Role-based access control method based on three-member management and expansion
A technology of role access control and roles, which is applied in data processing applications, digital data authentication, office automation, etc., can solve the problems of low flexibility of role access control strategies, difficulty in implementation, and coarse control granularity, so as to reduce the complexity of authorization The effects of improving flexibility, improving authorization flexibility, and subdividing control granularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to better understand the technical content of the present invention, specific embodiments are given together with the attached drawings for description as follows.
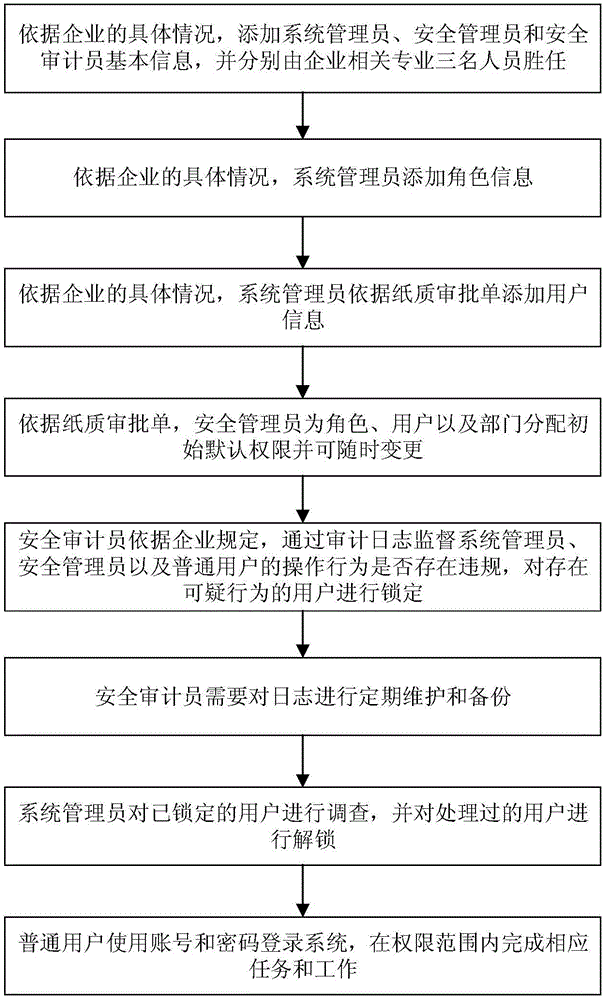
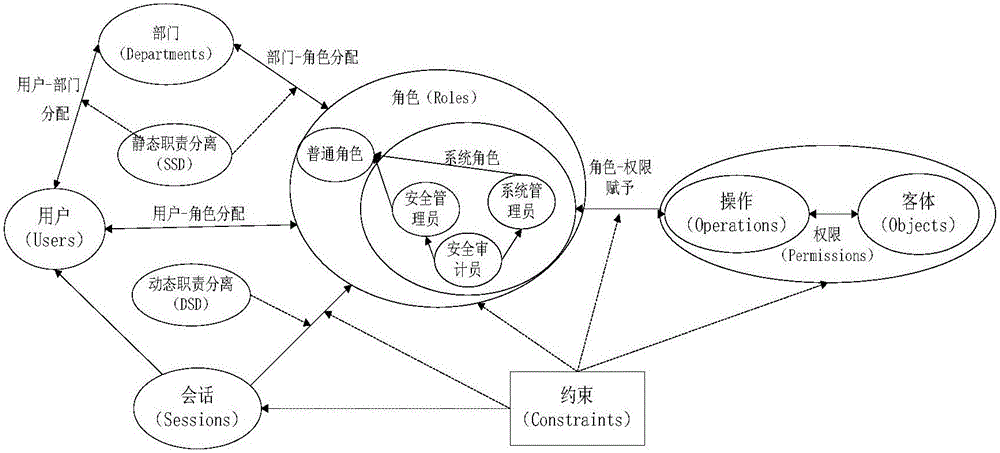
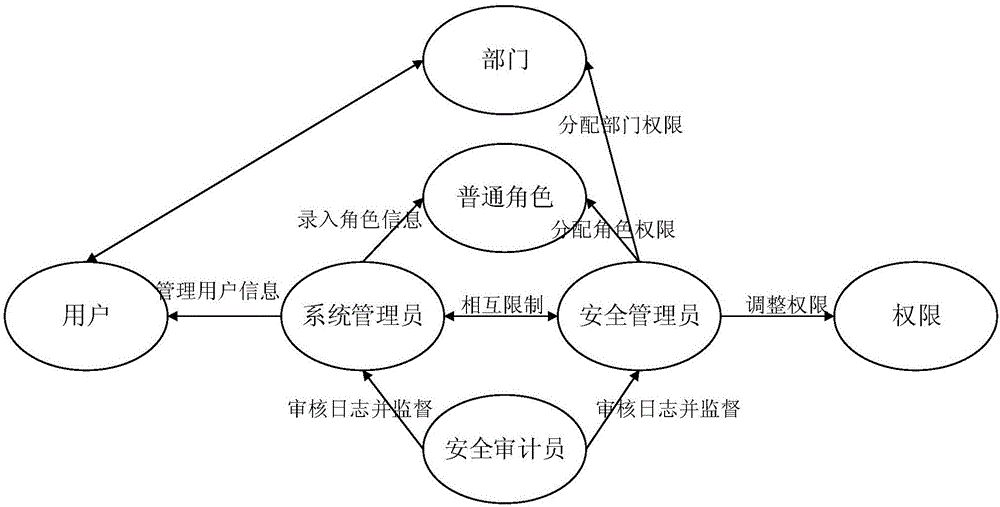
[0035] combine Figure 1-5 As shown, the role access control method based on three-person management and expansion proposed by the present invention enables the role access control strategy based on three-person management and expansion to be widely used in enterprise information systems, and through this strategy, users can be better assigned permissions , and at the same time, subdivided system roles can cooperate and restrict each other, which greatly avoids the abuse of permissions.
[0036] combine figure 1 , the role access control method based on three-person management and expansion includes the following steps:
[0037] Step 1. Establish a three-person management system in the information management system: a system administrator, a security administrator, and a security auditor, wherein...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com