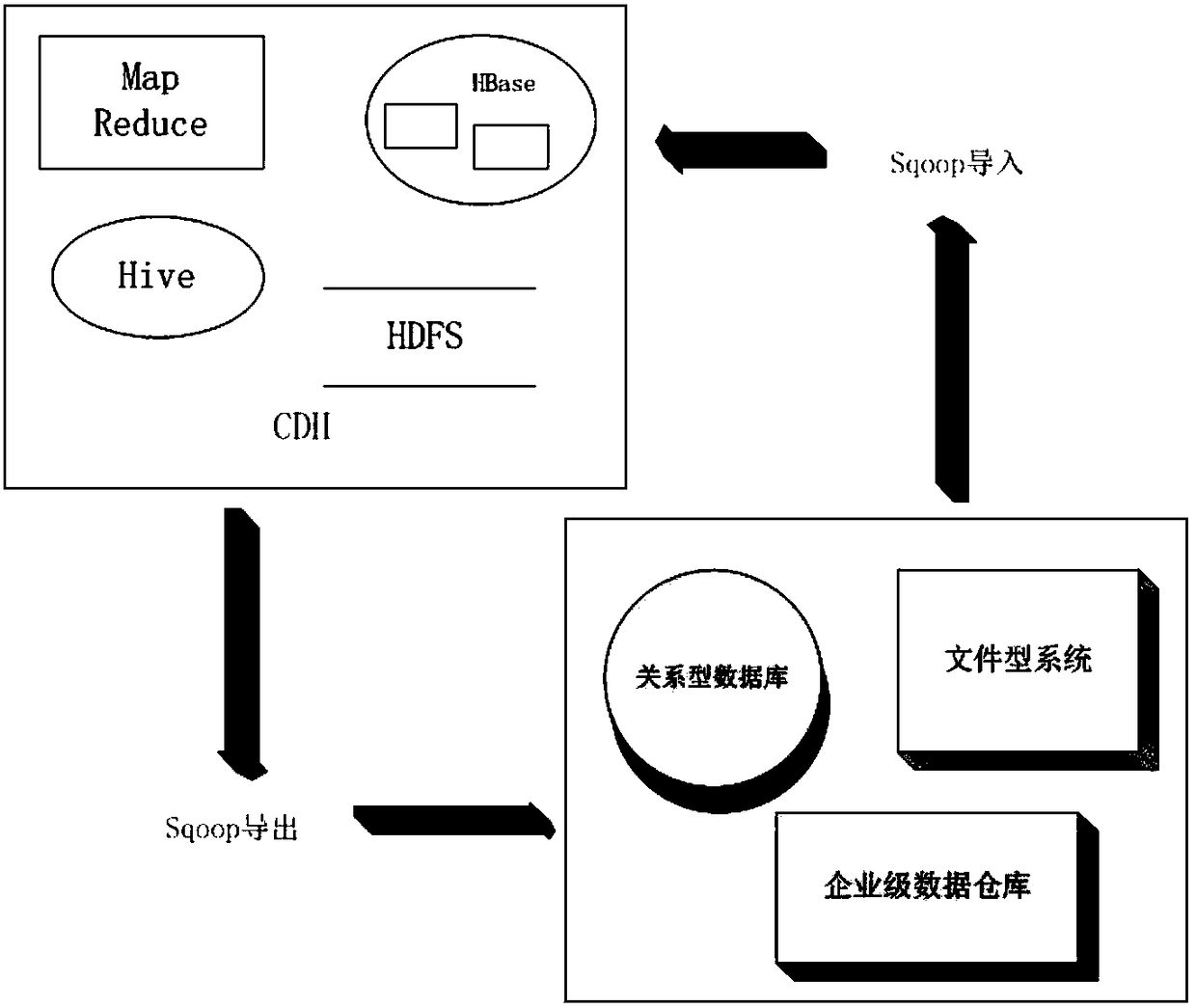
Patents
Literature
53 results about "Network information flow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
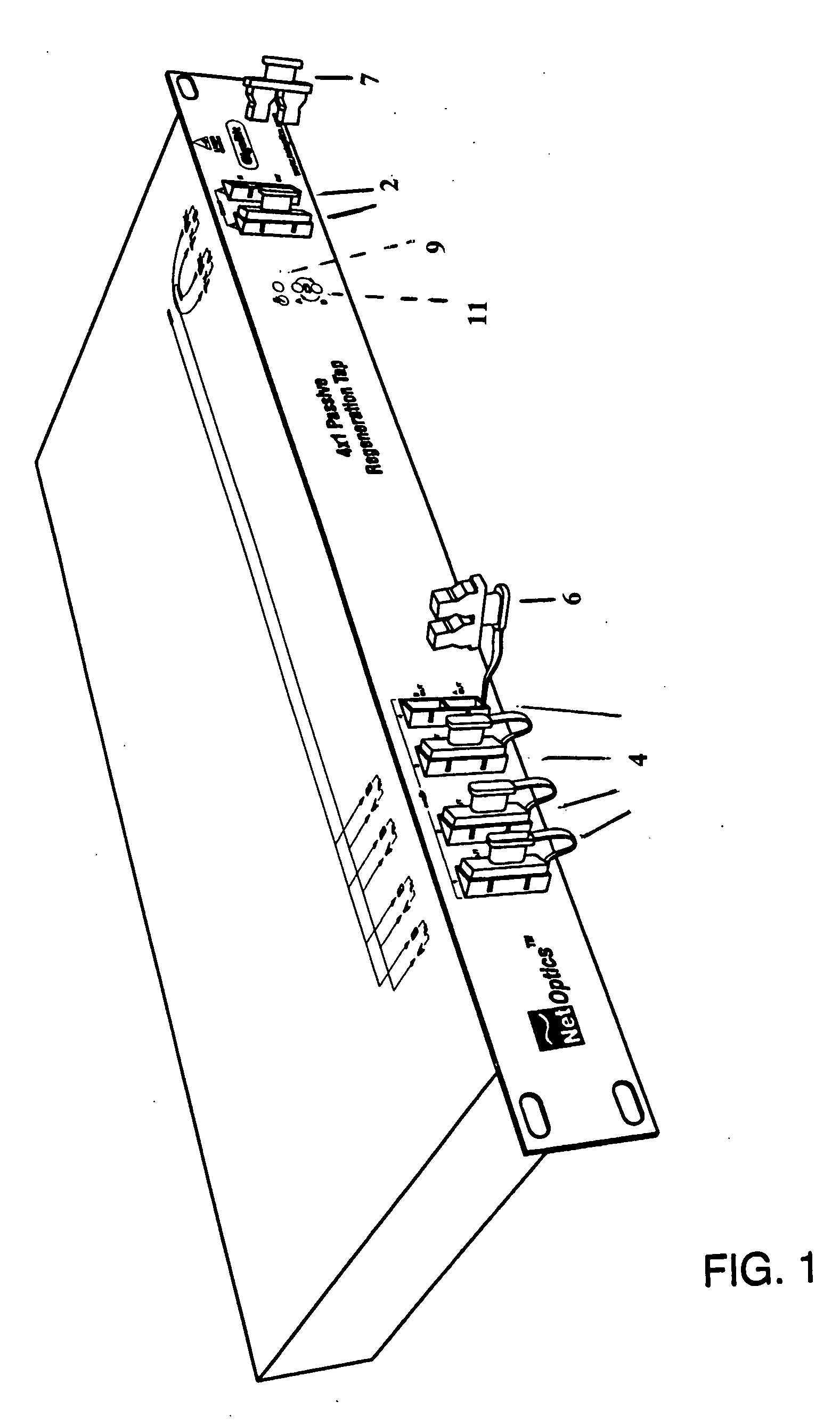
Zero-interrupt network tap
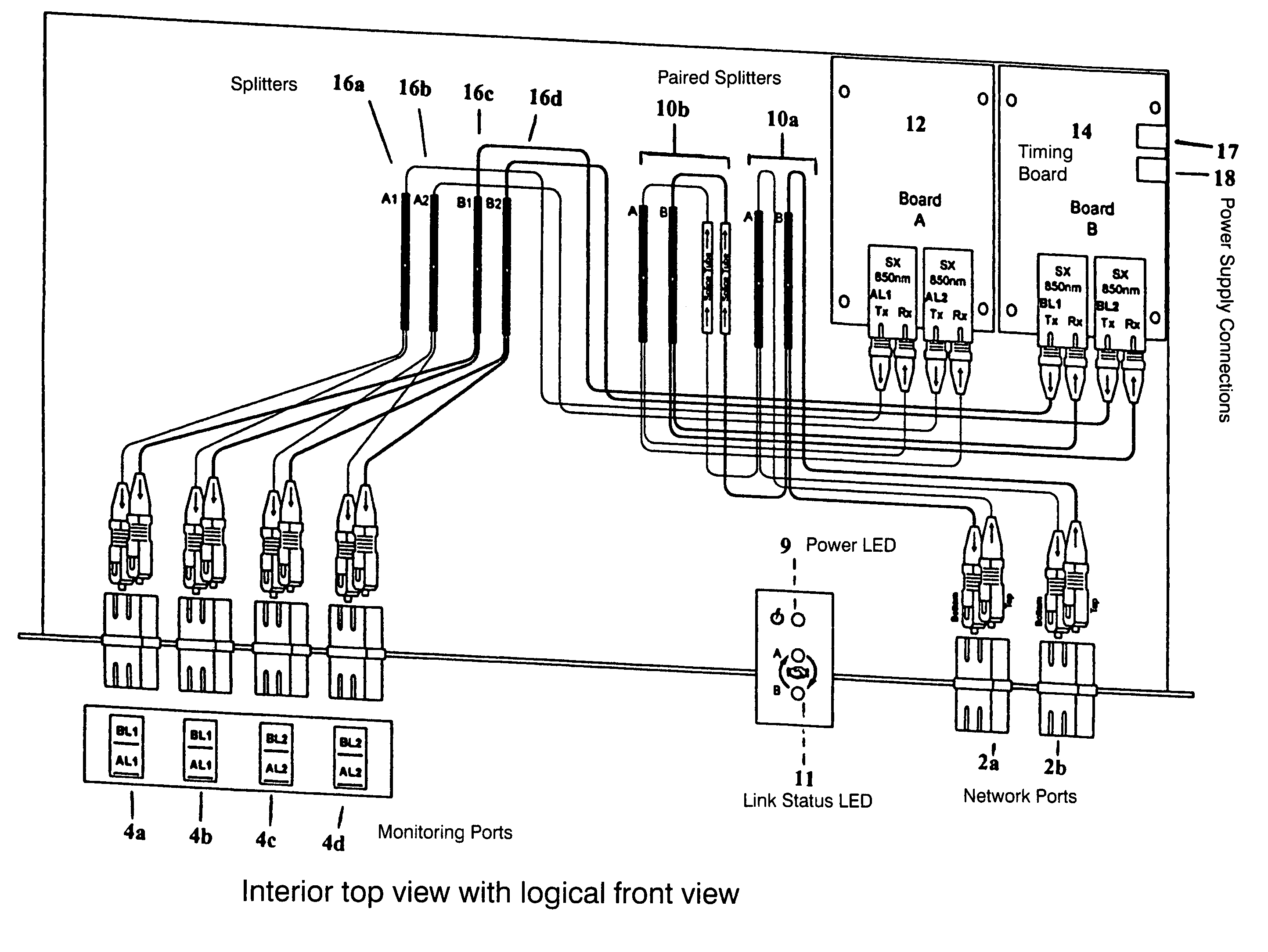
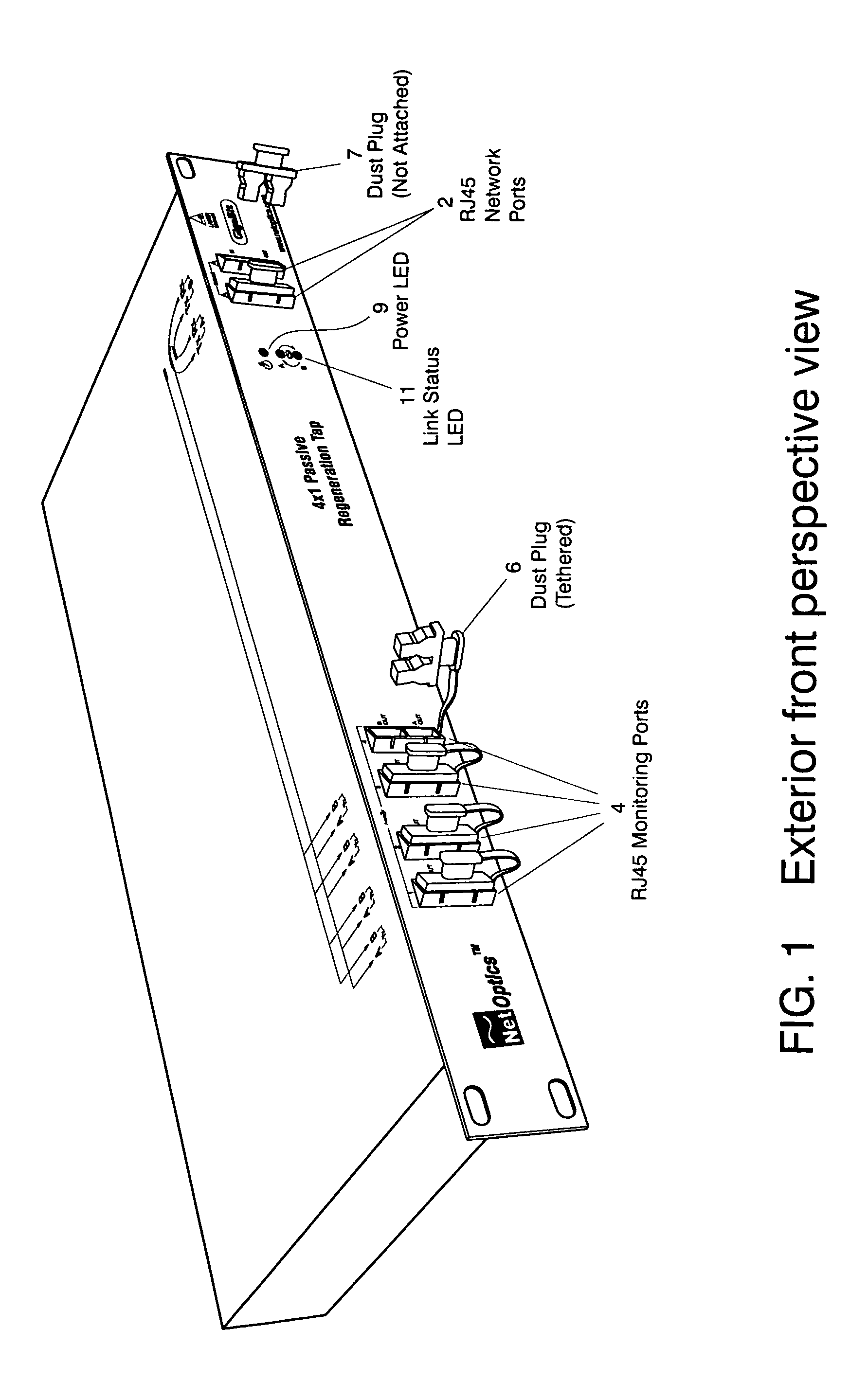
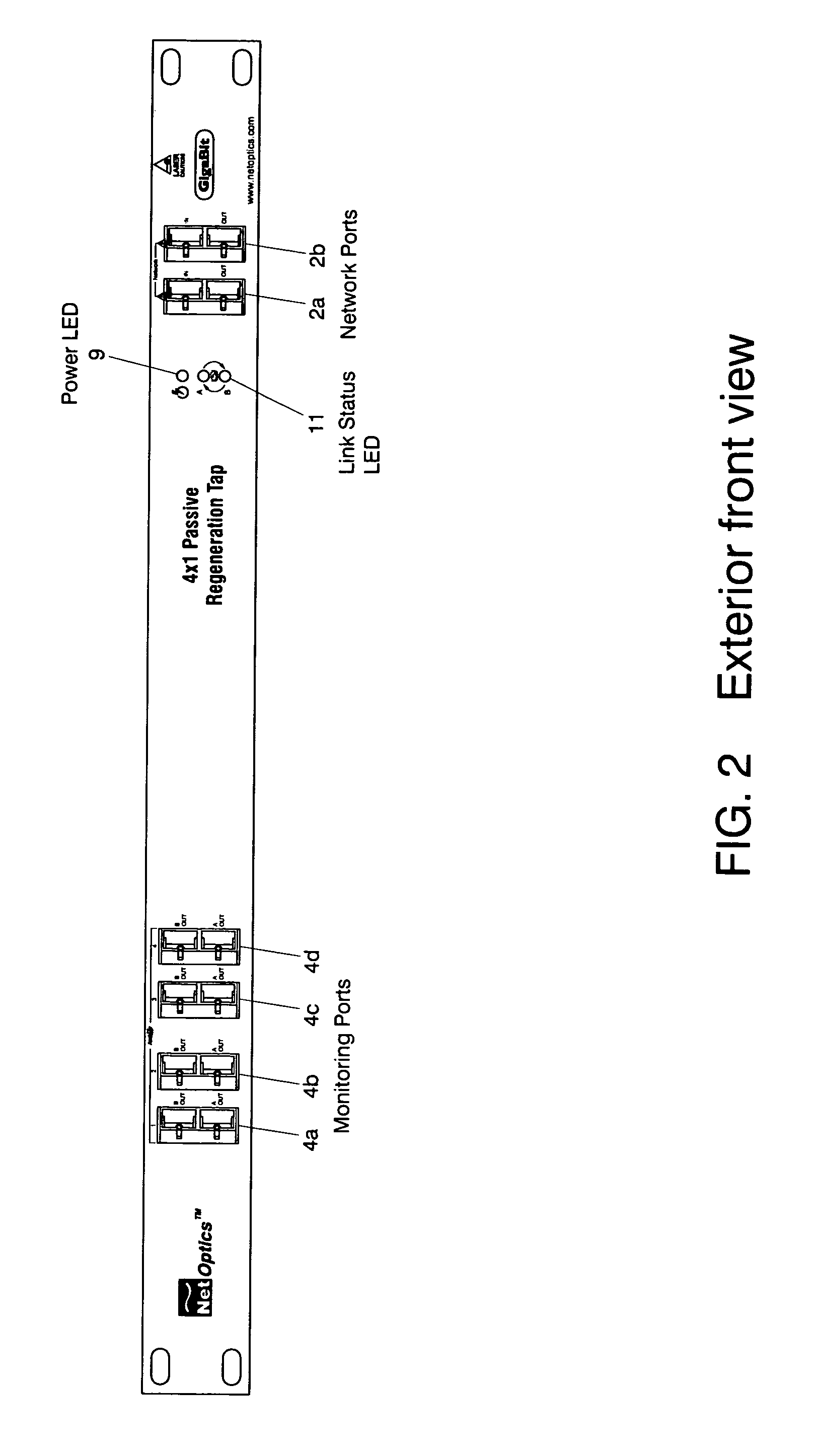
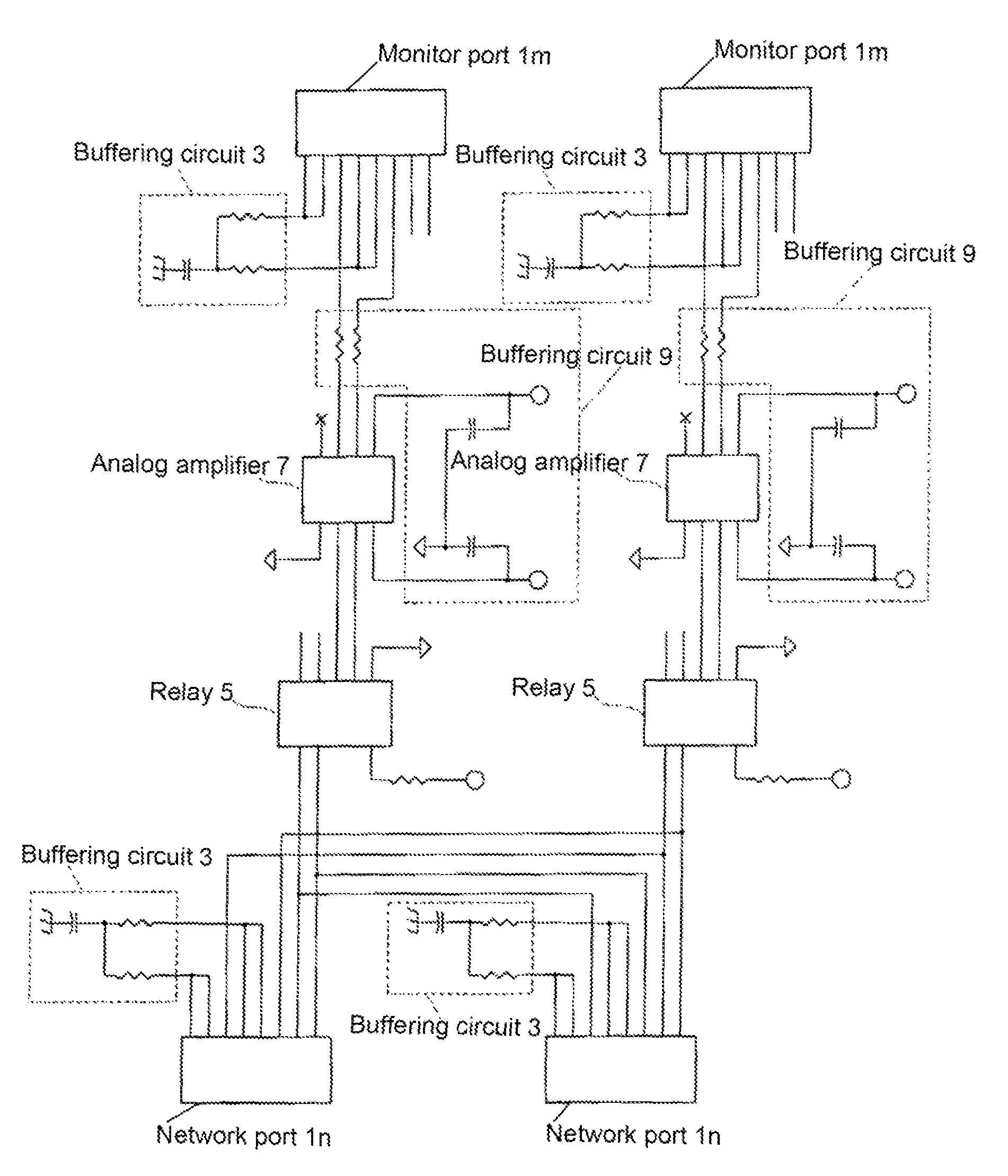
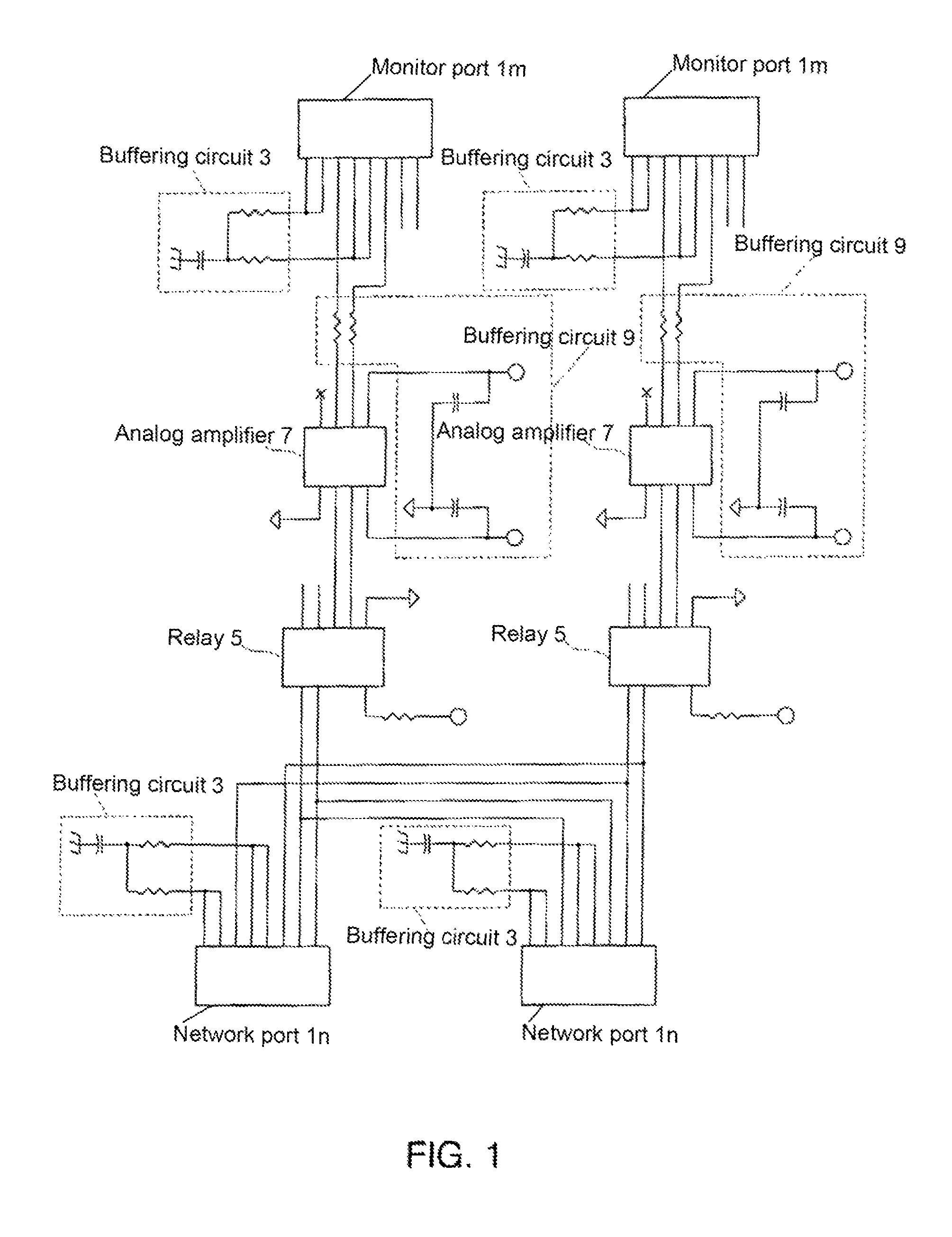
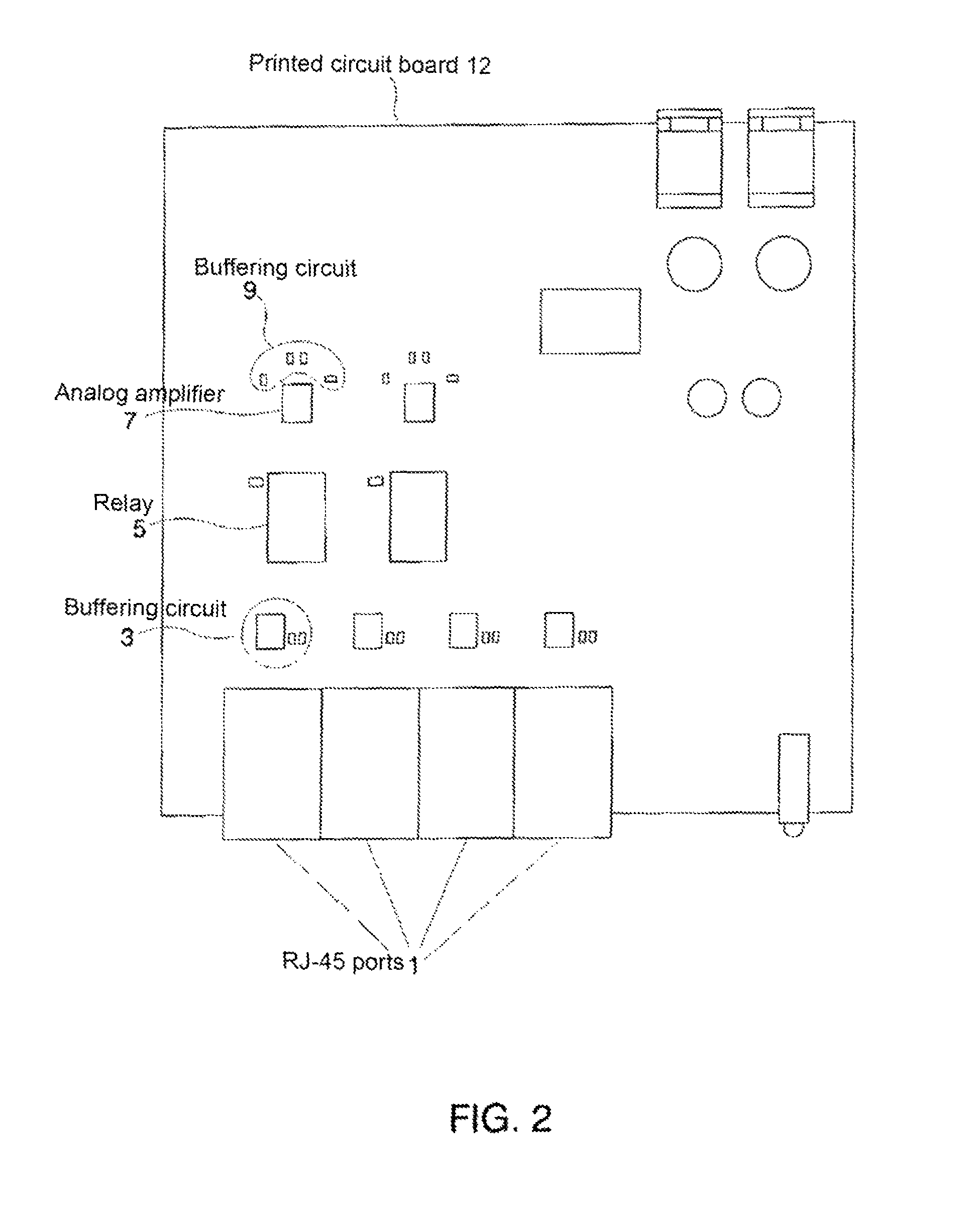
A network tap monitors network information flow over a particular connection. By duplicating the signal and diverting a copy, the information flow can be analyzed, both in real time and without interference through the monitoring process. When the power to the tap is either turned on or off, however, the change in impedance in the tap's circuit can create an interference spike in the connection that interrupts the information flow. By reducing or eliminating the impedance change in the tap circuitry, such disruptive interruptions can be eliminated.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
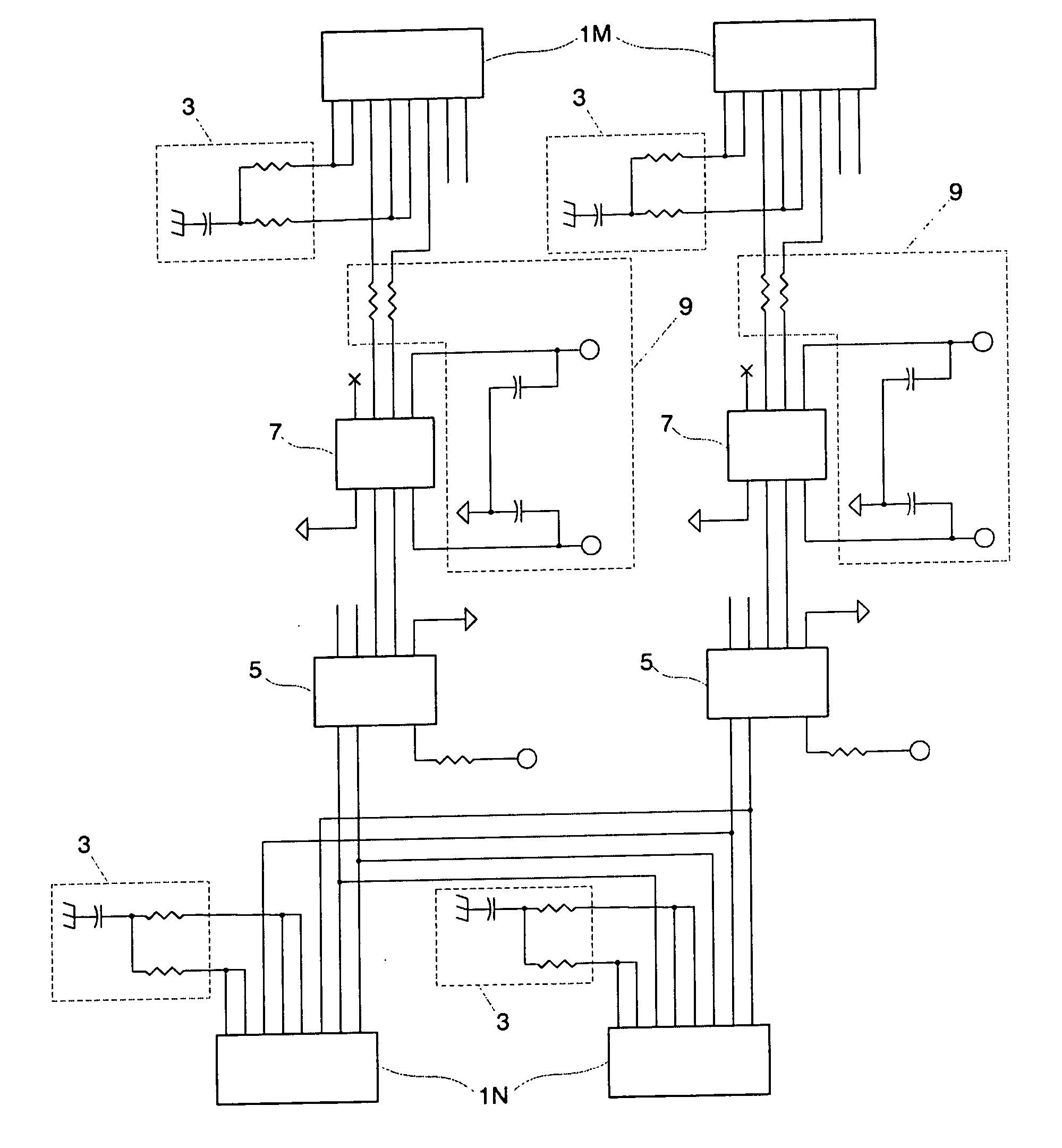
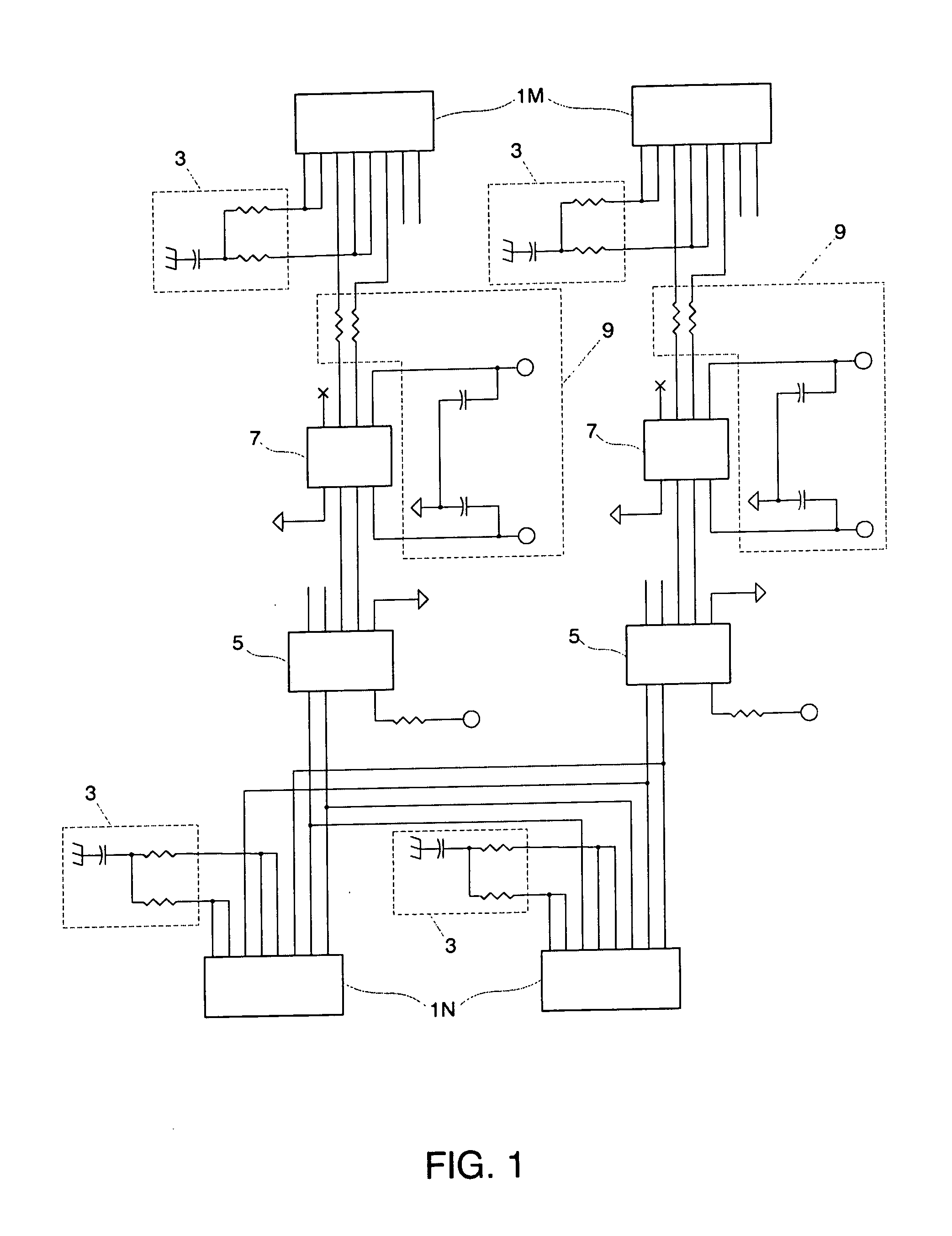
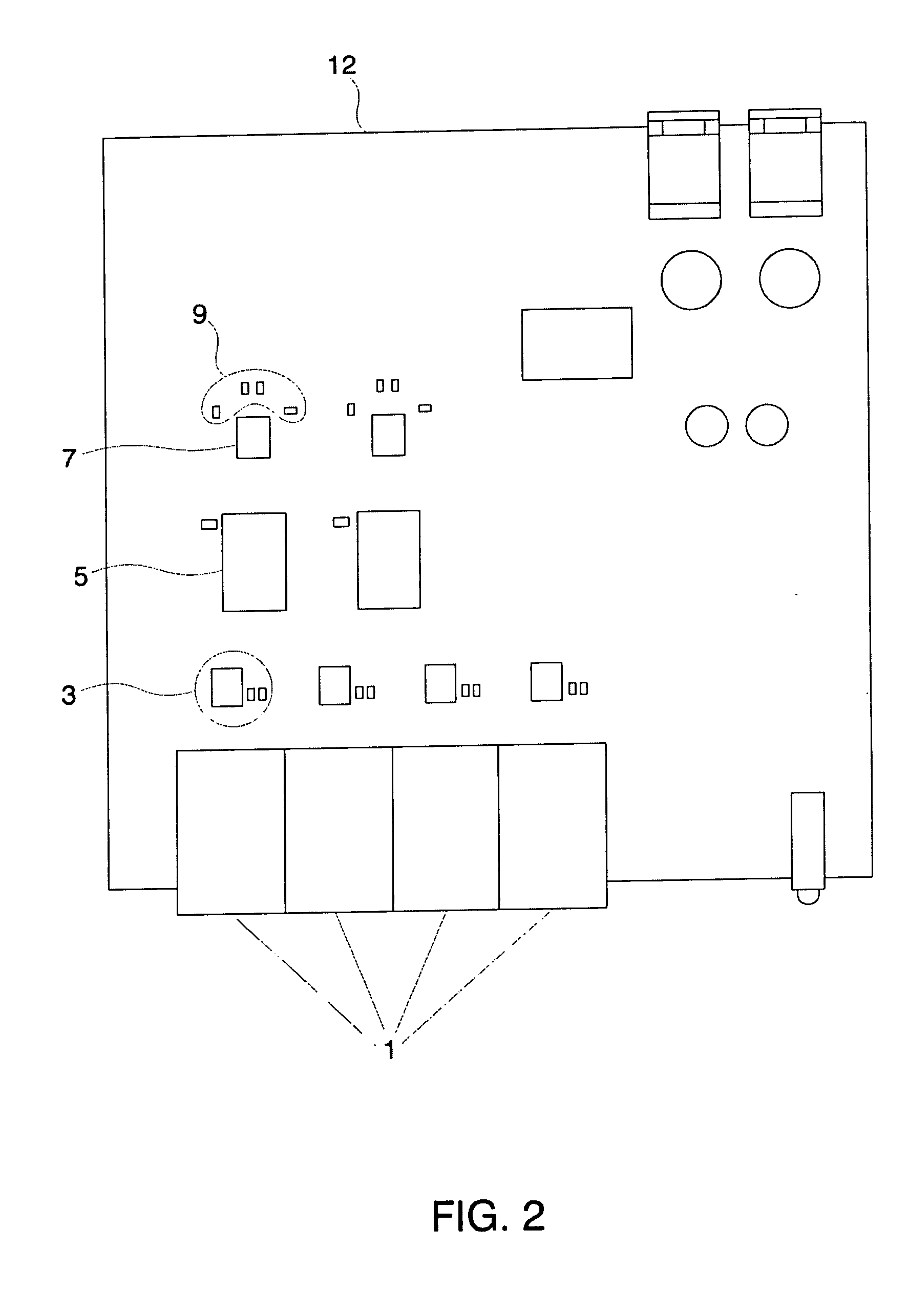
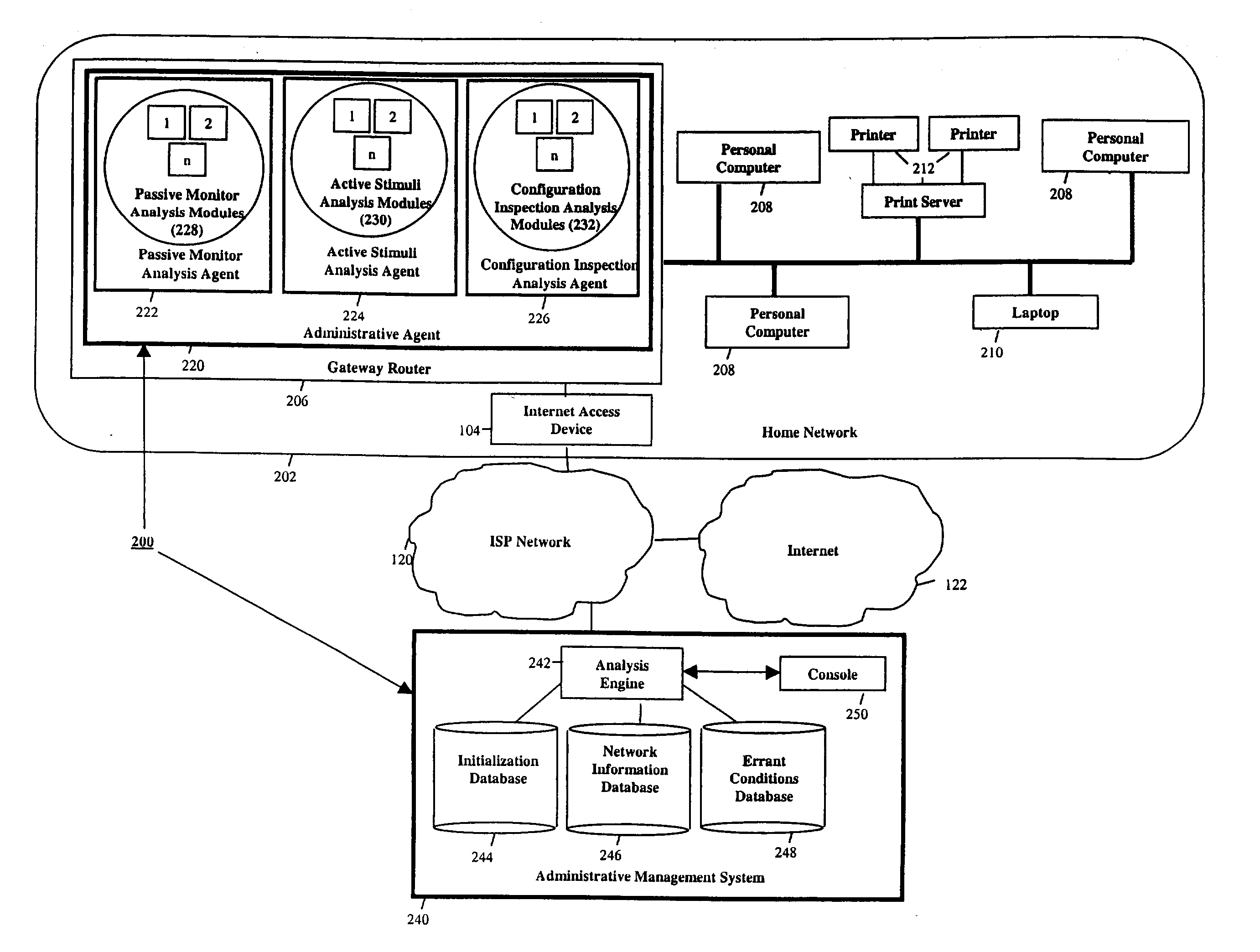
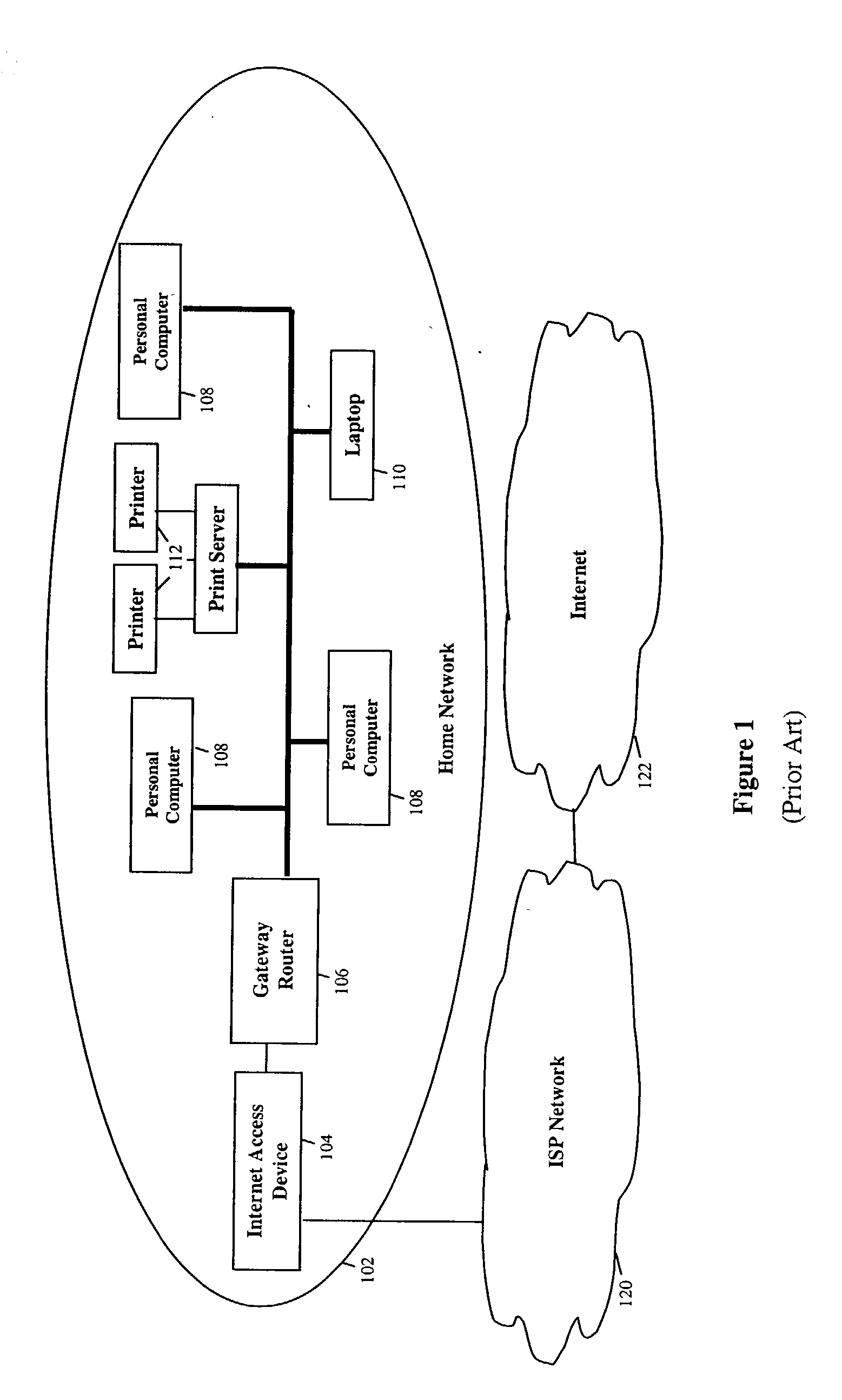
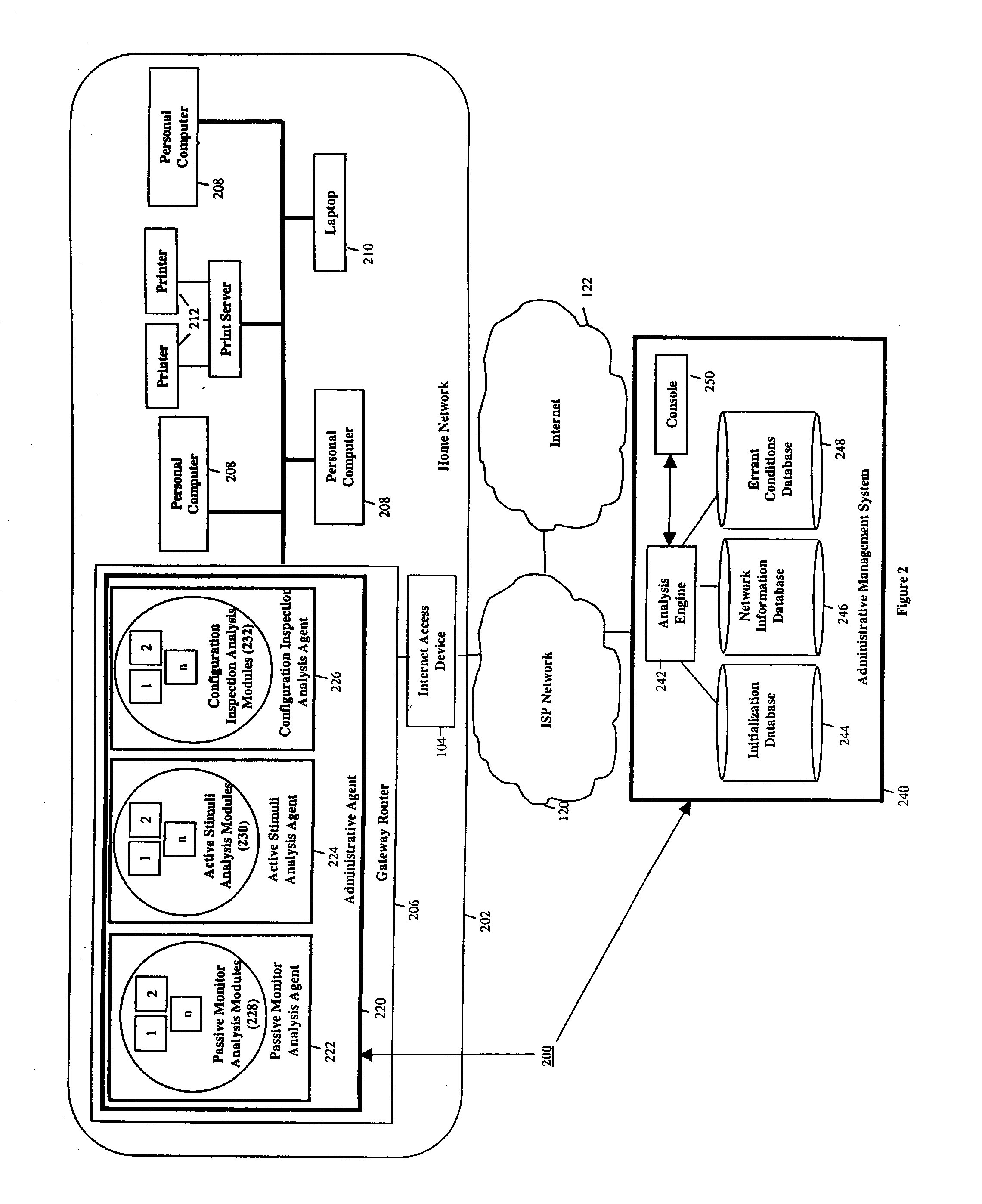
Detecting errant conditions affecting home networks
InactiveUS20040049714A1Hardware monitoringHome automation networksNetwork information flowAdministrative management
Errant conditions, including configuration issues, device / application failures, and performance problems, affecting a home network are detected by considering end-to-end information flows within the home network and between the home network and an external network. Specifically, errant conditions are detected by analyzing monitored network information flows, by analyzing responses resulting from the active stimuli of hardware / software components within the home and external network, and by considering in this analysis configuration information obtained from network devices. Gathered information and detected errant conditions are reported to an administrative management system for further analysis and for use by a help-desk administrator or home user in resolving the reported conditions.
Owner:TELCORDIA TECHNOLOGIES INC
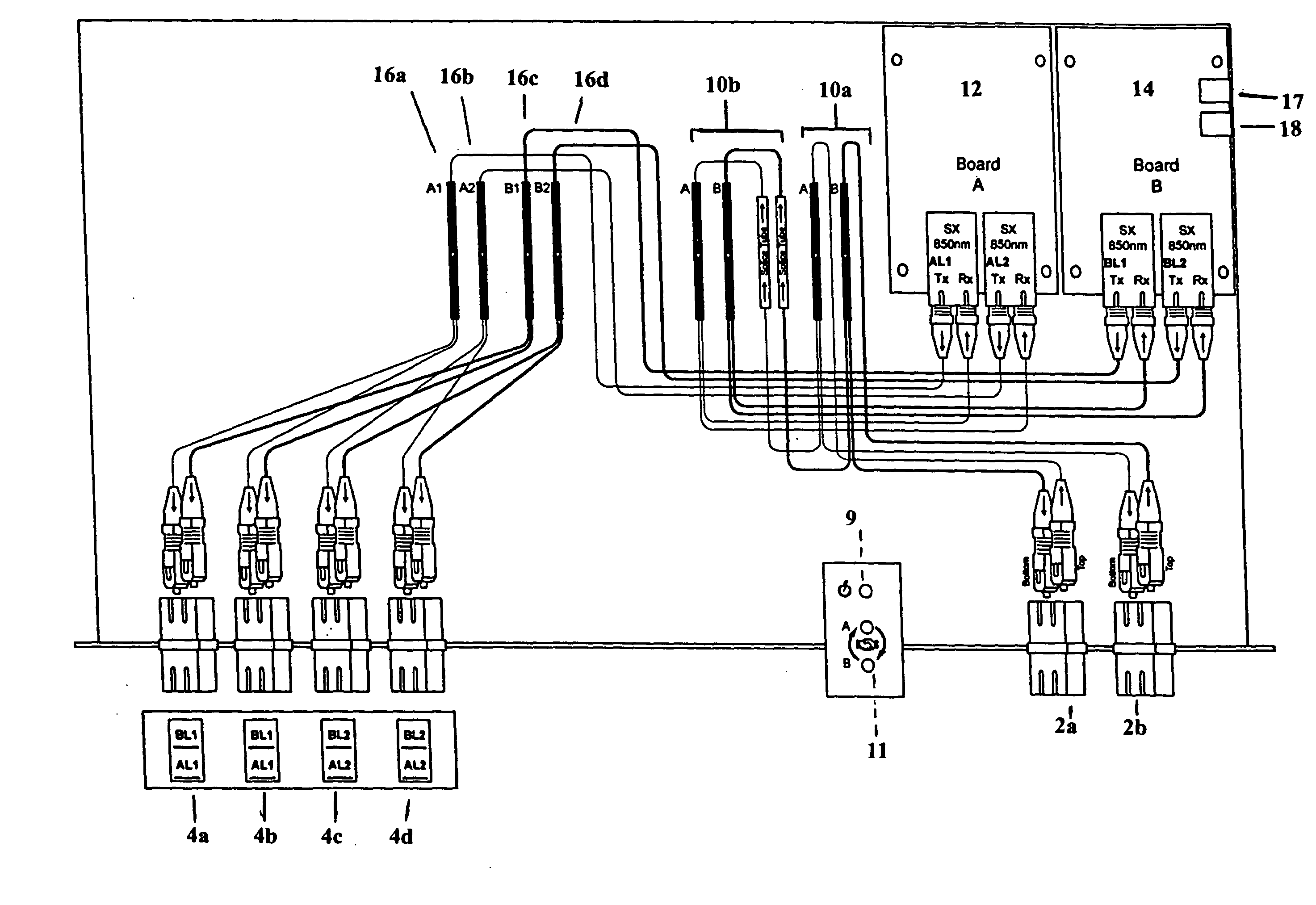
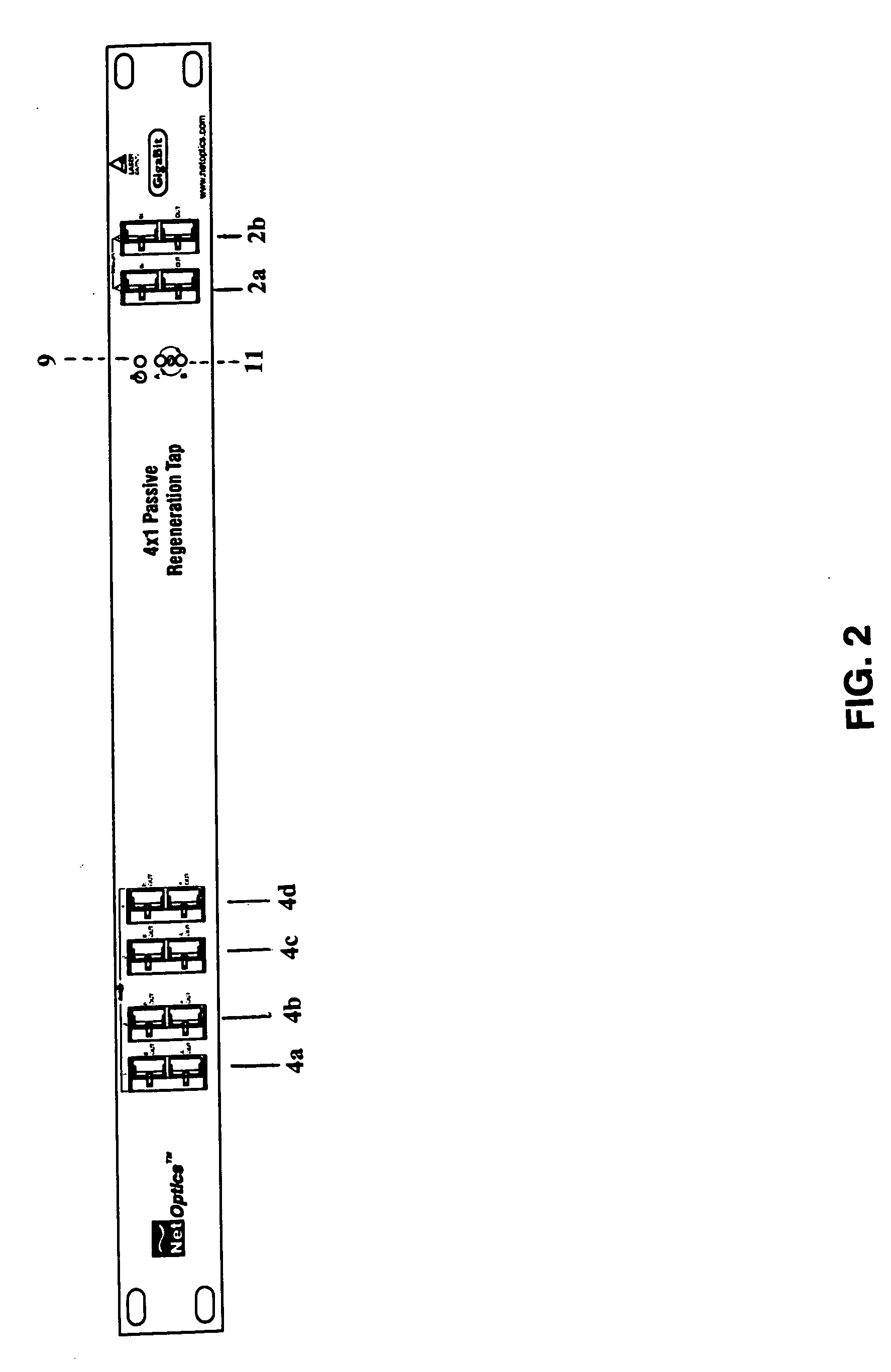
Multiple and parallel access network tap for gigabit internet lans
ActiveUS20050071711A1Avoid interferenceUndesired interferenceError preventionTransmission systemsTransmission protocolThe Internet
A single-usage network tap monitors network information flow over a particular connection. Instead of requiring a tap for each analytical device, by incorporating elements that regenerate, spread, and coordinate the timing of the signal, multiple, simultaneous, and parallel analytical devices can monitor a particular network connection through one tap, It incorporates four amplifiers preferably manufactured on the same IC die with high-impedance input terminals connected directly to the two conductors of a gigabit Ethernet local area network digital transmission line so as not to load or otherwise upset its impedance or other parameters. The output terminals of the operational amplifiers are connected to and match the input impedance of the digital transmission protocol Gigabit analyzer. The gain of the operational amplifiers is arranged so as to replicate at the input of the analyzer the signals appearing on the Gigabit local area network transmission line with uninterruptible power supply.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Method and system for predicting social network information popularity on basis of user characteristics
InactiveCN104281882APredictive propagationReduce lagForecastingWebsite content managementFeature extractionInformation propagation
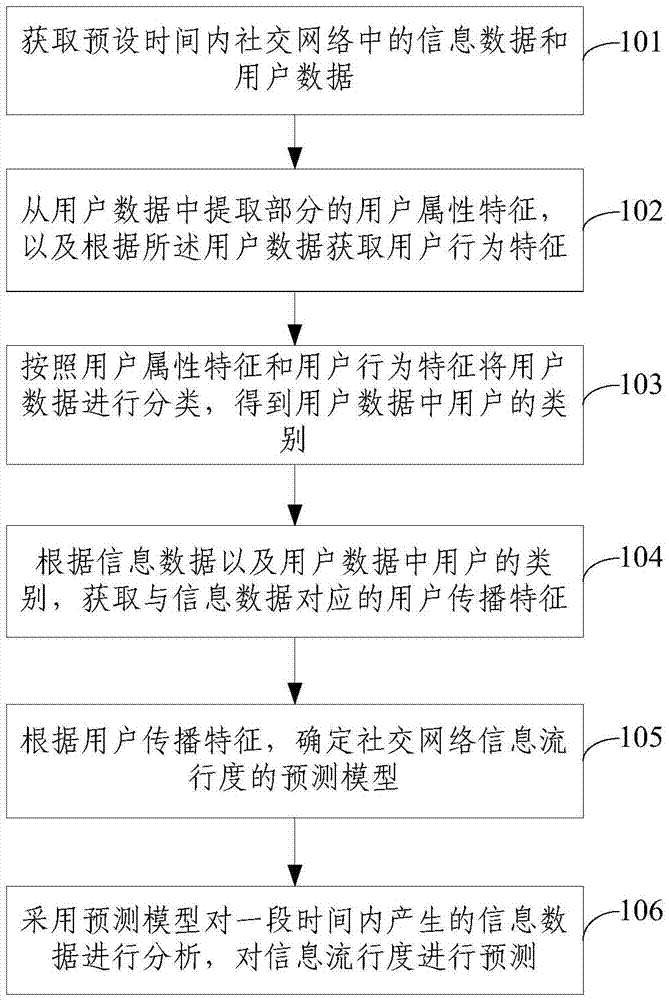
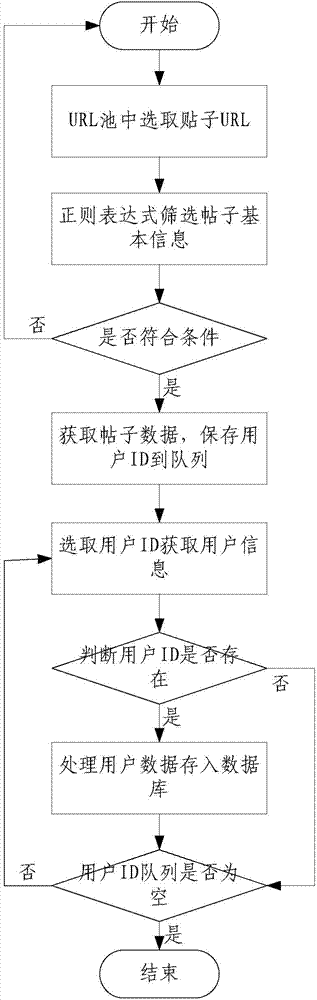
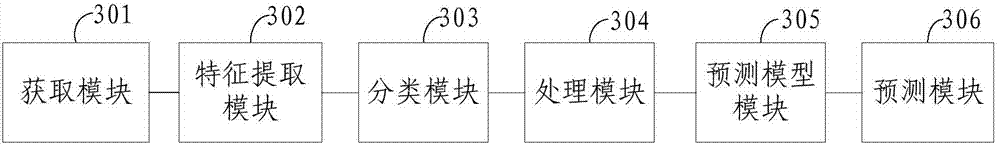
The invention provides a method for predicting social network information popularity on the basis of user characteristics. The method includes the steps of obtaining user data and information data in a social network, extracting part of user attribute characteristics and user behavior characteristics from the user data, classifying the user data according to the user attribute characteristics and the user behavior characteristics, obtaining user broadcasting characteristics corresponding to the information data according to the information data and the classification of a user, obtaining a social network information popularity prediction model according to the user broadcasting characteristics, and predicting the information popularity through the prediction model. The invention provides a system for predicting the social network information popularity on the basis of user characteristics. The system comprises an obtaining module, a characteristic obtaining module, a classification module, a processing module, a prediction model module and a prediction model. Through the combination with the features of user behavior characteristics, information propagation of the social network is more accurately predicted, and the problems that hot spot finding lags and the real-time performance of information pushing and online public opinion monitoring can be hardly ensured are solved.
Owner:INST OF INFORMATION ENG CAS
Multiple and parallel access network tap for gigabit internet LANS
ActiveUS7486624B2Avoid interferenceError preventionFrequency-division multiplex detailsTransmission protocolElectrical conductor
A single-usage network tap monitors network information flow over a particular connection. Instead of requiring a tap for each analytical device, by incorporating elements that regenerate, spread, and coordinate the timing of the signal, multiple, simultaneous, and parallel analytical devices can monitor a particular network connection through one tap, It incorporates four amplifiers preferably manufactured on the same IC die with high-impedance input terminals connected directly to the two conductors of a gigabit Ethernet local area network digital transmission line so as not to load or otherwise upset its impedance or other parameters. The output terminals of the operational amplifiers are connected to and match the input impedance of the digital transmission protocol Gigabit analyzer. The gain of the operational amplifiers is arranged so as to replicate at the input of the analyzer the signals appearing on the Gigabit local area network transmission line with uninterruptible power supply.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
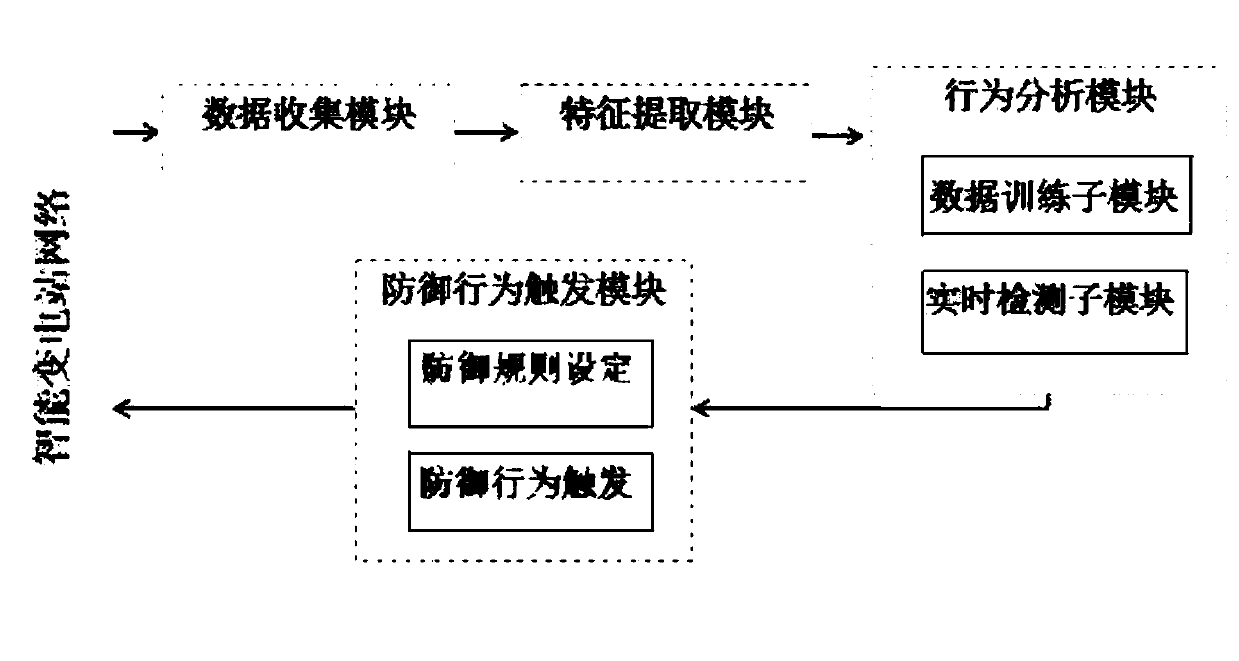
Intelligent substation network intrusion detection system and detection method based on deep learning
PendingCN110086776AAchieve defenseAchieve unificationTransmissionNeural learning methodsSmart substationFeature extraction
The invention belongs to the technical field of transformer substation network intrusion detection, and particularly relates to an intelligent transformer substation network intrusion detection systemand method based on deep learning. The system is used for intrusion detection aiming at network attacks of an IEC61850 communication protocol of an intelligent substation. The system comprises a datacollection module, a feature extraction module, a behavior analysis module and a defense behavior trigger module which are sequentially connected, wherein the data collection module is connected to an intelligent substation network to collect data, the defense behavior trigger module is connected to the intelligent substation network, the network information flow based on the IEC61850 protocol inthe intelligent substation is collected and analyzed in real time, and abnormal communication behaviors are detected and alarmed in real time.
Owner:ECONOMIC TECH RES INST OF STATE GRID HENAN ELECTRIC POWER
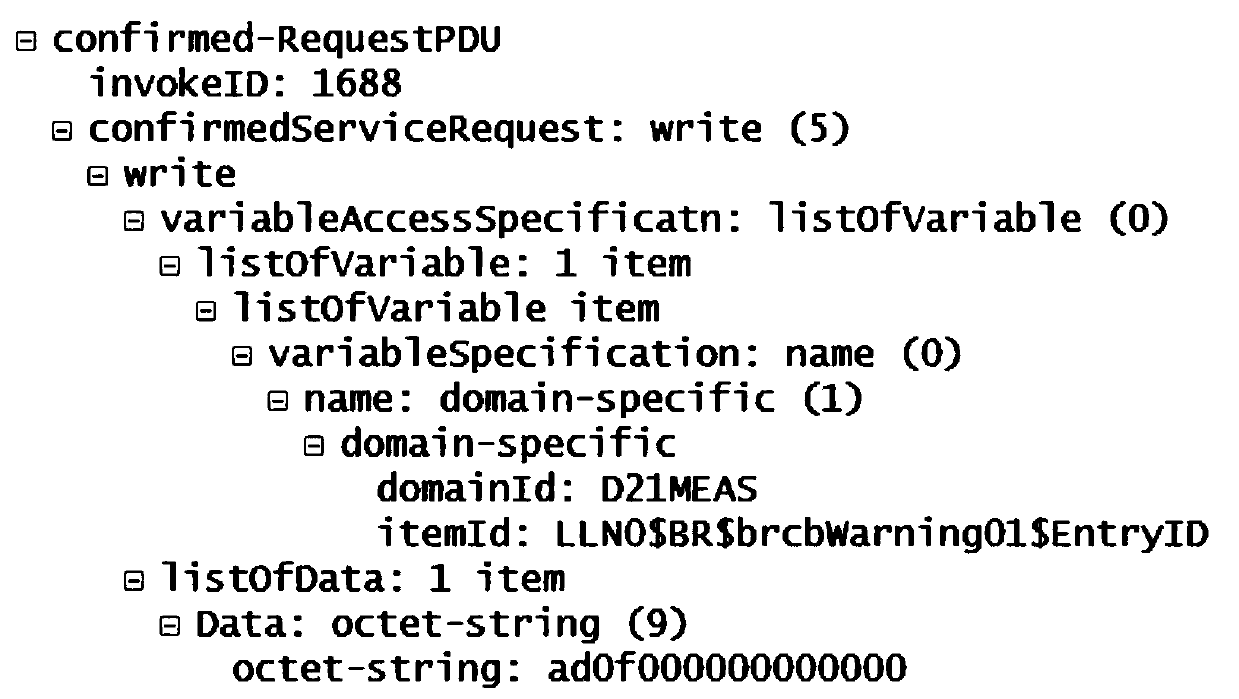
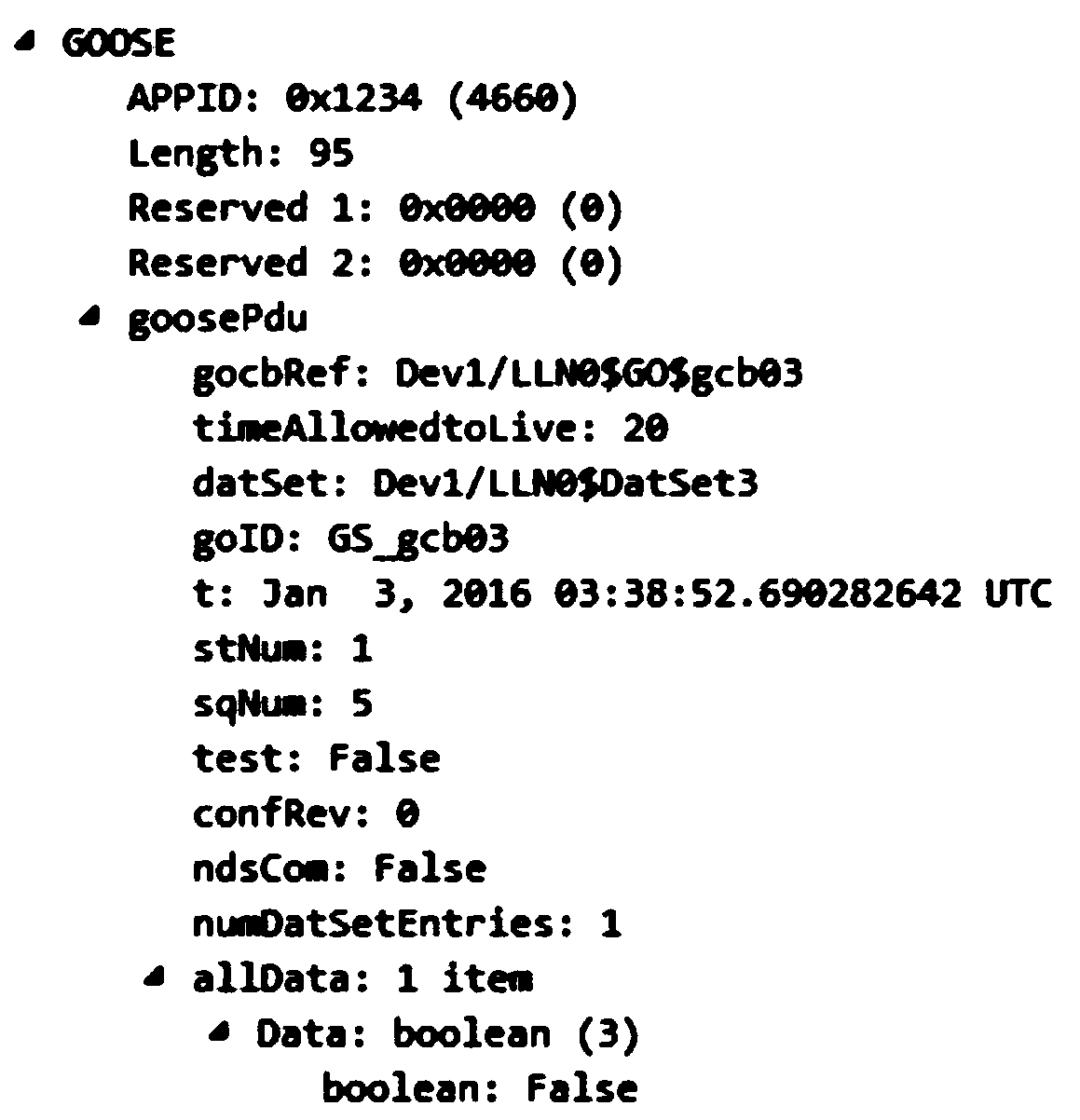
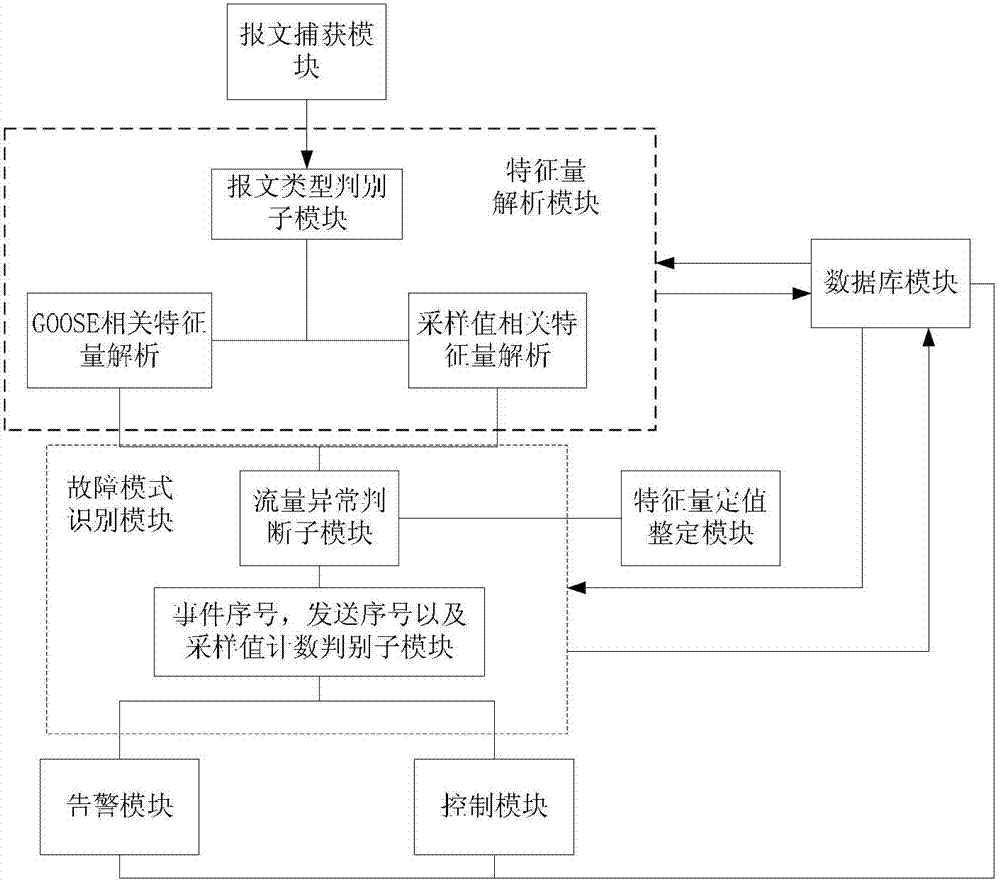
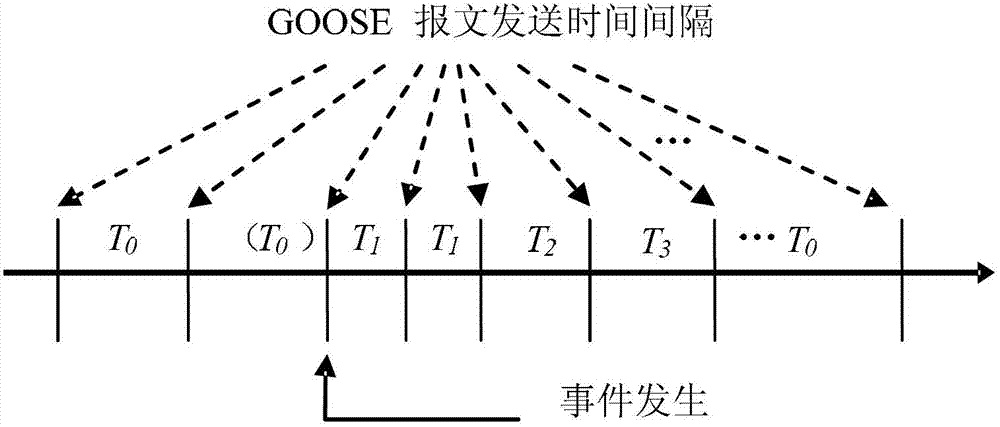
Information stream control method and system for improving relay protection reliability of intelligent substation
ActiveCN102932167AImprove reliabilityImprove performanceError prevention/detection by using return channelData switching networksValue setStream control
The invention relates to an information stream control method and system for improving the relay protection reliability of an intelligent substation. The information system control system comprises a message capturing module, a characteristic quantity analysis module and a fault mode identification module which are connected in sequence by a data line, wherein the characteristic quantity analysis module is further externally connected with a database module, the fault mode identification module is externally connected with a characteristic quantity fixed value setting module and the database module, and the fault mode identification module respectively outputs a control module and an alarm module. According to the information stream control method and system disclosed by the invention, control measures can be taken by judging a fault mode of a process level network information stream in accordance with different mode information, improvement of the transmission reliability of the process level network information stream is facilitated, furthermore, various performances of relay protection equipment of the intelligent substation are improved, the automation level of a secondary system is improved and favorable terms are provided for safety operation of the intelligent substation.
Owner:SOUTH CHINA UNIV OF TECH +1
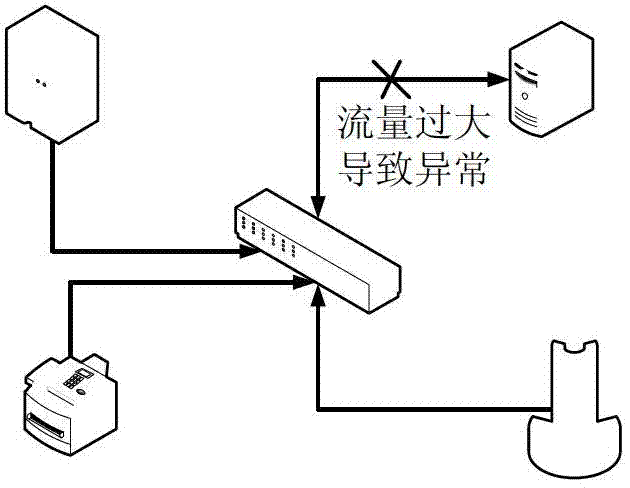
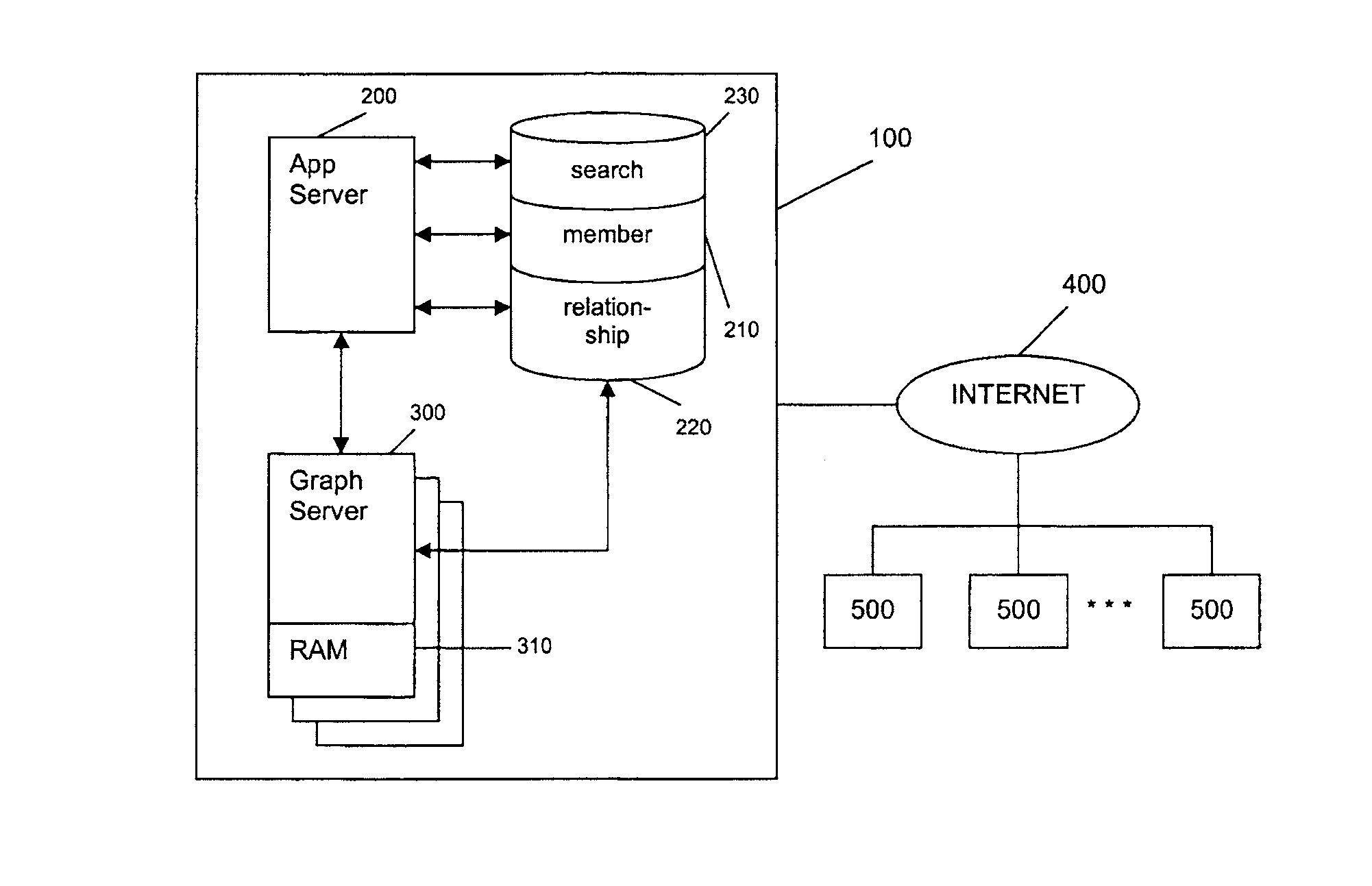
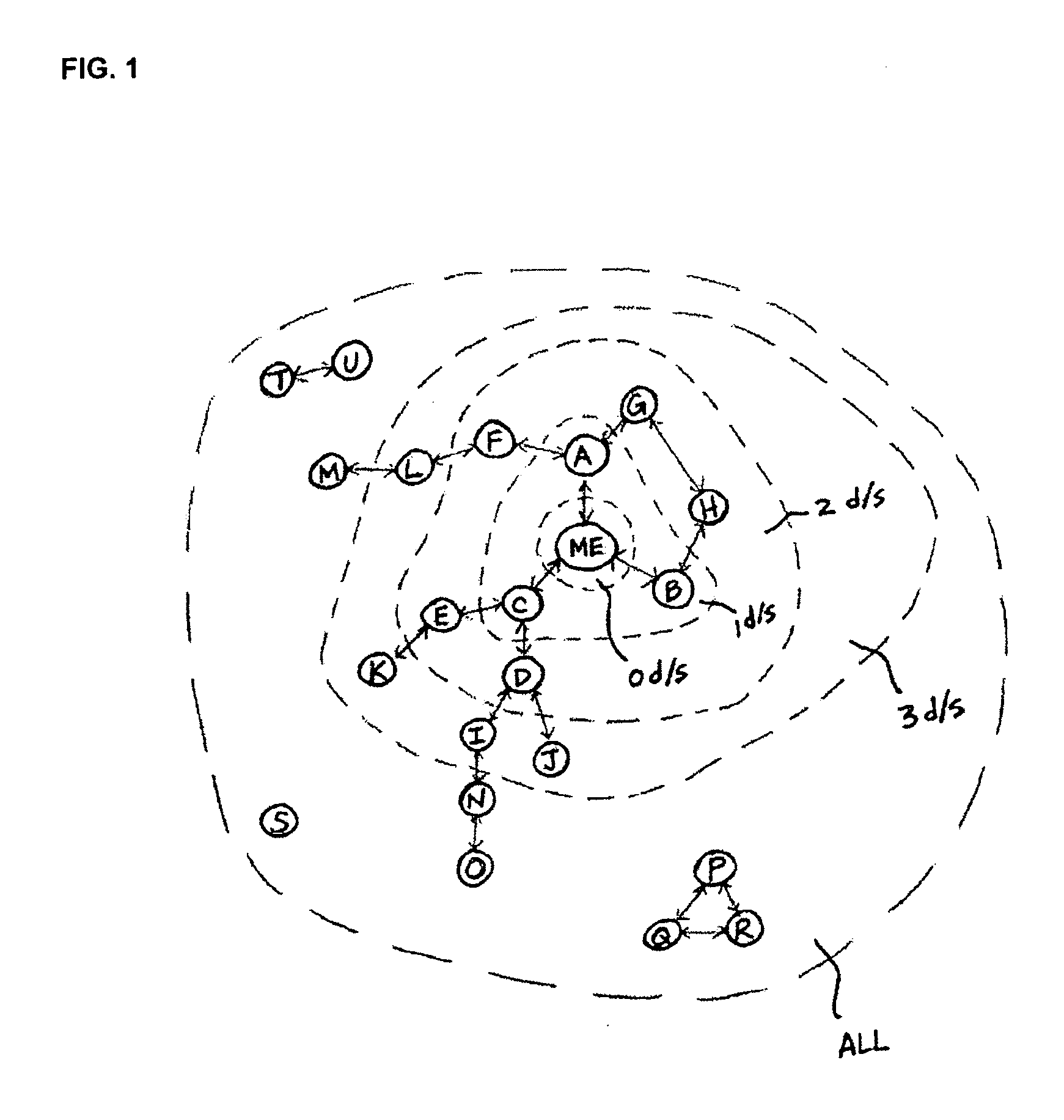
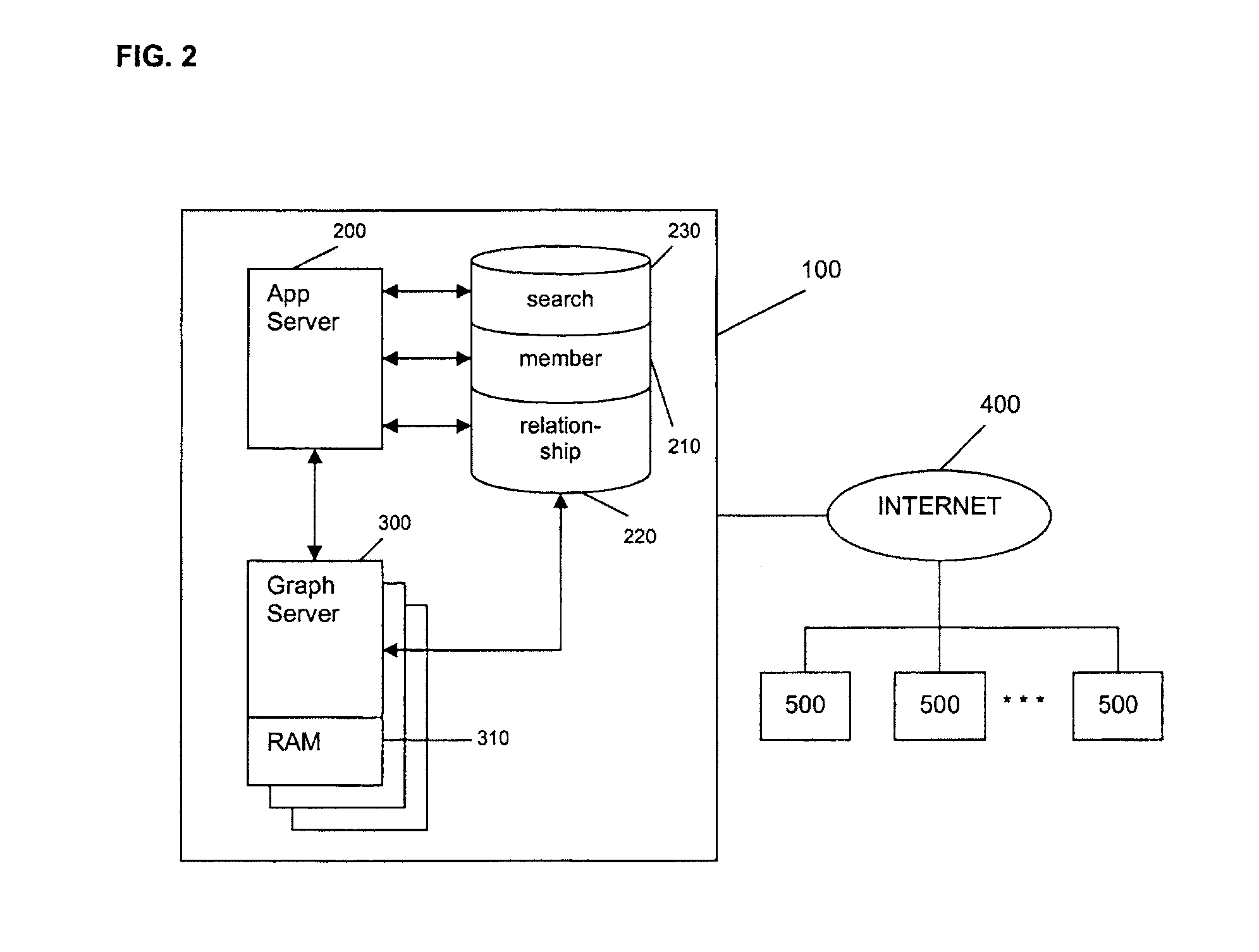
Graph Server Querying for Managing Social Network Information Flow
ActiveUS20110099167A1Improve processing efficiencyReduce in quantityDigital data processing detailsComputer security arrangementsGraphicsNetwork information flow
An online social network is managed using one server for database management tasks and another server, preferably in a distributed configuration, for CPU-intensive computational tasks, such as finding a shortest path between two members or a degree of separation between two members. The additional server has a memory device containing relationship information between members of the online social network and carries out the CPU-intensive computational tasks using this memory device. With this configuration, the number of database lookups is decreased and processing speed is thereby increased.
Owner:META PLATFORMS INC
Method for estimation of information flow in biological networks
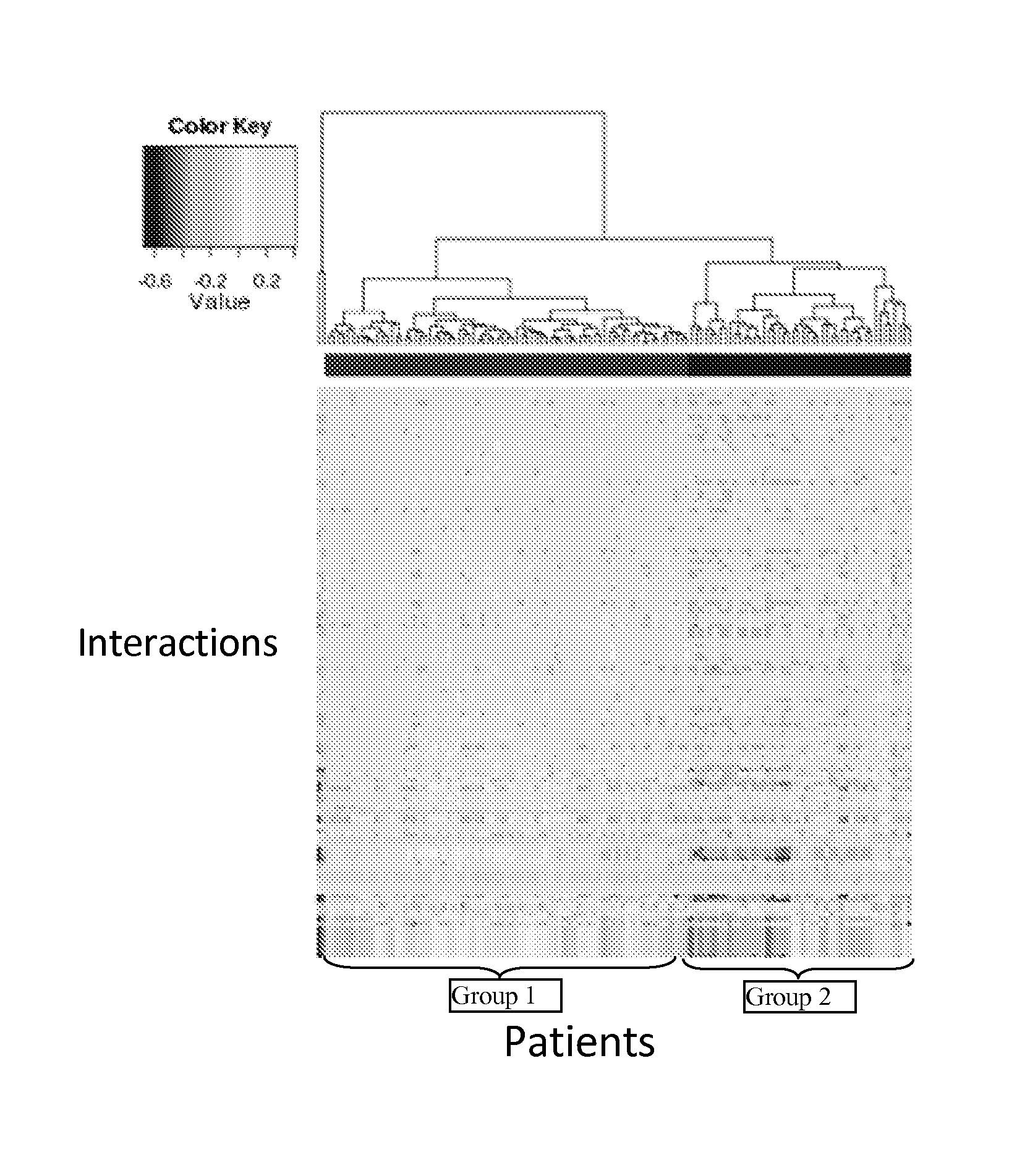
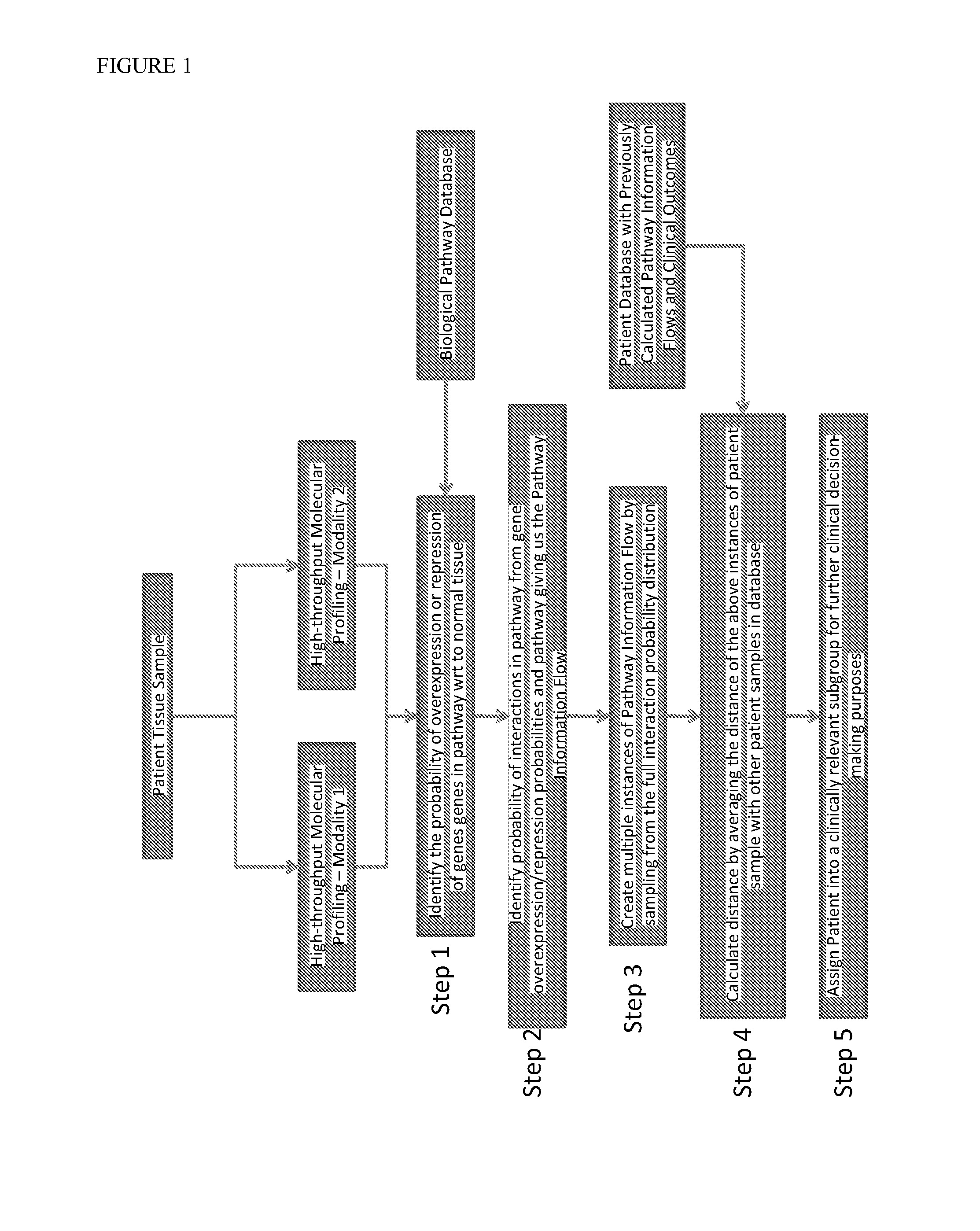
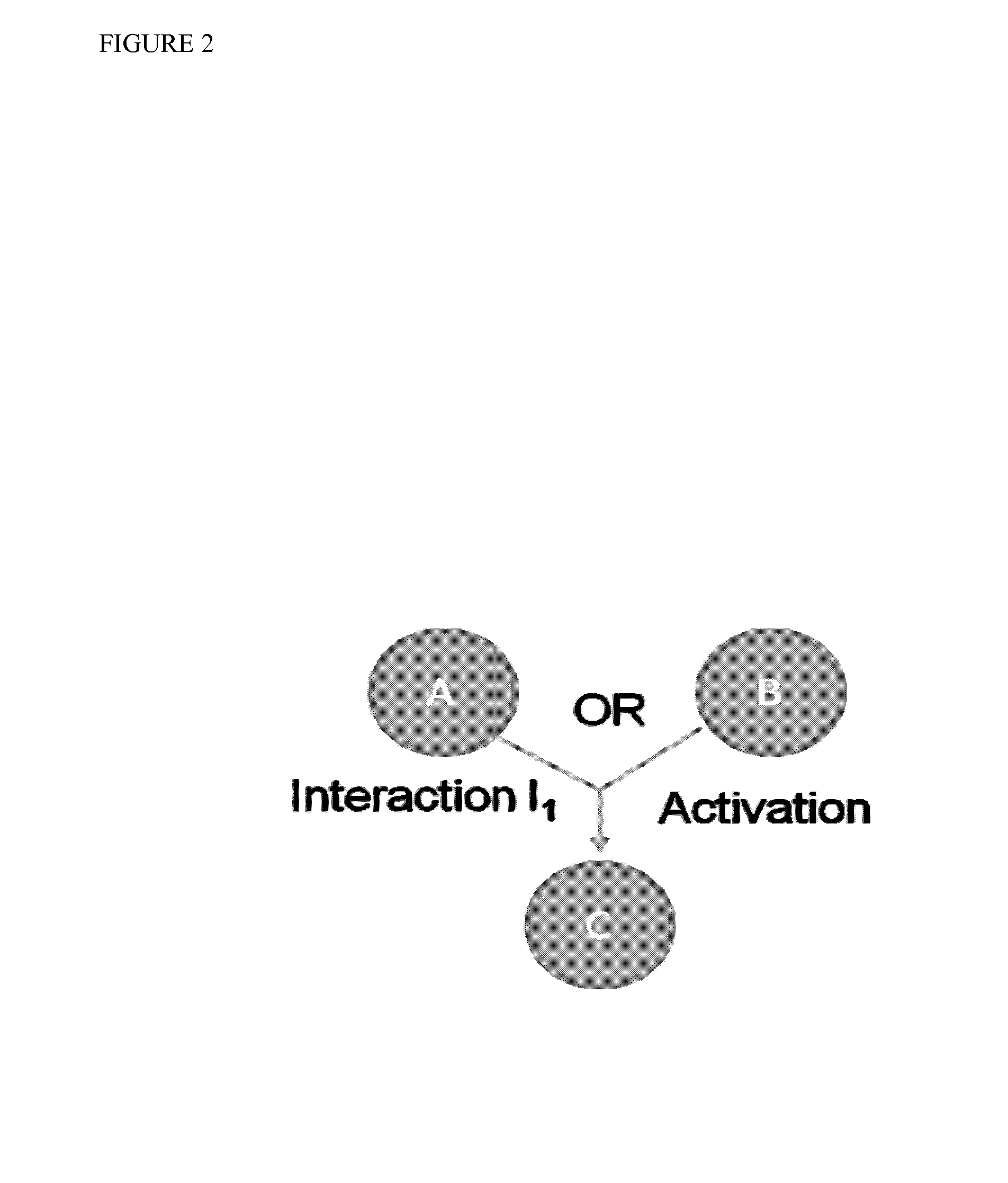
InactiveUS20140040264A1Stratify patients into clinically relevant groups very accuratelyAccurate layeringDigital data processing detailsBiostatisticsPatient databaseNetwork information flow
The present invention relates to a method for stratifying a patient into a clinically relevant group comprising the identification of the probability of an alteration within one or more sets of molecular data from a patient sample in comparison to a database of molecular data of known phenotypes, the inference of the activity of a biological network on the basis of the probabilities, the identification of a network information flow probability for the patient via the probability of interactions in the network, the creation of multiple instances of network information flow for the patient sample and the calculation of the distance of the patient from other subjects in a patient database using multiple instances of the network information flow. The invention further relates to a biomedical marker or group of biomedical markers associated with a high likelihood of responsiveness of a subject to a cancer therapy wherein the biomedical marker or group of biomedical markers comprises altered biological pathway markers, as well as to an assay for detecting, diagnosing, graduating, monitoring or prognosticating a medical condition, or for detecting, diagnosing, monitoring or prognosticating the responsiveness of a subject to a therapy against said medical condition, in particular ovarian cancer. Furthermore, a corresponding clinical decision support system is provided.
Owner:KONINKLJIJKE PHILIPS NV
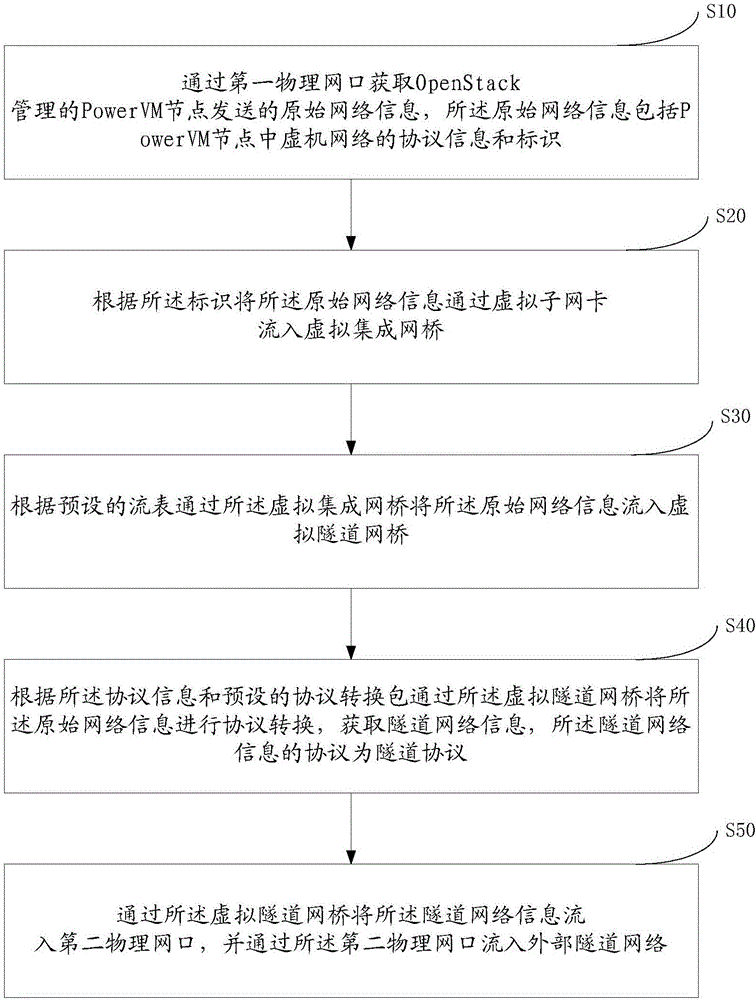
Power VM virtualized network management method and device based on Open Stack
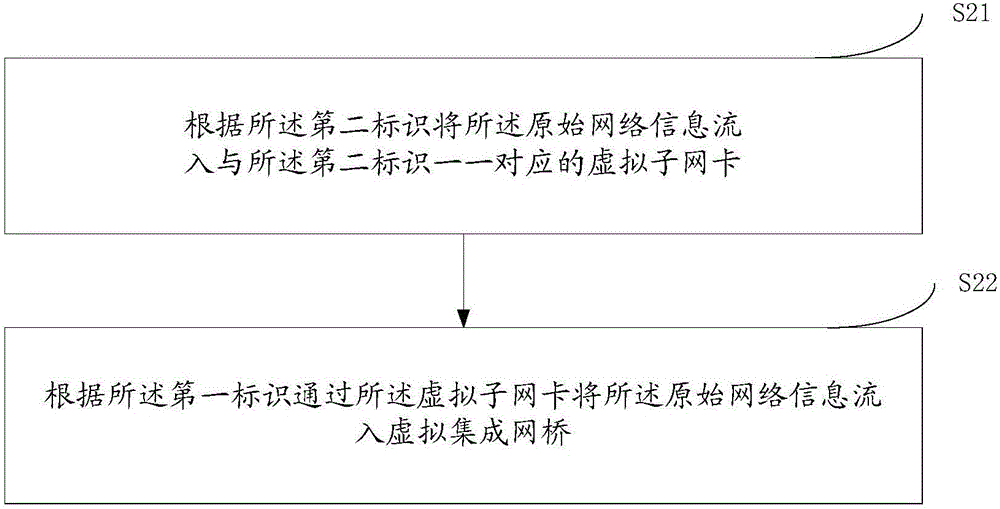
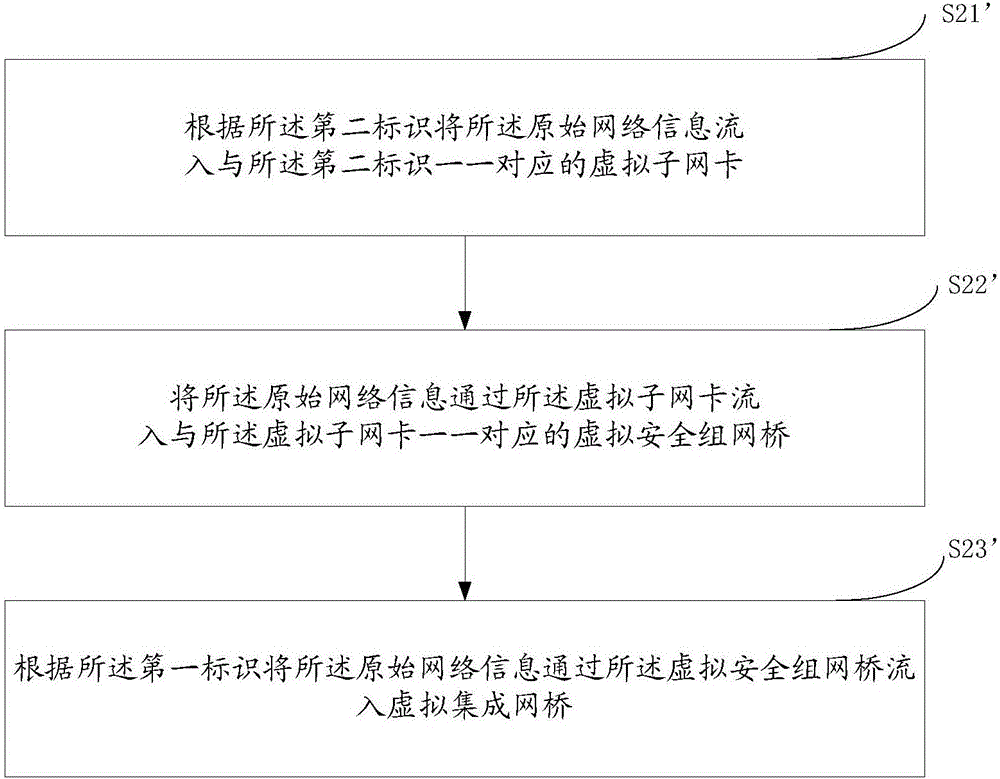
The invention provides a Power VM virtualized network management method and device based on Open Stack. The method comprises the following steps: acquiring original network information transmitted from a Power VM node managed by Open Stack through a first physical internet access, wherein the original network information comprises protocol information and identification; enabling the original network information to flow into a virtual integrated network bridge through a virtual secondary network card according to the identification; enabling the original network information to flow into a virtual tunnel network bridge through the virtual integrated network bridge according to preset flow table; carrying out protocol conversion on the original network information according to the protocol information and a preset protocol conversion package, and acquiring tunnel network information, and the protocol of the tunnel network information is a tunnel protocol; and enabling the tunnel network information to flow into a second physical internet access through the virtual tunnel network bridge, and enabling the tunnel network information to flow into an external tunnel network through the second physical internet access. By a mode of deploying a virtual machine, flowing-in and protocol conversion of a Power VM network are finished, and Power VM virtualized network management based on Open Stack is finished.
Owner:BEIJING TEAMSUN TECH
Method for mobile node's connection to virtual private network using mobile IP
InactiveCN101151849AData switching by path configurationWireless network protocolsPrivate IPPrivate network
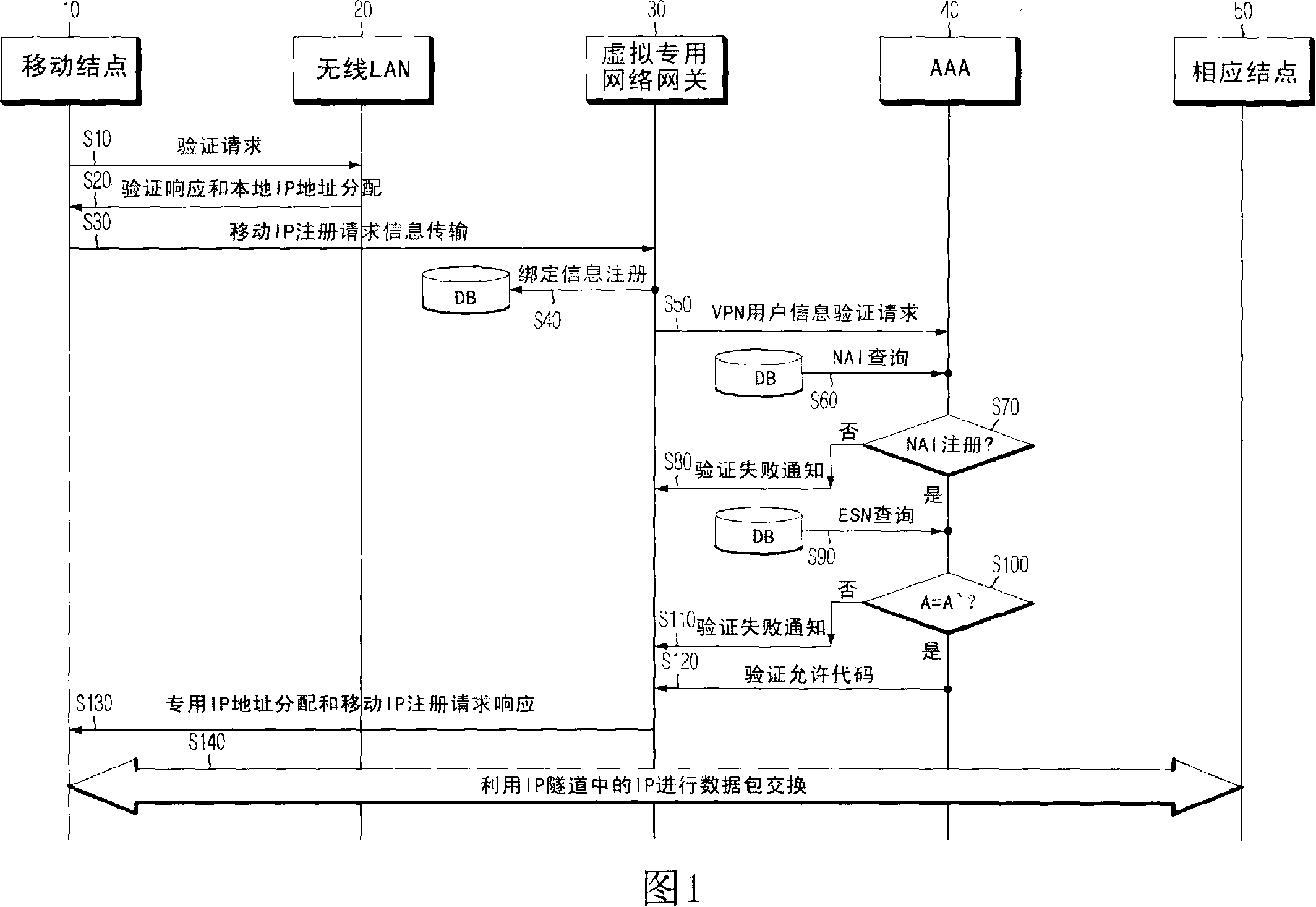
A method for a mobile node's connection to a virtual private network using a mobile IP under a mobile environment is provided. According to this method, the mobile node firstly makes a mobile IP registration request message including VPN user authentication information and transmits the message to VPN gateway. Then, the VPN gateway reads the VPN user authentication information from the message and inquires a database in which VPN user authentication information is already stored, to verify a VPN access authority of the mobile node. If the access authority is verified, private IP is recorded in a response message to the mobile IP registration request message, and the response message is transmitted to the mobile node to assign the private IP. Accordingly, a VPN having low construction cost, simple topology, less network traffic and low workig loads on the mobile node and the network under a mobile environment can be constructed.
Owner:KT FREETEL CO LTD
Flow control method for synchronous digital system network transmission data business
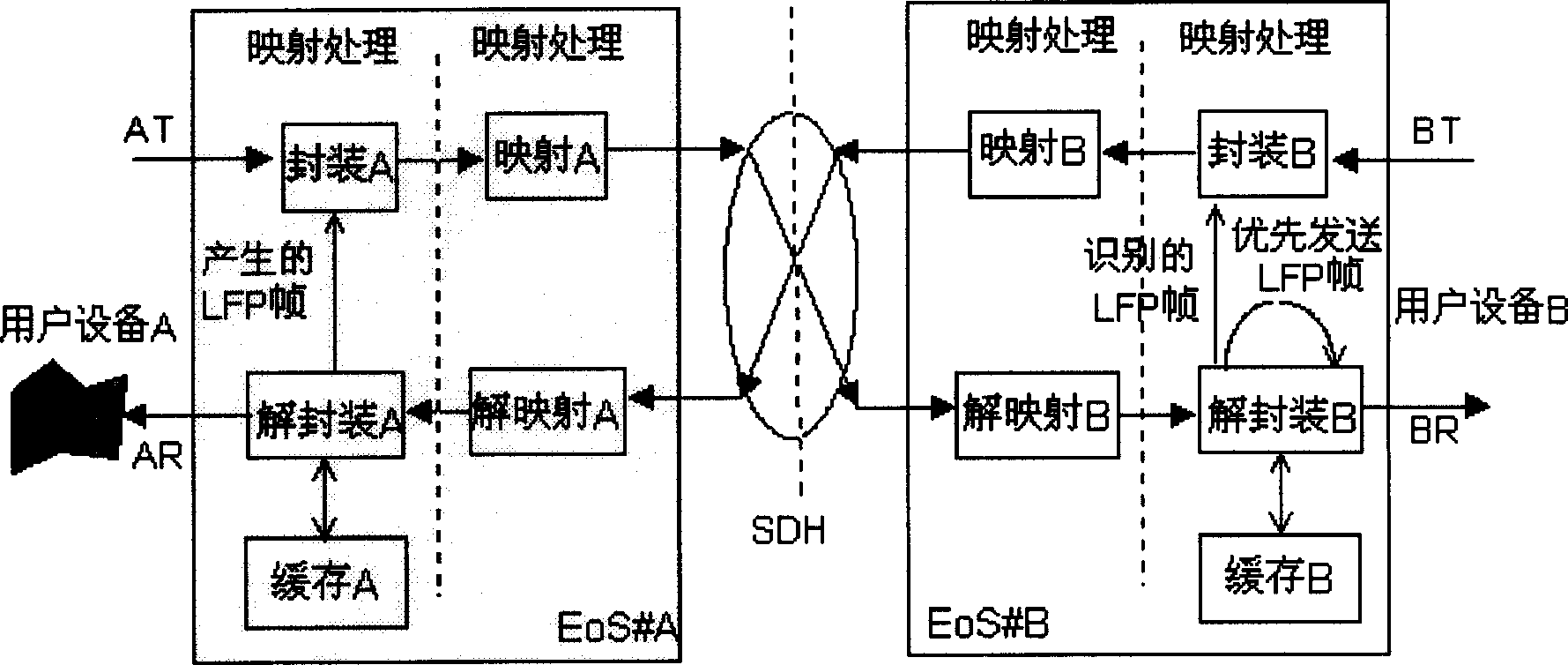
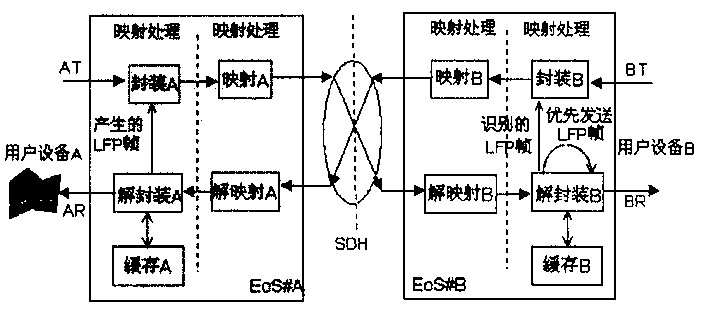
InactiveCN1474565AAvoid control failureGood application effectMultiplex communicationData switching networksTraffic capacityData information
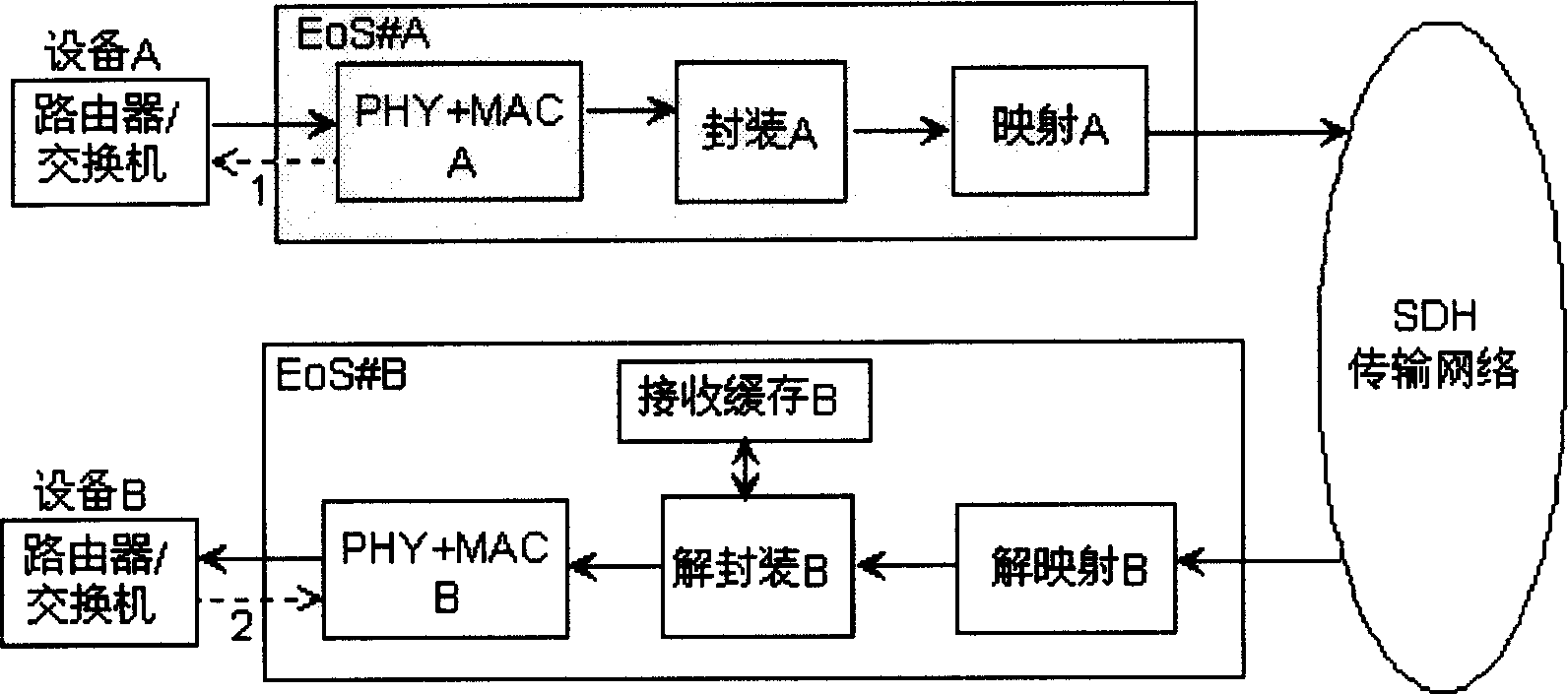
A flow control method relating to data information transmission used in transmitting data service of SDH network characterizing that, in the data transmission of SDH network, EOS equipment generates and packages LFP frames, images the E-E equipments transferred between destinated points in SDH net charge, the E-E equipment extracts LFP frames from SDH net charges and carries out the flow control information carried in LFP frame, which carrier can use PAUSE frame structure defined by standard 802.3x, the unpackage can be done applying a LFP transparent transmission way or regeneration way of LFP frame.
Owner:HUAWEI TECH CO LTD
Information network security posture sensing early-warning method based on big data
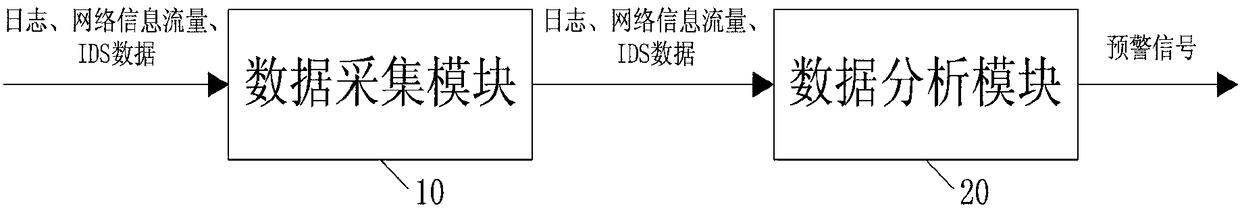
InactiveCN108156177AImprove the construction of intelligent network operation and maintenanceRealize early warning analysisRelational databasesTransmissionInformation networksData acquisition module
The invention belongs to the field of data collection and analysis excavation, and especially relates to an information network security posture sensing early-warning method based on big data. The early-warning method comprises a data collecting module and a data analysis module; the data collecting module collects logo, network information flow and IDS data, and sends the logo, network information flow and IDS data to the data analysis module; the data analysis module can perform early-warning analysis on the logo, network information flow and IDS data. The information network security posture sensing early-warning method can uniformly collect and store data, uniformly analyze the network running posture, and greatly promotes the intelligent network operation and maintenance construction;the early-warning method can analyze suspicious acts by combining with log data, network information flow and IDS data, and realizes the advanced warning and analysis. The information network security posture sensing early-warning method can timely find out and exactly determine safety hidden troubles in the network device and the terminal device, and position and improve the weak link of the information network safety.
Owner:STATE GRID CORP OF CHINA +1
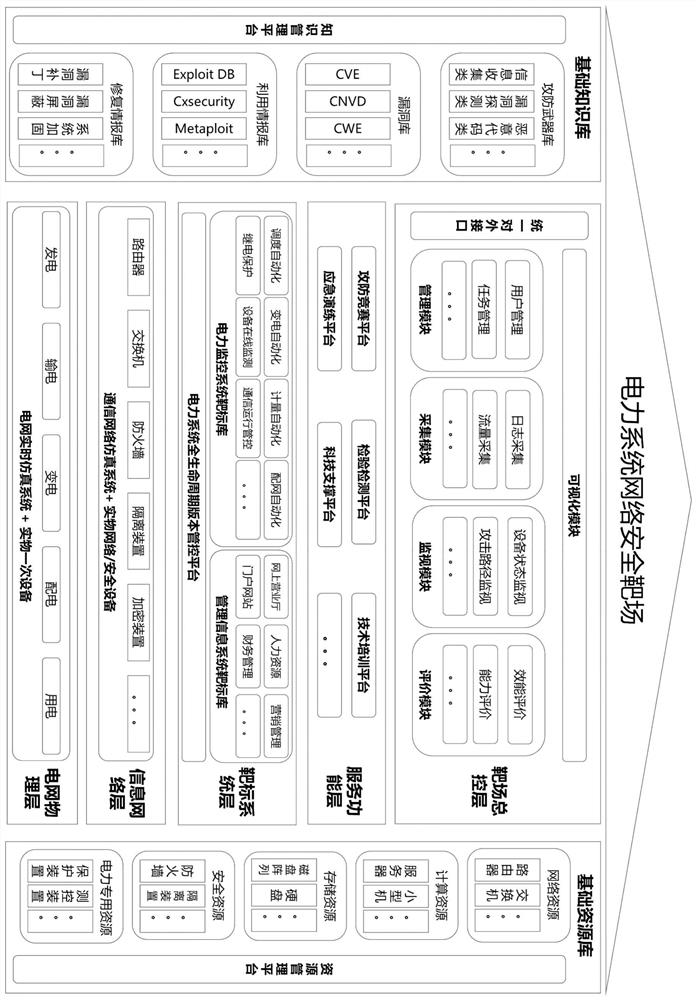
Network security target range system of power system
The invention provides a network security target range system of a power system. The network security target range system comprises a power grid physical layer, an information network layer, a targetsystem layer, a service function layer, a target range master control layer and a knowledge resource support module, wherein the power grid physical layer is used for simulating an interaction processof power grid energy flow; the information network layer is used for simulating an interaction process of power system network information flow; the target system layer is used for integrating and managing two types of power typical application systems, namely a power monitoring system and a management information system, and serves as a target of a target range; the service function layer is used for realizing multiple business service functions; the target range master control layer manages, collects, monitors, evaluates and displays the whole target range environment; and the knowledge resource support module provides knowledge support, tool support and resource support. The target range system provided by the invention has the simulation capability of covering all links of power generation, power transmission, power transformation, power distribution, power utilization and scheduling, and supports the business function requirements of attack and defense confrontation, inspection and detection, technical training, emergency drilling, science and technology research and development and the like.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
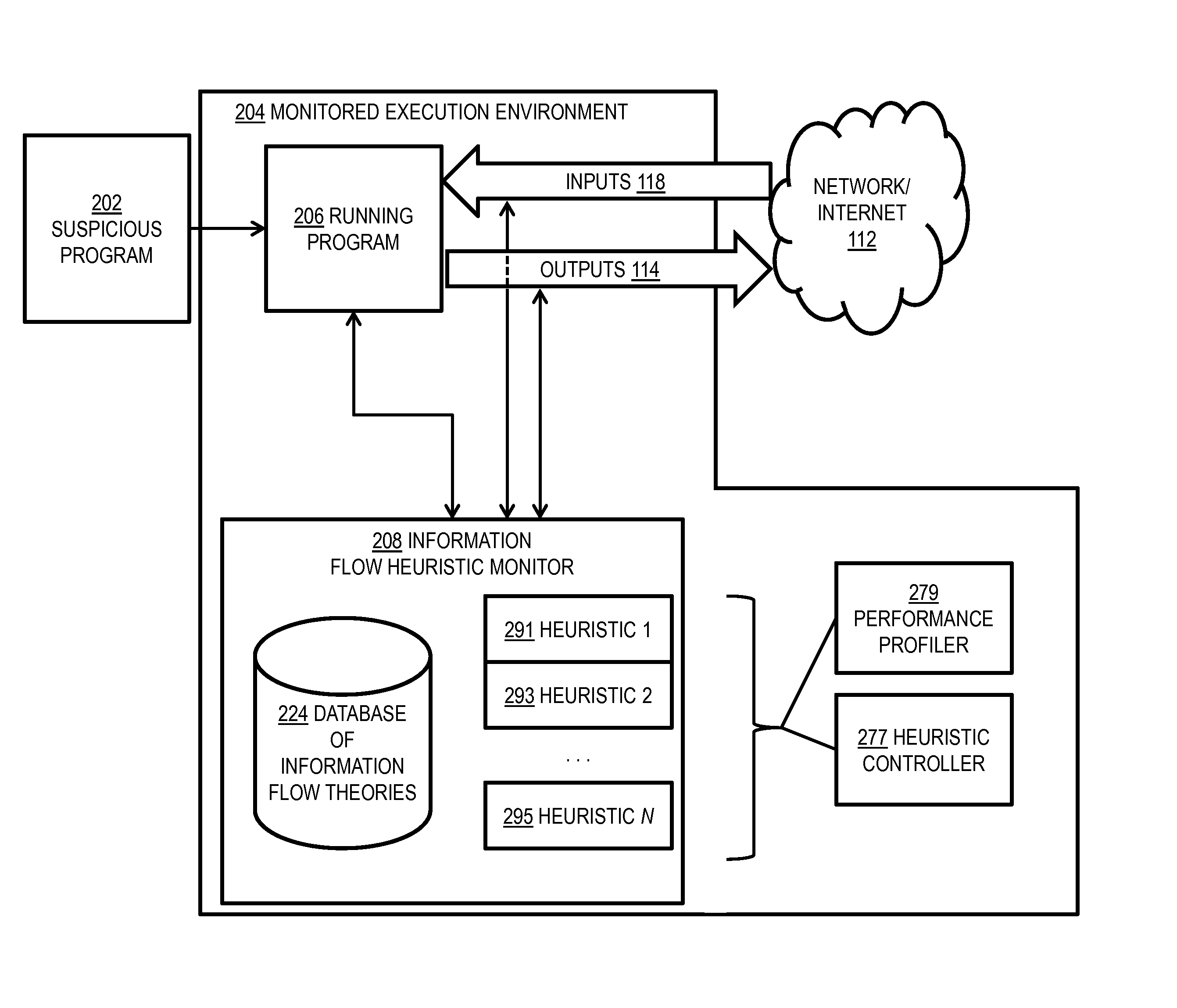
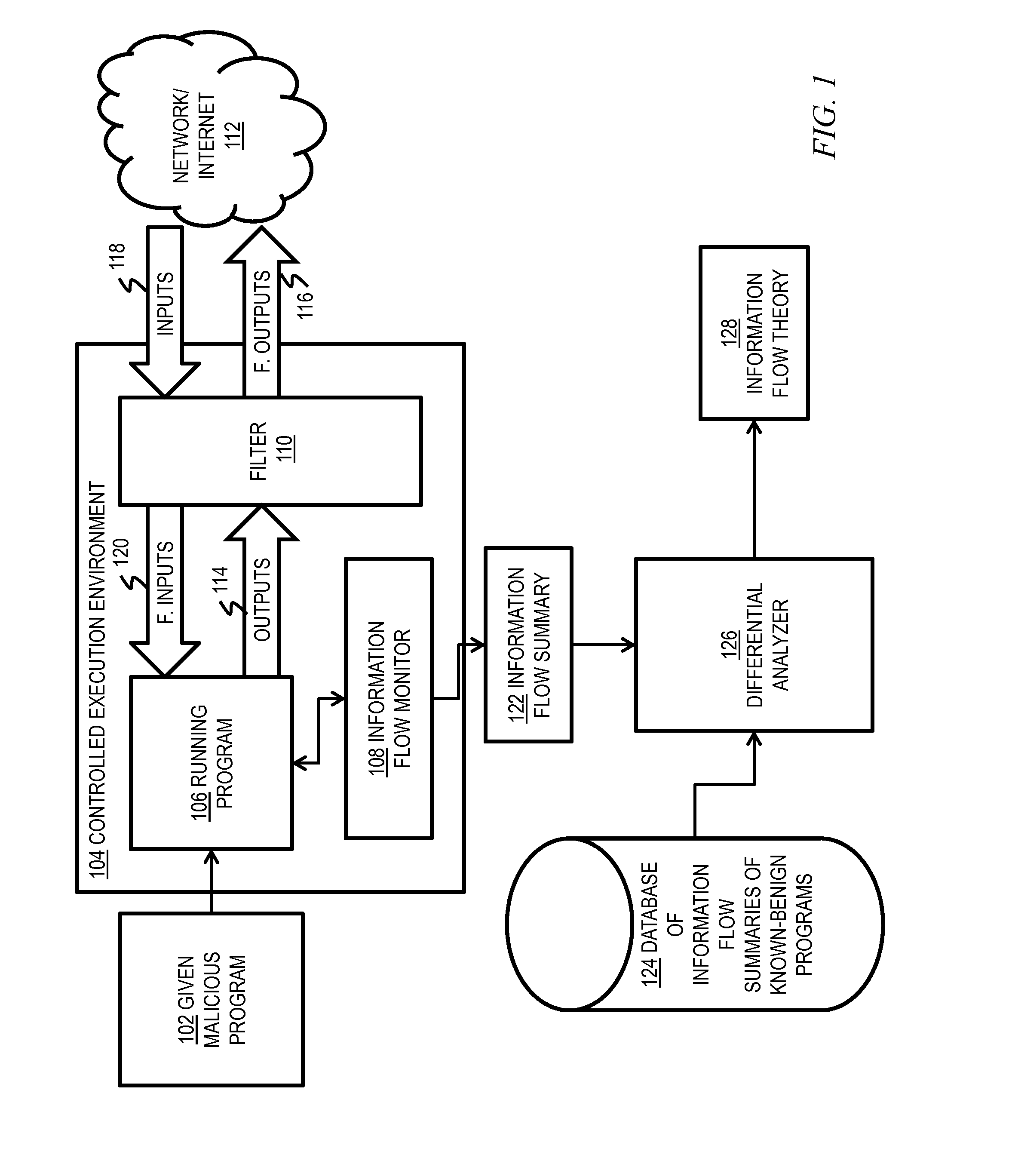
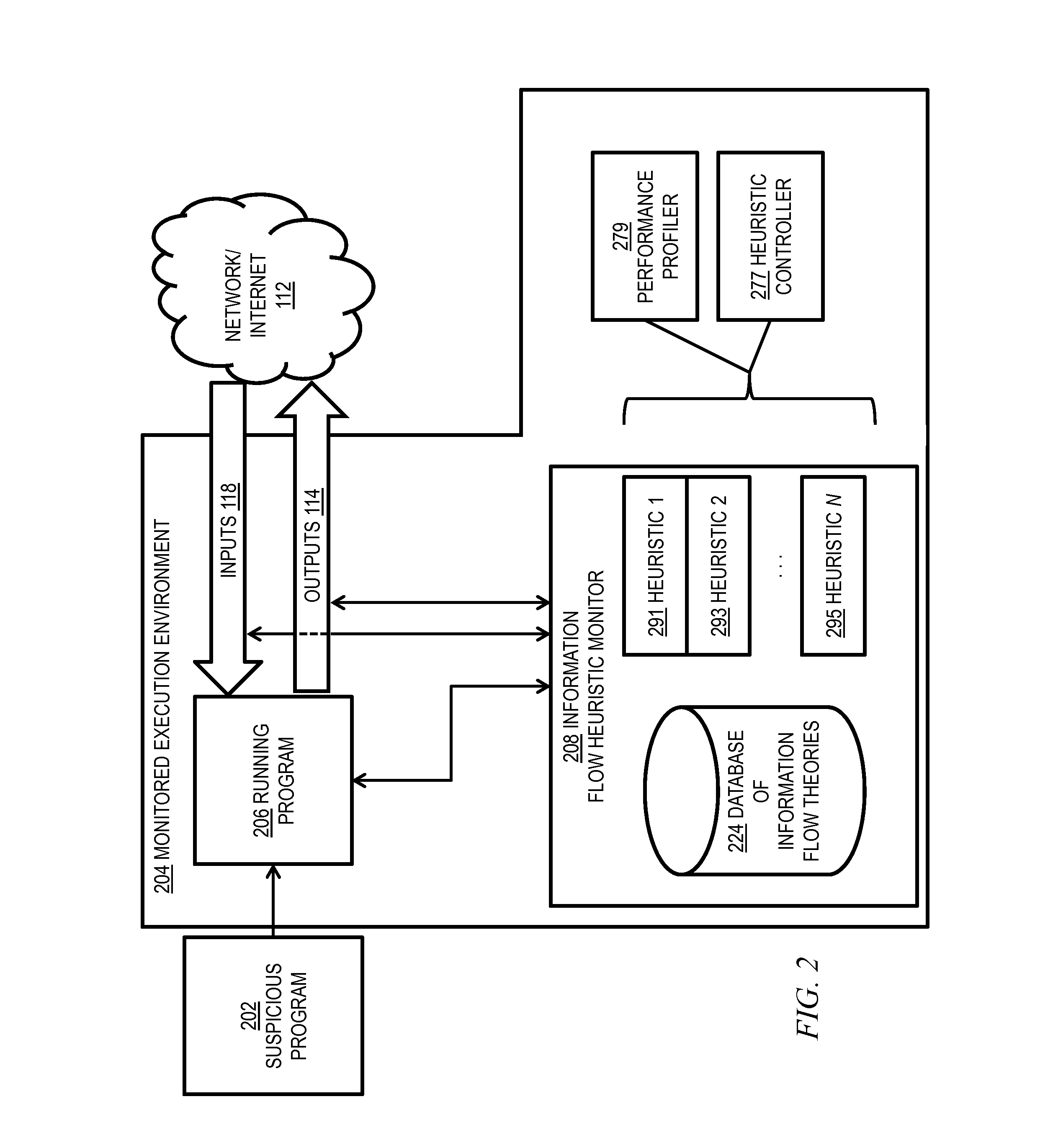
Malware detection via network information flow theories
InactiveUS20140223560A1Facilitate actionSimple actionMemory loss protectionError detection/correctionNetwork information flowMalware
Owner:IBM CORP
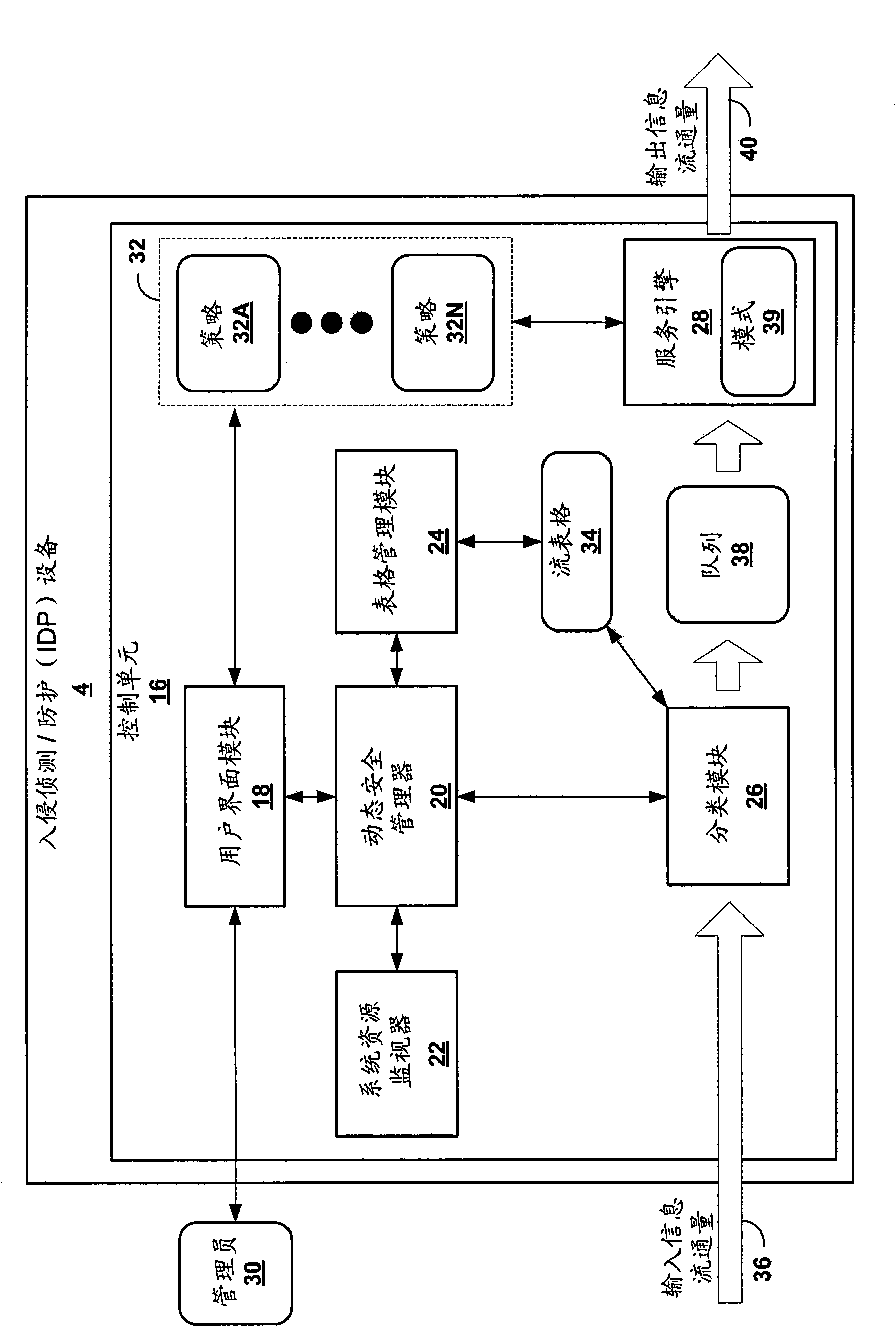
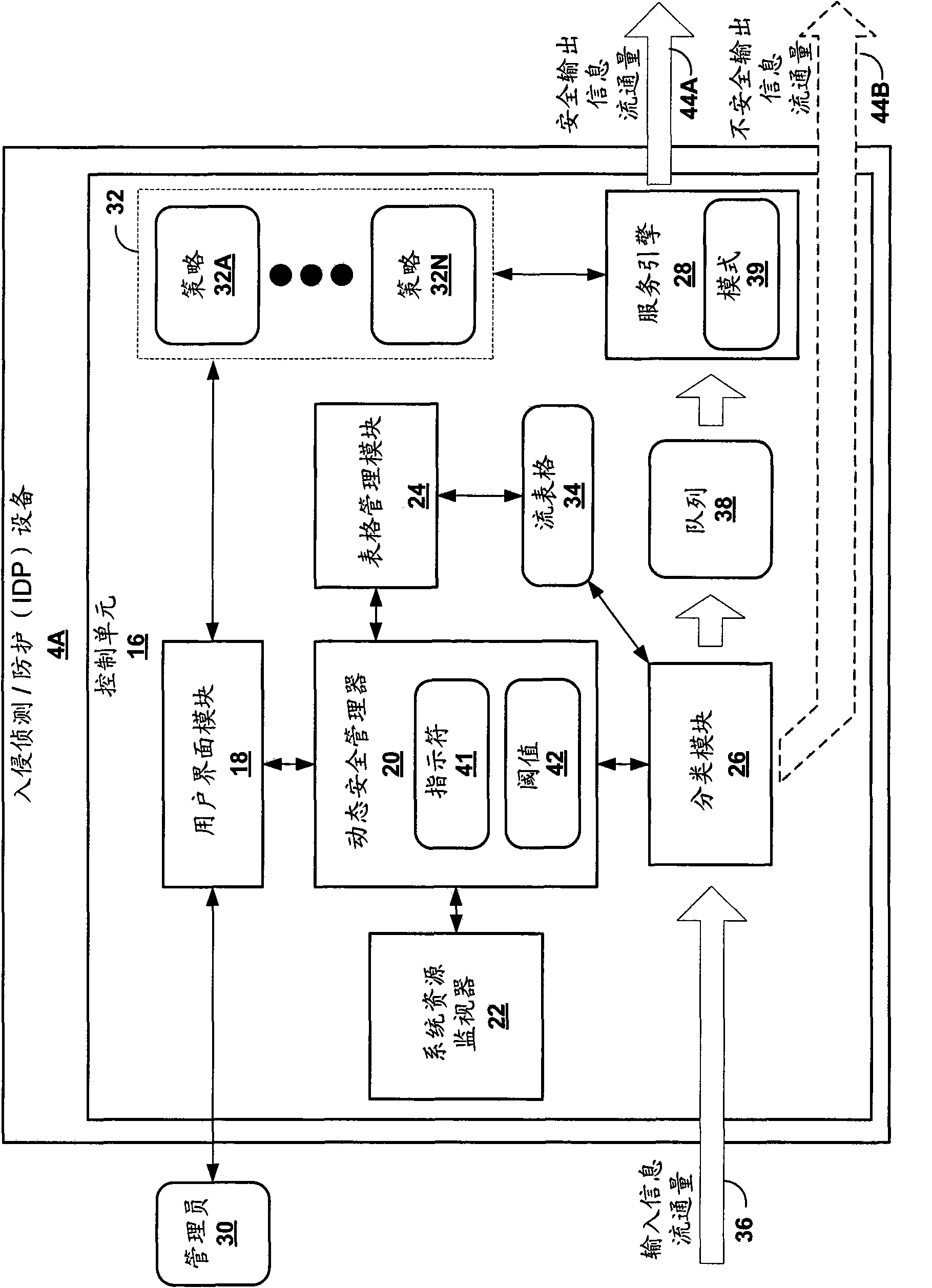
Dynamic strategy supply in network security device
The invention relates to a technology of dynamic strategy supply. A network security device comprises a memory, used for storing a first strategy and a second strategy of a first group mode corresponding to a first group network attack; and a control unit, used for applying the first strategy to network traffic to detect the first group network attack. When the first strategy is used, the control unit monitors parameters corresponding to one or more resources, and dynamically determines whether the second strategy is applied to network traffic based on the parameters. Thus, the control unit applies the second strategy to network traffic to detect a second group network attack, and transmits network traffic according to application of the second strategy. By this way, the network security device can realize the dynamic strategy supply technology.
Owner:JUMIPER NETWORKS INC
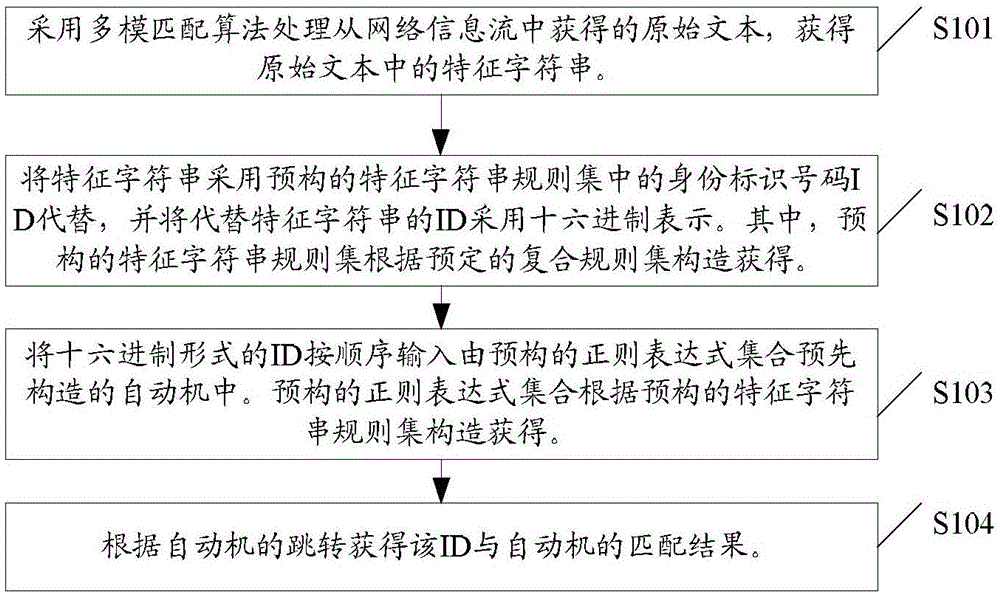
Composite rule set matching method and system
ActiveCN105045808AReduce the number of repeated readsDiminished independenceSpecial data processing applicationsNetwork information flowAutomaton
The present invention discloses a composite rule set matching method and system. The method comprises: using a multimode matching algorithm to process an original text obtained from a network information stream, to obtain a feature string in the original text; replacing the feature string with an identity identification number ID that is in a pre-constructed feature string rule set, and presenting the ID, with replaces the feature string, in hexadecimal; inputting the ID in hexadecimal in sequence to an automaton pre-constructed by using a pre-constructed regular expression set; and according to a jump of the automaton, obtaining a matching result between the ID and the automaton, wherein the pre-constructed feature string rule set is constructed in accordance with a preset composite rule set, and the pre-constructed regular expression set is constructed in accordance with the pre-constructed feature string. The scheme of the present invention can weaken independency between rules, reduce the number of times of repeated reading of text information and improve an actual matching speed.
Owner:BEIJING TIANYUAN TETONG SCI & TECH CO LTD
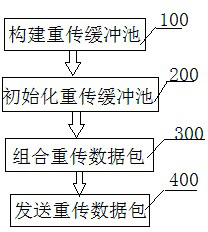
Transmitting terminal radio retransmission method and system based on network code
InactiveCN102594529AReduce latencyImprove transmission efficiencyError prevention/detection by using return channelLoss rateNetworked Transport of RTCM via Internet Protocol
The invention relates to a transmitting terminal radio retransmission method and a system based on a network code. The transmitting terminal radio retransmission method comprises the following steps: constructing a retransmission buffer pool, initializing the retransmission buffer pool and combining a retransmission data packet; and then transmitting the retransmission data packet to reduce the transmission frequency and improve the energy efficiency. The transmitting terminal radio retransmission method and system has the beneficial effects that when the data volume is larger, the network delay is reduced, the network transmission efficiency is improved, the network packet loss rate is reduced, the transmission reliability is increased; and the maximum network information flow can be achieved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
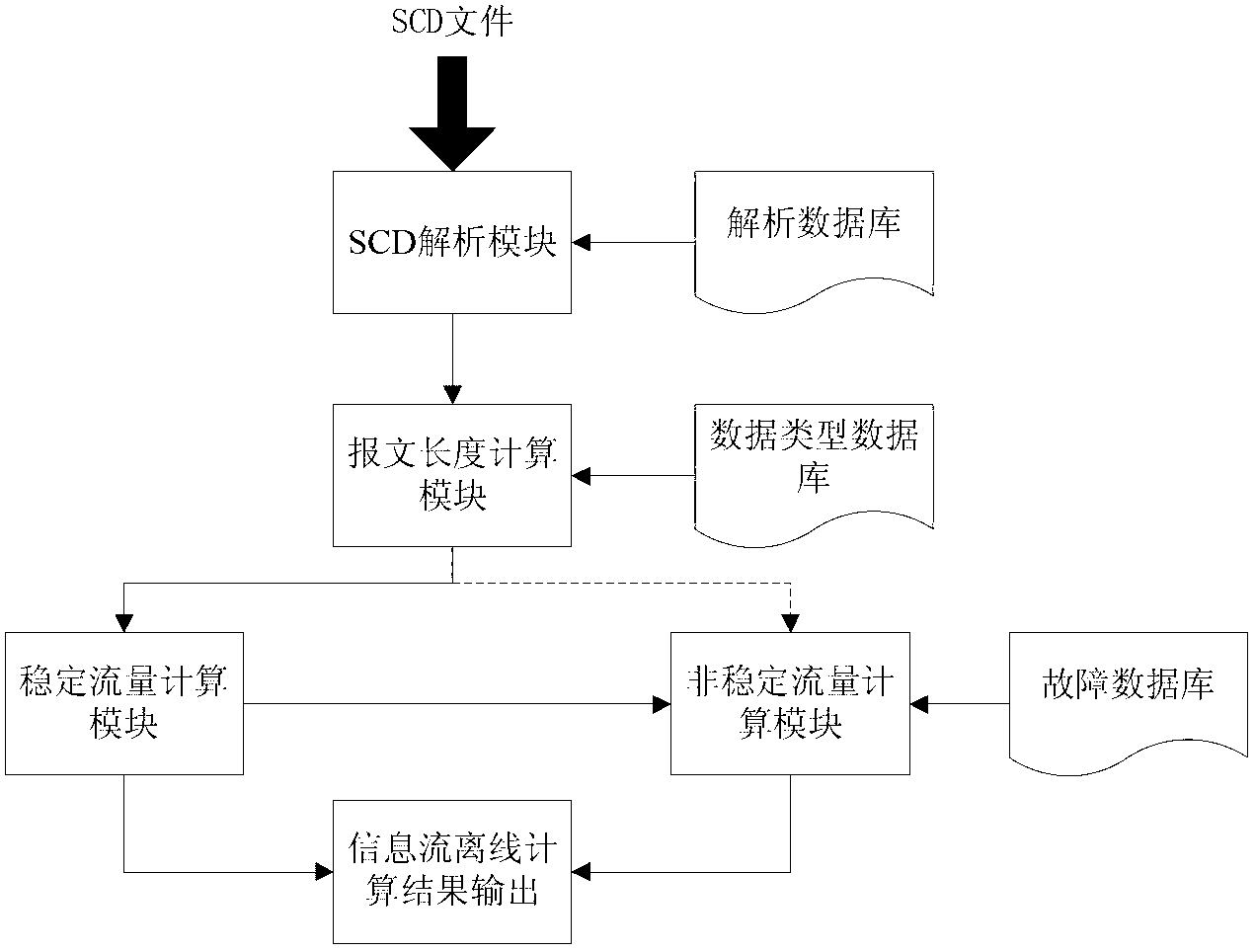
System and method for calculating and evaluating information flow of communication network of intelligent substation
ActiveCN102801580AImprove reliabilityImprove real-time performanceData switching networksMessage lengthSmart substation
The invention provides a system for calculating and evaluating the information flow of a communication network of an intelligent substation. The system comprises an SCD (Security Coding Device) analyzing module, a message length calculating module, a steady flow calculating module, a non-steady flow calculating module, a calculating result output module and other modules, an SCD analyzing database, a data type database and a fault database, wherein the SCD analyzing module externally receives an SCD message, is externally connected with an SCD analyzing sub database, and outputs the SCD message to the message length calculating module externally connected with the data type database, the steady flow calculating module and the non-steady flow calculating module respectively receive the outputs of the message length calculating module, the outputs are converged at the calculating result output module, and the non-steady flow calculating module also simultaneously receives the output of the steady flow calculating module and is externally connected with the fault database. The invention also relates to a method for calculating and evaluating the information flow of the communication network of the intelligent substation for the system. According to the system and the method, the design basis is provided for a designer in the design process of the communication network, and the enough predictability is provided for the designer and line personnel.
Owner:GUANGDONG POWER GRID POWER DISPATCHING CONTROL CENT
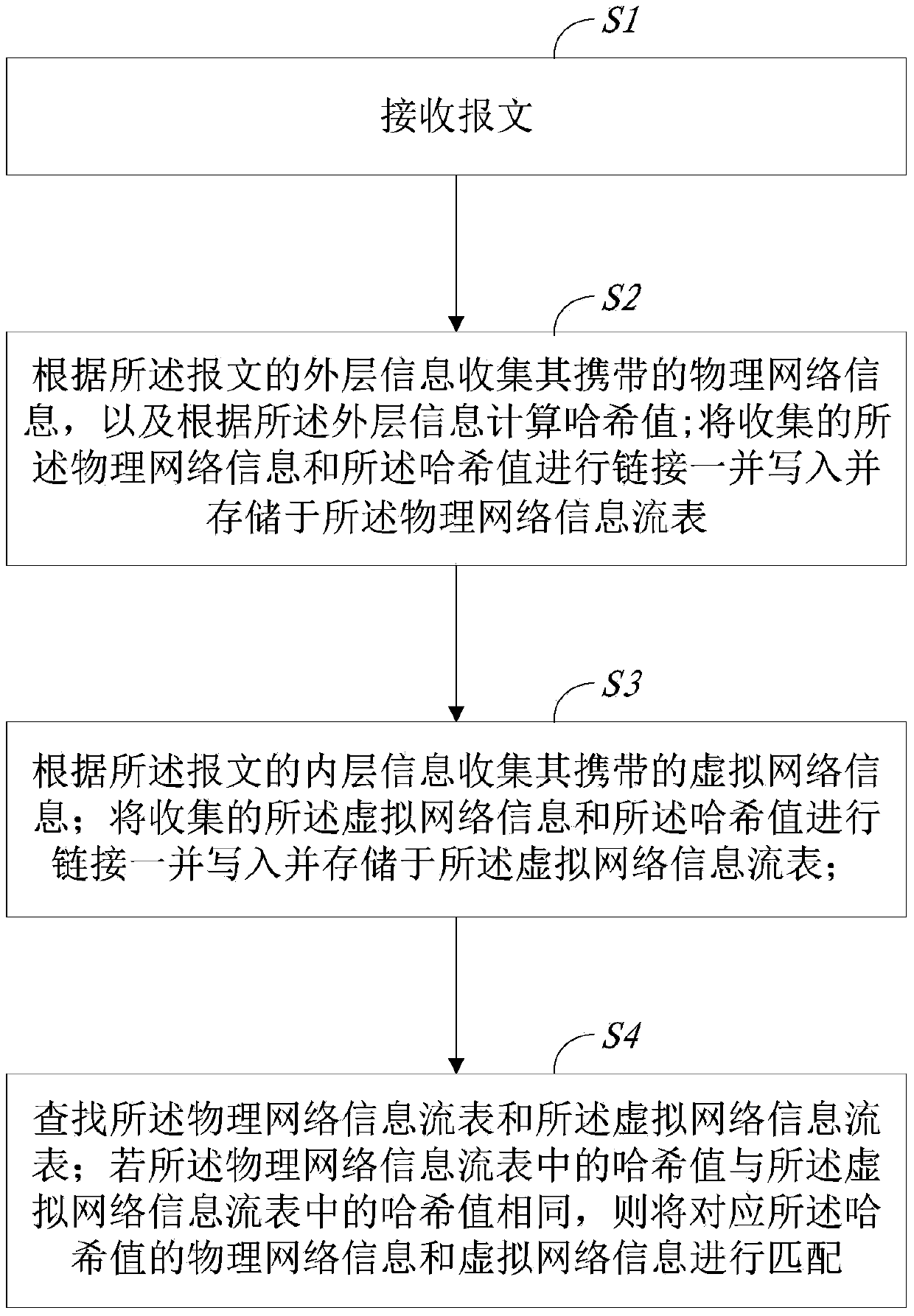
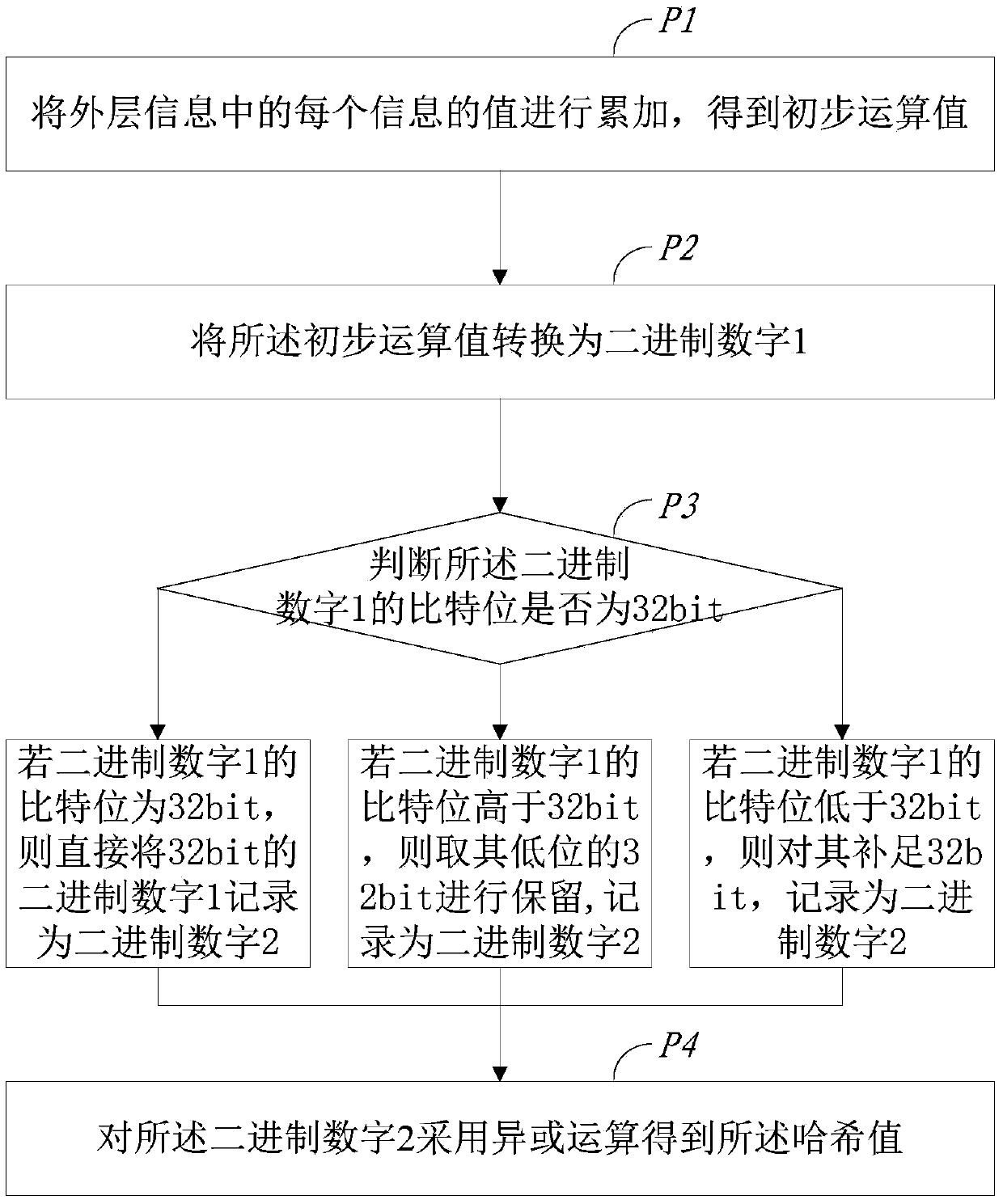
Method and system for collecting virtual network flow in data switch
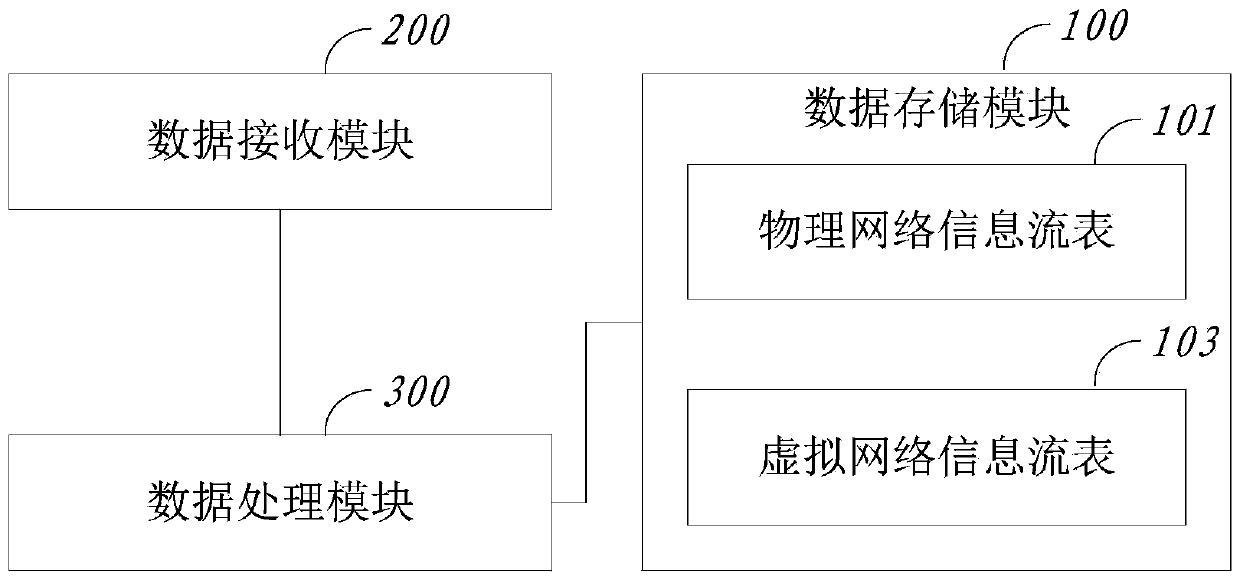
ActiveCN105376099AAvoid performance bottlenecksLower deployment costsData switching networksTraffic capacityNetwork information flow
The invention provides a method and a system for collecting virtual network flow in a data switch. The method comprises the following steps: receiving a message; collecting physical network information carried by the message according to outer layer information of the message, and calculating a hash value according to the outer layer information; linking the collected physical network information and the hash value to write and store the physical network information and the hash value in a physical network information flow table together; collecting virtual network information carried by the message according to inner layer information of the message; linking the collected virtual network information and the hash value to write and store the virtual network information and the hash value in a virtual network information flow table together; looking up the physical network information flow table and the virtual network information flow table; and if the hash value in the physical network information flow table is the same as the hash value in the virtual network information flow table, matching the physical network information and the virtual network information of the corresponding hash value. The method provided by the invention can be used for directly obtaining the virtual network flow through the data switch without the participation of a server, thereby reducing the deployment cost and the implementation complexity.
Owner:SUZHOU CENTEC COMM CO LTD
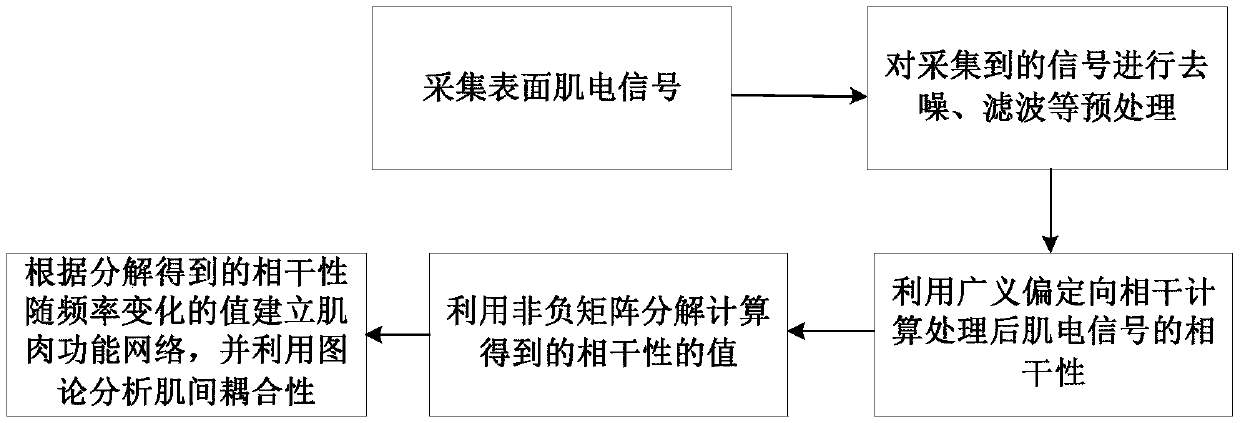
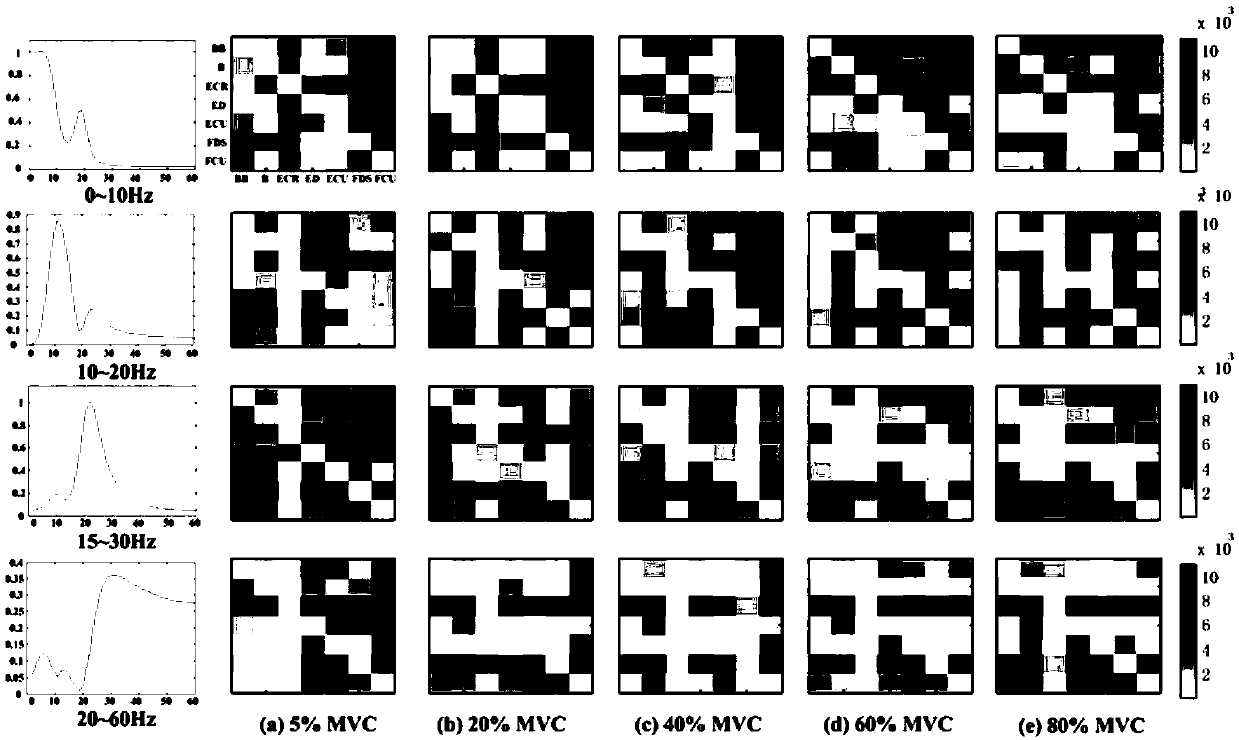
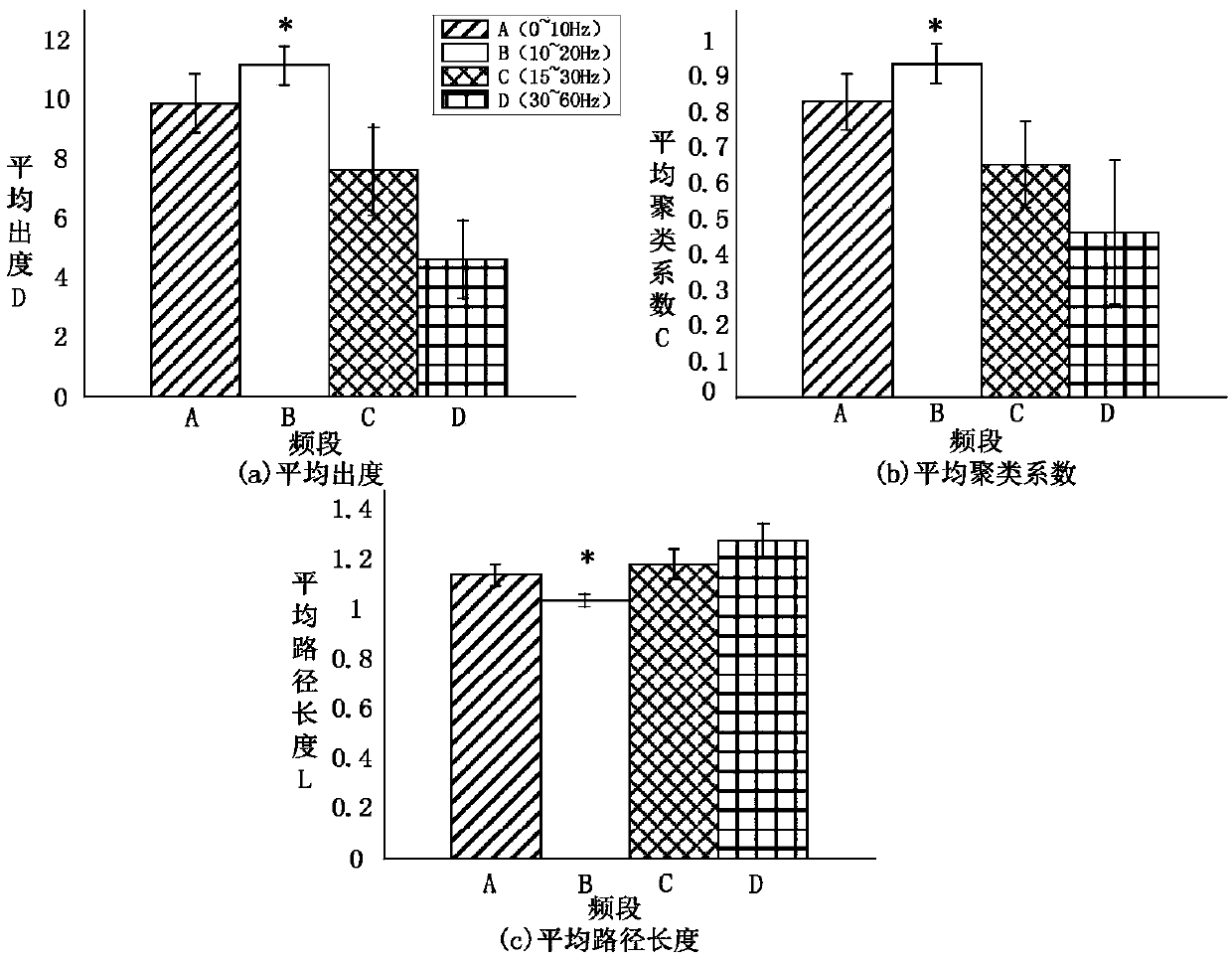
Intermuscular coupling analysis method capable of combining nonnegative matrix decomposition with complex network
The invention provides an intermuscular coupling analysis method capable of combining nonnegative matrix decomposition with a complex network. The method comprises the following steps: collecting seven-channel surface electromyogram signals when different grip strengths are output; firstly, adopting generalized partial directional coherence to calculate coherence among multiple channels; then, adopting a nonnegative matrix decomposition algorithm to decompose a coherence value; finally, adopting the complex network to establish muscle function networks under different conditions. The characteristic index of a graph theory is used for evaluating the transfer efficiency of a muscle function network information flow. A result displays that muscle activation degrees under different grip strengths have significant differences; intermuscular coupling is obvious on a waveband of 10-20 Hz; in addition, on the waveband of 10-20 Hz, the coupling degree of muscles is significantly changed along with different grip strength levels. According to the intermuscular coupling analysis method, multichannel intermuscular coupling analysis is carried out to embody the control pattern of a central nervous system for different output grip strengths, and a basis is provided for evaluating the diagnosis and rehabilitation effect of dyskinesia.
Owner:HANGZHOU DIANZI UNIV
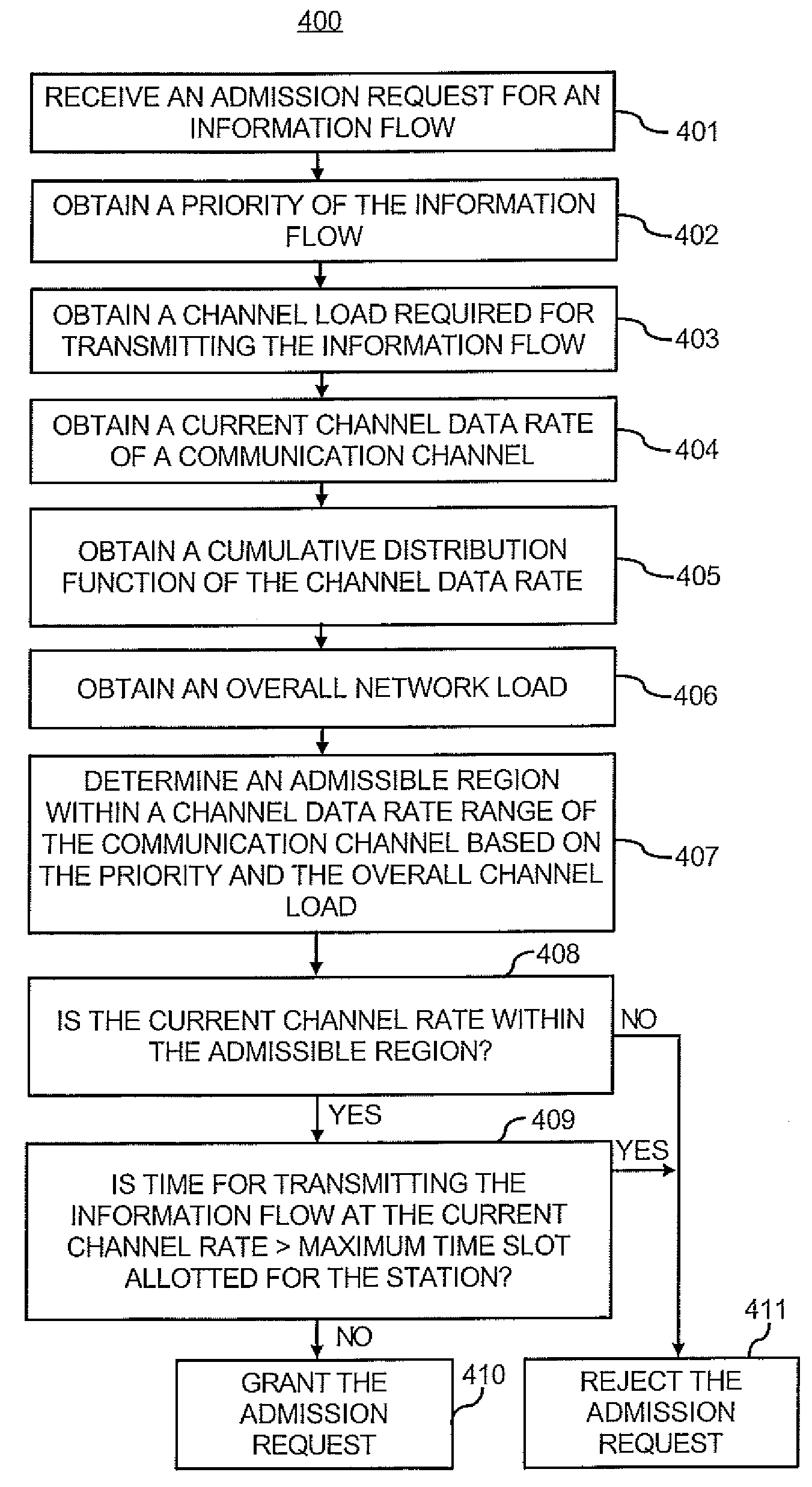
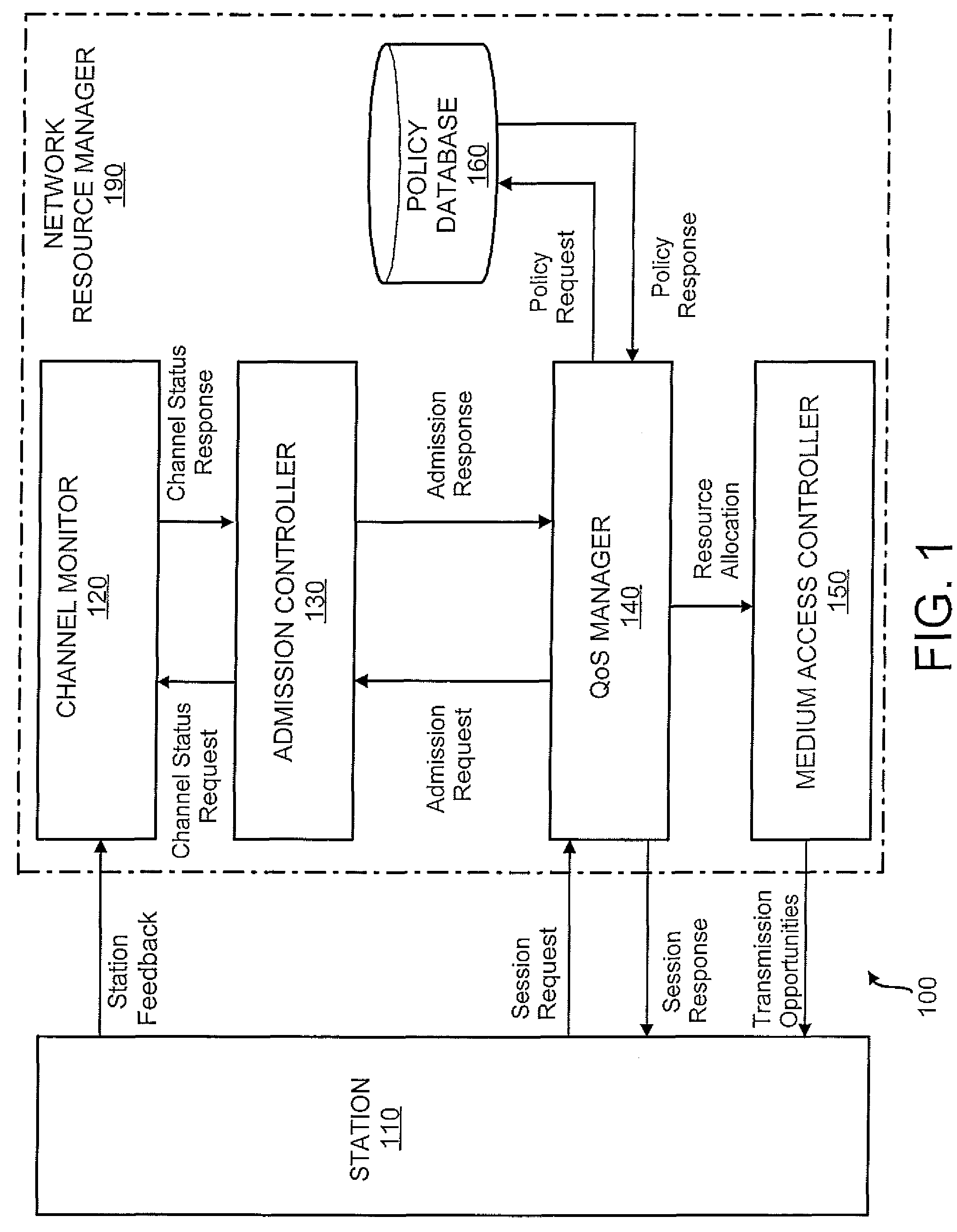
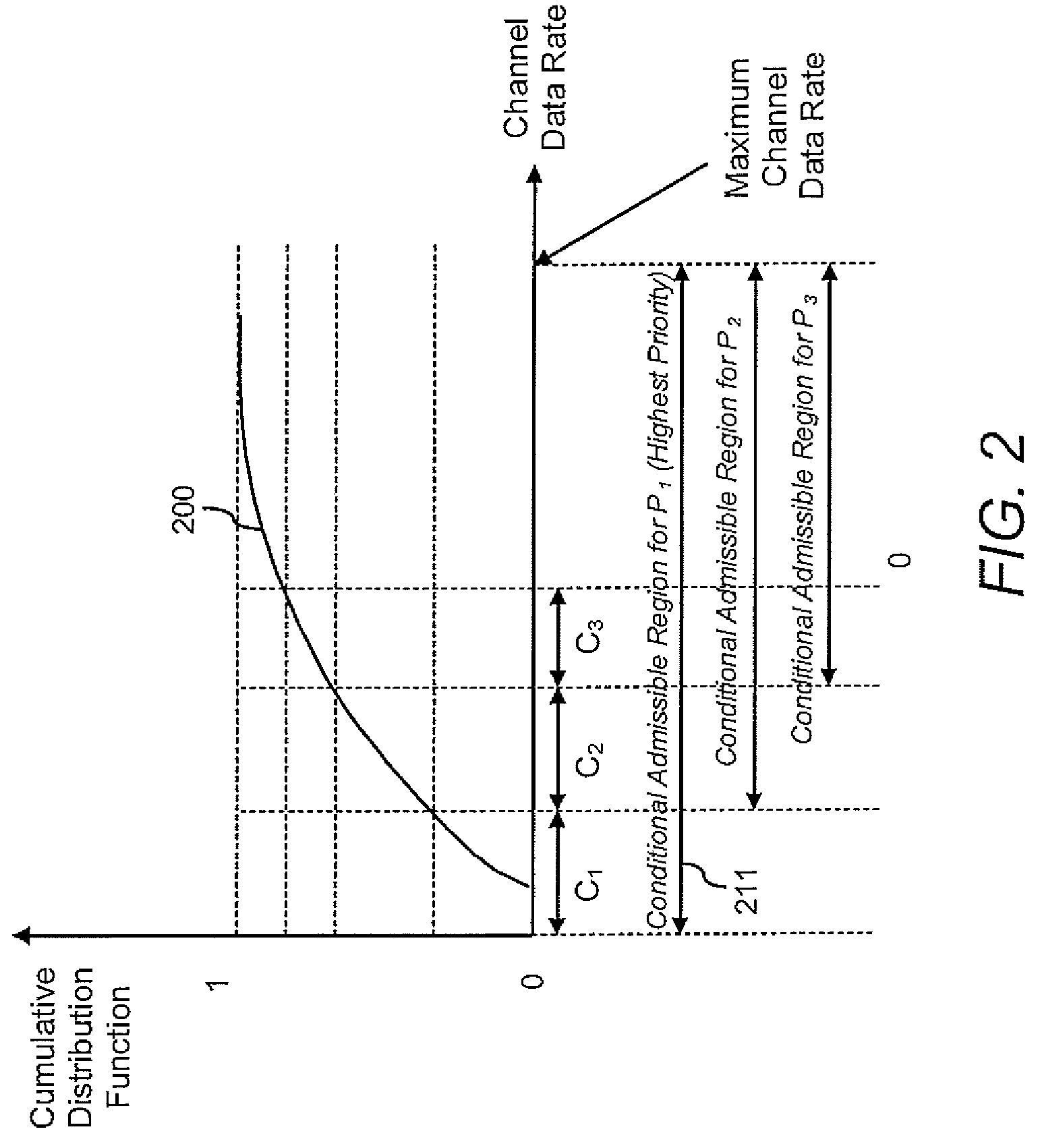
Priority-based admission control in a network with variable channel data rates
A method for priority-based admission control in a network, comprises receiving an admission request for transmitting an information flow to a network through a communication channel and determining an admissible region within a range of a channel data rate of a communication channel for an information flow in response to a priority of the information flow, where the priority of the information flow is one of a plurality of priorities of information flow. The admissible region is one of a plurality of admissible regions within the channel data rate range that correspond to different ones of the plurality of priorities of information flow, respectively, and each of the plurality of admissible regions within the channel data rate range is useable for transmitting information flow with a respective one of the plurality of priorities. Further included in the method is determining an available channel data rate of the communication channel for receiving the information flow by the network, and granting the admission request for the information flow after determining that the available channel data rate of the communication channel is within the admissible region of the channel data rate range.
Owner:GOOGLE TECH HLDG LLC
Zero-interrupt network tap
A network tap monitors network information flow over a particular connection. By duplicating the signal and diverting a copy, the information flow can be analyzed, both in real time and without interference through the monitoring process. When the power to the tap is either turned on or off, however, the change in impedance in the tap's circuit can create an interference spike in the connection that interrupts the information flow. By reducing or eliminating the impedance change in the tap circuitry, such disruptive interruptions can be eliminated.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Botnet network discovery technology and apparatus
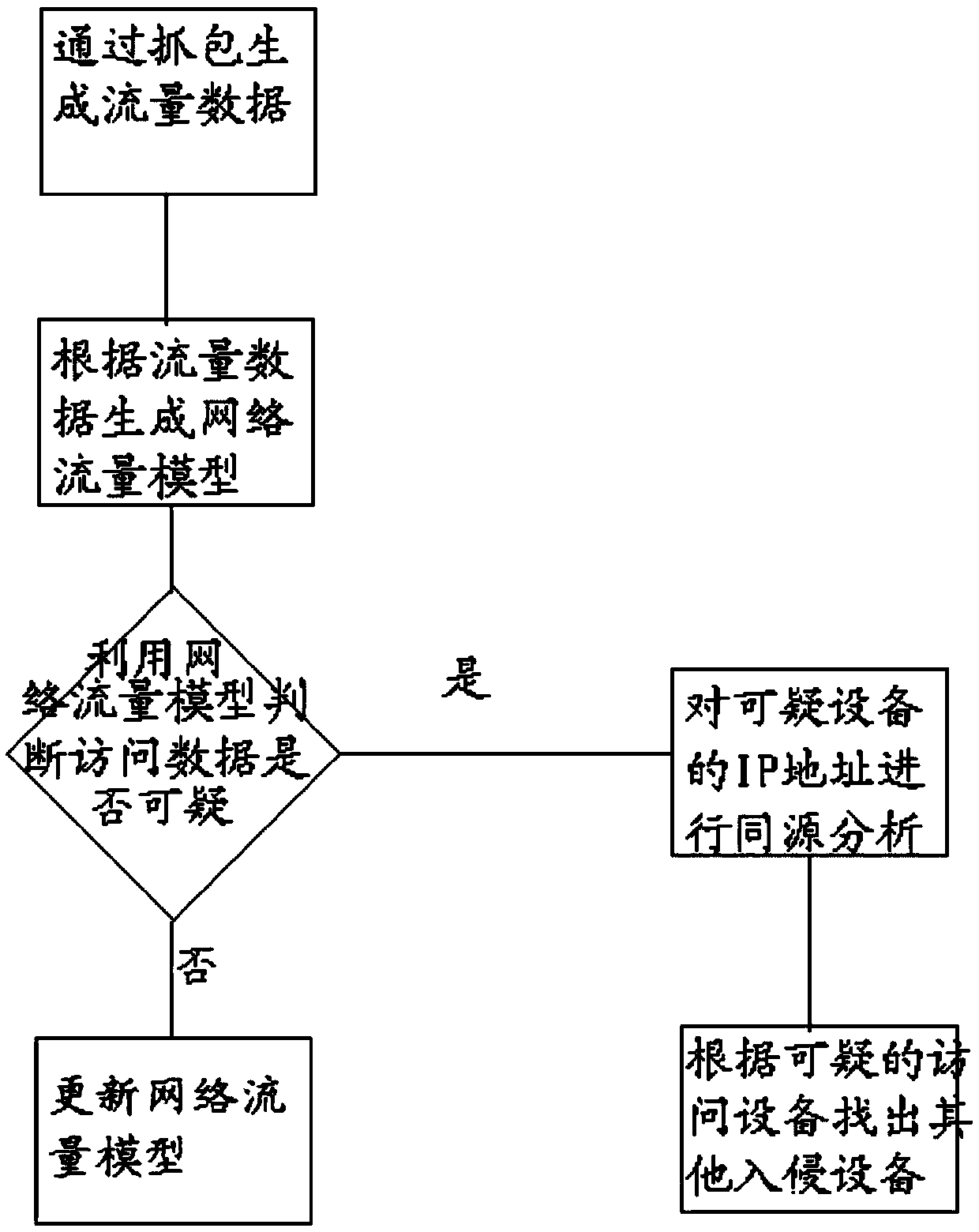
The invention discloses a botnet network discovery technology which comprises the following steps of: capturing network information traffic and generating traffic data; according to network segment information and VLAN (Virtual Local Area Network) partitioning information of an IP (Internet Protocol) address in the generated network data and behavior analysis of related data, partitioning a network device into a corresponding network organizational chart, and according to the network organizational chart, generating a network traffic model graph; according to the network traffic model graph and an access behavior of a device, carrying out comparison; and moreover, according to a comparison condition, judging a suspicious access source. The botnet network discovery technology has the beneficial effects that: a data traffic model is generated by capturing network information; moreover, traffic comparison is carried out by utilizing device information accessed by the data traffic model so as to judge safety of the access device; the related suspicious access source of the suspicious access device can be found; and use safety of the network device is ensured.
Owner:睿峰网云(北京)科技有限公司
Method for Transmitting Information Over an Integrated Telecommunications and Broadcast System and Integrated Telecommunications and Broadcast System
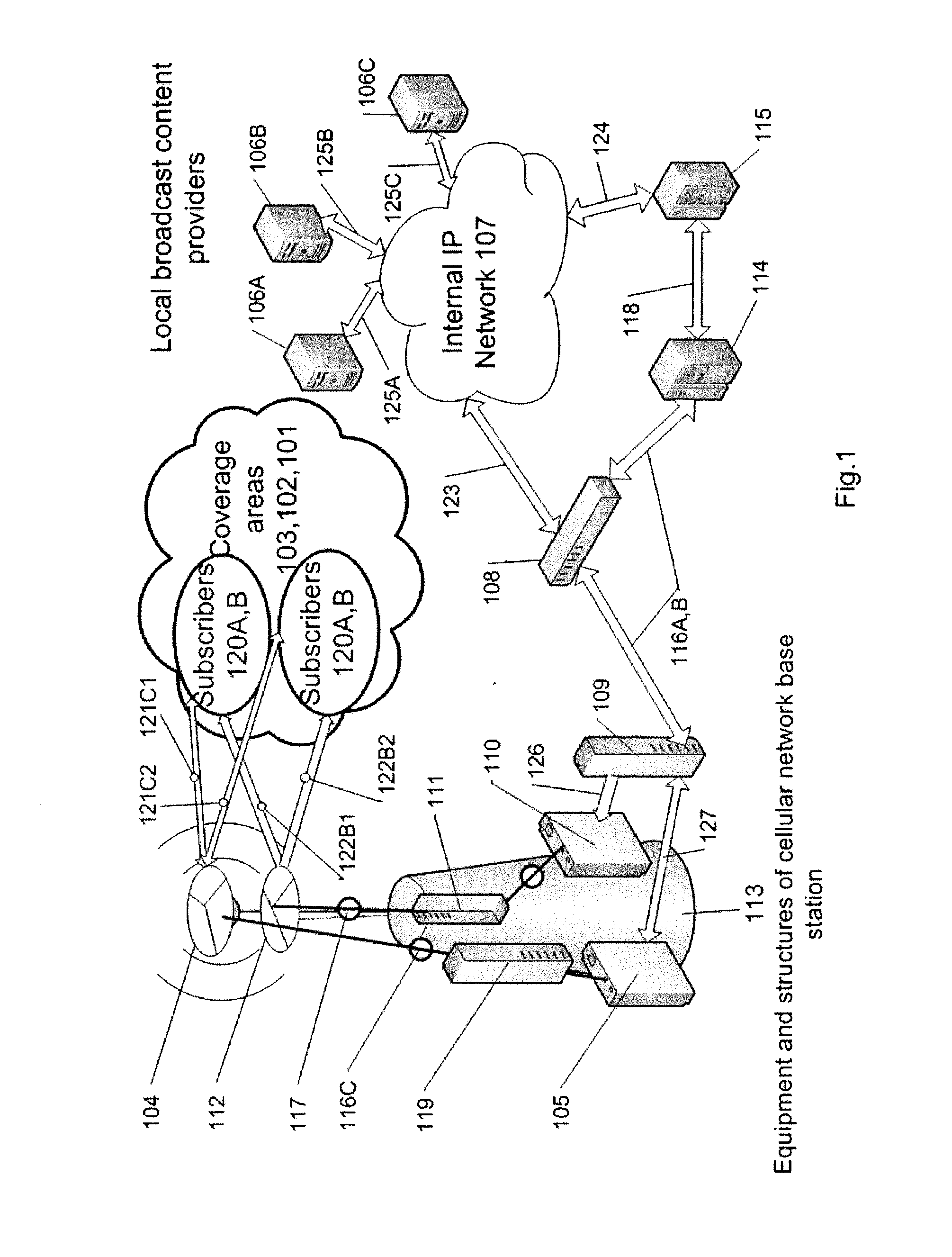
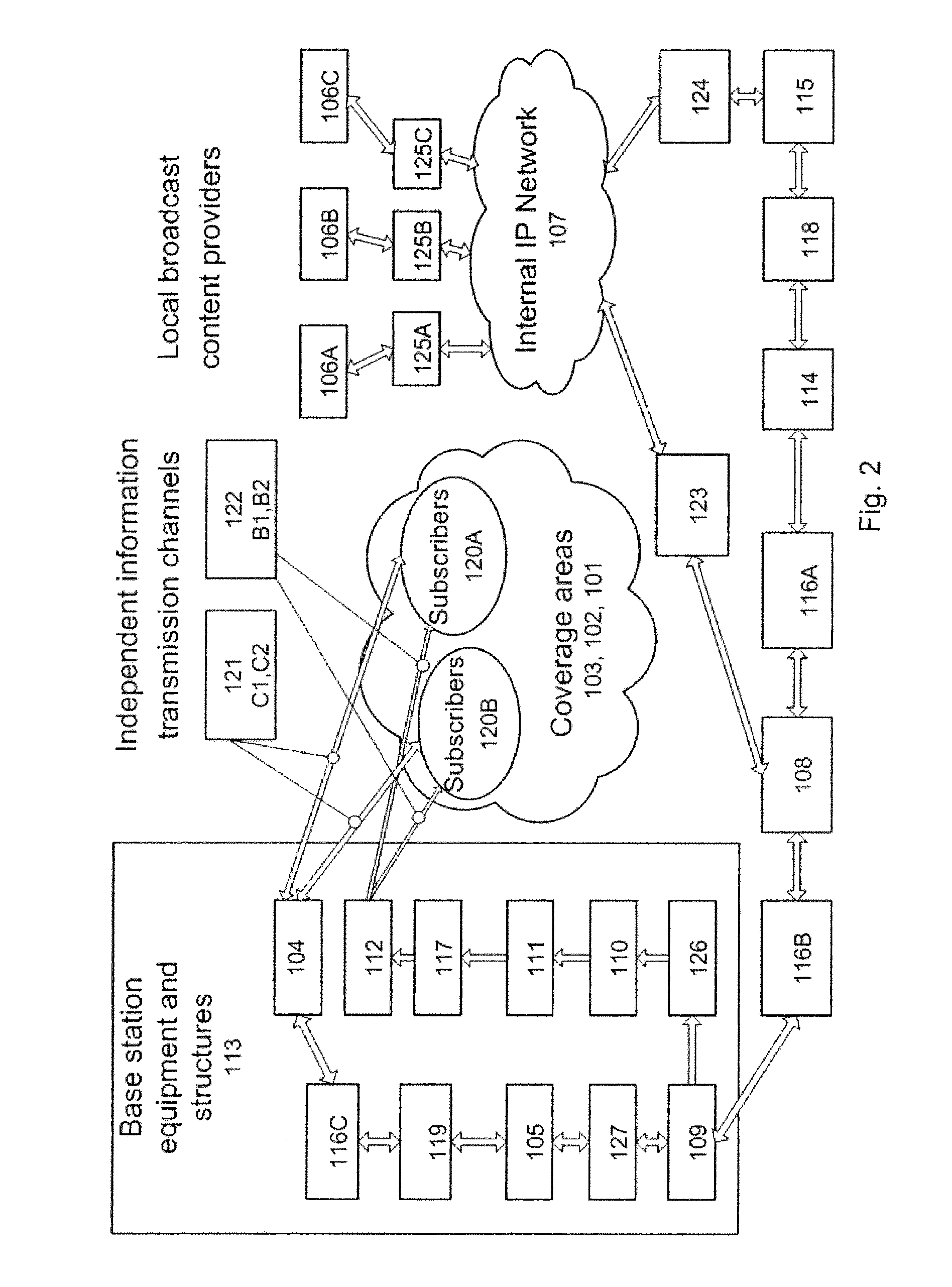
InactiveUS20120151534A1Pulse modulation television signal transmissionAnalogue secracy/subscription systemsTelecommunications linkInformation networks
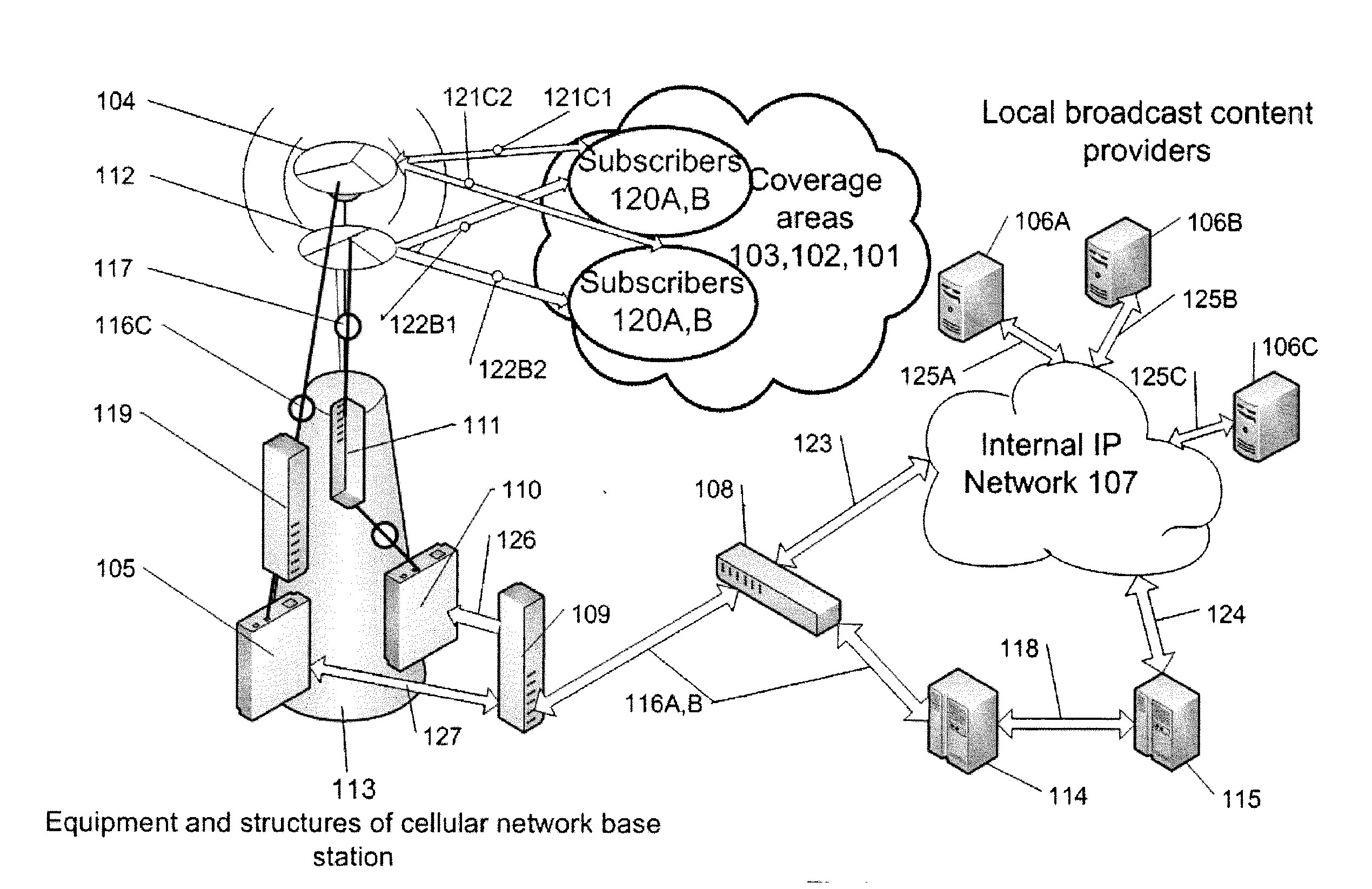
The present invention relates to methods and systems for transmitting information over different information networks and in particular to a method for transmitting information in an integrated telecommunications and broadcast system. The method for transmitting information across the integrated telecommunications and broadcast system incorporating a cellular network and a broadcast network with a plurality of broadcast content providers connectable to transmitter / receiver equipment installed at least one base station of the cellular network, consists of broadcast content generation by broadcast content providers, connecting the broadcast content providers to an internal IP network for broadcast program distribution, transfer of the broadcast content from the broadcast content providers by means of the internal IP network via communication links and line transmission equipment of the cellular network, transmission of cellular network information over the communication links and line transmission equipment of the cellular network, generation of a combined information stream of the broadcast content information and information of the cellular network for its transmission to at least one base station of the cellular network, separation of independent streams—the cellular network information stream and the broadcast network information stream from said combined stream, and transmission of the separated independent information streams to the above-mentioned transmitter / receiver equipment for their further transmission over appropriate independent channels to subscribers of the integrated telecommunications and broadcast system, located within the coverage area of the integrated system.
Owner:LIMITED LIABILITY COMPANY MERA NN
A network information circulating method
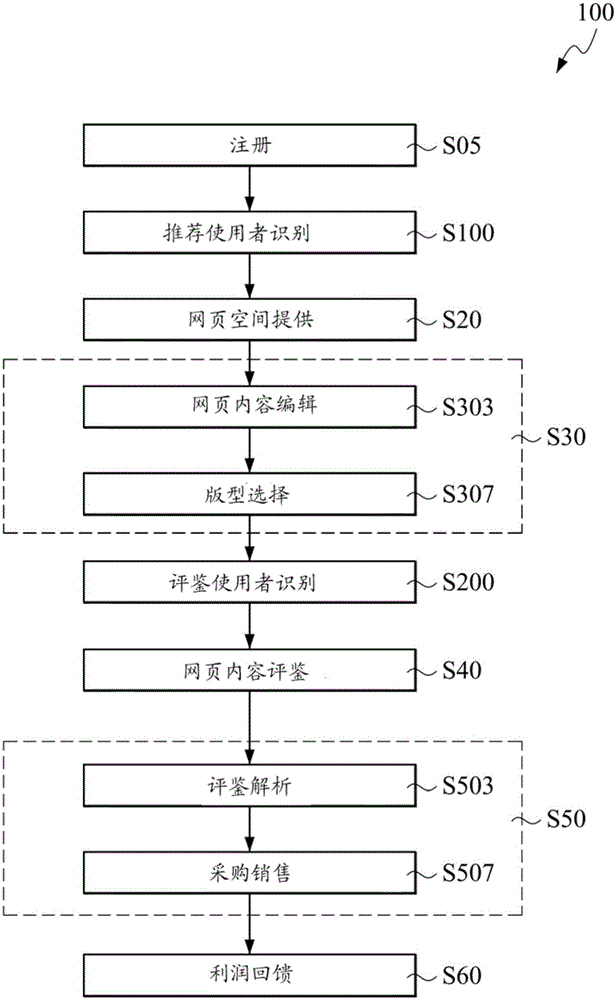
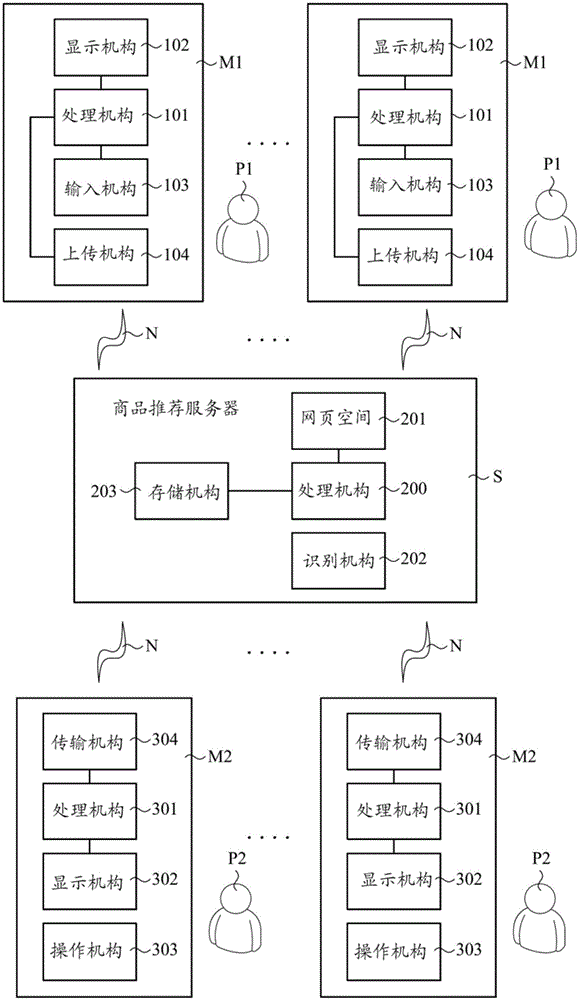
InactiveCN106204090AIncrease salesImprove turnover rateBuying/selling/leasing transactionsMarketingNetwork information flowWillingness to recommend
A network information circulating method comprises a user identification step, a web-page space providing step, a web page content displaying step, a web page content evaluation step, a sale step, and a profit feedback step, thereby, the web page space is provided to recommended users; through a page content editing step and a version selection step of the web content display steps, the convenience of page editing and overall aesthetics can be increased; through user evaluations on the displayed page content for recommended users, hot goods for sales can be formed; and the return of merchandise sales profits to the recommended users can enhance the sales of goods, turnover rate and the willingness to recommend.
Owner:潘仁杰
SpaceWire network interface bypass detection device
ActiveCN112291110AGuaranteed normal transmissionSimplified data detection methodData switching networksData streamNetwork information flow
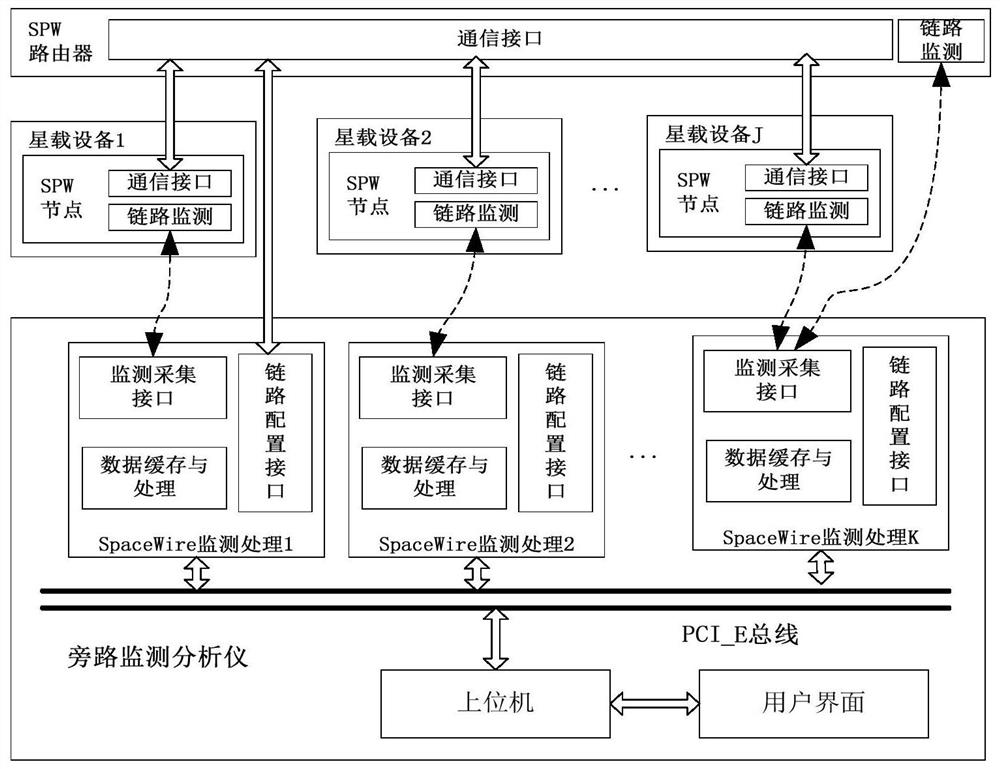
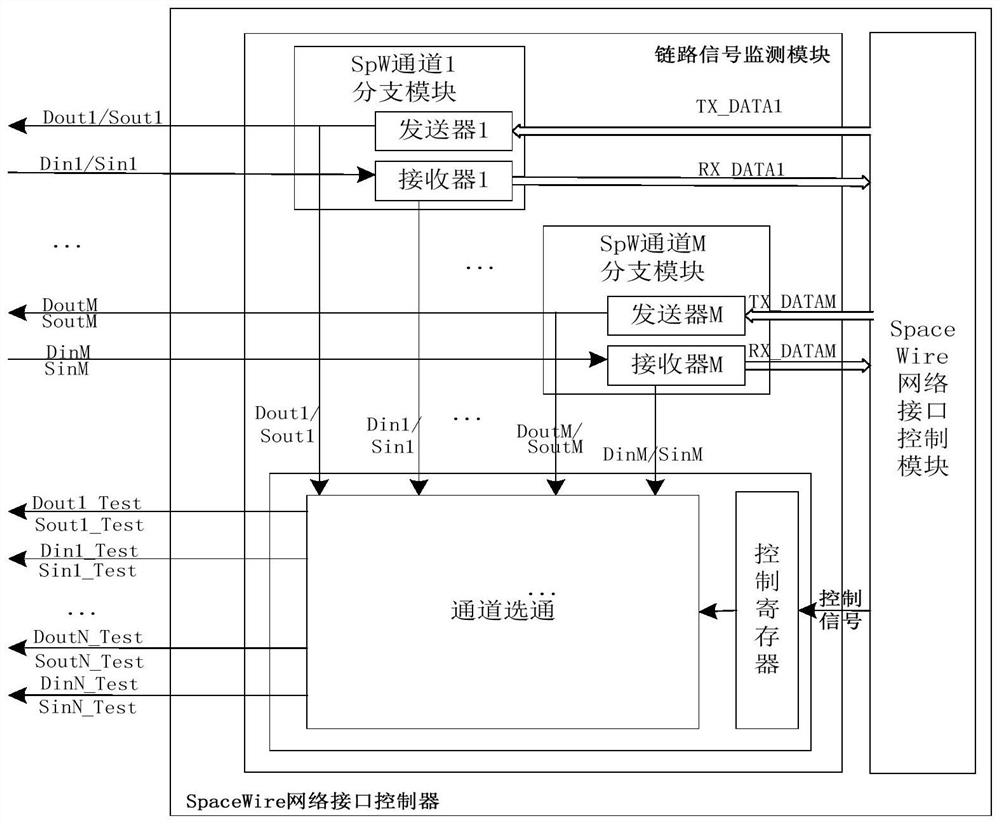
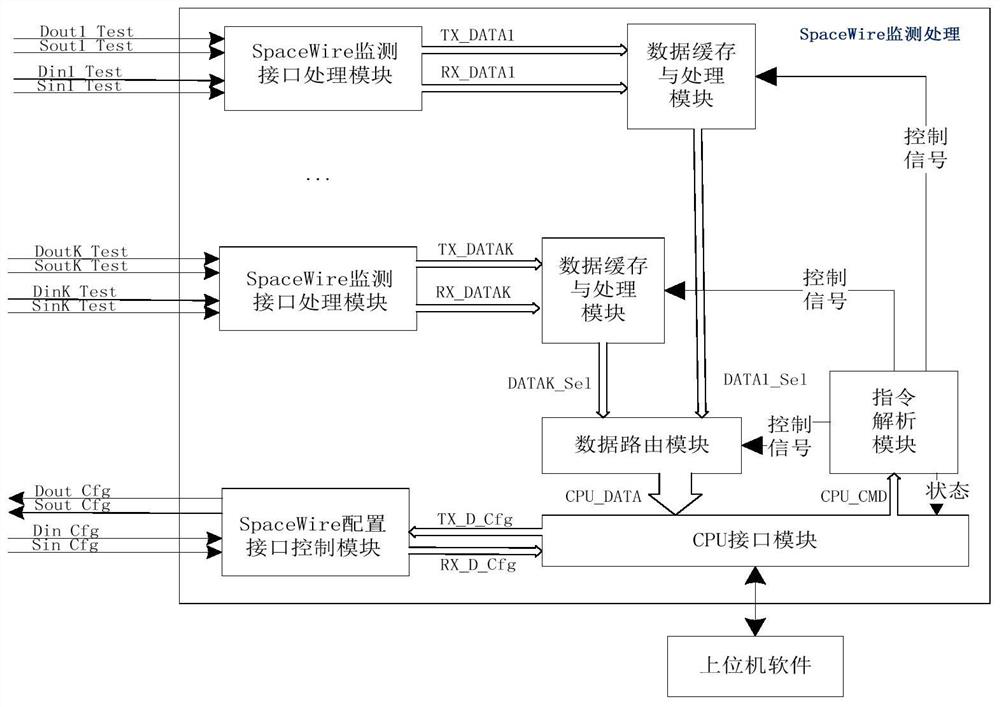
The invention discloses a SpaceWire network interface bypass detection device, which is characterized in that a link signal monitoring module breaks through the traditional monitoring mode that a monitoring device is inserted after an original link is disconnected, a link signal is extracted through a branch structure, meanwhile, the normal transmission of the link signal is ensured, a SpaceWire link data detection method is simplified, and the monitoring efficiency is improved. The device provides a nondestructive monitoring solution, can realize data flow online monitoring and analysis in the network node operation process, and solves the problem that the whole satellite system-level network information flow cannot be measured. The device has good hardware interface expandability, the link signal monitoring module supports instruction configuration monitoring interface gating, and the device is suitable for all SpaceWire interface control modules. The bypass monitoring analyzer can be used as a SpaceWire node to realize plug and play of the test equipment; according to the device, the combination mode of the link signal monitoring module and the bypass monitoring analyzer is flexible, and diversified detection modes such as single-link monitoring and full-network multipoint parallel monitoring can be realized.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
Network key point analysis method based on single-layer information flow transmission
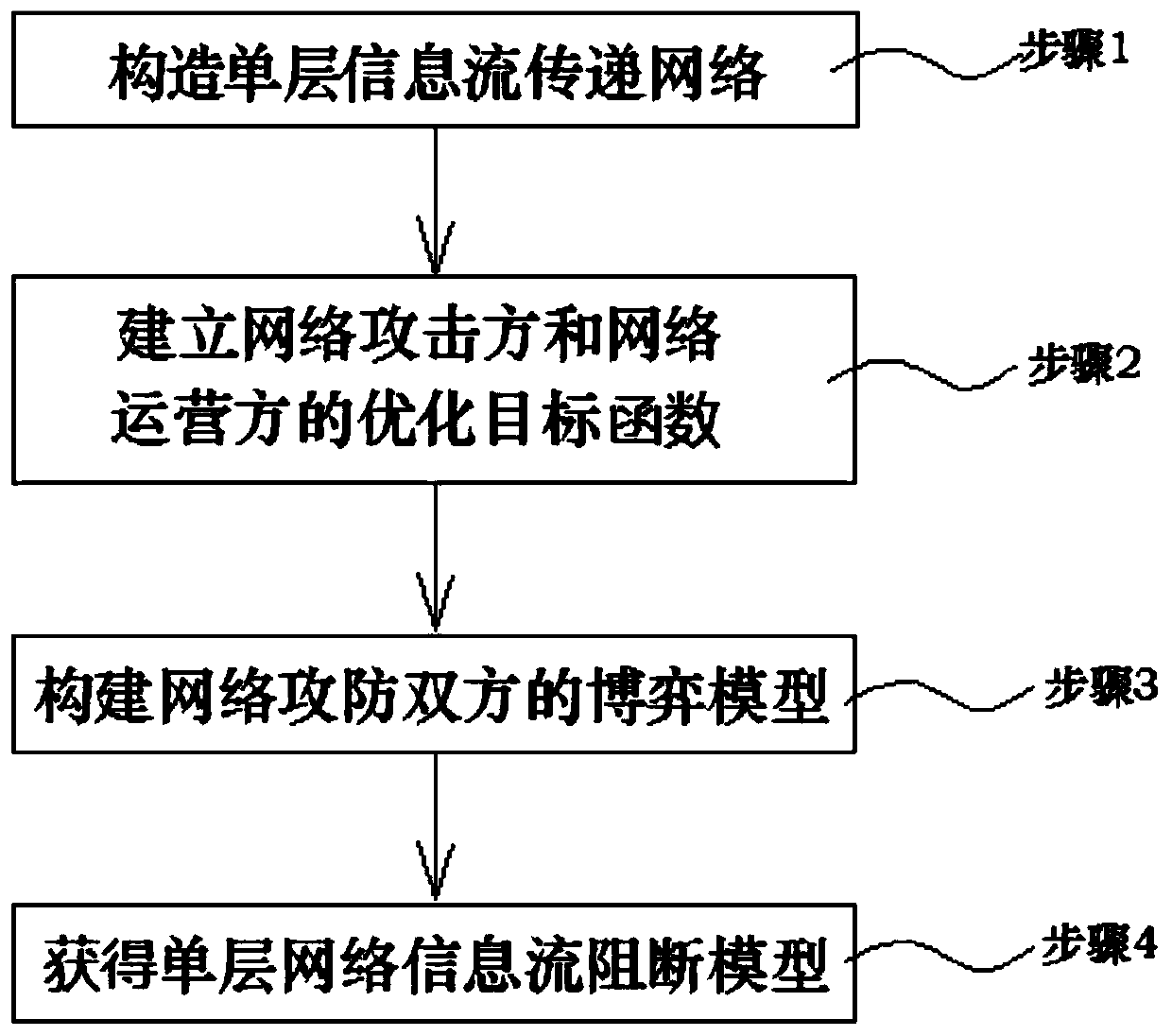
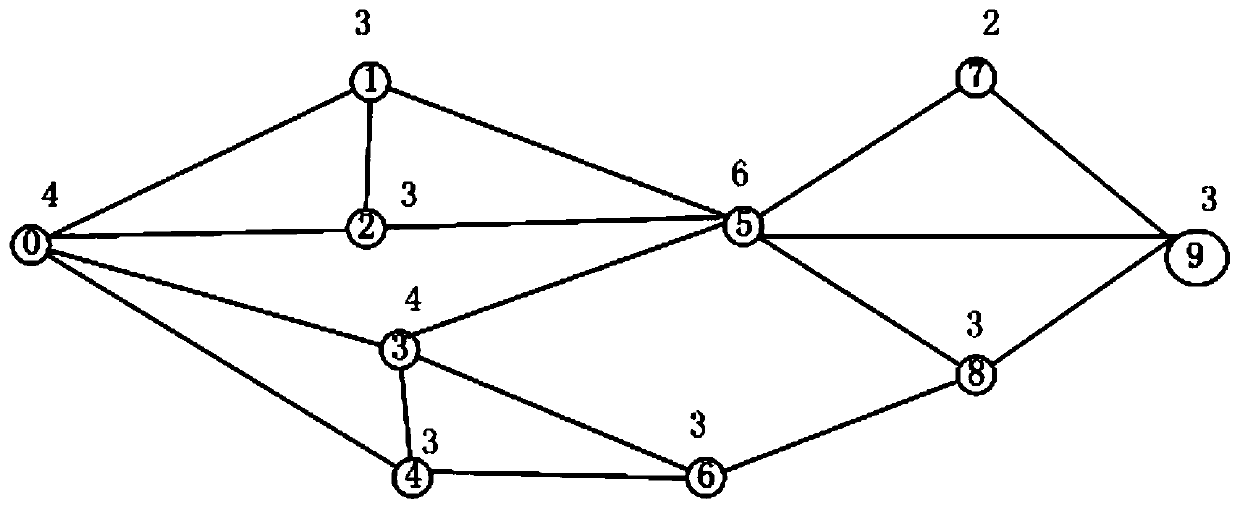
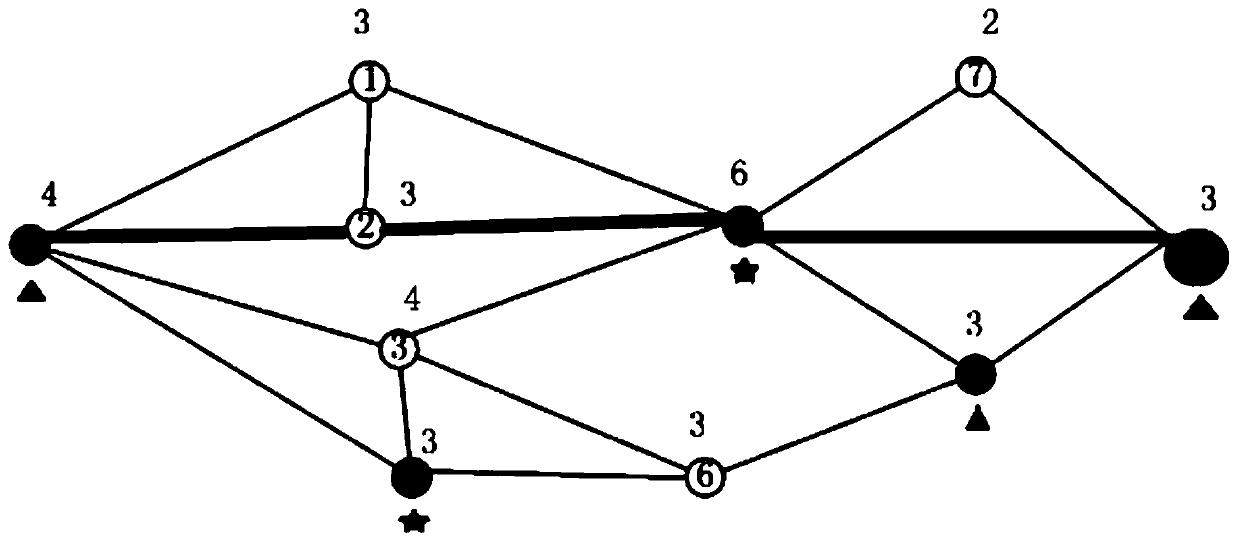
ActiveCN111478813AImprove securityImprove survivabilityData switching networksCyber operationsNetwork key
The invention discloses a network key point analysis method based on single-layer information flow transmission, and the method comprises the steps: obtaining network data based on a graph structure,and constructing a single-layer information flow transmission network according to the network data; preprocessing the single-layer information flow transmission network, and establishing an optimization objective function based on a network attacker and a network operator; constructing a game model according to the optimization objective functions of the network attacker and the network operator;establishing a single-layer network information flow blocking model from the perspective of the network attacker, and blocking nodes are determined as network key points. According to the invention,two concepts of a network attacker and a network operator are introduced to describe the problem of network security from different perspectives and construct a game model; and meanwhile, the targetsof the network attacker and the network operator are clearly described and are classified into the same model, so that a single-layer network information flow blocking model is established, and key nodes of the network are discovered while a blocking scheme is solved from the perspective of the attacker.
Owner:NAT UNIV OF DEFENSE TECH
Request processing method, device and equipment, and storage medium
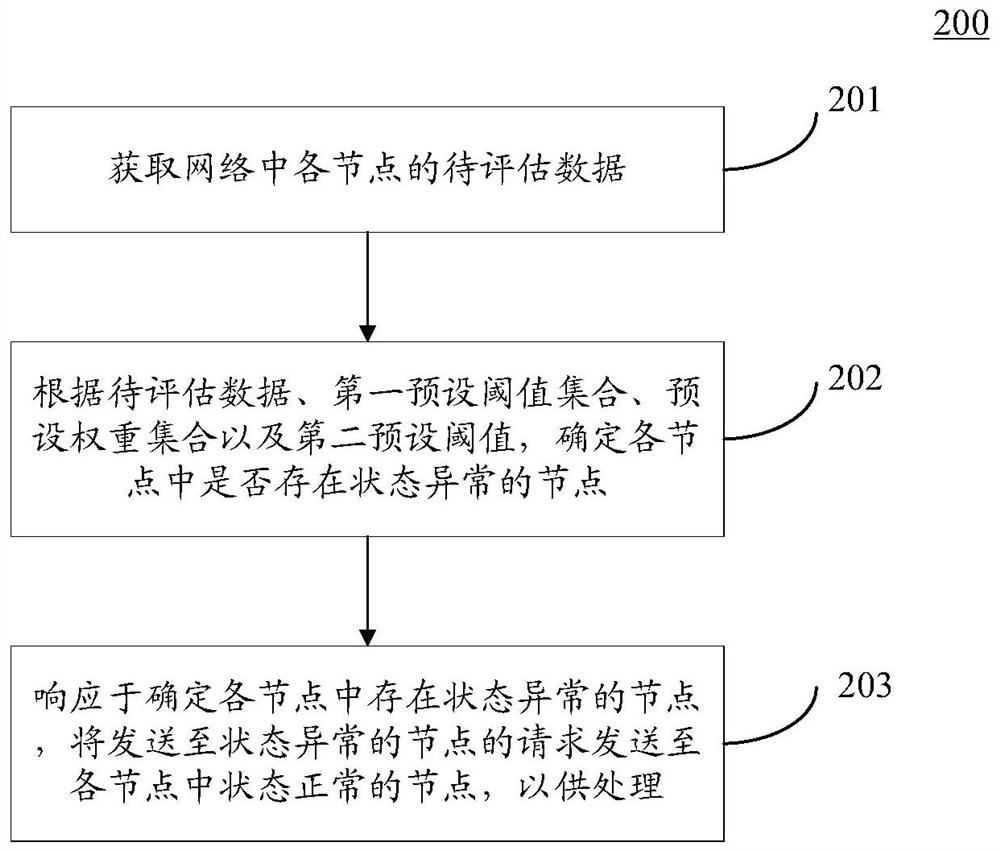
ActiveCN111865720ASolve the problem of inaccurate judgmentAvoid unmanageable risksData switching networksNetwork information flowEngineering
The invention discloses a request processing method, device and equipment and a storage medium, and relates to the field of cloud platforms, computer networks and information flows. The specific implementation scheme comprises the following steps: acquiring to-be-evaluated data of each node in a network; according to the to-be-evaluated data, a first preset threshold set, a preset weight set and asecond preset threshold, determining whether nodes with abnormal states exist in the nodes or not; and in response to the fact that the node with the abnormal state exists in the nodes, sending a request sent to the node with the abnormal state to the node with the normal state in the nodes for processing. According to the implementation mode, the state abnormal condition of the node can be accurately evaluated, the request sent to the node with the abnormal state is sent to the node with the normal state in time, and the risk that the user request cannot be processed is avoided.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Pushing method and device for deliverable entity
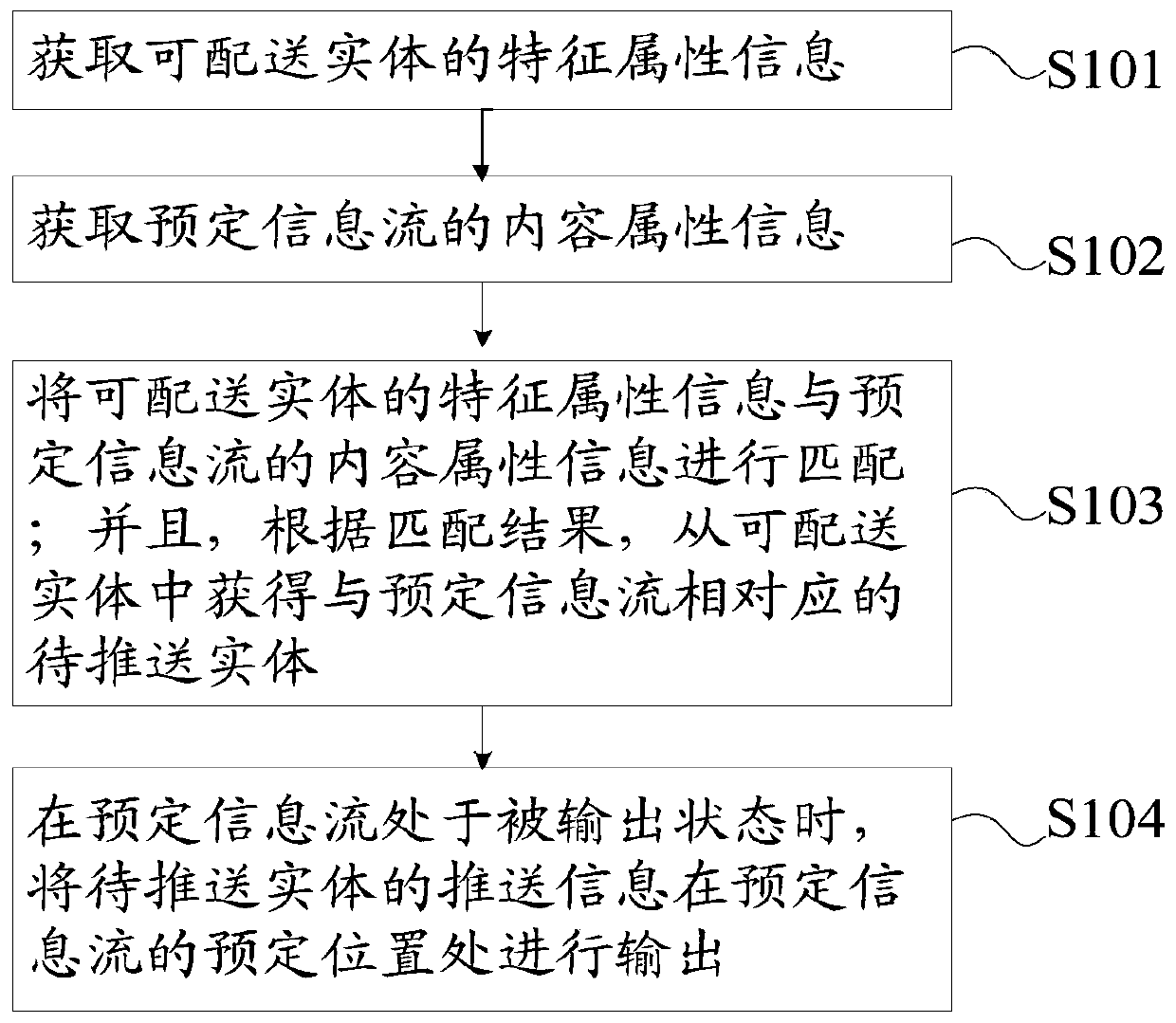
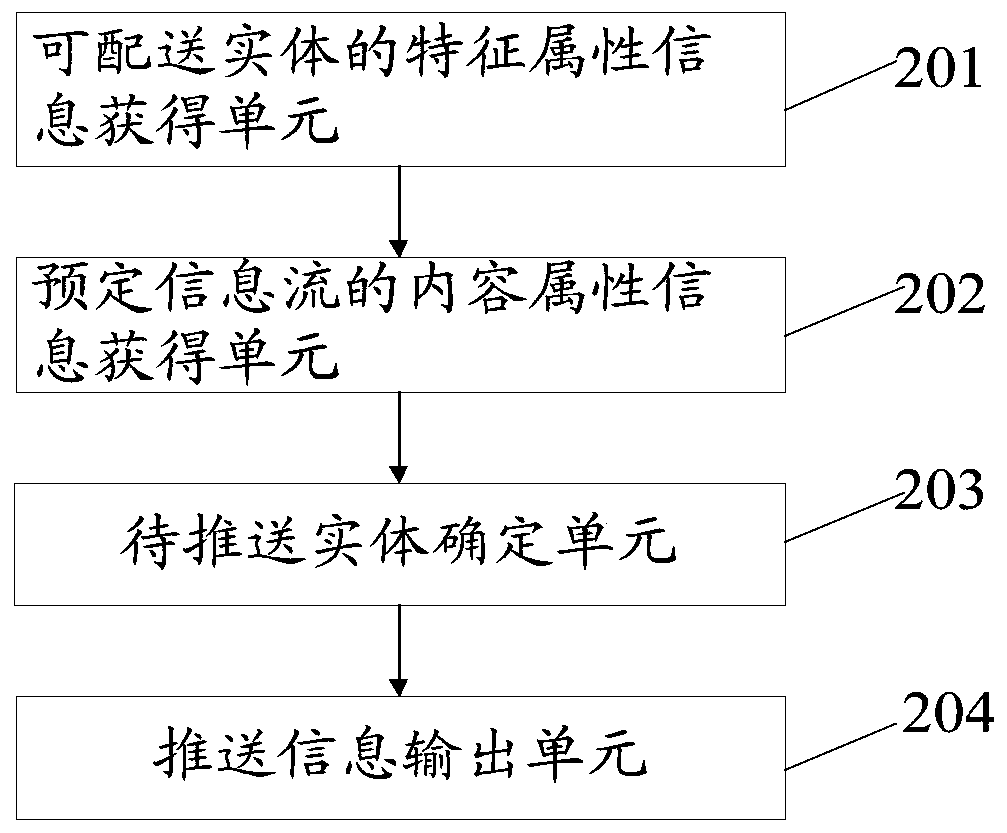
InactiveCN110035111AEfficient deliveryImprove experienceDigital data information retrievalBuying/selling/leasing transactionsPersonalizationNetwork information flow
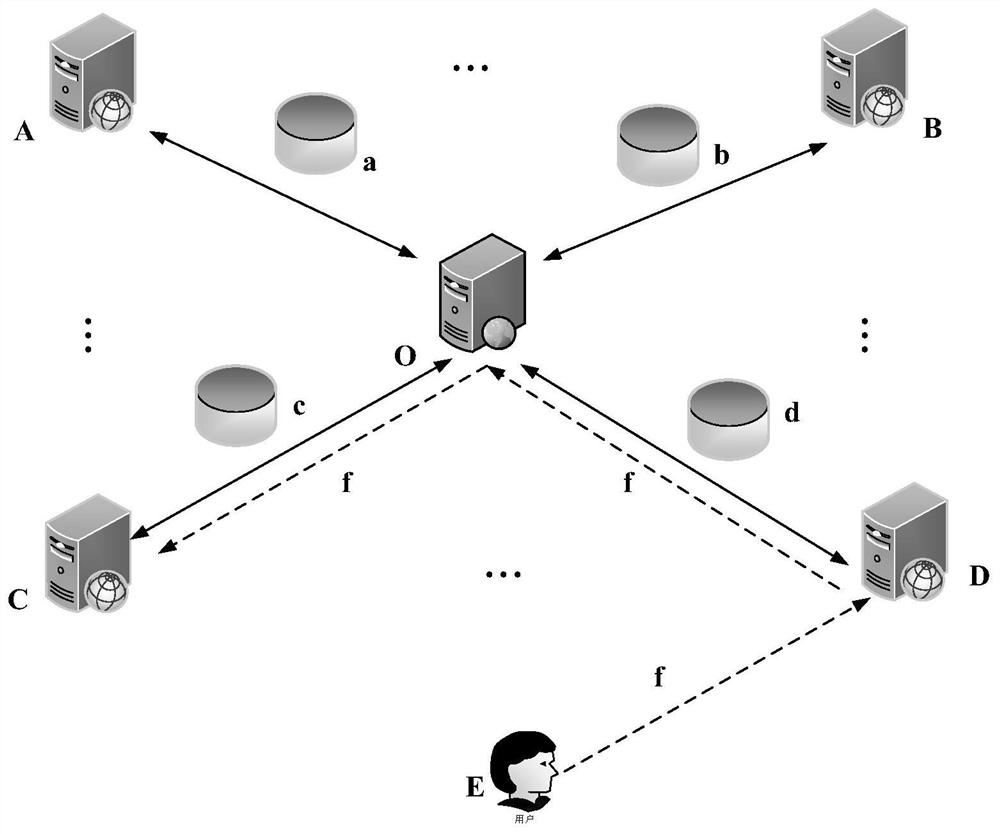
The invention discloses a pushing method and device for a deliverable entity. The method comprises the steps that feature attribute information of the deliverable entity is acquired; wherein the deliverable entity can be used for displaying promotion information; content attribute information of the predetermined information flow is obtained; the feature attribute information of the deliverable entity is matched with the content attribute information of the predetermined information flow, and a to-be-pushed entity corresponding to the predetermined information flow is obtained from the deliverable entity according to a matching result; and when the predetermined information flow is in the output state, the push information of the to-be-pushed entity is output on an output page of the predetermined information flow. By using the method, the user can browse the network information flow, the deliverable entity which is related to the network information flow and displays the promotion information is acquired, the relevance between the network information flow and the user is improved, the user experience is improved, the personalized push of the deliverable entity is realized, and theeffective release of the promotion information is realized while the output value and the browsability of the network information flow are enhanced.
Owner:FREELIFE SOLUTIONS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com