Patents
Literature
513 results about "Packet filtering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
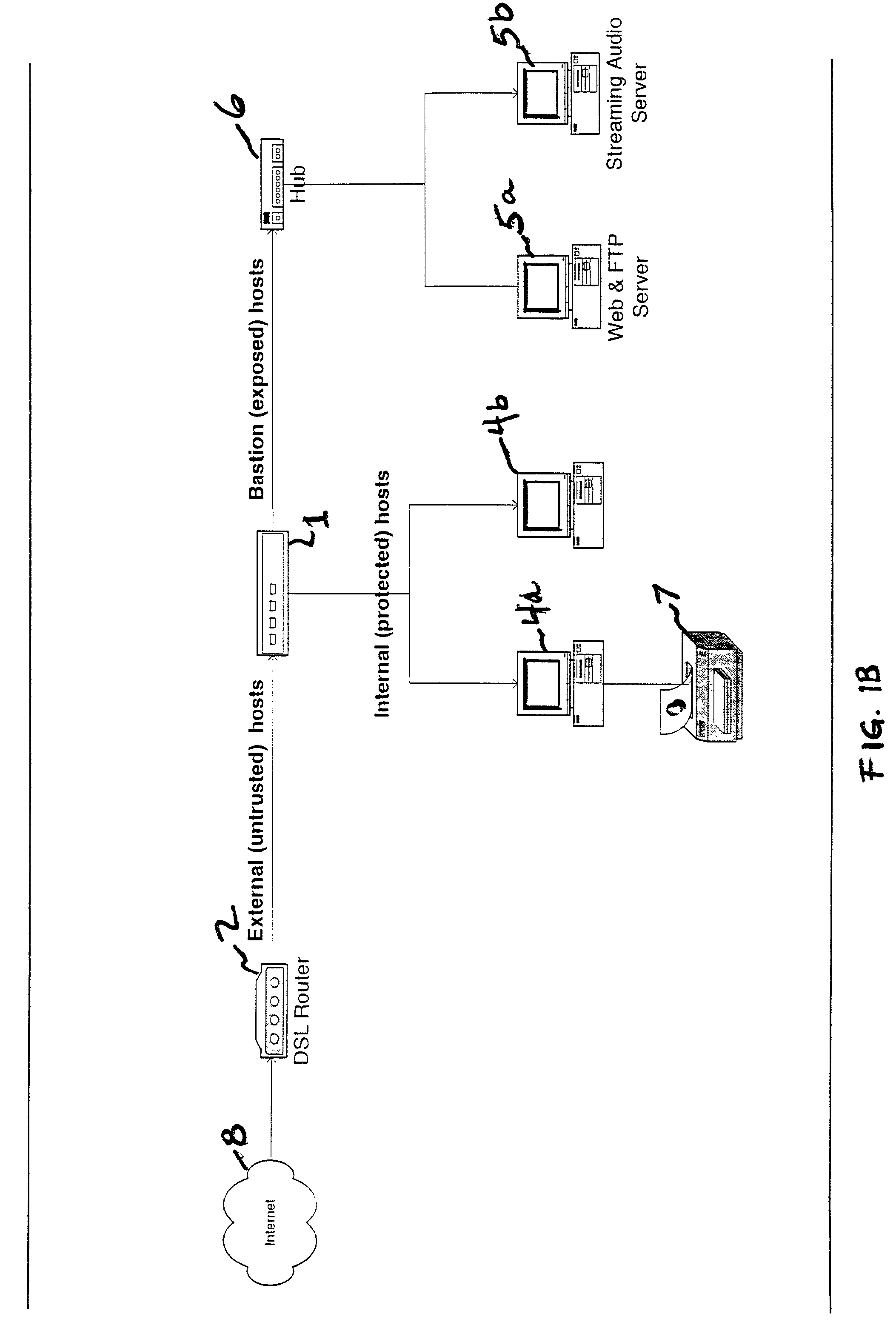
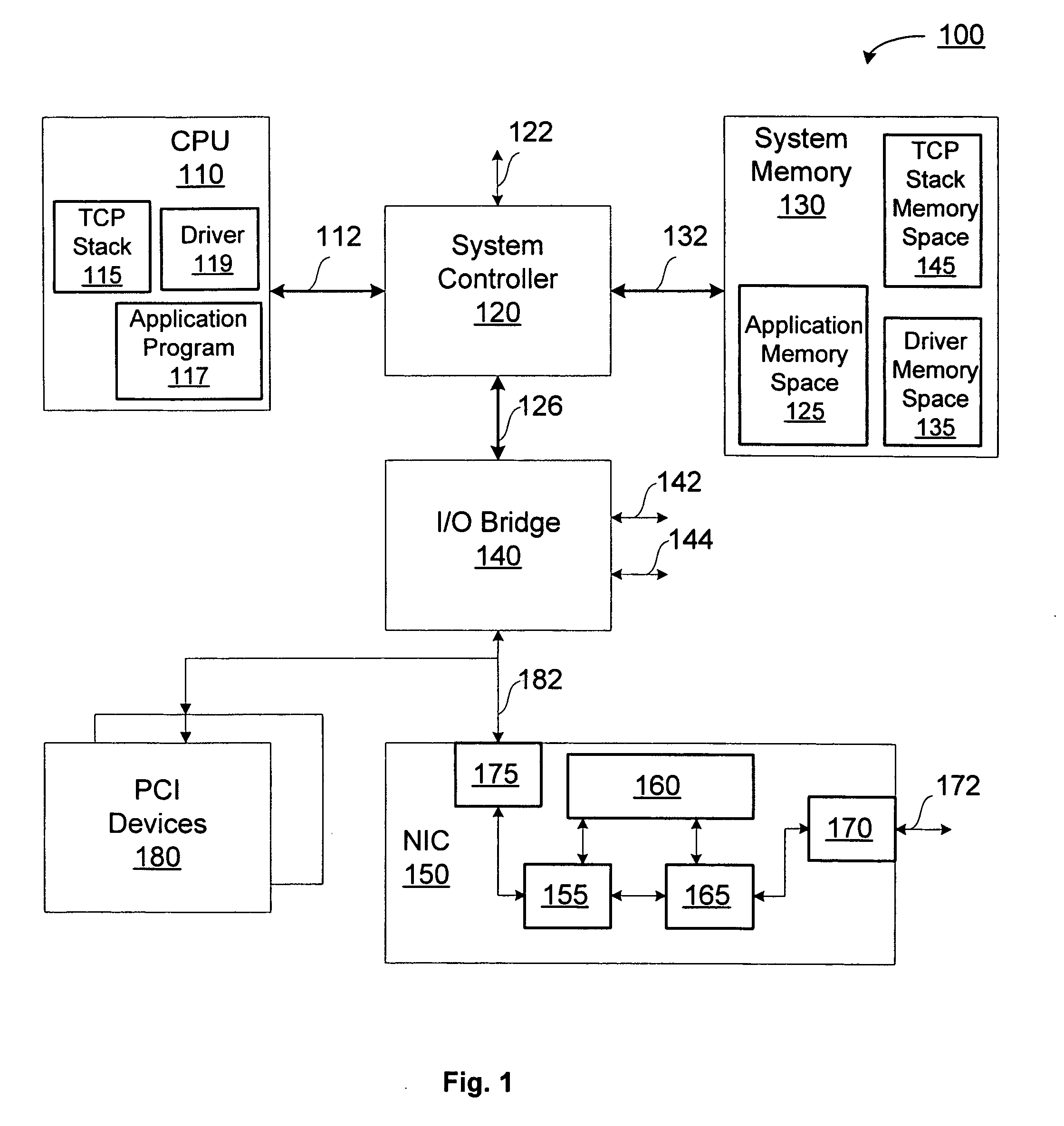
Systems and methods for processing packets
InactiveUS7215637B1Minimize occurrenceSize of output is increasedError preventionTransmission systemsPacket filteringTraffic analysis
Methods and devices for processing packets are provided. The processing device may include an input interface for receiving data units containing header information of respective packets; a first module configurable to perform packet filtering based on the received data units; a second module configurable to perform traffic analysis based on the received data units; a third module configurable to perform load balancing based on the received data units; and a fourth module configurable to perform route lookups based on the received data units.
Owner:JUMIPER NETWORKS INC
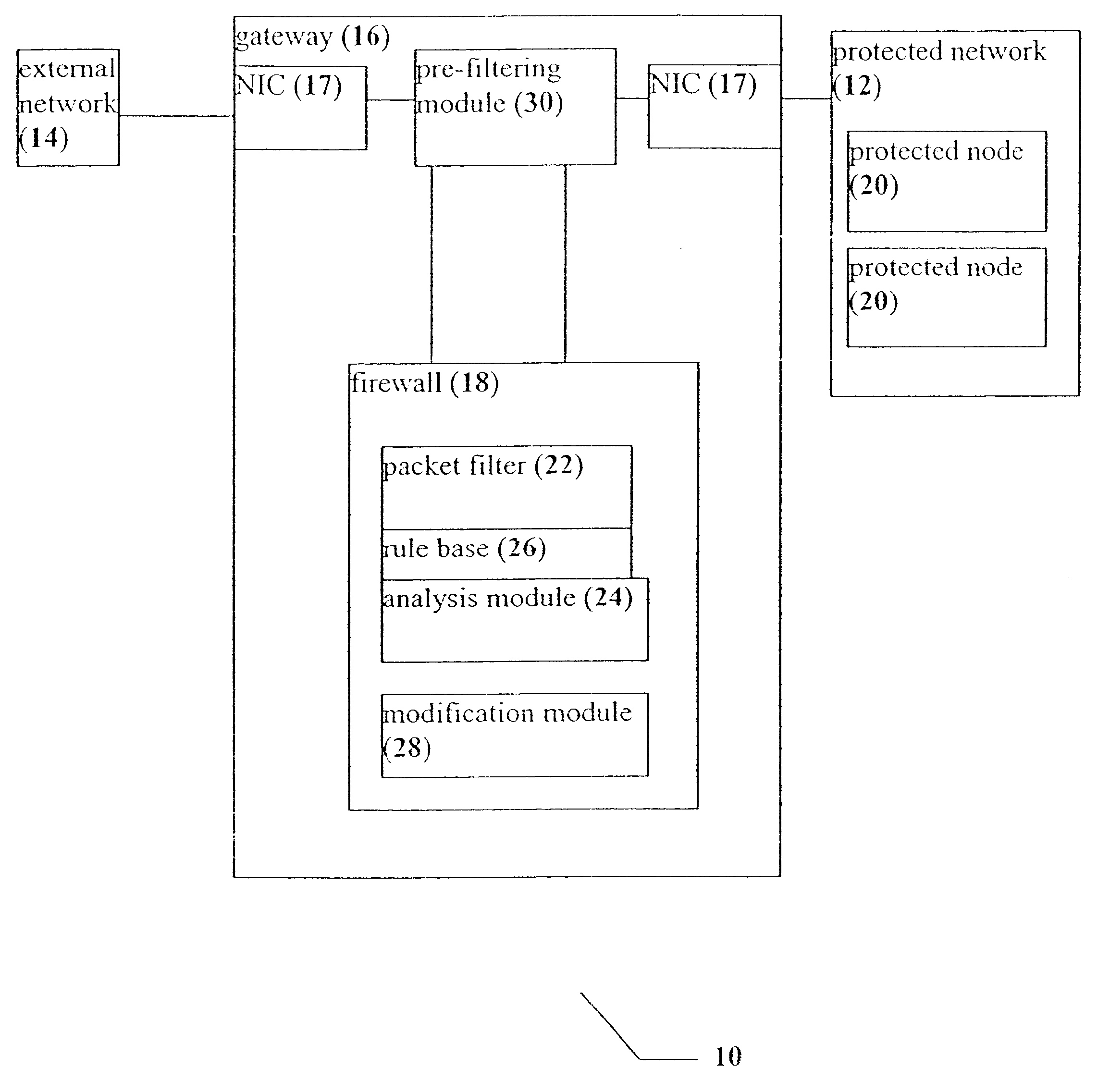
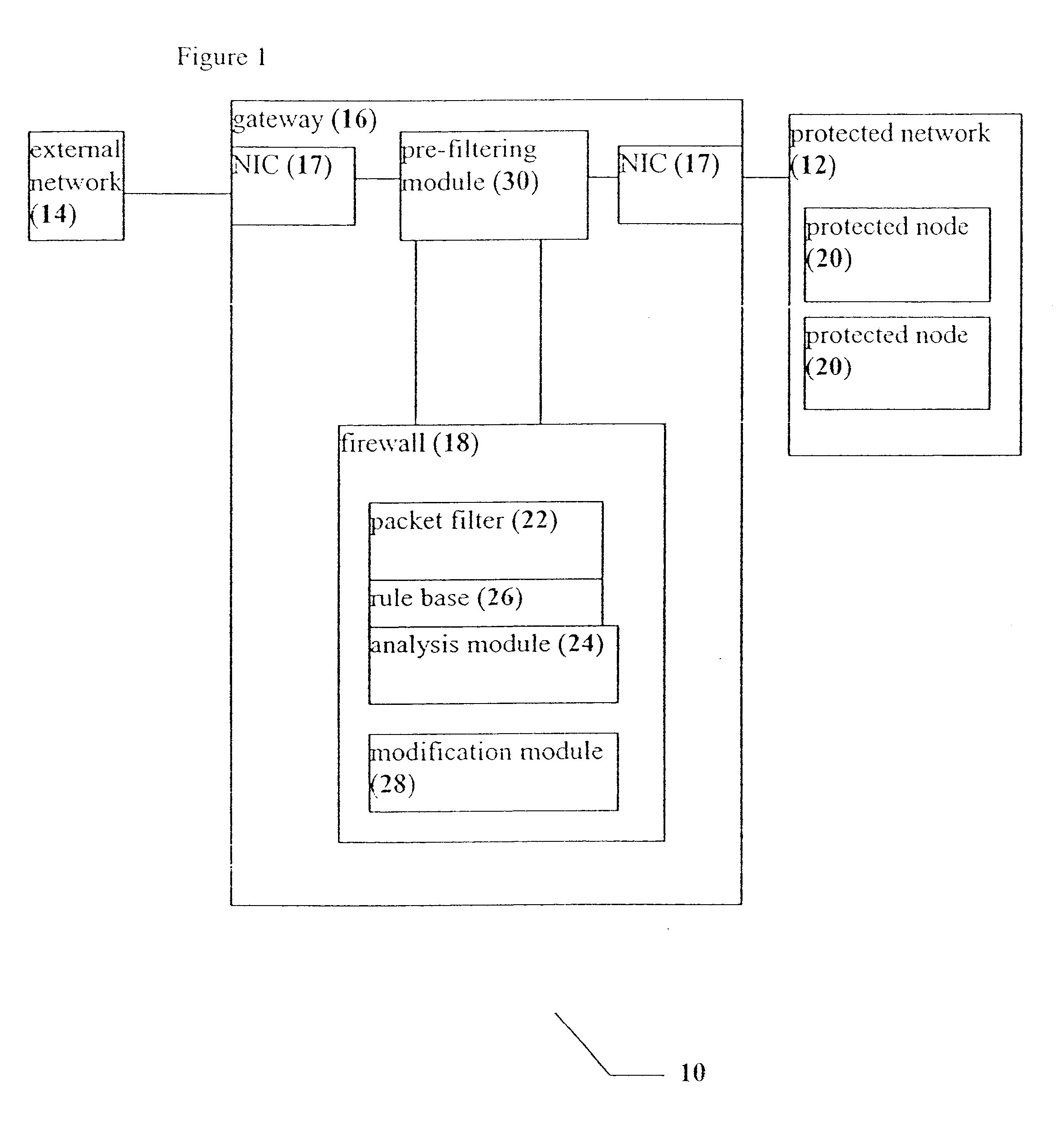
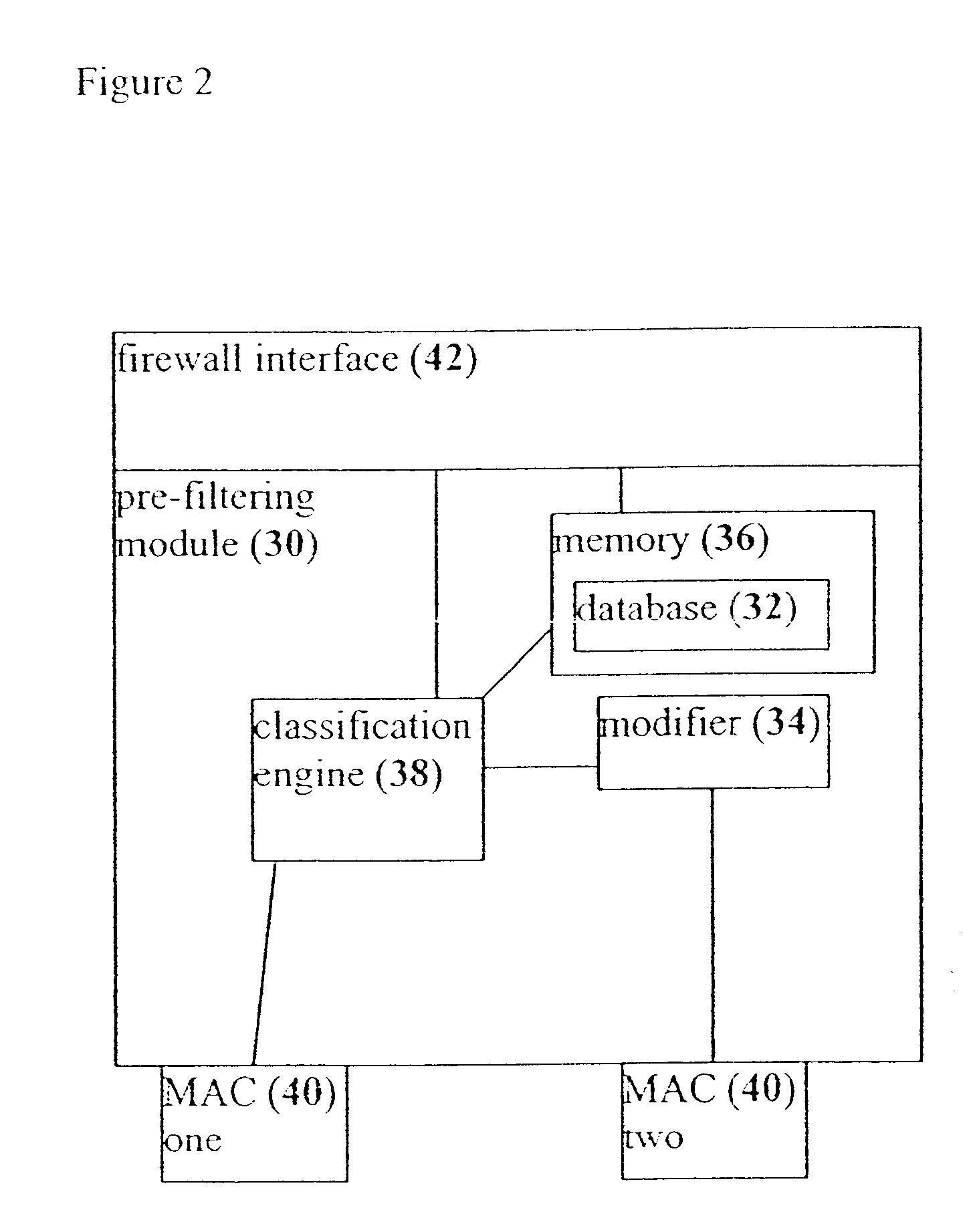
System, device and method for rapid packet filtering and processing
InactiveUS6496935B1Reducing and even eliminating amountImprove efficiencyLaser detailsData taking preventionFiltrationSession control
A system, a device and a method for accelerating packet filtration by supplementing a firewall with a pre-filtering module. The pre-filtering module performs a limited set of actions with regard to the packets, according to whether the packets are received from a connection which has been previously permitted by the firewall. If the packets are received from such a permitted connection, then the pre-filtering module forwards the packets to their destination, optionally performing one or more actions on the packets. Otherwise, the packets are forwarded to the firewall for handling. Preferably, once the firewall has transferred responsibility for the connection to the pre-filtering module, or "off-loaded" the connection, the firewall does not receive further packets from this connection until a timeout occurs for the connection, or a packet is received with particular session-control field values, such that the connection is closed. Optionally and preferably, the pre-filtering module is implemented as hardware.
Owner:CHECK POINT SOFTWARE TECH LTD
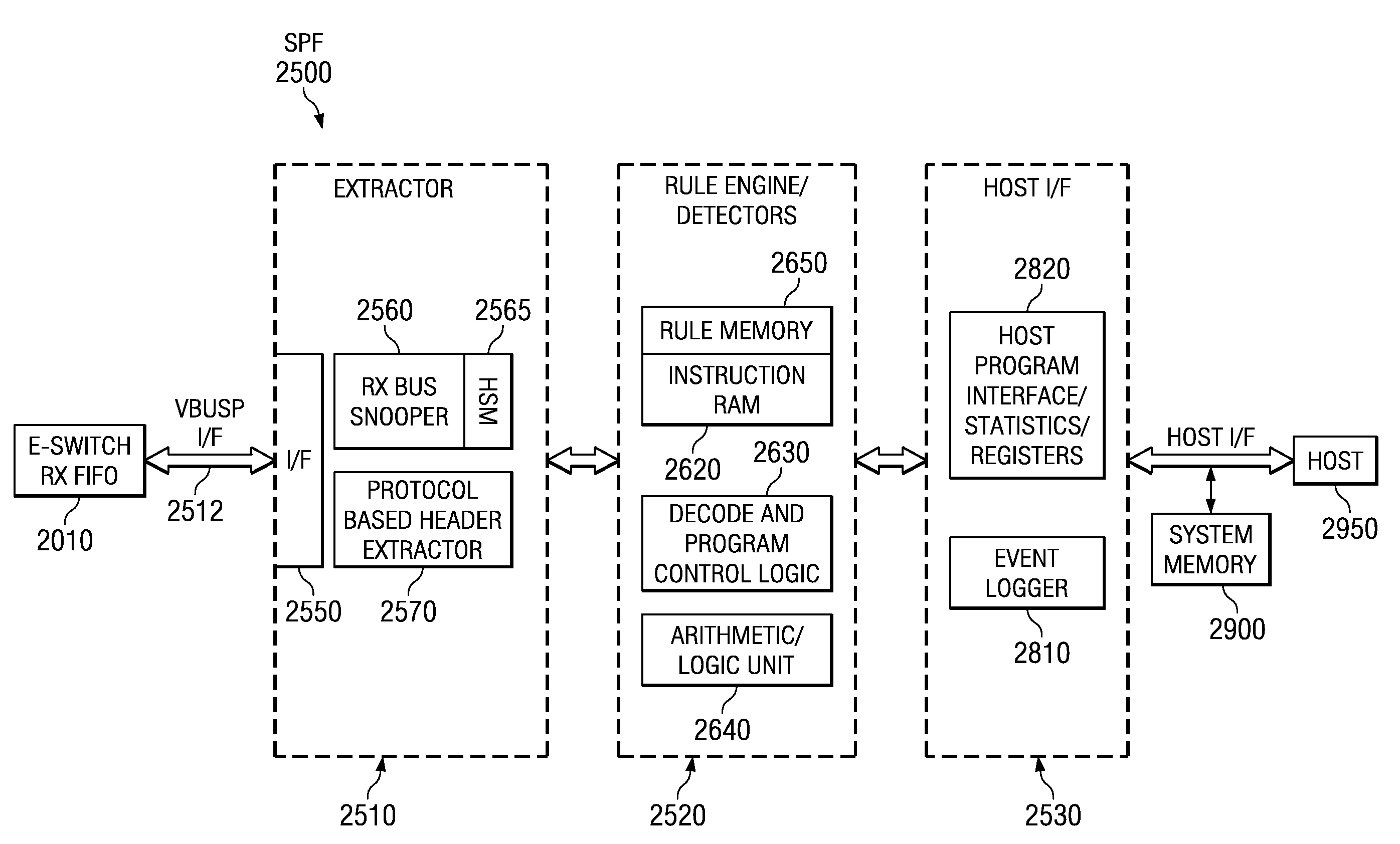
Packet processors and packet filter processes, circuits, devices, and systems
ActiveUS20070110053A1Data switching by path configurationProgram controlReal-time computingComputer network
A packet filter (2500) for incoming communications packets includes extractor circuitry (2510) operable to extract data from a packet, and packet processor circuitry (2520) operable to concurrently mask (3010) the packet data from the extractor circuitry (2510), perform an arithmetic / logic operation (3020) on the packet to supply a packet drop signal (DROP), and perform a conditional limit operation and a conditional jump operation (3030).
Owner:TEXAS INSTR INC
Device and method for detecting unauthorized, "rogue" wireless LAN access points
ActiveUS20050030929A1Improves receiver rangeImproves geolocation capabilityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsOutdoor areaGeolocation
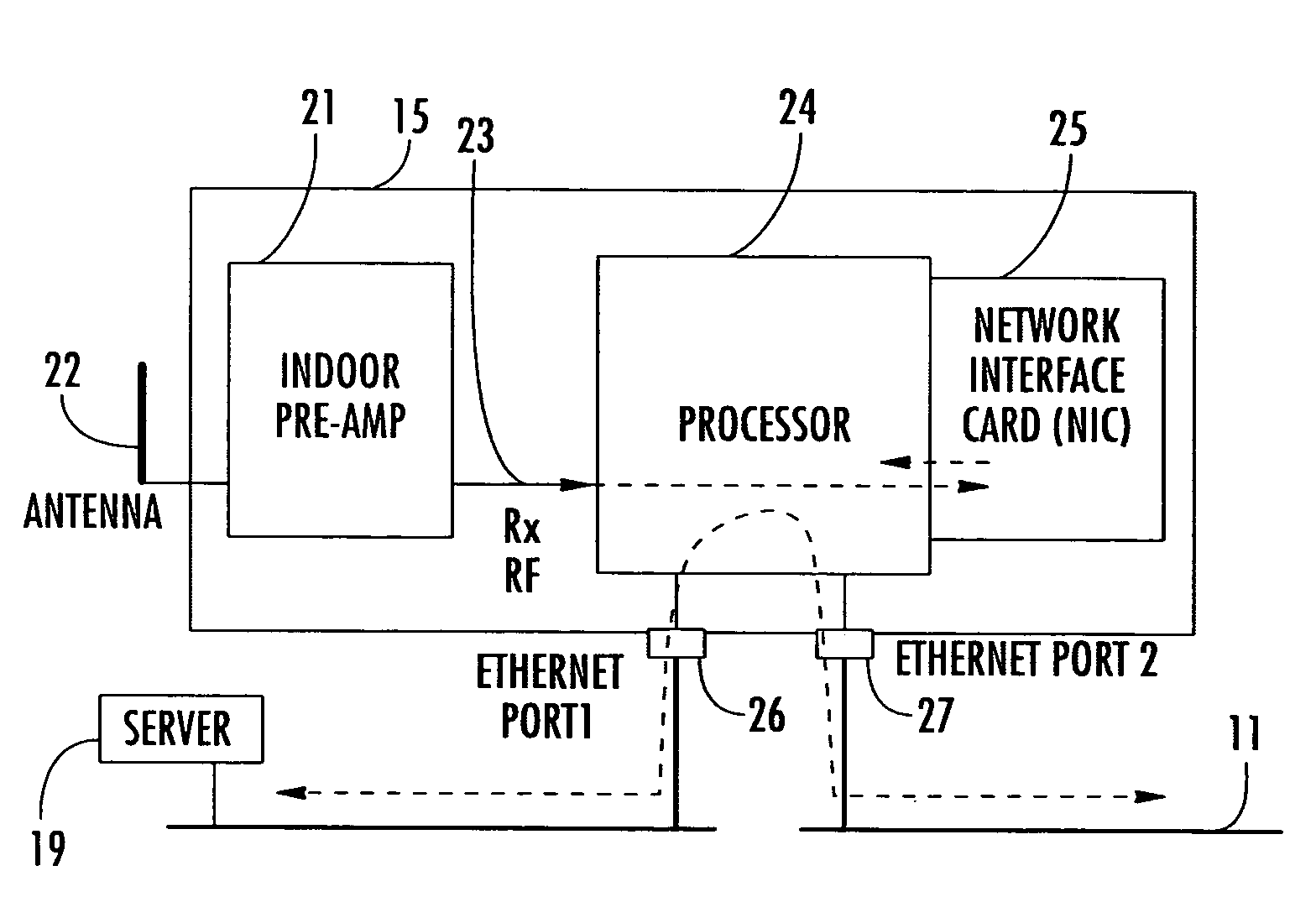
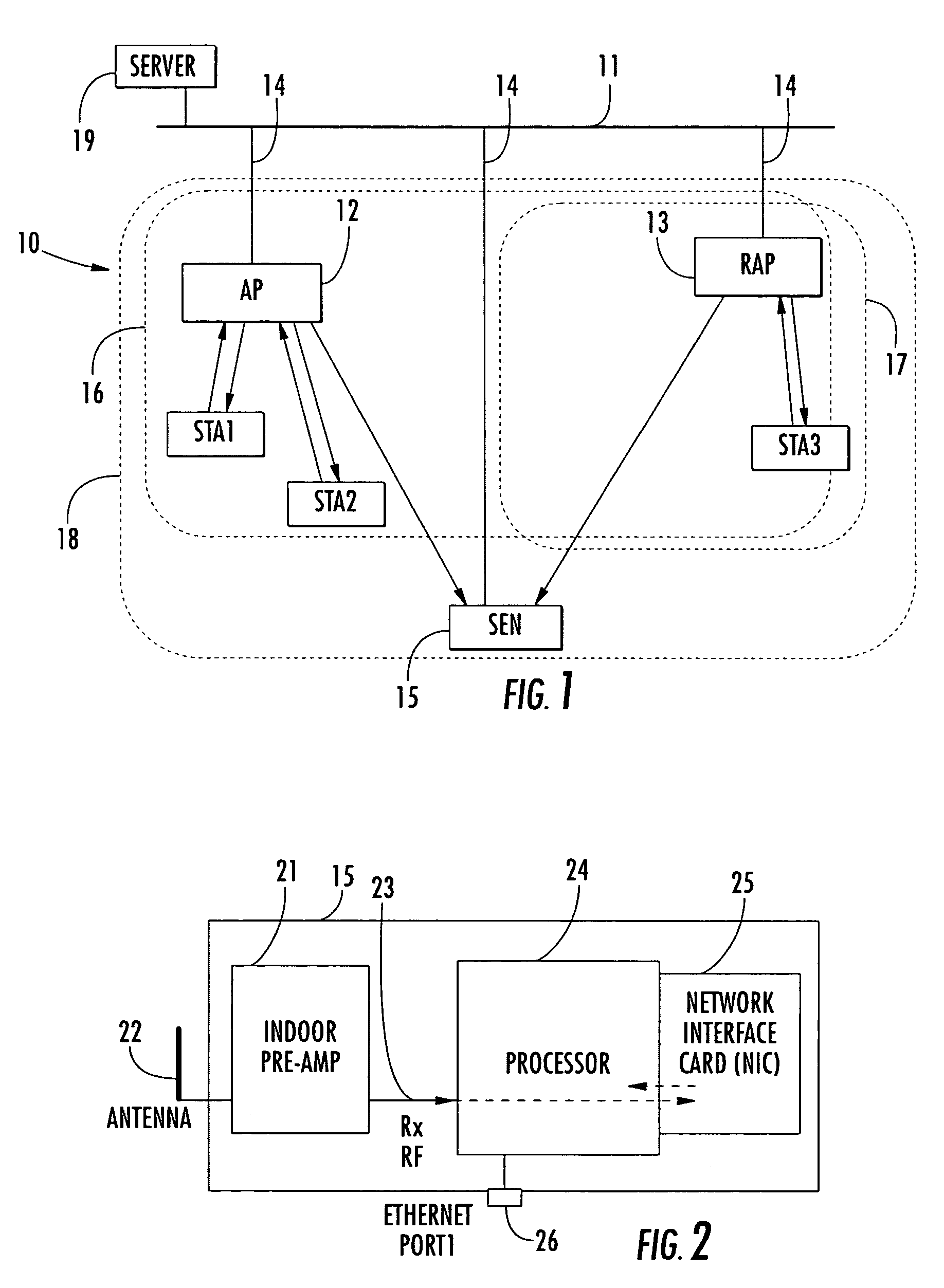
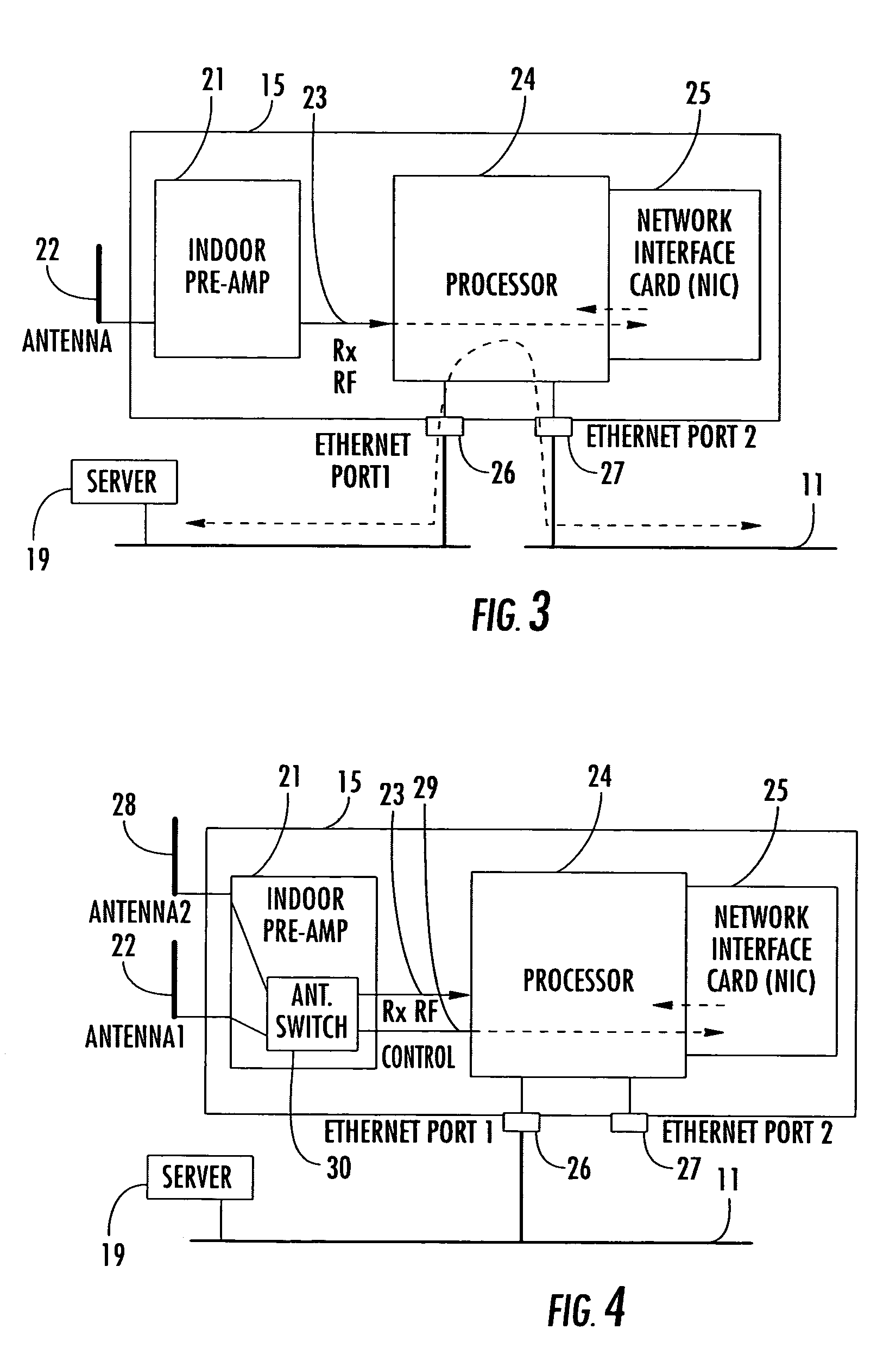
A system monitors and detects unauthorized wireless LAN access points and wireless devices. The system includes one or more wireless LAN monitoring devices, which detect and report the presence of unauthorized or “rogue” wireless LAN access points or wireless devices within a predetermined area, for example, within the vicinity of a wired LAN, including indoor and / or outdoor areas. Improved range is achieved through the use of preamplification and sectorized antennas. Larger areas may be covered using additional wireless LAN monitoring devices, which operate independently or cooperate together in the detection process. Geolocation is possible using single or multiple, cooperating monitoring devices. Provision can be made for monitoring devices to provide packet filtering on a wired LAN.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
System and method for multi-stage packet filtering on a networked-enabled device
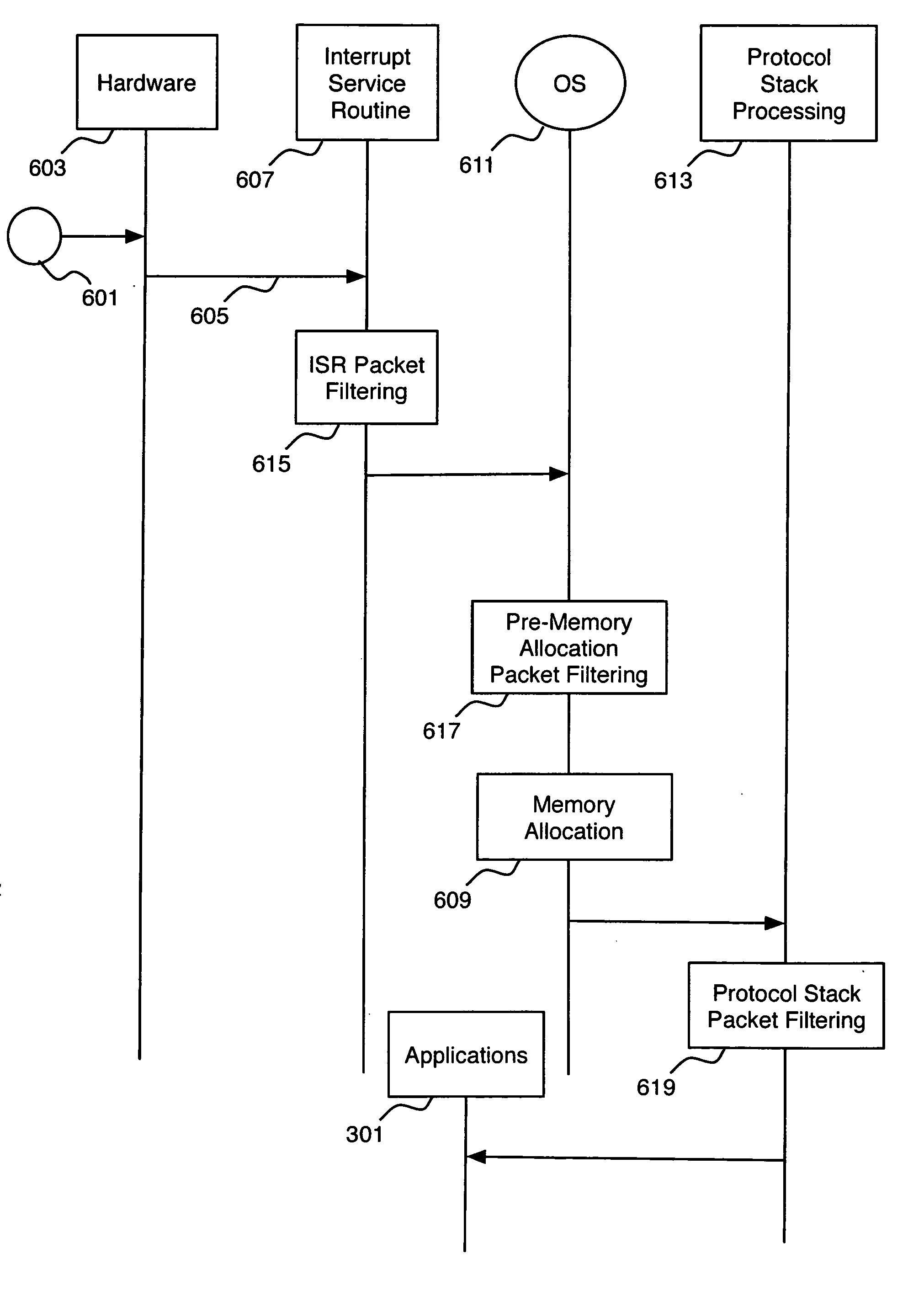
InactiveUS20070083924A1Avoiding allocating memory resourceAvoid resourcesMultiple digital computer combinationsProgram controlData packProtocol processing
A multi-stage packet filtering method and system. The multi-stage packet filtering according to the invention applies a set of filtering rules early in the processing of incoming communications packets by filtering incoming data packets using the filtering rules in a plurality of stages wherein the first stage is triggered by the receipt of a data packet by the device. Filtering rules that cannot be applied in the first stage may be deferred to a pre-memory allocation stage. Thus, preferable leaving only rules that must be executed in conjunction with protocol processing to be filtered at a filtering stage executed in a protocol processing filtering stage.
Owner:LU HONGQIAN KAREN
Methods and apparatus for a computer network firewall with multiple domain support
InactiveUS7143438B1Improve processing efficiencyIncrease access rule flexibilityUser identity/authority verificationHardware monitoringData packEngineering
The invention provides improved computer network firewalls which include one or more features for increased processing efficiency. A firewall in accordance with the invention can support multiple security policies, multiple users or both, by applying any one of several distinct sets of access rules. The firewall can also be configured to utilize “stateful” packet filtering which involves caching rule processing results for one or more packets, and then utilizing the cached results to bypass rule processing for subsequent similar packets. To facilitate passage to a user, by a firewall, of a separate later transmission which is properly in response to an original transmission, a dependency mask can be set based on session data items such as source host address, destination host address, and type of service. The mask can be used to query a cache of active sessions being processed by the firewall, such that a rule can be selected based on the number of sessions that satisfy the query. Dynamic rules may be used in addition to pre-loaded access rules in order to simplify rule processing. To unburden the firewall of application proxies, the firewall can be enabled to redirect a network session to a separate server for processing.
Owner:LUCENT TECH INC
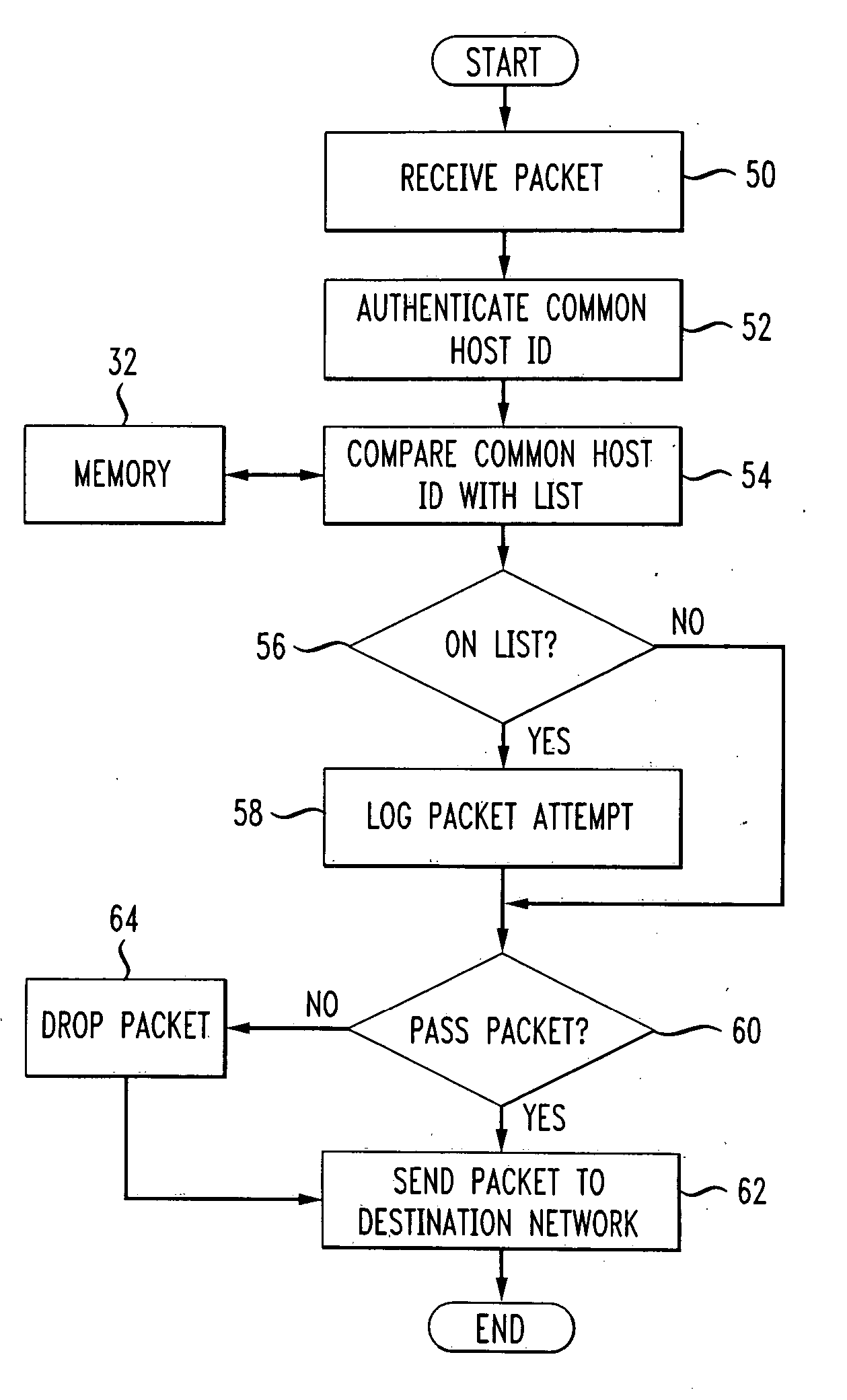
Methods for packet filtering including packet invalidation if packet validity determination not timely made
InactiveUS7013482B1Easy to switchEliminate requirementsMultiple digital computer combinationsProgram controlVisual feedbackElectric signal
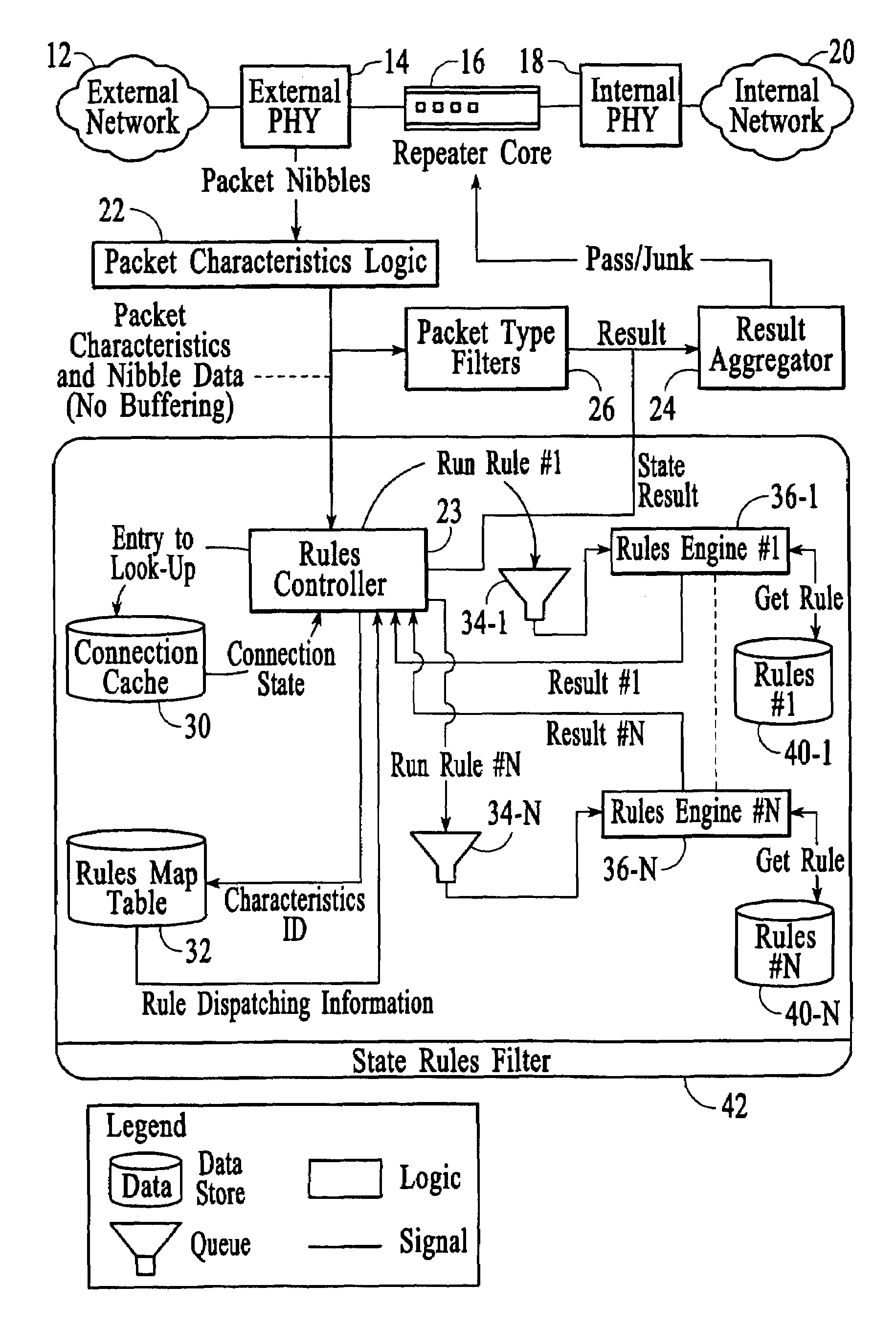
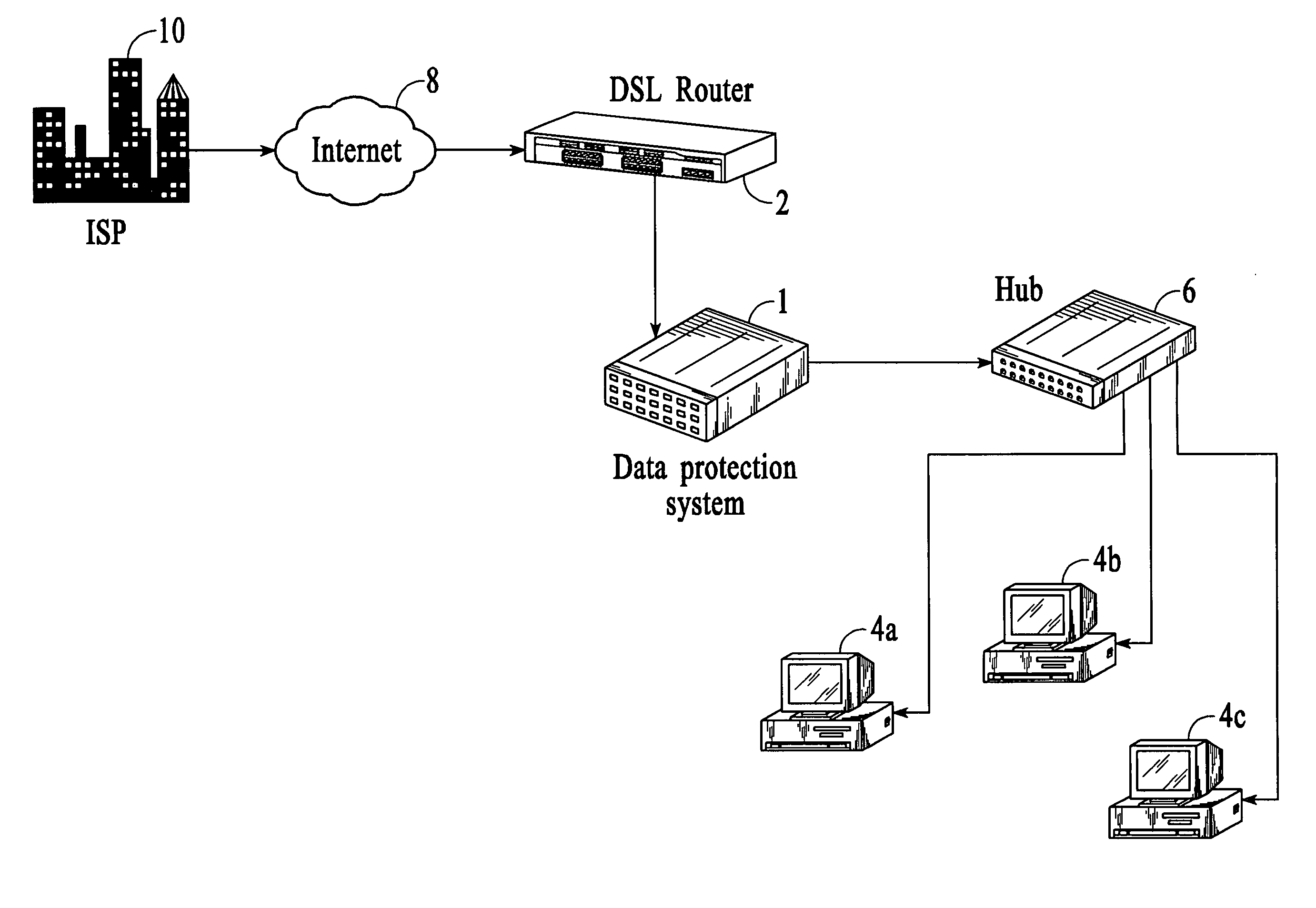
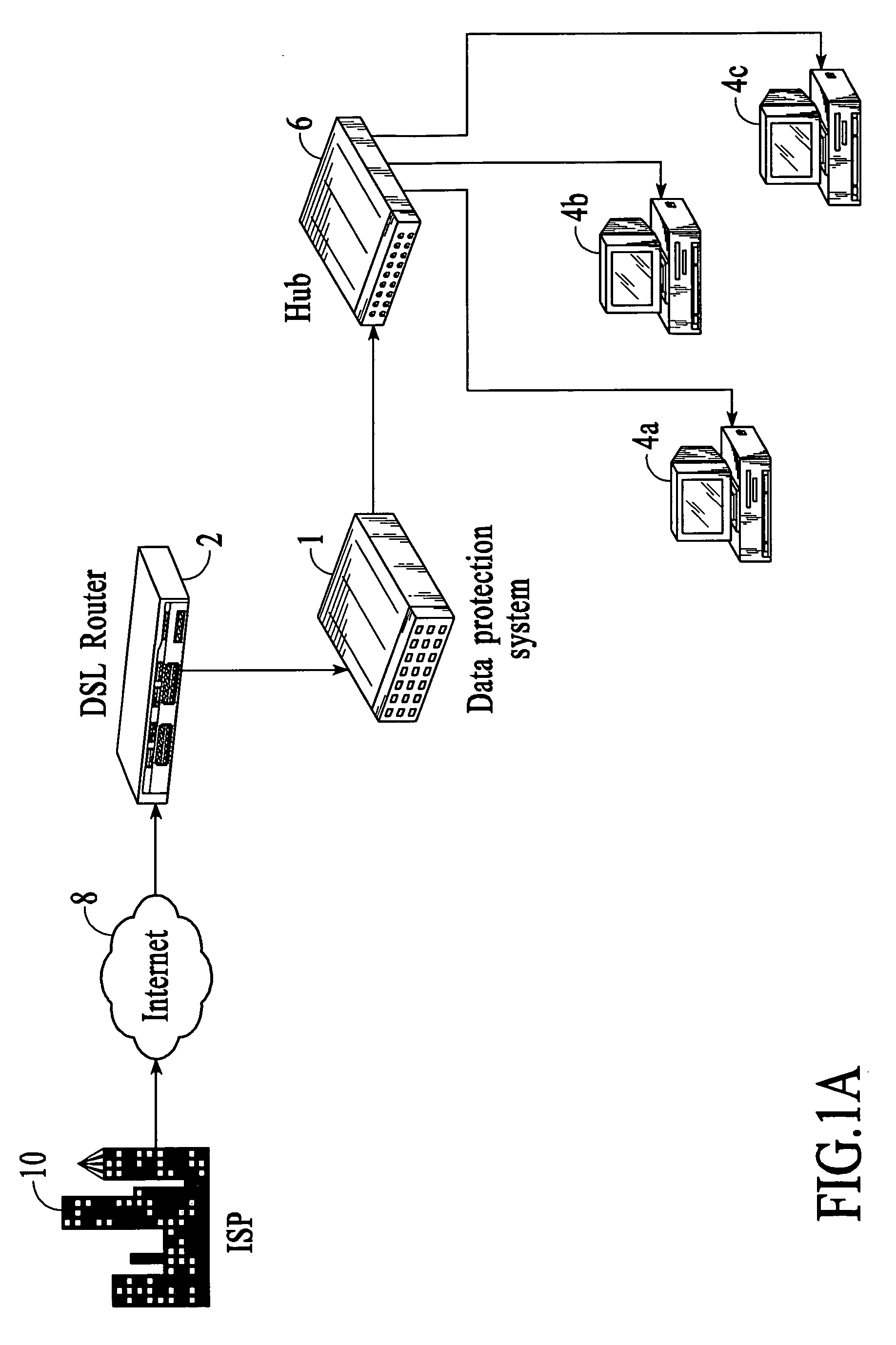
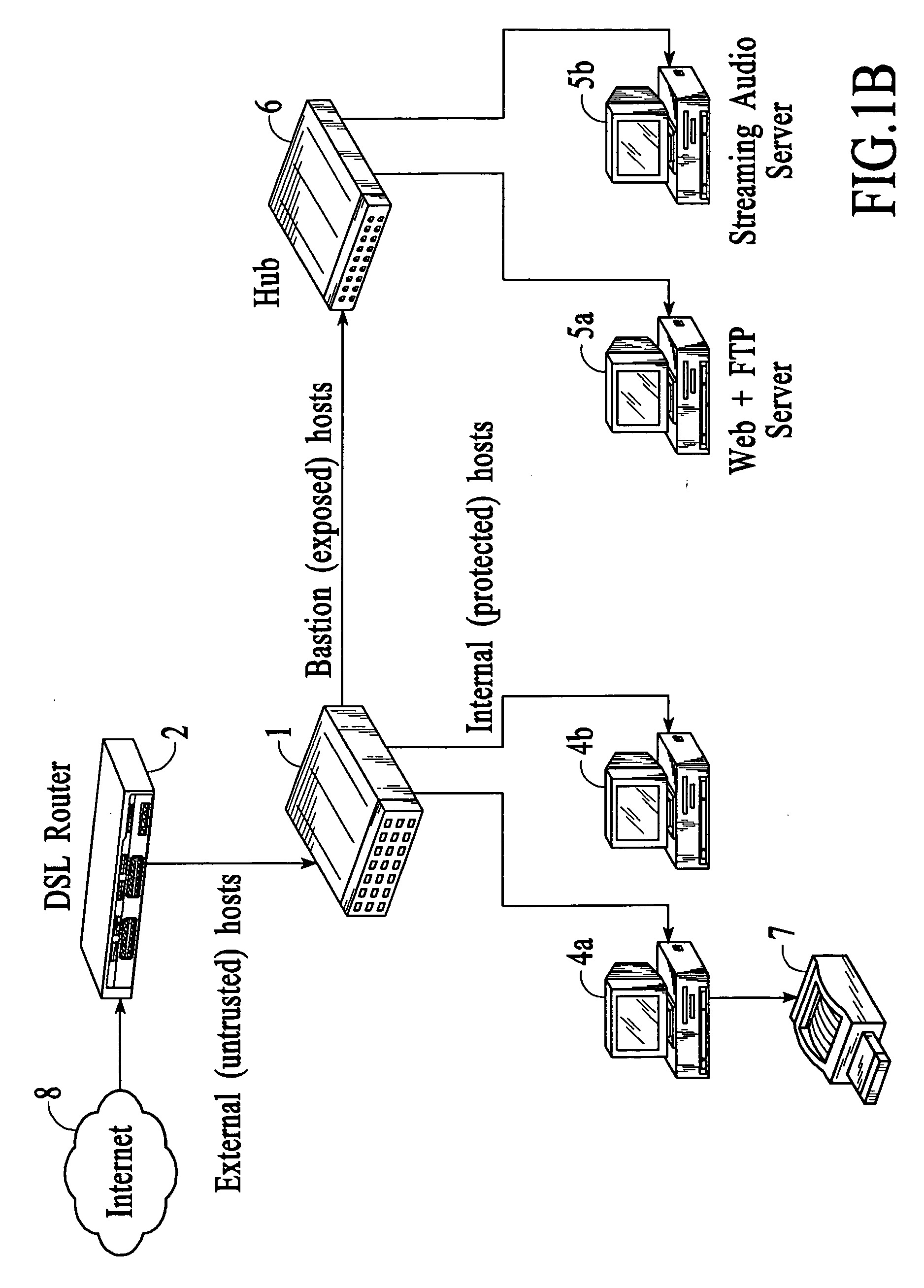
Methods and systems for firewall / data protection that filters data packets in real time and without packet buffering are disclosed. A data packet filtering hub, which may be implemented as part of a switch or router, receives a packet on one link, reshapes the electrical signal, and transmits it to one or more other links. During this process, a number of filters checks are performed in parallel, resulting in a decision about whether each packet should or should not be invalidated by the time that the last bit is transmitted. To execute this task, the filtering hub performs rules-based filtering on several levels simultaneously, preferably with a programmable logic or other hardware device. Various methods for packet filtering in real time and without buffering with programmable logic are disclosed. The system may include constituent elements of a stateful packet filtering hub, such as microprocessors, controllers, and integrated circuits. The system may be reset, enabled, disabled, configured, and / or reconfigured with toggles or other physical switches. Audio and visual feedback may be provided regarding the operation and status of the system.
Owner:802 SYST
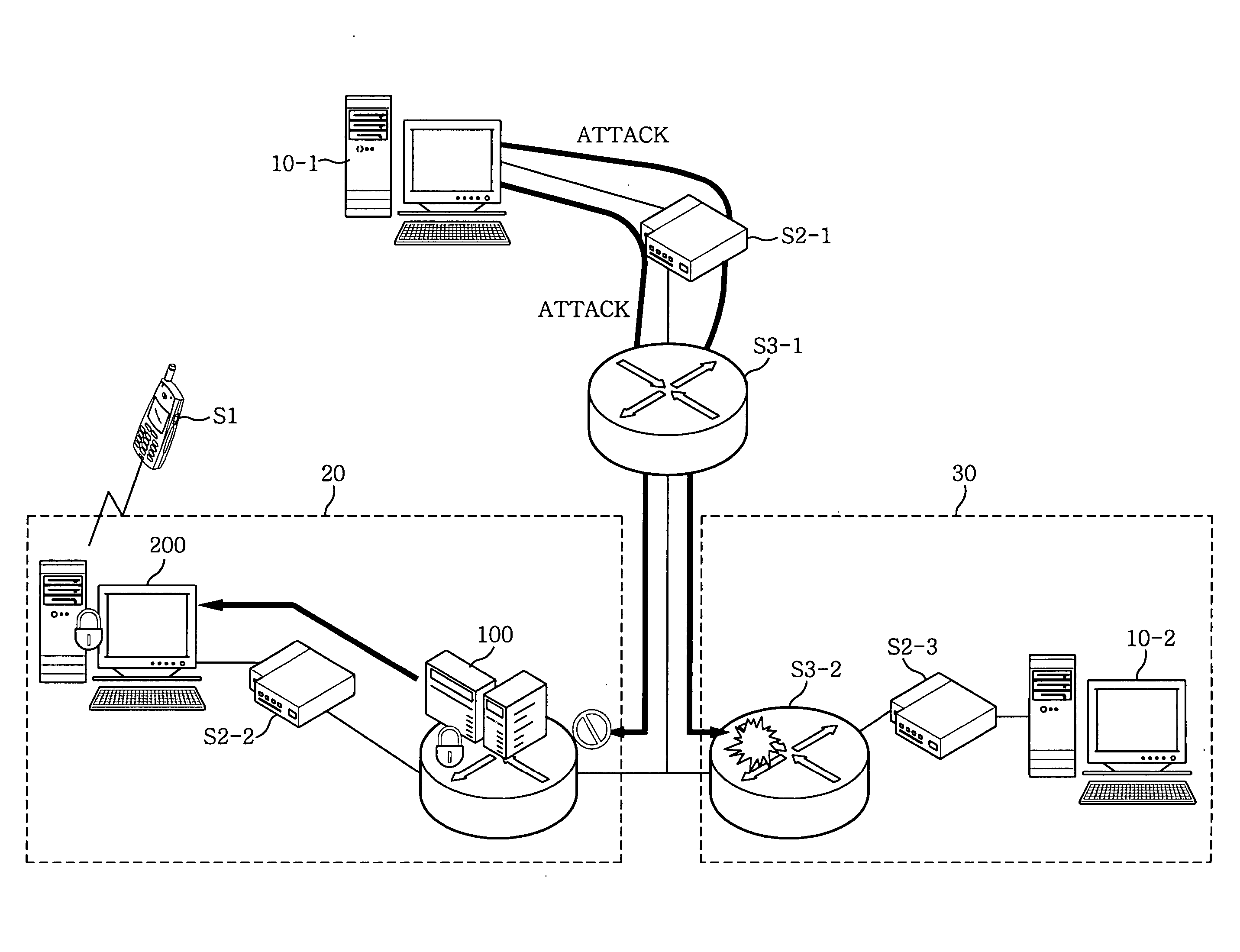
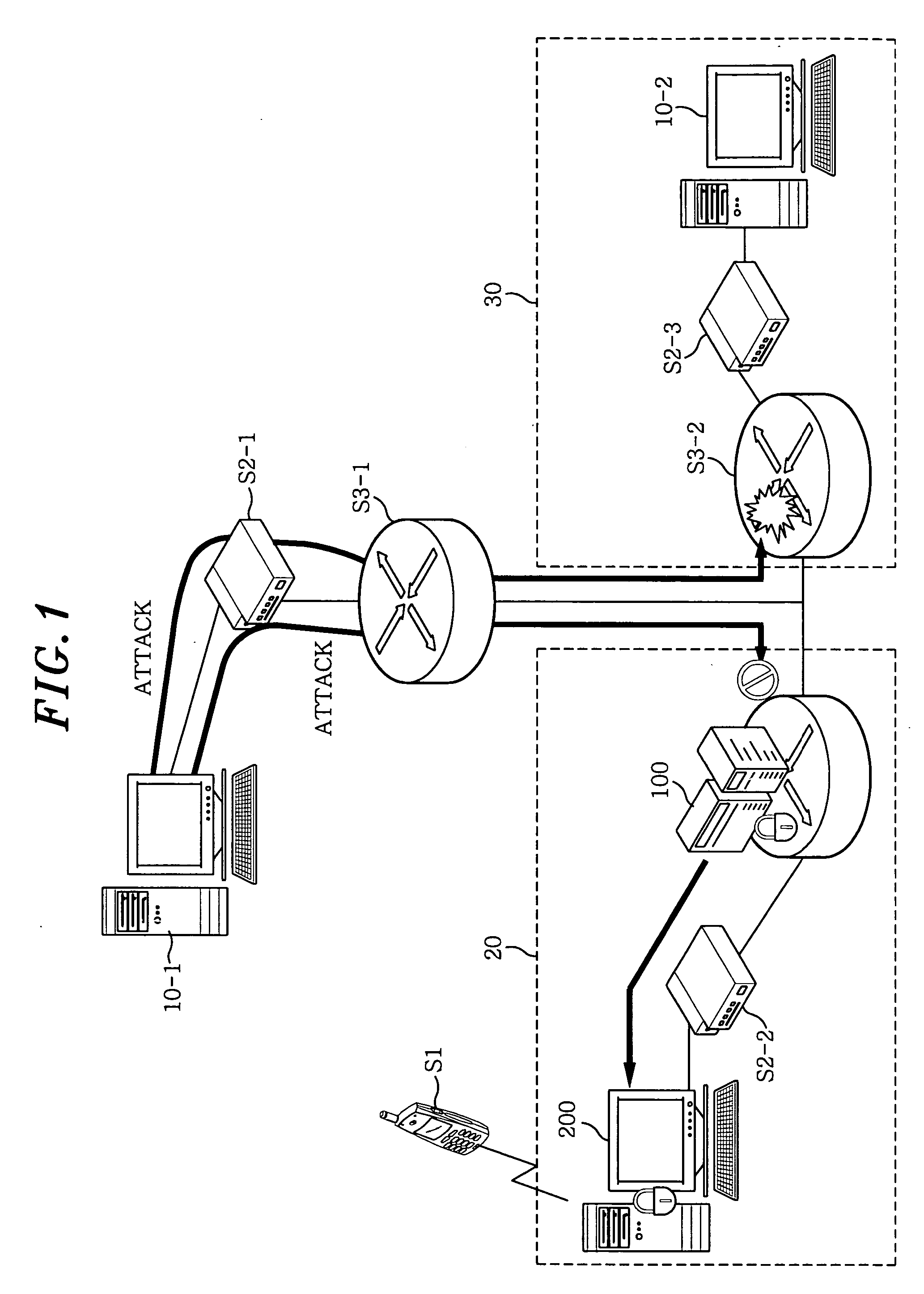
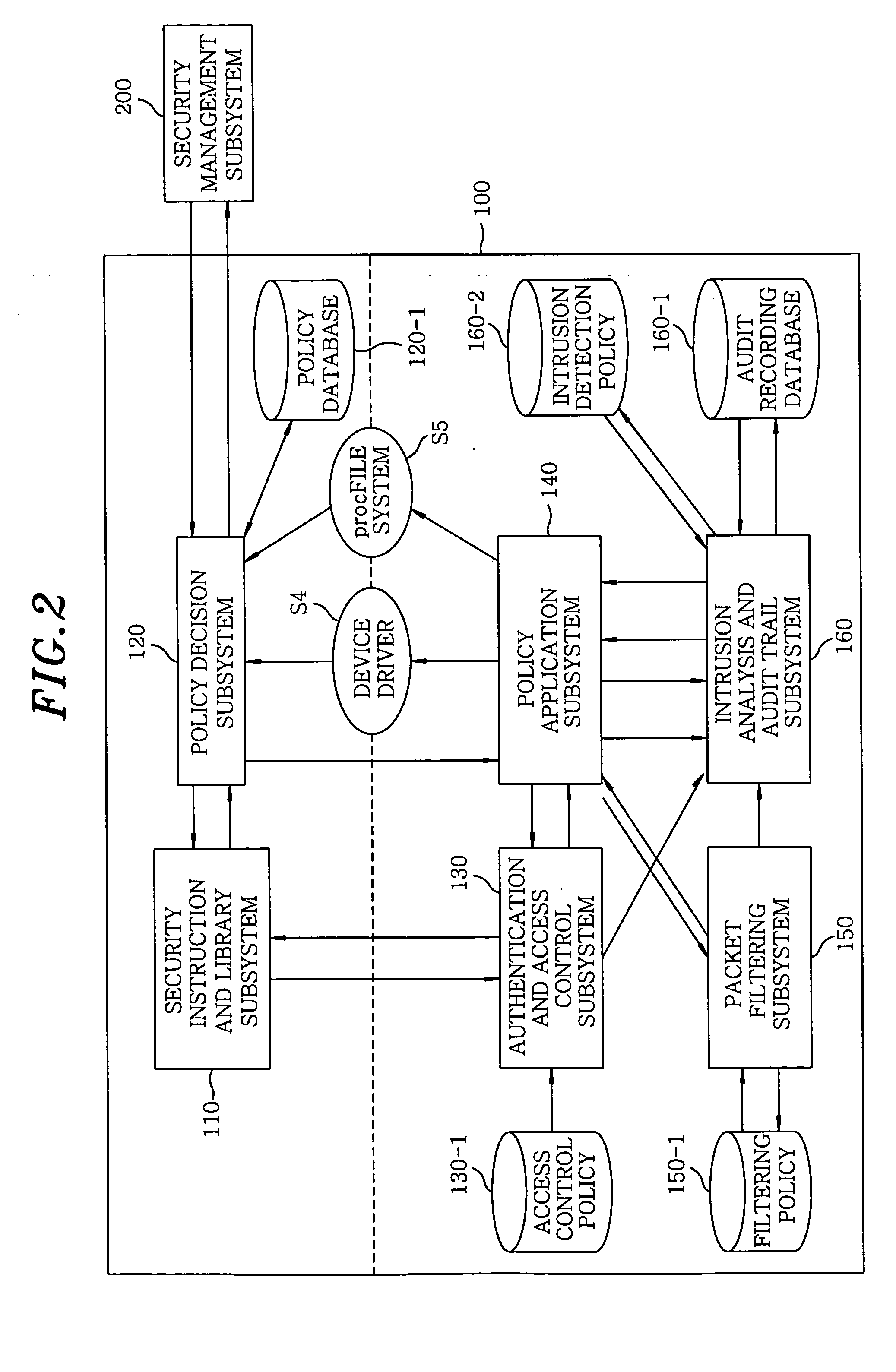
Method and apparatus for security engine management in network nodes
InactiveUS20050071650A1User identity/authority verificationDigital computer detailsPolicy decisionSystems management
In a security engine management apparatus in network nodes, a security instruction and library subsystem processes every application program and utility. A policy decision subsystem determines a filtering policy, an intrusion detection policy and an access control policy. An authentication and access control subsystem blocks an unauthorized user to access to a system and allows an authorized user to access thereto according to the access control policy. A policy application subsystem applies the policies. A packet filtering subsystem receives an allowed packet and denies a disallowed packet according to the filtering policy. An intrusion analysis and audit trail subsystem analyzes the intrusion according to the intrusion detection policy. A security management subsystem manages a security engine.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for a distributed firewall
InactiveUS20060070122A1Multiple digital computer combinationsProgram controlAuthenticationDistributed firewall
A method and apparatus for implementing a distributed firewall is described. A packet filter processor receives a packet sent from a first device to a second device. The packet filter processor authenticates an identifier for the packet. For example, authentication could be performed using a cryptographically-verifiable identifier. The packet filter processor determines whether to send the packet to the second device, based on the authentication and a set of policy rules. The packet filter processor sends the packet to the second device in accordance with the determination
Owner:RPX CORP
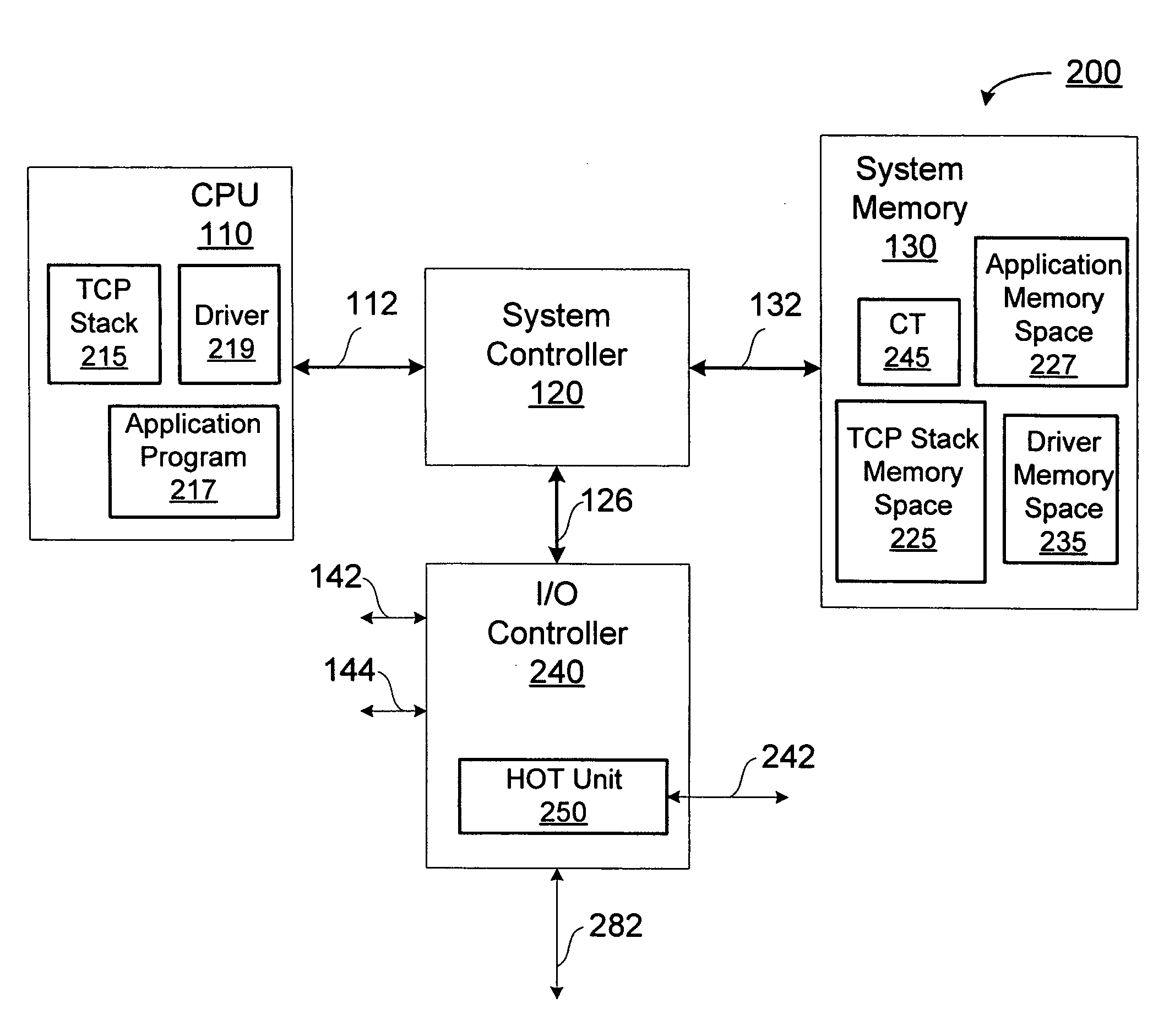
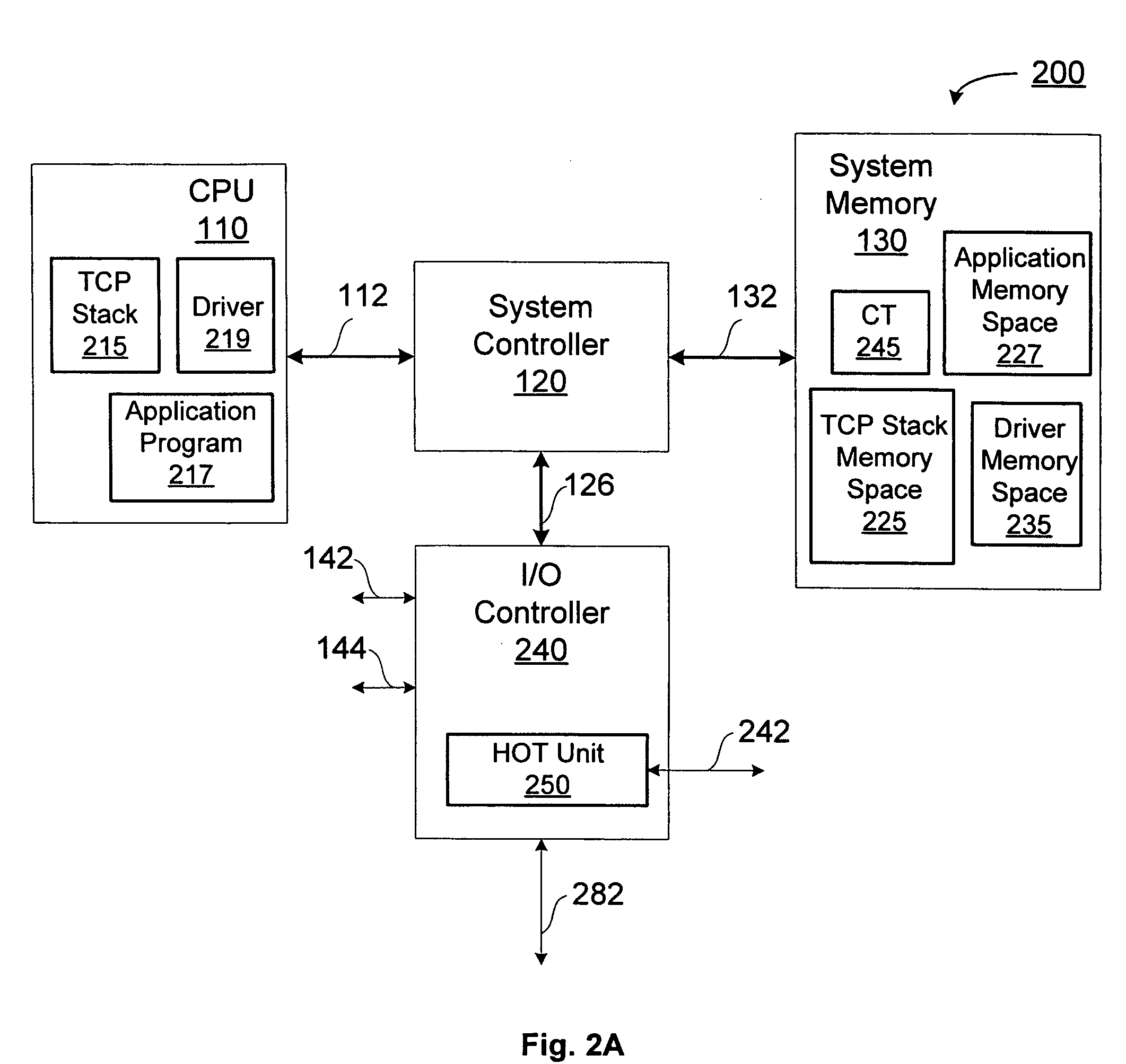
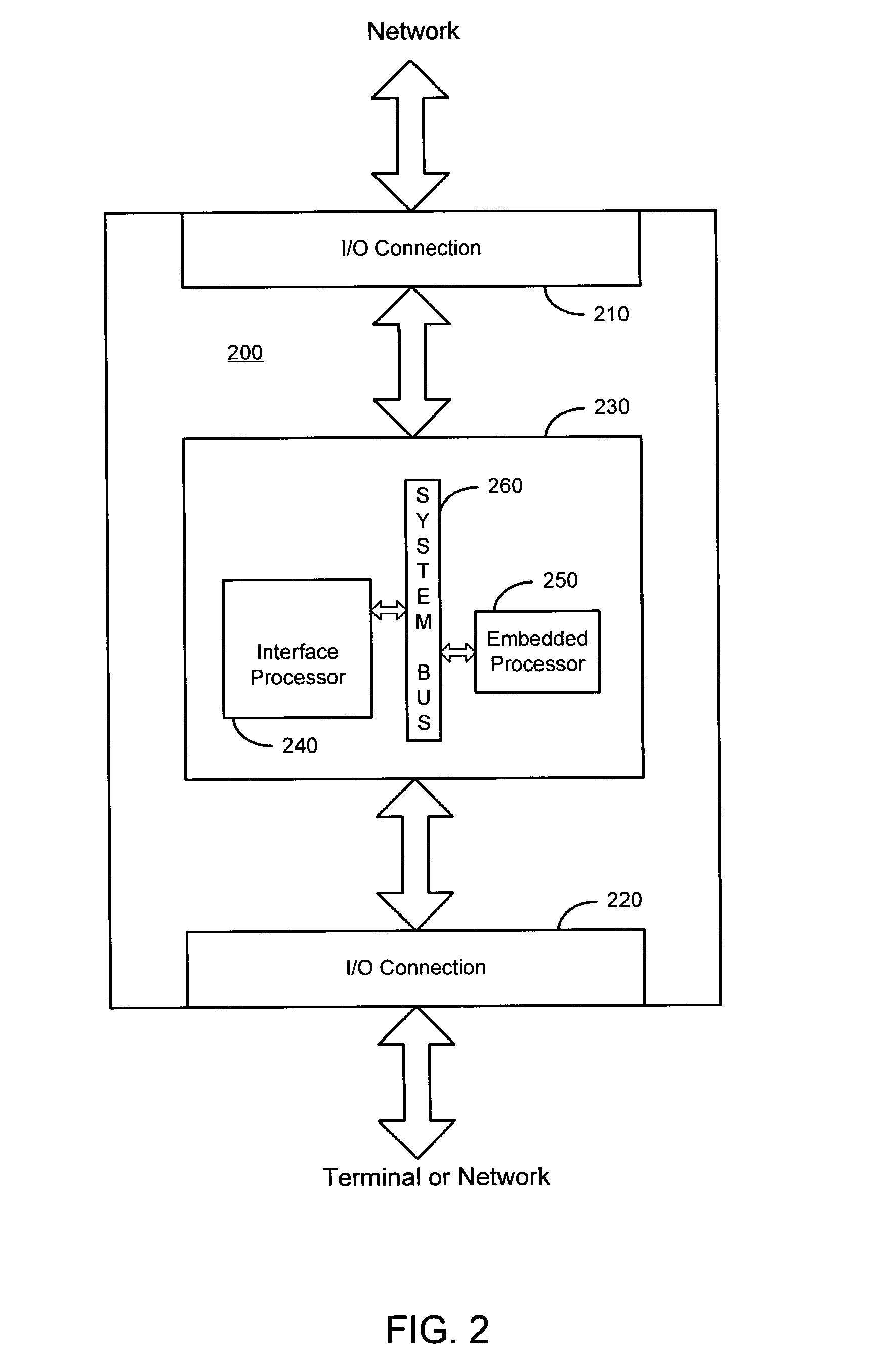
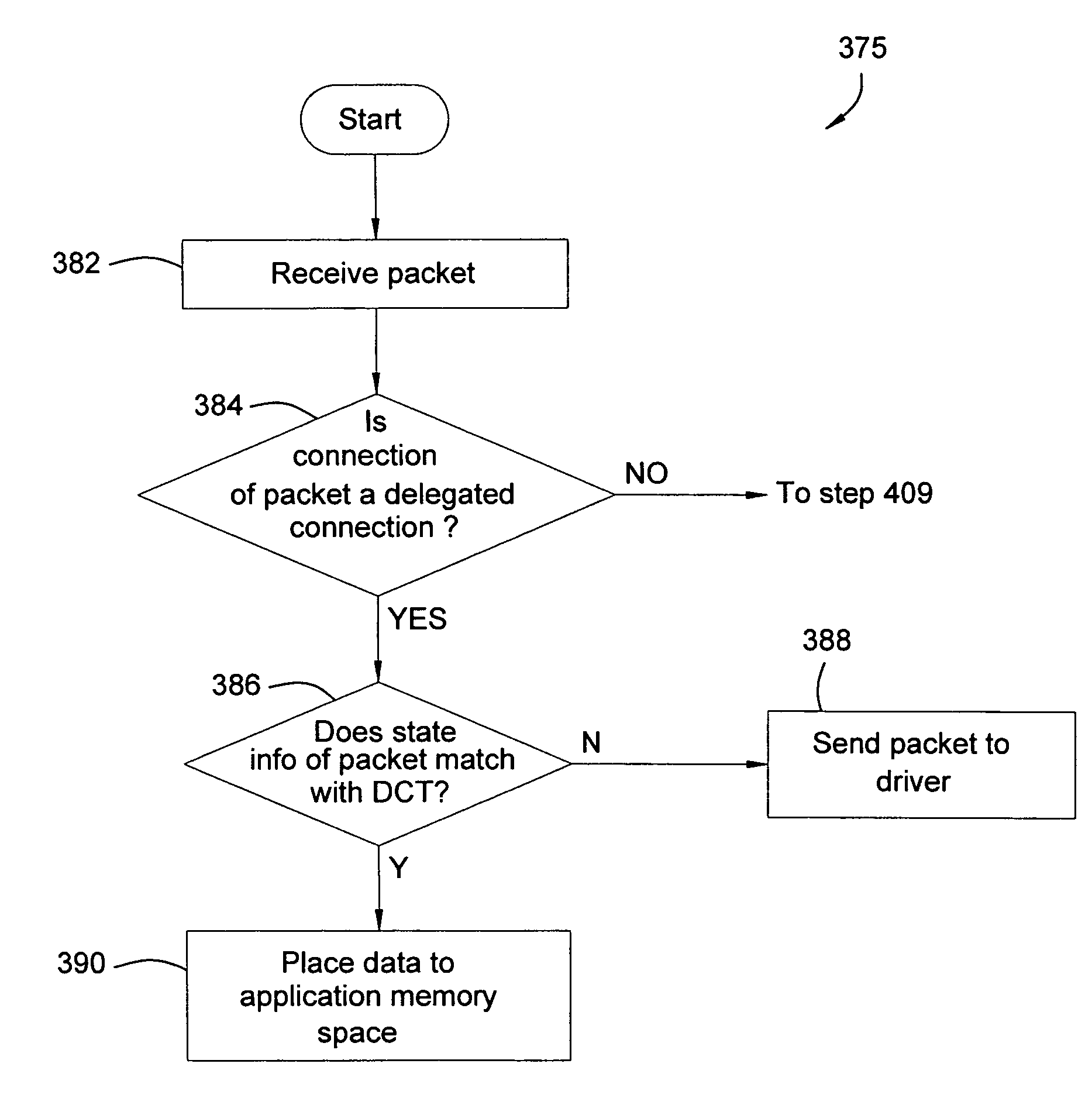
Using TCP/IP offload to accelerate packet filtering
A method and apparatus for filtering a packet on a connection within a computing system. In one embodiment, the method includes: receiving the packet; delegating the packet to an offload unit for filtering the packet; and determining, by the offload unit, whether the connection is a delegated connection.
Owner:NVIDIA CORP
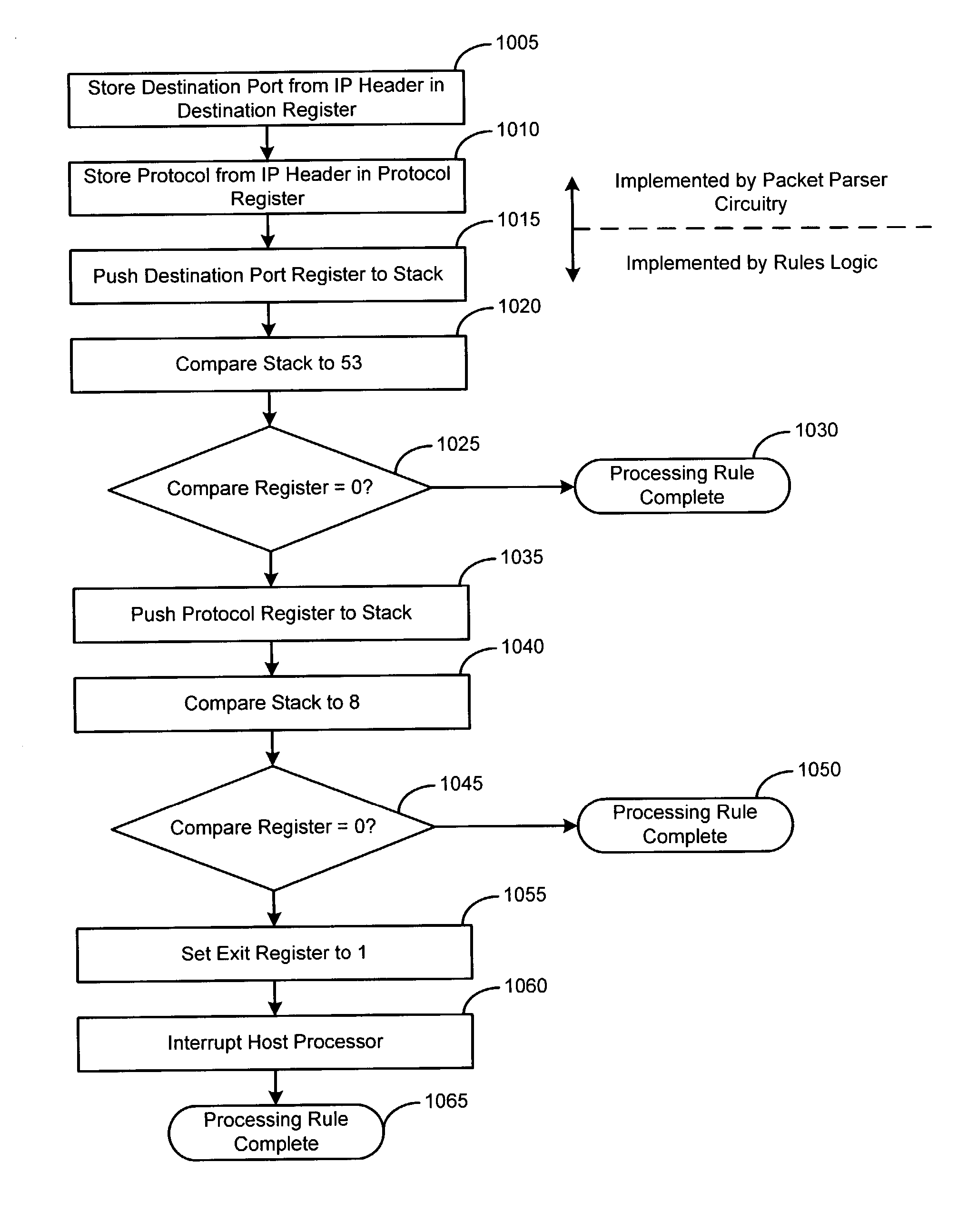
Hardware-based packet filtering accelerator
InactiveUS20040039940A1Digital computer detailsConcurrent instruction executionProcessor registerParallel computing
A data packet filtering accelerator processor operates in parallel with a host processor and is arranged on an integrated circuit with the host processor. The accelerator processor classifies data packets by executing a sequence machine code instructions converted directly from a set of rules. Portions of data packets are passed to the accelerator processor from the host processor. The accelerator processor includes packet parser circuit for parsing the data packets into relevant data units and storing the relevant data units in memory. A packet analysis circuit executes the sequence of machine code instructions converted directly from the set of rules. The machine code instruction sequence operates on the relevant data units to classify the data packet. The packet analysis circuit returns the results of the classification to the host processor by storing the classification results in a register accessible by the host processor.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Using TCP/IP offload to accelerate packet filtering
ActiveUS7420931B2Error preventionFrequency-division multiplex detailsComputing systemsPacket filtering
A method and apparatus for filtering a packet on a connection within a computing system. In one embodiment, the method includes: receiving the packet; delegating the packet to an offload unit for filtering the packet; and determining, by the offload unit, whether the connection is a delegated connection.
Owner:NVIDIA CORP
Methods, systems, and computer readable media for adaptive packet filtering
ActiveUS8495725B2Easy to processImprove performanceComputer security arrangementsMultiple digital computer combinationsSubject matterSelf adaptive
The subject matter described herein includes methods, systems, and computer readable media for adaptive packet filtering. One method includes identifying at least one subset of rules and an ordered set of firewall packet filtering rules that defines a firewall policy such that the subset contains disjoint rules. Disjoint rules are defined as rules whose order can be changed without changing integrity of the firewall policy. Rules in the subset are sorted to statistically decrease the number of comparisons that will be applied to each packet that a firewall encounters. Packets are filtered at the firewall using the sorted rules in the subset by comparing each packet to each of the sorted rules in the subset until the packet is allowed or denied and ceasing the comparing for the packet in response to the packet being allowed or denied and thereby achieving sub-linear searching for packets filtered using the sorted rules in the subset.
Owner:CENTRIPETAL NETWORKS LLC
Method and system for network management providing access to application bandwidth usage calculations
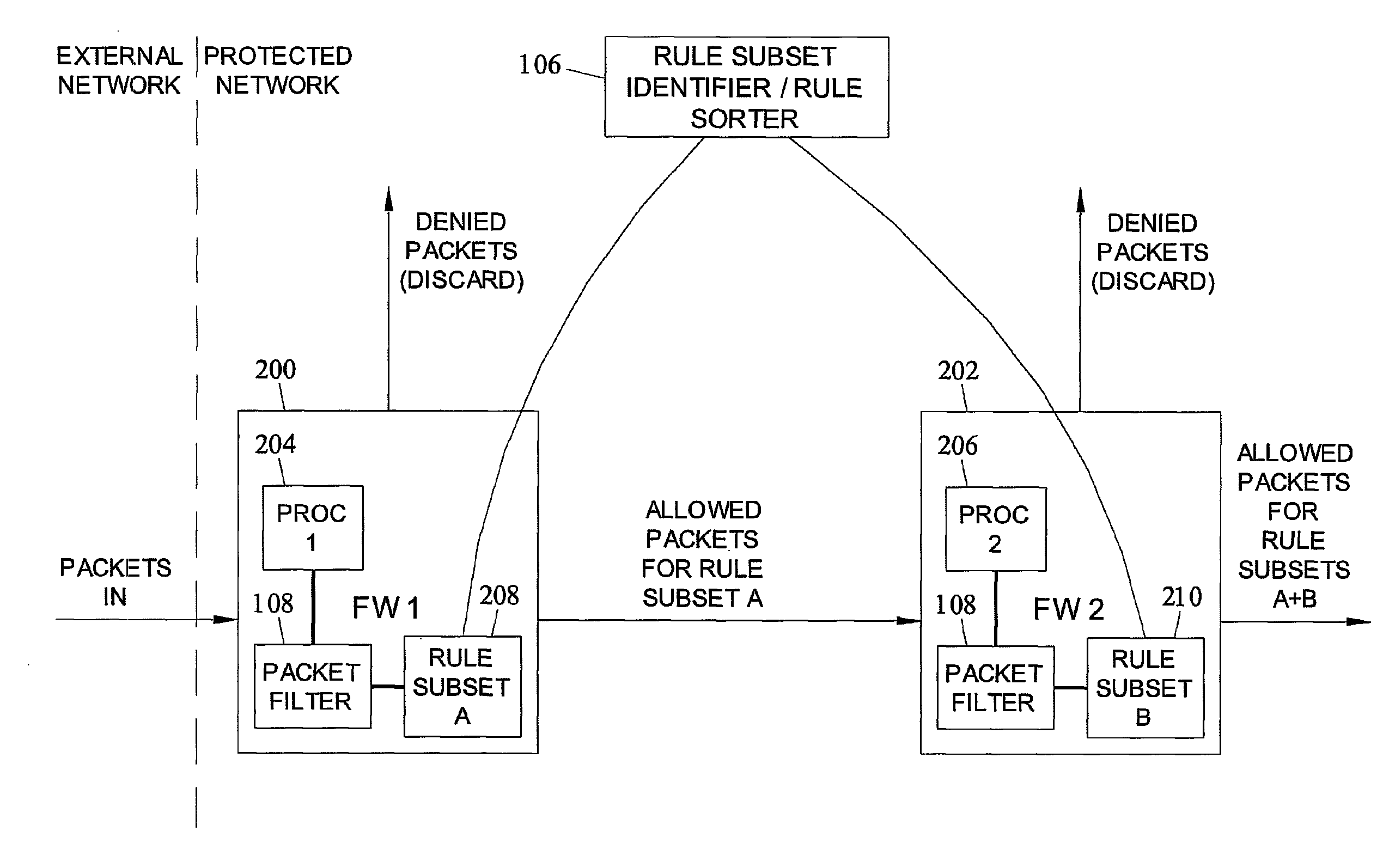
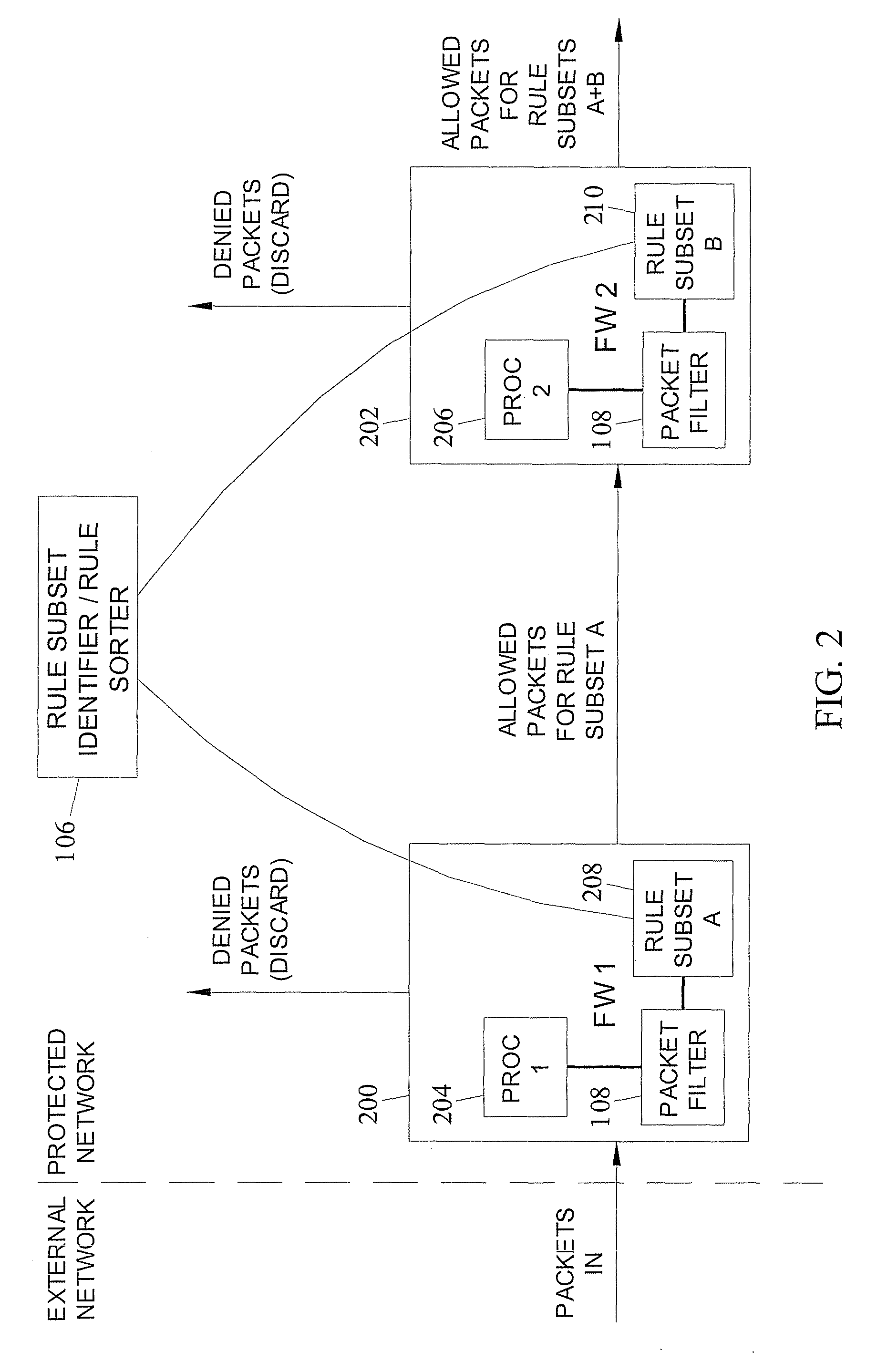
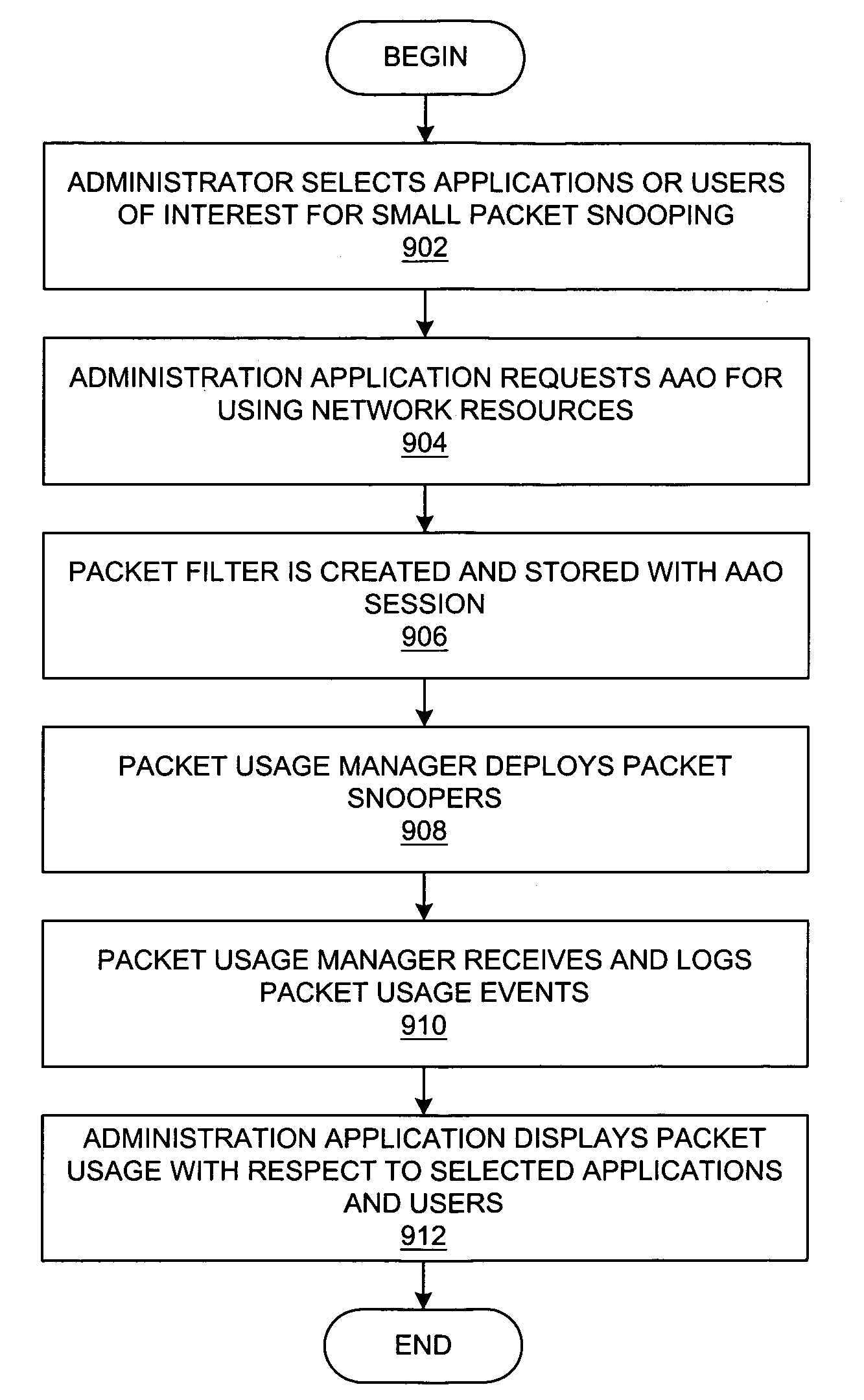
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. The network management framework is able to monitor multiple sources of network packets on various subnets within the distributed data processing system; distributed packet snoopers are deployed from a packet usage manager to monitor the multiple sources of network packets. The system administrator can request packet filtering based upon selected active users or active applications. A bandwidth history database is compiled from bandwidth usage data associated with multiple entities within the data processing system, including users, applications, and / or endpoints within the data processing system. In response to a requested action within the data processing system, bandwidth usage for the requested action can be predicted with reference to the bandwidth history database. The actual and predicted bandwidth usage of requested actions can be displayed to the system administrator in real time.
Owner:CITRIX SYST INT
Method and system for communication control in a computing environment
InactiveUS7200865B1Easy to useEasy to scaleMemory loss protectionError detection/correctionControl systemInterconnection
An access control system for a computing environment in which a number of processing nodes are interconnected to one another via an interconnection system. Multiple program applications, each made up of a number of application components, are installed in the environment, such that their components may be distributed among the various processing nodes of the platform. A set of rules is established, indicating allowed inter-node communications between the application components, and those rules are mapped onto a set of logic in the platform. The logic may be embodied in various forms, such as packet-filtering logic in a network interconnect switch, or firewall logic in a processing node. In turn, when an application component on one node attempts to communication with another application component on another node, a determination can be made whether the communication is allowed and, if the communication is not allowed, the communication can be blocked.
Owner:T MOBILE INNOVATIONS LLC
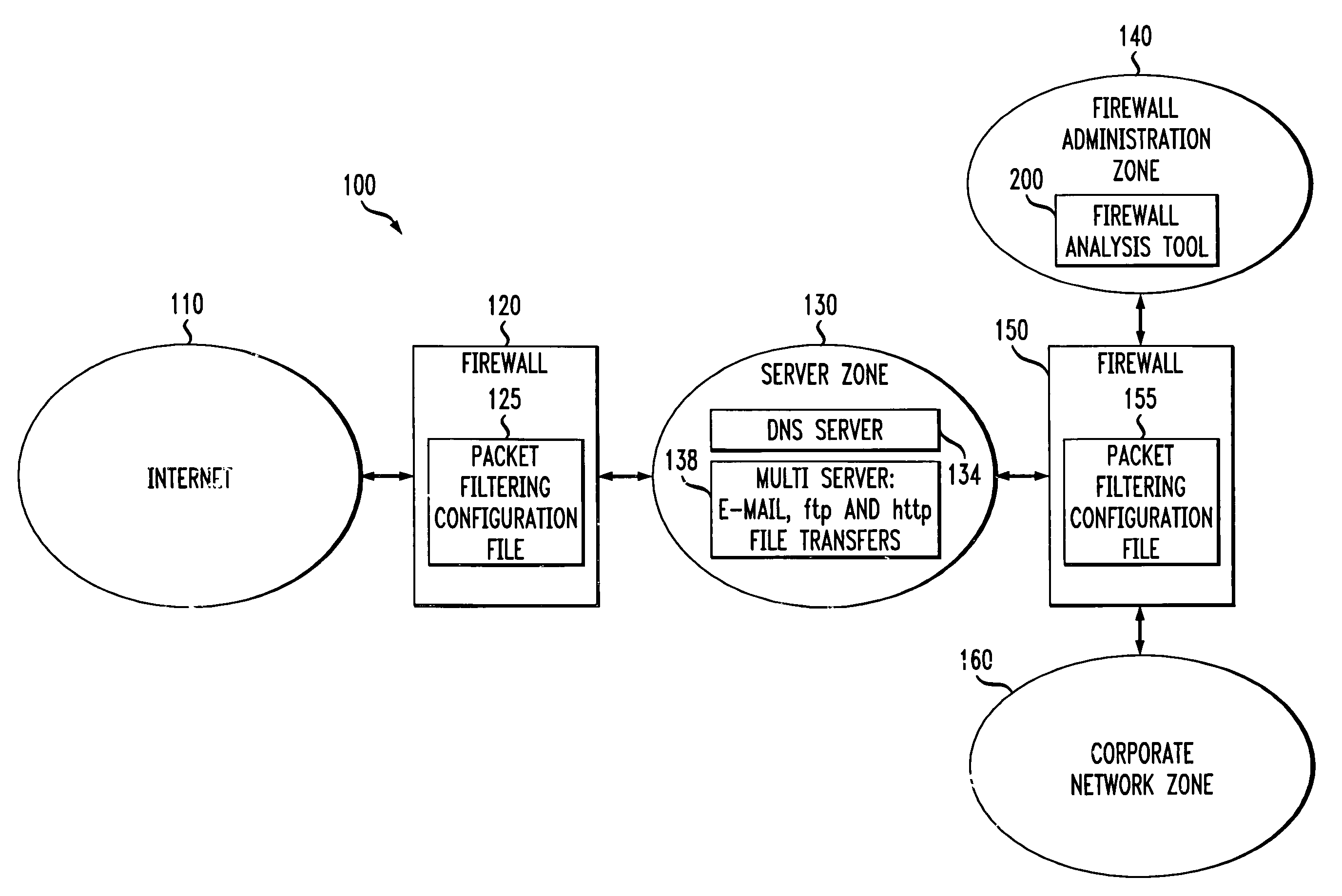
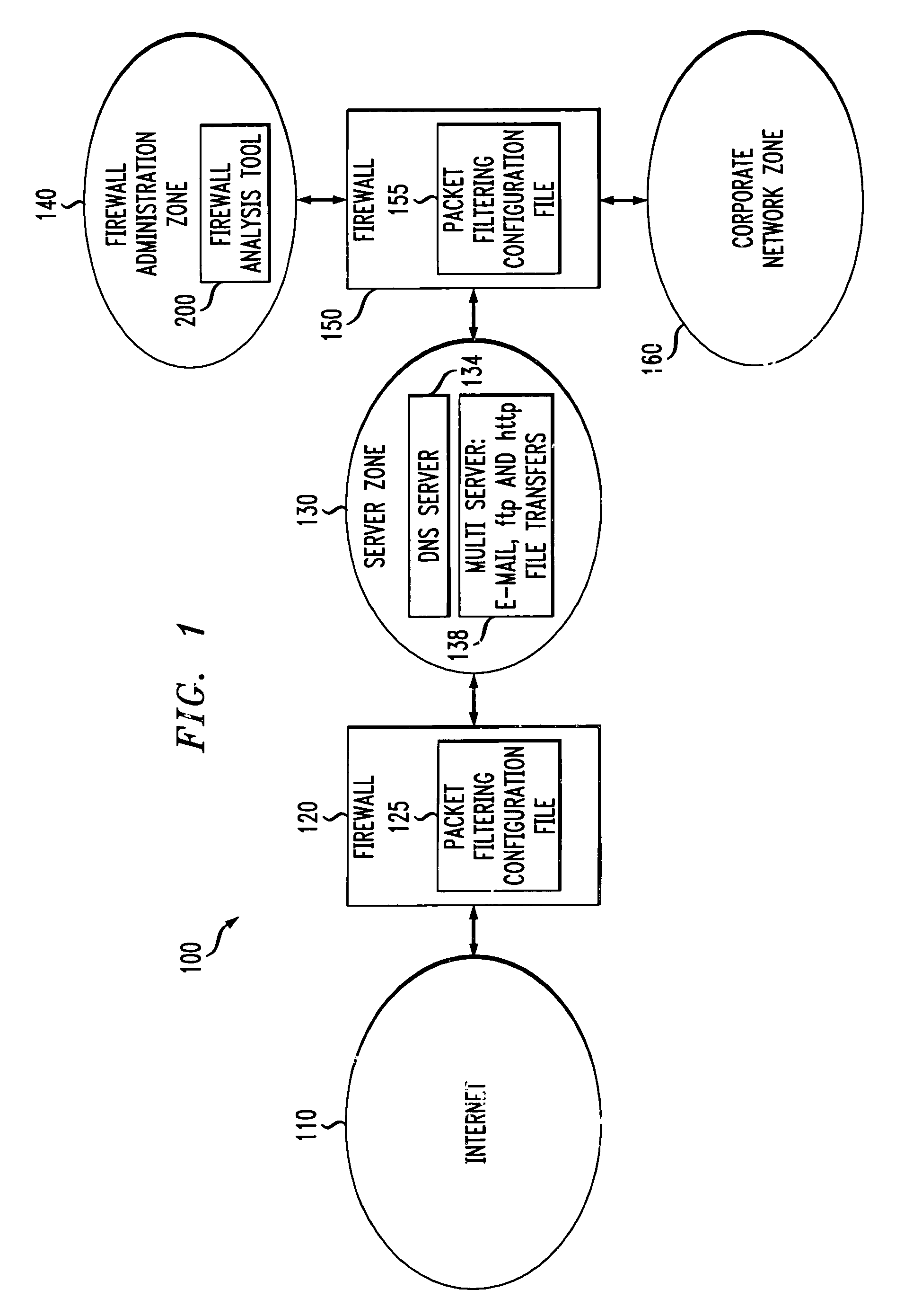
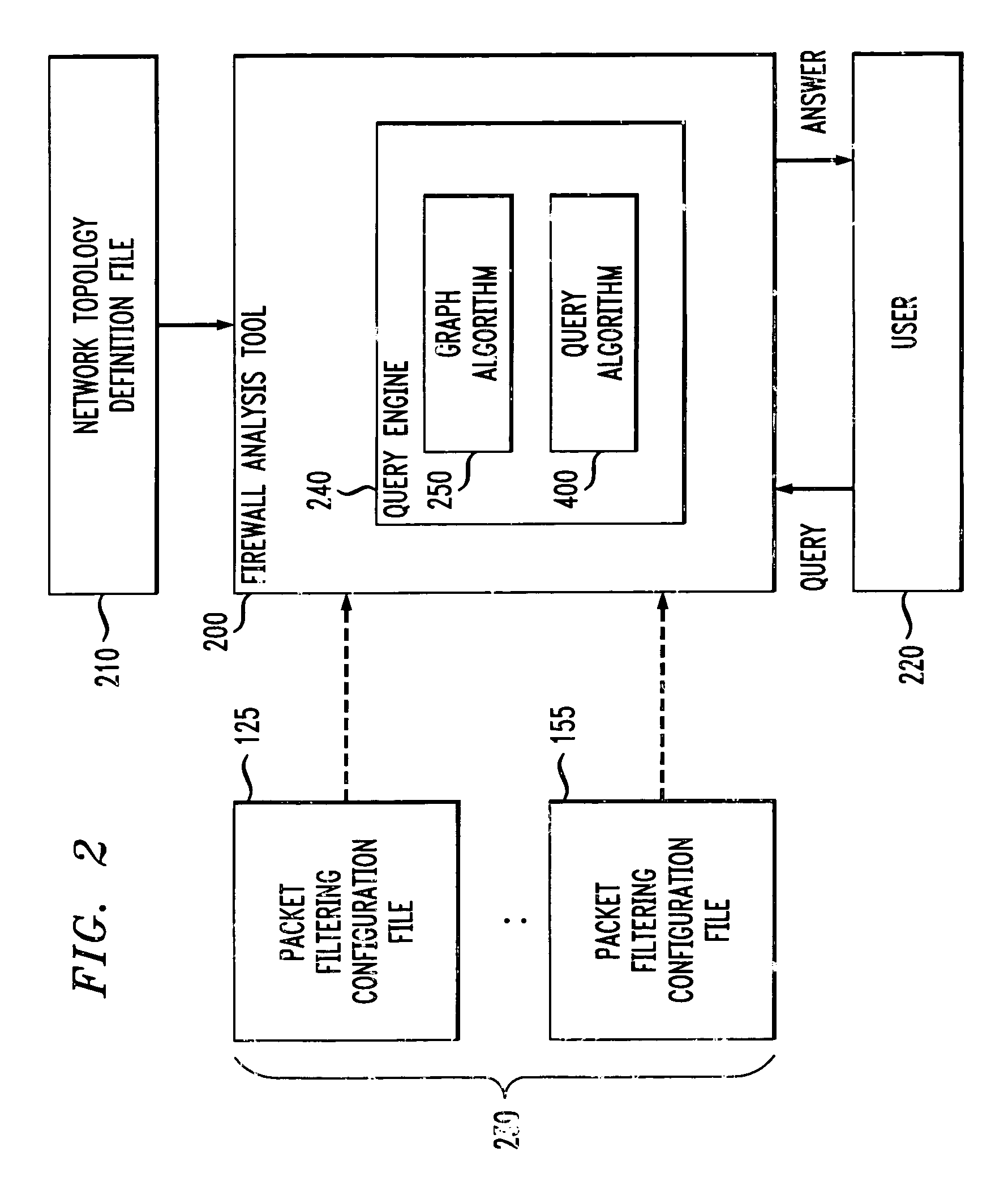
Method and apparatus for analyzing one or more firewalls
InactiveUS7016980B1Multiple digital computer combinationsProgram controlGraphicsGraphical user interface
A method and apparatus are disclosed for analyzing the operation of one or more network gateways, such as firewalls or routers, that perform a packet filtering function in a network environment. Given a user query, the disclosed firewall analysis tool simulates the behavior of the various firewalls, taking into account the topology of the network environment, and determines which portions of the services or machines specified in the original query would manage to reach from the source to the destination. The relevant packet-filtering configuration files are collected and an internal representation of the implied security policy is derived. A graph data structure is used to represent the network topology. A gateway-zone graph permits the firewall analysis tool to determine where given packets will travel in the network, and which gateways will be encountered along those paths. In this manner, the firewall analysis tool can evaluate a query object against each rule-base object, for each gateway node in the gateway-zone graph that is encountered along each path between the source and destination. A graphical user interface is provided for receiving queries, such as whether one or more given services are permitted between one or more given machines, and providing results. A spoofing attack can be simulated by allowing the user to specify where packets are to be injected into the network, which may not be the true location of the source host-group.
Owner:ALCATEL-LUCENT USA INC
Providing secure network access for short-range wireless computing devices
InactiveUS6851050B2Improve system performanceImprove scalabilityKey distribution for secure communicationUser identity/authority verificationEncrypted functionClient-side
The present invention provides methods, systems, and computer program instructions for providing location-independent packet routing and secure access in a wireless networking environment (such as that encountered within a building), enabling client devices to travel seamlessly within the environment. Each client device uses a constant address. An address translation process that is transparent to the client and server is automatically performed as the device roams through the environment, enabling efficient client migration from one supporting access point to another. The secure access techniques provide user-centric authentication and allow policy-driven packet filtering, while taking advantage of encryption capabilities that are built in to the hardware at each endpoint.
Owner:REEFEDGE
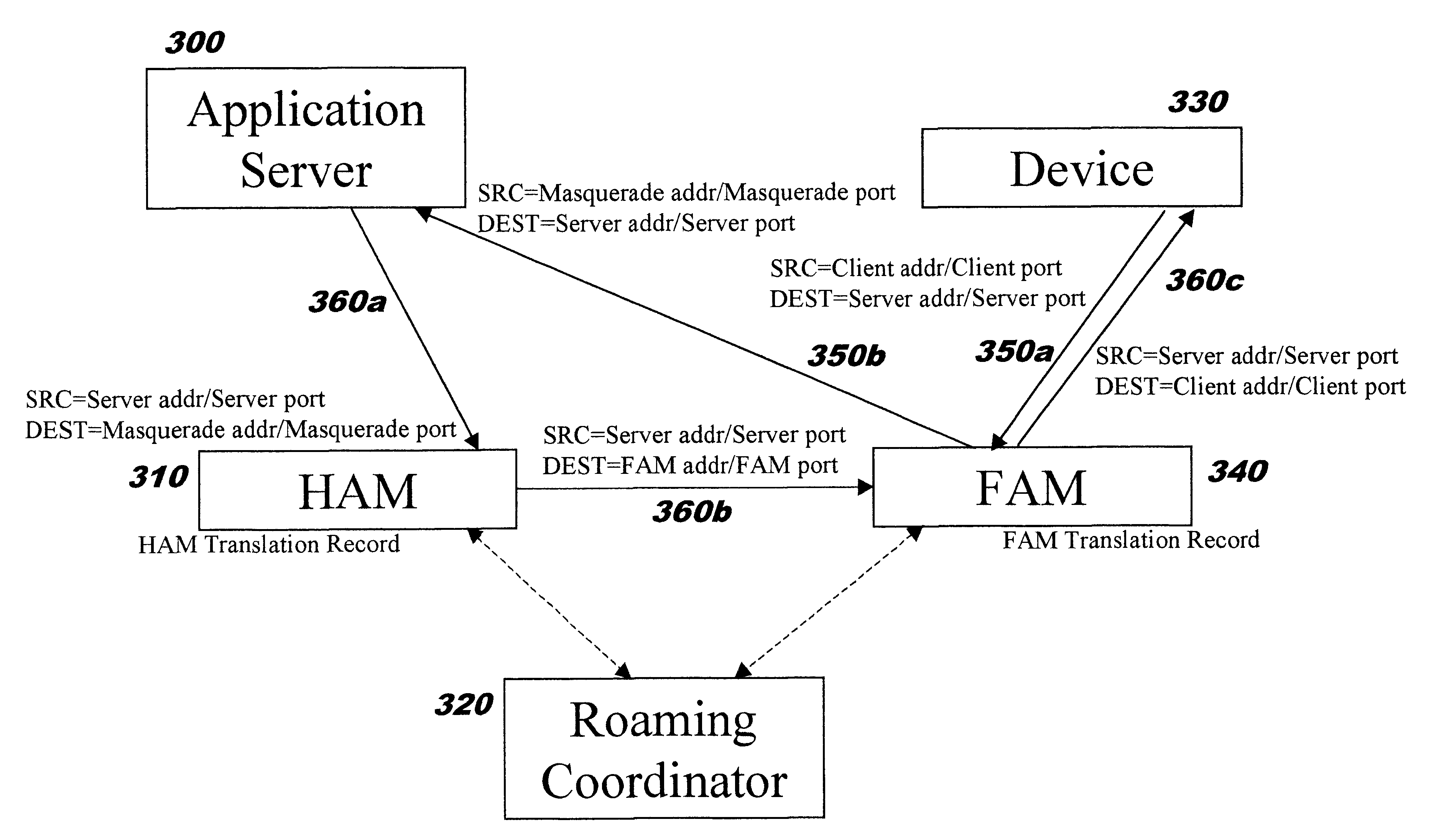
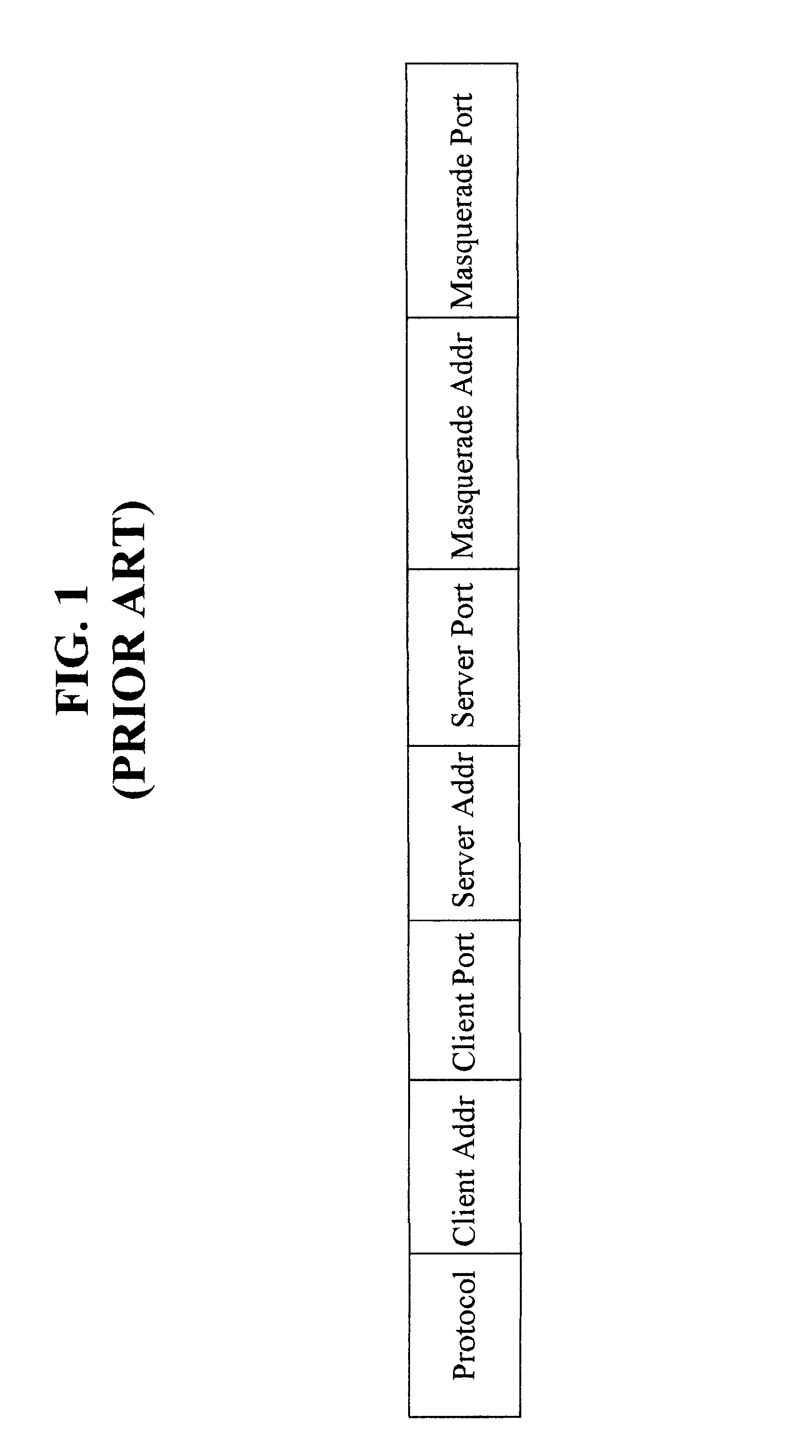
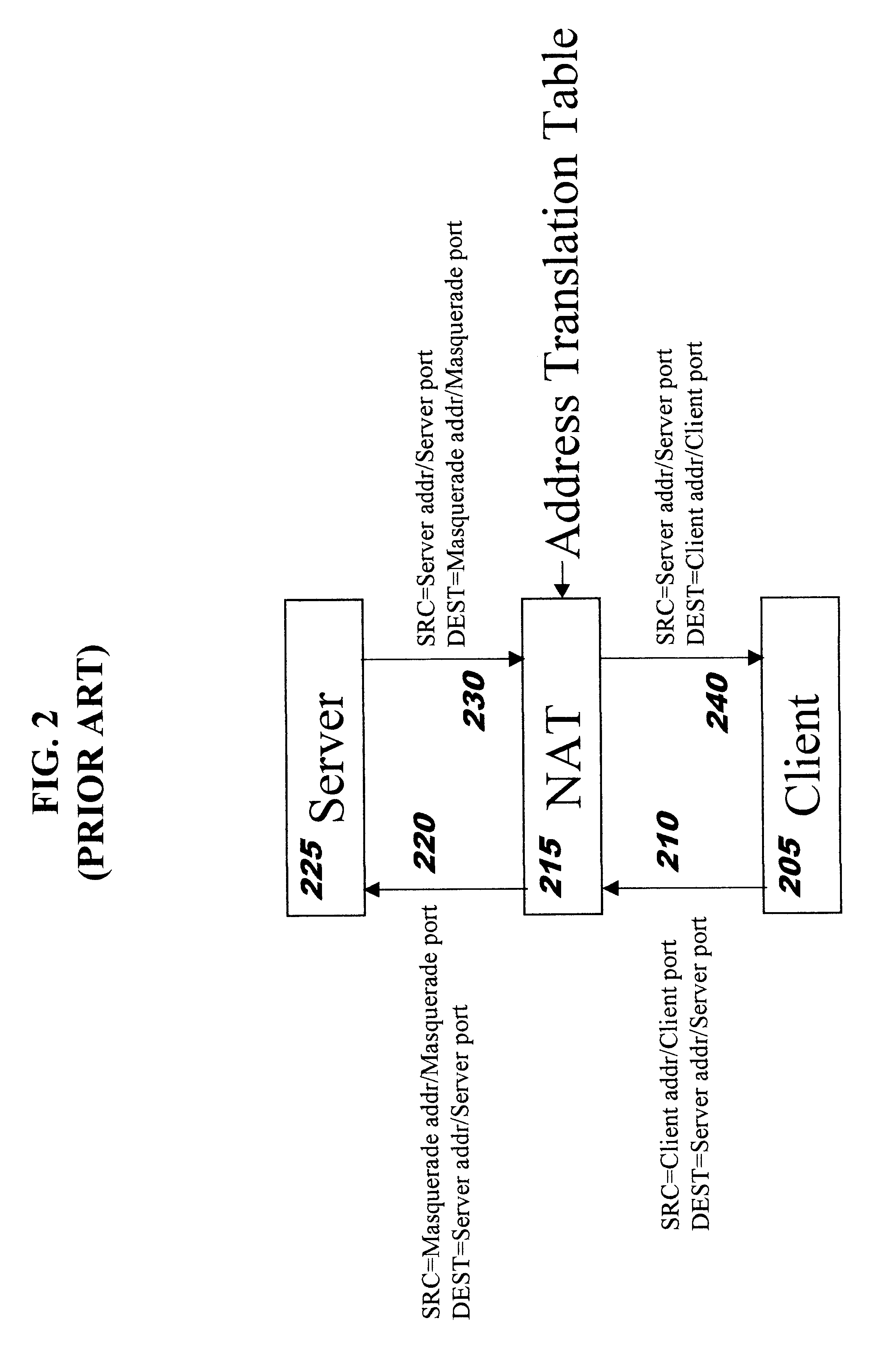
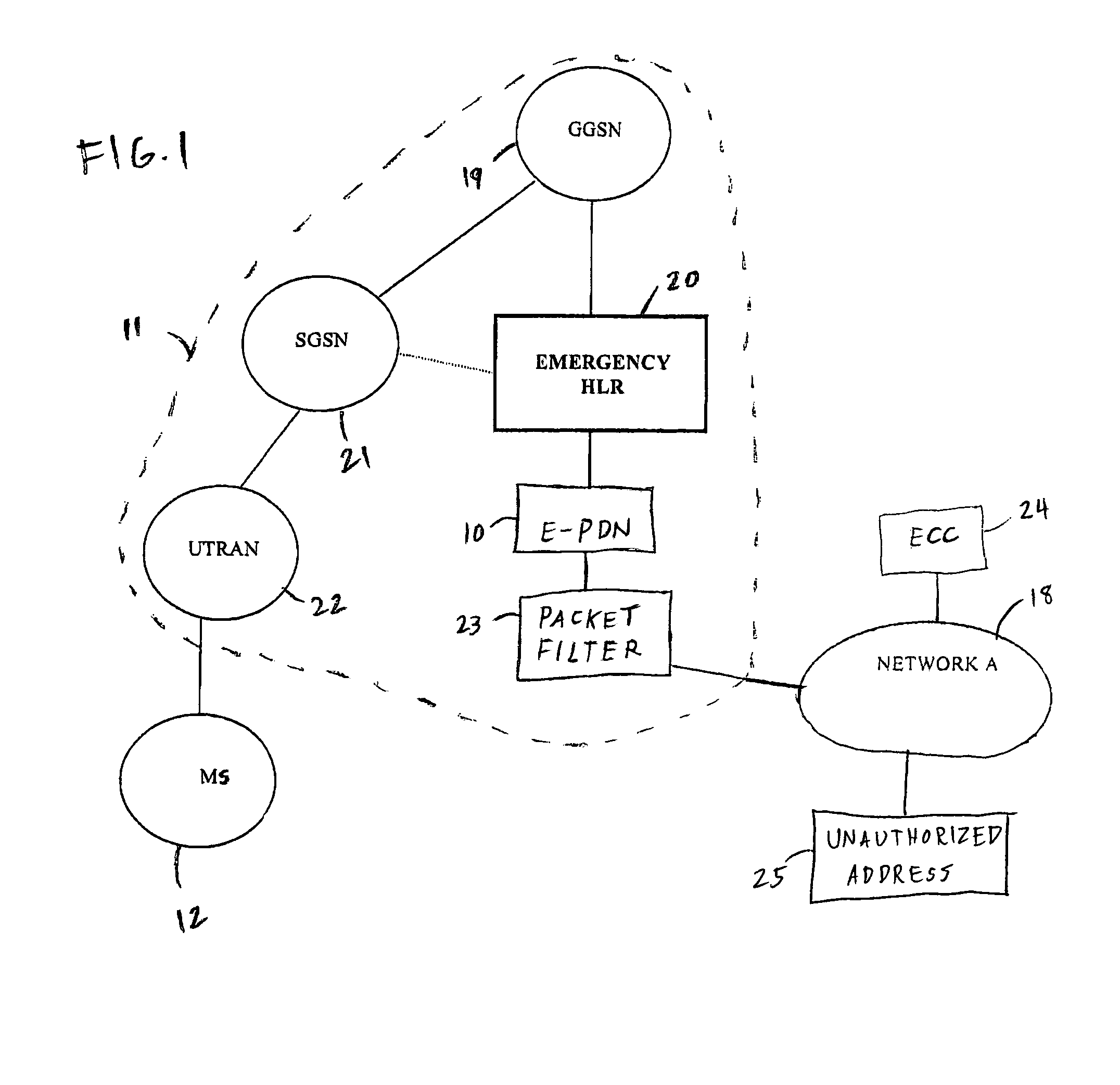
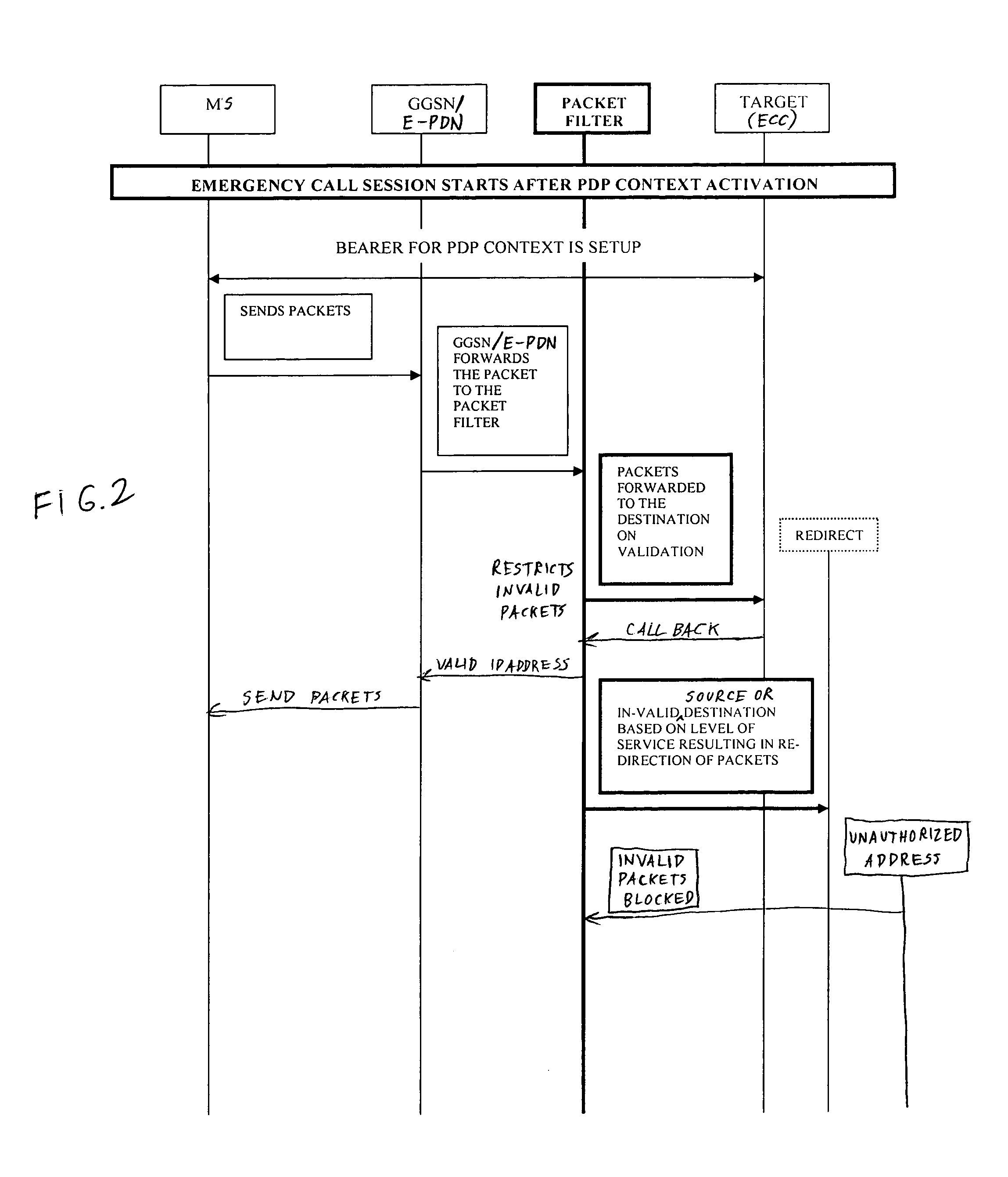
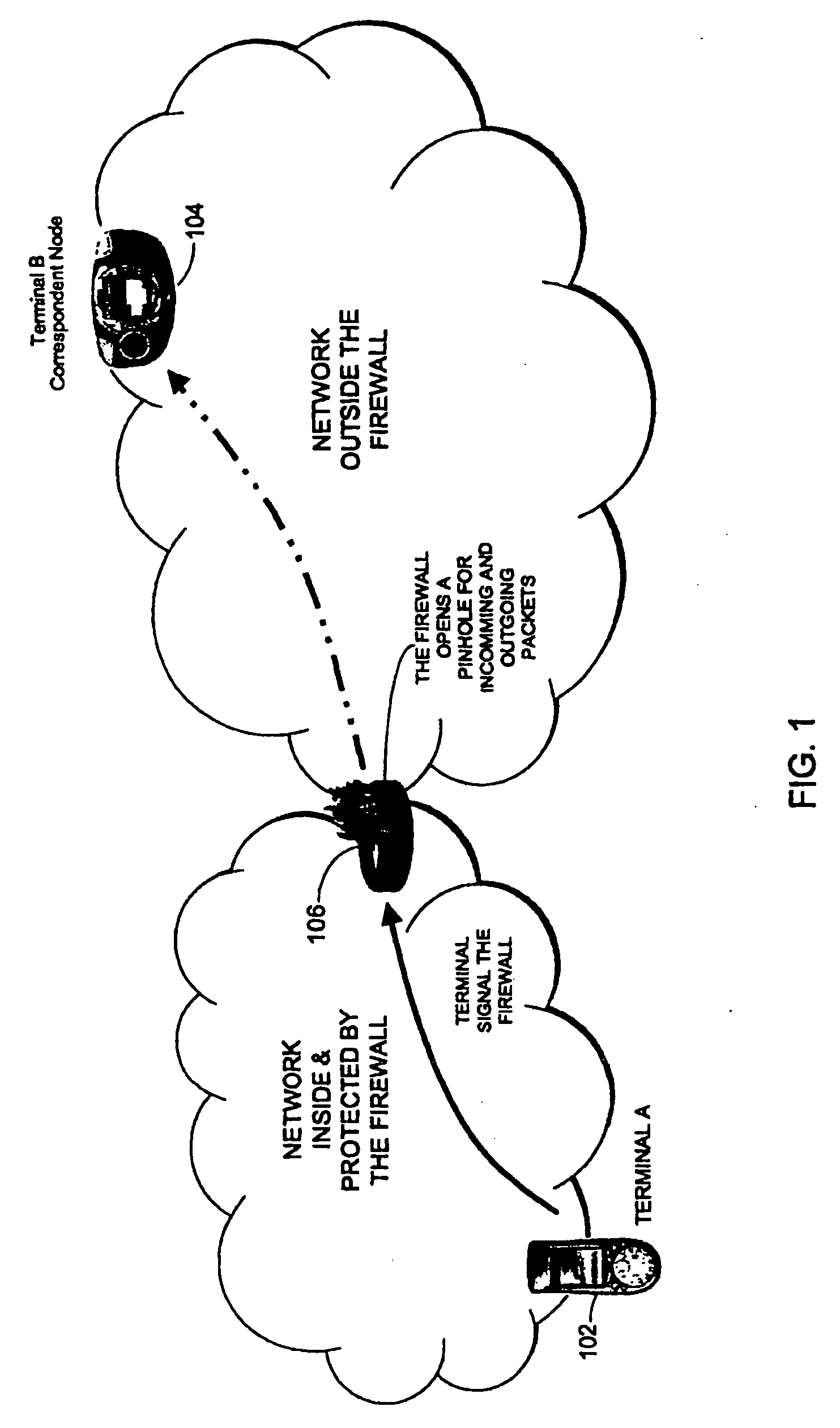
Packet filtering for emergency service access in a packet data network communication system
InactiveUS7539186B2Emergency connection handlingTelephonic communicationCommunications systemIp address
A method and apparatus method of filtering packet data for an anonymous user device in a packet data network communication system includes a first step of initiating a call from an anonymous user device on a home network. A next step includes assigning an interim identity and interim IP address to the user device. A next step includes determining a level of service access of the data packets from the user device. A next step includes mapping the level of service access of the user device to the IP address. A next step includes defining permissible routing identities per the level of service access. A next step includes routing the data packets of the call along with the associated IP address to only those location addresses from the defining step.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
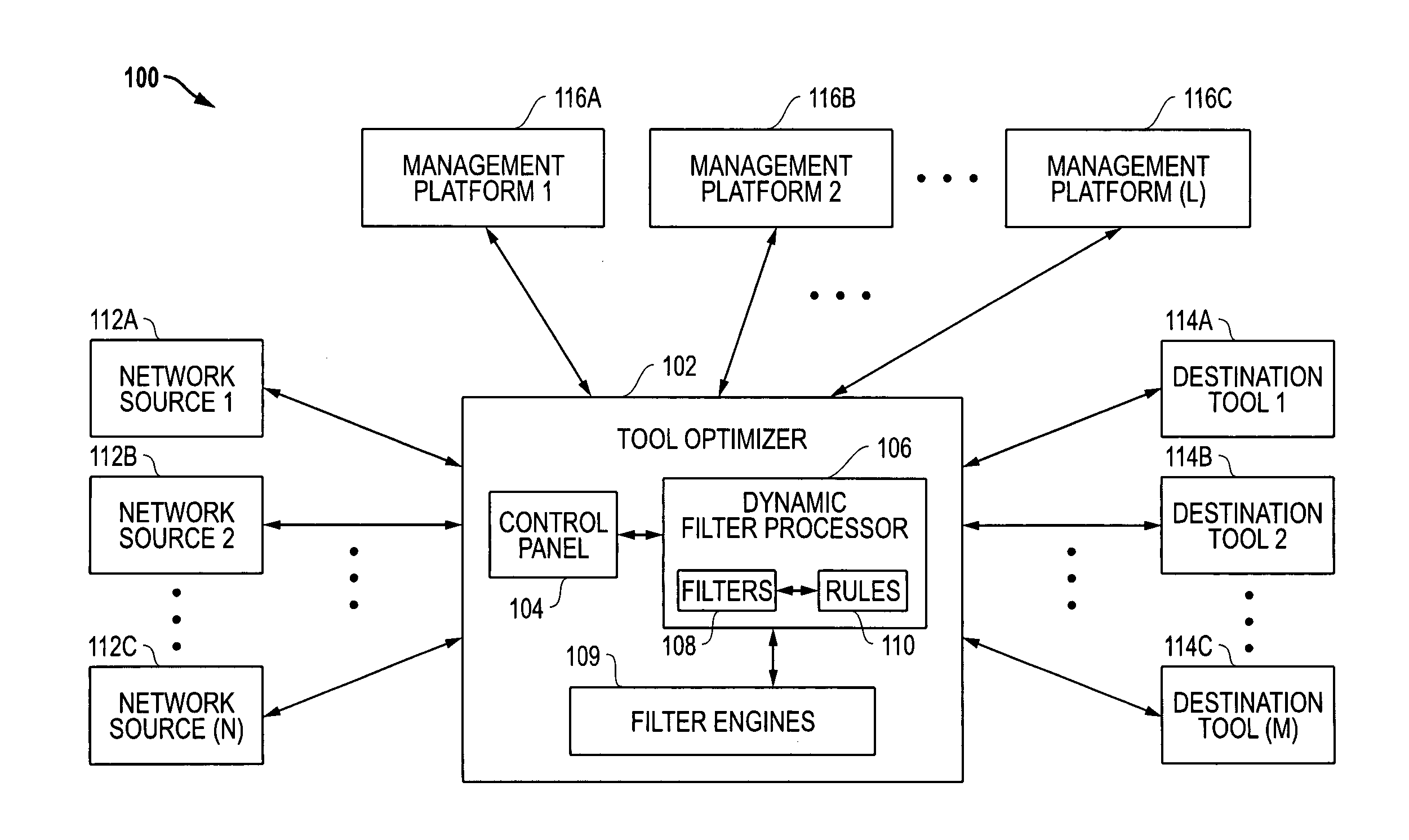
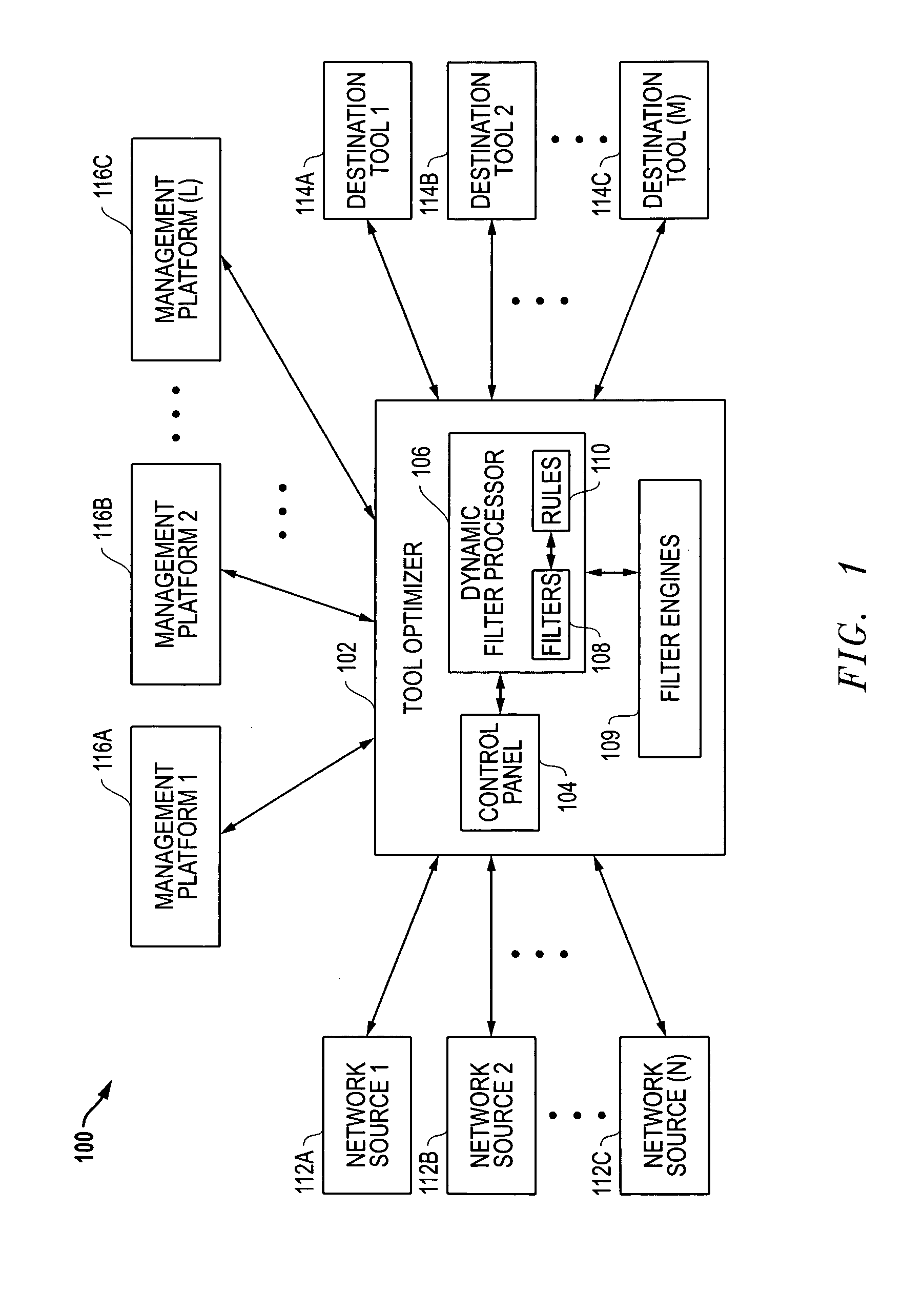
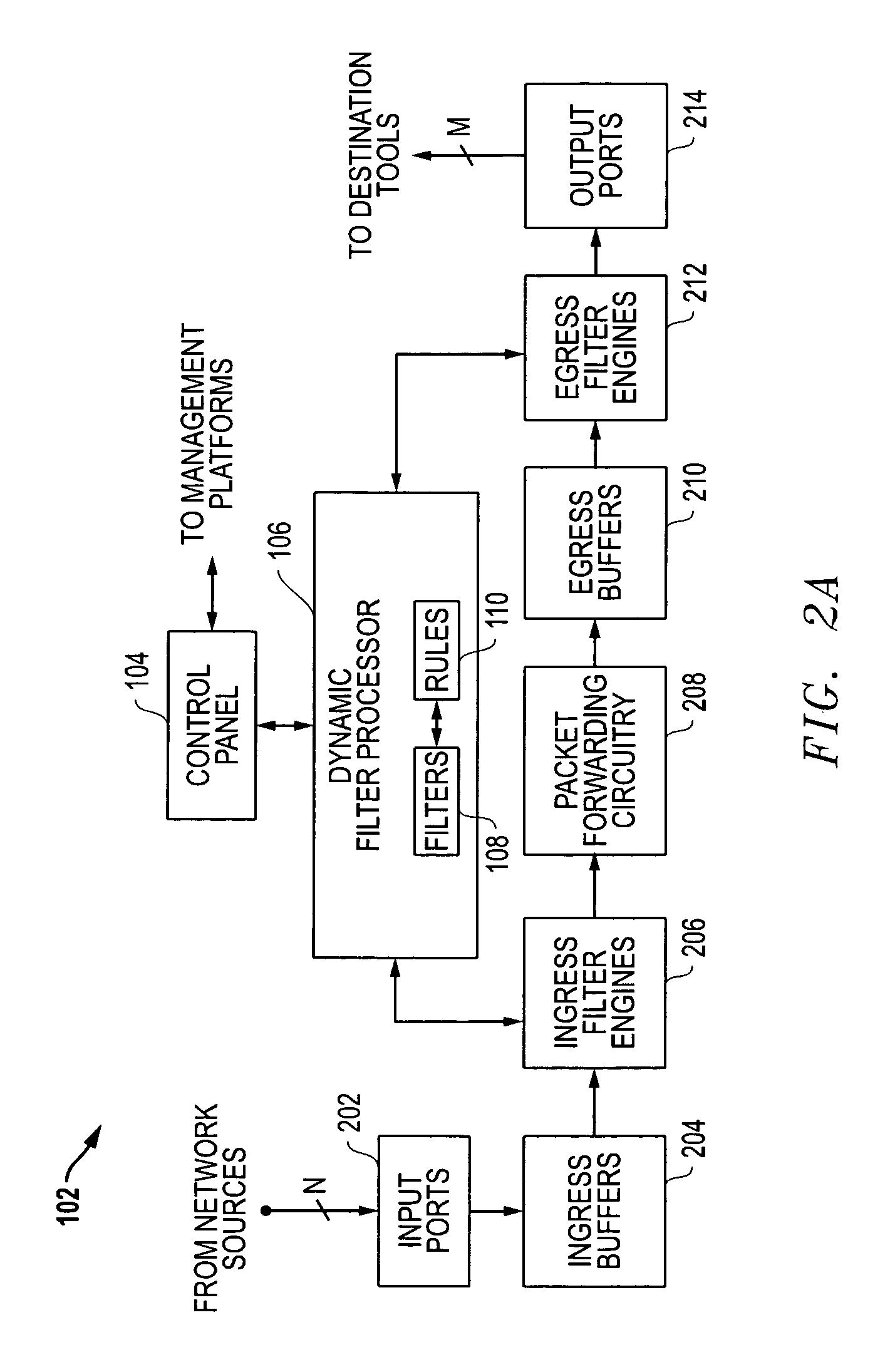
Automatic filter overlap processing and related systems and methods
ActiveUS8018943B1Easy to manageEasy to controlData switching by path configurationHandling systemNetwork monitoring
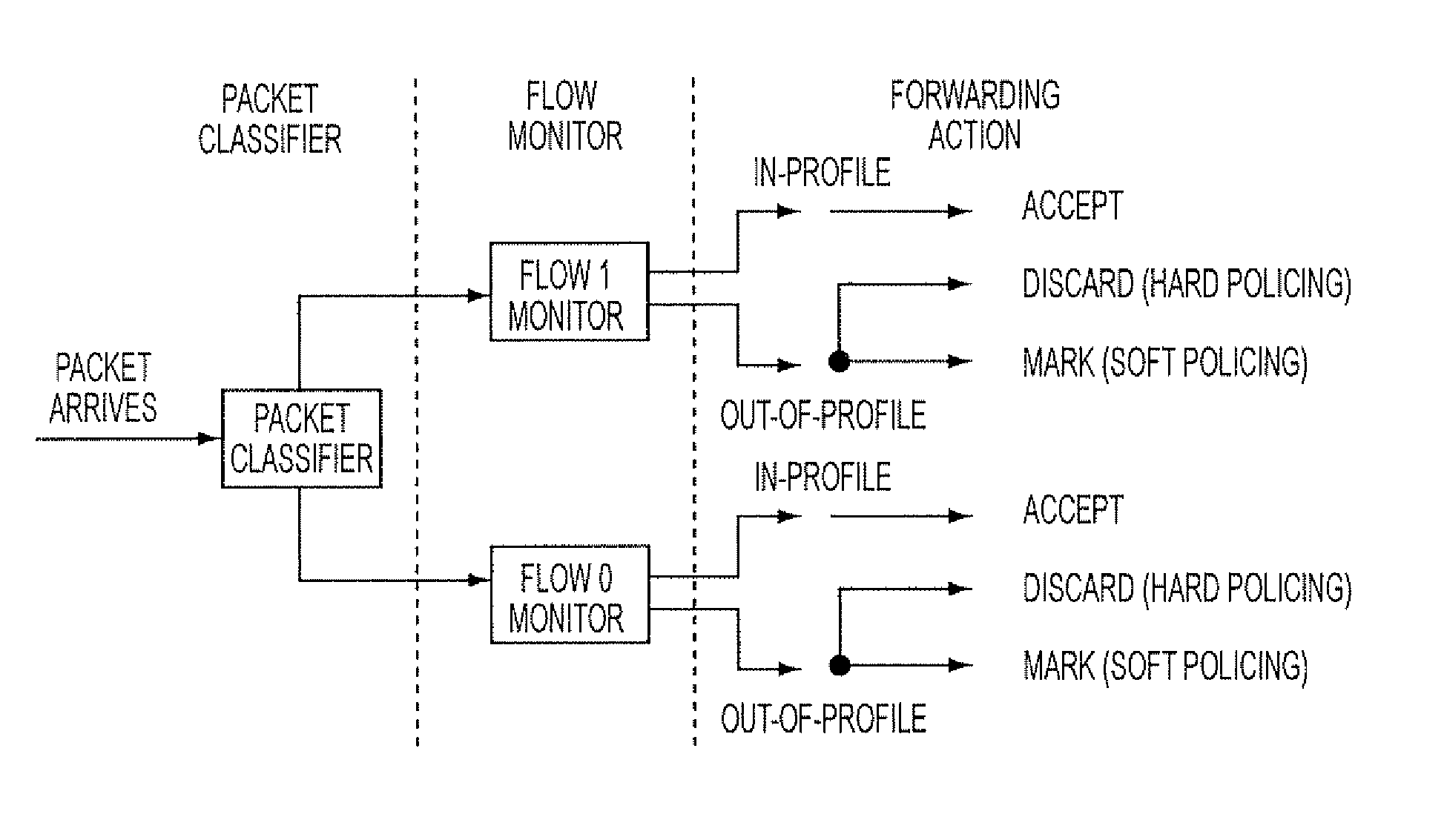
Systems and methods are disclosed that allow for improved management and control of packet forwarding in network systems. Network devices and tool optimizers and a related systems and methods are disclosed for improved packet forwarding between input ports and output ports. The input ports and output ports are configured to be connected to source devices and destination devices, for example, network sources and destination tools in a network monitoring environment. The network devices and tool optimizers disclosed can use a packet processing system whereby forwarding behavior is governed by matching packets in parallel against multiple user-specified packet filtering criteria, and by performing forwarding actions associated with all such matching filter criteria. The multi-action packet forwarding can be implemented using hardware configured to directly provide multi-action packet forwarding and / or hardware configured to provide single-packet-forwarding that has been subsequently configured using filter engines to provide multi-action packet forwarding.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Device and method for detecting unauthorized, "rogue" wireless LAN access points
ActiveUS7257107B2Improves receiver range and geolocation capability of systemUnauthorised/fraudulent call preventionDigital data processing detailsOutdoor areaGeolocation
A system monitors and detects unauthorized wireless LAN access points and wireless devices. The system includes one or more wireless LAN monitoring devices, which detect and report the presence of unauthorized or “rogue” wireless LAN access points or wireless devices within a predetermined area, for example, within the vicinity of a wired LAN, including indoor and / or outdoor areas. Improved range is achieved through the use of preamplification and sectorized antennas. Larger areas may be covered using additional wireless LAN monitoring devices, which operate independently or cooperate together in the detection process. Geolocation is possible using single or multiple, cooperating monitoring devices. Provision can be made for monitoring devices to provide packet filtering on a wired LAN.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Filtering and route lookup in a switching device
InactiveUS7688727B1Minimize occurrenceSize of output is increasedError preventionFrequency-division multiplex detailsTraffic capacityPacket filtering
Methods and devices for processing packets are provided. The processing device may Include an input interface for receiving data units containing header information of respective packets; a first module configurable to perform packet filtering based on the received data units; a second module configurable to perform traffic analysis based on the received data units; a third module configurable to perform load balancing based on the received data units; and a fourth module configurable to perform route lookups based on the received data units.
Owner:JUMIPER NETWORKS INC
Systems and methods that identify normal traffic during network attacks
A system protects against loss of communication during network attacks. In a first implementation, a system (120) models the behavior of normal users in a network in response to an application of a first packet filtering technique. The system (120) receives a group of packets from a first user subsequent to the application of the first packet filtering technique and creates one or more models reflecting the behavior of the first user based on the received packets. In another implementation, a system (130) receives a stream of packets subsequent to a filtering technique being applied, partitions the packets into groups, where each group corresponds to more than one packet, and classifies each group of packets as a normal group or an attack group using one or more models. Each model reflects a normal response to an application of the filtering technique. The system (130) forwards groups classified as normal groups, thus preventing network attacks from choking off all communication in the network.
Owner:TRI COUNTY EXCELSIOR FOUND +1
System, method and computer program product for updating the states of a firewall
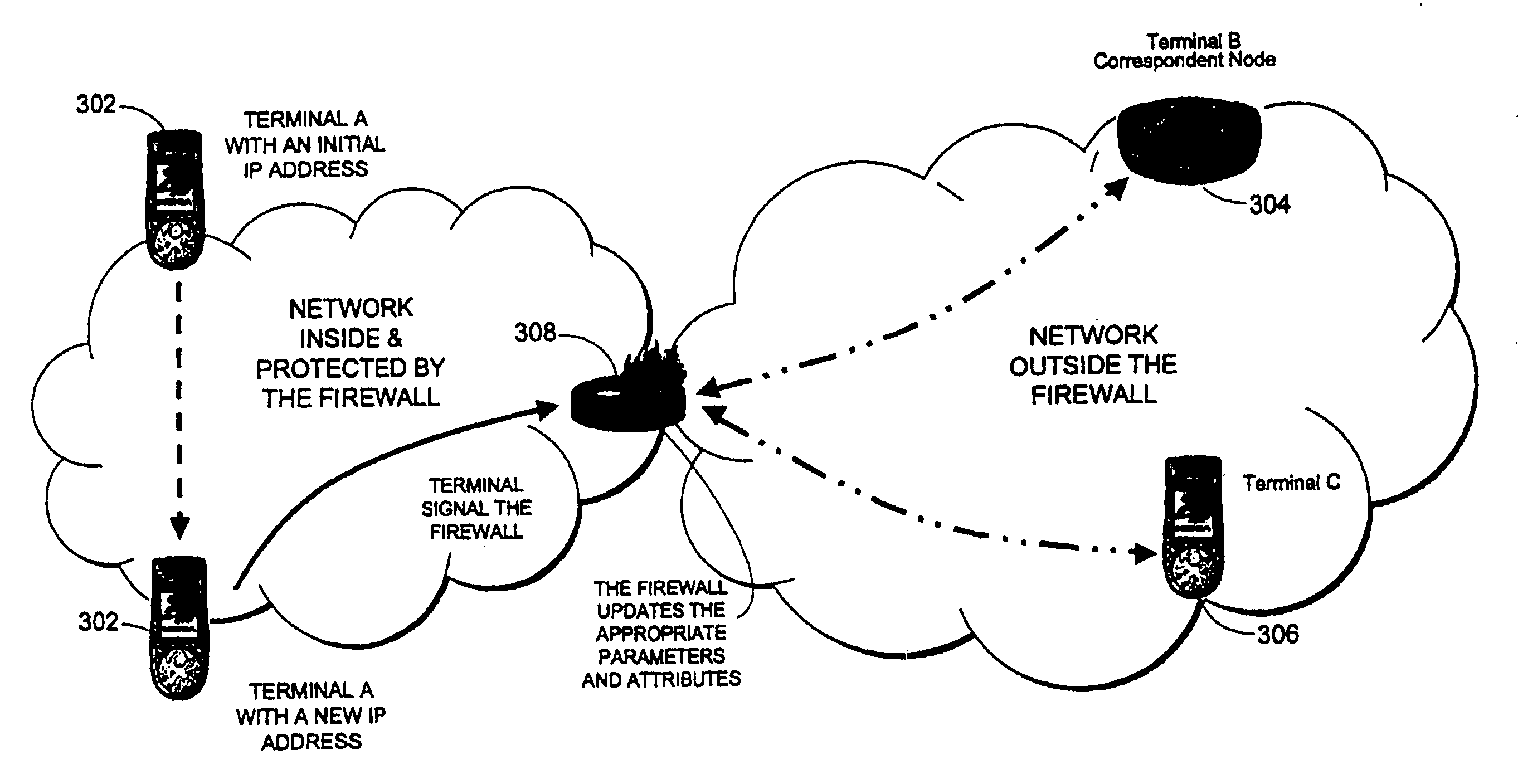
InactiveUS20050268335A1Multiple digital computer combinationsProgram controlIp addressTerminal equipment
The preferred embodiment of the present invention is a method and computer program product that specifies an array of elements to be incorporated into a firewall configuration protocol. When added to the configuration protocol, these added attributes allow the existing packet filtering mechanism to accommodate a terminal device that has moved and received a new IP address in a timely and efficient manner.
Owner:TRINITYECO
PLD-based packet filtering methods with PLD configuration data update of filtering rules
InactiveUS7031267B2Facilitate short time to carry-outEasy to switchTime-division multiplexData switching by path configurationPacket generatorOperational system
Methods and systems for a PLD-based network update transport (PNUT) protocol that utilizes UDP and other protocols for transmitting update or other commands or information over a packet-based or IP network. PNUT is a hardware-based network communication protocol that does not require the full TCP / IP stack and may be utilized for exchanging commands and information with such PLD-based and other devices. Protocols may include a set of core commands and a set of custom commands. Logic components within the PLD-based devices may consist of a command dispatcher, a transmitter / controller, a MAC receiver, a MAC transmitter, a packet parser, a packet generator, and core receiving and transmitting commands. The present invention may be implemented without requiring CPU cores, special controllers, stringent timings, or operating systems as compared with conventional network protocols. Various methods for exchanging and updating PNUT commands are disclosed. The methods and systems of the present invention may be utilized to provide other functions, such as filtering, logging, polling, testing, debugging, and monitoring, and may be implemented between a server and a PLD-based device or solely between PLD-based devices.
Owner:802 SYST
Filtering of dynamic flows
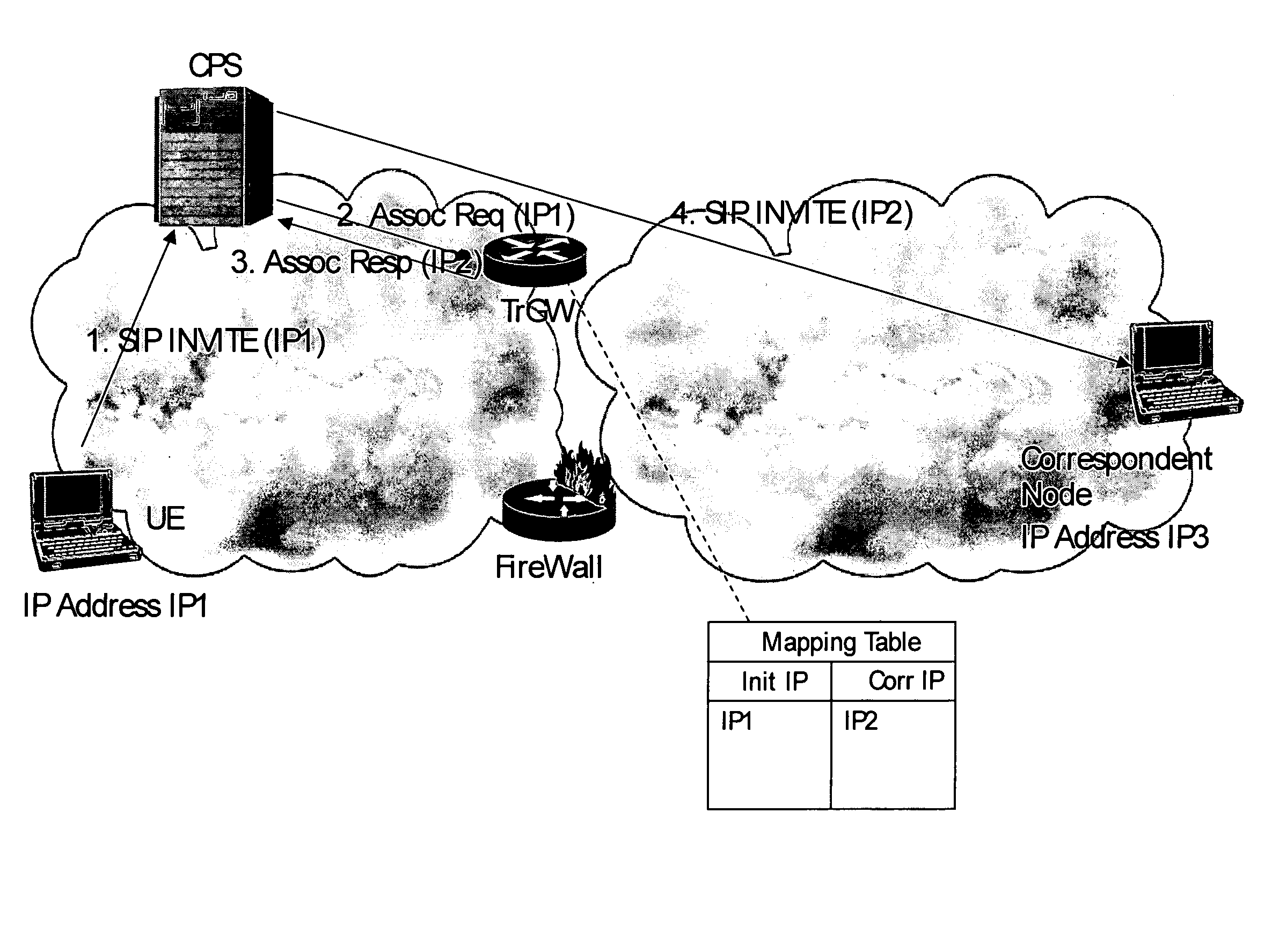
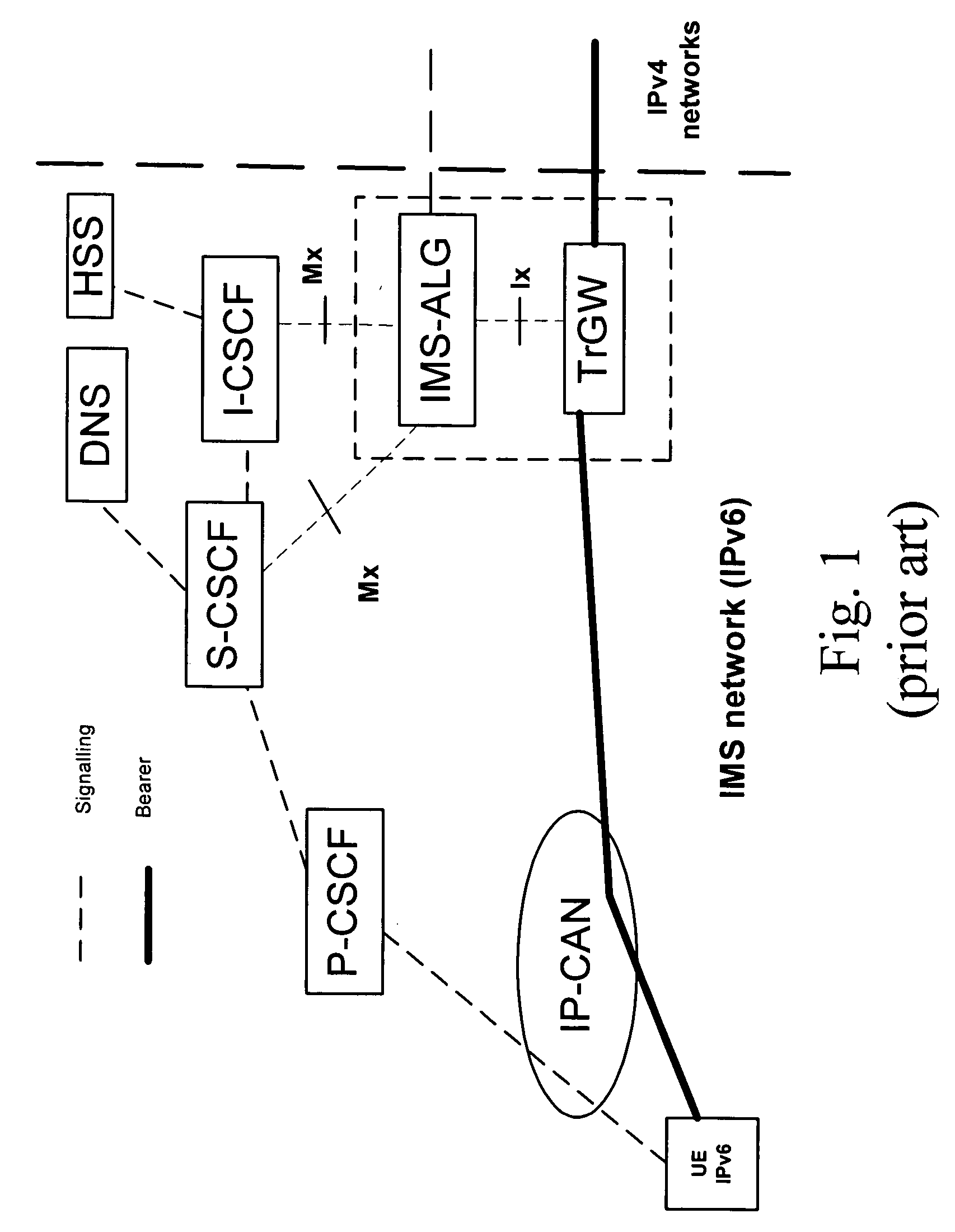
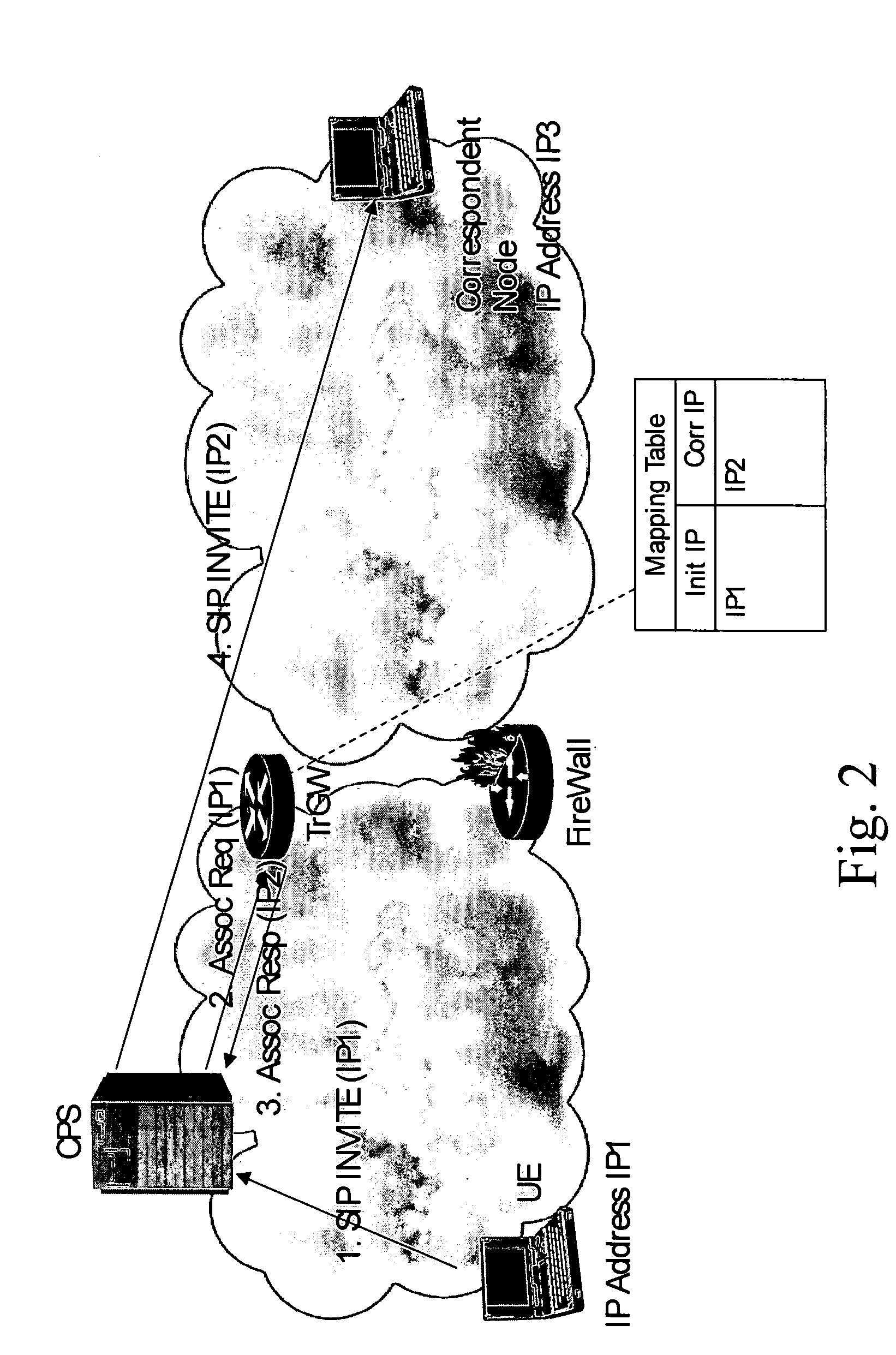
ActiveUS20050111382A1Short-term deploymentInterconnection arrangementsData switching by path configurationIp addressPacket filtering
Methods and correspondent nodes to filter IP communications through firewalls in scenarios where dynamic pinholes are created to ensure an appropriate level of security is disclosed. The invention is based on creating a secure and authorized anchor for communications where all the communications are routed through before a firewall performs the packet filtering. A Translator Gateway (TrGW) switches addresses in the header according to a stored Mapping Table and an interface between a CPS (or a SIP proxy) and the TrGW. This interface allows the CPS to request the TrGW to provide bindings data between IP addresses upon session initiation, the TrGW to provide the bindings data to the CPS and the CPS to release the bindings at session release. The firewall accepts incoming packets whose IP address belongs to the pool of addresses of the TrGW. Thus any incoming packet that does not correspond to an existing call will be dropped at the TrGW, and a valid packet will go through the firewall which will verify that the packet is not a malformed message or other attack.
Owner:RPX CORP
Filtering rule analysis method and system
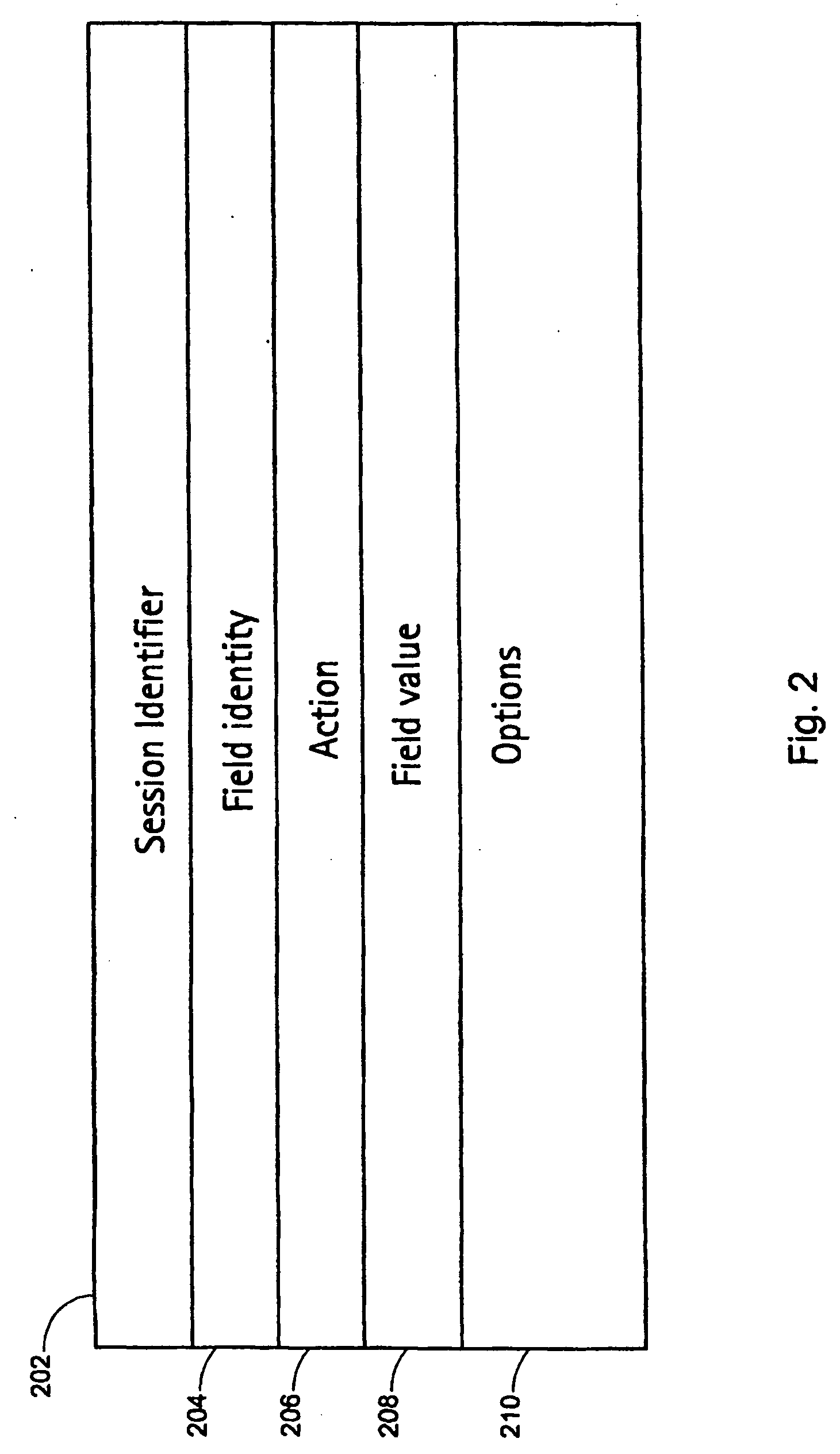
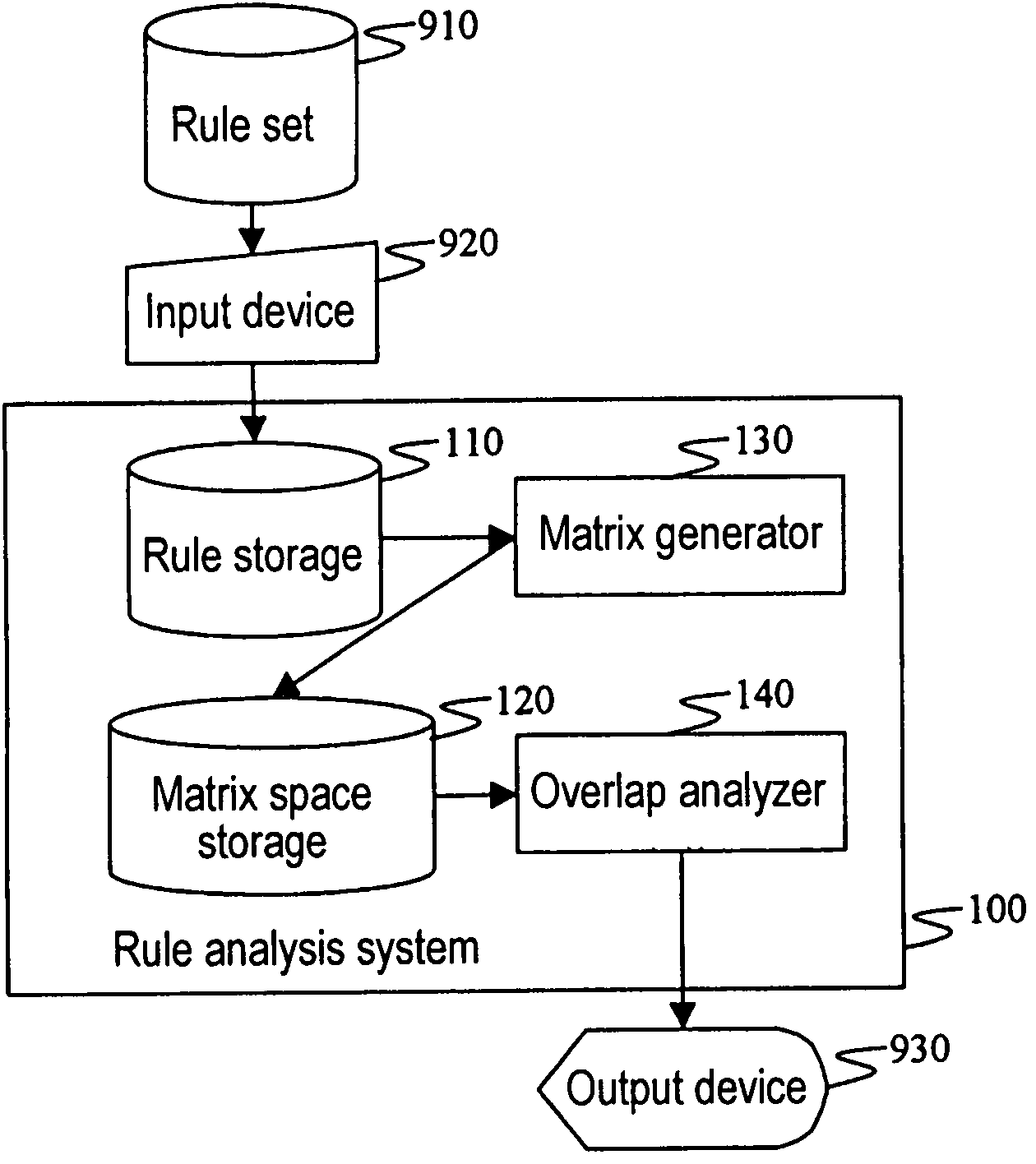
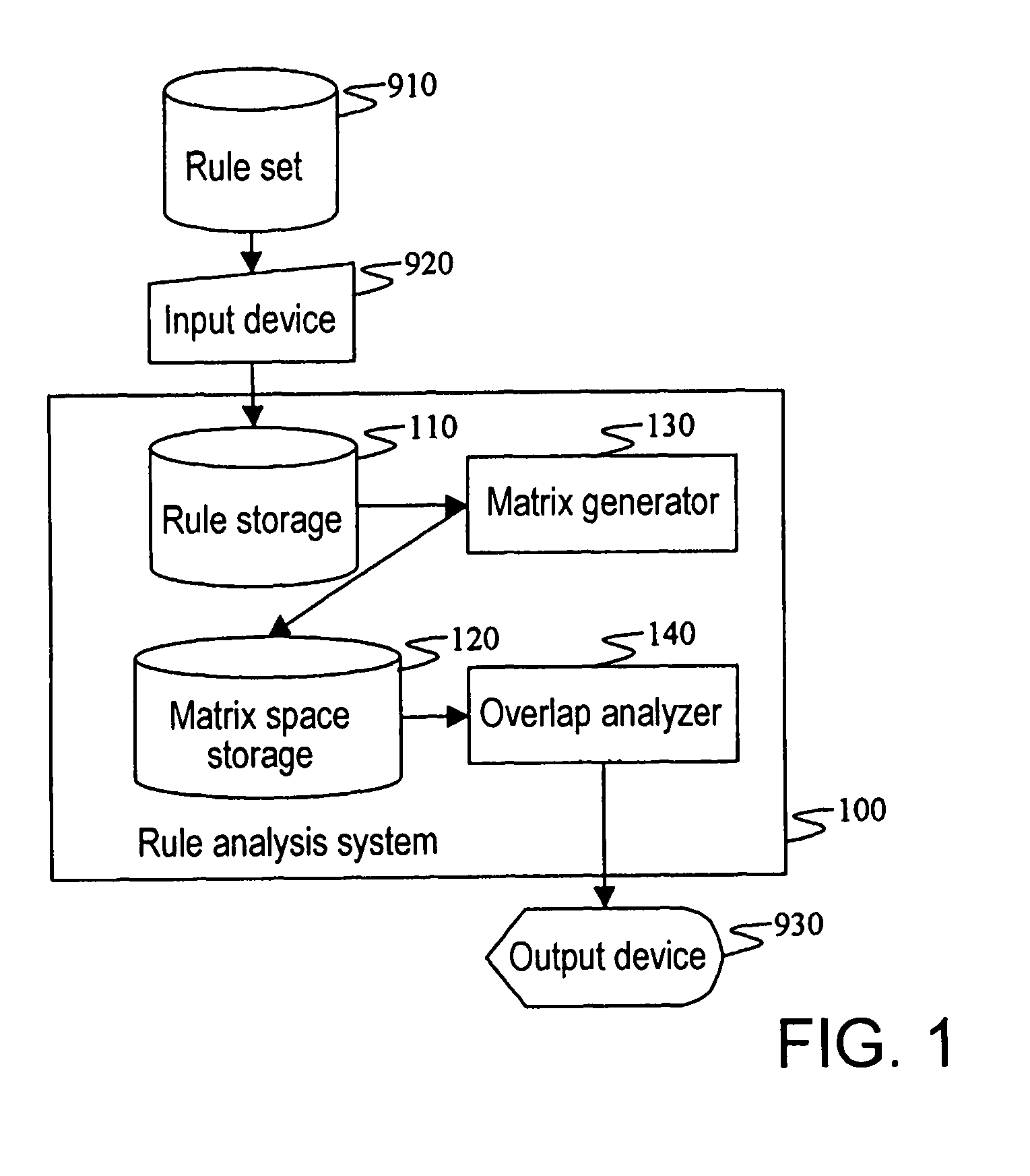
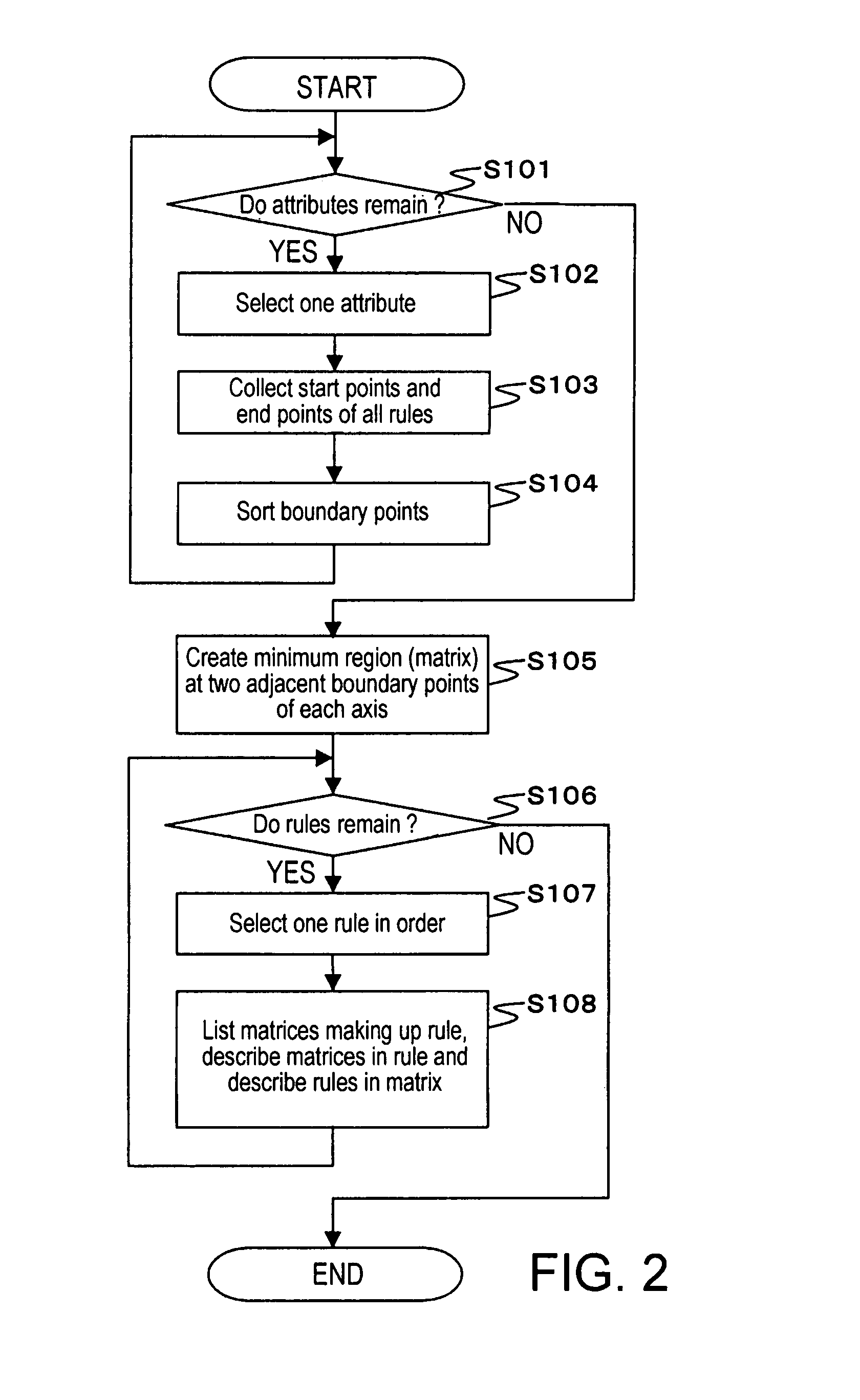
InactiveUS7792775B2Easy to understandKnowledge representationTransmissionFiltering rulesAnalysis method
A filtering rule analysis system for analyzing the rules of a packet filtering process that is set in network devices includes: a rule storage for storing sets of rules for which an order of priority has been established; a matrix generator for generating matrix spatial data that contains information of the order of priority and that indicates the correspondence relation between a minimum region identified by starting points and end points of ranges of packet attributes described in each rule as the condition of application of that rule and those rules; and an overlap analyzer for referring to the matrix spatial data to analyze overlap between the rules.
Owner:NEC CORP
Network packet tracking
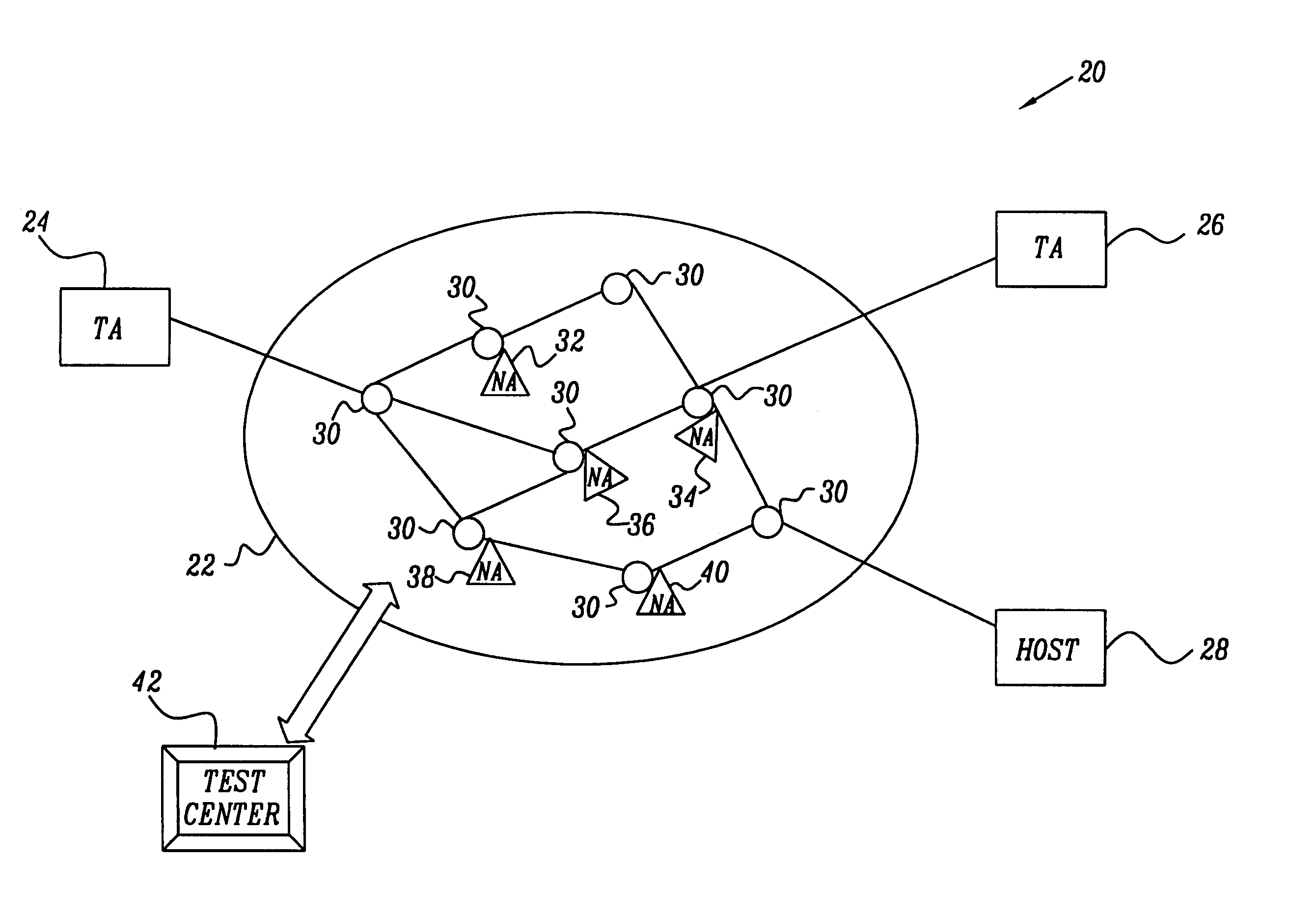
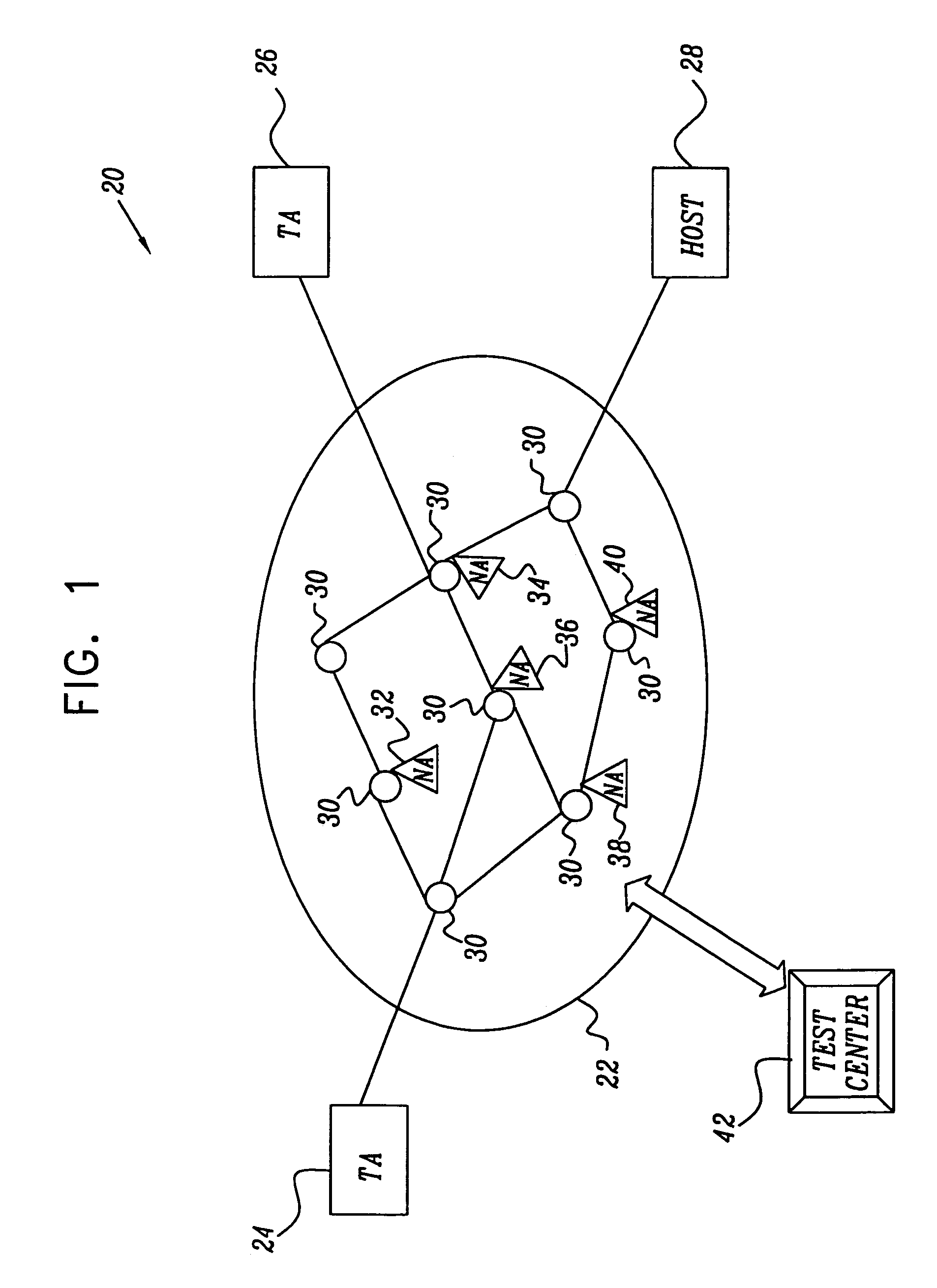
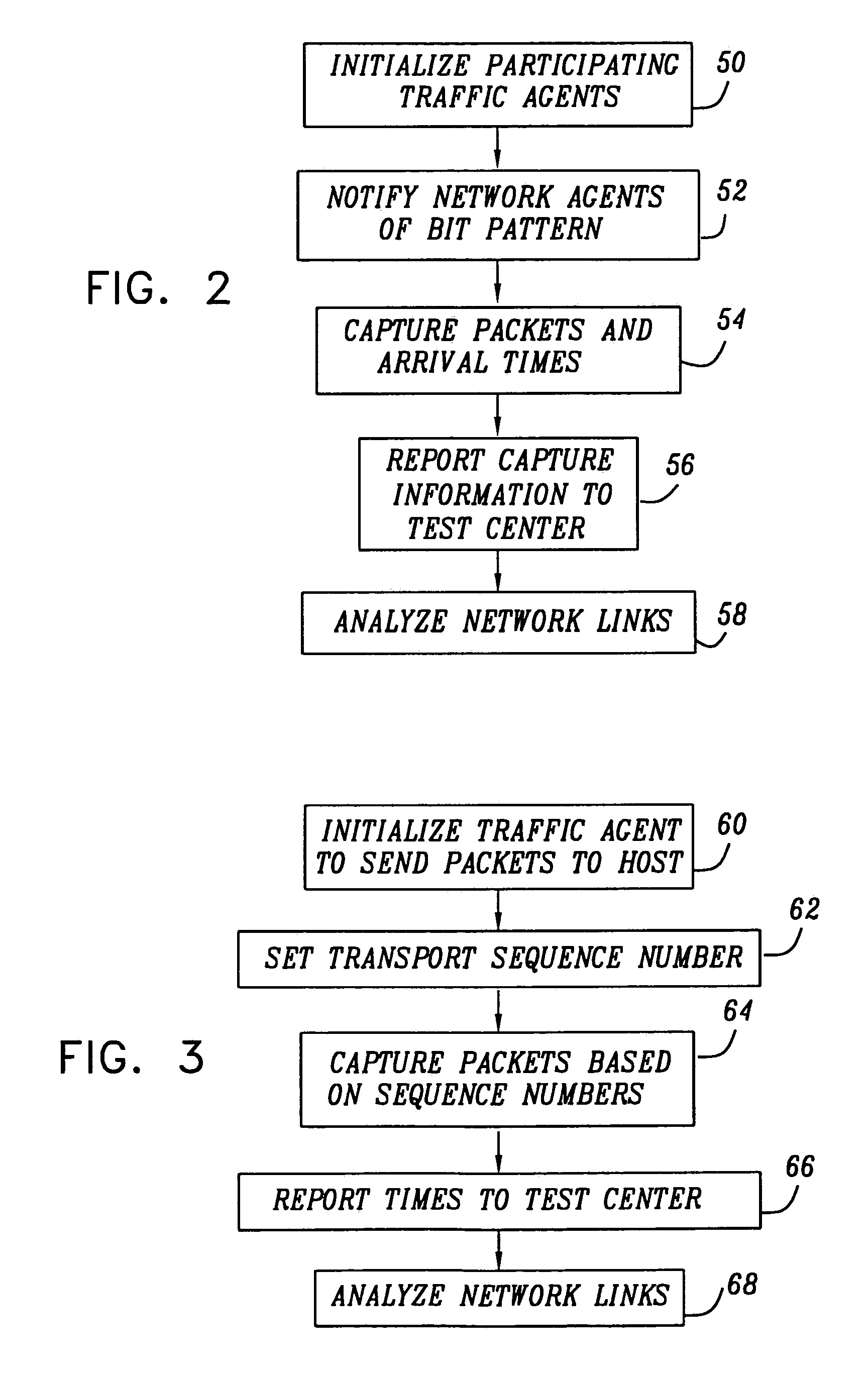
InactiveUS6958977B1Overcomes shortcomingError preventionTransmission systemsNetwork agentNetwork data
A method for testing of a communication network having a plurality of end-points, using one or more network agents coupled to the network at respective locations. The method includes specifying at least one packet filtering criterion, and transmitting one or more data packets meeting the at least one criterion through the network from one of the end-point to another. At least one of the data packets meeting the criterion is intercepted using the network agents at one or more of the respective locations in the network traversed by the at least one of the data packets. Information regarding the at least one intercepted packet at the one or more respective locations is recorded and processed to analyze a route of the at least one intercepted packet through the network.
Owner:CISCO TECH INC
Real time firewall/data protection systems and methods
InactiveUS20060253903A1Easy to switchEliminate requirementsMultiple digital computer combinationsProgram controlData packMicroprocessor controller
Methods and systems for firewall / data protection that filters data packets in real time and without packet buffering are disclosed. A data packet filtering hub, which may be implemented as part of a switch or router, receives a packet on one link, reshapes the electrical signal, and transmits it to one or more other links. During this process, a number of filters checks are performed in parallel, resulting in a decision about whether each packet should or should not be invalidated by the time that the last bit is transmitted. To execute this task, the filtering hub performs rules-based filtering on several levels simultaneously, preferably with a programmable logic or other hardware device. Various methods for packet filtering in real time and without buffering with programmable logic are disclosed. The system may include constituent elements of a stateful packet filtering hub, such as microprocessors, controllers, and integrated circuits. The system may be reset, enabled, disabled, configured, and / or reconfigured with toggles or other physical switches. Audio and visual feedback may be provided regarding the operation and status of the system.
Owner:802 SYST
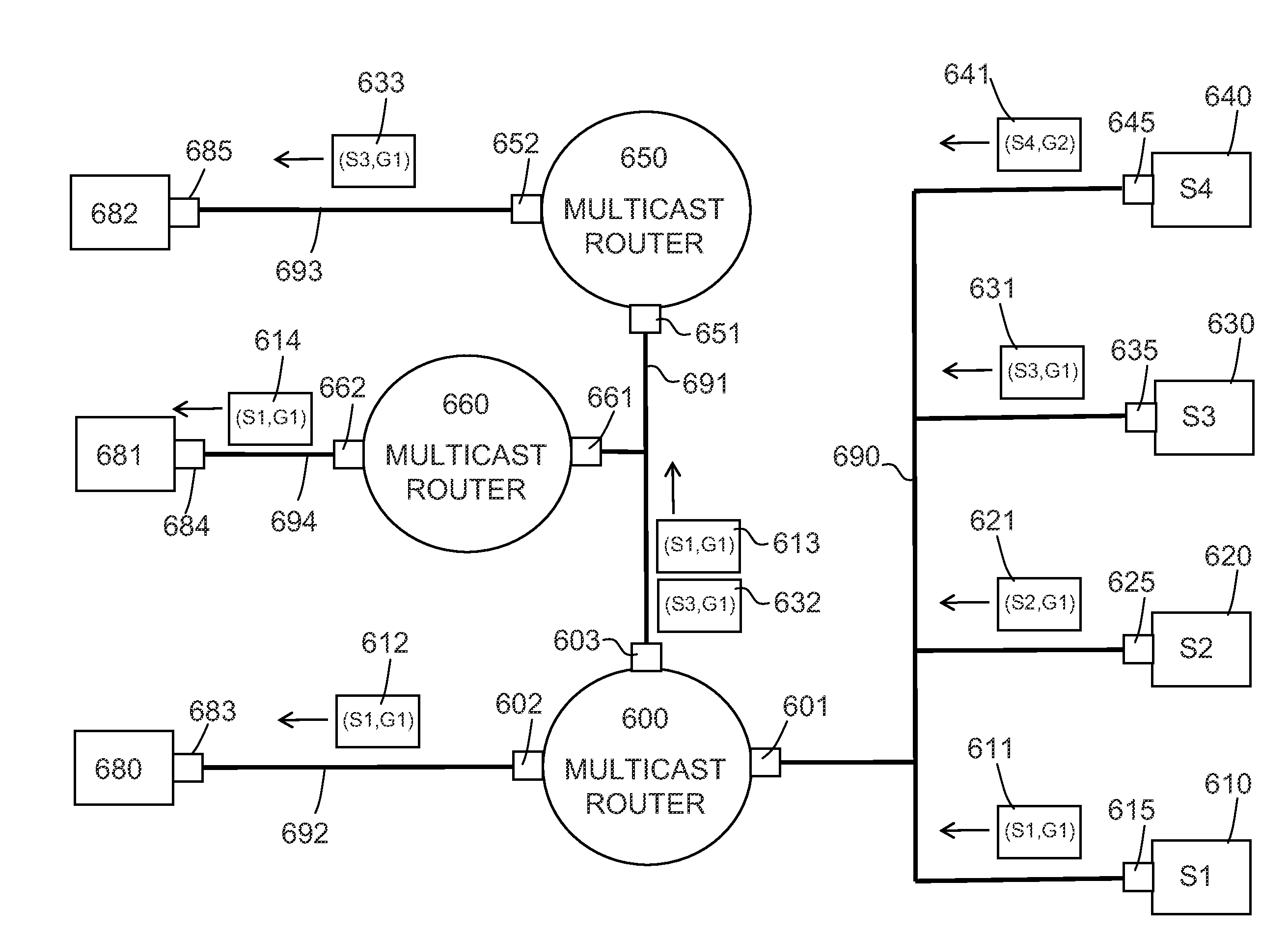
Method and apparatus for filtering multicast packets
InactiveUS20110149960A1Easy to detectSpecial service provision for substationData switching by path configurationTraffic capacityNetwork packet
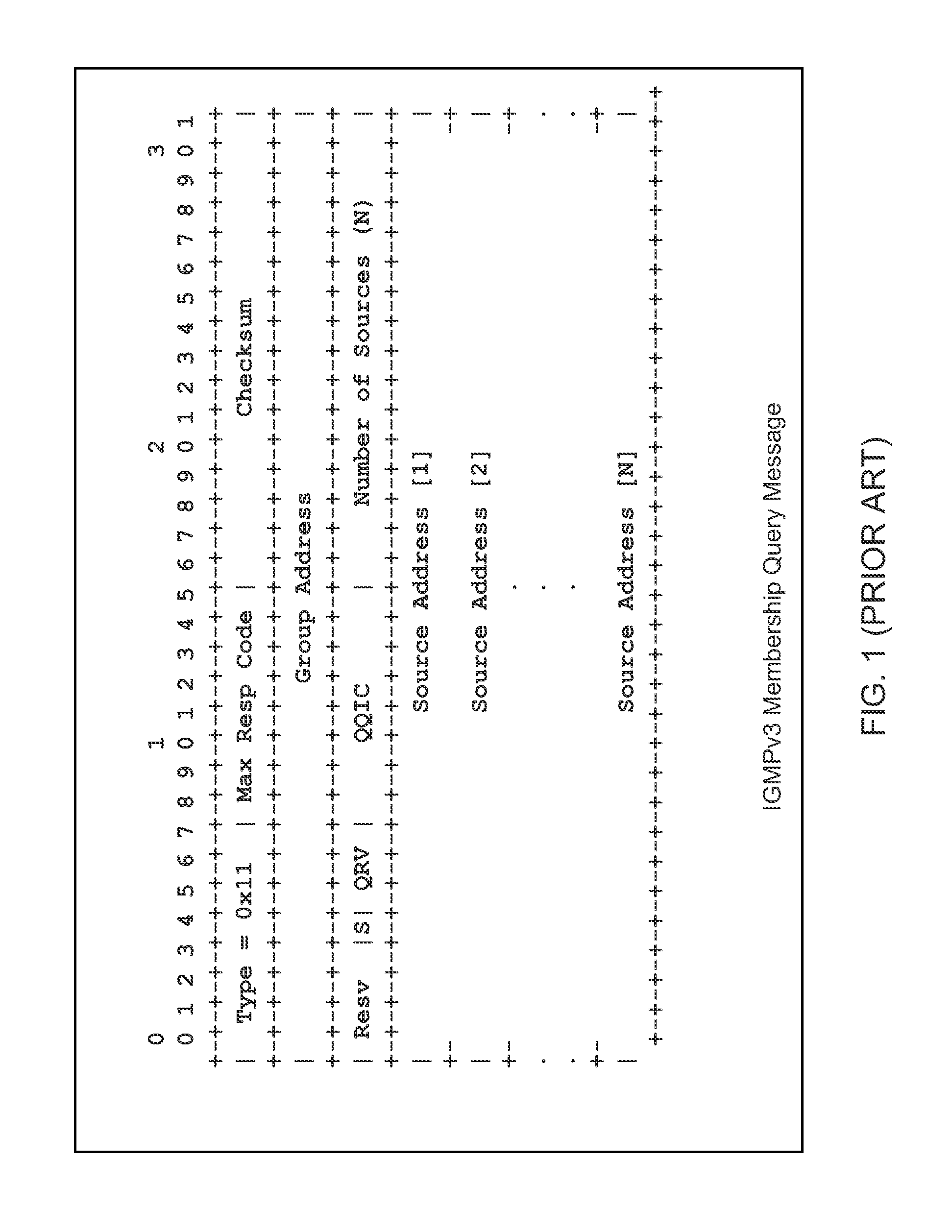
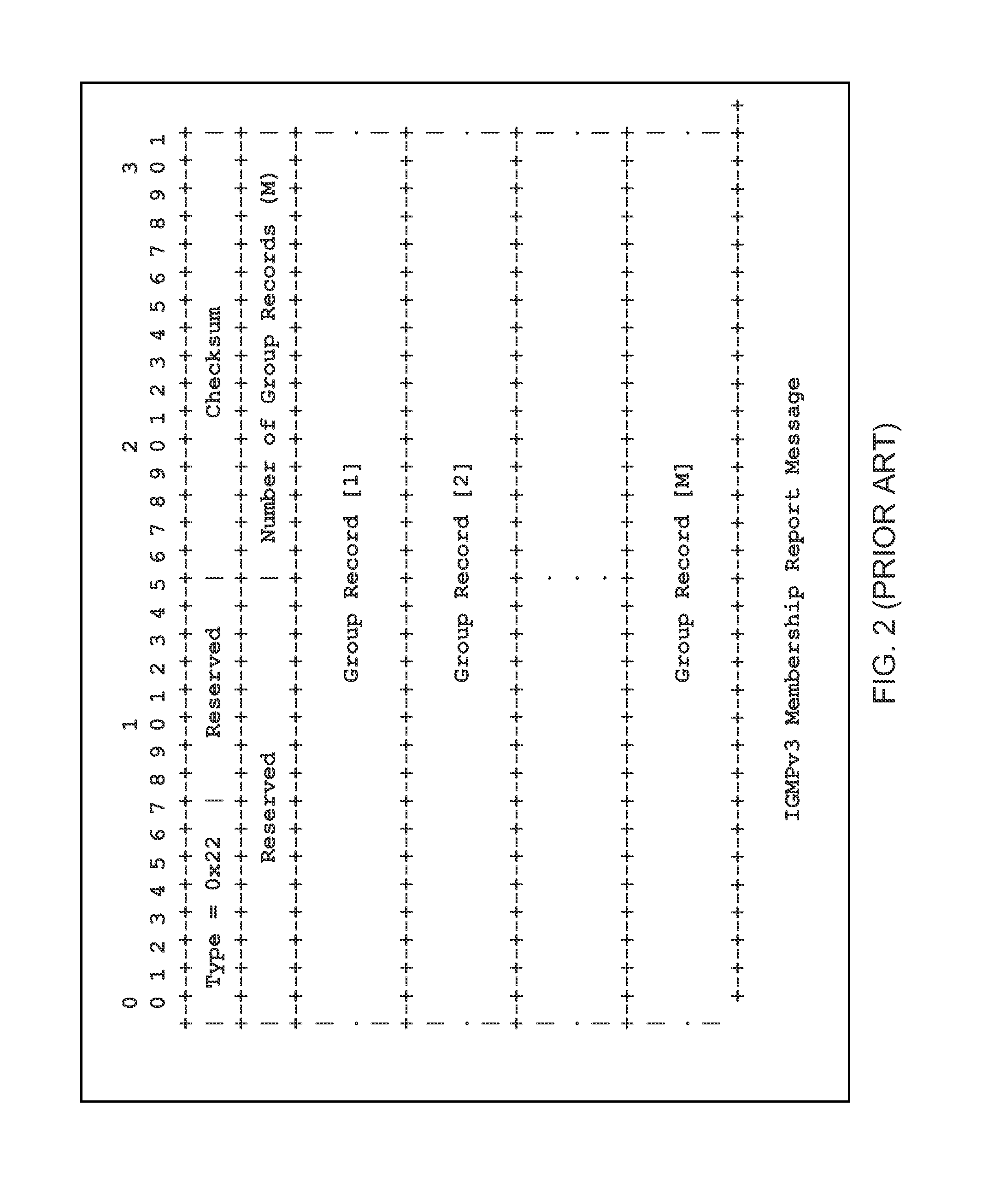
A method of filtering multicast packets received in a first network interface of a router is provided. The router receives multicast traffic in the first network interface from sources that send multicast packets to at least a first multicast group address. The router also having second and third network interfaces for receiving multicast traffic requests. In one implementation the filtering method includes receiving in the second network interface a first multicast traffic request for a first multicast group address according to a first multicast routing protocol including a first set of sources, receiving in the third network interface a second multicast traffic request for the first multicast group address according to a second multicast routing protocol, the multicast traffic request including a second set of sources, creating from the first and second multicast traffic requests a filter record having a third set of sources indicative of all of the sources of the first multicast group address requested to be transmitted through the second and third interfaces of the router; and filtering multicast packets received at the first network interface using the record. In alternative embodiments, multiple multicast state records (e.g., an Include source record and an Exclude source record) are stored for each network interface and multicast group address, the multiple multicast state records being used to create one or more multiple filter records that each have a set of sources that are used in combination to filter multicast packets received at the first network interface.
Owner:MEDIA PATENTS
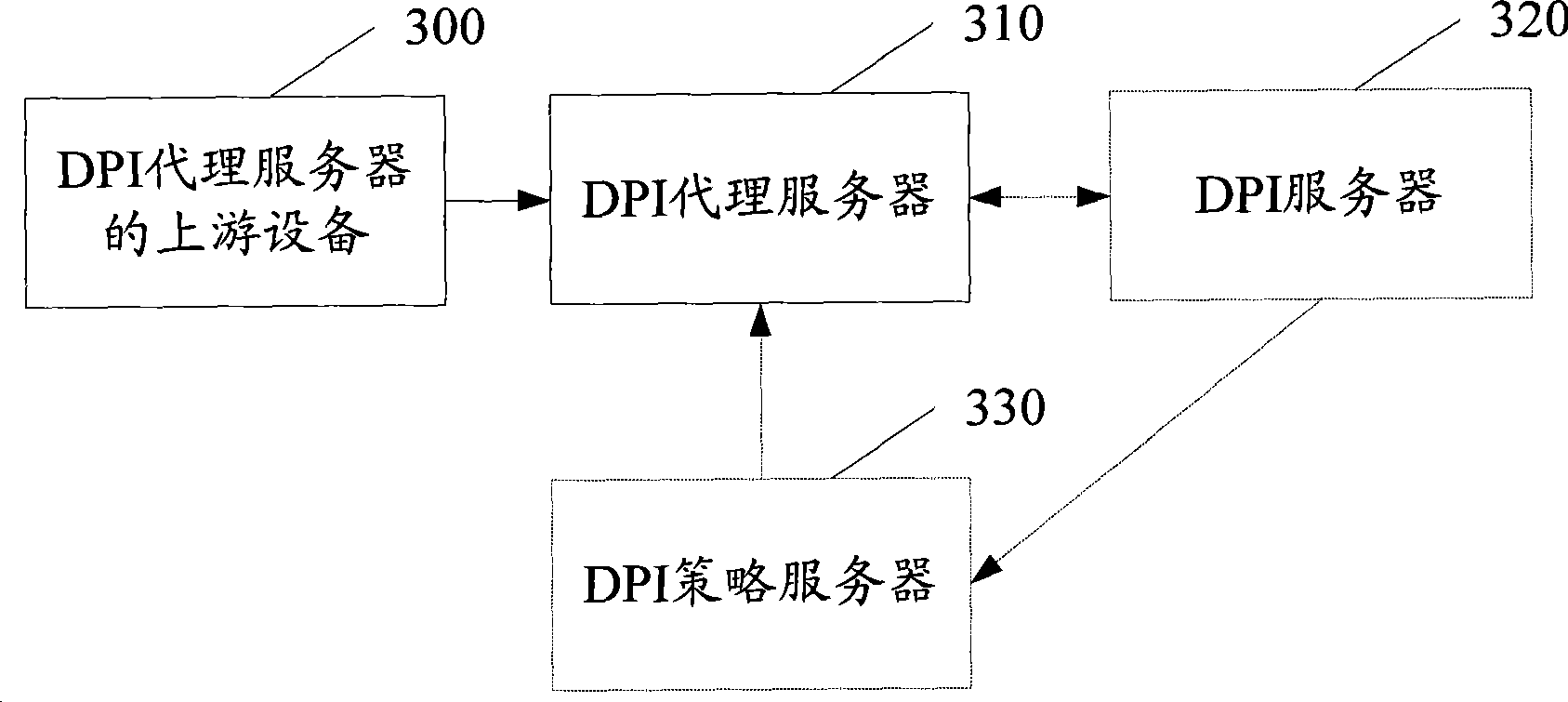
Method, system and device for packet filtering
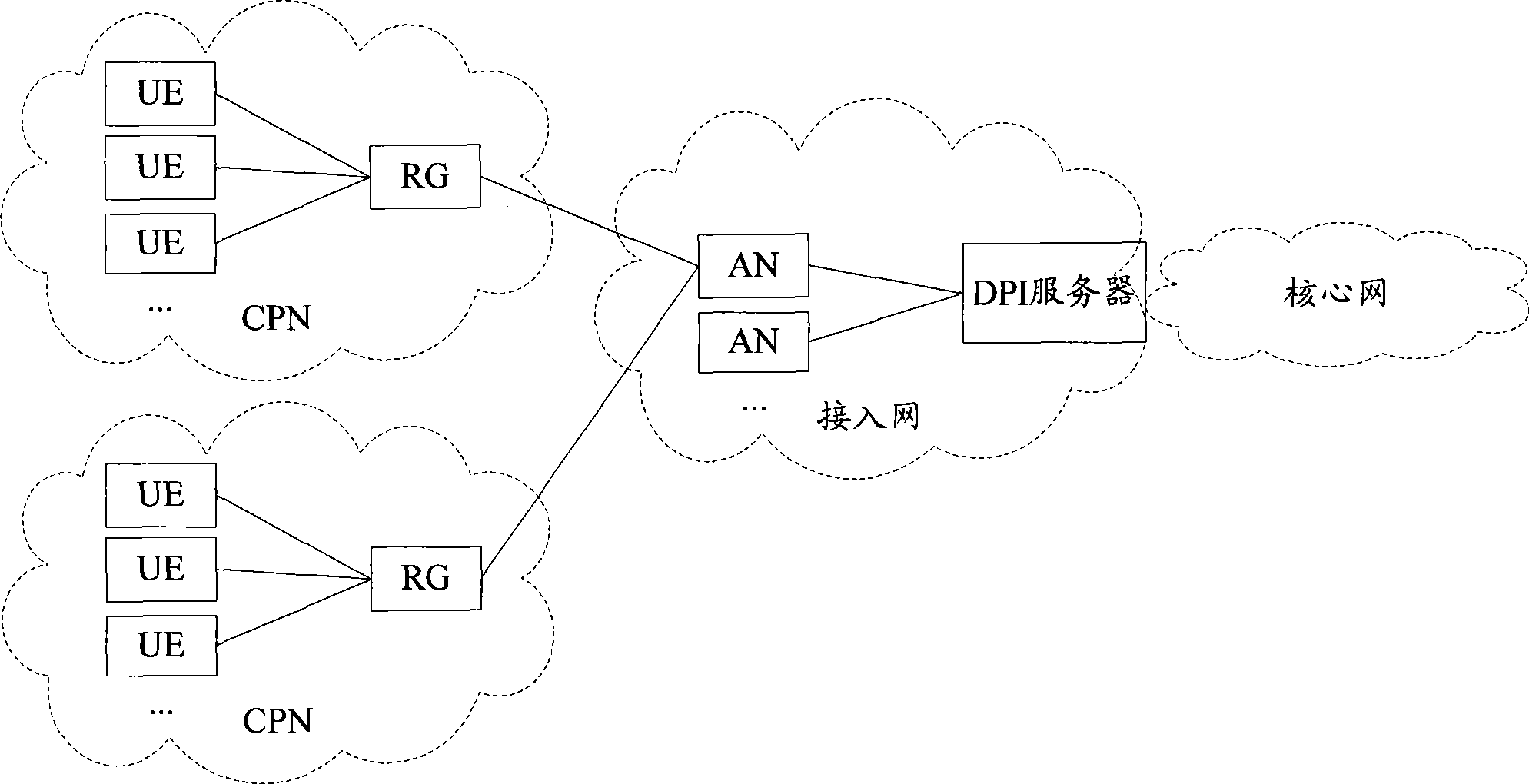
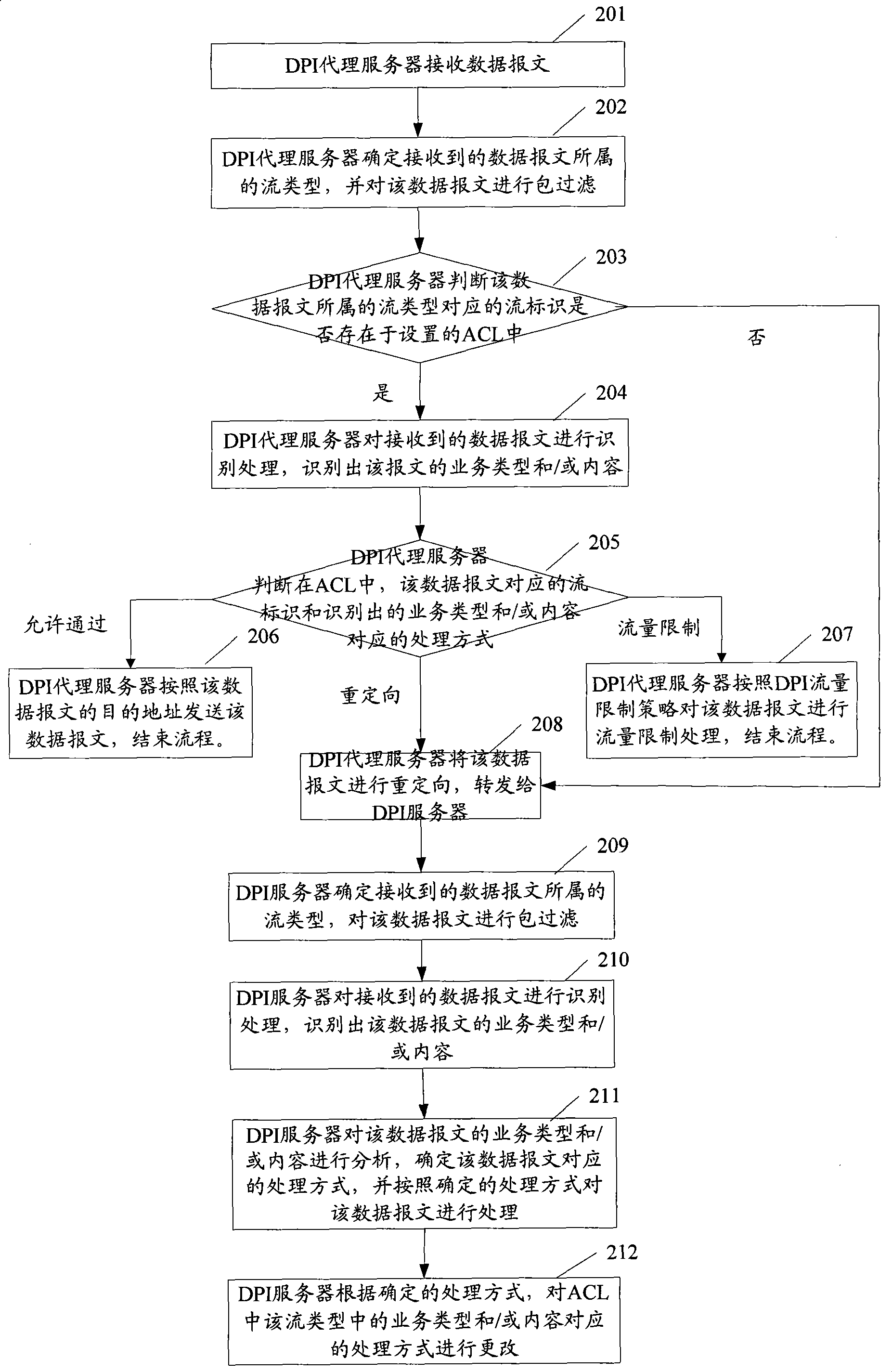
ActiveCN101399749AReduce trafficGuaranteed real-timeNetwork connectionsAccess networkTraffic capacity
The invention provides a message filtration method and a system and equipment thereof; DPI proxy servers which are arranged at the user side of the access network identify the service type and / or content of the received data message and then DPI filtration is implemented on the data message according to the set DPI filtration strategy and the identified service type and / or content. By adopting the mode, the DPI proxy servers can be distributed at the user side of the access network and the received data messages are only the messages transmitted by the user equipment of the corresponding user network; compared with the DPI servers which are arranged at the boundary of the core network and the access network, the data message flow which needs to be processed is reduced; therefore, the real-time deep packet inspection on the data message can be guaranteed.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com