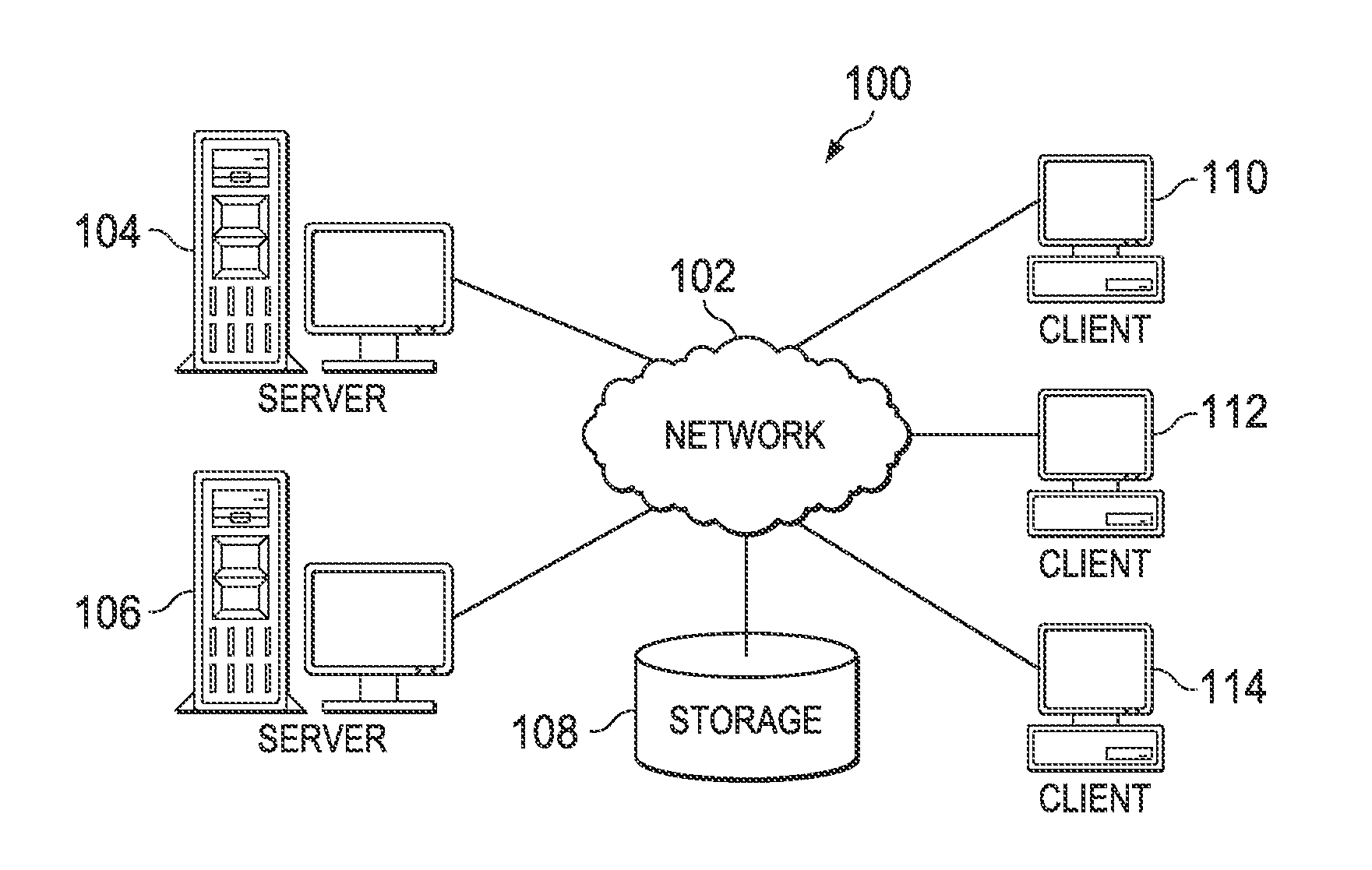
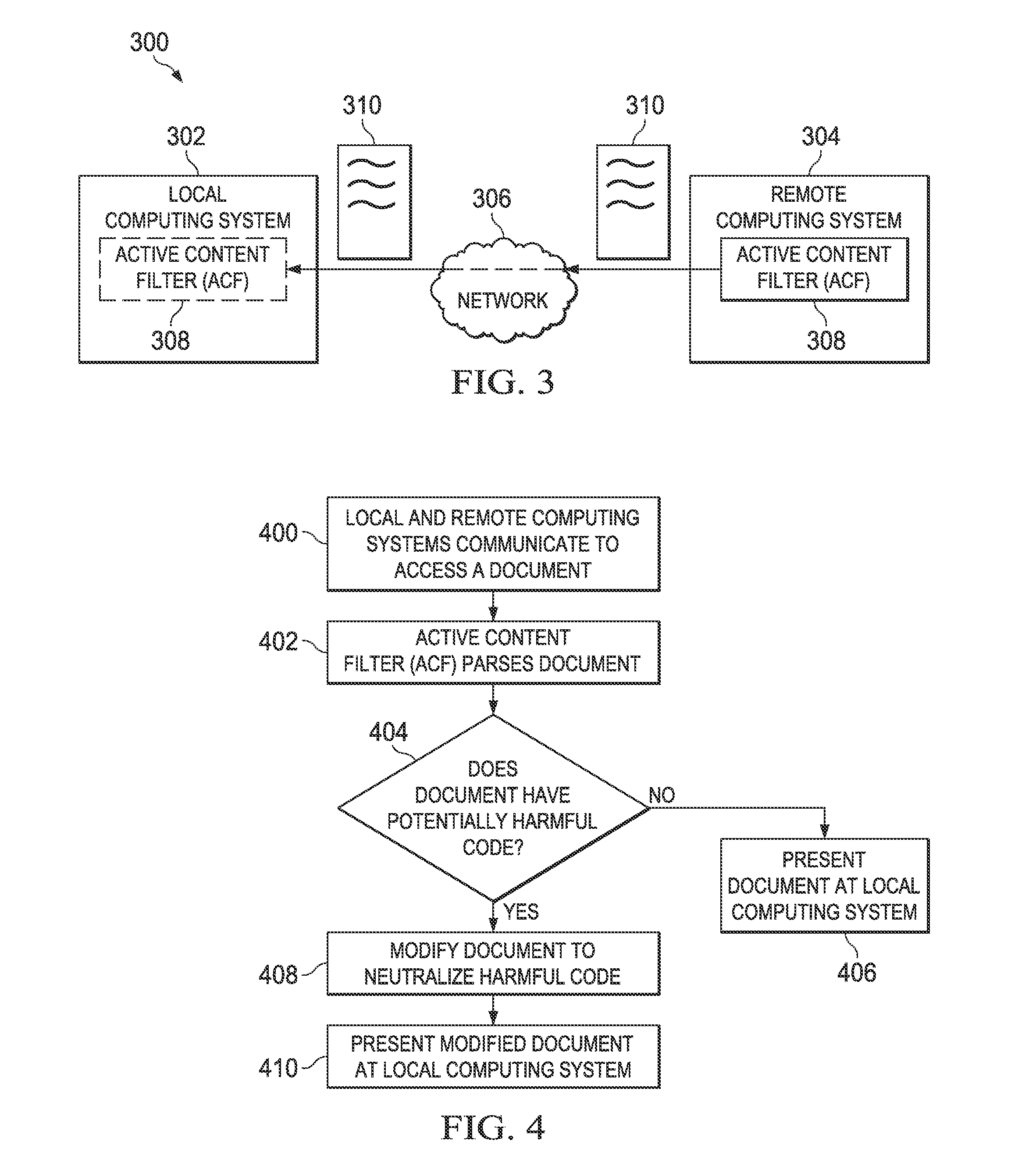
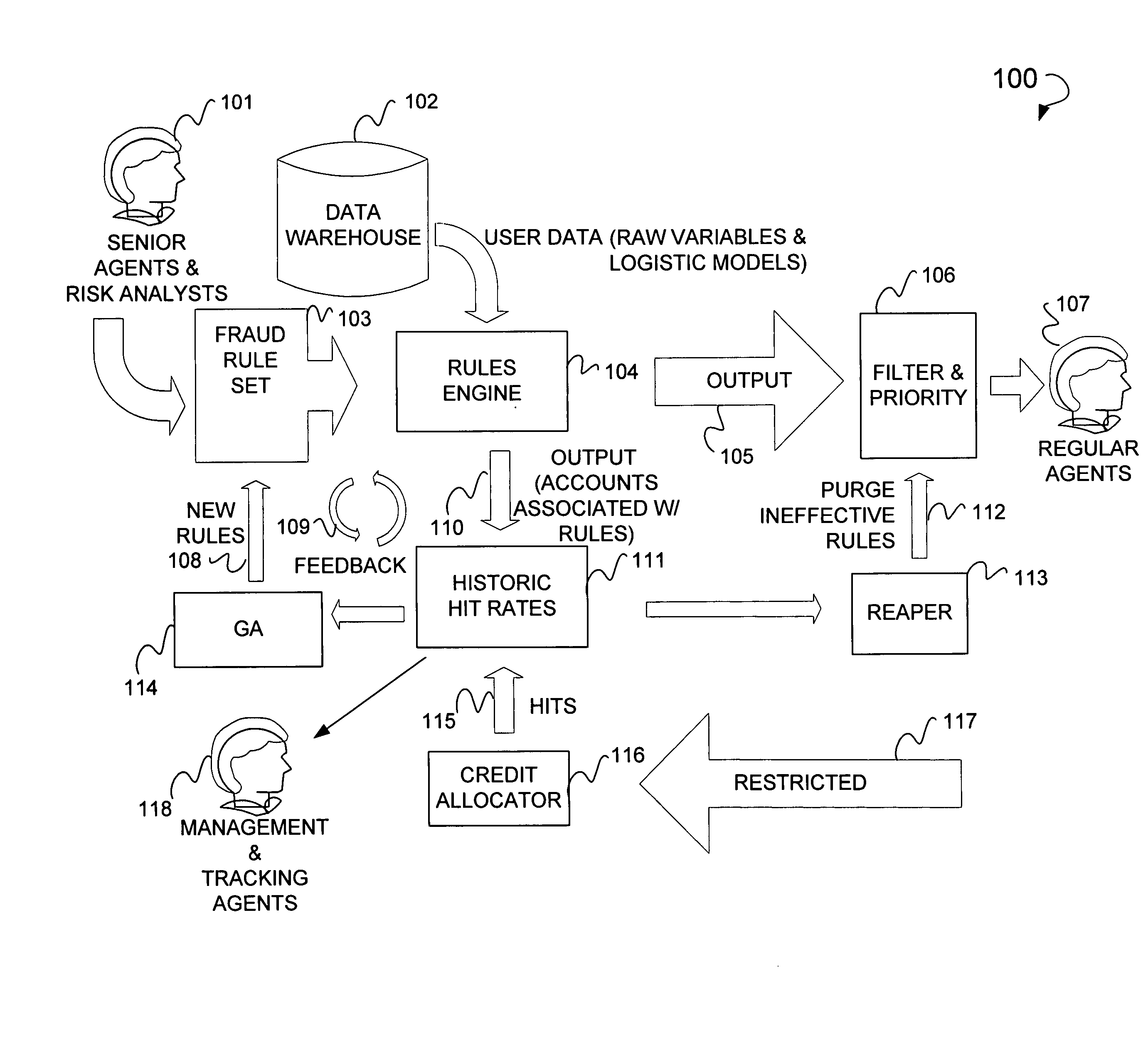
Patents
Literature
1077 results about "Filtering rules" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Filtering rules. Filtering rules allow you to exclude one part of the message target according to criteria defined in a query, such as quarantined profiles or profiles that have already been sent a certain number of emails.
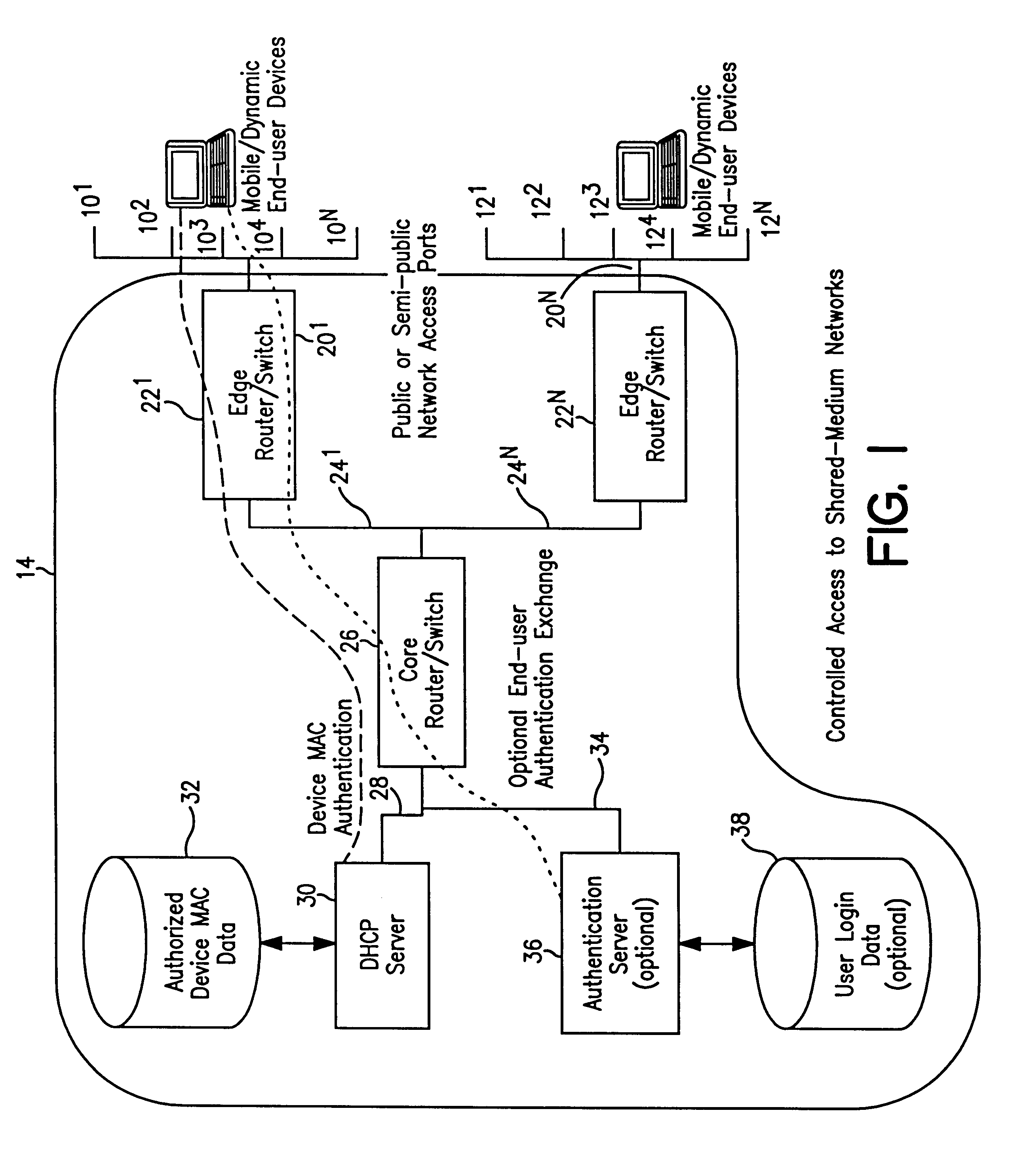
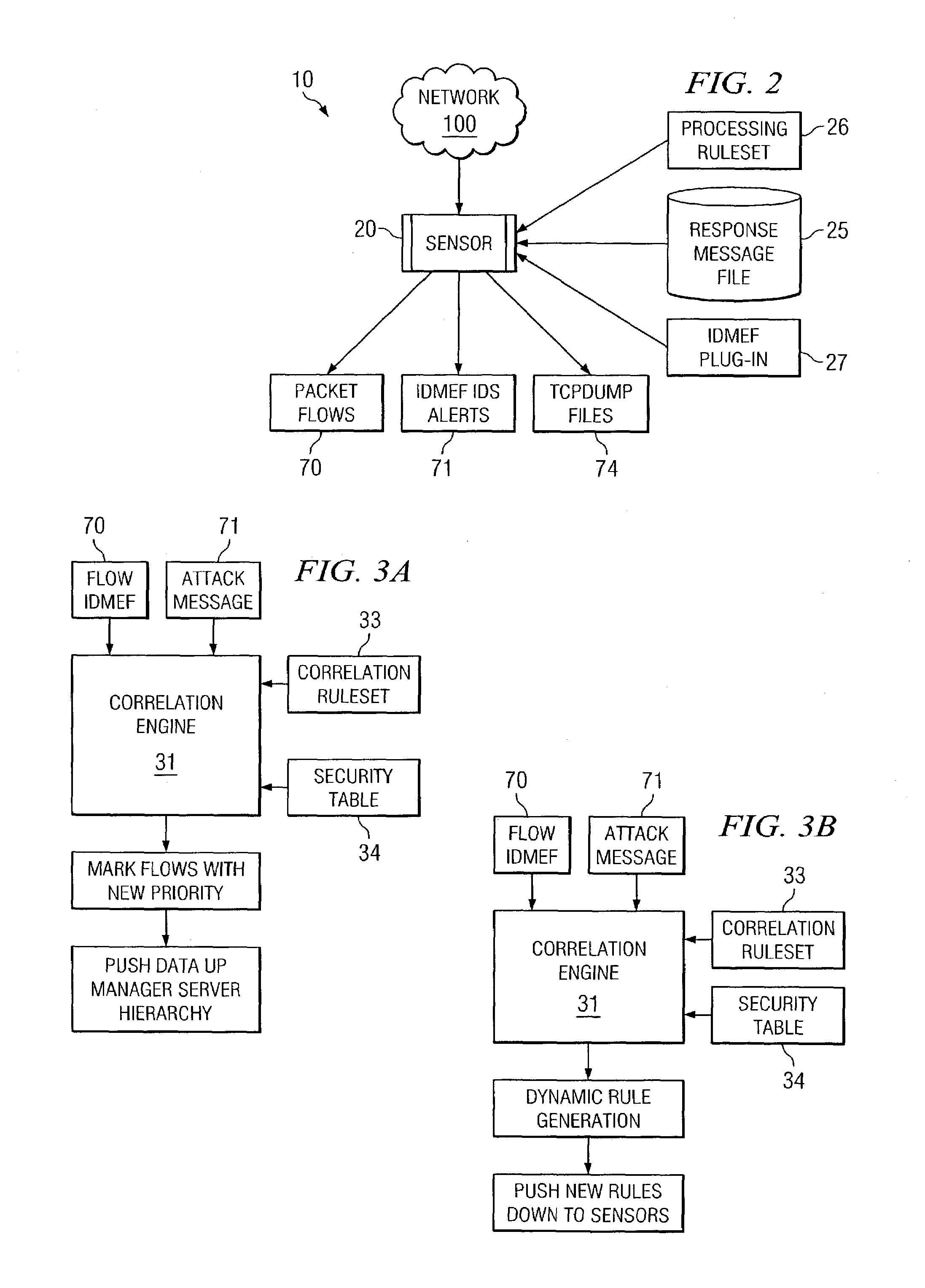
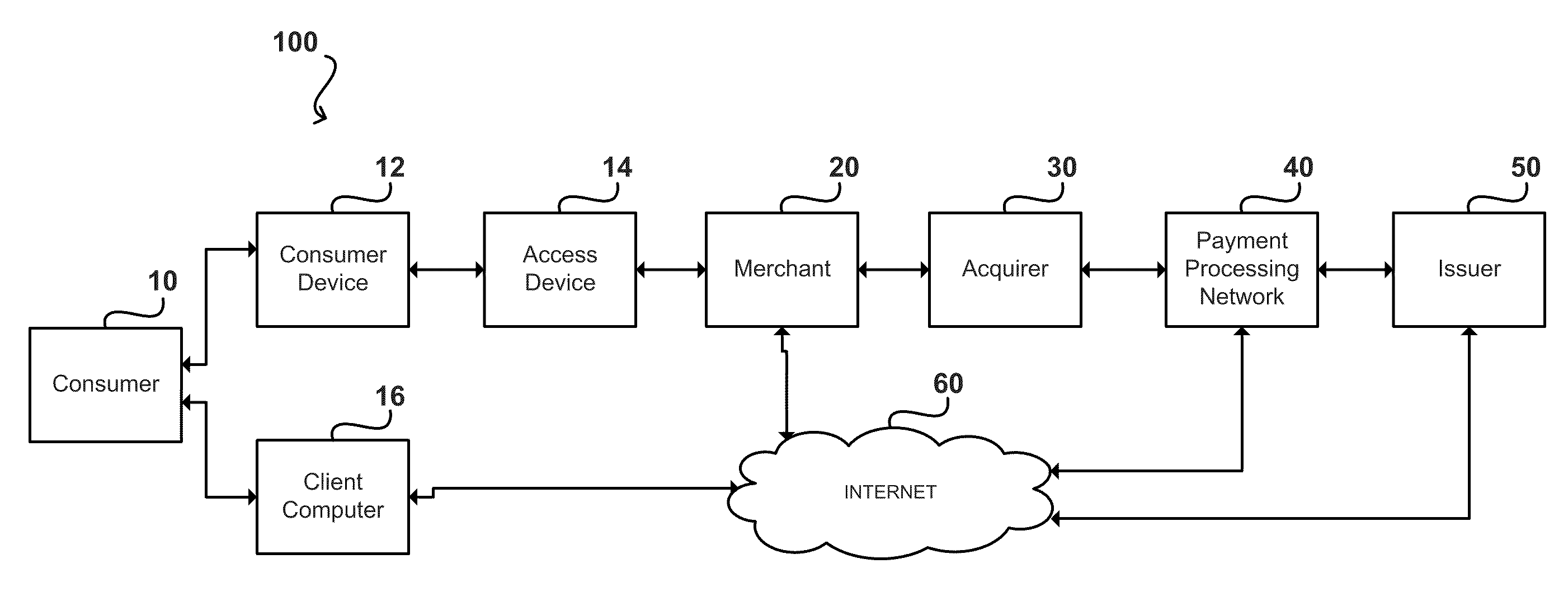
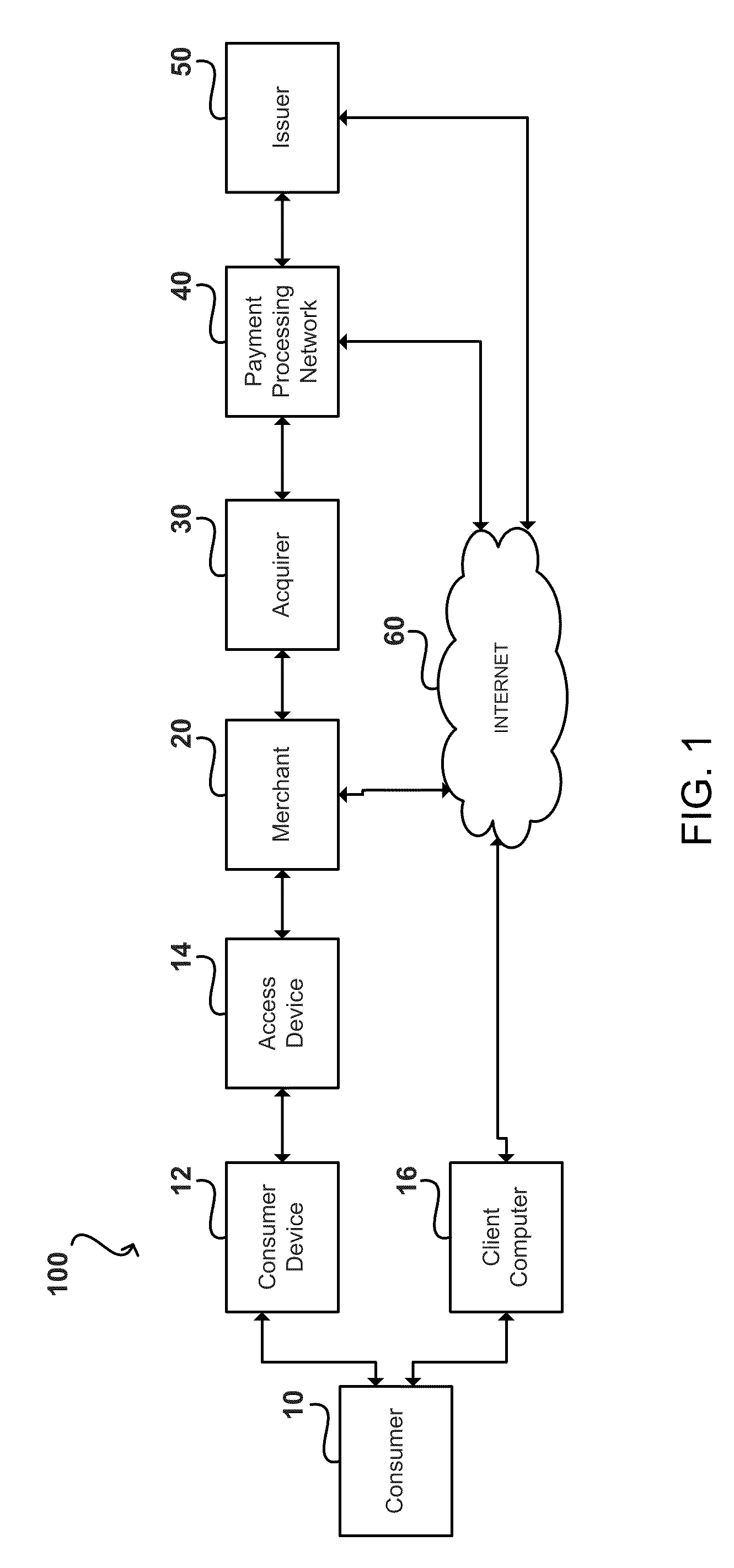
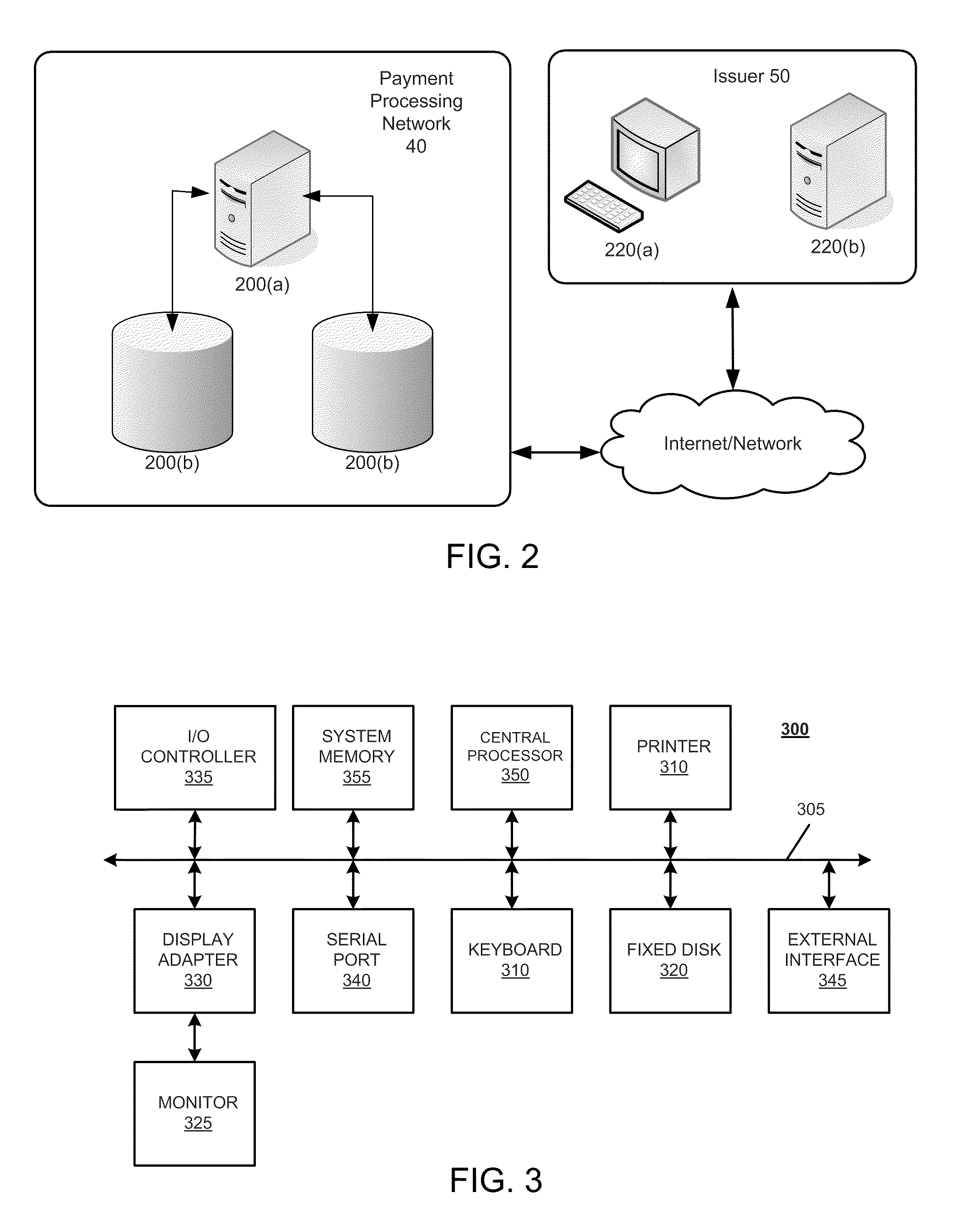
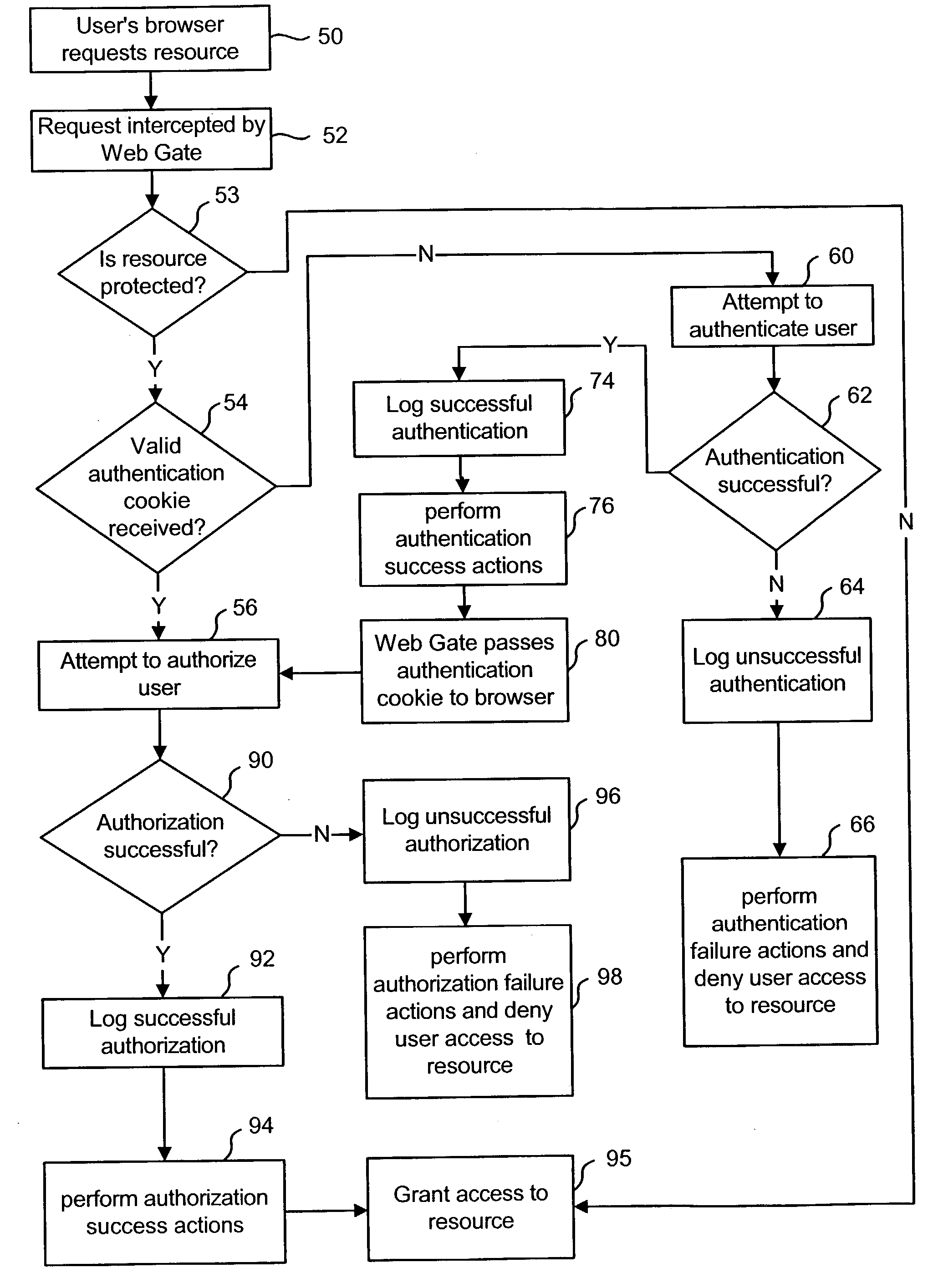
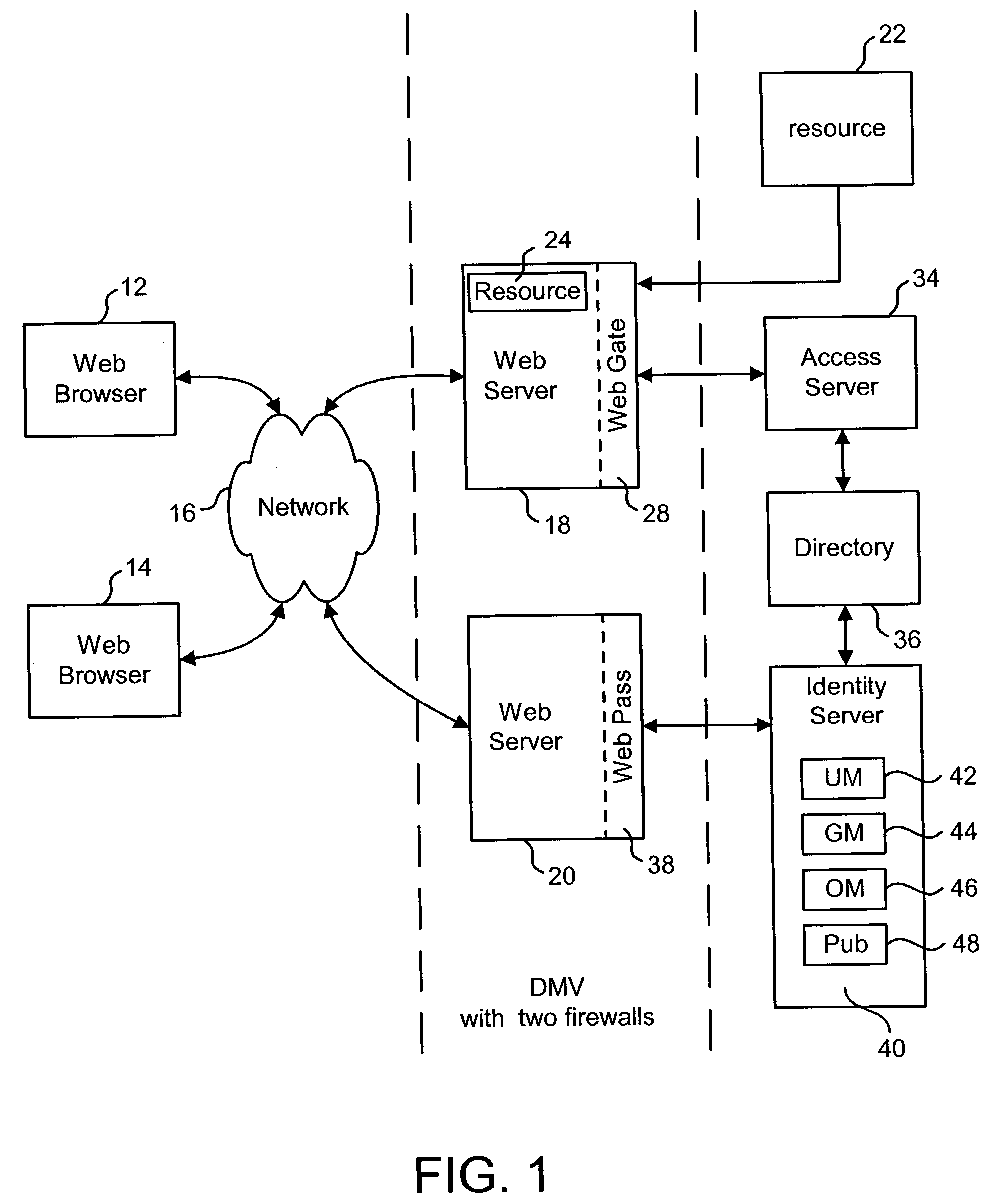
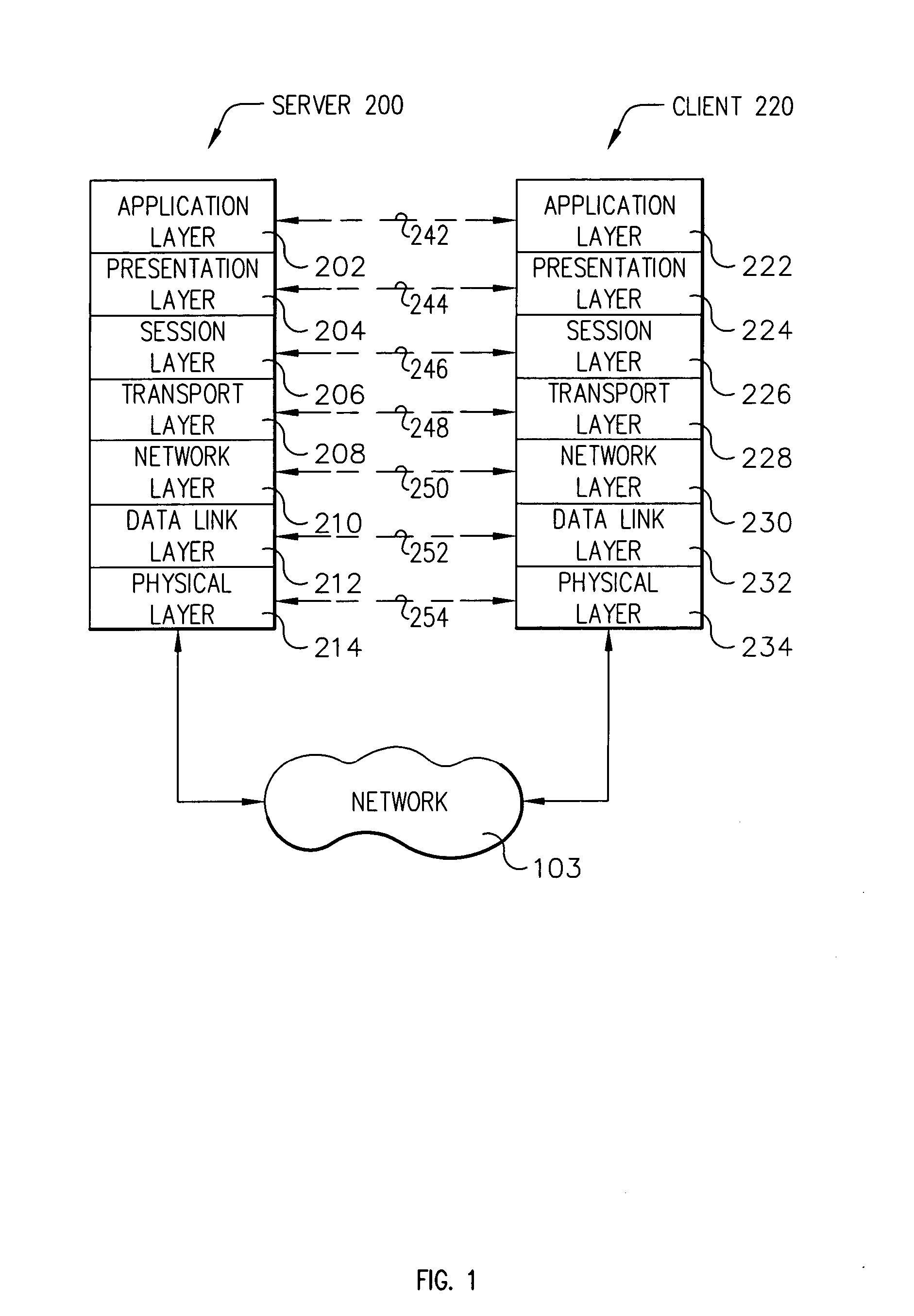
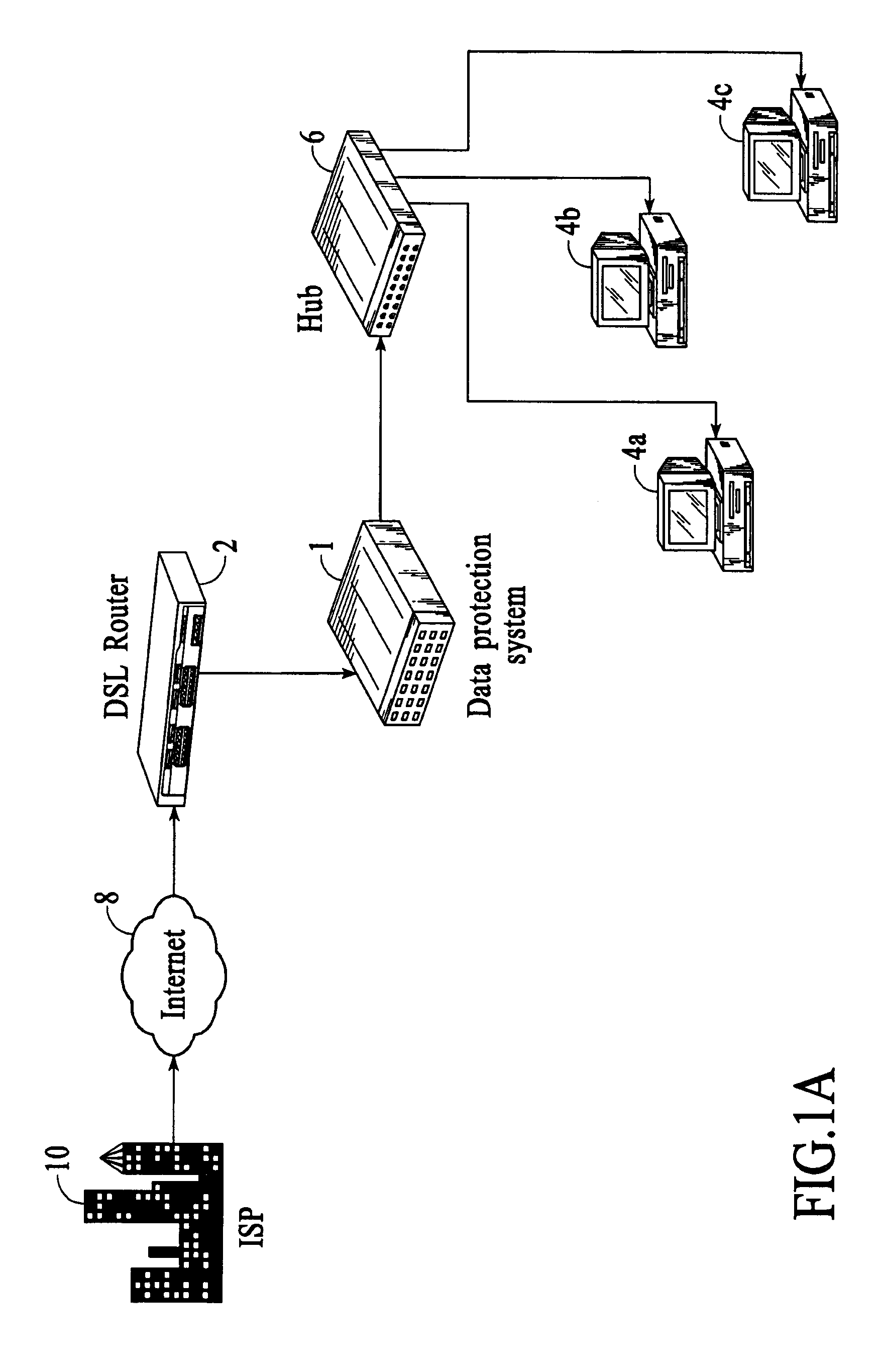
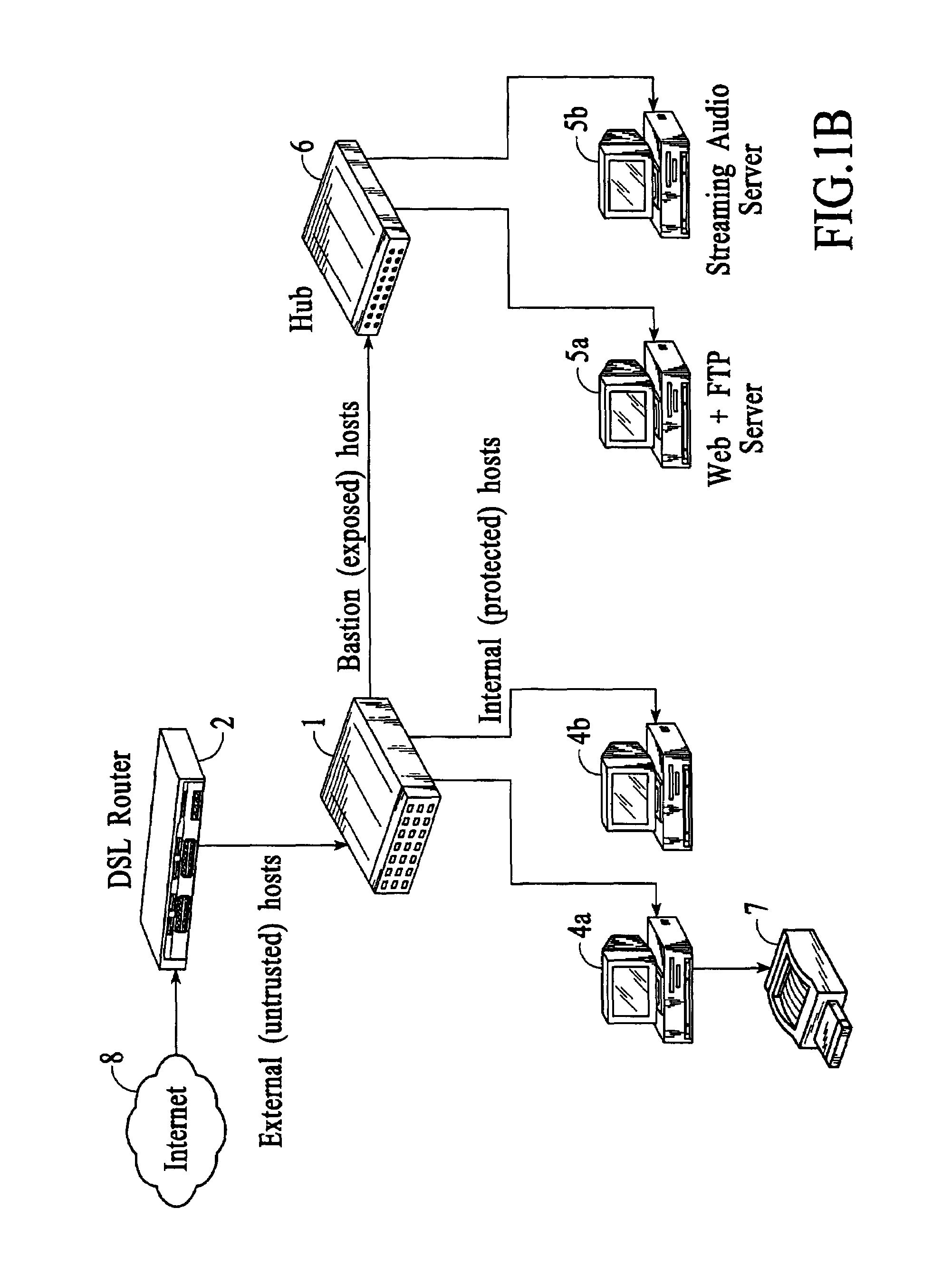
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
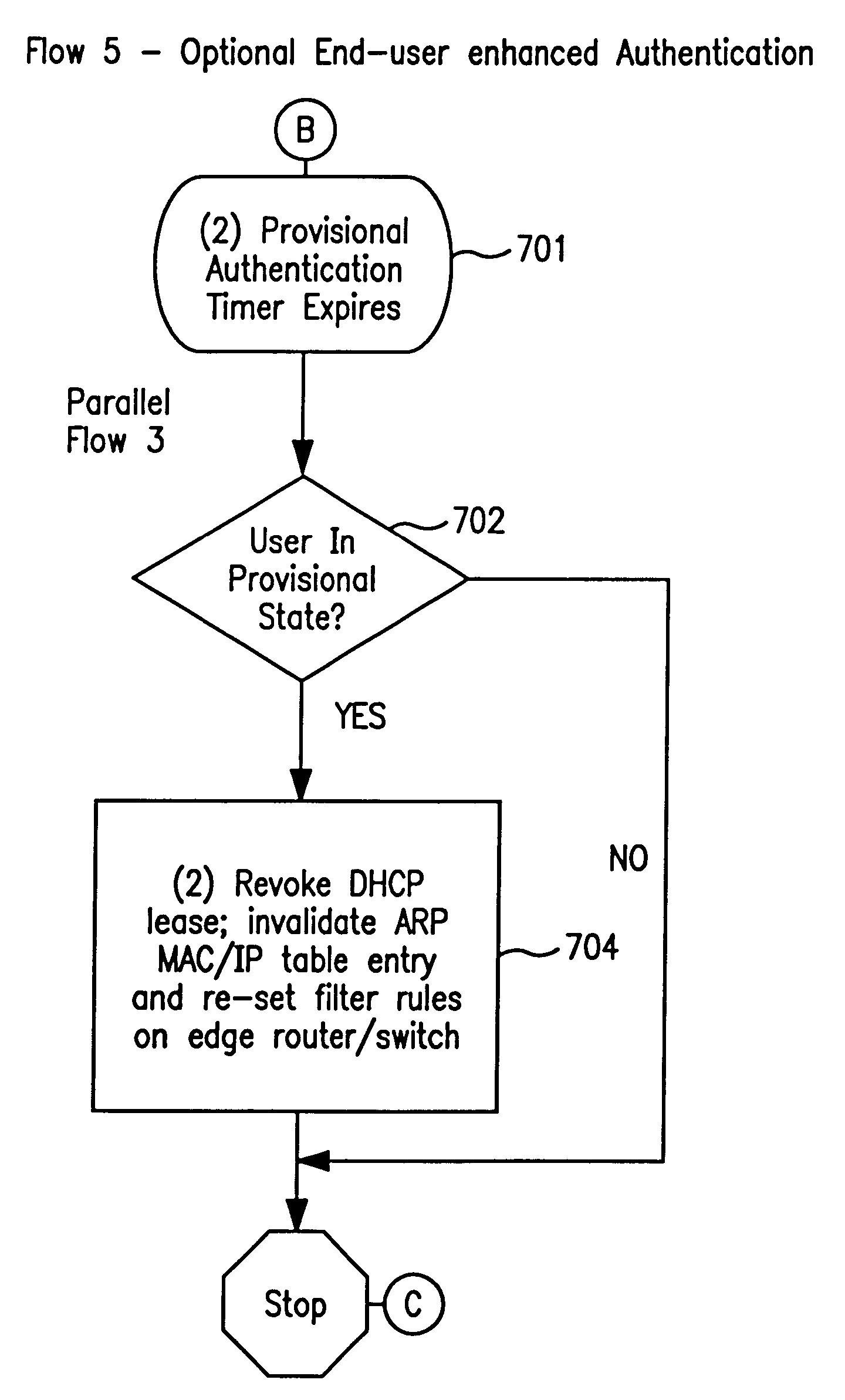
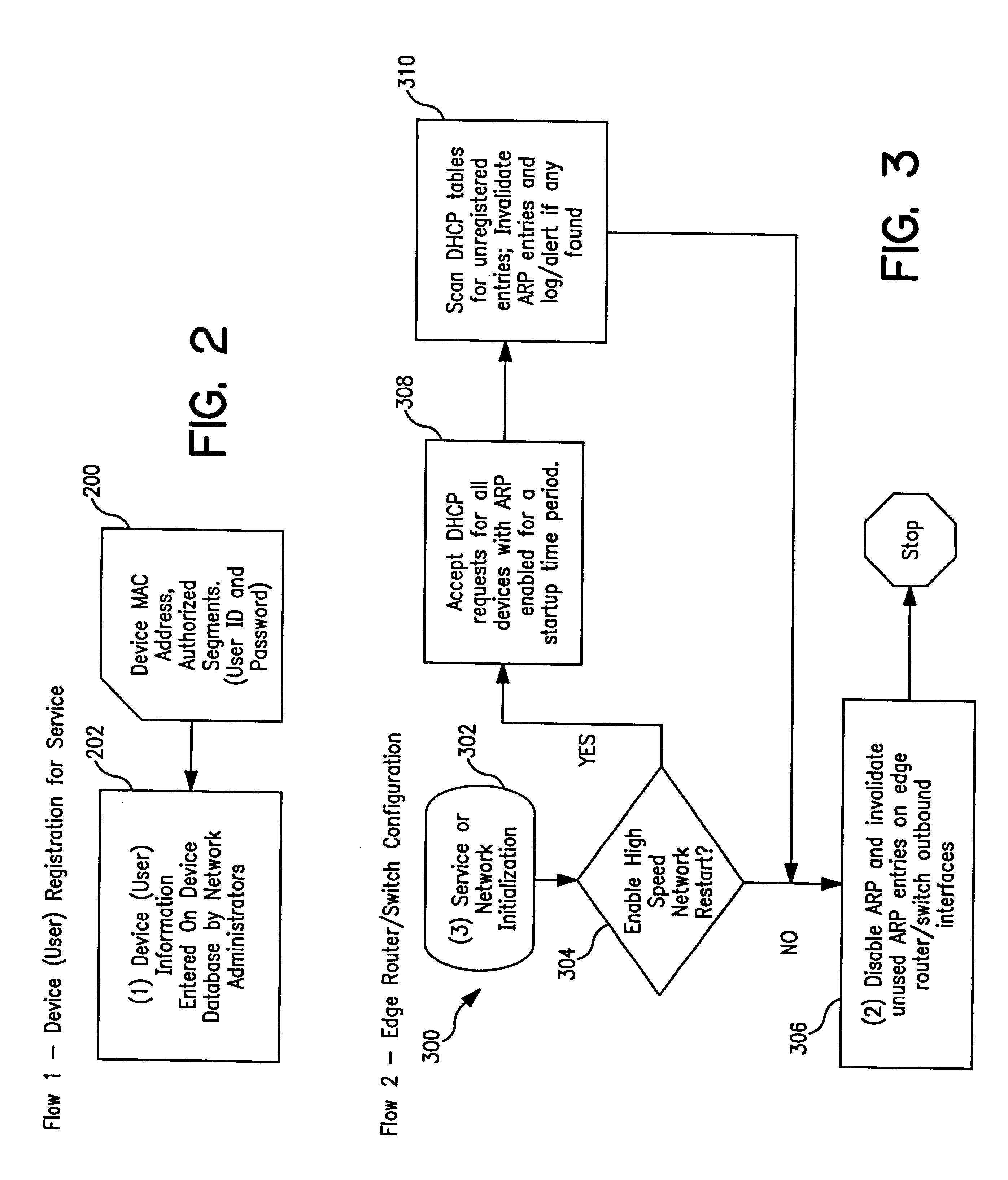
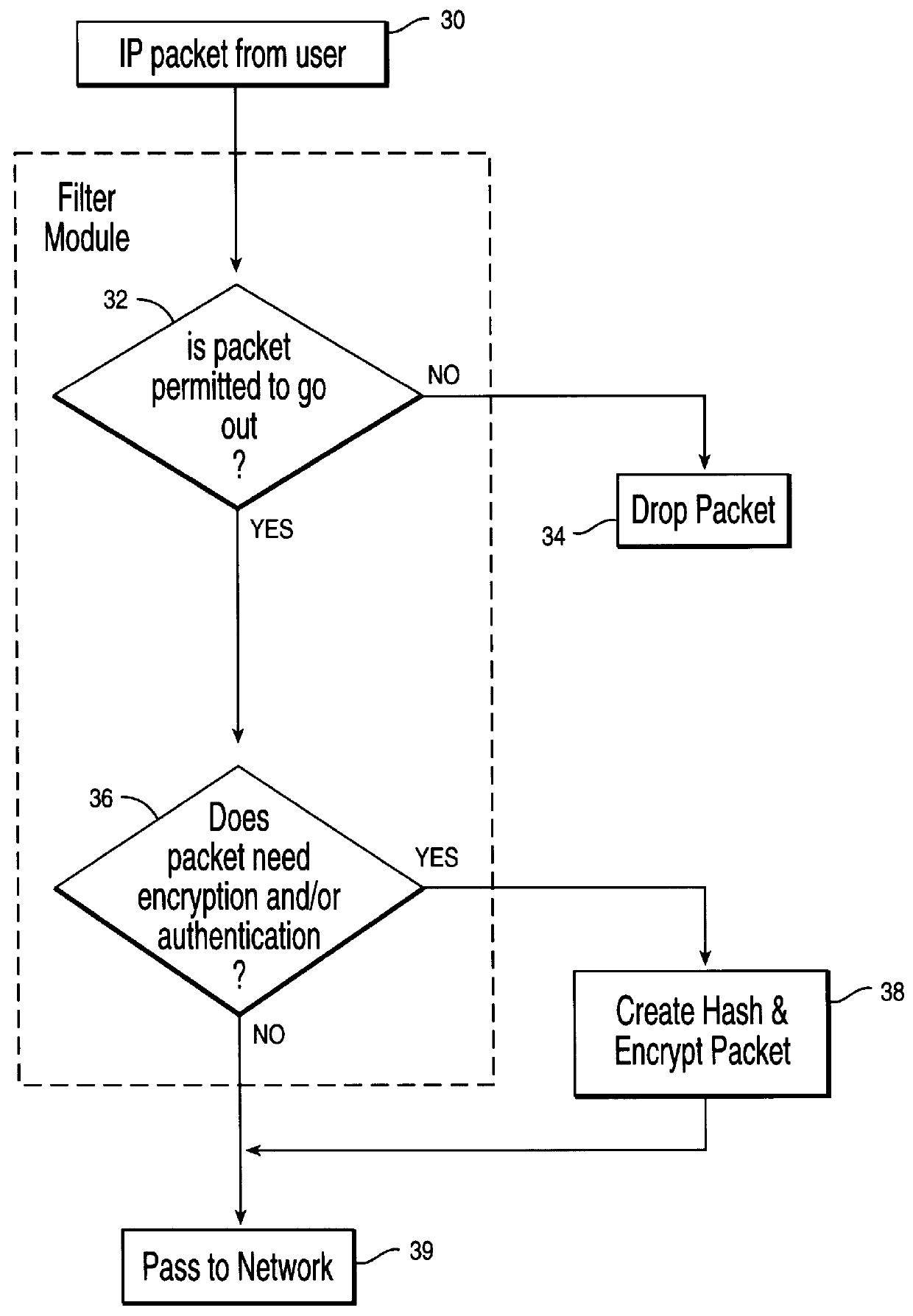
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
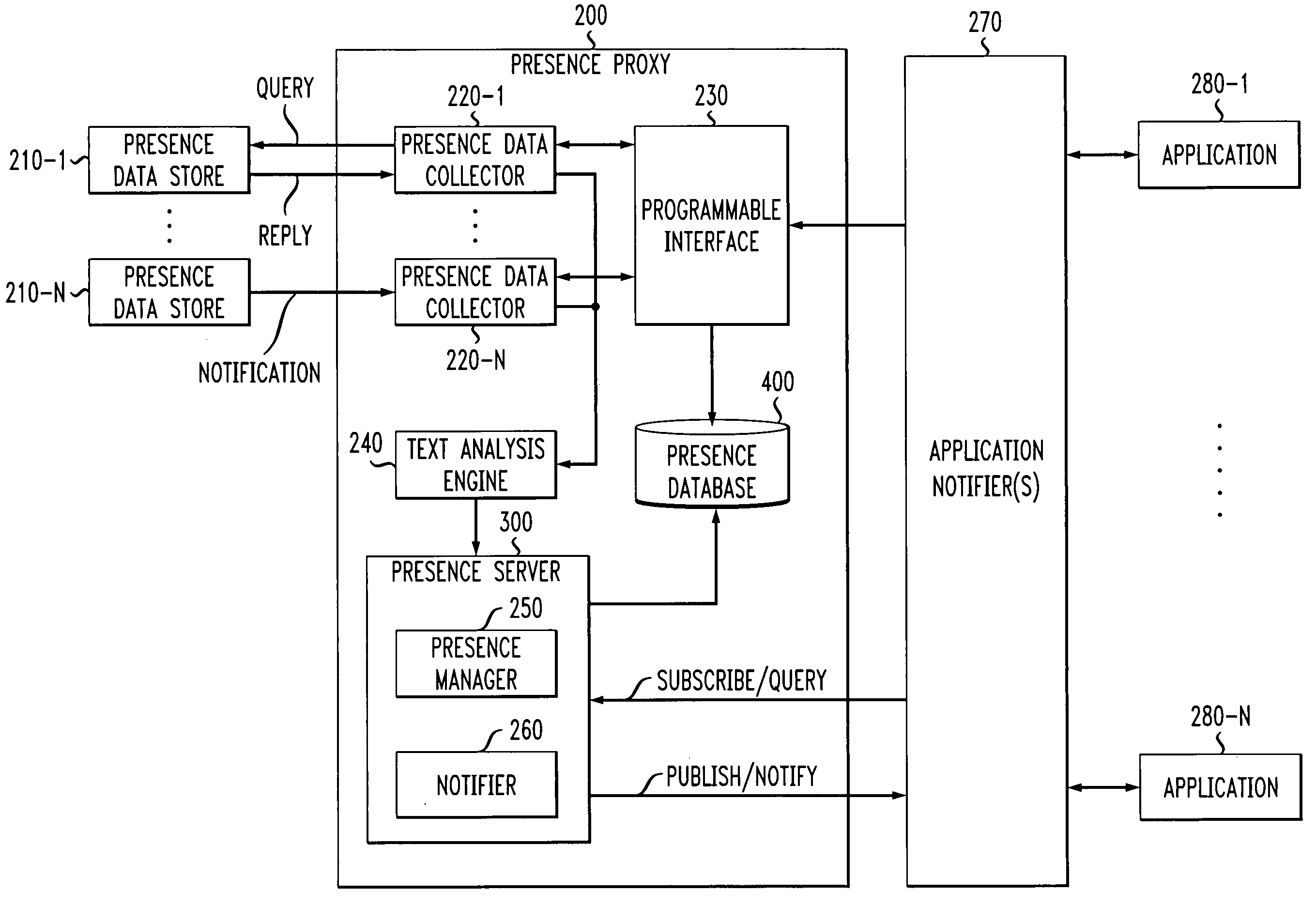
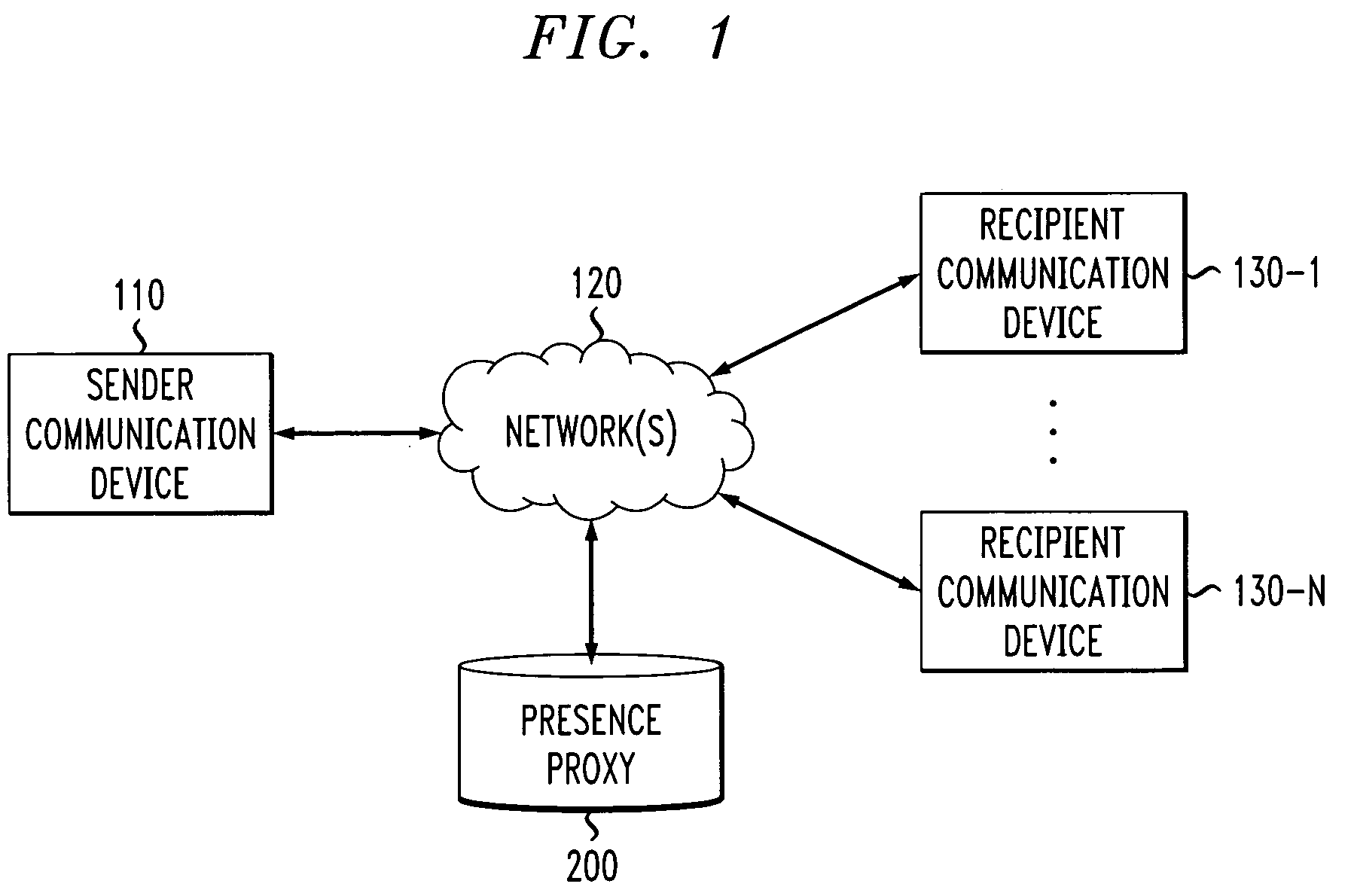
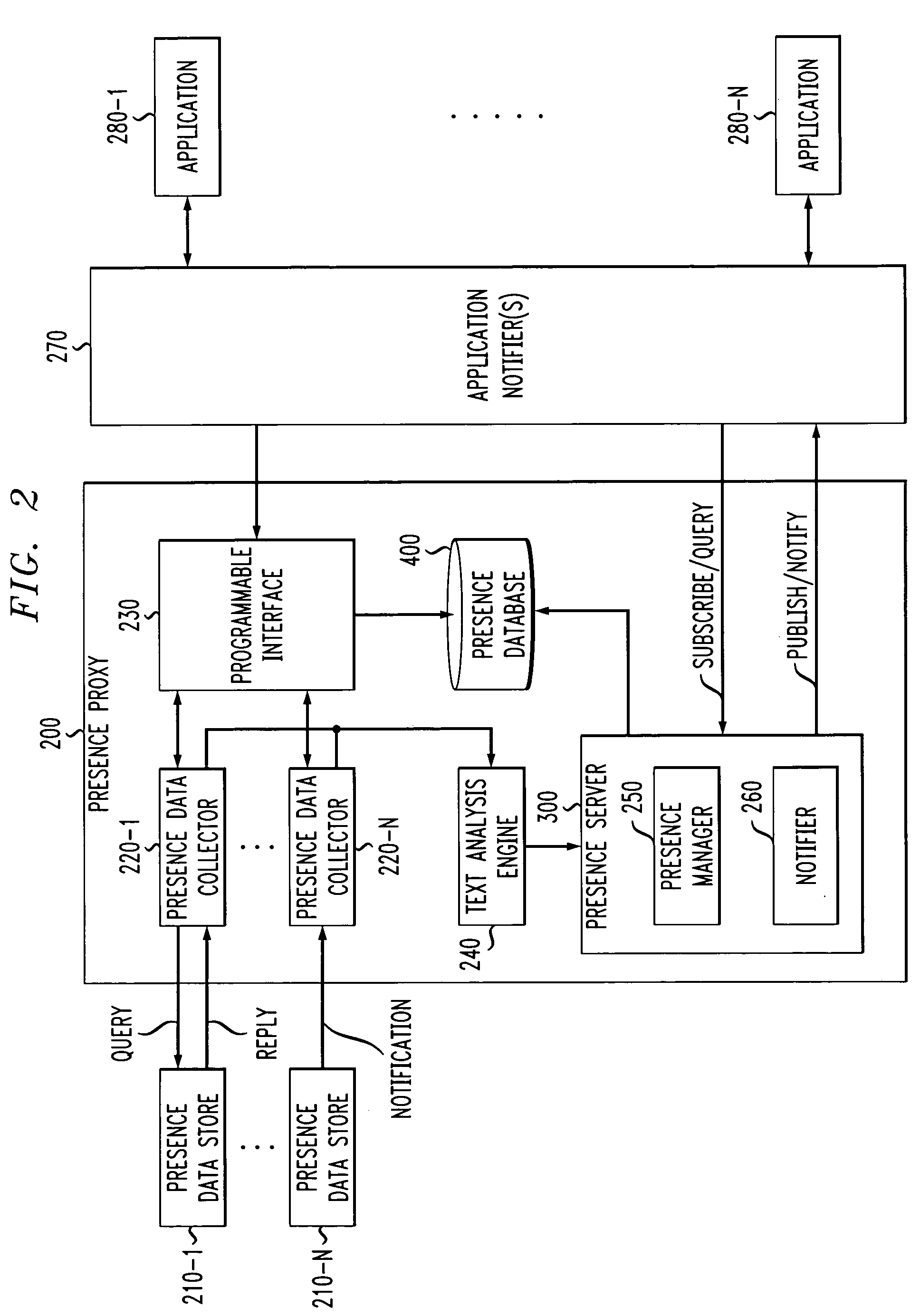
Programmable presence proxy for determining a presence status of a user
InactiveUS20050068167A1Frequency-division multiplex detailsTime-division multiplexFiltering rulesData storing
Owner:AVAYA TECH LLC
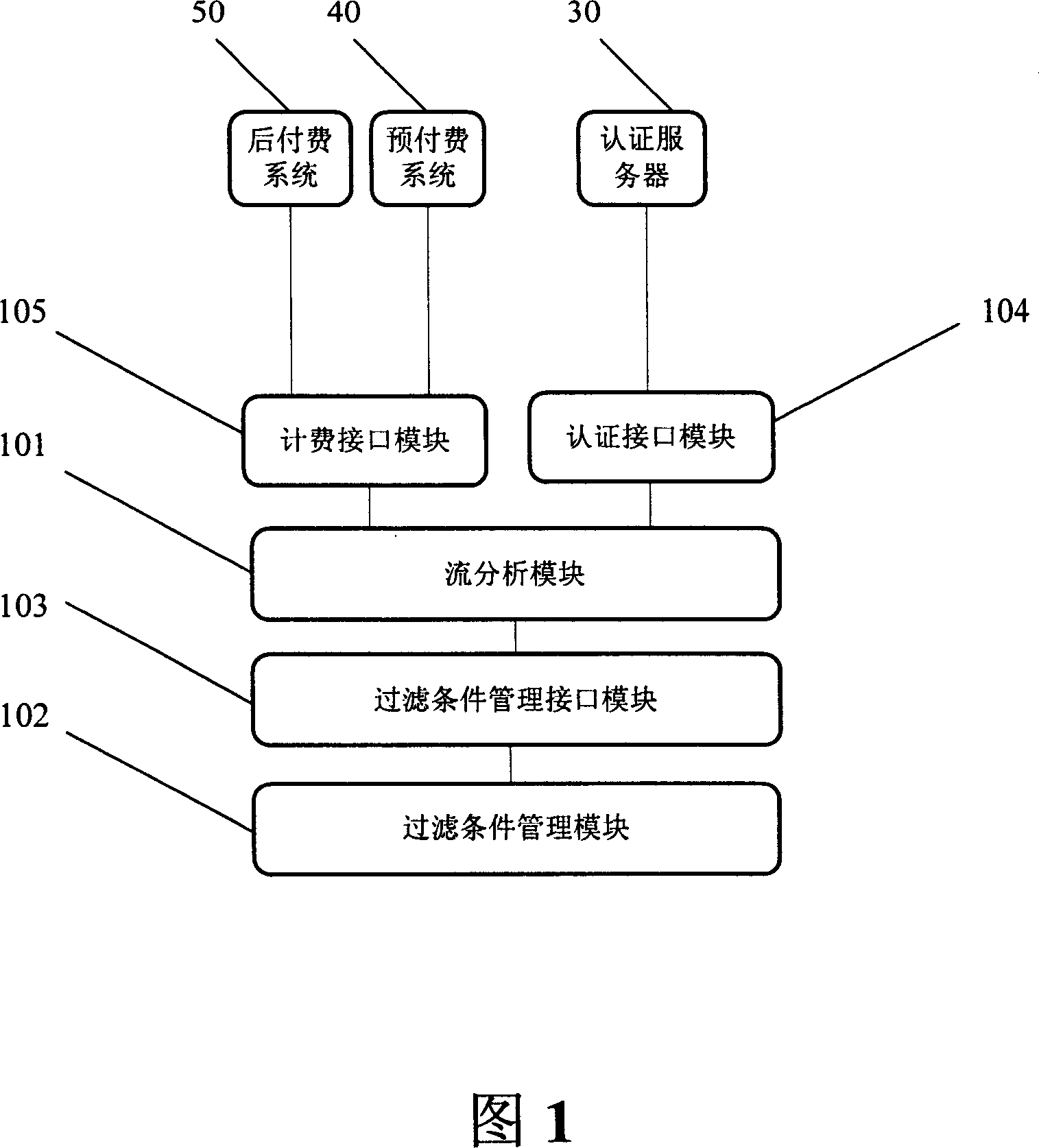
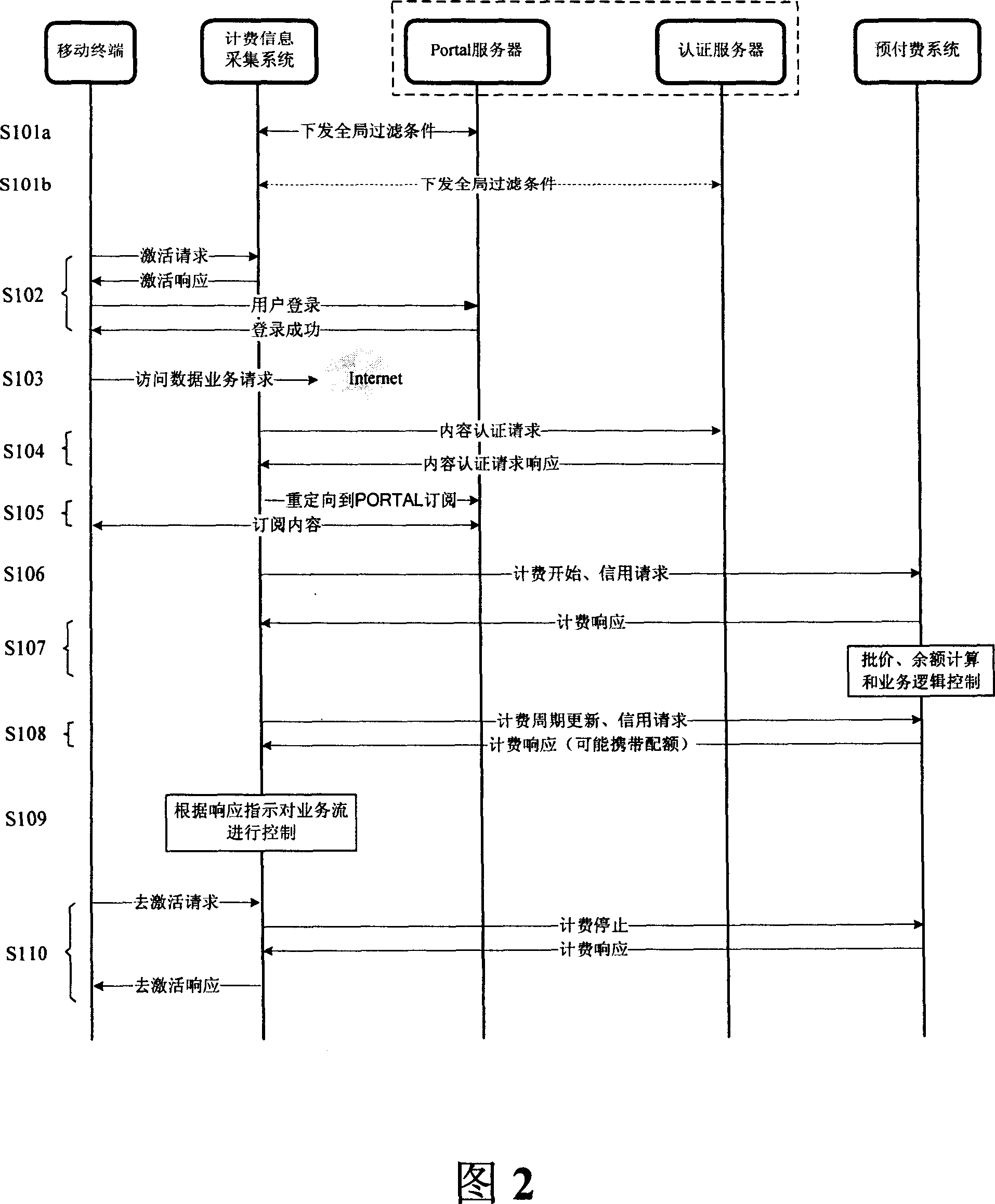
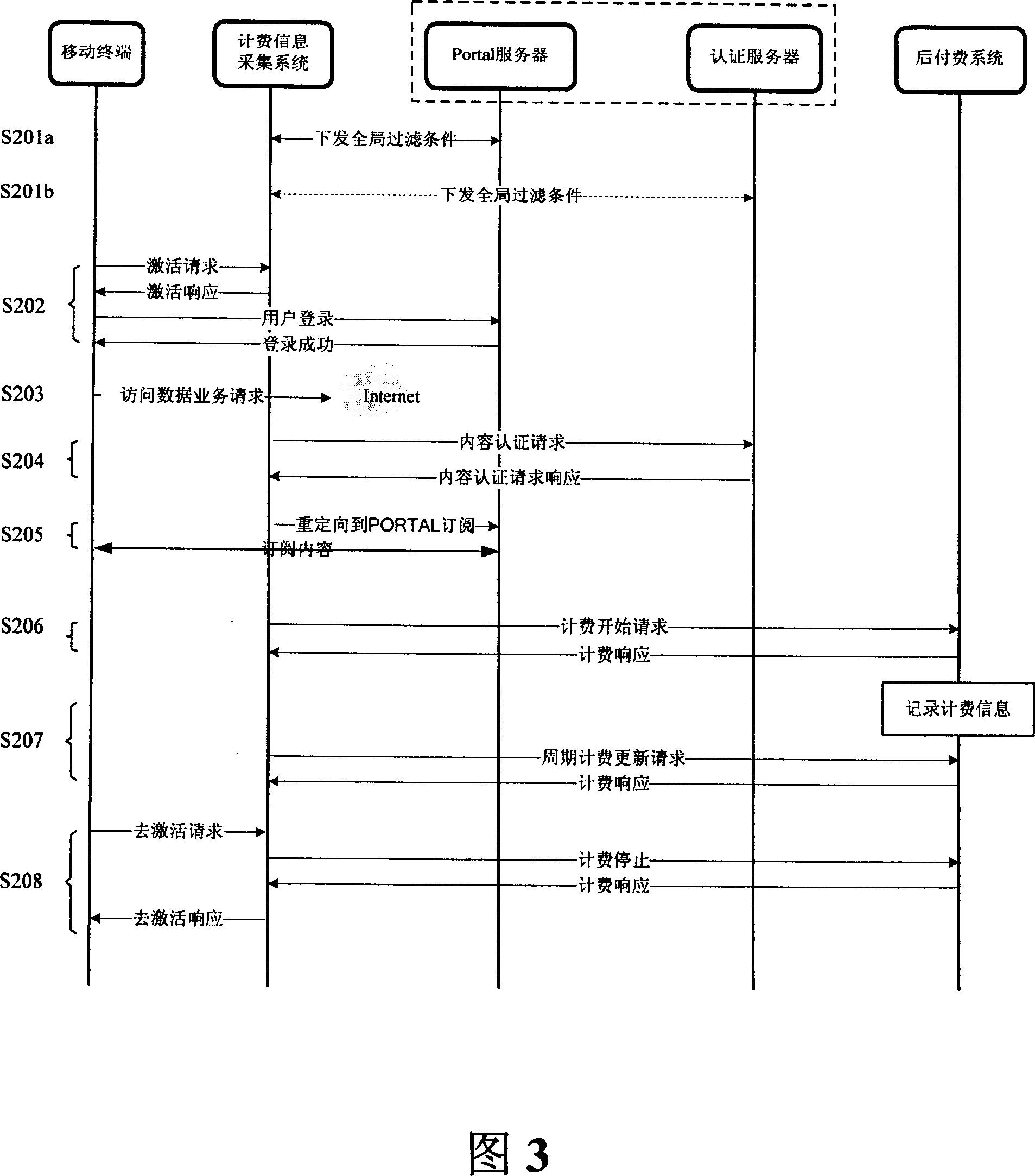
Charged information acquisition system and method, and charge realizing system and method
InactiveCN1937511AExtended business featuresMetering/charging/biilling arrangementsSoftware engineeringFiltering rules
The fare charging info collect system includes a filter condition management module (FCM) for setting and storing the filter condition being useful for flow analyze and control, a flow analyze module (FA), according to the filter condition, analyzes the business flow that mobile terminals access the data business, draws the data business content character code, business beacon and the business type info, a filter condition management interface module (FCMI) connecting FCM and FA, a authentication interface module (AI) sending the business content character code to the authentication server to authenticate. A fare charge interface module (FCI) sends the business beacon and the business type to the fare charging sub-system to charge. Via supporting user to set and modify dynamically the filter rule, this scheme extends user business features, e.g. QOS and safety features.
Owner:ZTE CORP
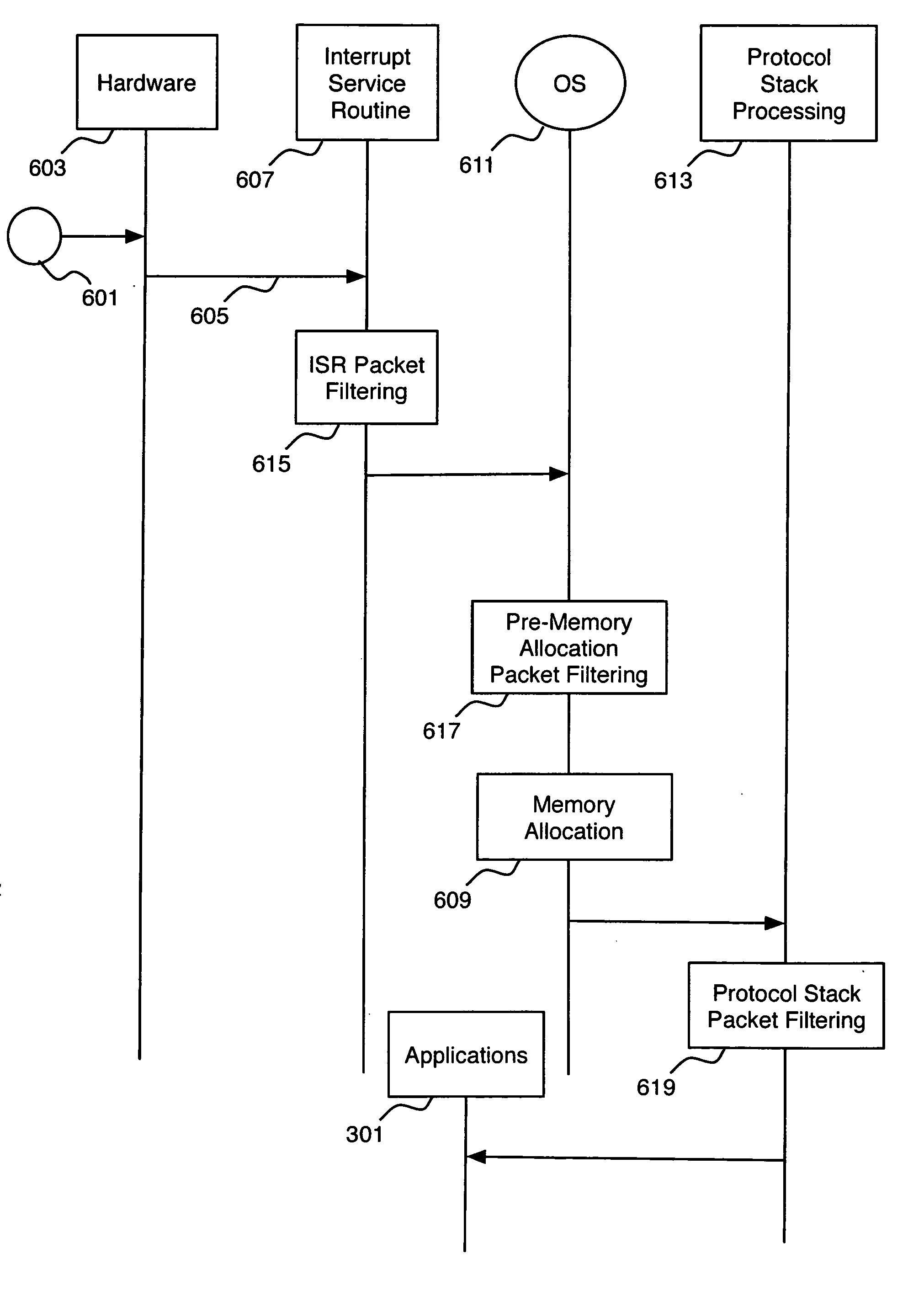
System and method for multi-stage packet filtering on a networked-enabled device
InactiveUS20070083924A1Avoiding allocating memory resourceAvoid resourcesMultiple digital computer combinationsProgram controlData packProtocol processing
A multi-stage packet filtering method and system. The multi-stage packet filtering according to the invention applies a set of filtering rules early in the processing of incoming communications packets by filtering incoming data packets using the filtering rules in a plurality of stages wherein the first stage is triggered by the receipt of a data packet by the device. Filtering rules that cannot be applied in the first stage may be deferred to a pre-memory allocation stage. Thus, preferable leaving only rules that must be executed in conjunction with protocol processing to be filtered at a filtering stage executed in a protocol processing filtering stage.
Owner:LU HONGQIAN KAREN
Disambiguating conflicting content filter rules
A content filtering mechanism is enhanced to resolve conflicts in filtering rules (e.g., those created by a whitelist, on the one hand, and a blacklist, on the other hand). Preferably, a conflict between or among content filtering rules is resolved by selecting among conflicting rules based on a notion of “risk” associated with the rules. According to this risk-based approach, when two or more rules conflict with one another, the particular rule whose risk value has a predetermined relationship (e.g., aligns most closely) with a risk level associated with the application (applying the rules) then takes precedence. By selecting among conflicting rules based on risk, the potential or actual conflicts are disambiguated, with the result being that the content is filtered appropriately.
Owner:IBM CORP
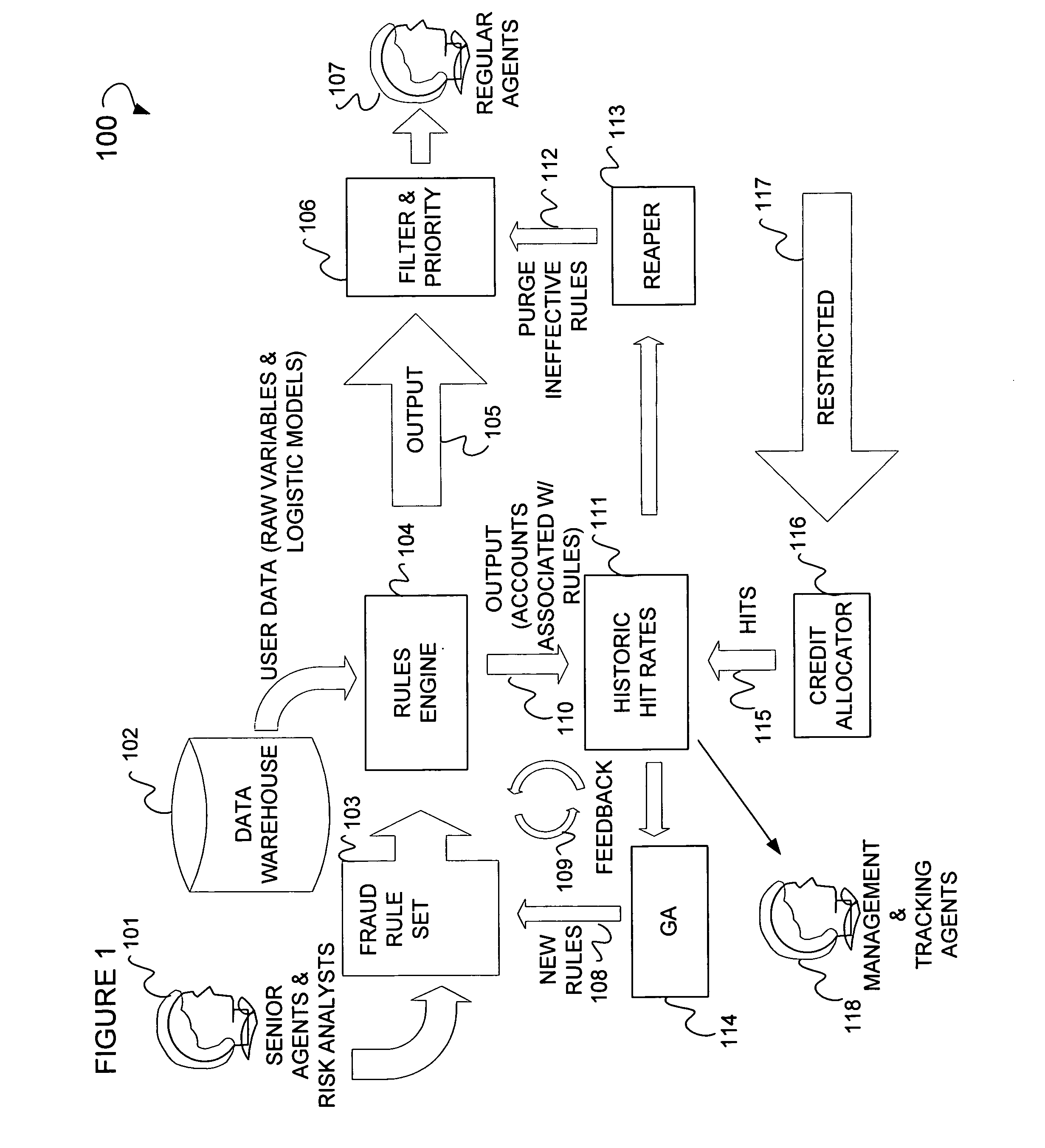
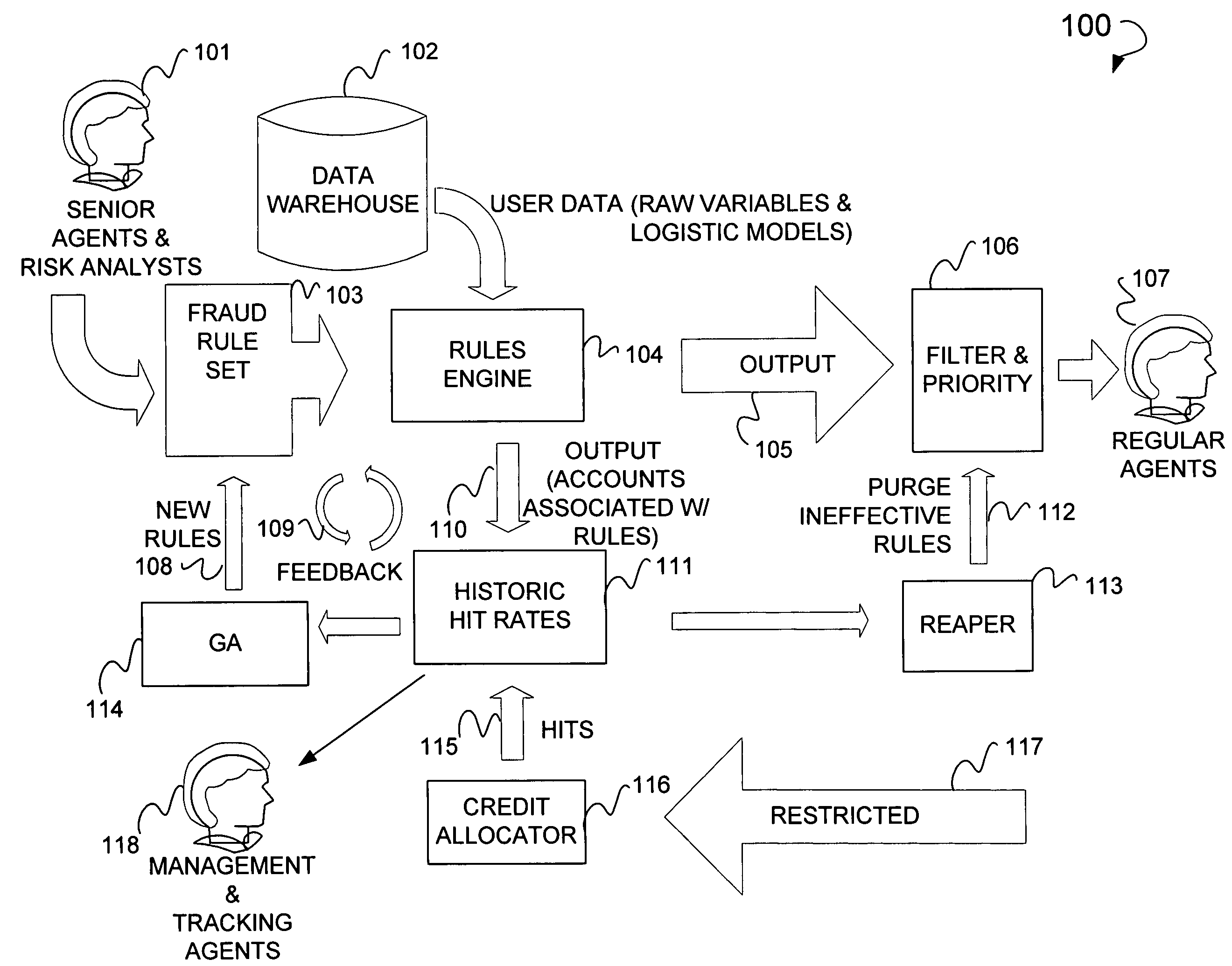
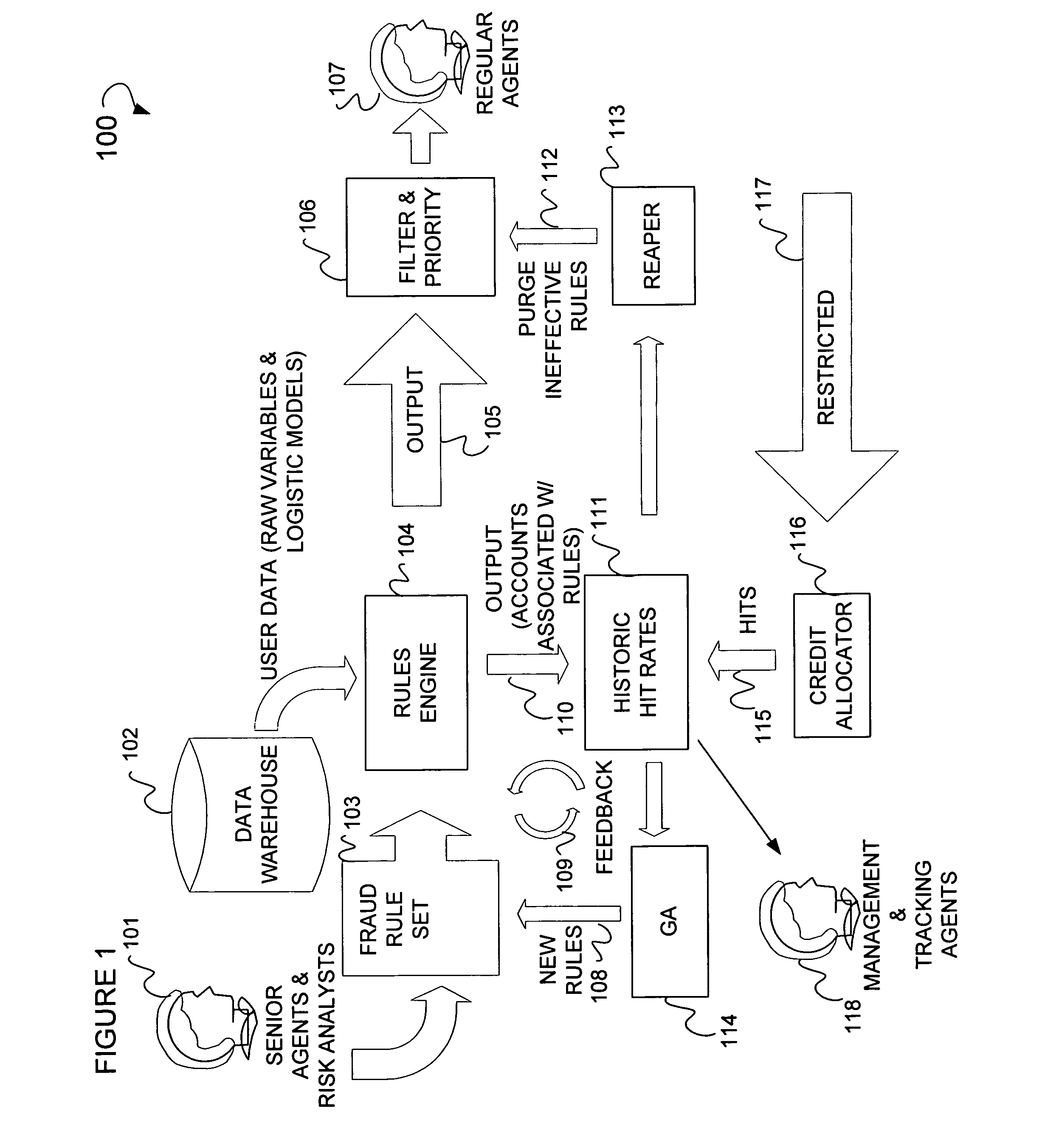
Online fraud prevention using genetic algorithm solution
Online fraud prevention including receiving a rules set to detect fraud, mapping the rules set to a data set, mapping success data to members of the rules set, filtering the members of the rules set, and ordering members of the data set by giving priority to those members of the data set with a greater probability for being fraudulent based upon the success data of each member of the rule set in detecting fraud. Further, a receiver coupled to an application server to receive a rules set to detect fraud, and a server coupled to the application server, to map the rules set to a data set, and to map the success data to each members of the rules set. The server is used to order the various members of the data set by giving priority to those members of the data set with a greatest probability for being fraudulent.
Owner:PAYPAL INC
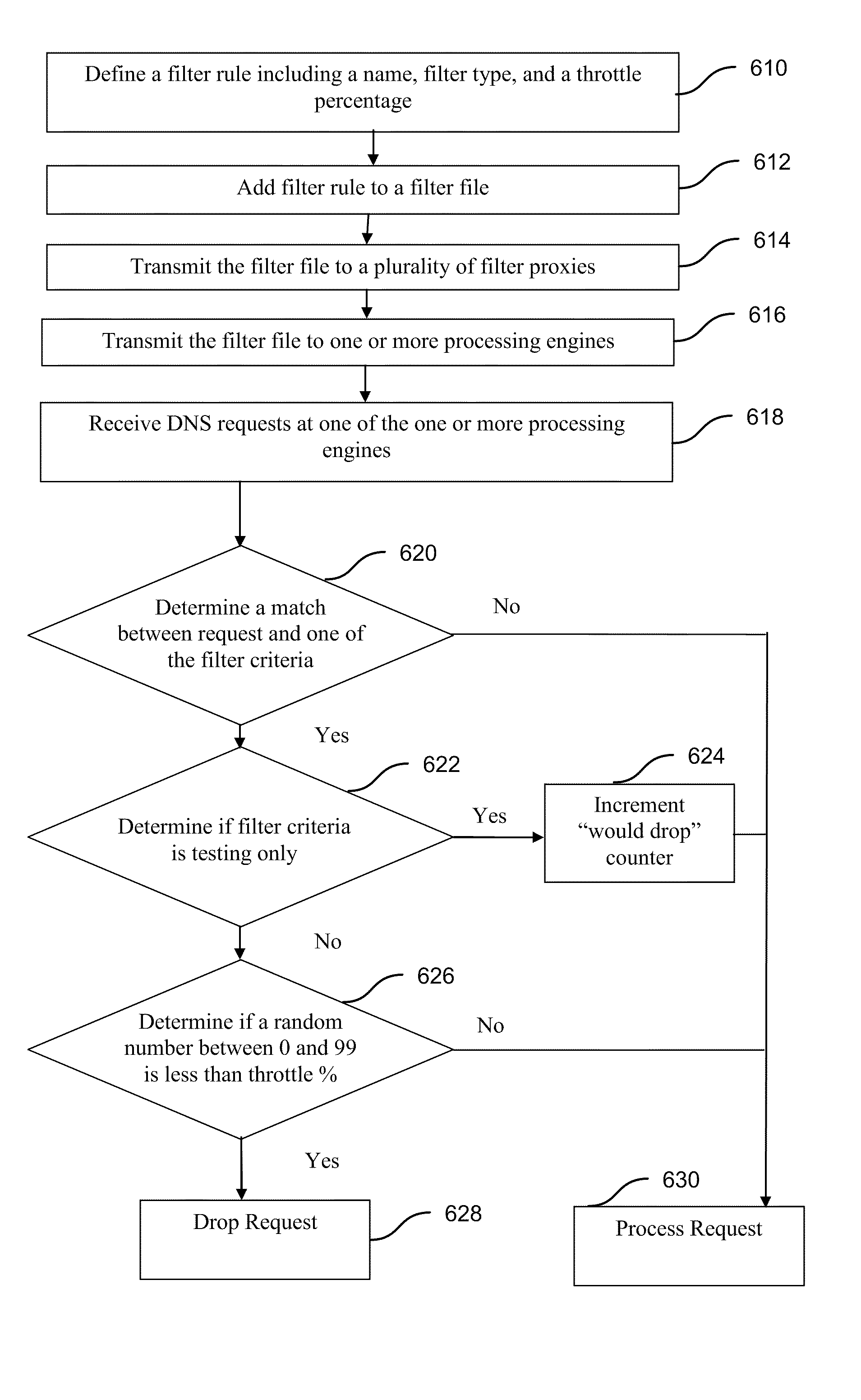
Method and system for filtering of network traffic
ActiveUS20110035469A1Quickly and efficiently distributingError preventionTransmission systemsDomain nameTraffic capacity
A method of filtering a plurality of DNS queries, wherein each DNS query includes a query name and a resource record type, includes defining a filter rule including a domain name, a filter type, and a throttle percentage and forming a filter file including the filter rule. The method also includes transmitting the filter file from a server to a plurality of filter proxies, transmitting the filter file from each of the plurality of filter proxies to one or more processing engines, and receiving the plurality of DNS queries at one of the one or more processing engines. The method includes determining a match between the domain name and the query name and between the resource record type and the filter type for a subset of the plurality of DNS queries, and blocking a predetermined percentage (equal to the throttle percentage) of the subset of the plurality of DNS queries.
Owner:VERISIGN
Action support method and apparatus
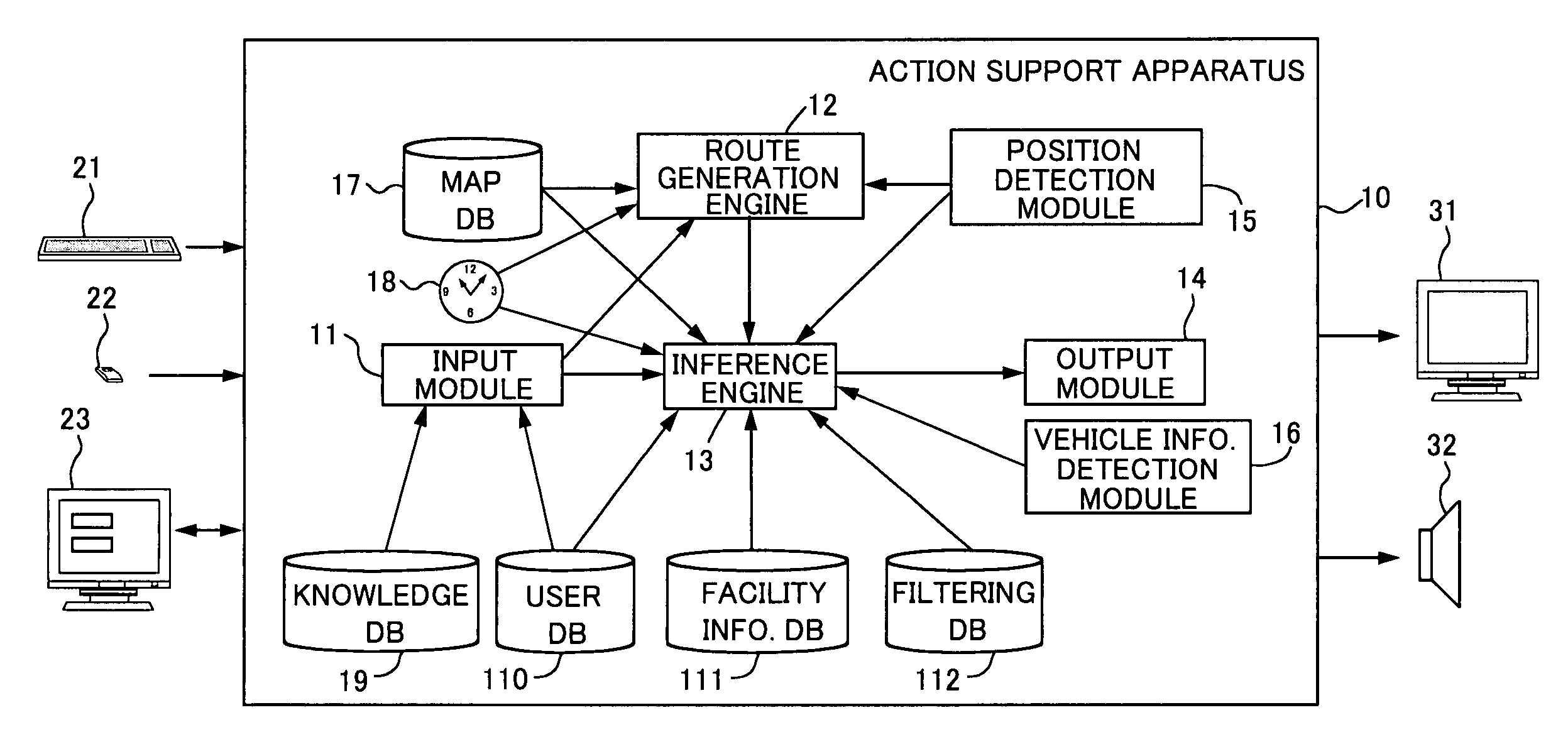
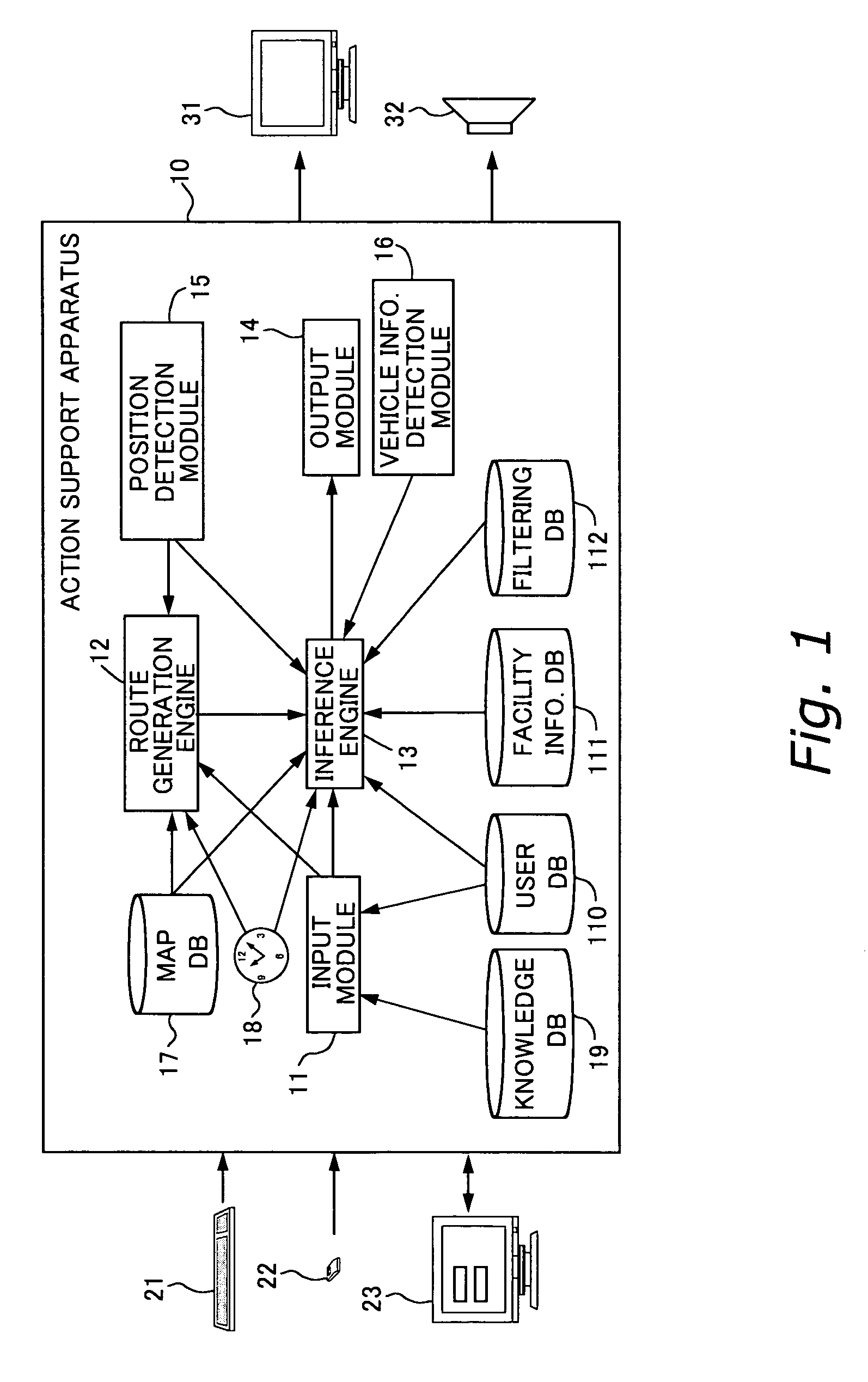
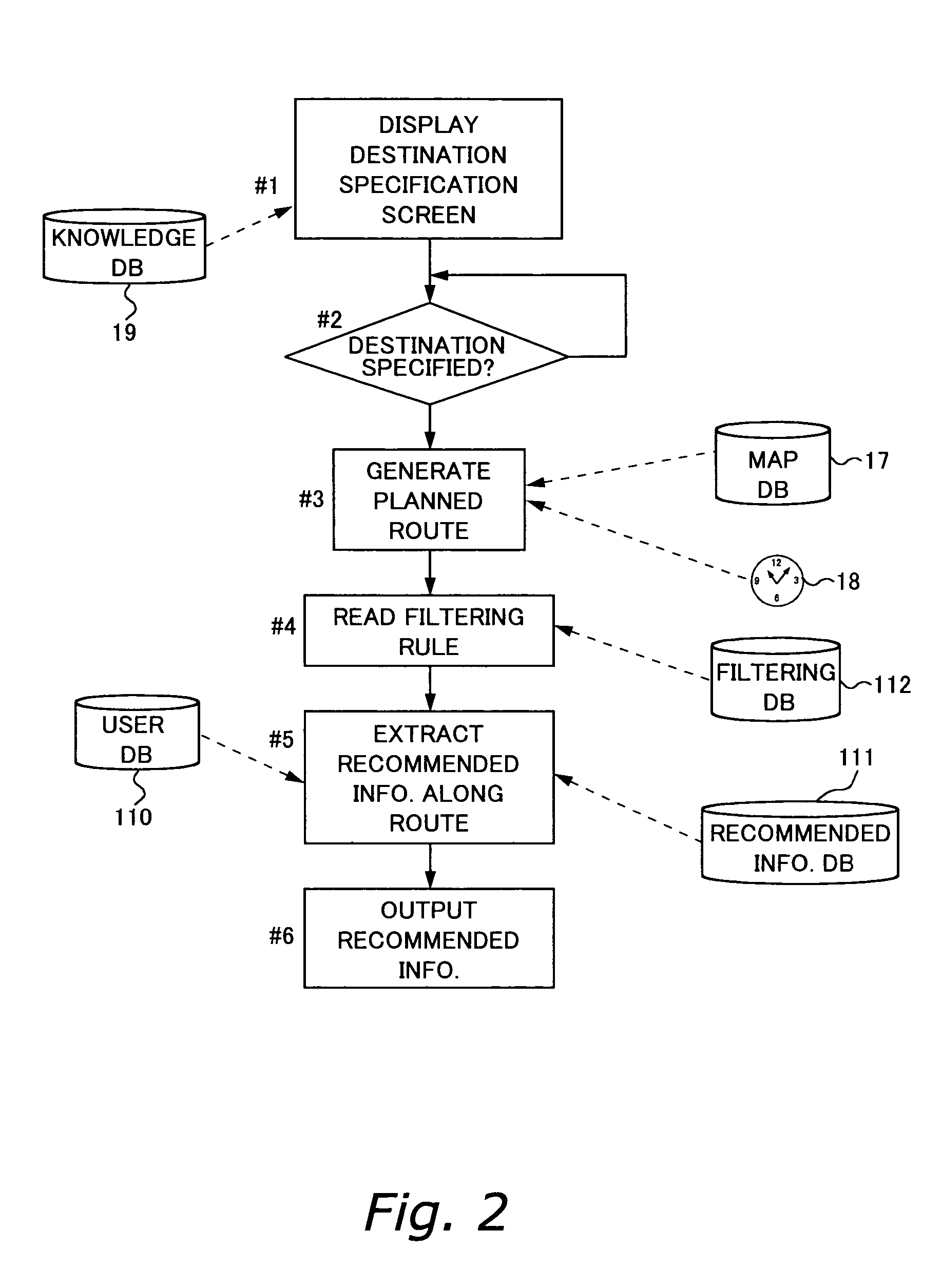
InactiveUS7254481B2Sure easyInstruments for road network navigationRoad vehicles traffic controlFiltering rulesComputer science
An action support apparatus displays a destination specification screen for specifying a destination, and receives from the user a specification of a general destination. If a general destination is specified, then the apparatus determines a detailed destination, referencing a knowledge DB. If there is a plurality of detailed destinations with respect to the general destination, then any one of them is set to the user's destination. Next, the apparatus sets the current location as the starting point, and generates a planned route from the starting point to the destination based on a map DB and an internal clock. Furthermore, the apparatus reads a filtering rule from a filtering DB, and extracts as recommended information facility information of facilities suited to the user from a facility information DB. Depending on the filtering rule, it is also acceptable to use user information in a user DB in the extraction of the recommended information. Subsequently, the apparatus associates the extracted recommended information with the planned route, and outputs them.
Owner:FUJITSU LTD
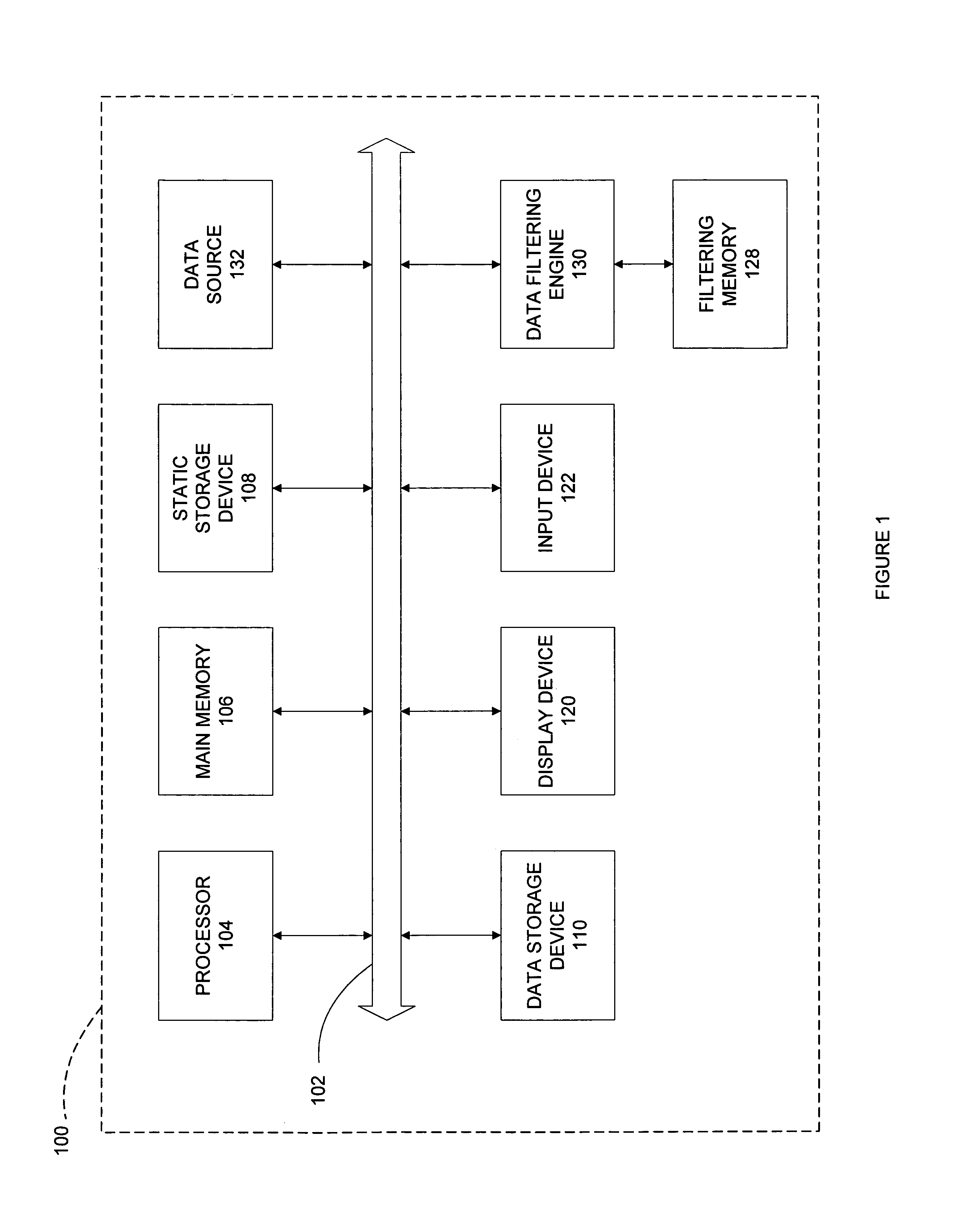
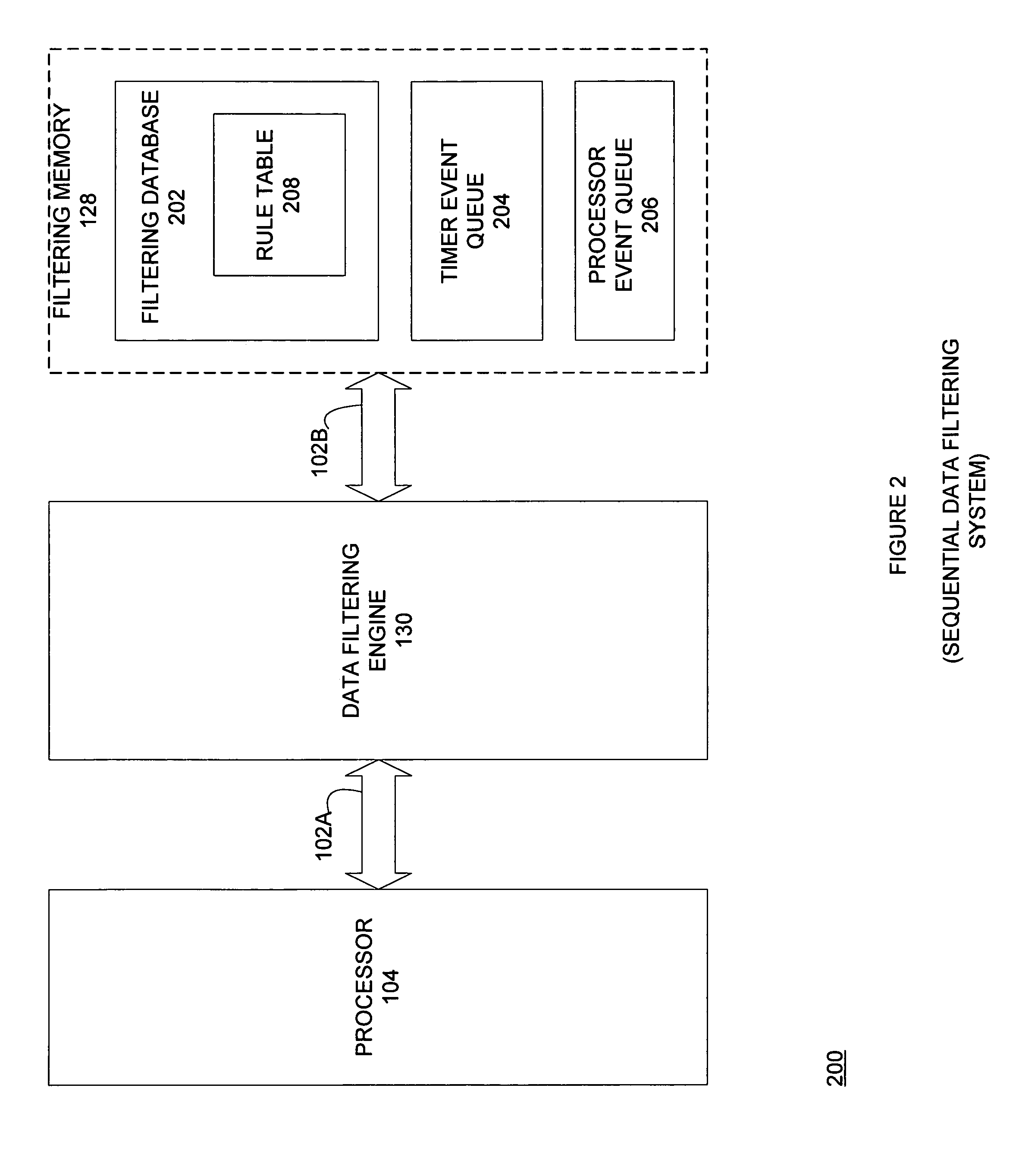
System and method for filtering data
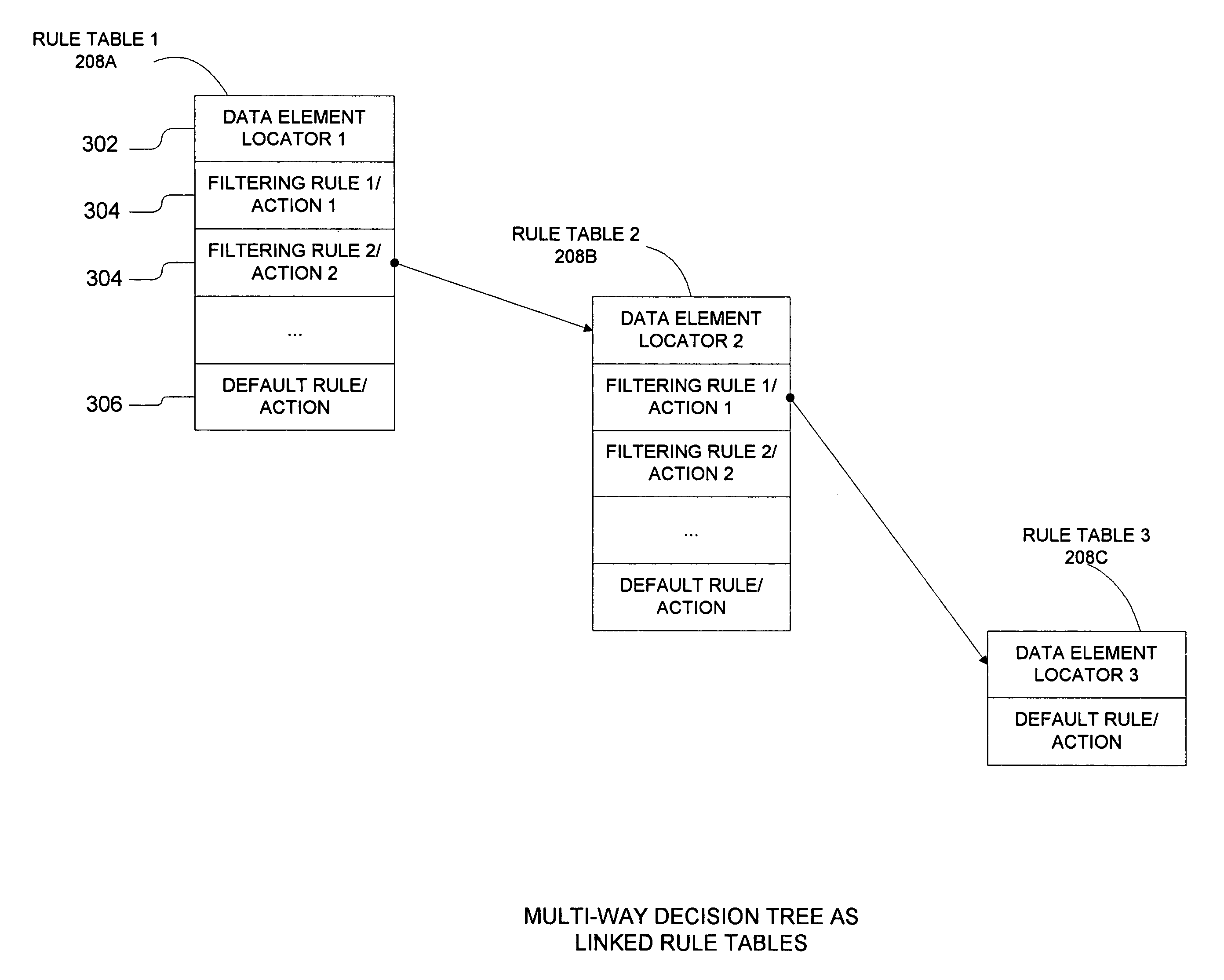
InactiveUS7133400B1Quickly and efficiently classifyQuickly and efficiently and filterDigital computer detailsData switching by path configurationFiltering rulesData element
A system for filtering data comprises a filtering database for storing layered rule tables and a data filtering engine coupled to the filtering database for filtering the input data using the layered rule tables. The data filtering engine filters or classifies input data using tests or rules performed on the data elements in the input data. The data elements are segments of data in the input data and are selected from the input data using a data element locator. Preferably, each rule table in the filtering database comprises a data element locator, a default rule, and zero or more filtering rules. The filtering rules comprise the tests or rules that are to be applied to the data elements. Each rule table corresponds to a single data element and each filtering rule in the rule table is to be applied to that data element.
Owner:INTEL CORP
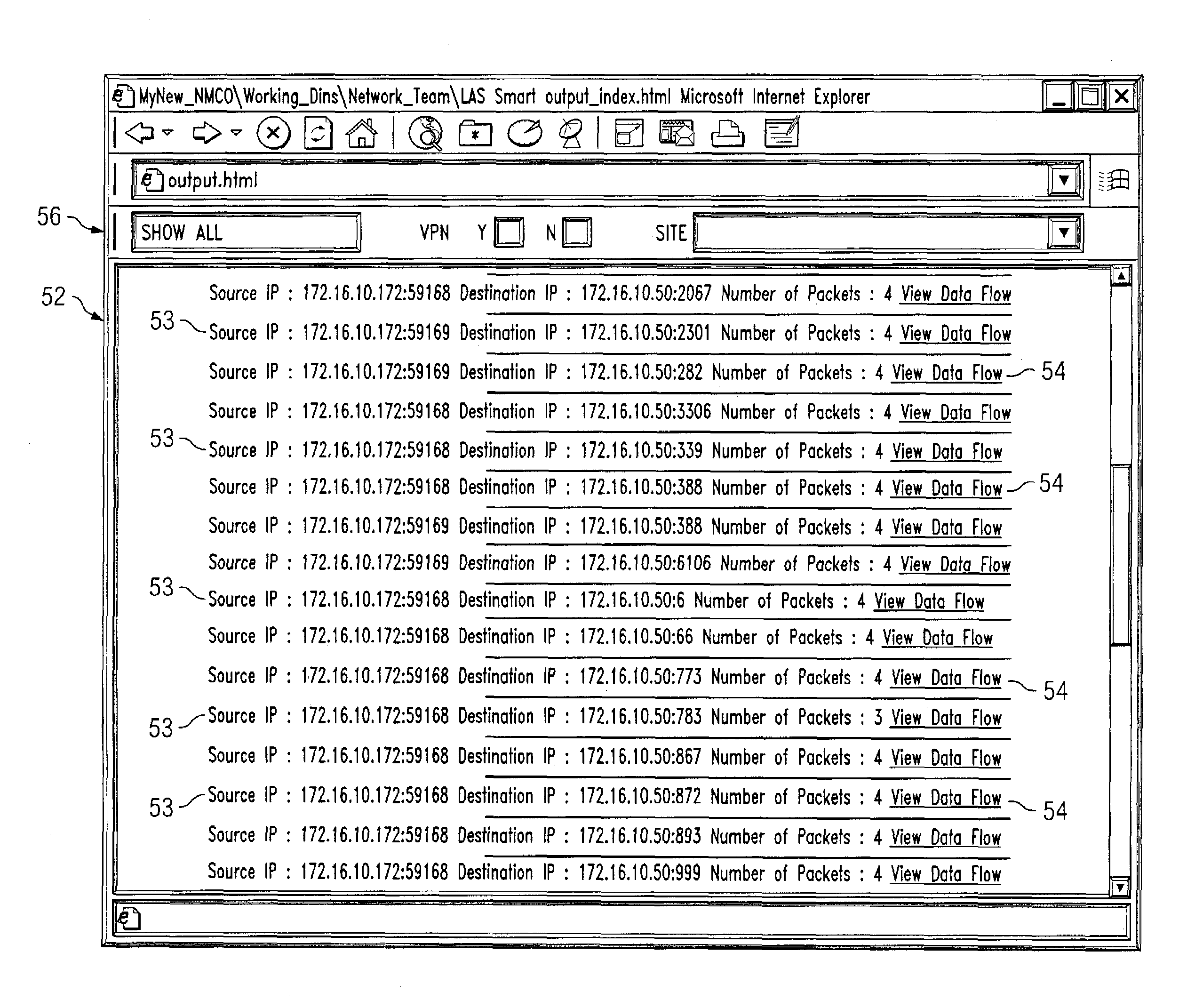
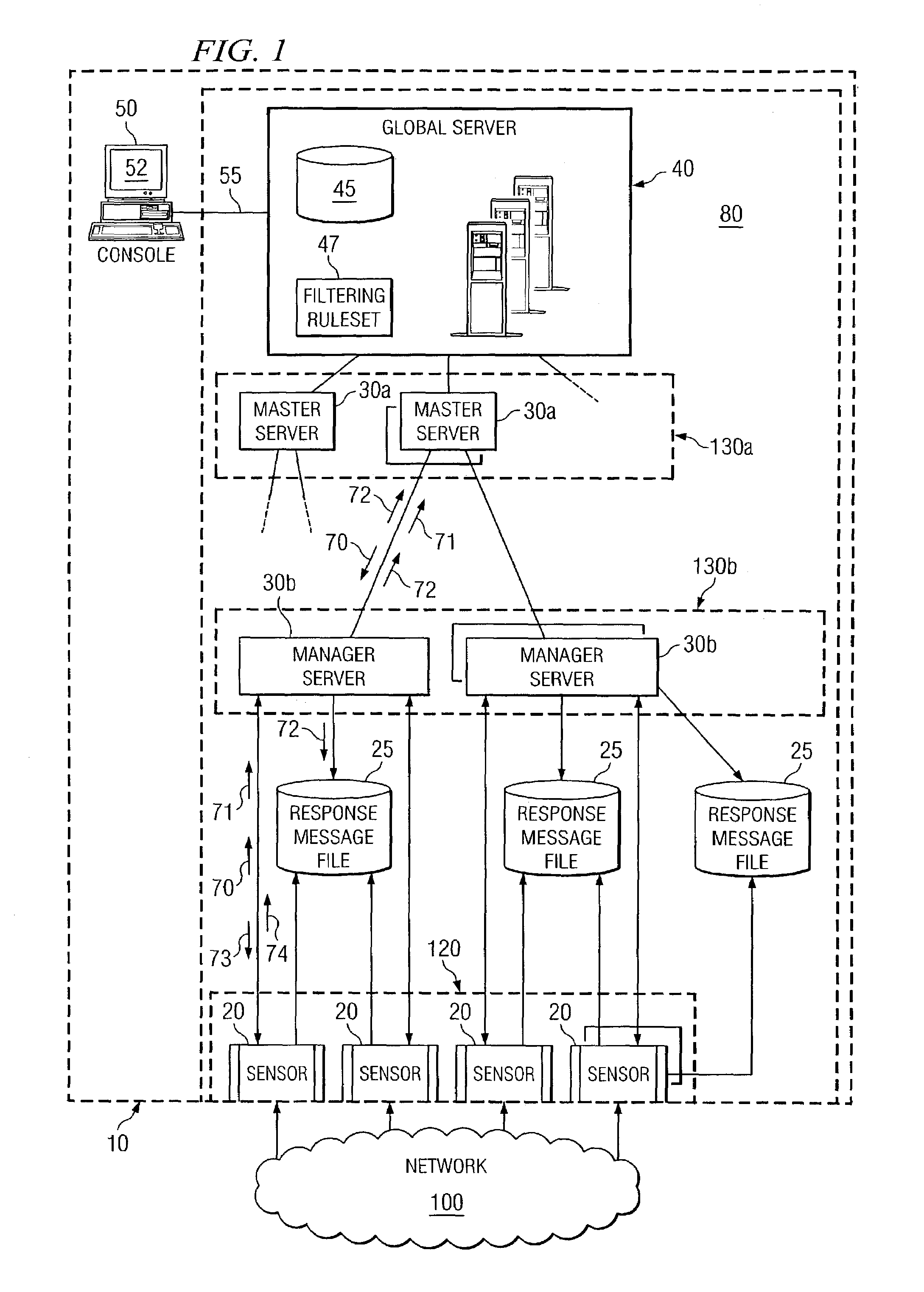
Graphical user interface for an enterprise intrusion detection system
ActiveUS7293238B1Improve efficiencyReliable detectionDigital computer detailsHardware monitoringGraphicsGraphical user interface
A method for interfacing with a user of an enterprise intrusion detection system, the method comprises receiving at least one packet flow, each packet flow originating from a unique node in the intrusion detection system and comprising descriptive information and a plurality of packet headers. The descriptive information of a first subset of the received packet flows is communicated to a user based at least in part on a filtering ruleset. A second subset of the received packet flows is concealed from the user based at least in part on the filtering ruleset. In response to receiving a command from the user, the plurality of packet headers for at least one packet flow in the first subset is communicated to the user.
Owner:FORCEPOINT FEDERAL
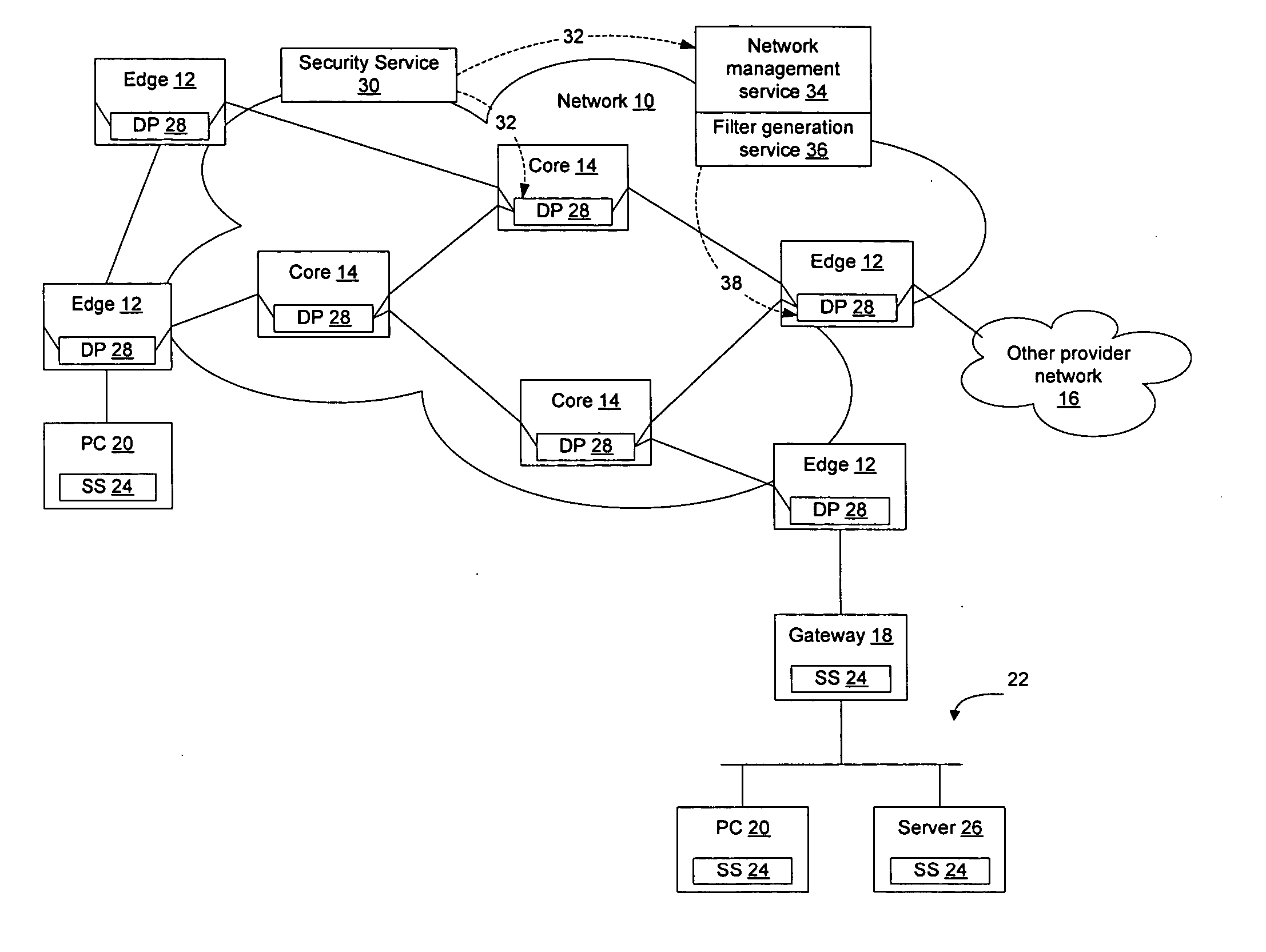
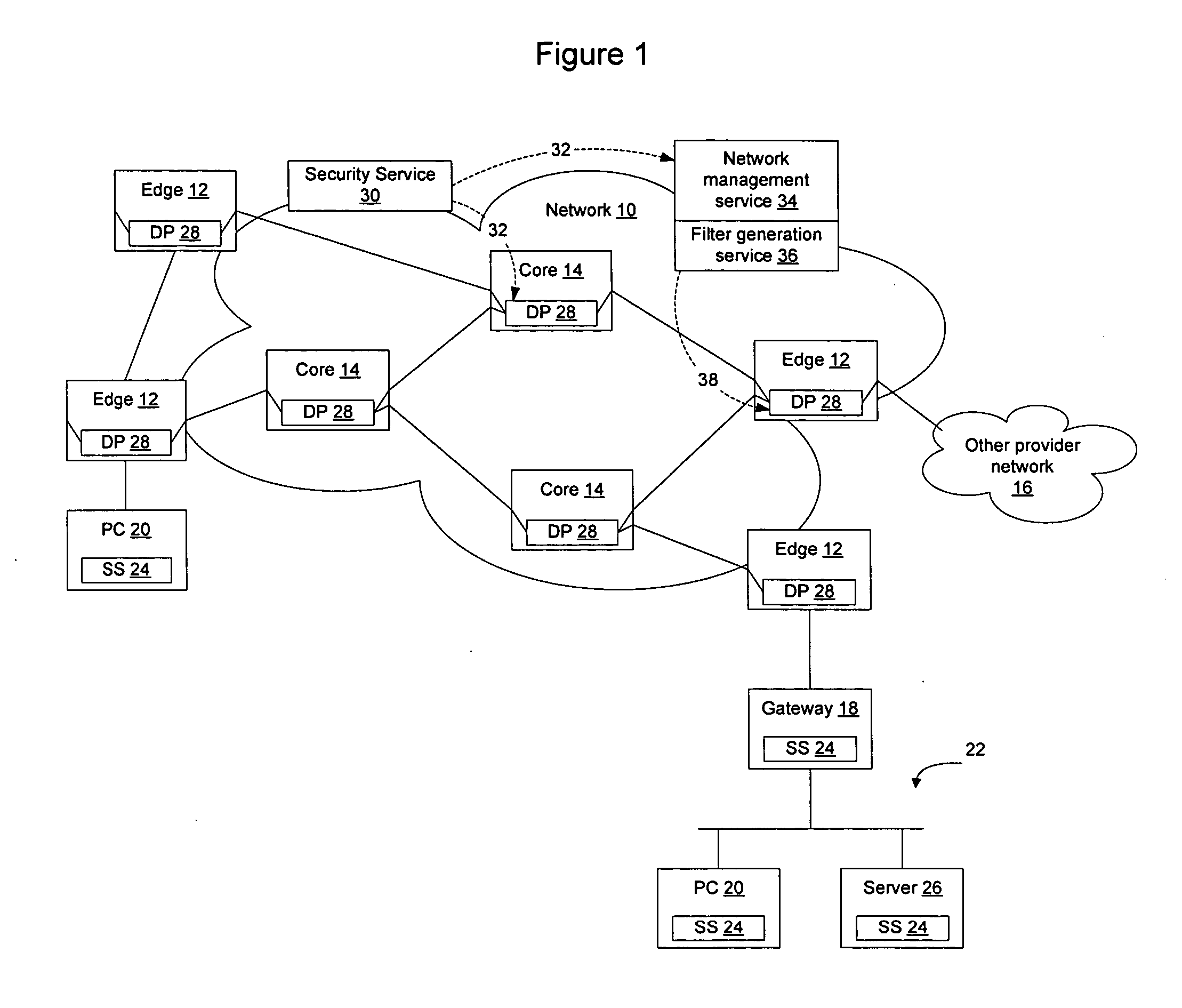
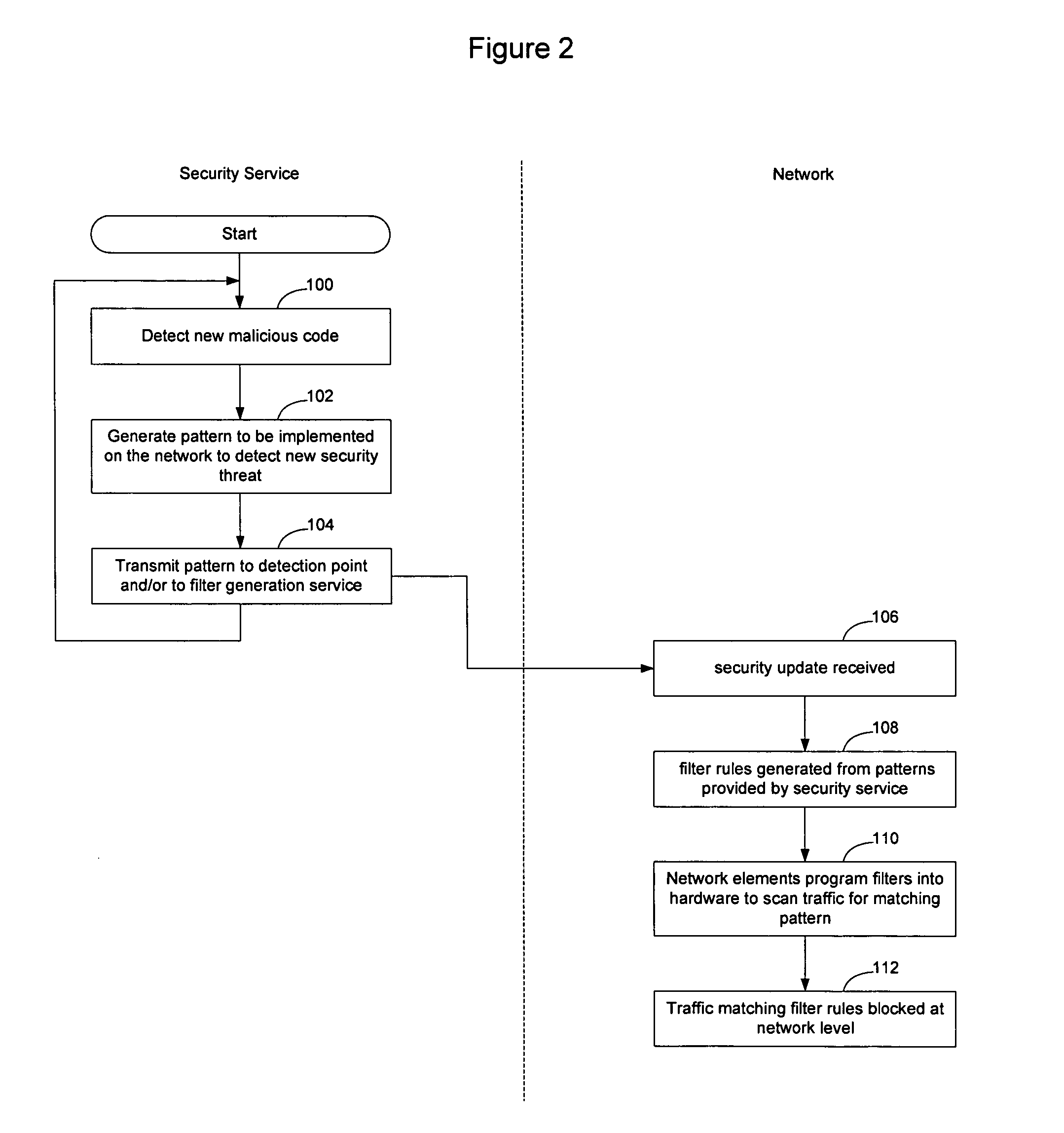
Method and apparatus for network immunization
InactiveUS20060123481A1Avoid dataAvoid spreadingMemory loss protectionError detection/correctionSecurity softwareFiltering rules
Network elements that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level. As new threats are identified by a security service, new patterns may be created for those threats, and the new patterns may then be passed out onto the network in real time. The real time availability of patterns enables filter rules derived from the patterns to be applied by the network elements so that malicious code may be filtered on the network before it reaches the end users. The filter rules may be derived by security software resident in the network elements or may be generated by a filter generation service configured to generate network element specific filter rules for those network elements that are to be implemented as detection points on the network.
Owner:AVAYA INC
Event Tracking and Velocity Fraud Rules for Financial Transactions
InactiveUS20110016052A1Reducing third-party processing feeReduce processing timeFinanceProtocol authorisationThird partyFiltering rules
A fraud rule can be applied to a transaction according to a first authorization parameter. The transaction is passed to a filtering rule which is applied to the transaction according to a second authorization parameter. The filtering rule can approve the transaction for processing or pass the transaction on to a third party analysis. The fraud and filtering rules can apply the same analysis to the transaction with the exception of the authorization parameters. The fraud rule and filtering rules can analyze historical attributes of a consumer account.
Owner:VISA INT SERVICE ASSOC
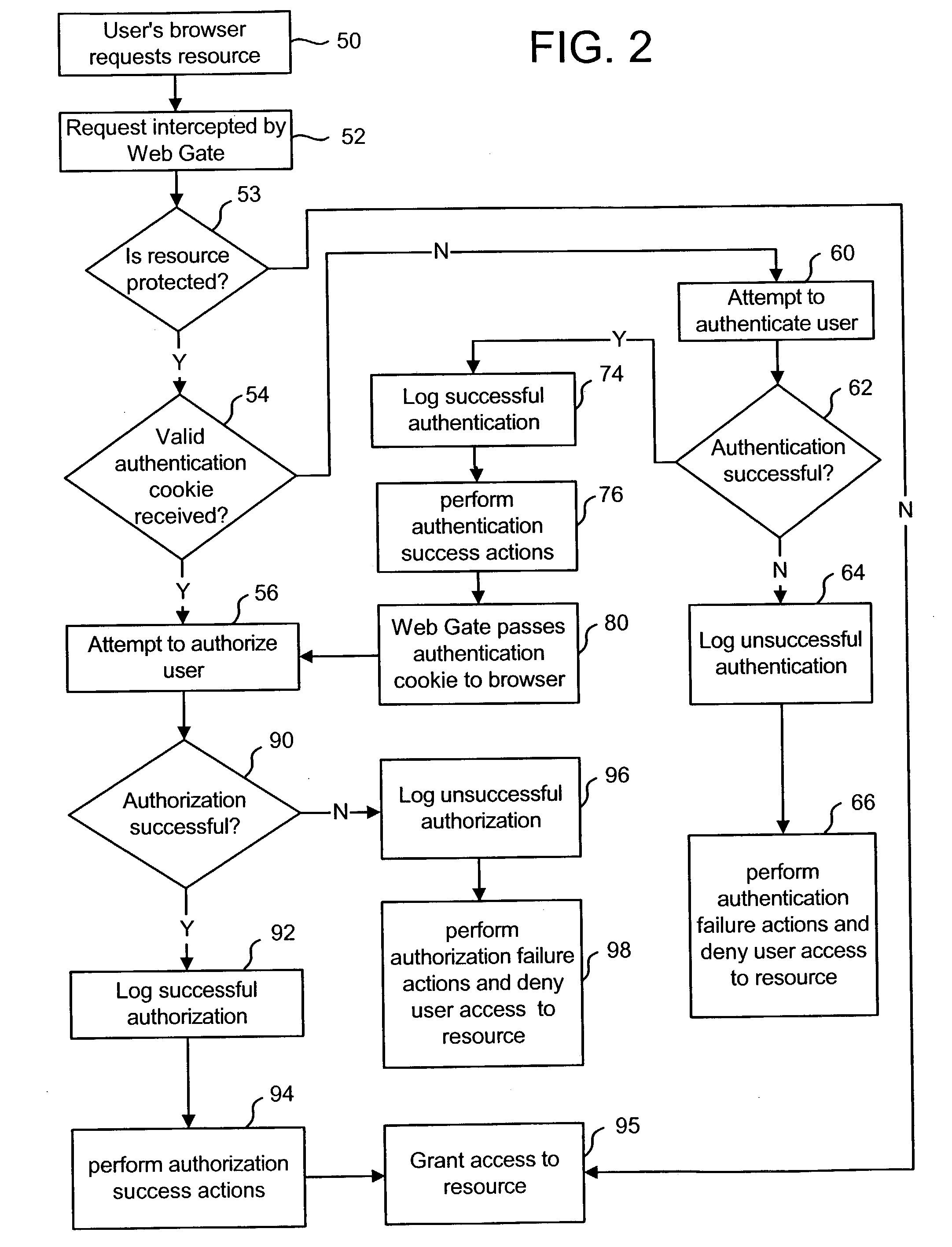
Rule based data management
ActiveUS20040010519A1Digital data information retrievalData processing applicationsDynamic populationFiltering rules
Data is acquired for an Identity System based on a one or more rules. The data can be from the same Identity System Component, another Identity System Component or a component external to the Identity System. The acquired data can be used to populate an Identity Profile, configure a workflow, or provide information to any other object, process, component, etc. of the Identity System. In one embodiment, the present invention combines dynamic identity value substitution and directory filter rules to enable rule based identity management. It enables dynamic population of identity data and real-time routing for identity management workflows. In other embodiments, the present invention can be applied to systems other than Identity Systems.
Owner:ORACLE INT CORP
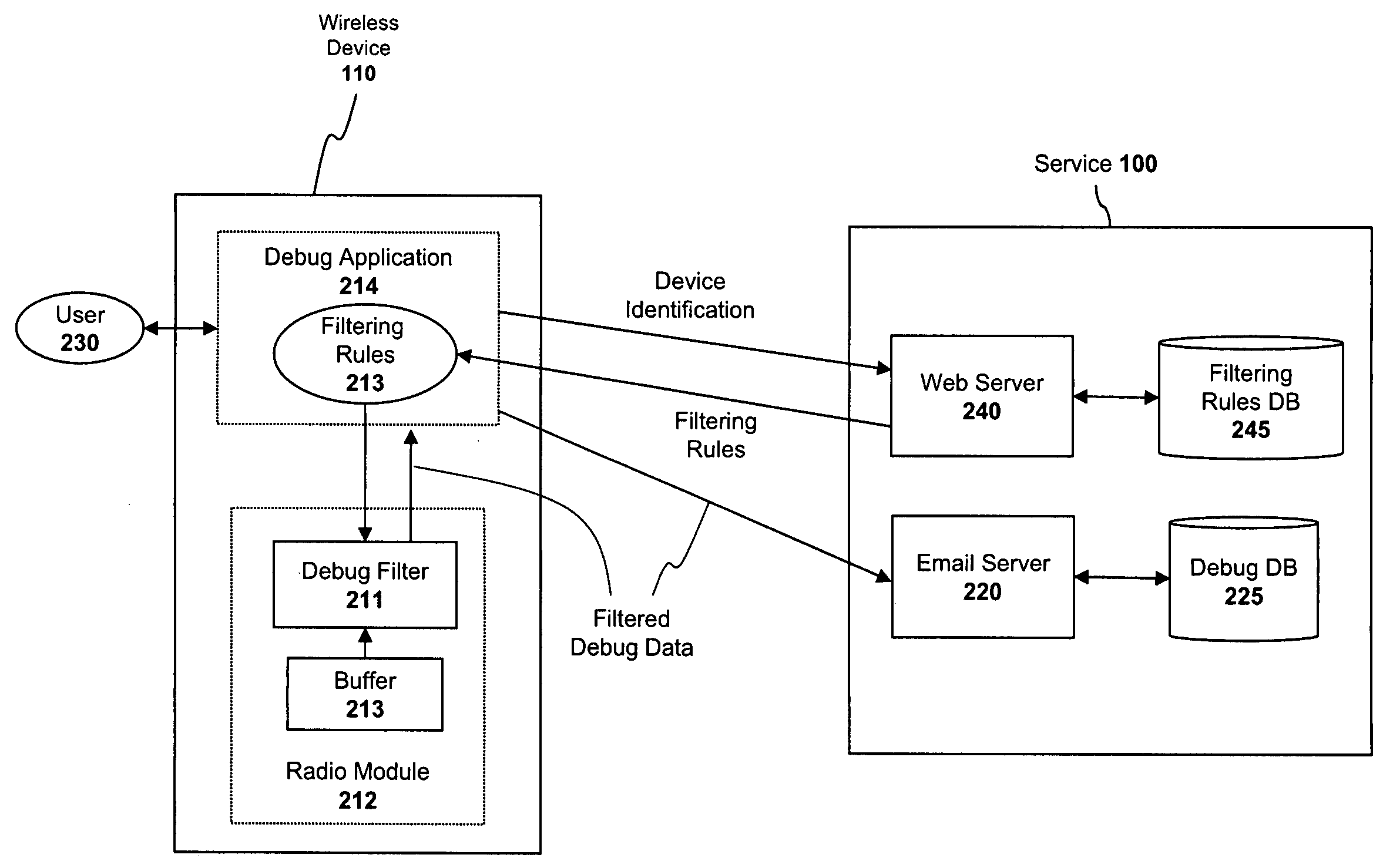
System and method for collecting debug data from a wireless device
ActiveUS20090138763A1Hardware monitoringMultiple digital computer combinationsComputer hardwareFiltering rules
A data processing apparatus having a memory for storing program code and a processor for processing the program code, the data processing apparatus comprising: a radio module to communicatively couple the data processing apparatus to a wireless network, the radio module generating a plurality of debug data in a plurality of signal classes; a set of debug data filtering rules specifying certain debug data within the plurality of signal classes to be collected from the radio module; and a debug application executed on the data processing apparatus, the debug application to apply the set of filtering rules, thereby causing only the specified set of debug data to be collected from the radio module.
Owner:MICROSOFT TECH LICENSING LLC
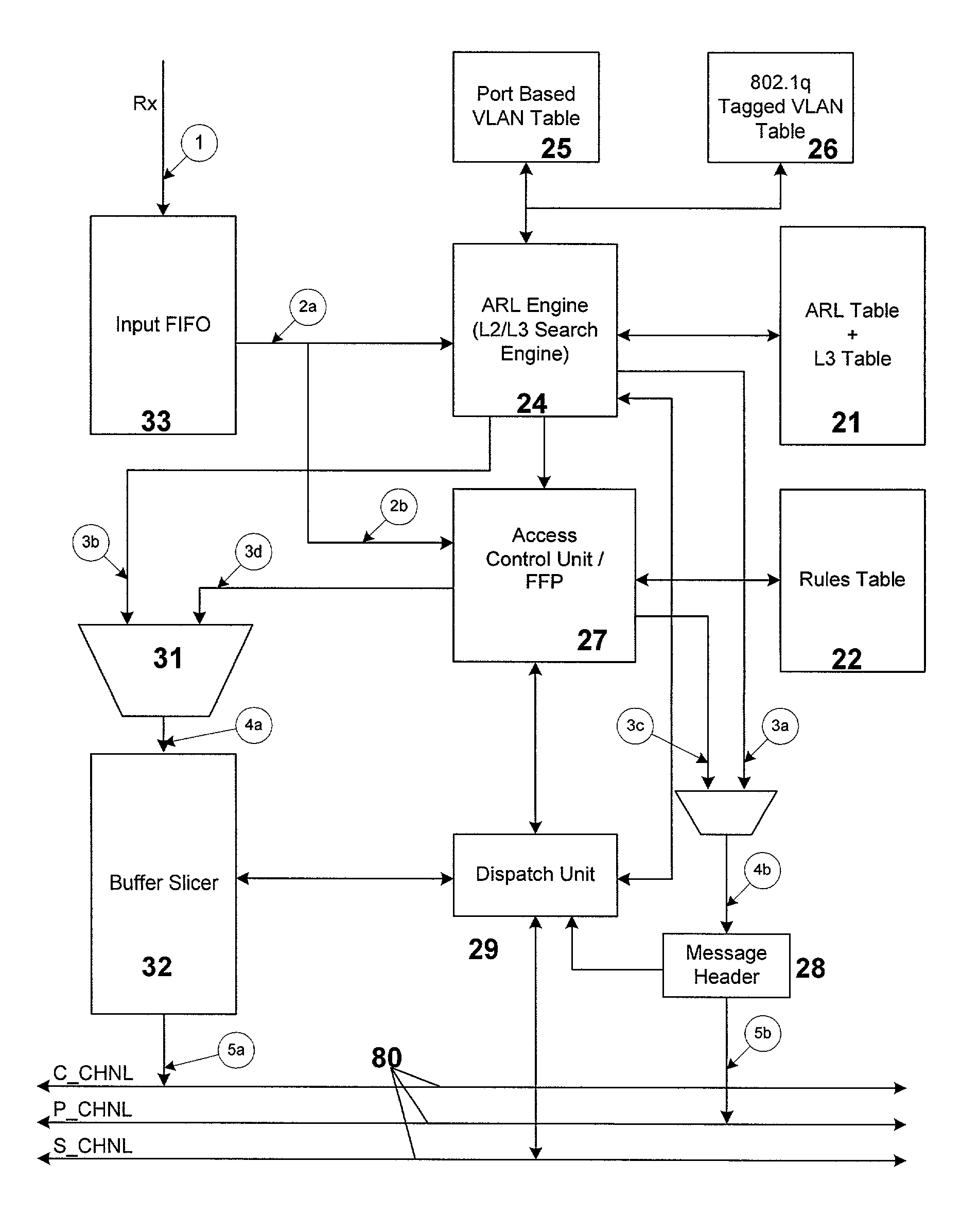
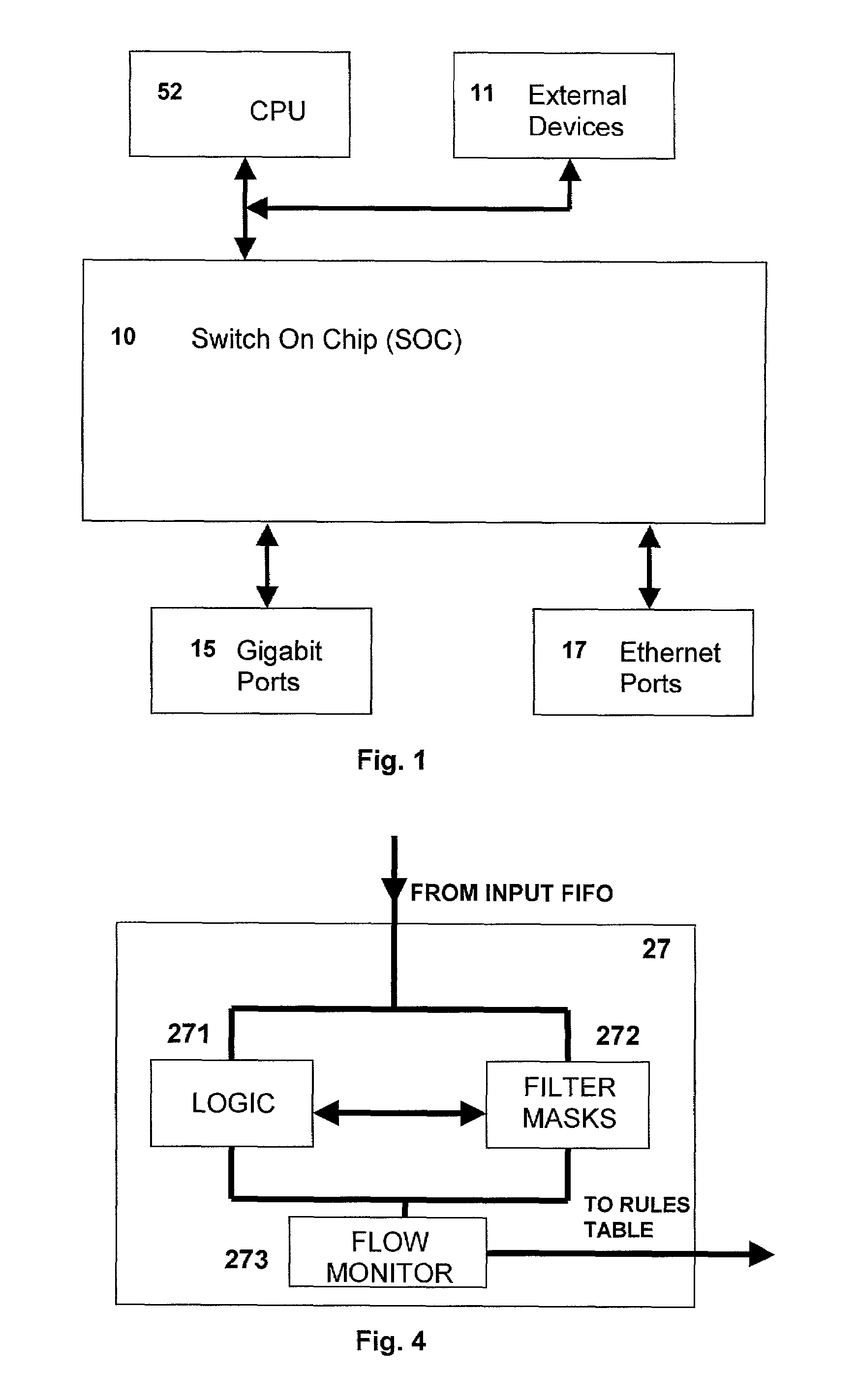
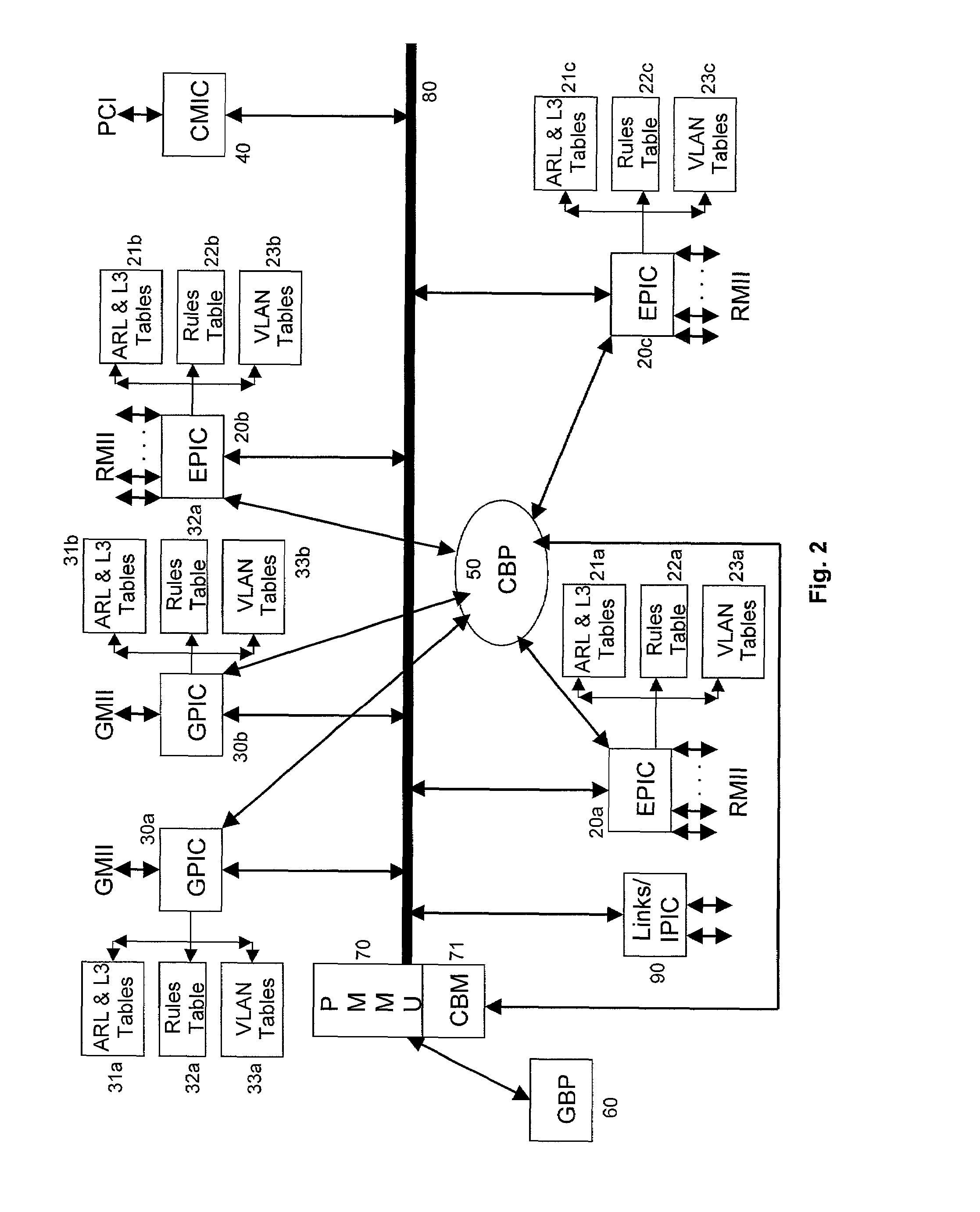
Method and apparatus for enabling access on a network switch
A data switch for network communications includes a data port interface which supports at least one data port which transmits and receives data. The switch also includes a CPU interface, where the CPU interface is configured to communicate with a CPU, and a memory management unit, including a memory interface for communicating data from the data port interface to the switch memory. A communication channel is also provided, communicating data and messaging information between the data port interface, the CPU interface, the switch memory, and the memory management unit. The data port interface also includes an access control unit that filters the data coming into the data port interface and takes selective action on the data by applying a set of filter rules such that access to the switch is controlled by the set of filter rules.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for filtering rules for manipulating search results in a hierarchical search and navigation system
ActiveUS20090125482A1Web data indexingDigital data processing detailsFiltering rulesNavigation system
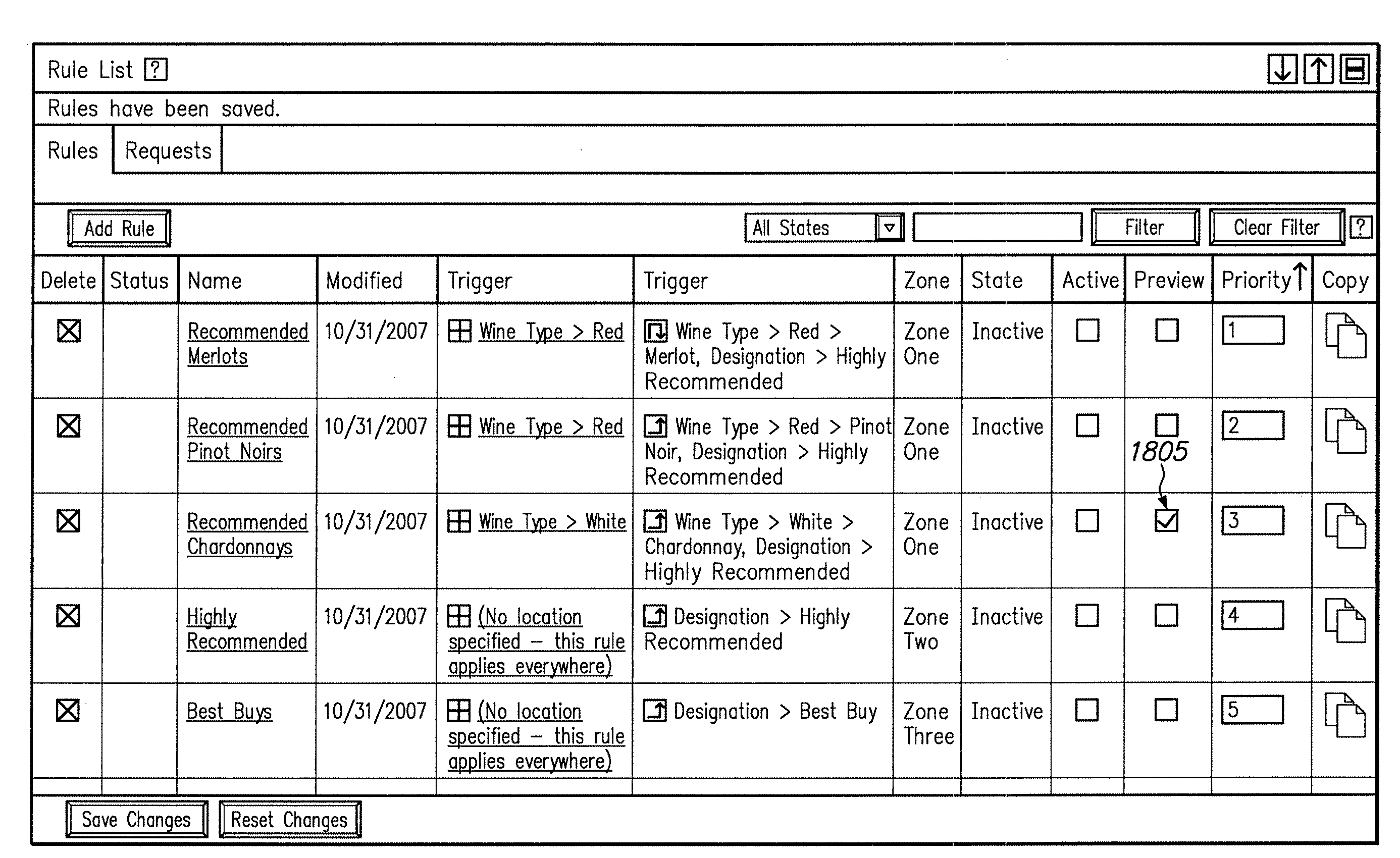
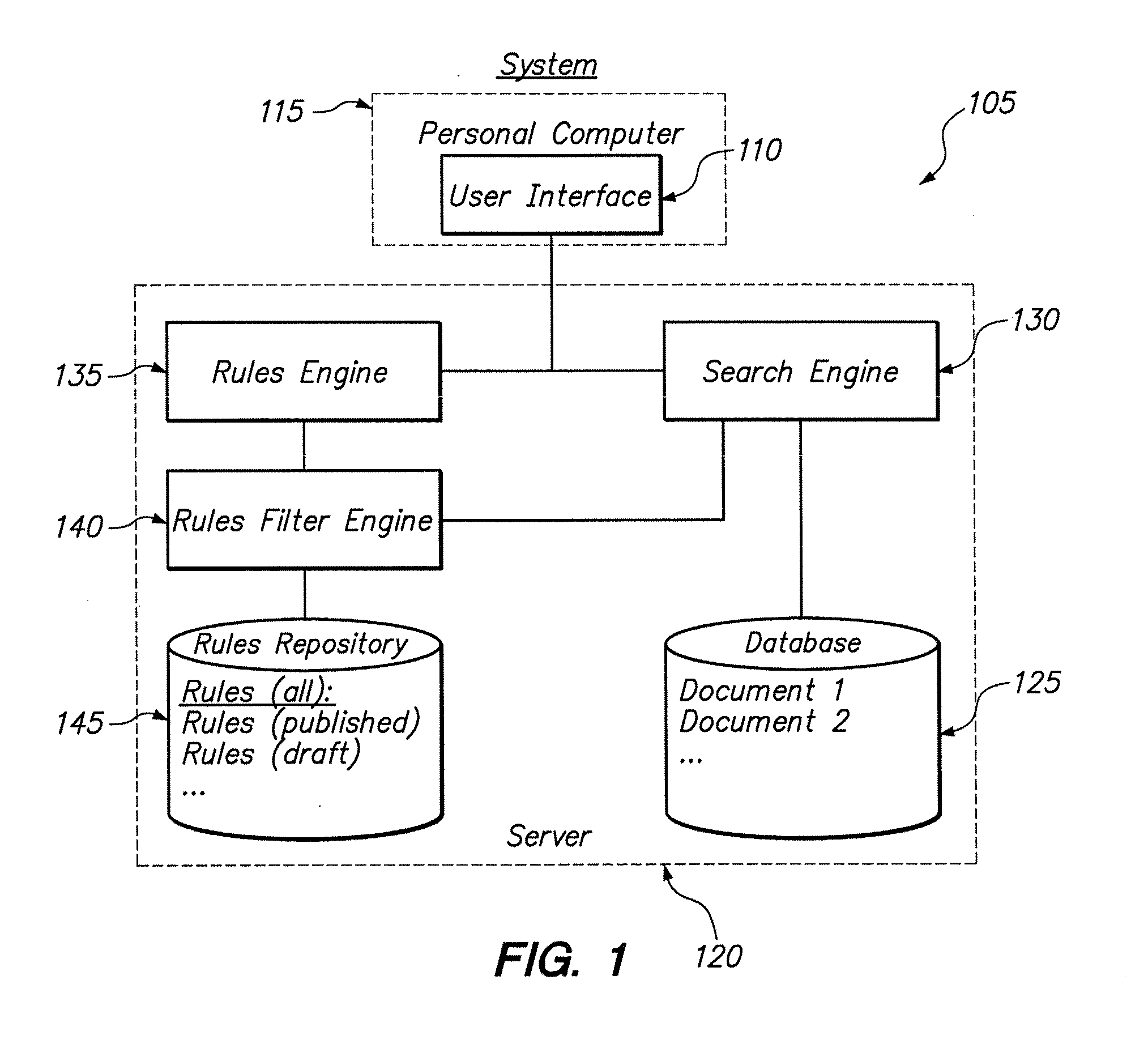
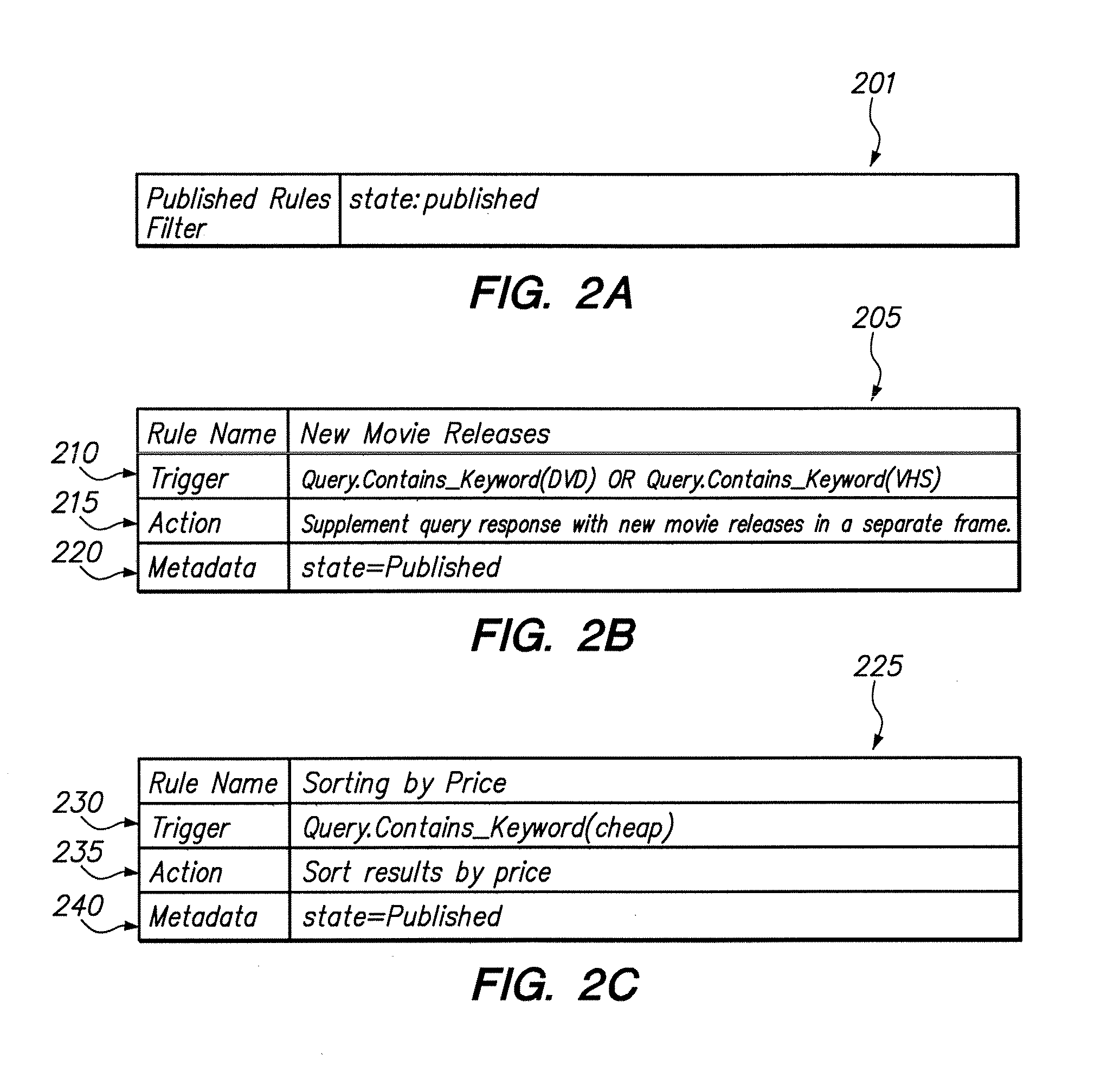
A method is disclosed for modifying the results of a search performed in a collection of items by a search and navigation system. The method includes receiving a query from a user interface and determining a navigation state, defined by expressions of attribute-value pairs, based on the received query. The user interface accepts both selecting and deselecting of any of the attribute-value pairs in an expression corresponding to a navigation state to obtain an expression corresponding to a different navigation state, and each selection and deselection forms a new query. The method further includes retrieving, from the collection, items associated with the navigation state to form a set of unmodified search results, the set of unmodified search results having an arrangement for presentation to the user. A rule filter that includes a metadata expression is applied to a set of rules, each rule having a trigger, an action, and metadata. The application of the rule filter to the set of rules includes evaluating the metadata expression of the rule filter based on the metadata of each rule and passing rules for which the metadata expression of the rule filter evaluates as logical true. The trigger of each rule passed by the rule filter is evaluated, and the action of each rule for which the trigger of the rule evaluates as logical true is executed to modify the unmodified search results to form modified search results.
Owner:ORACLE OTC SUBSIDIARY
Online fraud prevention using genetic algorithm solution
Online fraud prevention including receiving a rules set to detect fraud, mapping the rules set to a data set, mapping success data to members of the rules set, filtering the members of the rules set, and ordering members of the data set by giving priority to those members of the data set with a greater probability for being fraudulent based upon the success data of each member of the rule set in detecting fraud. Further, a receiver coupled to an application server to receive a rules set to detect fraud, and a server coupled to the application server, to map the rules set to a data set, and to map the success data to each members of the rules set. The server is used to order the various members of the data set by giving priority to those members of the data set with a greatest probability for being fraudulent.
Owner:PAYPAL INC
Simplified method of configuring internet protocol security tunnels
InactiveUS6076168AMultiple digital computer combinationsProgram controlTraffic capacityInternet protocol suite
A method of securing data traffic between a local and remote host systems is provided. The method includes autogenerating a filter having rules associated with a defined tunnel. The filter rules are used to permit or deny acceptance of transmitted data by the host system and to direct traffic to the tunnel. The tunnel, on the other hand, is used to keep data confidential. The method further includes autogeneration of a counterpart tunnel and associated filter to be used by the remote host when in communication with the local host. The method further autogenerates a new filter to reflect changes to any one of the tunnels and autodeactivates the filter associated with a deleted tunnel.
Owner:IBM CORP
Method for high speed packet classification
Owner:CISCO TECH INC
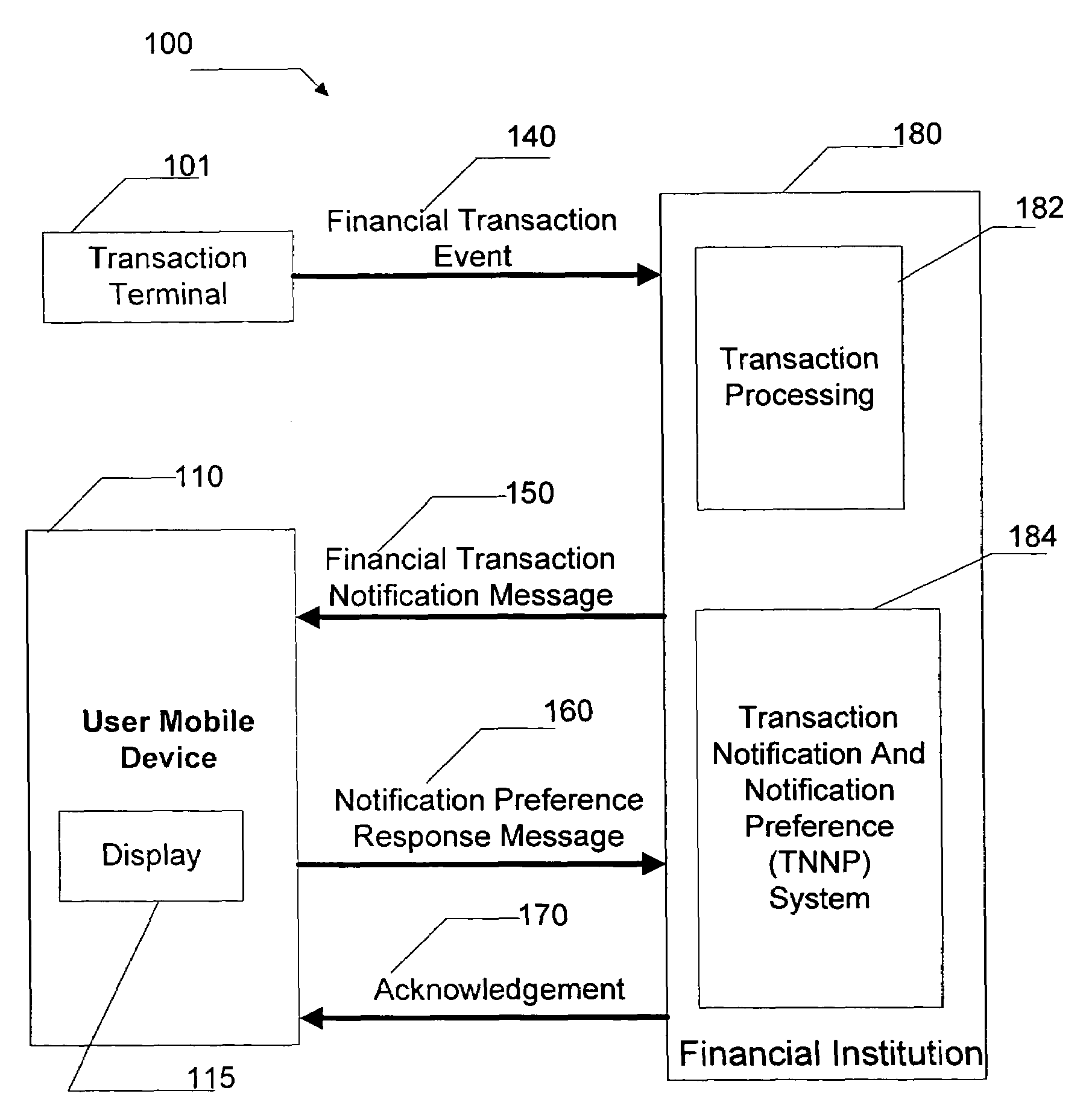
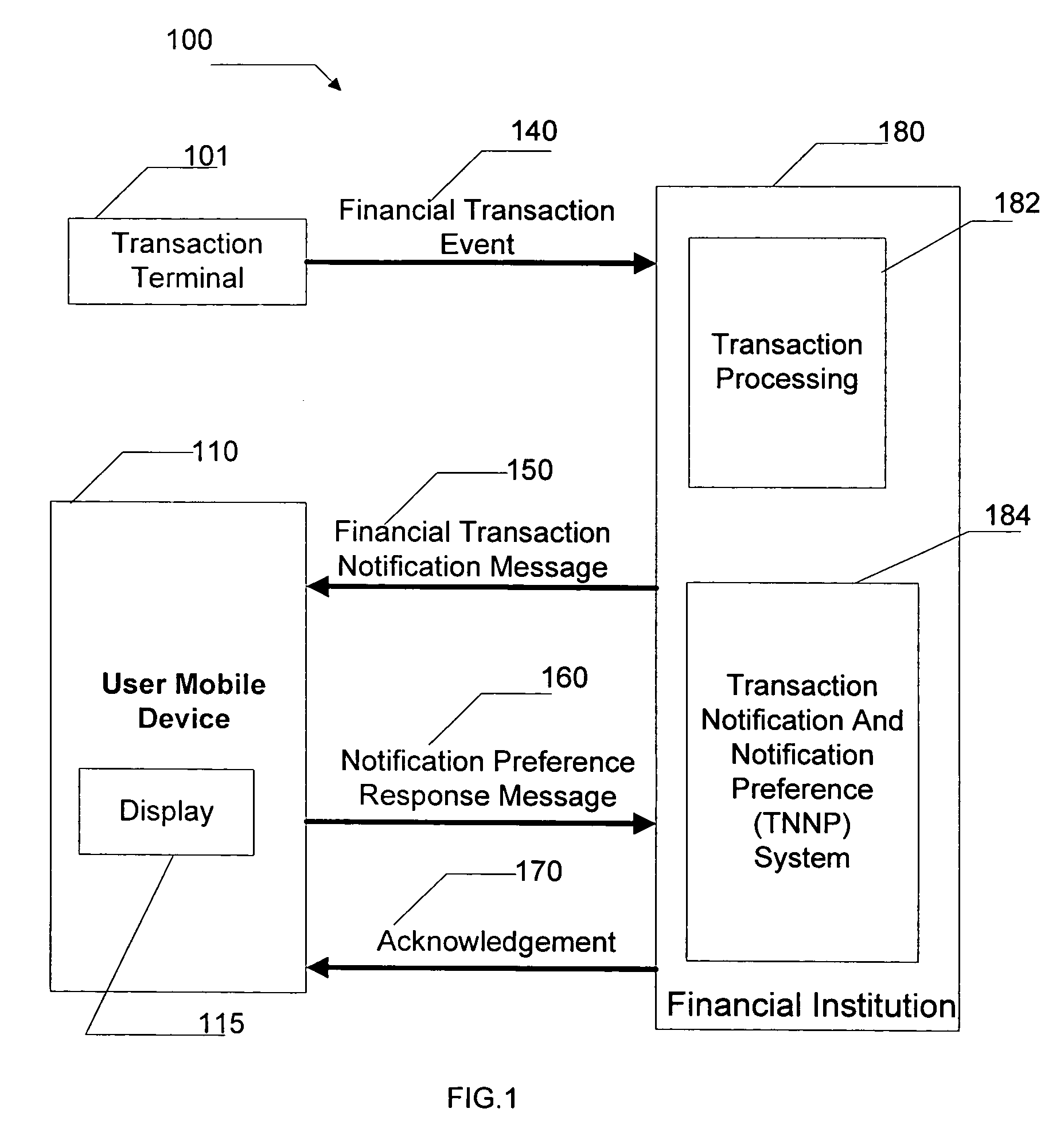
Method and system for defining financial transaction notification preferences
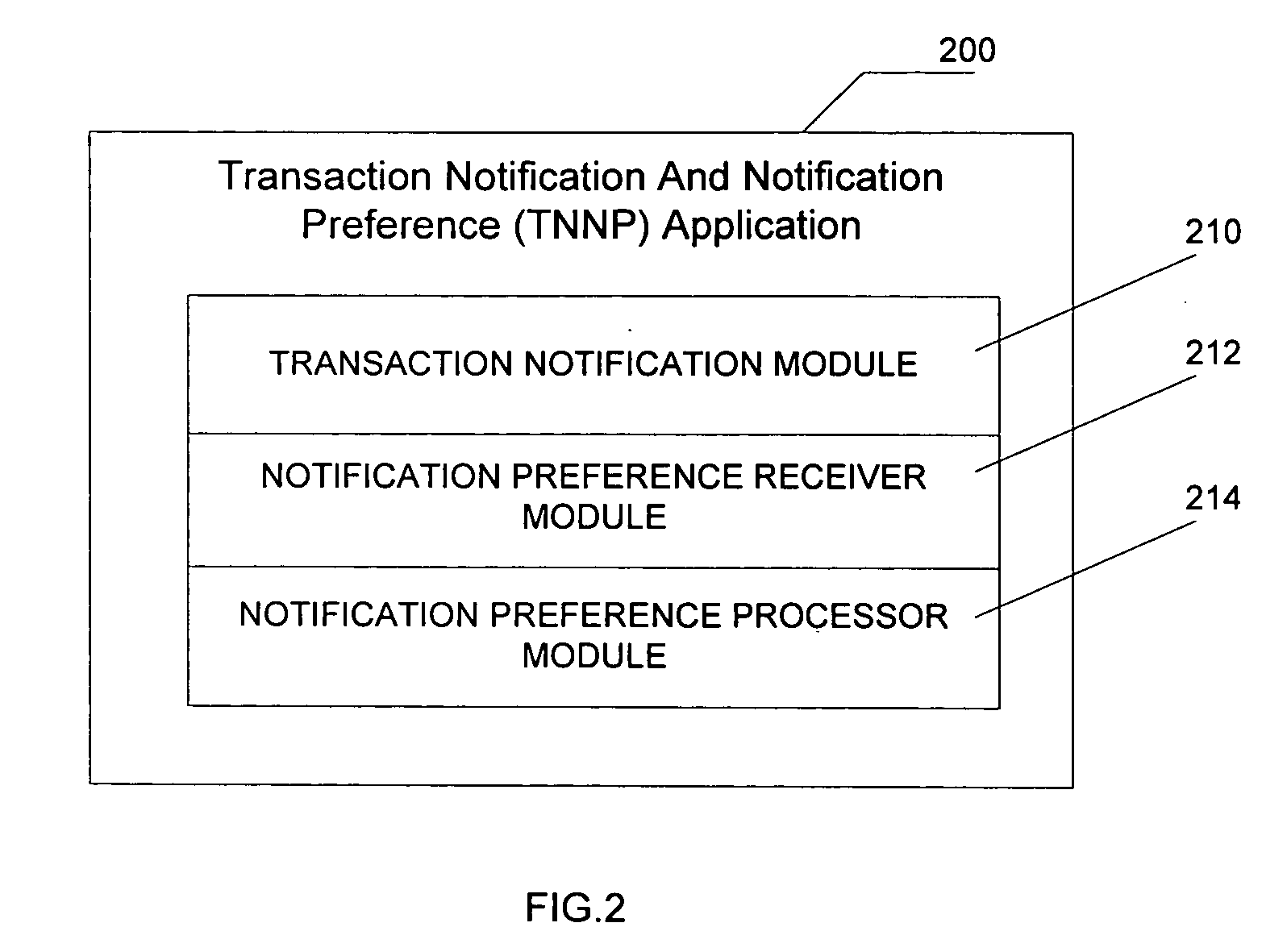
A method and system for defining financial transaction notification preferences is disclosed. A computer-implemented method for defining notification preferences using a financial transaction notification message served to a user on a mobile device and using properties of the financial transaction includes the steps of serving the financial transaction notification message, the financial transaction notification message being related to a financial transaction performed by the user, receiving a notification preference response message from the user, and defining at least one notification filtering rule based on the notification preference response message and the properties of the financial transaction. A system operable to implement the computer-implemented method includes a transaction notification module operable to serve the financial transaction notification message, the financial transaction notification message being related to a financial transaction performed by the user, a notification preference receiver module operable to receive a notification preference response message from the user, and a notification preference processor module operable to define at least one notification filtering rule based on the notification preference response message and the properties of the financial transaction.
Owner:BHOJWANI SANDEEP M +2
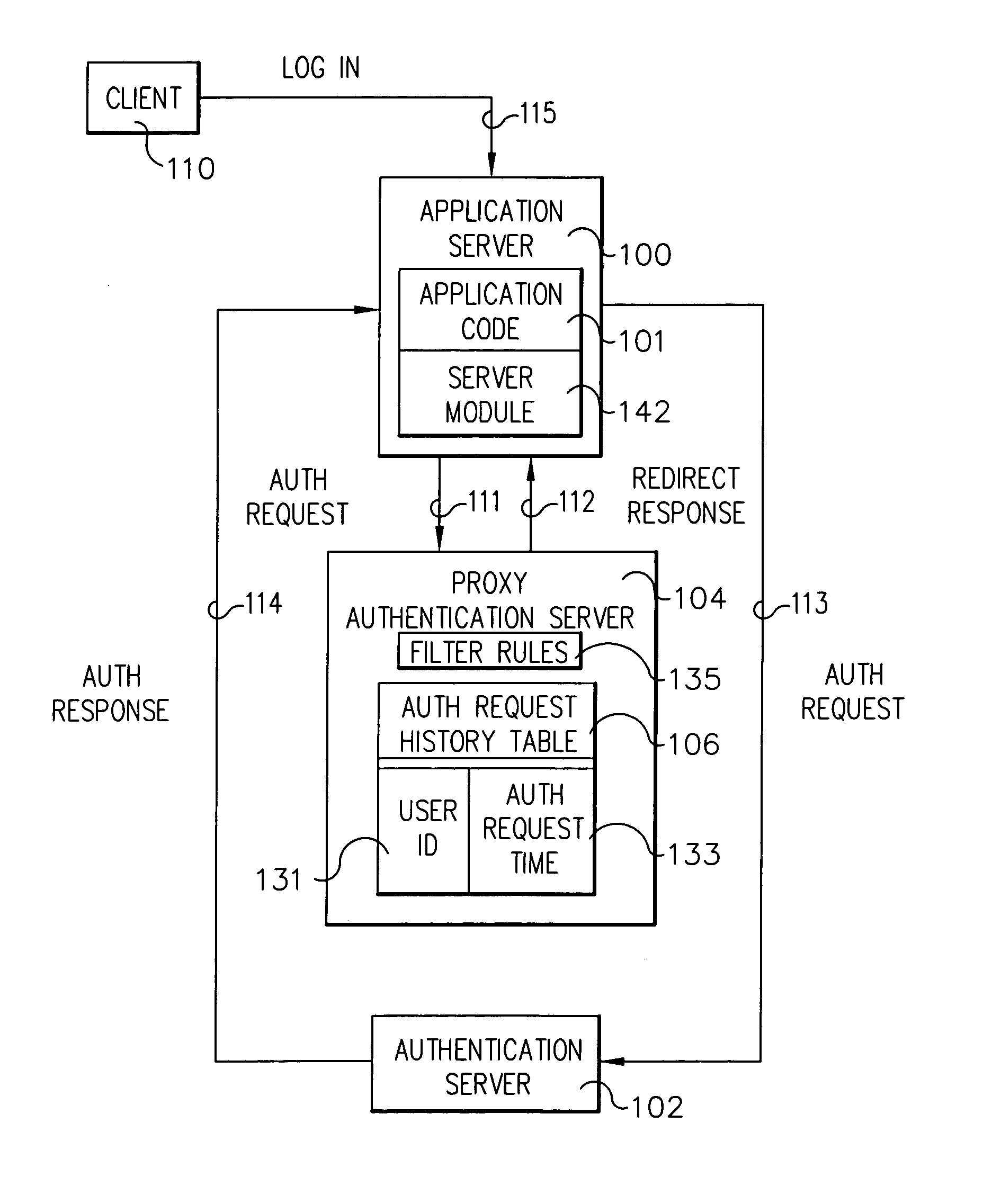
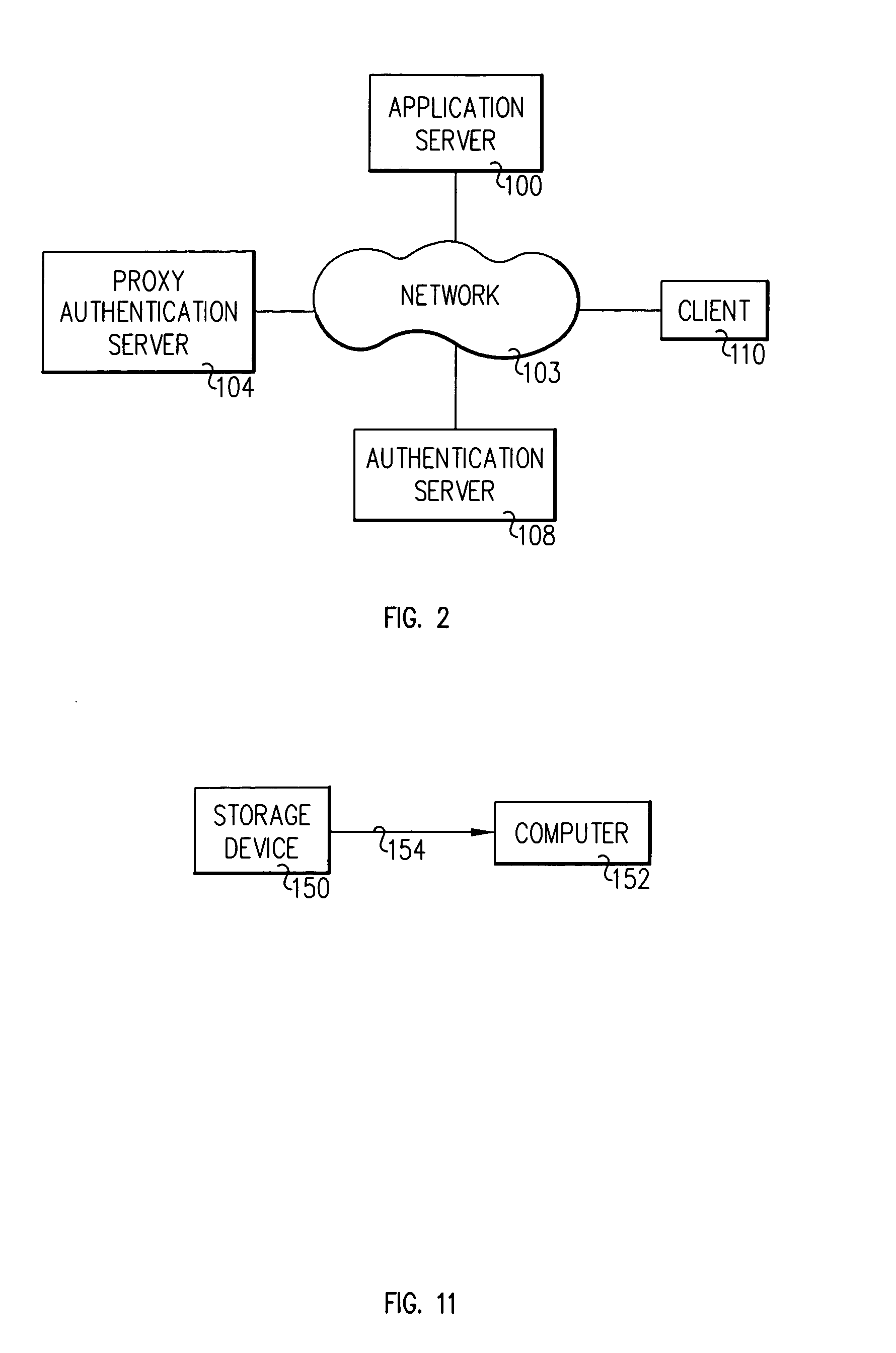
System and method for protecting a server against denial of service attacks
InactiveUS20060130140A1Memory loss protectionError detection/correctionApplication serverFiltering rules
A client application server includes a client server, a proxy authentication server, and an authentication server. The proxy authentication server maintains a set of one or more authentication rules and an authentication request table. The client server is responsive to an authentication request from a user including a user identifier for directing the authentication request to the proxy authentication server for searching the authentication request table for entries for the client; responsive to finding one or more entries, applying the filter rules; responsive failing a filter rule, rejecting the authentication request in a response message to the client server; and responsive to passing all relevant filter rules, directing the authentication request to the authentication server for authenticating the user.
Owner:IBM CORP
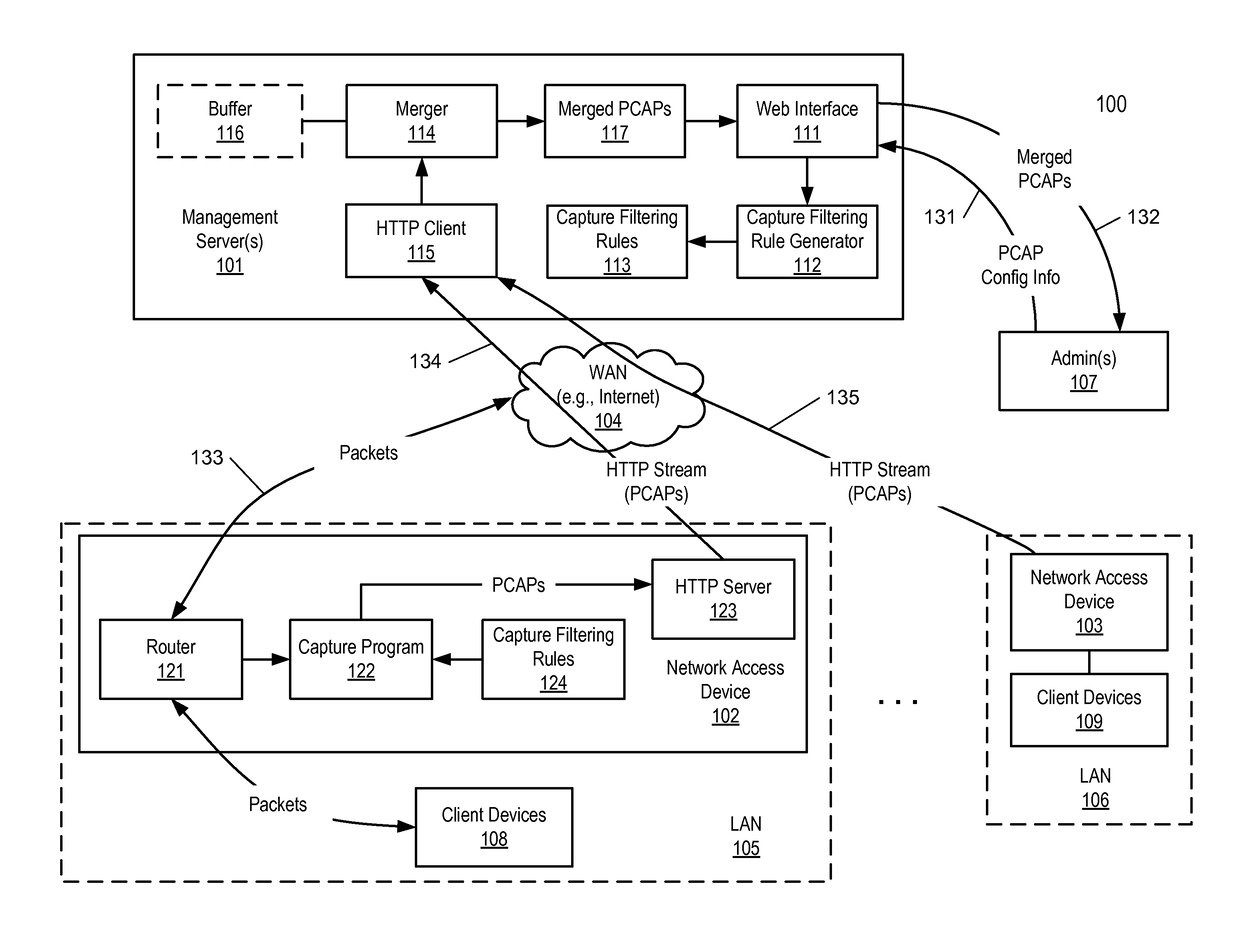
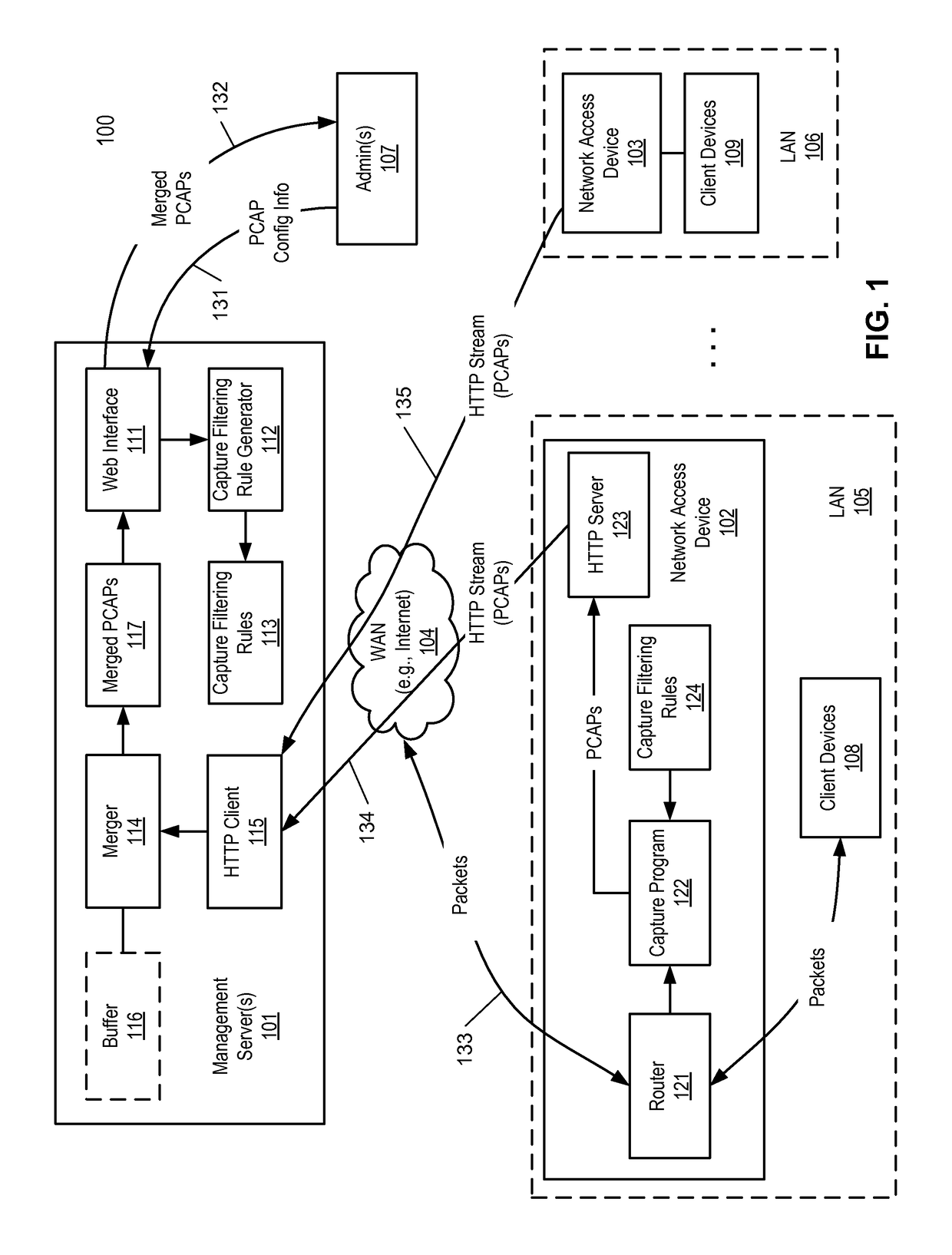
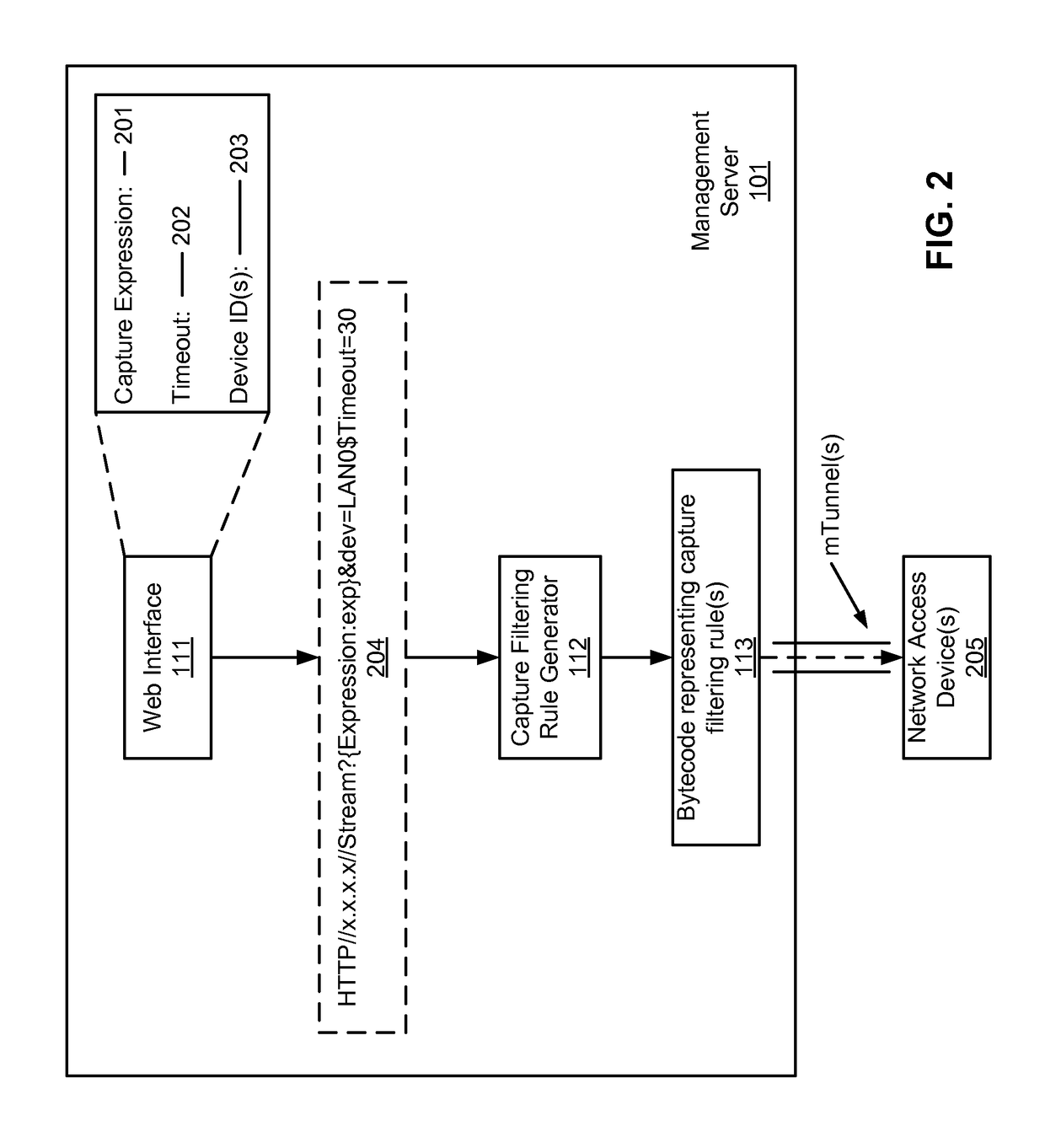
Method for streaming packet captures from network access devices to a cloud server over HTTP
ActiveUS9692802B2Multiple digital computer combinationsData switching networksNetwork access serverNetwork packet
A system for streaming packet captures over the Internet includes multiple network access devices, each operating as one of a gateway device, a wireless access point, and a network switch, and a management server communicatively coupled to the network access devices over the Internet for managing the network access devices. The management server maintains a persistent hypertext transport protocol (HTTP) connection with each of the network access devices over the Internet. The management server is to generate a bytecode based on a filtering expression for packet captures (PCAPs) representing one or more PCAPs filtering rules, transmit the bytecode to the network access devices without requiring the network access devices to compile the PCAPs filtering rules, receive PCAPs from the network access devices captured by the network access devices based on the PCAPs filtering rules, and merge the PCAPs received from the network access devices into merged PCAPs.
Owner:CISCO TECH INC
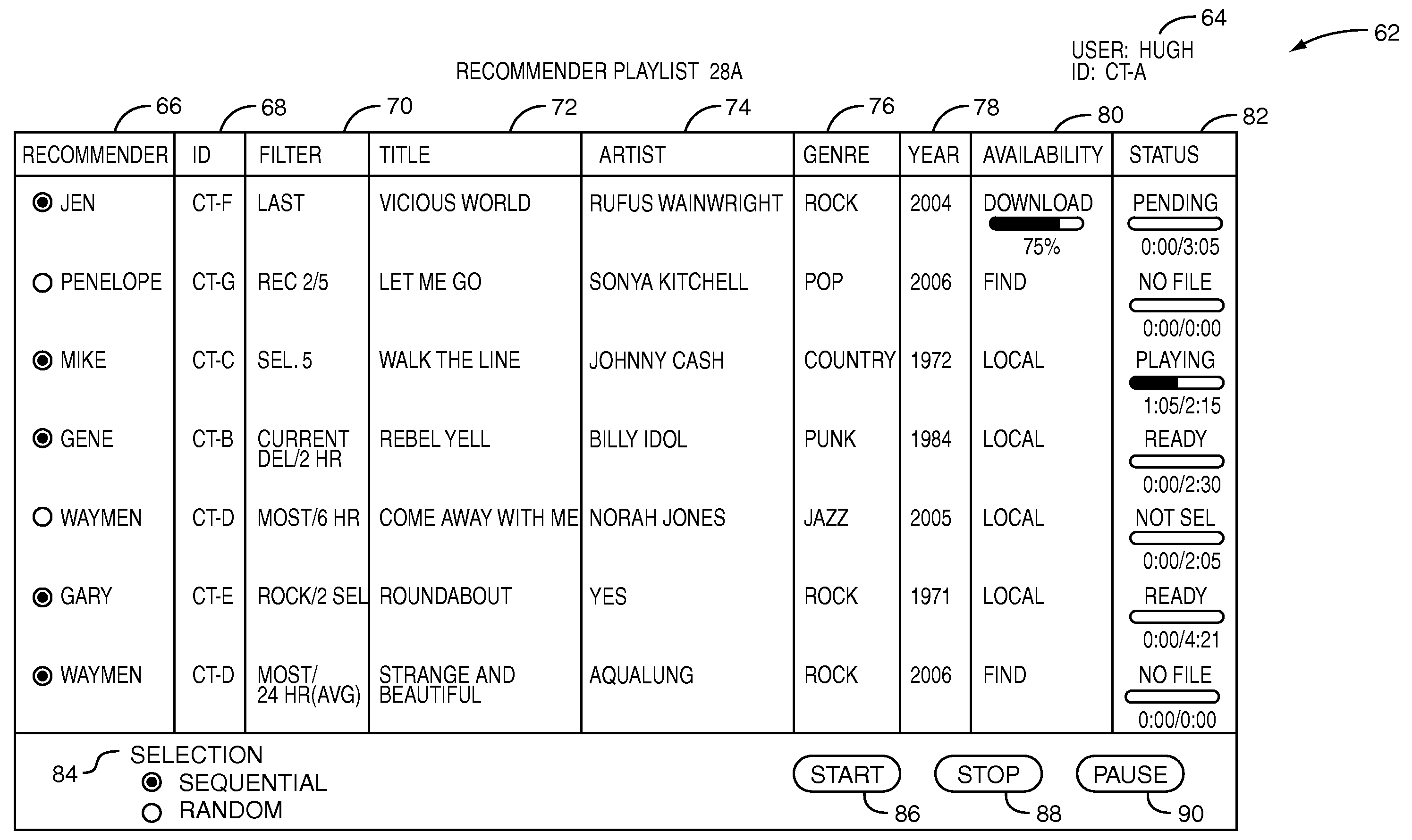
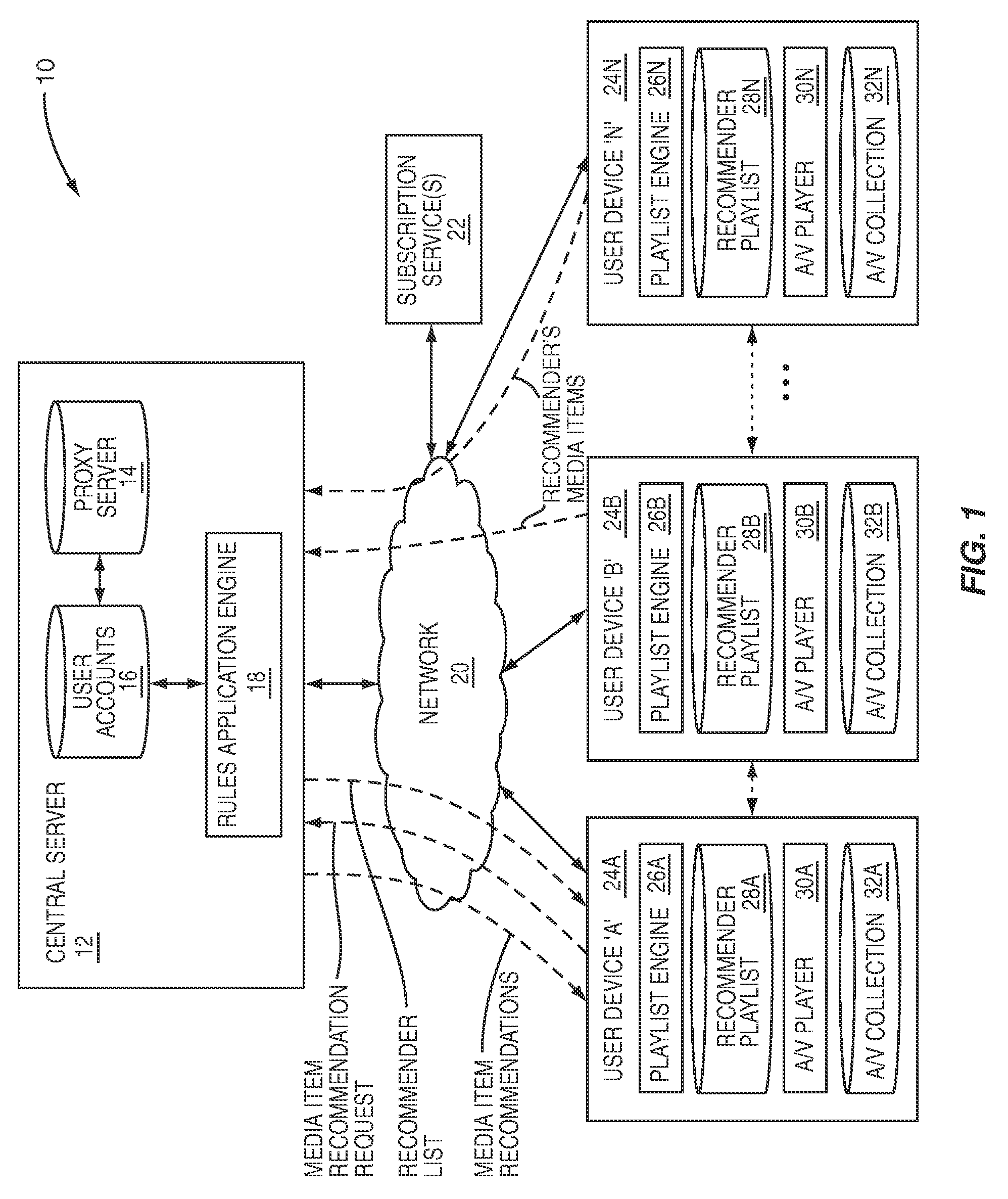
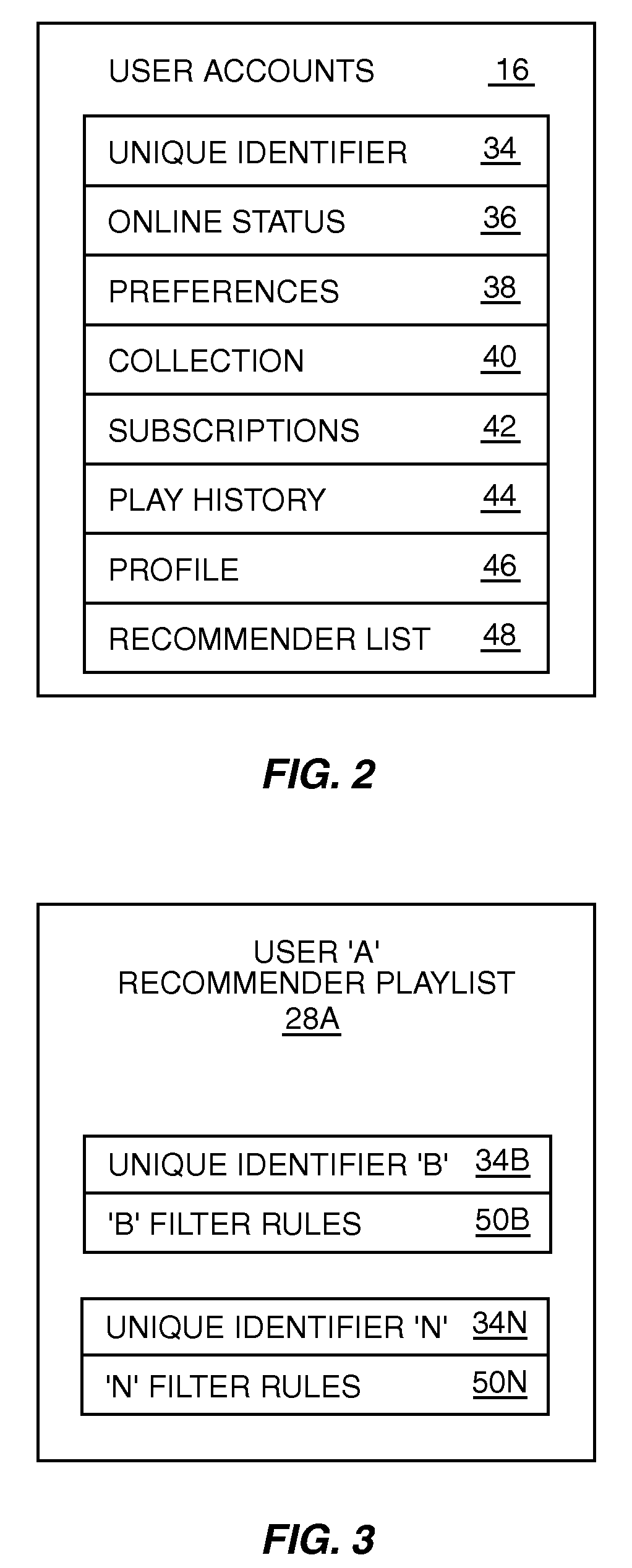
System and method for selectively identifying media items for play based on a recommender playlist
InactiveUS20080250067A1Extensive controlMaximum flexibilityDigital data information retrievalSpecial data processing applicationsFiltering rulesSocial web
A system and method for controlling media item recommendations received by a user based on the rendering of a user's pre-established recommender playlist. The recommender playlist is a list of identifiers that identify recommenders in the user's social network and a filter rule(s) associated with each recommender included in the recommender playlist. The filter rule(s) may be a rule associated with recommender's media items of the recommender. The user is able to control which media items from the recommender's media items of the recommender will be actually received by selecting the desired filter rule(s) for each of the recommenders in the user's recommender playlist. After the user establishes the recommender playlist and the user desires to actually receive recommendations from a recommender, the user renders the recommender playlist to receive a playlist consisting of the recommender's media items as filtered using filter rule(s) established by the user in the recommender playlist.
Owner:NAPO ENTERPRISES
Method, device, and system for monitoring a security network interface unit
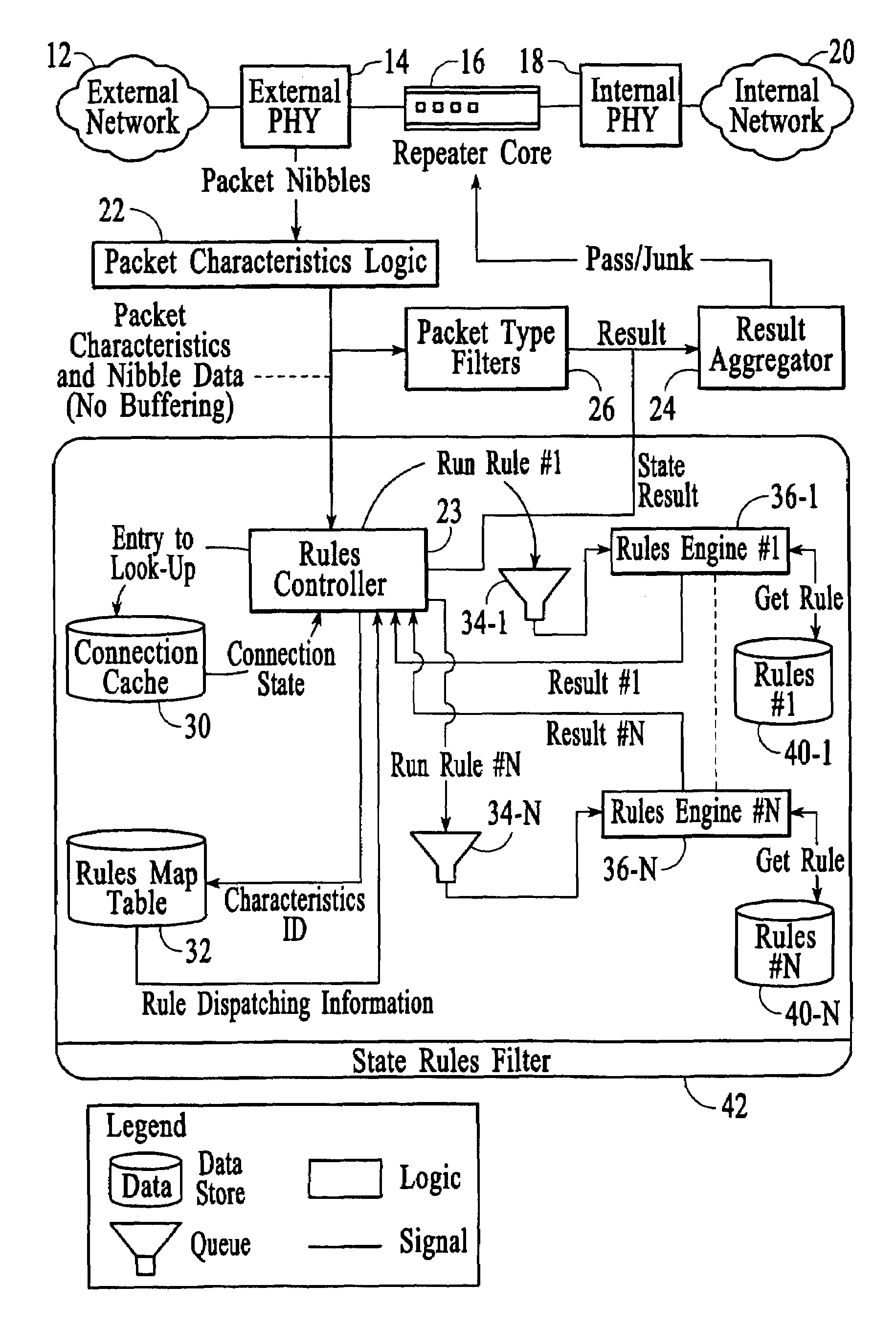
ActiveUS20160205069A1Facilitate initiationMultiple digital computer combinationsProgram controlData packFiltering rules
The invention relates to a method for monitoring a security network interface unit (23), FIG. 2 for example a firewall, which receives a stream of data packets via a first interface (21), checks said data stream with respect to filtering rules, and outputs said data stream to a second interface (22). The method has the steps of duplicating and outputting the data stream to the second interface (22), checking the output data stream for inadmissible data traffic, transmitting a warning message to the security network interface unit if inadmissible data traffic is detected in the data stream, and restricting the data stream by means of the security network interface unit if the warning message is received in the security network interface unit (23). The device or the system according to the invention comprises units which are designed to carry out the aforementioned method.
Owner:SIEMENS MOBILITY GMBH
PLD-based packet filtering methods with PLD configuration data update of filtering rules
InactiveUS7031267B2Facilitate short time to carry-outEasy to switchTime-division multiplexData switching by path configurationPacket generatorOperational system
Methods and systems for a PLD-based network update transport (PNUT) protocol that utilizes UDP and other protocols for transmitting update or other commands or information over a packet-based or IP network. PNUT is a hardware-based network communication protocol that does not require the full TCP / IP stack and may be utilized for exchanging commands and information with such PLD-based and other devices. Protocols may include a set of core commands and a set of custom commands. Logic components within the PLD-based devices may consist of a command dispatcher, a transmitter / controller, a MAC receiver, a MAC transmitter, a packet parser, a packet generator, and core receiving and transmitting commands. The present invention may be implemented without requiring CPU cores, special controllers, stringent timings, or operating systems as compared with conventional network protocols. Various methods for exchanging and updating PNUT commands are disclosed. The methods and systems of the present invention may be utilized to provide other functions, such as filtering, logging, polling, testing, debugging, and monitoring, and may be implemented between a server and a PLD-based device or solely between PLD-based devices.
Owner:802 SYST
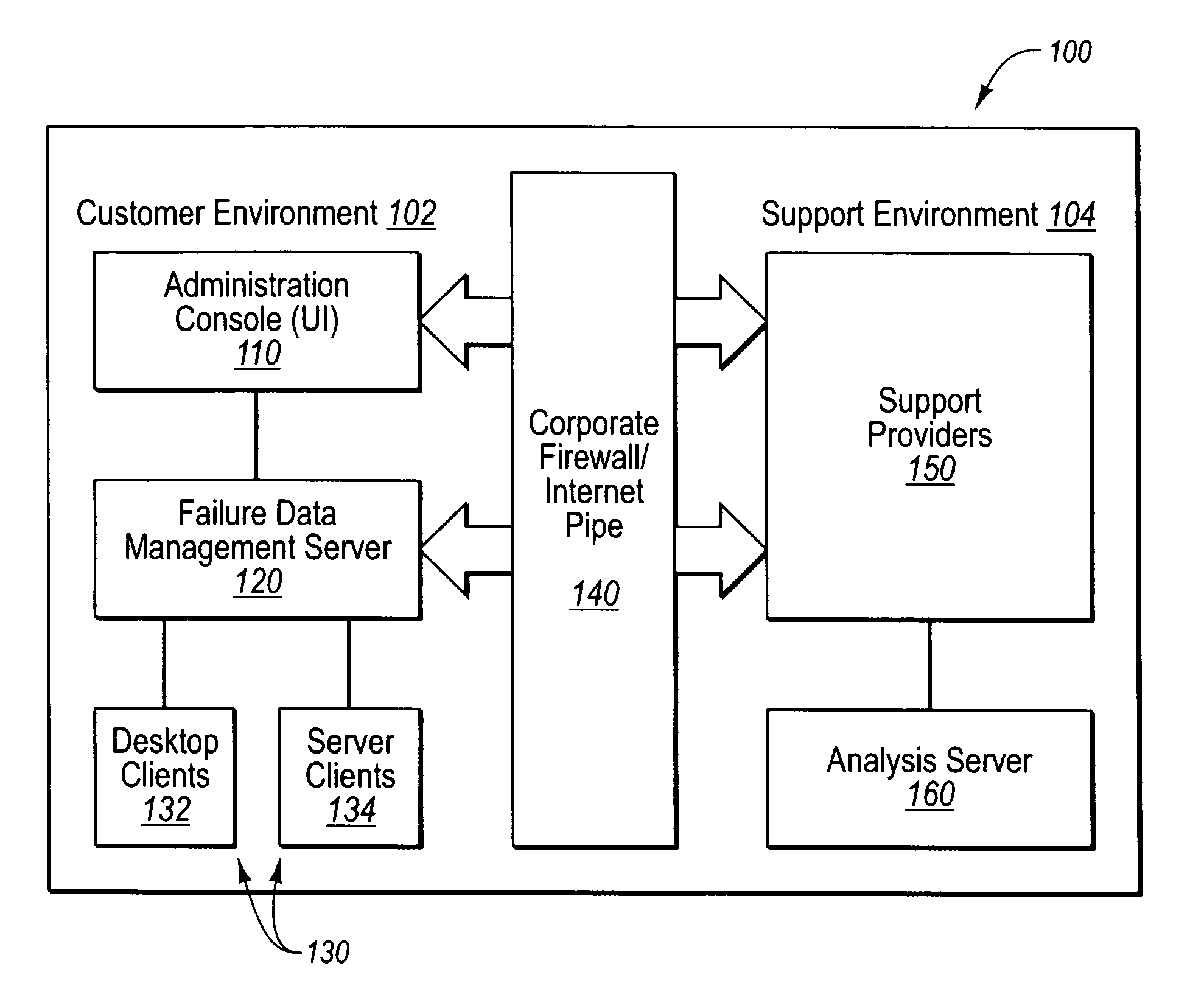
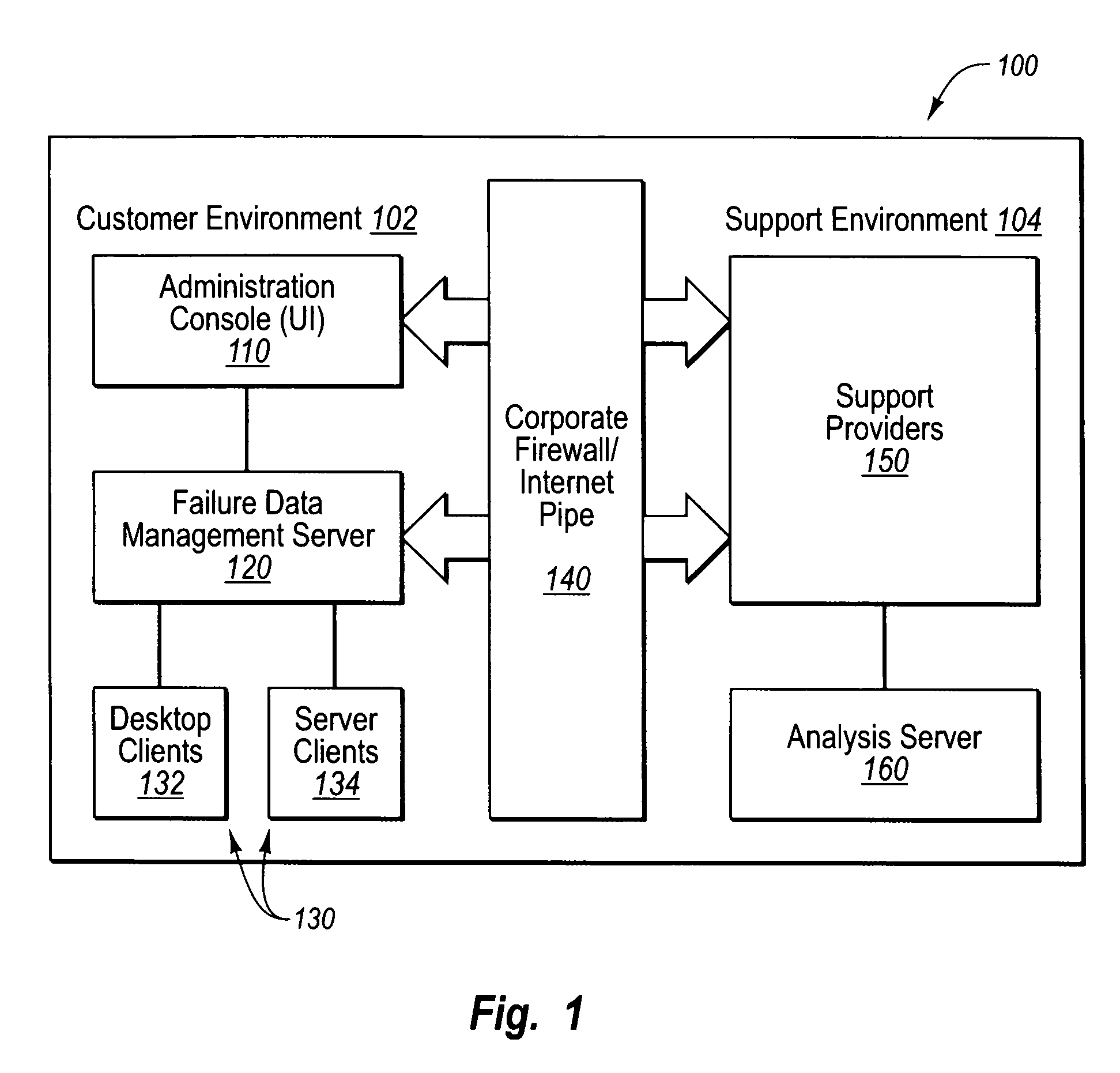
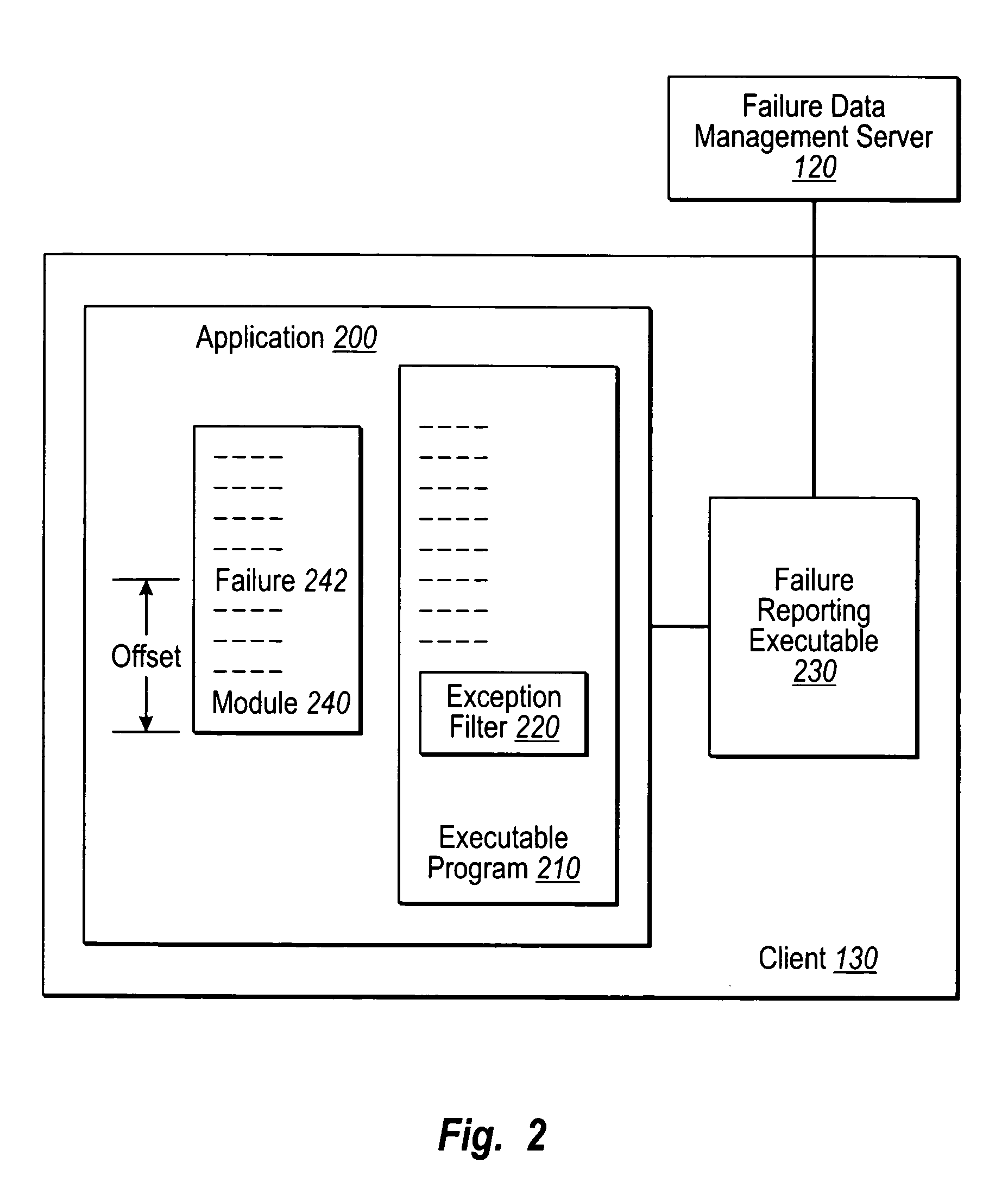
Controlling software failure data reporting and responses
User input defines transmission filter rules to be met when sending an error report to a support provider. User input also defines collection filter rules to be met when including failure data within an error report. Error reports corresponding to crash failures at clients are filtered with the transmission filter rules to determine which of the error reports to send to the support provider, and each error report to be sent to the support provider is further filtered to remove any failure data that fails to satisfy the collection filter rules. Each error report that satisfies the transmission filter rules, along with the failure data satisfying the collection filter rules, is sent to the support provider for analysis. Standard and or custom failure responses corresponding to the failures at the clients may be retrieved and sent to the clients in accordance with the collection filter rules.
Owner:MICROSOFT TECH LICENSING LLC
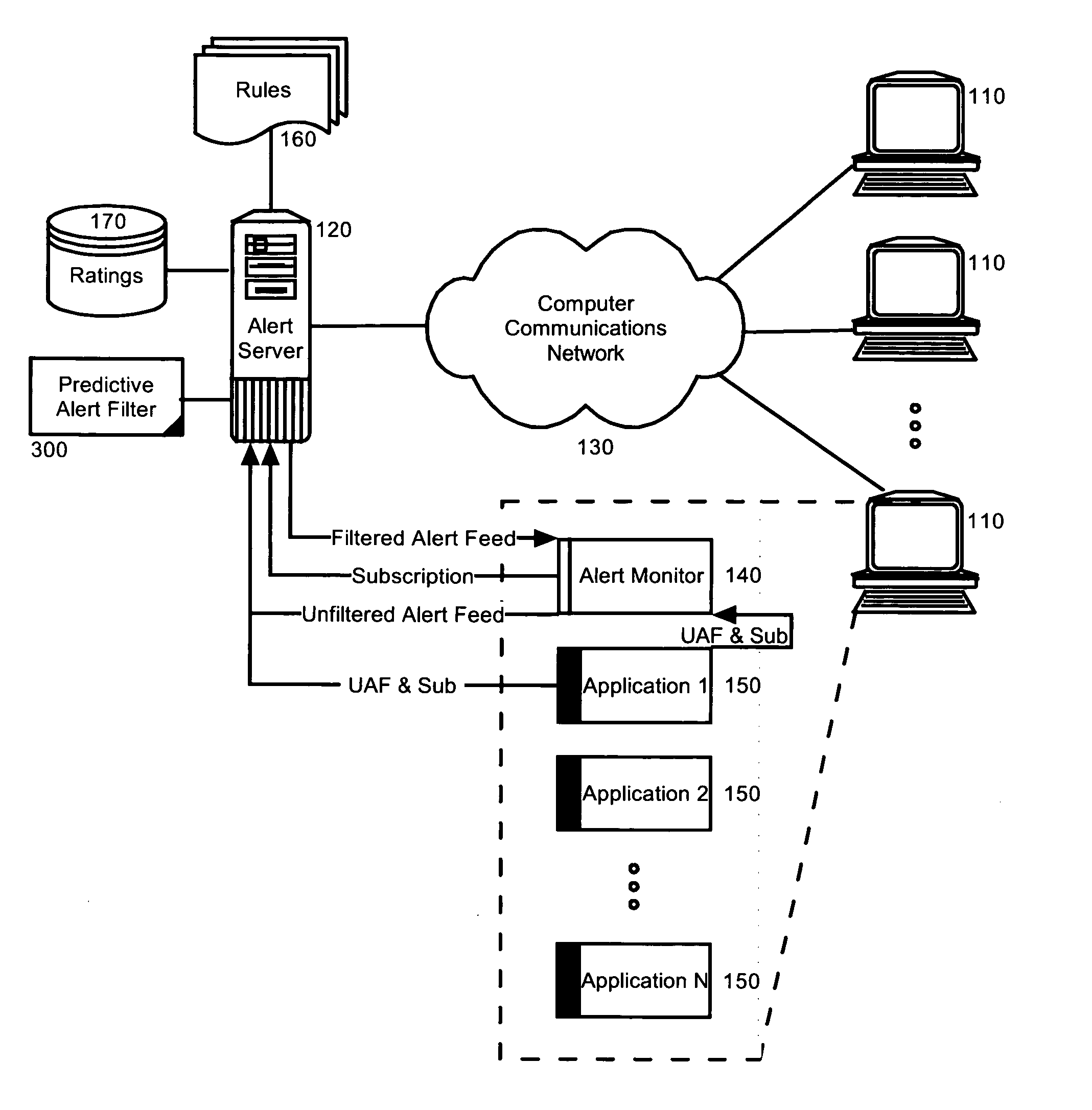
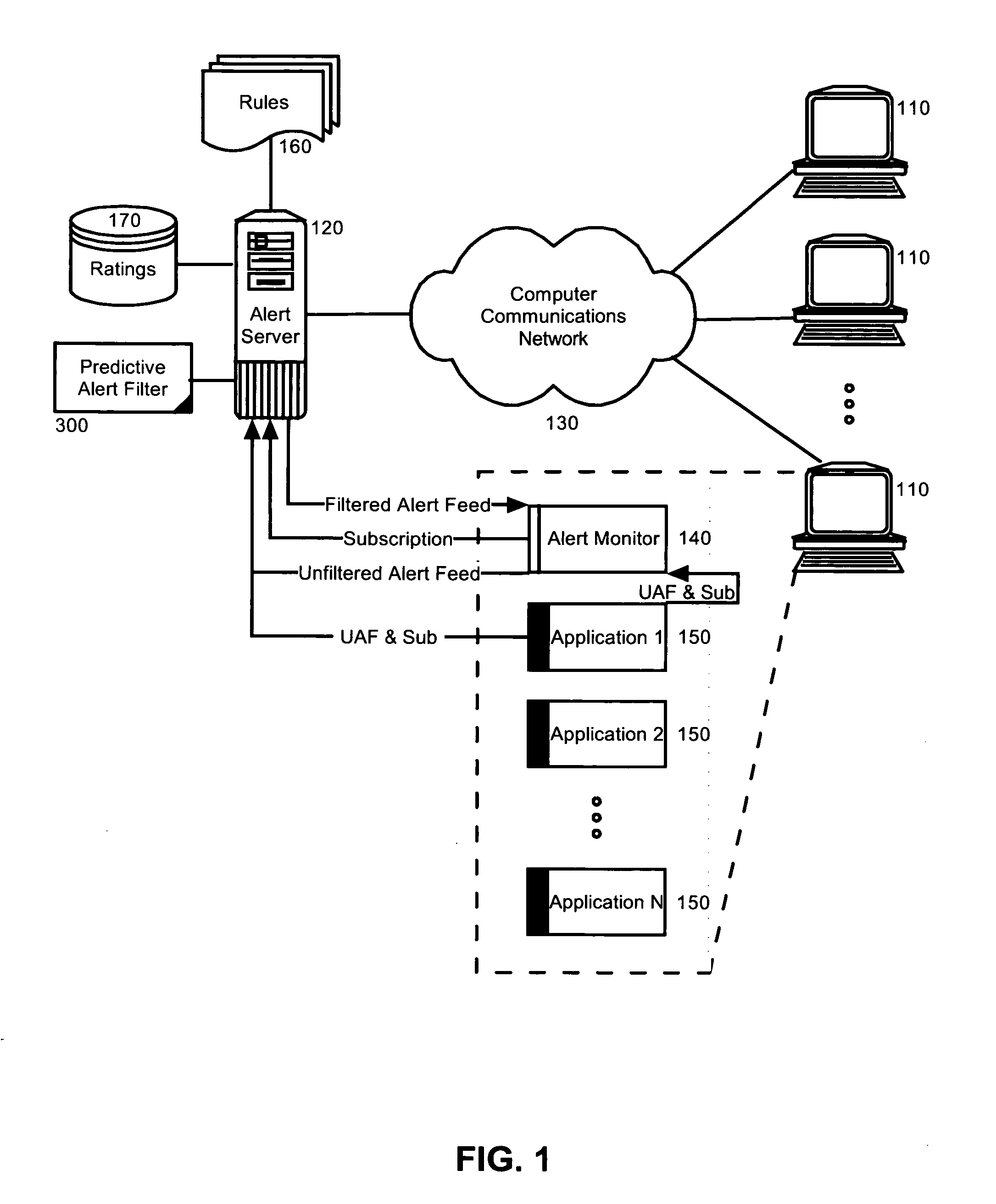
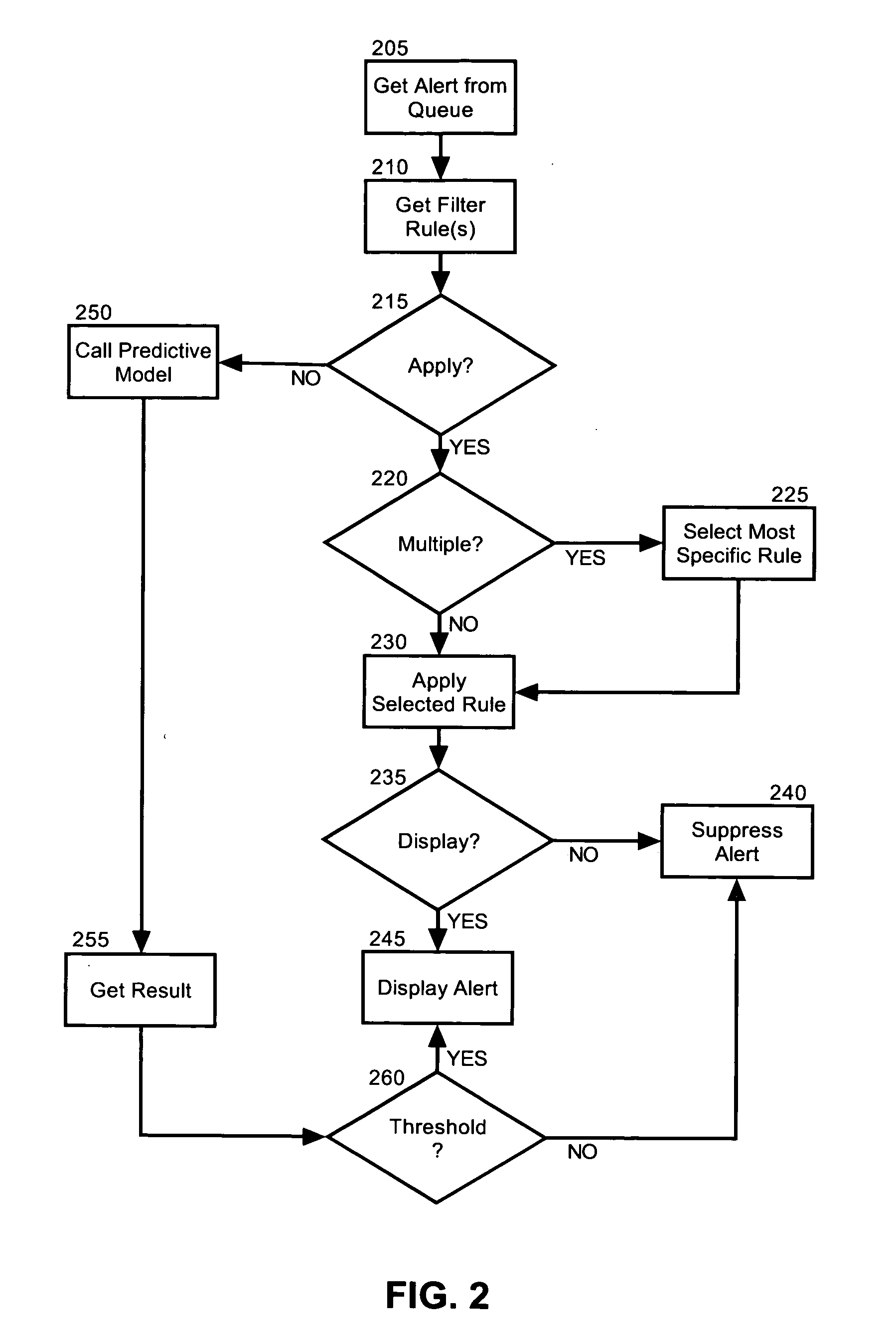
Adaptive alert management
Embodiments of the present invention address deficiencies of the art in respect to alert management and provide a method, system and computer program product for adaptive alert management. In one embodiment of the invention, an adaptive alert management data processing system can include an alert server and multiple different alert monitors disposed in corresponding application hosts. Each of the alert monitors can be configured to establish a subscription to the alert server on behalf of at least one application view of an application issuing alerts. Finally, the system can include multiple different filter rules accessible by the alert server. Each of the filter rules can specify whether or not to suppress or display an alert received in the alert server. The system further can include a data store of ratings previously applied to an alert, an established predictive rating for a target user for a received alert, and predictive alert filter logic enabled to refine the predictive rating for the received alert based upon ratings applied by a plurality of application users to the received alert in the data store.
Owner:IBM CORP
System and method for synchronizing medication configuration information among systems containing medication configuration information
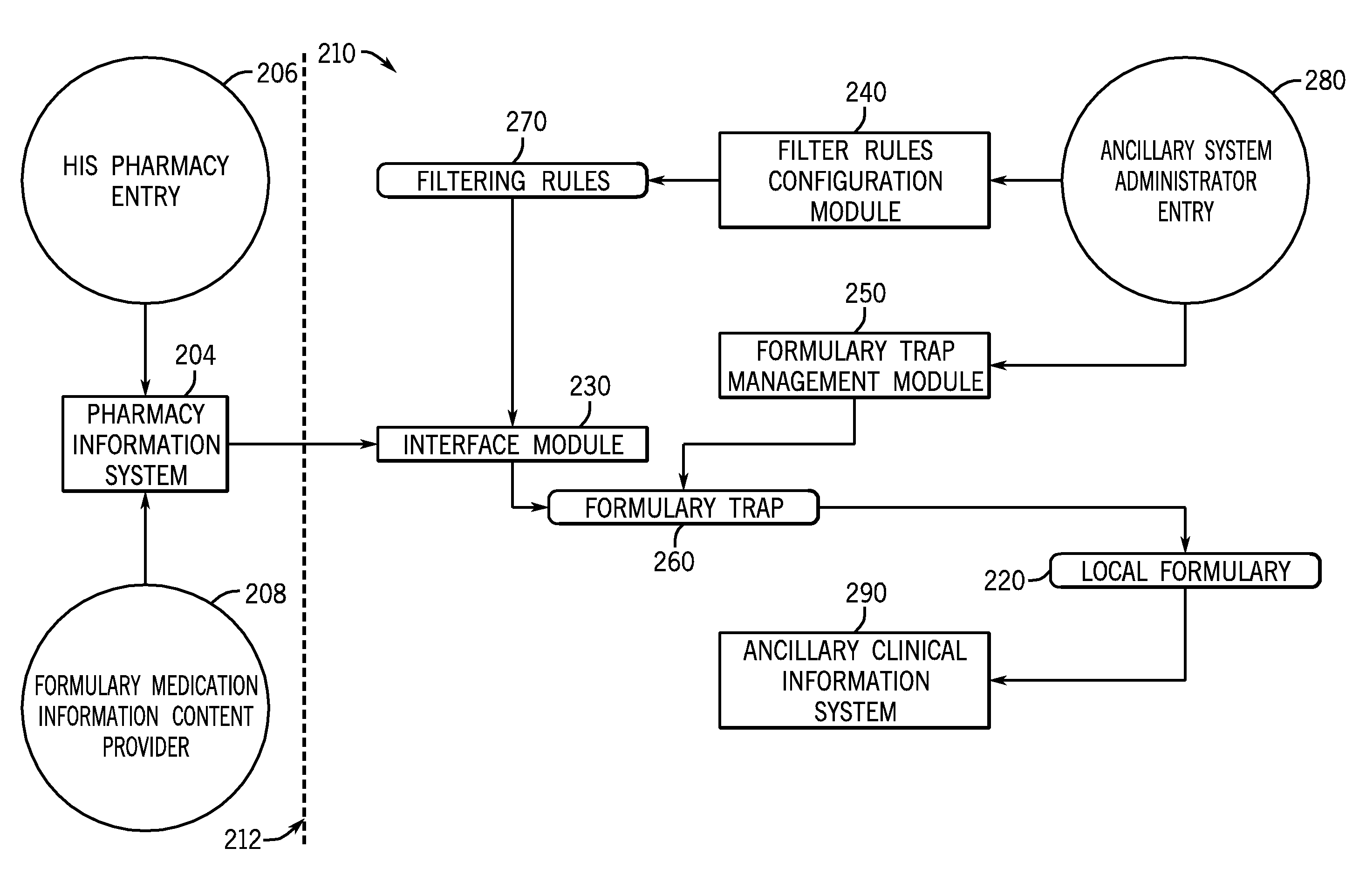
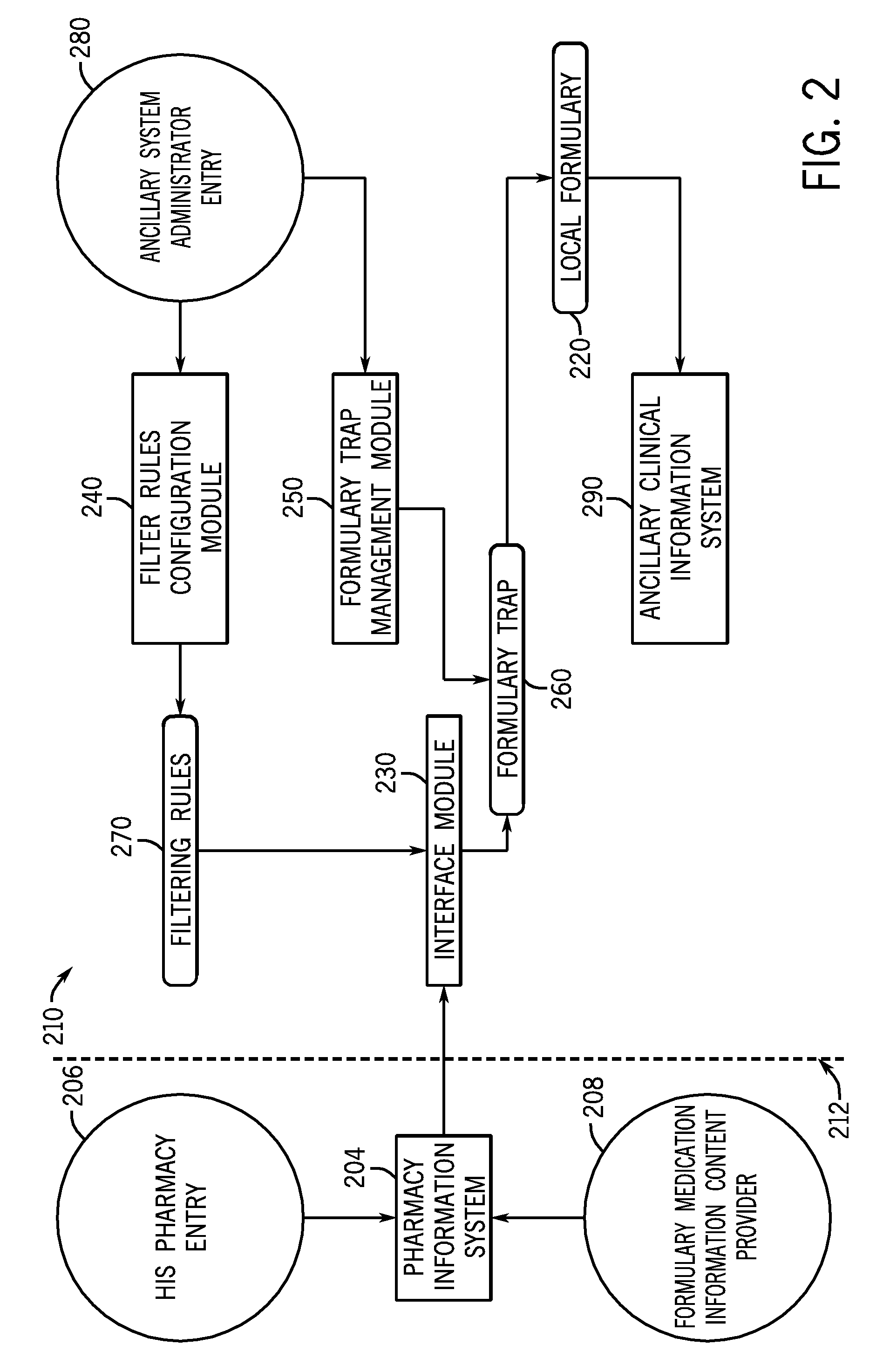
ActiveUS8660860B2Data processing applicationsLocal control/monitoringFiltering rulesAuxiliary system
A method and system for synchronizing medication configuration information. A primary medication configuration computer is adapted to receive medication configuration content from a medication configuration content source. The primary medication configuration computer is also adapted to generate medication configuration change information and transmit the medication configuration change information to an ancillary medication configuration computer, adapted to receive the medication configuration change information from the primary medication configuration computer. The ancillary medication configuration computer is also adapted to filter the medication configuration change information by applying a filtering rule to generate filtered medication configuration change information. The ancillary medication configuration computer is further adapted to store the filtered medication configuration change information in a repository and transmit at least a portion of the filtered medication configuration change information to a management client computer. The ancillary medication configuration computer is also adapted to receive an implementation decision about the portion of the filtered medication configuration change information, accepting or rejecting the portion of the filtered medication configuration change information. The ancillary medication configuration computer is also adapted to transmitting the accepted filtered medication configuration change information to an ancillary system database for integrating the accepted filtered medication configuration change information into the ancillary system database.
Owner:ICU MEDICAL INC
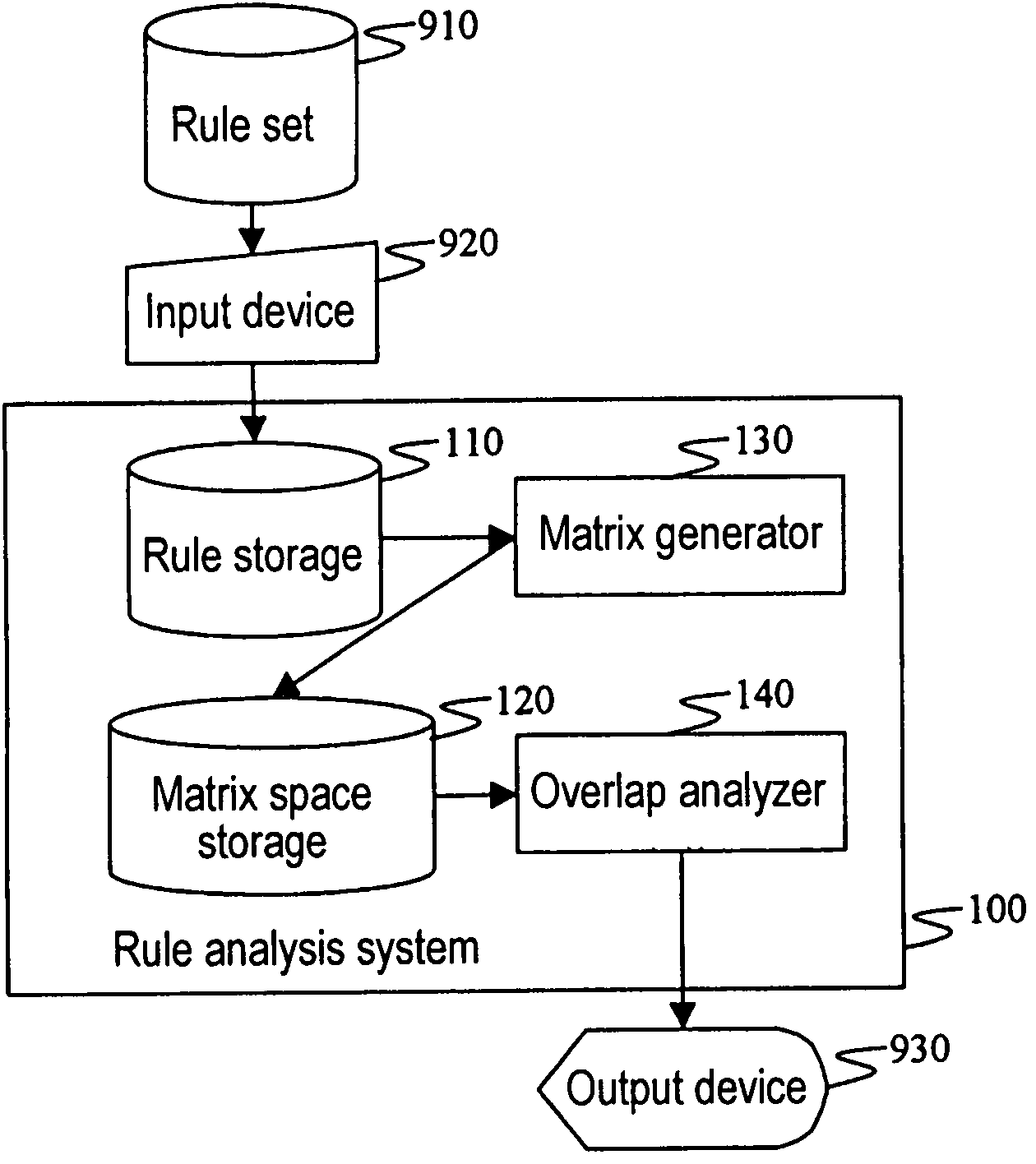
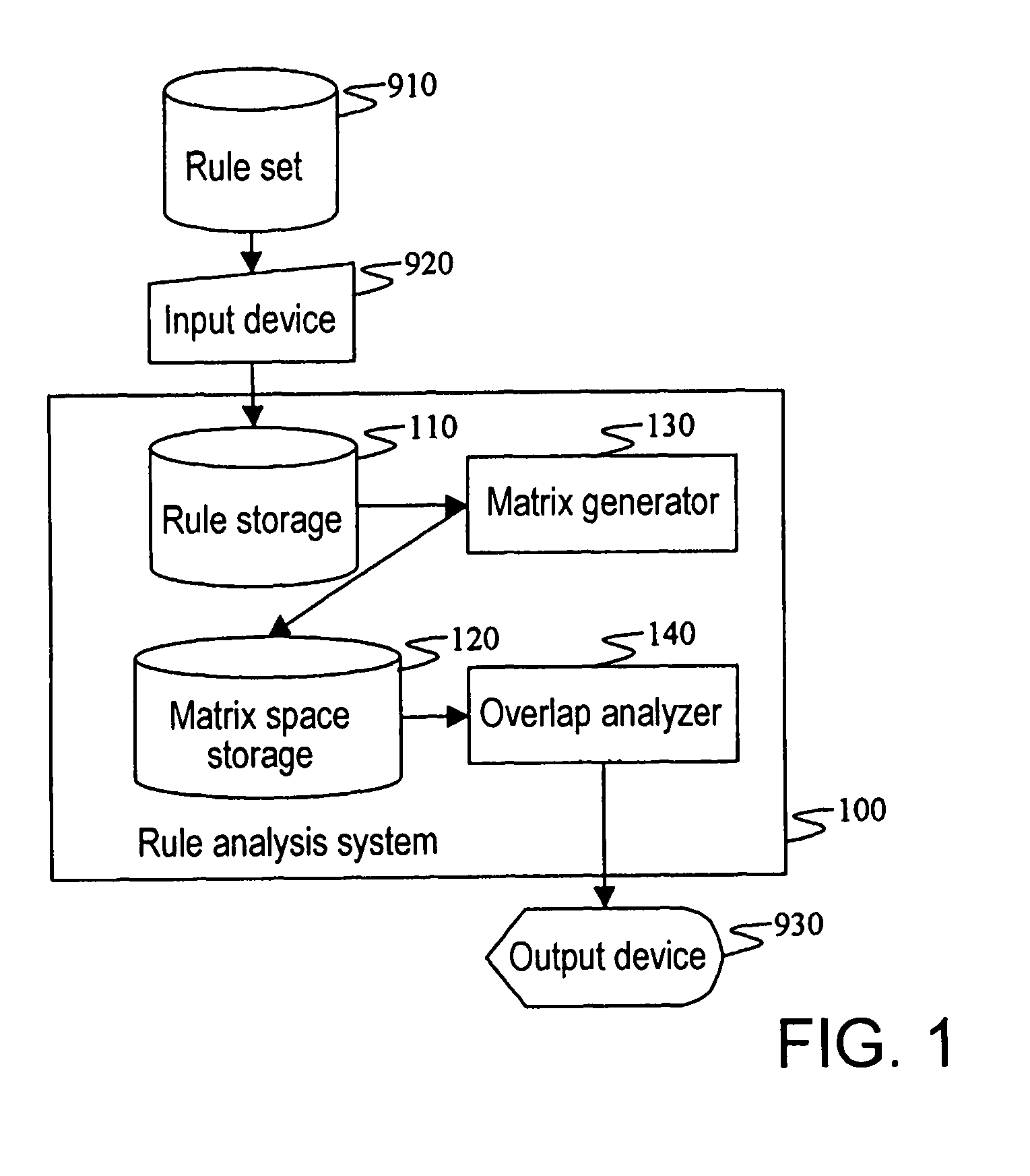
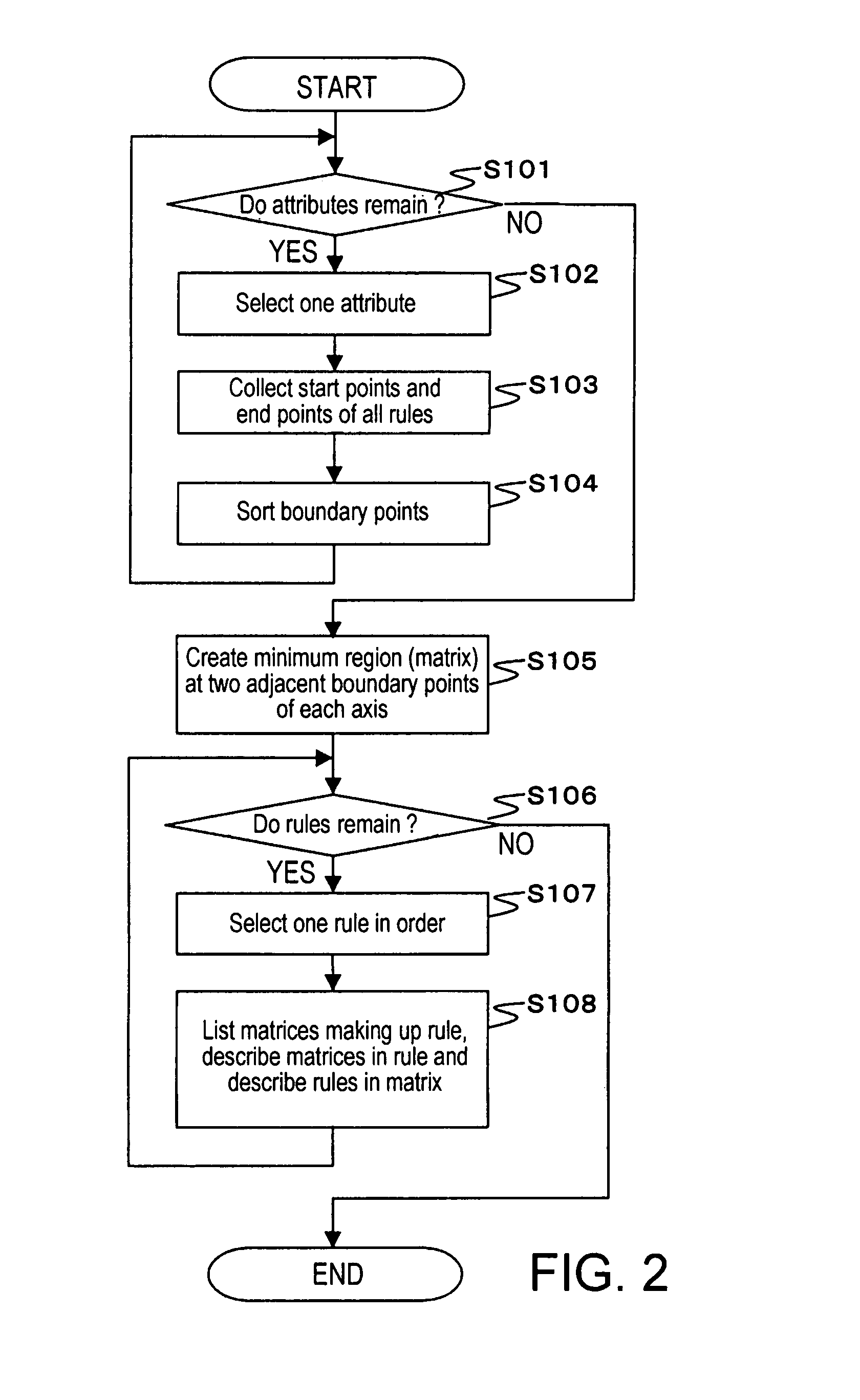
Filtering rule analysis method and system
InactiveUS7792775B2Easy to understandKnowledge representationTransmissionFiltering rulesAnalysis method
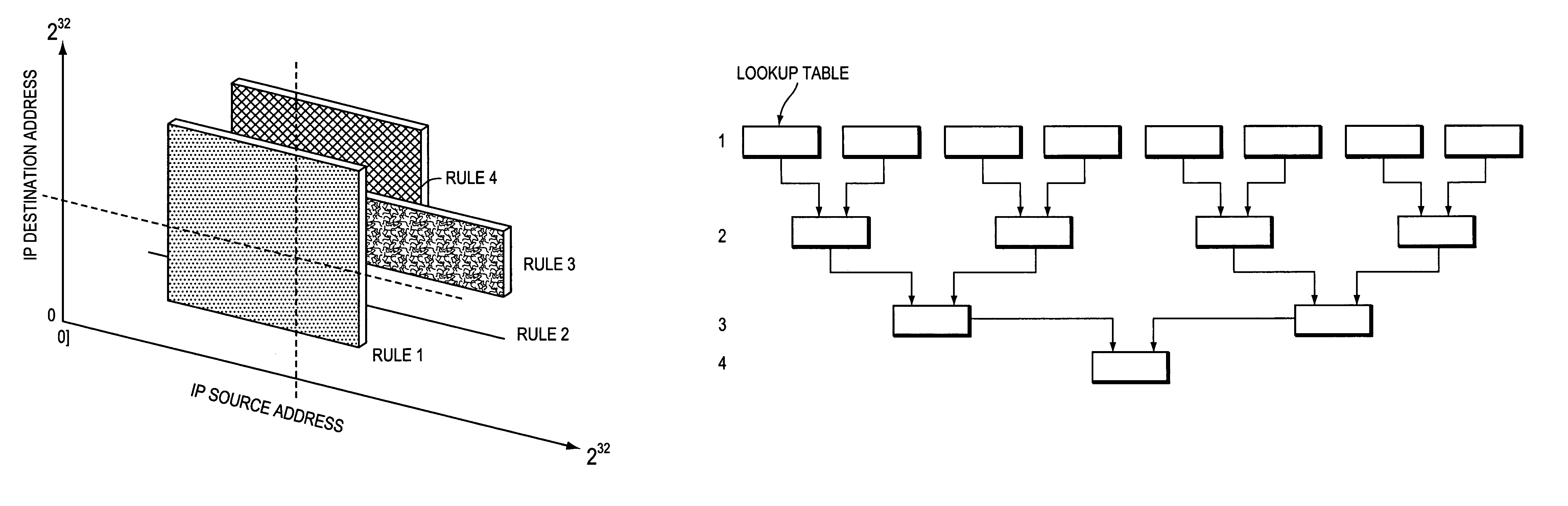
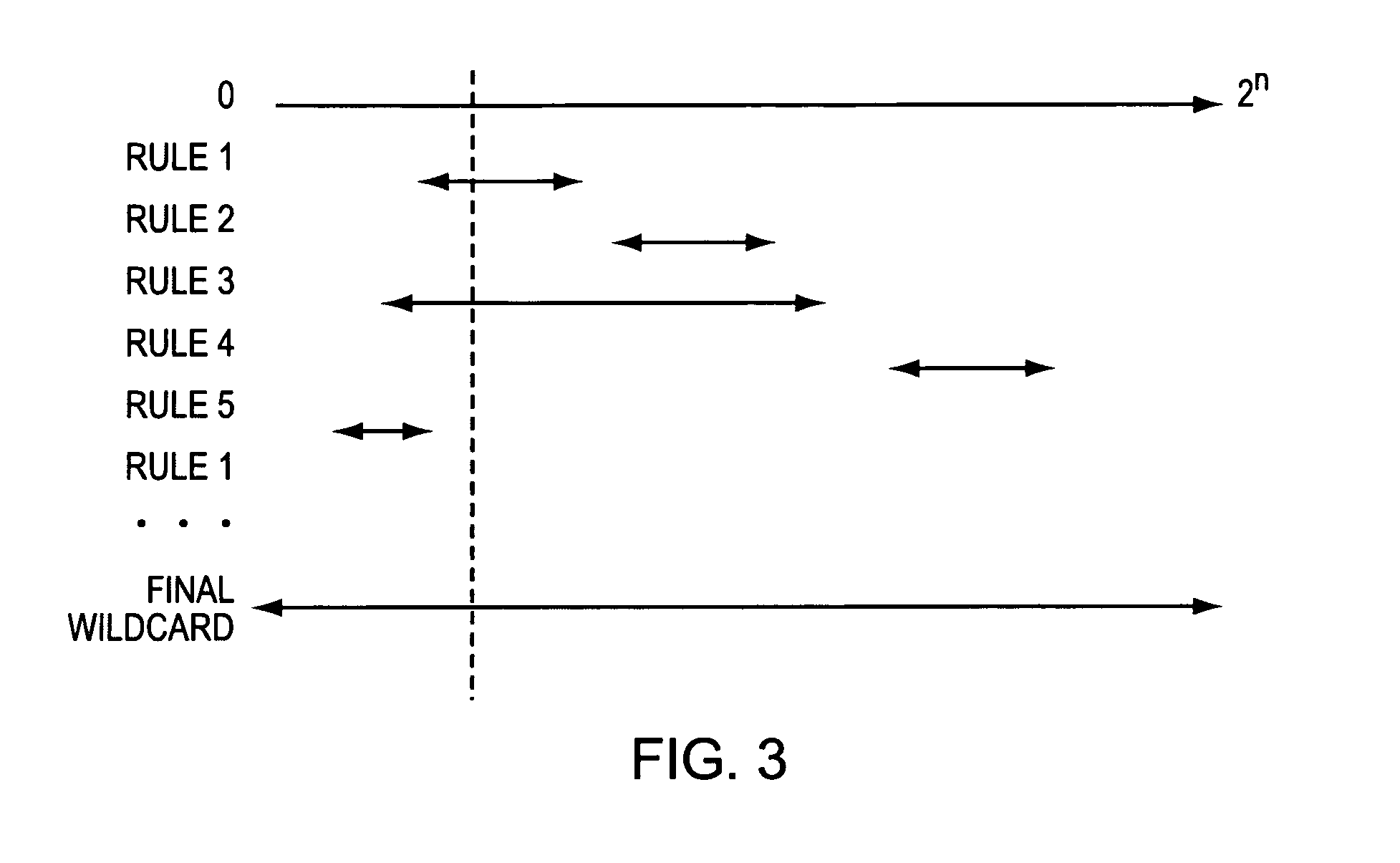
A filtering rule analysis system for analyzing the rules of a packet filtering process that is set in network devices includes: a rule storage for storing sets of rules for which an order of priority has been established; a matrix generator for generating matrix spatial data that contains information of the order of priority and that indicates the correspondence relation between a minimum region identified by starting points and end points of ranges of packet attributes described in each rule as the condition of application of that rule and those rules; and an overlap analyzer for referring to the matrix spatial data to analyze overlap between the rules.
Owner:NEC CORP
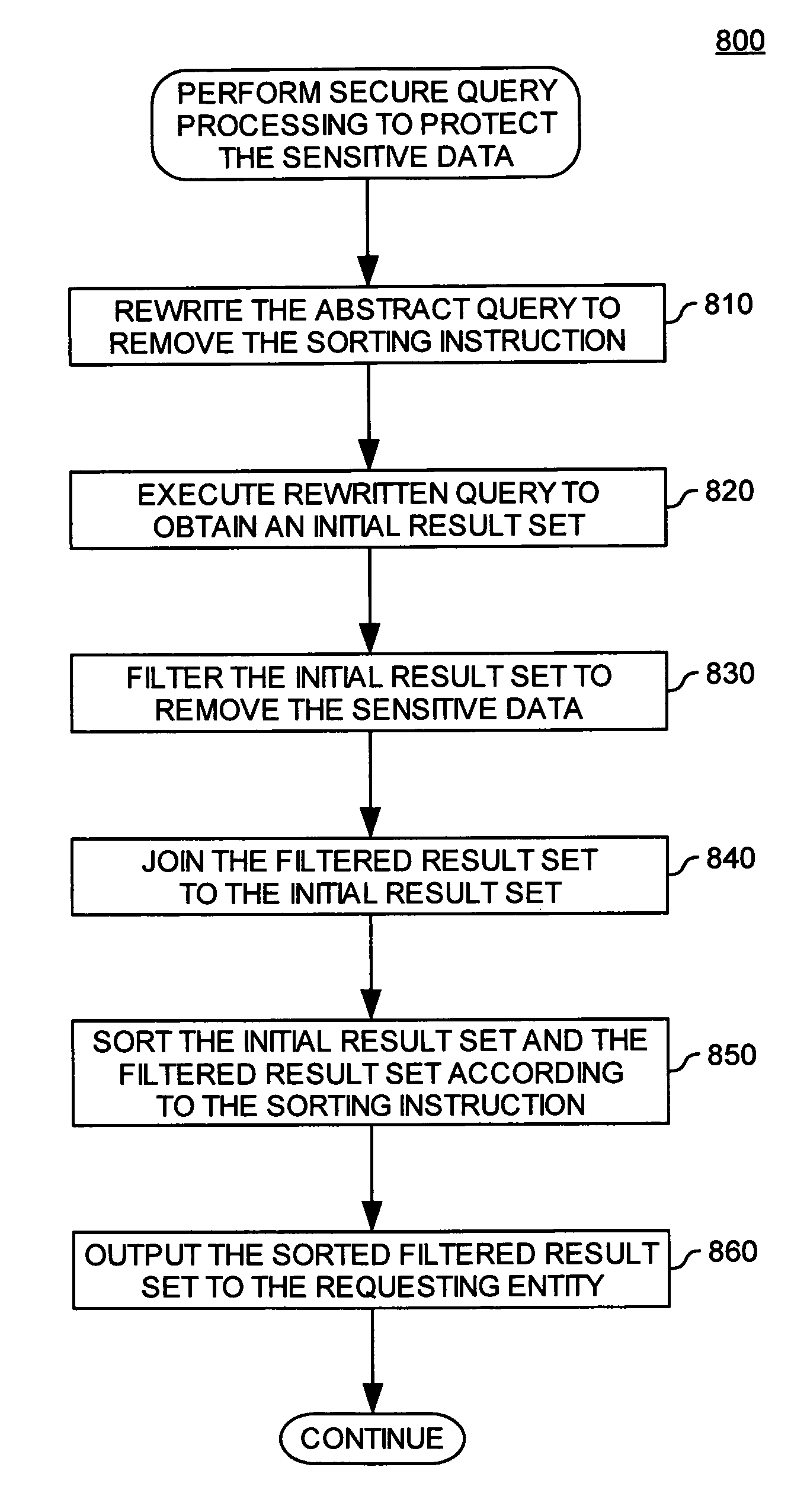
System and method for protecting sensitive data
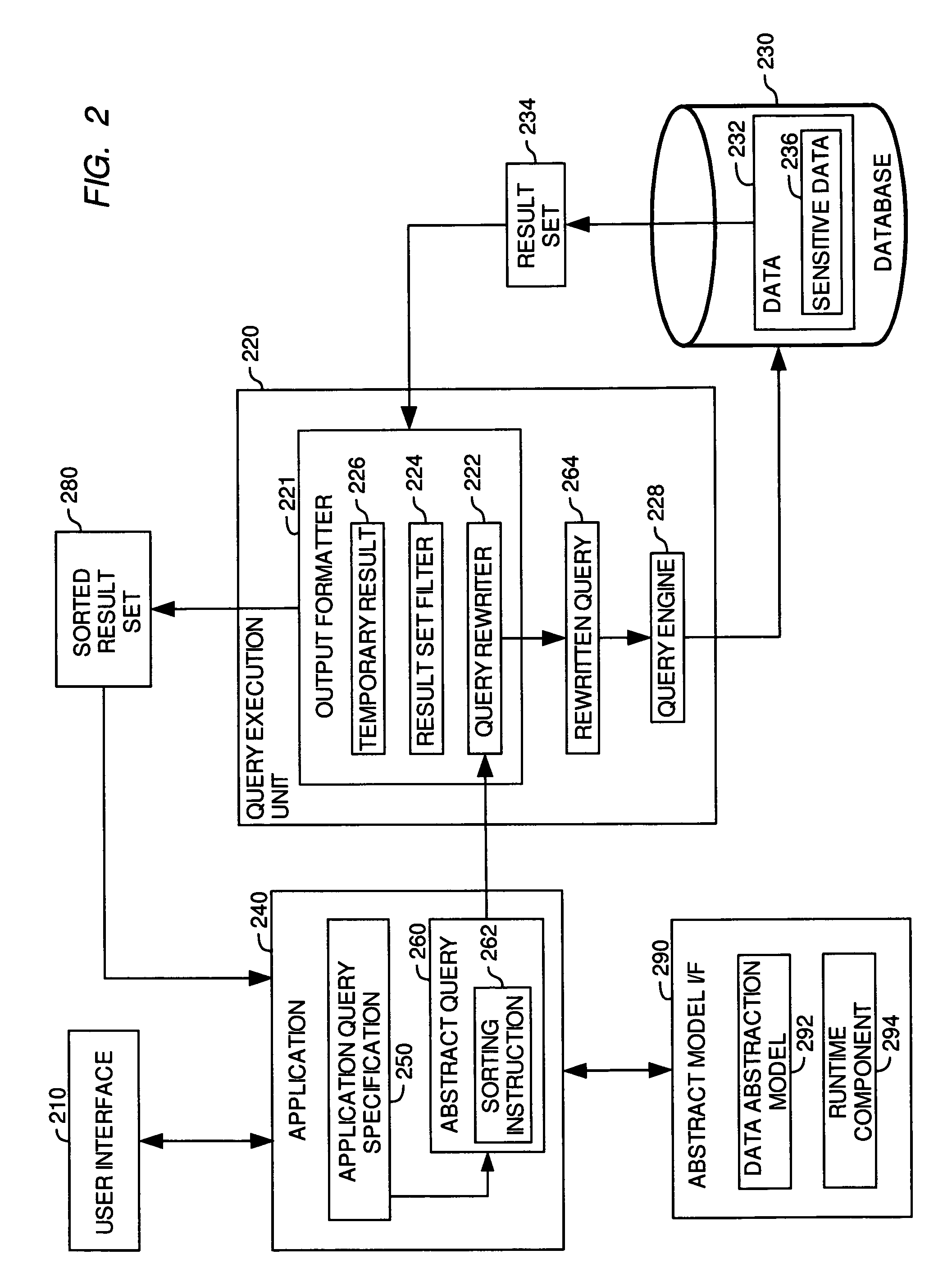
ActiveUS7752215B2Digital data information retrievalDigital data processing detailsField specificationFiltering rules
A method, system and article of manufacture for protecting sensitive data in databases and, more particularly, for managing access to sensitive data in a database. One embodiment comprises receiving a query against the data in the database comprising at least (i) a result field specification, and (ii) a sorting instruction. The method further comprises retrieving a result set from the database, and filtering the retrieved result set on the basis of predefined filtering rules to remove selected data from a selected result field of at least one data record included with the retrieved result set. The filtered result set is sorted according to the sorting instruction to produce the sorted result set, whereby the sorting is done independently of the removed selected data so that the sorted result set places the at least one data record at a position which is non-indicative of a value of the removed selected data.
Owner:TWITTER INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com