Website security monitoring and alarming system based on log analysis and firewall security matrixes
A security matrix and security monitoring technology, applied in the field of information security, can solve problems such as destroying the security matrix
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific implementation of this system is as follows:
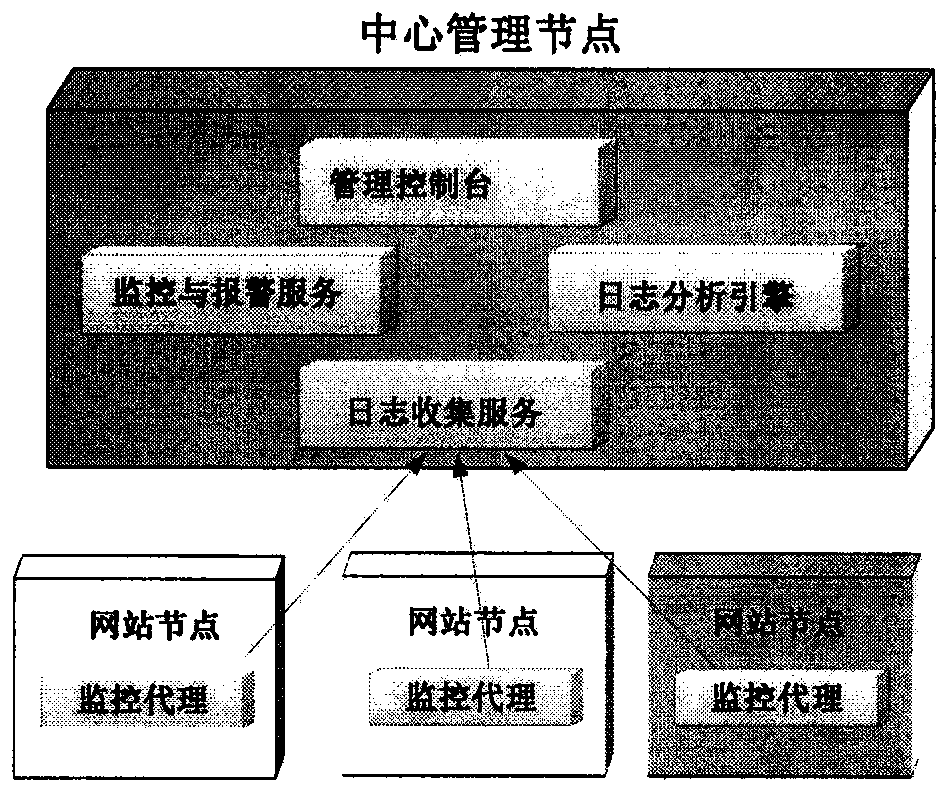
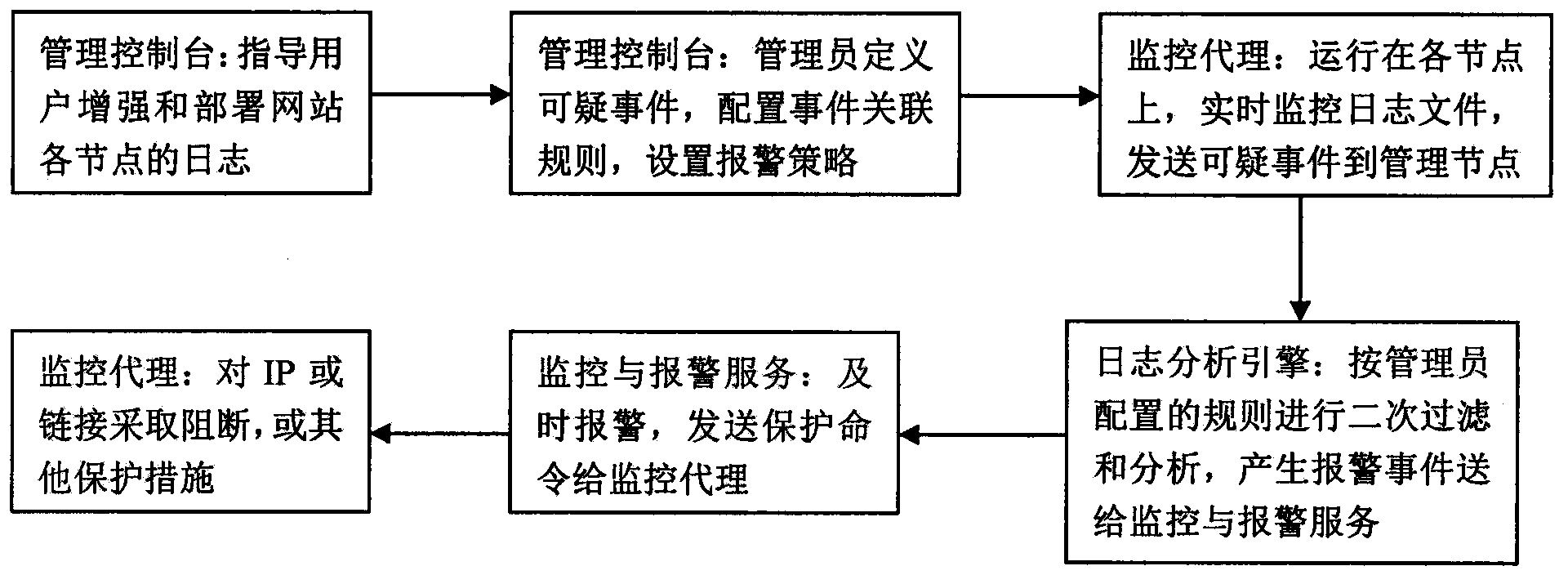
[0032] 1. Deploy the monitoring agent on all relevant host nodes of the website, and deploy the management center server on the local intranet or remotely.
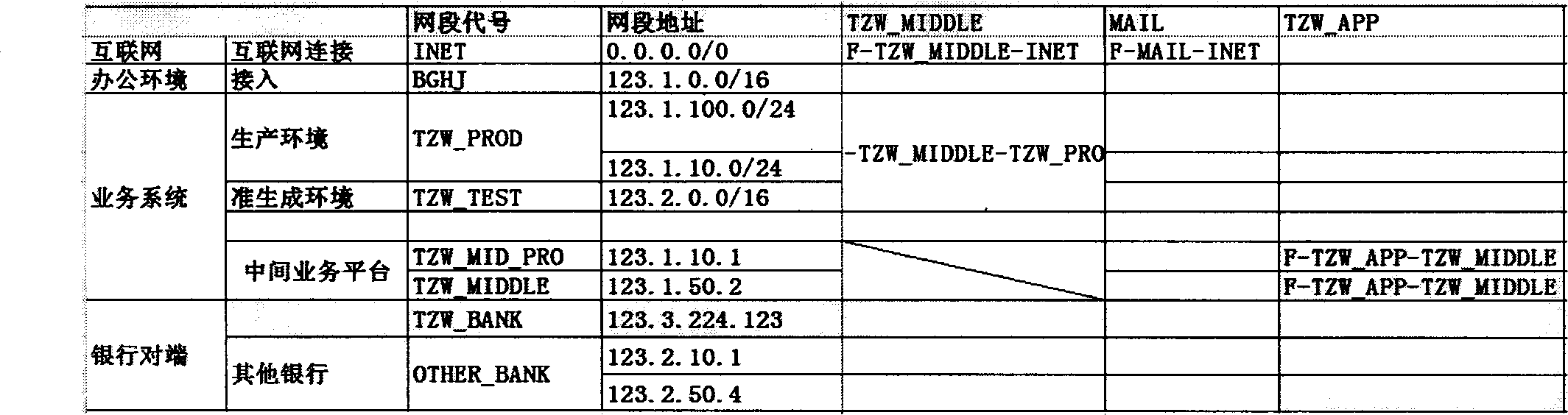
[0033] 2. The website security administrator designs the firewall security matrix of the entire website according to the guidance of this system, and configures the firewall equipment and hosts in the relevant environment of the website according to the requirements of the matrix.
[0034] 3. The administrator configures the monitoring parameters of the security matrix on the management node of the system, and the management node sends the monitoring requirements to each monitoring agent. The monitoring agent adopts direct and indirect methods to perform monitoring tasks to verify the validity of the matrix, and will report to the management node if any discrepancy is found. The direct monitoring method will regularly initiate access attempts (such as tel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com