Patents
Literature
53 results about "Network tap" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
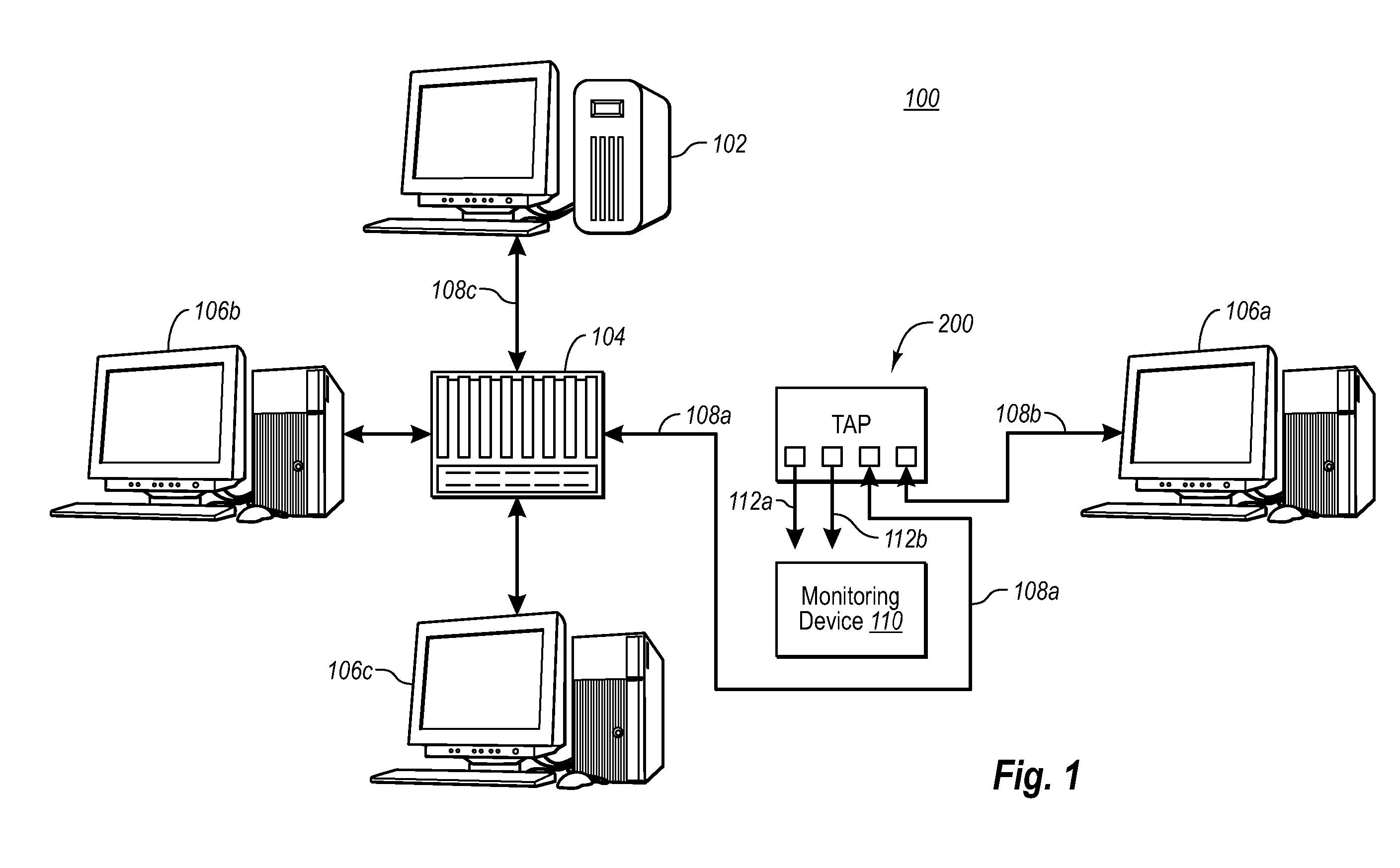
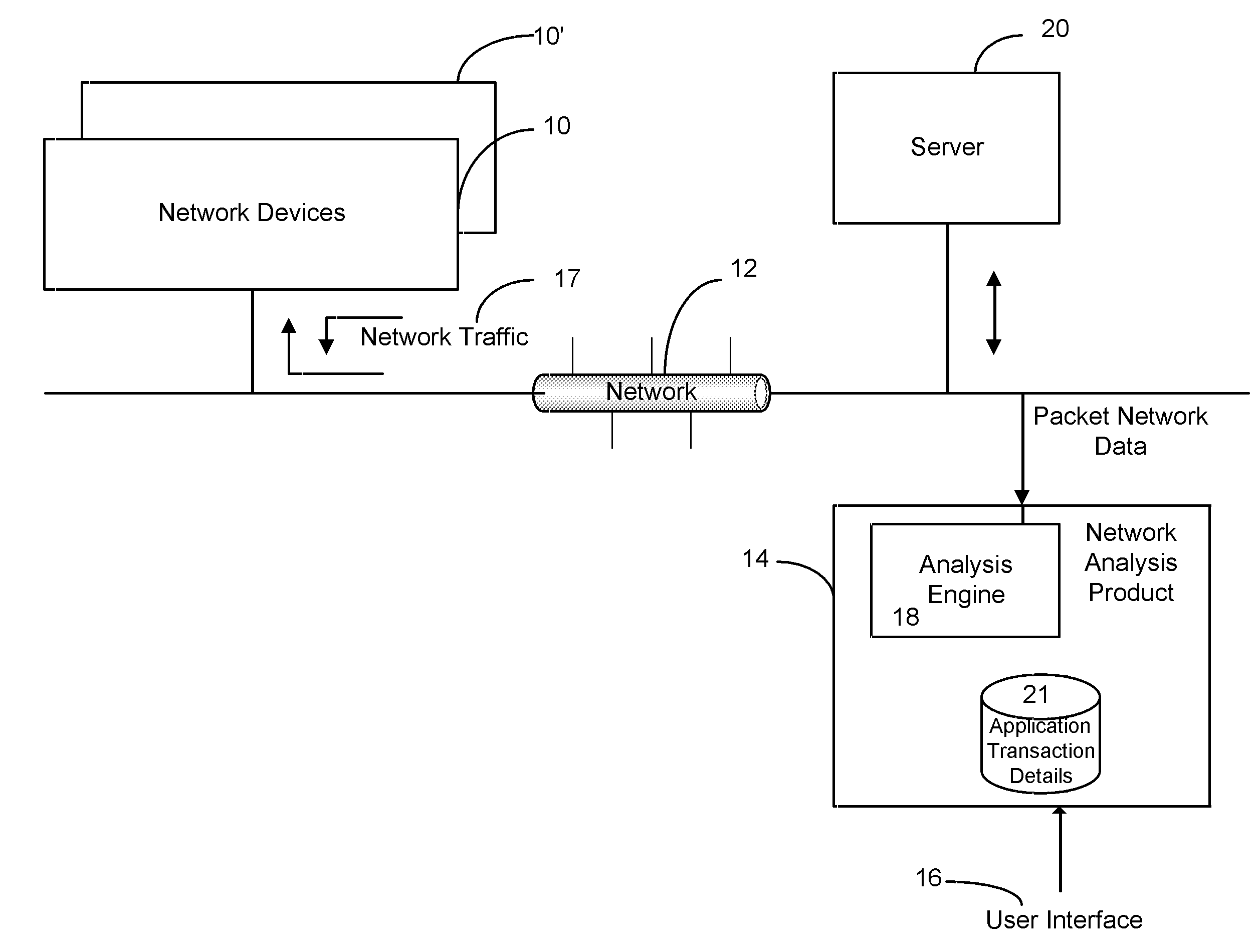
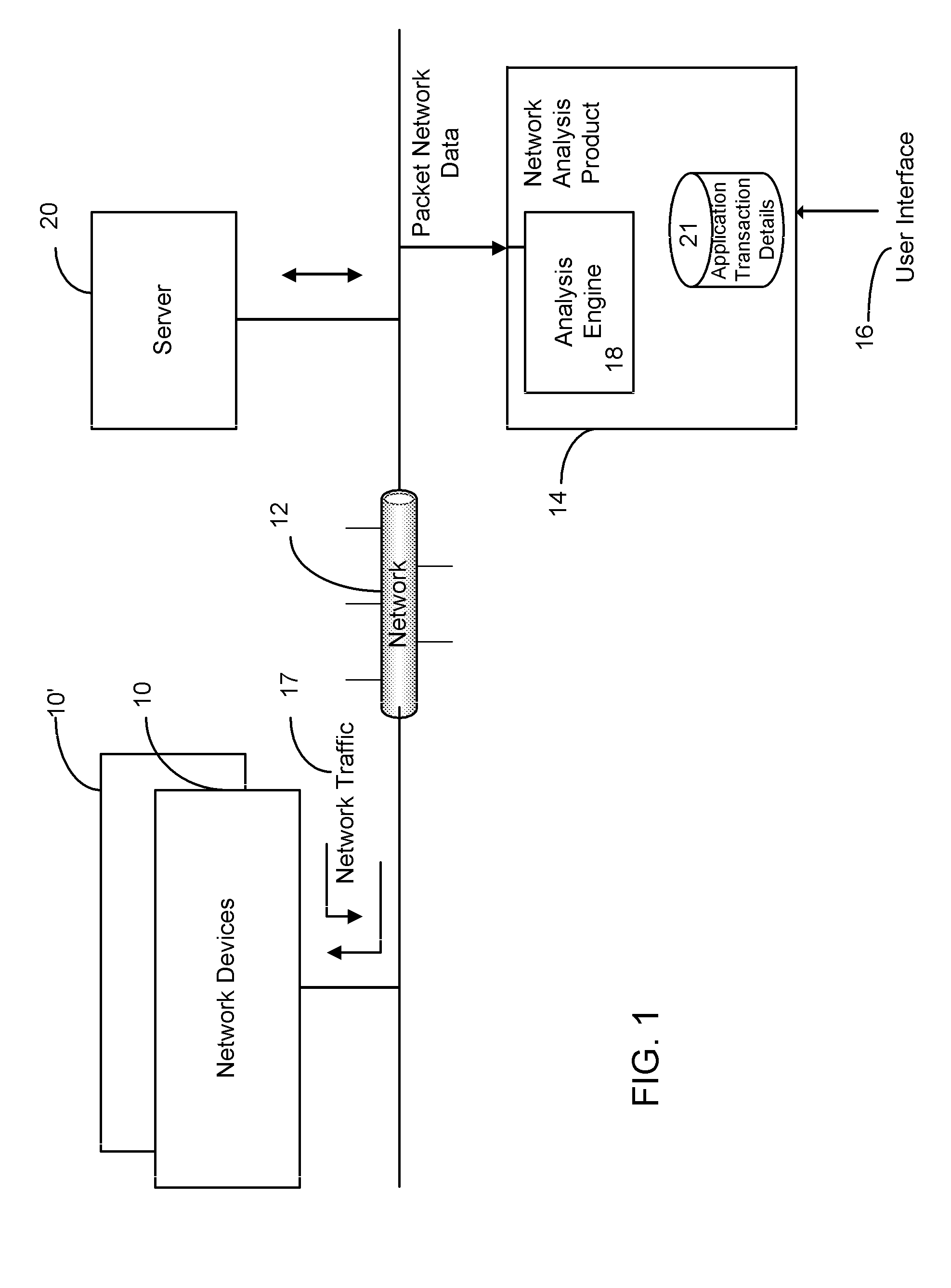
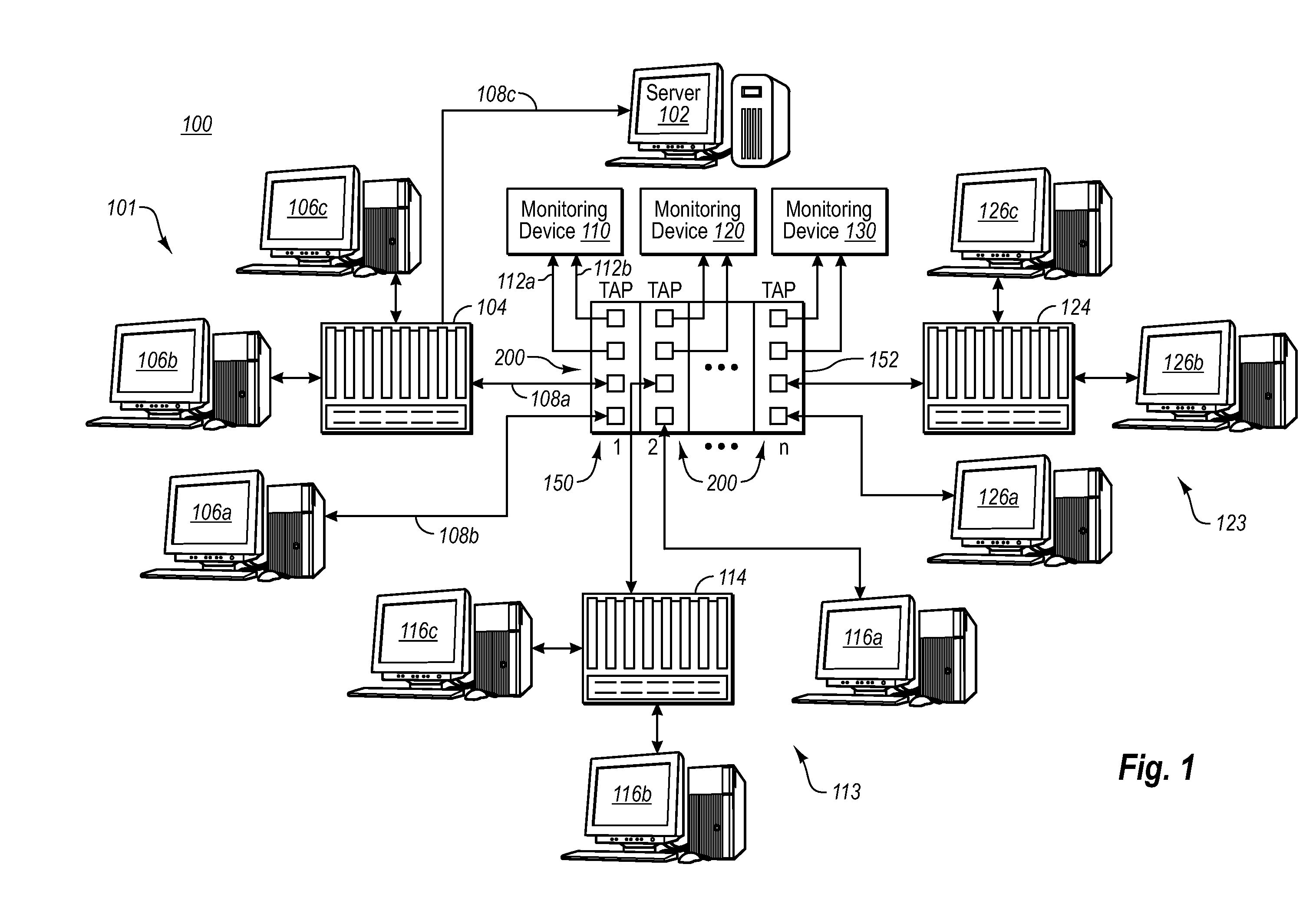
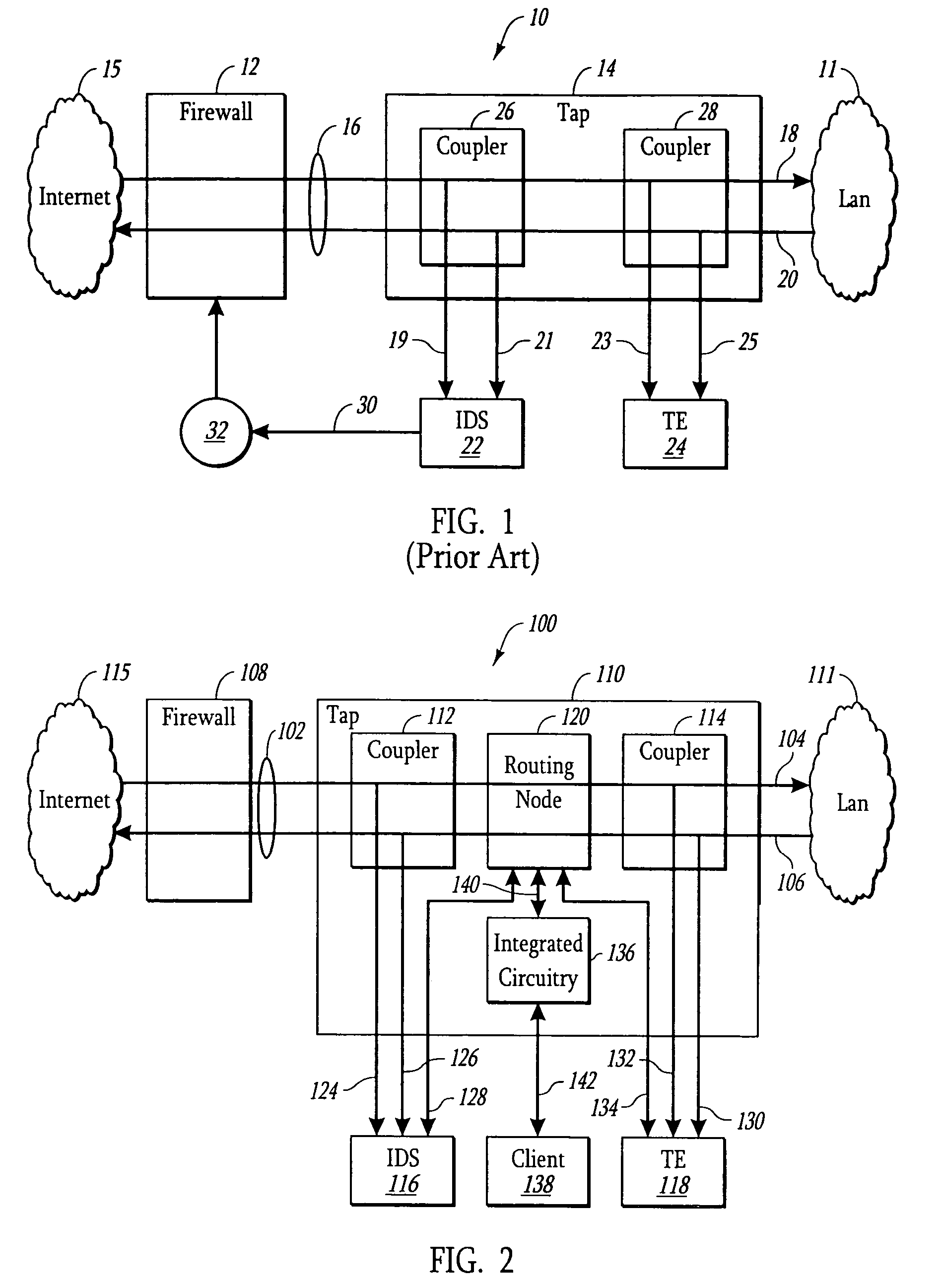
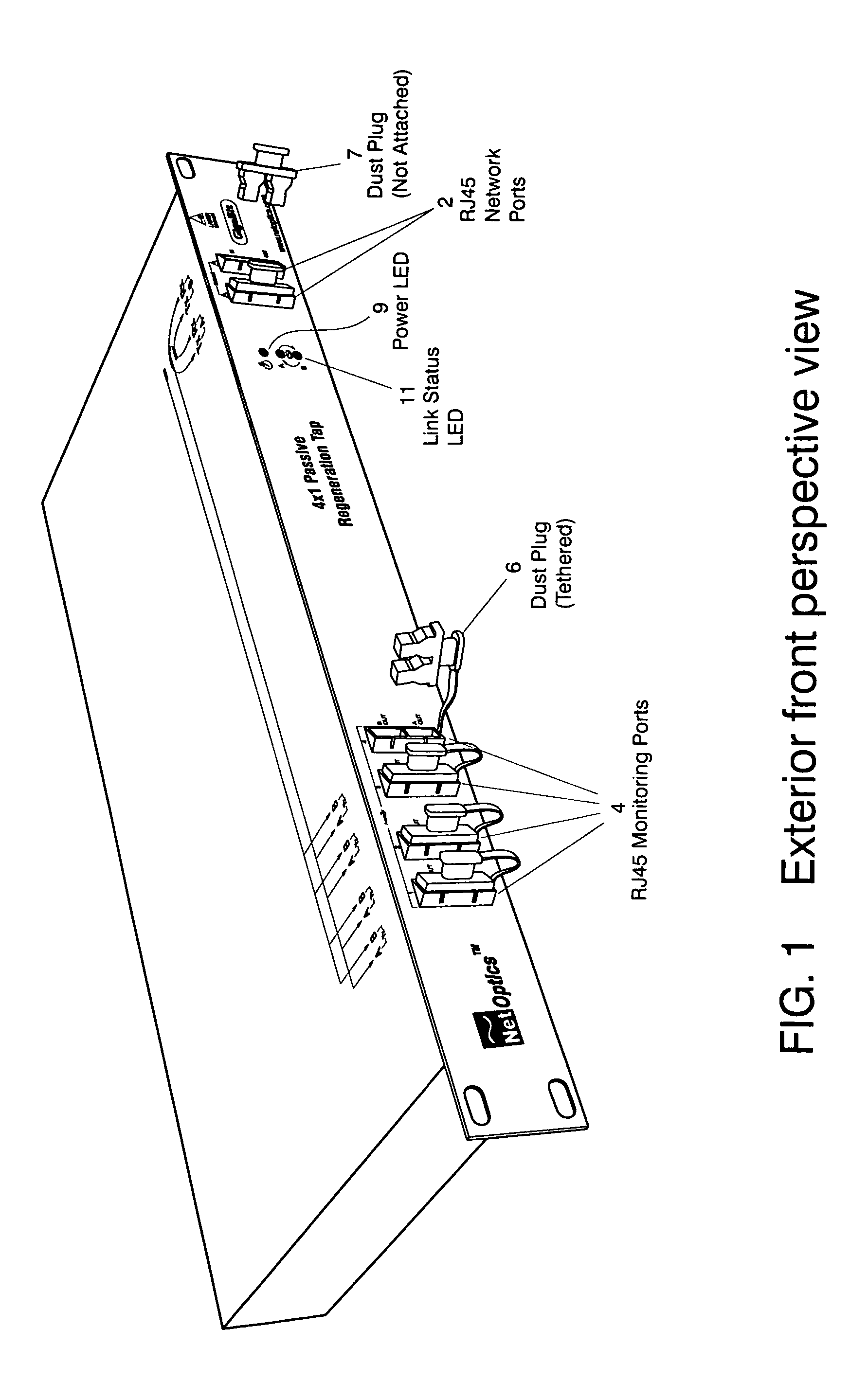
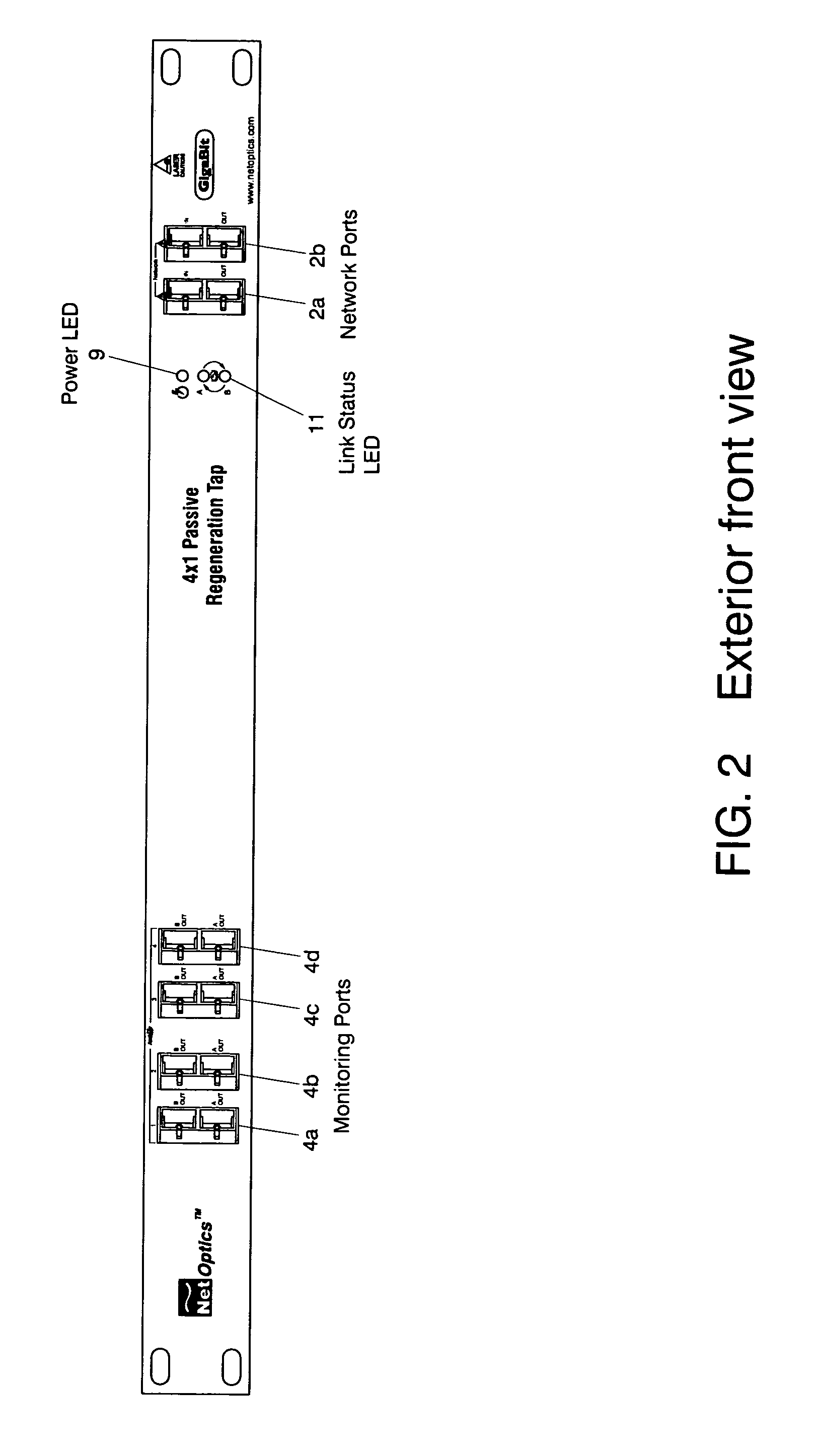
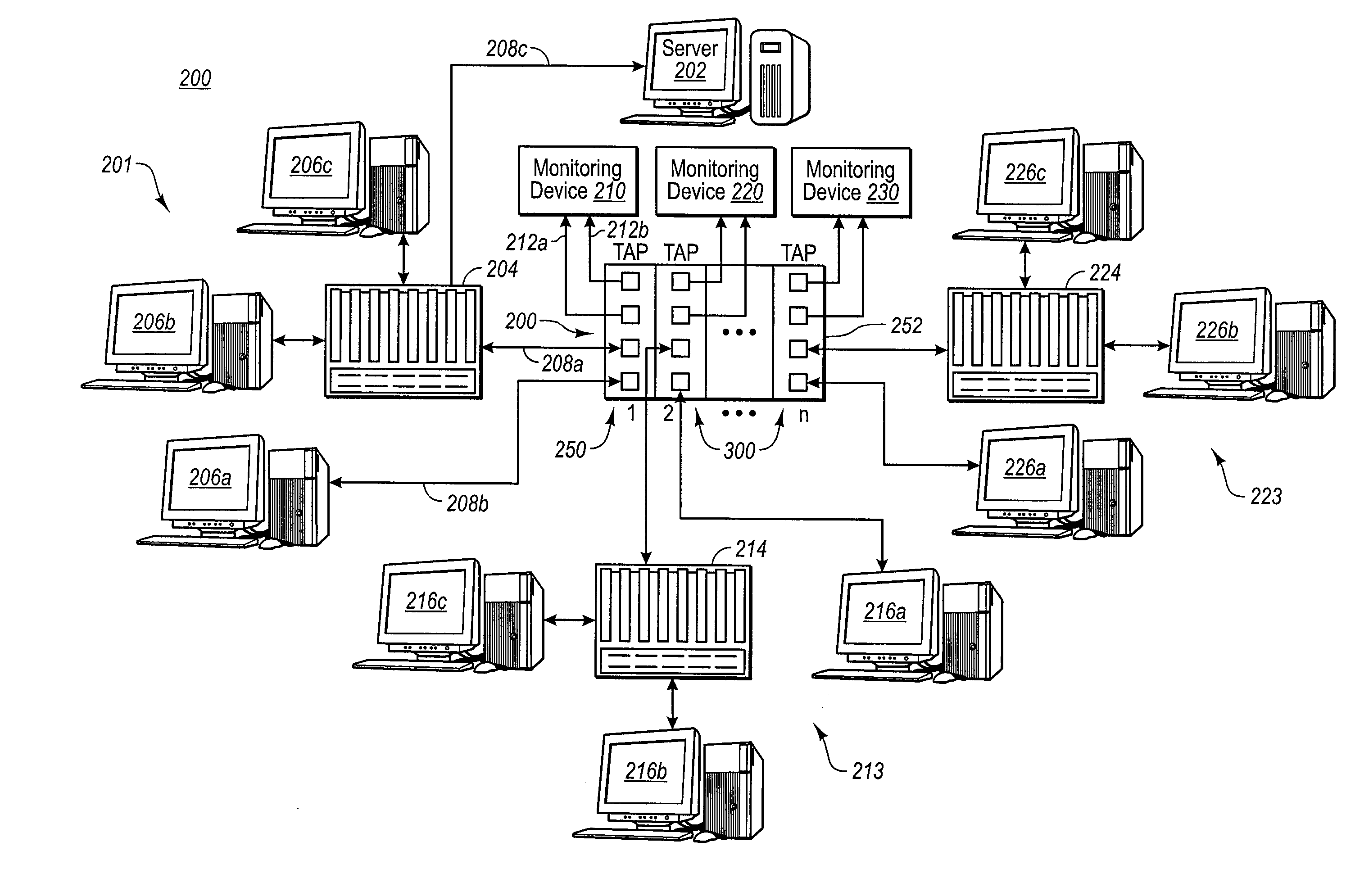
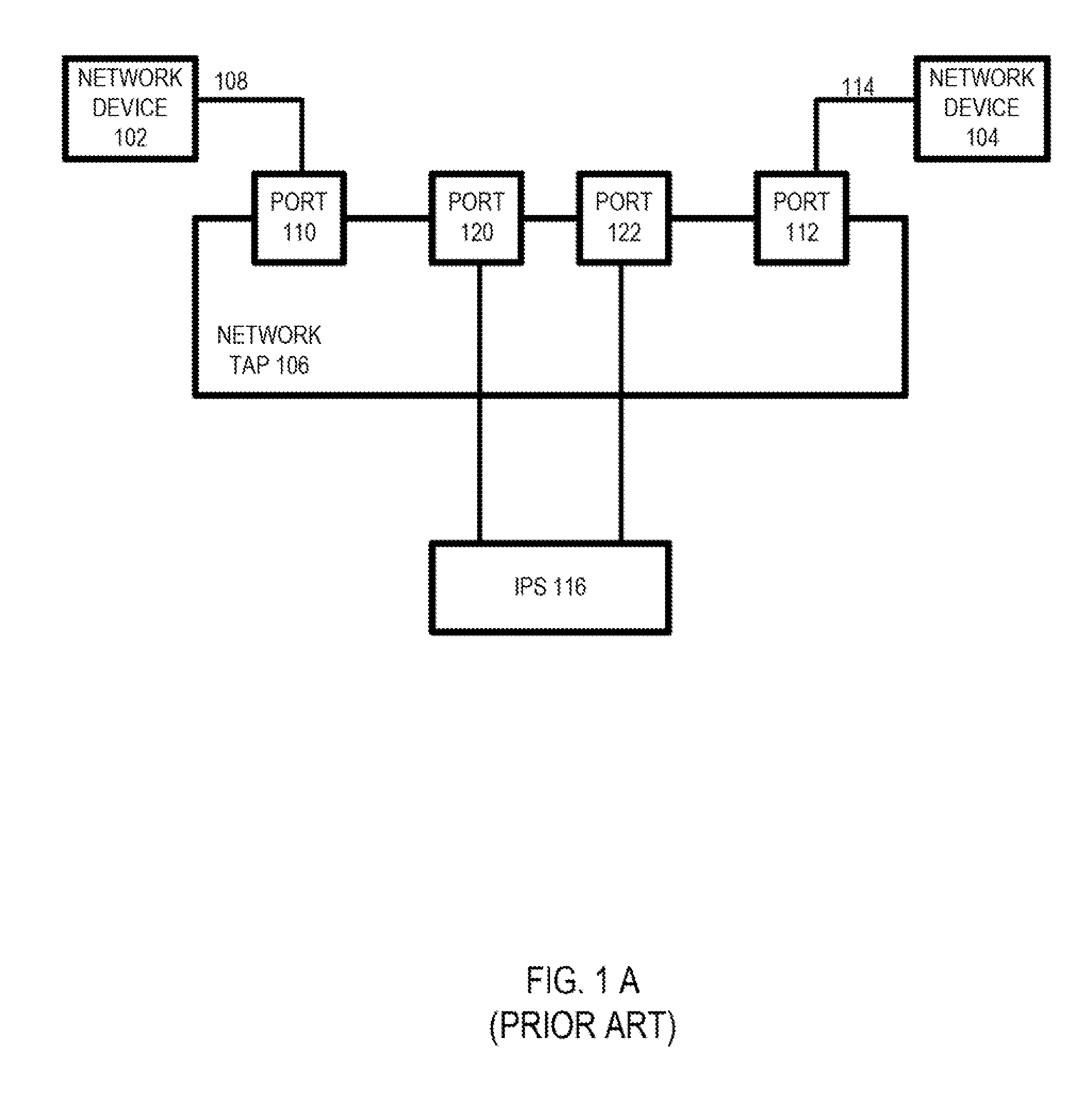
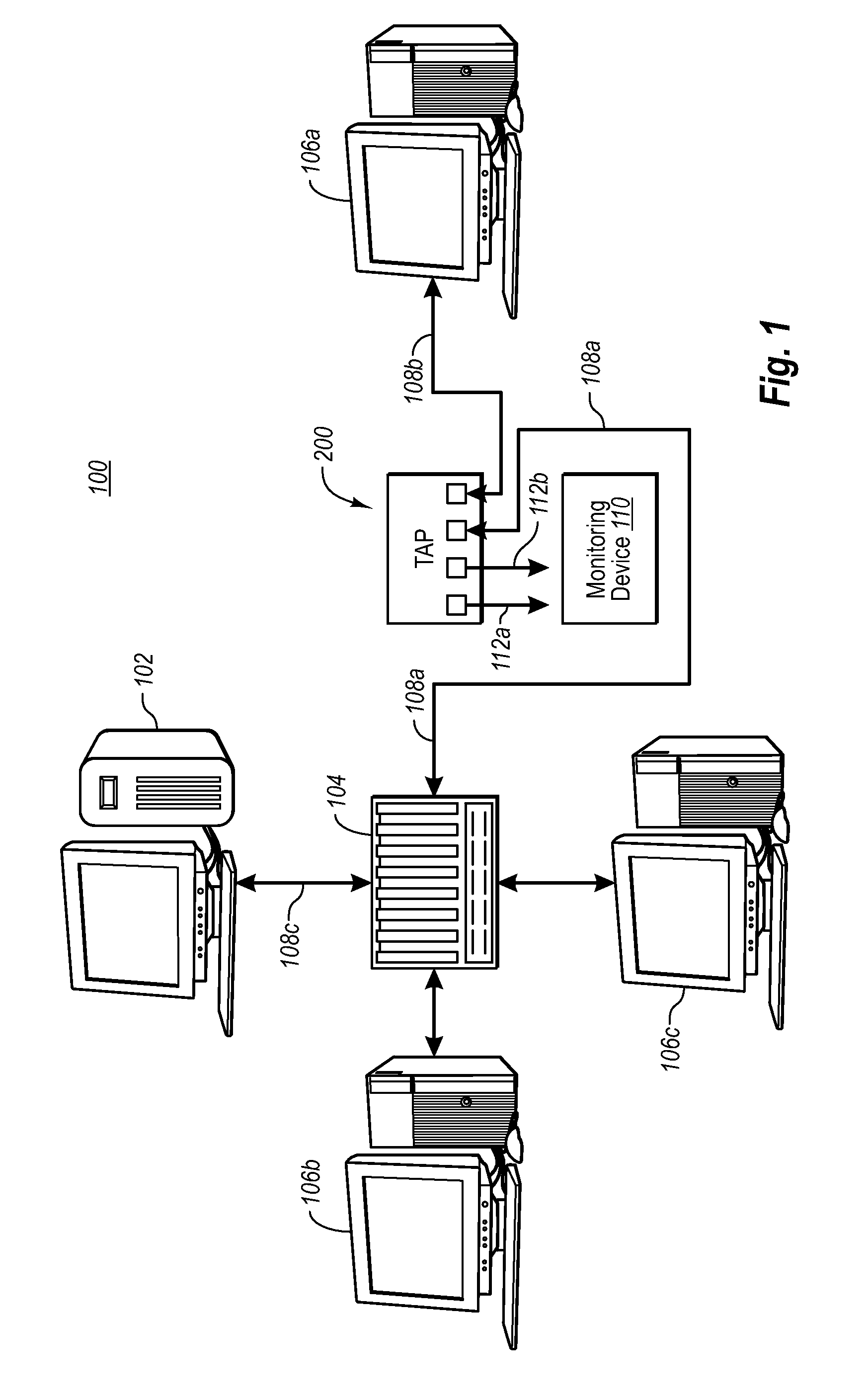
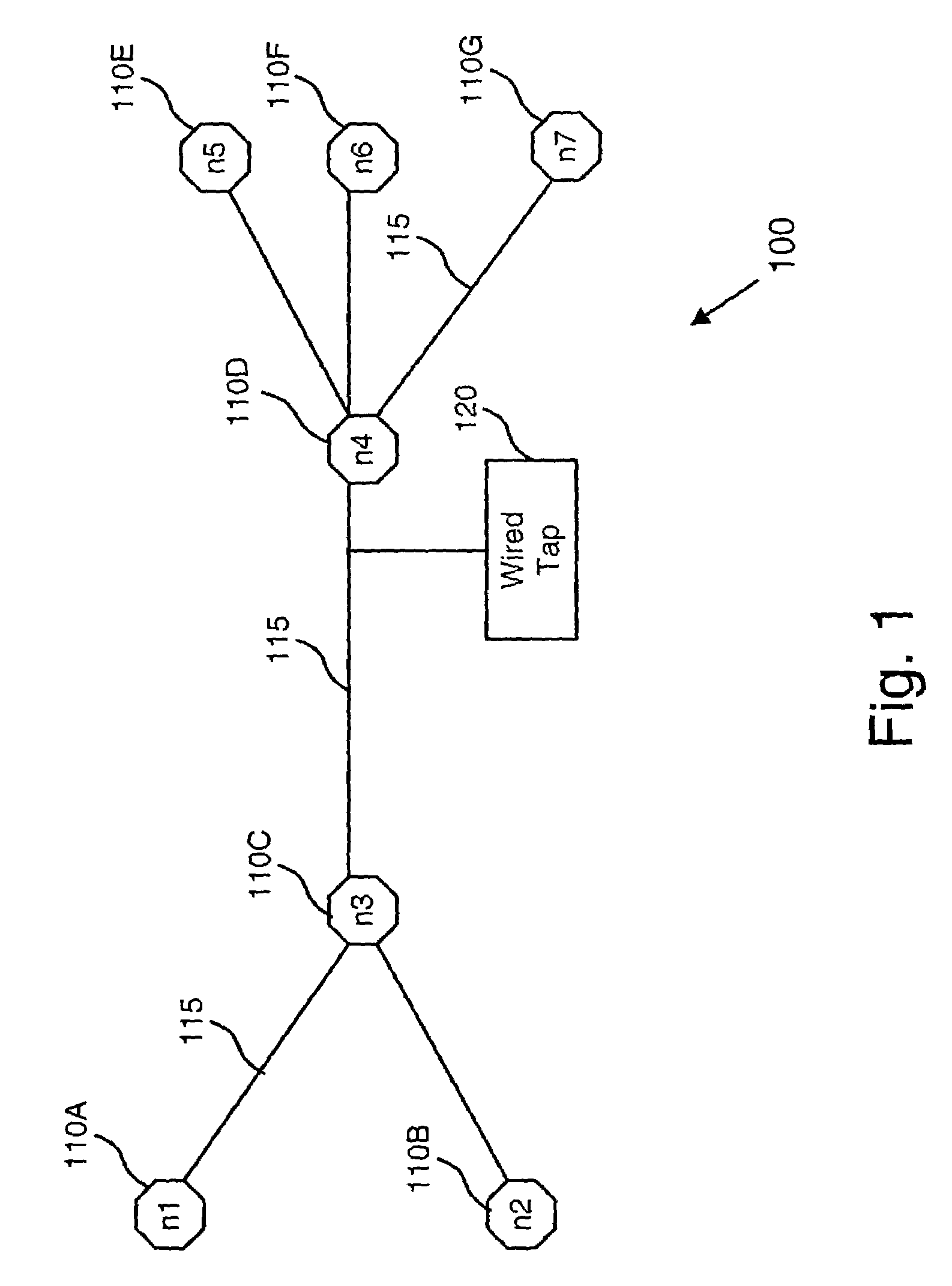
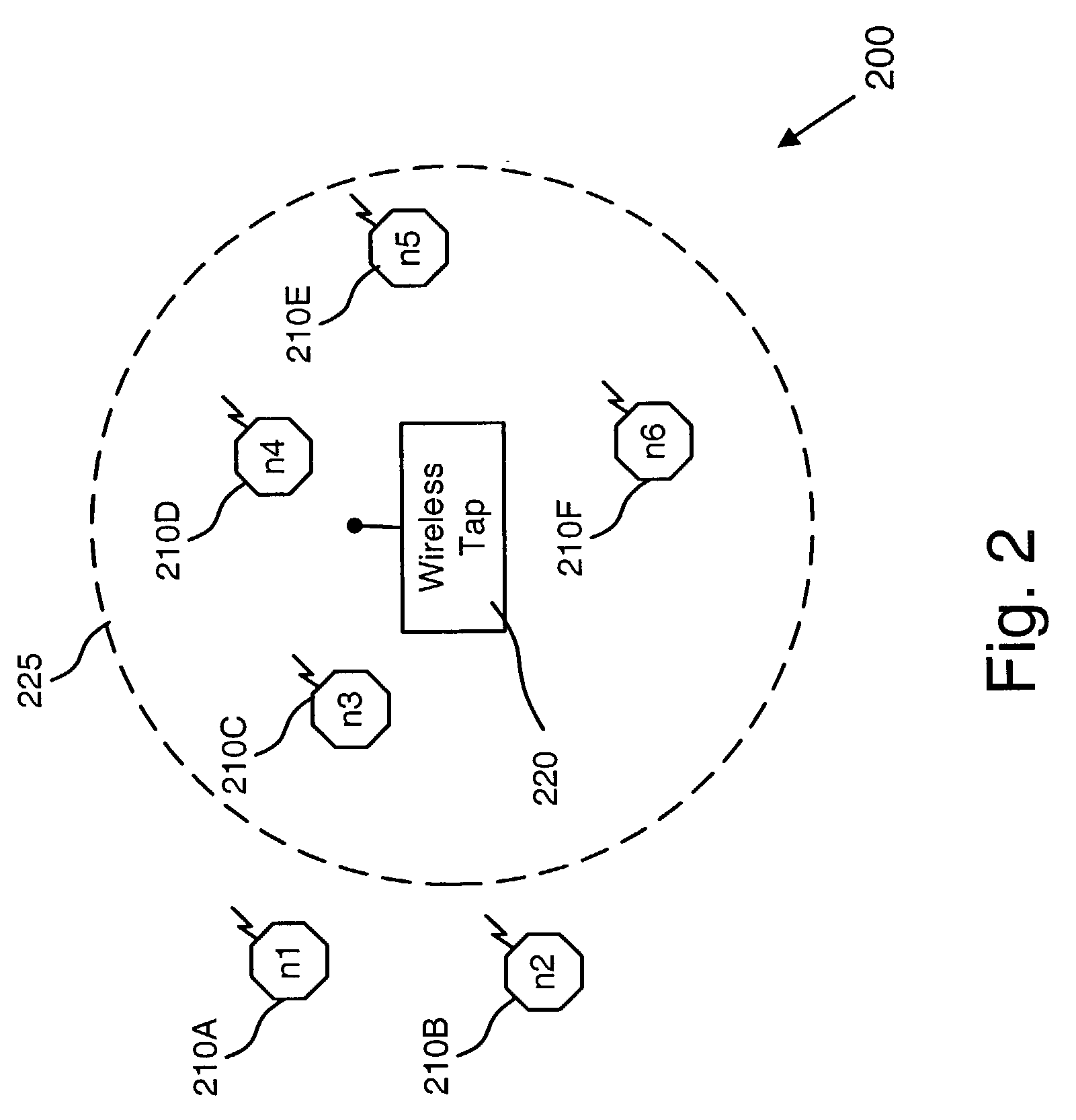
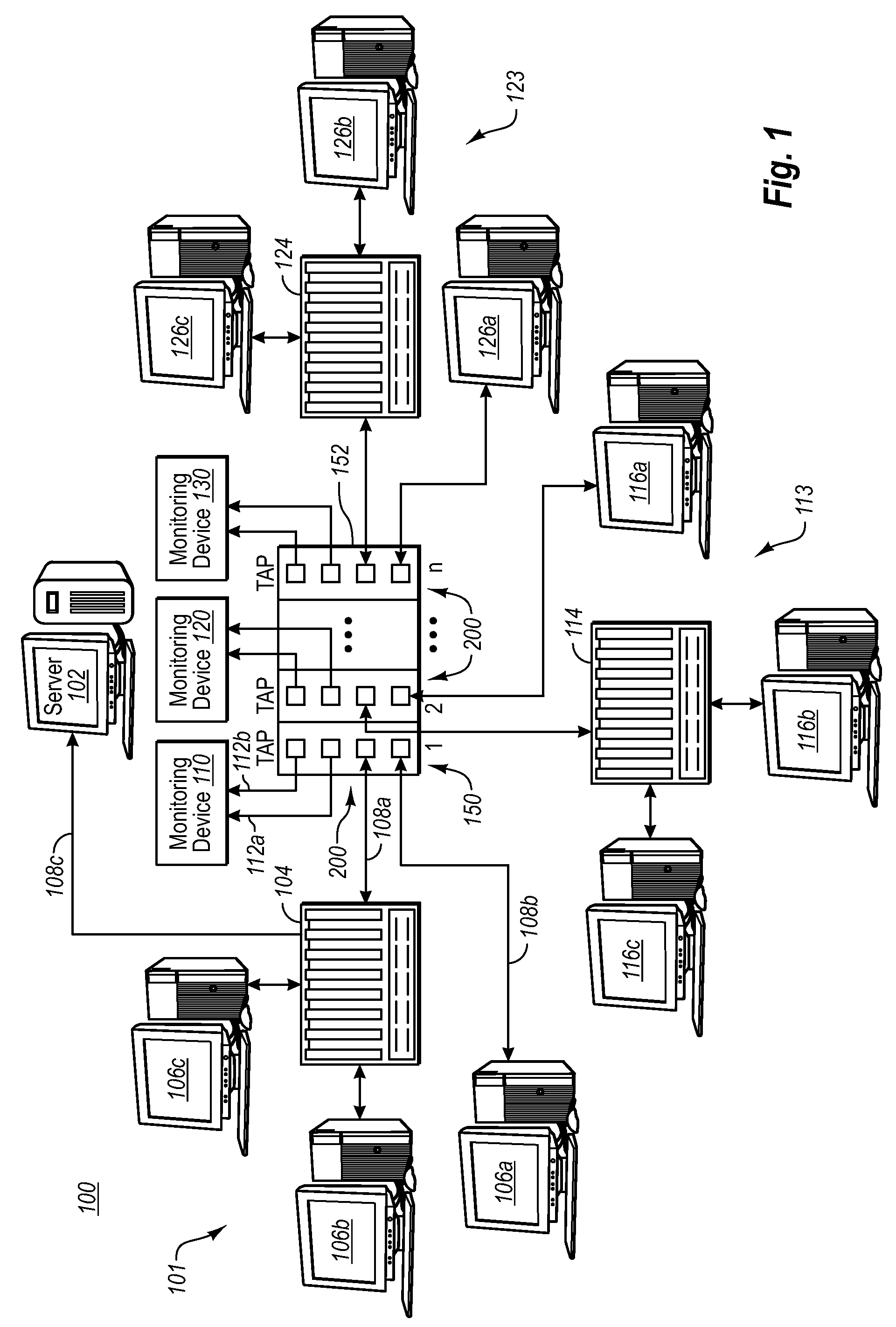
A Network TAP (Terminal Access Point) denotes a system that monitors events on a local network in order to aid administrators (or attackers) in analyzing the network. The tap itself is typically a dedicated hardware device, which provides a way to access the data flowing across a computer network. In many cases, it is desirable for a third party to monitor the traffic between two points in the network. If the network between points A and B consists of a physical cable, a "network tap" may be the best way to accomplish this monitoring. The network tap has (at least) three ports: an A port, a B port, and a monitor port. A tap inserted between A and B passes all traffic (send and receive data streams) through unimpeded in real time, but also copies that same data to its monitor port, enabling a third party to listen. Network taps are commonly used for network intrusion detection systems, VoIP recording, network probes, RMON probes, packet sniffers, and other monitoring and collection devices and software that require access to a network segment. Taps are used in security applications because they are non-obtrusive, are not detectable on the network (having no physical or logical address), can deal with full-duplex and non-shared networks, and will usually pass through or bypass traffic even if the tap stops working or loses power.
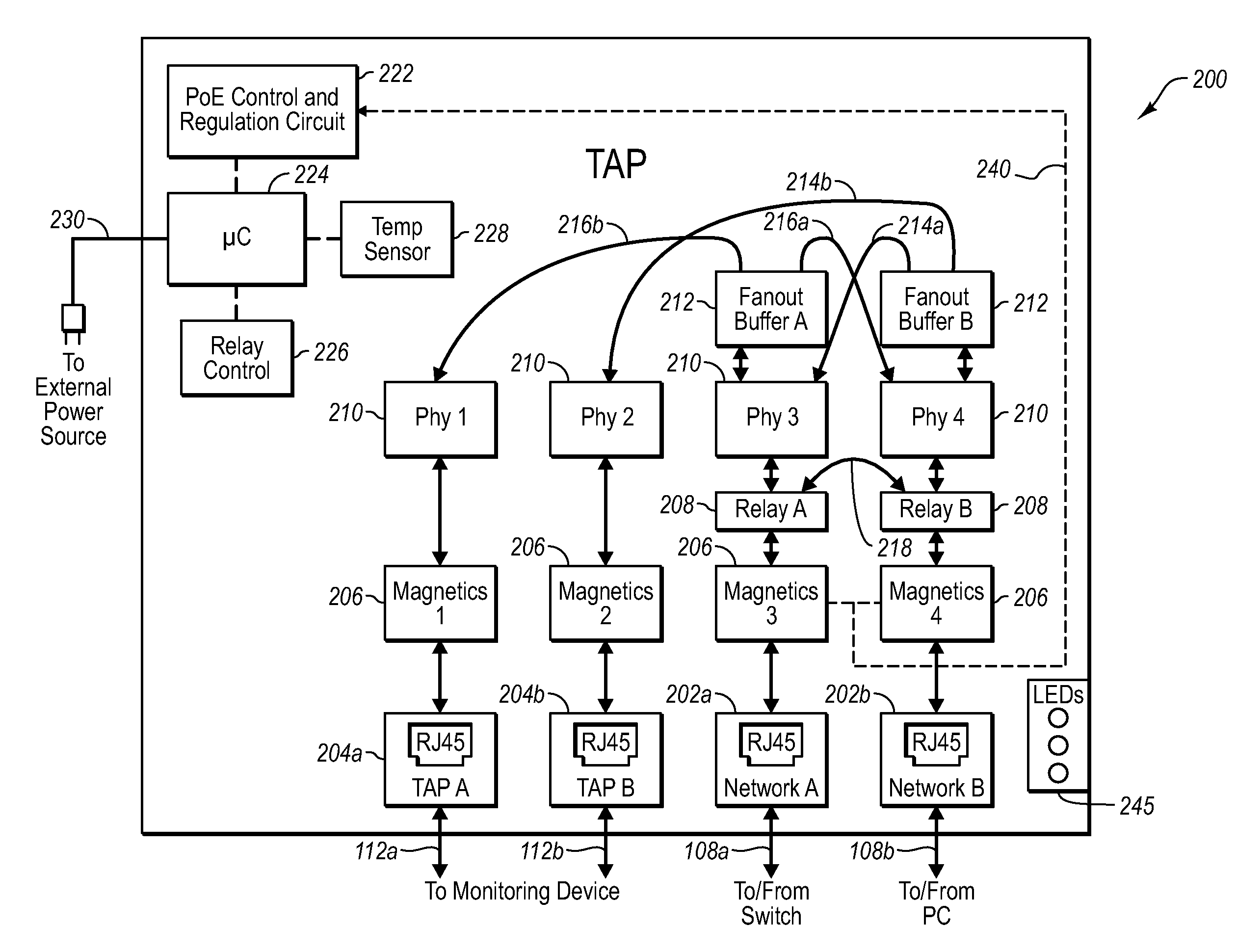
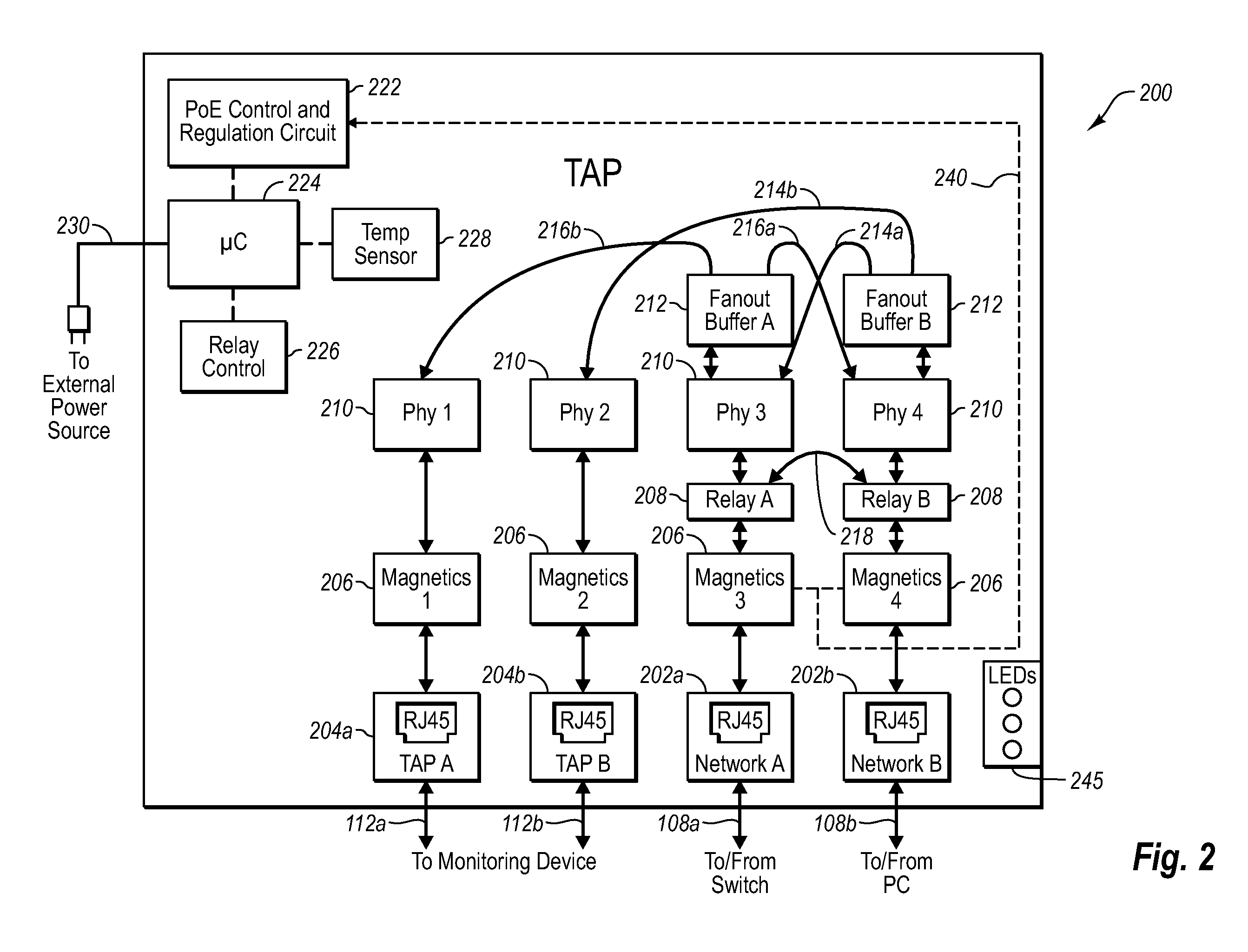
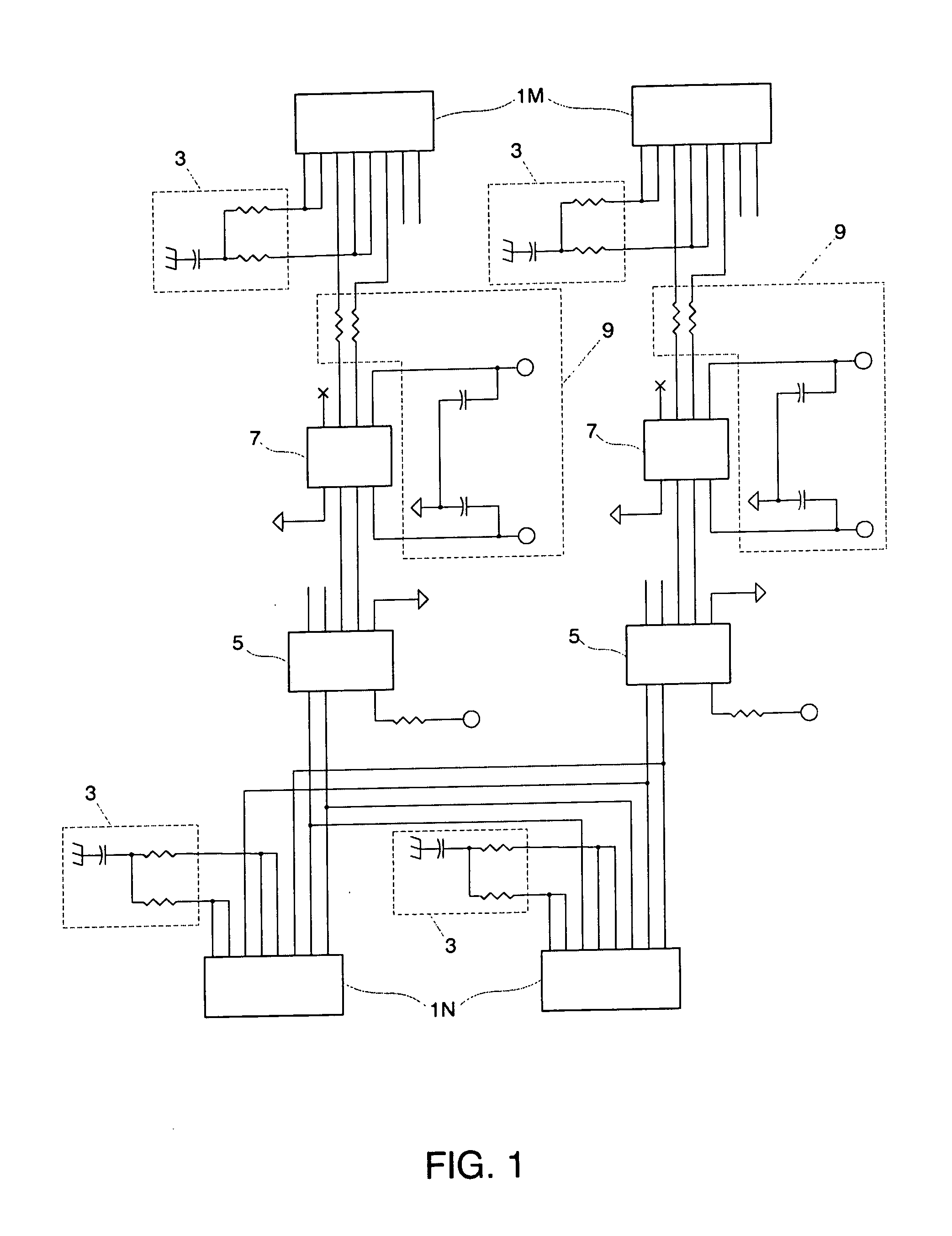
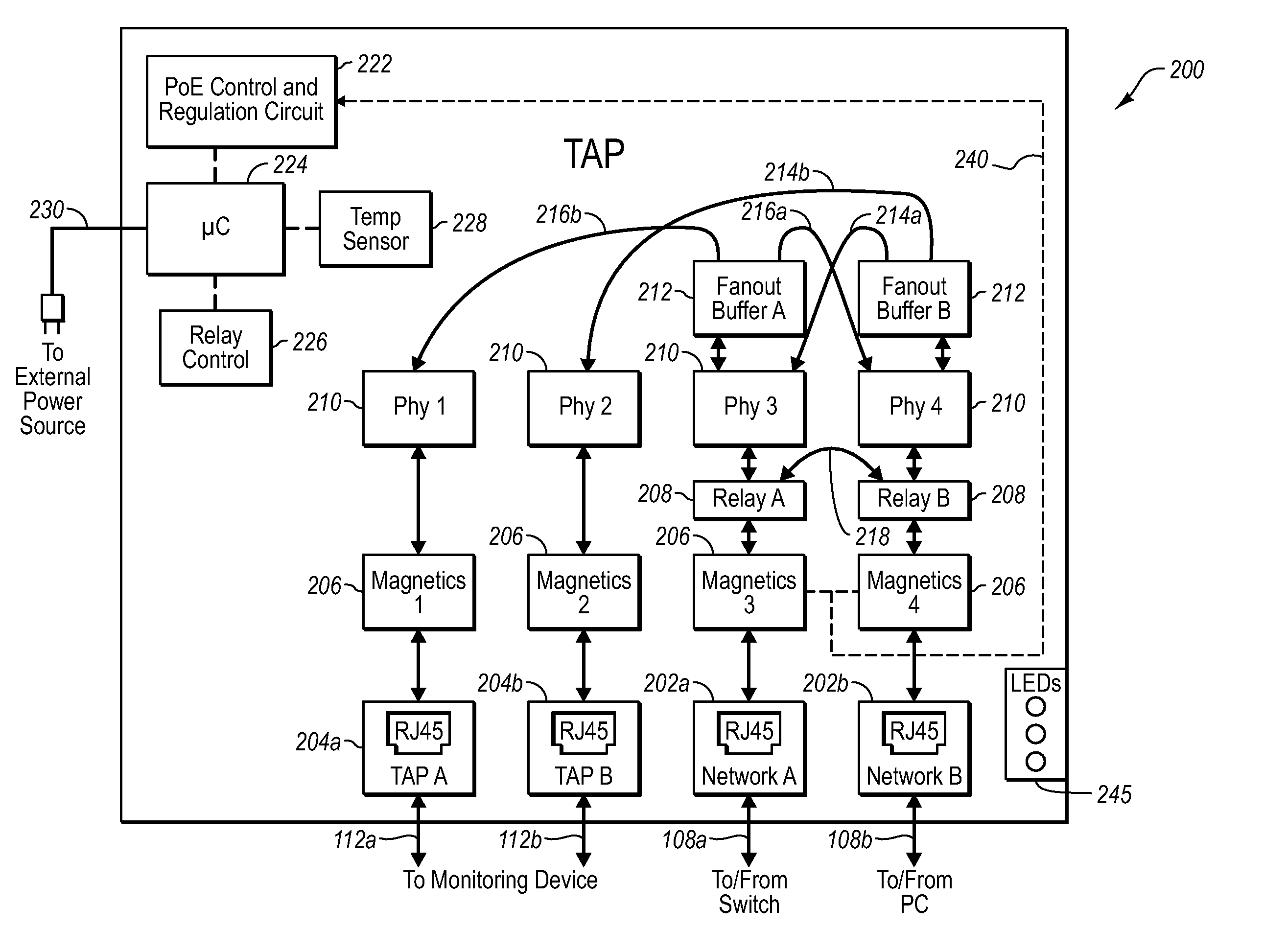
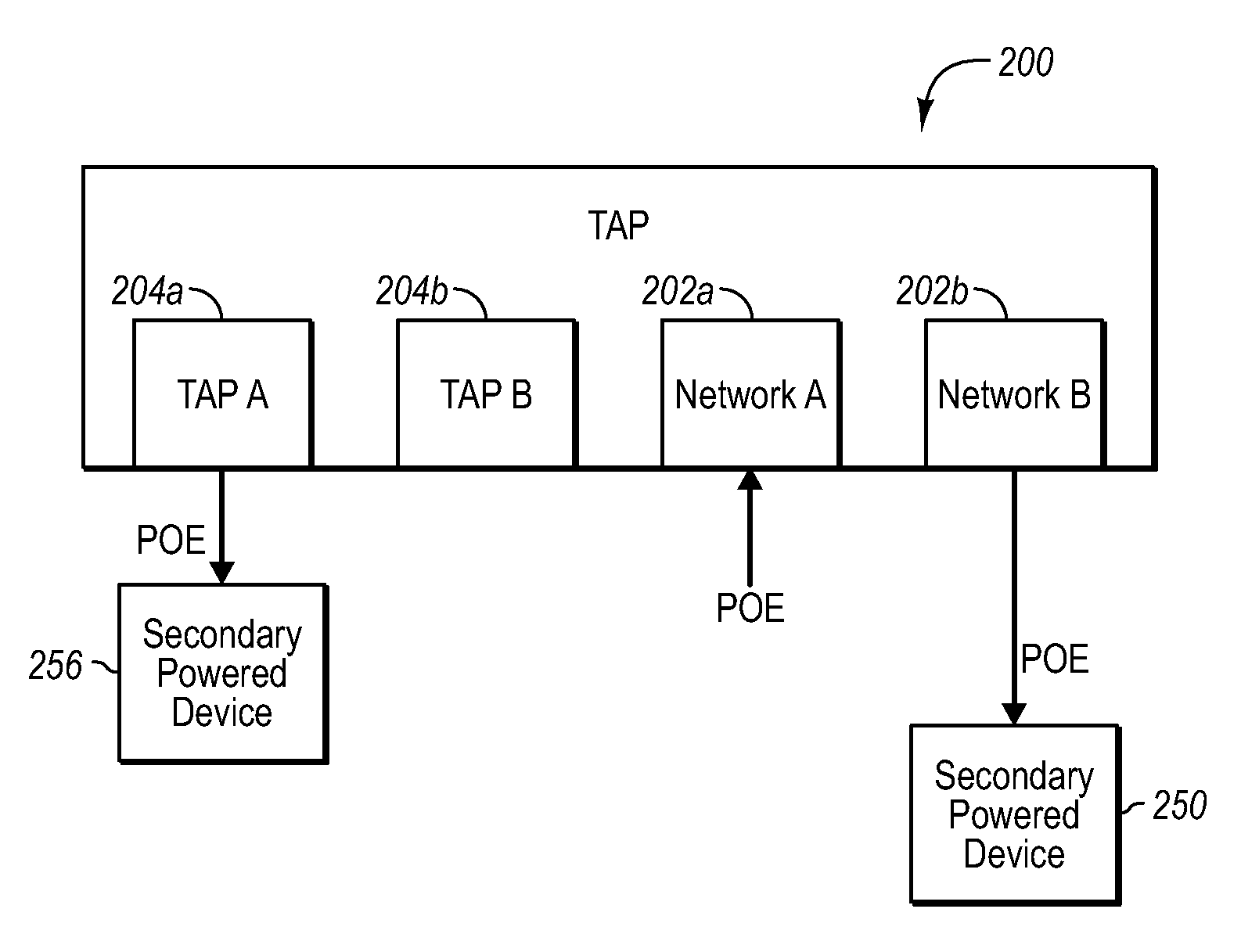
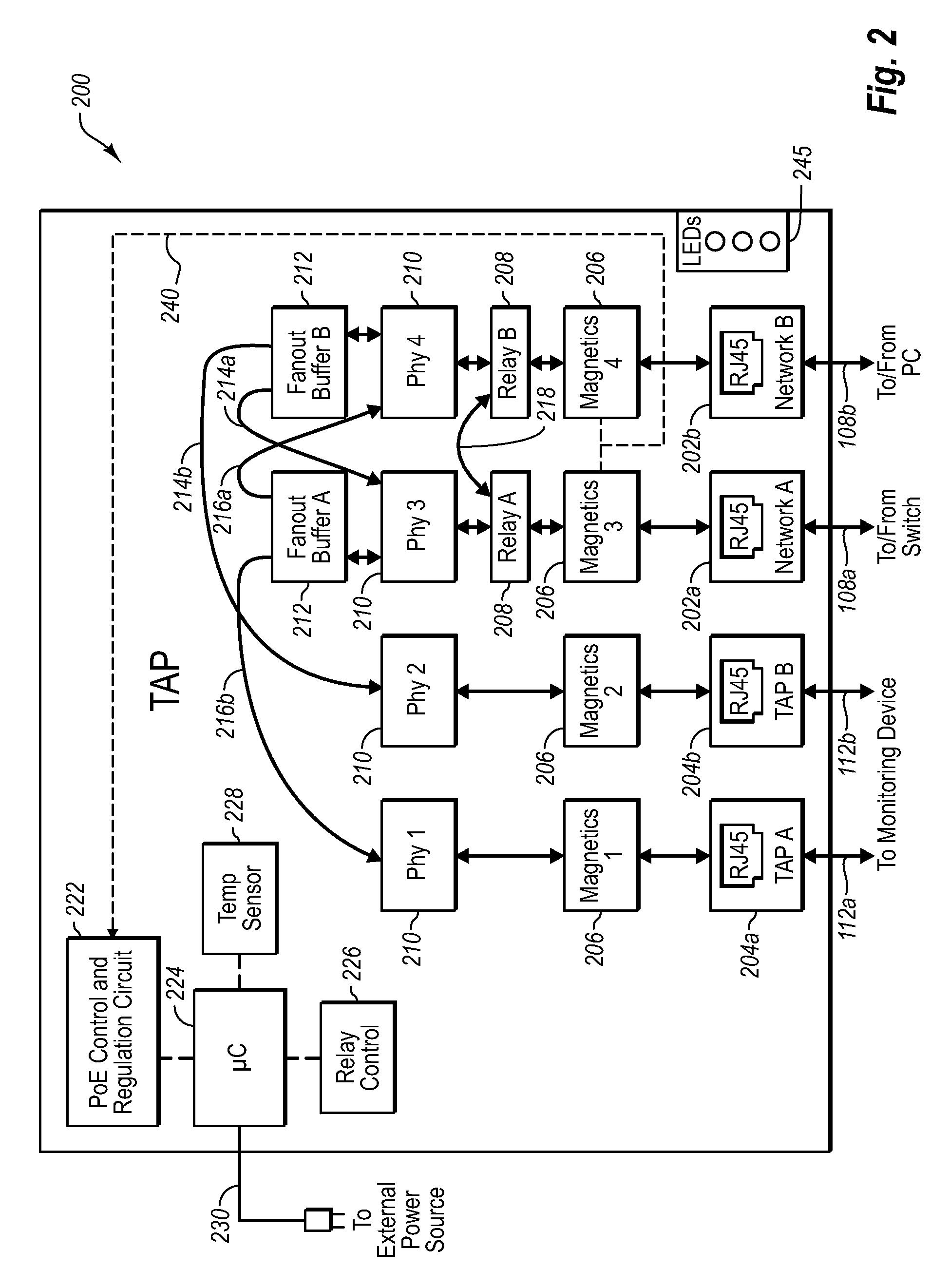
Network tap device powered by power over ethernet
ActiveUS20070081553A1Improve reliabilityImprove operationMechanical power/torque controlLevel controlNetwork tapMonitor equipment
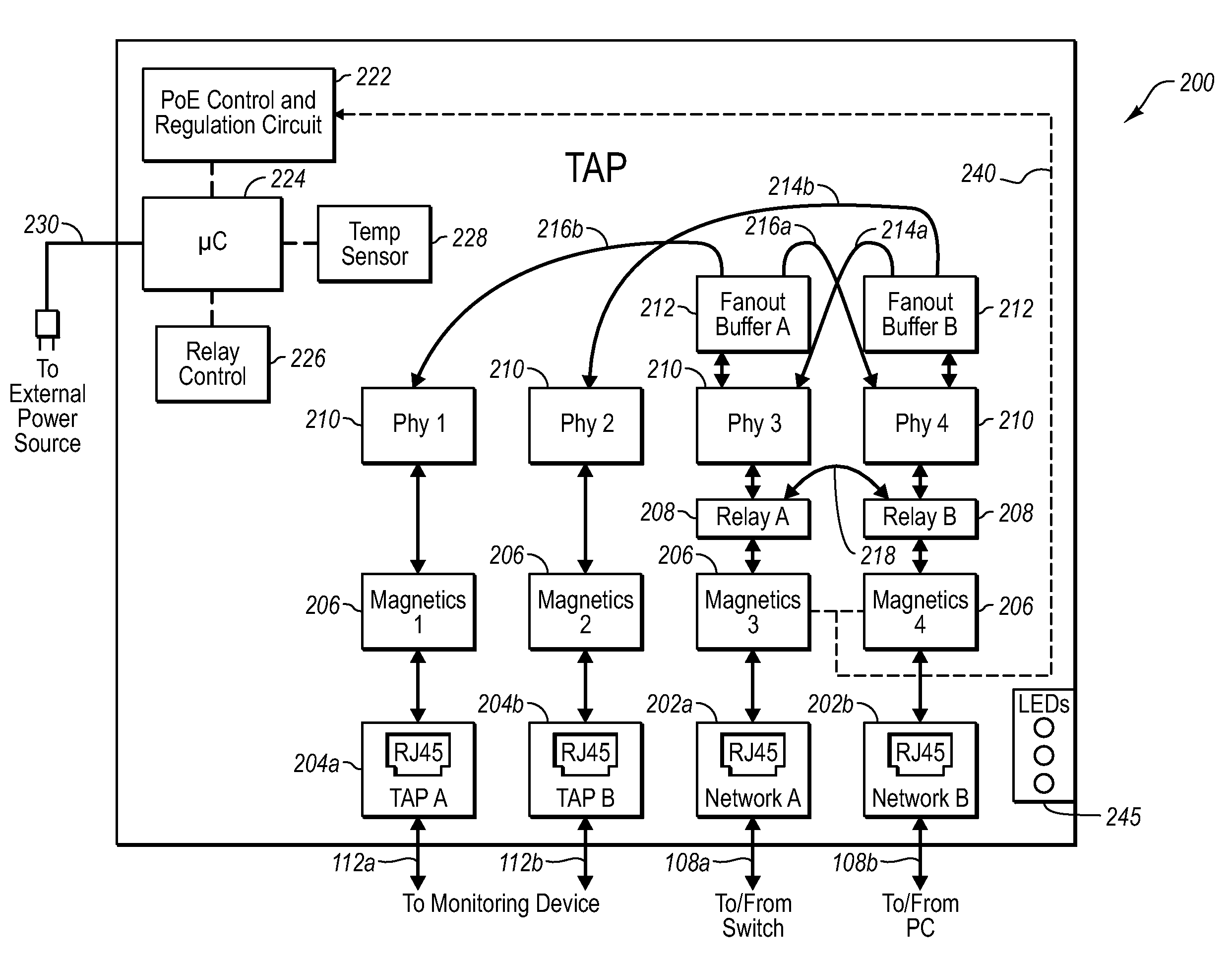
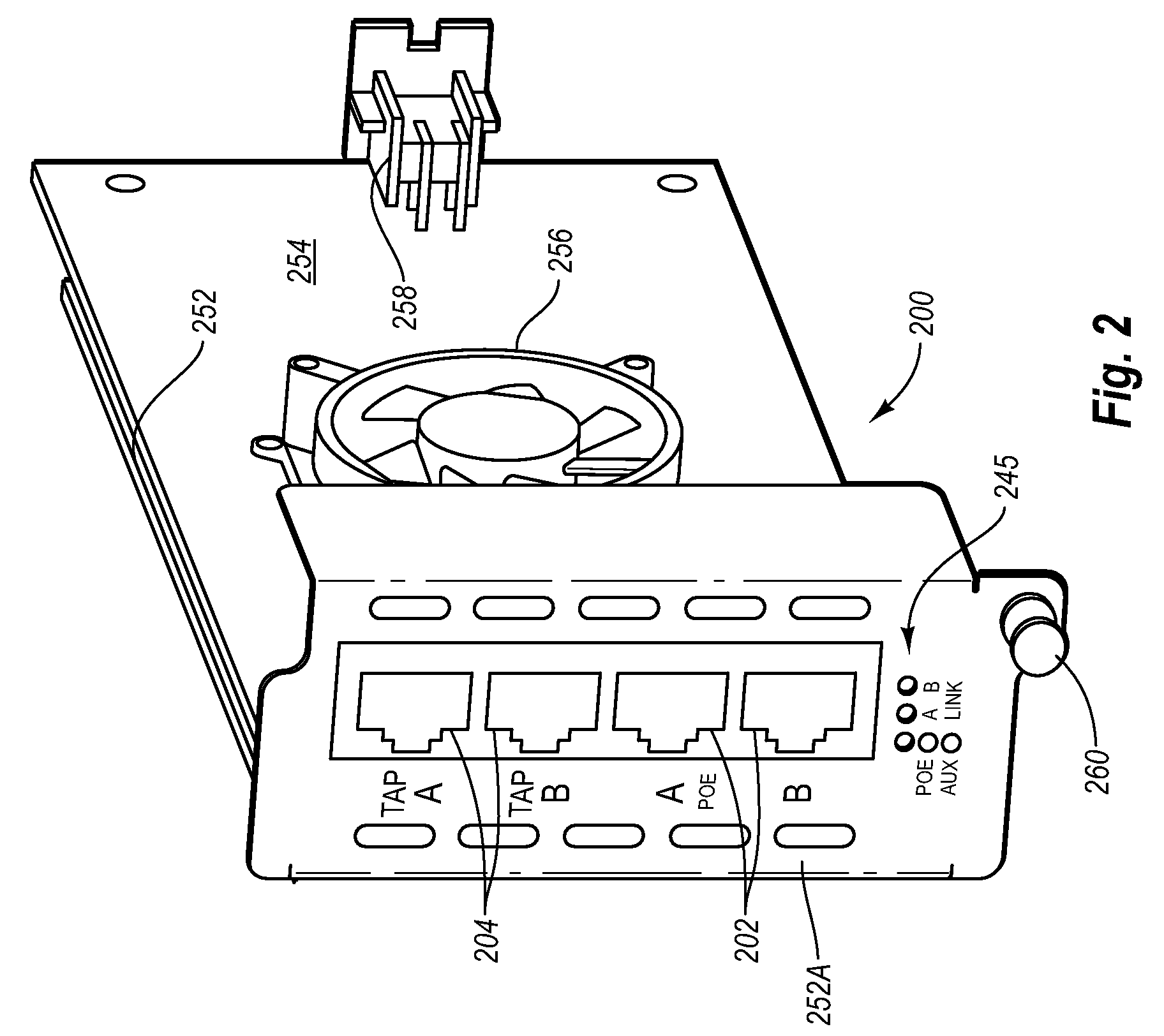
A network tap device that is configured for operation in a copper Gigabit Ethernet communications network using a power-over-Ethernet (“POE”) electrical supply is disclosed. In one embodiment, a network tap device powered by a POE supply is disclosed, comprising first and second network ports that are configured with receptacles for receiving communication cables. The communication cables are configured to carry both data signals and the POE supply to and from the network tap device. The network tap device further includes first and second tap ports that connect with additional communication cables to a monitoring device. The network tap device also includes control and regulation circuitry that is configured to receive the POE supply from the communication cables via the network ports and to enable components of the network tap device to be operated by the POE supply.
Owner:VIAVI SOLUTIONS INC
Zero-interrupt network tap
A network tap monitors network information flow over a particular connection. By duplicating the signal and diverting a copy, the information flow can be analyzed, both in real time and without interference through the monitoring process. When the power to the tap is either turned on or off, however, the change in impedance in the tap's circuit can create an interference spike in the connection that interrupts the information flow. By reducing or eliminating the impedance change in the tap circuitry, such disruptive interruptions can be eliminated.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Method and apparatus of measuring and reporting data gap from within an analysis tool
ActiveUS20090296593A1Enhanced authenticationAccurately determineError preventionTransmission systemsInternet trafficNetwork tap
Network data gap is determined and reported to enable a user to validate that all the traffic that was intended to be monitored is being monitored in monitoring and / or troubleshooting tools for observation of network traffic and network installation and maintenance. Span port oversubscription, incomplete span configuration, incorrectly placed network taps and monitoring device packet drop may thereby be detected and reported as data gap.
Owner:NETSCOUT SYSTEMS
Network tap for use with multiple attached devices
InactiveUS20050129033A1Function increaseEliminate needMultiplex system selection arrangementsData switching by path configurationNetwork tapData transmission
Owner:FINISAR
Network tap/aggregator configured for power over ethernet operation
ActiveUS20070081549A1Eliminates potentialImprovement in reliability and operationMechanical power/torque controlEnergy efficient ICTNetwork tapEngineering
A network tap device array capable of being powered by a power-over Ethernet (“POE”) supply is disclosed. The array enables data from multiple nodes in a communications network to be tapped and forwarded to a plurality of monitoring devices. In one embodiment the network tap device array includes a chassis that is configured to receive a plurality of network tap devices that are each powered by a POE supply. Each network tap device includes network ports for receiving and transmitting network data via communication cables and tap ports for forwarding the tapped network data to the monitoring device. In another embodiment, a sub-chassis includes a plurality of network tap devices and an aggregator that aggregates tapped data from each of the tap devices. The aggregator then forwards the aggregated data to the monitoring device. The sub-chassis can be included in a chassis that is configured to receive multiple populated chassis.
Owner:VIAVI SOLUTIONS INC
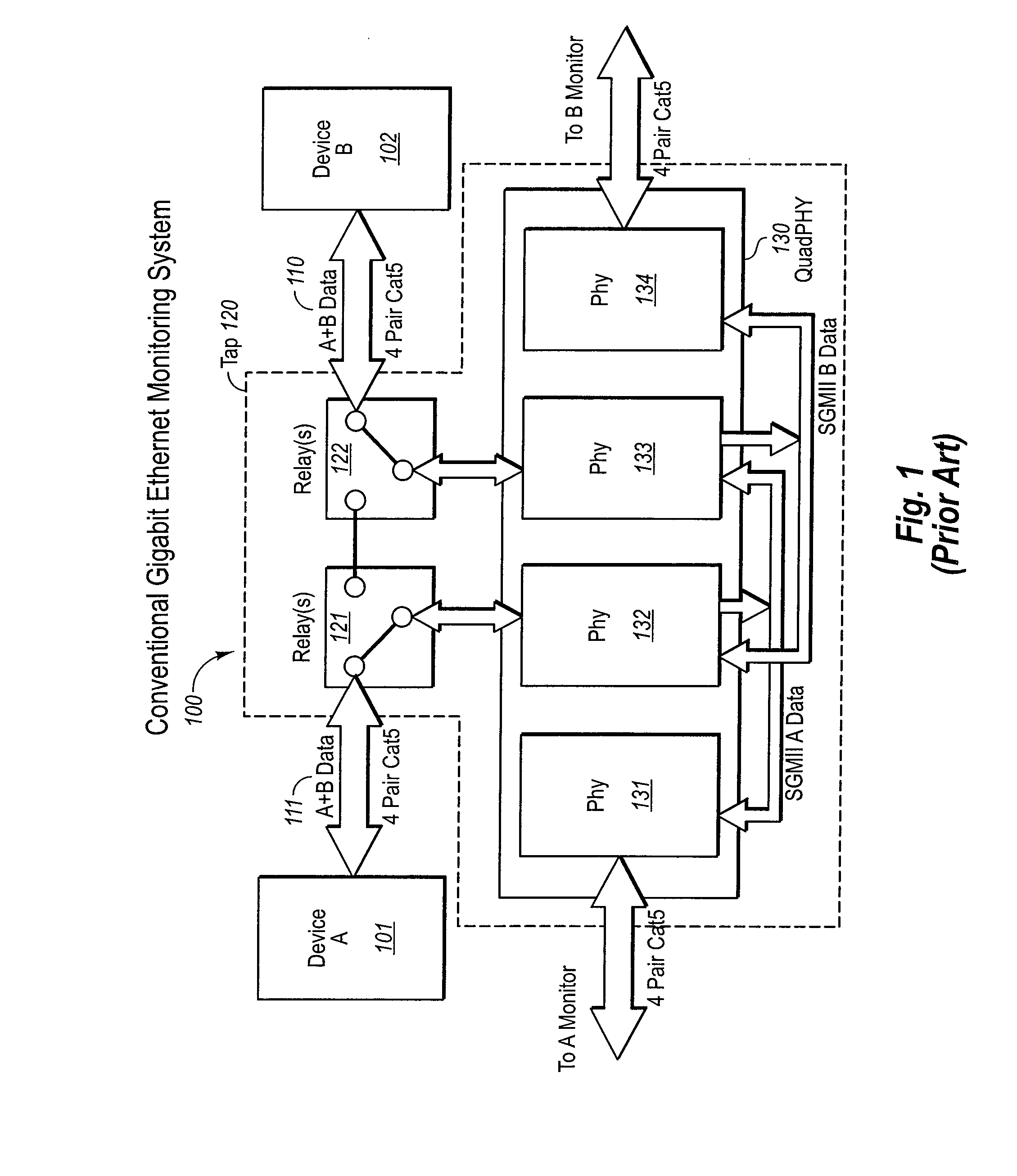
Multiple and parallel access network tap for gigabit internet lans
ActiveUS20050071711A1Avoid interferenceUndesired interferenceError preventionTransmission systemsTransmission protocolThe Internet
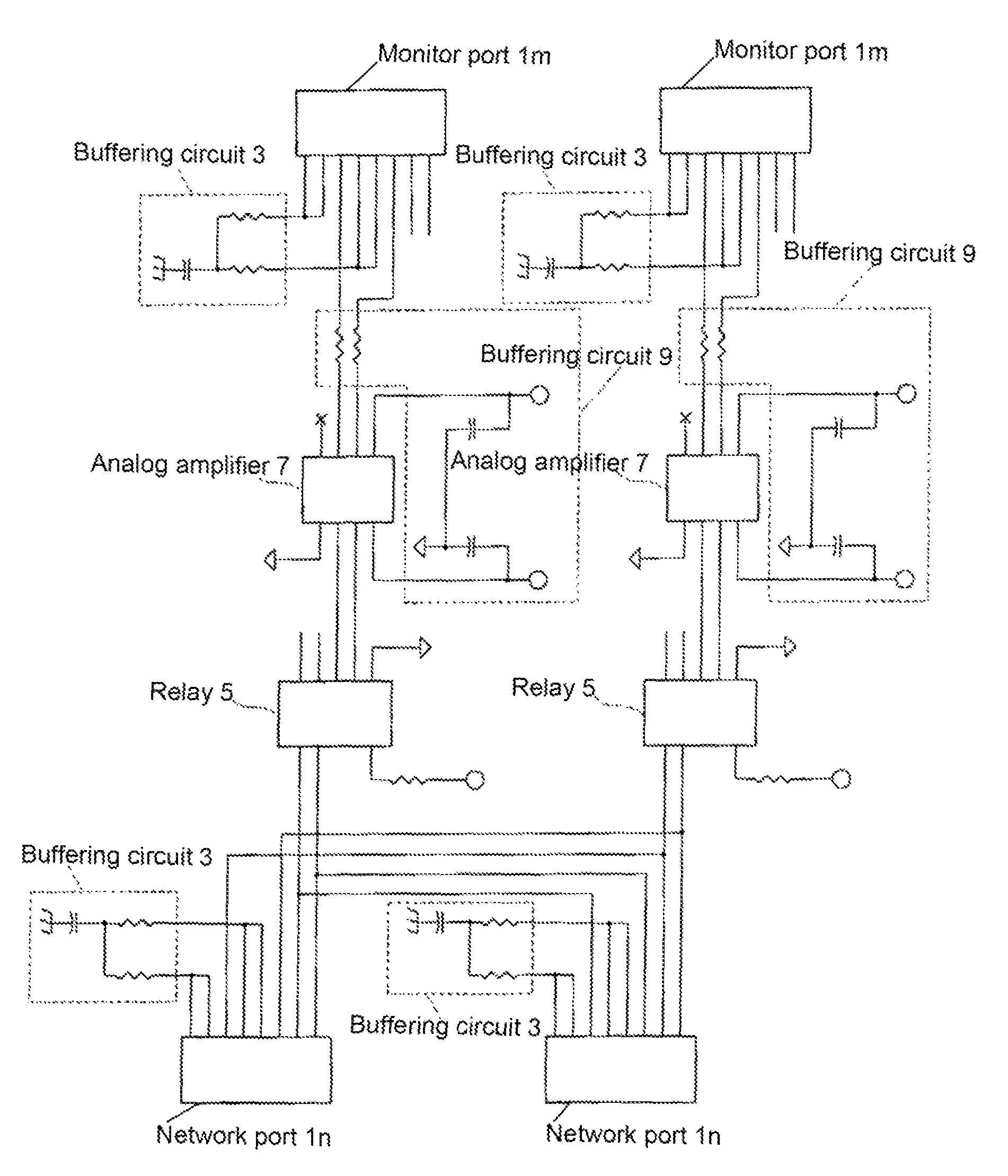
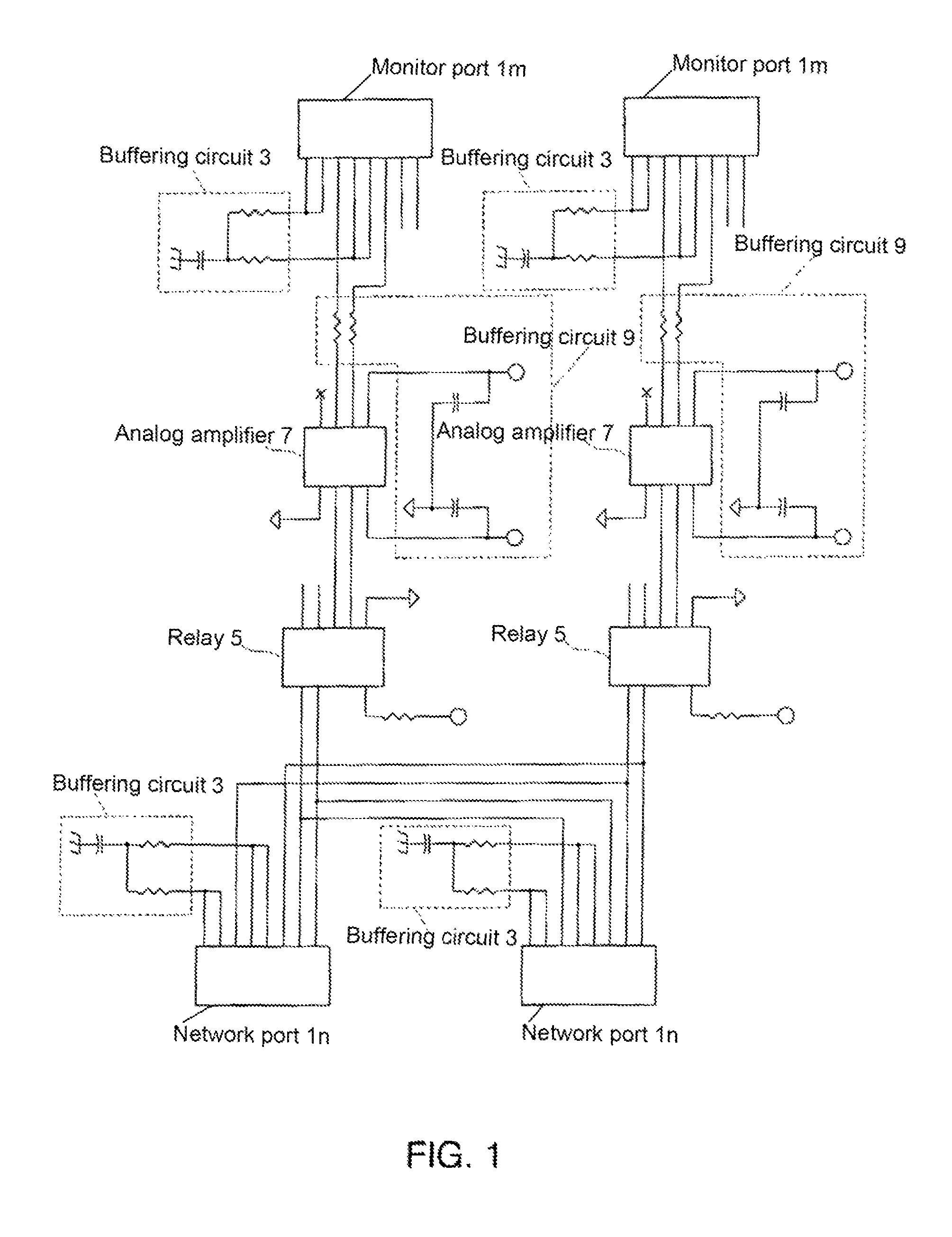
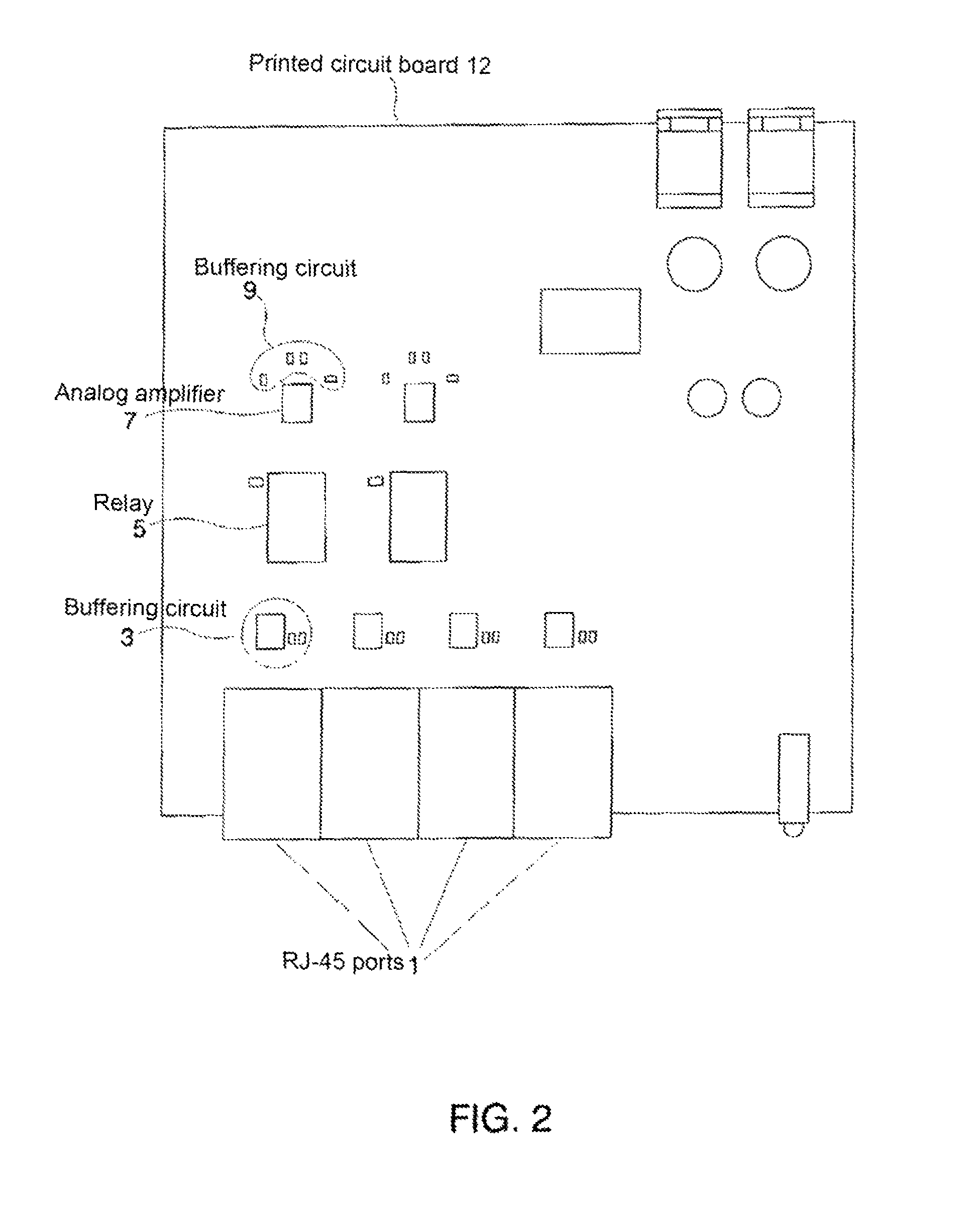
A single-usage network tap monitors network information flow over a particular connection. Instead of requiring a tap for each analytical device, by incorporating elements that regenerate, spread, and coordinate the timing of the signal, multiple, simultaneous, and parallel analytical devices can monitor a particular network connection through one tap, It incorporates four amplifiers preferably manufactured on the same IC die with high-impedance input terminals connected directly to the two conductors of a gigabit Ethernet local area network digital transmission line so as not to load or otherwise upset its impedance or other parameters. The output terminals of the operational amplifiers are connected to and match the input impedance of the digital transmission protocol Gigabit analyzer. The gain of the operational amplifiers is arranged so as to replicate at the input of the analyzer the signals appearing on the Gigabit local area network transmission line with uninterruptible power supply.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
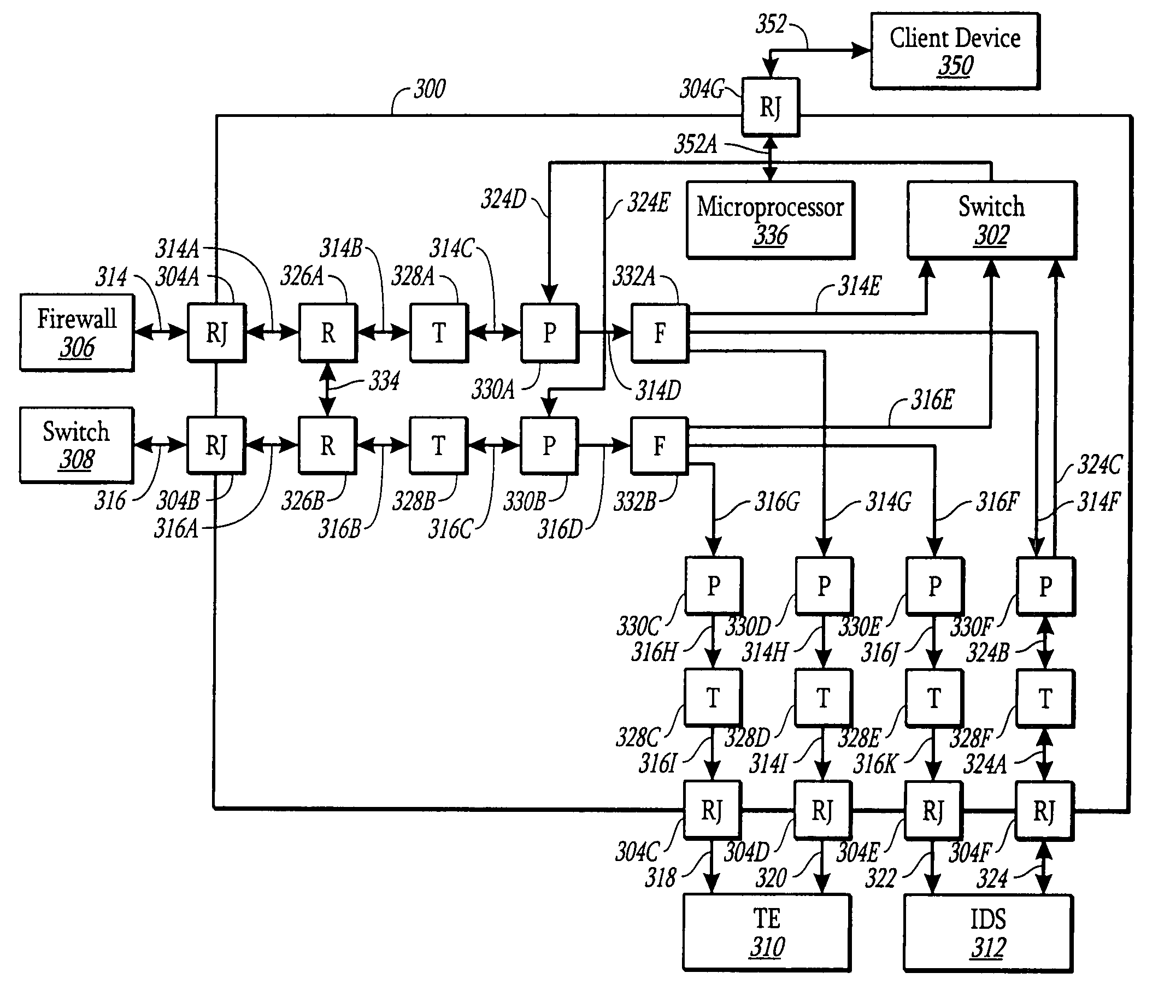
Network tap with integrated circuitry
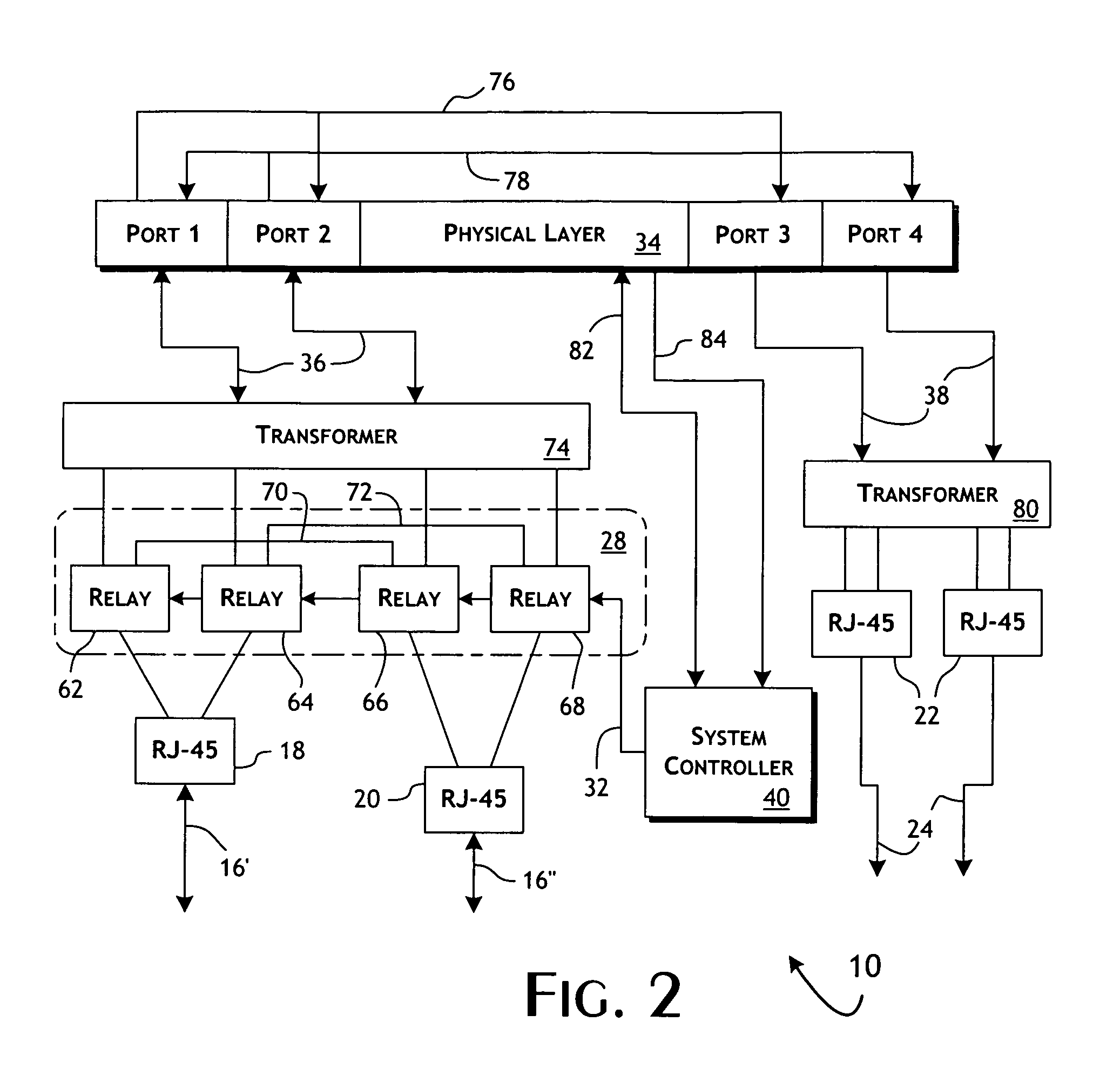
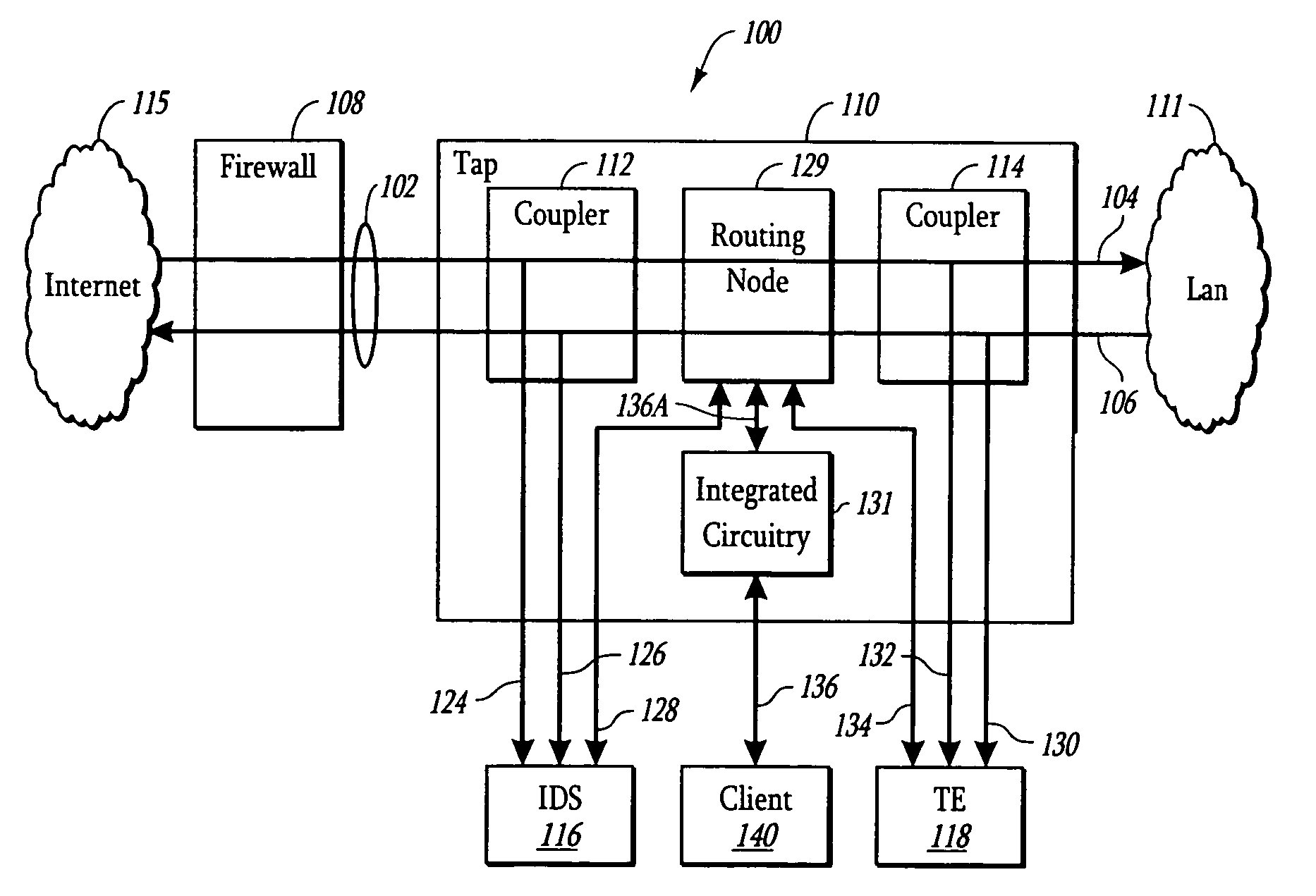
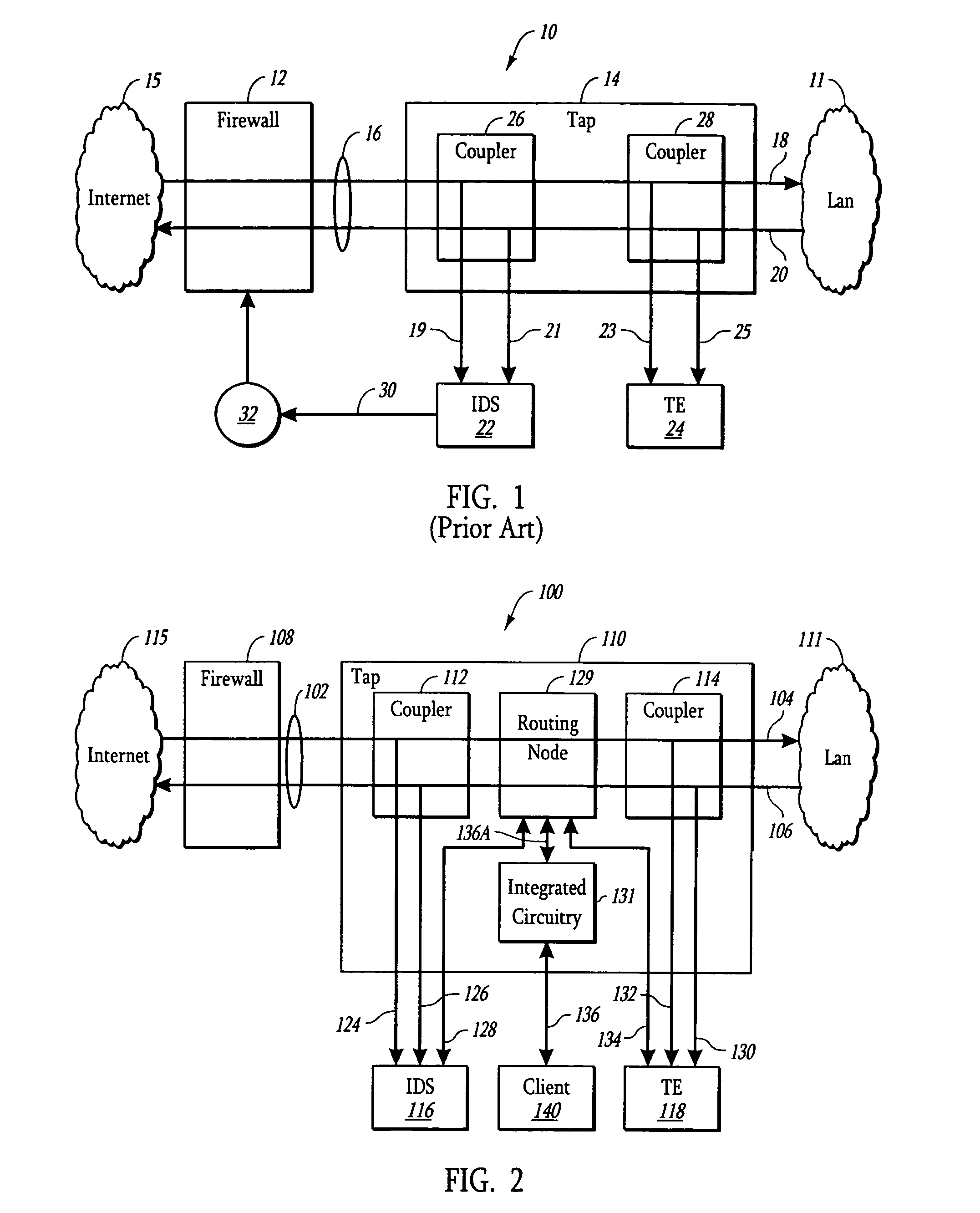
ActiveUS7505416B2Avoid Data ConflictsFunction increaseError preventionTransmission systemsTraffic capacityNetwork tap
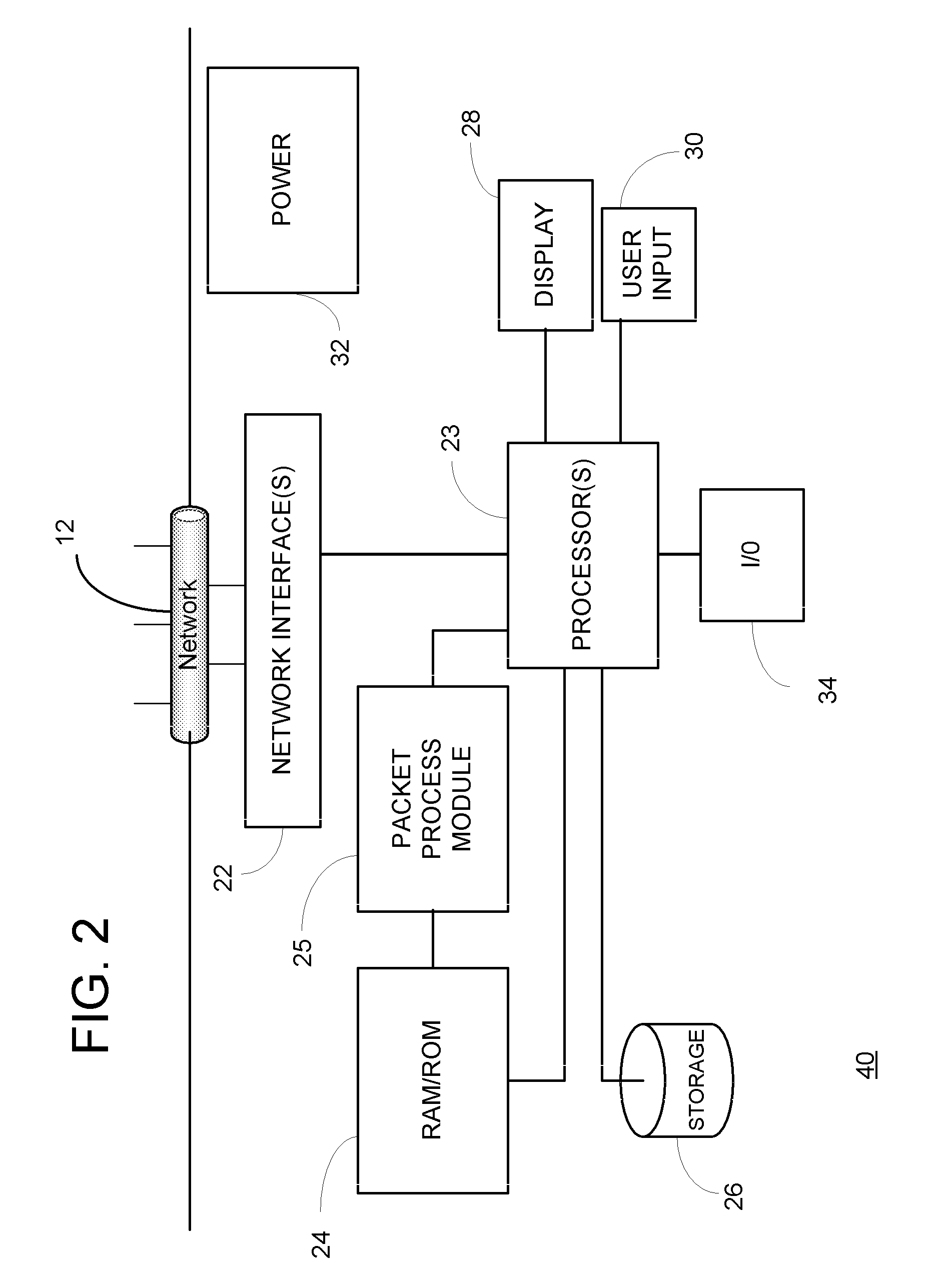
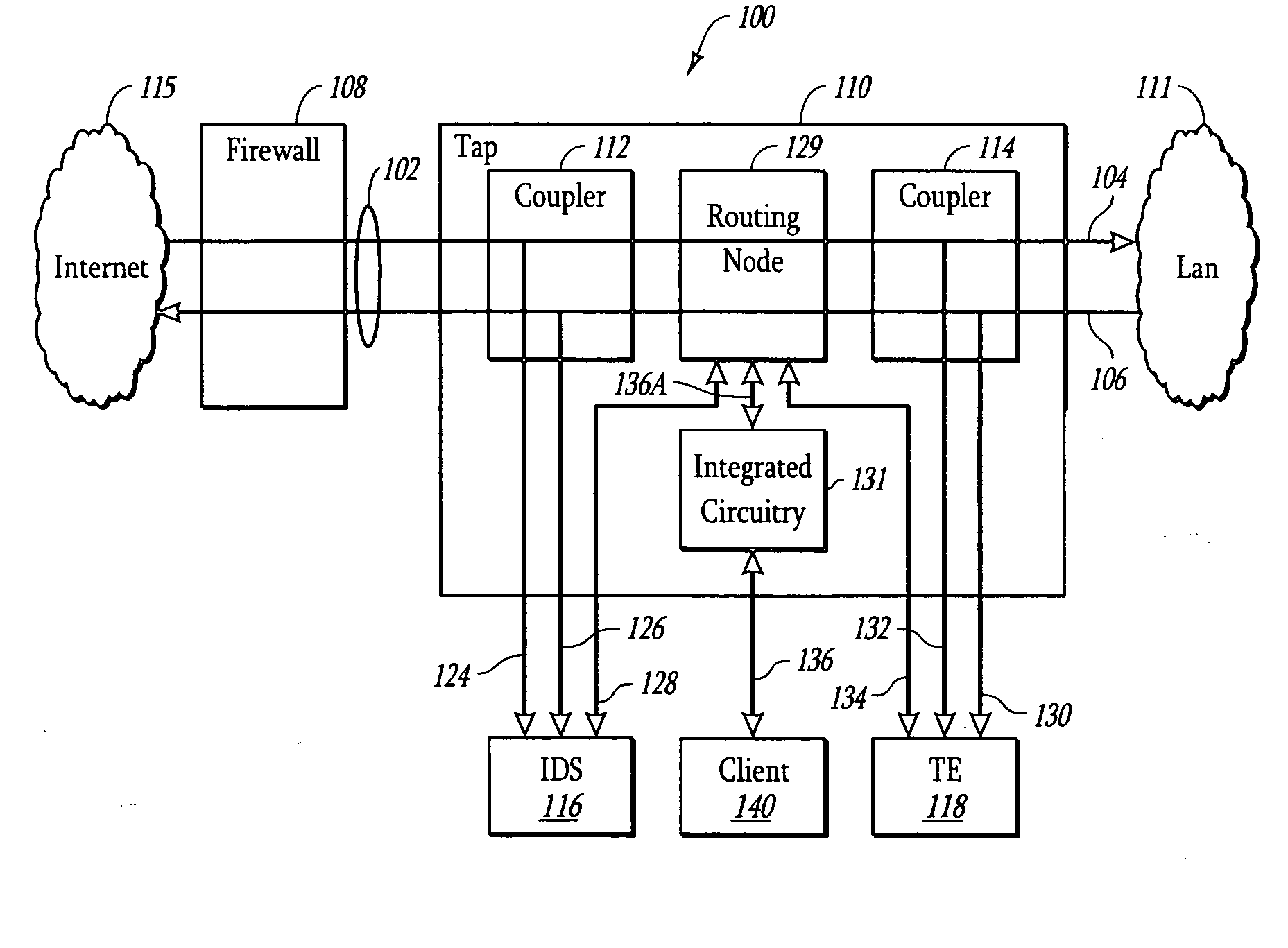
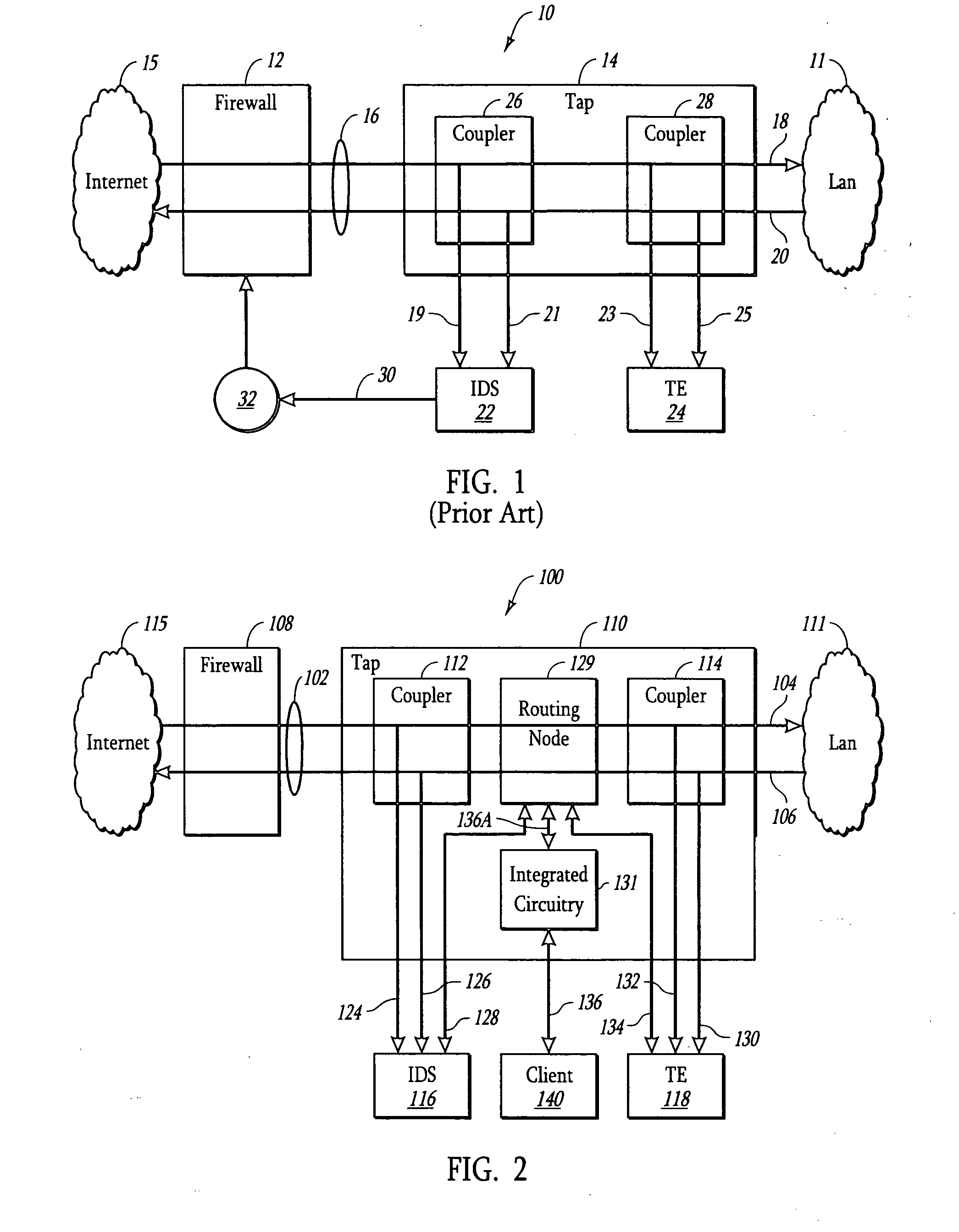
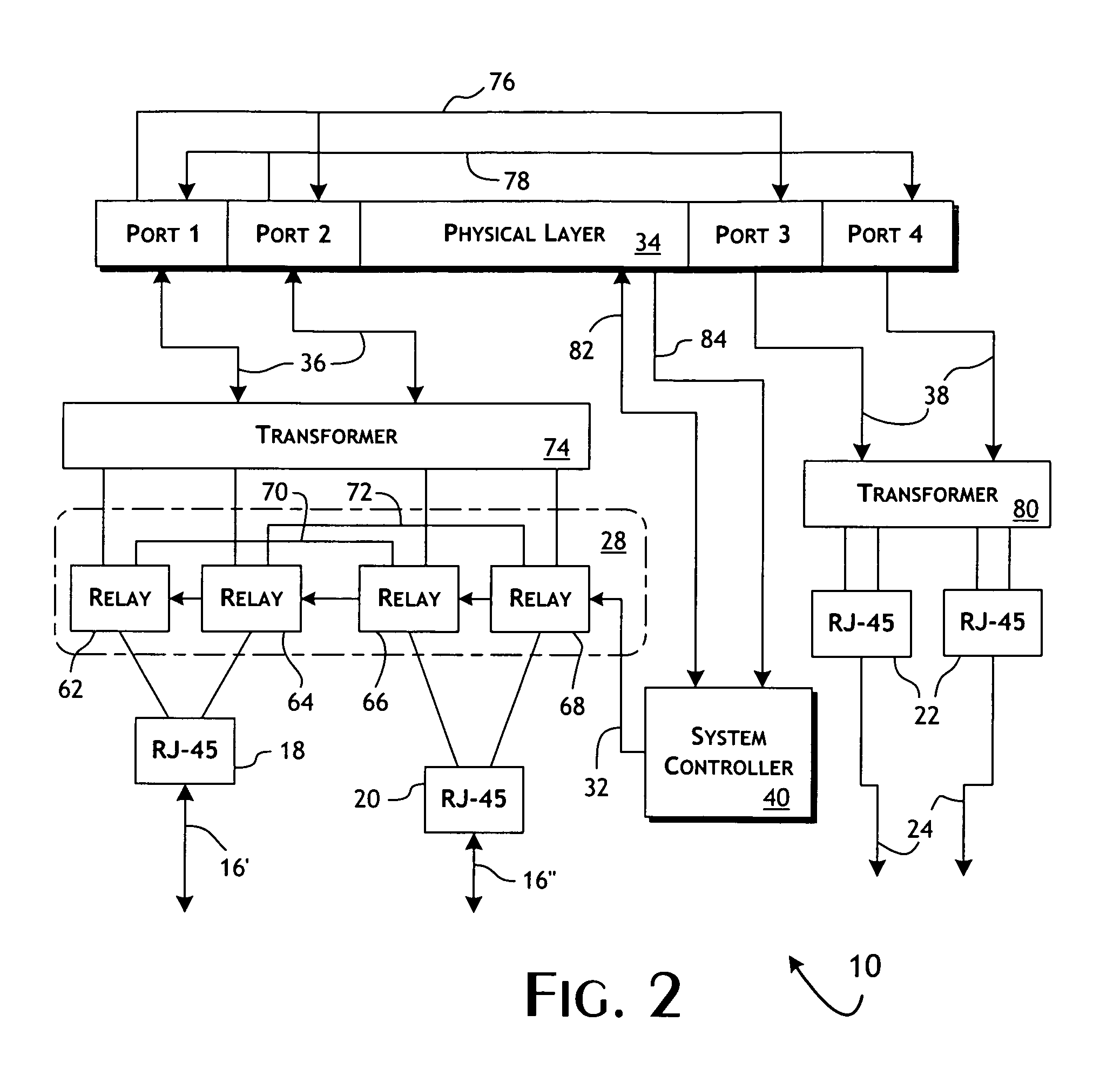
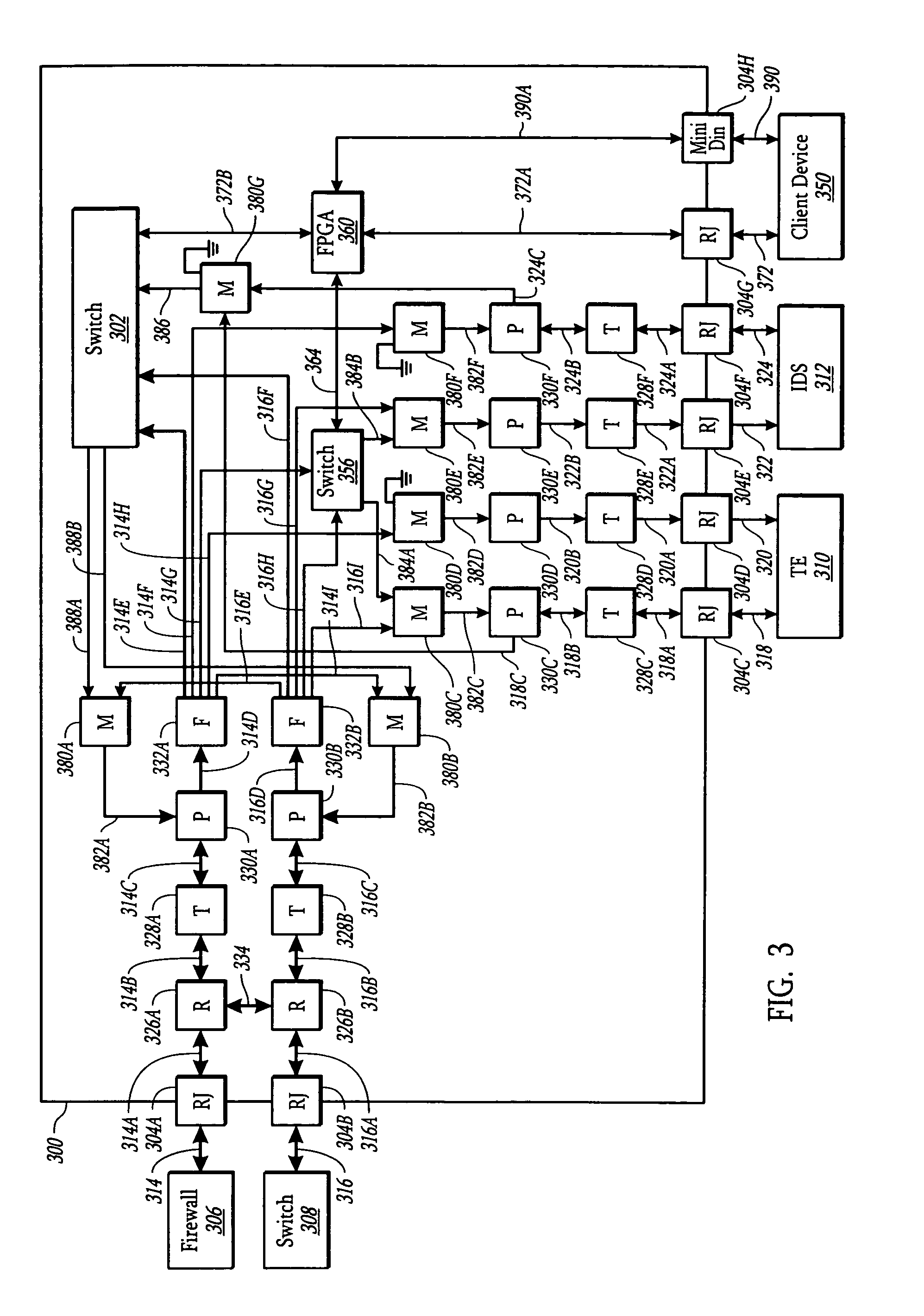
A system and method is presented for a network tap having integrated circuitry therein for obtaining statistics about a communication line. The network tap also has a routing node for allowing information to be transmitted back into the communication line from an attached device without disrupting the communication traffic. The routing node coordinates the transmission of device data from an attached device to avoid data collisions with data transmissions already existing in the communication line. The routing node may be an Ethernet switch or field programmable gate array (FPGA). The integrated circuit may be a microprocessor or FPGA. The integrated circuit also controls other components of the network tap. The integrated circuit may also be programmed or upgraded to provide other functions.
Owner:VIAVI SOLUTIONS INC
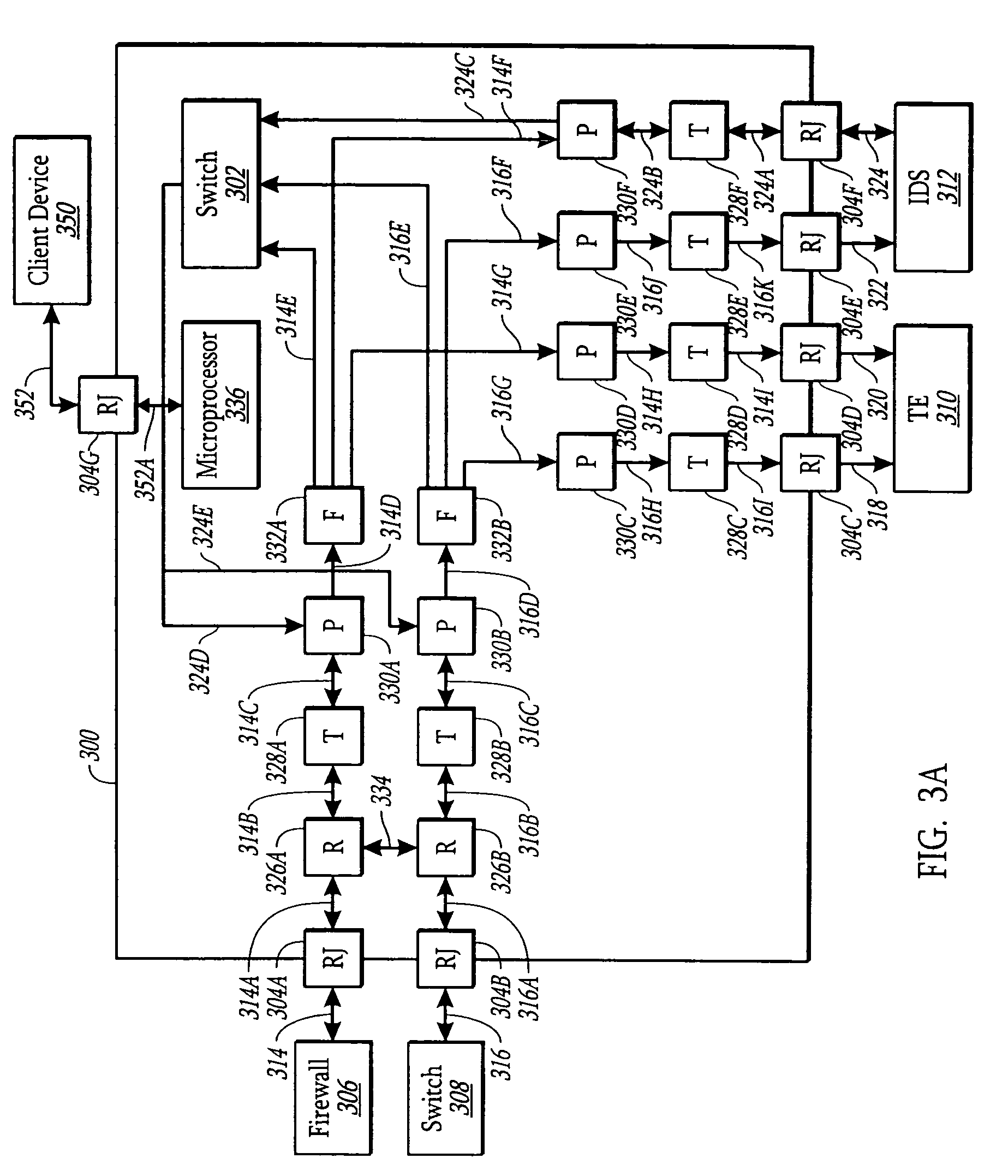
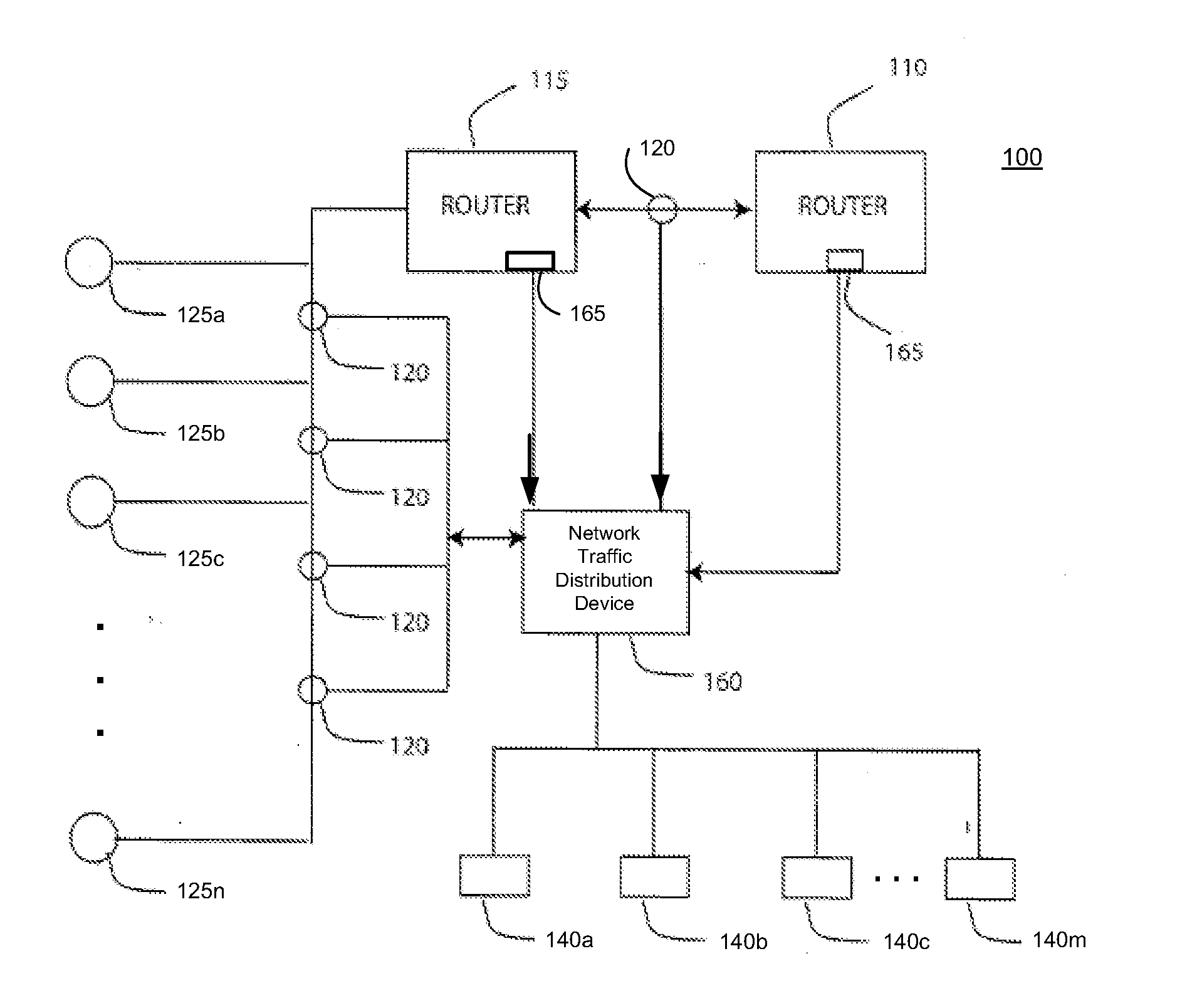
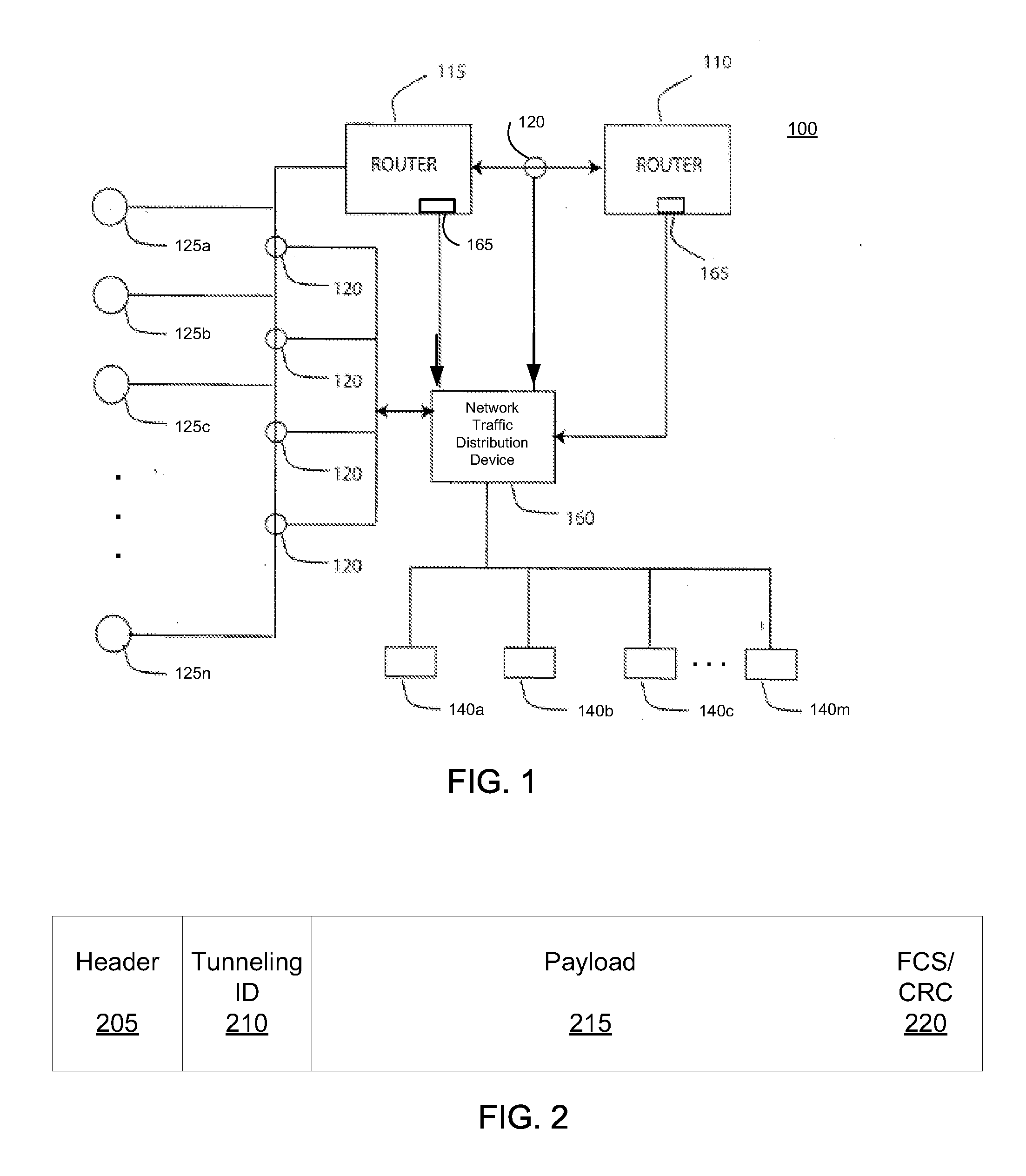
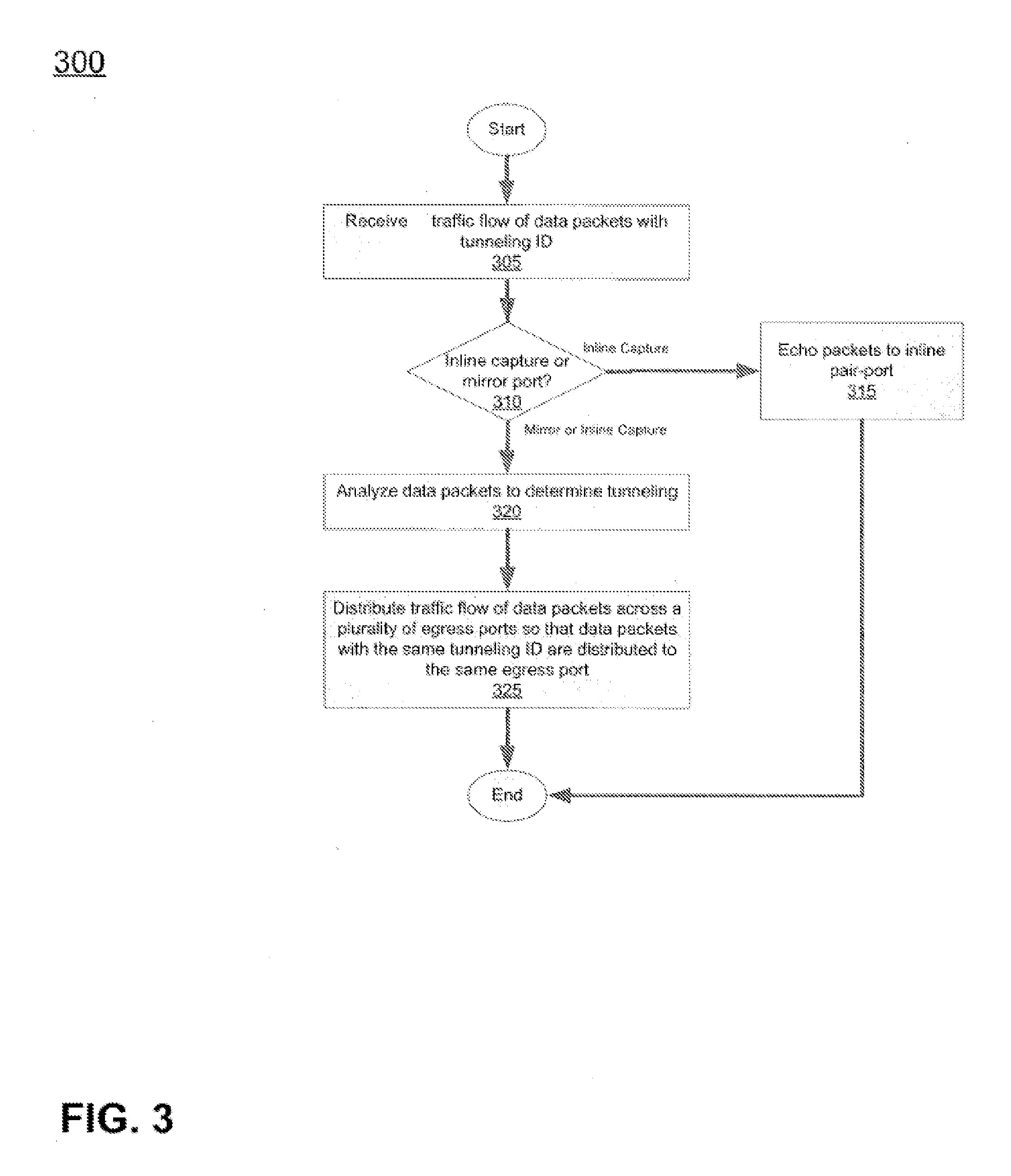
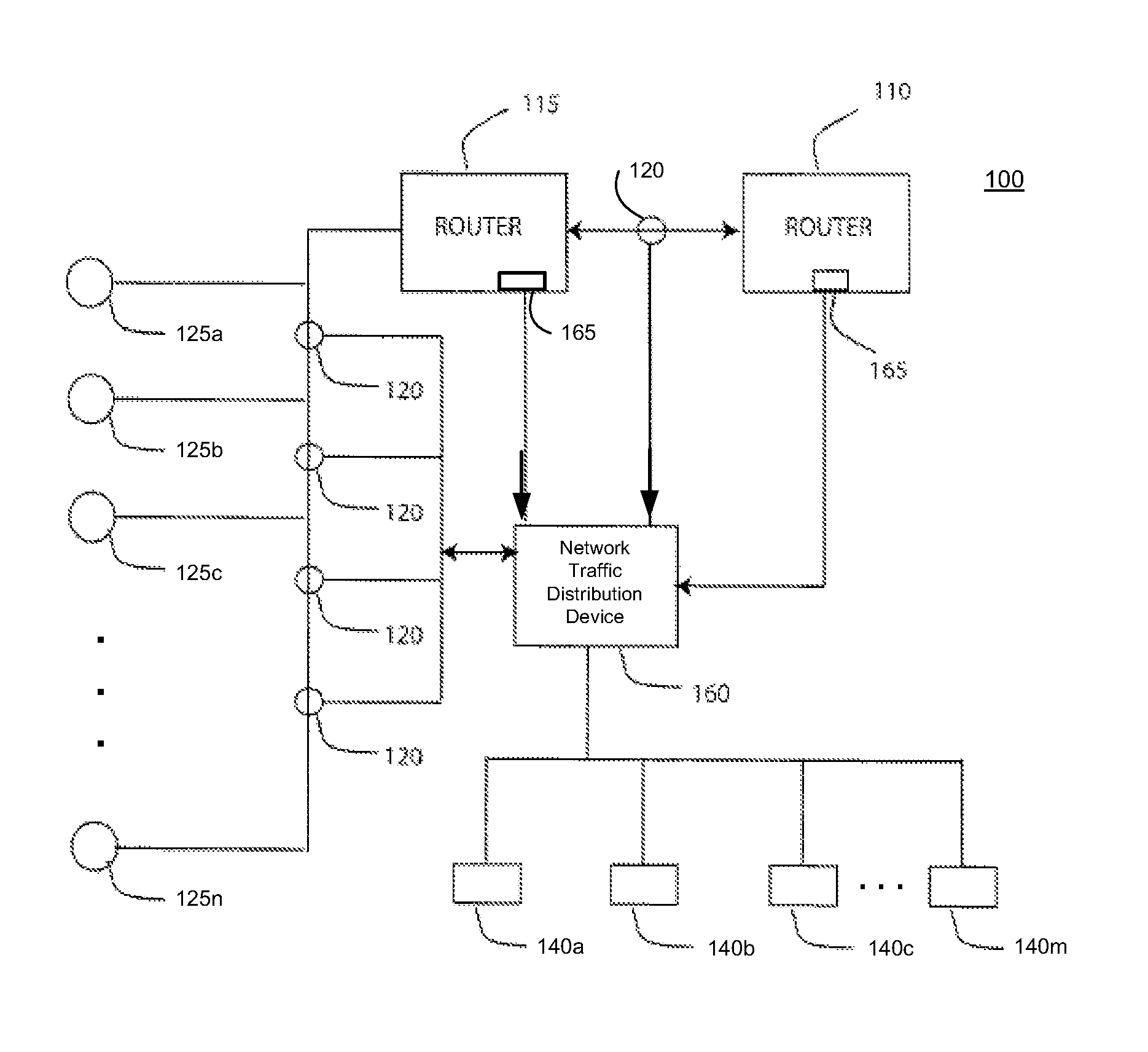
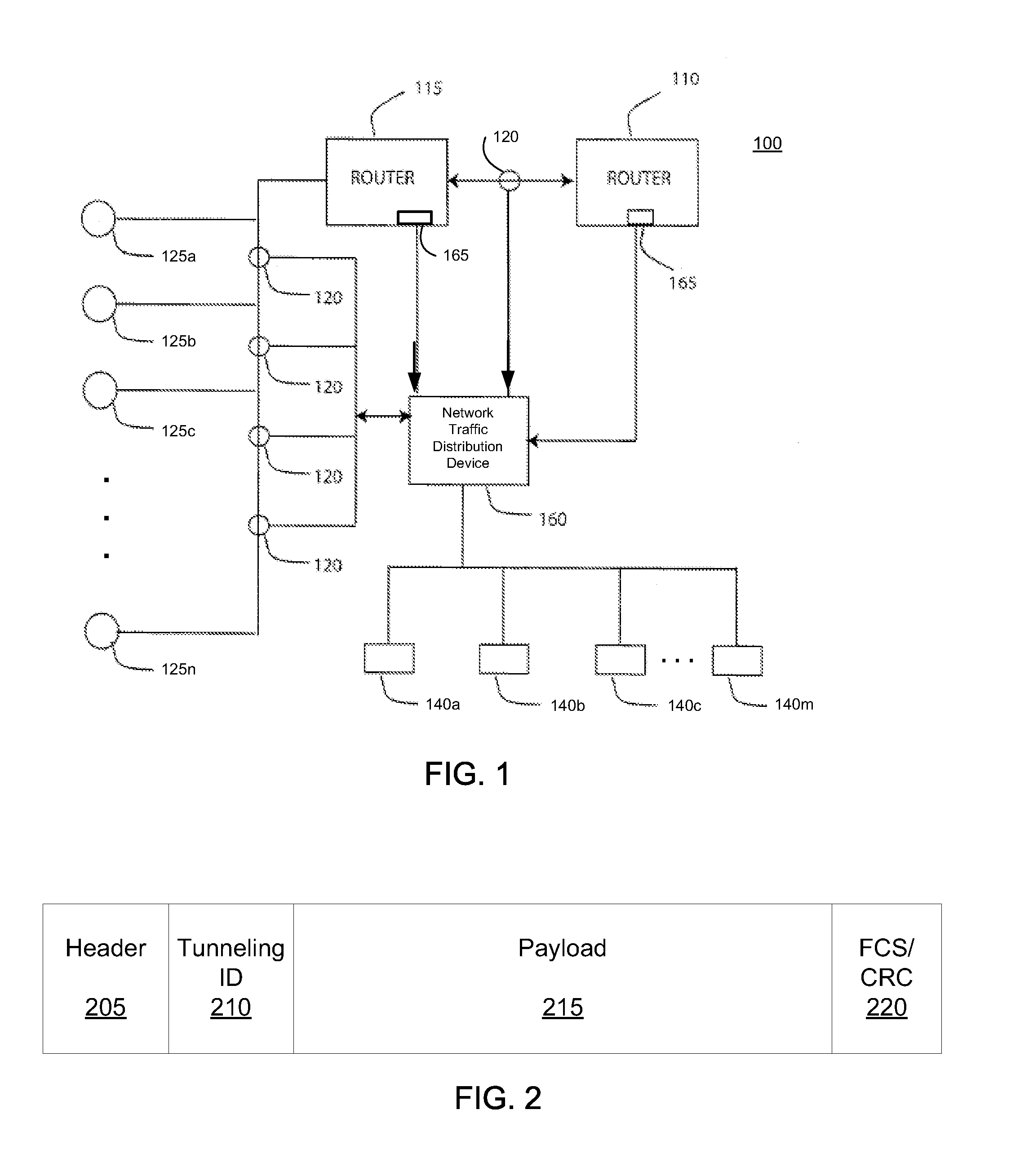
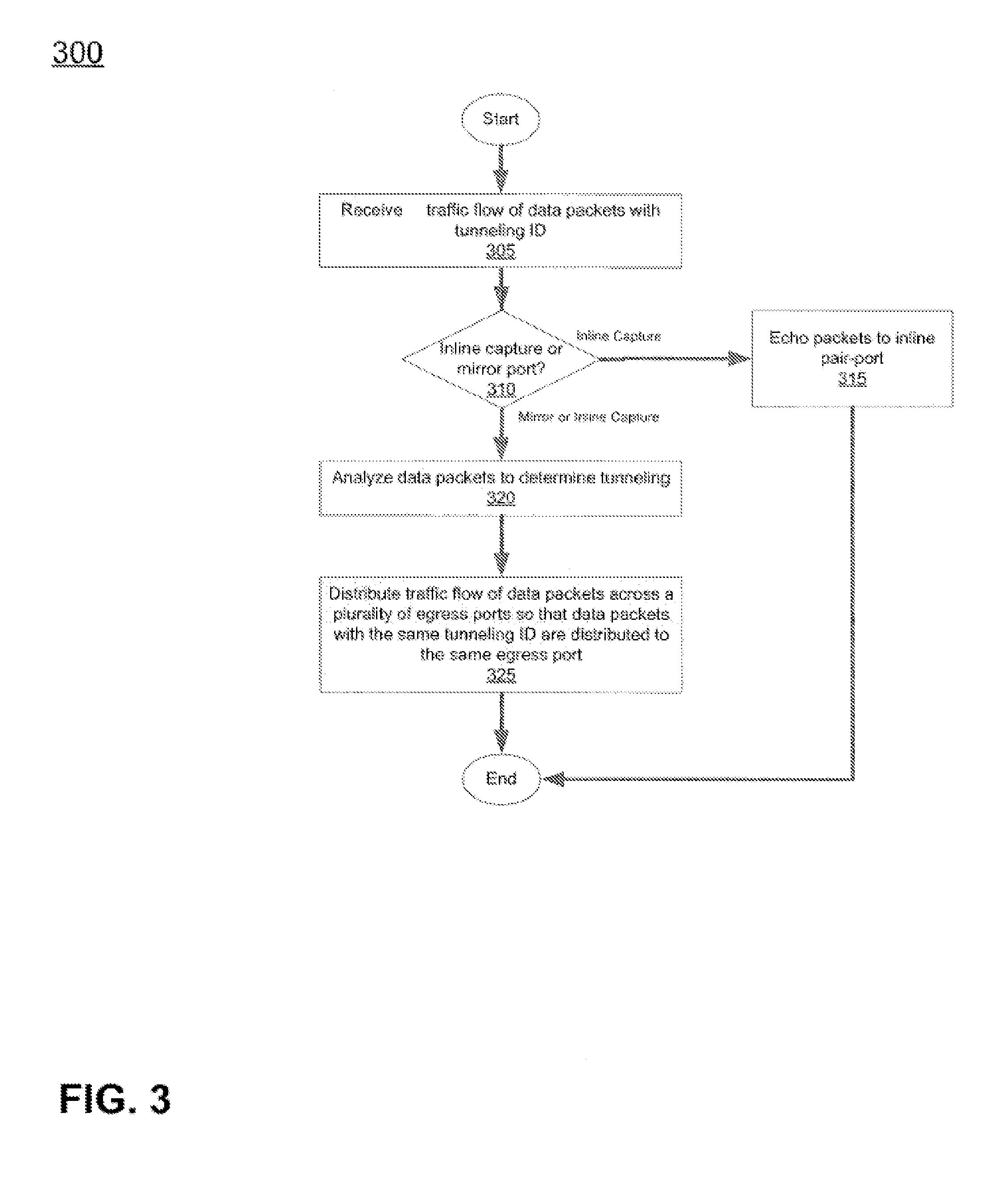
System, method and apparatus for distributing captured data packets including tunneling identifiers
A network traffic distribution device (e.g., a network tap or similar device) is configured to receive and analyze captured network traffic data packets that include tunneling IDs (e.g., GTP tunneling IDs) and, based on that analysis, to distribute those data packets in such a way that data packets with the same tunneling IDs are distributed to a common egress port of the network traffic distribution device. In some cases, each flow of data packets with a common tunneling ID is sent to a unique external device, while in other cases, two or more traffic flows, each with packets having respective, common tunneling IDs may be provided to the same external device, either via a common egress port of the network traffic monitoring device or via separate egress ports thereof.
Owner:NETSCOUT SYSTEMS
Enhanced communication network tap port aggregator arrangement and methods thereof
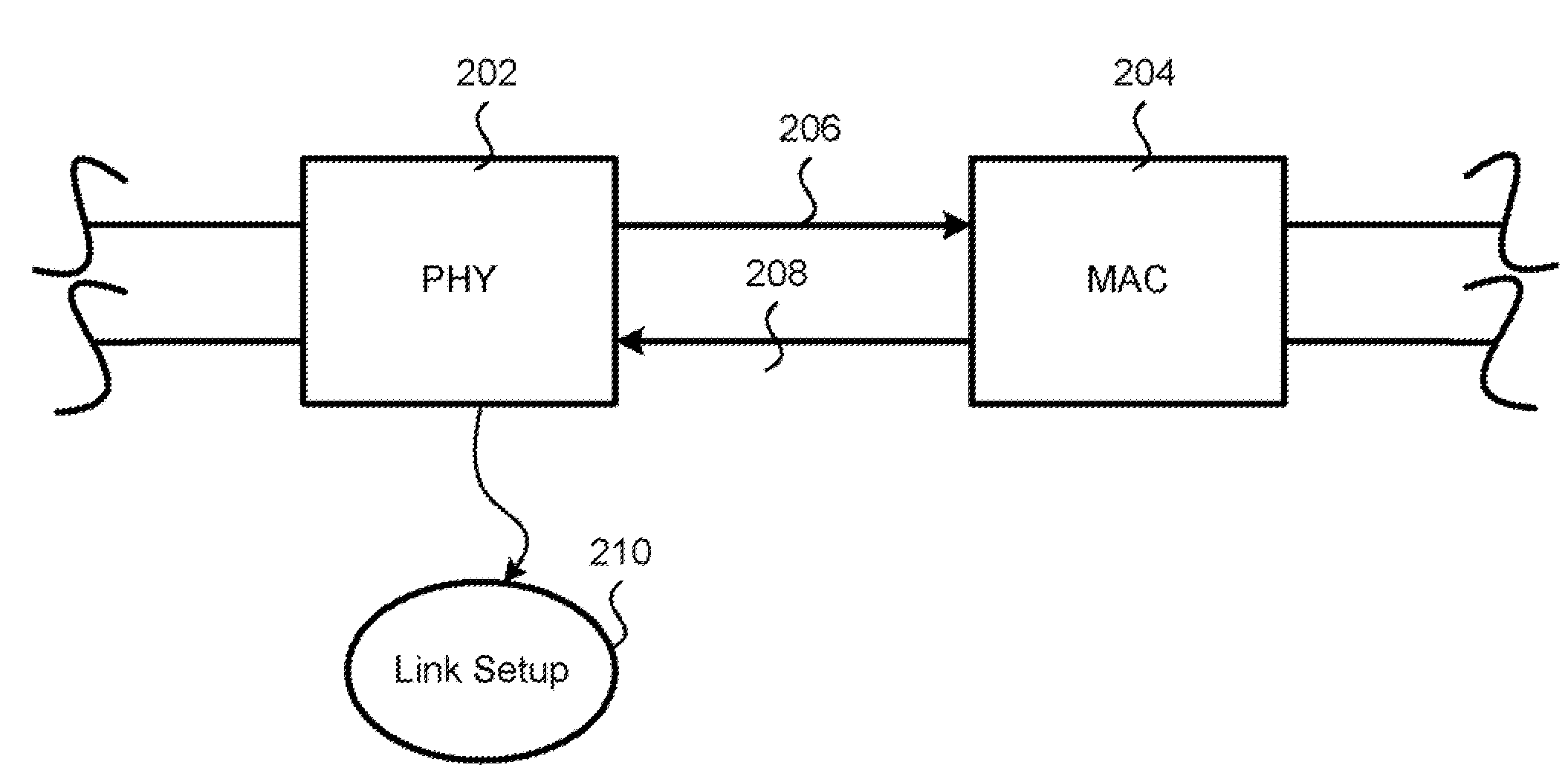
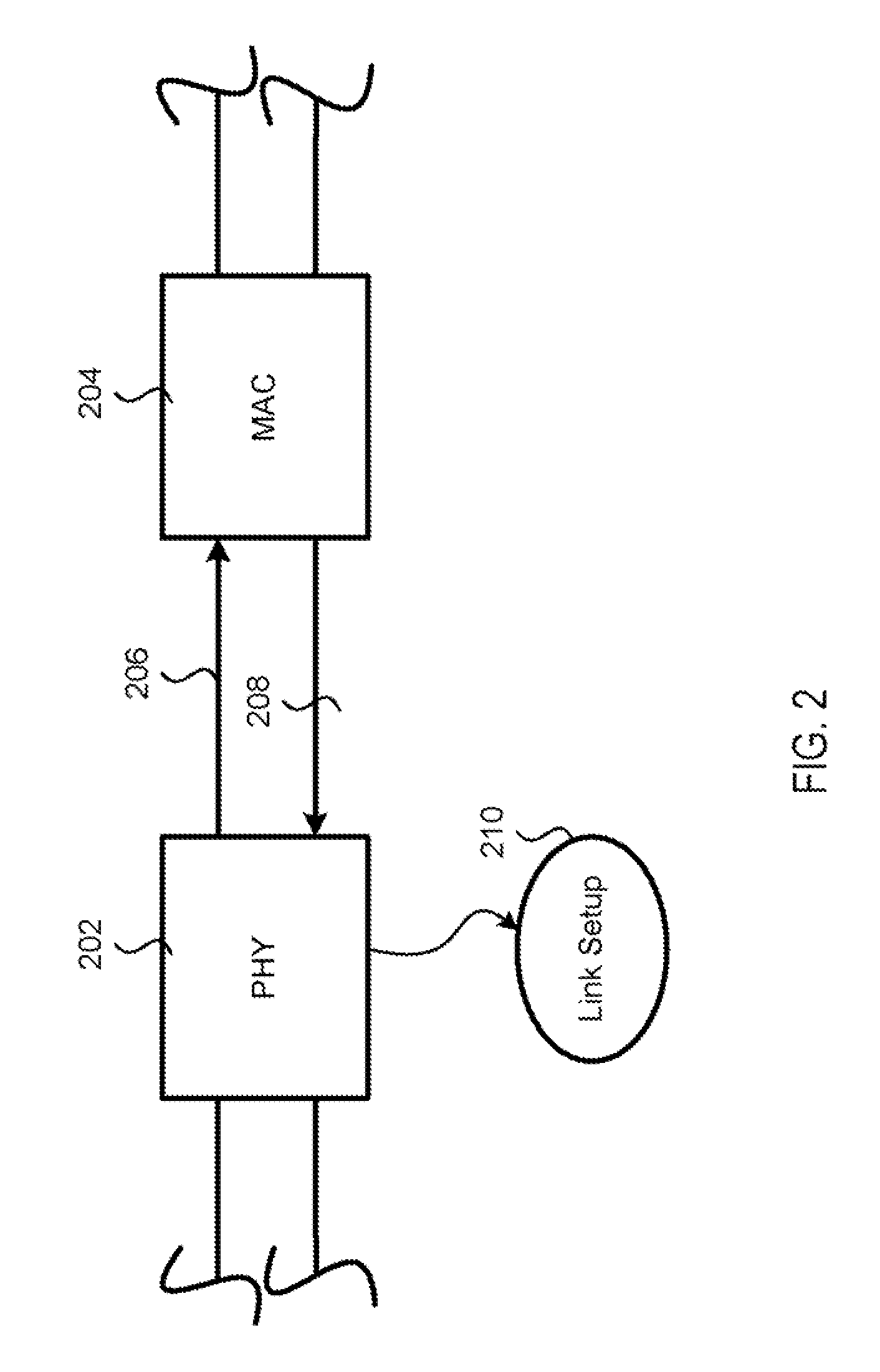
An arrangement in a network device for facilitating at least one of multiple connection speeds with a network, active response between a monitoring device and an end-device, and power over Ethernet (POE) over a network is provided. As a facilitator of multiple connection speeds, the arrangement includes a plurality of physical layer interface (PHY) and media access controller (MAC) that are configured to support multiple speeds. As a facilitator of active response, the arrangement includes a logic arrangement for multicasting a set of instructions that is sent from a monitoring port. As a facilitator of POE, the arrangement is configured to receive data traffic (e.g., data packets and / or power packets) through a first network port and to send the data traffic out a second network port.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Multiple and parallel access network tap for gigabit internet LANS
ActiveUS7486624B2Avoid interferenceError preventionFrequency-division multiplex detailsTransmission protocolElectrical conductor
A single-usage network tap monitors network information flow over a particular connection. Instead of requiring a tap for each analytical device, by incorporating elements that regenerate, spread, and coordinate the timing of the signal, multiple, simultaneous, and parallel analytical devices can monitor a particular network connection through one tap, It incorporates four amplifiers preferably manufactured on the same IC die with high-impedance input terminals connected directly to the two conductors of a gigabit Ethernet local area network digital transmission line so as not to load or otherwise upset its impedance or other parameters. The output terminals of the operational amplifiers are connected to and match the input impedance of the digital transmission protocol Gigabit analyzer. The gain of the operational amplifiers is arranged so as to replicate at the input of the analyzer the signals appearing on the Gigabit local area network transmission line with uninterruptible power supply.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Passive Network Tap With Bidirectional Coupler and Associated Splitting Methods
The principles of the present invention relate to passive full-duplex bidirectional Zero Packet Loss (ZPL) network taps that include single, dual, or dual differential couplers that are placed in the communication path between two network devices that communicate using a full-duplex bidirectional data stream that include a first and a second data component. The bidirectional couplers are configured to at least partially obtain a second data stream that includes at least the first data component and to obtain a third data stream that includes at least the second data component. In some embodiments, the bidirectional couplers may include a signal separation module or stage that is configured to further separate the first and second data components.
Owner:VIAVI SOLUTIONS INC
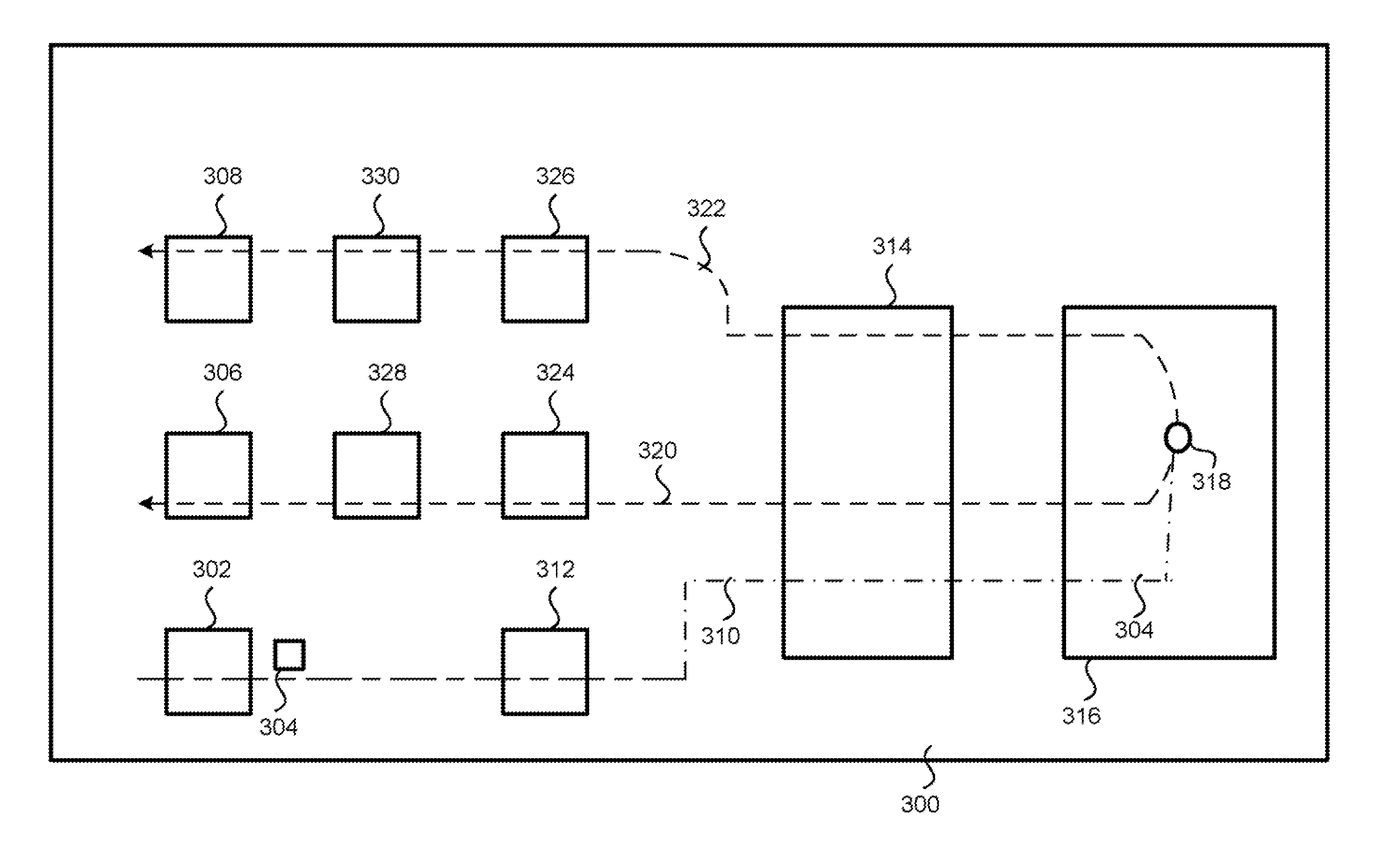
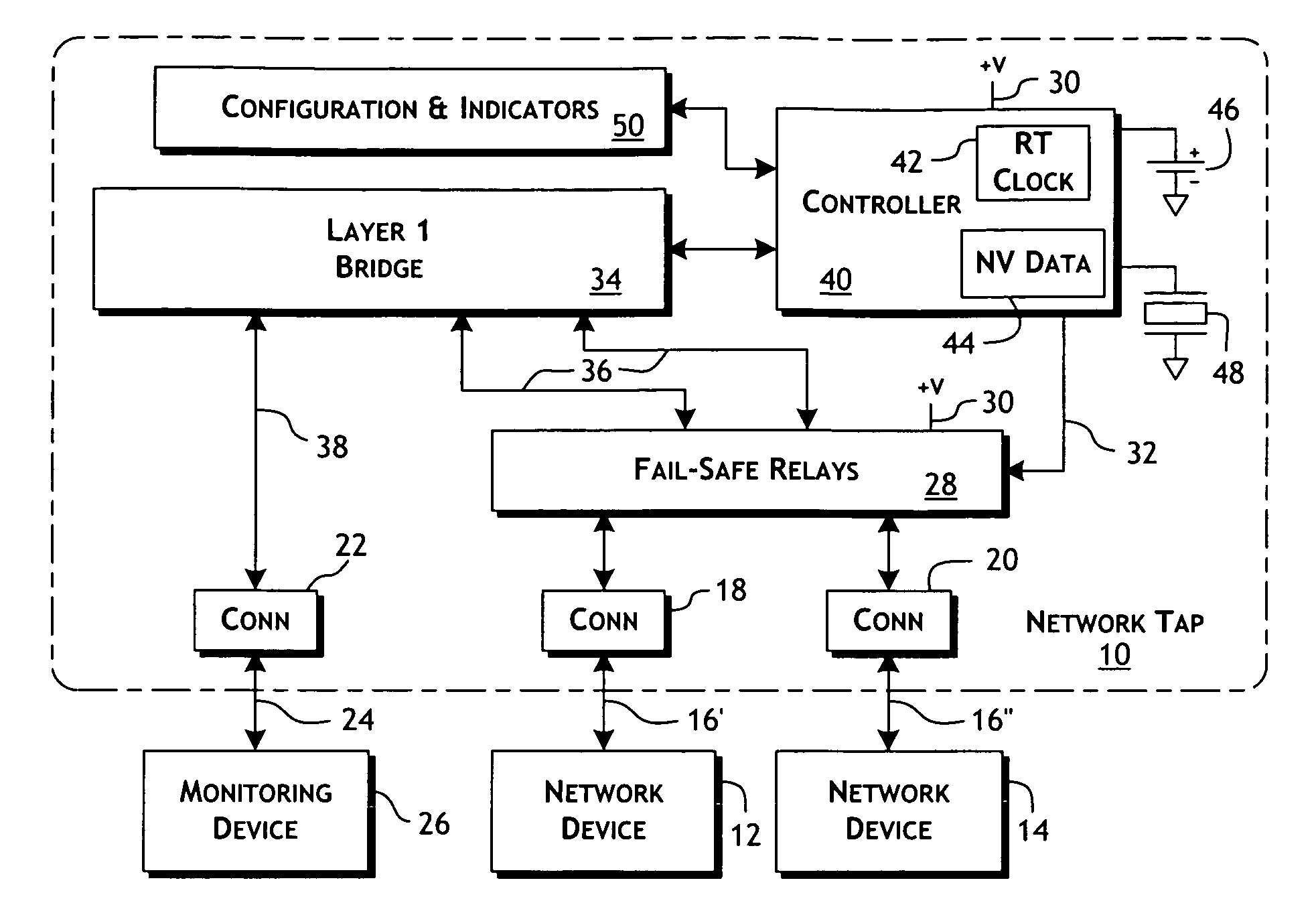
Intelligent fast switch-over network tap system and methods
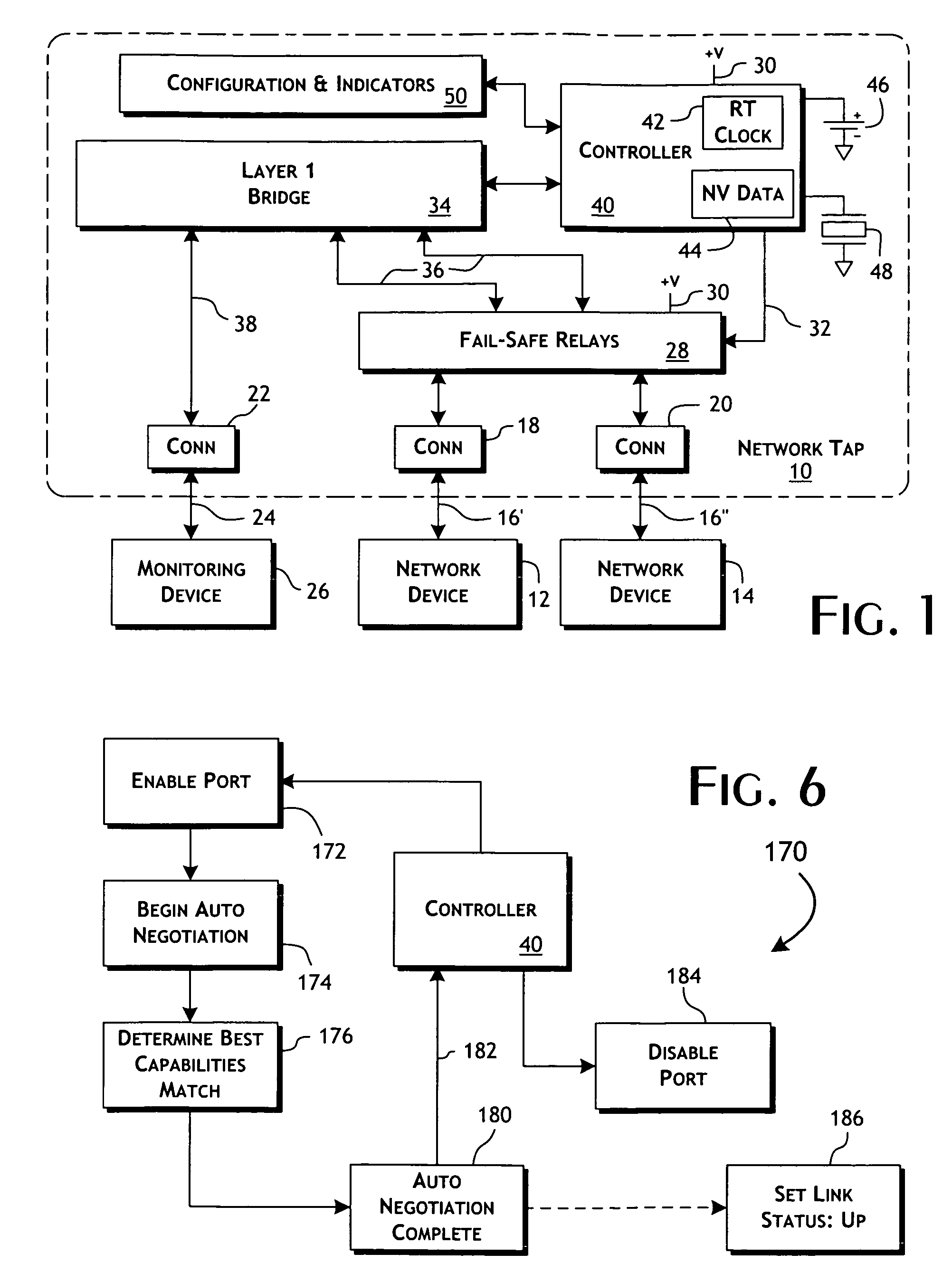
ActiveUS20100177644A1Effective maintenanceAvoiding wider networkError preventionTransmission systemsCross connectionActive monitoring
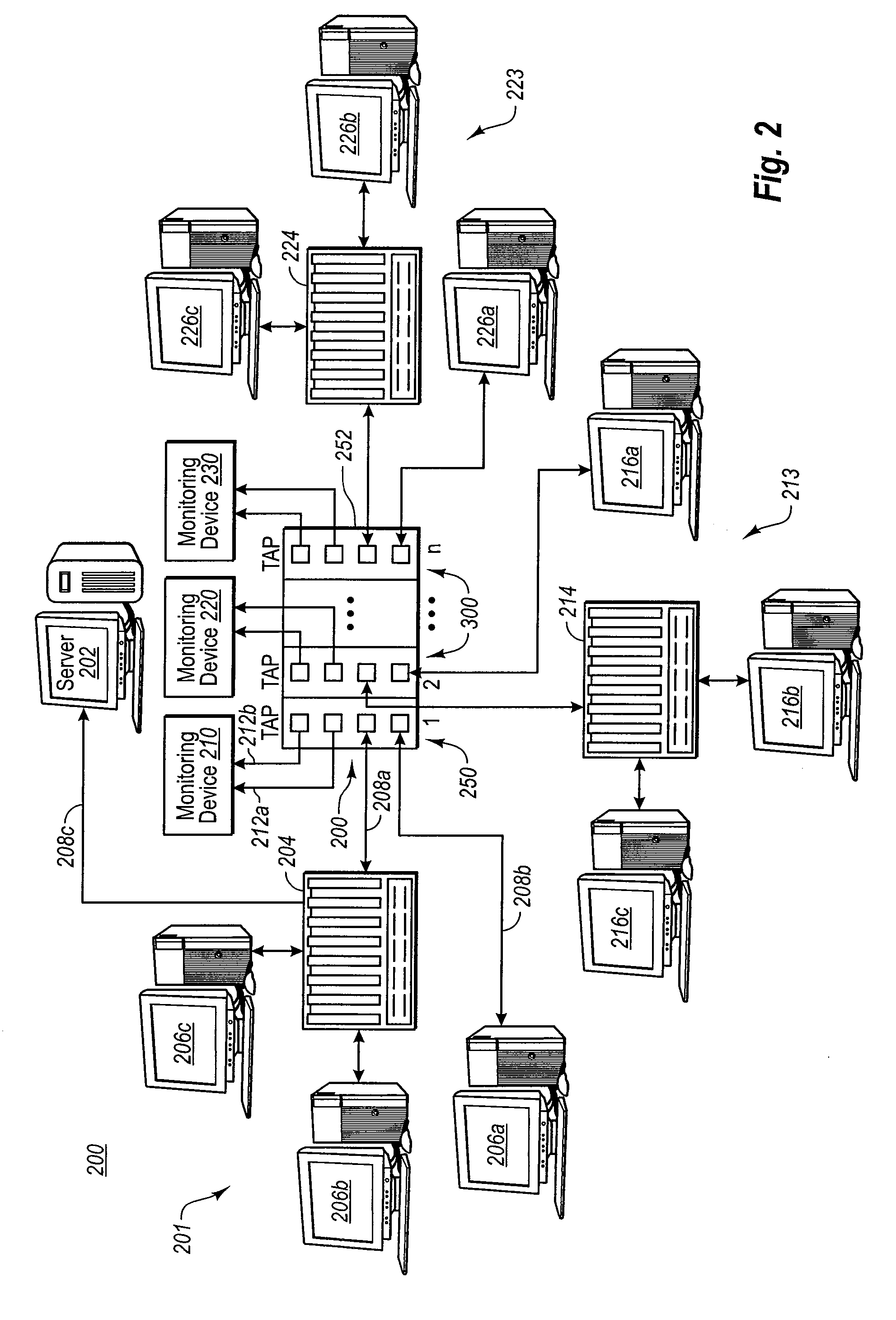
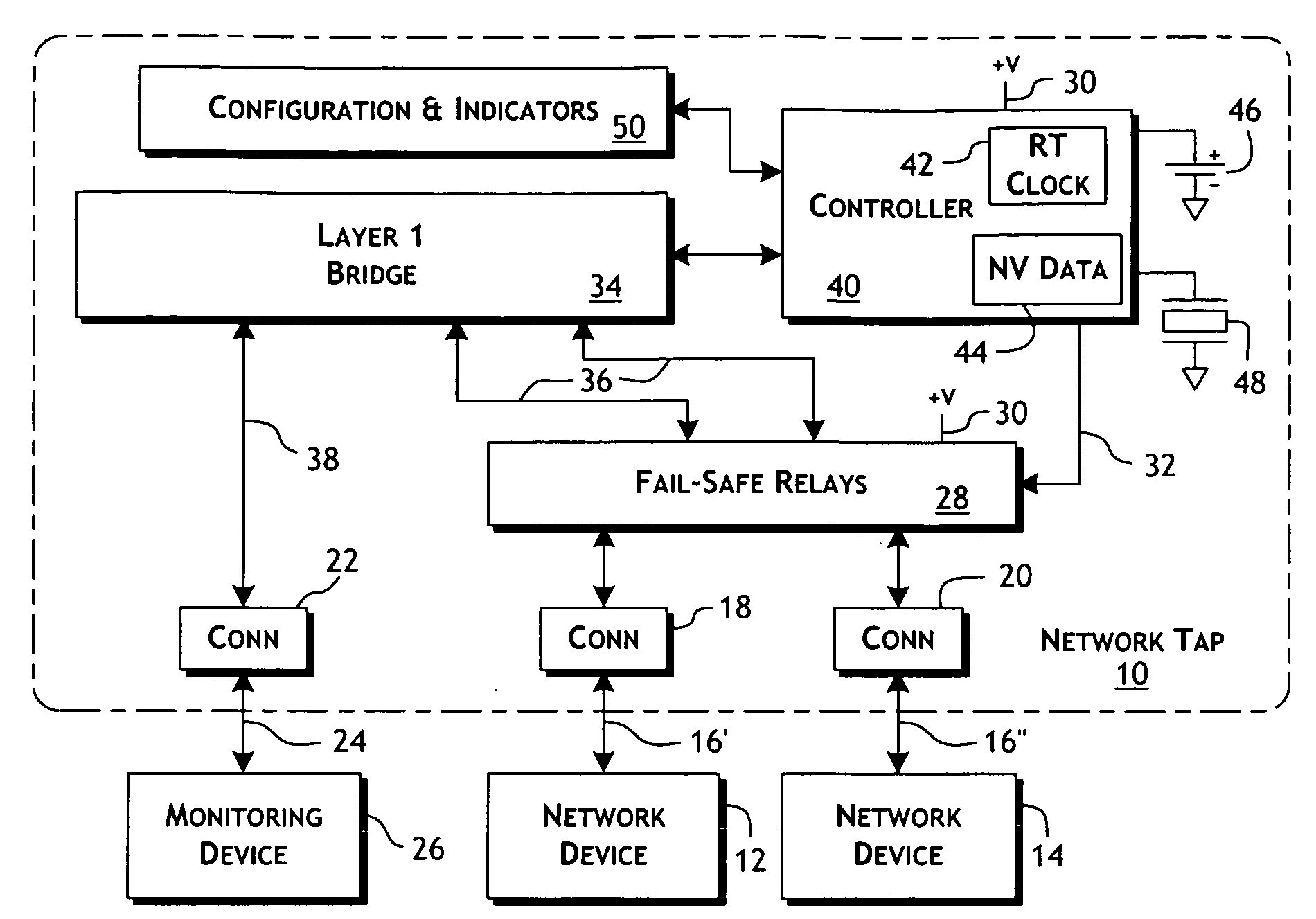
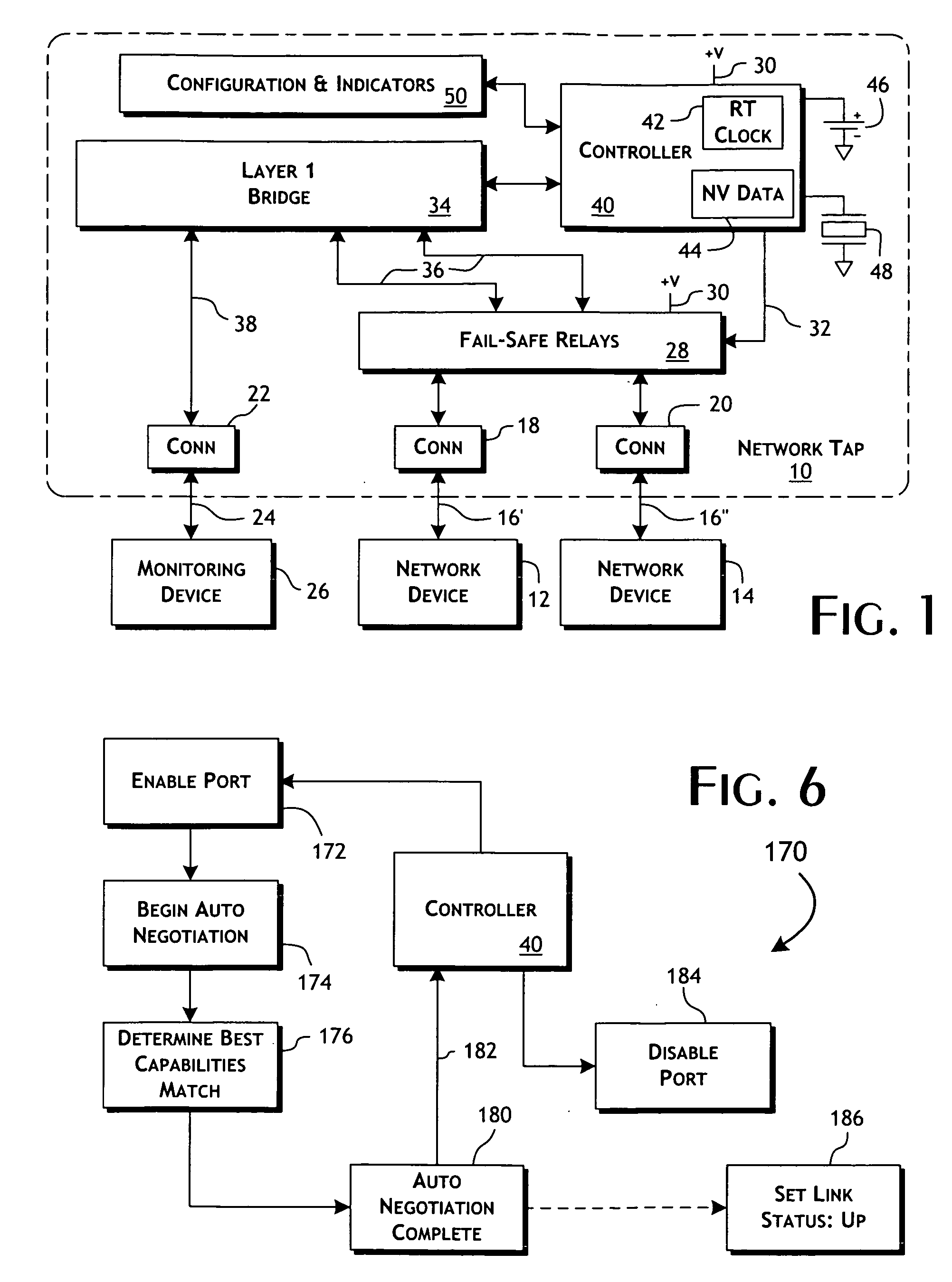
An intelligent fast switch-over network active tap system enables active monitoring of a network segment connected between network devices. A fail-safe relay subsystem is coupled between a pair of network ports, enabling transmission of network communications signals through a passive cross-connect between the network ports or through an active bridge subsystem. The active bridge subsystem is capable of independently establishing network links with the network devices, and a separate network link with a monitoring device. A controller manages operation of the relay and active bridge subsystems, including switches between passive and active network transmission through the tap system and to determine and establish the active network links subject to symmetric network link parameters and state. Thereby, the network link status of the connected network devices is preserved on switch between active and passive transmission and correctly reflected in the presence of link and power failures.
Owner:NETSCOUT SYSTEMS
Network Eavesdropping Detection
In one implementation, network taps are detected using impedance measurements from a network. A network device is configured to calculate a baseline impedance as a function of a sequence of impedance values. As impedance measurements subsequent to the sequence of impedance values are received, the network device is configured to calculate a difference between the impedance measurement and the baseline impedance. The network device generates a network tap warning message when the difference between the impedance measurement and the baseline impedance exceeds a threshold. The network device may be an endpoint computer, a data switch, or an external device remote from the network.
Owner:CISCO TECH INC
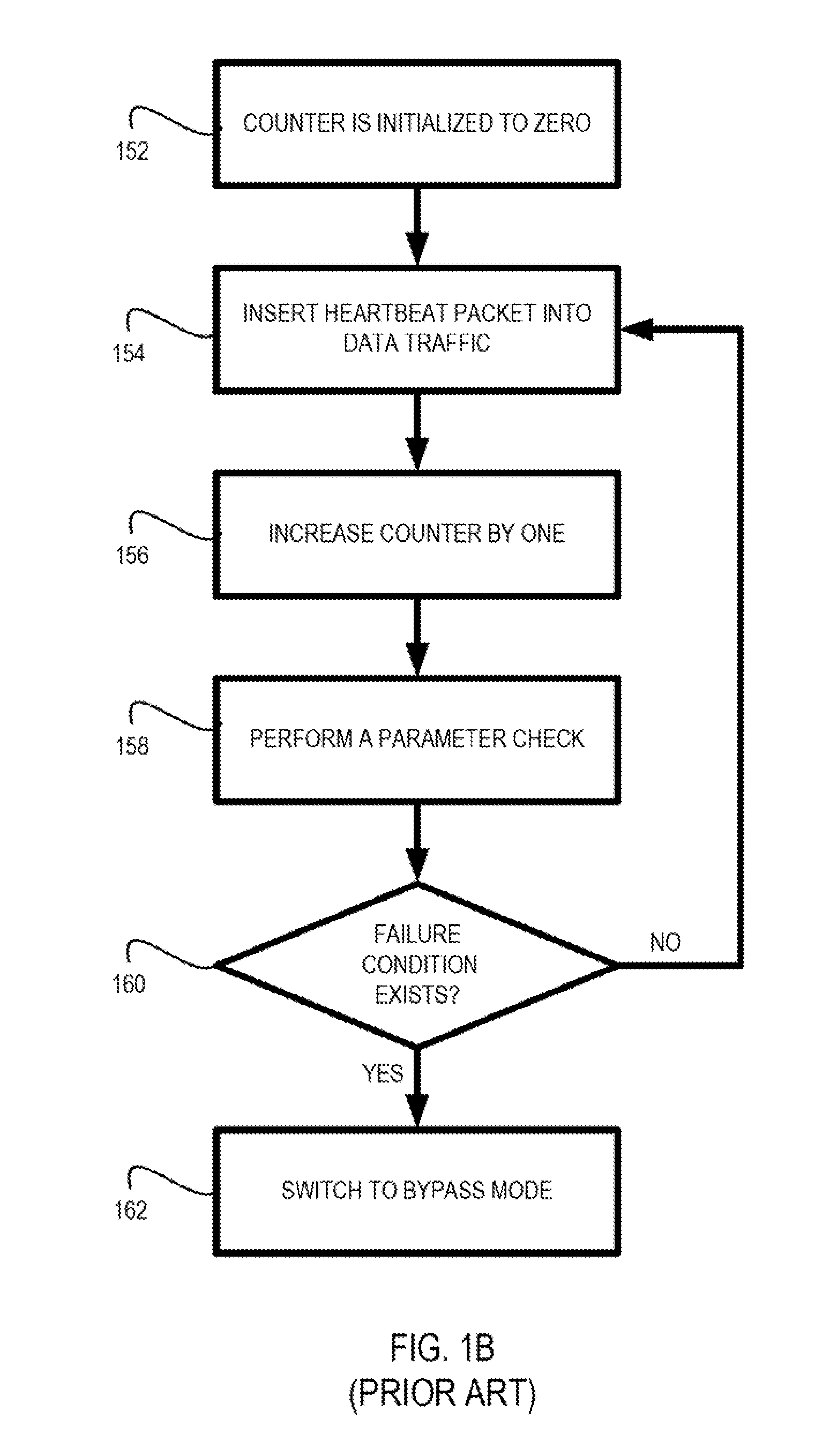
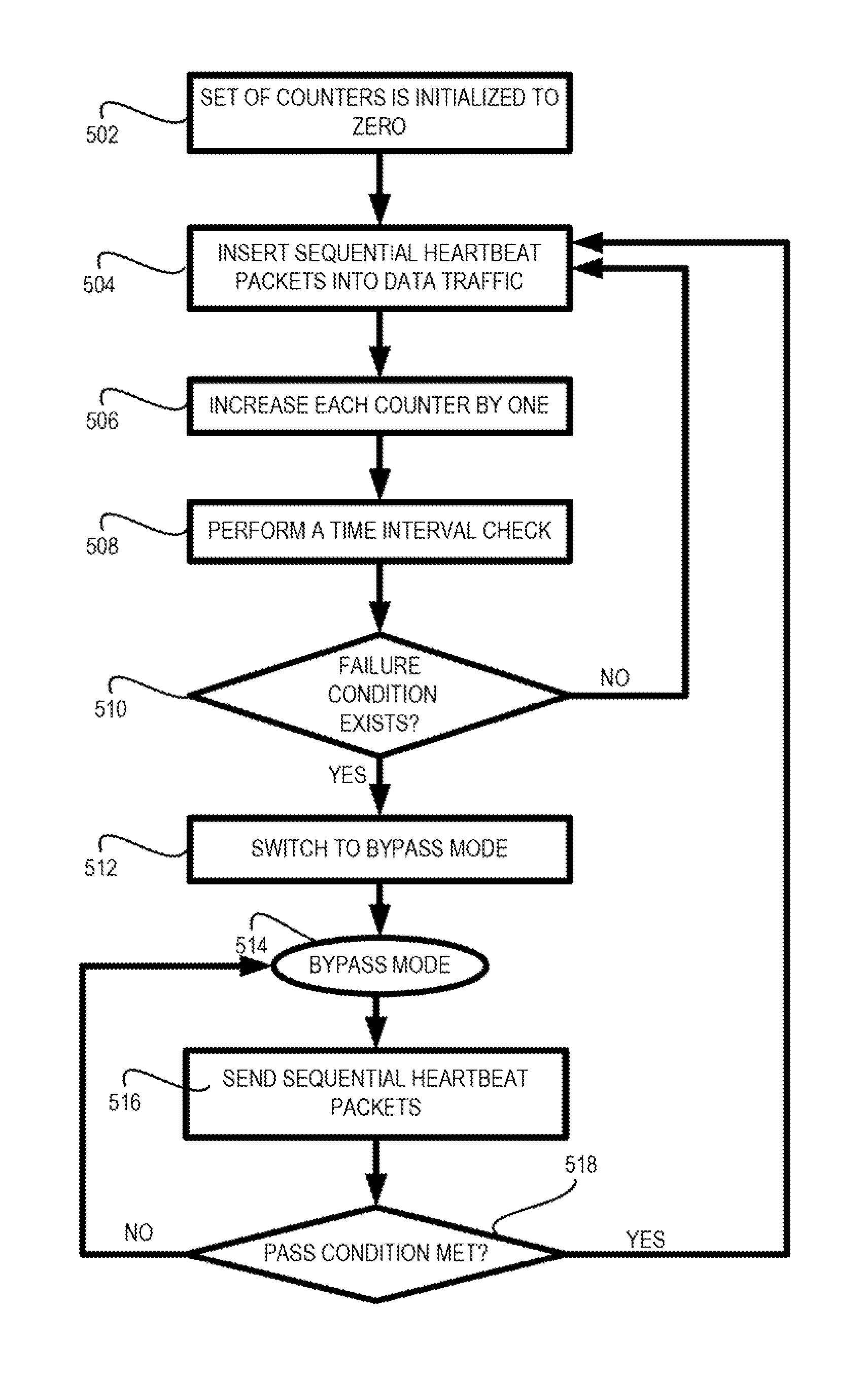
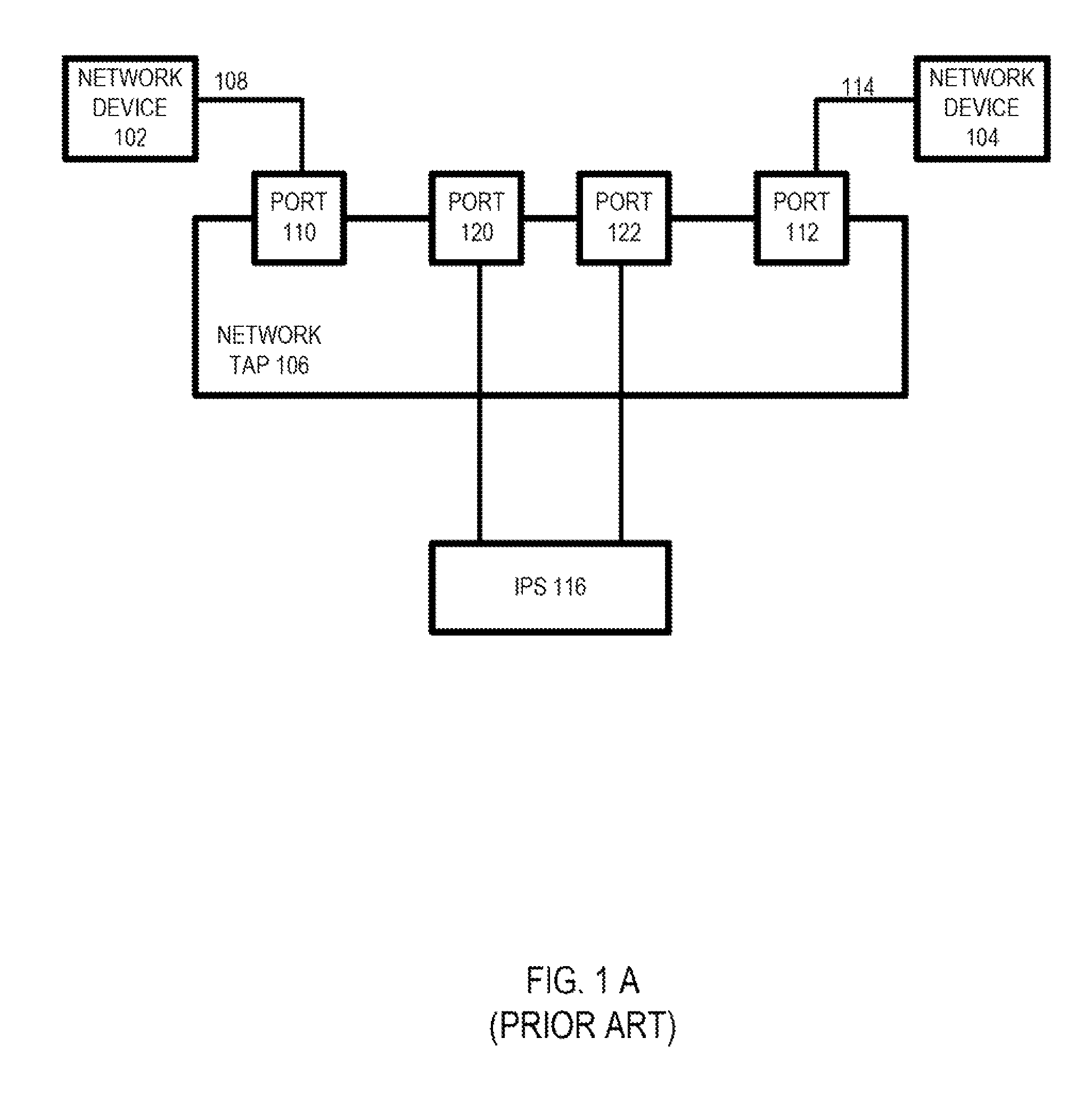
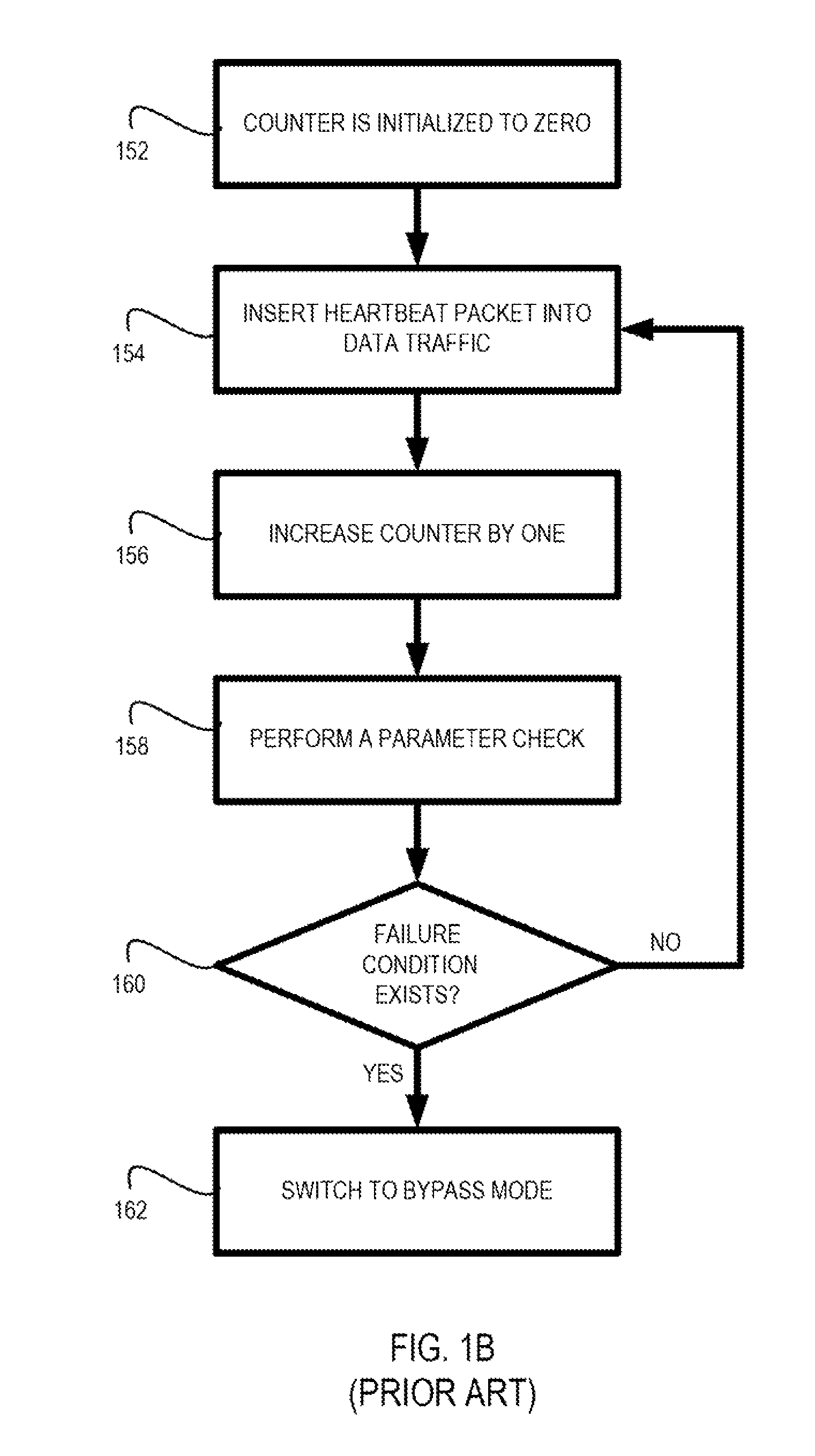
Sequential heartbeat packet arrangement and methods thereof
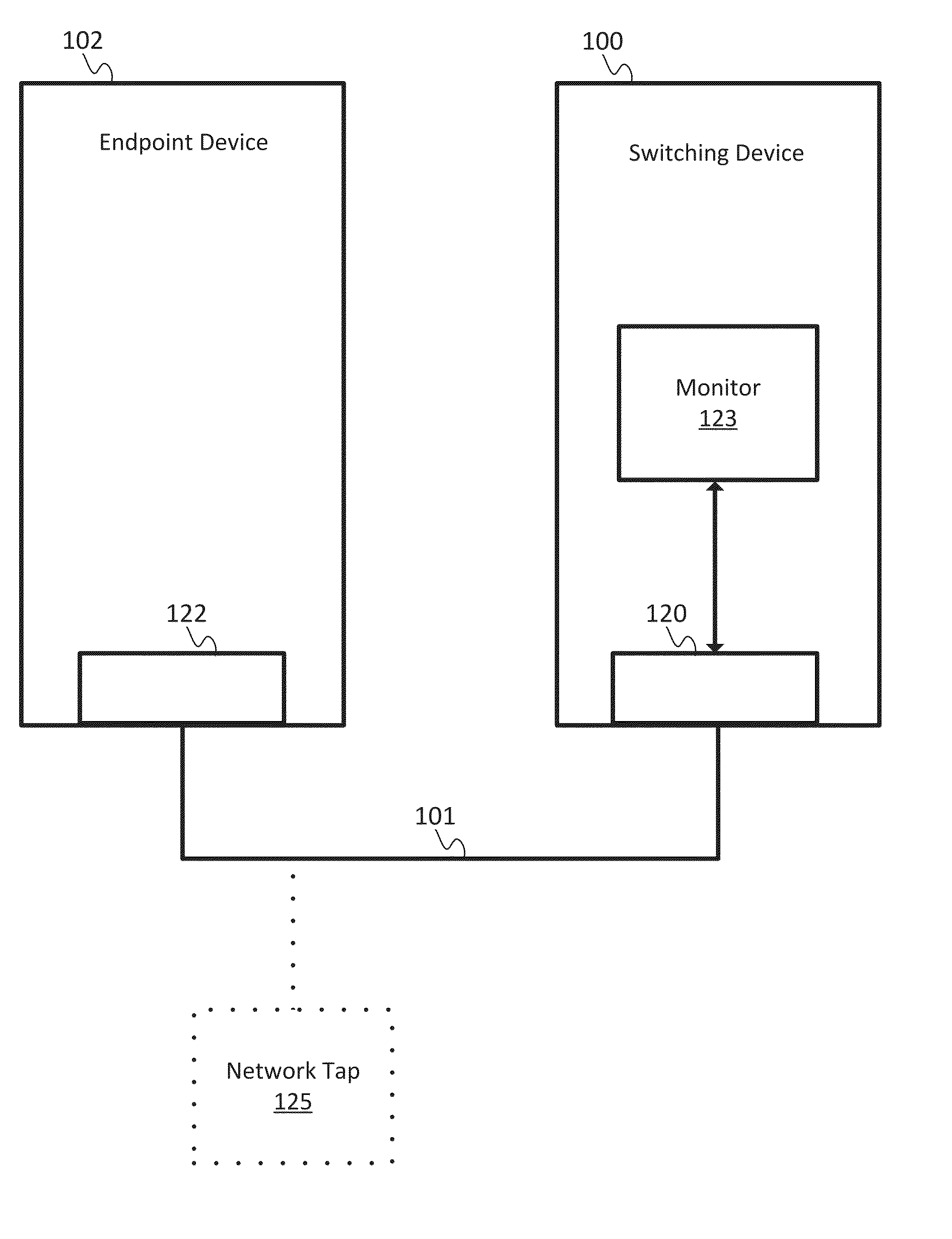
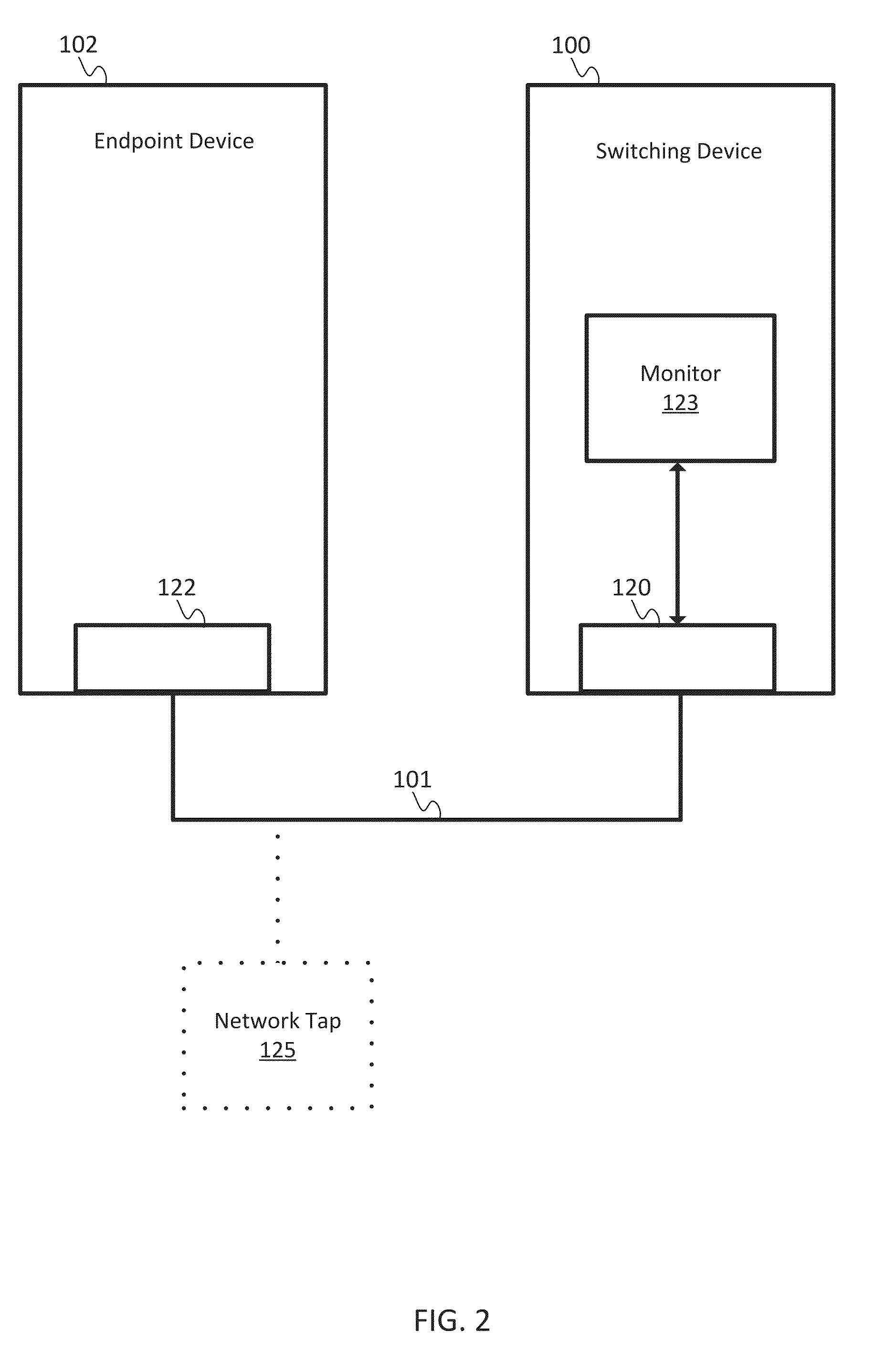
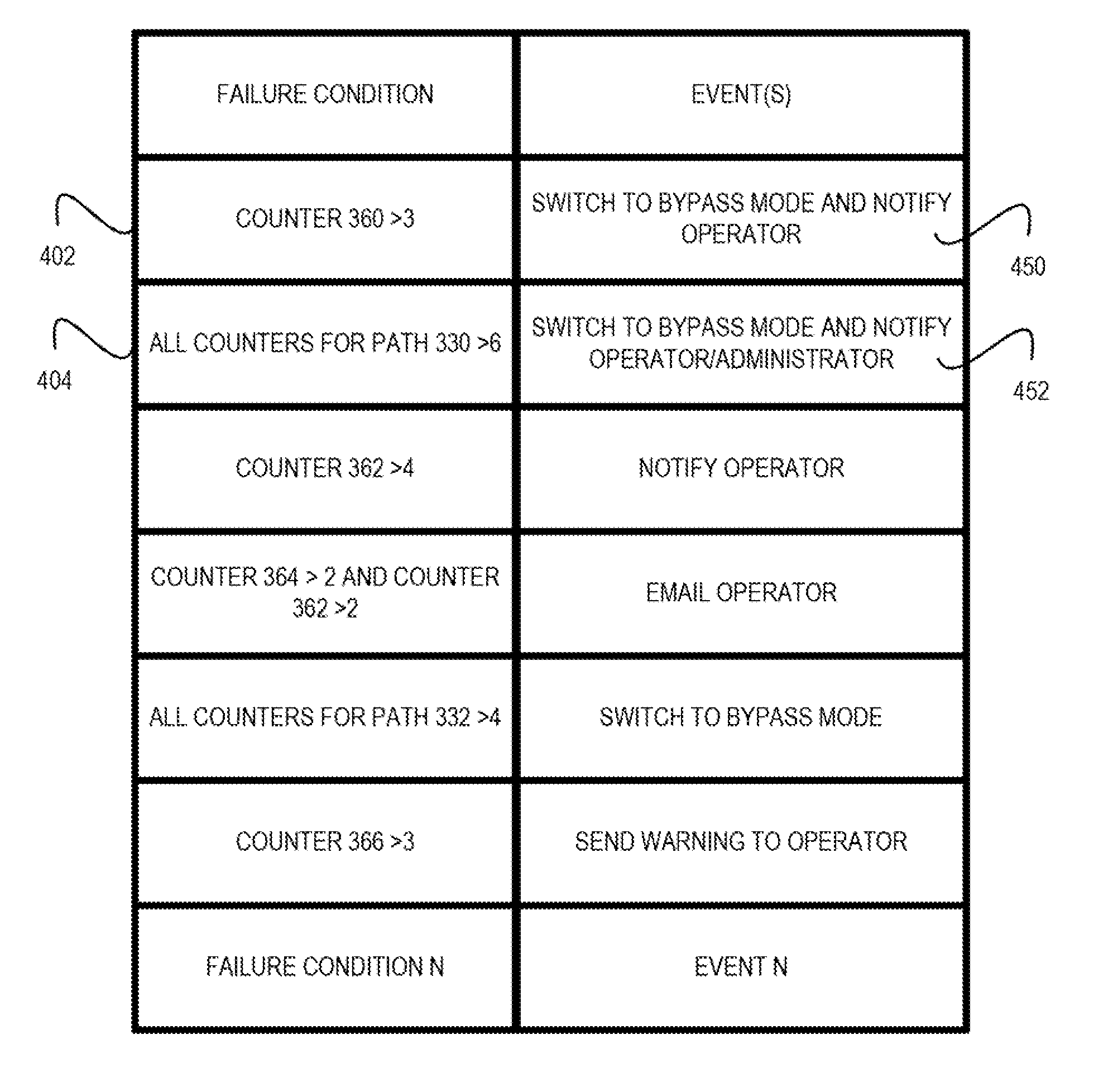
An arrangement in a network tap for monitoring state of a monitoring system is provided. The arrangement includes a set of network ports that includes a set of input network ports for receiving data traffic and a set of output network ports for outputting the data traffic from the network tap. The arrangement also includes a monitoring port that is configured to receive the data traffic from the set of network ports and to forward the data traffic onward to the monitoring system. The arrangement further includes a logic component configured for executing a sequential heartbeat diagnostic test. The sequential heartbeat diagnostic test is configured for providing a first set of sequential heartbeat packets for testing and determining the state of the monitoring system. The arrangement yet also includes a logic component for activating one or more events when a failure condition exists for the state of the monitoring system.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
System, method and apparatus for distributing captured data packets including tunneling identifiers
A network traffic distribution device (e.g., a network tap or similar device) is configured to receive and analyze captured network traffic data packets that include tunneling IDs (e.g., GTP tunneling IDs) and, based on that analysis, to distribute those data packets in such a way that data packets with the same tunneling IDs are distributed to a common egress port of the network traffic distribution device. In some cases, each flow of data packets with a common tunneling ID is sent to a unique external device, while in other cases, two or more traffic flows, each with packets having respective, common tunneling IDs may be provided to the same external device, either via a common egress port of the network traffic monitoring device or via separate egress ports thereof.
Owner:NETSCOUT SYSTEMS
Network tap device powered by power over ethernet
ActiveUS7809960B2Improvement in reliability and operationImpair operation of networkMechanical power/torque controlLevel controlNetwork tapMonitor equipment
A network tap device that is configured for operation in a copper Gigabit Ethernet communications network using a power-over-Ethernet (“POE”) electrical supply is disclosed. In one embodiment, a network tap device powered by a POE supply is disclosed, comprising first and second network ports that are configured with receptacles for receiving communication cables. The communication cables are configured to carry both data signals and the POE supply to and from the network tap device. The network tap device further includes first and second tap ports that connect with additional communication cables to a monitoring device. The network tap device also includes control and regulation circuitry that is configured to receive the POE supply from the communication cables via the network ports and to enable components of the network tap device to be operated by the POE supply.
Owner:VIAVI SOLUTIONS INC
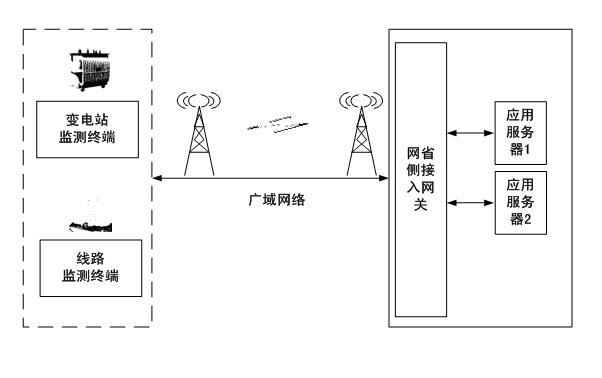
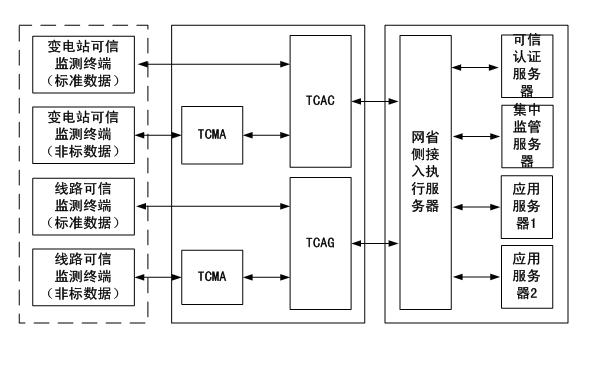
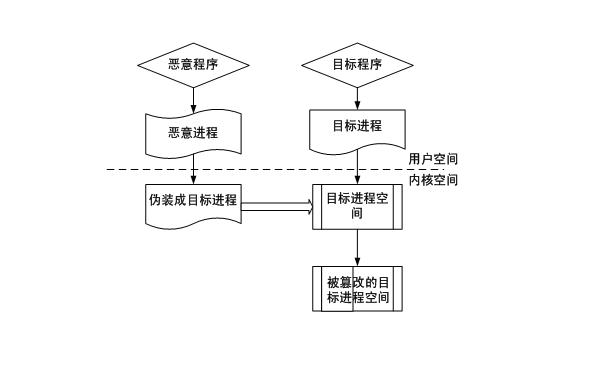
Power transmission and transformation equipment state monitoring system security protection method based on trust chain transmission
Owner:STATE GRID ELECTRIC POWER RES INST
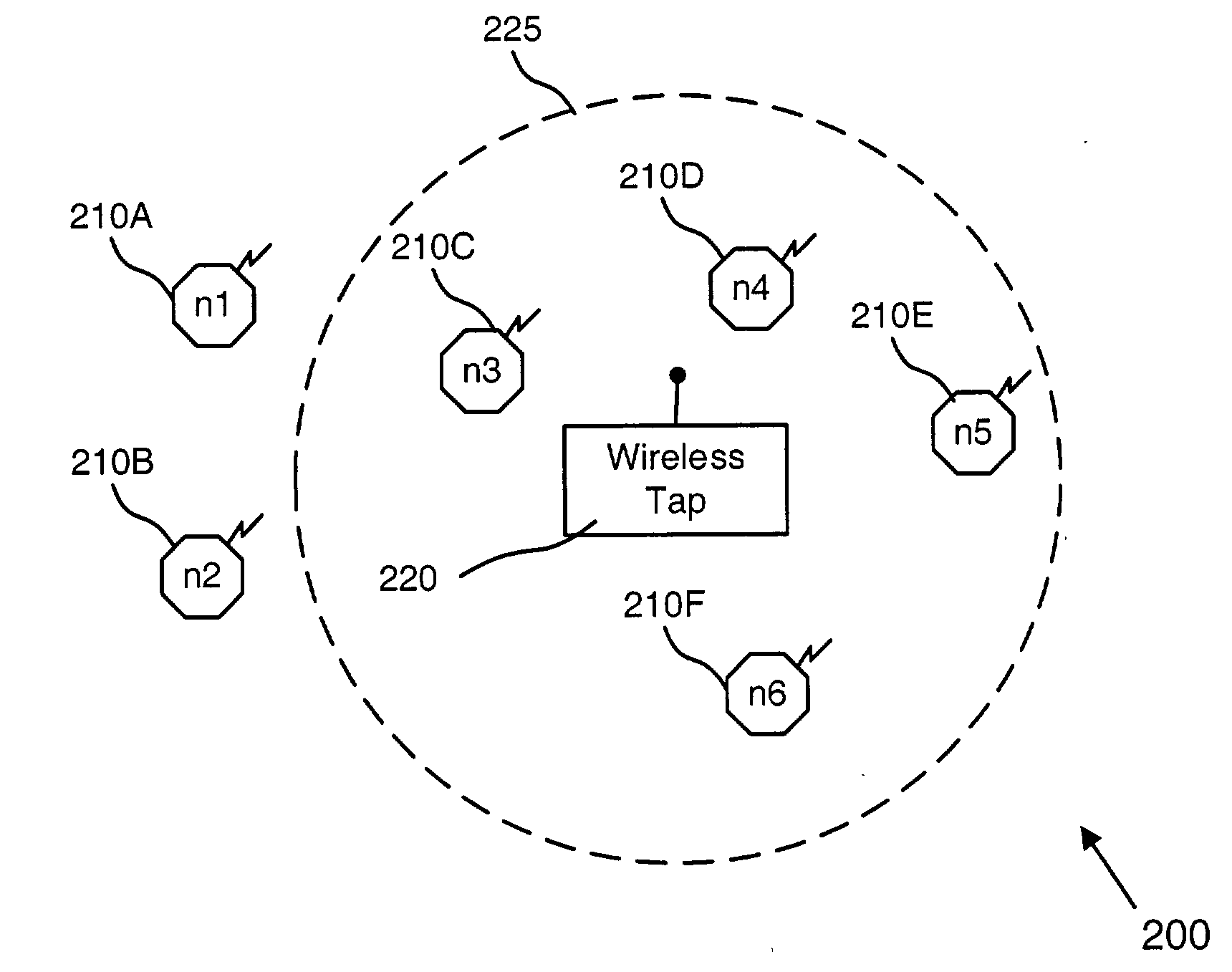
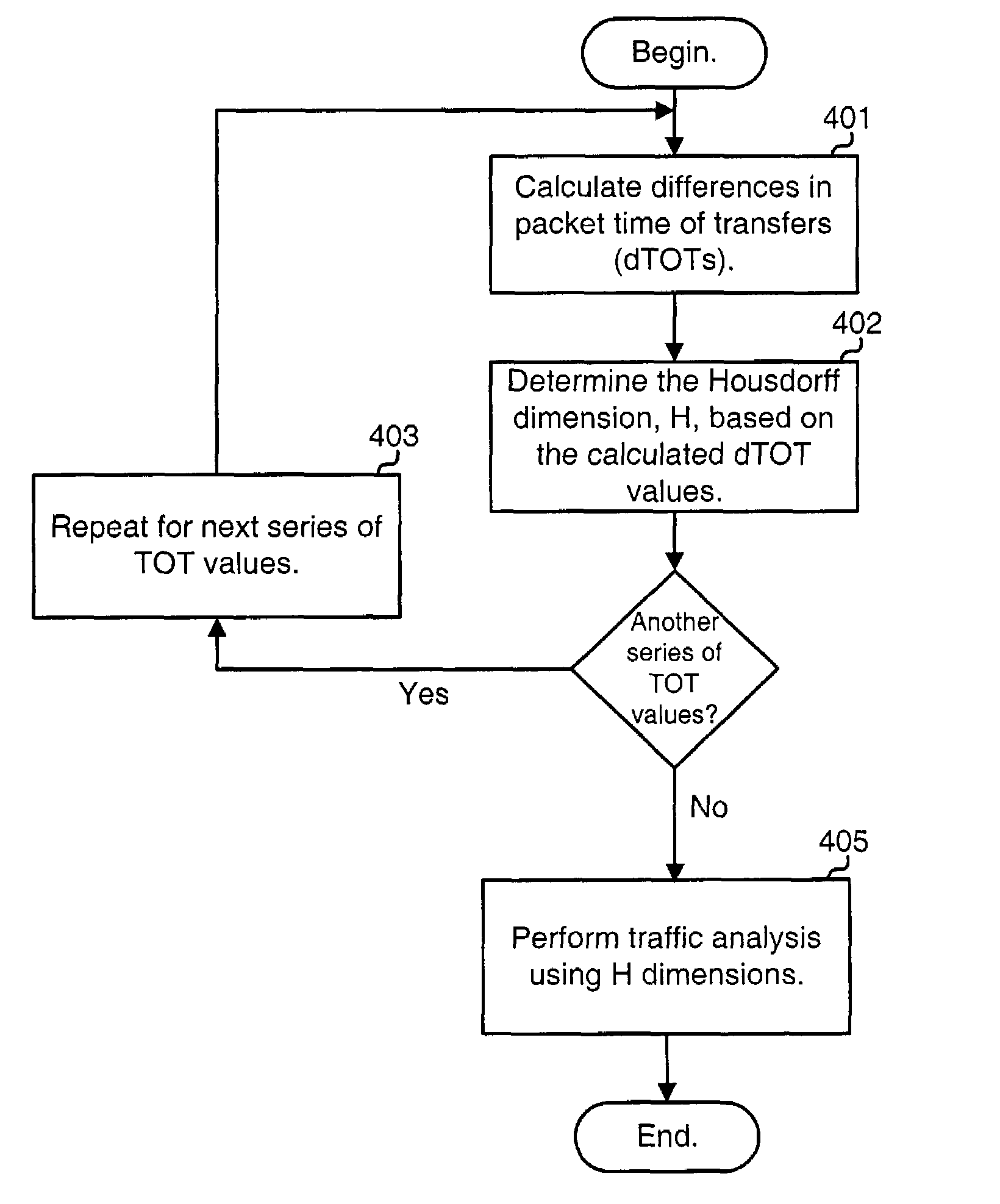
Fractal dimension analysis for data stream isolation
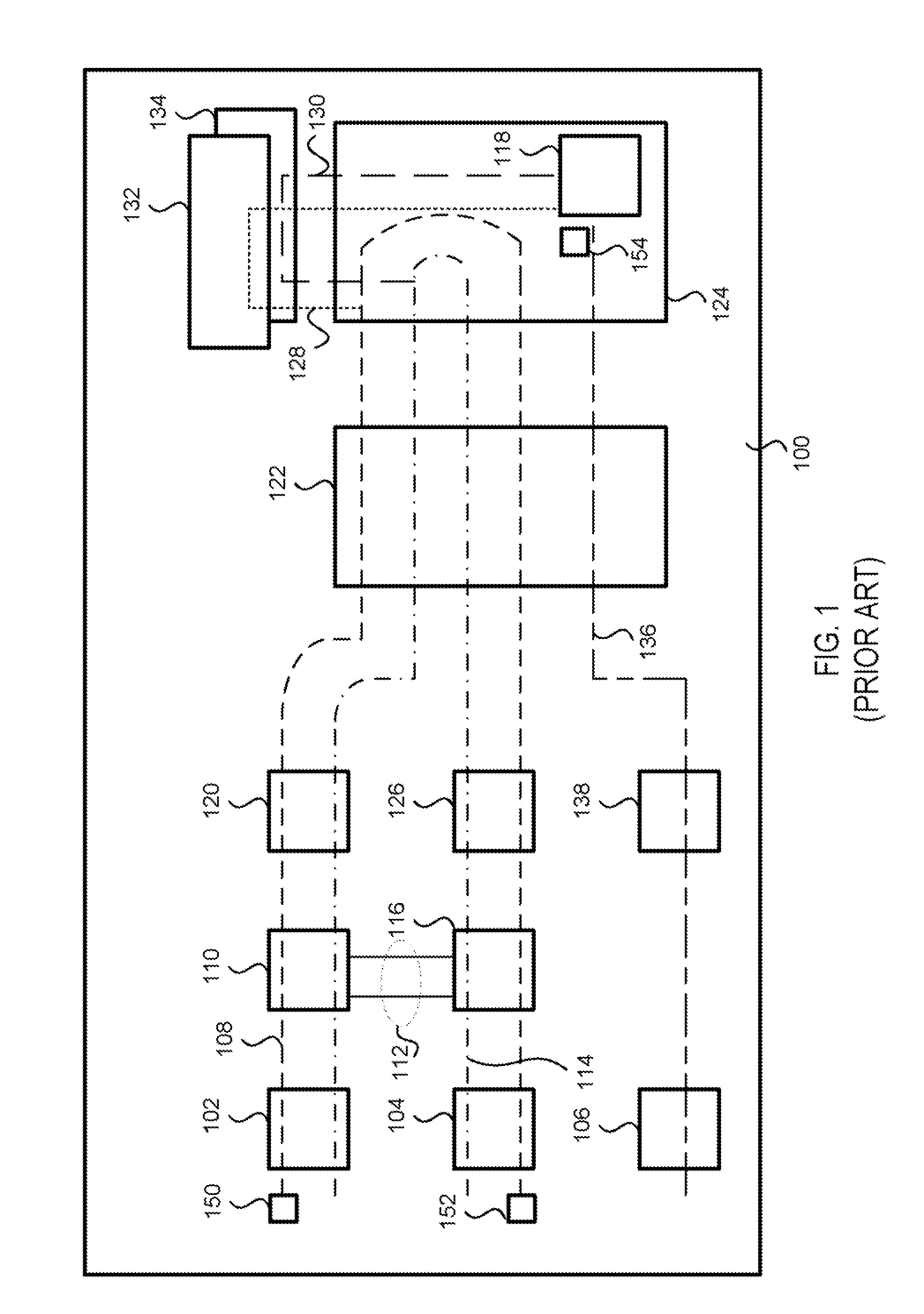
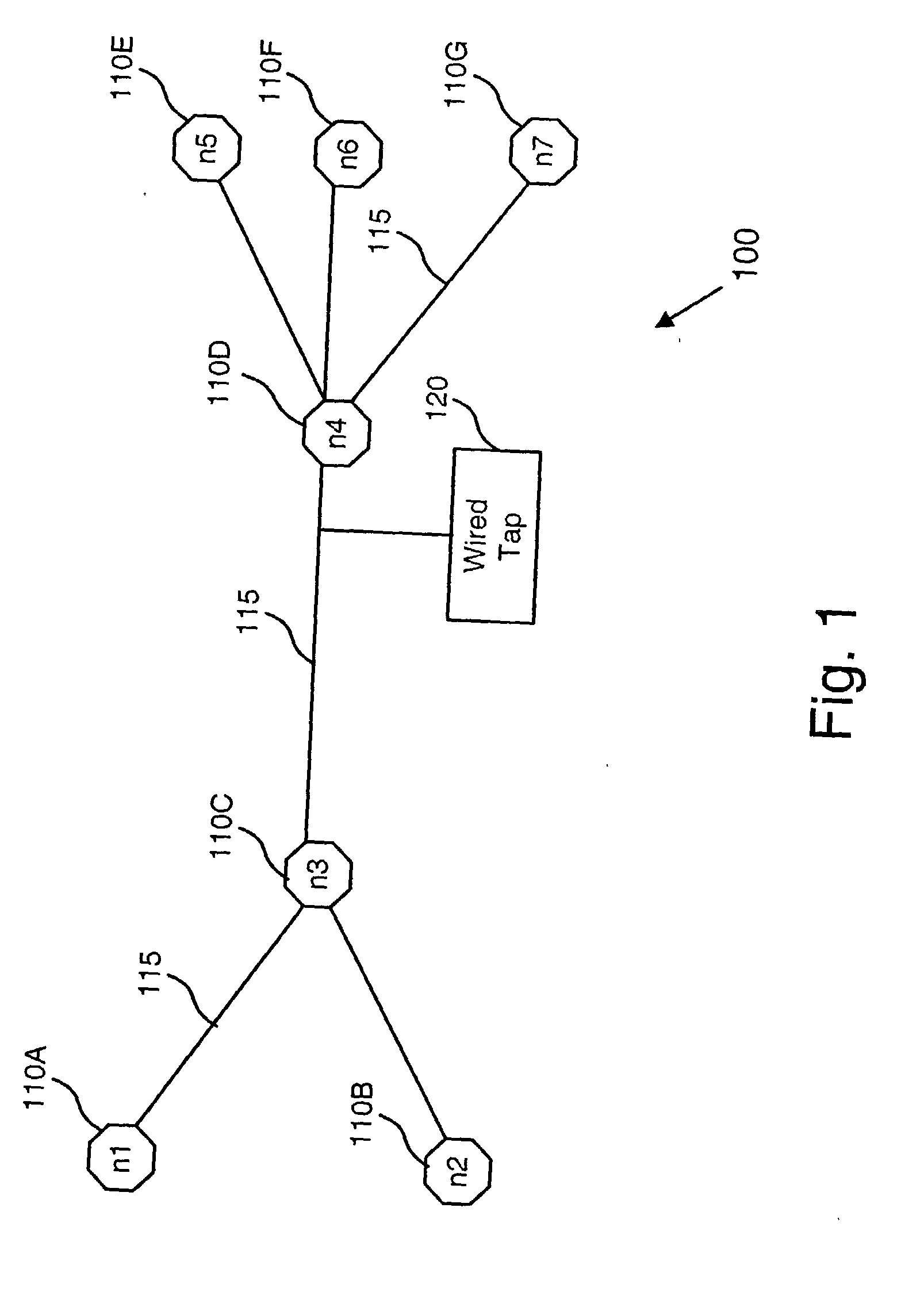
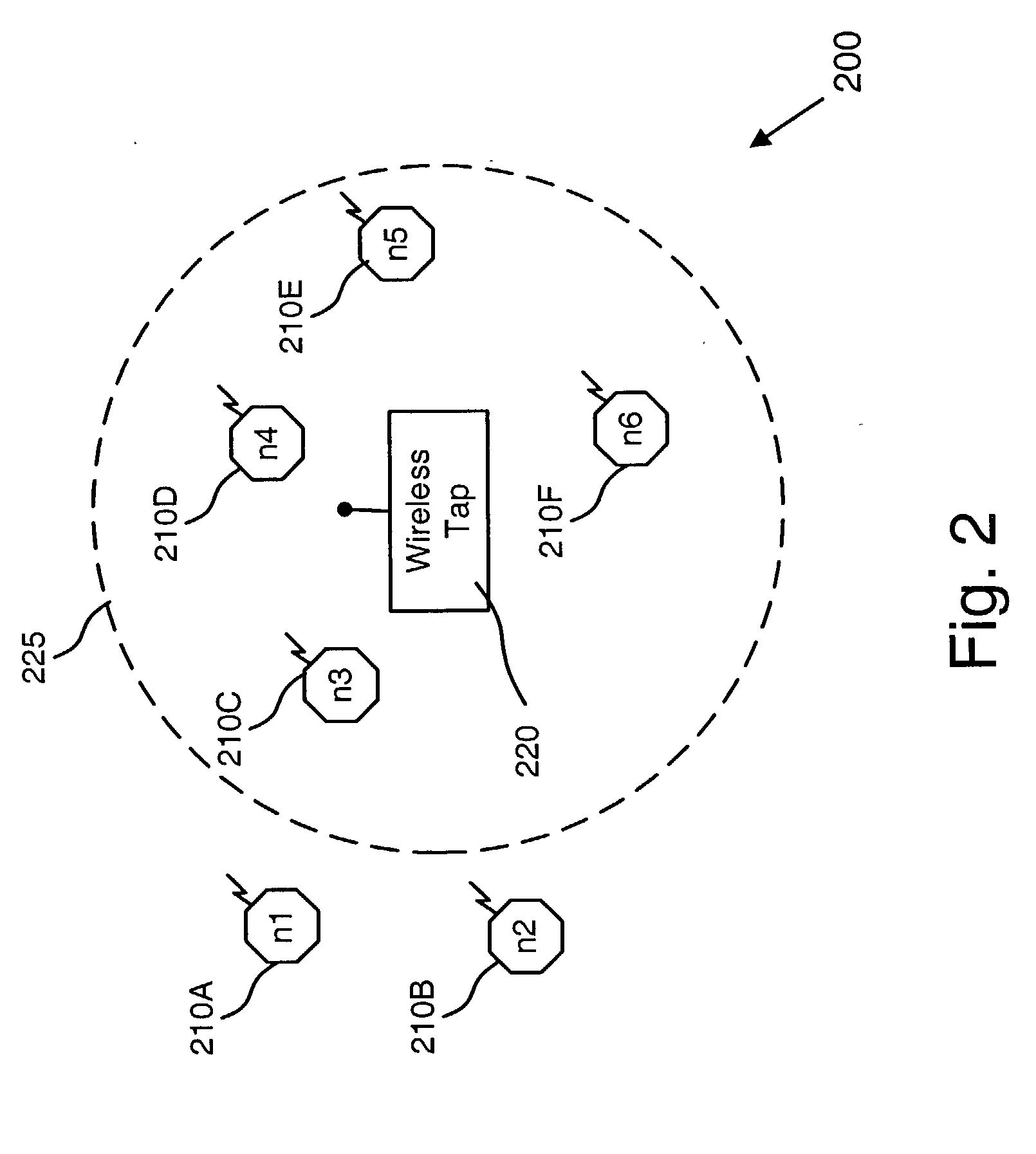
A network tap [120 / 220] monitors traffic transmissions in a network [100 / 200]. The tap records transmission time information [501] between data transmitted in the network. From the transmission time information, the tap calculates differences in transmission times [500], and assumes the differences in transmission times are distributed as fractional gaussian noise. Housdorff dimensions are calculated for the fractional gaussian noise distributions. The Housdorff dimensions are used to generate traffic analysis information for the network, even when the data transmitted on the network is encrypted.
Owner:RAYTHEON BBN TECH CORP
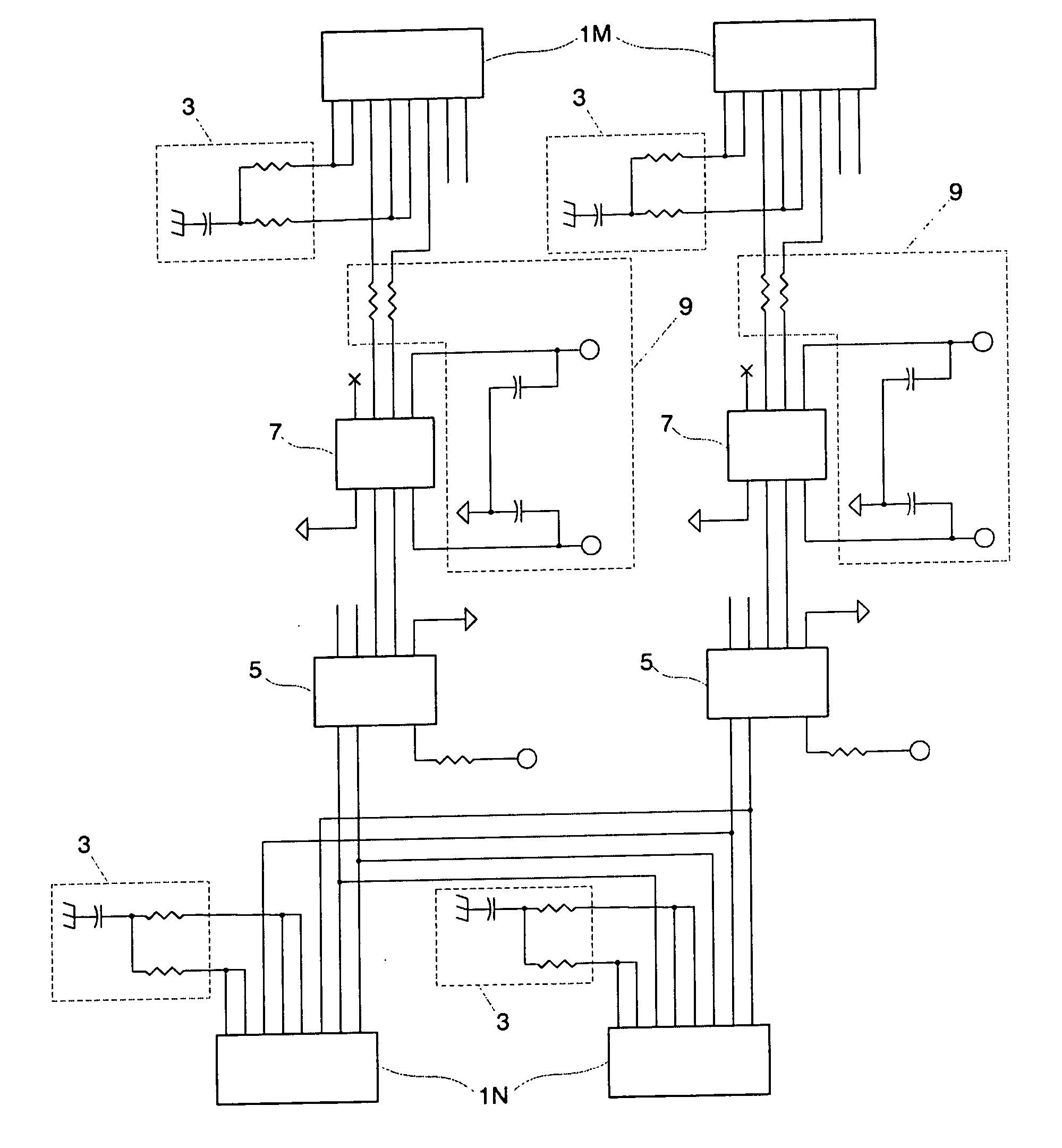
Adjustable circuit device and voltage measuring device
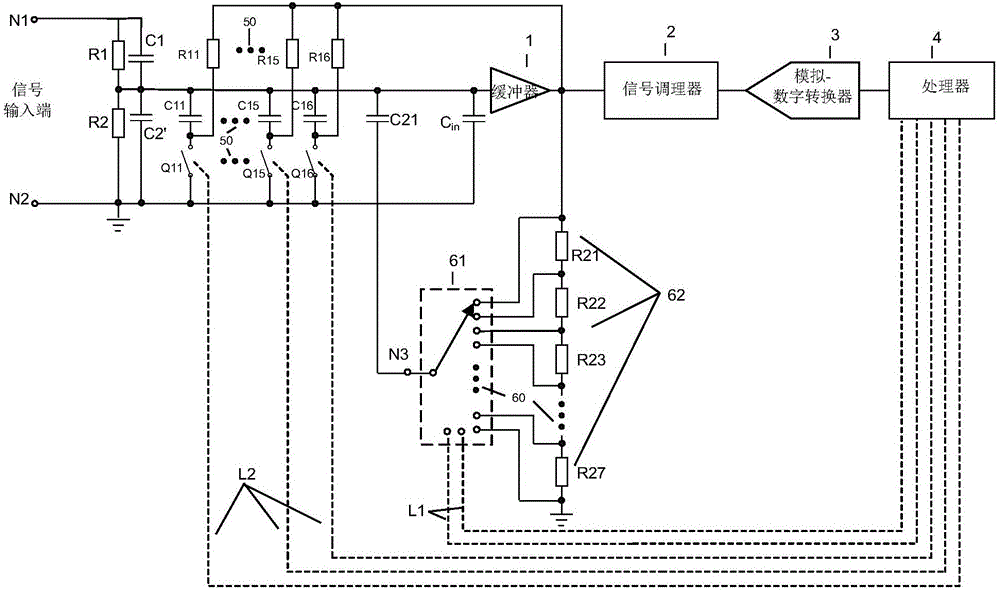
ActiveCN106353549ARealize inputRealize automatic adjustmentVoltage dividersVoltage measurements onlyCapacitanceControl signal
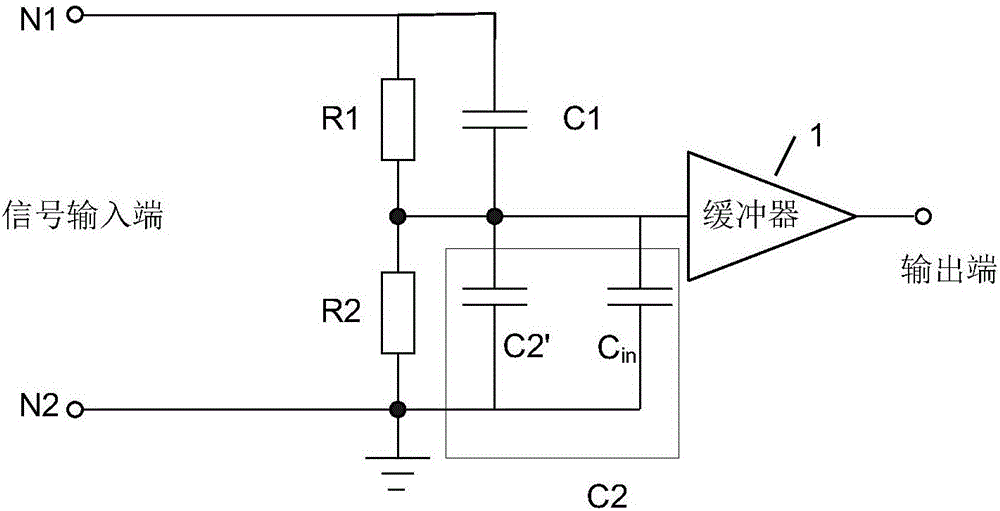
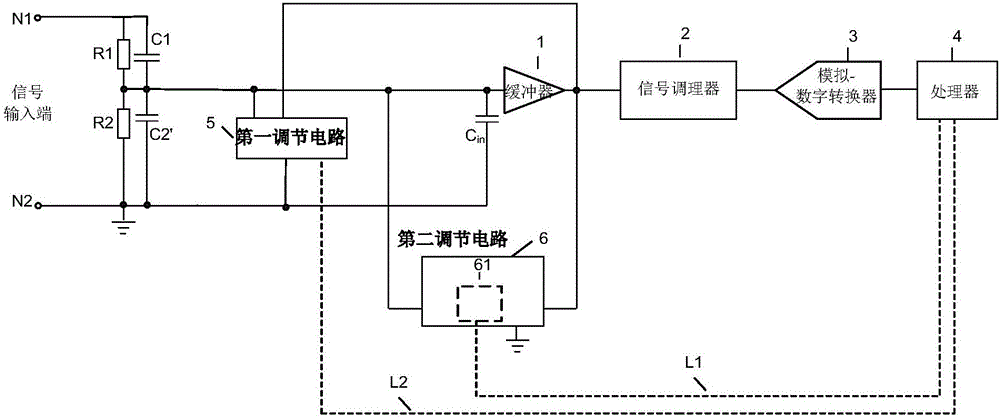
The invention provides an adjustable circuit device, comprising a first adjustment circuit, a second adjustment circuit, a signal conditioner, an analog-to-digital converter and a processor, wherein the processor receives the output signal converted by the signal conditioner and the analog-to-digital converter and analyzes the digital signal according to the pre-set rules; the equivalent capacitance of the first adjustment circuit is adjusted by the transmission of the control signal to control the opening and closing state of each switch in the first regulating circuit to realize the input or the cut of the adjustable capacitor according to the analysis result; and the fixed capacitance is simulated into an adjustable capacitance by controlling the gear connection state of the multiplexer in the second adjustment circuit, changing the connected voltage divider resistor network tap position so as to adjust the voltage across the fixed capacitor. The device realizes the automatic adjustment of the partial voltage capacitance through the program control, can reduce the human input and greatly improves the working efficiency.
Owner:广州致远仪器有限公司
Fractal dimension analysis for data stream isolation
Owner:RAYTHEON BBN TECH CORP
Enhanced communication network tap port aggregator arrangement and methods thereof
An arrangement in a network device for facilitating at least one of multiple connection speeds with a network, active response between a monitoring device and an end-device, and power over Ethernet (POE) over a network is provided. As a facilitator of multiple connection speeds, the arrangement includes a plurality of physical layer interface (PHY) and media access controller (MAC) that are configured to support multiple speeds. As a facilitator of active response, the arrangement includes a logic arrangement for multicasting a set of instructions that is sent from a monitoring port. As a facilitator of POE, the arrangement is configured to receive data traffic (e.g., data packets and / or power packets) through a first network port and to send the data traffic out a second network port.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Intelligent fast switch-over network tap system and methods
ActiveUS7936685B2Effective maintenanceAvoiding wider networkError preventionTransmission systemsCross connectionNetwork tap
An intelligent fast switch-over network active tap system enables active monitoring of a network segment connected between network devices. A fail-safe relay subsystem is coupled between a pair of network ports, enabling transmission of network communications signals through a passive cross-connect between the network ports or through an active bridge subsystem. The active bridge subsystem is capable of independently establishing network links with the network devices, and a separate network link with a monitoring device. A controller manages operation of the relay and active bridge subsystems, including switches between passive and active network transmission through the tap system and to determine and establish the active network links subject to symmetric network link parameters and state. Thereby, the network link status of the connected network devices is preserved on switch between active and passive transmission and correctly reflected in the presence of link and power failures.
Owner:NETSCOUT SYSTEMS
Network tap with interchangeable ports
InactiveUS7613837B2Function increaseEliminate needMultiple digital computer combinationsTransmissionTraffic capacityNetwork tap
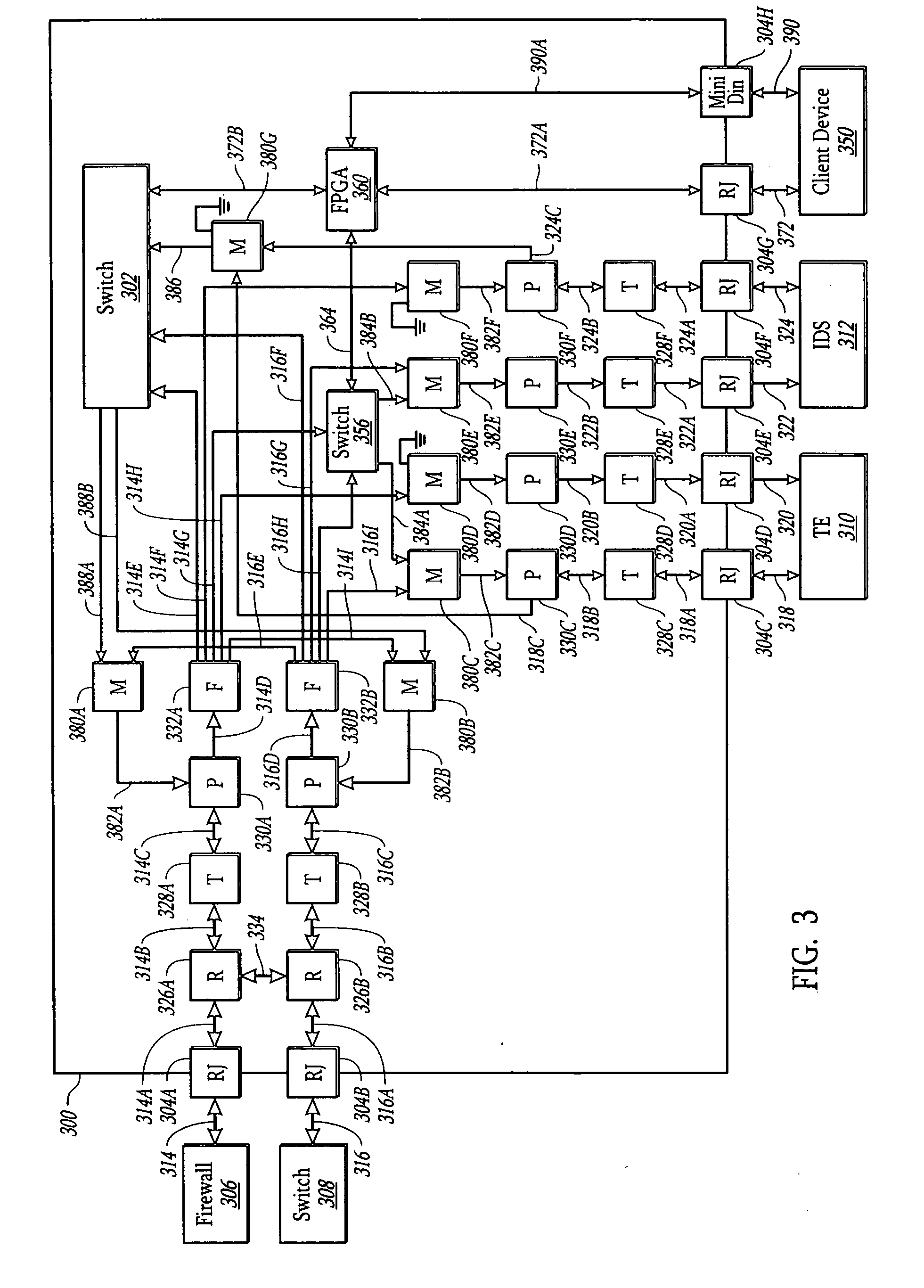
A network tap for enabling attached devices, such as an intrusion detection system, to transmit information into a communication line of the network without disrupting the network traffic on the communication line. When the attached device is an intrusion detection device, the network tap is connected to a firewall. An Ethernet switch or field programmable gate array (FPGA) is incorporated in the network tap to coordinate the transmission of device data to avoid data collisions with data transmissions already existing in the communication line. The network tap may be operated in various modes to accommodate different capabilities of attached devices. In addition, the network tap has various port configurations to allow a user to connect various attached devices through a single cable or dual cables.
Owner:VIAVI SOLUTIONS INC
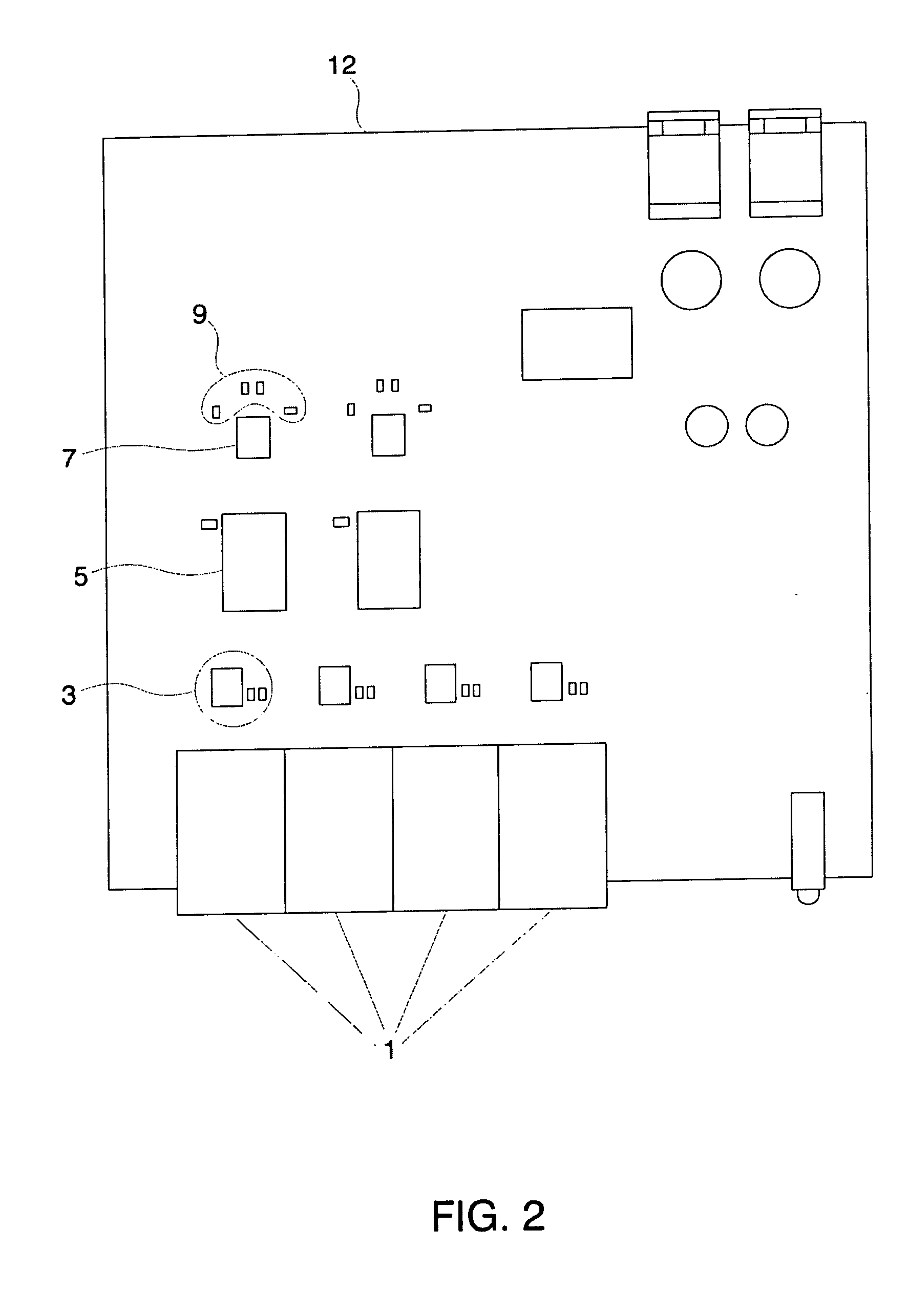
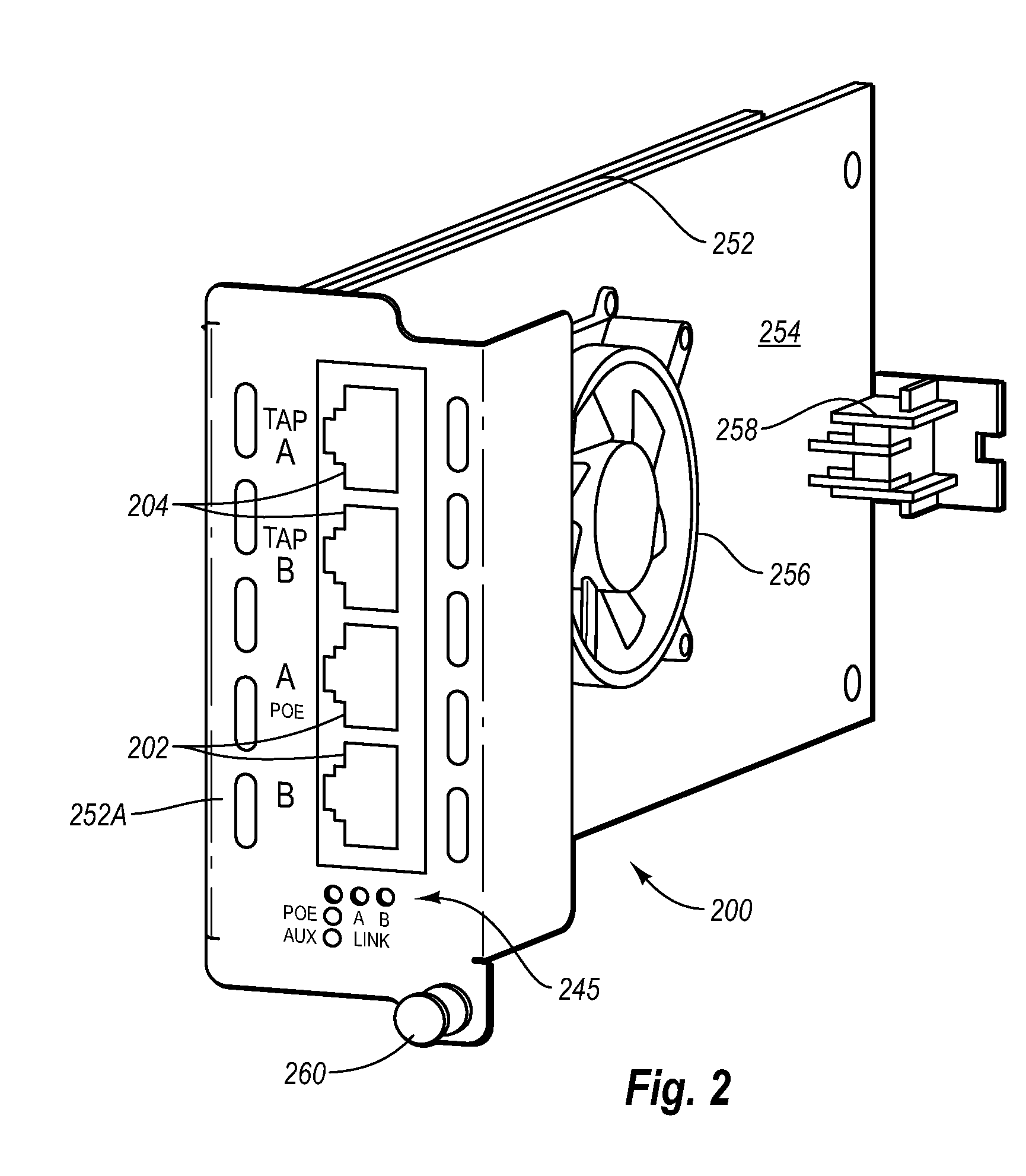
Displaceable card guide for high packing ratio housings
ActiveUS6976859B2Raise the ratioImprove usabilityEngagement/disengagement of coupling partsFibre mechanical structuresNetwork tapComputer module
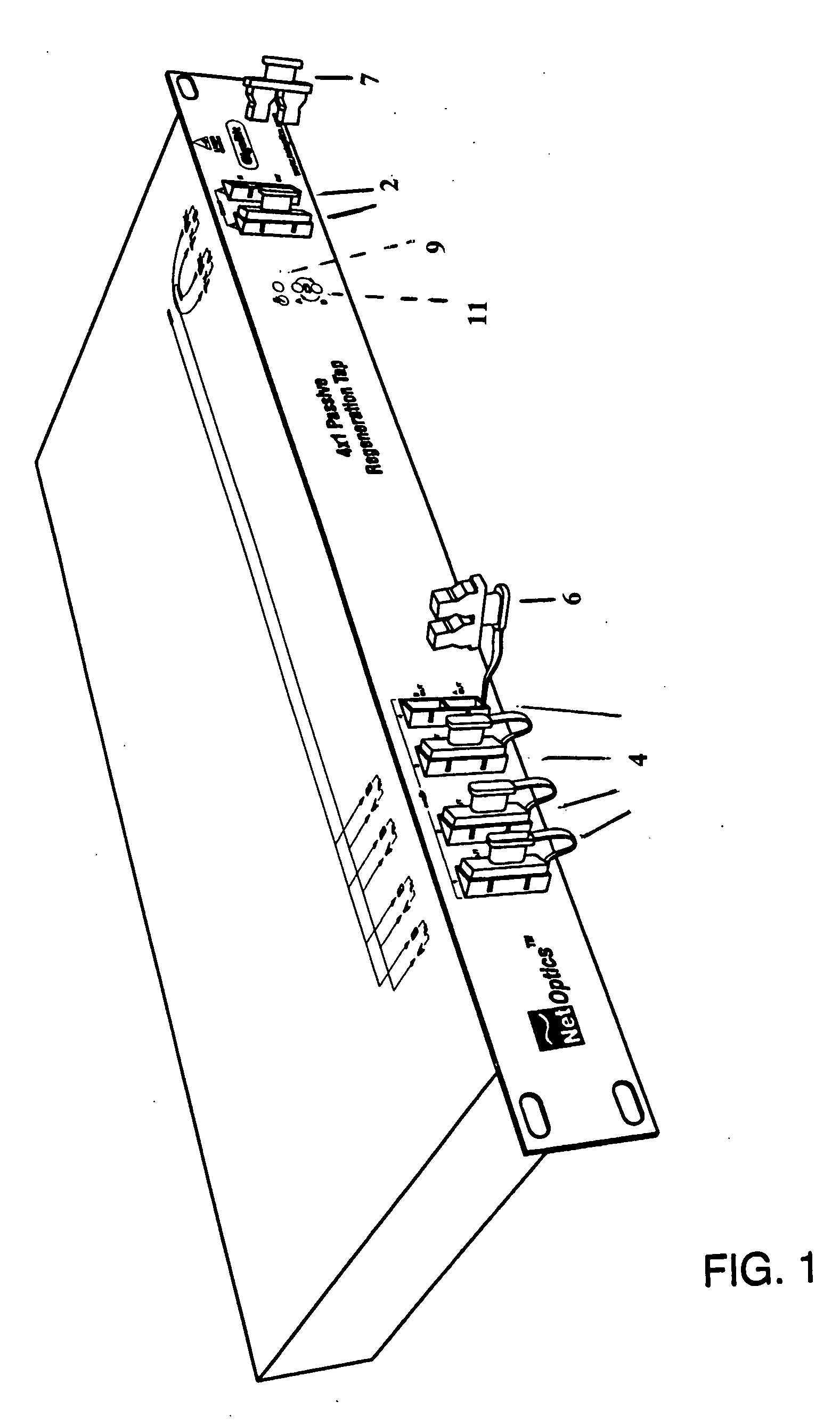
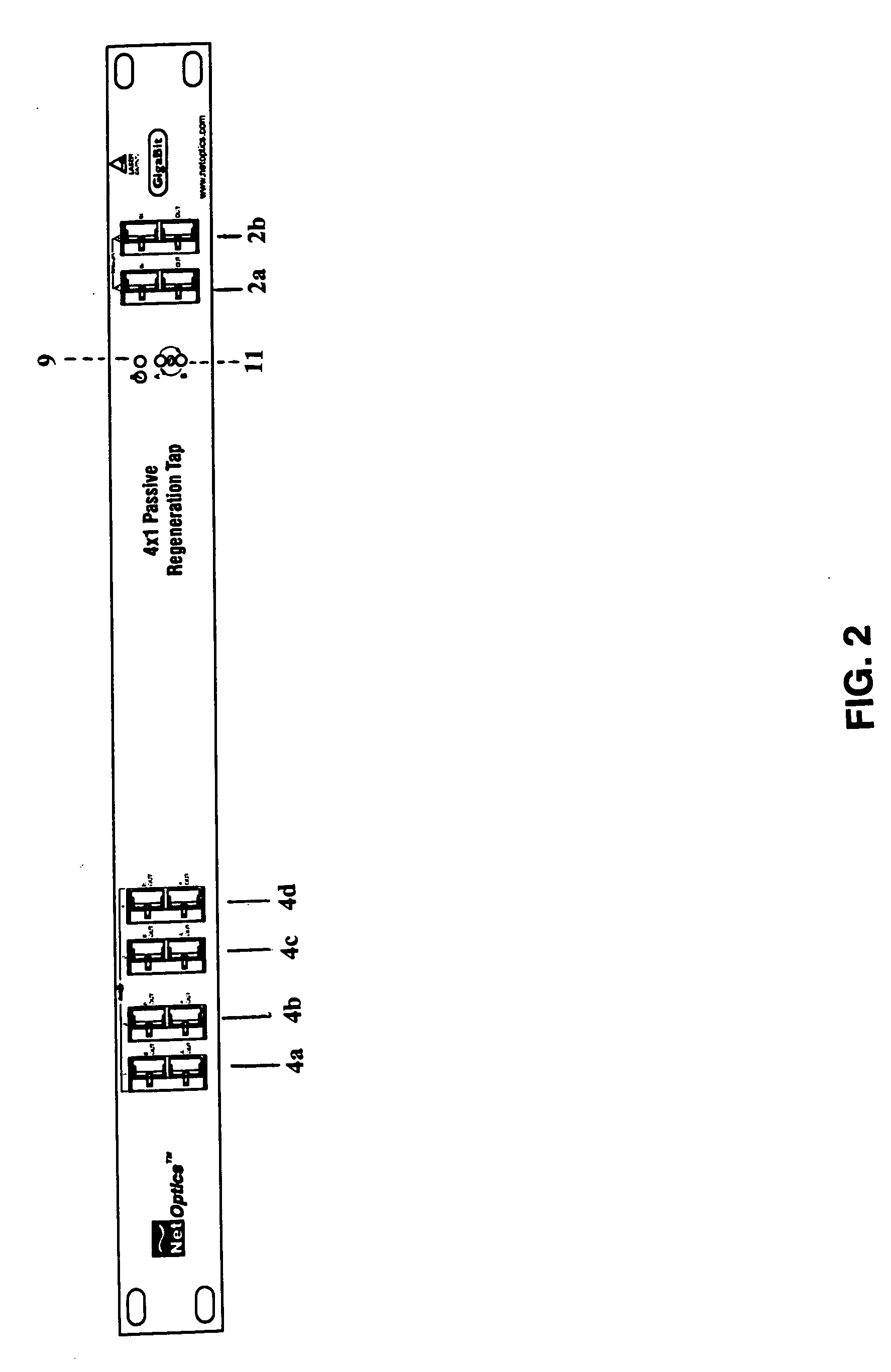
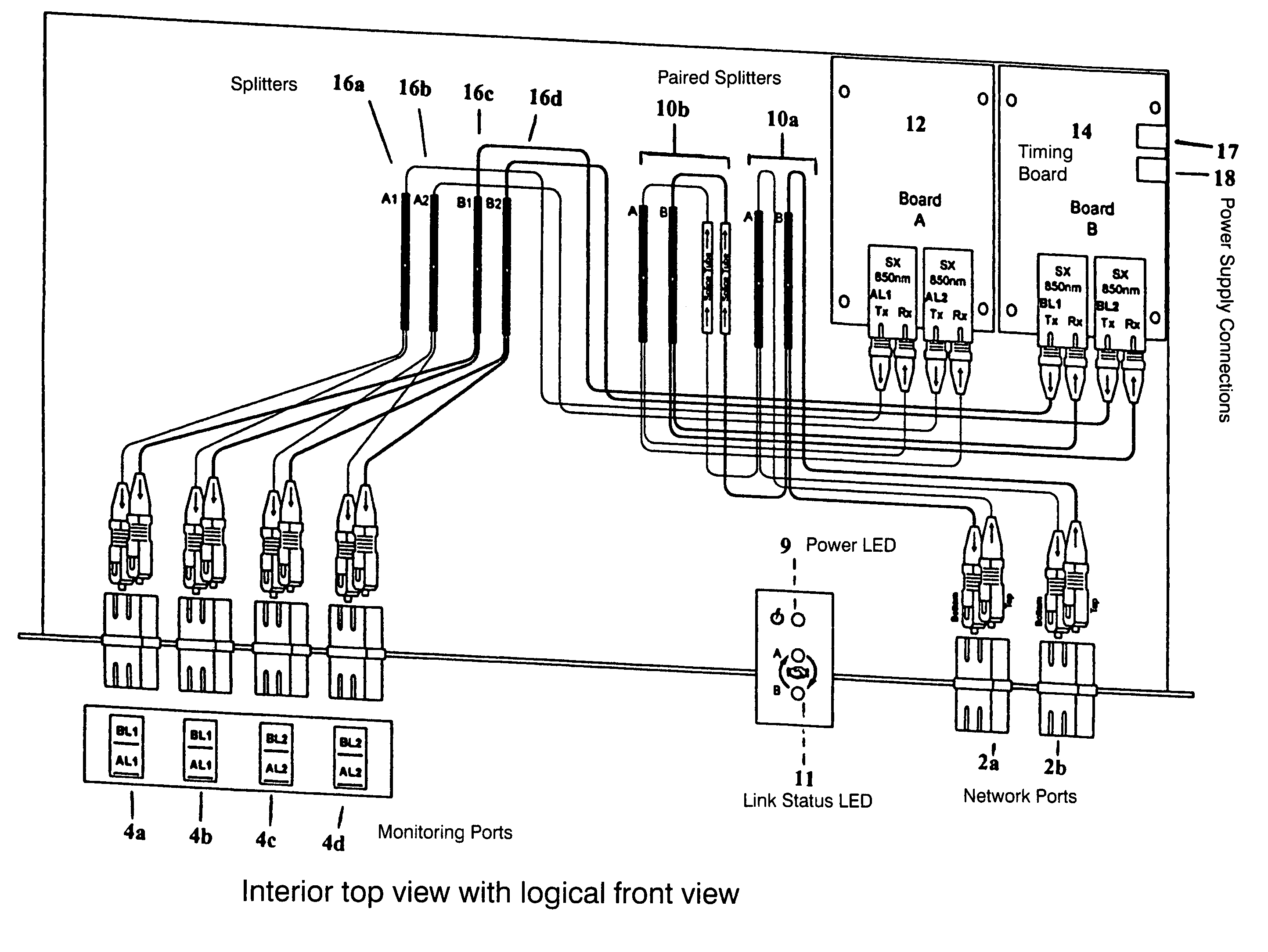
Displaceable card guides for use with high packing ratio housings for network tap modules. The housing allows the user to maintain all network taps in any given system in one housing and location. This increases the ease of maintaining multiple network taps and allows the network tap modules to be powered by a power supply included with the housing. The displaceable card guides enable a set network tap modules to be housed in a single housing with negligible or no spacing between adjacent modules. In addition, these card guides the associated housing are generally applicable to a number of other types of modular electrical or optical components.
Owner:VIAVI SOLUTIONS INC
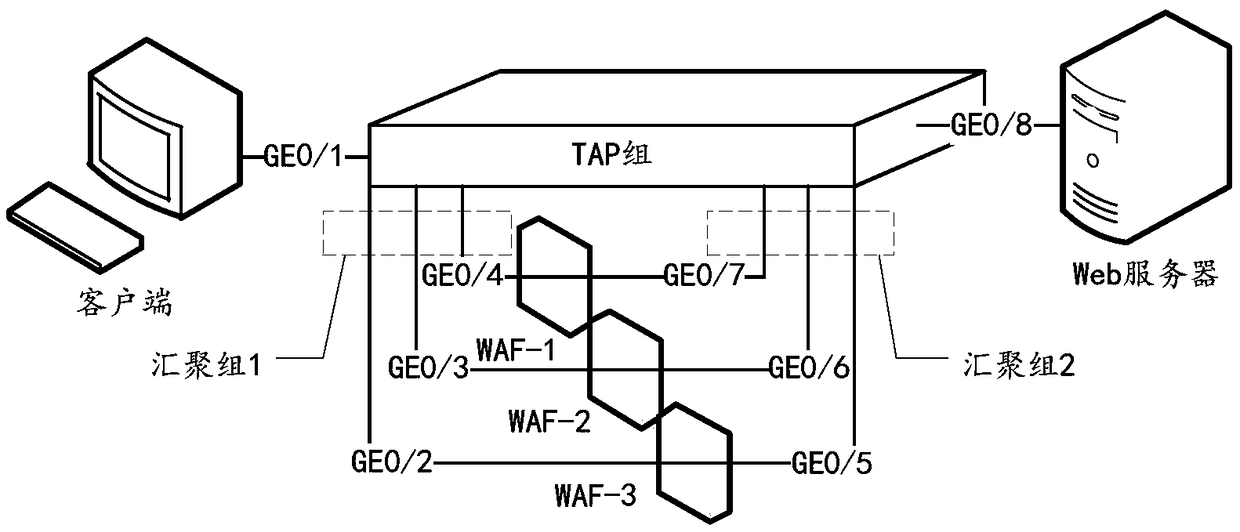
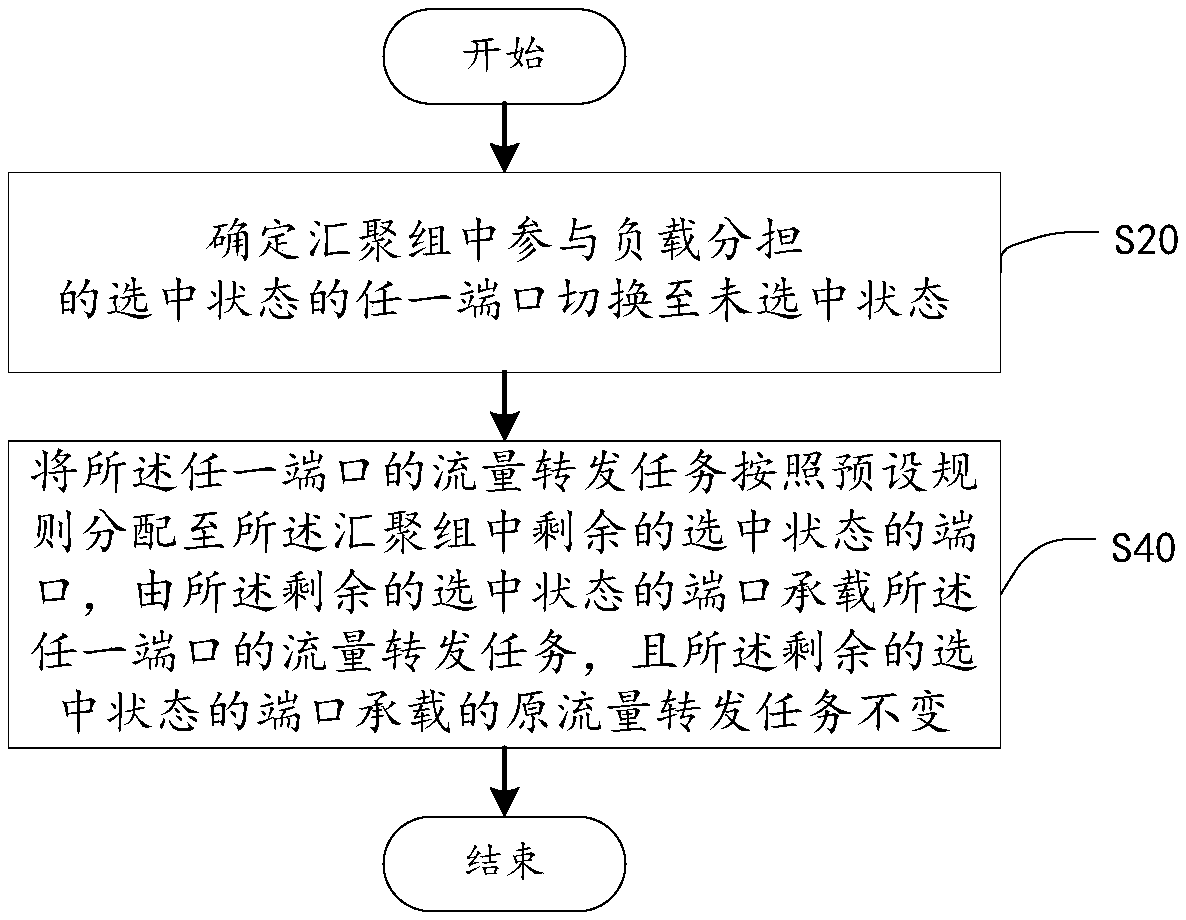
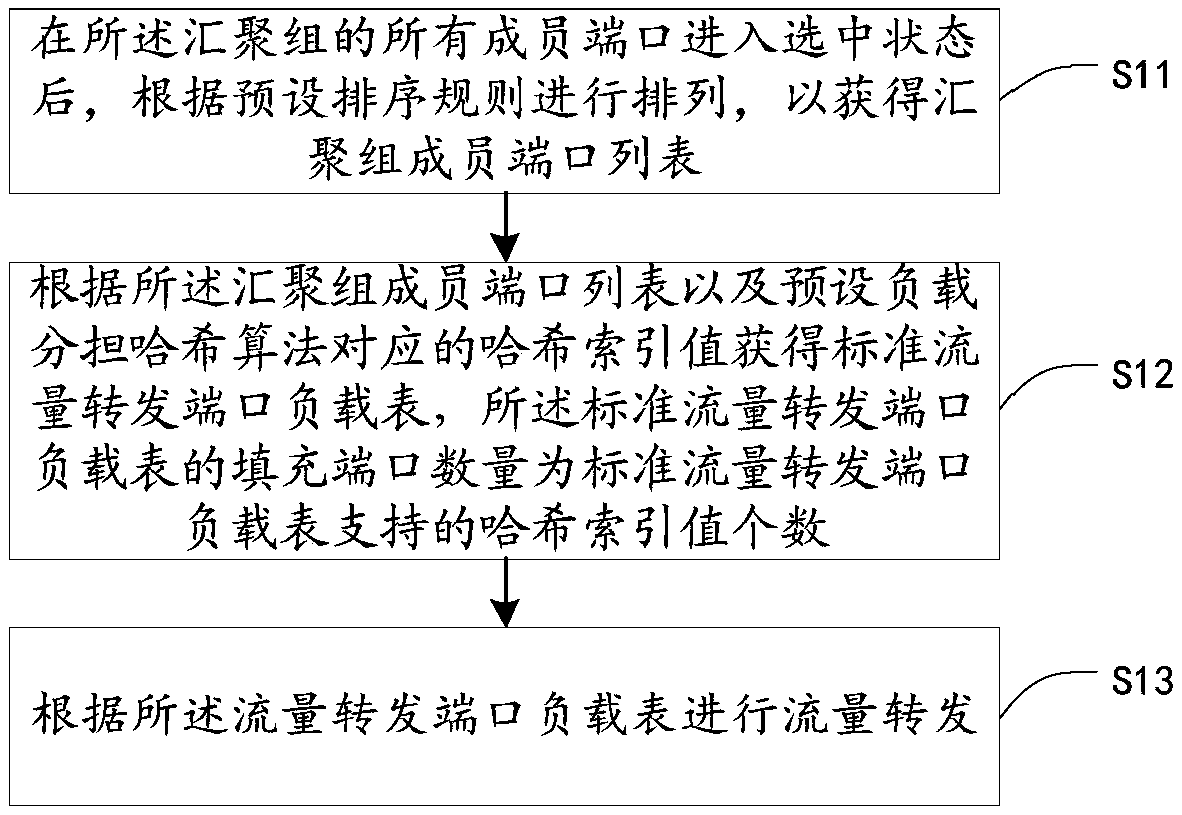
Load adjustment method, and load adjustment network tap
InactiveCN108965156AGuaranteed validityAvoid influenceData switching networksTraffic capacityNetwork tap
The embodiment of the invention belongs to the technical field of communication, and provides a load adjustment method and device. The load adjustment method comprises the following steps: determiningthat any port in an aggregation group that participates in load sharing is switched to an unselected status; and allocating traffic forwarding tasks of the port to other ports in the aggregation group, so that the traffic forwarding tasks can be carried out by the other ports in turn. The load adjustment method has the advantages that the traffic forwarding tasks are carried out by the ports other than the port in the unselected status in turn, and original traffic forwarding tasks of the other ports are not changed, so that load adjustments can be carried out after a status change to the port in the aggregation group without changes to the original traffic forwarding tasks of the other ports, and high traffic load consistency among the ports and the effect of ''same-origin and same-destination first'' can be further maintained.
Owner:MAIPU COMM TECH CO LTD
Sequential heartbeat packet arrangement and methods thereof
An arrangement in a network tap for monitoring state of a monitoring system is provided. The arrangement includes a set of network ports that includes a set of input network ports for receiving data traffic and a set of output network ports for outputting the data traffic from the network tap. The arrangement also includes a monitoring port that is configured to receive the data traffic from the set of network ports and to forward the data traffic onward to the monitoring system. The arrangement further includes a logic component configured for executing a sequential heartbeat diagnostic test. The sequential heartbeat diagnostic test is configured for providing a first set of sequential heartbeat packets for testing and determining the state of the monitoring system. The arrangement yet also includes a logic component for activating one or more events when a failure condition exists for the state of the monitoring system.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
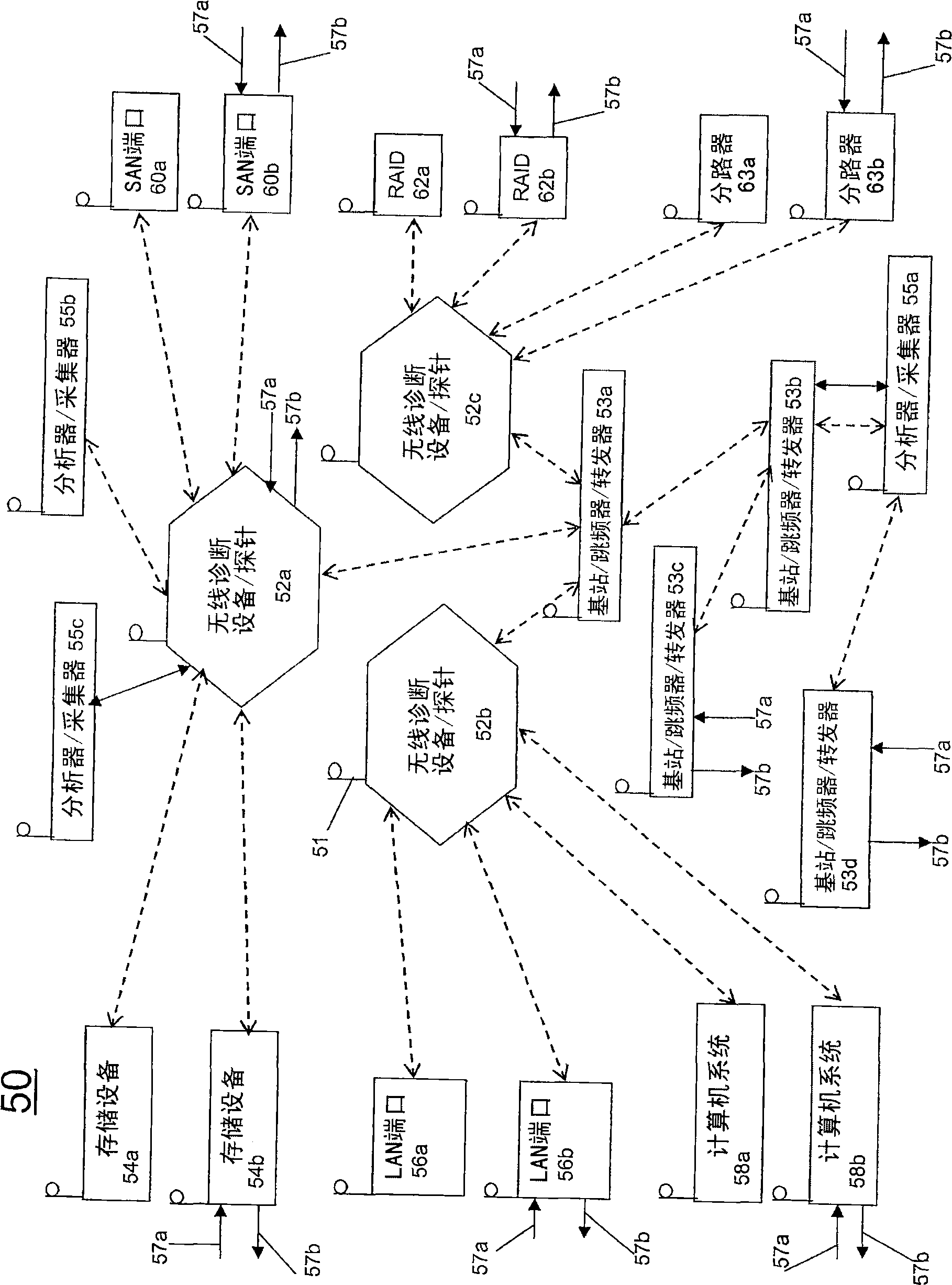
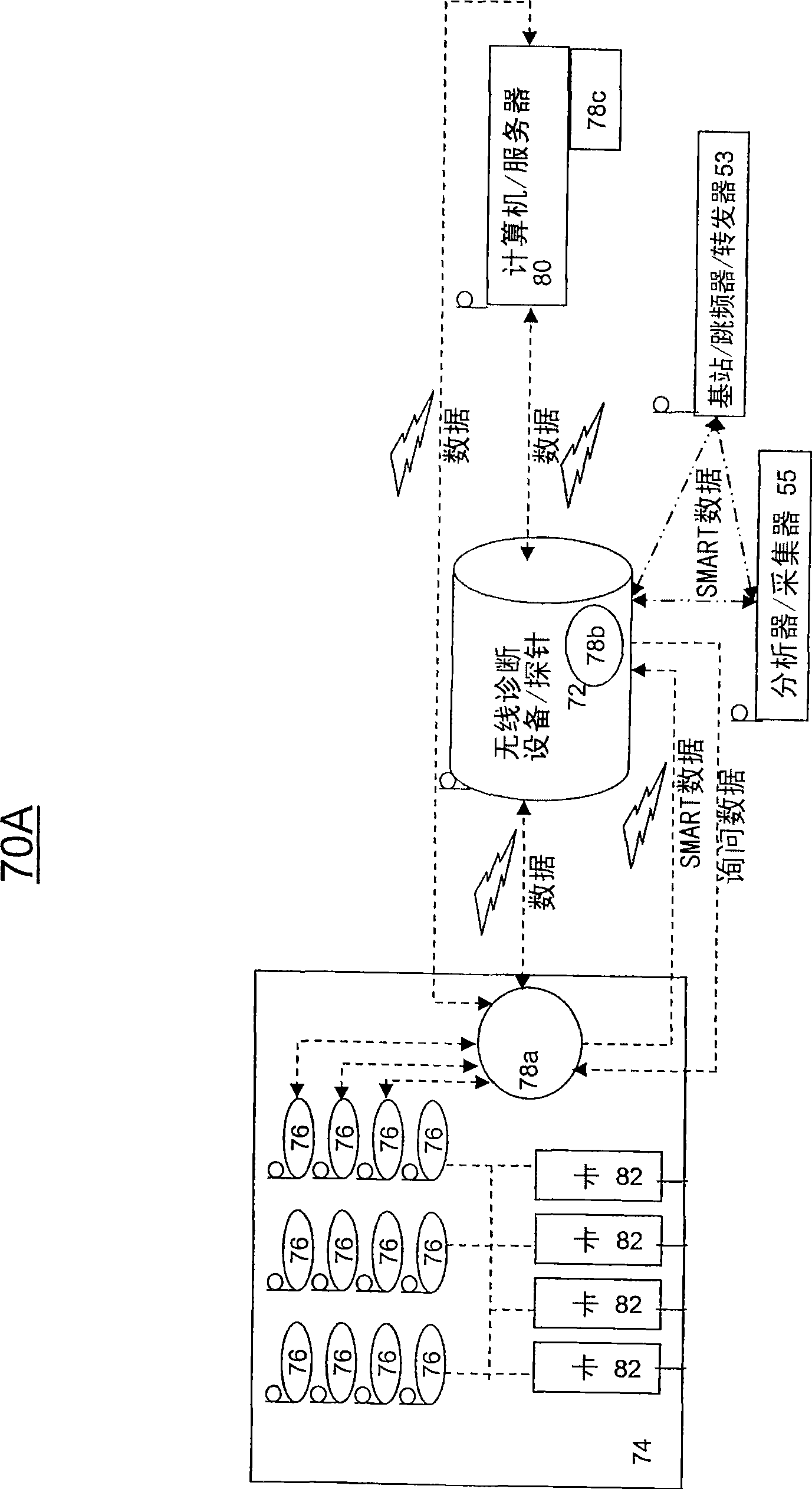
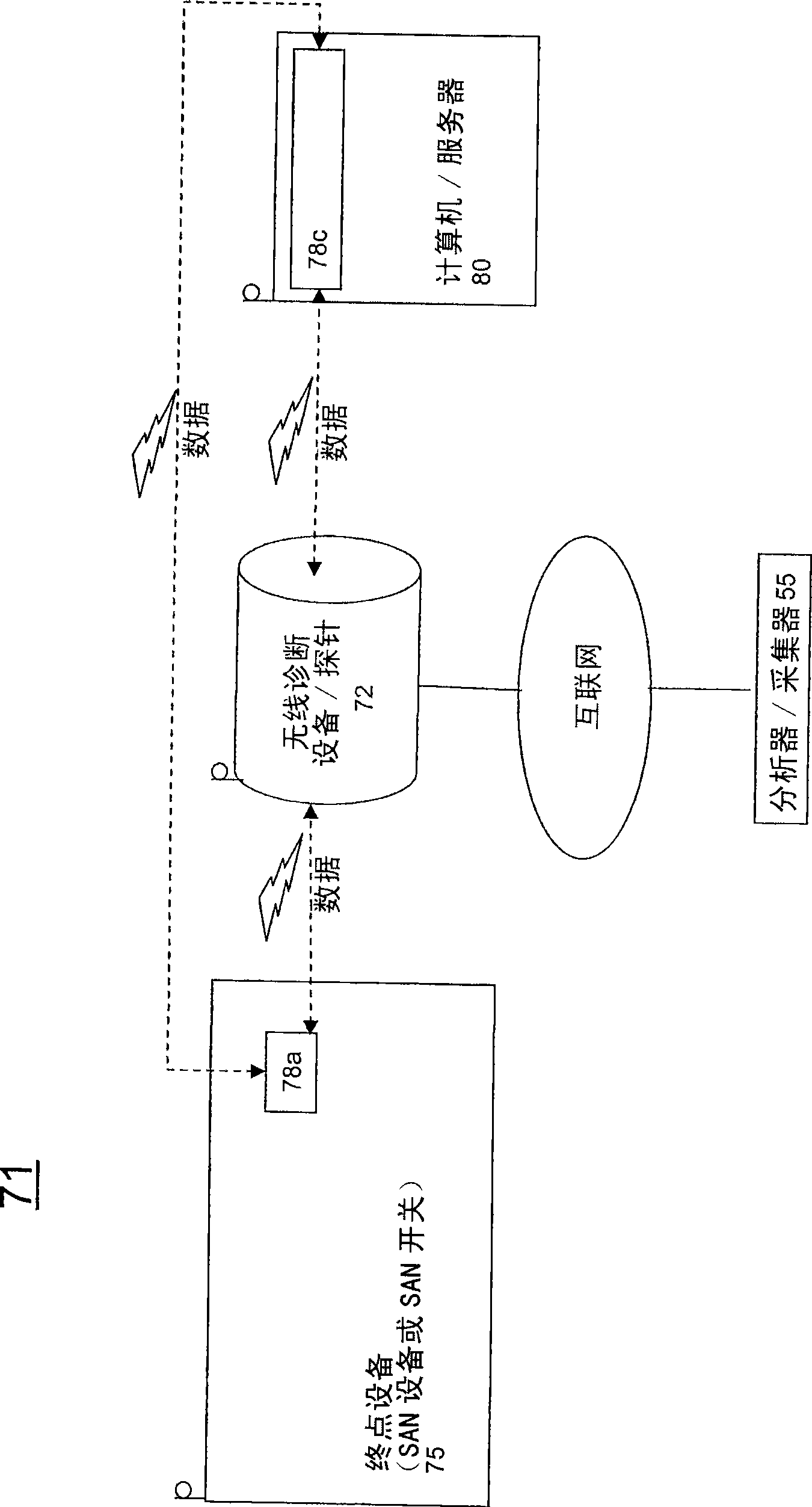
Wireless diagnostic systems
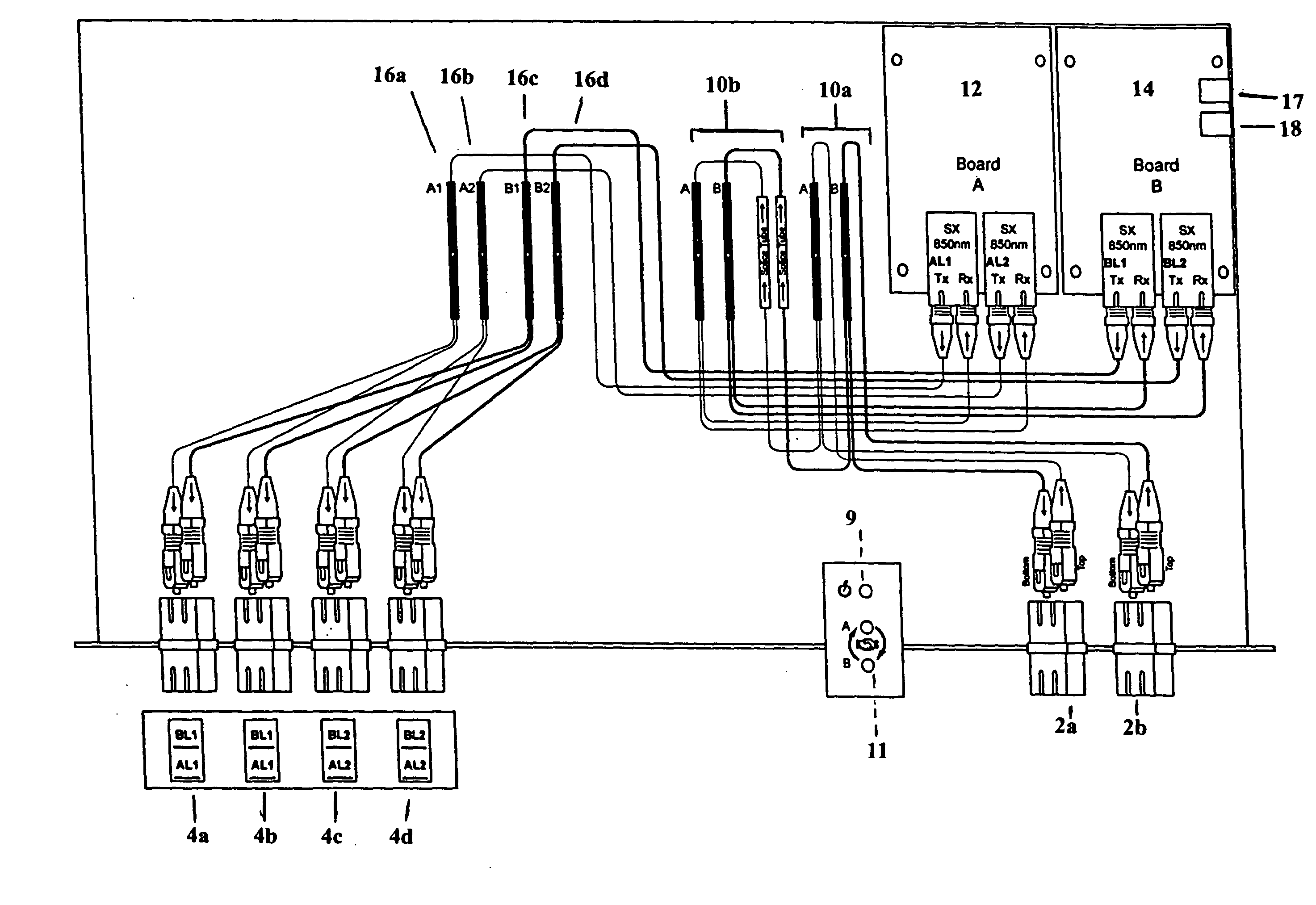
The invention discloses wireless diagnostic systems and methods of implementing wireless diagnostic analysis between at least one end point device and at least one wireless diagnostic device / probe, each including a wireless transceiver that enables wireless communication therebetween. The wireless diagnostic device could be a bit error rate tester, a protocol analyzer, a generator, a jammer, a monitor, and the like. The end point devices can be storage devices, LAN ports, computer systems, SAN ports, wireless RAIDS, network taps, and the like.
Owner:FINISAR
Zero-interrupt network tap
A network tap monitors network information flow over a particular connection. By duplicating the signal and diverting a copy, the information flow can be analyzed, both in real time and without interference through the monitoring process. When the power to the tap is either turned on or off, however, the change in impedance in the tap's circuit can create an interference spike in the connection that interrupts the information flow. By reducing or eliminating the impedance change in the tap circuitry, such disruptive interruptions can be eliminated.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Computer network tapping system
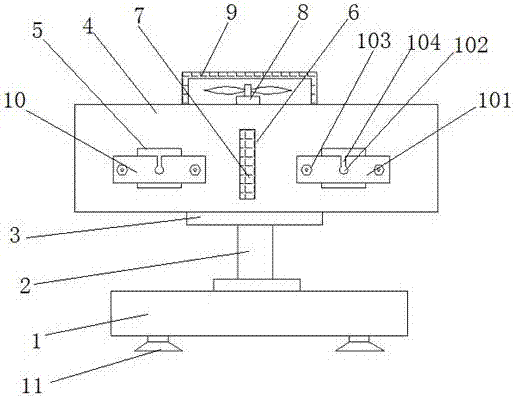
InactiveCN107305986AEasy to plug inEasy to set fastening on the connectorCouplings bases/casesCooling/ventilation/heating modificationsAir filterNetwork tap
The invention discloses a computer network branching system, which comprises a fixed seat, a rotating shaft, a turntable, a casing, a network cable connector, a side hole, a dust-proof net, a fan and a filter screen. The top of the fixed seat is provided with a vertical rotating shaft. The top of the rotating shaft is provided with a turntable, the turntable is provided with a casing, the casing is cylindrical, and a plurality of network cable connectors are uniformly arranged on the side wall of the casing, and there are The side hole is provided with a dust-proof net, the top opening of the shell is provided with a fan, and the fan cover is provided with a filter screen. The invention has the advantages of simple structure, convenient use, good heat dissipation effect, reduced bending of network cables, and significantly improved connection stability.
Owner:天津智涵科技有限公司
Network tap/aggregator configured for power over ethernet operation
ActiveUS7809476B2Eliminates potentialImprovement in reliability and operationEnergy efficient ICTMechanical power/torque controlNetwork tapEngineering
A network tap device array capable of being powered by a power-over Ethernet (“POE”) supply is disclosed. The array enables data from multiple nodes in a communications network to be tapped and forwarded to a plurality of monitoring devices. In one embodiment the network tap device array includes a chassis that is configured to receive a plurality of network tap devices that are each powered by a POE supply. Each network tap device includes network ports for receiving and transmitting network data via communication cables and tap ports for forwarding the tapped network data to the monitoring device. In another embodiment, a sub-chassis includes a plurality of network tap devices and an aggregator that aggregates tapped data from each of the tap devices. The aggregator then forwards the aggregated data to the monitoring device. The sub-chassis can be included in a chassis that is configured to receive multiple populated chassis.
Owner:VIAVI SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com