Method for penetrating the NAT and corresponding communication terminal and NAT device
A communication terminal and equipment technology, applied in the field of network communication, can solve the problems of not supporting address pool, not supporting TCP connection traversal, not supporting application protocols, etc., and achieve the effect of eliminating limitations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The above and other technical features and advantages of the NAT traversal method, NAT device, and communication terminal provided by the present invention will be described in detail as follows with reference to the accompanying drawings.
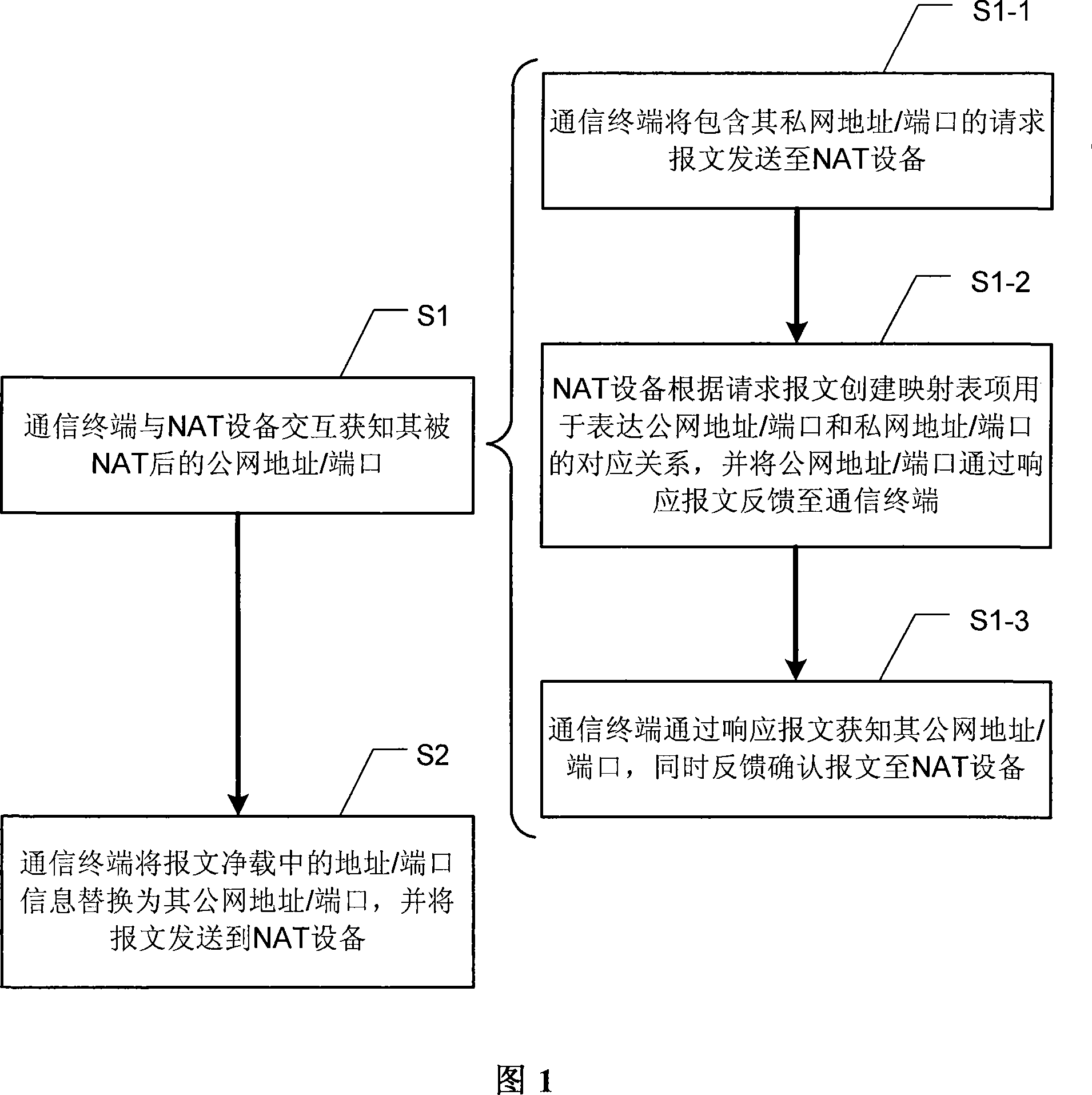
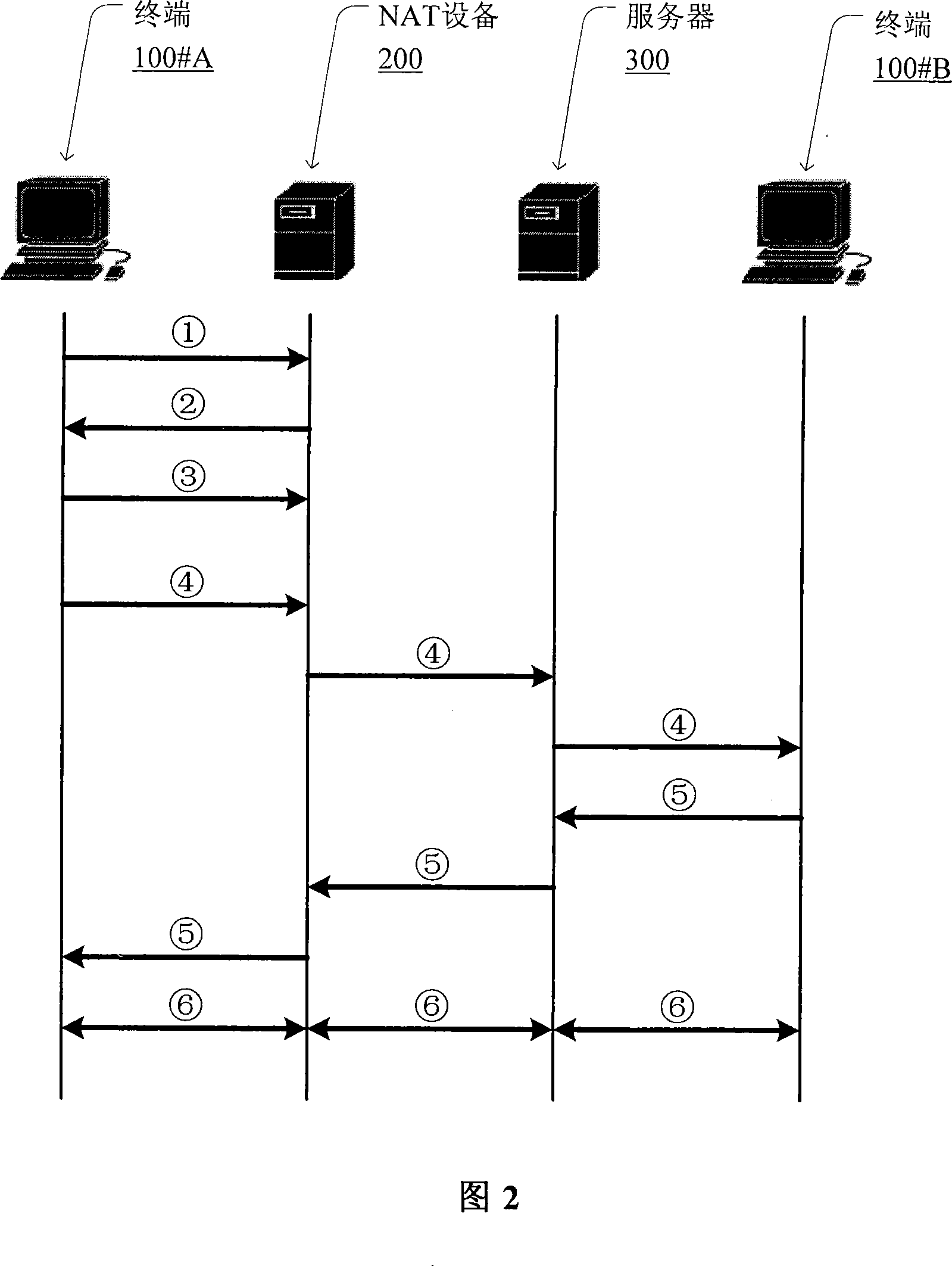
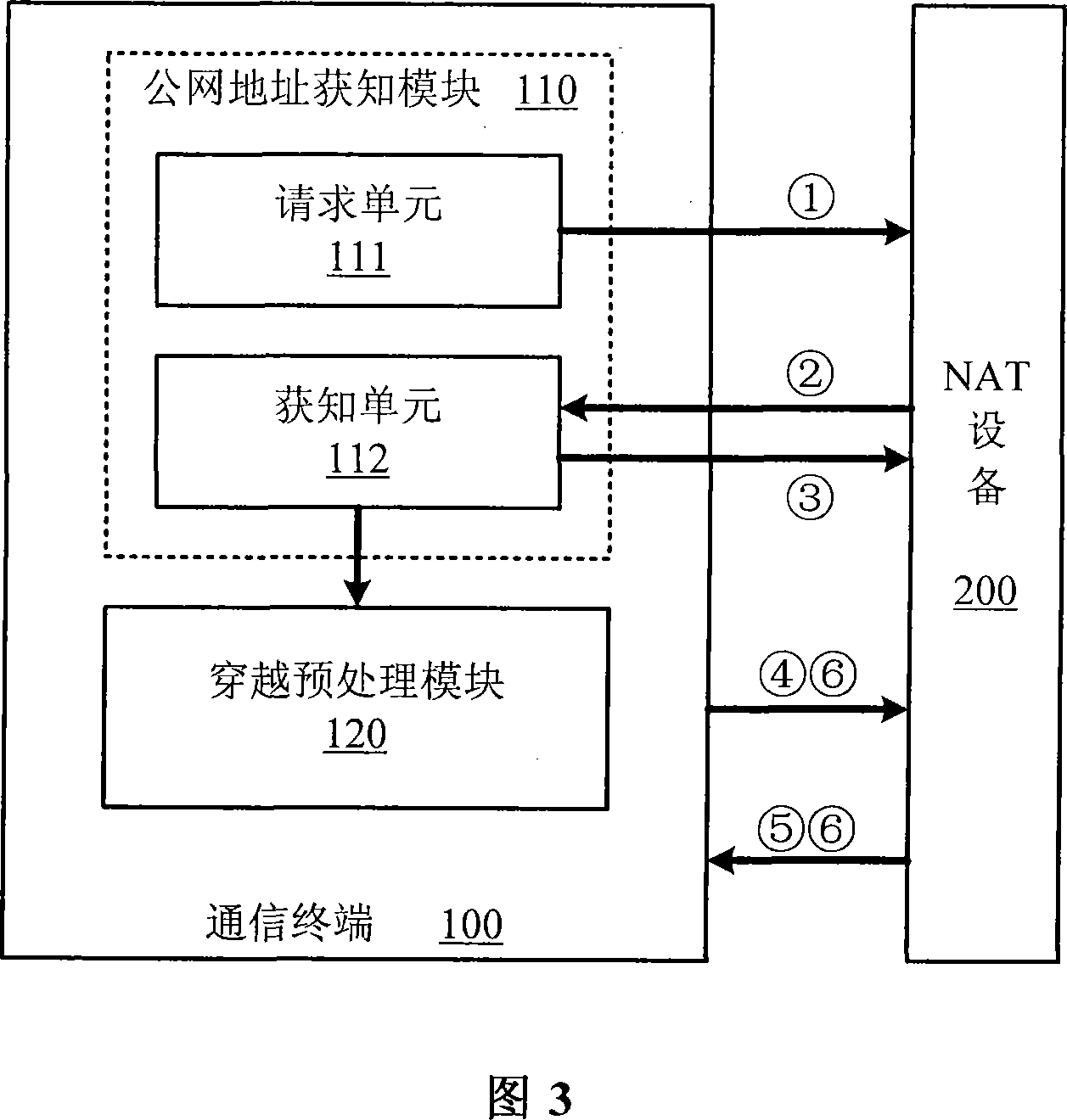
[0038] Fig. 1 shows a flow chart of a preferred embodiment of the NAT traversal method of the present invention. In order to realize NAT traversal on ordinary NAT devices, especially when address / port information is embedded in the message payload, the communication terminal behind the NAT device must first pass through the private network with the NAT device Inner interaction to learn its public network address / port after NAT, that is, to execute step S1 in Figure 1.
[0039] As shown in FIG. 1 , the interaction in the private network between the communication terminal and the NAT device can be realized by sequentially executing steps S1-1 to S1-3.
[0040] First, step S1-1 is executed: the communication terminal sends a request m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com