Patents
Literature
203 results about "STUN" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Session Traversal Utilities for NAT (STUN) is a standardized set of methods, including a network protocol, for traversal of network address translator (NAT) gateways in applications of real-time voice, video, messaging, and other interactive communications.
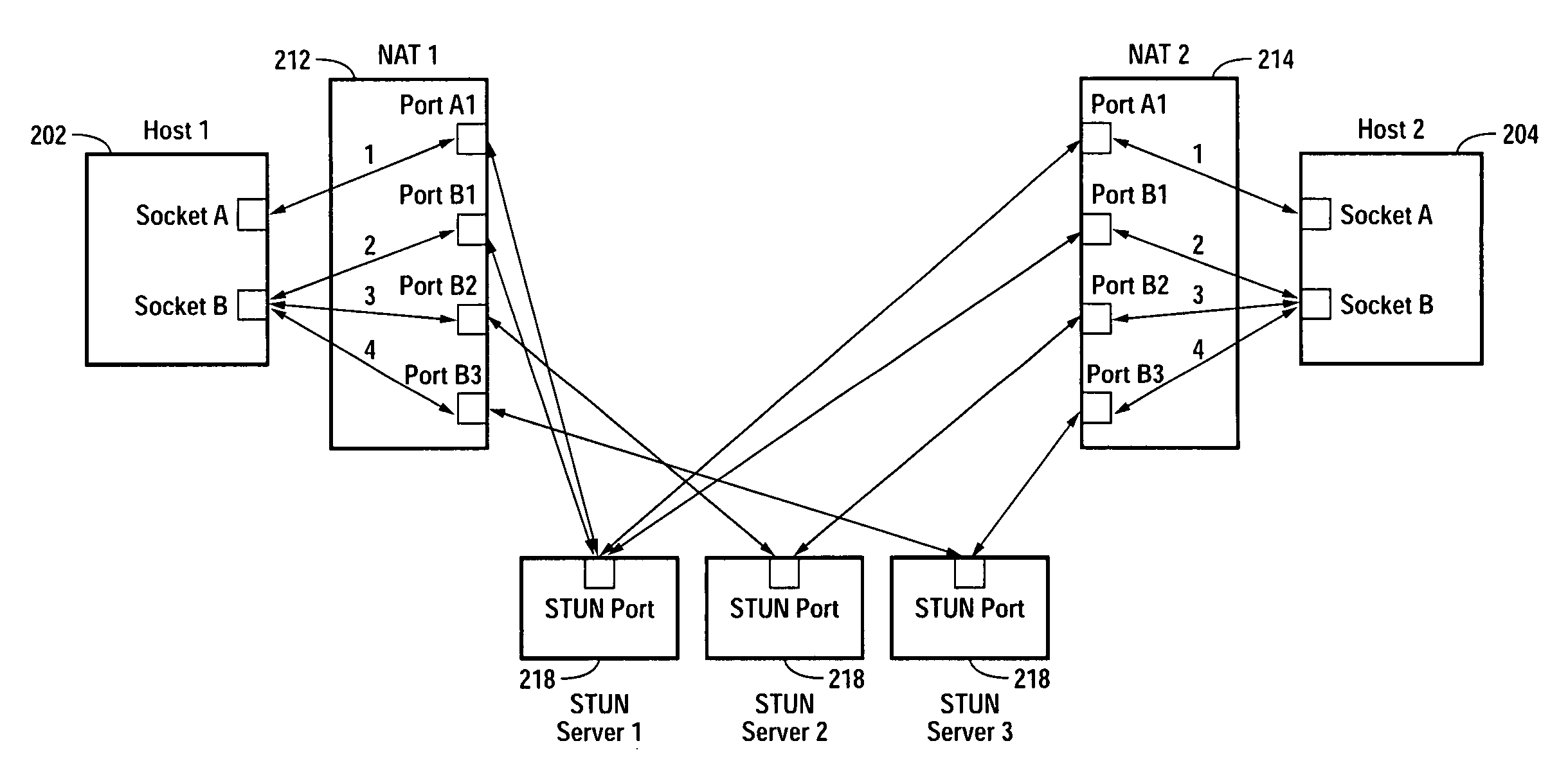
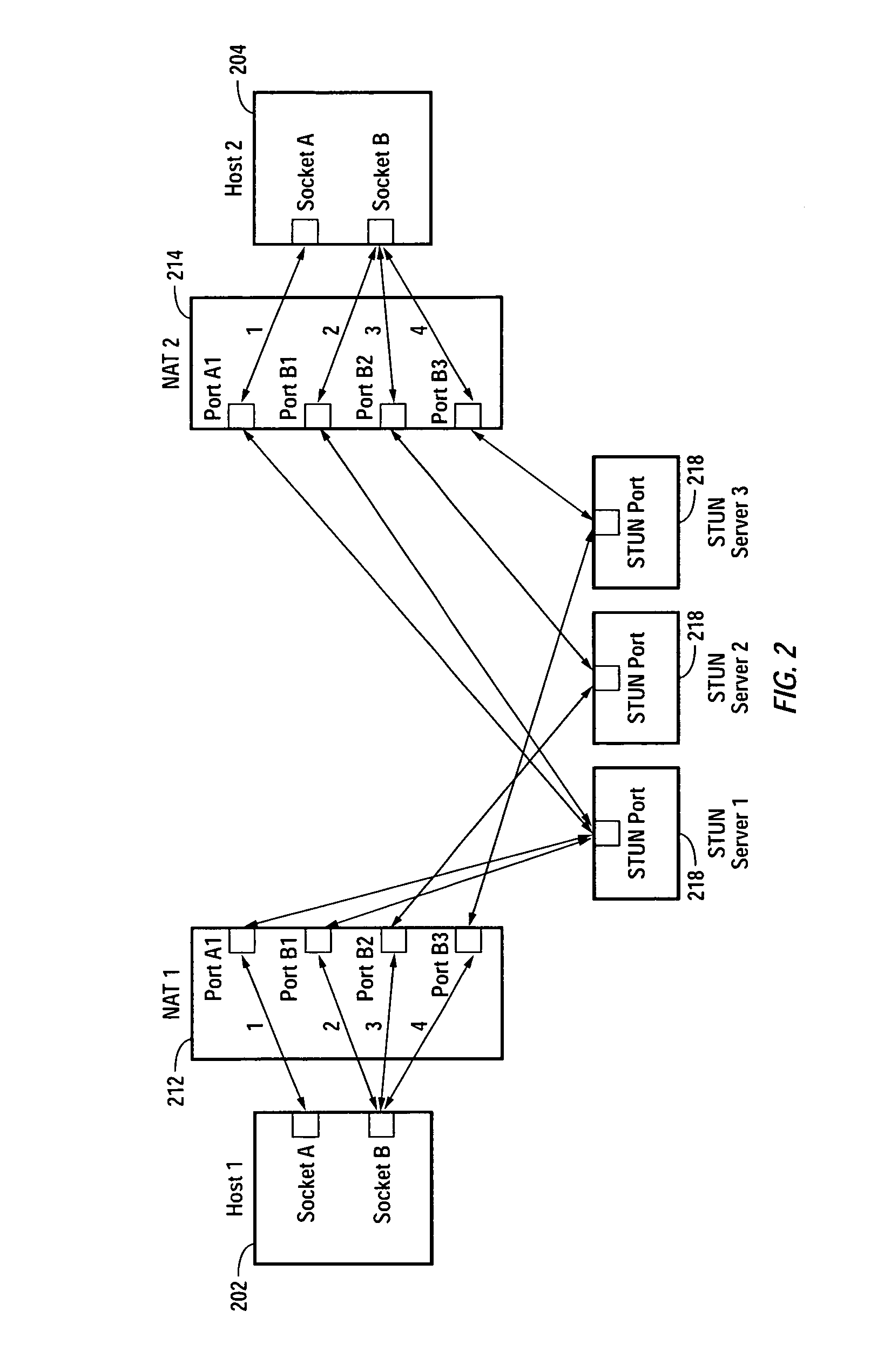
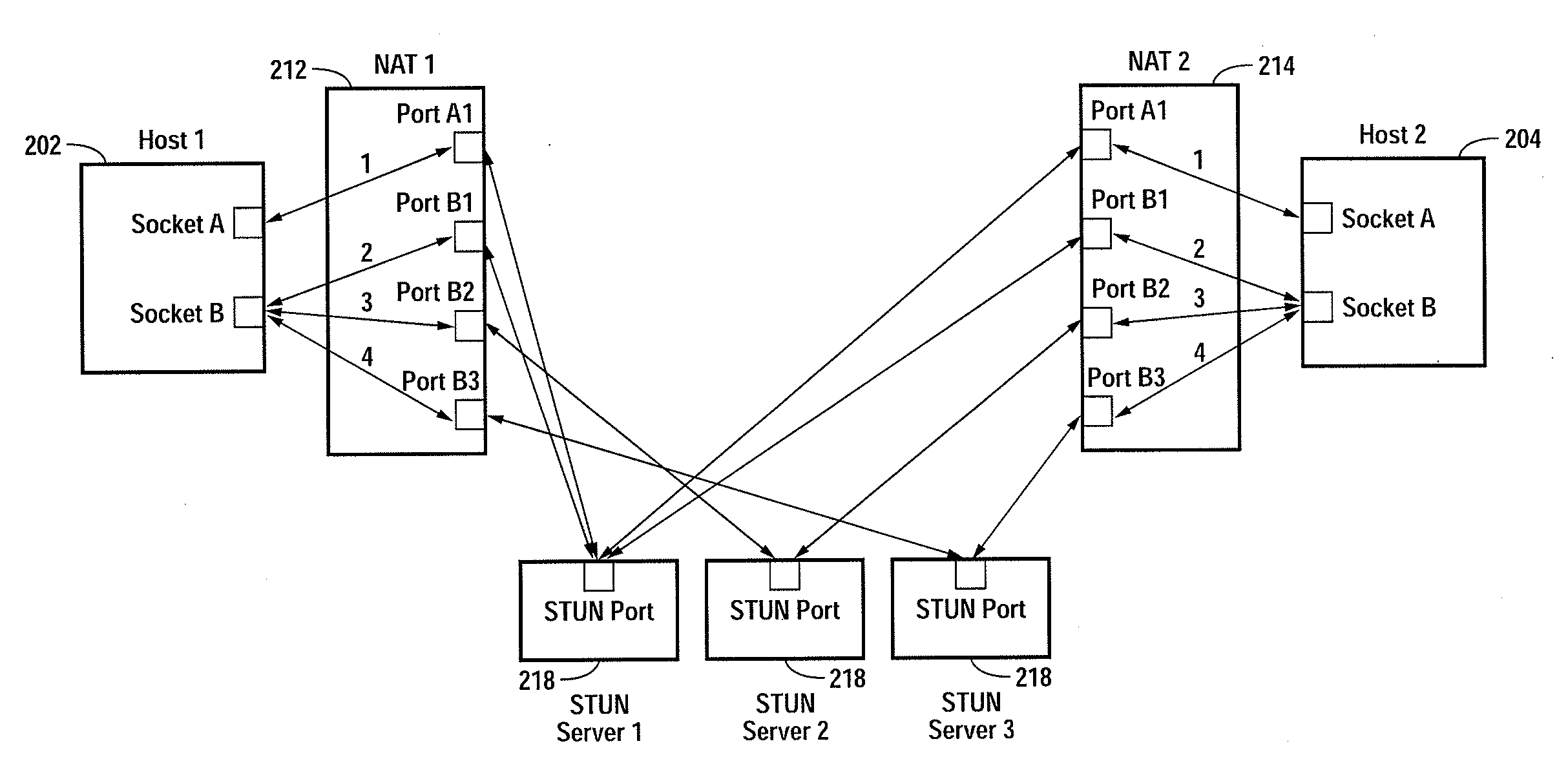
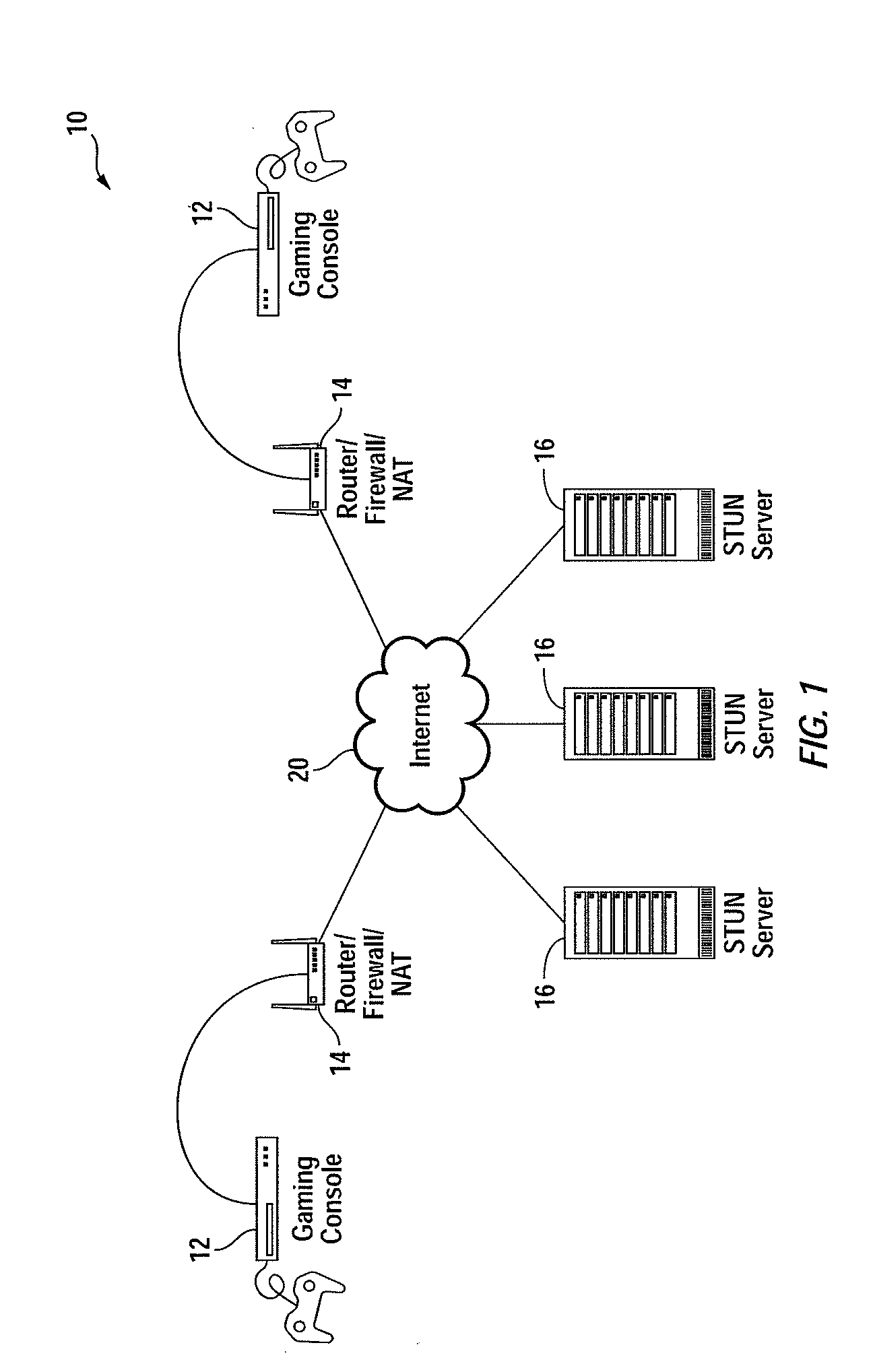
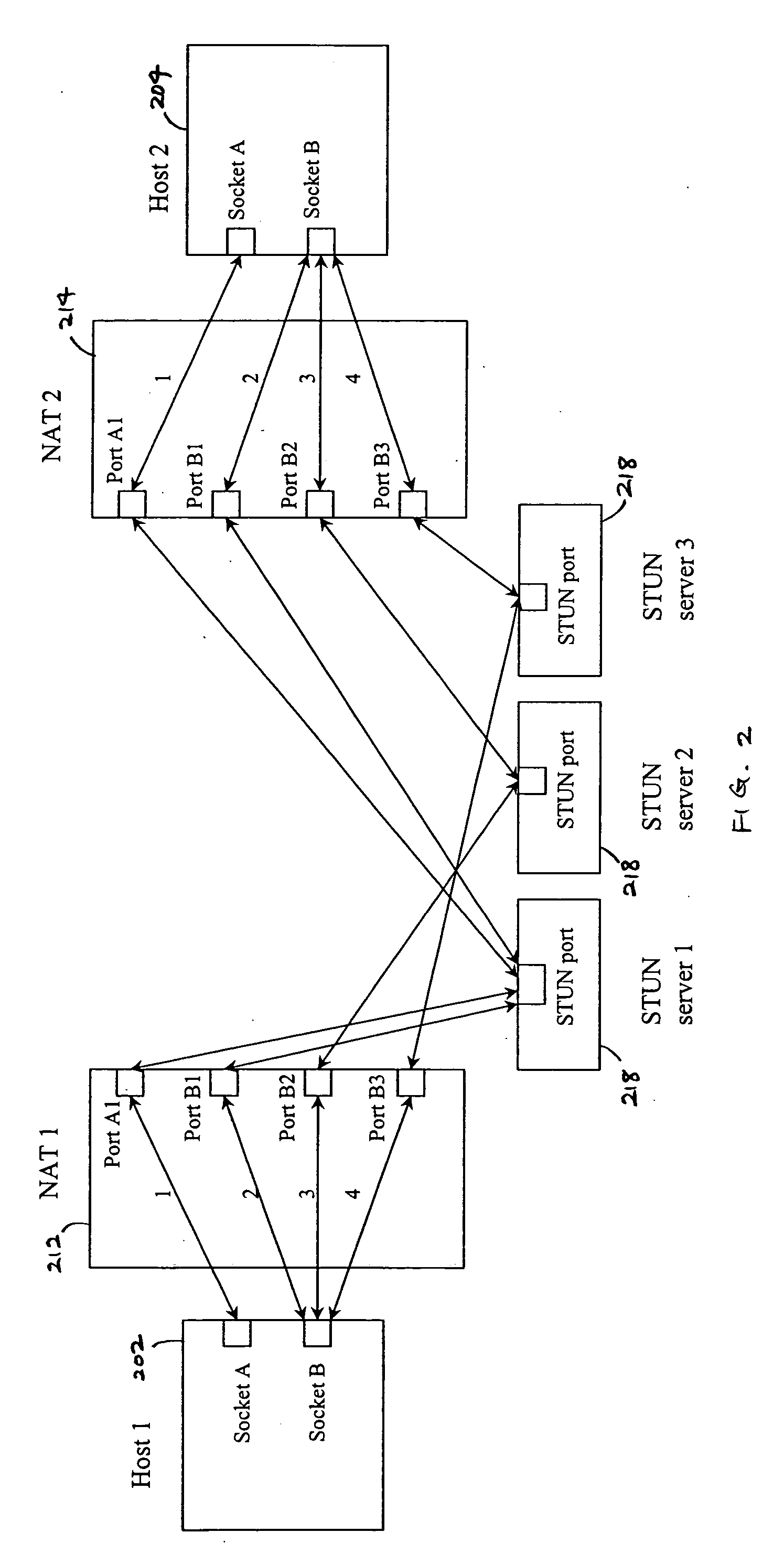
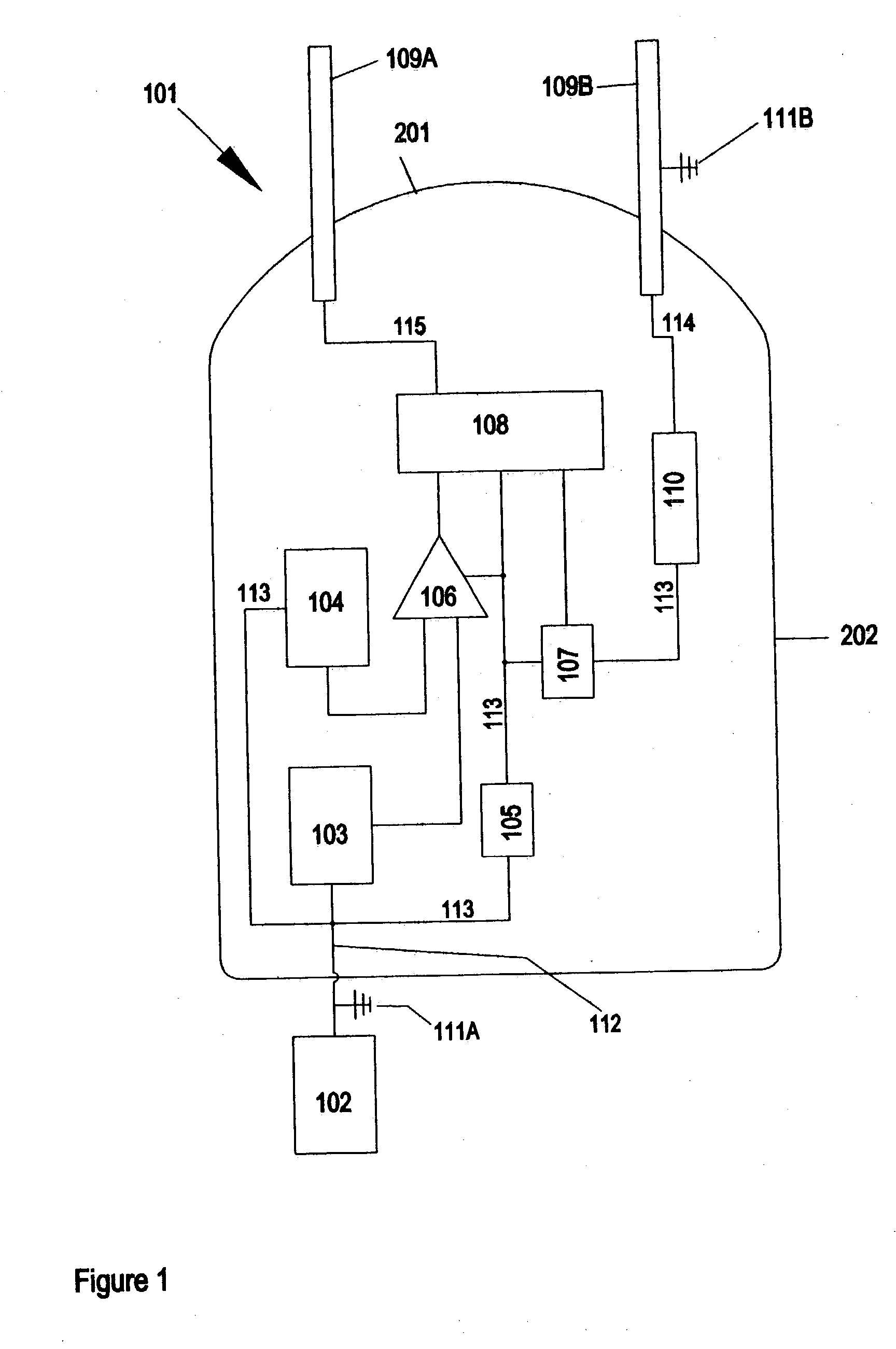
Multiplayer peer-to-peer connection across firewalls and network address translators using a single local port on the local host
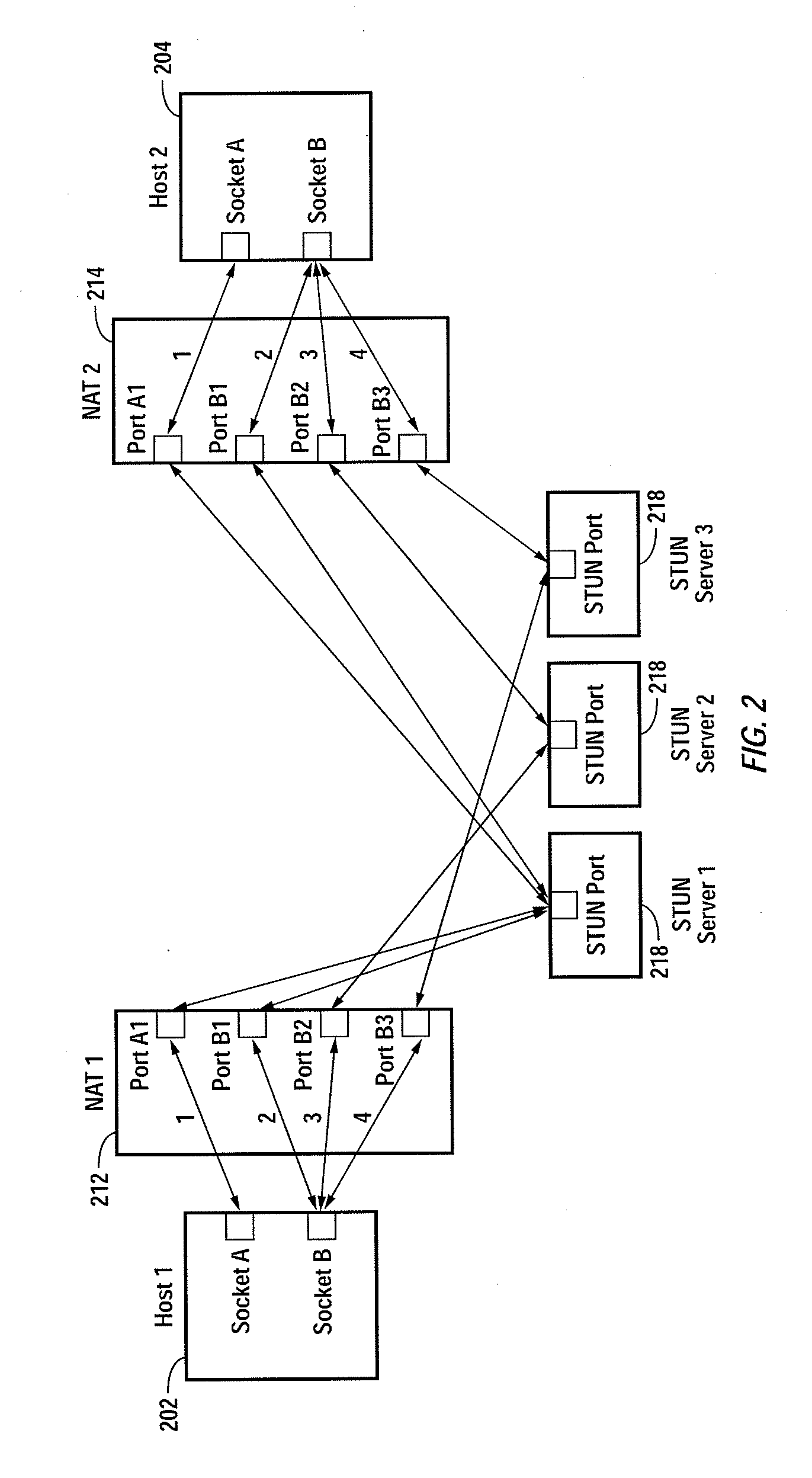
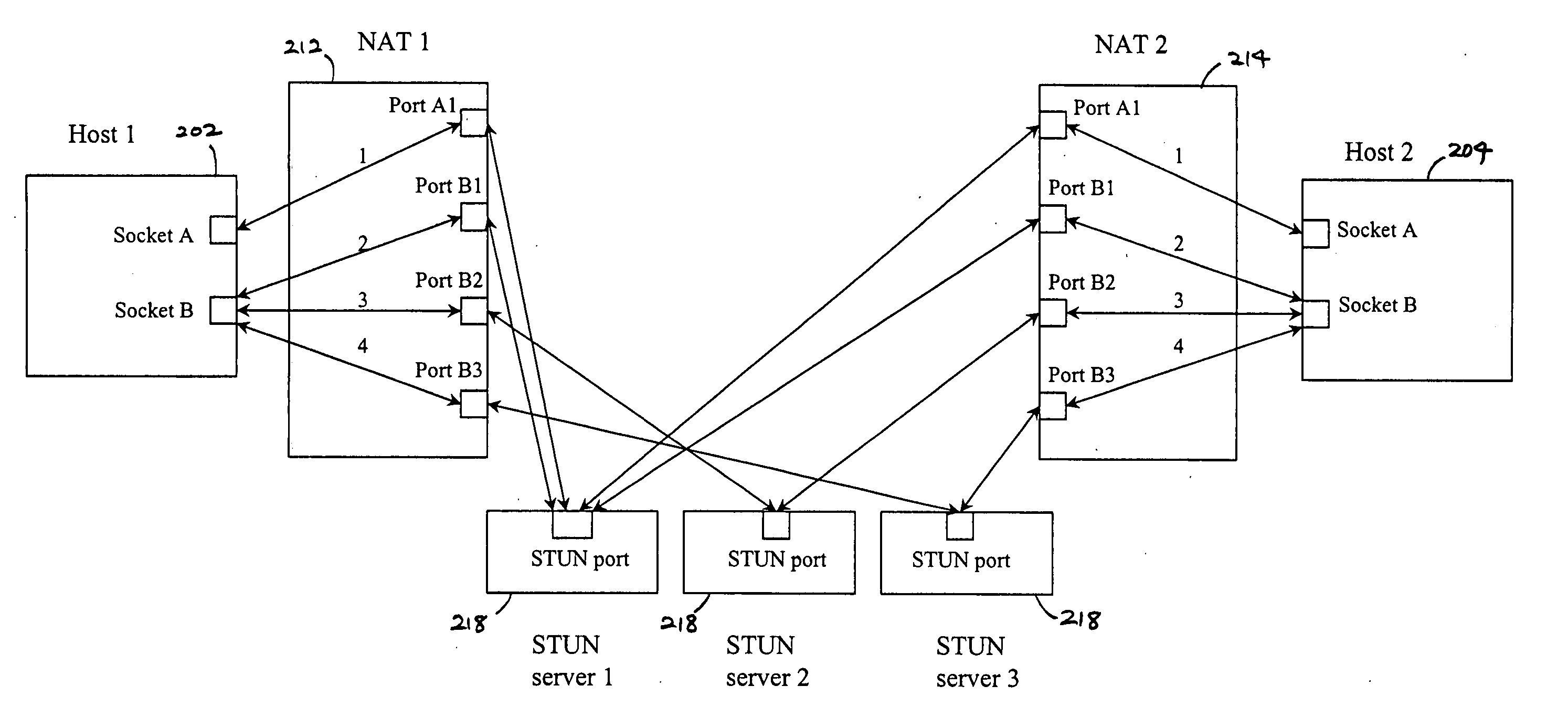
Embodiments of the invention achieve a very high success rate in multilayer peer-to-peer connection across firewalls and network address translators (NATs) using a single port on the local host. In one embodiment, a system of providing peer-to-peer connection comprises a plurality of host devices disposed behind corresponding NATs; and a plurality of STUN servers. Each host device includes a first socket bound to a first private port and a second socket bound to a second private port. Each host device sends a first STUN packet through the first socket to a first STUN server and a second group of STUN packets through the second socket to the STUN servers via public ports of the corresponding NAT. The STUN servers identify the public port numbers of the public ports. Each host device is configured to calculate a predicted public port number of the corresponding NAT for the second socket, based on the public port numbers of the public ports for the first socket and the second socket, the predicted public port number to be used for peer-to-peer connection between the second socket of the host device and other host devices.
Owner:LOGITECH EURO SA
Multiplayer Peer-to-Peer Connection Across Firewalls and Network Address Translators Using a Single Local Port on the Local Host
Owner:LOGITECH EURO SA
Multiplayer peer-to-peer connection across firewalls and network address translators using a single local port on the local host
Embodiments of the invention achieve a very high success rate in multilayer peer-to-peer connection across firewalls and network address translators (NATs) using a single port on the local host. In one embodiment, a system of providing peer-to-peer connection comprises a plurality of host devices disposed behind corresponding NATs; and a plurality of STUN servers. Each host device includes a first socket bound to a first private port and a second socket bound to a second private port. Each host device sends a first STUN packet through the first socket to a first STUN server and a second group of STUN packets through the second socket to the STUN servers via public ports of the corresponding NAT. The STUN servers identify the public port numbers of the public ports. Each host device is configured to calculate a predicted public port number of the corresponding NAT for the second socket, based on the public port numbers of the public ports for the first socket and the second socket, the predicted public port number to be used for peer-to-peer connection between the second socket of the host device and other host devices.
Owner:LOGITECH EURO SA
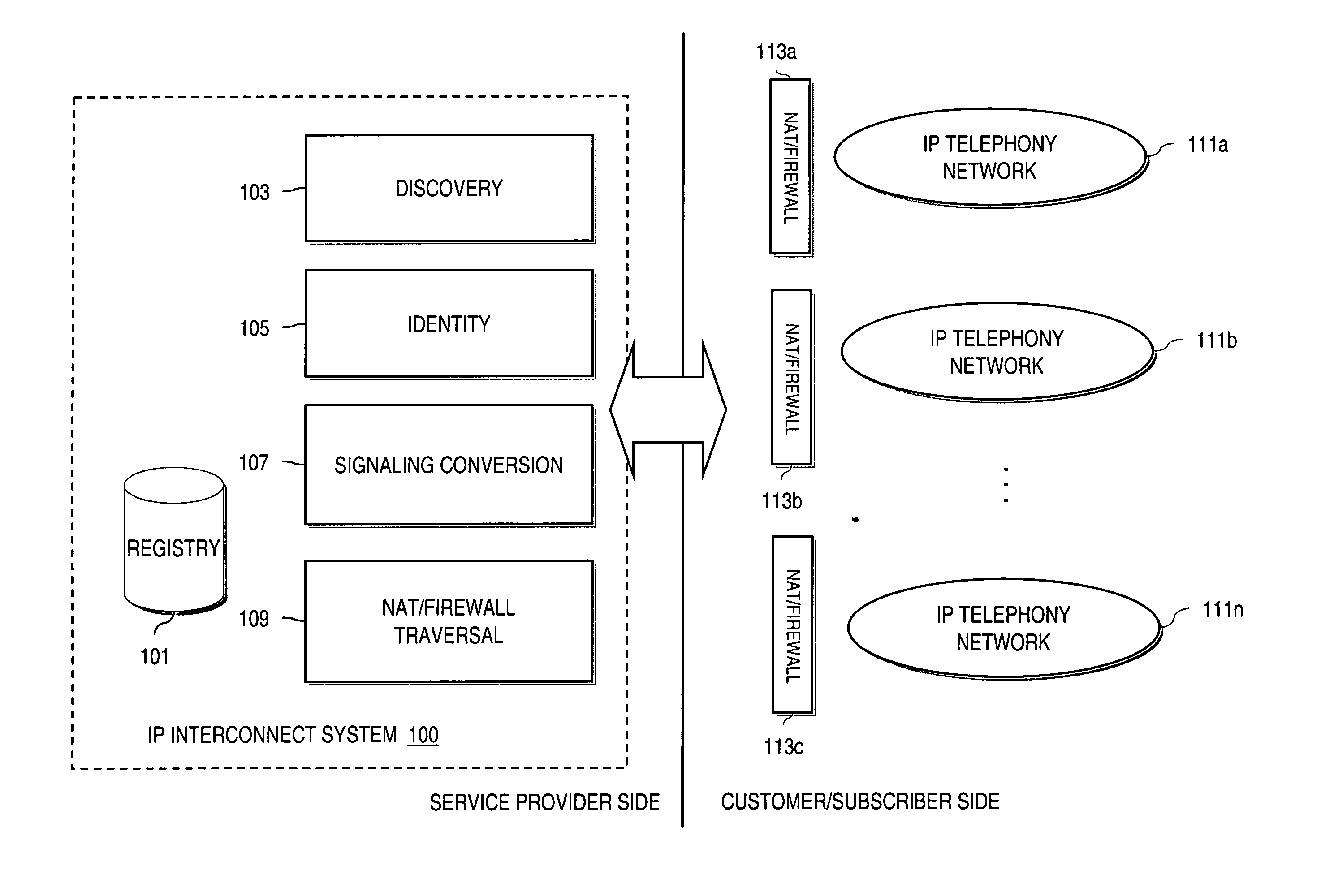
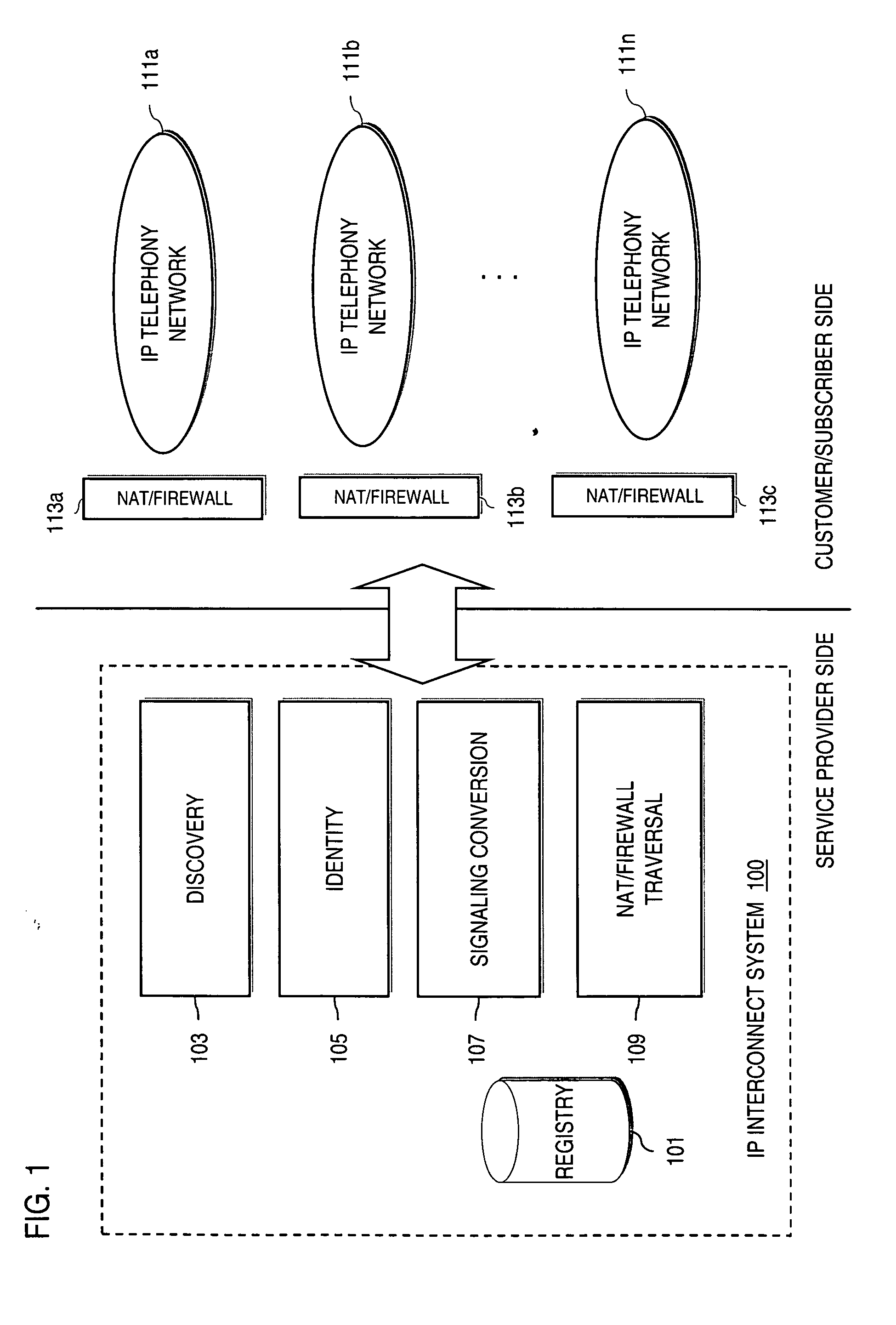
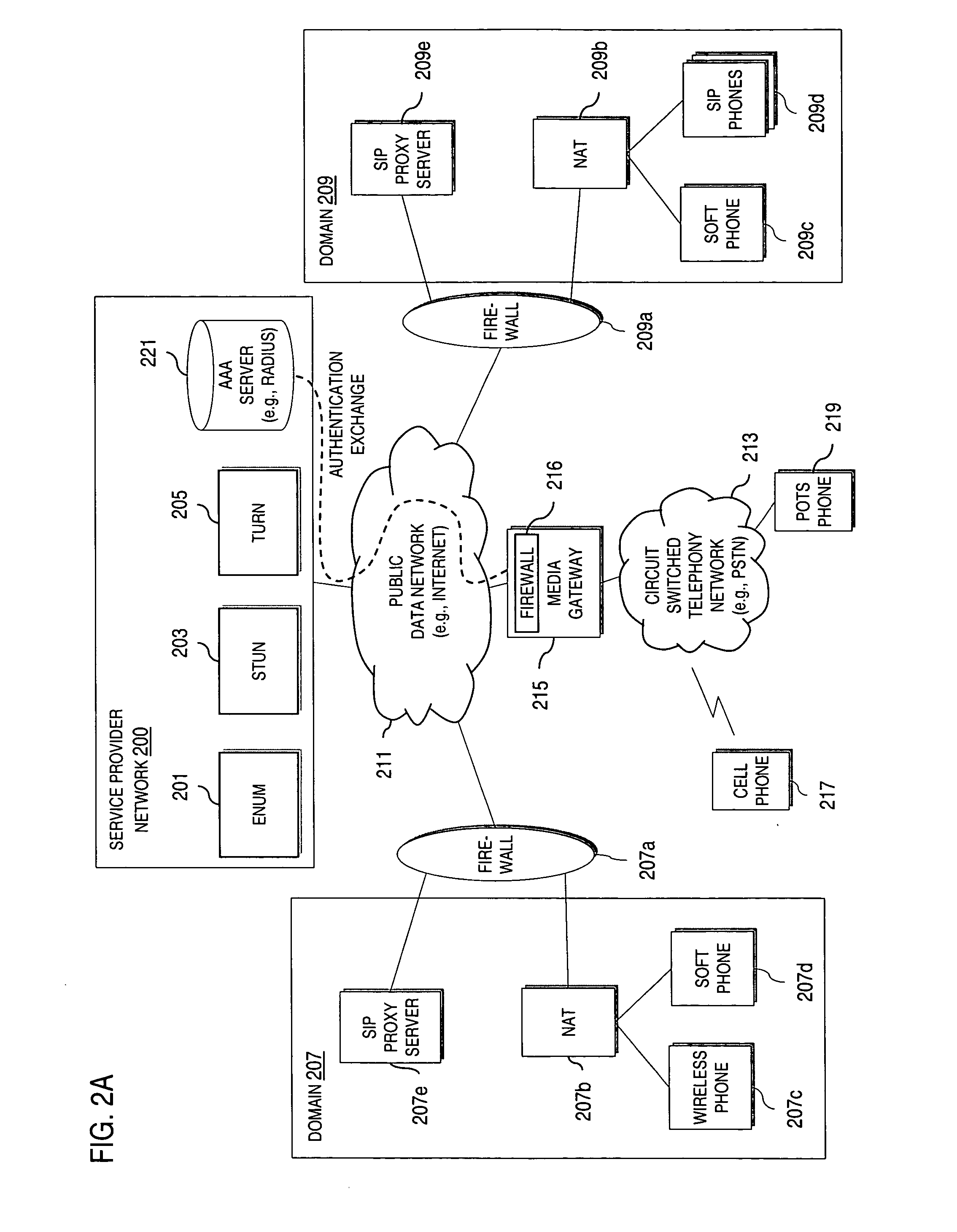
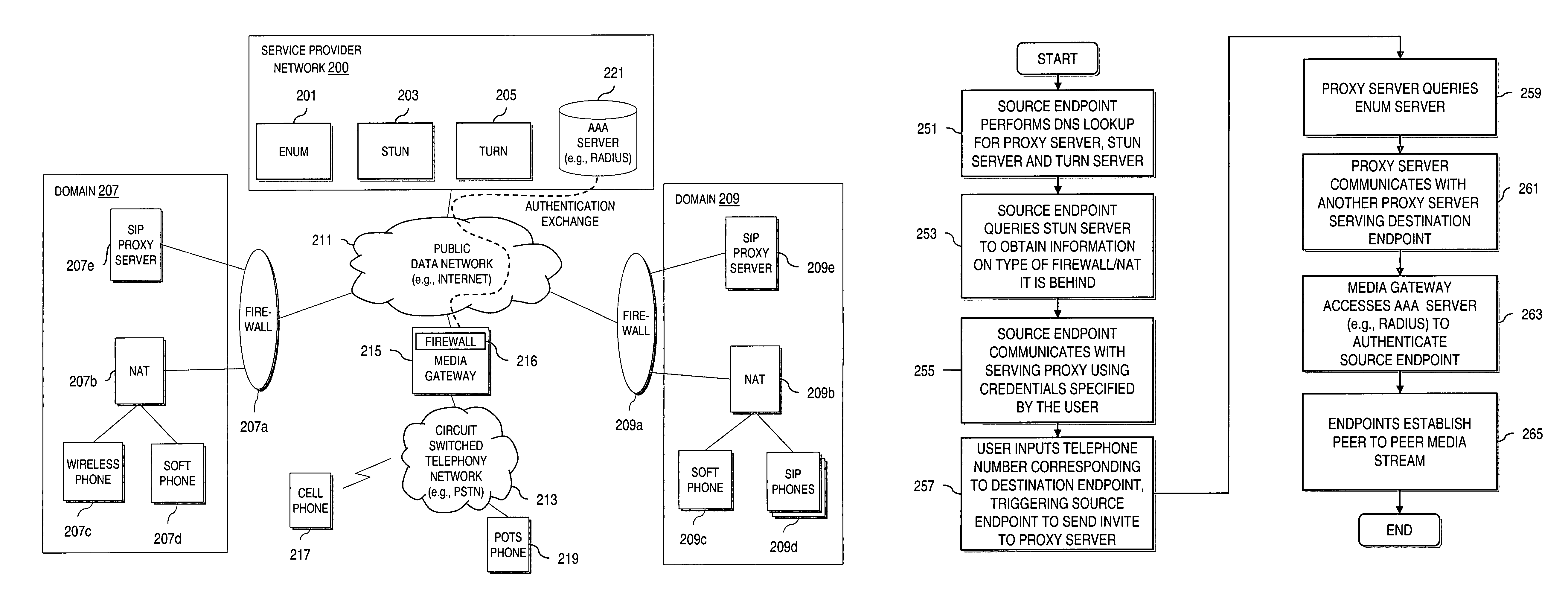
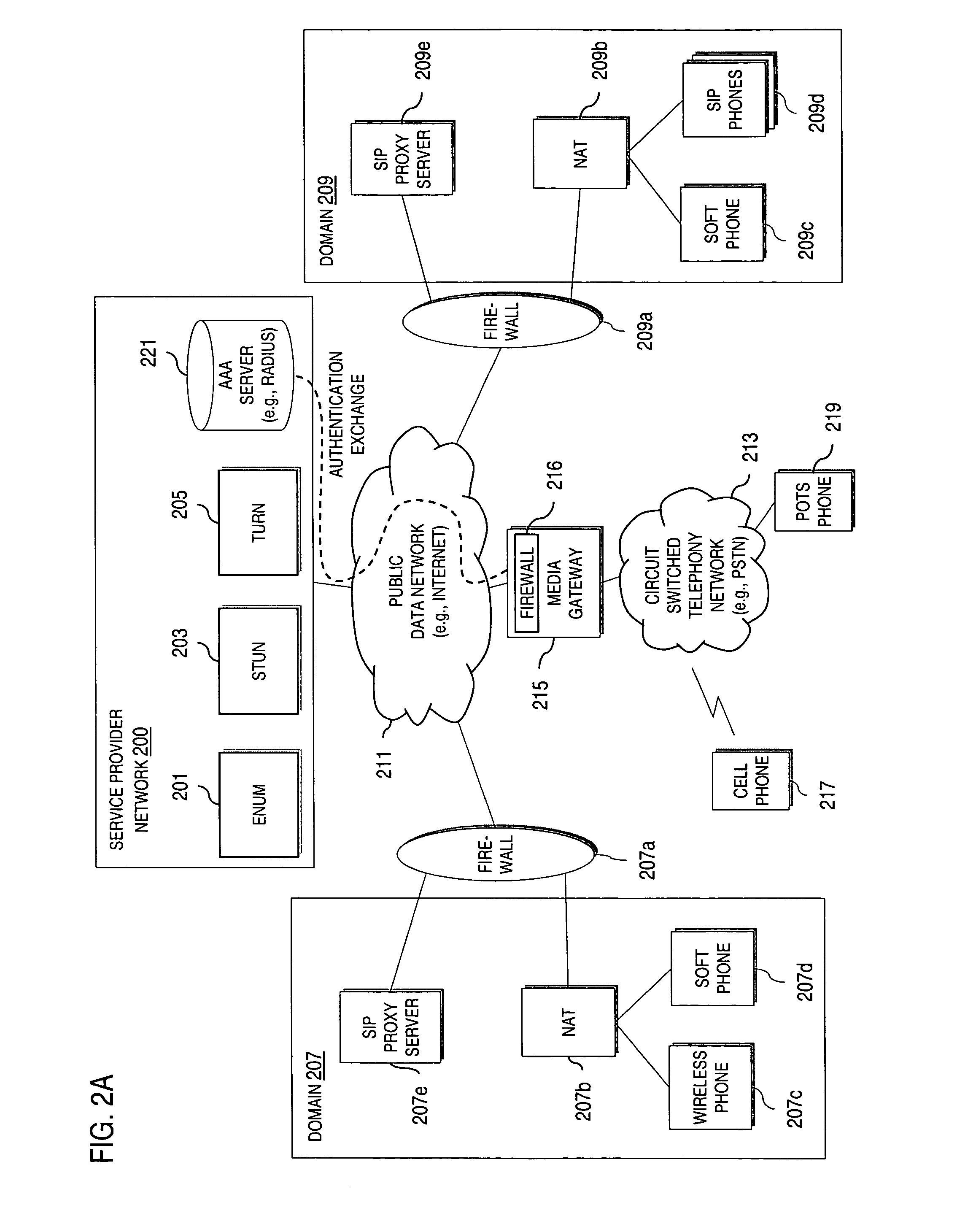
Method and system for providing secure media gateways to support interdomain traversal
ActiveUS20070019623A1Special service for subscribersData switching by path configurationNetwork addressNetwork address translation
An approach provides interdomain traversal to support packetized voice transmissions. A signaling message is received for establishing a voice call from a first endpoint associated with a first domain to a second endpoint associated with a second domain. The first endpoint queries a STUN (Simple Traversal of UDP (User Datagram Protocol)) server to determine information relating to a firewall and network address translator that the first endpoint is behind, and to log into a TURN (Traversal Using Relay NAT (Network Address Translation)) server configured to establish a media path between the first endpoint and the second endpoint. A first proxy server serving the first endpoint communicates with an ENUM (Electronic Number) server to convert a directory number corresponding to the second endpoint to a network address. The first proxy server communicates with a second proxy server serving the second endpoint to establish the voice call. The STUN server, the TURN server and the ENUM server are maintained by service provider. The first endpoint is authenticated to permit exchange of a media stream over the media path. The media stream is relayed, if the first endpoint is successfully authenticated.
Owner:VERIZON PATENT & LICENSING INC
Method and system for providing secure media gateways to support interdomain traversal
ActiveUS7920549B2Special service for subscribersData switching by path configurationNetwork addressNetwork address translation
An approach provides interdomain traversal to support packetized voice transmissions. A signaling message is received for establishing a voice call from a first endpoint associated with a first domain to a second endpoint associated with a second domain. The first endpoint queries a STUN (Simple Traversal of UDP (User Datagram Protocol)) server to determine information relating to a firewall and network address translator that the first endpoint is behind, and to log into a TURN (Traversal Using Relay NAT (Network Address Translation)) server configured to establish a media path between the first endpoint and the second endpoint. A first proxy server serving the first endpoint communicates with an ENUM (Electronic Number) server to convert a directory number corresponding to the second endpoint to a network address. The first proxy server communicates with a second proxy server serving the second endpoint to establish the voice call. The STUN server, the TURN server and the ENUM server are maintained by service provider. The first endpoint is authenticated to permit exchange of a media stream over the media path. The media stream is relayed, if the first endpoint is successfully authenticated.
Owner:VERIZON PATENT & LICENSING INC
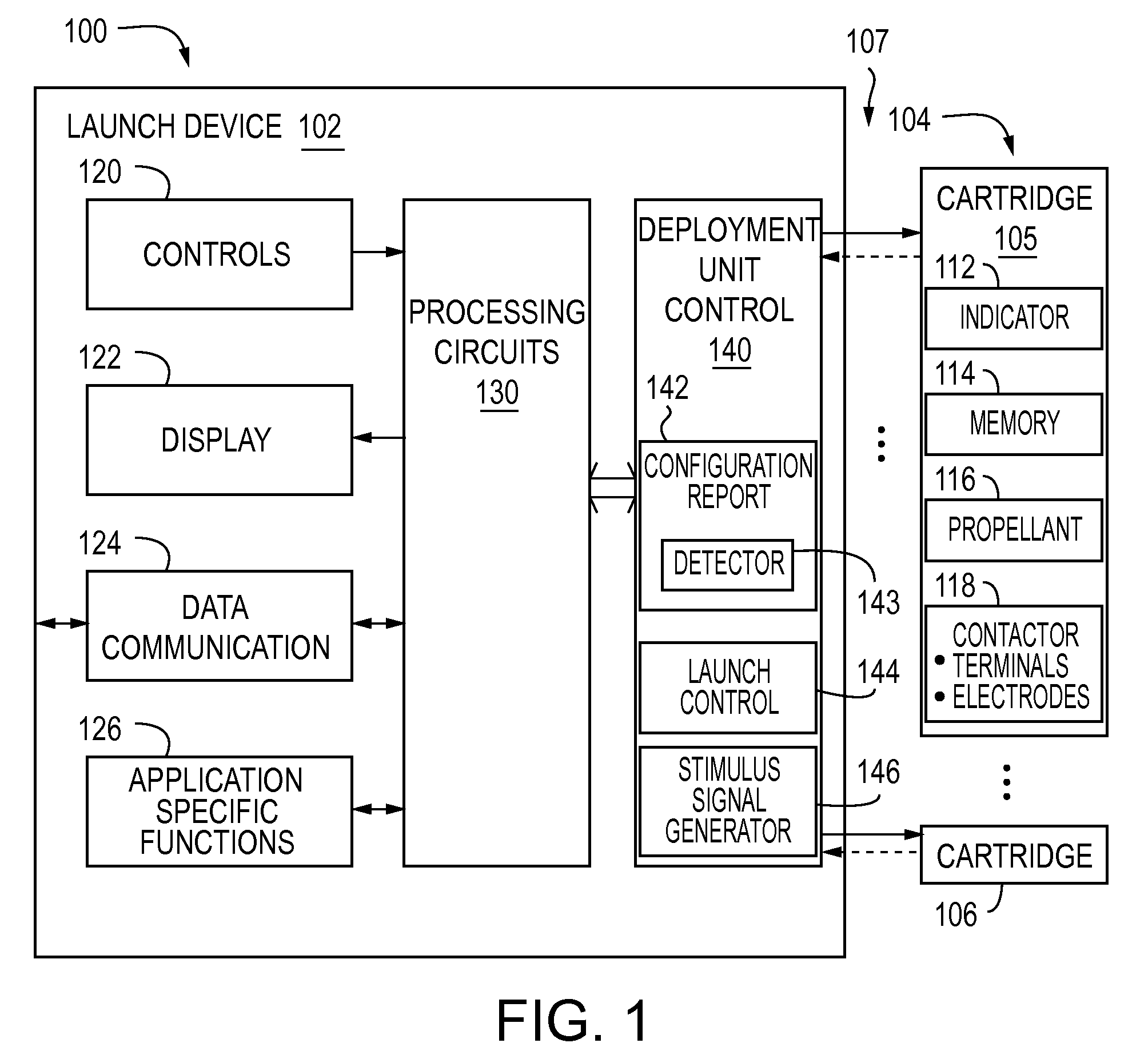
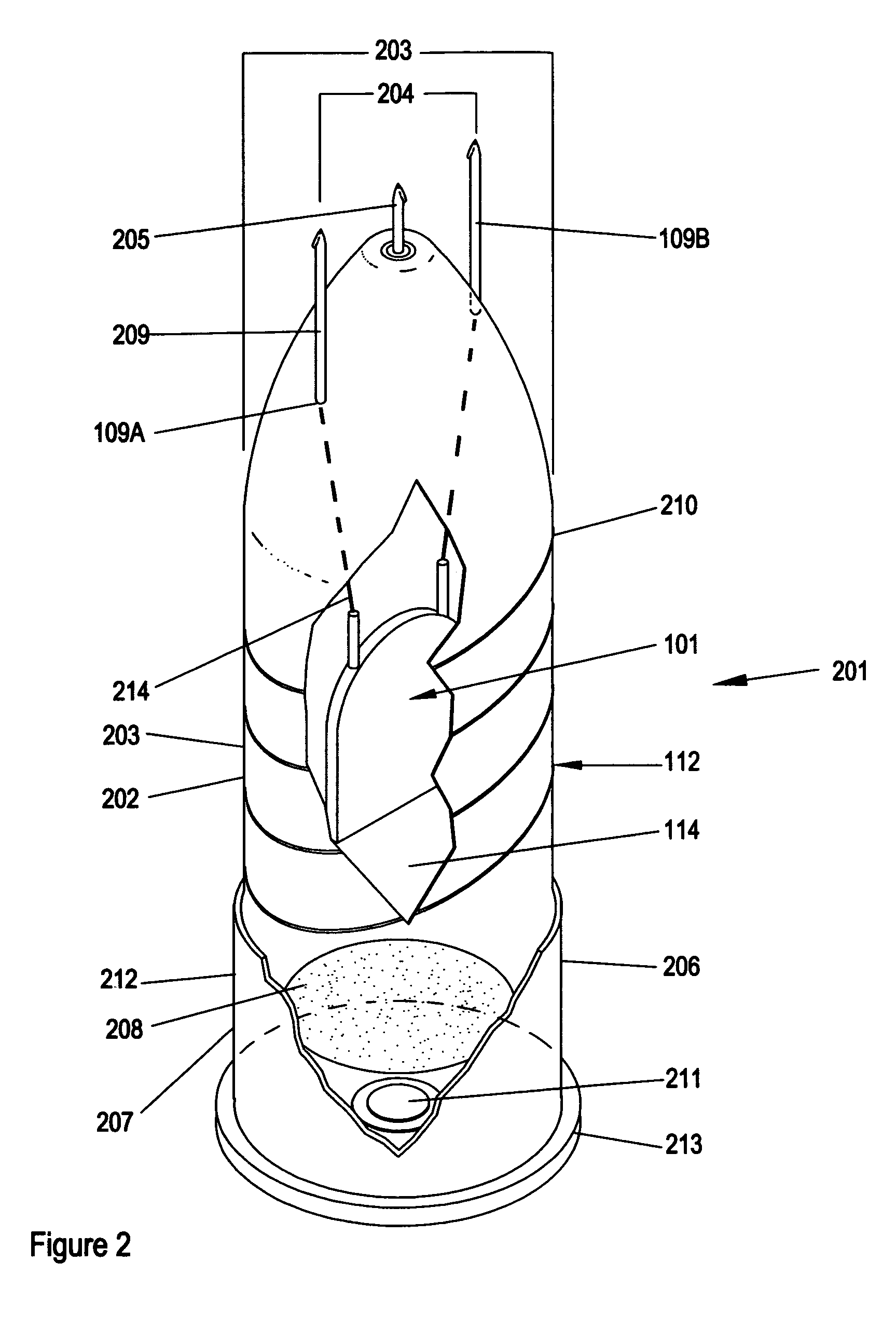
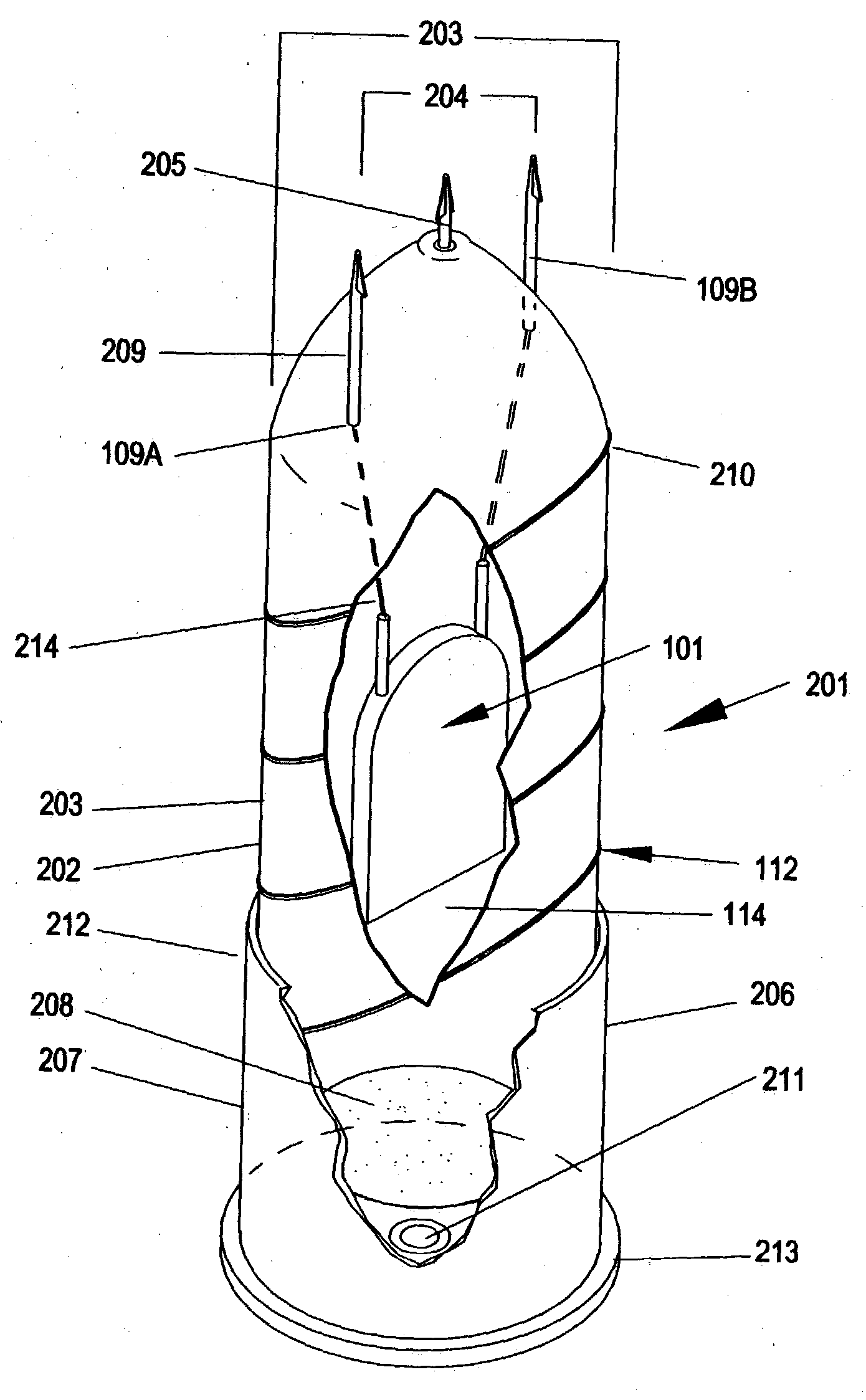
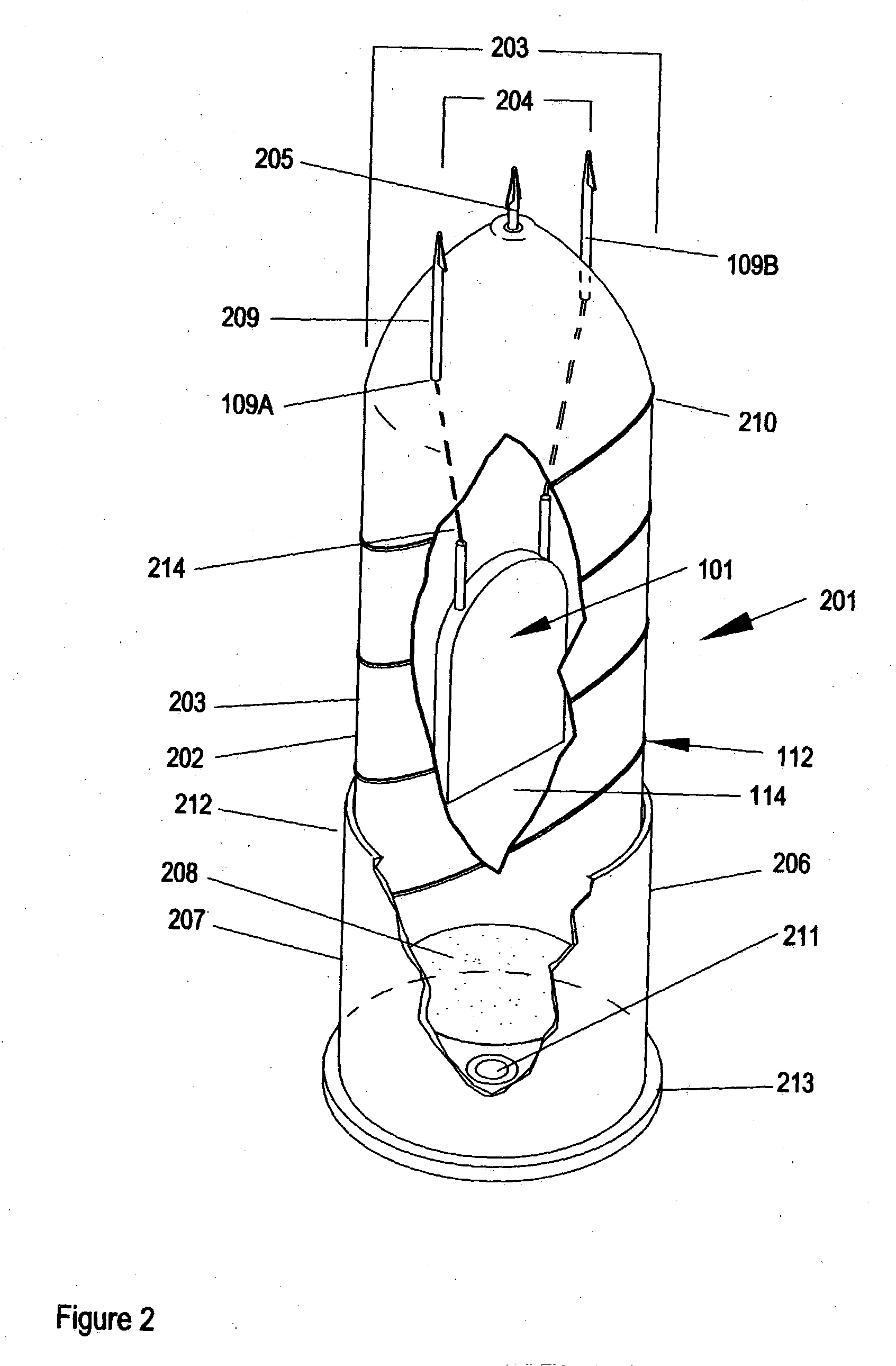
Sub-lethal, wireless projectile and accessories
InactiveUS6880466B2Increase energy levelReduce power levelAmmunition projectilesElectric shock equipmentsSTUNElectric discharge
The invention is a circuit capable of being positioned in a variety of wireless projectile and of delivering a series of pulsed electric discharges in two wave frequencies so as to stun and disable a target individual. The projectiles are adapted to be discharged from a different types of devices and powered by explosive, pneumatic, or manual means. At least one mode includes the ability to deliver a stunning physical blow in addition to the electric shock. The device is sub-lethal, but totally disabling in effects on a target individual.
Owner:CSA ENERGY
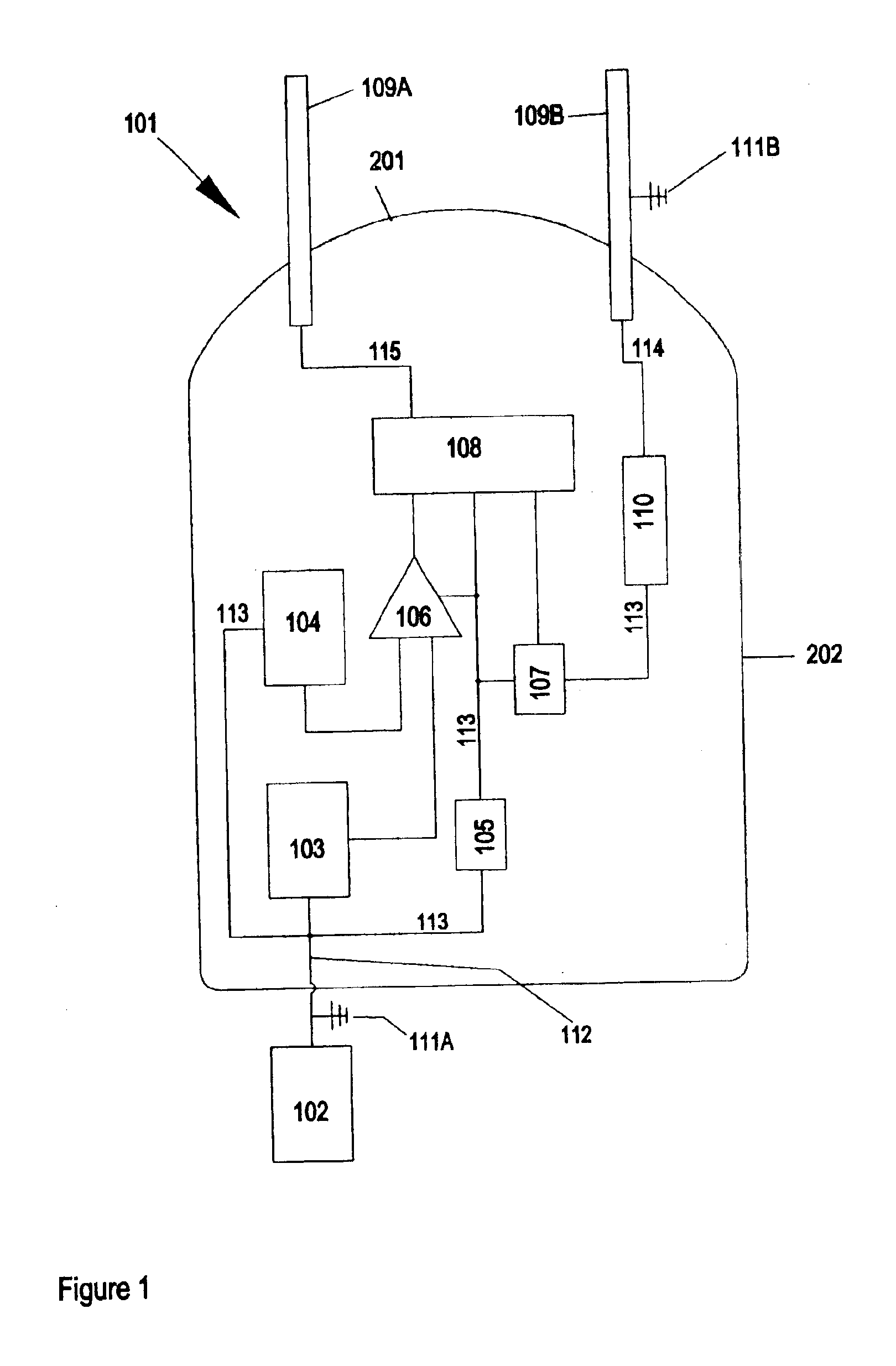
System and method of information communication, information processing apparatus and information processing method, program and recording medium
InactiveUS20050105543A1Low costLow-cost implementationMultiple digital computer combinationsStore-and-forward switching systemsInformation processingSTUN
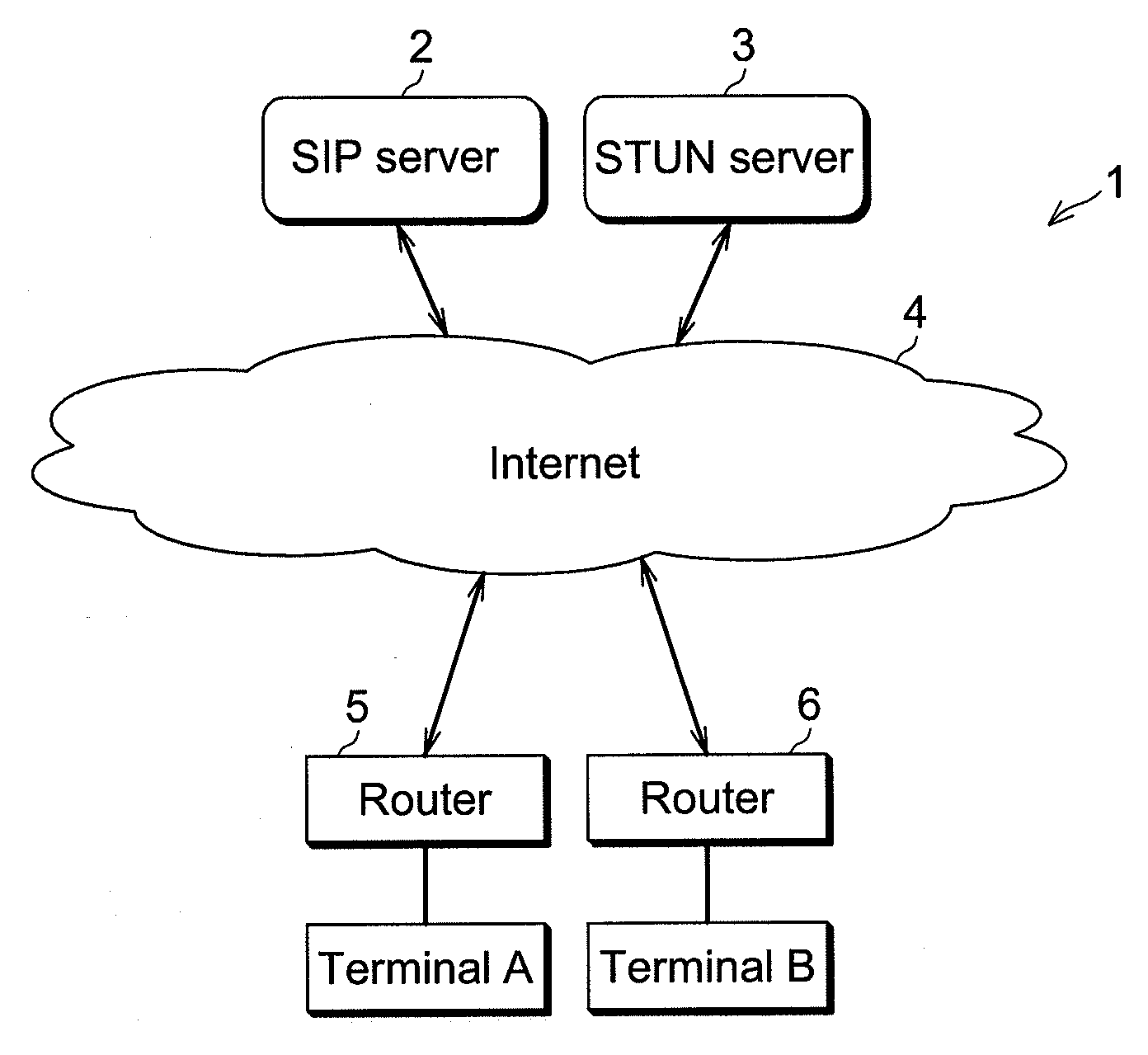
In order to realize NAT traversal communication at low cost and without fail, local communication terminals connected as subordinates of a first router having a UPnP™ function obtain an IP address and a port number, both to be converted by a NAT function of the first router, on the basis of a UPnP™ protocol to register them in a relay server as exchange information for the NAT traversal. Local communication terminals connected as subordinates of a second router without the UPnP™ function specify an IP address to be converted by the NAT function of the second router on the basis of a packet obtained from a STUN server and estimate a port number to be converted by the NAT function of the second router to register them in the relay server as the exchange information for the NAT traversal. The present invention may be applied to a personal computer.
Owner:SONY CORP
Stun gun
InactiveUS6256916B1Wider discharge gapImprove efficiencyElectric shock equipmentsSmallarmsSTUNEngineering
A stun gun having an electrically insulated protuberance that extends to a height above the line between the vertical terminations of the exposed electrical target contacts. Before the weapon's target probes can be brought in contact with the target, the insulative protuberance compresses the target's muscle. This action shortens the length of the muscle while increasing the area of tissue involved in a subsequent shocking discharge. This, in turn, increases the likelihood of a sustained involuntary flexing or extending contraction of the muscle. A rectangular ammunition bay may be placed in the weapon with a portion of one partially exposed probe touching the ammunition's negative contact and a portion of the other partially exposed probe touching the ammunition's positive contact. In the event of a ballistic deployment failure, without the addition of any circuitry, the weapon can still act as a manual contact weapon.
Owner:RESNICK BARNET
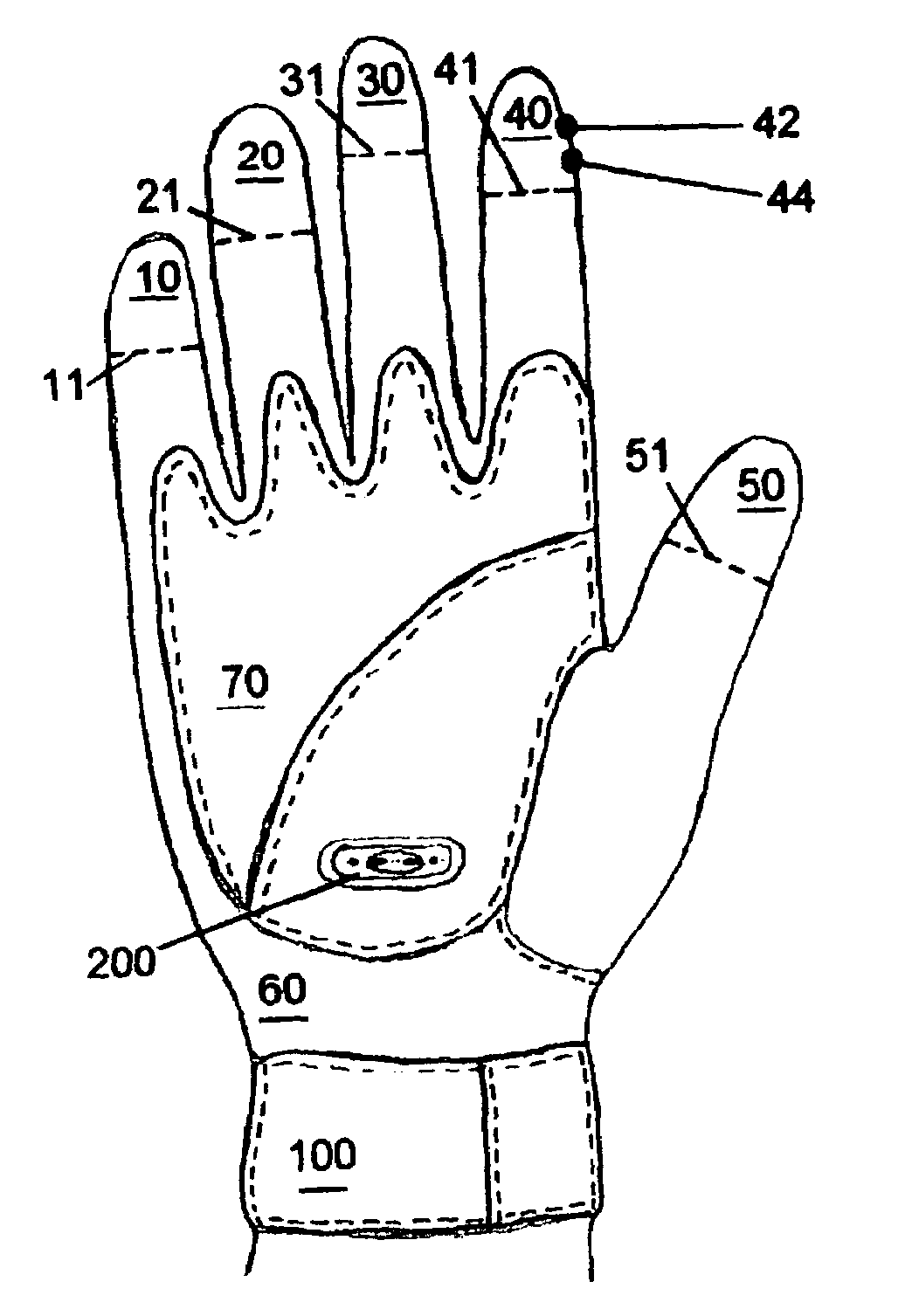
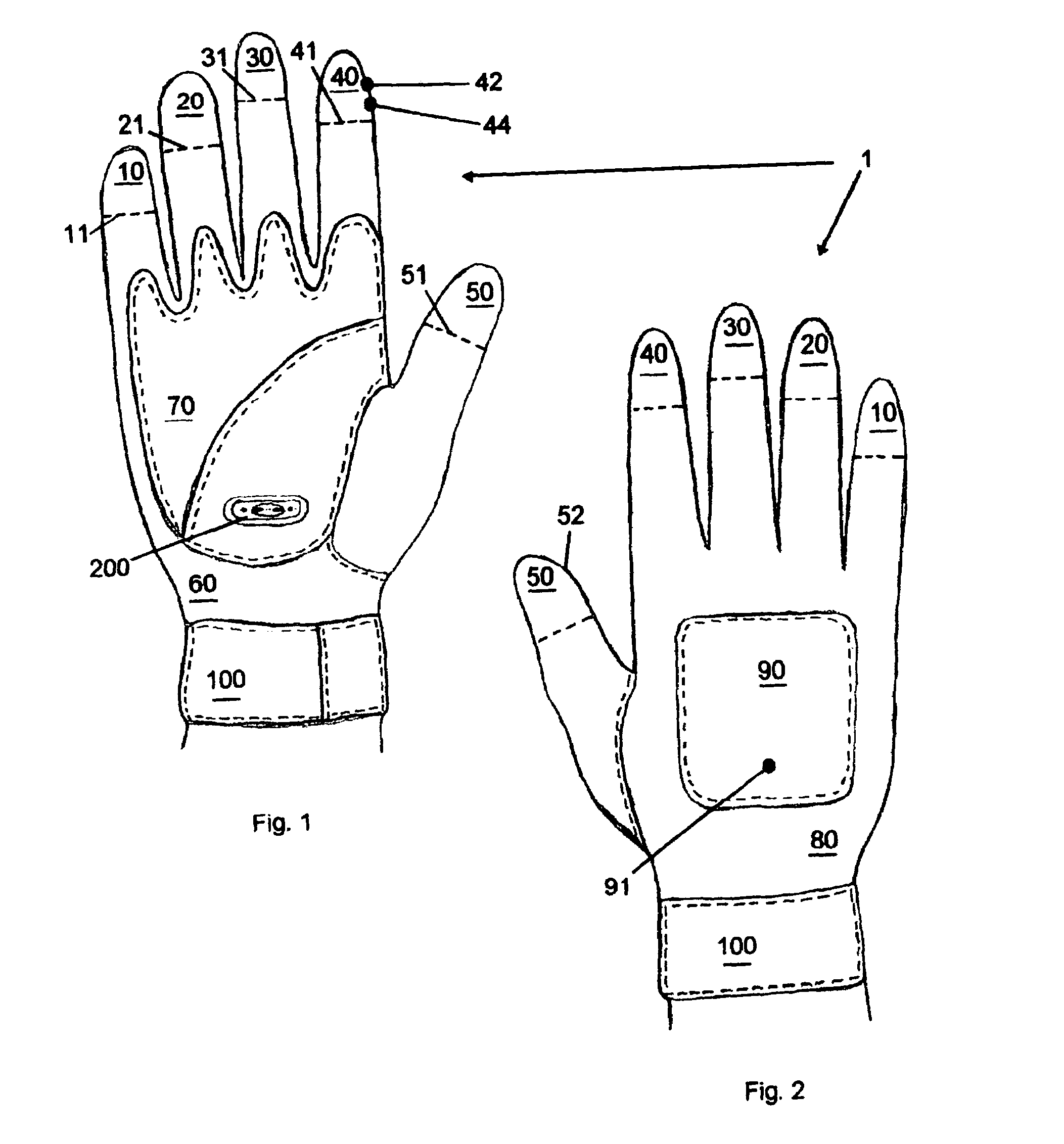
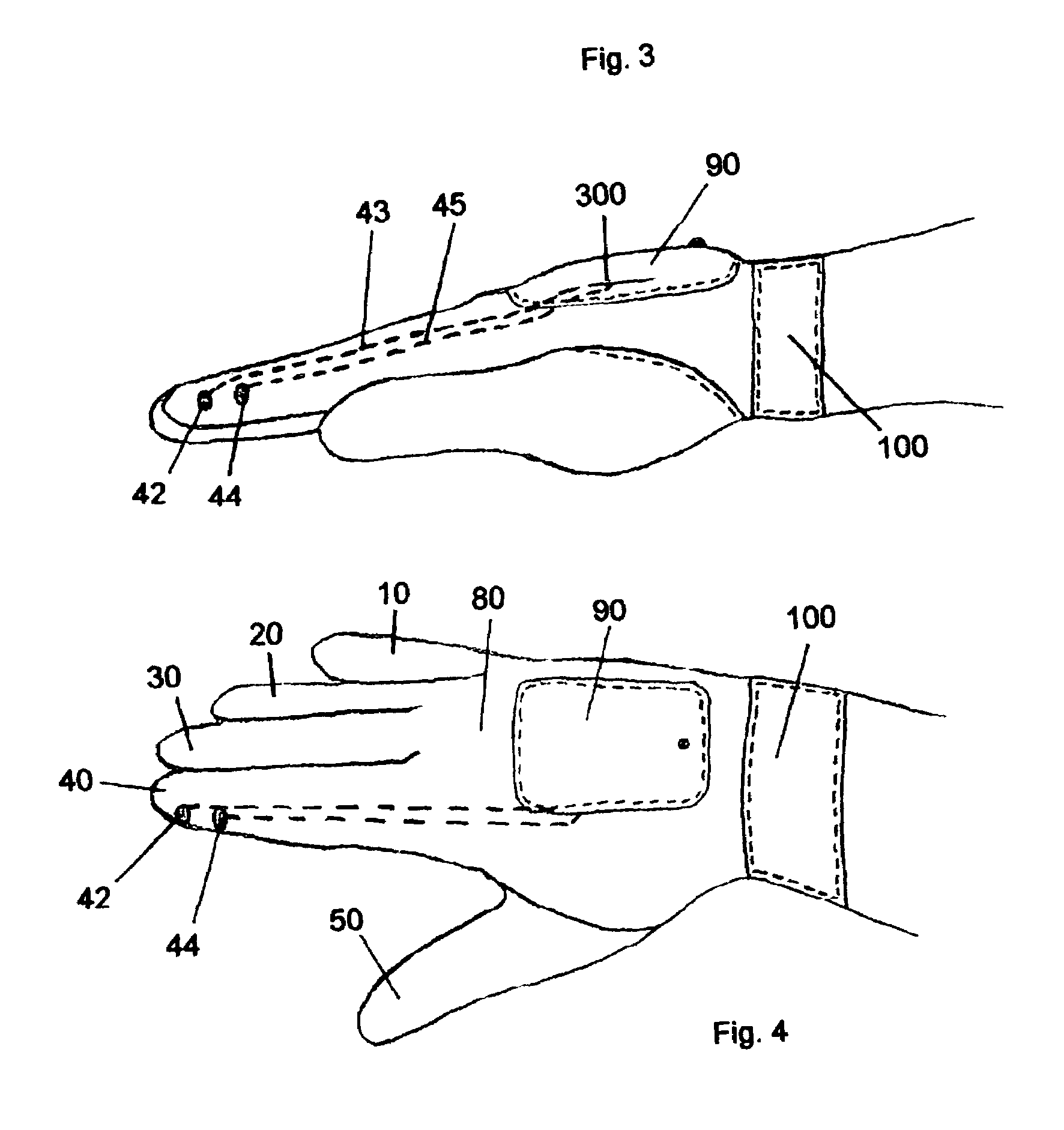
Versatile stun glove
InactiveUS7012797B1Promote activationWithout unnecessary delayElectric shock equipmentsApparelSTUNIndex finger
A versatile stun glove having at least two electrodes placed in the palm region, and / or on the back of the hand and / or on the fingers of the glove. A rechargeable power supply that uses simple thin diameter and thickness replaceable batteries for powering the electrodes. Batteries can include 9-volt battery, a double A, and triple A batteries. A thin watch battery can also be used so that no protrusions extend outward from the glove body. The power supply can be located in the palm region and / or on the back of the hand of the glove. The power supply can be accessed by a foldable panel cover that can be removed by hook and loop fasteners(Velcro®), snaps, a zipper and the like. The power can be activated by a simple switch located adjacent to the finger tip of the index finger of the user so that touching the tip of the thumb against the index finger tip activates the power. An alternative activation source can be a pressure sensor that is underneath one of the electrodes so that pressing the at least one electrode into an assailant activates the power. A novel stand and power supply recharge allows for the glove to be mounted to a vehicle cigarette lighter. The location of the stand allows for the glove to be easily accessible and reachable when needed by the user. A stun stick accessory can allow for the glove discharge to have greater reach to attackers and assailants.
Owner:C P D TECH
Method and apparatus for packet traversal of a network address translation device
A characterization method for a network address translation (NAT) device by an internal computer behind the NAT device includes creating a plurality of sockets; binding the plurality of sockets, respectively, to a plurality of ports; transmitting a plurality of STUN requests in user datagram protocol (UDP) packets to a plurality of STUN servers, wherein each STUN request is associated with one of the sockets; determining that the NAT device does support UDP packets if responses are not received from the STUN servers; and determining a set of NAT characteristics of the NAT device if a response is received from each of the STUN servers.
Owner:LOGITECH EURO SA
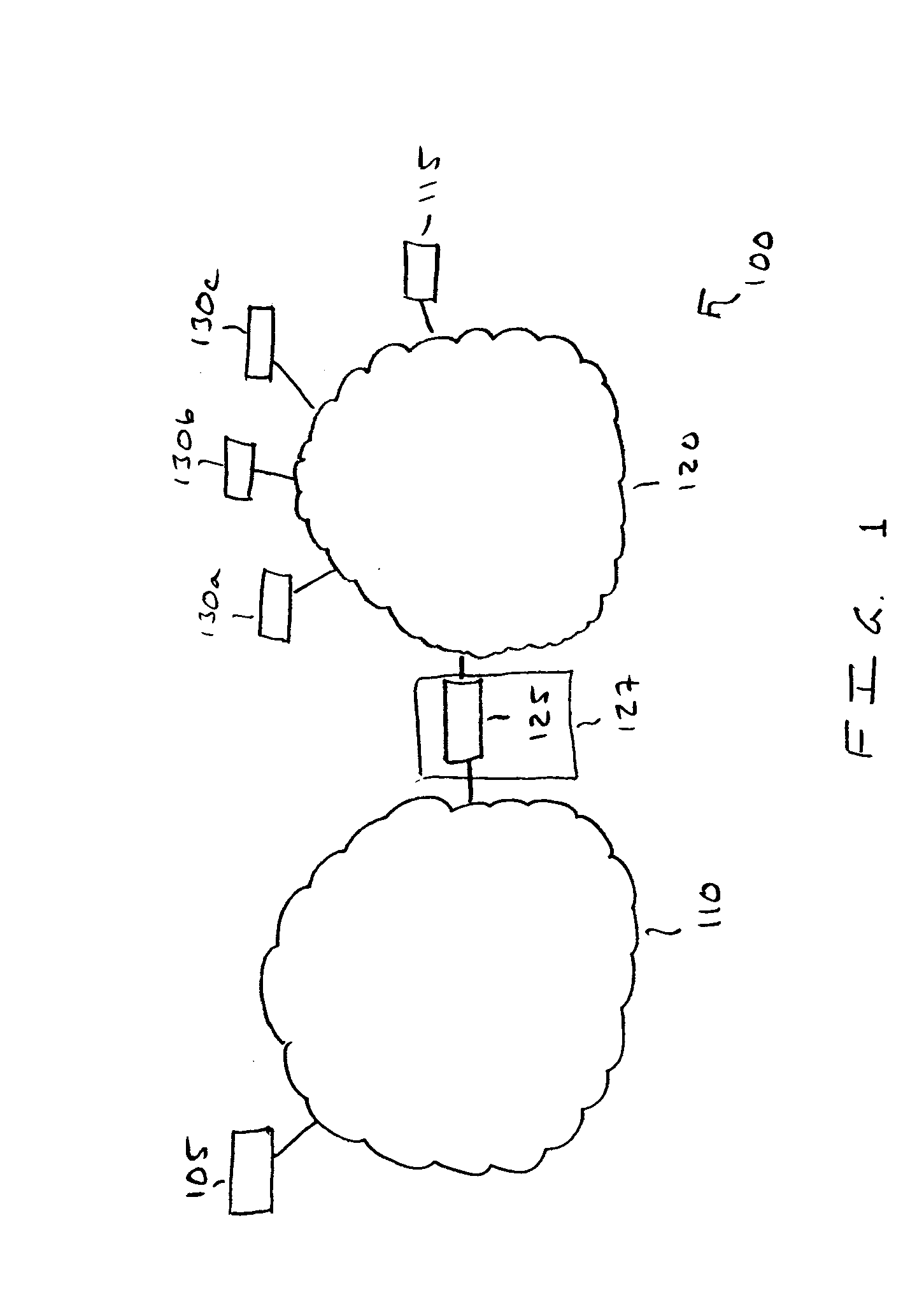
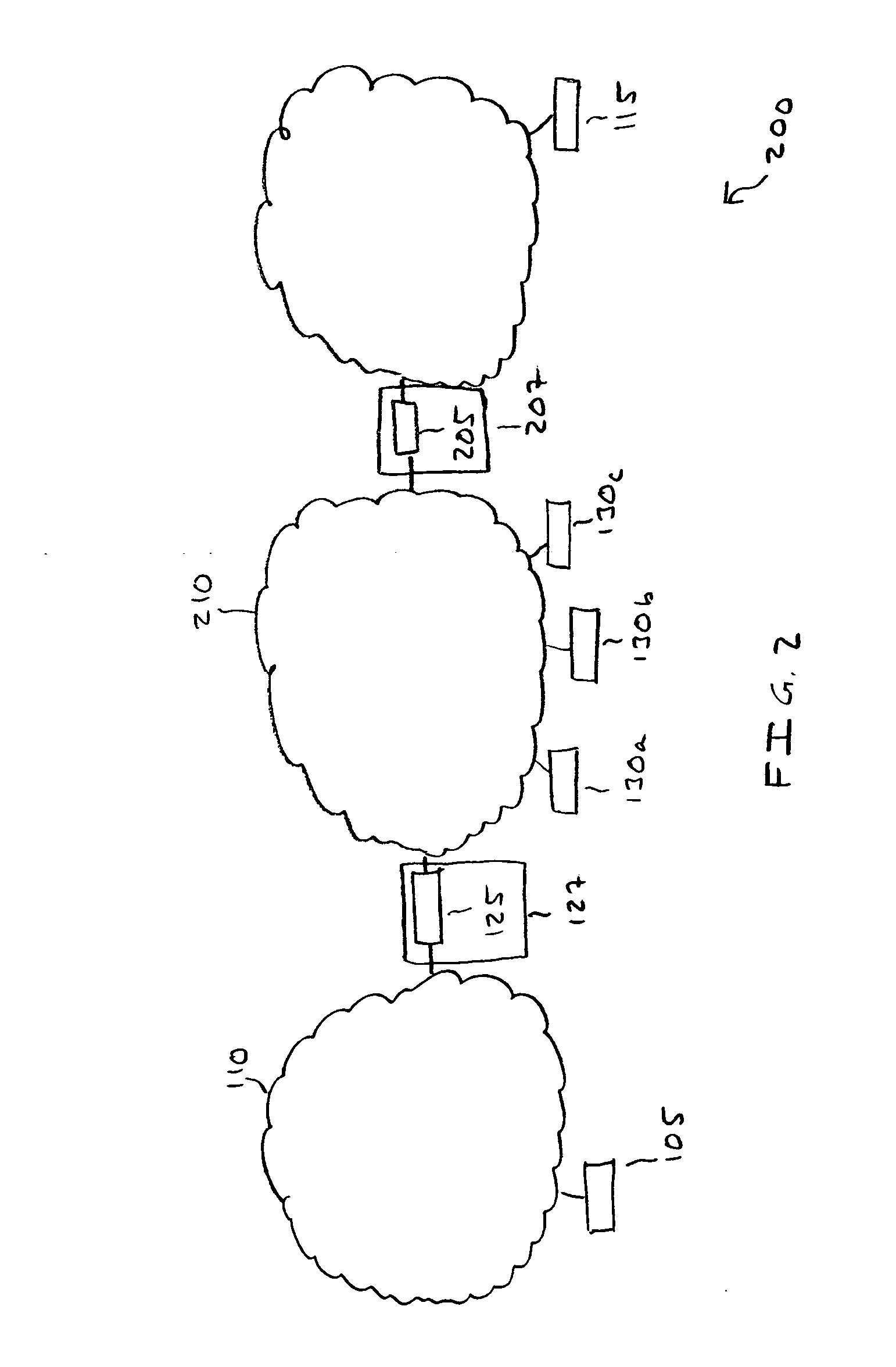
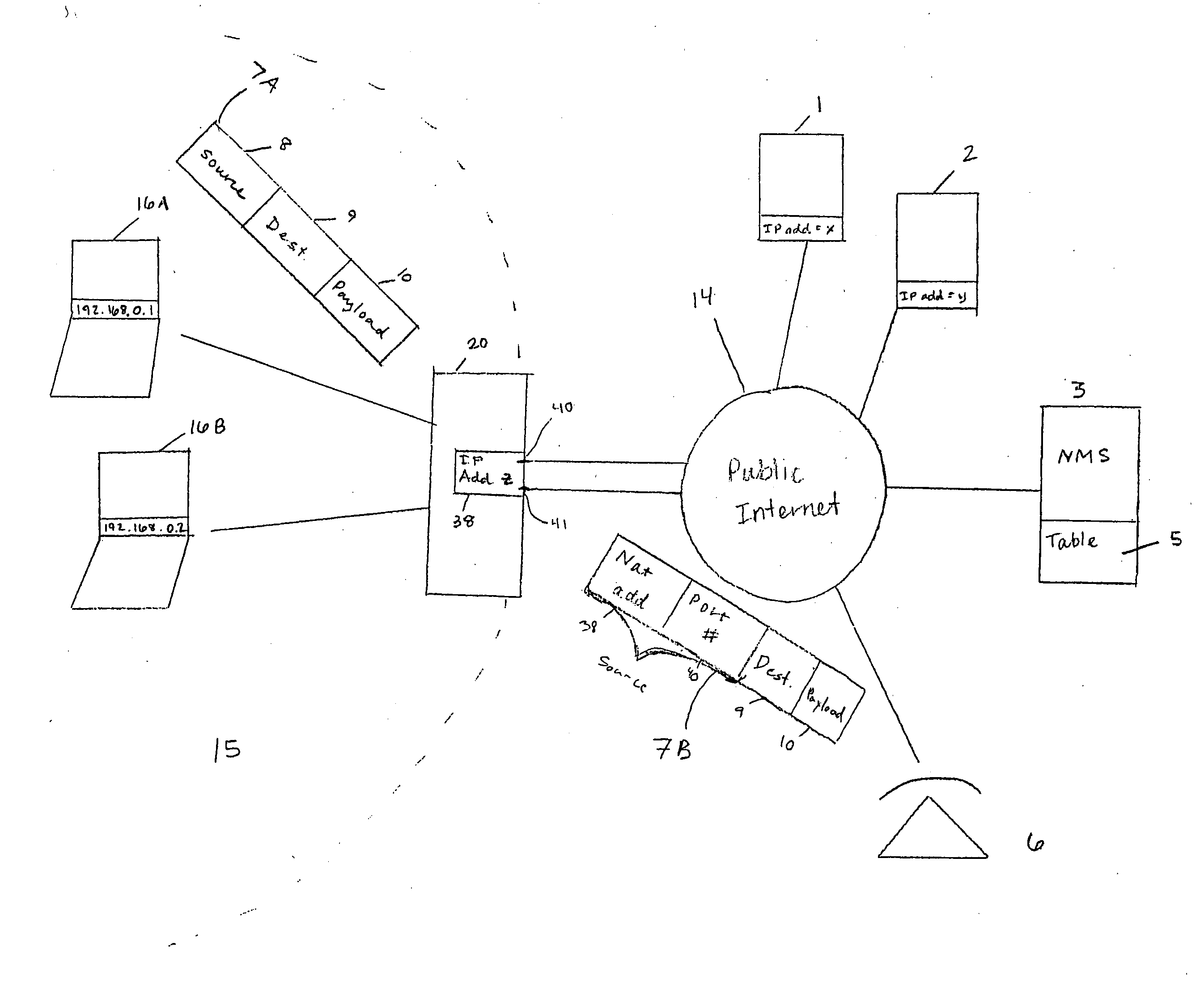
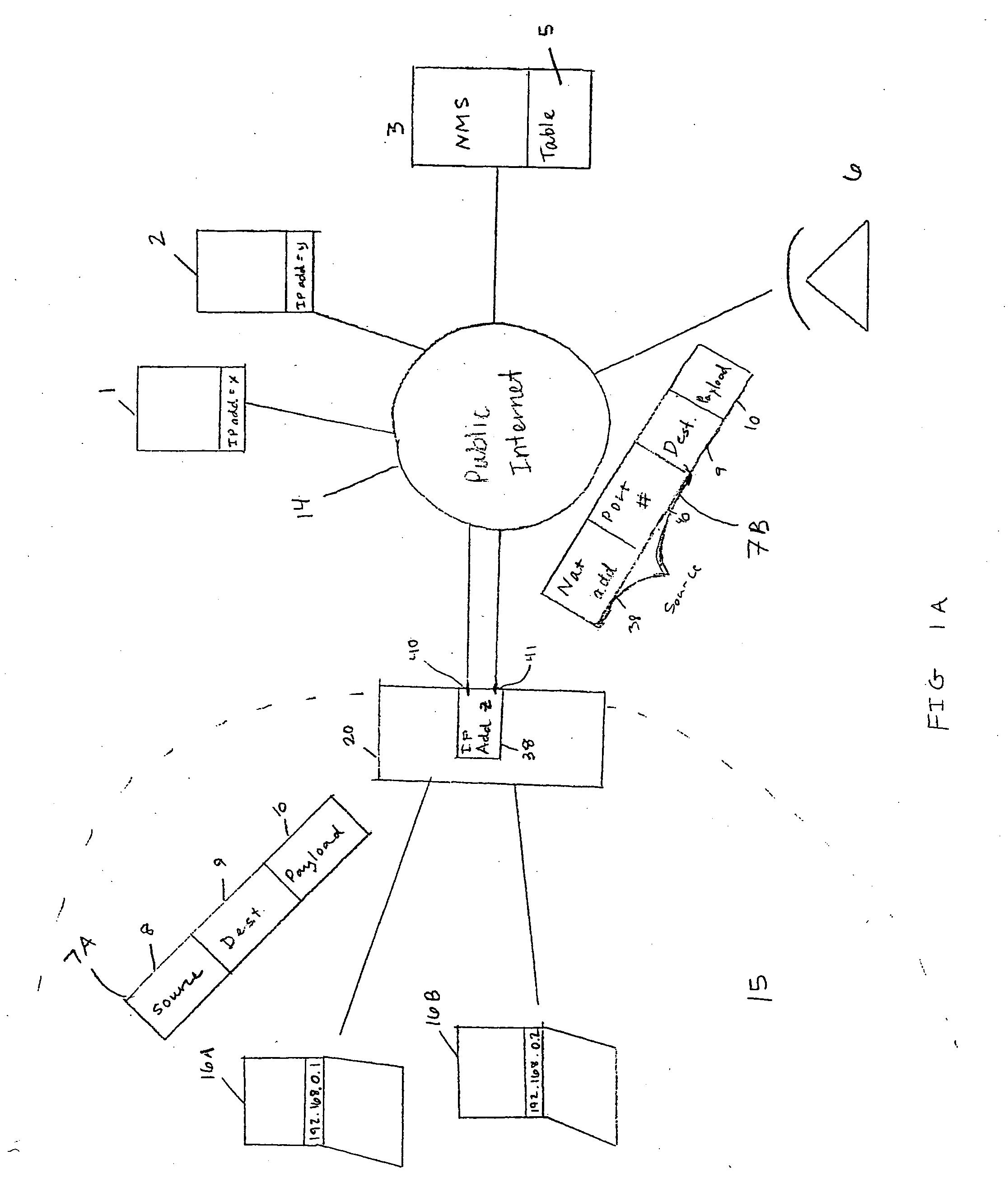
Managing devices across NAT boundaries
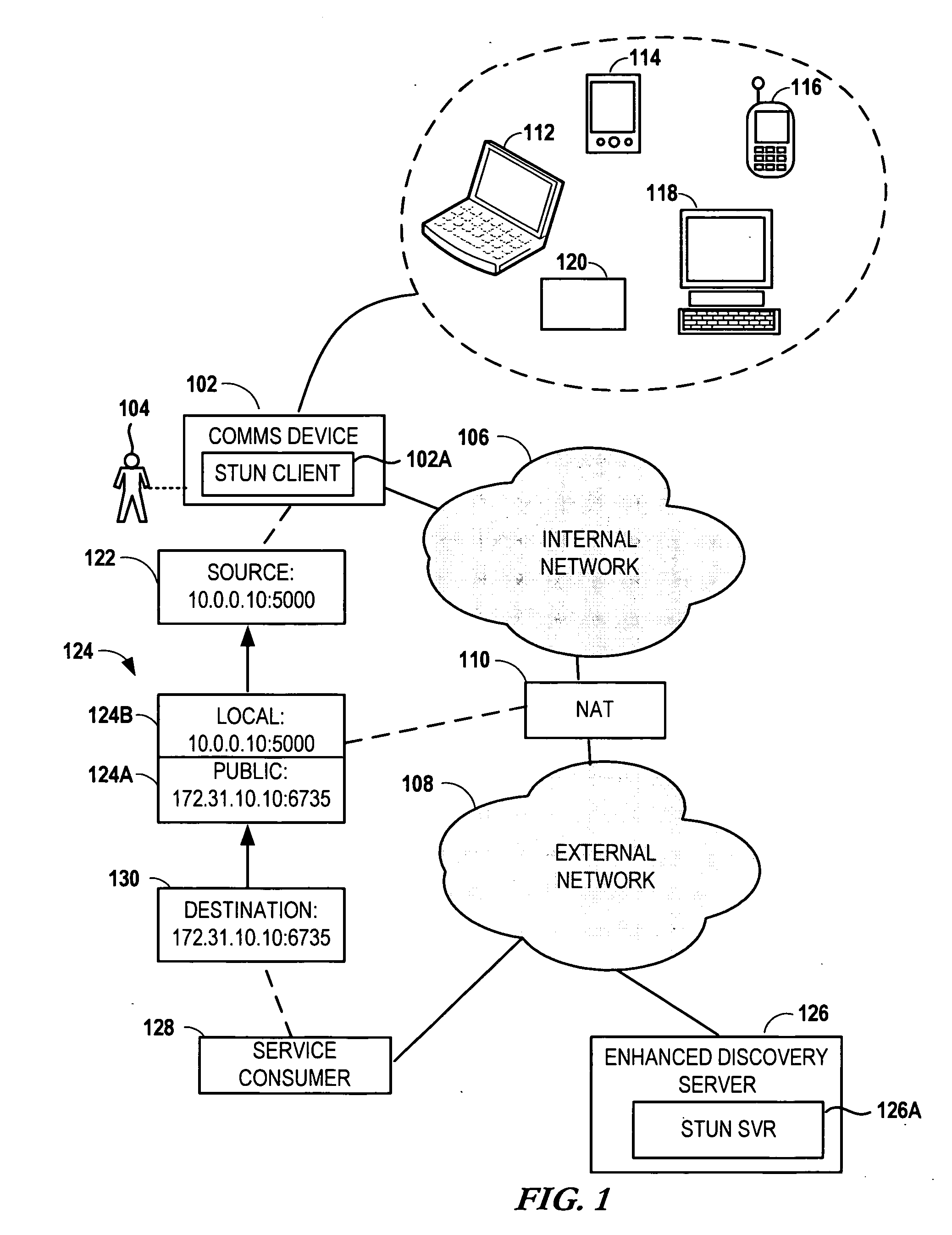
An address management scheme allows a Network Management System (NMS) to manage devices in a private network operating behind a Network Address Translator (NAT) boundary. A device operating in the private network sends a communication to a Simple Traversal of User Datagram Protocol (UDP) Through Network Address Translators (NATs) (STUN) server. The STUN server responds by communicating a public NAT IP address and a NAT port number back to the device. The device then provides the NMS with the public NAT IP address, a NAT port number associated with the device, a unique device identifier, and the private device IP address. The NMS stores this information in a table and then accesses this address information to manage the device in the private network. The device then uses the STUN server to identify any changes to the device address information and then sends the changes to the NMS.
Owner:CISCO TECH INC
Network-level access control management for the cloud
InactiveUS20140289791A1Facilitate actionSimple actionTransmissionSpecial data processing applicationsSTUNNetwork address translation
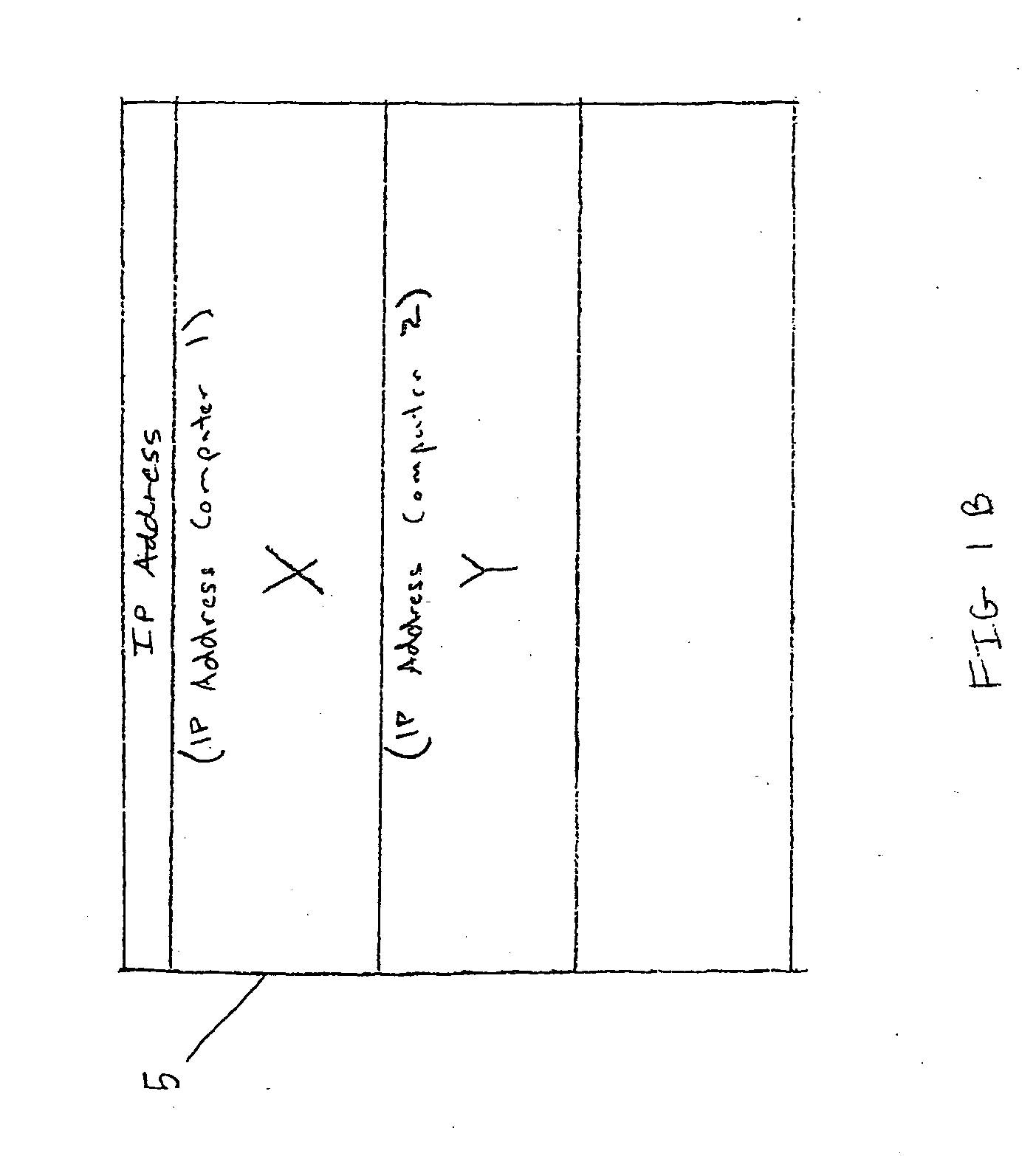
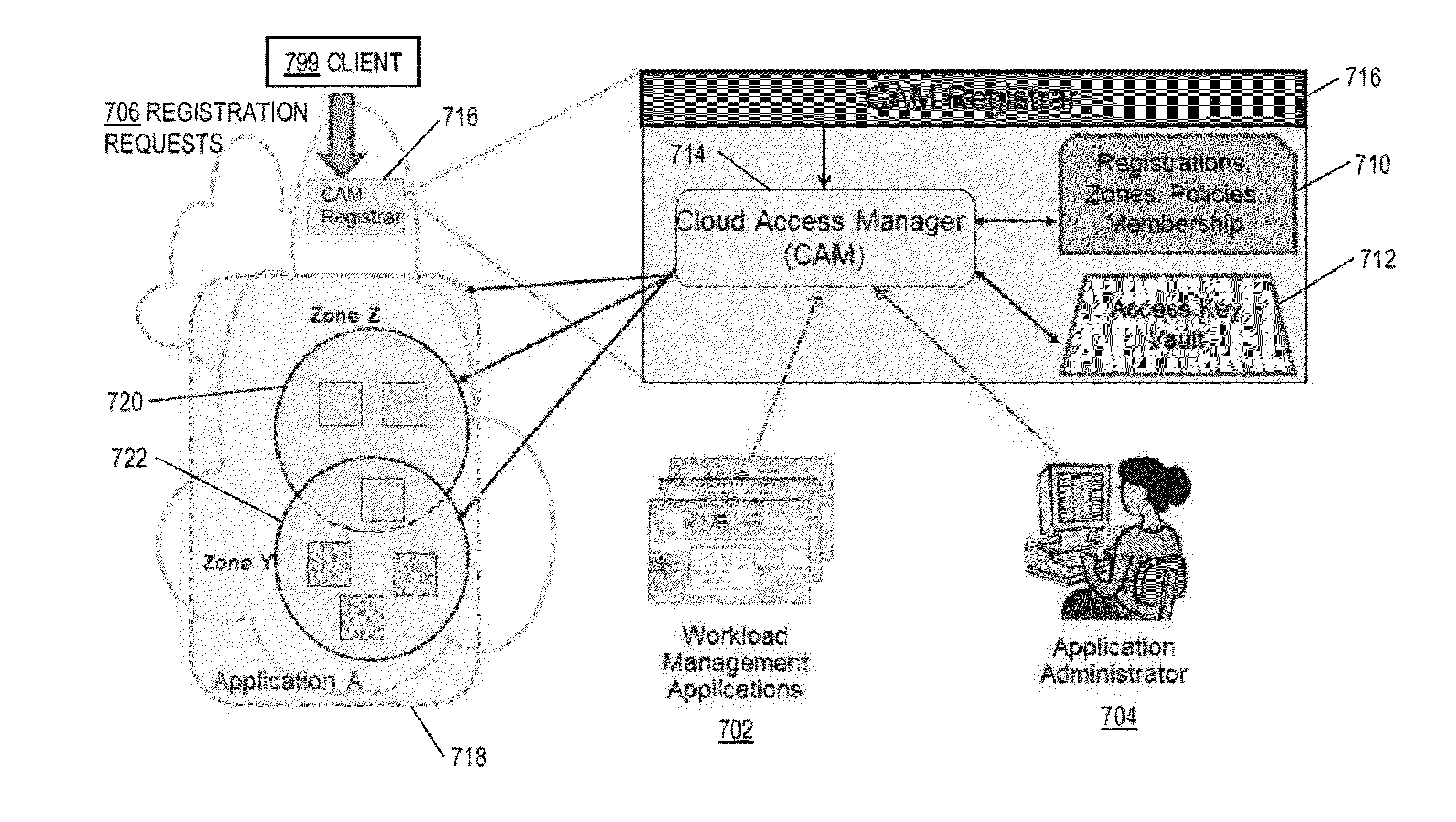
A cloud access manager obtains input regarding access control for at least one application deployed on a plurality of virtual machine instances in a cloud computing environment; the virtual machine instances are divided into at least first and second access zones. A cloud access manager registrar located in the cloud computing environment registers internet protocol addresses of external clients as seen from the cloud computing environment; at least some of the addresses are assigned to the clients via network address translation (NAT). Session traversal utility for NAT (STUN) is carried out to determine public internet protocol addresses assigned to the clients via NAT. The cloud access manager controls (i) access of the external clients to the plurality of virtual machine instances; and (ii) access of the plurality of virtual machine instances to each other, based on the registered internet protocol addresses, in accordance with the access zones.
Owner:IBM CORP
Non-lethal wireless stun projectile system for immobilizing a target by neuromuscular disruption
InactiveUS20070101893A1Reduce impact damageReduce momentumAmmunition projectilesMusical toysSTUNTransformer
A projectile launched from a conventional weapon; upon impact with a human target the projectile attaches to the target and stuns and disables the target by applying a pulsed electrical charge. The electric round is defined as non lethal ammunition directed to incapacitate a human, to prevent him from moving for a short time, to prevent him from committing a crime and to allow authorized personnel to arrest the target. A novel thin film technology transformer and thin film technology battery produce an electrical shock capable of stunning a human being in a device the size of a conventional bullet. The transformer and battery are smaller and lighter than conventional transformers and batteries with similar power output.
Owner:SECURITY DEVICES INT INC
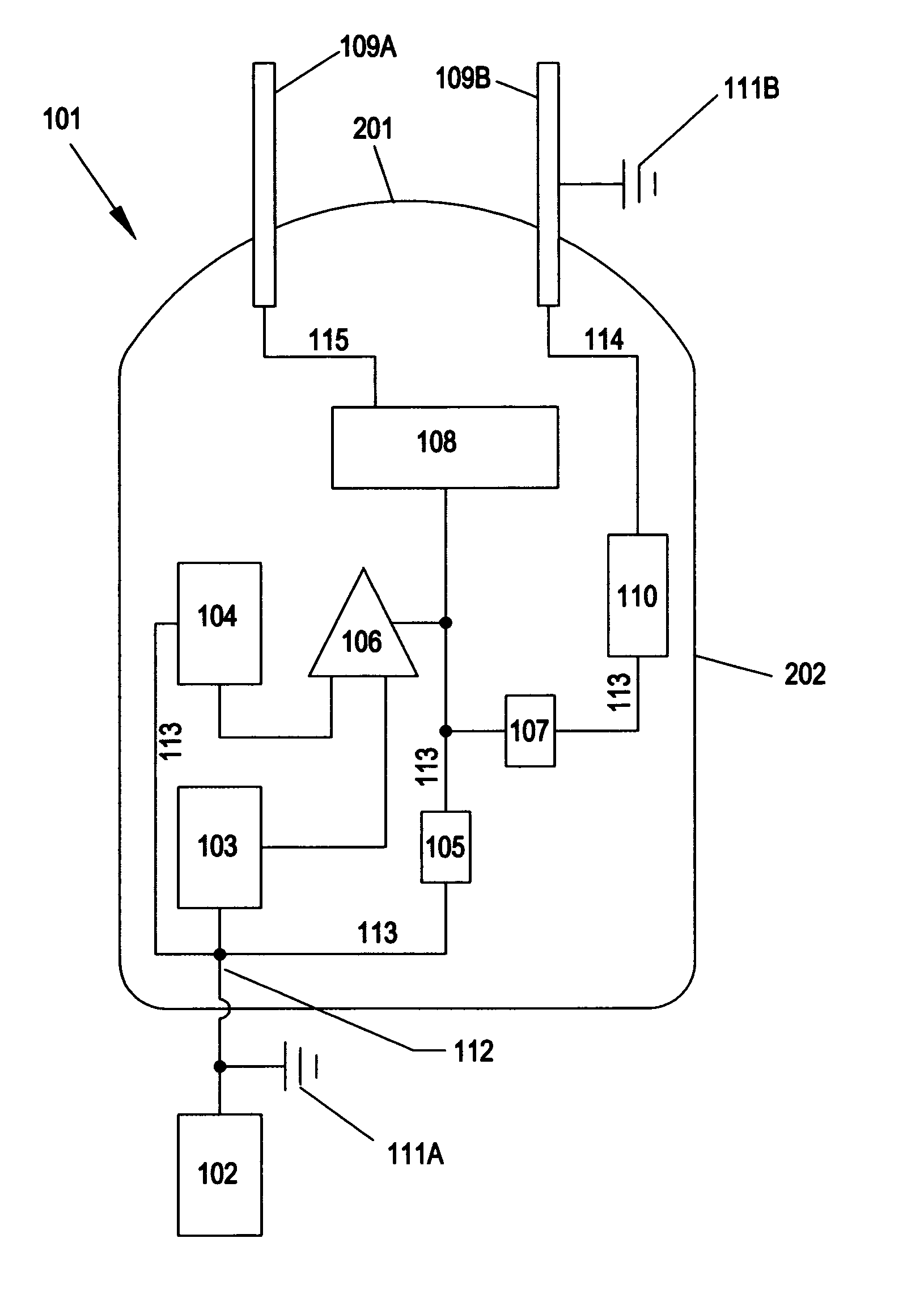
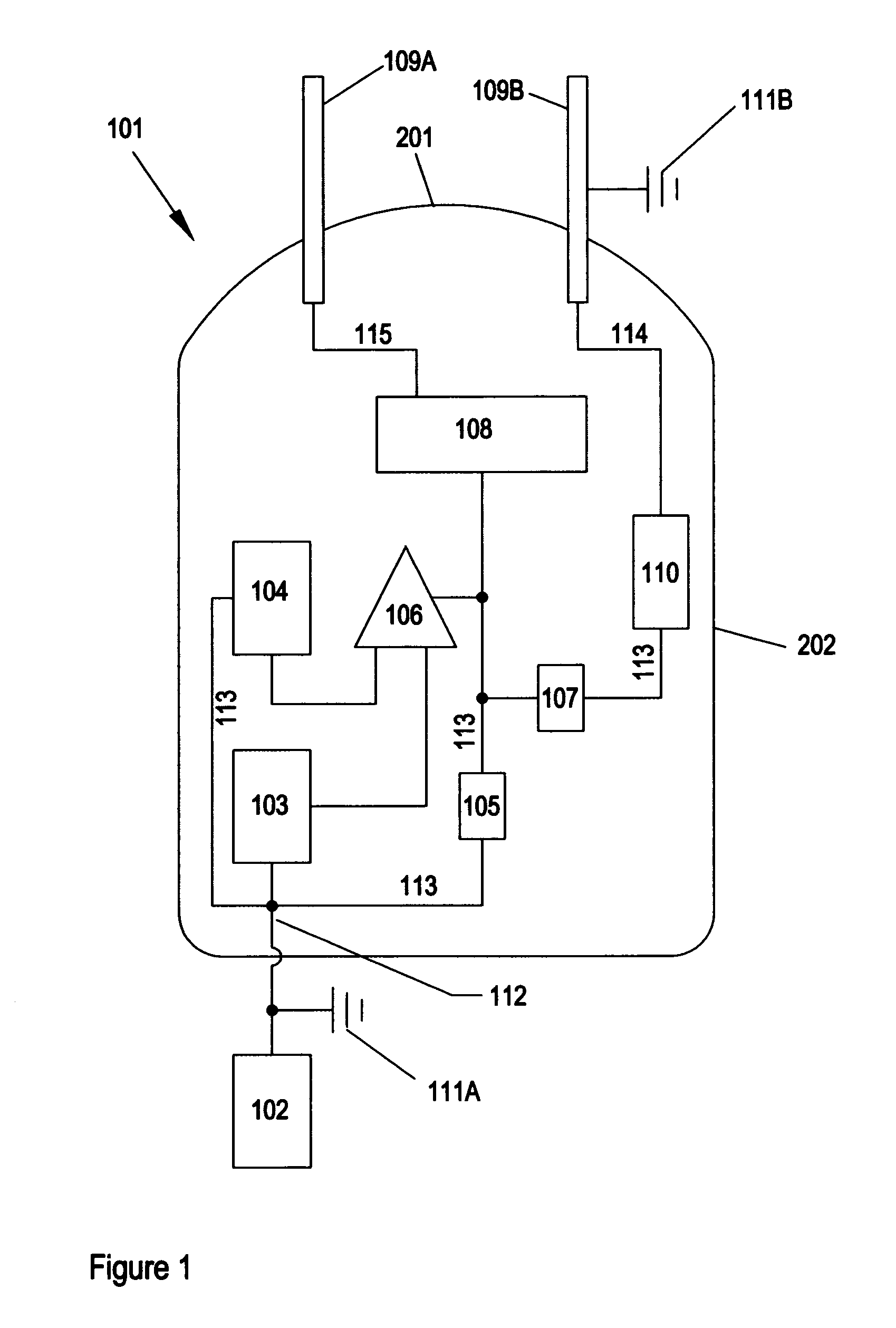
Systems And Methods For Immobilization Using A Compliance Signal Group
A method for immobilization of a human or animal target passes a current through a circuit that includes tissue of the target. The current causes pain compliance or interferes with skeletal muscle control by the target. The method includes in any practical order: (a) generating a first compliance signal of the current, the first compliance signal having a first maximum amplitude; and (b) generating a second compliance signal of the current, the second compliance signal having a second maximum amplitude. The absolute value of the second maximum amplitude is less than the absolute value of the first maximum amplitude. A system that performs such a method may include a processor, a signal generator, and electrodes or terminals for forming the circuit through tissue of the target. Systems, according to various aspects of the present invention, may include stun guns, dart weapons, electronic control devices, electrified projectiles, and mines, to name a few applications.
Owner:AXON ENTERPRISE INC
Sub-lethal, wireless projectile and accessories
InactiveUS7096792B1Increase energy levelReduce power levelAmmunition projectilesElectric shock equipmentsSTUNElectric discharge
The invention is a circuit capable of being positioned in a variety of wireless projectile and of delivering a series of pulsed electric discharges in two wave frequencies so as to stun and disable a target individual. The projectiles are adapted to be discharged from a different types of devices and powered by explosive, pneumatic, or manual means. At least one mode includes the ability to deliver a stunning physical blow in addition to the electric shock. The device is sub-lethal, but totally disabling in effects on a target individual.
Owner:CSA ENERGY
Sub-lethal, wireless projectile and accessories
InactiveUS20050039628A1Increase energy levelReduce power levelAmmunition projectilesElectric shock equipmentsSTUNElectric shock
The invention is a circuit capable of being positioned in a variety of wireless projectile and of delivering a series of pulsed electric discharges in two wave frequencies so as to stun and disable a target individual. The projectiles are adapted to be discharged from a different types of devices and powered by explosive, pneumatic, or manual means. At least one mode includes the ability to deliver a stunning physical blow in addition to the electric shock. The device is sub-lethal, but totally disabling in effects on a target individual.
Owner:CSA ENERGY
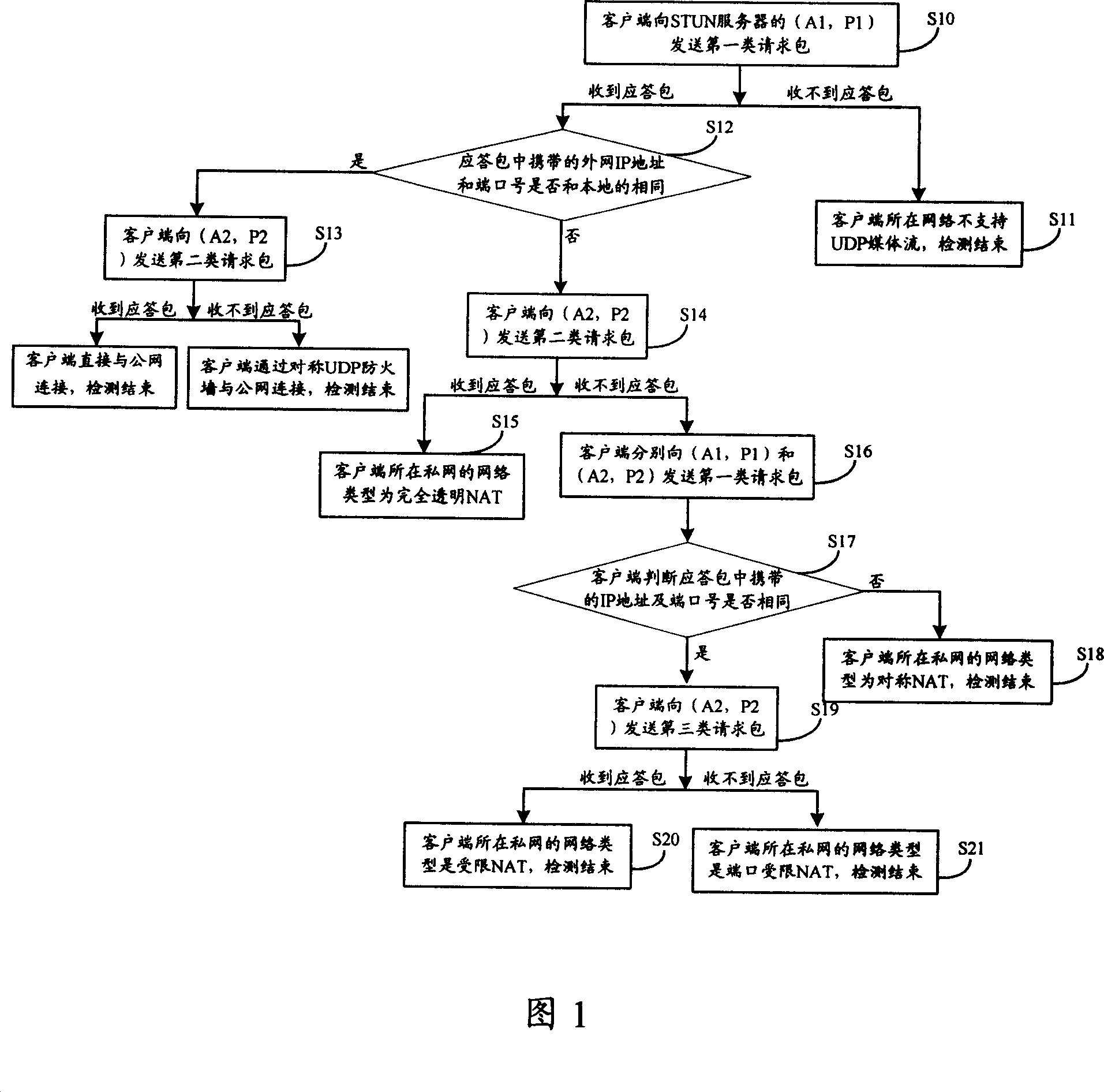
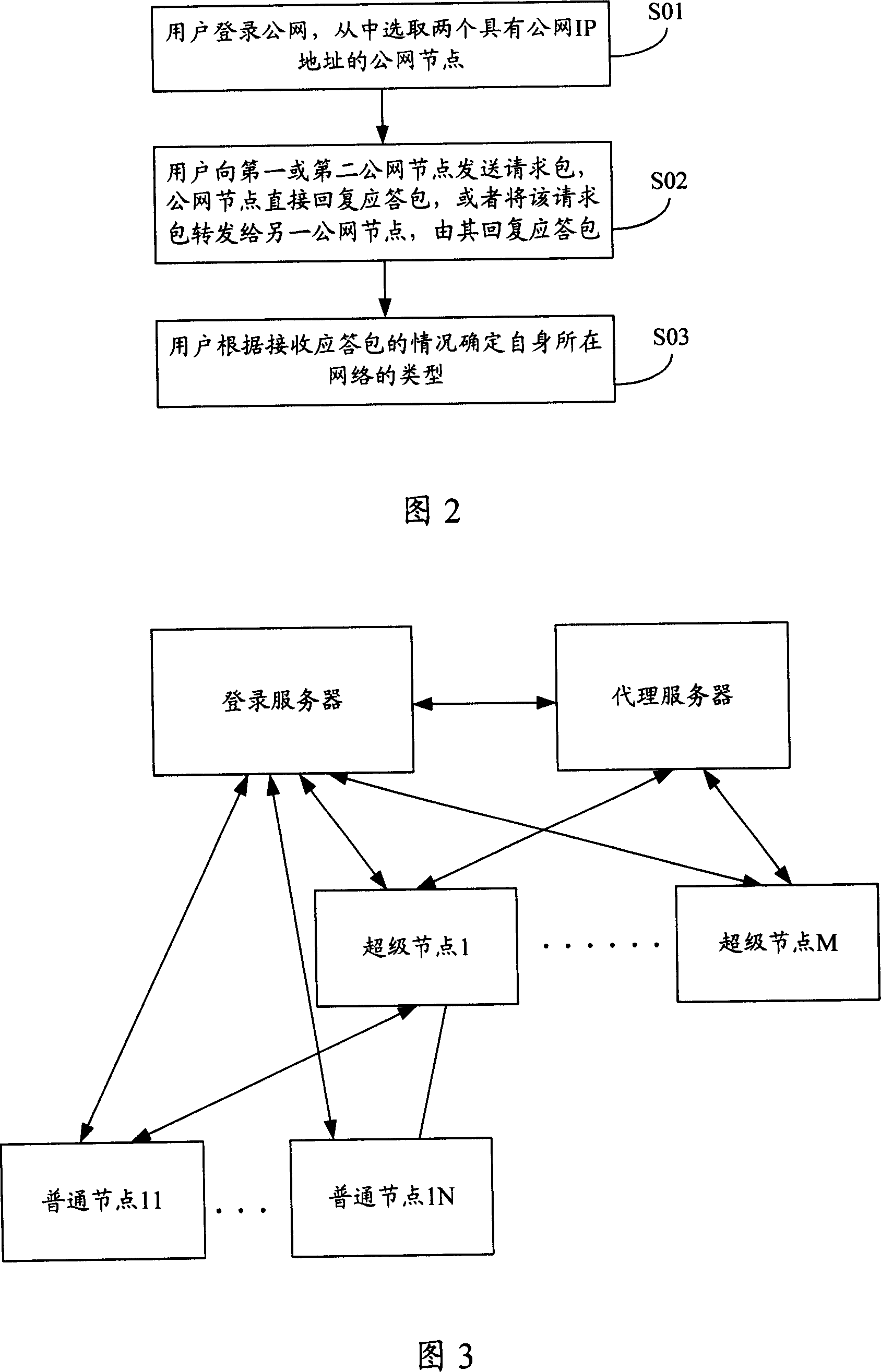
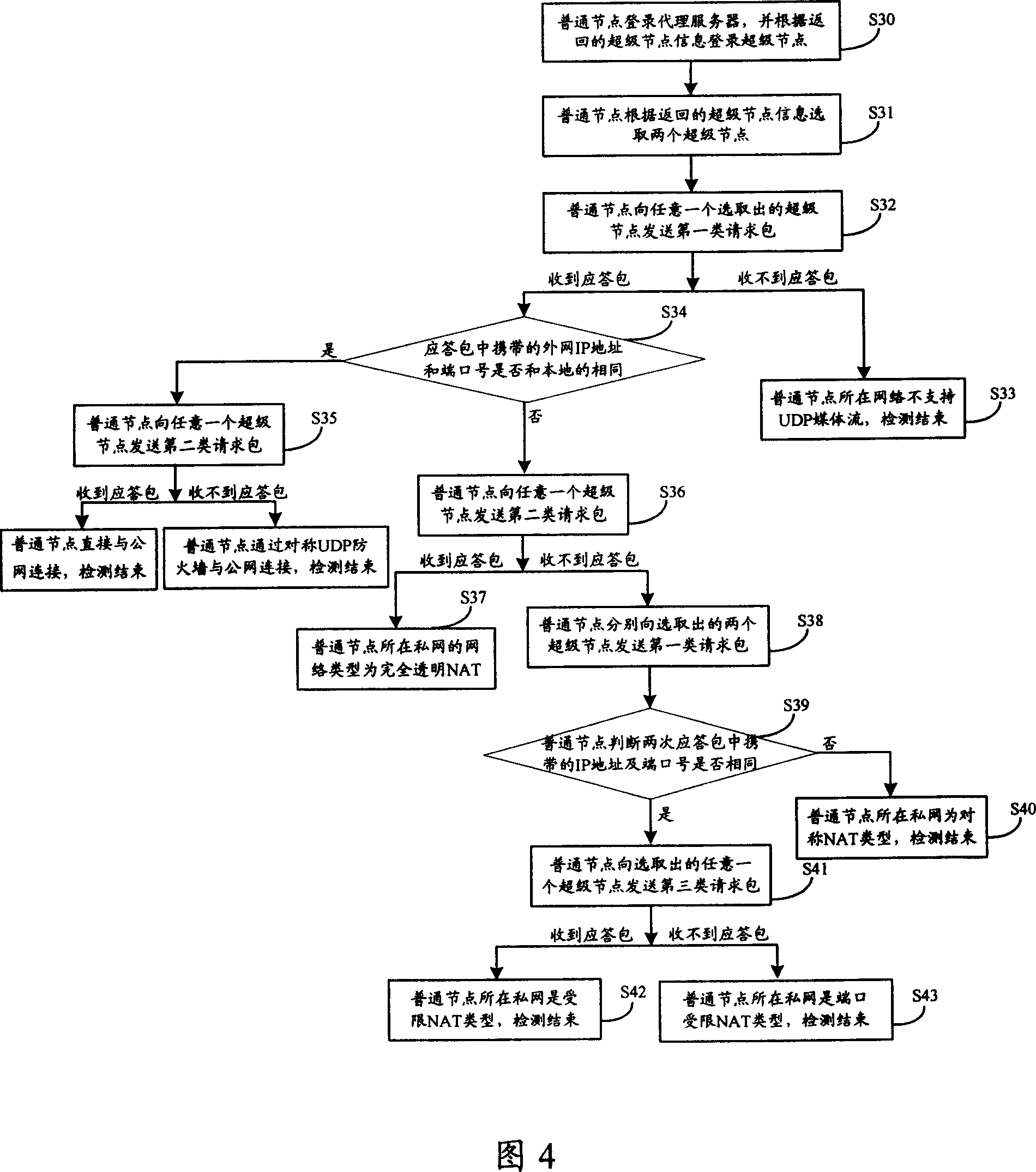
Method and system for detecting network types
ActiveCN101083565AReduce hardware costsAvoid single point of failureData switching networksSTUNIp address
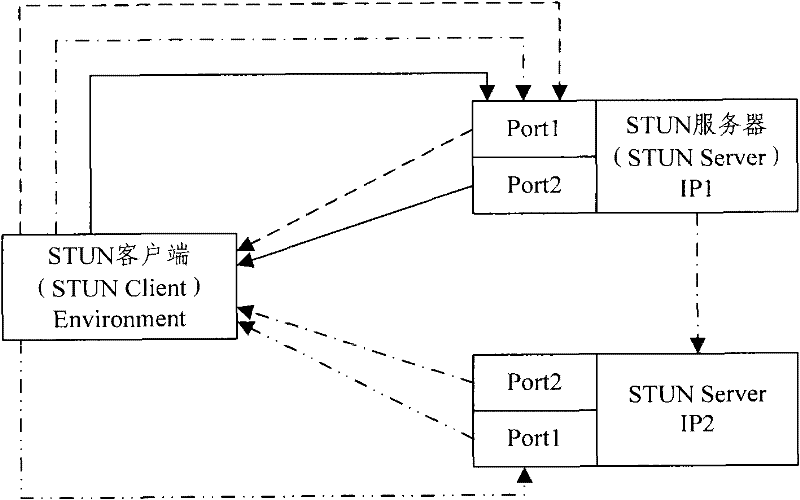
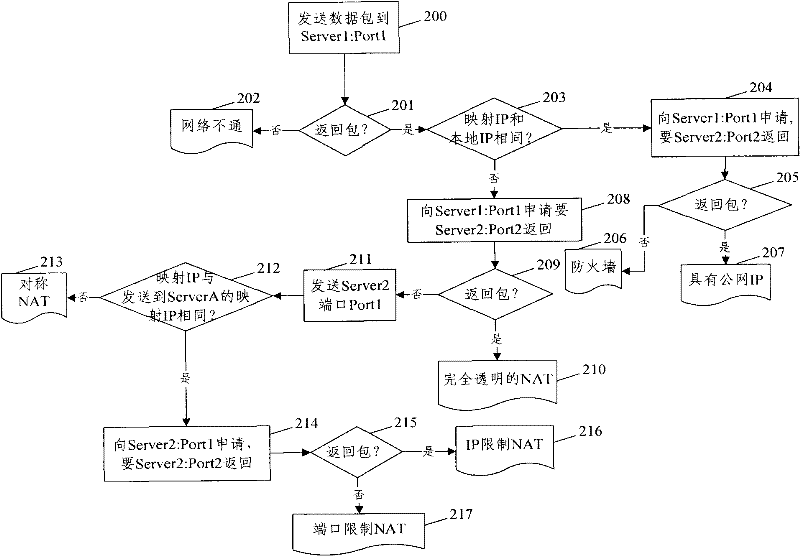
The invention discloses network type detecting method and system. It includes the following steps: loading public network; selecting public network nodes which has two IP addresses; sending request packet to the first or second nodes by STUN protocol; replying the response packet; confirming the network type. The invention can make the user detect the network type without STUN server which can greatly reduce hardware cost, avoid single point of failure.
Owner:TENCENT TECH (SHENZHEN) CO LTD
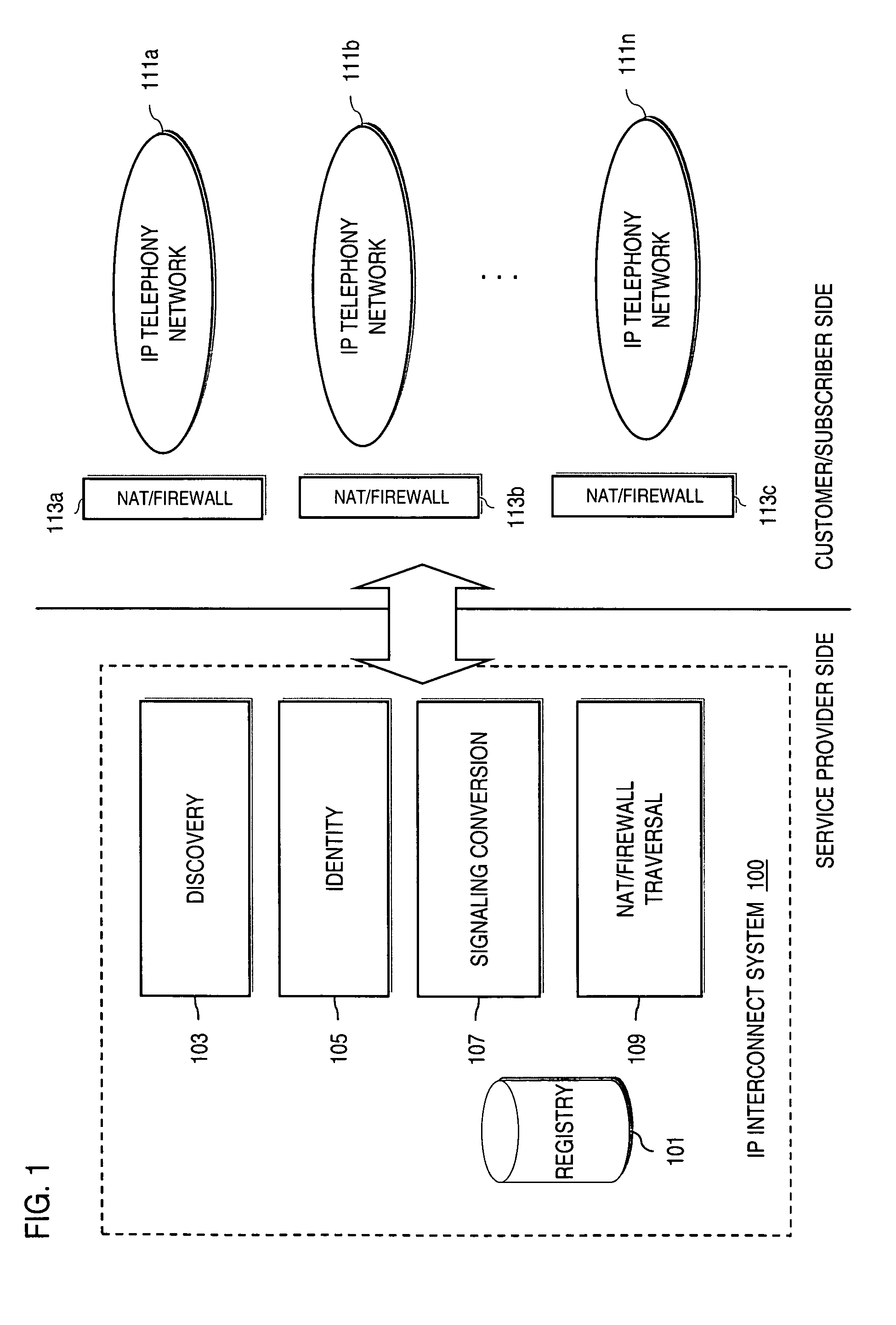
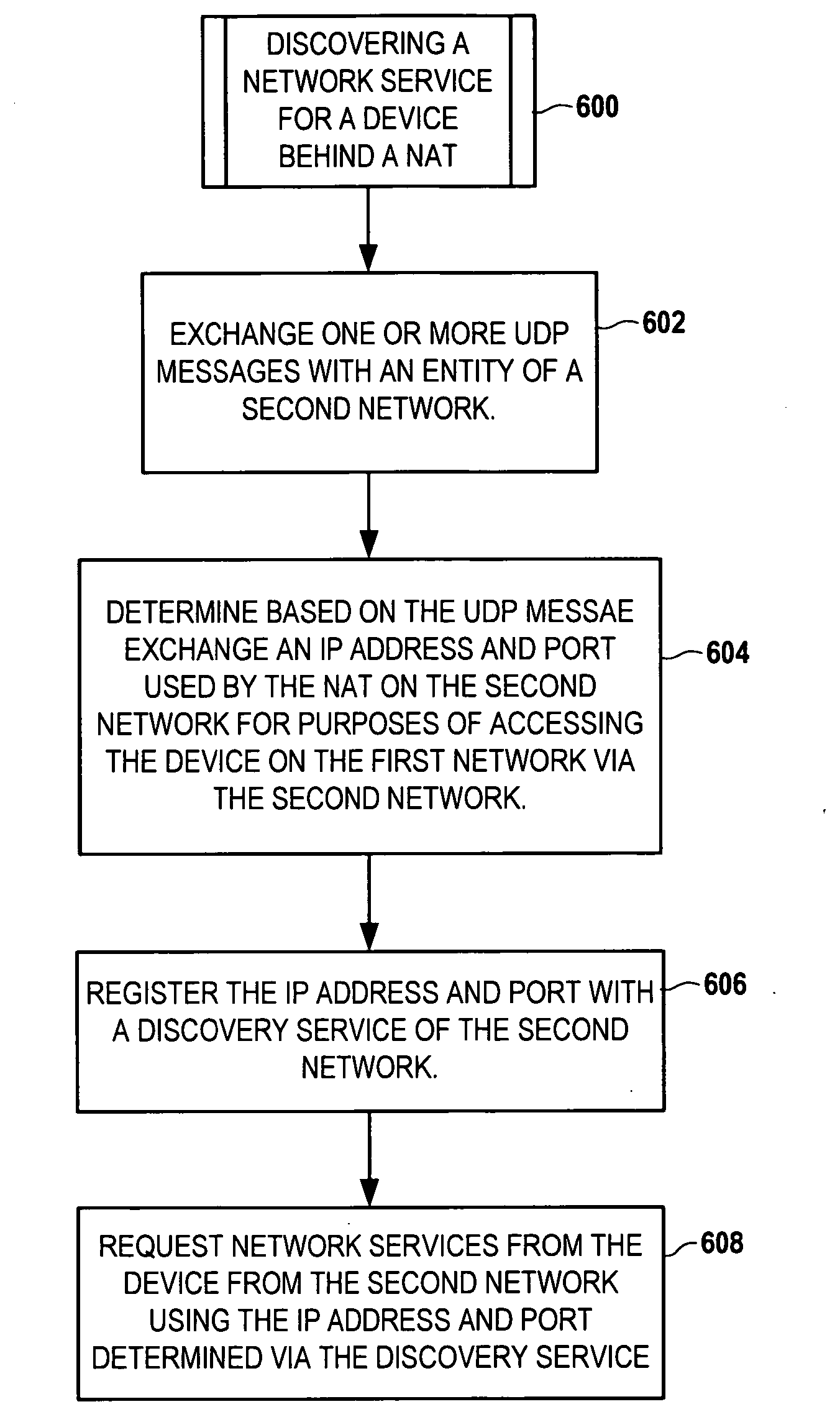
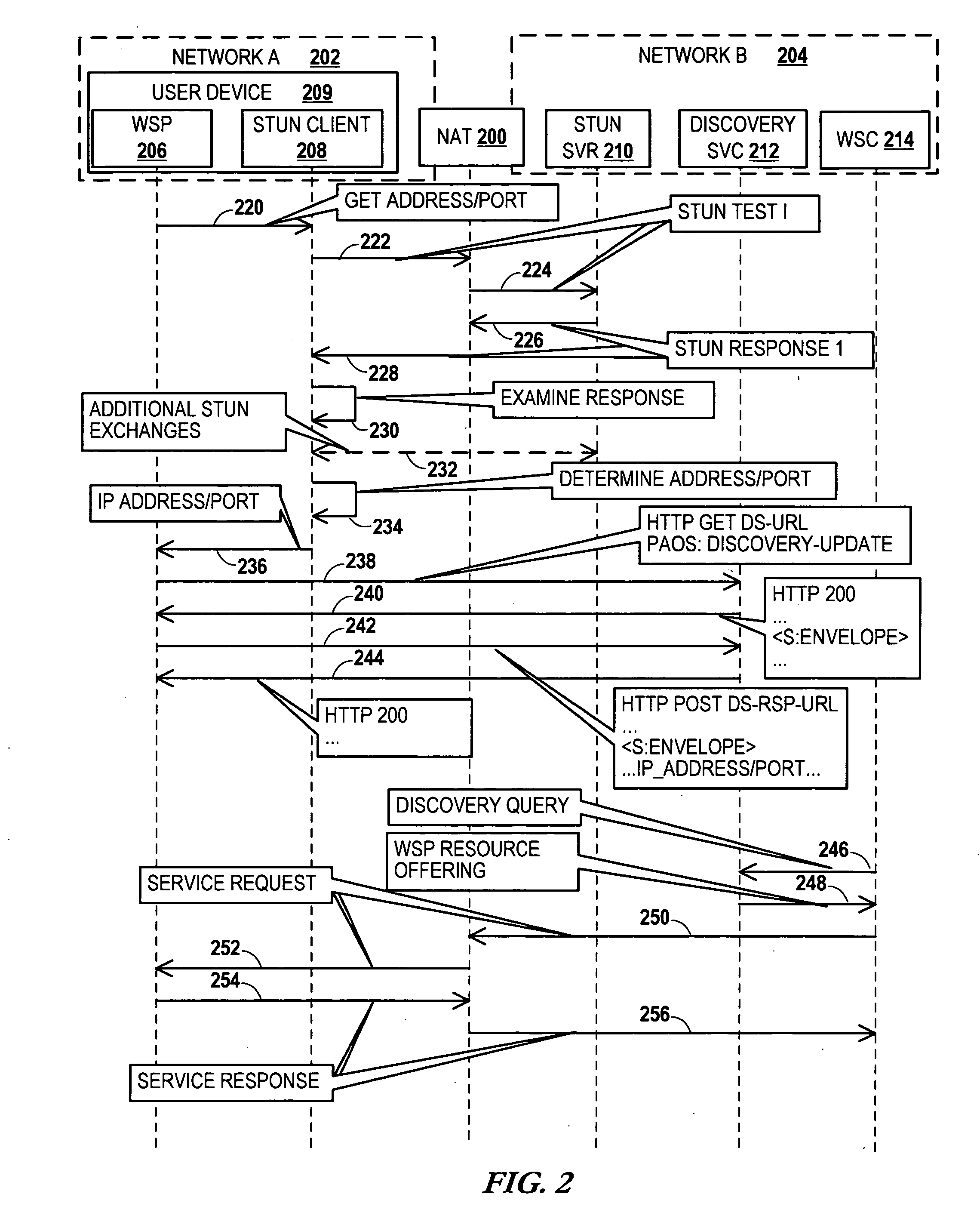
Dynamic discovery of a network service on a mobile device
InactiveUS20070153812A1Data switching by path configurationRadio/inductive link selection arrangementsSTUNIp address
A network service is made available on a device capable of operating on a first network that is coupled to a second network via a Network Address Translator (NAT). One or more User Datagram Protocol (UDP) messages with an entity of the second network. Based on the exchange of UDP messages, an IP address and port used by the NAT on the second network is determined for purposes of accessing the device on the first network via the second network. The IP address and port are registered with a discovery service of the second network. Network services are requested from the device via the second network using the IP address and port obtained via the discovery service. In one arrangement, the exchange of UDP messages involves the use of Simple Traversal of UDP Through NATs (STUN) messages.
Owner:NOKIA CORP
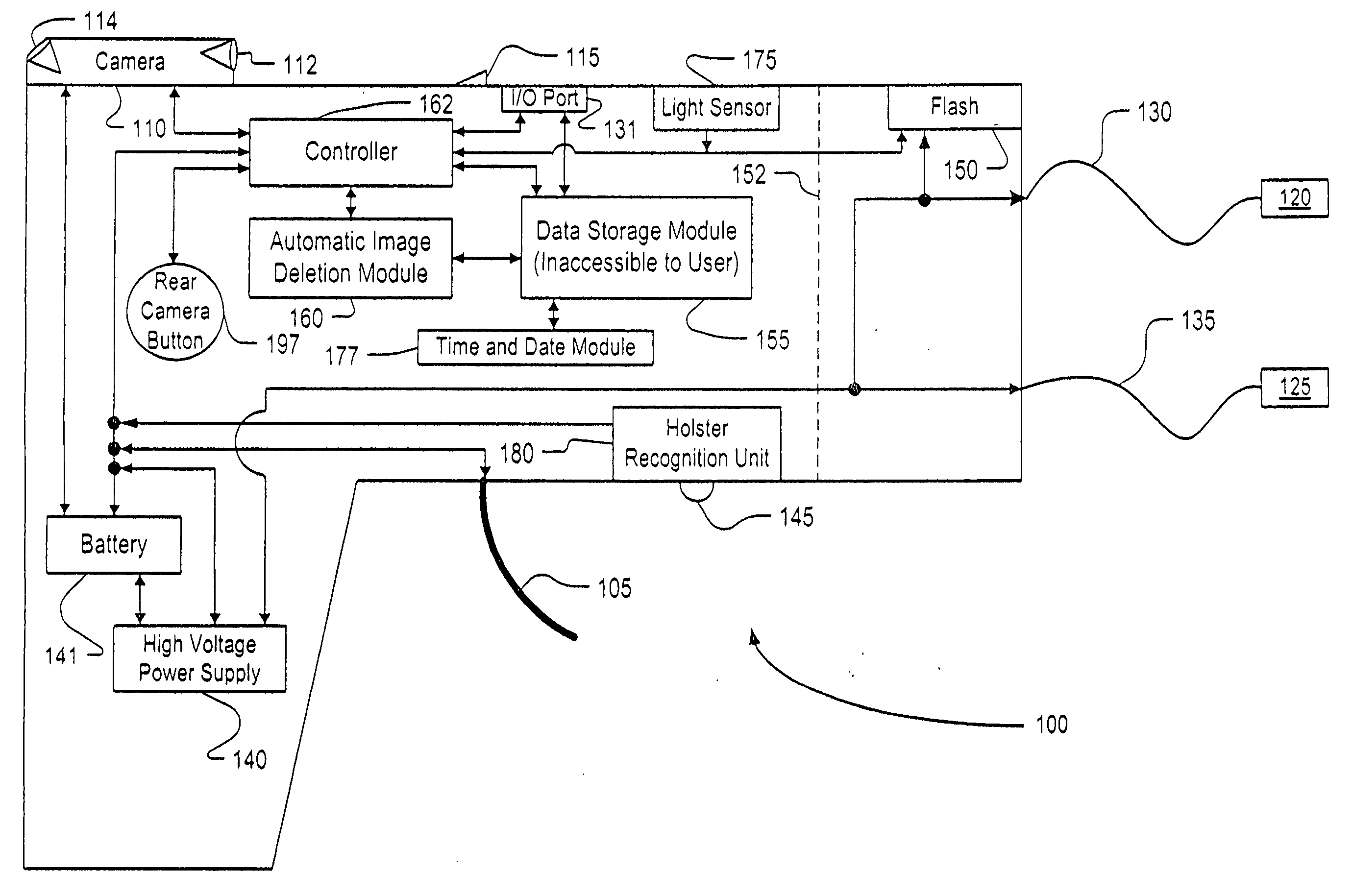
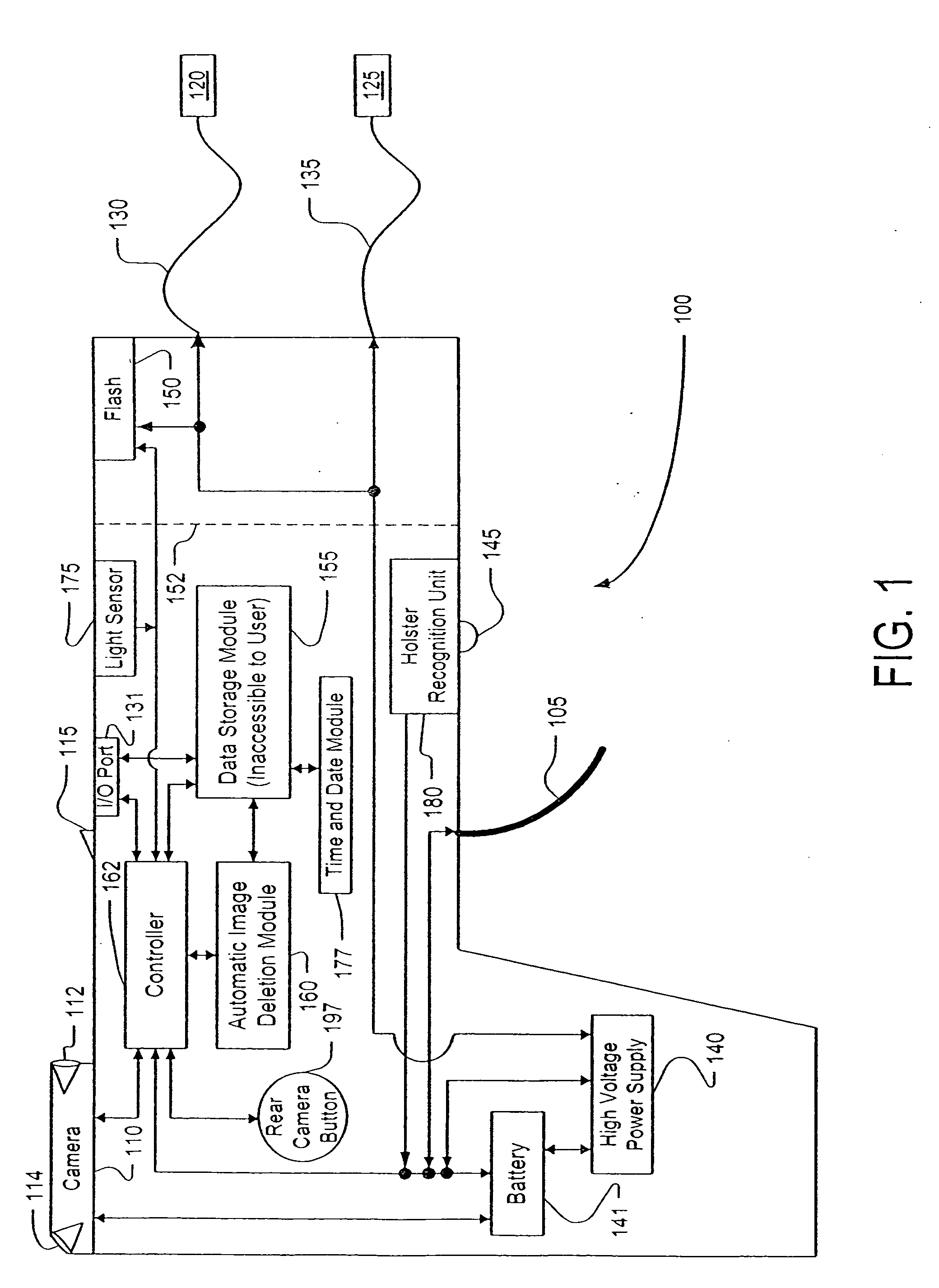
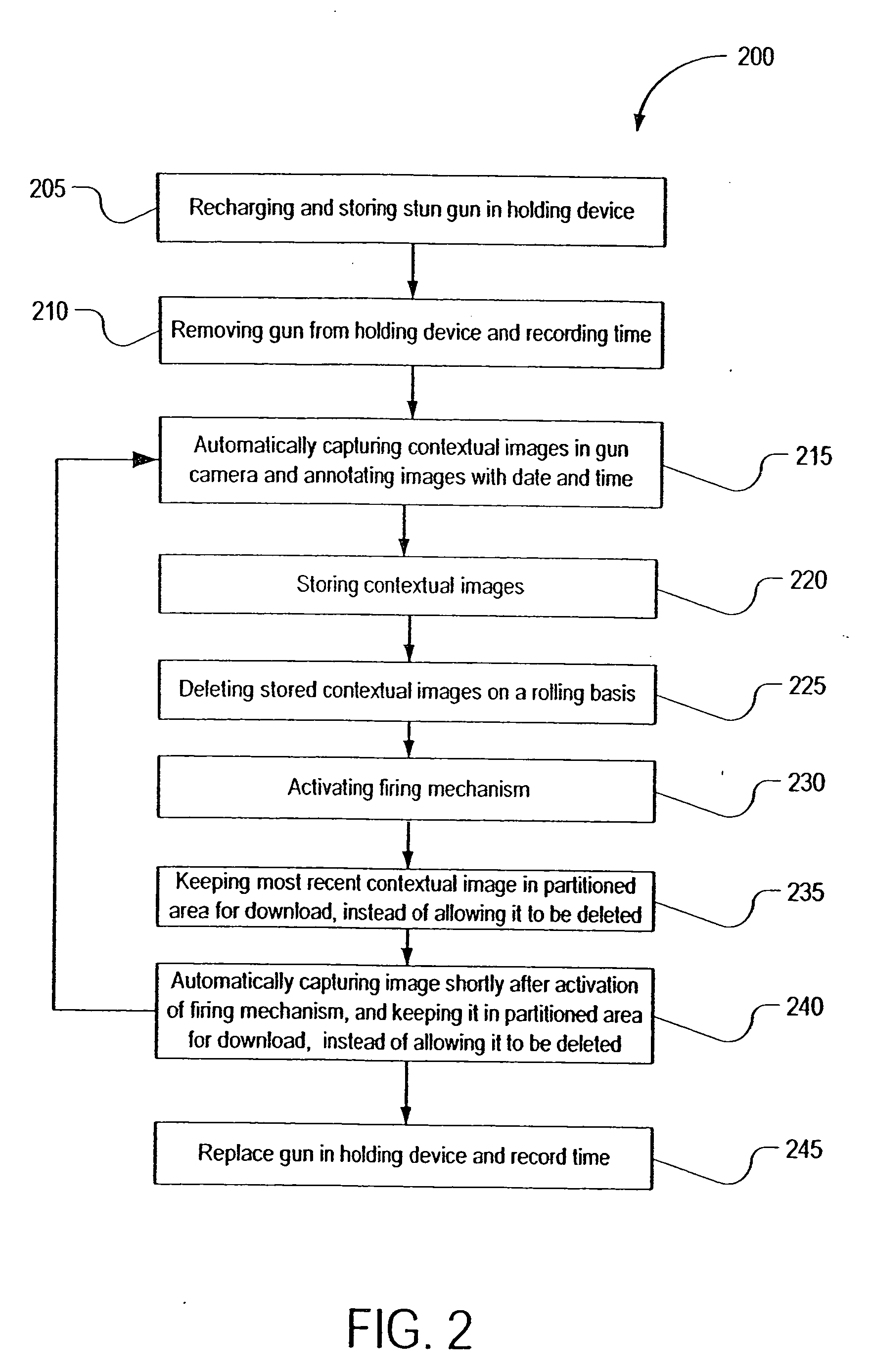
Gun equipped with camera
A stun gun is disclosed having a firing mechanism, and also having a camera for automatically capturing post-firing images after the firing mechanism is activated. The post-firing image is automatically and digitally marked, or partly marked, to indicate when the camera was used. A method of gun operation is also presented, along with a system that includes both the gun and a gun holder. Removal of the gun from the gun holder may activate the camera's visual or audio collection capabilities, and further actions such as removal of a gun safety may heighten activation of the camera. The camera's visual collection capabilities include viewing both the target and also the user of the gun.
Owner:FRESSOLA ALFRED A +2
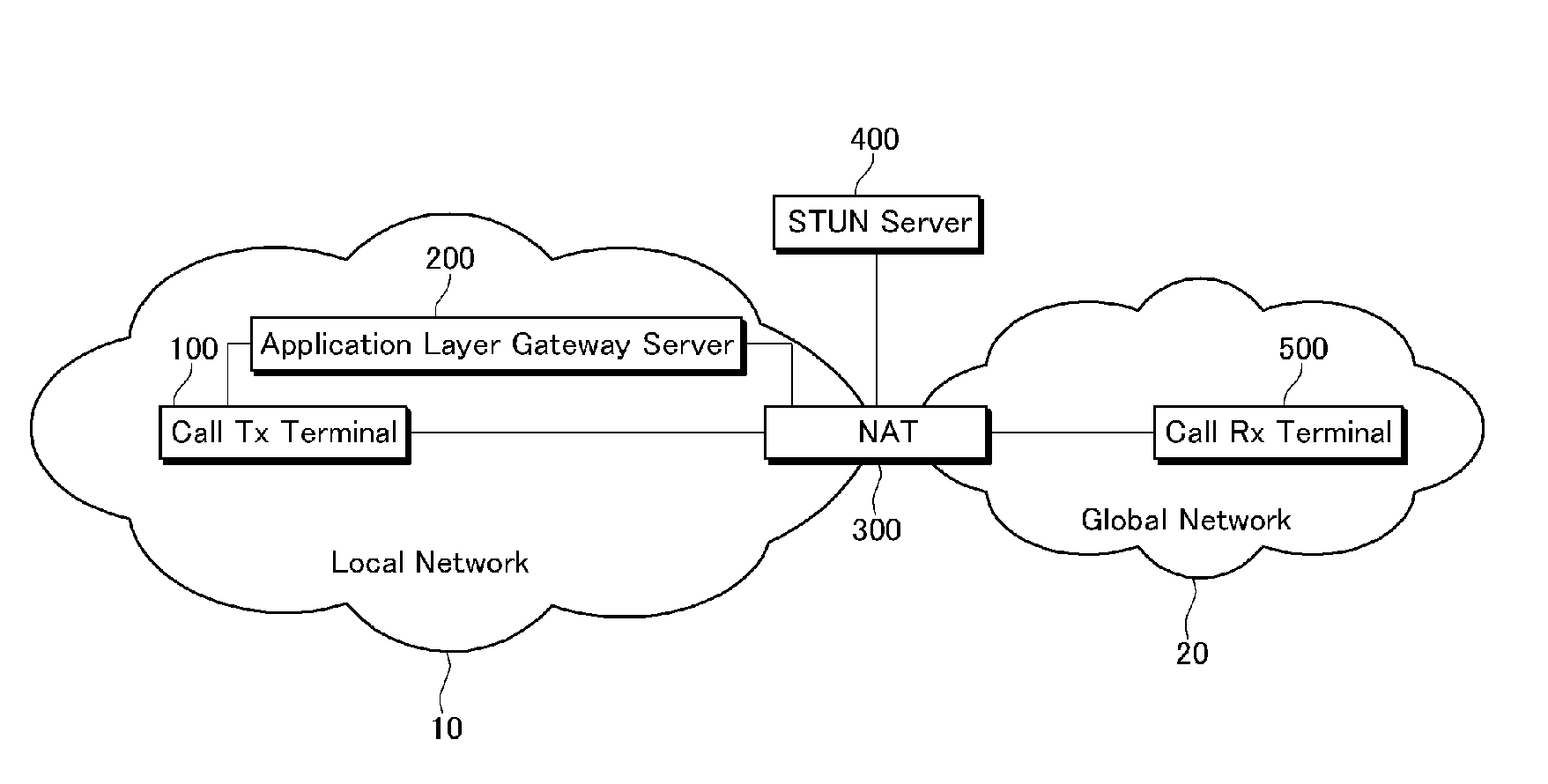
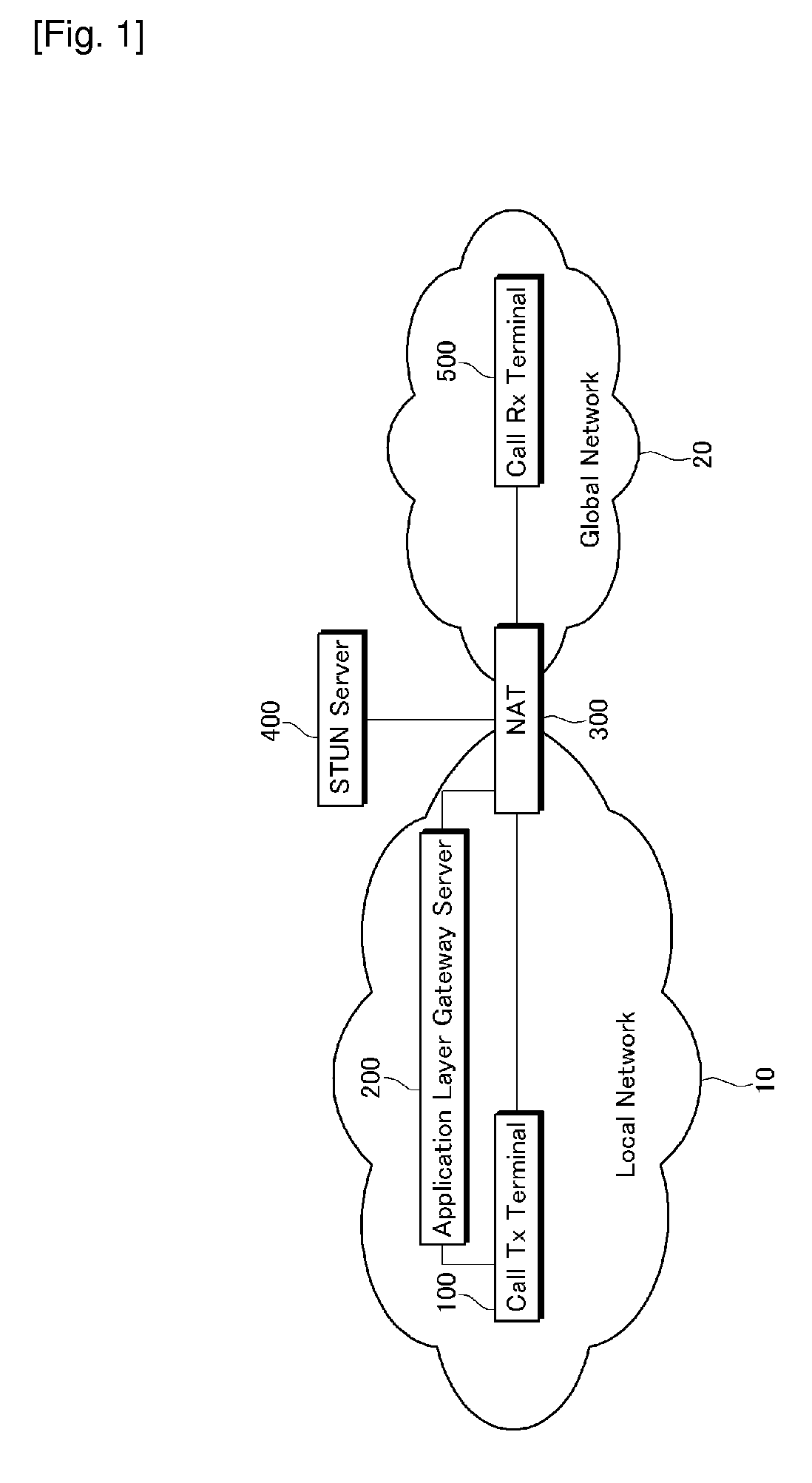
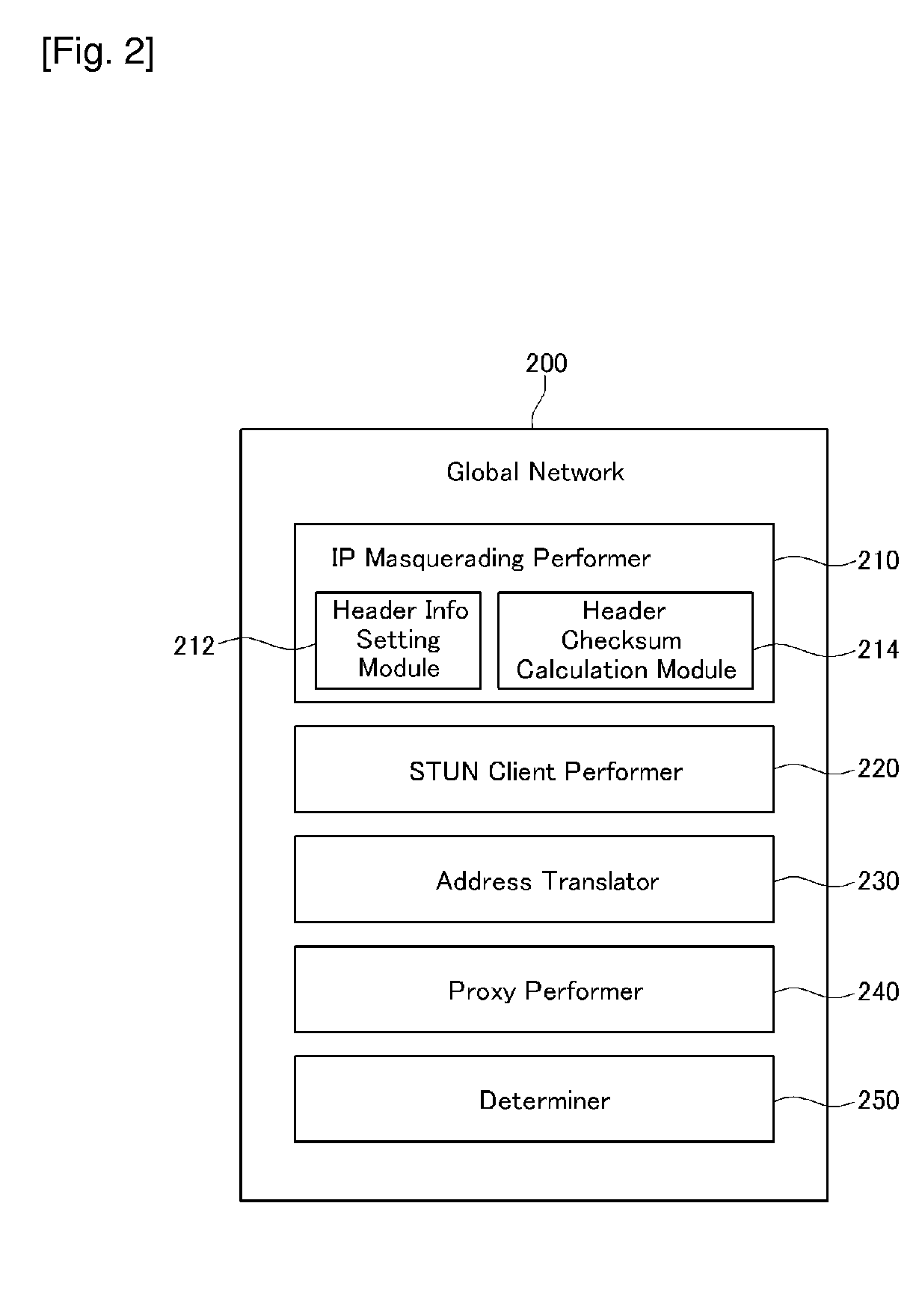
Inter working system between IP networks using different IP address format, application layer gateway (ALG) server, stun server, network address translator, interworking method thereof, and sIP message routing method thereof
ActiveUS20090180476A1Load minimizationMultiple digital computer combinationsNetworks interconnectionPrivate IPSTUN
Disclosed are an interworking system between IP networks using different IP address format, an application layer gateway (ALG) server, a network address translator, an interworking method, and a SIP message routing method. The interworking system between a local network using a private IP and a public network using a public IP includes a STUN server and an application layer gateway (ALG) server. The STUN server provides binding information of header information of a public IP binding request. The application layer gateway (ALG) server performs a public IP binding request with header information changed by IP masquerading, and performs routing by applying the received binding information to media receiving address information of a SIP message.
Owner:KT CORP
IP communication apparatus and NAT type determination method by the same
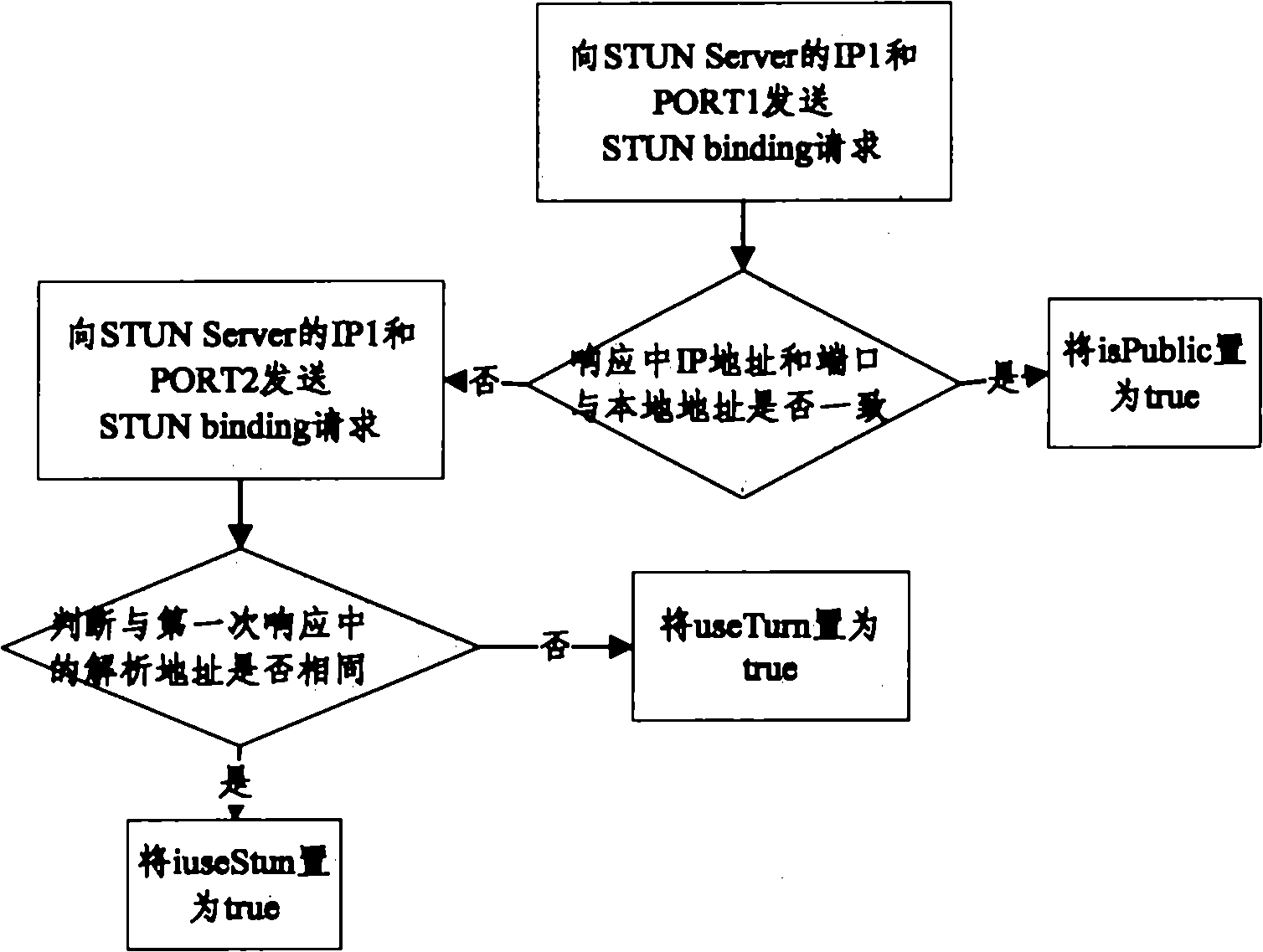
In a NAT type determination method pursuant to RFC 3489, address information added in a binding response from a STUN server in response to a binding request issued in a latest transmission test is compared with address information added in a binding response in response to any transmission test executed therebefore. When the address information are not identical, a NAT type is determined symmetric. Even when a router whose NAT type changes frequently according to a use status is connected, communication is capable without manual setting change by a user.
Owner:PANASONIC CORP
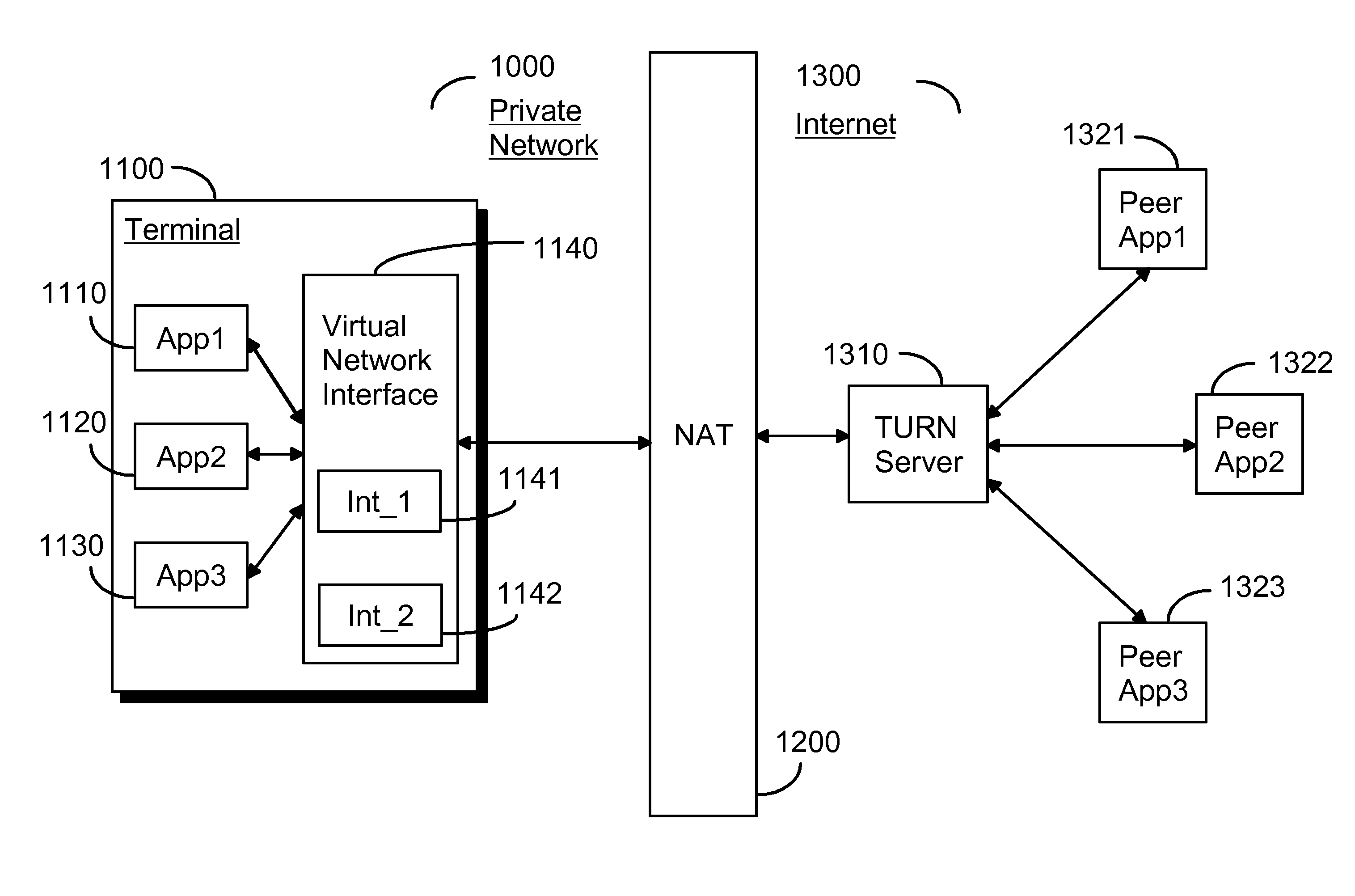
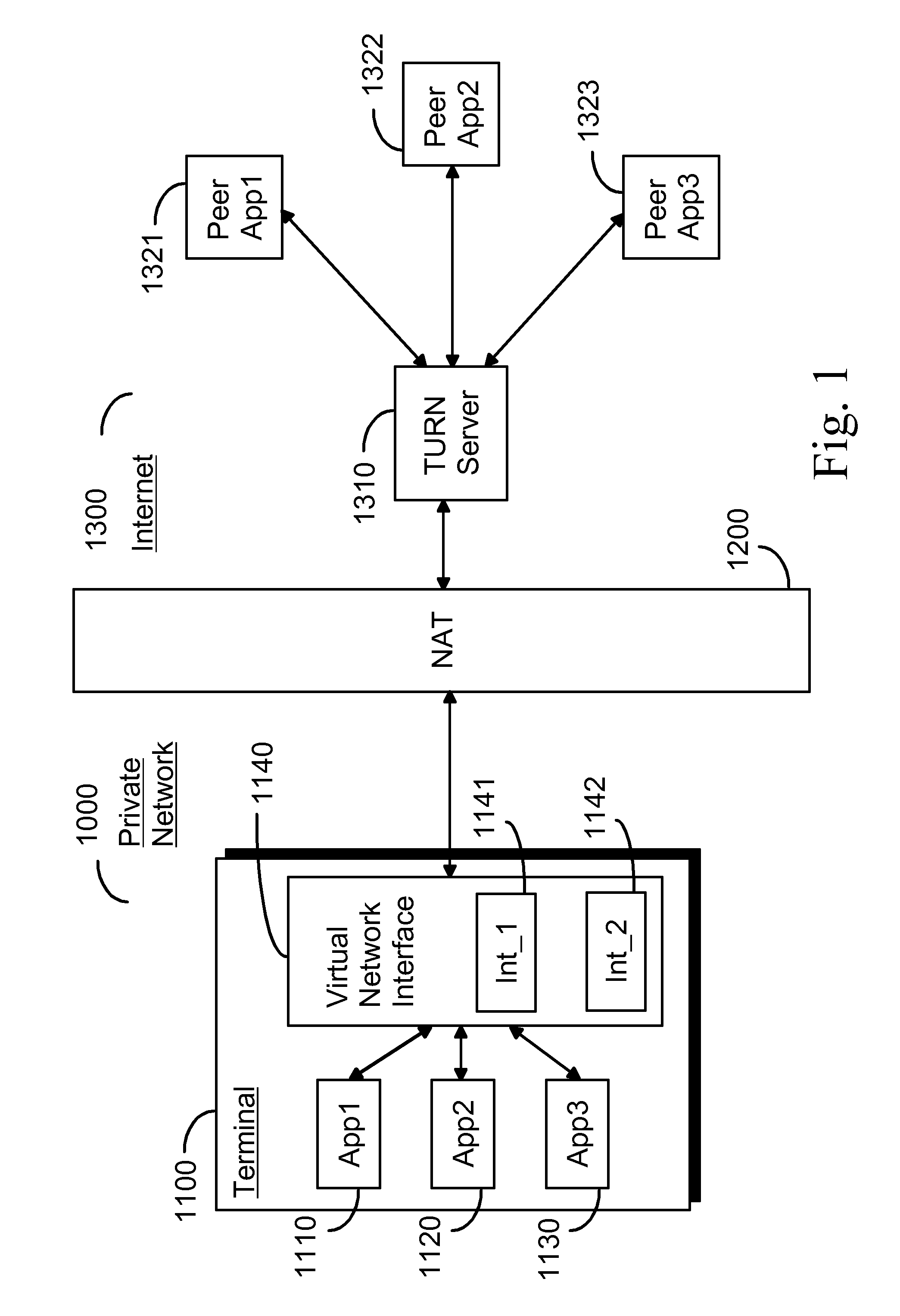
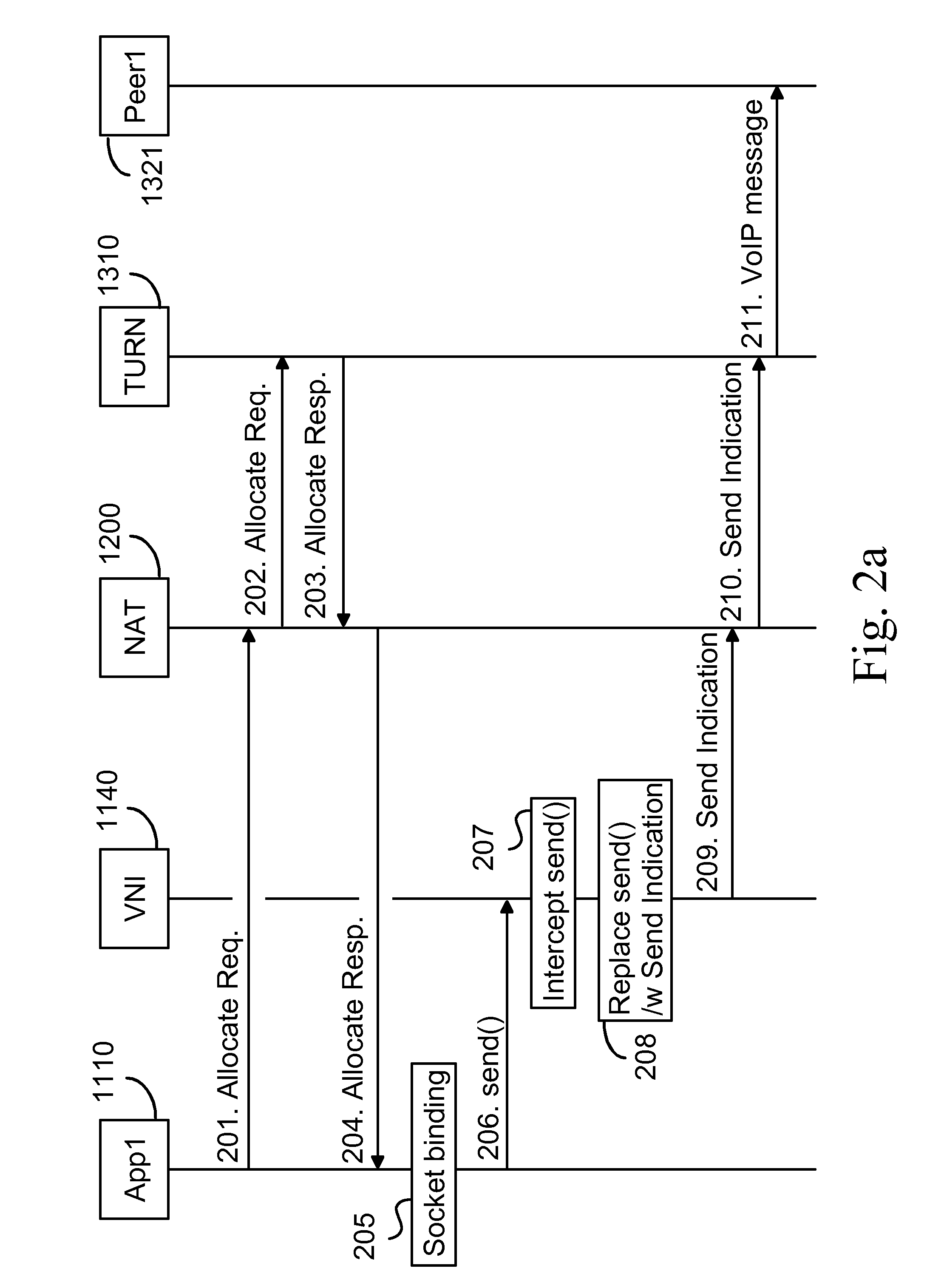
Virtual network interface for relayed NAT traversal
By providing a virtual network interface (1140) to a platform or an operating system wide implementation of the STUN protocol and its TURN extension, the invention allows applications (1110, 1120, 1130) located in a private network behind a NAT to communicate with their respective peers (1321, 1322, 1323) using sockets as usual while still getting the full benefit of the STUN protocol and its TURN extension for NAT traversal purposes.
Owner:NOKIA CORP
Network address translation (NAT) type determination method and device
The invention provides a network address translation (NAT) type determination method and an NAT type determination device. The method comprises that: a simple traversal of user datagram protocol through network address translators (STUN) client simultaneously transmits a request packet of a first test item and the request packet of a second test item to a first port and a second port of a first STUN server respectively; the first STUN server and a second STUN server return corresponding response packets; and the STUN client judges the NAT type of a client according to the received response packets. By the NAT type determination method provided by the invention, dependence on the sequence of test packets is avoided, and NAT type detection time is shortened by parallel testing. Moreover, the NAT type determination method provided by the invention is simpler and more highly efficient.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
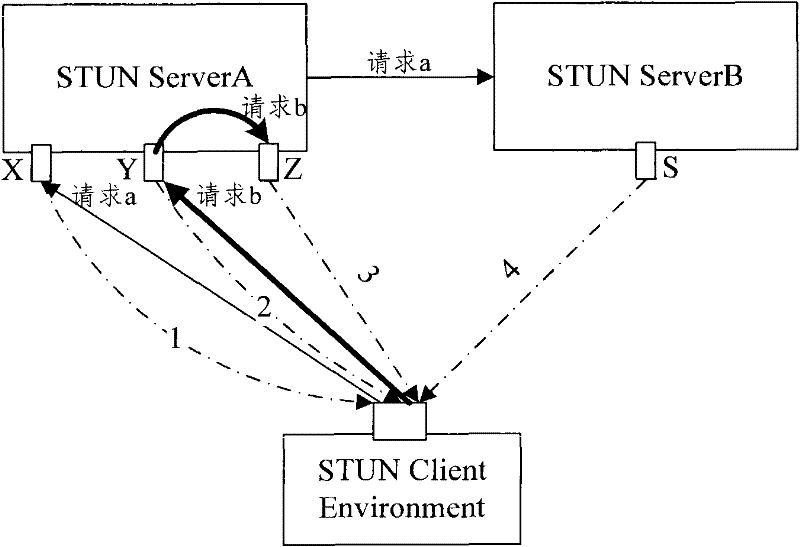
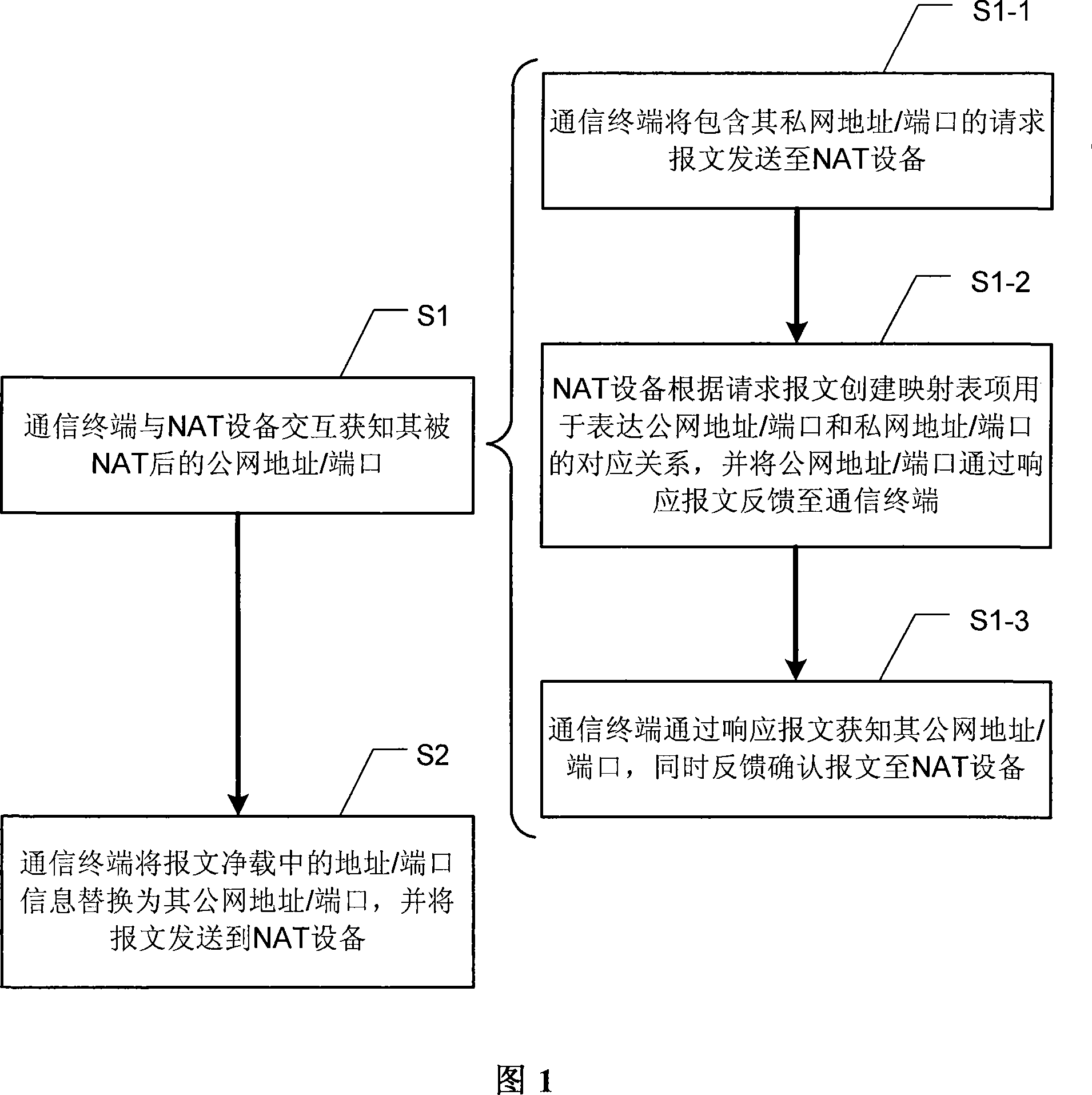
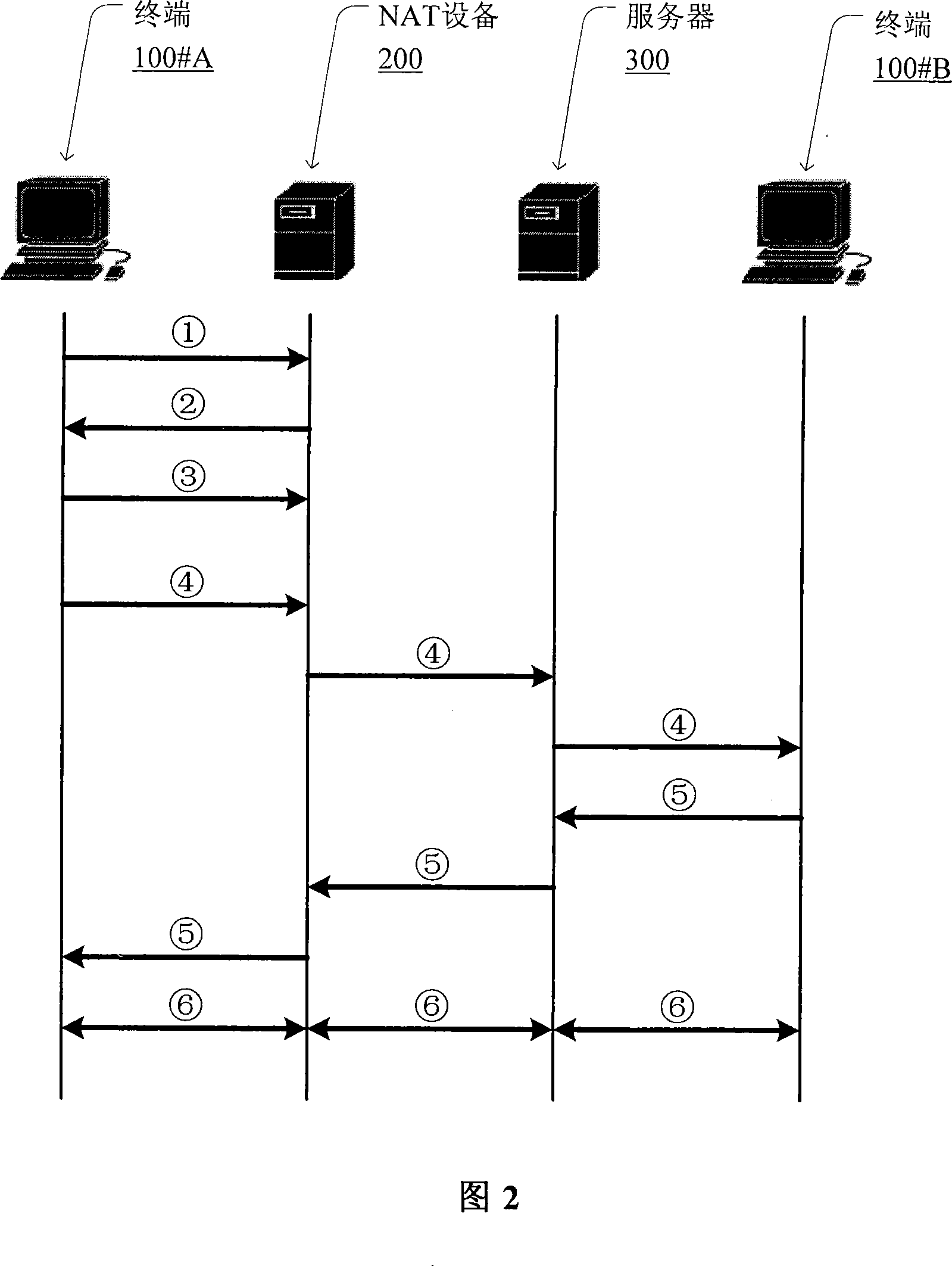
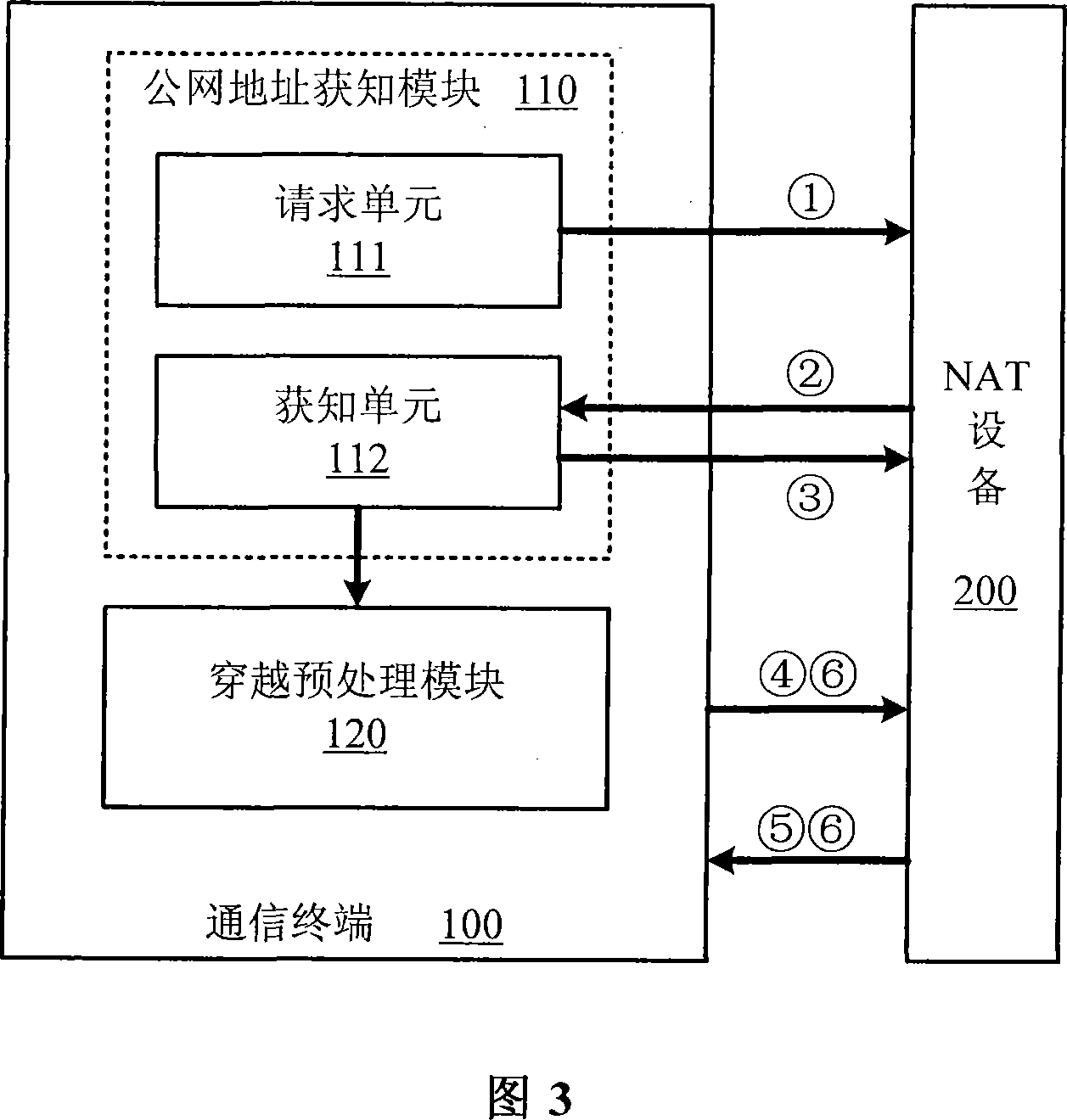
Method for penetrating the NAT and corresponding communication terminal and NAT device
The invention relates to a network communication area and discloses a method for penetrating the NAT. The method mainly includes: step S1: the communication terminal after the NAT device interacts with the NAT device to get the public network address and / or port behind the NAT from the NAT; step S2: the communication terminal fills the private network address and / or port information of the packet net payload as the public network address and / or port, and send the packets to the NAT device. The invention discloses the corresponding communication terminal and NAT device to support the implementation of the above method. Compared with the existing technology, the invention does not require NAT device to support the ALG (application layer gateway) and need not realize the STUN (UDP simple penetration mode of NAT) protocol, so it eliminates the limit of the static manual configuration.
Owner:NEW H3C TECH CO LTD
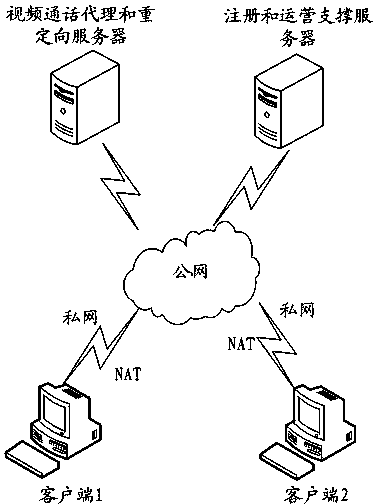
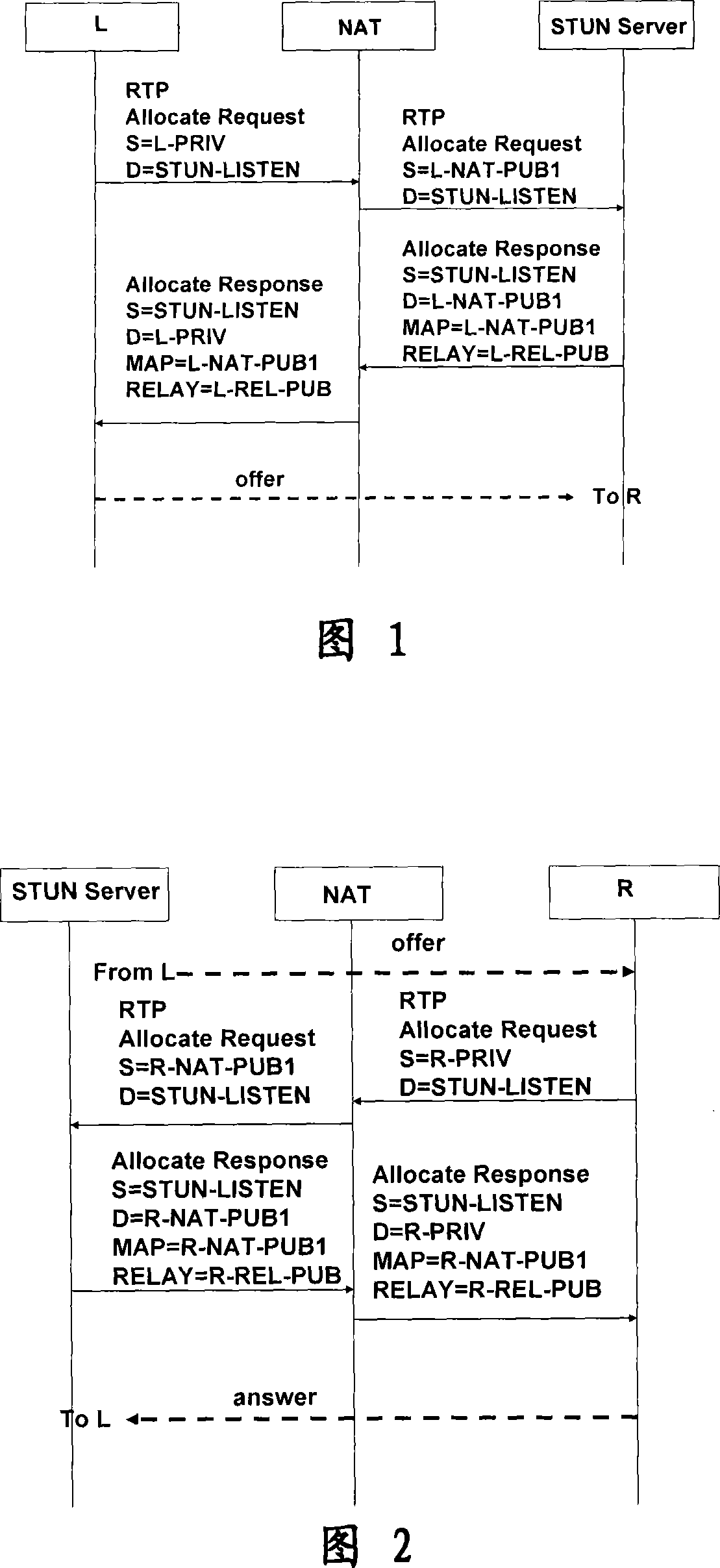
Audio and video communication method, device and system
InactiveCN103702062AHigh-quality communication effectTwo-way working systemsSelective content distributionSTUNInformation gain
The invention discloses an audio and video communication method, device and system. The method comprises the following steps that a first user registers via an XMPP (XML-based Messaging and Presence Protocol) server and acquires the identity information of a second user; the first user sends an audio and video communication request to the second user according to the identity information of the second user, receives the address information of the second user transmitted by an STUN (Simple Traversal of UDP over NATs) server and acquired according to the request information of the first user, and establishes a communication link with the second user according to the received address information of the second user; the first user processes extracted audio and video data via WEBRTC (Web Real-Time Communication), encapsulates in the form of an XMPP protocol to obtain audio and video data to be transmitted, and transmits the audio and video data to be transmitted on the communication link established between the first user and the second user to realize audio and video communication between two ends. By adopting the method, an end-to-end high quality communication effect can be realized among equipment without a server.
Owner:TCL CORPORATION
Method for performing media transmission using ICE relay candidate address
InactiveCN101179581ARelieve stressImprove forwarding real-time performanceData switching networksSTUNTransmission protocol
The invention relates to a method for performing media transmission by adopting an ICE relay candidate address. The method comprises the following steps: a user-end proxy sends the Allocate request to a STUN server and receives the Allocate response carrying the relay candidate address, and then sends a Binding request carrying the self-defined CHANGED-TUPLE attribute which meets the international communications standard to the relay candidate address that the server allocates so that the STUN server replaces the internal quintuple which is originally generated by the Allocate request and contains the monitoring address of the STUN server by using the new quintuple of the Binding request including the source address containing the IP address and the port number, the destination address containing the IP address and the port number (namely, the relay candidate address to which the STUN server containing the IP address and the port number allocate) and the transmission protocol after receiving the Binding request with the CHANGED-TUPLE attribute. The method forwards the media stream without occupying the monitoring address of the STUN server, thus greatly enhancing the transmitting efficiency of the STUN server, improving the transfer efficiency of the media stream and reducing the transmission delay of the media.
Owner:BEIJING UNIV OF POSTS & TELECOMM
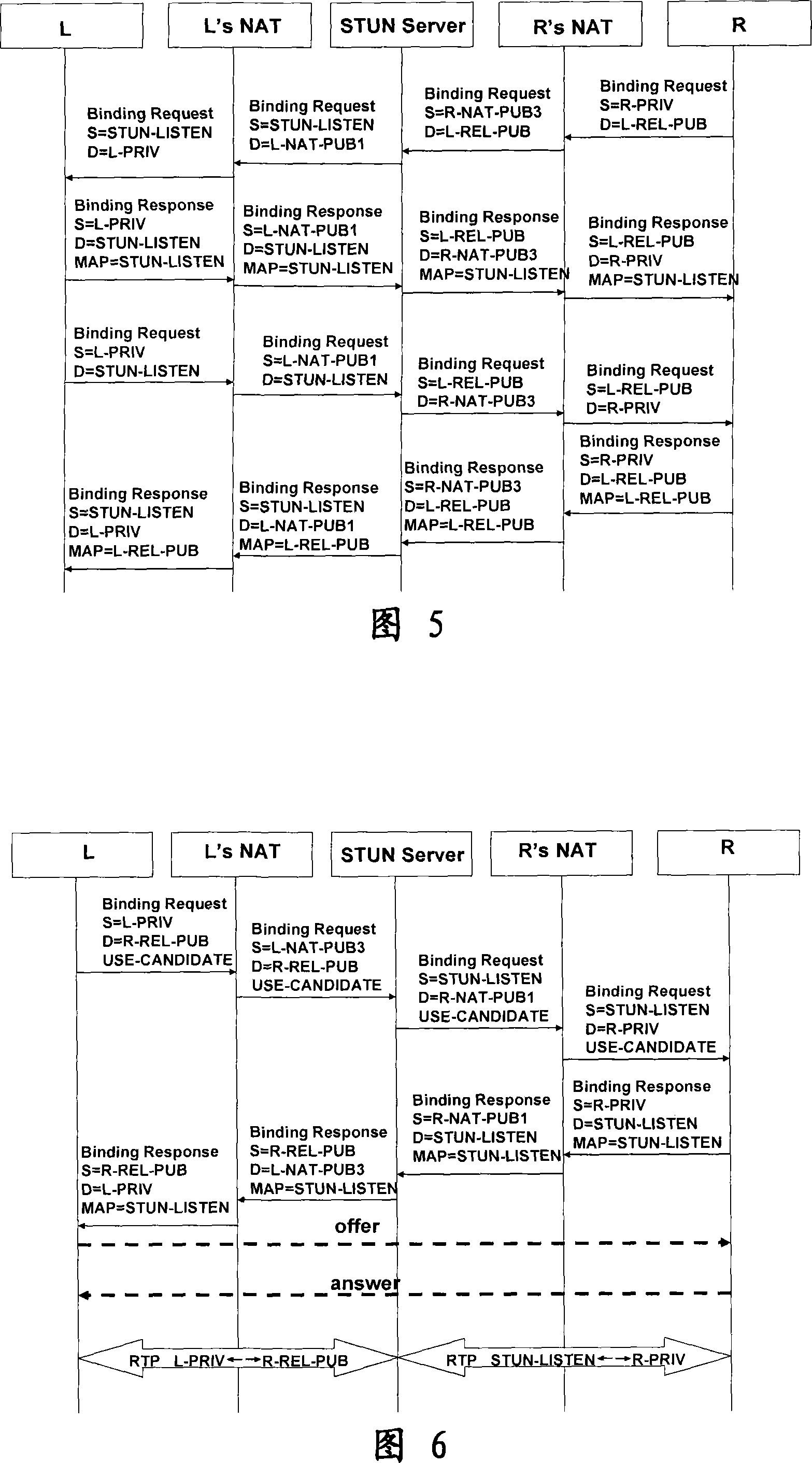
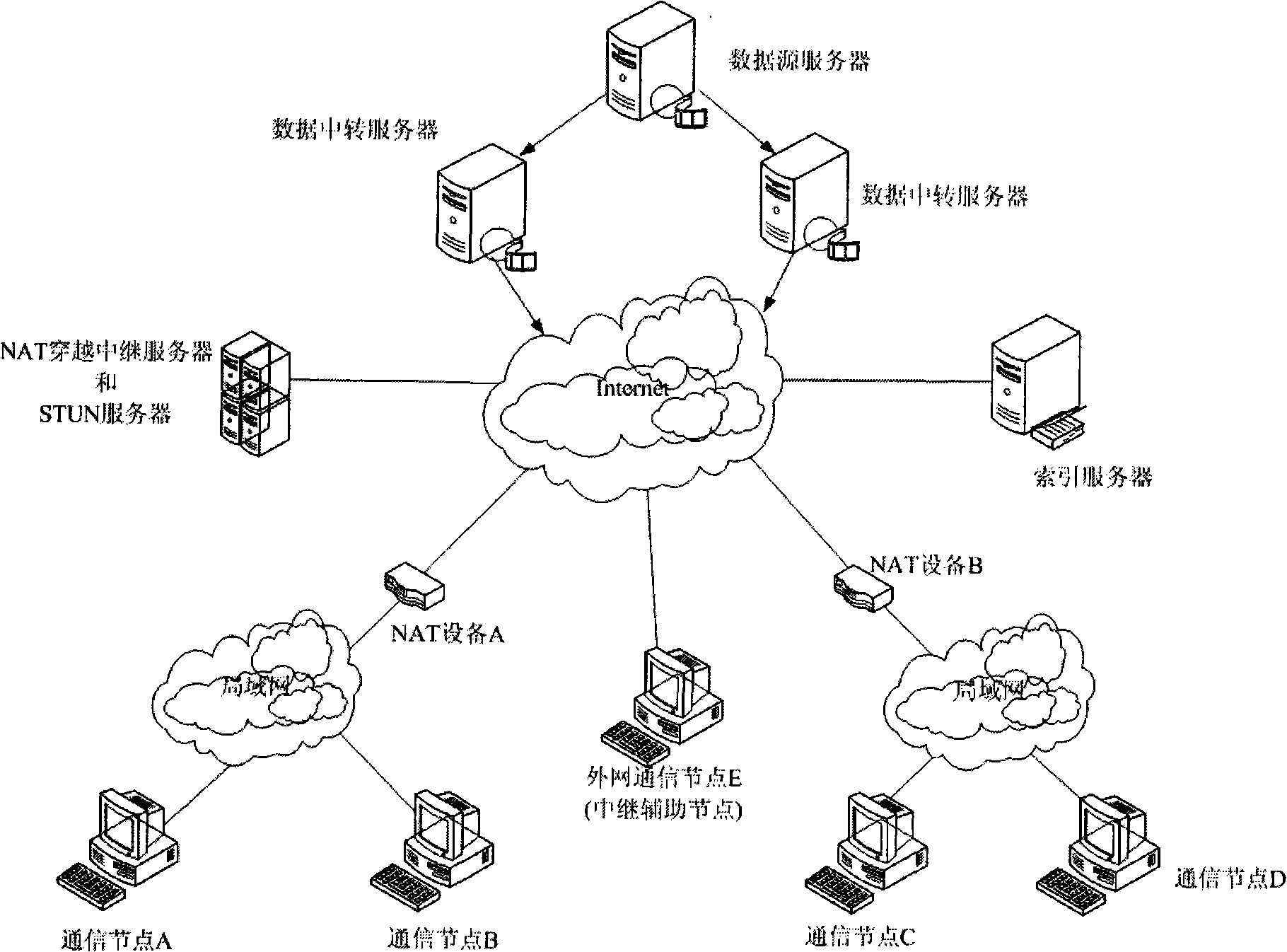
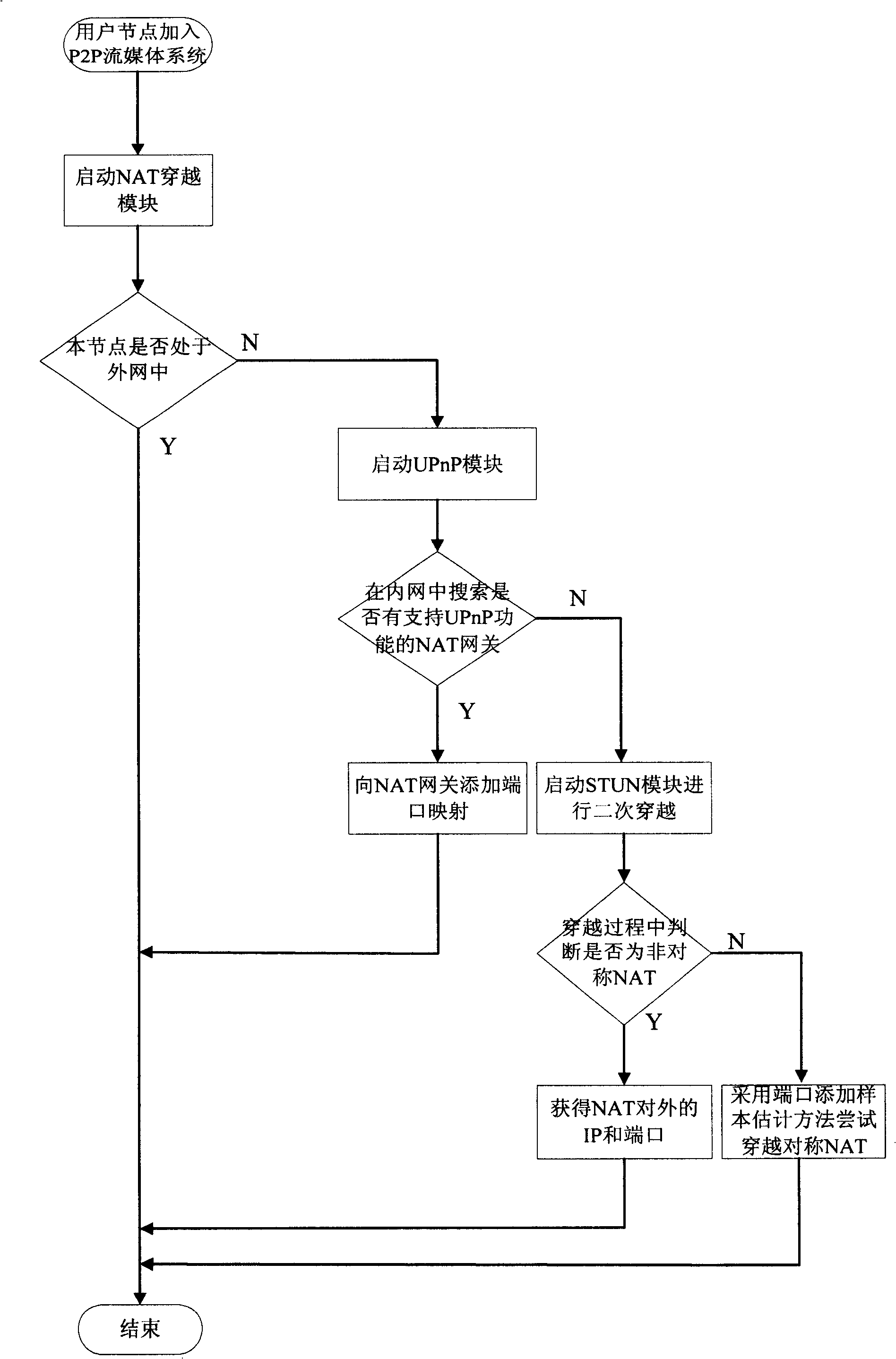
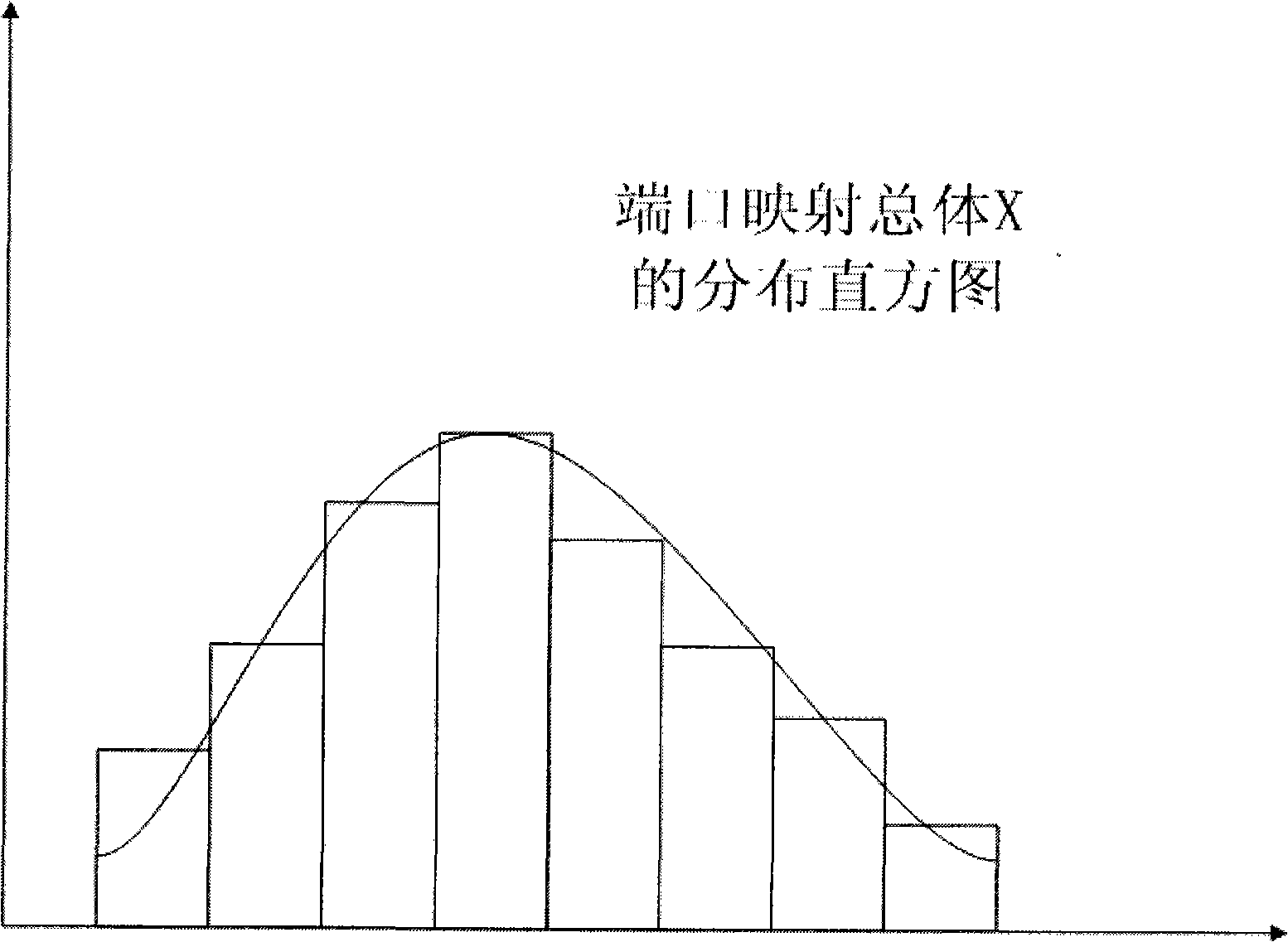
NAT traversing method based on combination of UPnP and STUN technologies
InactiveCN101557388AImprove the success rate of crossingAvoid blindnessData switching networksSTUNThe Internet
The invention relates to an NAT traversing method based on the combination of UPnP and STUN technologies, which effectively combines the UPnP and the STUN, adopts the STUN method to perform secondary transversal on the NAT after the UPnP fails to traverse the NAT and effectively enhances the success rate of the traversing by extracting respective advantages of the two traversing methods. As for traversing symmetrical NAT, the method carries out port guess in such a way that the port mapping distribution is estimated by adding port mapping sample value based on the NAT, thereby overcoming the deficiency caused by the transmitting carried out by sygate home networks and the blindness of increasing guess of simple ports; and as for the condition that both communicating sides in a P2P streamline media system are behind the NAT, the method relieves the pressure of a relay server by adopting part of common communication nodes which have abundant bandwidth and are at internet to serve as auxiliary relay nodes, thereby effectively eliminating the communication bottleneck of the system.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
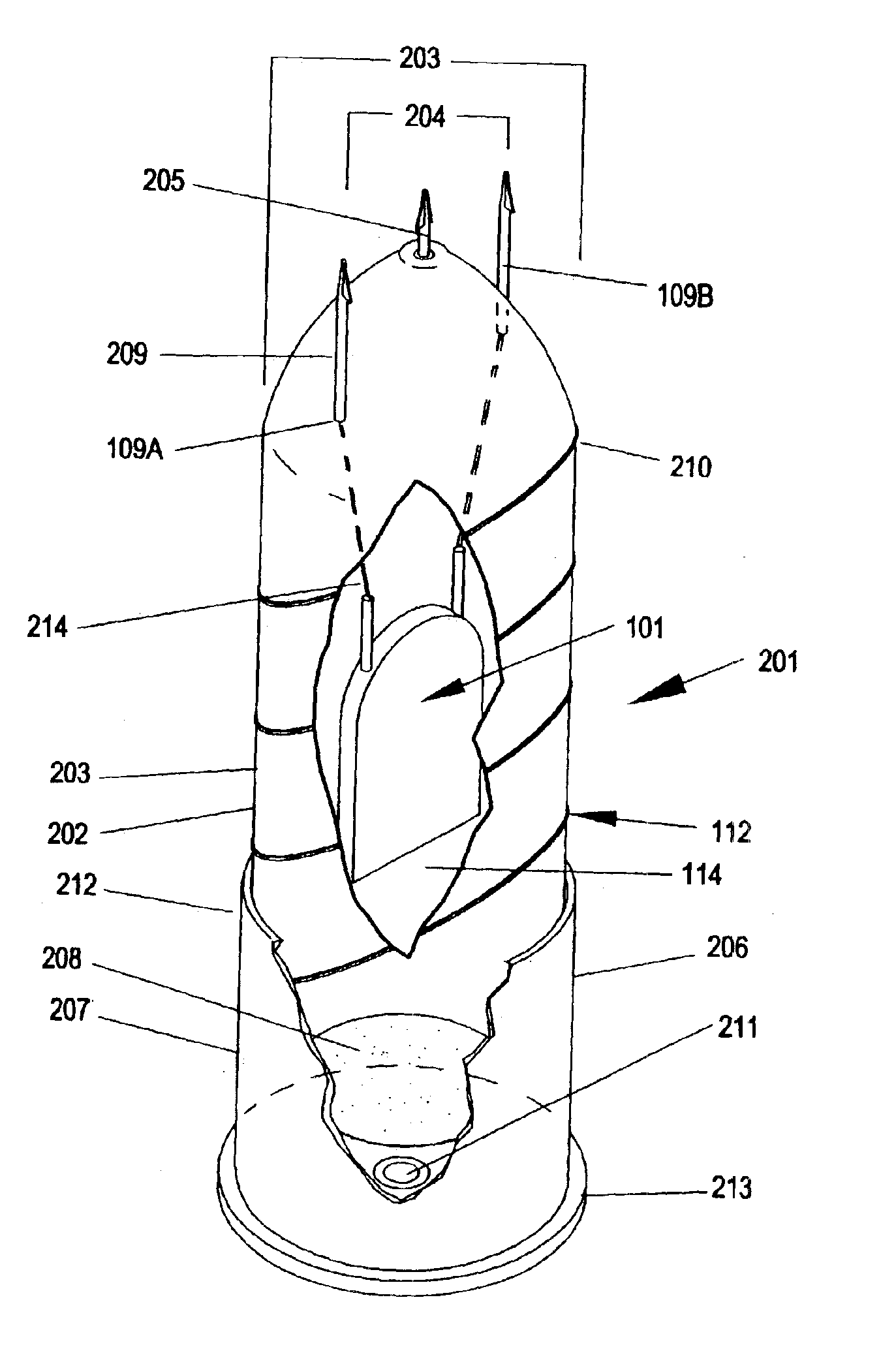
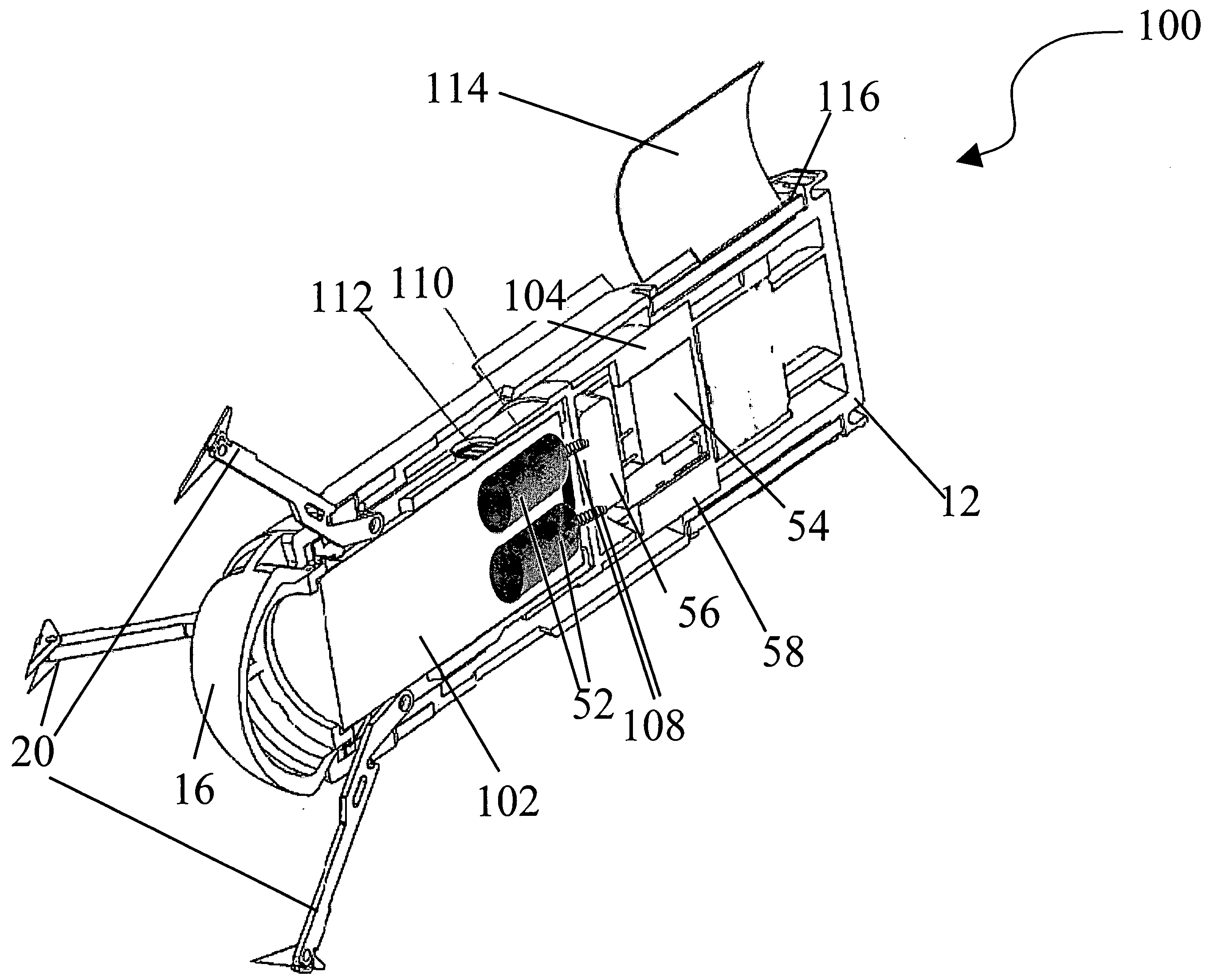
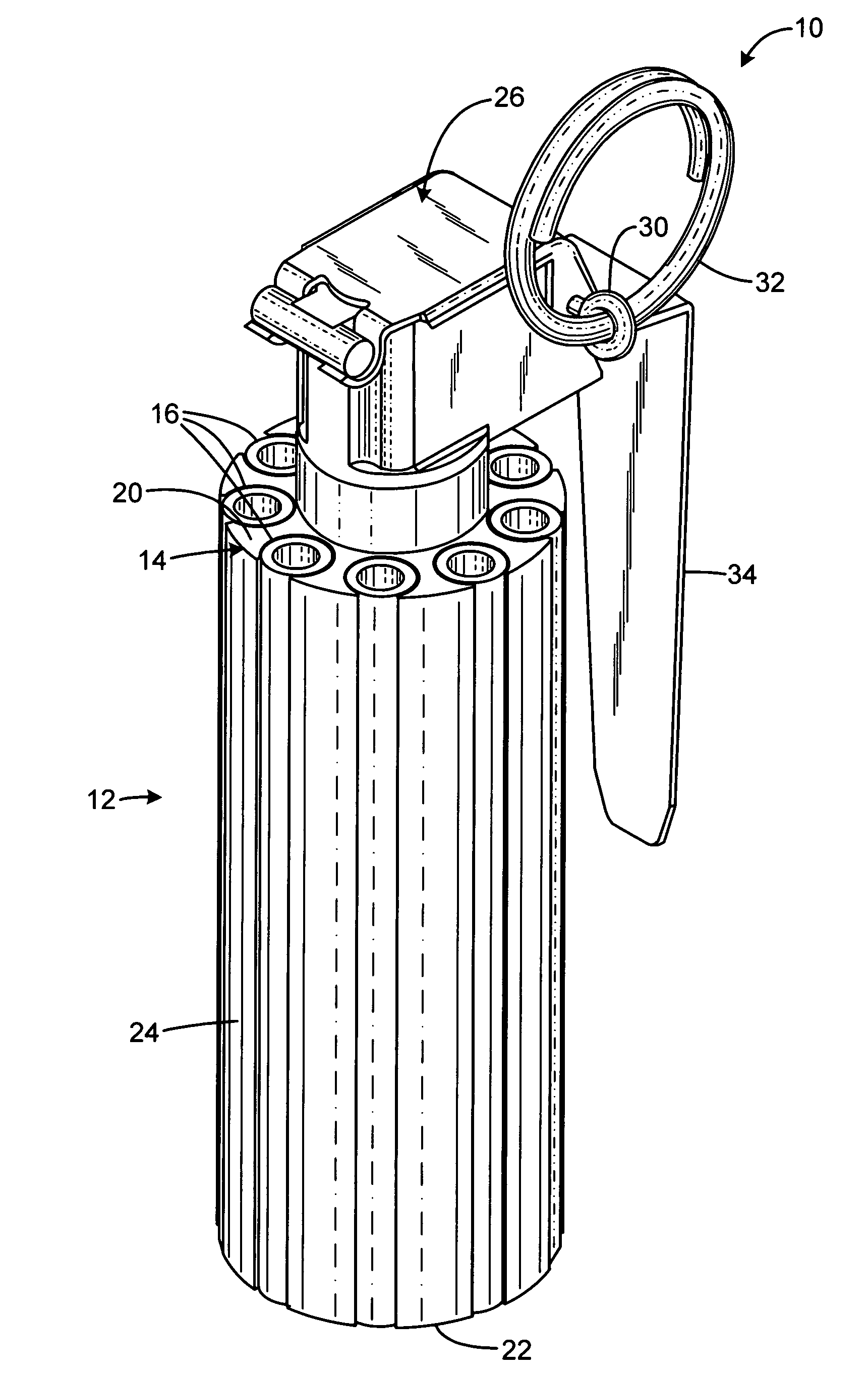
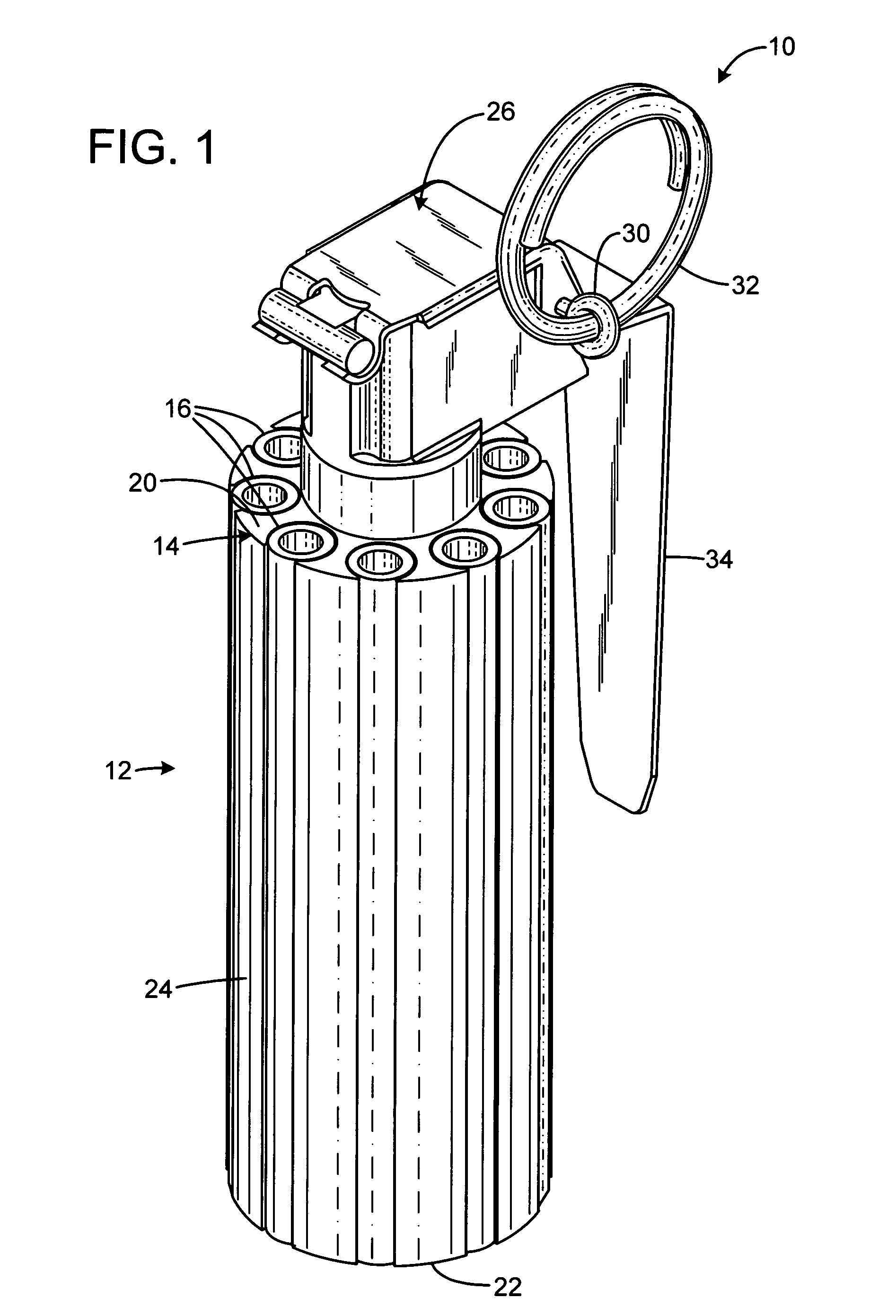
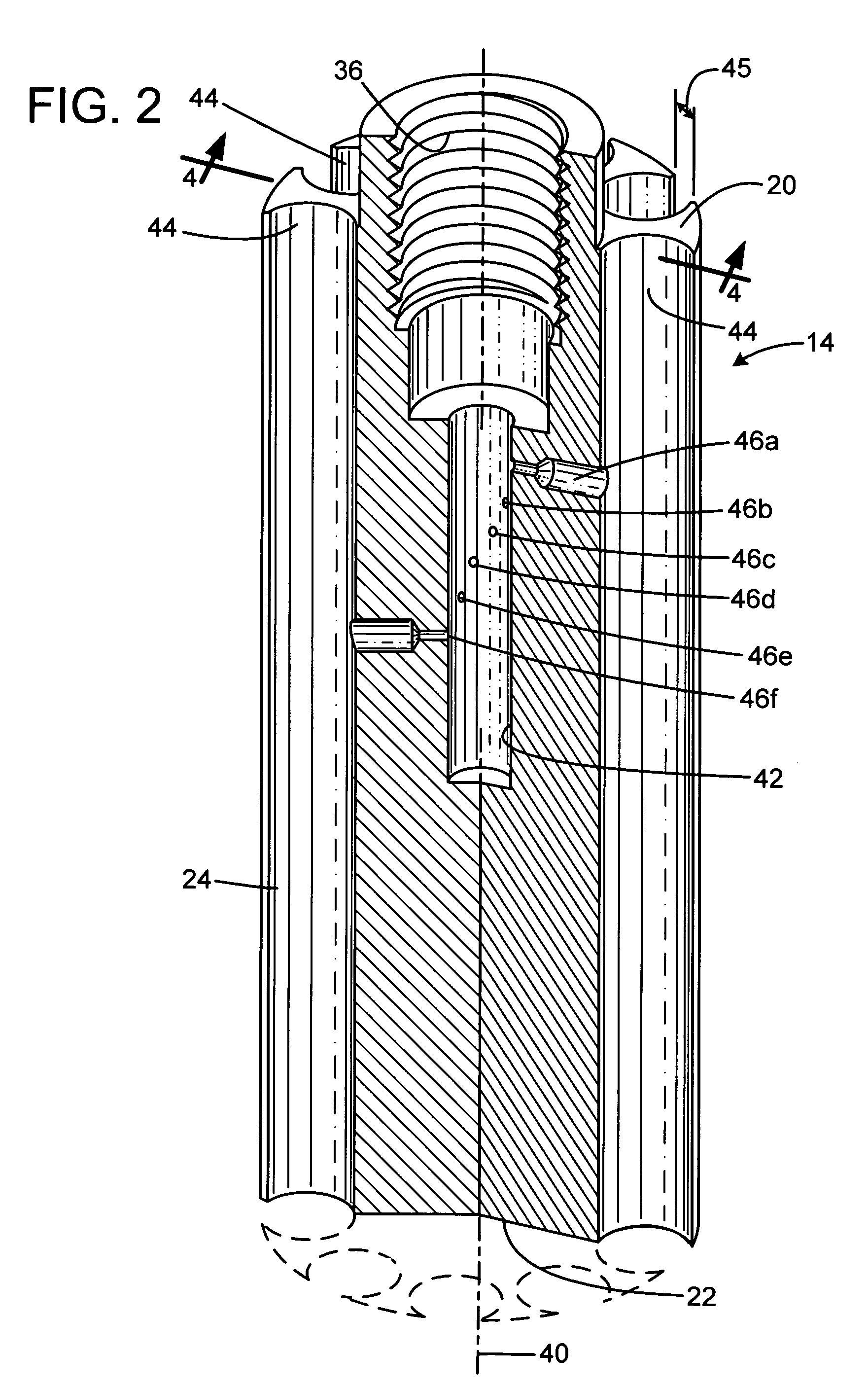
Multiple report stun grenade
The present invention overcomes the limitations of the prior art by providing a stun grenade device with an elongated cylindrical body having a cylindrical sidewall and opposed top and bottom end faces. The body includes a delay chamber containing a delay material, and has a number of flash charge chambers each containing a quantity of flash charge material. The body defines a number of ignition passages, each communicating from a respective flash charge chamber to the delay chamber. Each flash charge chamber has at least one exhaust aperture penetrating the top or bottom end face. Each flash charge chamber may be formed in an elongated tubular sleeve inset in a frame of a different material.
Owner:COMBINED SYST
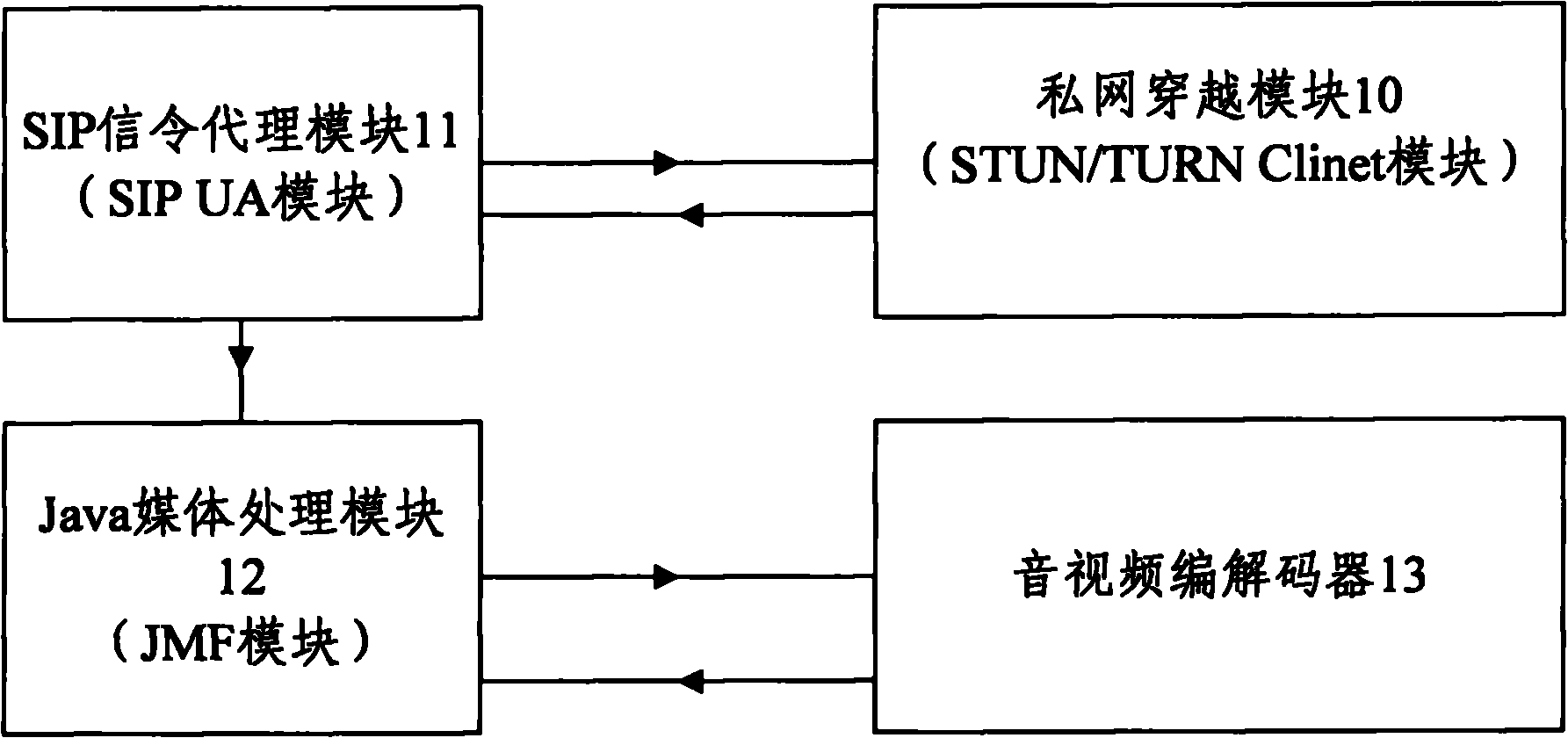
Private network access system based on SIP soft phone and method thereof
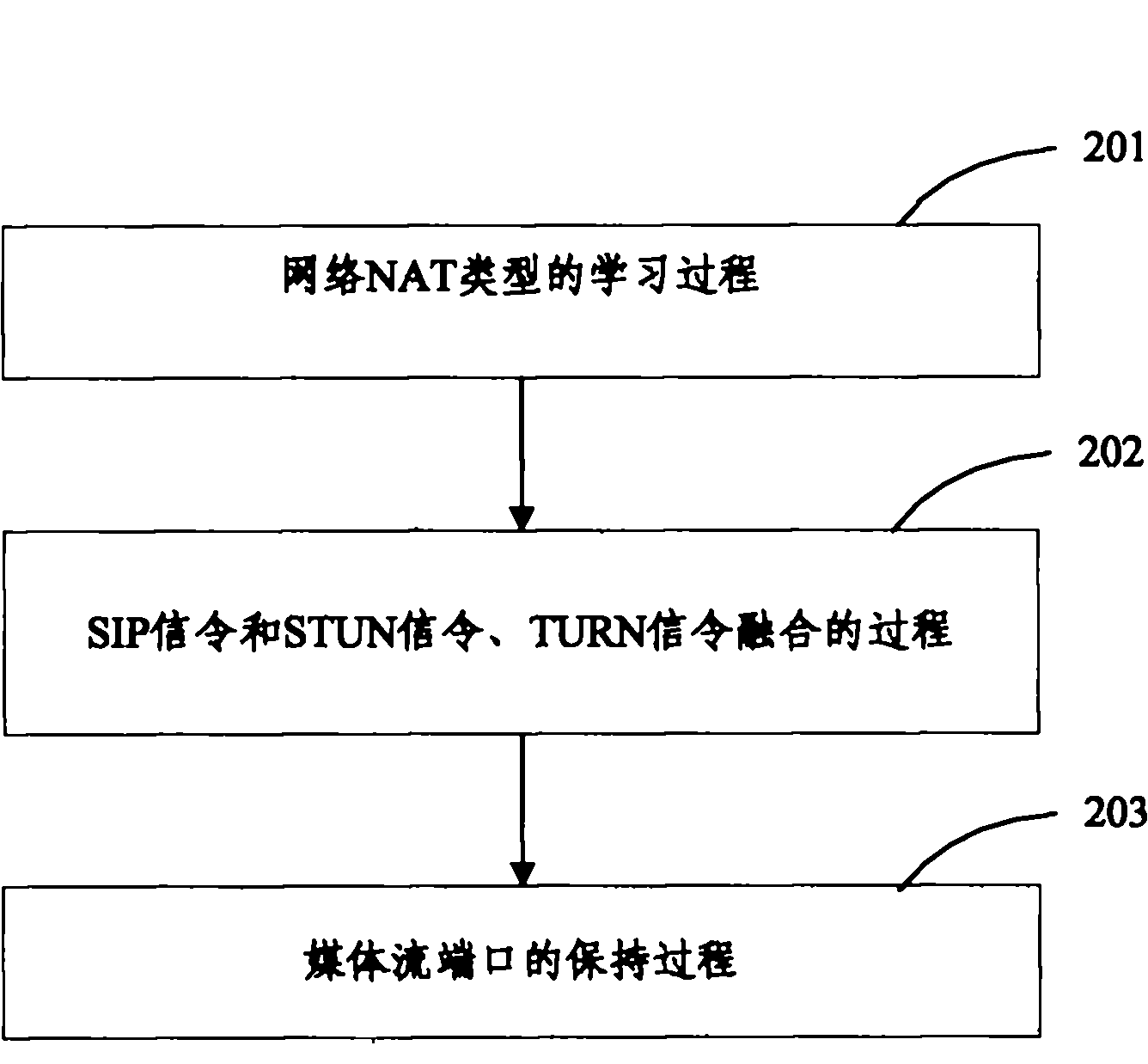
InactiveCN101860536AGuaranteed real-timeImprove efficiencyTransmissionSTUNSession Initiation Protocol
The invention discloses a private network access system based on a session initiation protocol (SIP) soft phone and a method thereof. The system comprises a private network access module, an SIP user agent module, a Java media framework module and an audio and video codec module. The method comprises the following steps that: SIP signaling is organically blended with an SIP extension protocol, an STUN message and a TURN message; and the SIP signaling adopts the extension protocol to coordinate with an SIP application server for communication, so that the SIP signaling without SDP can access without transmission of the STUN message and the TURN message, and only the SIP signaling with the SDP needs transmission of the STUN message and the TURN message for extraction of effective information in response. The invention can be used for communication when the public network and the private network are maintained accessible, thereby greatly improving the efficiency of communicating parties, ensuring the real-time communication, and realizing the access to the multi-level serial NAT.
Owner:BEIJING UNIV OF POSTS & TELECOMM
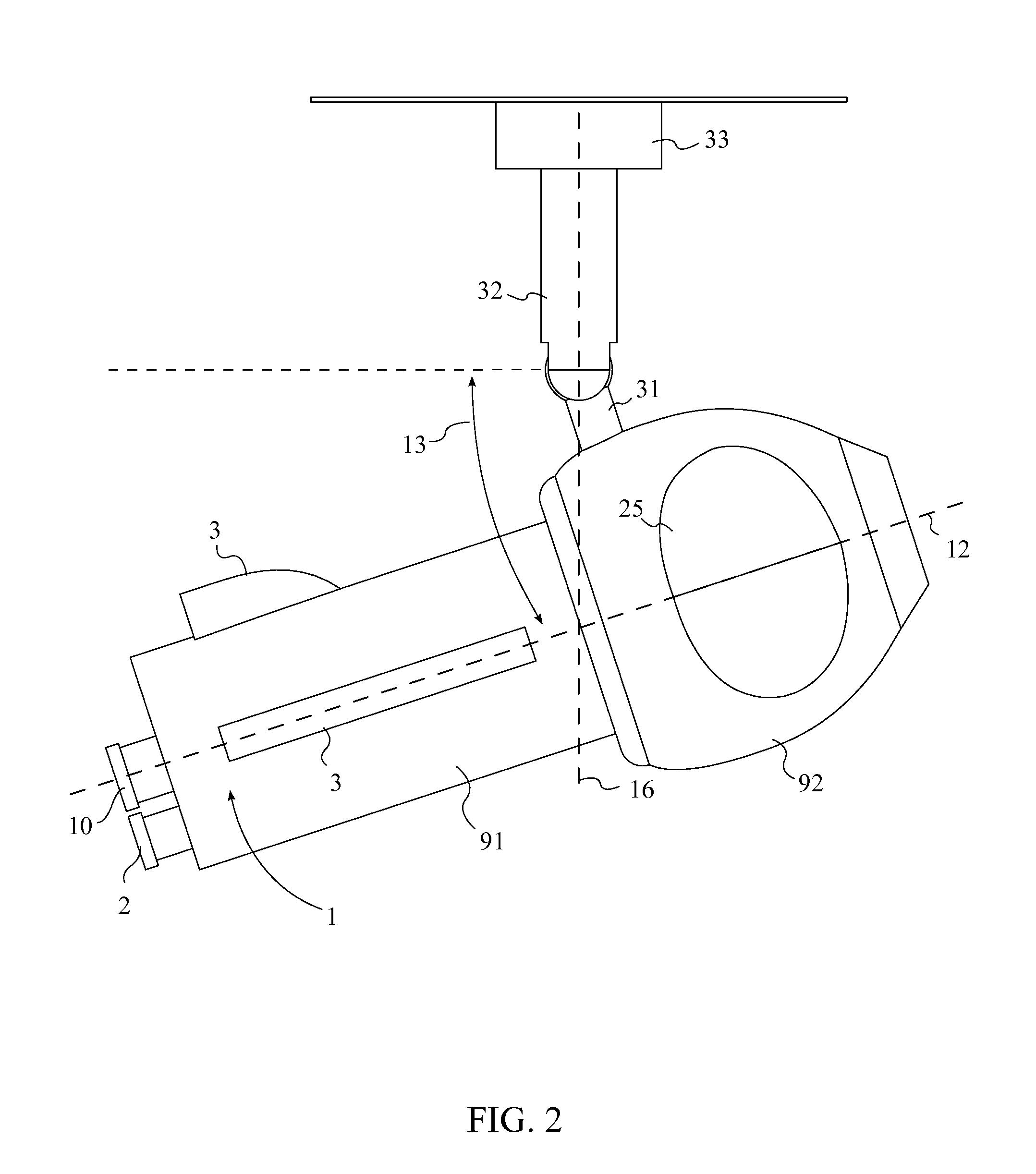
System of a Surveillance Camera For Identifying And Incapacitating Dangerous Intruders
A system of a surveillance camera for identifying and incapacitating dangerous intruders is a standard video camera with an additional infrared camera and an electrical stun gun. A data processing module in the camera utilizes body detection and tracking software to scan images received from the camera for human bodies, and a threat detection sensor communicates with the data processing module in order to identify a specific human body in the images as a threat. Once a threat is identified, the camera continually repositions itself so that at any given moment, a remote control can trigger the deployment of the electrical stun gun to incapacitate the threat. The data processing module also scans the facial and retina characteristics of the threat and stores the information in an information storage module at the back of the camera.
Owner:BUCKNOR VALENTINE A
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com