Patents
Literature
139 results about "Treatment error" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Error treatment (linguistics) In second language acquisition, error treatment refers to the way teachers respond to learners' linguistic errors made in the course of learning a second language. Many error treatment studies seek to address issues like when, how, and by whom such errors should be corrected.
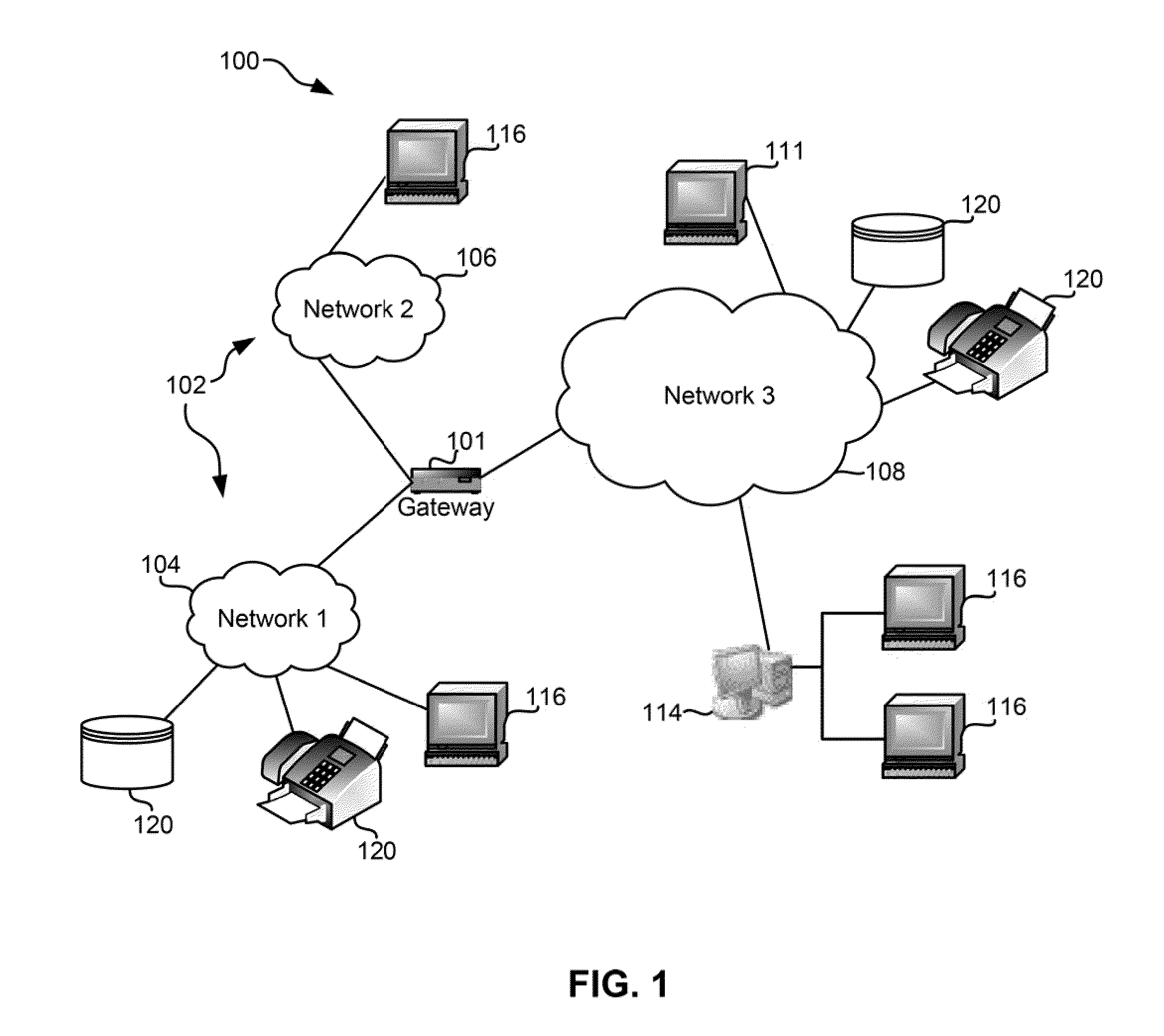
Embolic filtering method and apparatus
InactiveUS20060009799A1Obstruct passageEncourage and facilitate growth of tissueAnnuloplasty ringsDilatorsVenous bloodCardiac defects
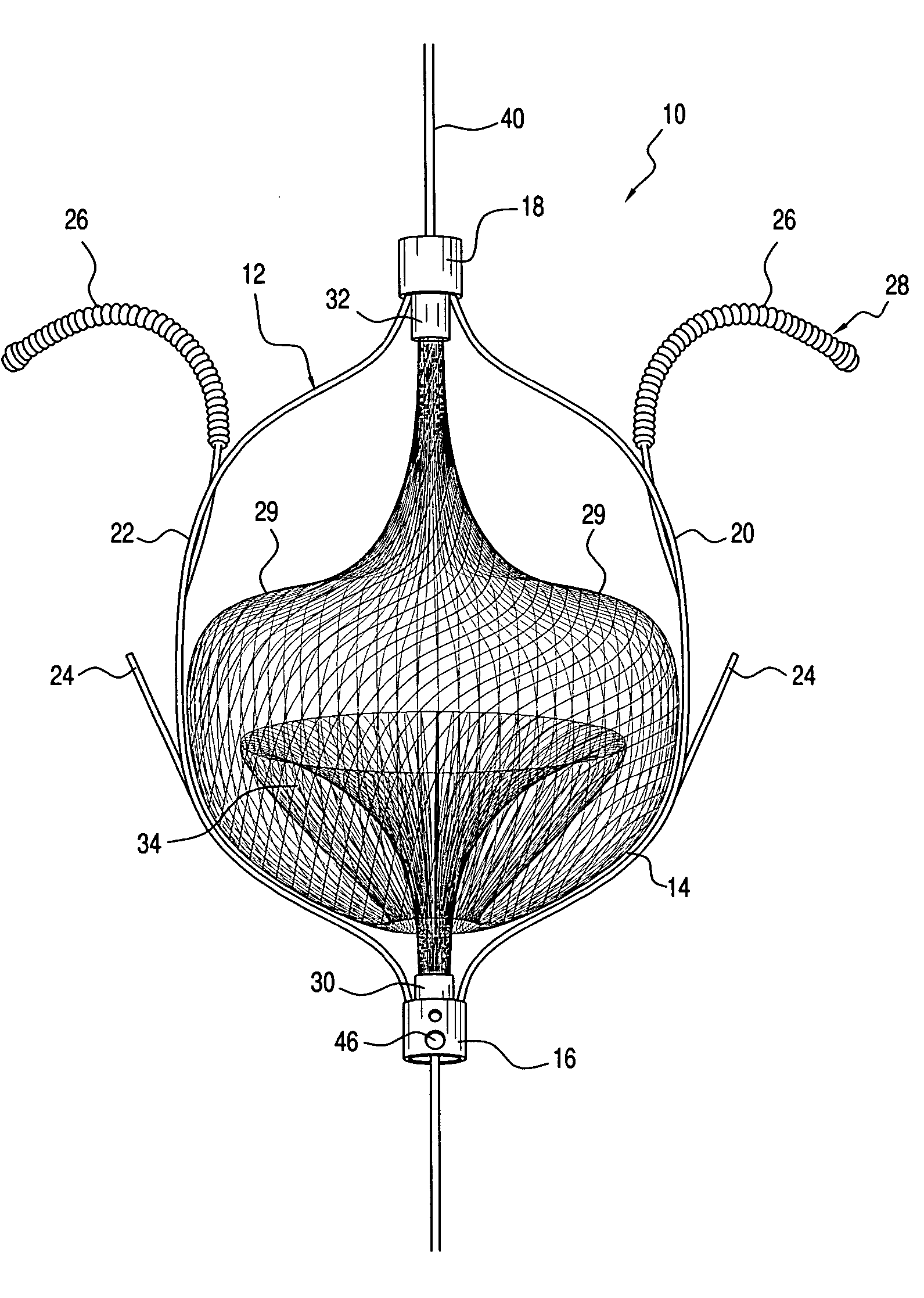
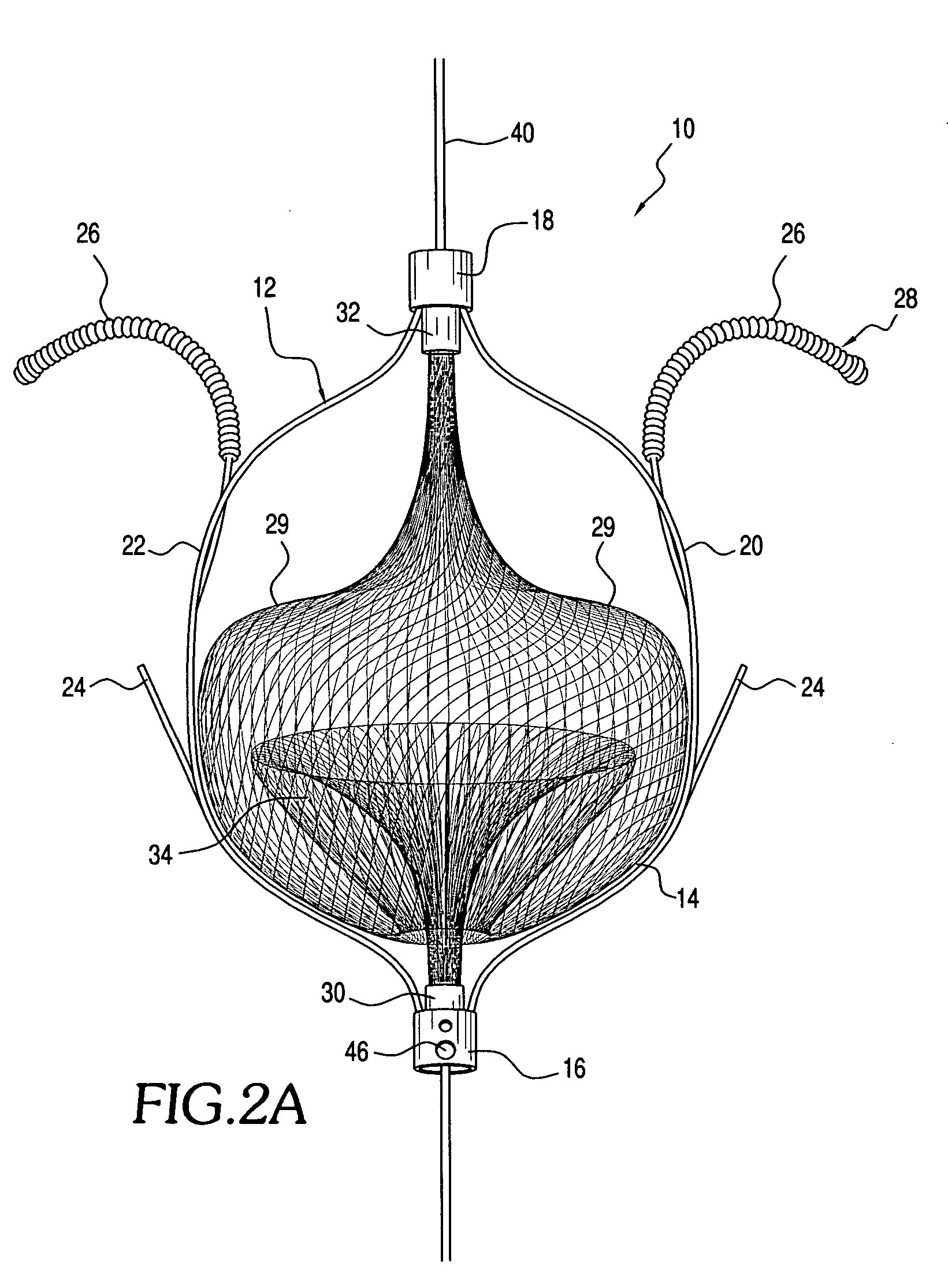
The present invention relates generally to a device and method for preventing the undesired passage of emboli from a venous blood pool to an arterial blood pool. The invention relates especially to a device and method for treating certain cardiac defects, especially patent foramen ovales and other septal defects, through the use of an embolic filtering device capable of instantaneously deterring the passage of emboli from the moment of implantation. The device consists of a frame, and a braided mesh of sufficient dimensions to prevent passage of emboli through the mesh. The device is preferably composed of shape memory allow, such as nitinol, which conforms to the shape and dimension of the defect to be treated.
Owner:SEPTRX
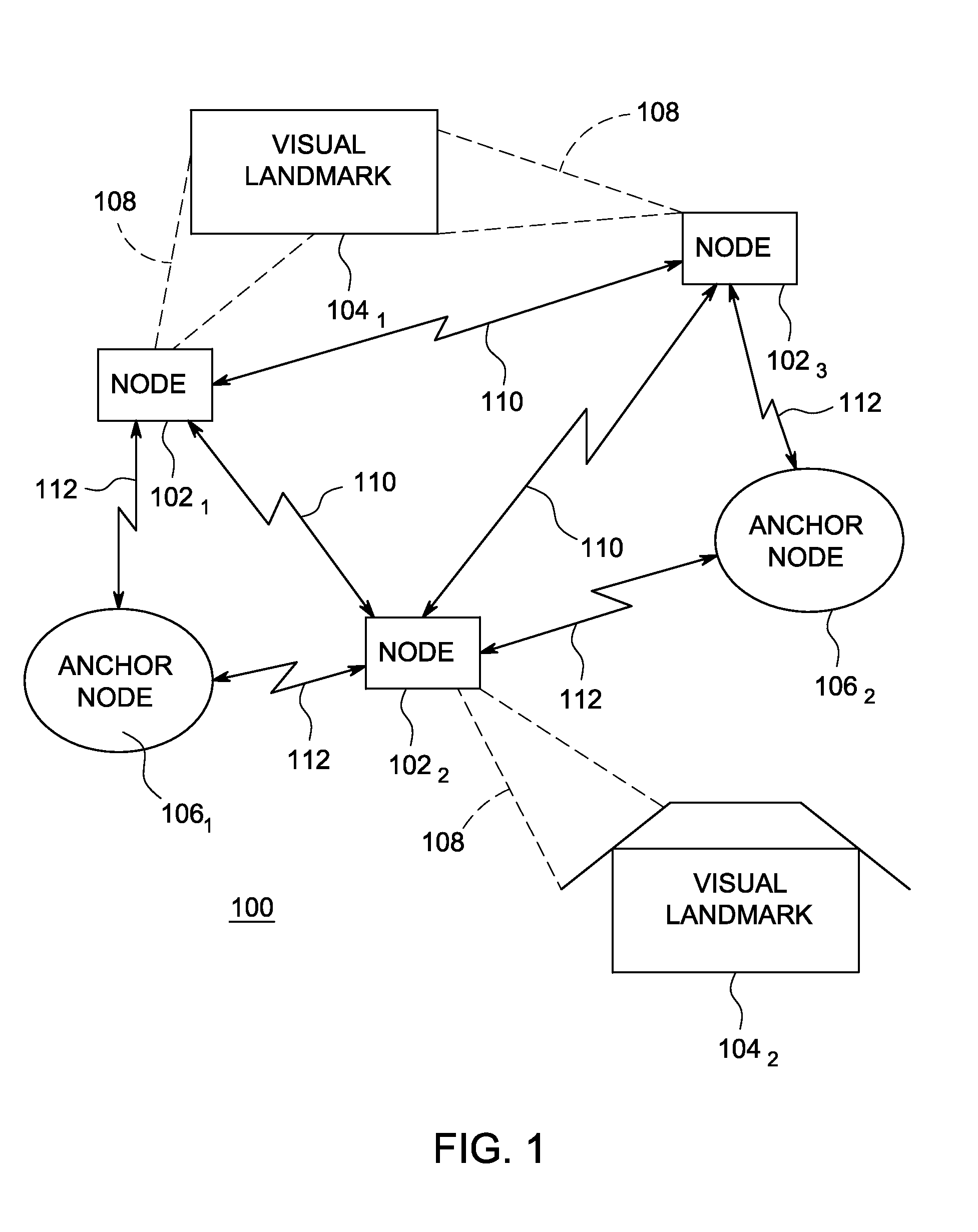
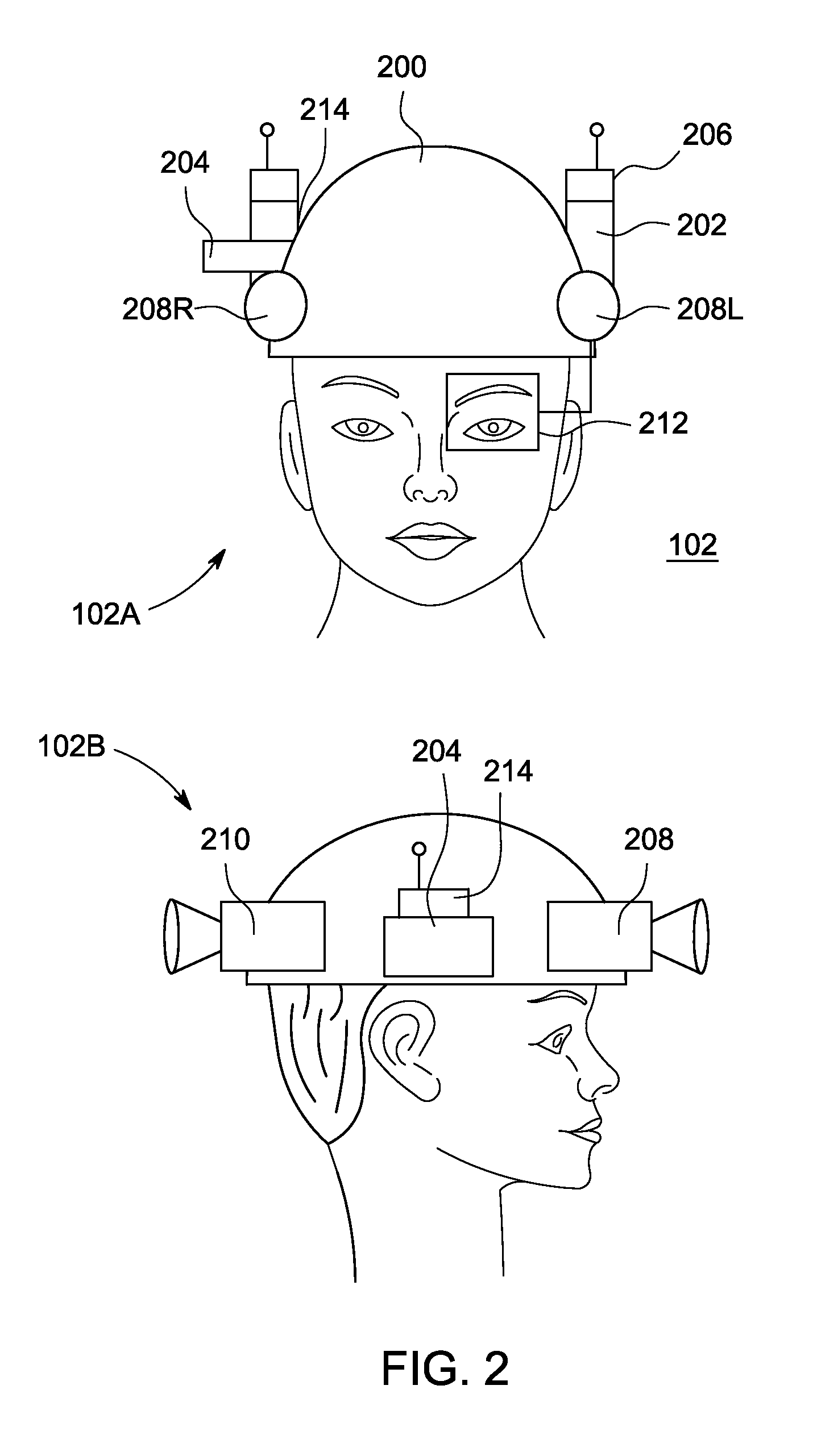
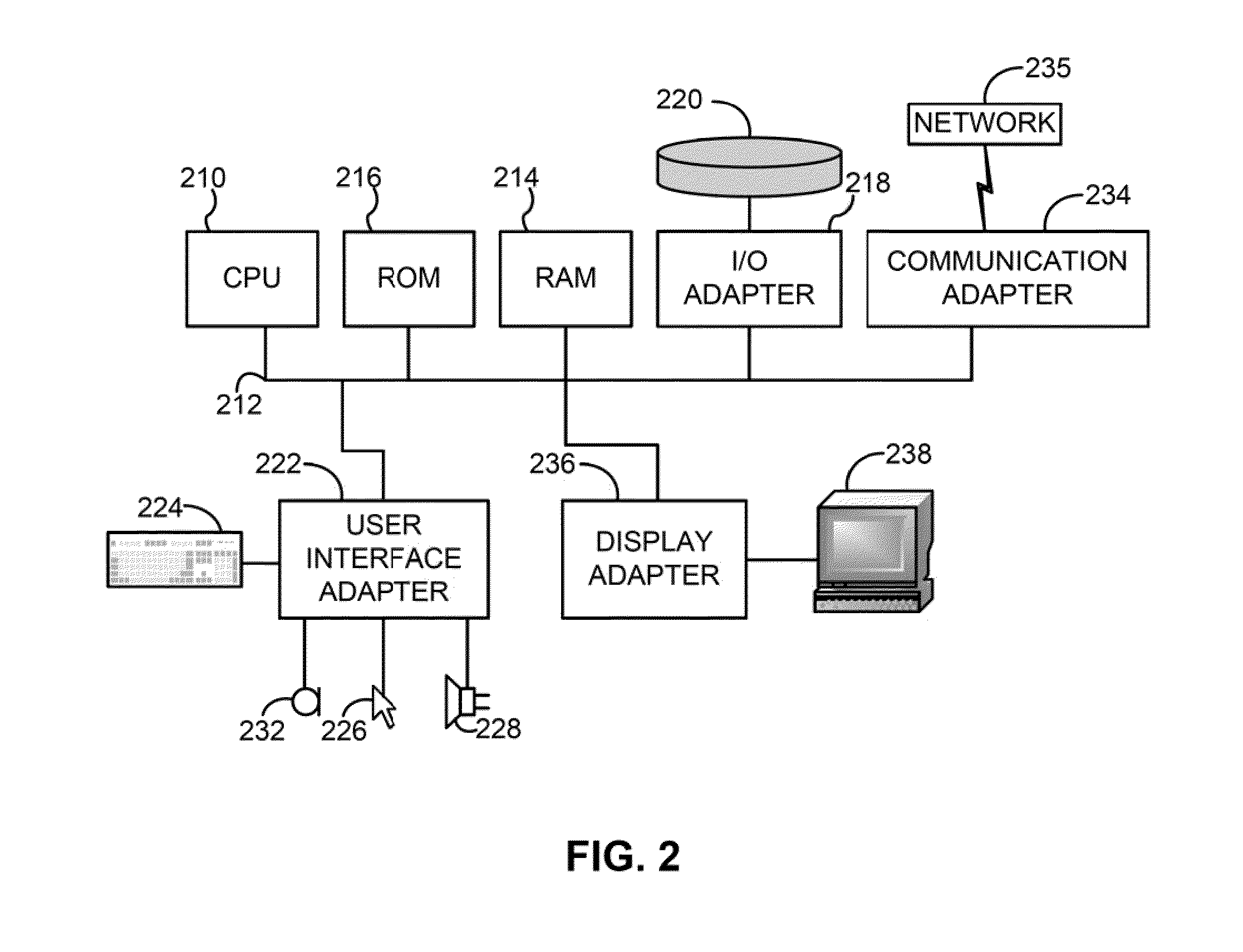
Method and apparatus for generating three-dimensional pose using multi-modal sensor fusion
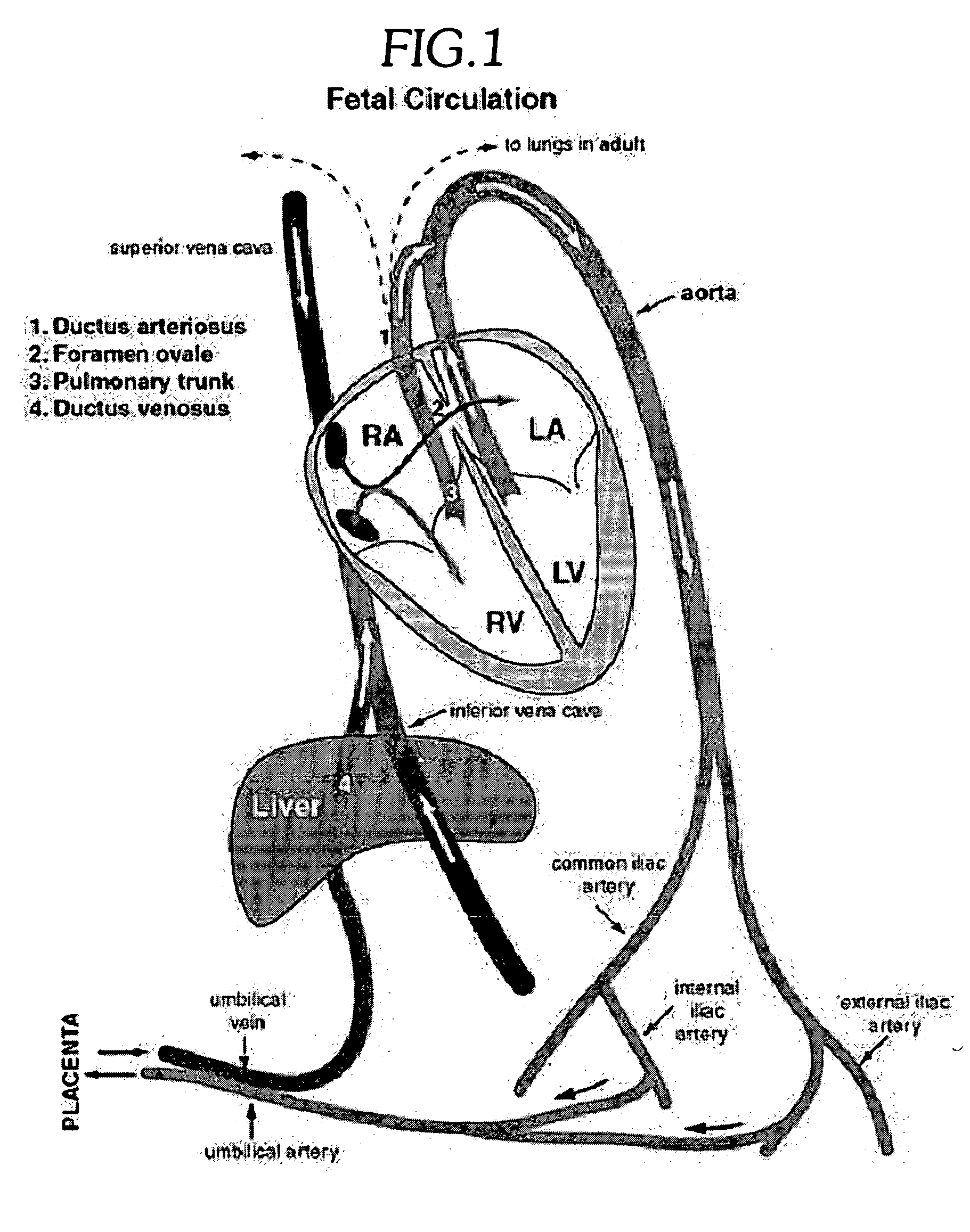
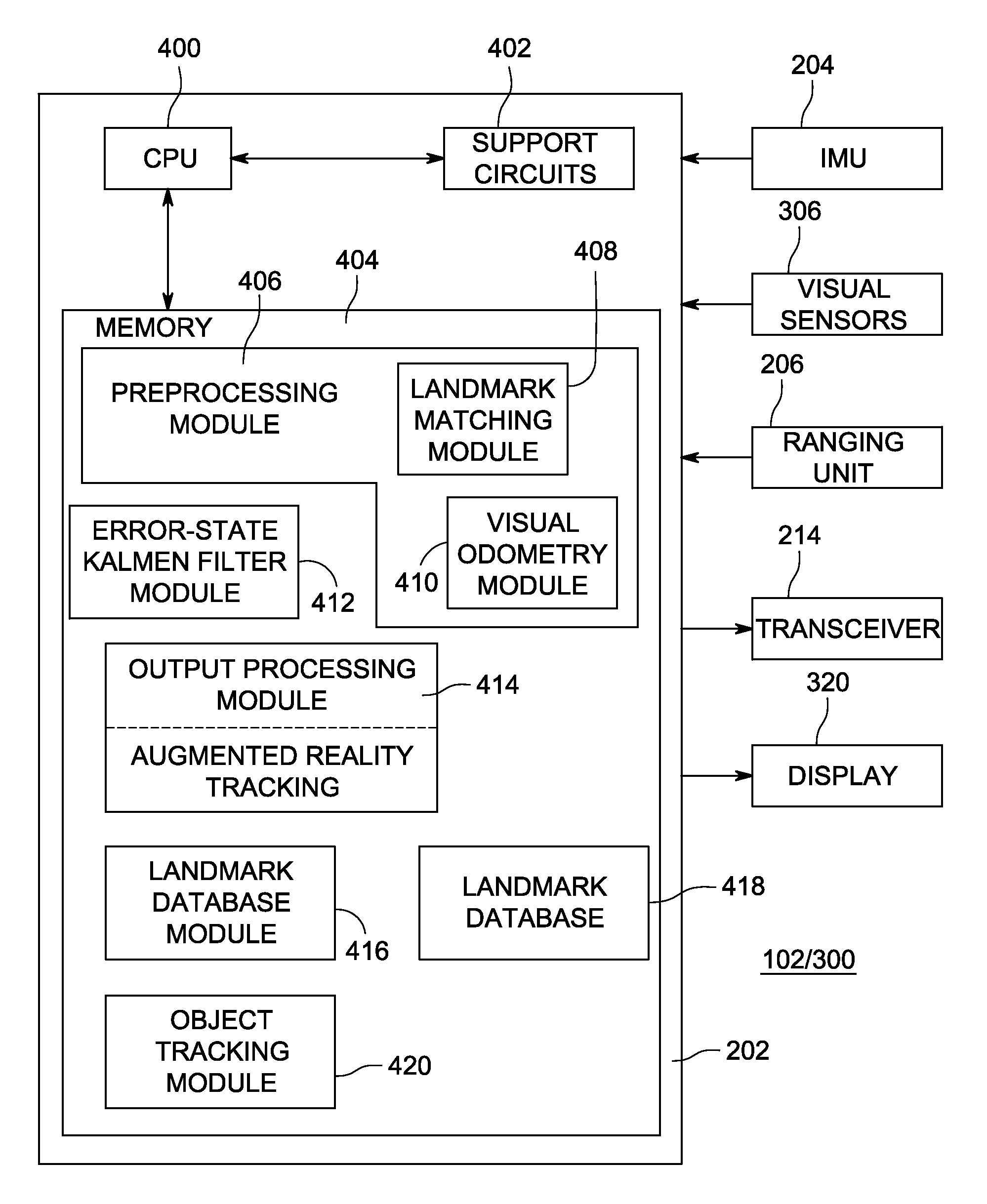
A method and apparatus for providing three-dimensional navigation for a node comprising an inertial measurement unit for providing gyroscope, acceleration and velocity information (collectively IMU information); a ranging unit for providing distance information relative to at least one reference node; at least one visual sensor for providing images of an environment surrounding the node; a preprocessor, coupled to the inertial measurement unit, the ranging unit and the plurality of visual sensors, for generating error states for the IMU information, the distance information and the images; and an error-state predictive filter, coupled to the preprocessor, for processing the error states to produce a three-dimensional pose of the node.
Owner:SRI INTERNATIONAL
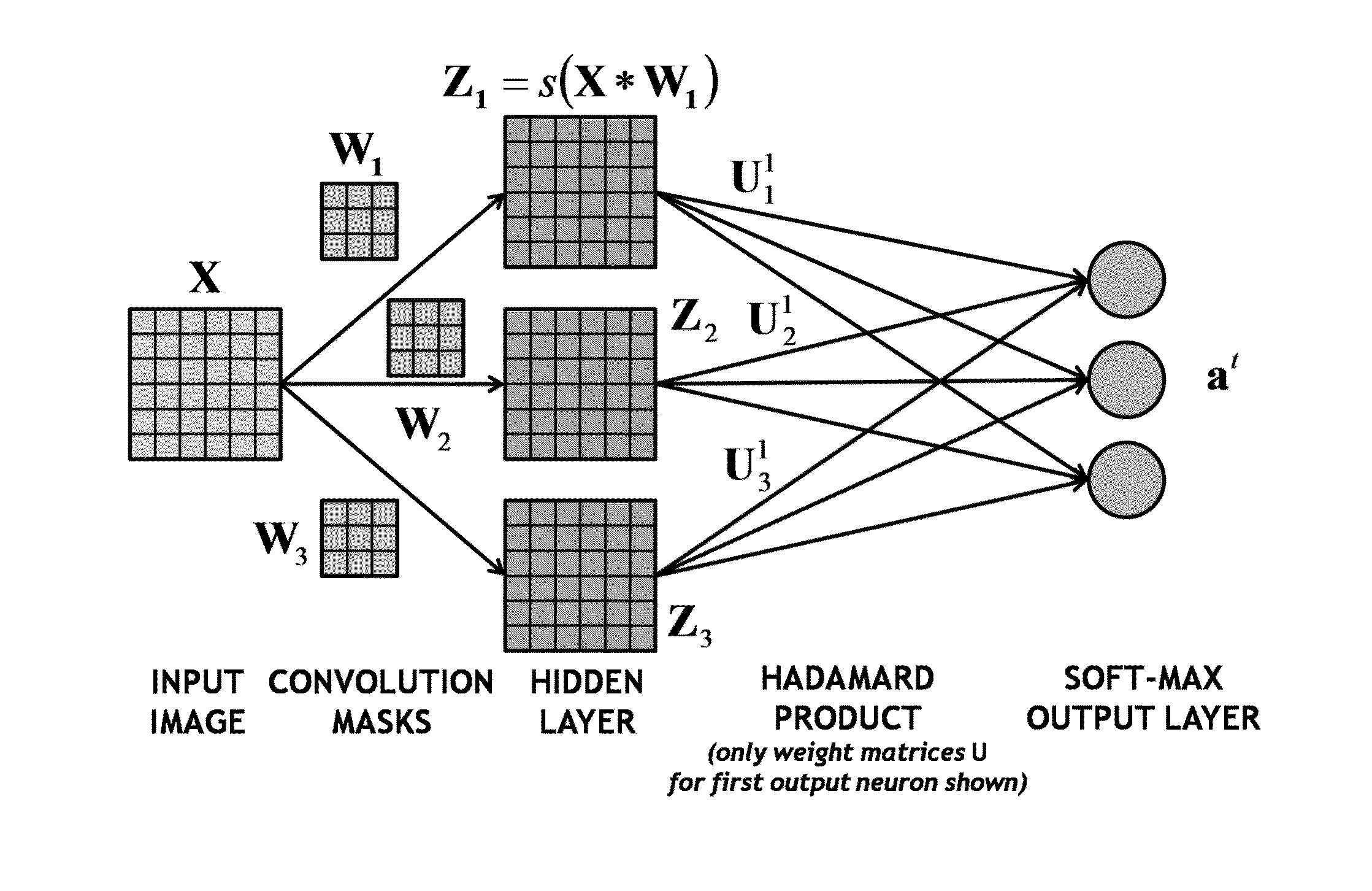
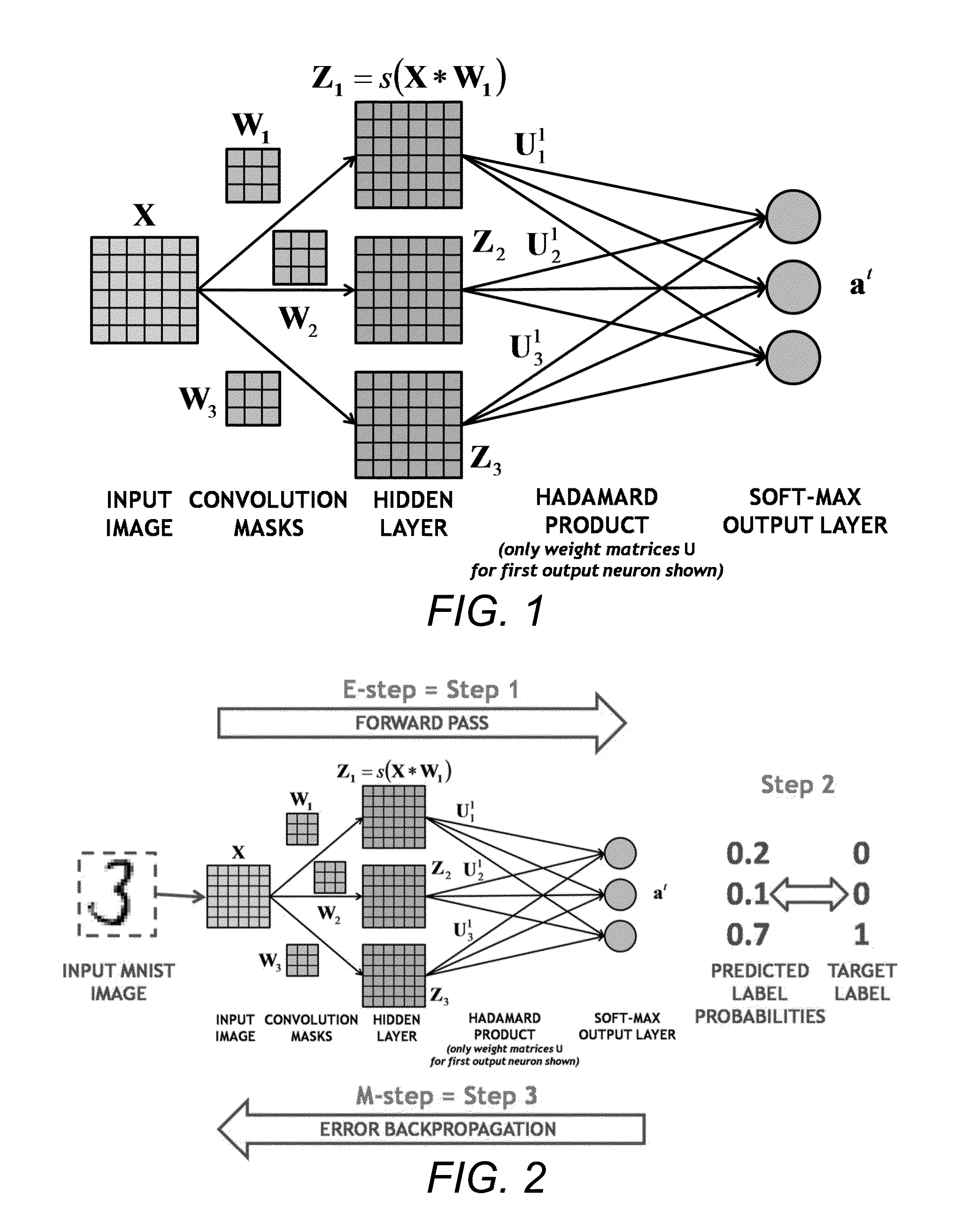
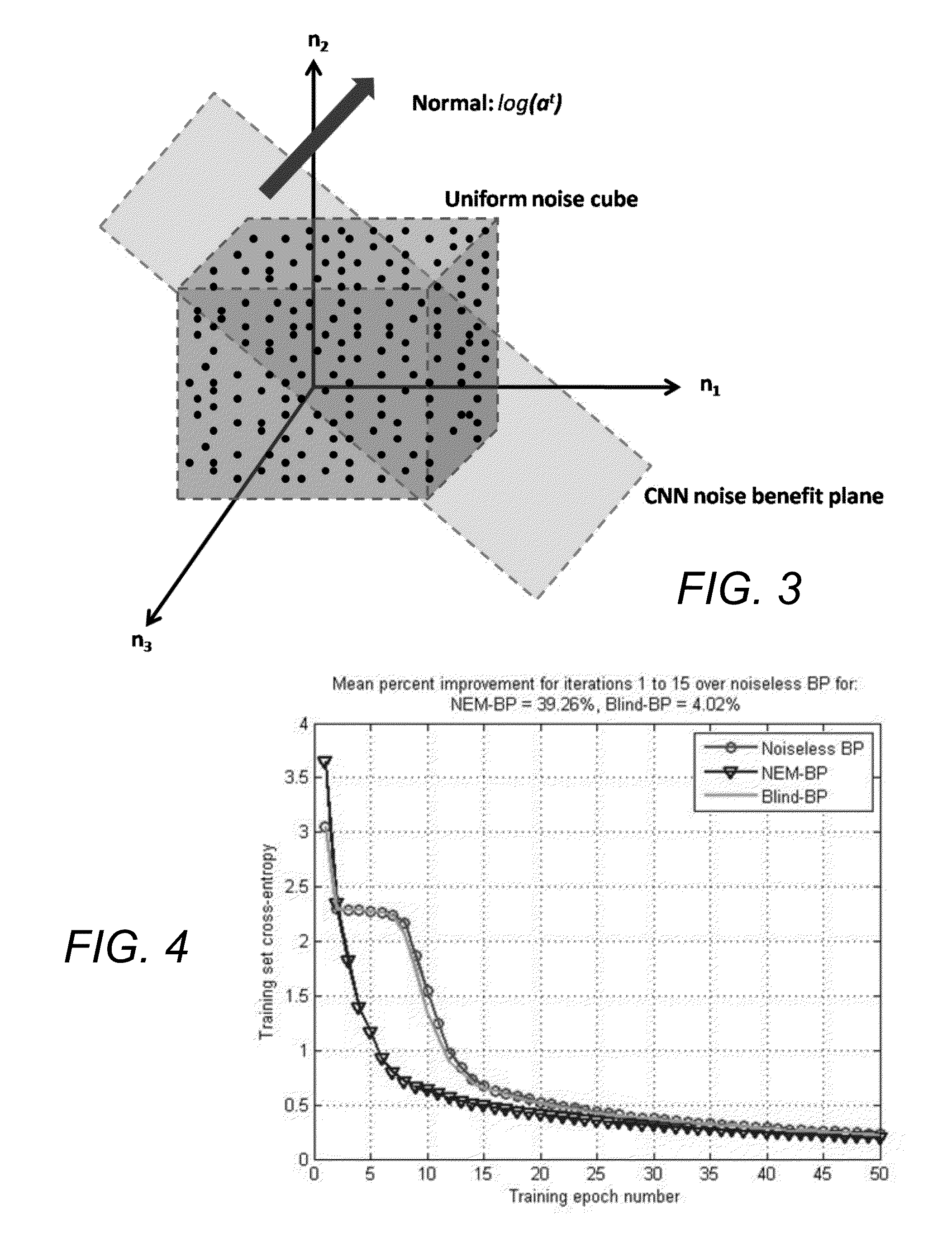
Noise-enhanced convolutional neural networks
ActiveUS20160019459A1Learning speedImprove accuracyMathematical modelsDigital computer detailsData processing systemComputerized system
A learning computer system may include a data processing system and a hardware processor and may estimate parameters and states of a stochastic or uncertain system. The system may receive data from a user or other source; process the received data through layers of processing units, thereby generating processed data; apply masks or filters to the processed data using convolutional processing; process the masked or filtered data to produce one or more intermediate and output signals; compare the output signals with reference signals to generate error signals; send and process the error signals back through the layers of processing units; generate random, chaotic, fuzzy, or other numerical perturbations of the received data, the processed data, or the output signals; estimate the parameters and states of the stochastic or uncertain system using the received data, the numerical perturbations, and previous parameters and states of the stochastic or uncertain system; determine whether the generated numerical perturbations satisfy a condition; and, if the numerical perturbations satisfy the condition, inject the numerical perturbations into the estimated parameters or states, the received data, the processed data, the masked or filtered data, or the processing units.
Owner:UNIV OF SOUTHERN CALIFORNIA
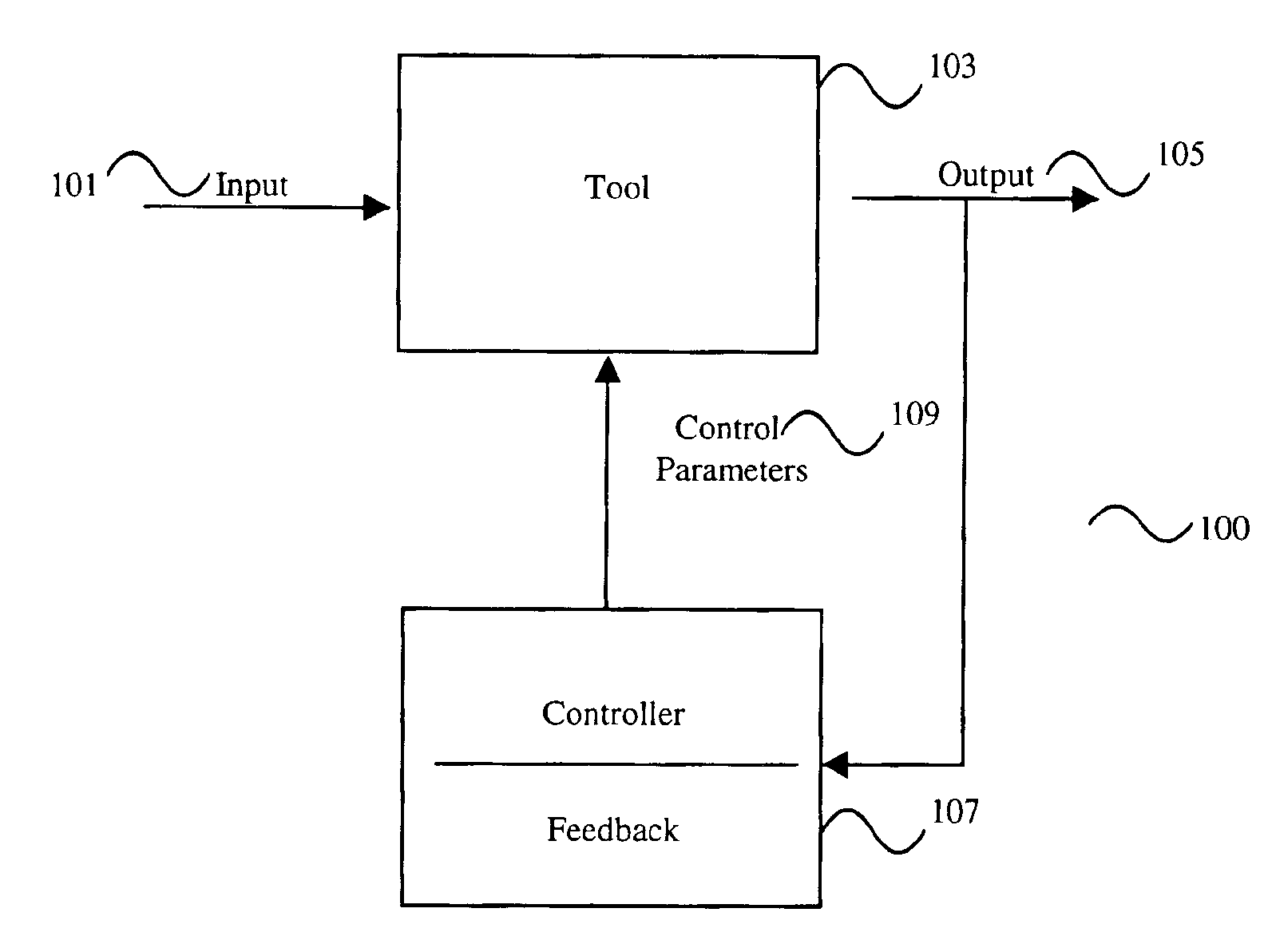
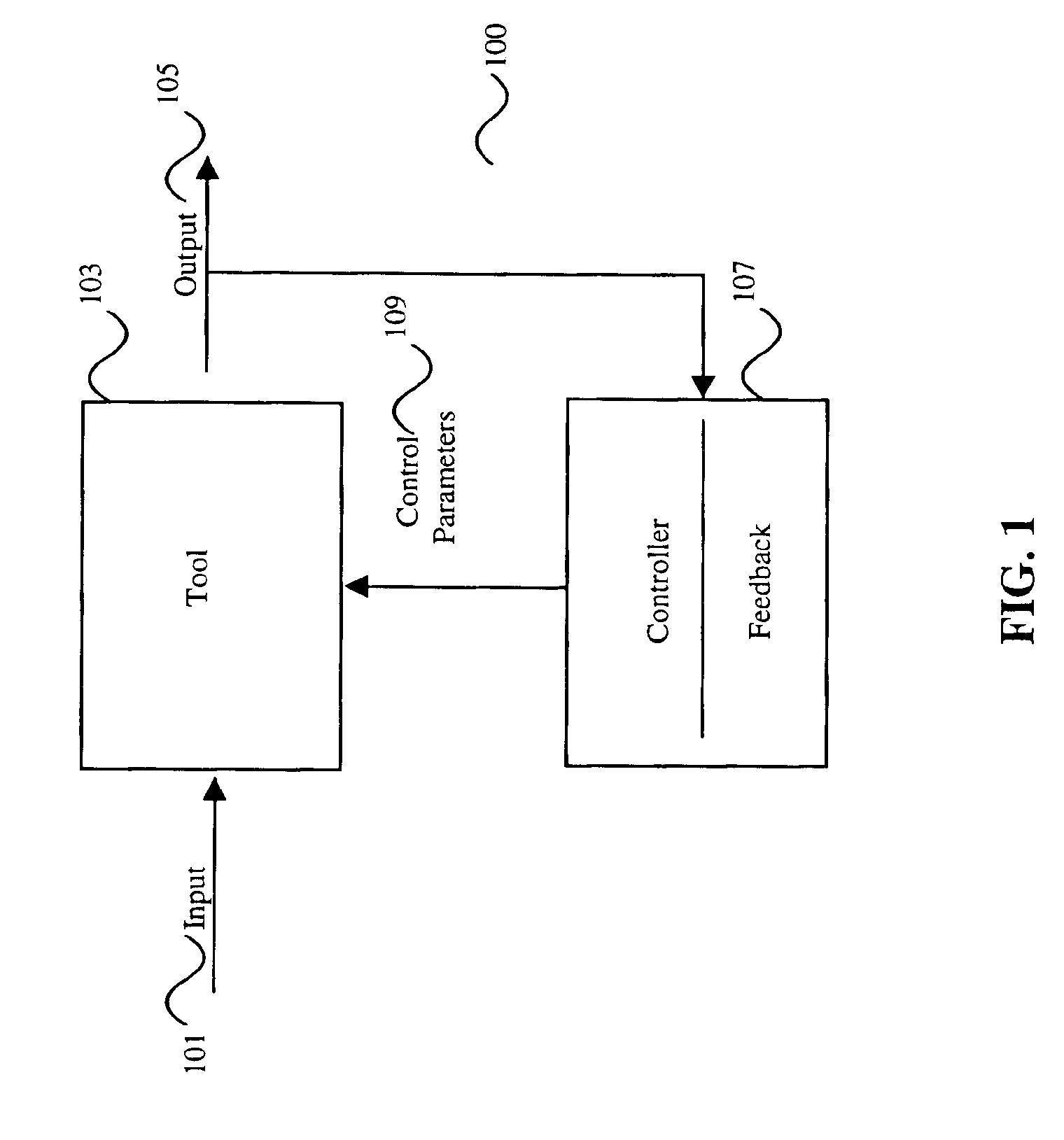
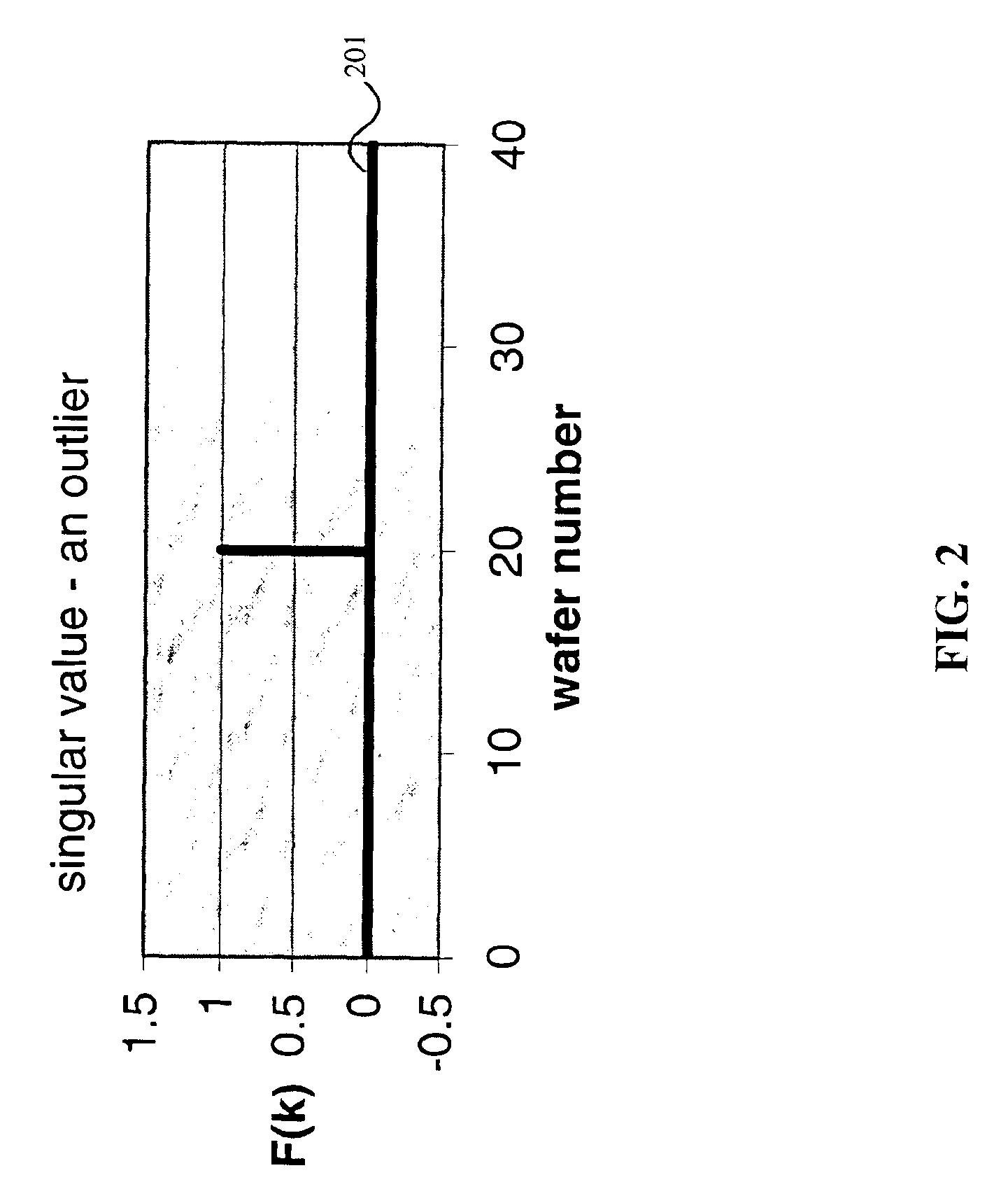
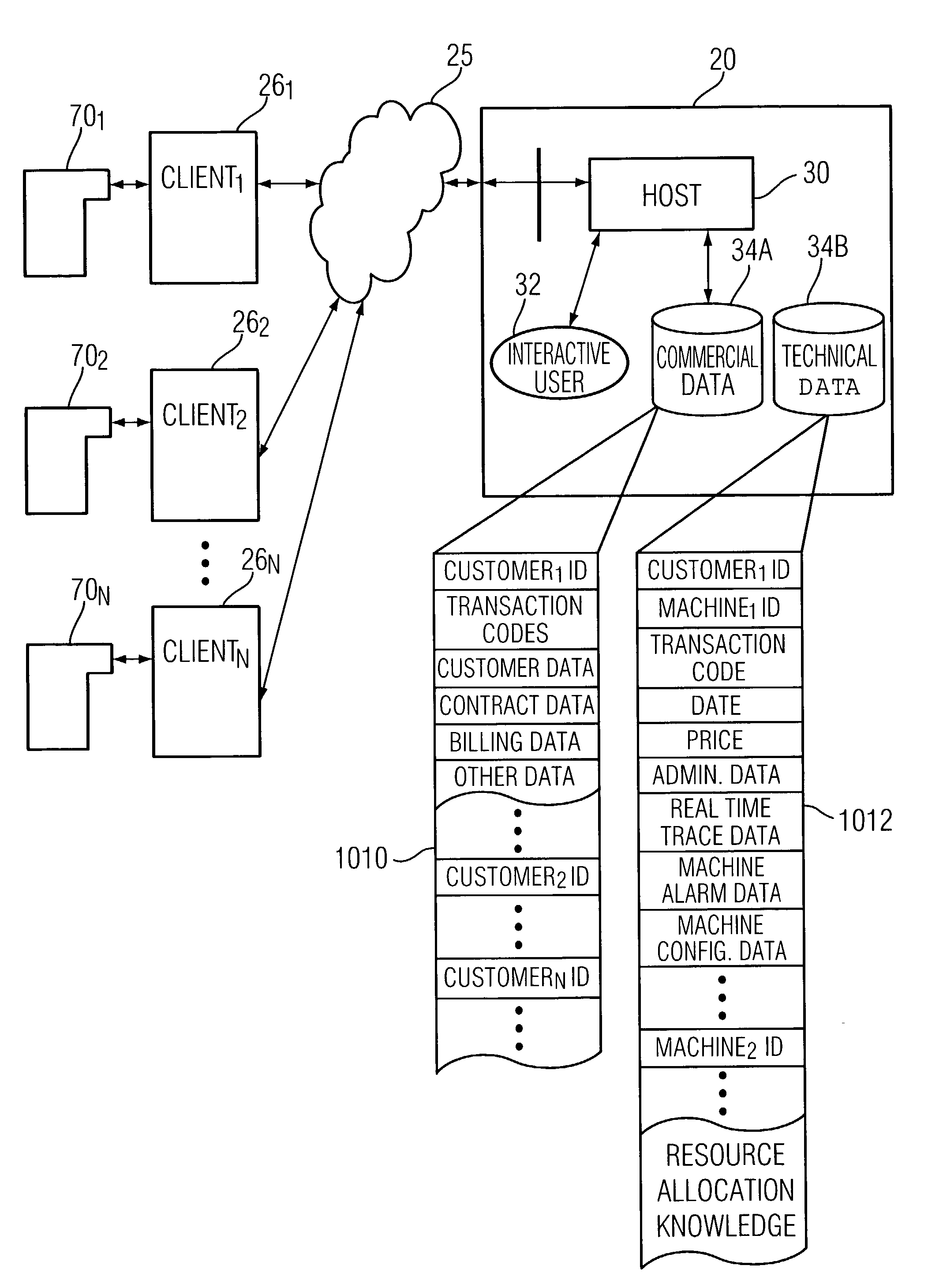
Method, system, and medium for handling misrepresentative metrology data within an advanced process control system
InactiveUS6999836B2Accurate measurementSampled-variable control systemsComputer controlMetrologyOutlier
A system, method and medium of controlling a semiconductor manufacturing tool using a feedback control mechanism. The feedback control mechanism includes features for receiving data points relating to an output of the tool. The data points include a current data point and at least one previous data point. The feedback control mechanism also includes features for determining whether the current data point is an erroneous outlier by comparing the current data point to a statistical representation of the at least one previous data point, and based on whether the at least one previous data point is an outlier. The feedback control mechanism further includes features for disregarding the current data point in calculating a feedback value of the feedback control mechanism if the current data point is determined as an erroneous outlier.
Owner:APPL MATERIALS ISRAEL LTD
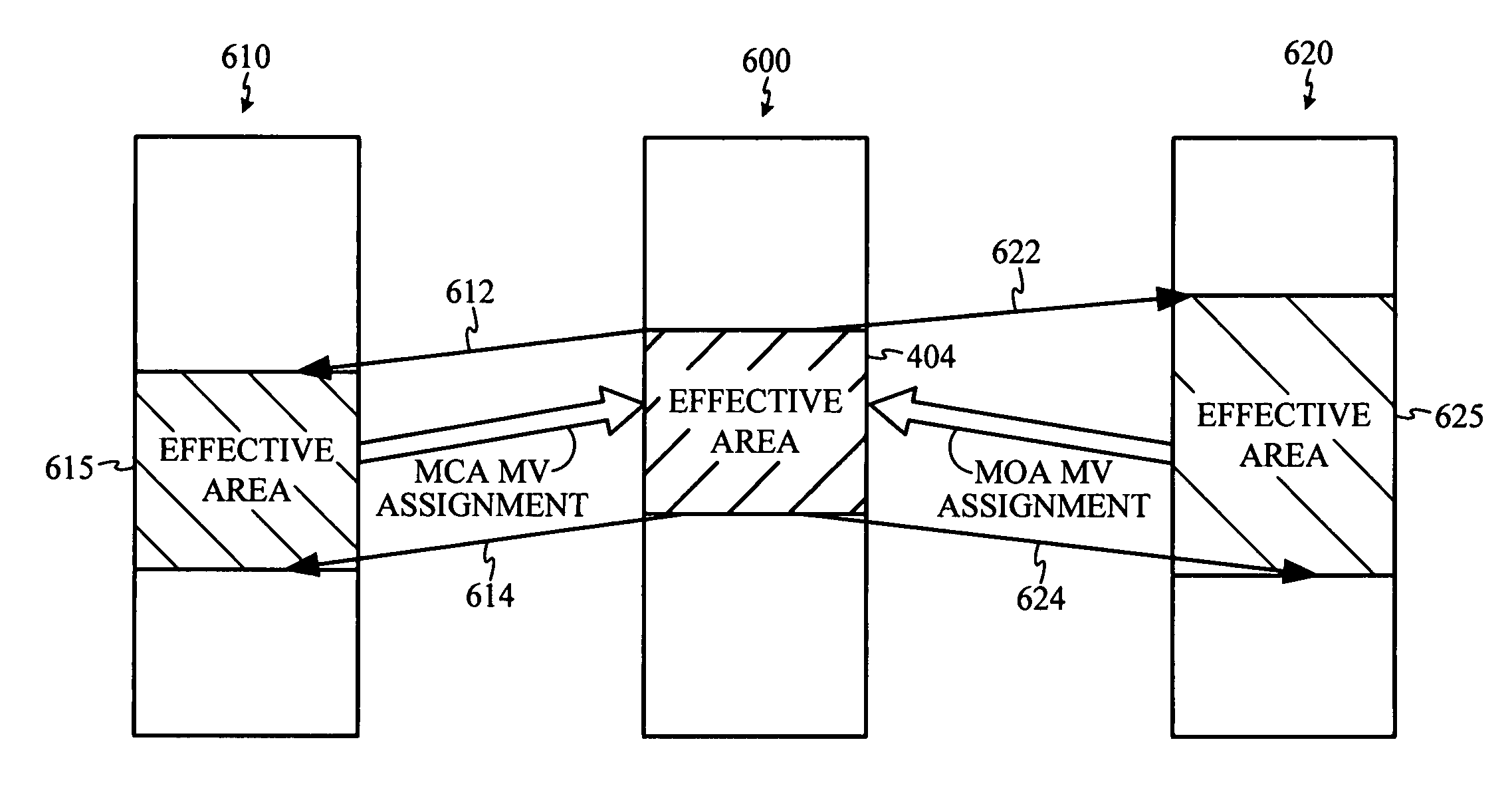
Temporal error concealment for bi-directionally predicted frames
ActiveUS7660354B2Color television with pulse code modulationColor television with bandwidth reductionMotion vectorError concealment
A method and apparatus to process erroneous bi-directionally predicted multimedia data is described. The method includes determining temporal prediction data for the erroneous multimedia data, and estimating the erroneous multimedia data based on the determined temporal prediction data. The temporal prediction data includes data that was used to predict a forward reference section and / or a backward reference section. In some aspects, the temporal prediction data comprises motion vector data of the reference frames which is scaled to correspond to a frame containing the erroneous data.
Owner:QUALCOMM INC
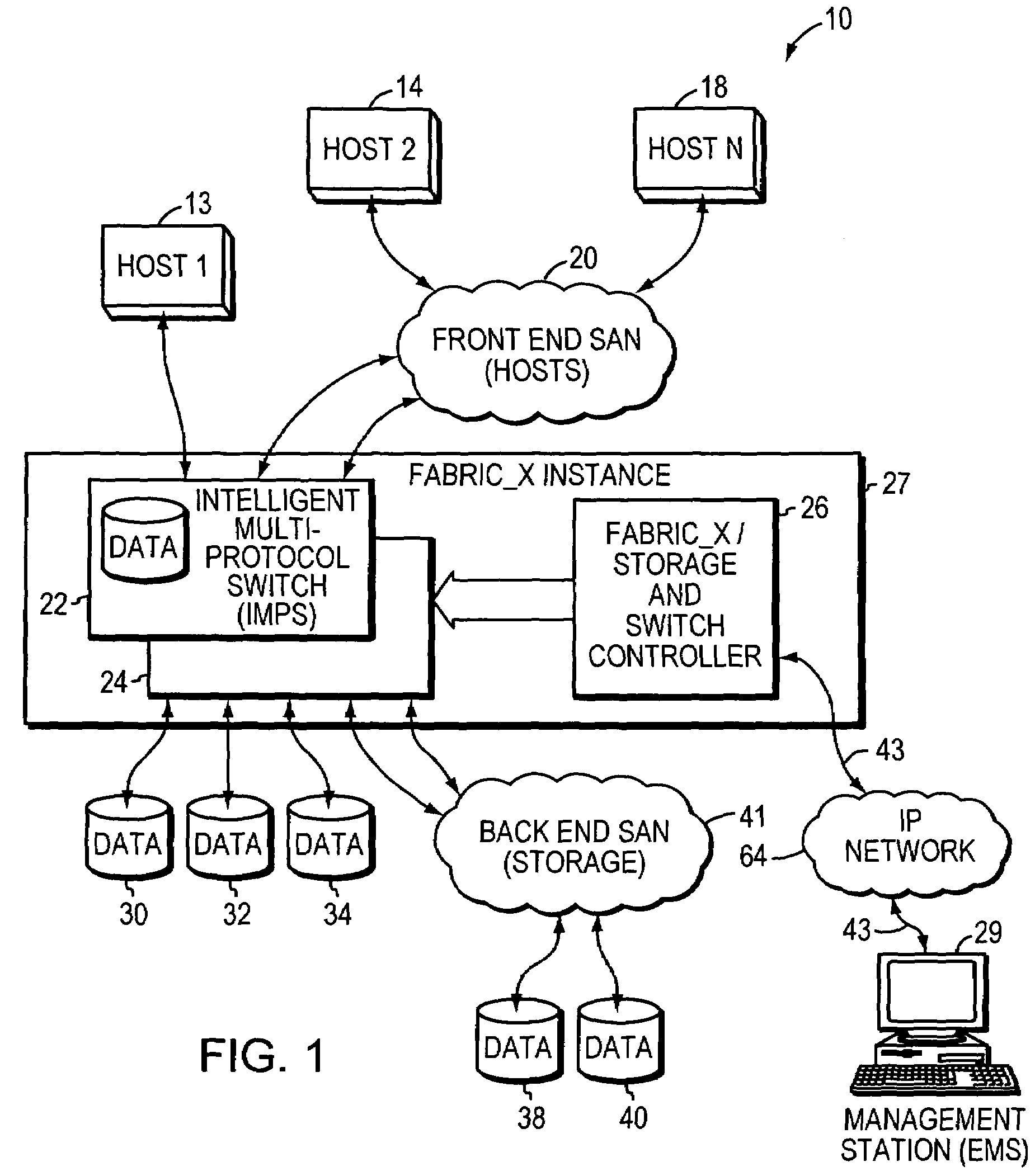
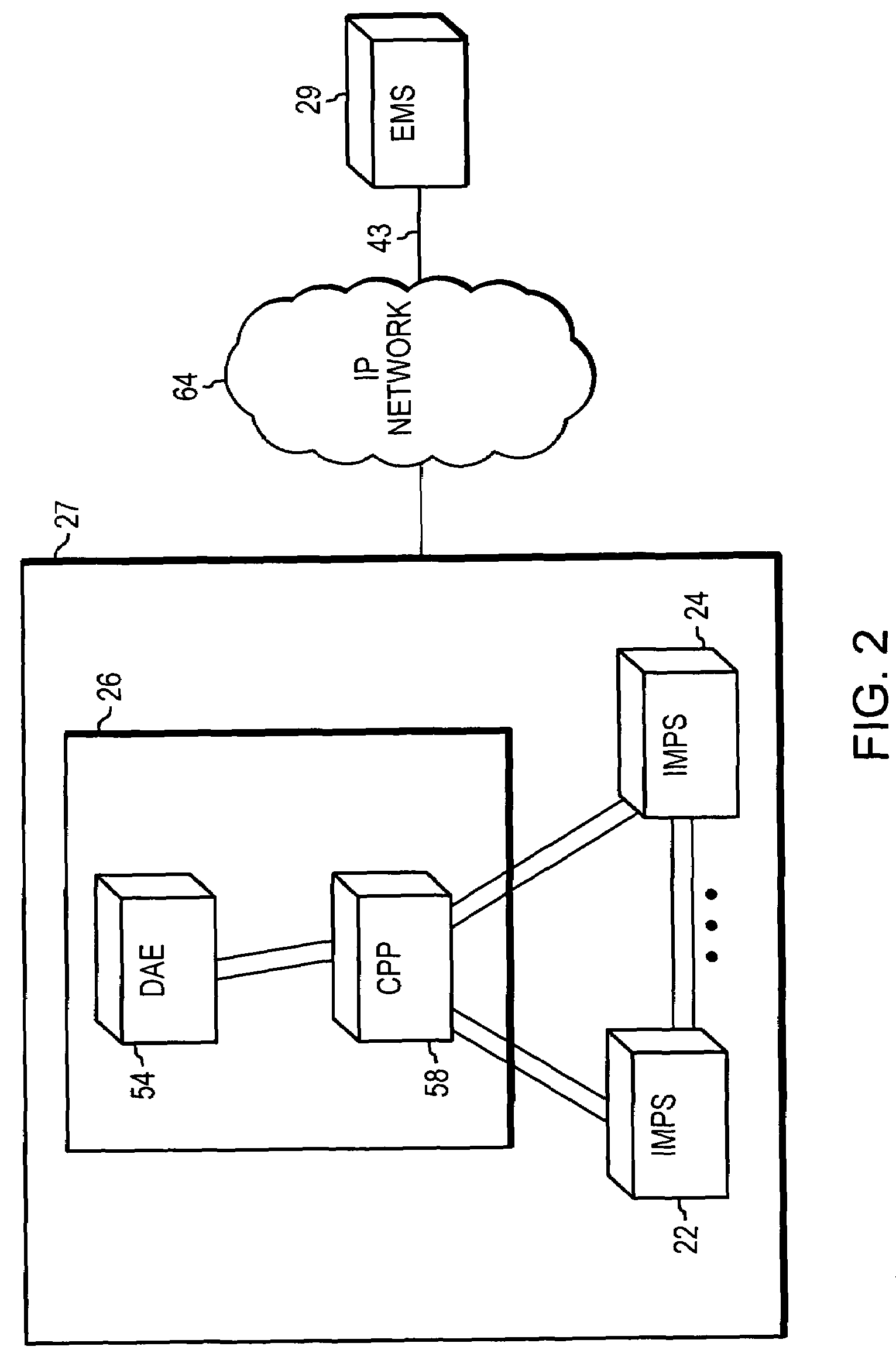
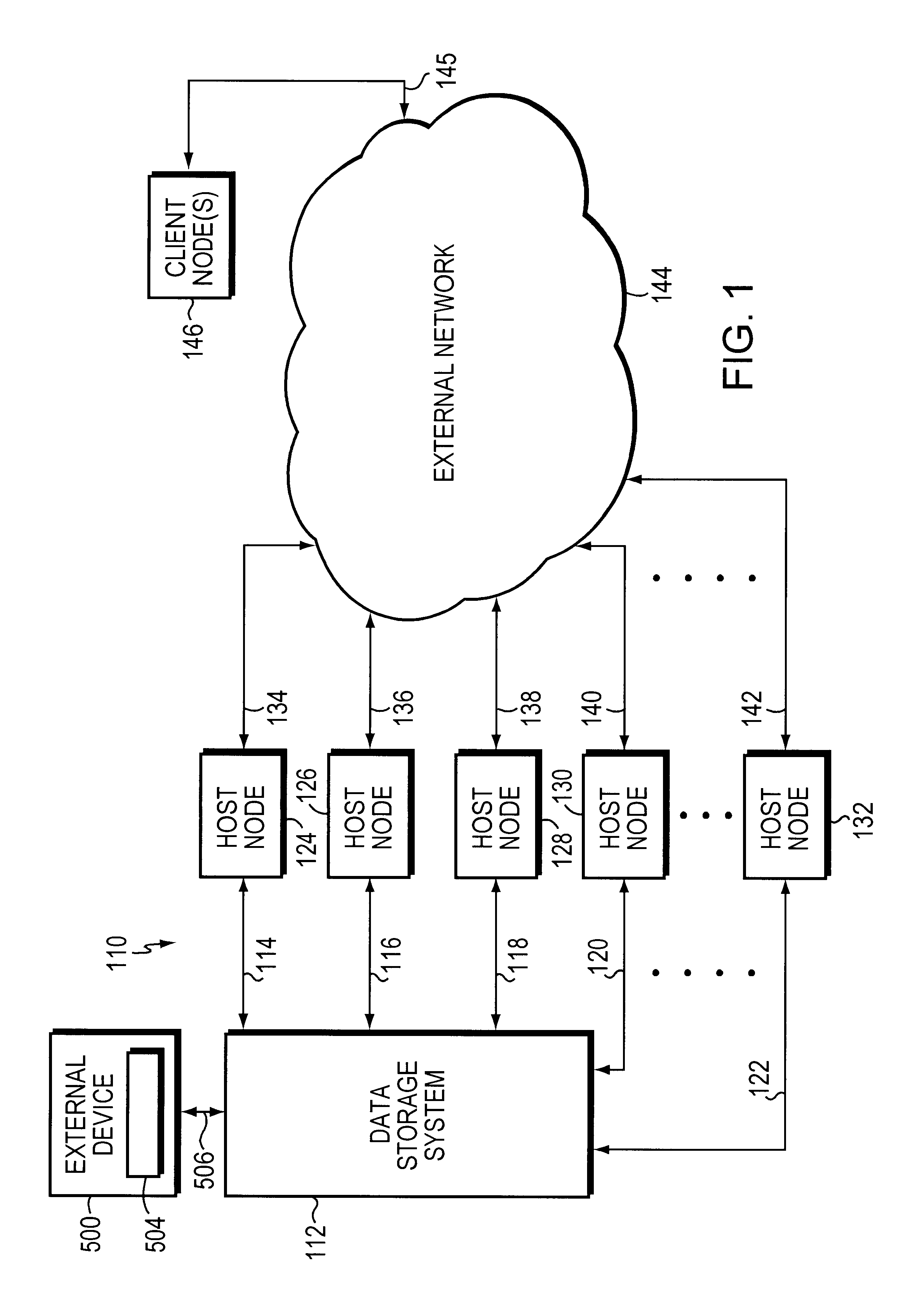
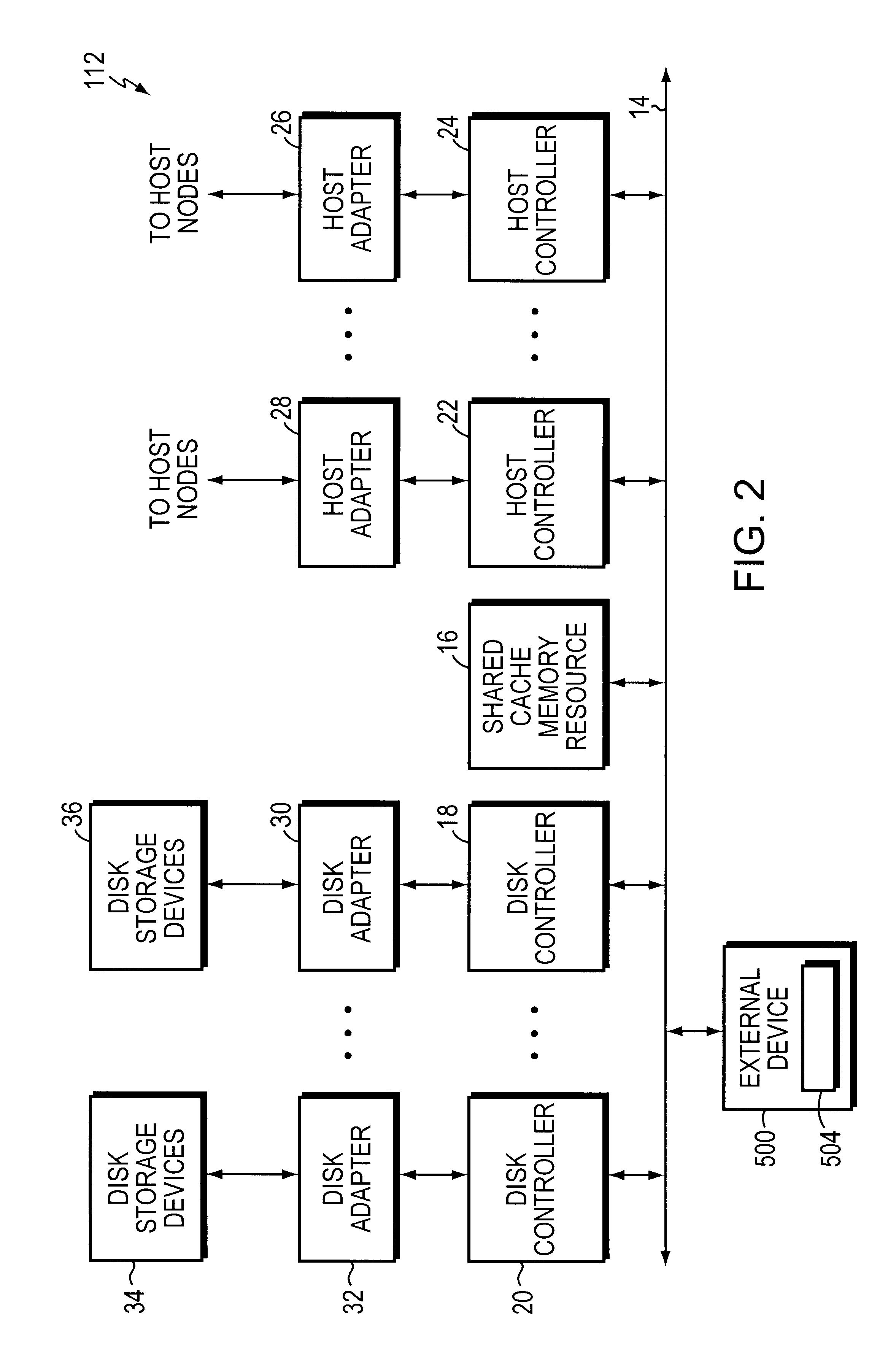
System and method for managing storage networks and providing virtualization of resources in such a network
InactiveUS7206863B1Input/output to record carriersResource allocationStorage area networkResource virtualization
This invention is a system and method for managing one or more data storage networks using a new architecture. A method for handling logical to physical mapping is included in one embodiment with the new architecture. A method for handling errors is included in another embodiment with the new architecture.
Owner:EMC IP HLDG CO LLC
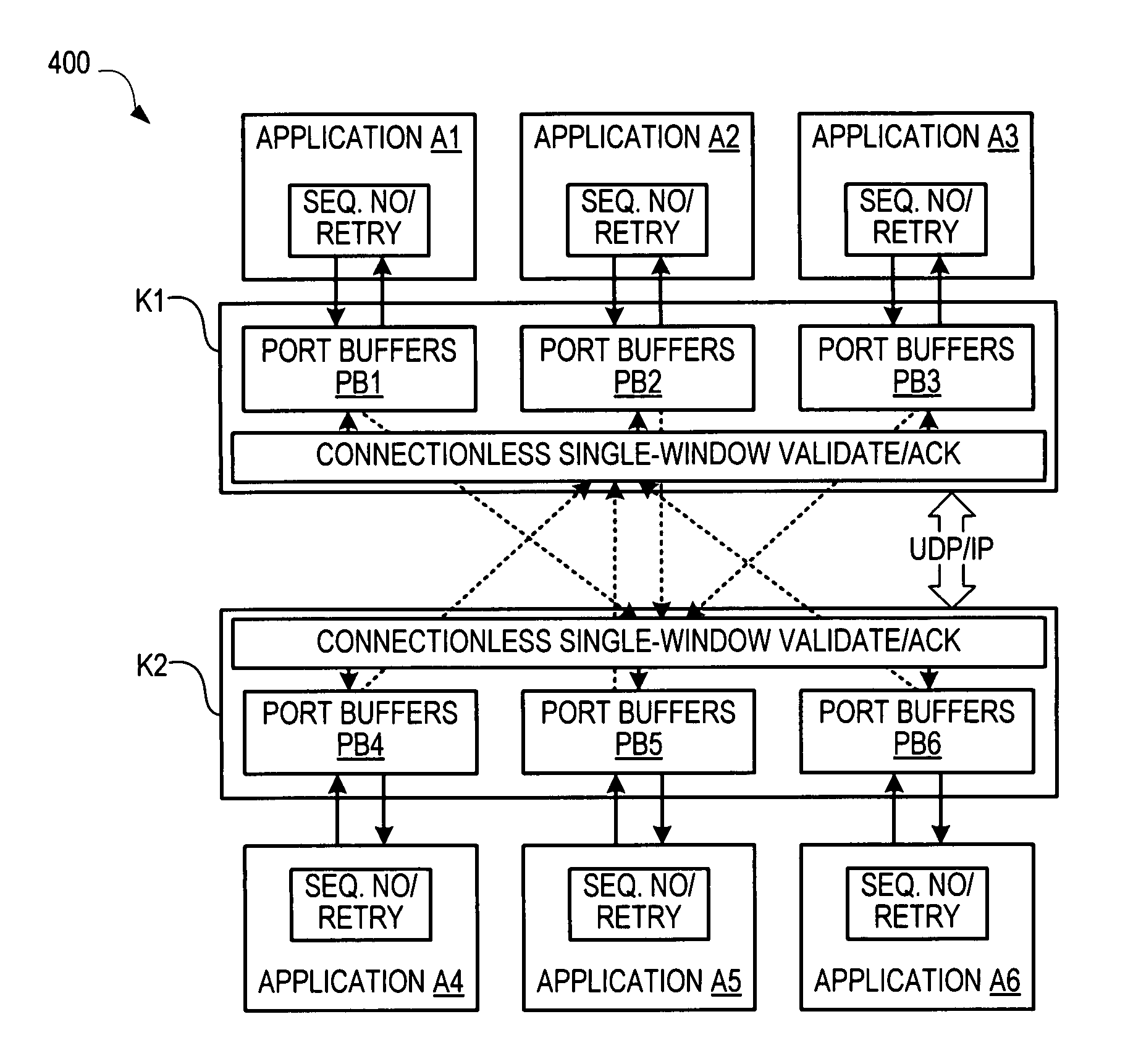
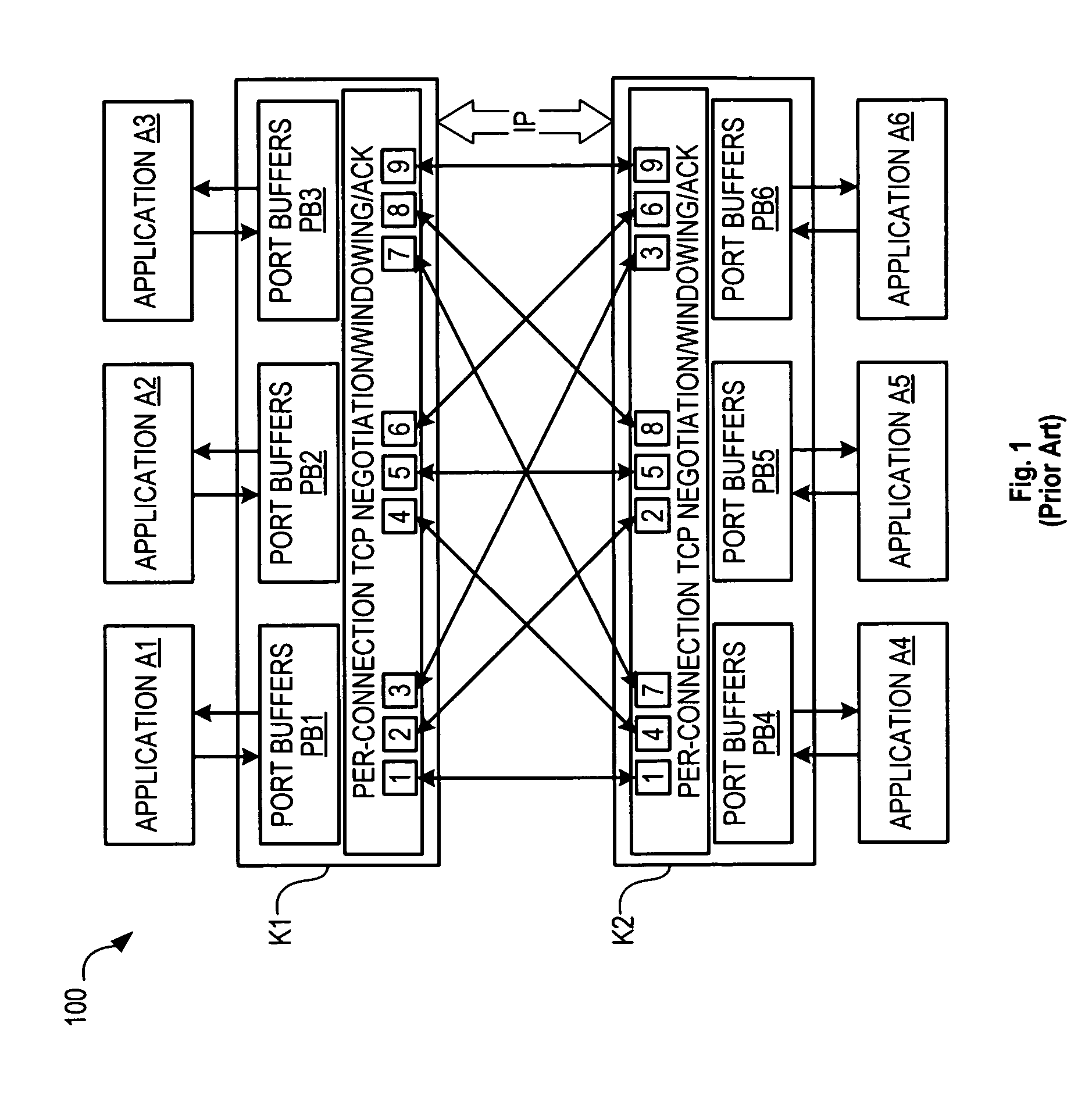
Guaranteed inter-process communication
ActiveUS8190960B1Error prevention/detection by using return channelTransmission systemsError checkingMessage processing
A multiprocessor system includes multiple processors executing multiple processes that send messages to each other. The system uses a connectionless single-window inter-process communication (IPC) protocol to avoid the high message-processing overhead of a connection-based protocol like TCP. The IPC protocol uses a central message-receive service that runs in the kernel on each processor to handle error-checking and sequence number checking and acknowledge received messages, while the single-window mechanism avoids out-of-order message reordering / buffering complexity. Since each process sending a message does not need to wait for the receiving process (which may be otherwise preoccupied or not even the focus of the receiving processor when the message is received and queued) before receiving acknowledgments, the protocol greatly reduces single-window message latency for all processes without resorting to complex connection-based multi-packet transmission windows.
Owner:DELL MARKETING CORP
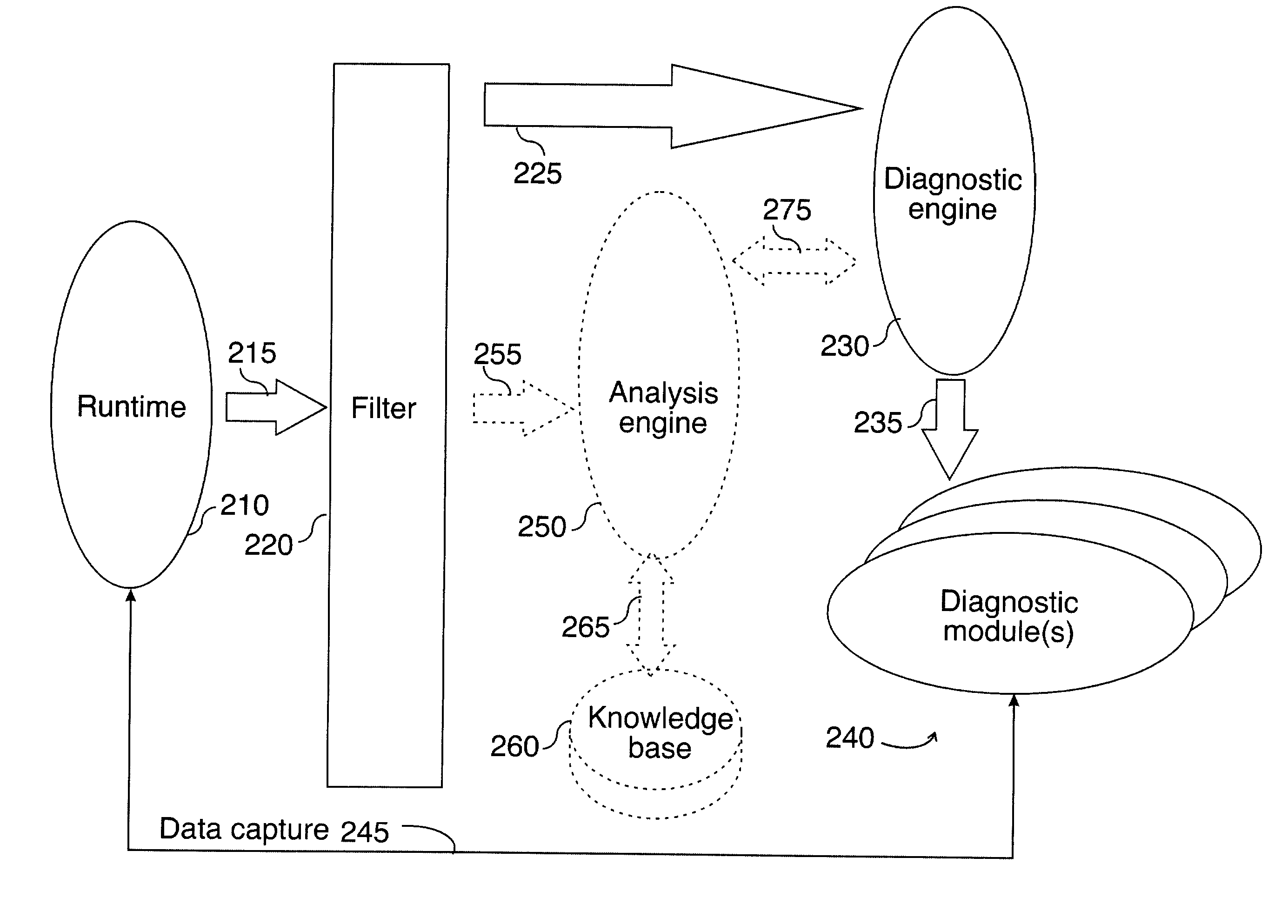
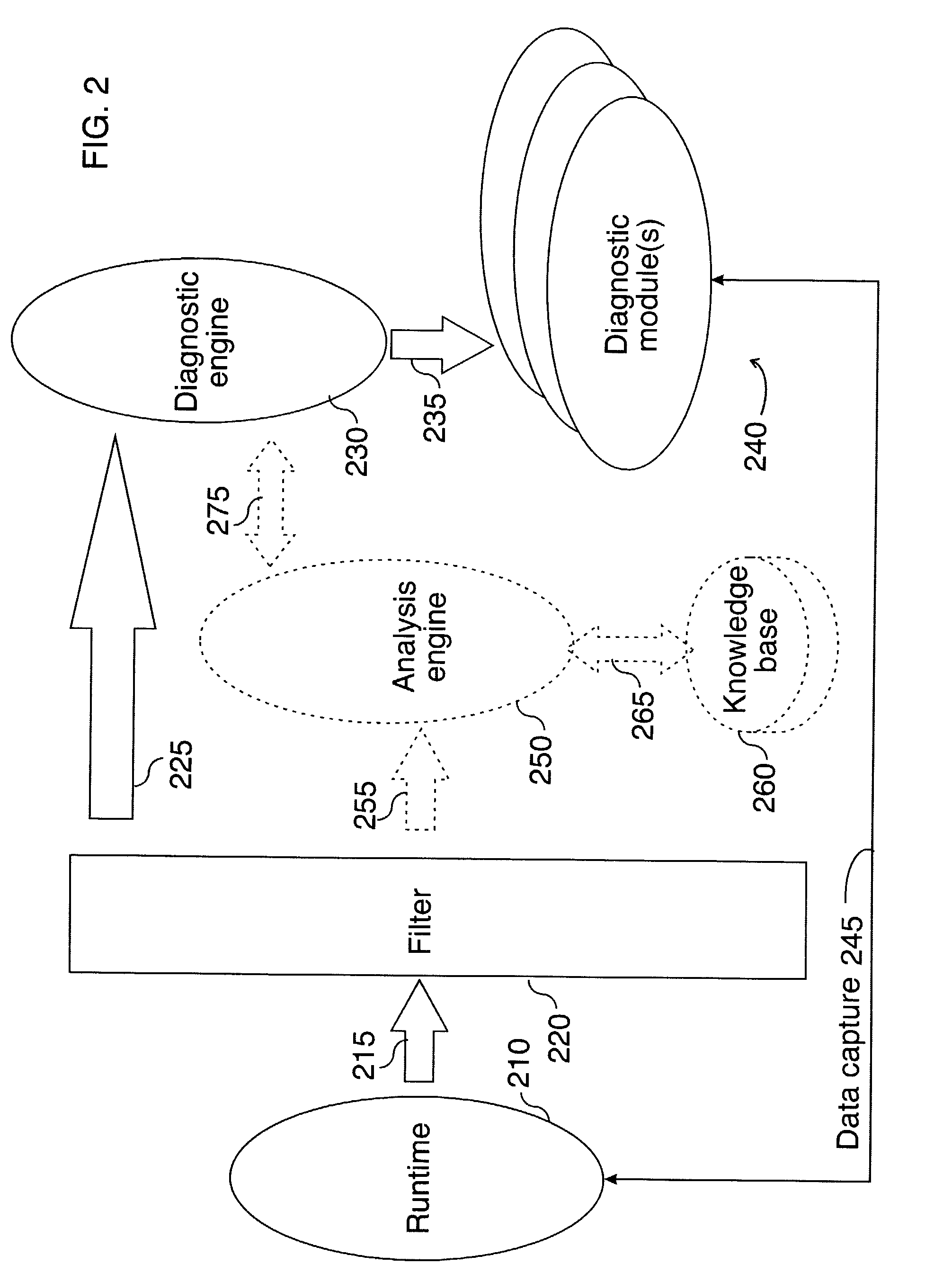
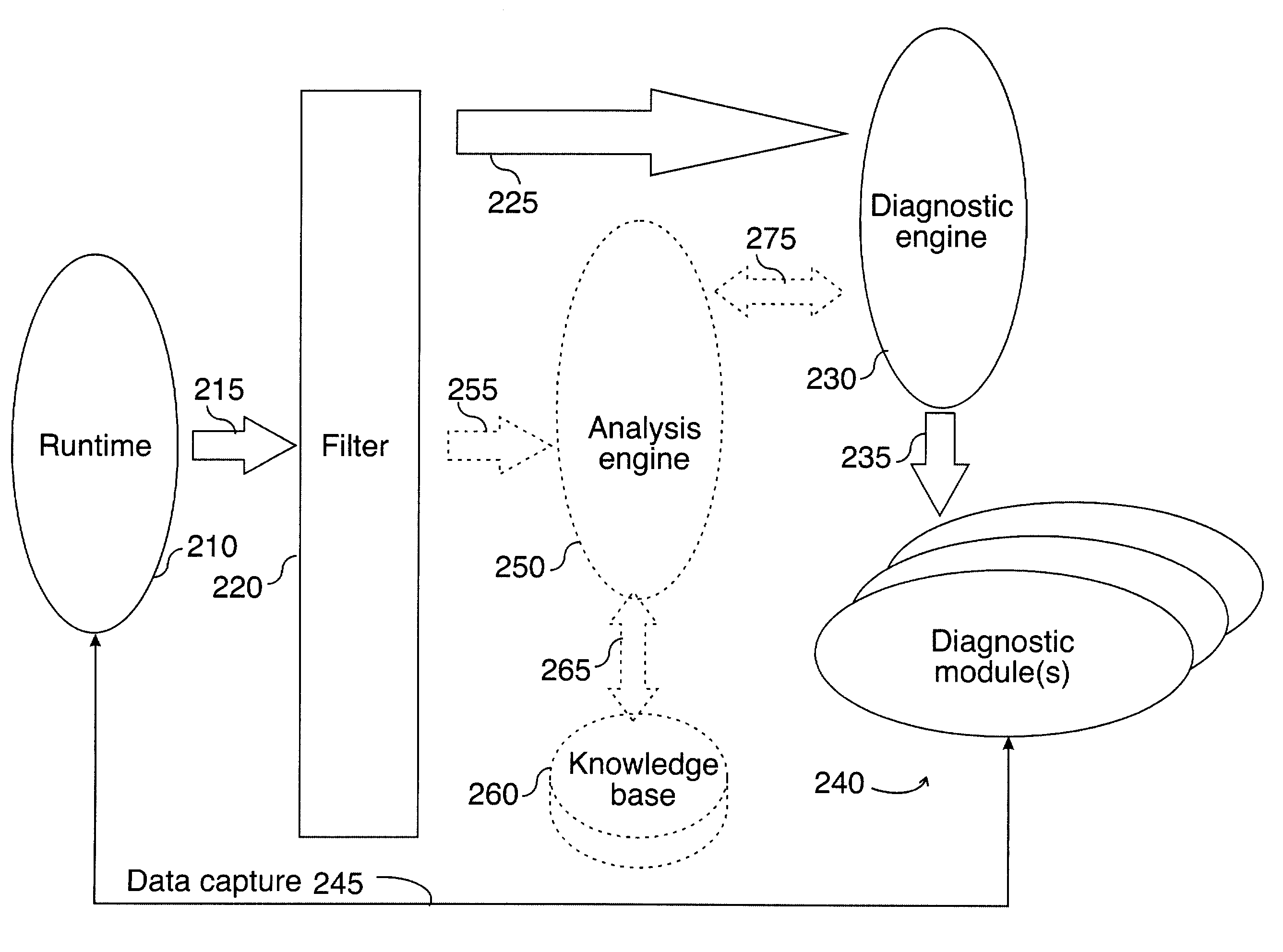
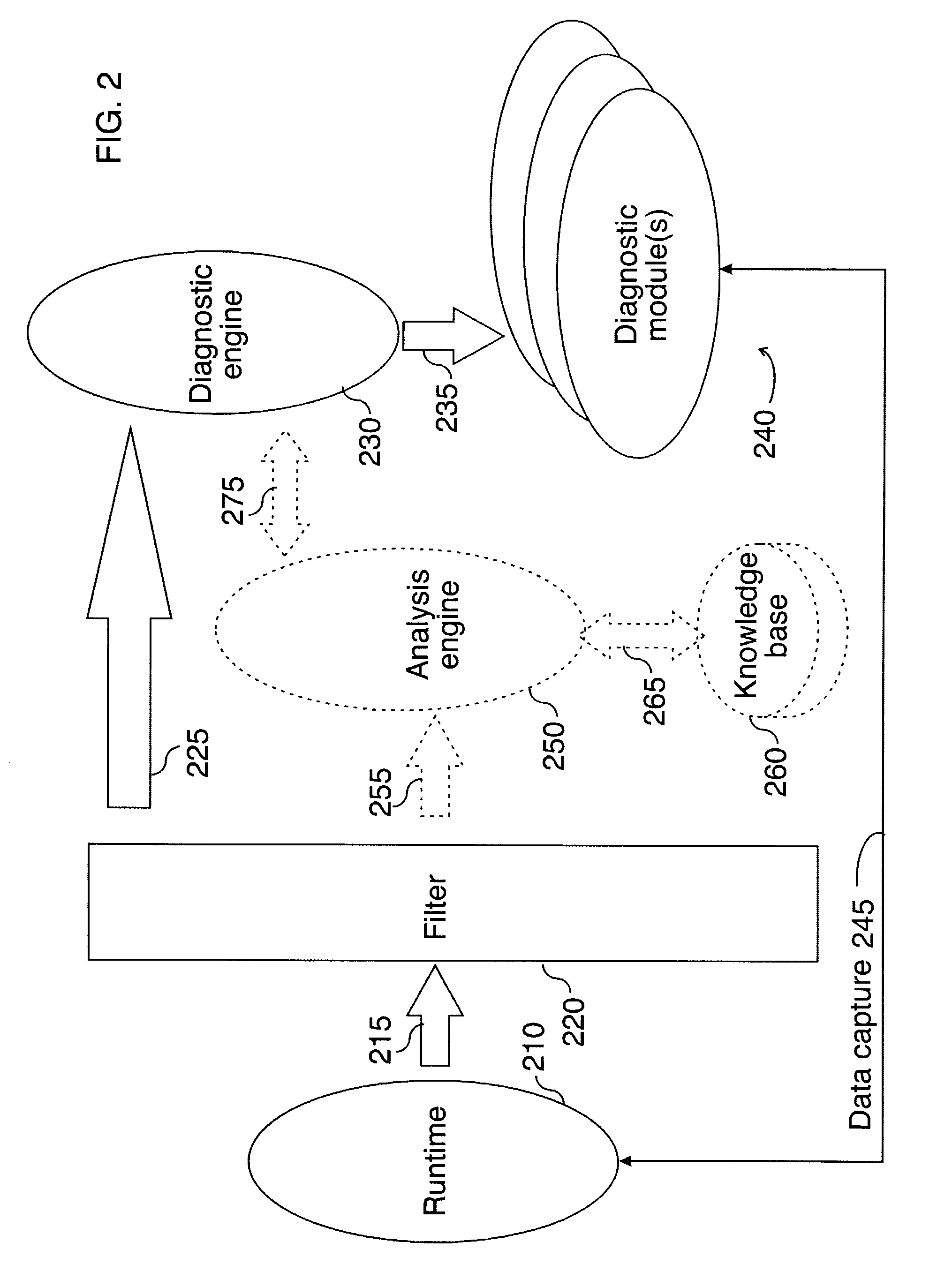
First failure data capture
InactiveUS7080287B2Digital data processing detailsSoftware testing/debuggingTreatment errorProblem solve
An example of a solution provided here comprises: selecting an incident that requires further processing, capturing data associated with said incident, outputting captured data, and outputting a description for said captured data, whereby problem-solving is promoted. Another example comprises: providing runtime features for data capture, selecting an incident that requires further processing, capturing data on a thread that encounters said incident, and outputting captured data. In some cases, such a solution might include comparing a current incident to known incidents, and if a match is found, retrieving information that is relevant to said current incident. In some cases, such a solution might include taking recovery action or corrective action in response to said incident. Methods for handling errors, systems for executing such methods, and instructions on a computer-usable medium, for executing such methods, are provided.
Owner:LINKEDIN
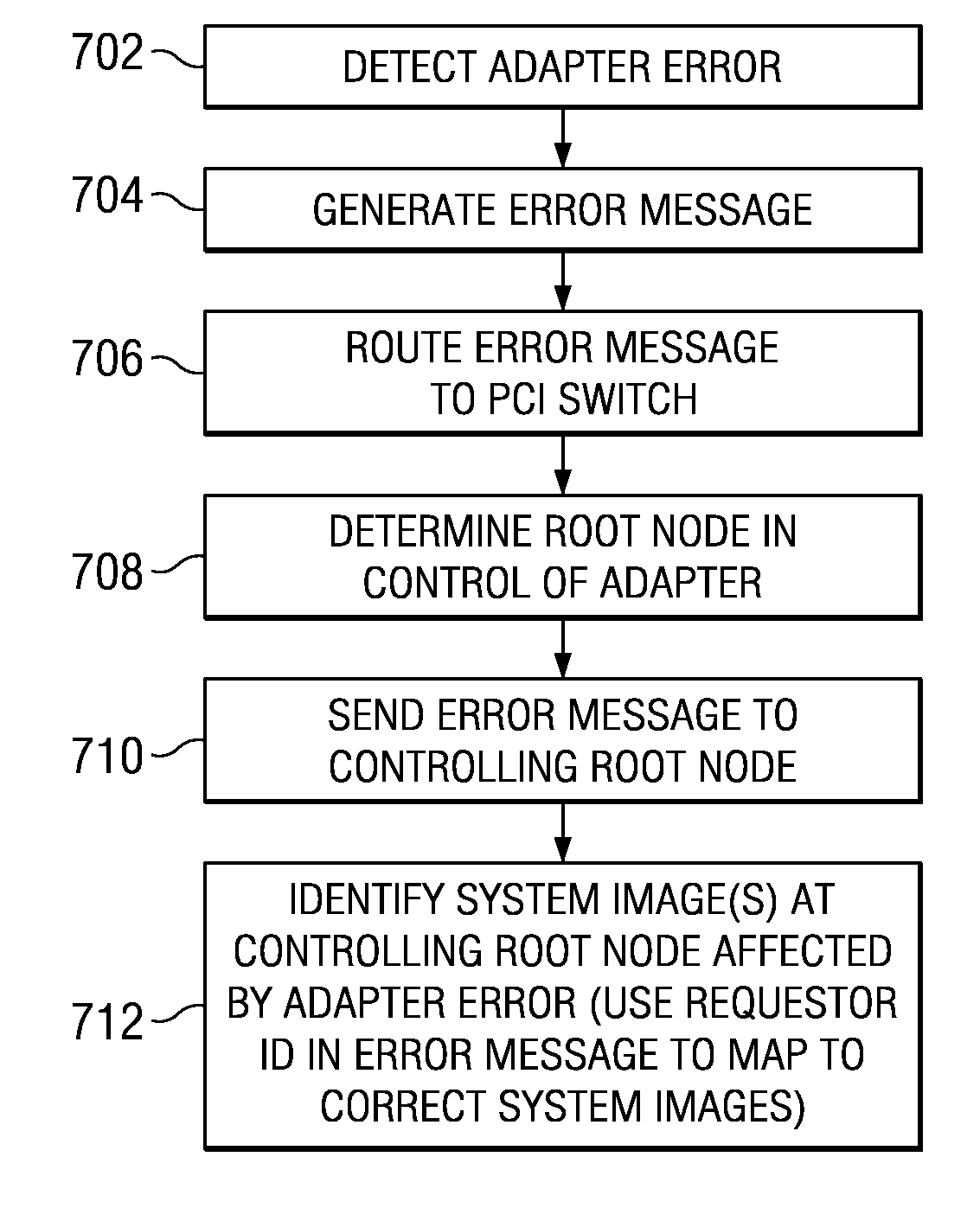
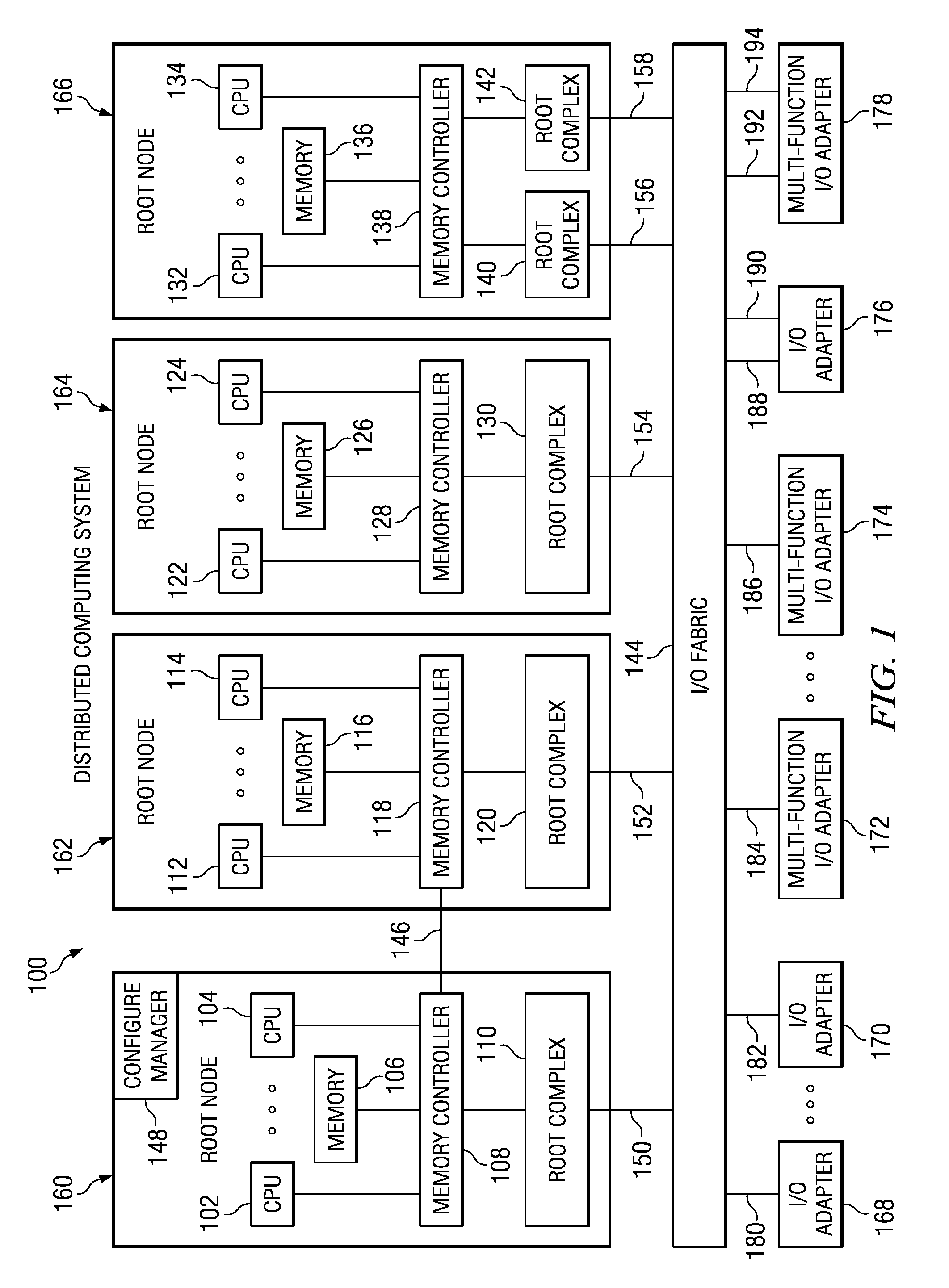
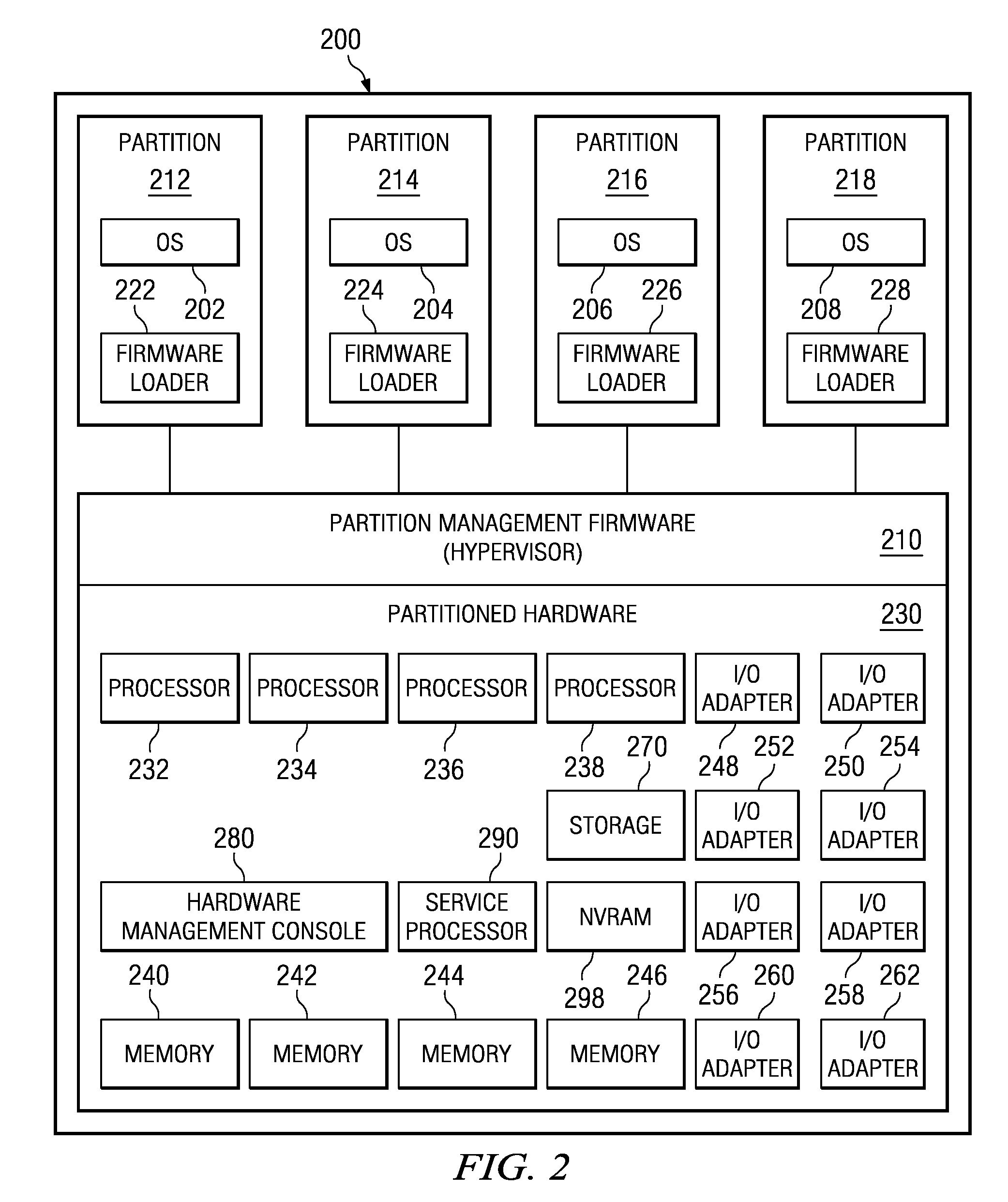
Method of Routing I/O Adapter Error Messages in a Multi-Host Environment
A method and apparatus is provided for routing error messages in a distributed computer system comprising multiple root nodes, and further comprising one or more PCI switches and one or more I / O adapters, wherein each root node includes one or more system images. In one useful embodiment, a method is provided for routing I / O error messages to root nodes respectively associated with the errors contained in the messages. The method includes detecting occurrence of an error at a specified one of the adapters, wherein the error affects one of the system images, and generating an error message at the specified adapter. The method further comprises routing the error message from the specified adapter to the particular root node that includes the affected system image. The error message is then selectively processed at the particular root node, in order to identify the affected system image. Usefully, the step of routing the error message includes using a bus / device / function number associated with the error, together with a routing table located in one of the PCI switches, to route the error message to the correct root node and system image.
Owner:LENOVO GLOBAL TECH INT LTD
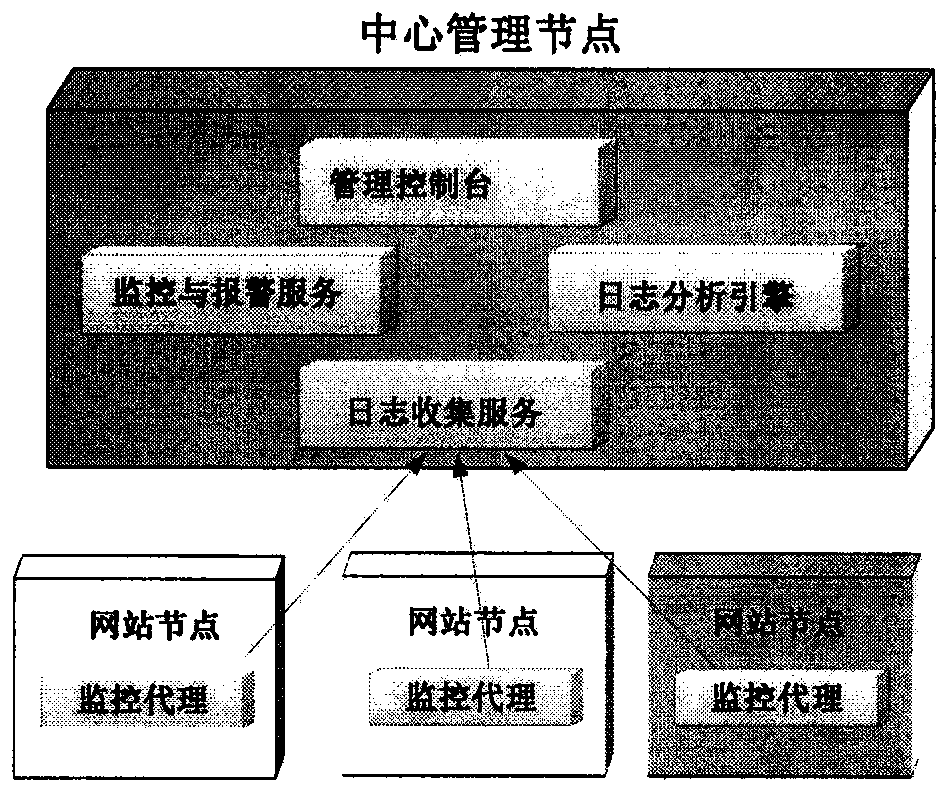
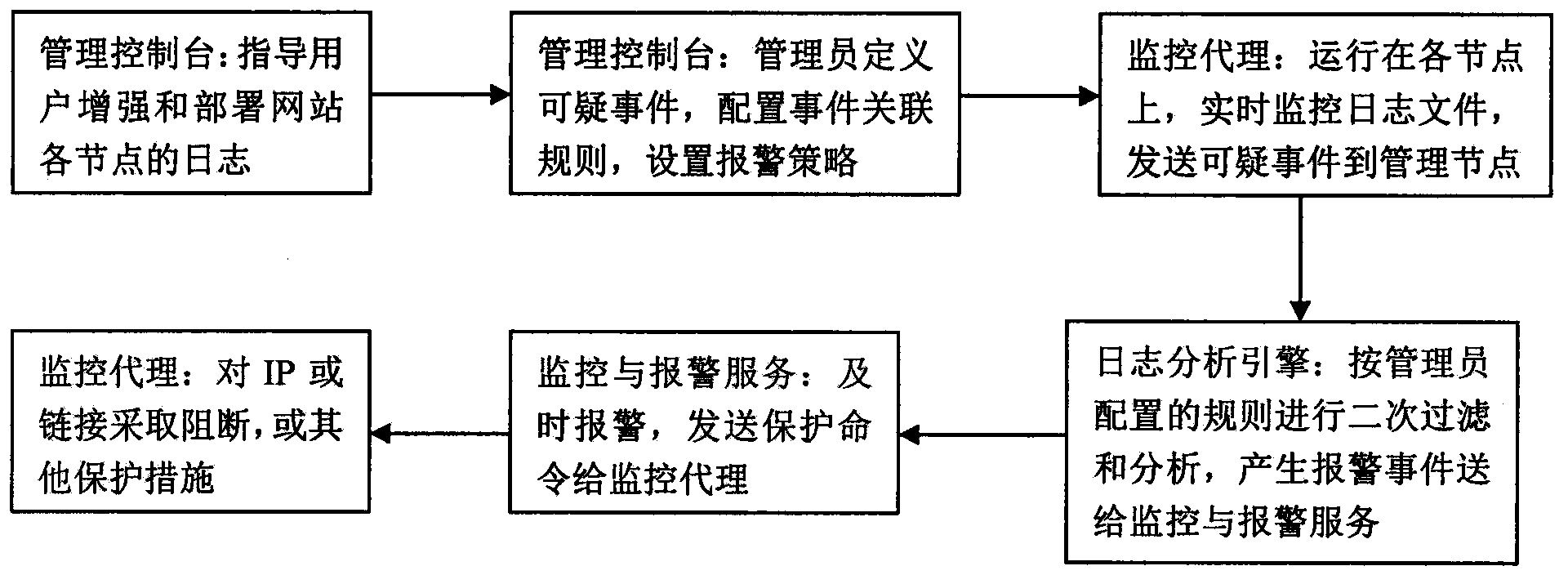
Website security monitoring and alarming system based on log analysis and firewall security matrixes
ActiveCN104144063ANo illegal accessEfficient discoveryData switching networksTreatment errorSecurity monitoring
The invention relates to a website security monitoring and alarming system based on log analysis and firewall security matrixes. The website security monitoring and alarming system aims at finding and stopping various security attacks on the website in time and is based on two work items which a website security administrator mostly depends on during actual security operation and maintenance. Log monitoring is characterized in that the known and unknown attacks are automatically found by conducting keyword / regular expression filtering on access of Apache / Tomcat / IIS or error logs or other environment logs, and meanwhile service processing errors caused by the hacker attacks in the early period are found in time through log customization in website service codes. The website security monitoring and alarming system is characterized in that the firewall security matrixes are defined, then the effectiveness of the firewall security matrixes is verified with the direct or indirect network connectivity detecting technology, and alarming is triggered once the firewall security matrixes are damaged. The website security monitoring and alarming system provides a simple and effective customization mode for the administrator, and sensing capacity for any attack or any suspicious action can be continuously improved.
Owner:朱烨 +1
Error analysis fed from a knowledge base
An example of a solution provided here comprises analyzing an incident, responding to said incident, and customizing the response, based on the result of the analysis. Another example of a solution comprises accessing a knowledge base, comparing a current incident to known incidents in said knowledge base, and if a match is found, retrieving information from said knowledge base, said information being relevant to the current incident. Methods for handling errors, systems for executing such methods, and instructions on a computer-usable medium, for executing such methods, are provided.
Owner:IBM CORP
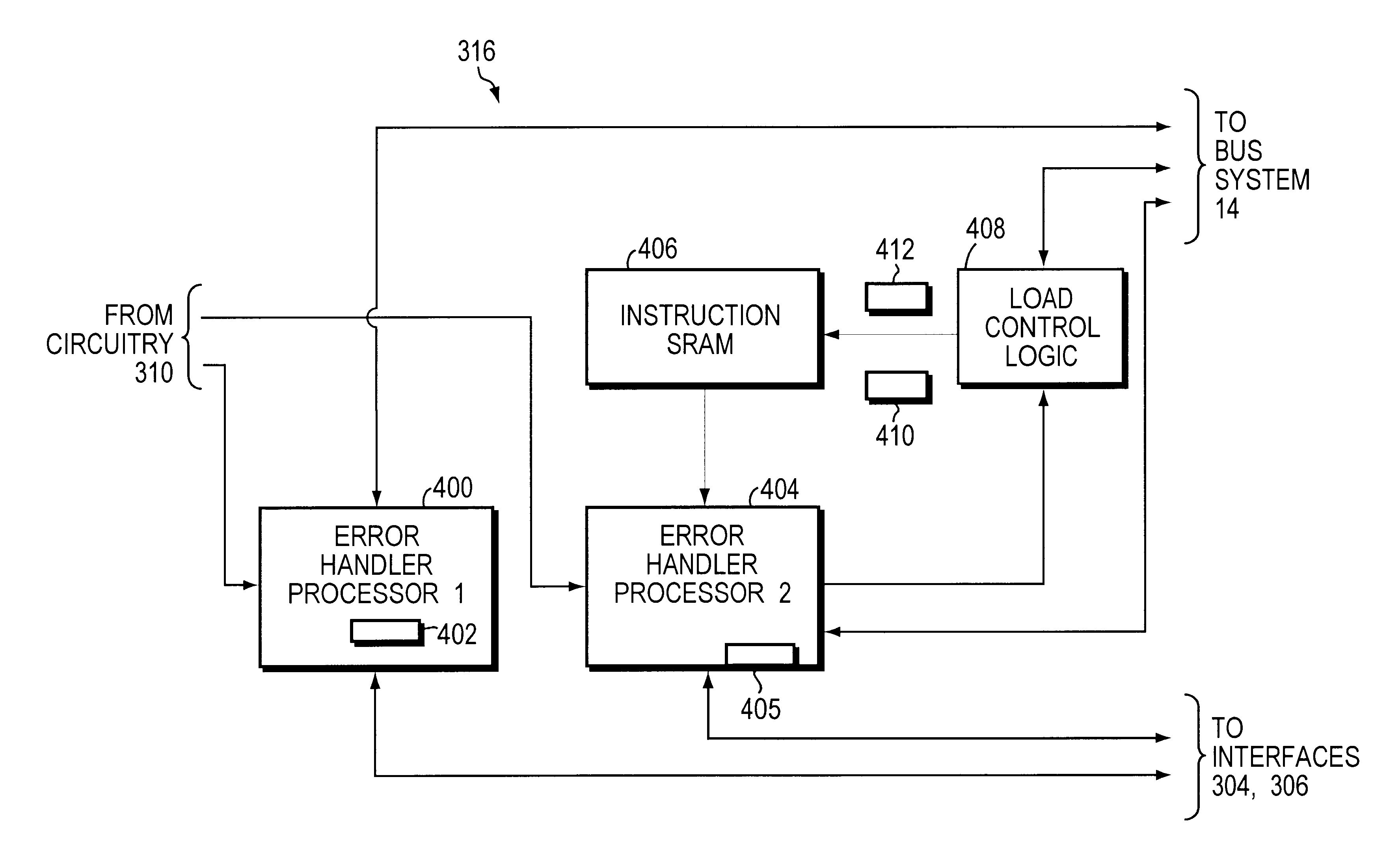
Error condition handling
InactiveUS6804794B1Good flexibilityAccurate processingNon-redundant fault processingError processingMemory controller
In one embodiment of the present invention, a memory controller is provided that includes both a first processor and a second processor. If a memory device controlled by the controller indicates to the controller that an error condition exists in the device, either the first processor or the second processor is selected to handle the error condition. If the first processor is selected to handle the error condition, the first processor handles the error condition according to one or more statically preprogrammed error handling routines. Conversely, if the second processor is selected to handle the error condition, the second processor handles the error condition according to one or more dynamically programmable error handling routines.
Owner:EMC IP HLDG CO LLC
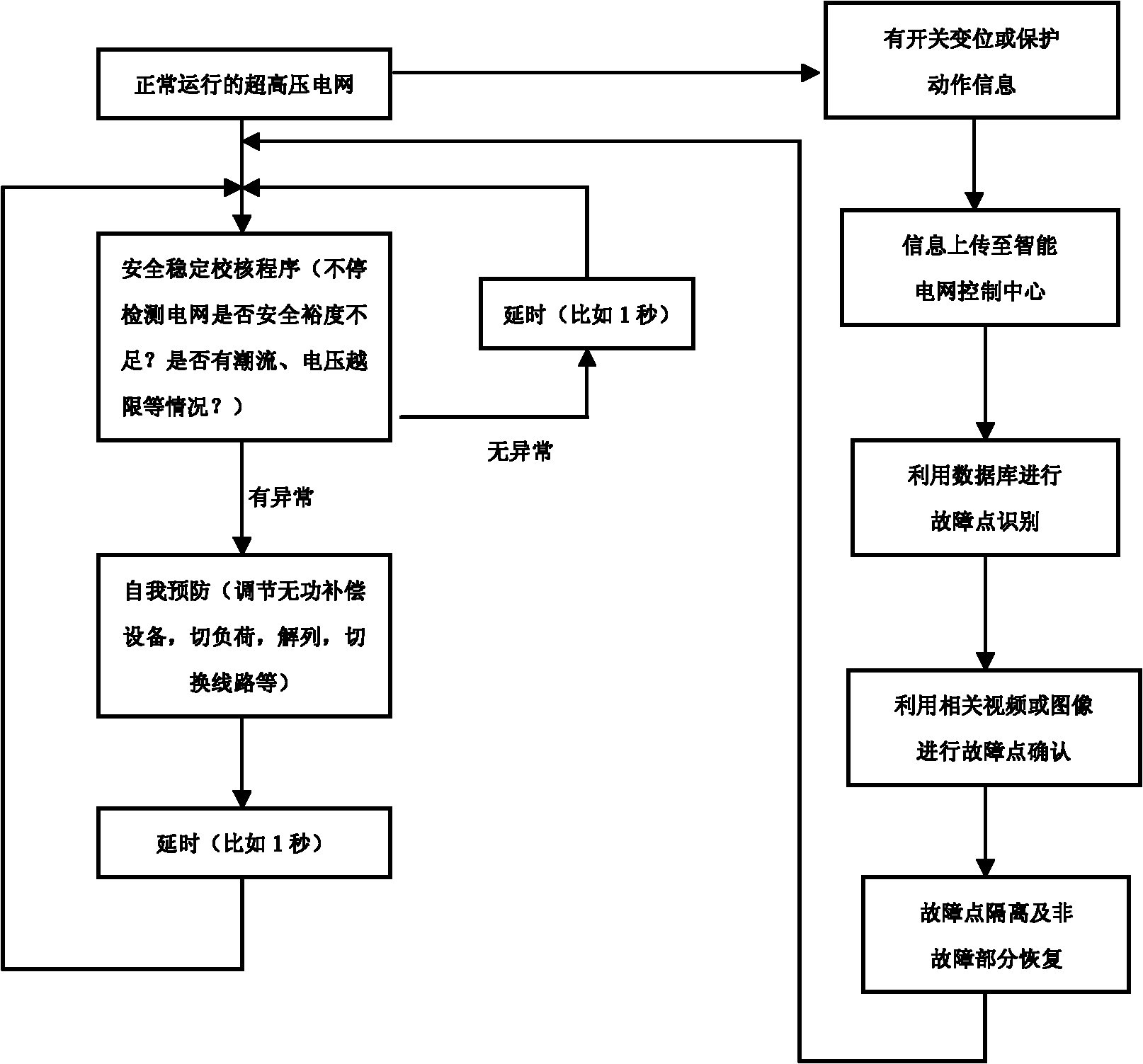
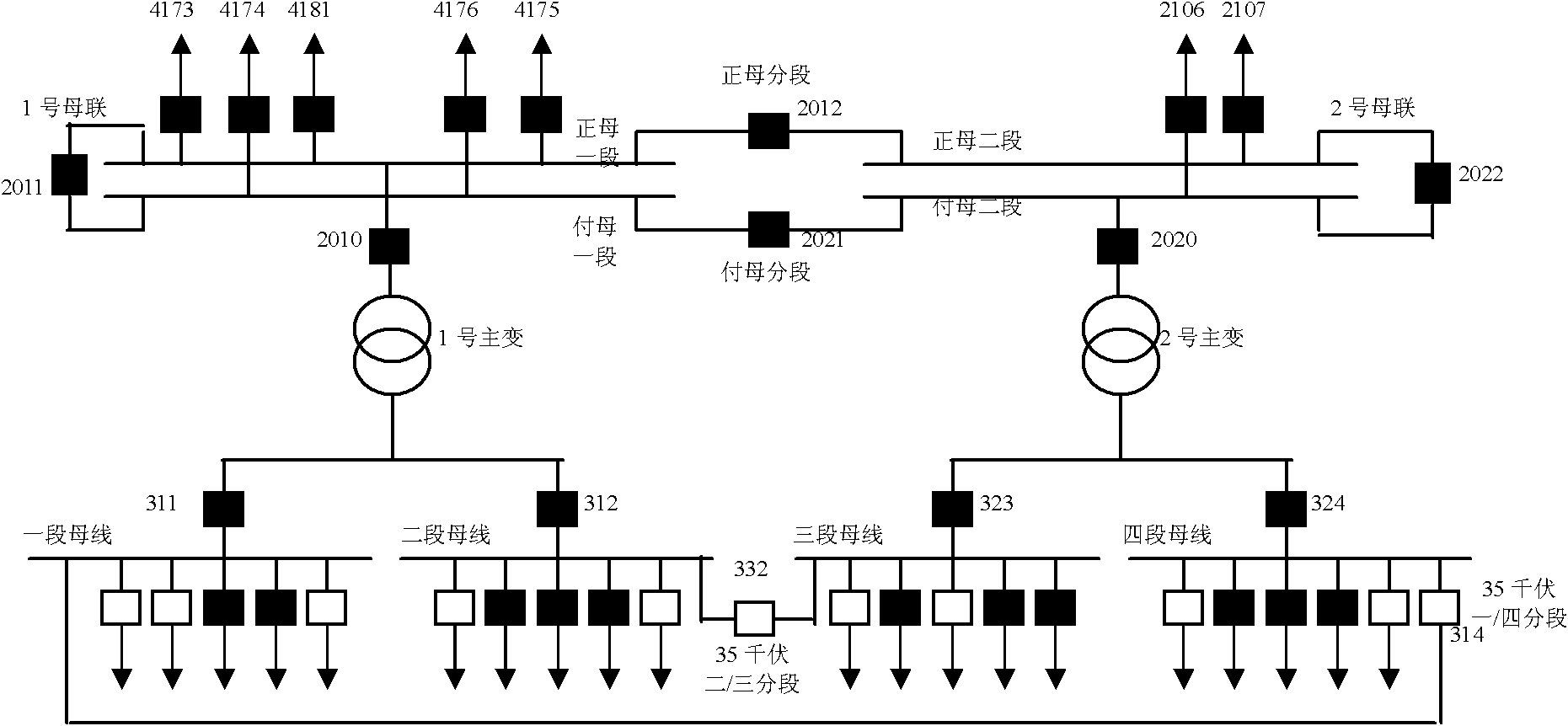
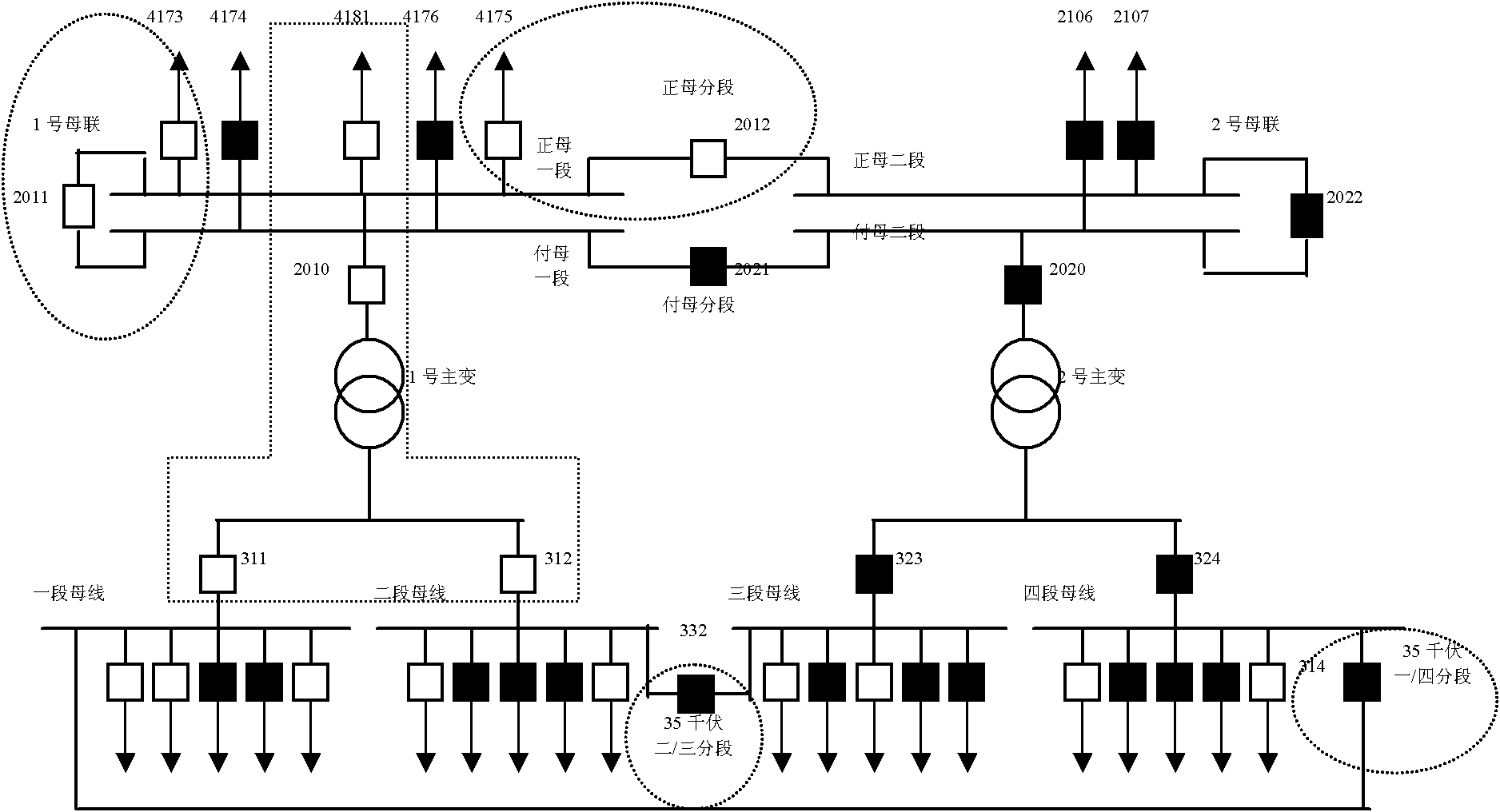
Intelligent self-healing monitoring method of extra high voltage power network
ActiveCN101944777ASecurity and Stability Additional ControlSolve self-healing problemsCircuit arrangementsSelf-healingFault coverage
The invention discloses an intelligent self-healing monitoring method of extra high voltage power network, belonging to the field of electric transformer and distribution. The invention uses the self-healing monitoring method that the power network control center collects the fault information, estimates the fault point according to the action information, judges the fault point according to the visualization technology, and starts the automatic recovery project. The method solves the self-healing problem of extra high voltage power network, performs the prevention and correction control, andmakes the dispose strategy based on the information quickly, thereby avoiding the cascade trip caused by load transfer, realizing the safe and stable addition control of the power network from the entire network perspective, and replenishing the disadvantages of area and in situ emergency control measure. Aiming at the specific characteristics in the aspects of running, dispatching and managing of the extra high voltage power network, the method can collect and use the information more comprehensive, and make the dispose strategy quickly to earn the time for the avoiding of cascade trip caused by load transfer, thereby avoiding the further enlargement of fault coverage due to wrong dispose, and solving the self-healing problem of the extra high voltage power network.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
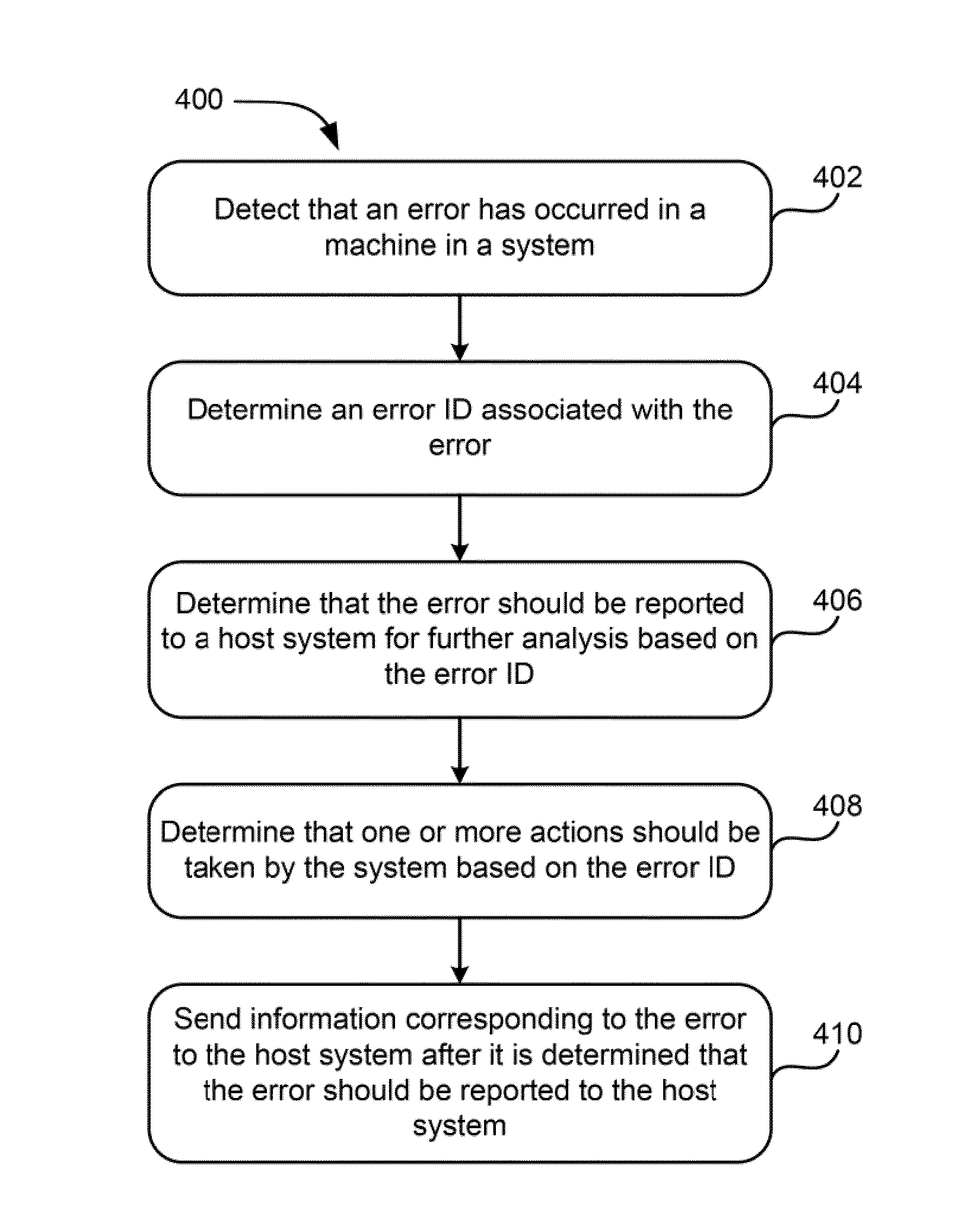
Systems for agile error determination and reporting and methods thereof
According to one embodiment, a method for handling errors includes detecting that an error has occurred in a machine in a system, determining an error ID associated with the error, determining that the error should be reported to a host system for further analysis based on the error ID, determining that one or more actions should be taken by the system based on the error ID, and sending information corresponding to the error to the host system after it is determined that the error should be reported to the host system. In another embodiment, a system includes a processor and logic for performing the method. According to another embodiment, a computer program product includes a computer readable storage medium having computer readable code embodied therewith for performing the method. Other methods, systems, and computer program products are also described according to more embodiments.
Owner:IBM CORP
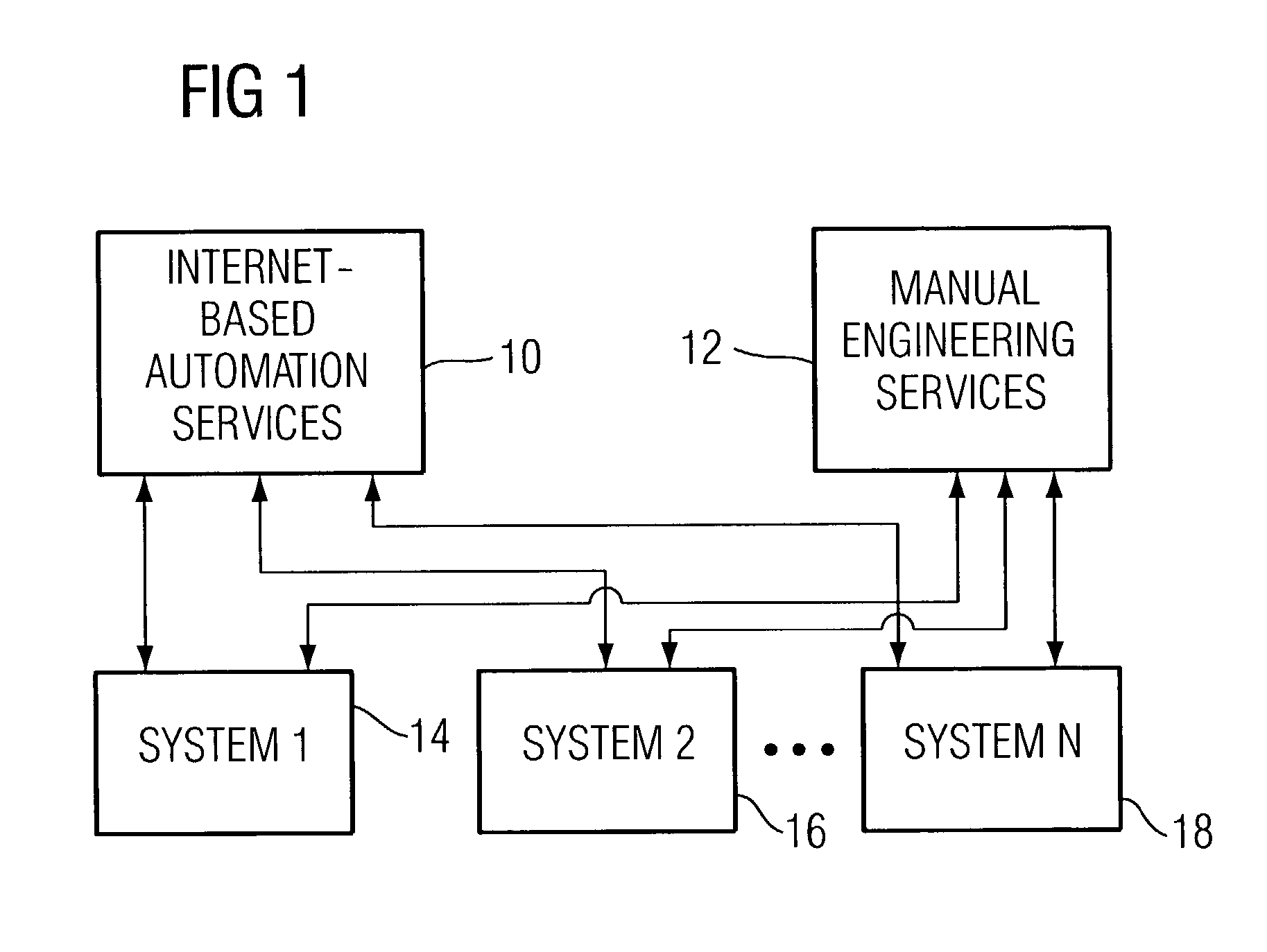
Active resource control system method & apparatus
Active resource control of added functionality in a numerical control process having at least one resource is provided. It can occur during run-time of the numerical control process, that an added functionality that uses at least a portion of the resource. On-line checking of the added functionality detects during run time whether the added functionality causes the numerical control process to reach a resource limit. Error handling handles errors upon reaching a resource limit. Off-line checking detects off-line, before the run time of the numerical control process, whether the added functionality causes the numerical control process to reach a resource limit of the resource. Multiple layers are provided that check at multiple layers of the numerical control process whether the added functionality causes the numerical control process to reach a resource limit of the resource. A flexible response to resource limit errors based on a degree of importance of the added functionality is provided.
Owner:SIEMENS AG
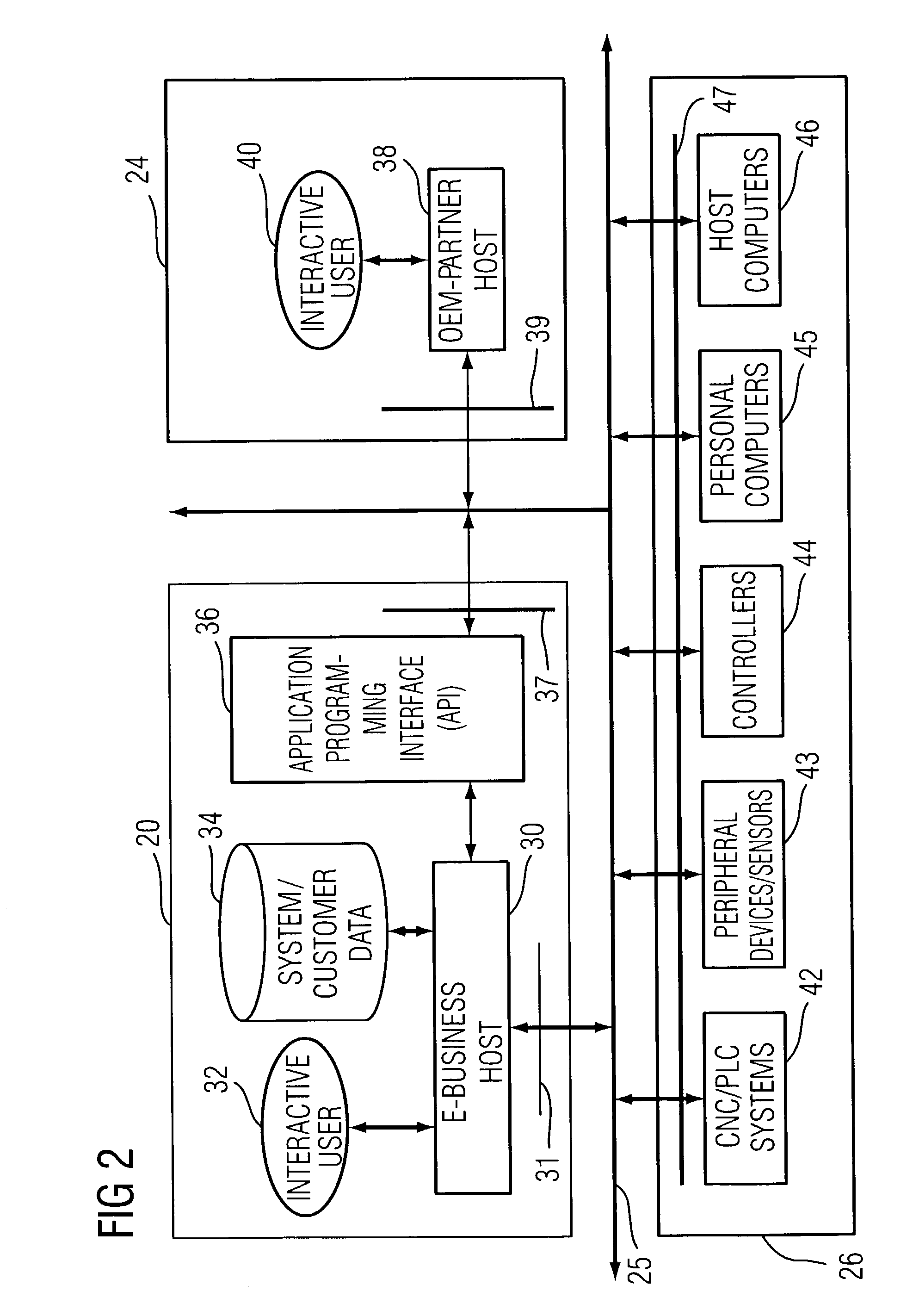
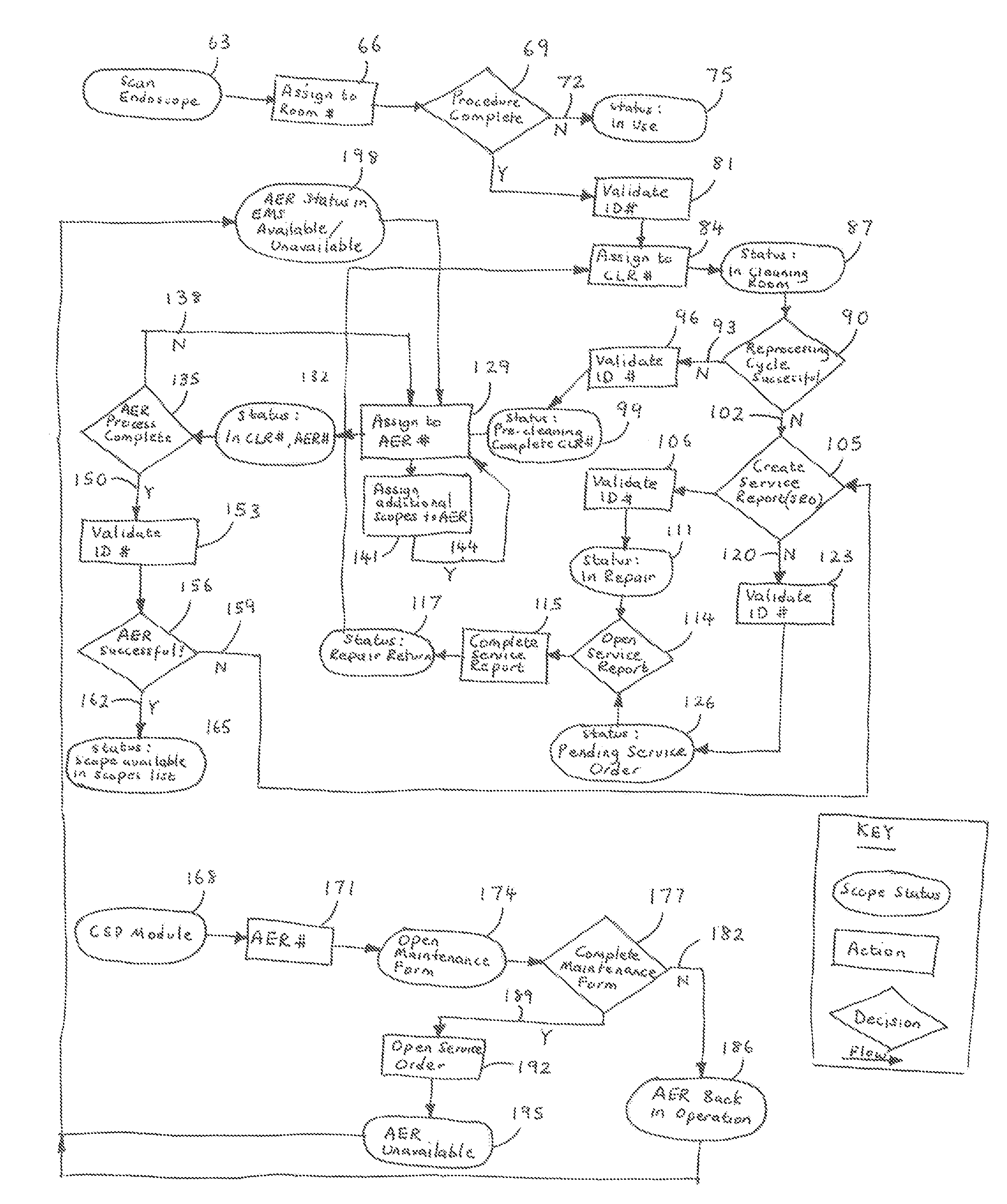
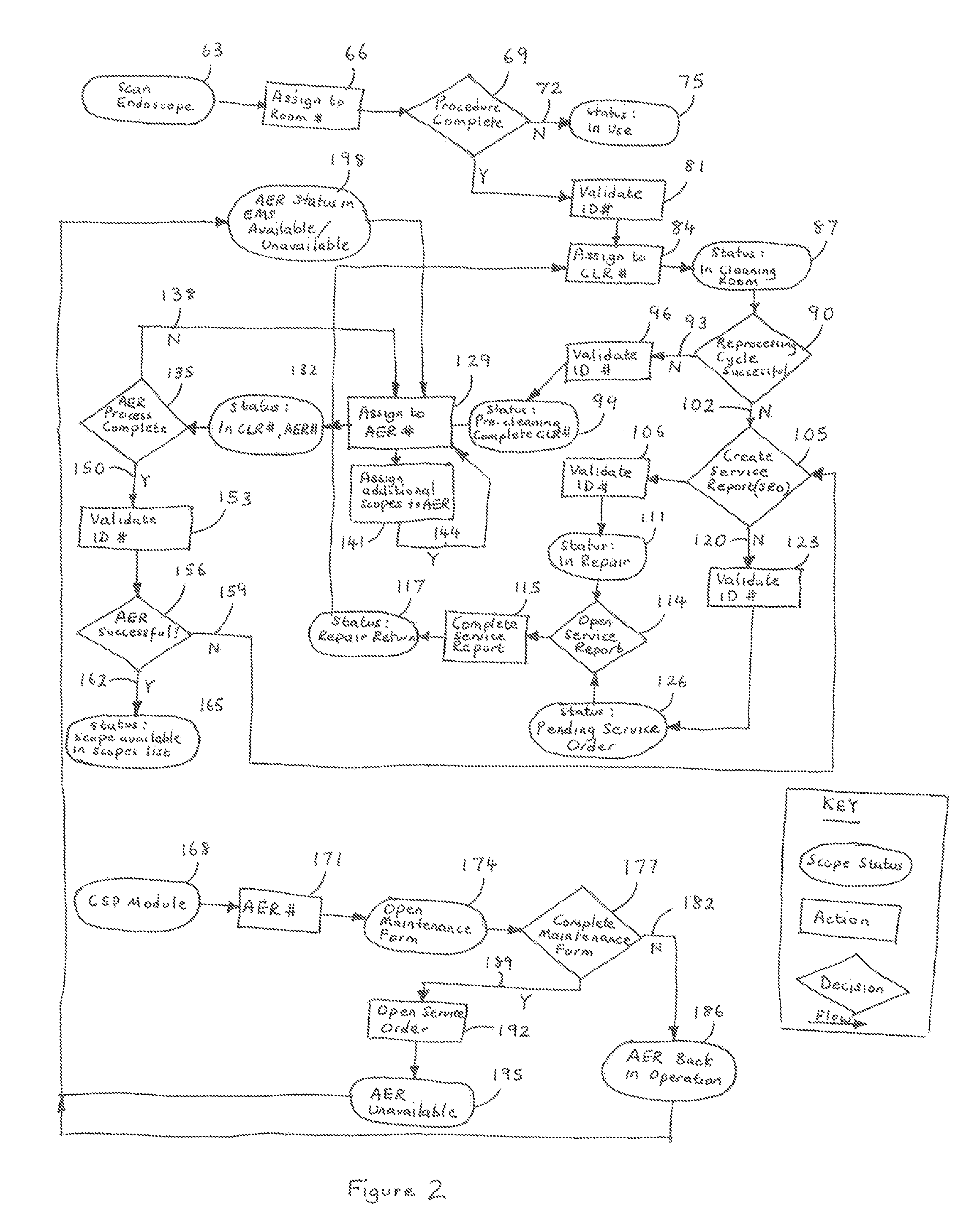
Endoscope management system
InactiveUS20090055215A1Highly user-friendly in operationEasy to set upData processing applicationsSurgical instrument detailsProgram EfficiencyDisplay device
A web-based endoscope management system and method for managing, scheduling and tracking in real-time the processing of endoscopy equipment in a single site or across multiple sites. The system allows various useful information relating to the managed endoscopy equipment and its processing history (such as equipment status, equipment movement, equipment repair history, cost and procedural efficiencies, what individuals have processed or come into contact with the equipment) to be tracked and analyzed. The system incorporates a user display and prompt to assist users in following the proper processing and cleaning protocols (preparation, pre-cleaning, automated reprocessing, repair, etc.) for the equipment. The system uses a colour-coded display so that pertinent information can be seen at a glance. This system is used in conjunction with a suitable colour-coded labeling scheme to reduce the possibility that users will process the wrong equipment or improperly store it.
Owner:ENDOLOGISTICS
Terminal with corrective maintenance in accordance with selected mode
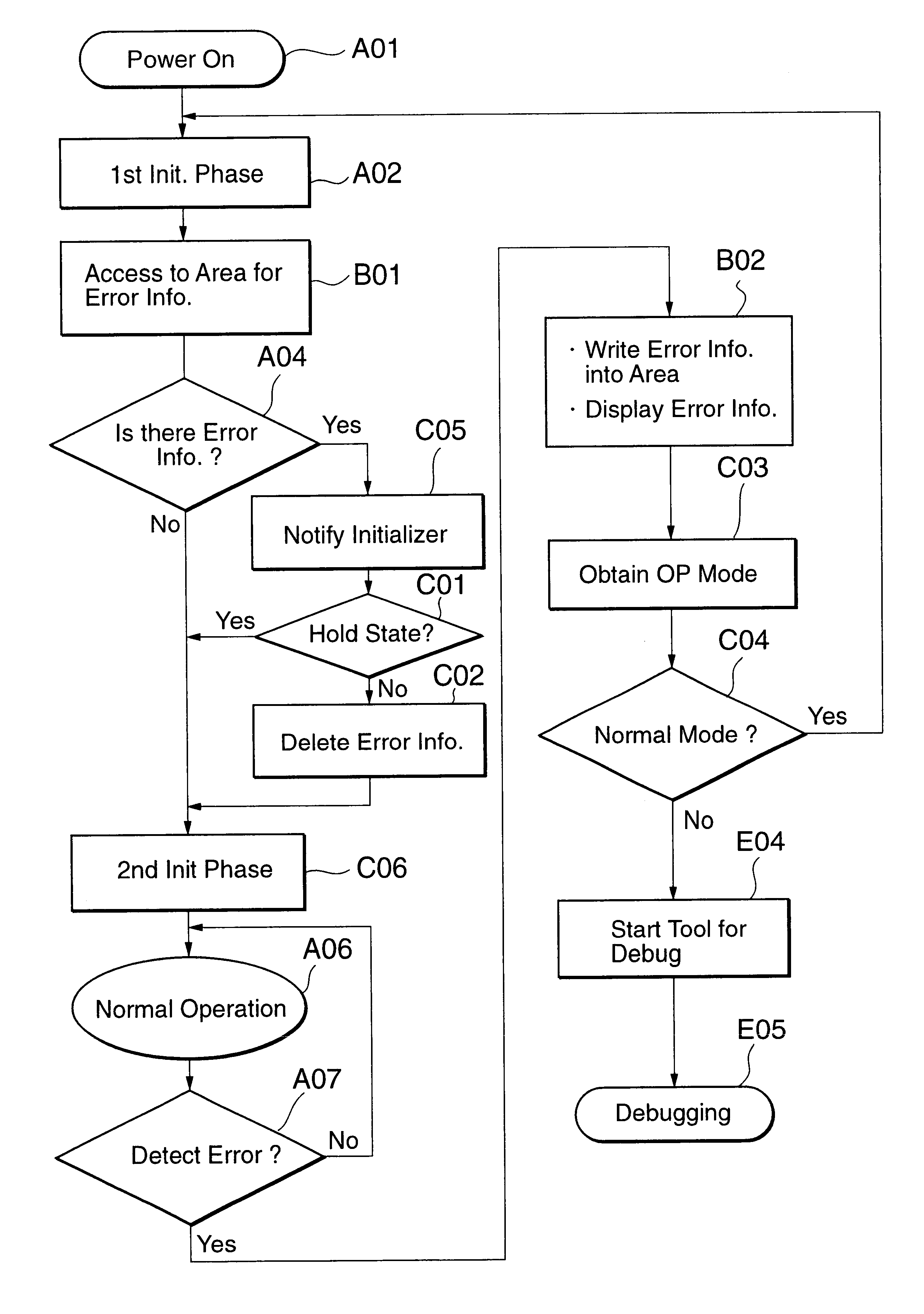
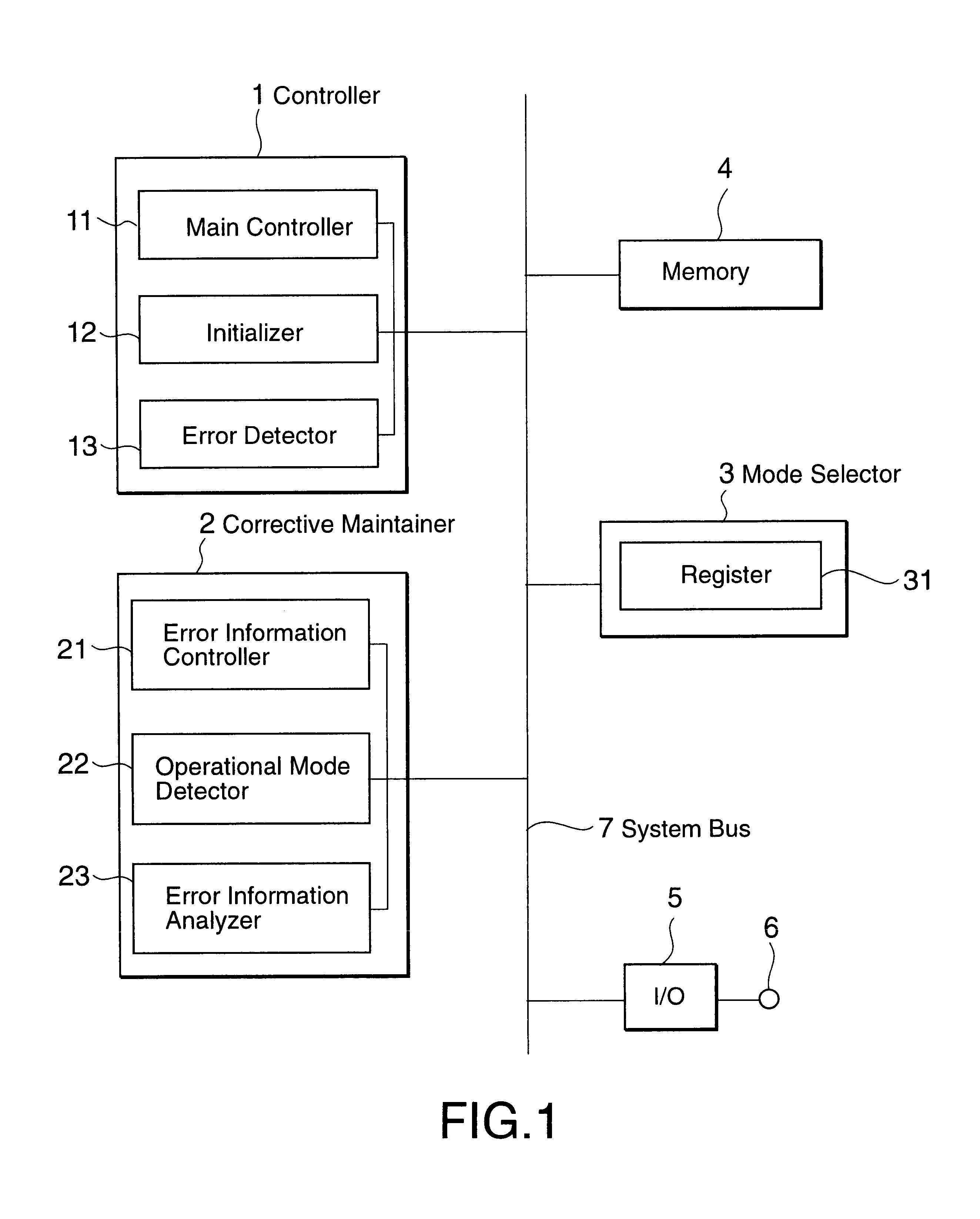
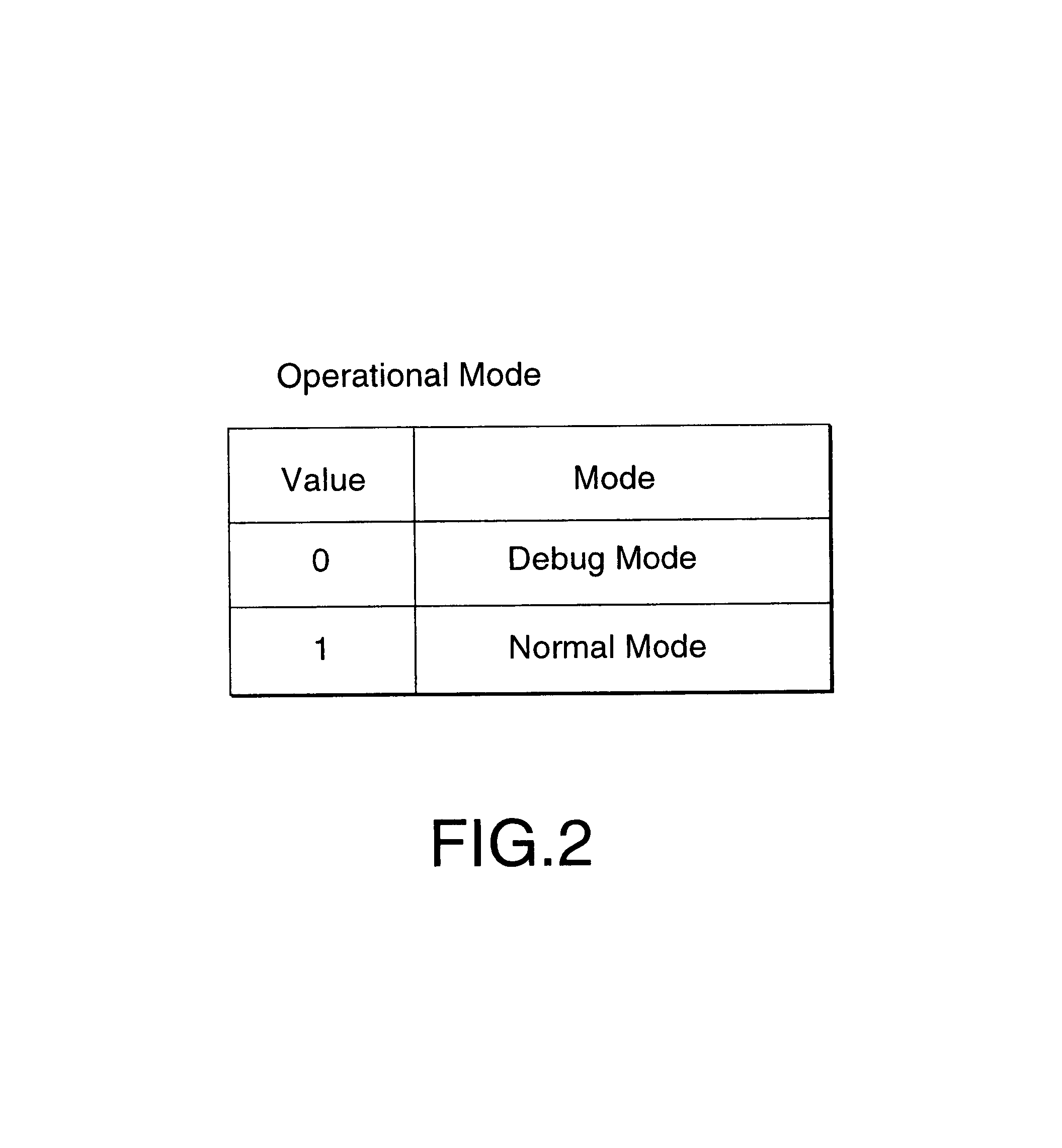
InactiveUS6868510B1Easy to handleHardware monitoringNon-redundant fault processingNormal modeEngineering
The terminal deals effectively with an error occurrence in accordance with a selected one of modes that comprise a normal mode and a debug mode. The terminal comprises a mode information holder, an error detector, a mode judge unit and a initializer. The mode information holder holds mode information that indicates which mode is the selected mode. For example, the holding of the mode information is carried out ahead of supplying power to the terminal. When an error occurs in the terminal, the error detector detects the error. Then the mode judge unit judges which mode is the selected mode, by referring to the mode information so as to produce an initialization request if the normal mode is the selected mode. The initializer initializes the terminal in response to the initialization request. On the other hand, the mode judge unit does not produce the initialization request if the debug mode is the selected mode. Accordingly, the initializer does not initialize the terminal so that the terminal continues to malfunction from the error.
Owner:NEC CORP
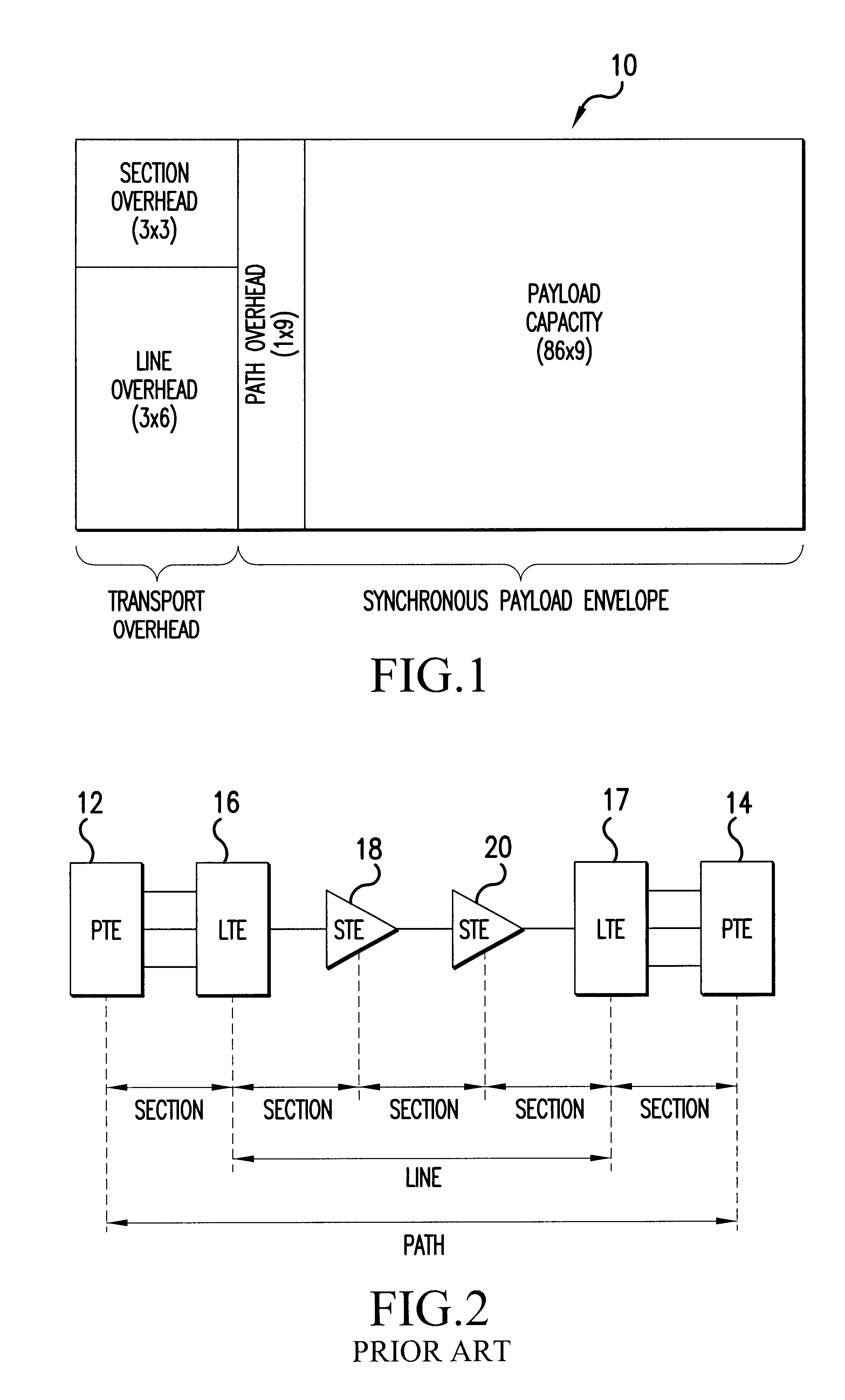
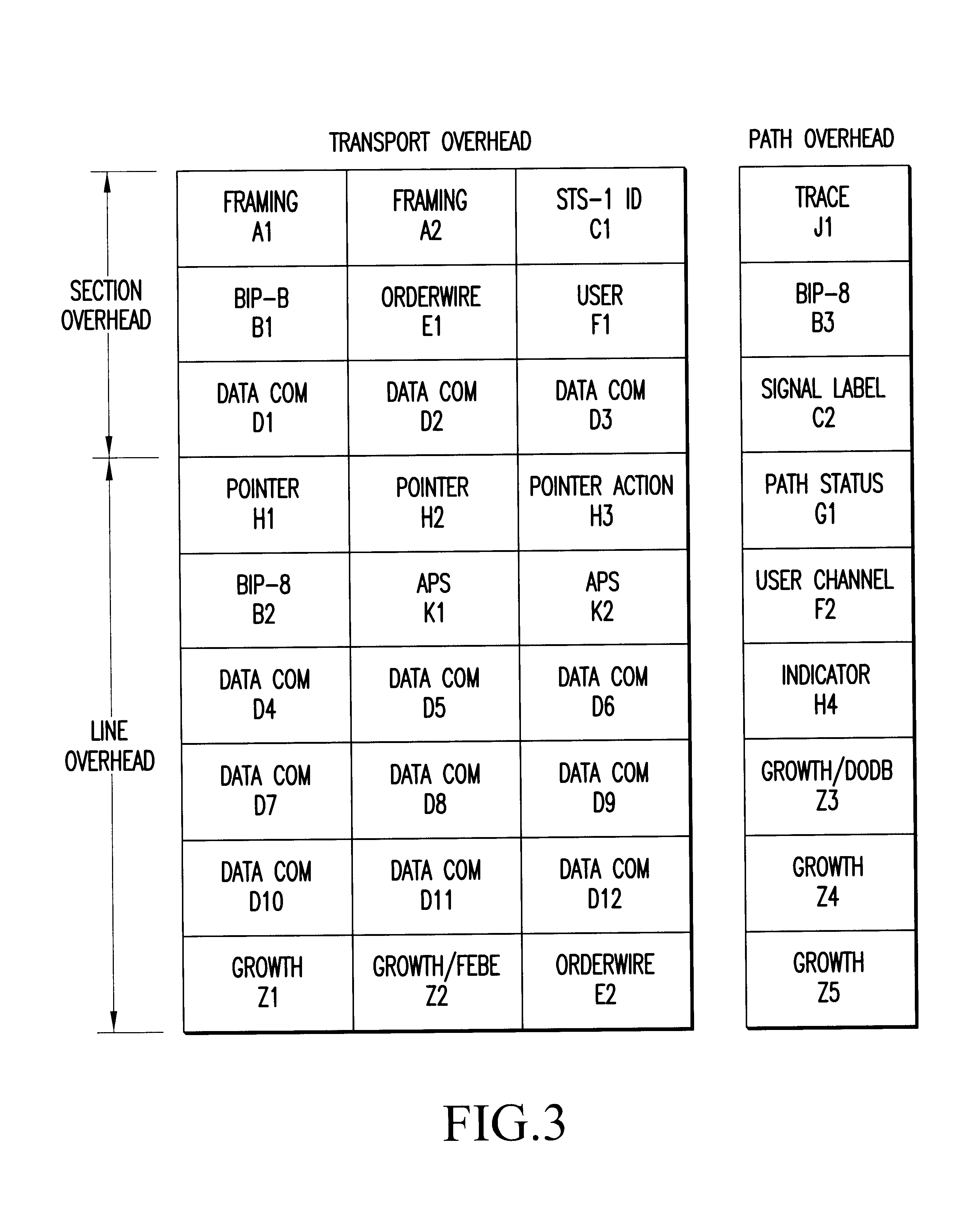
Semi-transparent time division multiplexer/demultiplexer
InactiveUS6870860B1TransparencyTime-division multiplexSynchronisation signal speed/phase controlHigh rateMultiplexer
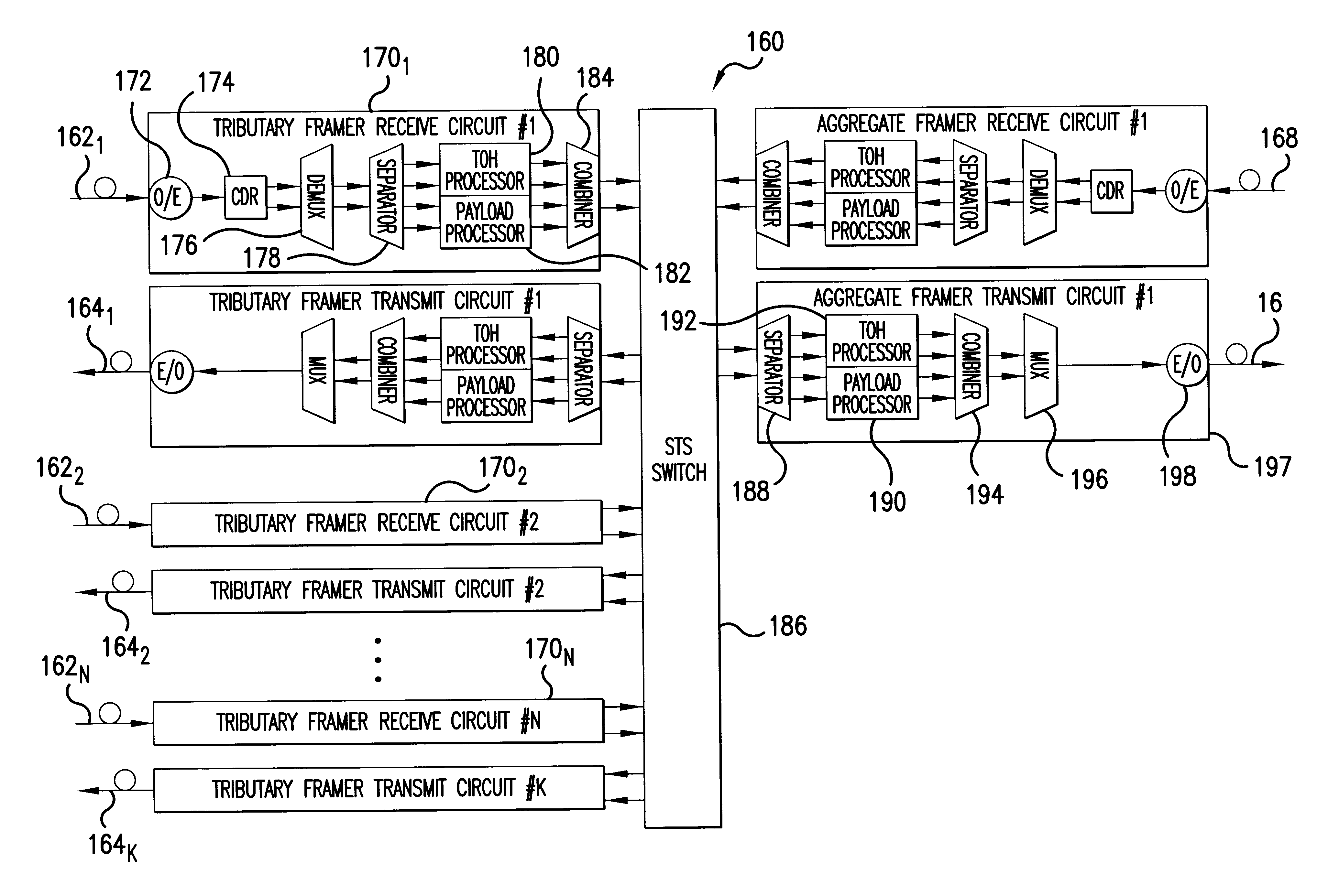
A semi-transparent time division multiplexer / demultiplexer that transmits low rate tributaries from one location to another using a high rate aggregate connection, while preserving substantially all of the TOH and payload for each tributary signal. Transparency of the tributary TOH is accomplished by interleaving both the TOH and the Payload of each tributary into the high rate aggregate signal. Some TOH bytes may be tunneled or re-mapped into unused / undefined TOH locations in the aggregate signal to allow transparency of the TOH without corrupting the aggregate. Errors may be handled by tunneling BIP bytes into unused / undefined aggregate locations and updating the tunneled bytes with error masks calculated at each network elements. Alternatively errors may be forwarded by using an error mask generated from the tributary BIP locations and inserting the mask into the associated aggregate BIP locations. The mask in the aggregate BIP is updated with error masks calculated at each network elements. Re-timing of TOH to a synchronized clock in the tributary framer circuits can be accomplished using controlled slips of overhead frames, whereby an entire frame is dropped or added depending on the relationship of the received clock and the synchronized clock. DCC bytes may be re-timed by adding or deleting flag bytes occurring between respective DCC packets. Re-timing of the aggregate TOH to a transmit clock may be accomplished in a similar manner.
Owner:CIENA
Secure program execution depending on predictable error correction
InactiveUS7353400B1ConfigurableUser identity/authority verificationUnauthorized memory use protectionTreatment errorComputer science
A CPU is provided with an ability to modify its operation, with respect to error correction, as a programmable feature. An error correction scheme is selected to be performed by the error correcting circuit. The compiled program may have intentionally introduced errors which are predictably corrected by the selected error correction scheme. When a program is compiled, the program is modified by the intentional insertion of errors which would result from the execution of the program. By providing error correction schema selected during program compilation, errors can be inserted in the program code, but are handled in a predictable manner by the error correction.
Owner:ORACLE INT CORP
Handling of errors in a data processing apparatus having a cache storage and a replicated address storage
ActiveUS20110047411A1Reduce power consumptionImprove system reliabilityError preventionTransmission systemsTreatment errorData value
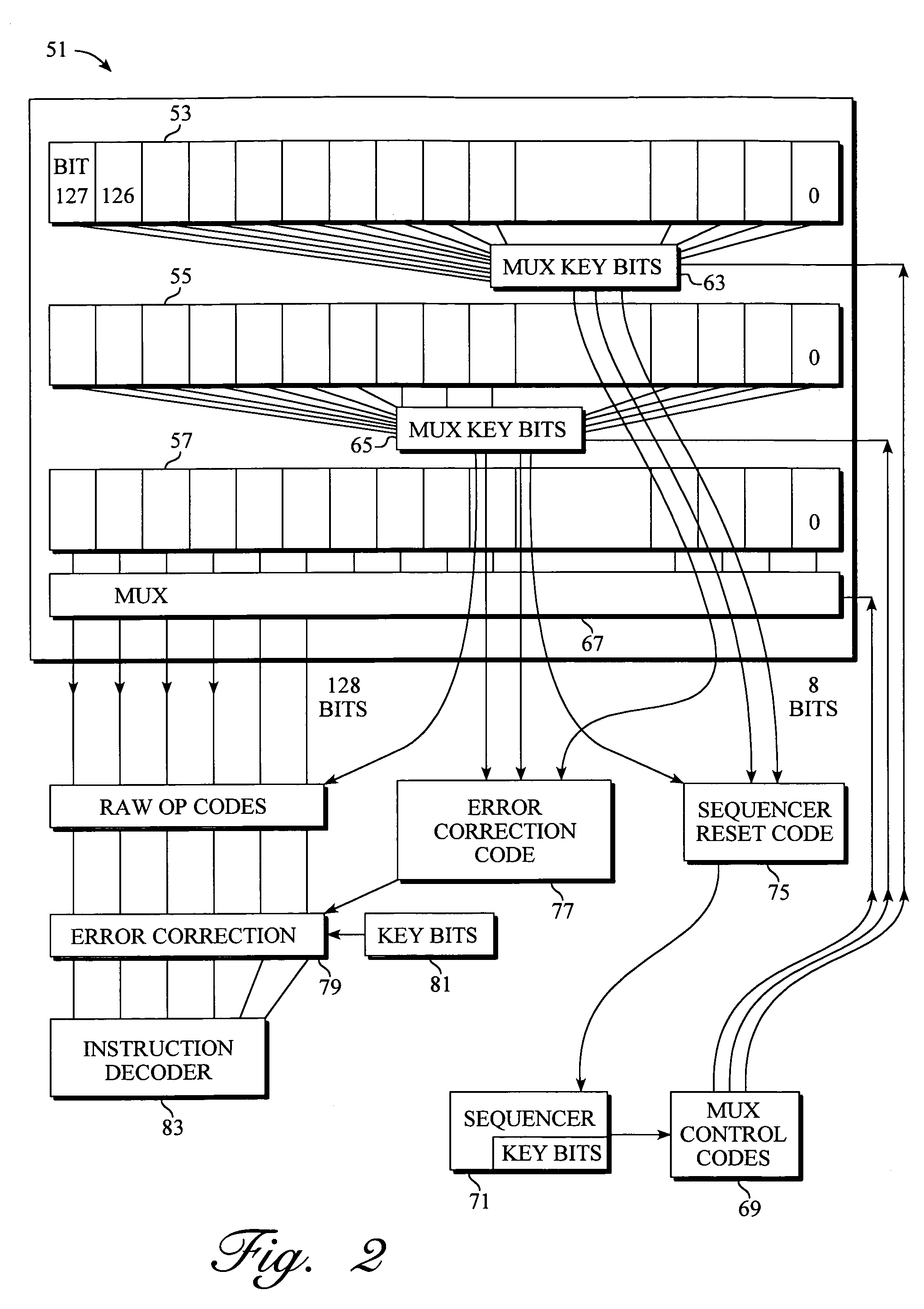
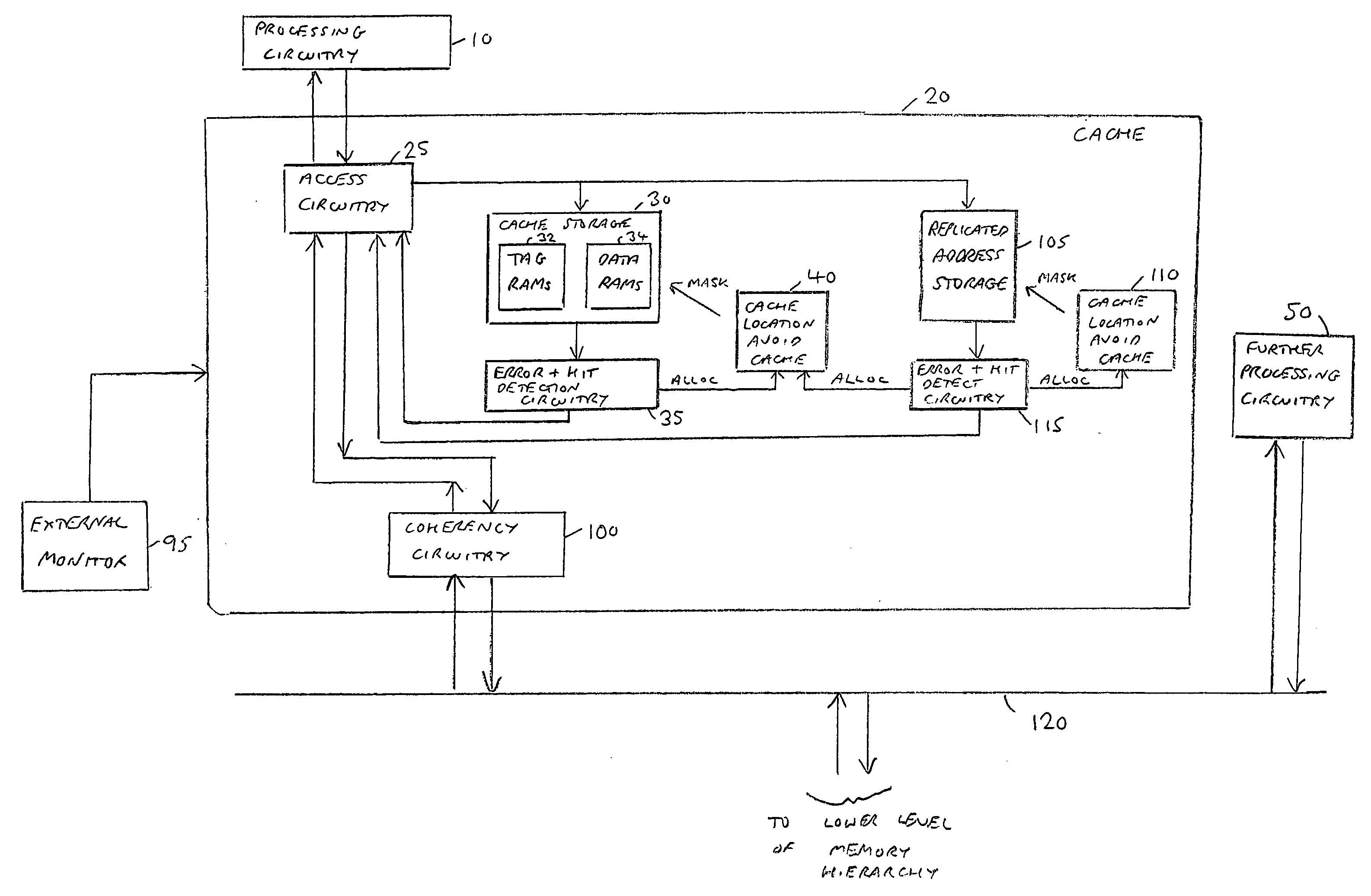
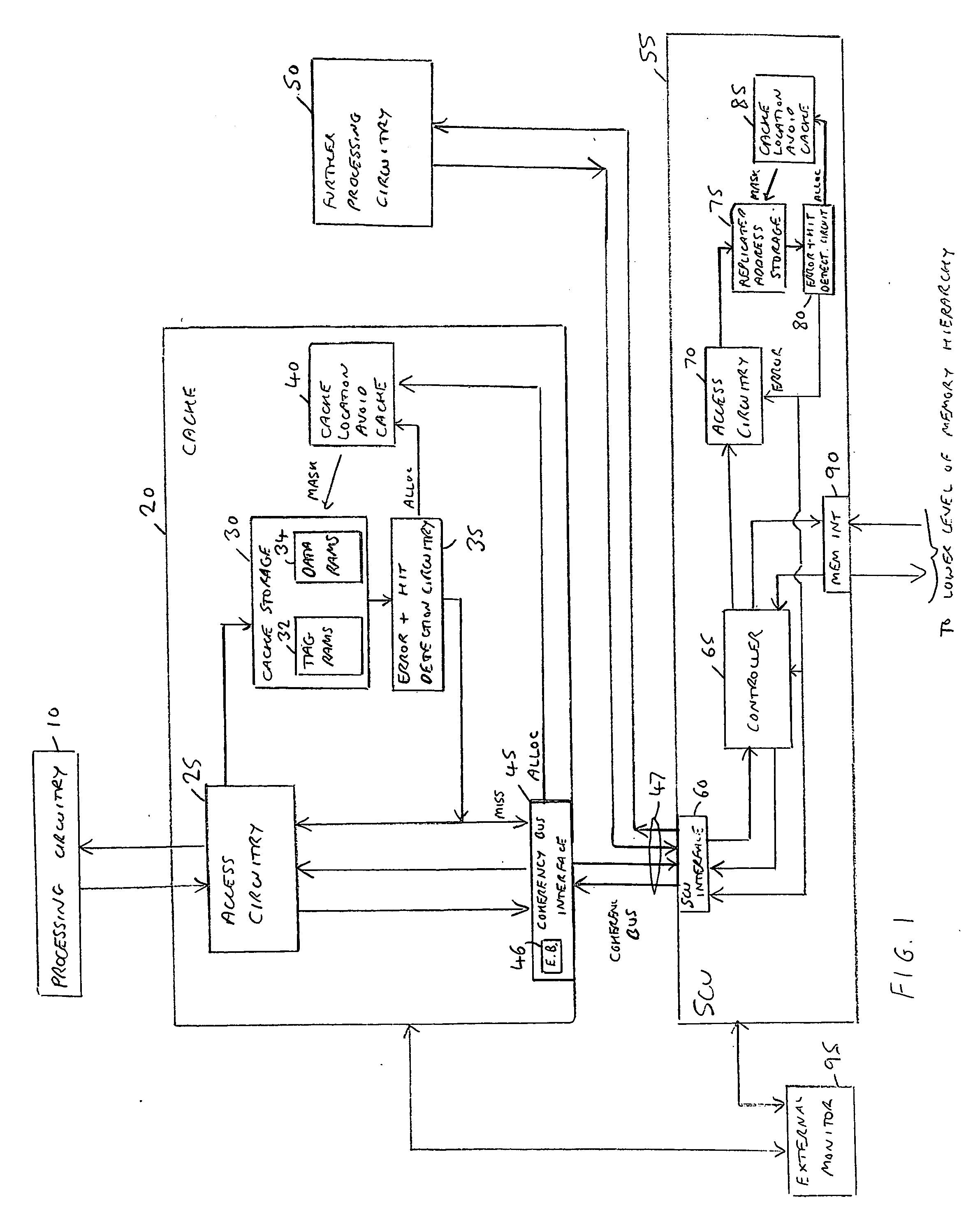
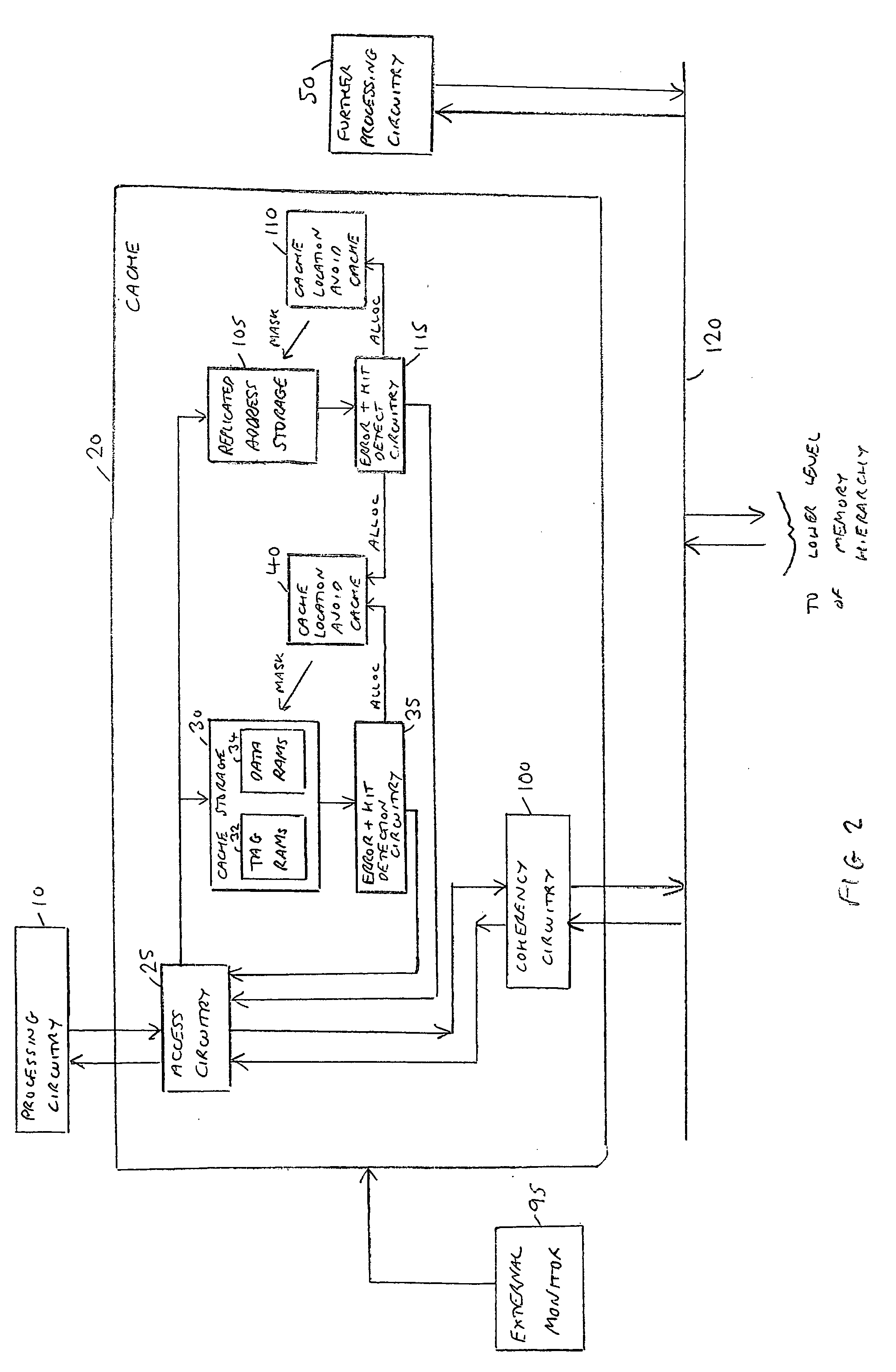
A data processing apparatus and method are provided for handling errors. The data processing apparatus comprises processing circuitry for performing data processing operations, a cache storage having a plurality of cache records for storing data values for access by the processing circuitry when performing the data processing operations, and a replicated address storage having a plurality of entries, each entry having a predetermined associated cache record within the cache storage and being arranged to replicate the address indication stored in the associated cache record. On detecting a cache record error when accessing a cache record of the cache storage, a record of a cache location avoid storage is allocated to store a cache record identifier for the accessed cache record. On detection of an entry error when accessing an entry of the replicated address storage, use of the address indication currently stored in that accessed entry of the replicated address storage is prevented, and a command is issued to the cache location avoid storage. In response to the command, a record of the cache location avoid storage is allocated to store the cache record identifier for the cache record of the cache storage associated with the accessed entry of the replicated address storage. Any cache record whose cache record identifier is stored in the cache location avoid storage is logically excluded from the plurality of cache records of the cache storage for the purposes of subsequent operation of the cache storage. Such an approach enables errors to be correctly handled, prevents errors from spreading in a system, and minimises communication necessary on detection of an error in a data processing apparatus having both a cache storage and a replicated address storage.
Owner:ARM LTD
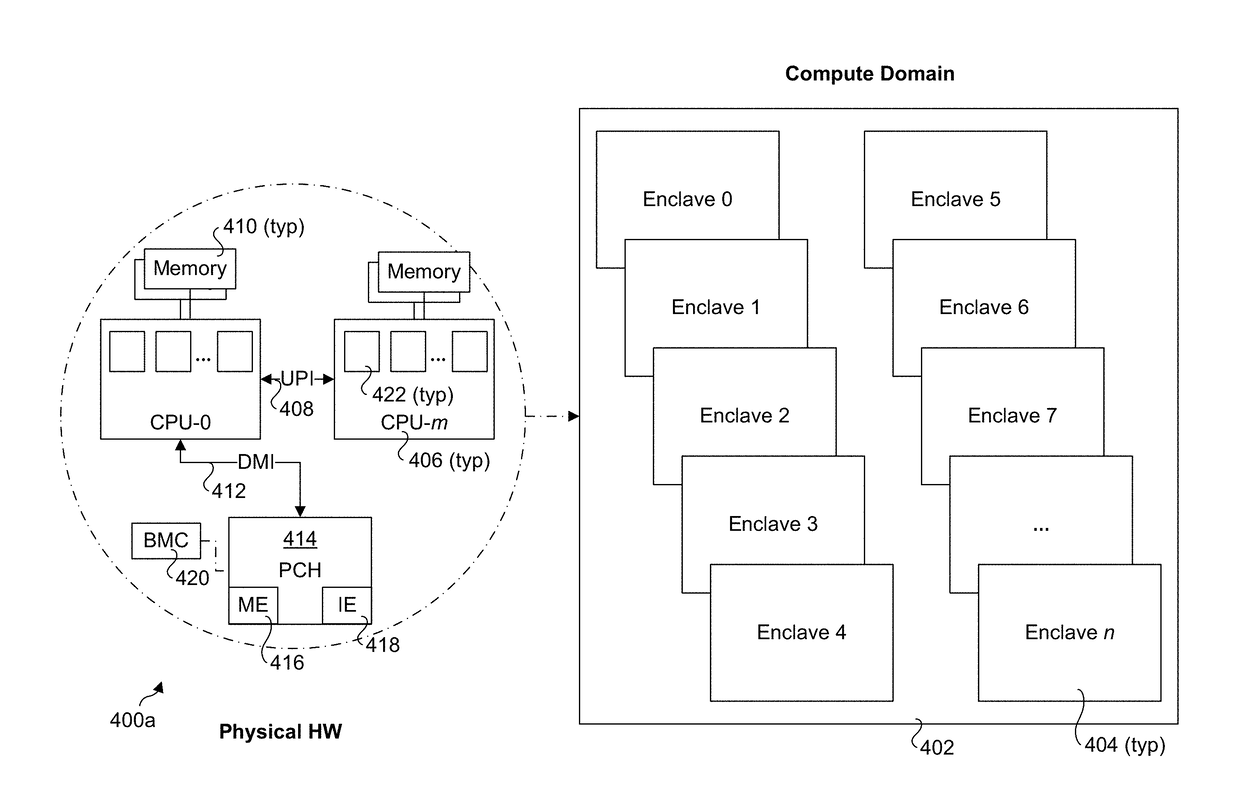
Method to increase cloud availability and silicon isolation using secure enclaves
ActiveUS20170177457A1Data resettingPlatform integrity maintainanceIntellectual propertyTreatment error
Methods and apparatus to increase cloud availability and silicon isolation using secure enclaves. A compute platform is configured to host a compute domain in which a plurality of secure enclaves are implemented. In conjunction with creating and deploying secure enclaves, mapping information is generated that maps the secure enclaves to platform / CPU resources, such as Intellectual Property blocks (IP) belong to the secure enclaves. In response to platform error events caused by errant platform / CPU resources, the secure enclave(s) belonging to the errant platform / CPU are identified via the mapping information, and an interrupt is directed to that / those secure enclave(s). In response to the interrupt, a secure enclave may be configured to one or more of handle the error, pass information to another secure enclave, and teardown the enclave. The secure enclave may execute an interrupt service routine that causes the errant platform / CPU resource to reset without resetting the entire platform or CPU, as applicable.
Owner:INTEL CORP
Fine-Grained Indoor Location-Based Social Network
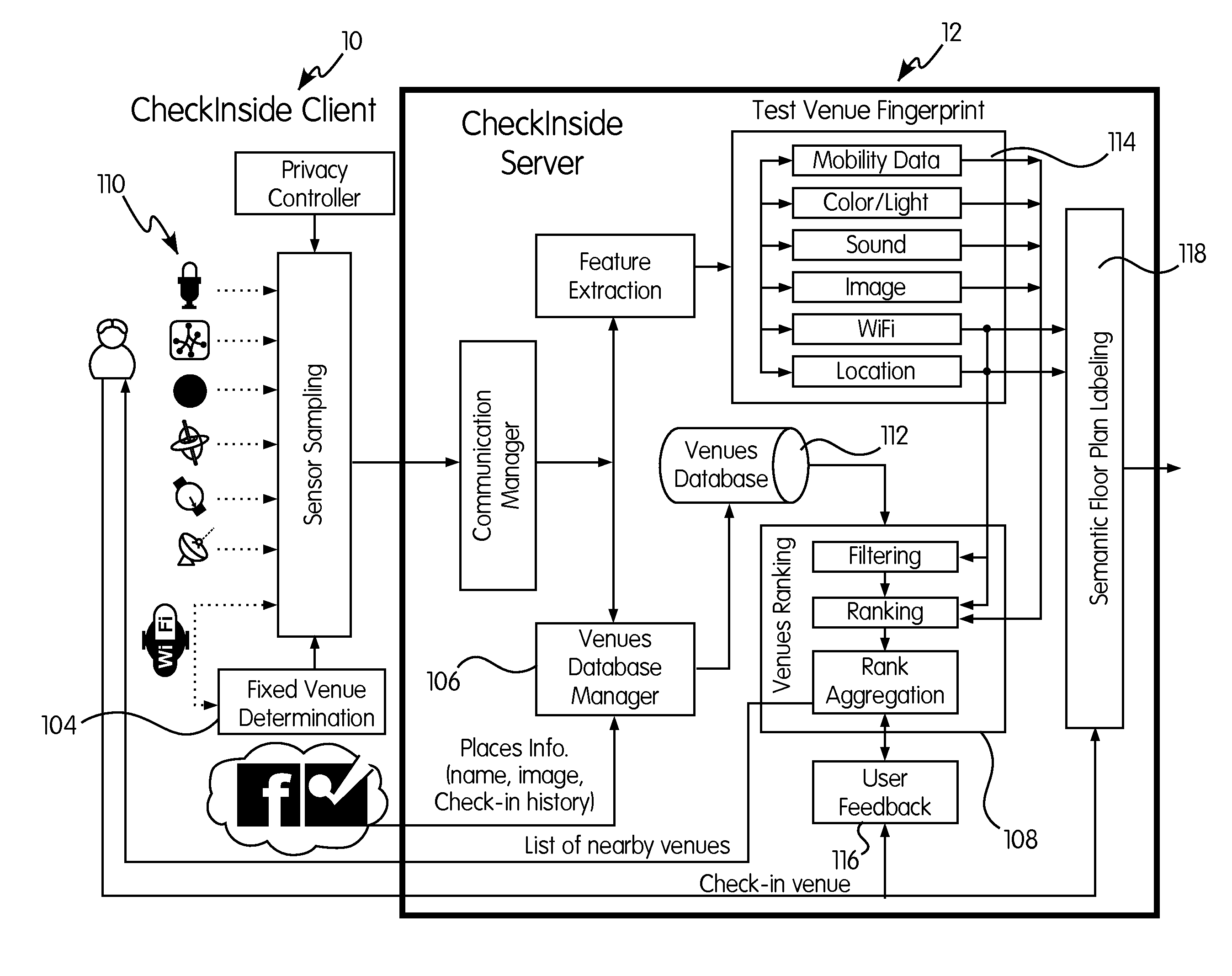
InactiveUS20160050541A1Improve accuracyReduce energy consumptionParticular environment based servicesNetwork topologiesSensing dataCrowds
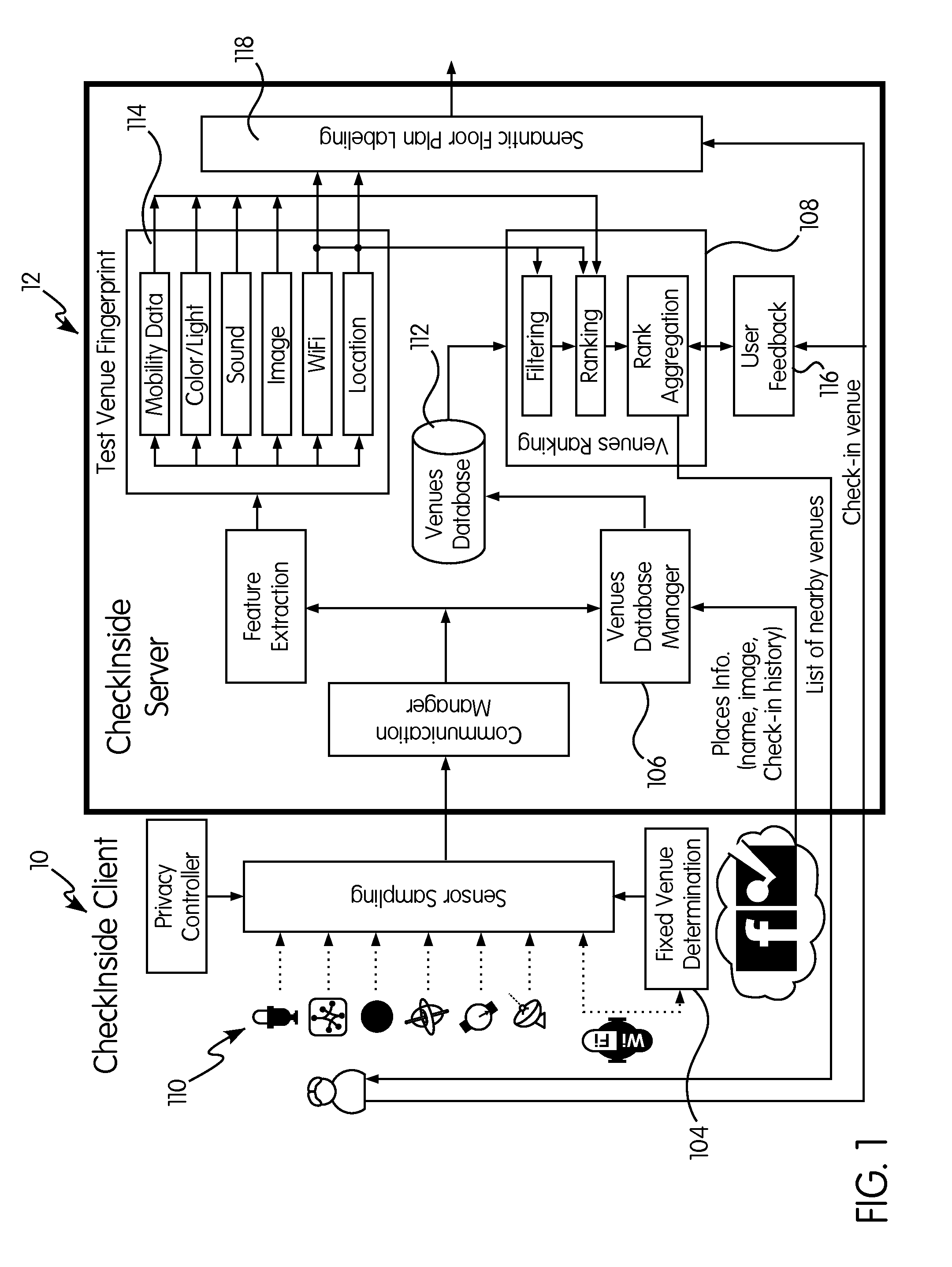
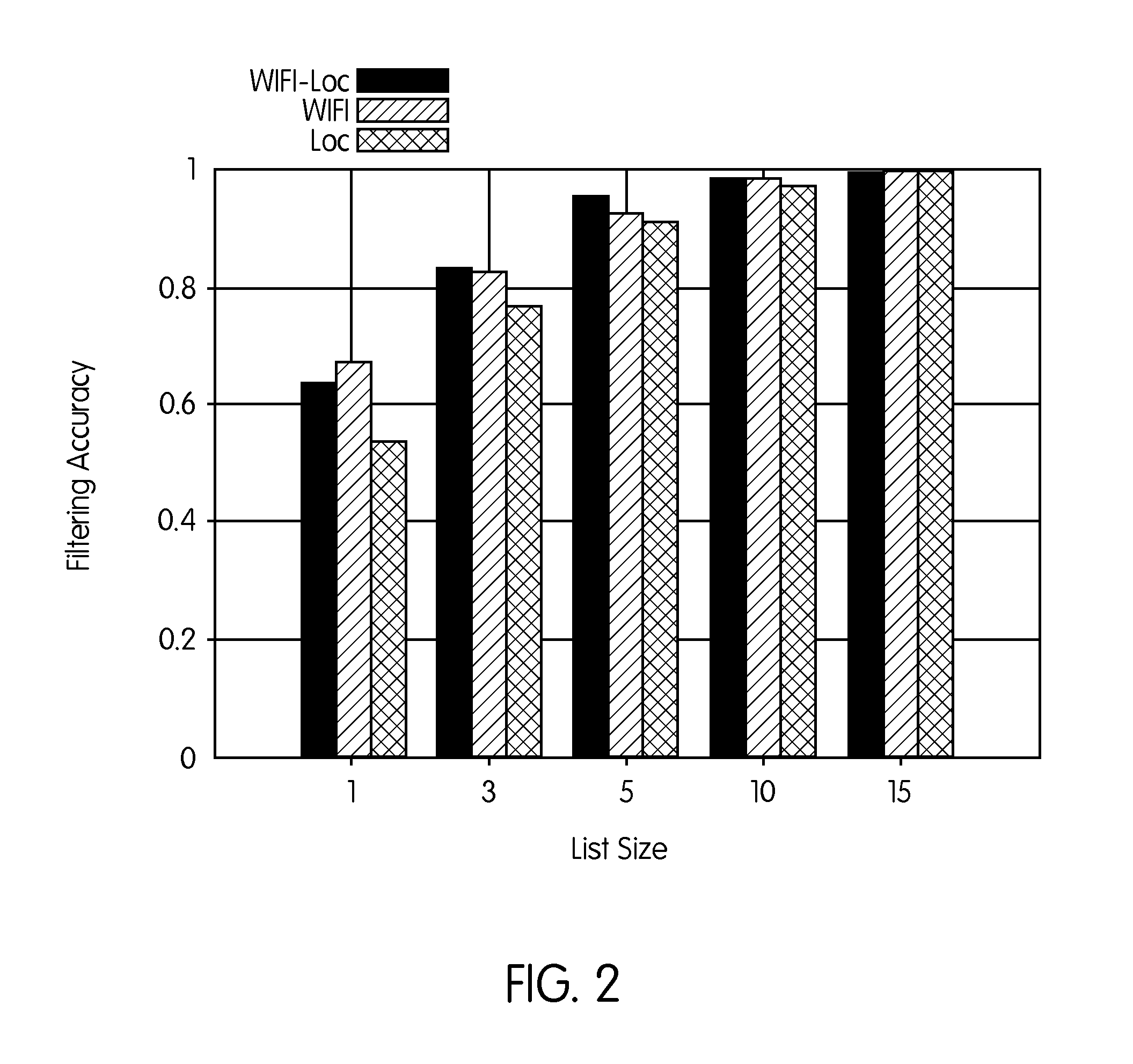
A system for providing a fine-grained indoor location-based social network (LBSN), the invention leverages the crowd-sensed data collected from a plurality of users' mobile devices during the check-in operation and knowledge extracted from current LBSNs to associate a place with its name and semantic fingerprint. This semantic fingerprint is used to obtain a more accurate list of nearby places as well as automatically detect new places with similar signatures. A novel algorithm for handling incorrect check-ins and inferring a semantically-enriched floorplan is proposed as well as an algorithm for enhancing the system performance based on the user implicit feedback.
Owner:EGYPT-JAPAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Methods, systems, and media for handling errors in script files
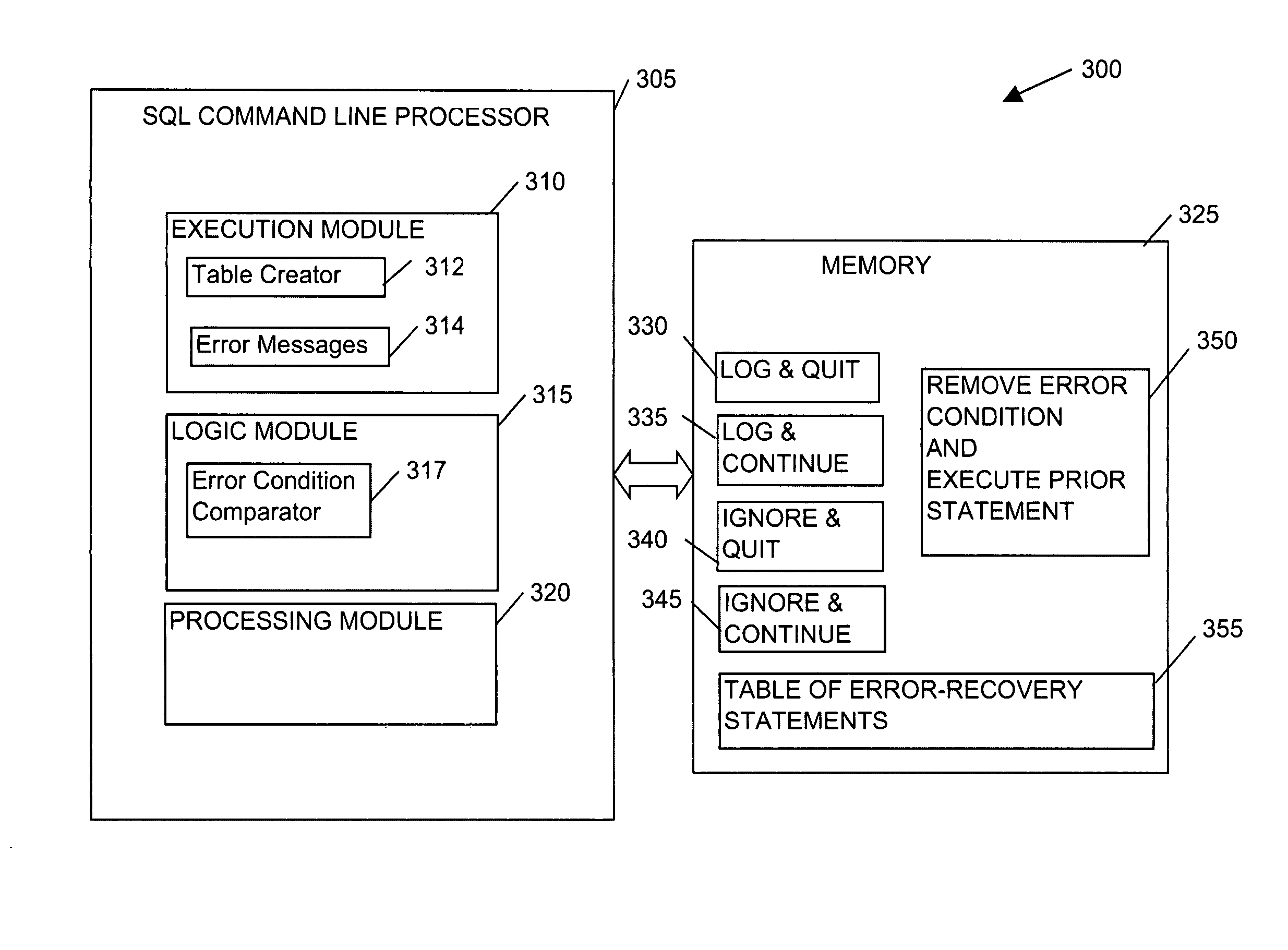
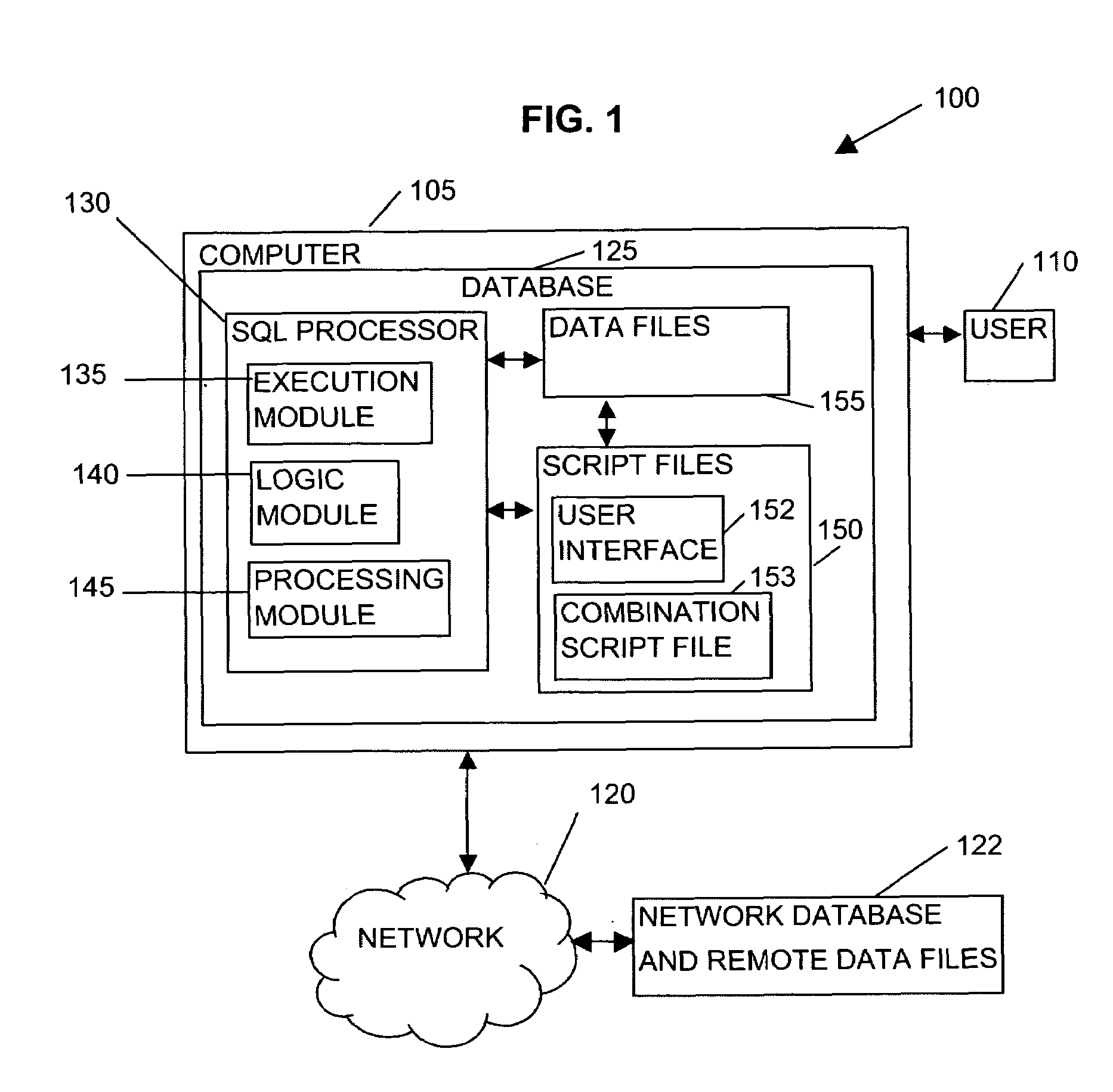
Methods, systems, and media are disclosed for handling errors resulting in error messages while executing a script file such as a Sequential Query Language (SQL) script. Embodiments may include one or more databases such as databases interconnected via a network, which include or have the ability to create and / or execute script files with on-error statements. Script files with on-error statements may include an error identifier and a resolution identifier. Each error identifier may identify one or more errors associated with the resolution identifier and the resolution identifier may identify a way to handle the error. Resolution identifiers may provide one or more error-recovery statements, calls for execution of a stored procedure, or other functions to correct, log, or ignore errors and continue or terminate execution of script files. Many embodiments include a command line processor that can recognize and implement the on-error statements.
Owner:INT BUSINESS MASCH CORP
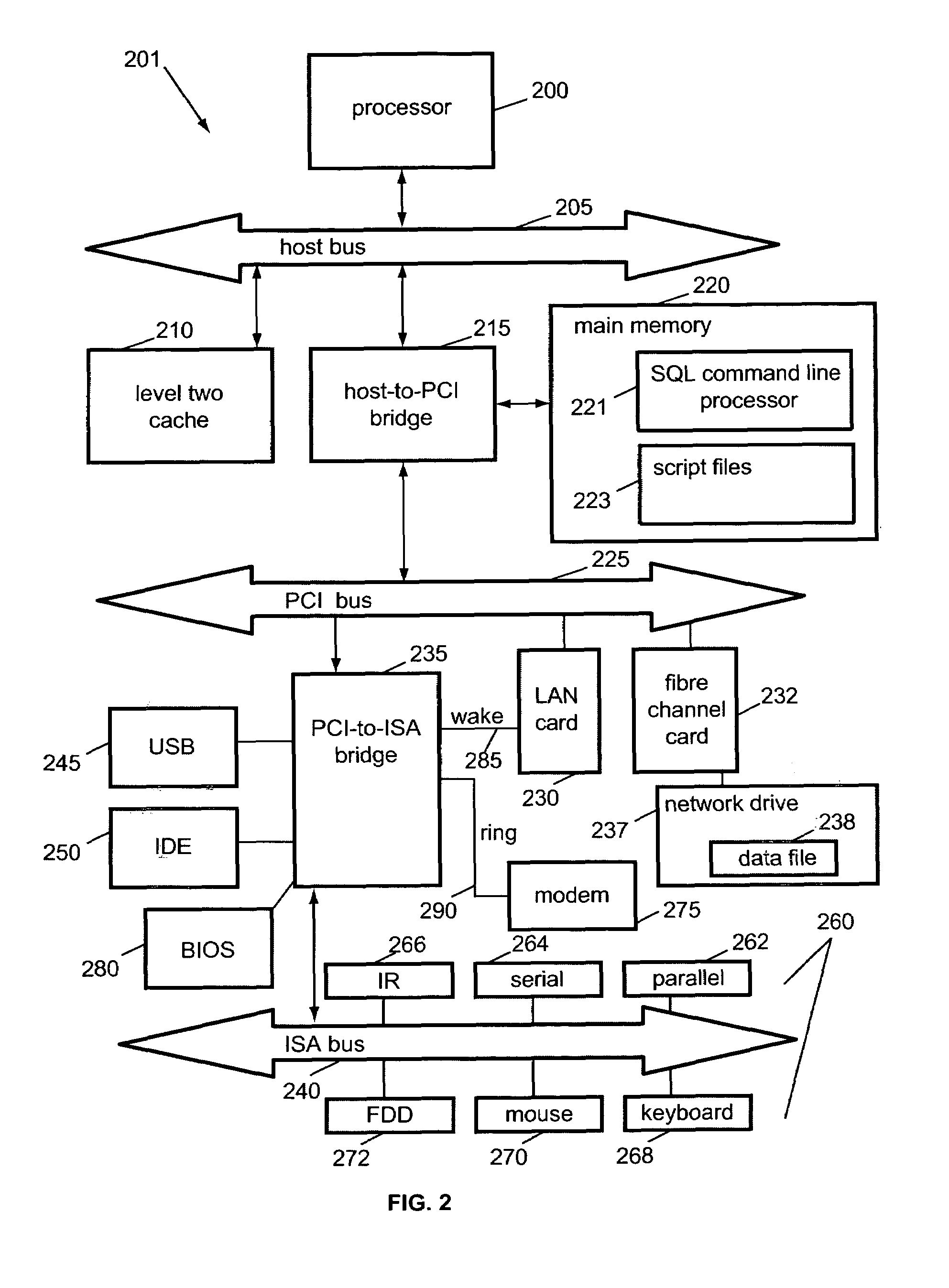
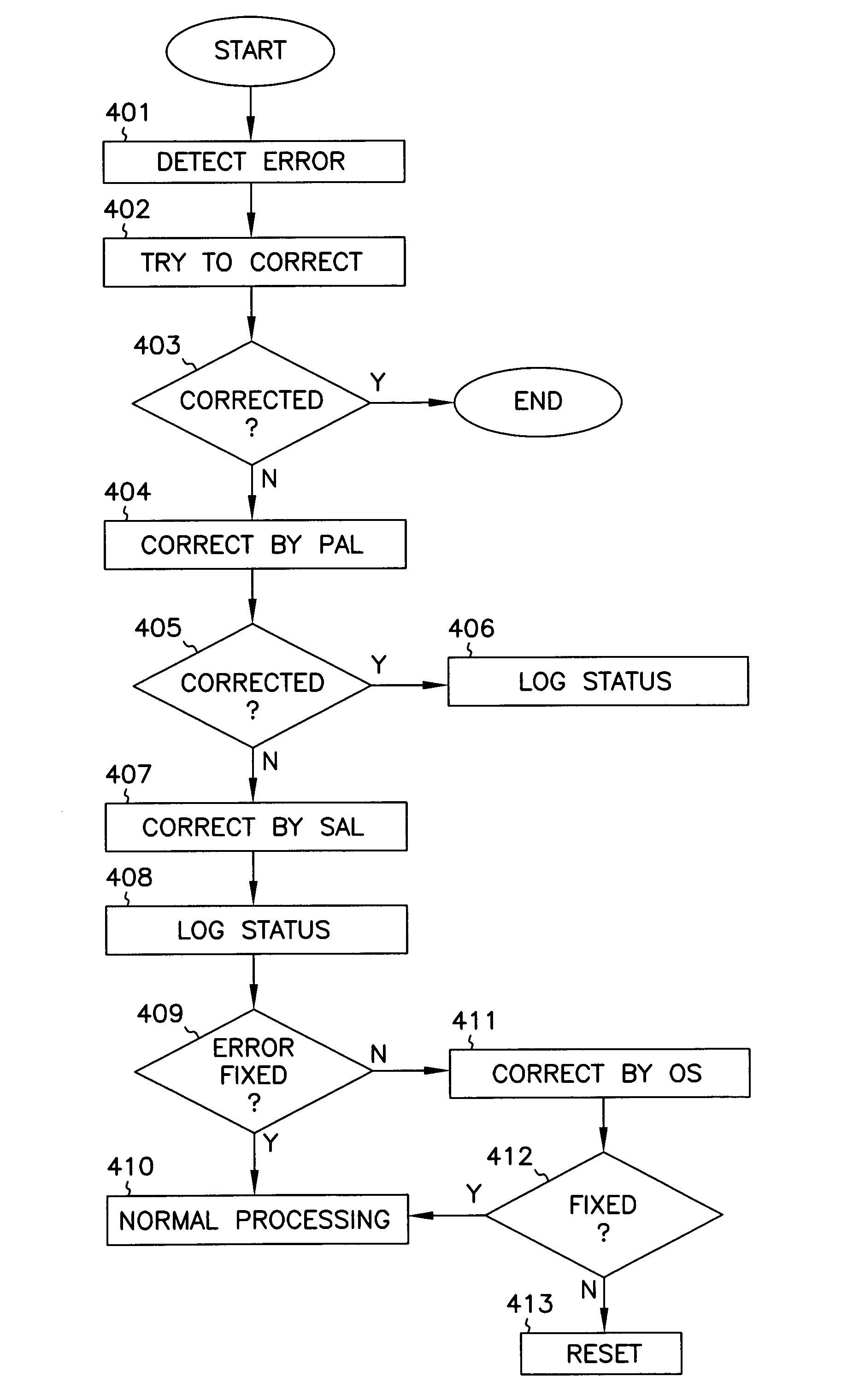
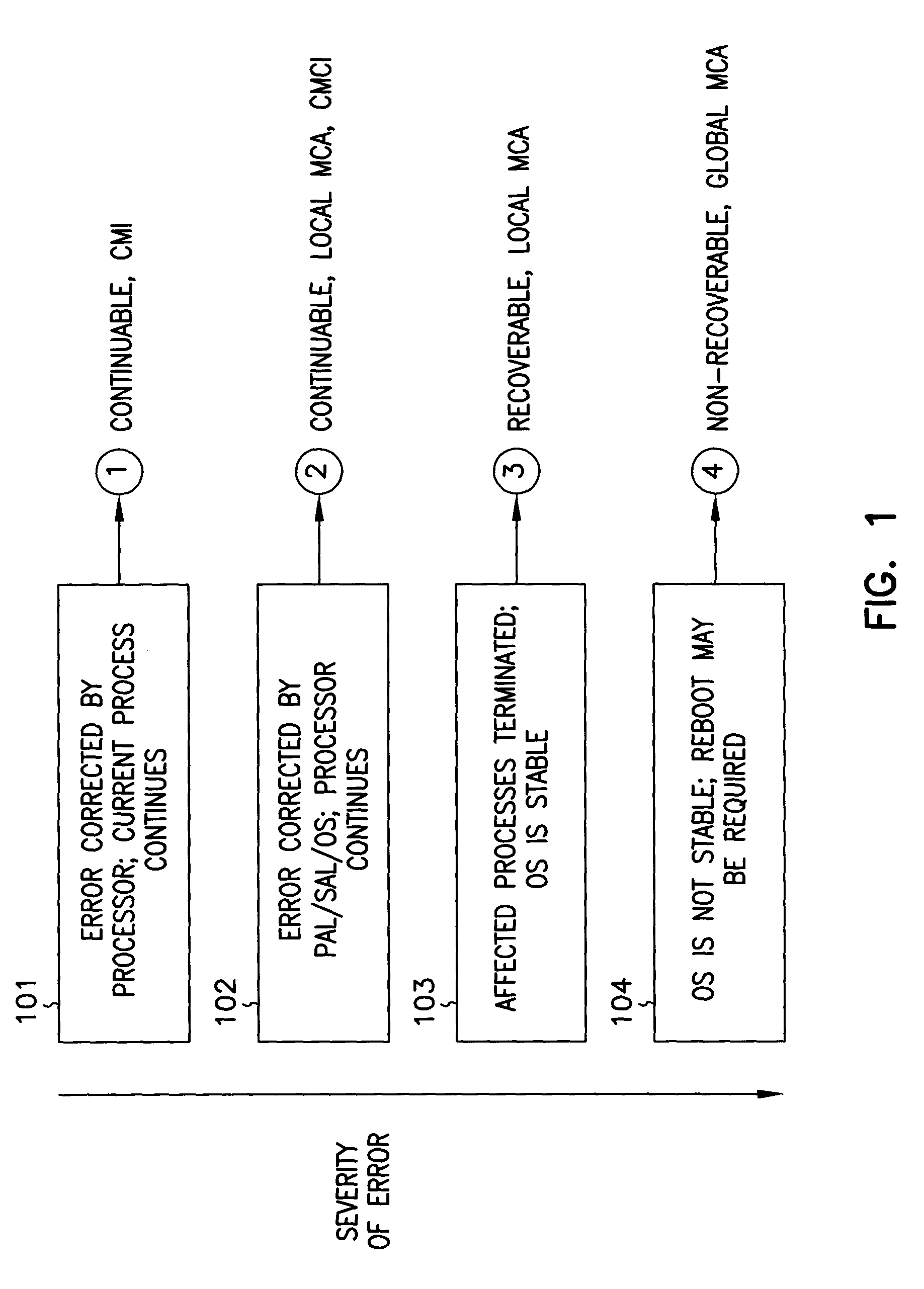
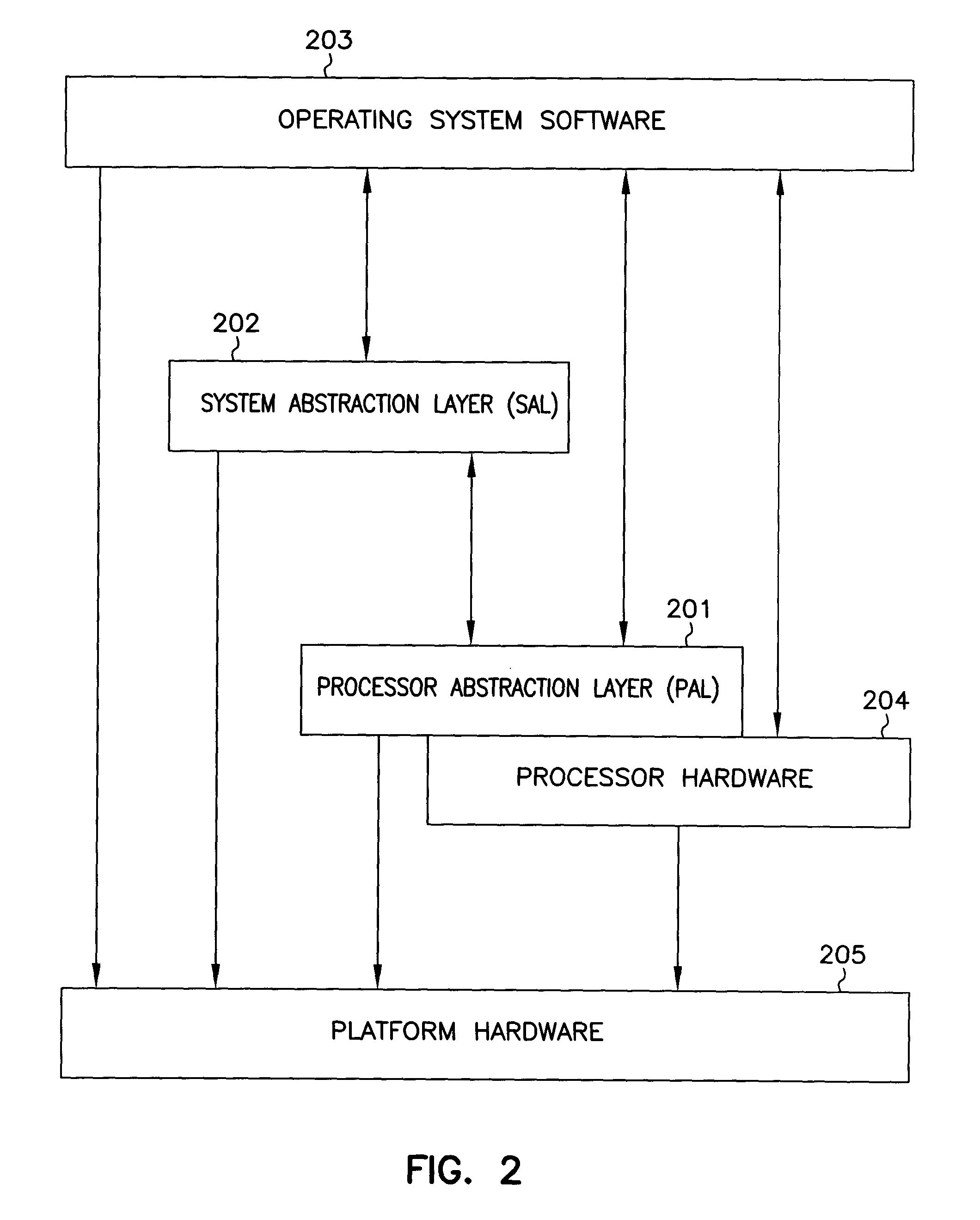
System abstraction layer, processor abstraction layer, and operating system error handling
Systems and methods for error handling are disclosed. The systems and methods may be utilized for single or multiple processor computer systems to handle errors in a coordinated manner between hardware and any firmware or software layers. A computer system includes a non volatile memory and at least one processor. A firmware error handling routine is stored on the non volatile memory. The firmware error handling routine is for handling errors. Each of the at least one processors detects errors. Each processor executes the firmware error handling routine on detecting an error. The executed firmware error handling routine handles the error. The executed firmware error handling routine also logs error information to a log.The systems and methods provide for coordinated error handling that enhance error recovery, provide error containment and maintain system availability.
Owner:INTEL CORP
Method and apparatus for processing navigation data in position determination
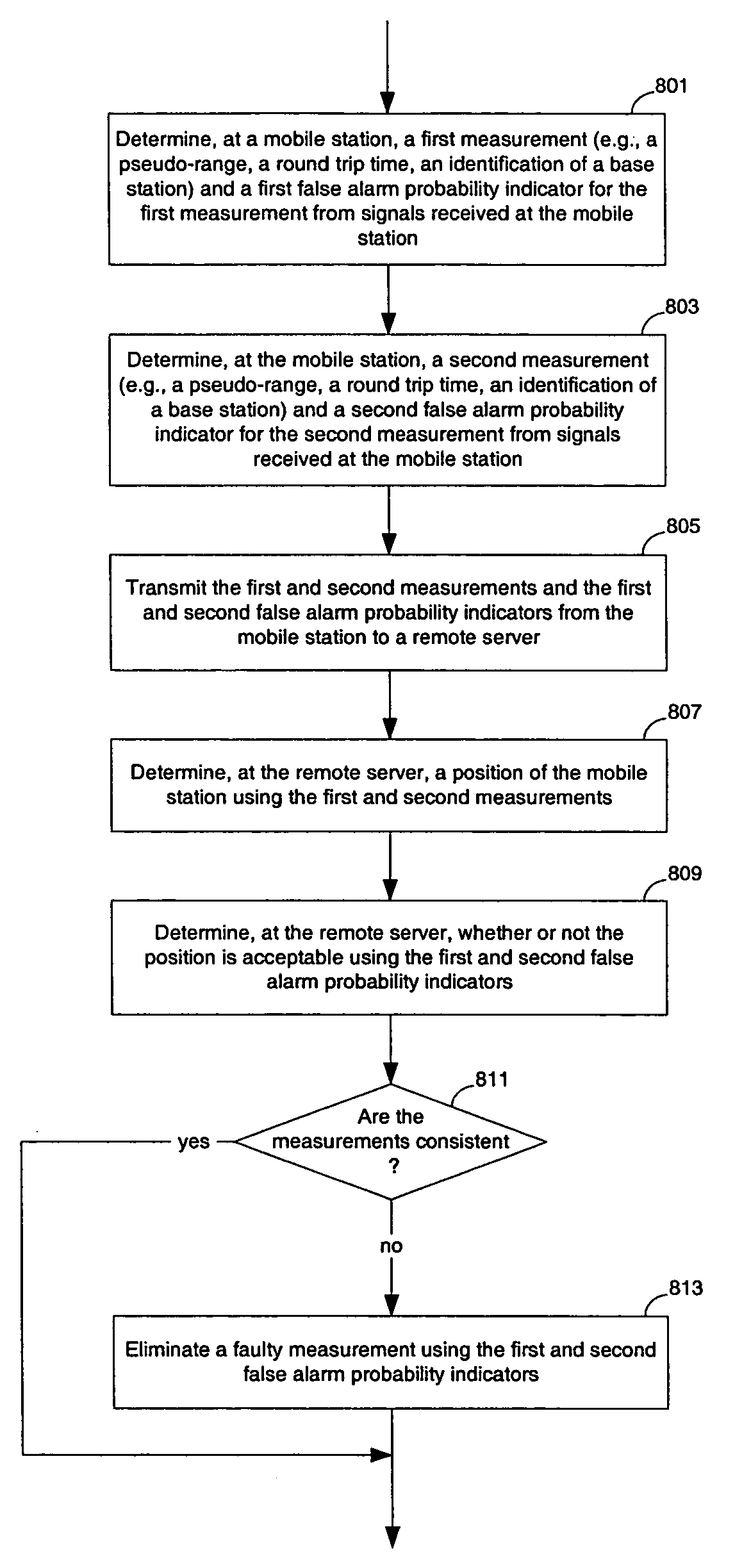
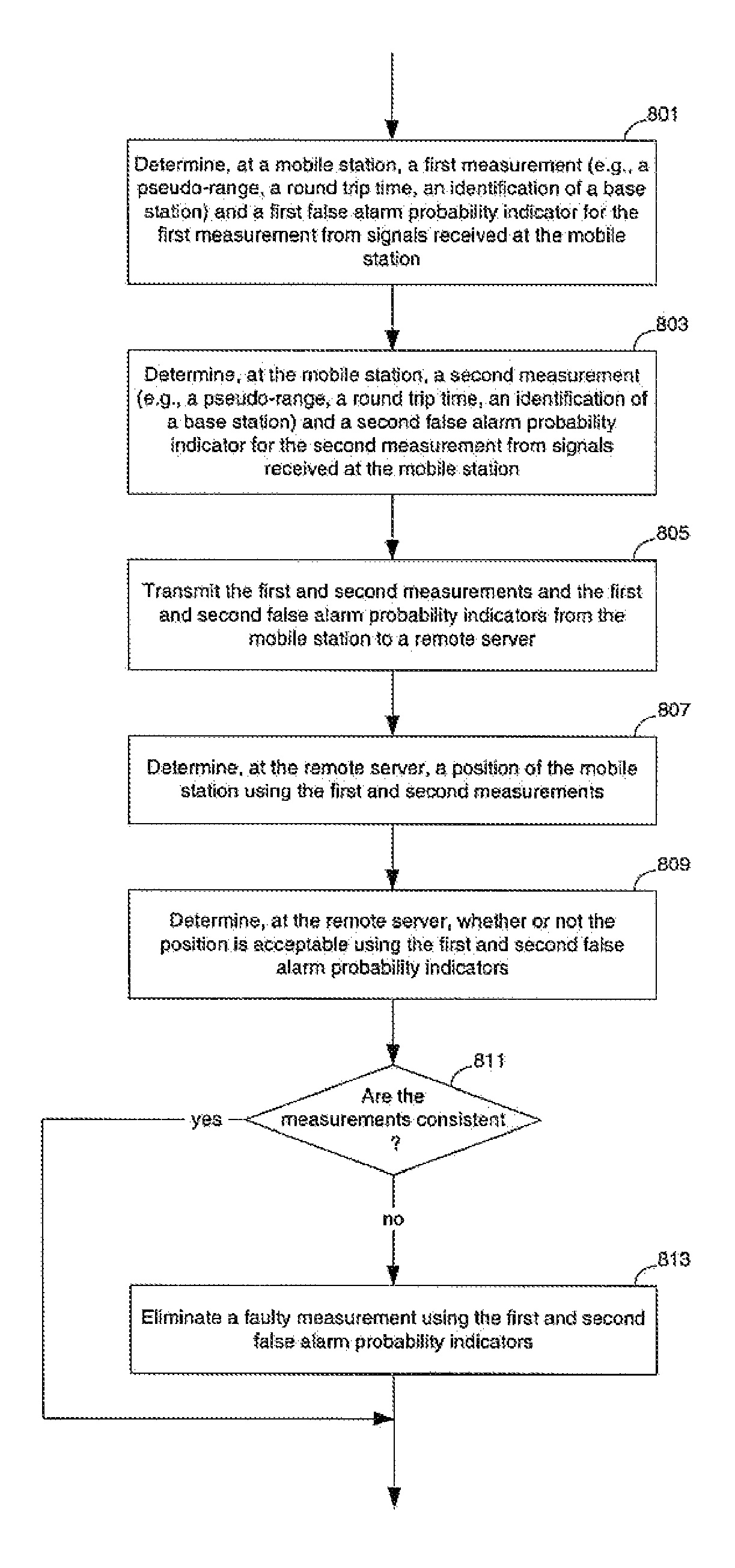
ActiveUS7170447B2SignalDirection finders using radio wavesPosition fixationTreatment errorData mining
Methods and apparatuses for the processing of false alarms in position determination. At least one embodiment of the present invention estimates and uses measurement false alarm probabilities in the position determination process. In one embodiment, the estimated measurement false alarm probabilities are combined to determine the reliability of the determined position solution or the reliability of the set of measurements as a collection. In one embodiment, the estimated measurement false alarm probabilities are used in the isolation and elimination of faulty measurements. For example, the traditional geometry based metric for identifying a faulty measurement is further weighted according to the measurement false alarm probabilities in order to determine the faulty measurement.
Owner:QUALCOMM INC
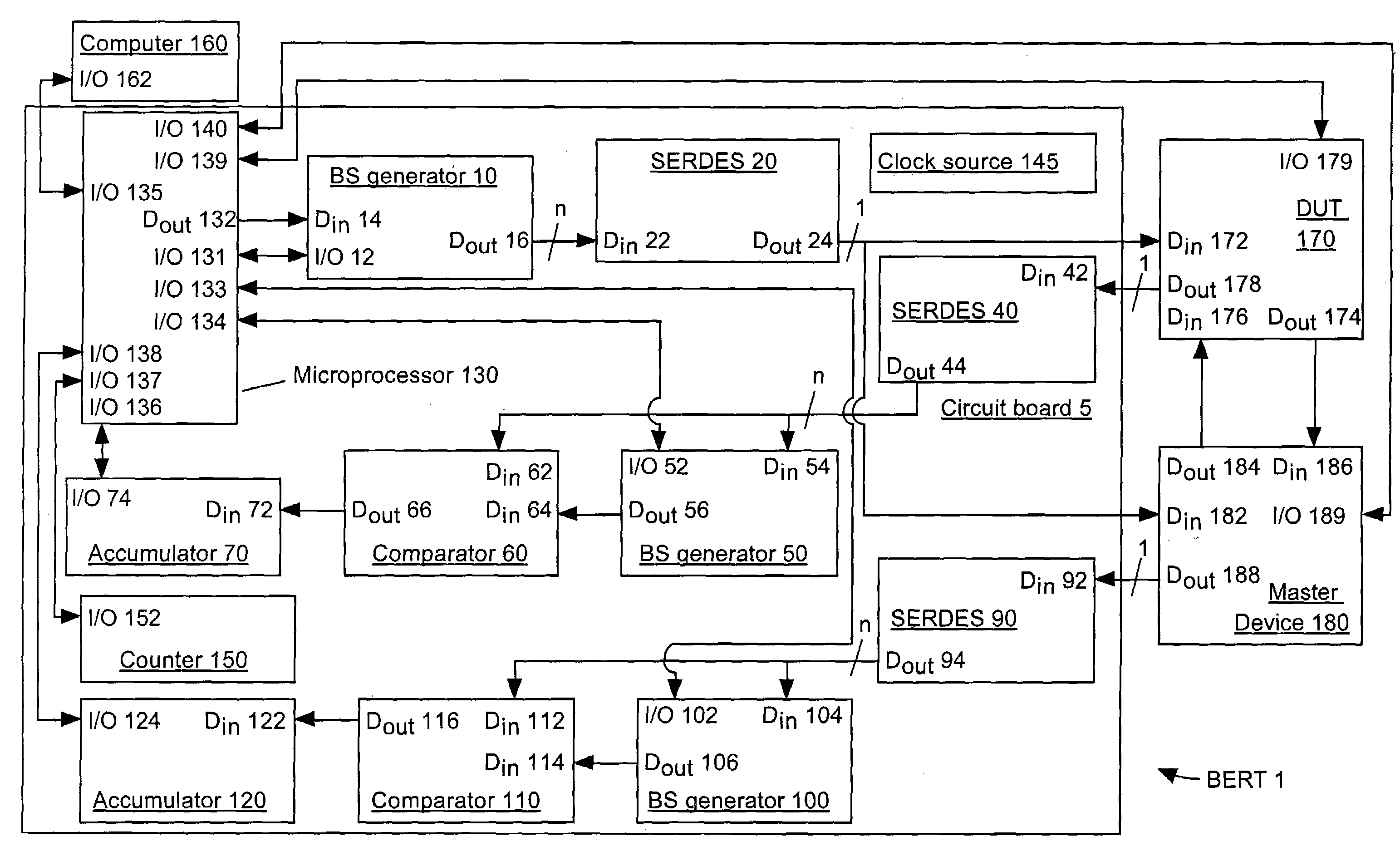
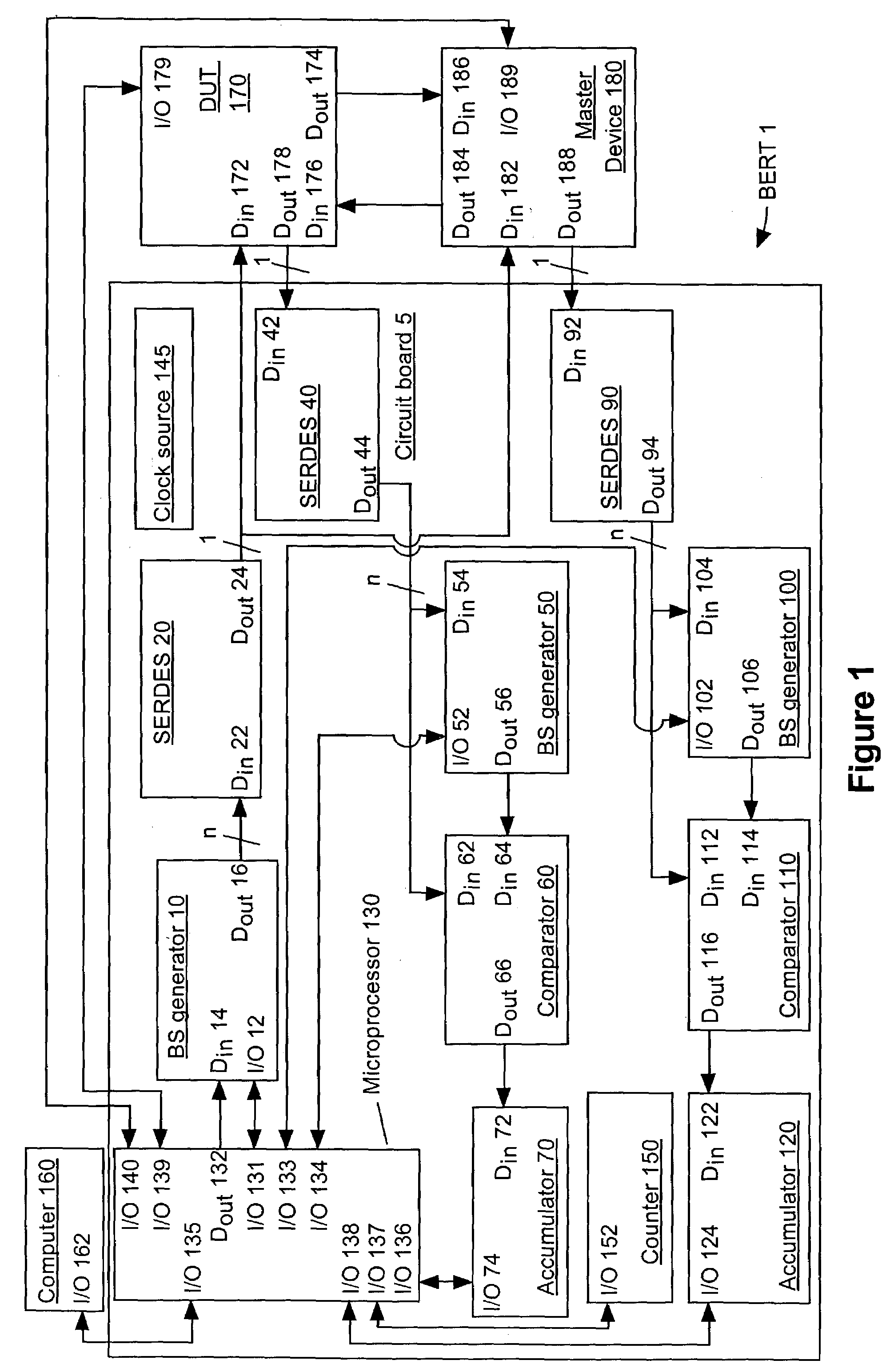
System and method of detecting a bit processing error
The present invention relates generally to an improvement in the ability of test systems to test bit processing capacities of electronic devices, and in particular an improvement in their ability to test the operation of an electronic device's transmitter and receiver circuitry. Data generated by a BERT is transmitted in an electrical form to a DUT and a master device. The DUT transmits data received in an electrical form to the master device in an optical form and the master device transmits data received in an electrical form to the DUT in an optical form. The master device and the DUT then transmit data received in an optical form back to the BERT in an electrical form. The data received from the DUT and the master device, respectively, is separately tested for bit errors. Do so enables to calculation of bit error rates for two distinguishable data paths through the DUT.
Owner:II VI DELAWARE INC
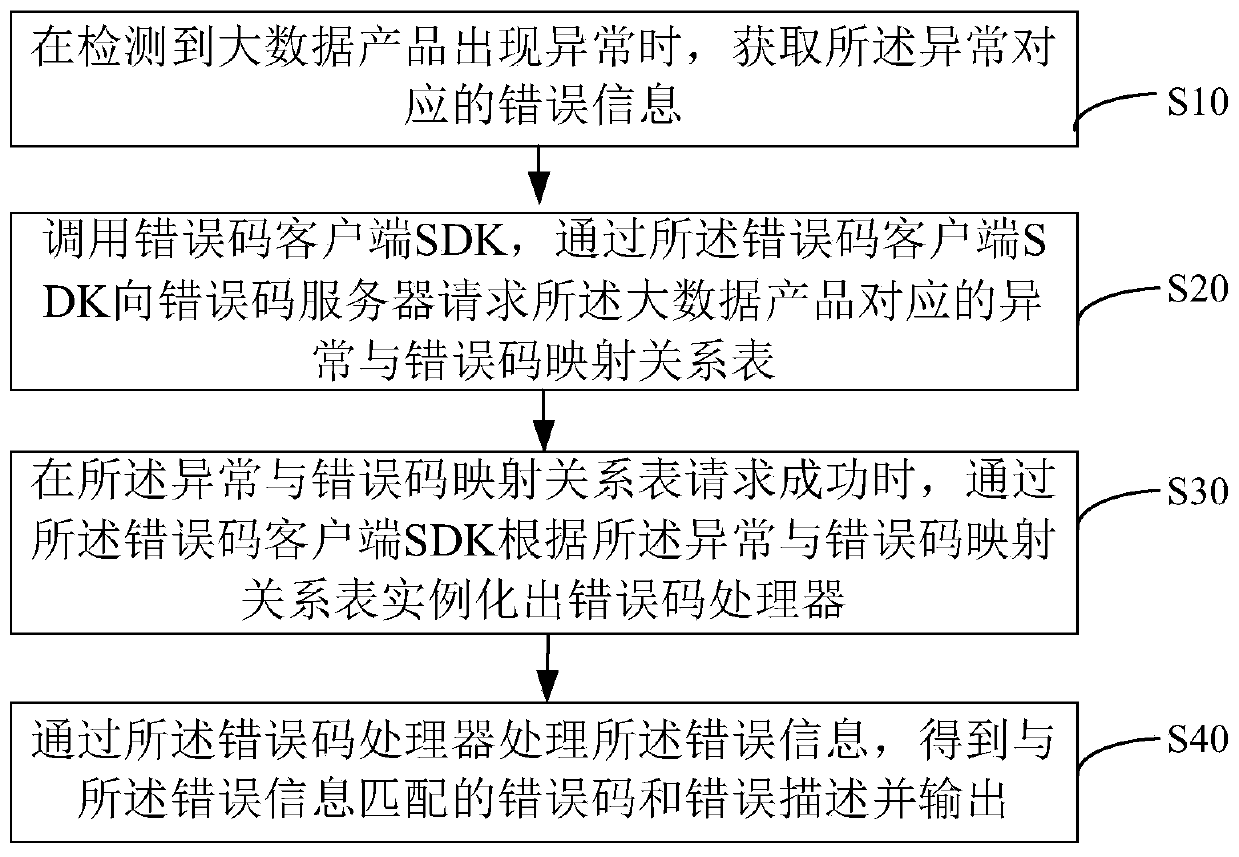
Exception prompting method, device and system for big data product, equipment and medium
ActiveCN110347560ARapid positioningReduce professional requirementsHardware monitoringComputer hardwareTreatment error
The invention relates to the technical field of big data of financial science and technology, and discloses an exception prompting method for a big data product, which comprises the following steps of: when it is detected that the big data product is exceptional, obtaining error information corresponding to the exception; calling an error code client SDK, and requesting an exception and error codemapping relation table corresponding to the big data product from an error code server through the error code client SDK; when the exception and error code mapping relation table is requested successfully, instantiating an error code processor through an error code client SDK according to the exception and error code mapping relation table; and processing the error information through an error code processor to obtain an error code and an error description matched with the error information, and outputting the error code and the error description. The invention further discloses an exceptionprompting device, system and equipment for the big data product and a medium. Error information of big data products is converted into error codes and error descriptions, so that operation and maintenance personnel can check the error codes and the error descriptions conveniently, and the efficiency is improved.
Owner:WEBANK (CHINA)
Method and apparatus for processing navigation data in position determination
Methods and apparatuses for the processing of false alarms in position determination. At least one embodiment of the present invention estimates and uses measurement false alarm probabilities in the position determination process. In one embodiment, the estimated measurement false alarm probabilities are combined to determine the reliability of the determined position solution or the reliability of the set of measurements as a collection. In one embodiment, the estimated measurement false alarm probabilities are used in the isolation and elimination of faulty measurements. For example, the traditional geometry based metric for identifying a faulty measurement is further weighted according to the measurement false alarm probabilities in order to determine the faulty measurement.
Owner:QUALCOMM INC
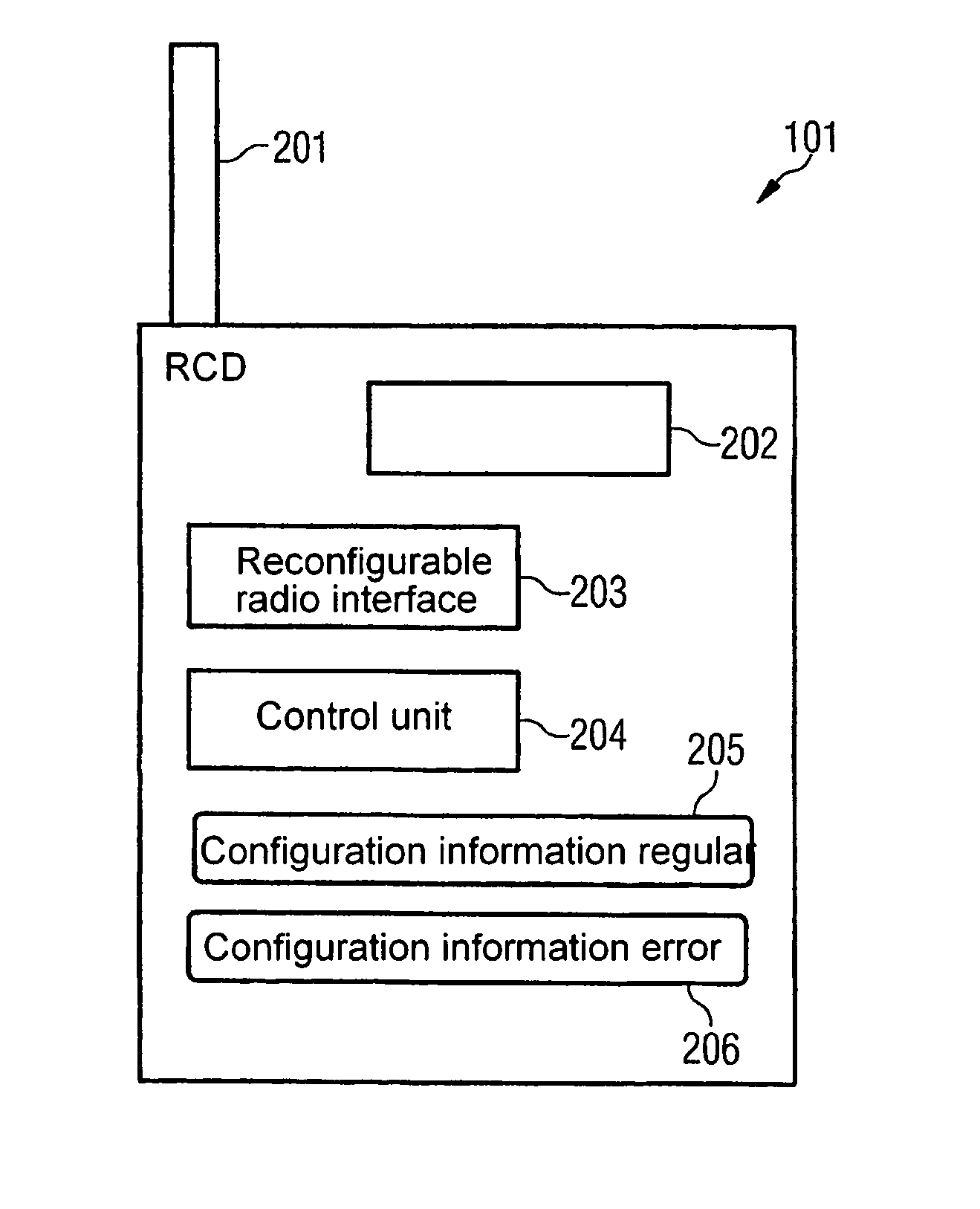
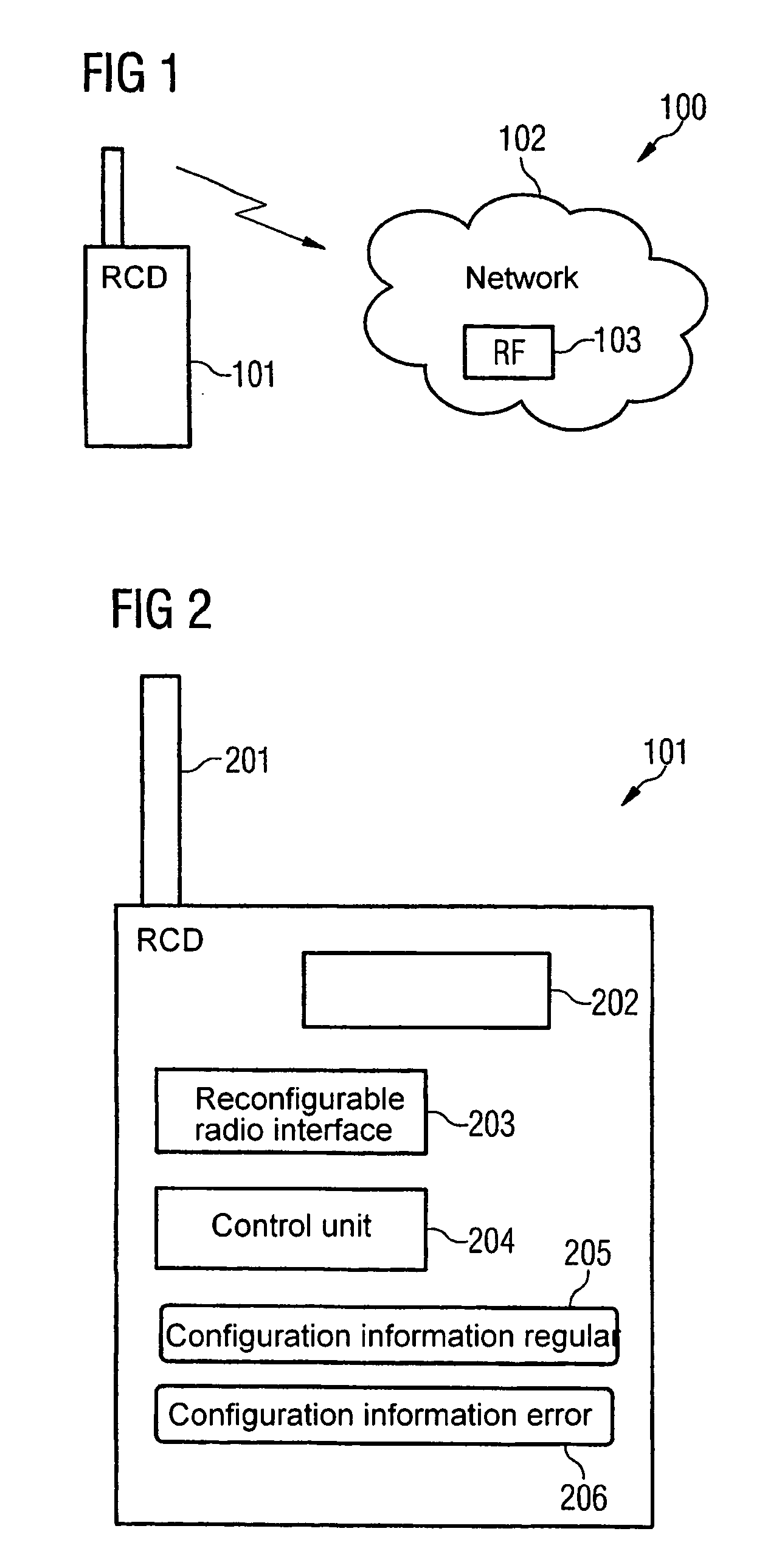
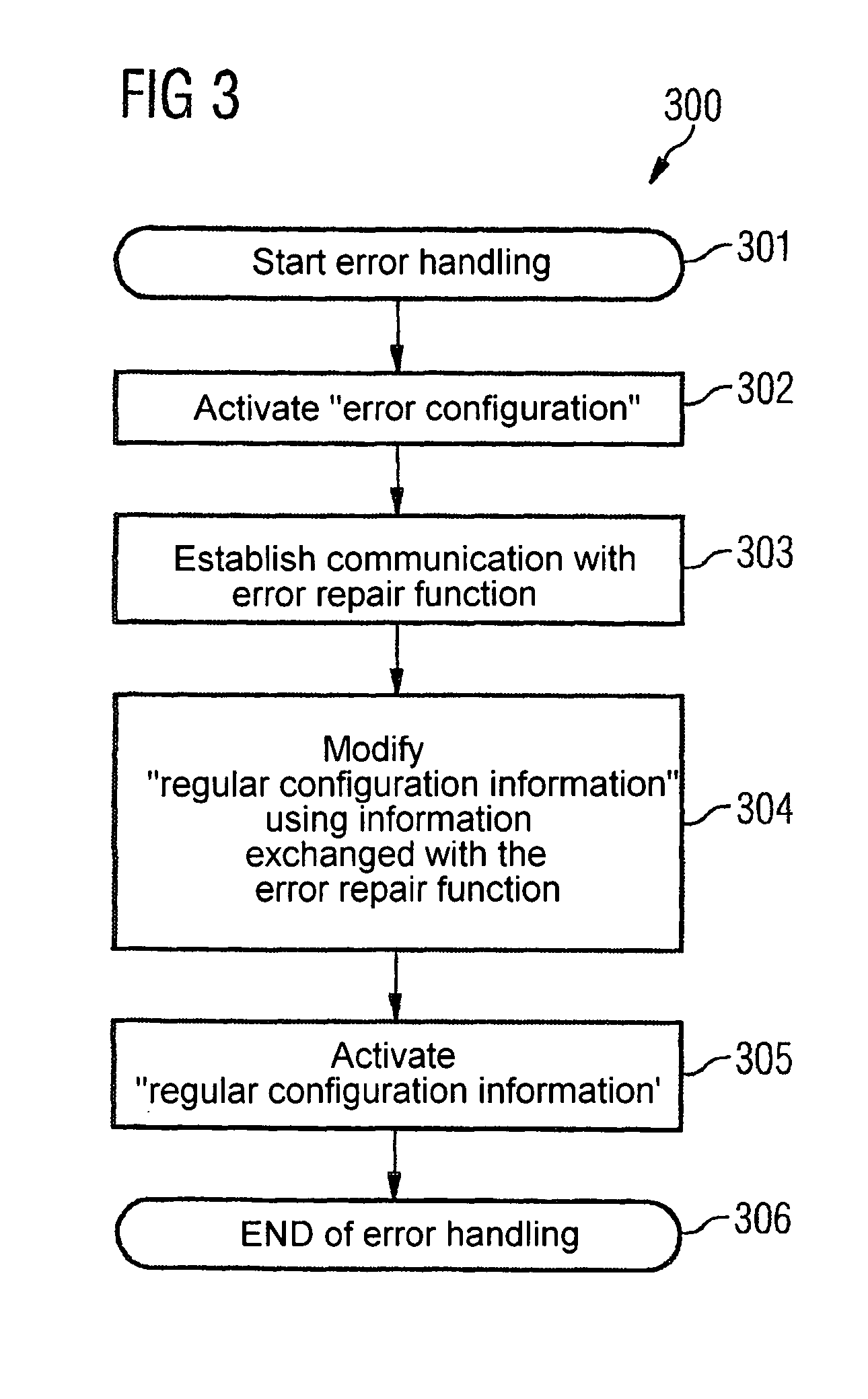
Reconfigurable radio system with error recognition and treatment
InactiveUS20070054662A1Simpler and more user-friendly solutionEasily damagedSubstation equipmentRadio/inductive link selection arrangementsComputer hardwareTreatment error
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
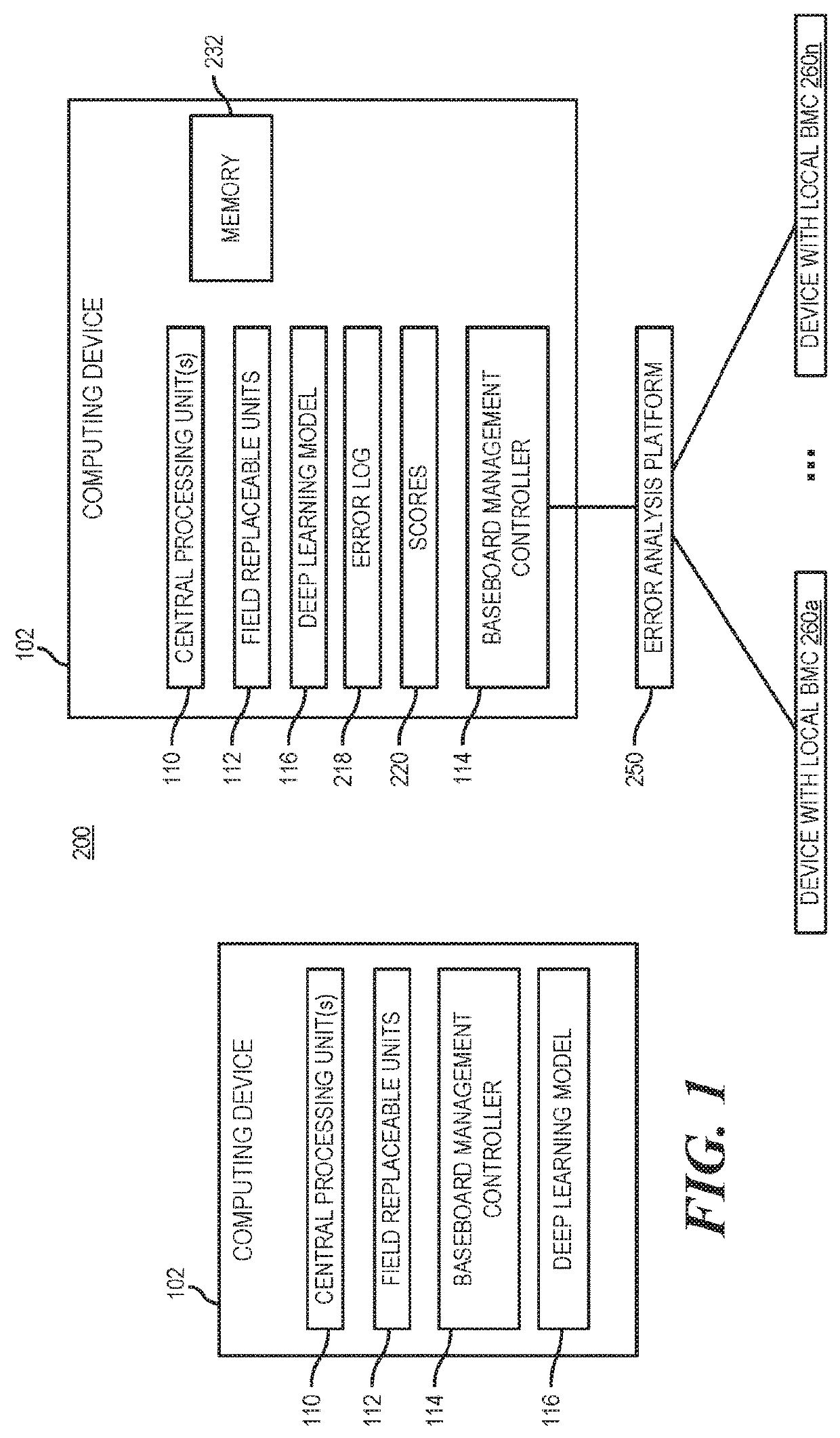
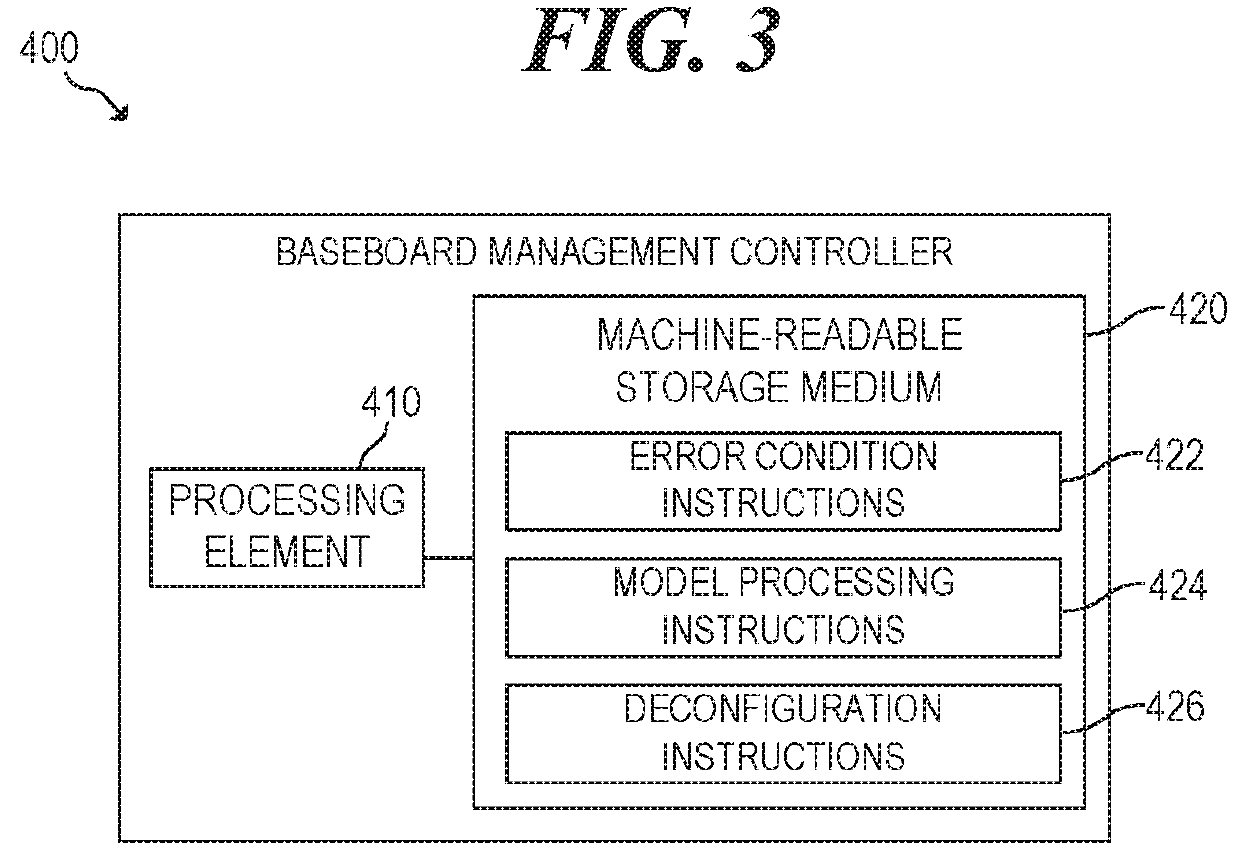
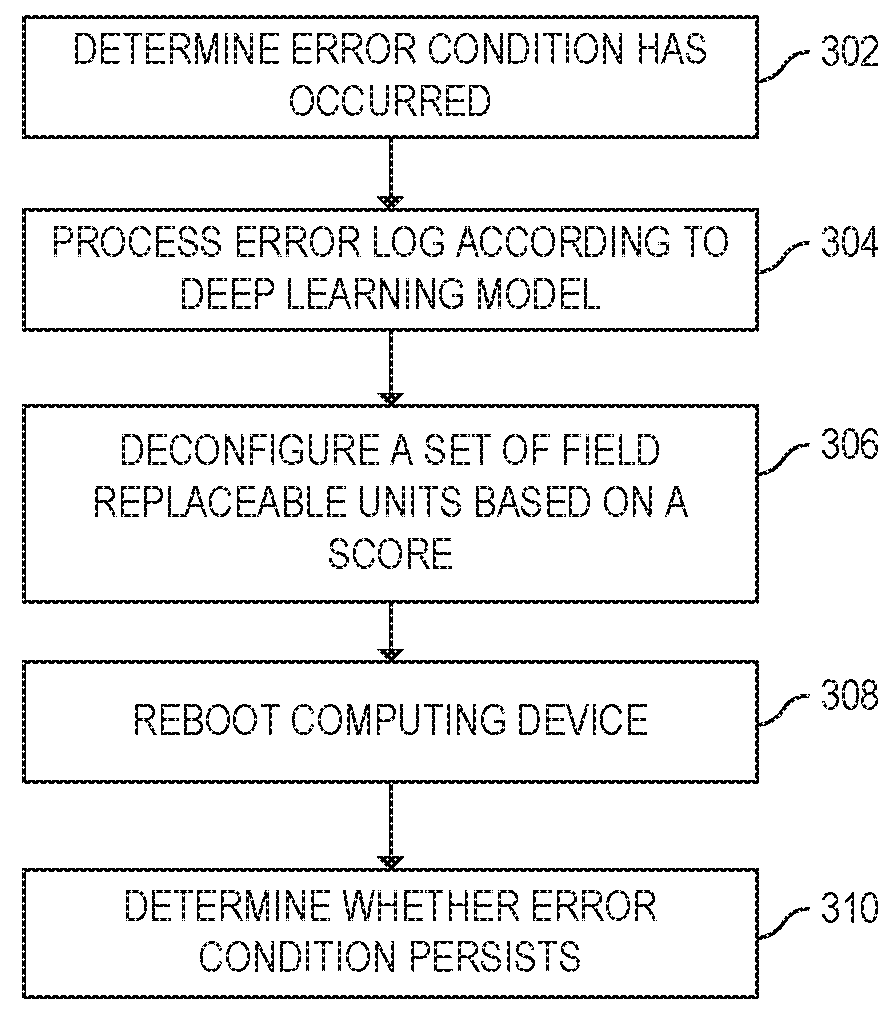
Baseboard Management Controller To Deconfigure Field Replaceable Units According To Deep Learning Model
Examples disclosed herein relate to a baseboard management controller (BMC) capable of execution while a computing device is powered to an auxiliary state. The BMC is to process an error log according to a deep learning model to determine one of multiple field replaceable units to deconfigure in response to the error condition. The BMC is to deconfigure the field replaceable unit. The computing device is rebooted. In response to the reboot of the computing device the BMC is to determine whether the error condition persists.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com