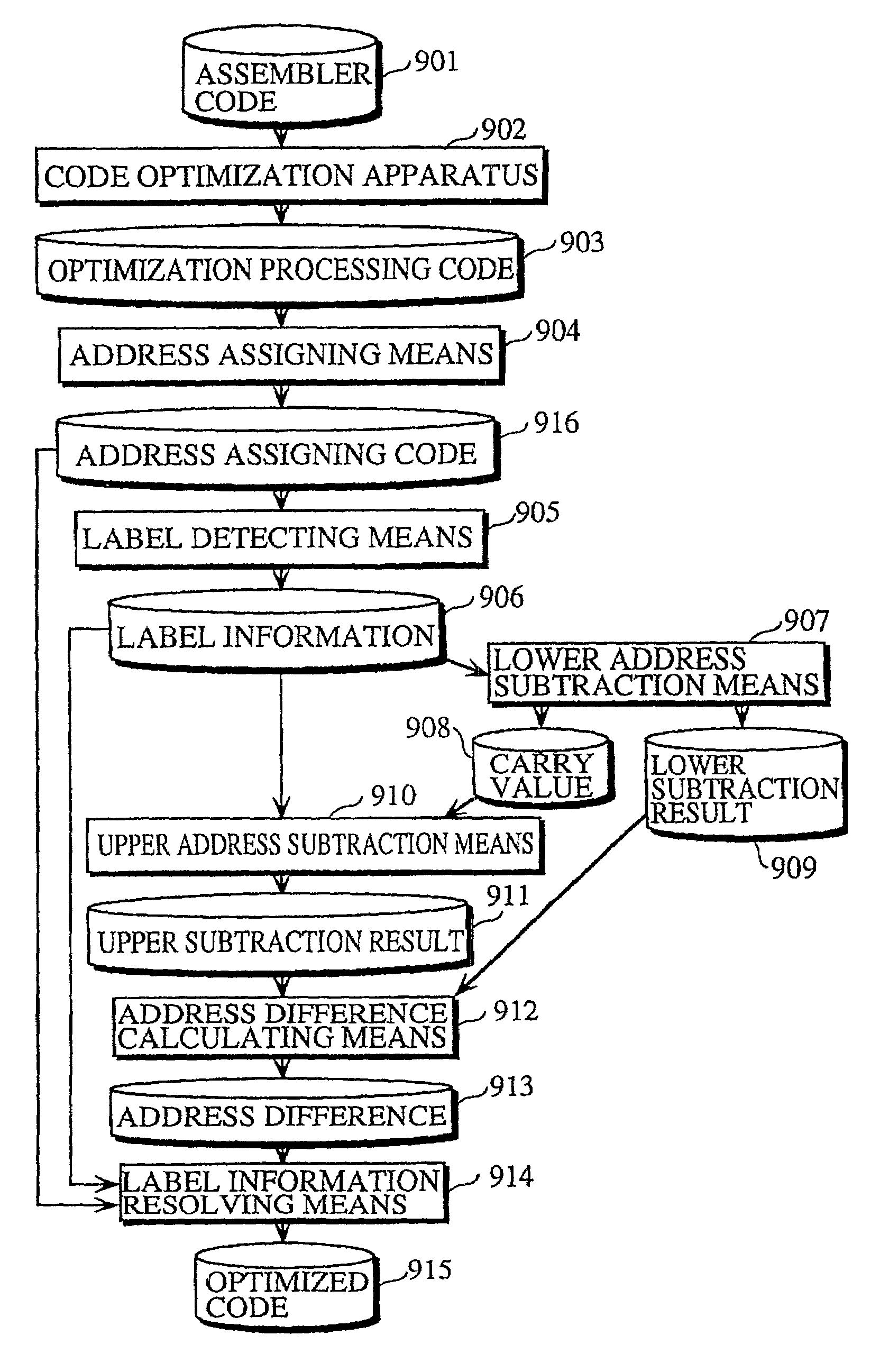
When a branch instruction is decoded by the instruction decoders 409a˜409c, the upper 29 bits of the PC relative value included in the branch instruction are sent to the upper PC calculator 411 and the lower 3 bits are sent to the lower PC calculator 405. The lower PC calculator 405 adds the lower 3 bits of the PC relative value and the lower 3 bits of the present lower PC 404 and sends the result to the lower PC 404 as the updated lower PC. The upper PC calculator 411 adds the upper 29 bits of the PC relative value, the upper 29 bits of the present upper PC 403, and a carry that may be received from the lower PC calculator 405, and sends the result to the upper PC 403 as the updated upper PC.
Owner:SOCIONEXT INC
Mining method for built-in application vulnerability of Android system
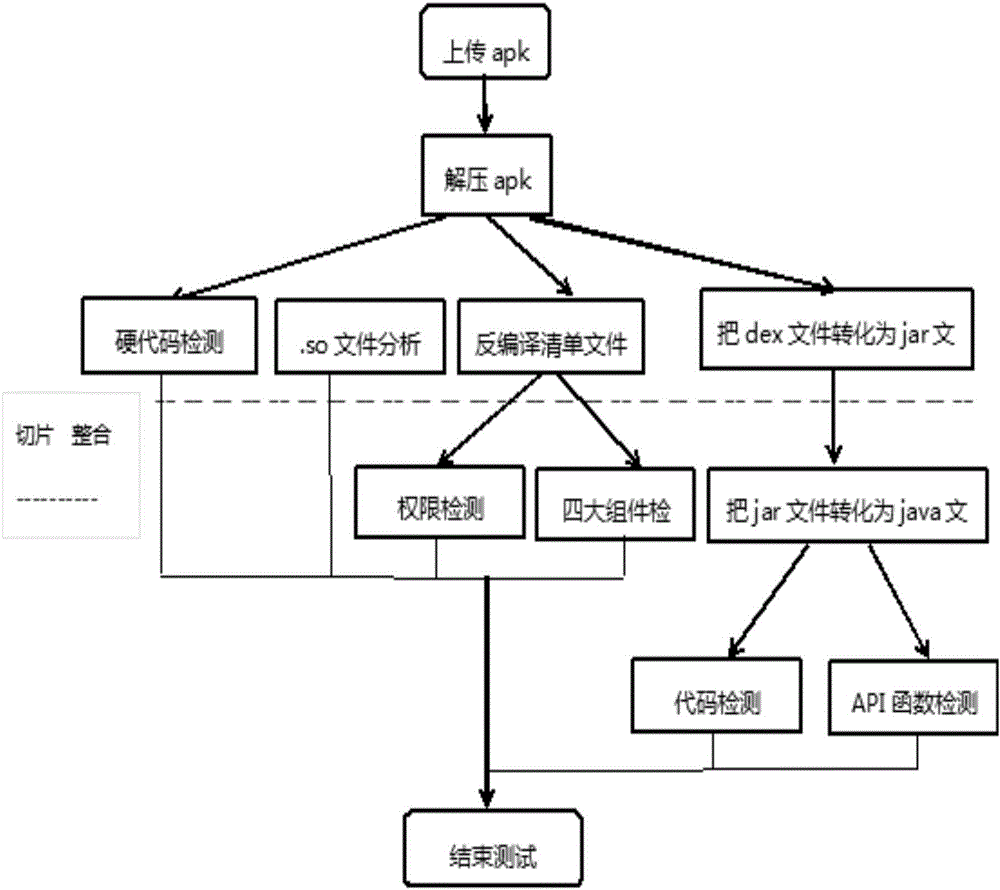
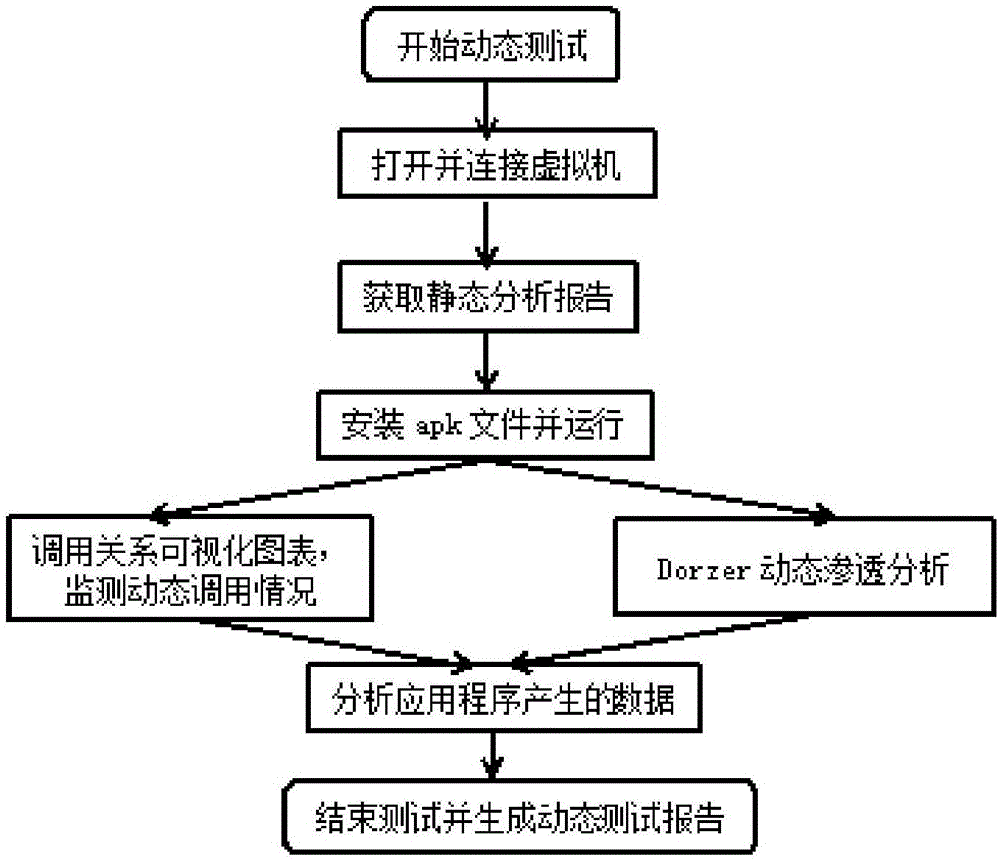
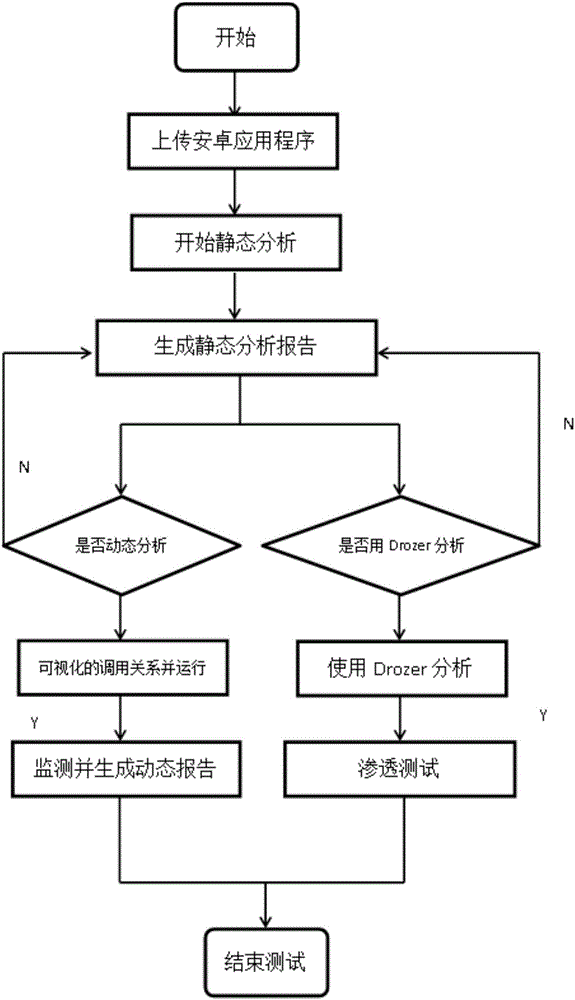
The invention belongs to the field of the information technology, and particularly relates to a mining method for the built-in application vulnerability of an Android system. The codes of each class of vulnerabilities are analyzed in detail, the class of vulnerability rule is sorted for each class of vulnerabilities, and different weights are attached according to the threat degree of each class of vulnerabilities; an APK (Android Package) file is decompiled, a corresponding executable file is disassembled, and a disassembling code is segmented; collected codes are generated into feature data, and an IDA (Interactive Disassembler) tool is imported to analyze a .so file; vulnerability matching is carried out; a .so file analysis result is combined to finally obtain a static weight report; before dynamic detection is started, an appointed APK file static report is obtained, the calling of an API (Application Program Interface) function is monitored; and through the integration of a Drozer dynamic analysis frame, various test commands are input in a command line, an attack surface is determined, and a test is carried out by aiming at an assaultable place. By use of the method, the safety of the developed APK can be quickly found, and the method has an important meaning for maintaining the stability and the business safety of the Android system.
Owner:BEIJING UNIV OF TECH
Processor for executing instructions in units that are unrelated to the units in which instructions are read, and a compiler, an optimization apparatus, an assembler, a linker, a debugger and a disassembler for such processor
When a branch instruction is decoded by the instruction decoders 409a˜409c, the upper 29 bits of the PC relative value included in the branch instruction are sent to the upper PC calculator 411 and the lower 3 bits are sent to the lower PC calculator 405. The lower PC calculator 405 adds the lower 3 bits of the PC relative value and the lower 3 bits of the present lower PC 404 and sends the result to the lower PC 404 as the updated lower PC. The upper PC calculator 411 adds the upper 29 bits of the PC relative value, the upper 29 bits of the present upper PC 403, and a carry that may be received from the lower PC calculator 405, and sends the result to the upper PC 403 as the updated upper PC.
Owner:SOCIONEXT INC
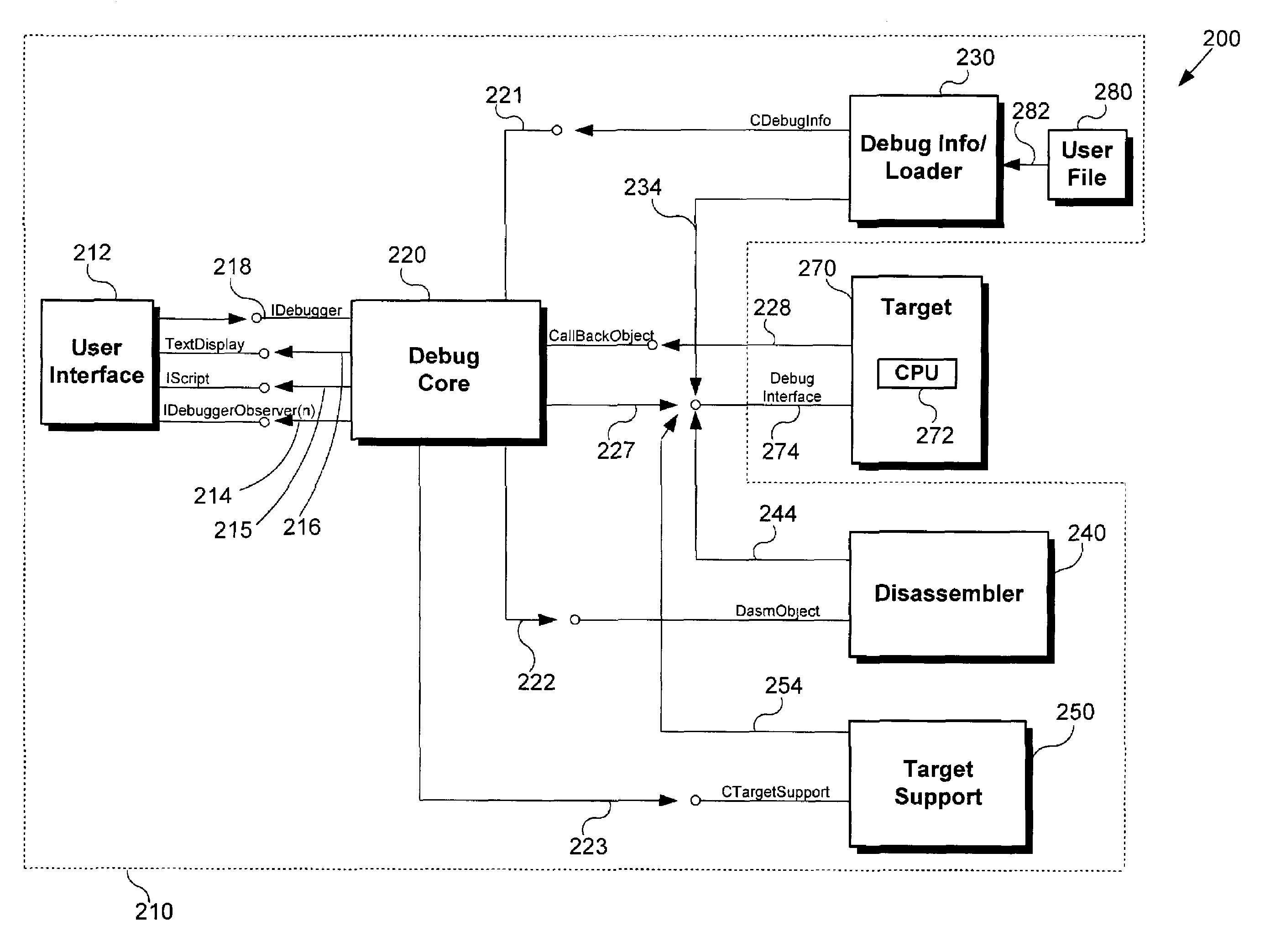
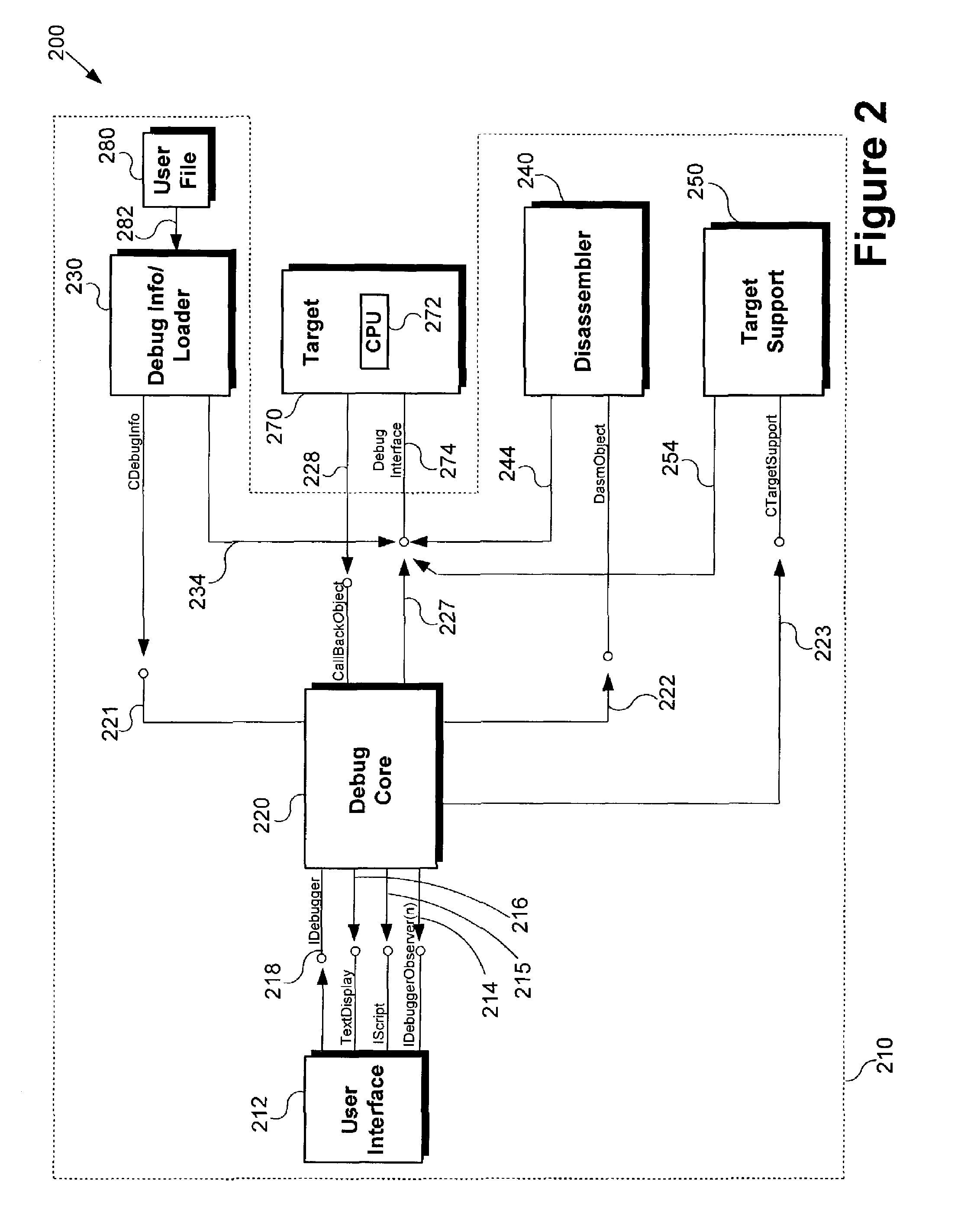
Method and system for adapting a debugger to new targets
ActiveUS6938185B1Effectively properly operateError detection/correctionSpecific program execution arrangementsDisassemblerTarget database
One disclosed embodiment is a method for adapting a debugger to a selected target. According to this embodiment, the debugger connects to the selected target. Thereafter a debug core in the debugger dynamically loads a module set from a target database that corresponds to the selected target. Next, a debug info / loader, a disassembler, and / or a target support are dynamically loaded based on the module set loaded by debug core. Thereafter, the debug info / loader, disassembler, and / or target support can directly connect to the selected target to retrieve additional target-specific information. By implementing the above method, the debugger can adapt to new or different targets without the need to rebuild different versions of the debugger to suit new or different targets. In other embodiments, a system for implementing the above method, and a computer readable medium containing a computer program for implementing the above method, are disclosed.
Owner:MACOM TECH SOLUTIONS HLDG INC
Systems and methods for instructions-based detection of sophisticated obfuscation and packing
ActiveUS20170099307A1Improve the detection rateReduce processing stepsComputer security arrangementsTransmissionObfuscationOpaque predicate
Disclosed herein are new methods and systems for detecting obfuscated programs. We build a recursive traversal disassembler that extracts the control flow graph of binary files. This allows us to detect the presence of interleaving instructions, which is typically an indication of the opaque predicate anti-disassembly trick. Our detection system uses some novel features based on referenced instructions and the extracted control flow graph that clearly distinguishes between obfuscated and normal files. When these are combined with a few features based on file structure, we achieve a very high detection rate of obfuscated files.
Owner:XU SHOUHUAI +2
Detection system and method for statically detecting applications
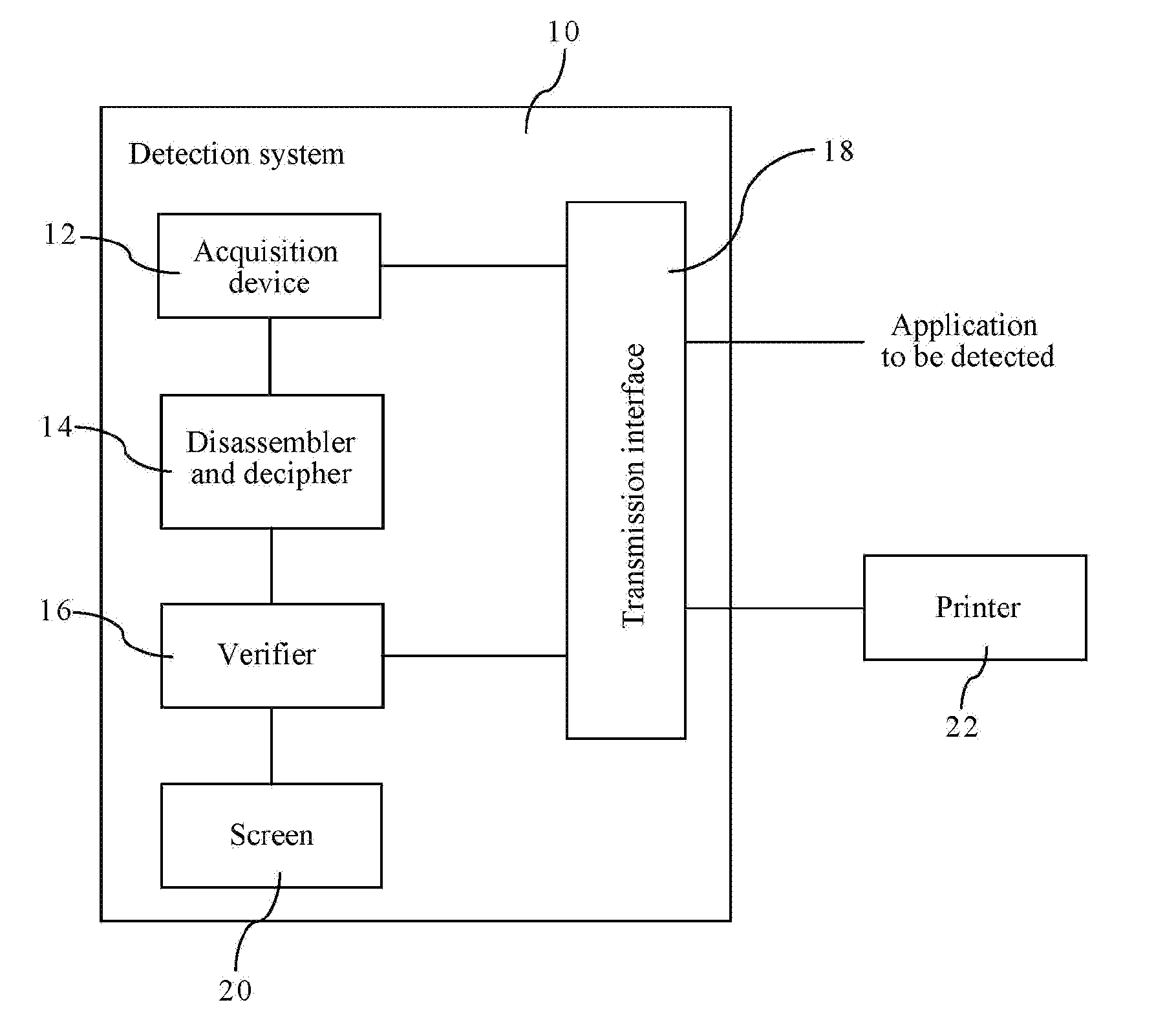
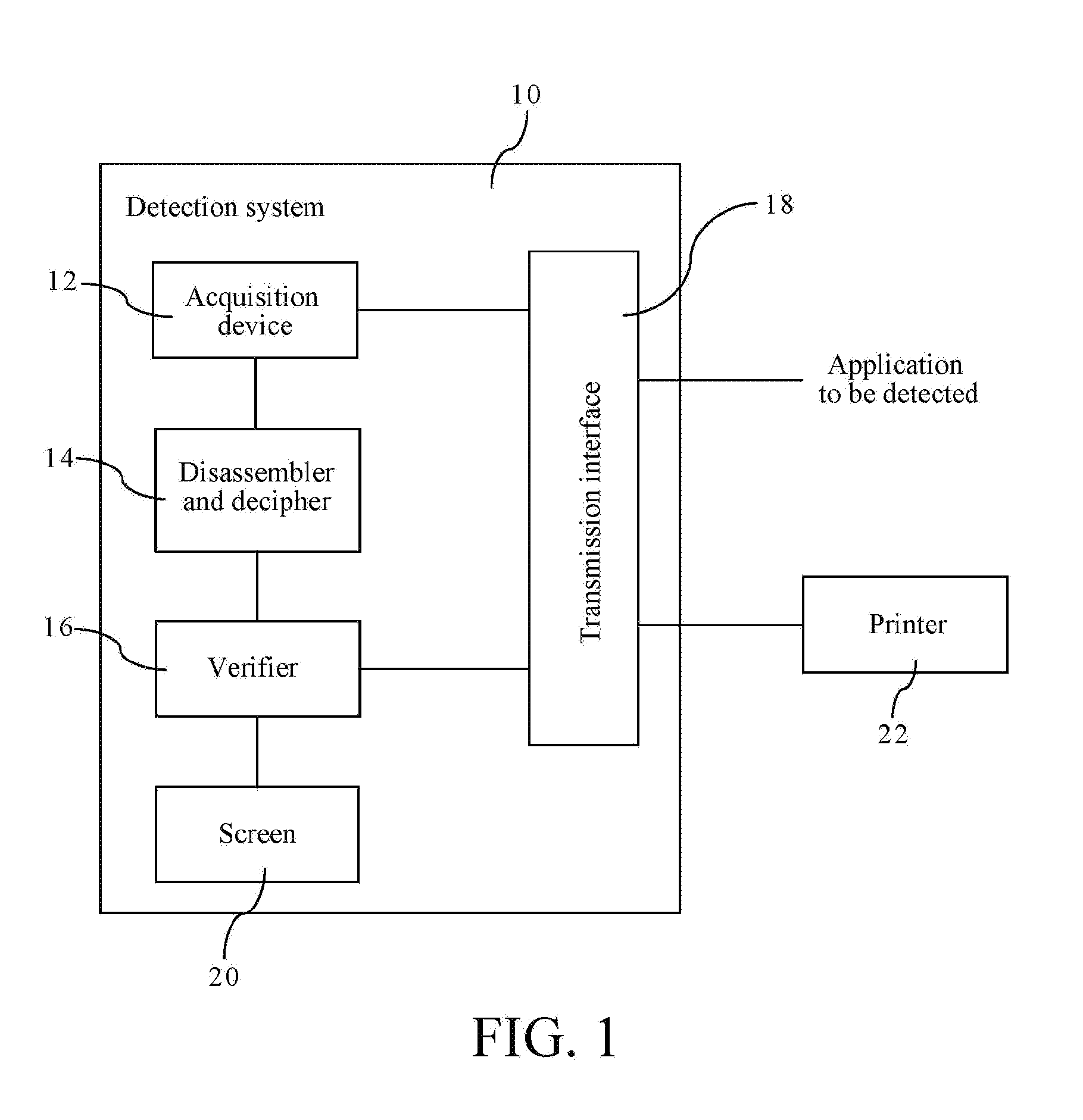
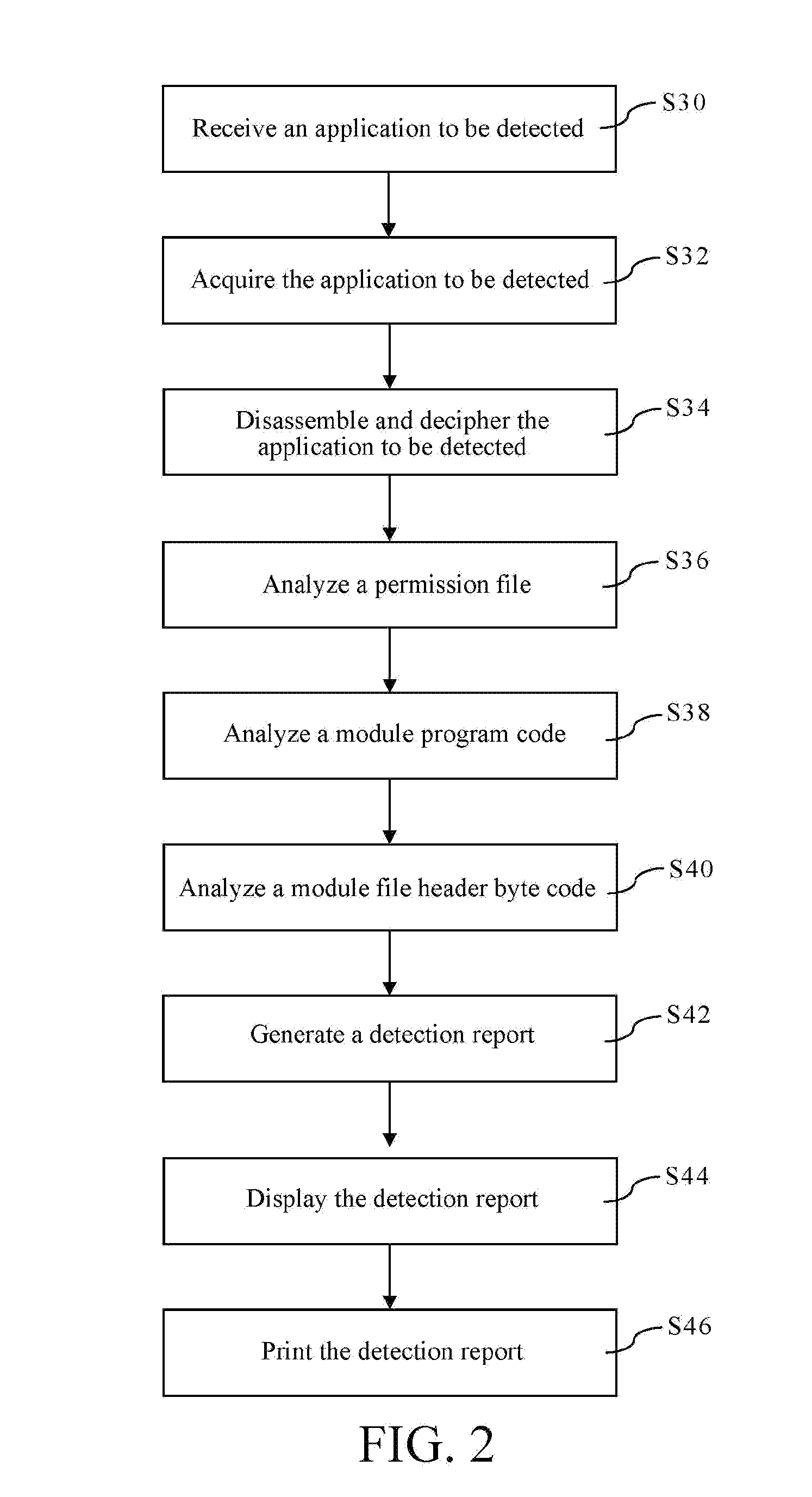
InactiveUS20160197950A1Save detection timeImprove the detection rateUnauthorized memory use protectionHardware monitoringApplication softwareDisassembler
Disclosed is a method for statically detecting applications, the method including: intercepting, by an acquisition device of the detection system, at least one module file header byte code, at least one module program code and a permission file in an application to be detected which have been complied and encrypted; disassembling and deciphering, by a disassembler and decipher of the detection system, the at least one module file header byte code, the at least one module program code and the permission file which have been complied and encrypted; analyzing, by a verifier of the detection system, the permission file, the at least one module program code and the at least one module file header byte code disassembled and deciphered, to judge whether to perform improper operations on the smart device; and generating, by the verifier, a detection report according to a result of judging whether to perform improper operations on the smart device.
Owner:RANGECLOUD INFORMATION TECH
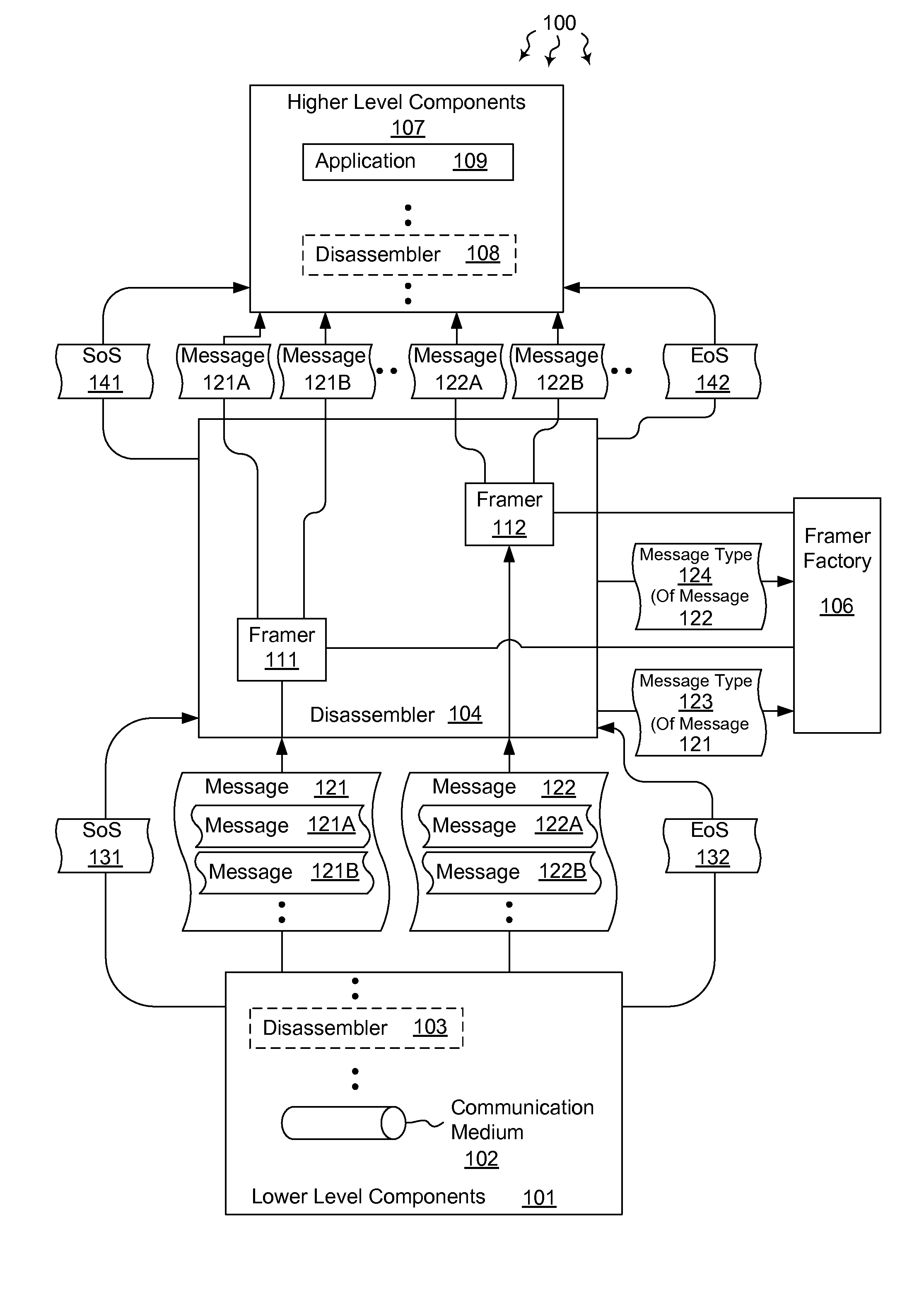
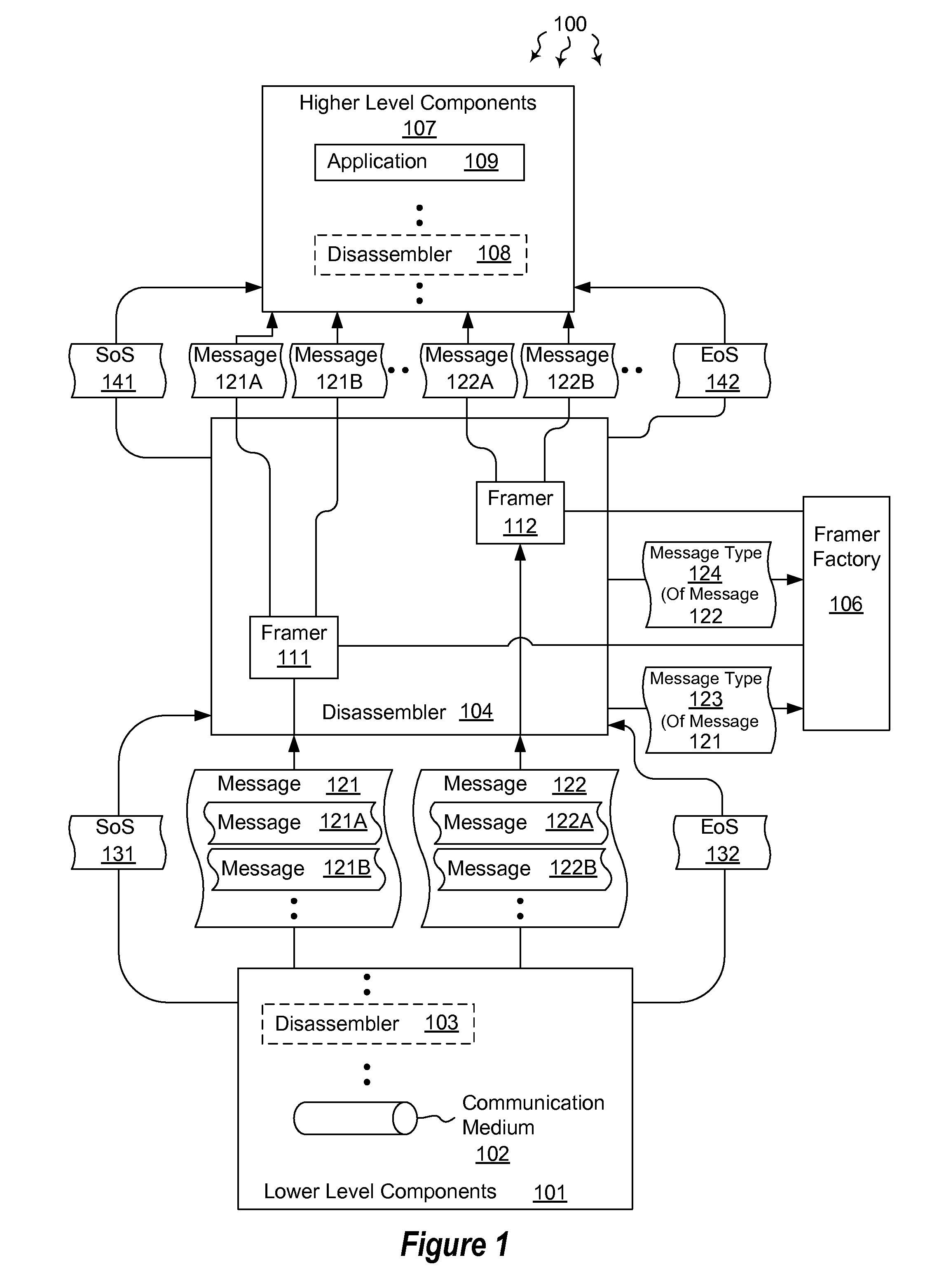
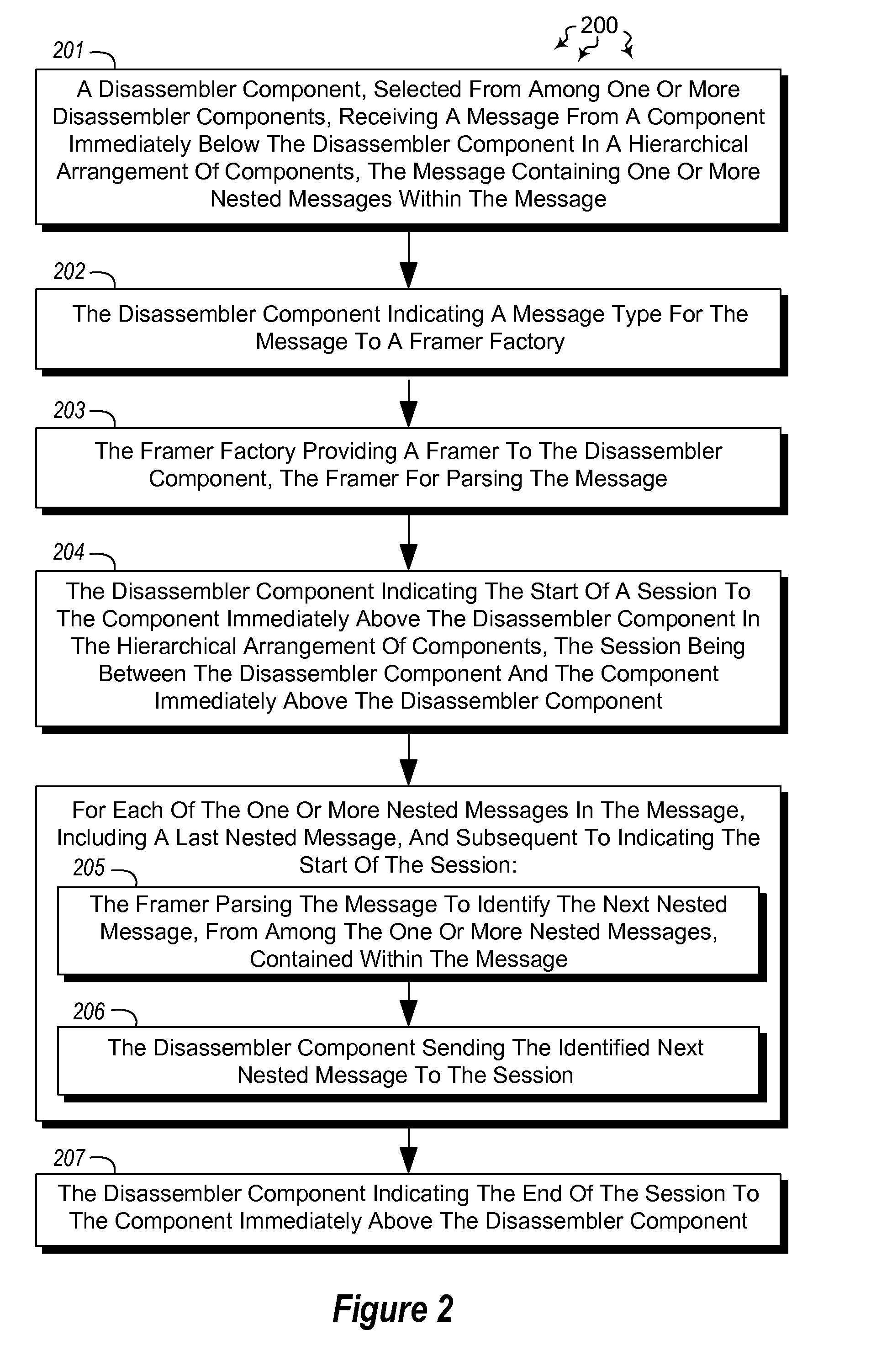
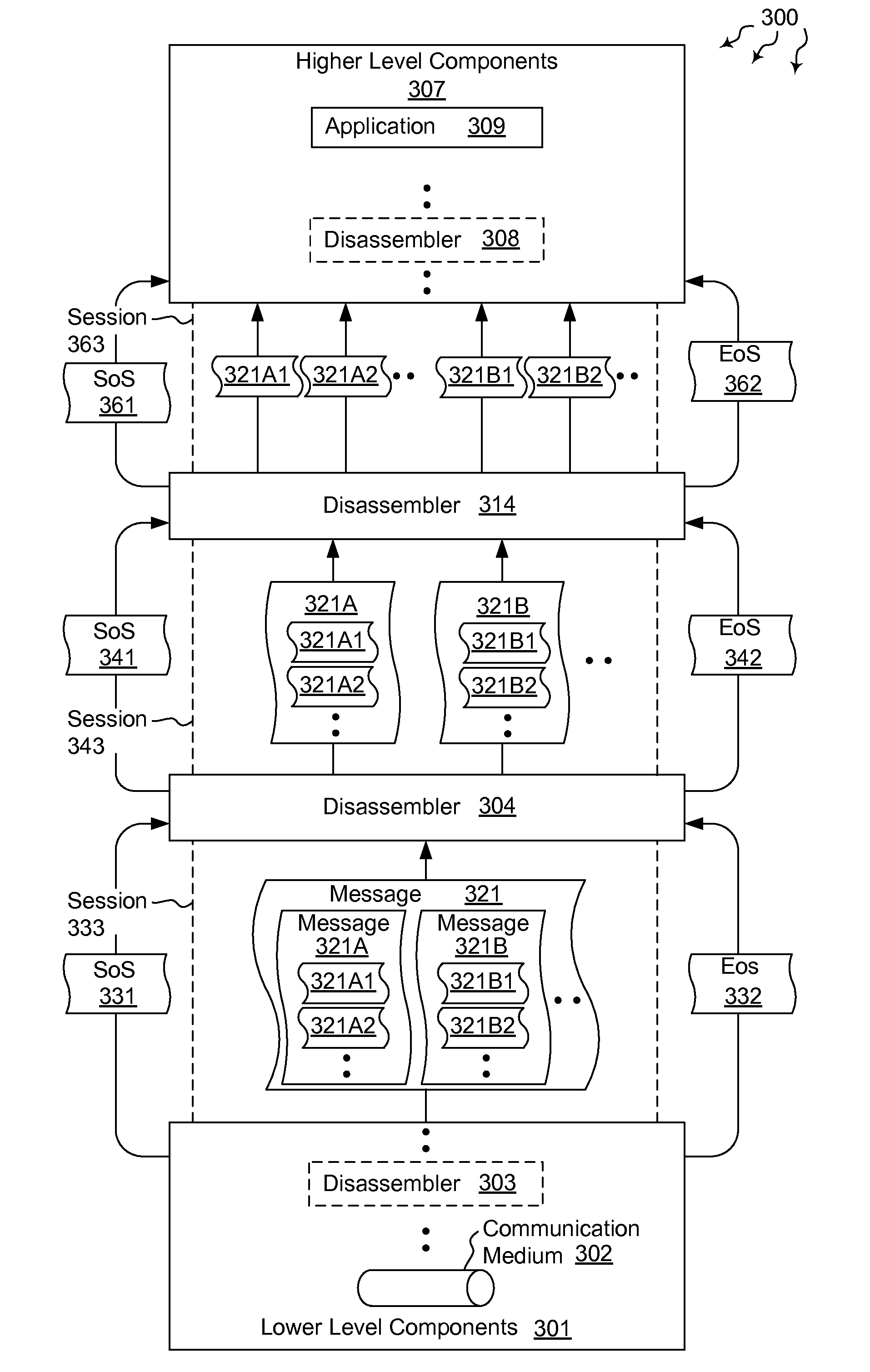
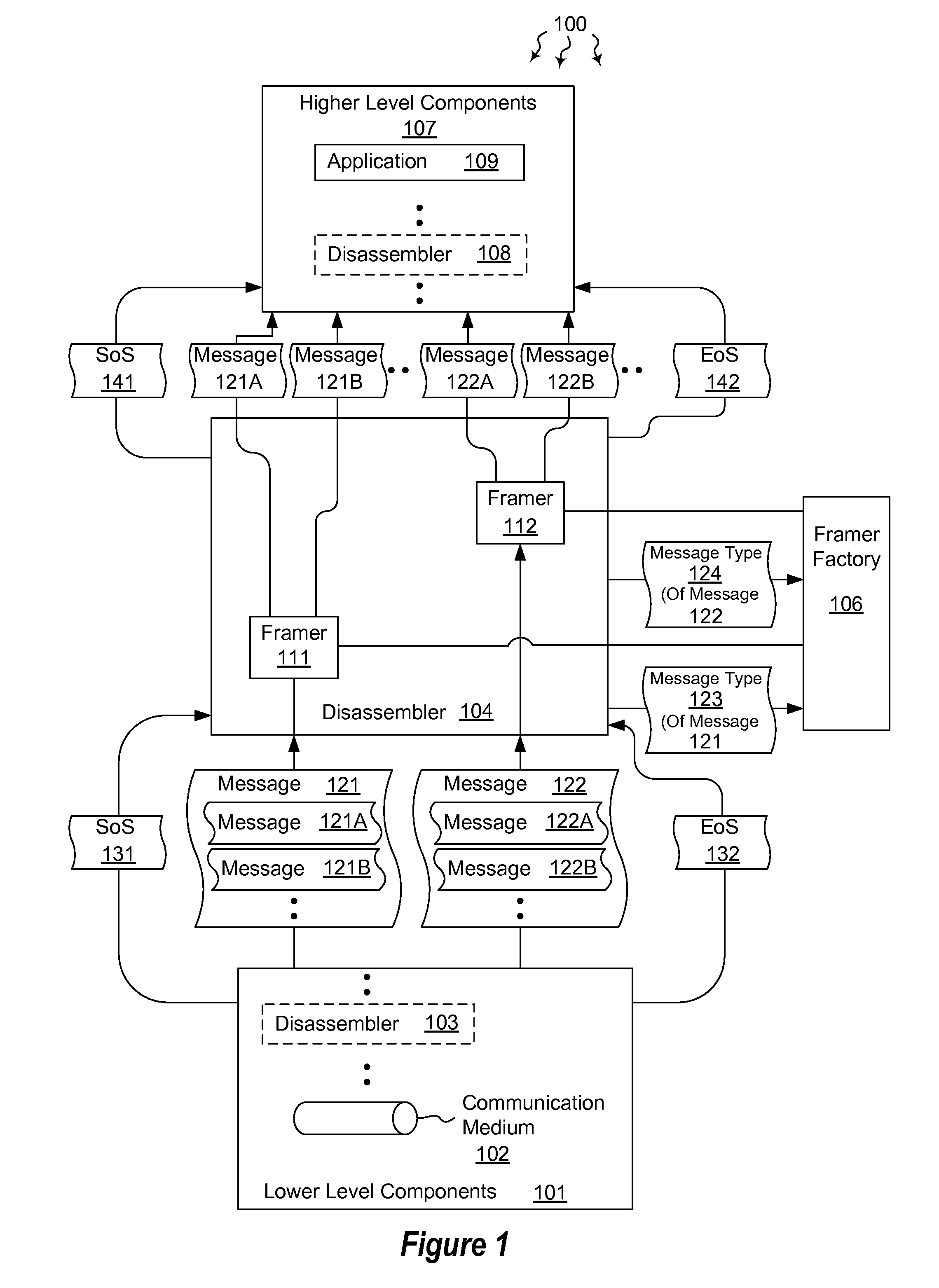
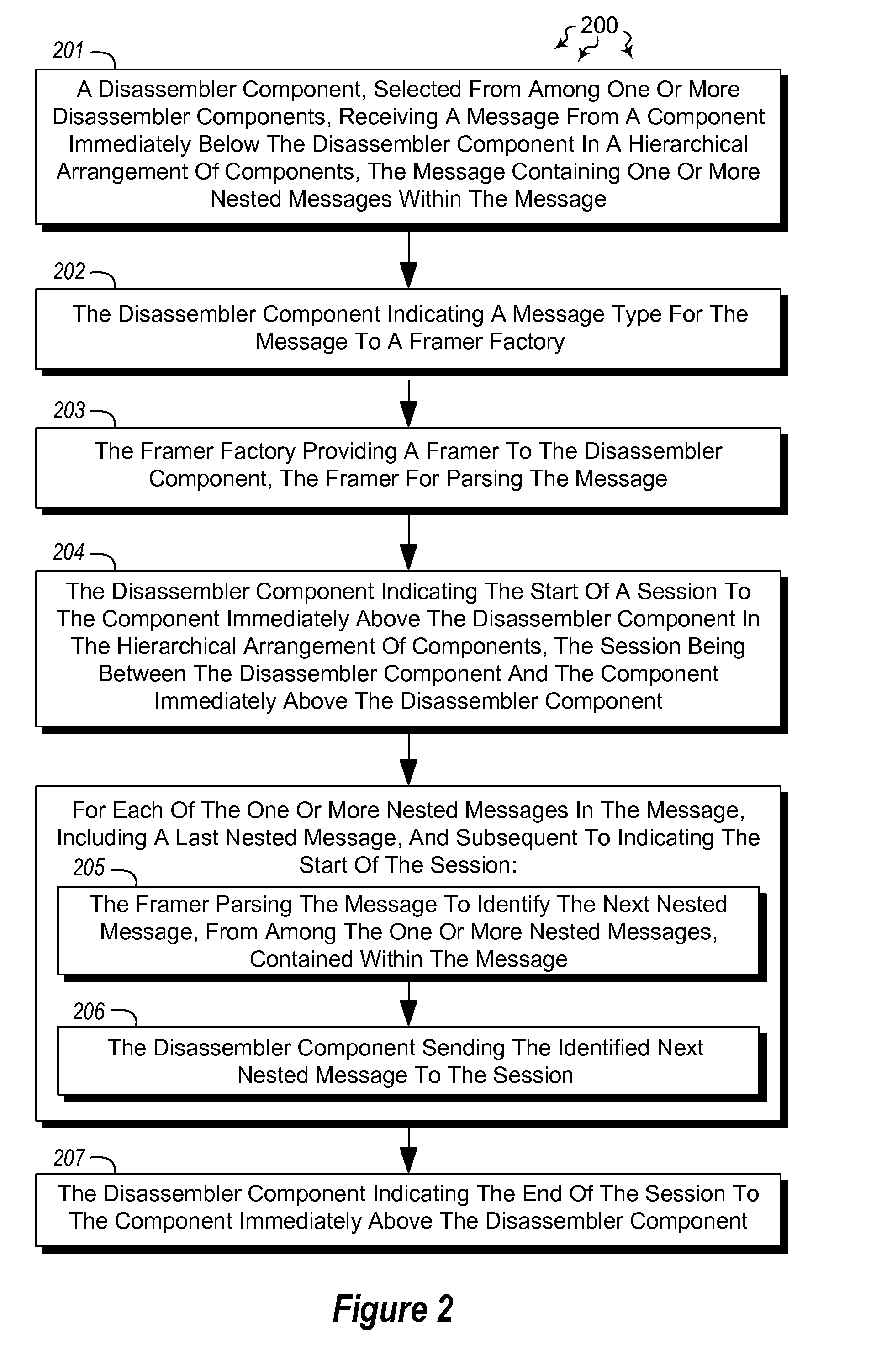
Hierarchically disassembling messages
The present invention extends to methods, systems, and computer program products for hierarchically disassembling messages. The functionality of disassemblers and framers is decoupled such that framers for different types of messages can be utilized at the same level in a hierarchy without having to also change disassemblers. Virtually any level of disassembly is possible to address any corresponding level of message nesting. Disassembly can be performed on a per message or per session basis.
Owner:MICROSOFT TECH LICENSING LLC
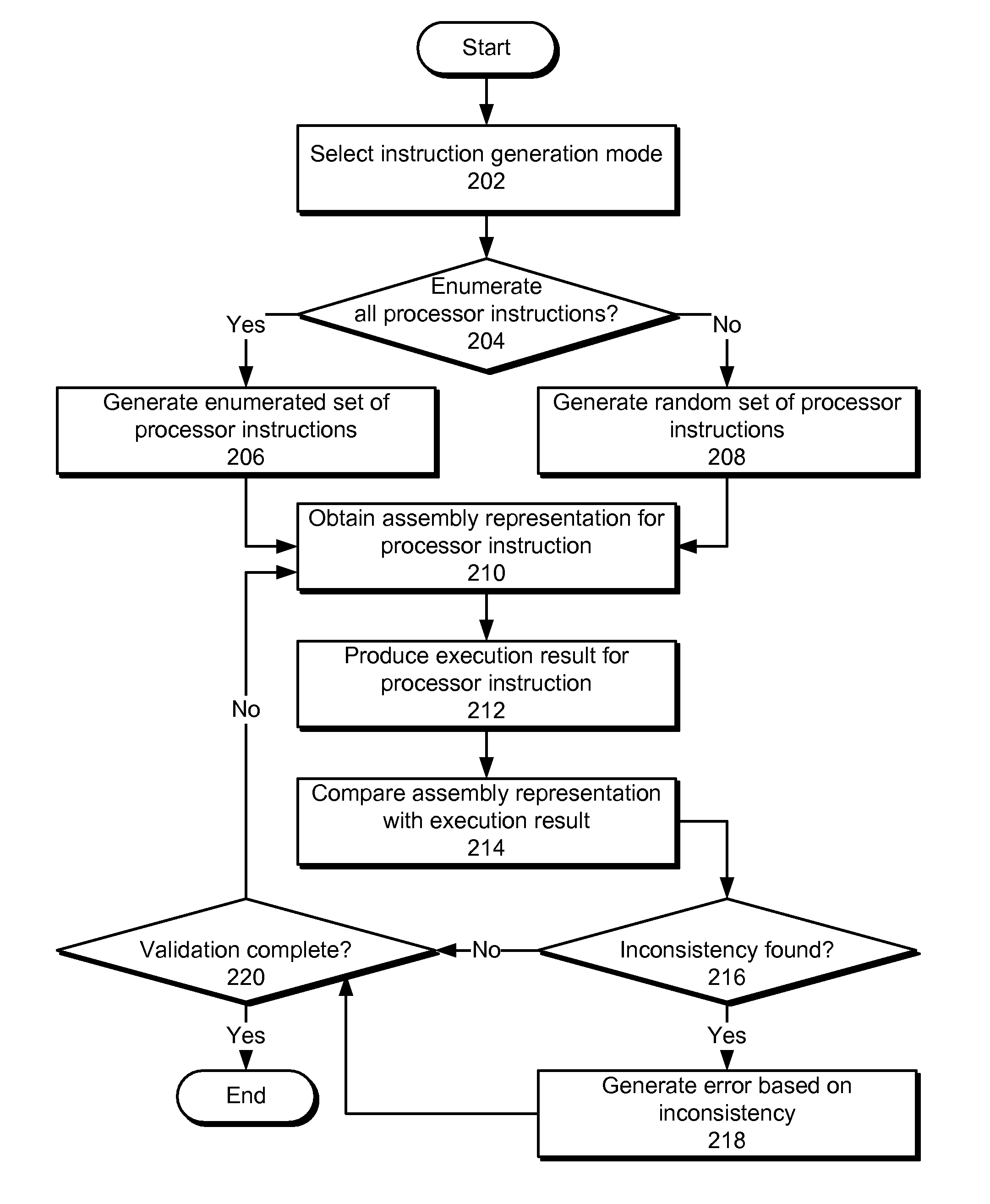
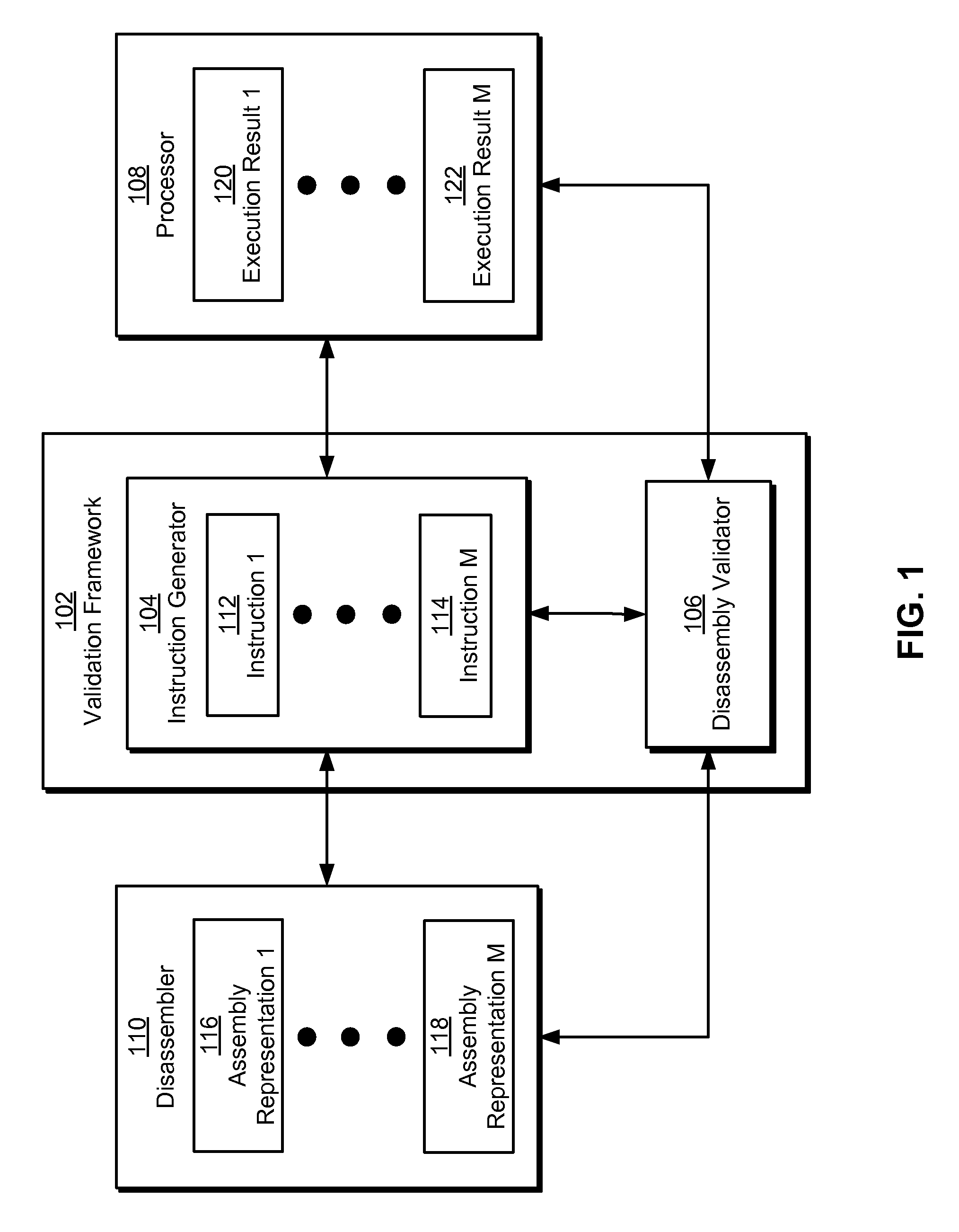
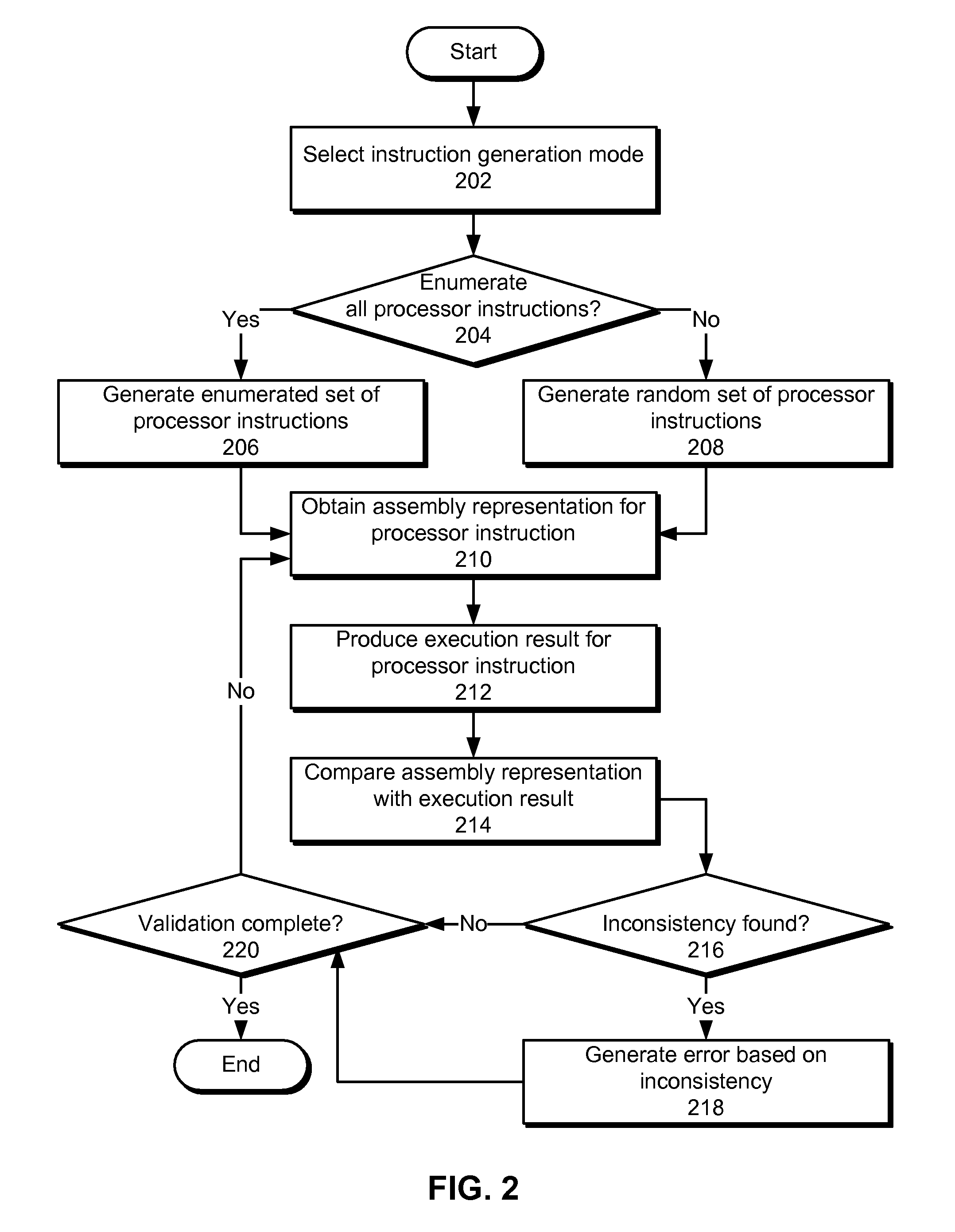
Method and system for validating a disassembler
InactiveUS8510713B1Decompilation/disassemblySoftware testing/debuggingParallel computingDisassembler
Some embodiments provide a system that analyzes the operation of a disassembler. The system starts by generating a set of processor instructions. Next, the system validates the disassembler using each processor instruction from the set of processor instructions by obtaining an assembly representation for the processor instruction using the disassembler. The system then monitors an execution of the processor instruction on a processor operating in single-step mode to produce an execution result for the processor instruction, and determines a correctness of the disassembler by comparing the assembly representation for the processor instruction with the execution result for the processor instruction.
Owner:GOOGLE LLC
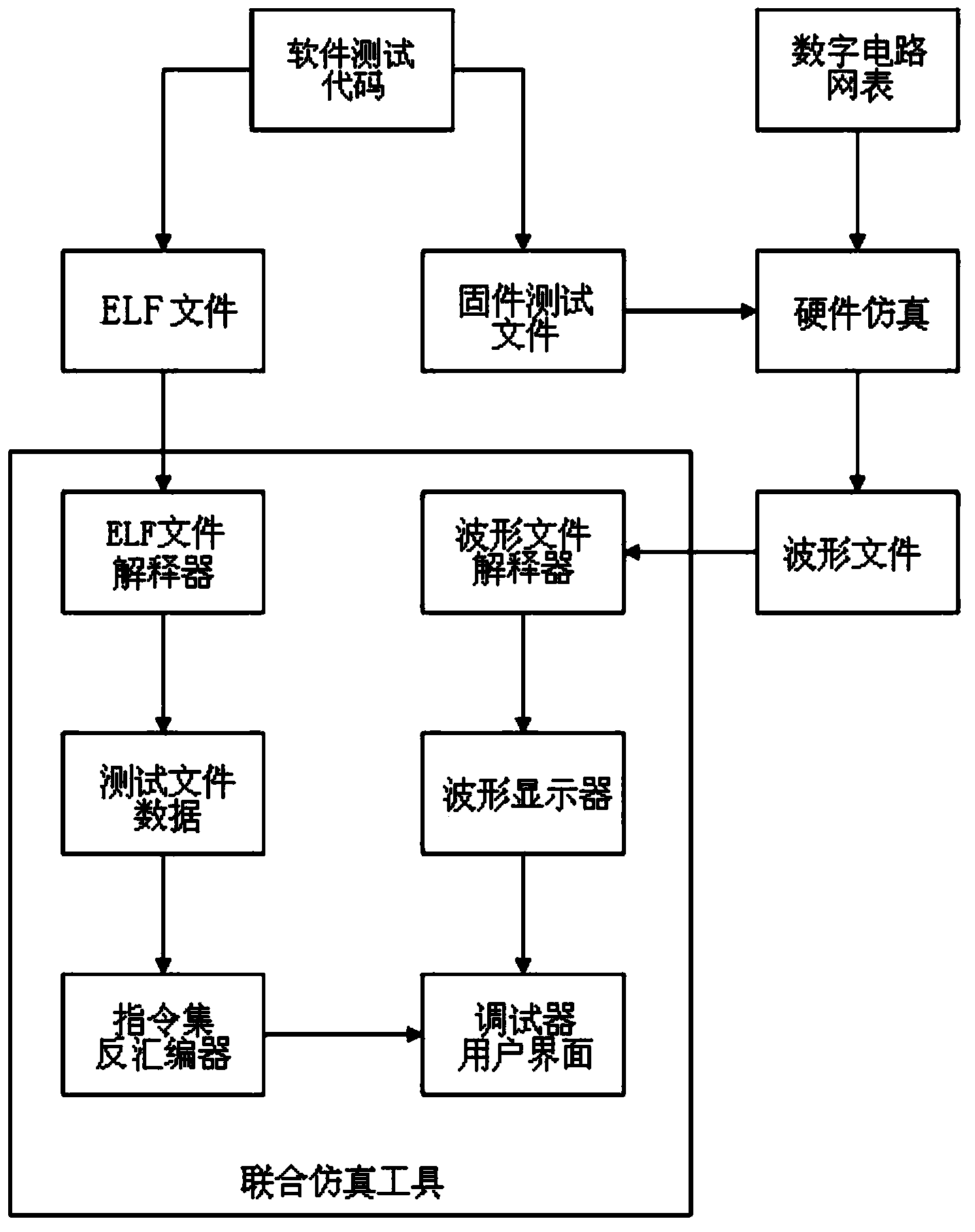
United simulation tool suitable for multi-type CPU
ActiveCN103678747AImprove work efficiencySpecial data processing applicationsInternal memoryDisplay device
The invention discloses a united simulation tool suitable for a multi-type CPU. The united simulation tool comprises a ELF file interpreter for extracting debugging information and data areas in ELF files, an instruction set disassemble for converting the debugging information and instructions in the inside into kernel assembly instruction codes of corresponding kernel instruction sets, a waveform file interpreter for reading and analyzing VCD files, interpreting multi-channel digital signal waveform information in the VCD files to generate waveform output modes and loading the waveform output modes into an internal memory, a waveform oscilloscope for processing interpreted multi-channel digital signal waveform information stored in the internal memory, a debugger user interface for displaying the kernel assembly instruction codes and multi-channel digital signal waveforms through respective windows and achieving automatic mutual correspondence between the multi-channel digital signal waveforms and the kernel assembly instruction codes. The united simulation tool can effectively improve the verification work efficiency.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
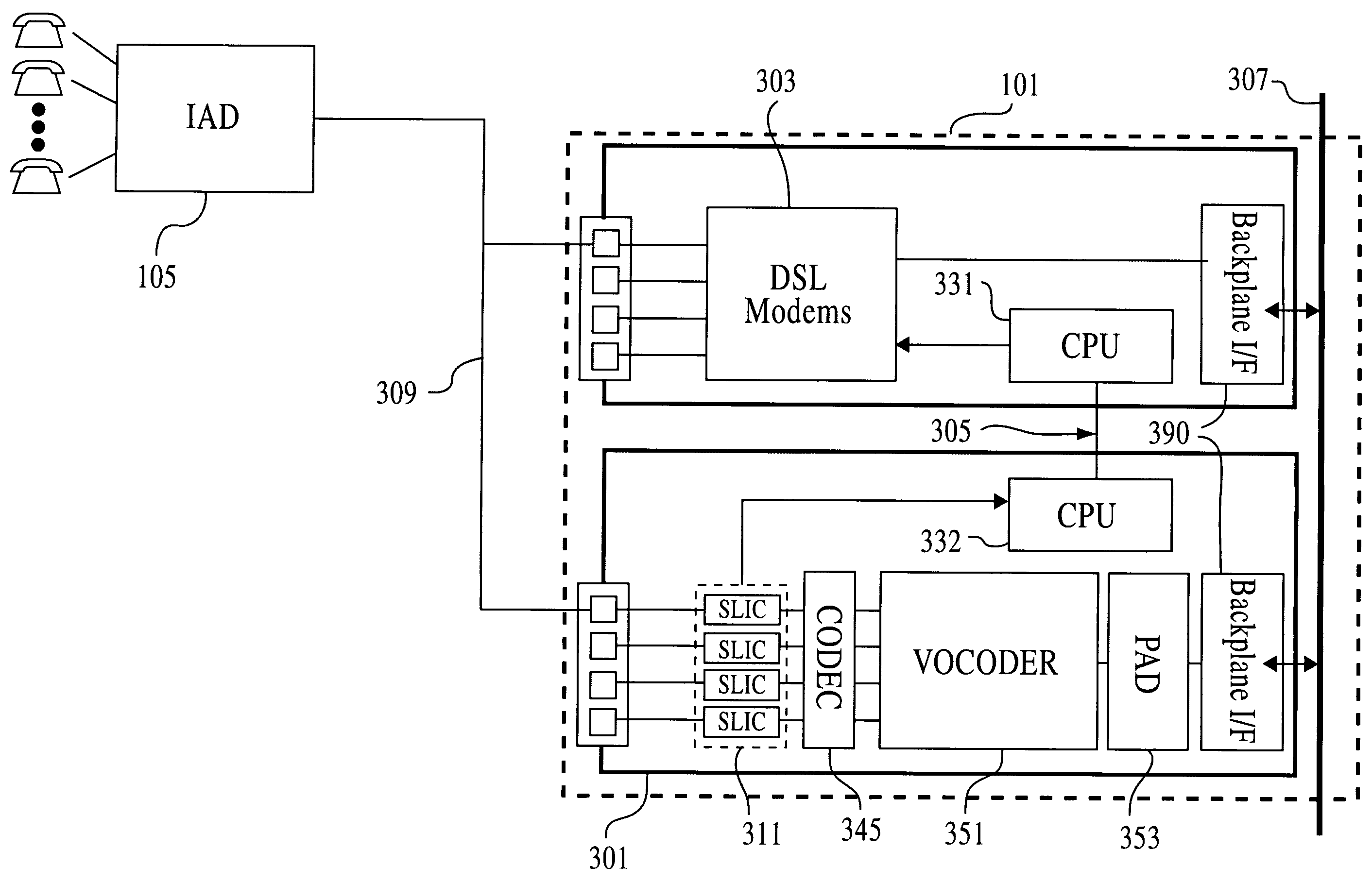
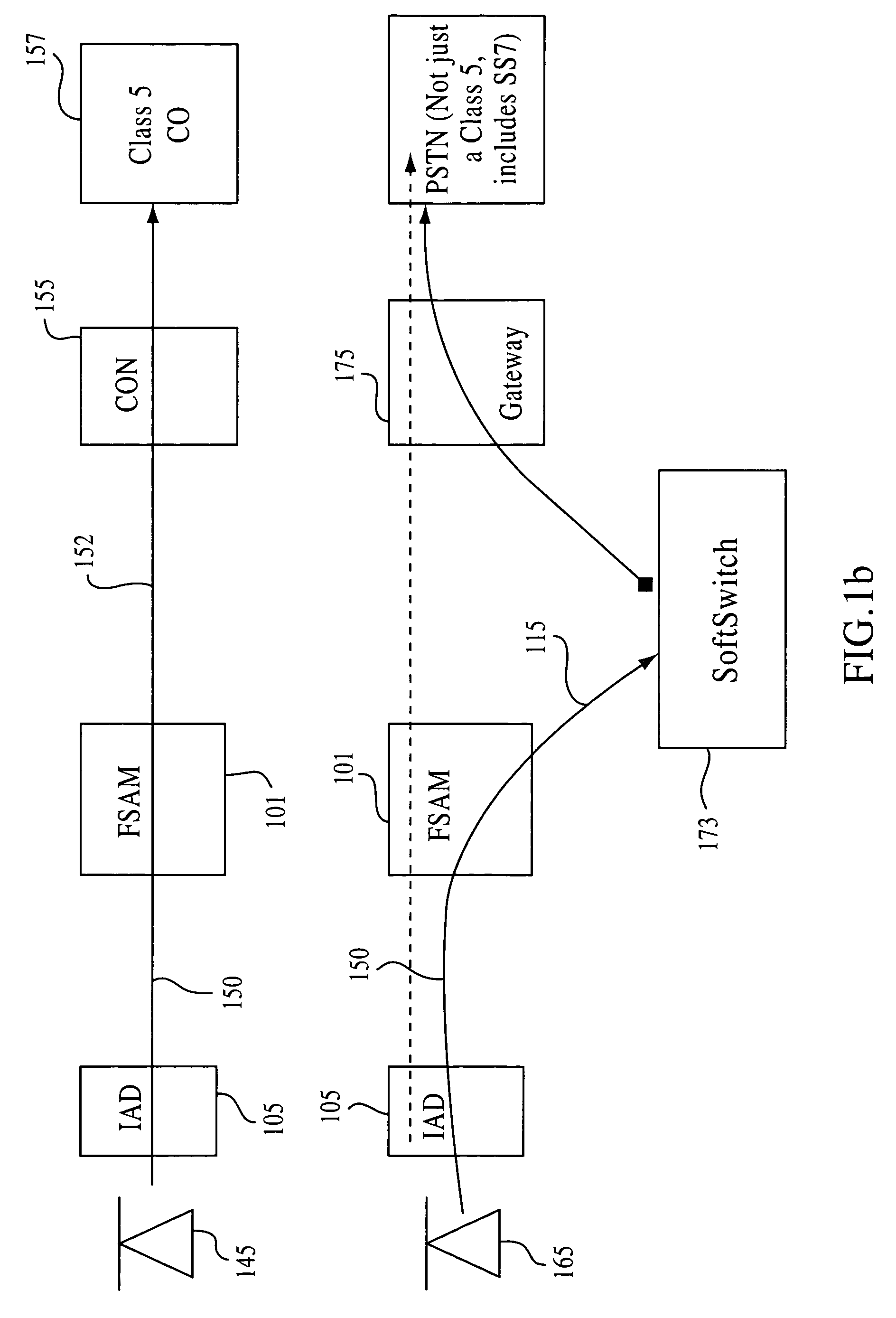
Pots extender for voice fallback in a subscriber line
InactiveUS7254110B2Error preventionFrequency-division multiplex detailsElectrical conductorModem device
A full services access multiplexer is described. A master digital subscriber line (master DSL) modem is coupled to a conductor pair. A POTS extender also is coupled to the conductor pair and may sense the operation of a fallback or other signal on the conductor pair. A suppression signal may be transmitted to a master DSL modem upon occurrence of the fallback. The suppression signal may travel over a control circuit. Traffic over a backplane or other network segment may be uninterrupted to a Integrated Access Device (IAD) by handling signals inbound and outbound to the backplane via a packet assembler and disassembler (PAD). The PAD may transmit a data stream to a vocoder and receive a data stream from the vocoder for injection onto the backplane. The vocoder connects duplexed traffic to the subscriber line interface circuit (SLIC) wherein traffic between the vocoder and the SLIC are in analog formats in or near the audible range of frequencies.
Owner:WI LAN INC
Automatic chain annular connecting and head riveting machine
The invention relates to an automatic chain annular connecting and head riveting machine. The machine comprises a machine body; and the machine body is provided with a chain positioning device, a transmission device, a feeding device, a head riveting device and a grabbing device. The chain positioning device realizes the butt joint positioning action of two ends of a chain by a guide rail, a positioning block and multiple cylinders; the feeding device realizes feeding of a chain plate and a pin shaft; the head riveting device realizes the annular connecting and head riveting actions of the chain; and finally, the chain is put in a material box through the grabbing device. The machine has the characteristics of reasonable structure design and annular riveting. The machine performs closed annular connecting and head riveting for one unfolded chain after the chain is charged from a section disassembler. The machine realizes automatic annular connection and automatic head riveting of the chain by using high-automation matching of all devices, and is quicker and labor-saved compared with a traditional method.
Owner:QINGDAO CHOHO IND CO LTD
Disassembler for iron sleeve of drag arm
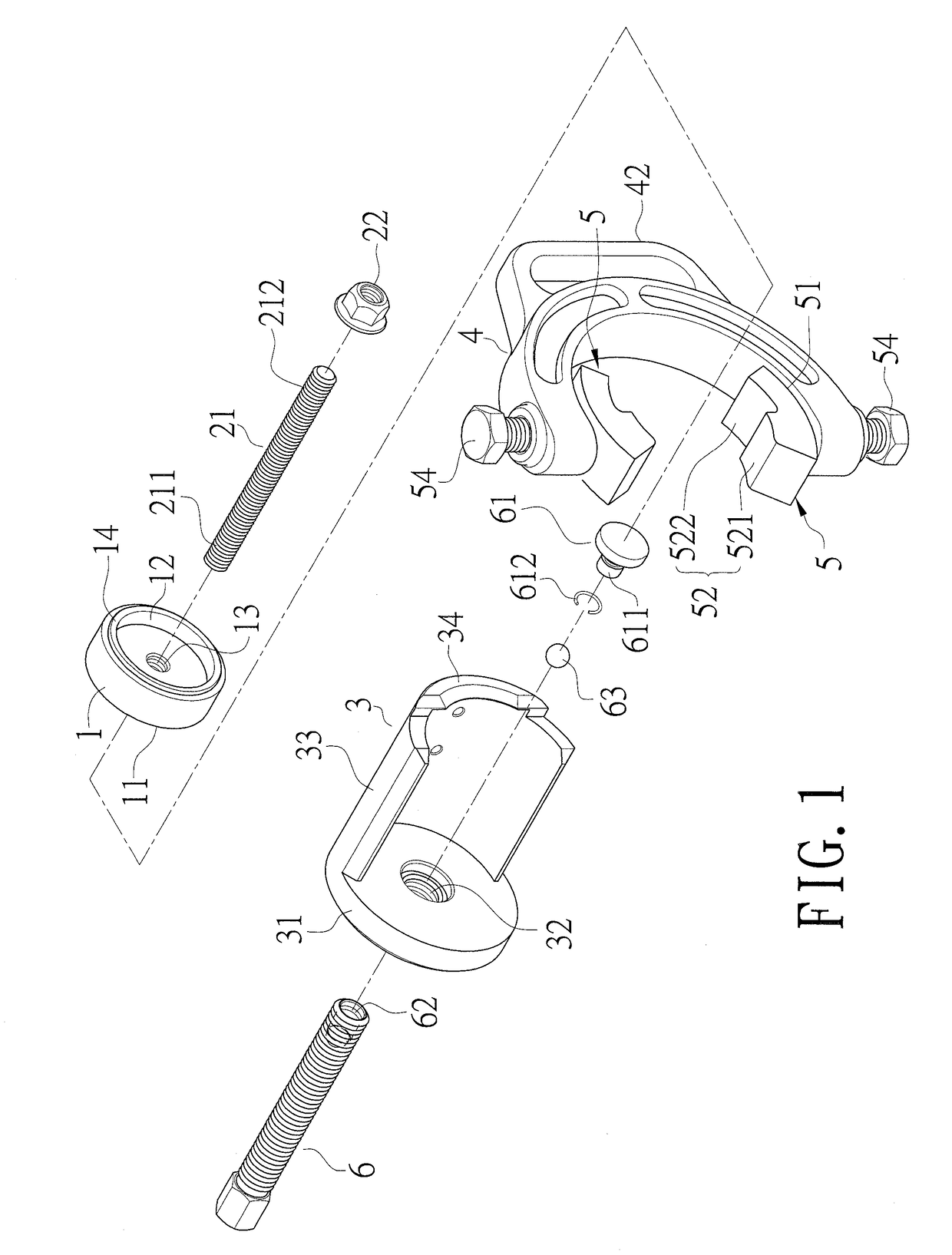
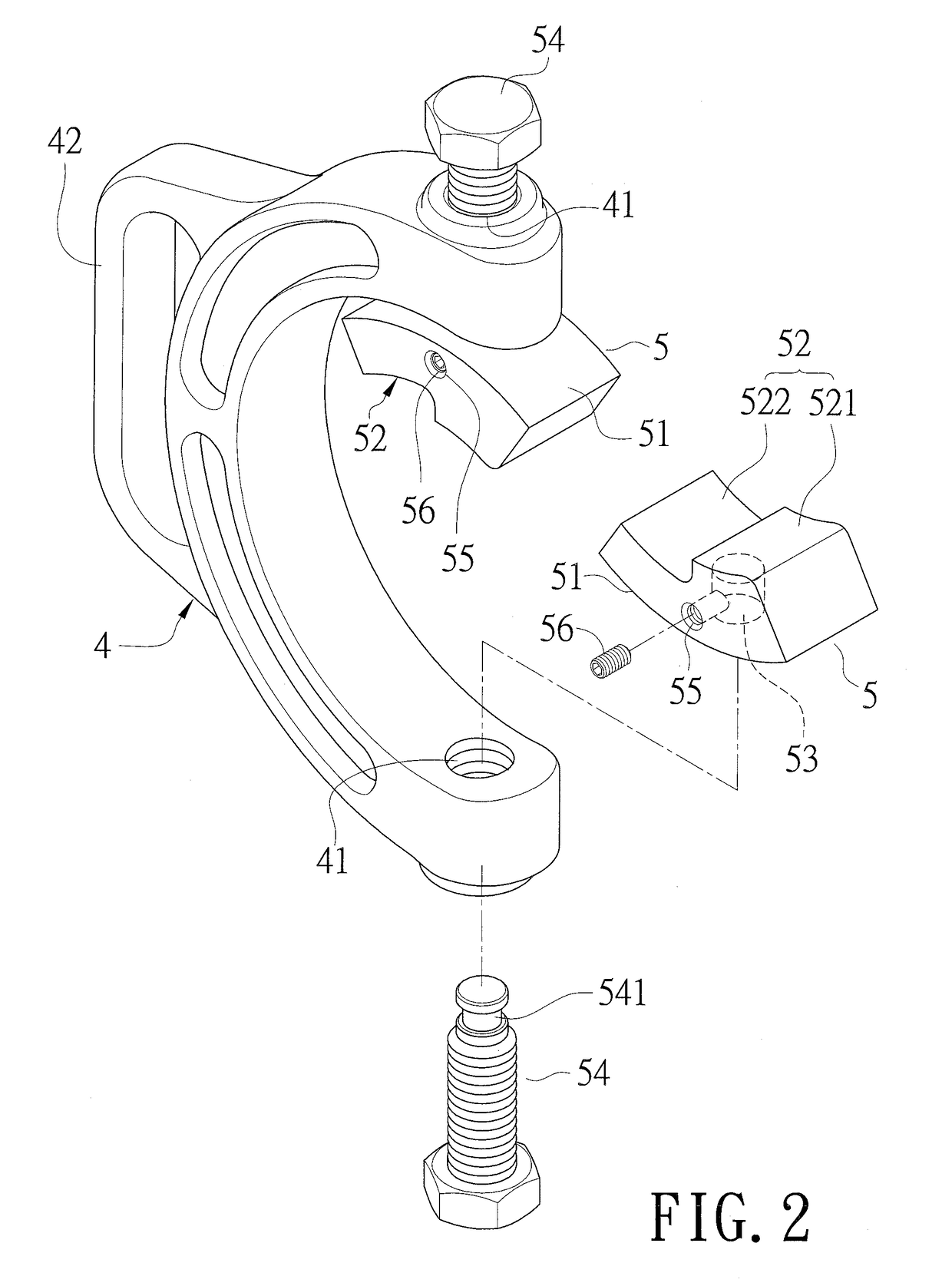
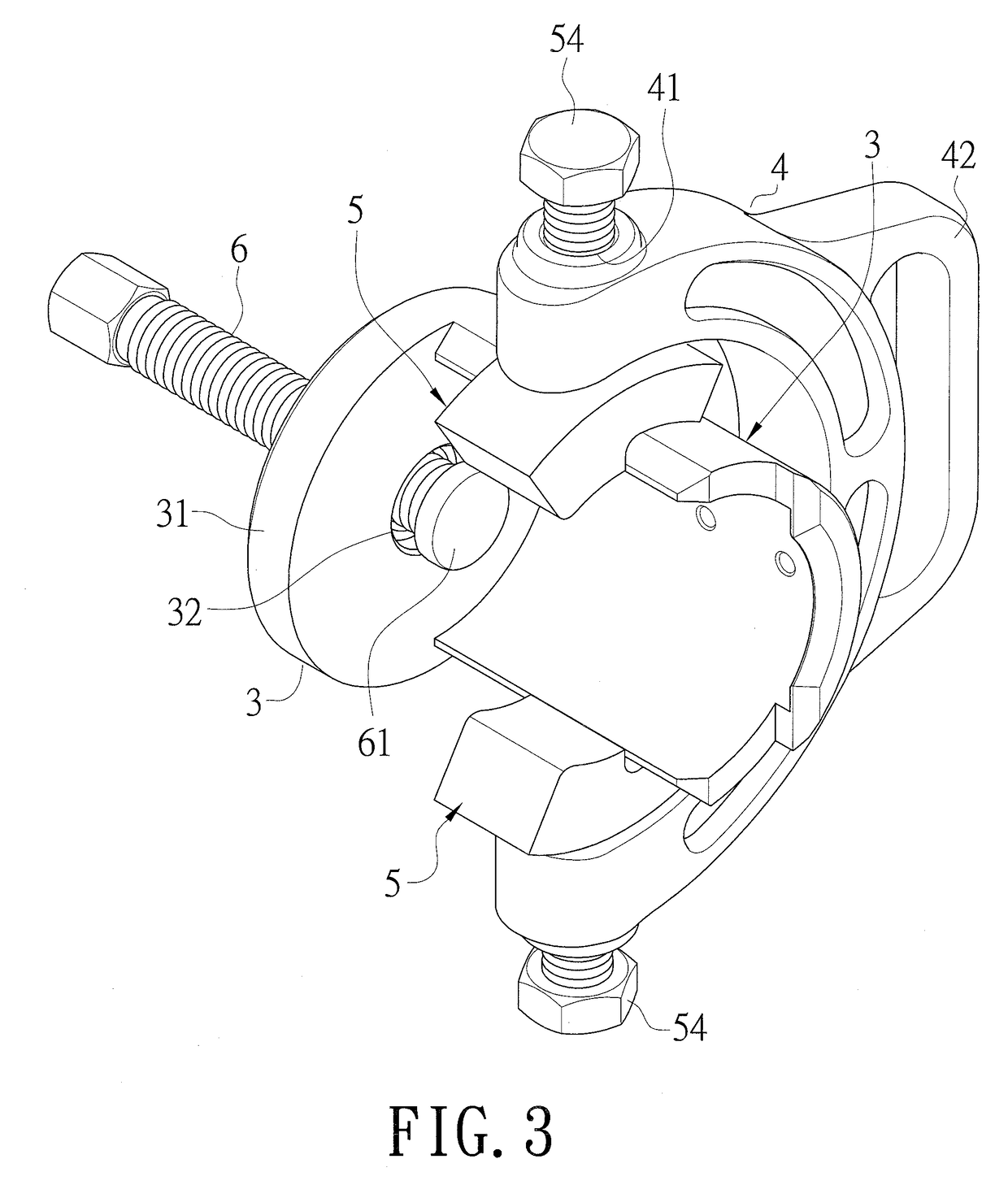
ActiveUS20190030700A1Improve practicalityAvoid damageSuspensionsMetal-working hand toolsTrailing armEngineering
A disassembler for an iron sleeve of a drag arm is disclosed. It comprises a top push casing, a bolt nut, a first screw inserted into an iron sleeve of a drag arm and screwed on the top push casing and the bolt nut, a casing for accommodating a bushing, a clamping seat, two positioning elements disposed on the clamping seat for clamping the casing and the bushing and for positioning the casing on the bushing, and a second screw screwed on the casing and contacting the top push casing in the bushing.
Owner:SIANG TOOLS DEV
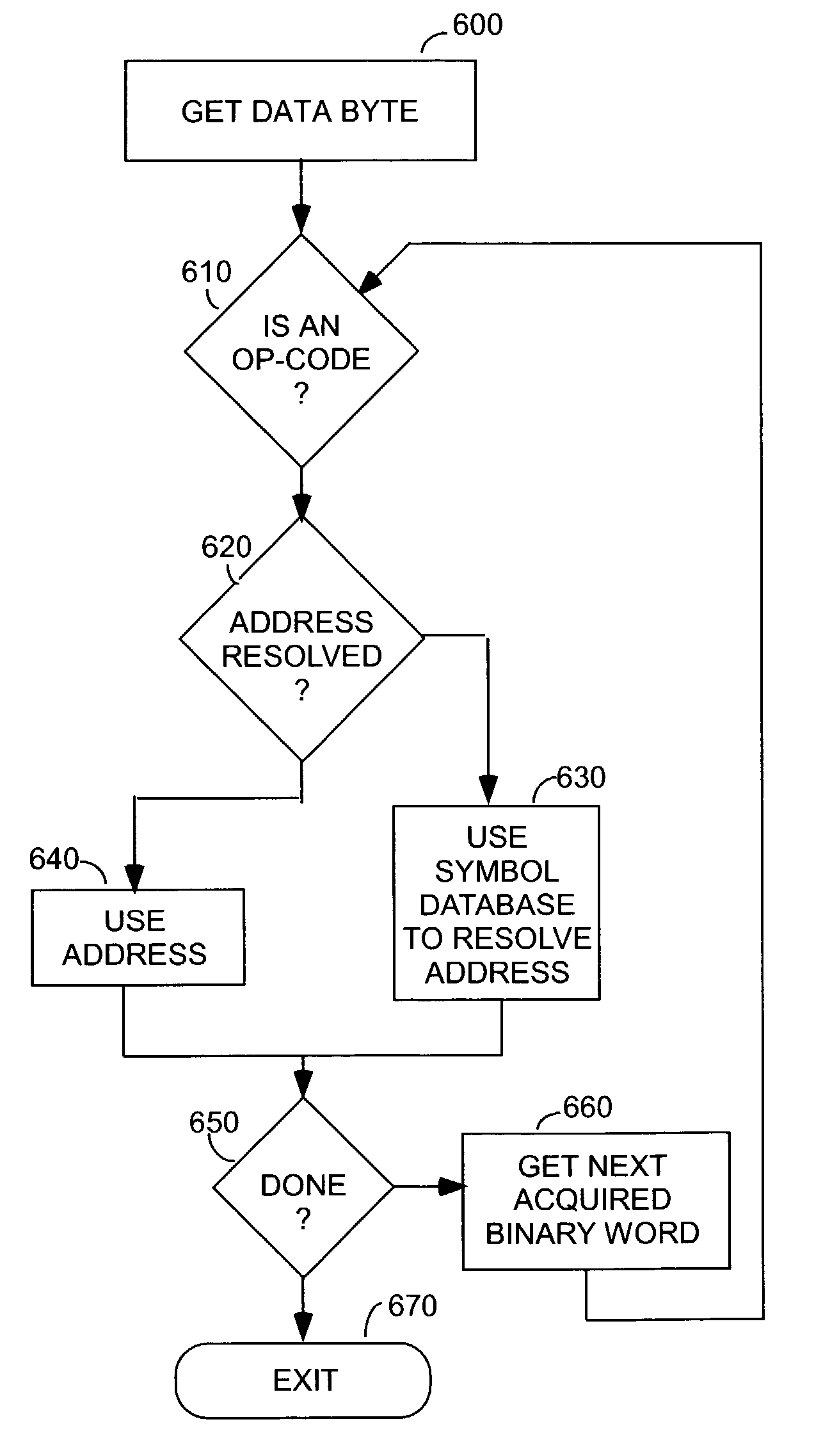
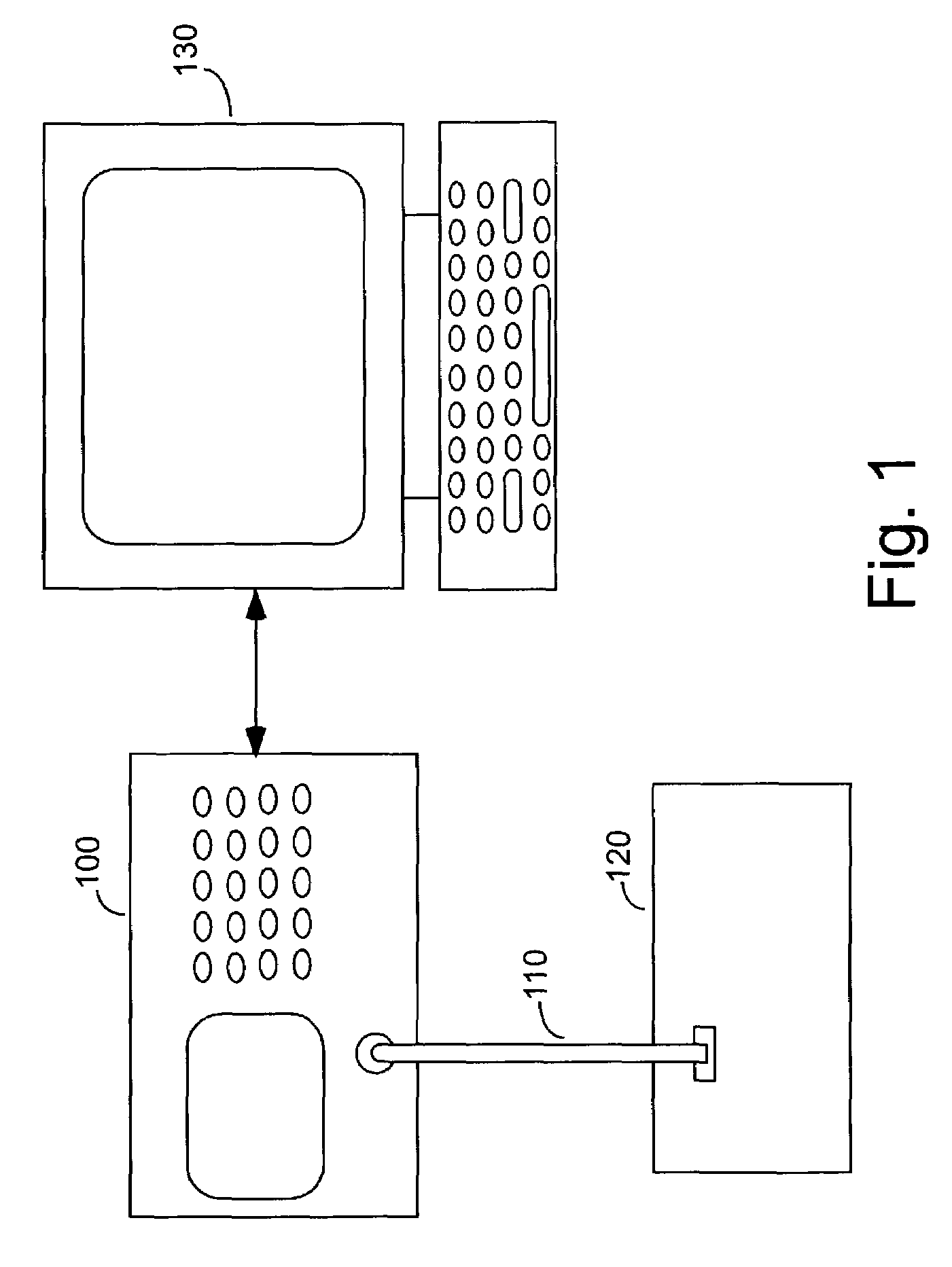
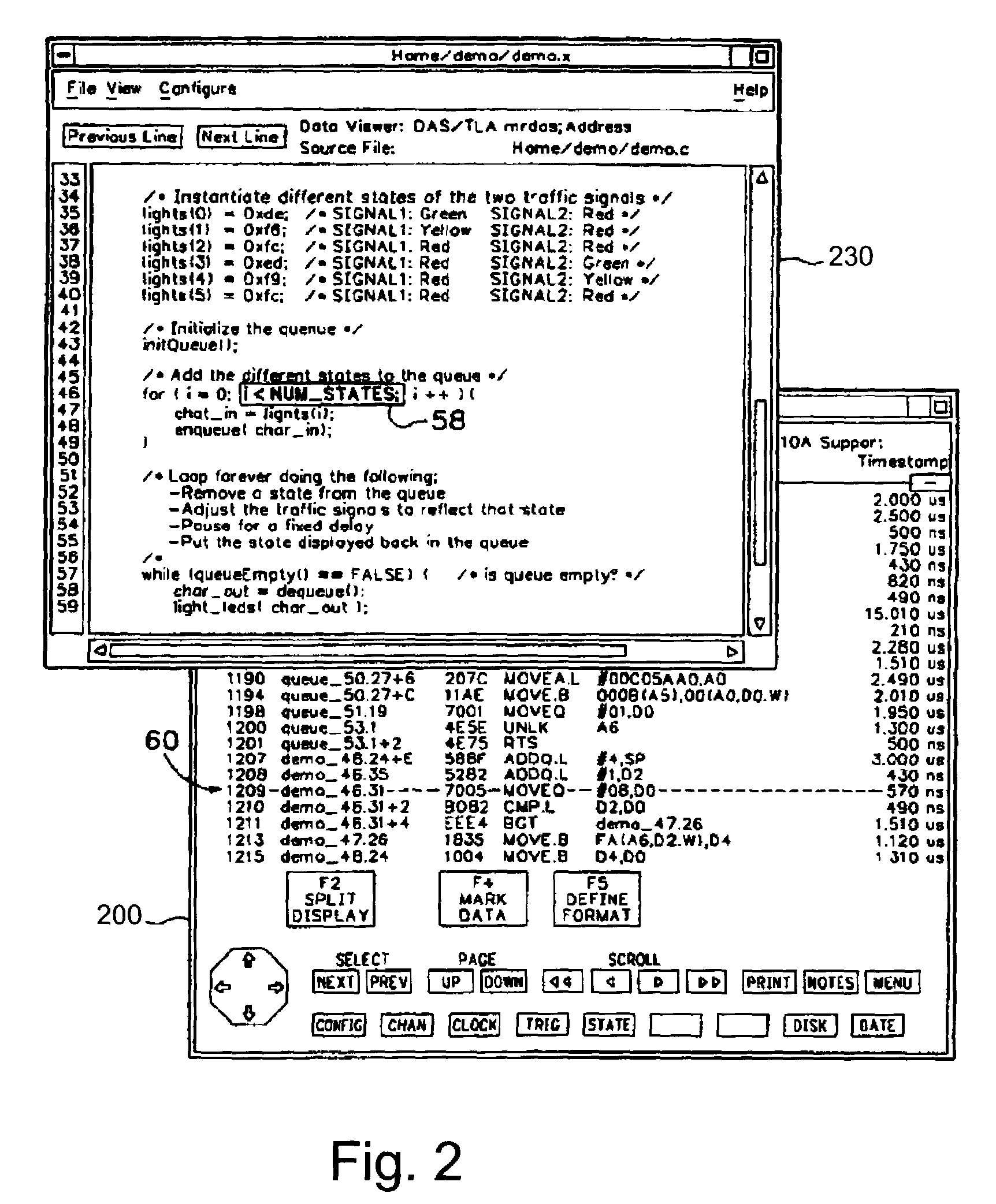
Logic analyzer having a disassembler employing symbol table information for identifying op-codes
A logic analyzer according to the subject invention includes a disassembler for disassembling object code. The disassembler automates the process of locating op-code addresses by utilizing information derived from an object file corresponding to the code whose execution is being disassembled. The object file includes addresses for the starting location of op-codes corresponding to individual source code lines. When the disassembler cannot determine the correct starting location for an op-code, it uses information from the object file to obtain the address of an op-code within a specified range of interest.
Owner:TEKTRONIX INC
Static and run-time anti-disassembly and anti-debugging
In order to prevent analysis by static and dynamic disassembly techniques, instruction level code obfuscation is performed to induce misalignment and mistaken analysis by disassemblers. Misalignment is induced by including a bypass which leads, during execution, to a legitimate location. During analysis, however, bogus data may be analyzed by the disassembler due to the bypass. Run-time modifications may also be included in code. Code is changed to an invalid state, and instructions inserted into the code which will return the code to a valid state during execution. During analysis, these invalid states may be analyzed by the disassembler as invalid instructions. Induced misalignments and run-time modifications can be chained together to produce sequences of code that will always produce invalid disassembly output from common disassemblers.
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatuses for reframing and retransmission of datagram segments
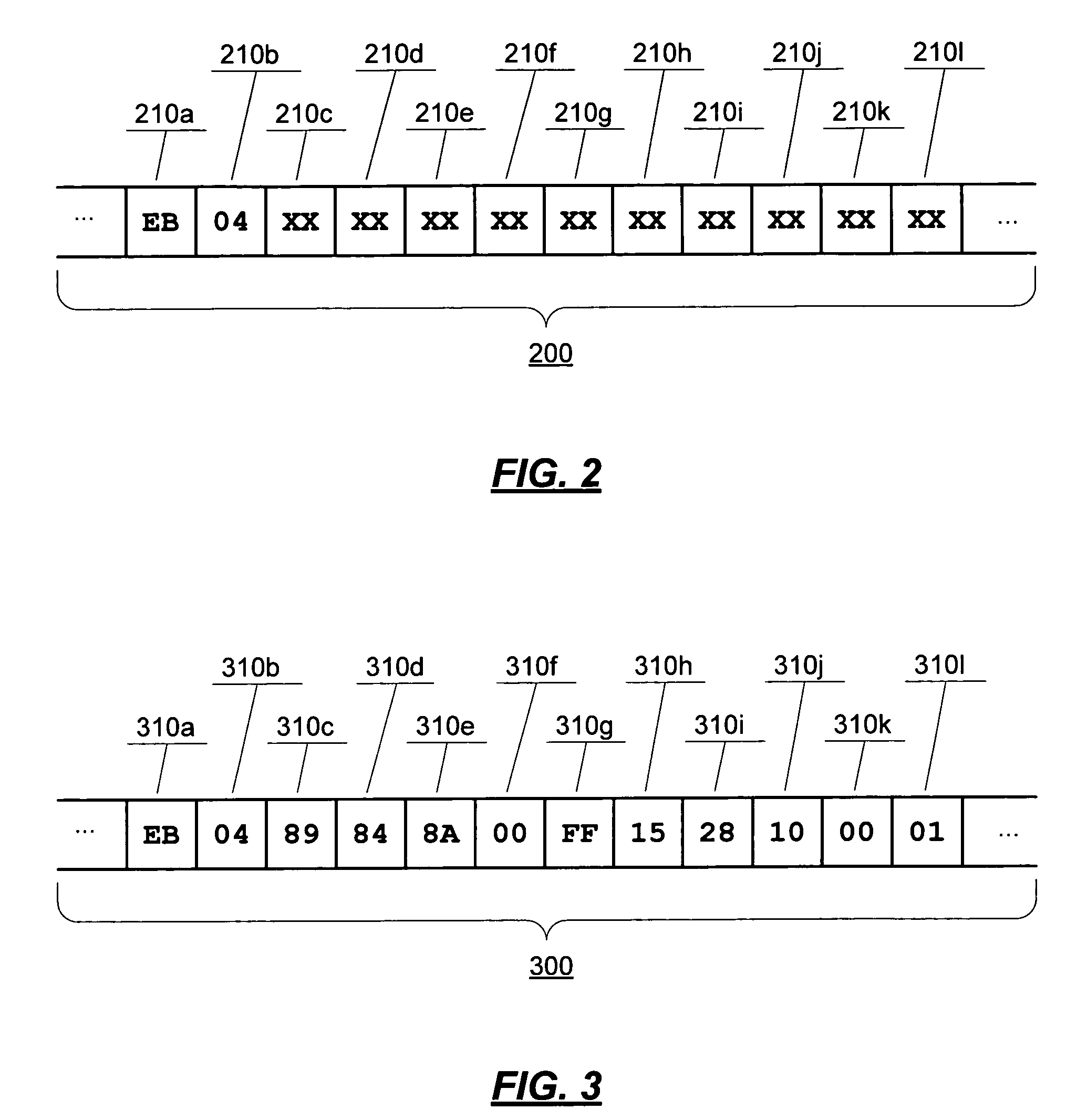
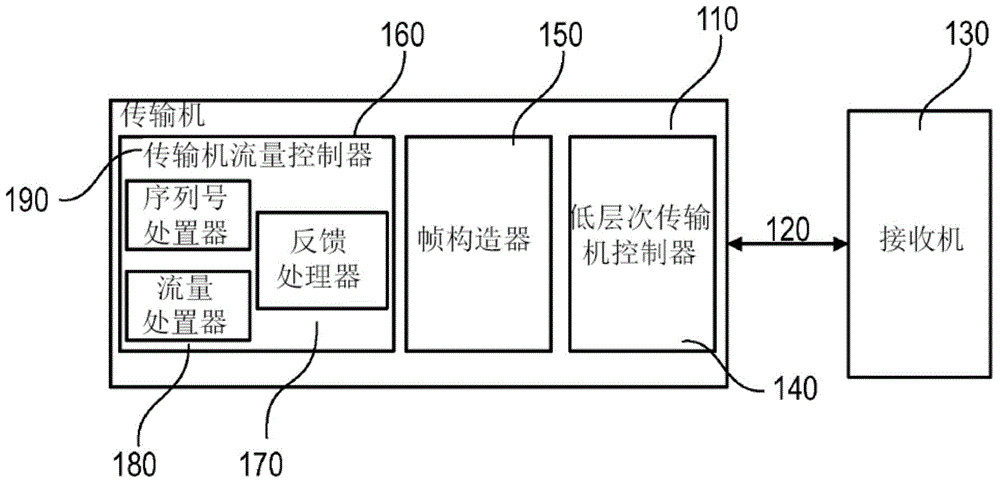
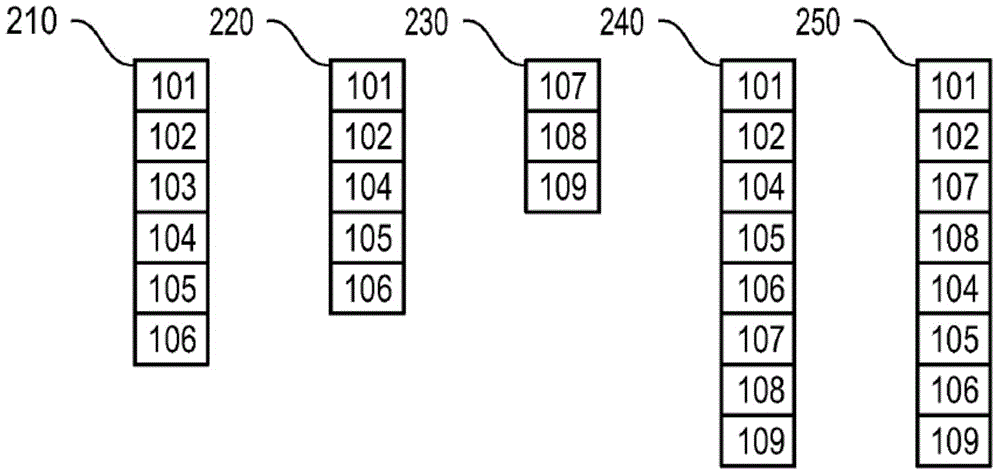
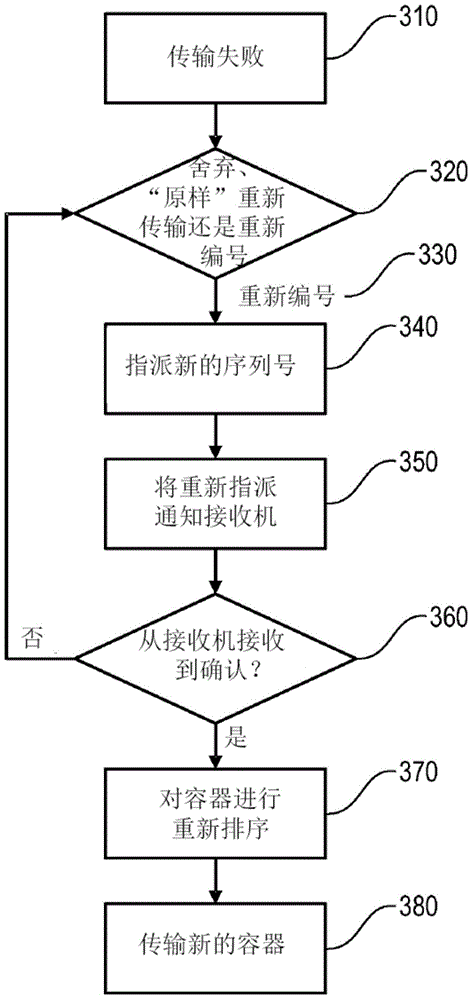
ActiveCN104956615AError prevention/detection by using return channelTransmitted data organisation to avoid errorsDisassemblerTransport engineering
A source device for sending datagrams contained in an aggregated packet structure comprising transport containers each containing one or more datagram segments of the datagram, the source device comprising a feedback processor configured to receive feedback that a transmission of a transport container has failed or a detector unit that detects that a transmission of a transport container will fail; a disassembler unit that disassembles the failed transport container the transmission of which has failed or will fail; a creating unit that creates at least one new transport container from less than all of the failed transport containers without splitting datagrams; and a sending unit that sends sequence information indicating a conversion between a sequence of the transport containers of the failed datagram and a sequence of the transport containers of the new datagram, where the source device is configured to reformat and retransmit datagrams whose transmission has failed.
Owner:LANTIQ ISRAEL
Disassembler instruction matching processing method
InactiveCN101290574AIntuitive and concise representationEasy to writeSpecific program execution arrangementsProcessing InstructionDisassembler
The invention discloses a method for processing instruction matching of a disassembler. A user represents the description of an instruction format on an instruction set manual as an 'instruction format representation string', and establishes the correlation of the 'instruction format expression string' and an 'instruction processing callback function'; the disassembler extends the 'instruction format representation string' as an 'expanded binary string of the instruction format representation string', further to establish the correlation of the 'expanded binary string of the instruction format representation string' and the 'instruction processing callback function'; when the disassembler disassembles, an input binary stream is matched with the 'expanded binary string of the instruction format representation string'; if the matching is successful, the corresponding 'instruction format expression string' is called; otherwise, the input string is not an effective instruction string. The representation method of the instruction format is intuitive and brief; the unfolding process of the representation is fixed without respectively compiling aiming at different platforms; and the utilization of the information provided by the presentation can conveniently quote an input string in the callback function.
Owner:ZHEJIANG UNIV
Hierarchically disassembling messages
ActiveUS20110264738A1Multiple digital computer combinationsProgram controlMessage passingDisassembler
The present invention extends to methods, systems, and computer program products for hierarchically disassembling messages. The functionality of disassemblers and framers is decoupled such that framers for different types of messages can be utilized at the same level in a hierarchy without having to also change disassemblers. Virtually any level of disassembly is possible to address any corresponding level of message nesting. Disassembly can be performed on a per message or per session basis.
Owner:MICROSOFT TECH LICENSING LLC
Lock free streaming of executable code data
A disassembler receives instructions and disassembles them into a plurality of separate opcodes. The disassembler creates a table identifying boundaries between each opcode. Each opcode is written to memory in an opcode-by-opcode manner by atomically writing standard blocks of memory. Debug break point opcodes are appended to opcode to create a full block of memory when needed. The block of memory may be thirty-two or sixty-four bits long, for example. Long opcodes may overlap two or more memory blocks. Debug break point opcodes may be appended to a second portion of the long opcode to create a full block of memory. A stream fault interceptor identifies when a requested data page is not available and retrieving the data page.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for performance efficient ISA virtualization using dynamic partial binary translation
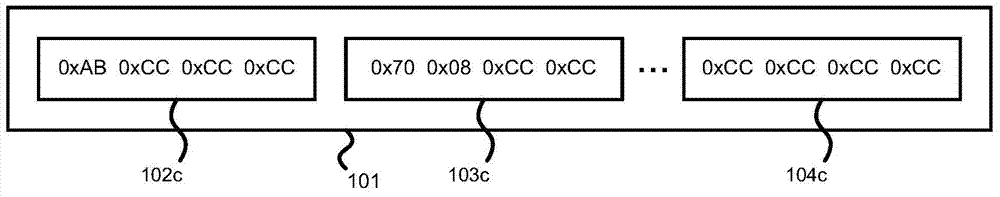
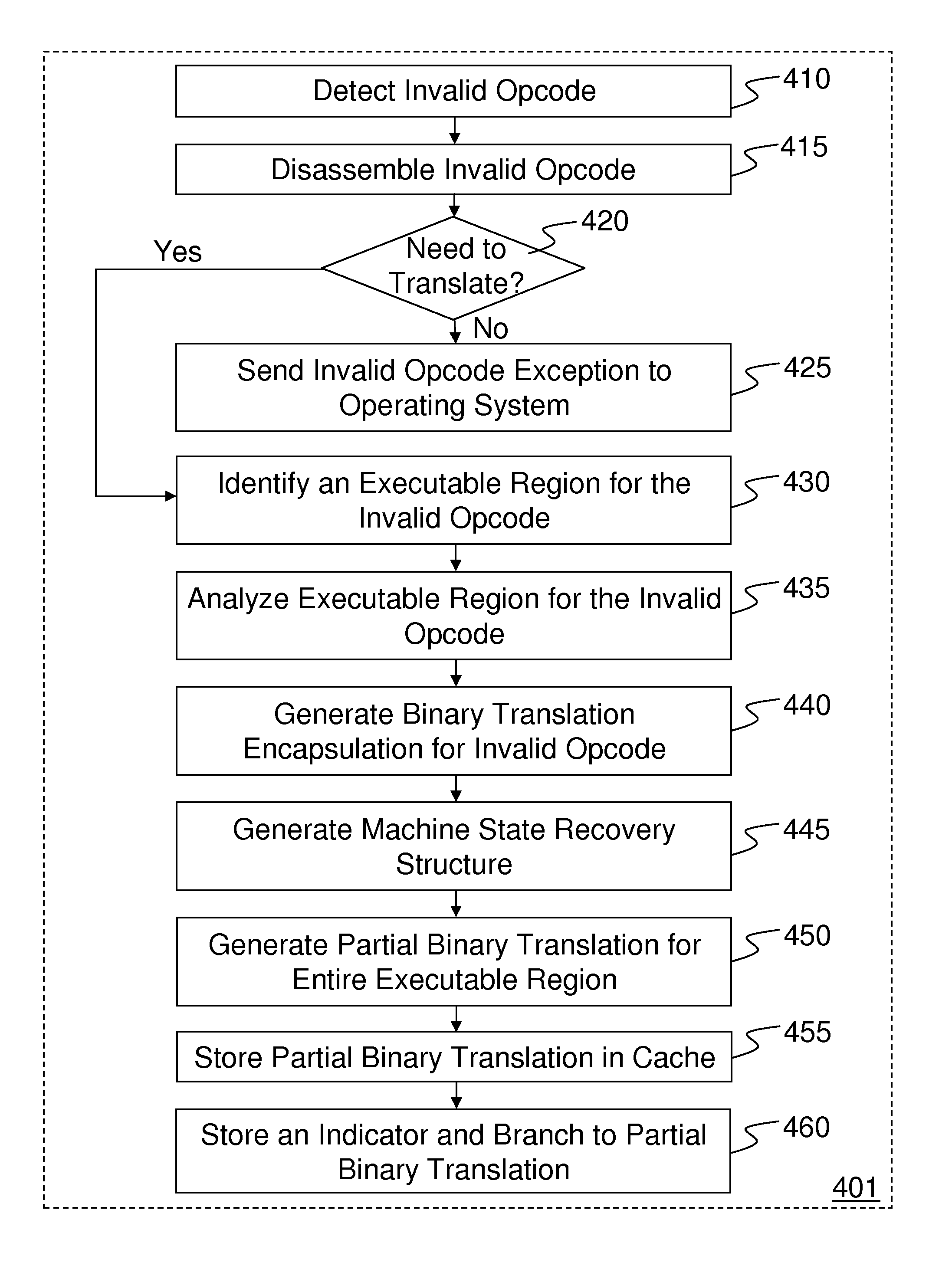
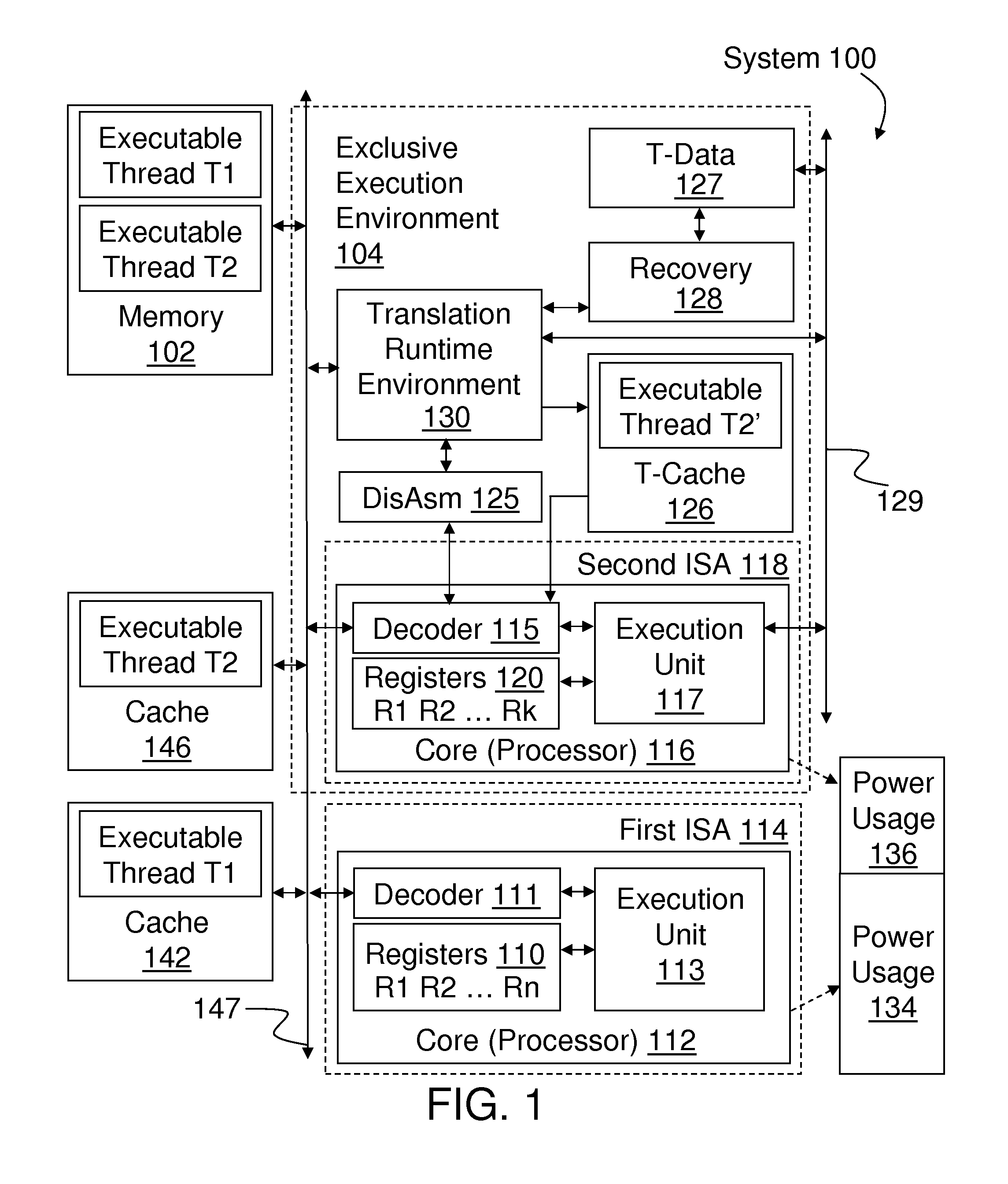
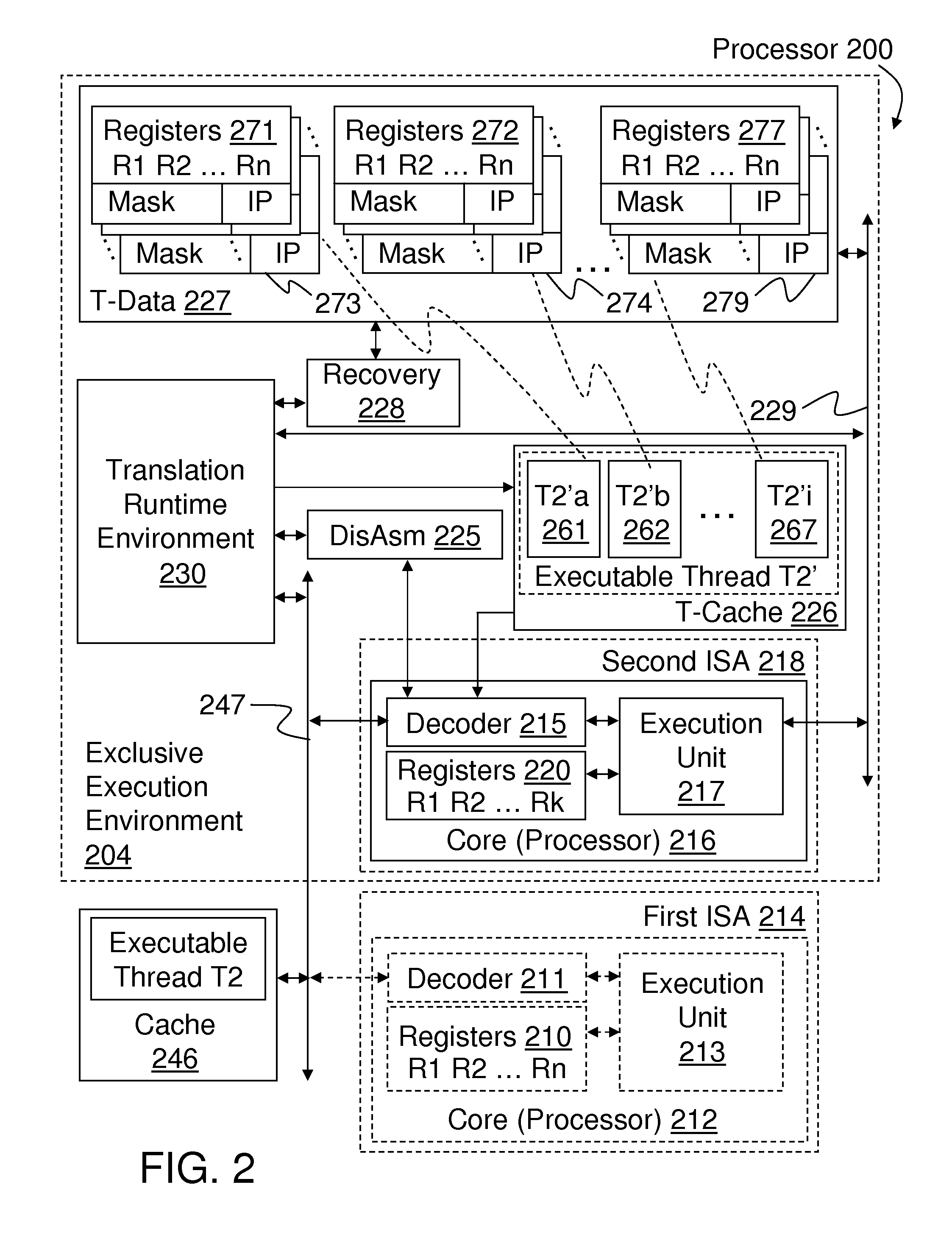
InactiveUS9141361B2Memory architecture accessing/allocationBinary to binaryVirtualizationDisassembler
Owner:INTEL CORP
Automatic recovery from failures of messages within a data interchange
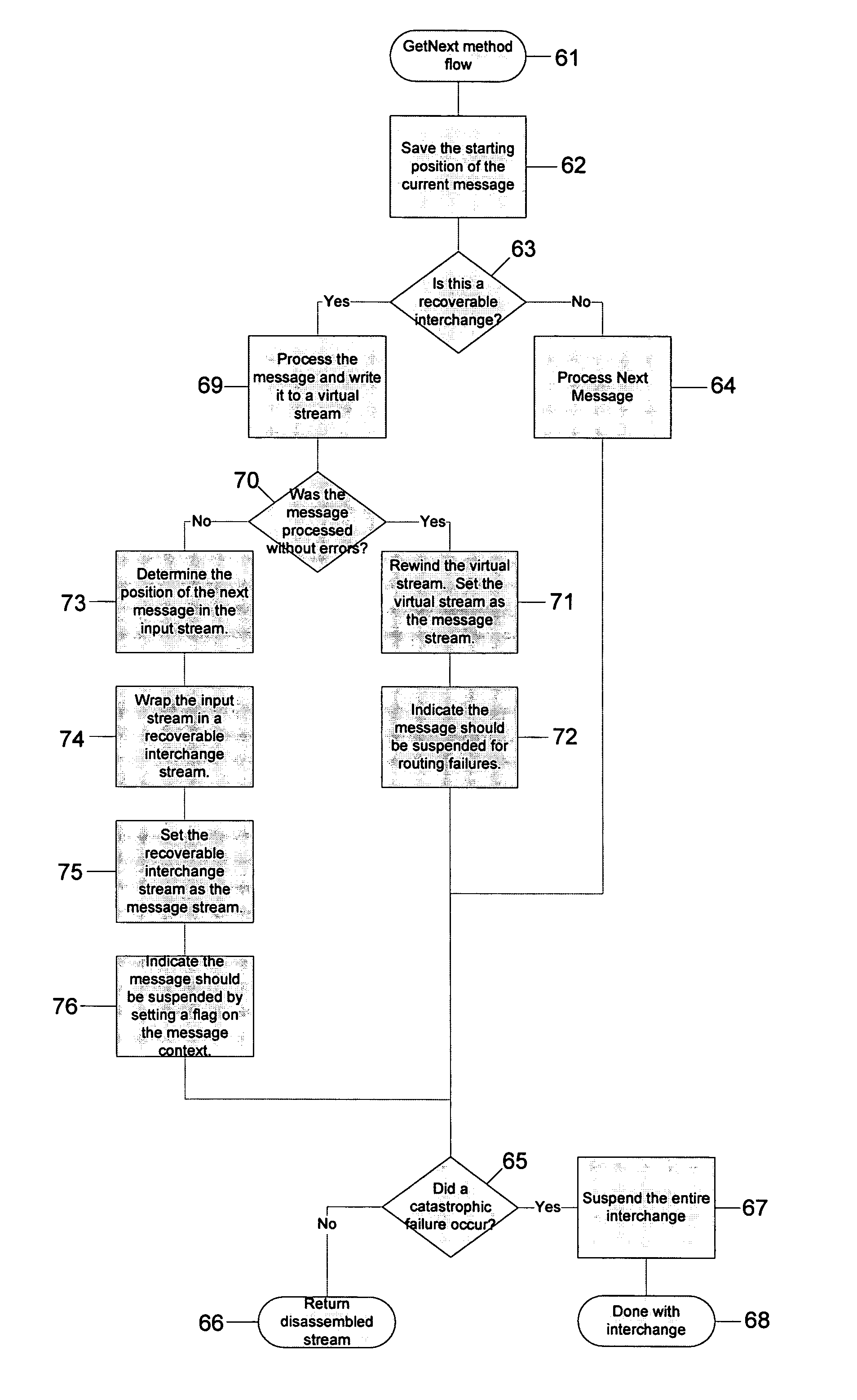
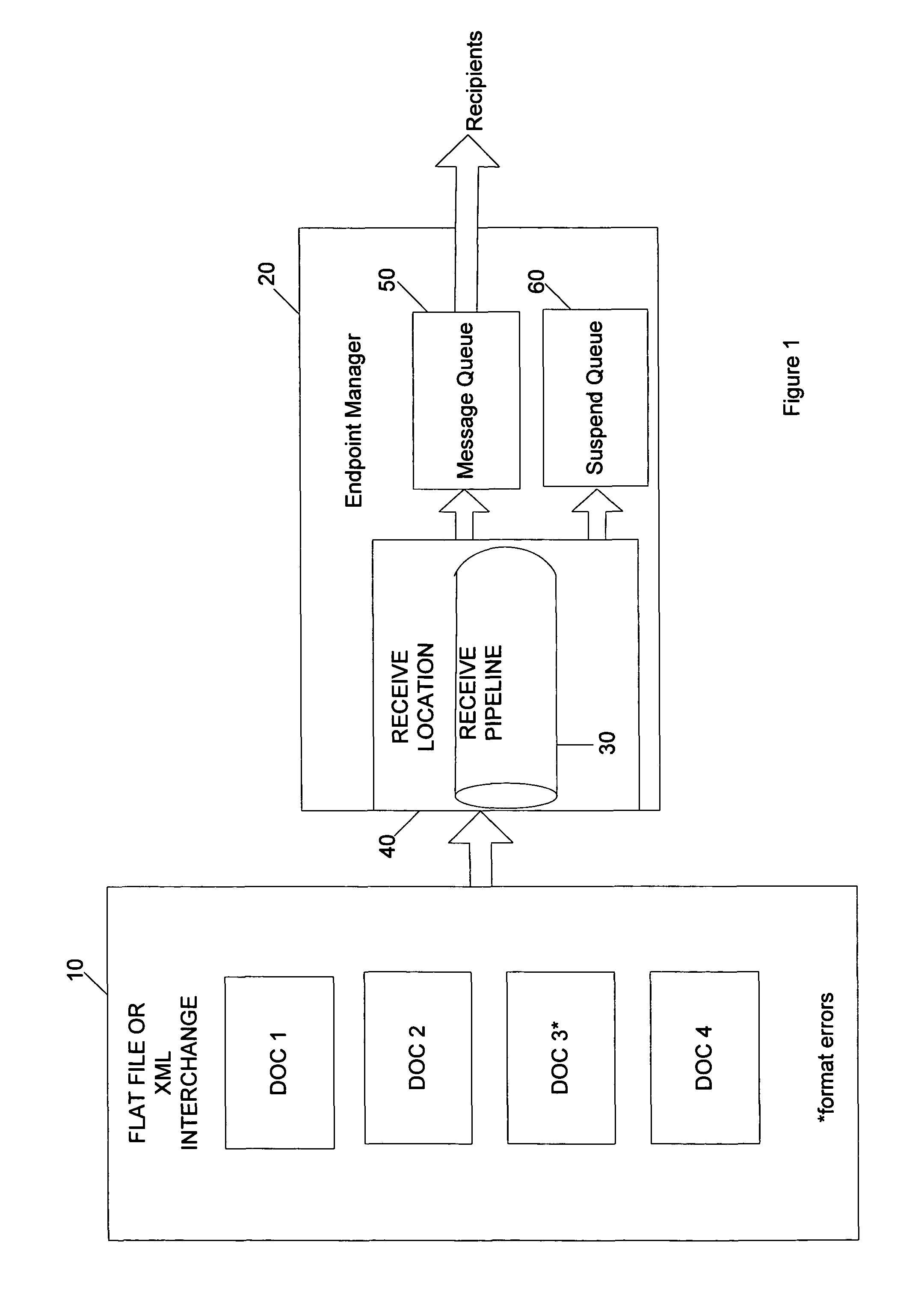
ActiveUS7954112B2Multiprogramming arrangementsMultiple digital computer combinationsComputer hardwareTreatment error
Data interchanges are processed so that problematic individual elements within the data interchanges do not cause the processing of the data interchanges to be suspended unless there is a catastrophic error. The data interchanges are split up by flat file and / or XML disassemblers of a message engine into independent messages even if some elements are incorrect or cause processing failures. Those messages in the interchange that may be processed are processed, while those that would cause processing errors are suspended in a suspend queue for recovery processing. Even when a message is placed in the suspend queue, processing continues with the next independent message in the data interchange. Messages that are placed in the suspend queue for lack of routing information may be resumed by providing the routing information and again attempting to route the previously suspended message. The method of the invention is scalable since it works regardless of the size of the interchange or its individual message elements.
Owner:MICROSOFT TECH LICENSING LLC
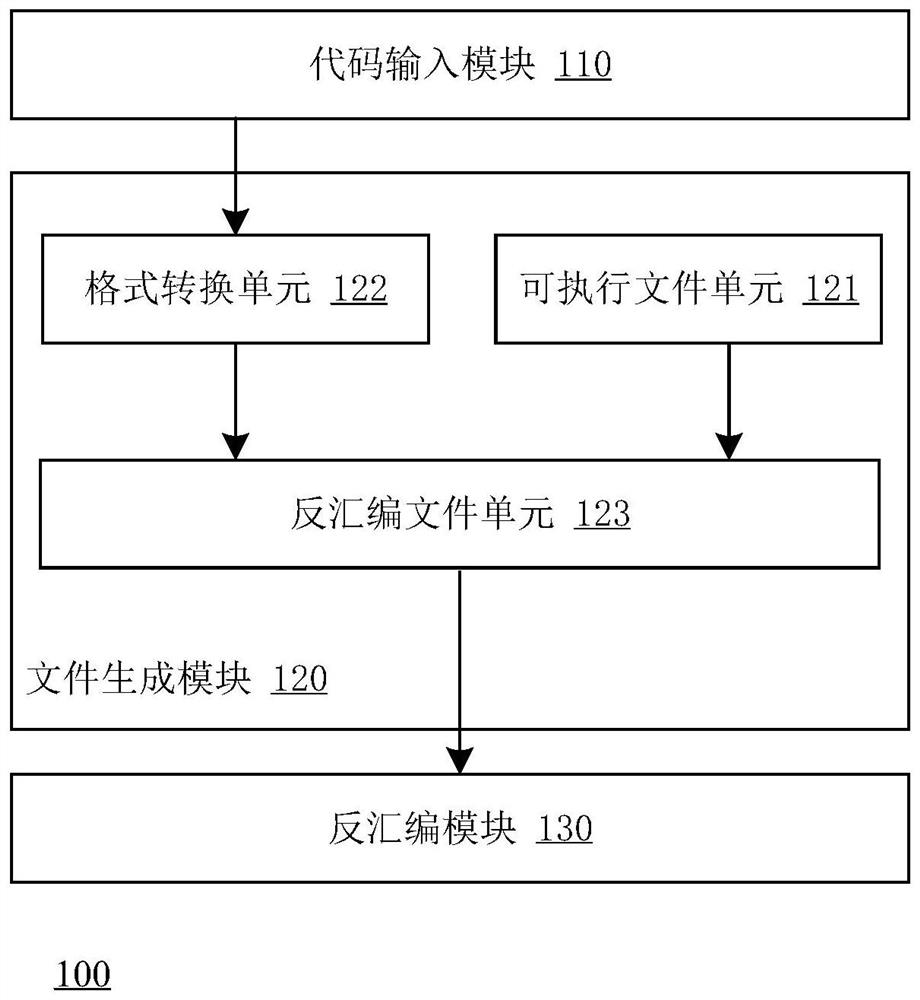
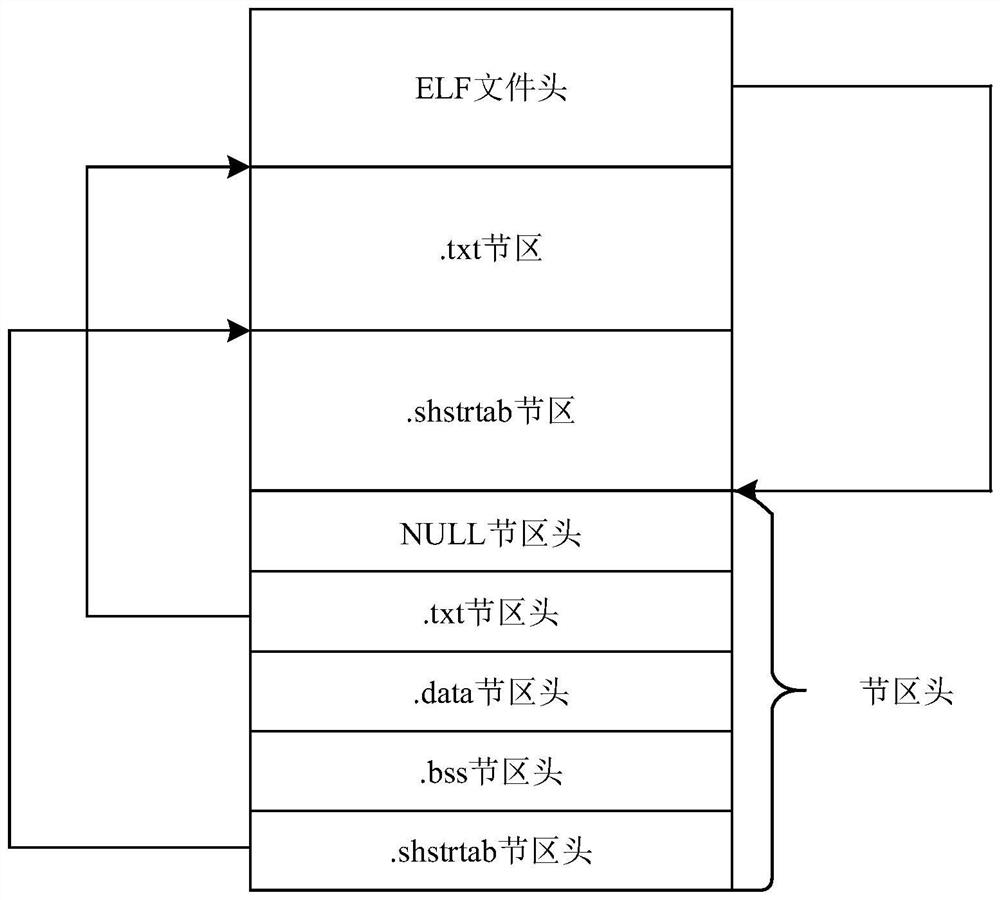
Machine code disassembling system and method, computer equipment and storage medium
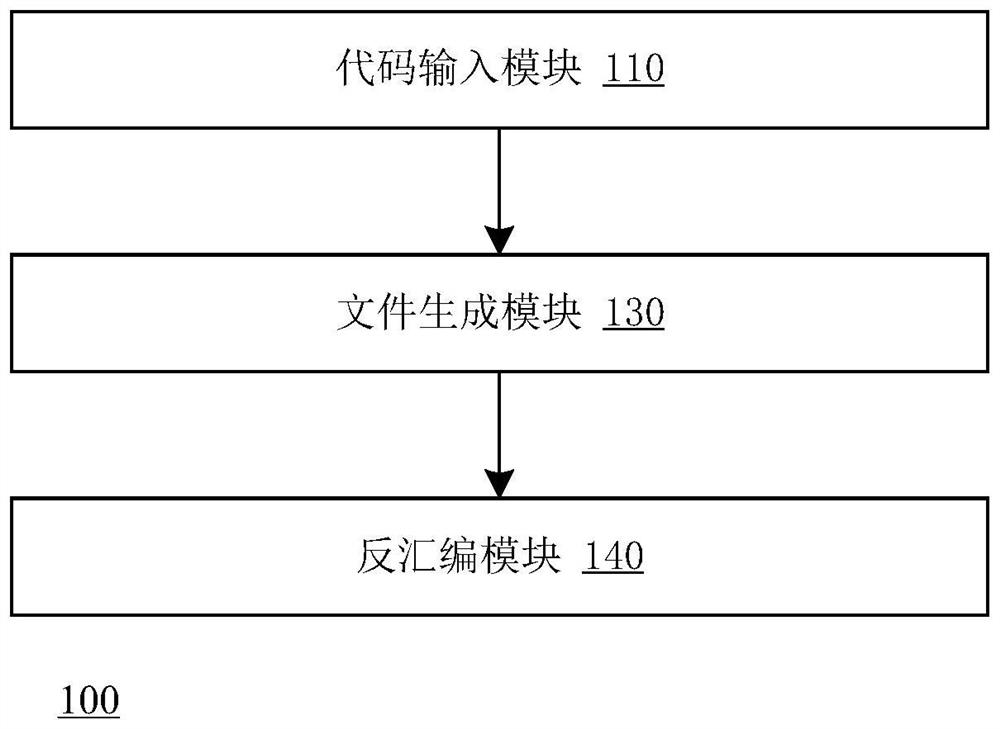
PendingCN114594962AConvenience to workReduce workloadDecompilation/disassemblyComputer architectureCpu architecture
The invention discloses a machine code disassembling system and method, computer equipment and a storage medium. The disassembling system of the machine code comprises a code input module which is configured to receive a machine code to be processed; the file generation module is configured to generate a disassembly file according to the machine code and an executable file in a predefined format, and the executable file comprises a file header, a code segment and a code segment header describing the segment; and the disassembling module is configured to perform disassembling processing on the disassembling file by utilizing a preset disassembling device so as to obtain an assembling instruction corresponding to the machine code. The disassembling method can be compatible with various CPU architectures, and machine codes in different CPU architectures can be disassembled.
Owner:BEIJING ESWIN COMPUTING TECH CO LTD
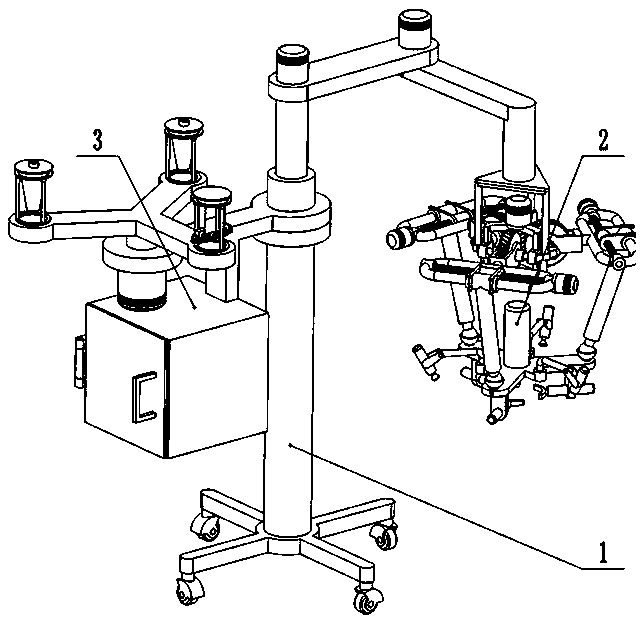
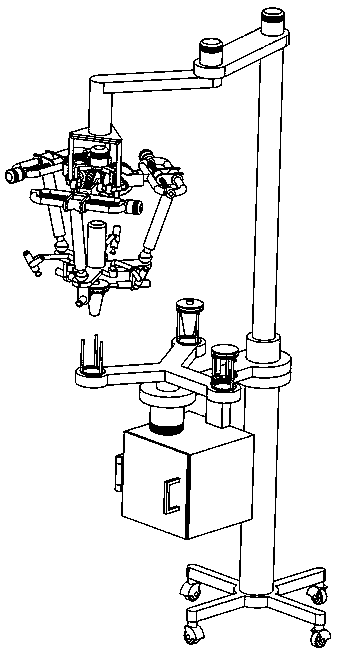
Multifunctional anesthesia assistant device in anesthesiology department
ActiveCN110025869ASimple structureEasy to operateAnaesthesiaMedical devicesDisinfectantThree degrees of freedom
The invention discloses a multifunctional anesthesia assistant device in anesthesiology department. The anesthesia assistant device comprises a three-degree-of-freedom bracket, a hybrid-connection platform, accessories, etc. A three-output worm gear-worm mechanism with three branches is in serial connection with three planar moving pairs, then a 3-RPS parallel mechanism is closed, and thus the hybrid-connection mechanism with variable workspace is constituted. The three-degree-of-freedom bracket is matched with the hybrid-connection platform with the variable workspace, a large operating rangeand high sensitivity are realized, and the anesthesia assistant device is suitable for various anesthesia applications. An ejector and a disassembler respectively aim at spraying anesthetization andanesthesia capsule anesthetization, and the anesthesia assistant device is adapted for various anesthesia occasions. A disinfection device is divided into an ejector with disinfectant and a disinfection box with ultraviolet lamp tubes, and skin can be disinfected by the ejector and instruments can be disinfected by the disinfection box.
Owner:丛静
Multi-mode specification-driven disassembler
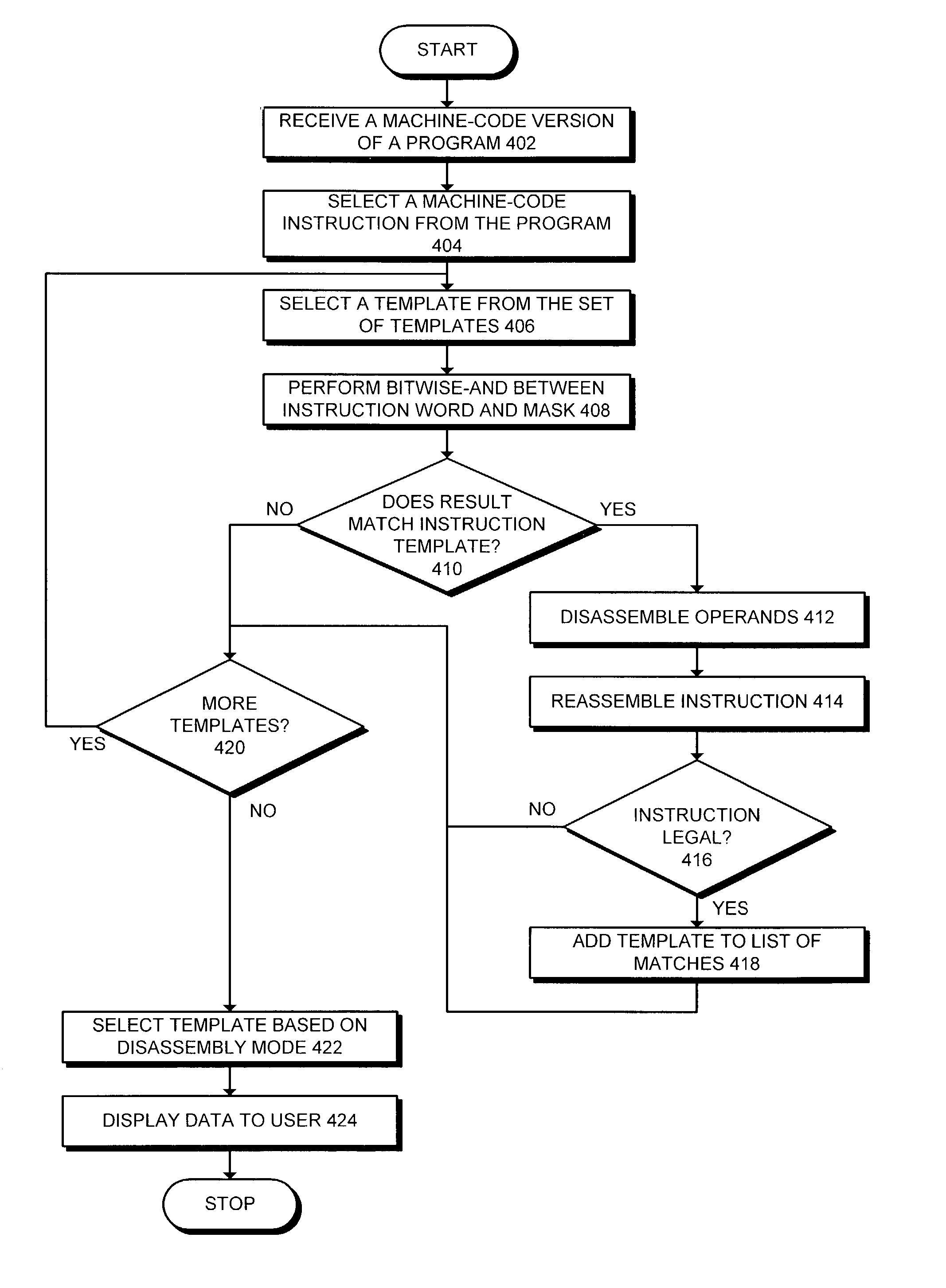
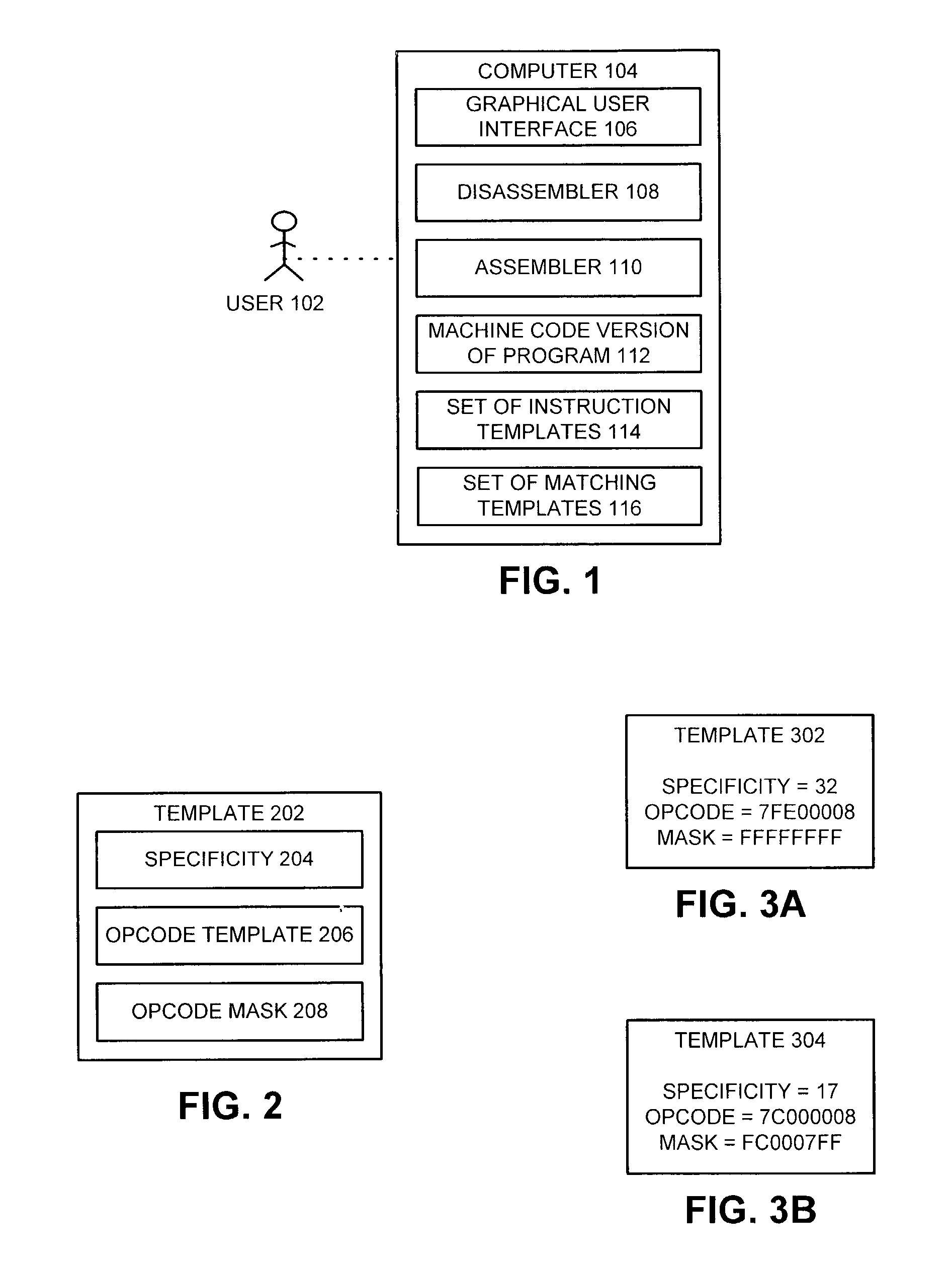
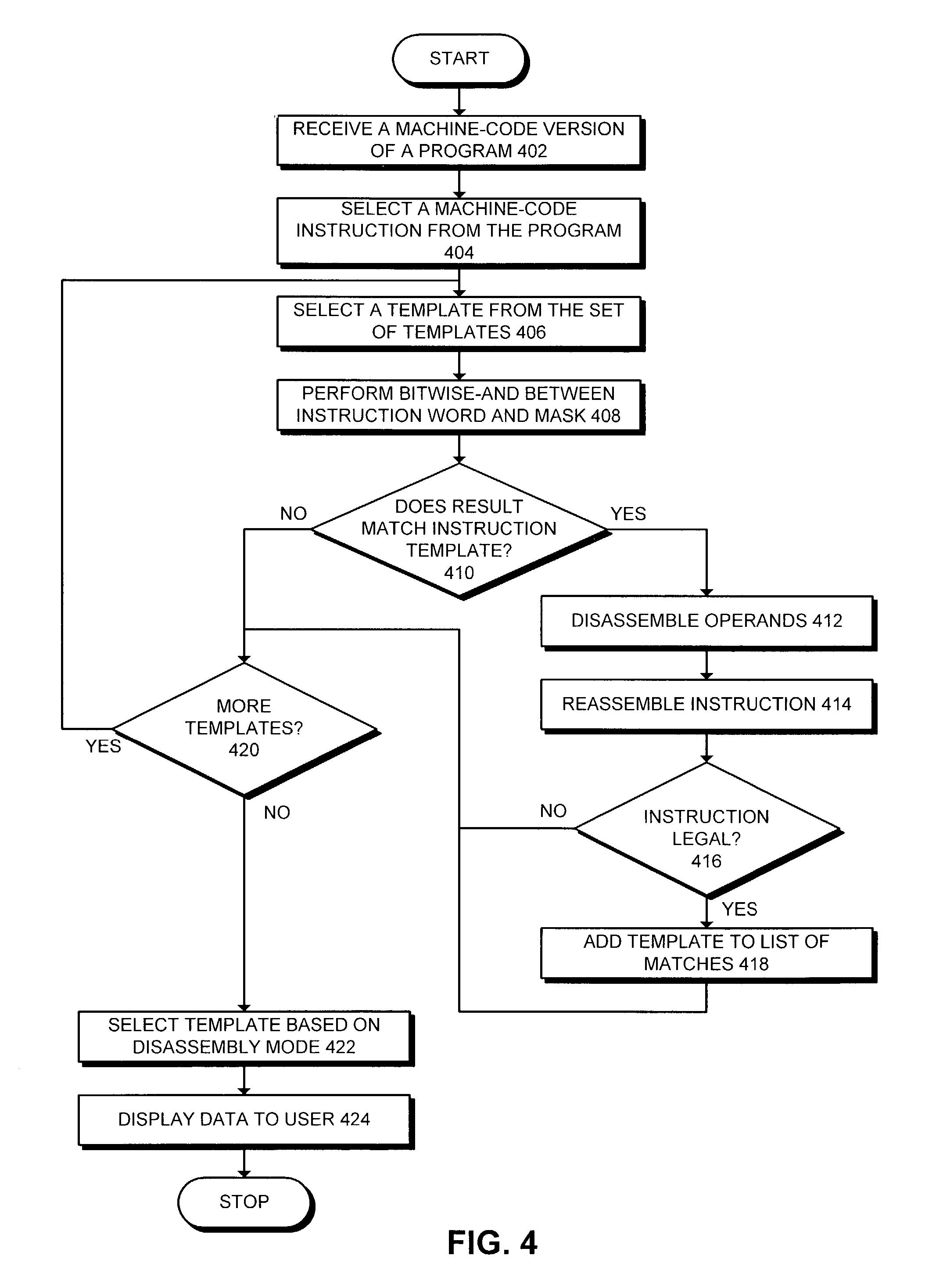
ActiveUS7036112B2Easy to implementDisassemble a specific machine-code instructionDecompilation/disassemblyGeneral purpose stored program computerTemplate basedOperand
One embodiment of the present invention provides a system that facilitates implementing multi-mode specification-driven disassembler. During operation, the disassembler receives a machine-code version of a computer program. In order to disassemble a specific machine-code instruction from this machine-code version, the system compares the machine-code instruction against a set of instruction templates for assembly code instructions to identify a set of matching templates. Next, the system selects a matching template from the set of matching templates based on the state of a mode variable, which indicates a specificity mode for the disassembler. The system then disassembles the machine-code instruction using the operand fields defined by the matching template to produce a corresponding assembly code instruction.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com