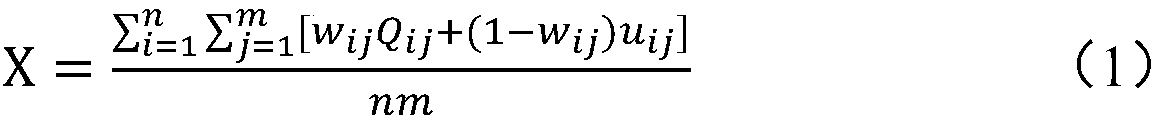Patents
Literature
1968results about How to "Accurate processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
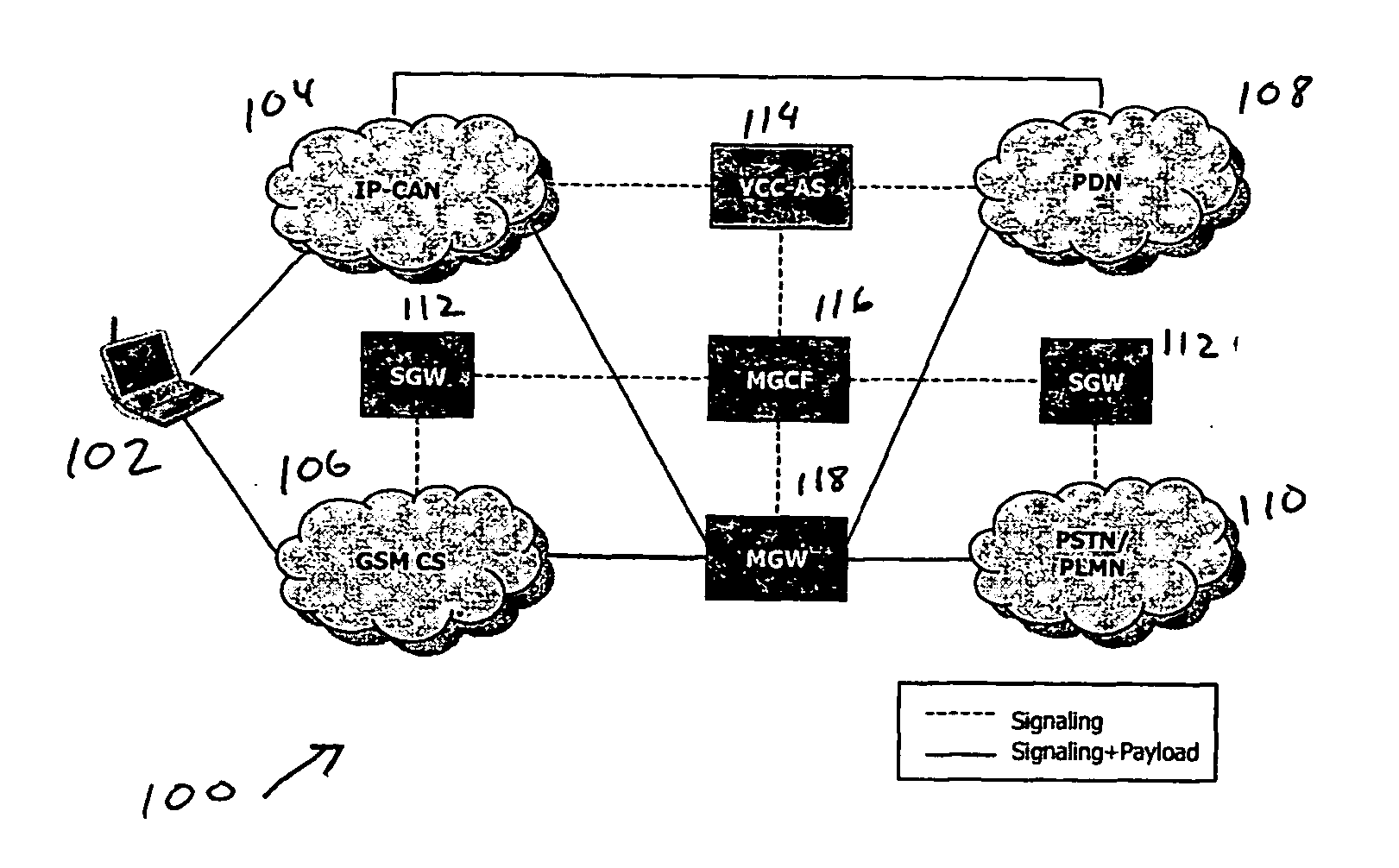
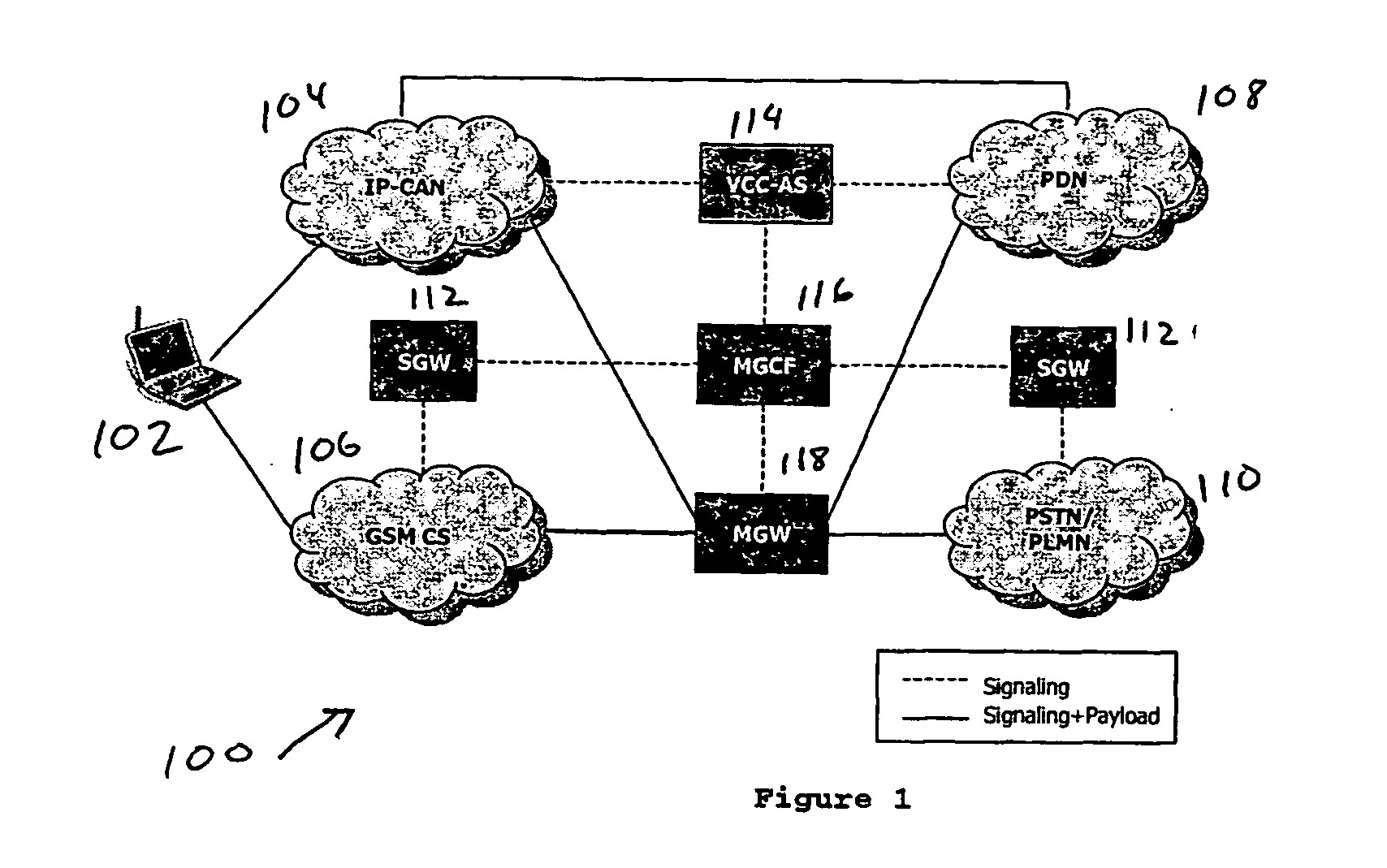
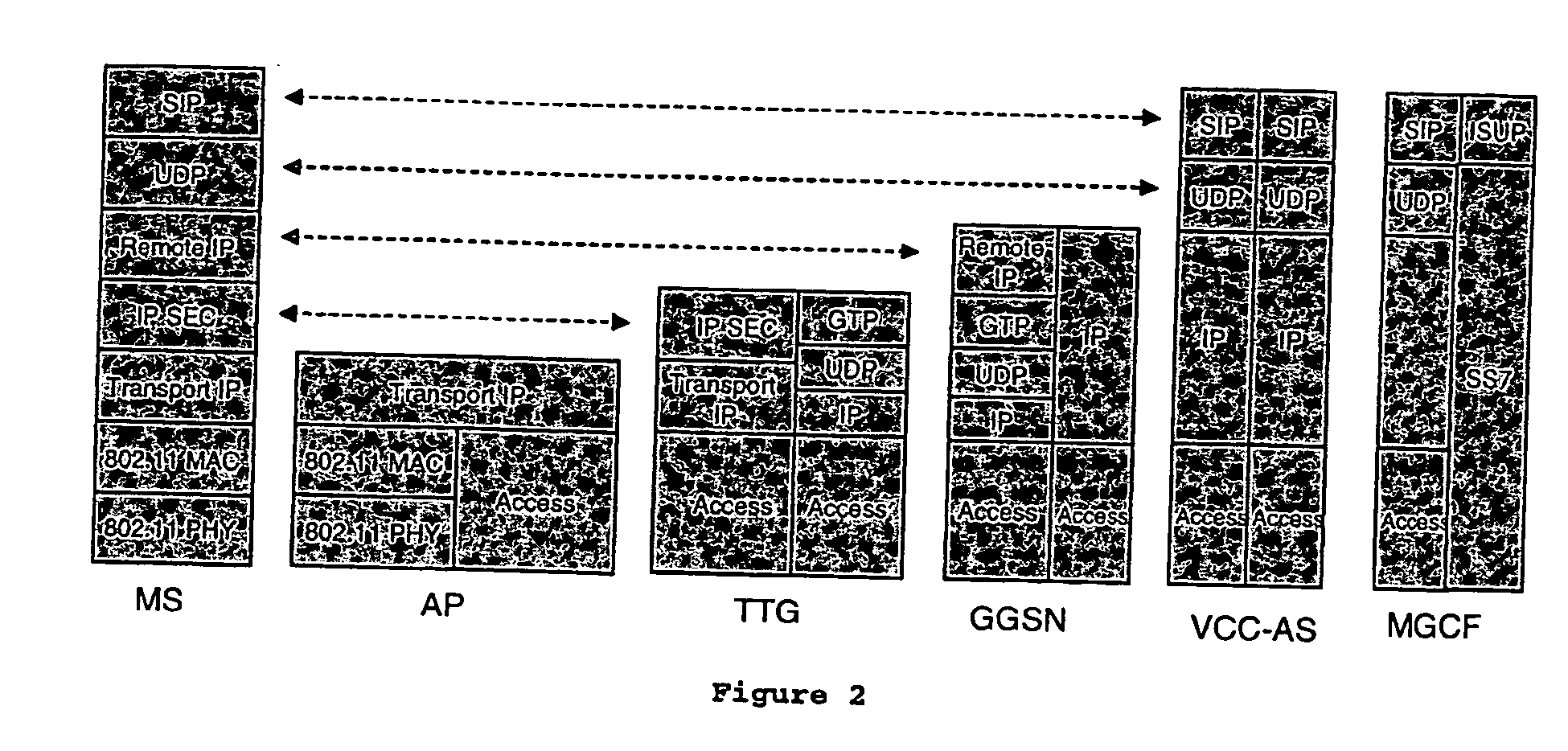
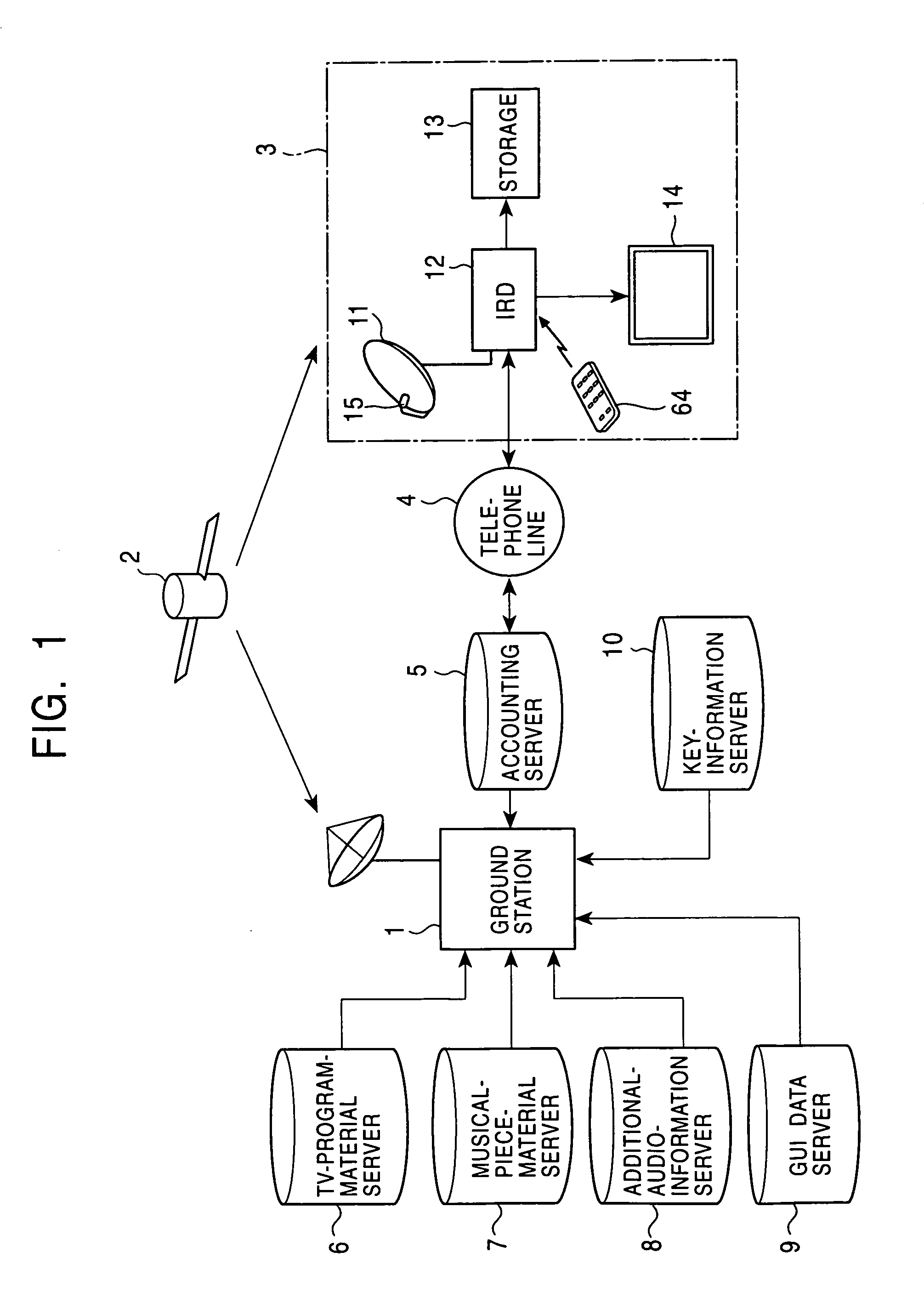
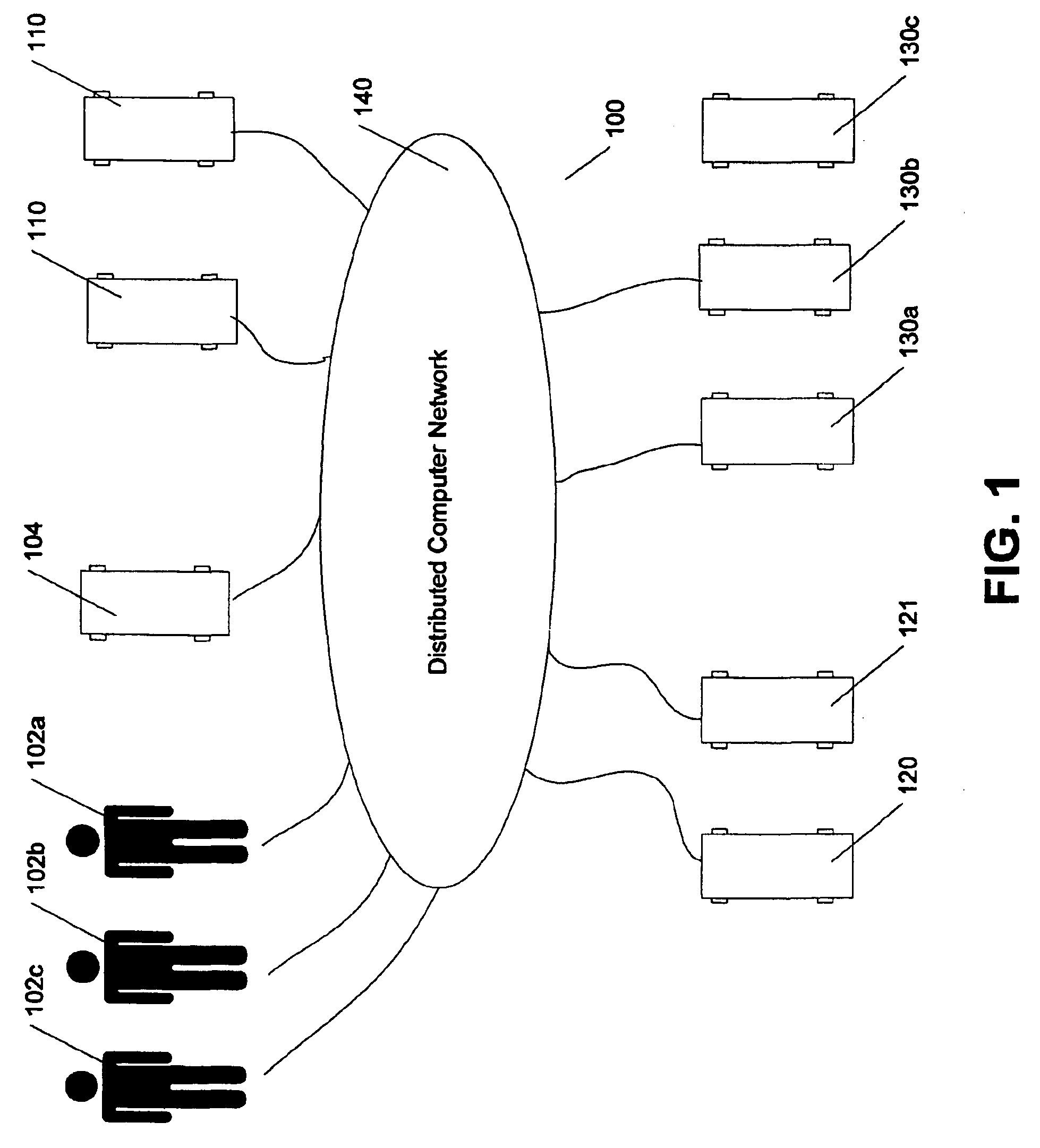
Voice call continuity application server between IP-CAN and CS networks
InactiveUS20070014281A1Accurate processingMultiplex system selection arrangementsConnection managementAccess networkApplication server
A system and method for continuous voice calls when a user switches between packet data and circuit switched access networks. In one example embodiment, the present innovations include an interworking system that supports voice call continuity for a user that moves between IP-CAN and CS networks (e.g., PSTN or GSM). In one example embodiment, the present innovations comprise a voice call continuity application server (VCC-AS) that serves as an anchor point for a voice call (i.e., it is the node from which a handover is initiated) and controls and handles voice calls to and from the user equipment (UE) regardless of the access network.
Owner:INTELLINET TECH
Apparatus and method for downloading desired data signal to user-selectable storage unit
InactiveUS6931198B1Facilitates user operationImprove reliabilityTelevision system detailsPulse modulation television signal transmissionData signalLog data
Owner:SONY CORP
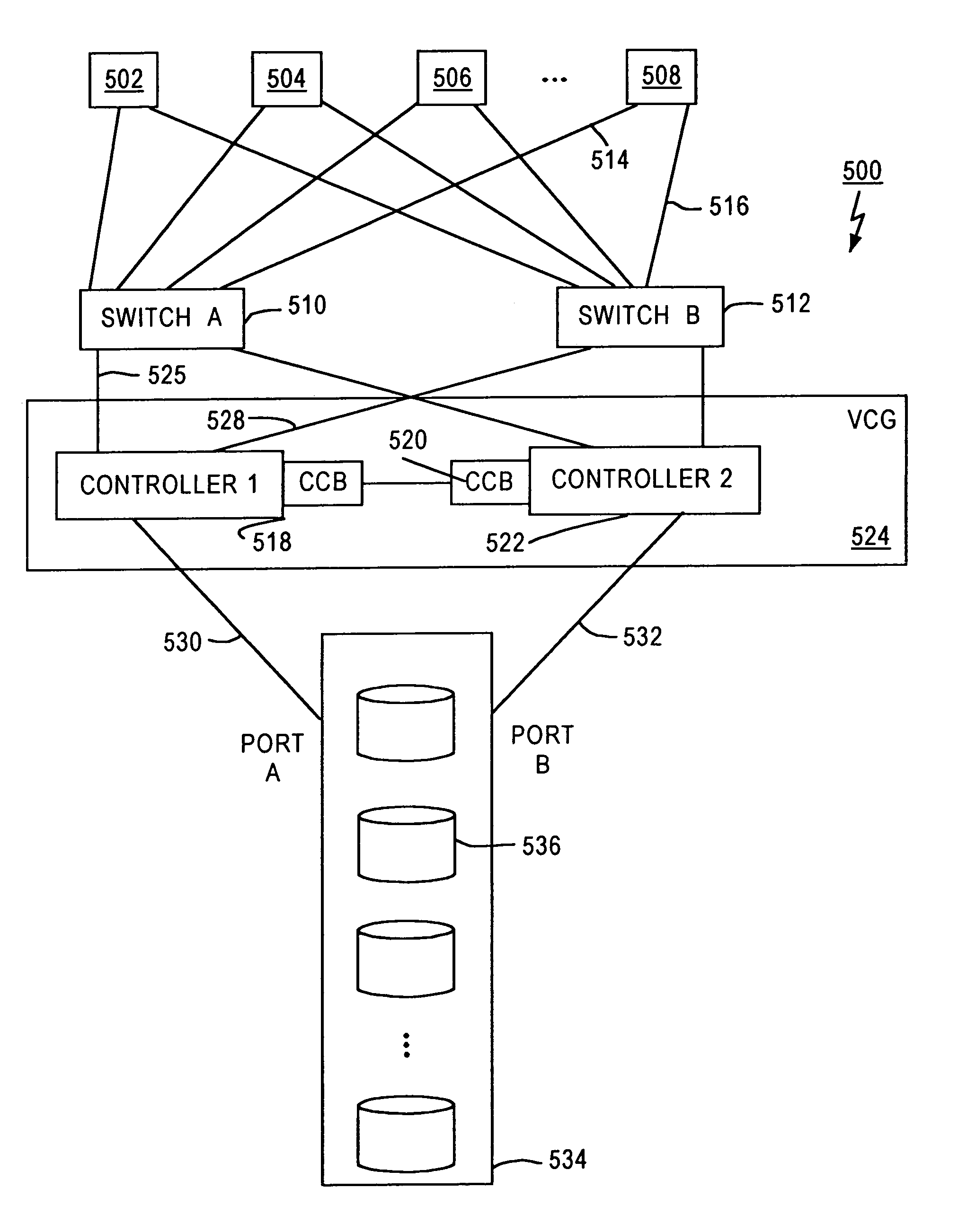
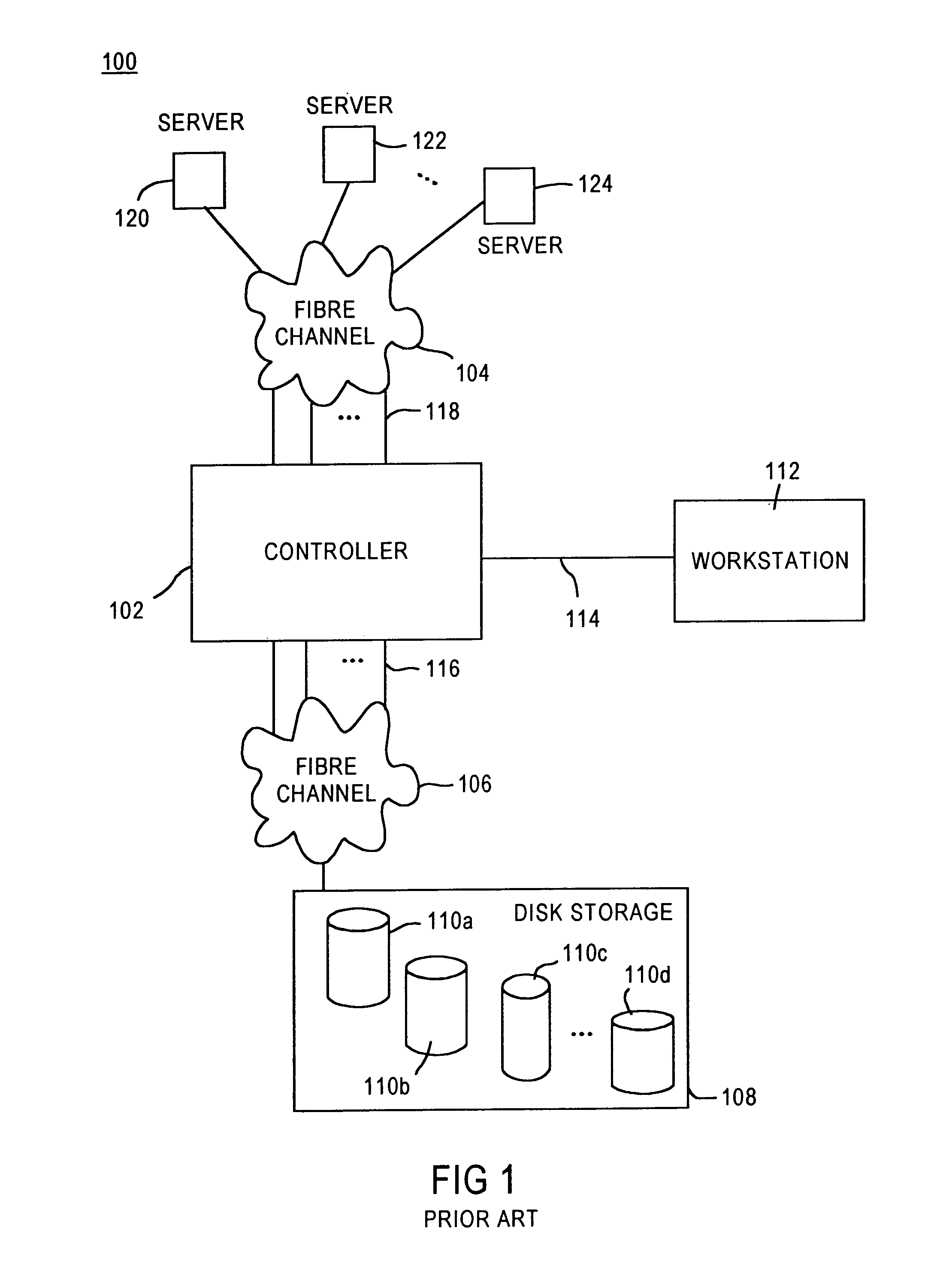
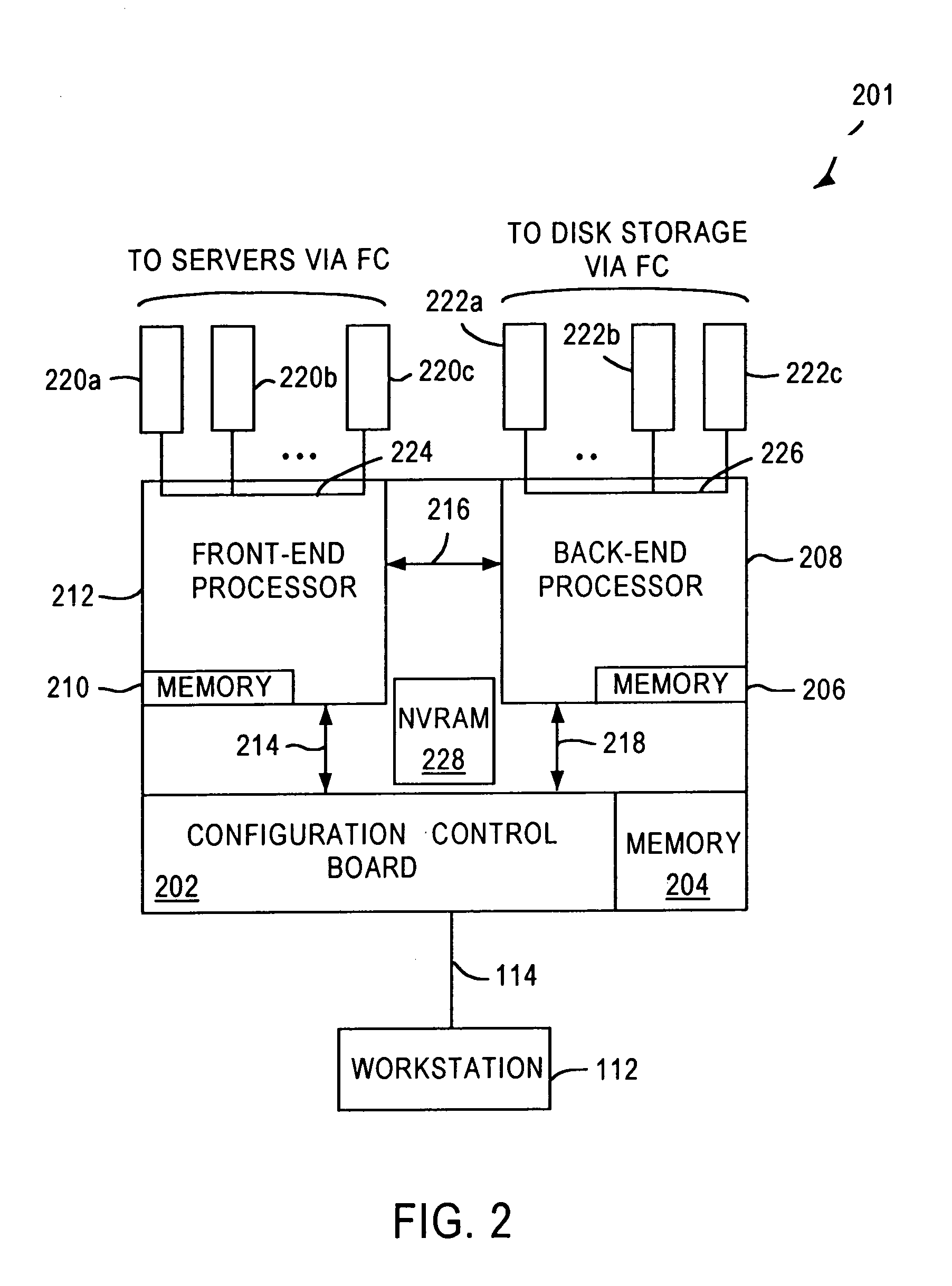
System and method to monitor and isolate faults in a storage area network
A fiber channel storage area network (SAN) provides virtualized storage space for a number of servers to a number of virtual disks implemented on various virtual redundant array of inexpensive disks (RAID) devices striped across a plurality of physical disk drives. The SAN includes plural controllers and communication paths to allow for fail-safe and fail-over operation. The plural controllers can be loosely-coupled to provide n-way redundancy and have more than one independent channel for communicating with one another. In the event of a failure involving a controller or controller interface, the virtual disks that are accessed via the affected interfaces are re-mapped to another interface in order to continue to provide high data availability. In particular, deadman timers, heartbeat signals internal to each controller, and heartbeat signals between different controllers are used to detect controllers that are no longer communicating with other controllers in order to identify those controllers which are failing or have failed.
Owner:XIOTECH CORP
Intelligent book management robot
ActiveCN104875177AMechanism design is exquisite and practicalRealization is likely to be largeManipulatorManipulatorEngineering
The invention provides an intelligent book management robot for fully automatically borrowing, returning and arranging of books of a library. The intelligent book management robot comprises an automatic moving trolley for polling and avoiding a barrier, a storing bookshelf, a book basket, a book picking and storing mechanism and a control device. The intelligent book management robot is characterized in that the moving trolley can move according to a ground mark and a mark line; a mechanism for avoiding the barrier and polling is mounted at a head part of the trolley; the storing bookshelf is of a special structure and is in the same direction as the trolley marching direction; the book picking and storing mechanism moves up and down, left and right and front and back based on the combination of guide rails; a composite manipulator consisting of a book expanding arm and a book picking arm is arranged at the tail end of the mechanism and has the functions of telescoping, expanding and clamping; the books can be picked and stored under the effects of imaging of a camera and controlling of a computer. The intelligent book management robot has the advantages that the book is automatically managed without reconstructing the bookshelf of the library, and thus the labor intensity of workers in the library can be reduced.
Owner:SHANGHAI JIAO TONG UNIV
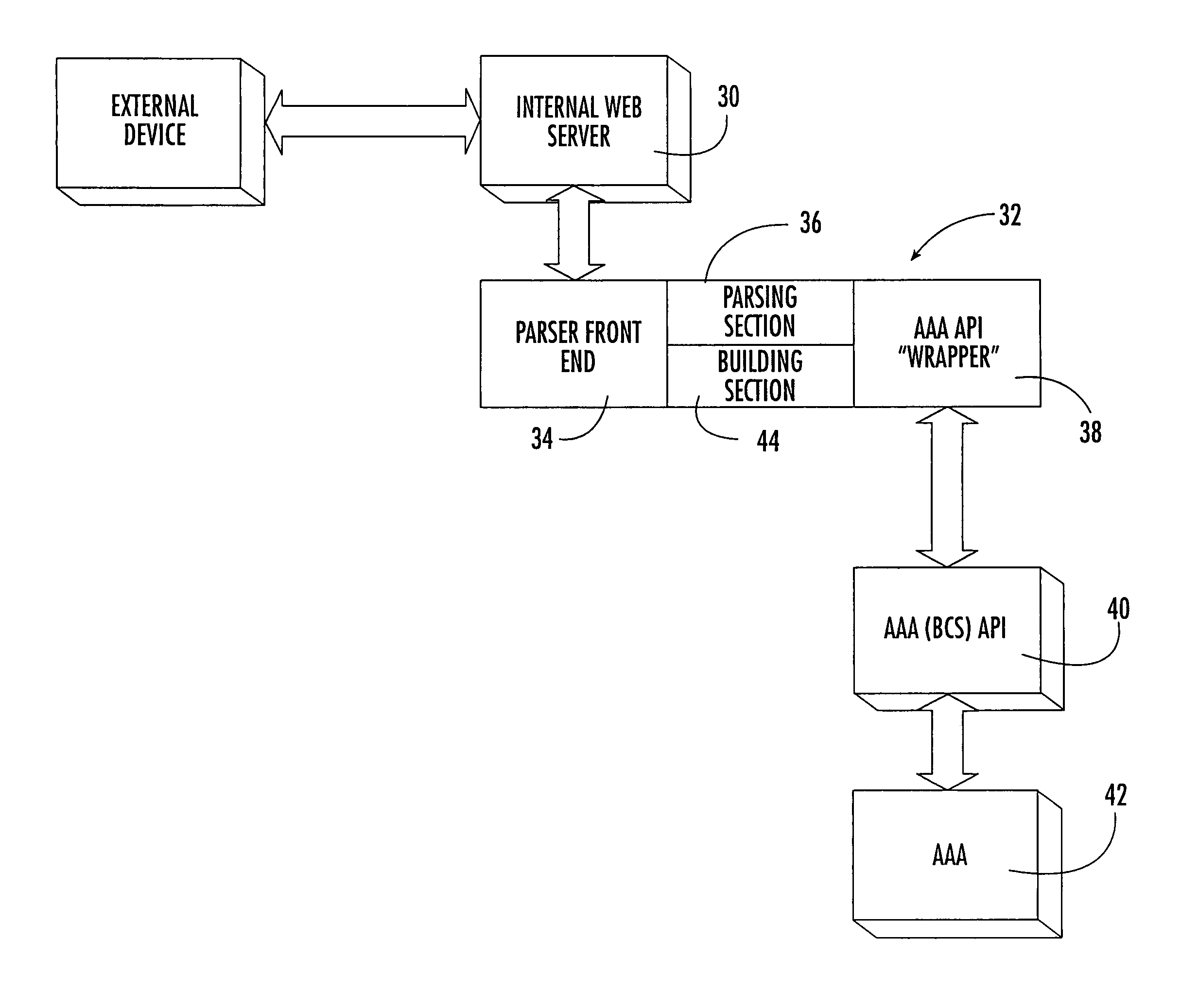
Gateway device having an XML interface and associated method
ActiveUS8190708B1Facilitate communicationSimple designMetering/charging/biilling arrangementsData switching by path configurationComputer networkXML
A gateway device and associated method are provided that facilitate communications with external devices by utilizing a uniform communications format. The gateway device includes a subscriber interface for adapting to a subscriber computer that is connected to the gateway device. The subscriber interface facilitates communications between the subscriber computer and at least one network or on-line service without requiring the subscriber computer to be reconfigured and without requiring the subscriber computer to support XML commands and responses. The gateway device also includes an XML interface for communicating with an external device via a series of XML commands and responses. The XML commands and responses can relate to a variety of matters, including various subscriber management matters.
Owner:NOMADIX INC
Method and system for synchronizing cached files
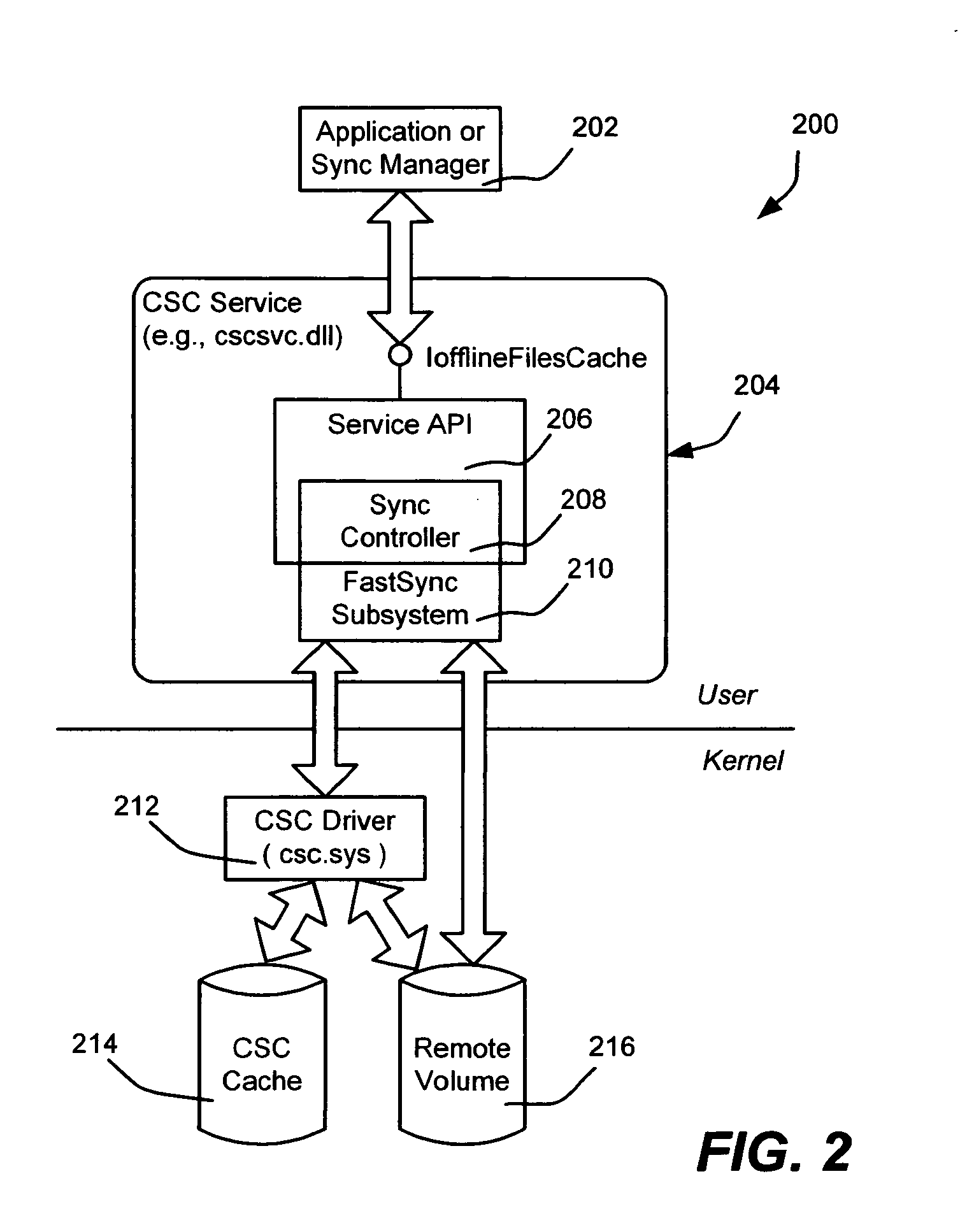
ActiveUS20060155776A1Accurate processingMemory architecture accessing/allocationDigital data processing detailsFile systemDatabase
Described is a system and method that synchronizes cached files and directories with a server's files and directories via a layered architecture, by collapsing state information into an index into a fixed set of known states, and looking up the action that synchronizes that state. The actions are then taken to synchronize the content. Any of fifty possible synchronization states are thus handled. A synchronization controller requests a subsystem to evaluate a local cache and remote file system to generate state flags for each item considered for synchronization. The synchronization controller processes the state information to identify a selected table from among a plurality of tables that contain the fifty values, and uses other flags to compute an index into the table. The selected table contains values that index into an action table containing actions that specify an operation set that is requested to synchronize the particular state scenario.
Owner:MICROSOFT TECH LICENSING LLC
Service providing apparatus and method that allow an apparatus to access unique information stored in transportable recording medium
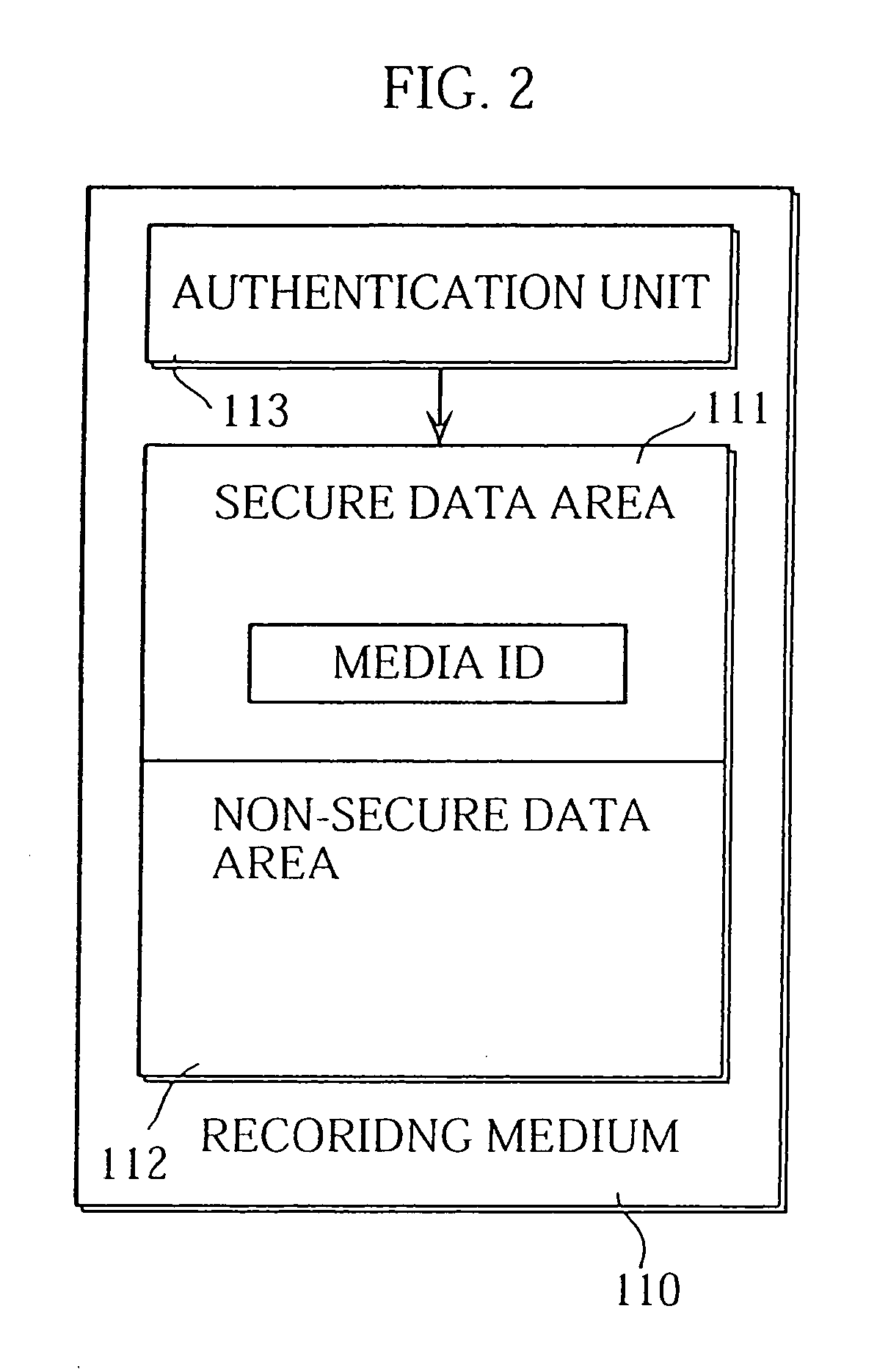
InactiveUS20060178996A1Improve securityAccurate processingComputer security arrangementsPayment architectureWeb siteService provision
A transportable recording medium includes an area for storing encrypted cookie information. The same cookie information is thus easy to use in different terminals and the cookie information becomes unique to respective users instead of respective terminals. A Web site reads the encrypted cookie information, decrypts the encrypted cookie information using a secret key stored in the Web site, customizes a requested service according to the decrypted cookie information, and provides the customized service to a terminal. If the Web site stores non-encrypted user information, the recording medium stores a media identification. The Web site stores the user information so that the user information of the user assigned to the recording medium is searched for according to the media identification. The Web site reads the media identification from the recording medium, searches for user information corresponding to the media identification, and customizes a requested service according to the user information.
Owner:PANASONIC CORP
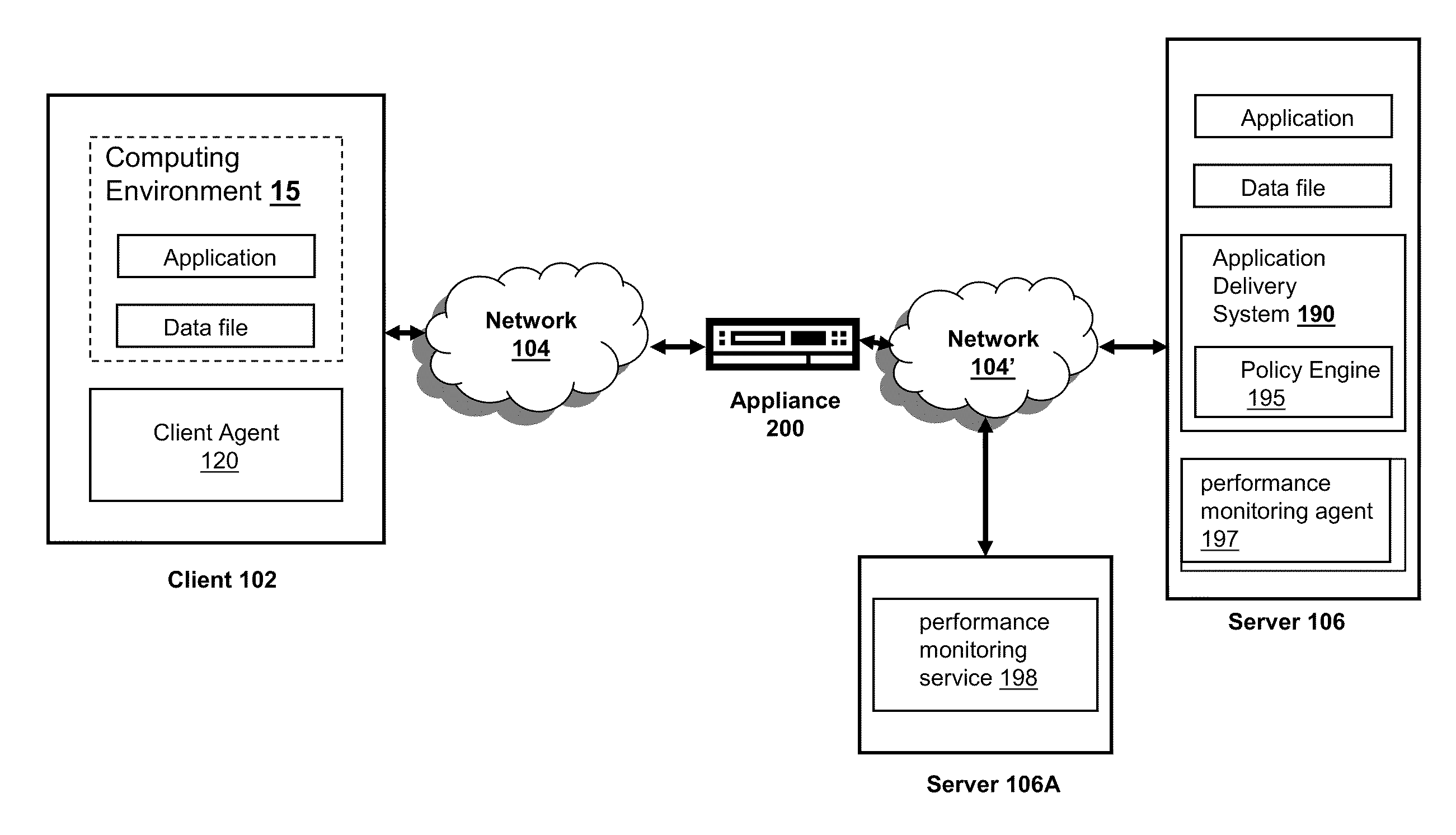
Methods, apparatuses and systems for transparently intermediating network traffic over connection-based authentication protocols
ActiveUS7343398B1Easy to deployTransparently fits into existing NTLM environmentMultiple digital computer combinationsTransmissionTraffic capacityComputer network
Methods, apparatuses and systems allowing for the transparent intermediation of network traffic over connection-based authentication protocols. In one embodiment, the present invention allows a proxy to be placed into an NTLM or HTLMv2 environment and have it transparently ensure that NTLM transactions are handled appropriately, such that the proxy can interact (optimize / accelerate) with the authenticated content without breaking the authentication scheme. Embodiments of the present invention provide a proxy solution that is easily deployed and transparently fits into an existing NTLM environment.
Owner:CA TECH INC
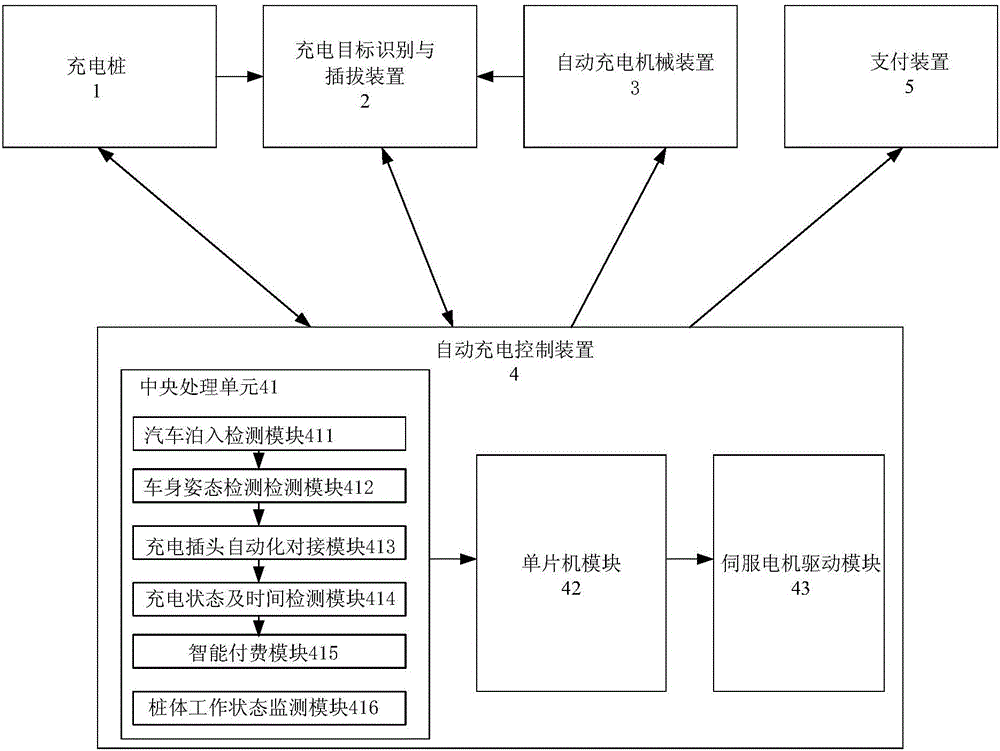
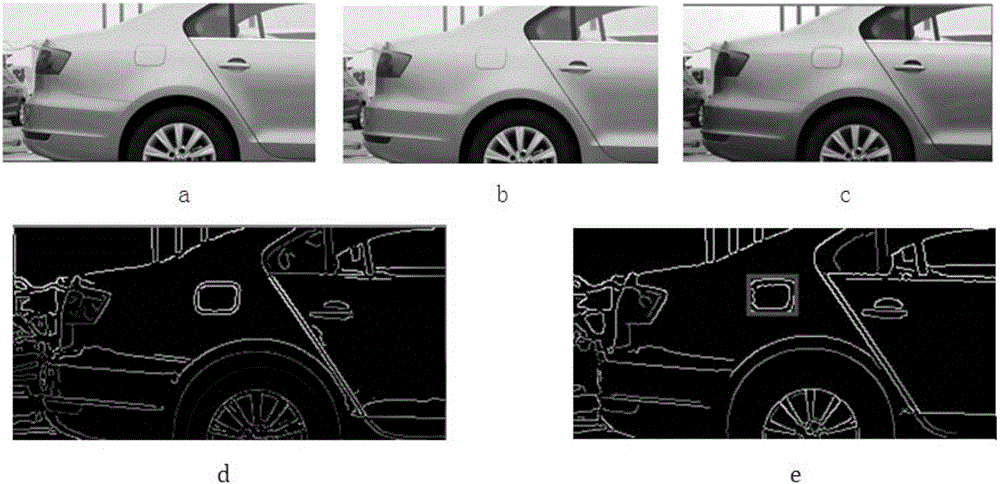
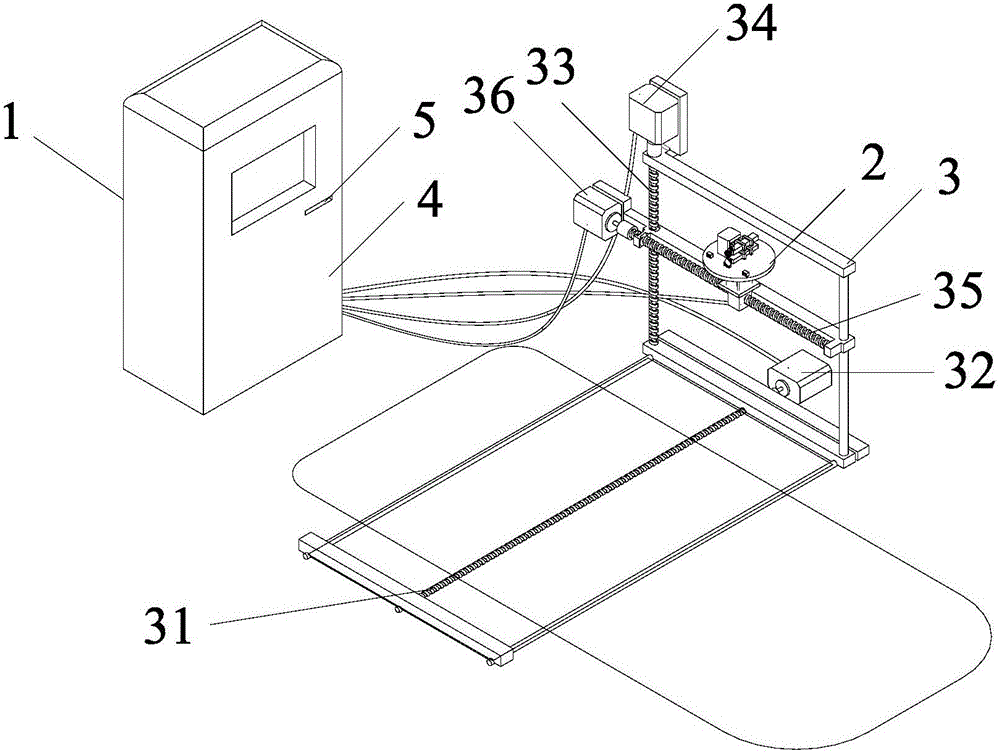
Automatic charging system of electric car and control method of automatic charging system
InactiveCN106696747ARealize intelligent operationReduce consumptionCharging stationsElectric vehicle charging technologyReal-time chargingCar model
The invention discloses an automatic charging system of an electric car and a control method of the automatic charging system. The automatic charging system and the control method thereof have the advantages that monitoring is started from parking of the car, a charging connection reset device is disconnected after charging of the car, a user's bill is generated, charging plug butt joint and real-time charging process monitoring are included, all related data in the whole charging process are monitored by a software system portion, a hardware mechanical portion is controlled to complete a next action, the hardware portion sends new semaphore to the software portion for new command calculation after completing a command, the software portion is combined with the hardware portion, and accordingly, systematicness and intellectuality of the whole charging system are improved; a charging interface butt joint scheme based on machine vision and a machine learning algorithm is applied, and feasibility and accuracy in butt joint are guaranteed; a three-dimensional lead screw guide rail mechanism with a long stroke is used, the range of activity of a charging connector is widened, and the charging connector is suitable for multiple car models; the automatic charging system is provided with a payment code scanner, payment of related charges can be completed through a payment bar code scanning function of a cellphone-side payment application, and accordingly, intelligent payment is achieved.
Owner:XIAMEN UNIV
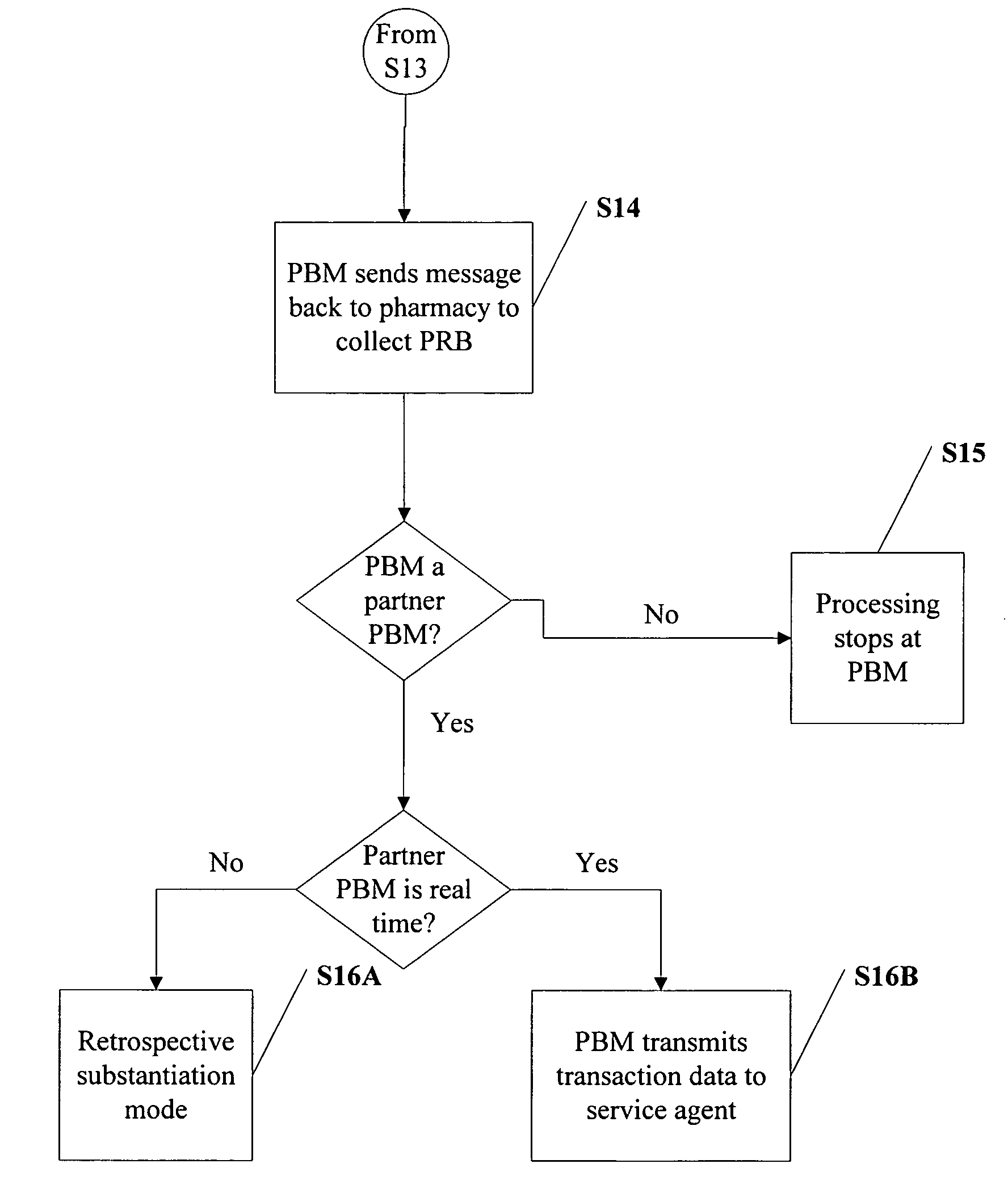
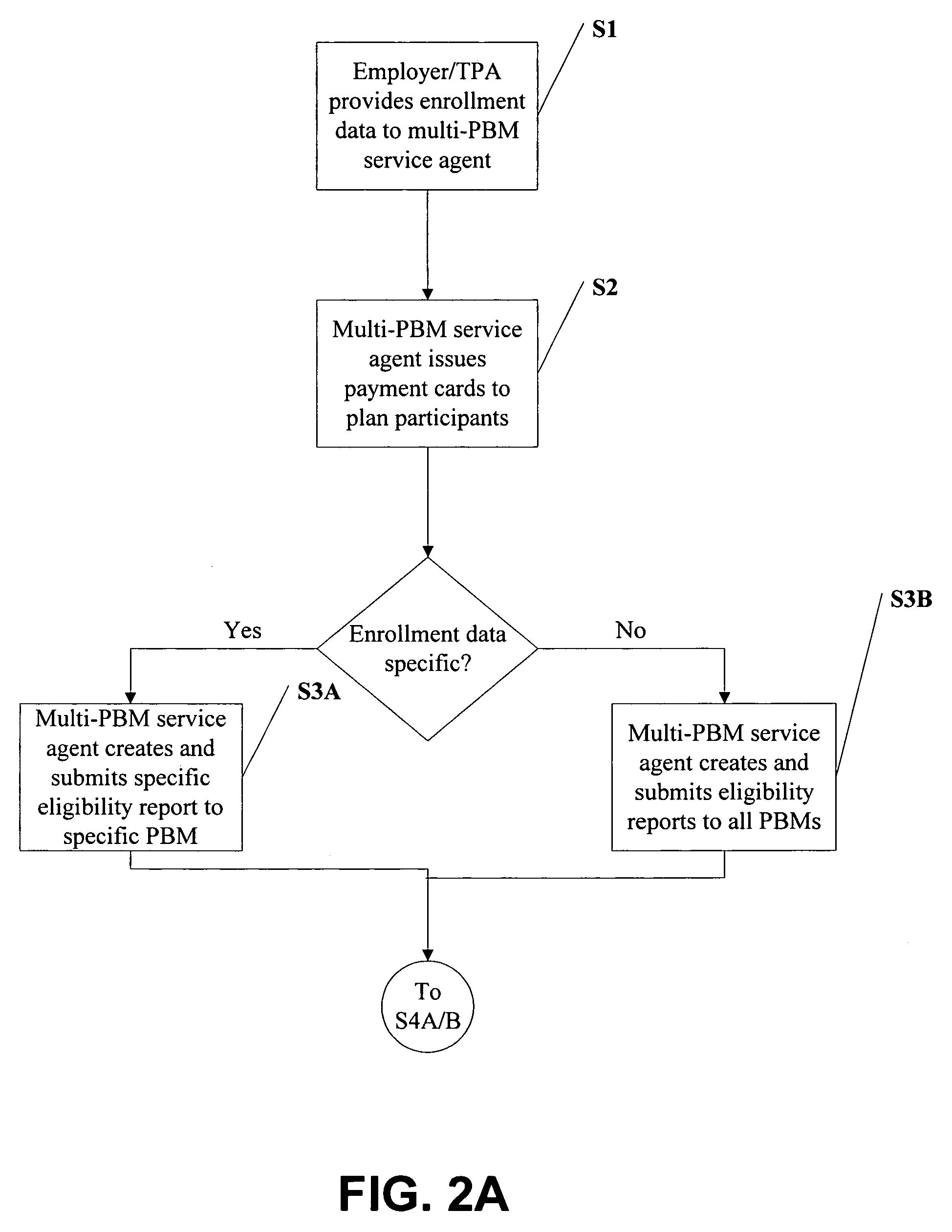
Method and system for processing transactions involving accounts for reimbursing medical expenses or patient responsible balances with multiple transaction substantiation modes
InactiveUS7197468B1Improve determinationAccurate processingCredit registering devices actuationFinanceMedical expensesComputer science
The present invention relates to a method and system for processing transactions involving accounts for reimbursing medical expenses or patient responsible balances, wherein the accounts may be handled by multiple payors having multiple transaction substantiation requirements. Examples of such accounts include flexible spending accounts, health reimbursement arrangement accounts, medical savings account, health savings account and the like. The system and method of the present invention allow an employer that uses multiple payors for administering the aforementioned accounts to distinguish its employees-based on their associated payors in order to determine the proper transaction substantiation requirement per each employee and associated payor without having required to collect payor data at the employee level.
Owner:WEX HEALTH INC
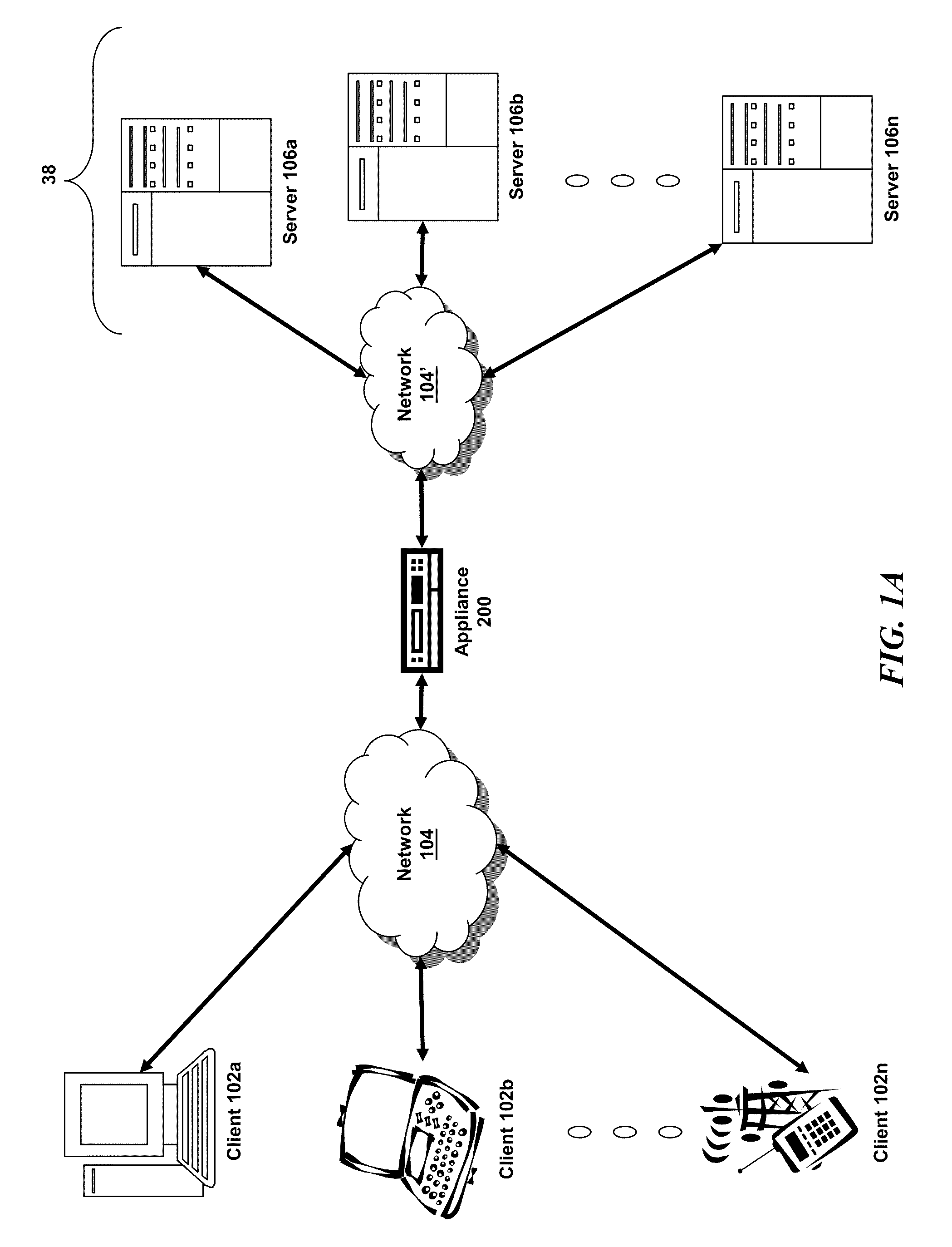
Systems and methods for managing ports for rtsp across cores in a multi-core system
ActiveUS20110161500A1Accurate processingMultiple digital computer combinationsTransmissionClient-sideProtocol for Carrying Authentication for Network Access
The present application is directed towards systems and methods for systems and methods for handling real-time streaming protocol sessions by an intermediary multi-core system. When a multi-core intermediary receives a setup request for a real-time streaming protocol session, the intermediary processes and forwards the request to a server providing the streaming media. The server sets up an RTSP session and transmits a session identification to the multi-core intermediary. A core of the intermediary receives the transmitted session identification and determines an owner core of the session, based on a hash of the session identification. The core transmits the session information to the determined owner core, which selects two consecutive ports on which to establish listening services. The owner core then notifies all other cores to establish listening services on the same consecutive ports, such that any core that receives an RTSP control message from a client can handle it properly.
Owner:CITRIX SYST INC
Parallel detecting, spectroscopic ellipsometers/polarimeters
InactiveUS6384916B1Minimization requirementsInexpensively adaptedPolarisation-affecting propertiesPolarisation spectroscopyPolarizerReal time analysis
The parallel detecting spectroscopic ellipsometer / polarimeter sensor has no moving parts and operates in real-time for in-situ monitoring of the thin film surface properties of a sample within a processing chamber. It includes a multi-spectral source of radiation for producing a collimated beam of radiation directed towards the surface of the sample through a polarizer. The thus polarized collimated beam of radiation impacts and is reflected from the surface of the sample, thereby changing its polarization state due to the intrinsic material properties of the sample. The light reflected from the sample is separated into four separate polarized filtered beams, each having individual spectral intensities. Data about said four individual spectral intensities is collected within the processing chamber, and is transmitted into one or more spectrometers. The data of all four individual spectral intensities is then analyzed using transformation algorithms, in real-time.
Owner:COLORADO SCHOOL OF MINES
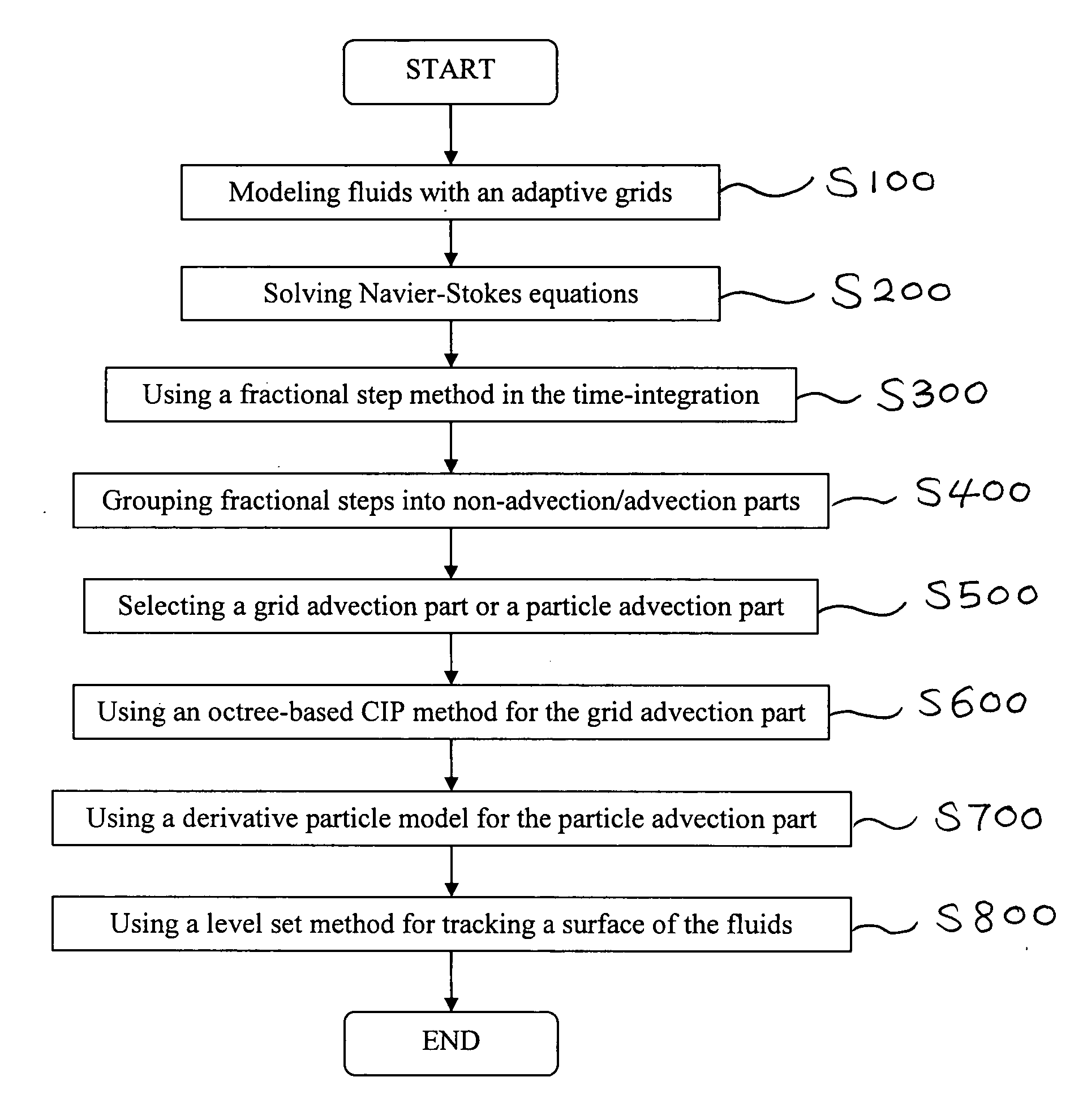
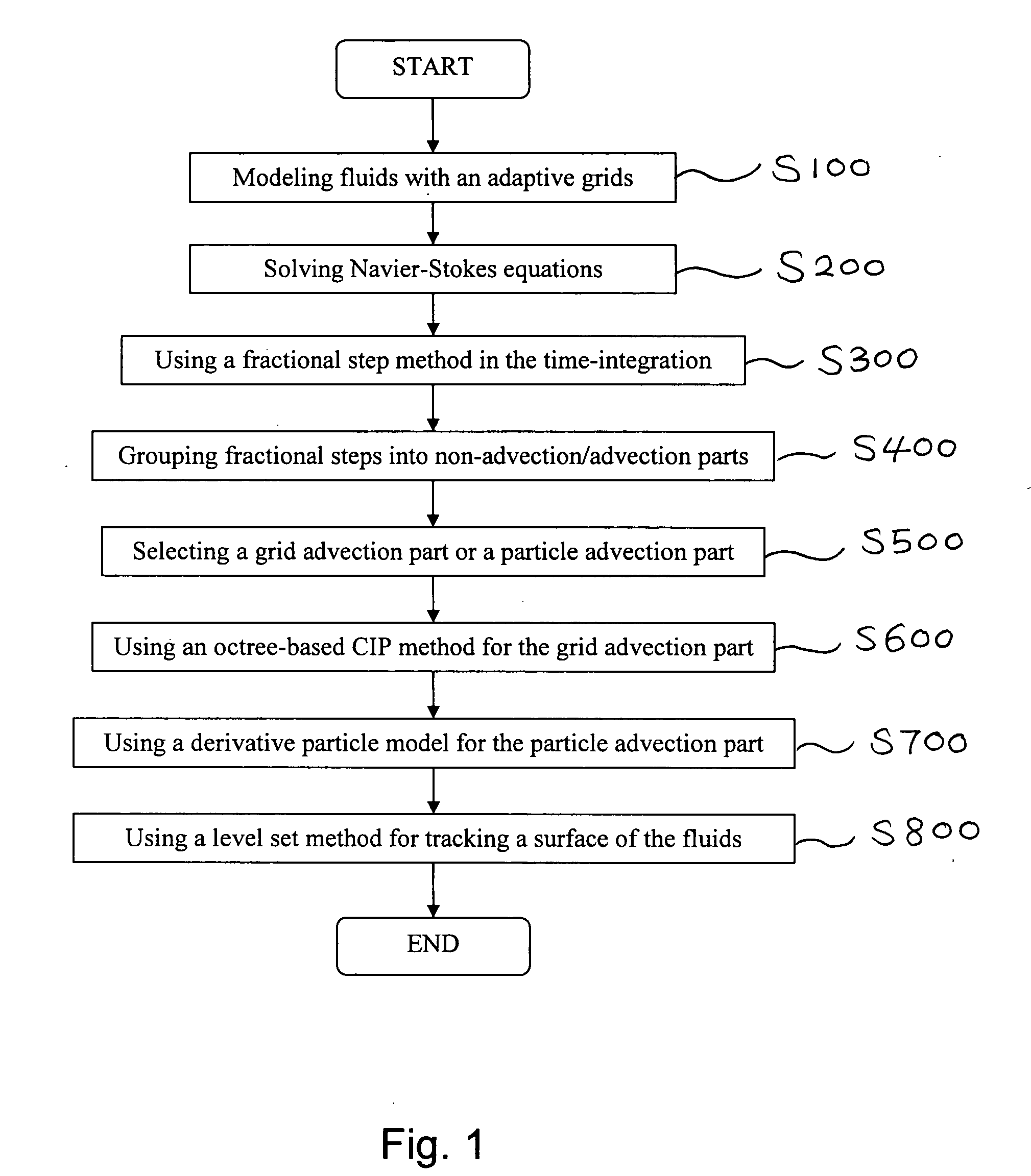
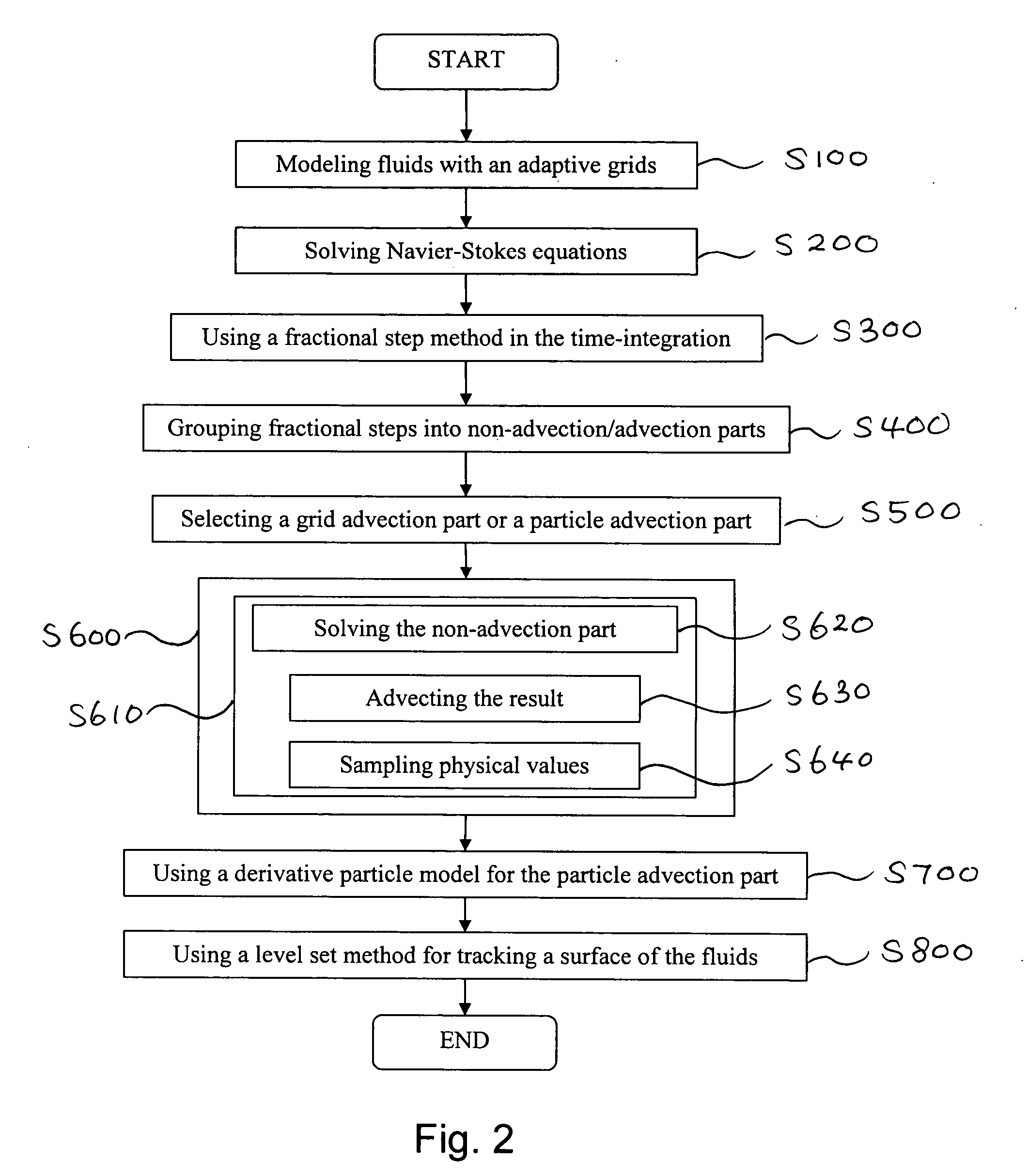
Method of simulating detailed movements of fluids using derivative particles
ActiveUS20070239414A1Reduce dissipationRealistic reproductionComputation using non-denominational number representationDesign optimisation/simulationAdvectionParticle simulation
The method provides a new fluid simulation technique that significantly reduces the non-physical dissipation of velocity using particles and derivative information. In solving the conventional Navier-Stokes equations, the method replace the advection part with a particle simulation. When swapping between the grid-based and particle-based simulators, the physical quantities such as the level set and velocity must be converted. A novel dissipation-suppressing conversion procedure that utilizes the derivative information stored in the particles as well as in the grid points is developed. Through several experiments, the proposed technique can reproduce the detailed movements of high-Reynolds-number fluids, such as droplets / bubbles, thin water sheets, and whirlpools. The increased accuracy in the advection, which forms the basis of the proposed technique, can also be used to produce better results in larger scale fluid simulations.
Owner:SEOUL NAT UNIV R&DB FOUND
Air filter
InactiveUS20060081528A1Easy to handleNot take up excessive spaceDispersed particle filtrationTransportation and packagingAir filterBiomedical engineering
A filter assembly for fluids including a filter element configured for axial through flow that has alternately sealed filter channels for axial through flow and a centrally disposed support member, which in conjunction with a mating part ensures that the filter element can be handled for servicing purposes. The mating part is preferably constructed as a retaining grid, which prevents damage to the axial end surface of the filter element.
Owner:MANN HUMMEL GMBH
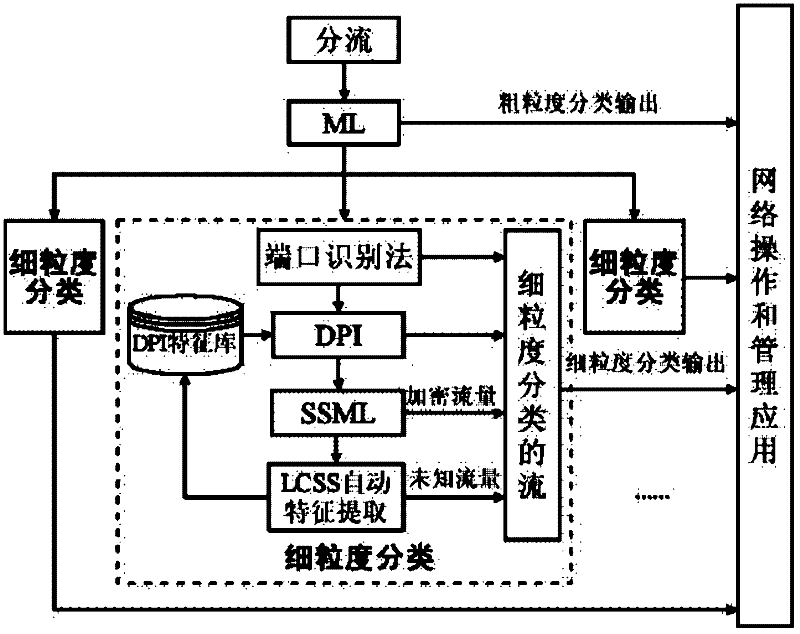
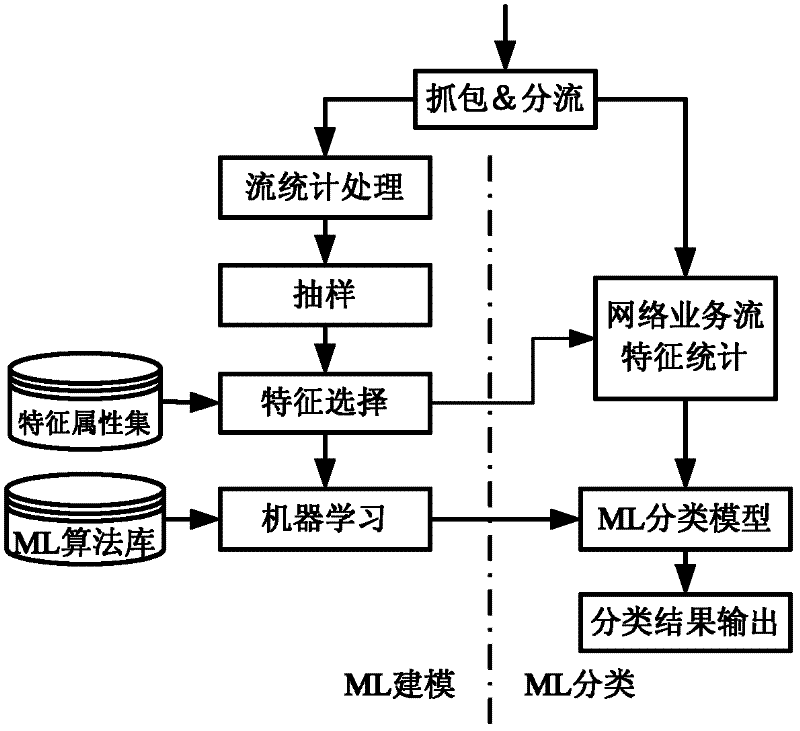
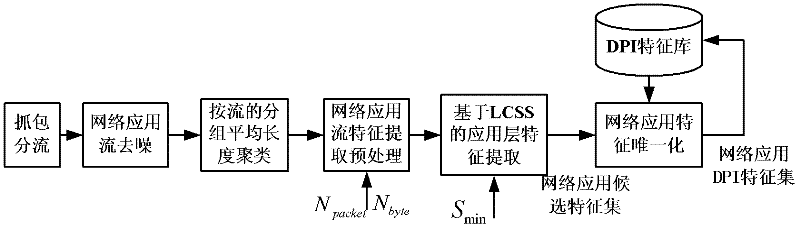
Hierarchical classification method for internet flow
InactiveCN102394827AImprove classification performanceAccurate identification and processingData switching networksTraffic volumeInternet traffic classification
The invention relates to a hierarchical classification method for internet flow, comprising the following steps: firstly, coarse grained classification is conducted as follows: a flow statistical property method based on machine learning is adopted for quickly classifying network flow, the network flow is divided into applied categories with different characteristics, if the flow distinguished by the coarse grained classification needs to be used, the flow can be output directly, and if the flow needs further classification, next step is conducted; and secondly, fine grained classification is conducted as follows: classification is further conducted on the applied categories distinguished by the coarse grained classification, the network flow can be intelligently, accurately and effectively identified in real time, good integrity and expandability are realized, and the requirements on the internet flow classification with different application targets and classification grain size can be met.
Owner:ZHEJIANG WANLI UNIV
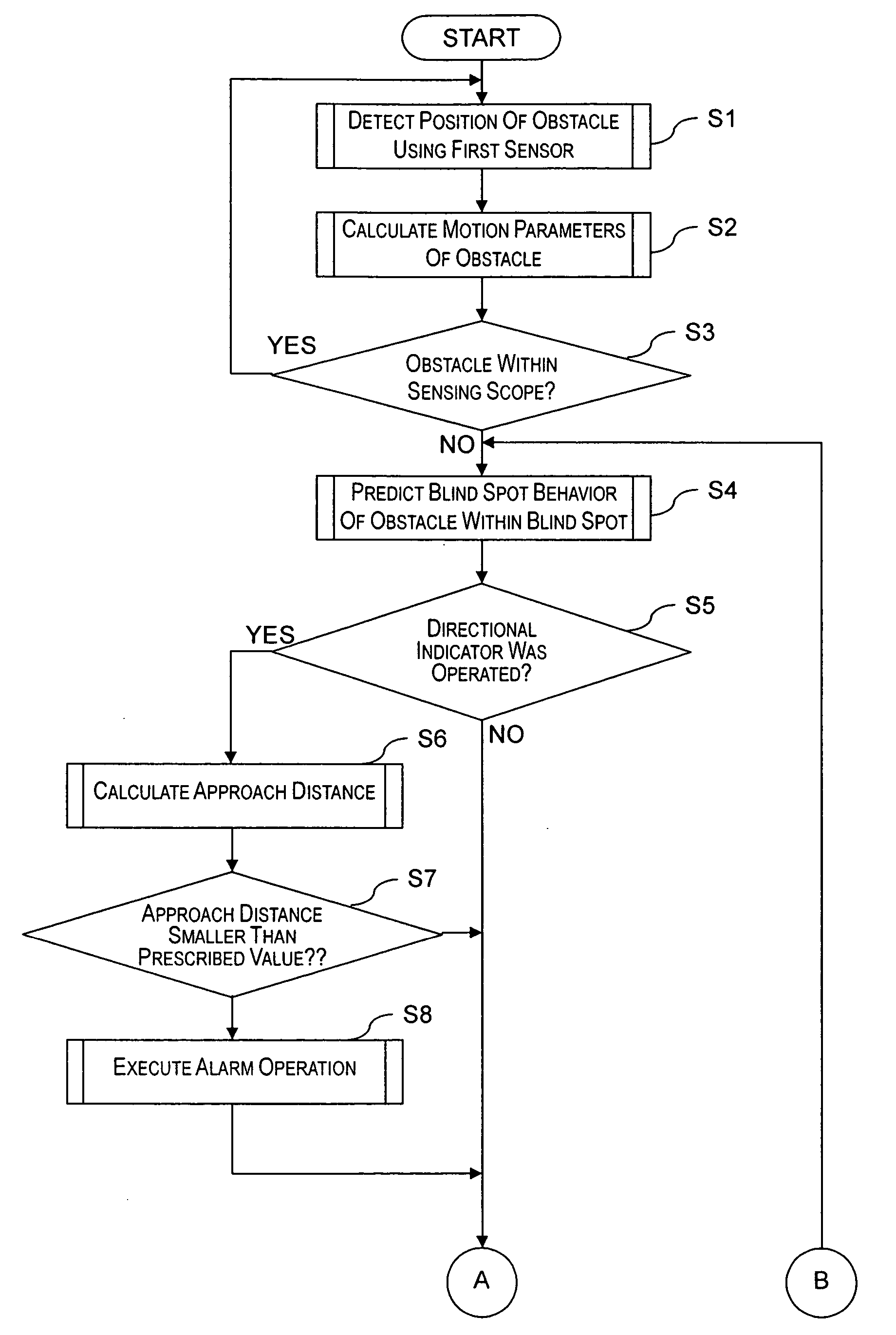
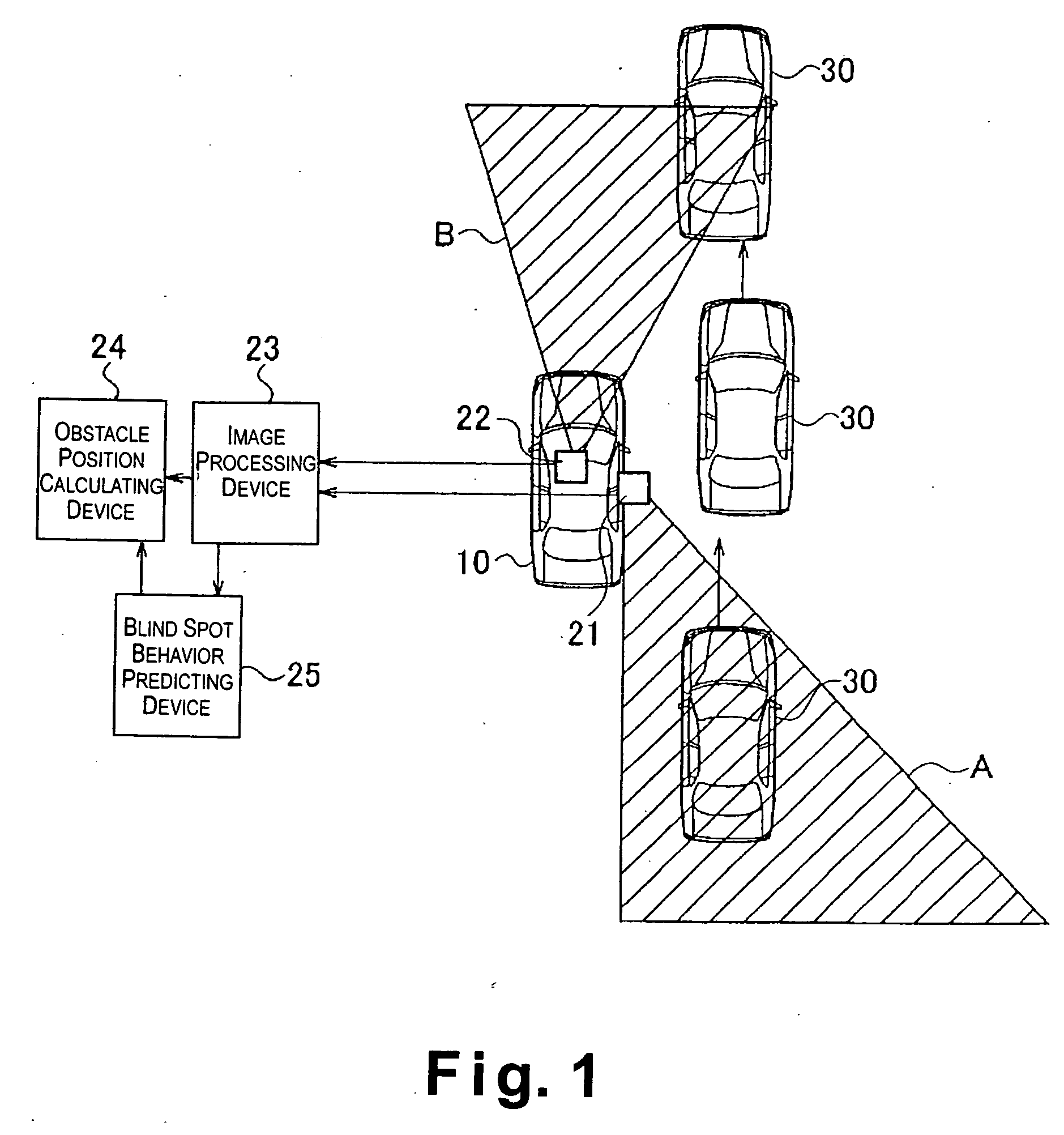
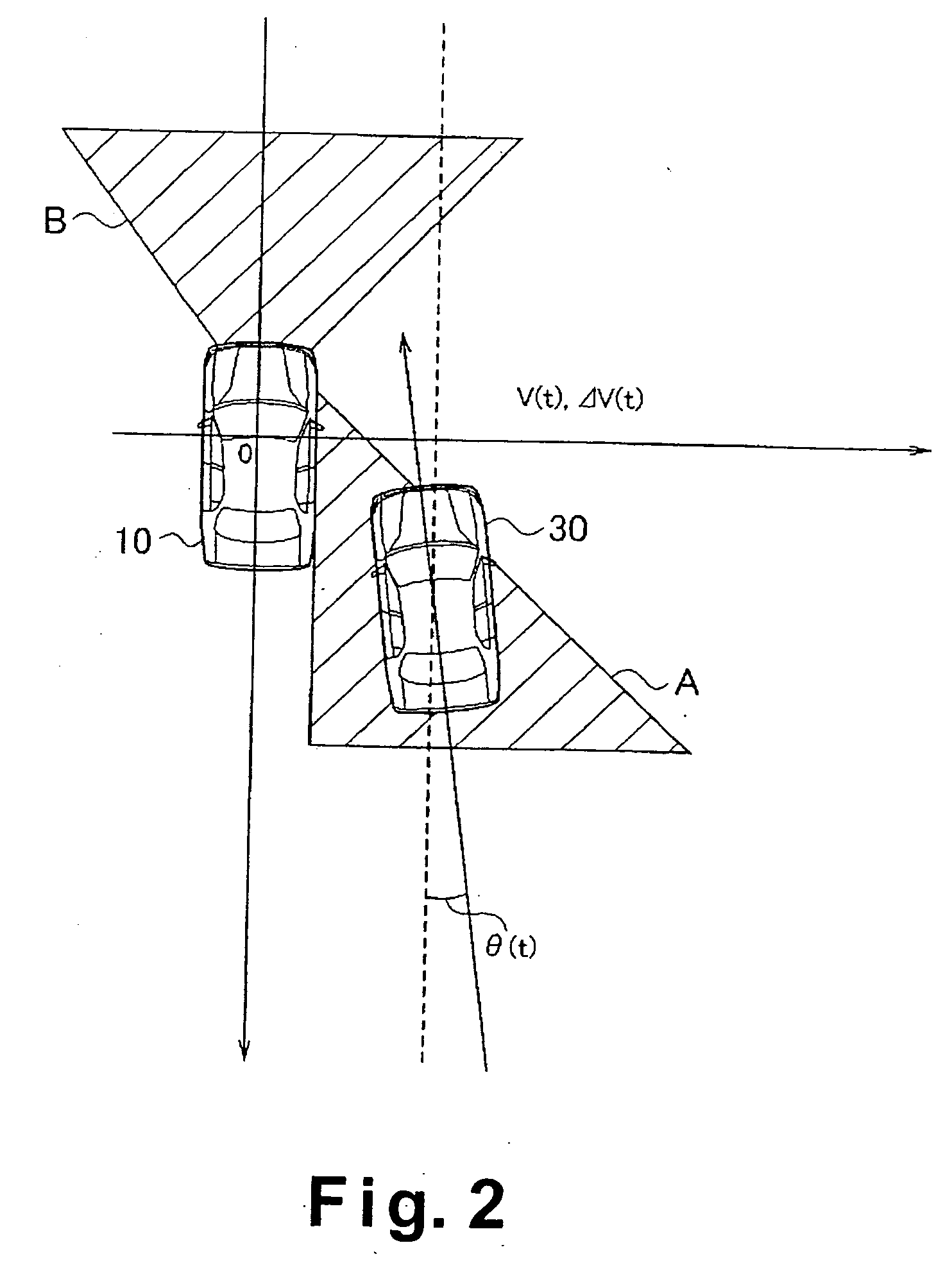
Vehicle obstacle detecting device
ActiveUS20050012604A1Improve detection reliabilityEfficient use ofPedestrian/occupant safety arrangementAnti-collision systemsEngineering
The vehicle obstacle detecting device improves safety of the vehicle by utilizing information detected by a plurality of sensors to appropriately handle situations in which an obstacle exists in a blind spot of the sensors. The vehicle obstacle detecting device includes at least first and second sensors arranged such that sensing scopes of the first and second sensors do not substantially overlap. The vehicle obstacle detecting device is configured to observe the behavior of an obstacle existing within the sensing scope of one of the first and second sensors and predict the blind spot behavior of the obstacle in a blind spot between the sensing scopes of the first and second sensors based on the observed behavior of the obstacle. Thus, the vehicle obstacle detecting device is configured to predict the existence of an obstacle in the blind spot where the first and second sensors cannot actually detect the obstacle.
Owner:NISSAN MOTOR CO LTD
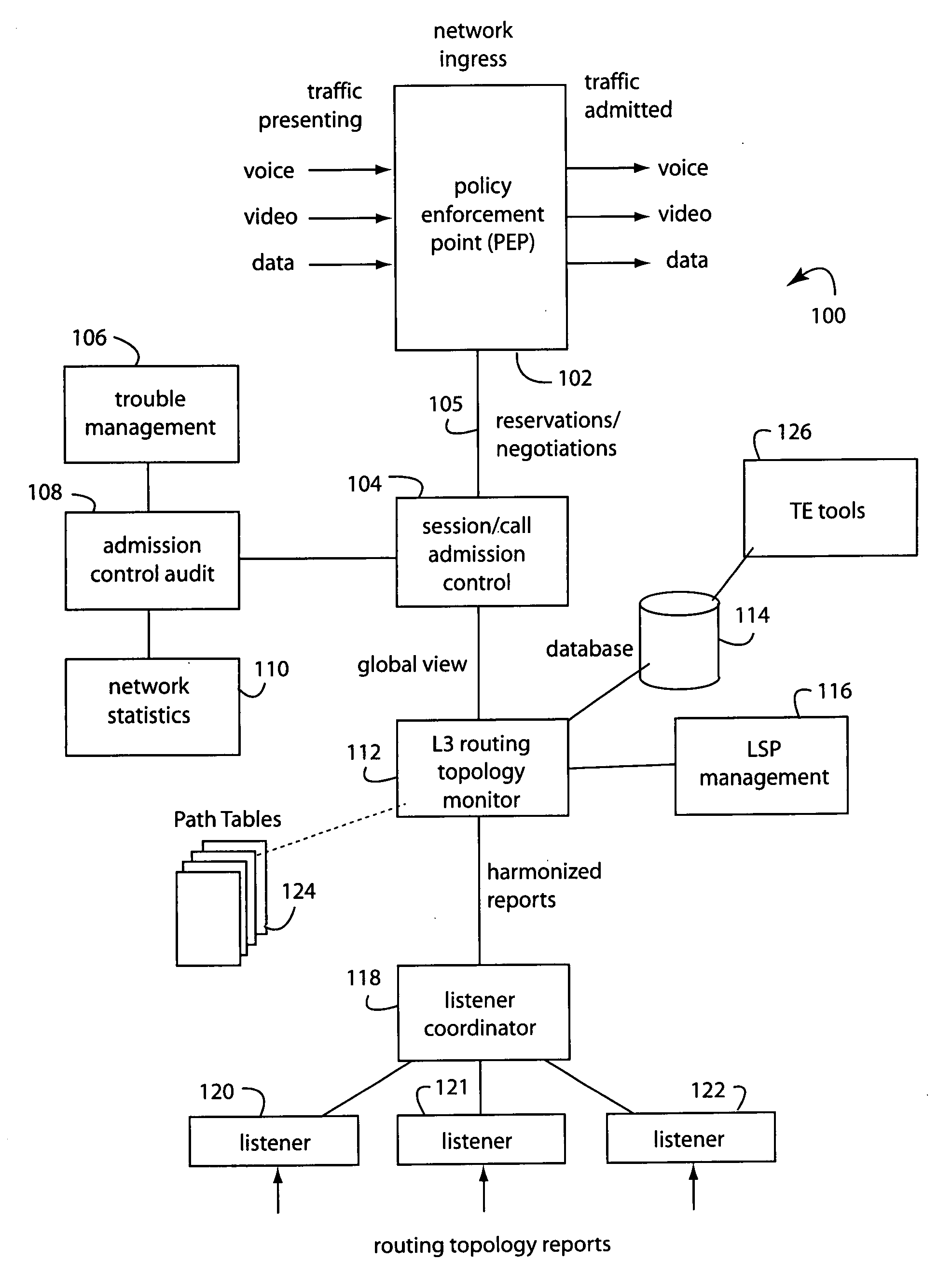
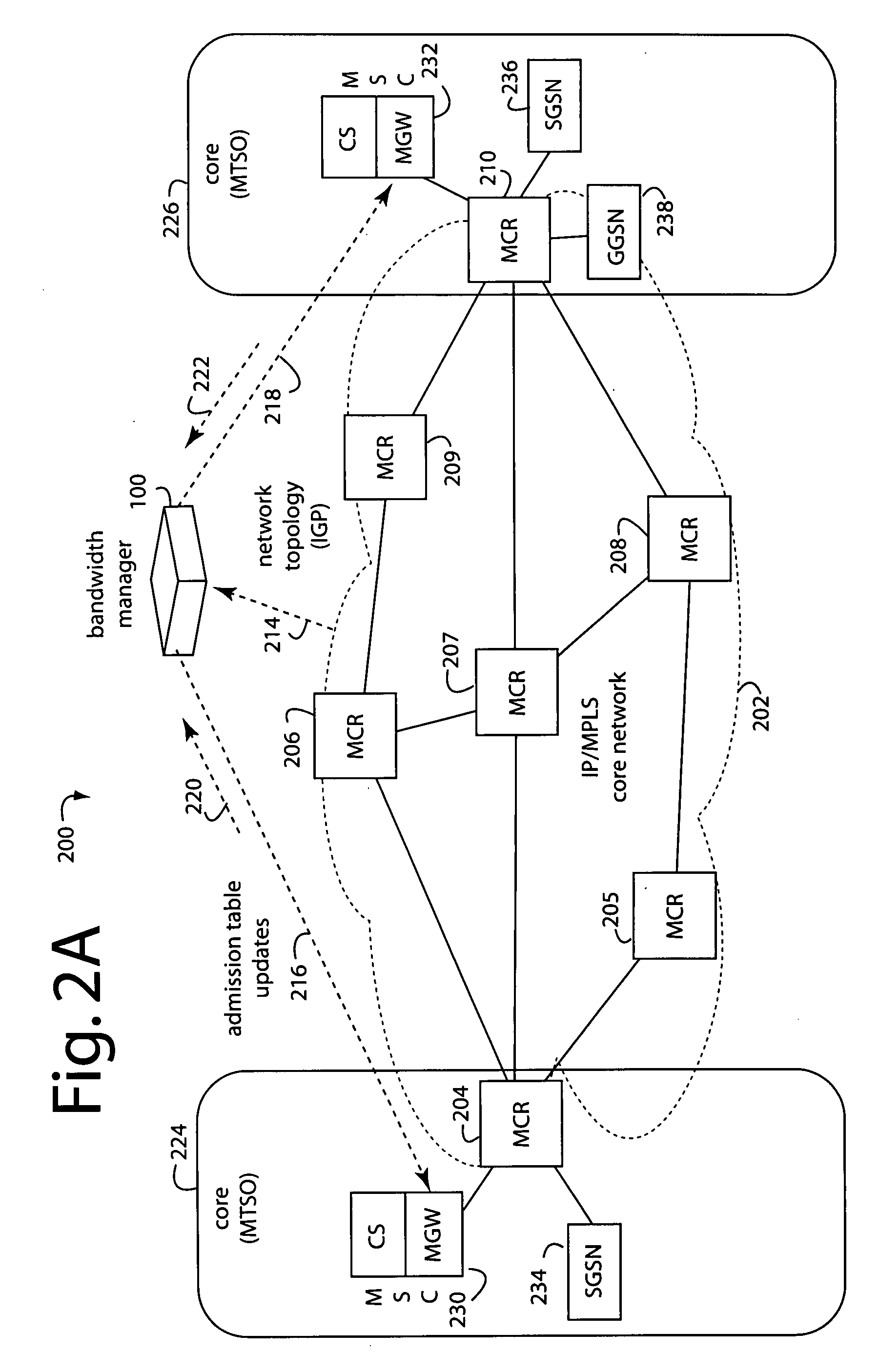
Low-impact call connection request denial
ActiveUS20080225857A1Economical in costPreserve quality of experienceTime-division multiplexData switching by path configurationTraffic volumeTraffic capacity
A policy enforcement point (PEP) attaches to the edge of a packet-switched network to manage loading when the network nears or exceeds its capacity due to changes in the network, e.g., component failures or incremental growth. Autonomous PEP's at the network's edges provide short-term, application-aware controls on their own that are applied to the corresponding network ingress traffic. Changes become necessary when a network event results in a loss of resilient bandwidth that effects the traffic class under admission control. Or, when an unexpected surge in traffic exceeds the PEP's reserved resources to a particular destination. The resources available across the network are recalculated for minimizing impact on existing sessions or calls, and it informs the PEP's of the new resources available. If the new maximum exceeds the current utilization to that destination, the PEP invokes a local priority drop mechanism to back off the traffic until it is under the new limit. A media gateway handling voice calls can keep all emergency calls up, and then invoke a local algorithm, such as random drop, for the remaining calls until calls to the constrained destination are under the new limit. In the second case, where there is an unexpected surge in demand, the PEP can request from the bandwidth manager additional resources to a particular destination.
Owner:RPX CORP
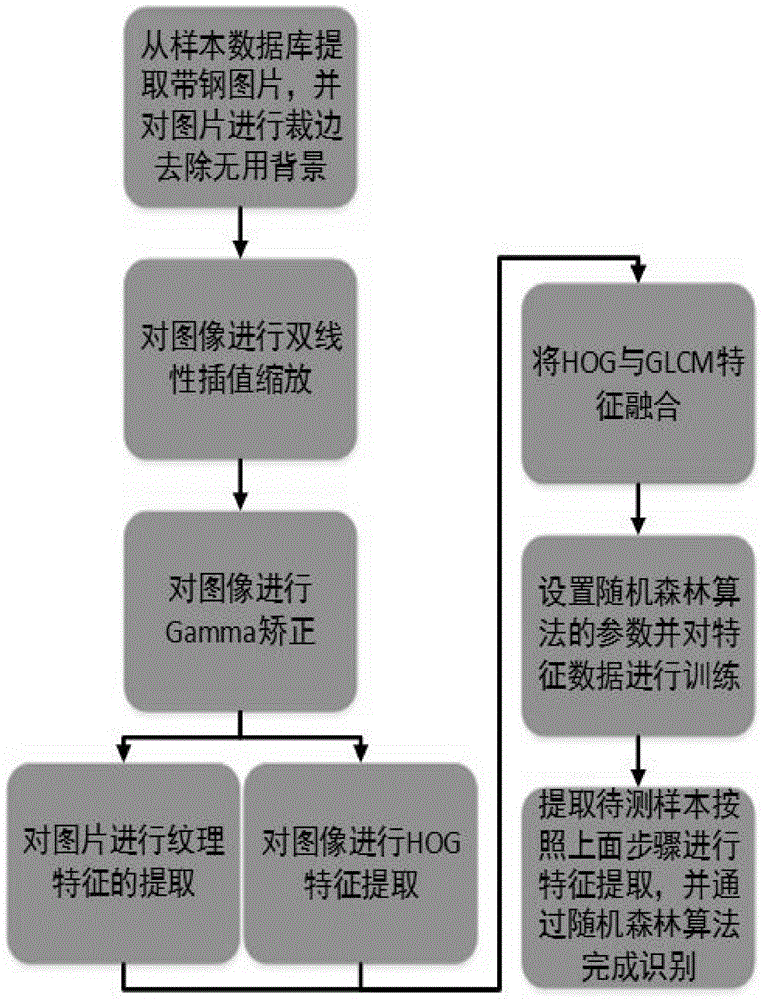
Strip steel surface area type defect identification and classification method
ActiveCN104866862AEasy to handleAccurate identificationCharacter and pattern recognitionFeature setHistogram of oriented gradients
The invention discloses a strip steel surface area type defect identification and classification method which comprises the following steps: extracting strip steel surface pictures in a training sample database, removing useless backgrounds and keeping the category of the pictures to a corresponding label matrix; carrying out bilinear interpolation algorithm zooming on the pictures; carrying out color space normalization on images of the zoomed pictures by adopting a Gamma correction method; carrying out direction gradient histogram feature extraction on the corrected pictures; carrying out textural feature extraction on the corrected pictures by using a gray-level co-occurrence matrix; combining direction gradient histogram features and textural features to form a feature set, which comprises two main kinds of features, as a training database; training the feature data with an improved random forest classification algorithm; carrying out bilinear interpolation algorithm zooming, Gamma correction, direction gradient histogram feature extraction and textural feature extraction on the strip steel defect pictures to be identified in sequence; and then, inputting the feature data into an improved random forest classifier to finish identification.
Owner:CENT SOUTH UNIV
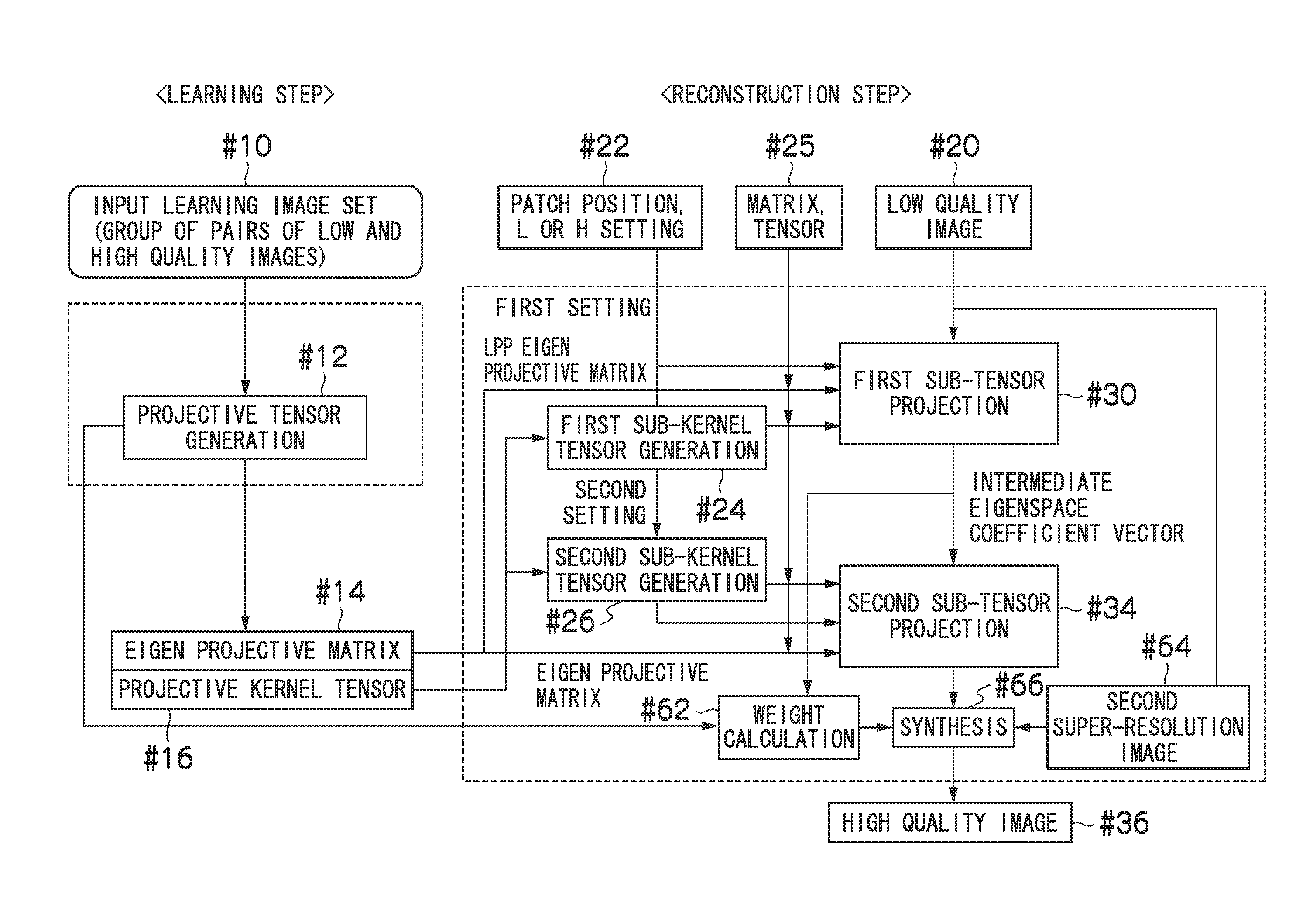
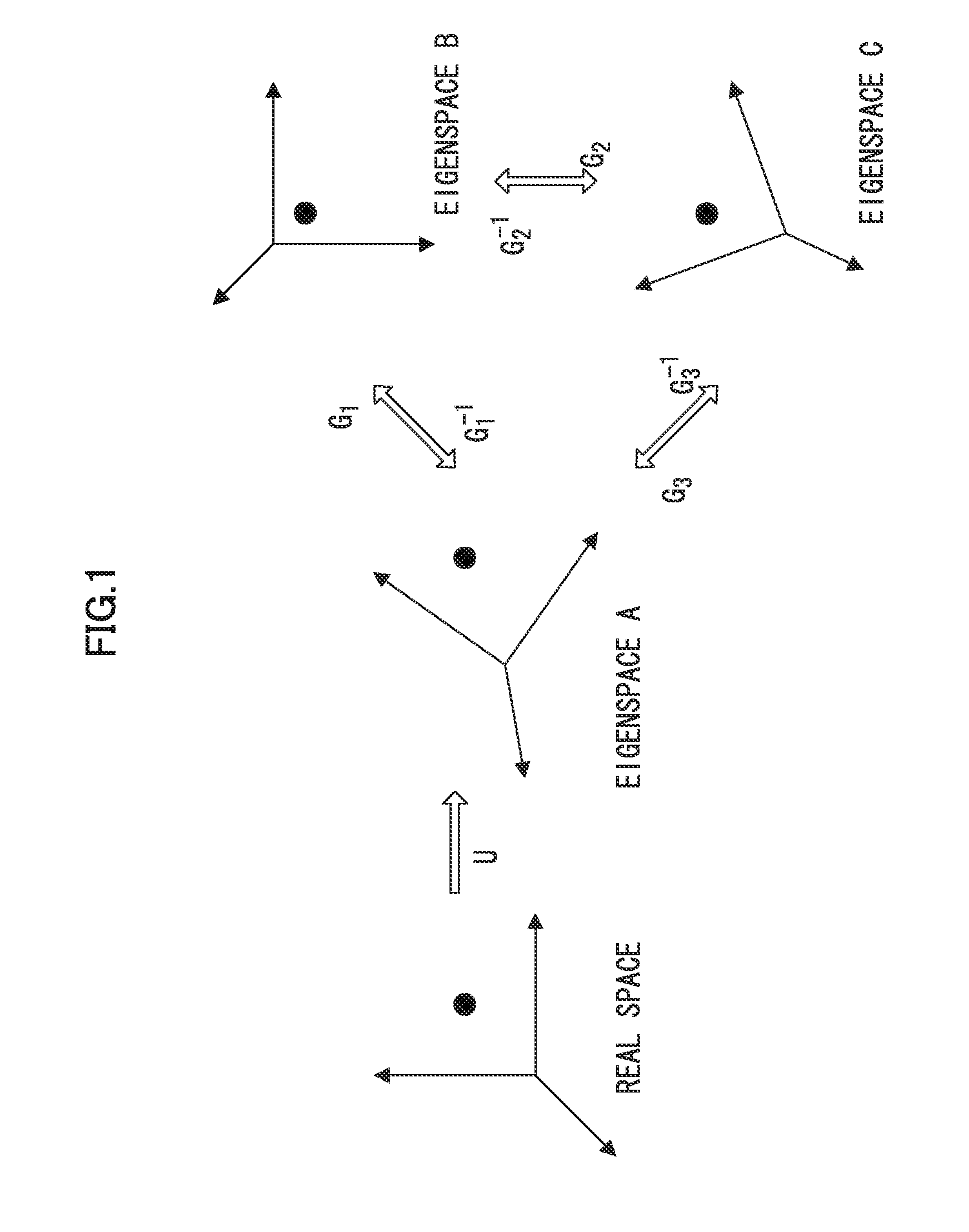
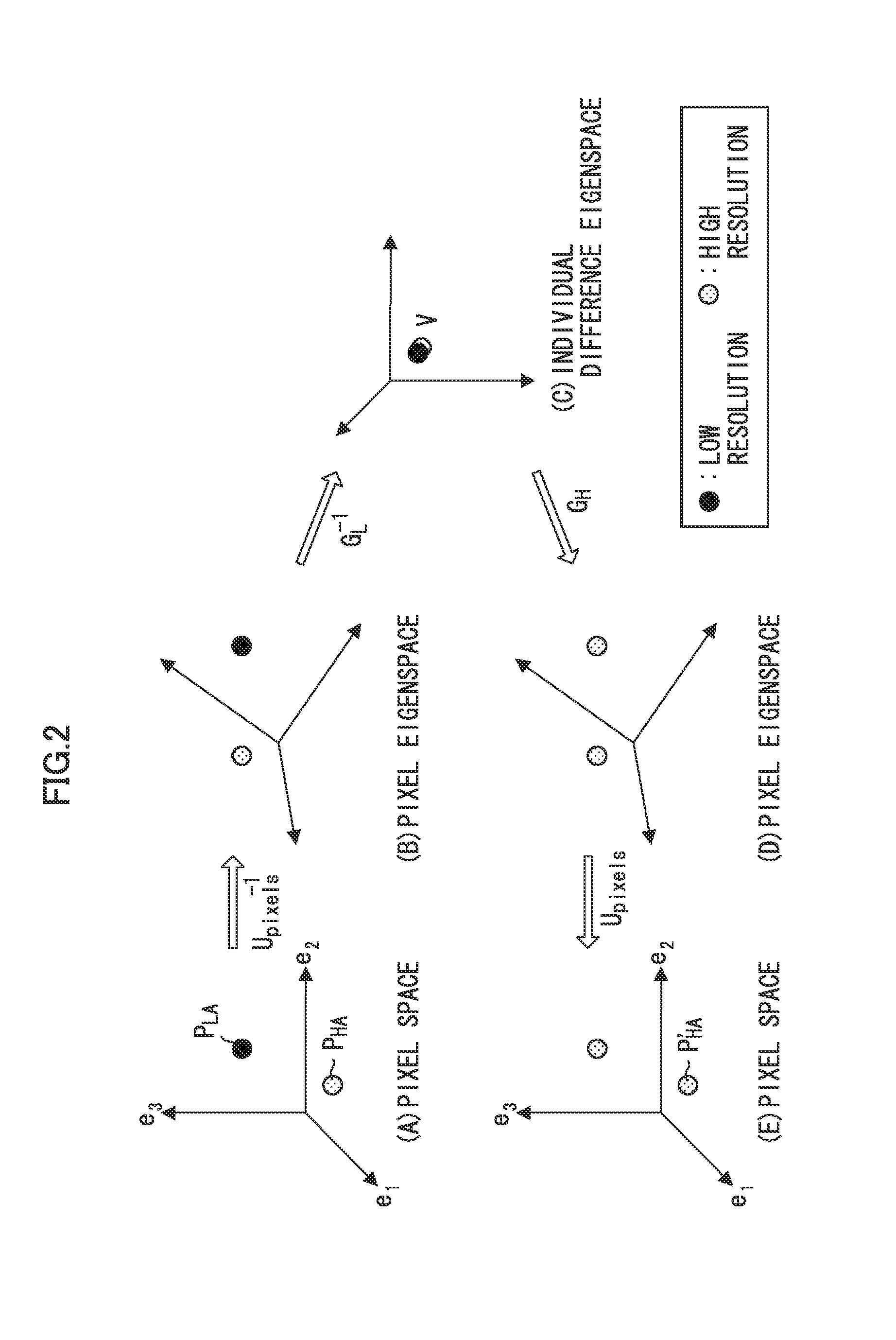
Image processing apparatus and method, data processing apparatus and method, and program and recording medium
InactiveUS20110026849A1Satisfactory reconstruction imageInhibit deteriorationGeometric image transformationAcquiring/recognising facial featuresImaging processingWeight coefficient
The present invention determines the adopting ratio (weight coefficient) between the high image quality processing using the tensor projection method and the high image quality processing using another method according to the degree of deviation of the input condition of the input image, and combines these processes as appropriate. This allows a satisfactory reconstruction image to be acquired even in a case of deviation from the input condition, and avoids deterioration of the high quality image due to deterioration of the reconstruction image by the projective operation.
Owner:FUJIFILM CORP
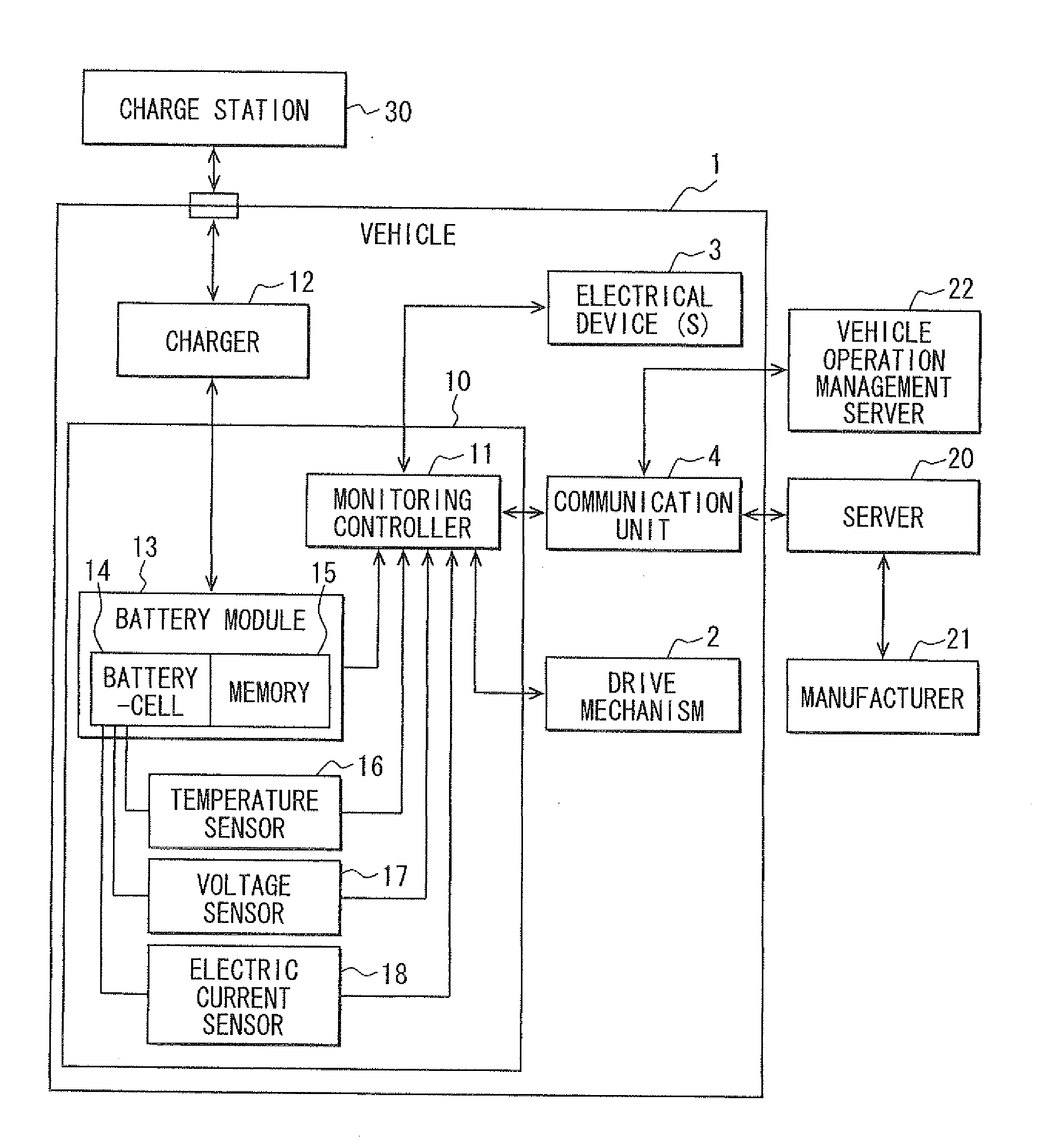
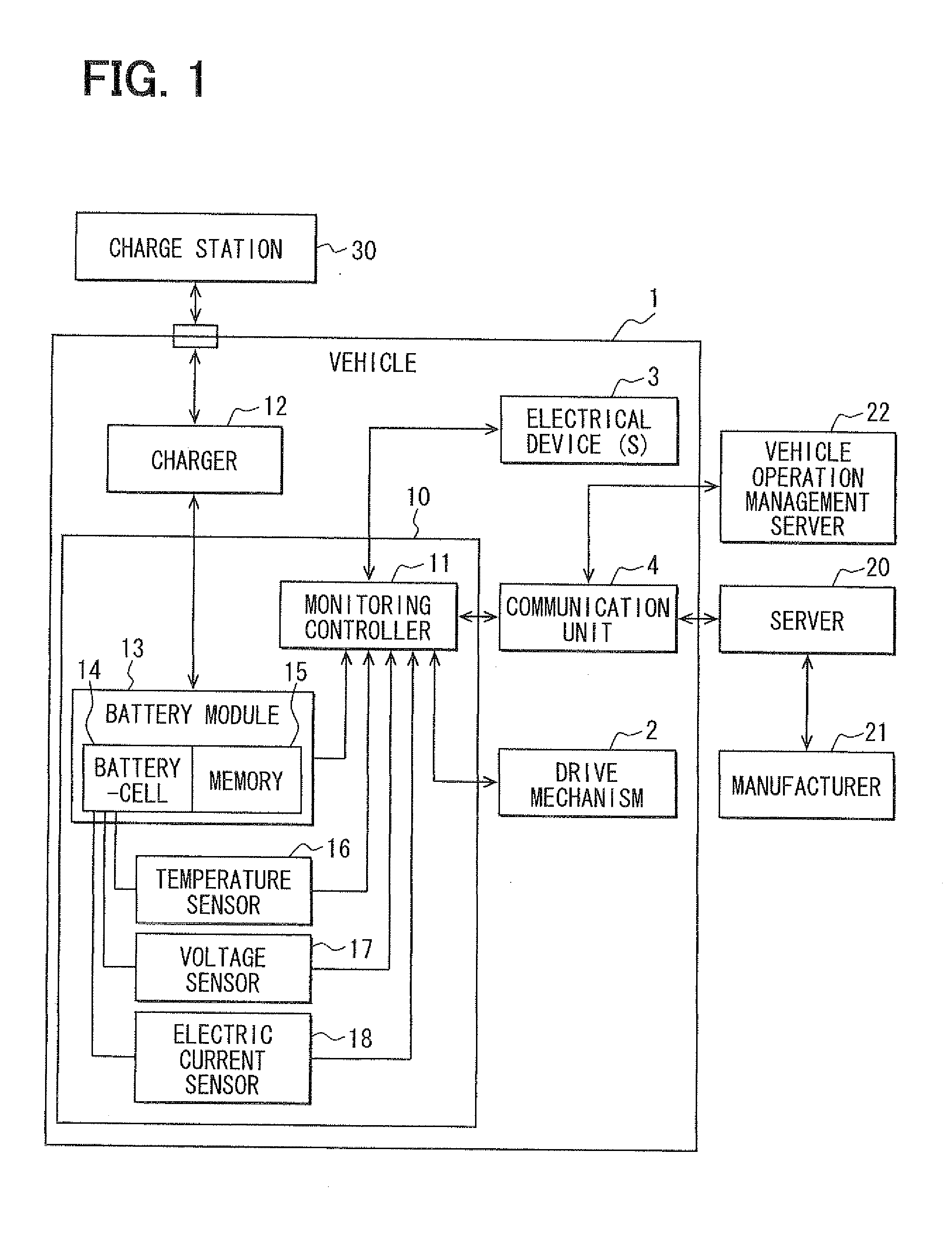
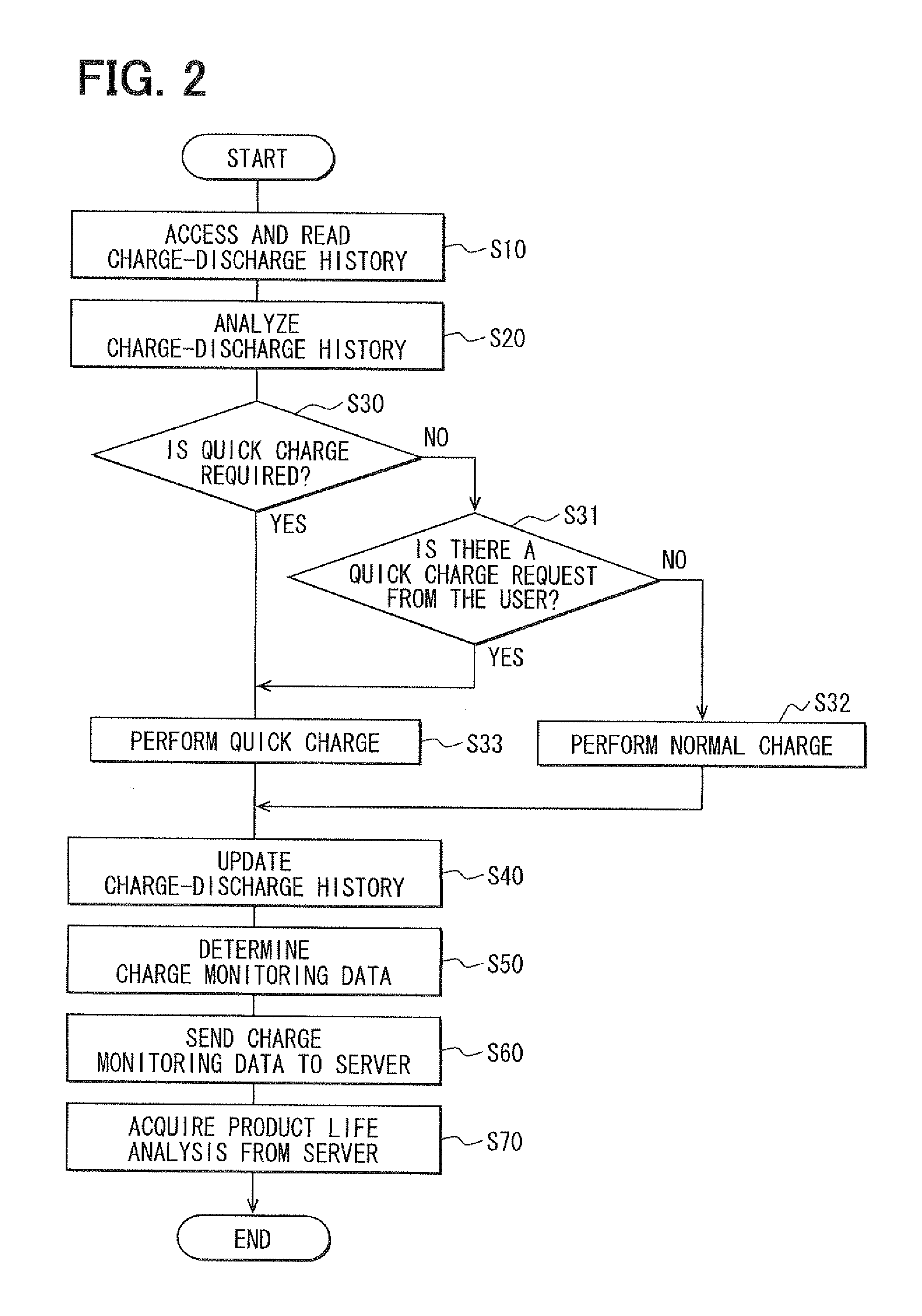
Vehicular battery pack
InactiveUS20120101755A1Timely/suitable maintenanceAccurate predictionCharging stationsReservationsElectricityCharge current
A battery pack includes a battery module that charges and discharges electricity to be used to drive a vehicle, and a monitoring controller for monitoring charge of the battery module. The monitoring controller stores past charge records and past discharge records in a charge-discharge history. Based on an analysis of learning data of a charge-discharge cycle in the charge-discharge history, the monitoring controller determines a charge operation, which may either be a normal charge or a quick charge, for charging the battery. The normal charge provides a charging electric current per unit time that is less than the charging current per unit time of the quick charge.
Owner:DENSO CORP
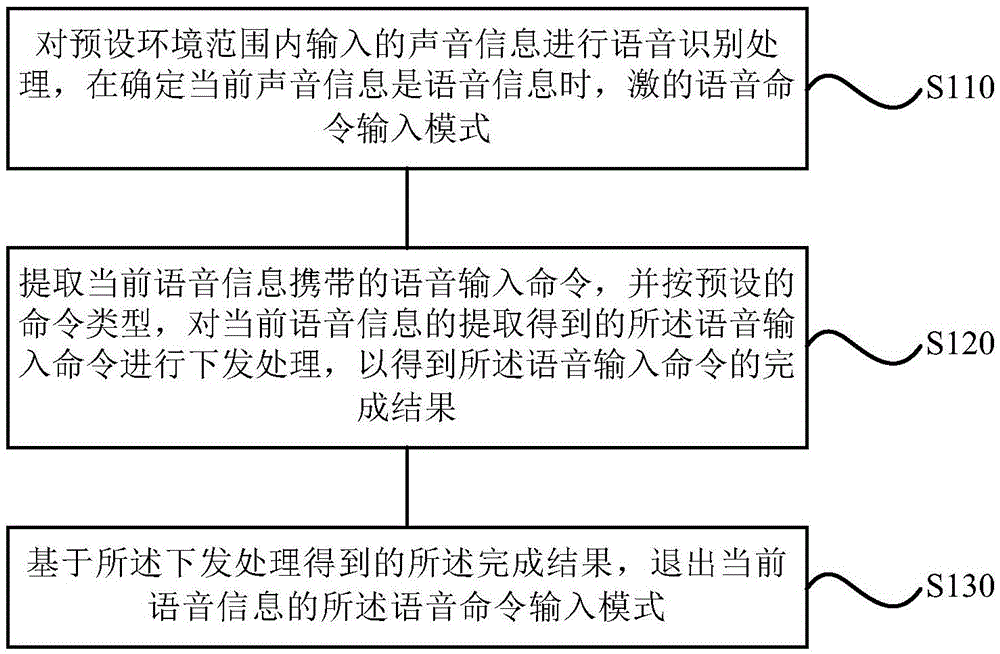
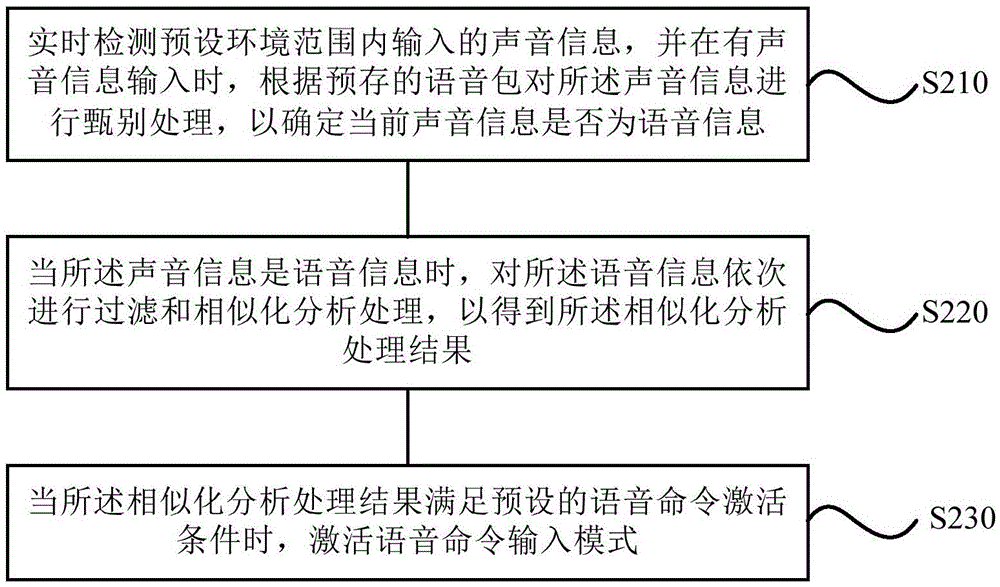
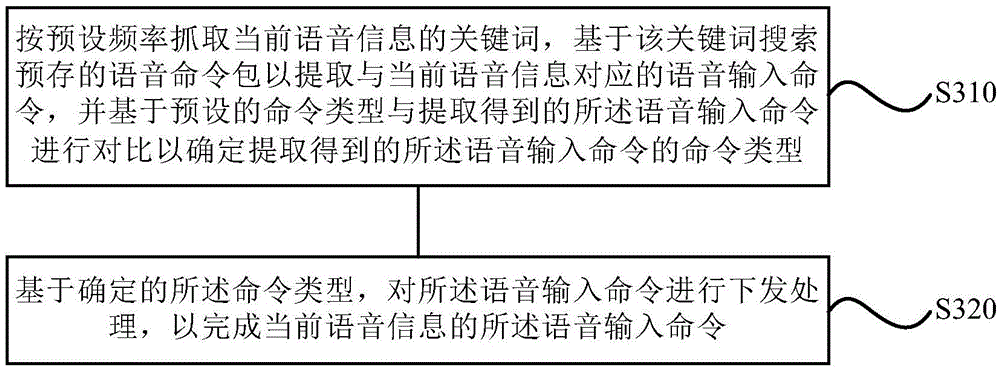
Display method and device based on speech recognition, display system and air conditioner
InactiveCN105679318AReduce dependenceIncrease flexibilityMechanical apparatusSpeech recognitionDisplay deviceSpeech identification
The invention discloses a display method and a display device based on speech recognition, a display system and an air conditioner. The display method comprises the steps of: carrying out speech recognition processing on sound information input within a preset environment range, and activating a speech command input mode when determining that the current sound information is speech information; extracting a speech input command carried by the current speech information, issuing the speech input command obtained through extraction according to a preset command type to obtain a completion result of the speech input command; and exiting the speech command input mode based on the completion result obtained through the issuing processing. The display method, the display device, the display system and the air conditioner can overcome defects of few functions, poor interactive flexibility, poor user experience and the like in the prior art, and achieve the beneficial effects of multiple functions, good interactive flexibility and good user experience.
Owner:GREE ELECTRIC APPLIANCES INC
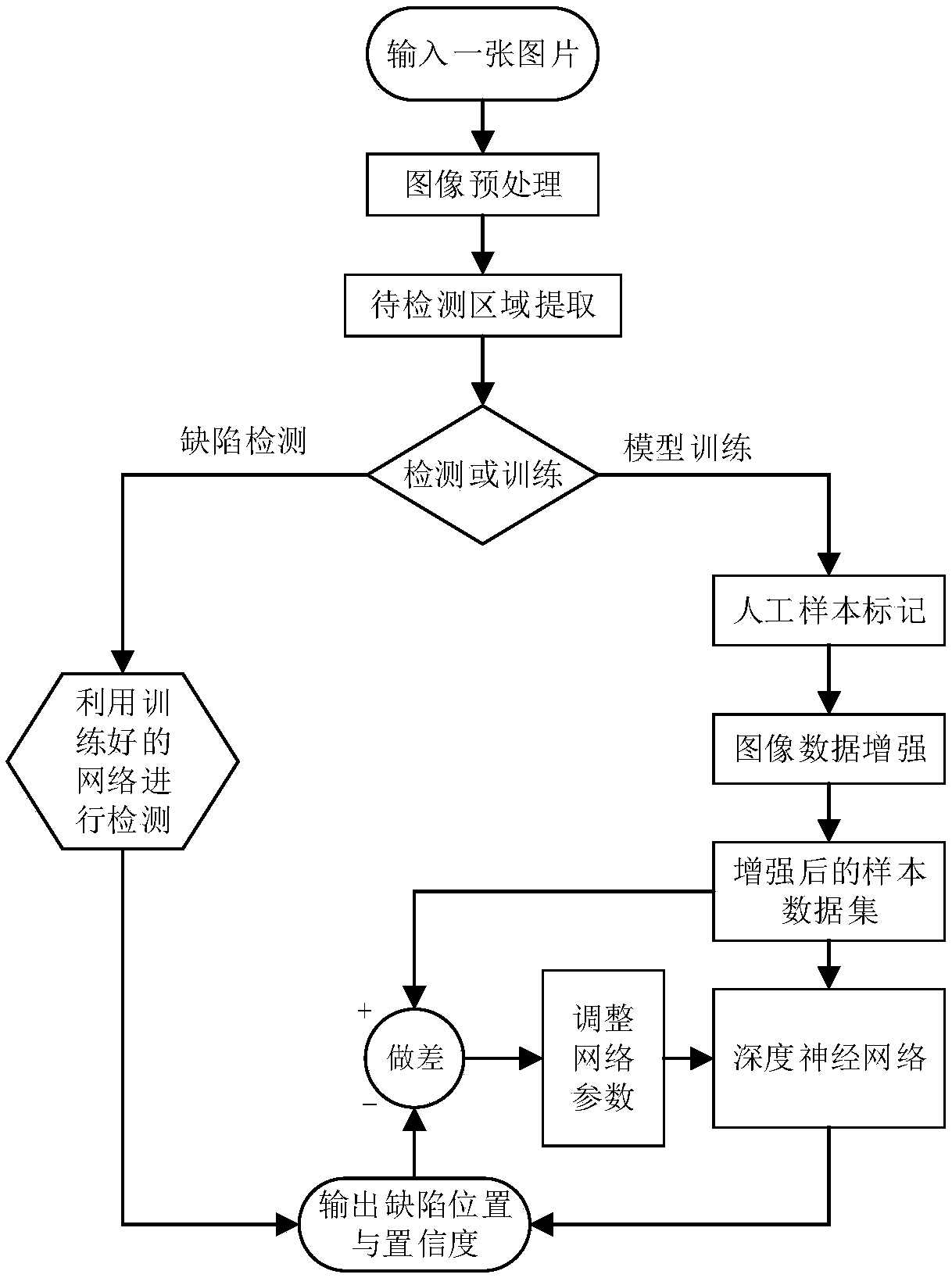
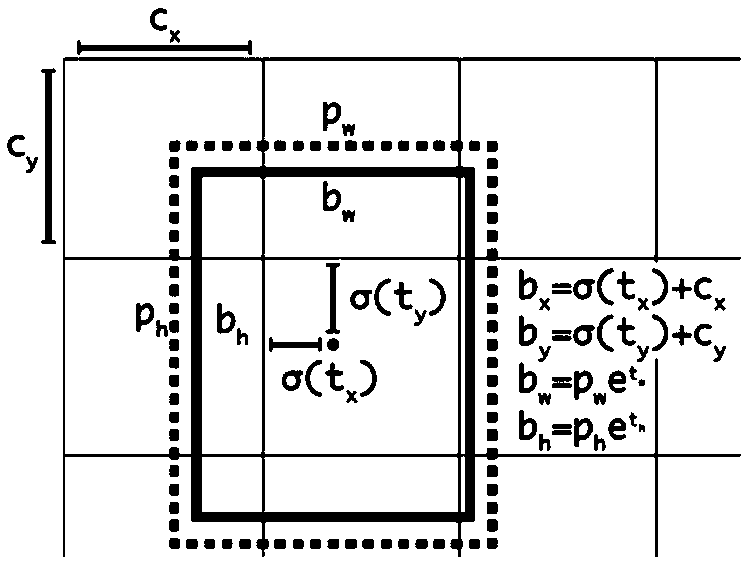
Defect detection method for irregular metal machining surface based on depth learning
PendingCN109636772ARun fastReduce processingImage enhancementImage analysisNetwork architectureImage enhancement
The invention relates to a defect detection method of an irregular shape metal working surface based on depth learning, By preprocessing the collected surface images of metal machining, image enhancement, YOLOv3-based network architecture, Deep learning network suitable for defect detection is built. The samples are labeled manually and the deep learning network is trained with labeled samples toobtain defect detection model. Finally, the defect detection model is used to detect the surface image of metal machining, and the defect detection results are obtained. Compared with the prior art, the network structure in the invention has good adaptability to the detection of small objects and small targets, and unifies the four basic steps of the candidate region generation, the feature extraction, the classification and the position refinement of the target detection into the same depth network framework, thereby improving the running speed and making the detection more accurate.
Owner:TONGJI UNIV
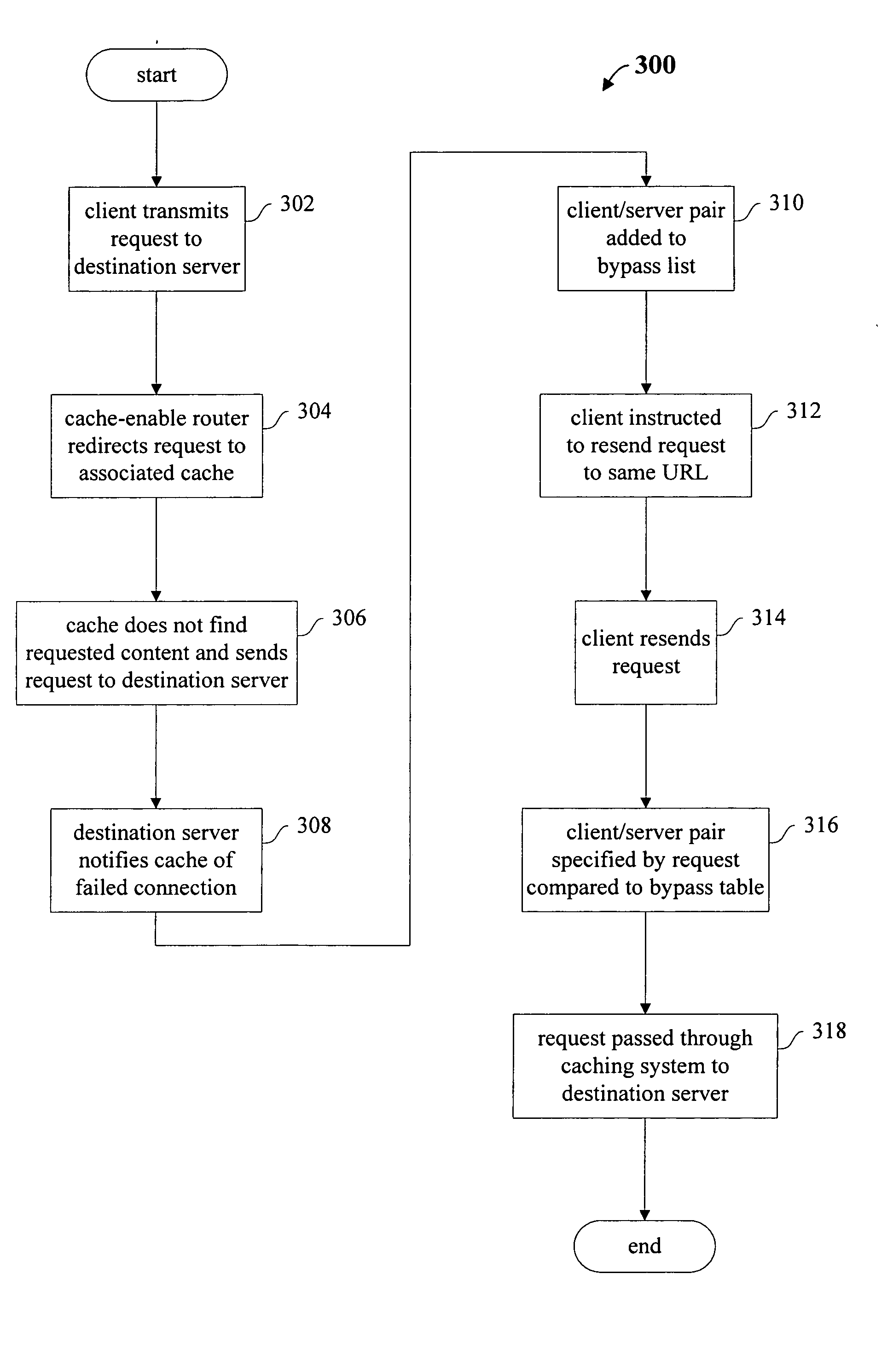
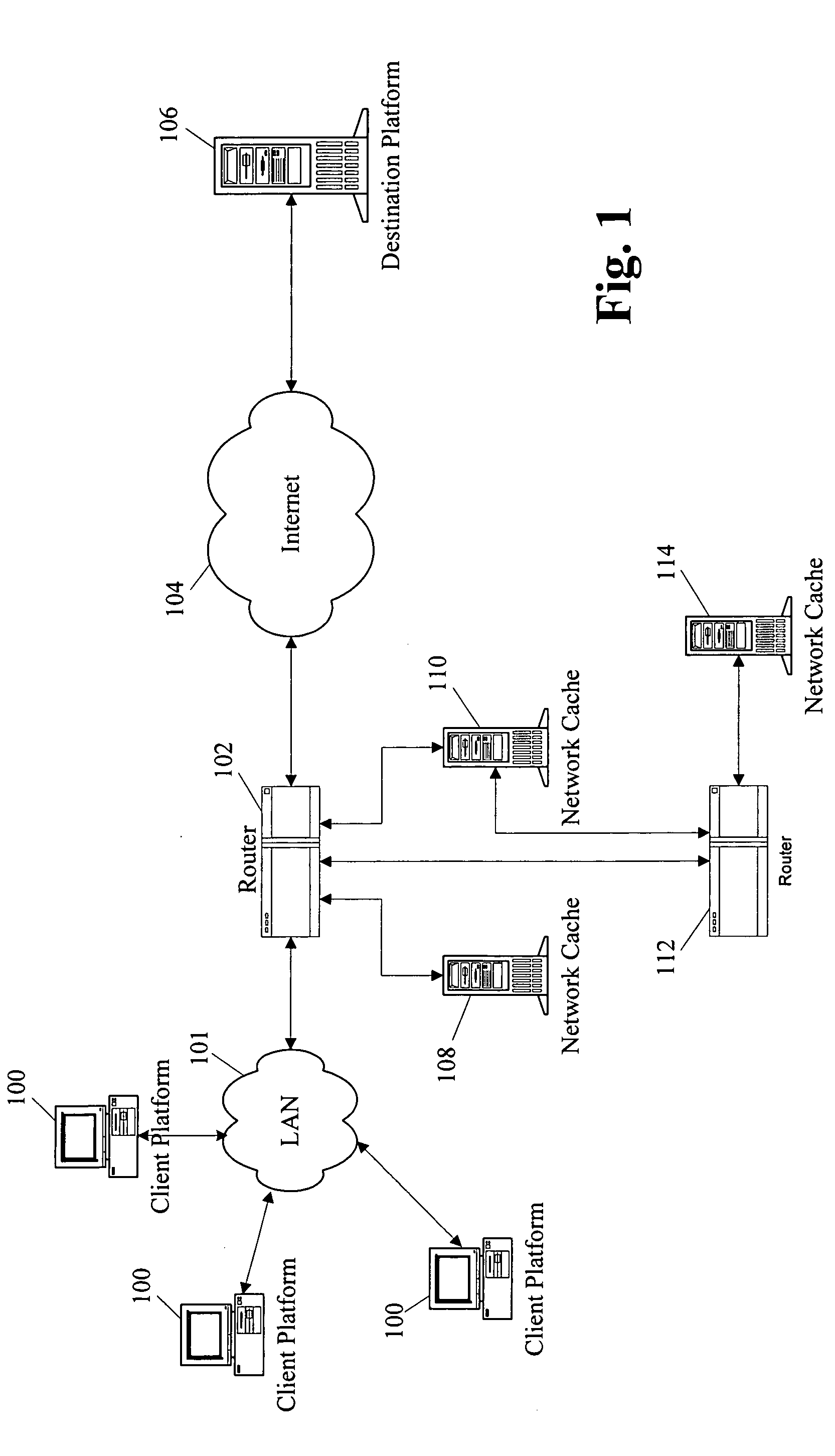
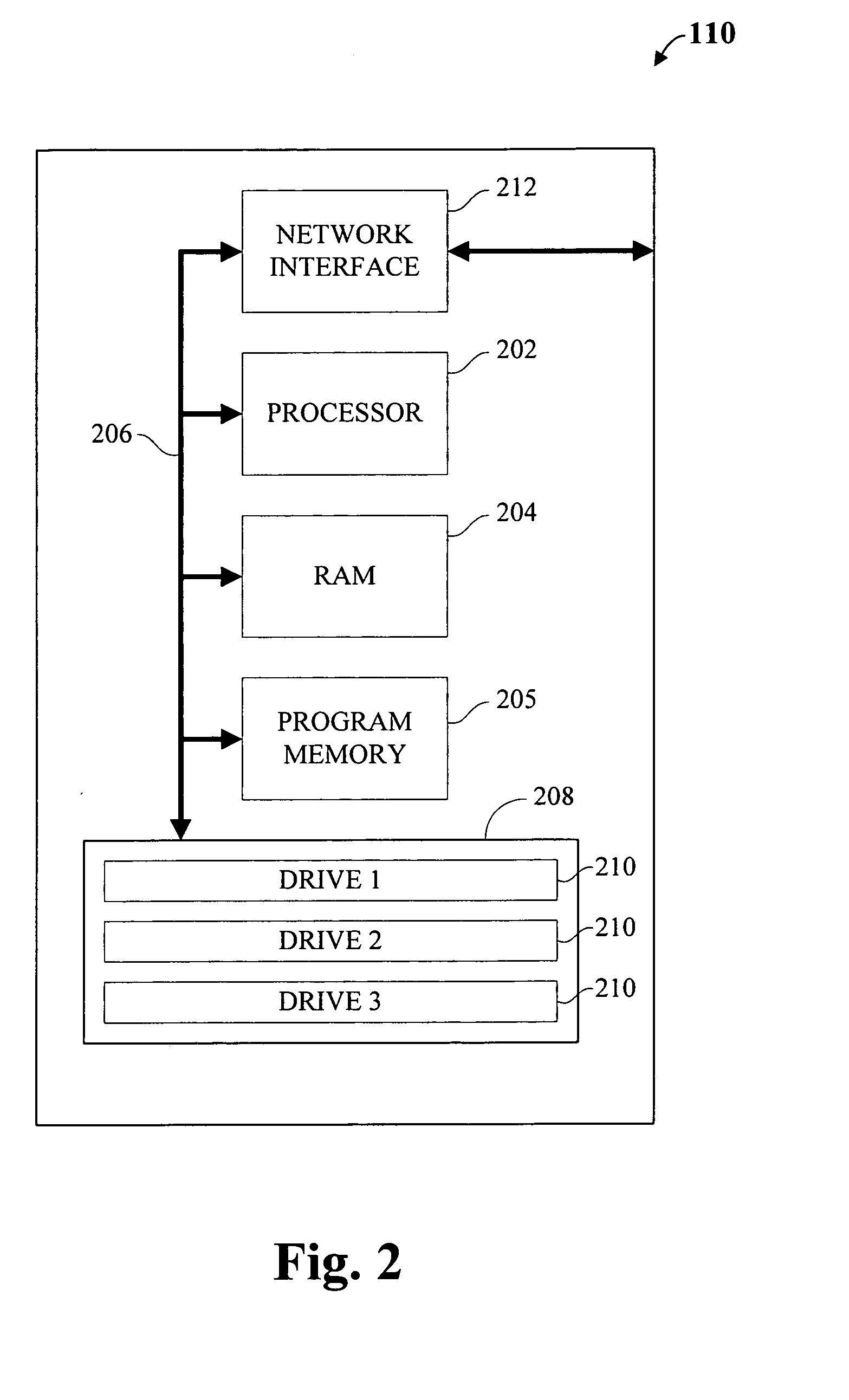
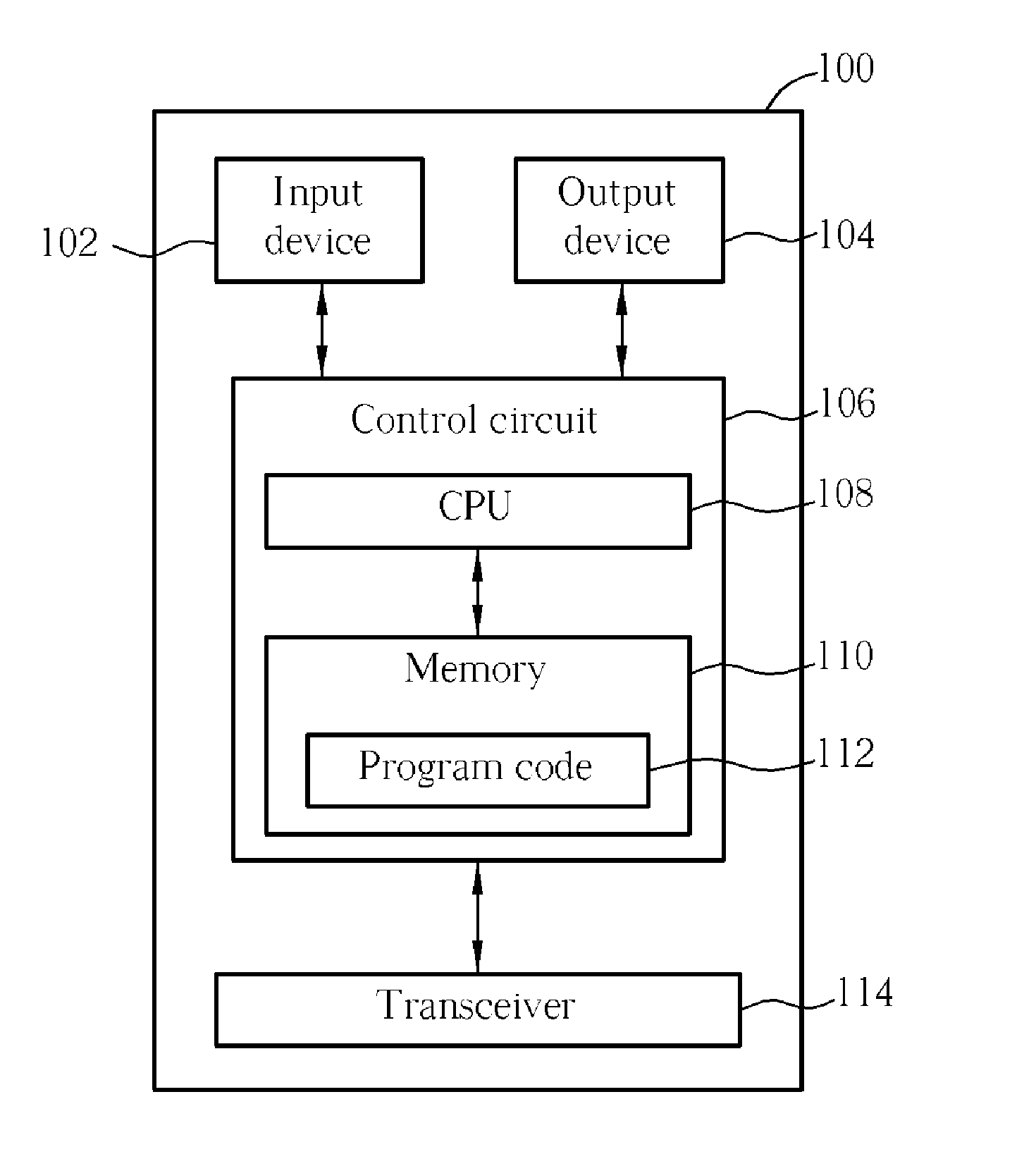
Methods and apparatus for redirecting network cache traffic
InactiveUS20060117093A1Easy to operateAccurate processingMultiple digital computer combinationsSecuring communicationOperating systemData request
Owner:CISCO TECH INC
Method and Apparatus for Handling Random Access Procedure in a Wireless Communications System
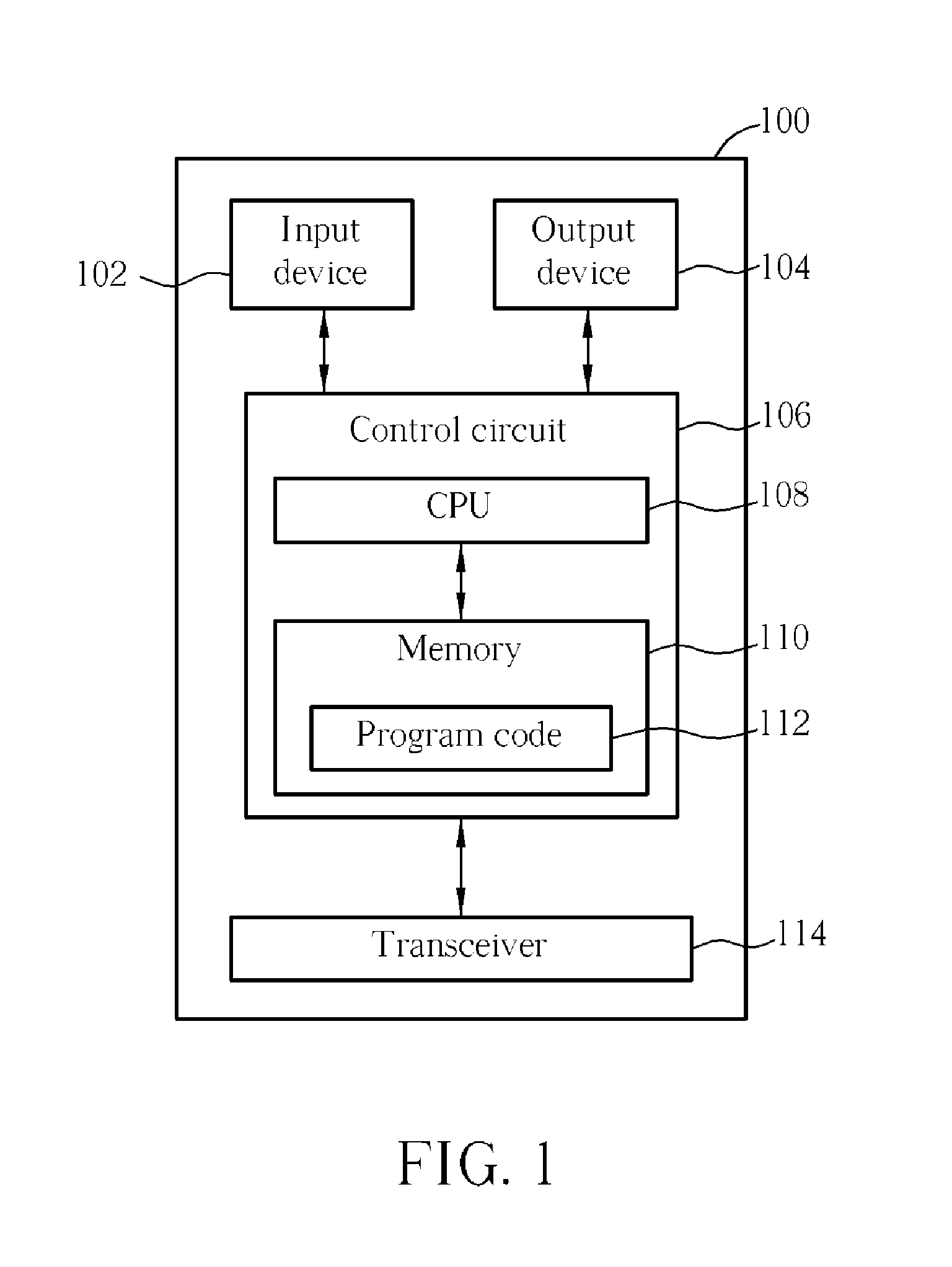
InactiveUS20080233940A1Accurate processingError prevention/detection by using return channelSignal allocationCommunications systemUser equipment
A method for handling a random access procedure in a user equipment, called UE hereinafter, of a wireless communications system includes sending a negative acknowledgement to a network or not sending an acknowledgement corresponding to a message 4 to request retransmission of message 4 when the message 4 is not successfully received from the network.
Owner:INNOVATIVE SONIC
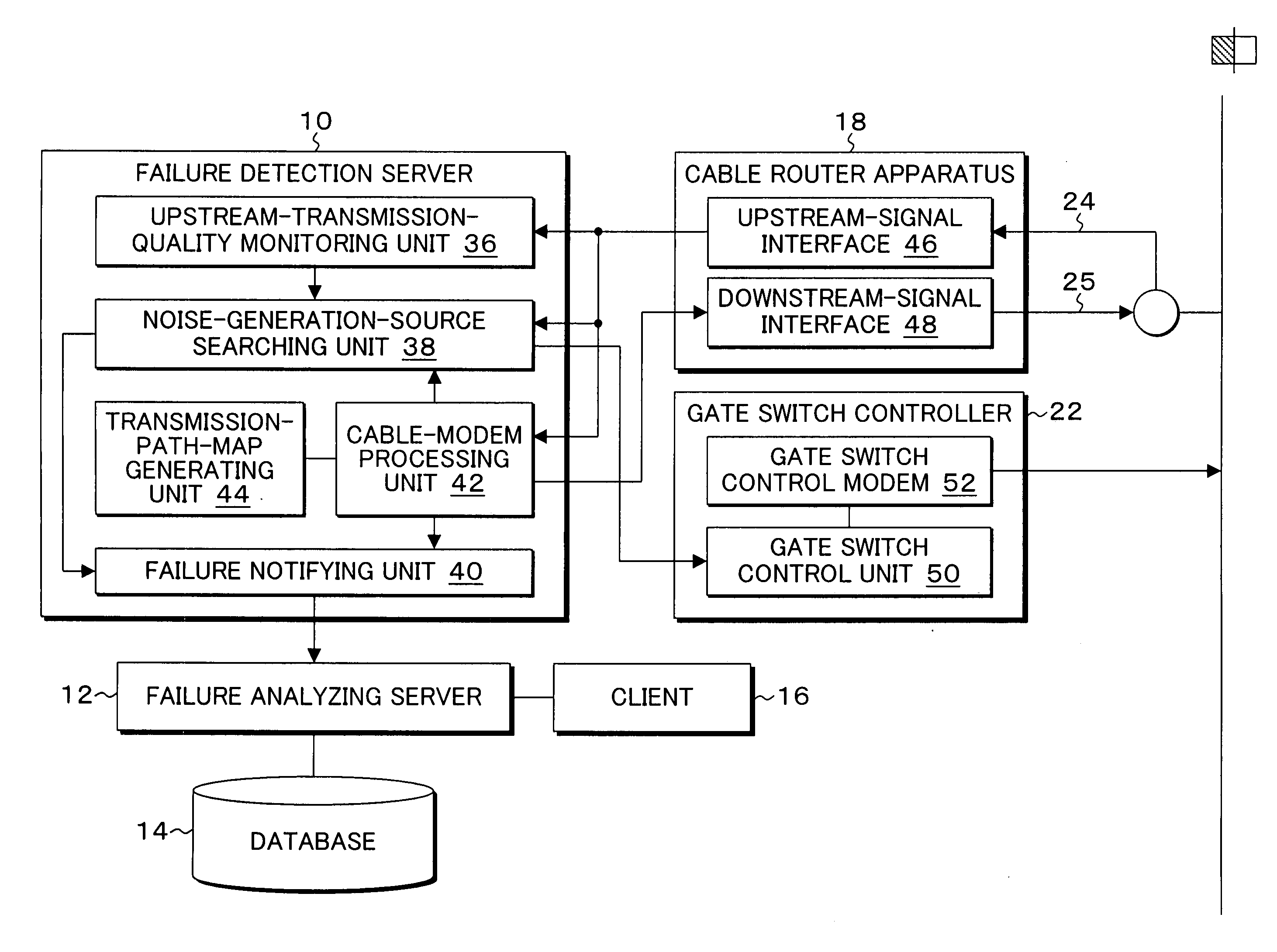
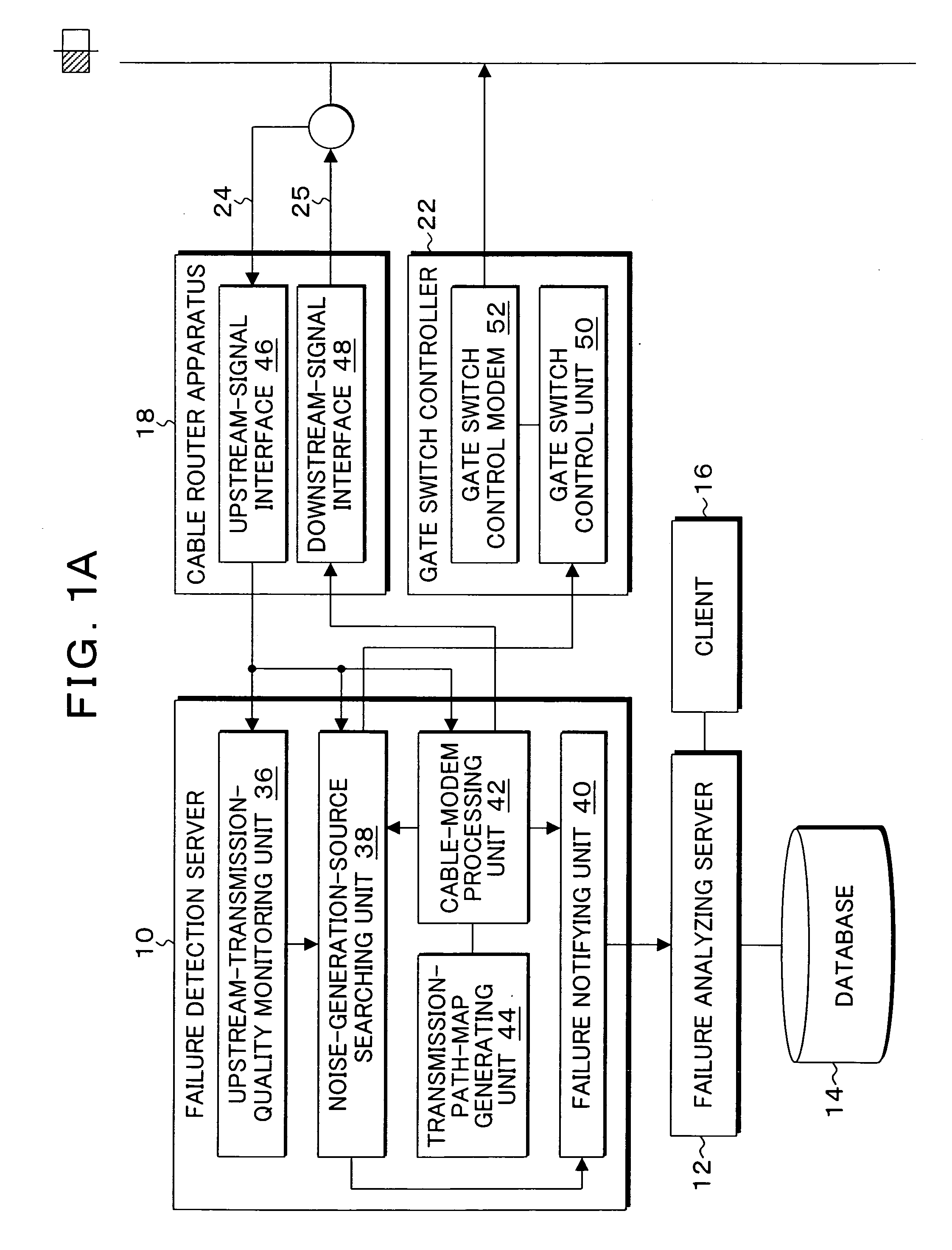
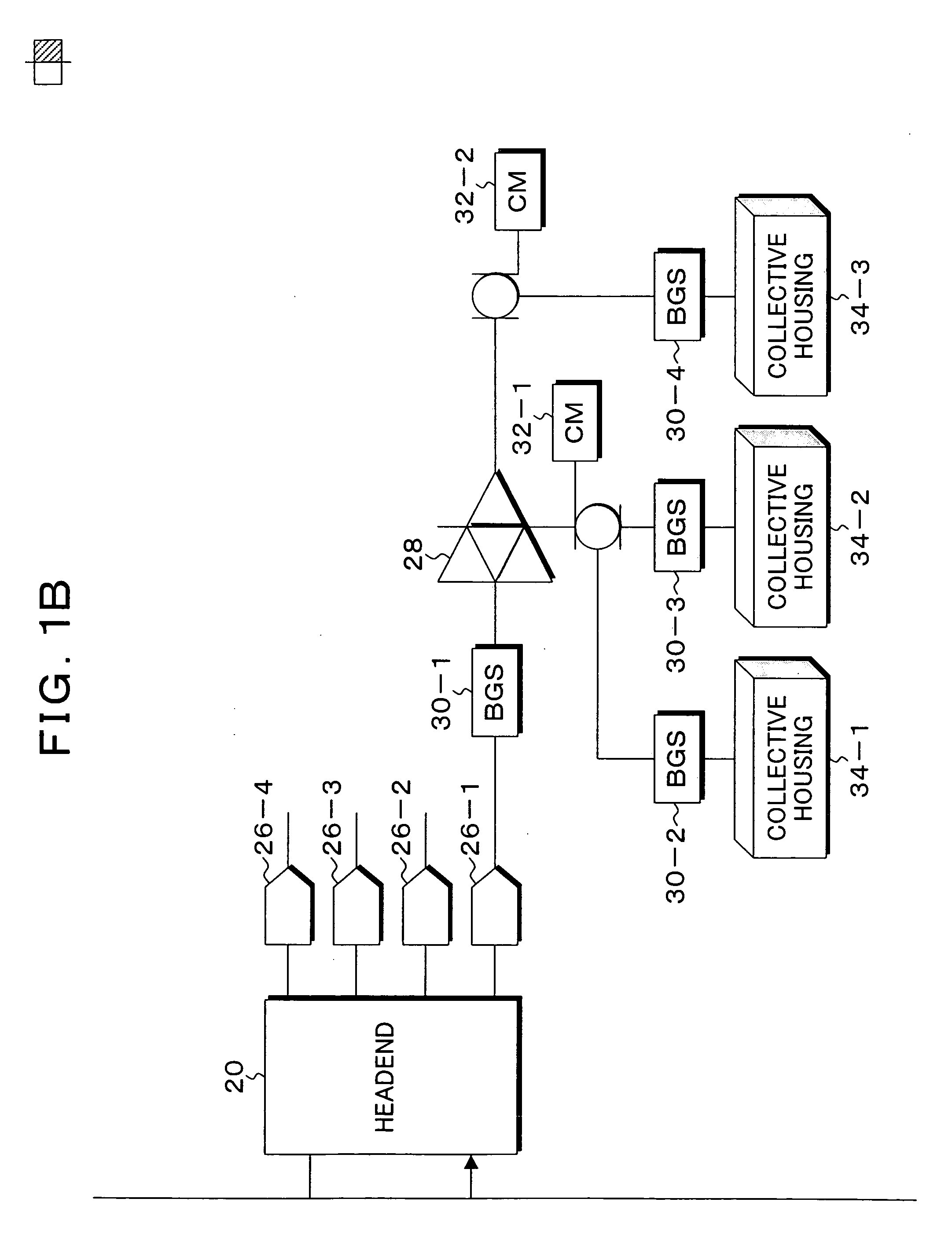
Apparatus, method, and program for CATV transmission-path monitoring
InactiveUS20090007210A1Transmission quality deterioratesReduce transmissionBroadcast-related systemsBroadcast transmission systemsNoise generationUltrasound attenuation
Gate switches can switch an amount of attenuation, and are set in a distributed manner on distribution lines and a trunk on subscribers' house side in a CATV transmission path having a tree structure with an optical node that follows a headend being taken as a starting point. An upstream-transmission-quality monitoring unit monitors an S / N ratio of an upstream signal obtained from an upstream port having the headend connected thereto to detect a decrease in upstream transmission quality based on a degree of decrease and a continuation state of an S / N ratio. When the upstream-transmission-quality monitoring unit detects a decrease in upstream transmission quality, a noise-generation-source searching unit performs a sequential switching control over the amount of attenuation at the gate switches provided on the CATV transmission path from upstream to downstream to search for a source of generation of upstream ingress noise.
Owner:OSS BROADNET
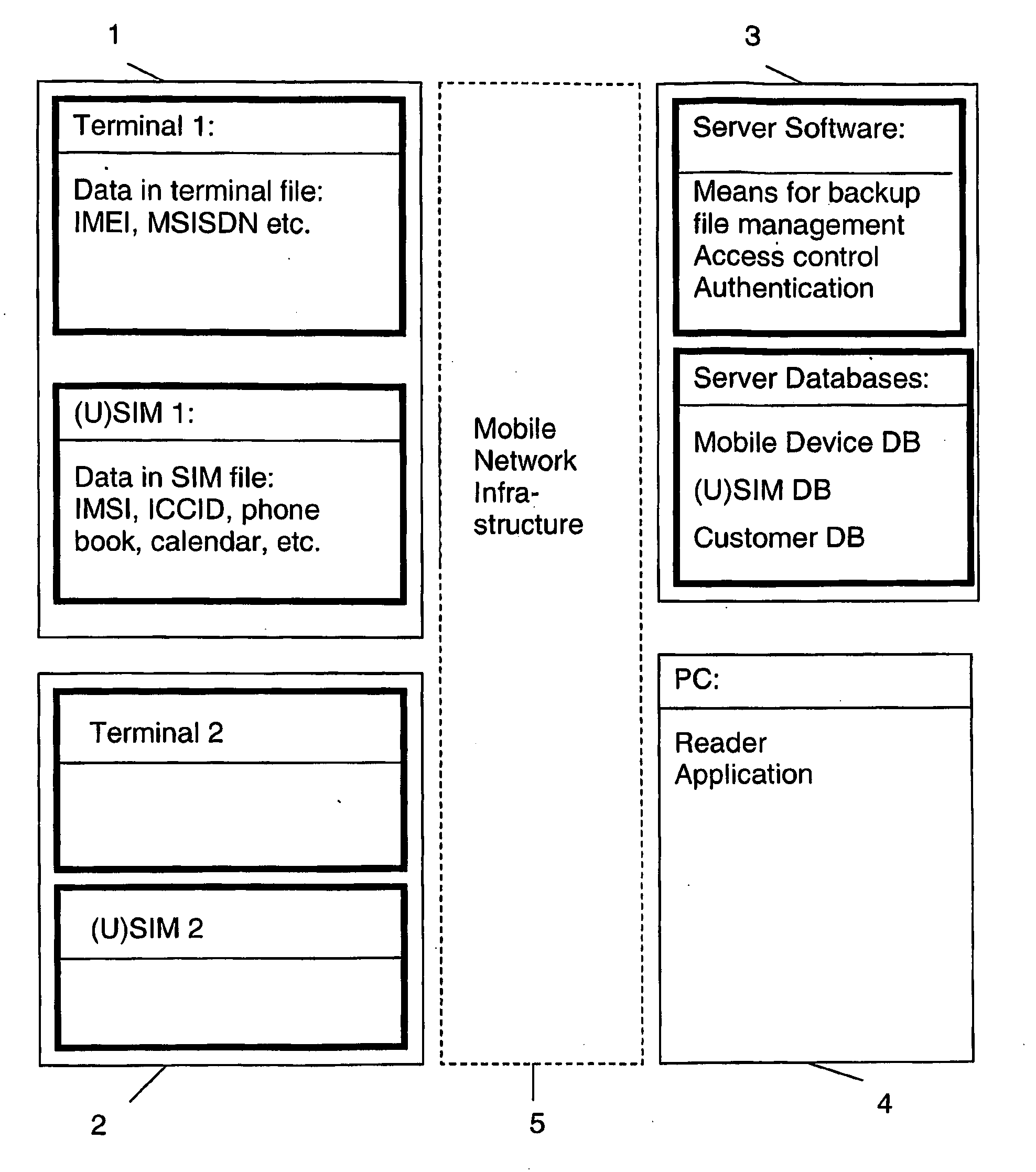
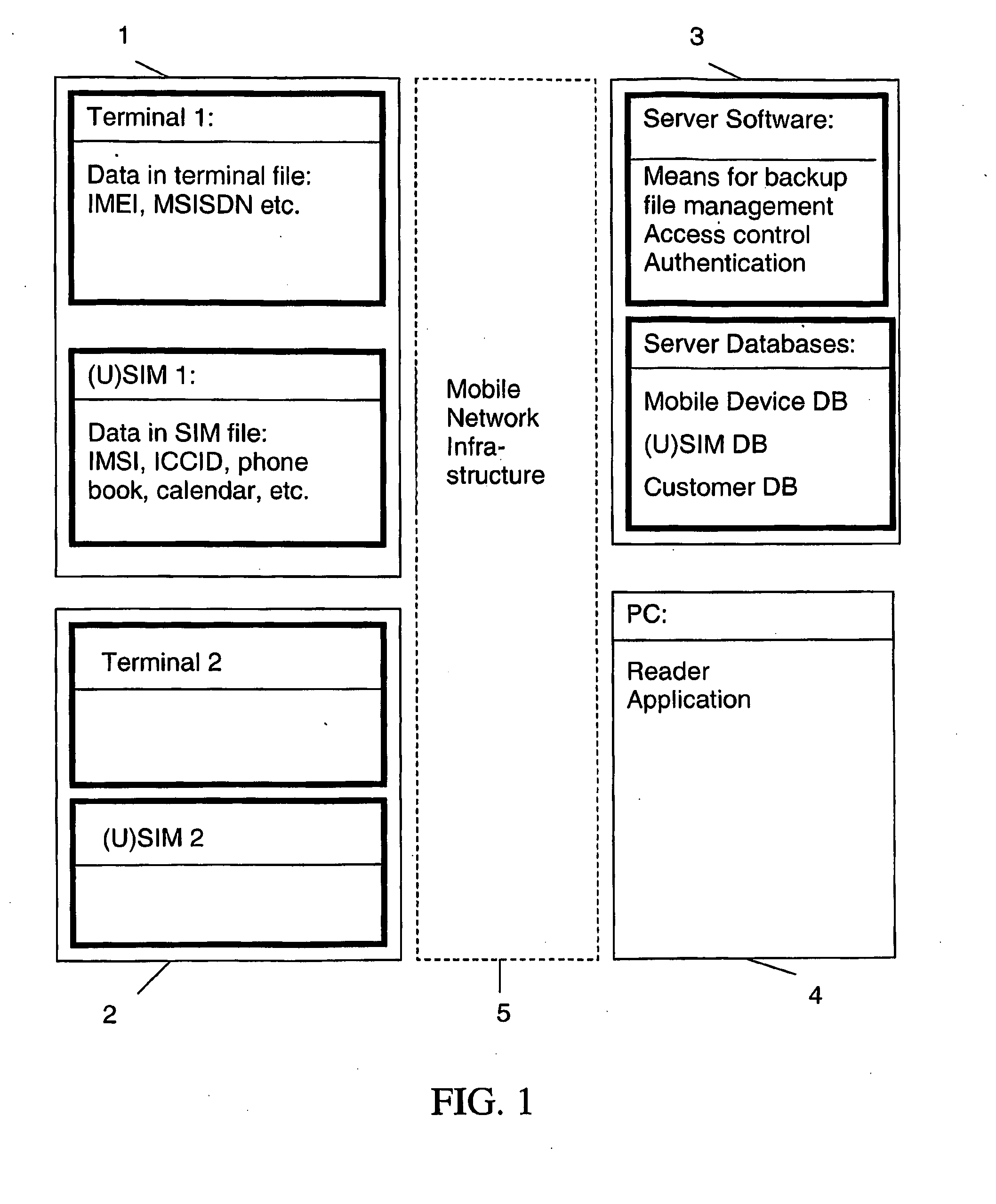
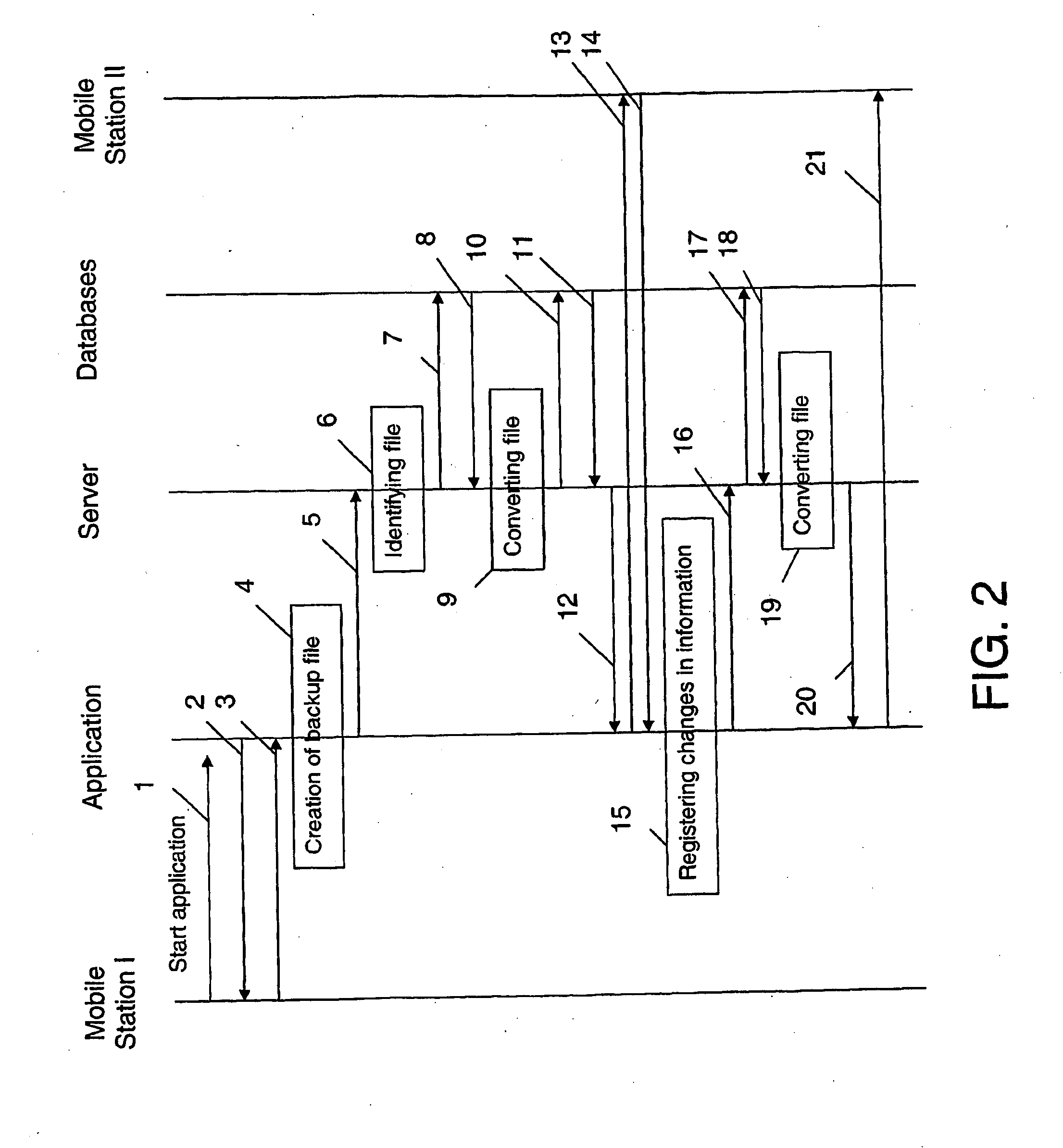
Backup system and method in a mobile telecommunication network
ActiveUS20100063960A1Good serviceAccurate processingMemory loss protectionDigital data processing detailsTelecommunications networkComputer terminal
The backup method is performed in a mobile telecommunication network for transferring data from one mobile station to another. The mobile stations have a terminal part and a subscription part. The method includes the steps of creating a backup file of data from a first mobile station, reading data from a second mobile station to which the data is to be transferred, converting the backup file into a format of the second mobile station, and downloading the resulting backup file of the foregoing step to the second mobile station.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
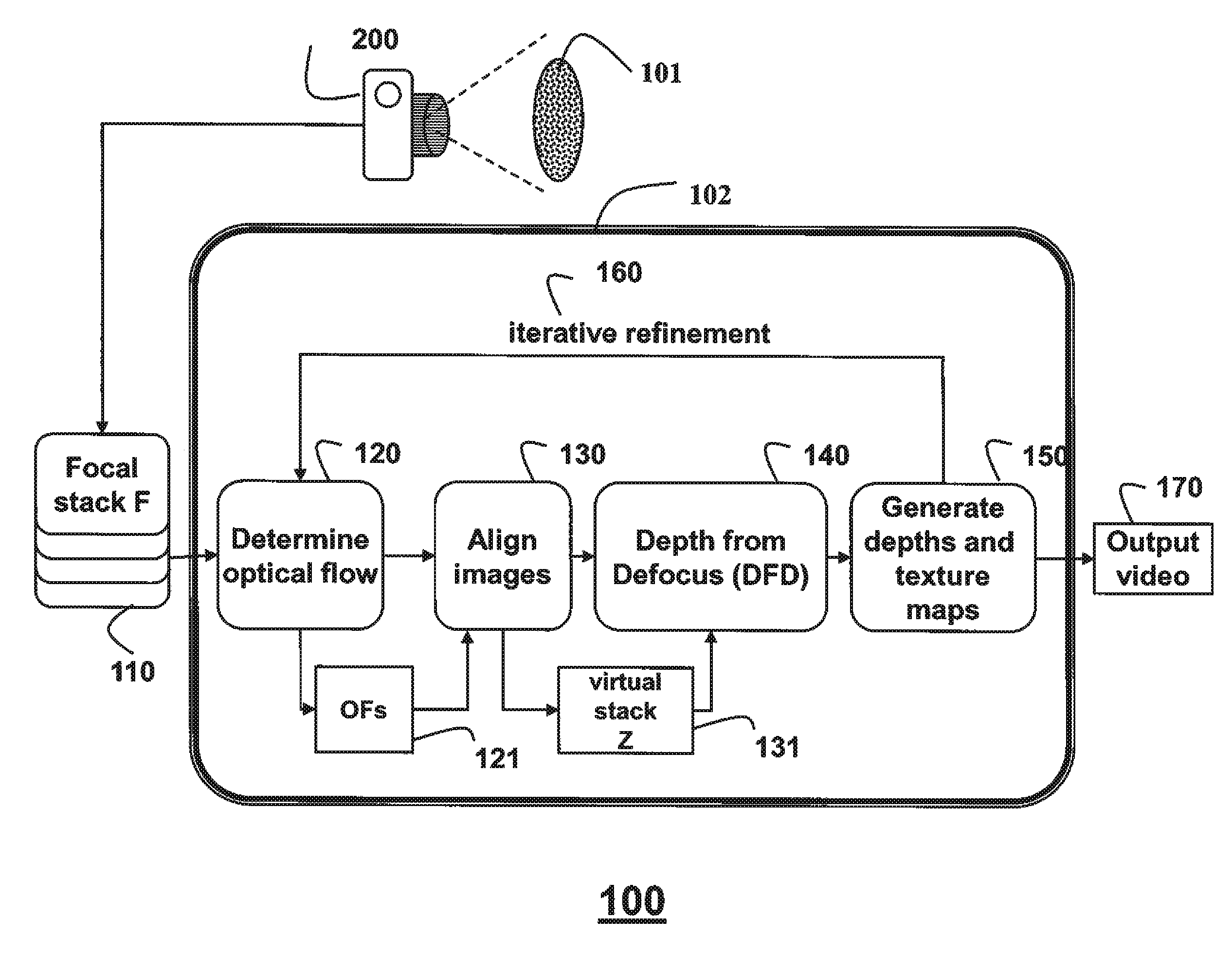
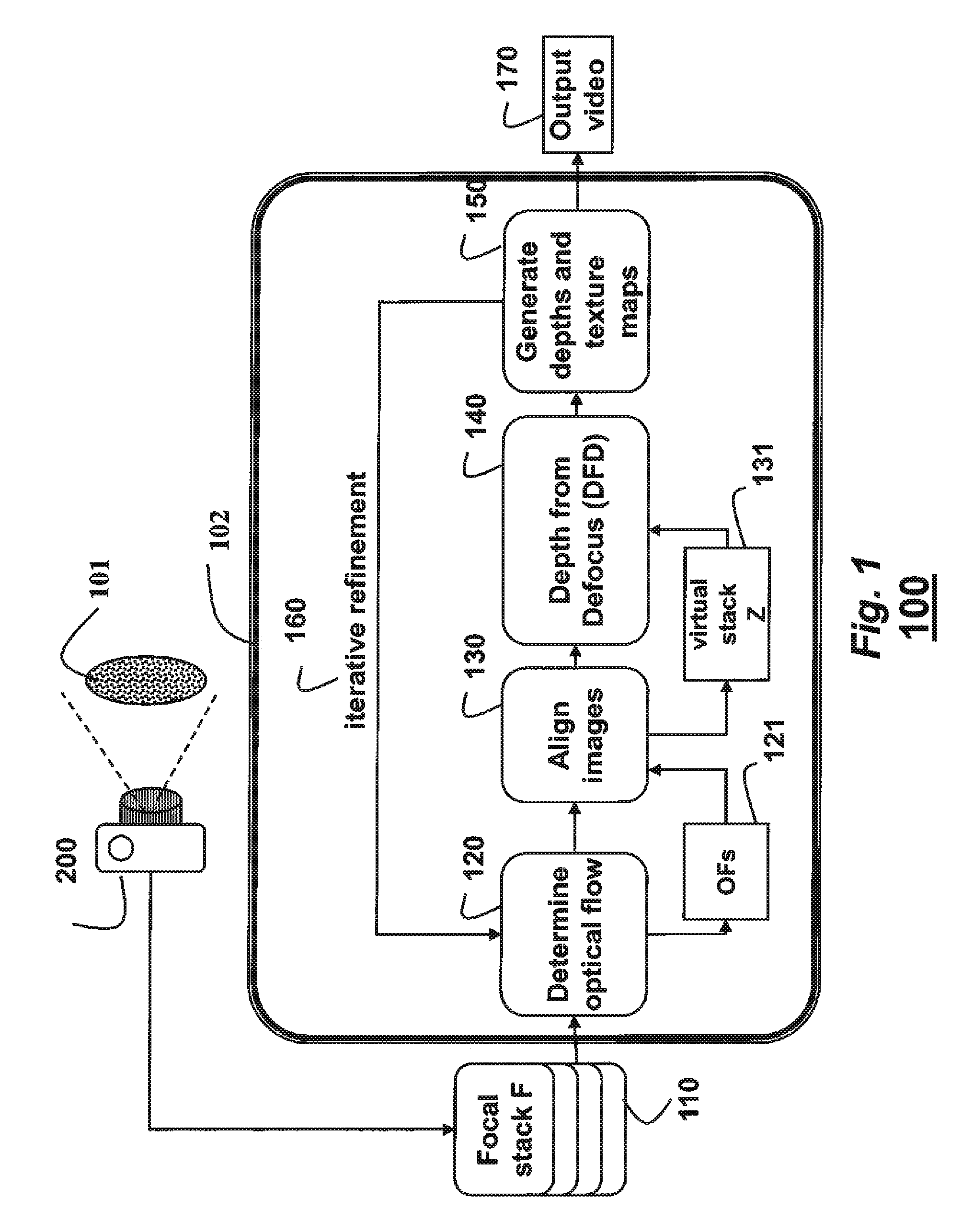
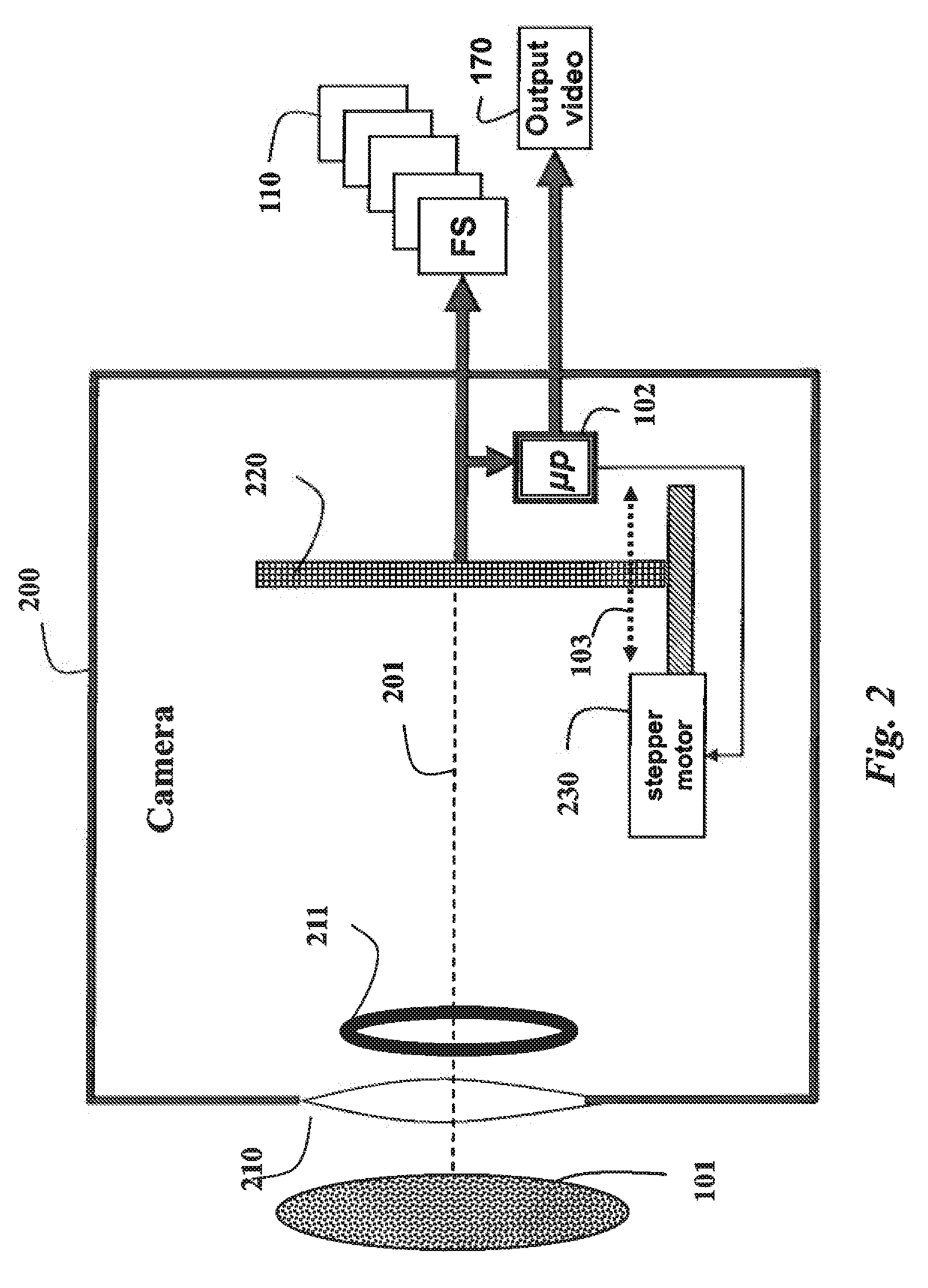
Camera and Method for Focus Based Depth Reconstruction of Dynamic Scenes
InactiveUS20130010067A1Accurate processingExtending and reducing depthTelevision system detailsCharacter and pattern recognitionOptical flowDepth of field
A dynamic scene is reconstructed as depths and an extended depth of field video by first acquiring, with a camera including a lens and sensor, a focal stack of the dynamic scene while changing a focal depth. An optical flow between the frames of the focal stack is determined, and the frames are warped according to the optical flow to align the frames and to generate a virtual static focal stack. Finally, a depth map and a texture map for each virtual static focal stack is generated using a depth from defocus, wherein the texture map corresponds to an EDOF image.
Owner:MITSUBISHI ELECTRIC RES LAB INC
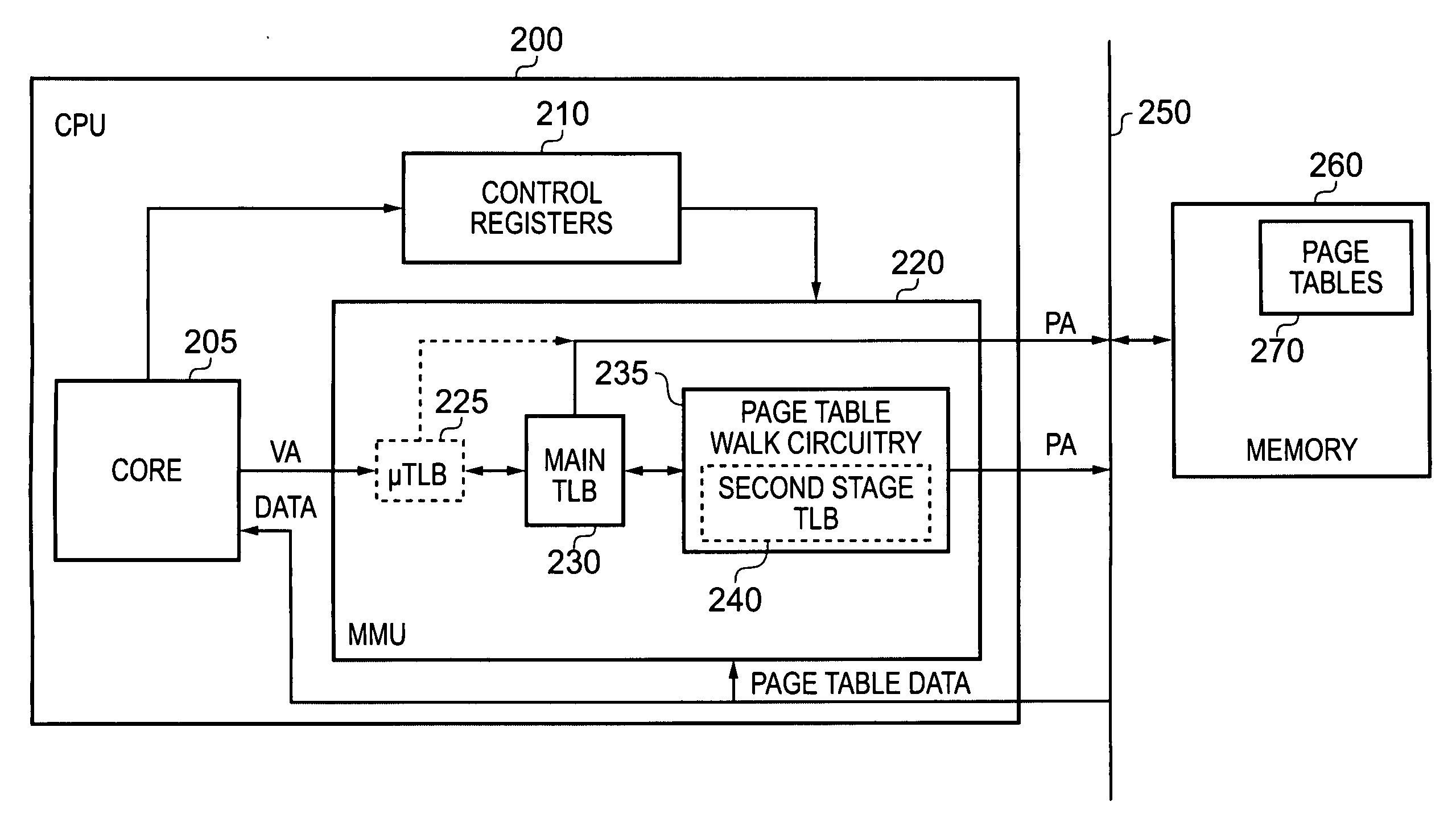
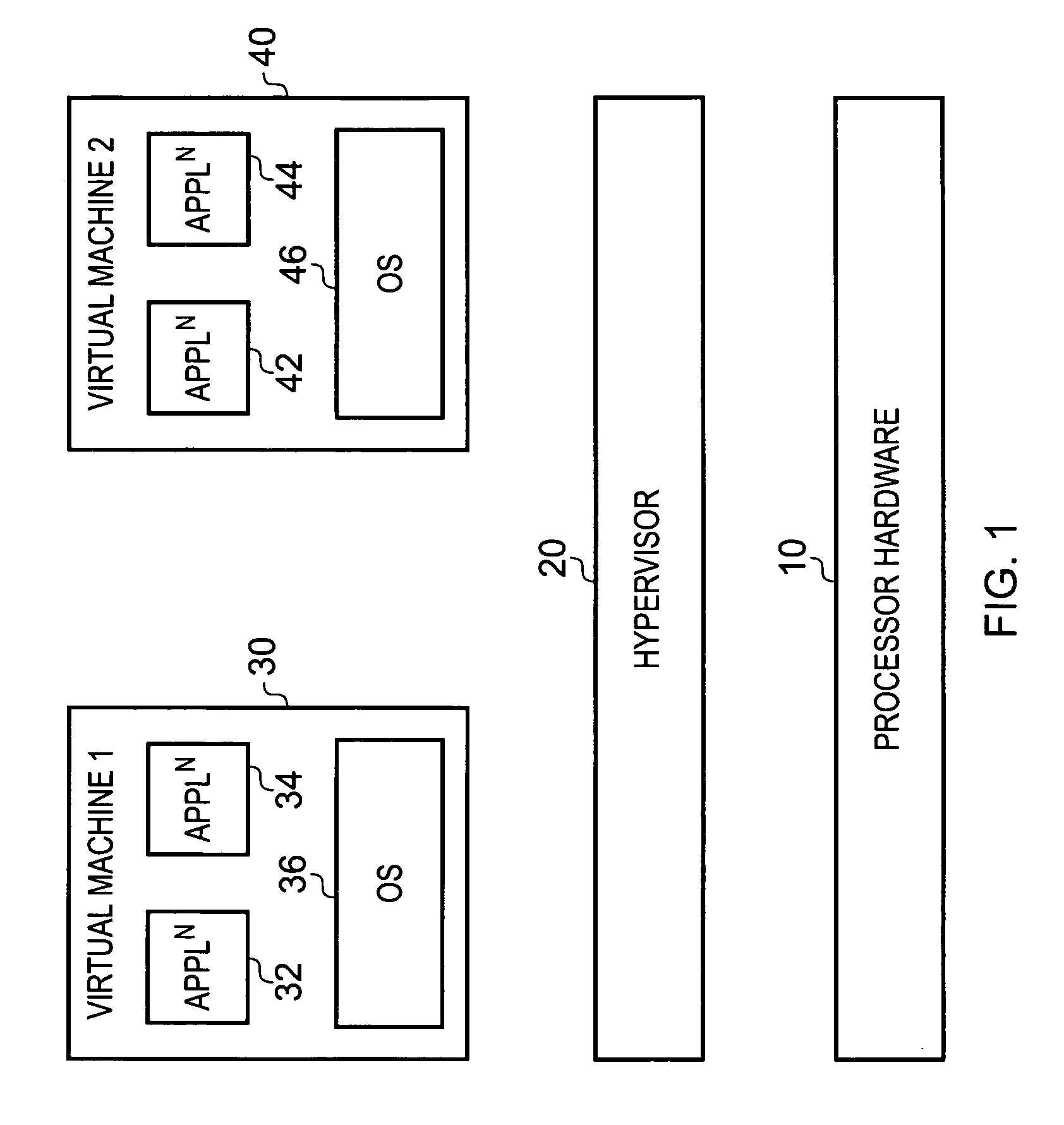
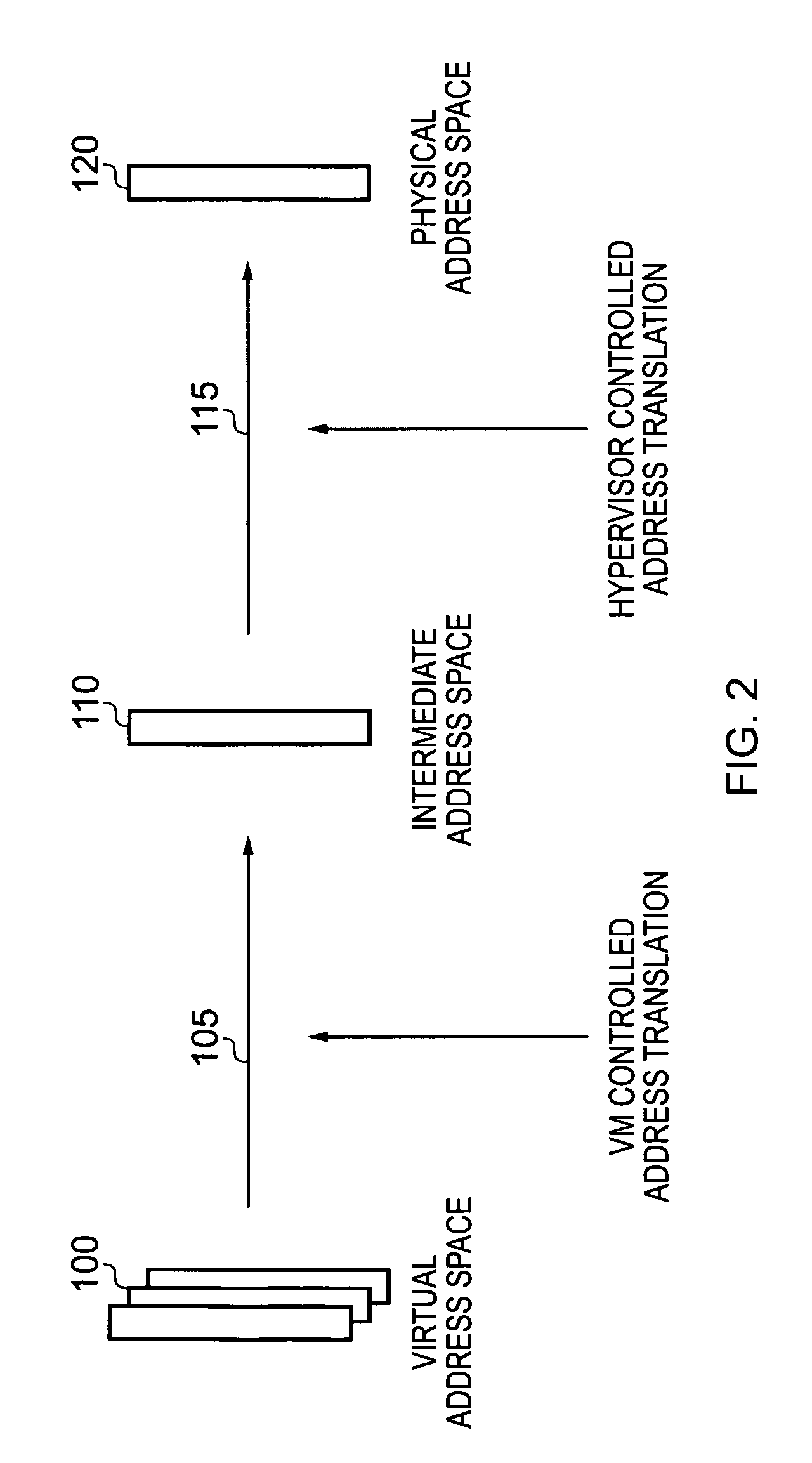
Data processing apparatus and method for handling address translation for access requests issued by processing circuitry
ActiveUS20090292899A1Improve efficiencyAccurate processingMemory adressing/allocation/relocationMicro-instruction address formationNetwork address translationVirtual address space
A data processing apparatus has address translation circuitry which is responsive to an access request specifying a virtual address, to perform a multi-stage address translation process to produce, via at least one intermediate address, a physical address in memory corresponding to the virtual address. The address translation circuitry references a storage unit, with each entry of the storage unit storing address translation information for one or more virtual addresses. Each entry has a field indicating whether the address translation information is consolidated address translation information or partial address translation information. If when processing an access request, it is determined that the relevant entry in the storage unit provides consolidated address translation information, the address translation circuitry produces a physical address directly from the consolidated address translation information. If on the other hand the relevant entry stores partial address translation information, the address translation circuitry produces an intermediate address from the partial address translation information and then performs the remainder of the multi-stage address translation process. Such an approach provides the performance benefits associated with a consolidated entry mechanism within the storage unit, whilst also allowing certain problem cases to be handled correctly and in an efficient manner.
Owner:ARM LTD
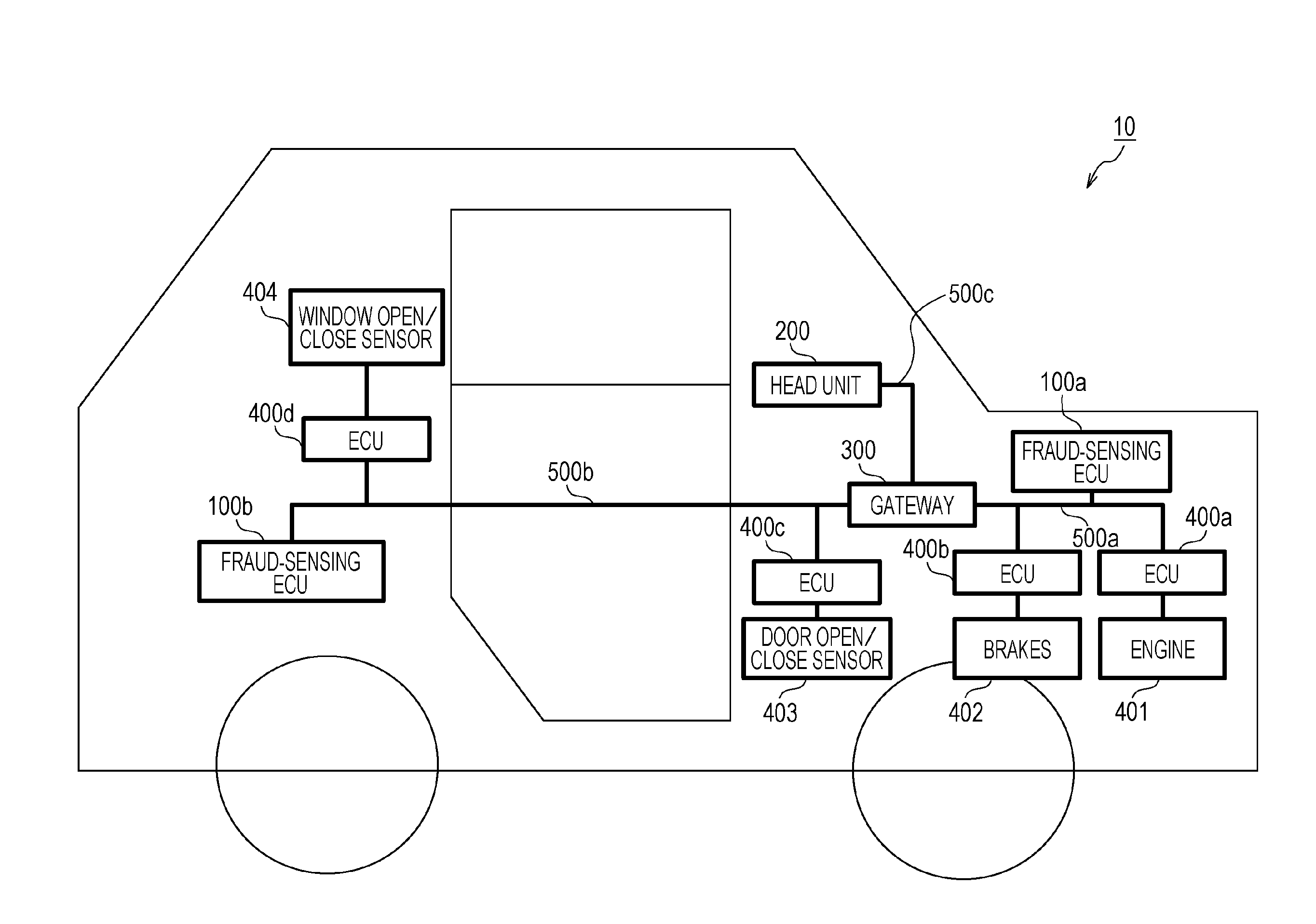
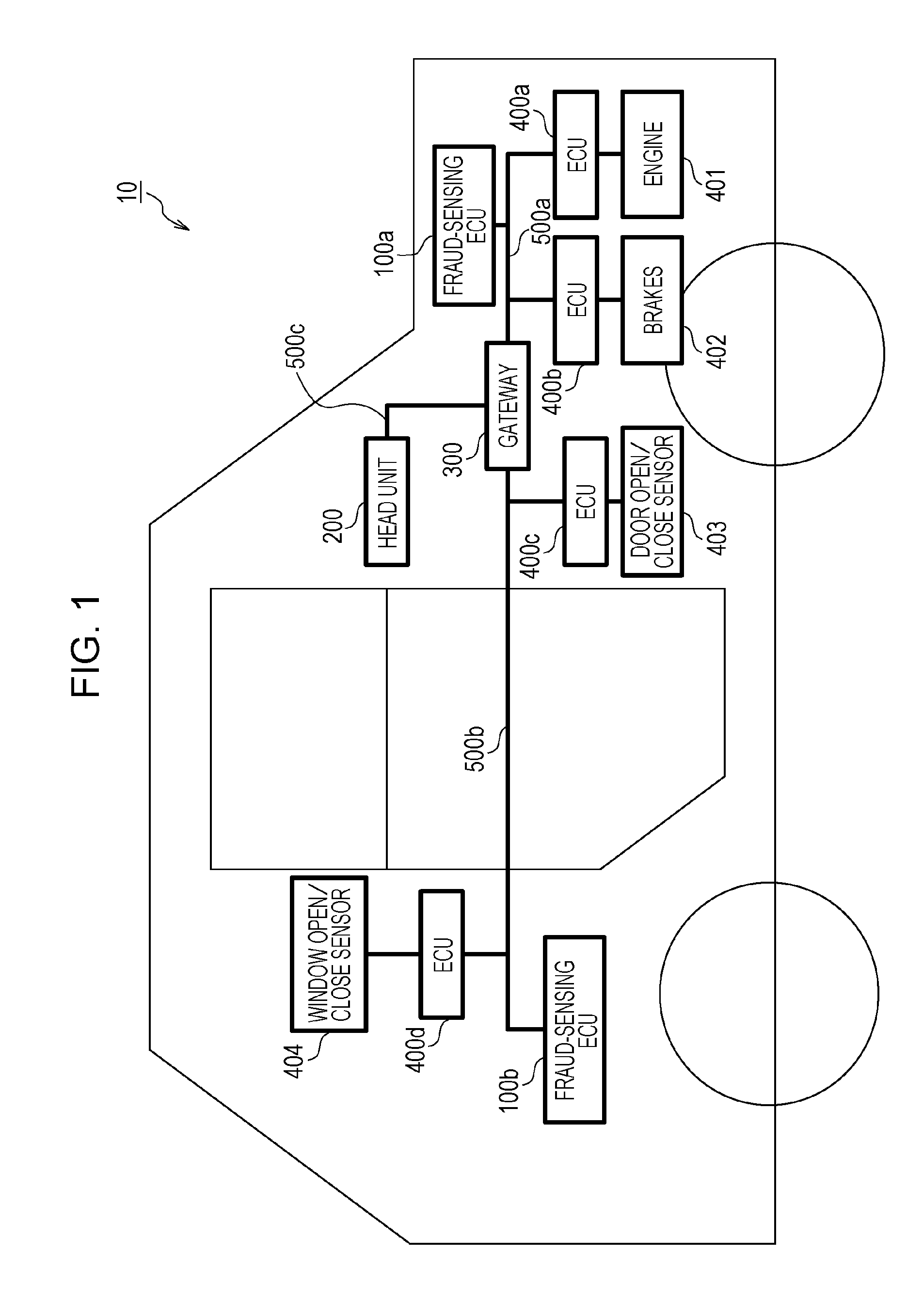
Method for handling transmission of fraudulent frames within in-vehicle network
ActiveUS20160297401A1Improve the immunityAccurate processingAnti-theft devicesSecuring communicationIn vehicleMessage authentication code
An anti-fraud method for use in an in-vehicle network system including a plurality of electronic control units that exchange data frames, each having added thereto a message authentication code (MAC), via at least one bus includes: receiving a data frame transmitted on the bus; generating a first MAC by using a MAC key and a value of a counter that counts the number of times a data frame having added thereto a MAC is transmitted; in a case where the verification has failed, (i) generating as second MAC by using an old MAC key; (ii) re-verifying that the received data frame has added thereto the generated second MAC; transmitting, in a case where the re-verification has succeeded, via the bus a key-update frame indicating a request for updating the MAC key; and updating the MAC key in response to the transmission of the key-update frame.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
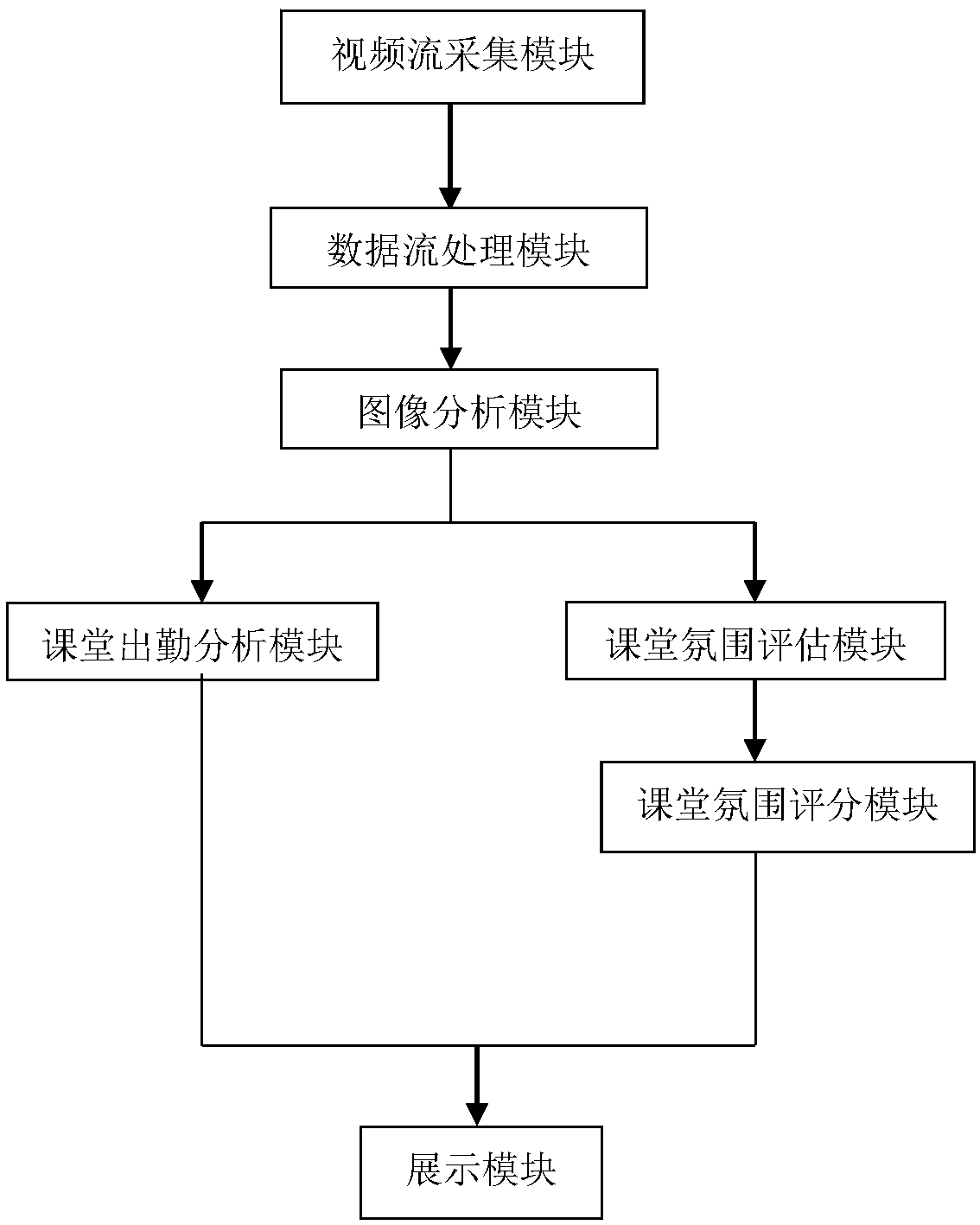
An online classroom atmosphere assessment system and method
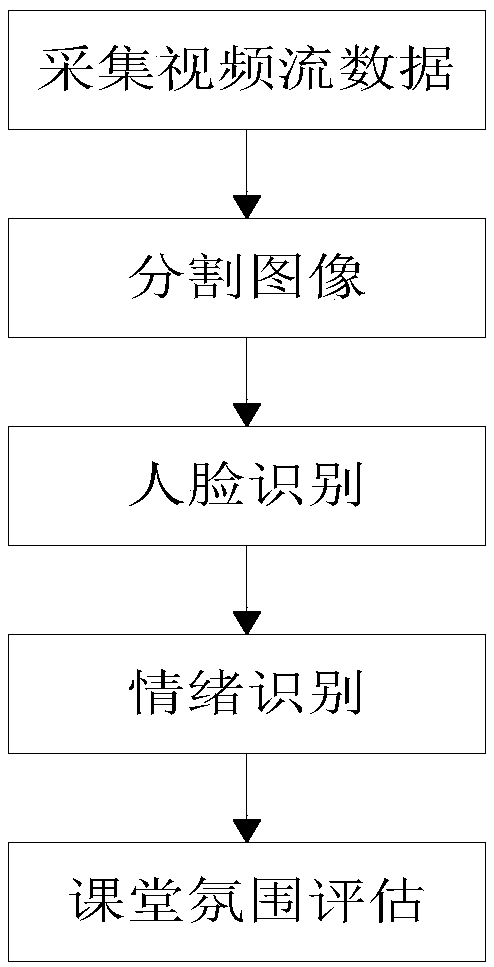
InactiveCN109035089AReduce the amount of parametersFast operationData processing applicationsAcquiring/recognising facial featuresImage analysisStreaming data
The invention provides an online classroom atmosphere evaluation system and method. The evaluation system comprises a video stream collection module, a data stream processing module, an image analysismodule, a classroom attendance analysis module, a classroom atmosphere evaluation module, a classroom atmosphere scoring module and a display module; . The invention collects classroom video stream data through a camera, and the captured video is captured frame by frame to obtain images; all the faces images are segmented and numbered sequentially, at the same time, the eigenvalues are assigned to the faces with the corresponding numbers, and then face recognition and facial expression recognition are carried out according to the number, so as to identify the number, emotion and movement posture of students in the video stream data; the score 0 is given to the students lowering heads in the image and the score 1 is given to students having interaction; according to the emotional analysisstrategy of students listening to the teacher, the current student listening student score is obtained and finally comprehensive evaluation of the classroom atmosphere score is obtained. The inventioncan evaluate the classroom quality on-line and in real time, and can effectively improve the evaluation effect.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com