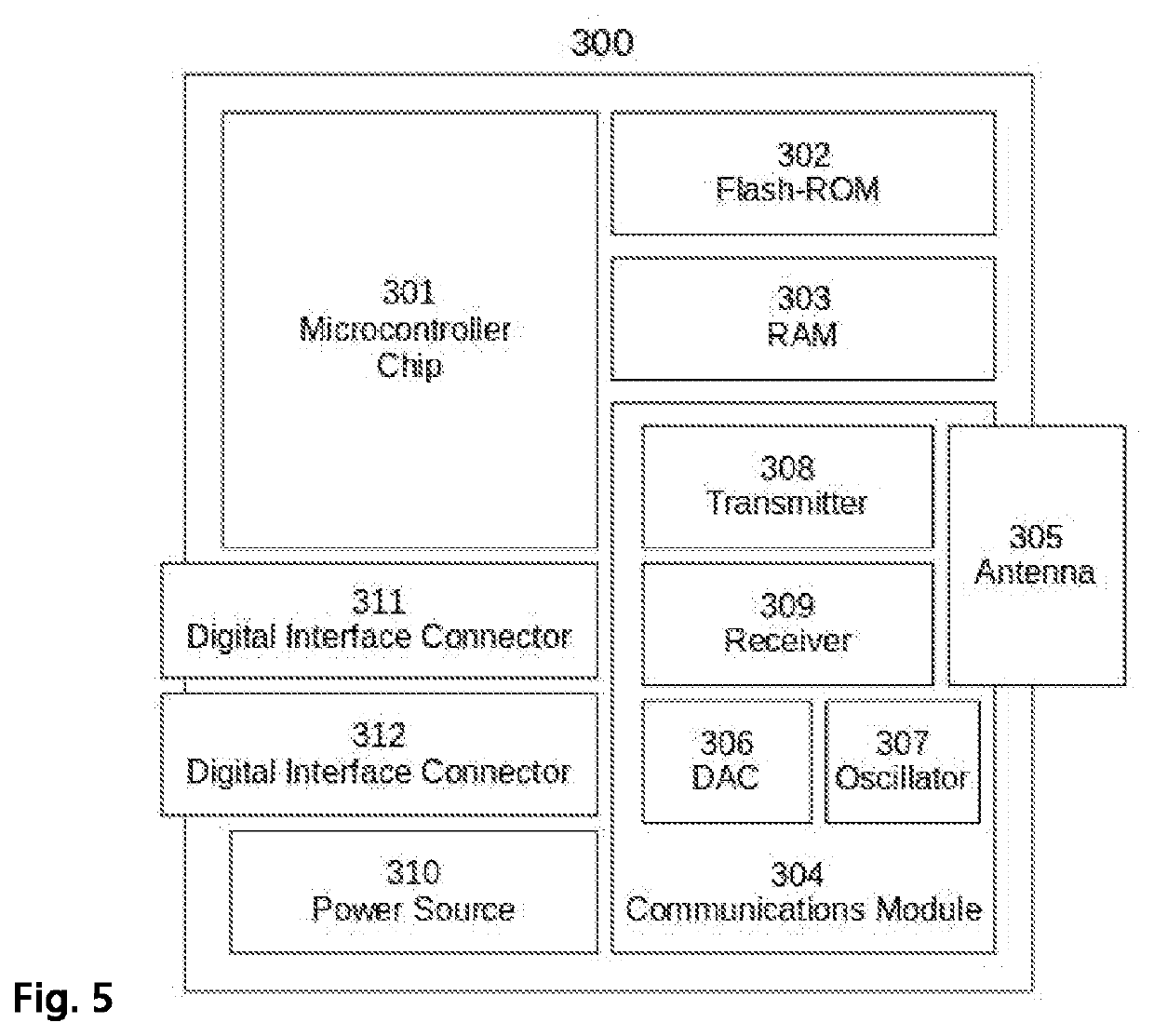
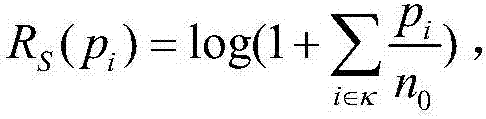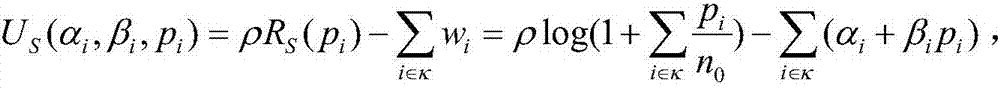Patents
Literature
51 results about "Symmetric network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
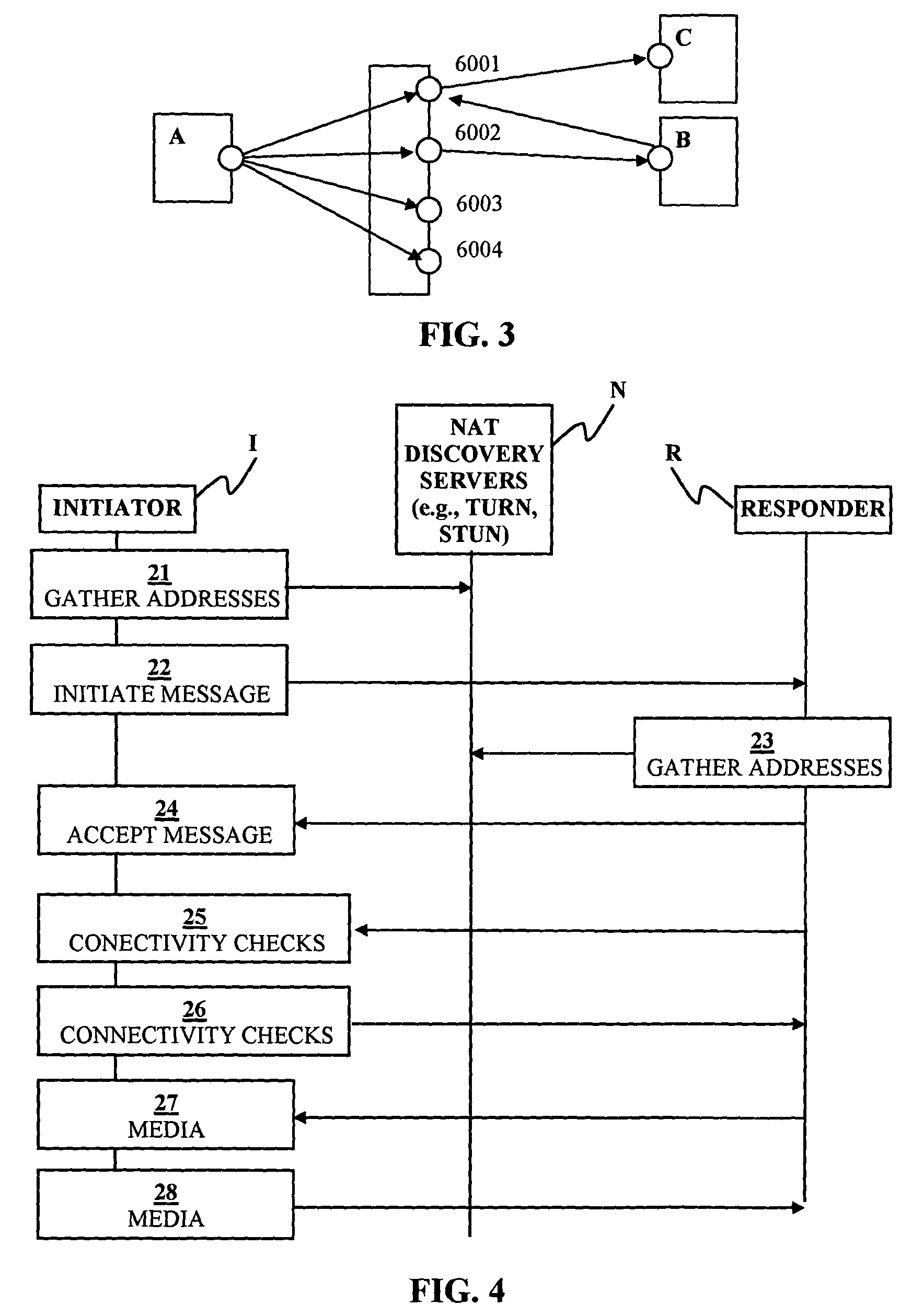
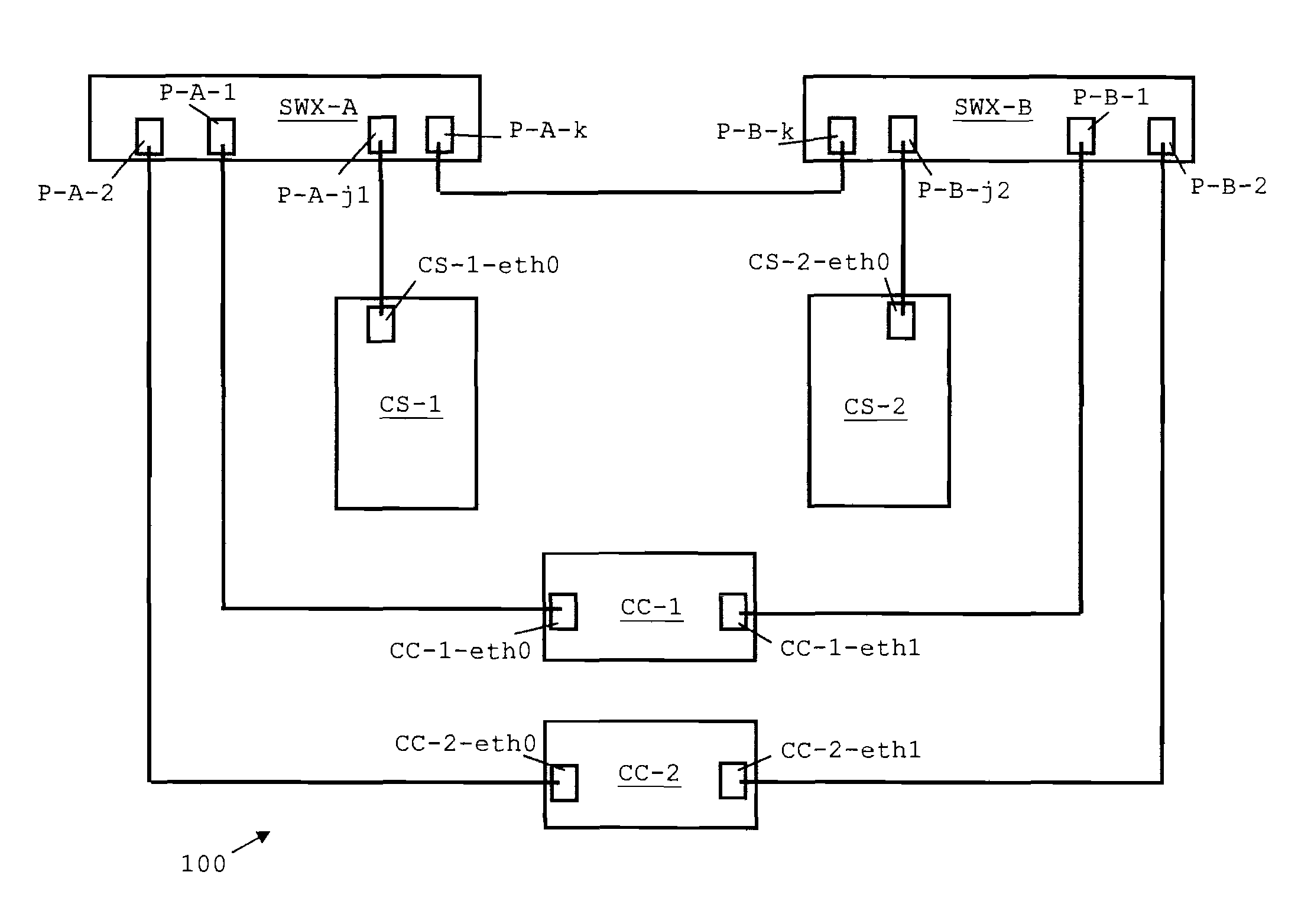
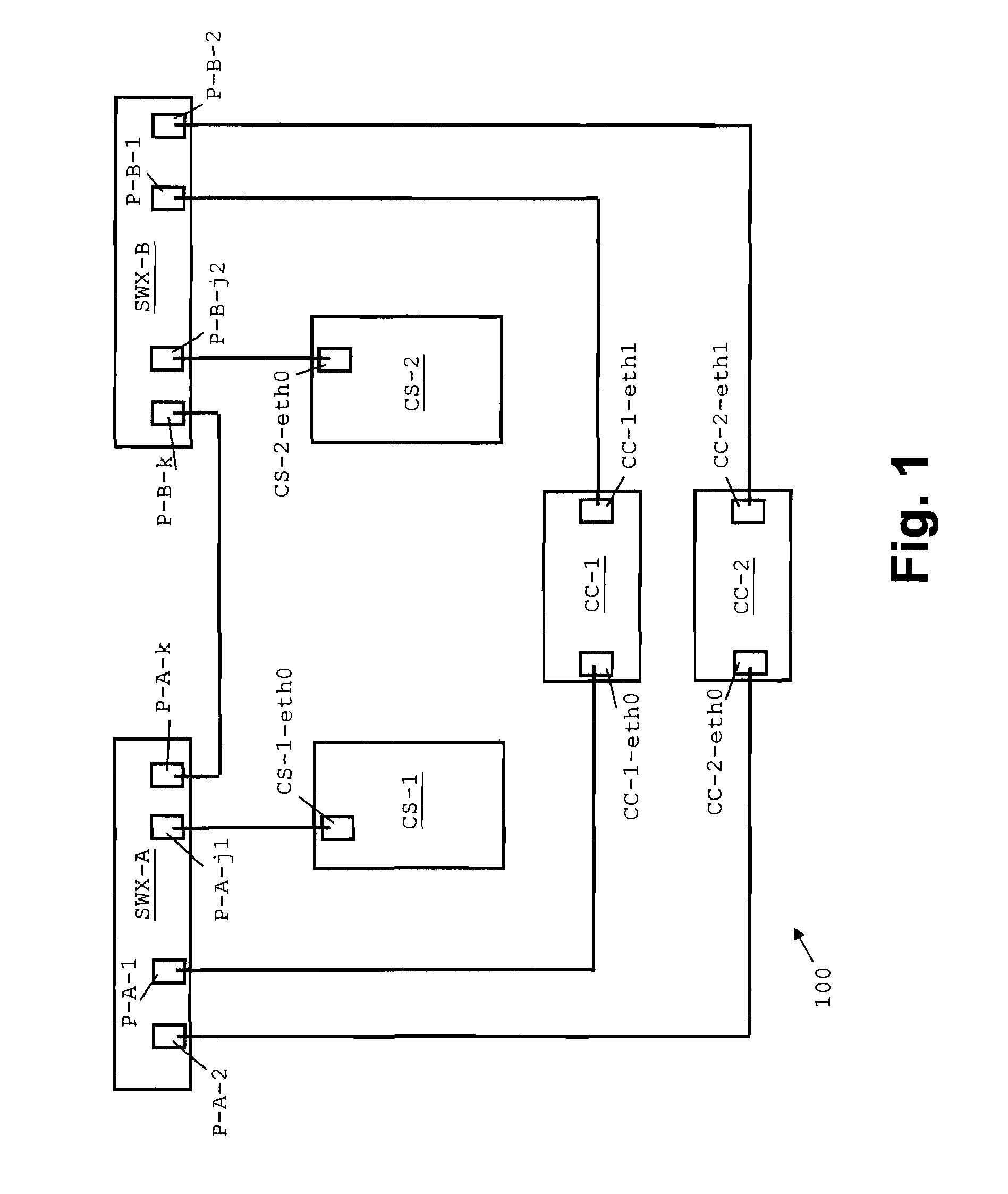
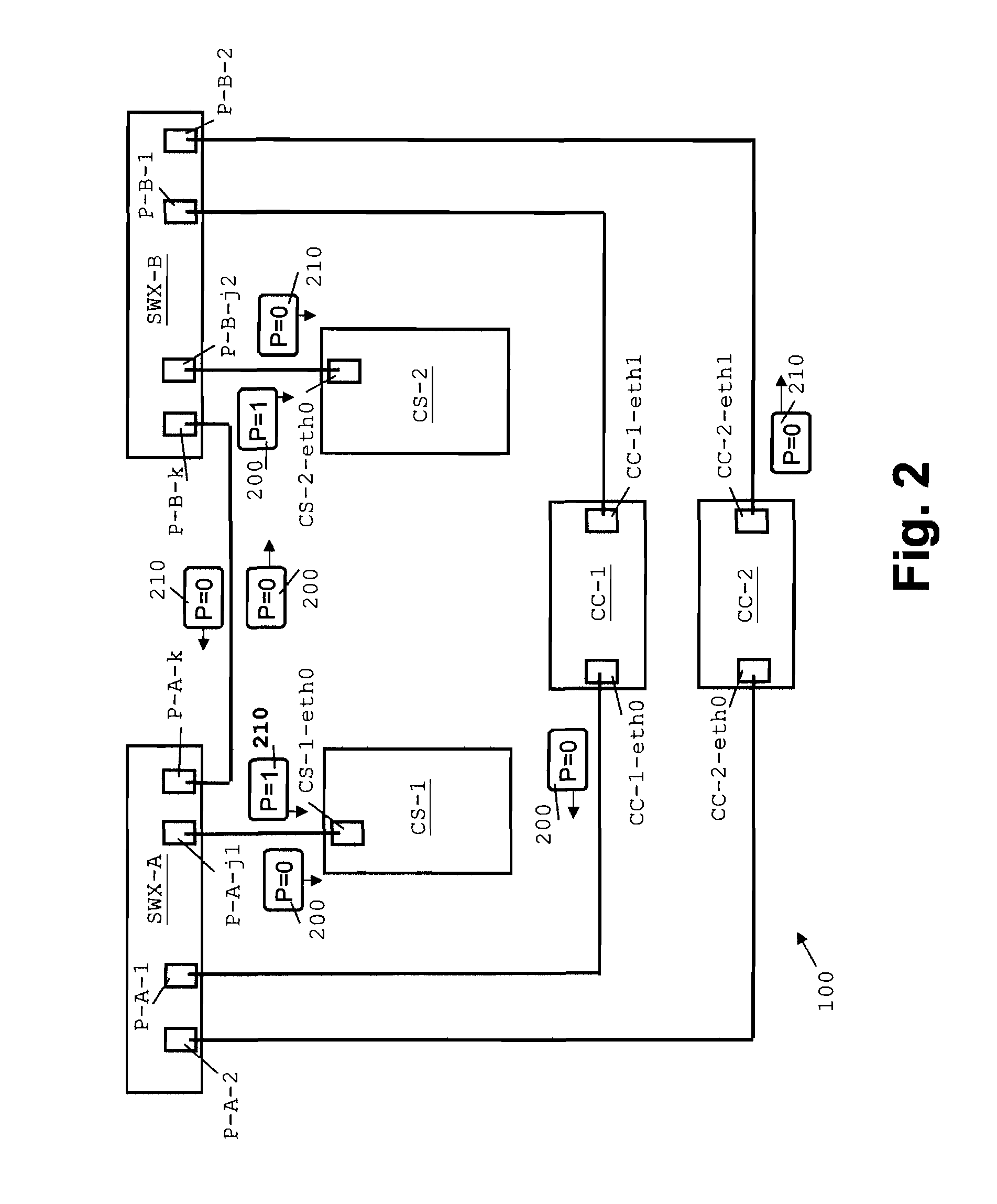
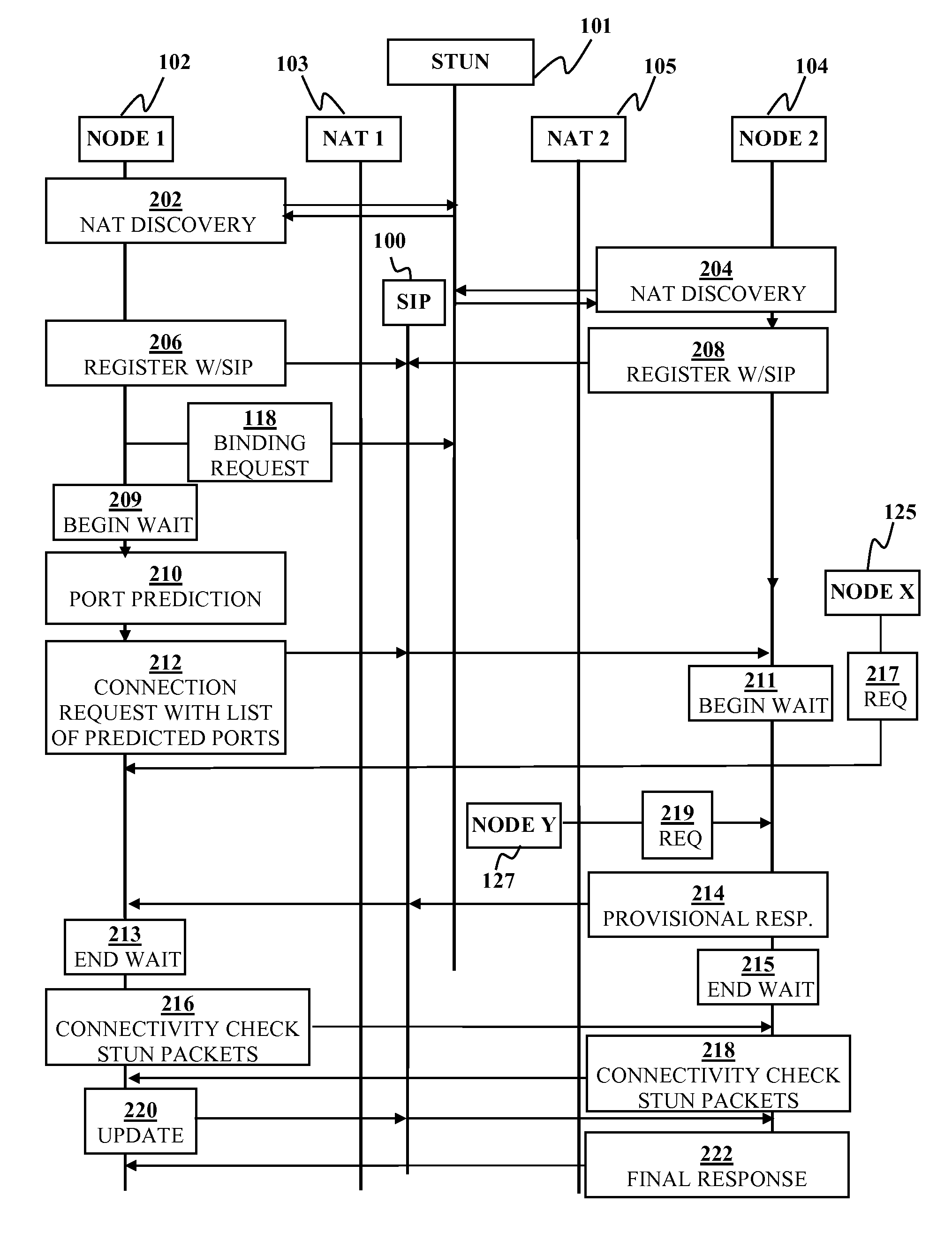
Peer-to-peer communication traversing symmetric network address translators
ActiveUS20070076729A1Data switching by path configurationMultiple digital computer combinationsNetwork addressingNetwork address
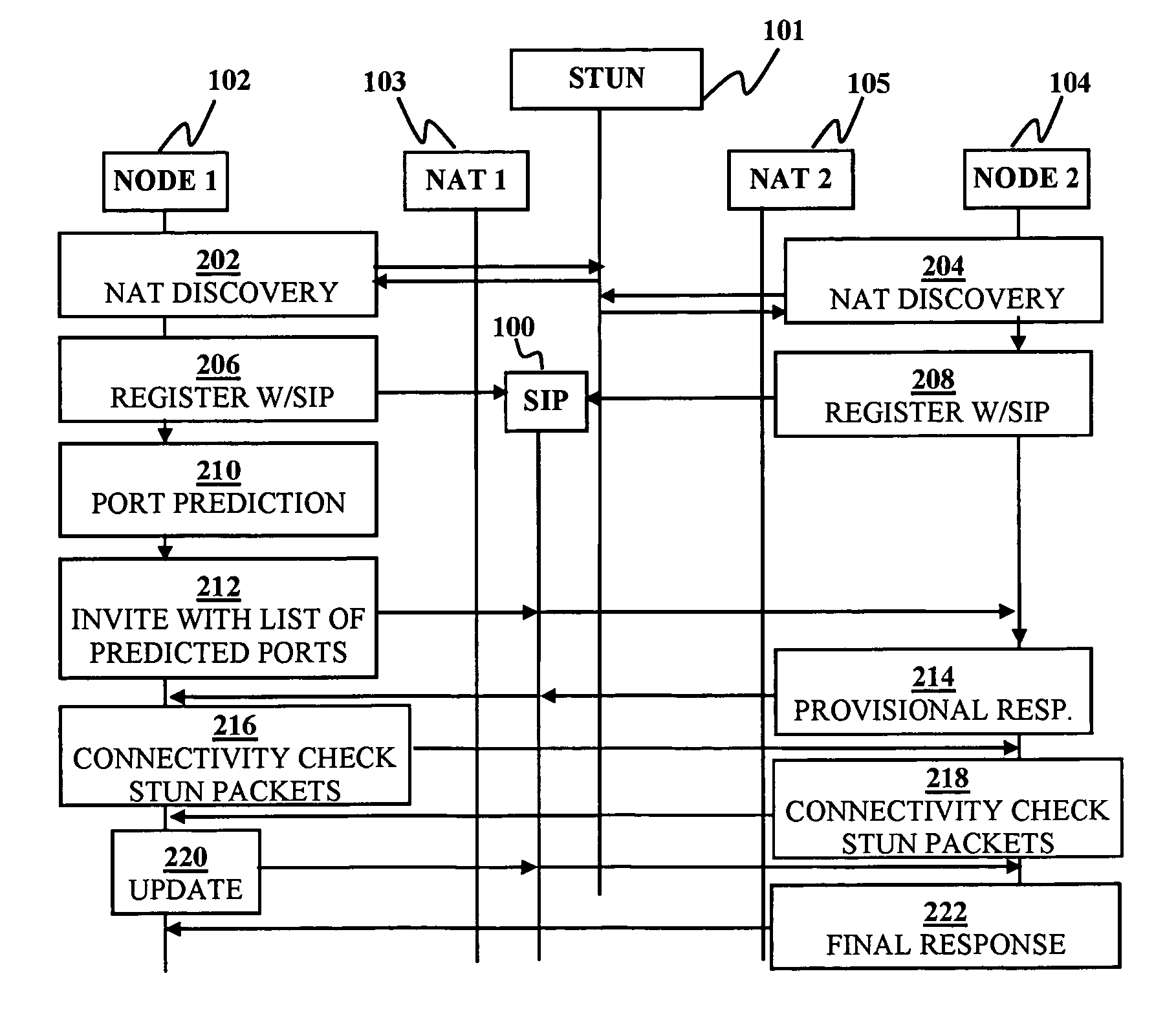
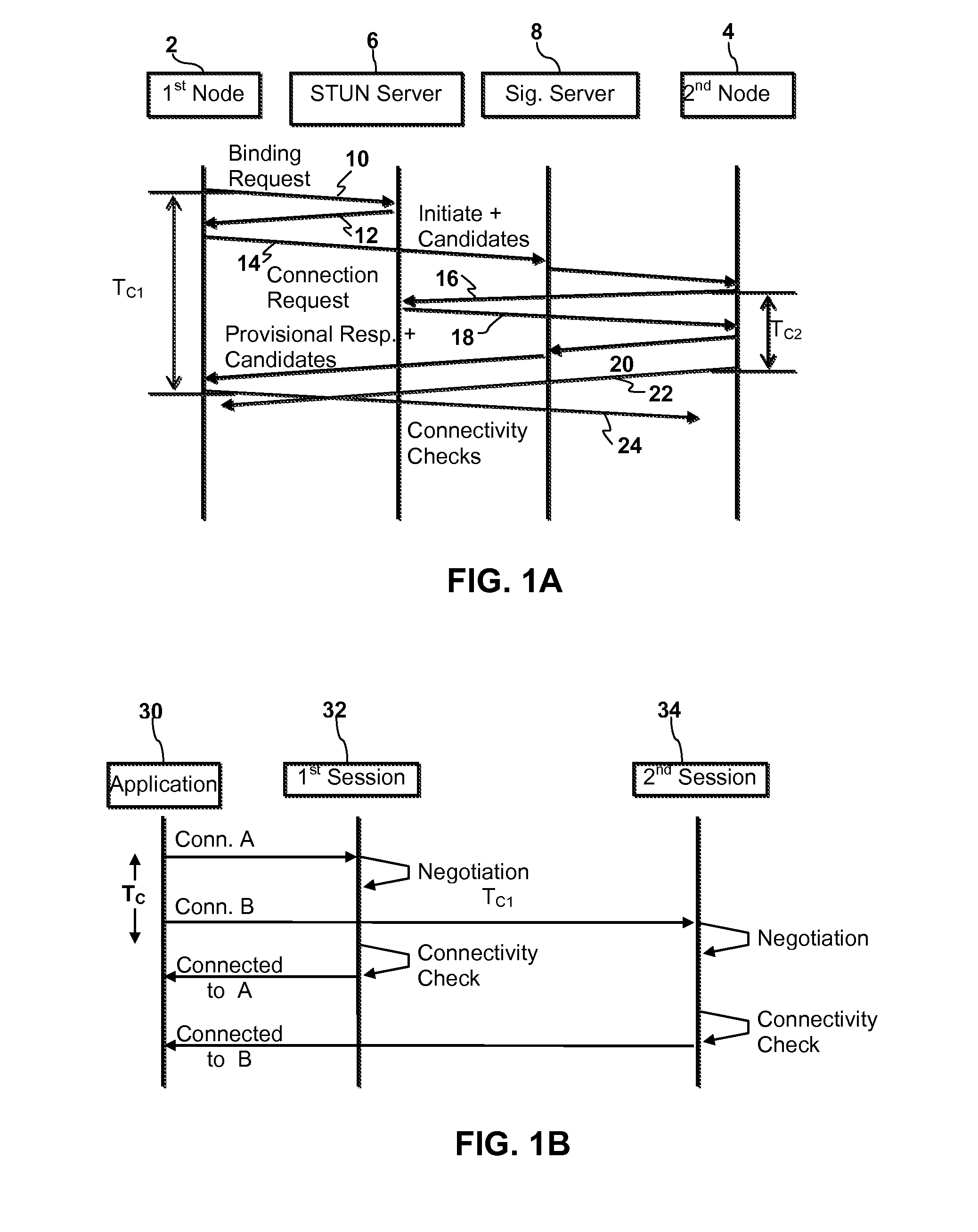
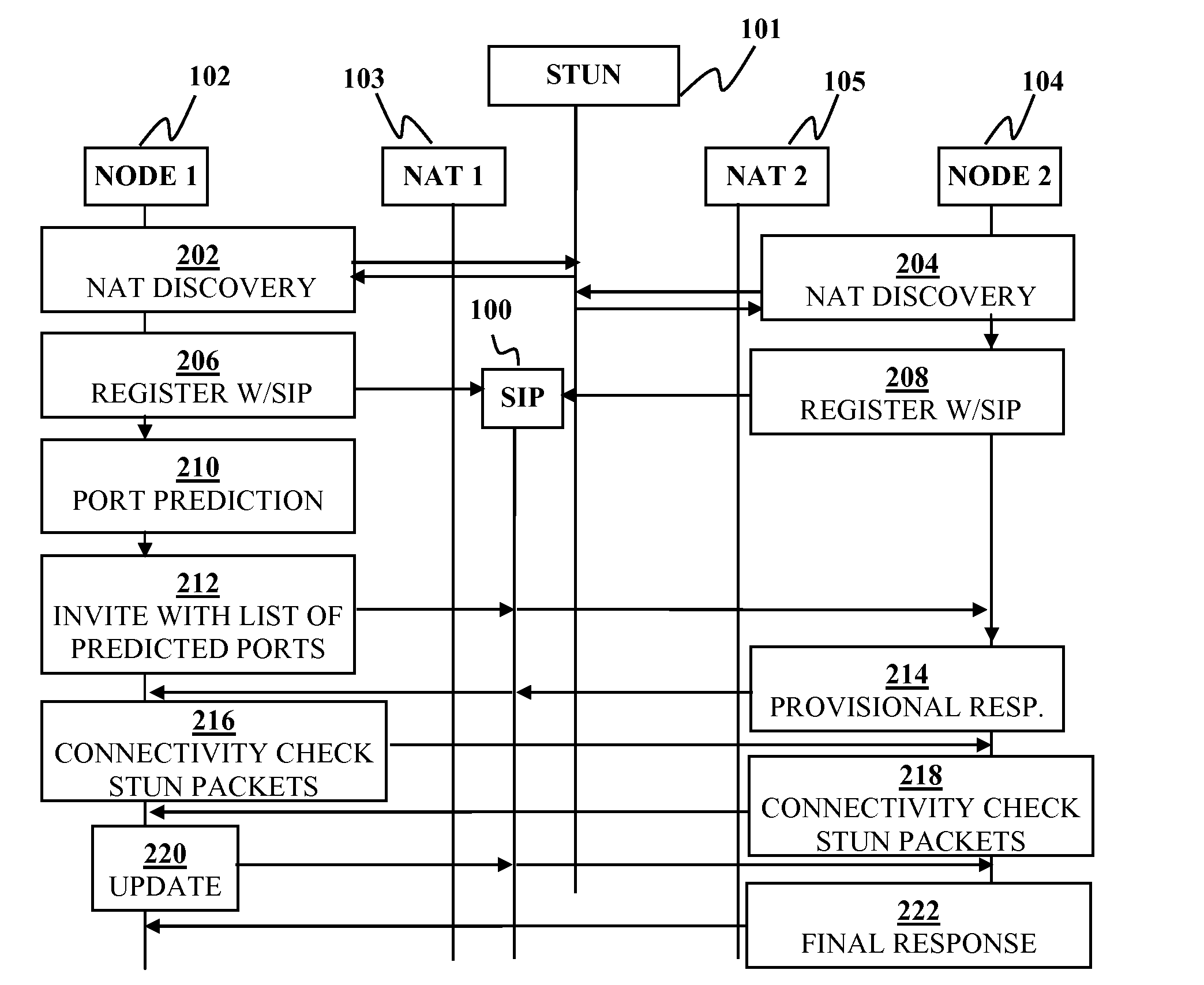
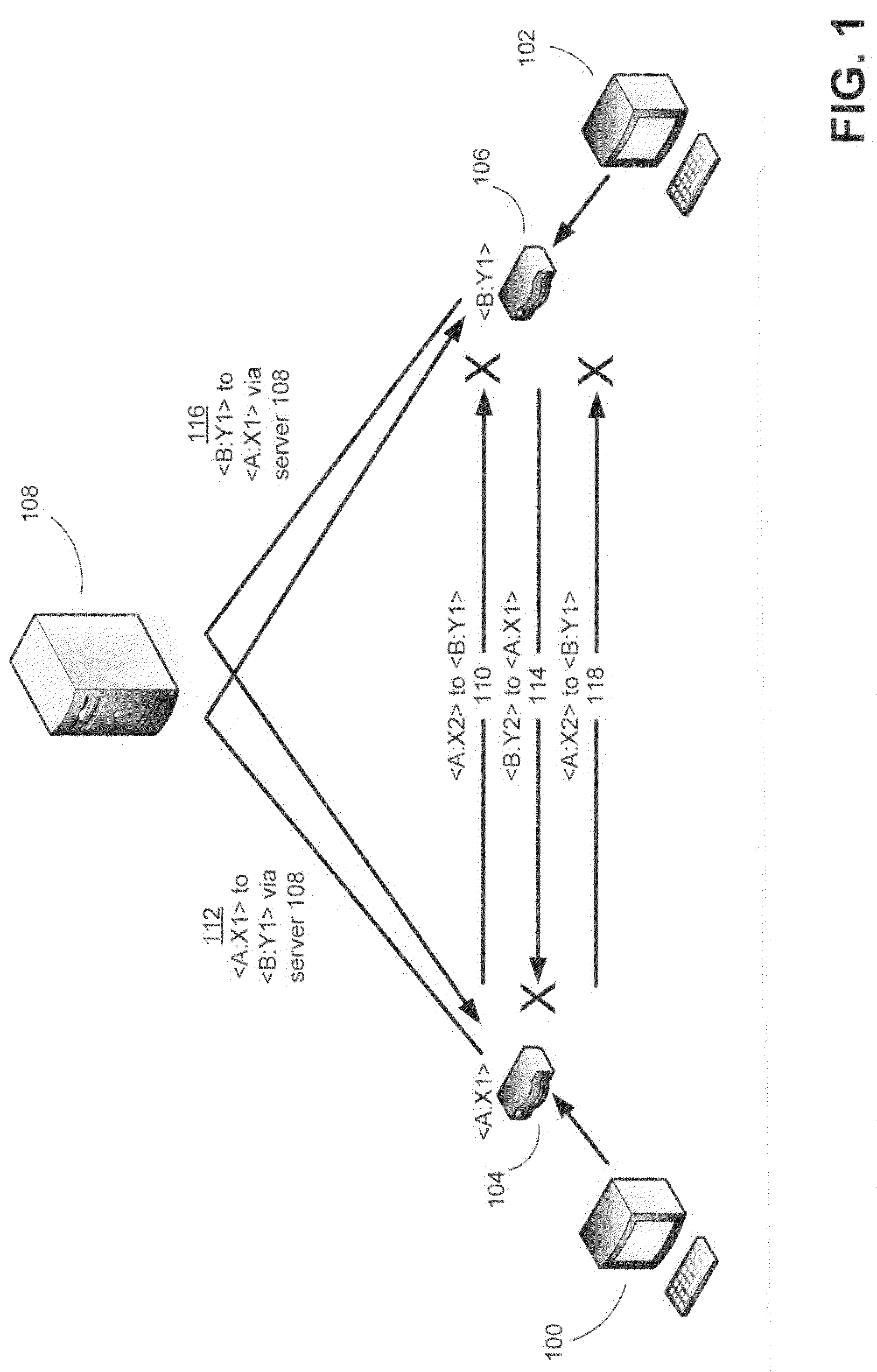
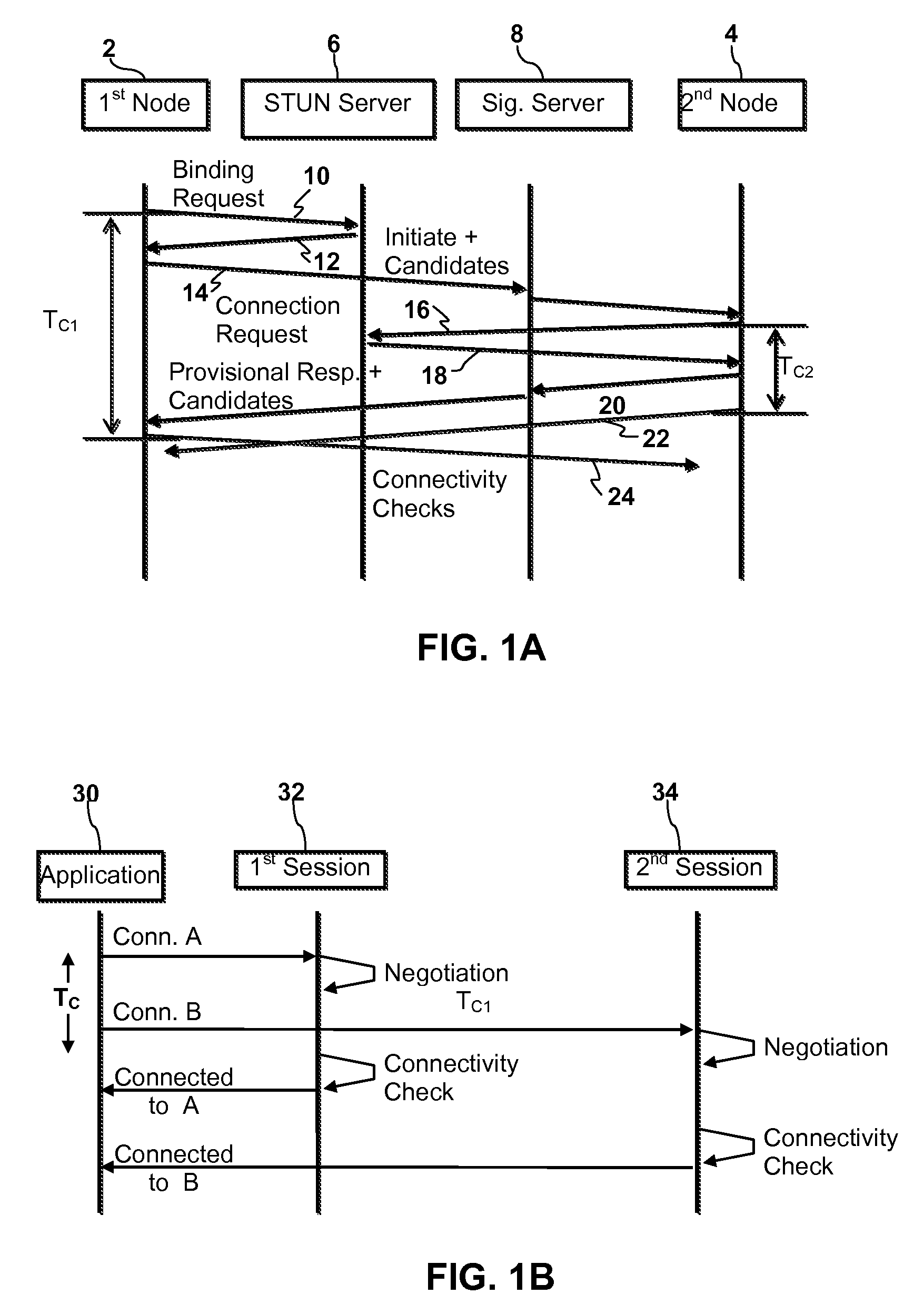
Disclosed are systems and methods for peer-to-peer communication over a network between a first node behind a first network address translator (NAT) and a second node behind a second NAT, despite the first NAT and the second NAT intervening between the first and second nodes. The first NAT is a Symmetric NAT. A port prediction is performed wherein the first node constructs a list of predicted transport addresses on the first NAT. A message containing the list of predicted transport addresses is sent from the first node to the second node. A connectivity check is performed with the second node using the predicted transport addresses.
Owner:SONY COMPUTER ENTERTAINMENT INC
Traversal of symmetric network address translator for multiple simultaneous connections
ActiveUS20090228593A1Easy to implementReduce the possibilityData switching by path configurationMultiple digital computer combinationsNAT traversalCritical time
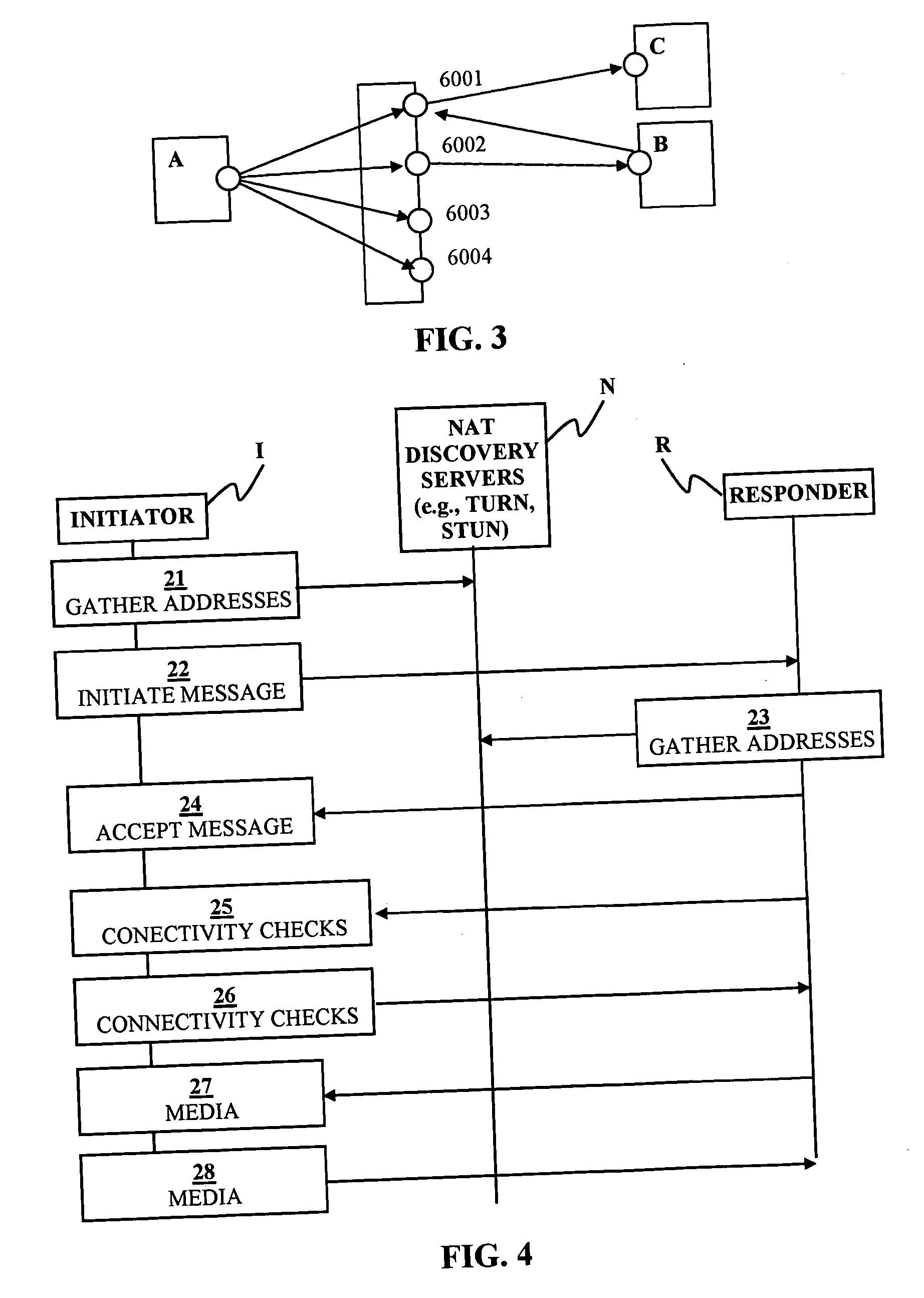
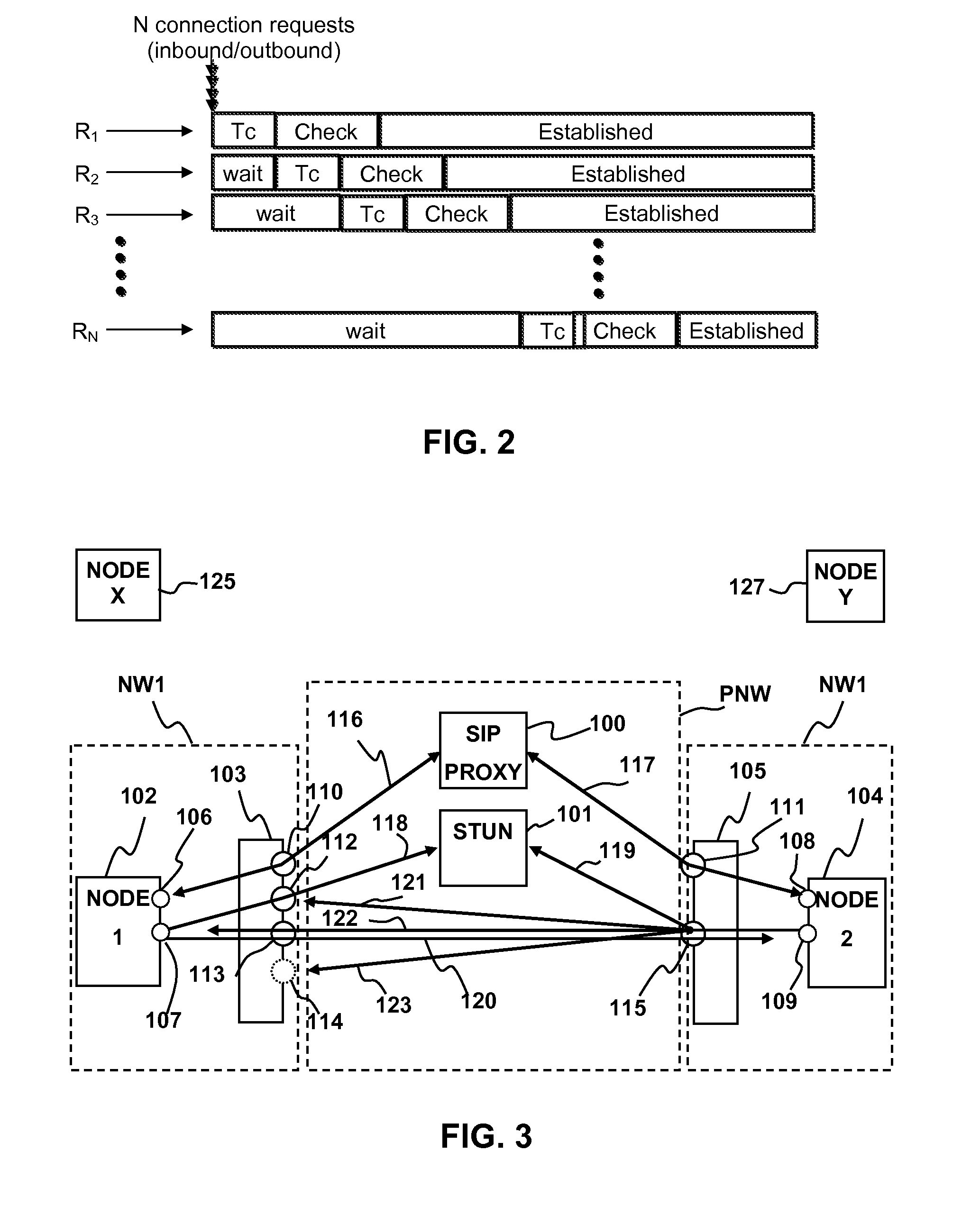
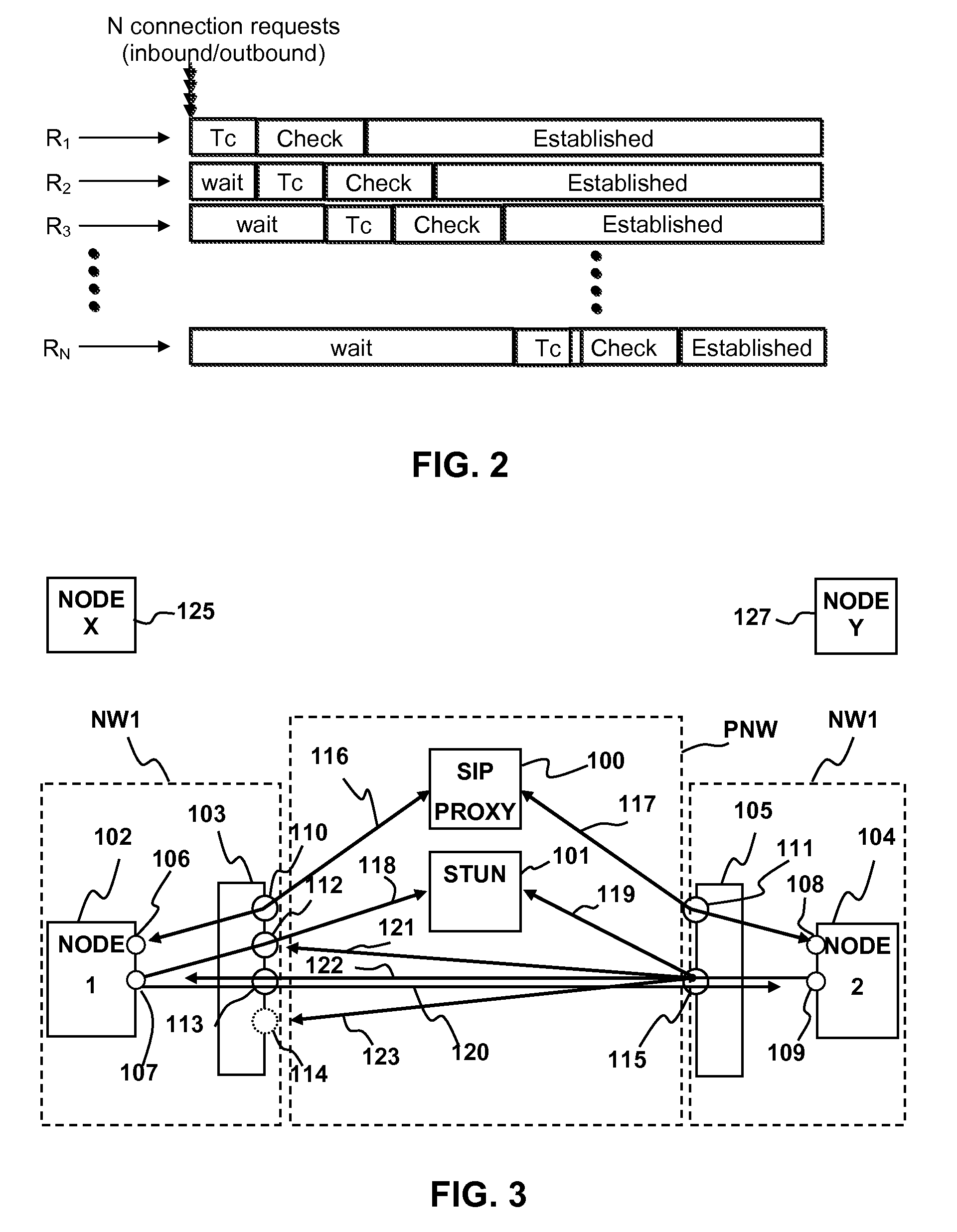
Handling of multiple connections during NAT traversal for a node behind a symmetric NAT is disclosed. The likelihood of connection failure during symmetric NAT traversal may be reduced by serializing critical time windows after port prediction. Once port prediction has begun for a first connection, port prediction for a subsequent connection may be delayed until a connectivity check has begun for the first connection. This process may be repeated to handle NAT traversal for multiple simultaneous connections to different nodes.
Owner:SONY COMPUTER ENTERTAINMENT INC
Peer-to-peer communication traversing symmetric network address translators
ActiveUS8224985B2Data switching by path configurationMultiple digital computer combinationsNetwork address translationNetwork address
Owner:SONY COMPUTER ENTERTAINMENT INC
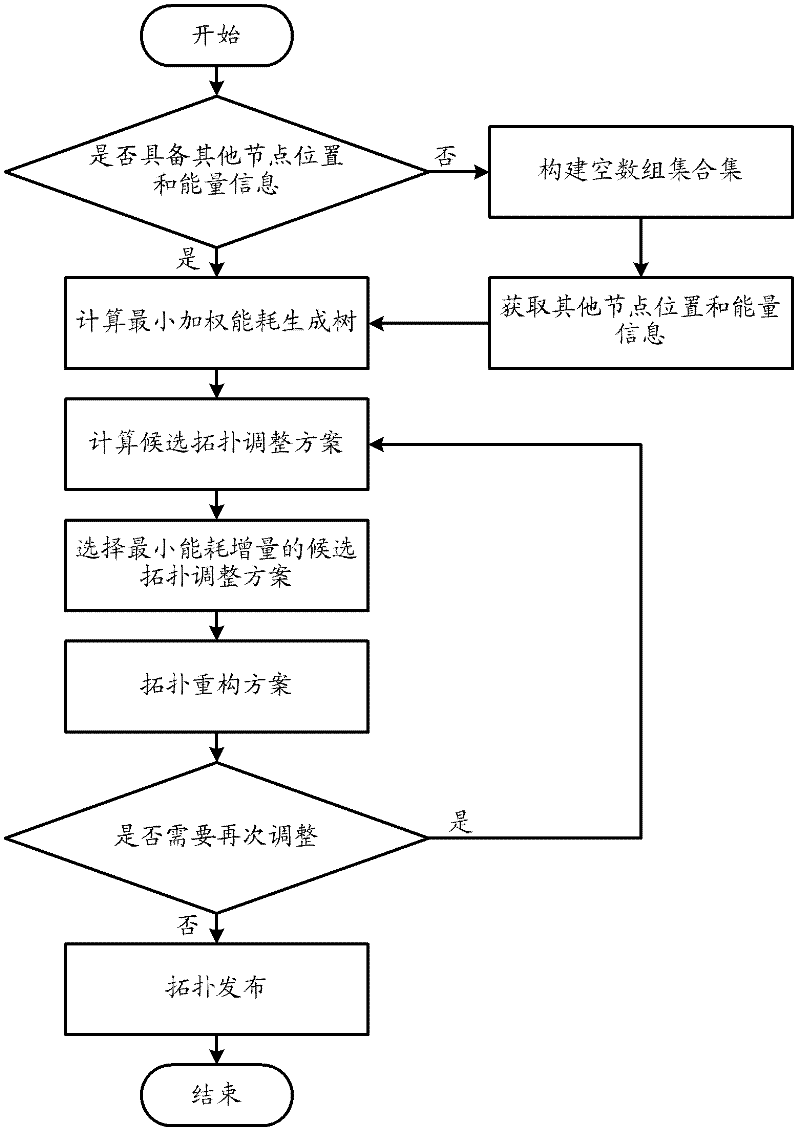
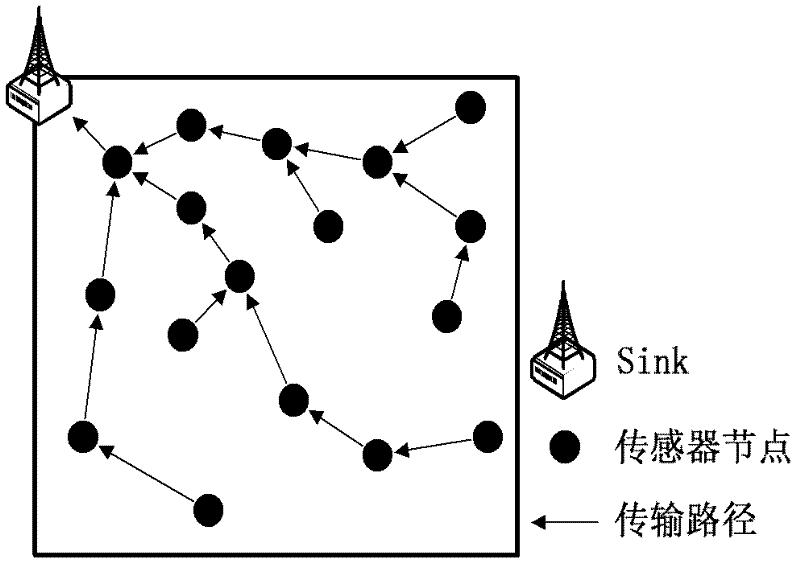
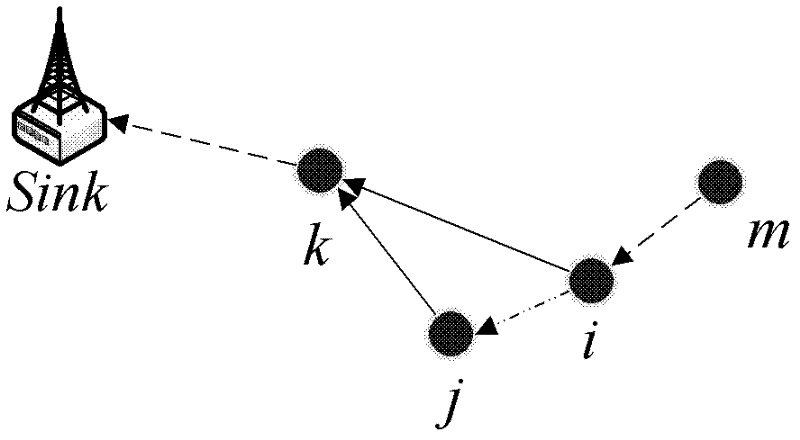
Construction method of time-delay-constrained energy consumption balance data acquisition tree in WSN (Wireless Sensor Network)
InactiveCN102413509ABalanced energy consumptionSimple and reliable evaluation criteriaNetwork traffic/resource managementNetwork topologiesMinimum weightData acquisition
The invention relates to a construction method of a time-delay-constrained energy consumption balance data acquisition tree in a WSN (Wireless Sensor Network). The construction method comprises the following steps: a data sink node calculates a weight of a node pair subjected to symmetrical network communication according to network topology information; the data sink node calculates shortest weighted paths from all nodes in the network to the data sink node, wherein a set of the shortest weighted paths forms a minimum weighted energy consumption generation tree; finding out the nodes in the minimum weighted energy consumption generation tree, which do not meet network time-delay limit, and calculating a corresponding topology adjusting scheme for each node as a candidate topology adjusting scheme; finding out one scheme with minimum adjustment on node transmission power from all the candidate topology adjusting schemes, and reconstructing the generation tree; and judging whether the nodes which do not meet hop count limit exist in the network, if so, continuously adjusting, and if not, ending the algorithm, wherein the generated generation tree is the final network topology result. According to the construction method disclosed by the invention, data effectiveness requirement is met, and energy consumptions of the nodes in the network are balanced.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
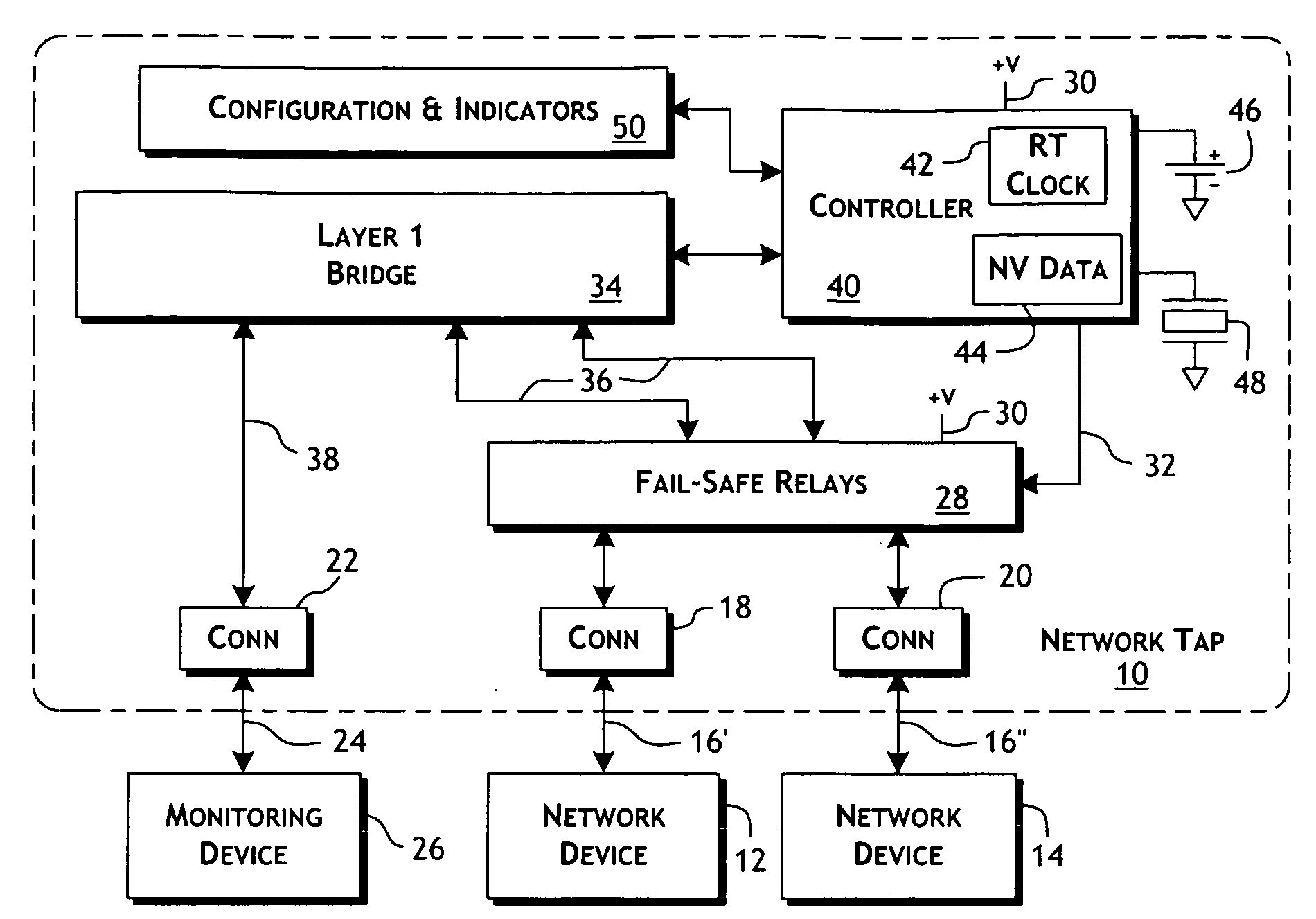
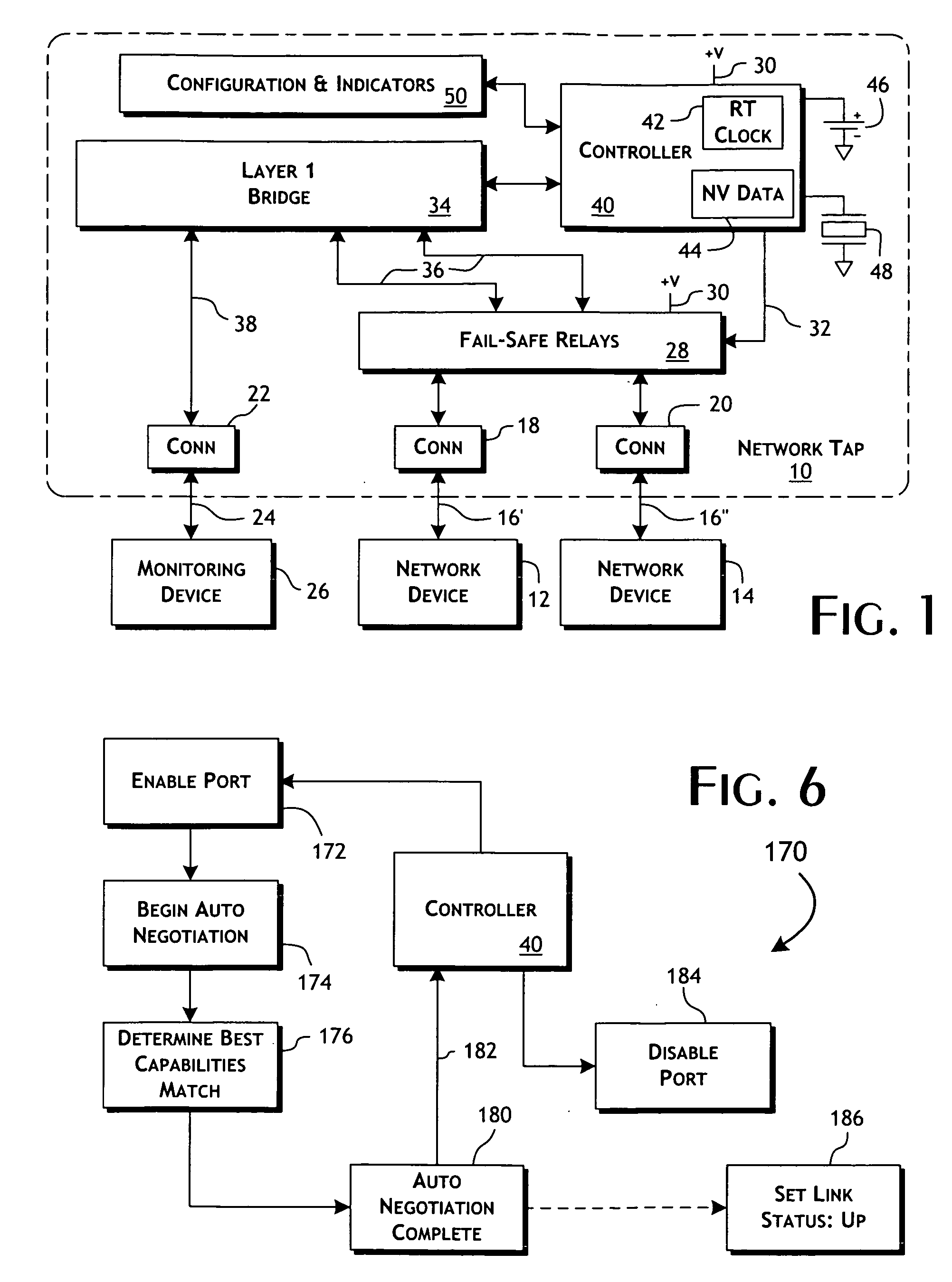
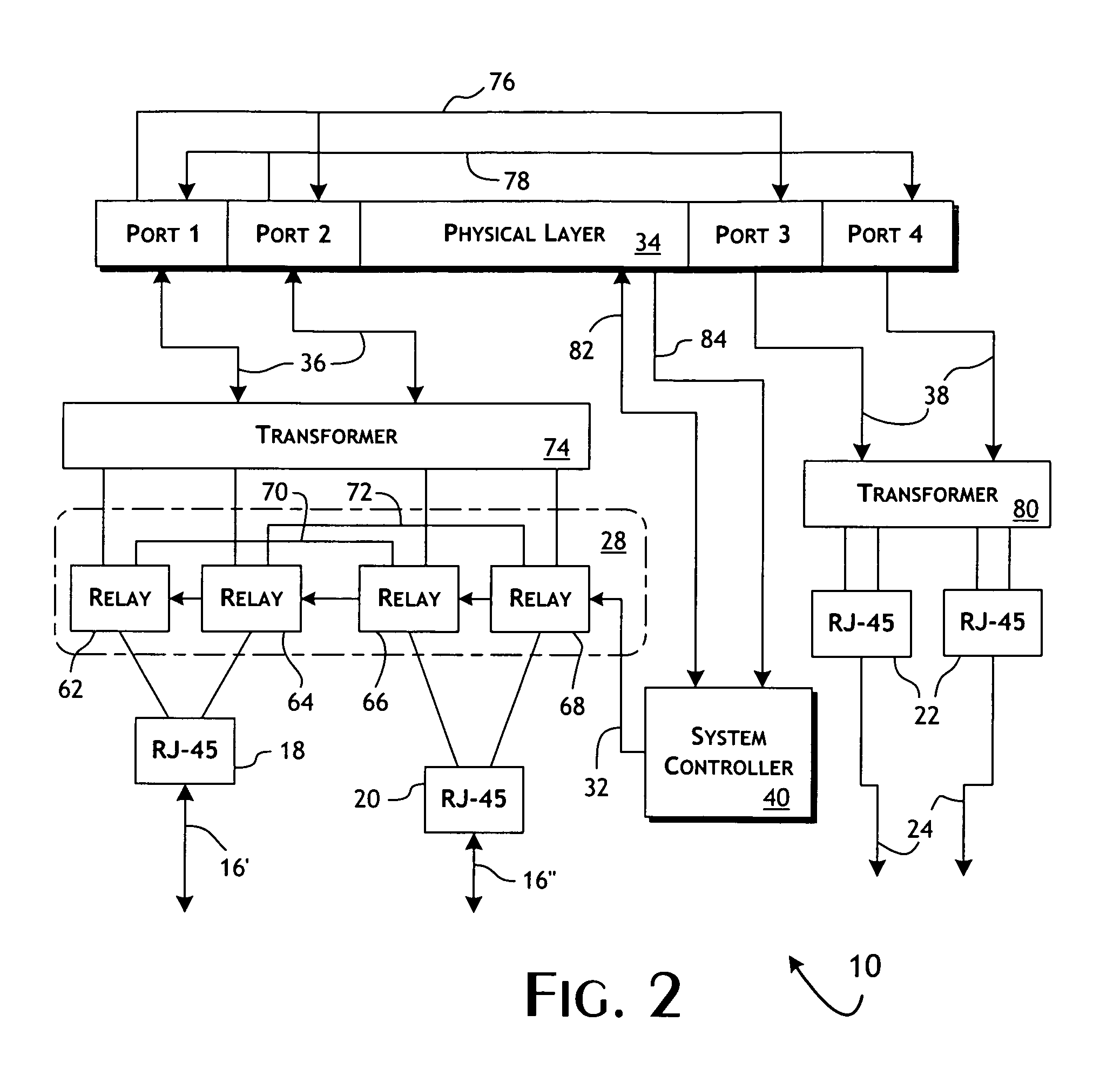
Intelligent fast switch-over network tap system and methods
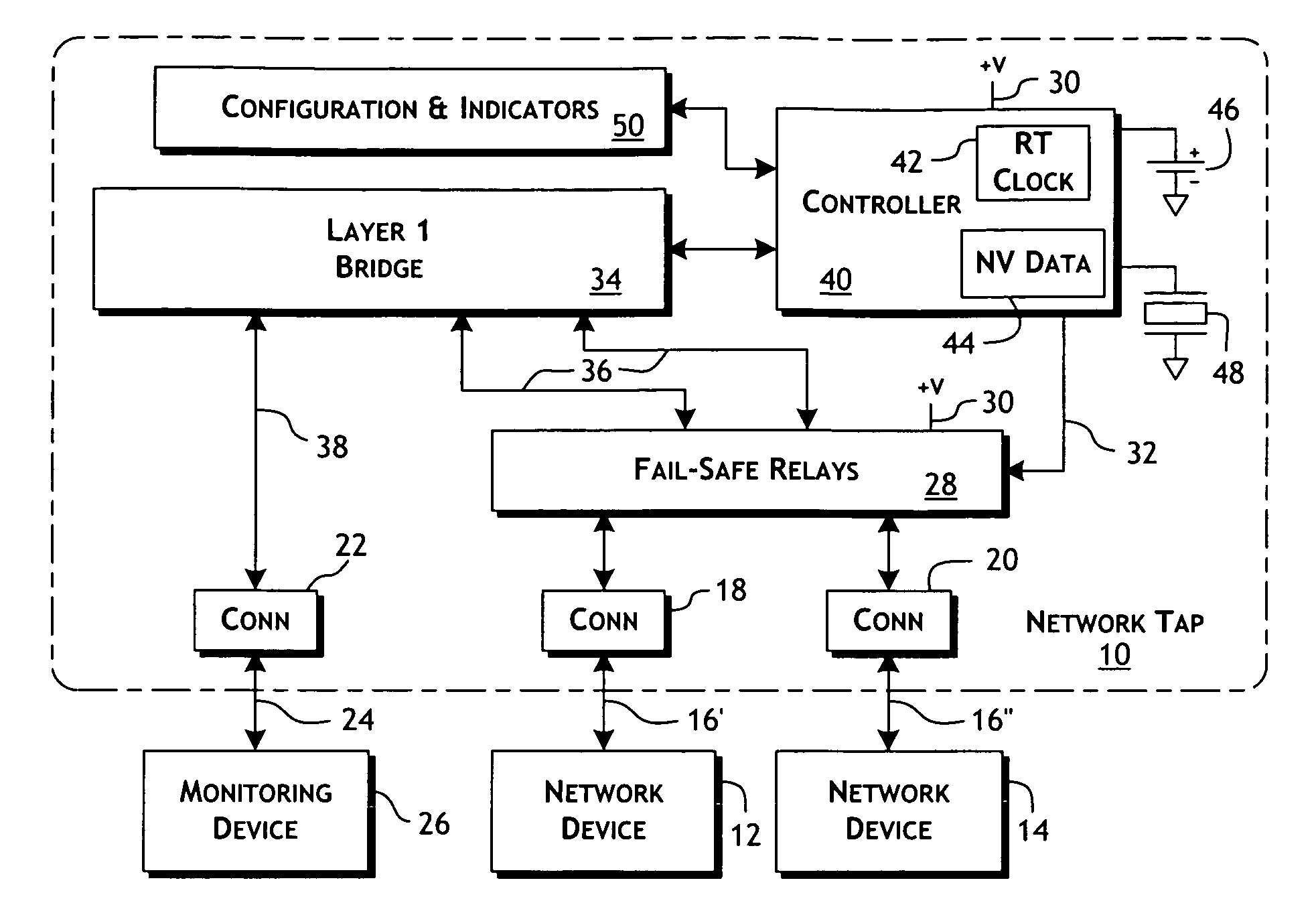
ActiveUS20100177644A1Effective maintenanceAvoiding wider networkError preventionTransmission systemsCross connectionActive monitoring
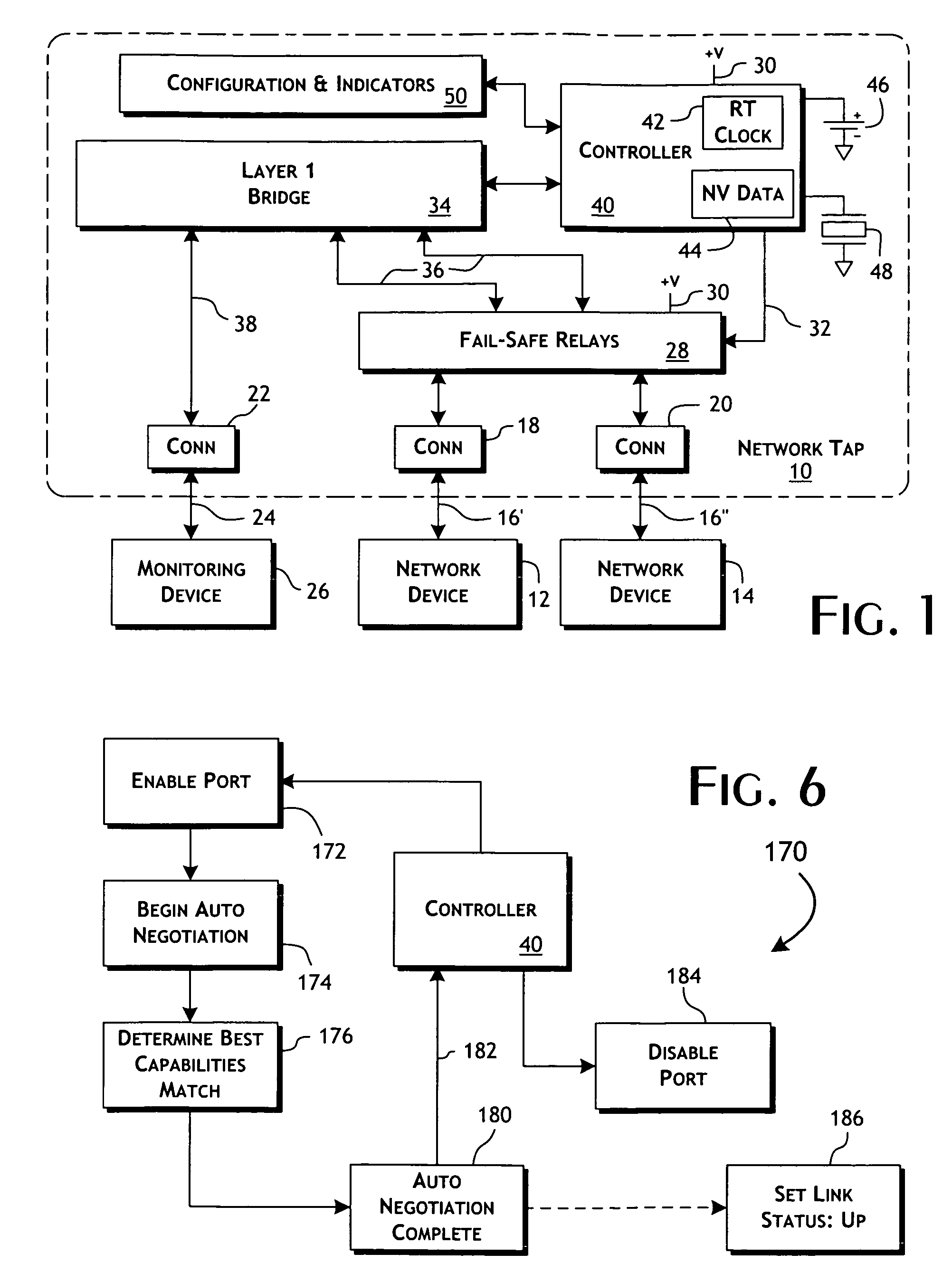
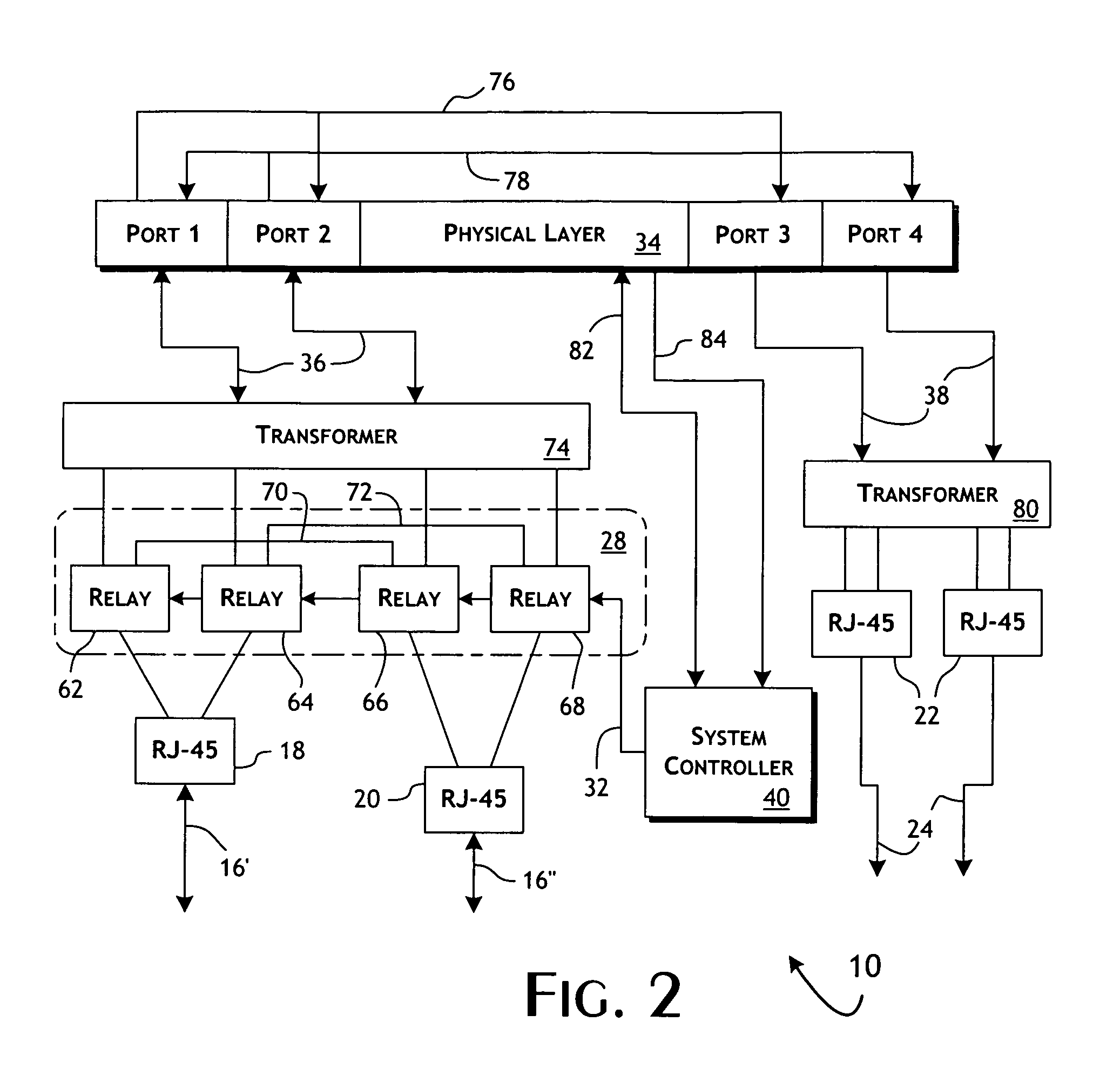
An intelligent fast switch-over network active tap system enables active monitoring of a network segment connected between network devices. A fail-safe relay subsystem is coupled between a pair of network ports, enabling transmission of network communications signals through a passive cross-connect between the network ports or through an active bridge subsystem. The active bridge subsystem is capable of independently establishing network links with the network devices, and a separate network link with a monitoring device. A controller manages operation of the relay and active bridge subsystems, including switches between passive and active network transmission through the tap system and to determine and establish the active network links subject to symmetric network link parameters and state. Thereby, the network link status of the connected network devices is preserved on switch between active and passive transmission and correctly reflected in the presence of link and power failures.
Owner:NETSCOUT SYSTEMS
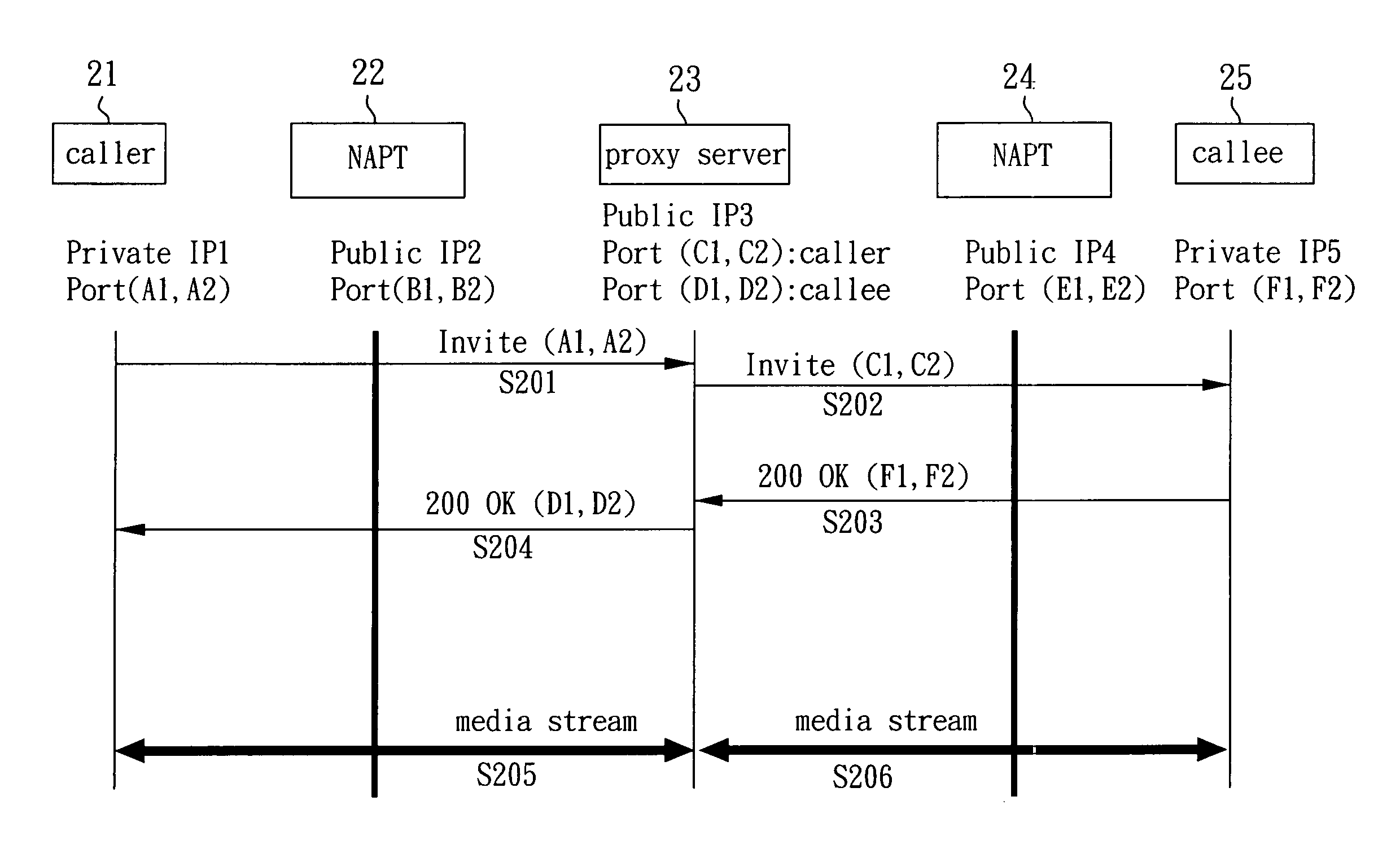
Method of reducing media relay of a network address translation apparatus
InactiveUS20050100047A1Reduce loadReduce unnecessary communicationTime-division multiplexData switching by path configurationNetwork address port translationNetwork addressing
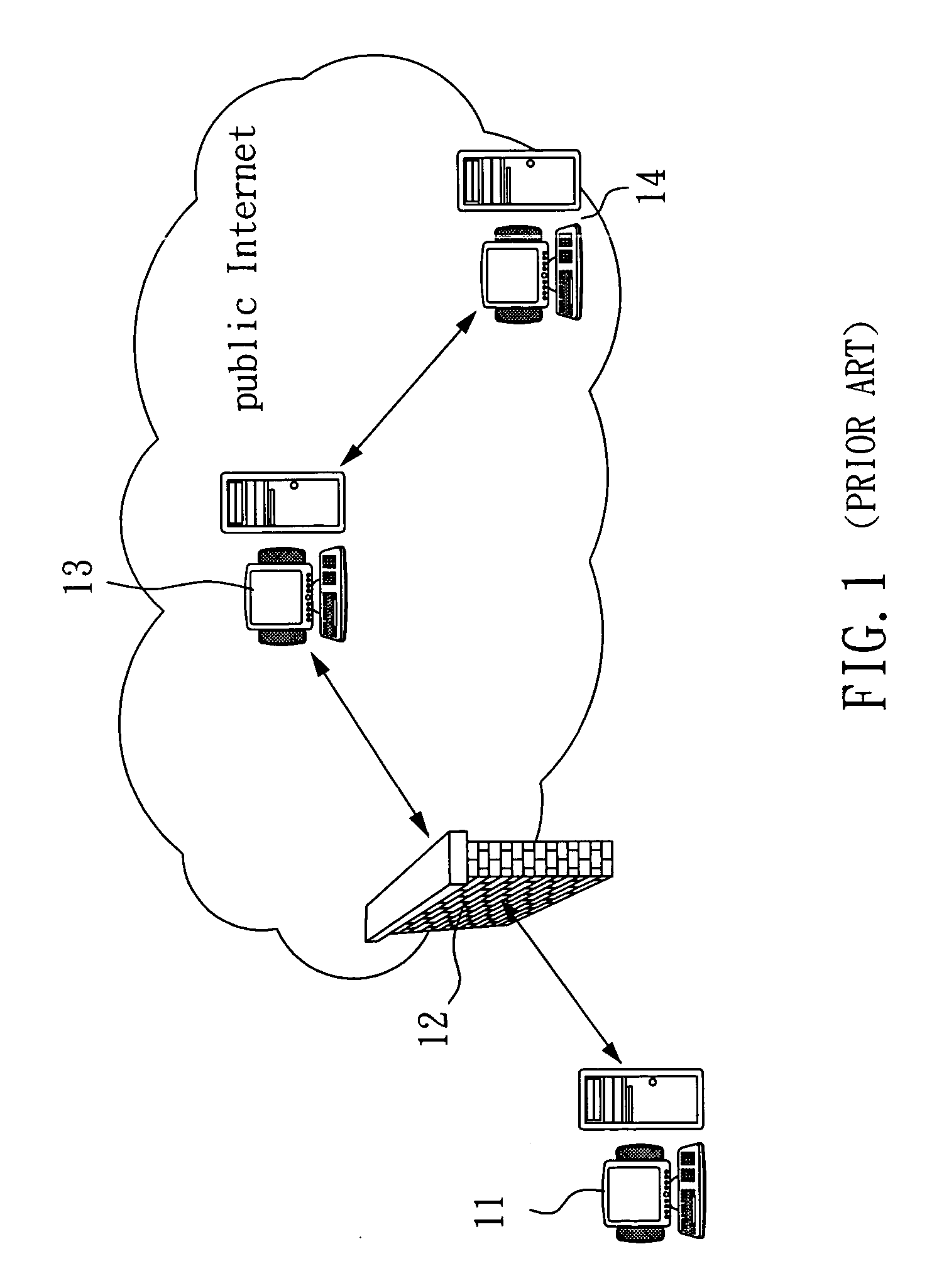
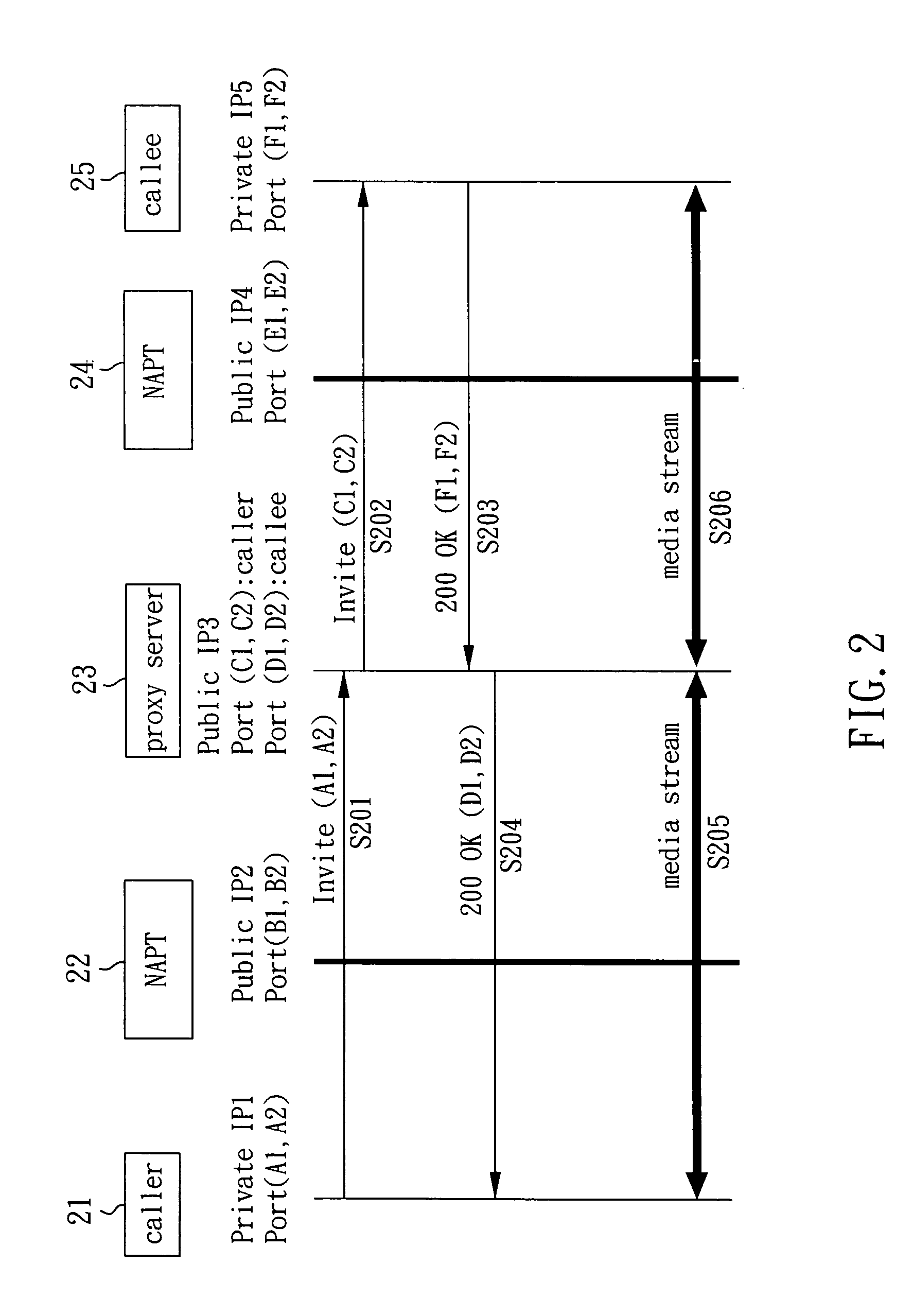
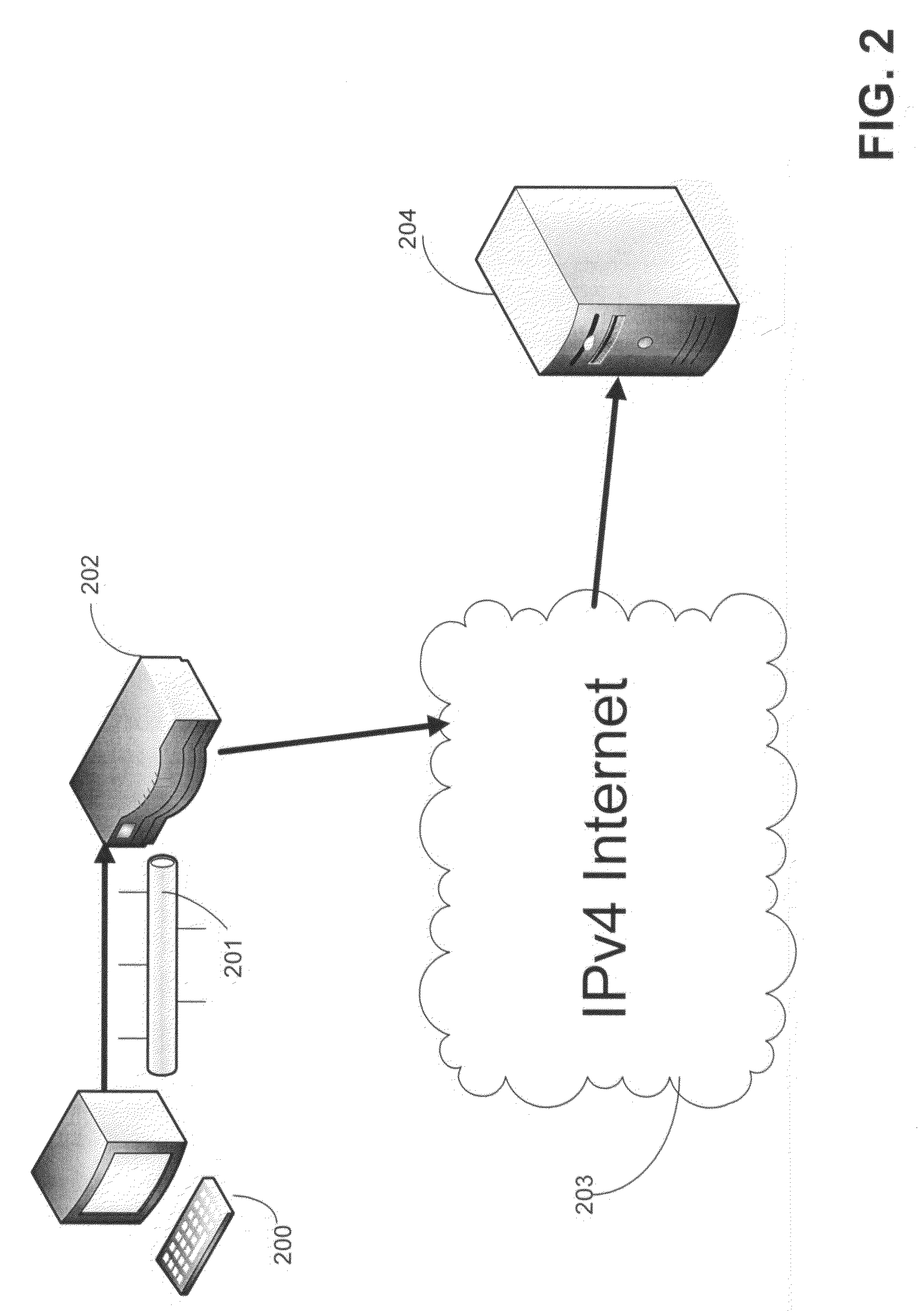
A method of reducing media relay of a network address translation (NAT) apparatus involves detecting a network type of a user agent (such as a network address port translator) to determine whether the user agent is a symmetric network type; if it is, a transmitting server is still required to relay a media stream; if it is not, a SIP standard structure and its communication protocol are utilized for changing a network address and its connecting port of an ‘invite’ packet via a proxy server so that the caller and the callee will send the media stream according to the changed network address and its connecting port.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
An ad-hoc network
PendingUS20200266989A1Minimal interventionPublic key for secure communicationUser identity/authority verificationSelf-organizing networkSymmetric network
Ad-hoc network comprising a configurator device and a plurality of nodes, wherein each node is an electronic device, wherein each node is connected by a communication connection with at least one of the other nodes and / or with the configurator device, wherein each node can be in different states comprising at least a non-commissioned state (NC), a commissioned state and a trust ring member state (TR) wherein a first node of the plurality of nodes being in the non-commissioned state (NC) is configured to send an non-commissioned advertisement message to the configurator device comprising an identifier of the first node, wherein the configurator device is configured to send an automated commissioning initialization (ACI) message to the first node containing a token, wherein the token is encrypted by a symmetric network key, wherein the first node is configured to send out a commissioning request message containing the received encrypted token, wherein the first node is configured to change its state, when it receives an authorisation message from another node or from the configurator device.
Owner:ELECTRIC SOC SA
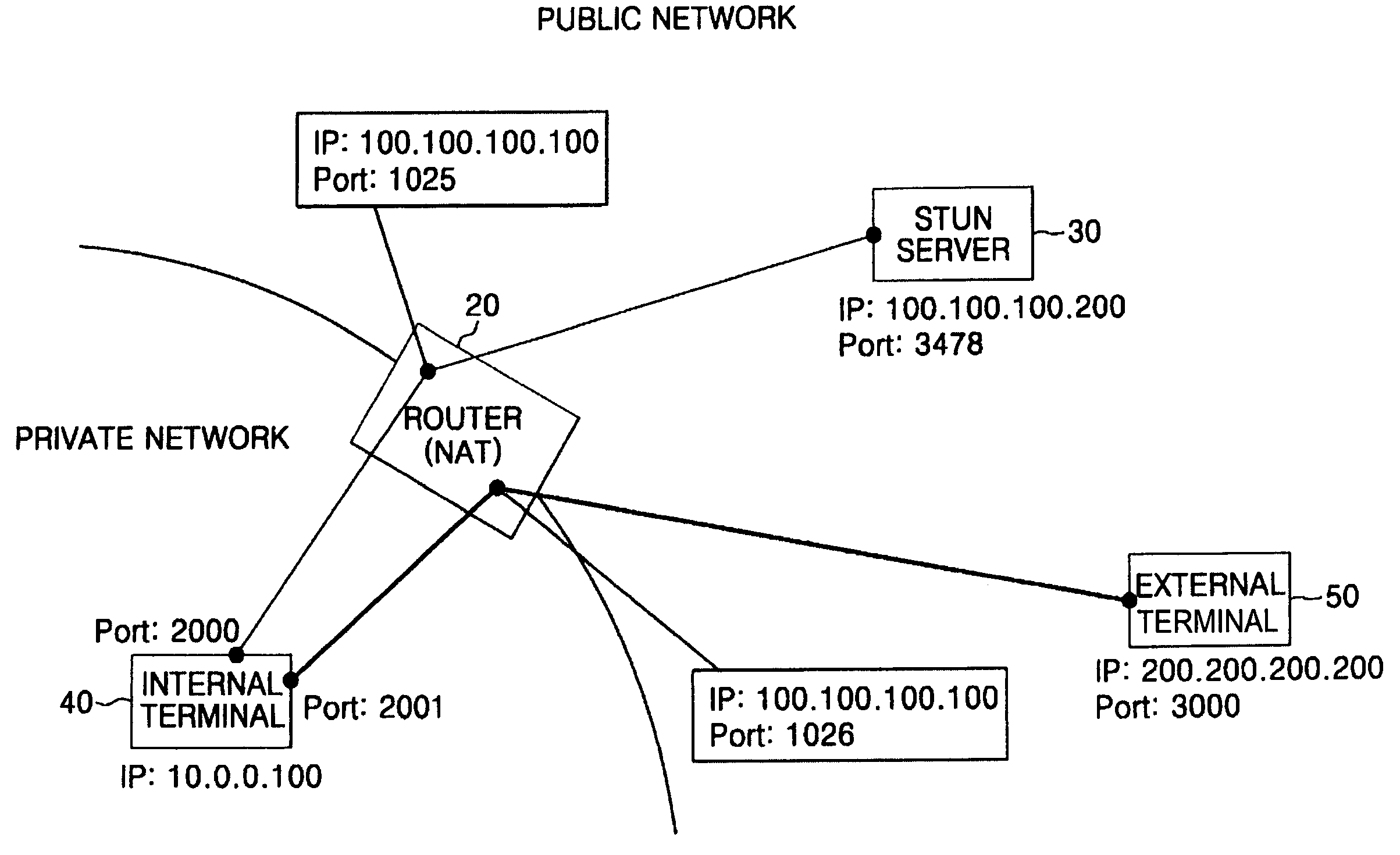
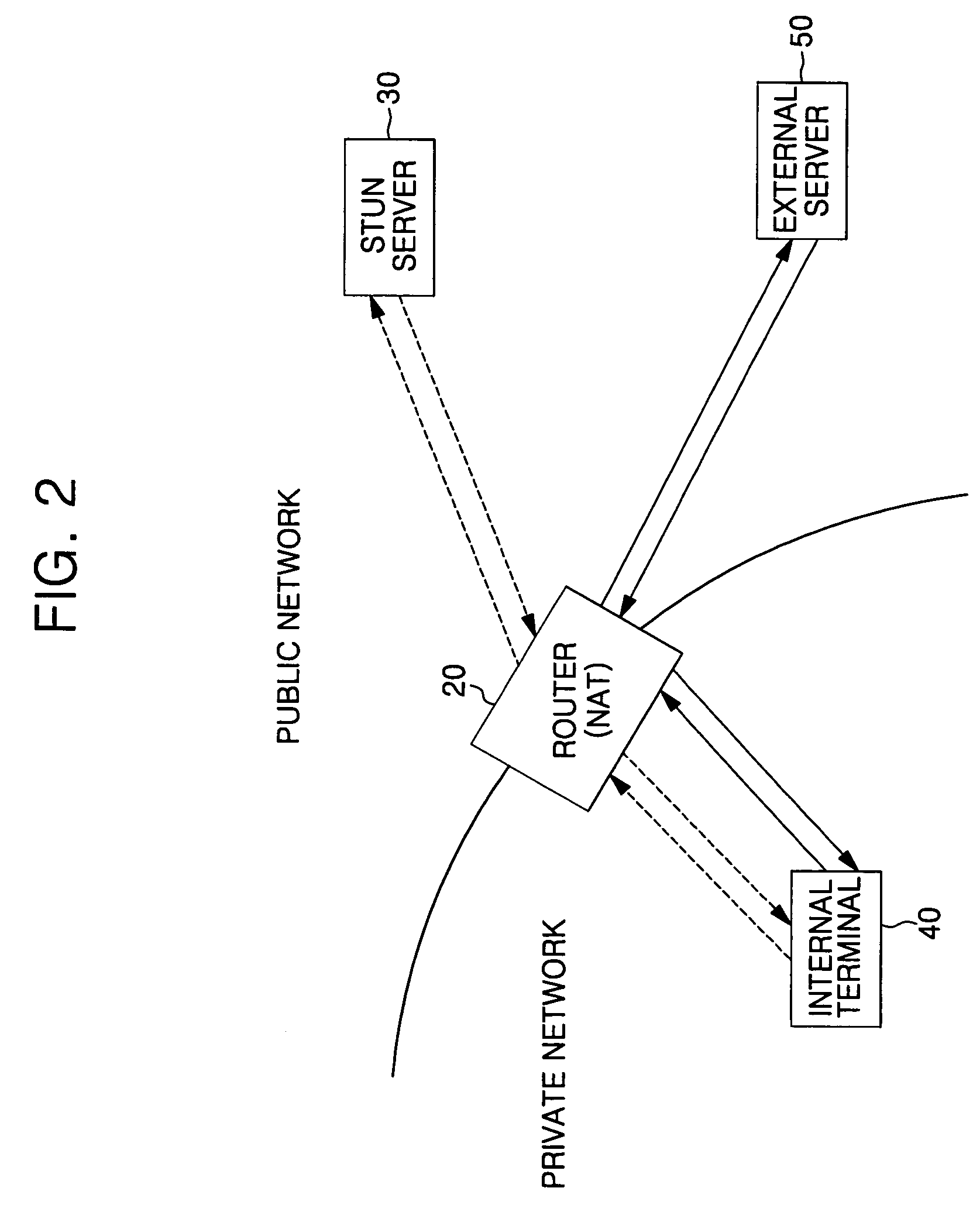
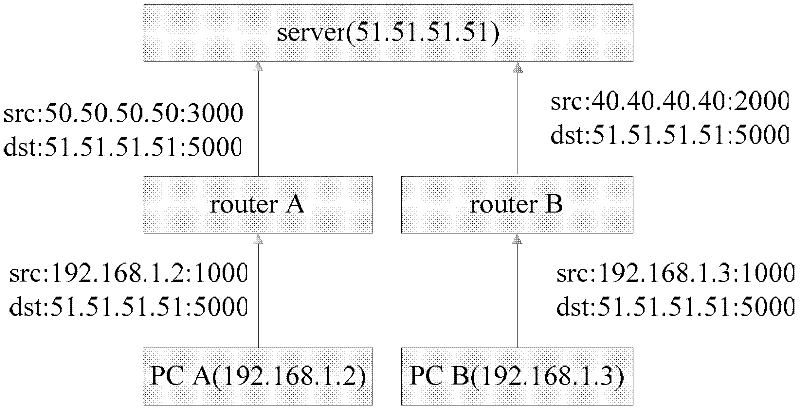
Symmetric network address translation system using STUN technique and method for implementing the same
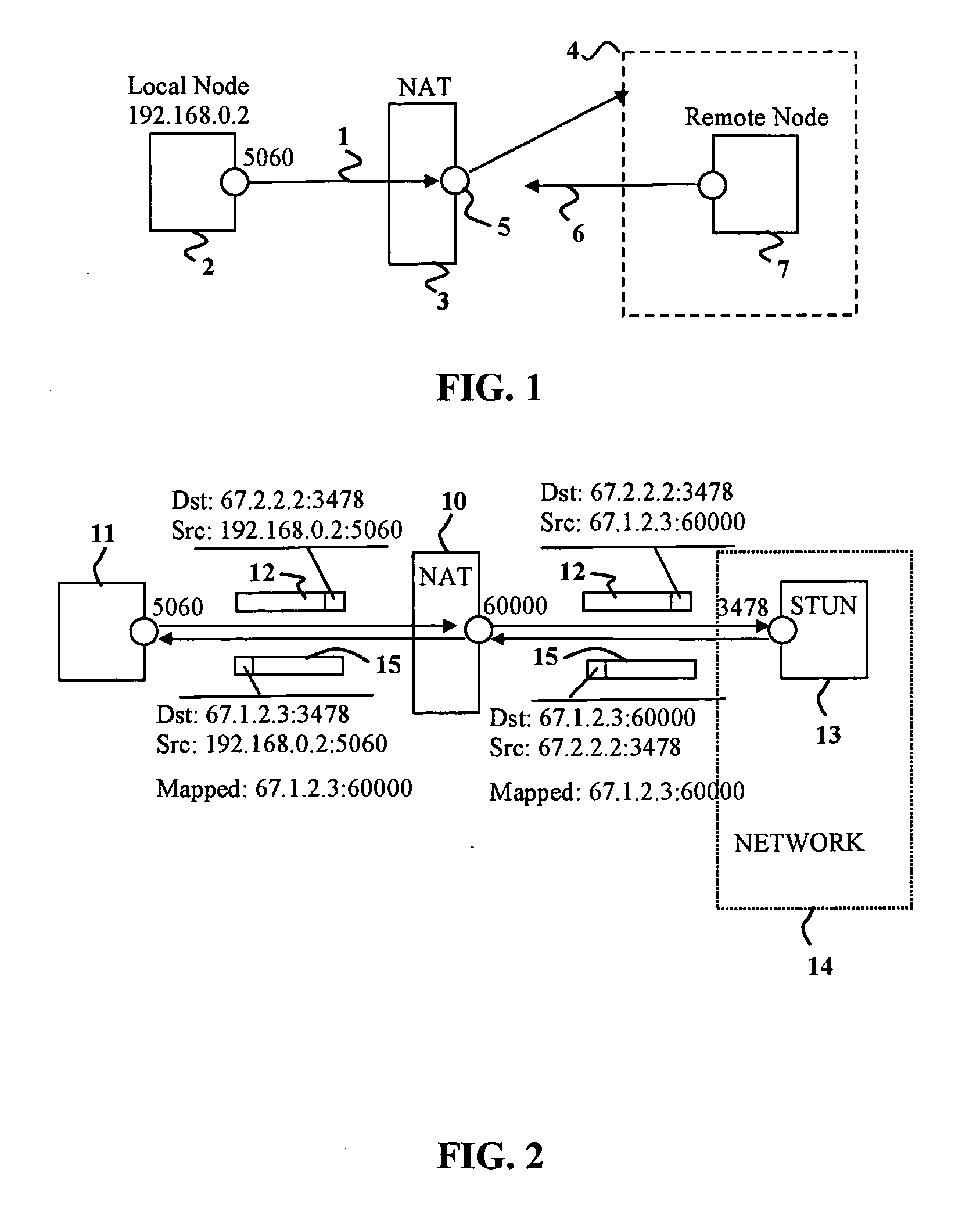
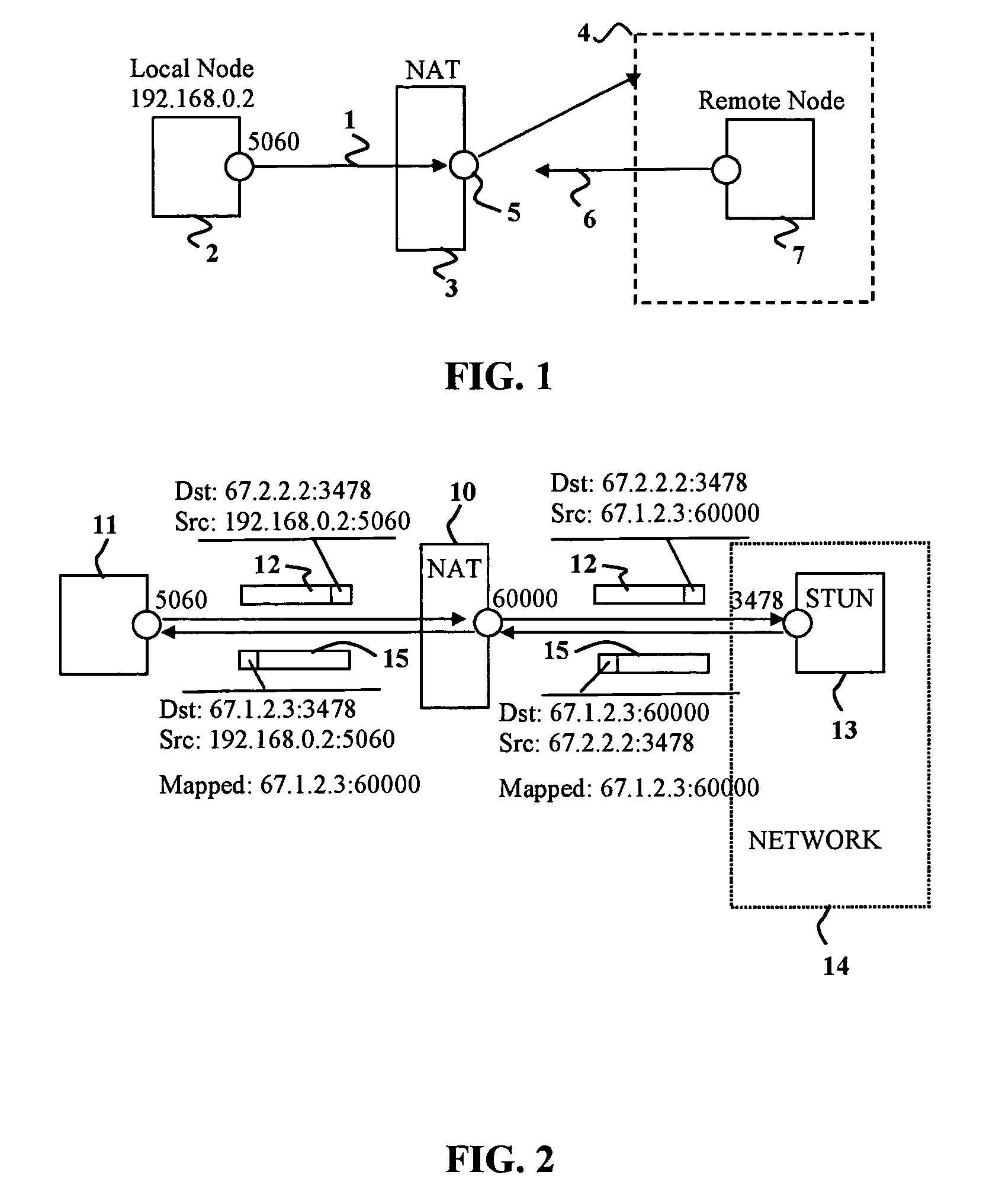
In a symmetric network address translation system using a Simple Traversal of UDP over NAT (STUN) technique and a method for implementing the same, a voice over Internet protocol (VoIP) network includes a STUN server for transmitting, to a private network terminal, a public Internet Protocol (IP) address and first port information of a router which is used for a VoIP call. The private network terminal transmits a session setup request message, including the public IP address and the first port information of the router, through its private IP address and a second port, and the router maps and stores the public IP address and the first port information of the router, and the private IP address and the second port of the private network terminal, and routes a packet received through the public IP address and the first port to the private IP address and the second port. Thus, a VoIP call is performed using the symmetric network address translation system to which the STUN technique is applied.
Owner:SAMSUNG ELECTRONICS CO LTD
Asymmetric ethernet network data transfer system and method
ActiveUS7403519B2High bandwidthImprove data transfer efficiencyBroadband local area networksTransfer systemTransfer mode
The present invention provides an asymmetric Ethernet network data transfer system and method. The present invention utilizes a network interface card being capable of an automatic transfer mode switch to form an asymmetric network data transfer system, and through which to modify the symmetry feature of the Ethernet and increase the transfer bandwidth.
Owner:VIA TECH INC
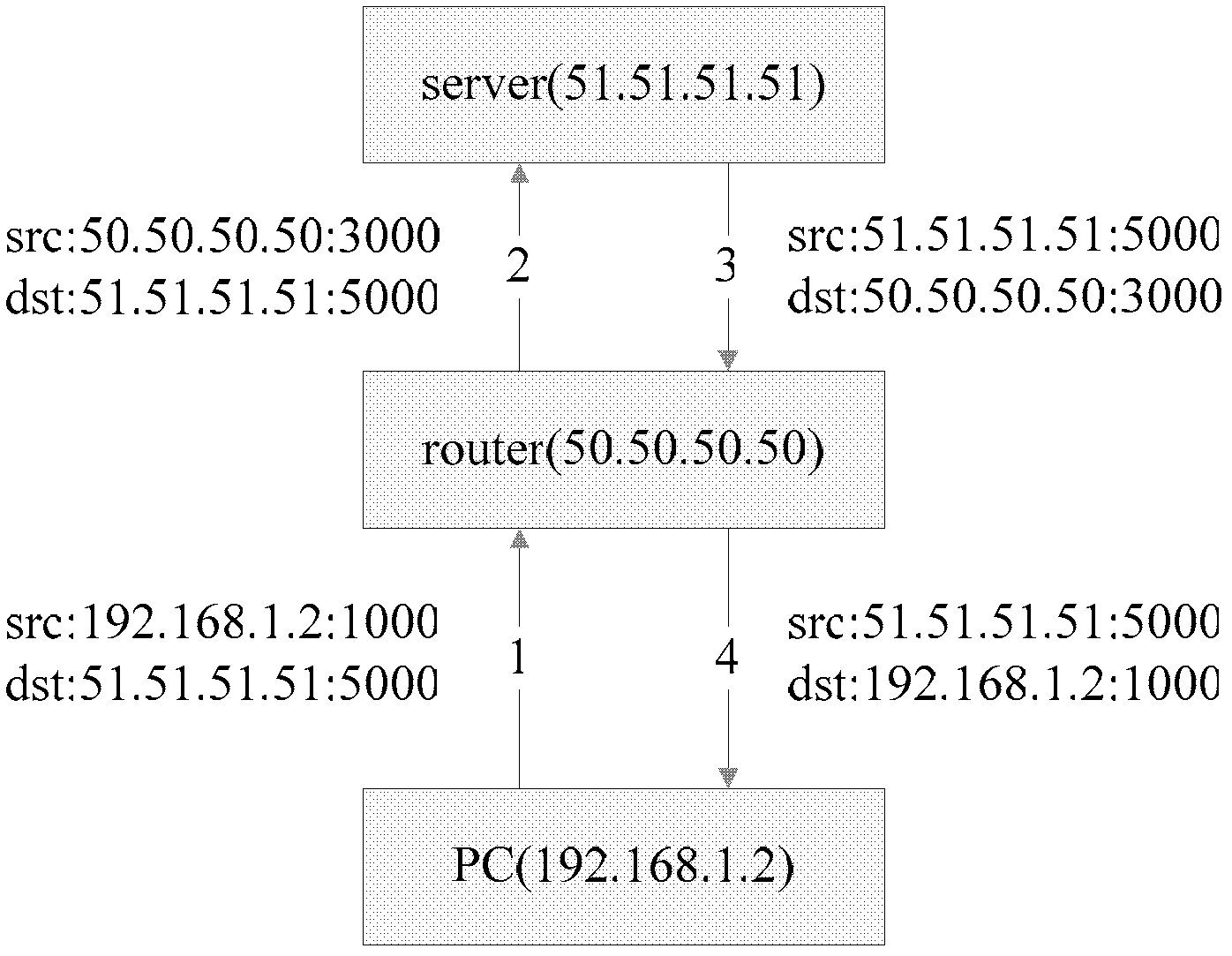
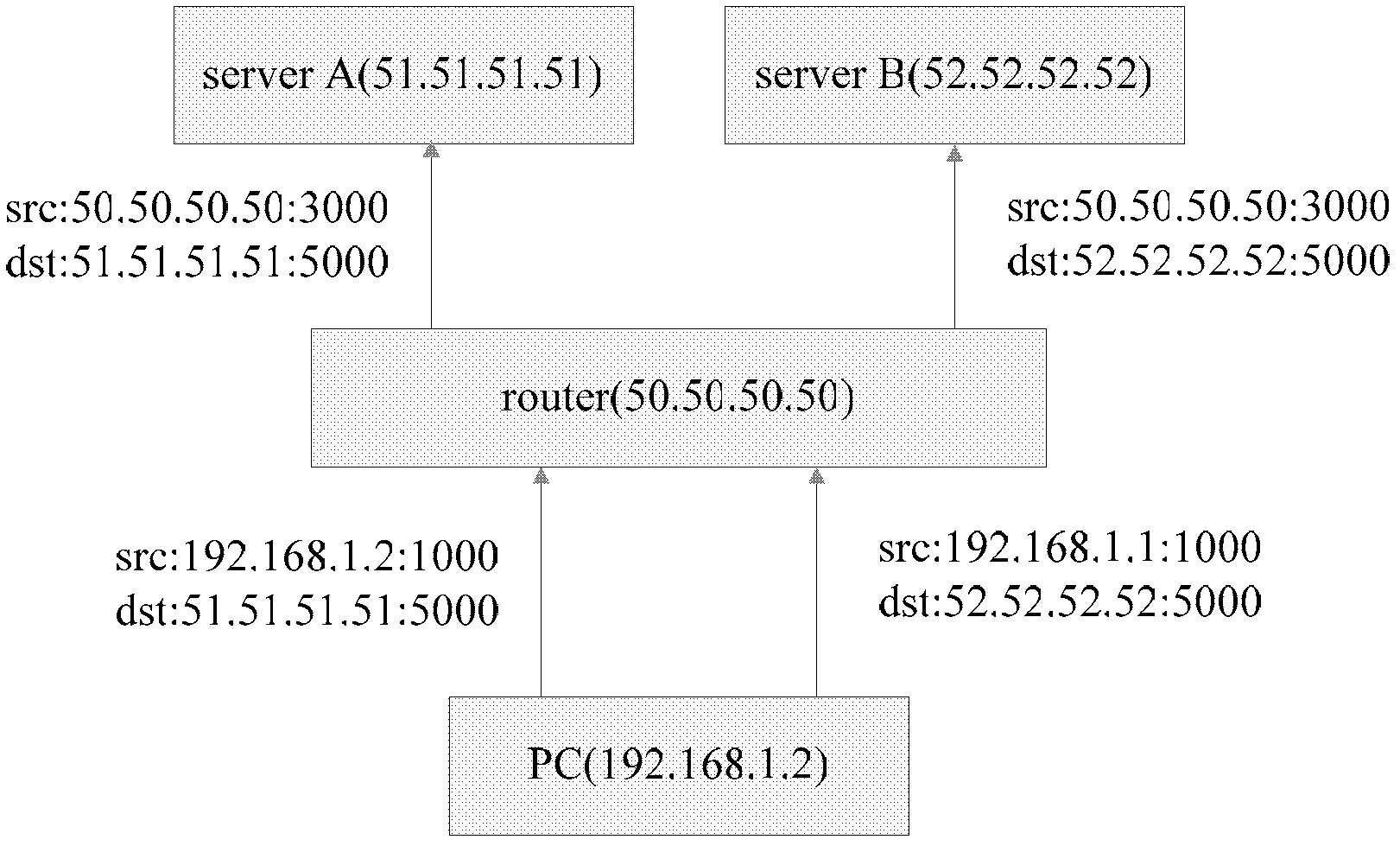
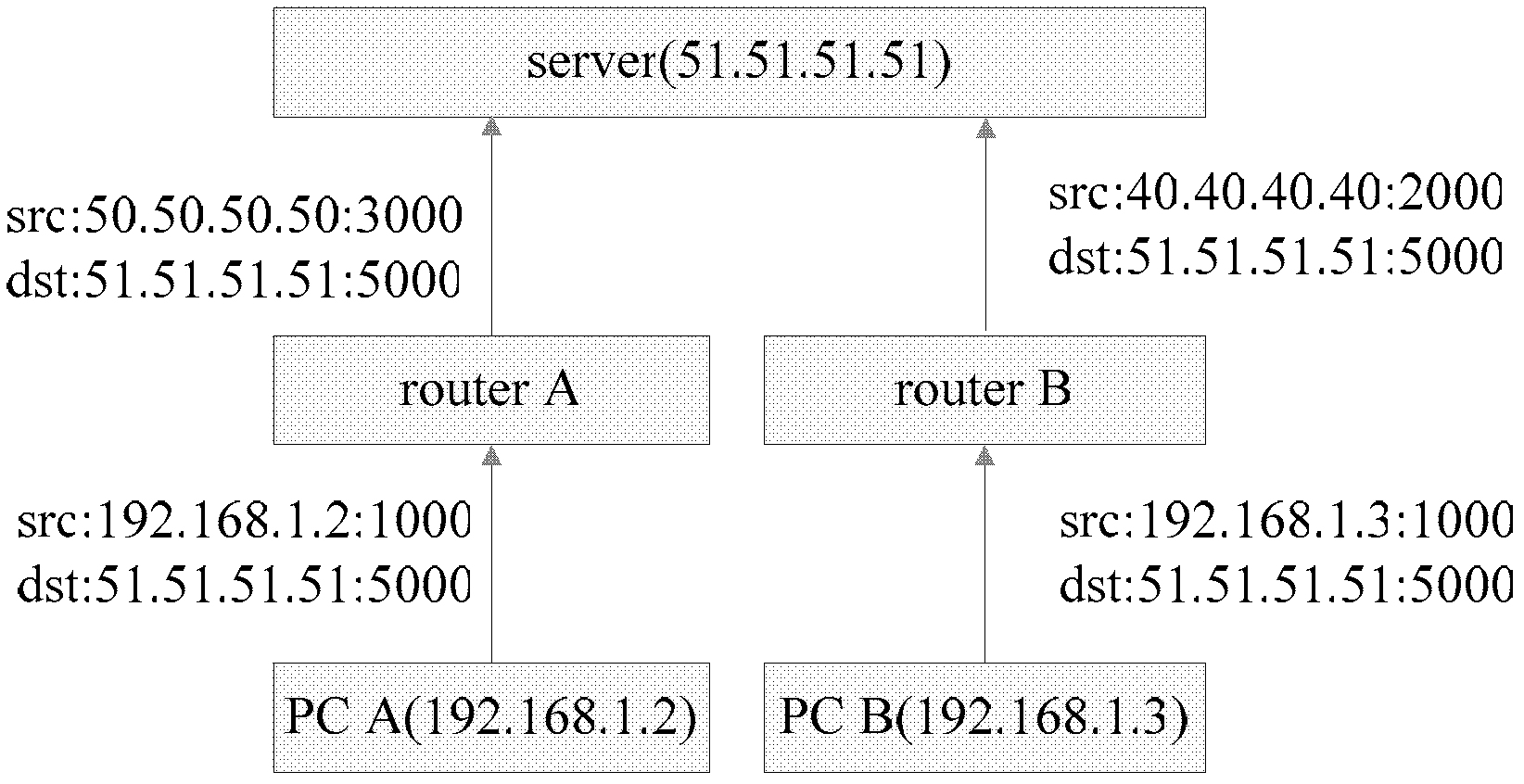
Method for operating a symmetric network address translation
ActiveUS20050165963A1Session-capacity of the NAT is advantageously significantly increasedMultiple digital computer combinationsTransmissionIp addressSymmetric network
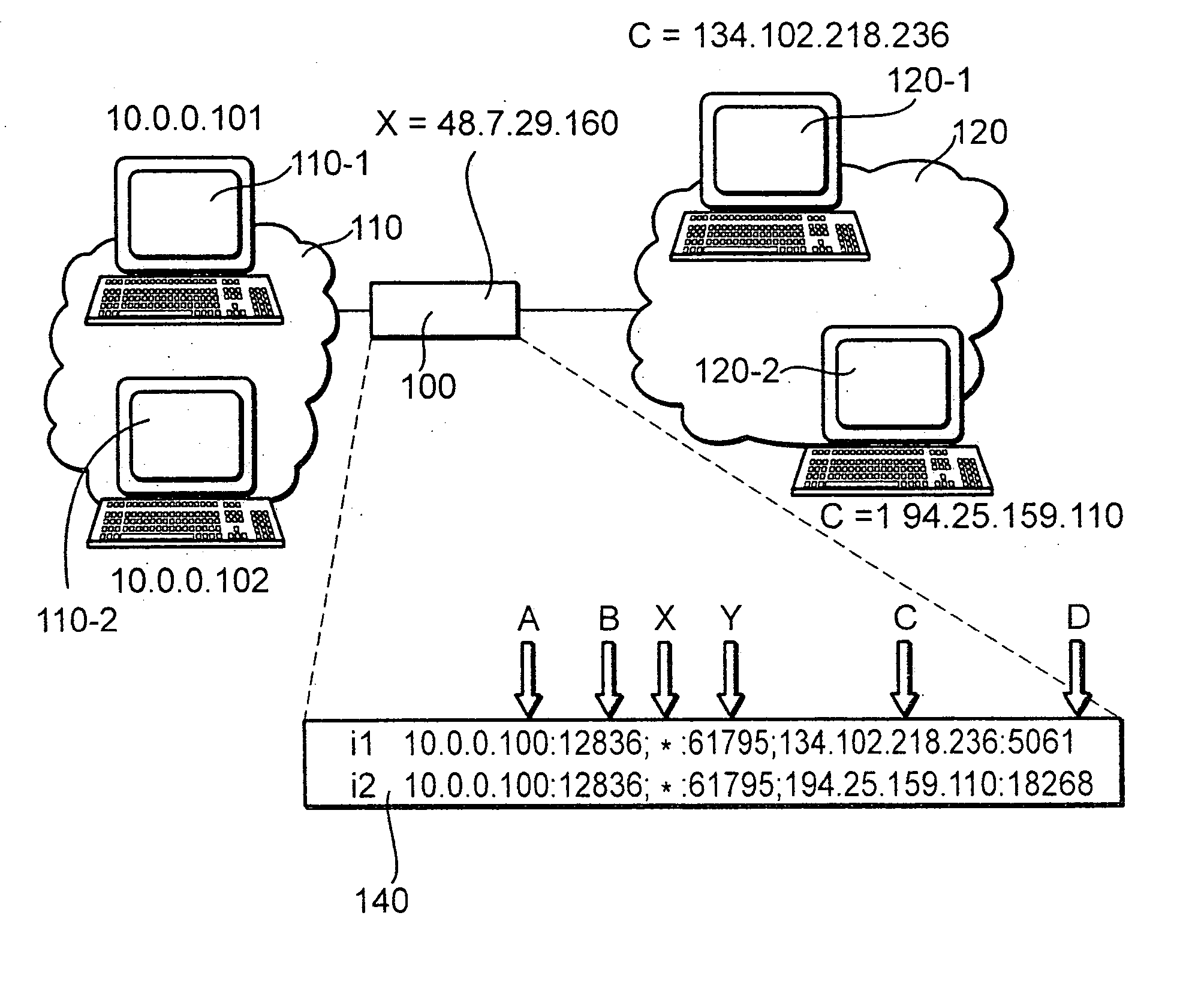
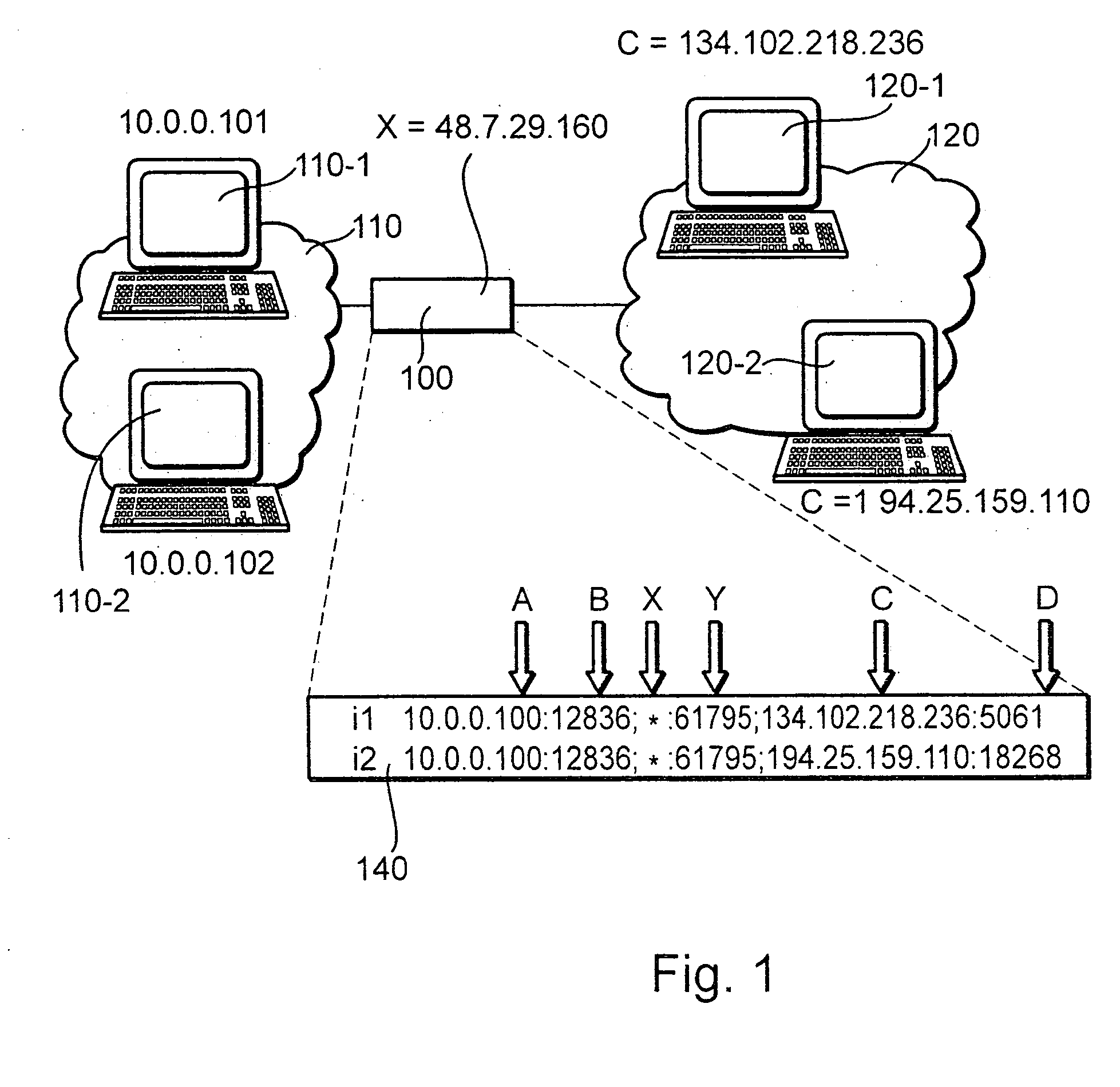
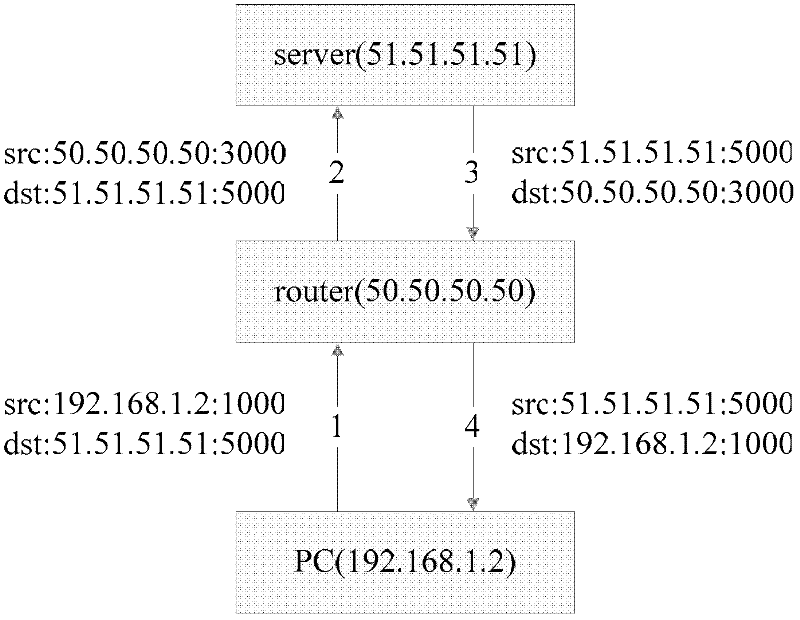
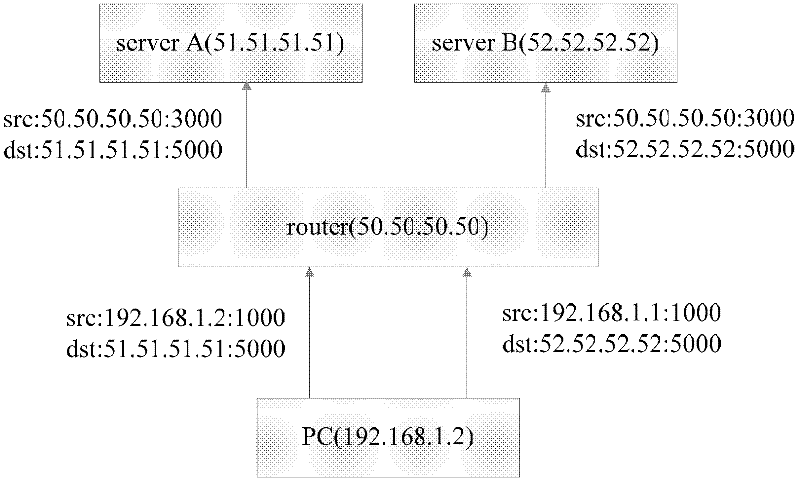
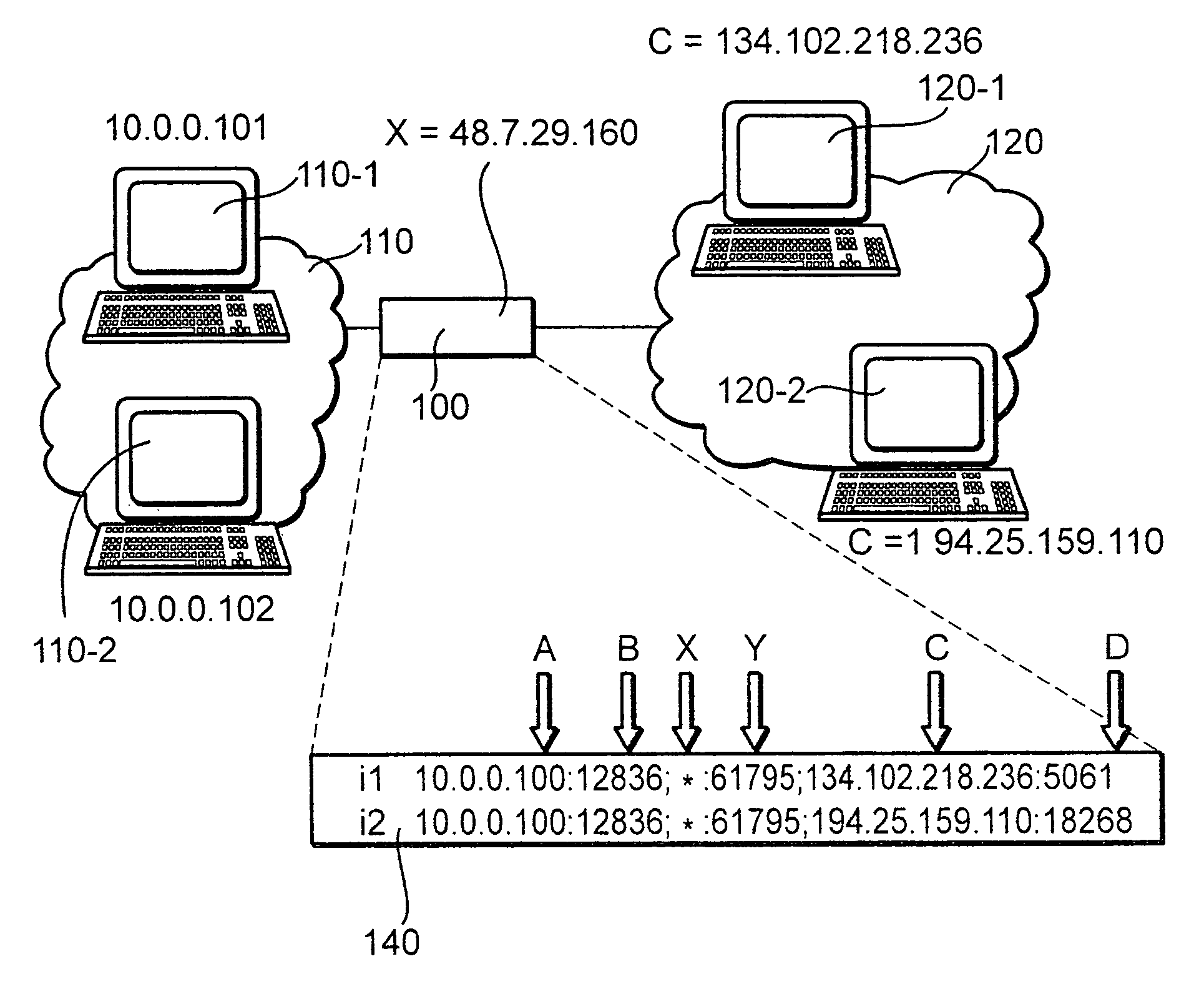
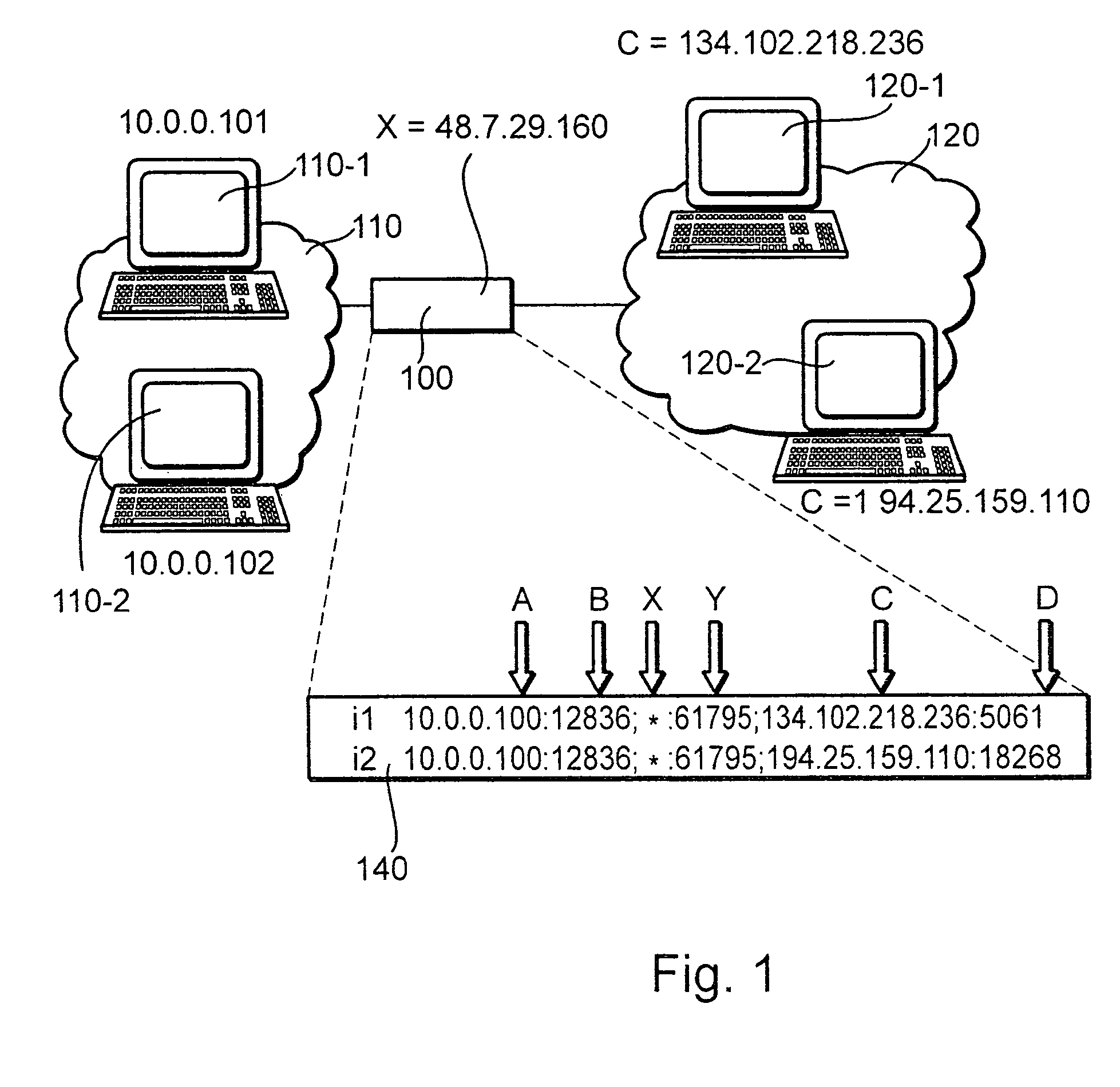
The invention relates to a method for operating a symmetric network address translation NAT (100) setting up sessions between a user terminal (110-1, 110-2) and a server (120-1, 120-2). If a new session is initiated by said user terminal an external IP-address (C) and port (D) representing the desired destination server as well as a public NAT-IP address (X) are determined. Further, a public NAT-IP port is selected. Finally, the NAT sets up the new session based on an appropriate entry representing said new session in a NAT table. In order to save available public NAT-IP ports a new session according to the invention not necessarily represented by a new public NAT-IP port, but by a tuple comprising the public NAT-IP address, the selected public NAT-IP port (Y), the external IP address (C) and the port (D). A new session is set up only if there is an entry of the whole tuple identifying said new session in said NAT-table.
Owner:ALCATEL LUCENT SAS
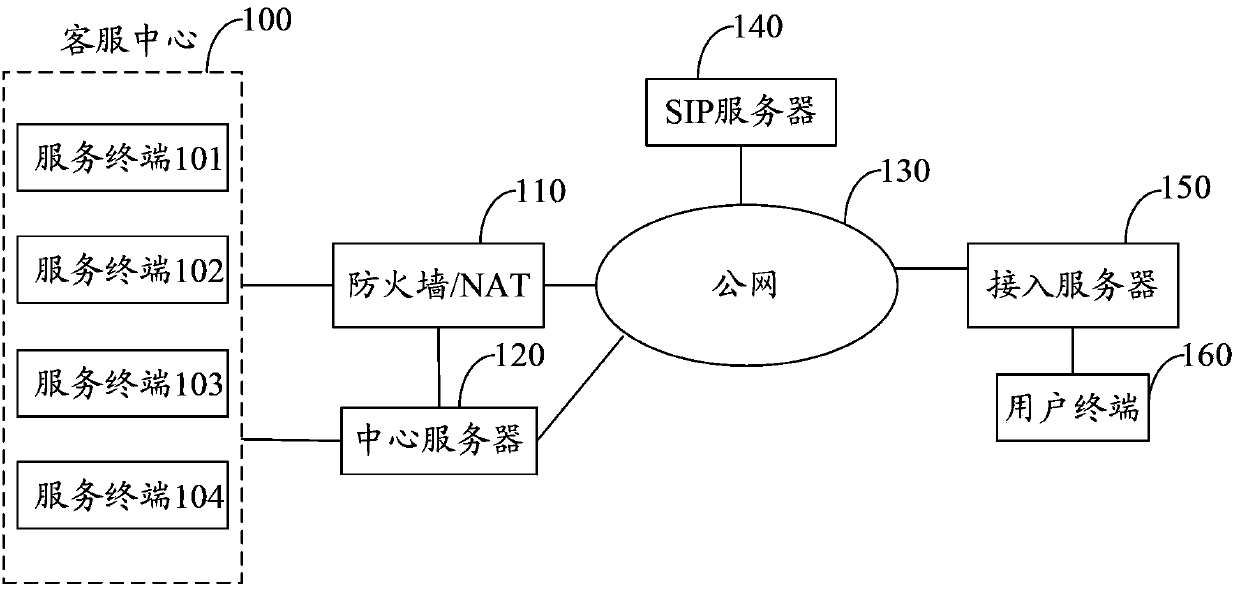
Method for realizing intranet penetration by using Internet group management protocol (IGMP) and intranet penetration system
ActiveCN102420774ARealize intranet penetrationGood effectData switching networksComputer networkUser Datagram Protocol
The invention discloses a method for realizing intranet penetration by using an Internet group management protocol (IGMP), and aims to overcome the shortcoming that a system using a Symmetric network address translator (NAT) cannot actively access another terminal by using one terminal. The method mainly comprises the following steps that: a first terminal transmits a request to a server, and is kept to be connected with the server; a second terminal transmits an IGMP message, establishes a multicast domain, is classified into a group, locally establishes a user datagram protocol (UDP) socket and performs snooping on a port; the second terminal transmits a multicast domain value and a port value to the server, and initiates an access request; the server forwards the access request to the first terminal; and the first terminal transmits data to a second router, and the second router forwards the data to the second terminal. The invention also discloses an intranet penetration system, which comprises at least two terminals, a router and the server. The method is applied to various systems of which each accesses another terminal by using one terminal, particularly to the system using the Symmetric NAT.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
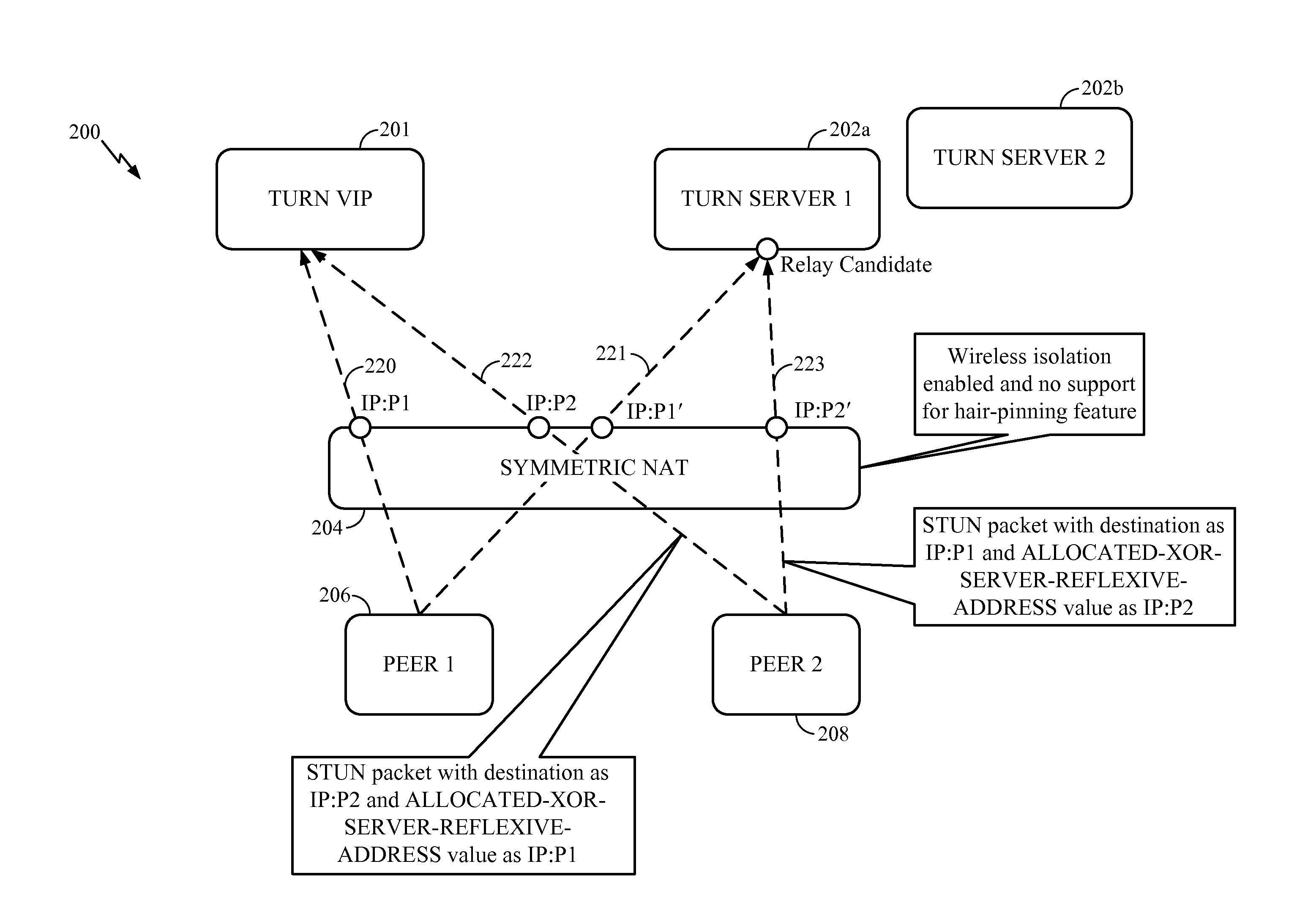
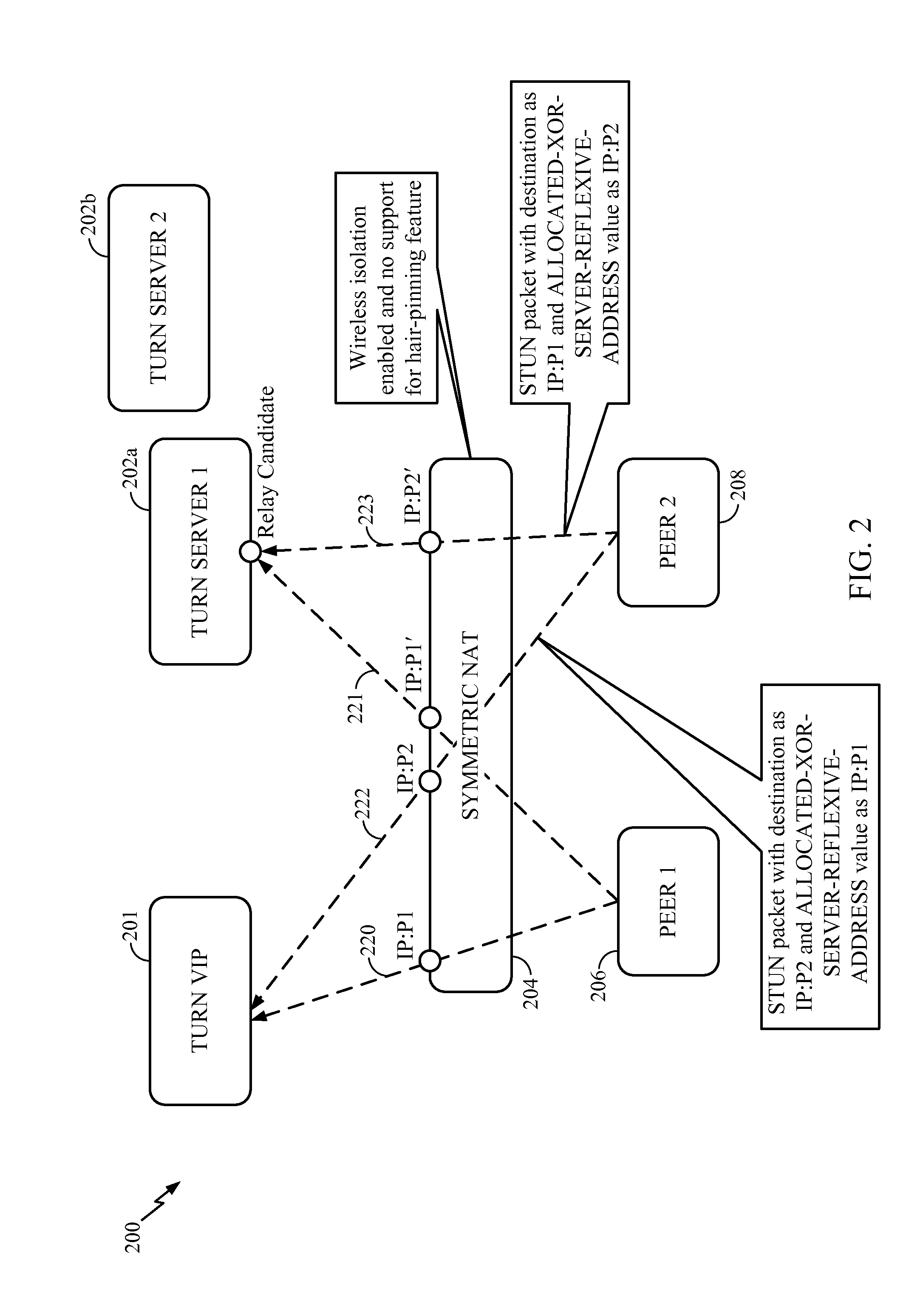
Peer-to-peer communication for symmetric NAT
InactiveUS20150113154A1Multiple digital computer combinationsTransmissionInteractive Connectivity EstablishmentThe Internet
Systems and methods for communicating between a first and a second peer using interactive connectivity establishment (ICE) protocol, the first and second peers sharing a symmetric network address translation (NAT) having wireless isolation enabled and no support for hair-pinning. At a first Traversal Using Relay NAT (TURN) server designated as a relay candidate by a TURN Virtual Internet Platform (VIP), it is determined that a first port allocated by the symmetric NAT for a first request for communication initiated by the first peer and directed to the TURN VIP, is different from a second port allocated by the symmetric NAT for a first packet transmitted from the first peer to the first TURN server, based on a first indication. The second port is mapped to the first port. Using a similar port mapping for the second peer, peer-to-peer communication between the first and second peers is enabled.
Owner:QUALCOMM INC
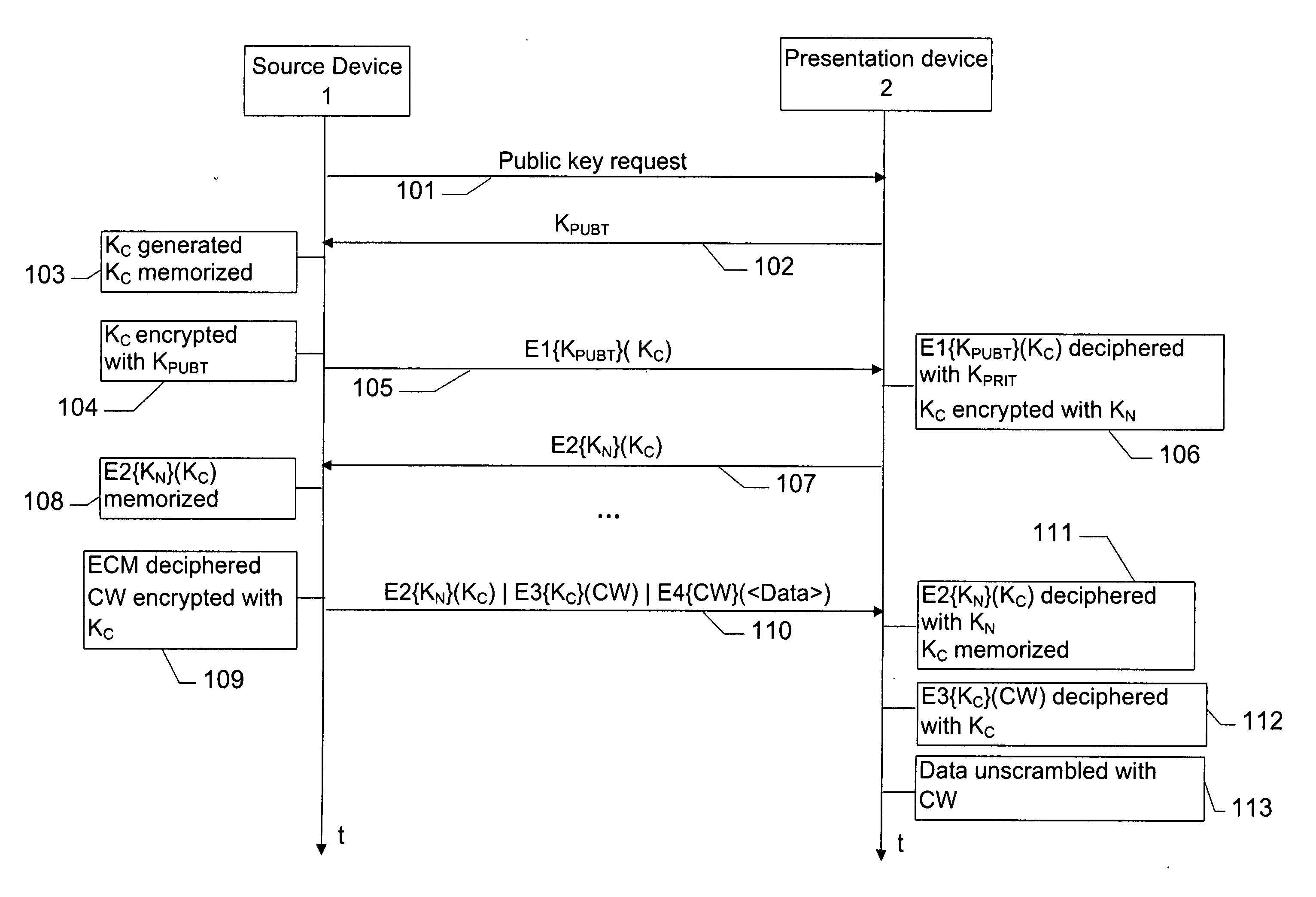
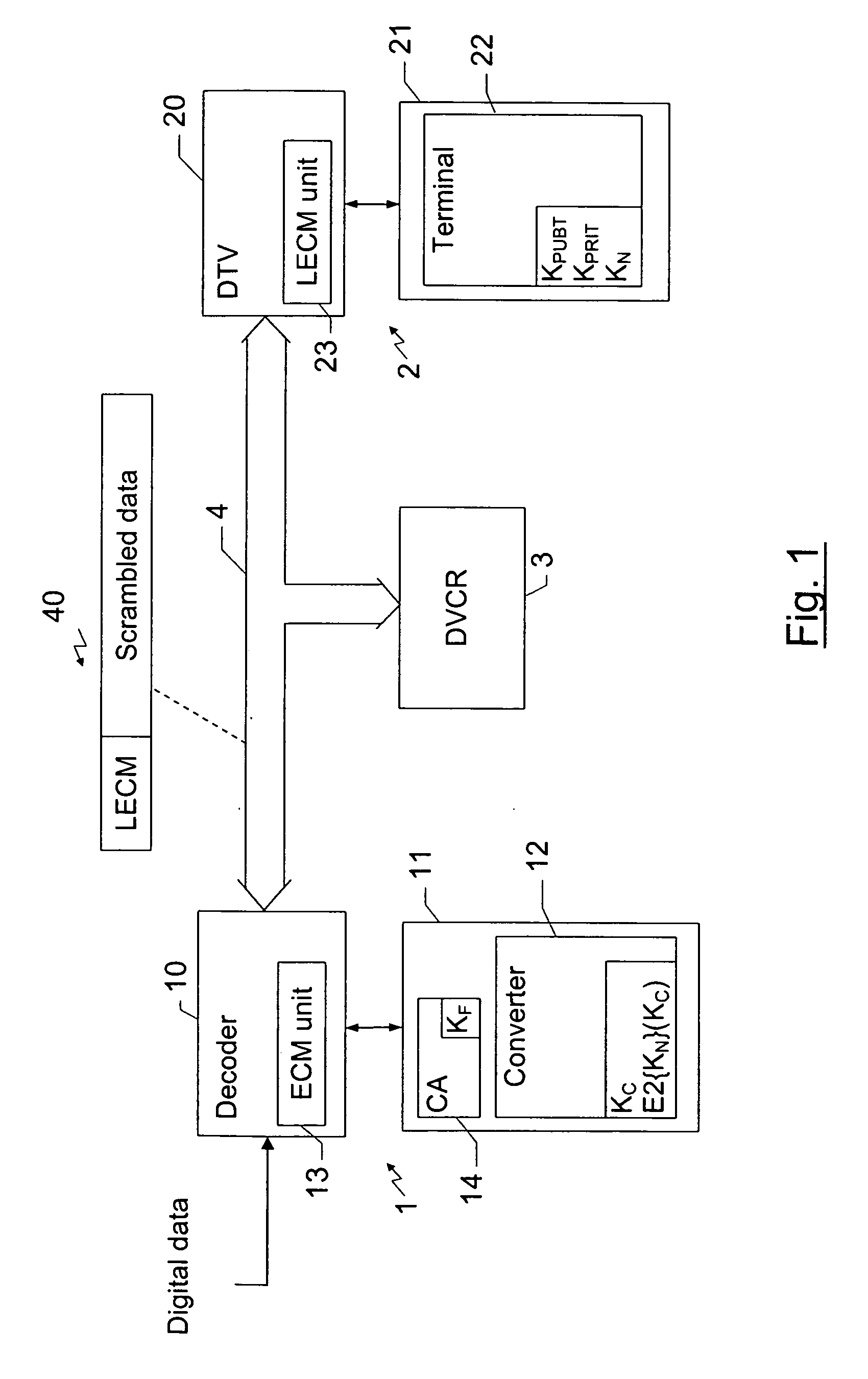
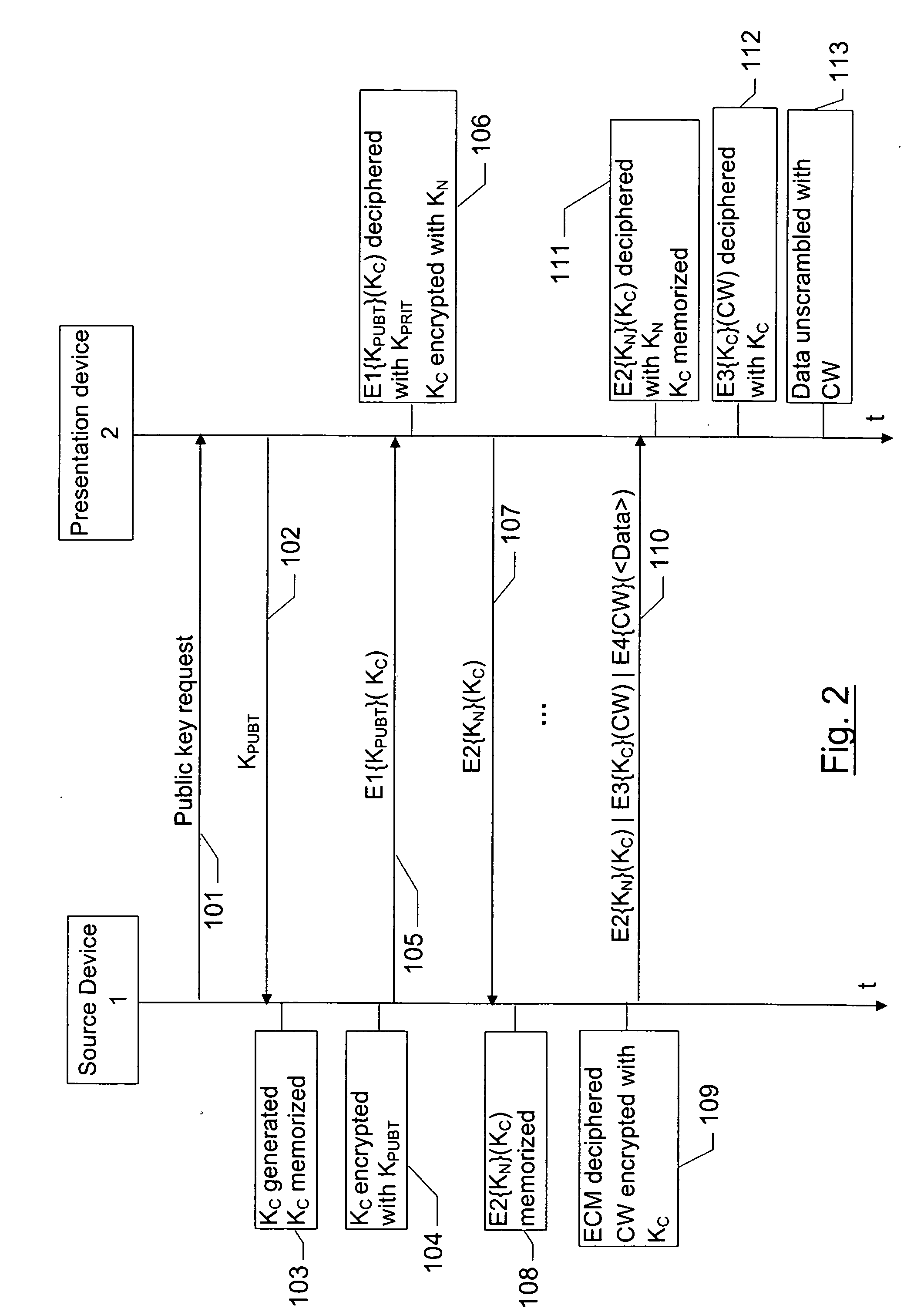
Simplified method for renewing symmetrical keys in a digital network
InactiveUS20060104440A1Key distribution for secure communicationUser identity/authority verificationDisplay deviceNetwork key
The invention concerns a method implemented in a communication network comprising a source device including: a first symmetrical key for encrypting data to be transmitted to a display device connected to the network; and the first symmetrical key encrypted with a second symmetrical network key known only to at least one display device connected to the network. When the source device needs to renew its first symmetrical key to encrypt new data, it generates a random number, then it calculates a new symmetrical key based on the first symmetrical key and on the random number. It then encrypts the data to be transmitted with the new symmetrical key and transmits to a display device, via the network: the data encrypted with the new symmetrical key, the random number, and the first encrypted symmetrical key with the second symmetrical network key.
Owner:THOMSON LICENSING SA
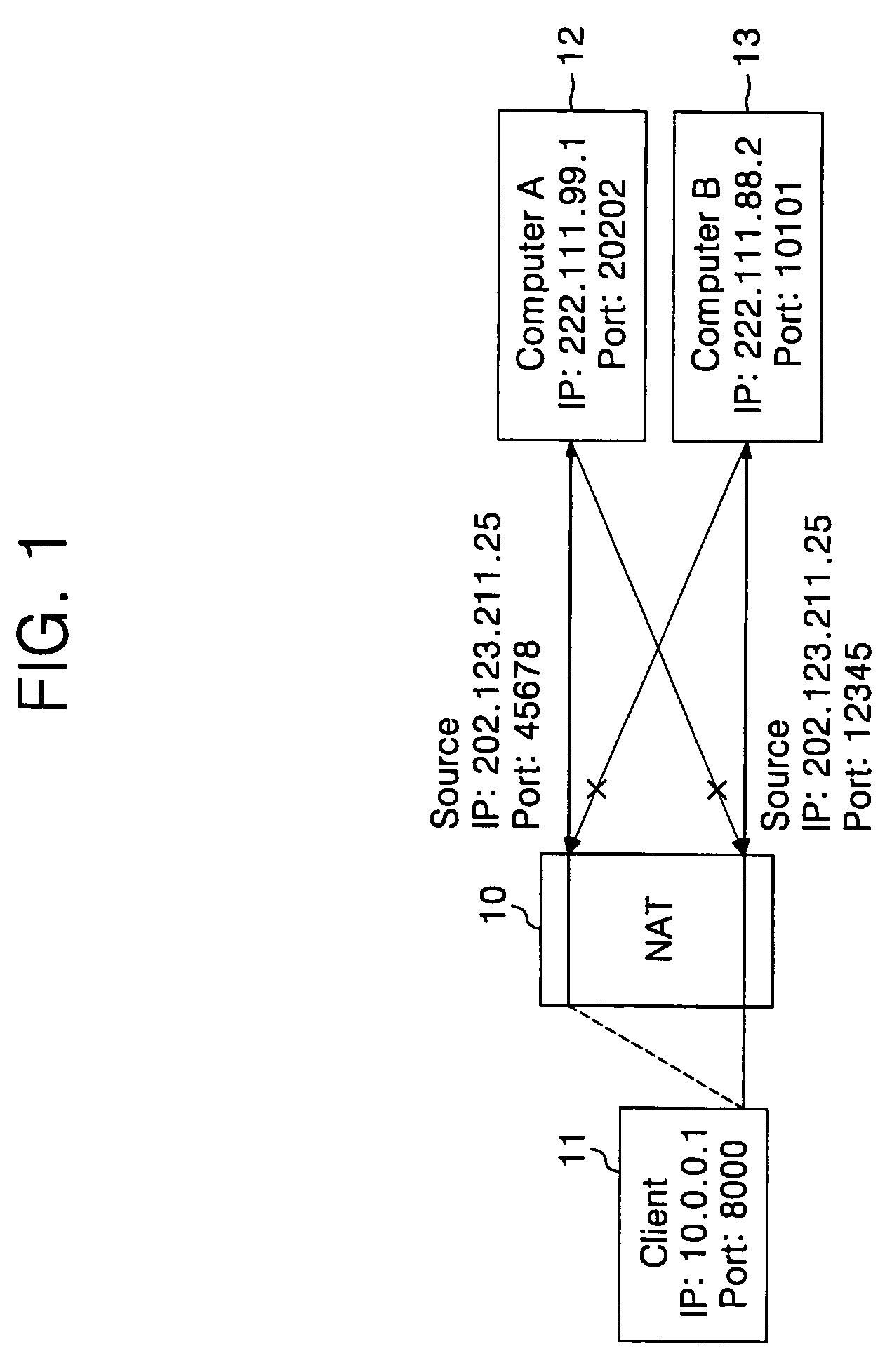
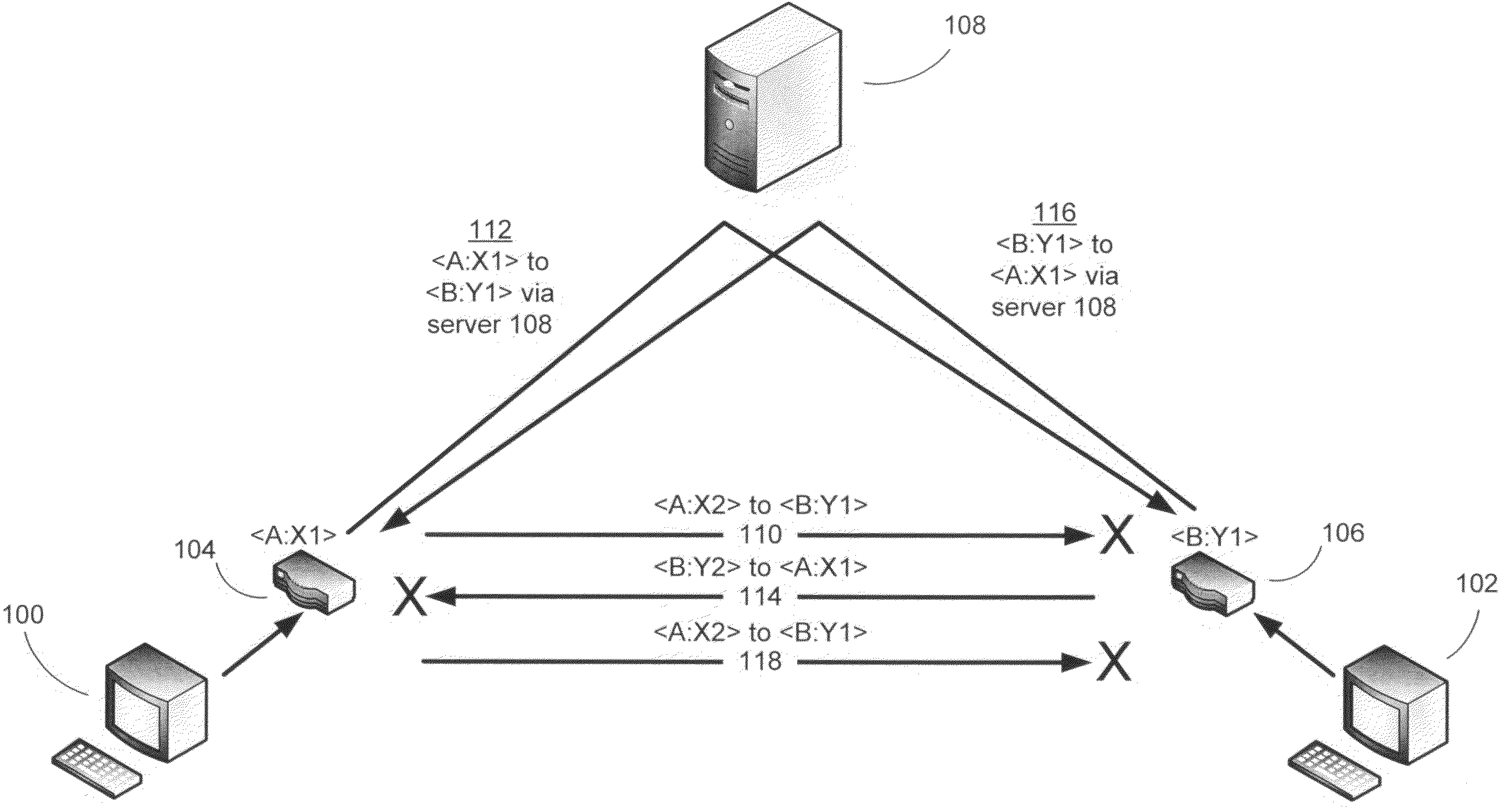
Communicating using the port-preserving nature of symmetric network address translators
InactiveUS20080253383A1Data switching by path configurationNetwork connectionsNetwork addressingNetwork address translation
Methods for establishing connections between computing devices when the computing devices are behind Network Address Translators (NATs). Embodiments of the present invention are directed to enabling a first client computer to communicate with a second client computer when both client computers are positioned behind NATs, wherein at least one of the NATs is a port-preserving NAT.
Owner:MICROSOFT TECH LICENSING LLC
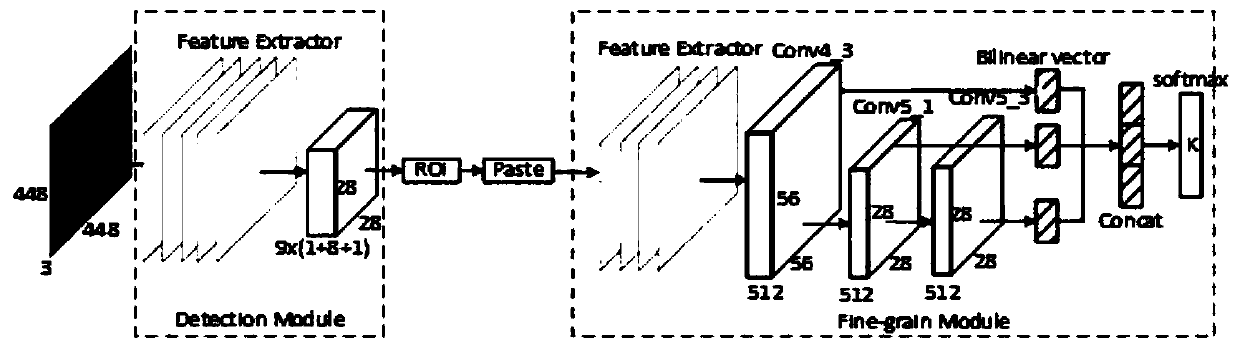
Image fine-grained recognition method based on multi-scale feature fusion
The invention discloses a retinal vessel segmentation method based on dense convolution and depth separable convolution. The method comprises the following steps: preprocessing an original image of aretinal vessel map; carrying out data enhancement on the data set; constructing a full convolutional neural network based on combination of dense convolution and depth separable convolution, and training the training set by using a loss function with weight; and testing and obtaining a final segmentation result graph. Encoding-decoding symmetric network is used as a backbone network. The additiondepth can separate convolution, so that the model parameter quantity is greatly reduced; dense convolution blocks are used, all layers are connected on a channel, information transmission is enhanced,and characteristic values of all scales are effectively utilized; in the image preprocessing process, self-adaptive gamma correction is carried out on the image, different gamma values are used for correcting different feature areas, and background noise is weakened while the feature contrast ratio is improved; during training, a loss function with weight is used to enhance the proportion of theblood vessel to be segmented during training.
Owner:SOUTHEAST UNIV
Identification method of social network spam account based on user relationship
InactiveCN109102418AEasy to identifyImprove accuracyData processing applicationsRelation graphFeature extraction
The invention discloses a social network garbage account identification method based on user relationship, which comprises the following steps: acquiring friend-fan relationship data of the social media account, constructing a local network relationship diagram, constructing a local symmetric network structure diagram and extracting symmetric characteristics of the network structure, and adoptinga supervised learning method to carry out garbage account identification. On the basis of constructing a user local network relation graph, as the network relationship extends from a single user network relationship to a two-way network relationship between the us and other users, the local network diagram is expanded and the new feature extraction method is adopted, which shows better stability in the garbage account identification, greatly reduces the content fraud of the garbage account identification, and makes the identification of the garbage account in the accuracy has been significantly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
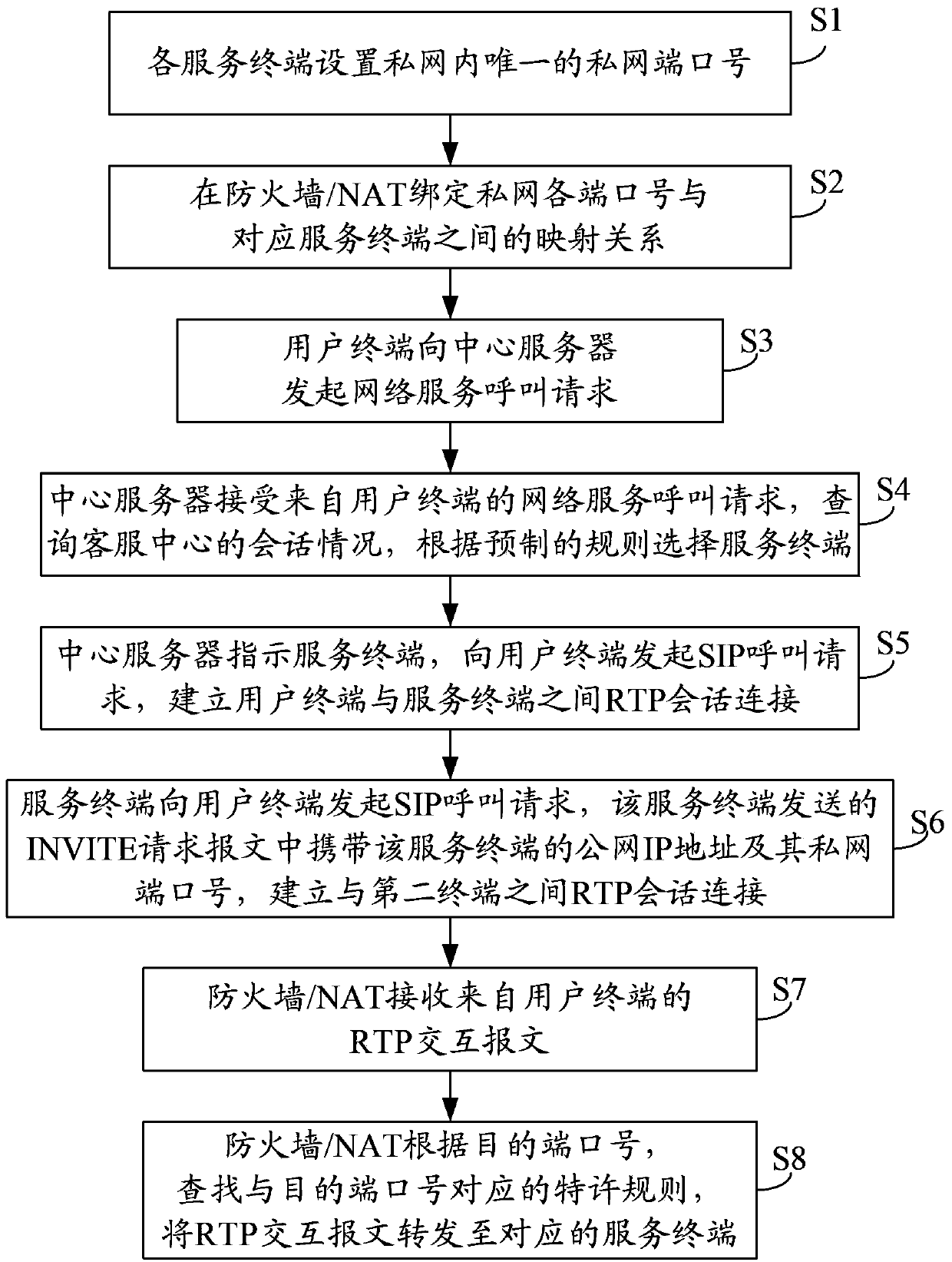
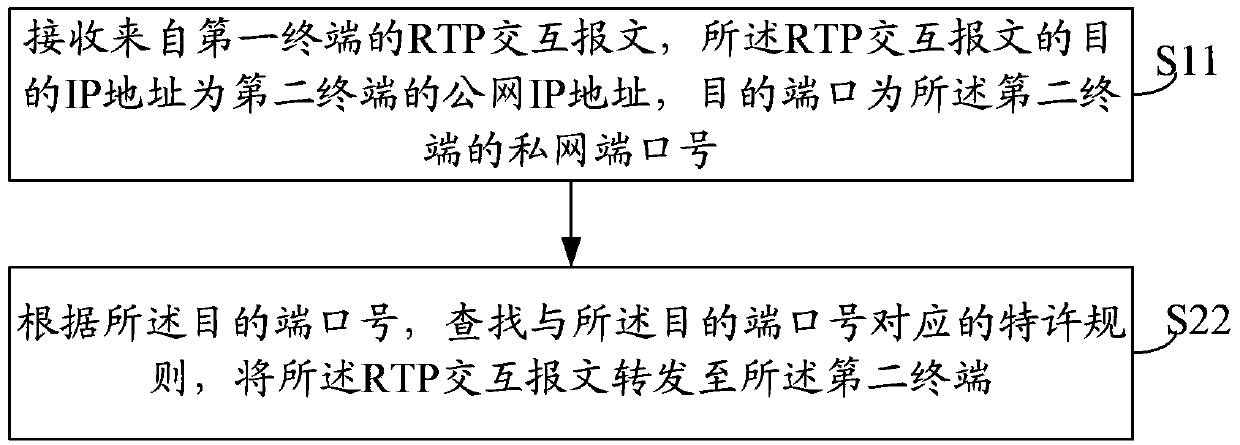
Network crossing method, device and system
ActiveCN103391334AThrough realizationReduce overhead costsTransmissionNetwork deploymentTime Protocol
An embodiment of the invention provides a network crossing method, device and system to achieve effective network crossing, particularly the network crossing of symmetric network address transmission (NAT) under the condition that network deployments are not changed. The network crossing method comprises that an NAT device receives a real time protocol (RTP) interaction message from a first terminal, the destination internet protocol (IP) address of the RTP interaction message is the public network IP address of a second terminal, and the destination port of the RTP interaction message is the private network port number of the second terminal; the NAT device searches a license rule corresponding to the destination port number according to the destination port number and forwards the RTP interaction message to the second terminal.
Owner:GUIYANG LONGMASTER INFORMATION & TECHNOLOGY CO LTD
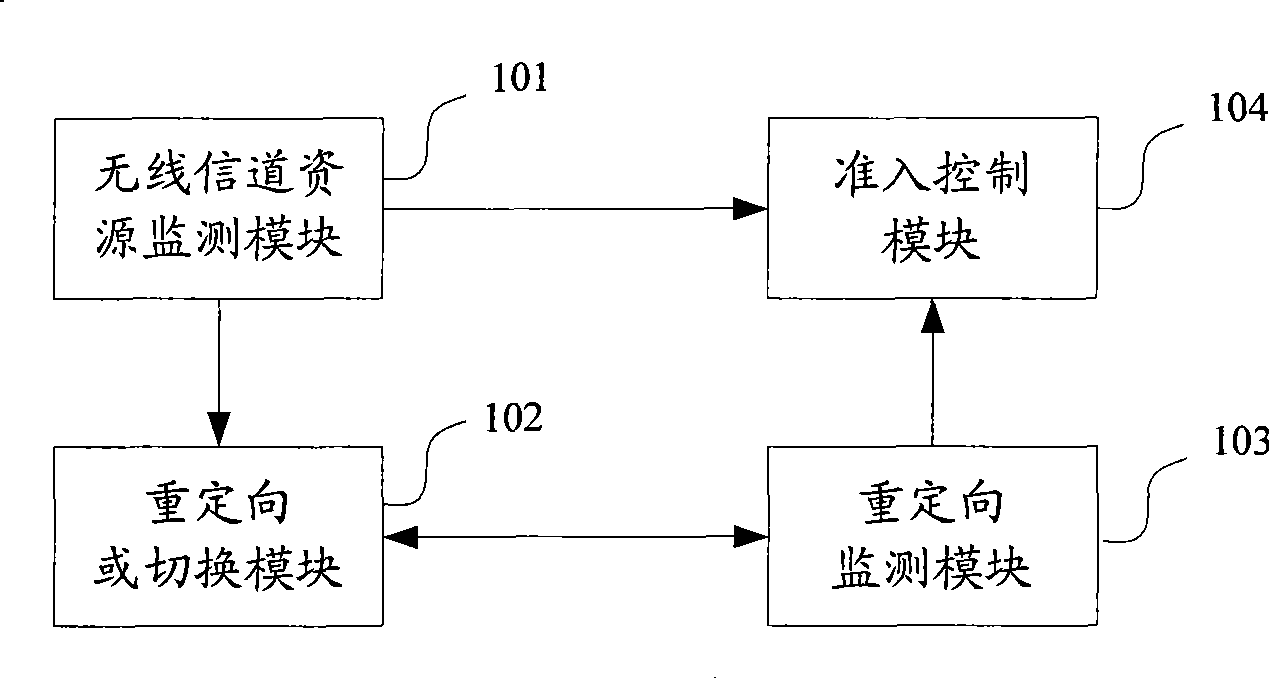
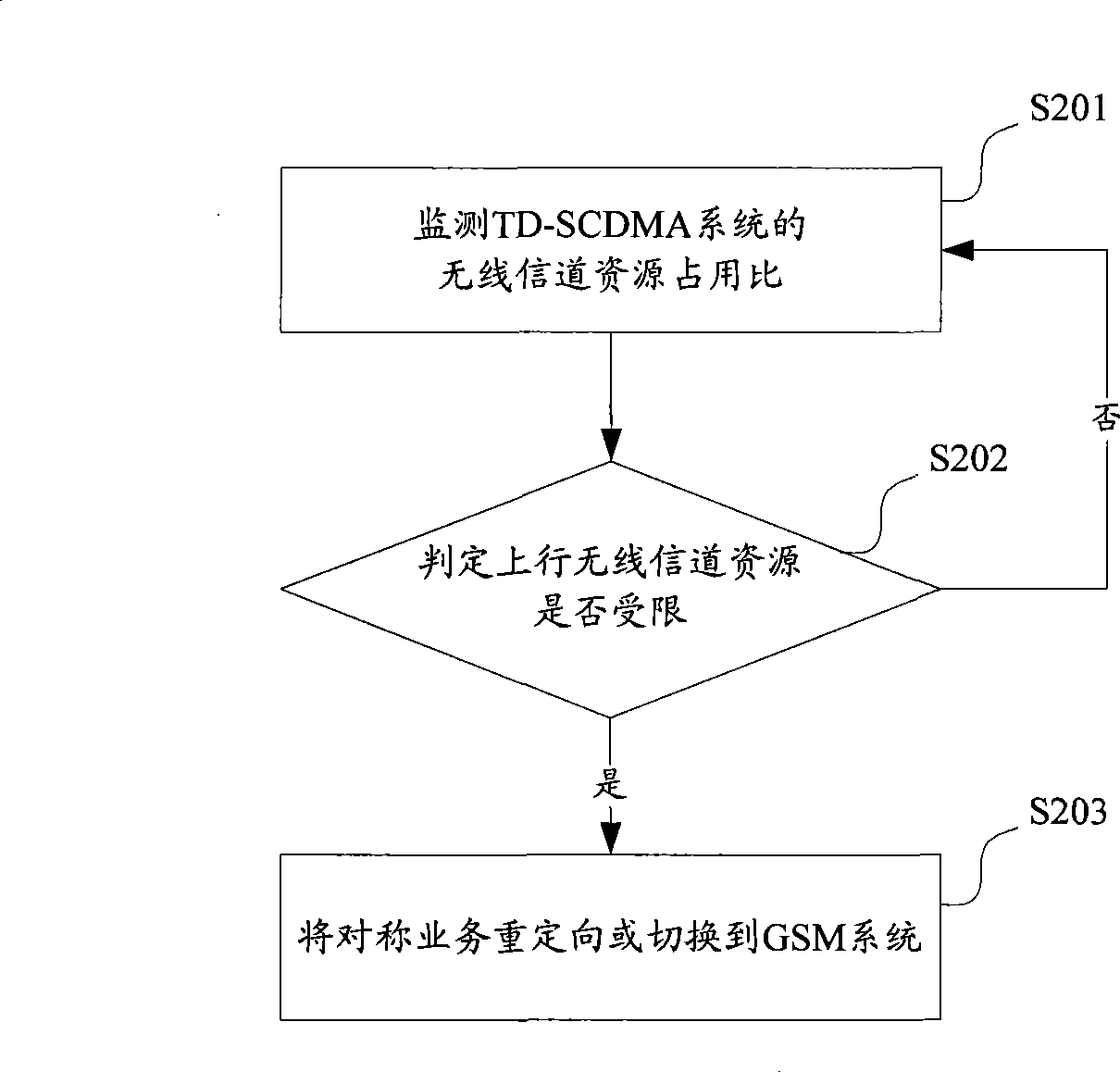
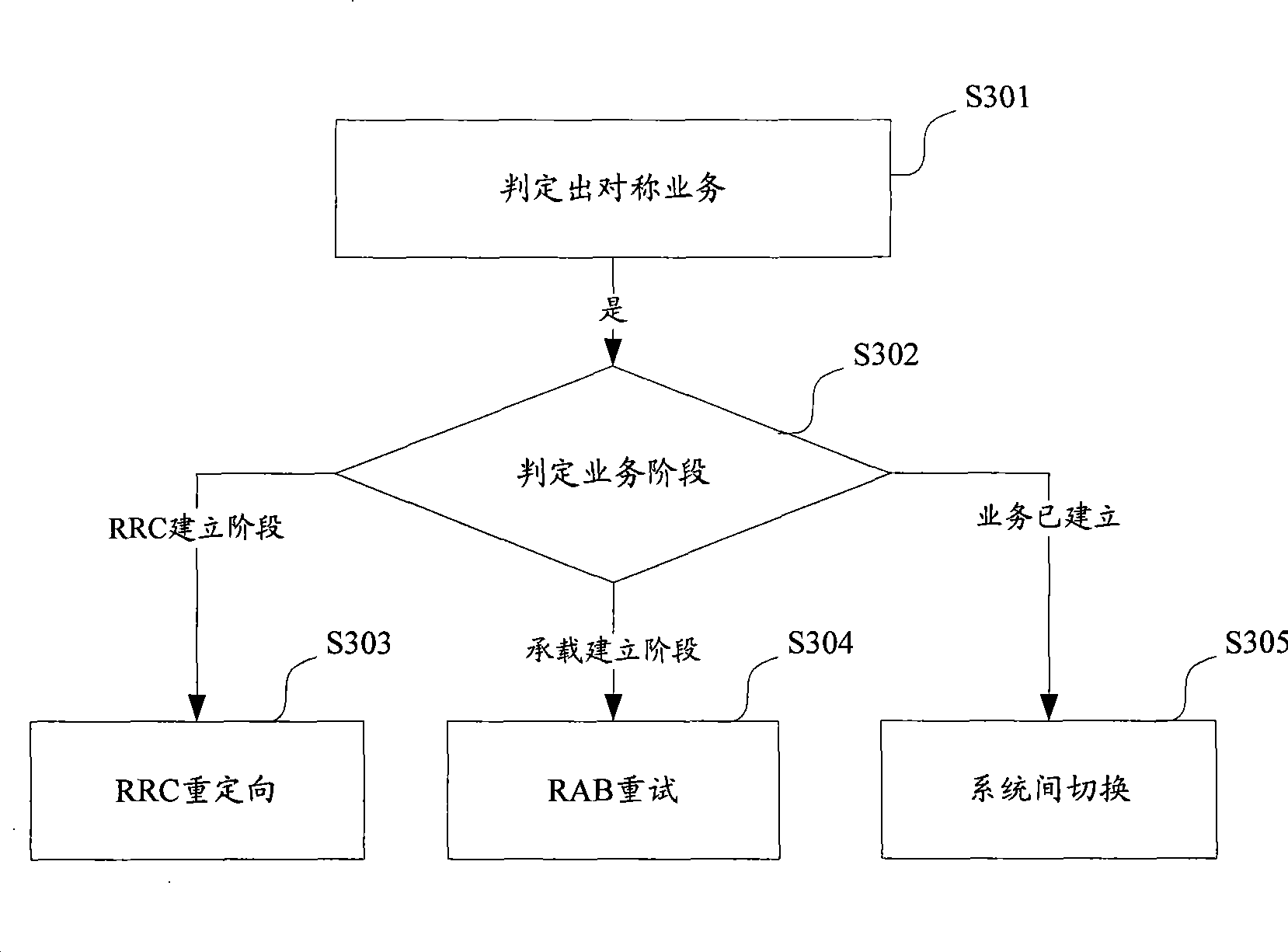
Load balance control method and apparatus
ActiveCN101453756ATake advantage ofGuaranteed experienceNetwork traffic/resource managementTelecommunicationsComputer science
The invention relates to the field of time division duplex communication networks, in particular to technique for balancing uplink and downlink load in a time division duplex communication network. A load balance control method comprises the following steps: monitoring an uplink wireless channel resource occupation rate and a downlink wireless channel resource occupation rate in an uplink and downlink asymmetric network; and re-orientating uplink and downlink symmetric services in the uplink and downlink asymmetric network or switching to a uplink and downlink symmetric network when determining the resources of the uplink and downlink asymmetric network are limited according to the uplink wireless channel resource occupation rate and the downlink wireless channel resource occupation rate. The invention also provides a load balance control device. Due to the switching of the uplink and downlink symmetric services from the uplink and downlink asymmetric network to the uplink and downlink symmetric network when determining the resources are limited, the method and the device flexibly adapt to the service change of a current system and achieve reasonable load balancing.
Owner:CHINA MOBILE COMM GRP CO LTD
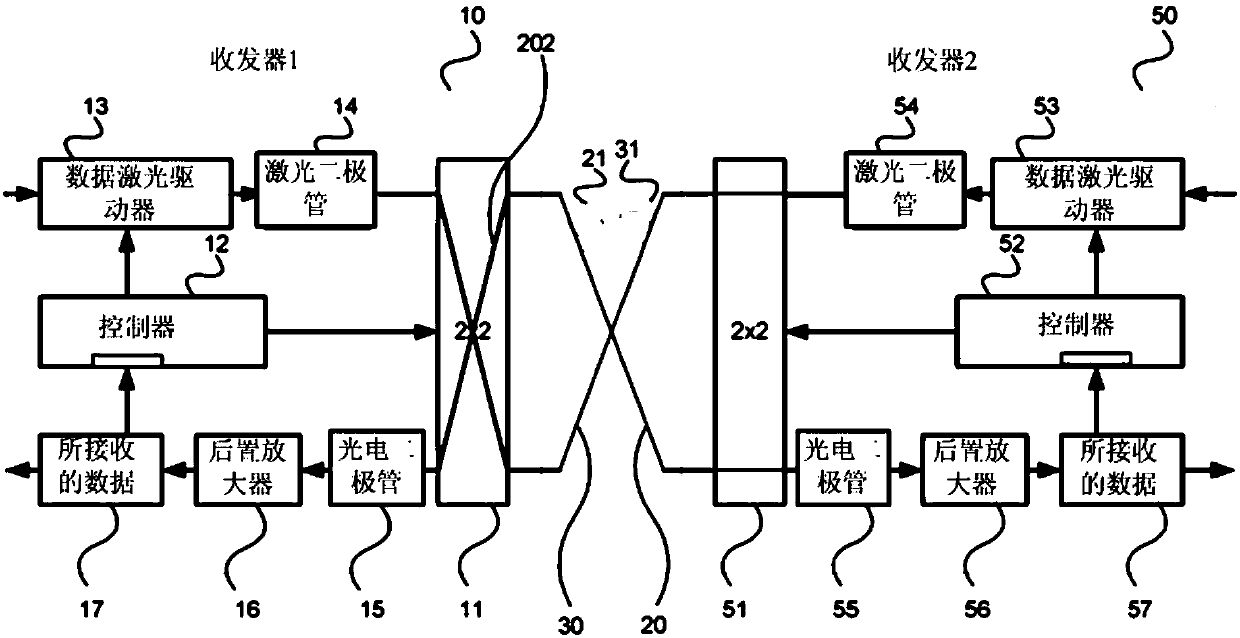
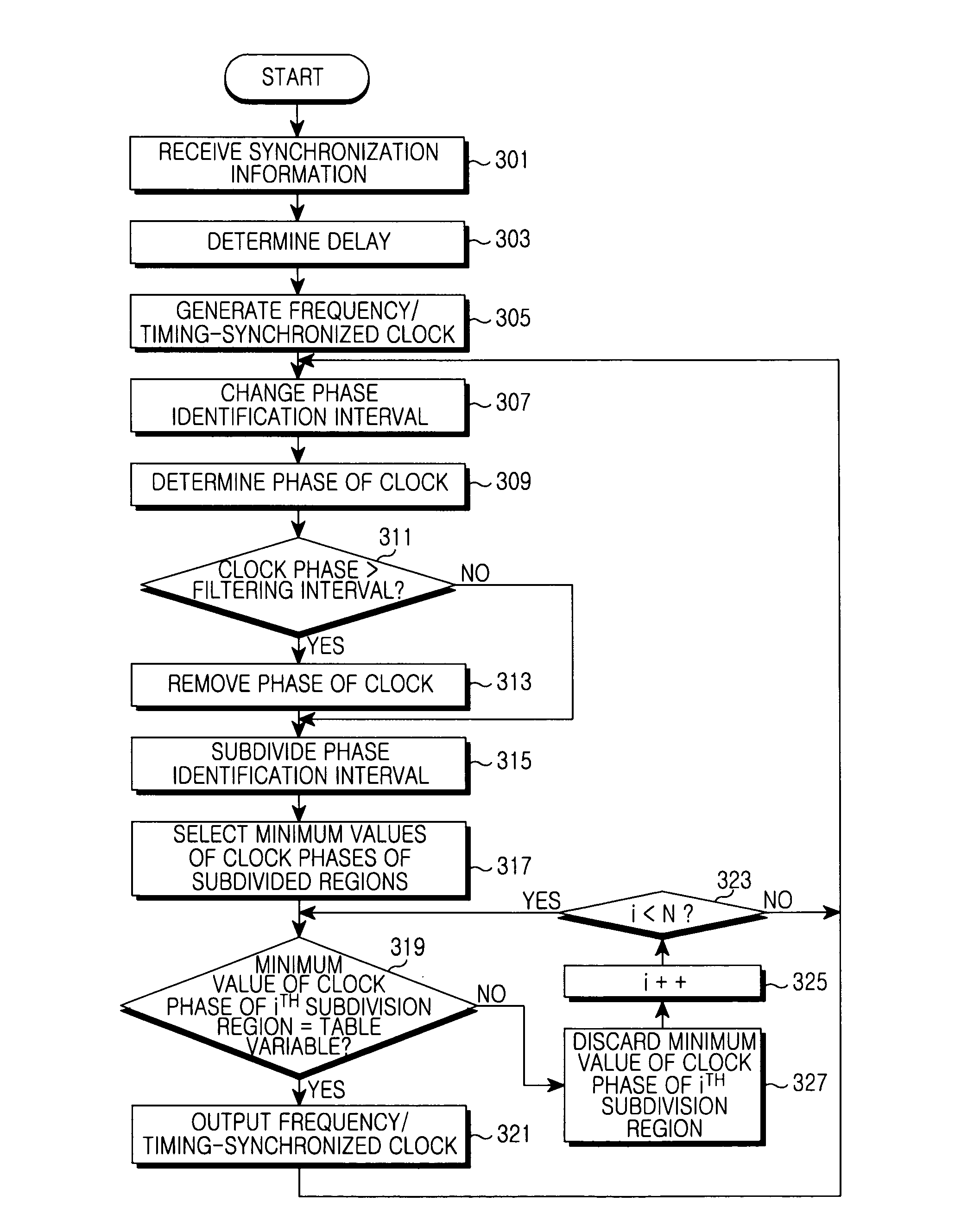
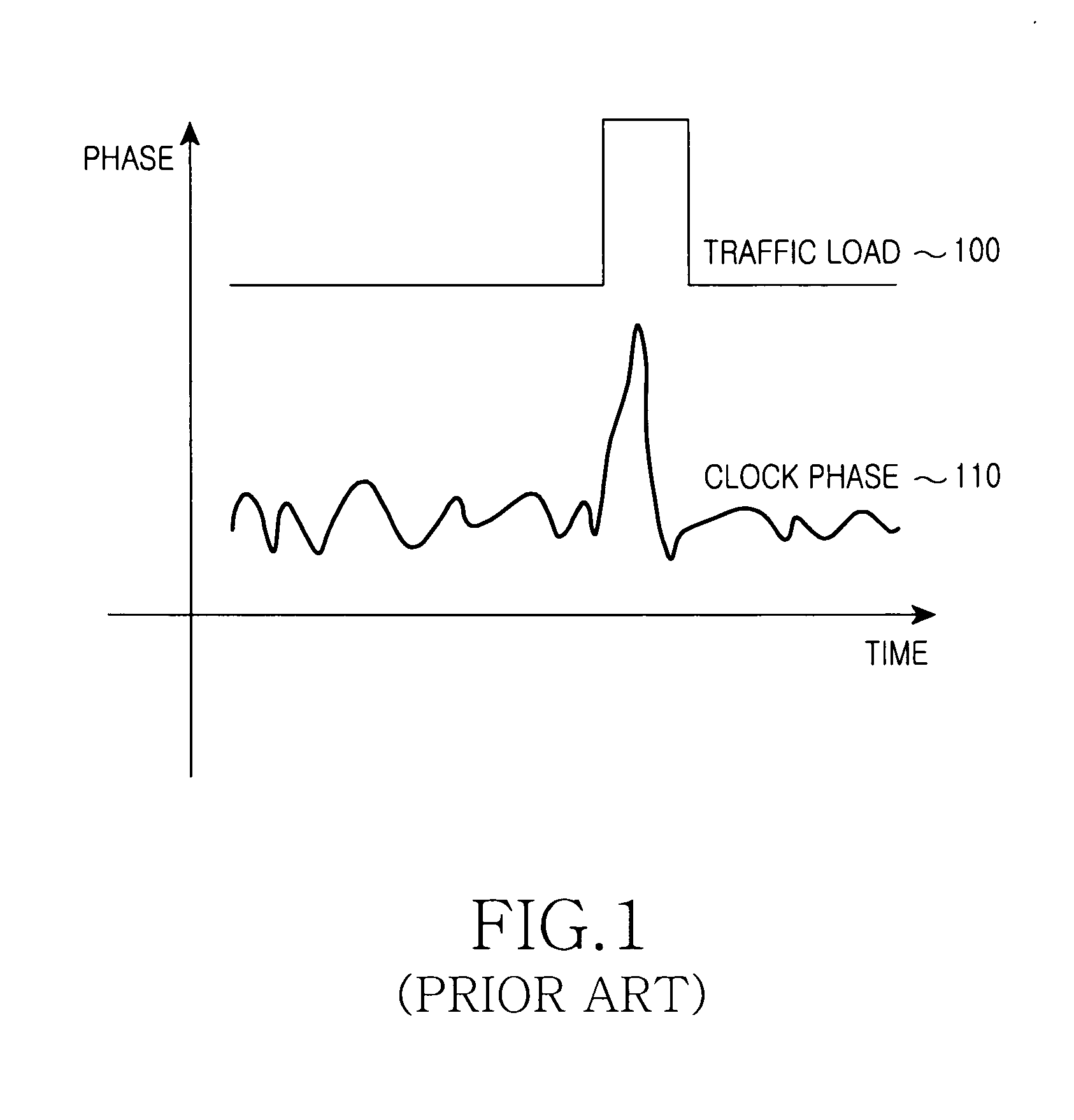
Apparatus and method for timing synchronization in a communication system
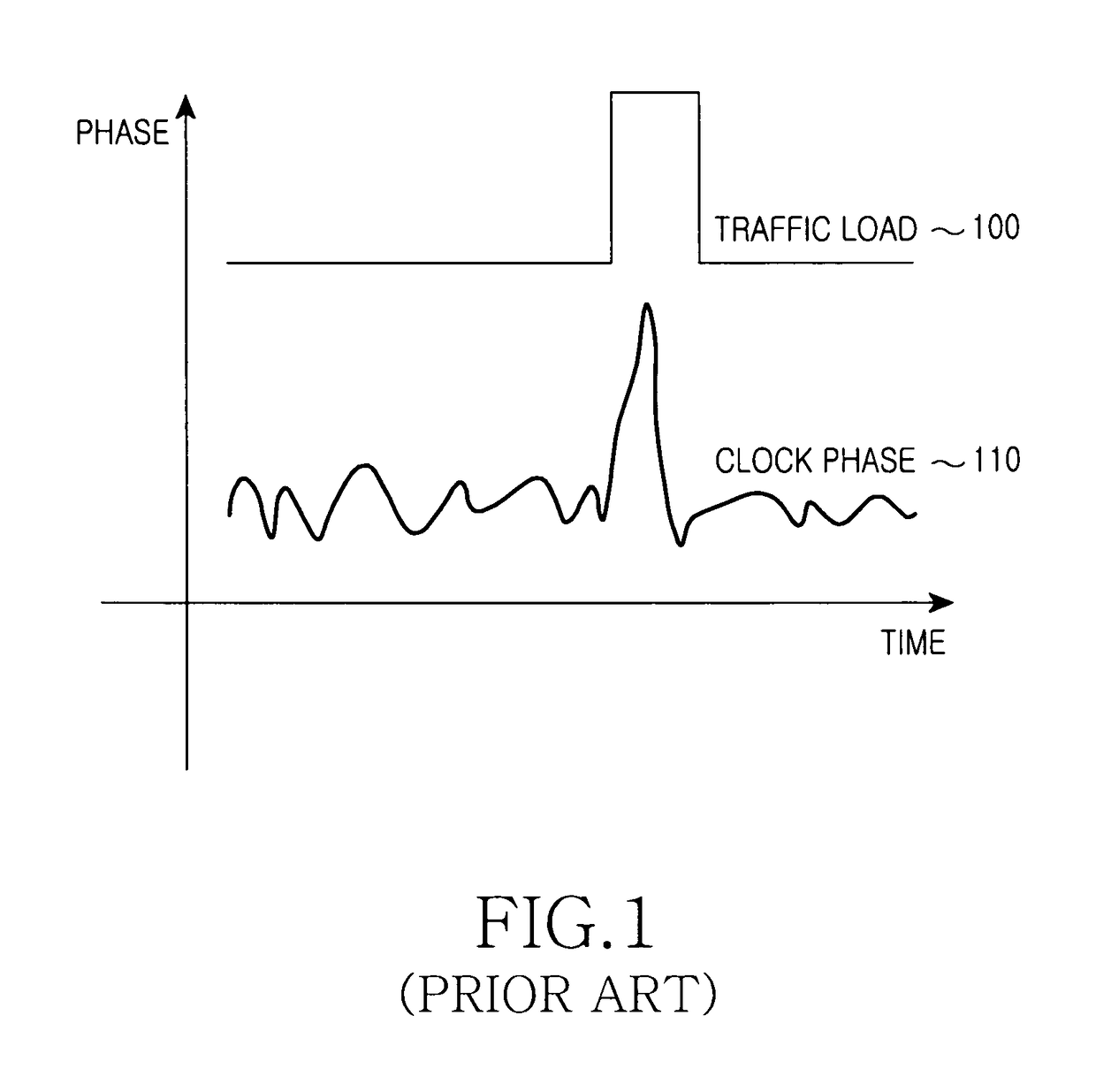
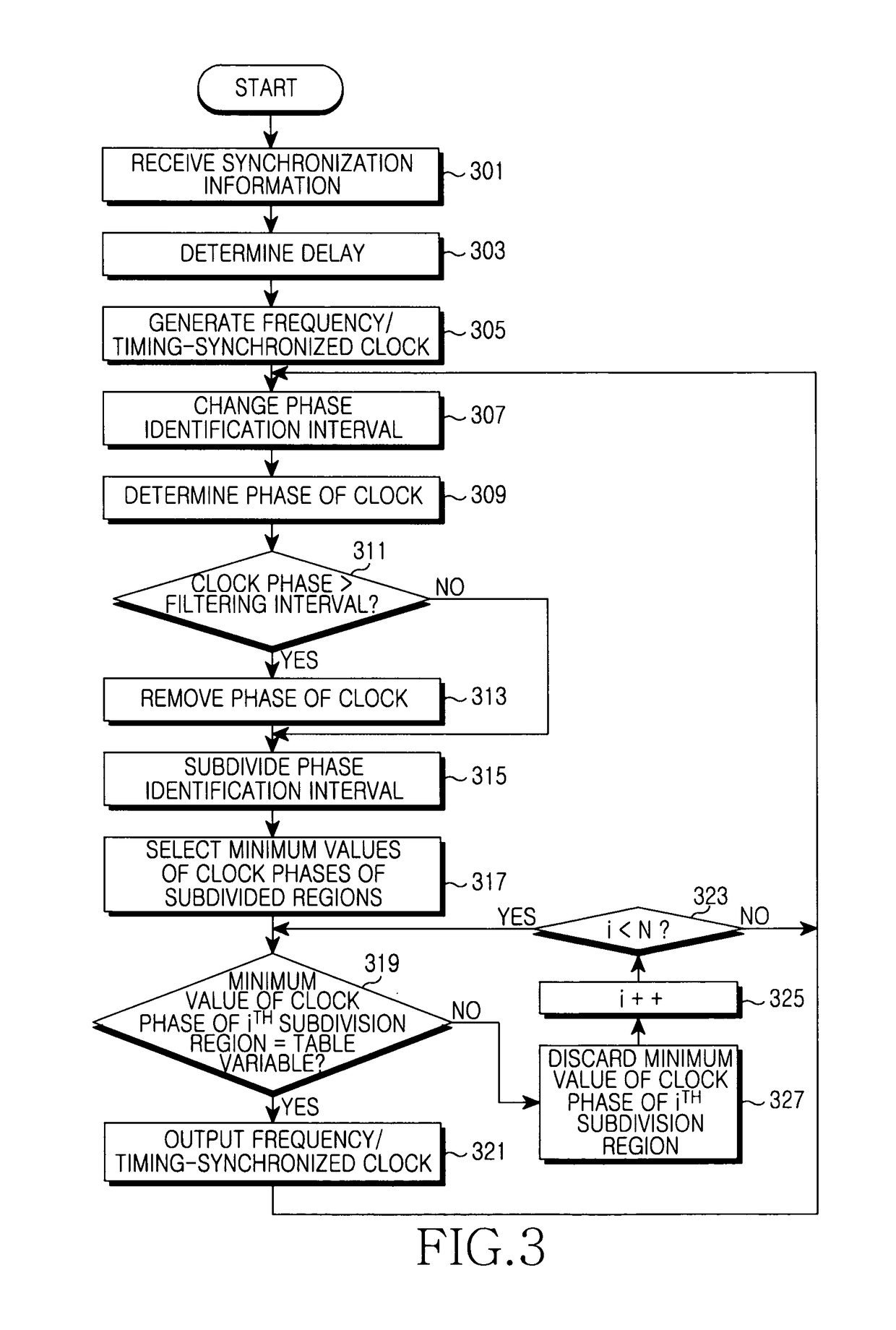
InactiveUS8472370B2Improve variationMinimize offsetTime-division multiplexSynchronisation signal speed/phase controlCommunications systemClock phase
An apparatus is capable of restoring a clock of a second node in a communication system with a symmetric network construction of a first node that is capable of receiving a Global Positioning System (GPS) signal, and the second node that is not capable of receiving a GPS signal. The method includes identifying synchronization information received from the first node, determining a delay with the first node, generating a clock using the synchronization information and delay, removing a clock phase being out of a reference range in a phase identification interval, dividing the phase identification interval into at least two subdivision intervals, and removing a clock phase being out of a normal operation range of a phase in each subdivision interval.
Owner:SAMSUNG ELECTRONICS CO LTD
Intelligent fast switch-over network tap system and methods
ActiveUS7936685B2Effective maintenanceAvoiding wider networkError preventionTransmission systemsCross connectionNetwork tap
An intelligent fast switch-over network active tap system enables active monitoring of a network segment connected between network devices. A fail-safe relay subsystem is coupled between a pair of network ports, enabling transmission of network communications signals through a passive cross-connect between the network ports or through an active bridge subsystem. The active bridge subsystem is capable of independently establishing network links with the network devices, and a separate network link with a monitoring device. A controller manages operation of the relay and active bridge subsystems, including switches between passive and active network transmission through the tap system and to determine and establish the active network links subject to symmetric network link parameters and state. Thereby, the network link status of the connected network devices is preserved on switch between active and passive transmission and correctly reflected in the presence of link and power failures.
Owner:NETSCOUT SYSTEMS
Multi-user cooperative communication incentive method in dual information asymmetric network environment
InactiveCN107018527AGuarantee normal implementationReduce overheadSite diversityData switching networksCommunications systemMarket driven
The invention belongs to the field of wireless cooperative communication system technology, and particularly relates to a multi-user cooperative communication incentive method in a dual information asymmetric network environment. The method comprises the following steps: mapping a cooperative communication network into a labor market, and establishing a source node model and a relay node model in combination with the characteristics of a market-driven contract theory; and in consideration of the selfish nature of the relay nodes and the constraints of individual rationality, establishing a multi-user cooperative communication incentive optimization model in the dual information asymmetric network environment for the adverse selection problem caused by the private information of the relay nodes before contract signing and the moral hazard problem caused by private behaviors of the relay nodes after contract signing. Thereby, the dual objectives of achieving cooperative information screening and cooperative effort incentive of the relay nodes can be realized, the win-win situation of benefits can be realized, and the implementation of cooperative communication can also be ensured.
Owner:HUBEI UNIV OF TECH
Adaptive asymmetric network connectivity probing system and method
InactiveUS6865510B2Easy data transferNuclear monitoringDigital computer detailsDatapathClient system
A system and method for analyzing network traffic between a client system and multiple mirror systems, to determine the most efficient data transfer paths for accessing the mirrored data. Accordingly, a set of network probes are passed between network point pairs. After doing so, the resulting figures are analyzed using a first-order linear equation to determine which pairs are “closest” in terms of data transfer efficiency in a specific direction. Using the closeness results, the optimal data paths for large data transfer are determined.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
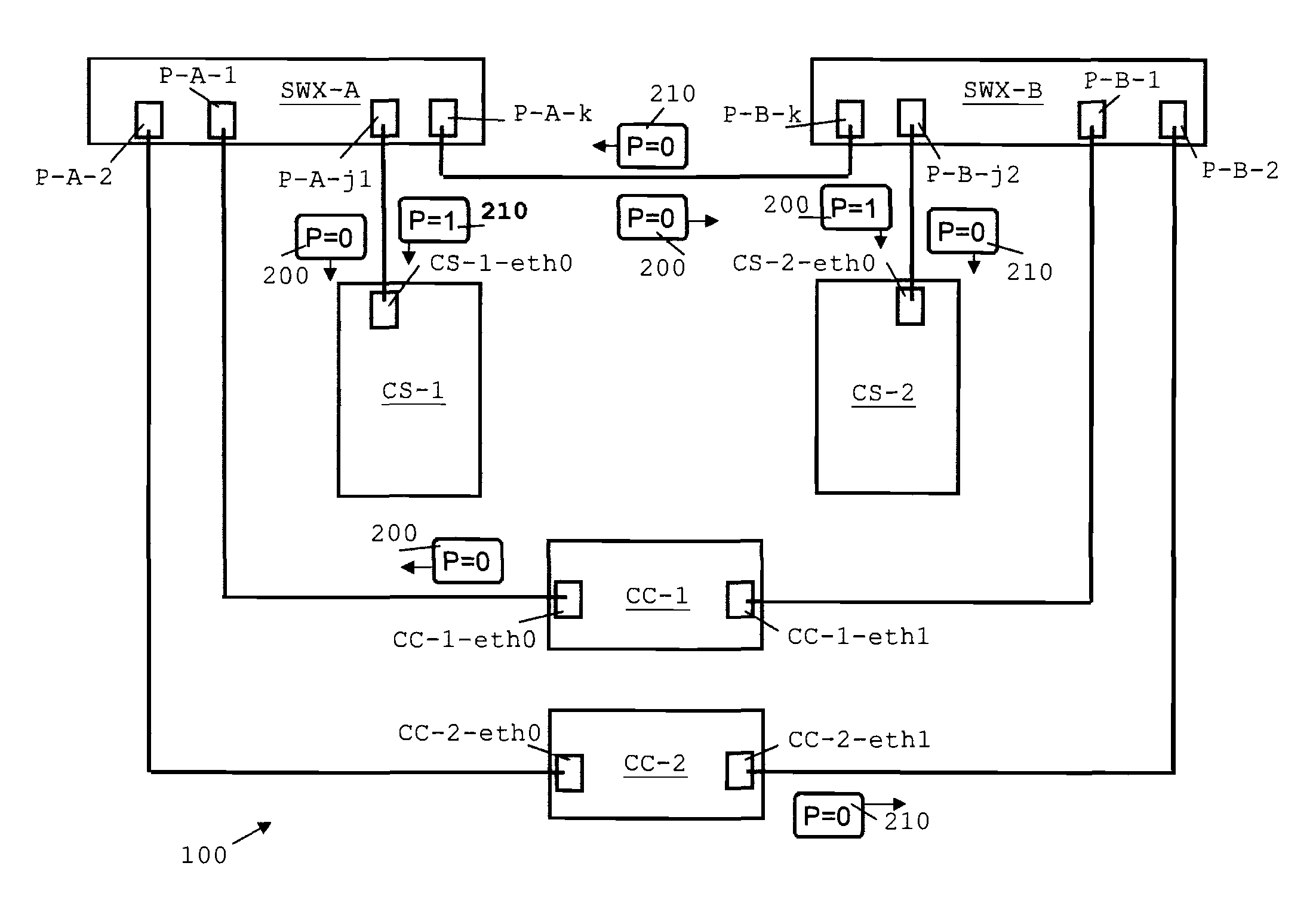
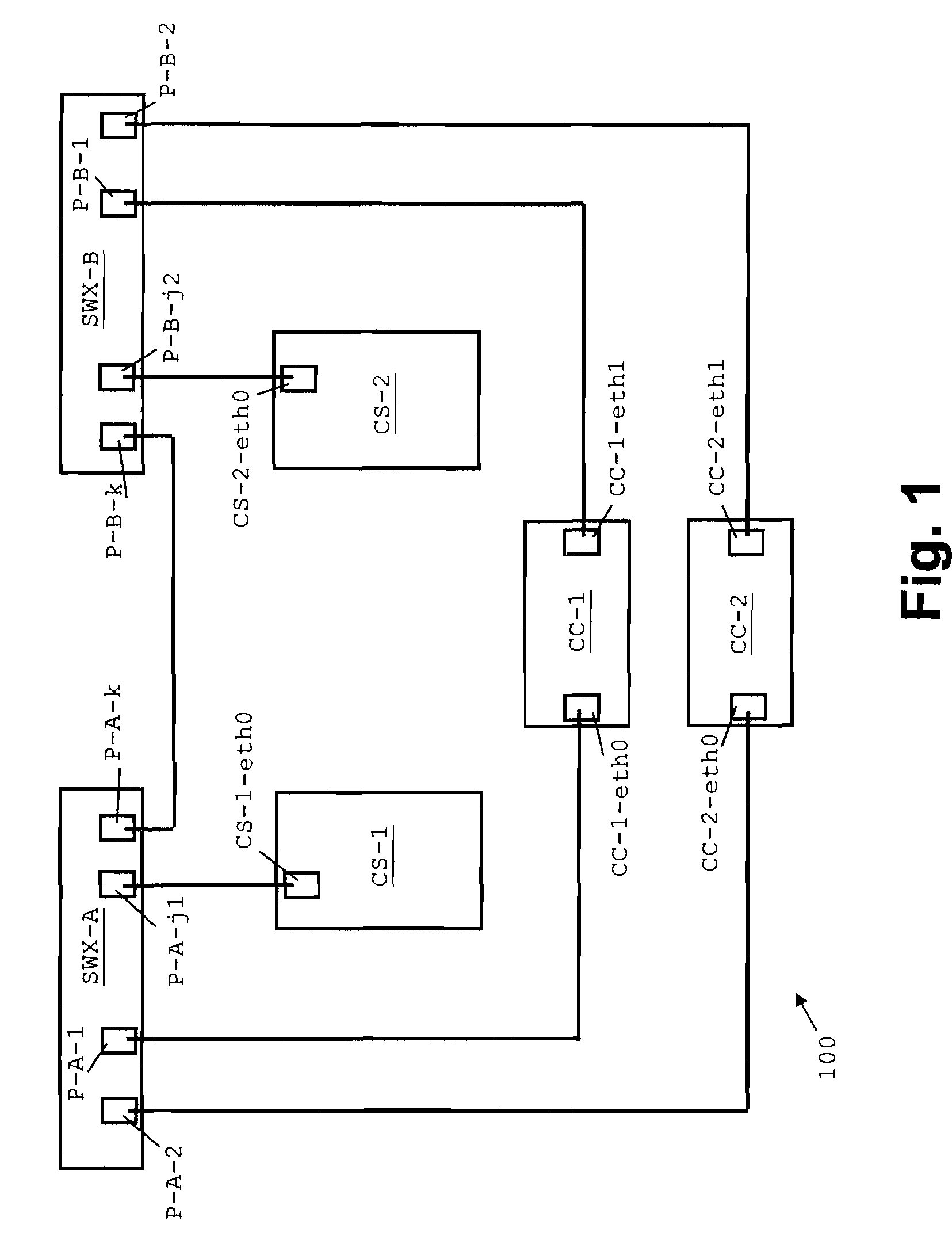
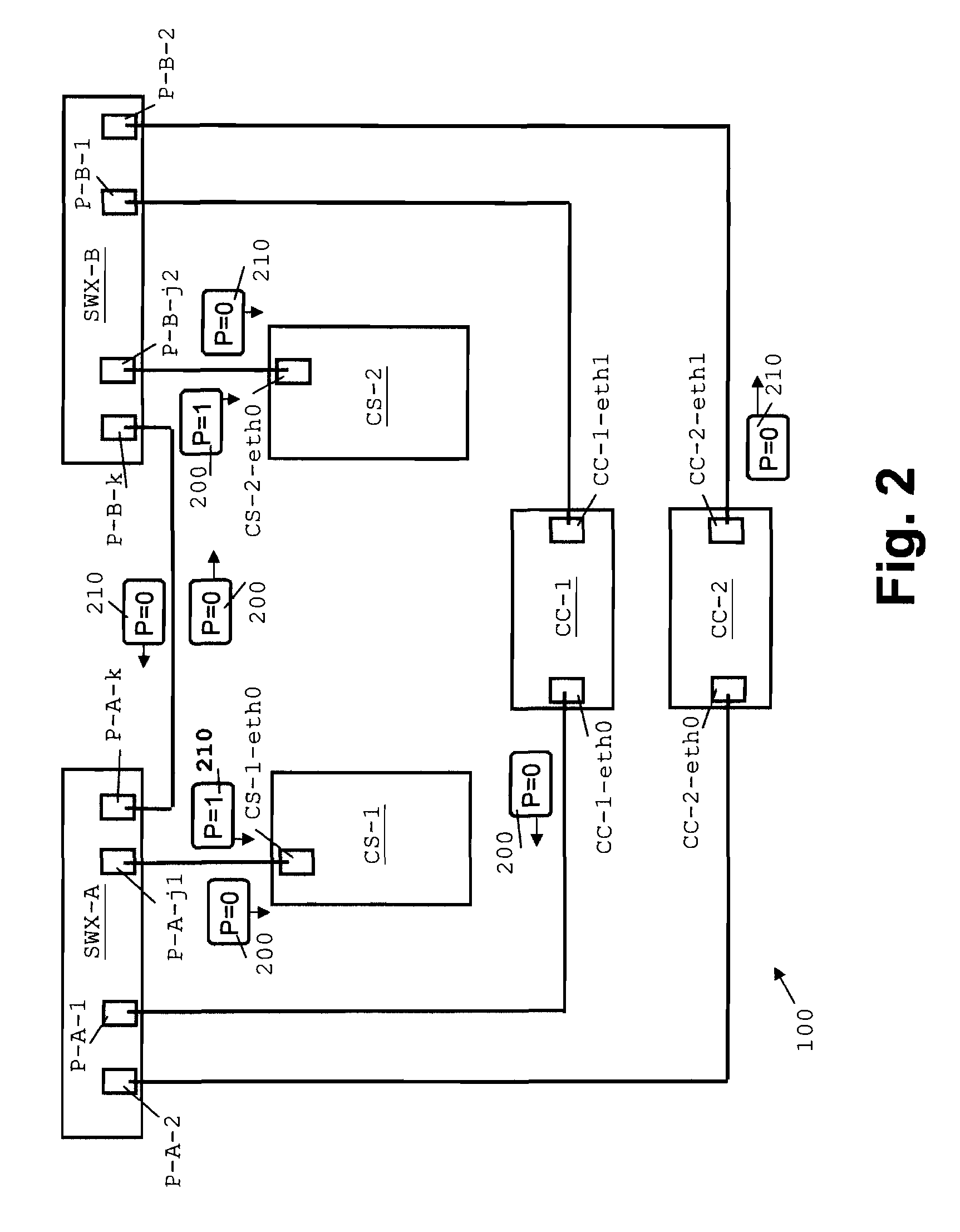
Network and Method for the Configuration Thereof
A method and corresponding apparatus is provided for determining the location of a configuration server being connected to a totally symmetric network infrastructure that does not exhibit any symmetry breakers on network level. The configuration server reaches a decision to determine its network-wide unique configuration in order to be able to serve controllers. This decision depends on the plug position of the configuration server under consideration and the assumption of plugging rules governing a “good” network infrastructure. The controllers periodically send network packets that will be marked if they traverse specific connection elements in the network. The origin and the path of a network packet can be determined. The decision making is based on a majority function based on the packets received by the configuration server. If a decision cannot be made, then errors in the cabling structure can be detected.
Owner:LENOVO GLOBAL TECH INT LTD
Traversal of symmetric network address translator for multiple simultaneous connections
ActiveUS7856506B2Improve abilitiesIncrease the number ofData switching by path configurationMultiple digital computer combinationsNAT traversalCritical time
Handling of multiple connections during NAT traversal for a node behind a symmetric NAT is disclosed. The likelihood of connection failure during symmetric NAT traversal may be reduced by serializing critical time windows after port prediction. Once port prediction has begun for a first connection, port prediction for a subsequent connection may be delayed until a connectivity check has begun for the first connection. This process may be repeated to handle NAT traversal for multiple simultaneous connections to different nodes.
Owner:SONY COMPUTER ENTERTAINMENT INC
System and methods for network synchronization
ActiveCN109565435ASynchronisation by photonic/optical meansTime-division multiplexPropagation delayTransceiver
One aspect of the disclosure is directed to a system and method for determining the propagation delay for a signal to traverse an optical fiber between two transceivers. The method is performed by a first network element and includes transmitting a message to a second transceiver over a first optical fiber. The method further includes configuring both network elements such that the first NE receives a reply message from the second NE on the first optical fiber. This reply message includes an indication of the internal time for the second NE to transmit the reply message. Accordingly the one way propagation delay on the first optical fiber can be determined. Another aspect is directed to a system and method for using the determined one way propagation delay to synchronize clocks of the twoNEs using a symmetric network synchronizing protocol such as precision timing protocol, and correcting for differences in the one way propagation delays which make up the round trip propagation delay.Some embodiments can do this without stopping the operation of the network while pausing (buffering) data flows while the one way propagation delays are determined.
Owner:HONOR DEVICE CO LTD
Apparatus and method for timing synchronization in a communication system
InactiveUS20100195565A1Improve variationMinimize offsetTime-division multiplexSynchronisation signal speed/phase controlCommunications systemClock phase
An apparatus is capable of restoring a clock of a second node in a communication system with a symmetric network construction of a first node that is capable of receiving a Global Positioning System (GPS) signal, and the second node that is not capable of receiving a GPS signal. The method includes identifying synchronization information received from the first node, determining a delay with the first node, generating a clock using the synchronization information and delay, removing a clock phase being out of a reference range in a phase identification interval, dividing the phase identification interval into at least two subdivision intervals, and removing a clock phase being out of a normal operation range of a phase in each subdivision interval.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for operating a symmetric network address translation
ActiveUS7774475B2Session-capacity of the NAT is advantageously significantly increasedMultiple digital computer combinationsTransmissionIp addressComputer terminal
The invention relates to a method for operating a symmetric network address translation NAT (100) setting up sessions between a user terminal (110-1, 110-2) and a server (120-1, 120-2). If a new session is initiated by said user terminal an external IP-address (C) and port (D) representing the desired destination server as well as a public NAT-IP address (X) are determined. Further, a public NAT-IP port is selected. Finally, the NAT sets up the new session based on an appropriate entry representing said new session in a NAT table. In order to save available public NAT-IP ports a new session according to the invention not necessarily represented by a new public NAT-IP port, but by a tuple comprising the public NAT-IP address, the selected public NAT-IP port (Y), the external IP address (C) and the port (D). A new session is set up only if there is an entry of the whole tuple identifying said new session in said NAT-table.
Owner:ALCATEL LUCENT SAS
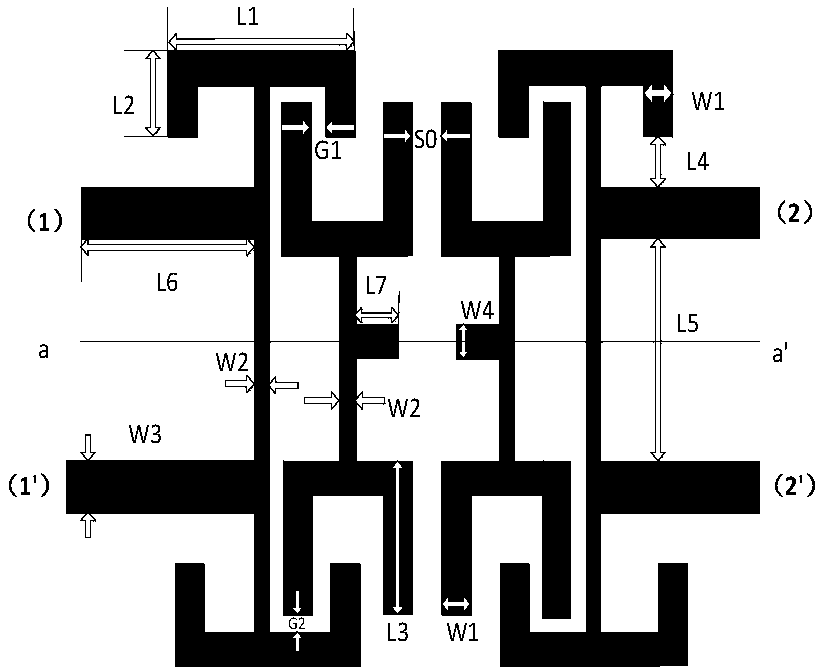
Micro differential filter based on T-shaped branch line structure
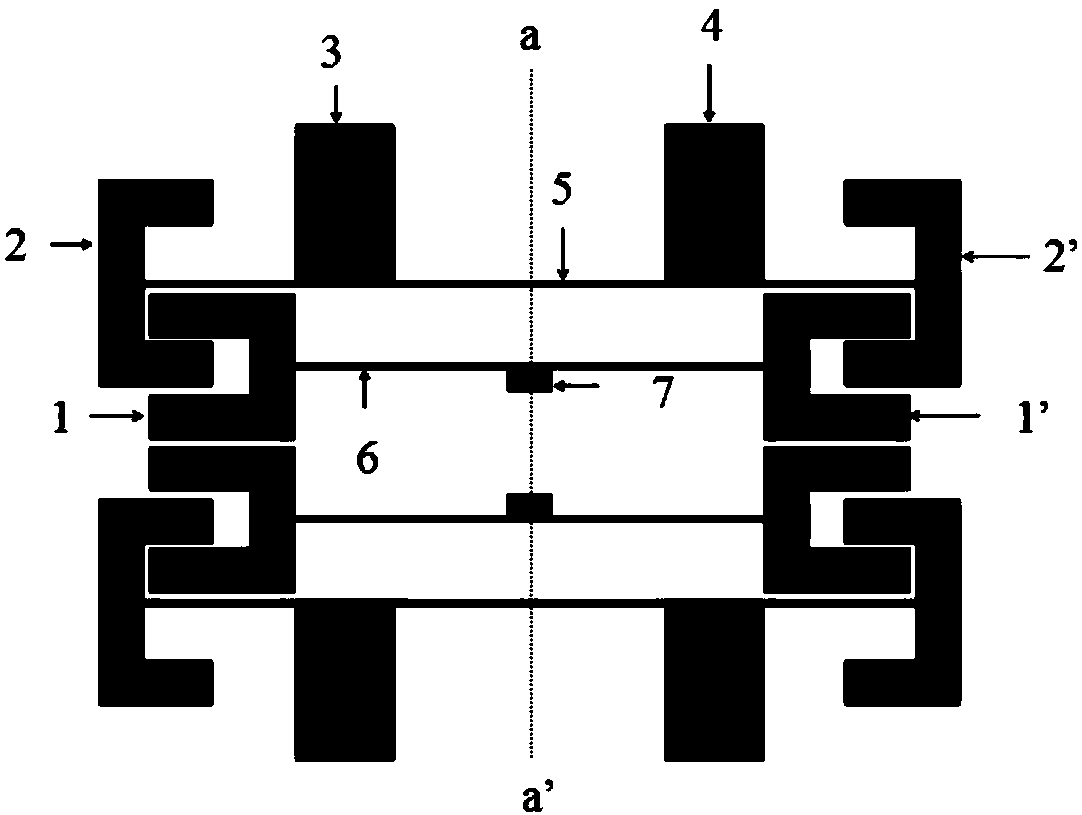
The invention discloses a novel patch topological structure, particularly relates to a micro differential filter based on the T-shaped branch line structure and belongs to the microwave communicationfield. The differential filter comprises four T-shaped resonators and the input and output of the feeder. The micro differential filter of the T-shaped branch line structure mainly employs a one-endshort circuit T branch and an open circuit T branch to design a filter microstrip line. According to the micro differential filter, the complementary symmetric network is utilized to analyze the differential filter, not only because the complementary symmetric network has characteristics of low loss and no mode power conversion, but also because any four-port networks can be seen as two-port differential mode signals and two-port common-mode signals. The micro differential filter is advantaged in that a tap-type feeding mode is employed, firstly, insertion loss can be reduced, impact of external factors on filter performance is reduced, and signal transmission capabilities are enhanced; and secondly, a feed line and a transmission line form a stepped impedance resonator, frequency responsecan be improved through adjusting the impedance ratio, and realization of miniaturization requirements is facilitated.
Owner:SHANGHAI MARITIME UNIVERSITY
Network and method for the configuration thereof
ActiveUS7809810B2OptimizationMultiple digital computer combinationsTransmissionNetwork packetNetwork data
A method and corresponding apparatus is provided for determining the location of a configuration server being connected to a totally symmetric network infrastructure that does not exhibit any symmetry breakers on network level. The configuration server reaches a decision to determine its network-wide unique configuration in order to be able to serve controllers. This decision depends on the plug position of the configuration server under consideration and the assumption of plugging rules governing a “good” network infrastructure. The controllers periodically send network packets that will be marked if they traverse specific connection elements in the network. The origin and the path of a network packet can be determined. The decision making is based on a majority function based on the packets received by the configuration server. If a decision cannot be made, then errors in the cabling structure can be detected.
Owner:LENOVO GLOBAL TECH INT LTD
Method for realizing intranet penetration by using Internet group management protocol (IGMP) and intranet penetration system
ActiveCN102420774BRealize intranet penetrationGood effectTransmissionComputer terminalUser Datagram Protocol
The invention discloses a method for realizing intranet penetration by using an Internet group management protocol (IGMP), and aims to overcome the shortcoming that a system using a Symmetric network address translator (NAT) cannot actively access another terminal by using one terminal. The method mainly comprises the following steps that: a first terminal transmits a request to a server, and is kept to be connected with the server; a second terminal transmits an IGMP message, establishes a multicast domain, is classified into a group, locally establishes a user datagram protocol (UDP) socket and performs snooping on a port; the second terminal transmits a multicast domain value and a port value to the server, and initiates an access request; the server forwards the access request to the first terminal; and the first terminal transmits data to a second router, and the second router forwards the data to the second terminal. The invention also discloses an intranet penetration system, which comprises at least two terminals, a router and the server. The method is applied to various systems of which each accesses another terminal by using one terminal, particularly to the system using the Symmetric NAT.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com