Method for self-adapting testing access of abnormal files
An adaptive detection and file access technology, applied in data exchange details, data collection and prevention, etc., can solve the problems of failure to propose detection system, time-varying, huge memory overhead, etc., and achieve simple and intuitive file access behavior. The effect of accurate model and easy reporting of results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
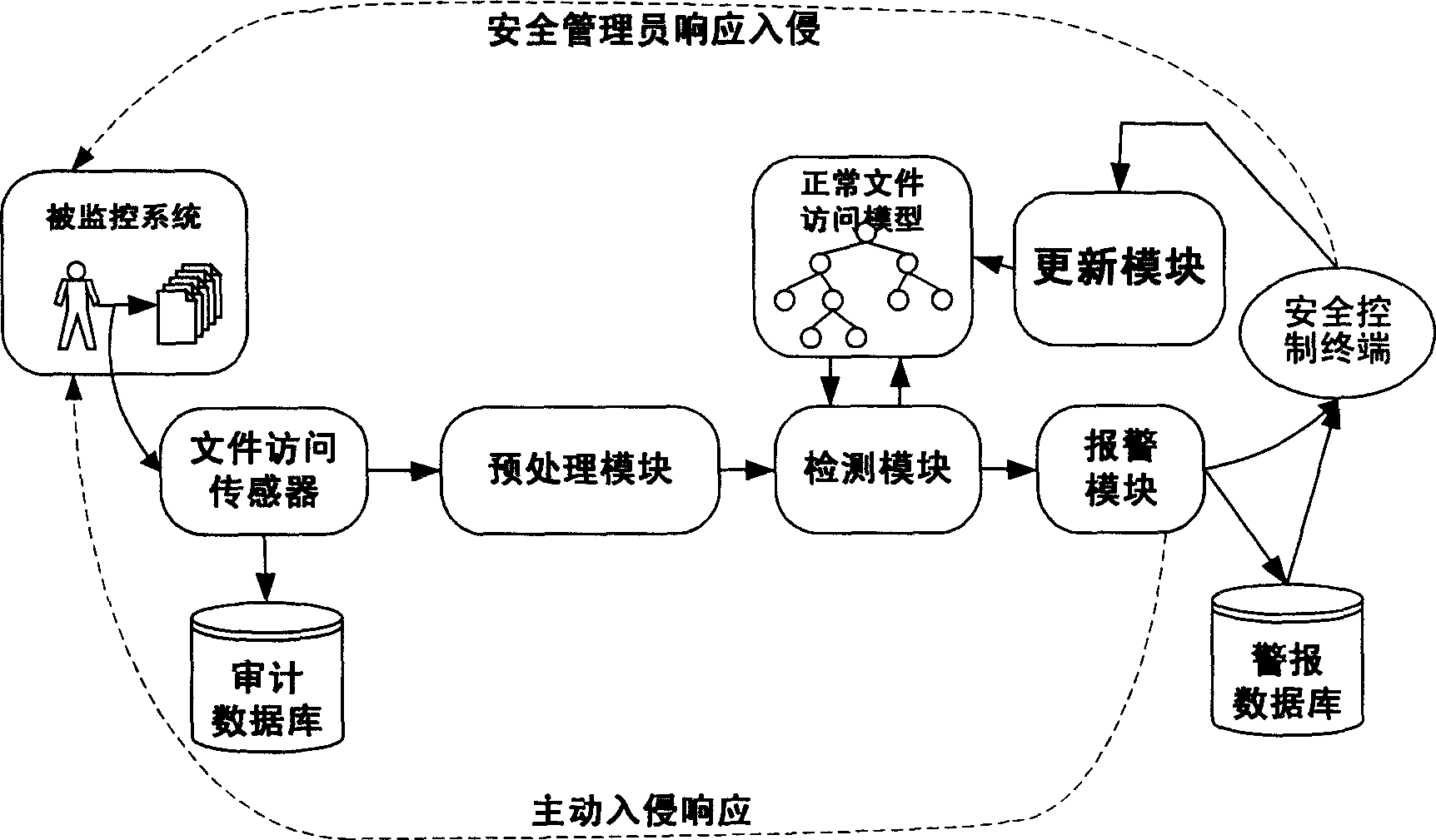
[0026] See figure 1 The specific implementation of the present invention can be based on an Adaptive Detection System for Abnormal File Accesses (ADSAFA). In ADSAFA, the file access sensor is connected to the monitored system, audit database and preprocessing module at the same time, and is connected to the detection module through the preprocessing module. The detection module is interconnected with the normal file access model, and is connected to the security control terminal and alarm database through the alarm module. Connected, the security control terminal and the alarm module are connected to the monitored system through a manual or automatic response mechanism, and the update module is connected to the normal file access model, and the normal model is automatically or compulsorily corrected under the command of the security control terminal.
[0027] The monitored systems are personal computers, various network servers (such as WWW, DNS, mail, database servers, etc.), an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com