Virtual-machine introspection collection system and method based on KVM
A technology of collection system and virtual machine, applied in the field of virtual machine introspection collection system, can solve the problems of internal collection failure of virtual machine, network paralysis, process death, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
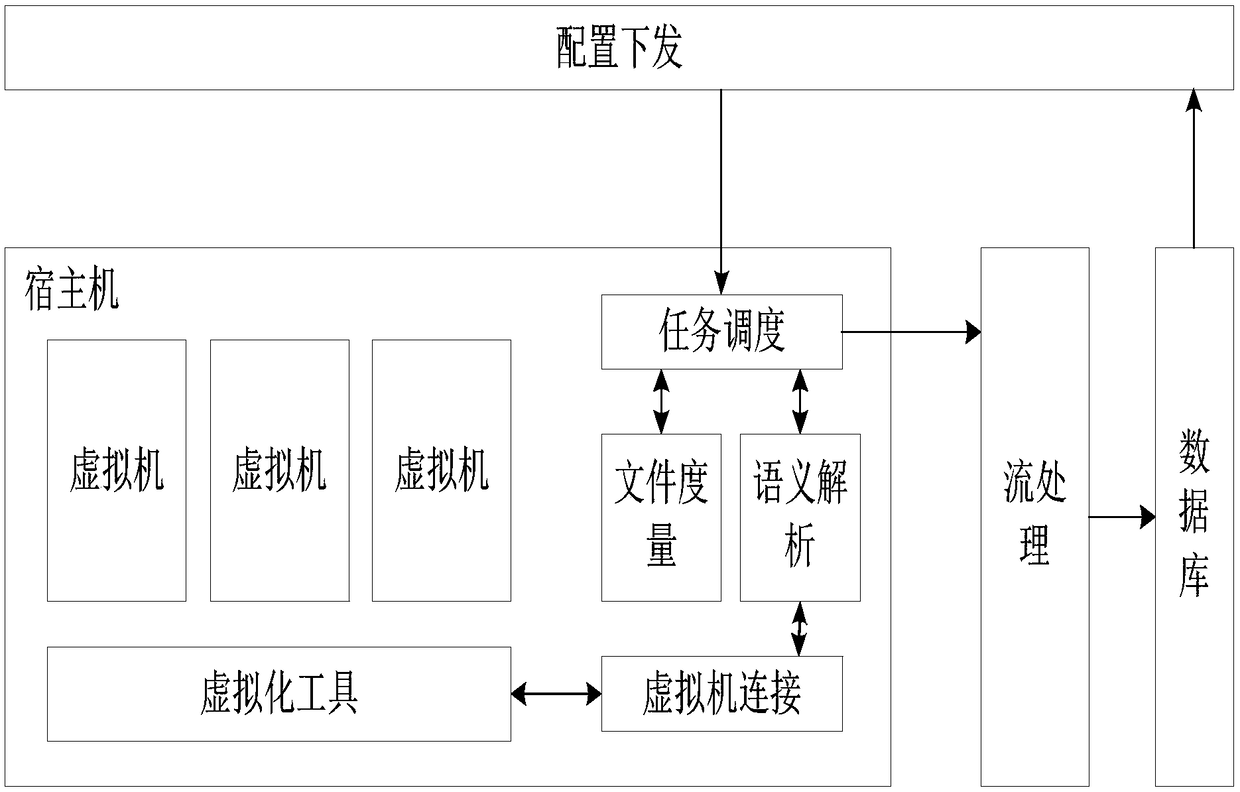
[0028] Specific Embodiment 1: A KVM-based virtual machine introspection acquisition system in this embodiment includes a configuration delivery module, a task scheduling module, a file measurement module, a semantic analysis module, a virtual machine connection module, a stream processing module and a database module. The system The structure diagram is as follows figure 1 ;
[0029] The full name of KVM is Kernel-based Virtual Machine;
[0030] The configuration delivery module is used to receive the request of the virtual machine collection task, such as starting or stopping the process information collection of the virtual machine B on the host machine A. The configuration delivery module is used to manage all serviceable virtual machines in the cloud platform, including which host machine the virtual machine is located under, the status of the virtual machine, and the operating system version of the virtual machine; when the configuration delivery module receives After c...
specific Embodiment approach 2
[0038] Specific embodiment two: the difference between this embodiment and specific embodiment one is: the semantic analysis module is responsible for the collection tasks of Windows and Linux virtual machine memory information, and the semantic analysis module is based on different virtual machine operating system versions and different collection tasks Start different acquisition configurations, analyze the virtual machine memory after the virtual machine connection module is initialized, and then obtain the corresponding Windows and Linux virtual machine information; specifically:
[0039] Adapt the kernel data structure and symbol table, fill the gap of the physical memory where the virtual machine memory is located, locate the object offset through the symbol table, locate the target information according to the kernel data structure, and then obtain the corresponding Windows and Linux virtual machine information.
[0040] Other steps and parameters are the same as those i...
specific Embodiment approach 3
[0041] Specific implementation mode three: a kind of KVM-based virtual machine introspection collection method specific process of this implementation mode is:
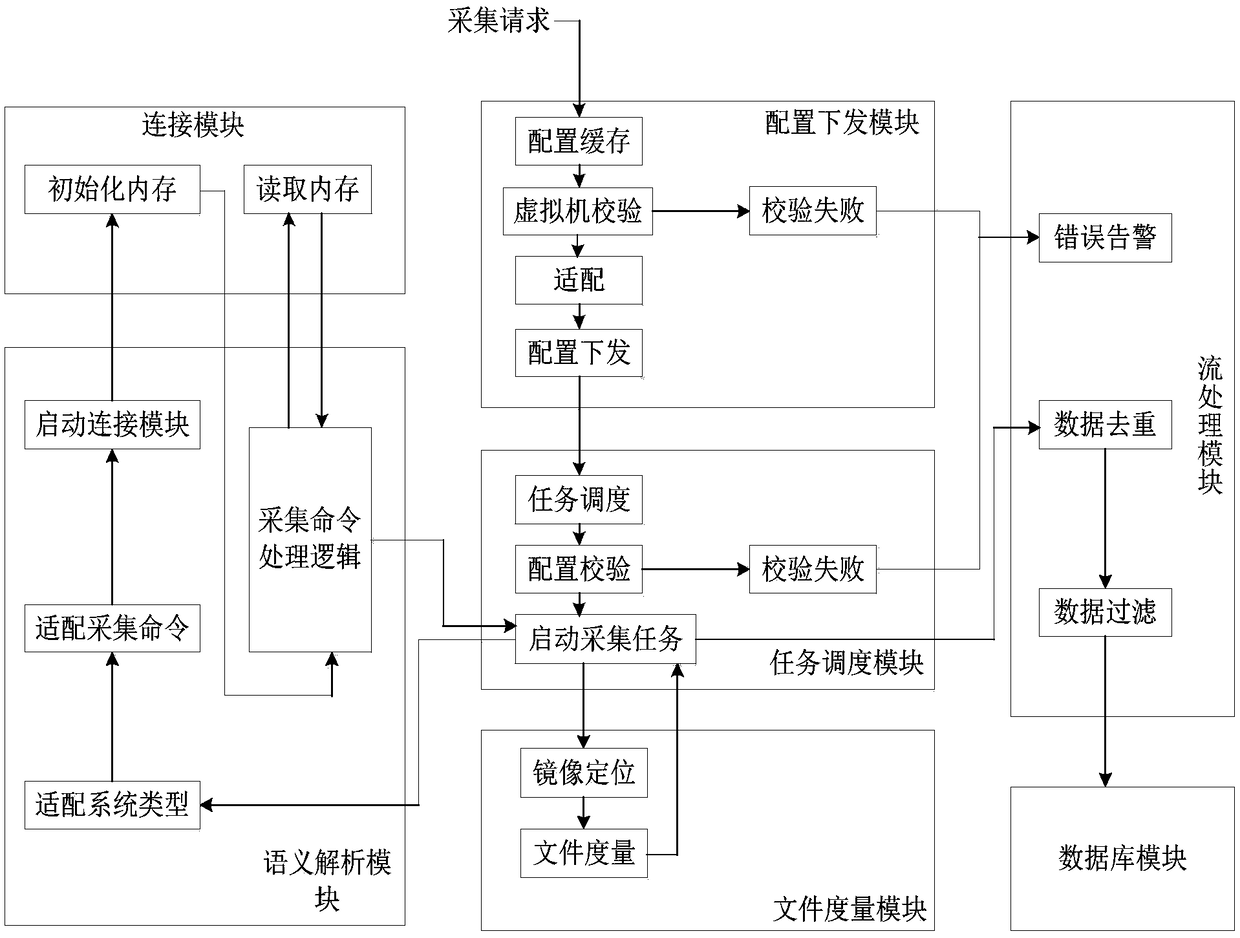
[0042] The information processing flow of the system is as follows: figure 2 .
[0043] When the system administrator sends a collection request, the collection request enters the configuration delivery module, and the configuration delivery module caches and verifies the collection request. If no relevant virtual machine information is found, the verification fails and the error message is sent to the streamer. Processing module; if relevant virtual machine information is found, it will adapt the operating system kernel version of the acquisition request and the configuration information related to the acquisition request, and after locating the host where the virtual machine is located, send the configuration information to the host;
[0044] The task scheduling module is located on the host machine, and performs co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com