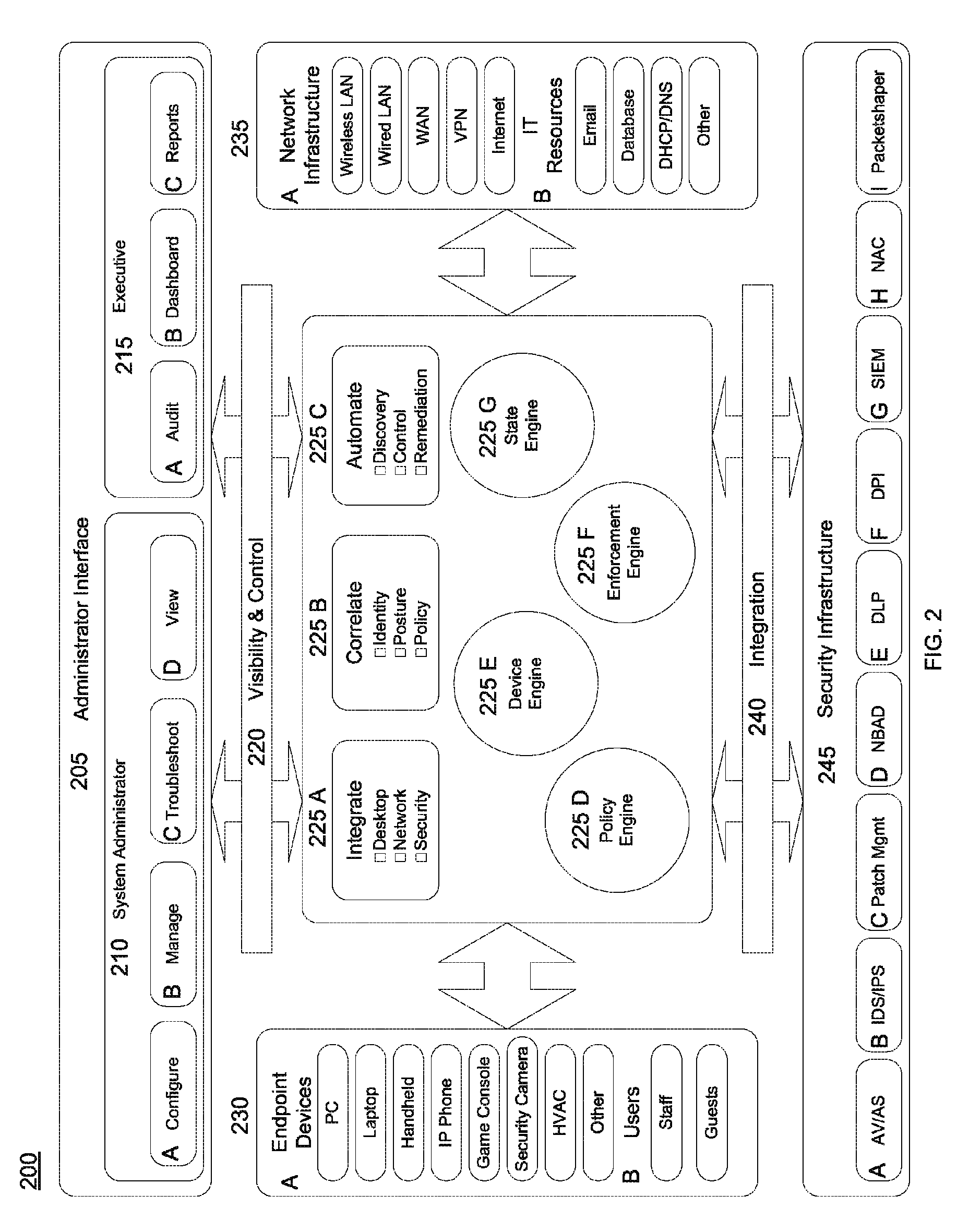
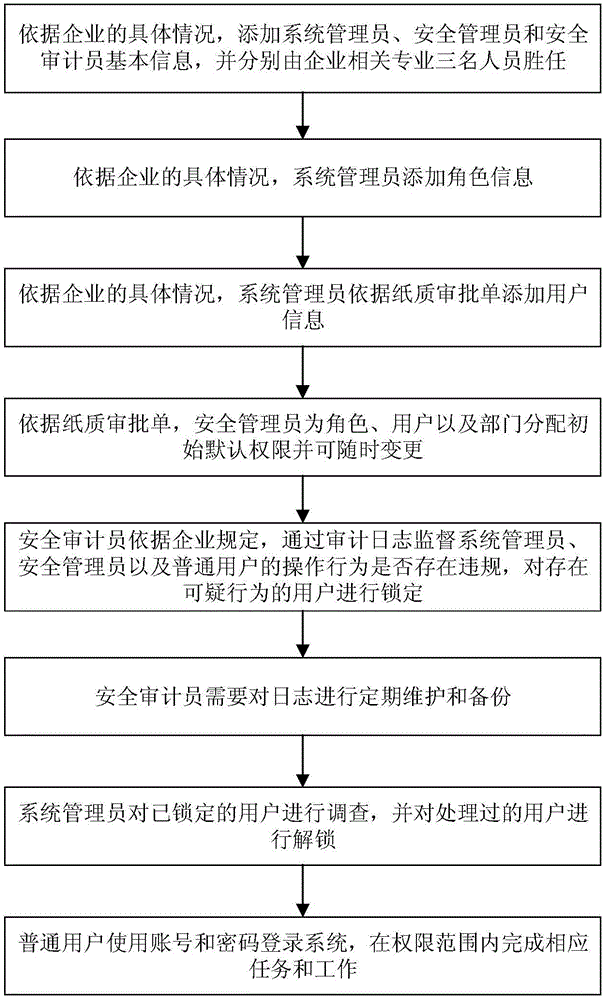
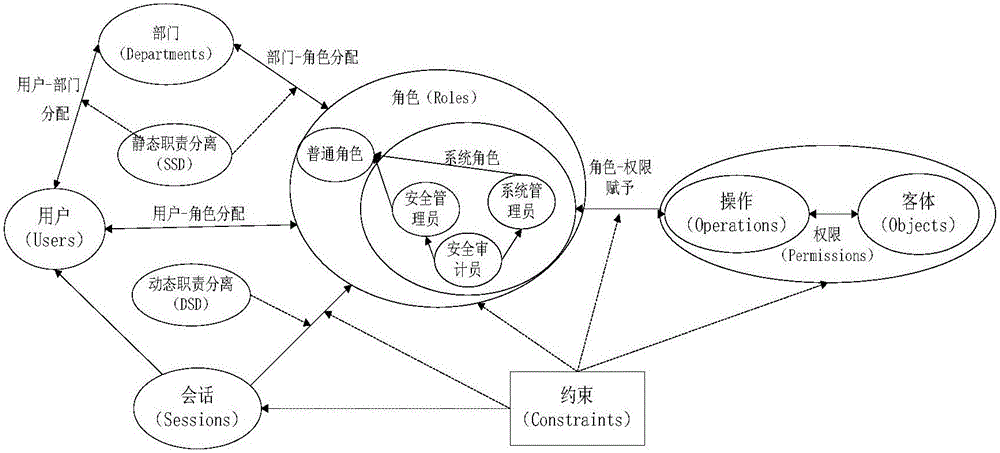
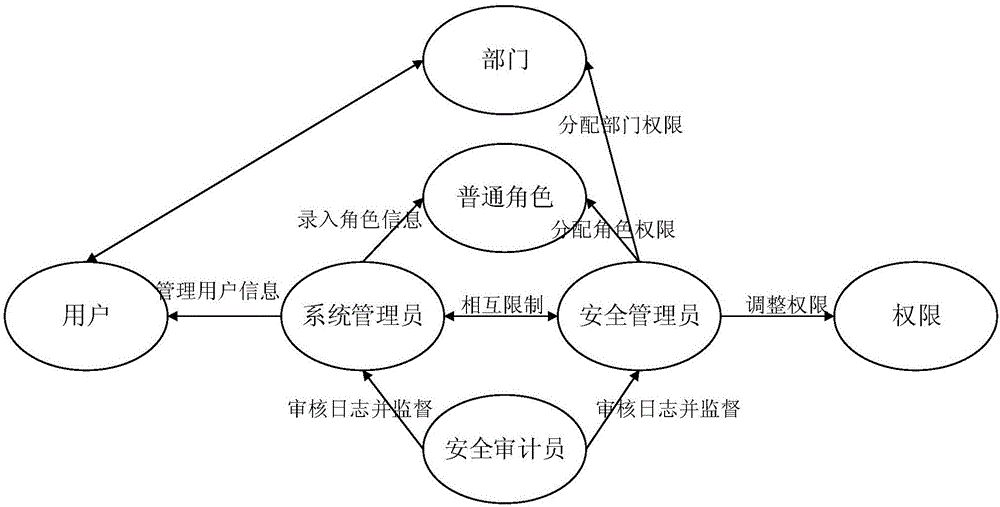
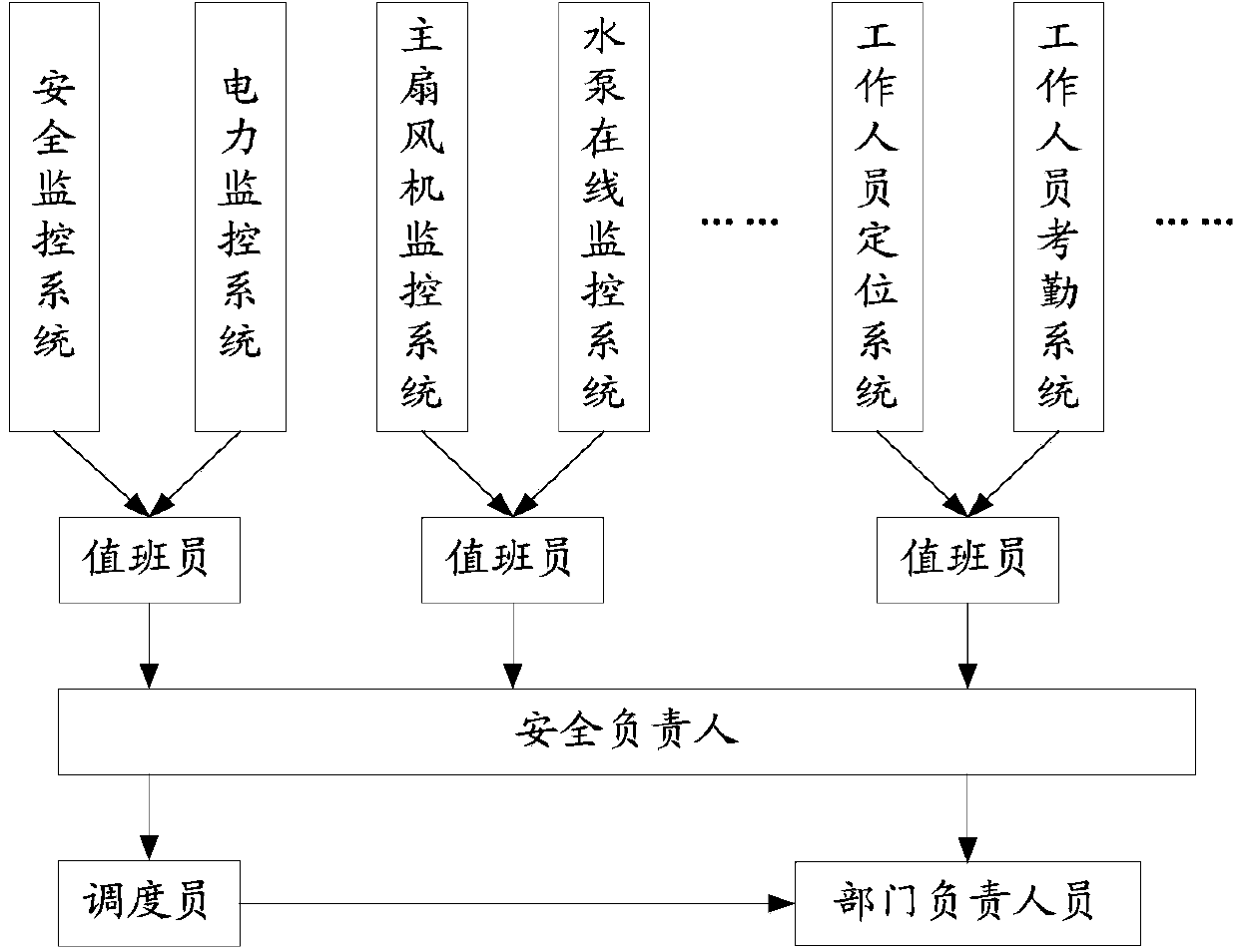
Patents
Literature
117 results about "Security administrator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
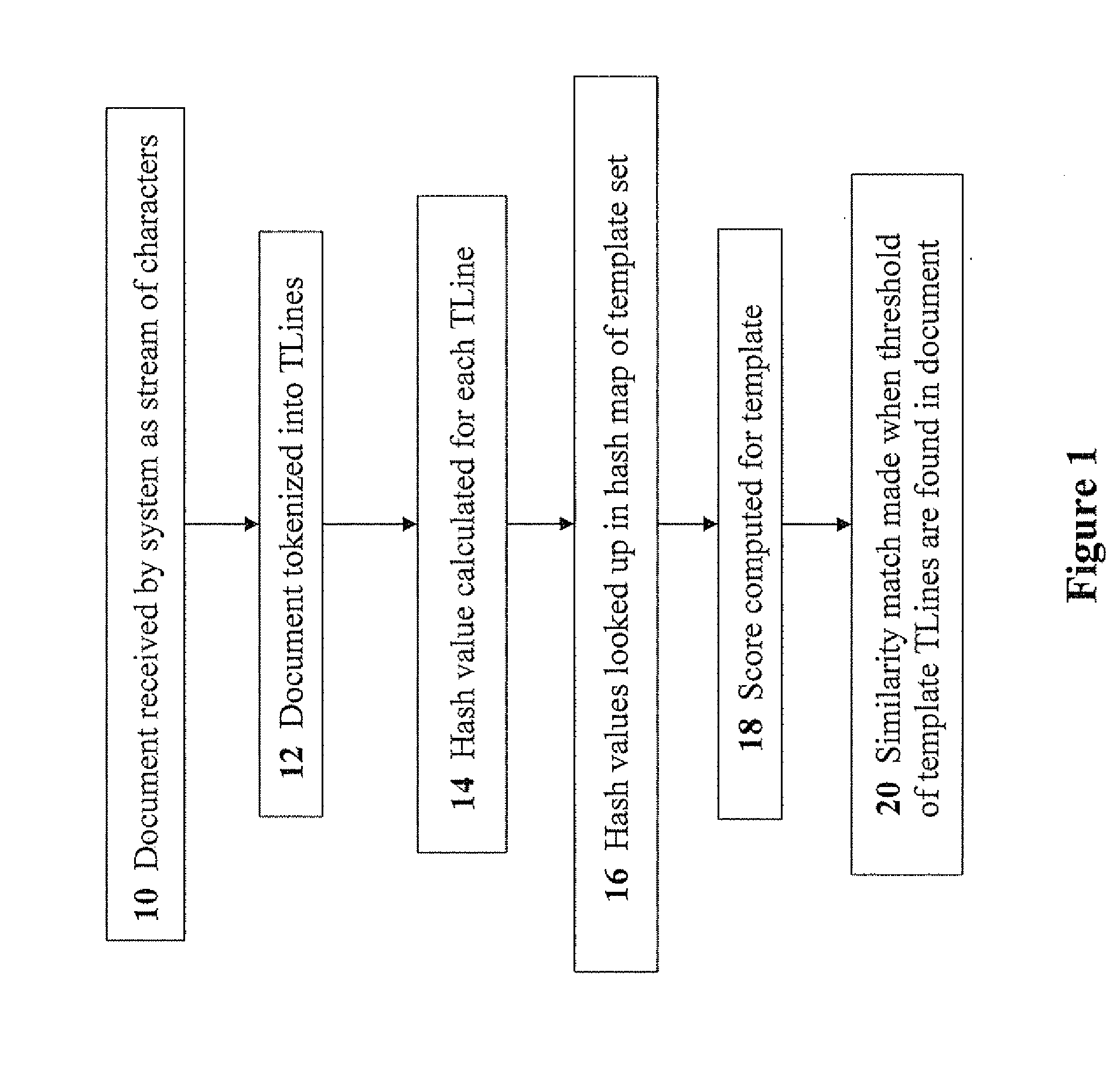
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
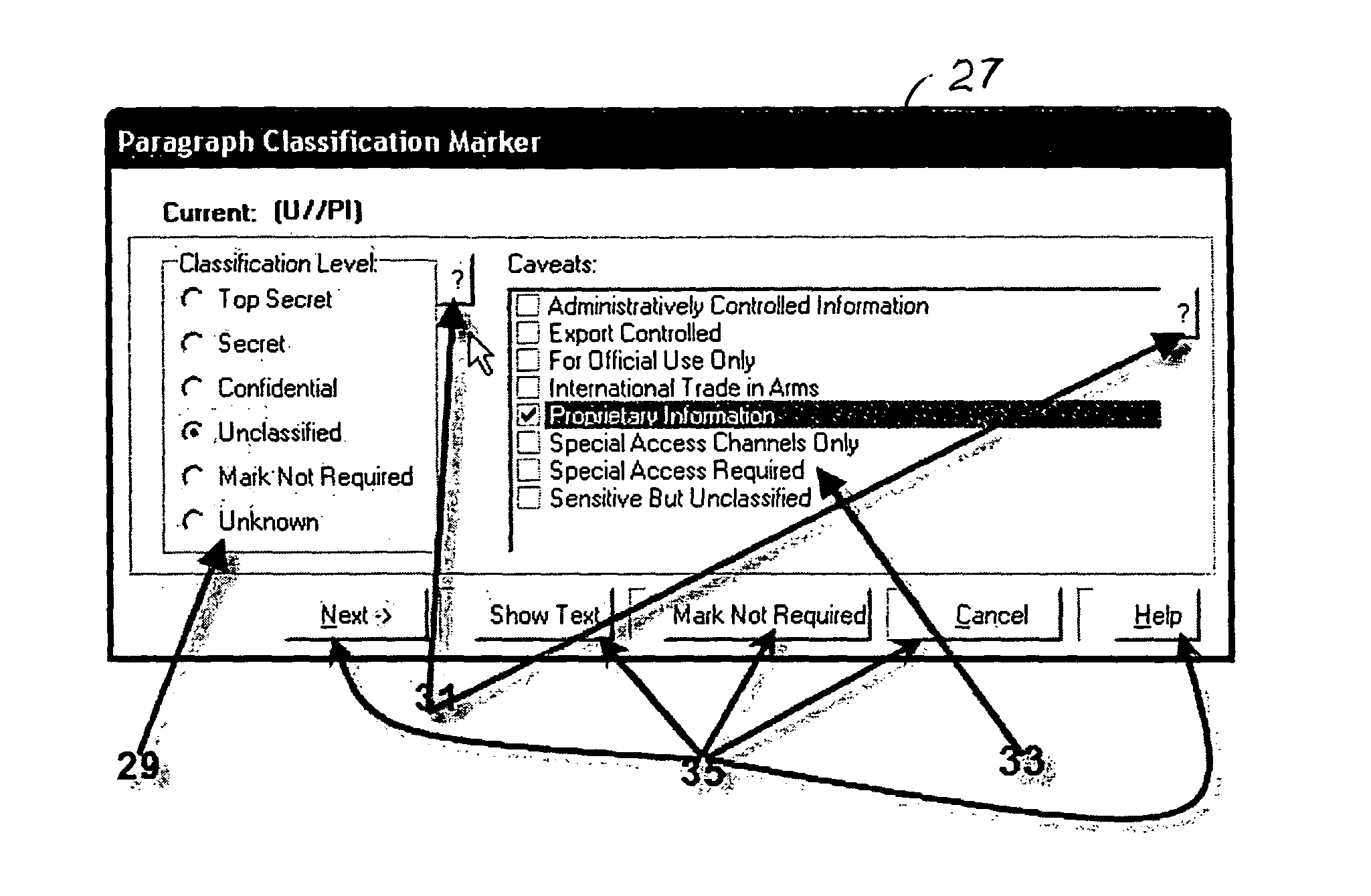
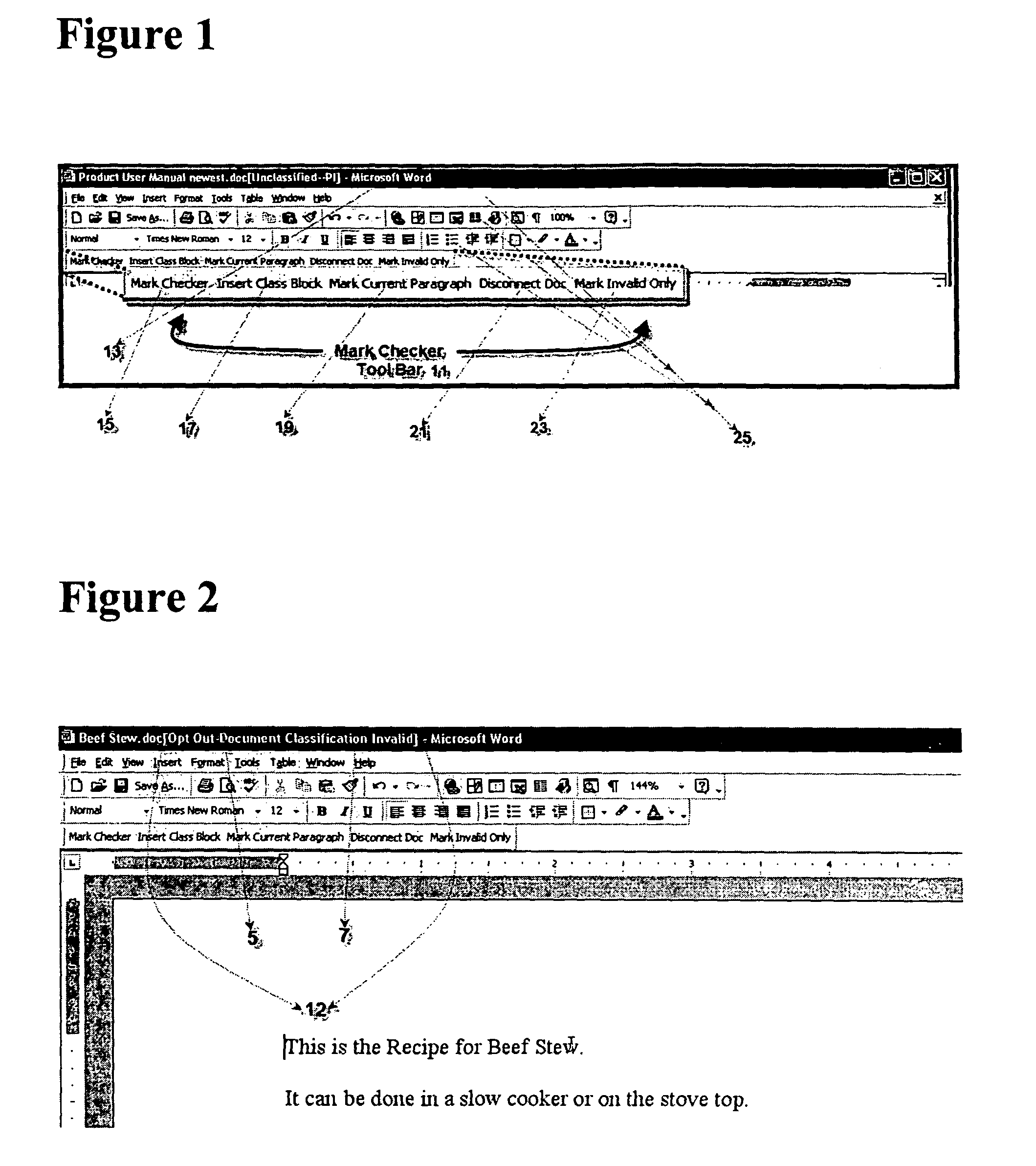
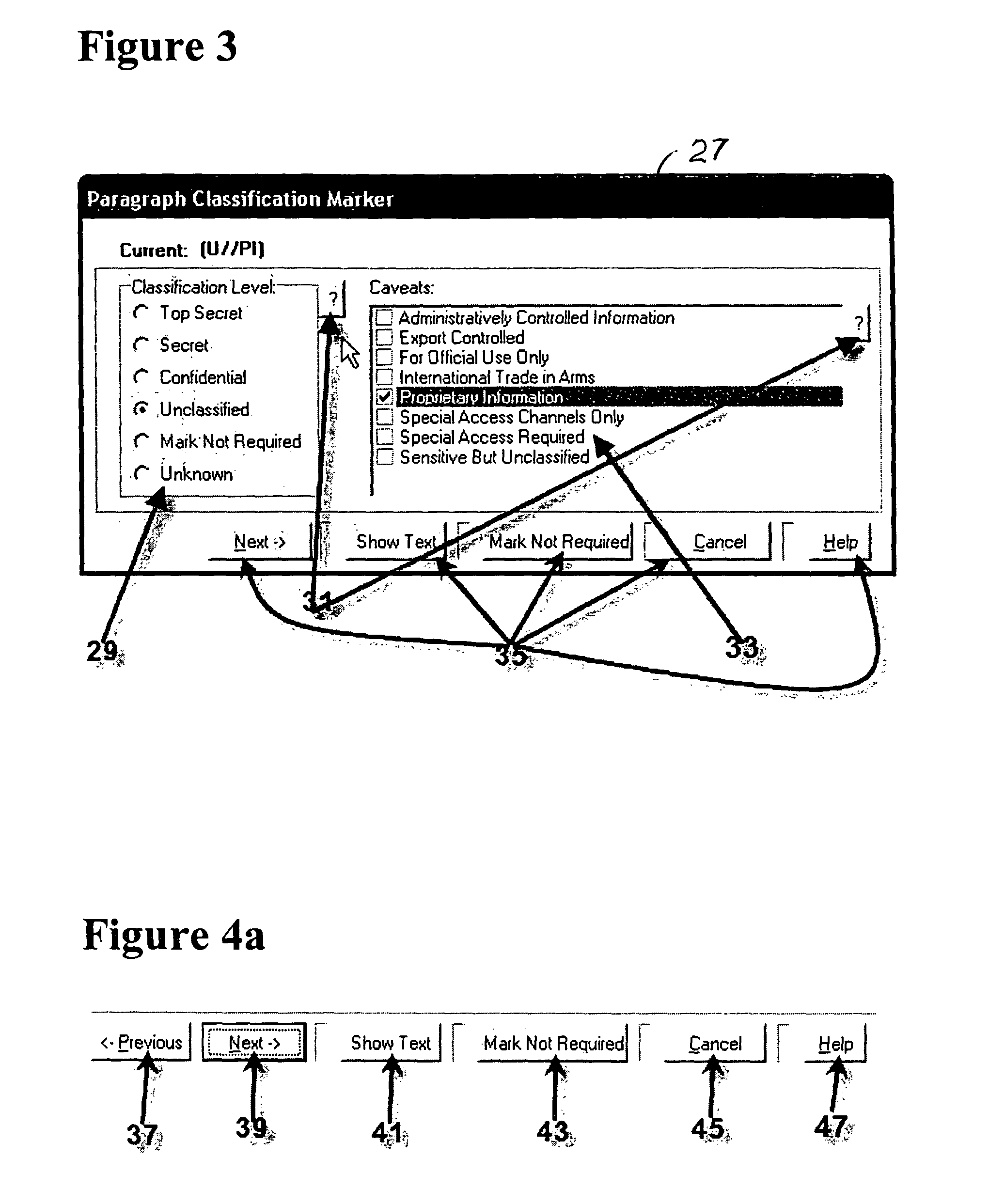
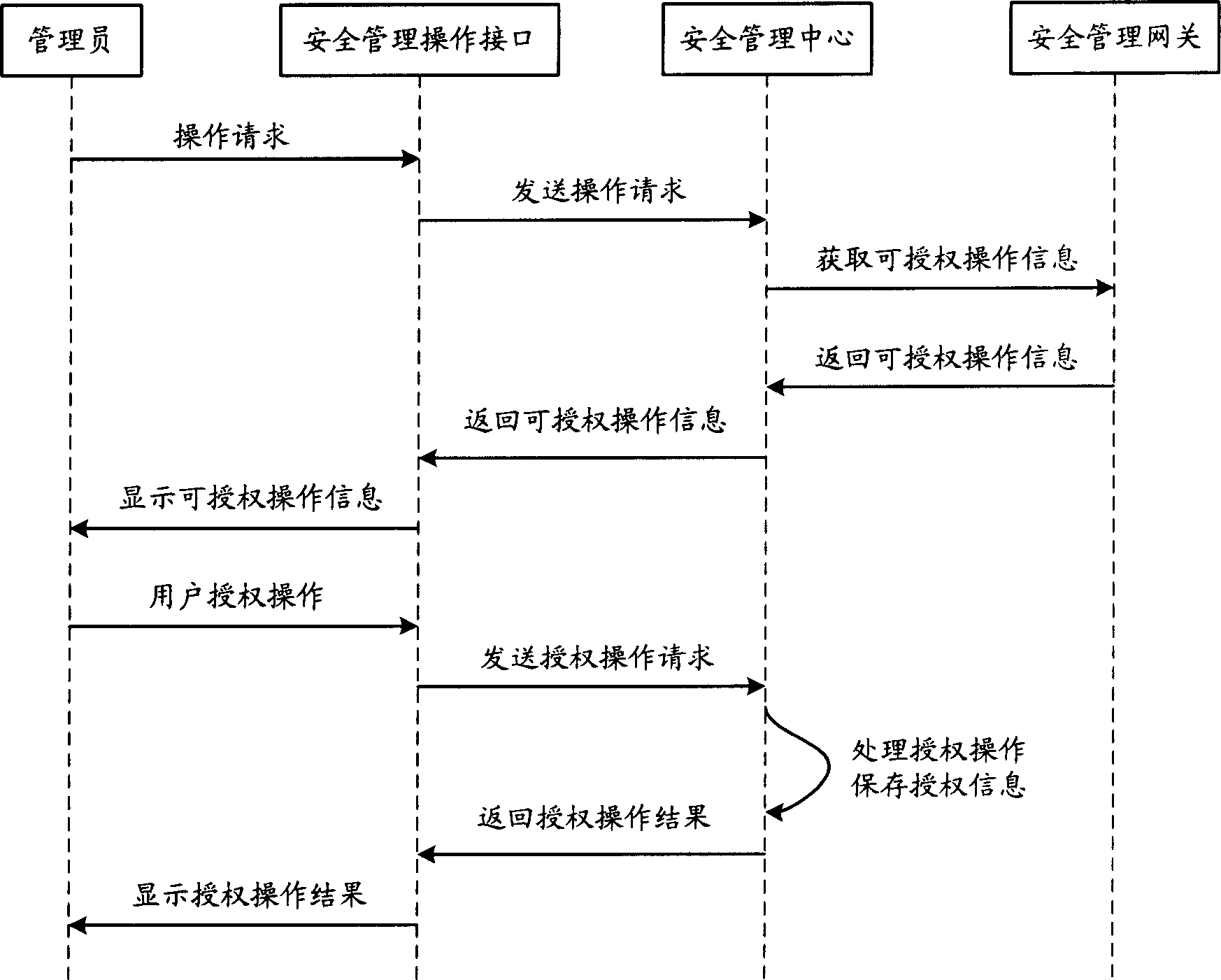
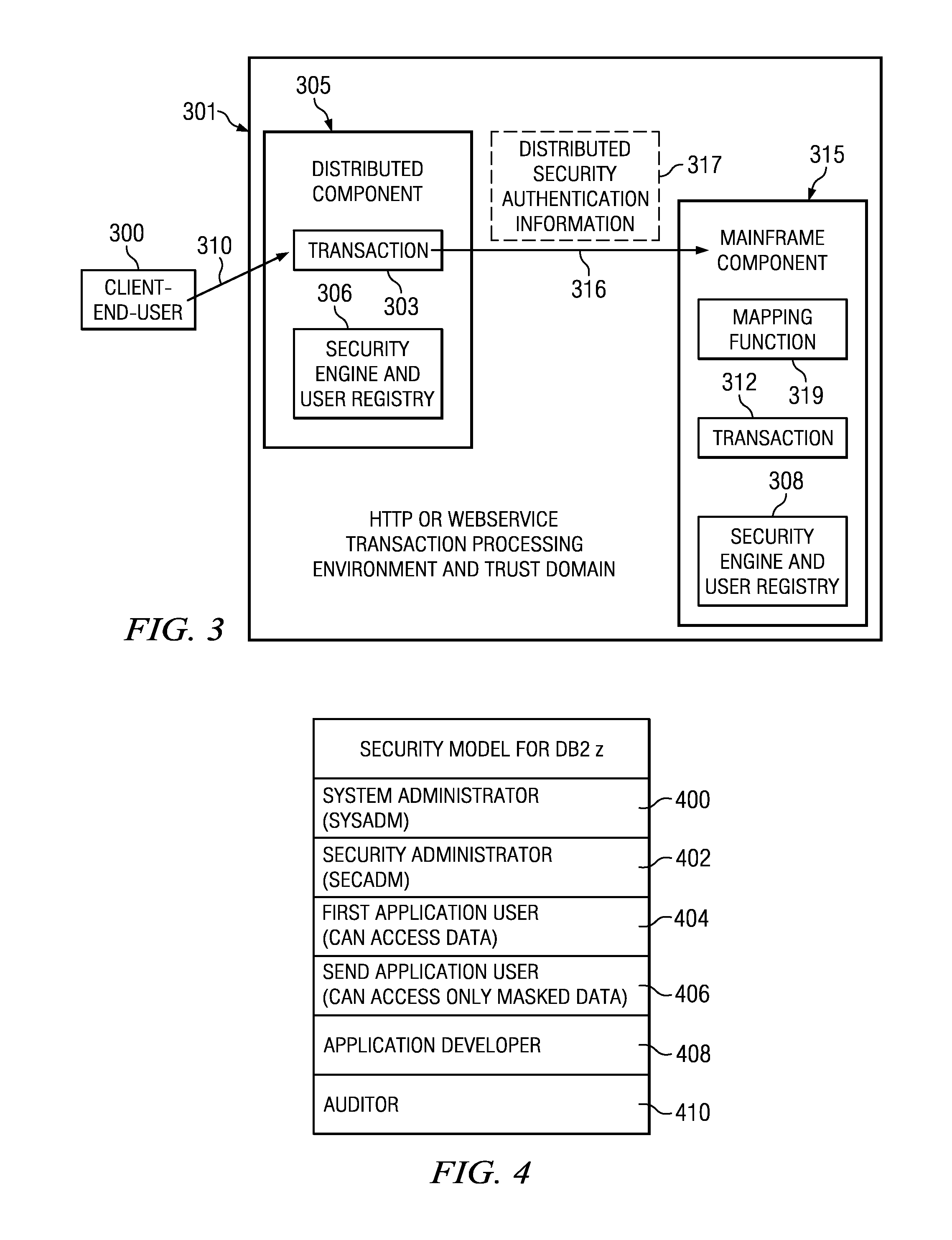
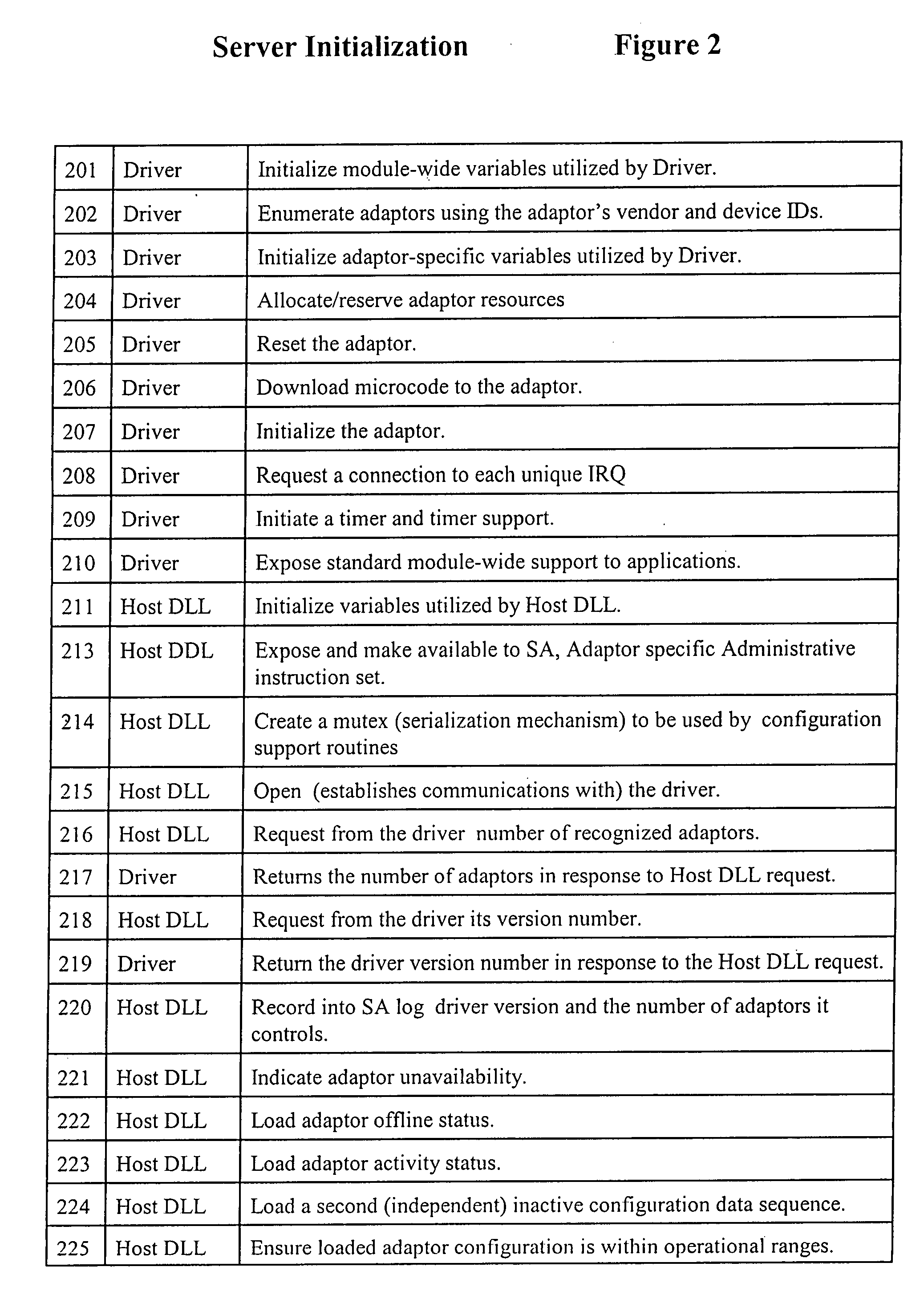
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
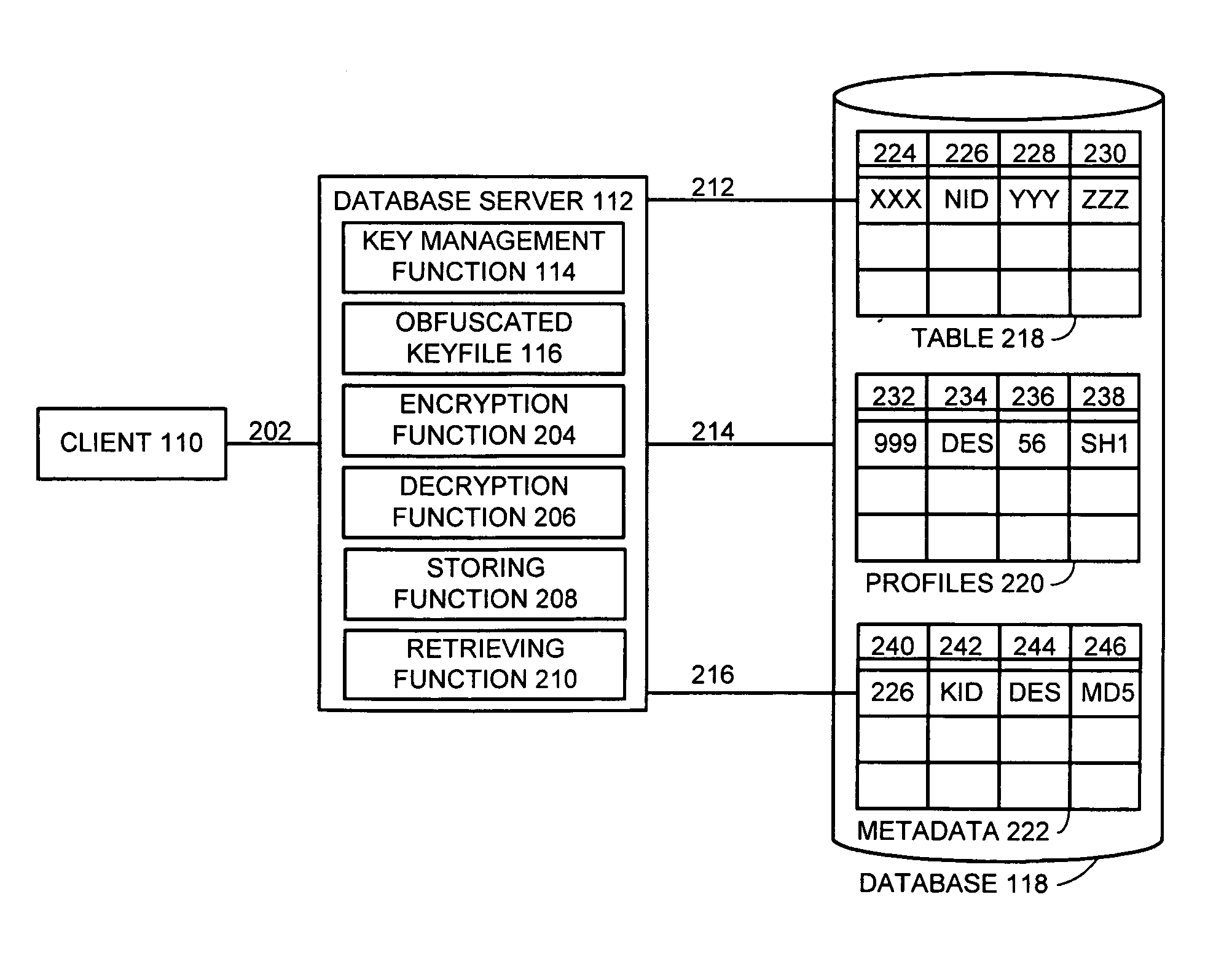
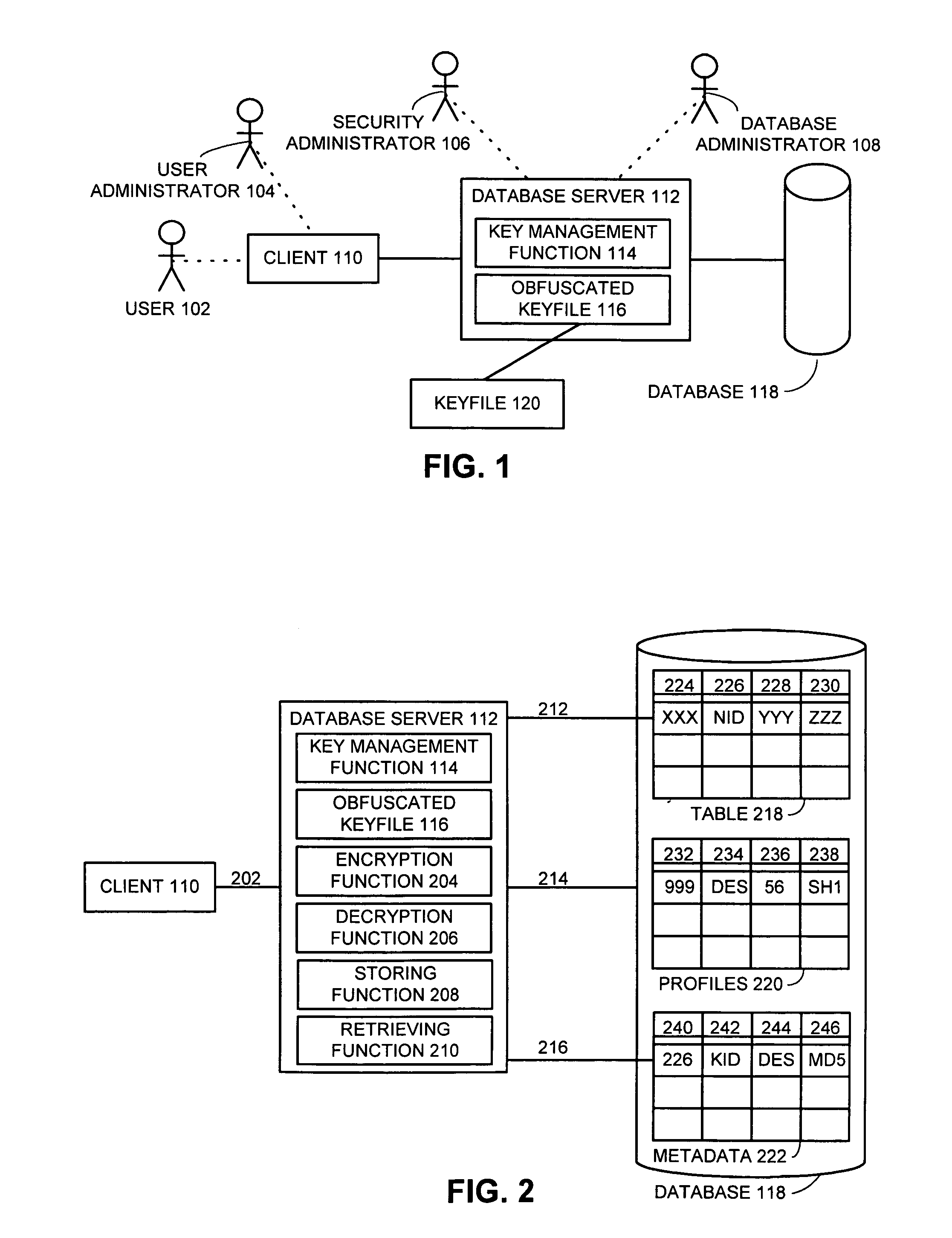
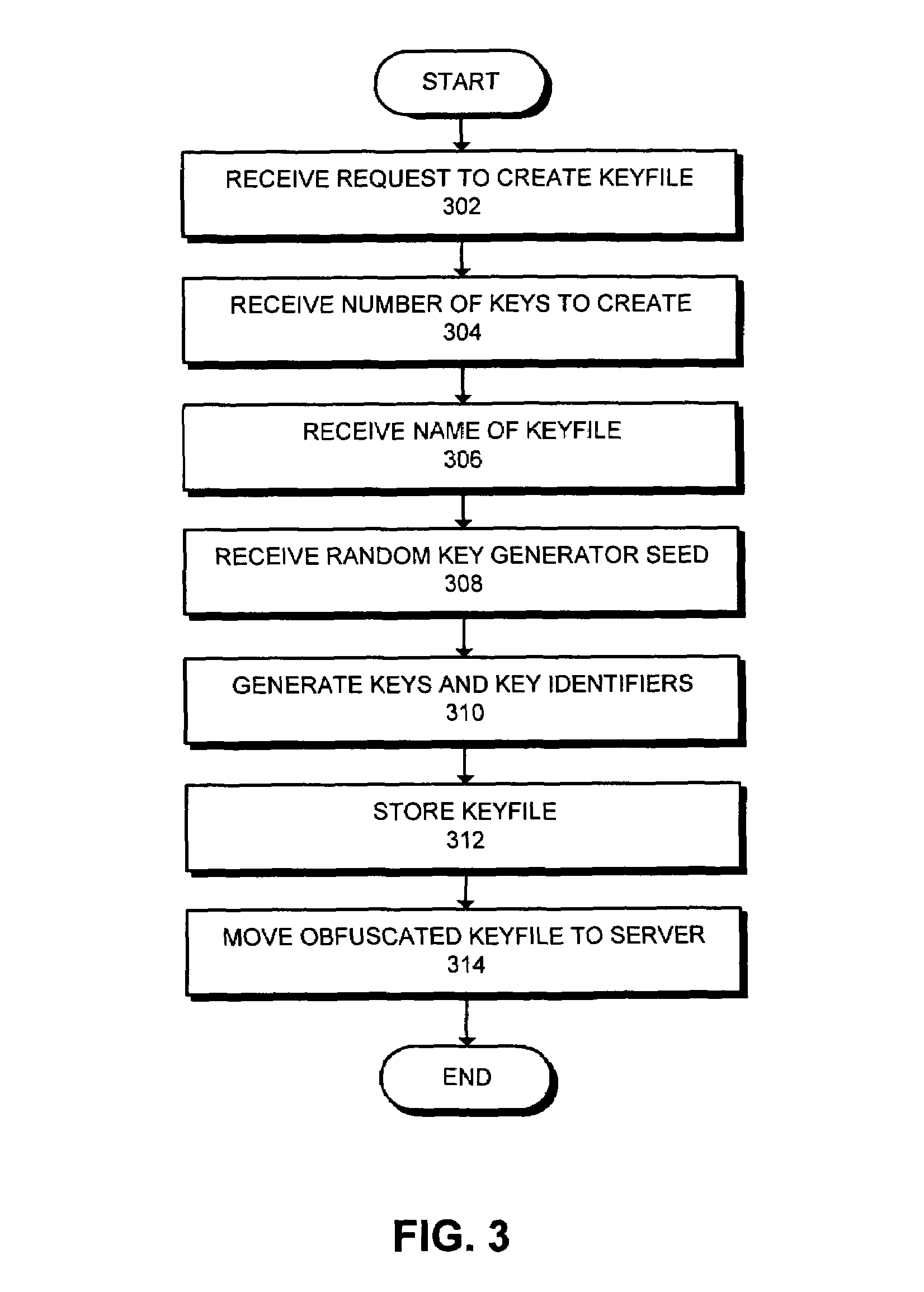
Method and apparatus for automatic database encryption
InactiveUS7111005B1Data processing applicationsMultiple keys/algorithms usageEncrypted functionDatabase encryption
One embodiment of the present invention provides a system for managing encryption within a database system that is managed by a database administrator, and wherein a user administrator not otherwise associated with the database system, manages users of the database system. This system performs encryption automatically and transparently to a user of the database system. The system operates by receiving a request to store data in a column of the database system. If a user has designated the column as an encrypted column, the system automatically encrypts the data using an encryption function. This encryption function uses a key stored in a keyfile managed by the security administrator. After encrypting the data, the system stores the data in the database system using a storage function of the database system.
Owner:ORACLE INT CORP
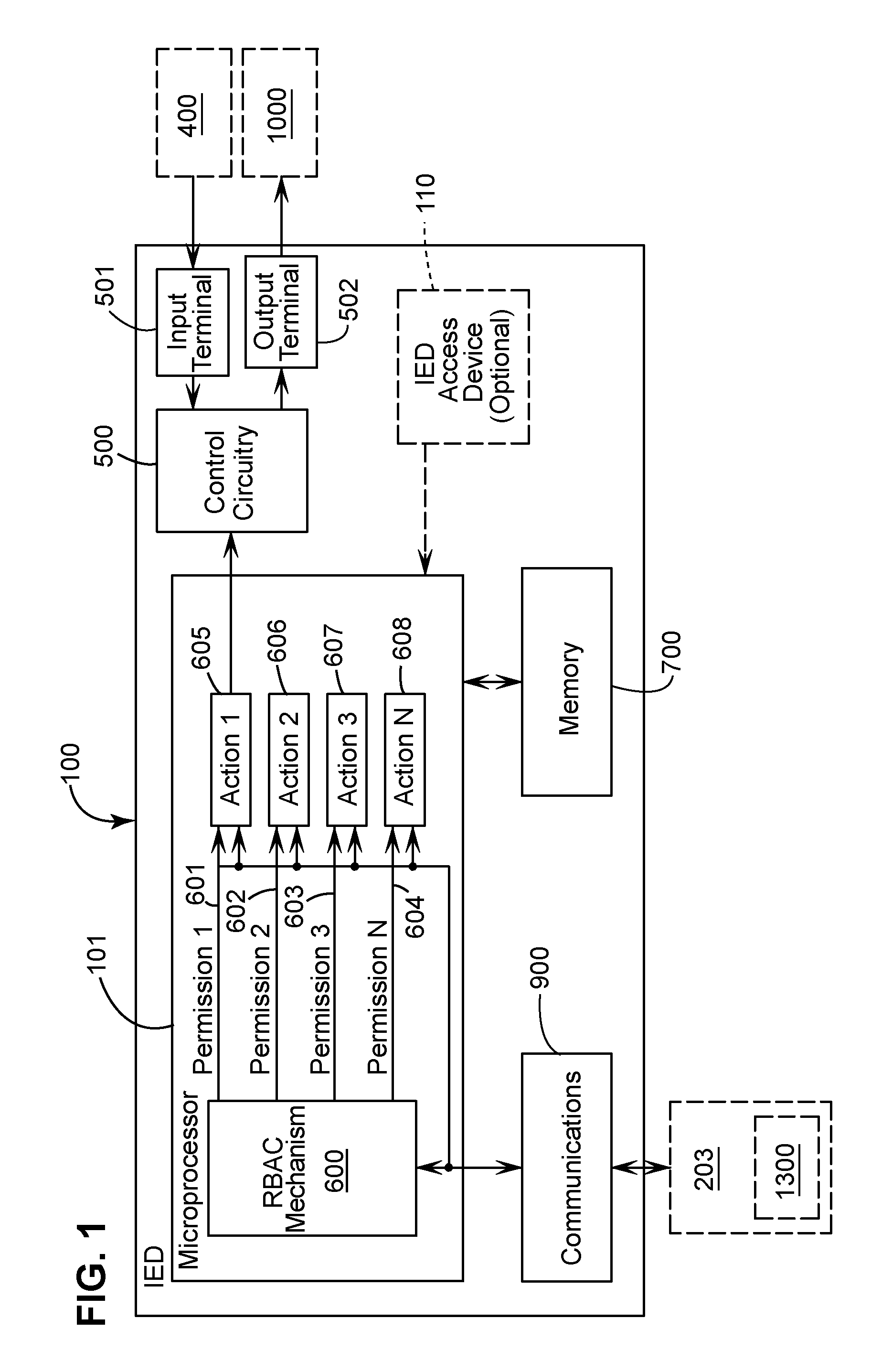
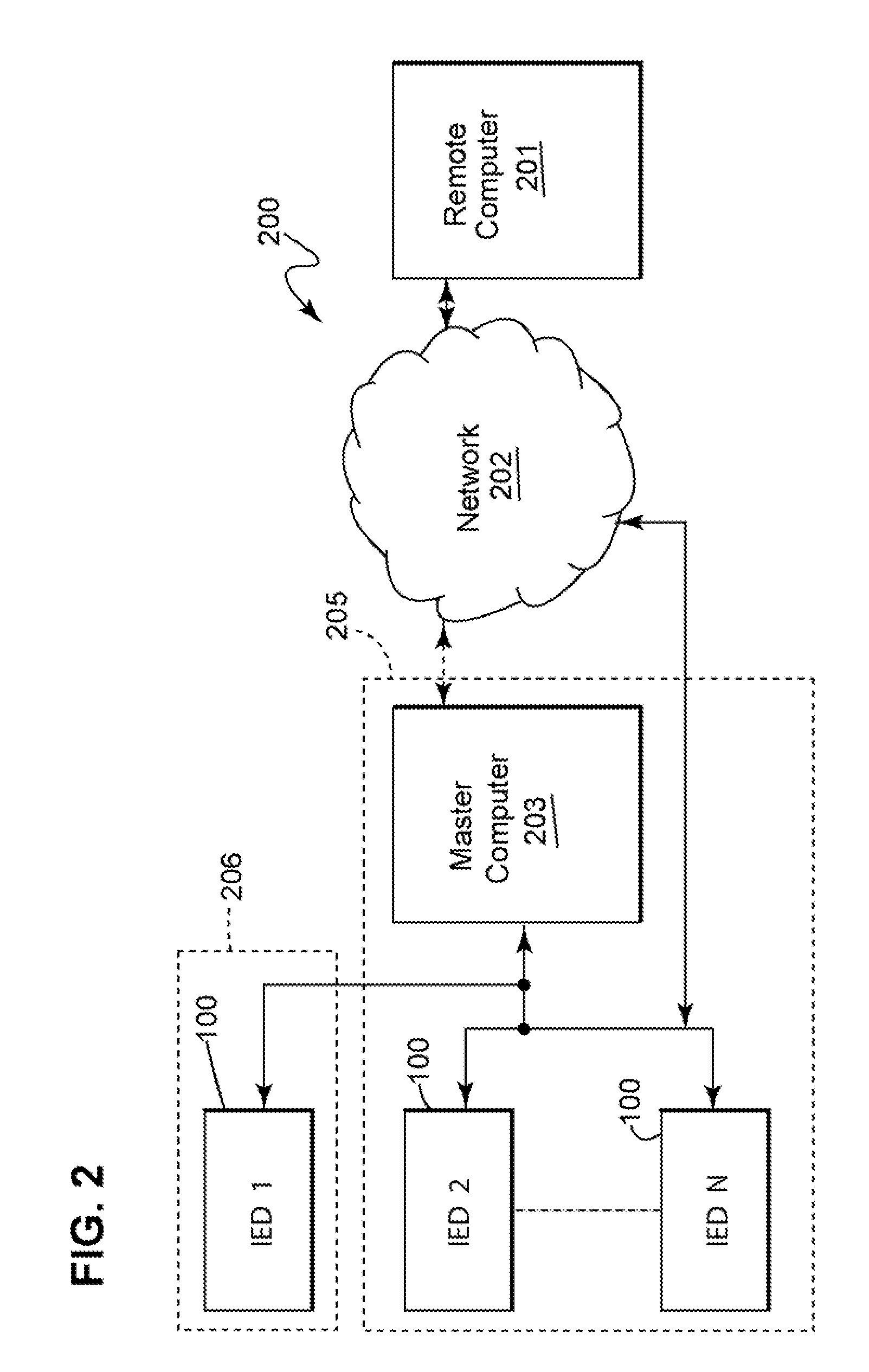
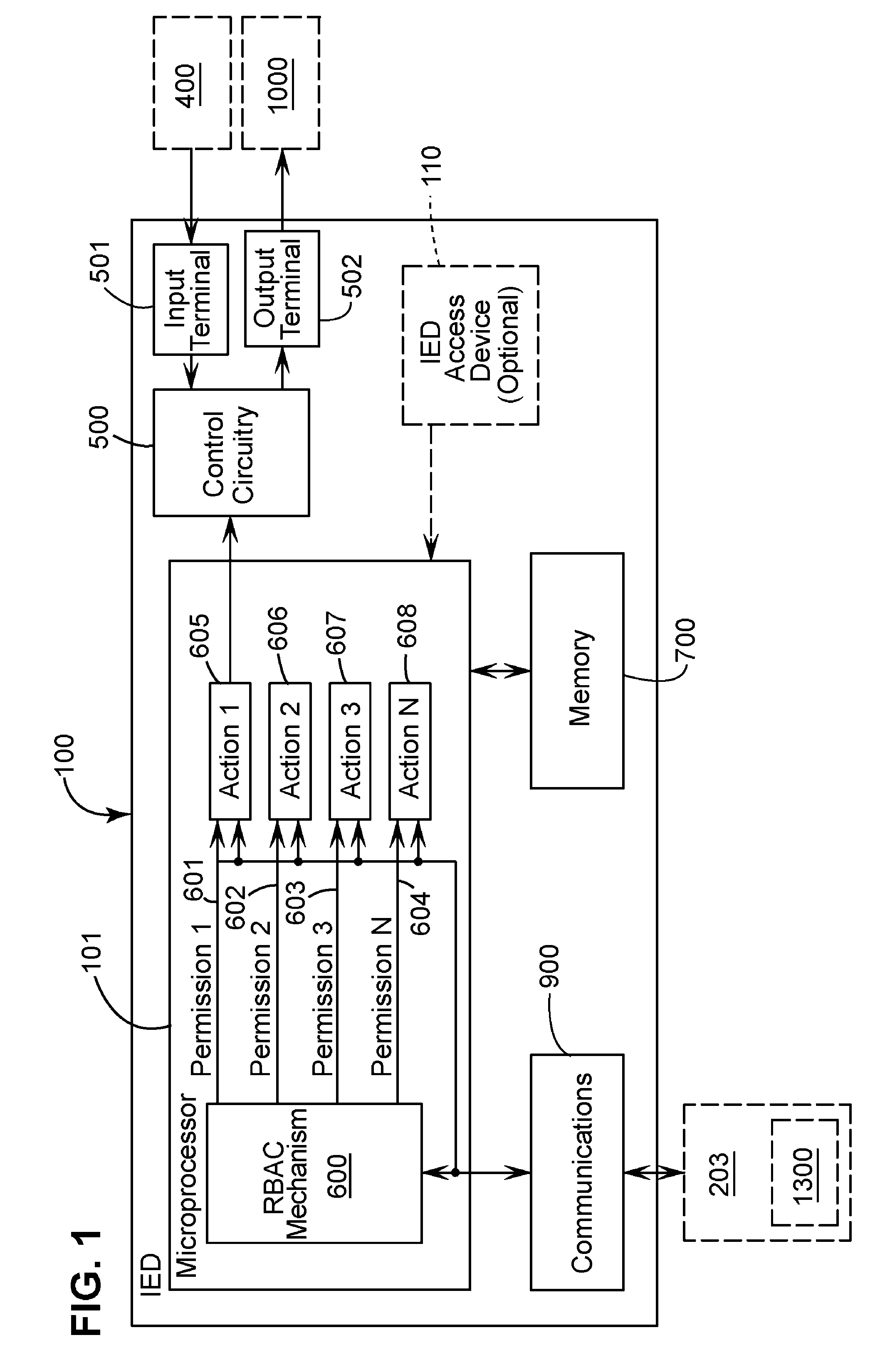
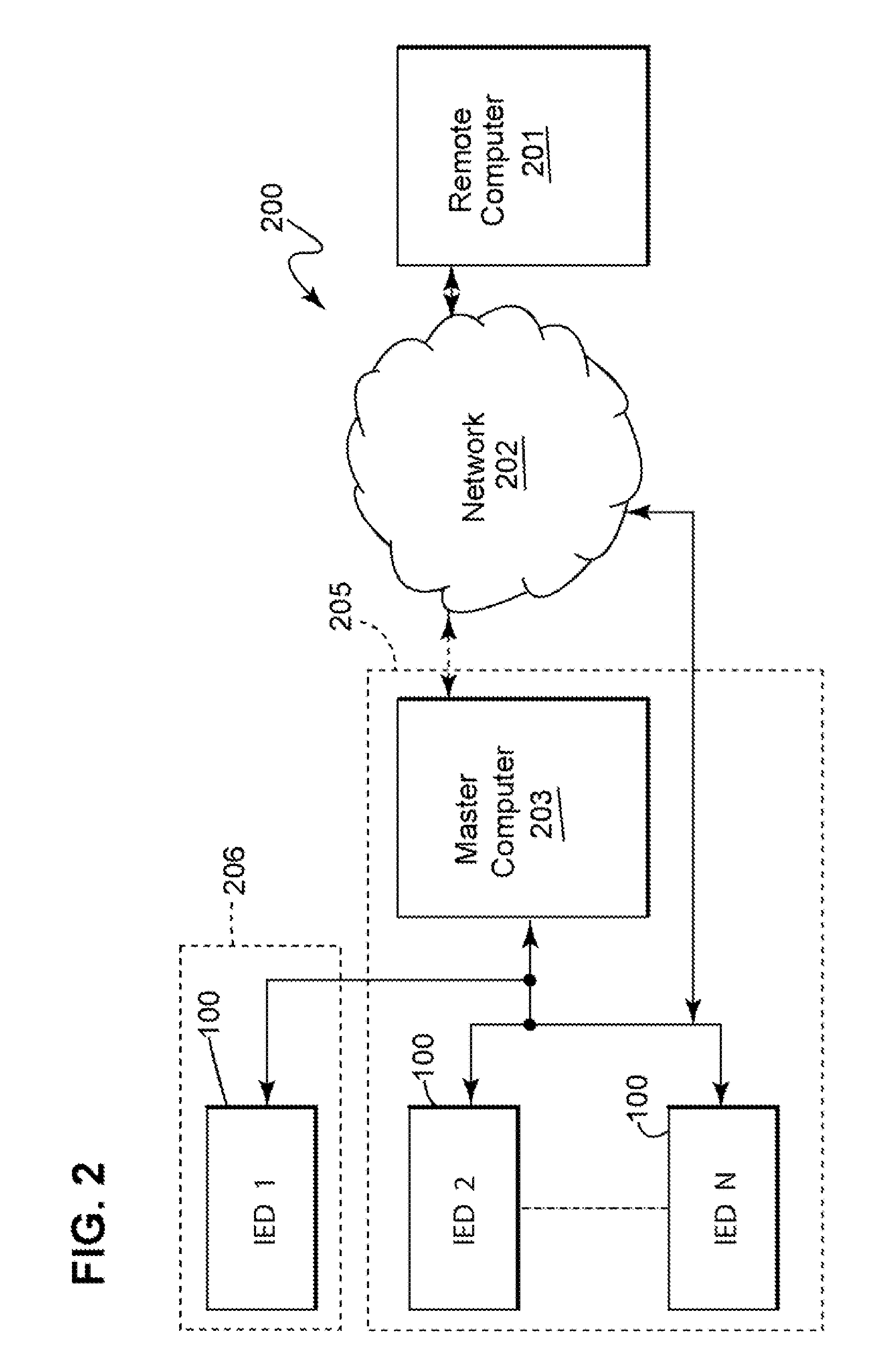
Apparatus, methods, and system for role-based access in an intelligent electronic device
ActiveUS20080162930A1Low costEasy to manageDigital data processing detailsUser identity/authority verificationProximatePassword
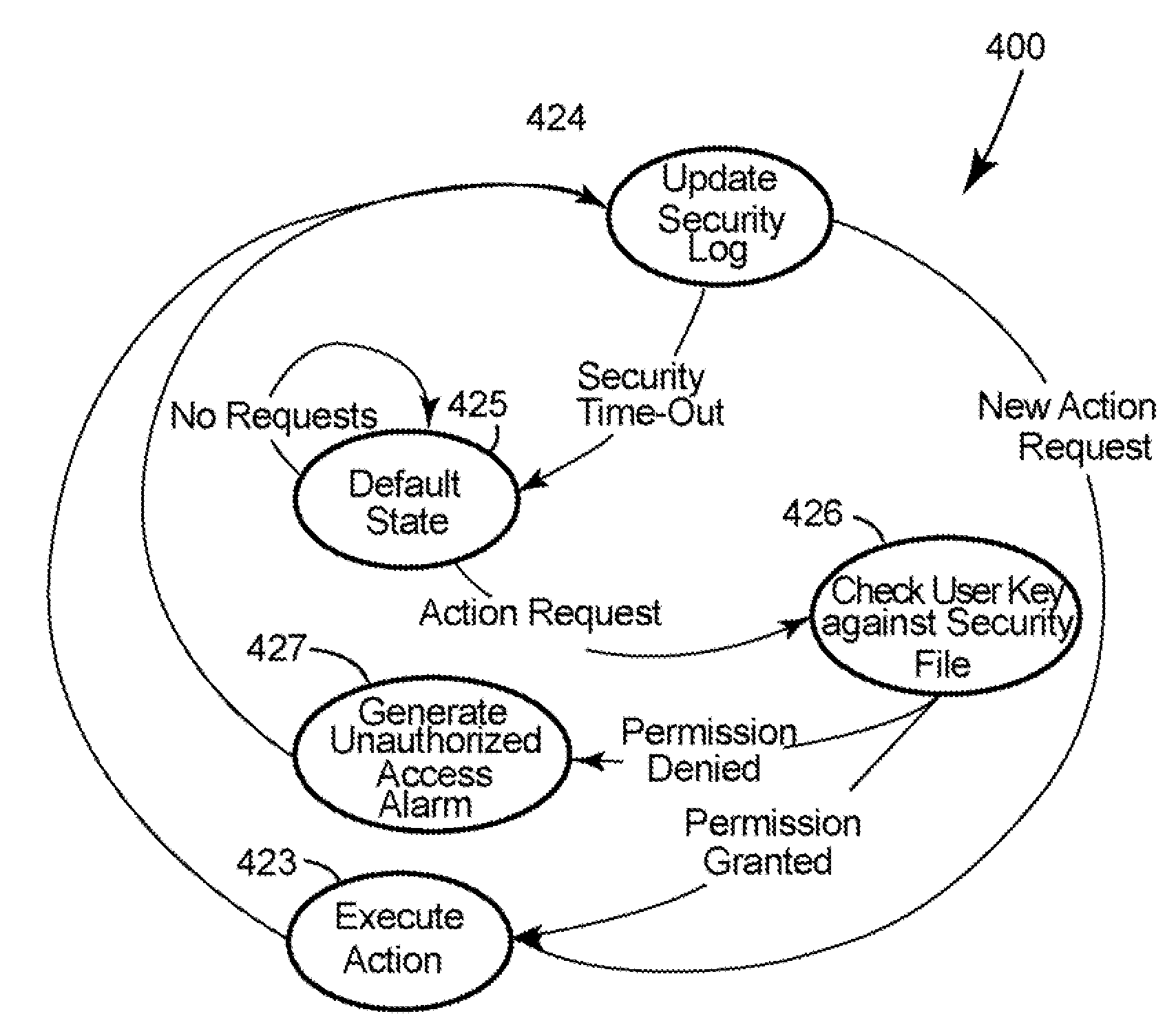
The present disclosure describes apparatus, methods, and system for secure access control of an intelligent electronic device (“IED”) by multiple personnel. Within the IED a set of basic permissions is defined. A software program allows a security administrator create specific roles from the basic permissions. The software program can then be used to assign to a user a specific role for one or more specific IEDs. This action creates a set of unique security keys for the user and a unique security file for each IED. When a user accesses an IED the system identifies the user from the security key and determines his / her permissions using the security file. The security key may take the form of a password inputted into the IED, an access device incorporated within the IED, and / or a remote access device positioned proximate the IED or removably positioned in the IED.
Owner:GENERAL ELECTRIC CO
Method and system for Synchronized Policy Control In A Web Services Environment
ActiveUS20080098453A1Digital data processing detailsUser identity/authority verificationVulnerability managementService-level agreement
Policy controls for Web service resource objects in a hierarchical resource space are loosely coupled so that policy changes are applied and enforced across the objects. This technique ensures that different policies are not applied unintentionally to the same resource (for example, one at the Web services entry level, and the other at the resource level). By synchronizing the object in the manner described, neither the entity that deploys the application nor the security administrator need to be aware of the differences between the various types of requests that occur within a Web services environment. In a representative embodiment, resource objects are linked within a hierarchical resource space to provide synchronized policy control, where the policy is an audit policy, a quality-of-service (QoS) policy, a service level agreement (SLA) policy, a governance policy, a compliance policy, a patch management / vulnerability management policy, a user management policy, or a rights management policy.
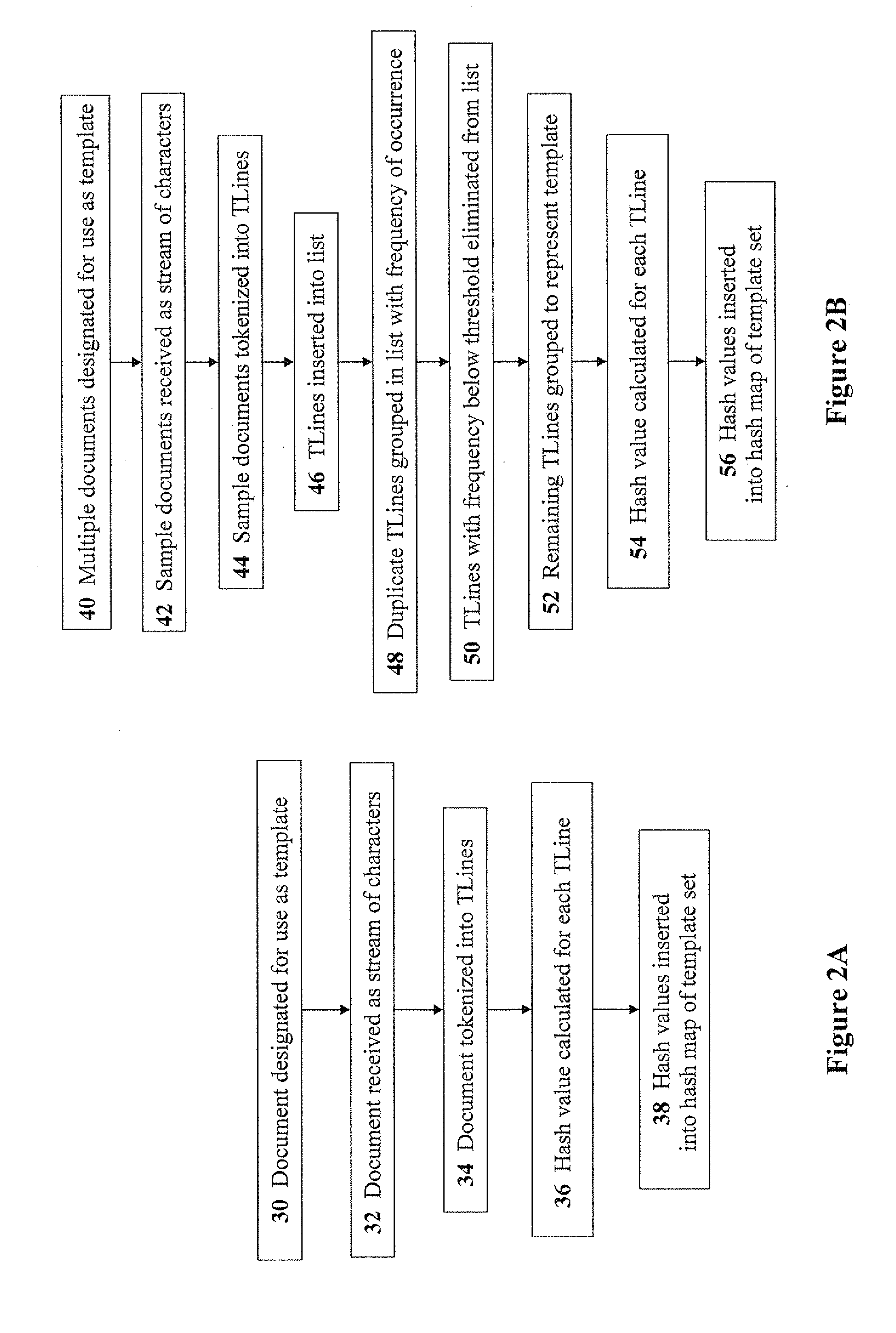
Owner:IBM CORP
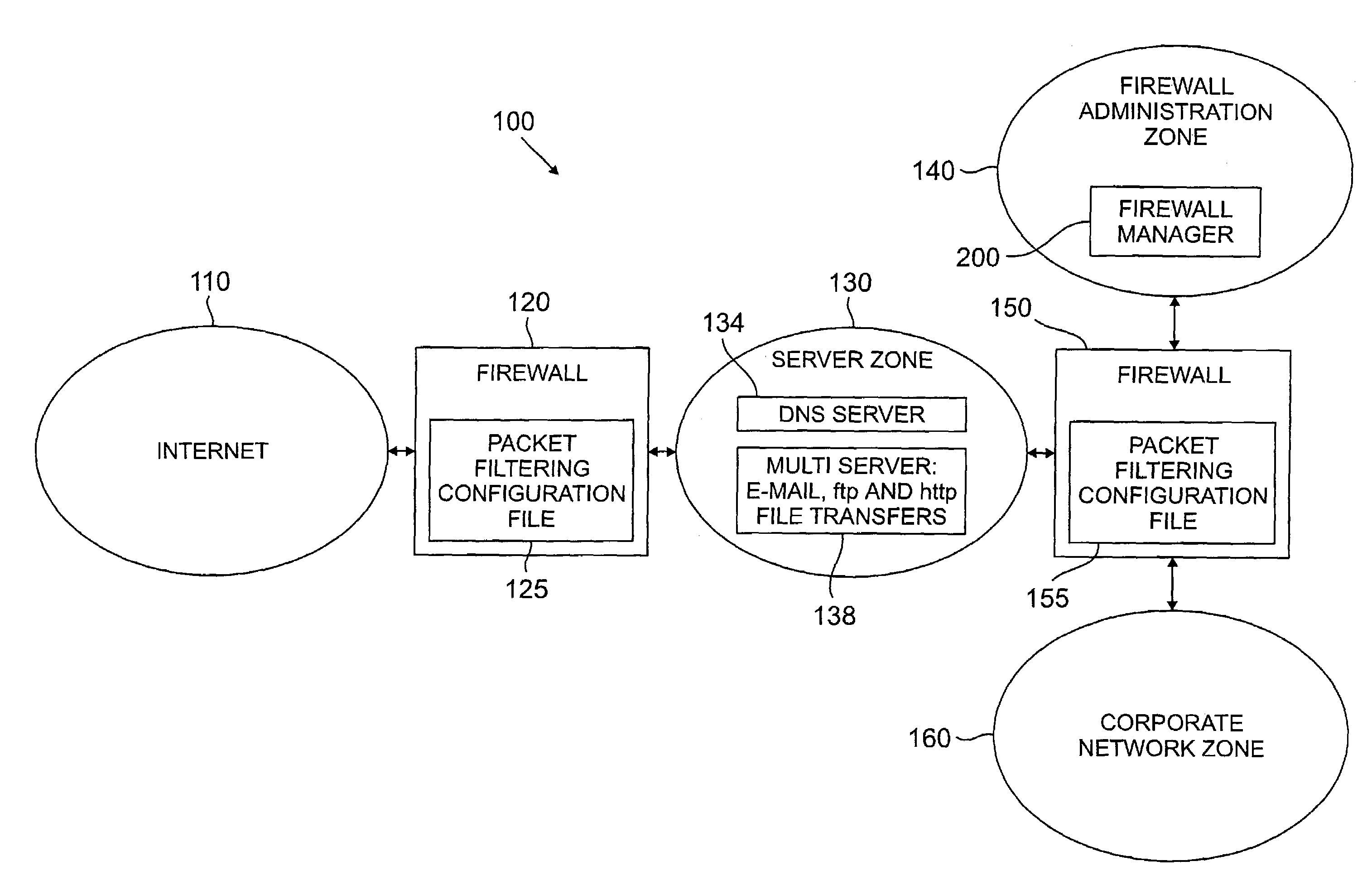
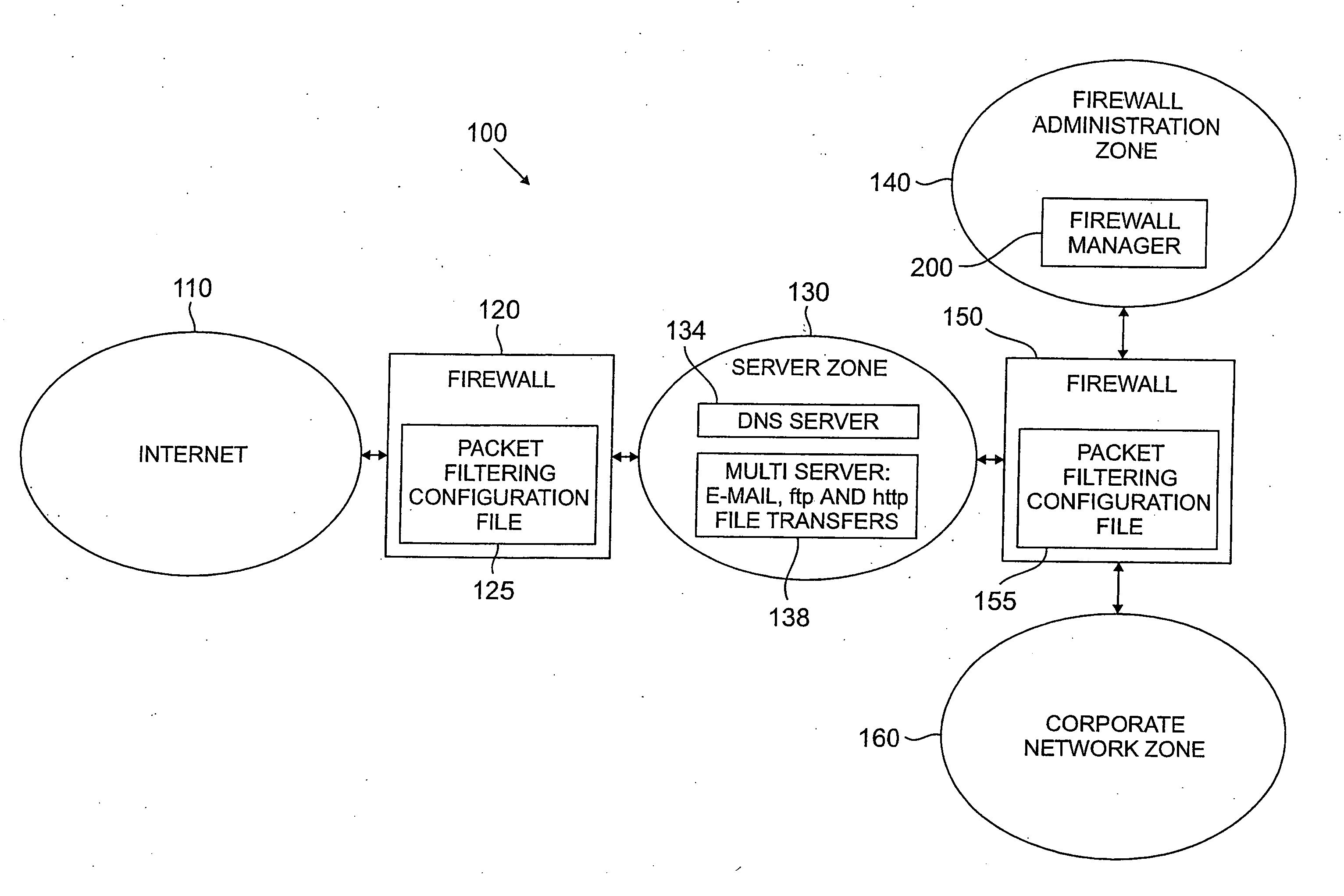
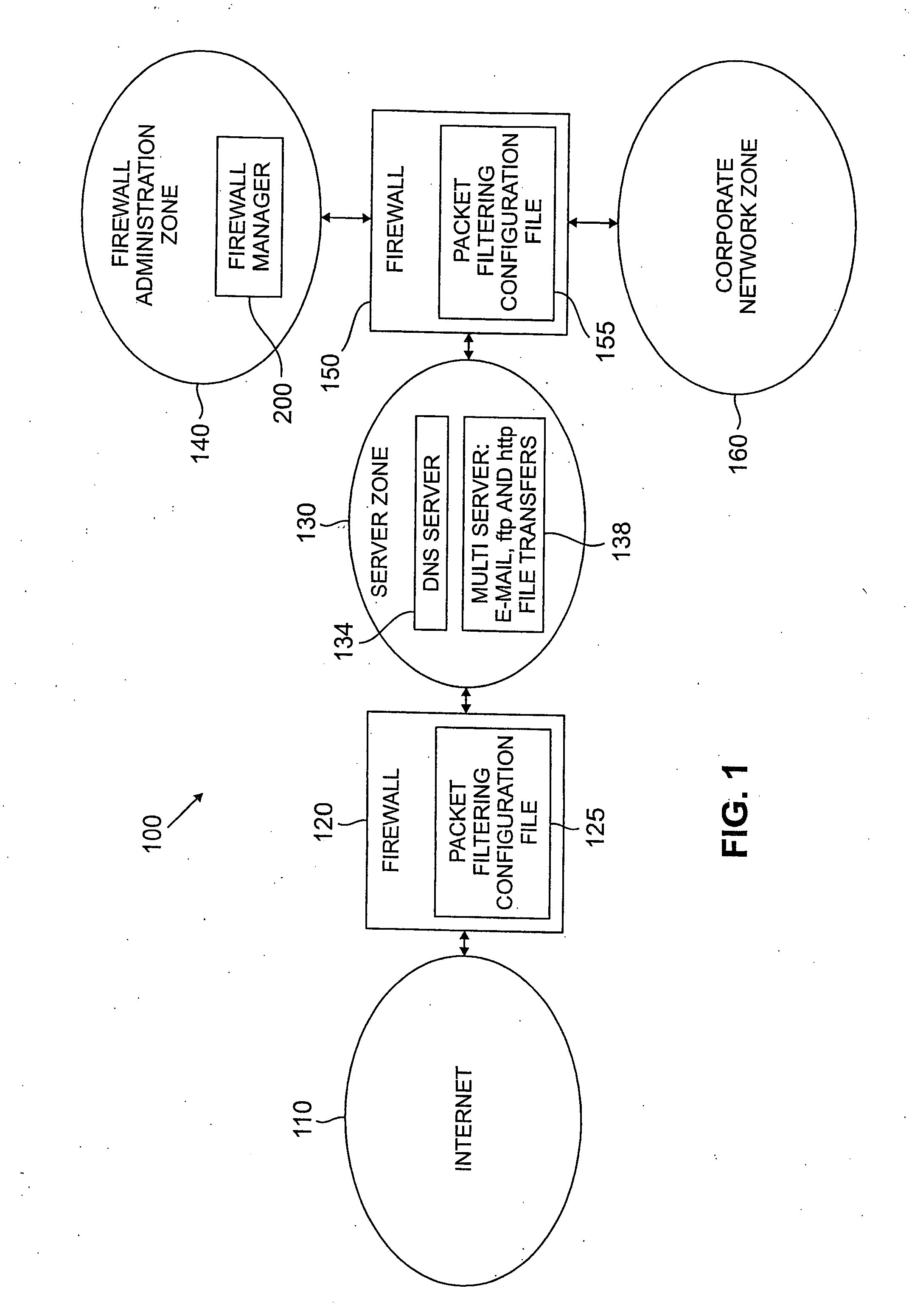
Method and apparatus for managing a firewall
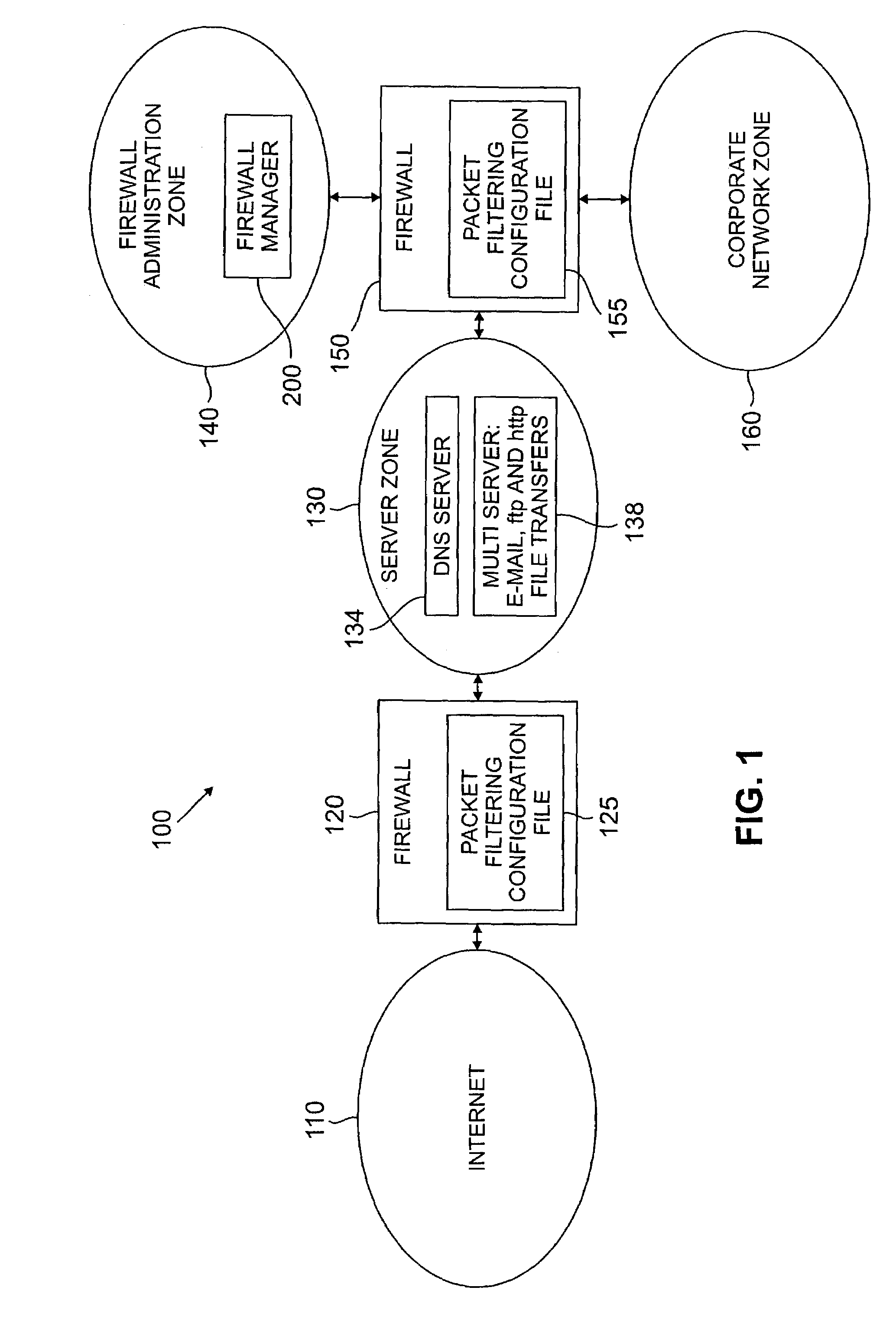
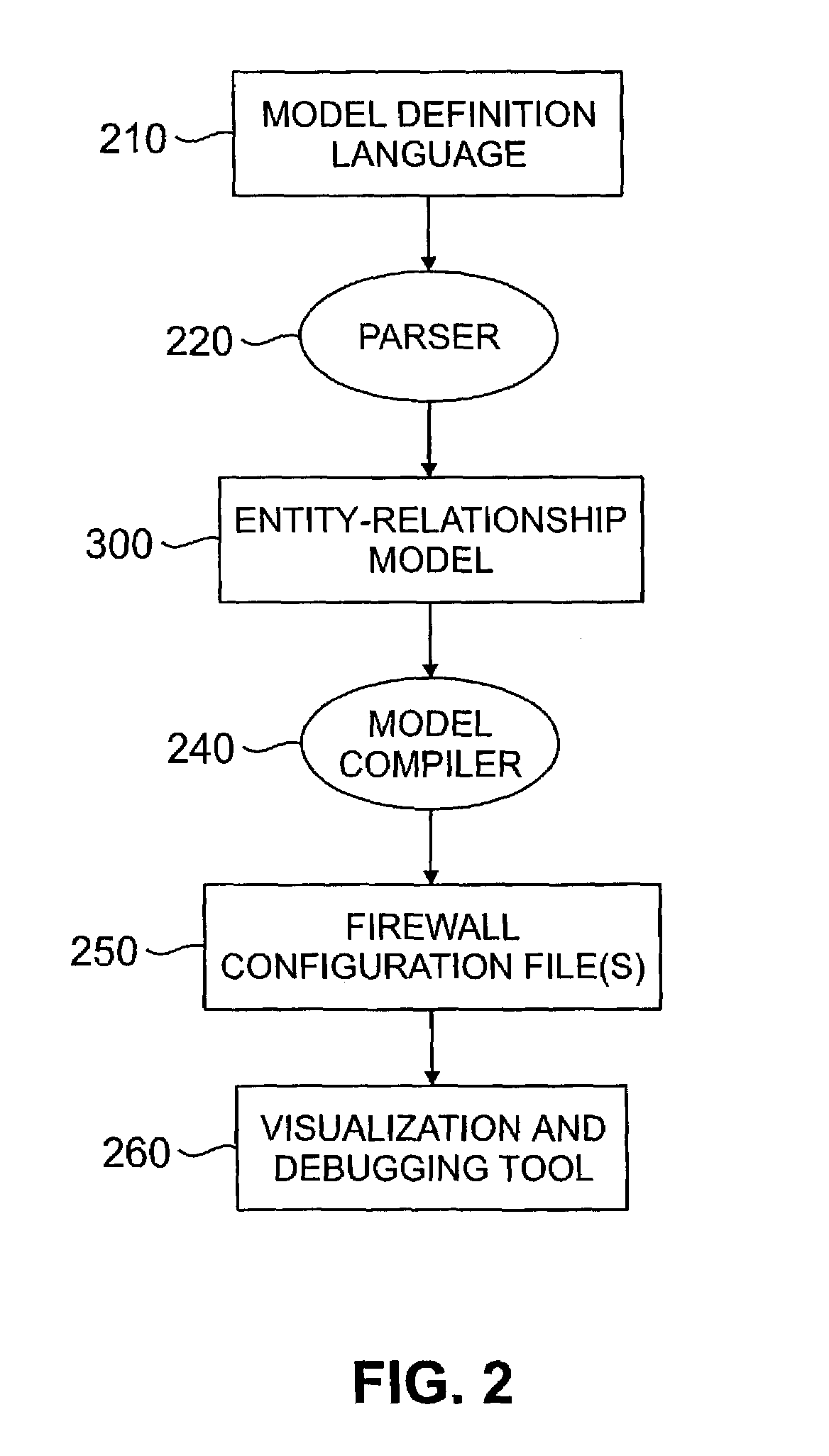
InactiveUS7146639B2Promote generationDigital data processing detailsMultiple digital computer combinationsNetwork topologyConfiguration Issue
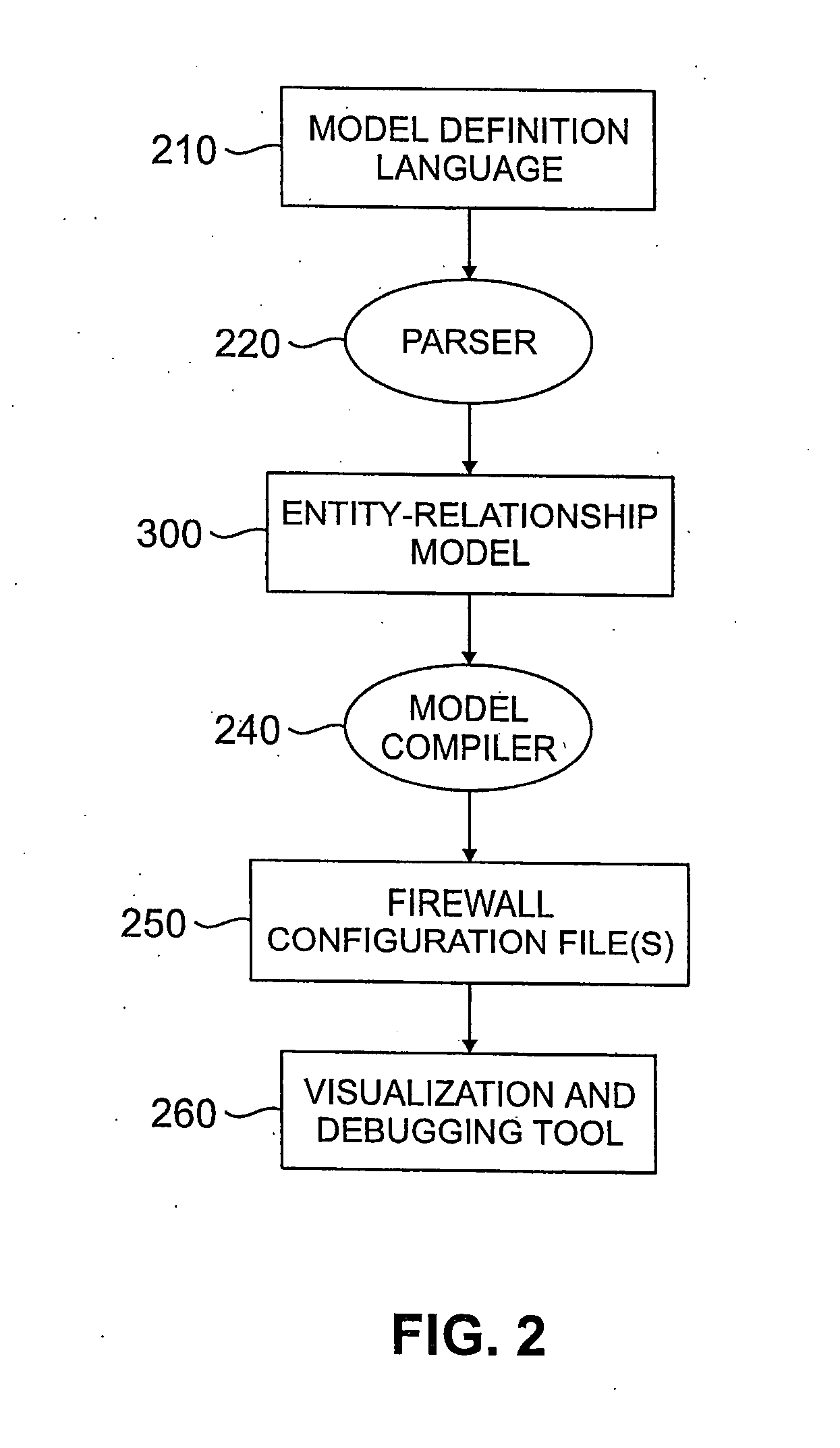
A method and apparatus are disclosed for managing a firewall. The disclosed firewall manager facilitates the generation of a security policy for a particular network environment, and automatically generates the firewall-specific configuration files from the security policy simultaneously for multiple gateways. The security policy is separated from the vendor-specific rule syntax and semantics and from the actual network topology. Thus, the security administrator can focus on designing an appropriate policy without worrying about firewall rule complexity, rule ordering, and other low-level configuration issues. In addition, the administrator can maintain a consistent policy in the presence of intranet topology changes. The disclosed firewall manager utilizes a model definition language (MDL) and an associated parser to produce an entity relationship model. A model compiler translates the entity-relationship model into the appropriate firewall configuration files. The entity-relationship model provides a framework for representing both the firewall-independent security policy, and the network topology. The security policy is expressed in terms of “roles,” which are used to define network capabilities of sending and receiving services. A role may be assumed by different hosts or host-groups in the network. A visualization and debugging tool is provided to transform the firewall-specific configuration files into a graphical representation of the current policy on the actual topology, allowing the viability of a chosen policy to be evaluated. A role-group may be closed to prevent the inheritance of roles.
Owner:LUCENT TECH INC
Electric power system interior APT attack detection and pre-warning system based on network architecture
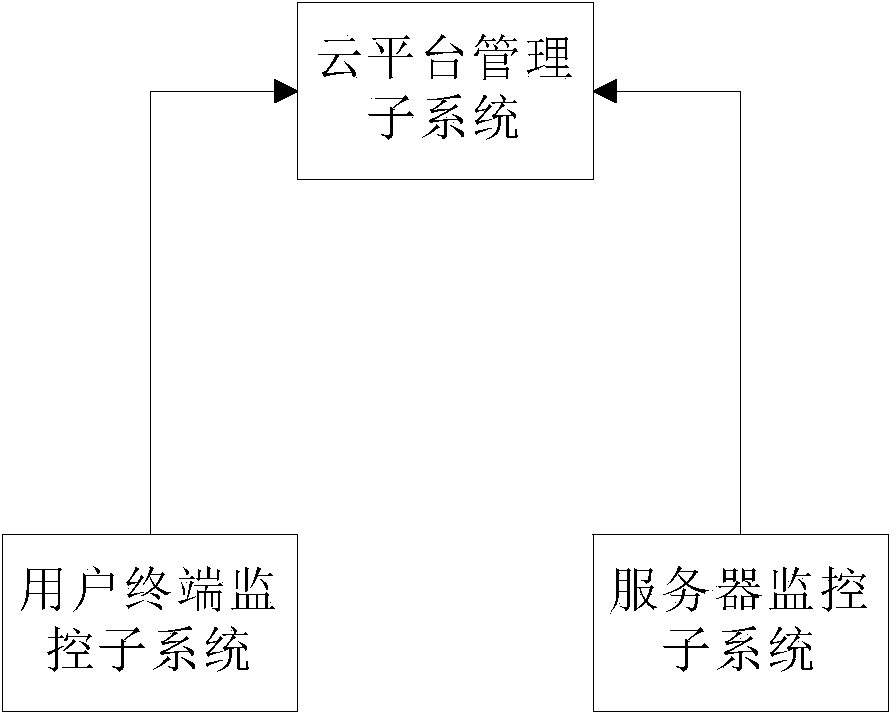
The invention provides an electric power system interior APT attack detection and pre-warning system based on network architecture. The system comprises a user terminal monitoring sub-system, a server monitoring sub-system and a cloud platform management sub-system. According to the characteristic that APT attacks are all pervasive, the APT attack detection and pre-warning system containing a user terminal and a system server is designed. The detection and pre-warning system has the common network security management function, meanwhile conducts analysis of exceptions on logs and events, and excavates and repairs loopholes of the system, after a network system is suffered from the APT attacks, data of attacked equipment can be quickly restored, and the system assists security managers in reversely tracking an attack source.
Owner:STATE GRID CHONGQING ELECTRIC POWER CO ELECTRIC POWER RES INST +1
Apparatus and method for secure object access
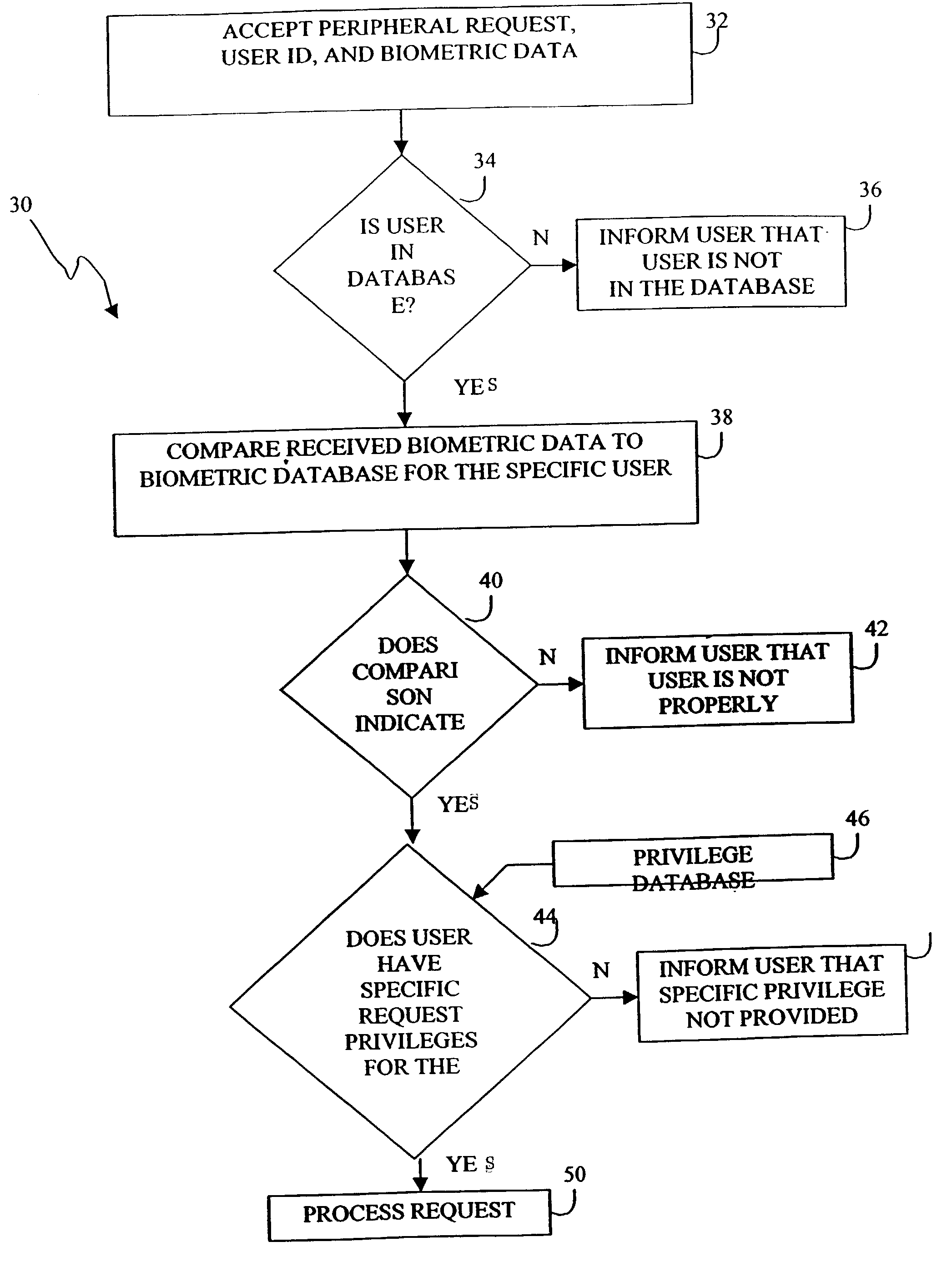
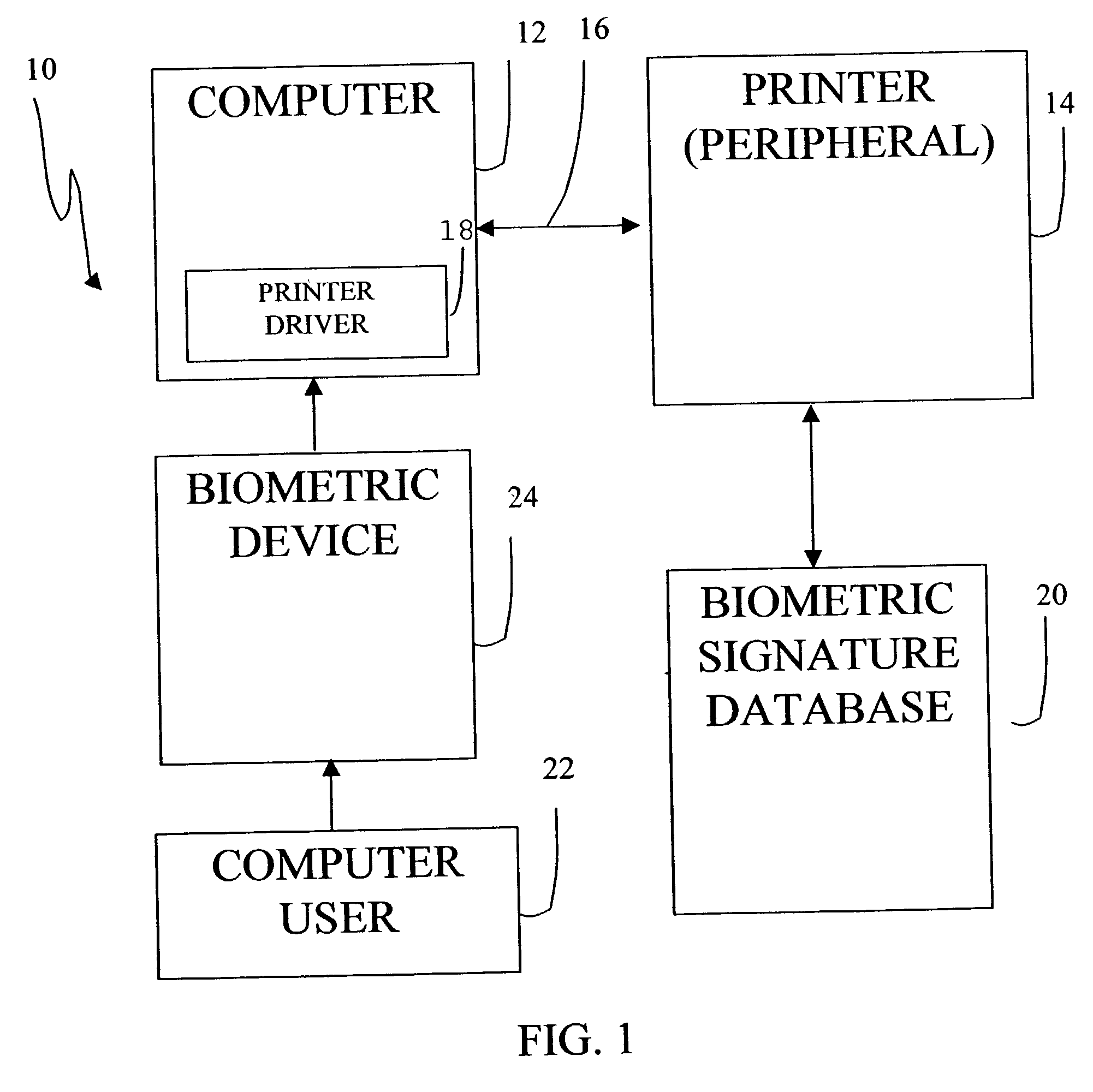
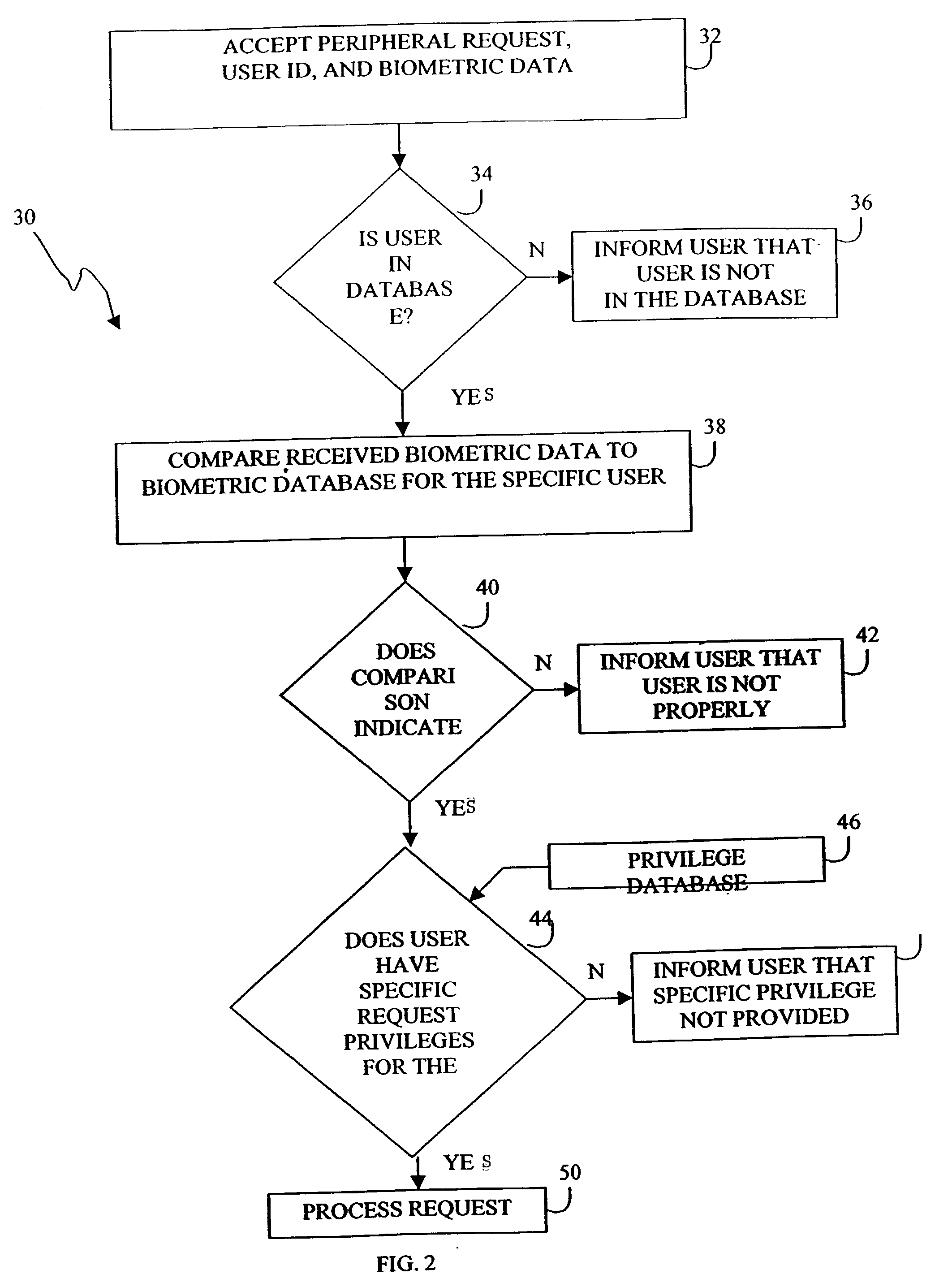
InactiveUS20030212709A1Digital data processing detailsInternal/peripheral component protectionBiometric dataComputer users
A method and apparatus to use biometric data to secure an object connected to a computer. The object maintains connections to one or more computers, and similarly to a biometric database that includes biometric data for computer users. Object requests from computers can be coupled with biometric data from a plurality of computer users. The biometric data can be entered on a periodic basis as scheduled by a security manager. Peripheral requests including biometric data can be subjected to a two-step analysis. First, the biometric data can be matched against the biometric database to ensure a match. If a match is not found, the request can be denied. If a match is found, the second analysis step includes determining whether the verified user has privilege for the requested object access. Multiple objects connected to multiple computers is anticipated, and the two-step analysis can be combined into a single step by providing a biometric database that includes only authorized user information. A single biometric database can be used for all peripherals, or multiple biometric databases can exist for multiple peripherals. The objects can be peripheral devices of any kind, they also can be smartcards, tokens or electronic cartridges. The peripheral devices can be inserted or removed from computer networks, computers, workstations, PDA's, other peripheral devices such as printers or storage drives, handheld devices or other computerized instruments.
Owner:DE SCHRIJVER STEFAAN
Automated configuration of network devices administered by policy enforcement
ActiveUS8458301B1Guarantee support safetyDigital computer detailsTransmissionAuto-configurationComputer science
A system and method for dynamic device configuration enabling network and security administrators to define policies that indicate event and alert conditions within their networks. The policies incorporate information about network devices, endpoints connected to those devices, input from external security systems, local endpoint policy compliance, and date / time-of-day to determine whether to generate an event or alert. Events and alerts can be associated with actions that effect changes to network device configurations in order to maintain a desired operational state of the network.
Owner:FORTINET
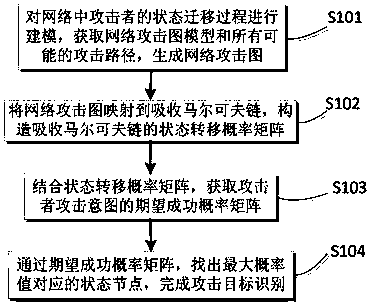
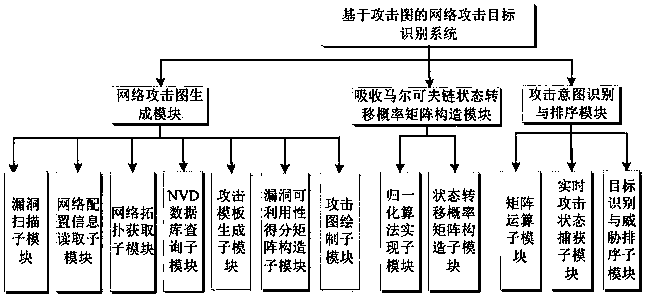
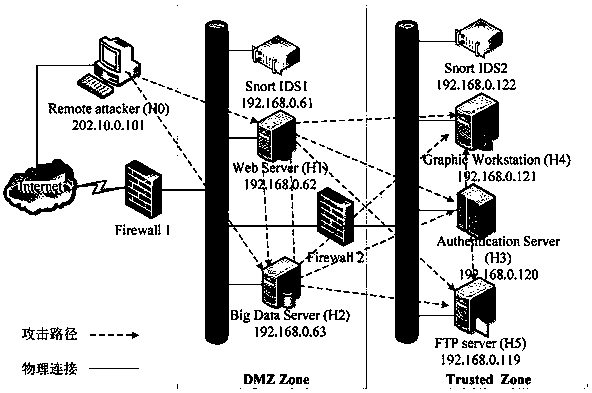
Network attack target identification method and network attack target identification system based on attack graph
ActiveCN108418843AObjective assessmentAccurate assessmentData switching networksNODALComputation complexity
The invention belongs to the technical field of network security, and particularly relates to a network attack target identification method and a network attack target identification system based on an attack graph, wherein the method comprises the following steps: modeling for a state migration process of an attacker in a network, acquiring a network attack graph model and all possible attack paths, and generating a network attack graph; mapping the network attack graph to a Markov chain, and constructing a state transition probability matrix which absorbs the Markov chain; and in combinationwith the state transition probability matrix, acquiring an expectancy for success probability matrix of attack intention of the attacker; through the expectancy for success probability matrix, finding out a state node corresponding to the maximum probability value, and completing attack target identification. With the method and the system provided by the invention, an average probability value of realizing different intentions of the attacker can be evaluated more objectively and accurately, a problem that the conventional method is limited by ideal cumulative probability when evaluating probability of occurrence of attacks is solved, computation complexity is low, operations are simple and convention to execute, and more reliable guidance is provided for assisting a security administrator to make a decision and improving network security performance.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
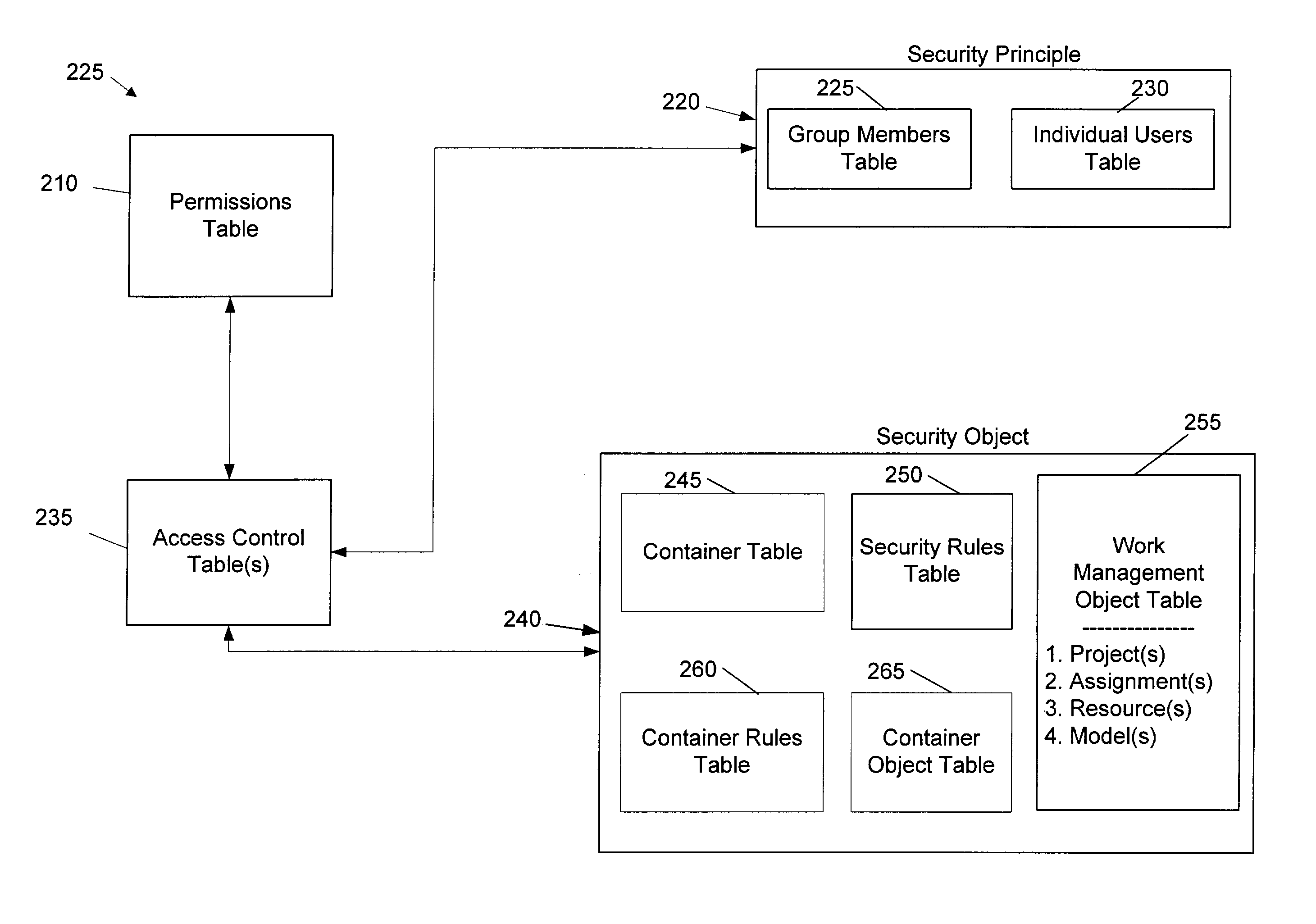
Controlling access to objects with rules for a work management environment
InactiveUS7127461B1Limited accessData processing applicationsDigital data processing detailsBiological activationSecurity rule
A security system uses rules to restrict access to objects of a database. These security rules are dynamic because they can adjust when the number of objects in the database is changing. In other words, the security rules can permit access to new objects when new objects are added to, modified, or deleted from the database. With this system, objects can be added to a container by a security administrator or they can be added based upon the triggering or activation of one or more rules. With this system, access to objects in a database is usually determined after each request for access instead of relying on a static permanent list.
Owner:MICROSOFT TECH LICENSING LLC
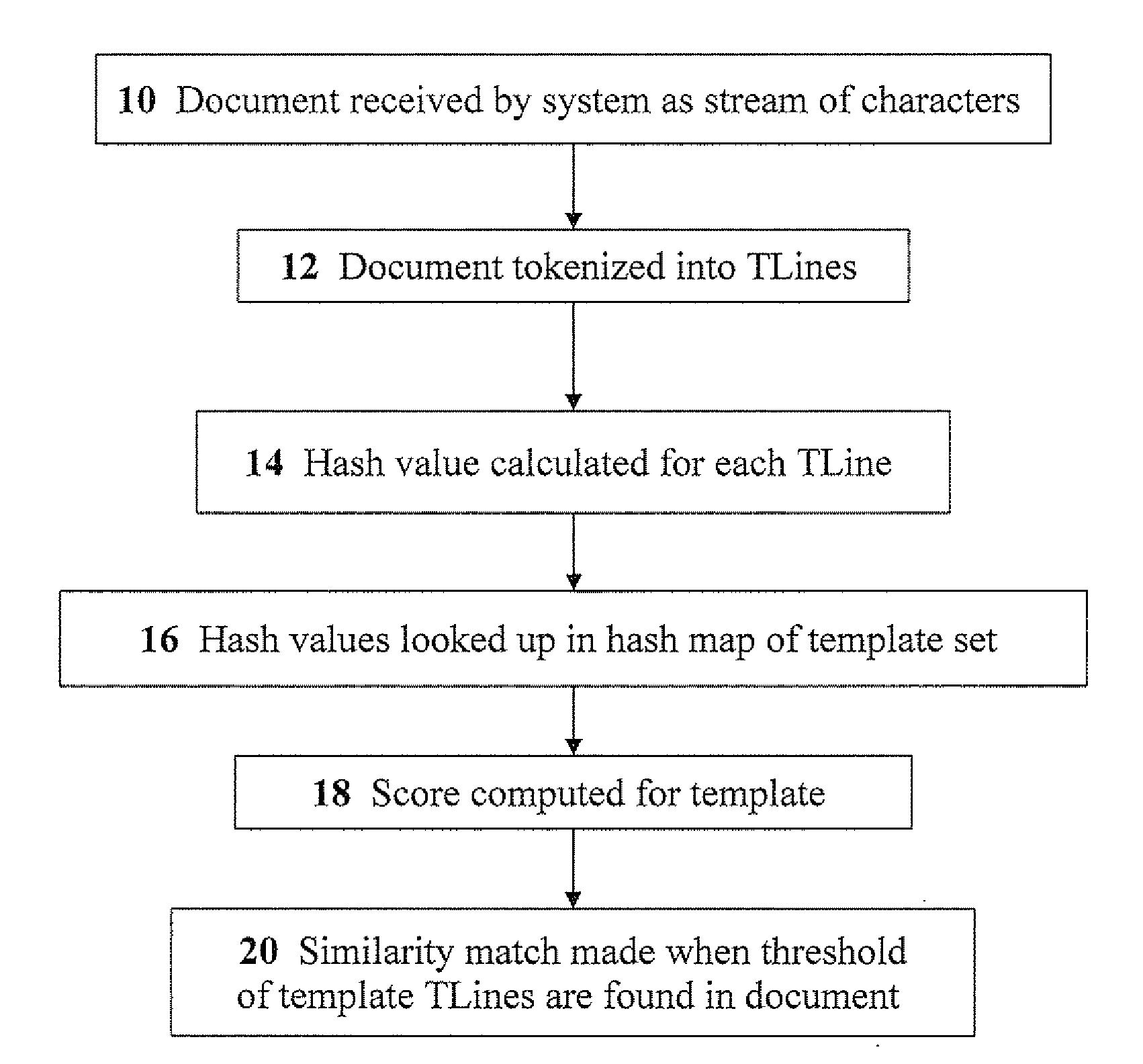
Methods for document-to-template matching for data-leak prevention
ActiveUS20100254615A1Memory loss protectionDigital data processing detailsTemplate matchingTemplate based
Owner:CHECK POINT SOFTWARE TECH LTD
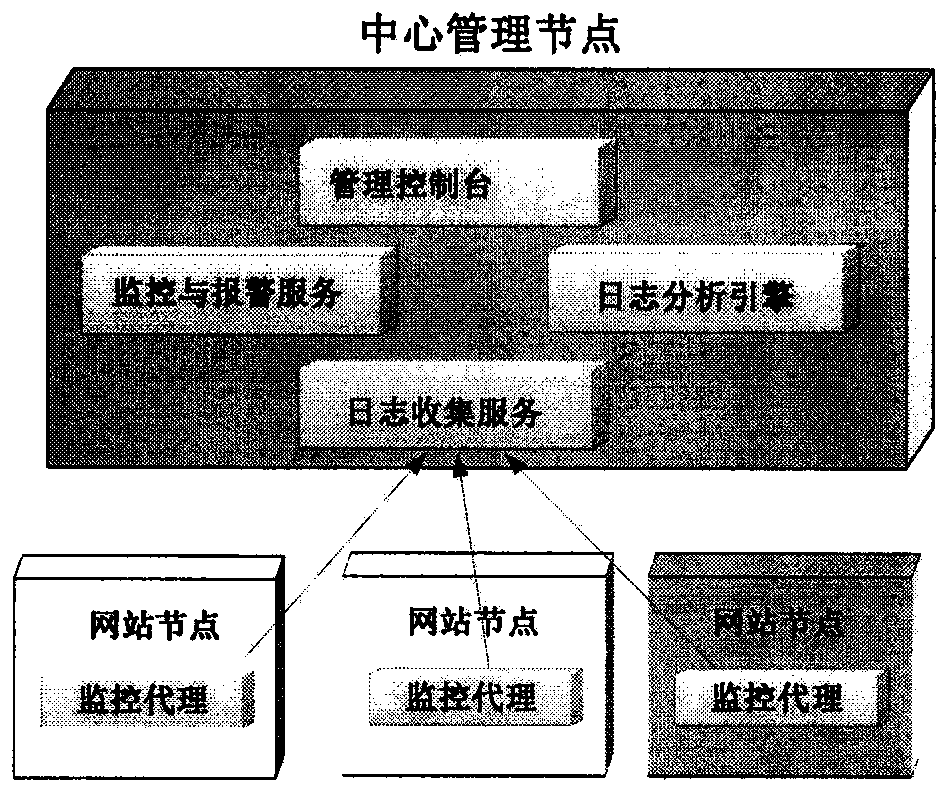
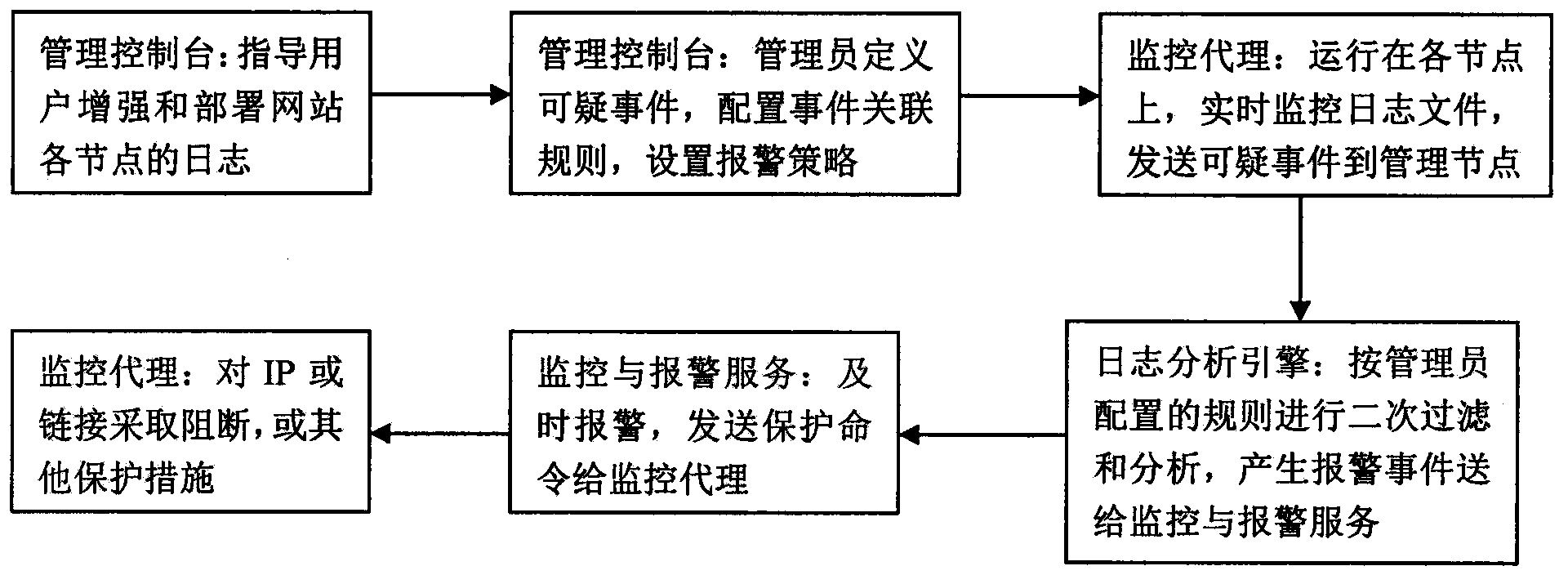
Website security monitoring and alarming system based on log analysis and firewall security matrixes
ActiveCN104144063ANo illegal accessEfficient discoveryData switching networksTreatment errorSecurity monitoring
The invention relates to a website security monitoring and alarming system based on log analysis and firewall security matrixes. The website security monitoring and alarming system aims at finding and stopping various security attacks on the website in time and is based on two work items which a website security administrator mostly depends on during actual security operation and maintenance. Log monitoring is characterized in that the known and unknown attacks are automatically found by conducting keyword / regular expression filtering on access of Apache / Tomcat / IIS or error logs or other environment logs, and meanwhile service processing errors caused by the hacker attacks in the early period are found in time through log customization in website service codes. The website security monitoring and alarming system is characterized in that the firewall security matrixes are defined, then the effectiveness of the firewall security matrixes is verified with the direct or indirect network connectivity detecting technology, and alarming is triggered once the firewall security matrixes are damaged. The website security monitoring and alarming system provides a simple and effective customization mode for the administrator, and sensing capacity for any attack or any suspicious action can be continuously improved.
Owner:朱烨 +1
Security information for updating an authorization database in managed networks
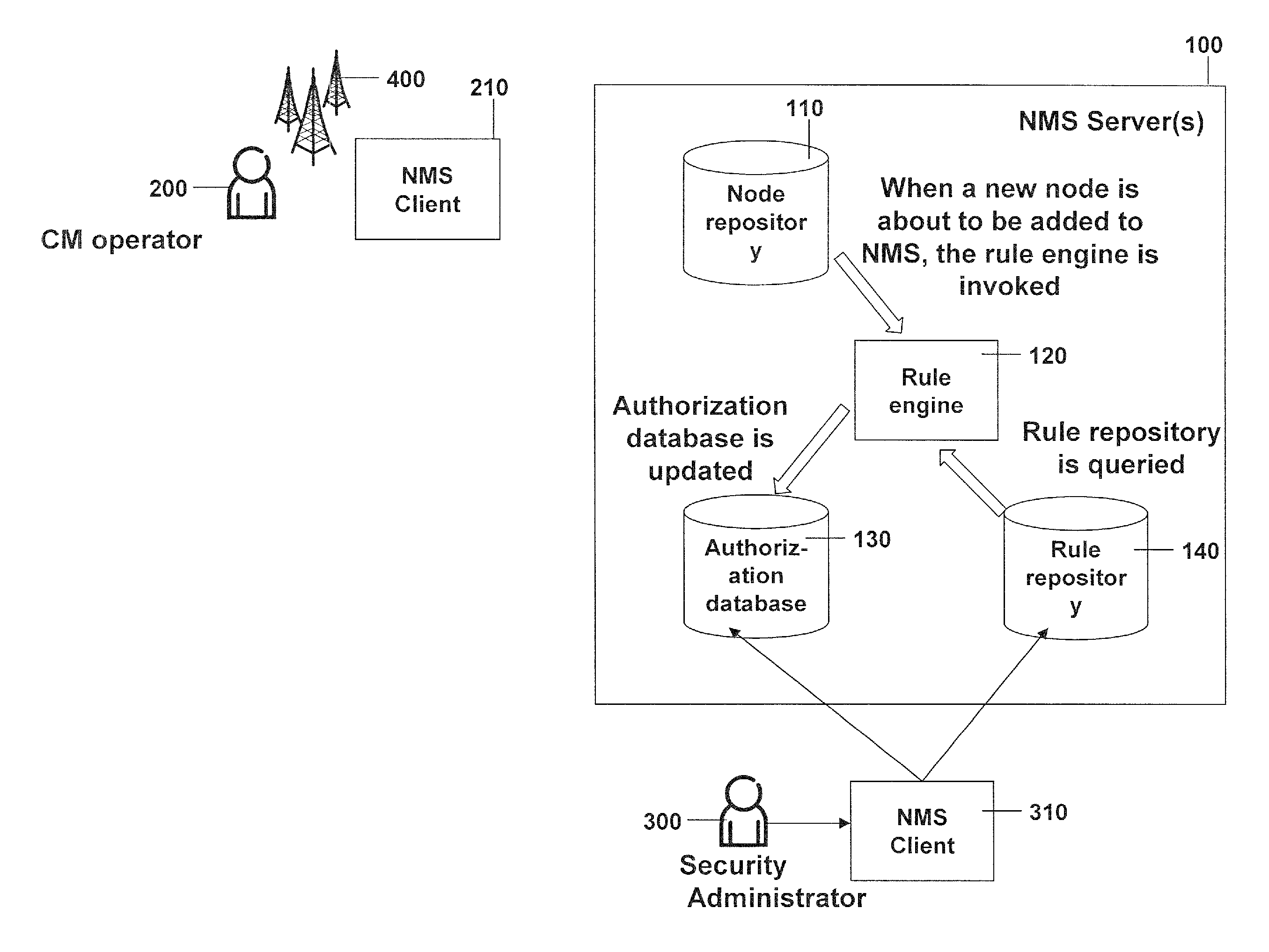
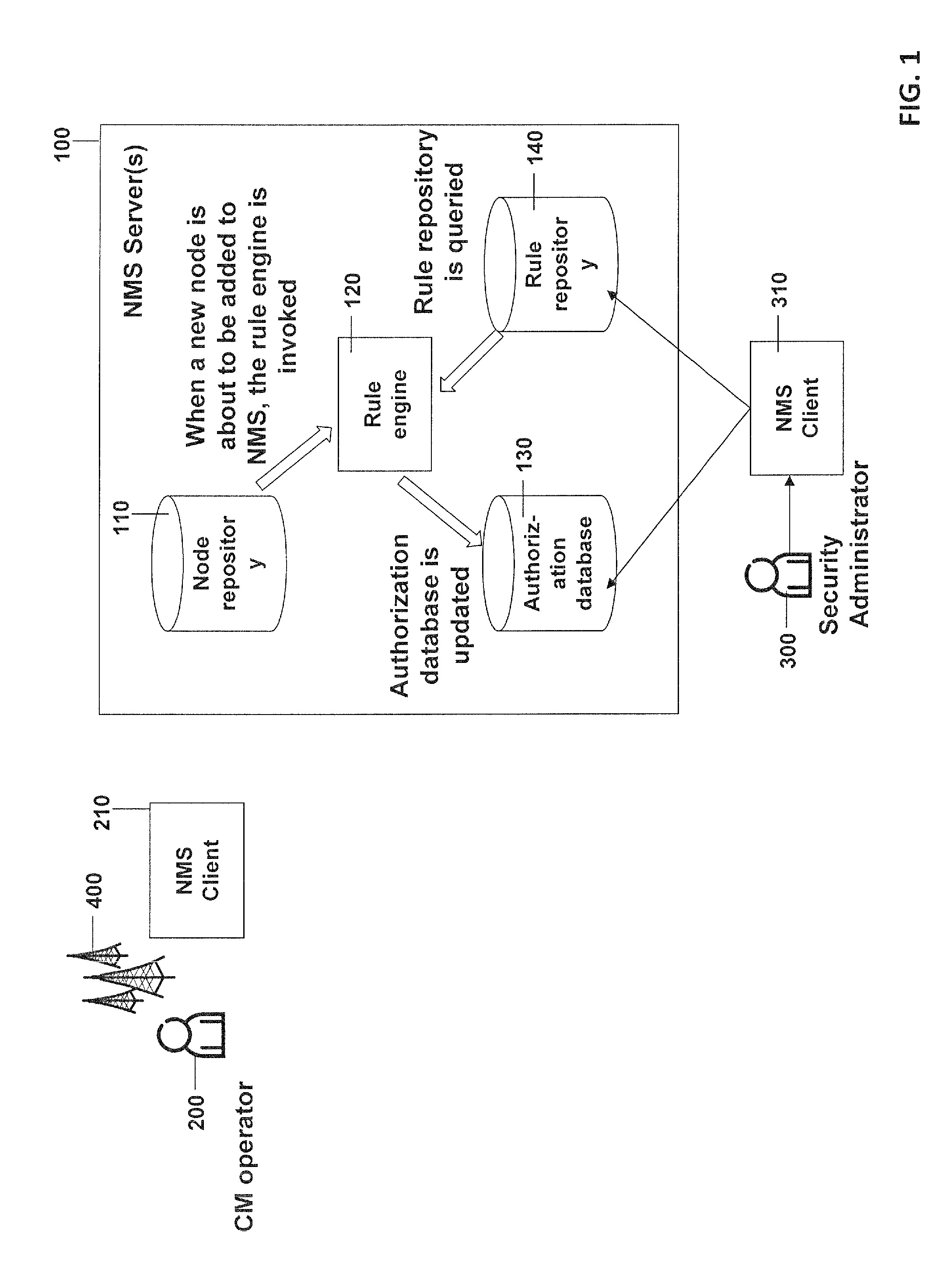
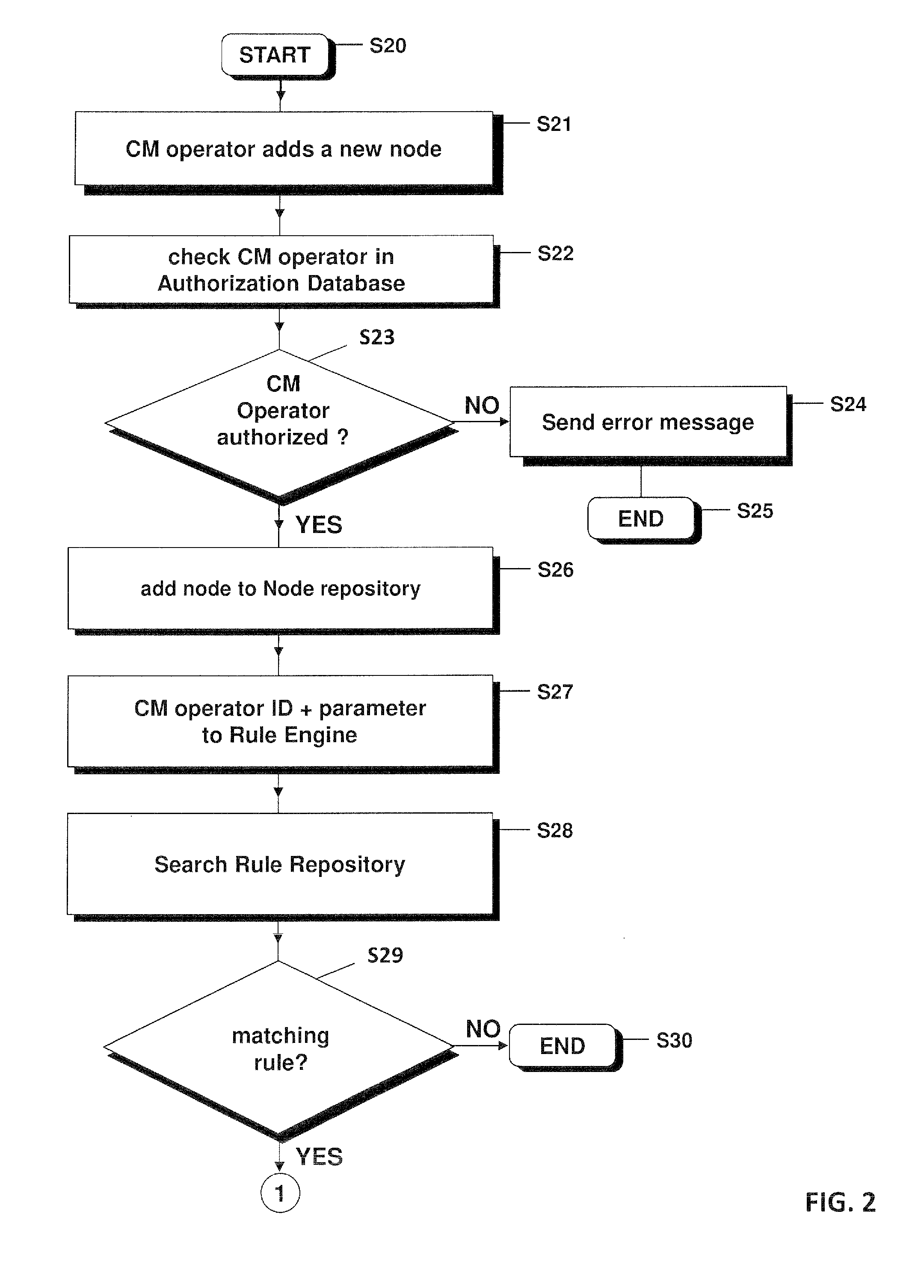
A method for amending, by a rule engine, a network element in a telecommunications network containing network elements each described by at least one parameter. An authorization database contains information for who and what extent configuring operators have access to the network elements, and a rule repository containing parameter dependent rules describing which activity is carried out for the network elements, and parameter dependent security information describing whether and how configuring operators are supervised by a security administrator when amending and how the authorization database is amended for a network element. A request for amending the network element in the network is identified and its parameter is determined. A rule is determined in the rule repository for which the parameter corresponds to the parameter of the amended network element and the security information for the determined rule is determined. The authorization database is updated using the security information.
Owner:TELEFON AB LM ERICSSON (PUBL)
Campus security system and method based on intelligent videos
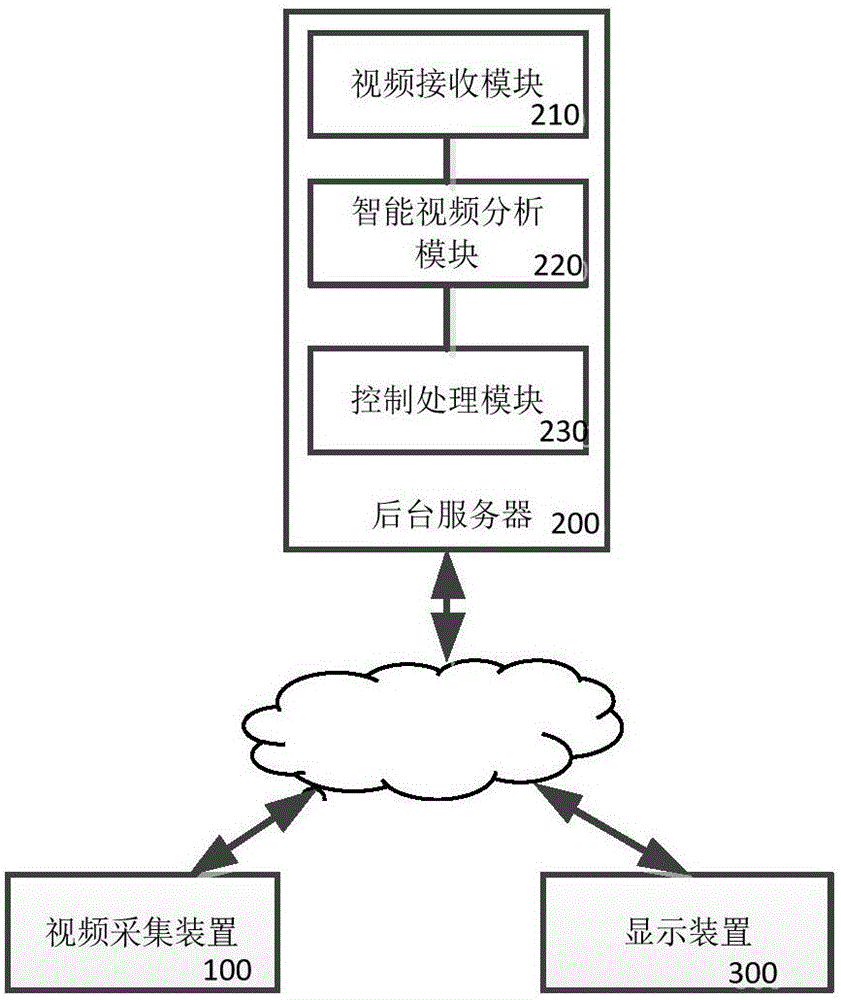
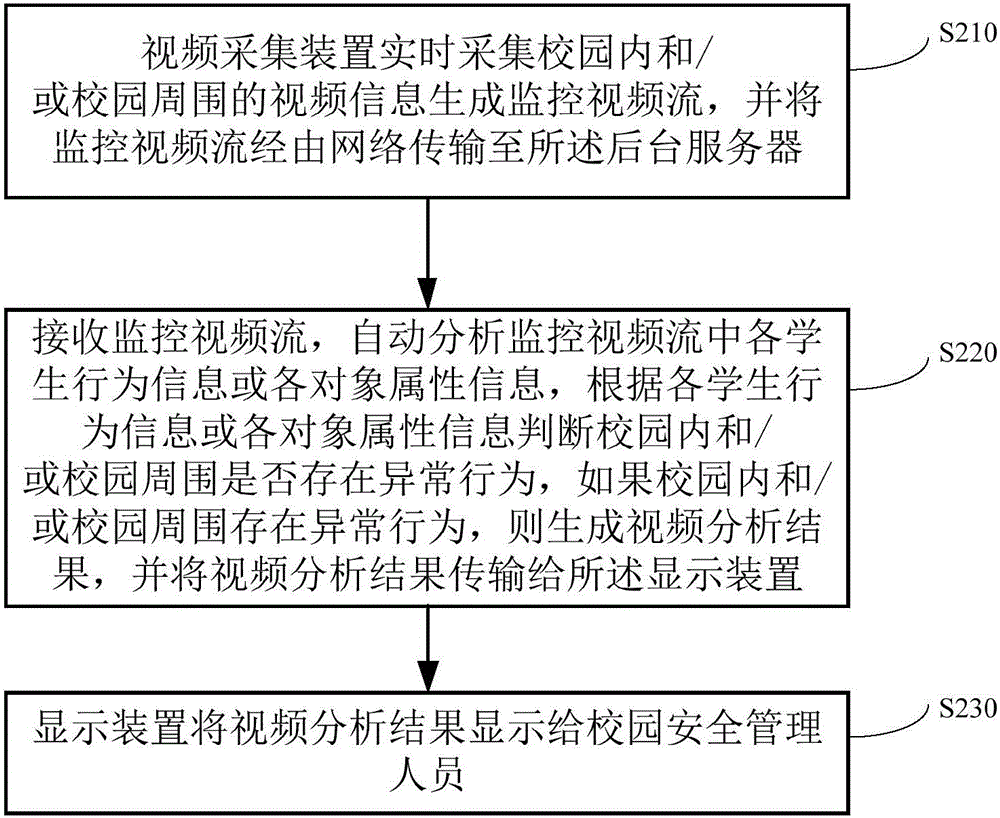
The invention provides a campus security system and method based on intelligent videos. The system comprises a video collection device used for collecting video information in a campus and / or in the vicinity of the campus to generate a monitoring video stream, a background server comprises: a video receiving module used for obtaining the monitoring video stream; an intelligent video analysis module used for automatically analyzing student behavior information or object attribute information in the monitoring video stream; a control processing module used for judging whether there is anomaly in the campus and / or in the vicinity of the campus according to the student behavior information or the object attribute information, generating a video analysis result if there is anomaly in the campus and / or in the vicinity of the campus, and transmitting the video analysis result to a display device; and the display device used for displaying the video analysis result to campus security administrators. The invention further provides a corresponding campus security method based on the intelligent videos.
Owner:CHONGQING KAIZE TECH
Common network management safety control system and method thereof
InactiveCN1889452ARealize centralized security managementImplement download cachingData switching networksCommunications systemSafety management systems
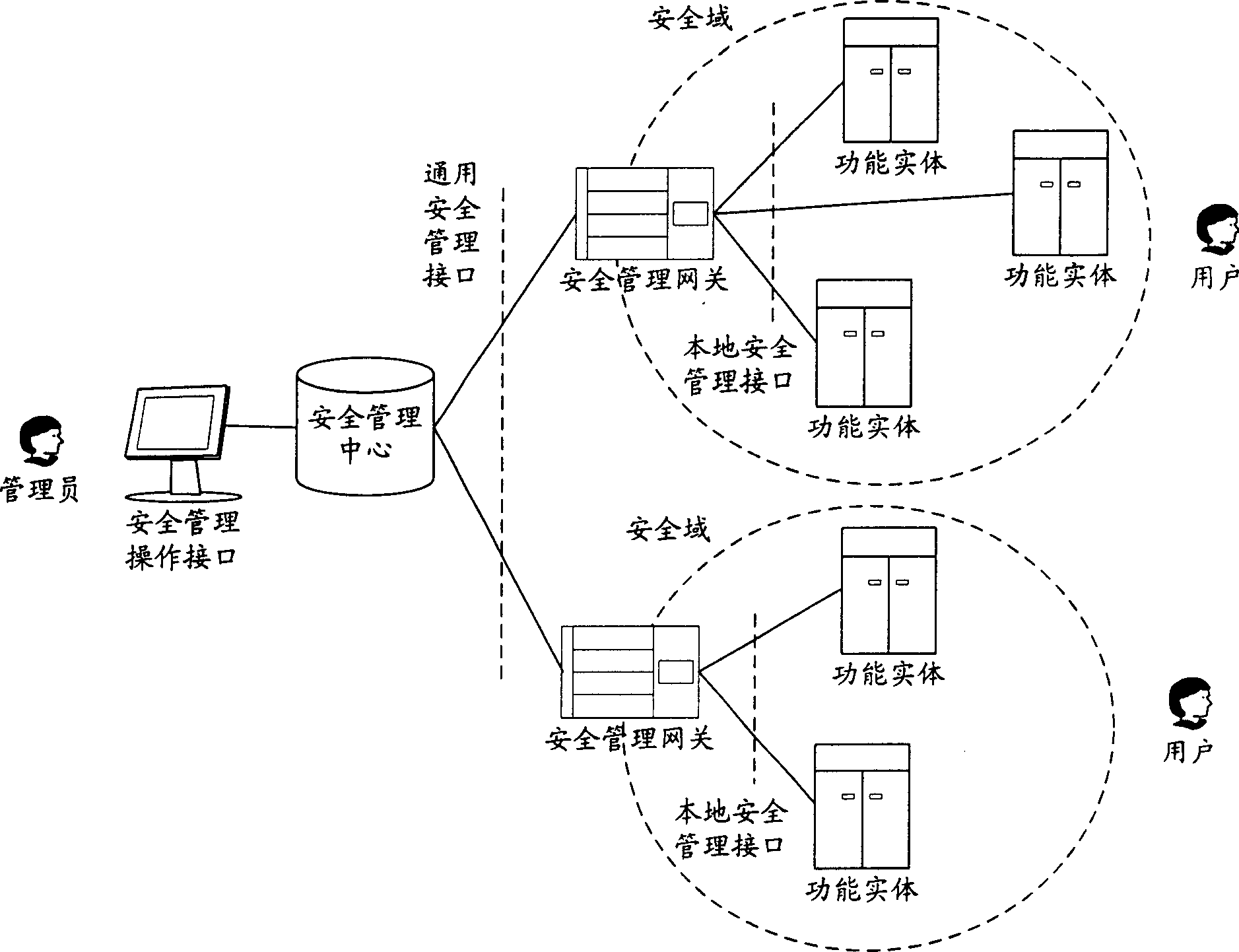
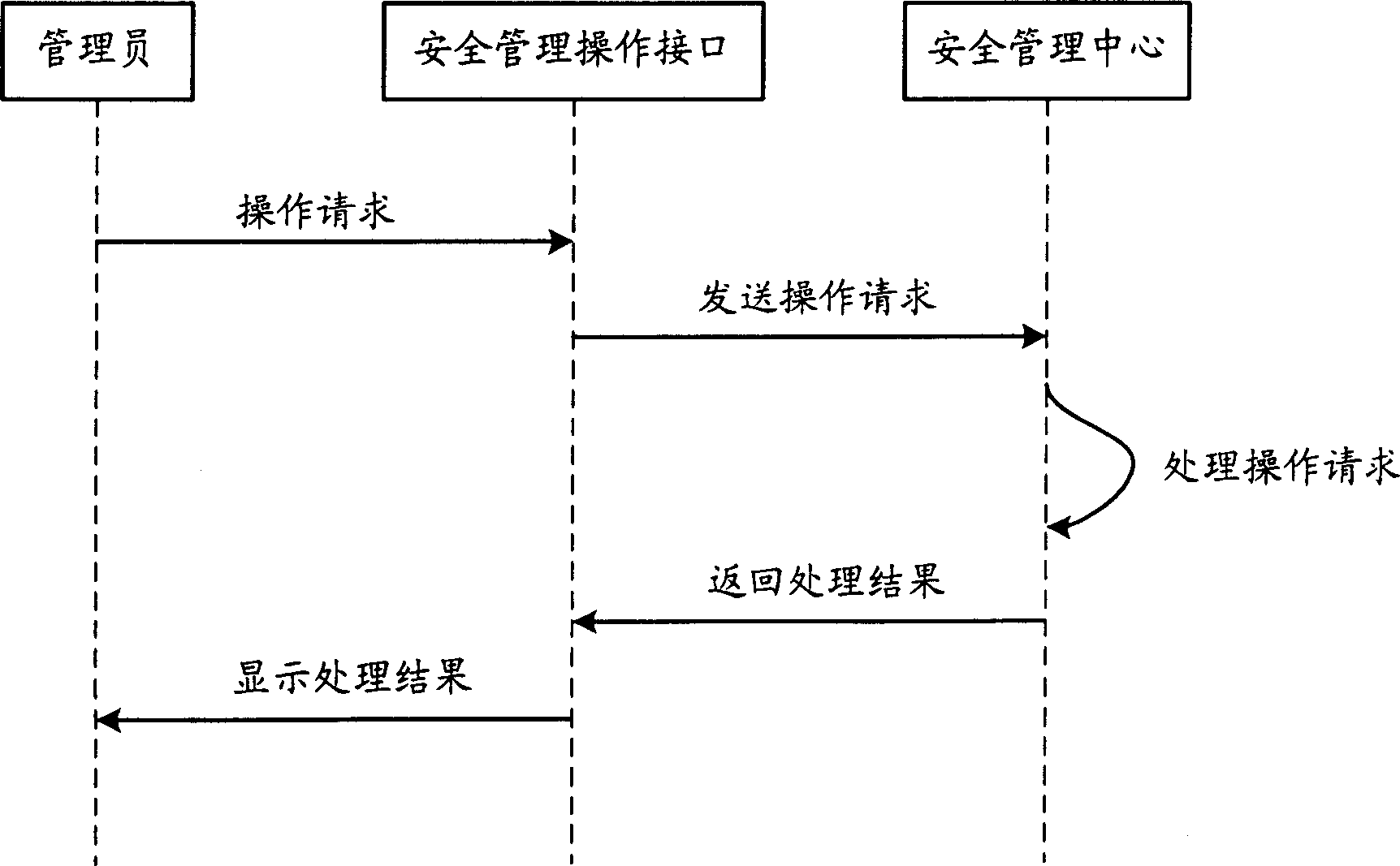
A network management technique of communication system includes dividing functional entities provided by different manufacture into different safety area and setting up a least one safety management gateway for each safety area to adapt safety management interface of safety area on universal safety management interface for realizing centralized safety management of all functional entities on network; additionally providing safety management-operation interface for supervisor to realize safety management system operation by utilizing user management, user authorization, user certification and user right identification.
Owner:HUAWEI TECH CO LTD
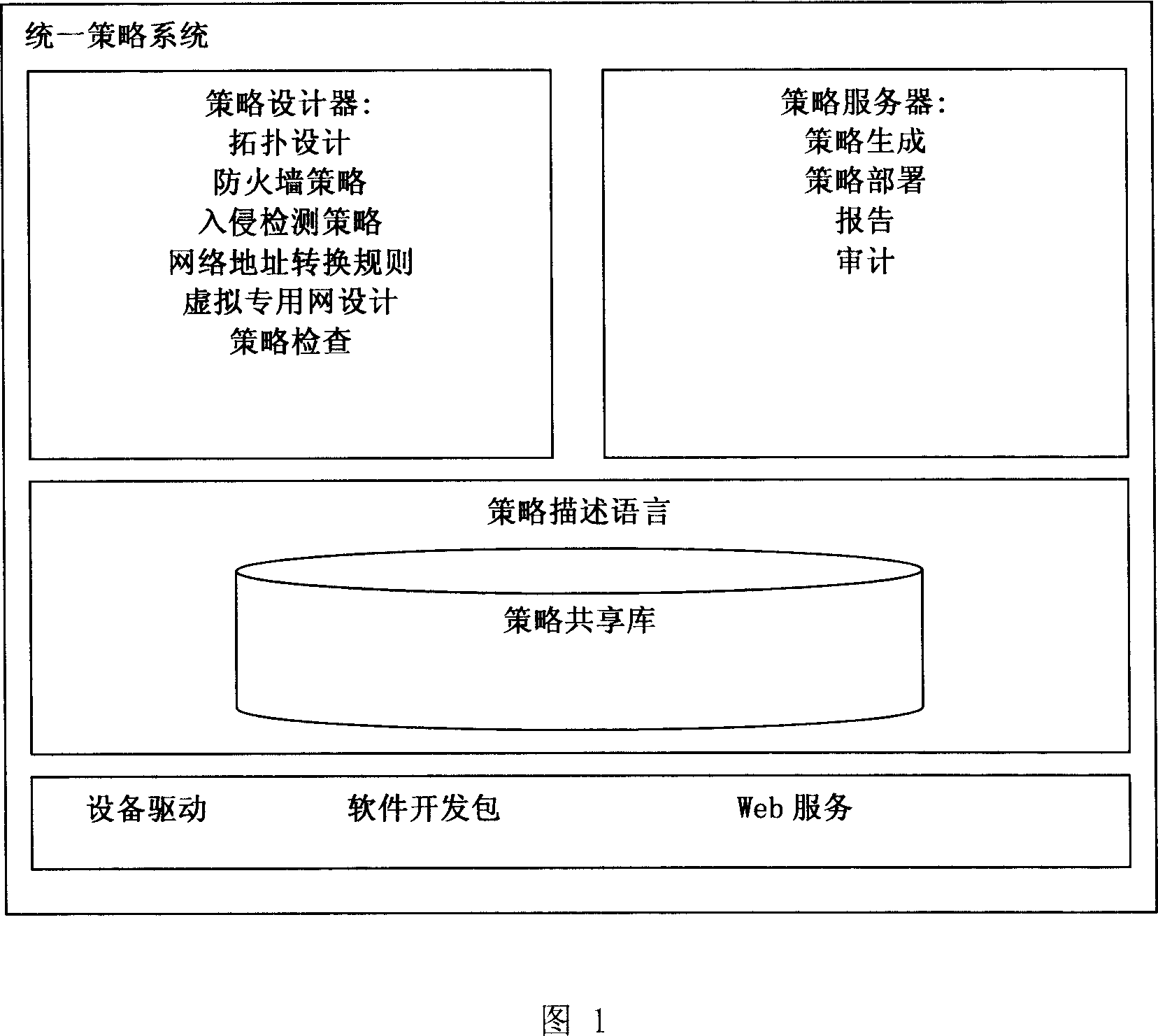
Integrated tactic managing system based on expandable label language
The invention relates to a unified strategy management system based on the extensible markup language in the computer security management filed, which includes a strategy server, a designer and a shared library. In which, the strategy designer makes a general security strategy for convenient management through visual strategy definition interface. The strategy server compiles a configuration rule of unified definition to the specific configuration rule of different products based on equipment type information field of unified strategy and presetting security equipment configuration files, and then distribute the rule to corresponding equipments in right order, they also provide a report system for security administrator to reflect the current state of the strategy and monitor equipment, issue a warning and report their activities. The strategy shared libraries store all security strategy defined by PDL uniformly for inquiring, generating reports or audit.
Owner:SHANGHAI JIAO TONG UNIV
Method and apparatus for managing a firewall
InactiveUS20060288409A1Promote generationMultiple digital computer combinationsProgram controlNetwork topologyConfiguration Issue
A method and apparatus are disclosed for managing a firewall. The disclosed firewall manager facilitates the generation of a security policy for a particular network environment, and automatically generates the firewall-specific configuration files from the security policy simultaneously for multiple gateways. The security policy is separated from the vendor-specific rule syntax and semantics and from the actual network topology. Thus, the security administrator can focus on designing an appropriate policy without worrying about firewall rule complexity, rule ordering, and other low-level configuration issues. In addition, the administrator can maintain a consistent policy in the presence of intranet topology changes. The disclosed firewall manager utilizes a model definition language (MDL) and an associated parser to produce an entity relationship model. A model compiler translates the entity-relationship model into the appropriate firewall configuration files. The entity-relationship model provides a framework for representing both the firewall-independent security policy, and the network topology. The security policy is expressed in terms of “roles,” which are used to define network capabilities of sending and receiving services. A role may be assumed by different hosts or host-groups in the network. A visualization and debugging tool is provided to transform the firewall-specific configuration files into a graphical representation of the current policy on the actual topology, allowing the viability of a chosen policy to be evaluated. A role-group may be closed to prevent the inheritance of roles.
Owner:BARTAL YAIR +2
Method for utilizing camera to automatically capture mine earthquakes and collapses of mine and timely record and alarm
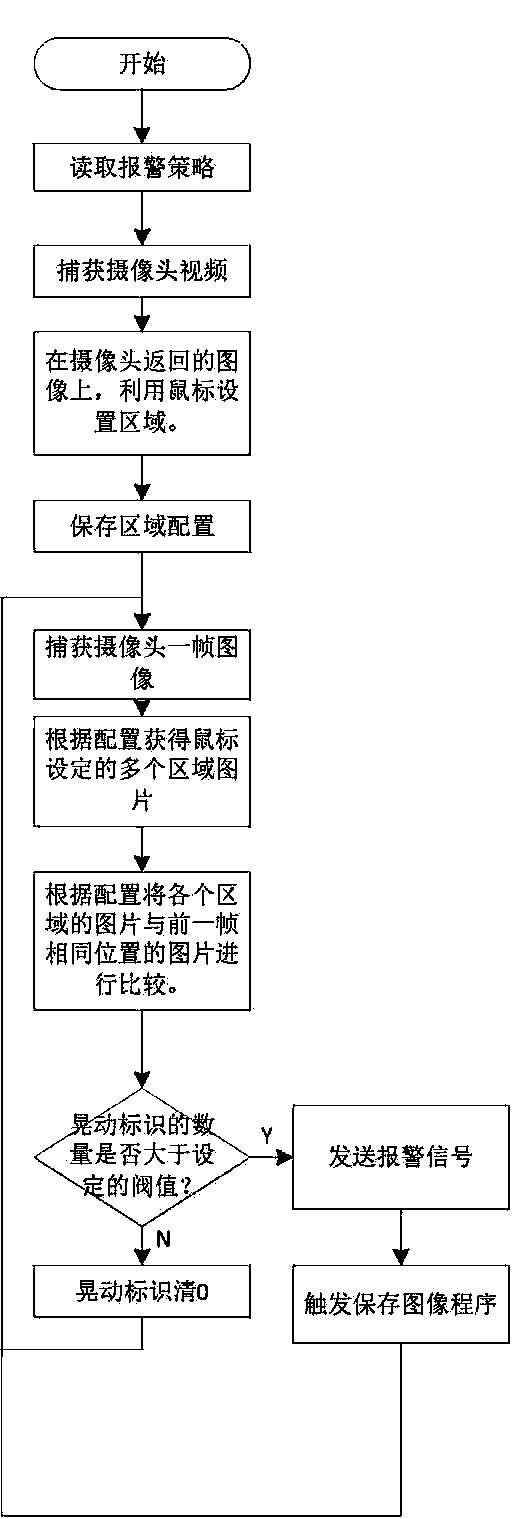
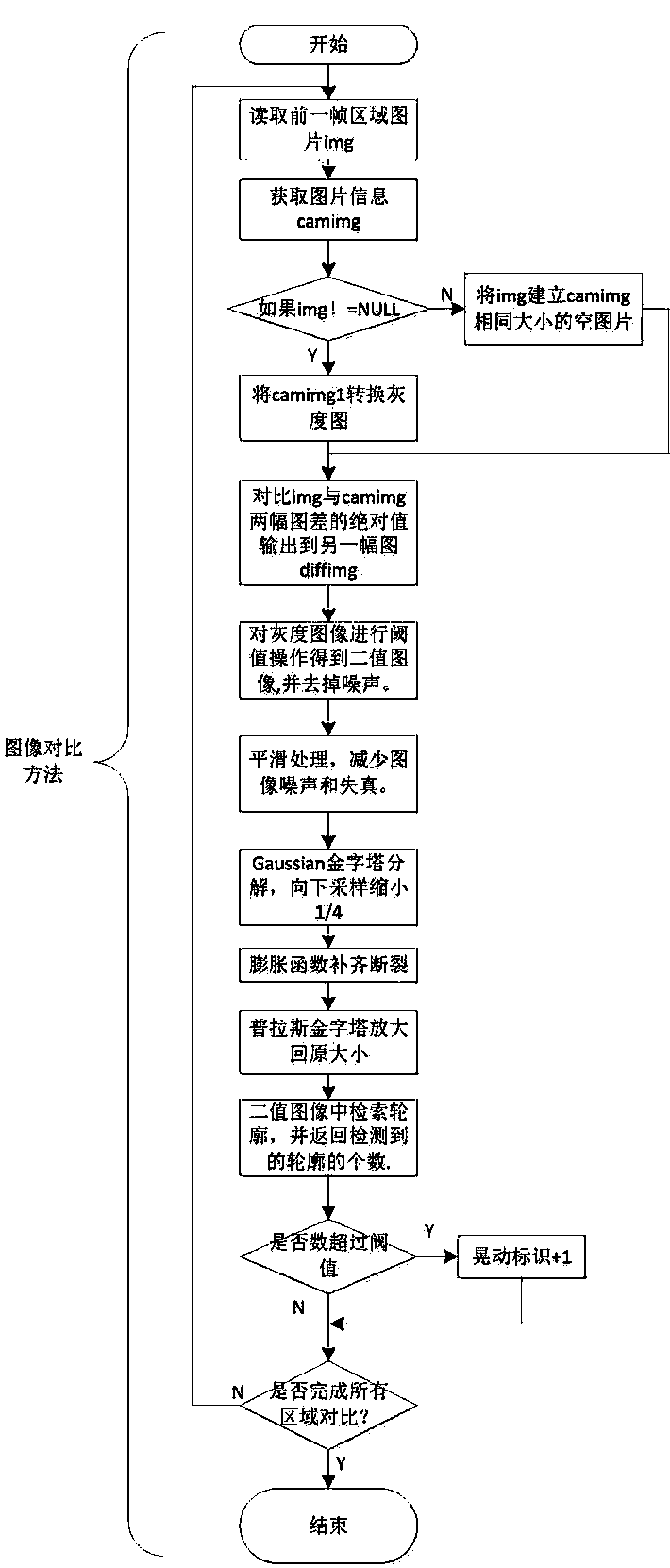
InactiveCN103726879AQuickly grasp the historical traceabilityMining devicesClosed circuit television systemsVideo monitoringAlarm message
The invention discloses a method for utilizing a camera to automatically capture mine earthquakes and collapses of a mine and timely record and alarm. Through the video surveillance technology and the image analysis technology, collapses and mine earthquakes inside the mine can be automatically found and timely alarmed, and video signals can be stored. The method includes that a plurality of monitoring zones are set on a same monitoring screen, and pictures of the zones are intercepted circularly and compared with a screen of same zones of the previous frame; once differences are found, counting is performed in a massage center; when counting value reaches a preset threshold, alarm information is triggered, recording of monitoring content is started, and the alarm information is transmitted to a mobile client side through a wireless network for a security guard to monitor and process. By the application of the method, the security guard can timely discover dangerous signals inside the mine, check on-site situations in real time and check on-site images in a history record, and thus quick master of on-site situations and historical retrospection of events is facilitated.
Owner:辽宁晟通系统集成工程有限公司
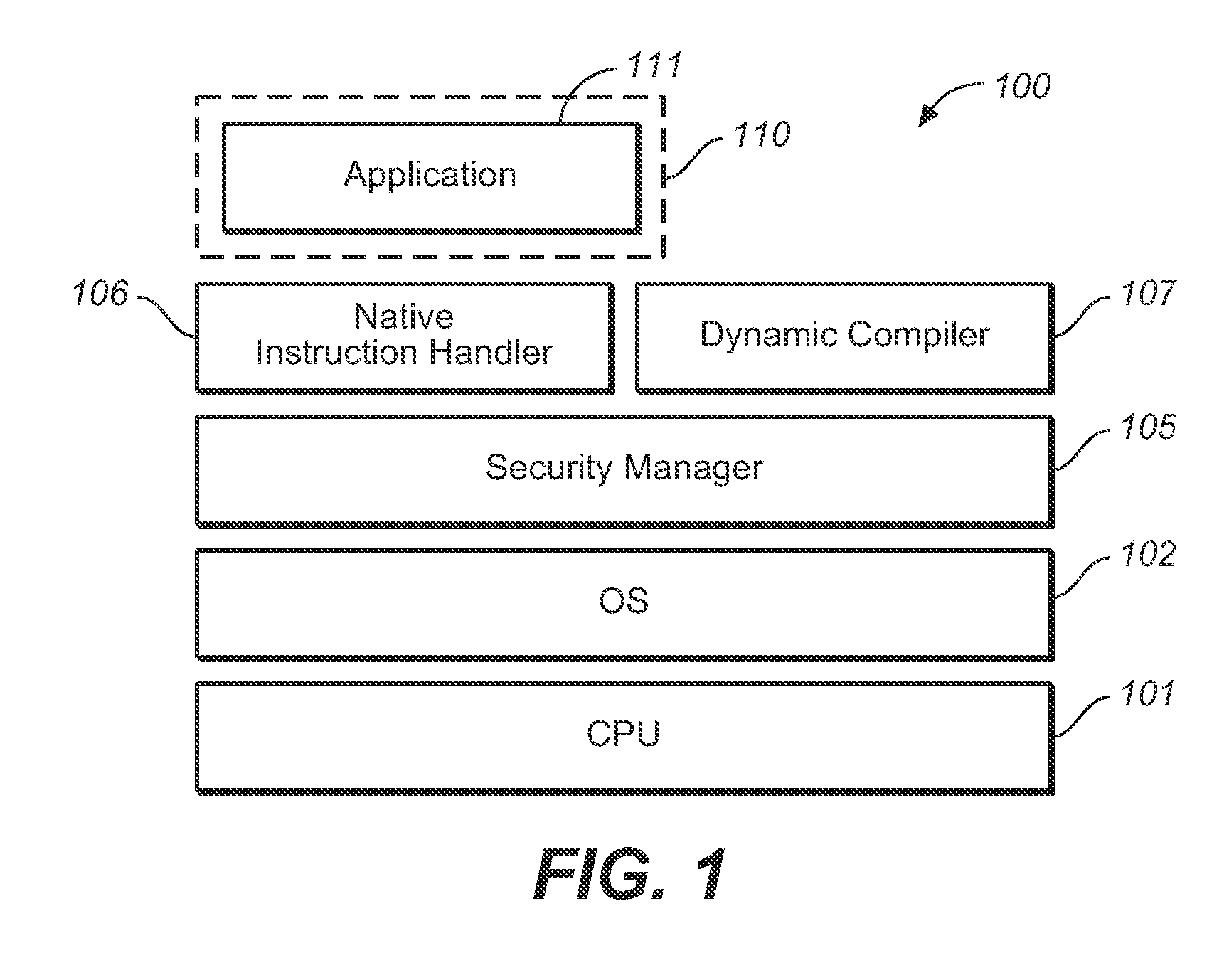
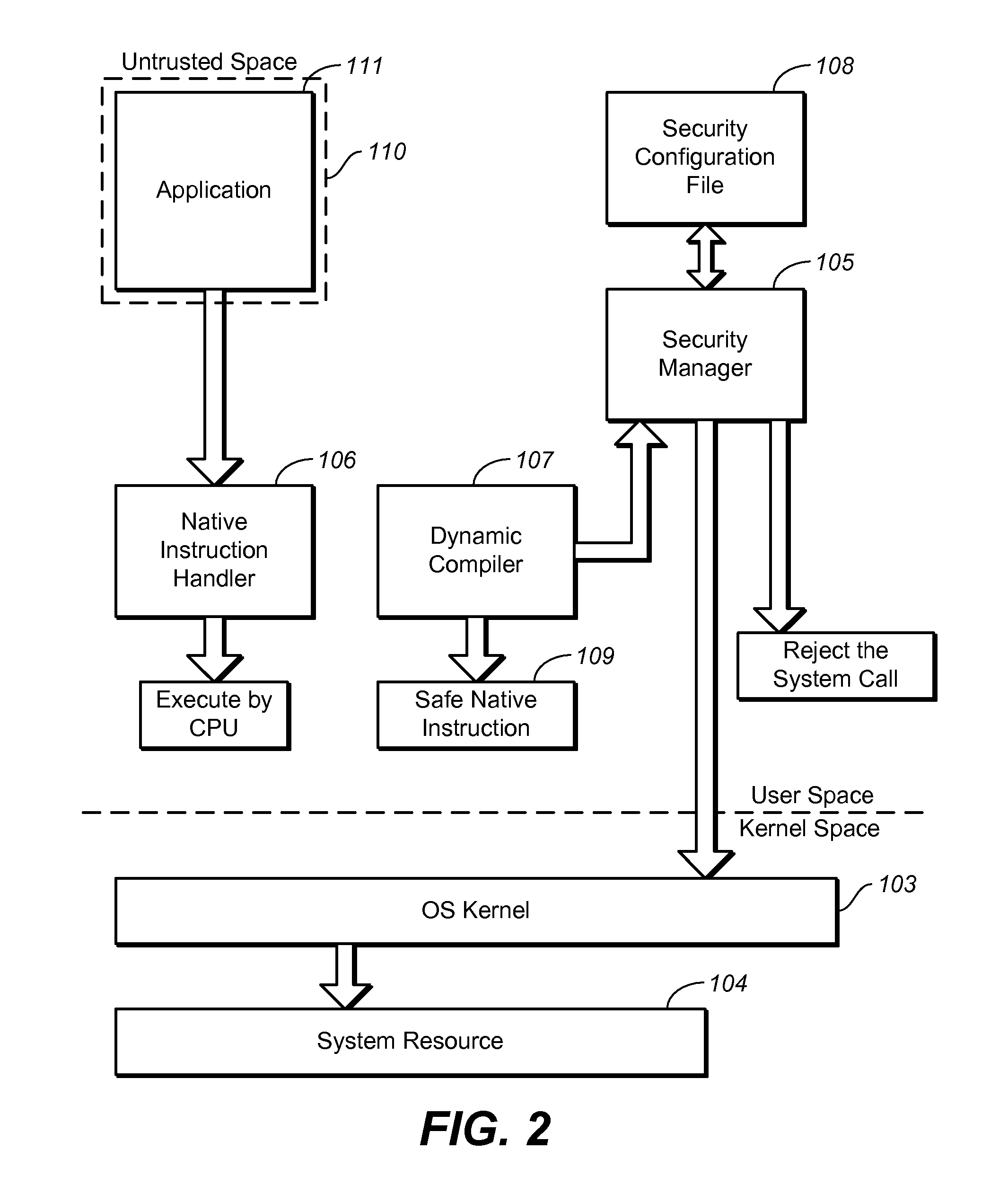
User space virtualization system
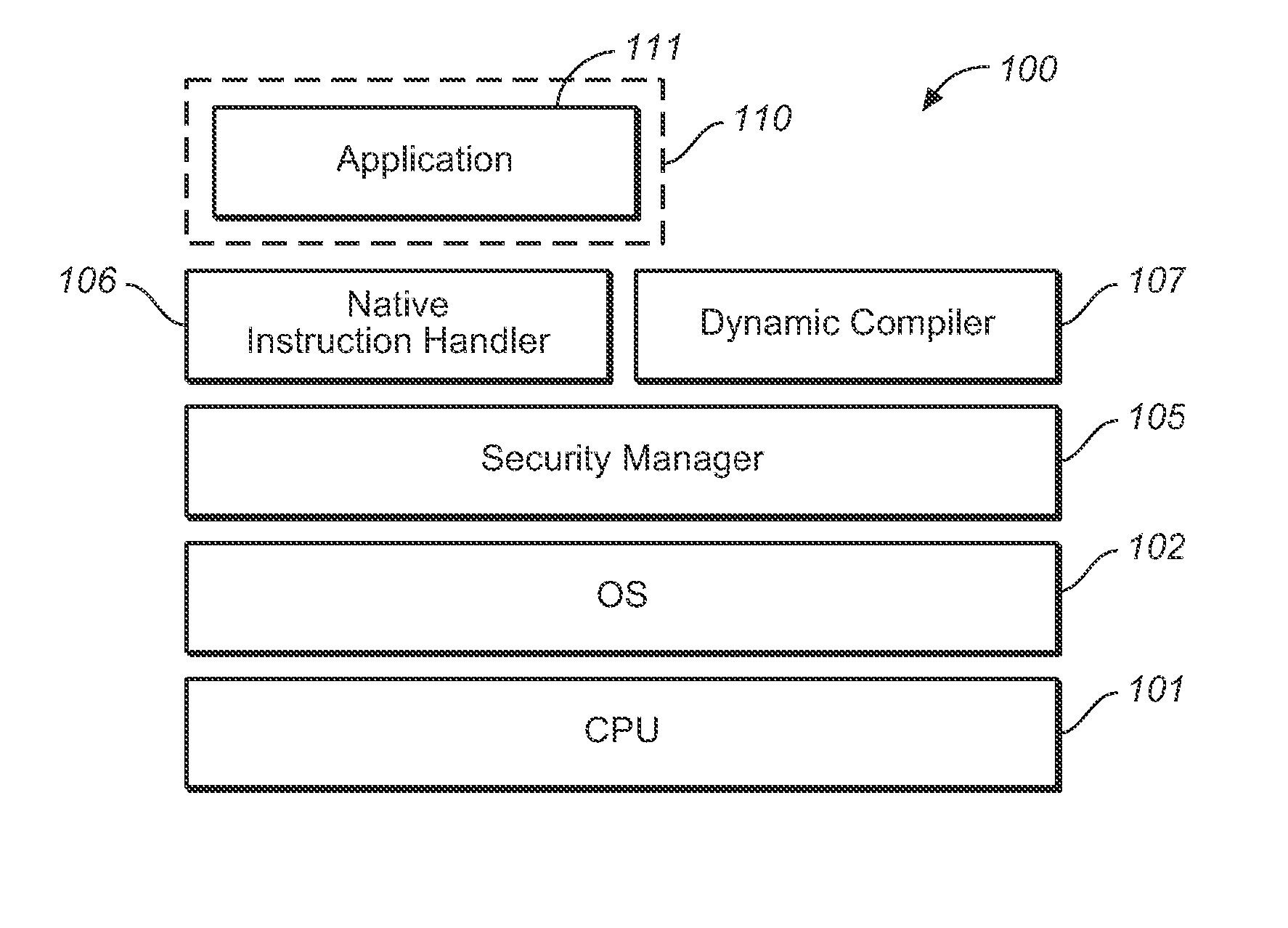
InactiveUS20080047023A1Improve performanceSame level of performanceDigital data processing detailsUser identity/authority verificationVirtualizationInstruction sequence
A user-space virtualization (USV) program to allow legacy applications in embedded systems to share resources without modification without compromising security is provided. A computer-implemented USV program may be characterized by a method in a user-space including retrieving a native code of an application, and identifying an instruction sequence. Further, identifying the instruction sequence includes, first, determining if executing the instruction sequence to perform processing is a possible security risk. If it is a possible security risk, then confirming that there is an execute authority for an active application. Execute authority may be confirmed by a security manager or a processor. If it is confirmed by the security manager that the active application has the execute authority for processing, then executing the instruction sequence with a processor. If the active application has no execute authority for processing, then not executing the instruction sequence. On the other hand, if executing the instruction sequence to perform processing is not a possible security risk, then executing the instruction sequence with the processor.
Owner:APLIX INC
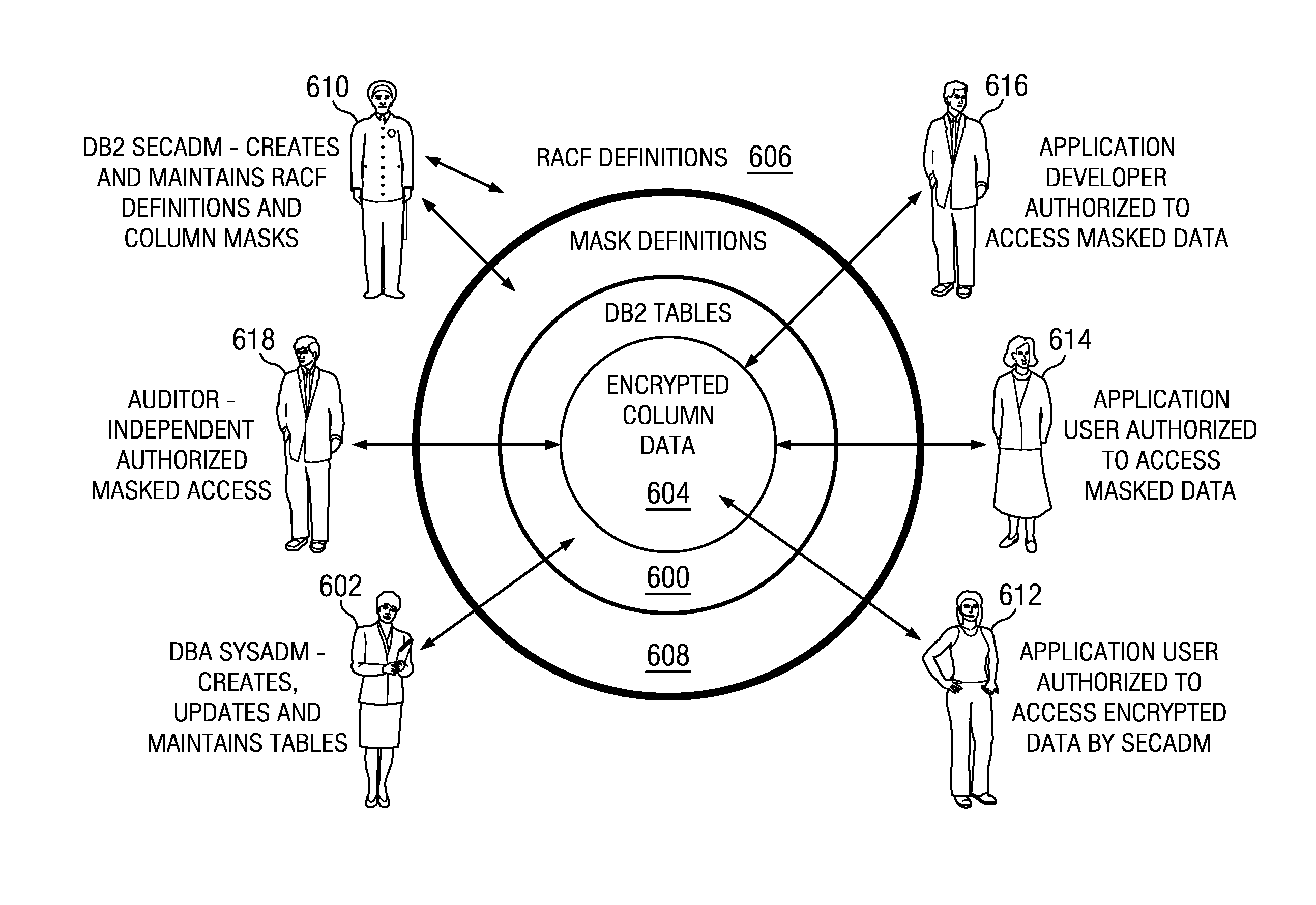
Role-oriented database record field security model
ActiveUS20140075571A1Supports accessDigital data processing detailsAnalogue secracy/subscription systemsEnd-to-end encryptionField data
A database management system implements a role-oriented authorization scheme that facilitates operating system (OS) supported encrypted field access for a table in the database. A security model provides for various roles that have varying responsibilities and rights with respect to the database tables and the data supported therein. In this approach, data that is considered sensitive is encrypted. A system administrator role is authorized to create, update, and maintain a table but is not authorized to view sensitive field data, i.e., data stored in encrypted columns of the table. A security administrator role is authorized to define column masks with OS-enforced security access control to the sensitive field data. By separating (fencing) these responsibilities, the security model enforces end-to-end encryption across the entire database management system.
Owner:IBM CORP
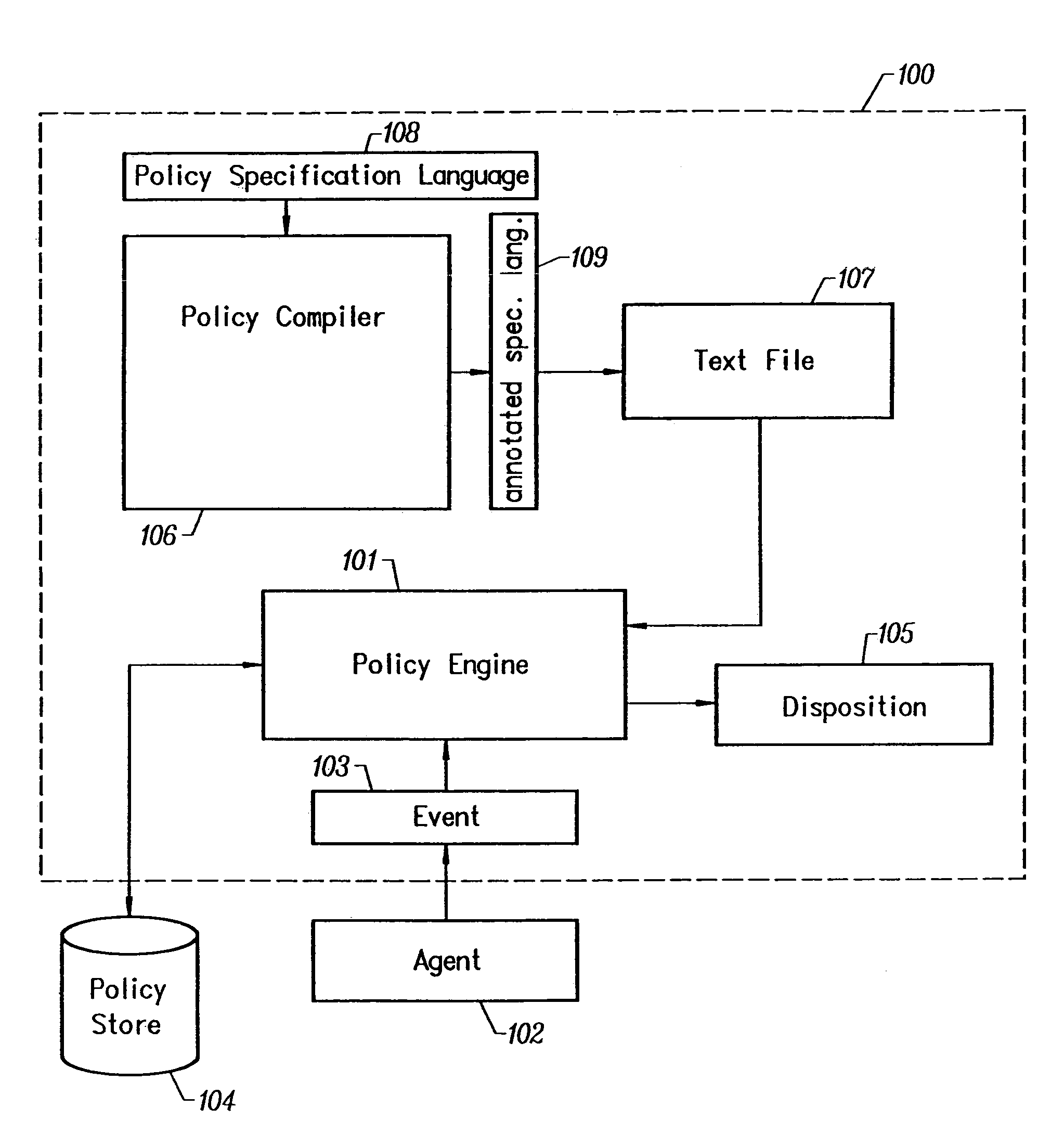
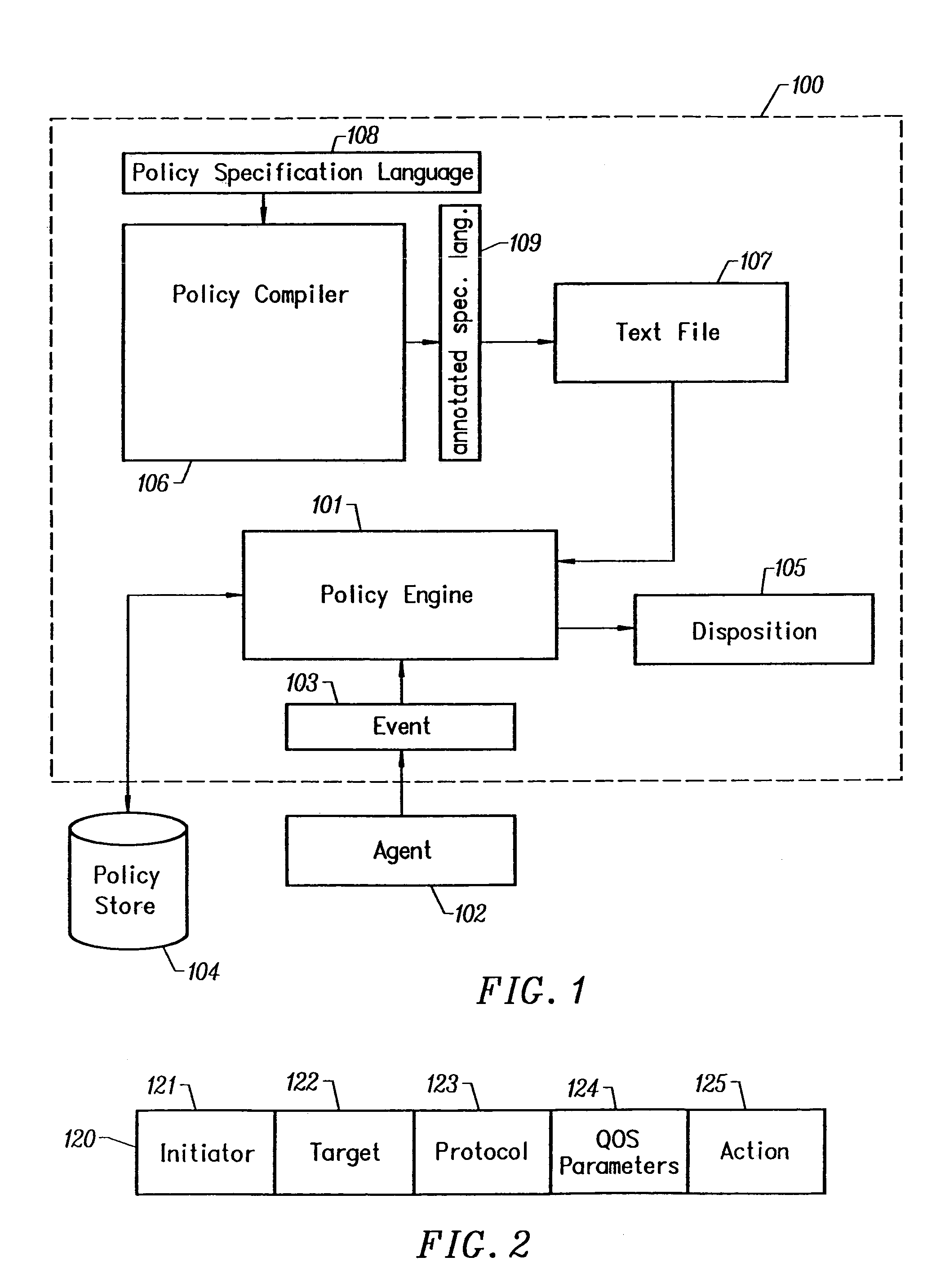
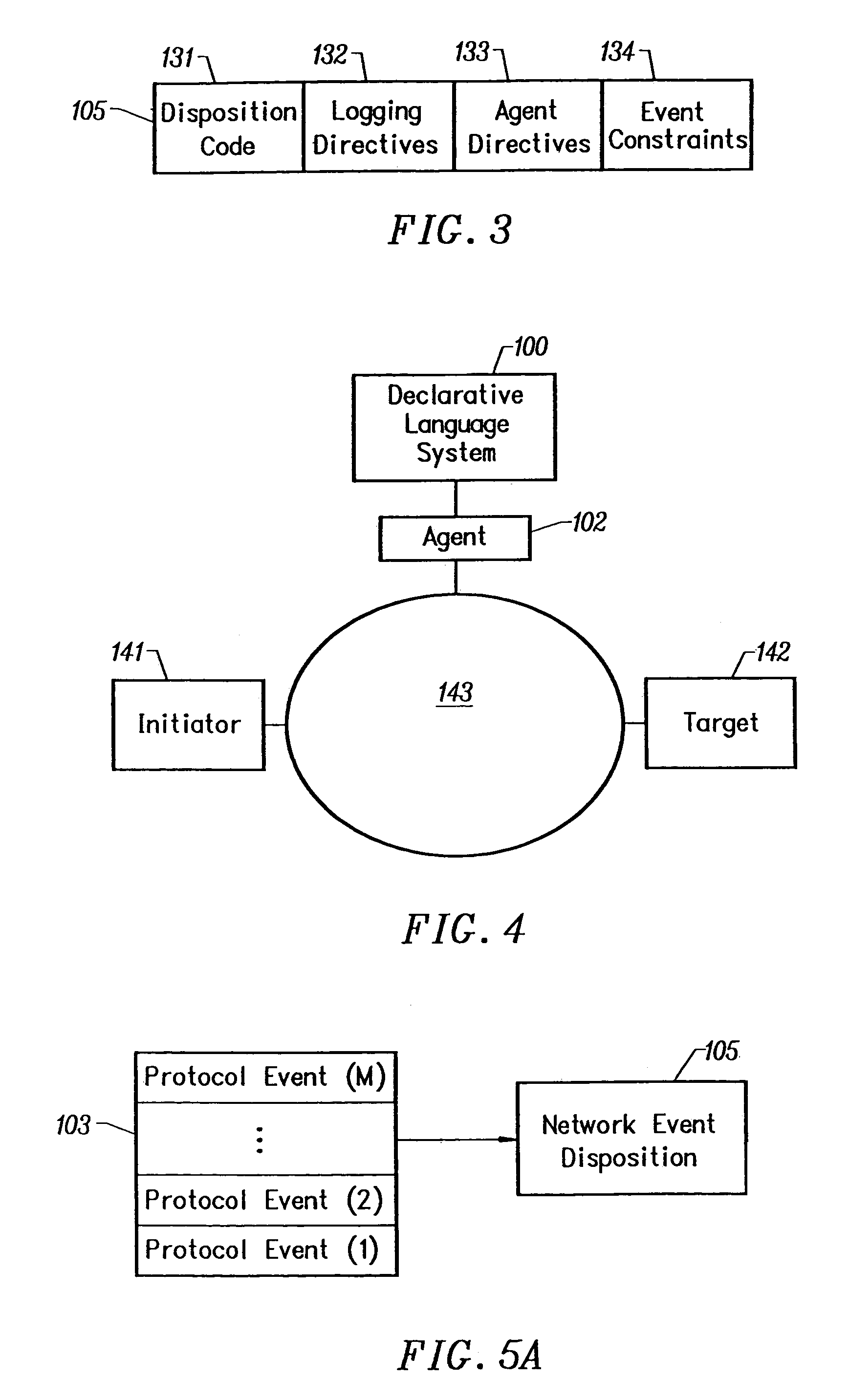
Declarative language for specifying a security policy
InactiveUS7478422B2Richer in termDigital data processing detailsMultiple digital computer combinationsNetwork security policyHuman operator
The invention is a declarative language system and comprises a language as a tool for expressing network security policy in a formalized way. It allows the specification of security policy across a wide variety of networking layers and protocols. Using the language, a security administrator assigns a disposition to each and every network event that can occur in a data communications network. The event's disposition determines whether the event is allowed (i.e. conforms to the specified policy) or disallowed and what action, if any, should be taken by a system monitor in response to that event. Possible actions include, for example, logging the information into a database, notifying a human operator, and disrupting the offending network traffic.
Owner:MCAFEE LLC
Role-based access control method based on three-member management and expansion
InactiveCN106228059AEnsure safetyGuaranteed Fair UseDigital data authenticationOffice automationGranularitySystems management
The invention provides a role-based access control (TMMERBAC) method based on three-member management and expansion. Roles are divided into ordinary roles and system roles, and the system roles are further divided into a system administrator, a security administrator and a security auditor for system management; department concept is introduced, the two authorization methods of user-department-role-authority and user-role-authority are adopted, the TMMERBAC strategy is applied to a specific project management system, and the advantages of the TMMERBAC strategy that authorization flexibility can be improved, authorization complexity can be reduced and control granularity can be divided are realized.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and system for intelligent supervision of coal mine safety production
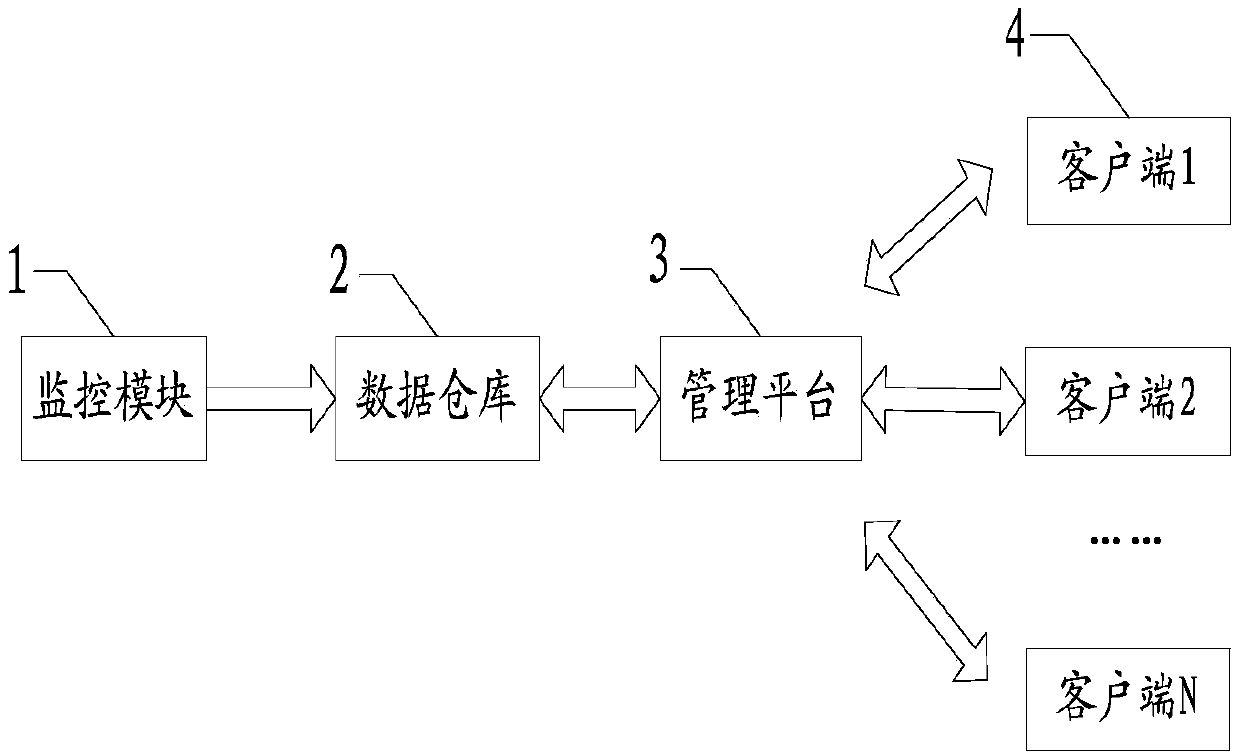
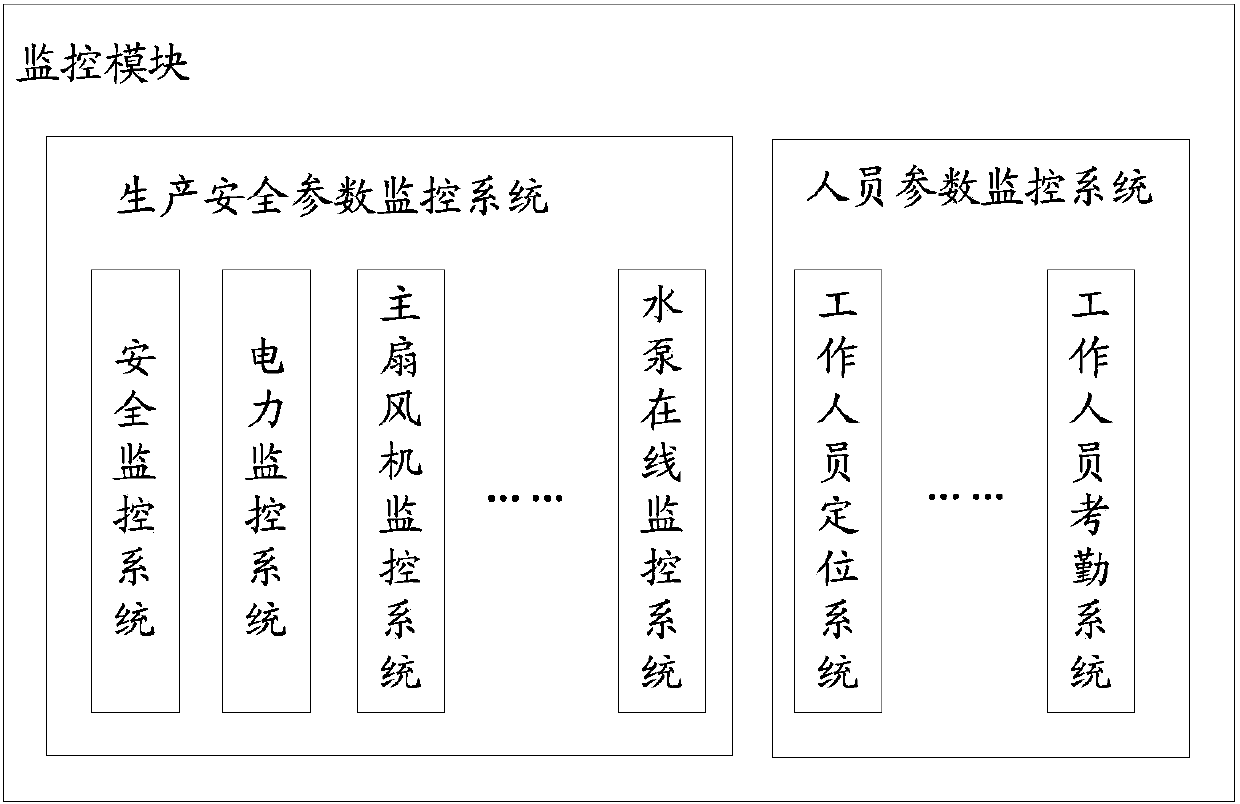
InactiveCN103473639ALearn about securityIncrease production capacityResourcesData warehouseComputer module
The invention relates to a method and system for intelligent supervision of coal mine safety production. The system comprises a monitoring module, a database, a management platform and a plurality of client terminals. The monitoring module is used for collecting monitoring data, processing the monitoring data through a data processing tool, and storing the processed monitoring data into the database in real time; the database is used for storing the monitoring data sent by the monitoring module; the management platform is used for conducting classification and optimization analysis on the data in the database according to the functional requirements and transmitting the analysis information to the corresponding client terminals; the client terminals are used for conducting data interaction with the management platform so that data in the management platform can be viewed. The monitoring data are loaded to the database through the monitoring module, classification and optimization analysis are conducted on the monitoring data by the management platform, and the monitoring data are transmitted to an intelligent terminal. The intelligent terminal is portable and flexible, enables safety managers in each level to know the safety conditions of production at any time and any place and efficiently direct production and dispose the potential safety hazards. Therefore, the safety of mine coal production is greatly improved.
Owner:BAISE MINING GRP CO LTD
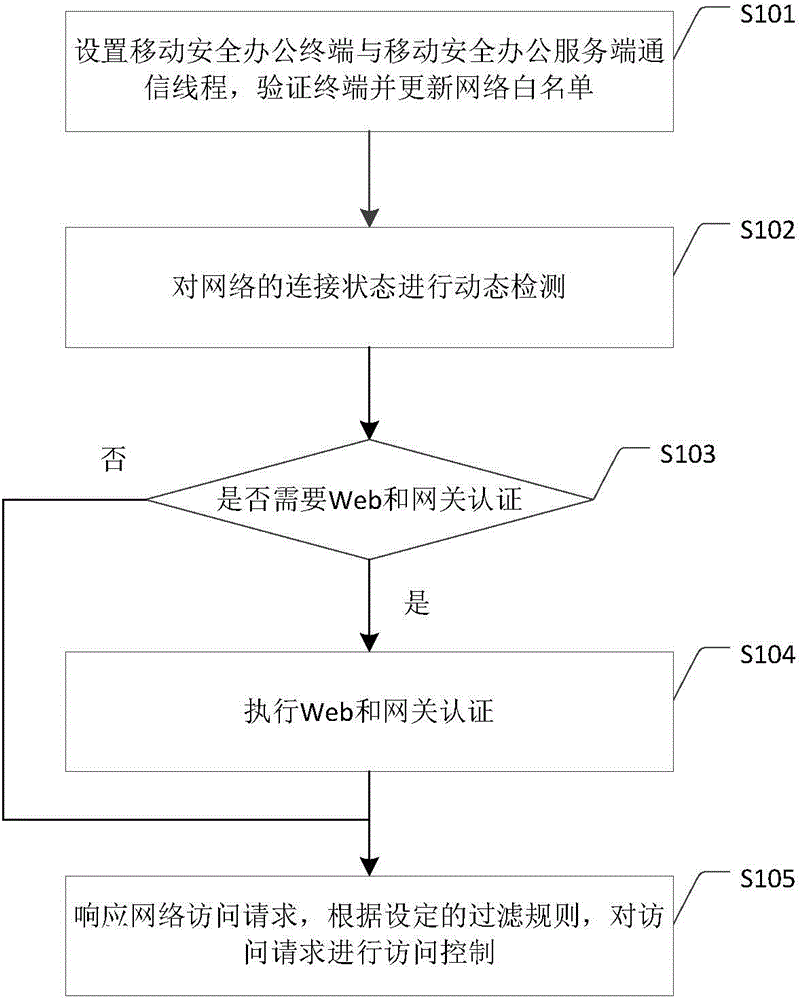
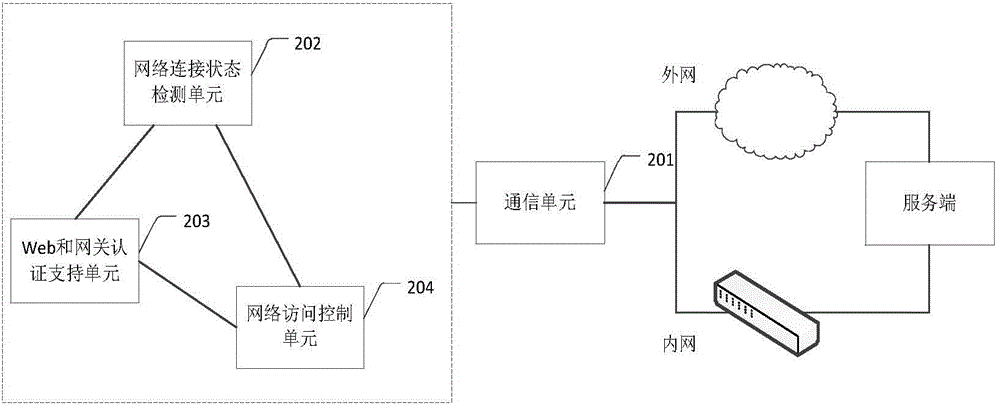
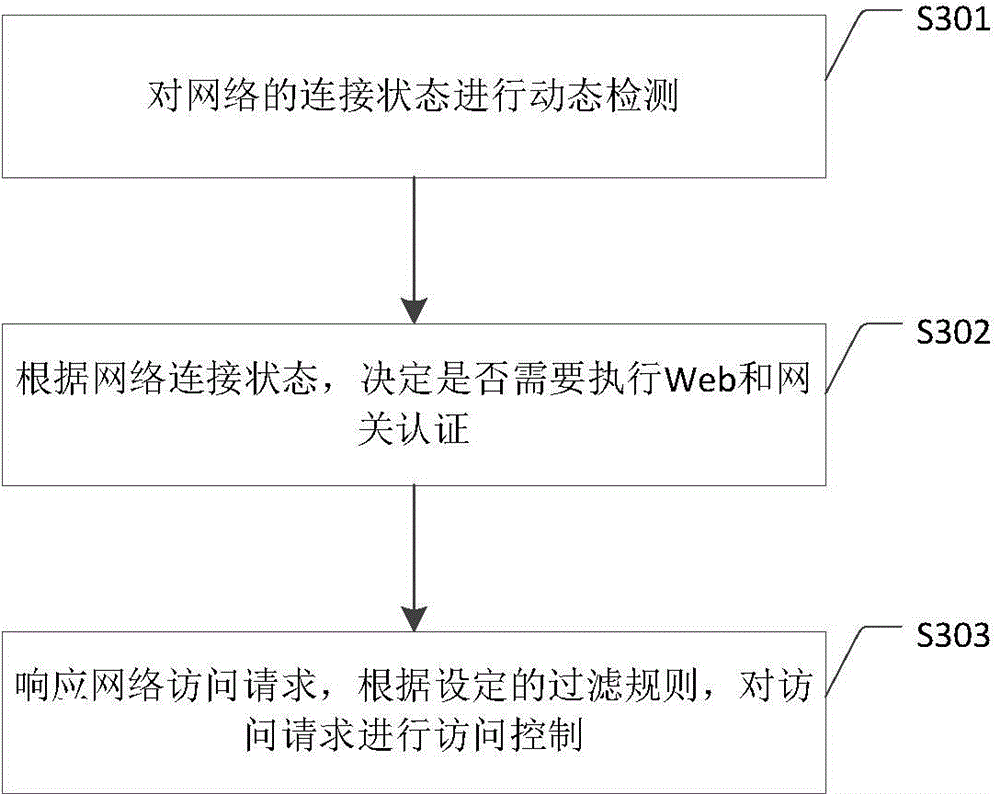
Method and system for network access control
The invention discloses a method and system for network access control, and relates to the technical field of network transmission security. When the mobile office terminal is under strict network access control, the network connection status of a terminal is dynamically detected, and the terminal can successfully pass the Web and gateway authentication according to the corresponding detection status. According to the method for network access control, the equipment is more compatible in complex changeful network environments, while the network security of the equipment is ensured, the effectiveness of network access control can be improved, the maintenance work of the security administrator can be reduced, and the support and guarantee can further be provided for the accessible network resources of the equipment.
Owner:BEIJING UNIV OF TECH
Method and system of file operation
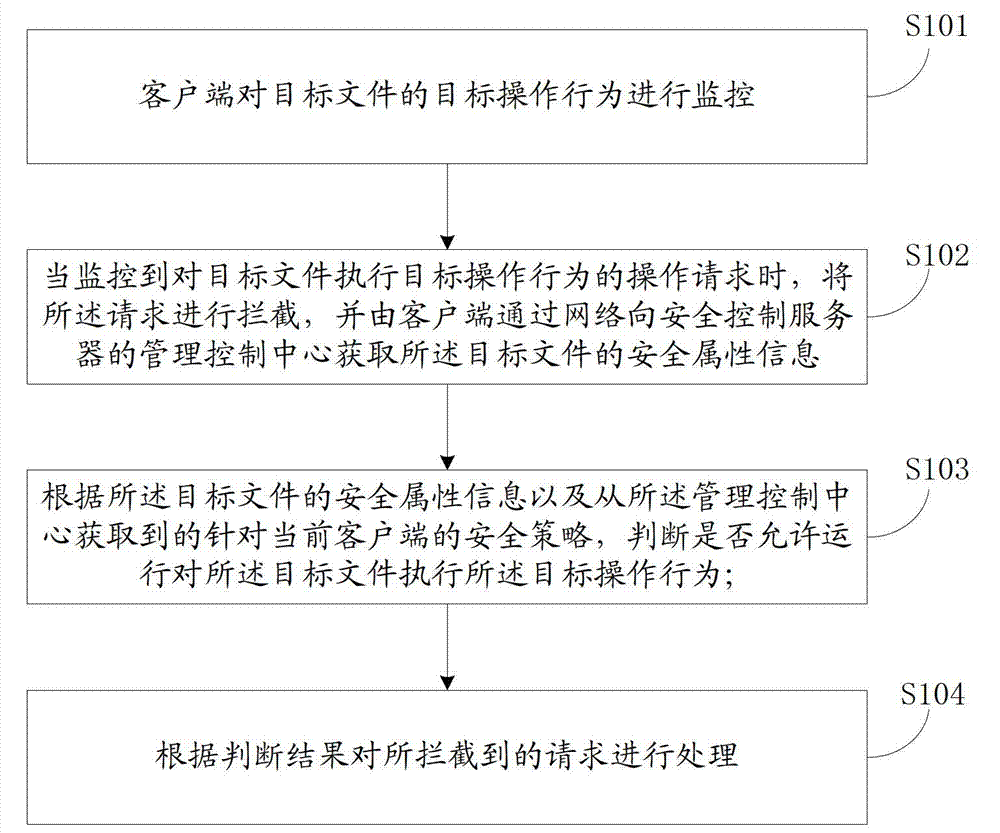
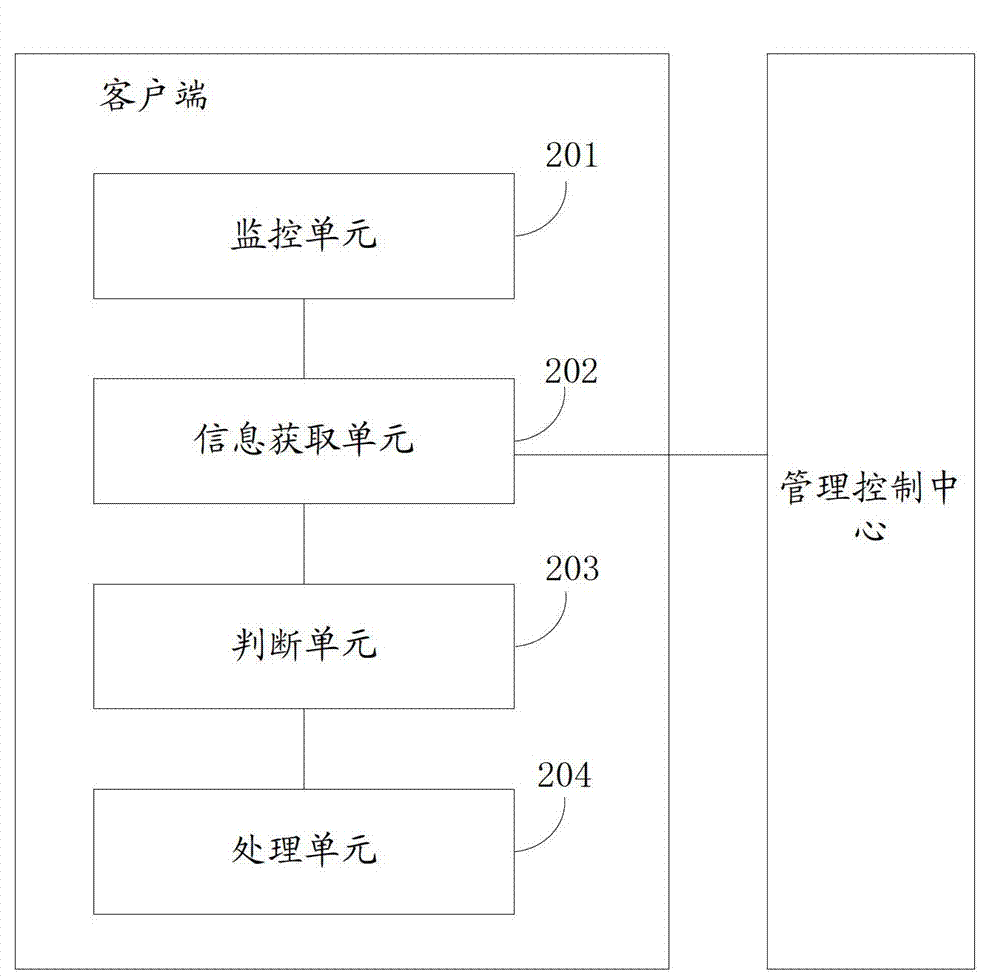
ActiveCN103198253AIncrease flexibilityPlatform integrity maintainancePersonalizationSecurity properties
The invention discloses a method and a system for controlling file operation. The method includes intercepting an operation request when the operation request of object operation to an object file is monitored and obtaining security attribute information which includes private attribute and public attribute of the object file from the management control center of a security control server through network by a client, wherein the private attribute is the security class information set for the object file by a security administrator of the management control center, determining whether permitting the object operation to the object file according to the security attribute information of the object file and a security strategy which is for the current client and obtained from the management control center, and processing the intercepted request according to the determining result. According to the method and the system of file operation and control, enterprise security products have individualized characteristics of different enterprises, and the great flexibility of the security control can be obtained.
Owner:BEIJING QIANXIN TECH
Apparatus, methods, and system for role-based access in an intelligent electronic device
ActiveUS7870595B2Low costEasy to manageDigital data processing detailsComputer security arrangementsPasswordIntelligent electronic device
The present disclosure describes apparatus, methods, and system for secure access control of an intelligent electronic device (“IED”) by multiple personnel. Within the IED a set of basic permissions is defined. A software program allows a security administrator create specific roles from the basic permissions. The software program can then be used to assign to a user a specific role for one or more specific IEDs. This action creates a set of unique security keys for the user and a unique security file for each IED. When a user accesses an IED the system identifies the user from the security key and determines his / her permissions using the security file. The security key may take the form of a password inputted into the IED, an access device incorporated within the IED, and / or a remote access device positioned proximate the IED or removably positioned in the IED.
Owner:GENERAL ELECTRIC CO
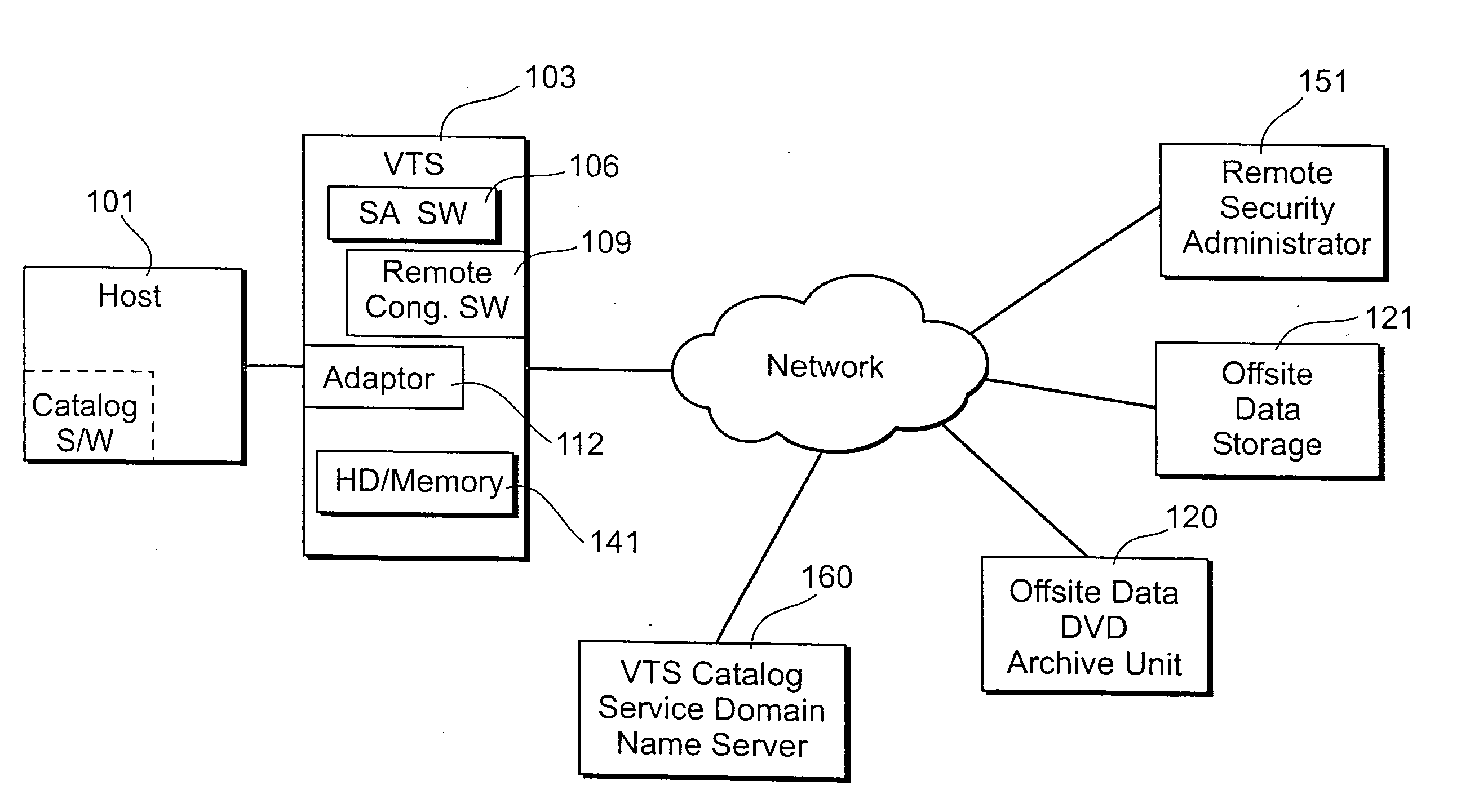
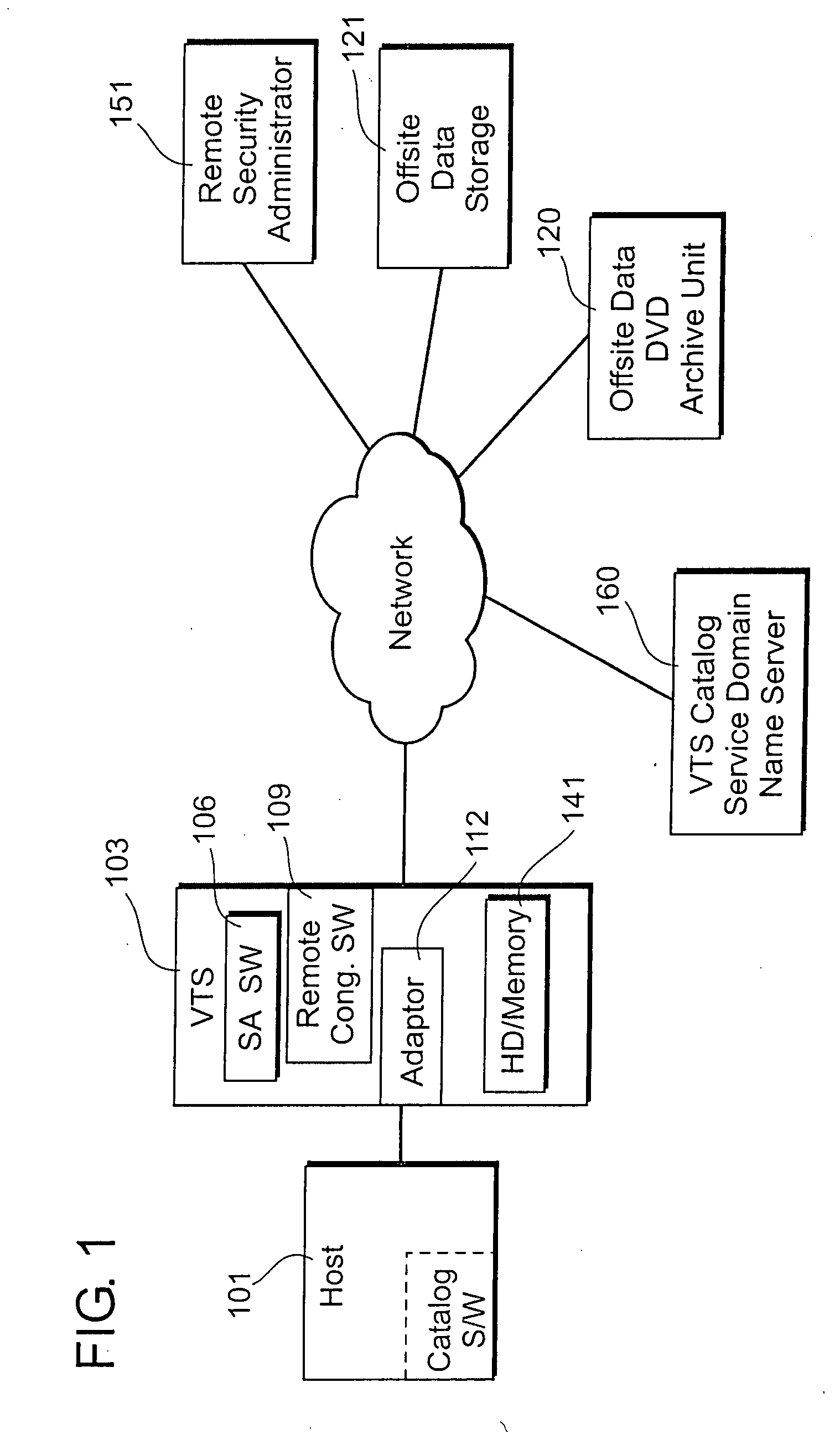
System and method for virtual tape management with remote archival and retrieval via an encrypted validation communication protocol
ActiveUS20070157294A1Improve data securityConnection securityInput/output to record carriersRandom number generatorsComputer hardwareMagnetic tape
Remote configuration and utilization of a virtual tape management system via communication of encrypted data. At least one security administrator CPU is communicably attached to a virtual tape management CPU. At least one remote data storage CPU is communicably attached to the virtual tape management CPU and to the security administrator. First software within the virtual tape management CPU validates authorized remote access to at least one remote data storage CPU and encrypts the data. Second software facilitates remote configuration and utilization of the virtual tape management CPU. At least one hardware adaptor card connects the virtual tape management CPU to a host.
Owner:GLOBAL INTERFACE SOLUTIONS INC D B A SECUREAGENT SOFTWARE
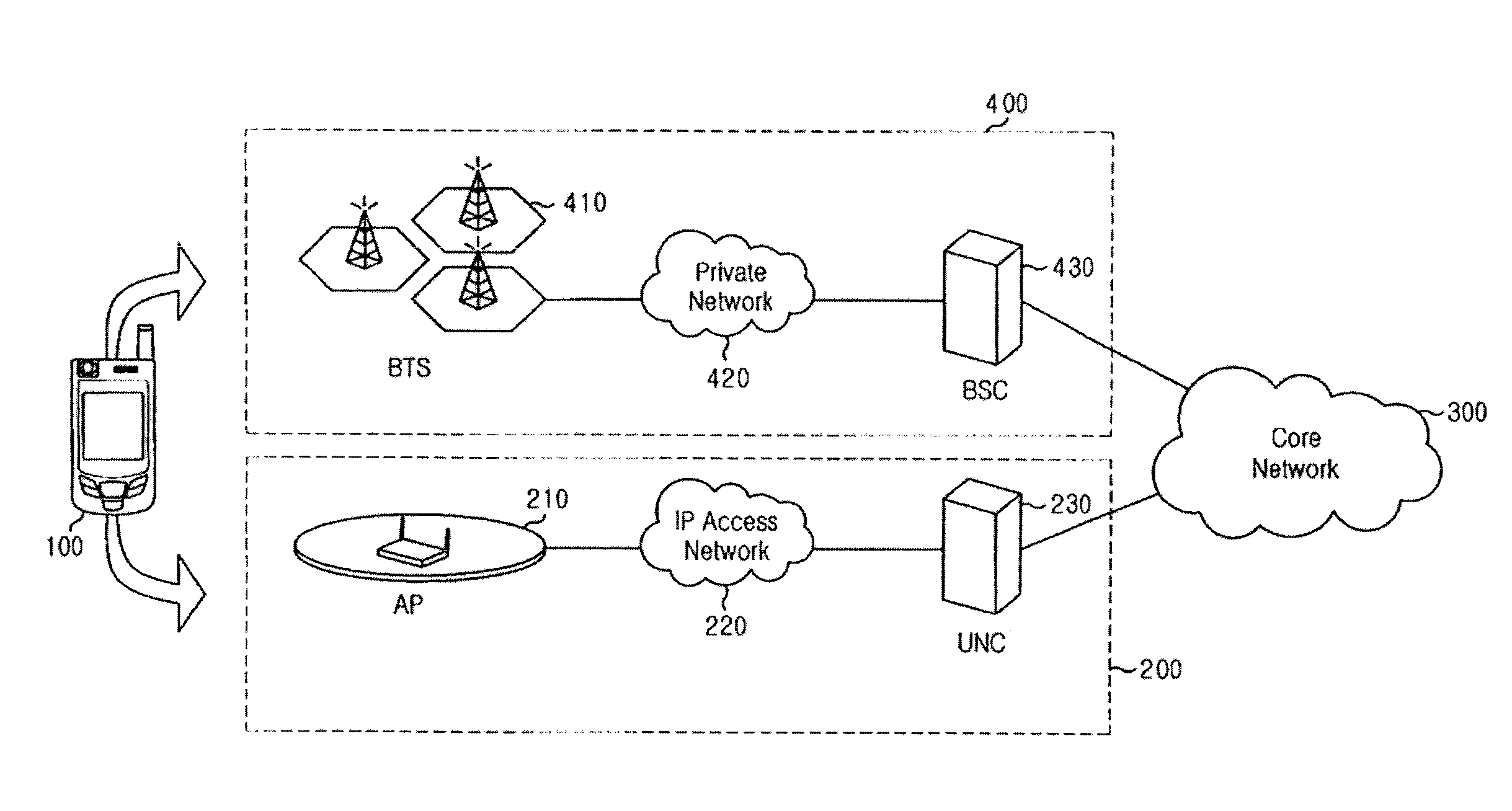
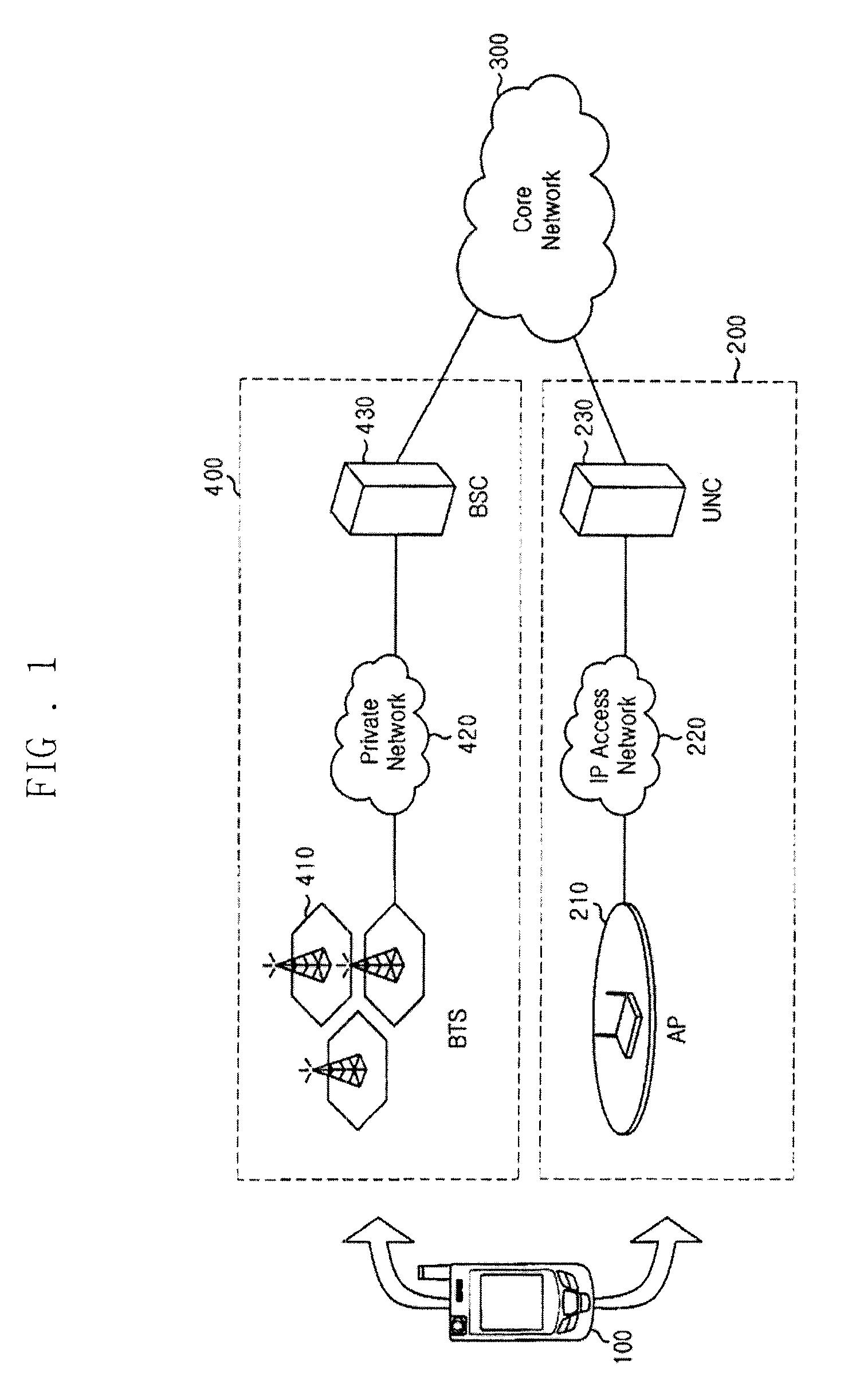
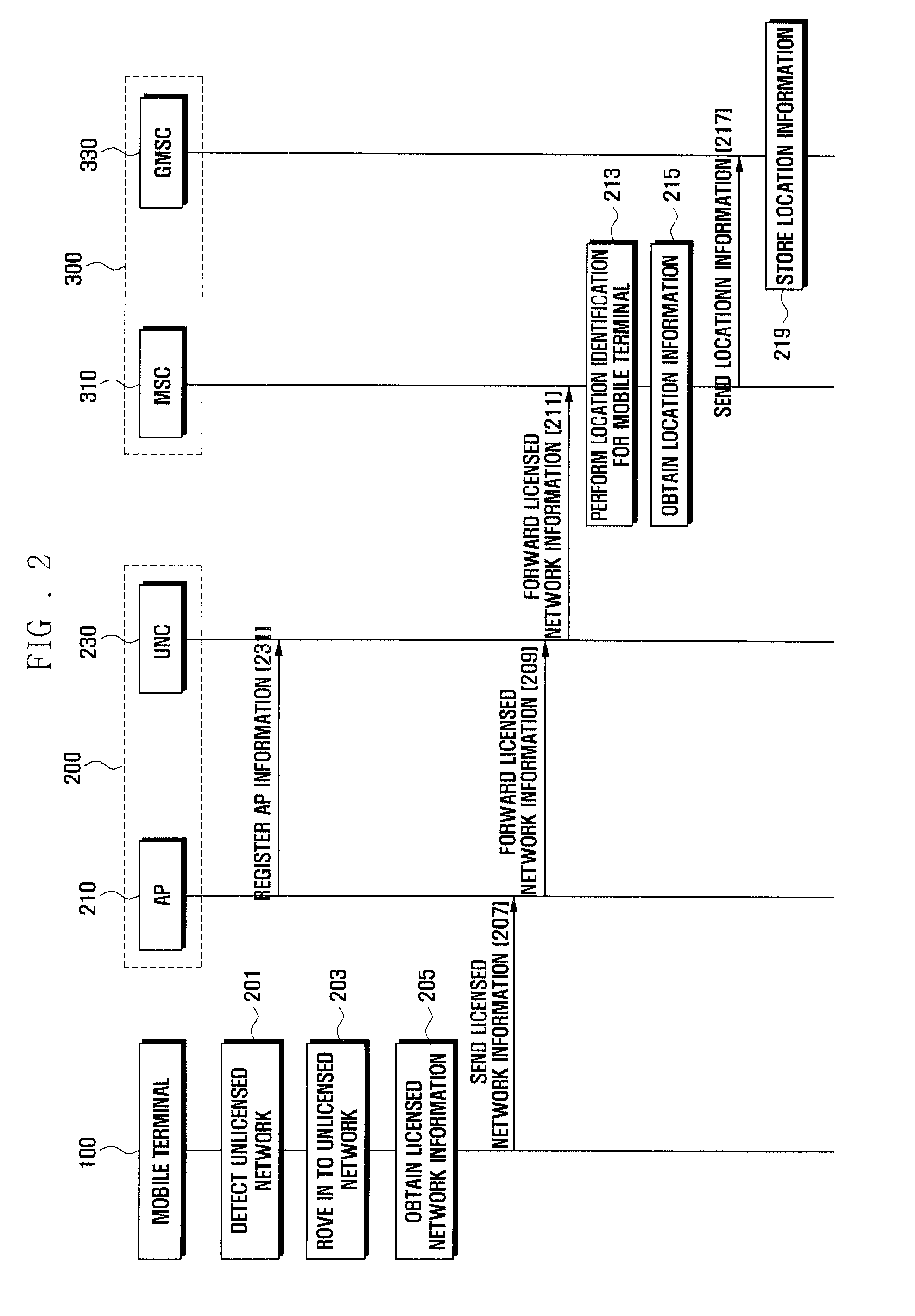
Method and system for emergency call service in unlicensed mobile access network
InactiveUS20100136947A1Shorten the timeEasy to handleEmergency connection handlingTelephonic communicationTelecommunicationsSecurity administrator
A method and system for an emergency call service in an unlicensed mobile access (UMA) network are disclosed. The emergency call service method includes: receiving, by a mobile terminal on an unlicensed network, an emergency call; forwarding, by the unlicensed network, the emergency call and an AP (access point) list related to an AP associated with the mobile terminal to a core network; searching for, by the core network, location information of the mobile terminal corresponding to the AP list; and sending, by the core network, an emergency report containing the location information of the mobile terminal to a safety manager.
Owner:SAMSUNG ELECTRONICS CO LTD
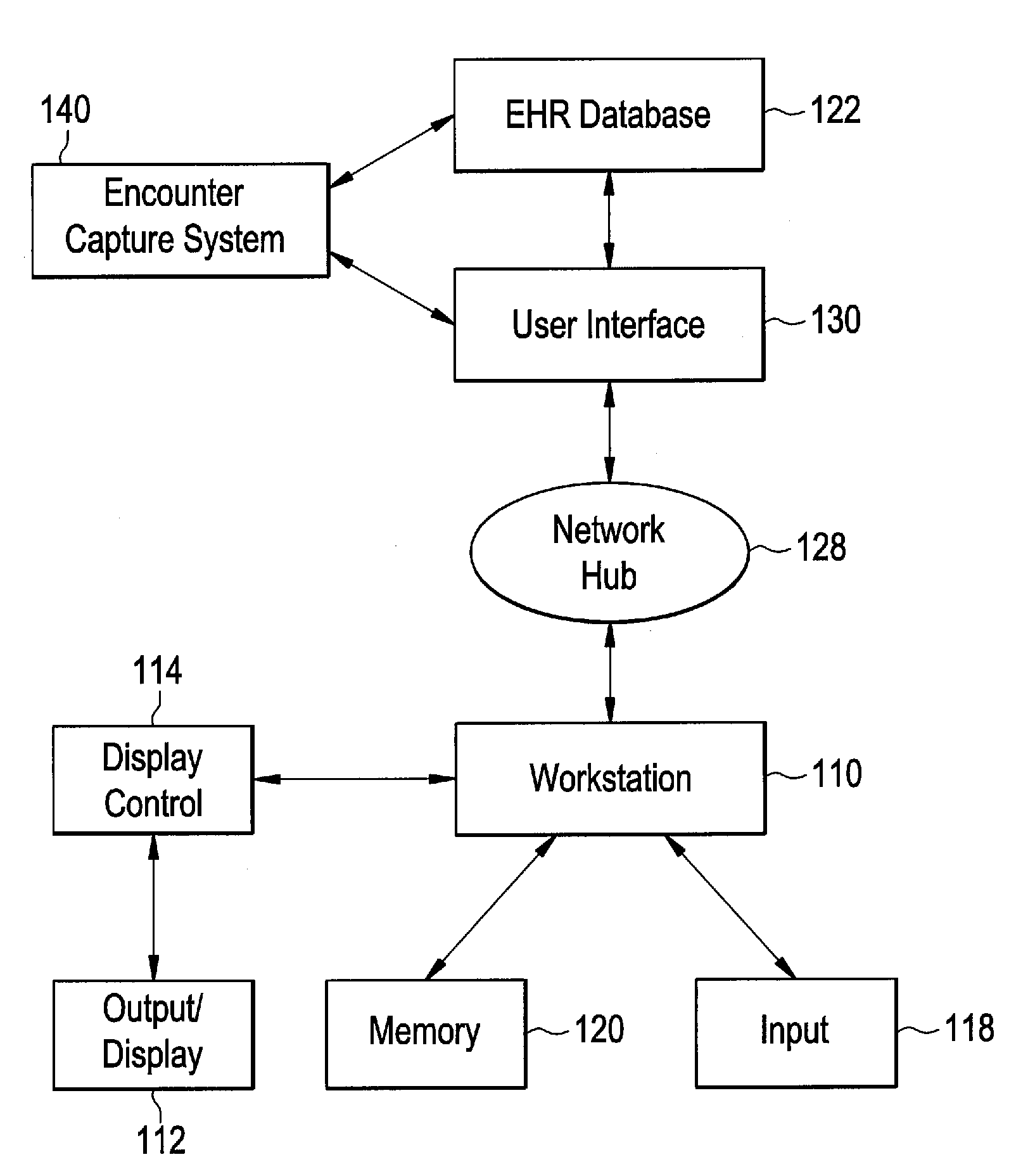
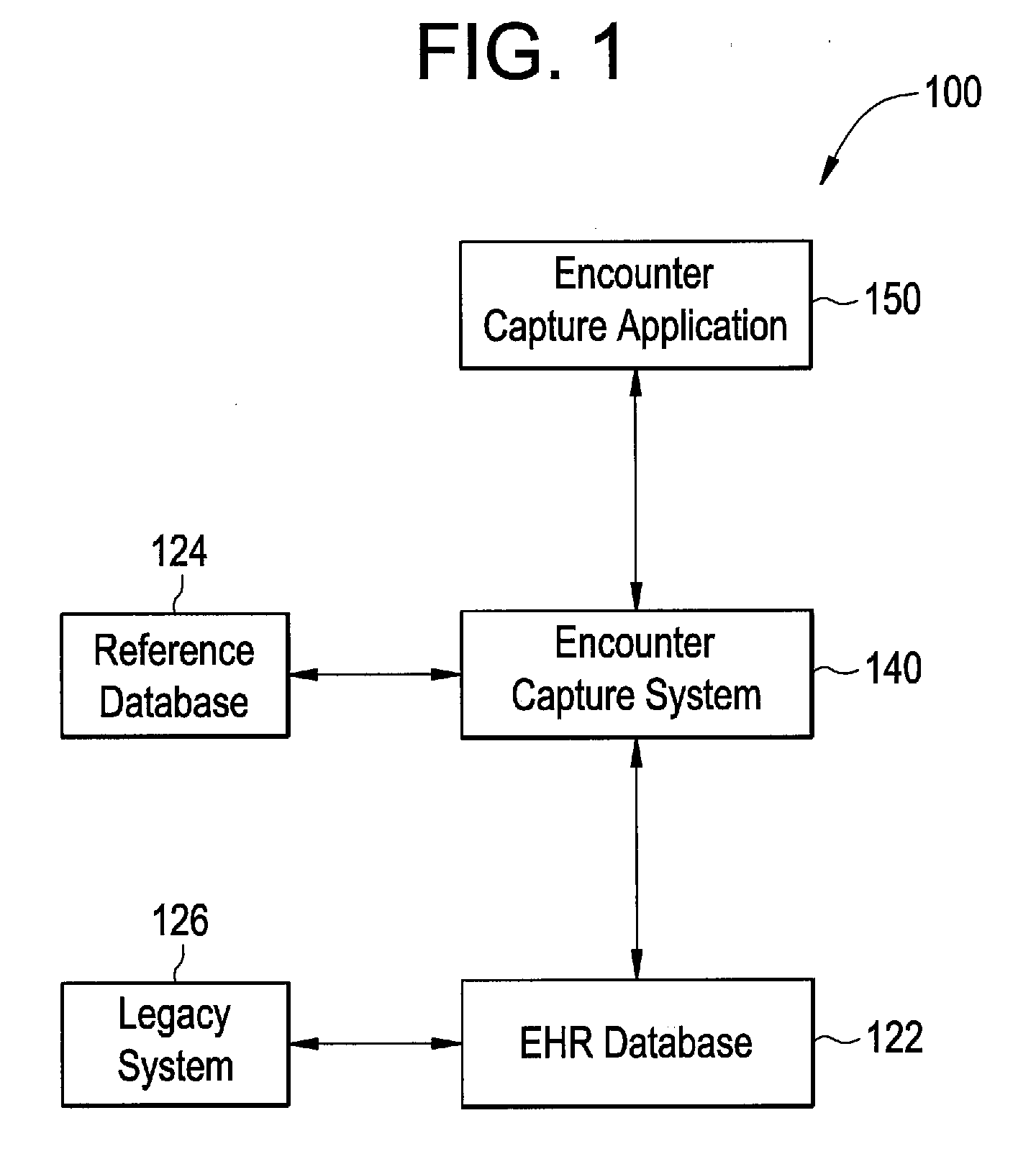
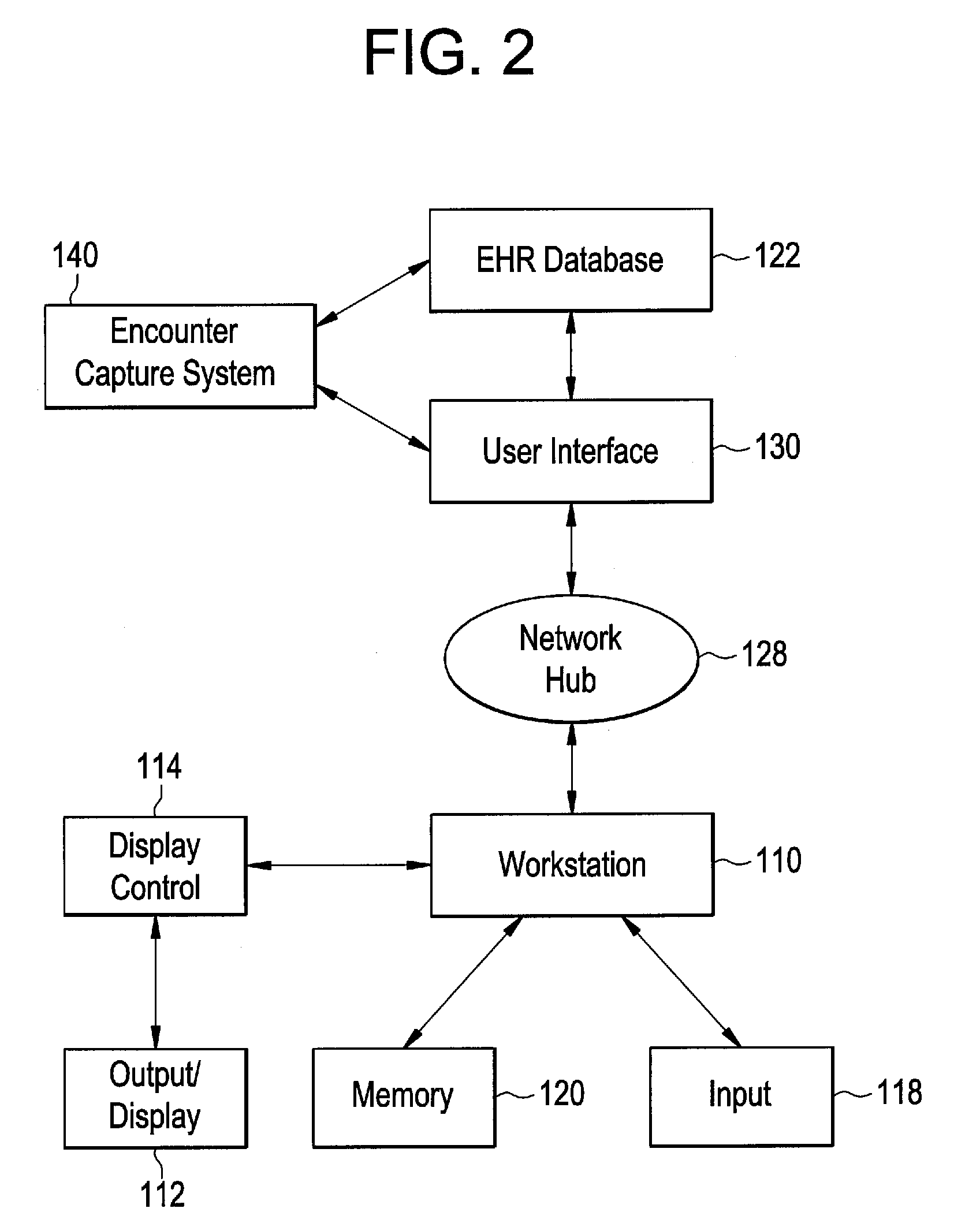
Systems and Methods for Allowing Patient Access to a Patient Electronic Health Records
Methods and systems are provided for providing patient and healthcare providers with access to a patient EHR a computer workstation. A user interface accessible via a network is provided that allows a user to access an EHR system comprising at least one patient EHR. The user is identified using a security administrator, and access is granted and denied based on user identification. The user obtains a patient EHR from the EHR system by providing instructions via the user interface. The user is provided with at least one functionality application allowing a user to add information to the patient EHR. The patient EHR is updated based upon the information entered by the user using the at least one functionality application and storing the updated patient EHR in the EHR database.
Owner:GENERAL ELECTRIC CO
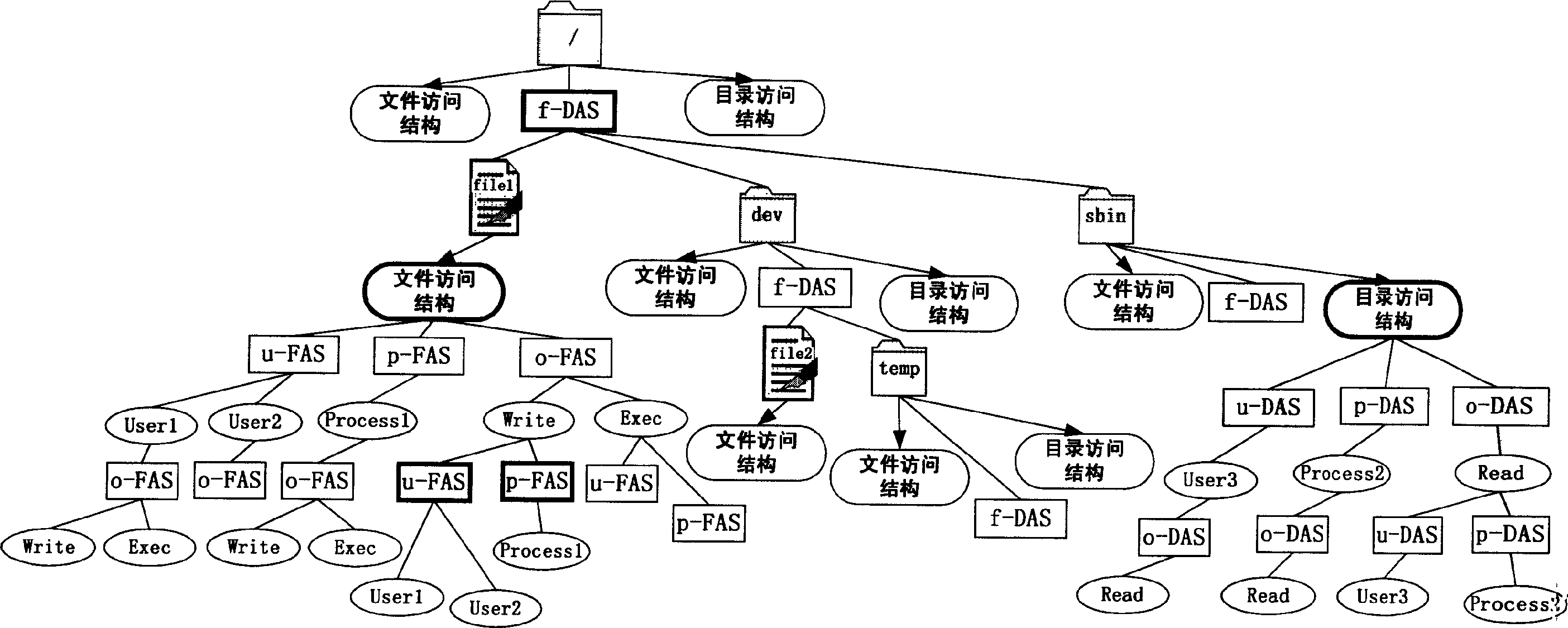
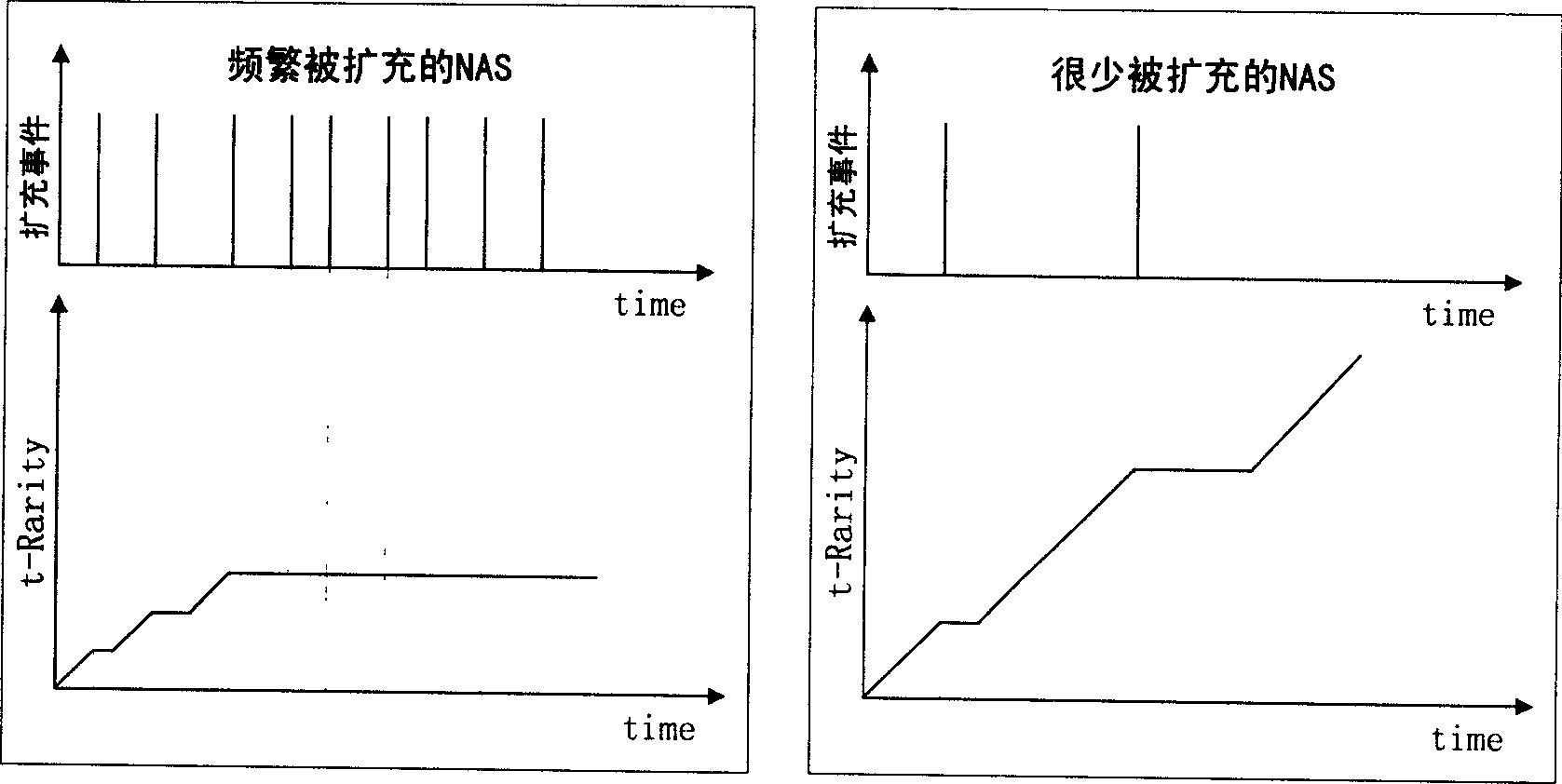
Method for self-adapting testing access of abnormal files
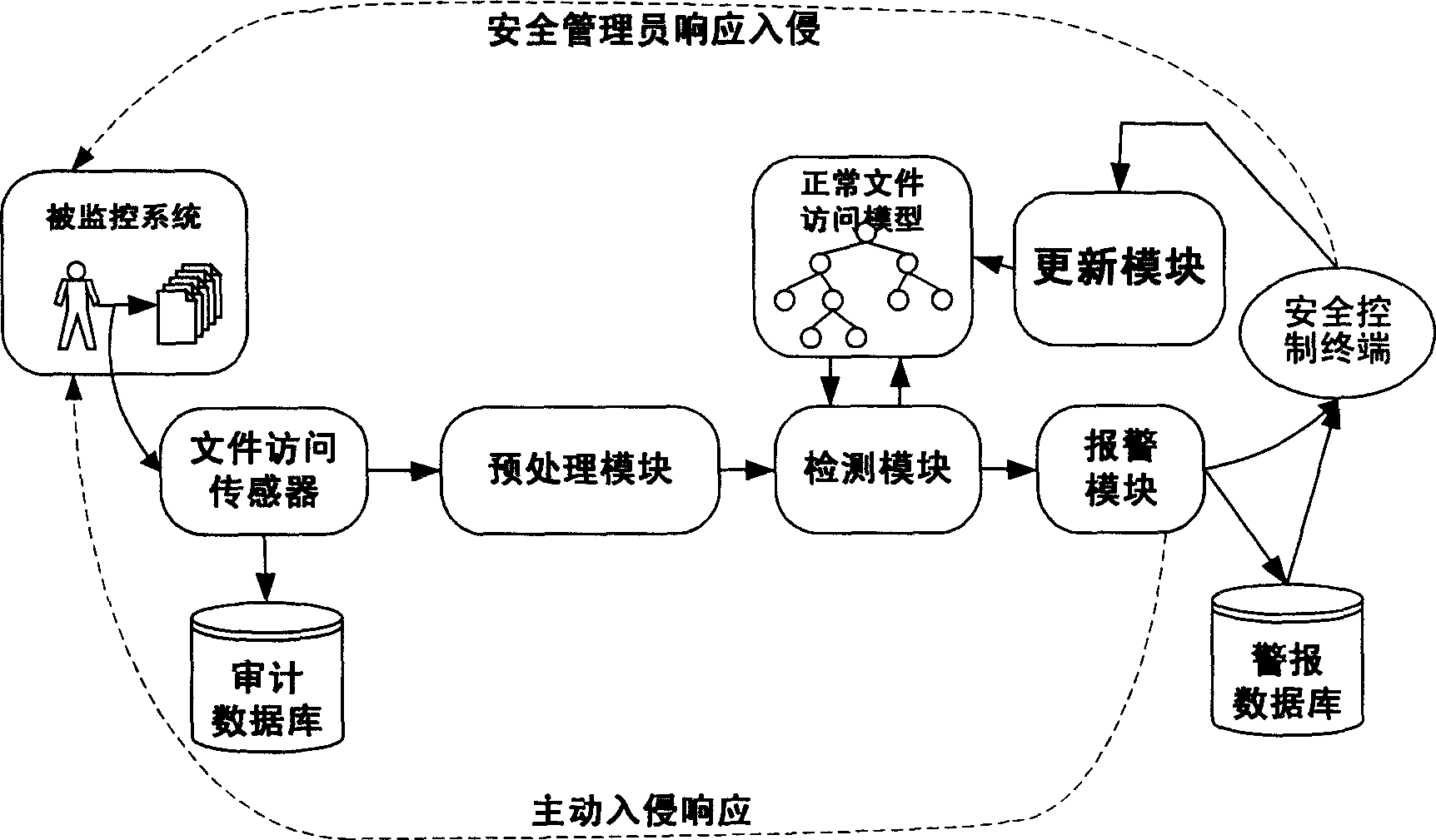
InactiveCN1627699AHandling Time Variation ProperlyBehavioral Models AccurateData taking preventionSelf adaptiveAction model
The method includes following steps: (1) recording request of accessing file resources generated in computer system in real time; (2) carrying out pretreatment for the recorded requests; (3) using relation tree of file access records relation of file access described in access records of normal files; (4) relation tree of file access is divided into two parts of fixed part and variation part based on rarity of time t-Rarity; (5) analyzing records of file access, and selecting normal actions of file access, and reporting abnormal actions of file access to safety officer; (6) updating relation tree of file access periodically, and deleting out outdated relation of file access recorded in relation tree of file access. Mechanisms of selective self-learning and self-adapting forgetting are adopted in the invention. Thus, safe and reliable normal action model is built automatically without manual intervention. The invention detects lots of malicious acts with high precision.
Owner:苏州赛博网垠信息科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com