Patents
Literature
55 results about "Configuration Issue" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
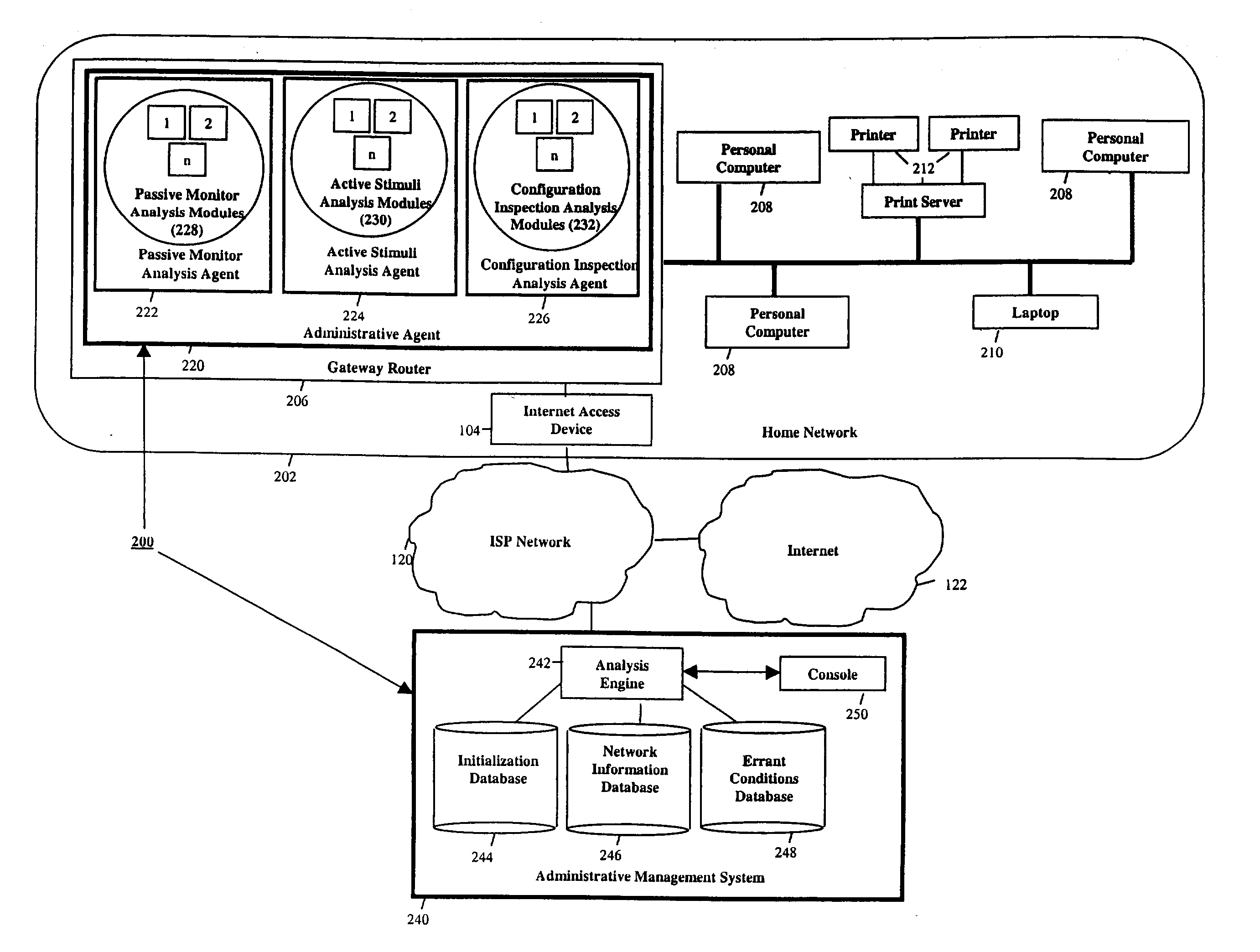
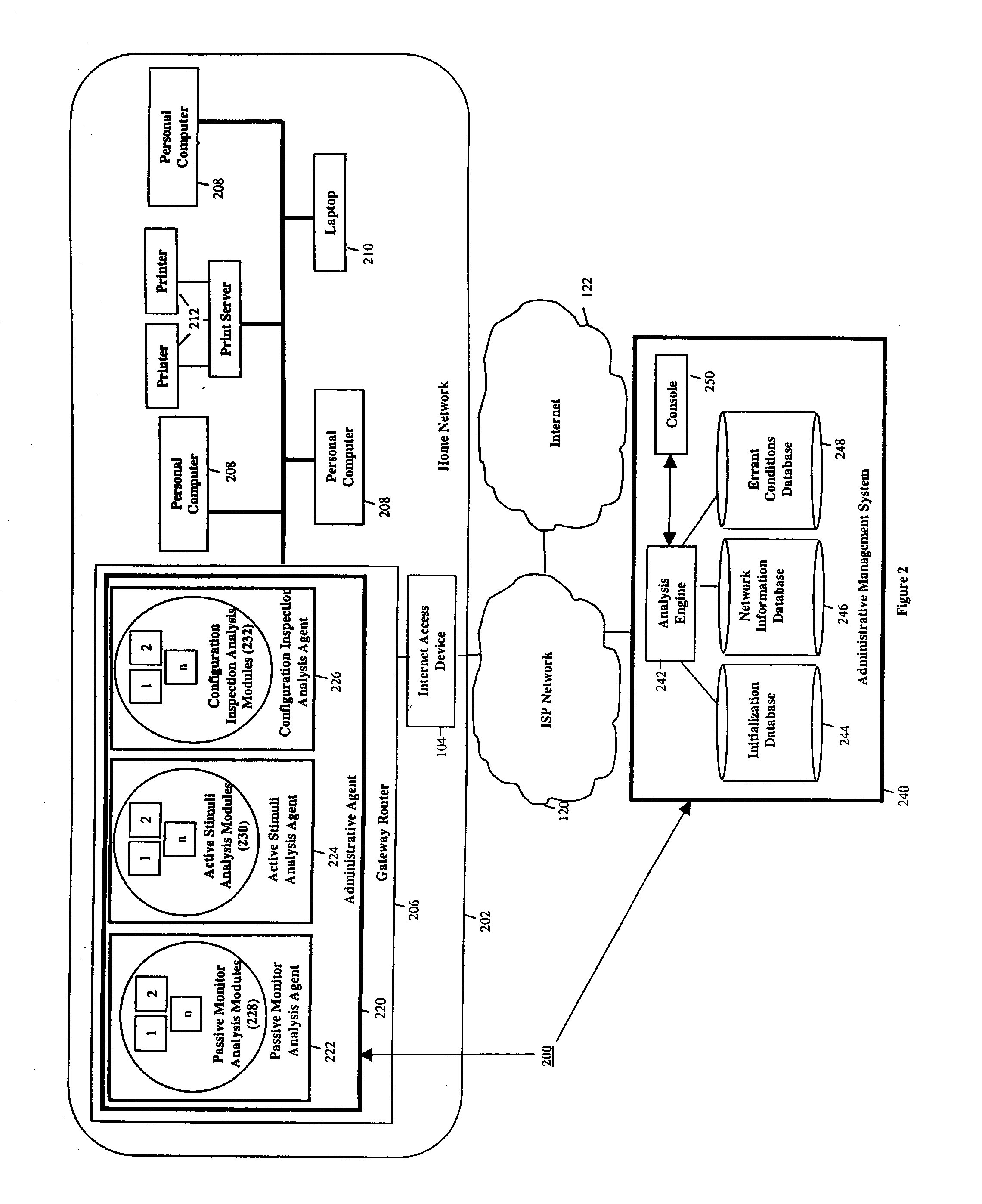
Detecting errant conditions affecting home networks
InactiveUS20040049714A1Hardware monitoringHome automation networksNetwork information flowAdministrative management
Errant conditions, including configuration issues, device / application failures, and performance problems, affecting a home network are detected by considering end-to-end information flows within the home network and between the home network and an external network. Specifically, errant conditions are detected by analyzing monitored network information flows, by analyzing responses resulting from the active stimuli of hardware / software components within the home and external network, and by considering in this analysis configuration information obtained from network devices. Gathered information and detected errant conditions are reported to an administrative management system for further analysis and for use by a help-desk administrator or home user in resolving the reported conditions.
Owner:TELCORDIA TECHNOLOGIES INC
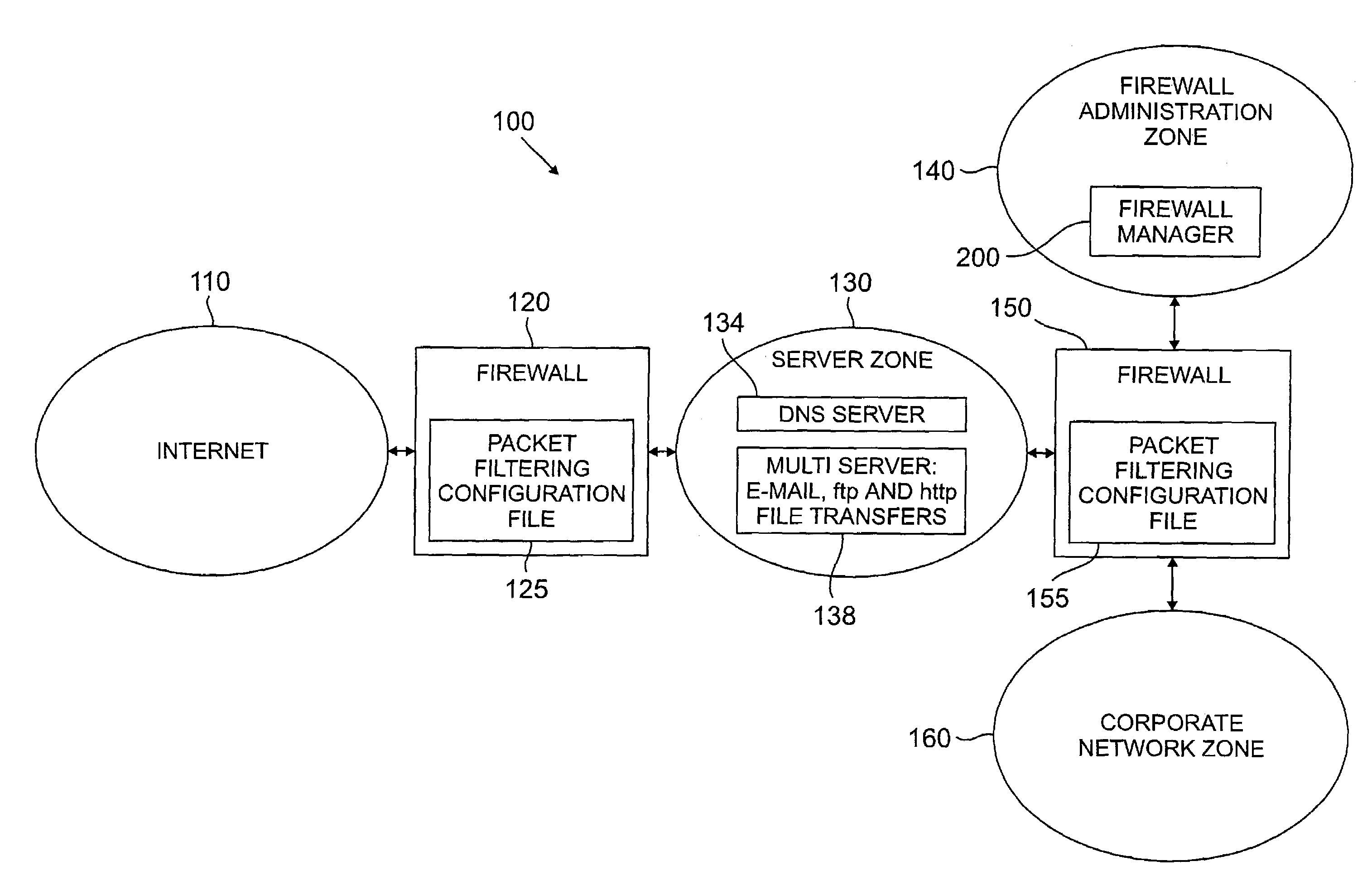
Method and apparatus for managing a firewall
InactiveUS7146639B2Promote generationDigital data processing detailsMultiple digital computer combinationsNetwork topologyConfiguration Issue
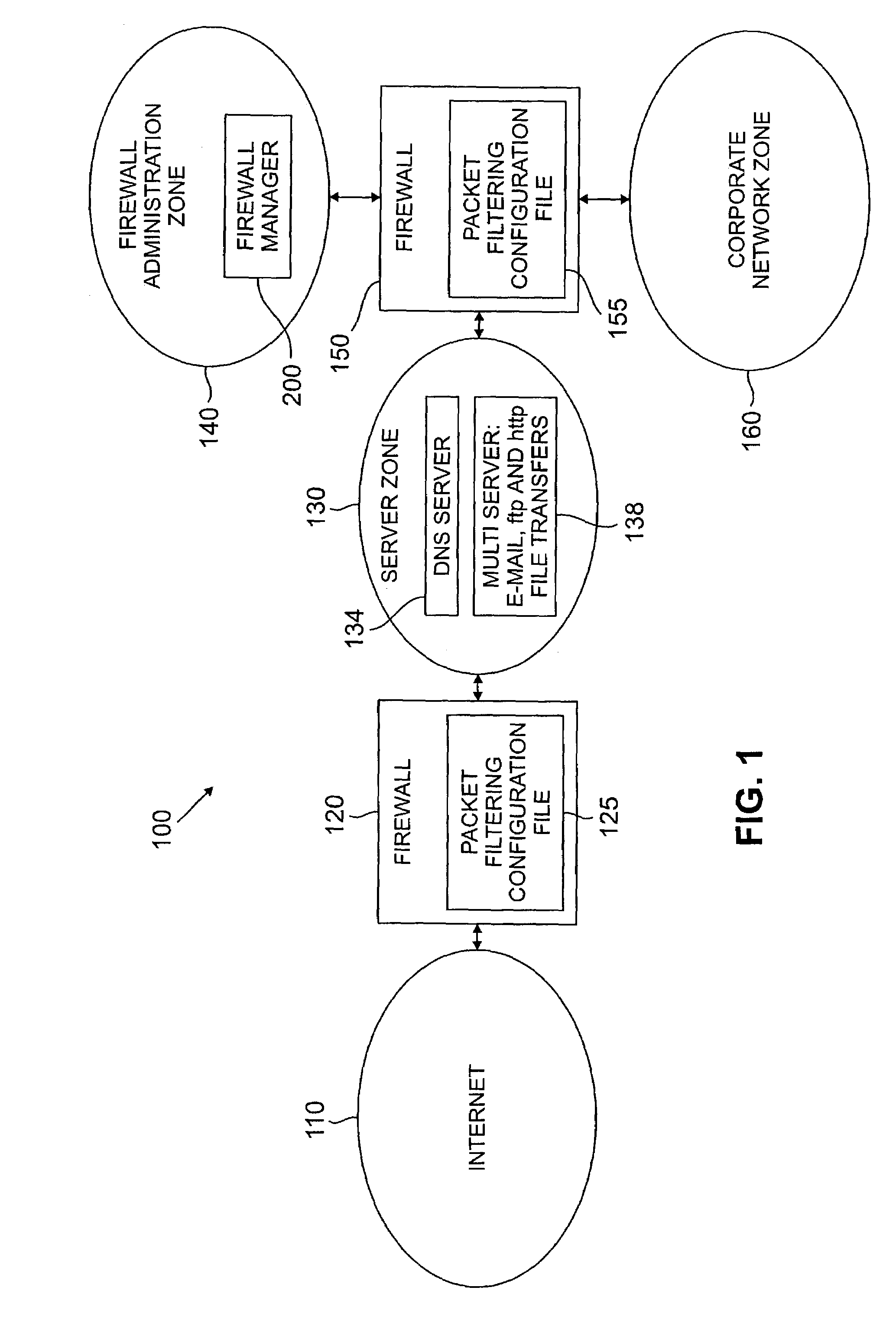
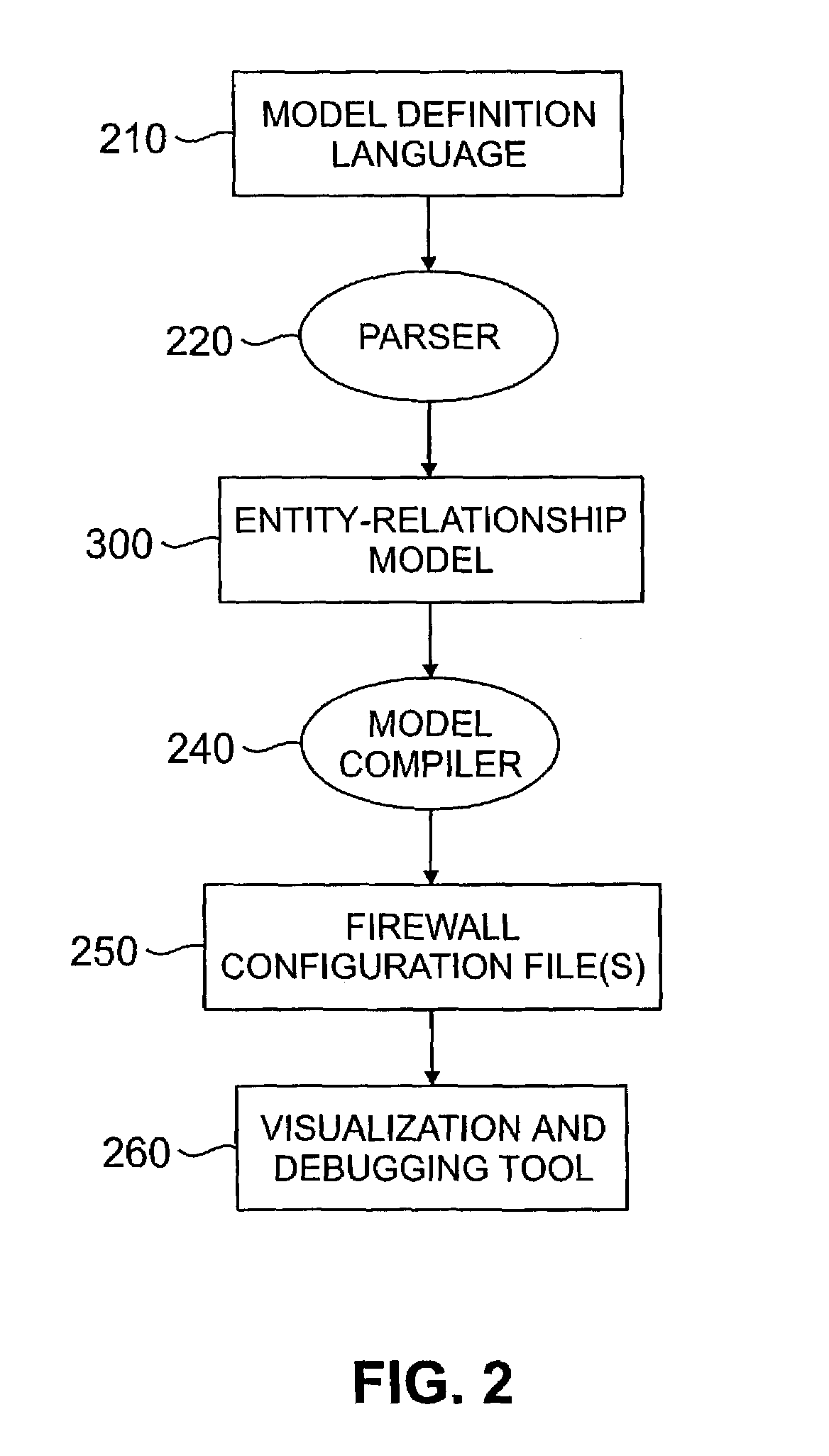
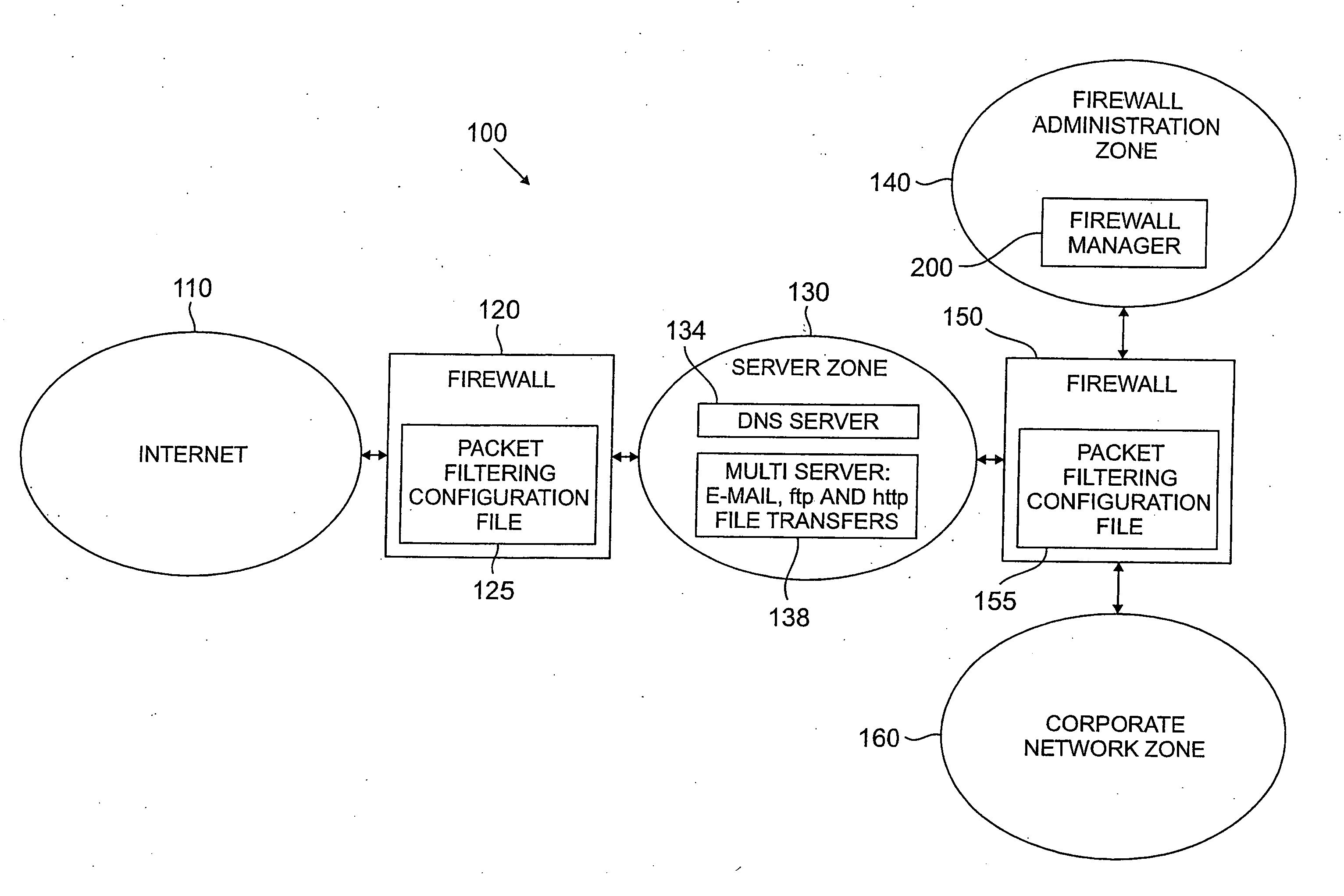
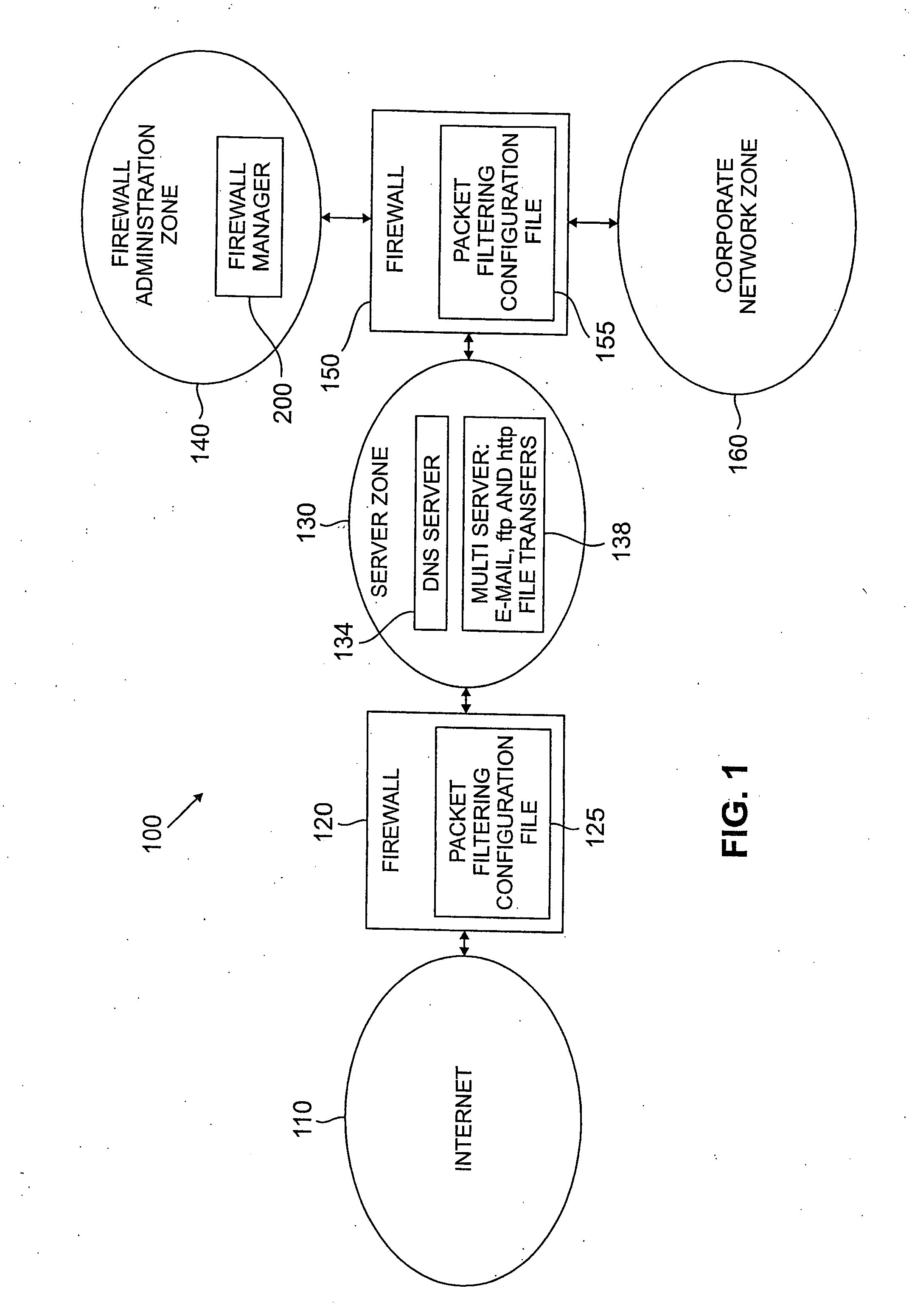
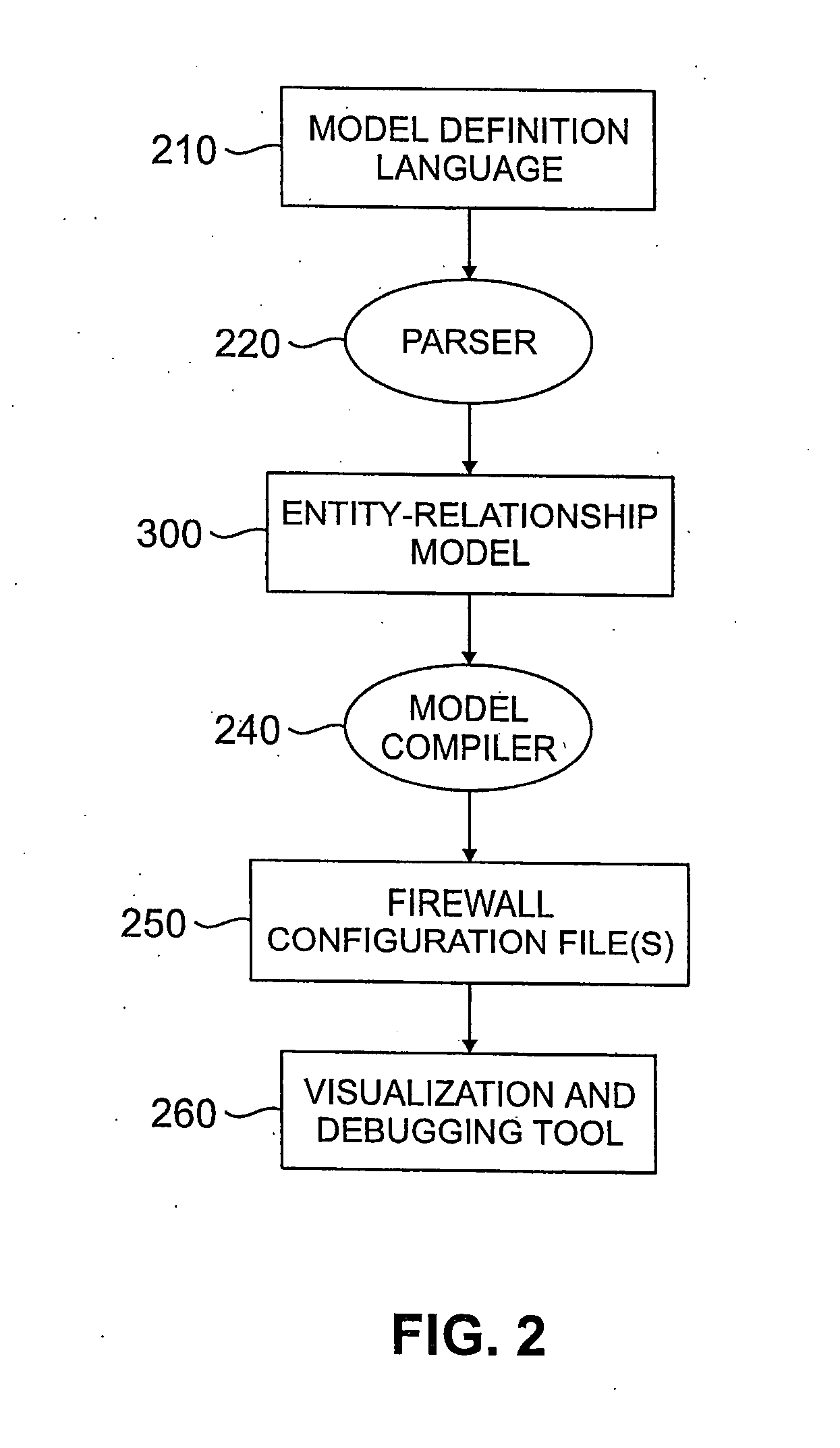
A method and apparatus are disclosed for managing a firewall. The disclosed firewall manager facilitates the generation of a security policy for a particular network environment, and automatically generates the firewall-specific configuration files from the security policy simultaneously for multiple gateways. The security policy is separated from the vendor-specific rule syntax and semantics and from the actual network topology. Thus, the security administrator can focus on designing an appropriate policy without worrying about firewall rule complexity, rule ordering, and other low-level configuration issues. In addition, the administrator can maintain a consistent policy in the presence of intranet topology changes. The disclosed firewall manager utilizes a model definition language (MDL) and an associated parser to produce an entity relationship model. A model compiler translates the entity-relationship model into the appropriate firewall configuration files. The entity-relationship model provides a framework for representing both the firewall-independent security policy, and the network topology. The security policy is expressed in terms of “roles,” which are used to define network capabilities of sending and receiving services. A role may be assumed by different hosts or host-groups in the network. A visualization and debugging tool is provided to transform the firewall-specific configuration files into a graphical representation of the current policy on the actual topology, allowing the viability of a chosen policy to be evaluated. A role-group may be closed to prevent the inheritance of roles.
Owner:LUCENT TECH INC
Method for measuring reference signal between UE (user equipment) and base station and base station
InactiveCN102711167ASwitch accuratelyAccurate measurementWireless communicationEngineeringUser equipment
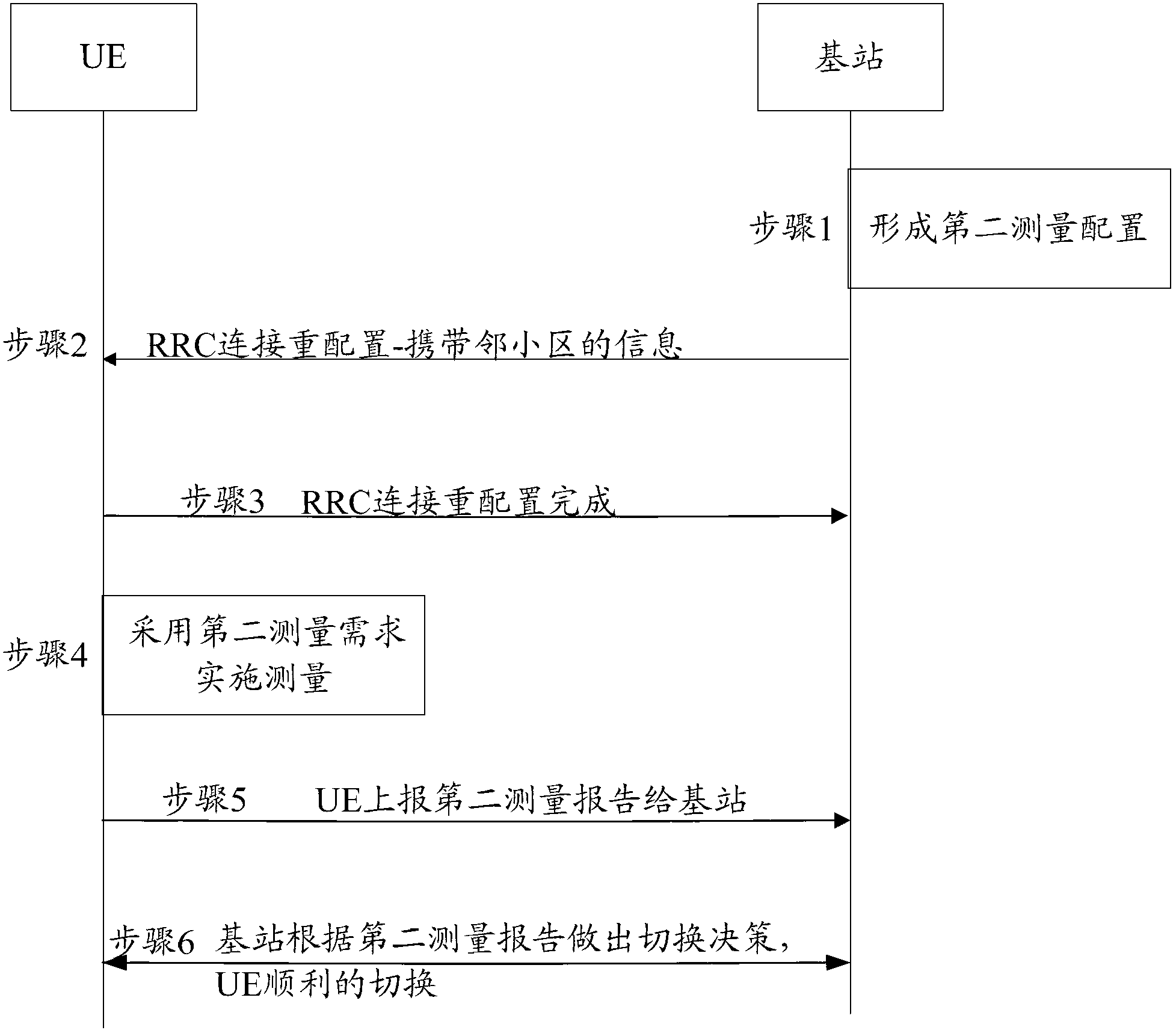
The embodiment of the invention provides a method for measuring a reference signal between UE (user equipment) and a base station and the base station. The method is applied to the base station and comprises the following steps: receiving a first measurement report reported by a first measurement configuration issued by the UE on the basis of the base station; when a distance between the position of the UE and an adjacent cell is determined to be smaller than a first distance threshold value according to the first measurement report, sending a second measurement configuration to the UE to indicate the UE to measure a reference signal of the adjacent cell according to an appointed second measurement period in the second measurement configuration, wherein the second measurement period is shorter than a corresponding first measurement period in the first measurement configuration; and receiving a measurement result which is acquired and encapsulated in a second measurement report by the UE after the adjacent cell is measured according to the second measurement period. In a moving process of the UE, after the second measurement configuration from the base station is received, the adjacent cell is measured in the second measurement period, and a more precise result is reported to the base station, so that the base station can be used for carrying out accurate switching between cells for the UE.
Owner:ZTE CORP
Method and apparatus for managing a firewall
InactiveUS20060288409A1Promote generationMultiple digital computer combinationsProgram controlNetwork topologyConfiguration Issue
A method and apparatus are disclosed for managing a firewall. The disclosed firewall manager facilitates the generation of a security policy for a particular network environment, and automatically generates the firewall-specific configuration files from the security policy simultaneously for multiple gateways. The security policy is separated from the vendor-specific rule syntax and semantics and from the actual network topology. Thus, the security administrator can focus on designing an appropriate policy without worrying about firewall rule complexity, rule ordering, and other low-level configuration issues. In addition, the administrator can maintain a consistent policy in the presence of intranet topology changes. The disclosed firewall manager utilizes a model definition language (MDL) and an associated parser to produce an entity relationship model. A model compiler translates the entity-relationship model into the appropriate firewall configuration files. The entity-relationship model provides a framework for representing both the firewall-independent security policy, and the network topology. The security policy is expressed in terms of “roles,” which are used to define network capabilities of sending and receiving services. A role may be assumed by different hosts or host-groups in the network. A visualization and debugging tool is provided to transform the firewall-specific configuration files into a graphical representation of the current policy on the actual topology, allowing the viability of a chosen policy to be evaluated. A role-group may be closed to prevent the inheritance of roles.
Owner:BARTAL YAIR +2
Method for realizing configuration synchronization of network elements and webmaster
ActiveCN102231679AQuickly locate configuration differencesSync configurationData switching networksConfiguration itemNetwork packet
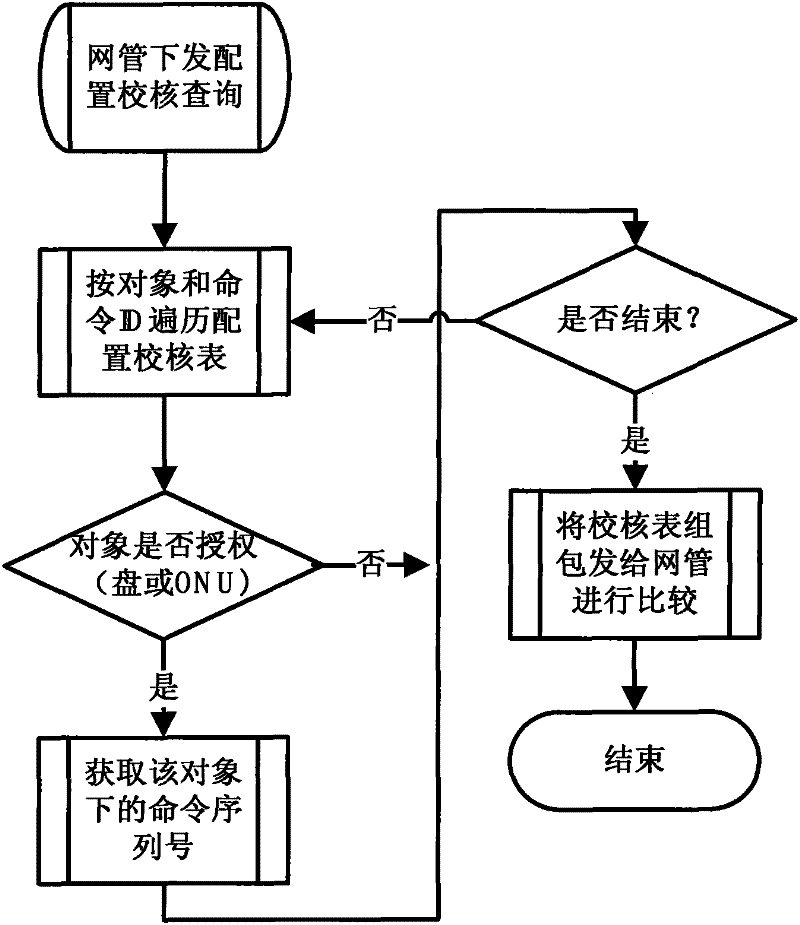
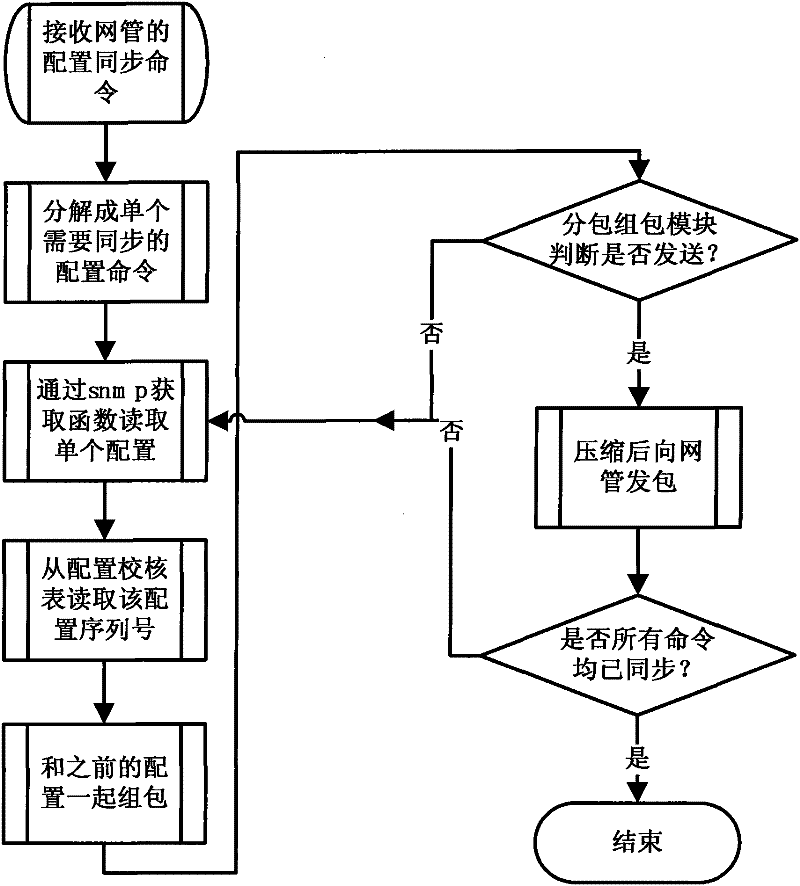
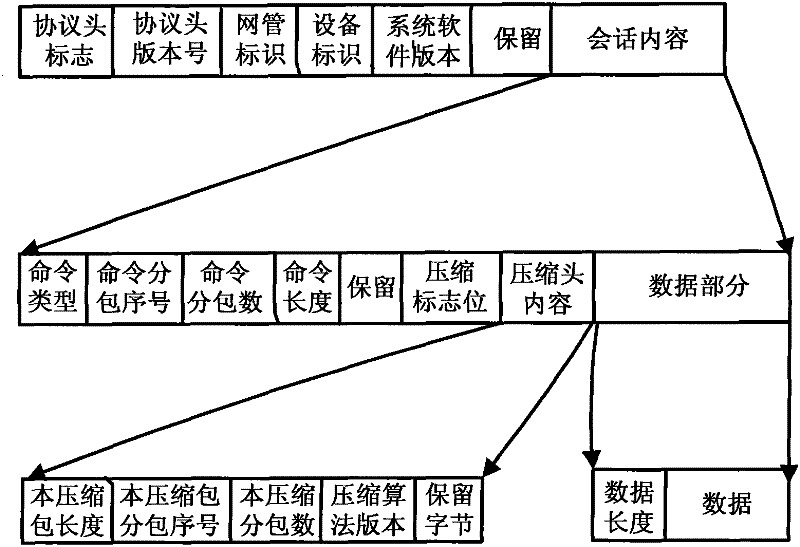
The invention discloses a method for realizing the configuration synchronization of network elements and a webmaster, and the method comprises the following steps: A. carrying out unique identification on each configuration of the network elements in a command ID (identifier) mode, loading a configuration item marked with a command ID into each network element, configuring a serial number for each command ID, and storing the configuration information of each network element in a master control disk reference table; B. when the network elements initiate the synchronization to the webmaster or the webmaster initiates the synchronization to the network elements, comparing the configuration item of each network element which is stored in the database of the webmaster and the master control disk reference table, adding the different configuration items in the comparison result into a configuration issuing sequence, and preparing the configuration of the data; and C. sending and receiving synchronization data packets in subpackage and compression package modes. The method disclosed by the invention can be used for reliably and effectively realizing the configuration synchronization of the network elements and the webmaster in a time saving mode.
Owner:FENGHUO COMM SCI & TECH CO LTD
Secure mobile office wireless local-area network application integration package running from CD-ROM
InactiveUS7464403B2Digital data processing detailsComputer security arrangementsOperational systemOff the shelf
This Invention permits very rapid installation of operating systems onto off-the-shelf hardware. Furthermore, this Invention addresses multiple configuration issues pertaining to the creation of unique “InterNet Hosts”, and thus enables the very rapid installation of operating systems preconfigured to boot into a “ready to internetwork” mode with no subsequent configuration needs. It integrates several different existing security and encryption models which are considered robust. Further, the media on which this Invention will be distributed, and from which it will be run, are read-only CD-ROM, providing further defense against InterNet-based attacks.A variety of scripts generates a series of CD-ROMs which will each boot an Intel-ix86-based PC to an individual network identity, all of which will have the characteristics listed above, and will automatically network if provided with the IEEE 802.11b standard wireless PC Cards.
Owner:HARDMAN JR THOMAS JAMES
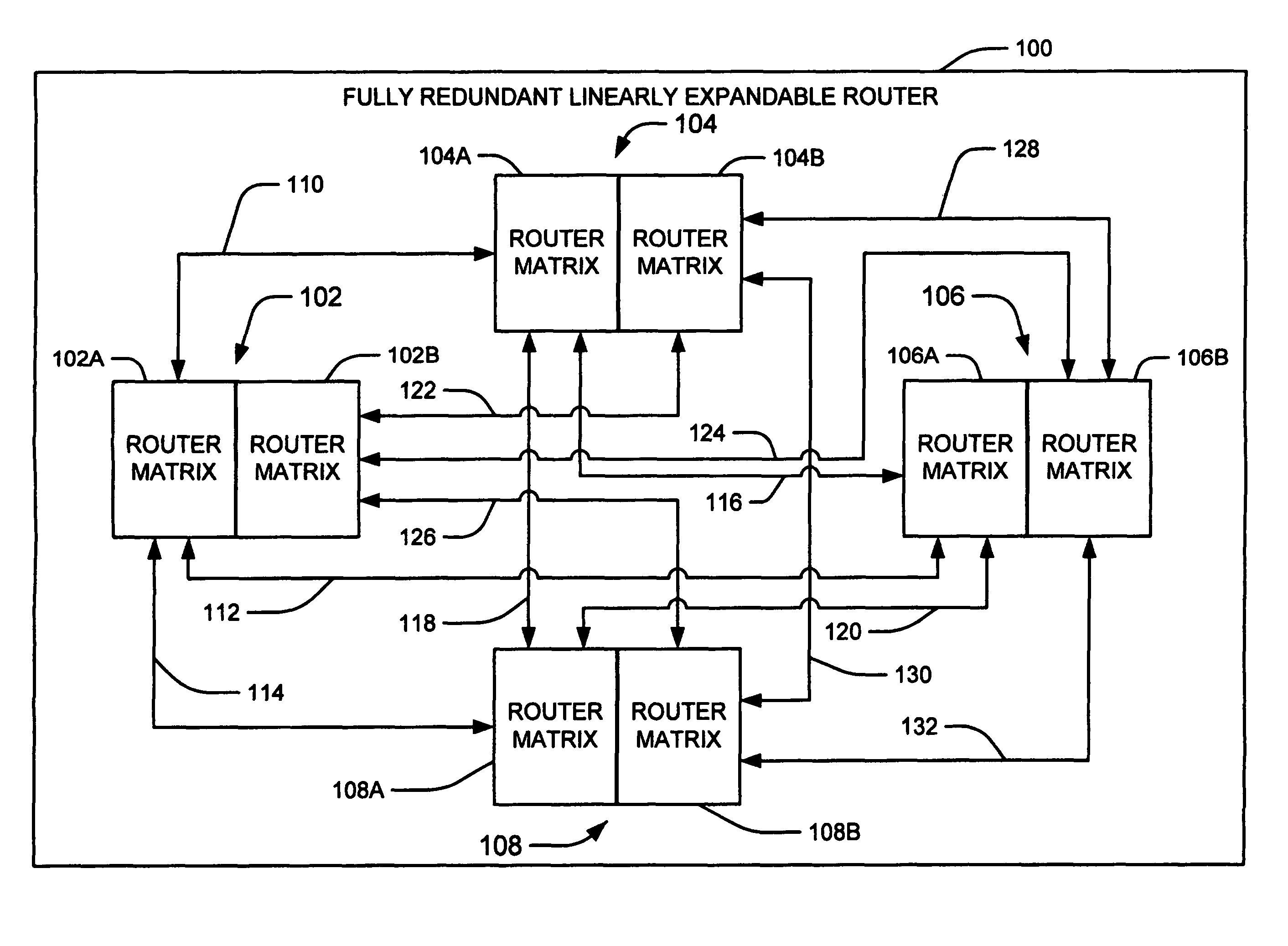
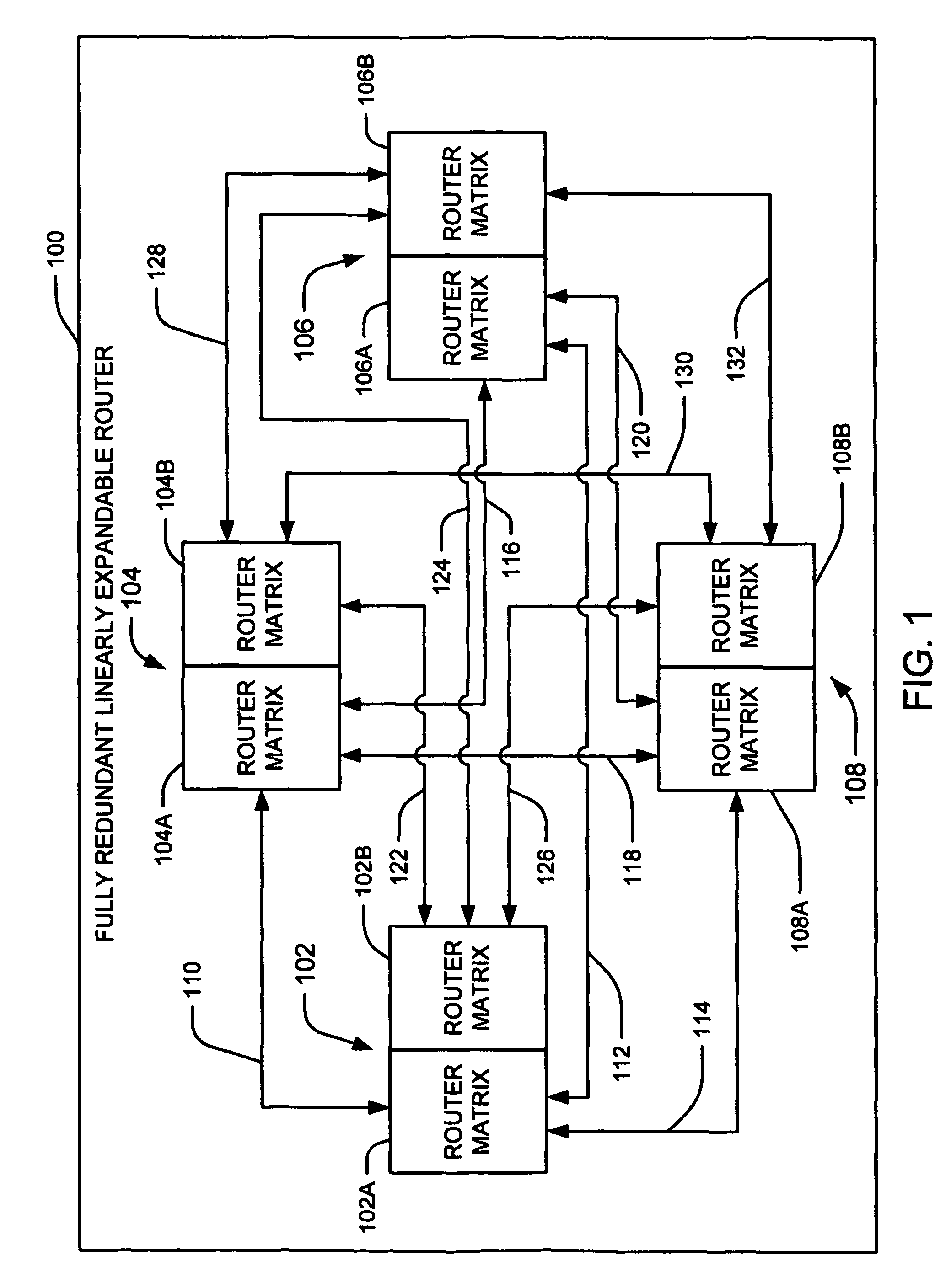
Broadcast router having a shared configuration repository
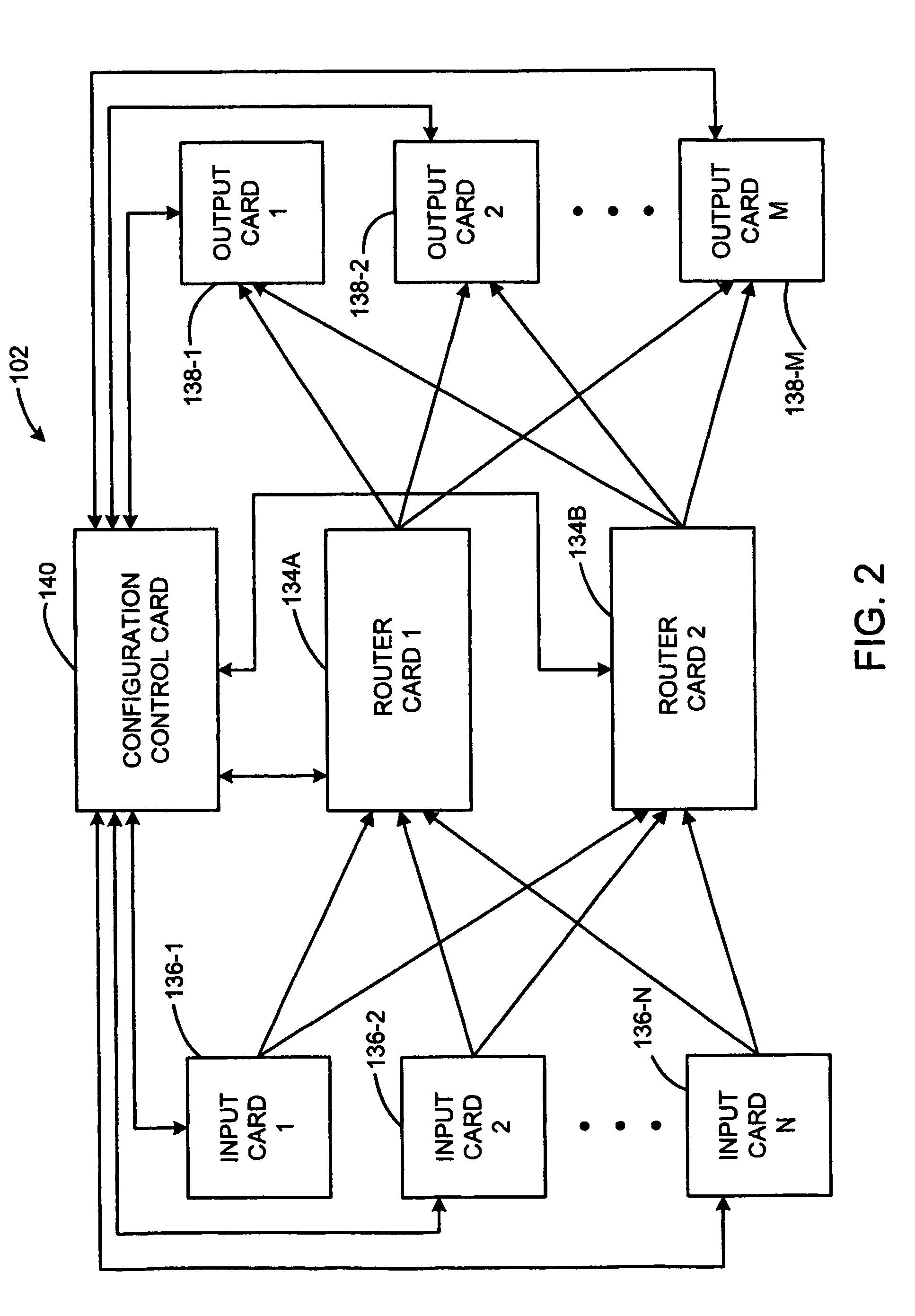
InactiveUS7805766B2Volume/mass flow measurementUnauthorized memory use protectionInformation repositoryBroadcasting
A broadcast router includes plural input cards, first and second router matrix card and plural output cards. Programmable devices residing on the cards requiring configuration issue a request for configuration to a main controller which resides, with a shared configuration information repository on a configuration control card. After a period of time which allows additional programmable devices to request configuration elapses, the main controller polls the programmable devices residing on the cards to determine which of the programmable devices had requested configuration and, using the configuration information maintained in the shared configuration information repository, configures each programmable device which had requested configuration.
Owner:THOMSON LICENSING SA
Complex configuration processing using configuration sub-models
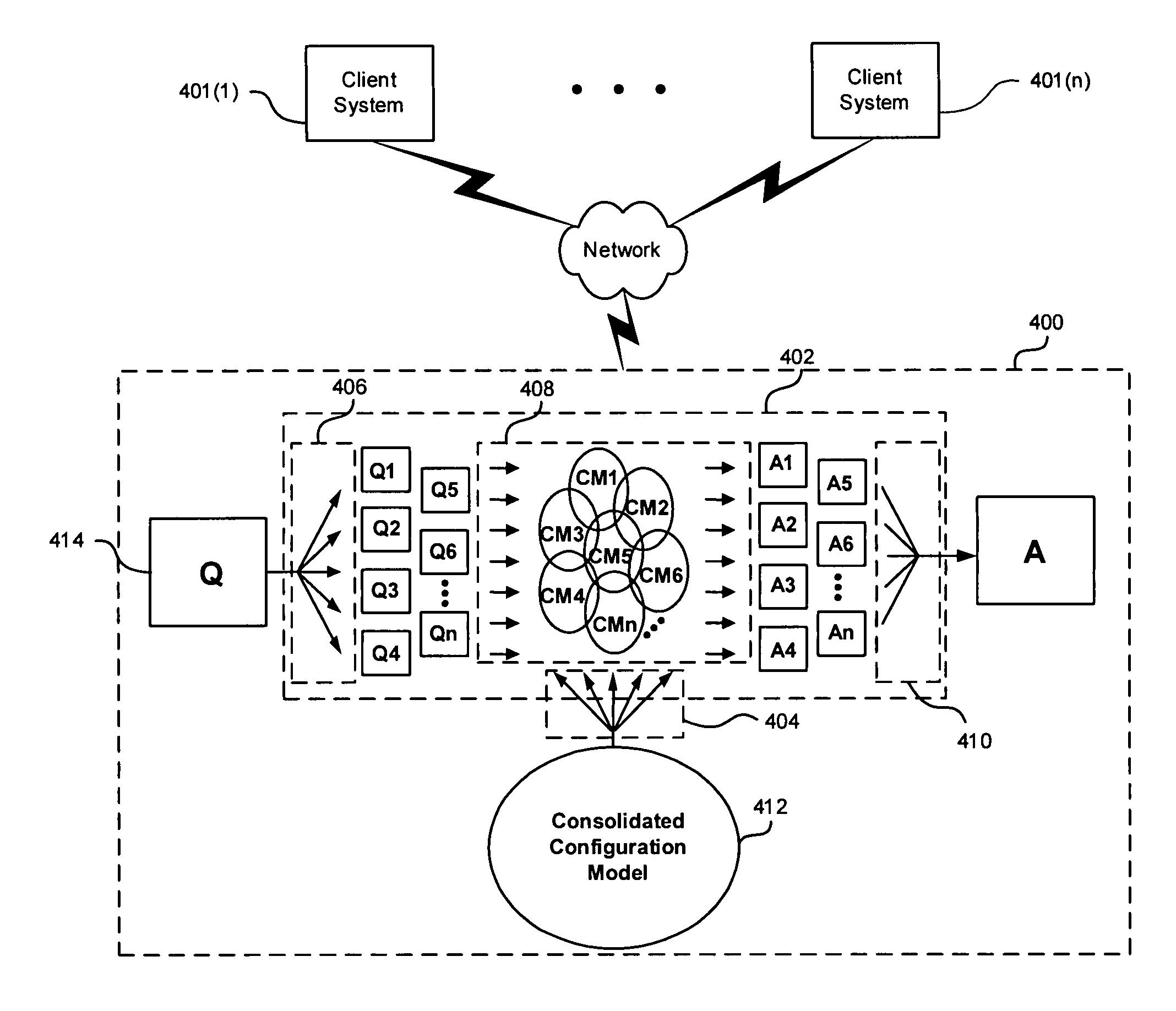
ActiveUS7882057B1Solve the real problemResourcesComputer aided designData processing systemAlgorithm
A configuration model dividing and configuration sub-model inference processing system and procedure addresses the issue of configuration model and query complexity by breaking a configuration problem down into a set of smaller problems, solving them individually and recombining the results into a single result that is equivalent to a conventional inference procedure. In one embodiment, a configuration model is divided into configuration sub-models that can respectively be processed using existing data processing resources. A sub-model inference procedure provides a way to scale queries to larger and more complicated configuration models. Thus, the configuration model dividing and configuration sub-model processing system and inference procedure allows processing by a data processing system of configuration models and queries whose collective complexity exceeds the complexity of otherwise unprocessable conventional, consolidated configuration models and queries.
Owner:VERSATA DEV GROUP
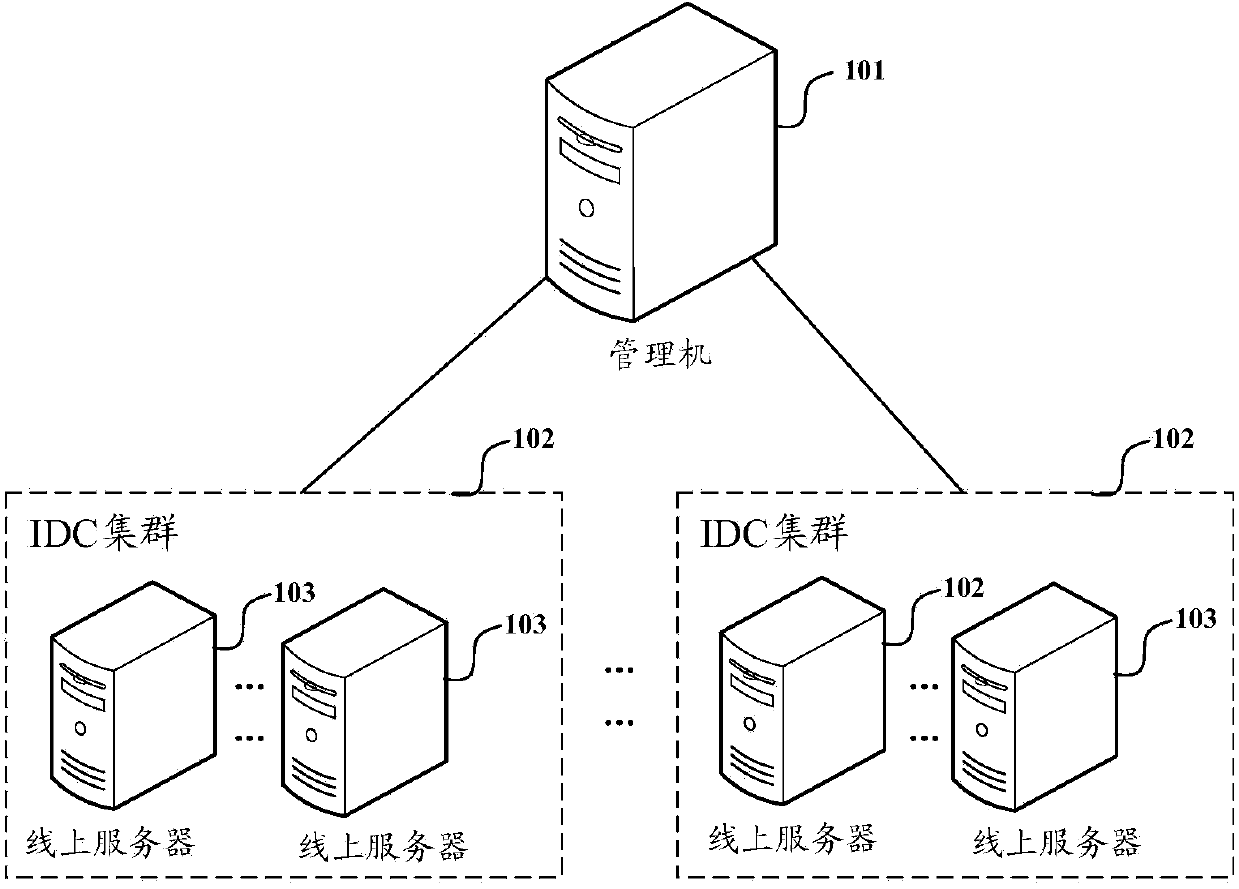
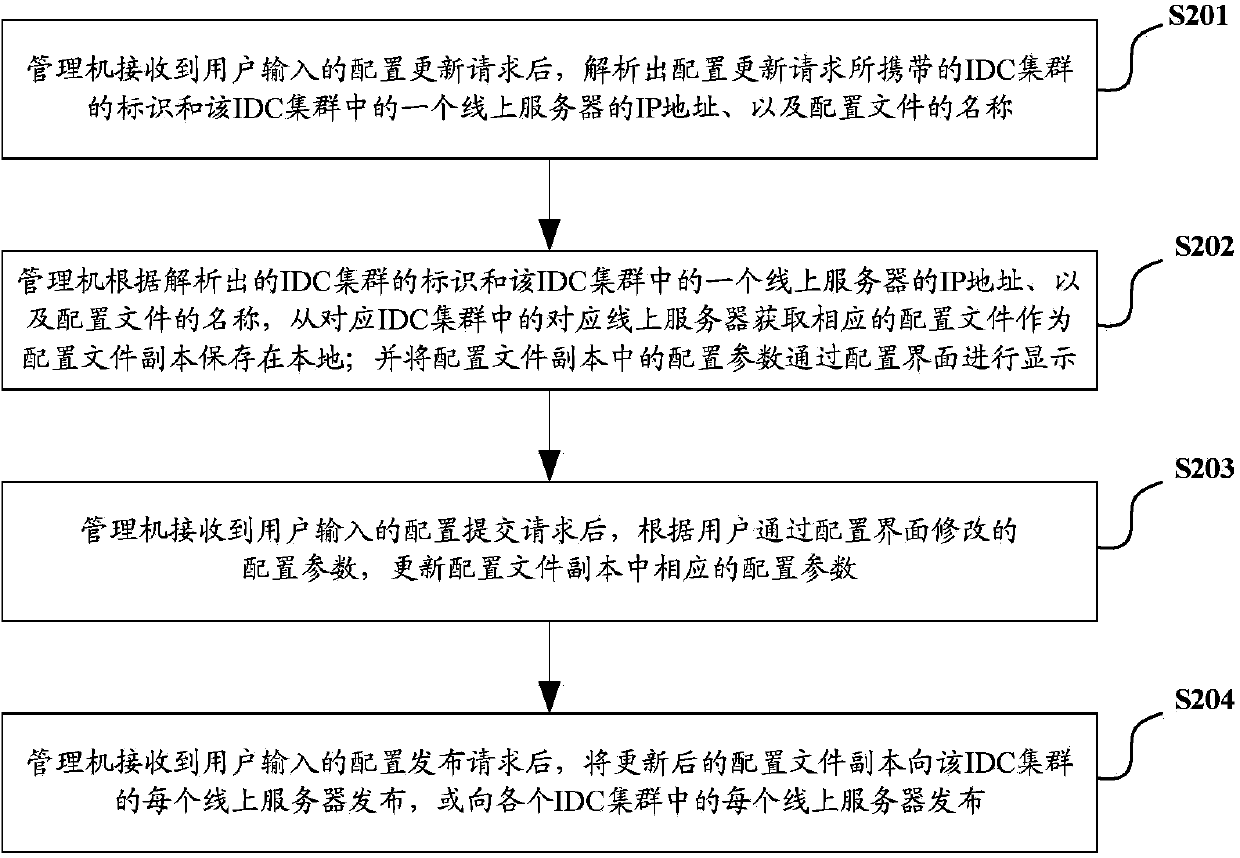
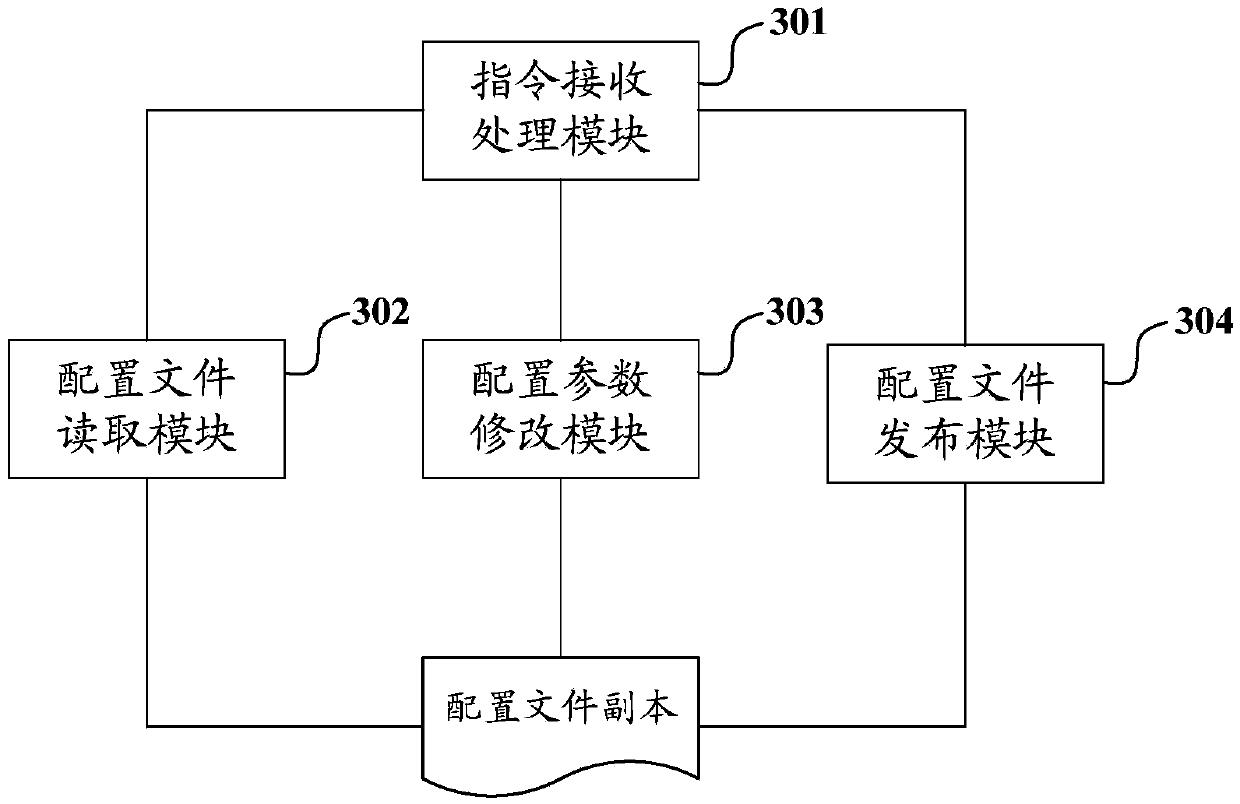
Method, system and equipment for managing multi-IDC (internet data center) cluster configuration file
ActiveCN103634144AEasy to manageReduce complexityData switching networksIp addressConfiguration Issue
The invention discloses a method, a system and equipment for managing a multi-IDC (internet data center) cluster configuration file. The method comprises the steps that according to the logo of the IDC cluster carried by a configuration updating request, the IP (internet protocol) address of one online server in the IDC cluster and the name of a configuration file, a supervisor acquires a corresponding configuration file as the copy of the configuration file to locally store the copy from the corresponding online server in the corresponding IDC cluster and displays configuration parameters in the copy of the configuration file by a configuration interface; after a configuration submit request is received, the corresponding configuration parameters in the copy of the configuration file are updated according to the configuration parameters modified through the configuration interface by a user; after a configuration issuing request is received, the copy of the configuration file is issued to each online server in the IDC cluster or is issued to each online server in each IDC cluster. Therefore, the management on the configuration file of multiple IDC clusters is realized by a simple logic, the management is more convenient and the stability of the online servers is higher.
Owner:新浪技术(中国)有限公司
Secure mobile office wireless local-area network application integration package running from CD-ROM
InactiveUS20070283339A1Digital data processing detailsComputer security arrangementsOperational systemCD-ROM
This Invention permits very rapid installation of operating systems onto off-the-shelf hardware. Furthermore, this Invention addresses multiple configuration issues pertaining to the creation of unique “InterNet Hosts”, and thus enables the very rapid installation of operating systems preconfigured to boot into a “ready to internetwork” mode with no subsequent configuration needs. It integrates several different existing security and encryption models which are considered robust. Further, the media on which this Invention will be distributed, and from which it will be run, are read-only CD-ROM, providing further defense against InterNet-based attacks. A variety of scripts generates a series of CD-ROMs which will each boot an Intel-ix86-based PC to an individual network identity, all of which will have the characteristics listed above, and will automatically network if provided with the IEEE 802.11b standard wireless PC Cards.
Owner:HARDMAN JR THOMAS JAMES
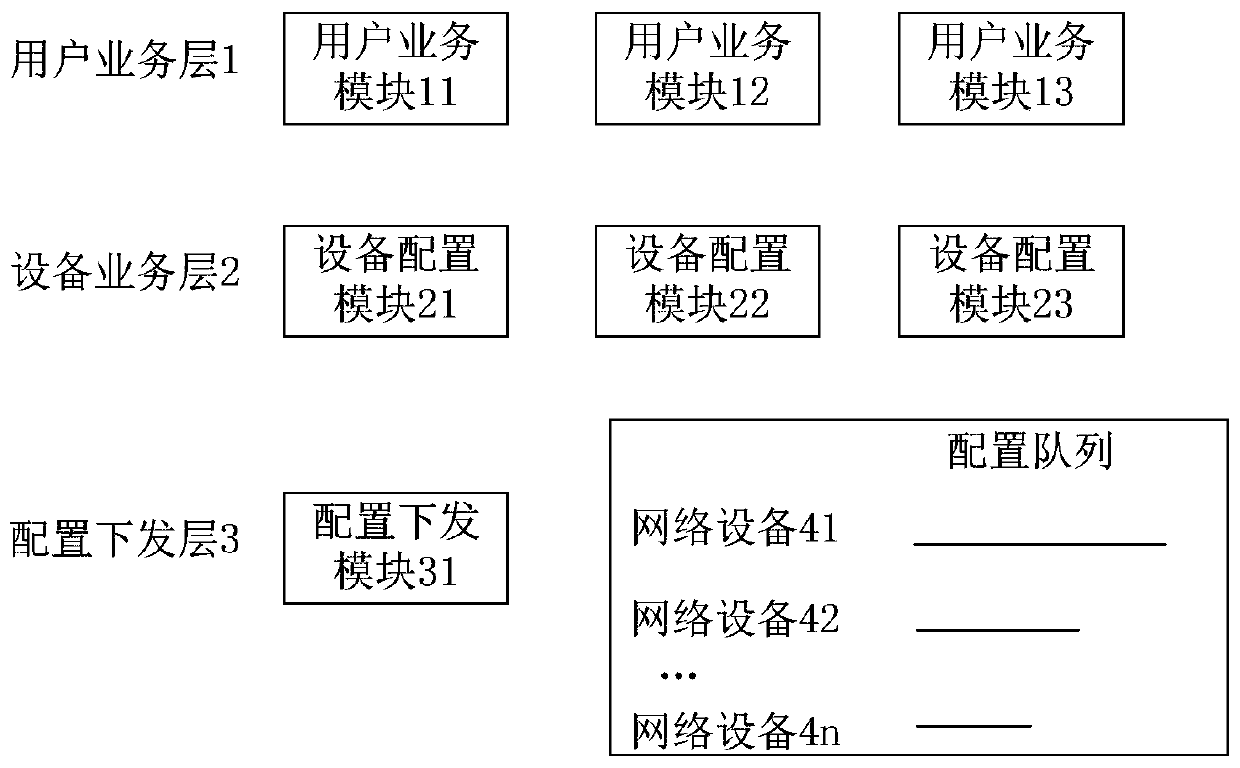
Method for configuring network equipment by SDN controller and SDN controller
ActiveCN110113197AAvoid repeated configurationReduce the number of timesData switching networksBusiness requirementsService module
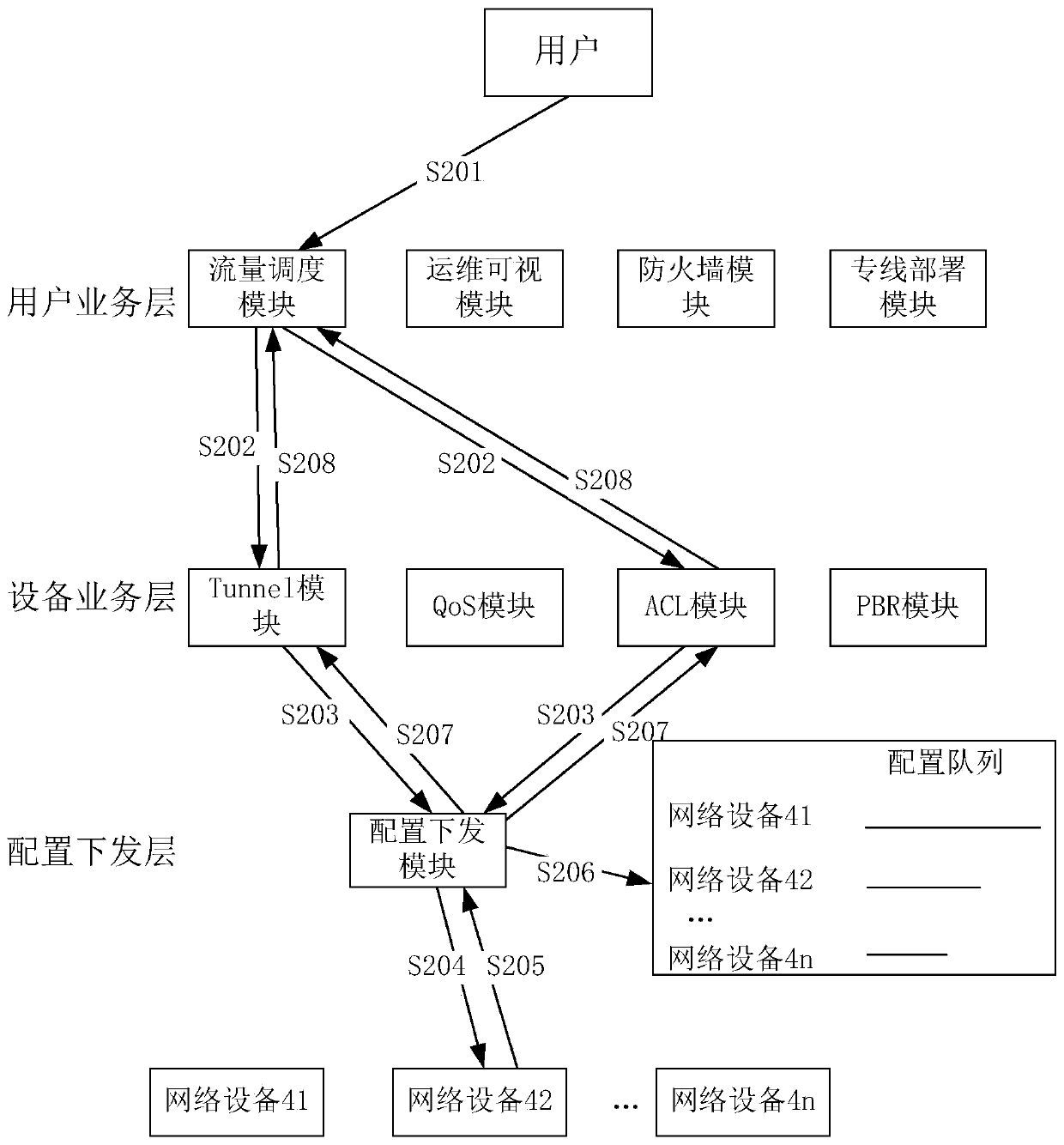
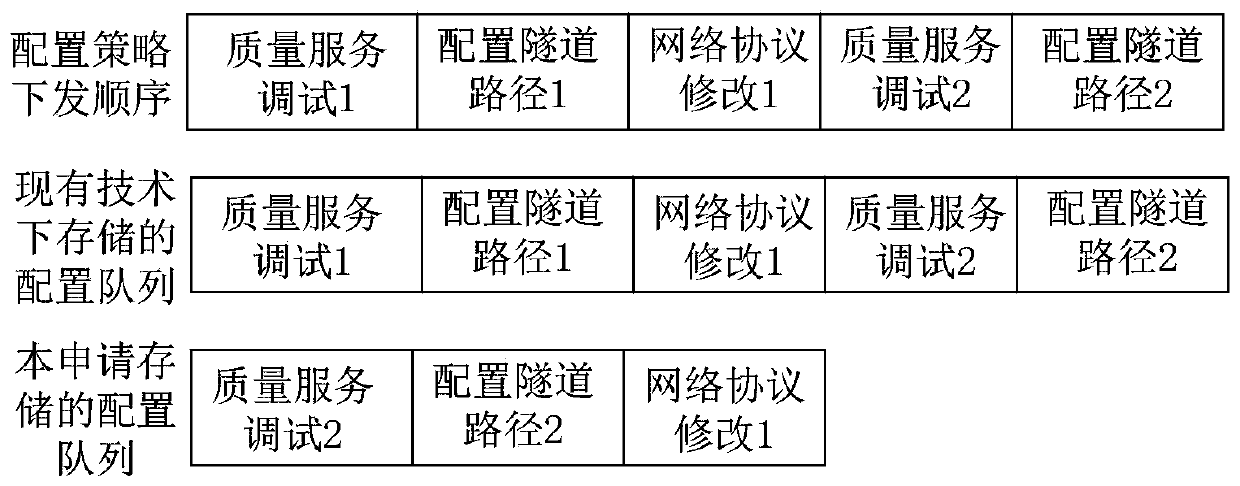
The invention provides a method for configuring network equipment by an SDN controller and the SDN controller, the method comprises steps of enabling a user service module of the SDN controller to determine a service type ID, a service entity ID, a configuration interface and configuration parameters according to service requirements; issuing a first request message to an equipment configuration module corresponding to the configuration interface, determining a configuration ID, an equipment configuration service ID and a configuration template by the equipment configuration module according to the received first request message, and issuing a second request message; enabling the configuration issuing module to receive the second request message and issue configuration information to the corresponding network equipment; after the configuration information is successfully issued, when a configuration list matched with the index information is found in a configuration queue of the network equipment, updating the configuration list by applying the configuration information. The mode of updating the configuration queue ensures that the same service in the configuration queue only stores the latest configuration information, avoids the problem that the network equipment repeatedly configures the same service, and improves the recovery efficiency of the service.
Owner:NEW H3C TECH CO LTD
Uplink transmission resource acquisition method, data transmission method and electronic equipment
ActiveCN110312312AReduce access delayImprove access efficiencySignal allocationPilot signal allocationUplink transmissionTerminal equipment
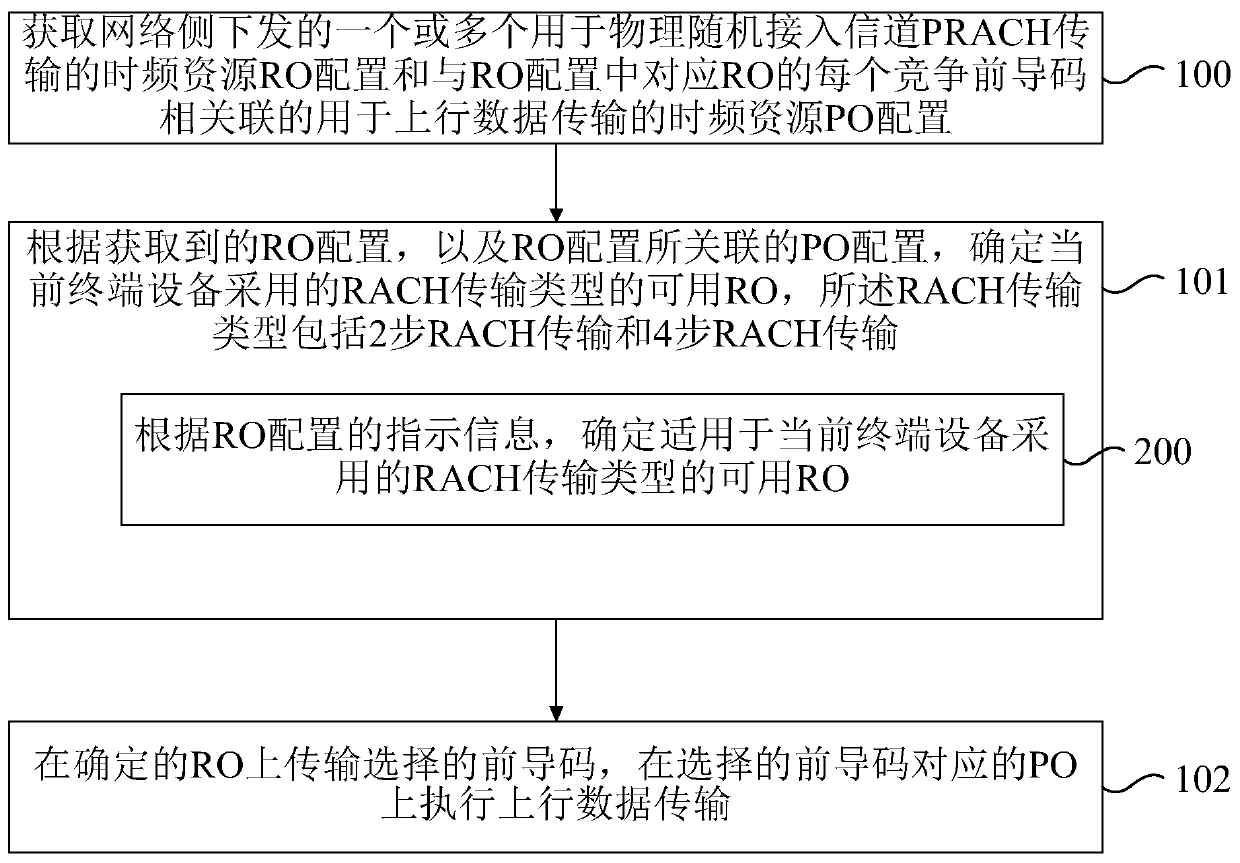
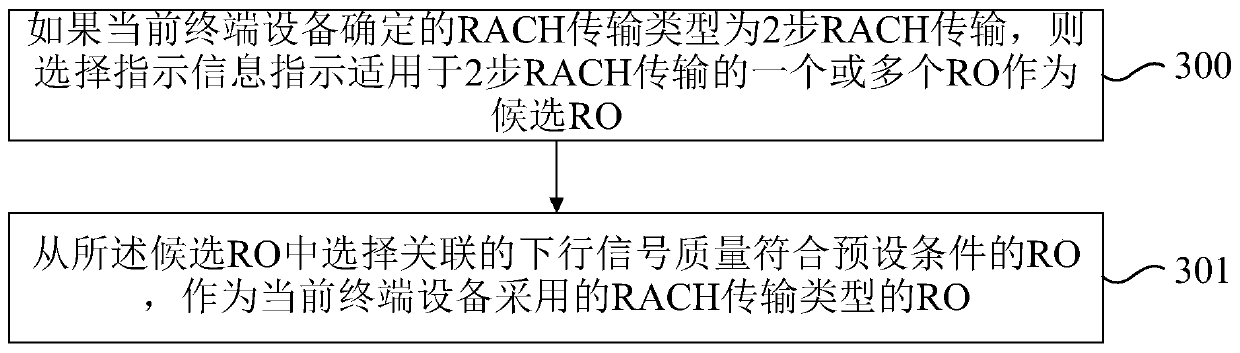
The invention relates to an uplink transmission resource acquisition method, a data transmission method and electronic equipment. The method comprises the following steps: acquiring one or more time-frequency resource RO configurations issued by a network side and used for physical random access channel PRACH transmission and time-frequency resource PO configurations associated with each competition preamble of a corresponding RO in the RO configurations and used for uplink data transmission; according to the acquired RO configuration and the PO configuration associated with the RO configuration, determining an available RO of an RACH transmission type adopted by the current terminal equipment, the RACH transmission type comprising two-step RACH transmission and four-step RACH transmission; and transmitting the selected preamble on the determined RO, and executing uplink data transmission on the PO corresponding to the selected preamble. According to the embodiment of the invention, the signaling overhead of the network side can be effectively reduced, the access delay of the terminal equipment is effectively reduced, and the access efficiency of the terminal equipment is improved.
Owner:BEIJING SPREADTRUM HI TECH COMM TECH CO LTD
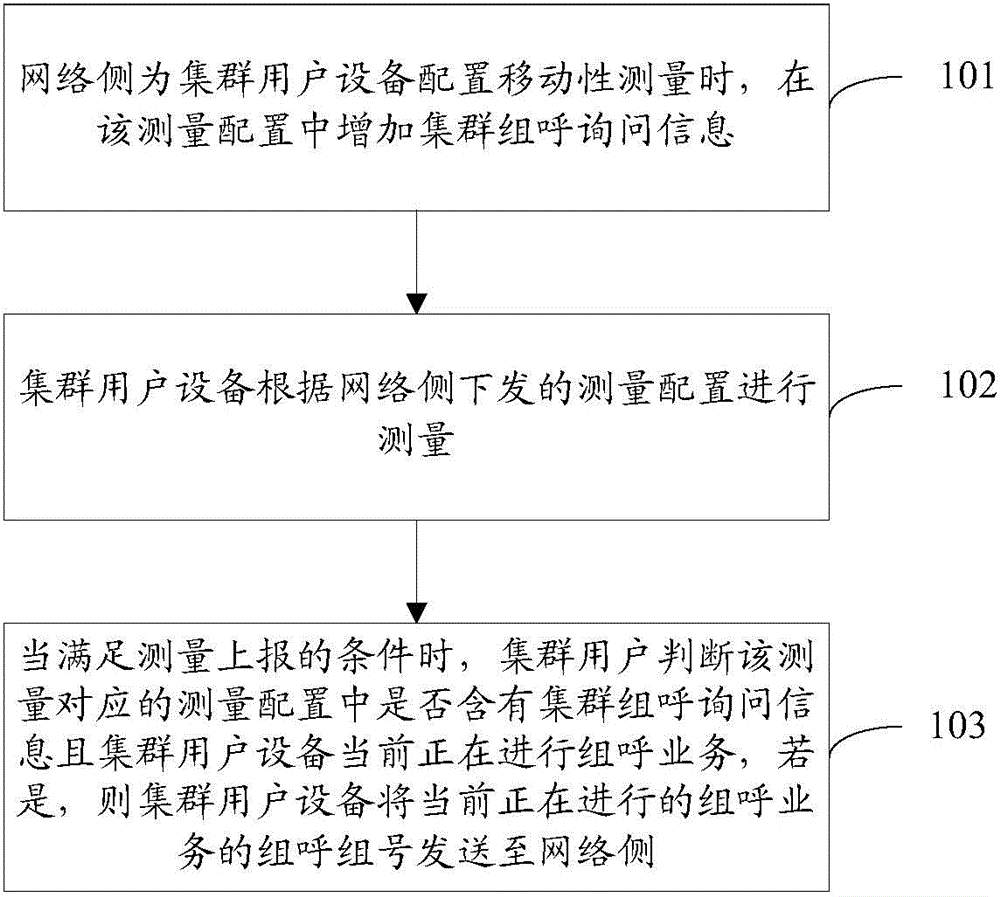
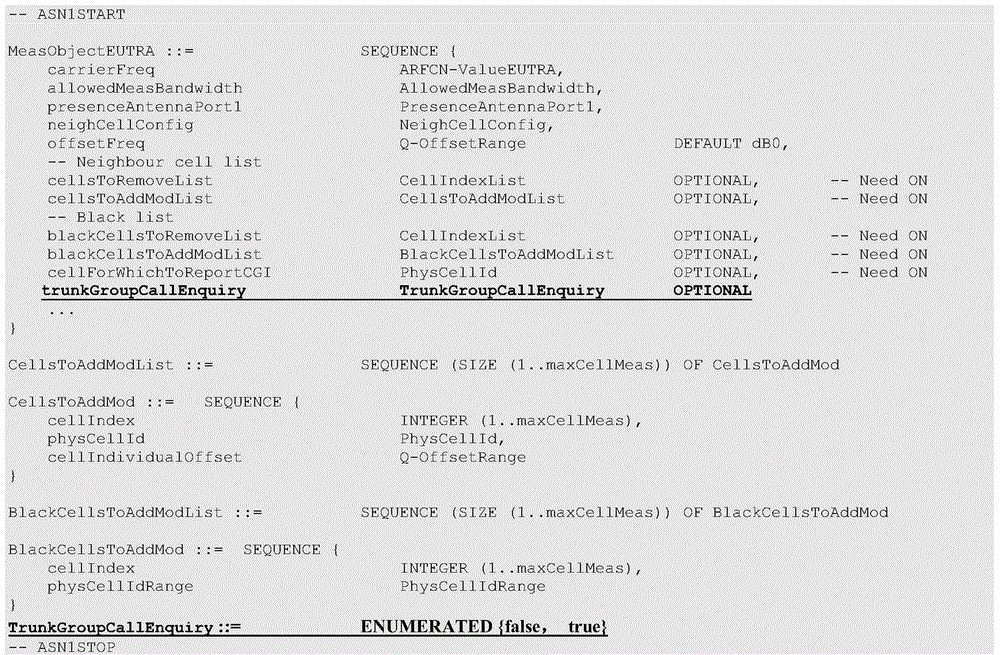
Mobility measurement method through cluster user equipment
ActiveCN104581809AAnswer the group call normallyGuaranteed continuityBroadcast service distributionTelecommunicationsCluster group
The invention discloses a mobility measurement method through cluster user equipment. The method comprises the following steps: A, a network side is used for configuring mobility measurement to the cluster user equipment, wherein cluster group calling inquiry information is added in the measurement configuration; B, the cluster user equipment carries out measurement according to the measurement configuration issued by the network side; C, when a measurement reporting condition is met, the cluster user equipment is used for determining whether the cluster group calling inquiry information exists in the measurement configuration corresponding to measurement or not while carrying out current group calling service, and if yes, the cluster user equipment is used for sending a group calling group number of the ongoing current group calling service to the network side. According to the technical scheme of the method, the network side can know a calling group of the cluster user equipment.
Owner:POTEVIO INFORMATION TECH
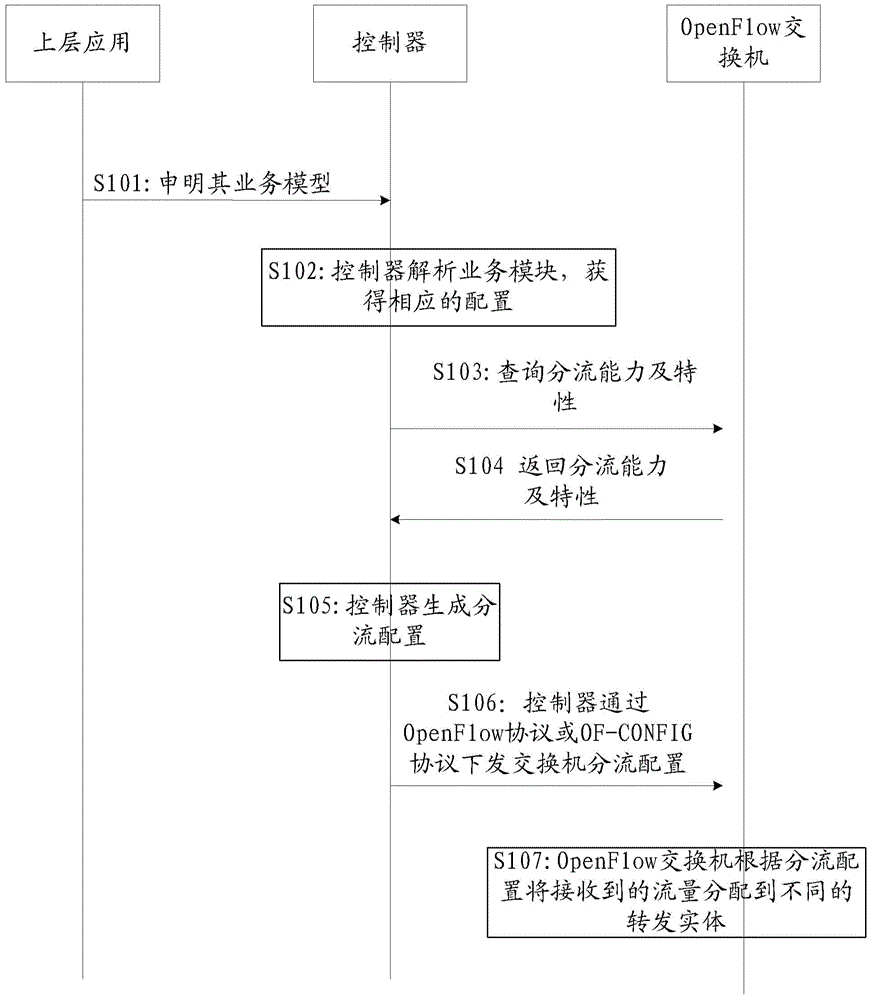
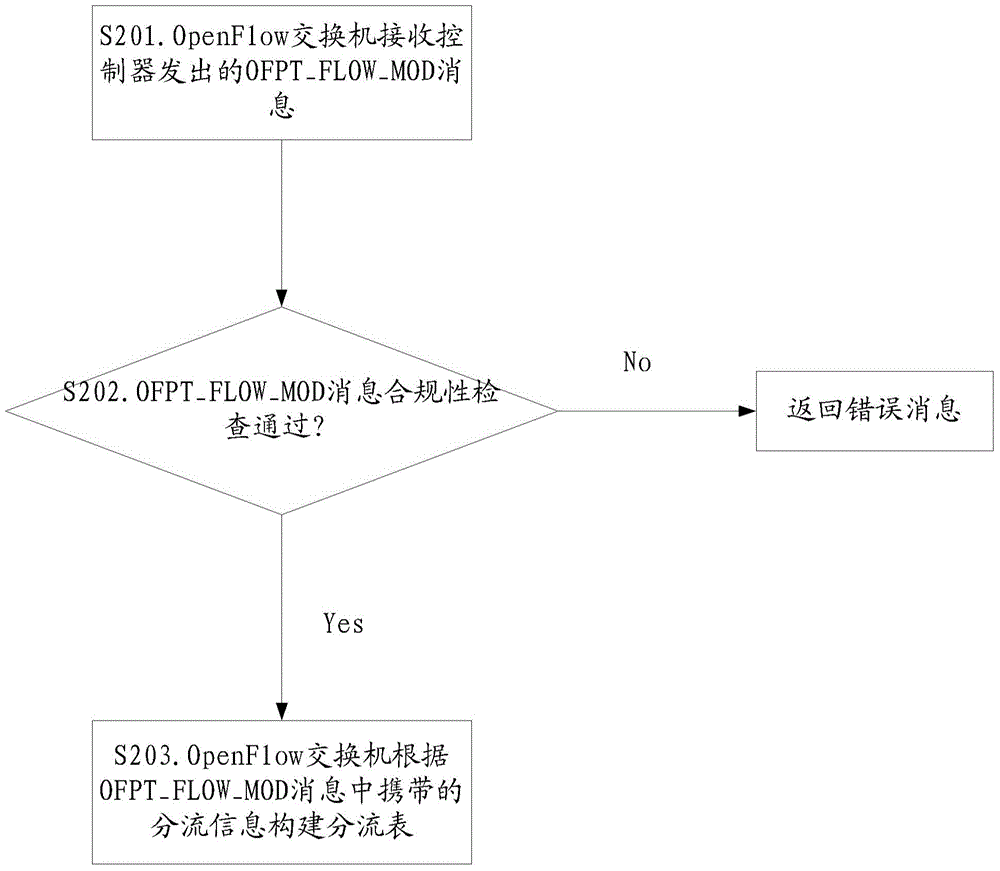
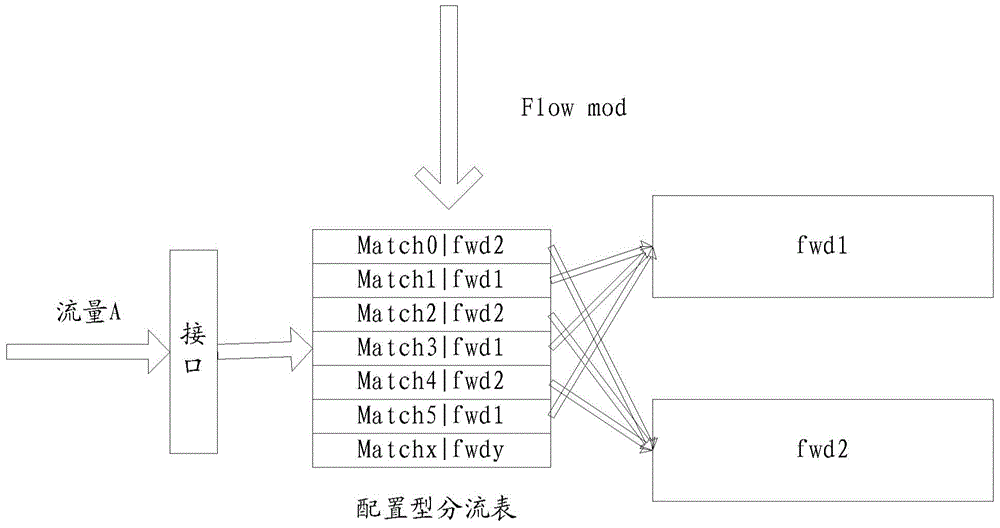
Shunting method, OpenFlow switch, controller and shunting system
InactiveCN105721329ARealize load sharingSolve the problem of load sharing mechanismData switching networksOpenFlowEmbedded system
The invention provides a shunting method, an OpenFlow switch, a controller and a shunting system, and relates to the communication field, being able to solve the problem of being short of a load sharing system under a new OpenFlow protocol framework. The shunting method includes the steps that an OpenFlow switch sends the switch configuration attribute to a controller, wherein the switch configuration attribute carries a shunting characteristic parameter which shows that the OpenFlow switch supports shunting; the OpenFlow switch receives shunting configuration issued from the controller; and according to the shunting configuration, the OpenFlow switch shunts the flow arrives in the OpenFlow switch to different forward entities. The shunting method, the OpenFlow switch, the controller and the shunting system are suitable for a new OpenFlow protocol framework network, and can realize load sharing under the new OpenFlow protocol framework.
Owner:ZTE CORP
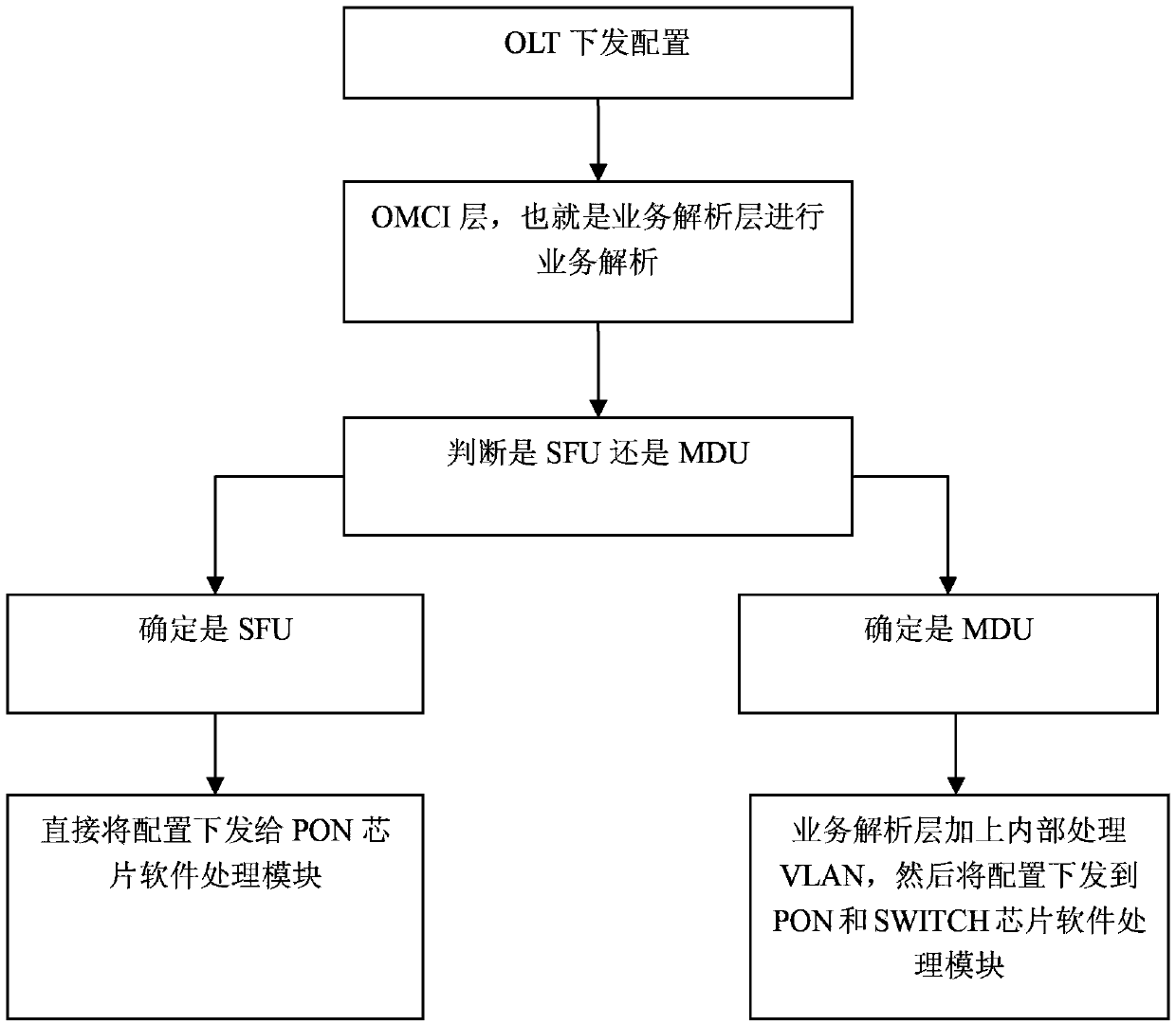
Configuration method of gigabit passive optical network terminal device
ActiveCN103369417AClear handlingAny porting and reuseMultiplex system selection arrangementsTerminal equipmentGigabit
The invention relates to the field of gigabit passive optical network, and especially relates to a configuration method of a gigabit passive optical network terminal device. The method comprises the following steps that: an OLT (Optical Line Terminal) issues configuration, and a business parsing layer parses out the configuration issued by the OLT according to a received OMCI (Ont Management And Control Interface) message; according to whether a MDU (Multi Dwelling Unit) or a SFU (Single Family Unit) works currently, if the SFU works currently, the business parsing layer directly issues the configuration to a chip bottom layer and a PON (Passive Optical Network) chip software processing module; if the MDU works, the business parsing layer adds the internal VLAN (Virtual Local Area Network) processing mechanism, and issues the configuration to corresponding SWITCH and the PON chip software processing module. The method is completely irrelevant to a hardware scheme, and has good portability and reusability. The configuration method can guarantee that development of MDU basic service can be finished around the same time when the SFU is developed.
Owner:TAICANG T&W ELECTRONICS CO LTD
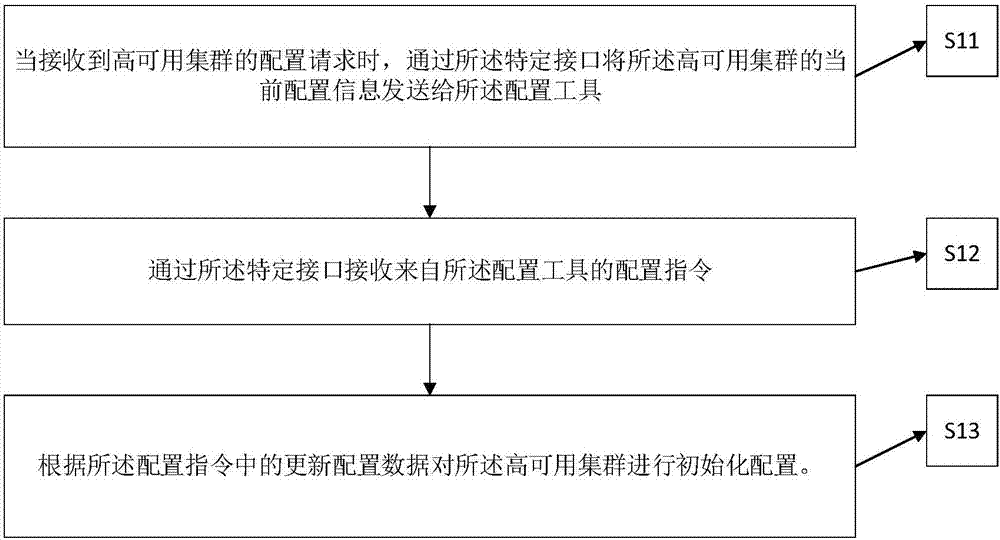
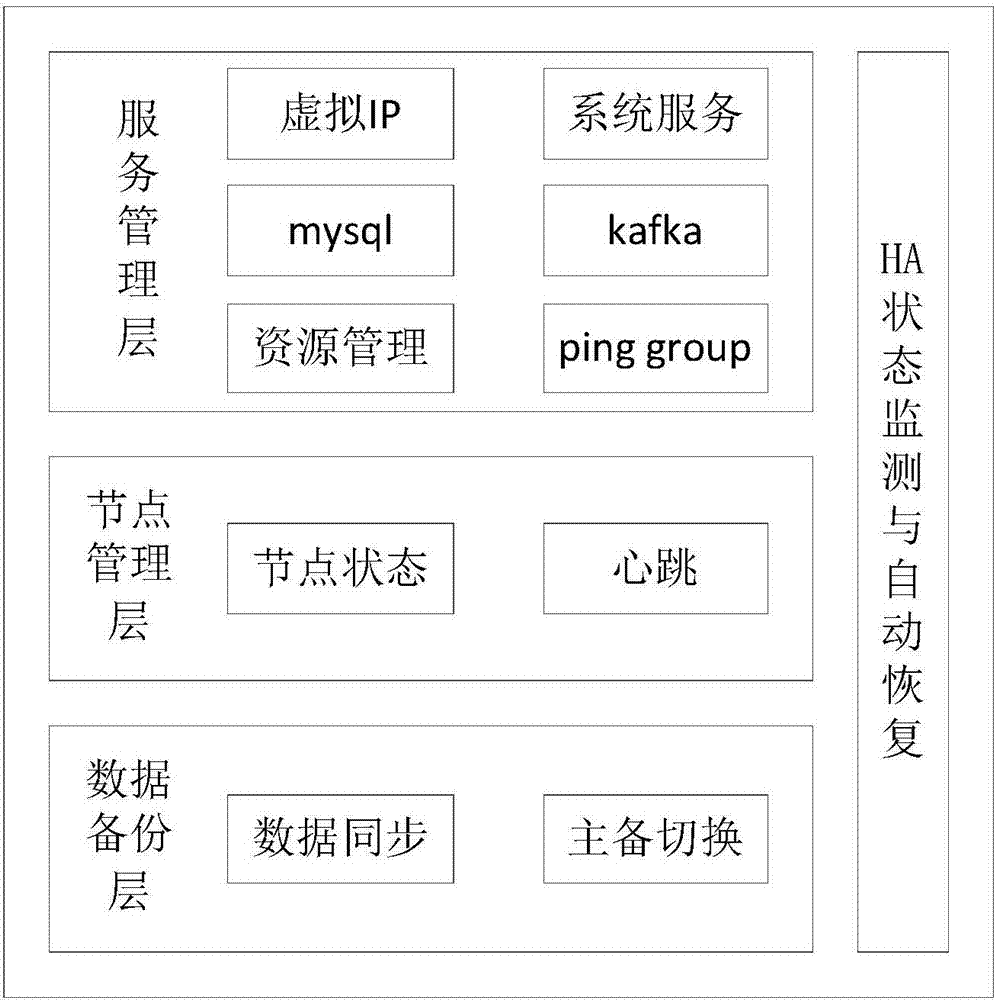
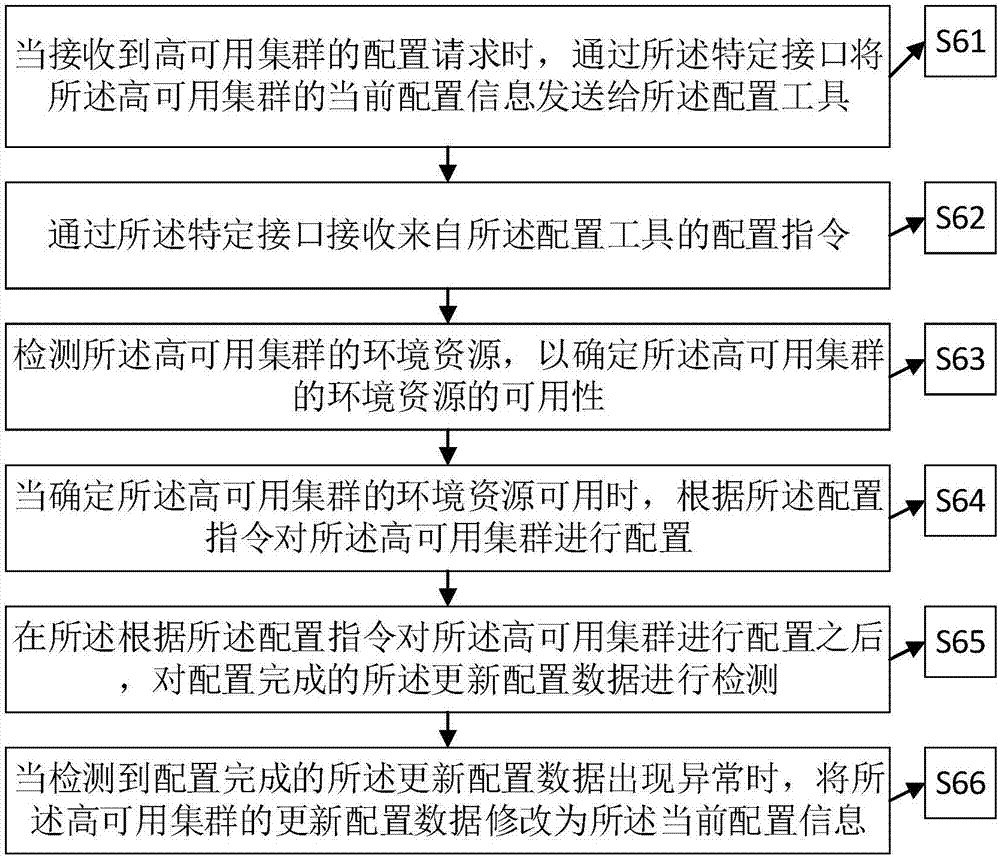
Configuration method, device and system for high availability cluster
PendingCN106972962AImplement automatic configurationNo human intervention requiredData switching networksAuto-configurationInteraction interface
The disclosure relates to the technology of HA deployment, and provides a configuration method, device and system for a high availability cluster, which can solve the problem of automatically configuring the high availability cluster in case that industrial control equipment and other resources are limited. The high availability cluster is provided with a specific interface, and the specific interface is an interaction interface between a configuration tool and the high availability cluster. The method comprises the following steps: when a configuration request of the high availability cluster is received, sending the current configuration information of the high availability cluster to the configuration tool through the specific interface; receiving a configuration instruction from the configuration tool through the specific interface; and implementing initialization configuration on the high availability cluster according to the updated configuration data in the configuration instruction. The configuration method, device and system provided by the disclosure are suitable for the configuration process of the high availability cluster.
Owner:BEIJING KUANGEN NETWORK TECH
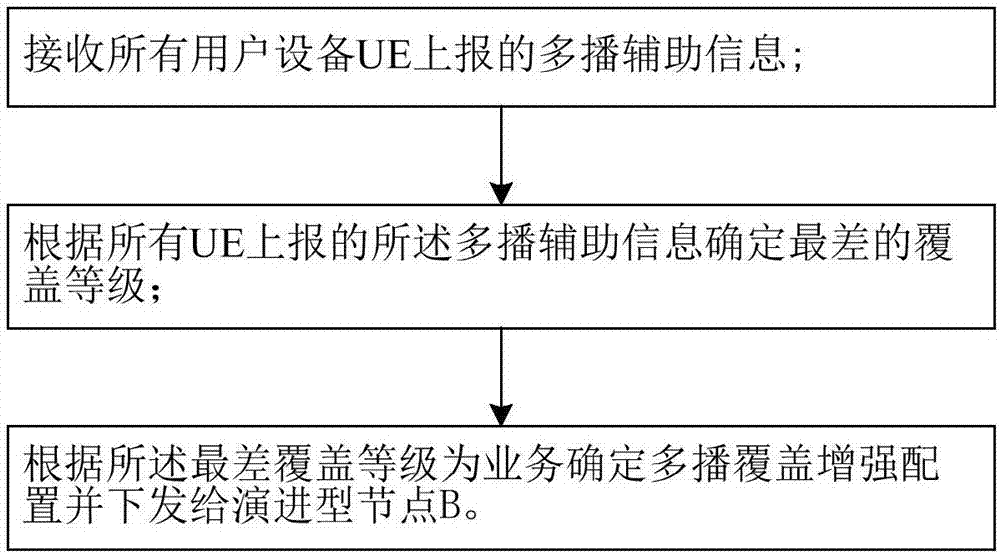
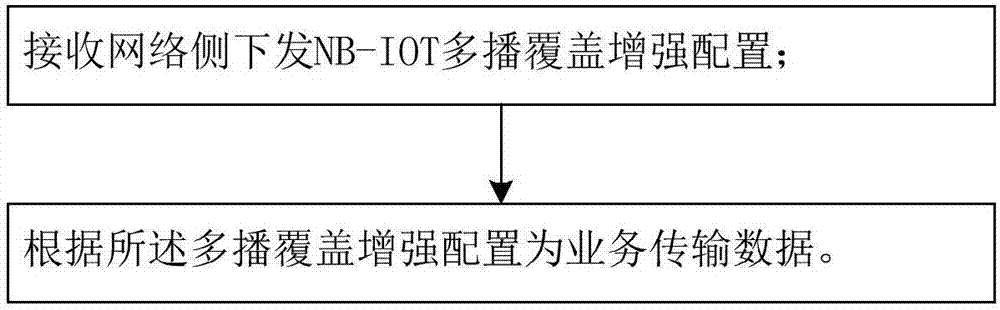
Method for realizing NB-IoT multicast coverage enhancement
InactiveCN107995595AResource optimizationBroadcast service distributionNetwork planningMobility managementConfiguration Issue
The invention provides a method for realizing NB-IoT multicast coverage enhancement. The method comprises the following steps: receiving multicast auxiliary information reported by all user equipmentUE through a mobility management entity MME; determining the worst coverage level according to the multicast auxiliary information reported by all UE; and determining the multicast coverage enhancement configuration for the service according to the worst coverage level, and issuing the multicast coverage enhancement configuration to an evolution node B, wherein the evolution node B receives the NB-IoT multicast coverage enhancement configuration issued by a network side; and transmitting data for the service according to the multicast coverage enhancement configuration.
Owner:BEIJING XINWEI TELECOM TECH
Controlling access to information over a multiband network
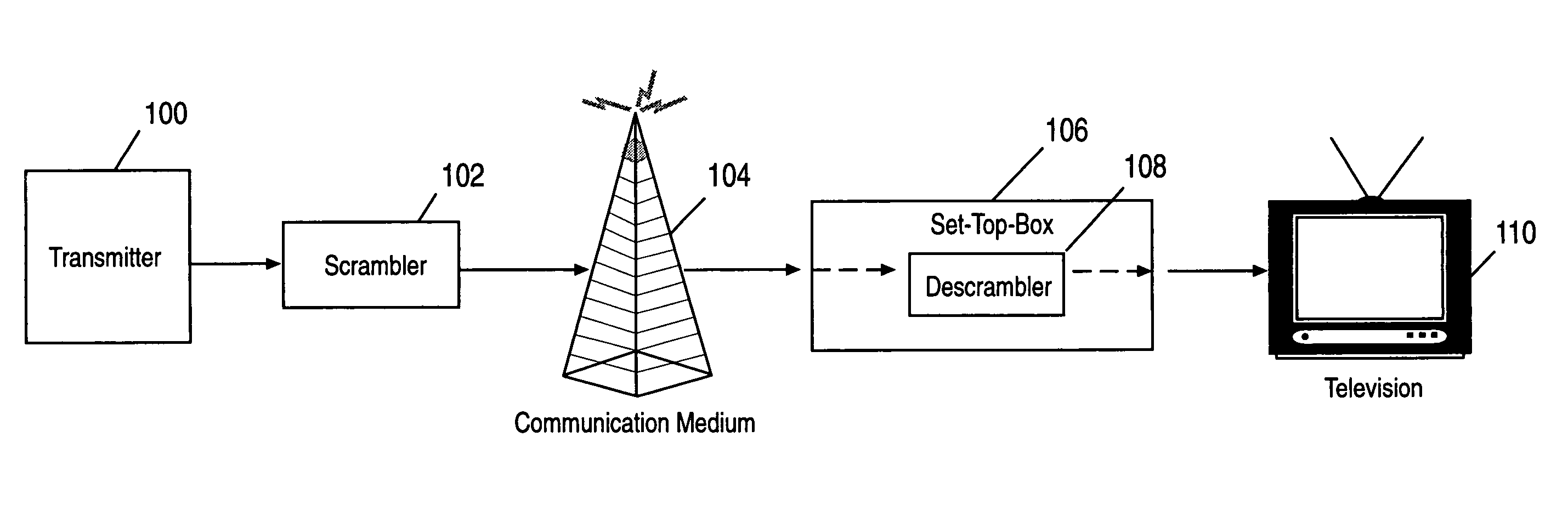
InactiveUS8069468B1Avoid viewingMaintain abilityDigital data processing detailsAnalogue secracy/subscription systemsTelevision stationSpecific time
A method and apparatus for controlling access to information over a network. Information and video / audio streams are transmitted across a network by a head end to a member space manager or set-top box where the information may be utilized or viewed. The frequency that a given stream of information is transmitted on is rotated or switched based on a switching algorithm. For example, a given stream (e.g., a motion picture on a pay-per-view station) may be transmitted on one frequency for a specified time interval, then switched to another frequency for a specified time interval, etc. To enable the member space manager to determine which frequency a given stream of information is transmitted on at a particular point in time, switching software may be provided by the head end server to the member space manager. Switching software may be encrypted prior to transmission to the member space manager. According to one or more embodiments of the invention, the stream-to-frequency mapping is determined, the mapping is transmitted to the member space manager where it is installed and executed, the stream of information is transmitted on varying frequencies to the member space manager, and the member space manager tunes into the appropriate frequency to receive and utilize a continuous stream of information. By transmitting information in this manner, all encryption, frequency / channel switching, configuration issues, etc. are transparent to the end user who merely has to select a virtual channel to view.
Owner:ORACLE INT CORP
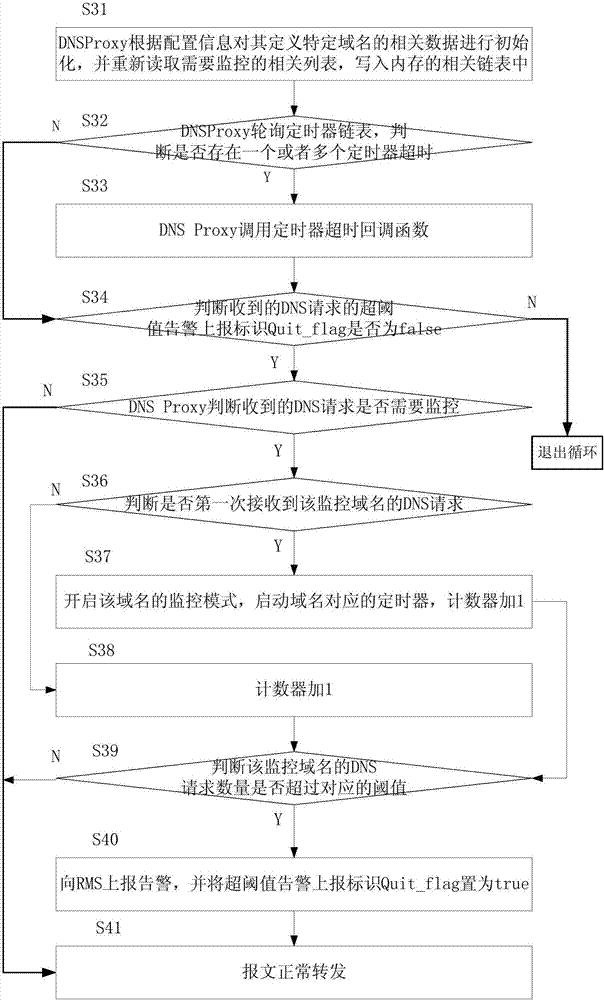
Method for monitoring DNS domain name attacks based on DNS Proxy
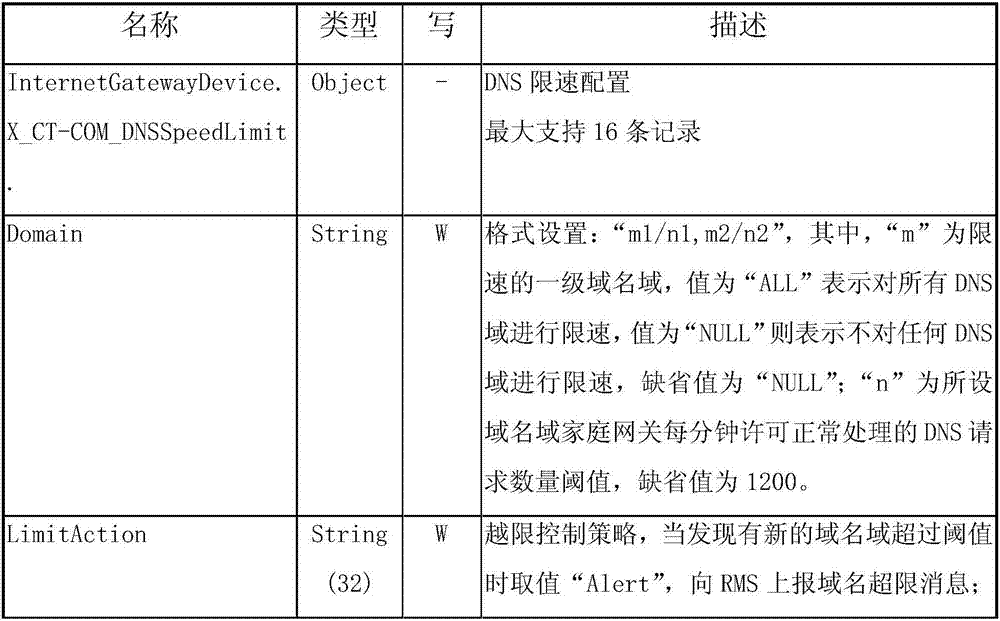
The invention discloses a method for monitoring DNS domain name attacks based on DNS Proxy. The method comprises the following steps: an RMS issues a configuration of an operation for monitoring specific domain names to home gateway equipment; a home gateway sends a message to notify a DNS Proxy process after receiving the configuration issued by the RMS; the DNS Proxy process initializes the monitoring of related data of the specific domain names based on configuration information, starts to monitor whether the number of DNS requests of the specific domain names exceeds a corresponding threshold, and reports the domain names that exceed the threshold and related information of the corresponding home gateway to the RMS in the form of alarm; the RMS analyzes whether the DNS requests that exceed the threshold are in normal access states, and sends the domain names in abnormal access states to the home gateway; and the DNS Proxy process of the home gateway directly discards the DNS requests in the abnormal access states. The method disclosed by the invention can avoid the network paralysis caused by the DNS domain name attacks, is easy to operate and implement, ensures the high performance of networks, and has very good reusability.
Owner:FENGHUO COMM SCI & TECH CO LTD
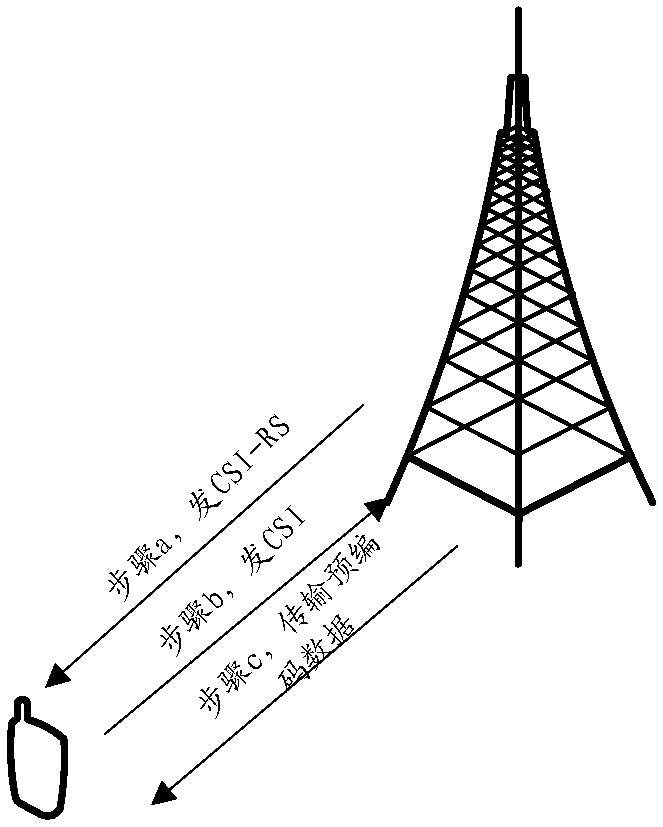
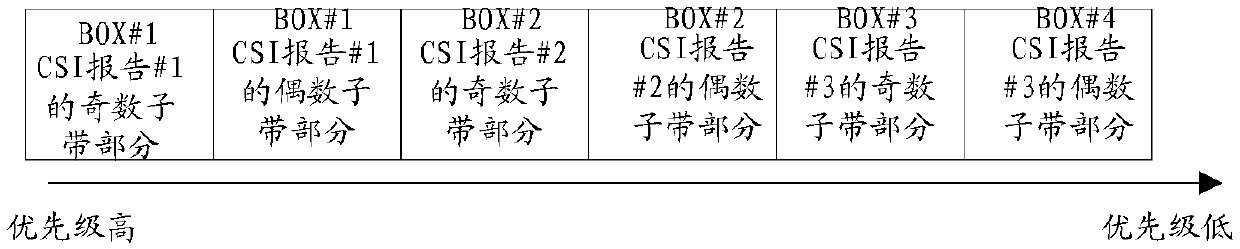
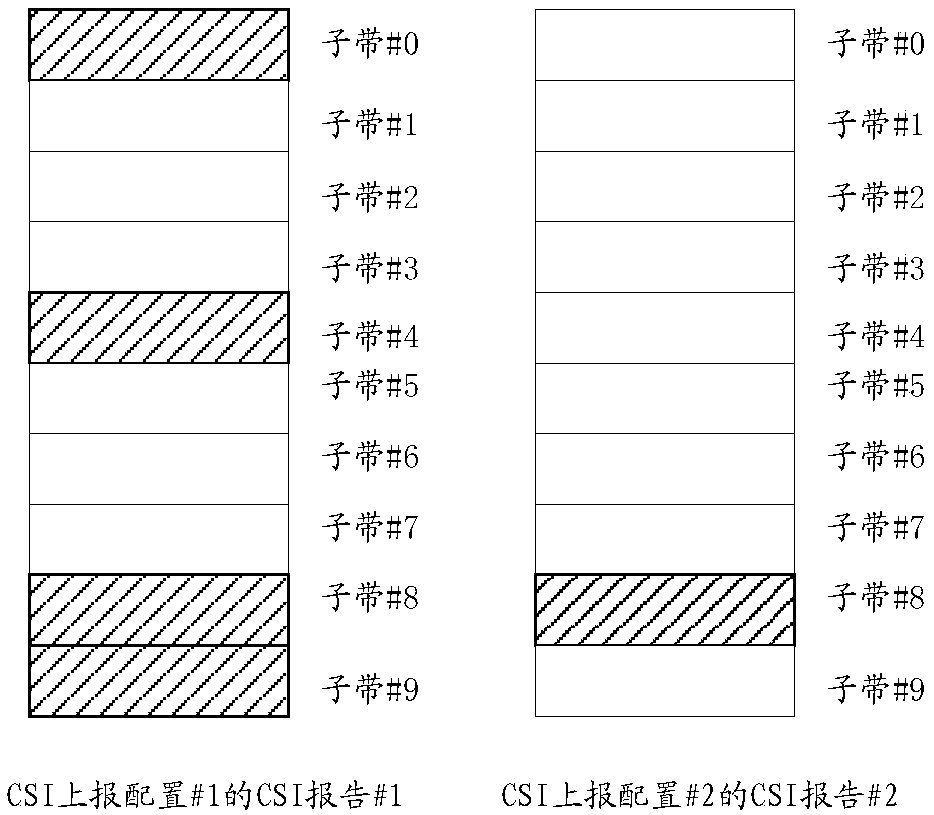
CSI reporting method and terminal equipment
The invention discloses a CSI reporting method and a terminal device. The method comprises the steps that the terminal device receives M CSI reporting configurations issued by a base station, configurations of first CSI-RS resources associated with each CSI reporting configuration, and first signaling; For a first CSI-RS resource associated with any CSI reporting configuration, the terminal devicedetermines a second CSI-RS resource corresponding to the CSI reporting configuration according to the first signaling; The terminal device configures a corresponding first CSI-according to each CSI report, determines the priority order of the M CSI reporting configurations by using the RS resources and the second CSI-RS resources; The terminal device sends a CSI report to the base station according to the priority order; The method is used for solving the problem that a CSI report reported by current terminal equipment is incomplete, downlink resource scheduling of the UE is limited by a basestation, and the utilization rate of downlink resources is reduced.
Owner:HUAWEI TECH CO LTD
Cloud configuration method and system based on proxy service
InactiveCN110474983AImprove performanceHigh cloud configuration functionData switching networksApplication softwareCentralized management
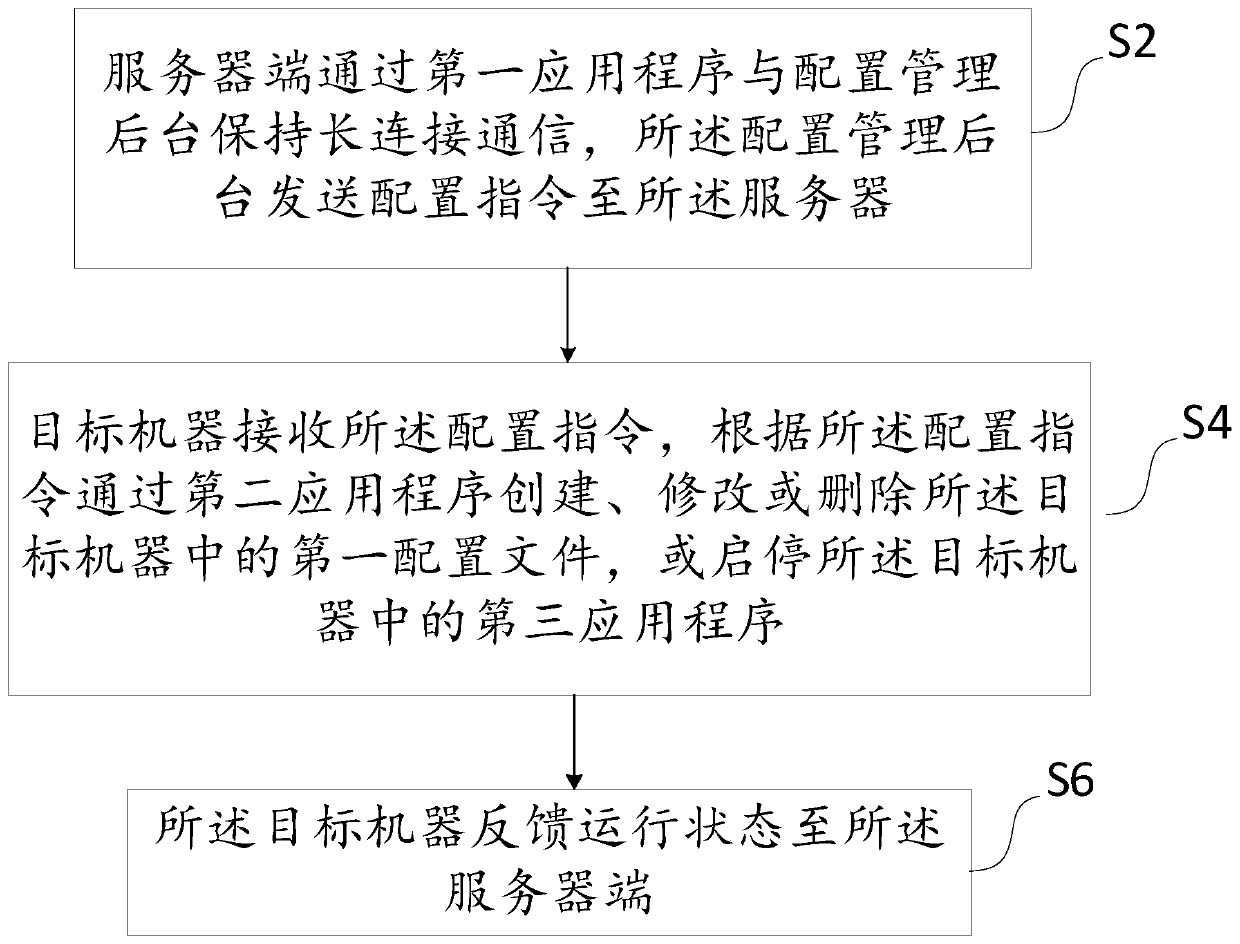
The invention discloses a cloud configuration method and a system based on proxy service, and the method comprises the steps that a server terminal maintains long-connection communication with a configuration management background through a first application program, and the configuration management background sends a configuration instruction to a server; a target machine receives the configuration instruction, creates, modifies or deletes a first configuration file in the target machine through a second application program according to the configuration instruction, or starts and stops a third application program in the target machine; and the target machine feeds back the operation state to the server terminal. The cloud configuration method based on the proxy server provided by the invention has the following advantages: centralized management: all configuration information can be subjected to centralized management in a configuration center management background, and can also be managed according to role permission, so that the operation is very convenient. Configuration is flexible, the configured content can be published according to a specified version and can also be published to a specific machine in a specified mode, and the whole configuration issuing operation is very flexible.
Owner:车轮互联科技(上海)股份有限公司
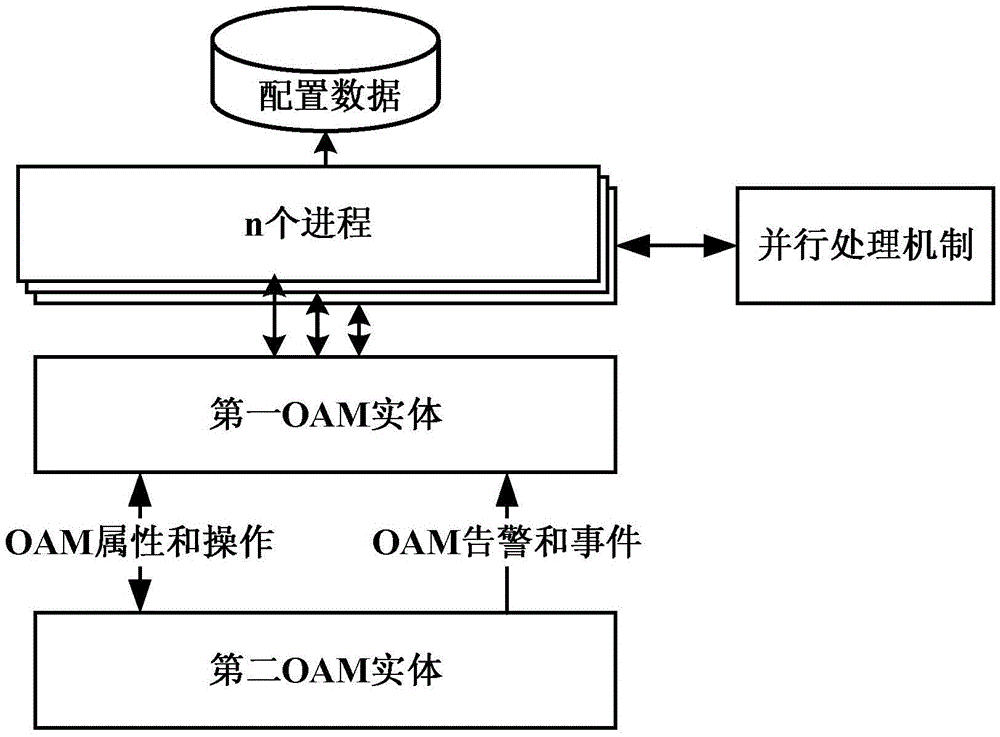
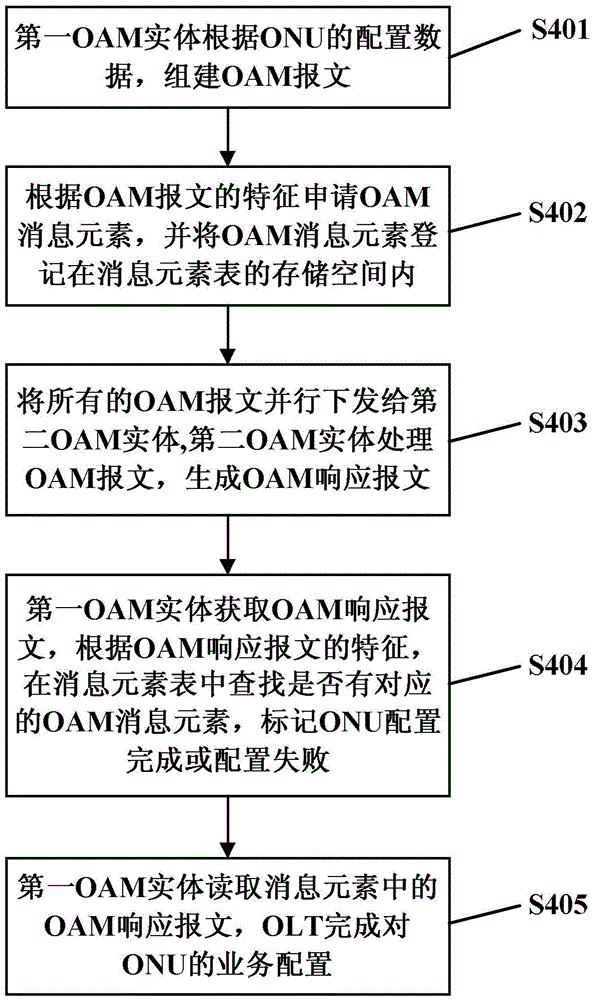
Parallel OAM configuration management method in EPON system and system thereof
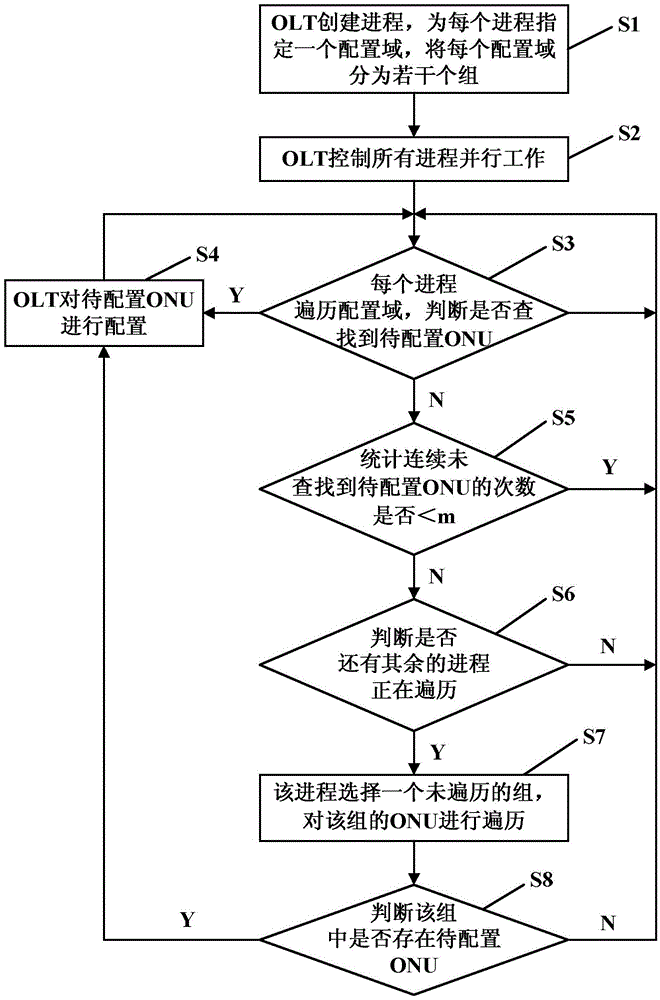
ActiveCN105610601AImprove configuration delivery efficiencySave configuration timeData switching networksService configurationComputer science
The invention discloses a parallel OAM configuration management method in an EPON system and a system thereof and relates to the OAM technology field in the EPON system. The system comprises an OLT and an ONU. The OLT comprises one configuration module, n first determination modules and n second determination modules. The method comprises the following steps that the OLT creates n processes which need to carry out service configuration on the ONU and assigns one configuration domain for each process; the OLT controls parallel work of all the processes; each process loops through the ONU in the corresponding configuration domain and the ONU to be configured is configured; when the number of times for one process which does not find the ONU to be configured continuously in the corresponding configuration domain is m, the process loops through other groups which are not looped through, configures the ONU to be configured and then loops through the ONU in the corresponding configuration domain again. In the invention, a parallel mechanism is introduced, configuration issuing efficiency of an OAM channel can be increased and ONU service configuration time is shortened.
Owner:FENGHUO COMM SCI & TECH CO LTD
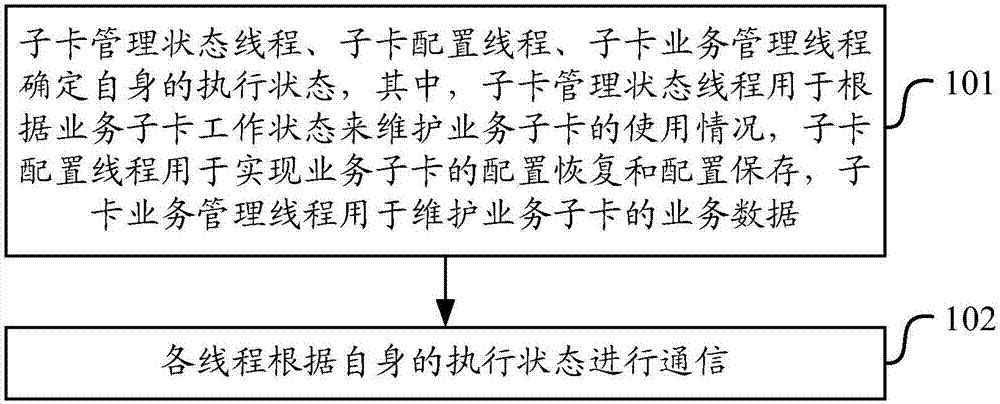
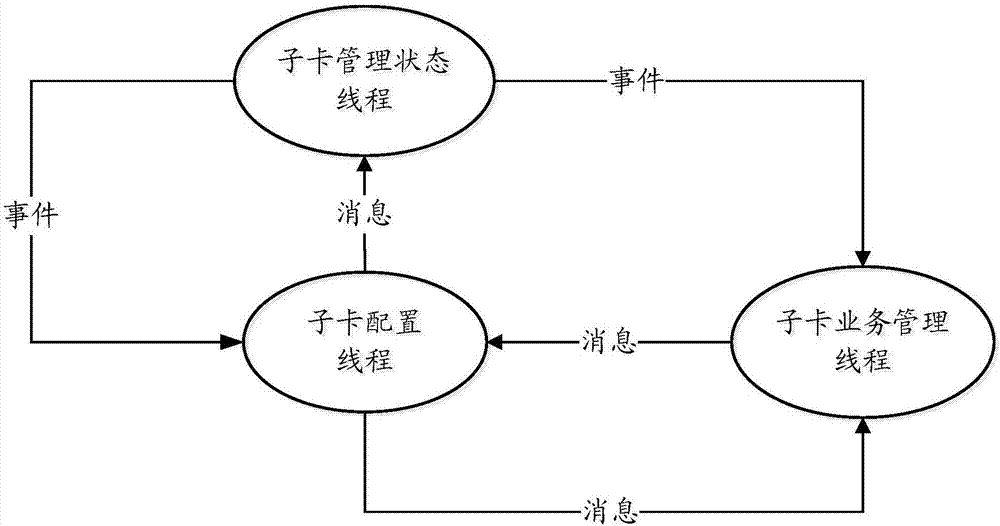
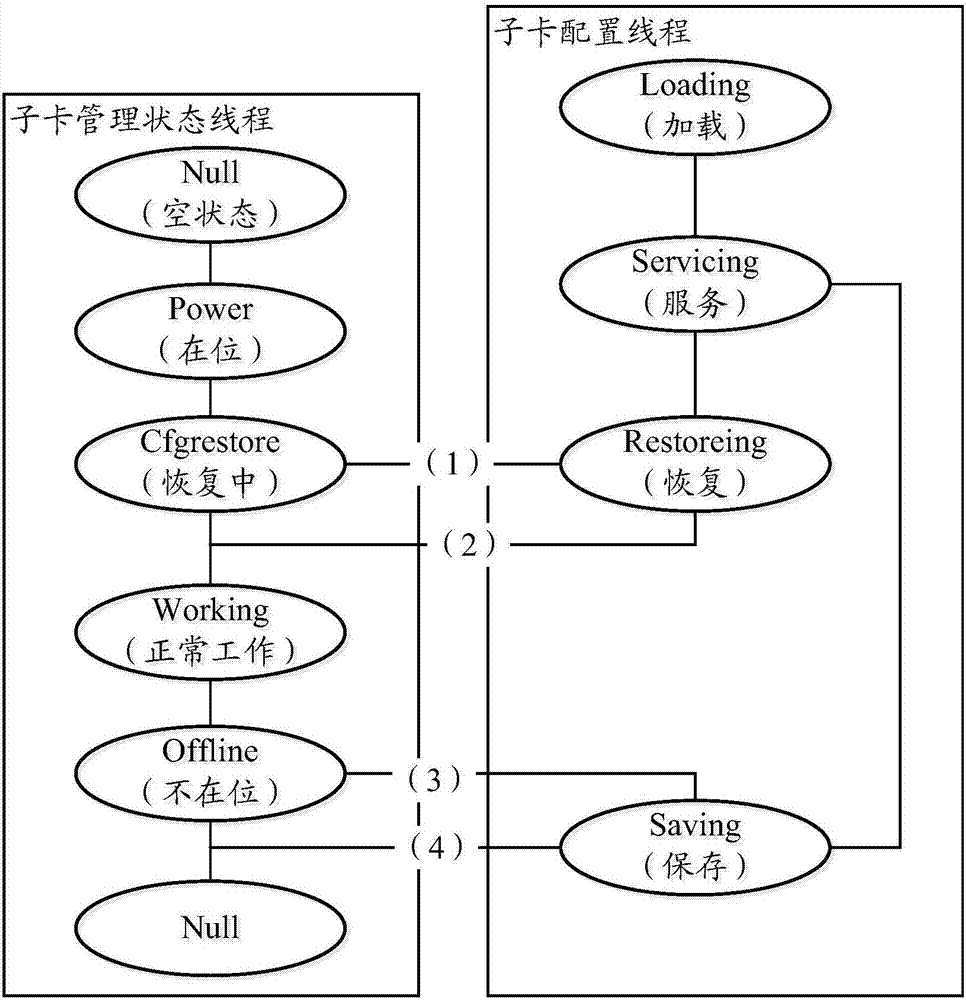
Business daughter card management method and device
ActiveCN107122251ALower hang deadPrevent hangingProgram initiation/switchingInterprogram communicationBusiness managementDaughterboard
The invention discloses a business daughter card management method and device. The method comprises the steps that a daughter card management state thread, a daughter card configuration thread and a daughter card business management thread determine respective execution states; and all the threads perform communication according to respective execution states, wherein the daughter card management state thread performs inter-thread communication with the daughter card configuration thread and the daughter card business management thread in the form of events, the daughter card configuration thread performs inter-thread communication with the daughter card management state thread and the daughter card business management thread through messages, and the daughter card business management thread performs inter-thread communication with the daughter card configuration thread through a message. By the adoption of the business daughter card management method and device, a shutdown of a management system can be effectively prevented, operating efficiency of business daughter card management is substantially improved, and positioning of configuration issue failure and configure failure problems is facilitated.
Owner:RAISECOM TECH
Software change management, configuration substitution and remote administration of datacenters
InactiveCN102160029ADatabase updatingDigital data processing detailsChange managementRelational database
Change management in a relational database may be implemented by indexing changes by copying the database to a new revision when a change is made to one or more items in the database. The new revision may be committed as a single unit and all changes stored together under a single revision. Database users may be notified of the new revision that is available for use. Software configuration issues may be simplified through the use of a configuration language that separates the logical configuration between software components from the specific configuration of those components. Secure data center administration may be handled through the use of control hosts.
Owner:美国索尼电脑娱乐有限责任公司
Configuration Checker for Application
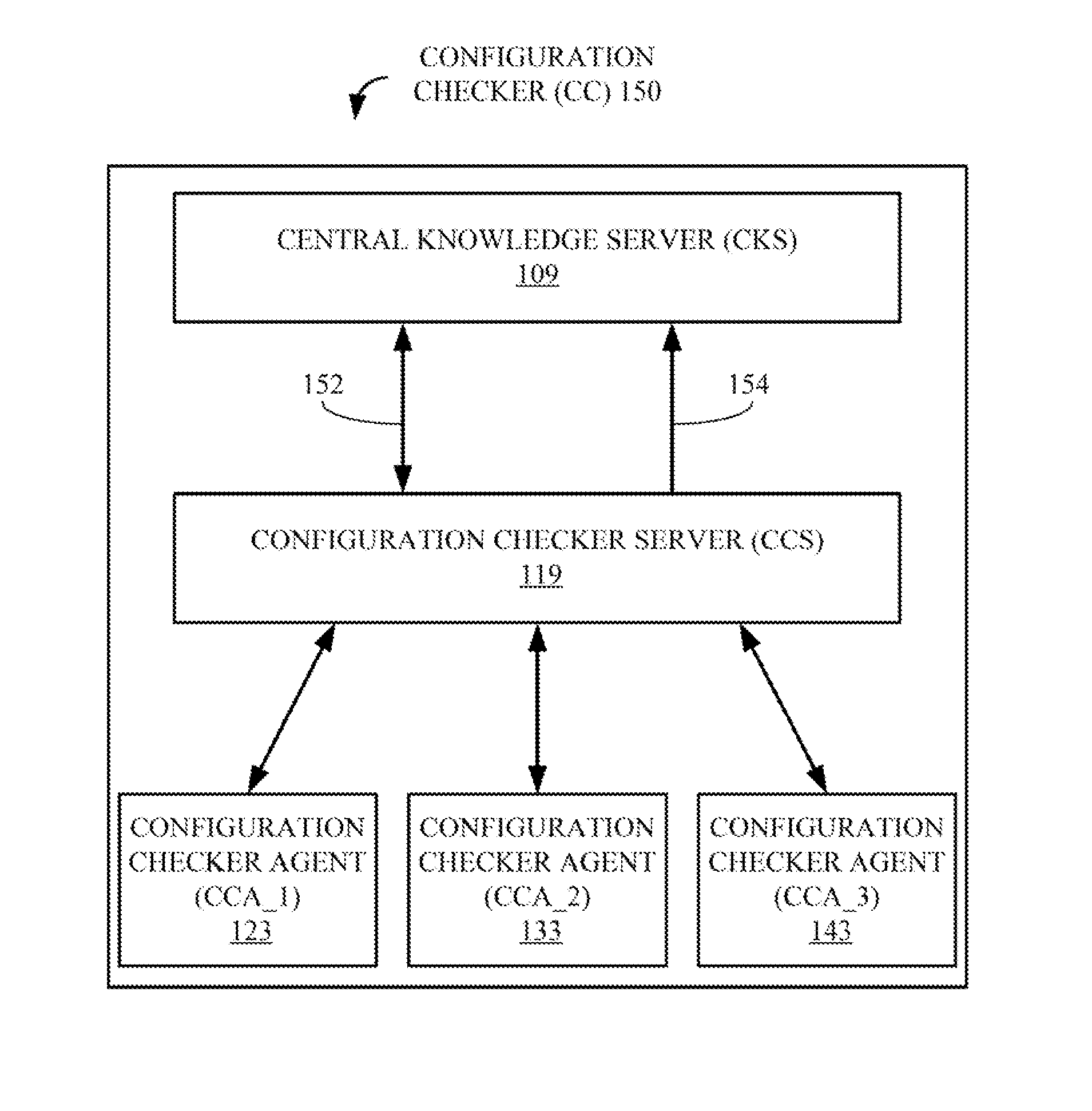
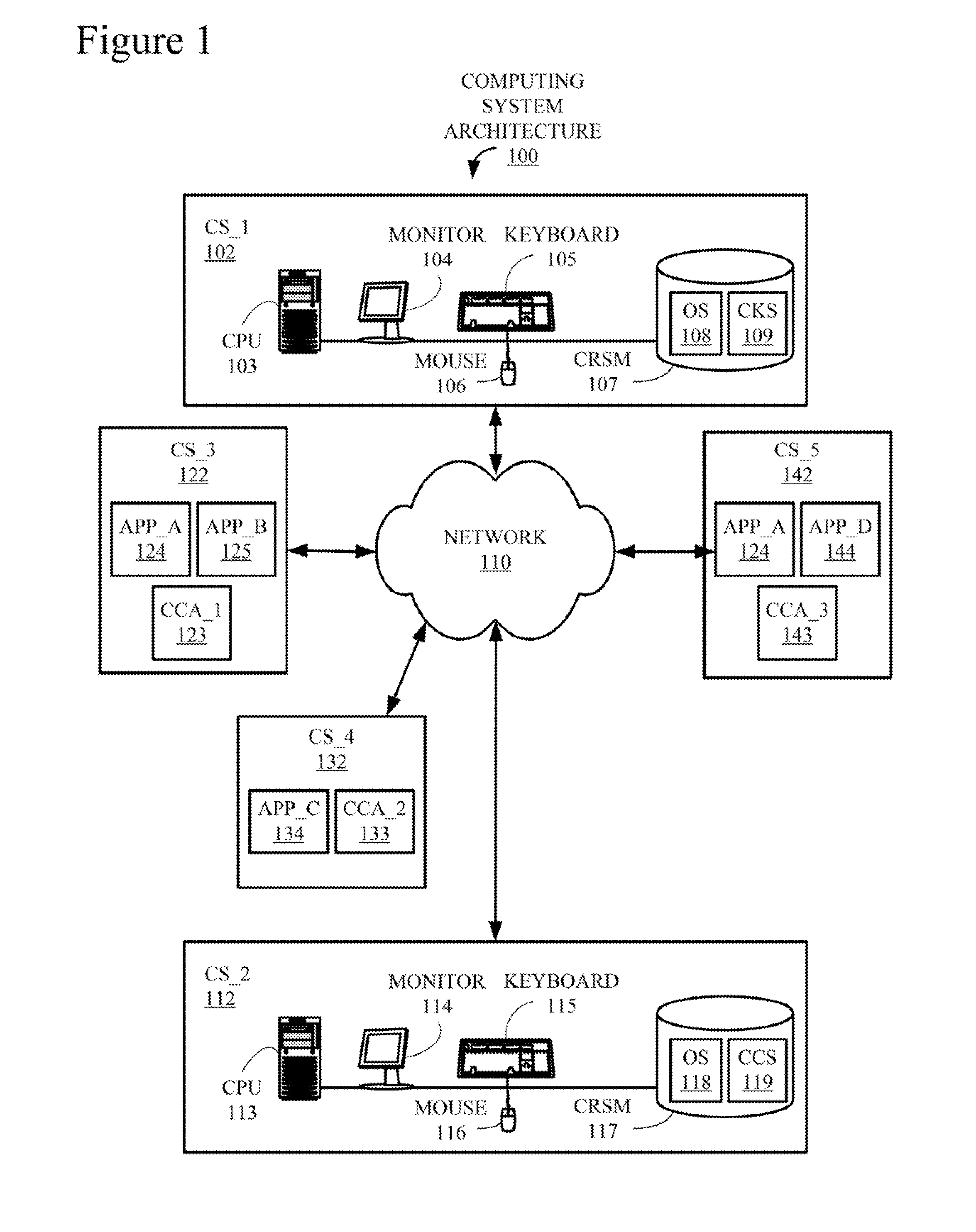
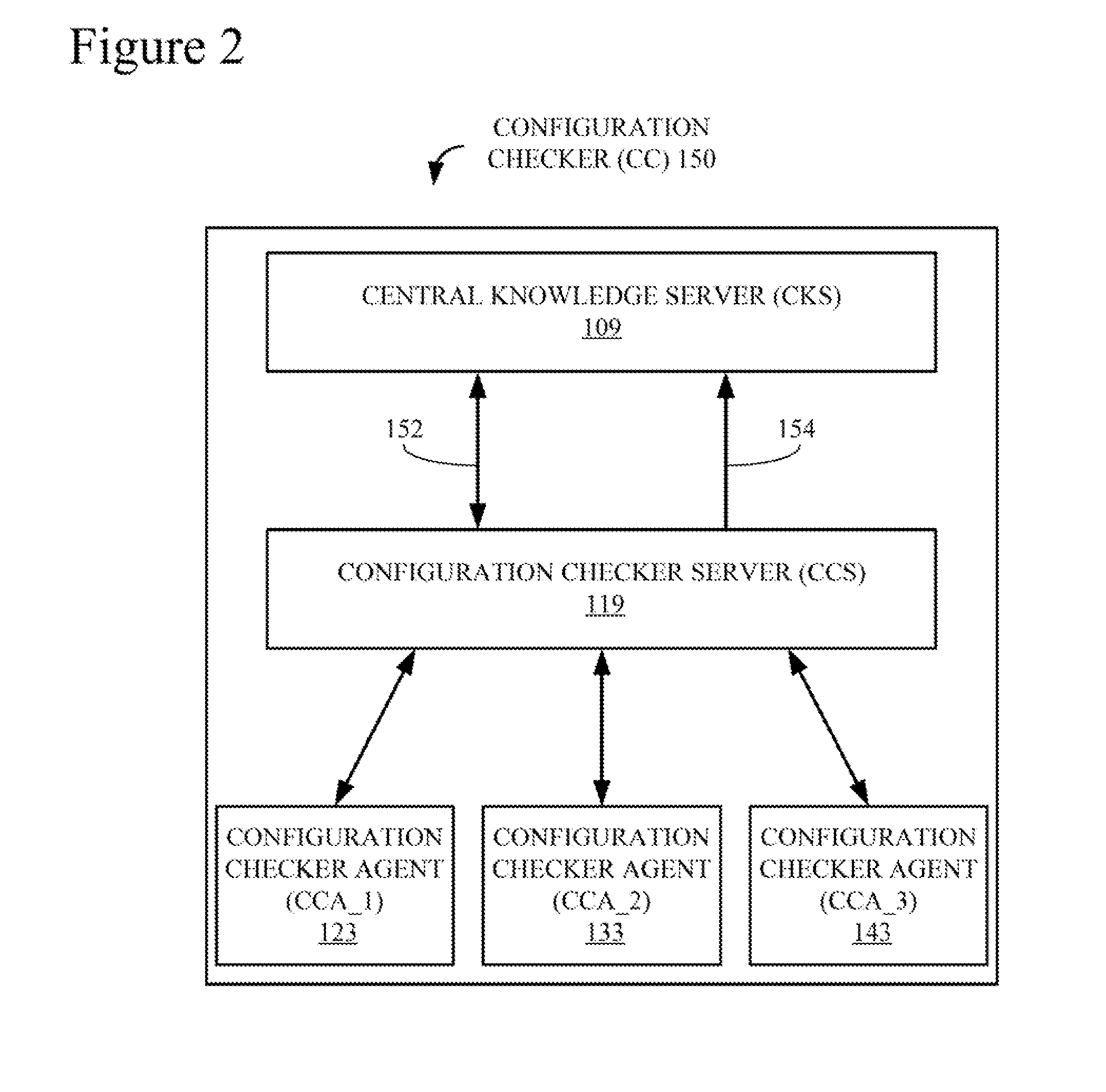
ActiveUS20160291991A1Interprogram communicationProgram loading/initiatingComputer compatibilityApplication software
Provided are techniques for verifying application compatibility, comprising providing a configuration knowledge server (CKS) to store information about configuration issues; detecting, by a configuration checking agent (CCA), a reconfiguration of a computing system; signaling, by the CCA, a configuration checking service (CCS), in response to the detecting; in response to the signaling, requesting, by the CCS, a compatibility report, from the CKS, about potential configuration issues with respect to the reconfiguration; transmitting the compatibility report from the CKS to the CCS; parsing, by the CCS, the compatibility report to identify a compatibility issue with respect to the reconfiguration; and in response to identifying the compatibility issue, dynamically performing an action to mitigate the compatibility issue.
Owner:IBM CORP
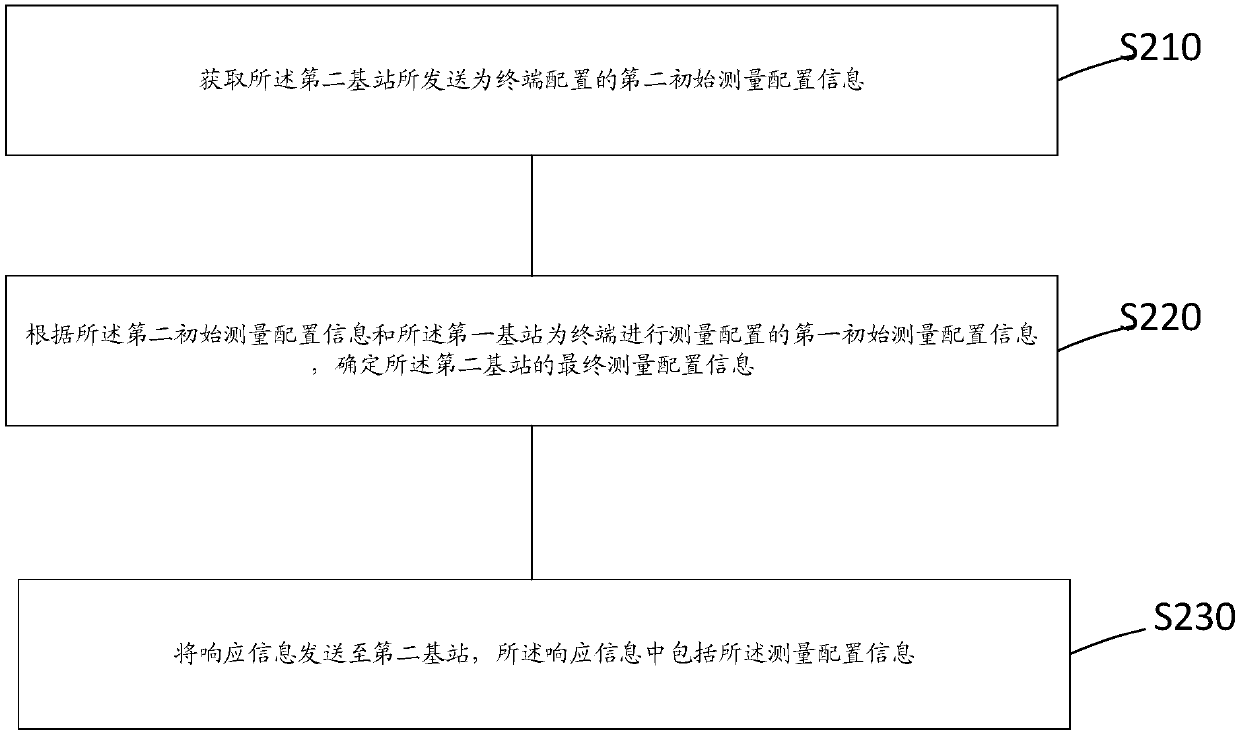
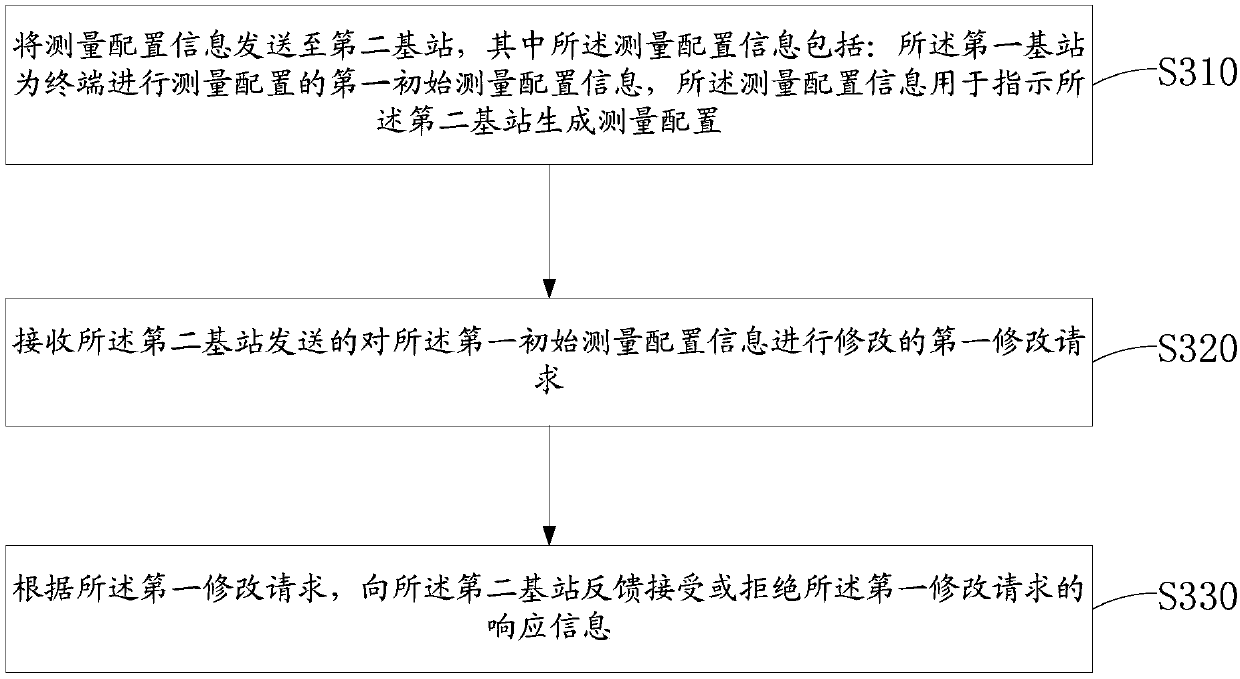
Negotiation method of measurement configuration under inter-system double connections, base station and terminal
The invention provides a negotiation method of measurement configuration under inter-system double connections, a base station and a terminal. The method is applied to a first base station and comprises the steps that measurement configuration information is sent to a second base station, the measurement configuration information is used for indicating measurement configuration issued by the second base station to a terminal, and the terminal is connected to the first base station and the second base station at the same time. According to the negotiation method, the first base station sends measurement configuration information used for indicating the second base station to perform measurement configuration on the terminal to the second base station, so that the first base station has a decision-making right of the measurement configuration, and the problems that the measurement configuration information of the two base stations conflicts with each other, the UE may perform measurementtwice for the same frequency point, and the measurement overhead is wasted are avoided.
Owner:CHINA MOBILE COMM LTD RES INST +1
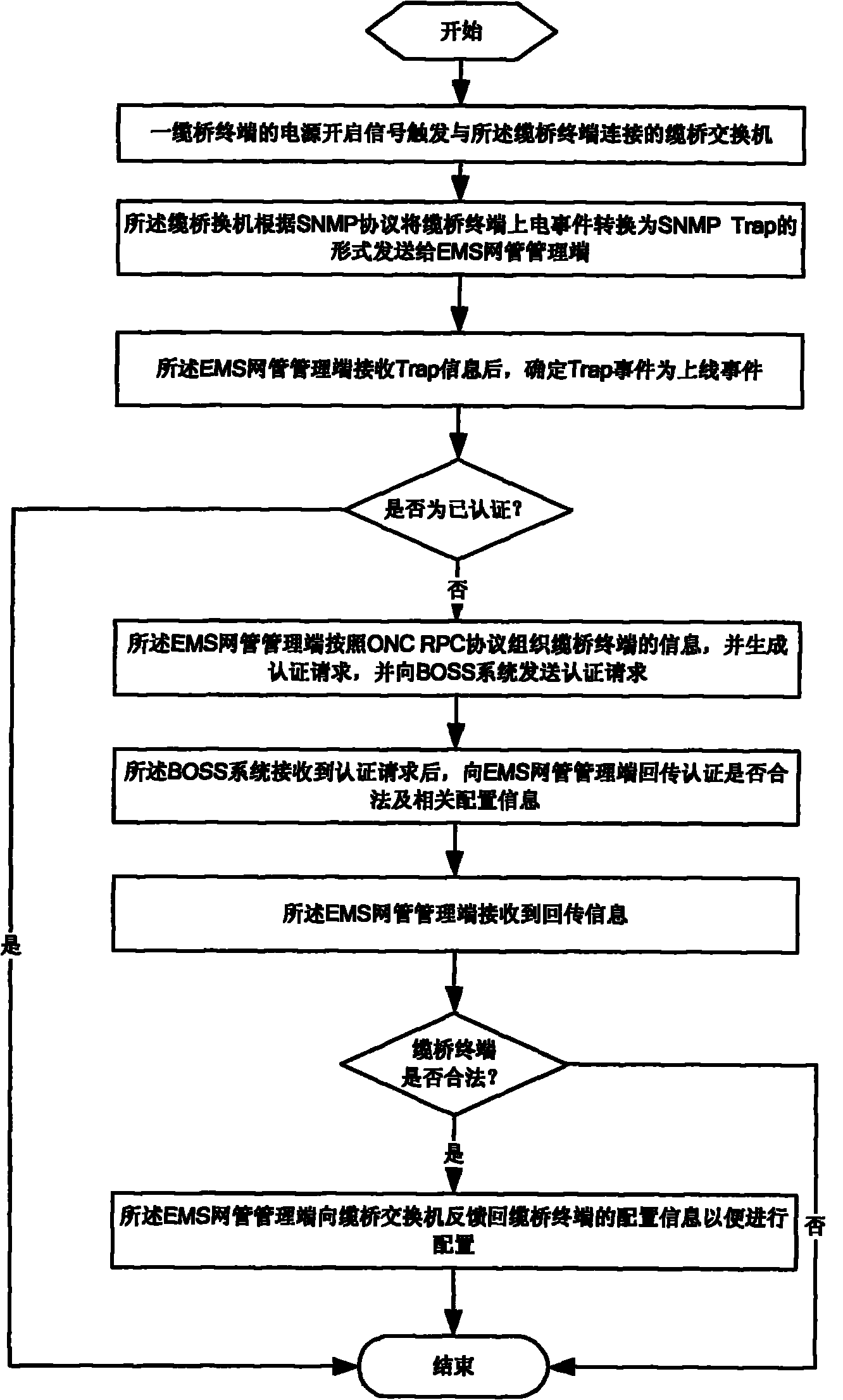
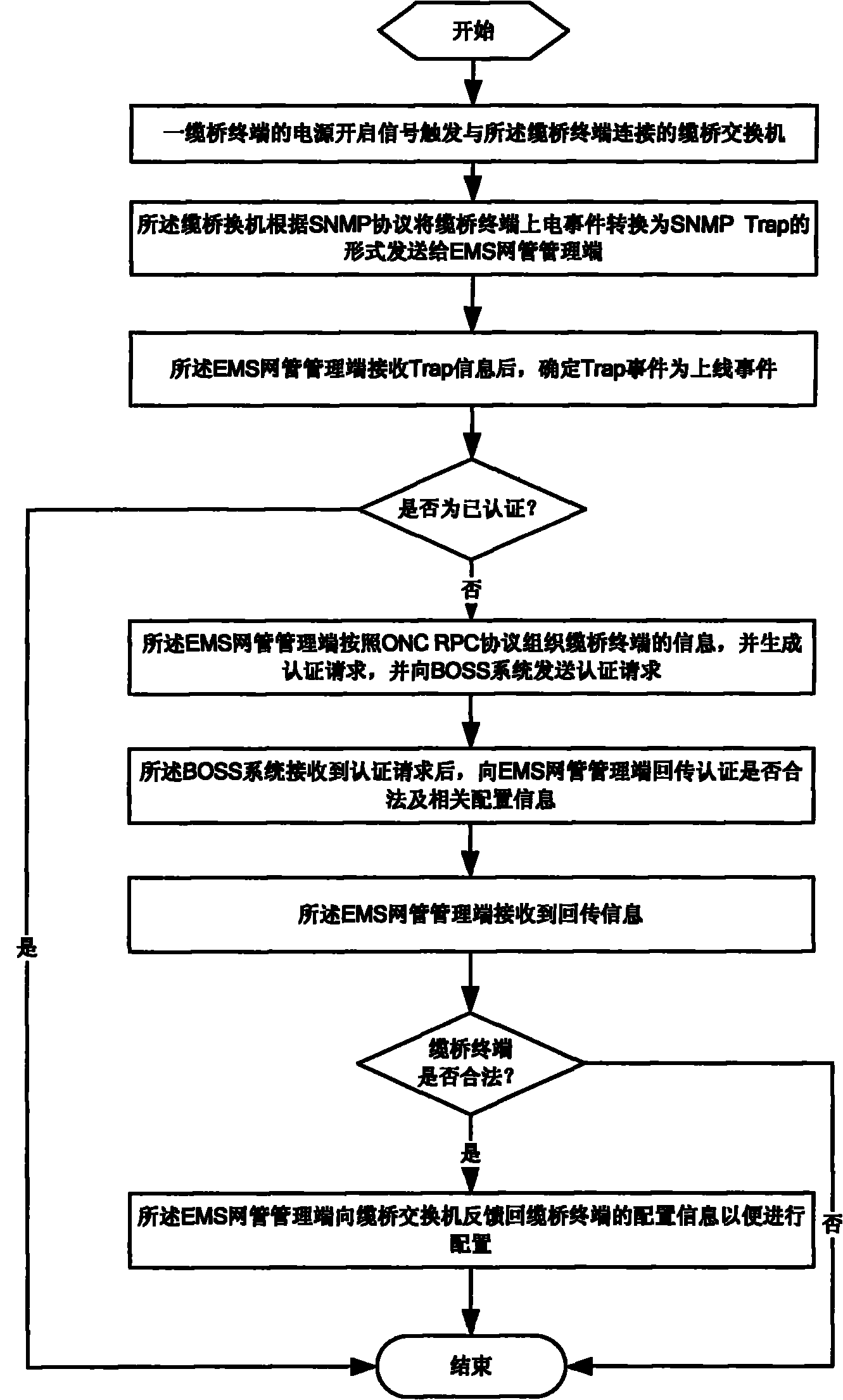
Method for automatic authentication and configuration issue of cable bridge terminal with utilization of BOSS system
ActiveCN102377587AImplement automatic authenticationImplement configurationData switching networksEngineeringSimple Network Management Protocol
The invention relates to a method for automatic authentication and configuration issue of a cable bridge terminal with utilization of a BOSS system. The method comprises the following steps that: a power supply starting signal of a cable bridge terminal triggers a cable bridge switch that is connected with the cable bridge terminal; according to a simple network management protocol (SNMP), the cable bridge switch converts a mode of a power-on event of the cable bridge terminal into an SNMP Trap mode and then the converted Trap information is sent to a management terminal of EMC network management; after the management terminal of the EMC network management receives the Trap information, a Trap processing flow is entered; and according to an open network computing remote procedure call (ONC RPC) procotol, unauthorized Trap information of the cable bridge terminal is converted into an authentication request and the converted request is sent to the BOSS system; the BOSS system returns whether the authentication is legal or not and correlated configuration information; and according to the returned information, the management terminal of the EMC network management determines whether the authentication of the cable bridge terminal is legal or not; if so, the configuration information of the cable bridge terminal is feedbacked to the cable bridge switch, so that corresponded configuration is carried out on the cable bridge terminal; and therefore, automatic authentication and configuration issue on the cable bridge terminal are realized.
Owner:SHANGHAI BROADBAND TECH
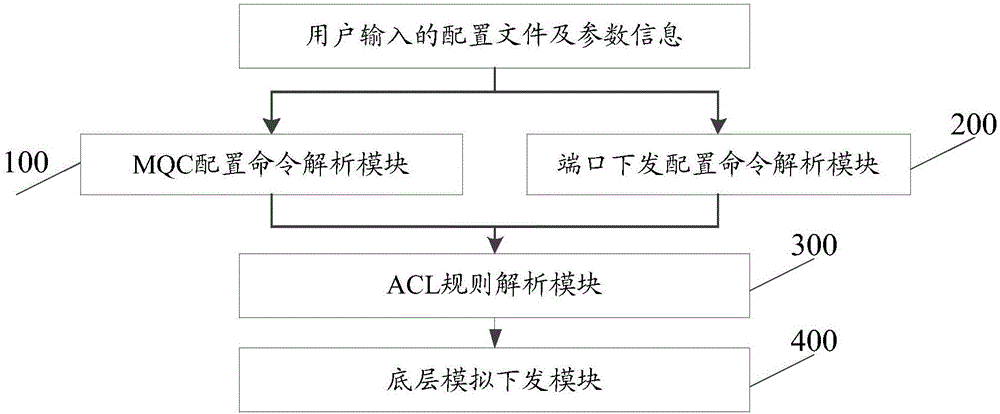
Switch configuration simulated issuing method, system and computer
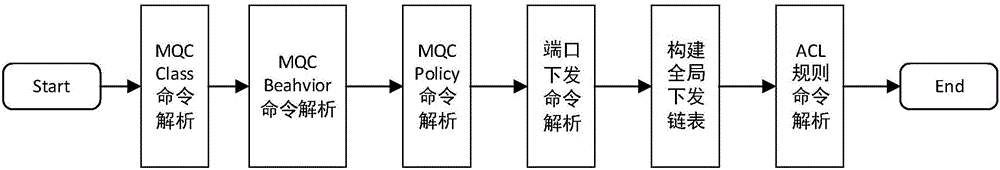
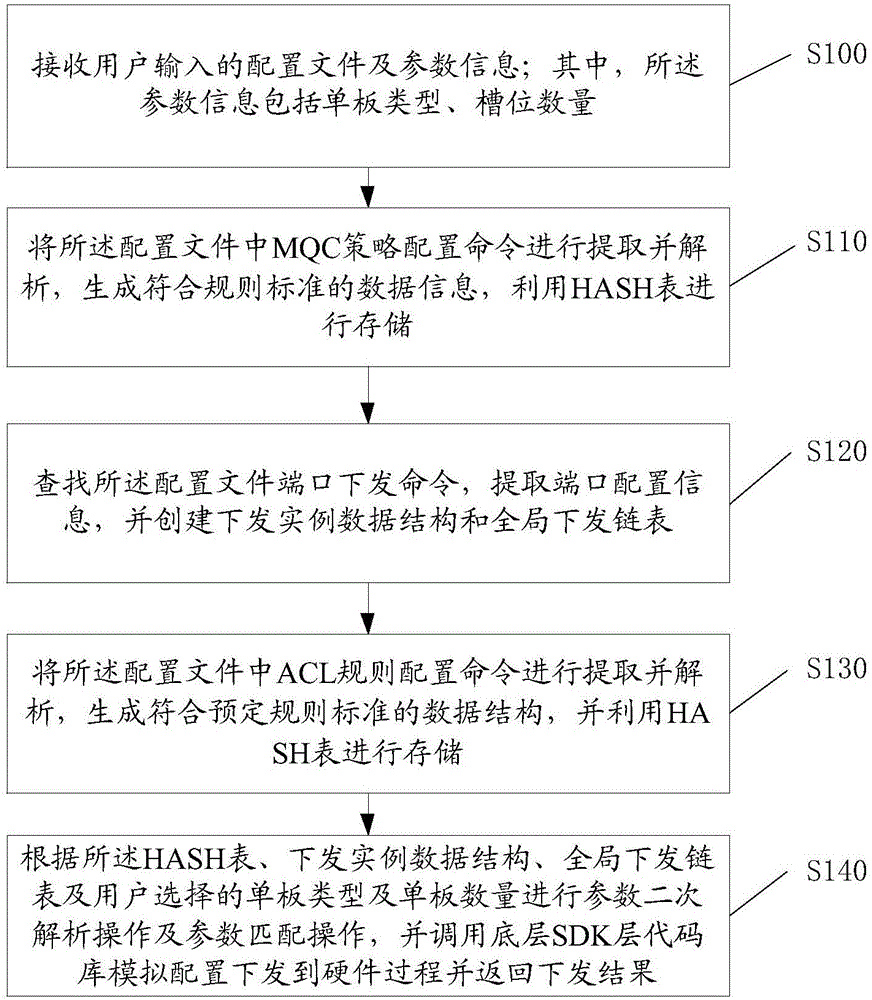
The invention discloses a switch configuration simulated issuing system. The system comprises an MQC configuration command analysis module, a port issuing configuration command analysis module, an ACL rule analysis module, and a bottom layer simulated issuing module; the front three modules belong to analytic layer module for analyzing configuration files according to the configuration files input by a user and information of the single board type, slot number and the like, when the analytic layer is accurately executed, an interface of the bottom layer simulated issuing module can be called to enter the simulated issuing stage and return a simulated issuing result; the system enables the user to be divorced from real physical equipment and performs configuration issuing through software simulation, and the issuing effects of the current configuration on different equipment can be conveniently and rapidly checked, thereby evaluating the performance of single equipment, and selecting a product most suitable for the need of the user himself through comparison. The invention further discloses a switch configuration simulated issuing method and computer which have the abovementioned effect.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method and device for processing internet group management protocol (IGMP) Snooping
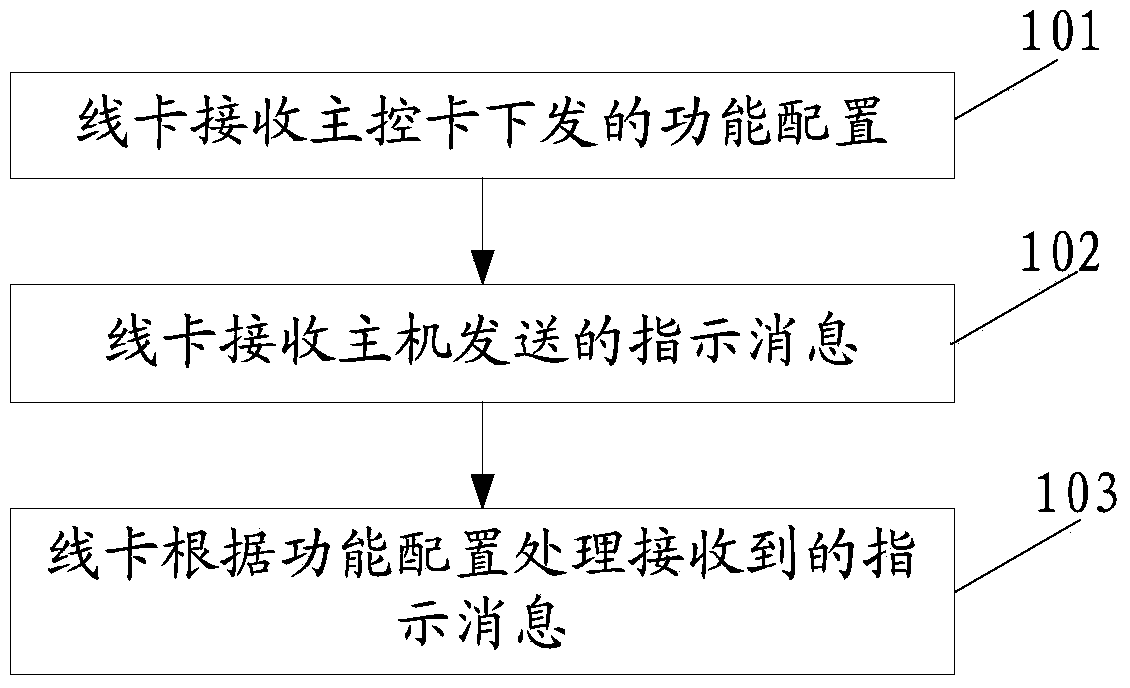
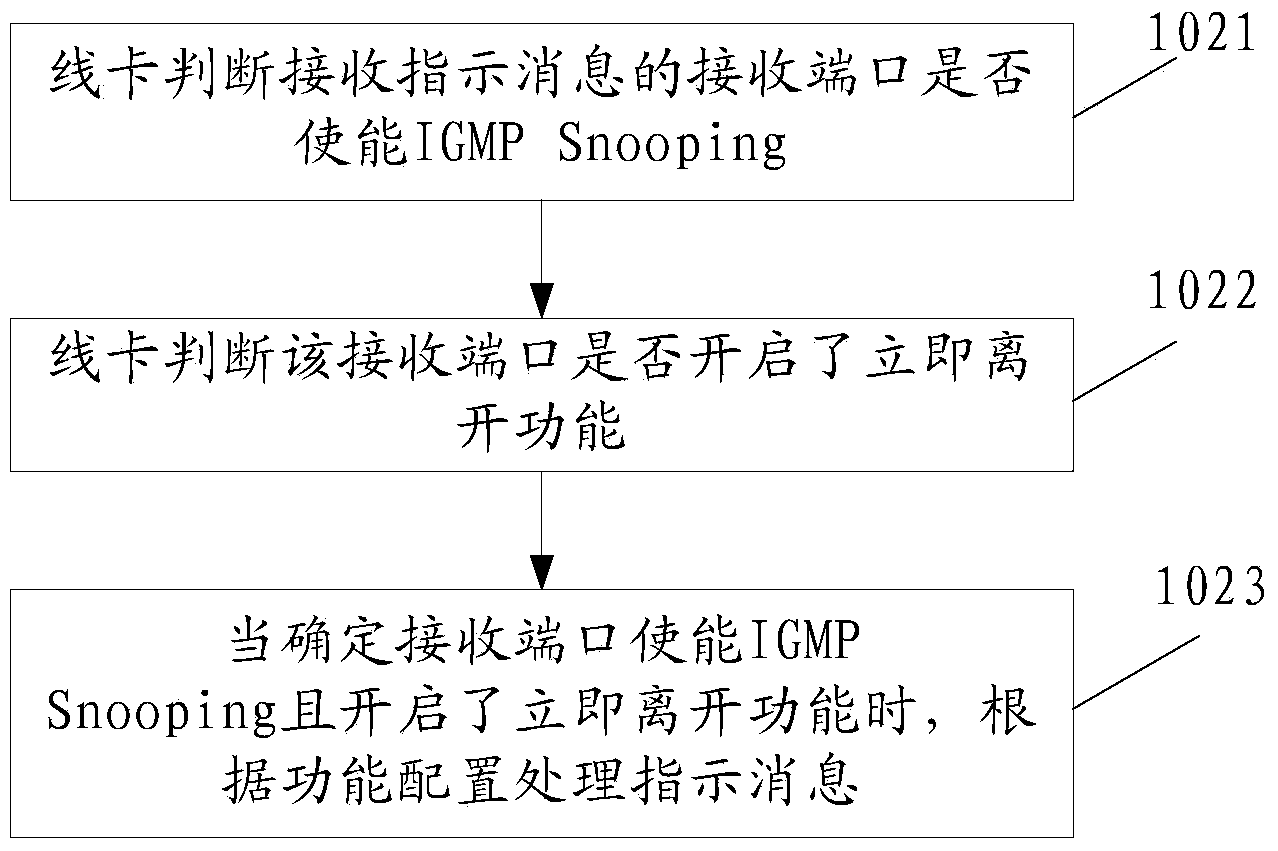
The invention discloses a method and device for processing internet group management protocol (IGMP) Snooping and relates to the technical field of multicast. Accession and departure time delay of IGMP Snooping is remarkably reduced, channel switching time is reduced, and user experience is improved. The method comprises the steps of directly enabling a line card to process indication messages after the line card receives IGMP Snooping enabling and instant departure function starting configuration issued by a main control card and receives the indication messages sent by a mainframe. The method and the device are mainly applied to a processing flow of the IGMP Snooping.
Owner:MAIPU COMM TECH CO LTD
Virtual-machine introspection collection system and method based on KVM
ActiveCN108897602ARealize acquisitionThere will be no collection failureProgram initiation/switchingPlatform integrity maintainanceCollection systemComputer module
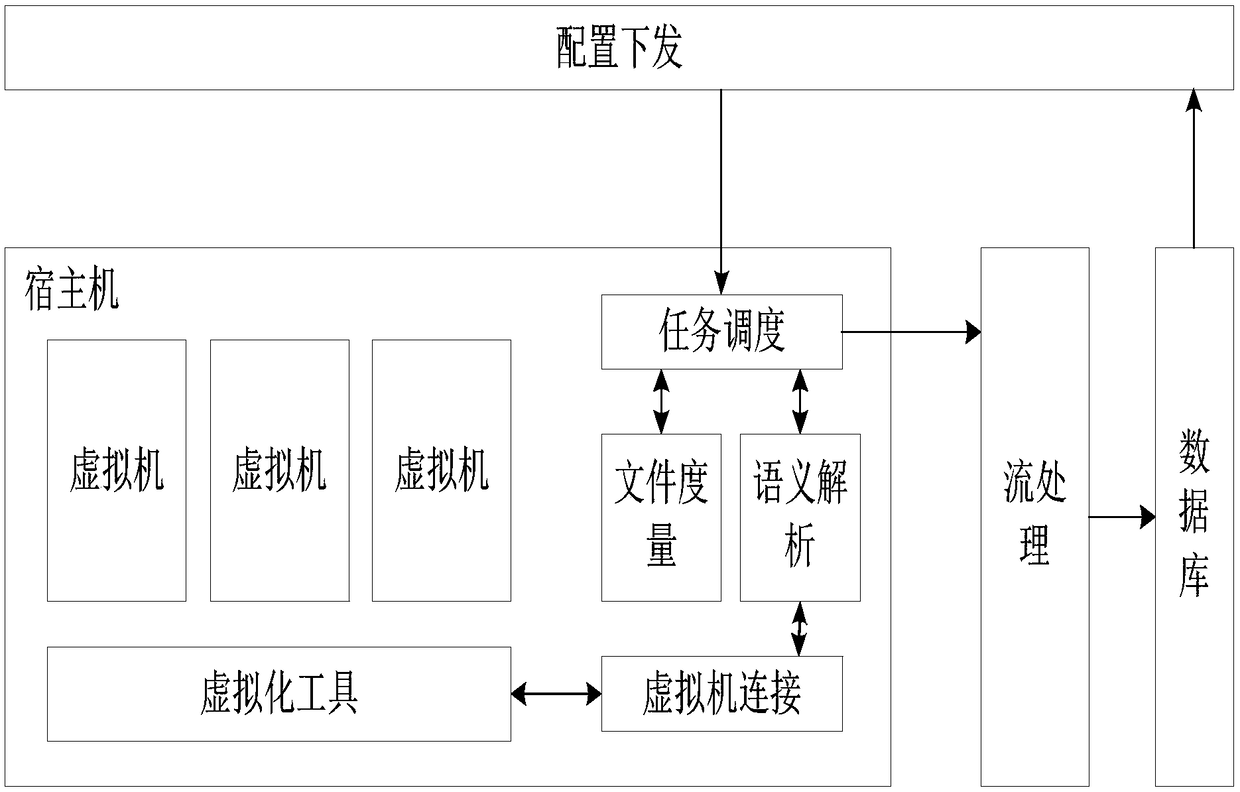
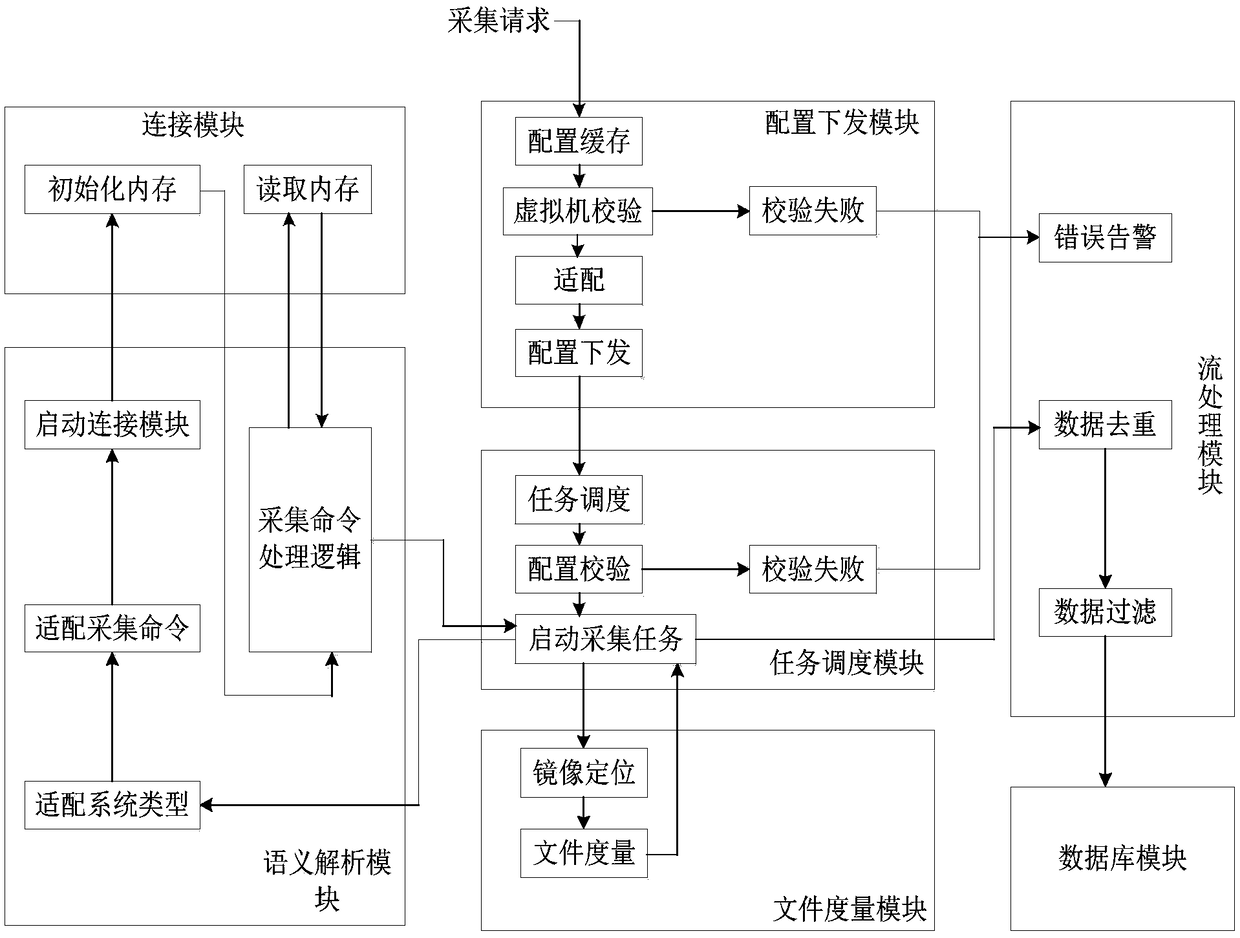
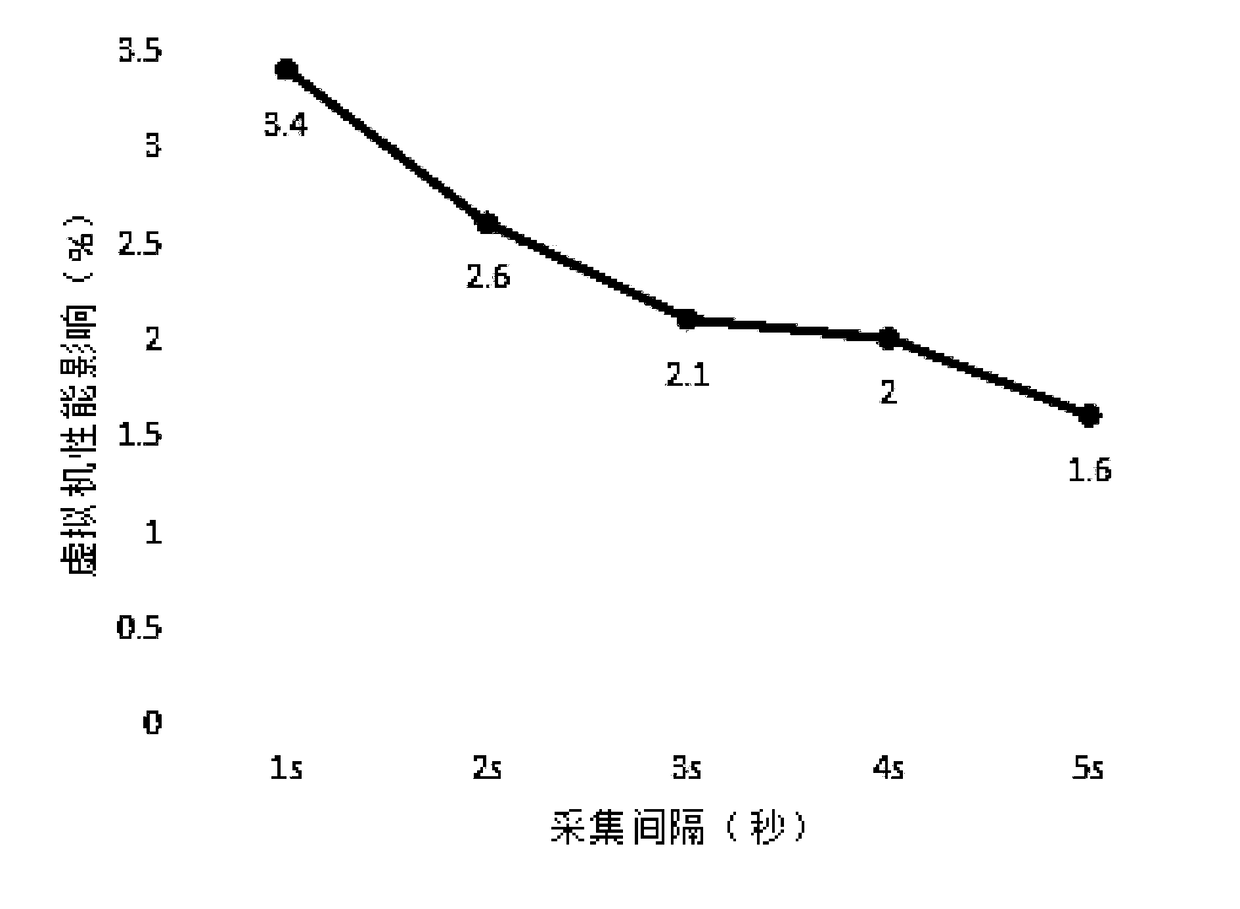
The invention discloses a virtual-machine introspection collection system and method based on a KVM. The virtual-machine introspection collection system and method based on the KVM aim at solving theproblem that when existing foreign network attack appears, due to process death or network paralysis, virtual-machine internal collection fails. The virtual-machine introspection collection system based on the KVM comprises a configuration issuing module, a task scheduling module, a file measurement module, a semantic analysis module, a virtual-machine connection module, a stream processing moduleand a database module; multidimensional information collection of a virtual machine is achieved, and includes virtual-machine memory information collection and virtual-machine file information collection, and supports collection of a Windows virtual machine and a Linux virtual machine. The virtual-machine introspection collection system and method based on the KVM is used for the field of virtual-machine introspection collection.
Owner:HARBIN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com